Login method based on confidential order of trusted equipment
A login method and password technology, applied in the field of system login, can solve problems such as user name + password no longer safe, security incidents, lack of security awareness of system manufacturers and users, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
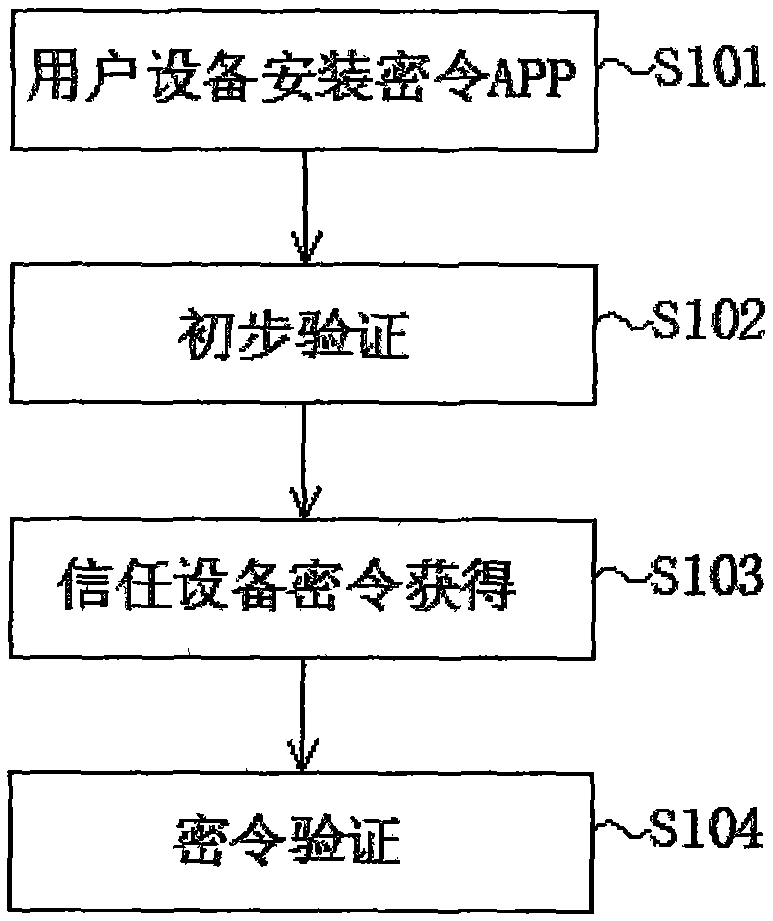
[0037] Such as figure 1 As shown in the present invention, a login method based on a trusted device password includes the following steps,
[0038] Step S101: the user device installs the password APP, and after logging into the APP, binds the device under the user's account to make it a trusted device, thereby obtaining the corresponding login password.
[0039] Step S102: Preliminary verification, the user completes the preliminary verification when entering the user name and password during the login process;
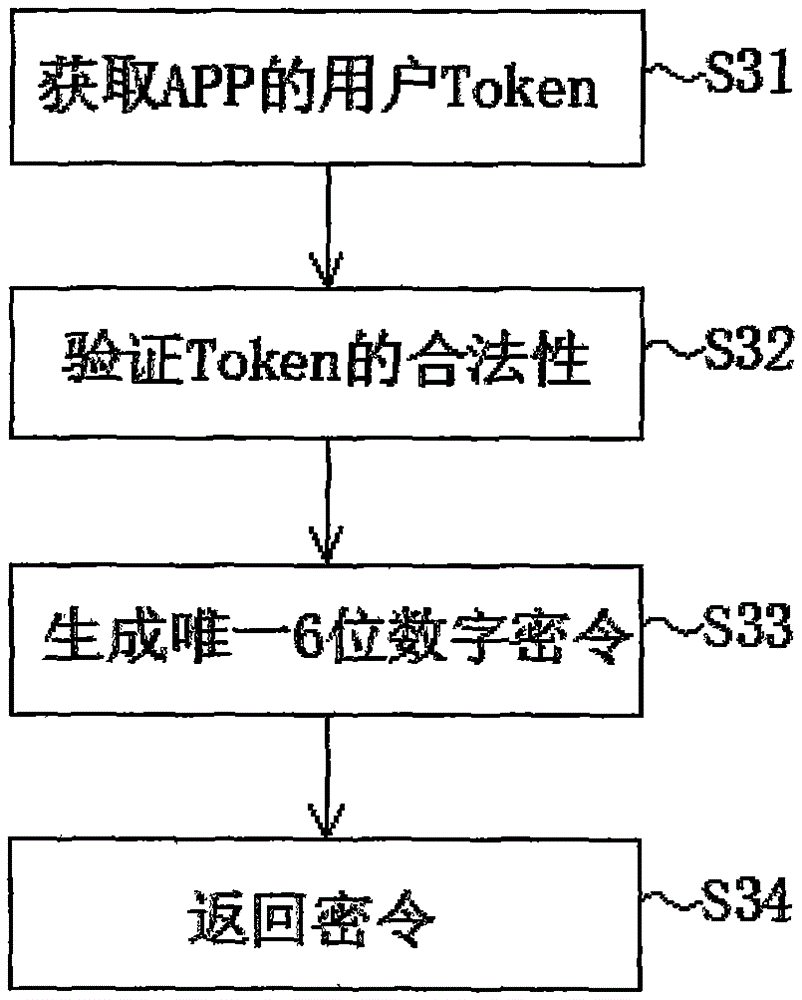
[0040] Step S103: Obtain the password of the trusted device; after the preliminary verification is completed, the system will send a unique password to the APP of the trusted device, and at the same time, the system will remind the user to enter the password displayed by the APP. Such as figure 2 As shown, the step S103 of obtaining the trusted device password specifically includes the following steps,
[0041] Step S31: Obtain the user Token of the APP;
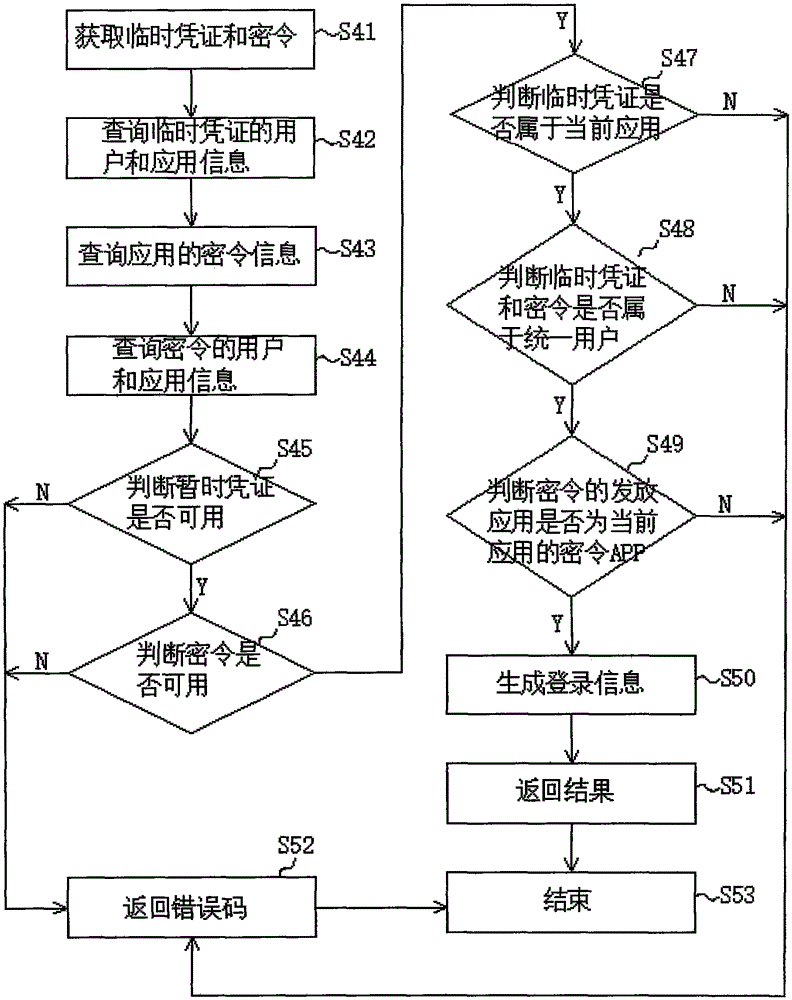
[0042...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com