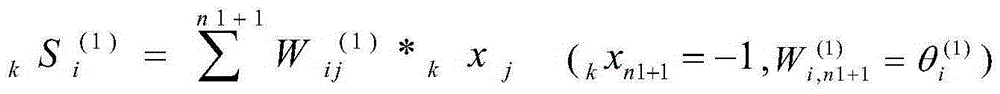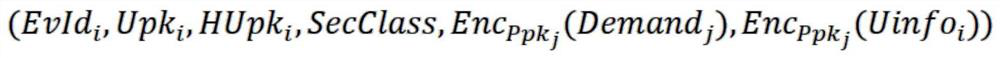Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1446 results about "Node count" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
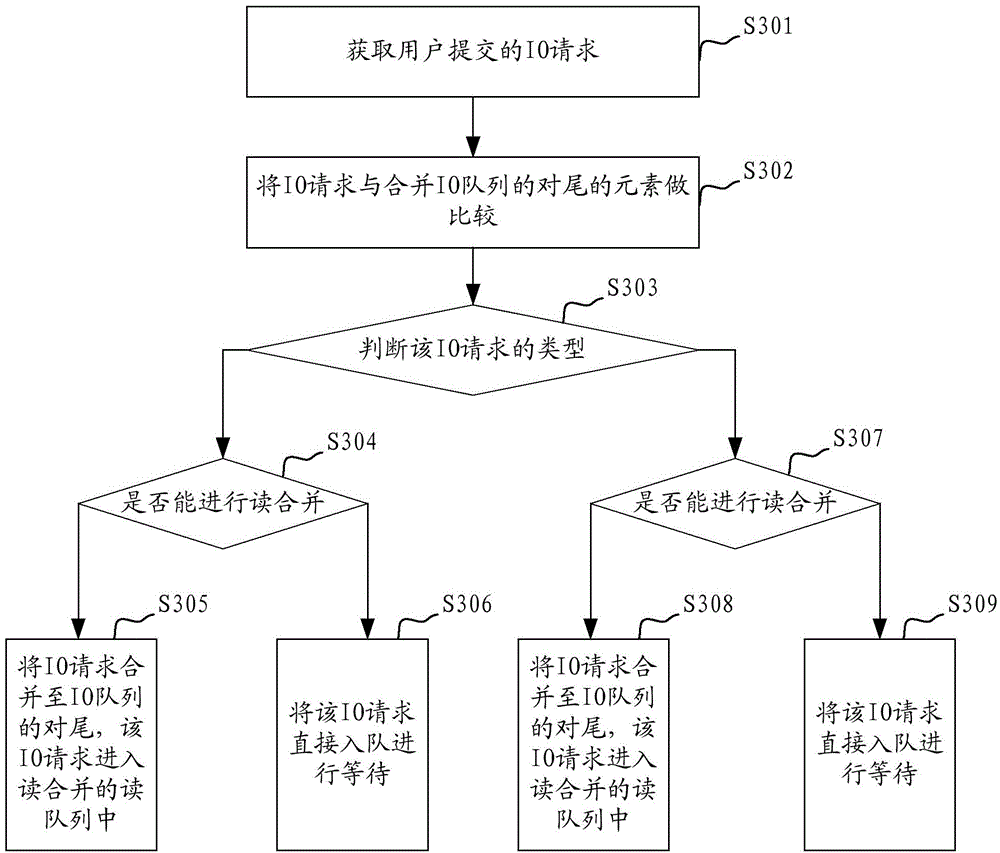
Instead of counting nodes on the fly, Term Node Count keeps track of all term's node counts in its own database table and exposes that data to views. This makes displaying node counts for a list of terms much easier and much more efficient. If at any time the data stored by this module is corrupted by outside influences (i.e.
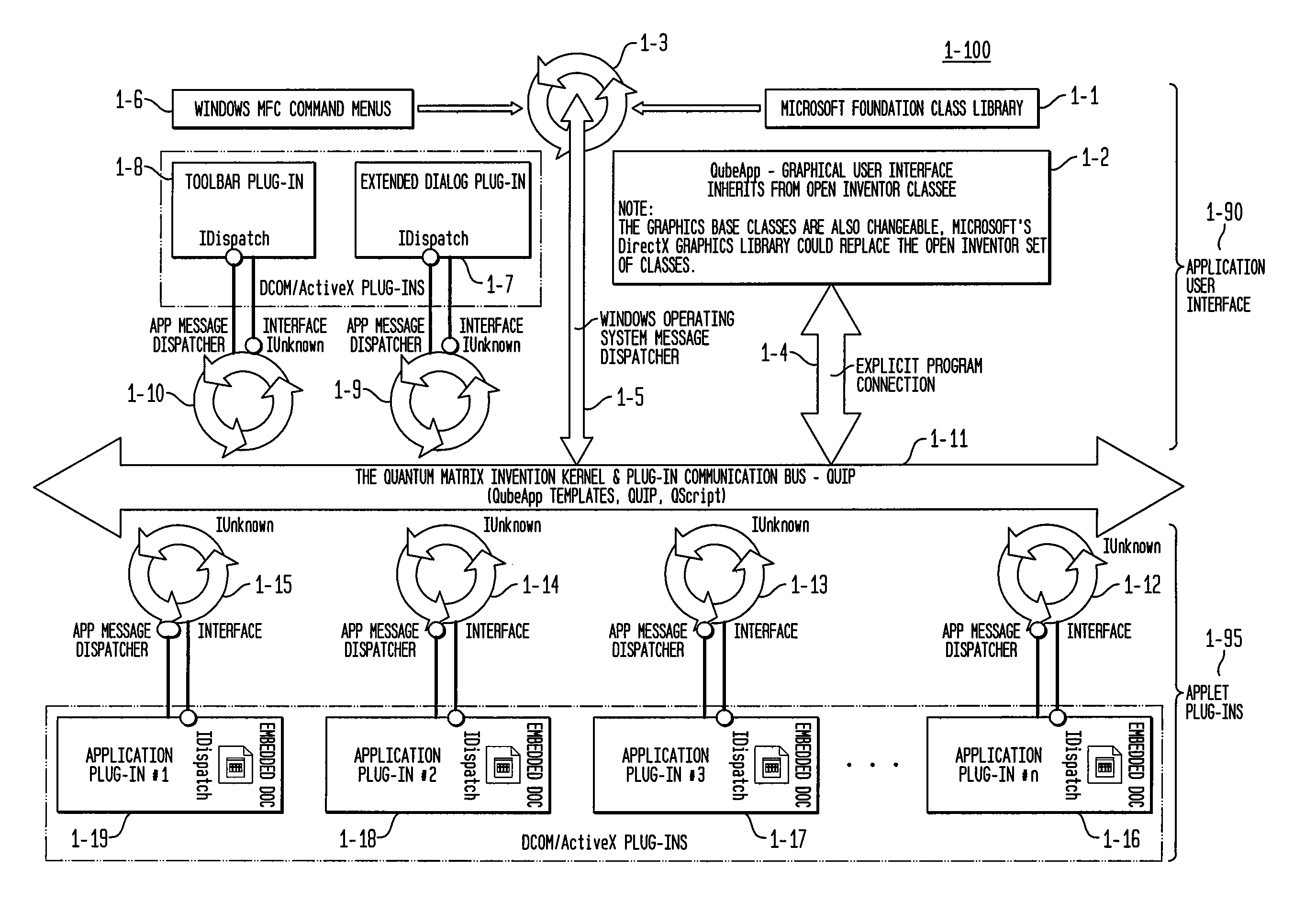
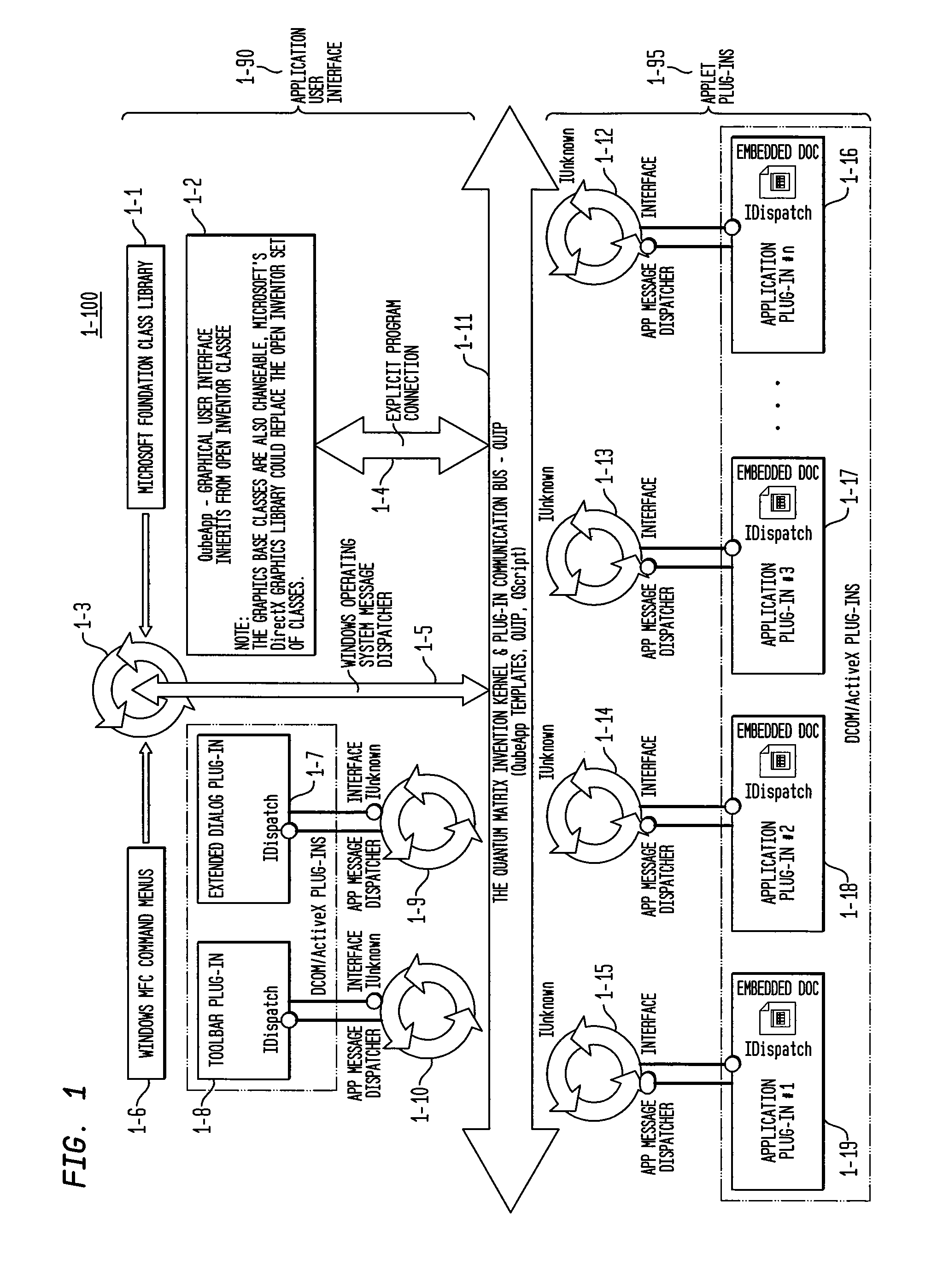
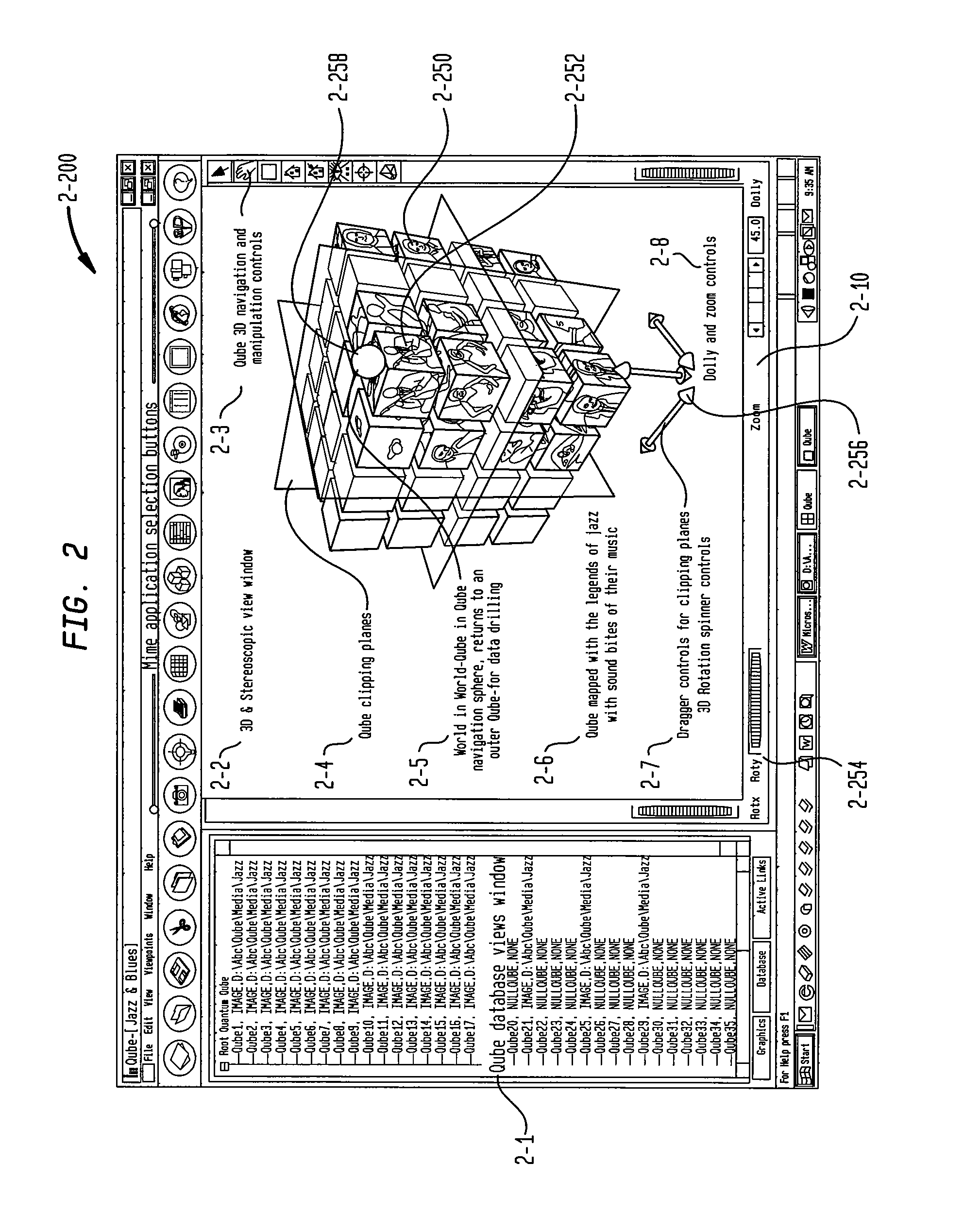
System and method for multi-dimensional organization, management, and manipulation of data
ActiveUS20050131924A1Data processing applicationsDigital data processing detailsScripting languageFile system
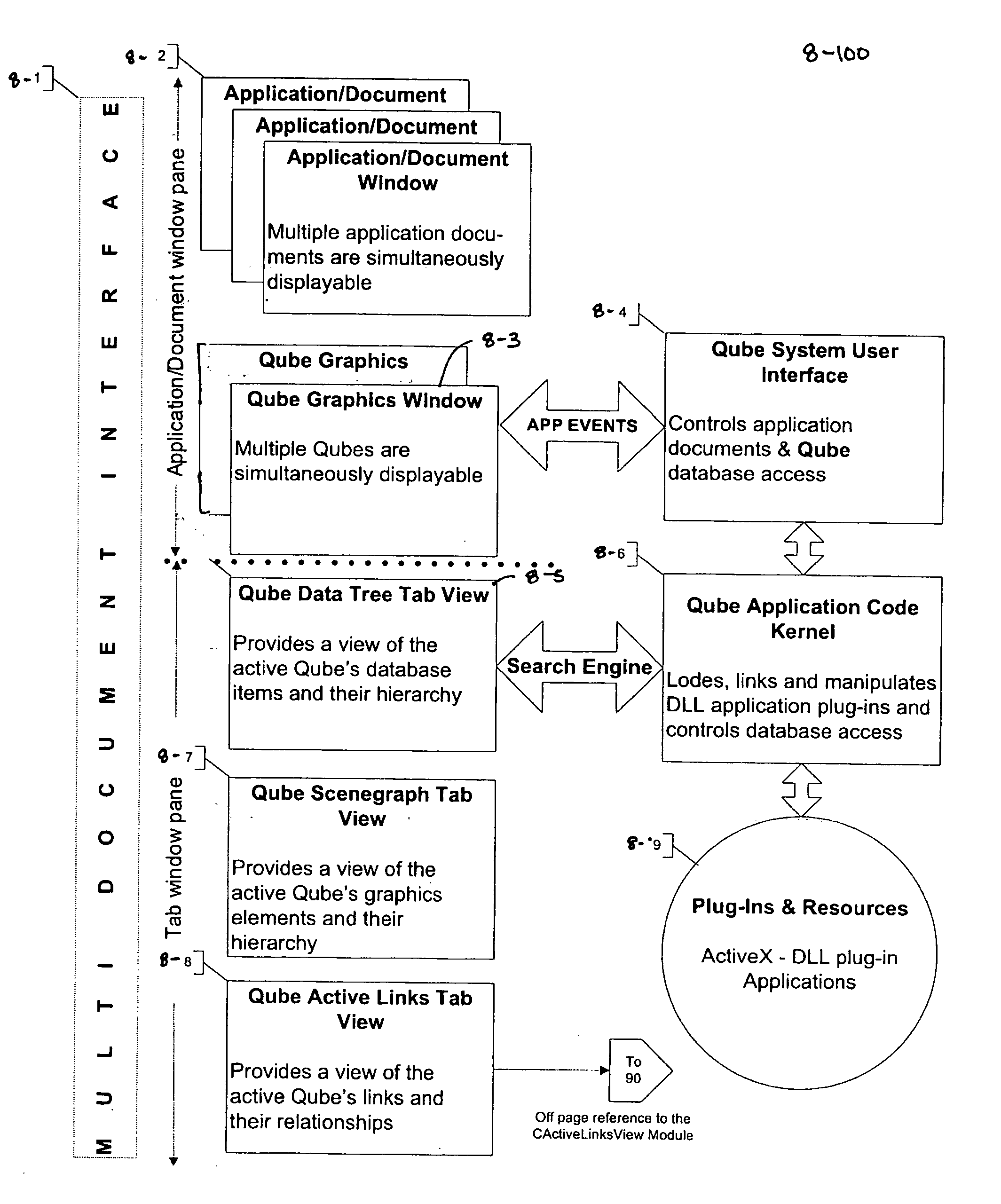
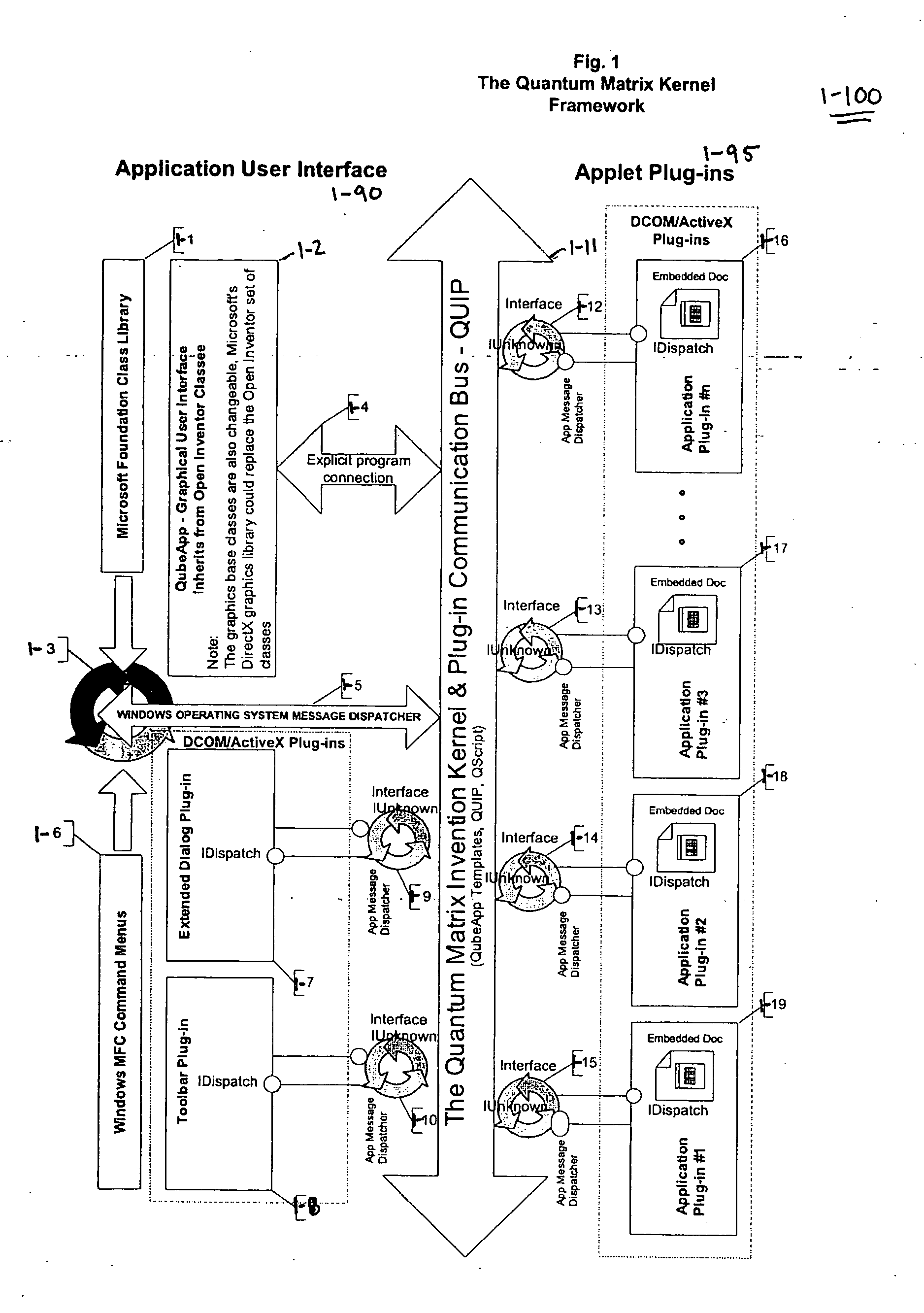
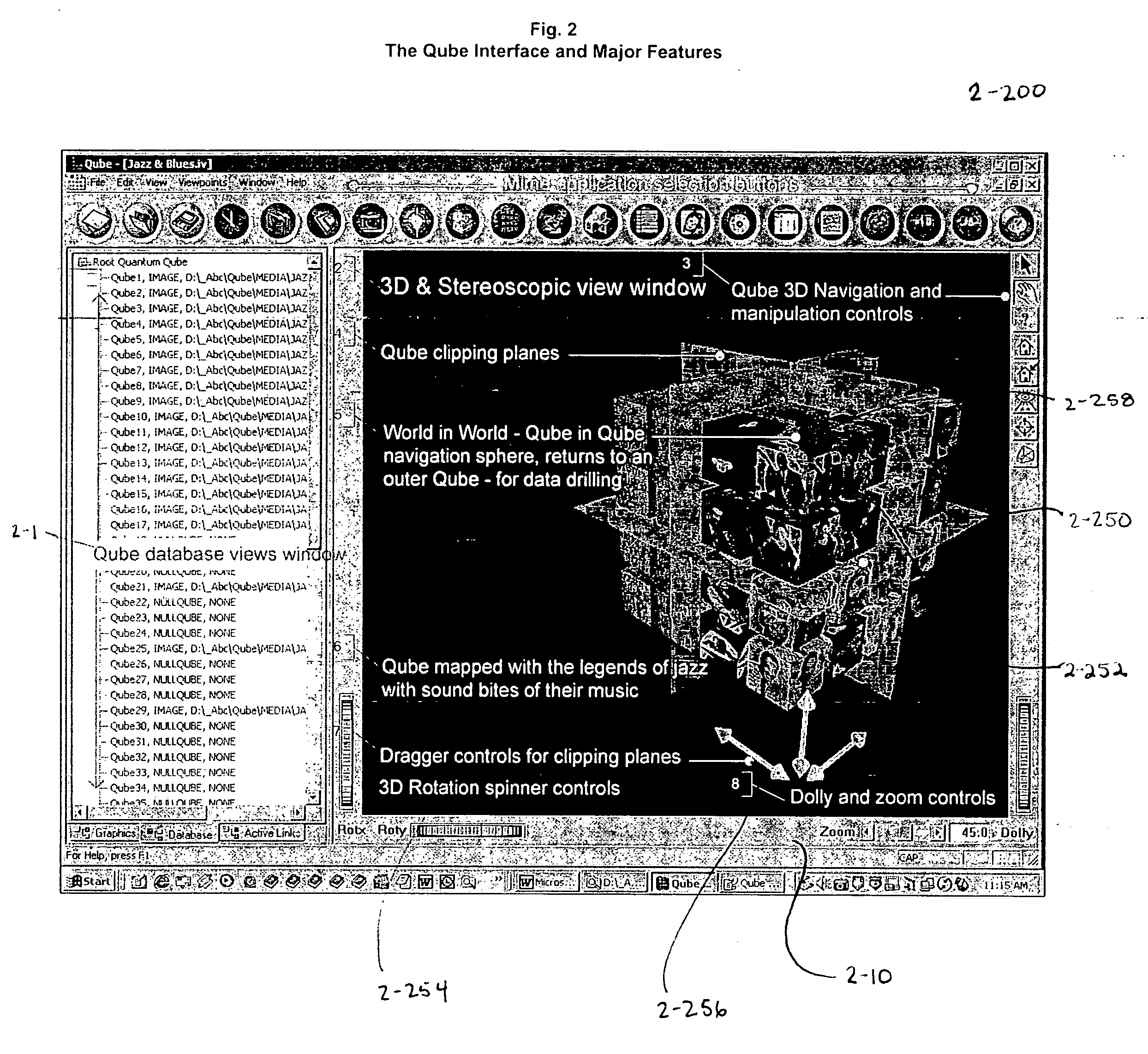
The Quantum Matrix system is a multi-dimensional, multi-threaded exchange environment for data organization, management, and manipulation. Data is organized into a multi-dimensional structure of nodes. Nodes may represent data, absence of data, or another set of nodes. The multi-dimensional structure or portions of it can be automatically created from a file system. One or more associations are also defined for the multi-dimensional structure. An association indicates a relationship between a node and another node, data, or a set of nodes. The multi-dimensional structure is then displayed three-dimensionally and navigated. Relational logic, Boolean algebra, or a scripting language can be applied to the nodes, data, and associations to produce a resultant set of nodes. Furthermore, portions of the multi-dimensional structure can be isolated with the use of planes to ease navigation. Furthermore, Avatars may be displayed and used for collaborative purposes and to automate the navigation of the multi-dimensional structure.
Owner:QUANTUM MATRIX HLDG
Method and system for partial-order analysis of multi-dimensional data
InactiveUS6931418B1Improve performanceEfficient combinationDigital data information retrievalData processing applicationsFuzzy pattern matchingData profiling
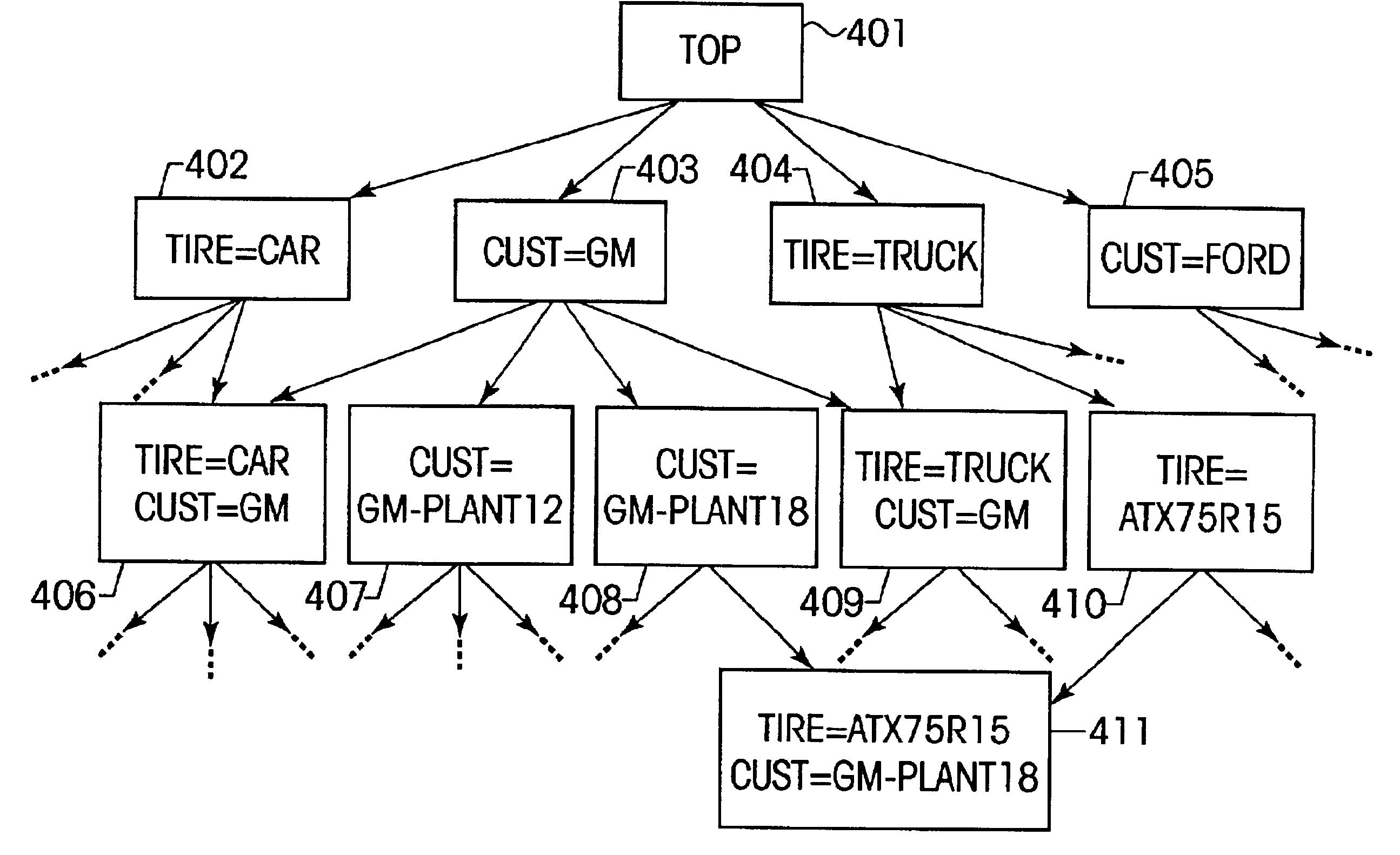
A method and system for performing data analysis where multiple, categorical dimensions and statistical measures are used. The method includes preparing multi-dimensional data into nodes and arranging them logically in the form of a partial-order database. The database may then be traversed by a data-mining tool, or queried in an OLAP manner. Queries are answered through a process of associative partial-order search, which includes optional support for “children-of” requests, and optional support for fuzzy pattern-matching. By aggregating measures on-the-fly, this method is able to preform well without requiring a large number of summary nodes, when taken as a percentage of the total node count.
Owner:GULA CONSULTING LLC
Methods and apparatus for dynamic topology configuration in a daisy-chained communication environment
InactiveUS6055228AImprove effective communication performanceDigital computer detailsNetworks interconnectionFiberCommunications system
A loop isolation circuit (LIC) to enable subdivision of a single daisy-chained communication loop (e.g., FC-AL) into smaller loops and to enable joining of smaller loops into a single larger loop. An LIC comprises essentially two multiplexors configured so as to permit controlled subdivision or joining of two loop portions. In a first selected state, the LIC subdivides a communication loop in which it is inserted into two loops. This configuration sacrifices accessibility among some devices previously on the larger loop for the benefit of enhanced bandwidth and reduced overhead due to node count. Bandwidth is enhanced by enabling simultaneous operation of two (or more) loop portions for establishing and communicating over logical circuit connections. However, when a failure of a redundant loop precludes access to devices, the LIC may be set to a second state to rejoin previously subdivided loops into a larger loop. This configuration restores access among all devices sharing common access to the larger loop. The LIC of the present invention therefore enables communication loop controllers to dynamically reconfigure a daisy-chained loop communication system to enhance performance in normal operation. The LIC of further enables restoration of the larger loop to restore redundant loop configurations. The LIC of the present invention is applicable in many daisy-chained loop communication environments including, but not limited to, Fiber Channel Arbitrated Loop (FC-AL).
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System and method for multi-dimensional organization, management, and manipulation of data
ActiveUS7433885B2Data processing applicationsDigital data processing detailsScripting languageFile system
The Quantum Matrix system is a multi-dimensional, multi-threaded exchange environment for data organization, management, and manipulation. Data is organized into a multi-dimensional structure of nodes. Nodes may represent data, absence of data, or another set of nodes. The multi-dimensional structure or portions of it can be automatically created from a file system. One or more associations are also defined for the multi-dimensional structure. An association indicates a relationship between a node and another node, data, or a set of nodes. The multi-dimensional structure is then displayed three-dimensionally and navigated. Relational logic, Boolean algebra, or a scripting language can be applied to the nodes, data, and associations to produce a resultant set of nodes. Furthermore, portions of the multi-dimensional structure can be isolated with the use of planes to ease navigation. Furthermore, Avatars may be displayed and used for collaborative purposes and to automate the navigation of the multi-dimensional structure.
Owner:QUANTUM MATRIX HLDG
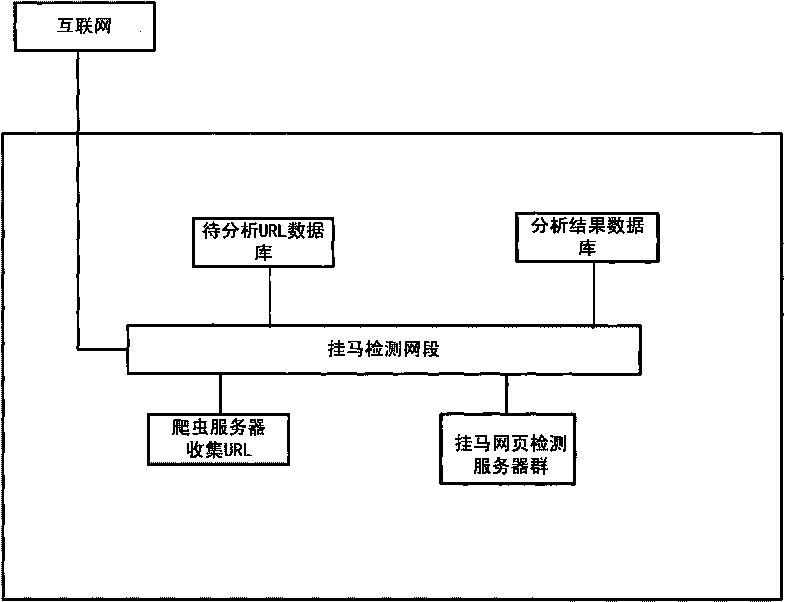
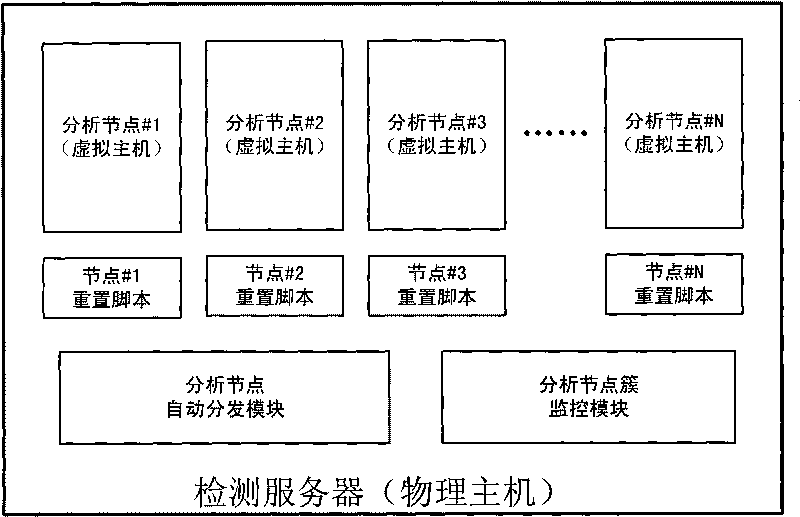
Method and system for detecting large-scale malicious web pages
InactiveCN101692267AWill not affect operationDoes not affect functionalityPlatform integrity maintainanceProgram loading/initiatingSelf maintenanceNode clustering
The invention discloses a method and a system for detecting large-scale malicious web pages by using a three-layer parallel architecture and a layered control guarantee method: in the first layer, a plurality of detection servers interconnected via networks are arranged in parallel, so as to construct a detection server cluster, and a task set to be analyzed is set up on one detection server; in the second layer, a plurality of analysis nodes are arranged in parallel in each detection server, and a node cluster monitoring module is arranged so as to monitor and analyze the operating condition of the nodes; and in the third layer, a sandbox environment is constructed in parallel in each analysis node, so as to achieve the paralleled detection of the task to be analyzed. The architecture of the invention ensures the mutual independence and self-maintenance among the detection servers and among the analysis nodes, the overall operation of the system is free from the dynamic expansion of physical hosts and node numbers, and the overall function thereof is not affected by the invalidity of the single analysis node; and various tasks can be detected in a multi-channel and paralleled manner at the same time in the same node, thereby improving the analysis efficiency of the system.
Owner:PEKING UNIV
Differentiated secondary index maintenance in log structured nosql data stores
InactiveUS20140279855A1Accelerate point queryEffectively avoids broadcasting queriesDatabase updatingDigital data processing detailsData storingData store
There is provided a method for operating multi-node data stores. A data table is stored in a first computing node and an index table is stored in a second computing node. The index table provides keys used for accessing data in the first computing node and other multi-node data stores. Operations that update or read the data table accessed from the first computing node and the index table accessed from the second computing node are performed. The operations optimize between latency in updating or reading the data table and the index table and data consistency maintained between data entries in the data table and data entries pointed by indices in the index table
Owner:IBM CORP
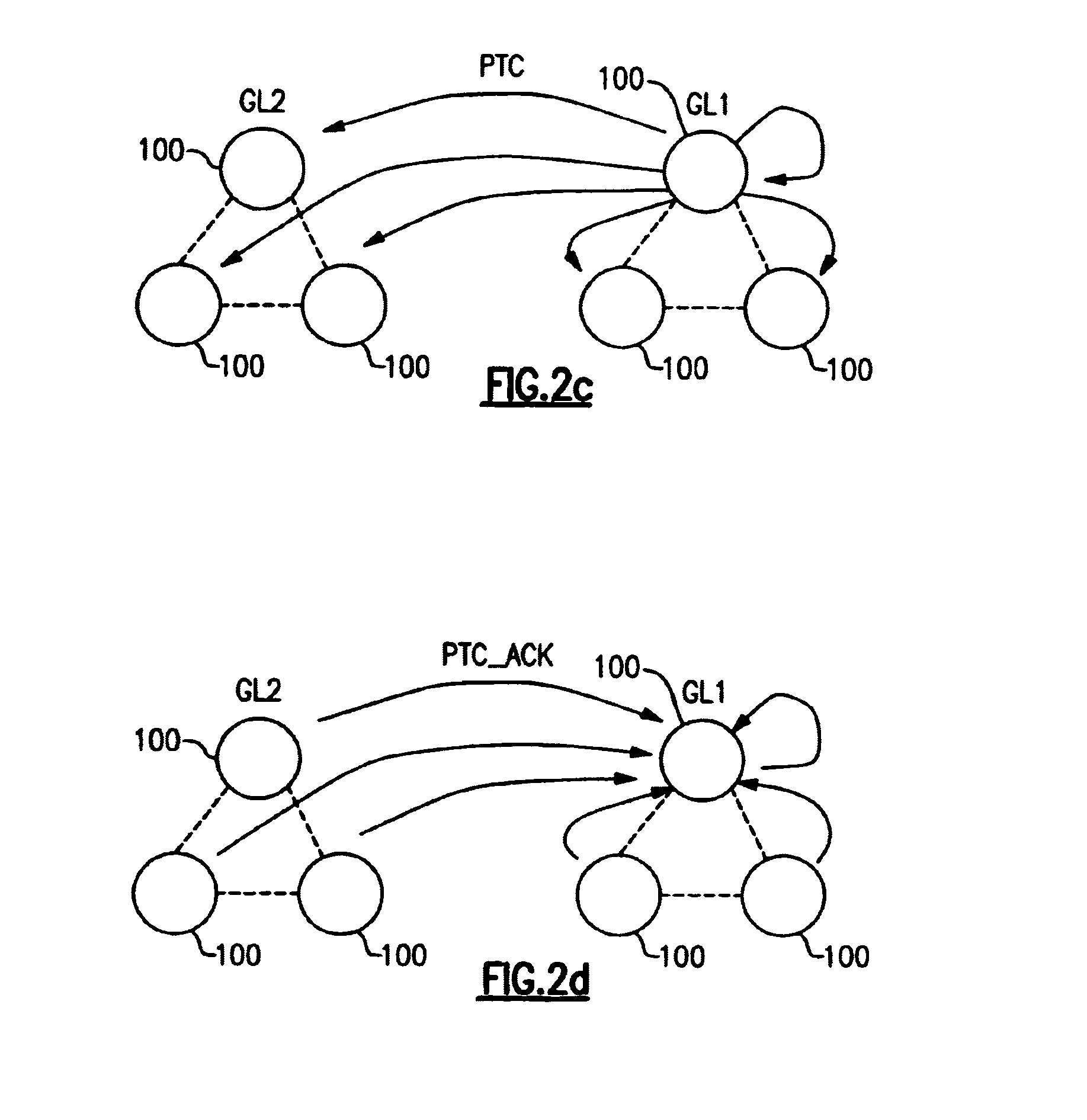
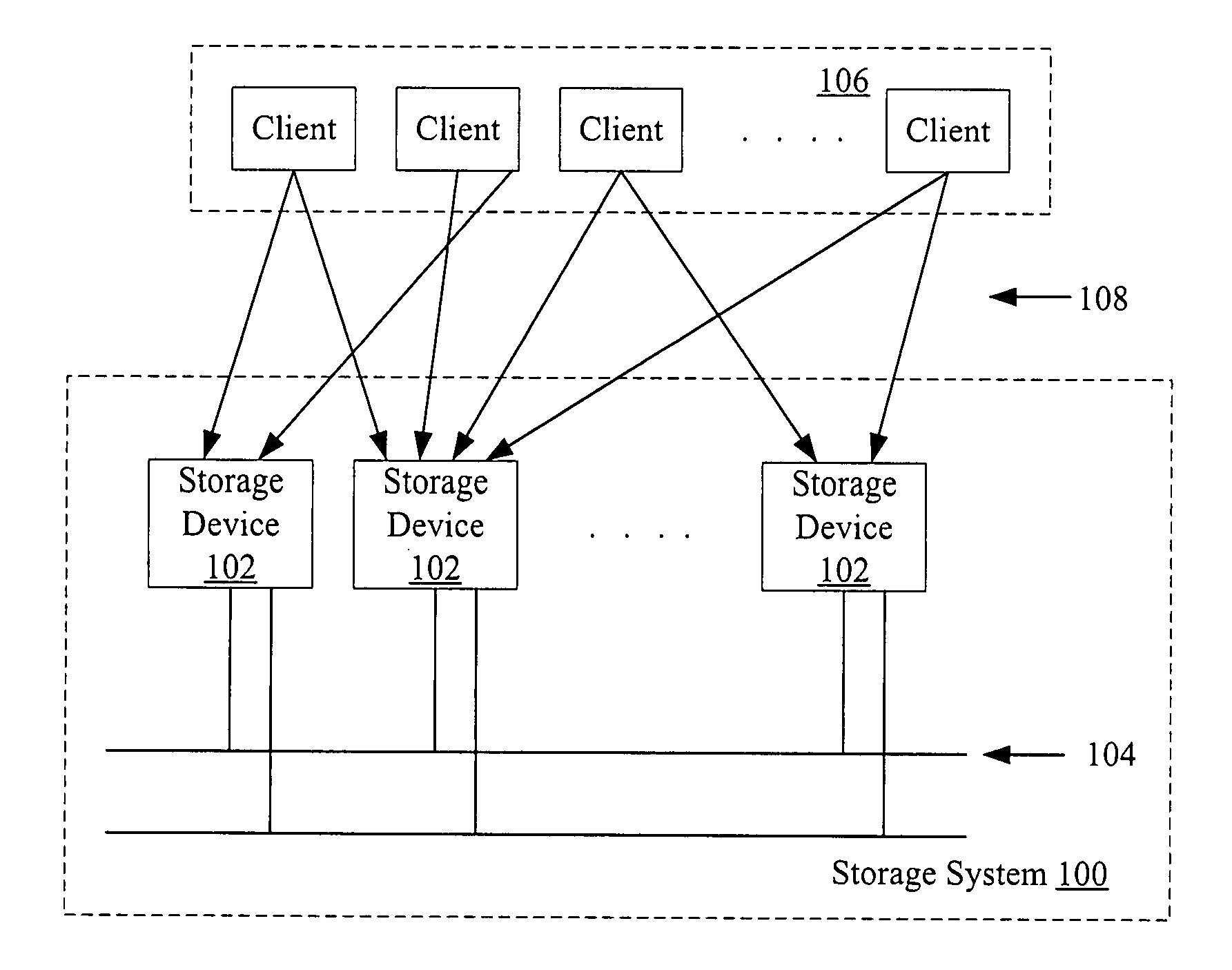
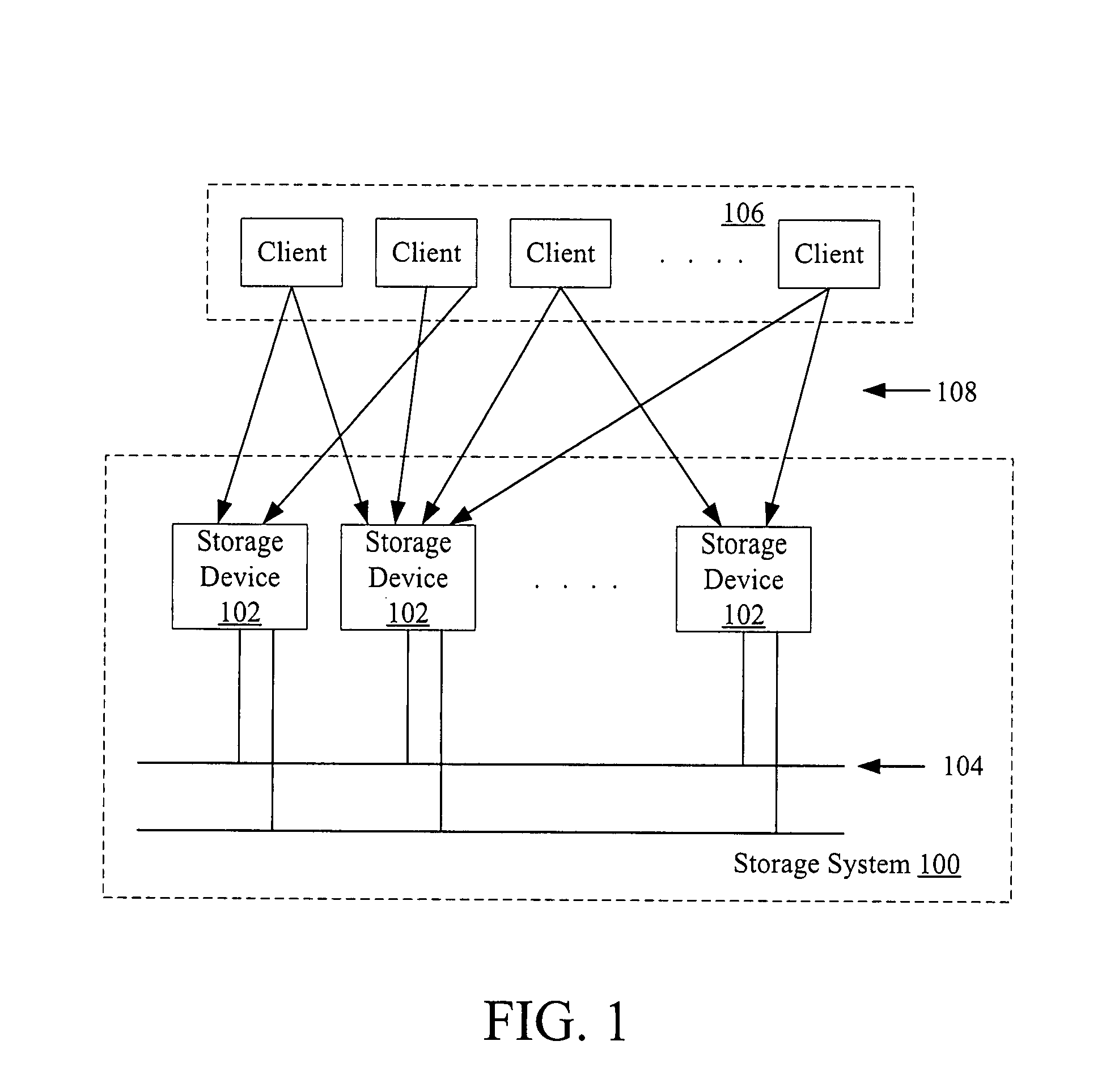
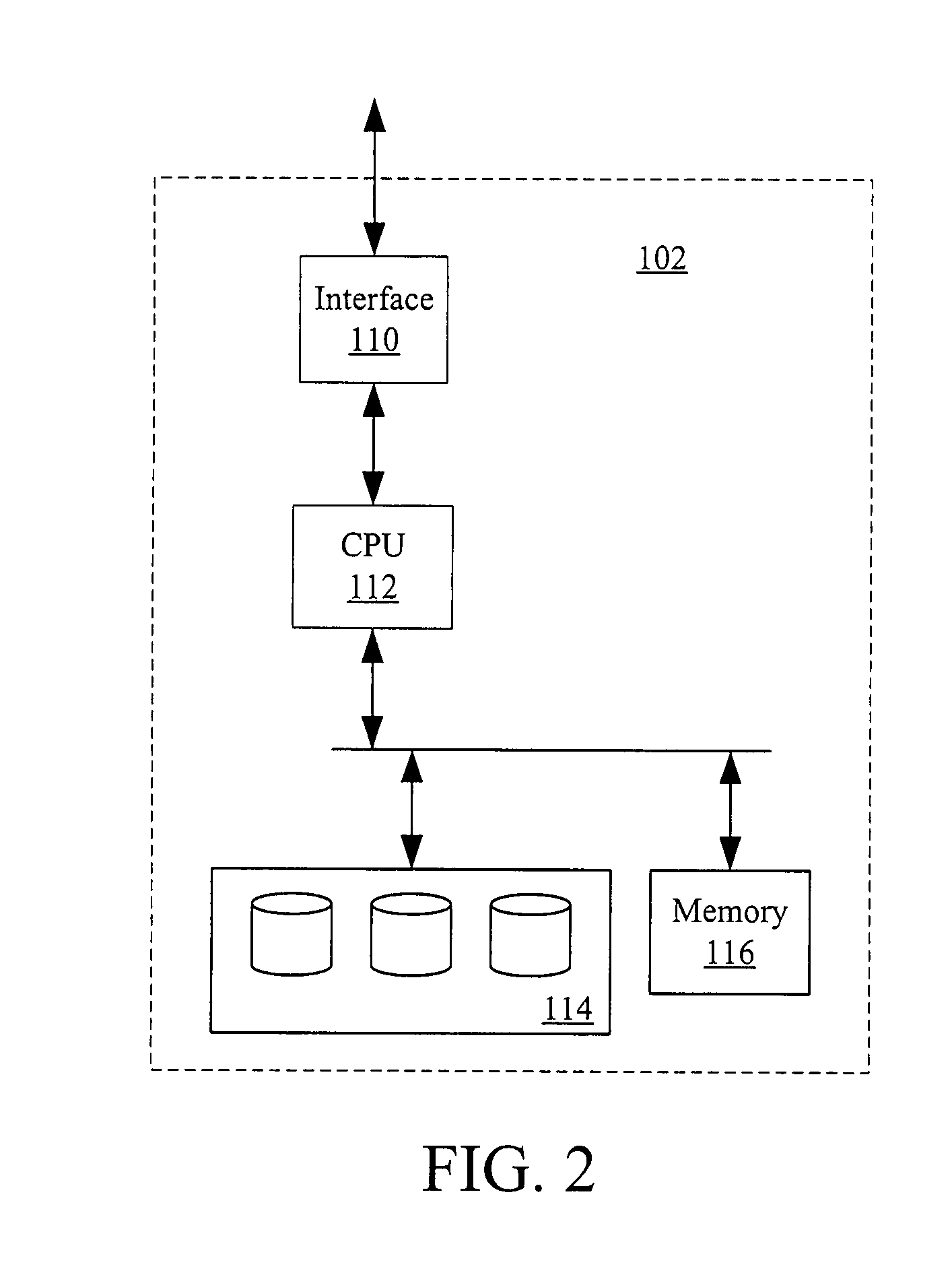
[01] cost-efficient repair for storage systems using progressive engagement
ActiveUS20150303949A1Minimal costMinimize the numberError detection/correctionCode conversionNode countDistributed database
An apparatus or method for minimizing the total accessing cost, such as minimizing repair bandwidth, delay or the number of hops including the steps of minimizing the number of nodes to be engaged for the recovery process using a polynomial-time solution that determines the optimal number of participating nodes and the optimal set of nodes to be engaged for recovering lost data, where in a distributed database storage system, for example a dynamic system, where the accessing cost or even the number of available nodes are subject to change results in different values for the optimal number of participating nodes. An MDS code is included which can be reused when the number of participating nodes varies without having to change the entire code structure and the content of the nodes.
Owner:RGT UNIV OF CALIFORNIA
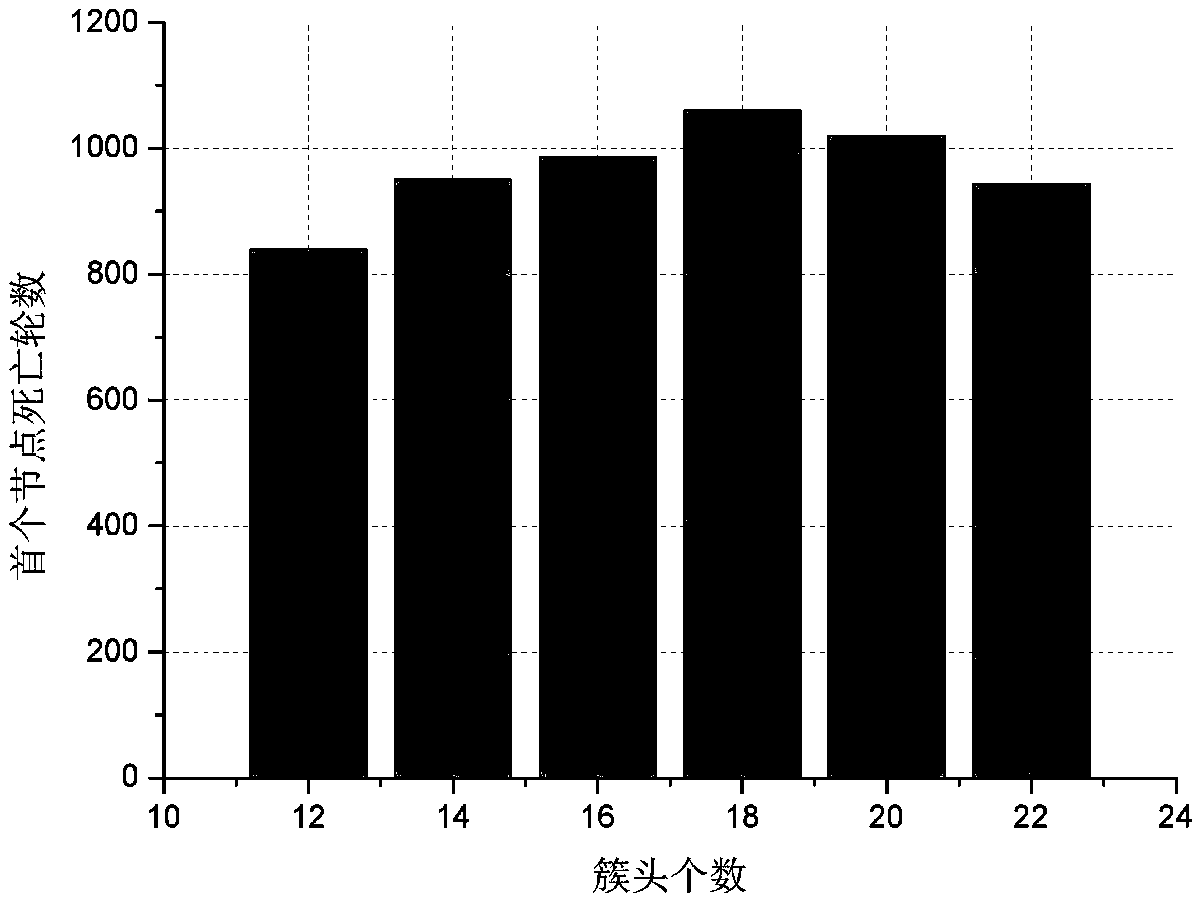
Energy balancing wireless sensor network clustering method
ActiveCN102036308AEvenly distributedShorten the timePower managementEnergy efficient ICTEnergy balancingExtensibility
The invention relates to an energy balancing wireless sensor network clustering method, which comprises the following three steps of: selecting cluster heads, building a cluster and transmitting data, wherein in the process of selecting the cluster heads, the priorities of nodes to be selected as the cluster heads are set by parameters such as the energy of the nodes, the number of neighboring nodes and the like, so that the cluster heads are more uniformly distributed; in the process of building the cluster, an energy threshold is set as the rebuilding condition of the cluster, so that the aim of reducing the rebuilding frequency of the cluster is fulfilled; meanwhile, a single-hop and multi-hop combined data transmission model is adopted, so that hot problems in a network are solved. Bythe method, the energy can be effectively utilized, the stability of the network is improved, the energy consumption of the network can be balanced, the service life of the network is effectively prolonged, and the network has higher extensibility and safety.
Owner:JIANGSU HILLSUN INFORMATION IND
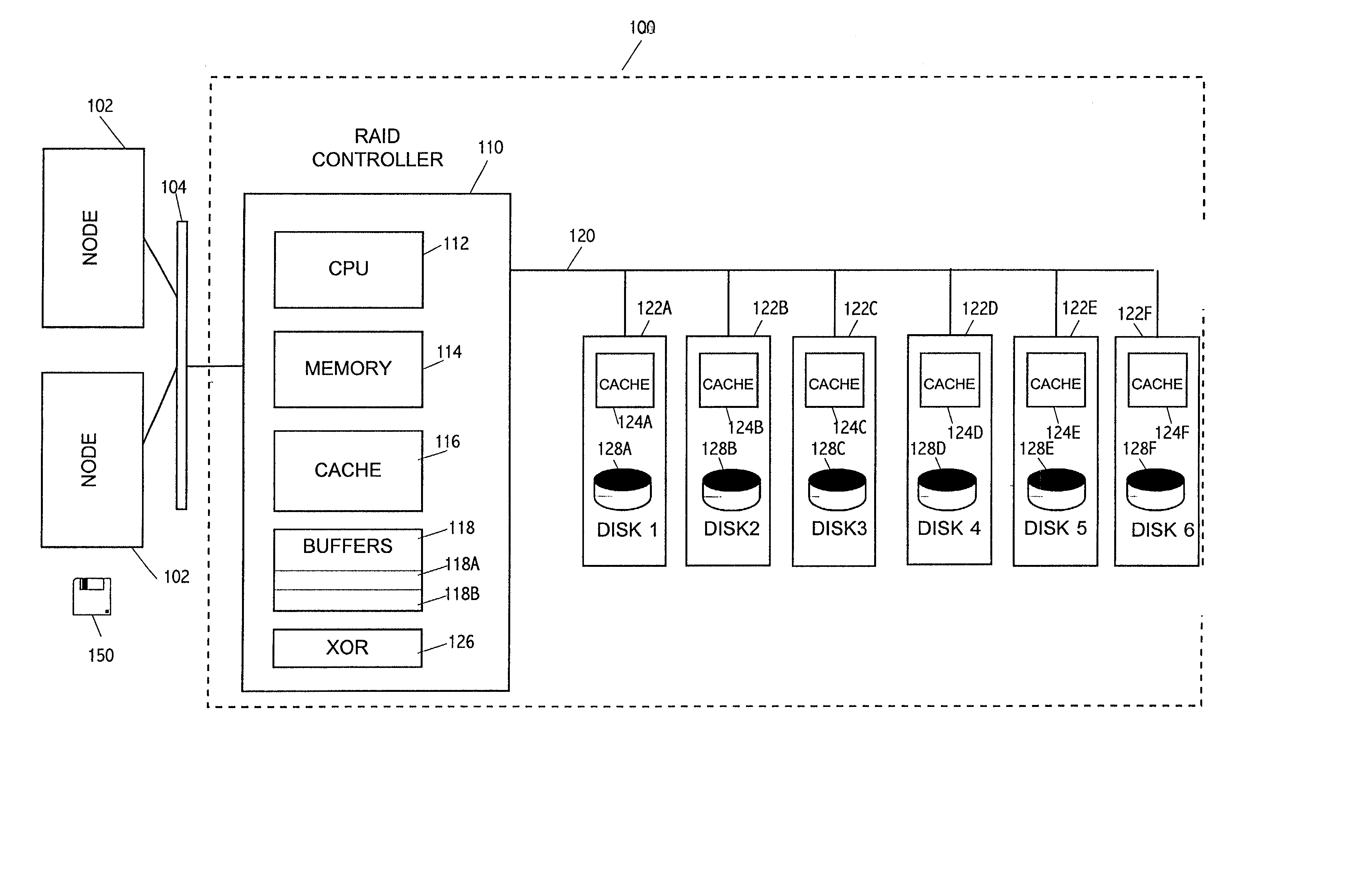
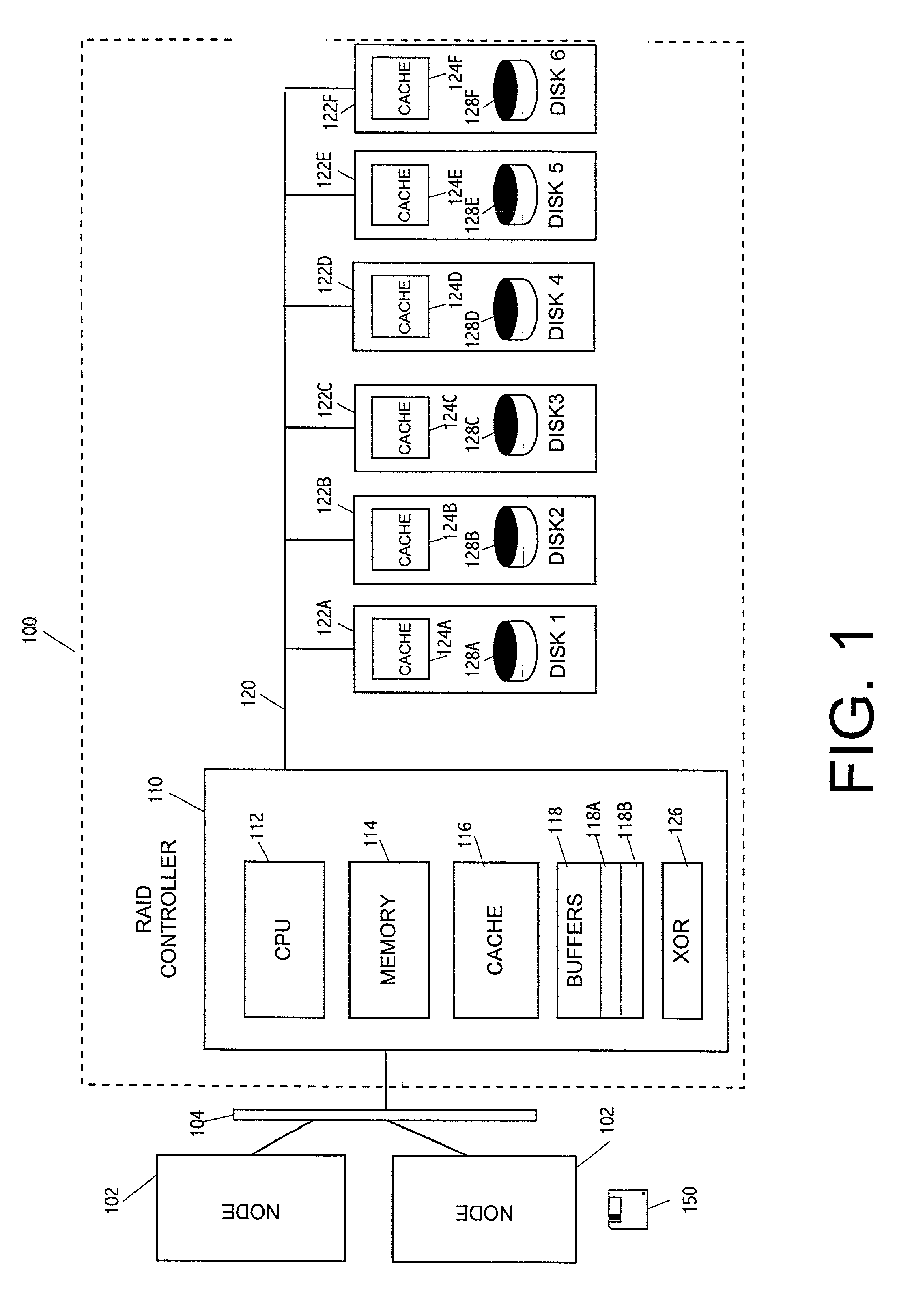
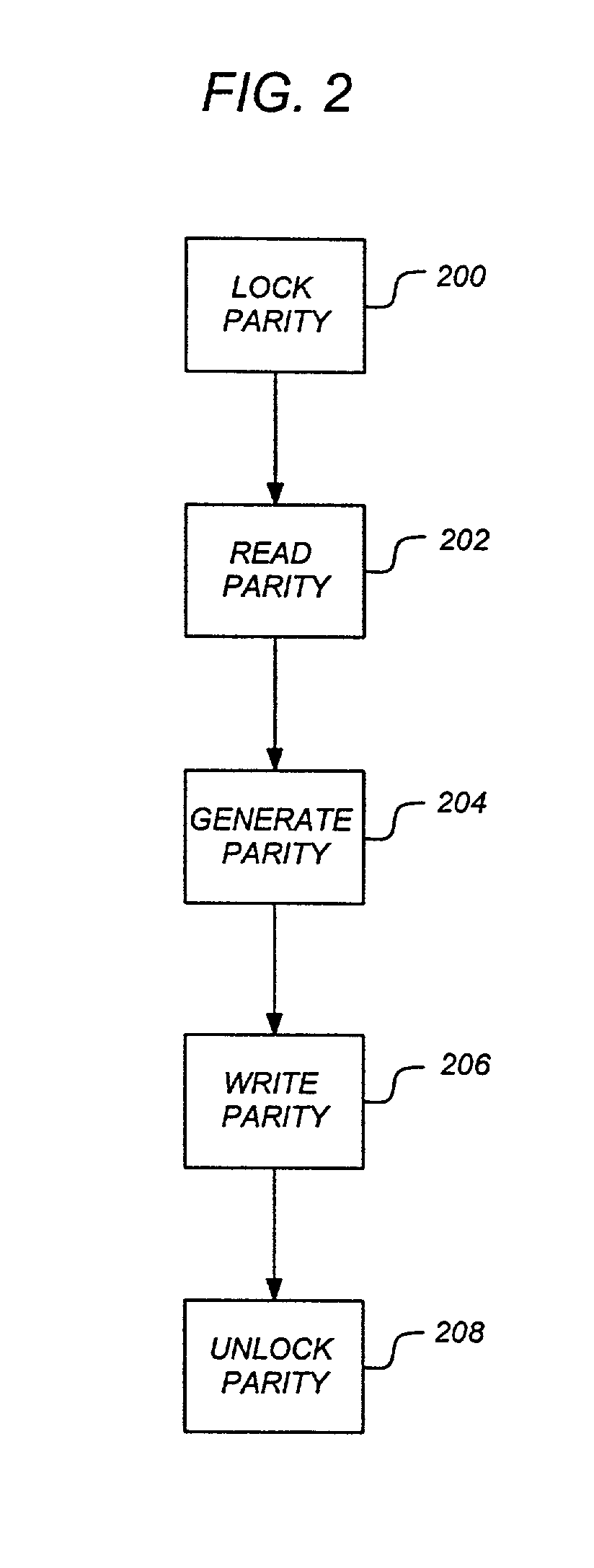
Method and apparatus for supporting parity protected raid in a clustered environment
To address the requirements described above, the present invention discloses a method, apparatus, article of manufacture, and a locking structure for supporting parity protected RAID in a clustered environment. When updating parity, the parity is locked so that other nodes cannot access or modify the parity. Accordingly, the parity is locked, read, generated, written, and unlocked by a node. An enhanced protocol may combine the lock and read functions and the write and unlock functions. Further, the SCSI RESERVE and RELEASE commands may be utilized to lock / unlock the parity data. By locking the parity in this manner, overhead is minimized and does not increase as the number of nodes increases.
Owner:IBM CORP
Method for controlling group membership in a distributed multinode data processing system to assure mutually symmetric liveness status indications
ActiveUS7043550B2Indication of stabilityImprove reliabilityMultiple digital computer combinationsElectric digital data processingData processing systemLiveness
In distributed multinode data processing systems, mechanisms are employed to insure that the nodes are continually informed about the liveness of the other nodes within node groups in the network and across networks. The method of the present invention employs the concept of node stability which it uses to provide indications of membership in a previous stable group as part of messages transmitted in a protocol for forming, maintaining and dissolving node groupings in such a way as to assure that all of the nodes in the group have a consistent indication of liveness status for all of the nodes within any given group of nodes.
Owner:TWITTER INC
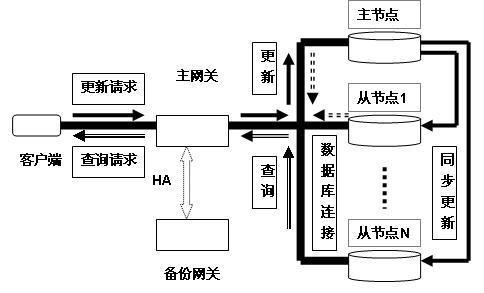
Batch processing request-based Microsoft SQL server database cluster
InactiveCN102254031AImprove execution efficiencyGuaranteed uptimeSpecial data processing applicationsData setBatch processing
The invention relates to a batch processing request-based Microsoft SQL server database cluster. The cluster consists of two parts, wherein a gateway and backups thereof are arranged at the front end of the cluster, and two or more of database server nodes are arranged at the rear end of the cluster; each node is provided with a structured query language (SQL) Server example and a cluster proxy and is not provided with a shared disk structure; and each node has an independent and consistent data set, and the cluster is only provided with a host. The gateway is used for managing the integral cluster; and for each client link, the gateway opens a database link corresponding to each node simultaneously to receive, analyze and optimize all client requests, wherein the client requests are divided into two classes, namely the read-only query requests and the data updating requests; for the read-only query requests, the gateway sends the requests to any one node to execute the requests according to a set load balancing algorithm so as to realize the real database access load balancing and improve the performance of a system; and the updating requests are sent to the host of the cluster to be executed, and are subjected to synchronous data by the host to other nodes to keep the data set of each node real-time and consistent, eliminate a single-point fault source and realize system fault tolerance. The integral cluster can improve the performance, availability and reliability of the system obviously and solve various problematic issues of the performance, single-point faults, zero data loss and the like in the field of databases, and is a comprehensive database cluster scheme.
Owner:无锡浙潮科技有限公司
Proximal relevancy ranking in a layered linked node database
InactiveUS20110105143A1Improve rankingDigital data processing detailsGeographical information databasesNode countData mining
A system and method for determining node relevancy by proximal weighting and pruning in a layered linked node database, such as that used to represent connections between a set of objects. The weights of connections between nodes in the layered linked node database is used as a distance metric, with propagation semantics determining how the summed relevancy is determined. This is particularly useful for determining, for a given node in a given layer, which nodes in another layer, or on the same layer, are most relevant. In the context of mobile device users, this is particularly useful for dynamically determining which people, places, events etc. are of greatest relevance in a scalable manner.
Owner:GEOSOLUTIONS
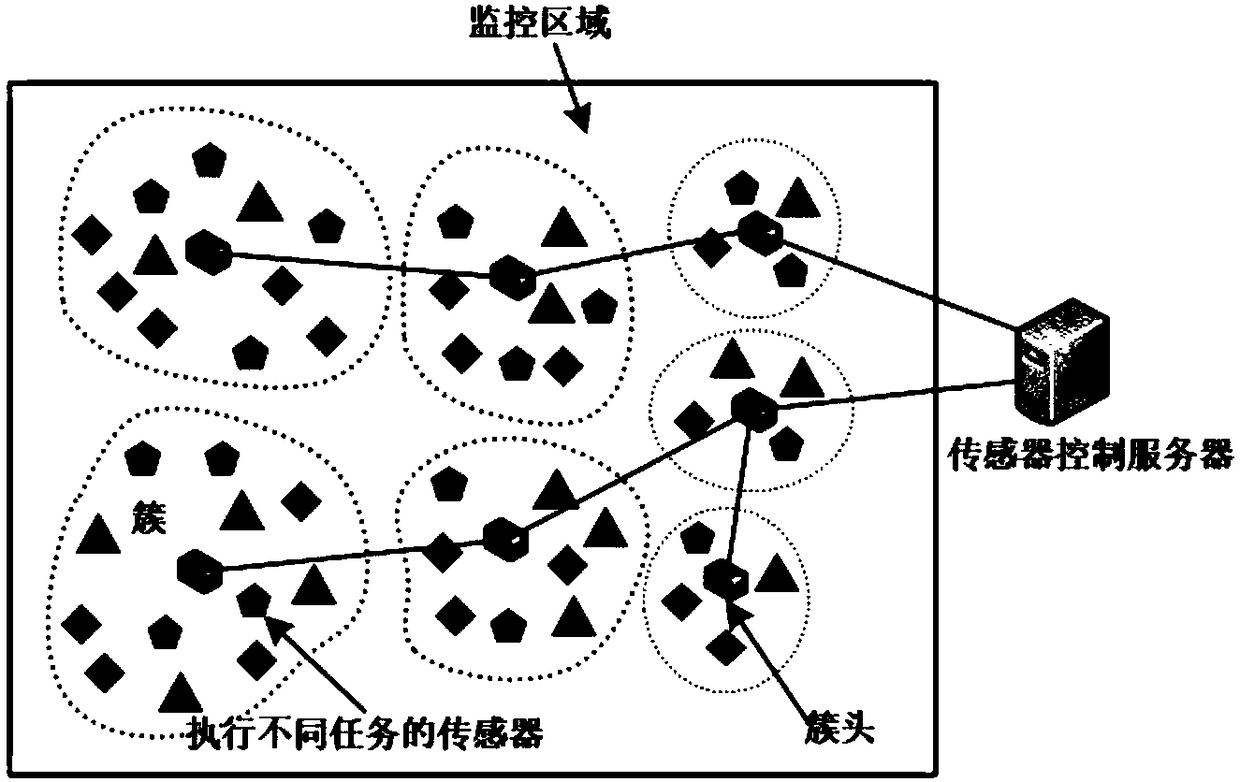
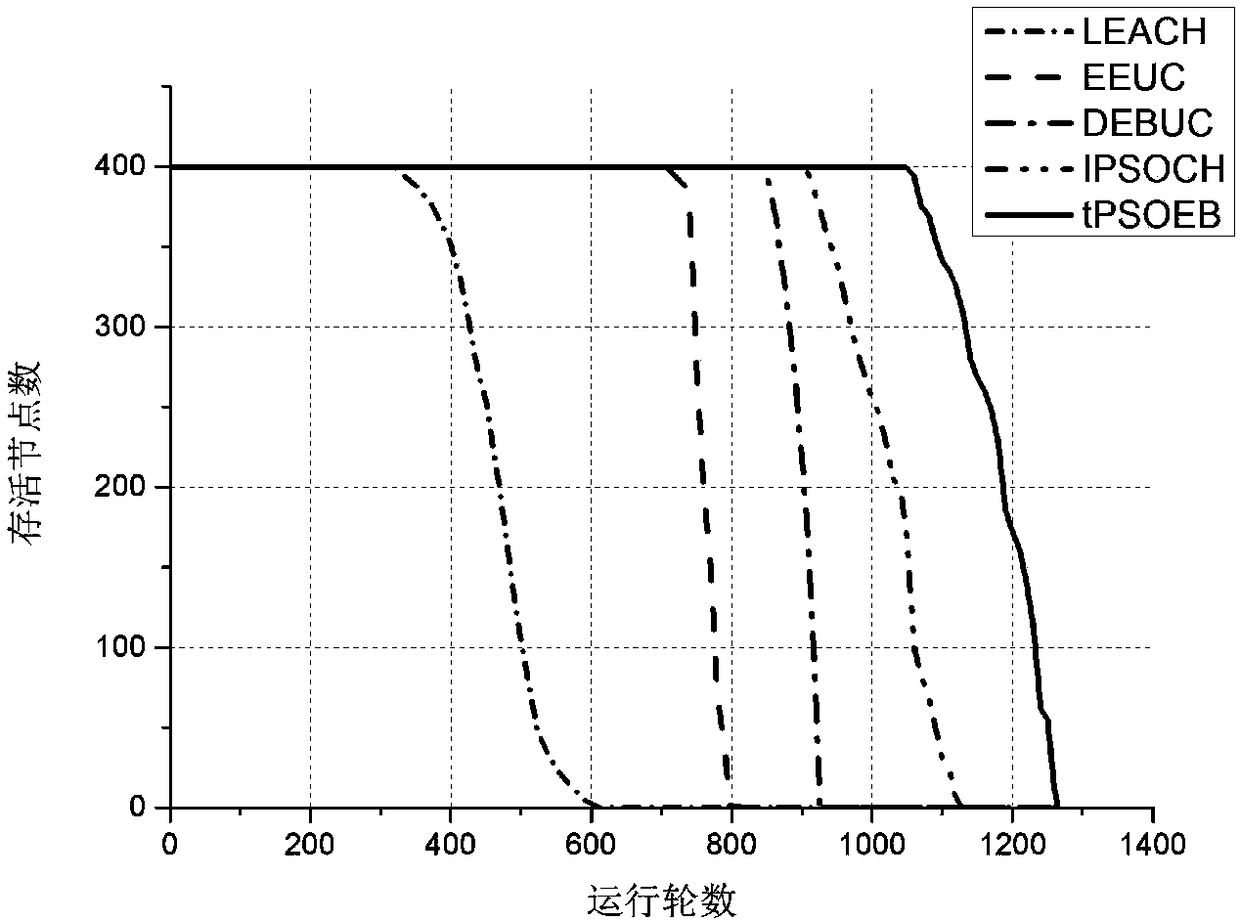
Extremum disturbed particle swarm optimization based SDWSN energy-balanced routing algorithm
ActiveCN108566663AExtend the life cycleFlexible deploymentHigh level techniquesWireless communicationEnergy balancingWireless sensor networking
The invention relates to an extremum disturbed particle swarm optimization based SDWSN energy-balanced routing algorithm and belongs to the technical field of wireless sensor networks. The algorithm comprises the steps of firstly selecting a cluster head by giving consideration to residual energy, position and energy balanced information of nodes and utilizing improved extremum disturbed particleswarm optimization algorithm, and dividing the whole network dynamically into clusters different in size based on a distance from the nodes to the base station, node residual energy and the number ofneighbor nodes; and secondly, saving energy consumption during cluster division by adopting a way of performing global clustering and k local cluster head updating per each period; and finally, building a shortest routing tree based on factors such as link energy consumption, node residual energy and in-cluster node number by adopting a centralized mode by a sensor control server when multi-hop routing is built. The extremum disturbed particle swarm optimization based SDWSN energy-balanced routing algorithm can efficiently save energy and balanced network energy consumption and prolong the life circle of the network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
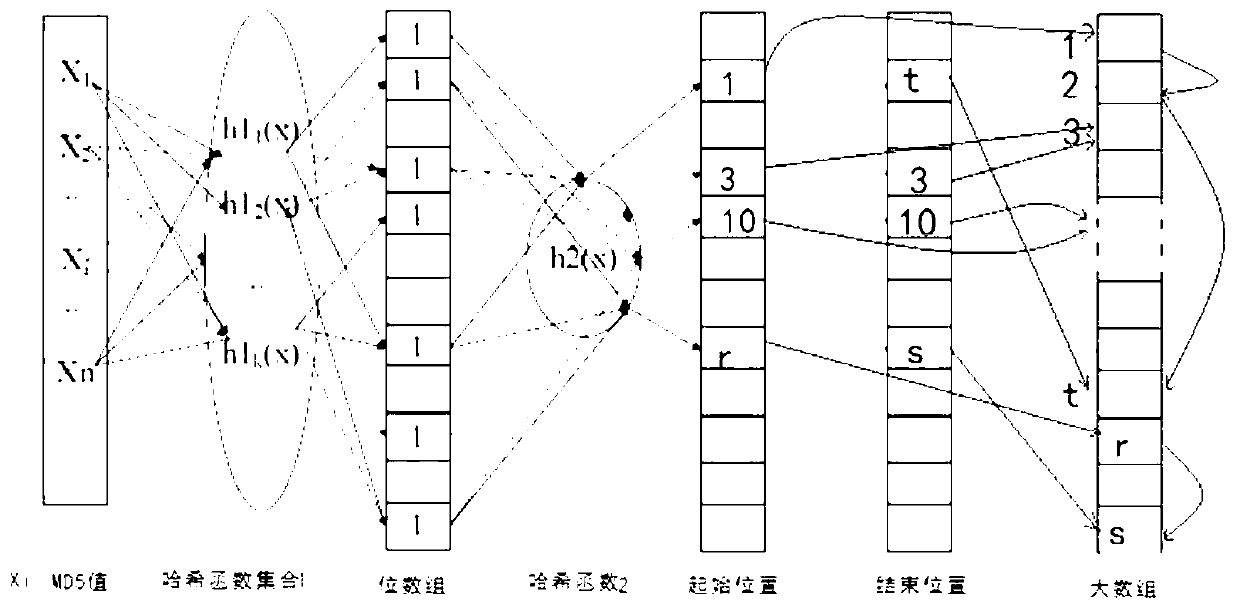
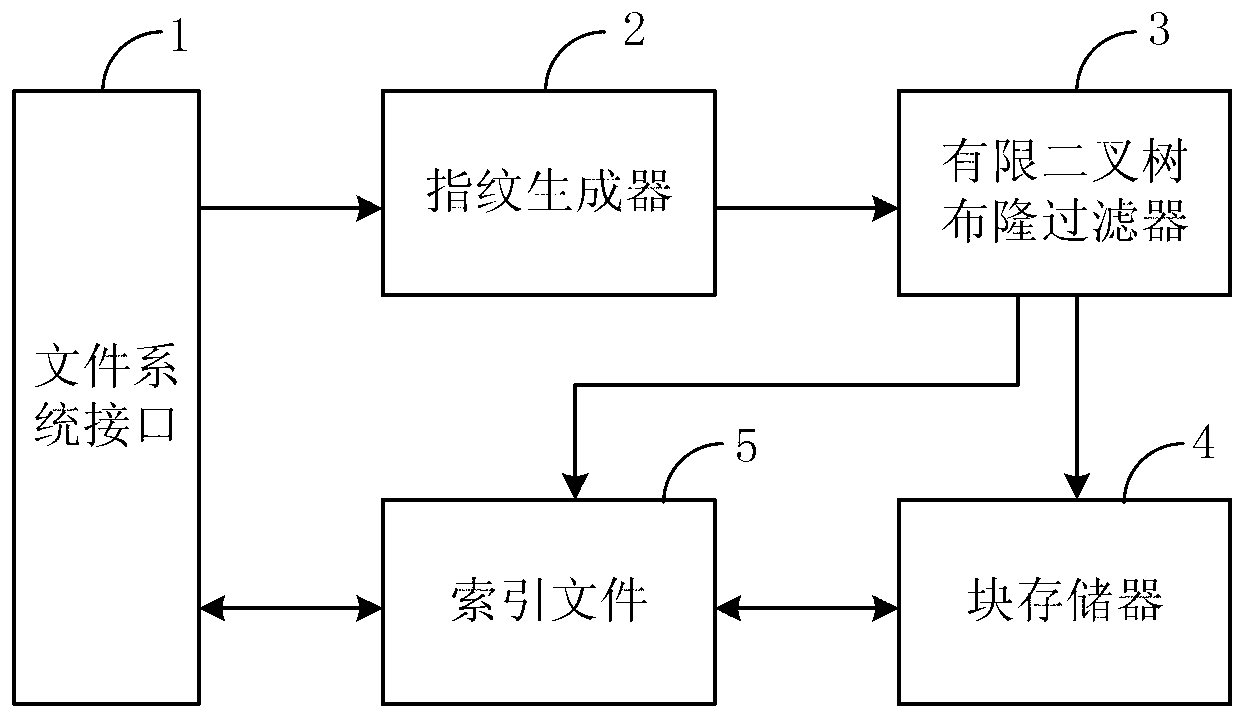
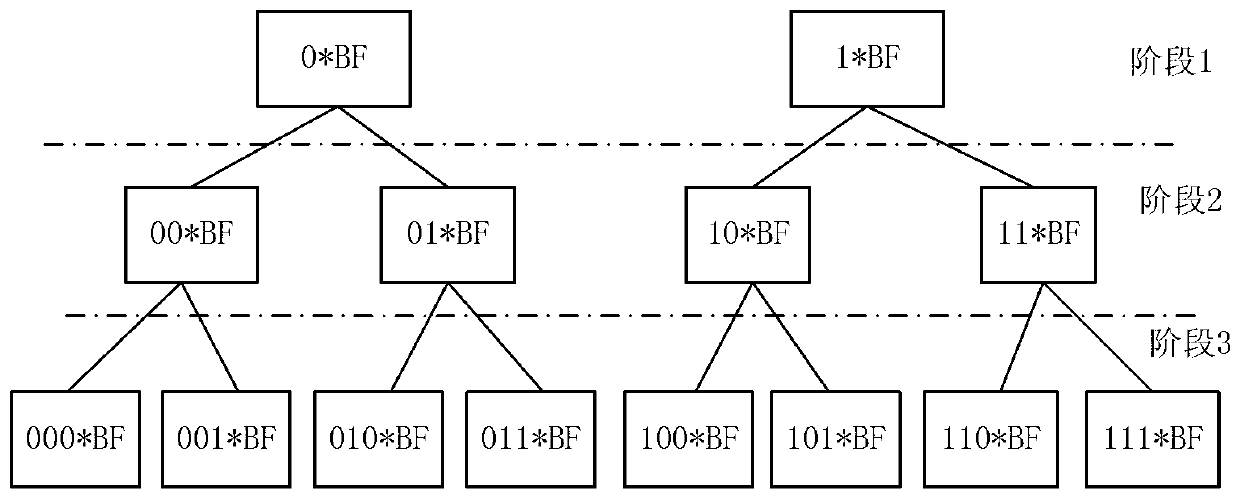
Redundancy removal file system based on limited binary tree bloom filter and construction method of redundancy removal file system
InactiveCN103345472AReduce misjudgmentHigh Deduplication Rate AccessSpecial data processing applicationsMemory footprintFile system
The invention provides a limited binary tree bloom filter, a redundancy removal file system based on the limited binary tree bloom filter, and a construction method of the redundancy removal file system based on the limited binary tree bloom filter. According to the limited binary tree bloom filter, an upper limit is arranged for the number of nodes of each layer, each node is a two-stage bloom filter, and each two-stage bloom filter comprises a standard bloom filter body and a second portion which contains fingerprints and addresses of data blocks in a stored mode. Firstly, a fingerprint of each data block is searched in the standard bloom filter bodies; when the fingerprint of each data block is not found, a node misses, otherwise, search is continuously carried out in the second portions, the node hits the target when a completely matched fingerprint is found in the second portions, and otherwise the node misses. The redundancy removal file system and the construction method of the redundancy removal file system achieve write-in, reading and deletion of files on the basis of the limited binary tree bloom filter. Misjudgment is reduced through a secondary query, and the limited binary tree bloom filter, the redundancy removal file system based on the limited binary tree bloom filter, and the construction method of the redundancy removal file system based on the limited binary tree bloom filter have the advantages of being low in occupation of the memory, low in usage of a CPU, low in occupation of additional space, high in redundancy removal ratio, and excellent in access performance and extensibility.
Owner:BEIHANG UNIV
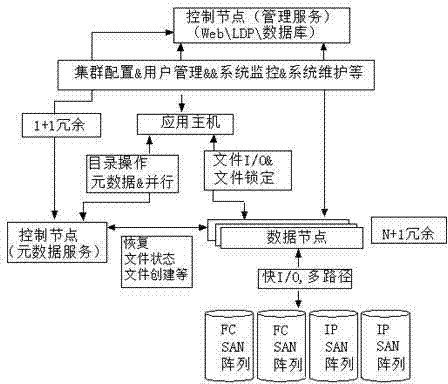
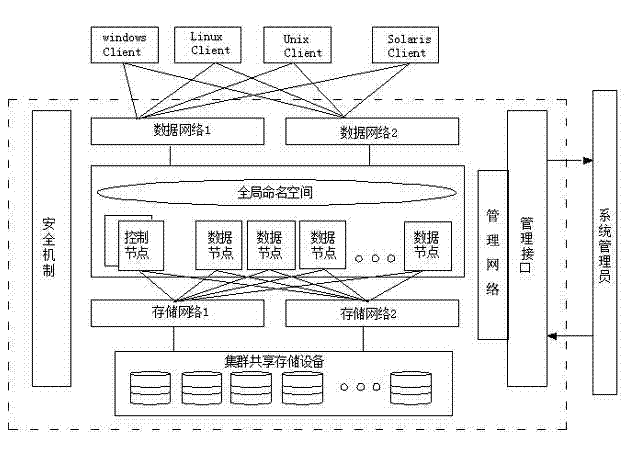
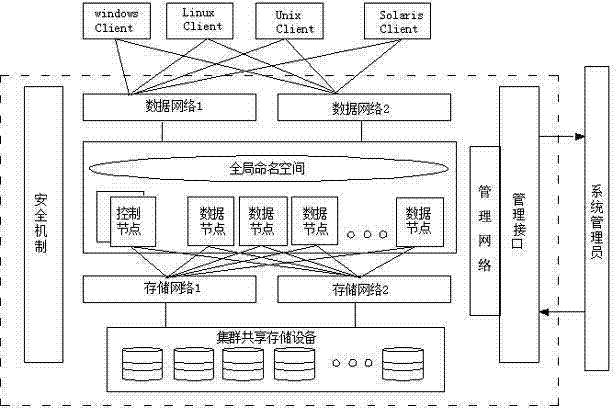
Construction method of NAS cluster system based on modularization design
InactiveCN102571904AImprove availabilityImprove stabilityTransmissionFile systemSoftware engineering
The invention provides a construction method of an NAS cluster system based on a modularization design. The modularization design-based NAS cluster system is composed of a control node, a data node, a storage network, a management network and a data network. All the above-mentioned parts work independently but are mutually connected to form an organic integral body, so that the complete NAS cluster system with high reliability, high expandability and high performance can be provided for a user. Functions of all the parts of the NAS cluster system are described as follows: in the aspect of the control node, each set of NAS cluster system contains two control nodes; hardware composition is a rack server or a blade server; and functions of cluster service configuration file system establishment, catalog management, user management, and system monitoring and maintenance and the like are completed.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
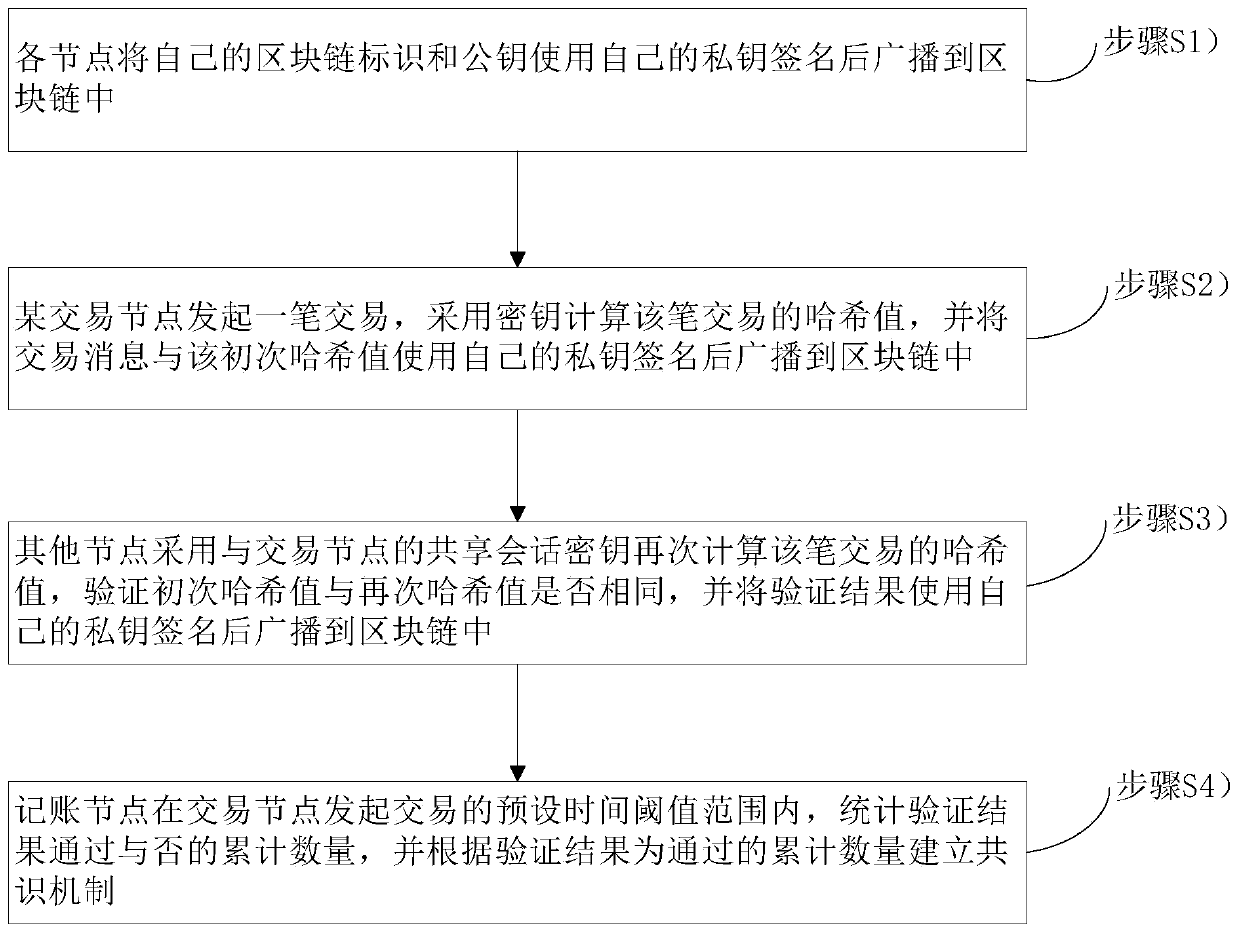
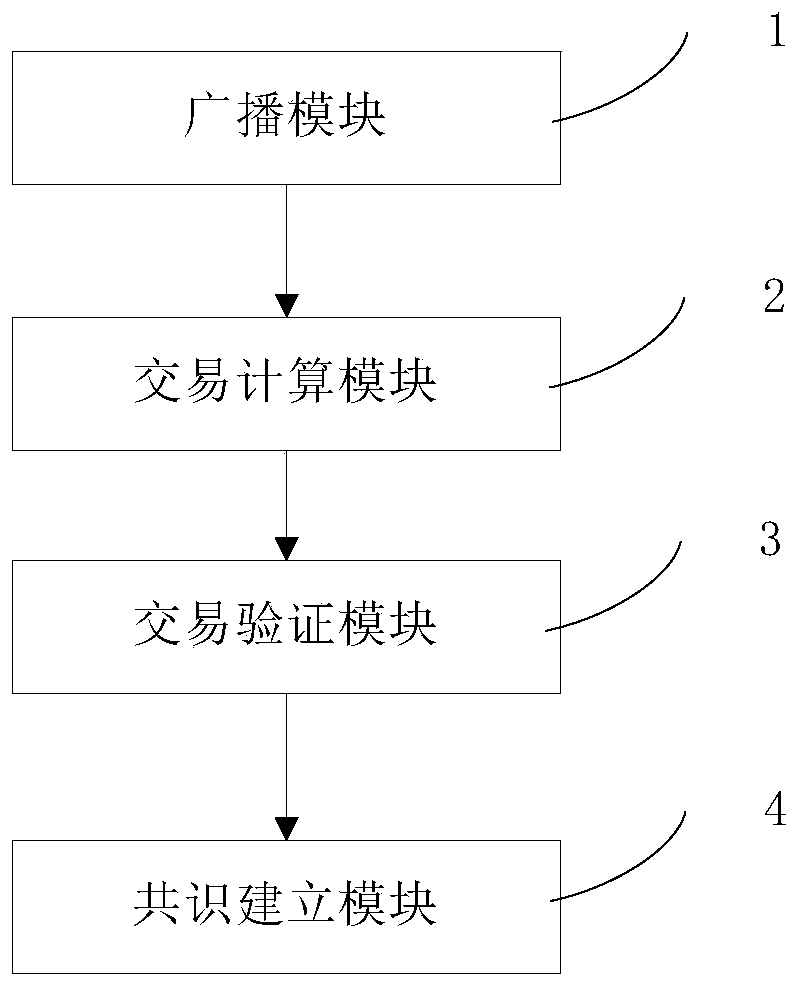
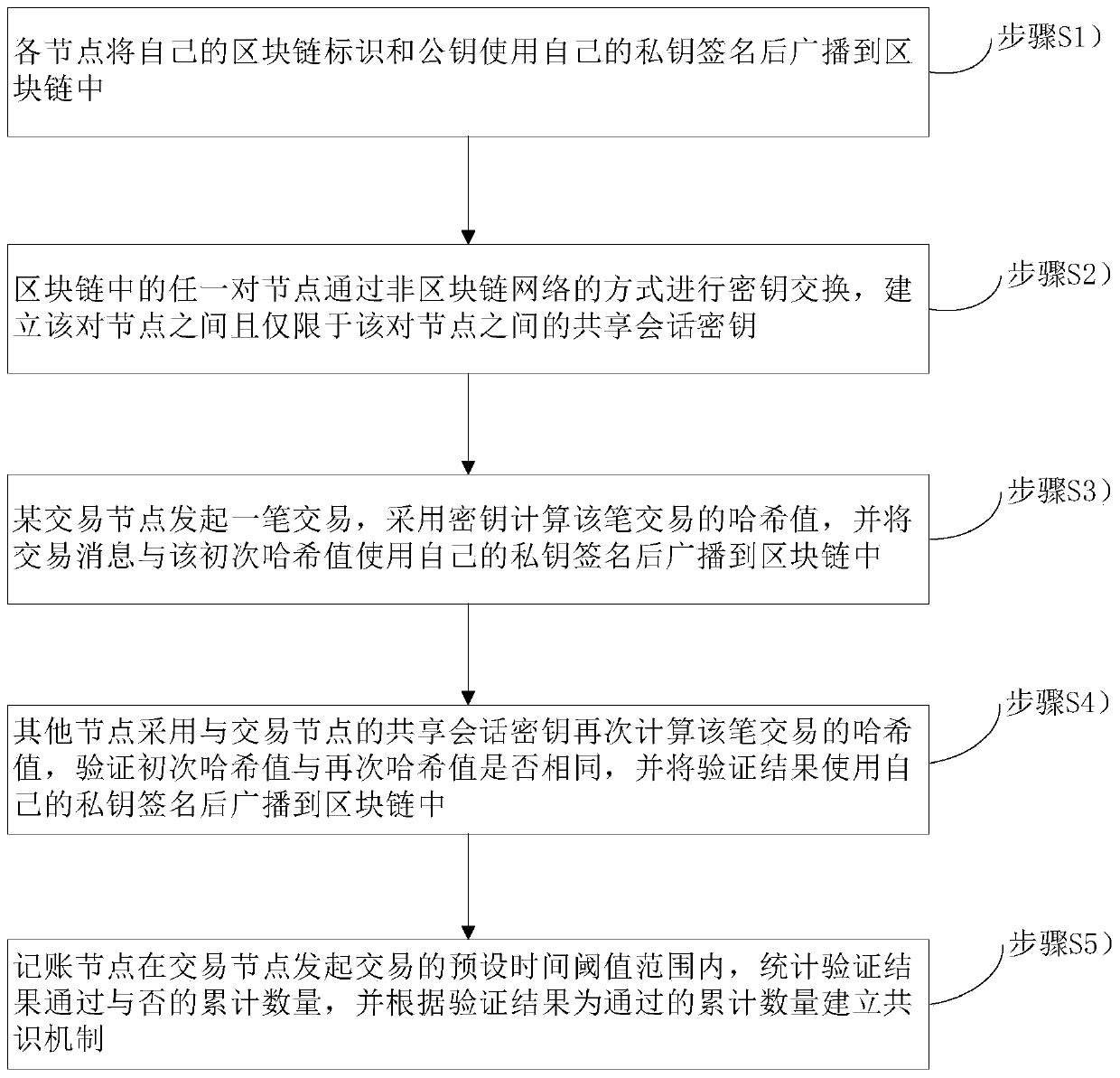
Blockchain-based transaction method and a blockchain-based transaction system
ActiveCN109767220AImprove transmission efficiencyIncrease communication loadPayment protocolsNode countSession key
The invention belongs to the technical field of block chains, and relates to a block chain-based transaction method and a block chain-based transaction system. The method comprises the following steps: each node signs a block chain identifier and a public key of the node by using a private key of the node and broadcasts the block chain identifier and the public key to a block chain; A certain transaction node initiates a transaction, calculates a Hash value of the transaction by adopting a secret key, signs the transaction message and the primary Hash value by using a private key of the transaction node, and broadcasts the transaction message and the primary Hash value to the block chain; The other nodes calculate the Hash value of the transaction again by adopting the shared session key with the transaction node, verify whether the primary Hash value is the same as the secondary Hash value or not, and broadcast the verification result to the block chain after using the own private keyto sign the verification result; And the accounting node counts whether the verification result is passed or not within a preset time threshold range of the transaction initiated by the transaction node, and establishes a consensus mechanism according to the verification result which is the passed accumulated number. The communication burden of the block chain and the size of the block can be reduced, and the transmission efficiency of the block chain is greatly improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Redundant data assigment in a data storage system
The present invention provides techniques for assignment and layout of redundant data in data storage system. In one aspect, the data storage system stores a number M of replicas of the data. Nodes that have sufficient resources available to accommodate a requirement of data to be assigned to the system are identified. When the number of nodes is greater than M, the data is assigned to M randomly selected nodes from among those identified. The data to be assigned may include a group of data segments and when the number of nodes is less than M, the group is divided to form a group of data segments having a reduced requirement. Nodes are then identified that have sufficient resources available to accommodate the reduced requirement. In other aspects, techniques are providing for adding a new storage device node to a data storage system having a plurality of existing storage device nodes and for removing data from a storage device node in such a data storage system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Byzantine fault tolerance method of data block chain authorization participation consensus based on reward and punishment and reward and punishment method thereof
InactiveCN107423962ABlock transactionFinanceNon-redundant fault processingByzantine fault toleranceAuthorization
The invention discloses a Byzantine fault tolerance method of a data block chain authorization participation consensus based on reward and punishment and a reward and punishment method thereof, relating to the technology of fault tolerance of a data block chain. A node reward and punishment algorithm is used to ensure that commands sent by nodes in a Byzantine fault tolerant data block chain which is authorized to participate in the consensus are honest. The technical points of the invention are that the method comprises the steps of (1) selecting consensus nodes in the data block chain, wherein the number of the consensus nodes is smaller than a node total number in the data block chain, (2) allowing the consensus nodes to carry out consensus games to reach a consensus on authenticity judgment of the commands sent by the nodes in the data block chain, and (3) carrying out reward and punishment on the nodes in the block chain based on a result that the consensus nodes reach the consensus.
Owner:CHENGDU LEEREY ENTERPRISE MANAGEMENT LTD
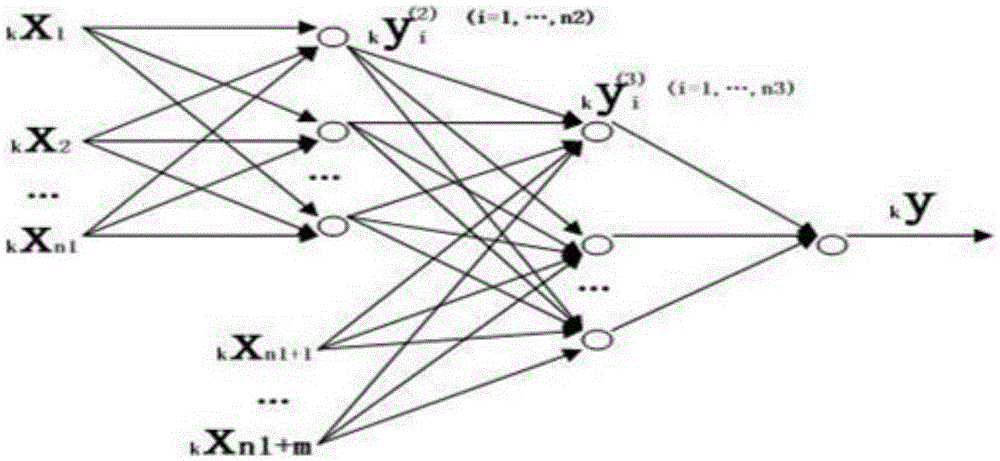
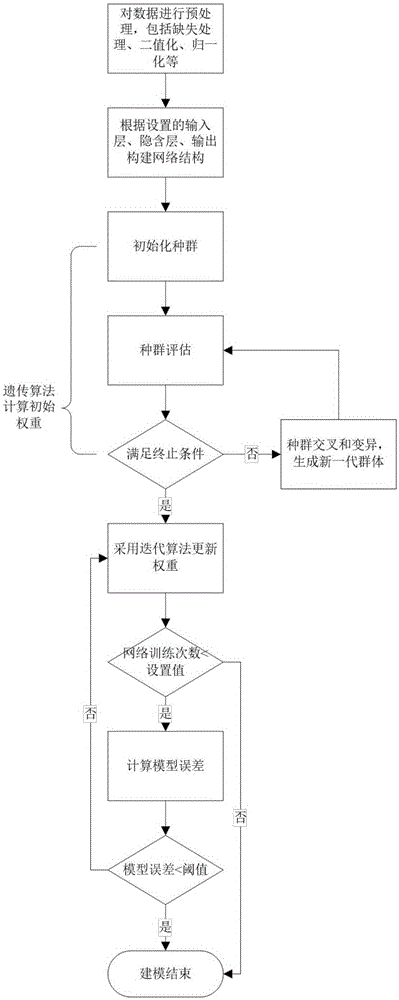
Multi-stage nerve network model training method based on genetic algorithm
The invention relates to a multi-stage nerve network model training method based on a genetic algorithm. The multi-stage nerve network model training method is technologically characterized by comprising the steps of preprocessing data for eliminating the physical dimension effect of a field; constructing a multi-input-layer network structure according to the number of nodes in an input layer, the number of nodes in a hidden layer and the number of nodes in an output layer; training an initial weight and a threshold by means of the genetic algorithm; updating the weight by means of an iterative algorithm; determining whether a model termination condition is satisfied according to the number of iteration times and a model error, terminating the model if the model termination condition is satisfied, and otherwise updating the weight again. According to the multi-stage nerve network model training method, a multi-stage nerve network structure is constructed for aiming at a problem that parameters in process control are periodical and deteriorate output. According to a fact that the genetic algorithm has a global searching characteristic, the multi-stage nerve network model training method is used for selecting a group of relatively reasonable initial weight for the network structure, thereby preventing local minimum point in network training, and settling a problem that the nerve network structure with only one input layer cannot settle a problem of product processing speed reduction caused by incapability of settling the parameters in a time sequence in engineering control.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
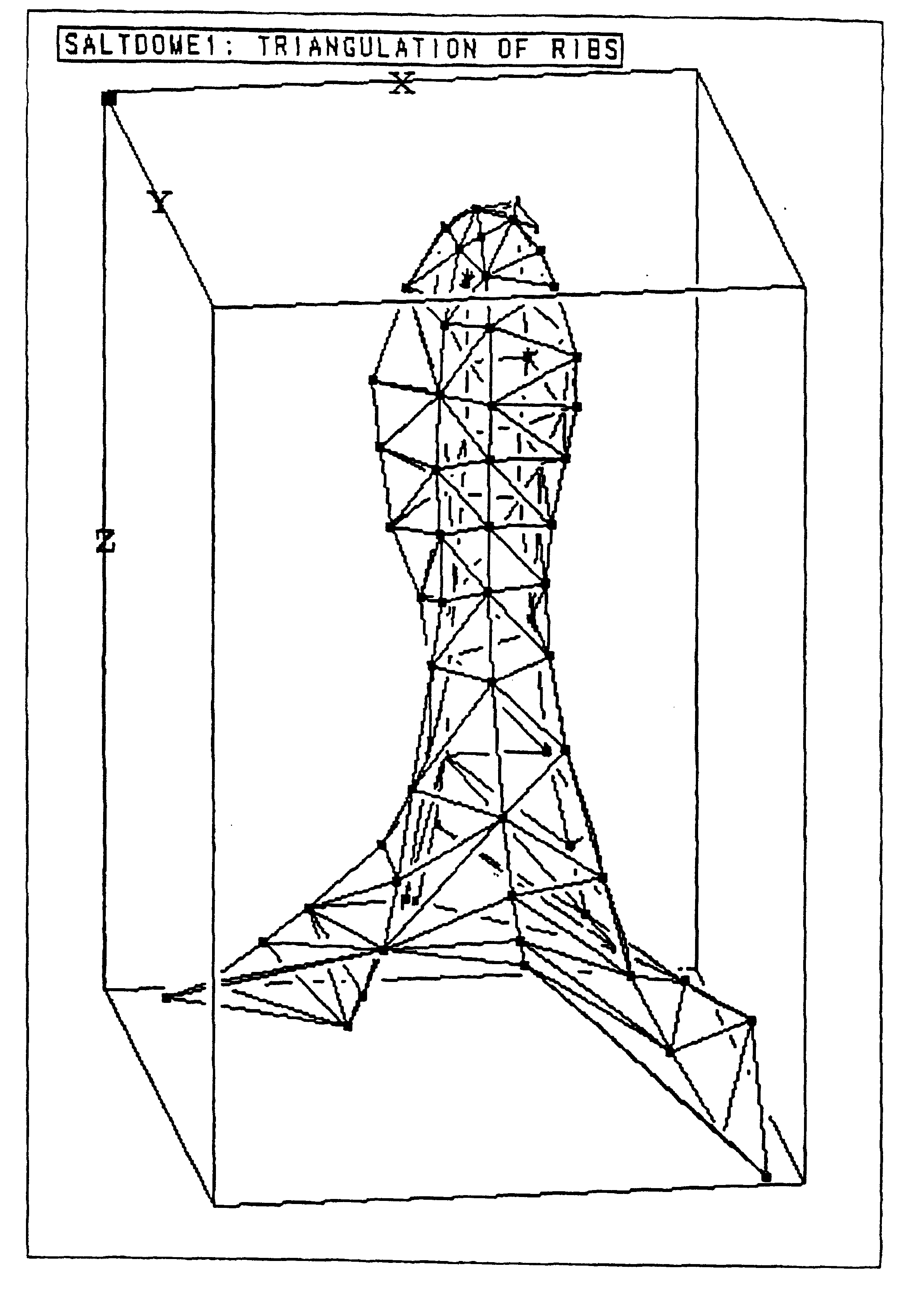
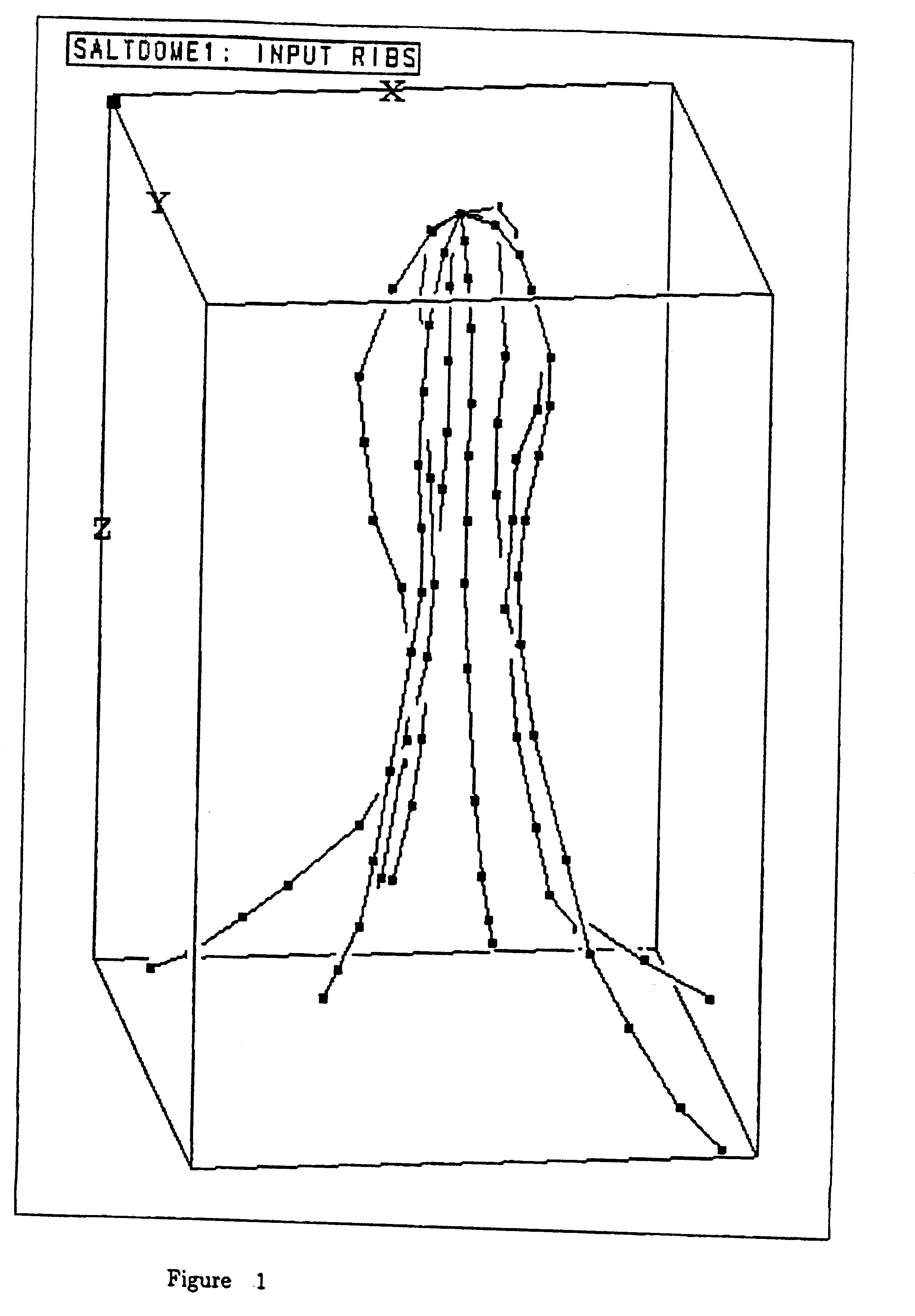
Method and apparatus for creating representations of geologic shapes
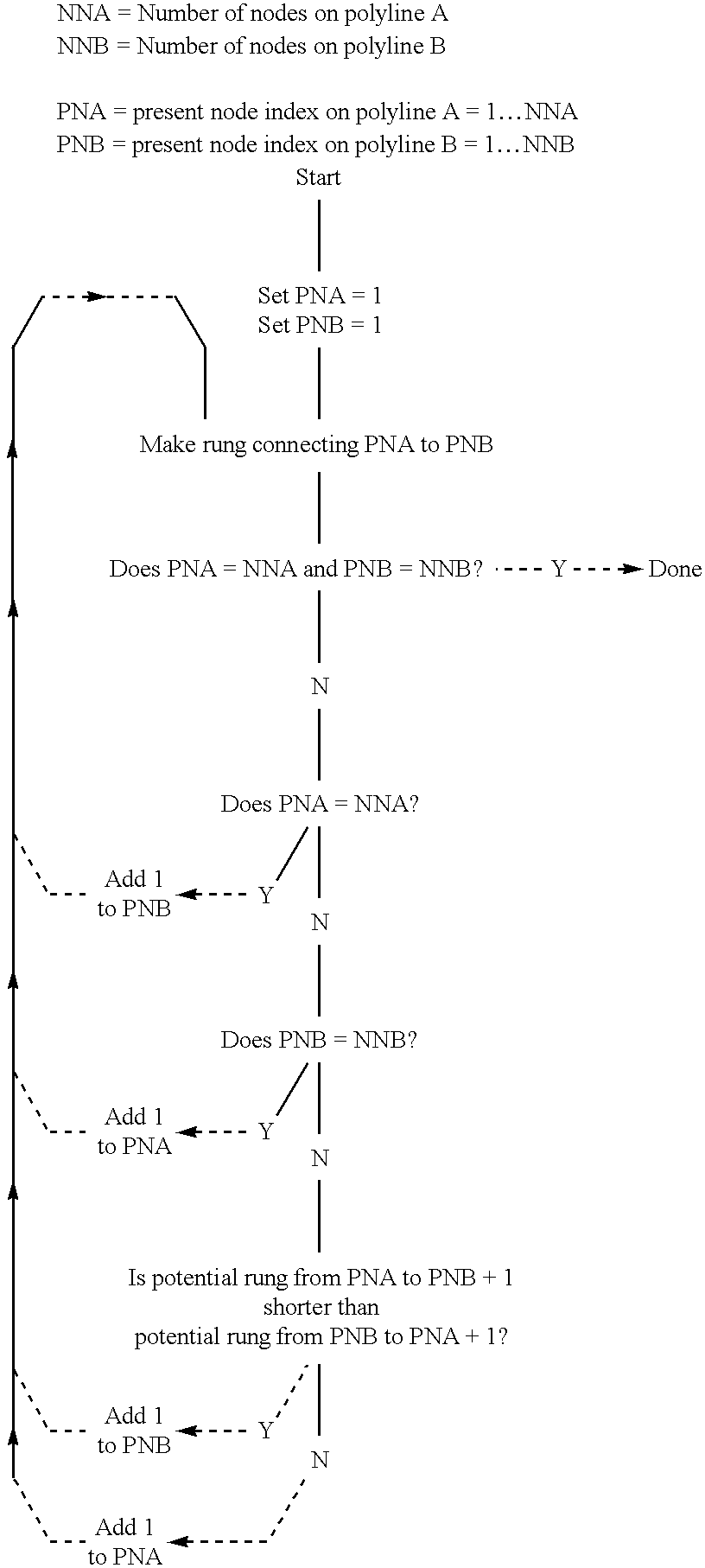
A method for filling the space between two neighboring polyline ribs is disclosed. The method, called ladder triangulation, likens two ribs, which generally outline a complex structure, to the two rails of a ladder. The ladder triangulation is built by adding rungs, each rung connecting a node on one rib to a node on the other rib and thereby (after the first rung) creating one more triangle. In essence the first rung connects node 1 of polyline 1 to node 1 of polyline 2, and the second rung connects either node 1 polyline 1 to node 2 polyline 2 or else node 1 polyline 2 to node 2 polyline 1, whichever rung is shorter. There are (n1+n2) / 2 such rungs where n1 and n2 are the respective node counts of the two polylines, and computation is linear with node count. Where there are multiple polylines, the same process is repeated between polylines 2 and 3, 3 and 4, etc. and may also be repeated between the last polyline and the first one (cyclic rib fill). The entire set of ribs is filled in time proportional to the total node count. Moreover, if a single rib is subsequently modified by an editing process, a triangulation can be updated rapidly by recomputation of just the two ladder triangulations involving that rib.
Owner:LANDMARK GRAPHICS
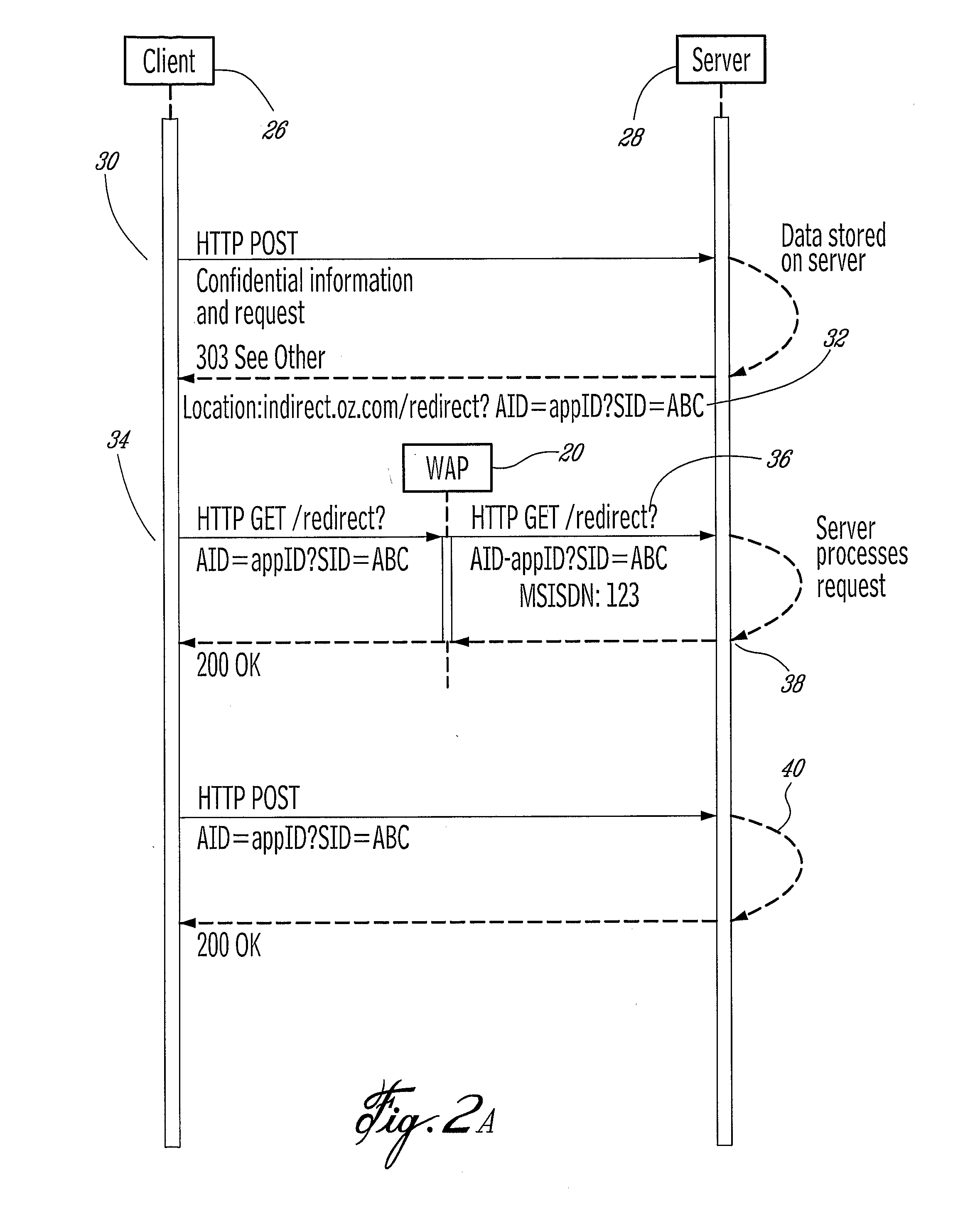
Method for Securely Associating Data with Http and Https Sessions
ActiveUS20080307517A1Digital data processing detailsUser identity/authority verificationInternet privacyTrunking
A computing system, method and product comprising a server, a mobile device comprising a client interconnected with the server via a data network, the client identified by a credential which is unavailable to the client and an intermediate node interconnected to the client and the server via the data network wherein the credential is available to the intermediate node. Upon reception of a service request from the client at a first server address the server redirects the client to transmit the service request to a second server address via the intermediate node together with a token, wherein the intermediate node appends a credential identifying the client to the redirected service request and the token and relays the redirected service request, the token and the credential to the second server address.
Owner:SYNCHRONICA
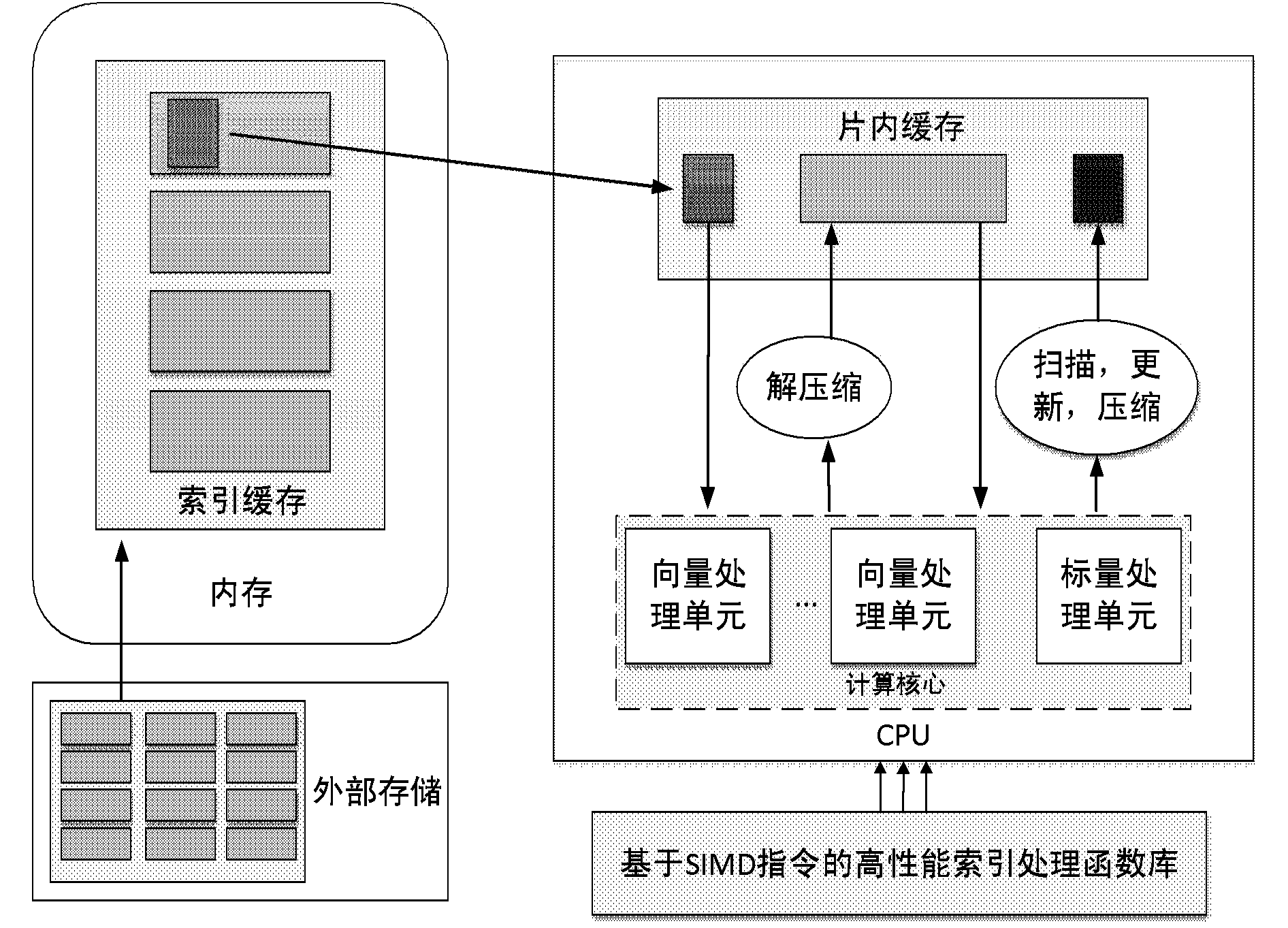
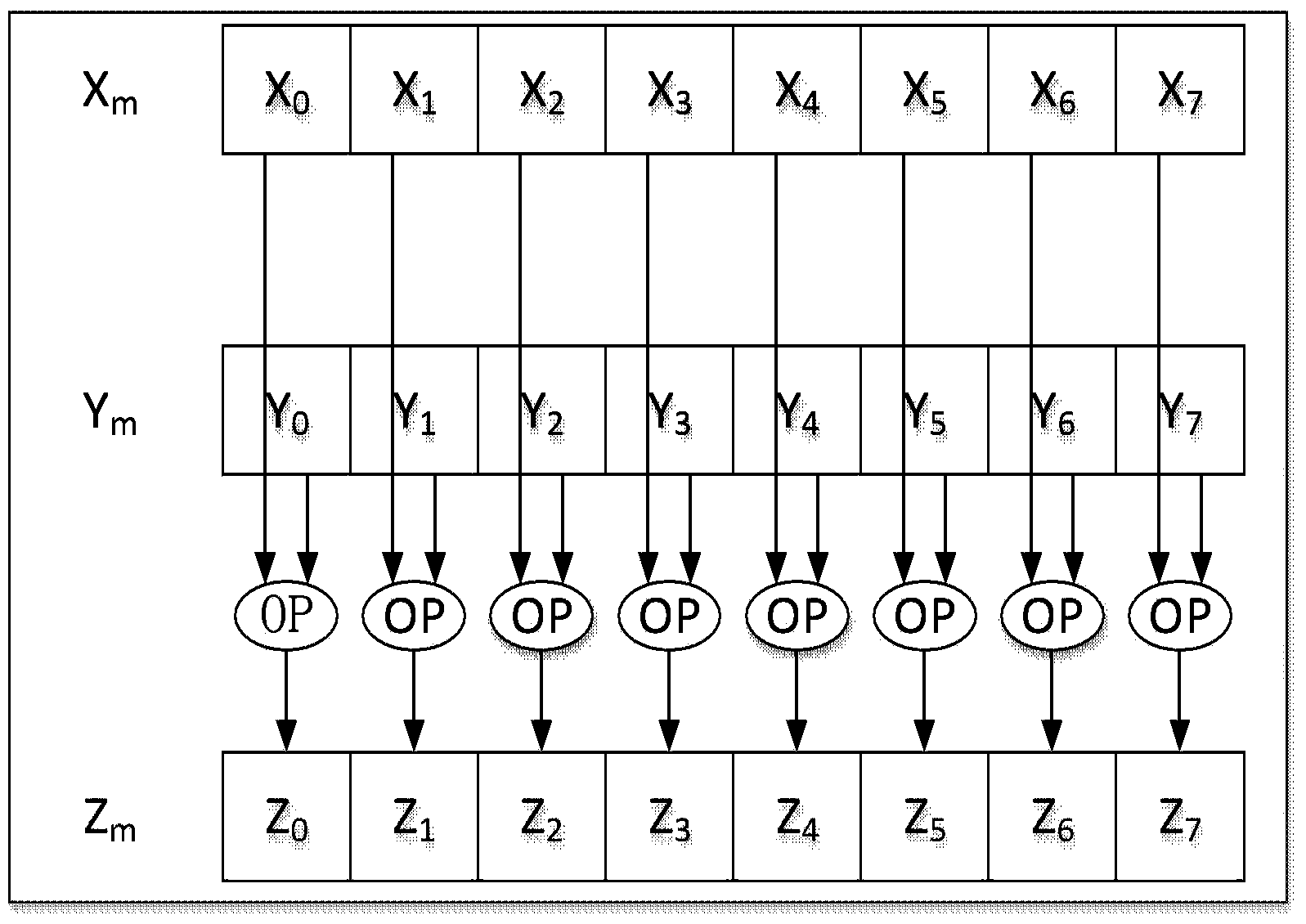
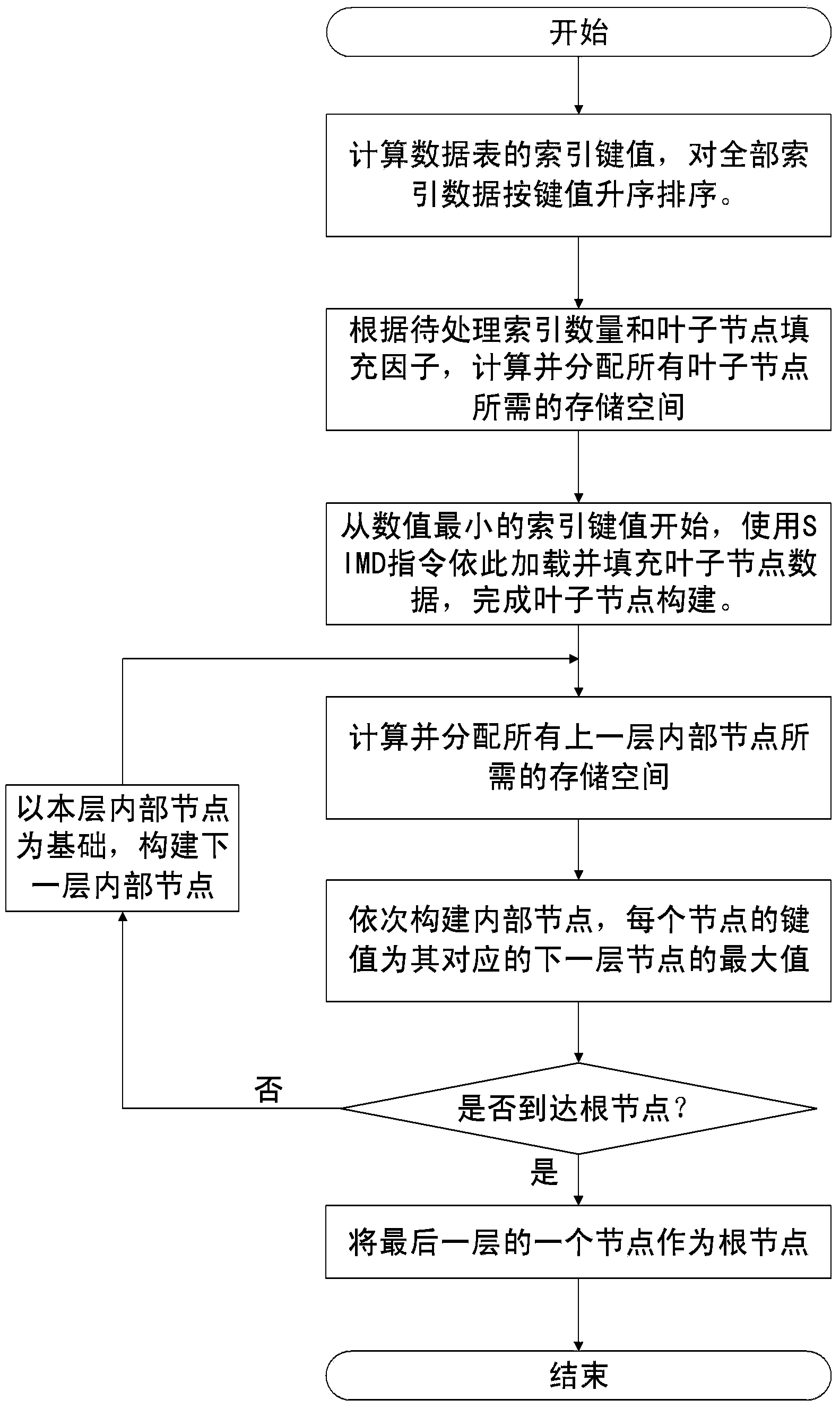
Method and device using vector instruction to process file index in parallel mode
InactiveCN104331497AReduce usageImprove parallelismSpecial data processing applicationsNode countData mining
The invention discloses a method and a device using a vector instruction to process a file index in a parallel mode. The method comprises the following steps of calculating and sorting index key values of data in a data table, distributing needed storing space of all leaf nodes, using an SIMD (single instruction multiple data) instruction to load a plurality of index key values once, sequentially filling the data in all the leaf nodes, distributing the needed storing space of the internal nodes of the upper layer, building the internal nodes, continuously building the internal nodes of the upper layer until the node number of the upper layer is one, regarding the node as a root node, and finishing the building of an index tree; building a buffer pool in internal storage, using an inquiring queue to temporarily store all received inquiring requests, taking the inquiring requests out of the buffering pool when the length of the inquiring queue reaches a preset threshold value, sorting the inquiring requests, and forming a sorted to-be-inquired queue; sequentially obtaining a to-be-inquired term in the sorted inquiring queues, sequentially searching from the root node of the built index tree, and using the SIMD method to search the to-be-inquired term in a parallel mode inside the internal nodes and the leaf nodes.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
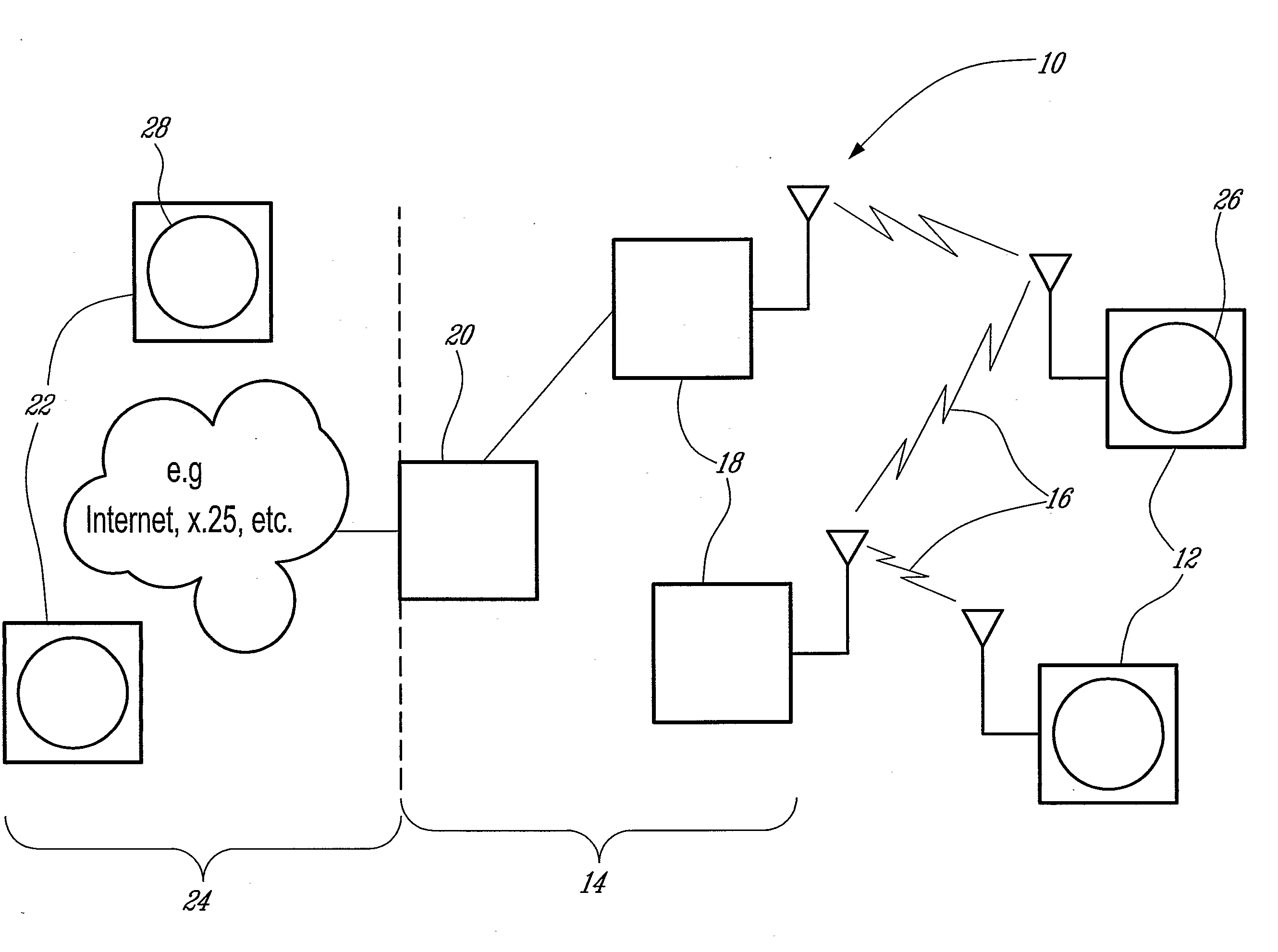
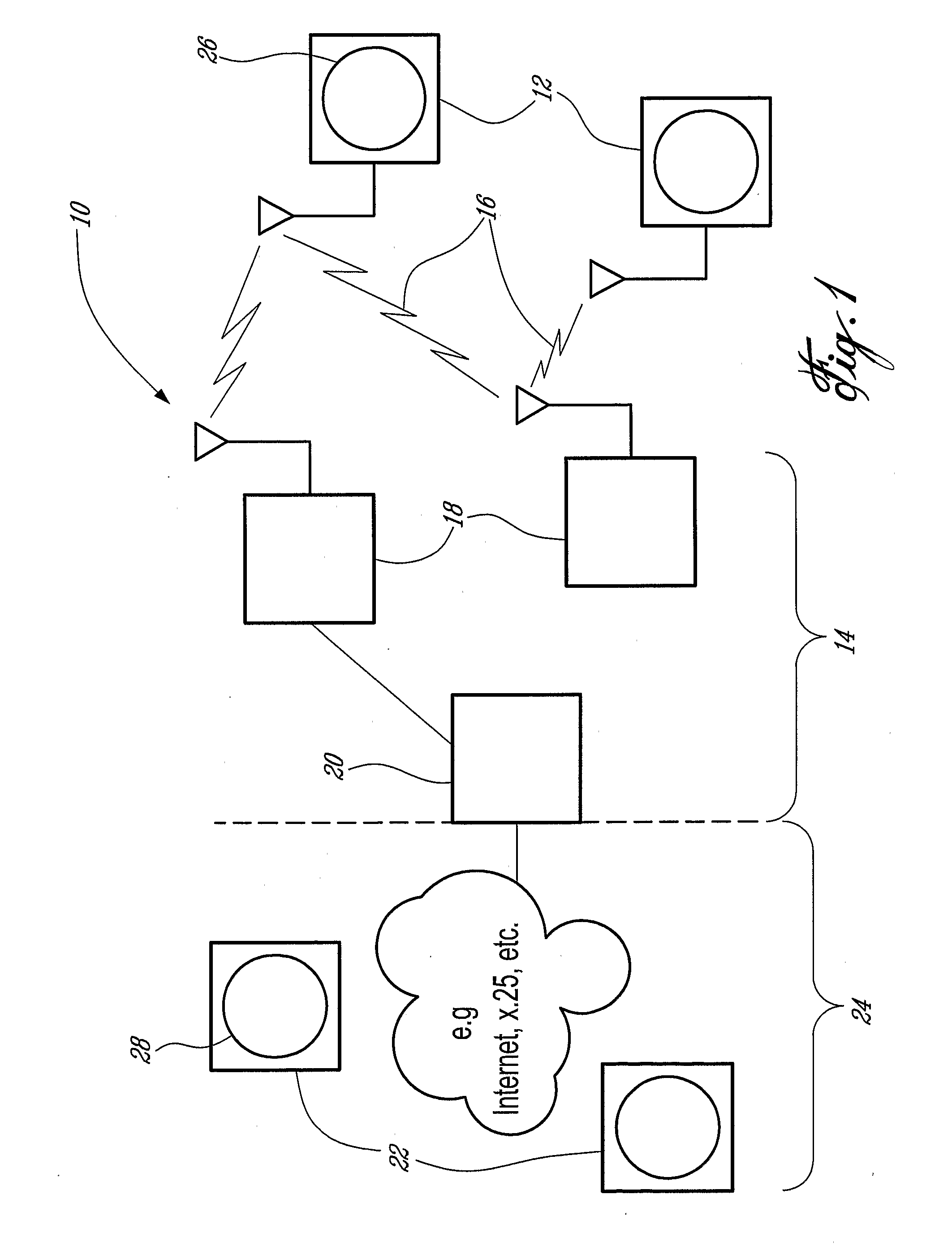
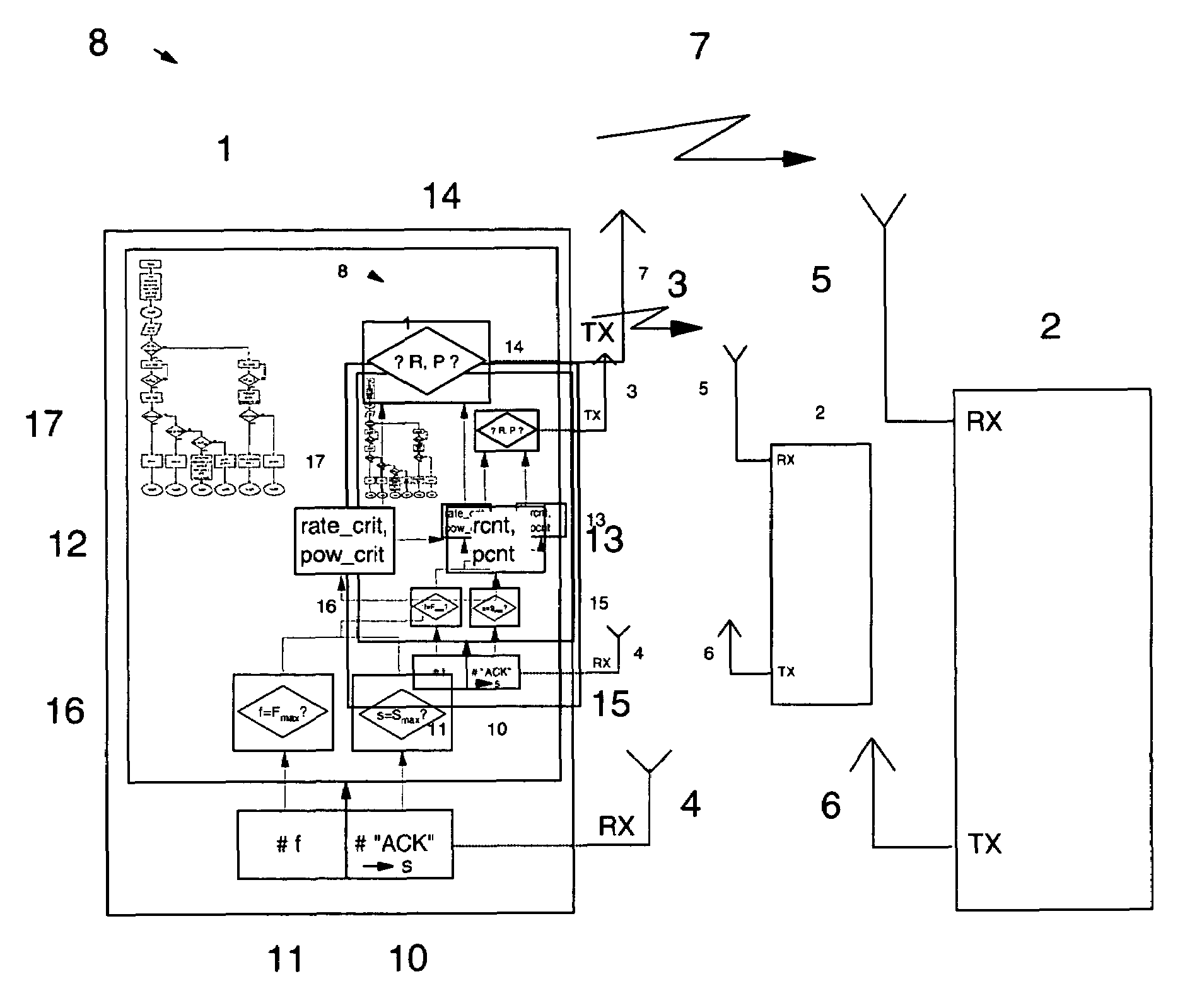
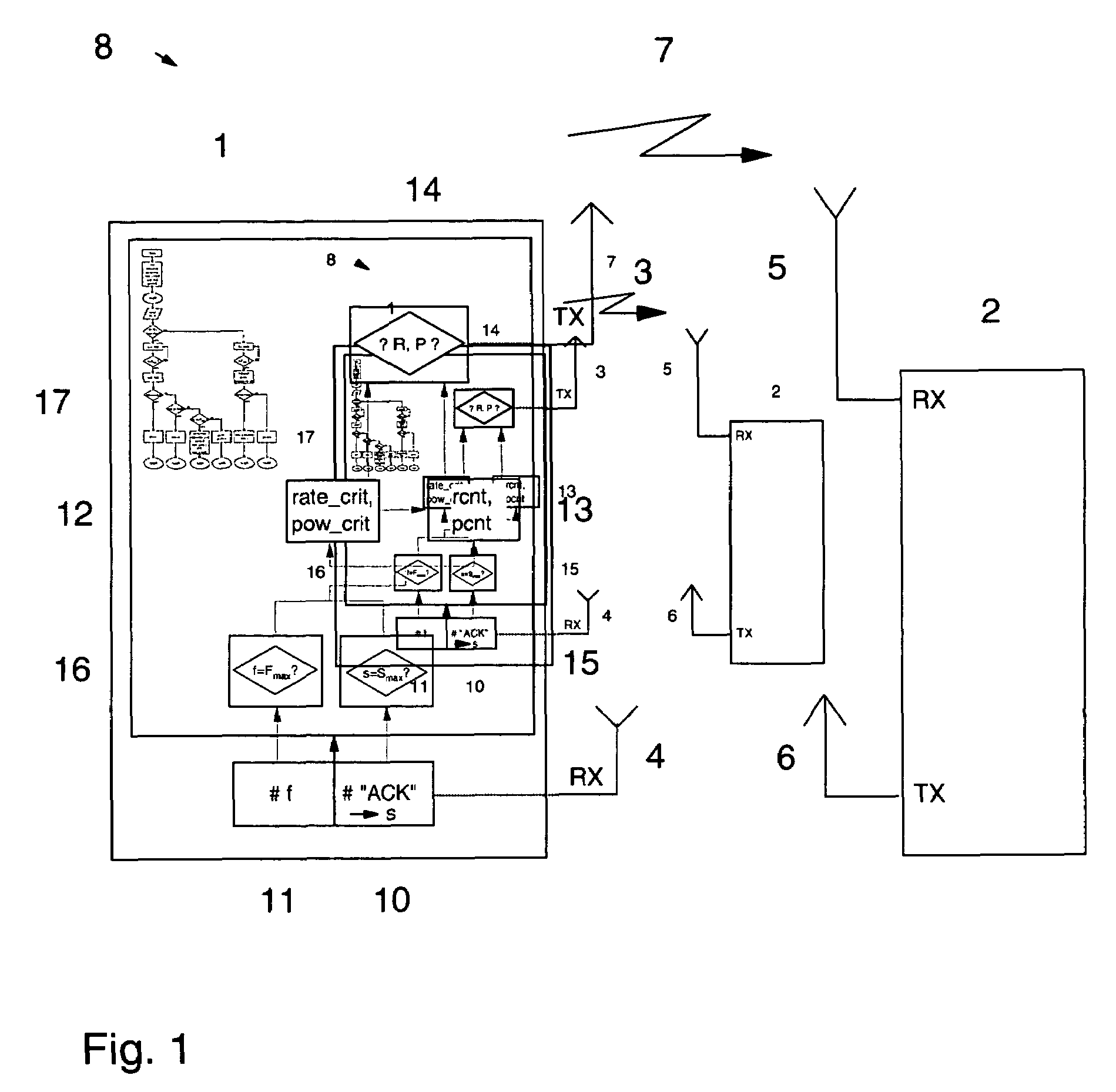
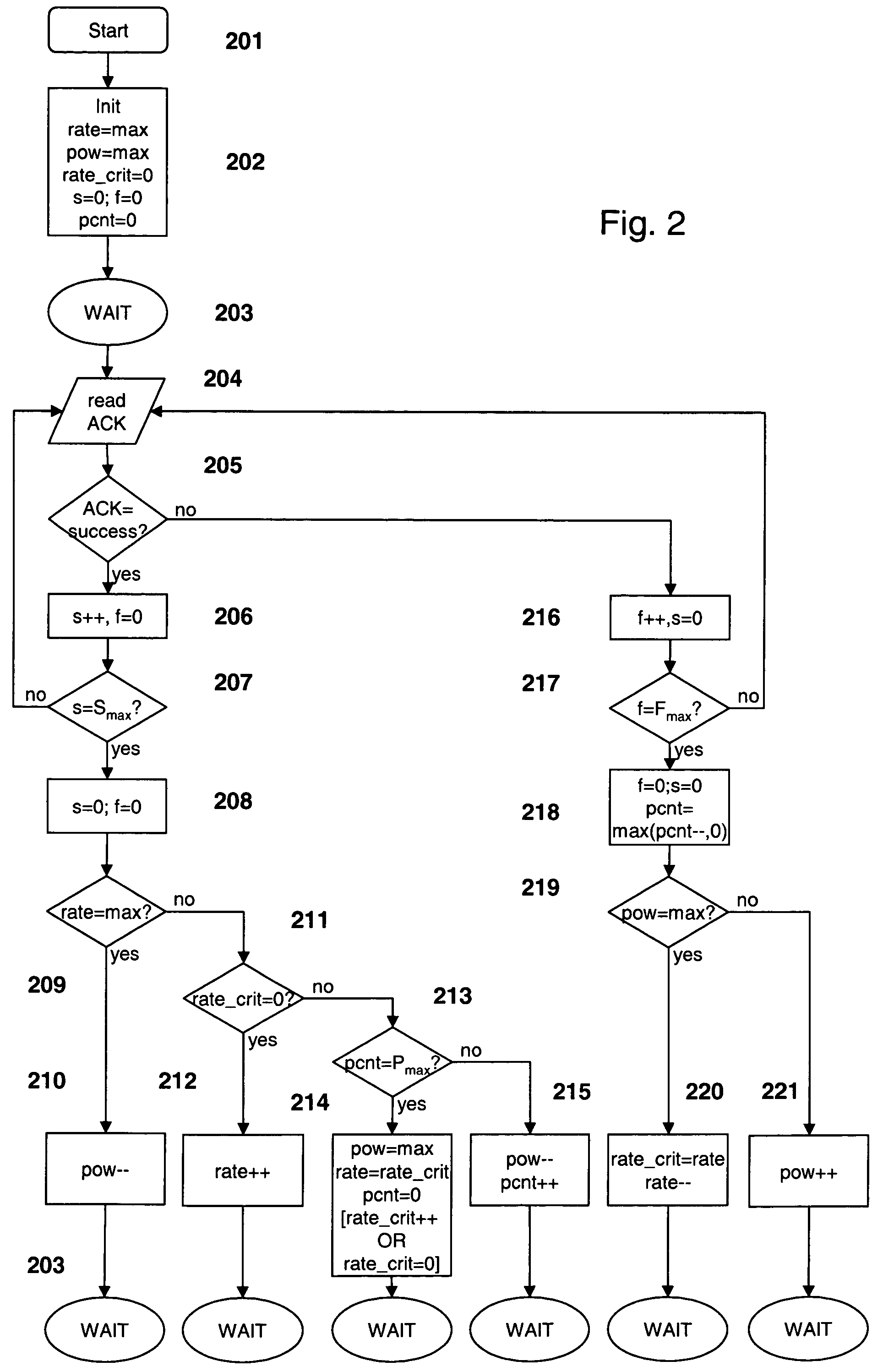
Adapting transmission parameters in a transmitting node of a data communication system to the current link quality of a data communication channel
InactiveUS7512097B2Error prevention/detection by using return channelTime-division multiplexSuccessful transmissionCommunications system
Provides apparatus, systems and methods for adapting a first and second transmission parameter R, P in a transmitting node of a data communication system to the current link quality of a data communication channel. A method comprises in the transmitting node counting the number of successful transmissions s, each successful transmission bases on a receipt of an acknowledgment “ACK”, and comparing the number of successful transmissions s against a threshold value Smax. In the event of reaching the threshold value Smax and operating with the first and second transmission parameter R, P in a predetermined parameter space, the method further comprises adapting at least one of the first and second transmission parameters R, P in dependence on a critical value that due to the current link quality corresponds to a temporarily unsupported value of one of the first and second transmission parameters R, P.
Owner:IBM CORP
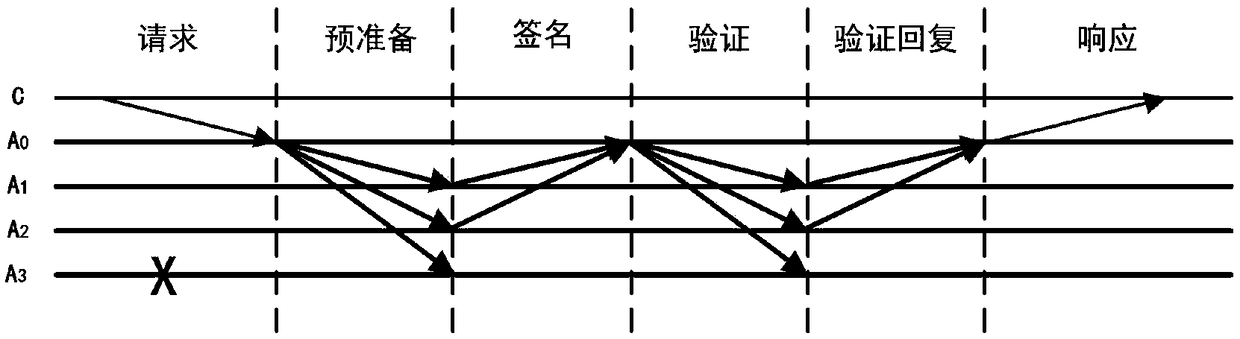
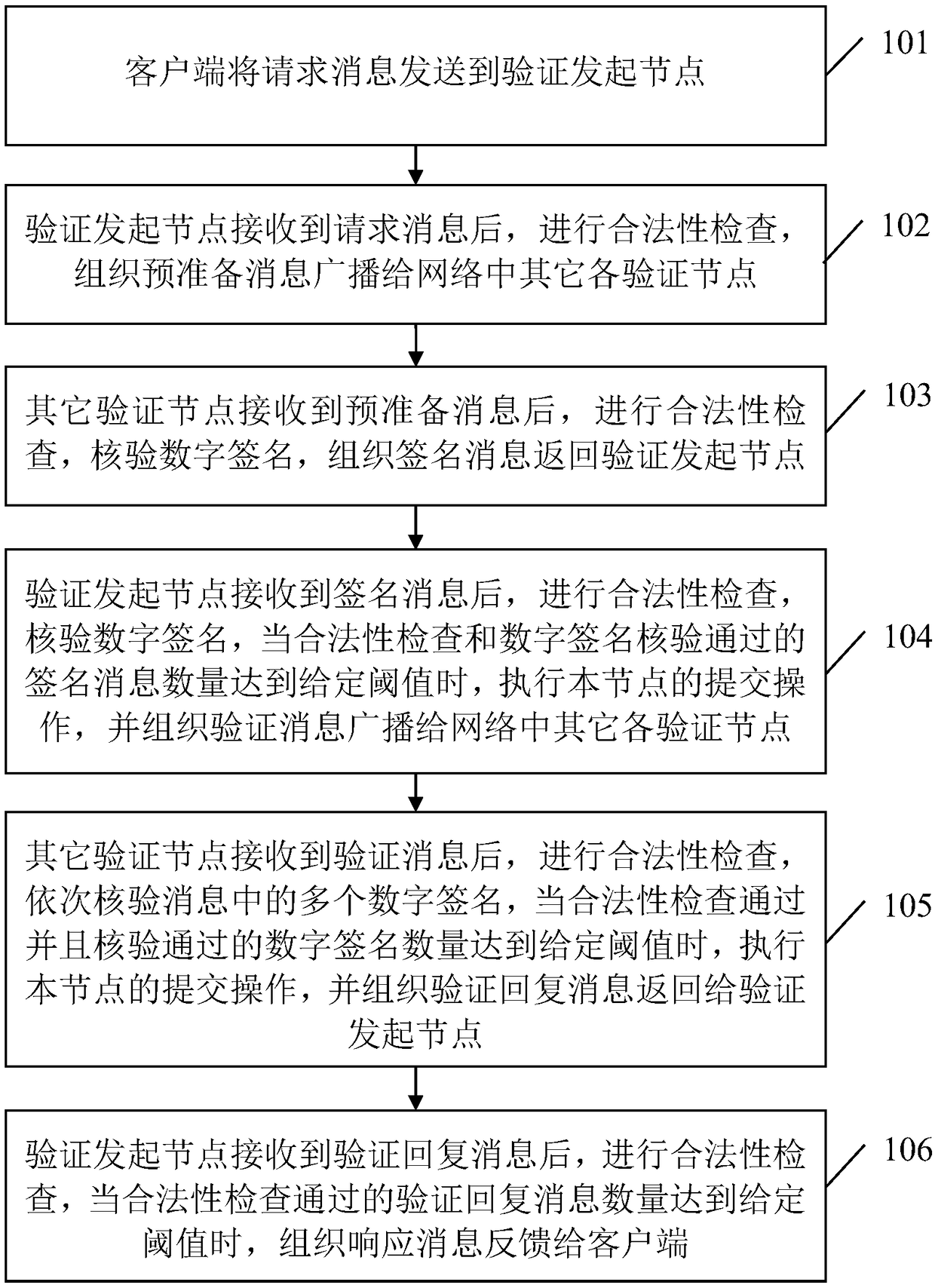
Verification based blockchain common recognition method
ActiveCN108848056AReduce the number of communicationsReduce communication data volumeUser identity/authority verificationByzantine fault toleranceDigital signature
The invention relates to a verification based blockchain common recognition method. A client sends a request message to a verification initiation node; the verification initiation node organizes a pre-preparation message and broadcasts the message to other verification nodes in the network; the other verification nodes organize signature messages and return the signature messages to the verification initiation node respectively; the verification initiation node counts the signature messages which are received correctly, submission of the present node is executed when the number of the signature messages which are received correctly reaches a given threshold, and a verification message is organized and sent to the other verification nodes; each of the other verification nodes checks digitalsignatures in the message successively, when the number of the digital signature that passing checking reaches a given threshold, submission operation of the present node is executed, and a verification reply message is organized and returned to the verification initiation node; and the verification initiation nodes organizes a response message and back feeds the response message to the client. Compared with a practical Byzantine fault tolerant method, the network communication frequency and communication data bulk are reduced, and the common recognition efficiency is improved.
Owner:NANJING UNIV OF SCI & TECH
Cloud data migration method
The invention discloses a cloud data migration method. The cloud data migration method comprises the following specific steps: dividing one file into one or more blocks to store, and distributing and storing on a cluster server by taking the block as a unit, wherein each block is an independent storage unit; taking each block as one partition, and taking the partition as a basic unit for data migration and load monitoring; respectively classifying all storage nodes in an immigration node set and an emigration node set according to the relationship of standardized load values and the total node number of a system; and achieving load balance of the system among various nodes in a cloud environment through a data migration algorithm. Compared with the prior art, the cloud data migration method disclosed by the invention has the advantages that: a data migration strategy is made on the basis of the balance degree; an optimal data migration operation is selected; therefore, the load balance of the system is achieved; the load skew is reduced; and the cloud data migration method is high in practicability and easy to popularize.
Owner:QILU UNIV OF TECH
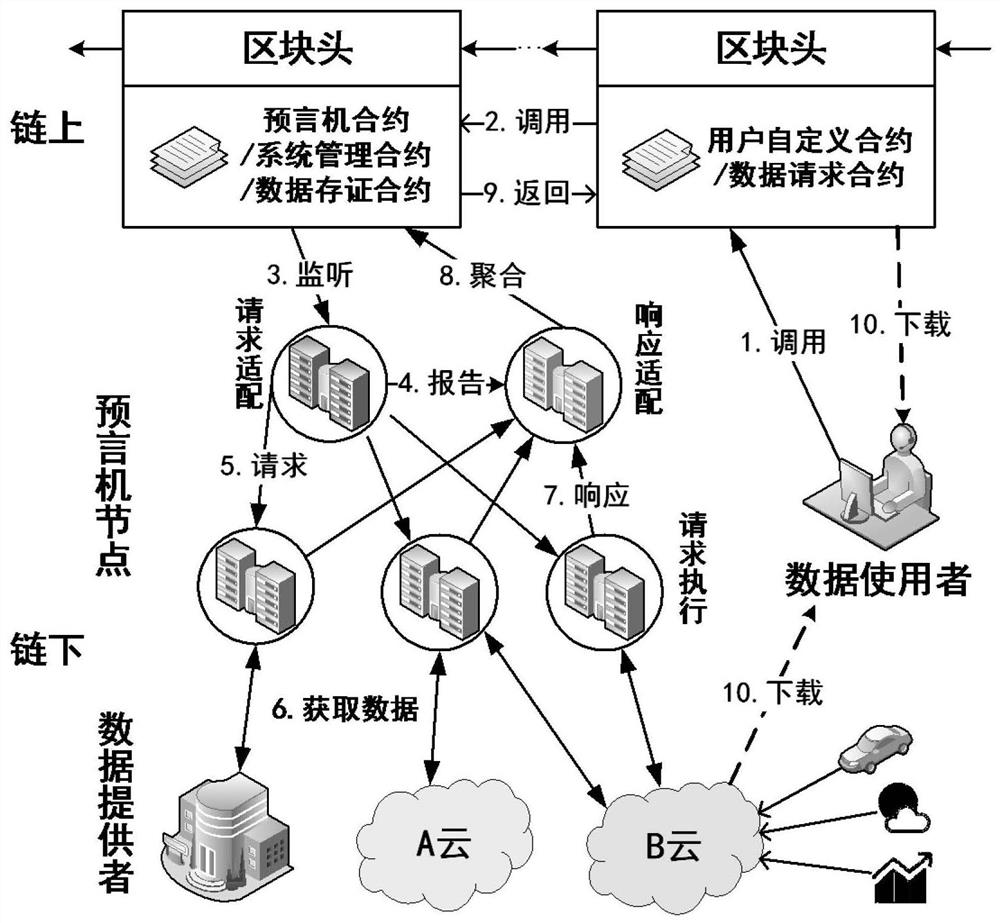
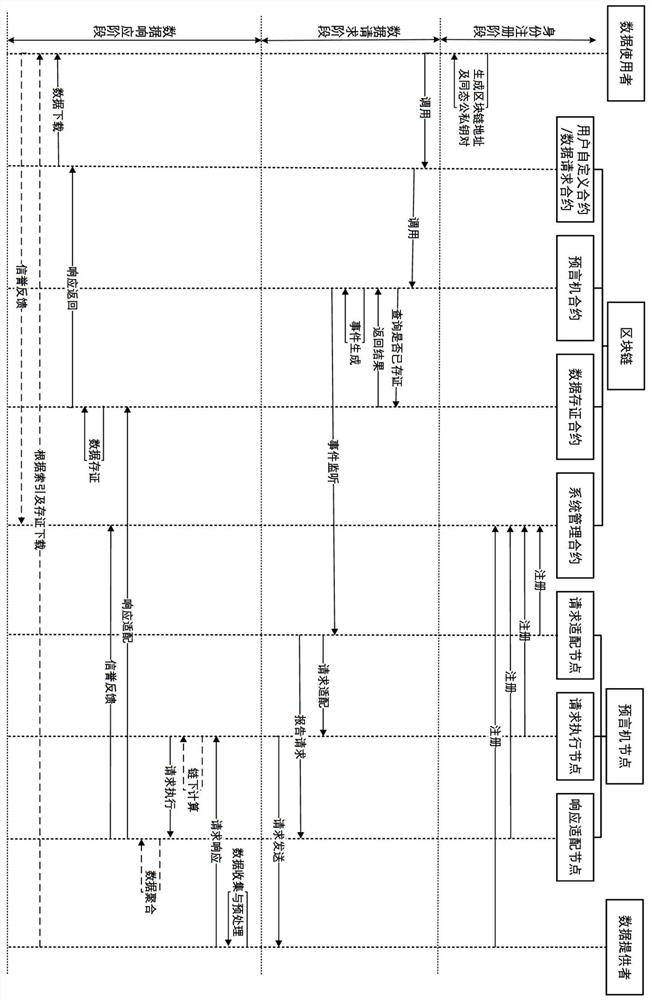
On-chain and off-chain data sharing scheme based on distributed oracle machine and homomorphic encryption
ActiveCN112016105ATake the initiative to obtainImprove timelinessDigital data protectionCommunication with homomorphic encryptionData integrityData provider
The invention belongs to the technical field of block chains. The scheme comprises four kinds of entities including a data user, a block chain, an oracle machine node and a data provider, and the block chain deploys a system management contract, an oracle machine contract, a data storage contract, a data request contract and a user-defined contract; wherein the oracle machine node comprises a request adaptation node, a response adaptation node and a request execution node; according to the scheme, cooperative sharing of the on-chain data and the off-chain data is realized by using the distributed oracle machine, the network bandwidth and the on-chain storage space demand are reduced, and the data integrity can be verified through the on-chain evidence storage; according to the scheme, homomorphic encryption is used for protecting data privacy in the processing process of the oracle machine and realizing basic under-chain computing capacity, better universality and verifiable safety areachieved. Meanwhile, data aggregation operation is set under a chain, and the processing performance is improved compared with on-chain aggregation.
Owner:东北大学秦皇岛分校
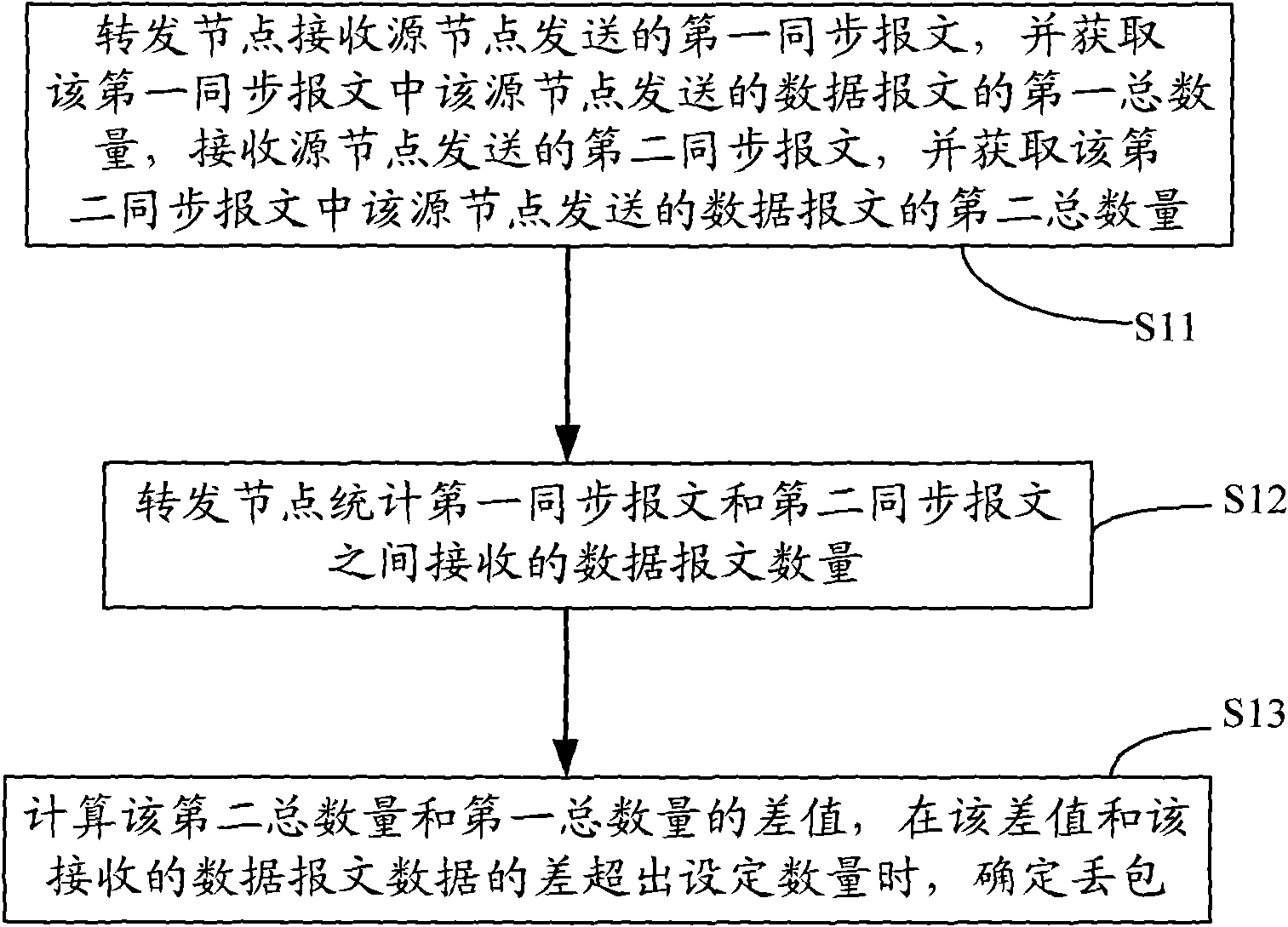
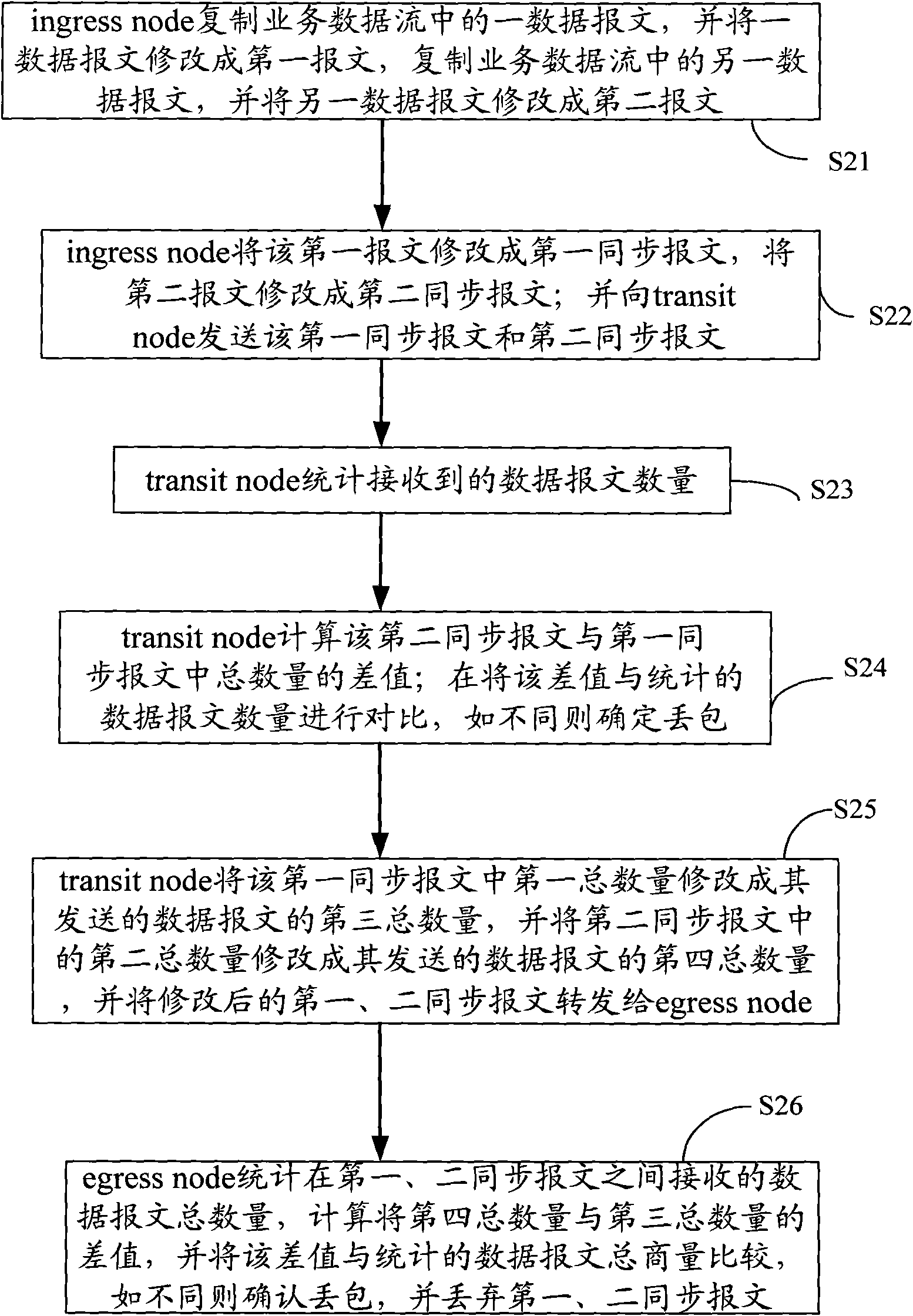
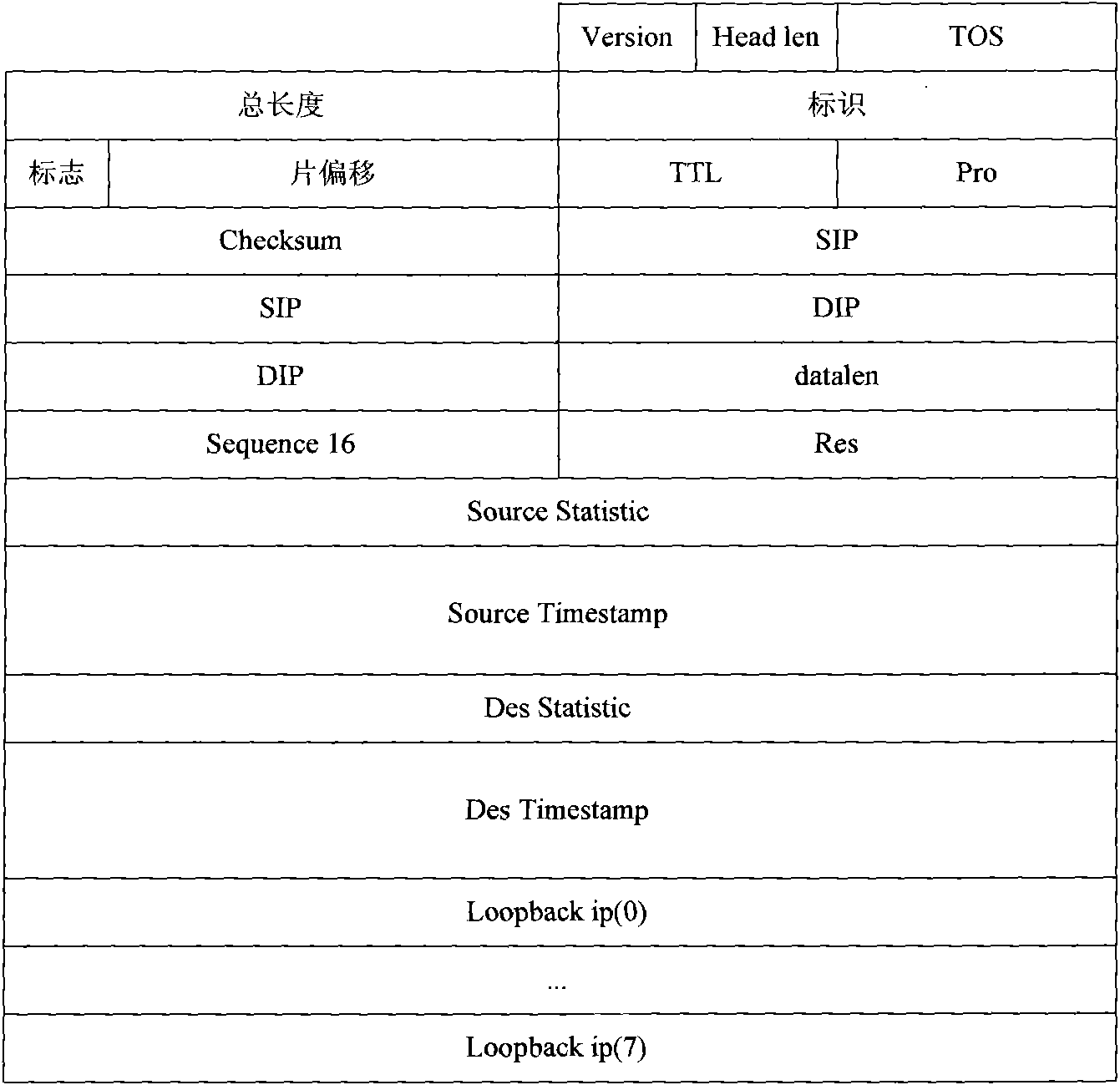
Detection method, device and system of packet loss in network communication
The implementation mode of the invention provides a detection method, a device and a system of packet loss in network communication, belonging to the field of network communication. The method comprises the following steps: a forwarding node receives a first synchronous message sent by a source node, wherein, the first synchronous message carries the first total quantity of a data message sent by the source node, and the first total quantity is acquired; the forwarding node receives a second synchronous message sent by the source node, the second synchronous message carries the second total quantity of the data message sent by the source node and the second total quantity is acquired; the forwarding node counts the data message quantity received between the first synchronous message and the second synchronous message; the forwarding node calculates the difference value of the first total quantity and the second total quantity; when the difference and the difference of the data message quantity are larger than threshold, the packet loss is determined. The technical proposal has the advantages of carrying out packet loss position and having good detection effect.
Owner:HUAWEI TECH CO LTD
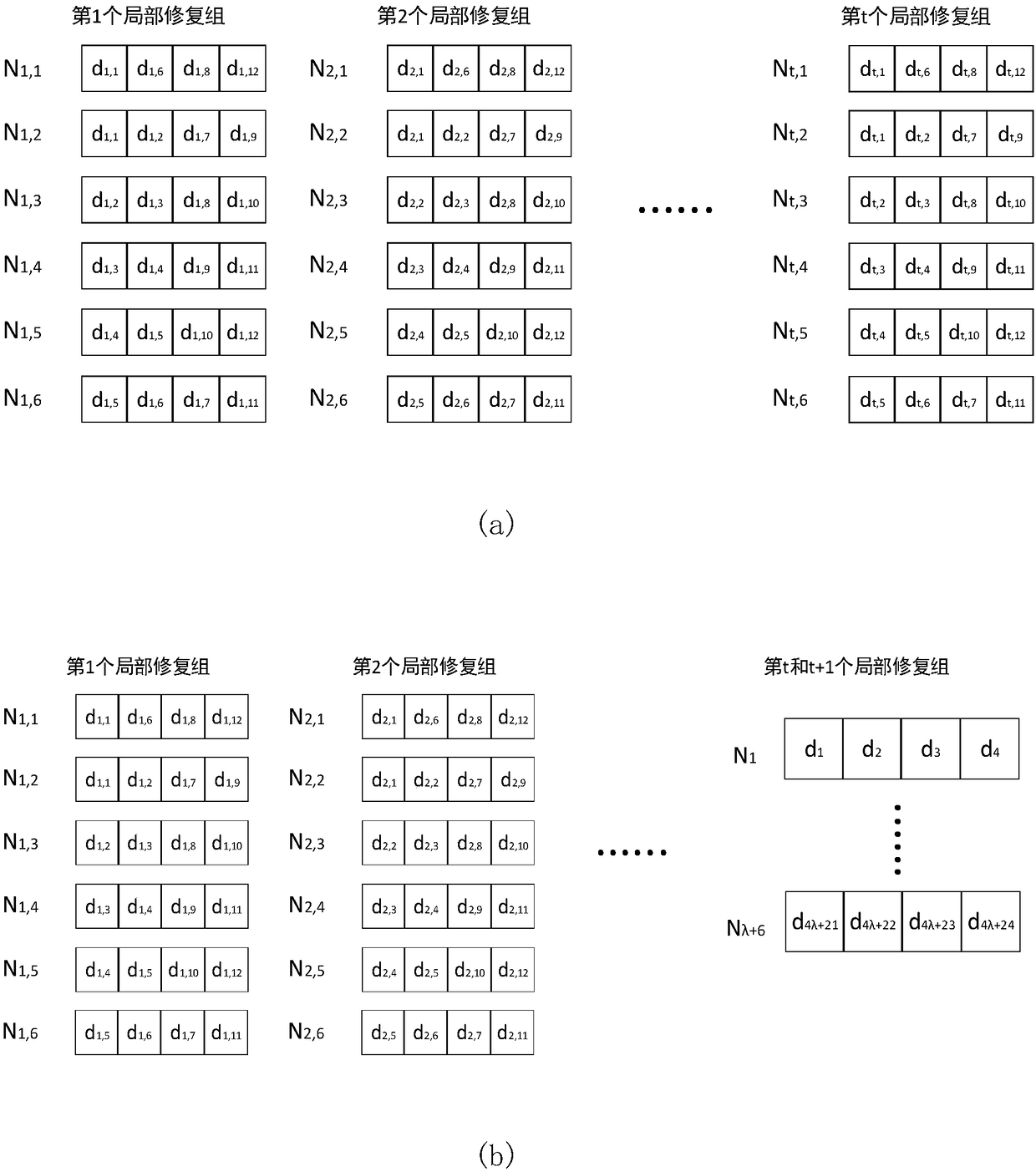
Local repairing coding method based on fractional repetition codes and node failure repairing method
ActiveCN108540520AGuaranteed Storage OverheadControl the amount of stored dataForward error control useData switching networksAlgorithmTheoretical computer science
The invention discloses a local repairing coding method based on fractional repetition codes and a node failure repairing method, the local repairing coding method based on the fractional repetition codes is used for realizing storage of data, the number of nodes in a local repairing group and the quantity of stored data in the local repairing group can be controlled, and thus, storage overhead ofthe nodes can be guaranteed; and when single node failure and two-node failure exist in the local repairing group, data reconstruction of the failed nodes in the local repairing group can be realizedquickly just by finite live nodes in the local repairing group, and data of the failed nodes can be recovered quickly.
Owner:CHANGAN UNIV
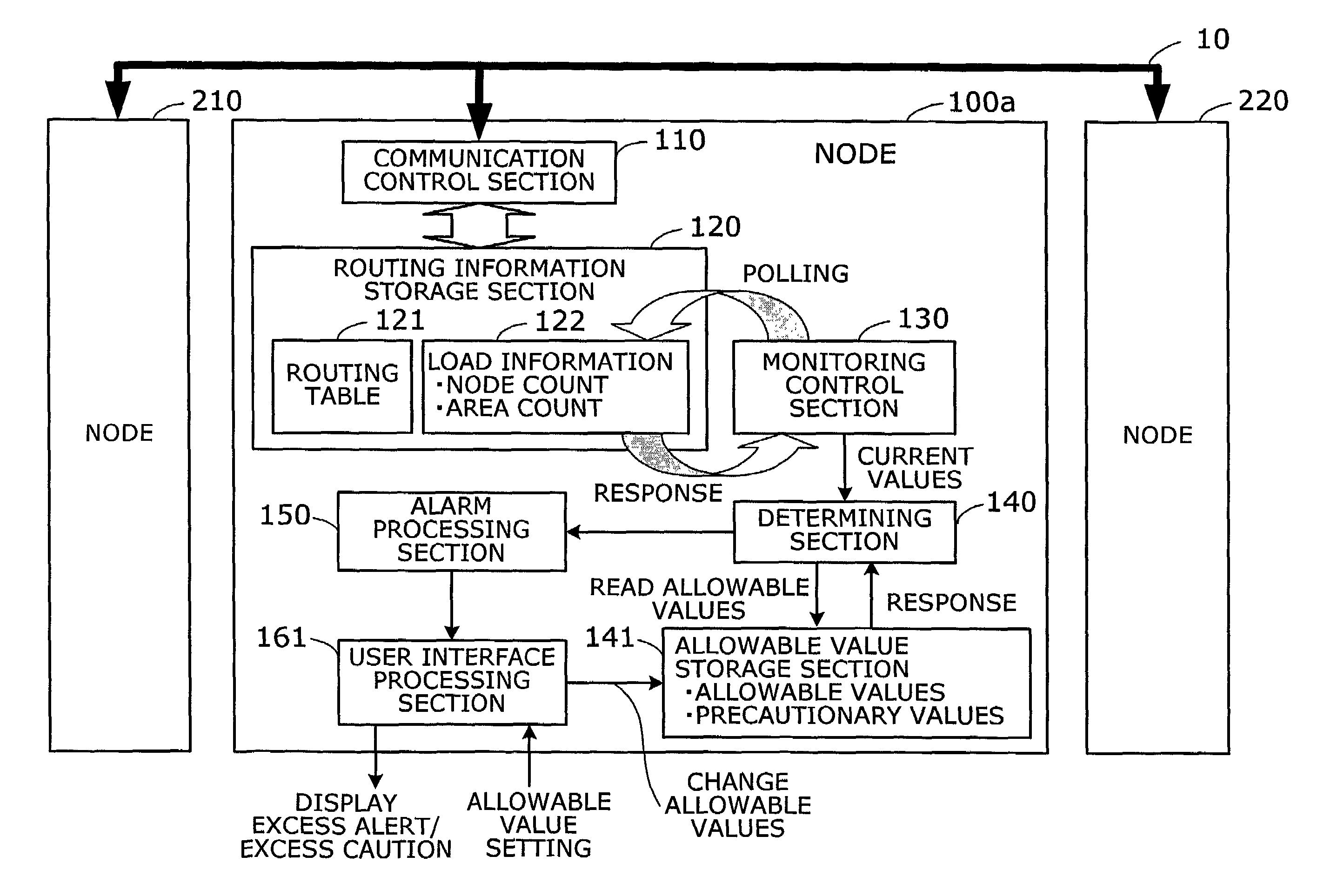
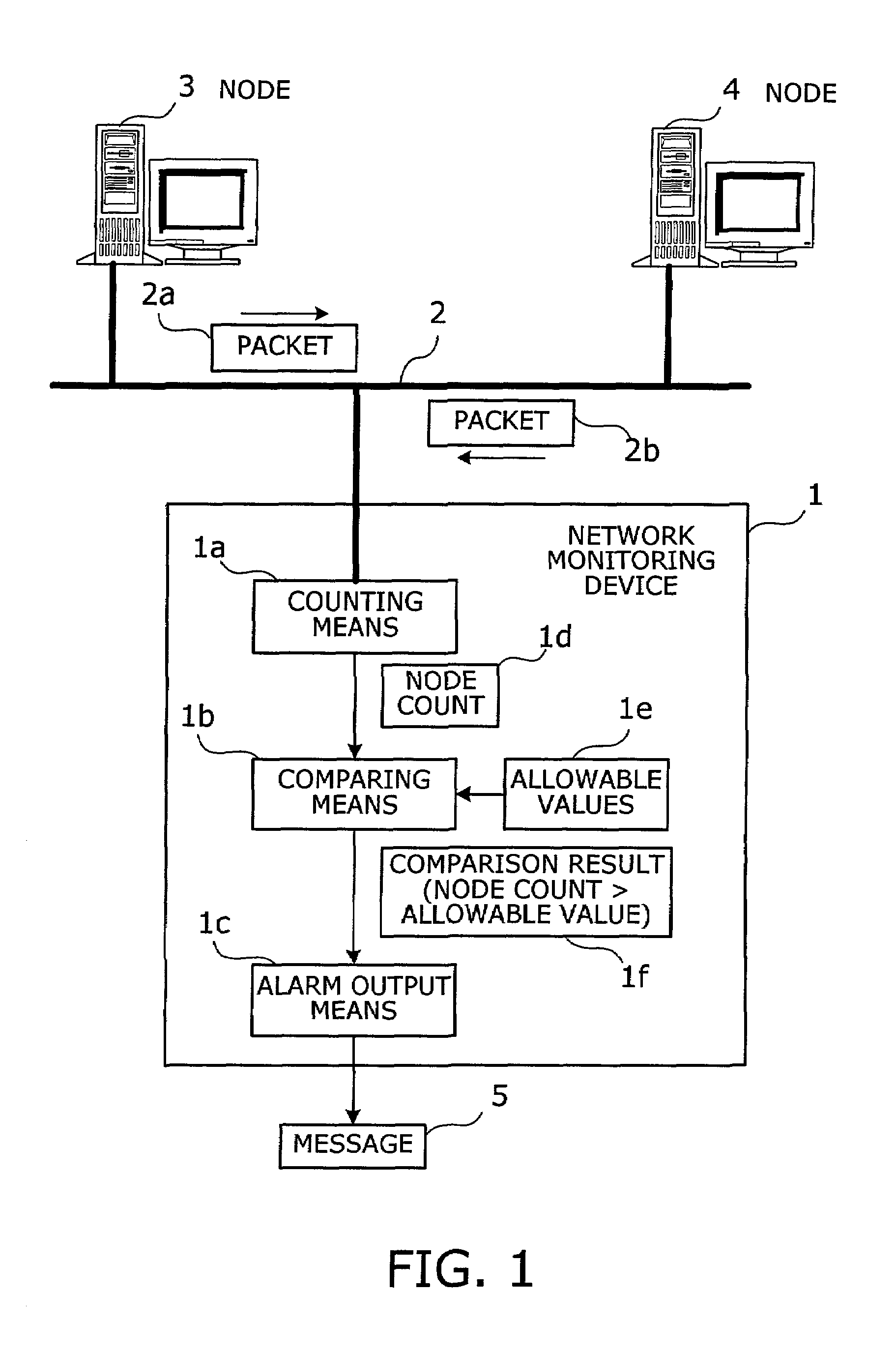
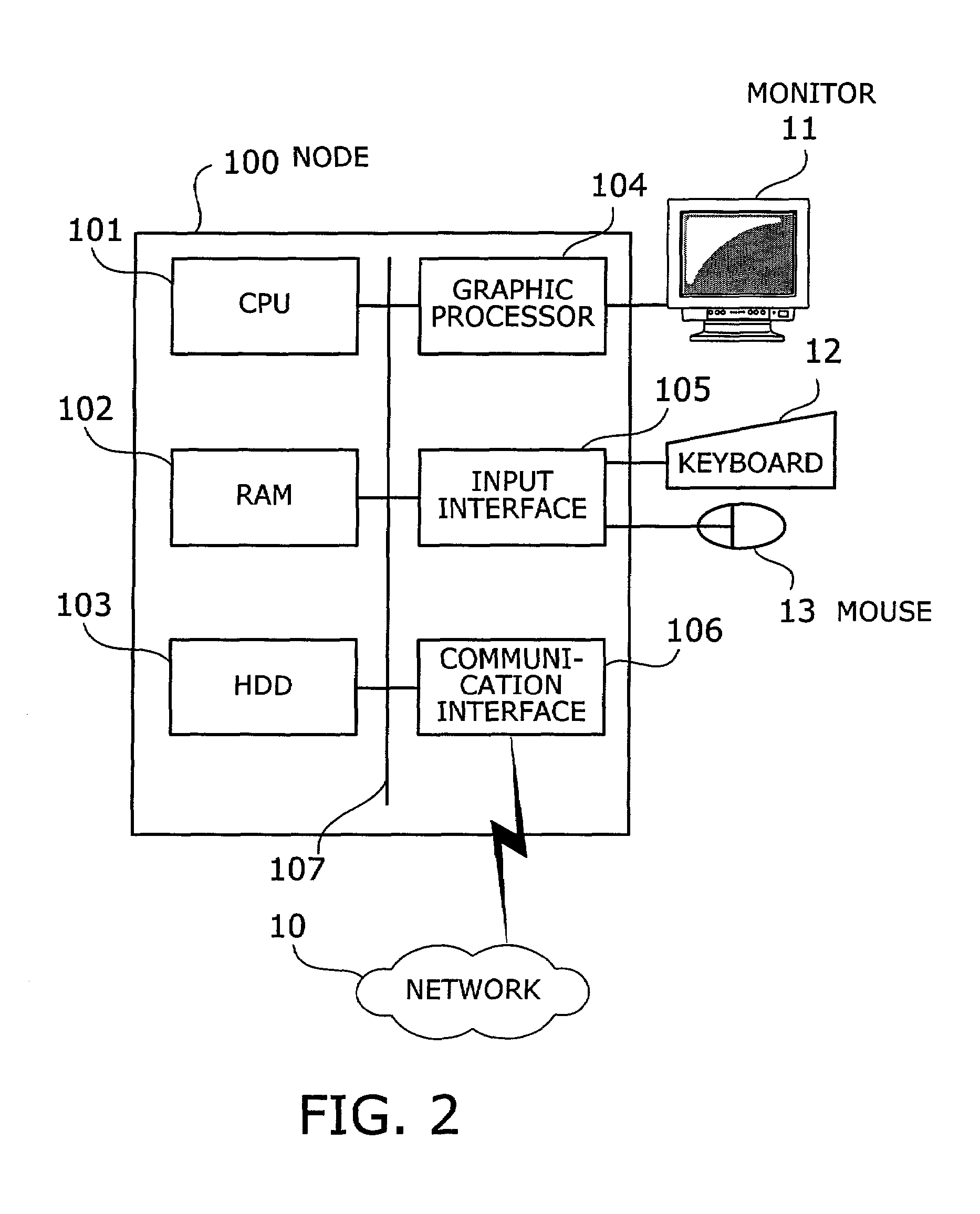
Network monitoring device and method
Network monitoring device and method whereby the user can be given an alarm before a guaranteed limit of packet routing is exceeded. Counting section counts the number of nodes based on packets exchanged between the nodes, and comparing section compares the node count with an allowable value. If the node count is larger than the allowable value, alarm output section outputs a message that the node count is excessively large.
Owner:FUJITSU LTD
Distribution-based task scheduling method and system
InactiveCN105335219AControllable energy consumptionLow costInput/output to record carriersMultiprogramming arrangementsData centerData access
The invention is suitable for the technical field of data storage, and provides a distribution-based task scheduling method and system. The method comprises the following steps: setting an accessed datanode threshold value of each rack in a distributed cluster; obtaining an amount of the datanodes accessed in each rack, and judging whether the amount of the datanodes accessed in each rack at present exceeds the threshold value or not; and if the amount of the datanodes accessed in each rack at present exceeds the threshold value, distributing a new distributed task to other racks, or scheduling the new task to a task queue to wait. On the basis of a control algorithm based on IO (Input / Output) access, the single-cabinet power of cold storage data access and the energy consumption of an integral cold data center can be controllable, the relationship between flash memory media service and energy consumption is fully utilized, and the characteristics of data distribution type storage / access are combined to lower cold data backup cluster expense.
Owner:ALIBABA GRP HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com



![[01] cost-efficient repair for storage systems using progressive engagement [01] cost-efficient repair for storage systems using progressive engagement](https://images-eureka-patsnap-com.libproxy1.nus.edu.sg/patent_img/a9653ab0-f18e-444f-8212-6db105d9530a/US20150303949A1-20151022-D00000.PNG)
![[01] cost-efficient repair for storage systems using progressive engagement [01] cost-efficient repair for storage systems using progressive engagement](https://images-eureka-patsnap-com.libproxy1.nus.edu.sg/patent_img/a9653ab0-f18e-444f-8212-6db105d9530a/US20150303949A1-20151022-D00001.PNG)
![[01] cost-efficient repair for storage systems using progressive engagement [01] cost-efficient repair for storage systems using progressive engagement](https://images-eureka-patsnap-com.libproxy1.nus.edu.sg/patent_img/a9653ab0-f18e-444f-8212-6db105d9530a/US20150303949A1-20151022-D00002.PNG)