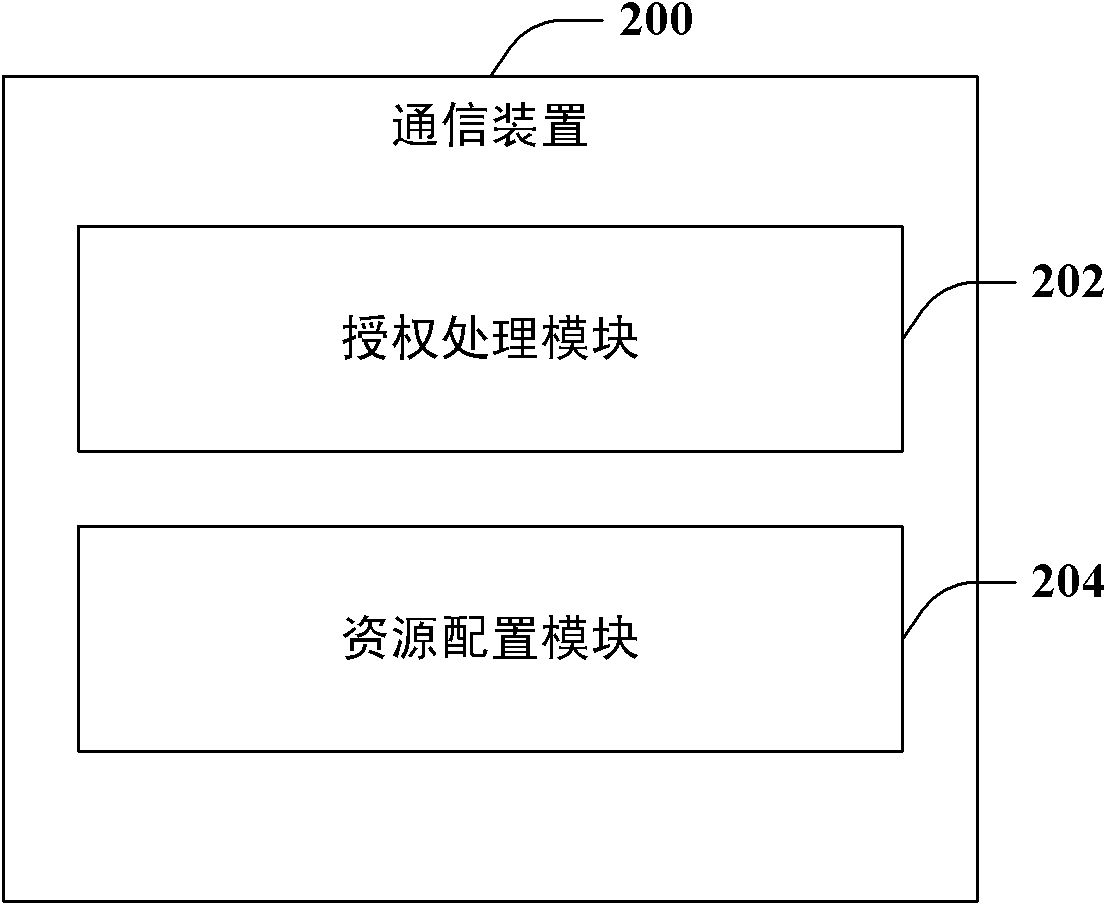
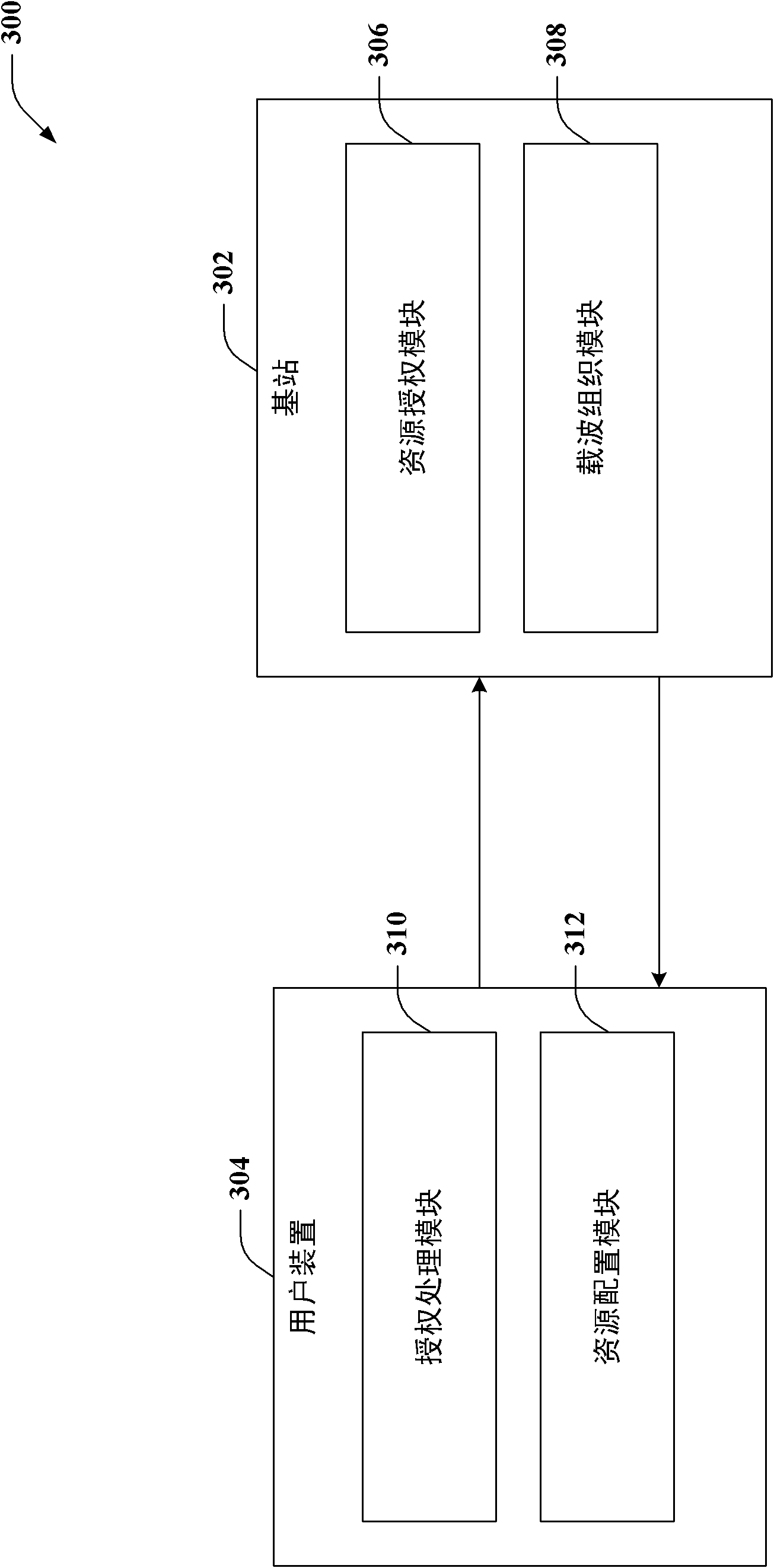
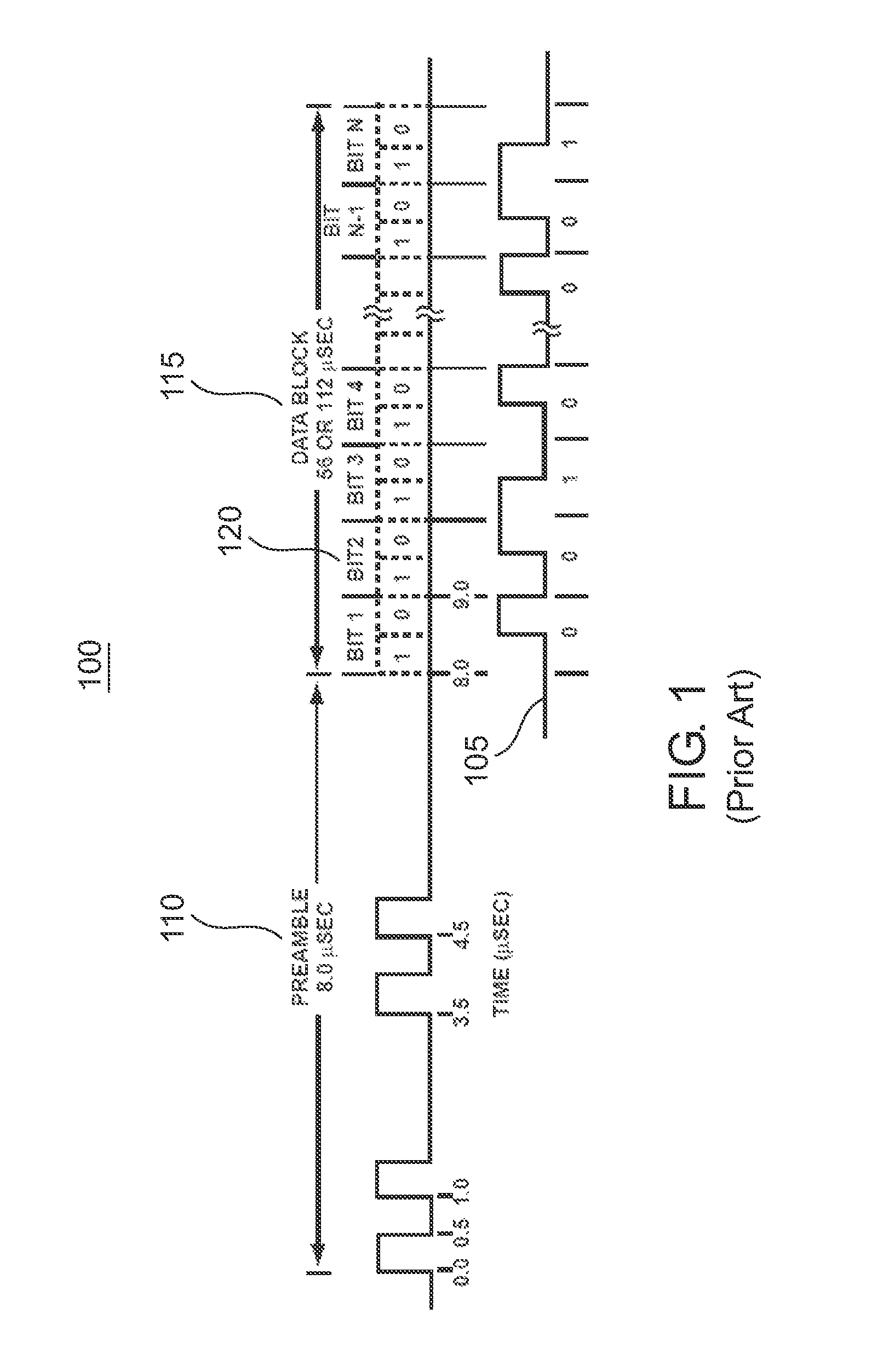
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
82 results about "Legacy mode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
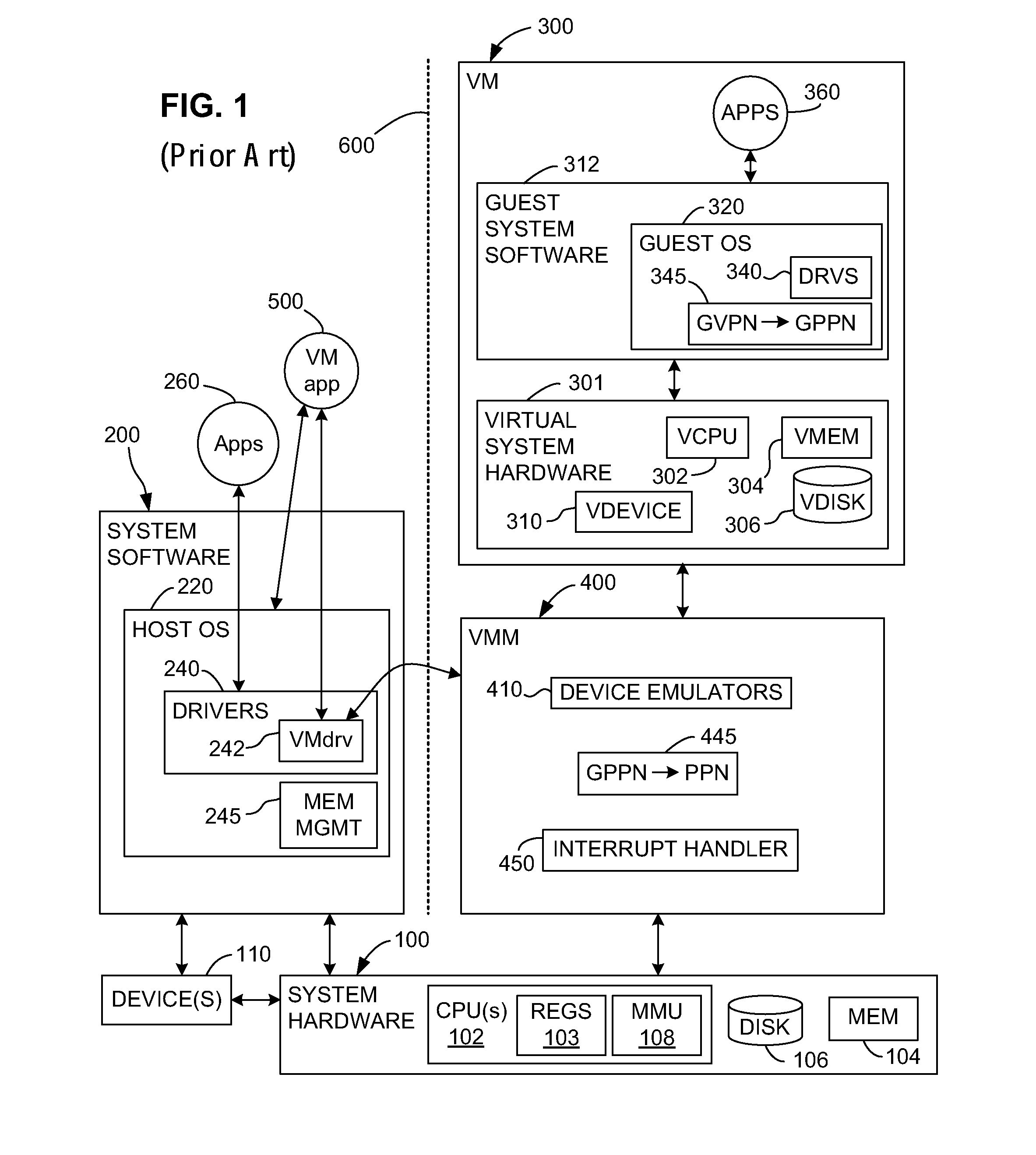
In computing, legacy mode is a state in which a computer system, component, or software application behaves in a way different from its standard operation in order to support older software, data, or expected behavior. It differs from backward compatibility in that an item in legacy mode will often sacrifice newer features or performance, or be unable to access data or run programs it normally could, in order to provide continued access to older data or functionality. Sometimes it can allow newer technologies that replaced the old to emulate them when running older operating systems.
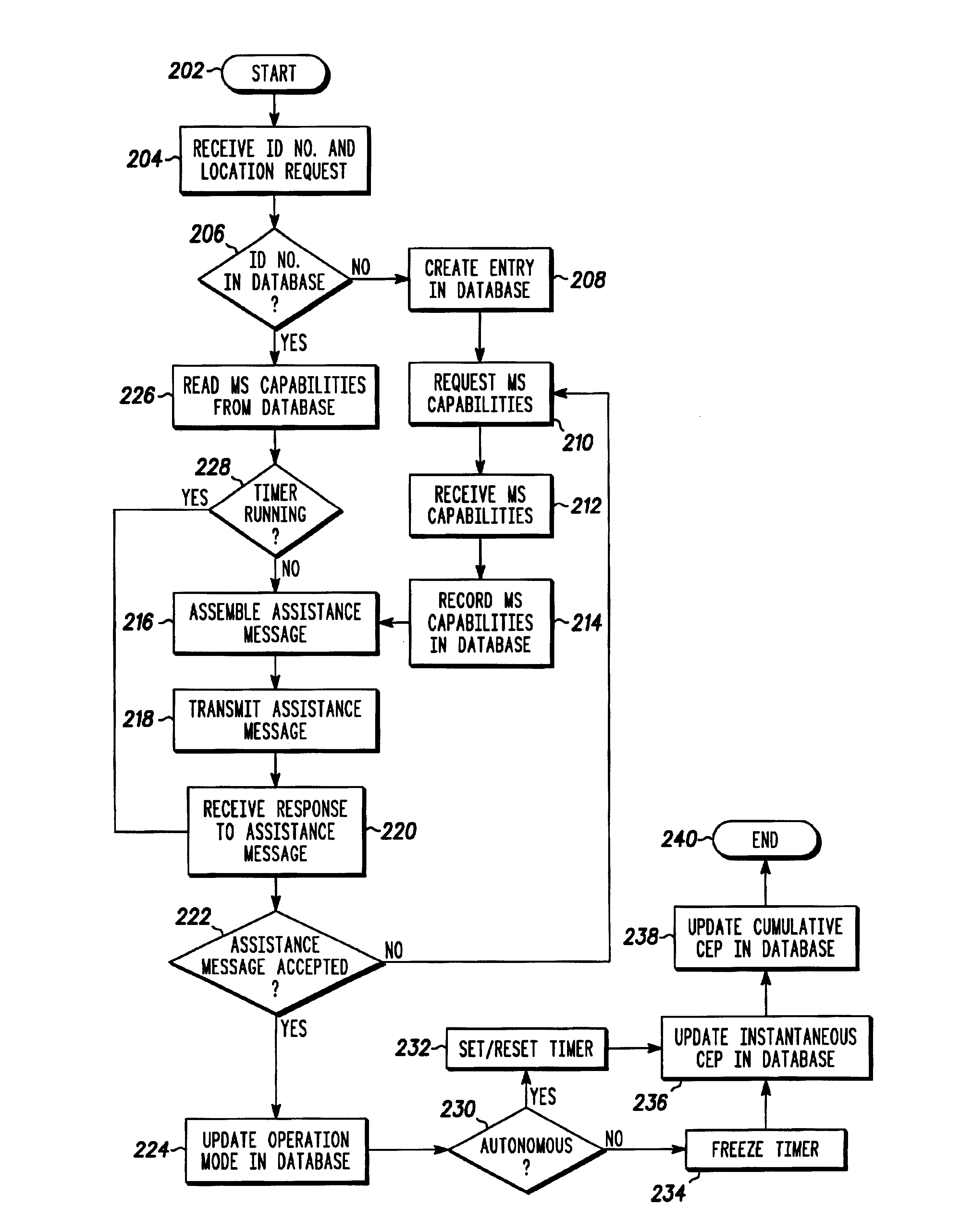
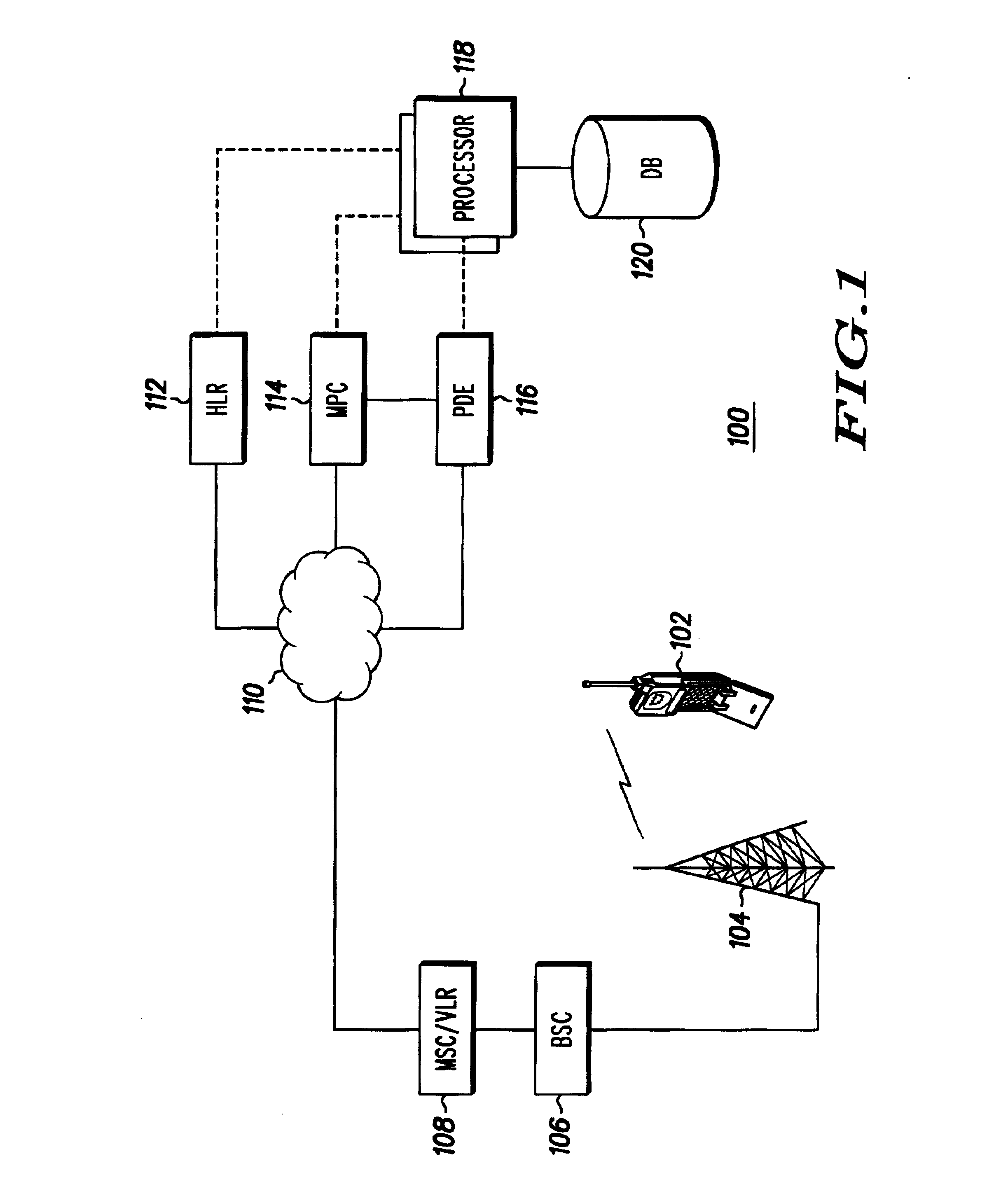
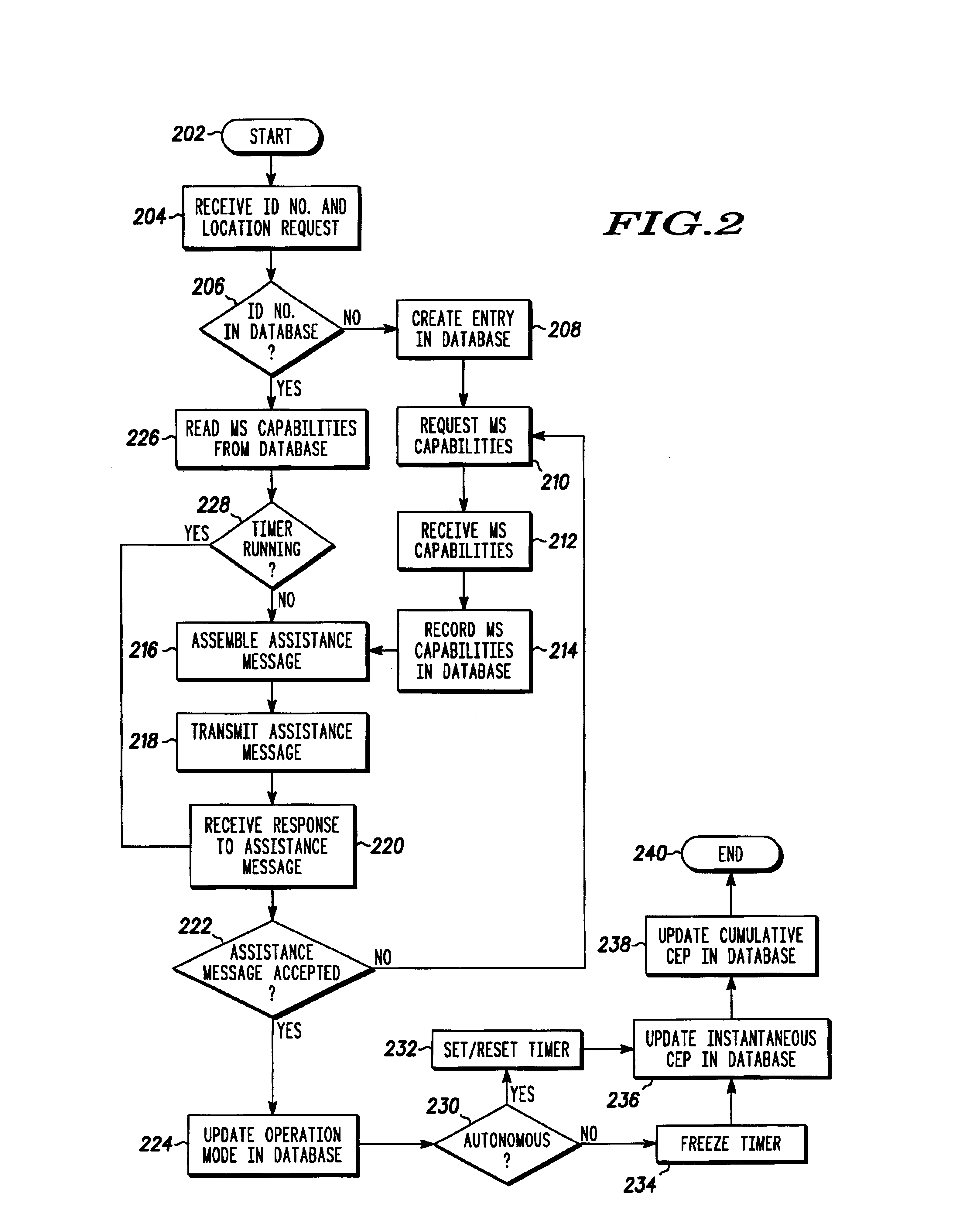
Network and method for monitoring location capabilities of a mobile station
InactiveUS6912395B2Instruments for road network navigationDirection finders using radio wavesTelecommunicationsMobile station
The present invention is a communication network (100) and method for monitoring location capabilities of mobile stations (102) in a database (120) of a communication network. Initially, the network receives an identification number from a mobile station (102). If the database (120) does not include a location capability corresponding to the identification number, then a processor (118) requests the location capability from the mobile station (102) and stores the requested location capability in the database (120). The location capability includes one or more of the following capabilities: an autonomous mode capability, an assisted mode capability and a legacy mode capability. To retrieve an entry from the database (120), the network reads the location capability corresponding to the identification number from the database (120). The network then assembles an assistance message based on the location capability of the mobile station (102) and transmits the assistance message to the mobile station (102).
Owner:GOOGLE TECH HLDG LLC
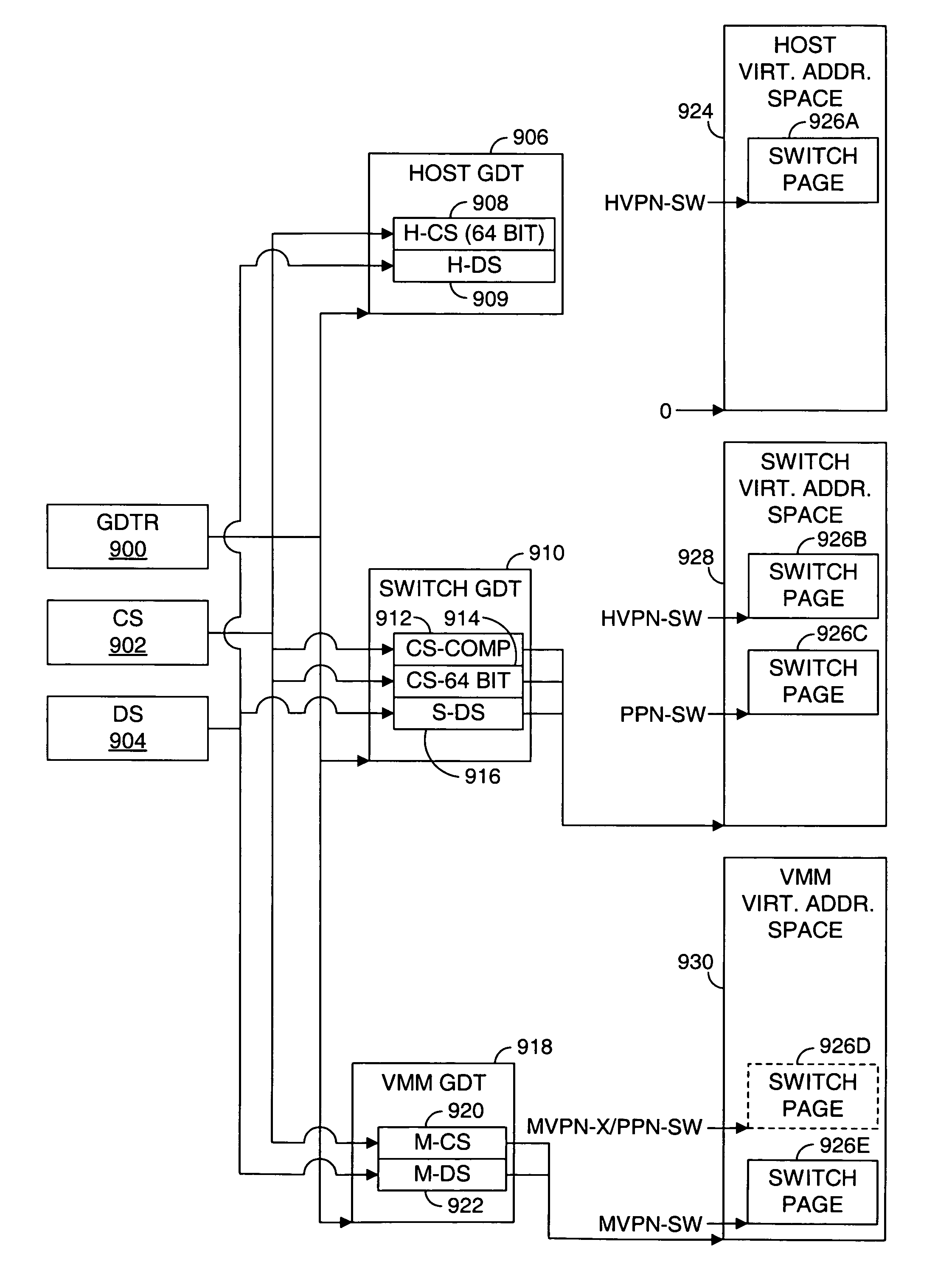
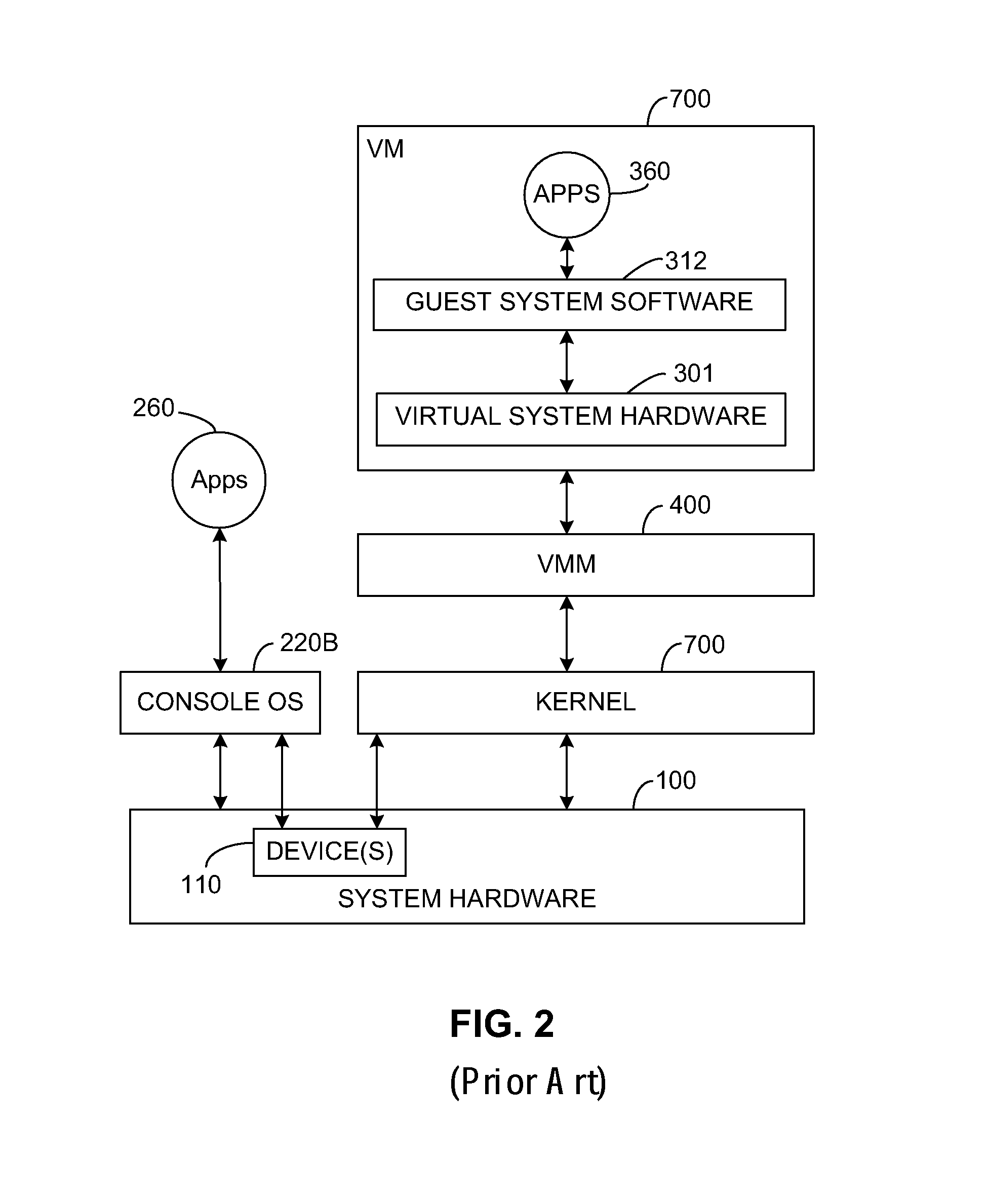
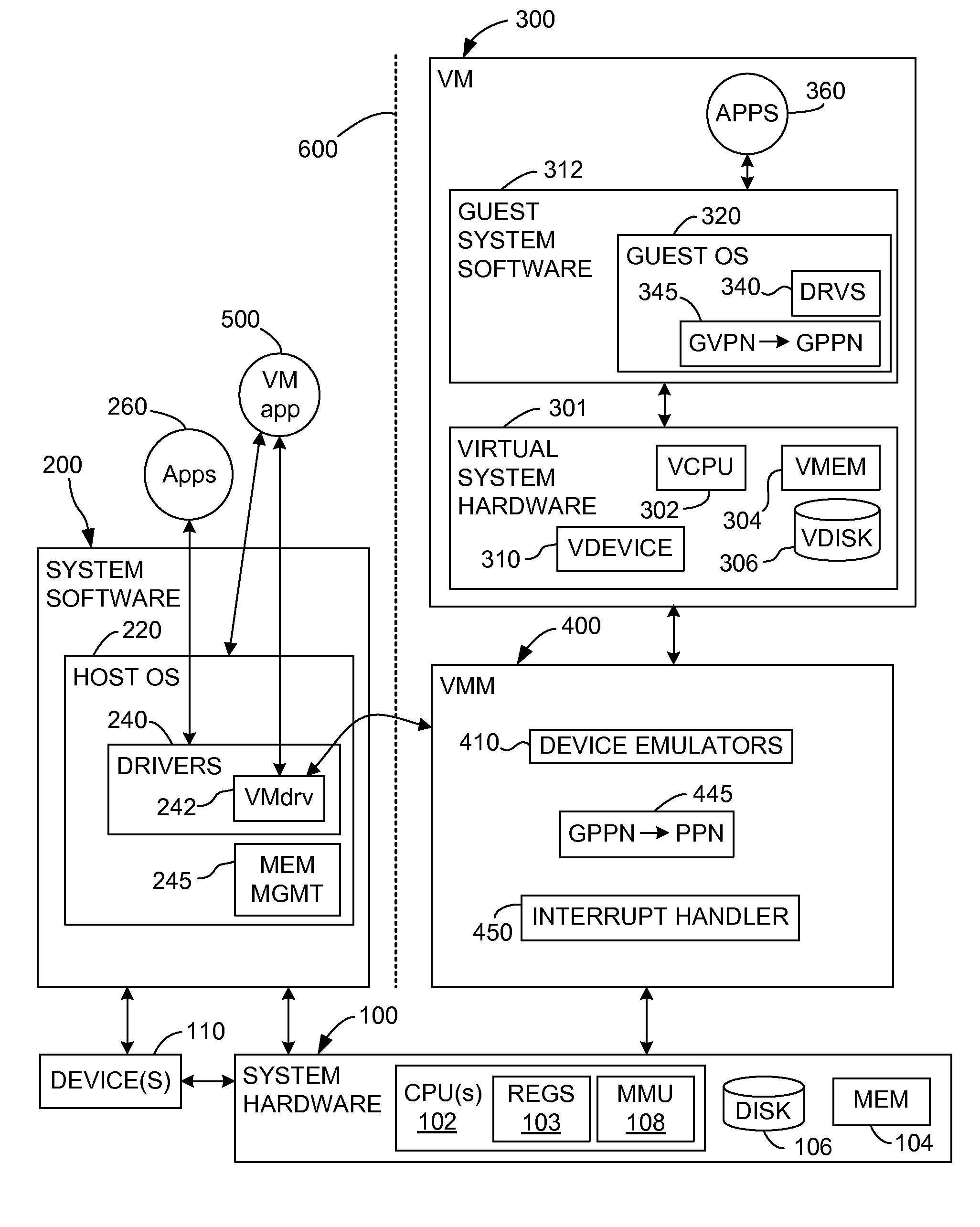
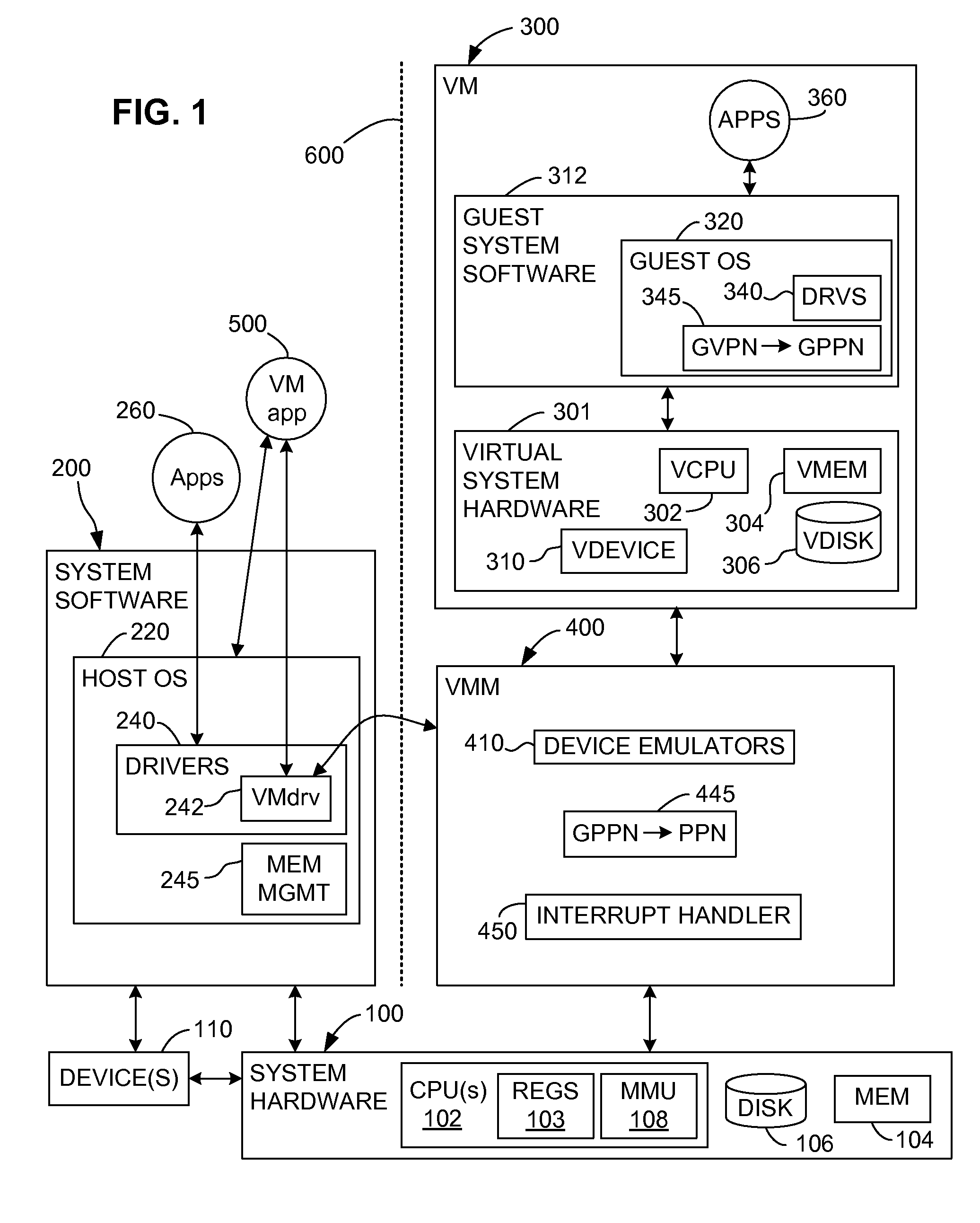
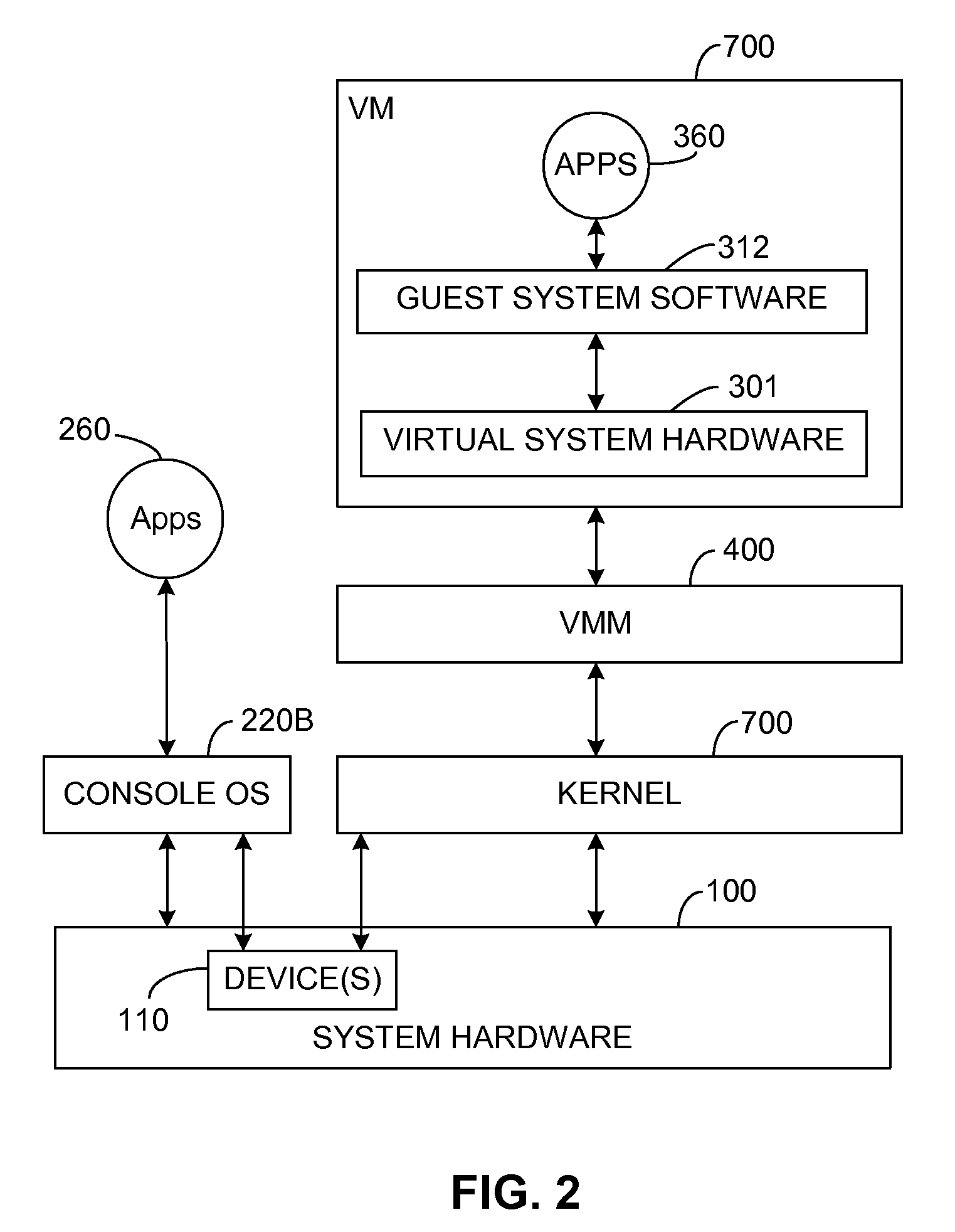
Switching between multiple software entities using different operating modes of a processor in a computer system
ActiveUS7478388B1Restoring contextSoftware simulation/interpretation/emulationMemory systemsLong modeOperational system
A processor has multiple operating modes, such as the long / compatibility mode, the long / 64-bit mode and the legacy modes of the x86-64 microprocessor. Different software entities execute in different ones of these operating modes. A switching routine is implemented to switch from one operating mode to another and to transfer control from one software entity to another. The software entities may be, for example, a host operating system and a virtual machine monitor. Thus, for example, a virtual computer system may comprise a 64-bit host operating system and a 32-bit virtual machine monitor, executing on an x86-64 microprocessor in long mode and legacy mode, respectively, with the virtual machine monitor supporting an x86 virtual machine. The switching routine may be implemented partially or completely in an identity-mapped memory page. Execution of the switching routine may be initiated by a driver that is installed in the host operating system of a virtual computer system.
Owner:VMWARE INC
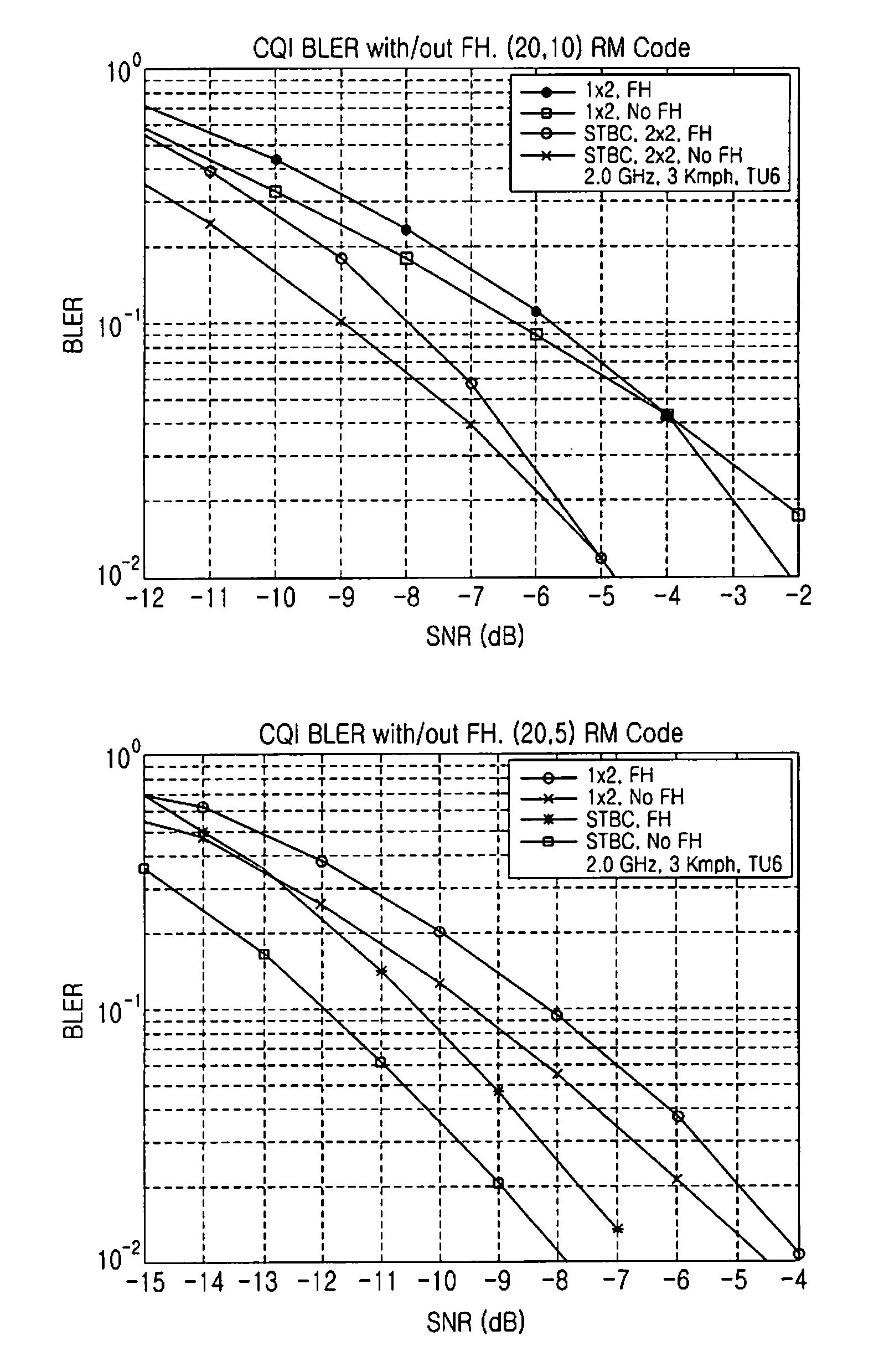
Selective application of frequency hopping for transmission of control signals
A Method and apparatus for selectively applying, by a User Equipment (UE), Frequency Hopping (FH) for a transmission of Uplink Control Information (UCI) signals in a Physical Uplink Control CHannel (PUCCH). The UE applies FH when the UCI is of a first type and does not apply FH when the UCI is of a second type. The UE applies FH when transmission diversity is not applied to the UCI transmission and does not apply FH when transmission diversity is applied to the UCI transmission. UEs operating in a legacy mode do not apply FH to the UCI transmission while UEs operating with additional functionalities may apply FH to the UCI transmission according to the UCI type and the use of transmission diversity.
Owner:SAMSUNG ELECTRONICS CO LTD
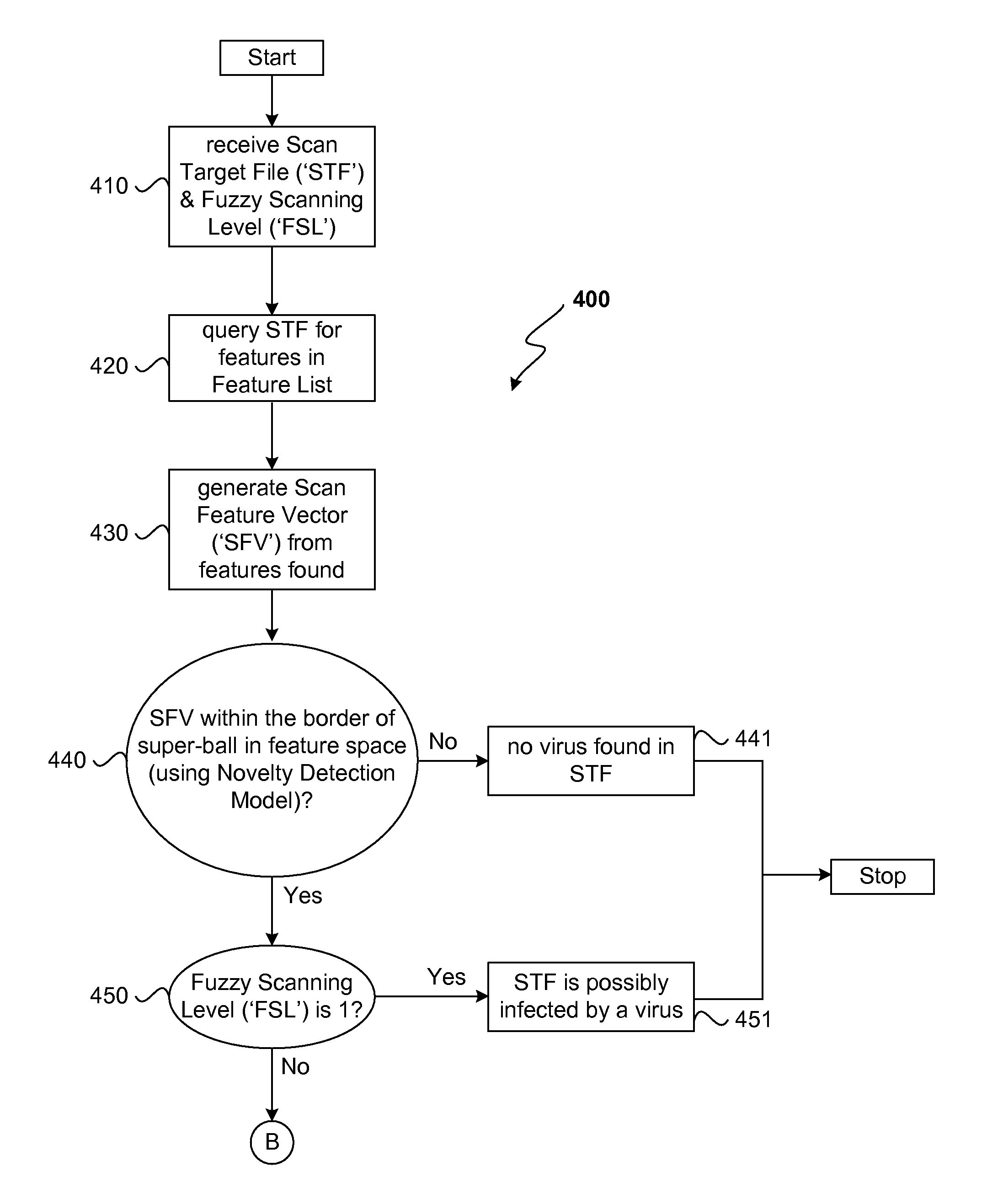
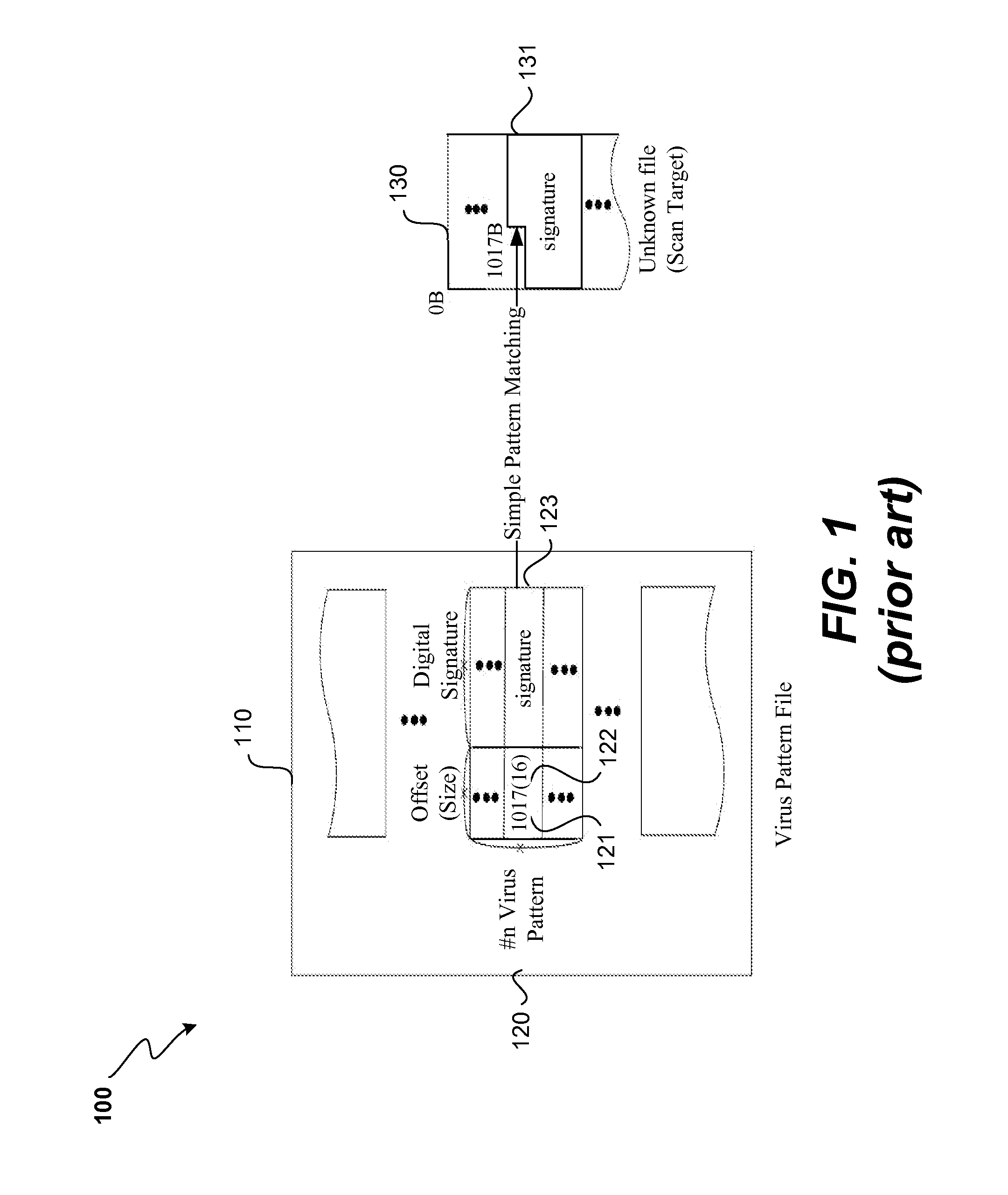
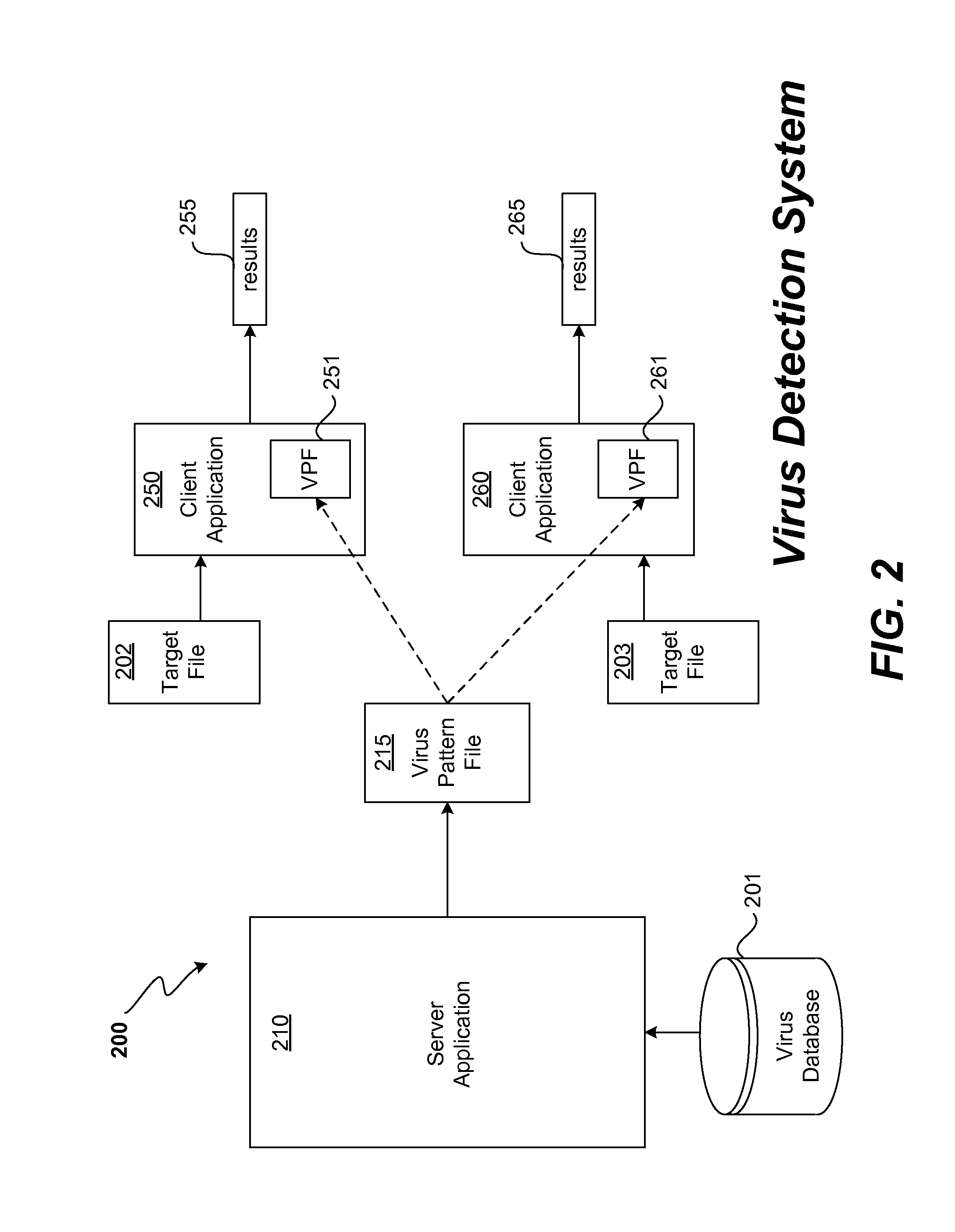
Two stage virus detection
ActiveUS8935788B1Improve efficiencyLess iterationMemory loss protectionUnauthorized memory use protectionPattern matchingPhases of clinical research
A two stage virus detection system detects viruses in target files. In the first stage, a training application receives a master virus pattern file recording all known virus patterns and generates a features list containing fundamental virus signatures from the virus patterns, a novelty detection model, a classification model, and a set of segmented virus pattern files. In the second stage, a detection application scans a target file for viruses using the generated outputs from the first stage rather than using the master virus pattern file directly to do traditional pattern matching. The results of the scan can vary in detail depending on a fuzzy scan level. For fuzzy scan level “1,” the existence of a virus is returned. For fuzzy scan level “2,” the grant virus type found is returned. For fuzzy scan level “3,” the exact virus name is returned. This invention provides a solution for the problems caused by traditional virus detection solution: slow scanning speed, big pattern file, big burden on computation resource (CPU, RAM etc.), as well as heavy pattern updating traffic via networks.
Owner:TREND MICRO INC
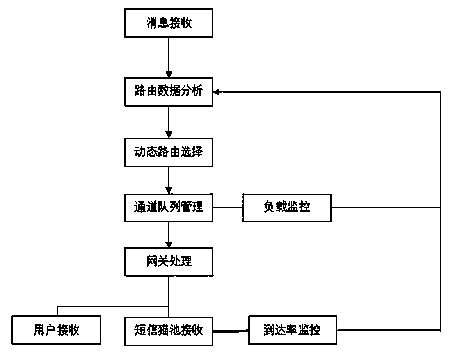
Method for establishing intelligence communication channels
InactiveCN103856963AReduce misjudgment of delivery rateReduce the possibility of human interventionWireless communicationModem deviceCommunications system
The invention provides a method for establishing intelligence communication channels. According to the method, a channel list and a route list in a communication system are maintained, the current status of the channels is detected, the queue loading situation is monitored and arrival rates of the channels are analyzed, so the optimum route and the optimum sending path of a system at current can be selected dynamically. The phenomena that fixed route rules and channel faults can not be found timely in traditional communication models, and manual detection, analysis and interference are needed are avoided. In addition, the method that the arrival rates are monitored through a modem pool is innovated, so the defect that the arrival rates can not be fed back timely due to the fact that status reports are limited to user cell phones and network situations in traditional modes is overcome. By the adoption of the model, the manual maintenance cost is lowered, the speed for exception handling is increased, the maintenance difficulty is reduced, the sending efficiency is improved, and waste of channel resources is reduced.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
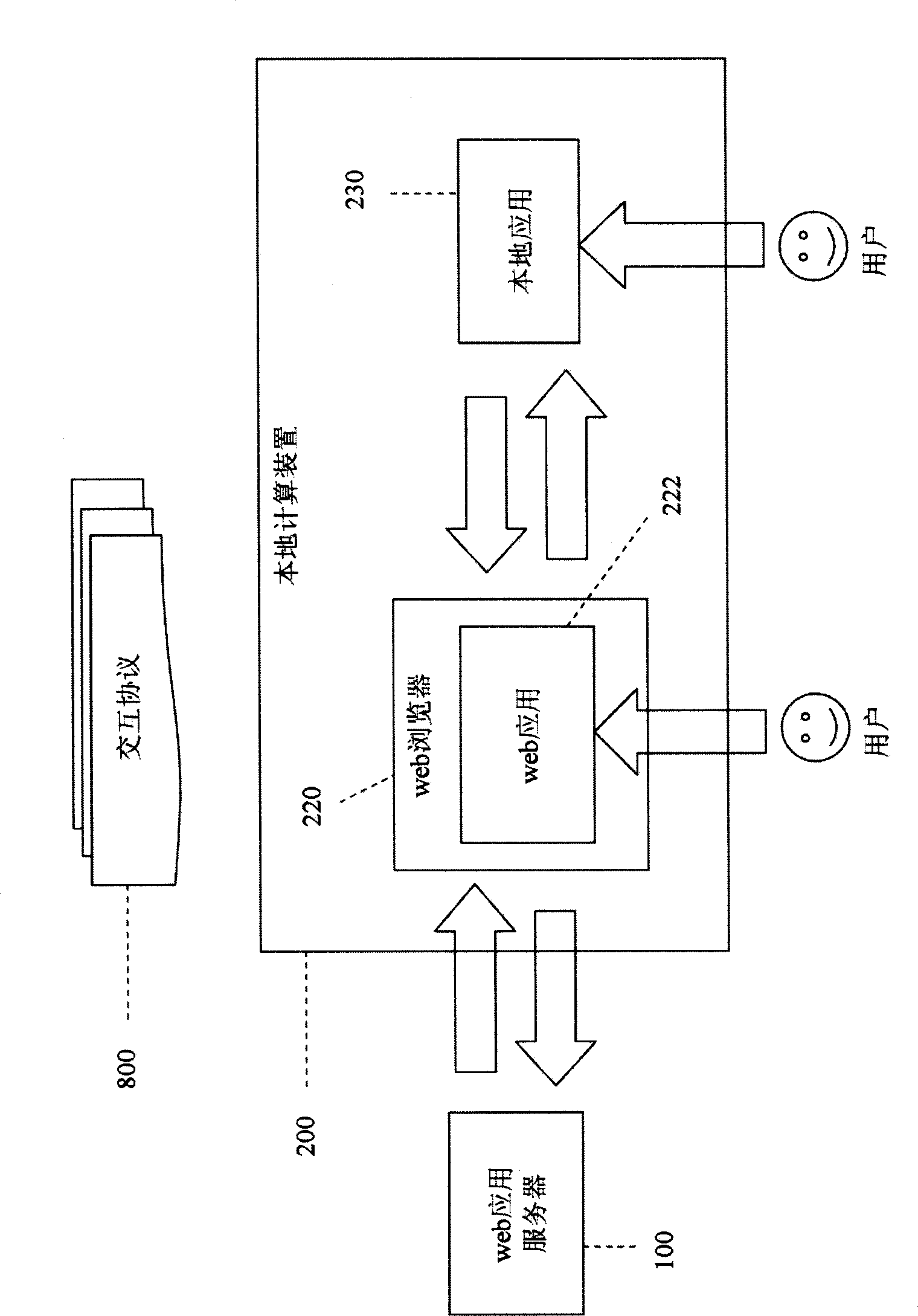
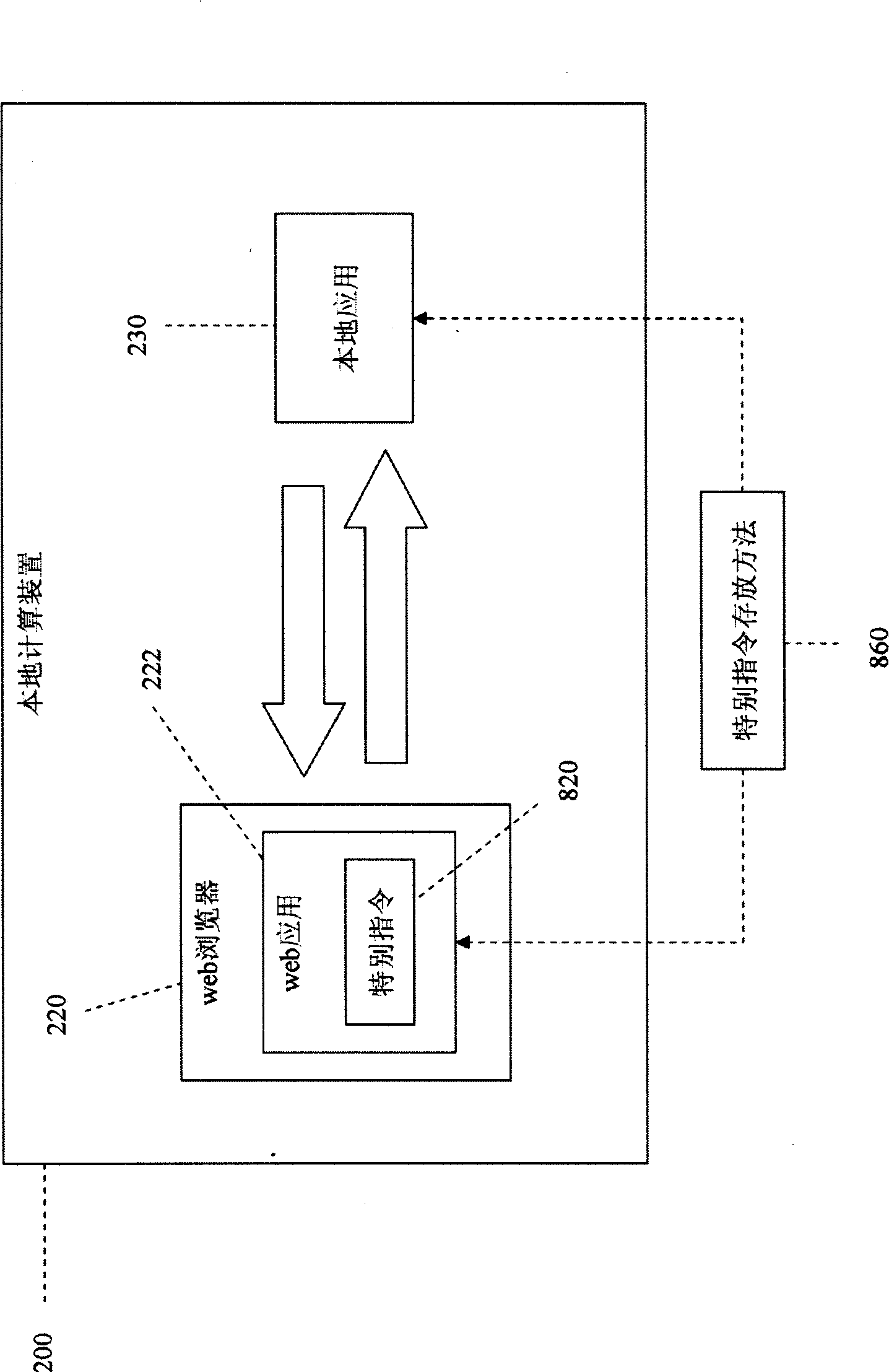
Novel web application and local application interaction mode
The invention provides a novel interactive mode of web application and local application. The novel mode breaks through the traditional mode in which the web application directly calls ActiveX control or Java Applet installed on a local calculating device by a script when the browser is in operation and adopts a mode that the local application drives HTML document object model (DOM) of the web application in the web browser according to requirements of the web application to realize the interaction between the web application and the local application, thereby breaking through limits brought by the traditional mode.
Owner:CHONGQING ANRUAN INFORMATION TECH
Switching between multiple software entities using different operating modes of a processor
ActiveUS20090100250A1General purpose stored program computerMultiprogramming arrangementsVirtualizationSoftware engineering
The computer program includes a virtualization software that is executable on the new processor in the legacy mode. The new processor includes a legacy instruction set for a legacy operating mode and a new instruction set for a new operation mode. The switching includes switching from the new instruction set to the legacy instruction set and switching paging tables. Each of the new operating mode and the legacy operating mode has separate paging tables. The switch routine is incorporated in a switch page that is locked in physical memory. The switch page has a first section to store a part of switching instructions conforming to the new instruction set and a second section to store another part of the switching instructions conforming to the legacy instruction set.
Owner:VMWARE INC
Method for detecting network nonlicet nodes by adjacent supervise
This invention belongs to computer safety field, which is used to test network illegal points and uses adjacent points to test mechanism of network identification servo and internet computer legal property to improve traditional mode passive identification to send requirement data not reliable for monitoring service test.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
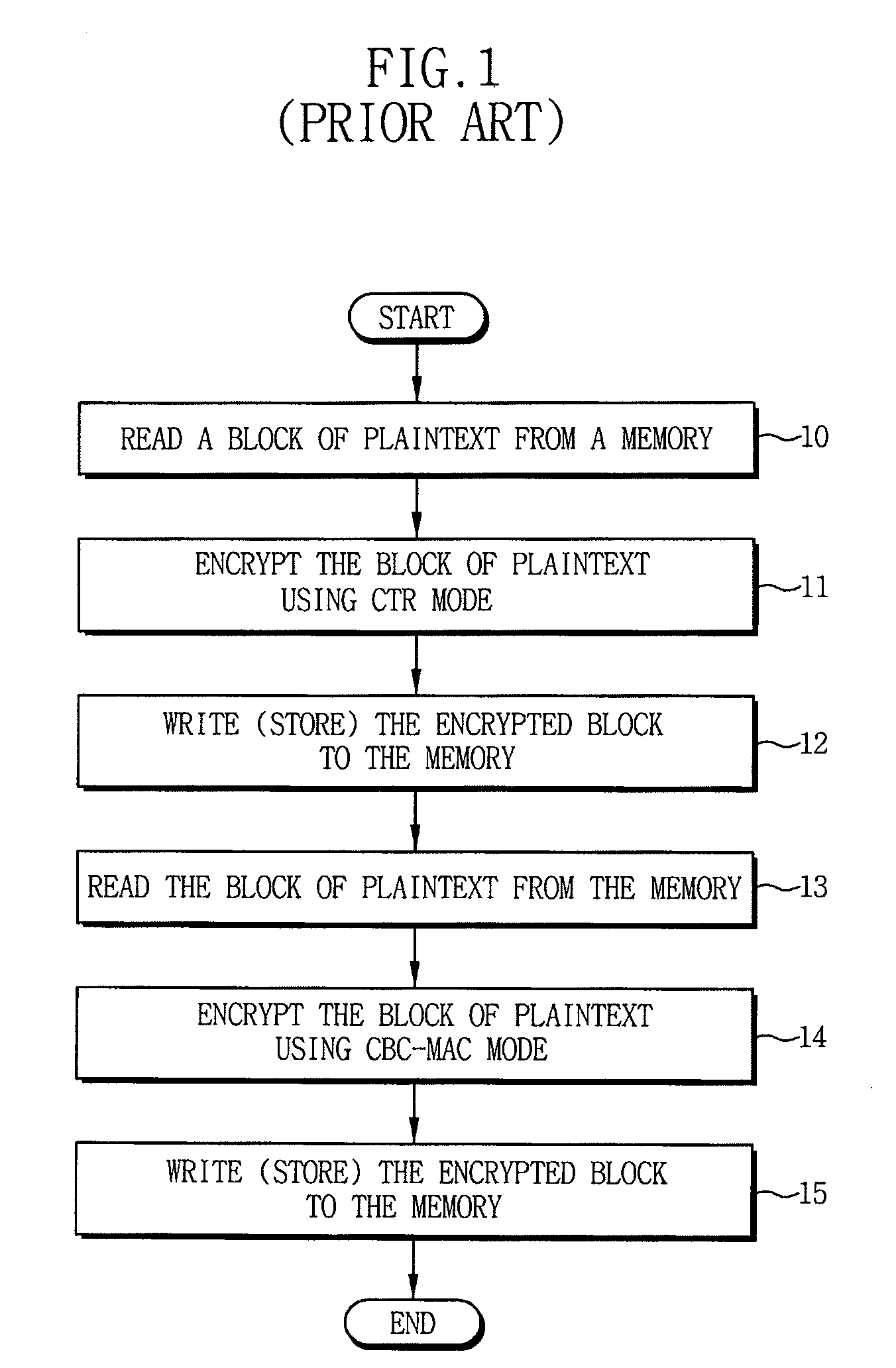
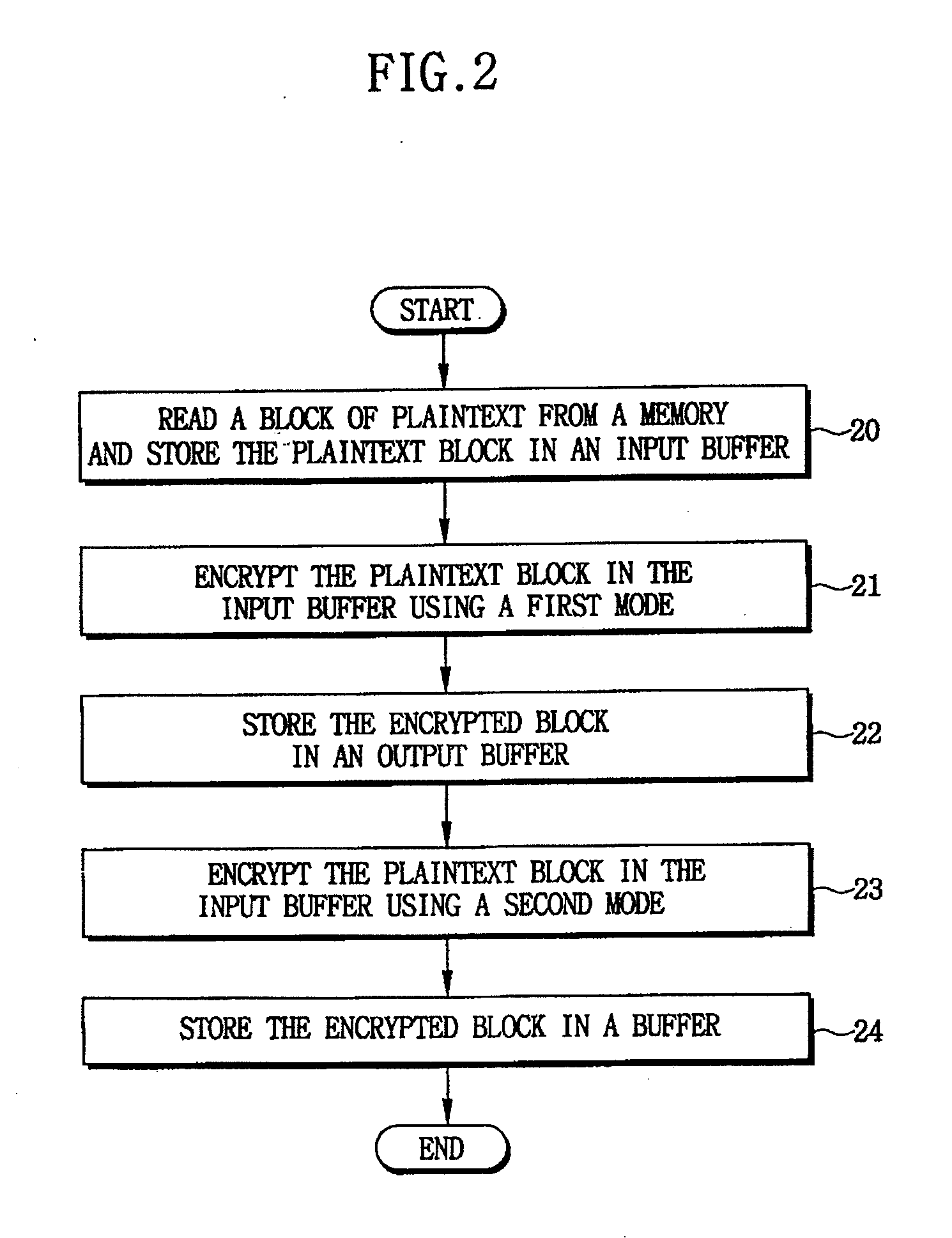
Cryptographic systems and methods supporting multiple modes
InactiveUS20080240424A1Reduce in quantityIncrease ratingsEncryption apparatus with shift registers/memoriesSecret communicationPlaintextCiphertext
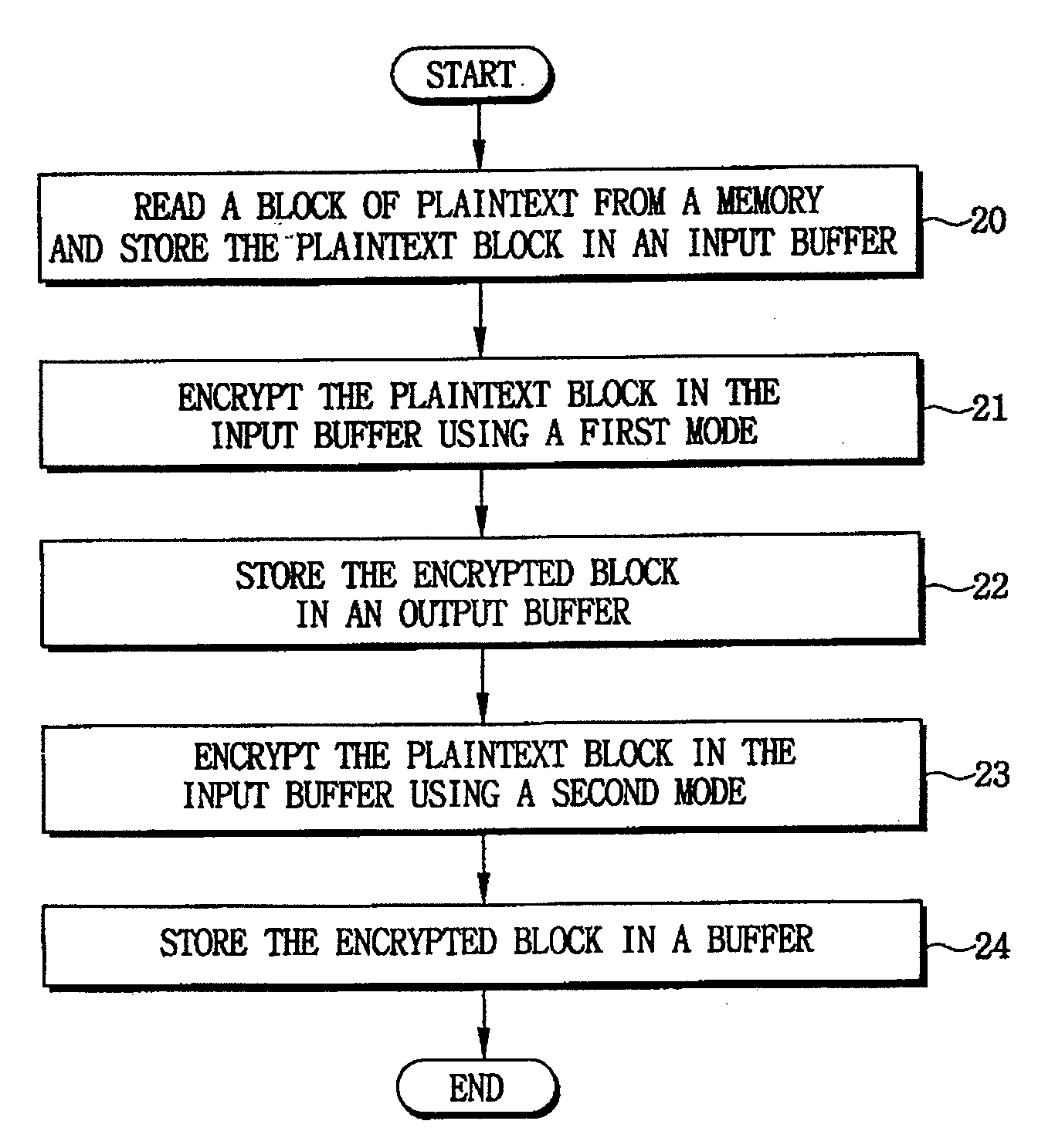
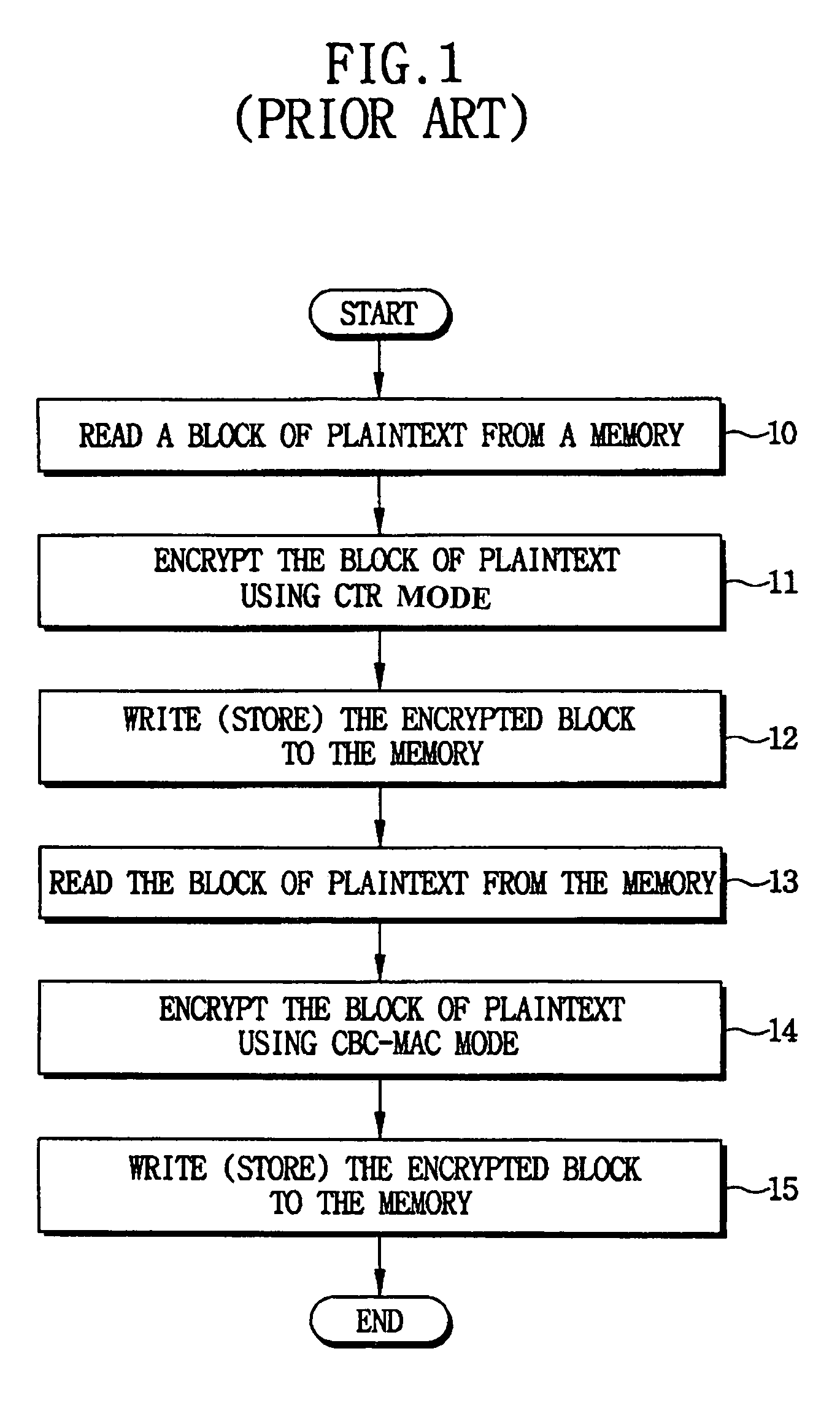
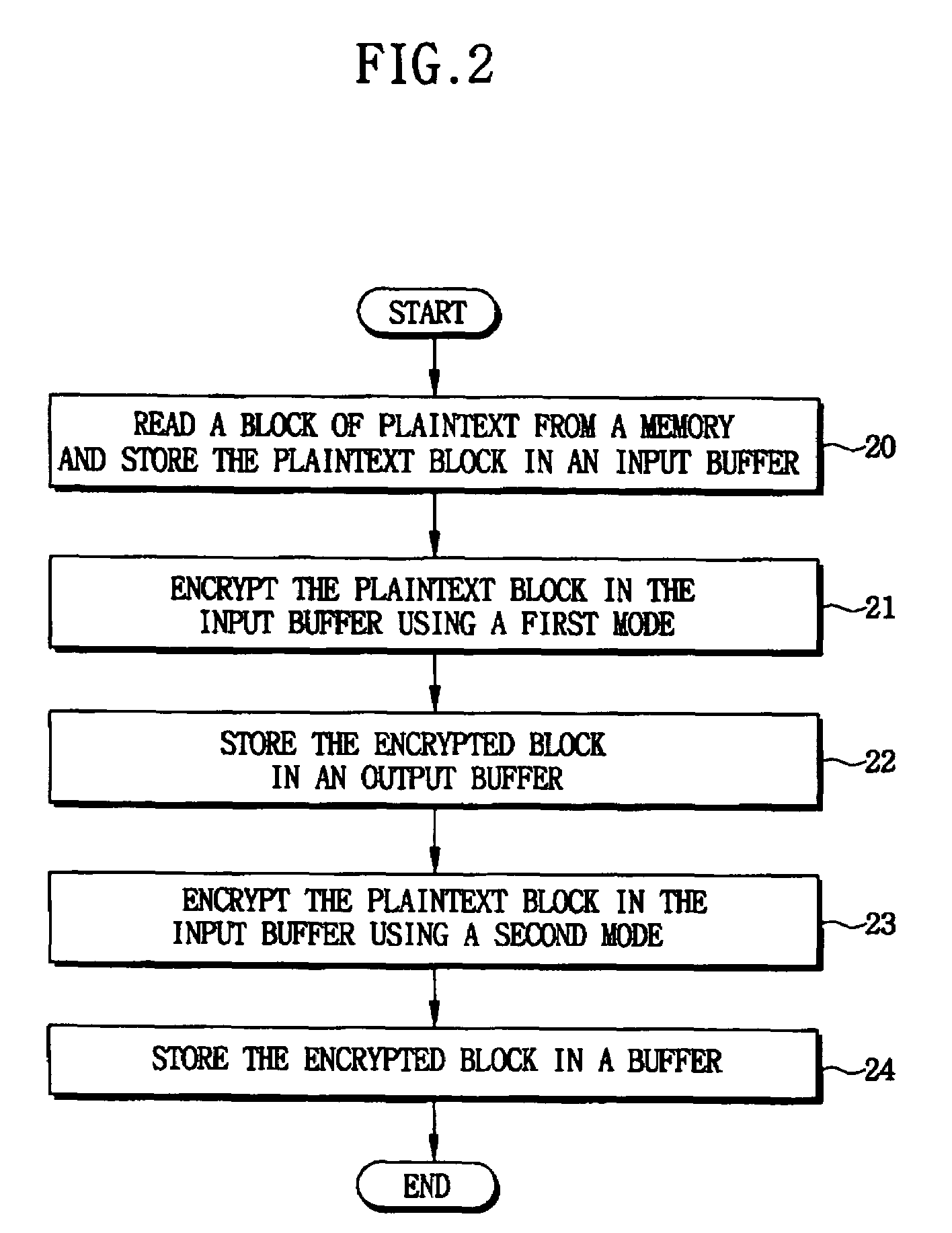
Cryptographic systems and methods that support multiple modes of operation, such as CBC, CTR and / or CCM modes. In one aspect, a method for encrypting data includes reading a plaintext data block from a memory, storing the plaintext data block in an input buffer, encrypting the plaintext data block in the input buffer using a first mode to generate a first ciphertext, storing the first ciphertext in an output buffer, encrypting the plaintext data block in the input buffer using a second mode to generate a second ciphertext. For example, in a CCM mode of operation wherein the first mode is a CTR (counter) mode and the second mode is a CBC (cipher block chaining) mode, the block of plaintext that is initially read from memory and stored in the data input register is applied to both the CTR and CBC modes, thereby reducing a number memory read operations as in conventional CCM modes.
Owner:SAMSUNG ELECTRONICS CO LTD
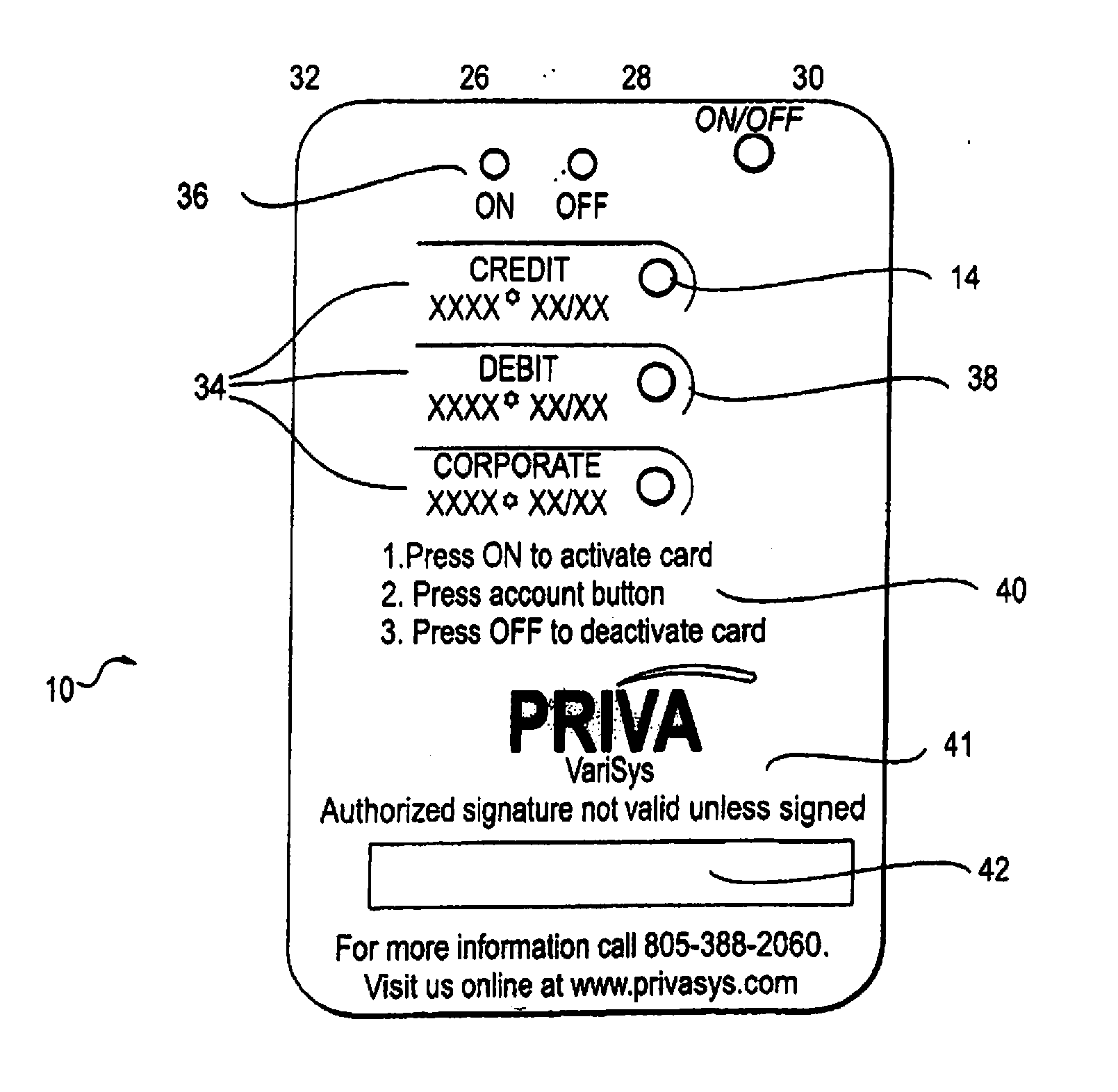
Electronic Financial Transaction Cards and Methods
ActiveUS20120205451A1Alter functionalitySensing record carriersRecord carriers used with machinesElectricityNetwork packet
An electronic card has a card body with a power source electrically coupled to a general processor which is electrically coupled to a secure processor and a broadcaster. At least one sensor sends a signal to the general broadcaster when a physical act of swiping the card body through a legacy magnetic stripe reader having a magnetic read head commences. The card is usable as a legacy mode Smart card, the broadcaster is operable to broadcast a transaction specific data packet so that it is read by the magnetic stripe reader, and the secure processor is an ISO 7816 compliant processor.
Owner:DFS SERVICES
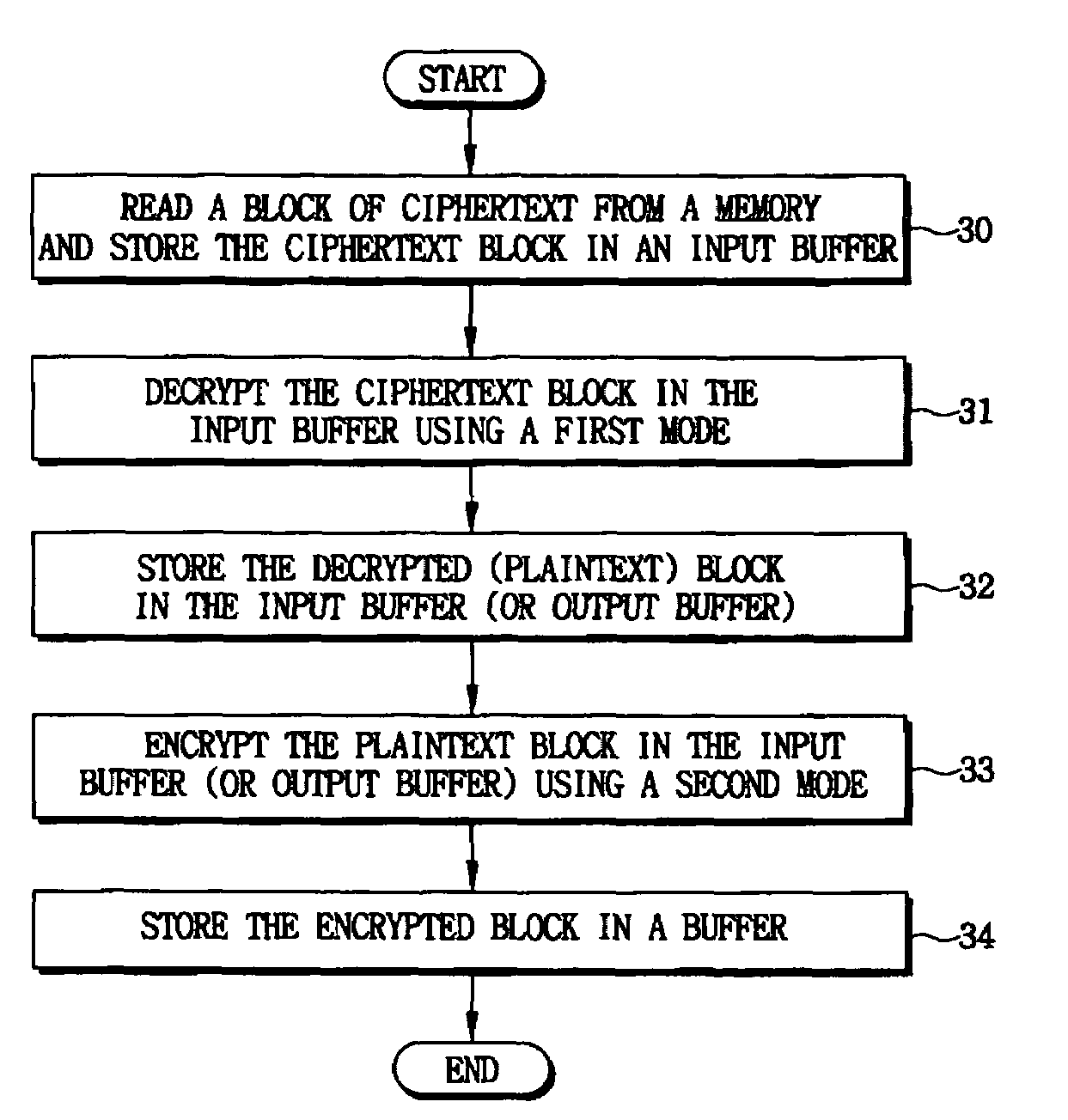
Cryptographic systems and methods supporting multiple modes
ActiveUS7336783B2Increased encryption/decryption rateReduce in quantityEncryption apparatus with shift registers/memoriesSecret communicationPlaintextCiphertext
Cryptographic systems and methods that support multiple modes of operation, such as CBC, CTR and / or CCM modes. In one aspect, a method for encrypting data includes reading a plaintext data block from a memory, storing the plaintext data block in an input buffer, encrypting the plaintext data block in the input buffer using a first mode to generate a first ciphertext, storing the first ciphertext in an output buffer, encrypting the plaintext data block in the input buffer using a second mode to generate a second ciphertext. For example, in a CCM mode of operation wherein the first mode is a CTR (counter) mode and the second mode is a CBC (cipher block chaining) mode, the block of plaintext that is initially read from memory and stored in the data input register is applied to both the CTR and CBC modes, thereby reducing a number memory read operations as in conventional CCM modes.
Owner:SAMSUNG ELECTRONICS CO LTD
Multi-satellite remote sensing data processing system
InactiveCN105094982AImprove efficiencyImplementation of load balancing schedulingProgram initiation/switchingResource allocationHandling systemSatellite remote sensing
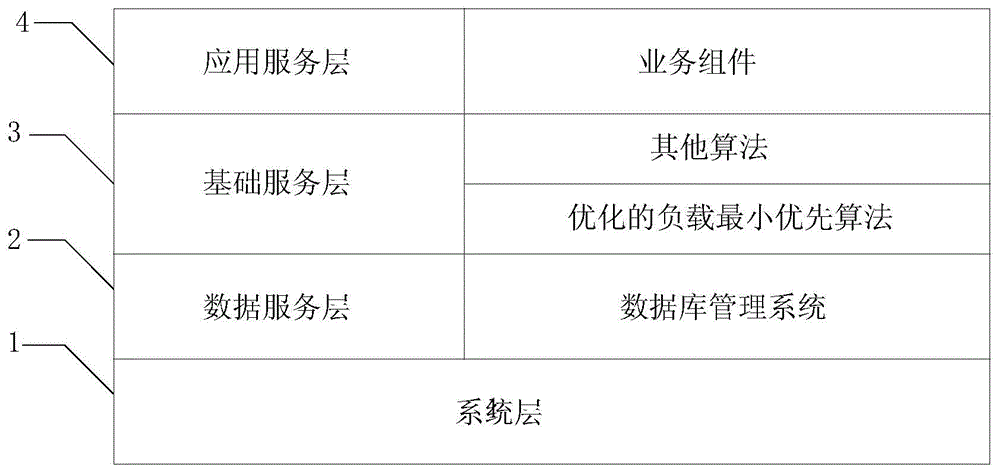
The present invention discloses a multi-satellite remote sensing data processing system, comprising: a system layer, a data service layer, a basic service layer and an application service layer, wherein the system layer is used for providing a software supporting environment; the data service layer is used for storing remote sensing data and configuration information; the basic service layer is used for controlling different resource nodes to process remote sensing data of different satellites by a load balancing scheduler according to a scheduling algorithm; and the application service layer is used for performing task scheduling and process control of the multi-satellite remote sensing data by a service component and the load balancing scheduler of the basic service layer. Adoption of the multi-satellite remote sensing data processing system solves the problem of establishing a plurality of sets of processing systems for a plurality of satellites in a conventional mode and a load balancing mechanism of multi-task scheduling is provided.
Owner:SPACE STAR TECH CO LTD
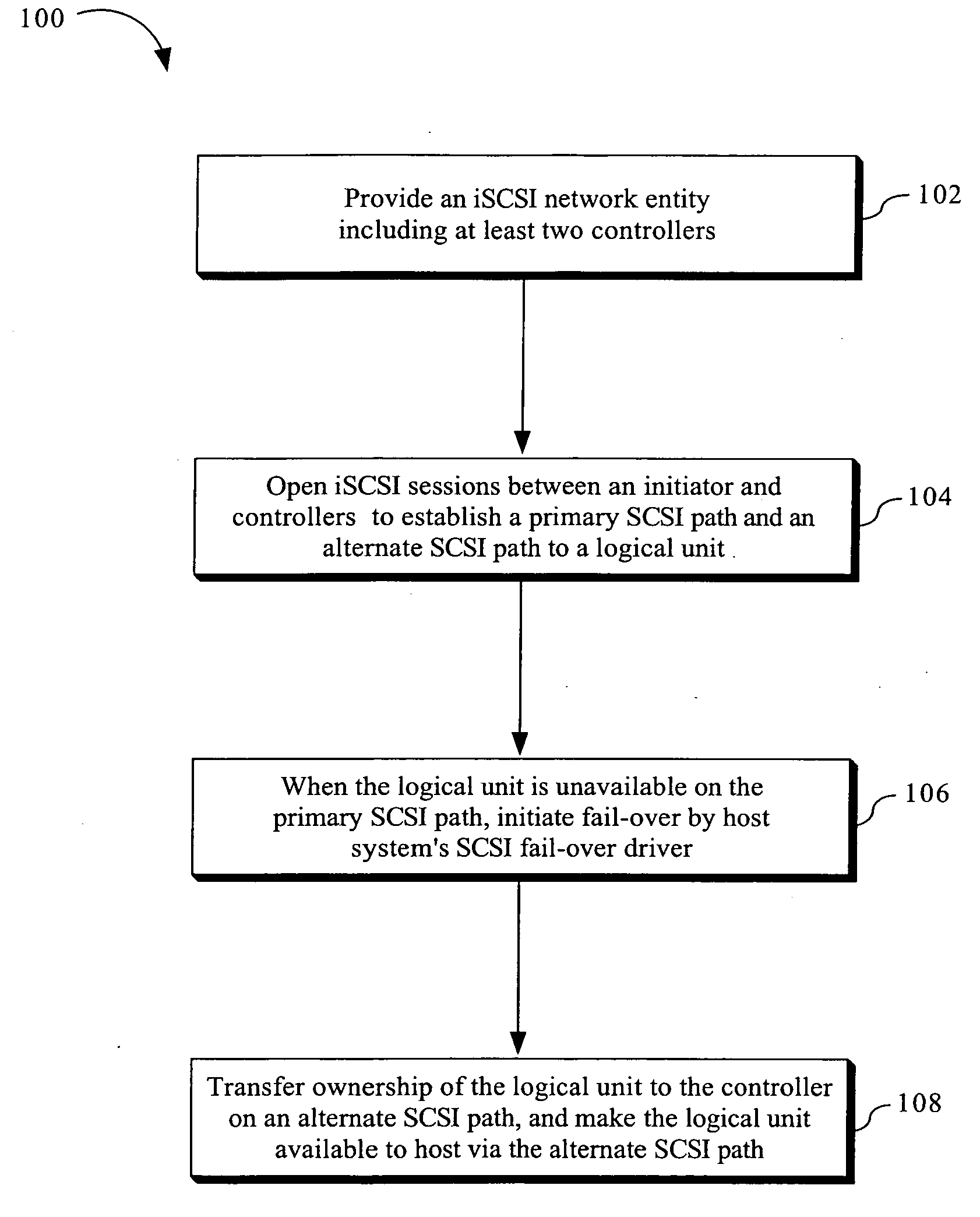
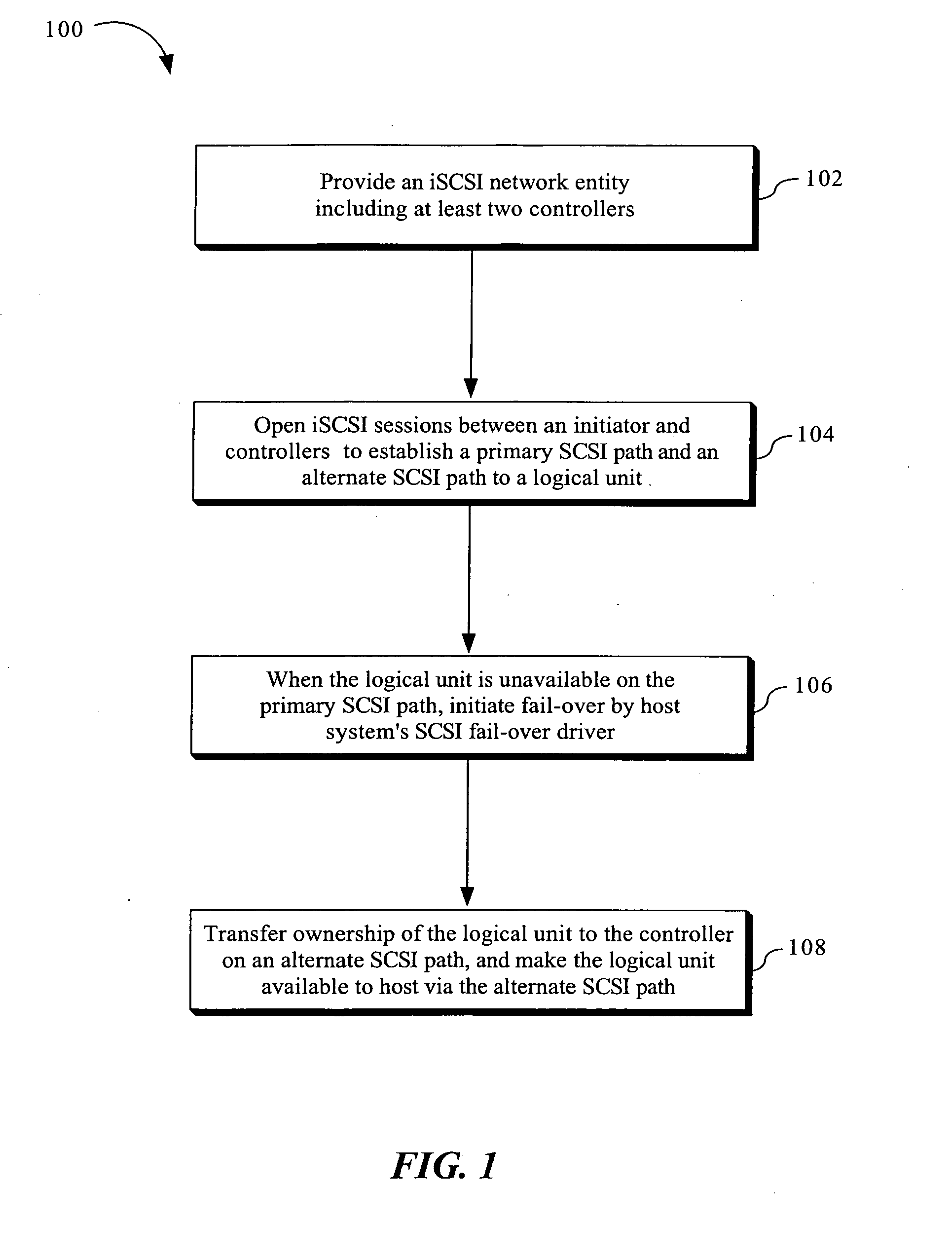
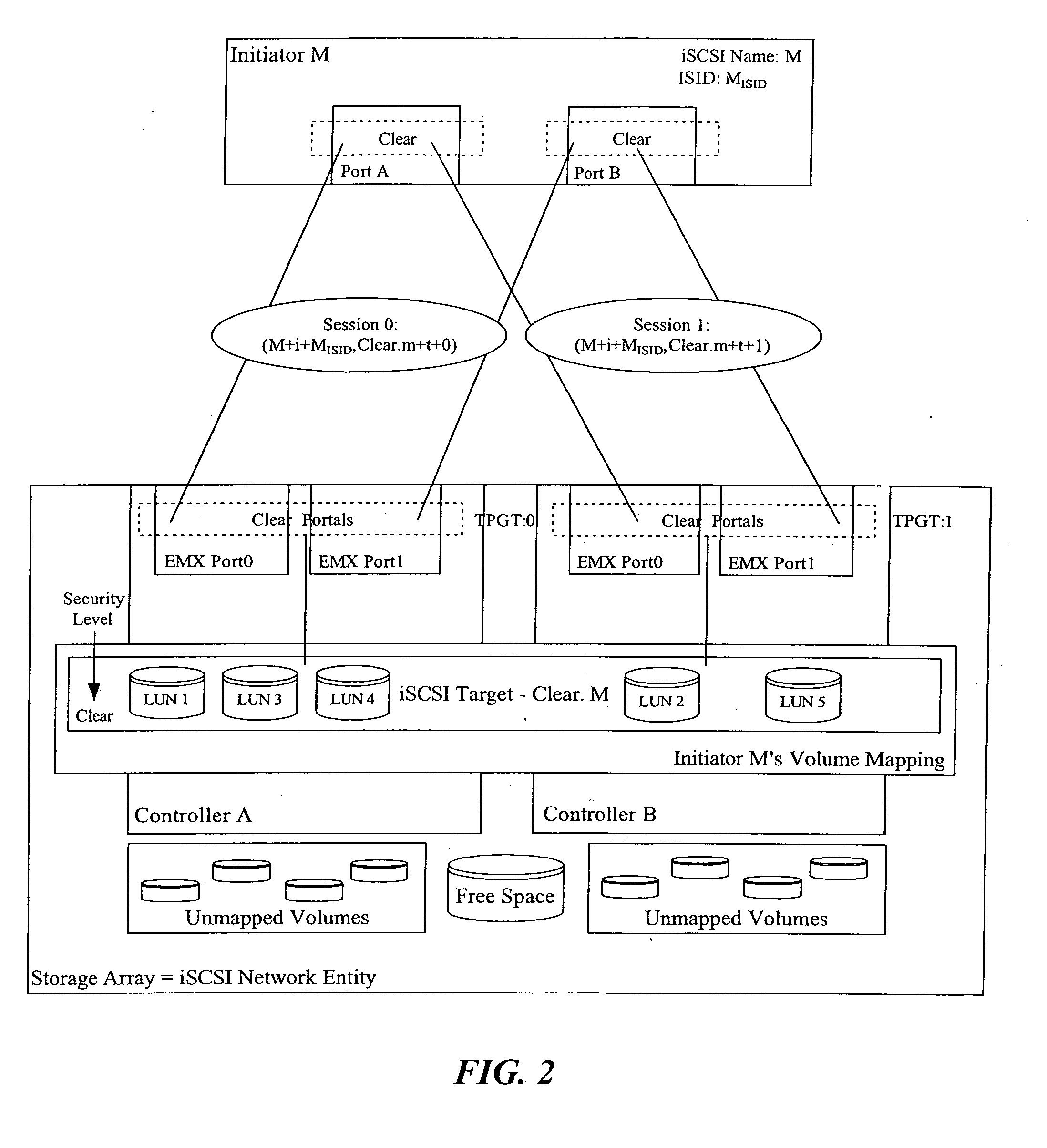
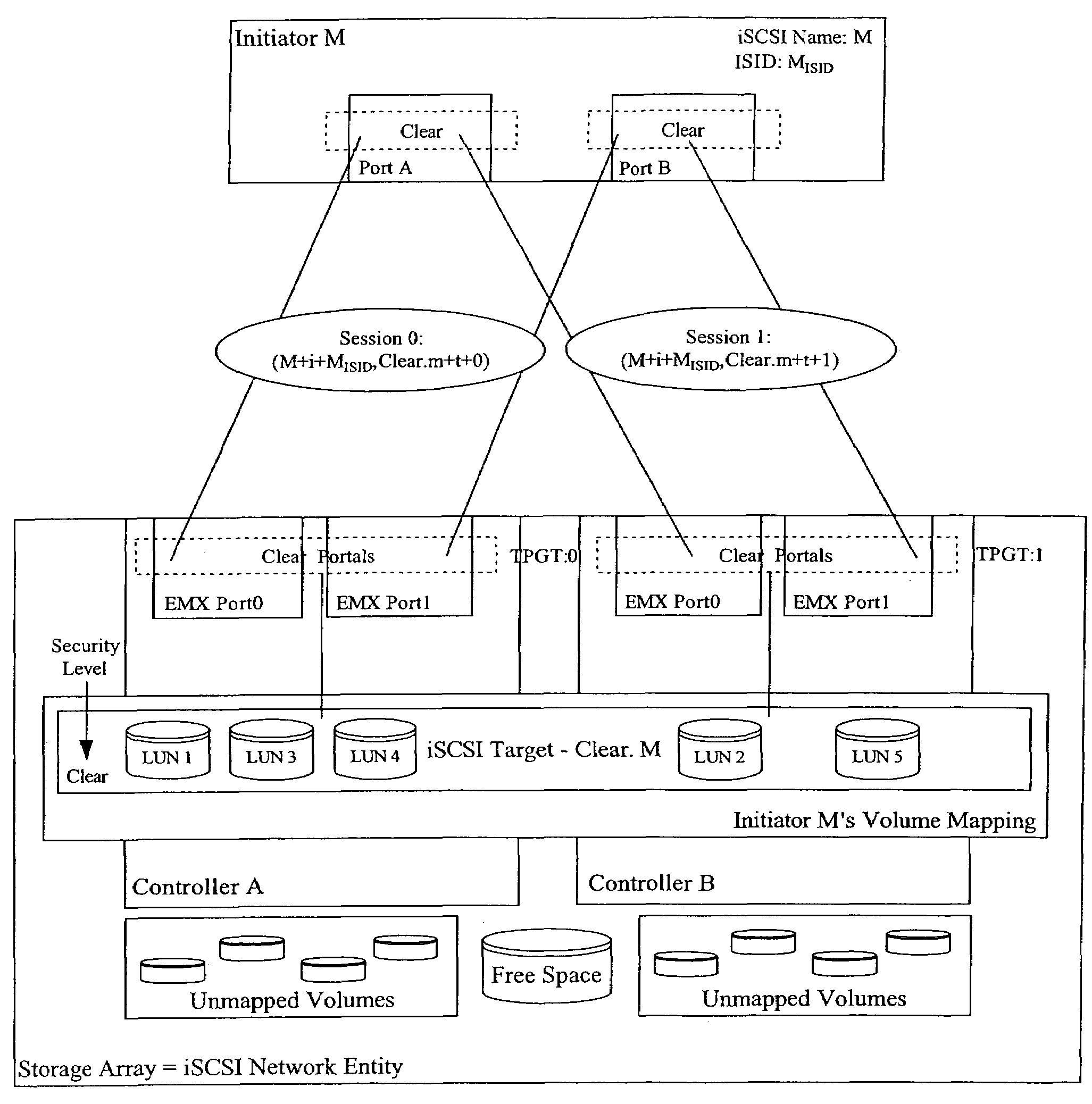
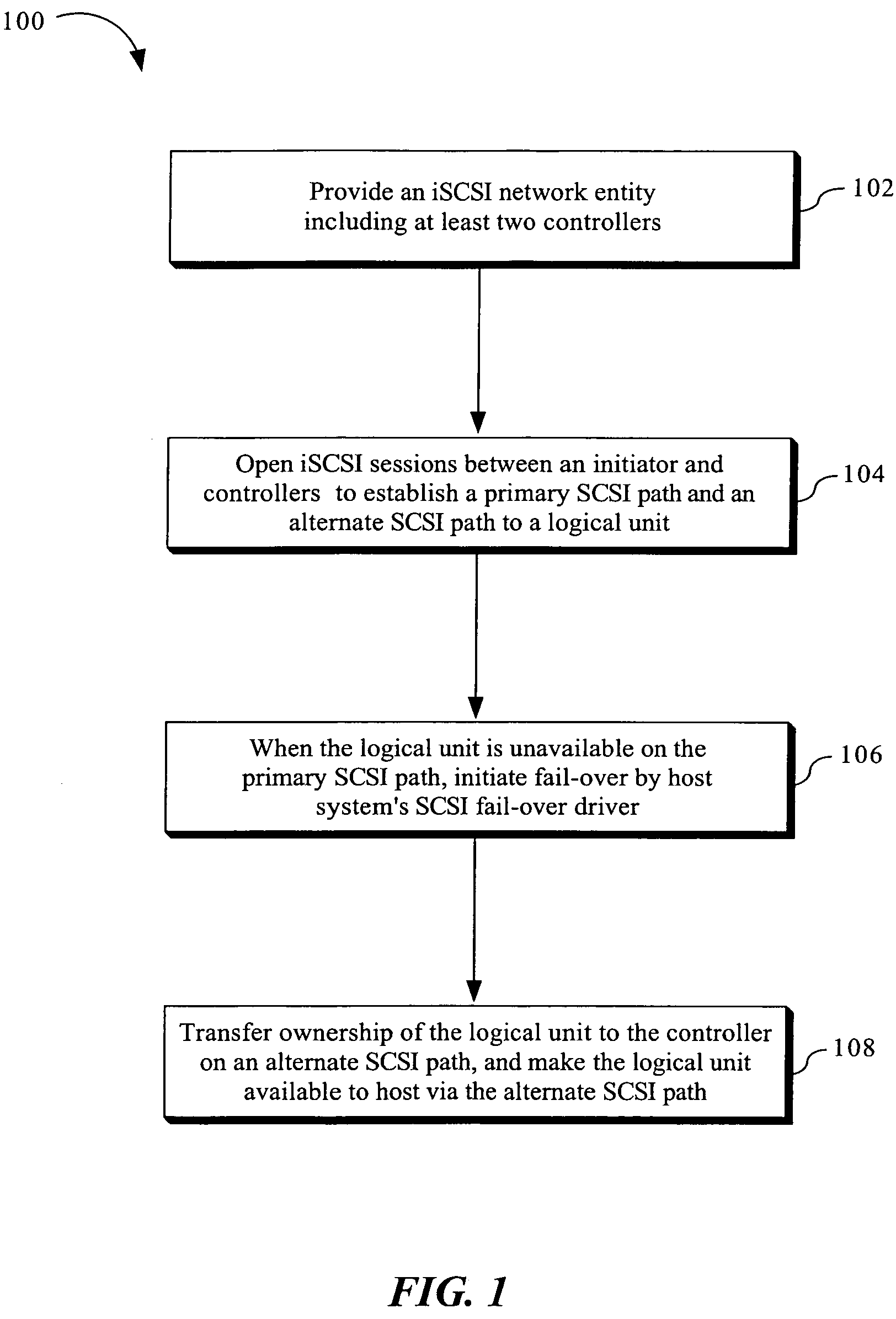
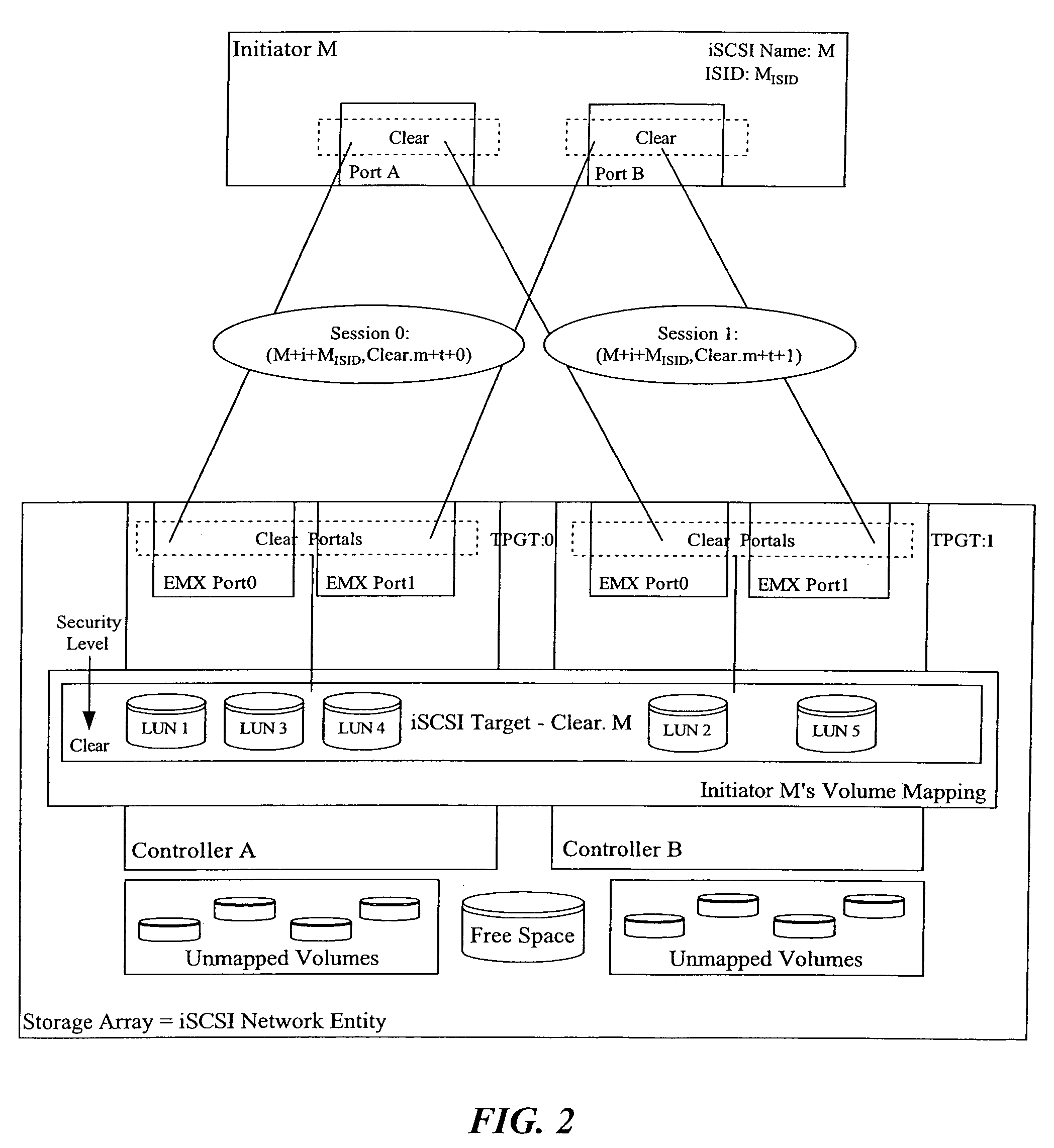
Method and apparatus for supporting legacy mode fail-over driver with ISCSI network entity including multiple redundant controllers
The invention is directed to a method and apparatus for supporting legacy mode fail-over drivers with an iSCSI network entity including multiple redundant controllers. In an exemplary aspect of the present invention, to support legacy mode fail-over drivers with an iSCSI network entity including multiple redundant controllers, the following configuration constraints may be placed on the iSCSI network entity and its iSCSI configuration: (1) the network device need have two or more redundant controllers; (2) the portals on each controller may or may not be formed into portal groups; (3) the portal groups may not span controllers (i.e., the target portal groups are limited in scope to a single controller); (4) the same iSCSI target name need be exported by all redundant controllers (i.e., the targets span all controllers of the iSCSI network entity, making the LUNs available to all controllers); (5) the target portal group numbers on the redundant controllers need have unique target portal group tags (i.e., all target portal group tags are unique across all portal groups in the iSCSI network entity. However, the target portal group tags do not need to be unique for different iSCSI targets); and (6) all targets are available from at least one target portal group on each controller. In addition, the initiator may use a single ISID for all sessions, use a different ISID for a different session, or the like. The present configuration constraints may enable the normal behavior of the legacy mode SCSI driver to locate and use redundant SCSI paths to the SCSI devices on the iSCSI target.
Owner:NETWORK APPLIANCE INC
Method of controlling computer random procedure and its peripheral equipment by using hand mobile equipment
InactiveCN1794212AImprove the office environmentIncrease profitRadio/inductive link selection arrangementsElectric digital data processingComputer usersTerminal equipment
This invention discloses a method for carrying out information interaction with fixed digital terminal devices by cordless or radio handheld mobile devices aiming at solving the shortcoming of the functions of the current personal used fixed digital terminal and display devices including input and output devices of sounds and images and they can be separated physically, in which, computer users can break away from the traditional mode of connecting to the host computer by signal lines and interact in the wireless mode and control the behavior of the host computer and its surrounding devices to improve the office environment.
Owner:王宏源
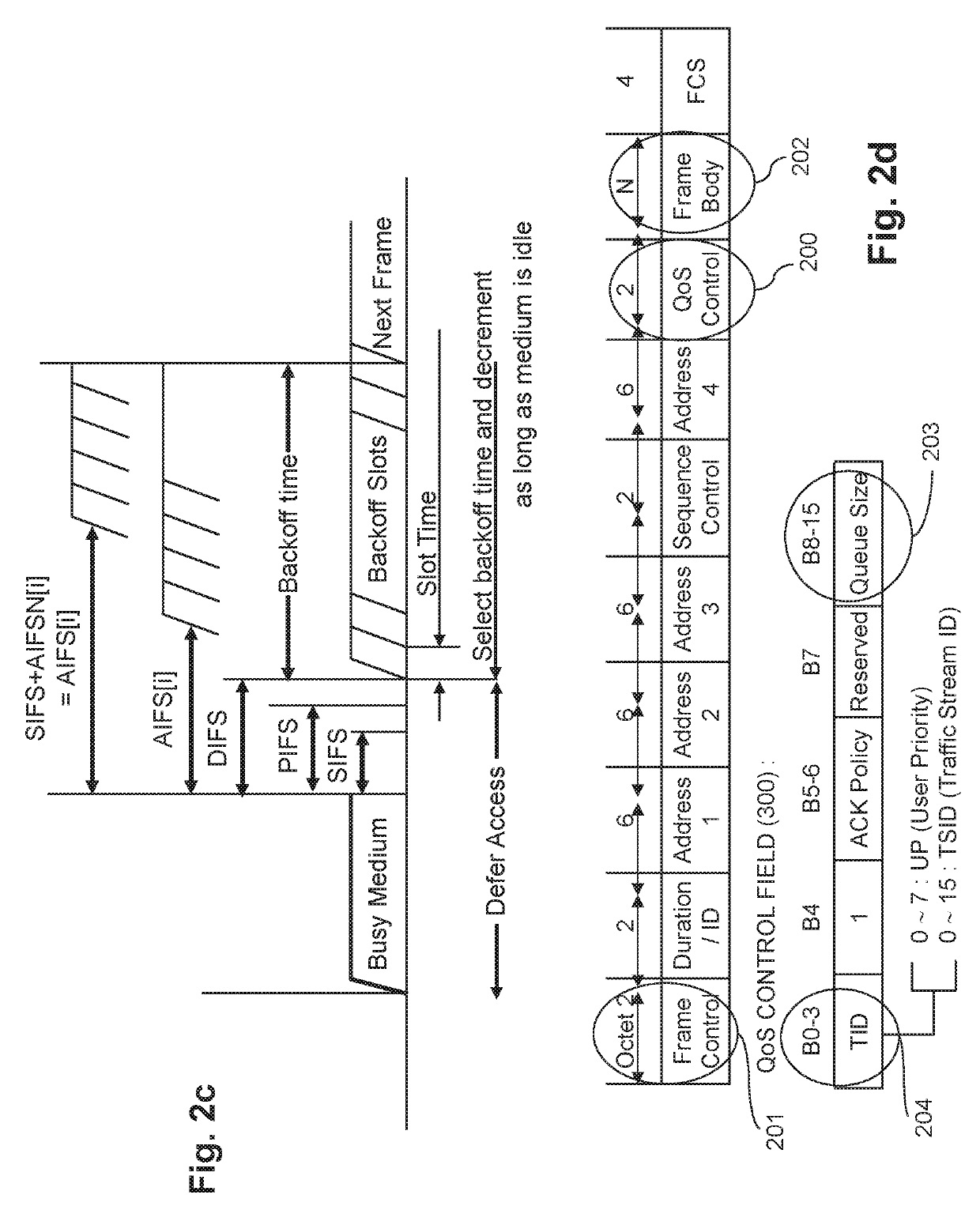
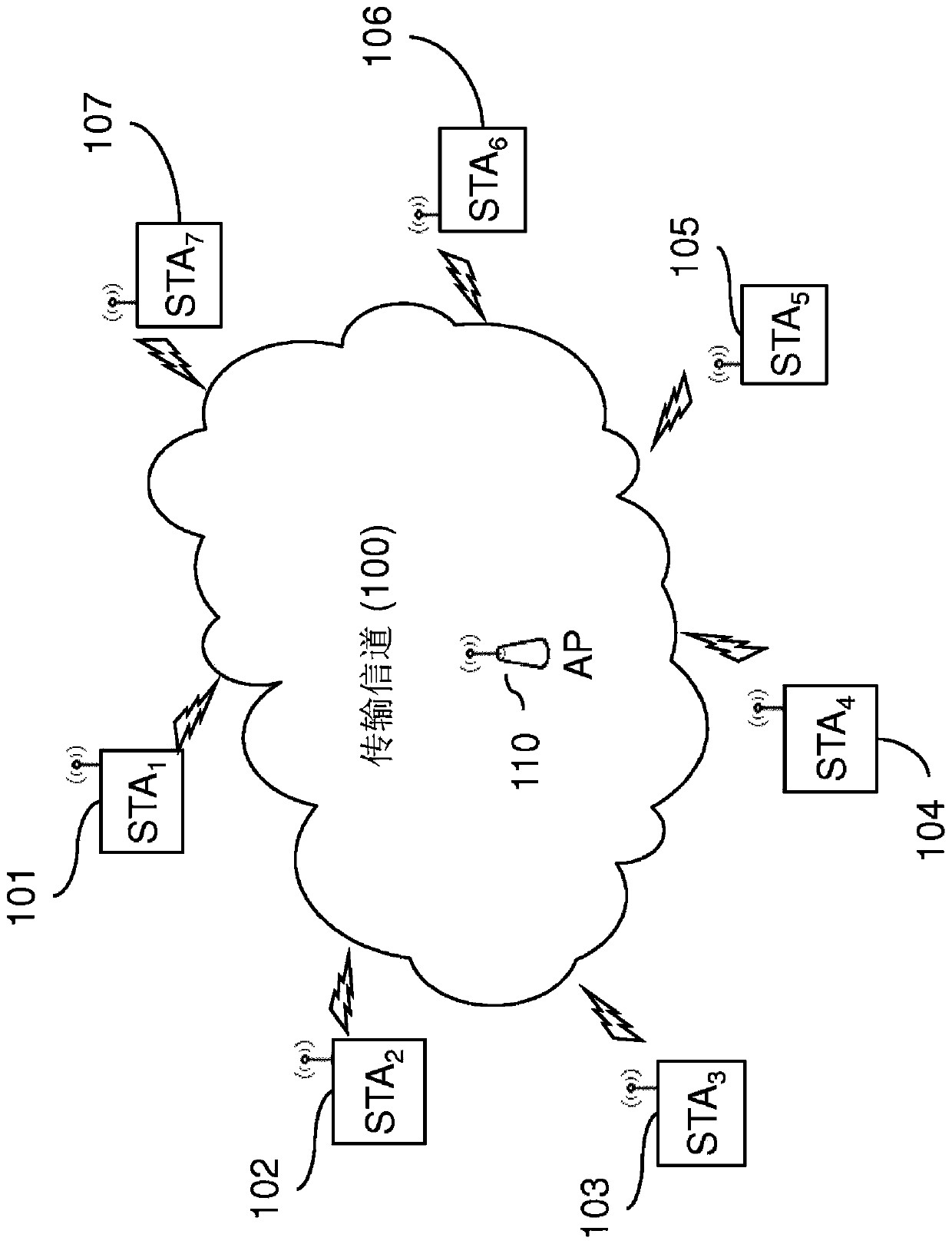
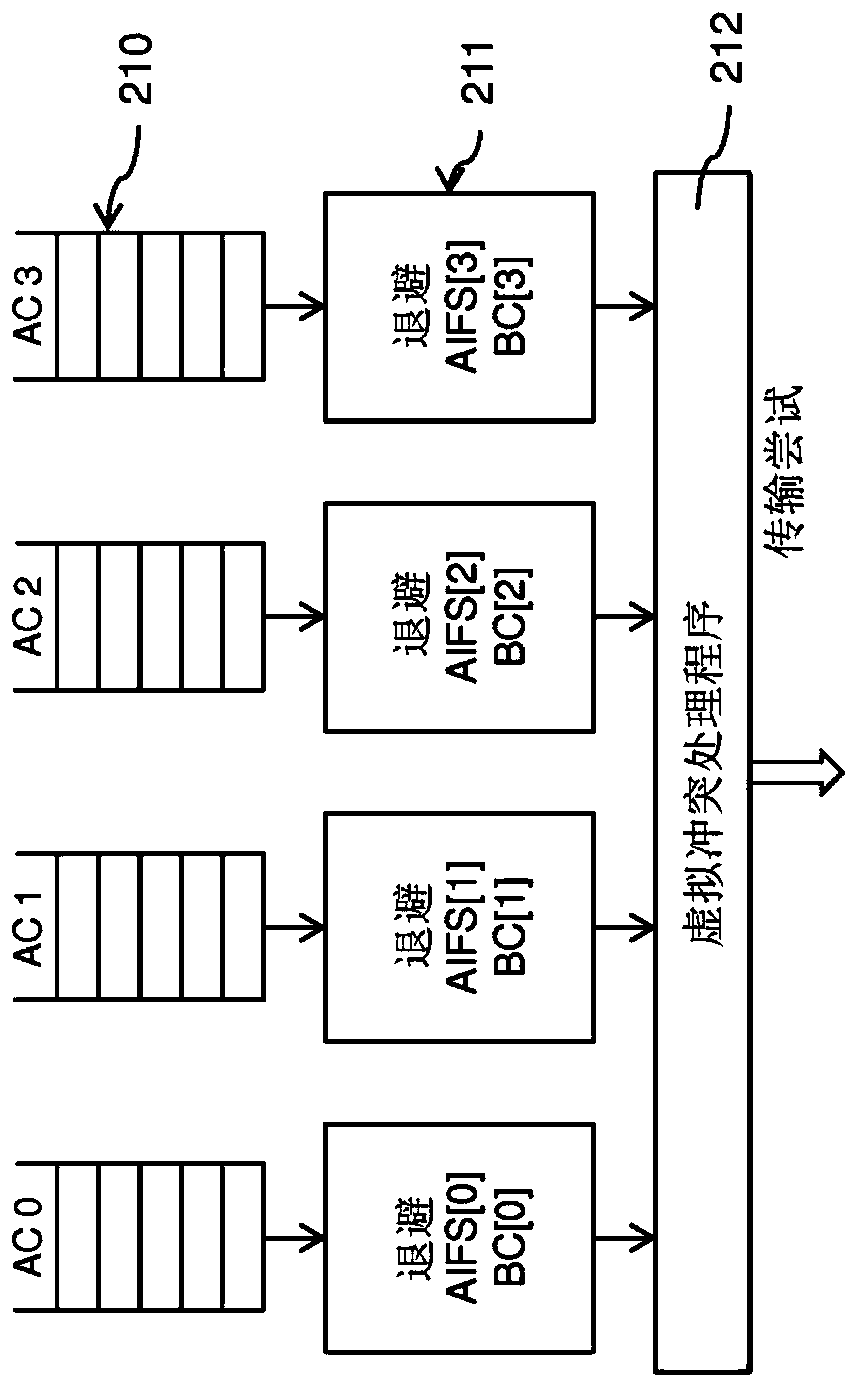
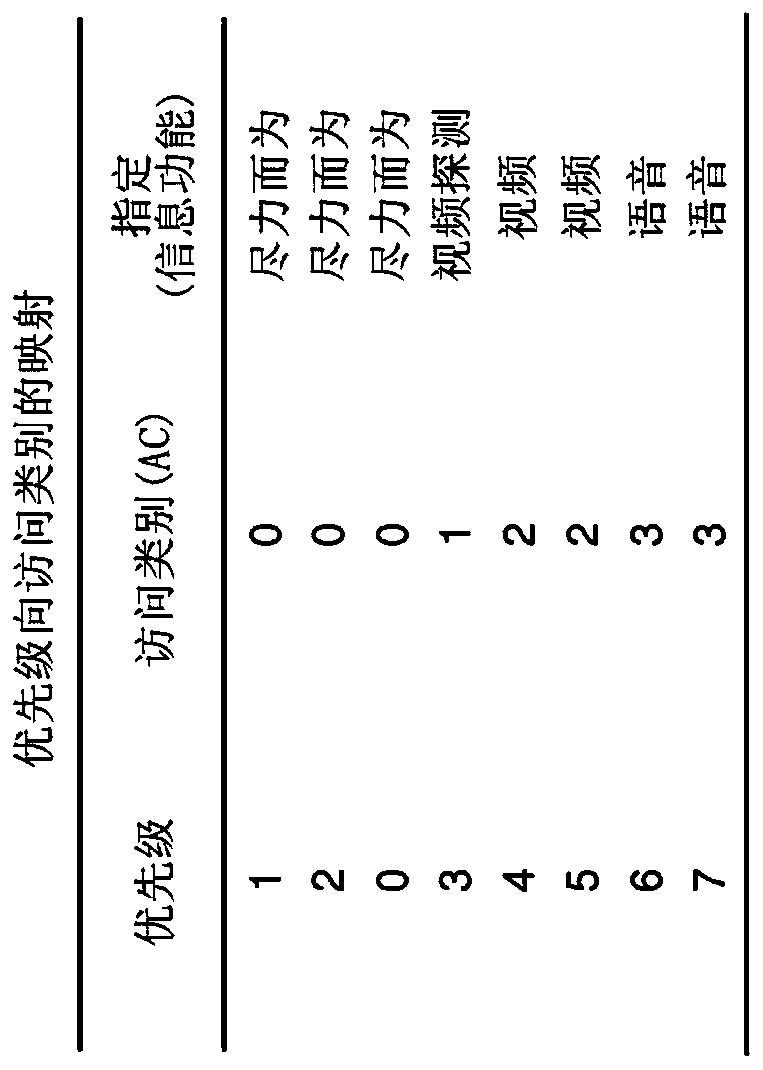
QoS MANAGEMENT FOR MULTI-USER EDCA TRANSMISSION MODE IN 802.11AX NETWORKS
ActiveUS20190274171A1Improve network efficiencyNetwork traffic/resource managementTransmission path divisionTraffic capacityQos management
The invention relates to wireless network comprising an access point and non-AP stations. The station has traffic queues and associated a backoff counters which are decremented over time upon continuously sensing the medium as free during more than respective AIFS durations. To compensate additional opportunities provided by OFDMA RUs, a queue switches to an MU mode upon transmitting its data in an RU provided by the AP. To restore dynamicity of the backoff counters, frozen in the MU mode in the known techniques, embodiments provide the following at each expiry of one of the queue backoff counters: the current mode of the expiring traffic queue is determined; in case of legacy mode, the station accesses the channel to transmit data from the queue; whereas in case of MU mode, a new backoff value is drawn to reset the expiring backoff counter, without having data from the queue being transmitted.
Owner:CANON KK
Method and apparatus for supporting legacy mode fail-over driver with iSCSI network entity including multiple redundant controllers
The invention is directed to a method and apparatus for supporting legacy mode fail-over drivers with an iSCSI network entity including multiple redundant controllers. In an exemplary aspect of the present invention, to support legacy mode fail-over drivers with an iSCSI network entity including multiple redundant controllers, the following configuration constraints may be placed on the iSCSI network entity and its iSCSI configuration: (1) the network device need have two or more redundant controllers; (2) the portals on each controller may or may not be formed into portal groups; (3) the portal groups may not span controllers (i.e., the target portal groups are limited in scope to a single controller); (4) the same iSCSI target name need be exported by all redundant controllers (i.e., the targets span all controllers of the iSCSI network entity, making the LUNs available to all controllers); (5) the target portal group numbers on the redundant controllers need have unique target portal group tags (i.e., all target portal group tags are unique across all portal groups in the iSCSI network entity. However, the target portal group tags do not need to be unique for different iSCSI targets); and (6) all targets are available from at least one target portal group on each controller. In addition, the initiator may use a single ISID for all sessions, use a different ISID for a different session, or the like. The present configuration constraints may enable the normal behavior of the legacy mode SCSI driver to locate and use redundant SCSI paths to the SCSI devices on the iSCSI target.
Owner:NETWORK APPLIANCE INC
Method for automatically constructing target file based on container technology
PendingCN111399865AAvoid wastingSave yourself the hassle of typing commandsVersion controlProgram code adaptionProject environmentConfigfs
The invention discloses a method for automatically constructing a target file based on a container technology. The method comprises the following steps: 1, acquiring a project code and copying the project code to a server; 2, judging whether a configuration file stored with project environment information exists on the server or not; if so, executing the step 3; if not, executing the step 6; 3, reading configuration file information to obtain an environment required by the current project; 4, judging whether an environment mirror image exists on the server or not, and generating the environment mirror image if the environment mirror image does not exist: if yes, the docker container is started through the docker mirror image; 5, executing a predefined target file construction command in the docker container; 6, ending the construction operation. The compiling construction problem based on the standard architecture project is effectively solved, and different development environments, test environments and deployment environments are rapidly provided by using the container mirror image. In addition, in the environment migration process, the method is faster than a traditional mode,and it is guaranteed that the environment is completely consistent after migration.
Owner:贵州新致普惠信息技术有限公司
Selective application of frequency hopping for transmission of control signals
A Method and apparatus for selectively applying, by a User Equipment (UE), Frequency Hopping (FH) for a transmission of Uplink Control Information (UCI) signals in a Physical Uplink Control CHannel (PUCCH). The UE applies FH when the UCI is of a first type and does not apply FH when the UCI is of a second type. The UE applies FH when transmission diversity is not applied to the UCI transmission and does not apply FH when transmission diversity is applied to the UCI transmission. UEs operating in a legacy mode do not apply FH to the UCI transmission while UEs operating with additional functionalities may apply FH to the UCI transmission according to the UCI type and the use of transmission diversity.
Owner:SAMSUNG ELECTRONICS CO LTD
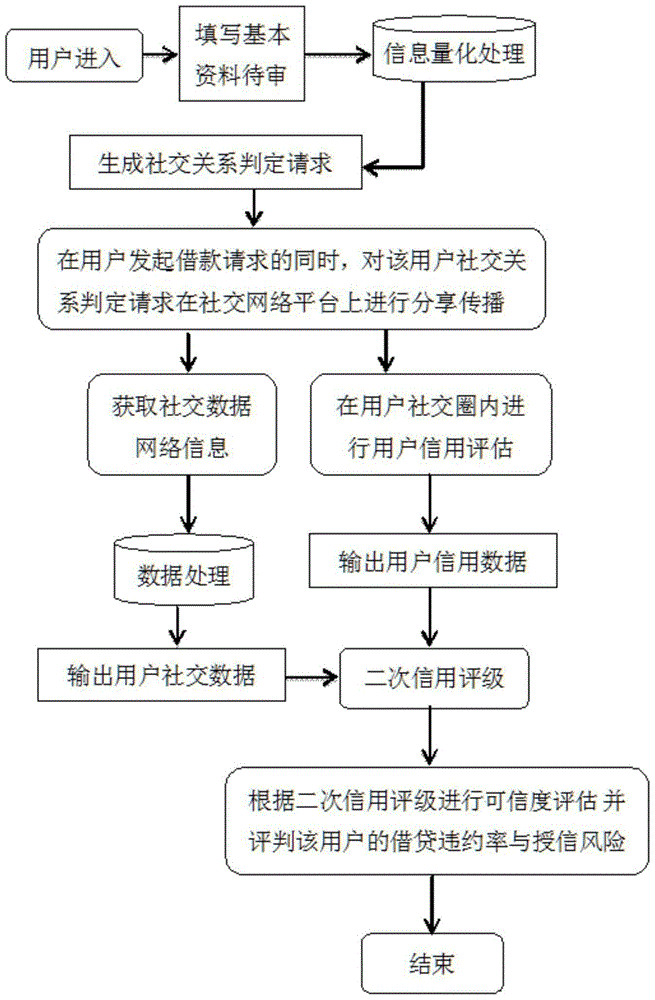
Method for processing user credibility social network data
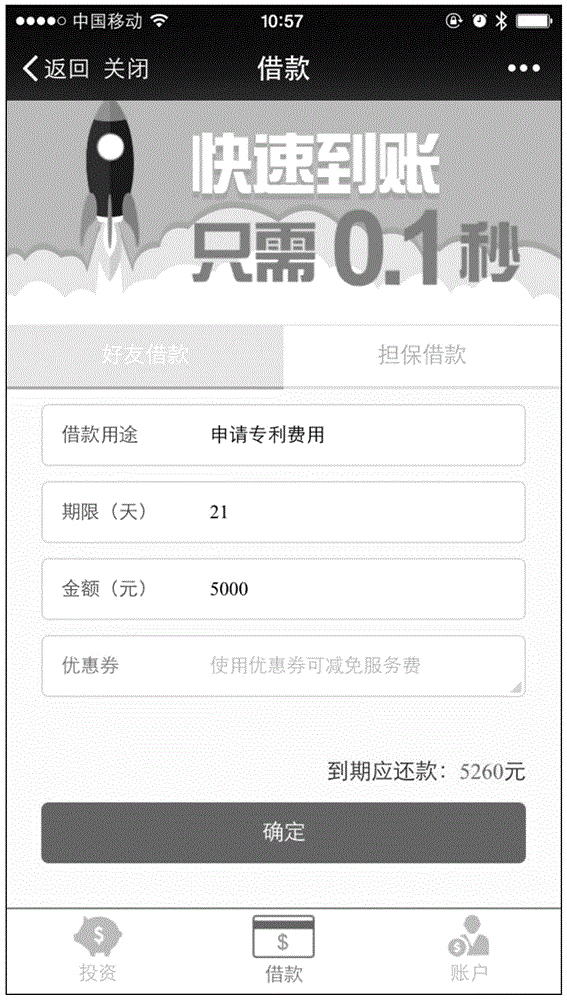
A method for processing user credibility social network data provided by the invention is provided with a social network platform including WeChat, and includes: a step of user registration and generation of a corresponding social relation judging request; a step of obtaining different levels and types of social contact data network information while a user initiates a loan request; a step of data entry, cleaning and combing and output of user social contact data; a step of performing user credit assessment in a user social circle to obtain user credit data; and a step of performing secondary credit granting rating and a step of performing credibility assessment and judging the loan default rate and credit granting risk of the user. The method has the advantages that through estimation of the overdue rate of users, an assessed value of a model used for distinguishing user quality can reach above 40, an assessed value of a traditional model is only about 35, and the identification rate of user assessment can reach above 70%, i.e., repayment results of 70% of users can be accurately identified through the model. Remarkable effects are achieved in practical application compared with credit granting in a traditional mode.
Owner:先花信息技术(北京)有限公司 +1
Transportation information publishing and retrieving method based on named data networking (NDN)
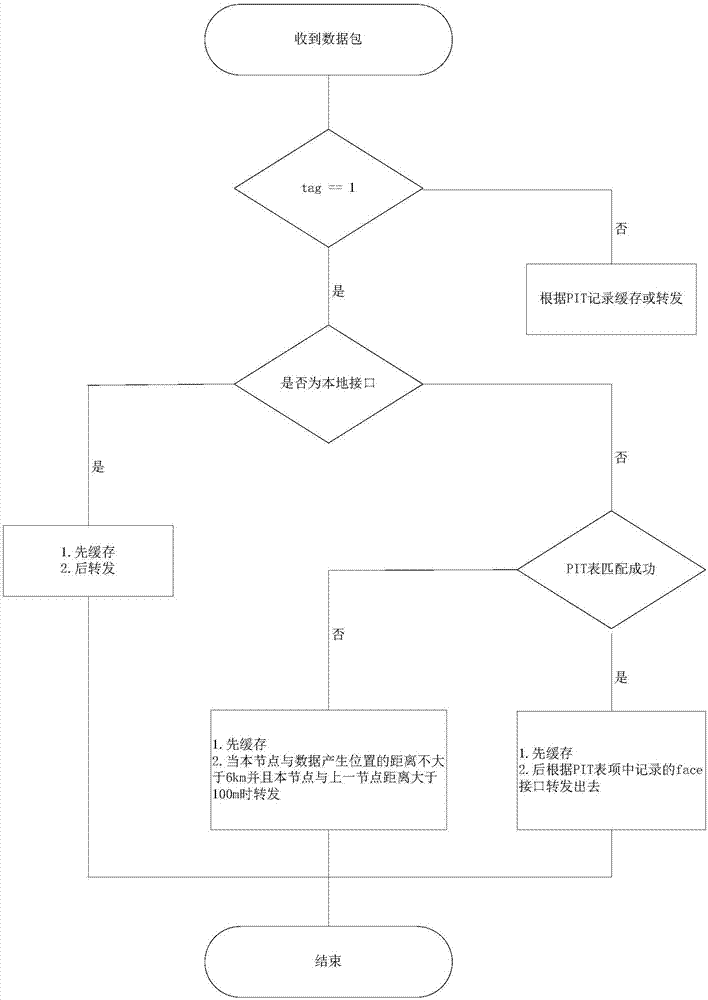
InactiveCN106936909AEfficient queryTransmissionSpecial data processing applicationsGeographic siteNetwork packet
The invention discloses a transportation information publishing and retrieving method based on named data networking (NDN). The method comprises the following specific steps: recommending a data naming mechanism: names are partitioned into five basic layers; publishing transportation information: a source vehicle node forwards a generated data packet to the periphery, and vehicle nodes receiving the data packet cache the data packet and continually forward the data packet outwards in a broadcasting way; and retrieving the transportation information: a requester vehicle node transmits an interest packet outwards, and returns the data packet according to a naming prefix matching rule of the NDN. According to the transportation information publishing and retrieving method based on an NDN mechanism without any central server in a VANET (Vehicular Ad-hoc Network), vehicles in a whole network are self-organized, and each vehicle node plays the roles of a producer, a consumer and a forwarder, so that the vehicles can forward and cache information through the NDN mechanism, and vehicle drivers can rapidly and efficiently inquire relevant transportation information of a certain geographical position through other vehicles without the assistance of the central server used in a conventional mode.
Owner:BEIJING UNIV OF TECH
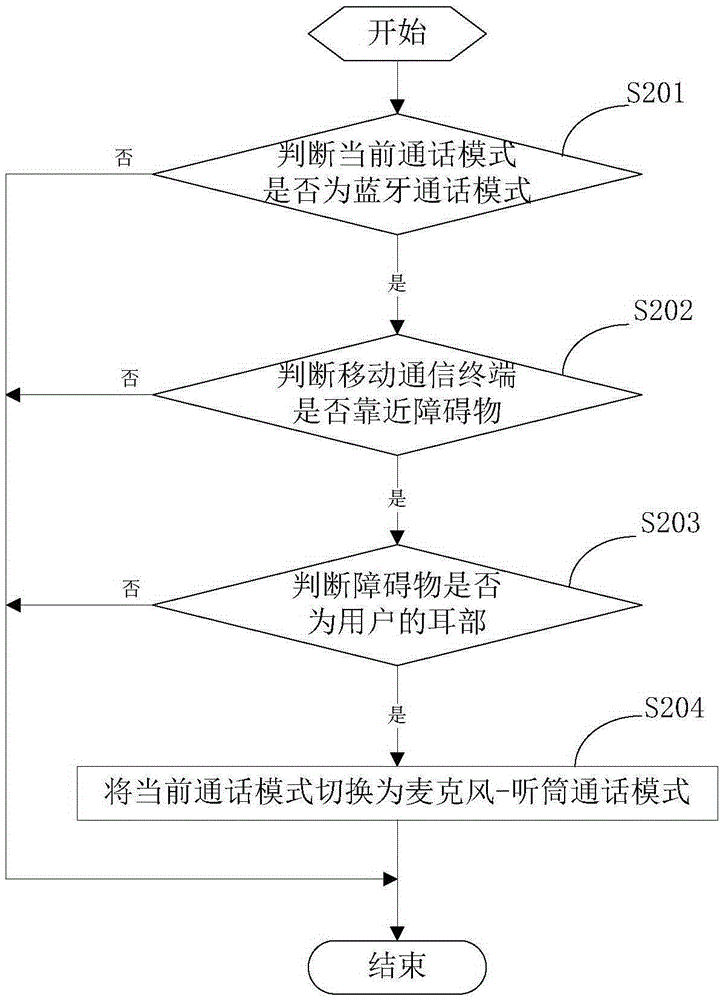
Communication mode switching method and mobile communication terminal
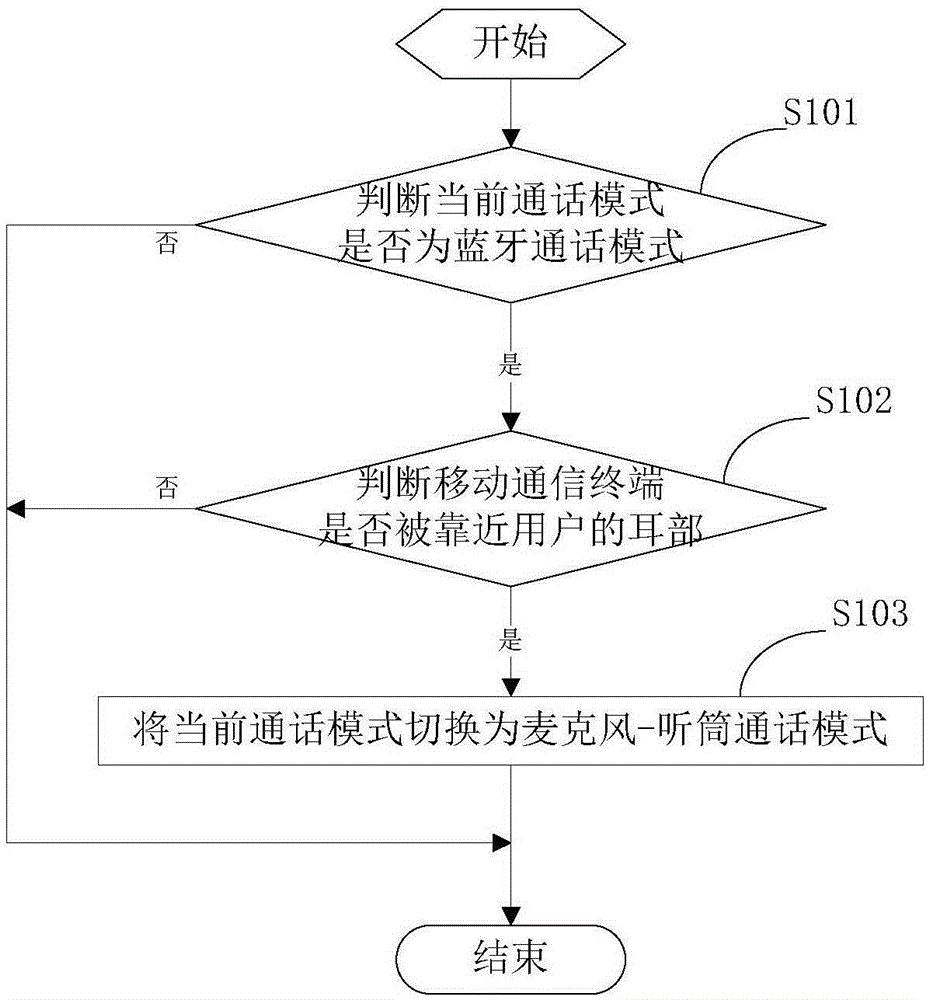
InactiveCN105827812AEasy to answerSatisfy the habit of callingSubstation equipmentComputer engineeringLegacy mode
The present invention provides a communication mode switching method and a mobile communication terminal. According to the communication mode switching method, firstly, whether the mobile communication terminal is in the Bluetooth communication mode or not is judged during the conversation process of the mobile communication terminal. On the condition that the mobile communication terminal is in the Bluetooth communication mode, whether the distance between the mobile communication terminal and the ear part of a user is less than a preset distance or not is further judged. If the distance between the mobile communication terminal and the ear part of the user is less than the preset distance, the user wants to answer a call in the conventional mode. At this time, the current communication mode is switched to the microphone-earphone communication mode, so that the requirements of the user in realizing the conversation in the microphone-earphone mode can be met. Through detecting the actions of the user, the current communication mode of the mobile communication terminal is timely switched to the microphone-earphone communication mode. Therefore, the above purpose can be realized without the multiple operations of the user. As a result, the user can answer calls more conveniently.
Owner:VIVO MOBILE COMM CO LTD
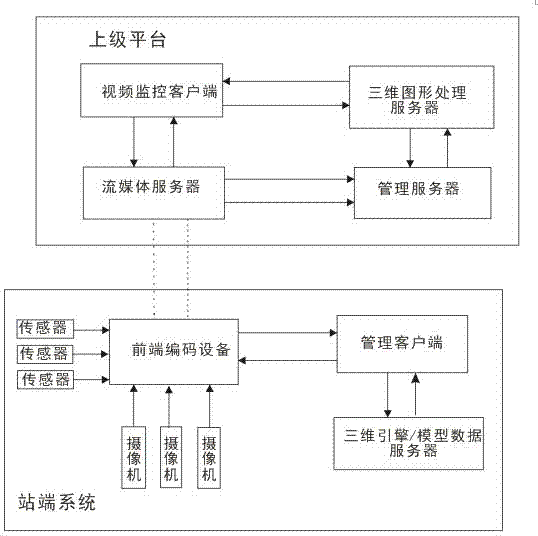
Method for realizing 3D scene display by transformer station video monitoring system
InactiveCN103780873AFully analyzedImprove the quality of management workClosed circuit television systemsSelective content distributionVideo monitoringGraphics
The invention discloses a method for realizing 3D scene display by a transformer station video monitoring system. The method comprises a station end system and an upper platform, wherein the station end system comprises a 3D engine / model data server, a management client, a front coding device and multiple cameras; and the upper platform comprises a management server, a streaming media server, a 3D figure processing server and a video monitoring client. The method provided by the invention realizes the 3D scene display through establishing a 3D model by use of Unity 3d software, the application of the method can optimize the conventional working mode of an electric power department, post-processing is converted to prediction in advance, management personnel have sufficient time to integrate, analyze and solve problems occurring in a system operation and maintenance process, and the quality of management work is improved accordingly.
Owner:INFORMATION & TELECOMM COMPANY SICHUAN ELECTRIC POWER
QoS MANAGEMENT FOR MULTI-USER EDCA TRANSMISSION MODE IN 802.11AX NETWORKS
ActiveCN109923930ANetwork traffic/resource managementTransmission path divisionQos managementCurrent mode
The invention relates to wireless network comprising an access point and non-AP stations. The station has traffic queues and associated a backoff counters which are decremented over time upon continuously sensing the medium as free during more than respective AIFS durations. To compensate additional opportunities provided by OFDMA RUs, a queue switches to an MU mode upon transmitting its data in an RU provided by the AP. To restore dynamicity of the backoff counters, frozen in the MU mode in the known techniques, embodiments provide the following at each expiry of one of the queue backoff counters: the current mode of the expiring traffic queue is determined; in case of legacy mode, the station accesses the channel to transmit data from the queue; whereas in case of MU mode, a new backoffvalue is drawn to reset the expiring backoff counter, without having data from the queue being transmitted.
Owner:CANON KK
Multi-carrier grant design
Systems and methodologies are described that facilitate assigning resources for an anchor carrier and an additional carrier with a grant message. The grant message communicated with an anchor carrier can include resource information a plurality of carriers. Moreover, the systems and methodologies that facilitate identifying control information for an anchor carrier and / or an additional carrier based upon an operating mode, wherein the operating mode is a legacy mode or an extended mode. Based on the operating mode, particular resources associated with control regions are monitored for control information for respective anchor carrier(s) or additional carrier(s).
Owner:QUALCOMM INC
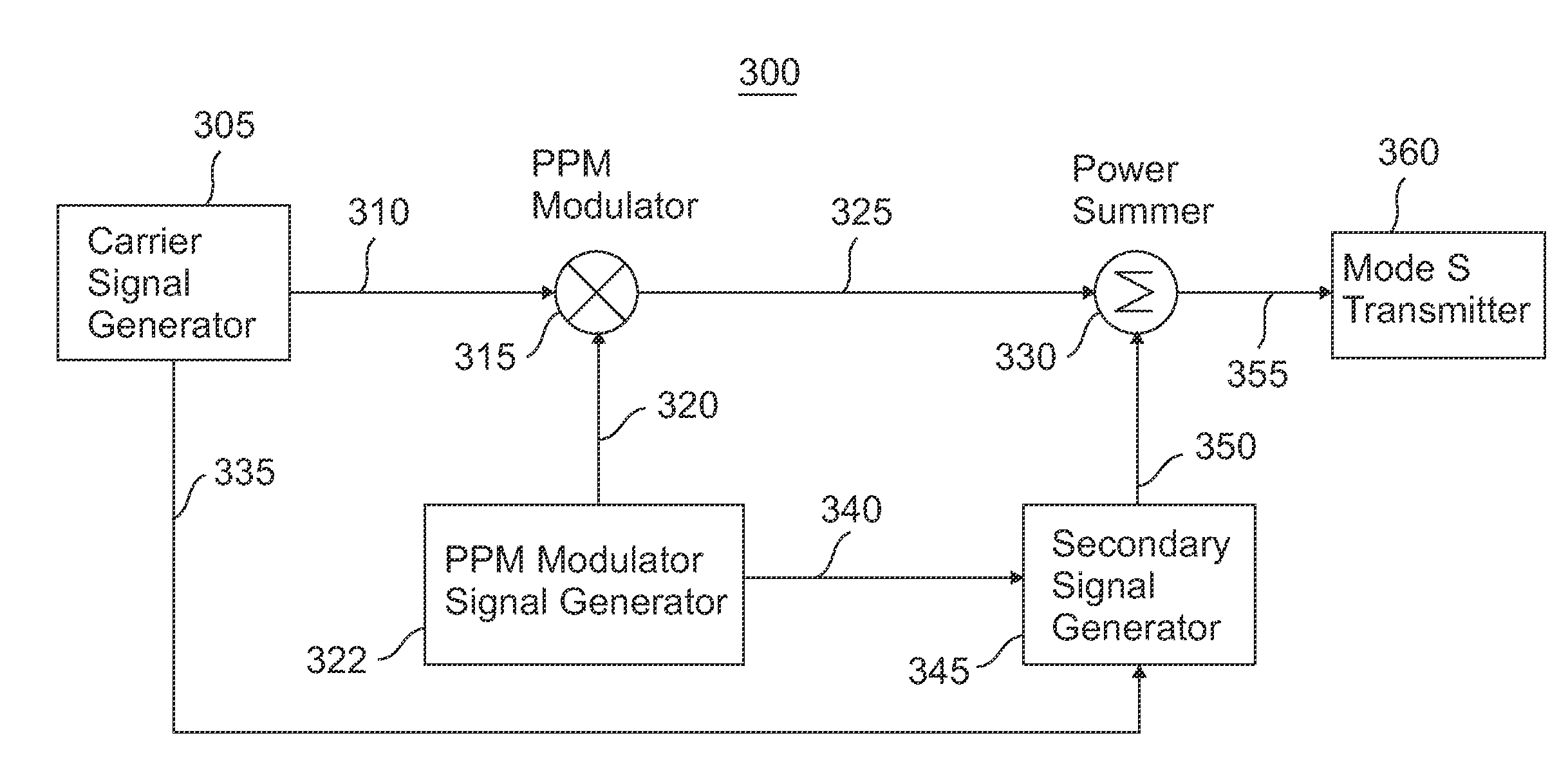
Secondary communication signal method and apparatus
InactiveUS8665985B1Increase data rateIncrease rangeSimultaneous amplitude and angle modulationAmplitude-modulated carrier systemsData rateComputer science
A low level secondary communication signal is summed with an existing primary communication signal in a manner that prevents interference to the existing primary communication signal while providing secondary communication signal benefits such as increased data rate, range, or interference immunity. Examples are presented in which a M-QAM secondary signal is summed with either an ATC Mode S PPM reply or DPSK interrogation primary signal. Legacy Mode S transponders, TCAS, and ADS-B equipment continue to demodulate and decode the primary signal information in accordance with preexisting formats while new enhanced equipment obtains the benefits of the secondary signal.
Owner:PIESINGER GREGORY HUBERT
Automatic construction method and system for table-driven cloud model software
PendingCN108427554ASimplify the development processImprove development efficiencyTransmissionCreation/generation of source codeSoftware development processSystem requirements
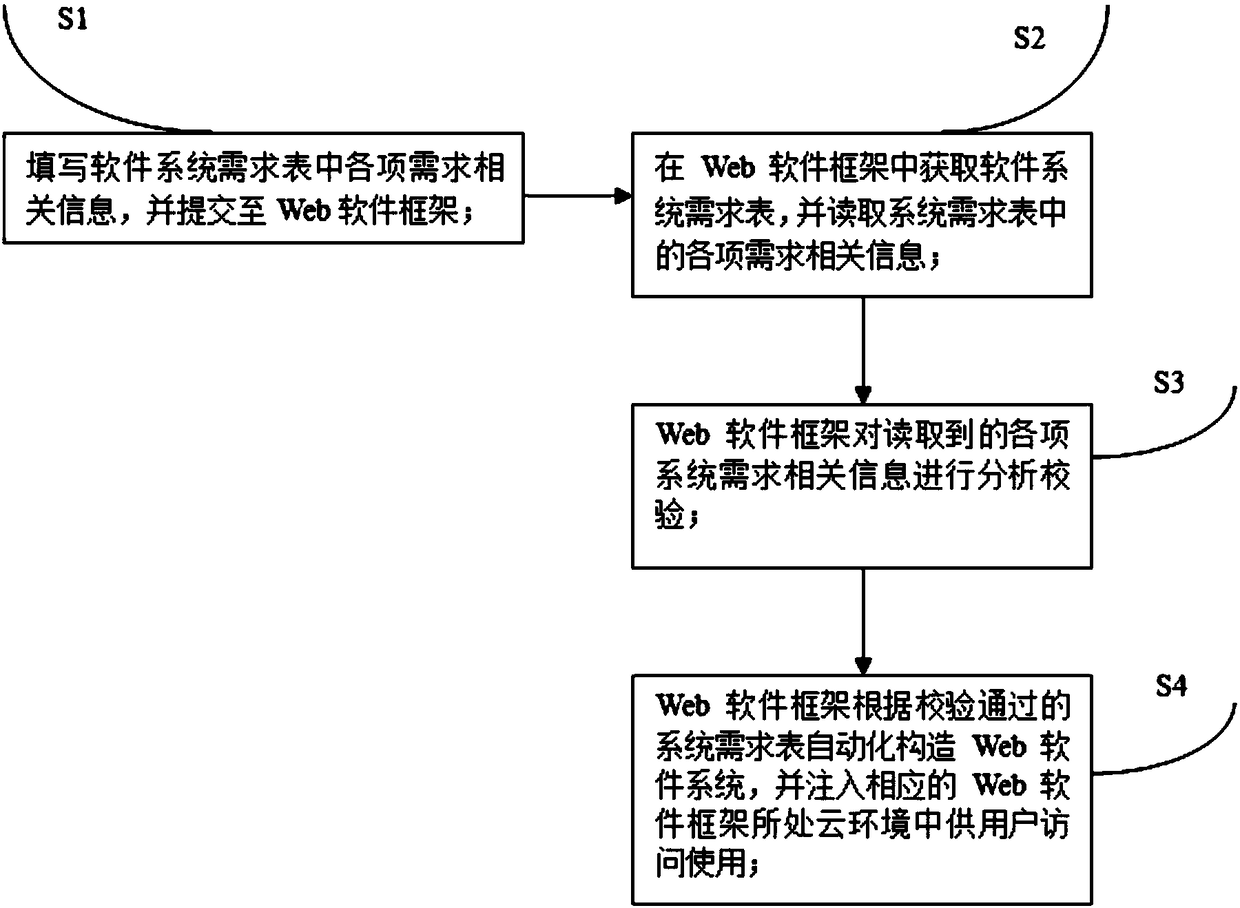
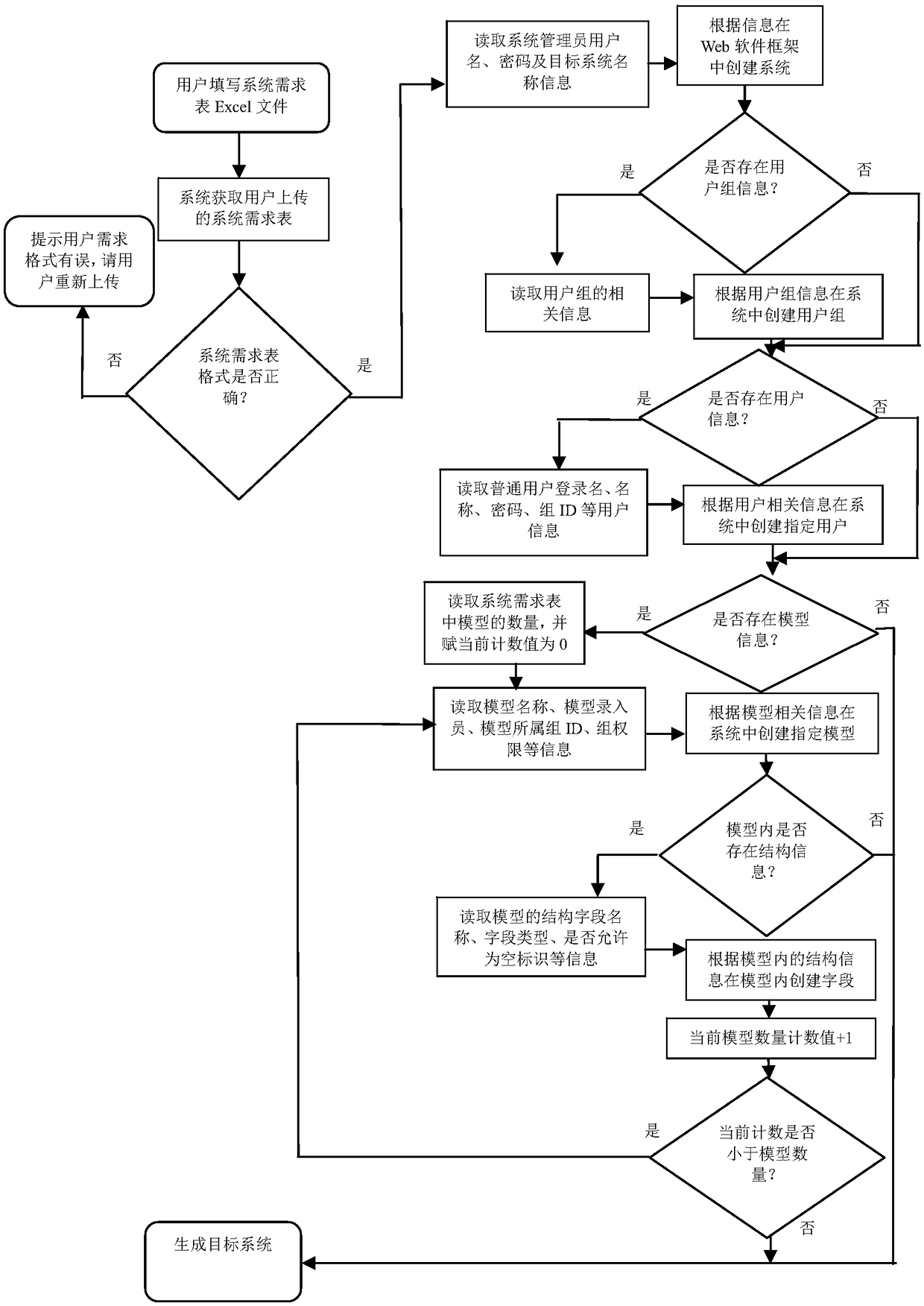
The invention discloses an automatic construction method and system for table-driven cloud model software. The method comprises the following steps that a user fills related requirement information ina software system requirement table and submits the table, various requirement related information in the received software system requirement table is automatically read through an automatic web software construction framework, the various read system requirement related information is analyzed and checked, and a web software system matched with the requirement is automatically constructed according to the verified software system requirement table information and is injected into a cloud environment where the corresponding web software framework is located. The automatic construction methodand system for the software have the advantages that the complicated software development process in a traditional mode is simplified, multi-tenant software, namely a service cloud model is supported, the programming and deploying links in the conventional information management system software development process are omitted for the user, and therefore the user can quickly and efficiently construct the web software system meeting the requirement by just focusing on the requirement of a defined system, and the software development efficiency is greatly improved.
Owner:SOUTH CHINA UNIV OF TECH
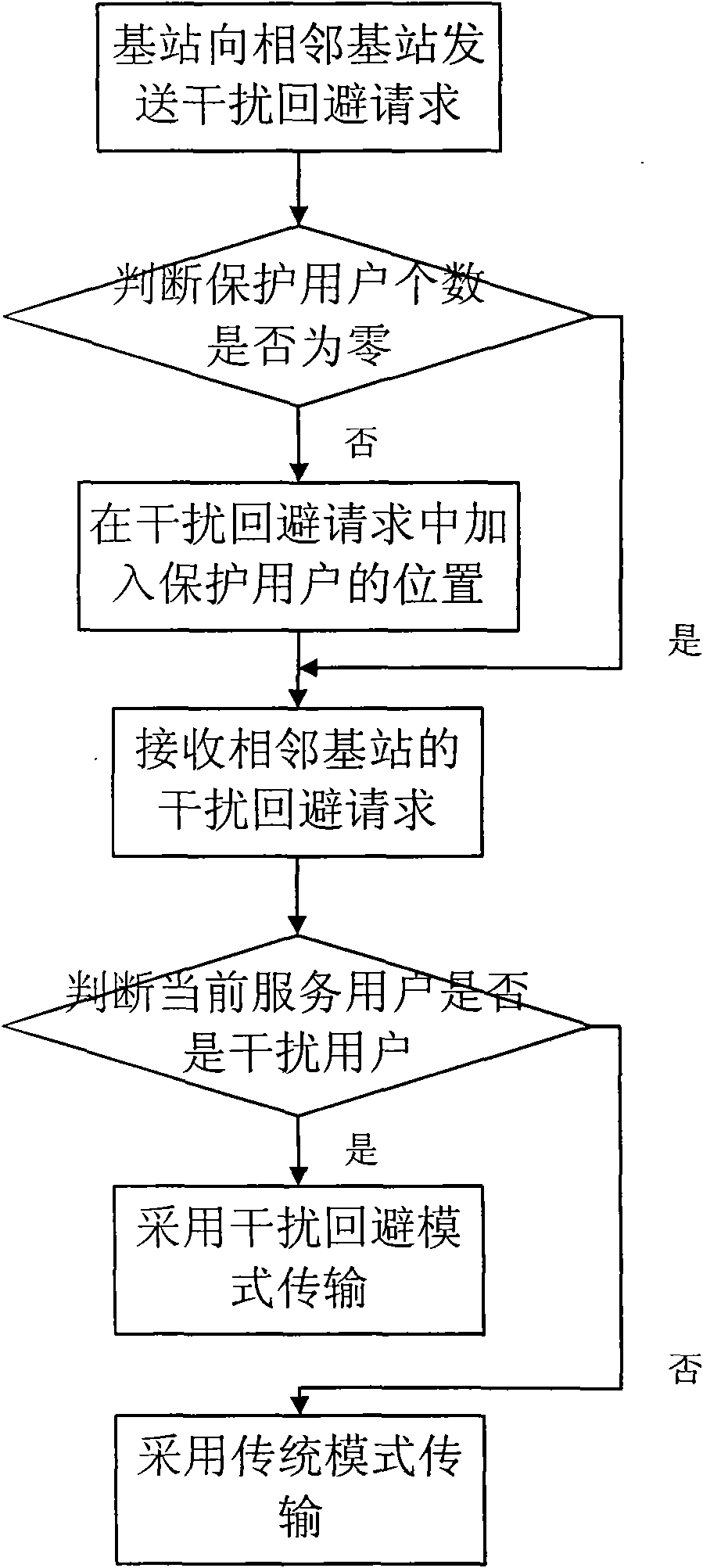
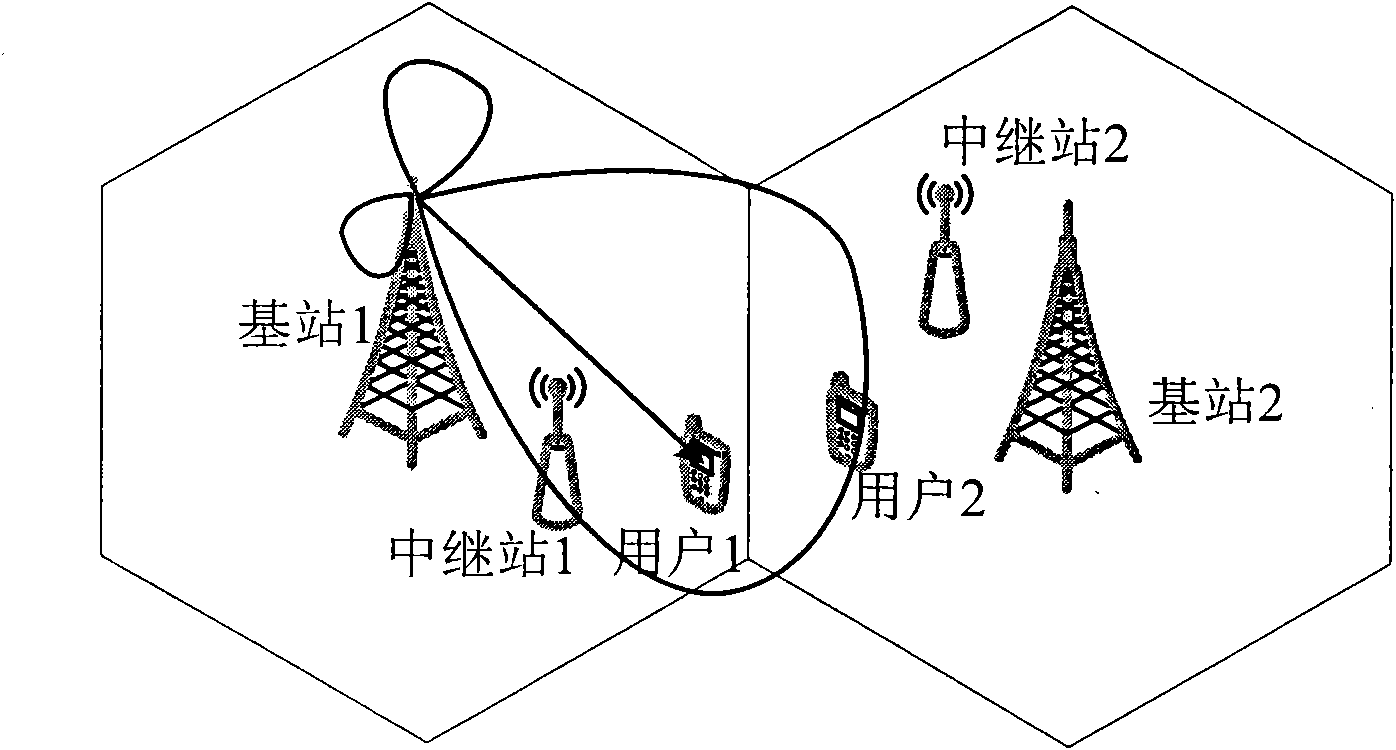
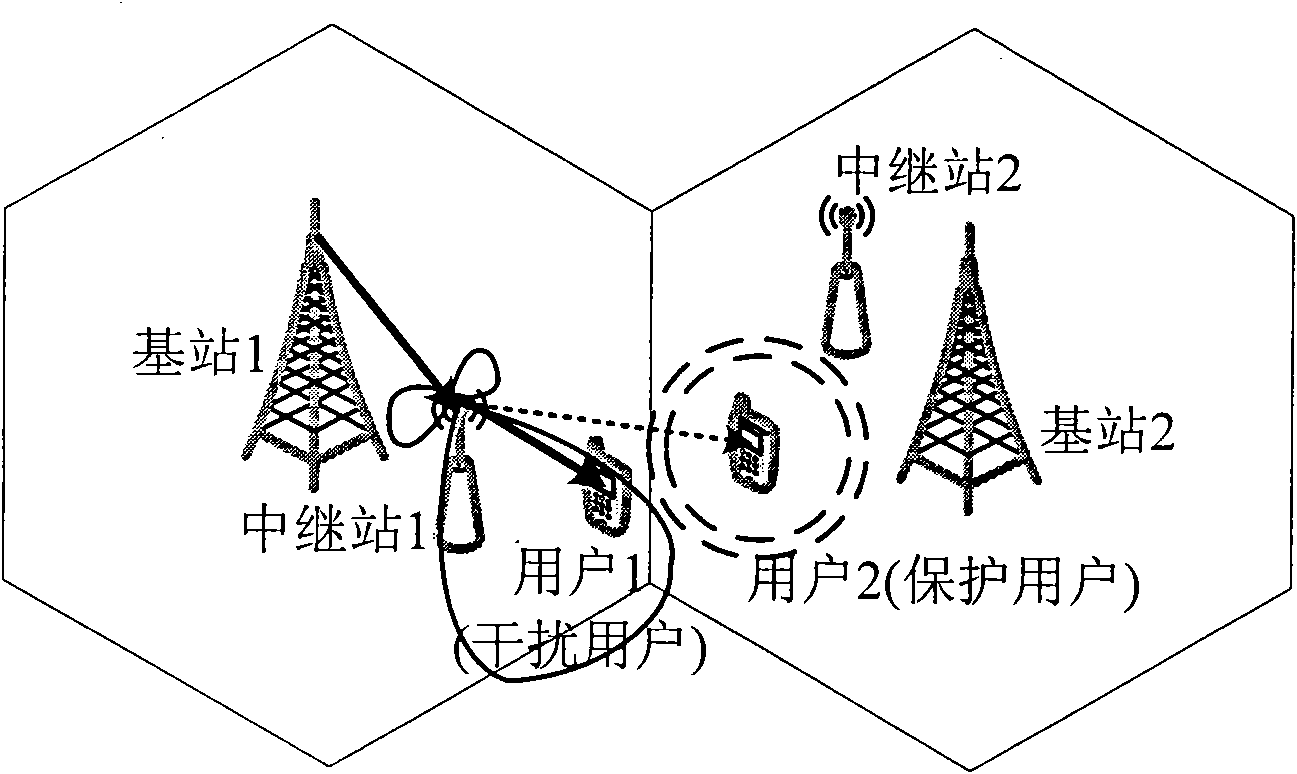
Interference coordination method among downlink cells in relay wireless communication network
The invention relates to an interference coordination method among downlink cells in a relay wireless communication network, belonging to the technical field of wireless communication. The base station of the downlink of the relay wireless communication network divides the user area of the cell into non-interference user and interference user according to amount and position of users on the adjacent cell service edge, traditional transmission mode is adopted for the non-interference user, and interference evaded transmission mode is adopted for the interference user. In the interference evaded transmission mode, a relay carries out wave beam forming on the position information of the adjacent cell-edge user and the channel information of the cell interference user so that the interferenceof the adjacent cell-edge user is effectively evaded. In the method, when all cells adopt the interference evading policy, the performance of all cell-edge users can be effectively protected so that the throughput of the cell-edge user can be improved.
Owner:BEIHANG UNIV
Service parameter configuration method
PendingCN111078313AIncrease flexibilityImprove adaptabilityVersion controlProgram loading/initiatingCentralized managementComputer science
The invention discloses a service parameter configuration method, which relates to the technical field of computers, analyzes and classifies service parameters, carries out centralized management through a unified parameter management standard, carries out parameter remapping according to data structure differences of parameter tables of target subsystems, and publishes the service parameters to the target subsystems. The configuration of the service parameters adopts a mode of'generating a service scene driving system function '; a traditional mode that a service scene depends on technology implementation is broken through; when a new service demand is generated, the service is restarted; secondary code development is not needed; the parameter configuration requirements under different service scenes can be met through simple interface configuration, so that the parameter configuration can flexibly and quickly adapt to different service scenes, the parameter synchronization efficiencyis improved while the flexibility and the adaptability of the parameter configuration are improved, and the error rate and the cost of the parameter synchronization are reduced.
Owner:神州数码融信软件有限公司
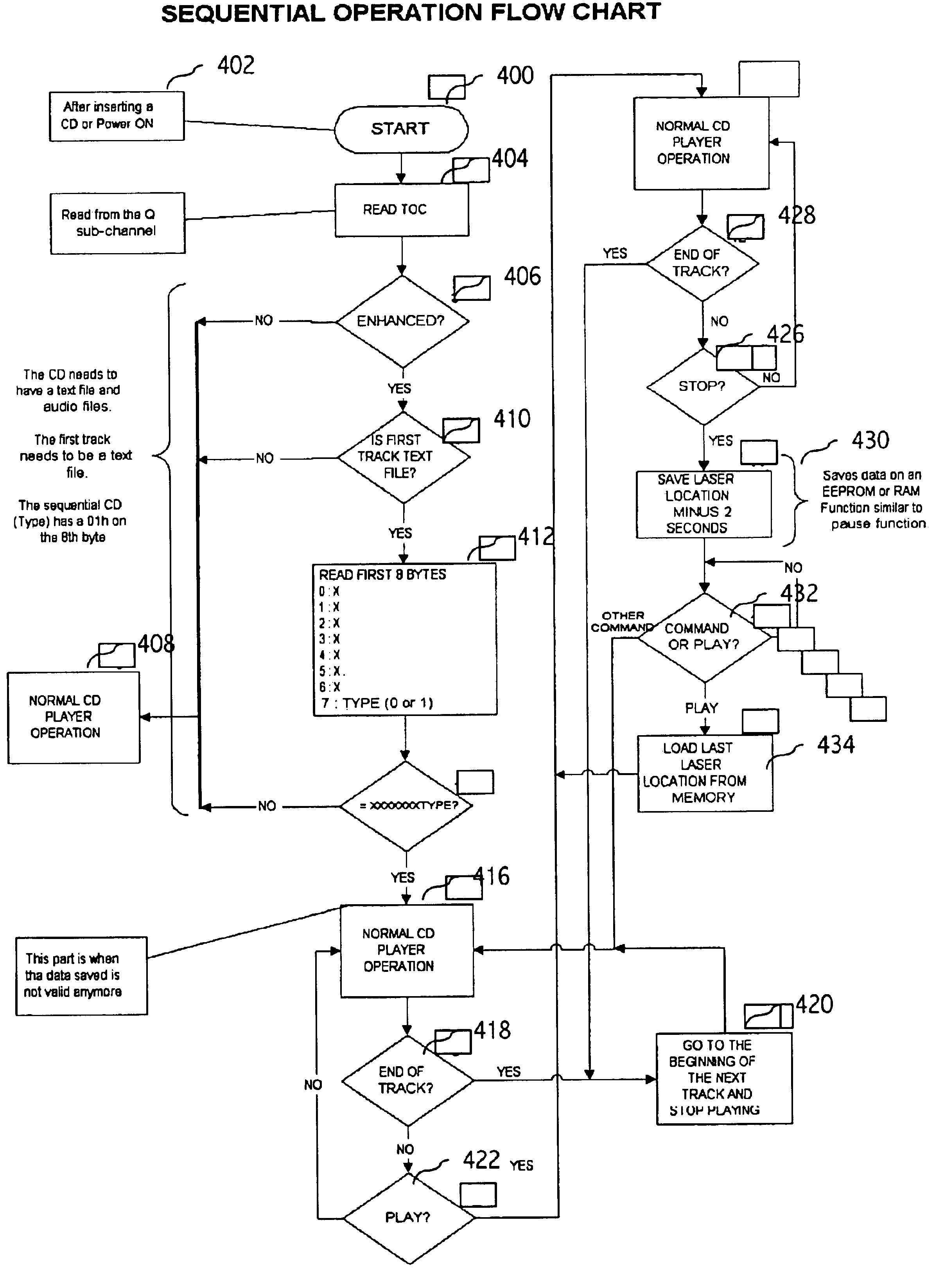
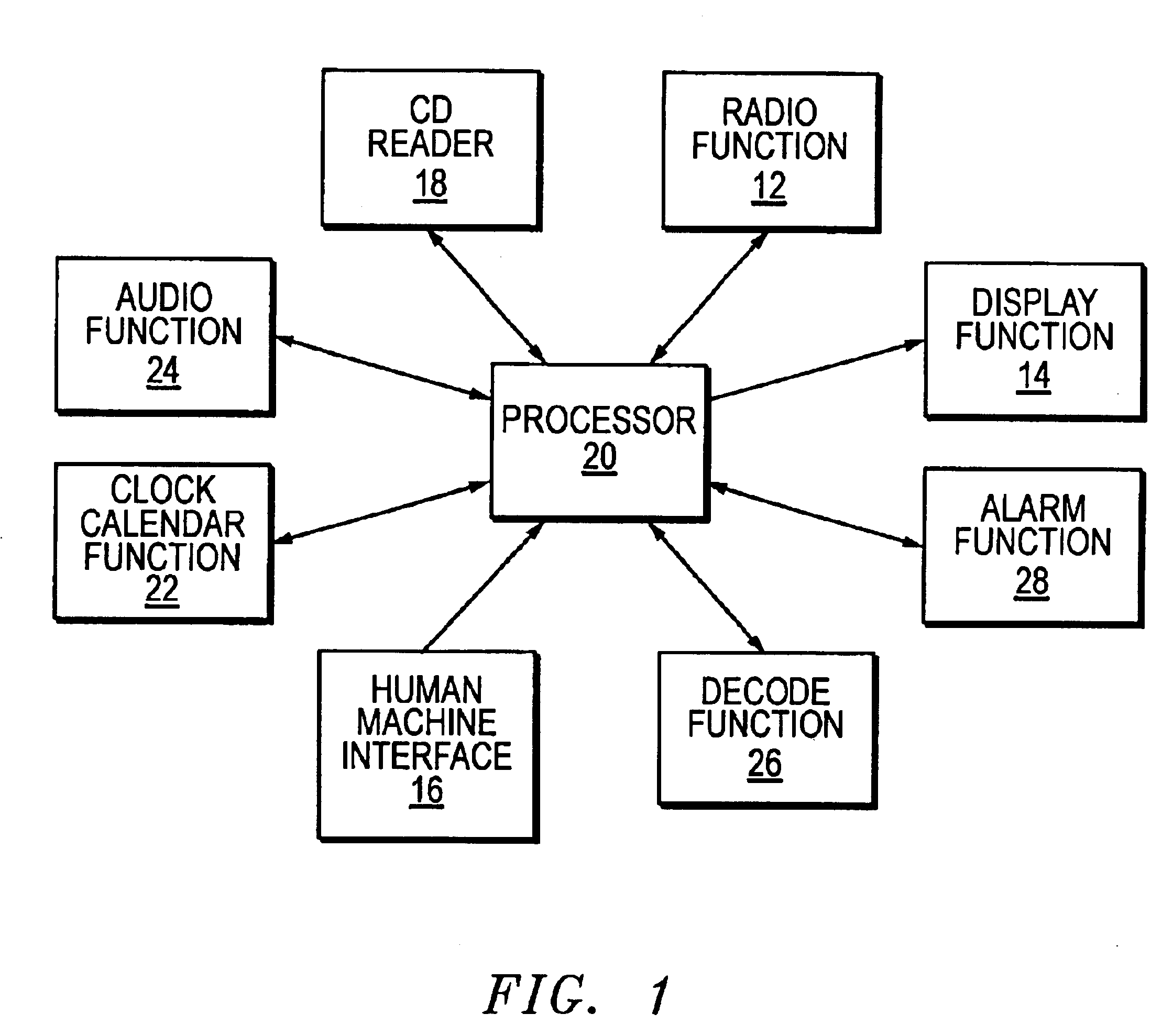
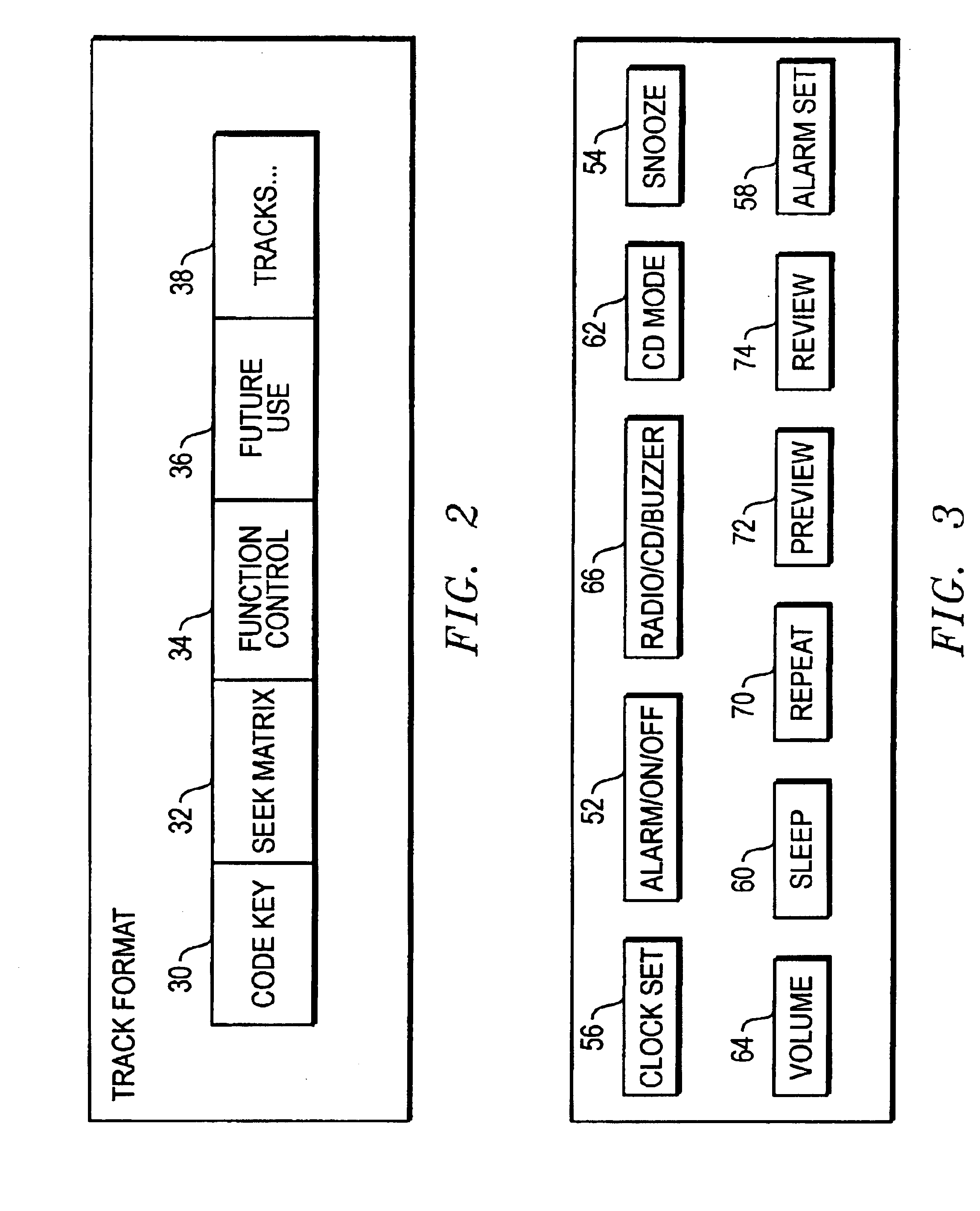
System and method for delivery of audio content correlated to the calendar date and/or time of day
InactiveUS6920089B1Eliminates and reduces disadvantageEliminates and reduces and problemAcoustic time signalsElectric indicationComputer scienceTime of day
An apparatus and method are provided for automatically playing a recorded message, from a uniquely formatted encrypted CD, correlated to a specific date and a time of day as an option on a CD clock radio or the like. Disclosed are means for distinguishing the unique CD format and thereafter following a prescribed process for decrypting and playing. Otherwise all device functions and options operate in their conventional modes.
Owner:STEINBACH SCOTT BOWMAN
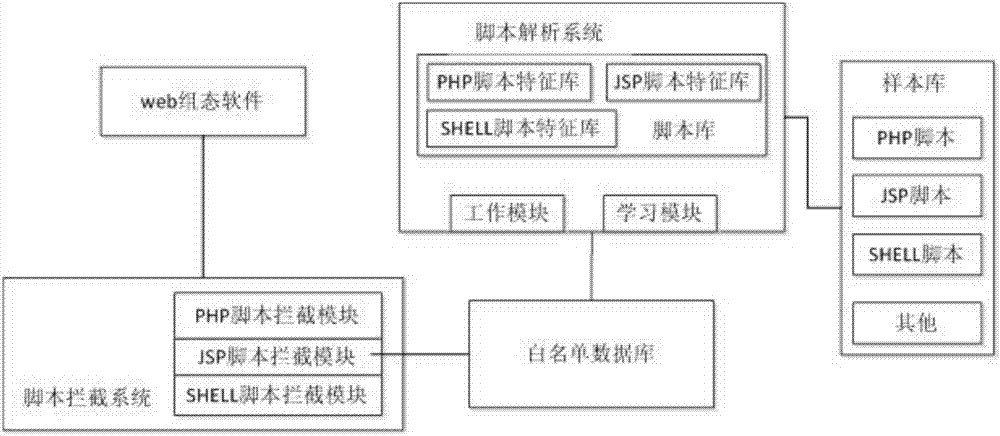
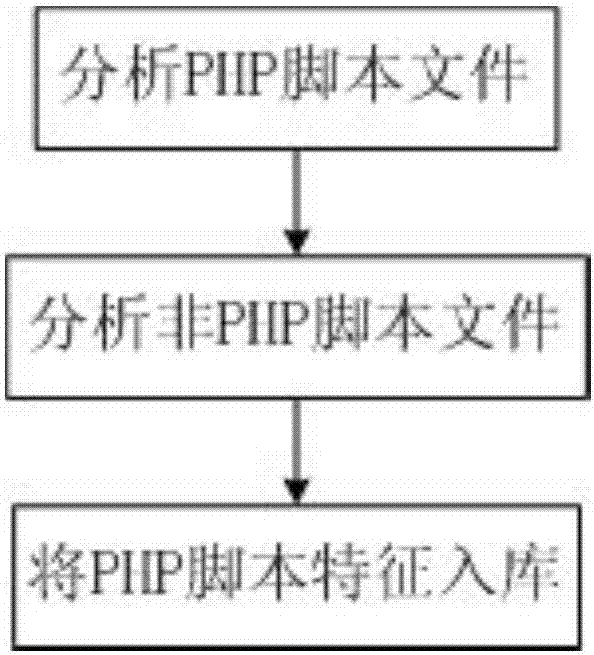
Script control method for web configuration
InactiveCN107341371ALoading forbiddenNo impact on workflowProgram/content distribution protectionIndustrial control systemParsing
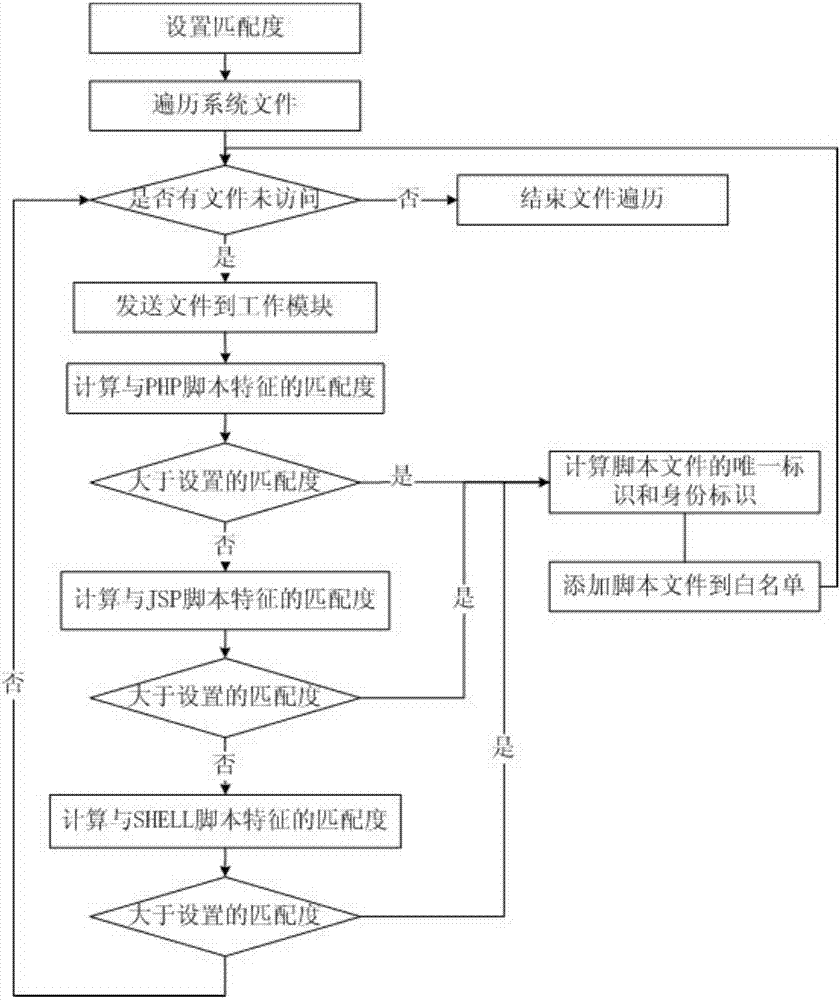
The invention discloses a script control method for web configuration. The script control method is characterized by comprising the steps that a corresponding script feature library is generated in a self-learning mode according to the features of various scripts, real-time interception and verification are conducted on the scripts when web configuration software loads the scripts, the condition that the malicious scripts operate to threaten the security of the web configuration software is prevented, and threats to an industrial control system are fundamentally blocked. The script control method has the advantages that the learning mode is adopted, the features of the scripts can be automatically extracted to recognize and classify script files, the file parsing method for conducting specific parsing on the specific file forms in the traditional mode is eliminated, and later extension and maintenance are convenient while the script file recognition speed is increased.
Owner:BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com