Method for detecting network nonlicet nodes by adjacent supervise
A technology for adjacent nodes and monitoring networks, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problem of lack of detection mechanism for illegal node access, and achieve the effect of reducing harm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
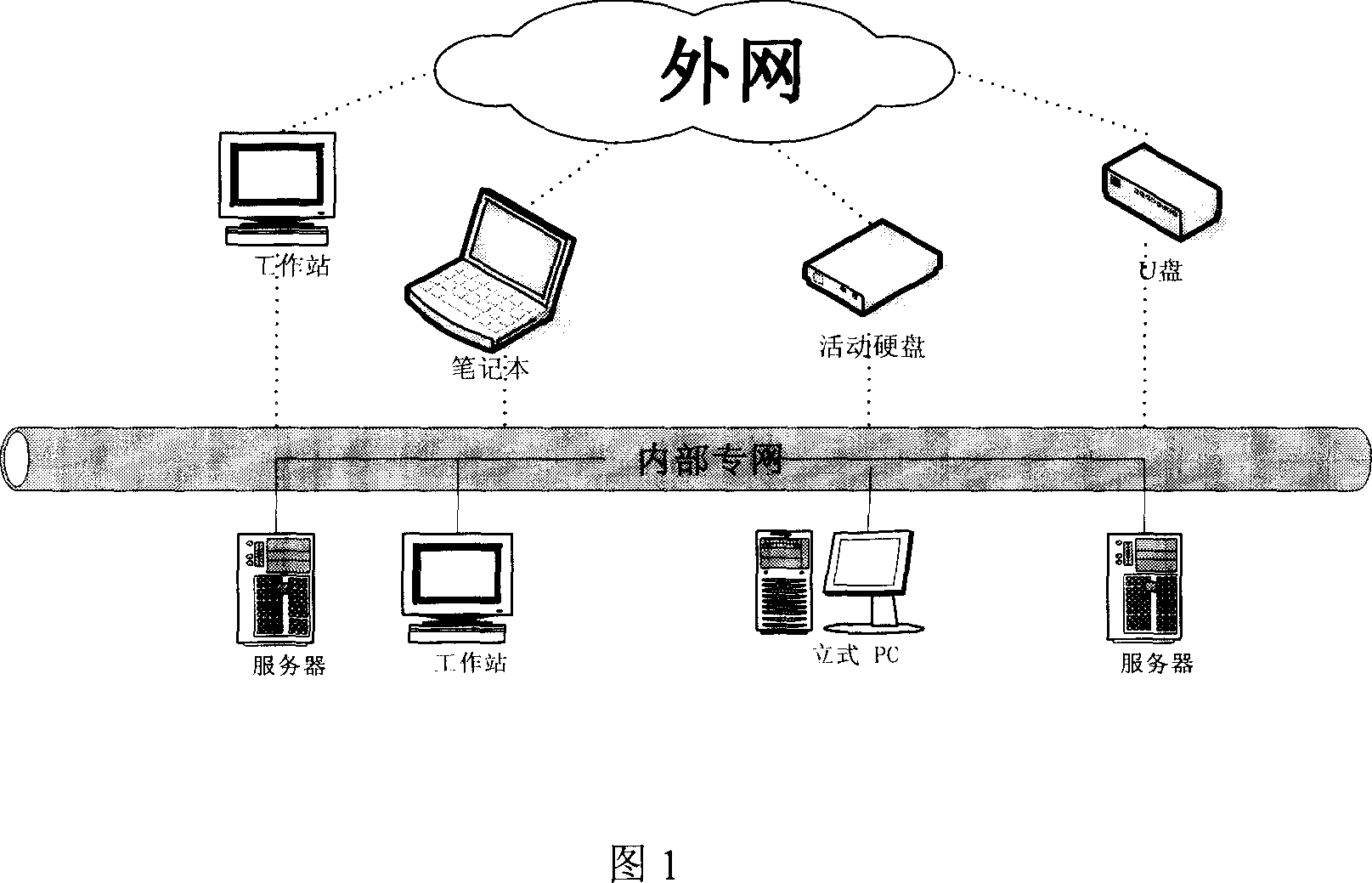
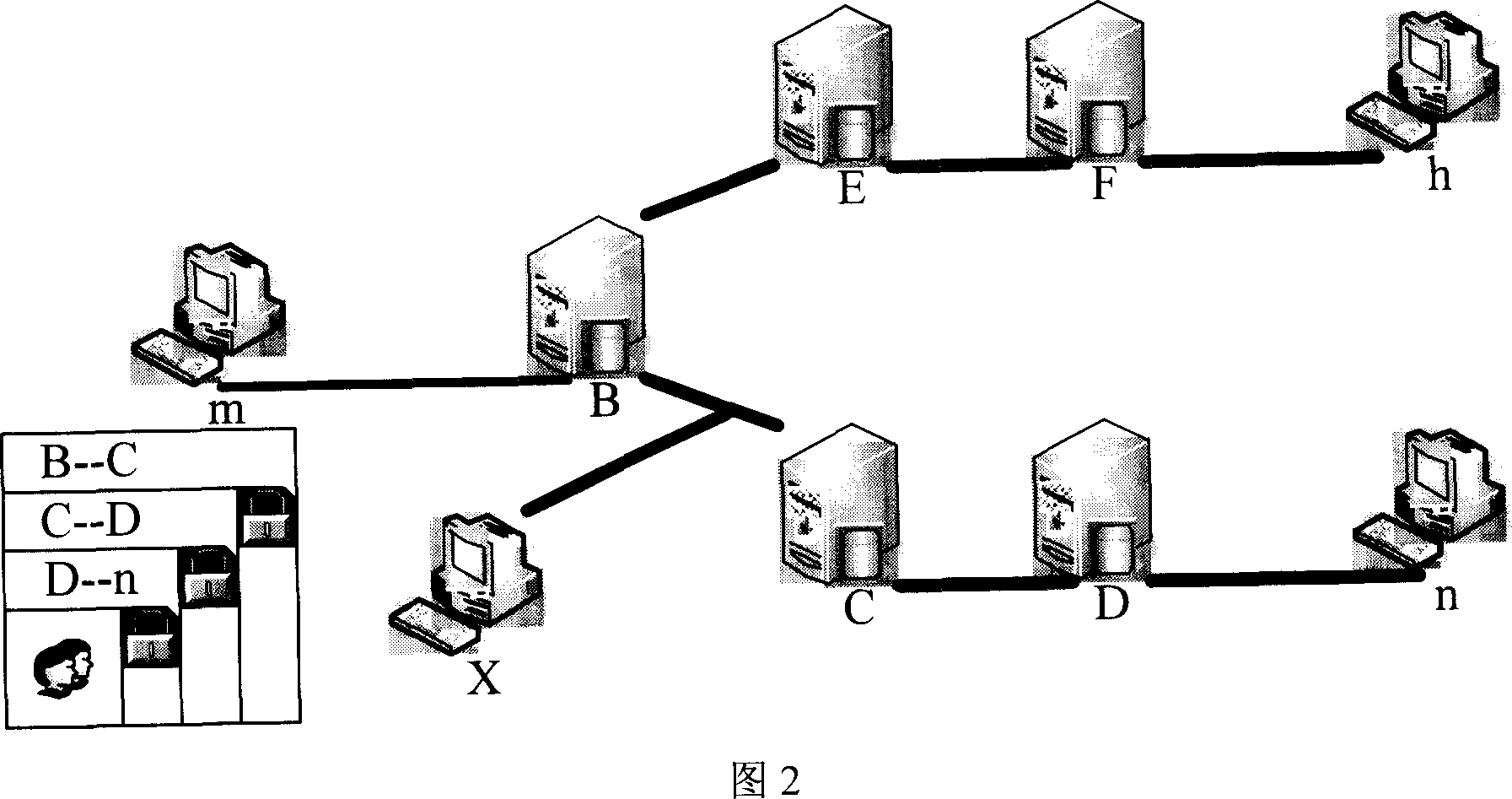
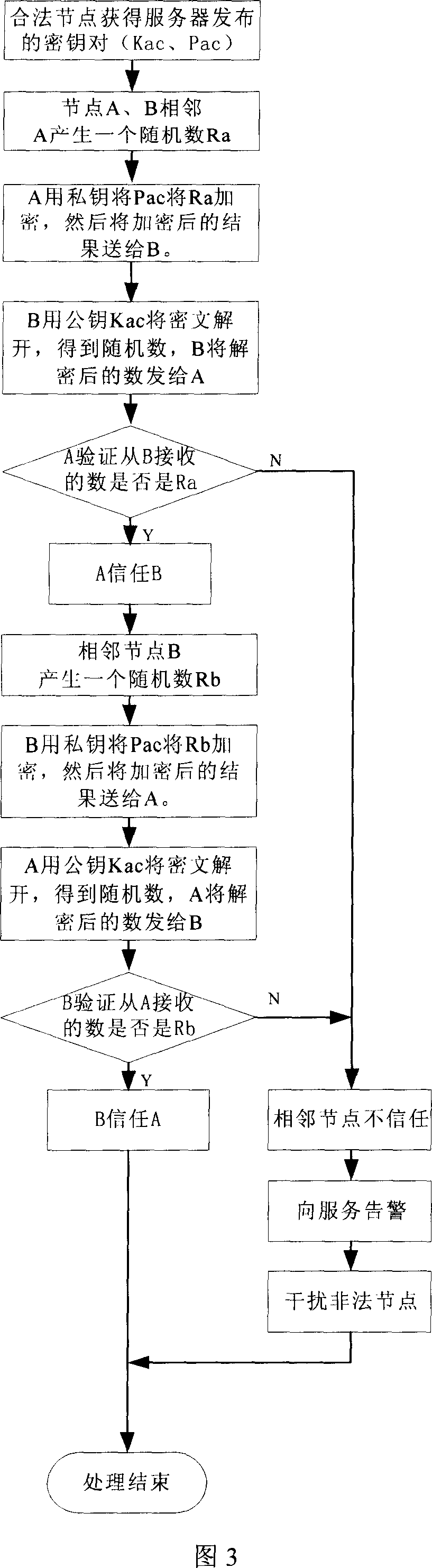
[0049] There are many uncertain factors in the discrete state, and its prevention needs to be considered carefully. At the same time, effective methods are needed to detect the existence of illegal nodes and issue warnings in time. The authentication of legitimate nodes uses public key\private key pairs to authenticate with the authentication server. The daily file operation key needs to be changed constantly, but it must be able to decrypt previously encrypted files. Timestamps can be used as encryption and decryption seeds. The storage time of each file is used as a time stamp, and the operation key of each time stamp is stored in the management server. For the detection of illegal nodes, the multi-level authentication structure shown in Figure 2 can be used.
[0050] The host computer m communicates with n, and the computer m carries the access password assigned by the proxy server that allows it to access the network segment of the host computer. Every time it passes throu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com