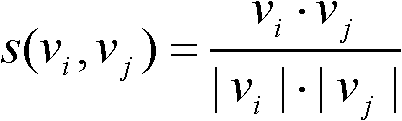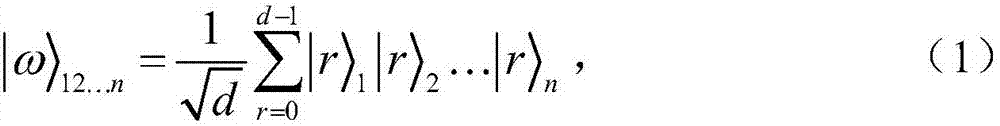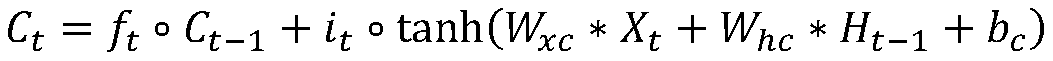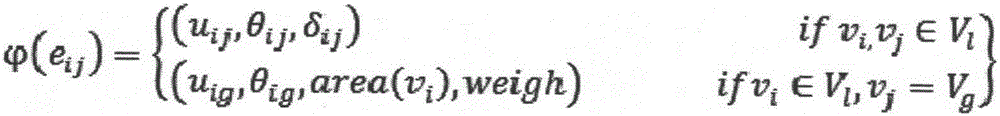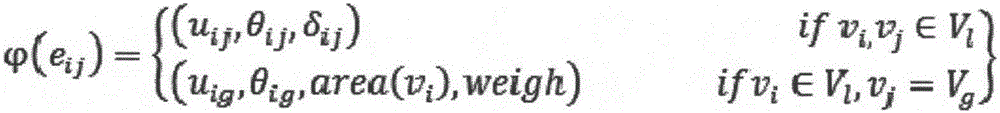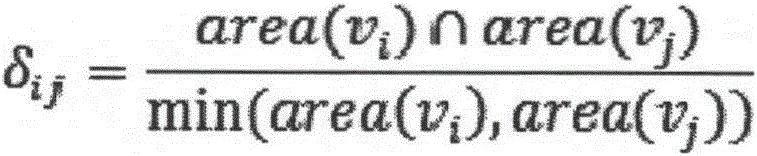Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
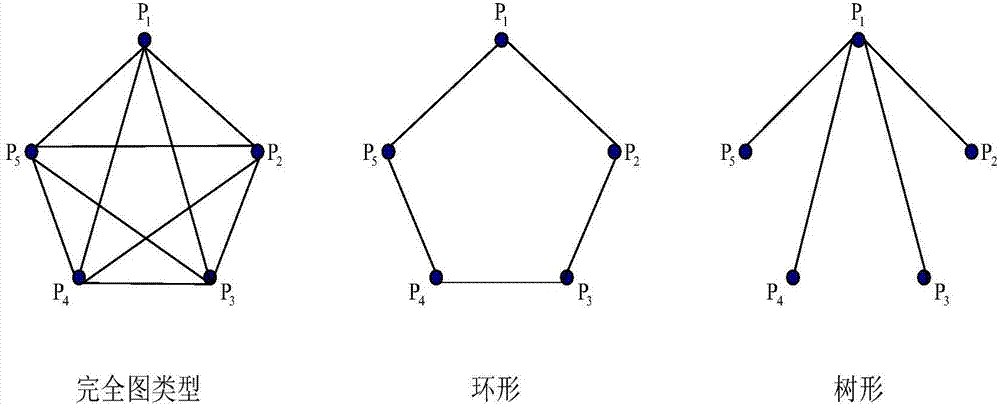
108 results about "Complete graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
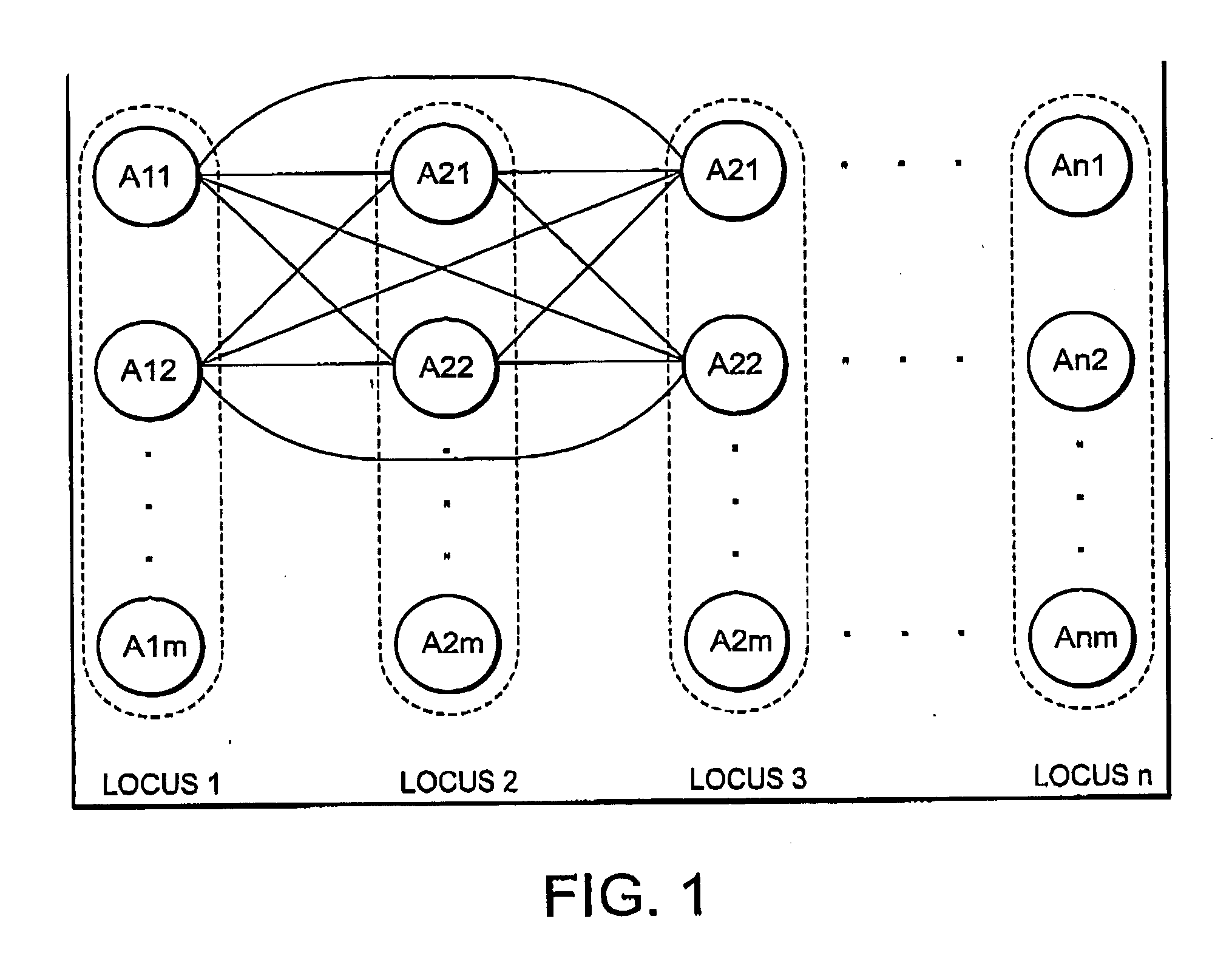
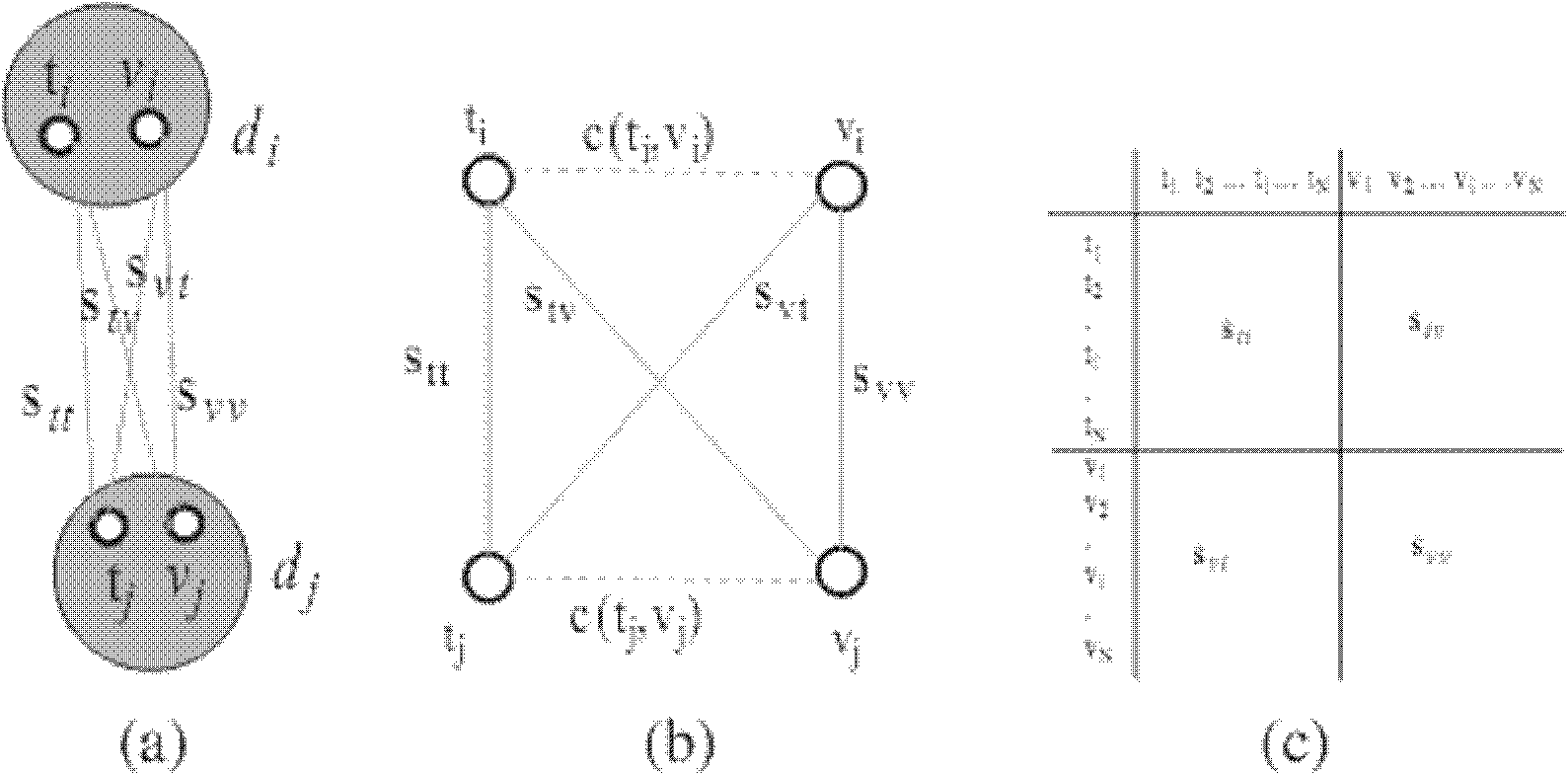
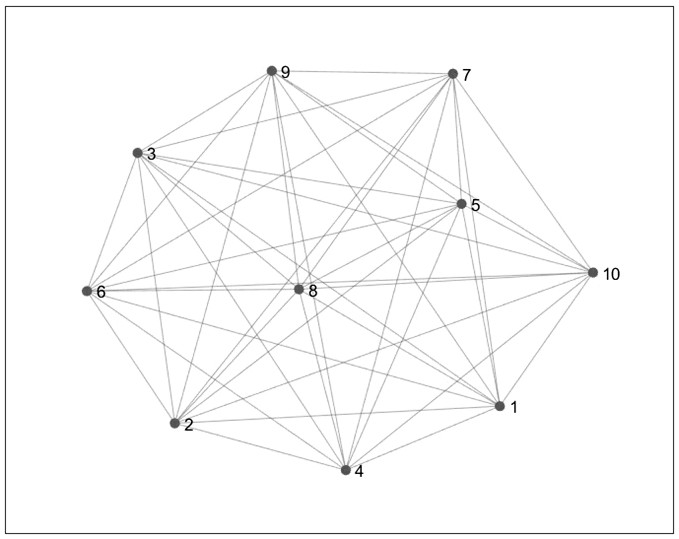
In the mathematical field of graph theory, a complete graph is a simple undirected graph in which every pair of distinct vertices is connected by a unique edge. A complete digraph is a directed graph in which every pair of distinct vertices is connected by a pair of unique edges (one in each direction).
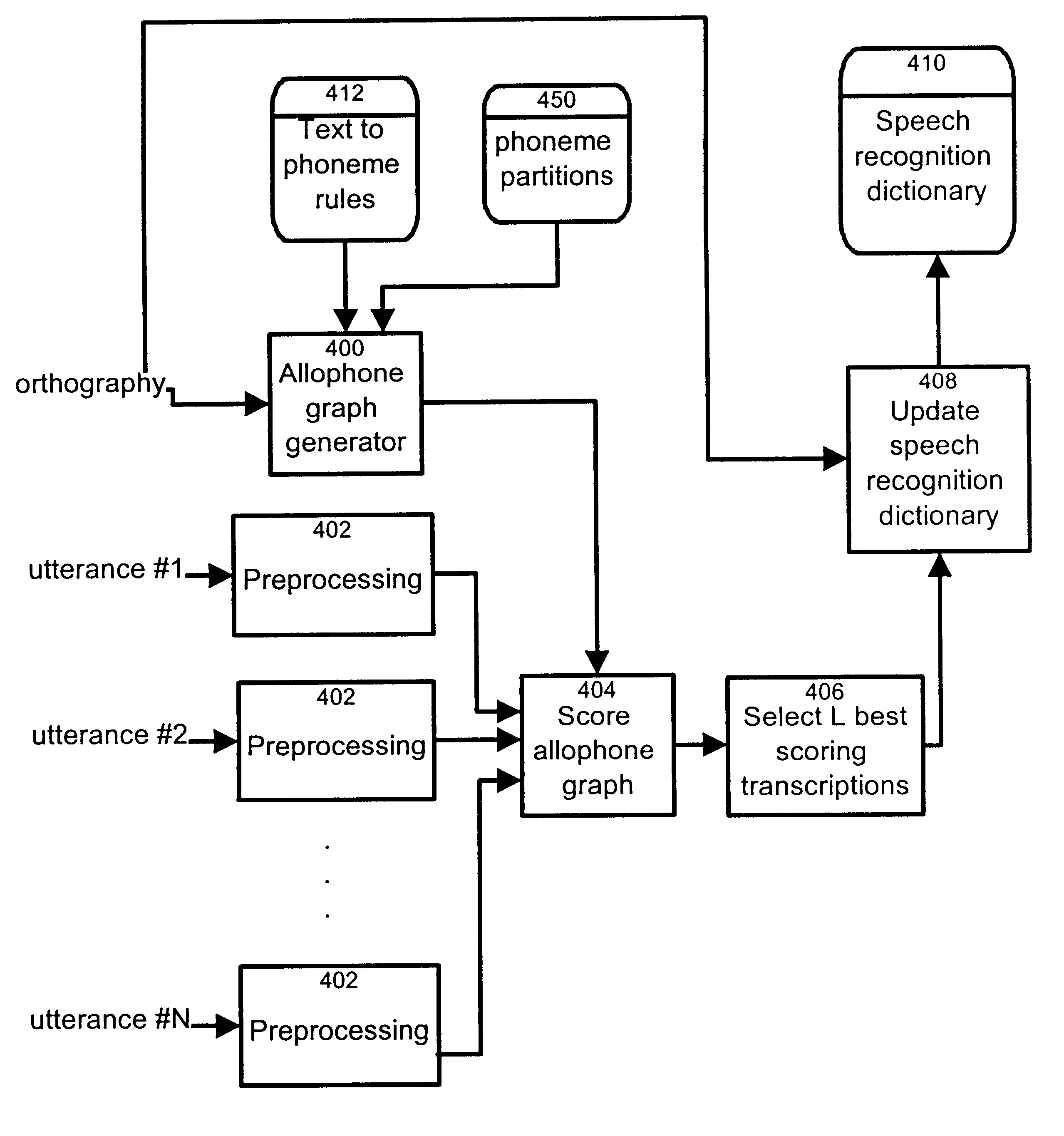
Method and apparatus for obtaining a transcription of phrases through text and spoken utterances
A method and an apparatus for adding a new entry to a speech recognition dictionary, and more particularly a system and method for generating transcriptions from multiple utterances and a textual representation of a given word is provided. The method and apparatus combine acoustic information obtained from each of the training utterances to generate the most likely transcriptions. It also provides a method and apparatus for transcribing multiple utterances into a single transcription that can be added to a speech recognition dictionary. In a first step, a graph representative of possible pronunciation of the word or combination of words is generated on the basis of the textual representation of the word and a letter to phoneme set of rules. Phonemes perceptually close to the phonemes in the transcriptions obtained using the letter to phoneme rules are added on parallel branches in the generated graph. Following this, each branch in the graph is replaced with its allophones and the complete graph is scored using training utterances to obtain the most likely allophone sequence on the basis of the multiple utterances of the word.
Owner:AVAYA INC
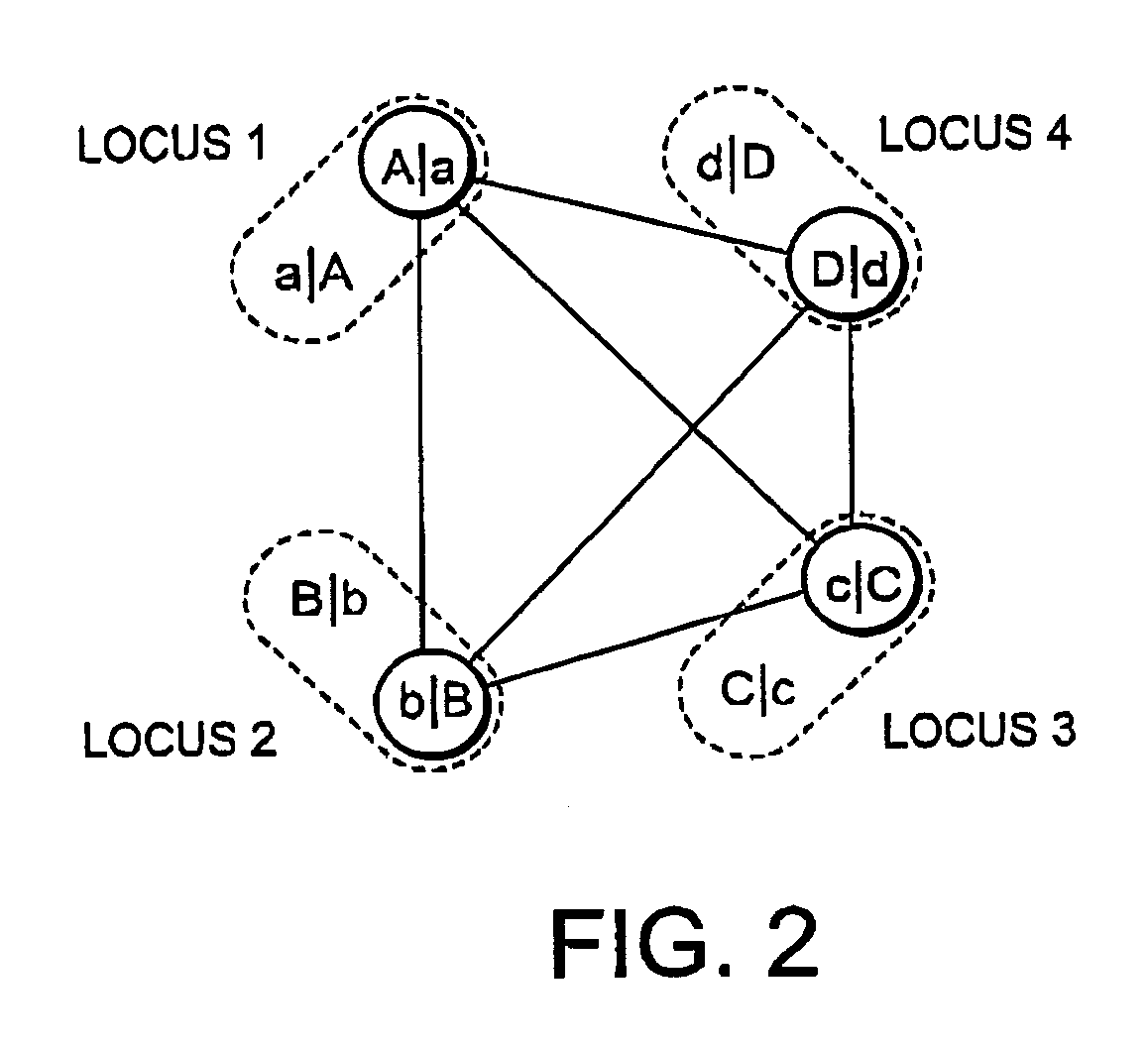
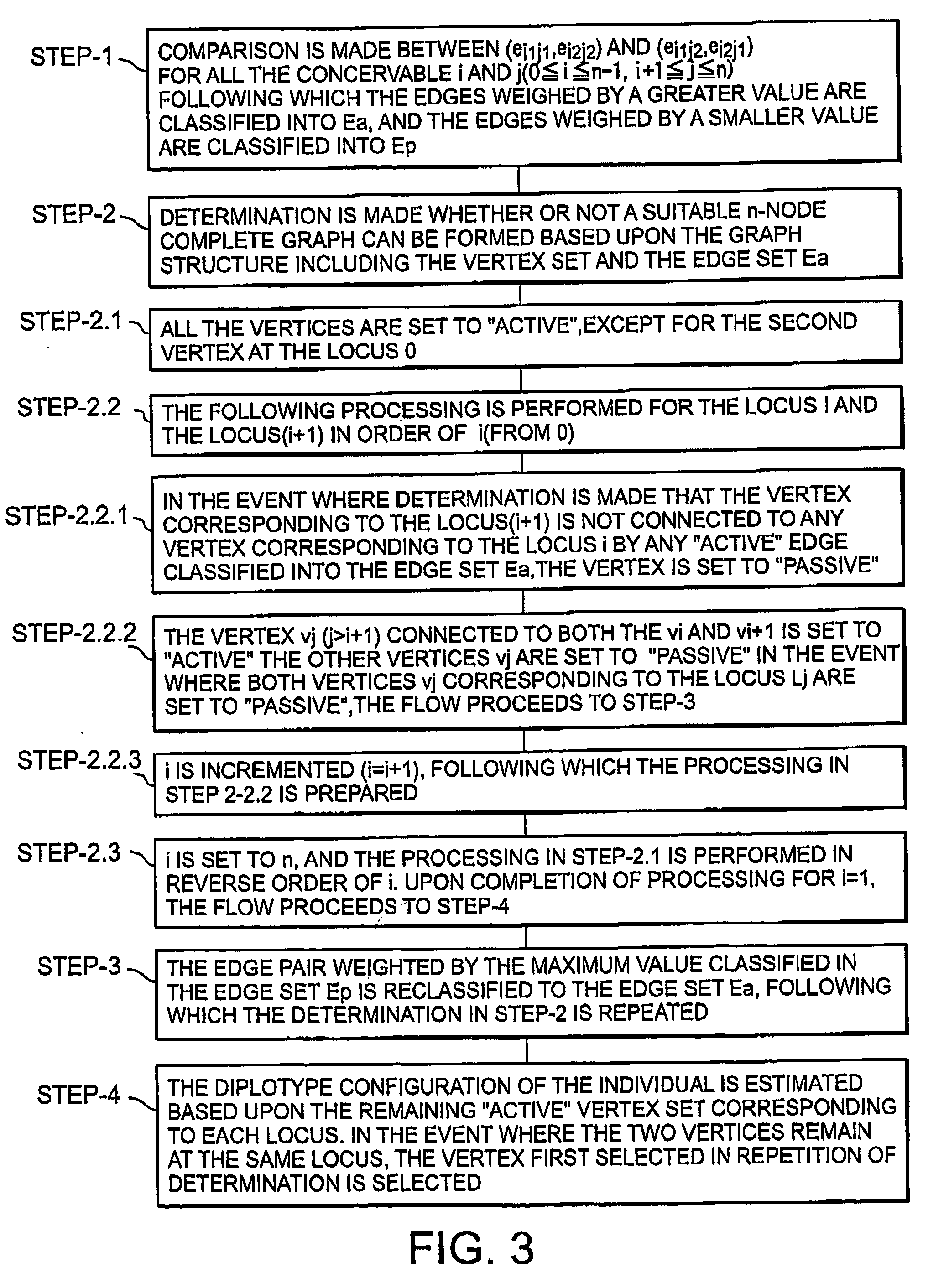
Haplotype estimation method
InactiveUS20050089906A1Reduce processing timeImprove accuracyMicrobiological testing/measurementBiostatisticsAlgorithmHaplotype estimation
An EM algorithm and a graph structure are combined so that all haplotype information to be assumed is kept, thus changing a problem into one for searching for a complete graph having a maximum score for haplotype estimation.
Owner:NEC CORP +1
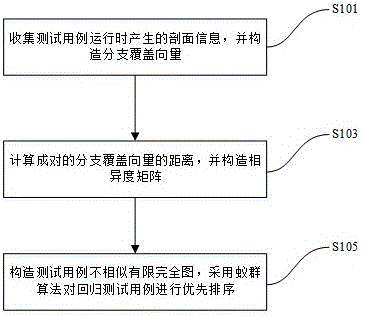
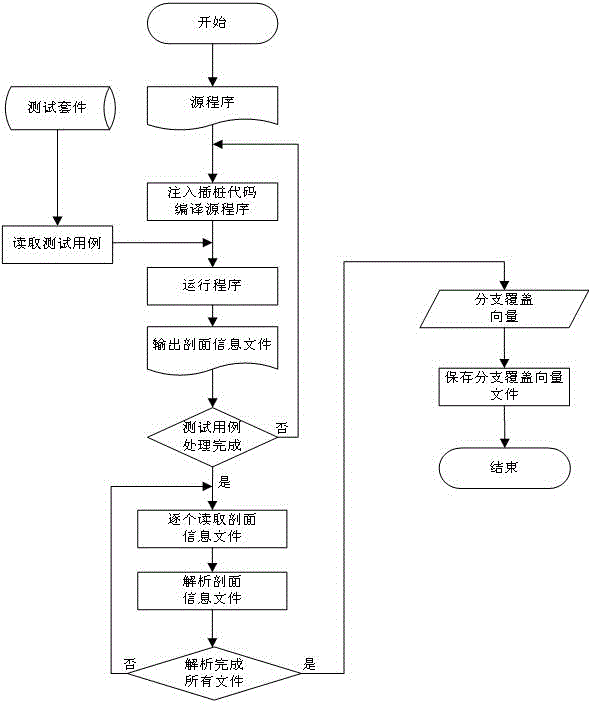
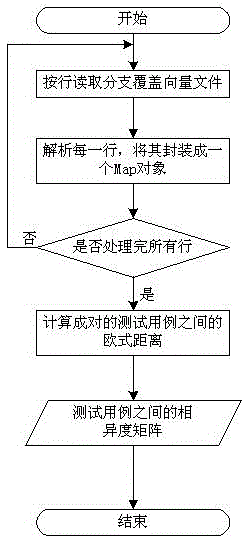
Regression test case prioritization method based on branch coverage and similarity
InactiveCN105528289AImprove scalabilityImprove efficiencyArtificial lifeSoftware testing/debuggingRegression testingComplete graph
The present invention provides a regression test case prioritization method based on branch coverage and similarity. The regression test case prioritization method comprises the following steps of (1) collecting profile information when test cases are operated, and constructing branch coverage vectors; (2) calculating the distance between the coupled vectors through an Euclidean distance function, and constructing a dissimilarity matrix of the test cases; and (3) constructing a test case nonsimilarity limited complete graph by using the test cases as vertexes and using connecting lines and distances between the test cases respectively as edges and edge weights. The test case prioritization sequence having the longest distance is searched in the graph through ant colony optimization. The problems that in the prior art, for a regression test case prioritization method, error detection efficiency is not high, and stability of results is poor are solved, regression test error detection efficiency, stability and expandability are largely improved, automation degree of software regression test is also increased, and therefore software testing work efficiency is improved.
Owner:CHINA UNIV OF MINING & TECH
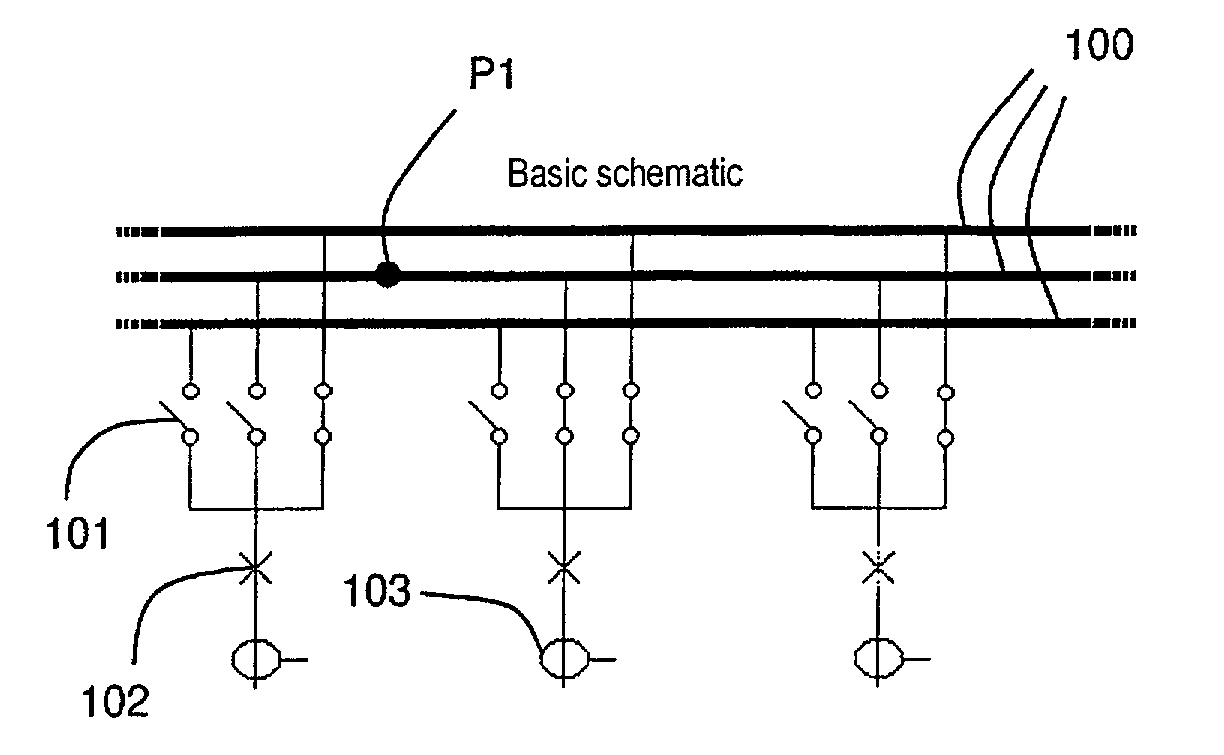
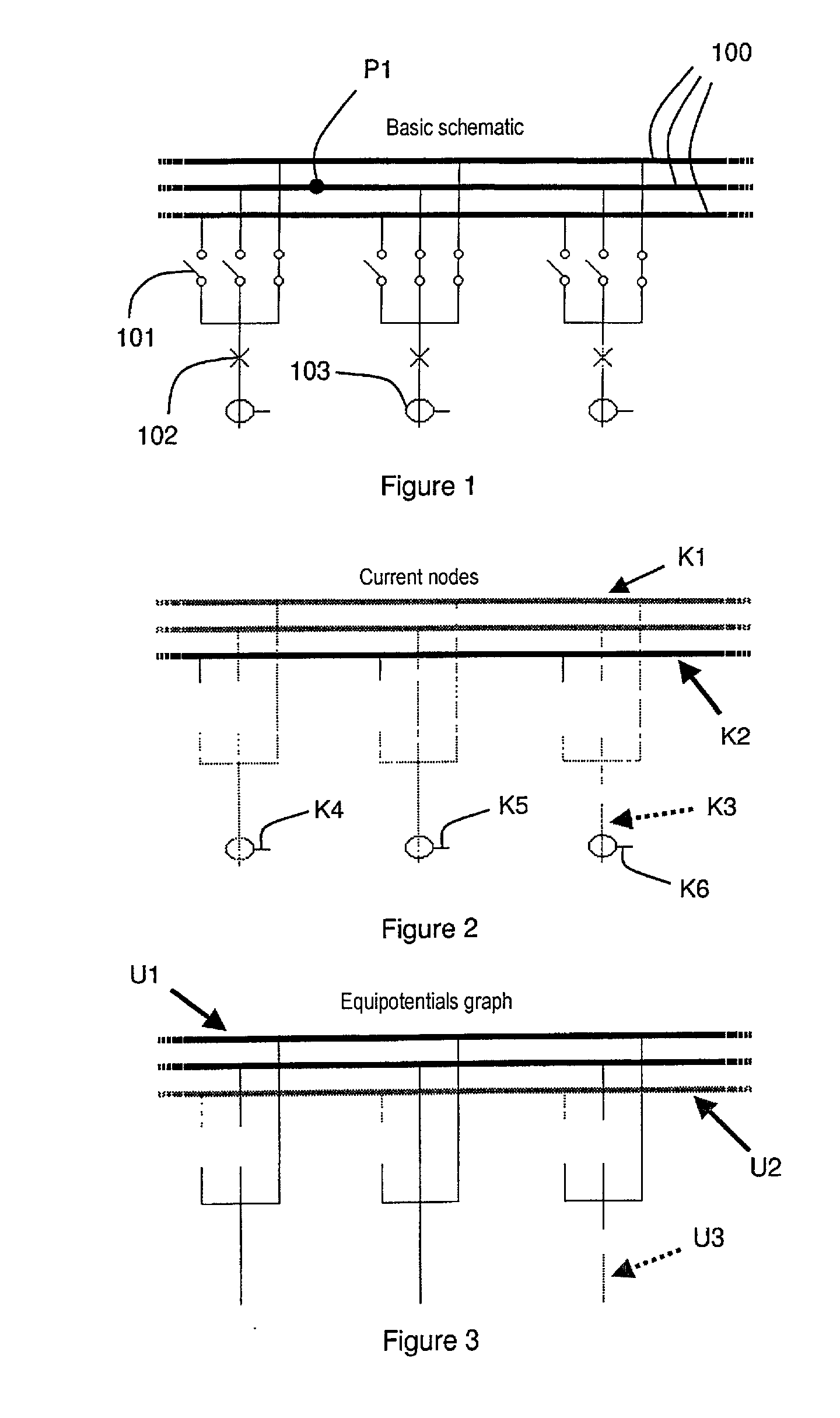
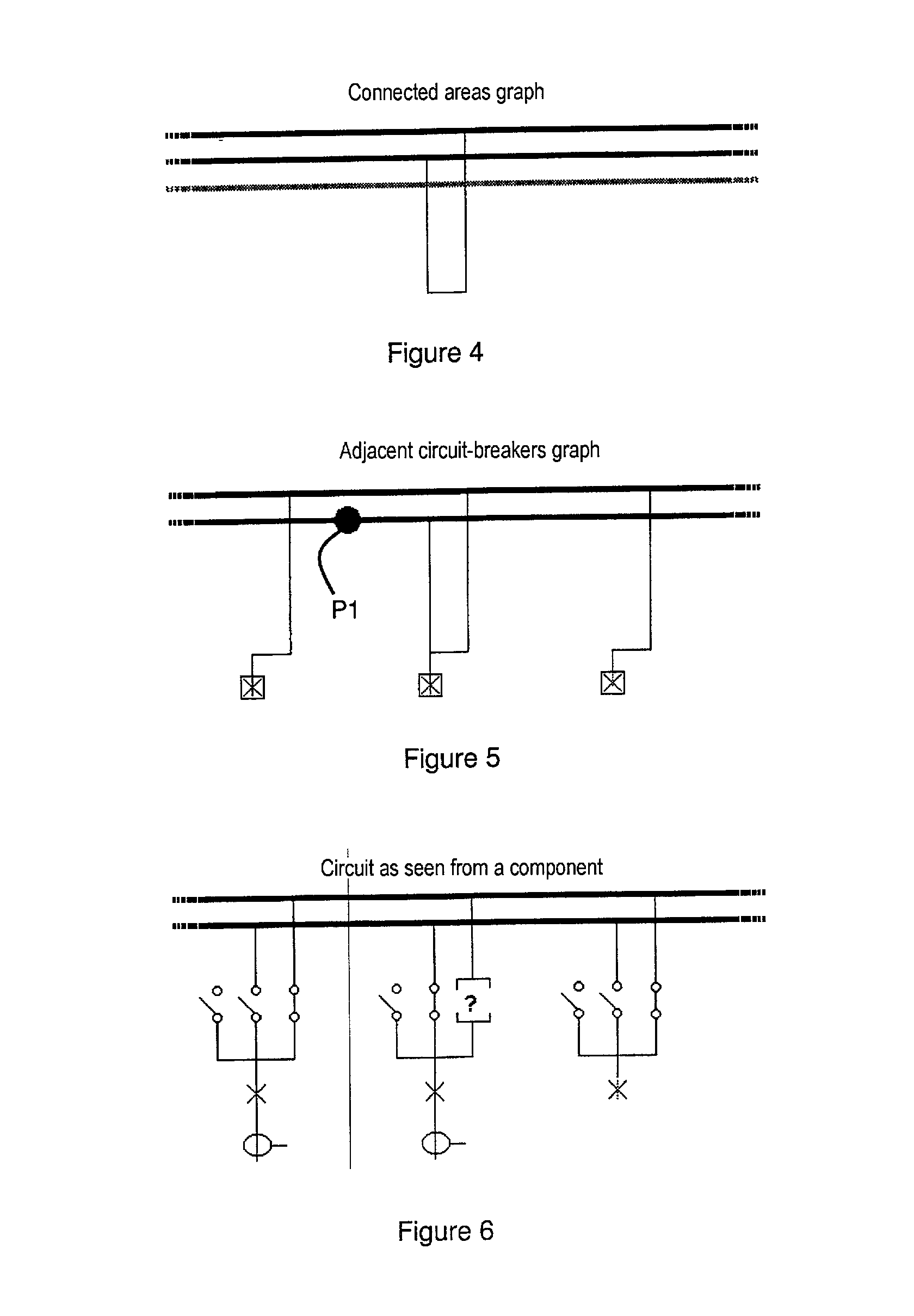
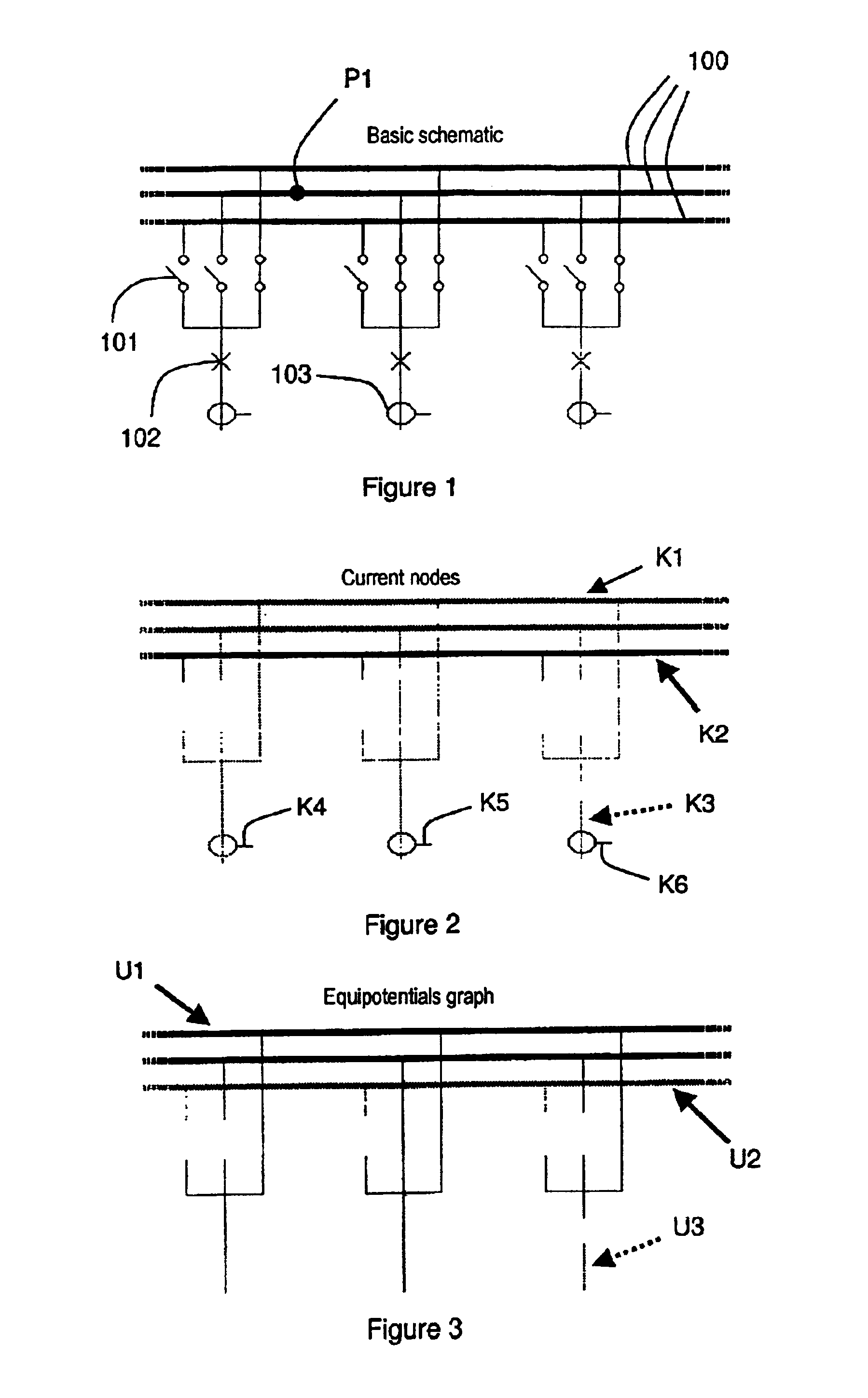
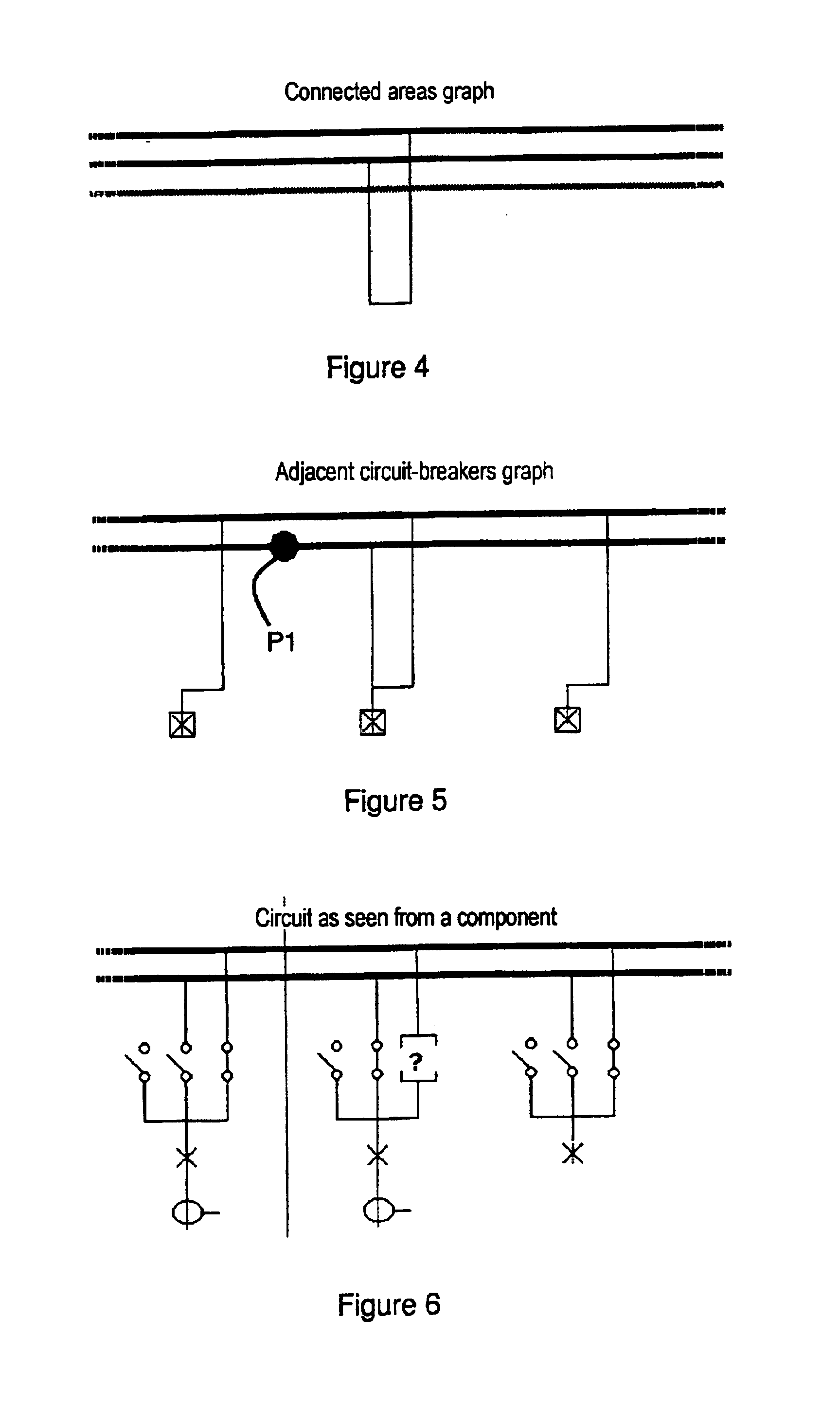
Process for initializing and updating the topology of a high-voltage or medium-voltage electrical power station
InactiveUS20020091503A1Simple taskEasy to operateGeometric CADAnalogue computers for nuclear physicsPower stationManagement unit
The process is intended to optimize the operation of a digital protection system for protecting sets of busbars in the power station and uses a basic schematic of the electrical configuration of the power station obtained from information on the type of components used in the power station, and on the possible connections and accesses to said components. The information is assigned to management units of the digital protection system, said management units comprising peripheral measurement units and at least one centralization unit. A topological compilation process is implemented to provide a compiled schematic topology, and to provide a compiled assignment topology of the components in the power station and of their connections to the management units. A partial graph, whose structure depends on the type of information searched for and the status of each component of the power station, is obtained for each peripheral unit. A complete graph is then computed in one or more centralization units by algorithms which superpose partial graphs.
Owner:ALSTOM SA
Multicast routing method based on particle swarm algorithm
InactiveCN101447936AFast convergenceImprove robustnessBiological modelsData switching networksParticle swarm algorithmComputer science
The invention aims at solving the multicast routing problem by applying a particle swarm algorithm. Firstly, a connecting network is converted into a distance complete graph based on a Floyd algorithm, and then the particle swarm algorithm is applied to searching for an optimal multicast tree on the basis of the distance complete graph. In the particle swarm algorithm, each particle is encoded into a binary character string to represent a node for constructing the multicast tree, wherein, '1' means that the node is used while '0' means that the node is not used. Each particle constructs the multicast tree by a Prim algorithm based on the binary character string; and a constructed multicast tree can be evaluated when redundant parts of the multicast tree are cut off. Experimental results prove that a better result can be obtained by the particle swarm algorithm of the invention compared with the traditional heuristic algorithm.
Owner:SUN YAT SEN UNIV
Multimode-combined image reordering method
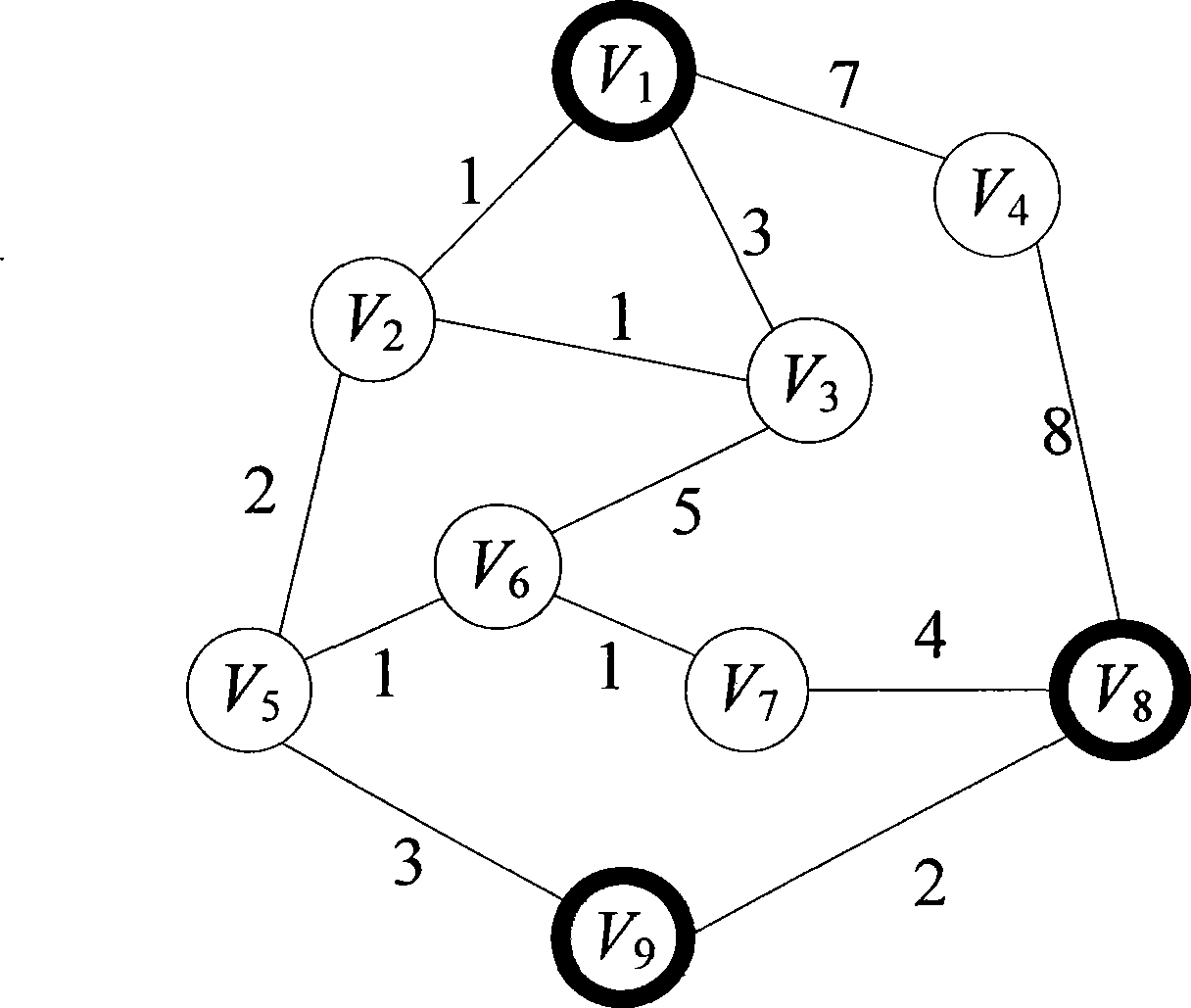
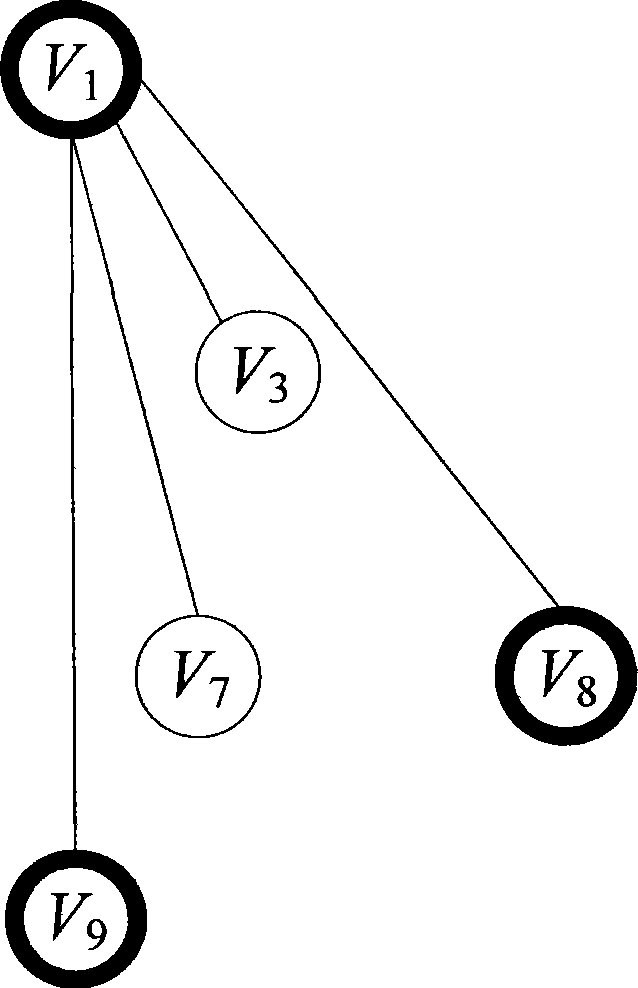
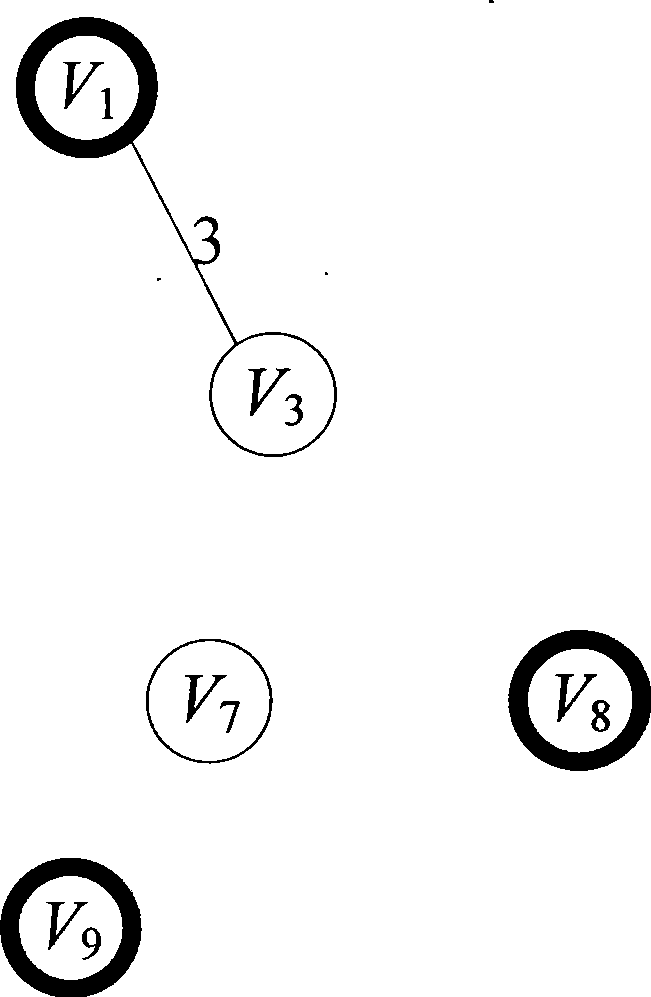
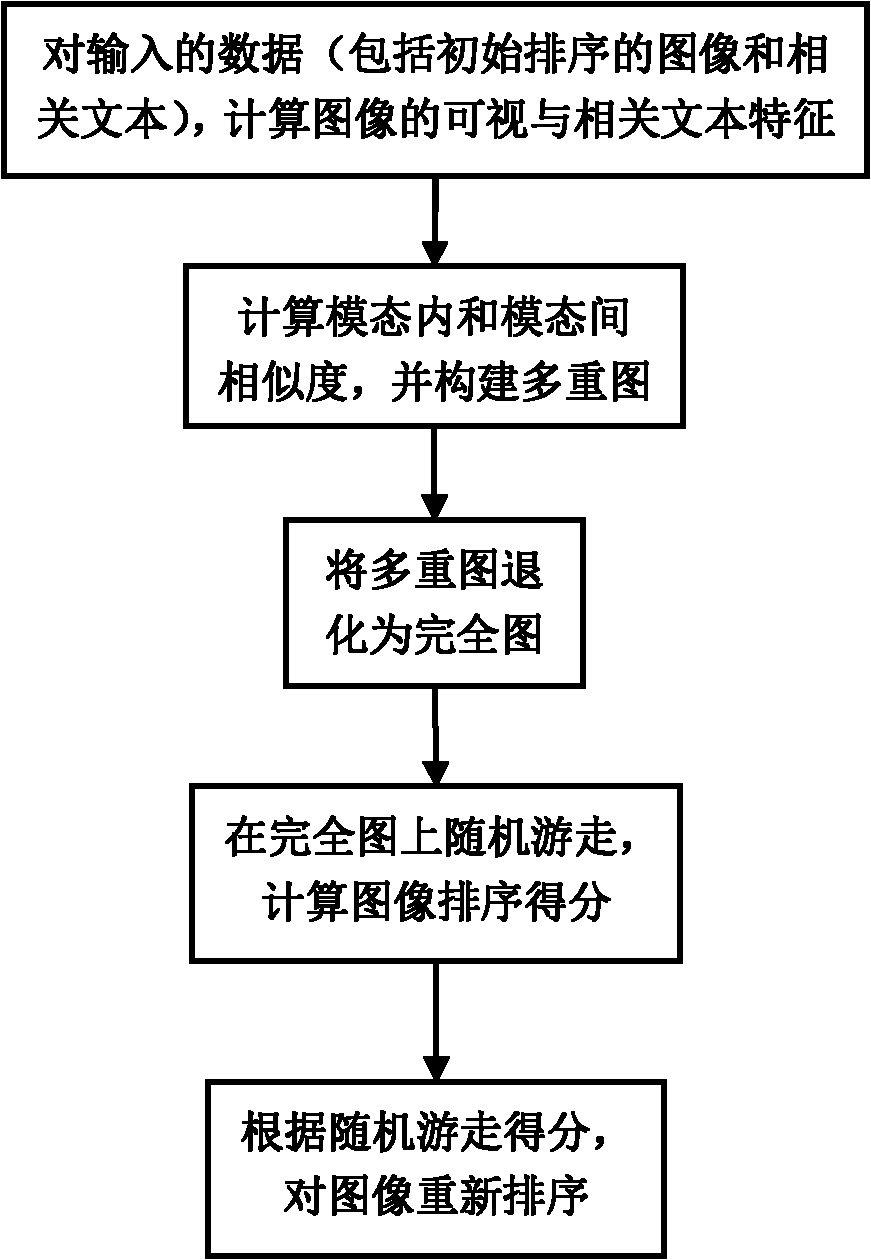
InactiveCN102129477AOvercoming the problem of image multimodal separation considerationsSort results improvedCharacter and pattern recognitionSpecial data processing applicationsMultigraphImage retrieval
The invention discloses a reordering method aiming at image retrieval result, which can make full use of multimode information in the process of image ordering, can further improve the image ordering result on the basis of the current retrieval result to enhance the accuracy, and is extraordinarily suitable for the use by an image retrieval system under a network environment or on the basis of a local system. The method of the invention comprises the following steps of: (1) extracting visual and textual characteristics of images; (2) retrieving the similarity in the modes (between single modes) and the similarity between the modes (between multiple modes) between the images, and constructing a multigraph according to the similarities; (3) processing the multigraph so that the multigraph is deteriorated to a complete graph; (4) performing random walk on the complete graph and calculating image ordering scores; and (5) reordering the images according to the condition of the image ordering scores to obtain a final result.
Owner:SHANDONG UNIV
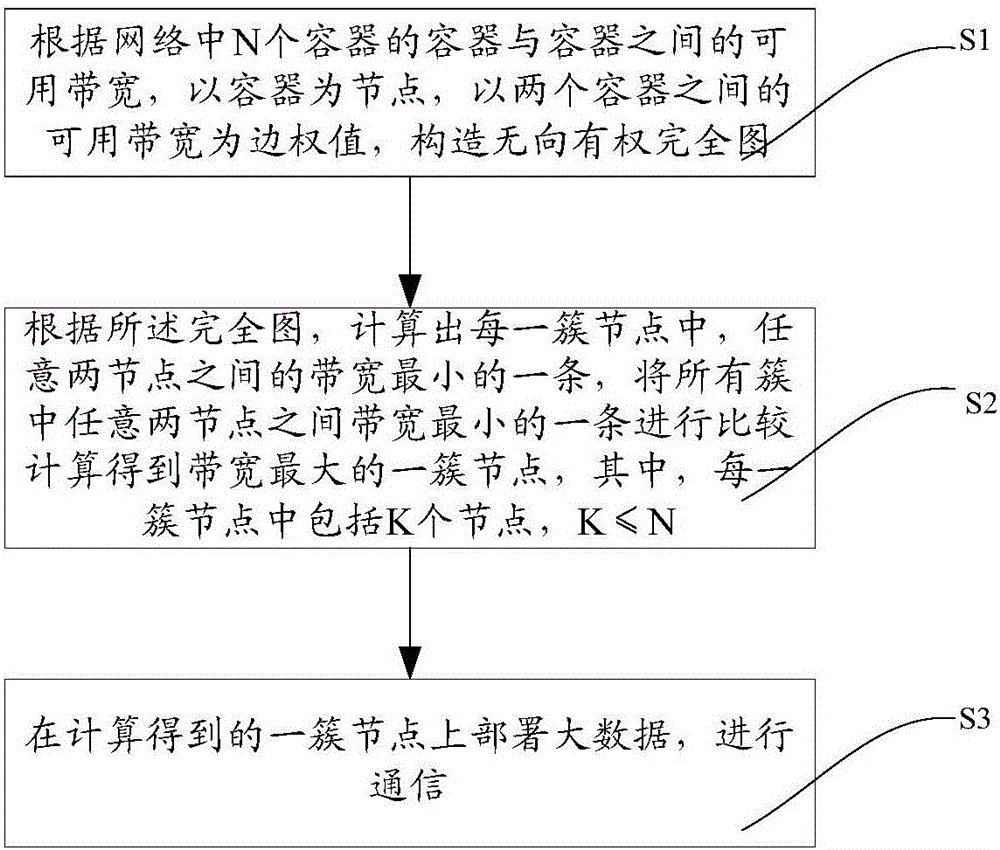
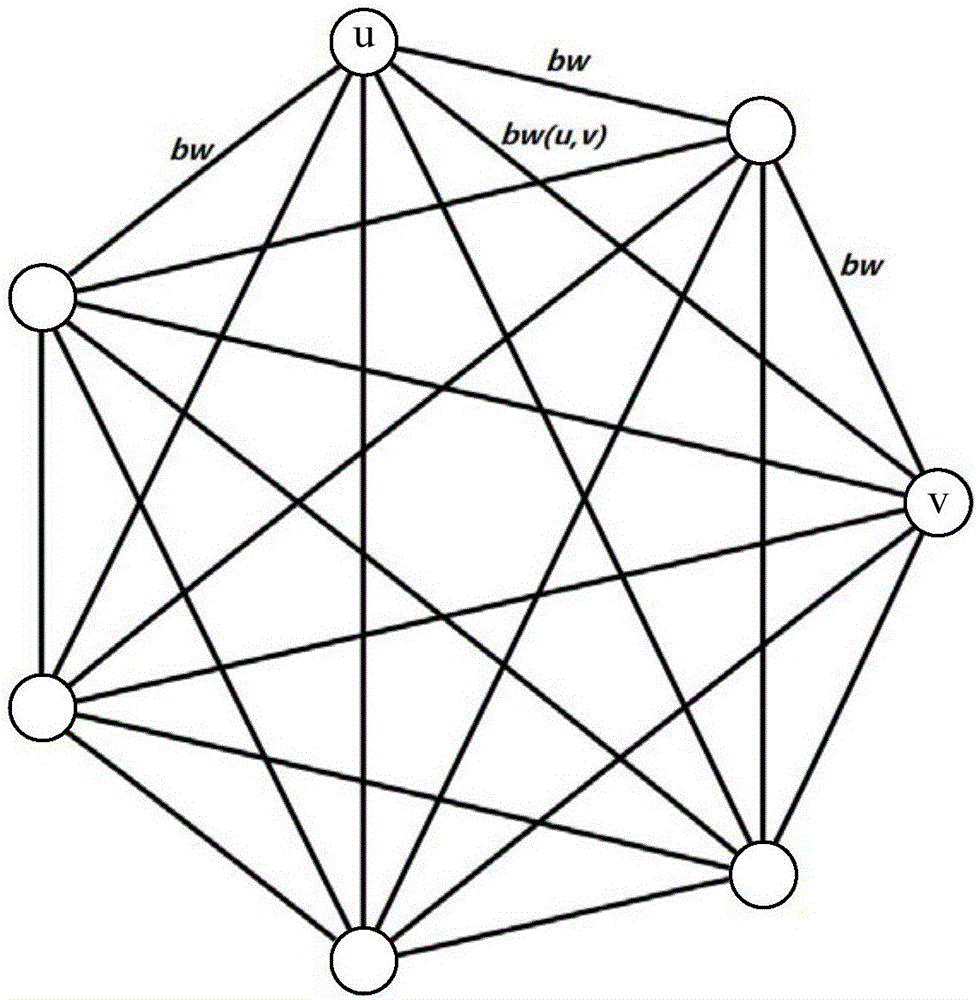
Container resource allocation method and device
ActiveCN106095579ALarge aggregation bandwidthSave bandwidthResource allocationComplete graphResource allocation
The invention provides a container resource allocation method and device, and belongs to the technical field of communications. The container resource allocation method comprises the steps that 1, according to available bandwidths between N containers in a network, an undirected weighted complete graph is structured by taking the containers as nodes and taking the available bandwidths between every two containers as edge weights; 2, according to the complete graph, the smallest bandwidth between any two nodes in each cluster node is calculated, and the smallest bandwidths between any two nodes in all clusters are compared and calculated to obtain the cluster node with the largest bandwidth, wherein each cluster node comprises K nodes, and K is smaller than or equal to N; 3, big data is deployed on the cluster node obtained through calculation, and communication is conducted.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
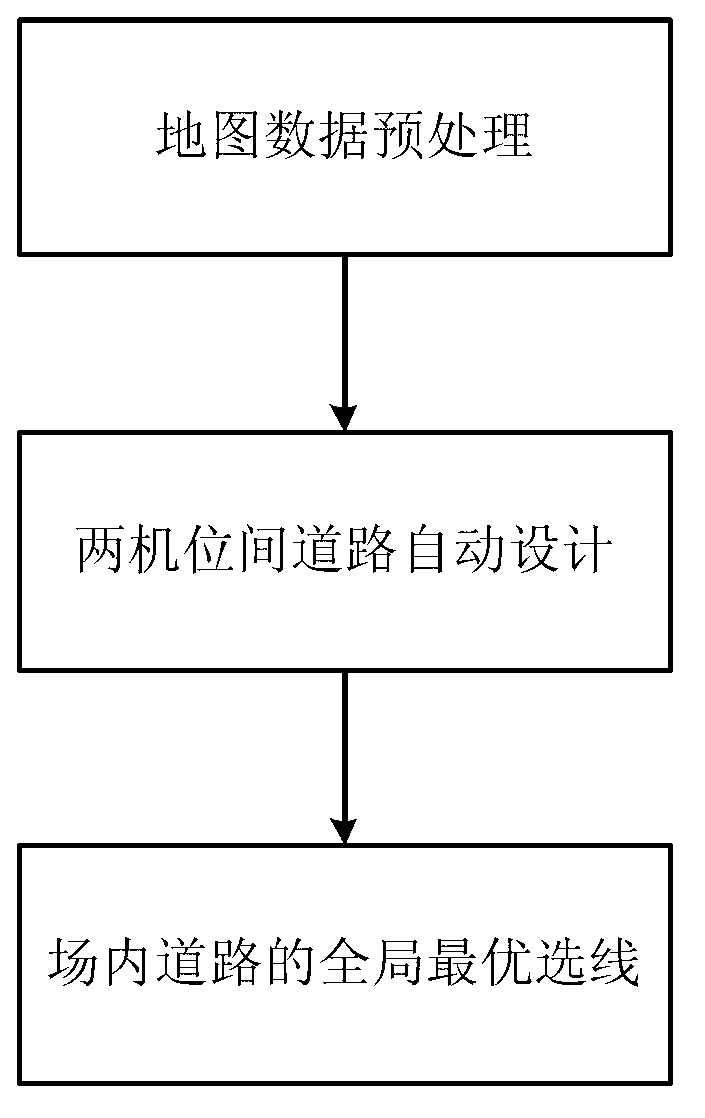
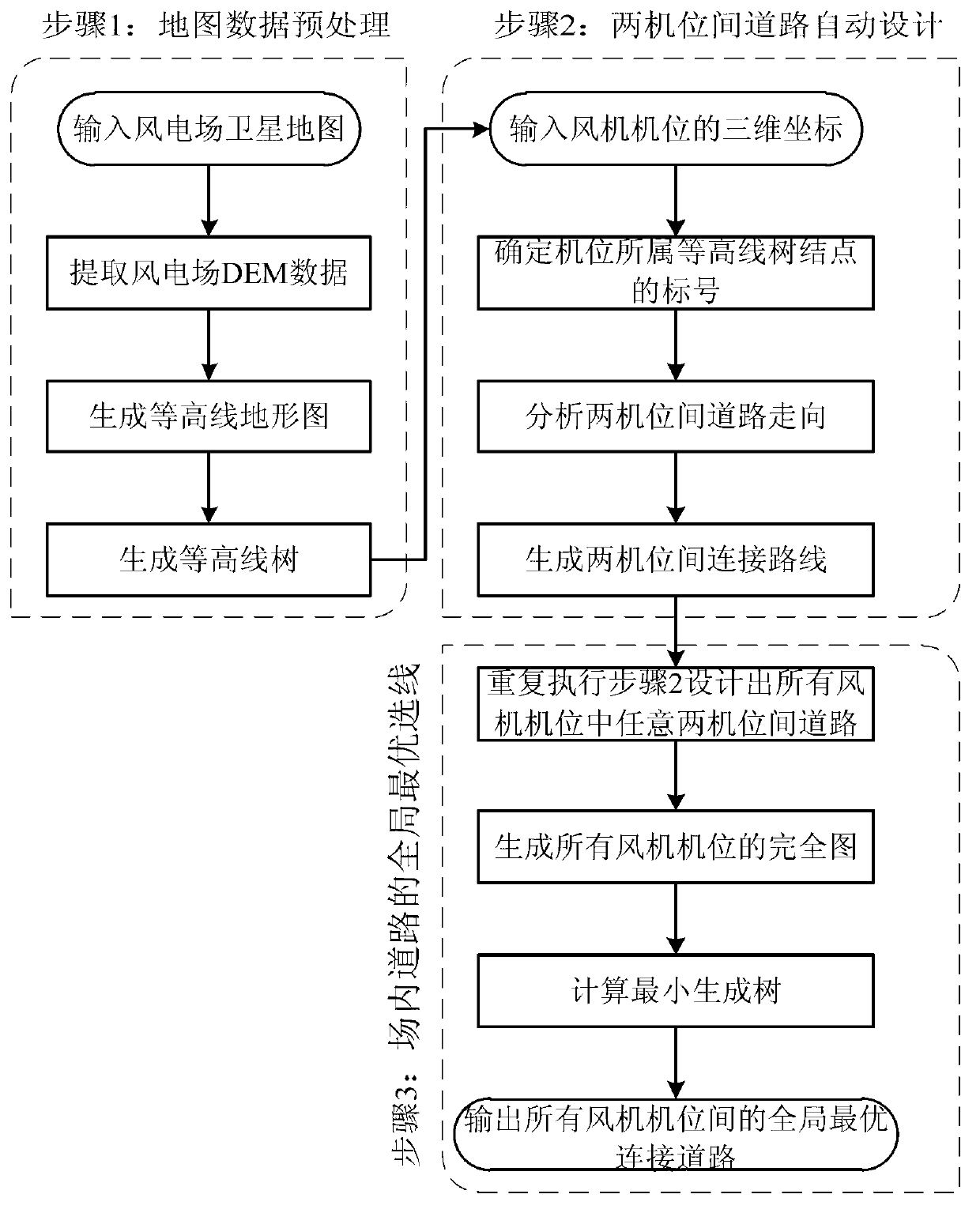
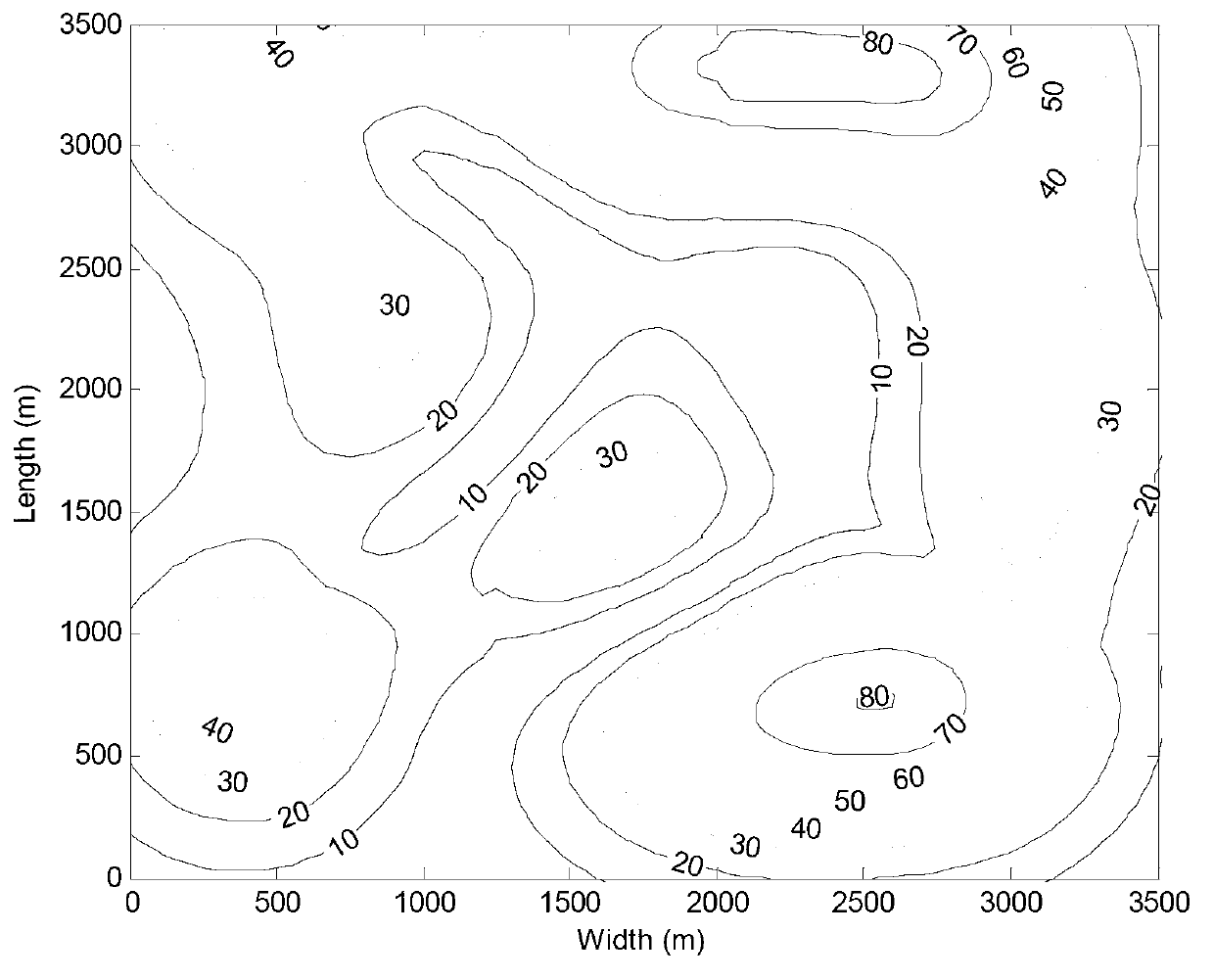
Automatic optimization route-selection method for route design in wind power plant
InactiveCN103106300ASpeed up the construction processJudging the feasibilitySpecial data processing applicationsInformation technology support systemPeaking power plantWorkload
The invention relates to an automatic optimization route-selection method for a route design in a wind power plant. The automatic optimization route-selection method comprises the following steps: (1) pre-processing a satellite map of the wind power plant to obtain a hypsographic map and a hypsographic tree of the wind power plant, (2) defining a connection route between any two fan positions in the wind power plant according to the hypsographic tree and the hypsographic map, and (3) repeating the step (2) until a complete graph of the connection routes of all fan positions is generated, and optimizing the overall route selection of the complete graph to obtain the best connection route of roads in the wind power plant. Compared with the prior art, the automatic optimization route-selection method is capable of rapidly optimizing the roads in the wind power plant which is complex in landform, lightens workloads, improves the efficiency of optimized route selection, and has high engineering practicability.
Owner:TONGJI UNIV
Security multi-party quantum summation consultation method based on quantum Fourier transform
ActiveCN107508677AKey distribution for secure communicationPhotonic quantum communicationFast Fourier transformQuantum Fourier transform
The invention discloses a security multi-party quantum summation consultation method based on quantum Fourier transform, wherein transmitted particles are transmitted in a complete graph mode. The method disclosed by the invention can resist to an external attack and a participant attack. Particularly, a participant in a non-minimum subset cannot successfully and separately decide a shared summation calculation result. In addition, according to the method disclosed by the invention, a module d is calculated, and both calculation and summation are carried out in a mode of adding integers and integers instead of a mode of adding bits and bits.
Owner:嘉兴市顺凯鹿科技有限公司
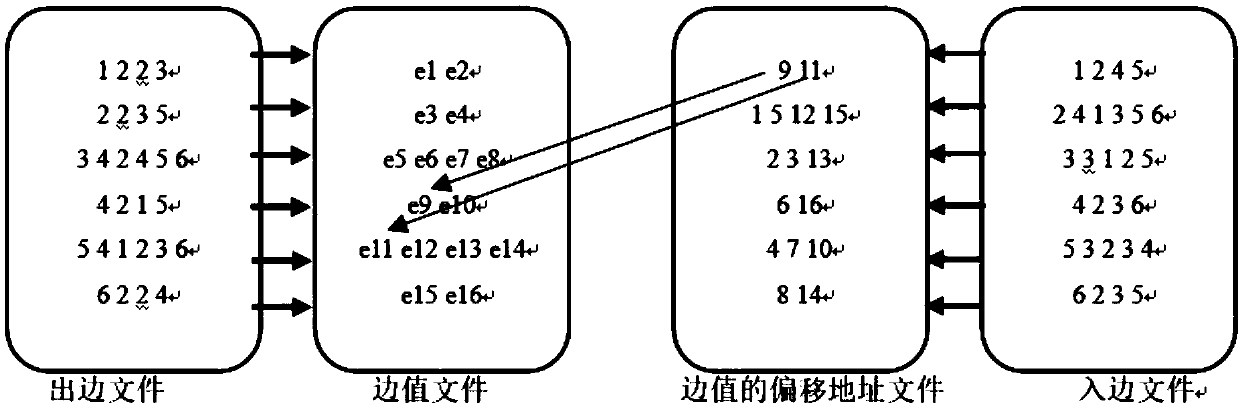
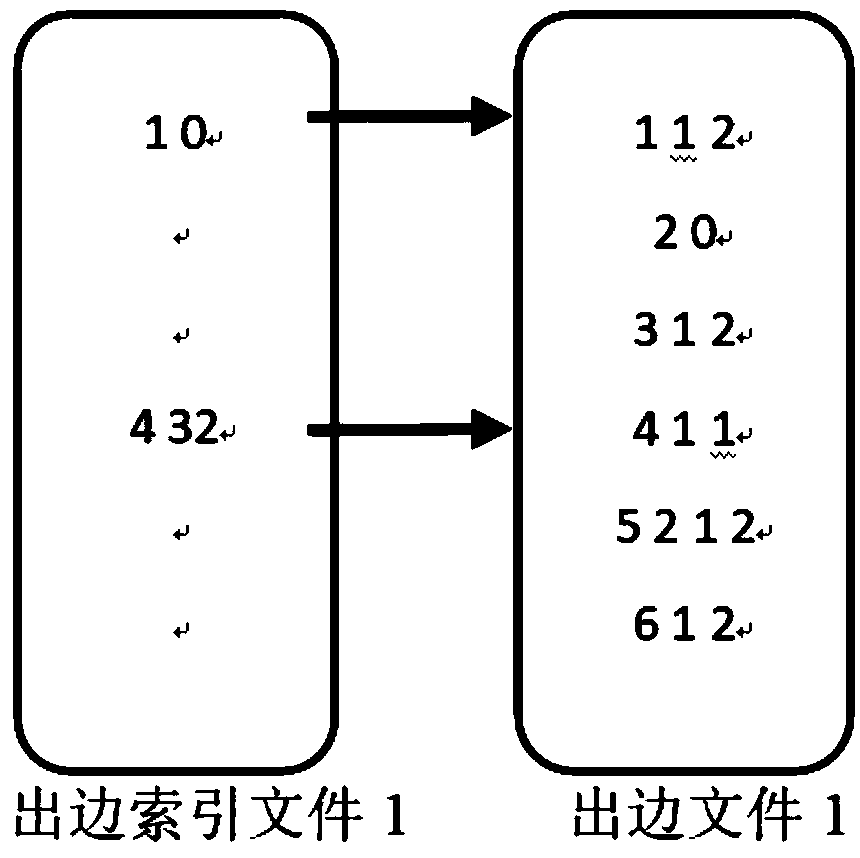
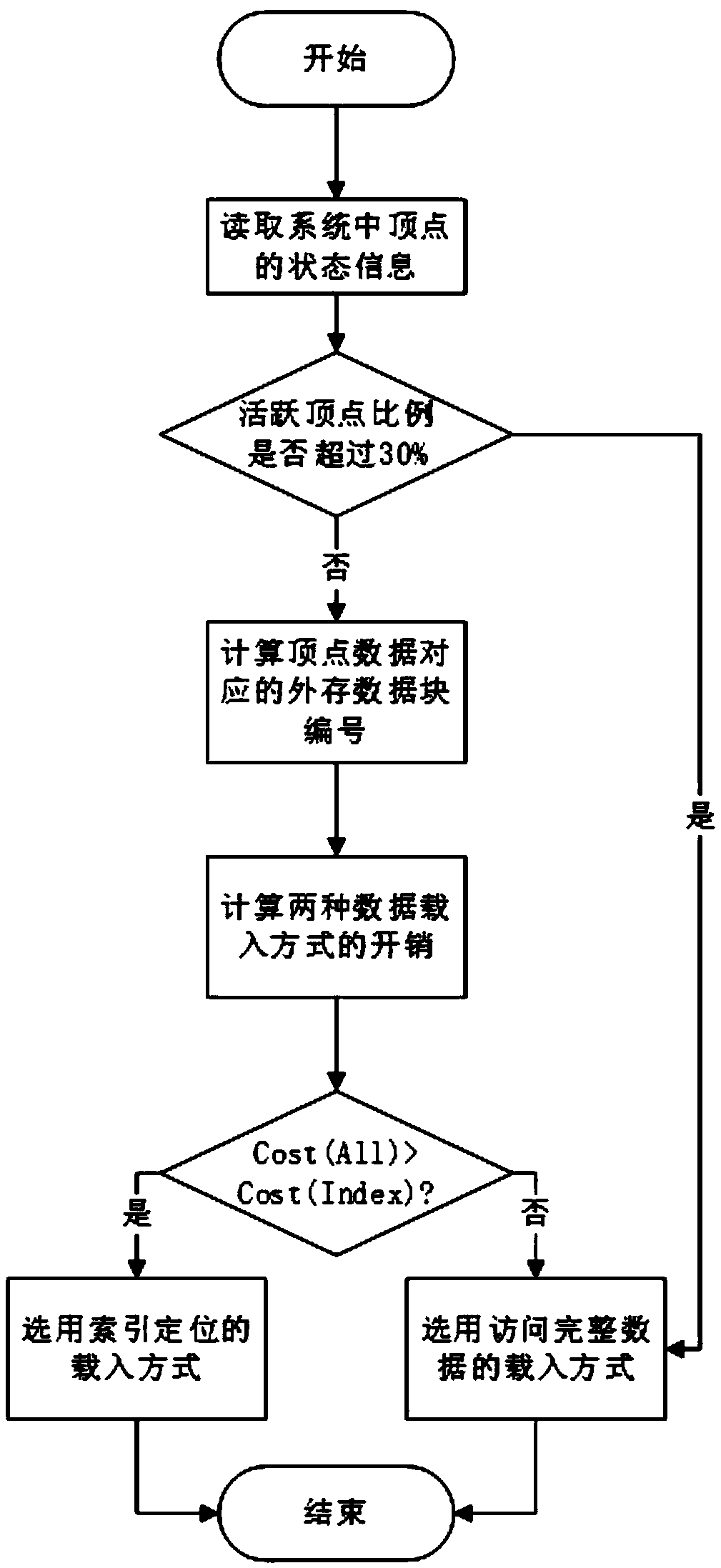
External memory access method of a graph computing system based on index positioning
The invention discloses an external memory access method of a graph computing system based on index positioning, which comprises the following steps: dividing complete graph data into a plurality of sub-graphs; sorting The edges of each subgraph according to the source vertex number and the target vertex number respectively. Writing The sorted sub-graphs into the external storage file and indexedfor the source vertex number and the target vertex number respectively. Choosing the best loading mode from the loading mode of index positioning and the loading mode of accessing complete data; Loading the subgraphs in the external memory into memory in an optimal load manner. The invention redesigns the external storage data structure, improves the data loading mode, enables the system to analyze the effective data in the external storage before loading, and remarkably reduces the I / O data quantity and the random access times. This paper analyzes the time cost of accessing complete data andindex positioning, dynamically determines the optimal data loading mode of the system, and reduces the time cost of data loading.
Owner:HUAZHONG UNIV OF SCI & TECH
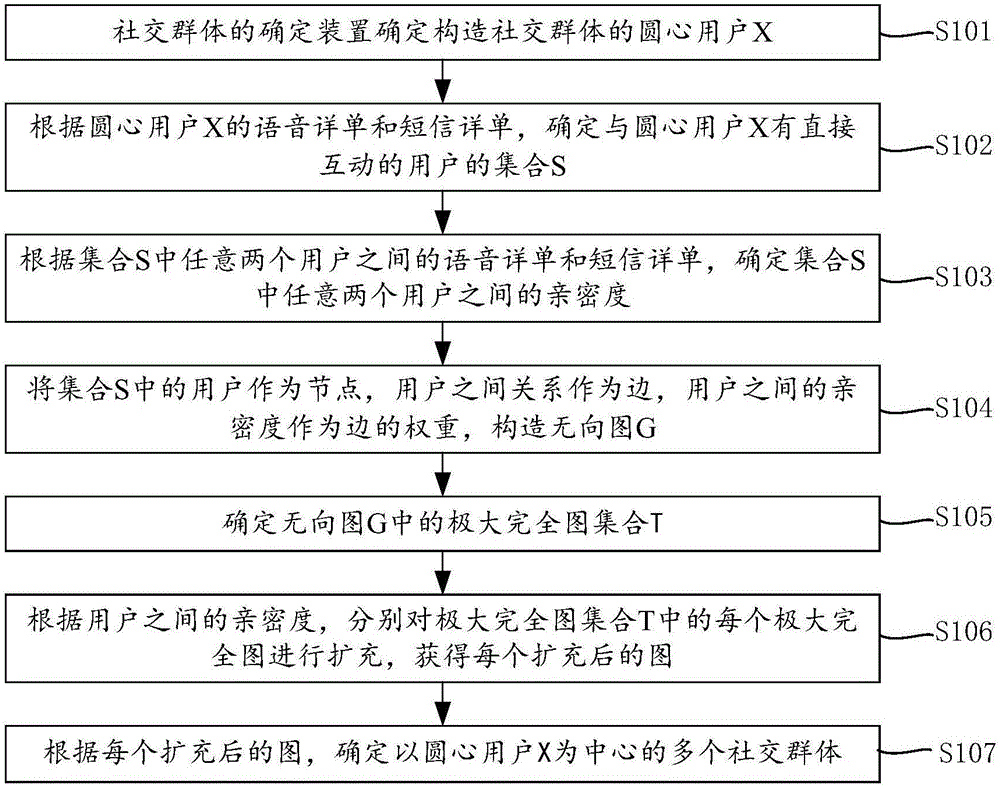
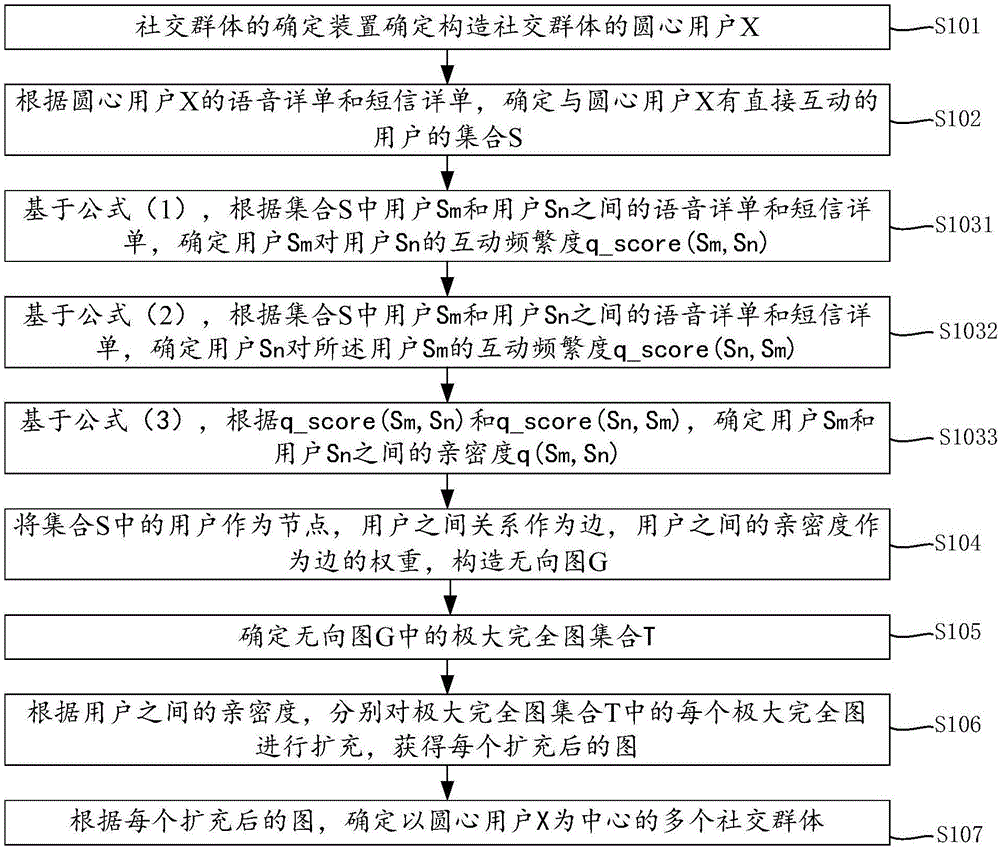
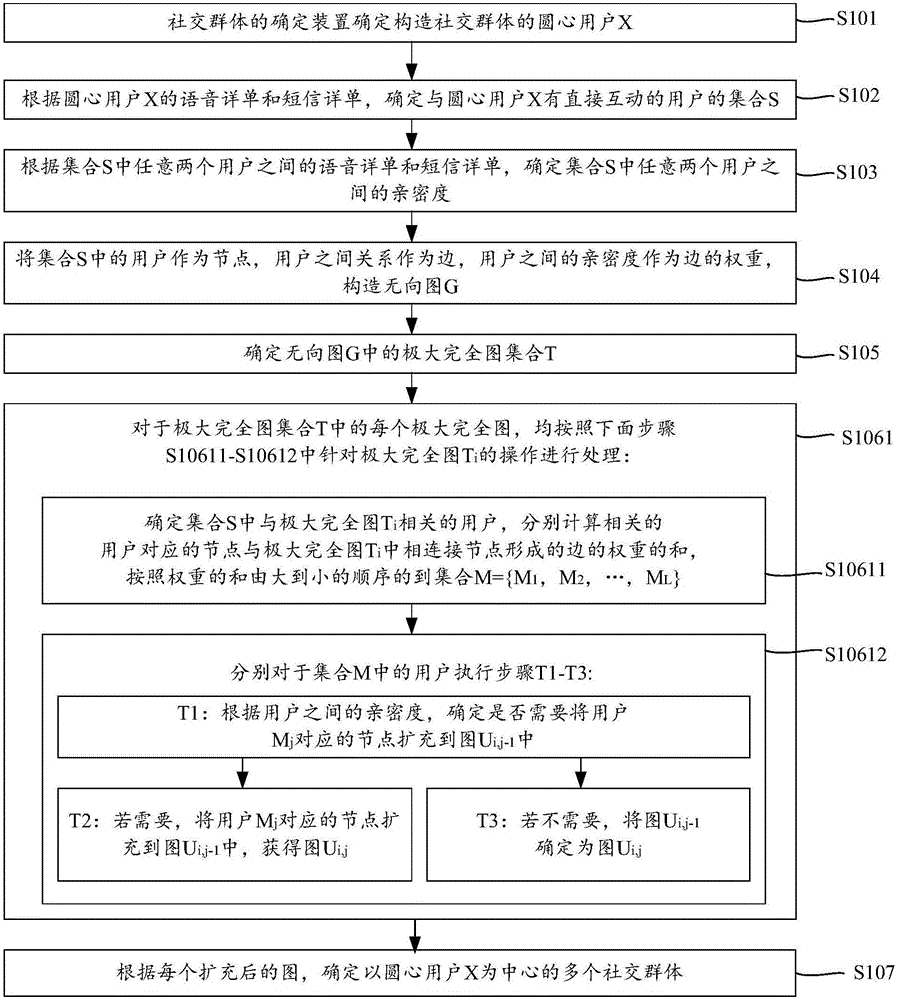
Determination method and apparatus of social groups
The embodiment of the invention provides a determination method and apparatus of social groups, relates to the field of communication, and solves problems of deep mining of the social attribute of users and determination of the social groups with a larger range according to the association relation including calling and text messages among the users with "strong ties". The method includes: determining a center of circle user X for constructing the social groups; determining a set S of users having direct interaction with the user X according to a voice detailed list and a text message detailed list of the user X; determining the intimacy between any two users in the set S according to the voice detailed list and the text message detailed list between any two users in the set S; constructing an undirected graph G by regarding the users in the set S as nodes, the relations among the users as edges, and the intimacies among the users as the weights of the edges; expanding each maximal complete graph in the undirected graph G according to the intimacies among the users; and determining a plurality of social groups regarding the user X as the center according to each expanded graph.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
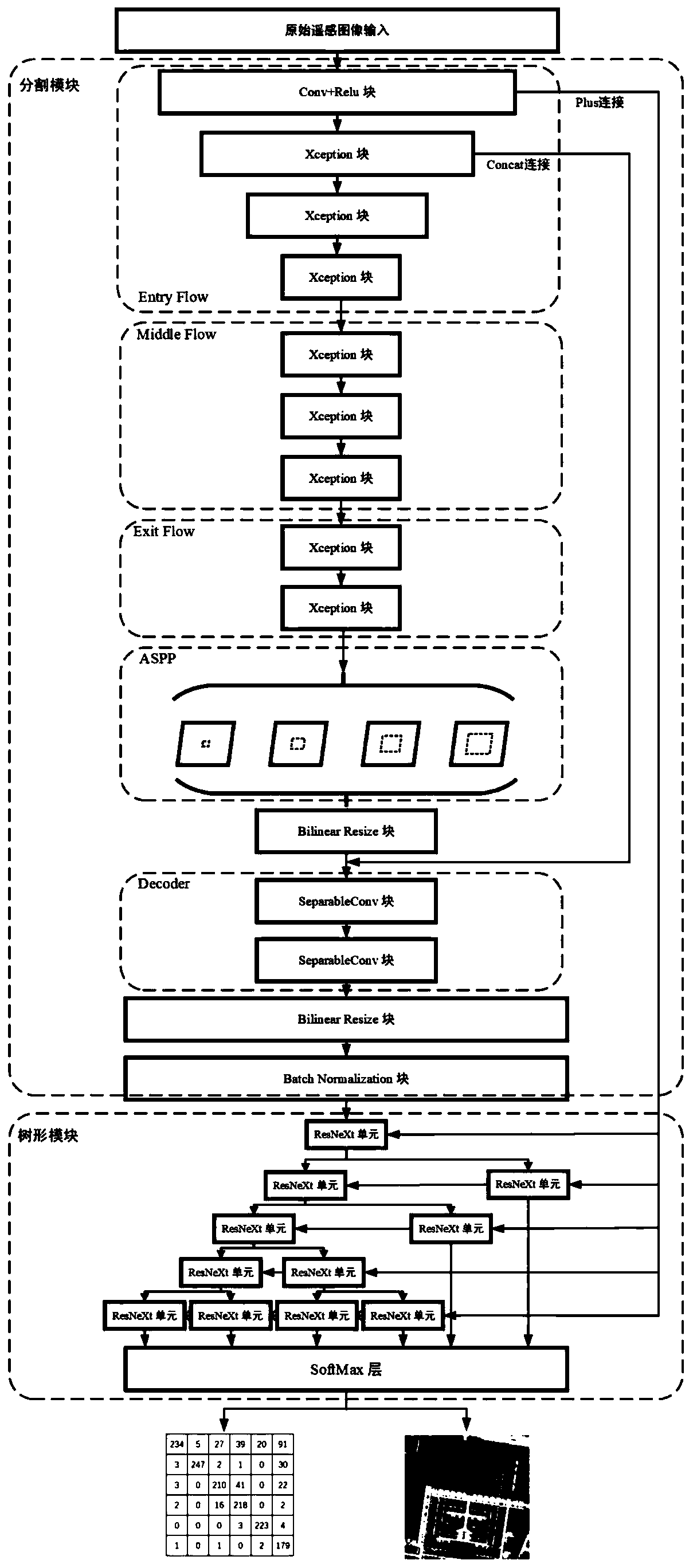
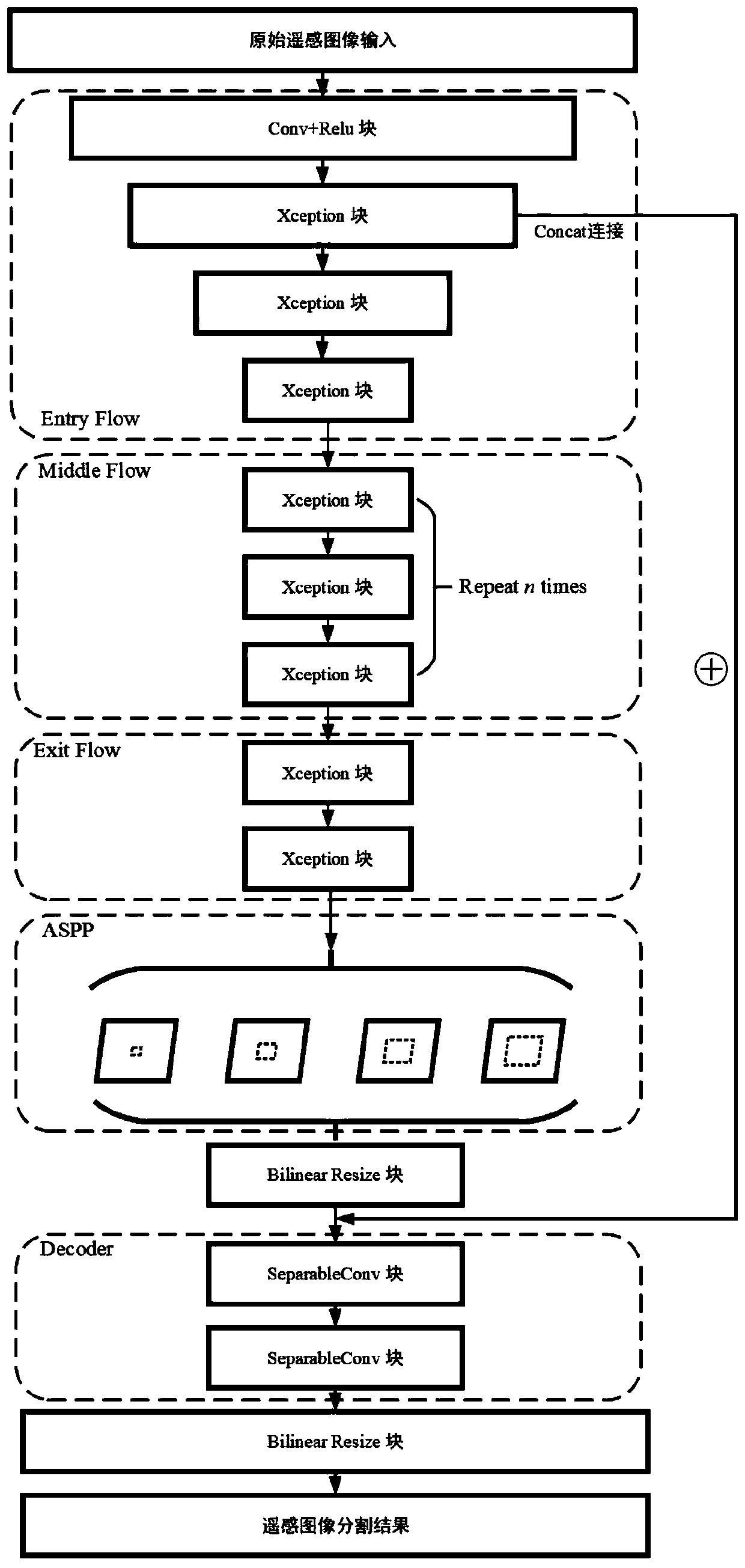
Remote sensing image segmentation network based on tree structure
ActiveCN110009637AImprove Segmentation AccuracyEasy to distinguishImage enhancementImage analysisVisual technologyProcess module
The invention relates to a remote sensing image segmentation network based on a tree structure, and belongs to the technical field of computer vision. The remote sensing image segmentation network isa DeepLab V3 + structured tree network model, and the tree network model comprises a segmentation module and a tree processing module which are connected in sequence; the segmentation module is a DeepLab V3 + network model, and the DeepLab V3 + network model comprises an encoder part and a decoder part. The construction method of the tree-shaped processing module comprises the steps of constructing a confusion matrix, calculating a lower triangular matrix, establishing a confusion undirected complete graph, performing iterative edge cutting operation on the confusion undirected complete graph,and obtaining the tree-shaped processing module shown in the specification. The confusable pixels can be better distinguished, a more accurate segmentation result is obtained, the overall semantic segmentation precision of the high-resolution remote sensing image is effectively improved, and the segmentation accuracy of the confusable category data is remarkably improved.
Owner:BEIJING UNIV OF CHEM TECH
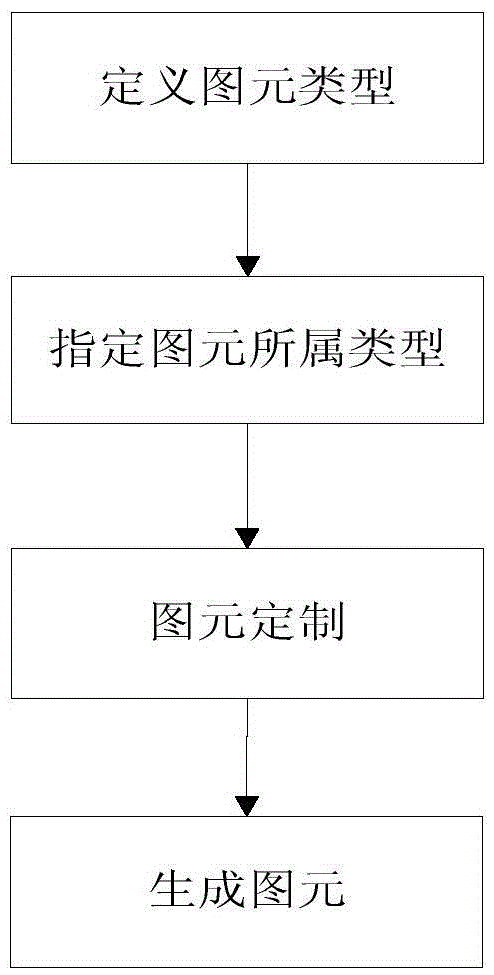
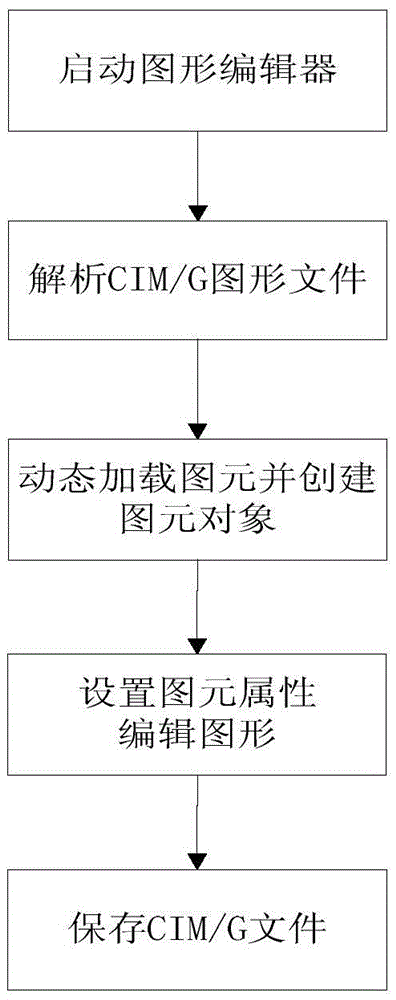
Method for maintaining graphic file of power system off line
InactiveCN105653515AEasy to installImprove production efficiencyData processing applicationsNatural language data processingGraphicsControl system
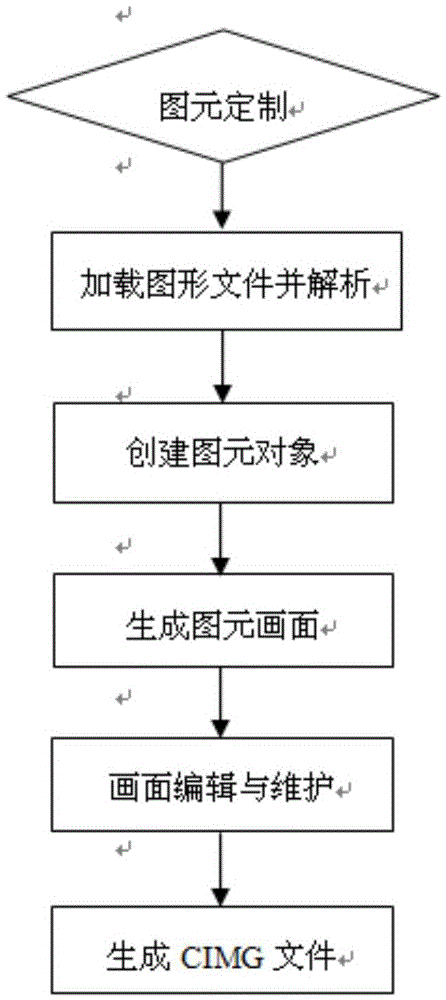
The invention discloses a method for maintaining a graphic file of a power system off line. The method comprises the following steps: (1) defining a primitive; (2) loading the graphic file; (3) establishing a primitive object and displaying a graphic picture: dynamically loading a required primitive file from a primitive warehouse according to the primitive attribute, locally caching the primitive file, dynamically generating a corresponding primitive object in the cached information, drawing a complete graph according to the primitive attribute in a memory pool, coloring with a corresponding voltage class color according to the attribute of the voltage class; (4) performing graphic maintenance and panoramic storage: selecting the primitive object from the memory pool, instantiating the specific primitive object according to the factory class, selecting a required position according to a user demand, modifying the primitive attribute, defining an equipment name in a database, editing a graph, and saving the primitive attribute into the graphic file with a CIM / G format. Under an environment separated from an intelligent power grid dispatching control system, the method is universal and effective by meeting requirements for editing and maintaining a CIM / G file.
Owner:NARI TECH CO LTD +5
Process for initializing and updating the topology of a high-voltage or medium-voltage electrical power station
InactiveUS6922661B2Simple taskEasy to operateGeometric CADComputation using non-denominational number representationPower stationManagement unit
The process is intended to optimize the operation of a digital protection system for protecting sets of busbars in the power station and uses a basic schematic of the electrical configuration of the power station obtained from information on the type of components used in the power station, and on the possible connections and accesses to said components. The information is assigned to management units of the digital protection system, said management units comprising peripheral measurement units and at least one centralization unit. A topological compilation process is implemented to provide a compiled schematic topology, and to provide a compiled assignment topology of the components in the power station and of their connections to the management units. A partial graph, whose structure depends on the type of information searched for and the status of each component of the power station, is obtained for each peripheral unit. A complete graph is then computed in one or more centralization units by algorithms which superpose partial graphs.
Owner:ALSTOM SA
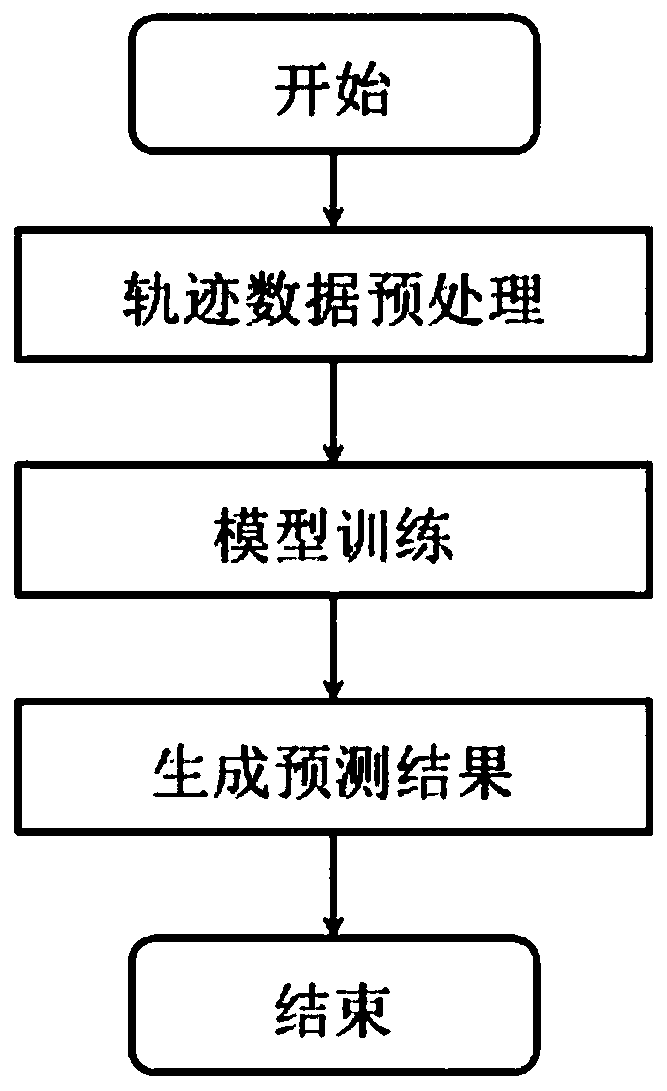
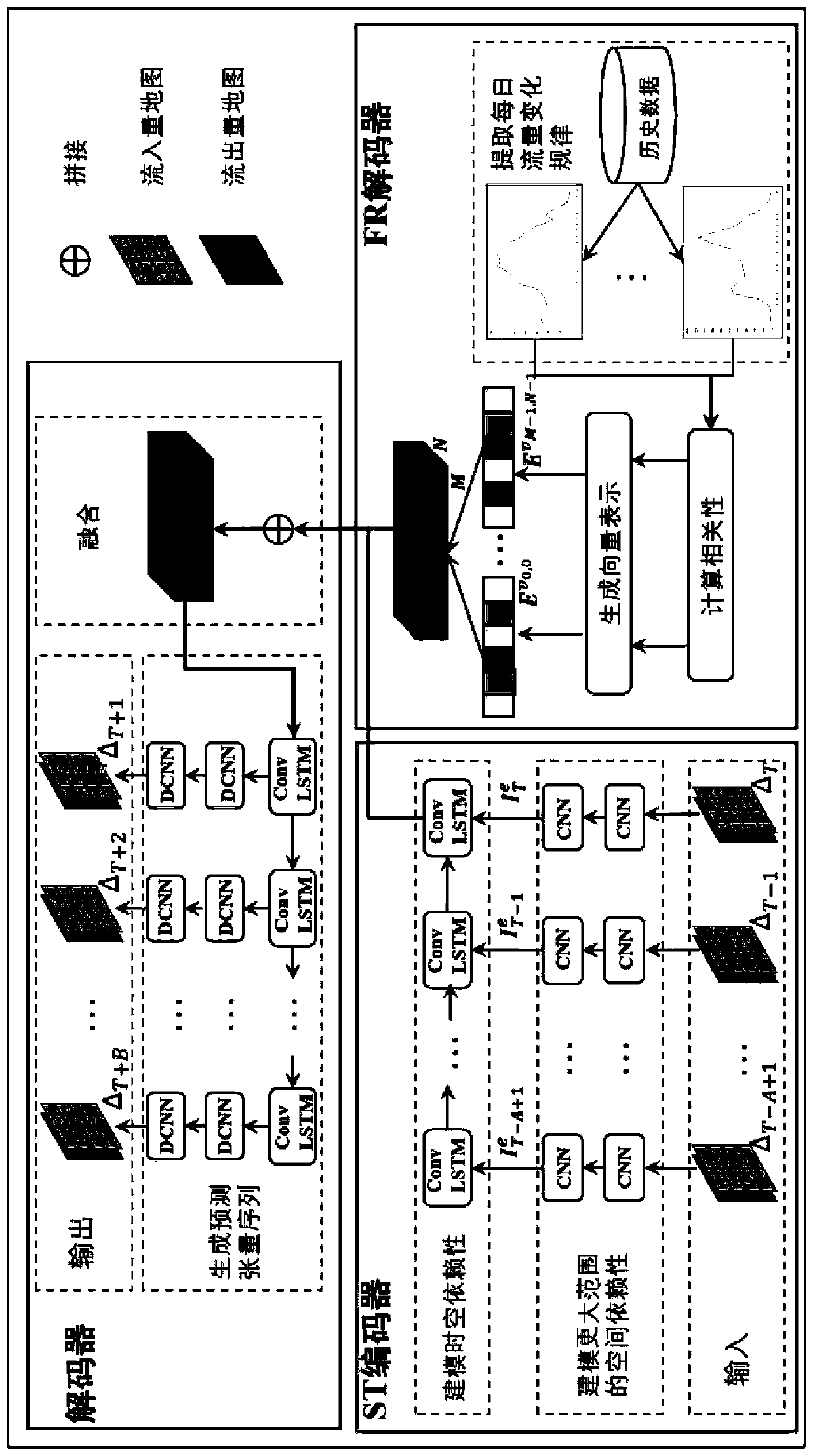
Pedestrian volume prediction system capable of simultaneously modeling space-time dependence and daily flow correlation
The invention discloses a pedestrian volume prediction system capable of simultaneously modeling space-time dependence and daily flow correlation. The system comprises an ST encoder module, an FR encoder module and a decoder module. According to the invention, the convolutional long-term and short-term memory network is used for simultaneously realizing dependence and time dependence of adjacent regions in space; spatial dependencies in different ranges in a geographic space are captured hierarchically by superposing a convolutional neural network; meanwhile, a complete graph reflecting the flow correlation between all the areas in the whole city range is generated based on the daily flow change mode of the areas, fixed-dimensional vector representation is generated for each area through agraph embedding method, and a pedestrian flow prediction result is generated through a layer of long-short-term memory network and two layers of deconvolution neural networks.
Owner:SHANGHAI JIAO TONG UNIV
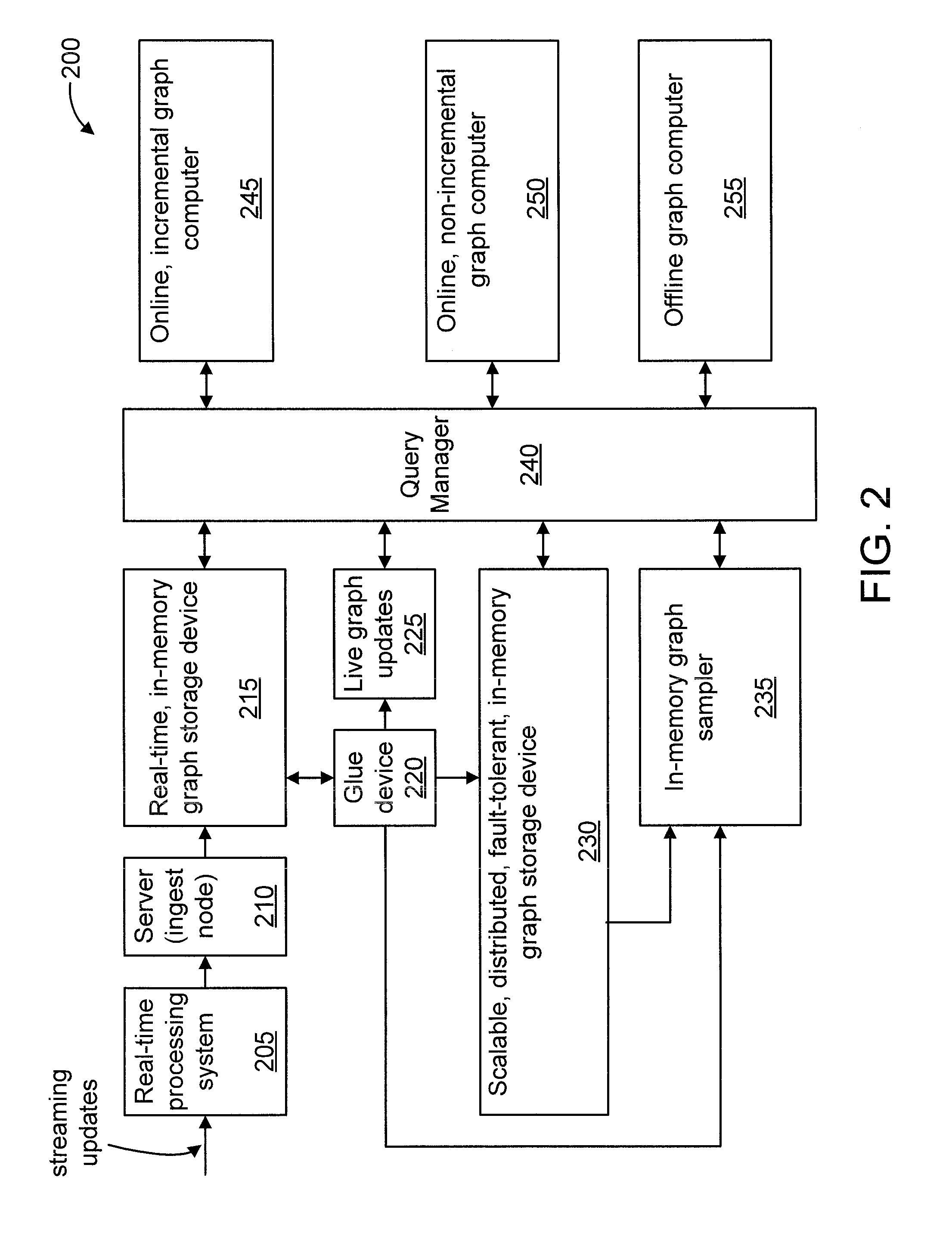
Large-Scale, Dynamic Graph Storage and Processing System
A graph storage and processing system is provided. The system includes a scalable, distributed, fault-tolerant, in-memory graph storage device for storing base graph data representative of graphs. The system further includes a real-time, in memory graph storage device for storing update graph data representative of graph updates for the graphs with respect to a time threshold. The system also includes an in-memory graph sampler for sampling the base graph data to generate sampled portions of the graphs and for storing the sampled portions of the graph. The system additionally includes a query manager for providing a query interface between applications and the system and for forming graph data representative of a complete graph from at least the base graph data and the update graph data, if any. The system also includes a graph computer for processing the sampled portions using batch-type computations to generate approximate results for graph-based queries.
Owner:NEC CORP
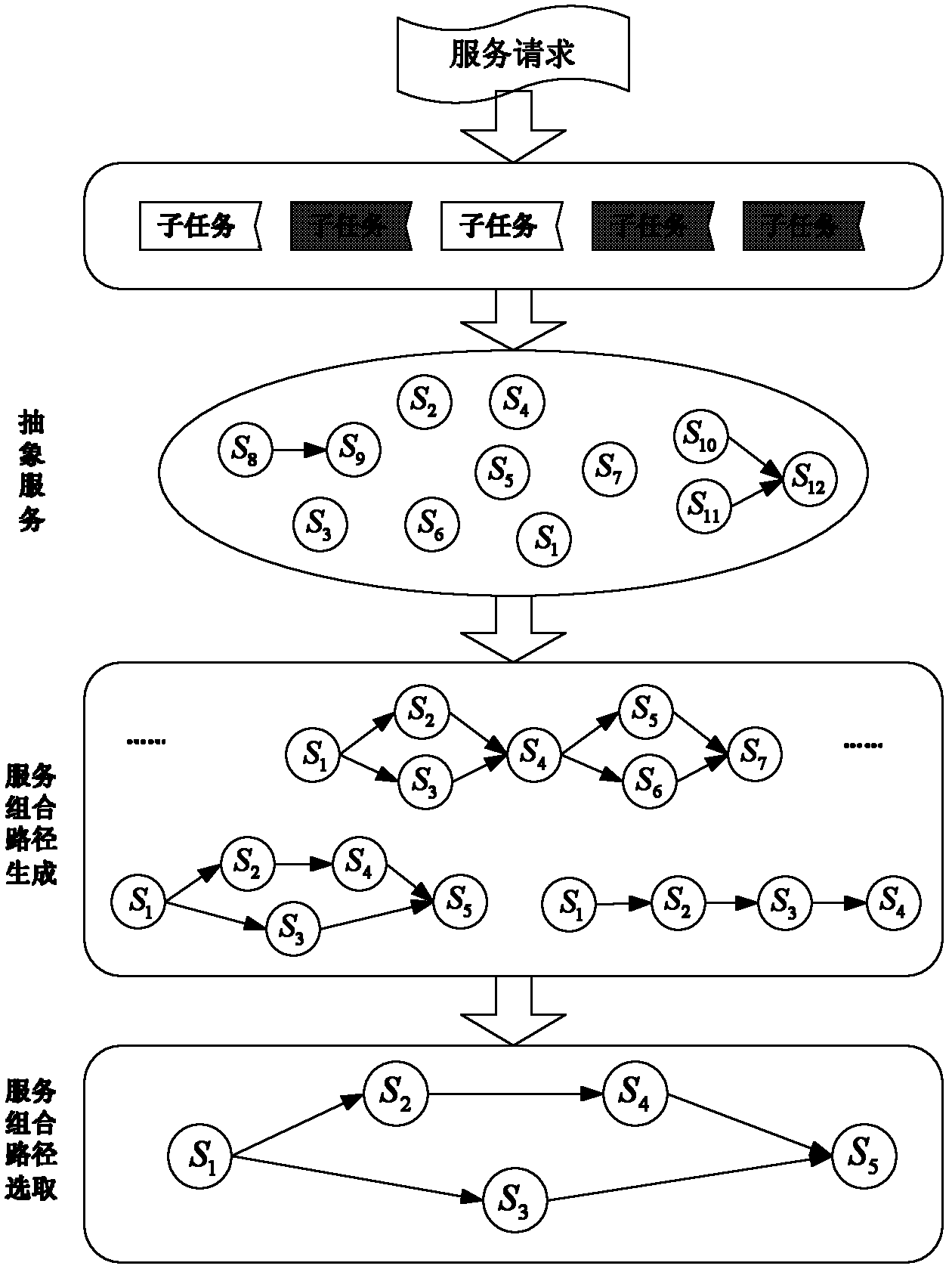
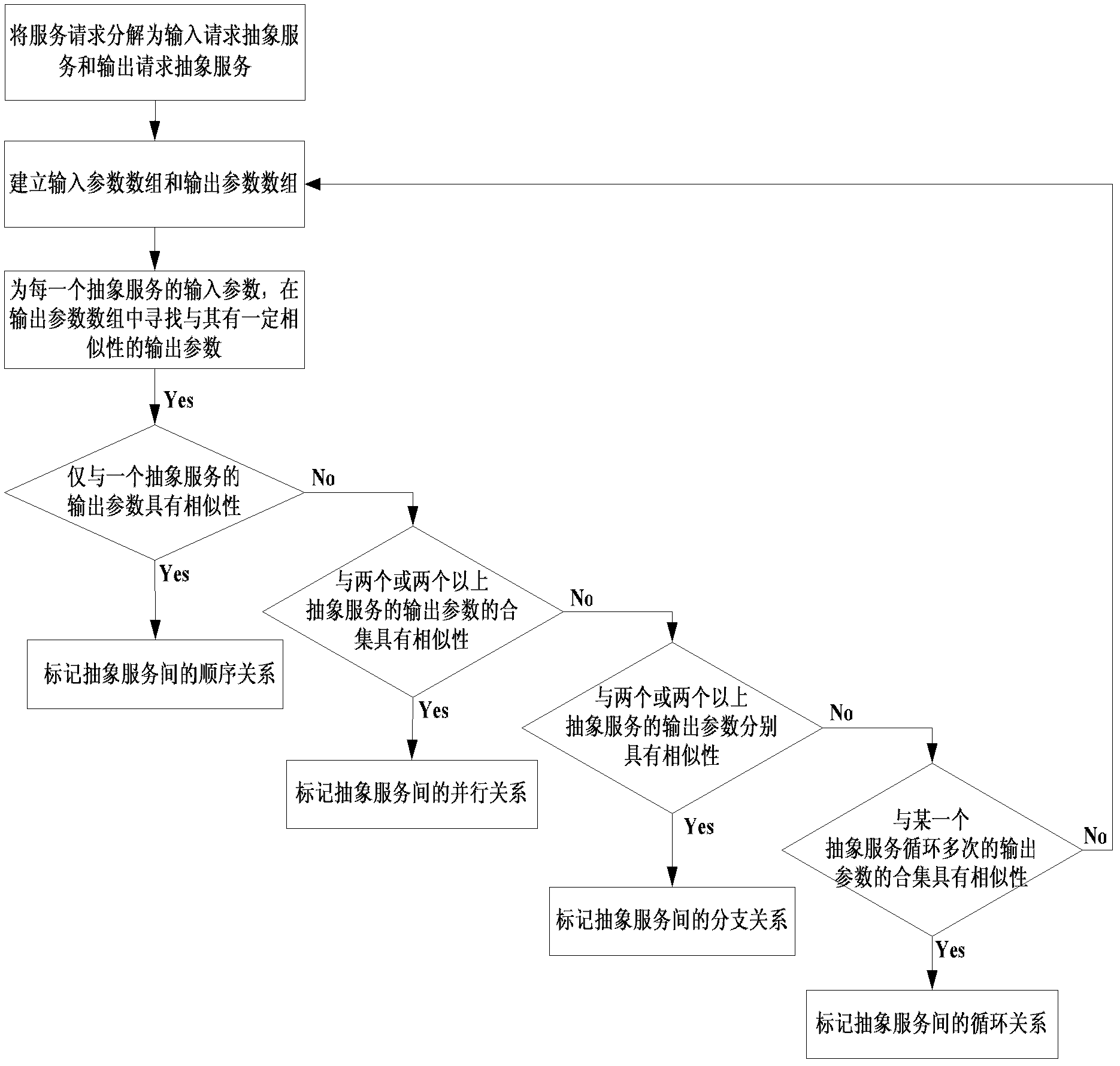
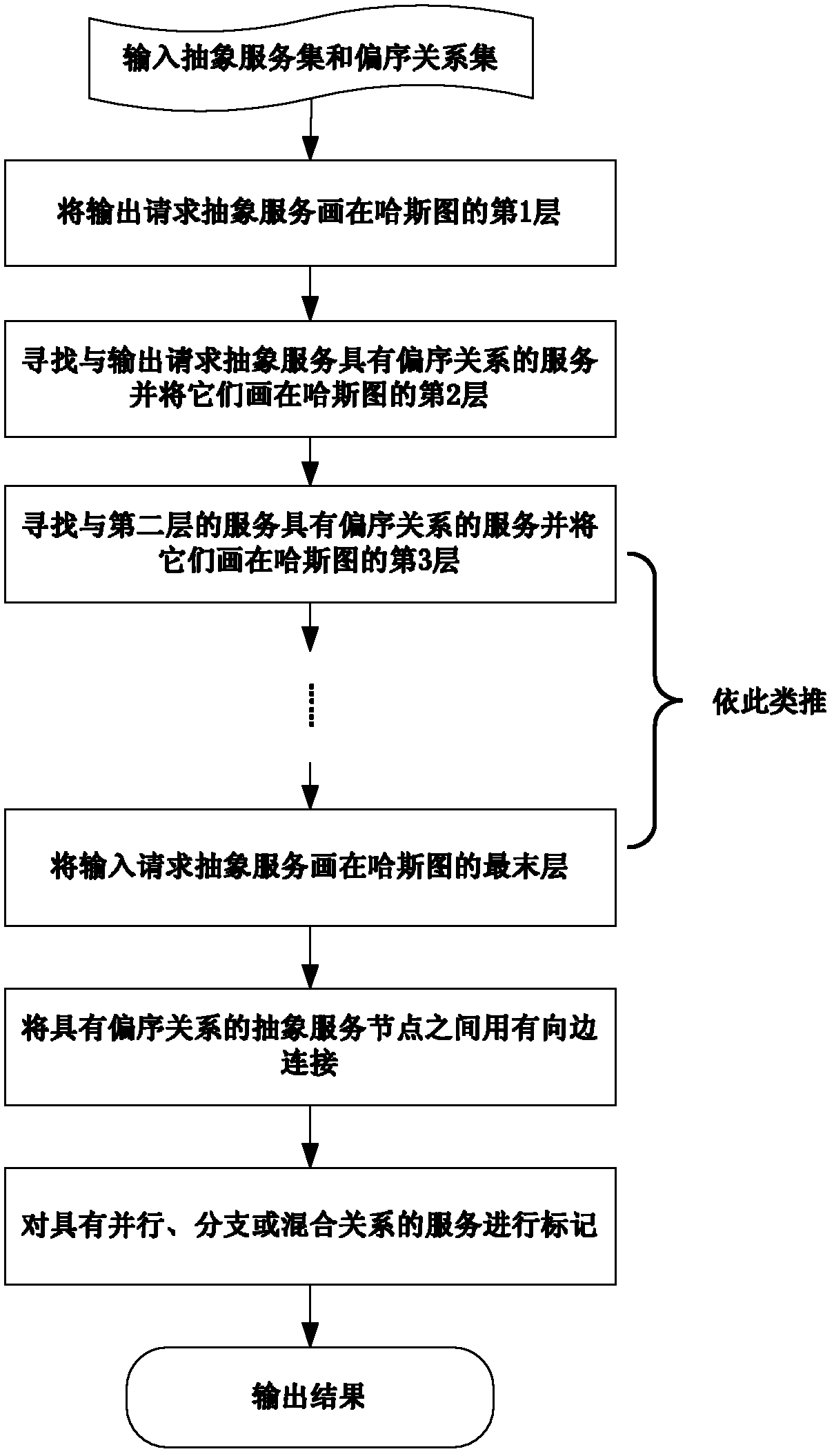
Service composition path construction method for cloud manufacturing
InactiveCN102571962ARealize the structureGenerate accuratelyTransmissionService compositionComputing Methodologies
The invention relates to a service composition path construction method for cloud manufacturing, in particular to a method for achieving mapping from complicated service request to service combination paths from top to bottom in a cloud manufacturing mode based on driving of user service request. The method comprises the steps of finding partial order relations among abstract services based on combinable association relations among services to achieve aggregation of the abstract services, utilizing the idea of Hasse diagram to build a complete graph of the service combination paths, and selecting the service combination paths by solving the largest combinable degree based on a computing method for combinable degree of the service combination paths. The service composition path construction method for the cloud manufacturing has the advantages of being simple in construction method, strong in applicability and operability and good in expandability.
Owner:BEIHANG UNIV
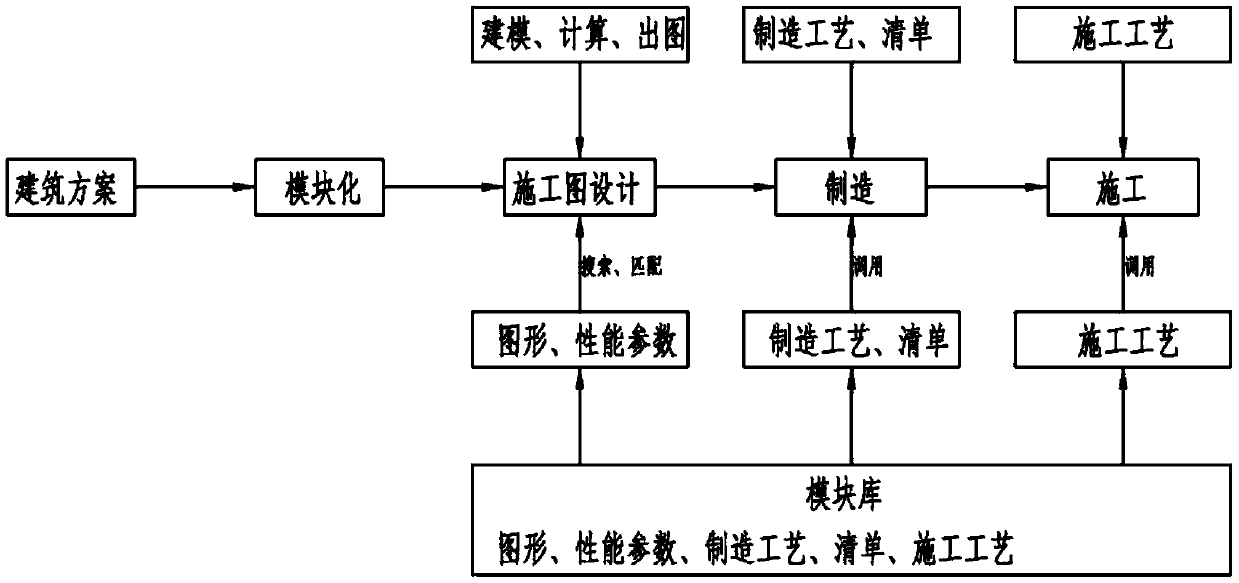
Modularization method for building design, manufacturing and construction
InactiveCN110287591AOutstanding FeaturesHighlight significant effectGeometric CADCAD network environmentInformatizationModularity
The invention discloses a modularization method for building design, manufacturing and construction. The modular method comprises the following steps: (1) dividing a building into different standard modules; (2) modeling, calculating and drawing by a designer corresponding to each standard module, so that each standard module contains all information such as a complete graph, a list, performance parameters, a manufacturing process, a construction process and the like; (3) establishing a standardized module library shared by all industries by utilizing a big data platform; (4) importing the standard module information of the step (1) and the step (2) into the module library of the step (3); (5) a building designer matching the credit of the module library of the big data platform with a standard module required by a self building scheme through a search engine; and (6) directly calling manufacturing and construction related data from the selected standard module by a building manufacturing and construction worker, and carrying out manufacturing and construction. Redundant workload of design, manufacturing and construction links is reduced, comprehensive cost is reduced, efficiency is improved, the environment is protected, quality is improved, and modularization, standardization, universalization and informatization are achieved.
Owner:CHANGSHA BROAD HOMES IND GRP CO LED
Three-dimensional multi-head assembly dynamic inclined scanning 3D printing method
InactiveCN108407288AHigh resolutionImprove printing efficiencyAdditive manufacturing apparatusIncreasing energy efficiencyGraphicsDecomposition
The invention discloses a three-dimensional multi-head assembly dynamic inclined scanning 3D printing method. The method mainly adopts multi-head laser engine arrays; multiple laser engine arrays synchronously print to effectively improve the printing capacity; graph decomposition and multi-head assembly exposure are performed; graphs needing to be printed are decomposed to Nx*Ny parts according to the number Nx, Ny of laser engines; all the graphs needing to be printed are distributed to the engines in appointed positions for area synchronous printing of complete graphs; the method dose not theoretically limit lengths, widths and heights of 3D graphs and internal fineness degrees of the graphs; the printing speed is not influenced by the lengths and the widths of workpieces needing to beprinted; and compared with traditional 3D printing capacity, the method is multiple times of the traditional 3D printing speed, and belongs to a parallel high-speed dynamic scanning 3D printing technology.
Owner:ZHONGSHAN AISCENT TECH
Method for implementing complete k communication of wireless sensing network based on part k communication
InactiveCN101437306AImprove reliabilityMaintain connectivityNetwork topologiesCycle controlAlgorithm
The invention discloses a method for realizing full k connection of a wireless sensor network based on partial k connection. The method uses a graph theory mode and a partial k connection method to realize the full k connection of the wireless sensor network. Based on a partial k mechanism, the method adopts a cycle control strategy to realize full k connection of the sensor network. The method comprises: for any wireless sensor network, a unit disc graph is used to find all abstract each node of the network respectively to form a wireless sensor network model graph first; then a weighted complete graph of the network model graph is solved and a greed algorithm is used to solve the k connected subgraphs of the weighted complete graph; the partial k connection mechanism is used to increase new nodes to form a new wireless sensor network model graph; and finally the formed new wireless sensor network model graph is used to do cycle treatment till the full k connection is realized.
Owner:BEIHANG UNIV
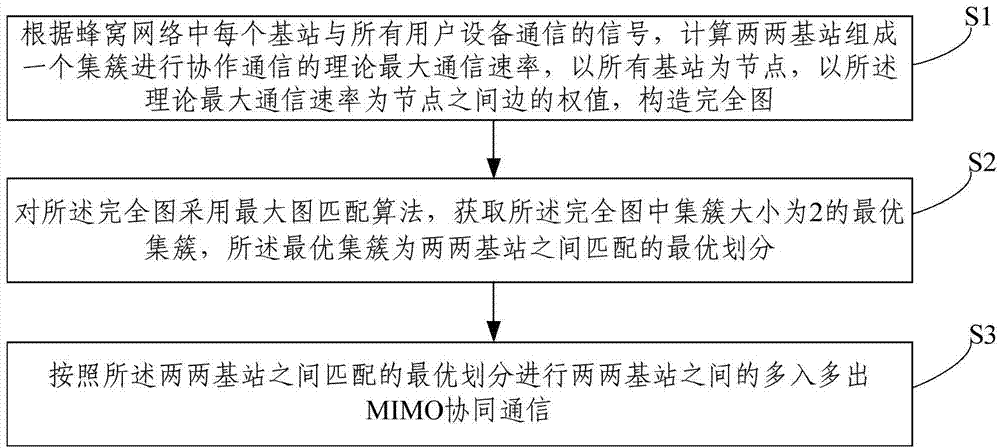
Cluster-based cooperative communication method and device in cellular network
ActiveCN104507111AReduce Inter-Cell InterferenceEnhanced signalRadio transmissionWireless communicationCluster cellCluster based
The invention provides a cluster-based cooperative communication method and device in a cellular network. The method includes: calculating the theoretical maximum communication rate of a cluster, formed by every two base stations, performing cooperative communication according to the communication signals of each base station in the cellular network and all user equipment, and using all the base stations as nodes and the maximum communication rate as the edge weight among the nodes to build a complete graph; using a maximum graph matching algorithm on the complete graph to acquire the optimal cluster, with the cluster size being 2, in the complete graph, wherein the optimal cluster is the matched optimal division between every two base stations; performing MIMO cooperative communication between every two base stations according to the optimal division. The method has the advantages that an optimal cell cluster scheme can be selected, signals in a cluster cell can be enhanced, interference among cells in the cellular network is lowered, and data transmission rate is increased.
Owner:TSINGHUA UNIV
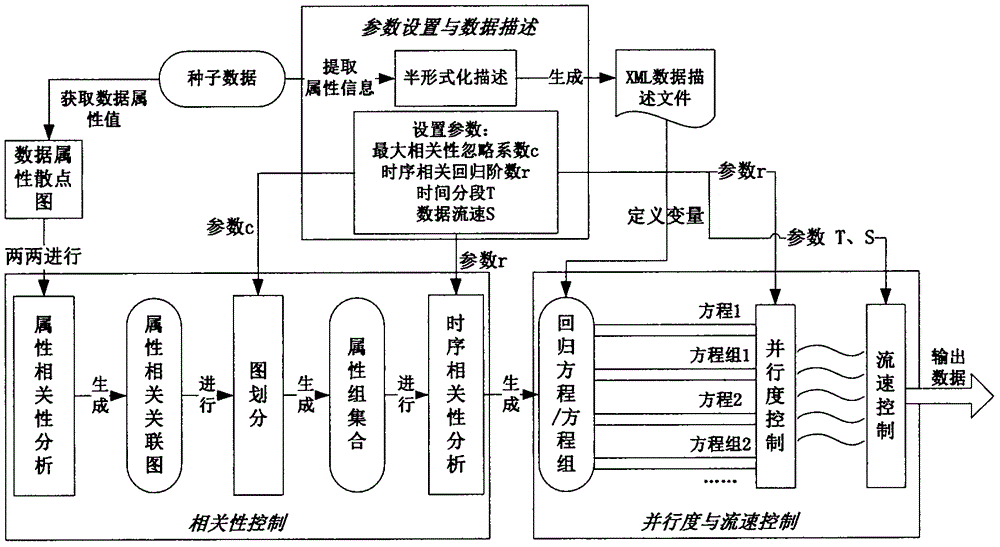
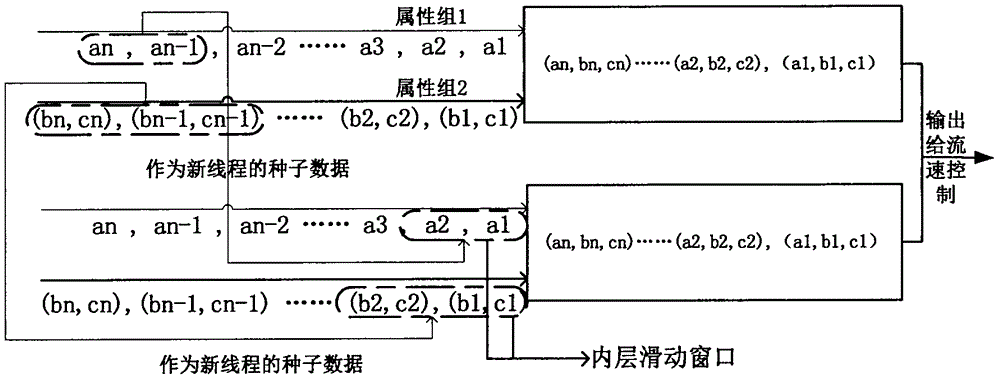
Correlativity feature-containing simulative stream big data generation method for system test
InactiveCN106294131AImprove parallelismImprove production efficiencySoftware testing/debuggingNODALStreaming data
The invention discloses a correlativity feature-containing simulative stream big data generation method for a system test, and solves the problem in simulative data generation in a stream big data system test. The method comprises the steps of firstly, analyzing a seed data set of a real scene, and giving out a scatter diagram of every two attributes; secondly, describing the correlativity between every two attributes by adopting a maximum mutual information coefficient, and generating a weighted undirected complete graph of N nodes (N is the number of data attributes and a weight value is a calculated related coefficient); thirdly, proposing a c-prim algorithm to divide an attribute set so as to enable the decomposed attribute sets to have the characteristics similar to highly cohesive and low coupling, giving out a time sequence model selection policy, and performing simulation by adopting different time sequence models according to different characteristics of the attribute sets, thereby ensuring the correlativity of finally generated data in time sequence; and finally, proposing a double-layer sliding window method to control a degree of parallelism and a stream data output speed. According to the method, stream big data with data features relatively close to those of the real scene can be generated and the stream speed of a generated data stream can be simply and effectively controlled.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Network flow anomaly detection method based on intuitionistic fuzzy time series graph mining
ActiveCN111460026AImplement miningTake advantage ofVisual data miningStructured data browsingData setAnomaly detection
The invention discloses a network flow anomaly detection method based on intuitionistic fuzzy time series graph mining. The method comprises the following steps: step 1, constructing an IFTS graph; step 2, IFTS graph mining; and step 3, determining an anomaly judgment criterion. The method has the beneficial effects that an intuitionistic fuzzy time sequence diagram is constructed, so that the vertex relationship information in the diagram is comprehensively mined and fully utilized, and the network traffic abnormality can be more accurately detected. The method firstly converts original one-dimensional network flow prediction into more accurate five-dimensional prediction by combining information entropy and an IFTS prediction technology; in addition, heuristic variable-order IFTS prediction not only has efficient prediction performance on an incomplete data set, but also can enable a prediction result to be closer to reality. A complete graph established by using a more accurate prediction result can reflect the change of the flow attribute more accurately, so that a more accurate exception report is obtained through frequent sub-graph mining.
Owner:AIR FORCE UNIV PLA
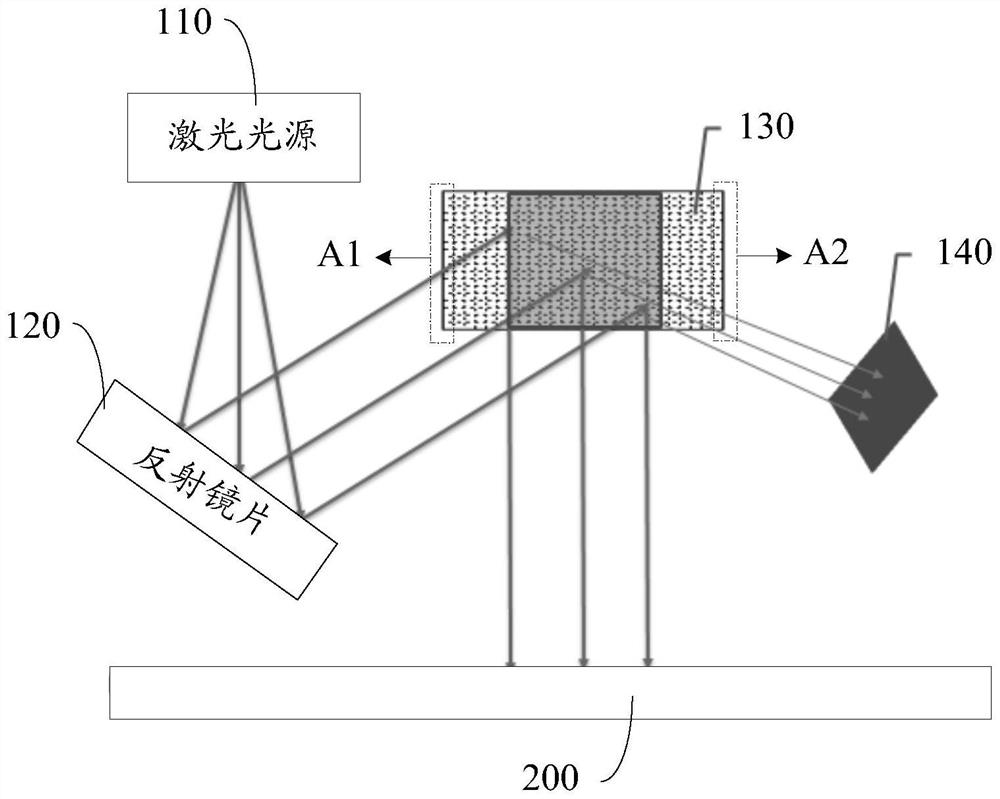
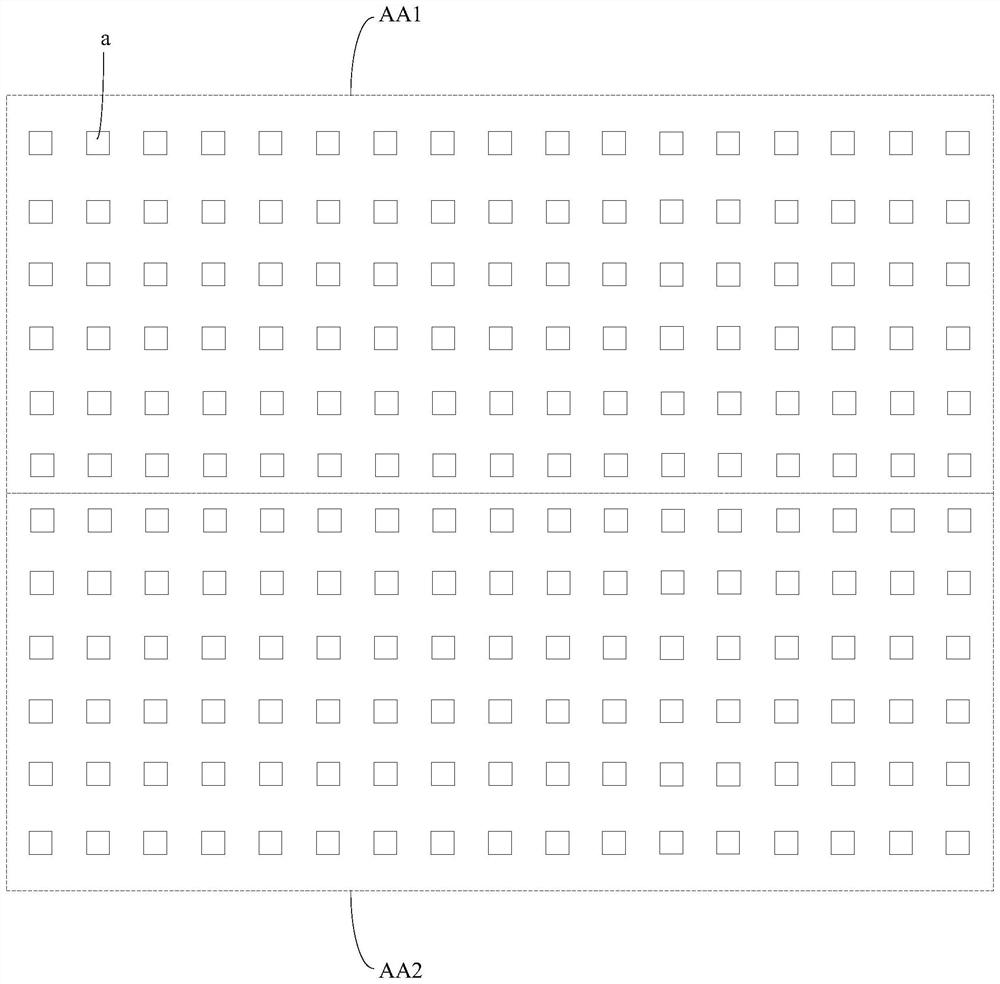
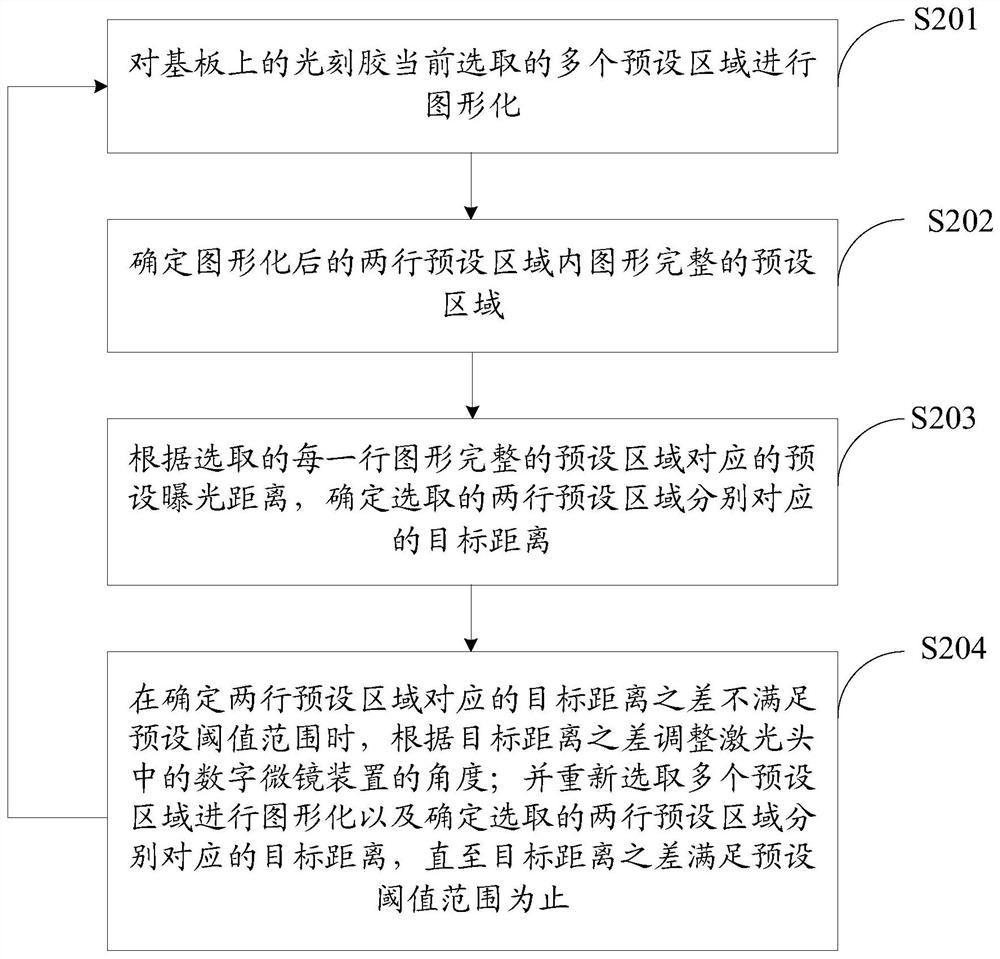
Exposure machine adjusting method and device
ActiveCN111694222AGuaranteed parallelAvoid unevennessPhotomechanical exposure apparatusMicrolithography exposure apparatusGraphicsEngineering
Owner:BOE TECH GRP CO LTD +1
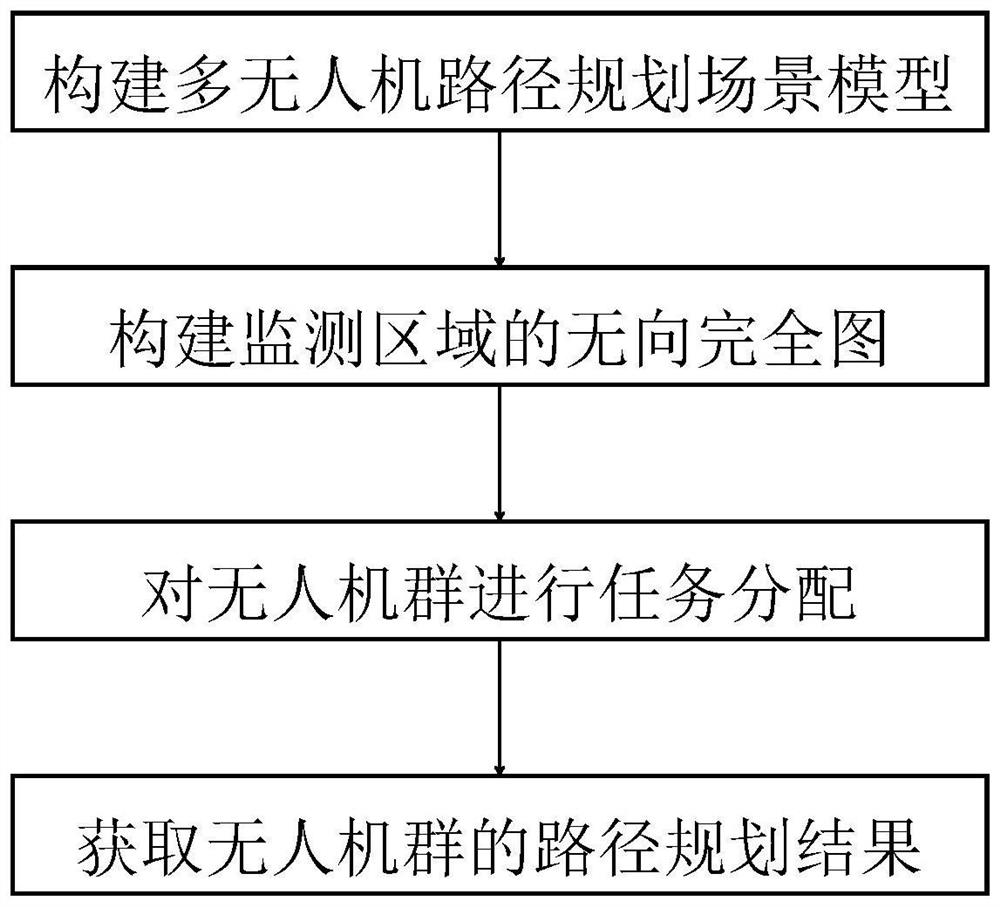
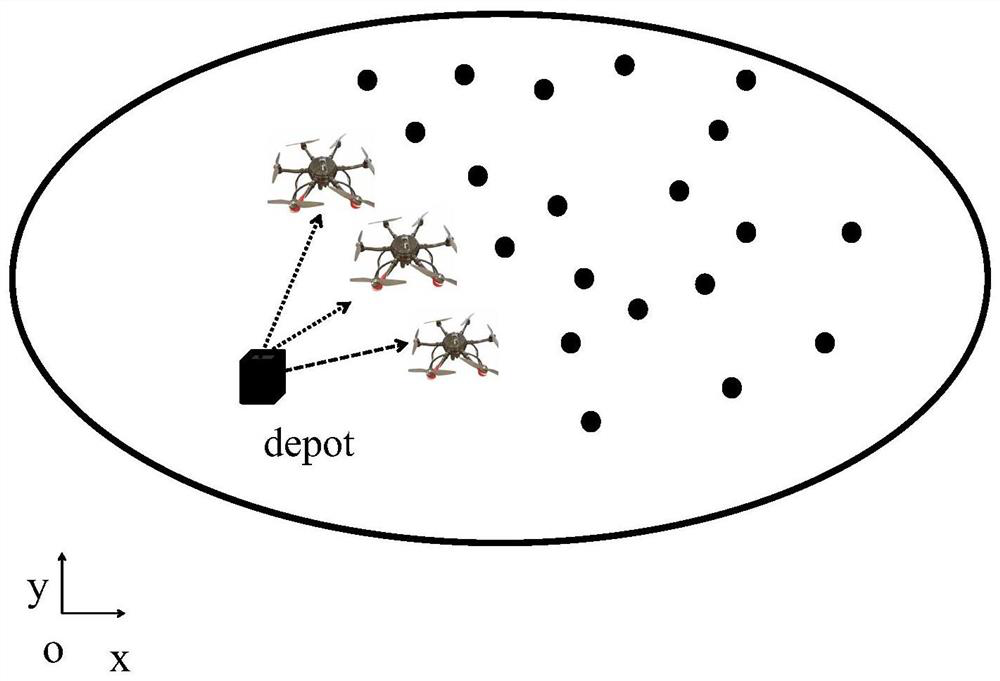
Multi-unmanned aerial vehicle path planning method
ActiveCN112629539AReduce flight distanceOptimize task assignment resultsNavigational calculation instrumentsMonitoring siteSimulation
The invention provides a multi-unmanned aerial vehicle path planning method. The method comprises the following steps: constructing a multi-unmanned aerial vehicle path planning scene model; constructing an undirected complete graph of the monitoring area; carrying out the task allocation on the unmanned aerial vehicle group; and obtaining a path planning result of the unmanned aerial vehicle group. An undirected complete graph of a monitoring area is constructed, a monitoring point traversed by each unmanned aerial vehicle and a starting point are modeled into the undirected complete graph, point transfer and exchange operations are carried out between the undirected complete graphs to continuously optimize a task allocation result, and a minimum Hamiltonian ring of each unmanned aerial vehicle is obtained on the basis of the optimized task allocation result; point transfer is carried out between the minimum Hamiltonian rings, the task allocation result is further optimized, and the path planning result of the unmanned aerial vehicle group is obtained, so the flight distance of the unmanned aerial vehicle with the maximum flight distance in the multiple unmanned aerial vehicles is minimum, and the flight time is the shortest.
Owner:XIDIAN UNIV +1
Attribute graph based image representation method
ActiveCN106778763ACategory fitGood effectCharacter and pattern recognitionSemanticsBackground information
The invention provides an attribute graph based image representation method. The image representation method is characterized in that an indirect complete graph (V, E), which called as an attribute graph, is adopted to represent an image; V={V1, Vg} is vertexes of the graph; V1 represents local nodes and describes all objects contained in the image; Vg represents global nodes and describes background information or the whole scene information of the image; E represents edges of the graph, wherein the edges are divided into local edges and global edges; and the edges in the attribute graph represent a spatial relationship between objects in the image and spatial positions of the objects in the whole image. According to the method provided by the invention, the attribute graph is adopted to represent an image, and images which contain the same objects but represent different image semantics can be accurately classified. The attribute graph not only considers local features of the image, but also considers global features of the image. Meanwhile, information of the edges is used to describe the spatial relationship between objects and the spatial positions of the objects in the whole image, thereby having positive significance for image classification and recognition.
Owner:SHANGHAI DIANJI UNIV
Network construction and evolution method based on weighting technique
InactiveCN107247813ADescribe the inner connectionData processing applicationsText database queryingNODALCo-occurrence
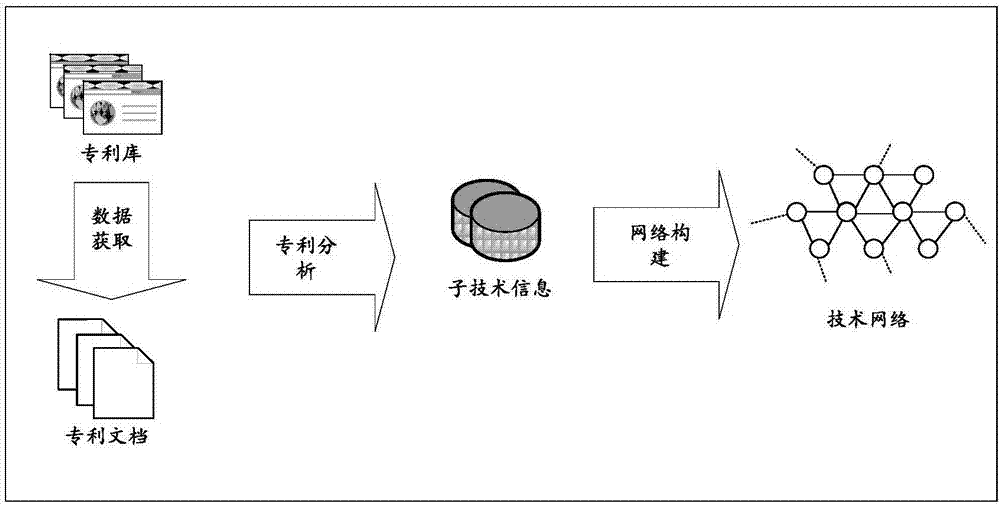
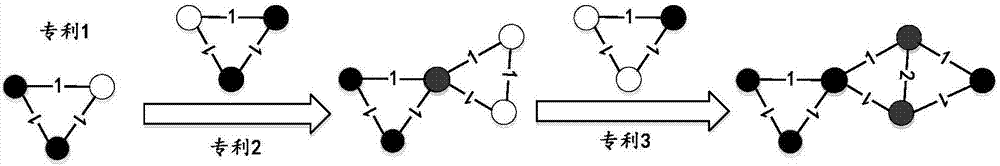
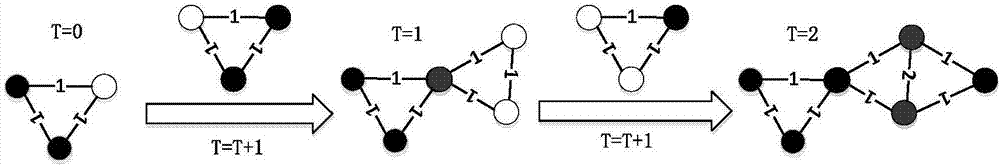
The invention provides a network construction and evolution method based on a weighting technique in order to construct a network by existing product techniques and predict technical development trend by the network. The method comprises: first, processing data, to be specific, analyzing existing patent documents, and extracting structural information composing the patient system as sub-technique information; second, constructing a technical network, to be specific, describing each patent document, in co-occurrence relation of patient documents, as a plurality of complete graphs composed of a plurality of nodes according to the sub-technique information, connecting the complete graphs through same sub-technique nodes in the complete graphs to form a weighted undirected technical network; third, evolving the technical network, to be specific, performing evolution process of a weighted technical network based on the second step.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
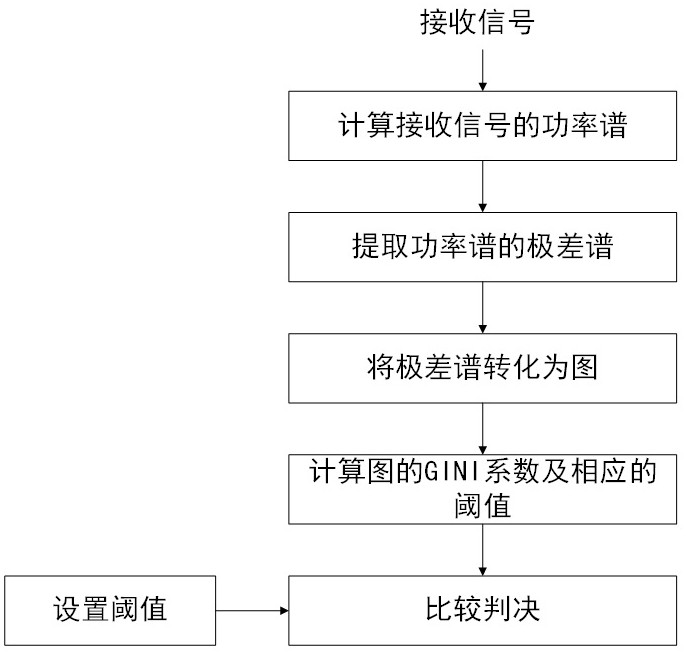
Weak signal detection method based on grouping range map
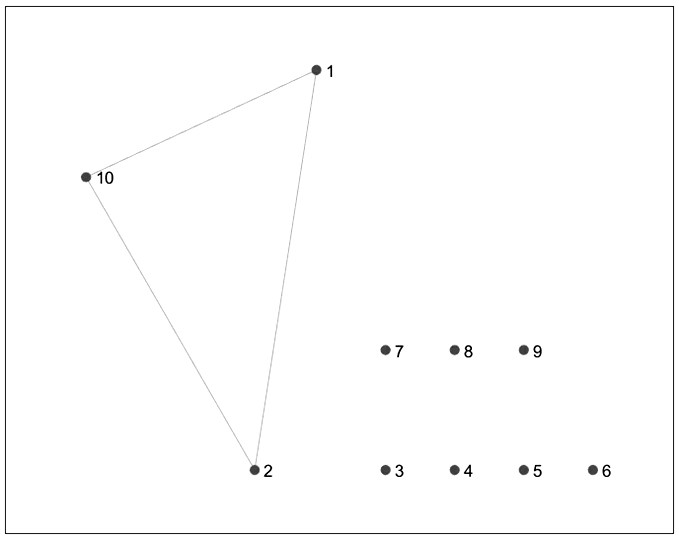
The invention discloses a weak signal detection method based on a grouping range map, which comprises the following steps of: firstly, Fourier transform is carried out on an oversampled receiving signal for further calculation to obtain a power spectrum of the receiving signal; a range spectrum is then extracted from the power spectrum and converted into a specific undirected simple graph having a plurality of vertexes and edges; finally, the GINI coefficient of the graph is used as a judgment index, and whether a signal is detected or not is judged by checking whether the graph is a complete graph or not. The performance of the method provided by the invention is superior to that of a conventional signal detection algorithm under the conditions of small signal-to-noise ratio and medium samples.
Owner:JINLING INST OF TECH
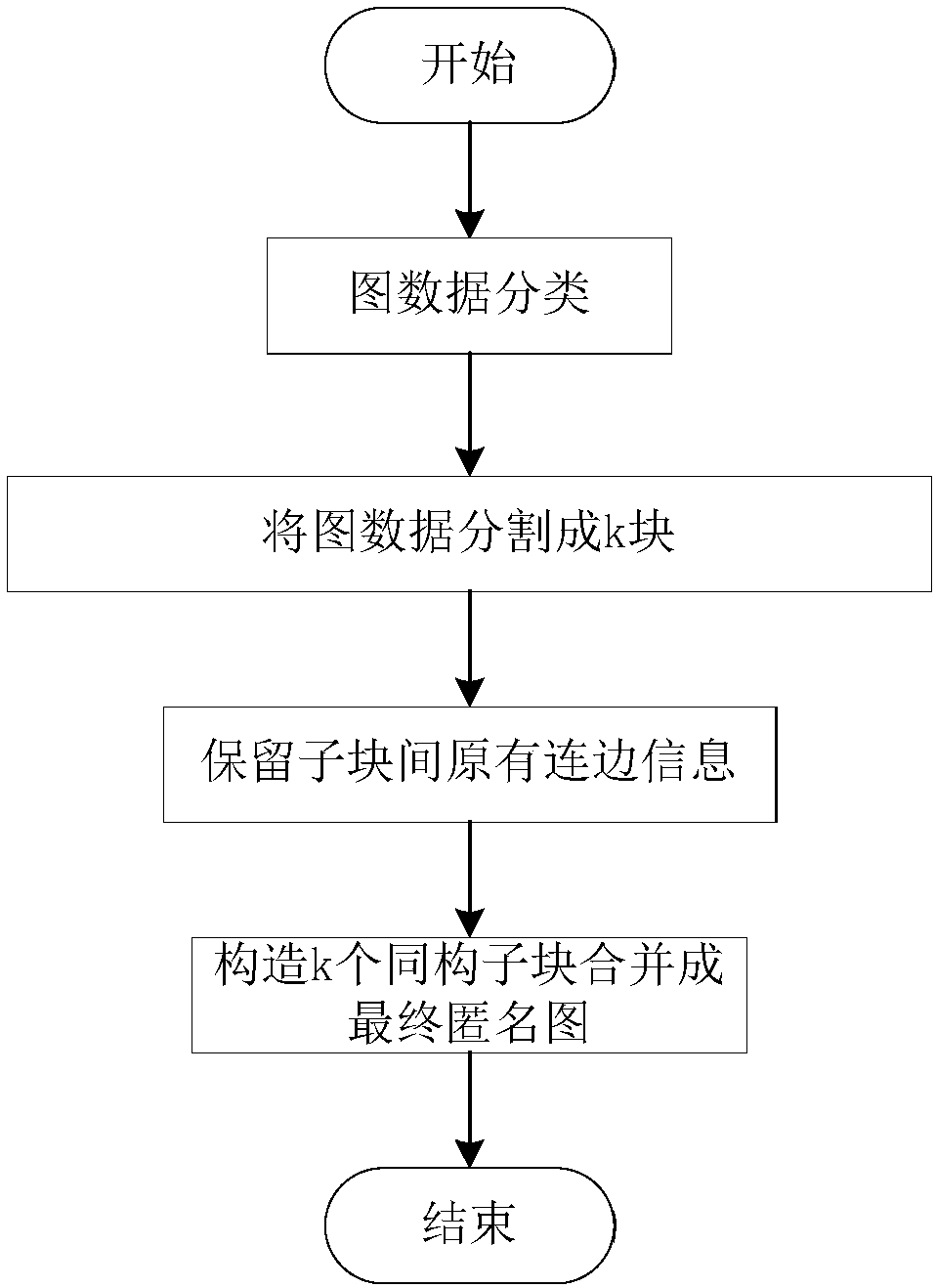
Privacy protection method and system oriented to large-scale graph data dissemination
ActiveCN107742083AImprove usabilityGuaranteed retentionDigital data protectionNODALPrivacy protection
The invention discloses a privacy protection method oriented to large-scale graph data dissemination. The privacy protection method specifically comprises the steps of 1, uniformly dividing original graph data into multiple subsidiary blocks; 2, reading cut connection sides, comparing node degrees of the two ends of each cut connection side, newly adding noise nodes in a subsidiary block of each node with a large node degree, and reserving the cut connection sides through a ligature of the corresponding node with the large node degree and the corresponding noise node; 3, constructing an isomorphism block matrix, wherein subsidiary block structure information is compared with the isomorphism block matrix, and isomorphism is conducted in the mode of adding the noise sides to complete graph data anonymous protection. The time needed for the overall graph data anonymous protection is lowered by one order of magnitudes, and the efficiency of an anonymization process is achieved; finally ananonymous graph satisfies a k anonymous mechanism, and the safety of anonymization is achieved. By means of the privacy protection method oriented to the large-scale graph data dissemination, it is guaranteed that the balance performance of the anonymous graph among usability, safety and efficiency is improved by a large margin.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for evolutionary analysis on anonymous graph data
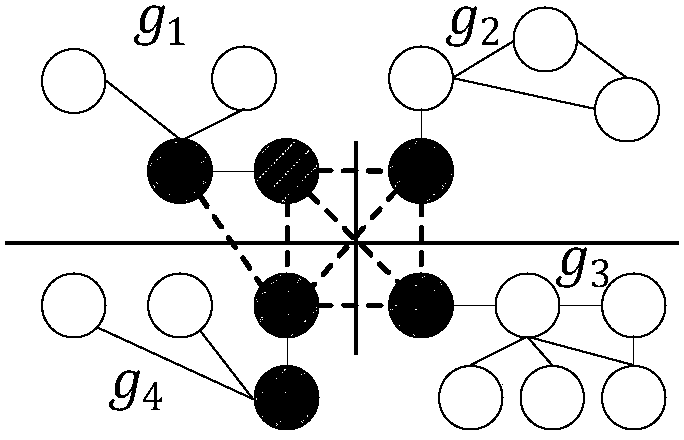
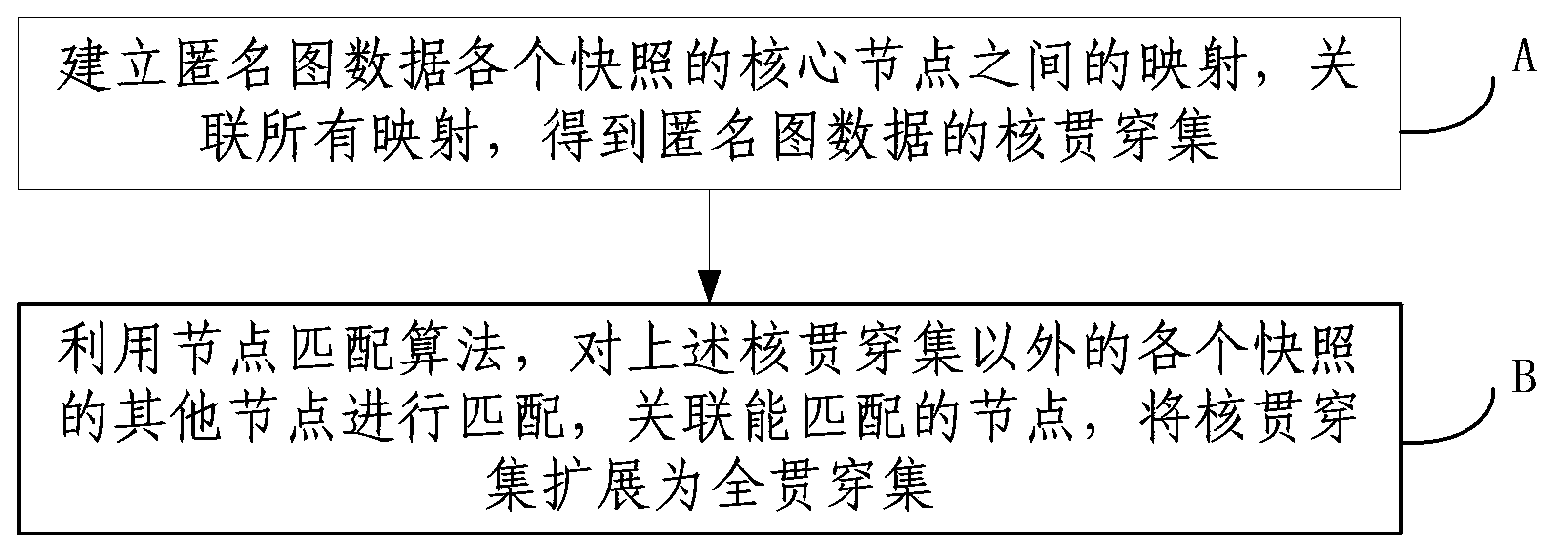
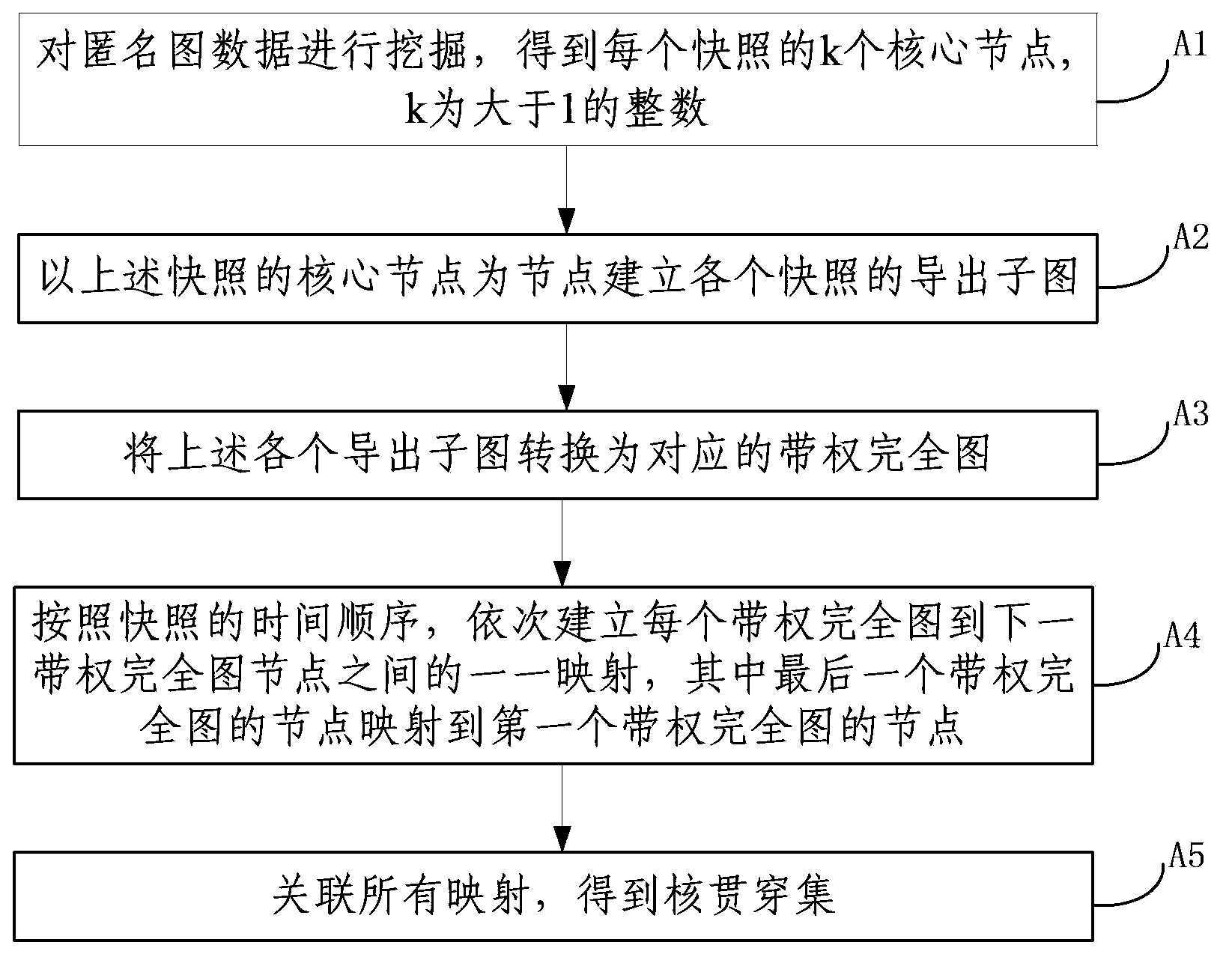
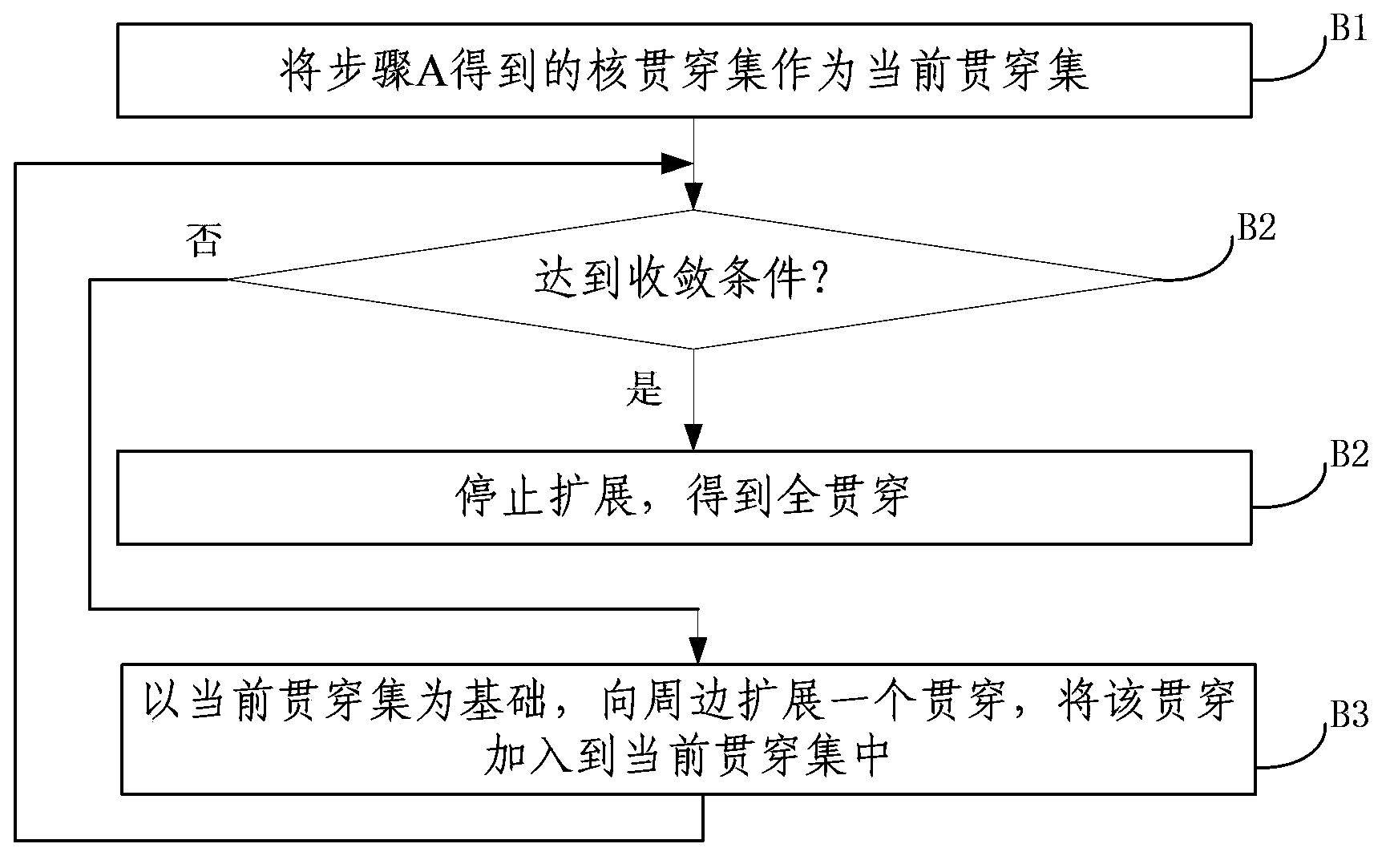
ActiveCN103440263AChange the status quo that evolution analysis cannot be performedImprove accuracySpecial data processing applicationsData dredgingInduced subgraph
The invention discloses a method for evolutionary analysis on anonymous graph data, and belongs to the field of graph data mining and analysis. The method comprises the following steps of mining the anonymous graph data to obtain the first k core nodes of each snapshot; for each snapshot, obtaining an induced subgraph taking the core nodes of the snapshot as vertexes; converting each induced subgraph into a corresponding weighted complete graph; establishing a mapping from each weighted complete graph to the next weighted complete graph; associating all the mappings to obtain a core penetration; iteratively extending a penetration towards the periphery in each snapshot of the anonymous graph data on the basis of a current penetration set; stopping extension under a condition of convergence to obtain a full penetration. The method provided by the invention can be used for the evolutionary analysis on a plurality of snapshots of the same graph data source which is published by adopting an anonymization technology at different time points, and the problem that the anonymous graph data cannot be evolutionarily analyzed in the prior art is solved.
Owner:TSINGHUA UNIV
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com