Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
218 results about "Channel analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Channels Analysis. Channels Analysis provides a comprehensive view of the key issues affecting the sales, marketing and distribution of technology products and helps channel managers develop strategies that deliver business results.
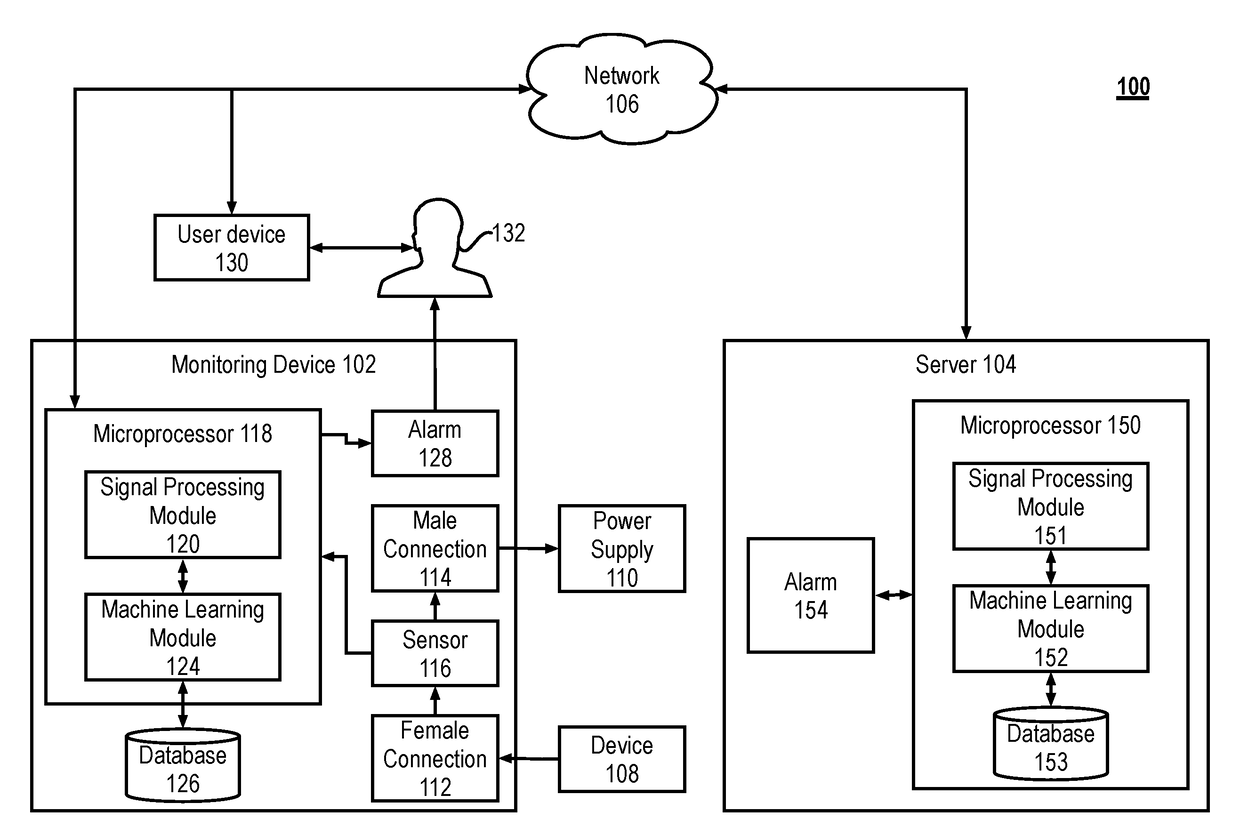
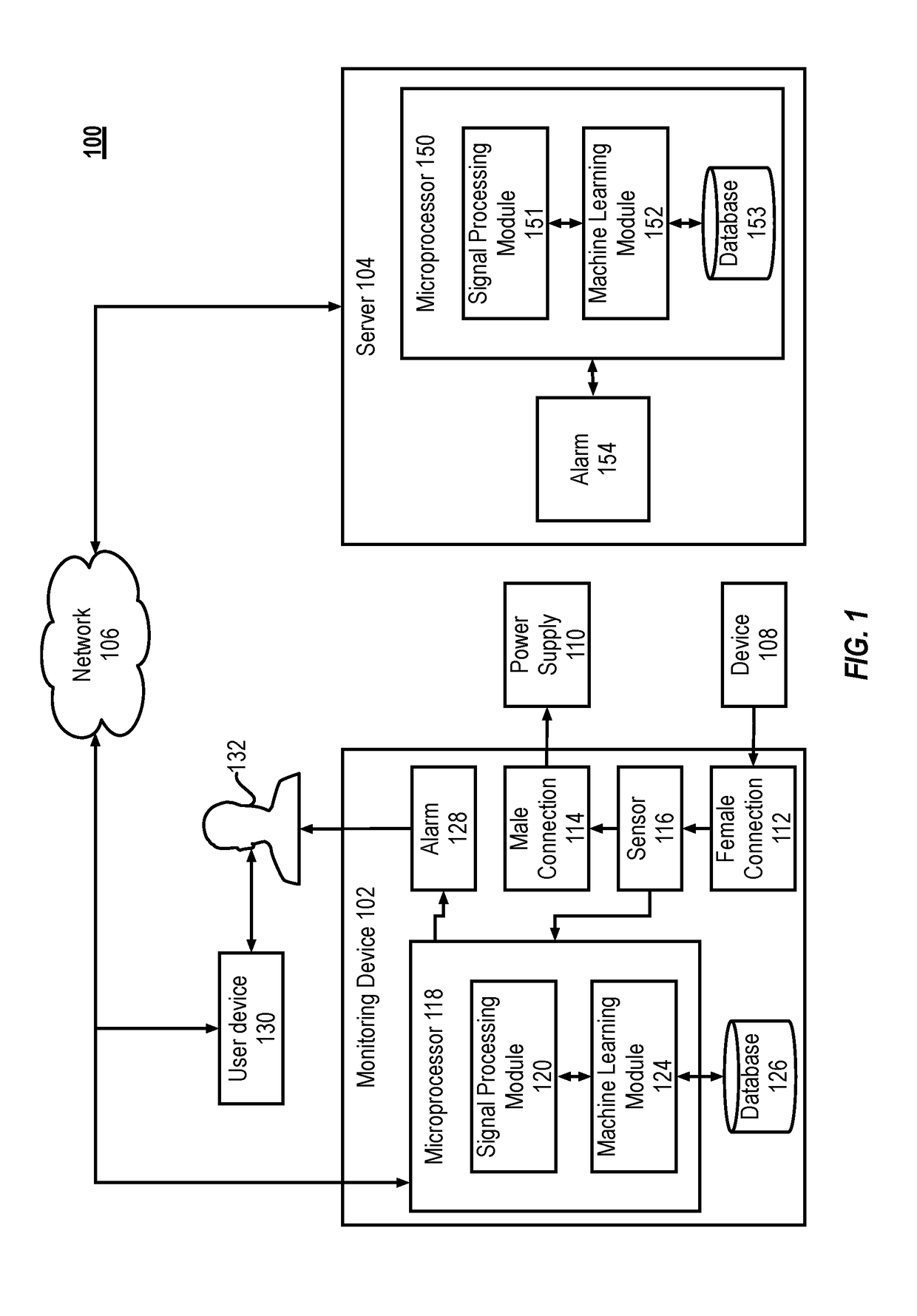
Anomaly and malware detection using side channel analysis
ActiveUS20180007074A1Telemetry/telecontrol selection arrangementsPower supply for data processingAnomaly detectionCloud base
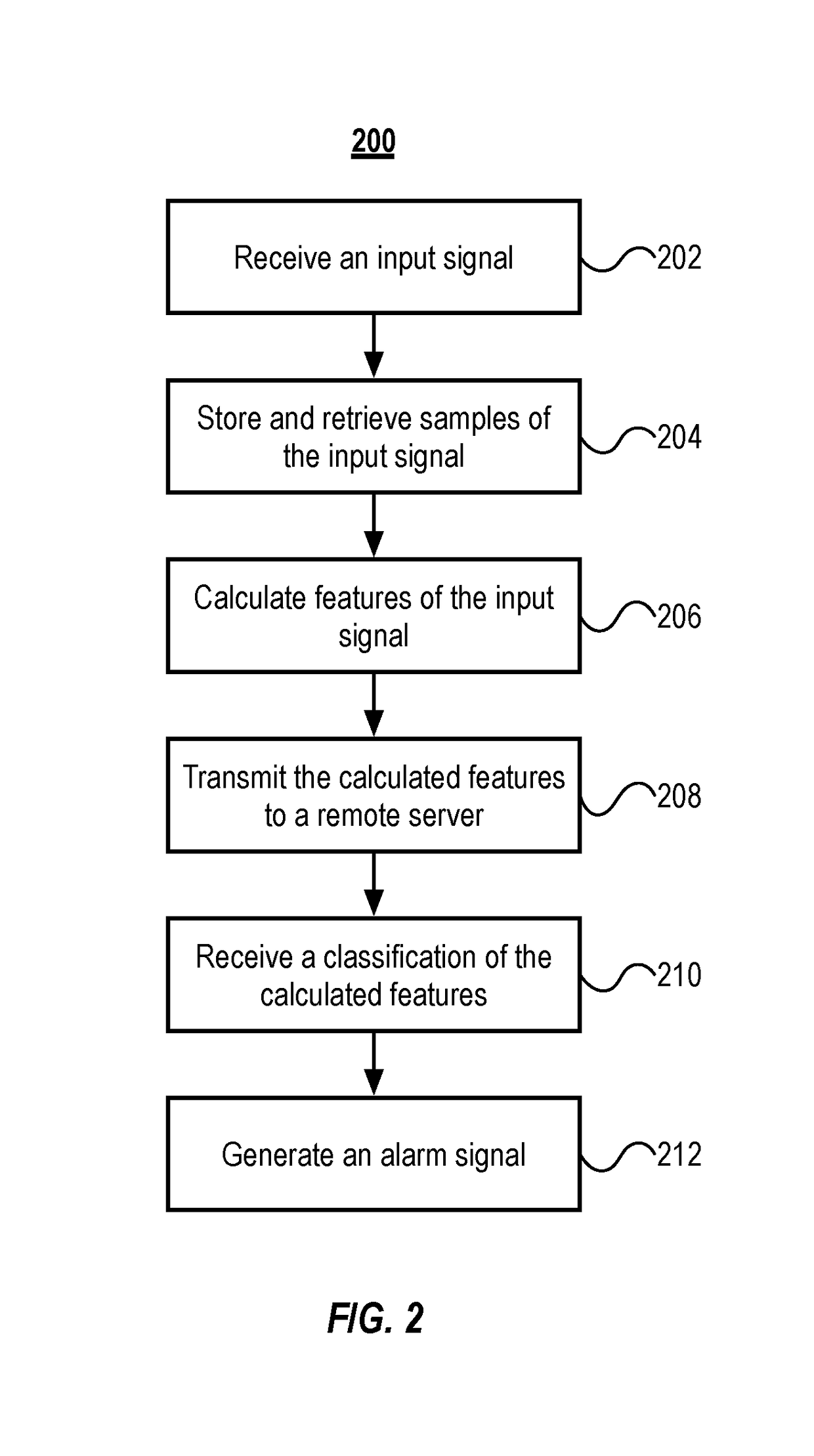
The present disclosure describes systems and methods for detecting malware. More particularly, the system includes a monitoring device that monitors side-channel activity of a target device. The monitoring device that can work in conjunction with (or independently of) a cloud-based security analytics engine to perform anomaly detection and classification on the side-channel activity. For example, the monitoring device can calculate a first set of features that are then transmitted to the security analytics engine for anomaly detection and classification.
Owner:VIRTA LAB INC
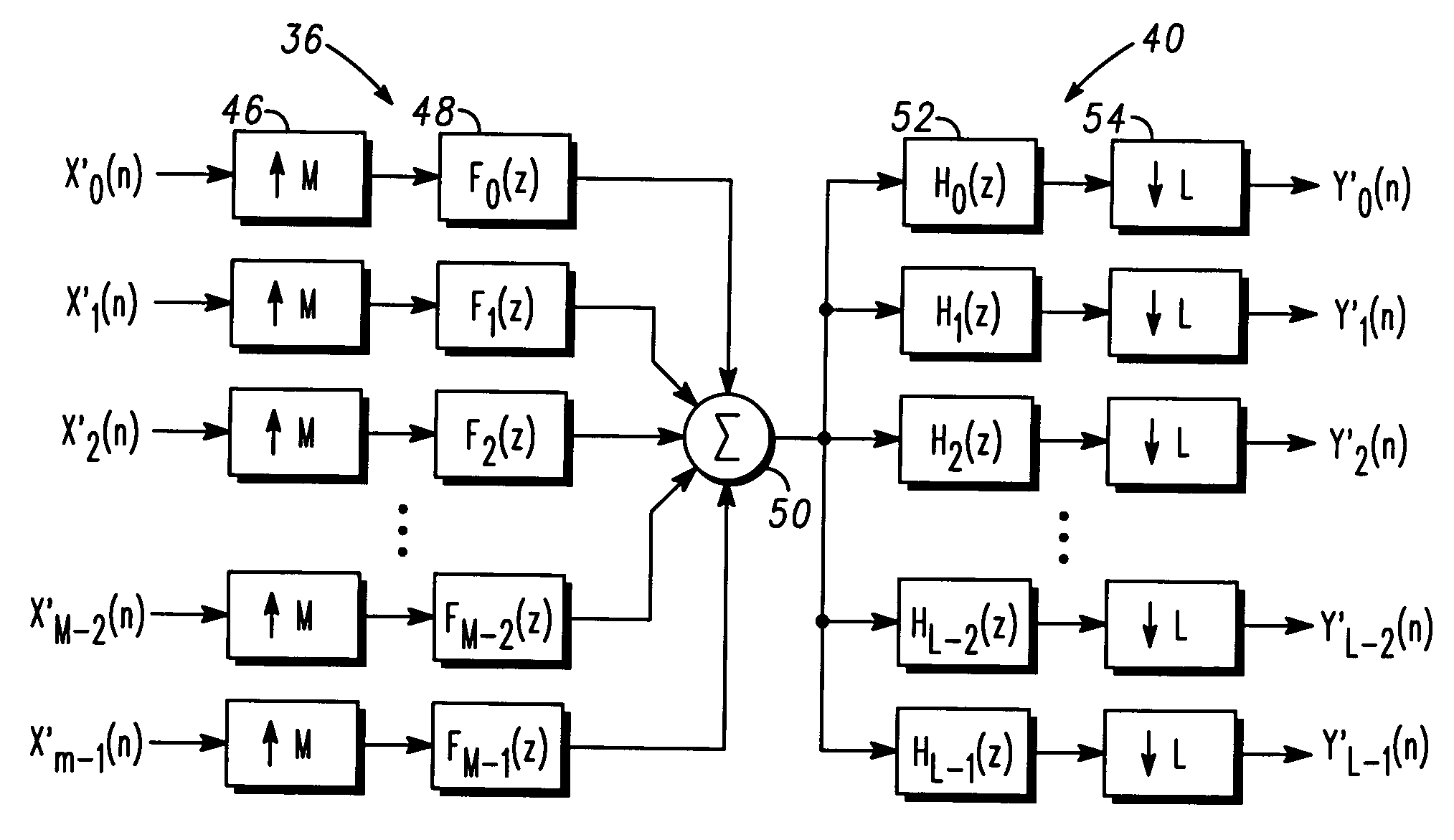
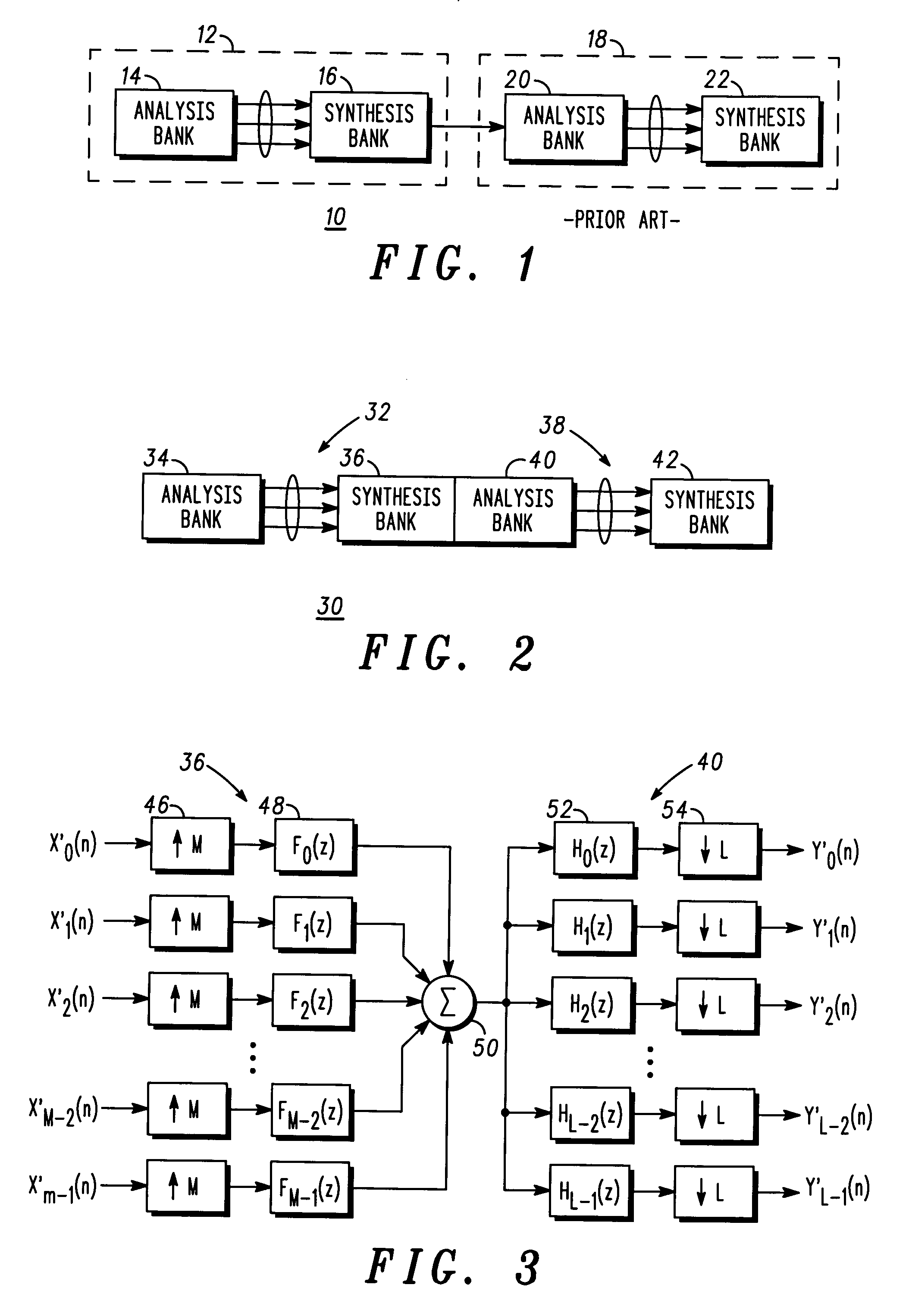
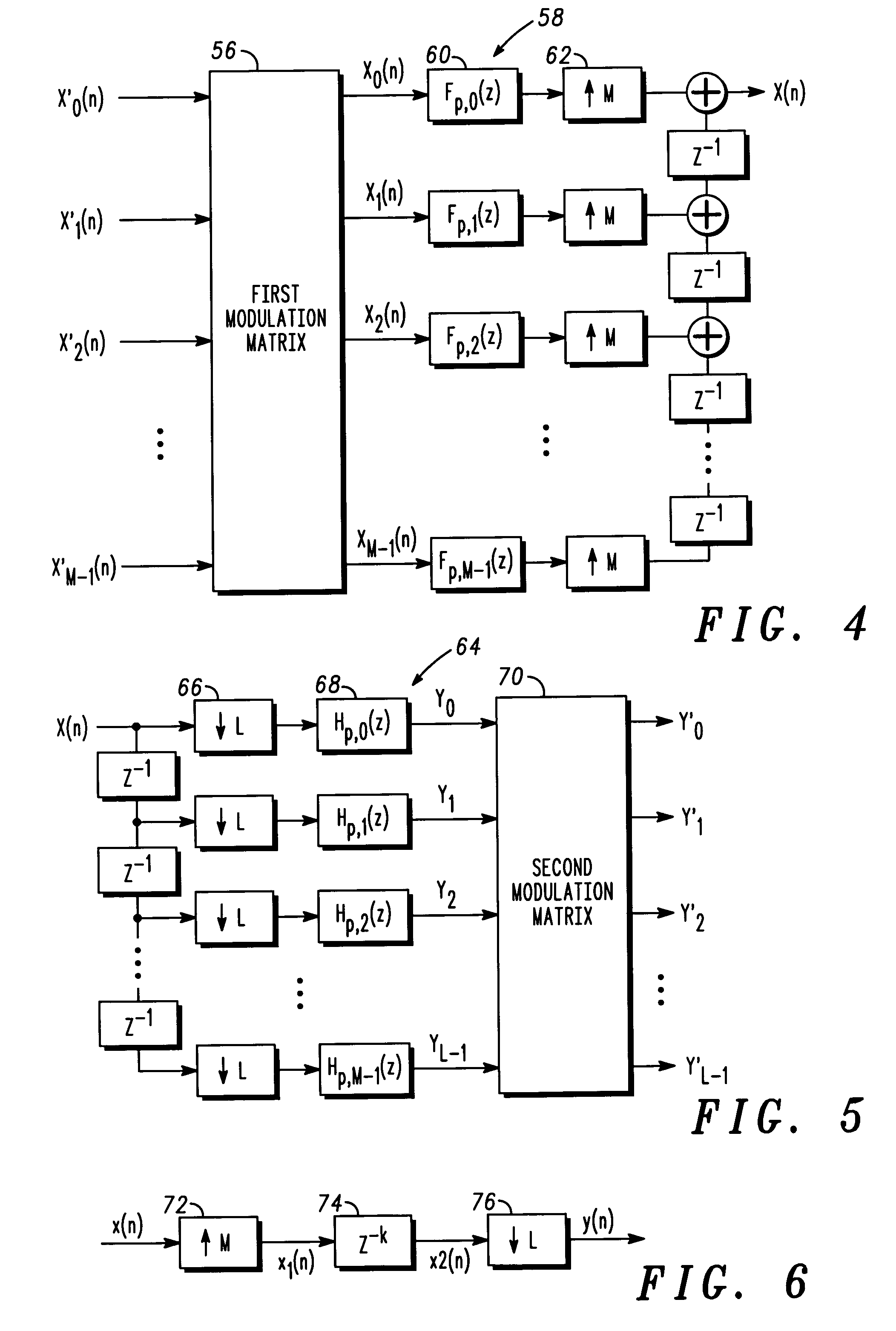
Method of combining an analysis filter bank following a synthesis filter bank and structure therefor
An efficient method and structure for combining an M-channel synthesis filter bank followed by an L-channel analysis filter bank.
Owner:MOTOROLA INC
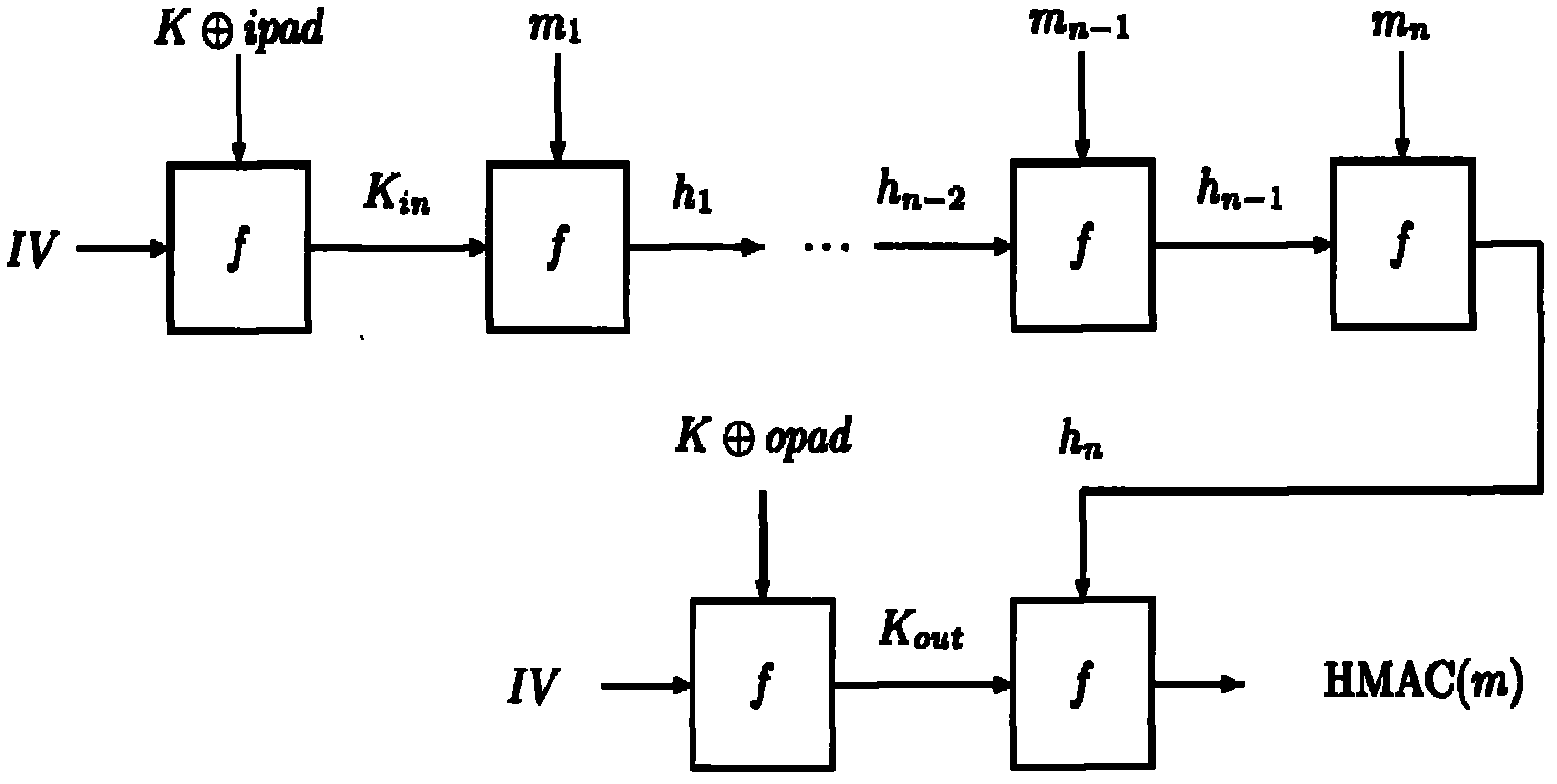
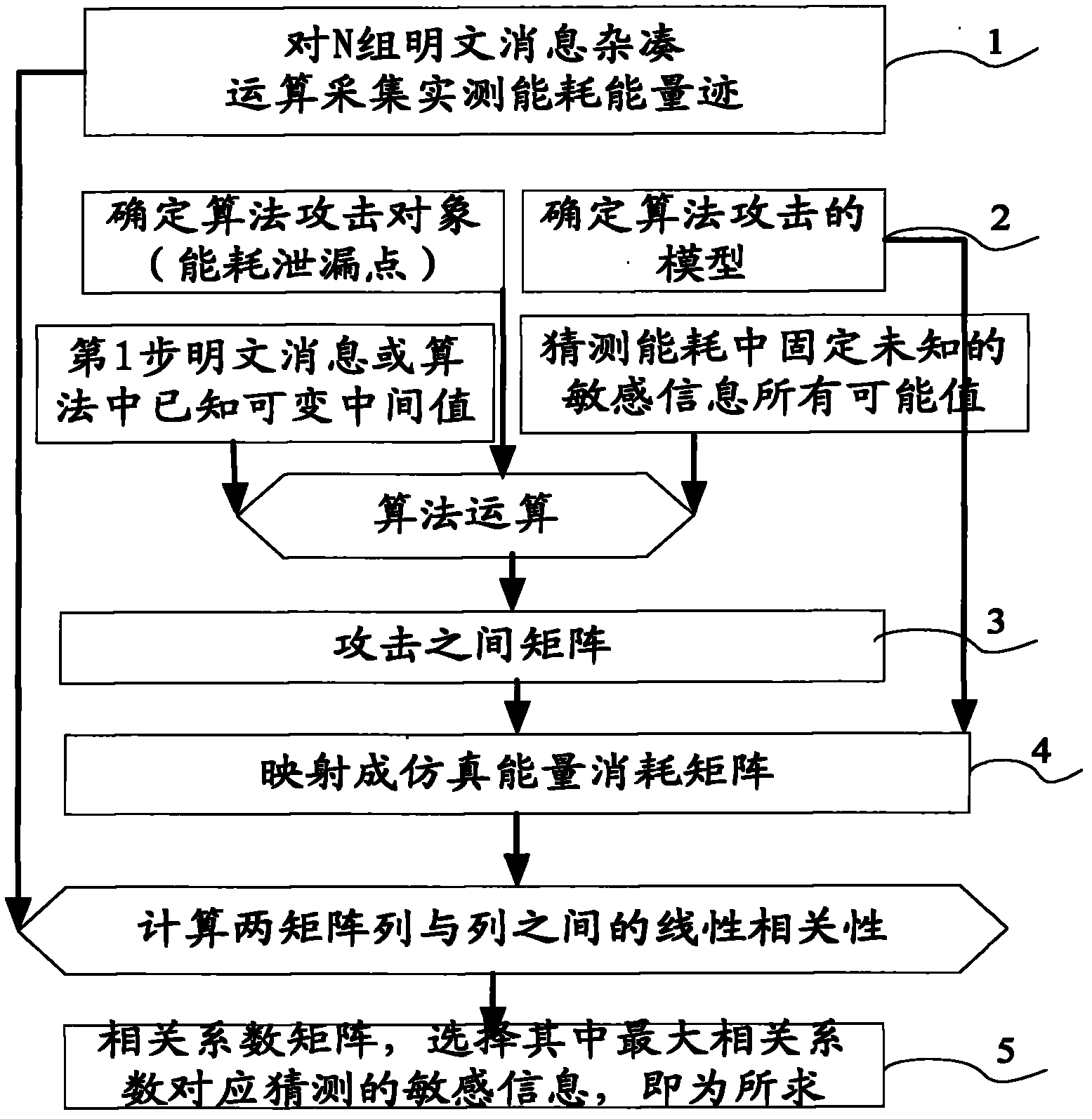
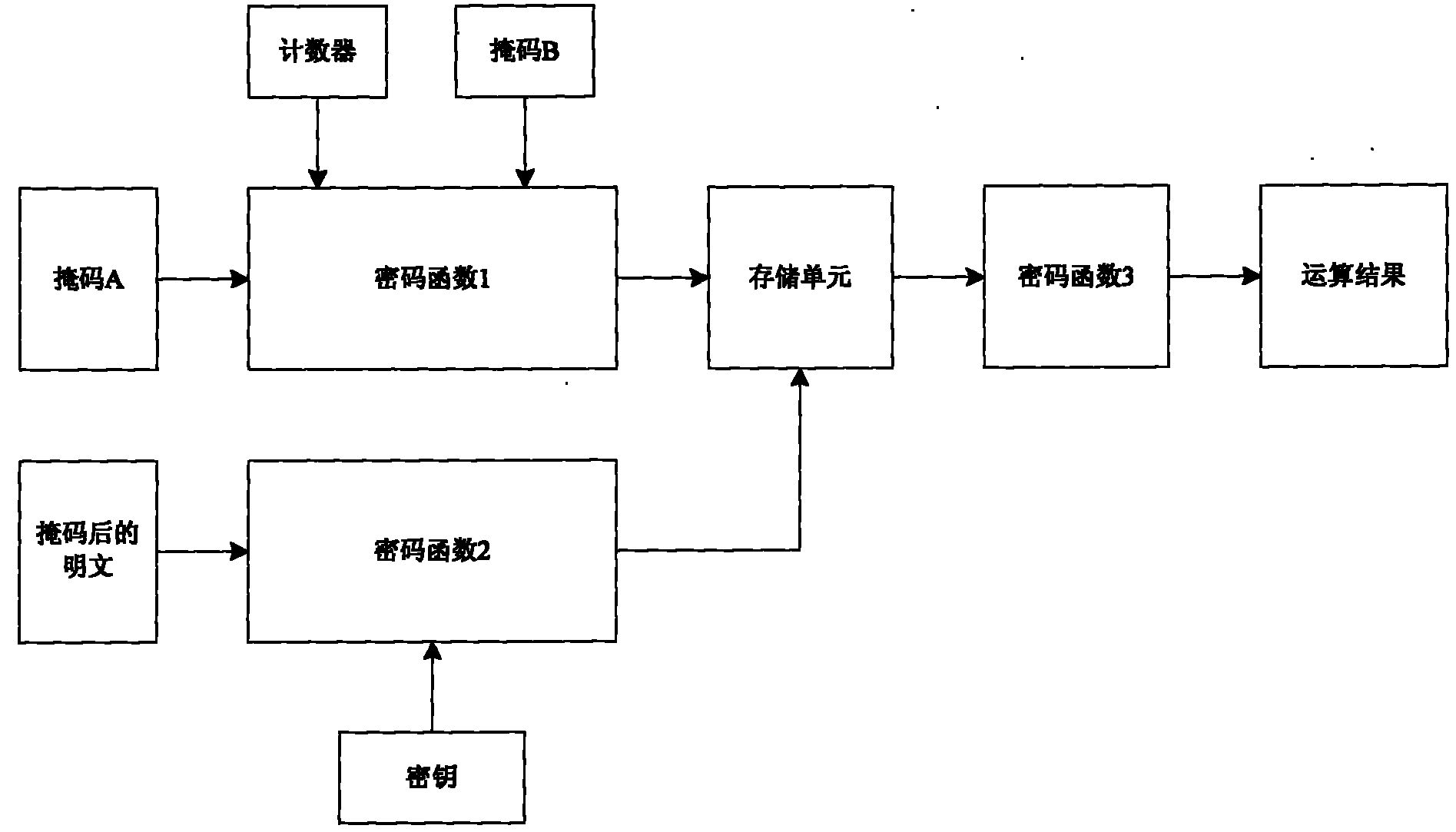
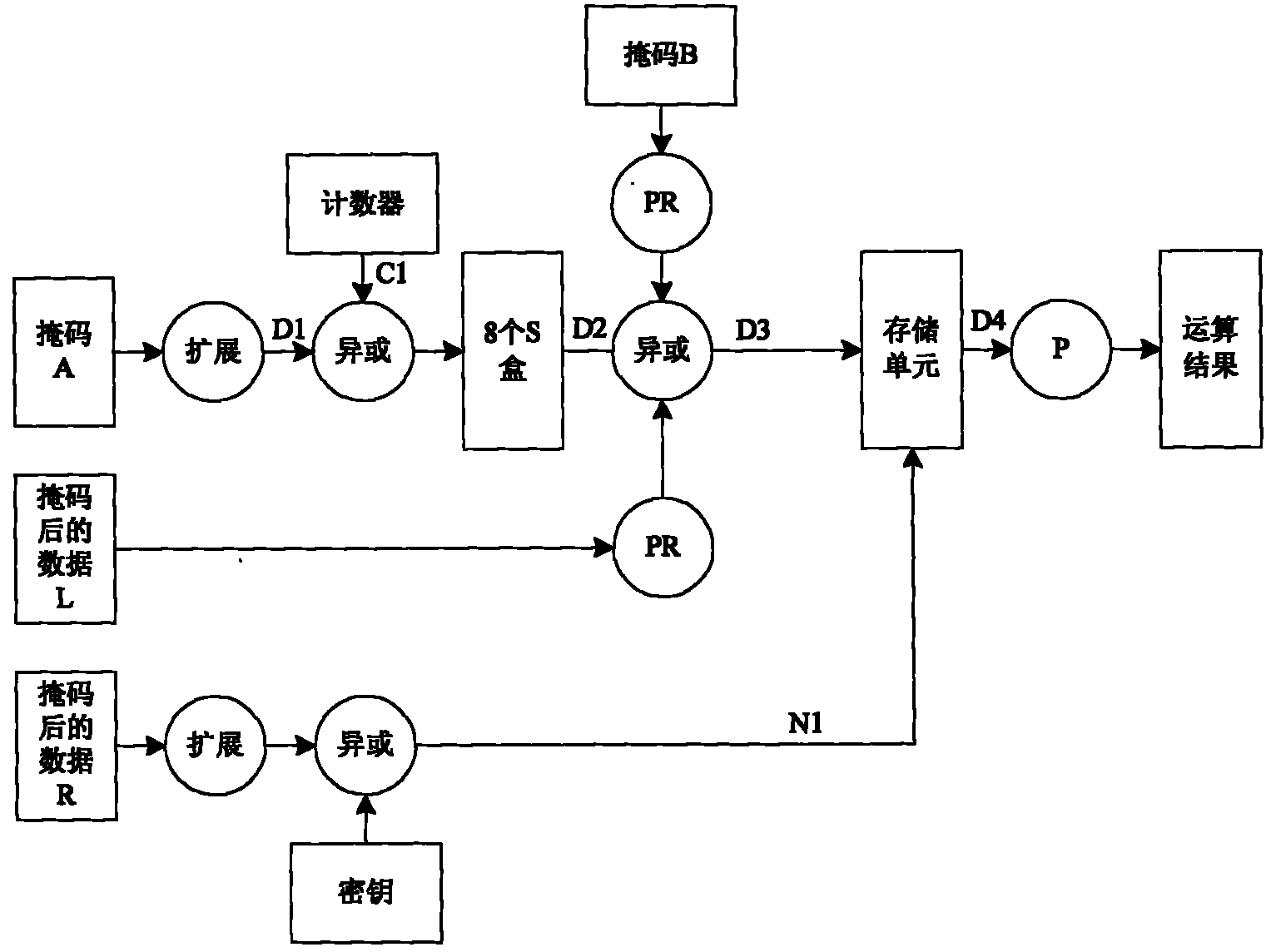
Side channel energy analysis method for SM3 cryptographic algorithm HMAC mode
ActiveCN103457719AEncryption apparatus with shift registers/memoriesComputer security arrangementsPower analysisChannel analysis
The invention discloses a side channel energy analysis method for an SM3 cryptographic algorithm HMAC mode. The method performs analyses on implementation characteristics of a SM3 cryptographic algorithm and the HMAC mode of the SM3 cryptographic algorithm. Based on a DPA attack method and a CPA attach method, the SM3 cryptographic algorithm HMAC mode is successfully cracked in combination with the characteristics of the SM3 cryptographic algorithm HMAC mode and energy consumption leakage points, and output summaries can be freely fabricated. According to the technical scheme, the method includes the steps that 1, energy traces of HMACs are collected; 2, a K[in] is obtained through analyses and the K[in] is an intermediate state value in a first hash algorithm; 3, a K[out] is obtained through analyses and the K[out] is an intermediate state value in a second hash algorithm. The method in the step 3 is the same as that in the step 2. According to the technical scheme, the method provides a solution for side channel analysis implementation of the SM3 cryptographic algorithm.
Owner:国家密码管理局商用密码检测中心
Radioactive detection system and radioactive detection method
InactiveCN105137469AReduce operating hazardsKeep healthyX-ray spectral distribution measurementDosimetersPhysicsEnergy spectrum
Embodiments of the invention disclose a radioactive detection system and a radioactive detection method, and relate to the technical field of radiation monitoring. By adopting the system and the method, personnel do not need to approach or enter a radiation area or suspected radiation area with an instrument in hand for detection just like that in a traditional measurement method, and the risk is reduced. The system is composed of an unmanned rotor aircraft and a ground control terminal. The unmanned rotor aircraft comprises an unmanned rotor flying platform, and a radiation measuring platform borne on the unmanned rotor flying platform. The radiation measuring platform comprises a storage module used to store all measurement data and detection results, an energy spectrum detection module used to acquire energy spectrum information in a current environment, a multi-channel analysis module used to preliminarily process the energy spectrum information, a data processing module used to integrate and package location information, preliminary processing result data and dose rate monitoring information, and a wireless radio-frequency transmission module used to send a data packet to the ground control terminal. The radioactive detection system and the radioactive detection method of the invention are suitable for remotely detecting the radiation dose rate.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method and device for identifying channels
InactiveCN103002328ADigital data information retrievalSelective content distributionServer Side IncludesChannel analysis
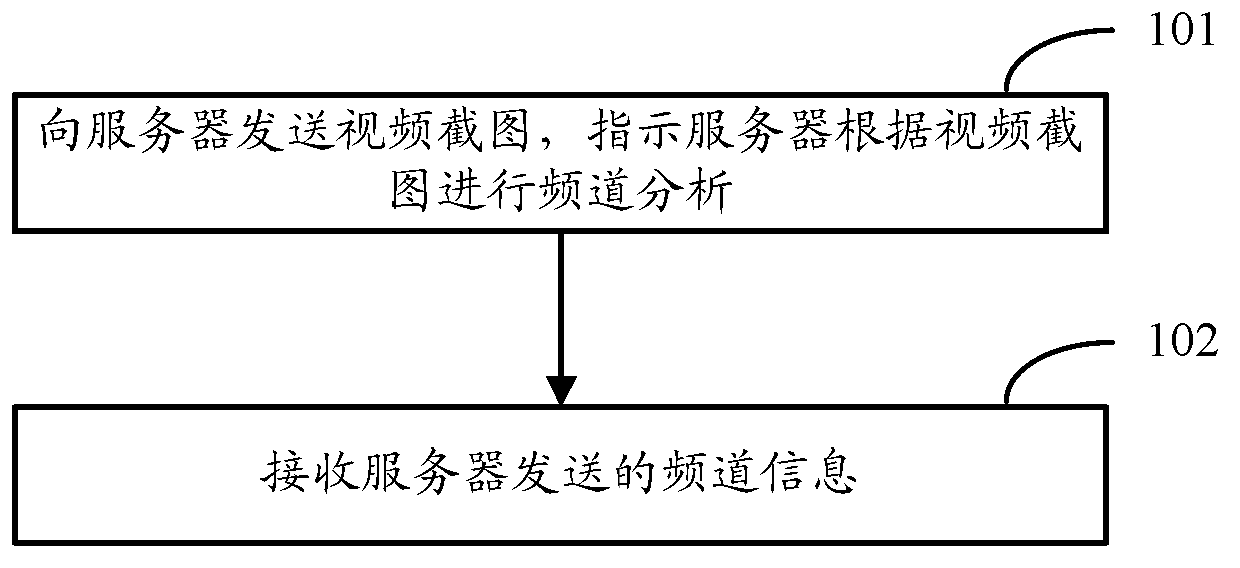
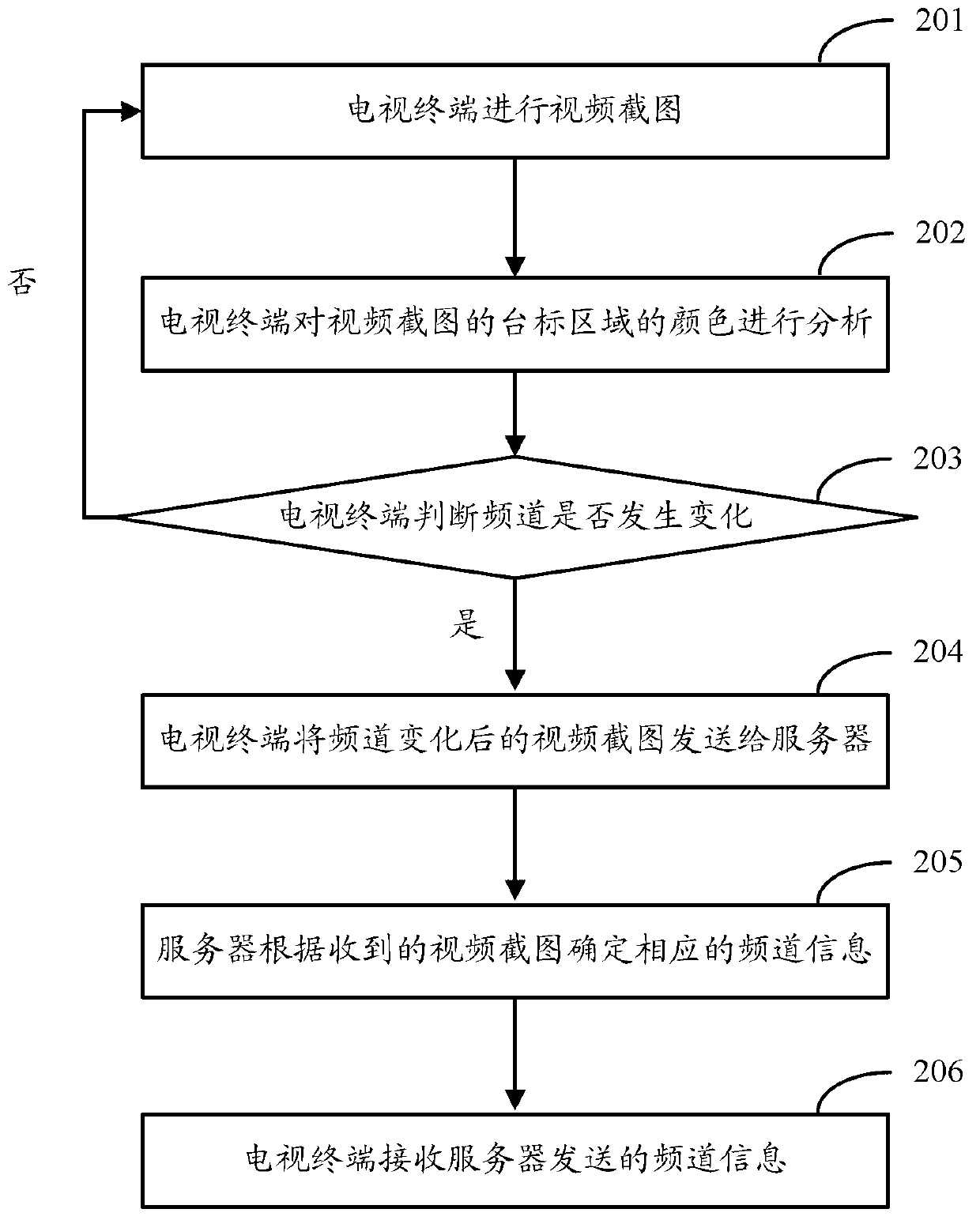
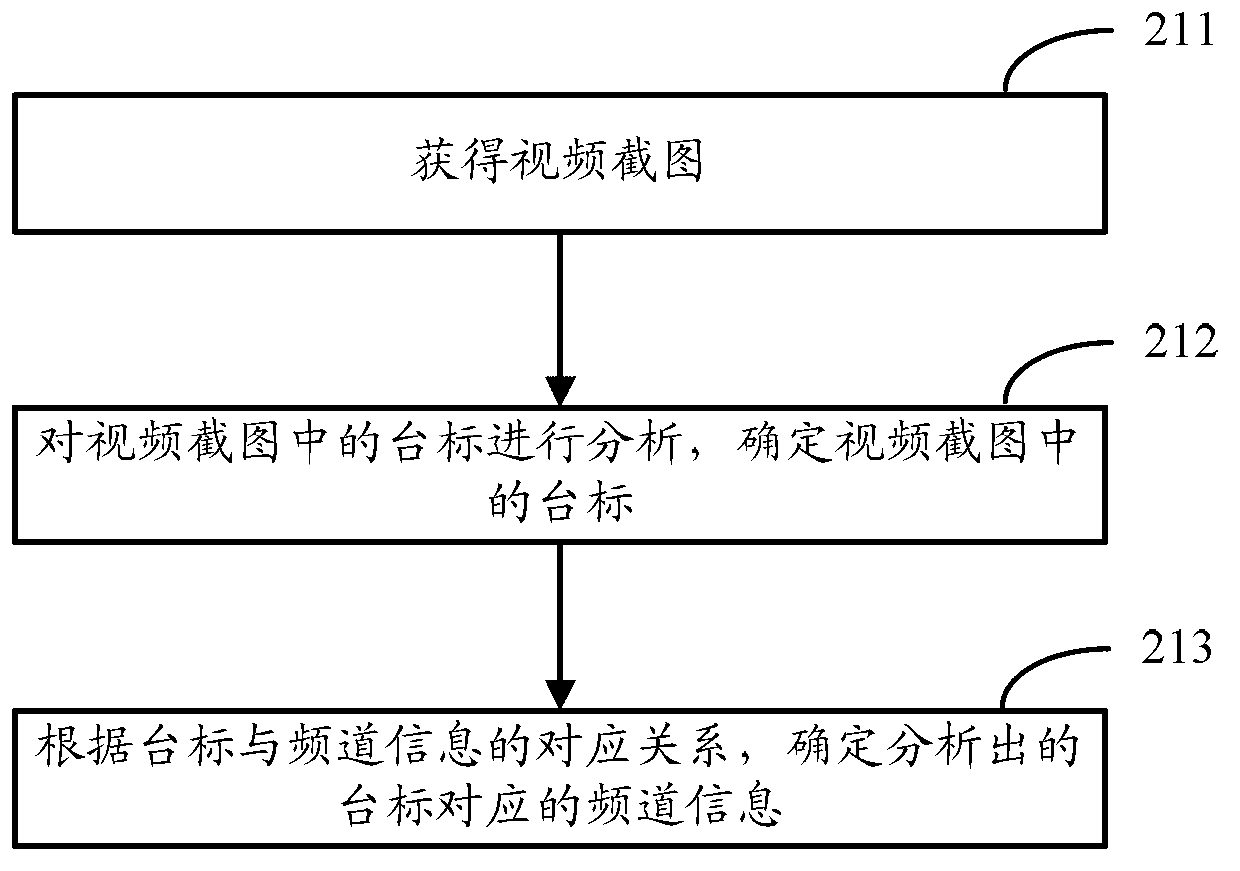
The invention discloses a method for identifying channels and a device for implementing the method. The method is used for informing a television terminal of channel information. The method of a television terminal side includes sending a video screenshot to a server, indicating the server to perform channel analysis according to the video screenshot and receiving the channel information sent by the server. The method of a server side includes receiving the video screenshot sent by the television terminal, analyzing a station caption in the video screenshot, determining the station caption in the video screenshot, determining the channel information which the analyzed out station caption corresponds to according to a corresponding relationship between the station caption and the channel information and sending the determined channel information to the television terminal.
Owner:KUYUN INTERACTIVE TECH
Integrated circuit protected against horizontal side channel analysis
ActiveUS20110246789A1Easy to implementReduce in quantityDigital computer detailsUnauthorized memory use protectionChannel analysisComputer science
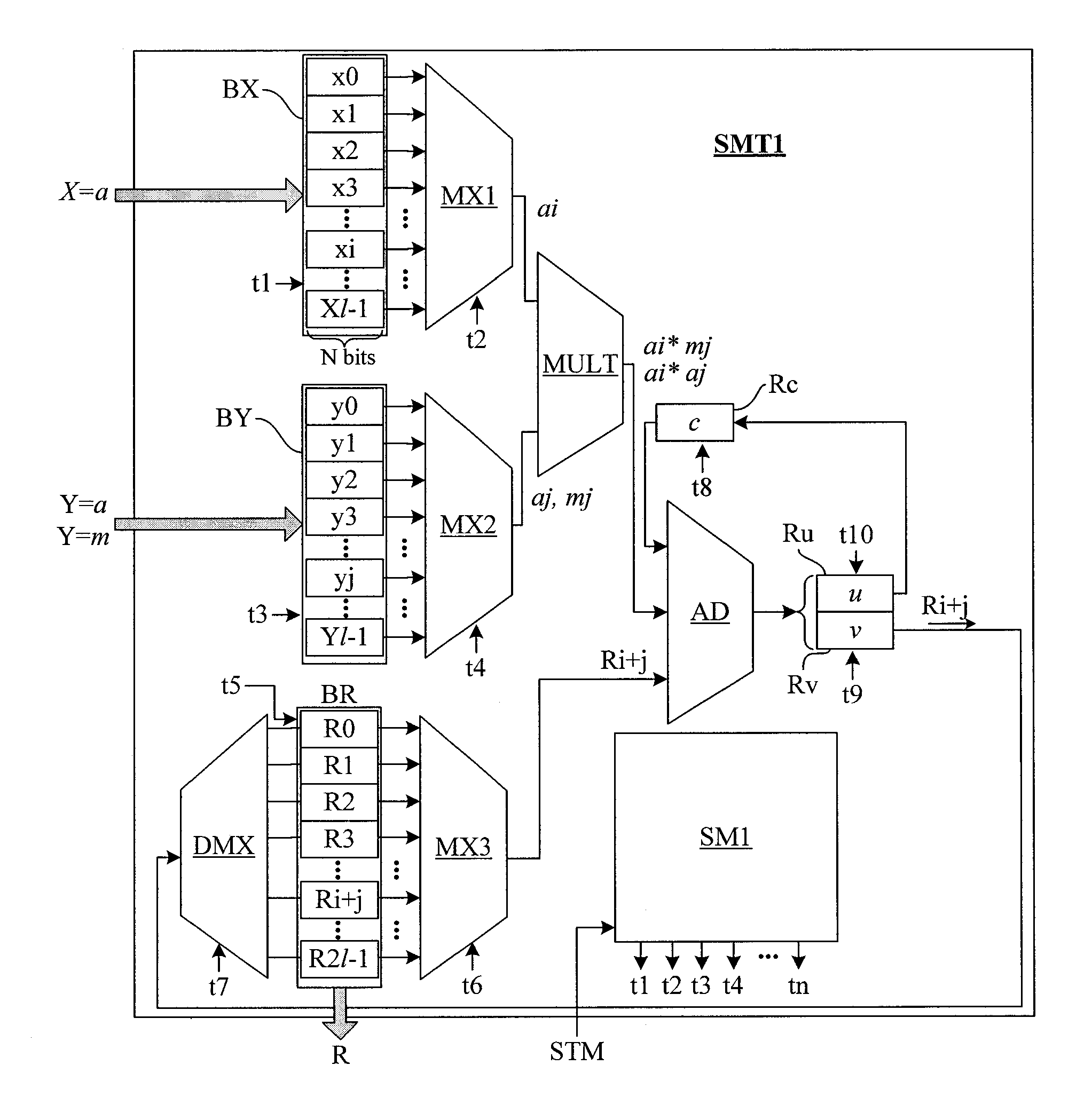
An integrated circuit including a multiplication function configured to execute a multiplication operation of two binary words x and y including a plurality of basic multiplication steps of components xi of word x by components yj of word y is described. The multiplication function of the integrated circuit is configured to execute two successive multiplications by modifying, in a random or pseudo-random manner, an order in which the basic multiplication steps of components xi by components yj are executed.
Owner:CRYPTOGRAPHY RESEARCH
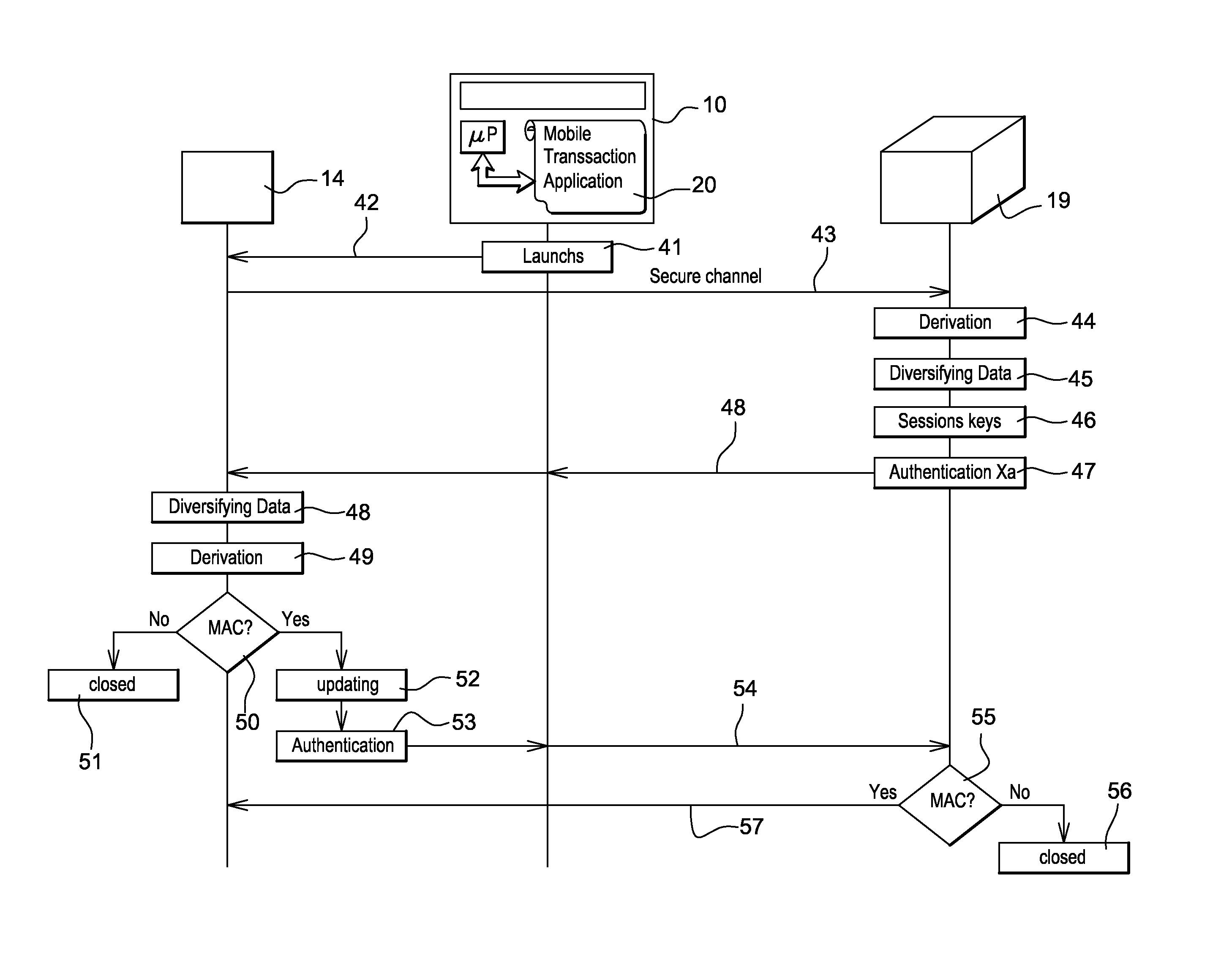
System and method for securing communications between a card reader device and a remote server
InactiveUS20160295404A1Reduced flexibilityImprove securityKey distribution for secure communicationSecurity arrangementSecure communicationEnd to end security
The present invention concerns the implementation of end-to-end security for the communication between a low cost card reader and the remote server. The purpose of the present invention is the establishment of a secure channel between the card reader and the remote server through an un-trusted communication device (e.g. a smart phone or a tablet) that is intrinsically resistant to some basic differential side-channel analysis in a context where there is no secure random number generator and no source of entropy in the card reader, while providing the following characteristics:—Mutual authentication between the card reader and the server—Secure channel based on session keys such that the keys of the secure channel related to a past transaction cannot be re-played, or the session keys of a future transaction cannot be pre-computed by the card reader and later re-use by the card reader in a legitimate transaction.
Owner:GEMPLU
Process for testing the resistance of an integrated circuit to a side channel analysis
ActiveUS20110246119A1Easy to implementReduce in quantityDigital data processing detailsElectrical testingElectrical resistance and conductanceEngineering
A process for testing an integrated circuit includes collecting a set of points of a physical property while the integrated circuit is executing a multiplication, dividing the set of points into a plurality subsets of lateral points, calculating an estimation of the value of the physical property for each subset, and applying to the subset of lateral points a step of horizontal transversal statistical processing by using the estimations of the value of the physical property, to verify a hypothesis about the variables manipulated by the integrated circuit.
Owner:CRYPTOGRAPHY RESEARCH
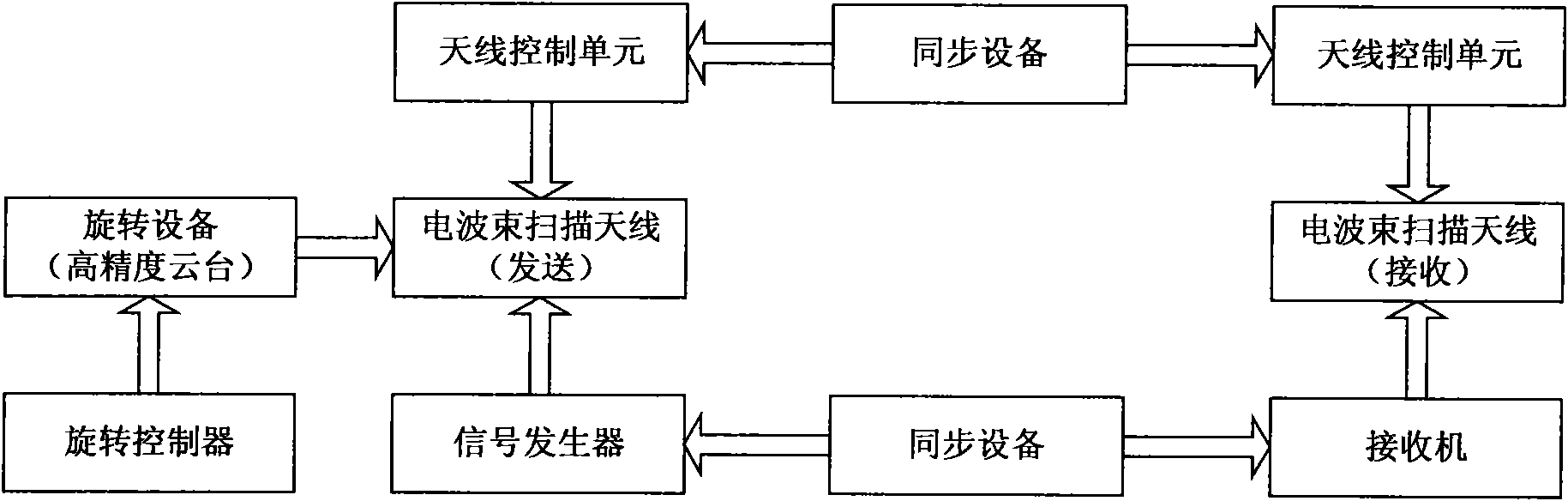
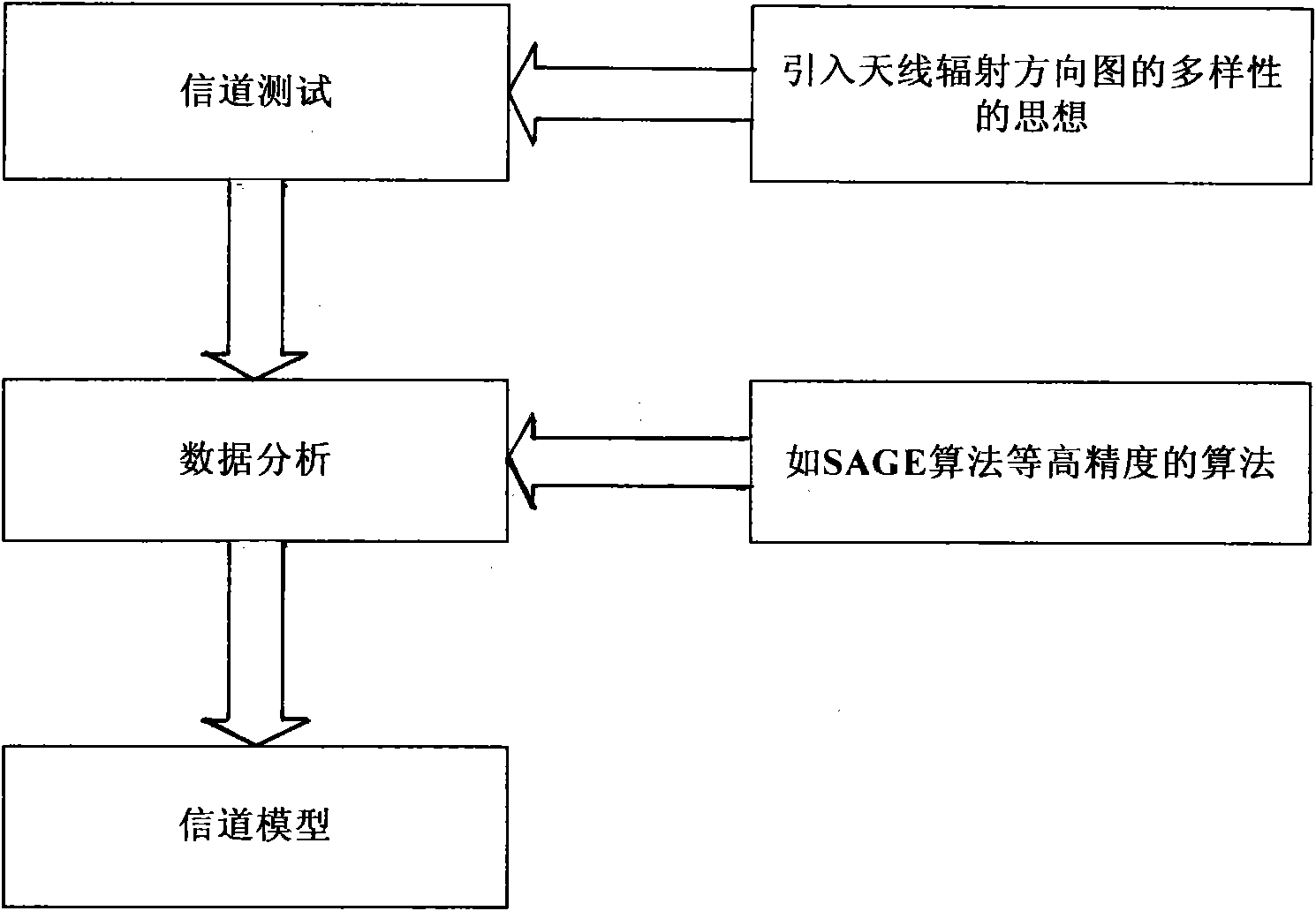
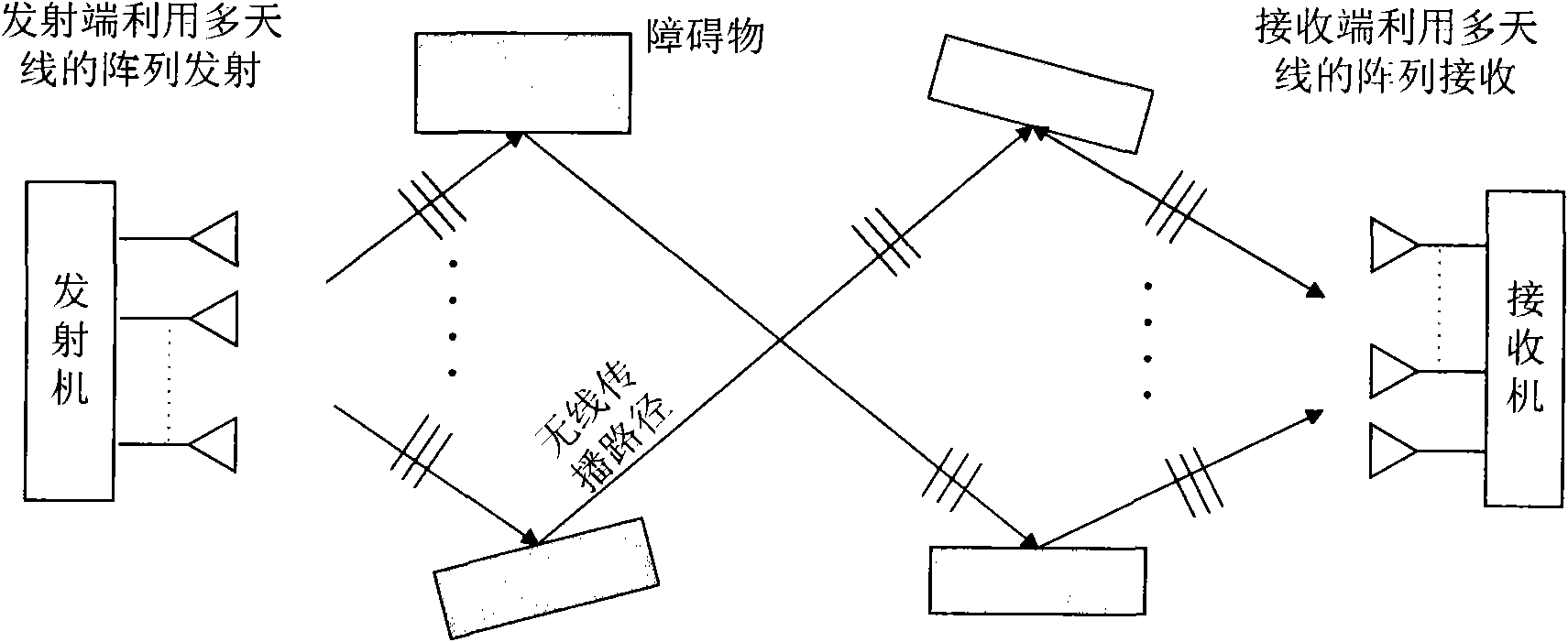
Diverse wireless channel analysis platform based on antenna radiation directional diagram and method thereof
InactiveCN101631318ALower requirementGood orthogonalityDiversity/multi-antenna systemsNetwork planningProblem of timeAntenna radiation patterns
A diverse wireless channel analysis platform based on antenna radiation directional diagram and a method thereof are disclosed; a transmitting antenna and a receiving antenna are respectively fixed at certain positions in the space and transmits and receives data through different radiation directional diagram of the antenna, the diversity of the antenna radiation directional diagram is used as a sampling space of the wireless transmission channel response on the space domain, and simultaneously high precision parameter estimation algorithm is used for obtaining detailed features of the wireless transmission channel in the directions of incident and exit through a manner of array signal processing, and conclusion and model construction are carried out on the feature of the wireless transmission channel by combining the feature estimation results of the channel on the time domain and time delay domain. The invention eliminates the fuzzy judgment problem of time and space of the traditional channel analysis method and improves the preciseness of channel analysis.
Owner:TONGJI UNIV
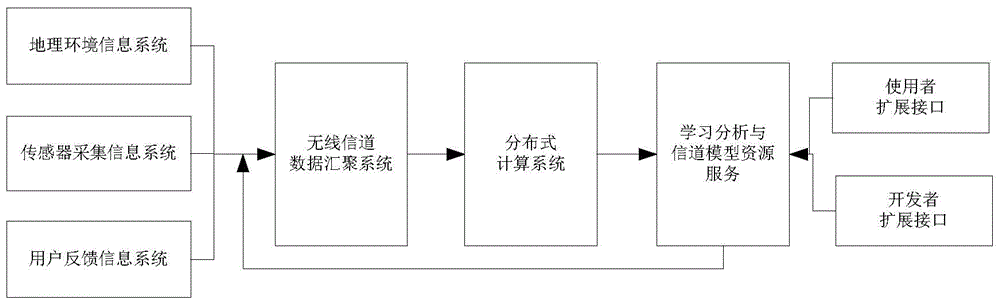
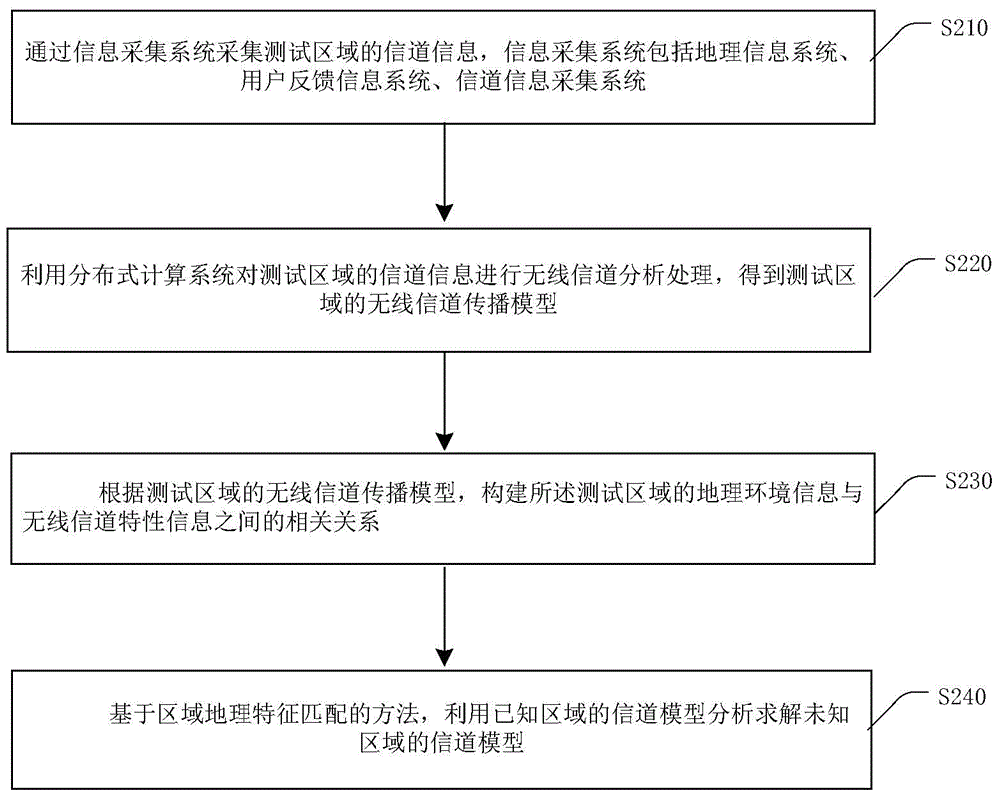
Collected data-based wireless channel transmission model establishing method and system
InactiveCN104618045AHigh precisionTransmission monitoringSpecial data processing applicationsChannel analysisTest region
The embodiment of the invention provides a collected data-based wireless channel transmission model establishing method and system. The method mainly comprises collecting the channel information of a tested region through an information collecting system, which comprises a geographic information system; performing wireless channel analysis on the channel information of the tested region through a distributed computation system to obtain the wireless channel transmission model of the tested region; according to the wireless channel transmission model of the tested region, structuring the correlation between the geological information of the tested region and wireless channel characteristic information. The collected data-based wireless channel transmission model establishing method helps obtain the wireless channel transmission model by mining mass data, performing wireless channel analysis on the mass channel correlated information through the distributed computation system and analyzing the correlation of the mass channel correlated information, thereby improving the accuracy of the wireless channel transmission model and wireless channel prediction.
Owner:BEIJING JIAOTONG UNIV
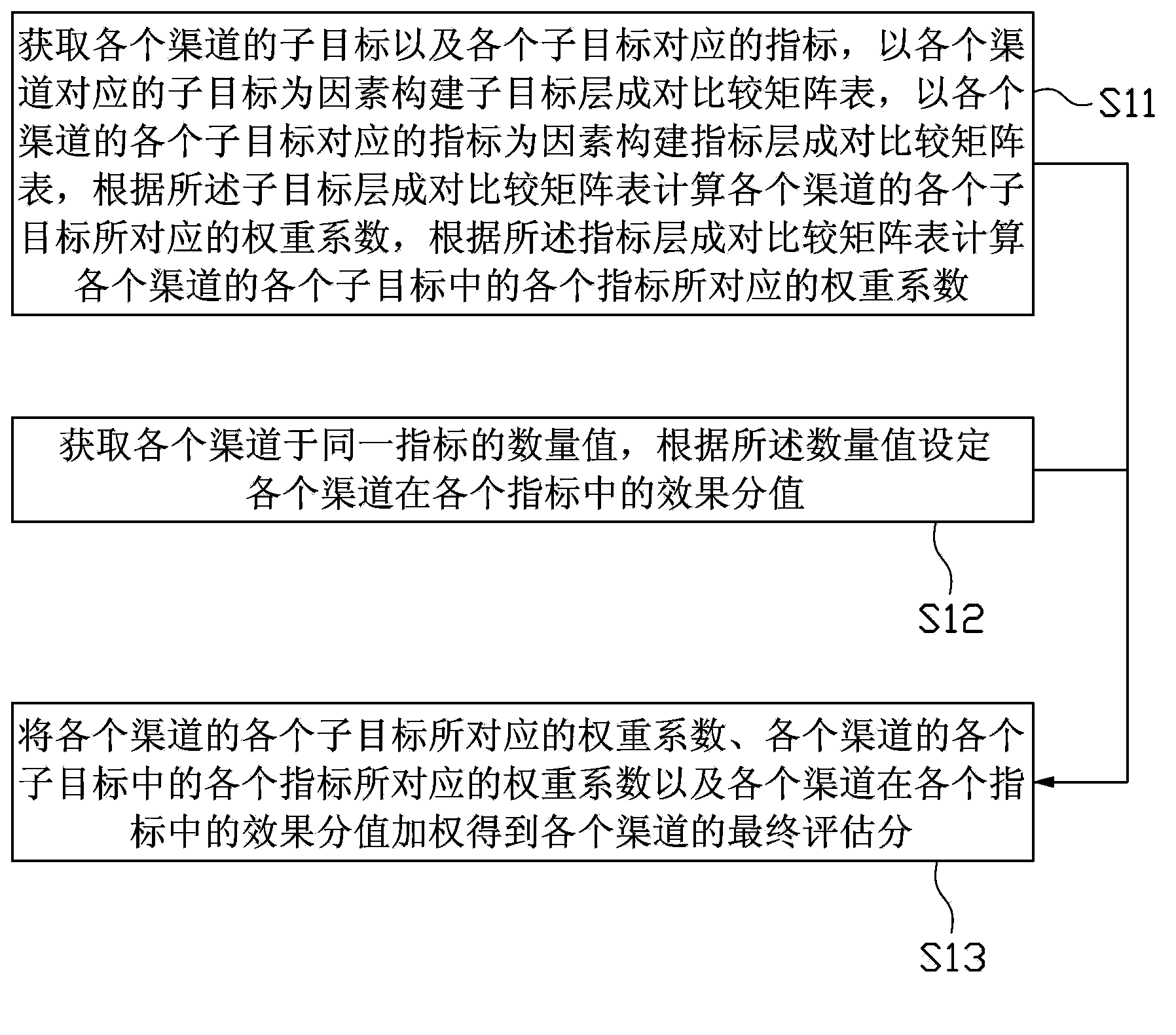
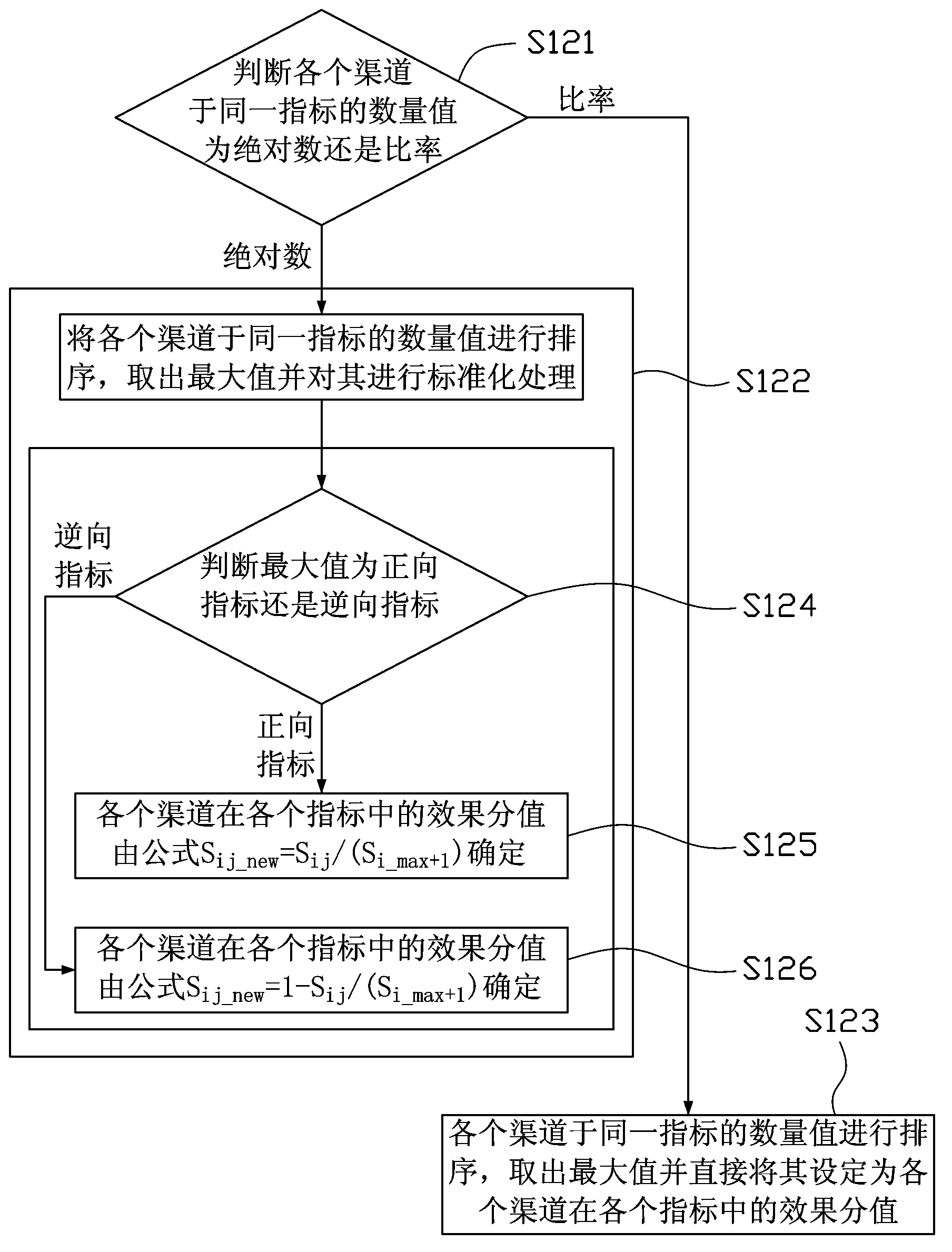
Multi-channel analysis method and device based on analytic hierarchy process
InactiveCN103886168AScience of Assessment ResultsThe assessment results are accurateSpecial data processing applicationsPairwise comparison matrixWeight coefficient
The application provides a multi-channel analysis method and a multi-channel analysis device based on an analytic hierarchy process. The method comprises the steps of: acquiring a sub-target of each channel and an index corresponding to each sub-target, building a sub-target layer paired comparison matrix table by using the sub-targets corresponding to the channels as factors, building an index layer paired comparison matrix table by using the indexes corresponding to the sub-targets of the channels as factors, computing a weight coefficient corresponding to each sub-target of each channel according to the sub-target layer paired comparison matrix table, computing a weight coefficient corresponding to each index in each sub-target of each channel according to the index layer paired comparison matrix table, acquiring a quantity value of each channel at the same index, setting an effect value of each channel at each index according to the quantity value, and weighting the weight coefficients and the effect values to obtain a final assessing score of the channel. According to the multi-channel analysis method and device based on the analytic hierarchy process, a more scientific and accurate multi-channel assessing result can be provided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for atomicity for elliptic curve cryptosystems
InactiveUS20090046851A1Digital data processing detailsPublic key for secure communicationEllipseChannel analysis
A method and system are provided for atomicity for elliptic curve cryptosystems (ECC-systems). The method includes a side channel atomic scalar multiplication algorithm using mixed coordinates. The algorithm including repeating a sequence of field operations for each elliptic curve addition or doubling operation to provide an atomic block, wherein an atomic block appears equivalent by side-channel analysis. The mixed coordinates are chosen based on a ratio of I / M where I and M are the time required to execute an inversion and a multiplication in the ground field respectively. If the I / M ratio is less than 60, a mixture of affine and Jacobian coordinates are used during scalar multiplication. If the I / M ratio is 60 or more, a mixture of Chudnovsky-Jacobian and Jacobian coordinates are used during scalar multiplication. The method is optimized for elliptic curves over Fp defined by an equation of the form y2=x3+ax+b, where a, b ε Fp, having a=−3.
Owner:DOORDASH INC
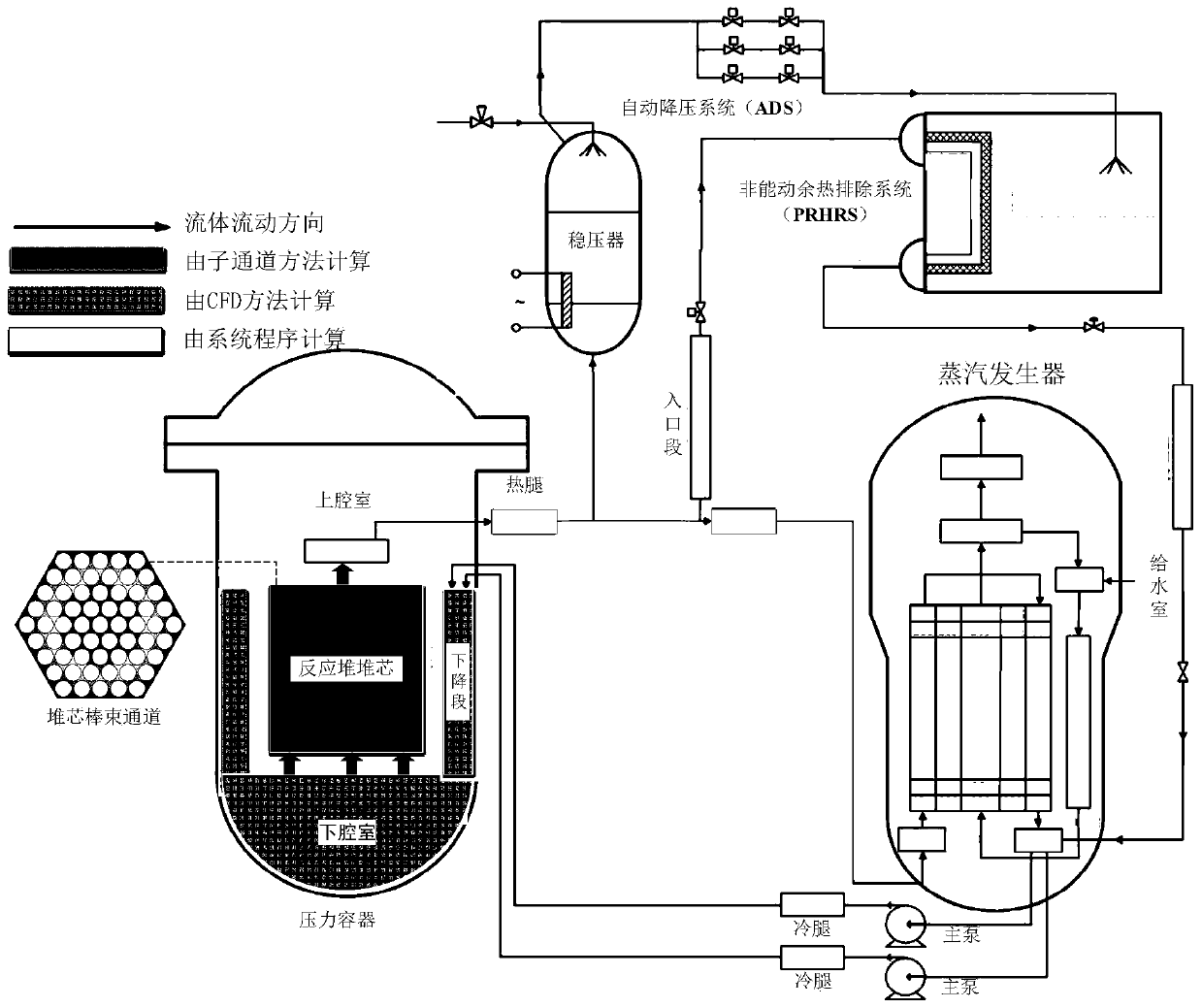
Nuclear power system interdimensional coupling simulation method
ActiveCN109903870ADo not change modeling propertiesEasy to implementNuclear energy generationNuclear power plant controlSystems analysisCoupling
The invention discloses a nuclear power system interdimensional coupling simulation method which includes the steps: firstly, performing modeling on components of a nuclear power system through different reactor thermal hydraulics analysis programs; secondly, preliminarily calculating a reactor thermal hydraulic system analysis program and a reactor thermal hydraulic sub-channel analysis program according to set initial boundary conditions; thirdly, taking calculation results of the reactor thermal hydraulic system analysis program and the reactor thermal hydraulic sub-channel analysis programas boundary conditions of computational fluid dynamics software to perform calculation; fourthly, taking calculation results acquired in the third step as boundary conditions of the reactor thermal hydraulic system analysis program to calculate thermal hydraulic parameters of next time step reactor; fifthly, taking calculation results acquired in the fourth step as boundary conditions of the thermal hydraulic sub-channel analysis program to calculate thermal hydraulic parameters of a reactor core; sixthly, repeating the third step to the fifth step until full time calculation is completed.
Owner:XI AN JIAOTONG UNIV
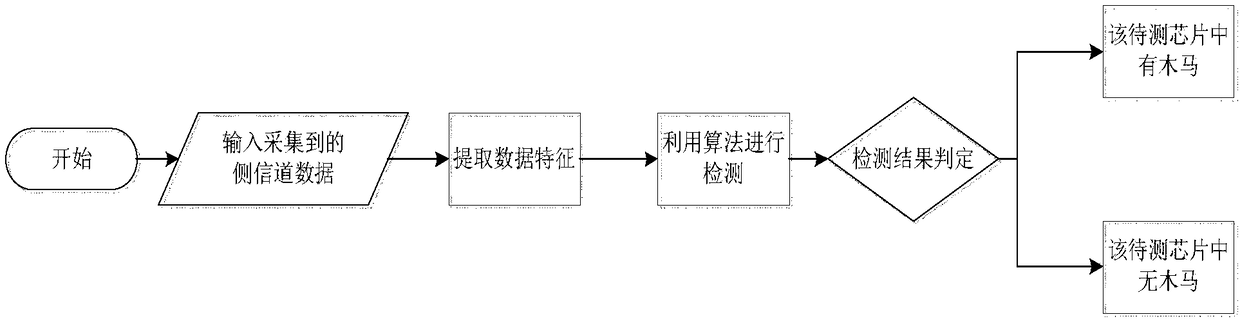
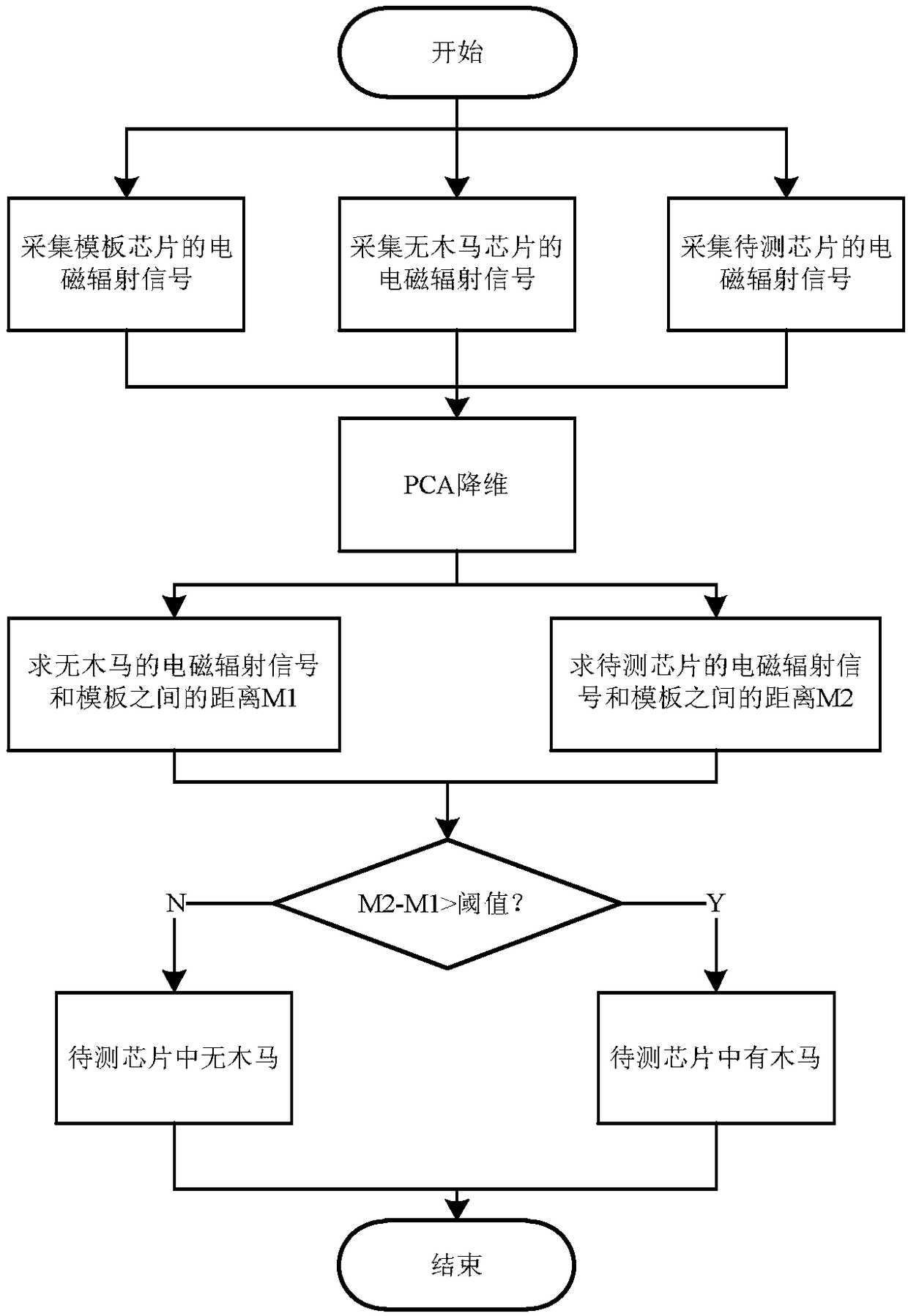
Hardware-Trojan-horse detection method based on side-channel analysis
InactiveCN108062477AImprove detection efficiencyInternal/peripheral component protectionPlatform integrity maintainanceChannel analysisChannel data
The invention belongs to the field of chip security, and particularly relates to a hardware-Trojan-horse detection method based on side-channel analysis. The method includes: establishing a chip side-channel signal collection and detection platform; utilizing a principal component-based analysis method to carry out dimension reducing on collected side-channel data to reduce the amount of the dataand extract valid information; and selecting a detection algorithm to analyze the data to obtain a detection result. According to the method, the chip side-channel signal collection platform is built,the detection algorithm is selected to detect hardware Trojan horses, thus a user can realize hardware-Trojan-horse detection simply by inputting related parameters according to prompting, Trojan-horse detection can be realized simply without the need for manually importing the data or inputting code of the detection algorithm, detection efficiency and accuracy are improved, detection of multipledetection algorithms can be realized at the same time, and the algorithms can also be extended according to user needs.
Owner:BEIJING ELECTRONICS SCI & TECH INST
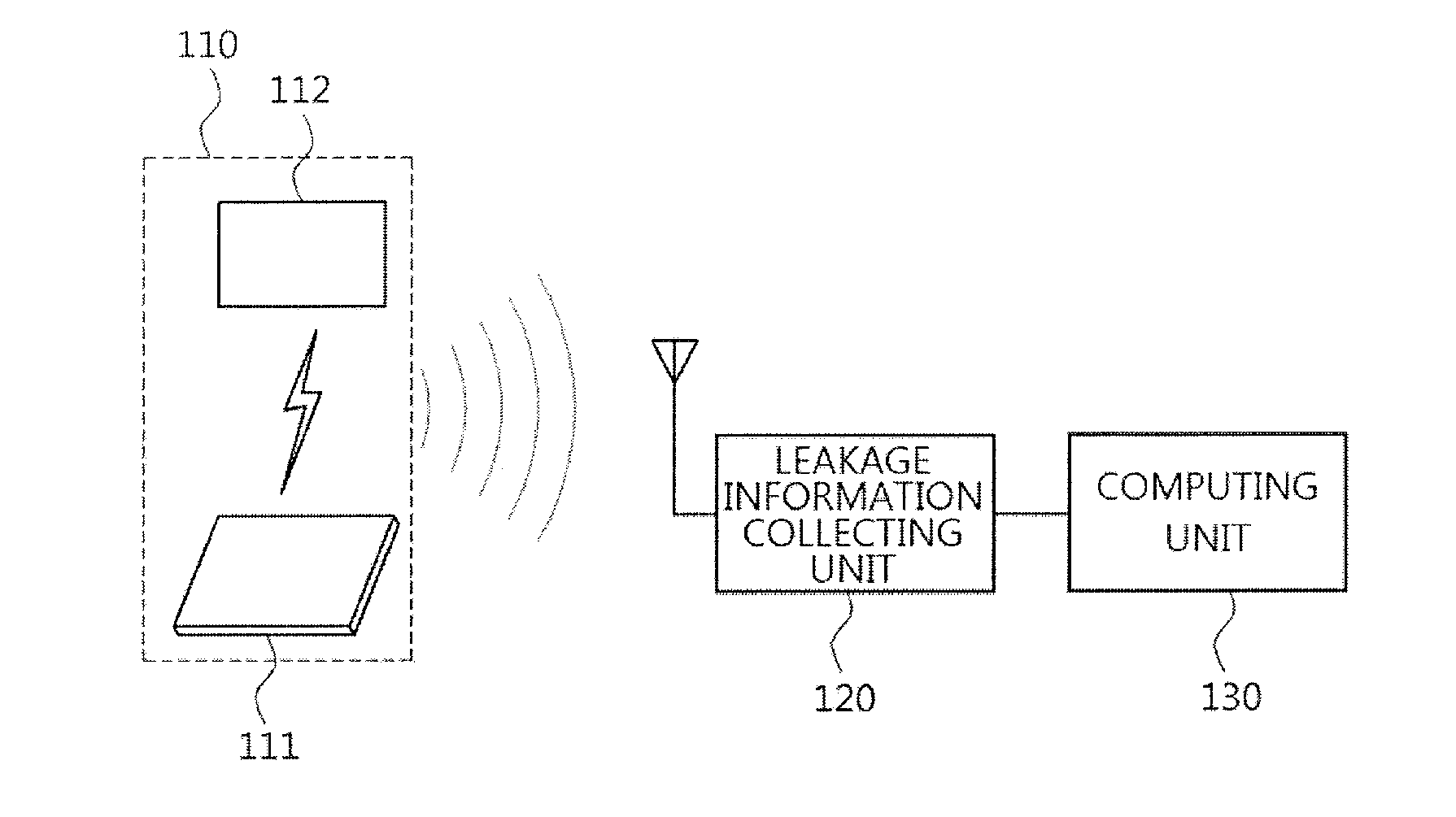
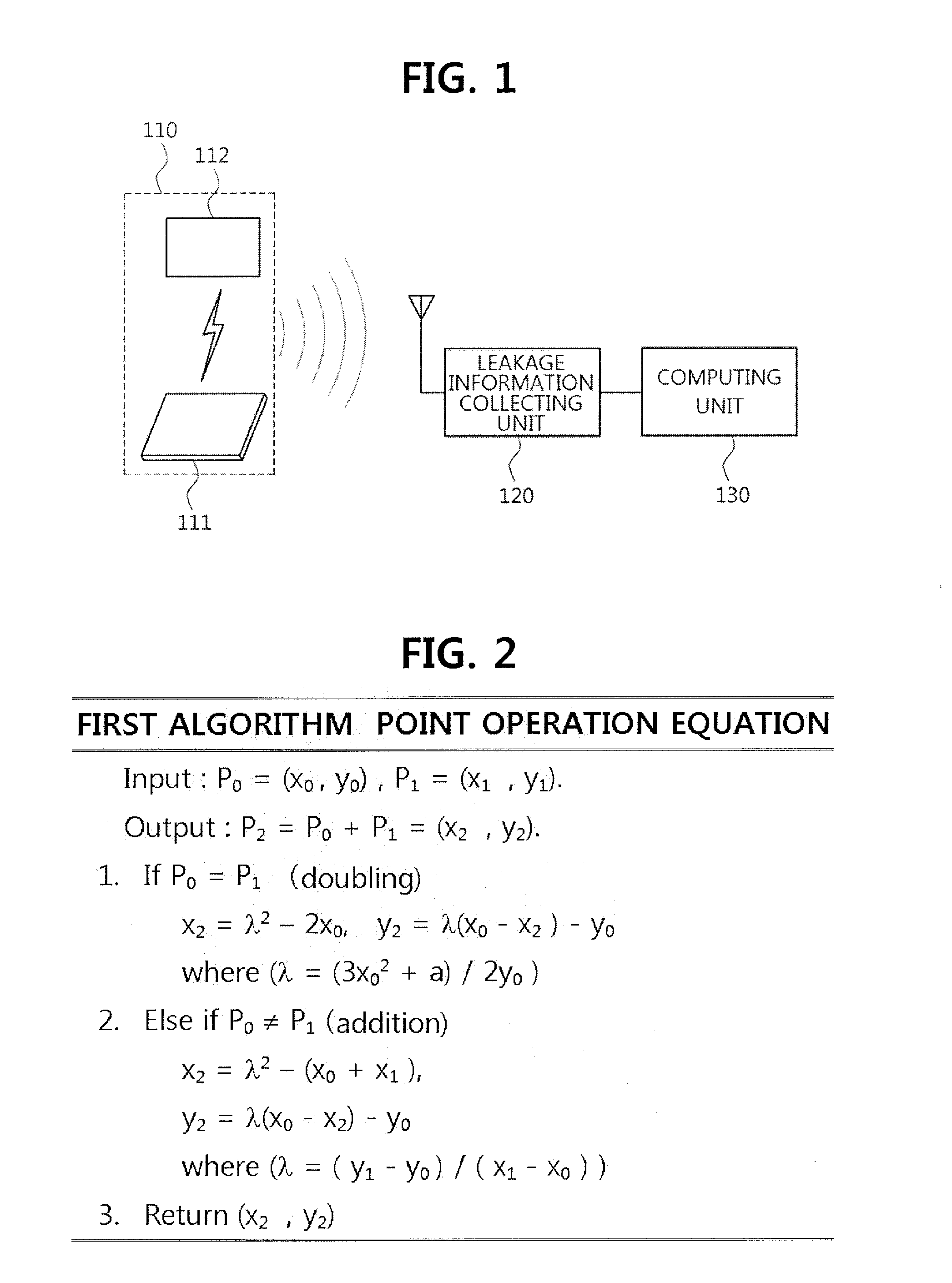
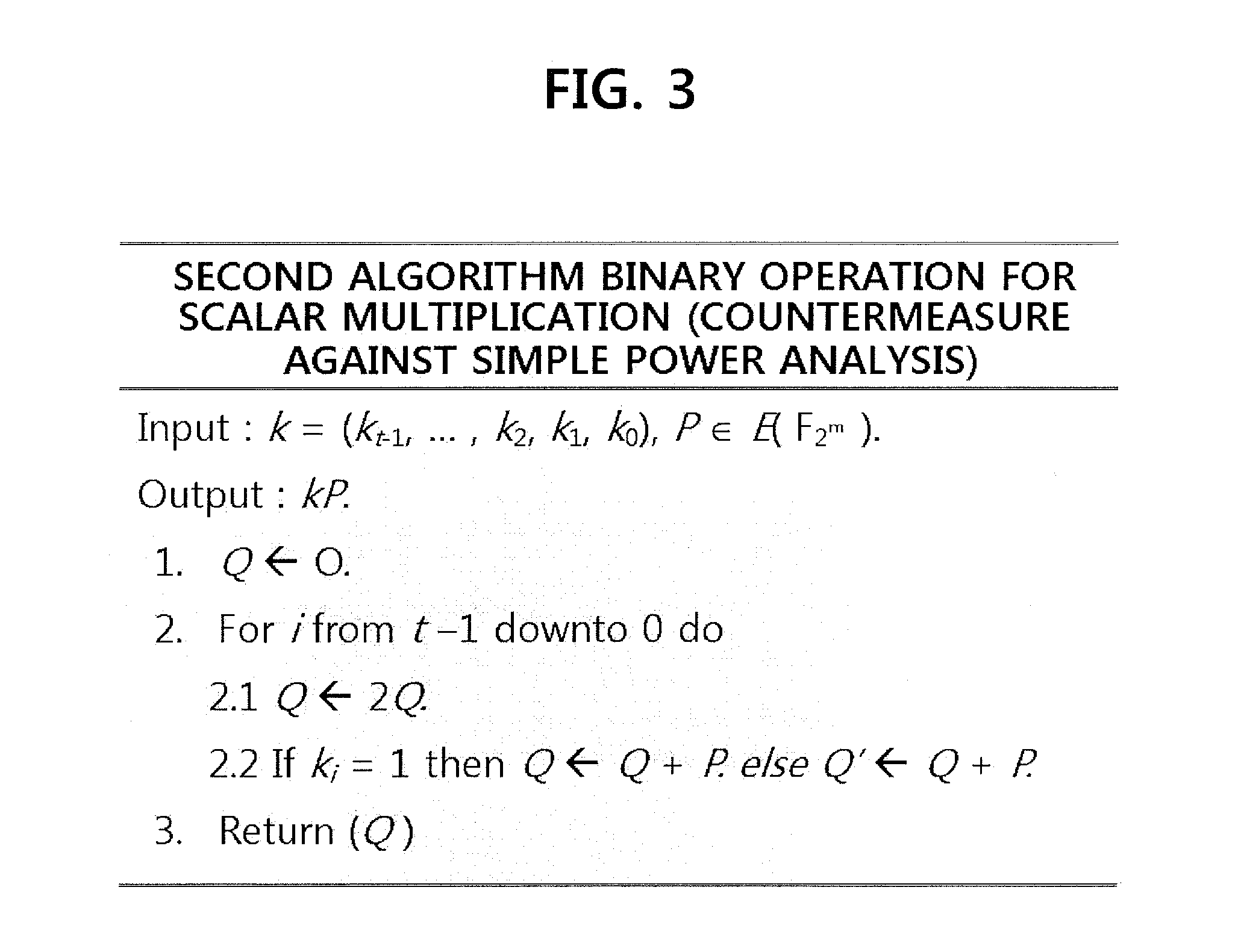
Method for elliptic curve cryptography with countermeasures against simple power analysis and fault injection analysis and system thereof
InactiveUS20140098951A1Easy to analyzeSecret communicationCryptographic attack countermeasuresPower analysisCountermeasure
There are provided a method for elliptic curve cryptography with countermeasures against simple power analysis and fault injection analysis, and a system thereof. According to an aspect, there is provided a method for elliptic curve cryptography, in which an elliptic curve point operation is performed to generate an elliptic curve code, including: receiving a first point and a second point on the elliptic curve, wherein the first point is P0=(x0, y0) and the second point is P1=(x1, y1); and performing doubling if the first point is the same as the second point, and performing addition if the first point is different from the second point, to thereby obtain a third point, wherein the third point is P2=P0+P1=(x2, y2). Accordingly, it is possible to provide countermeasures against a side channel analysis attack.
Owner:ELECTRONICS & TELECOMM RES INST
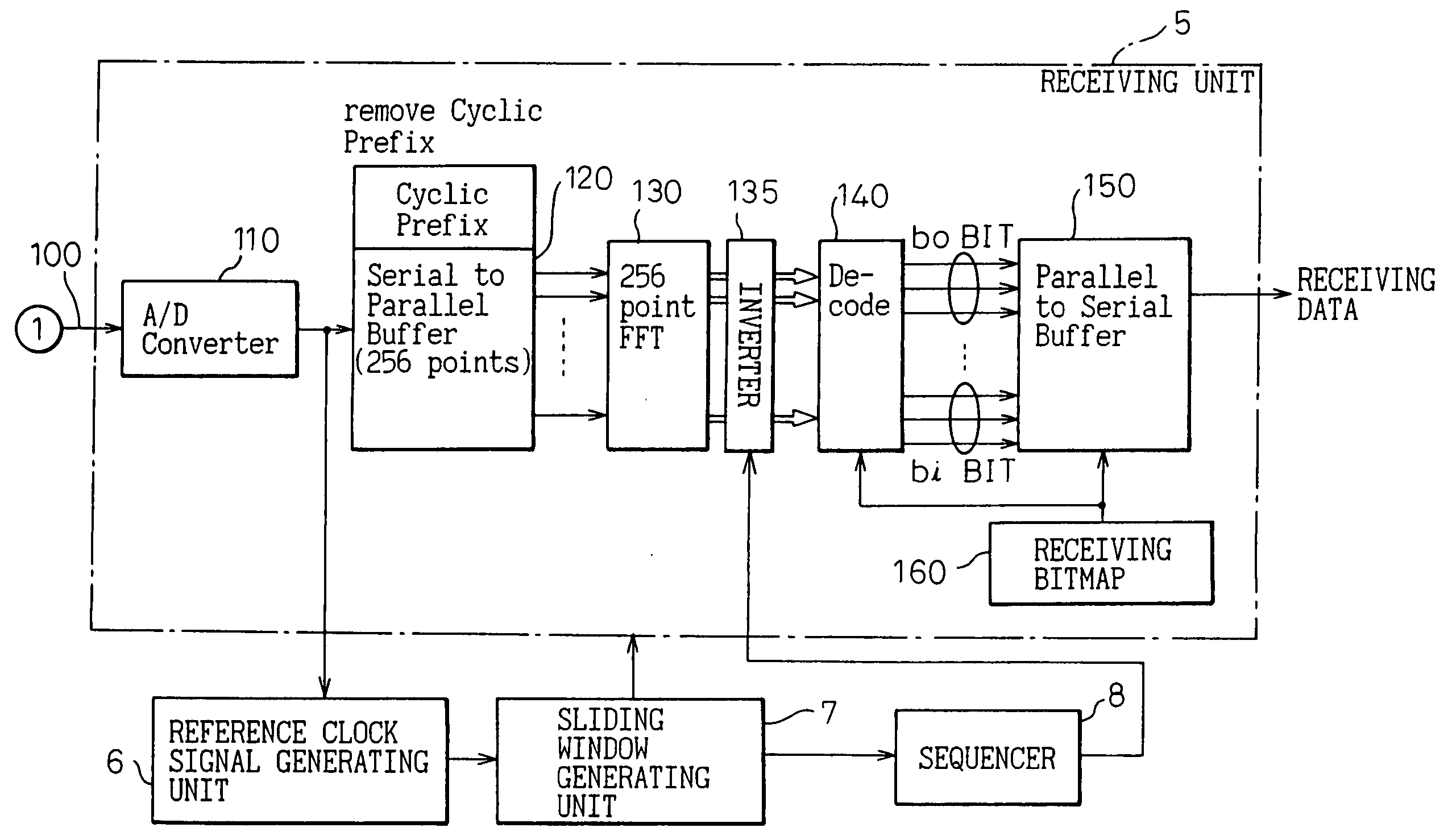
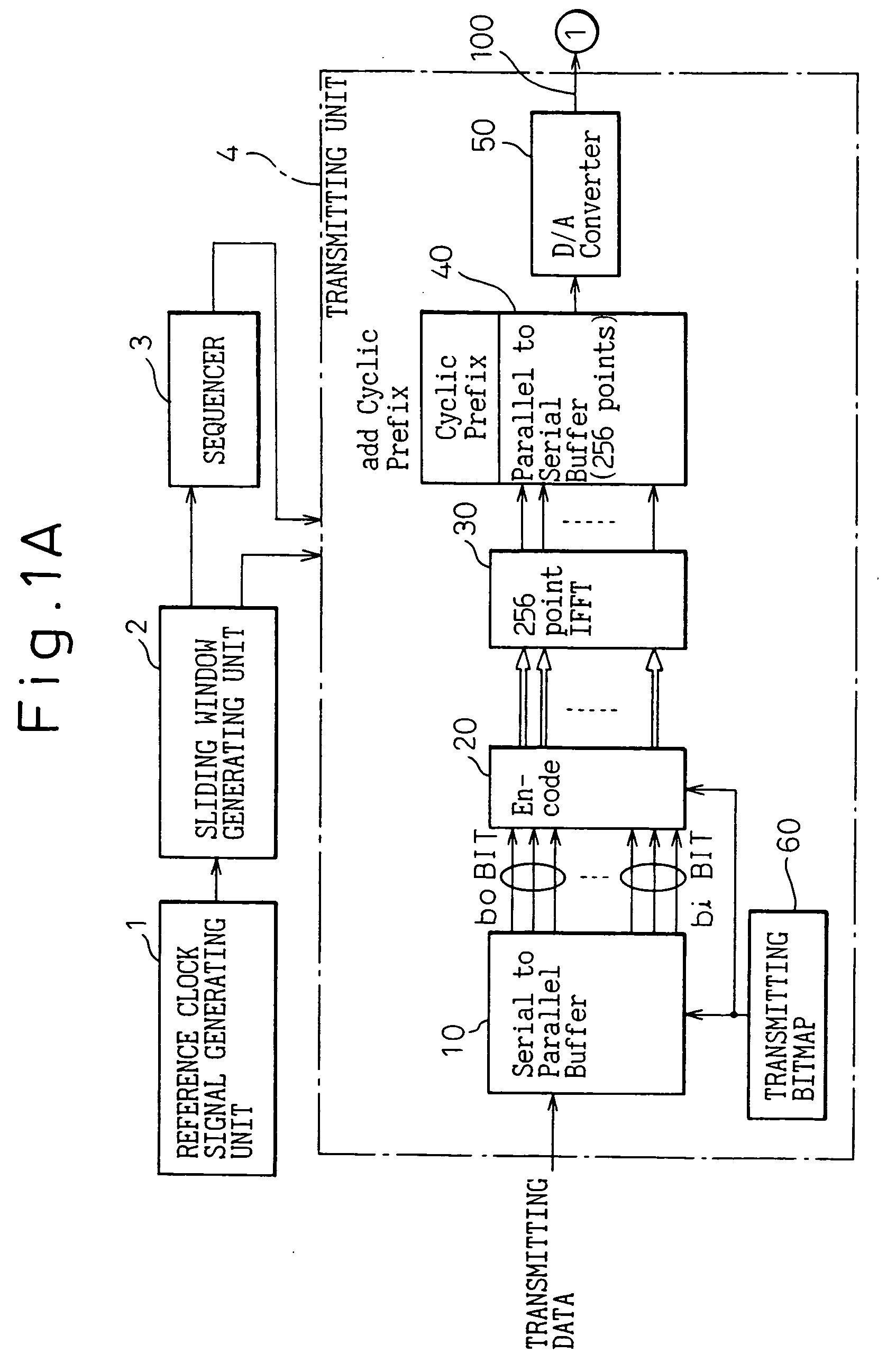
Digital subscriber line communicating system and a transceiver in the system
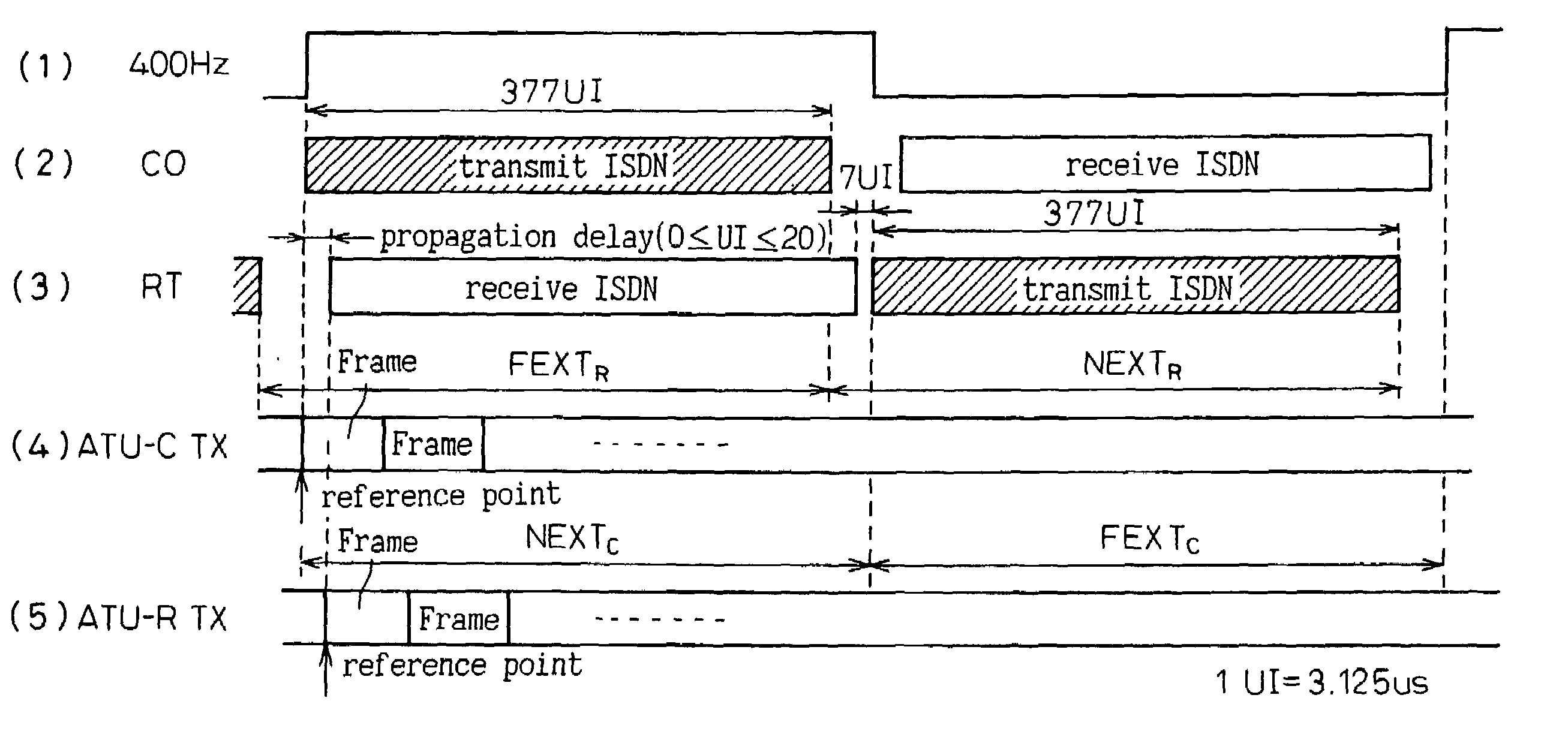
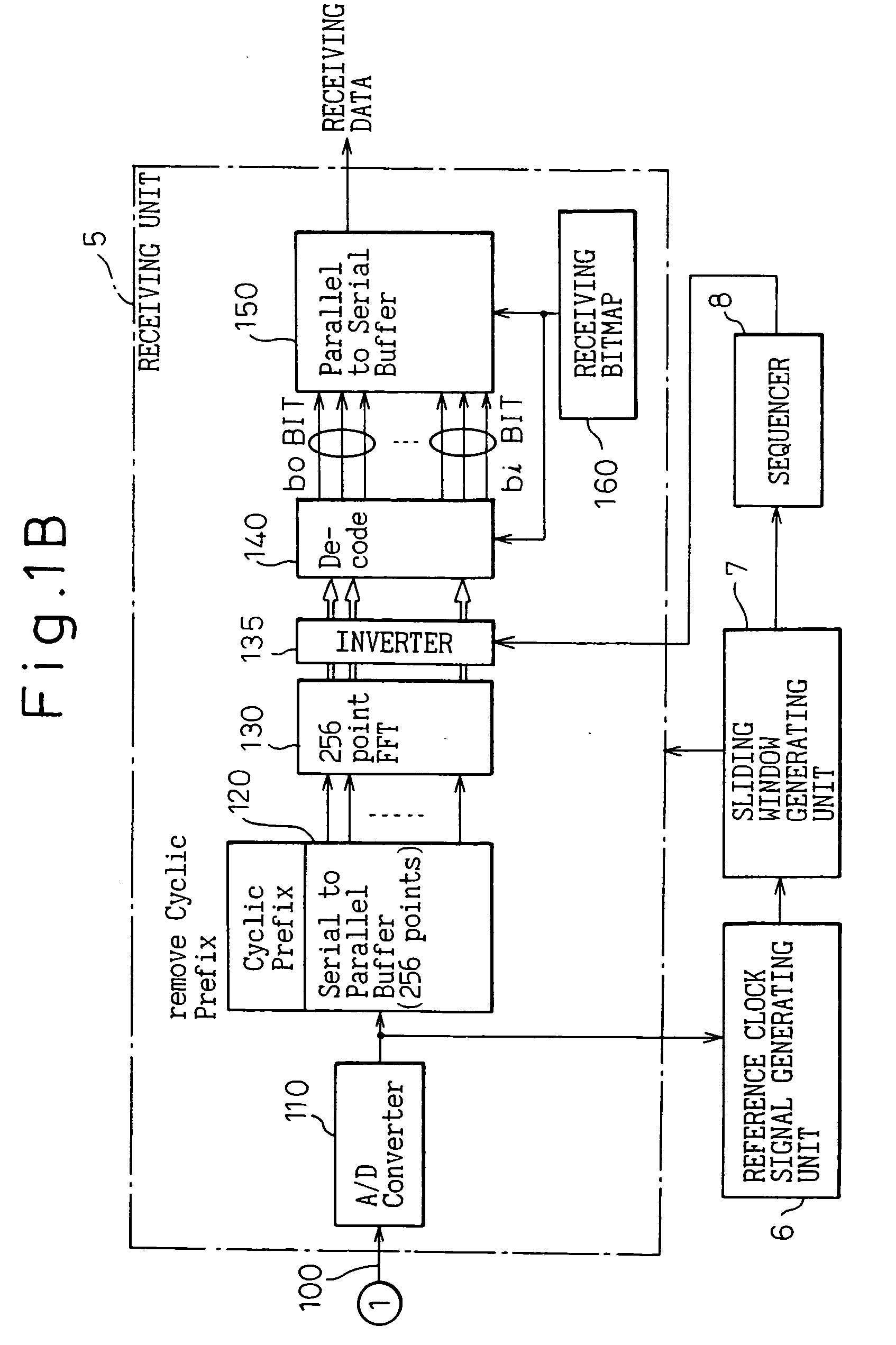
InactiveUS7167509B2Cross-talk reductionAutomatic exchangesDigital subscriber lineCommunications system
A digital subscriber line communicating system for communicating between a transmitting side and a receiving side tough a communication line, the system including a hyperframe counter for periodically counting a predetermined number of continuous transmitting data symbols constituting a hyperframe synchronized with a timing signal, and a decoder for discriminating, based on the count value of the hyperframe counter, whether a transmitting data symbol belongs to a FEXTR, or a NEXTR.A sequencer is provided for initializing the status during an initialization period before starting usual communication. The initialization period includes an activation and acknowledgement sequence, a transceiver training sequence, a channel analysis sequence, and an exchange sequence. According to a single bitmap mode, the initialization is carried out by transmitting modulated symbols through only inside of the sliding window. According to a dual bitmap mode, the initialization except for an S / N measuring sequence in the channel analysis sequence is carried out by transmitting modulated symbols through only inside of the sliding window, and the S / N measuring sequence is carried out by transmitting modulated symbols through both inside and outside of the sliding window.
Owner:WI LAN INC
Multiscale reactor core thermal hydraulic analysis method
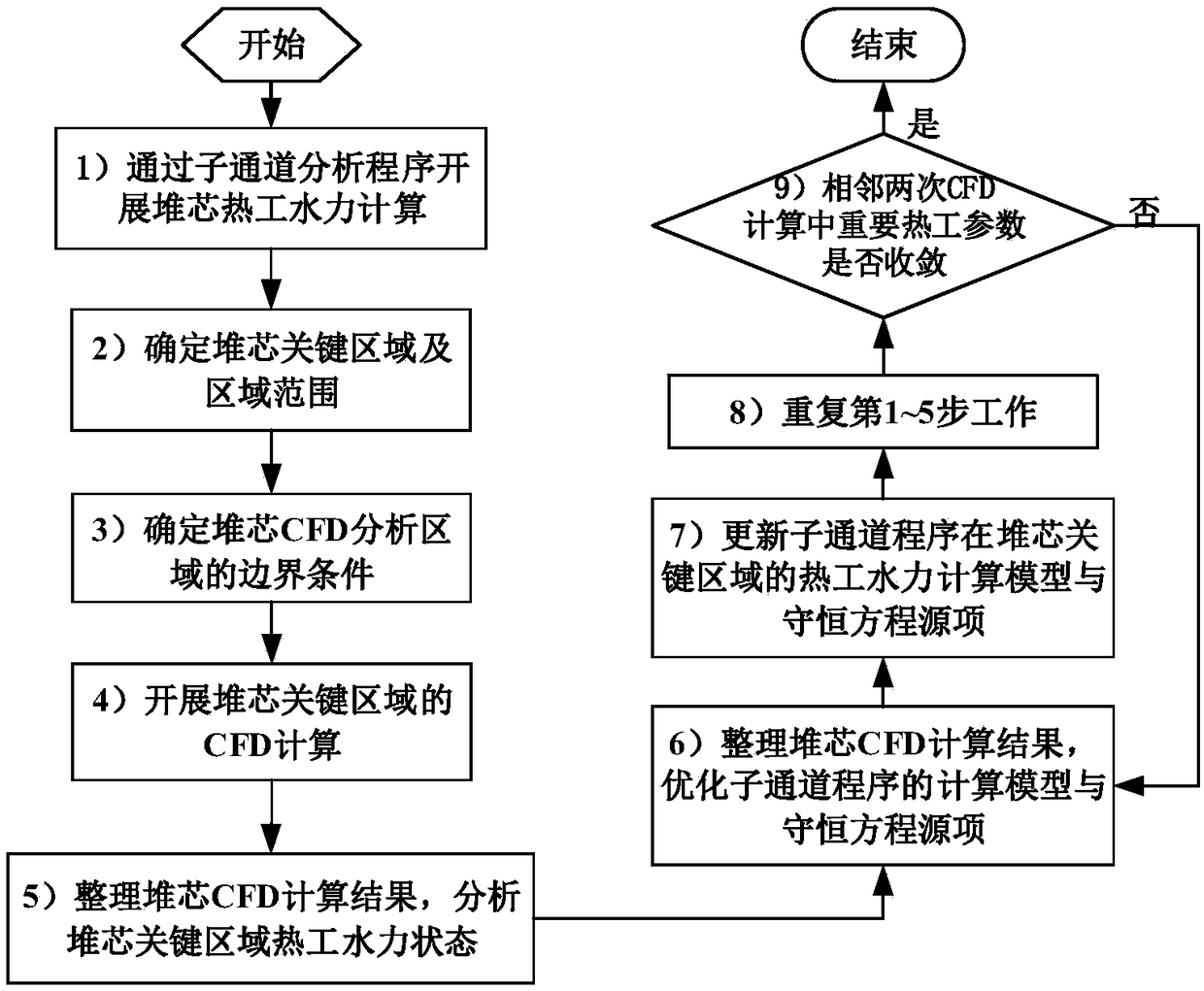
ActiveCN108875213AImprove applicabilityGuaranteed analytical efficiencyGeometric CADDesign optimisation/simulationState predictionNuclear engineering
The invention provides a multiscale reactor core thermal hydraulic analysis method. The method comprises the following steps of: 1, carrying out reactor core thermal hydraulic calculation through a reactor core sub-channel analysis program; 2, determining a position and an area range of a reactor core key area; 3, determining a boundary condition of a reactor core CFD analysis area; 4, carrying out CFD calculation on the reactor core key area; 5, arranging the CFD calculation result ad analyzing states of thermal hydraulic important parameters of the reactor core key area; 6, arranging the CFDcalculation result and optimizing a calculation model and a conservation equation source item of the sub-channel program; 7, updating a thermal hydraulic calculation model and a conservation equationsource item, in the reactor core key area, of the sub-channel program; 8, repeating the steps 1 to 5 via the updated sub-channel program; and 9, comparing important parameter values of the key area in two adjacent key area CFD calculations so as to judge whether convergence is carried out or not. The method is capable of comprehensively ensuring the accuracy and efficiency of thermal hydraulic state prediction for reactor cores.
Owner:HARBIN ENG UNIV
Countermeasure method against side channel analysis for cryptographic algorithms using boolean operations and arithmetic operations
InactiveUS20150110266A1Thorough understandingPreventing statistical analysisEncryption apparatus with shift registers/memoriesPublic key for secure communicationCountermeasureModularity
The present invention relates to a countermeasure method against side channel analysis for cryptographic algorithm using Boolean operations and arithmetic operation. To protect a cryptographic algorithm combining Boolean and arithmetic instructions against first order side channel analysis, it is necessary to perform conversions between Boolean masking and arithmetic masking. The present invention proposes a new conversion method from arithmetic masking to Boolean masking, using only one precomputed table T. Said table T being configured so that to convert from arithmetic to Boolean masking k-bit nibble by k-bit nibble for integers having a size greater than k bits while adding a masked carry from the modular addition to the nibble.
Owner:GEMPLU
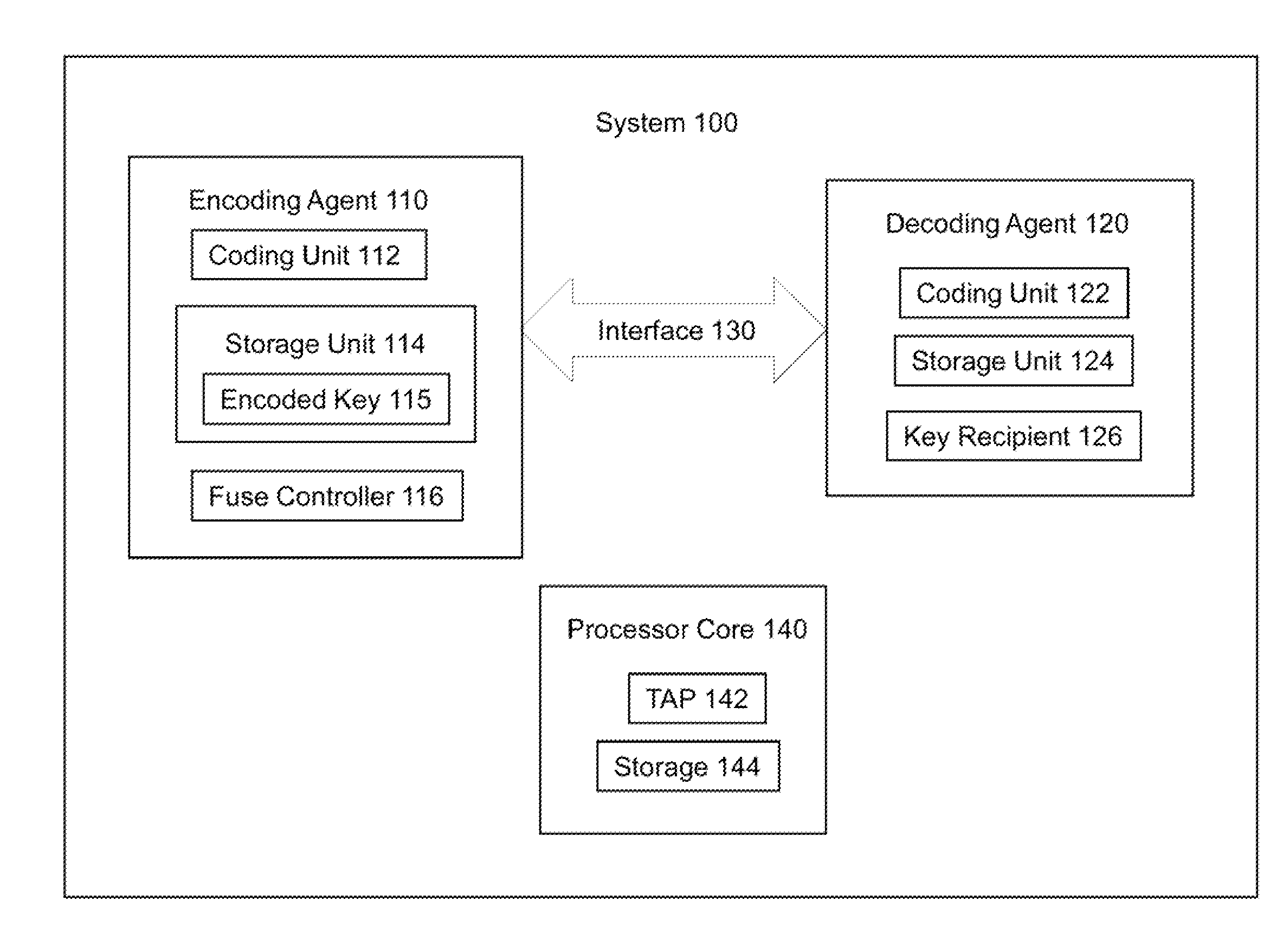
Hardening data transmissions against power side channel analysis
ActiveUS20150033338A1Memory loss protectionError detection/correctionComputer hardwareChannel analysis
Embodiments of an invention for hardening data transmissions against power side channel attacks are disclosed. In one embodiment, a system includes a first agent and a second agent. The first agent is to transmit an encoded datum through an interface in a plurality of encoded packets. The second agent is to receive each of the plurality of encoded packets from the interface and decode each of the encoded packets to generate a plurality of decoded packets. Each of the encoded packets has the same Hamming weight. The Hamming distance between any two consecutively transmitted encoded packets is constant.
Owner:INTEL CORP
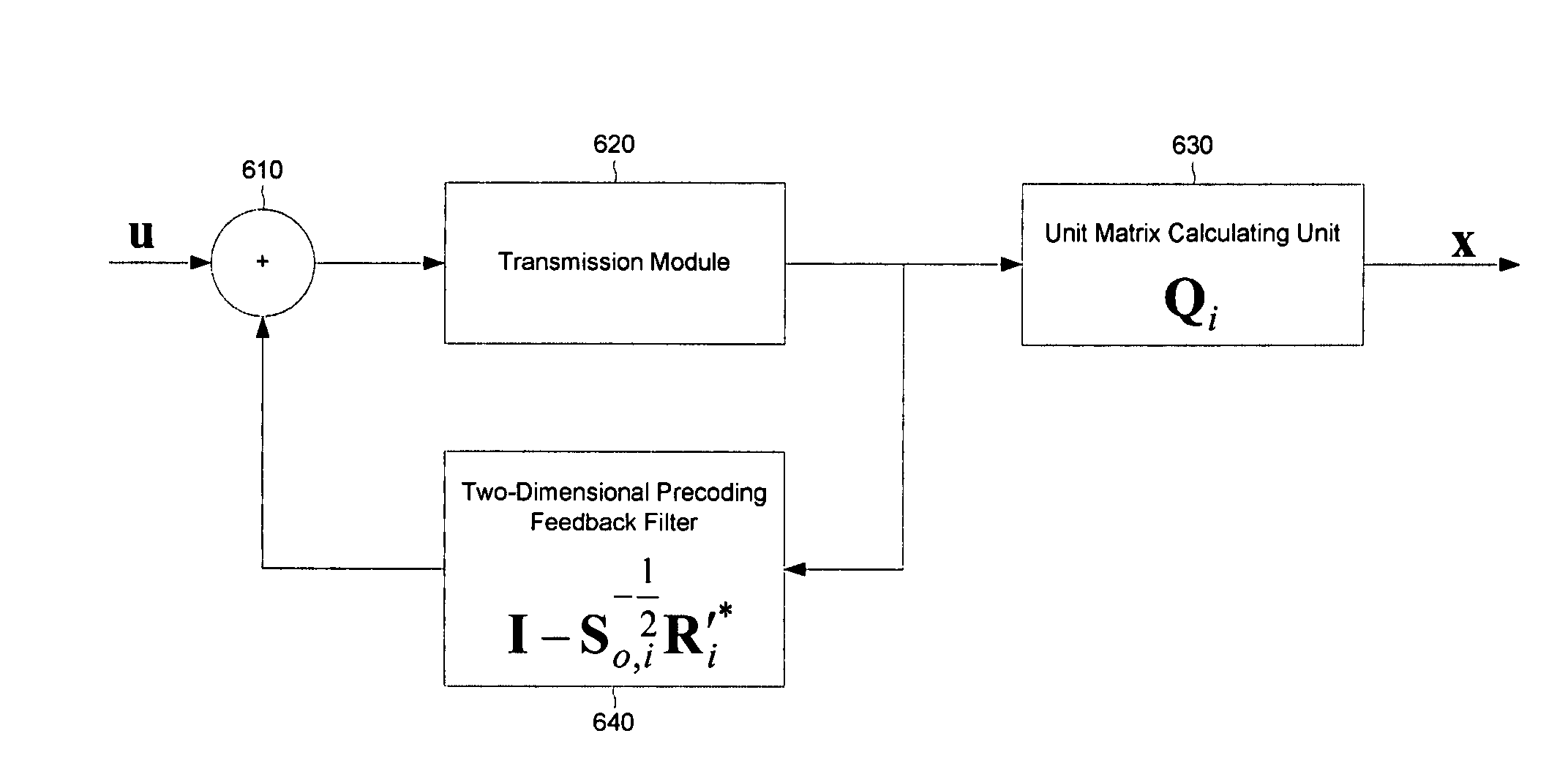
Method and apparatus for cancellation of cross-talk signals using multi-dimensional coordination and vectored transmission
In a method of canceling crosstalk signals, decoding or precoding through a diagonal channel analysis of the user domain and the time domain is performed, in addition to decoding or precoding in the user and time domains.
Owner:ELECTRONICS & TELECOMM RES INST
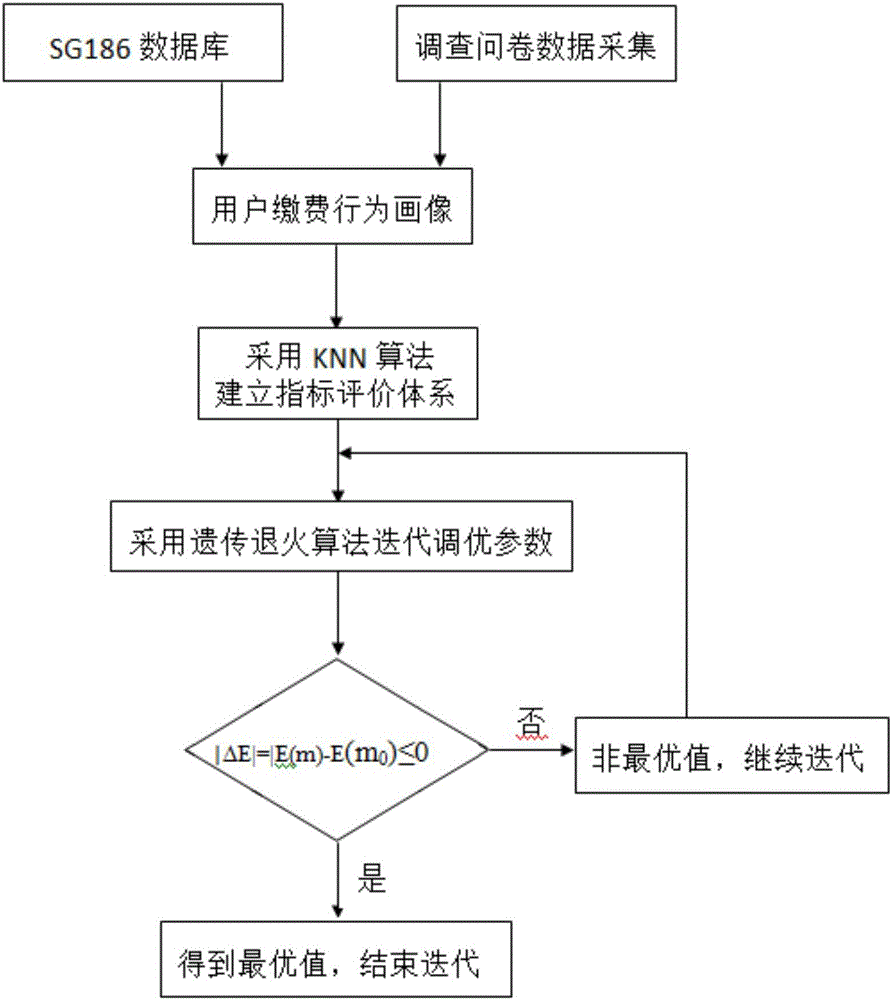
Calculating method of index selection, weight optimization and channel planning of electric power payment channel analysis
InactiveCN106650763AConvenient paymentImprove the level of lean managementCharacter and pattern recognitionCharge recoveryNear neighbor
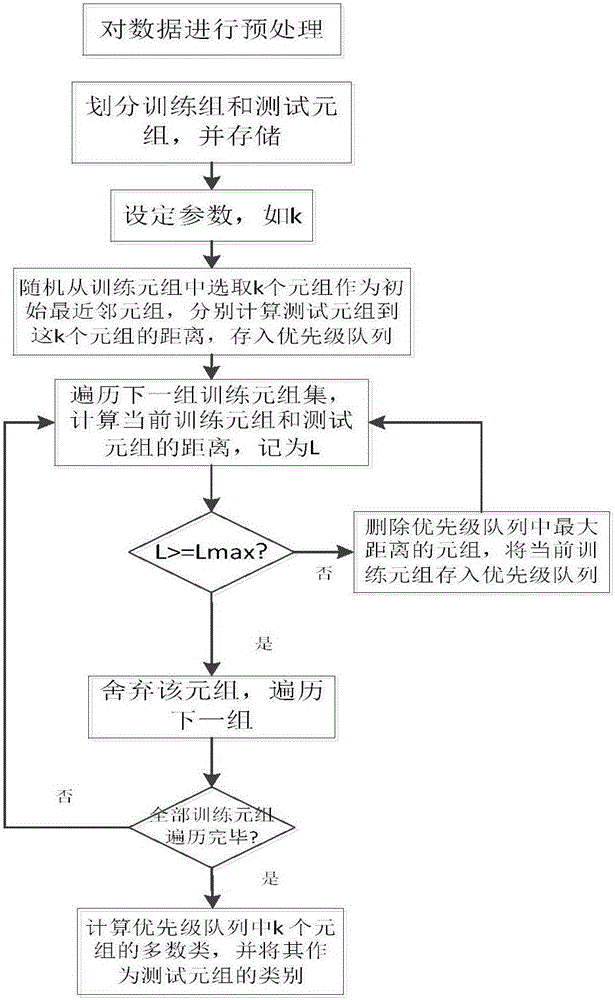
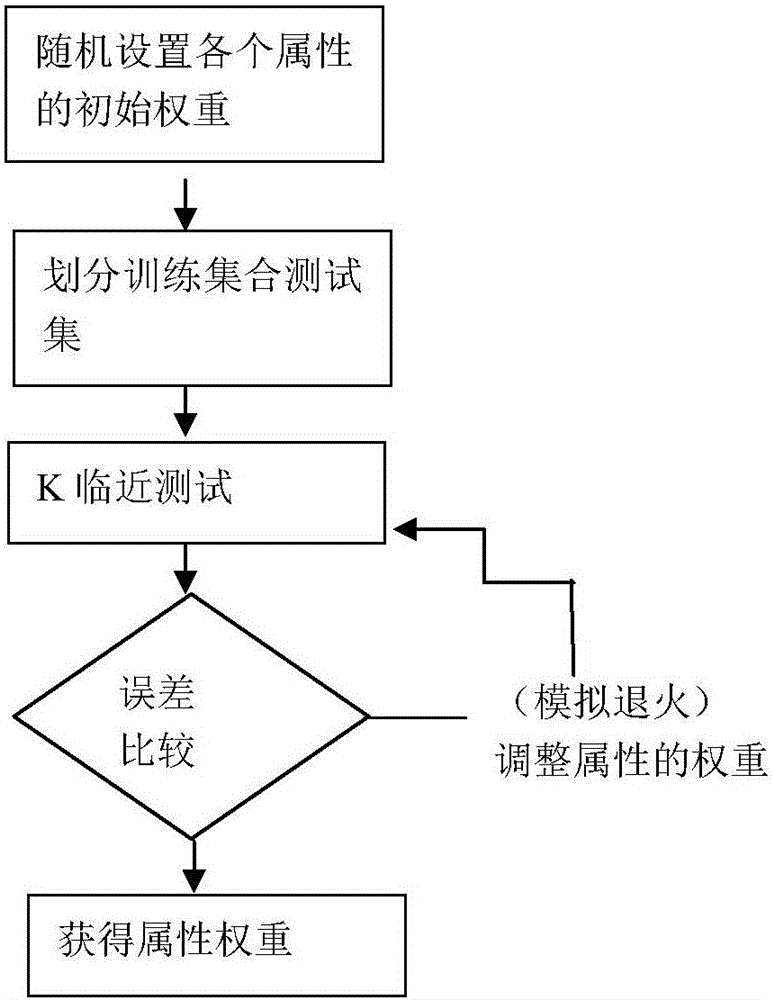
A calculating method of index selection, weight optimization and channel planning of electric power payment channel analysis is disclosed. The method comprises the following steps of step1, through a SG186 system or a questionnaire, acquiring data of basic attribute information and payment habit attribute information of a user who pays; step2, using a characteristic weight optimization method to optimize each weight in an individual user figure, acquiring an optimal individual user figure, and through a clustering algorithm, establishing a group user payment behavior figure; step3, using a K-nearest neighbor classification algorithm to establish an index evaluation system; step4, using a genetic annealing algorithm to calculate a weight value of each attribute index; and step5, determining whether the value is an optimal value and determining an optimal payment channel. In the invention, based on user payment large data, a lean management level of marketing electricity charge recovery work is increased and finally a payment service channel through which the user can pay conveniently and which is satisfied by the user is realized.
Owner:ELECTRIC POWER RES INST OF EAST INNER MONGOLIA ELECTRIC POWER +2
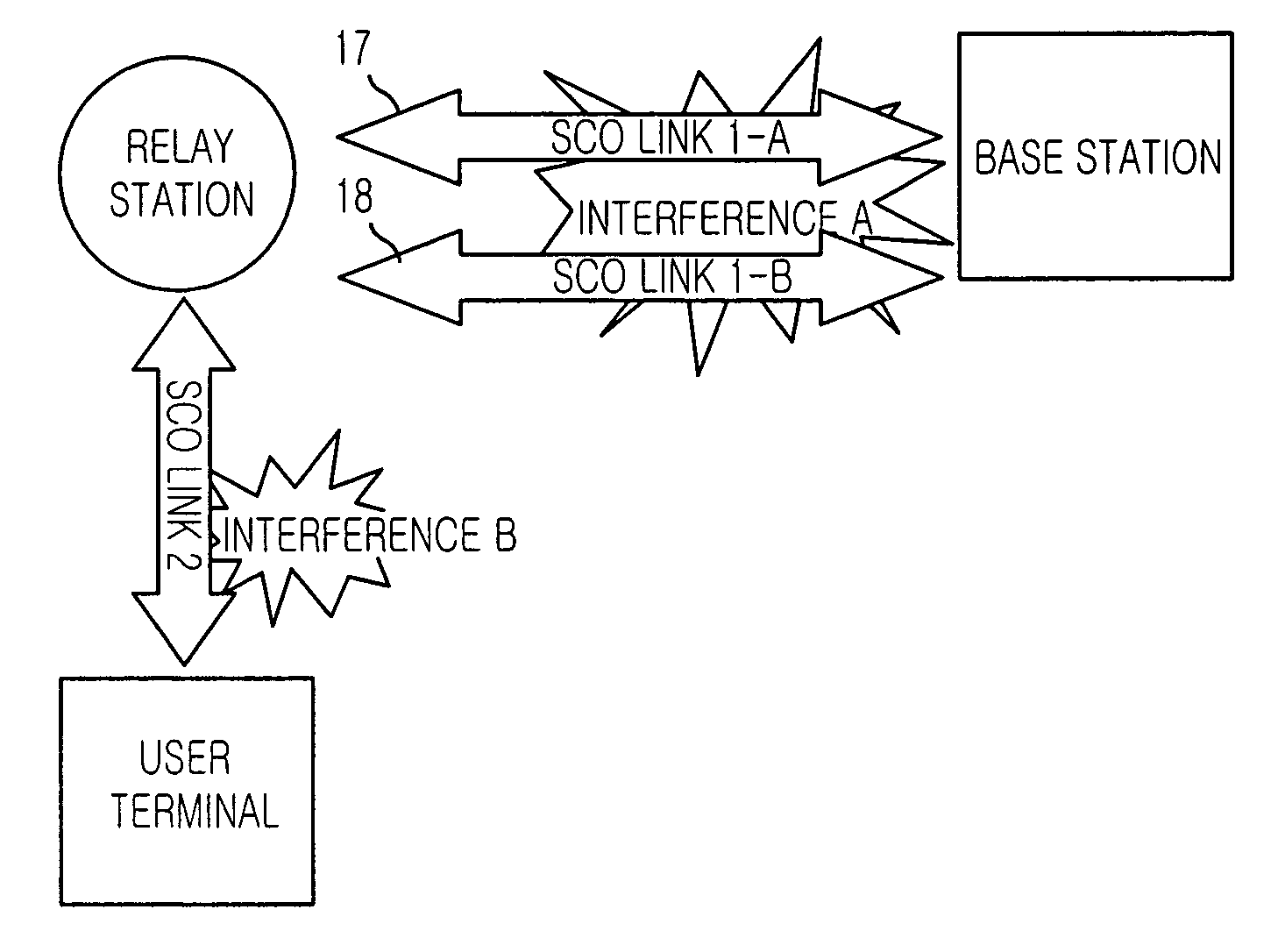
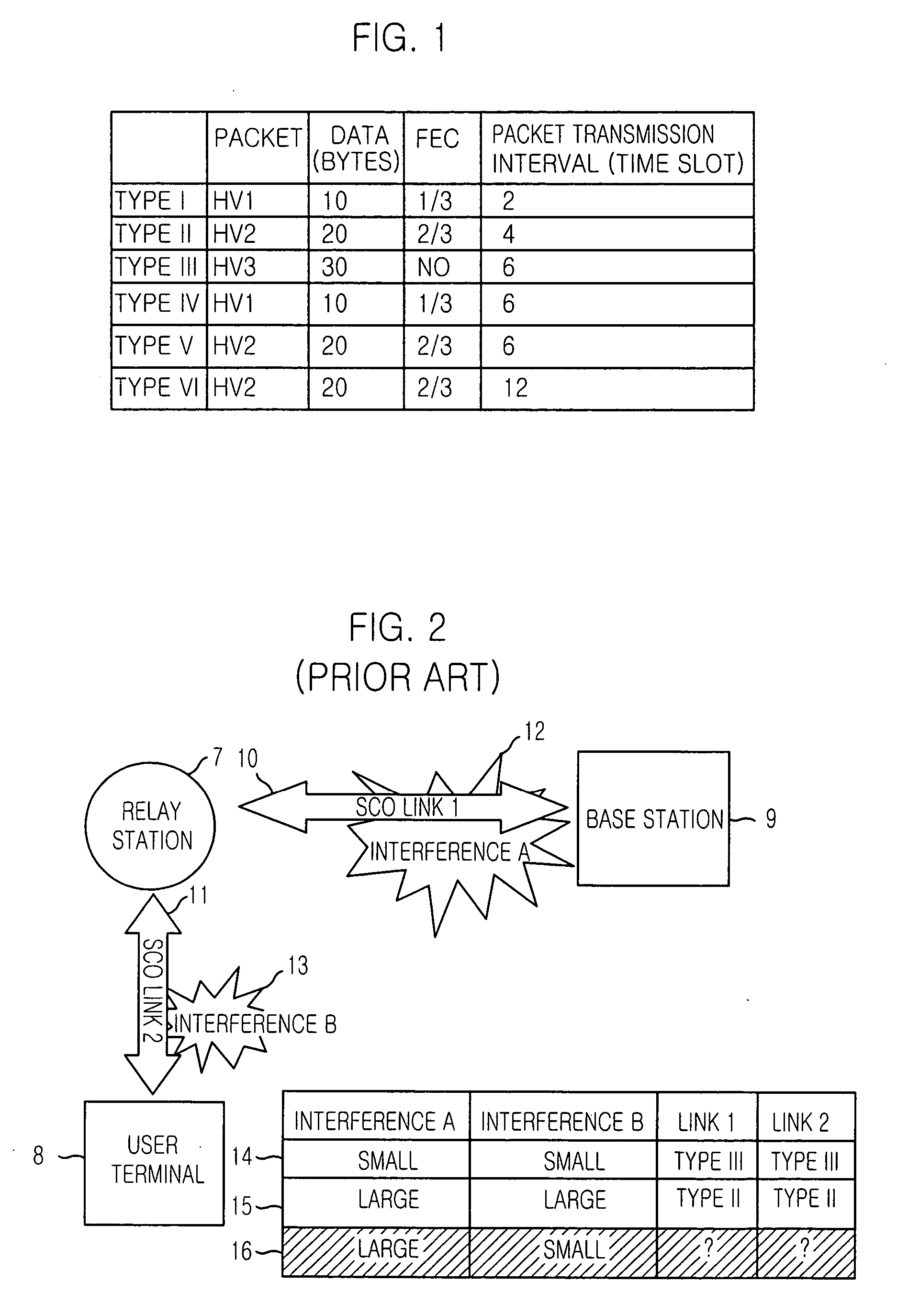
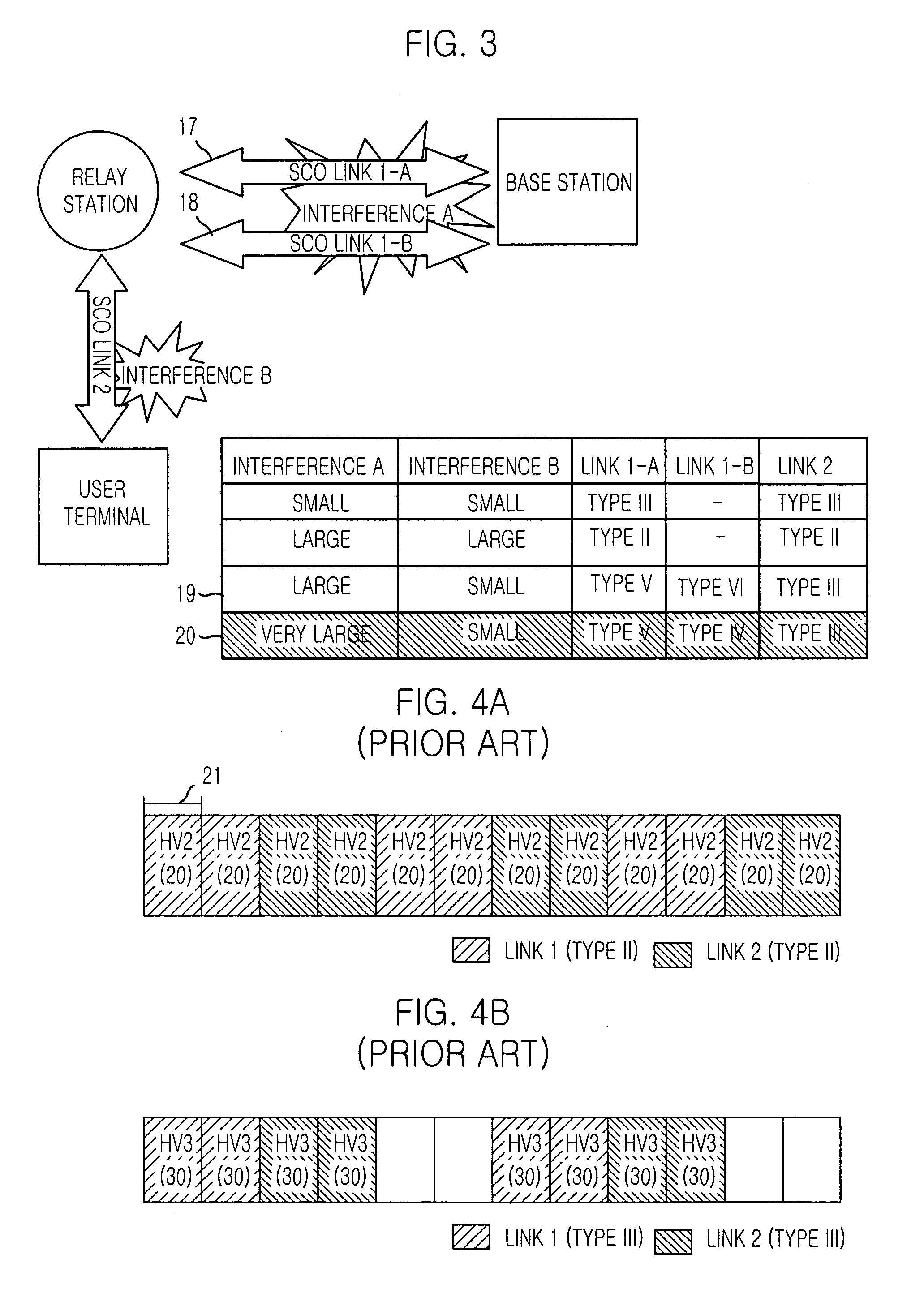
Method for dynamically managing SCO links in bluetooth system
InactiveUS20040120341A1Data switching by path configurationRadio transmissionChannel analysisData transmission
The present invention provides a method for managing SCO links dynamically in a Bluetooth system, which can reduces energy consumption in a Bluetooth system and provides better quality of data transmission by managing synchronous connection-oriented (SCO) links according to channel environment. The method includes the steps of: (a) analyzing communication channels in order to secure a quality of data transmission in the Bluetooth system; and (b) changing types of SCO links according to the channel analysis.
Owner:ELECTRONICS & TELECOMM RES INST
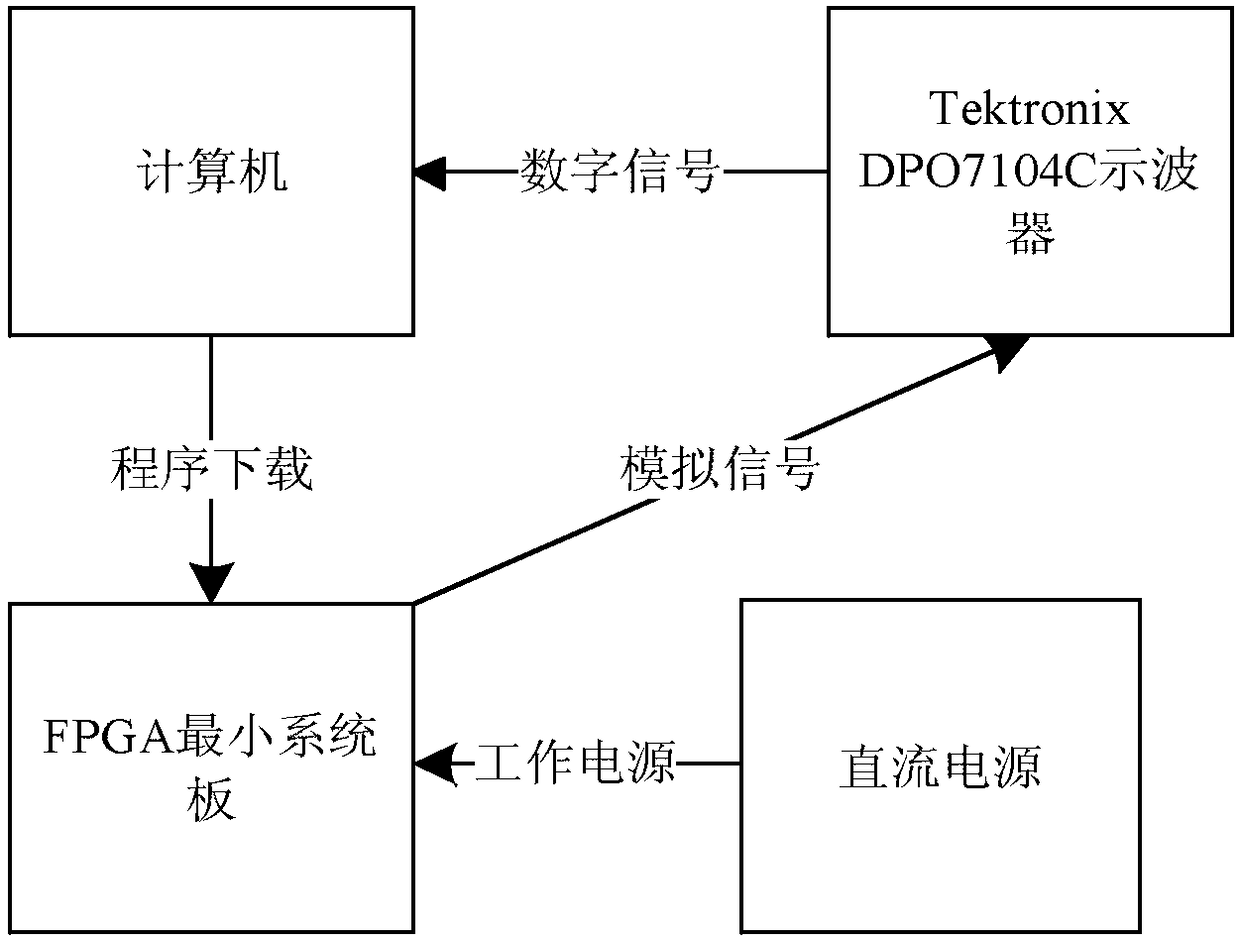
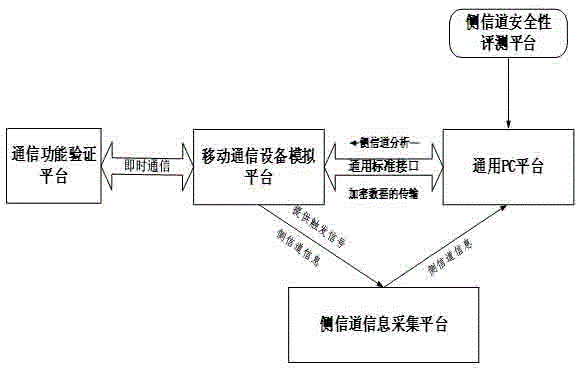
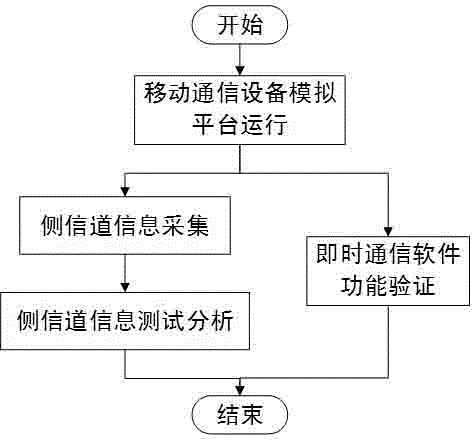
Instant messaging software side channel testing system for mobile communication platform
ActiveCN104023352AImprove applicabilityStrong practical significanceWireless communicationExtensibilityCommunications software
The invention discloses an instant messaging software side channel testing system for a mobile communication platform. The instant messaging software side-channel testing system comprises the mobile communication equipment simulation platform, a side channel information acquisition platform, a universal PC platform and a communication function verification platform. The mobile communication equipment simulation platform is connected with the universal PC platform through a universal standard interface and used for being controlled by the universal PC platform. The mobile communication equipment simulation platform conducts information interaction with the communication function verification platform through a network. The universal PC platform is used for controlling input and output of enciphered data and storing side channel information. Testing pins of the side channel information acquisition platform are connected with the mobile communication equipment simulation platform and used for capture of the side channel information. A side channel analysis platform is arranged on the universal PC platform and used for testing the correctness of instant messaging software encryption execution results, analyzing collected power consumption curves and forming side channel analysis results. The instant messaging software side channel testing system for the mobile communication platform has the advantages of being convenient to use, low in cost, high in expandability and the like.
Owner:WUHAN UNIV
Method for symmetric cryptographic algorithm to resist side-channel analysis
The invention relates to a method for a symmetric cryptographic algorithm to resist side-channel analysis. The method can be used for resisting side-channel attack for a symmetric cryptographic algorithm and preventing an attacker from acquiring a computation key of the symmetric algorithm through side-channel analysis. The symmetric cryptographic algorithm can be realized by hardware and software. In the computation process, a realization carrier leaks key information of computation through a side channel, such as carrying out differential power analysis attack with the use of power consumption information in the computation process. Side-channel analysis poses a great threat to software and hardware realization security of the symmetric cryptographic algorithm. The invention provides a method for the symmetric cryptographic algorithm to resist side-channel analysis. In the whole process of symmetric cryptographic computation, no clear data known to attackers participates in computation, an intermediate result in symmetric cryptographic computation has a random mask, and the mask of each round of computation is different from masks of other rounds, which makes it extremely difficult for attackers to acquire key information from side-channel analysis and realizes protection on the key of the symmetric cryptographic algorithm.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Digital subscriber line communicating system and a transceiver in the system
InactiveUS20050157779A1Guaranteed normal transmissionCross-talk reductionAutomatic exchangesDigital subscriber lineCommunications system
A digital subscriber line communicating system for communicating between a transmitting side and a receiving side through a communication line, comprising a hyperframe counter for periodically counting a predetermined number of continuous transmitting data symbols constituting a hyperframe synchronized with a timing signal, and a decoder for discriminating, based on the count value of the hyperframe counter, whether a transmitting data symbol belongs to a FEXTR or a NEXTR. A sequencer is provided for initializing the status during an initialization period before starting usual communication. The initialization period includes an activation and acknowledgement sequence, a transceiver training sequence, a channel analysis sequence, and an exchange sequence. According to a single bitmap mode, the initialization is carried out by transmitting modulated symbols through only inside of said sliding window. According to a dual bitmap mode, the initialization except for an S / N measuring sequence in the channel analysis sequence is carried out by transmitting modulated symbols through only inside of said sliding window, and the S / N measuring sequence is carried out by transmitting modulated symbols through both inside and outside of said sliding window.
Owner:WI LAN INC
Methods and devices against a side-channel analysis
ActiveUS20170373832A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesExclusive orChannel analysis
A method for executing by a circuit a bit permutation operation by which bits of an input data are mixed to obtain an output data including at least two words, may include: generating a first mask set including mask parameters, the mask set having one word column per word of the input data, each word column comprising a same number of occurrences of all possible values of one input data word in relation to a size of the input data word; generating an input set by combining the input data with each mask parameter of the first mask set by Exclusive OR (XOR) operations; and computing an output set including output data resulting from the application of the bit permutation operation to each data in the input set, where the first mask set may be generated such that the output set includes columns of output words, and each output word column including a same number of occurrences of all possible values of one output word in relation with a size of the output word.
Owner:ESHARD
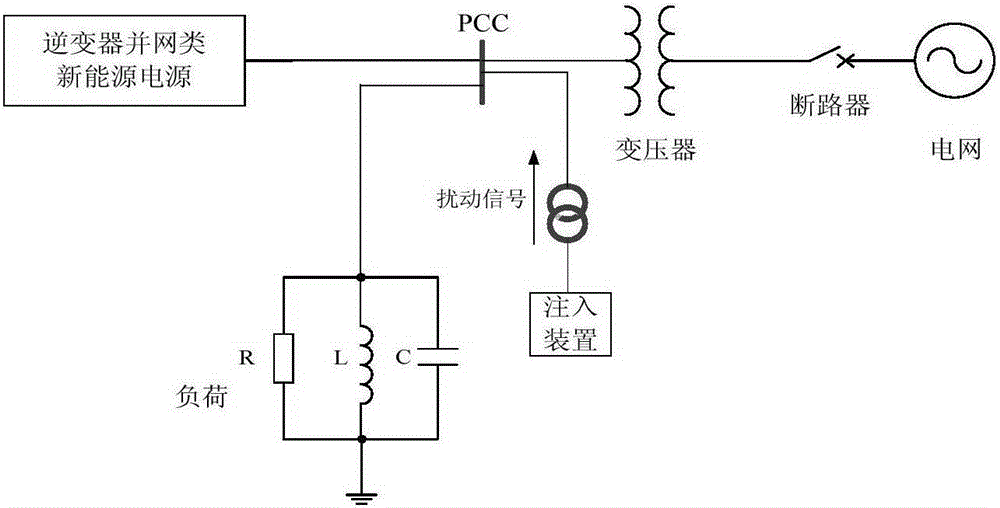
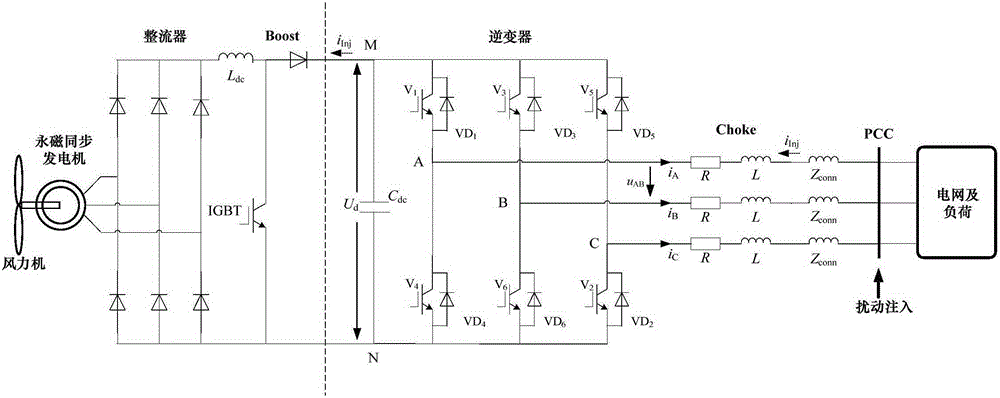
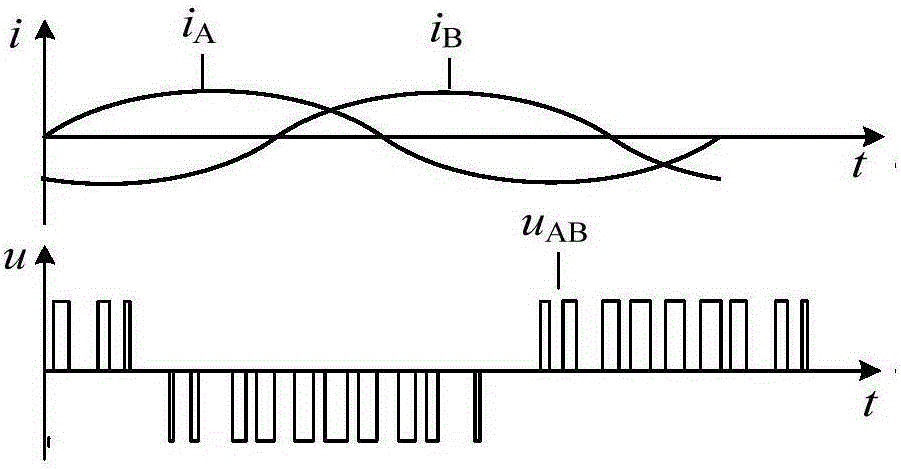
Inverter grid connected type power source impedance measurement model optimization method under the condition of external disturbance signals
ActiveCN105305483AUniversalPracticalSingle network parallel feeding arrangementsPower inverterMulti machine
The invention belongs to the new energy generating grid connected technology field of an electric power system and particularly relates to an inverter grid connected type power source impedance measurement model optimization method under the condition of external disturbance signals. The method is characterized by comprising steps that, dynamic channels through which the external disturbance signals enter an inverter and conversion rulers are acquired through analysis according to inverter on-ff rules; the signal channels are classified, for each type of the channels, subsequent channels after the signals passing through the inverter are further analyzed; according to the signal channel analysis result, external impedance measurement characteristics of an inverter grid connected type power source are solved through conclusion and equivalence; on the basis of the external impedance measurement characteristics, conversion from dynamic time-variable impedance to constant state impedance is carried out. The method is not limited by generator types, inverter grid connected requirement is only necessary, operation conditions and different control strategies are further not restrained, a voltage source type PWM inverter is only satisfied, principle universality is realized, the method is suitable for complex multi-machine clustering, and the method has high precision.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
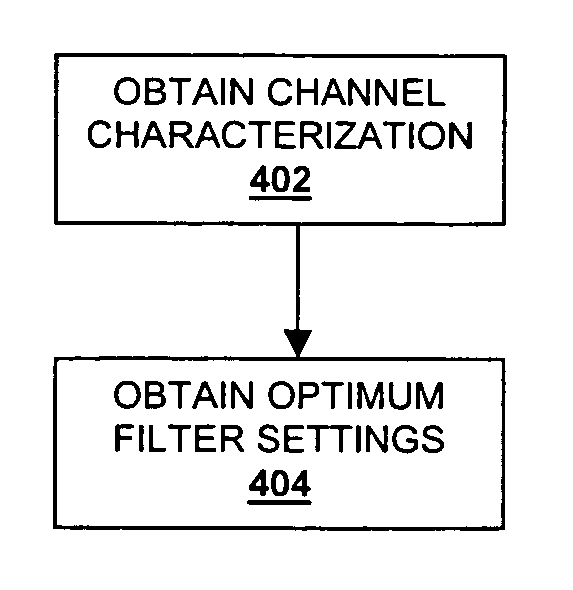
Method and system for performing channel analysis
ActiveUS7627463B2Reduce in quantityIncrease the amount of dataCAD circuit designSpecial data processing applicationsTime domainWave form
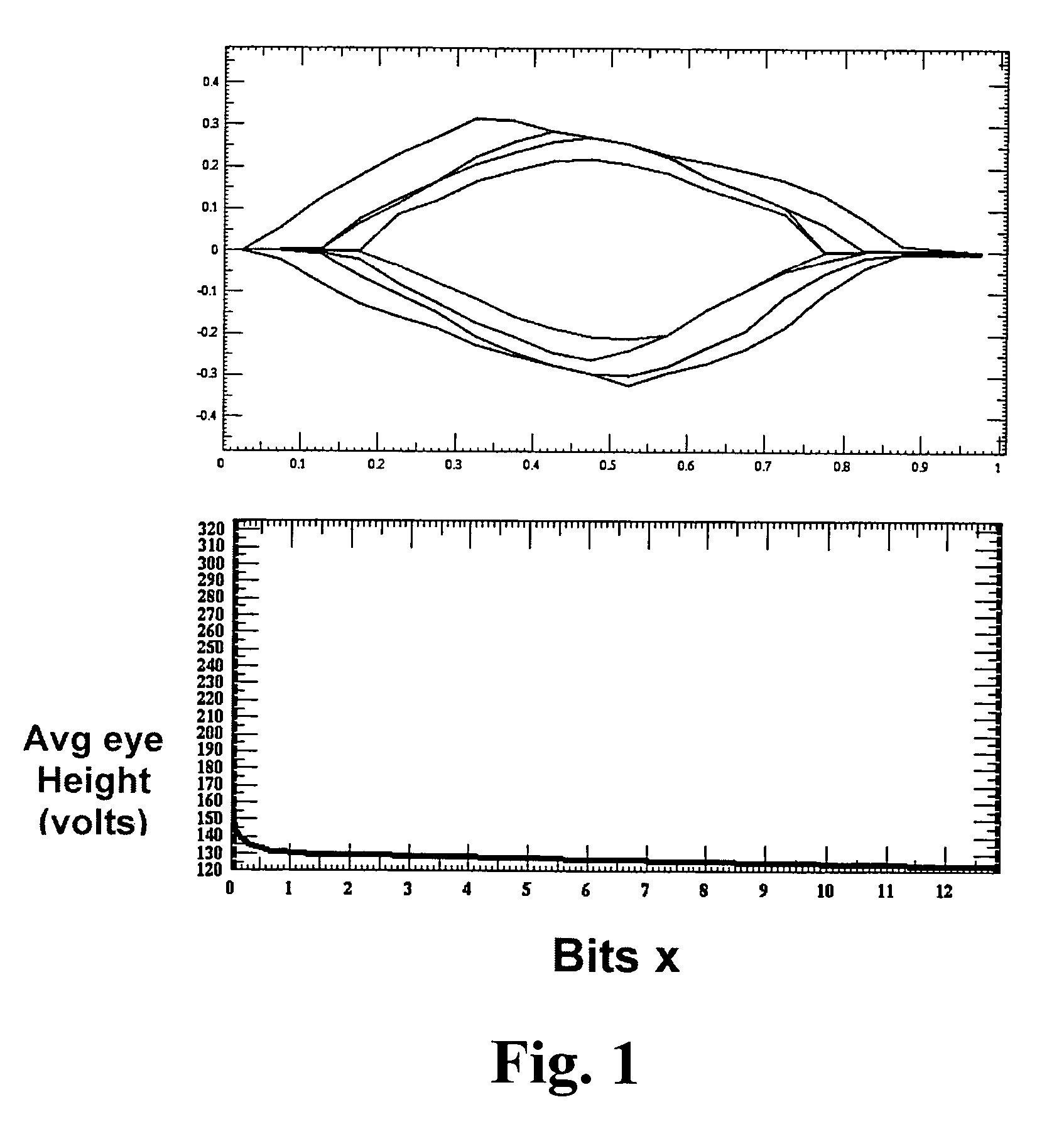
A system, method, computer program and article of manufacture for channel analysis. Channel analysis is a multi gigahertz capacity time domain circuit simulation which uses the impulse response of the channel to determine optimum filter settings and to produce wave form plots in a fraction of the time of circuit simulation.
Owner:CADENCE DESIGN SYST INC
Concealed channel identification method
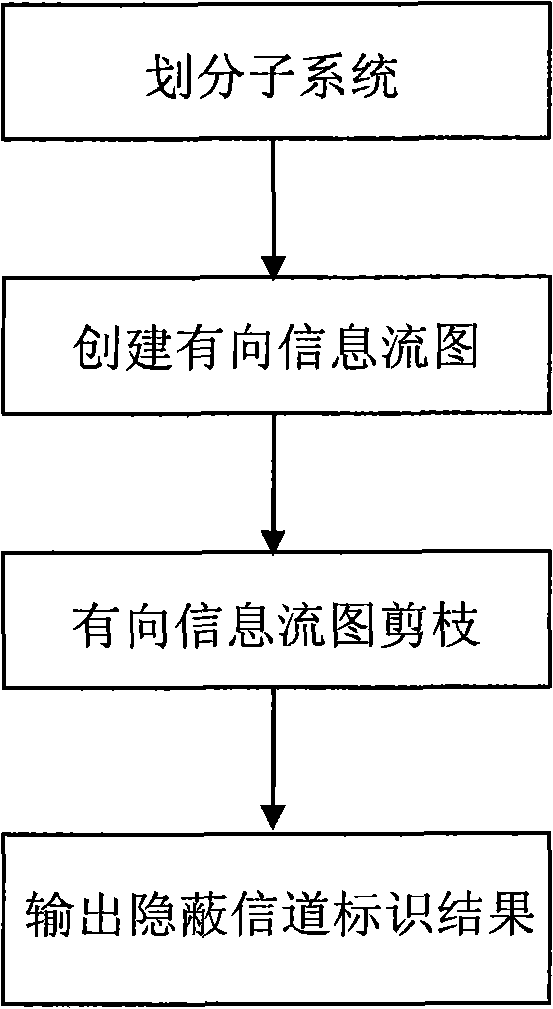
InactiveCN102045158AMeet the requirements of the analysisReduce analysis sizeSecuring communicationNODALOperational system
The invention discloses a concealed channel identification method. A system source code is used as an analysis object. The method comprises the following steps of: formally describing a concealed channel in a secure information system as (V, PAh, PVl, P); then dividing a system to be analyzed into relatively independent subsystems; searching related function calling branches in the subsystems by using a shared variable as a basic unit, and further constructing directed information flow graphs according to an information flow relationship; and pruning each information flow graph according to the formal description of the concealed channel to eliminate invalid flow branches and variable aliases in the code, wherein all flow nodes and function calling branches in the finally obtained information flow graphs are potential concealed channel forming factors. The method is suitable for source codes of information systems such as an operating system, a database, a network and the like of high security level, has wide application range, high execution efficiency and low error report rate and missing report rate, can identify the potential concealed channel in the system, and meets the requirement of security standards on concealed channel analysis.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Content based video package priority assignment method
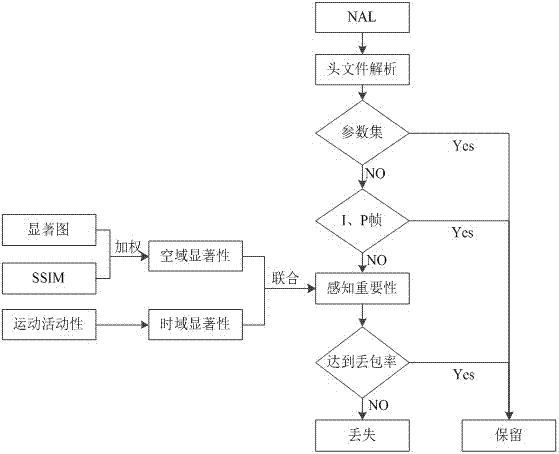
ActiveCN107371029AImprove fault toleranceReduce computational complexityDigital video signal modificationTransmissionTime domainSpace time domain
The invention discloses a content based video package priority assignment method. First, an initial slice priority sequence is obtained according to an NAL type. The priority of parameter set is the highest and the priority of I frame and P frame is second to the highest level. Then structural similarity of significance weight is used for indicating space domain perception importance and motion activity is used for indicating time domain perception importance, and space time domain perception priority is obtained through combination. The priority information is written into an NAL head file, so that external code flow cost is avoided. Channel analysis is performed on the NAL head file, and NAL type and time space domain perception priority indicators are acquired, so that the priority of each video package is determined. In a packet dropout network environment, packages with low priority are dropped first and video packages with high priority are protected. Error concealment is performed by adopting a simple method of copying the former frame at a decoding end, and then a decoded video is obtained. According to the invention, in a condition with identical package dropout rate, the video quality is higher than that employing a random package dropout method, so that video transmission robustness is improved.
Owner:SHANGHAI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com