Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
622results about How to "Increase the amount of data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
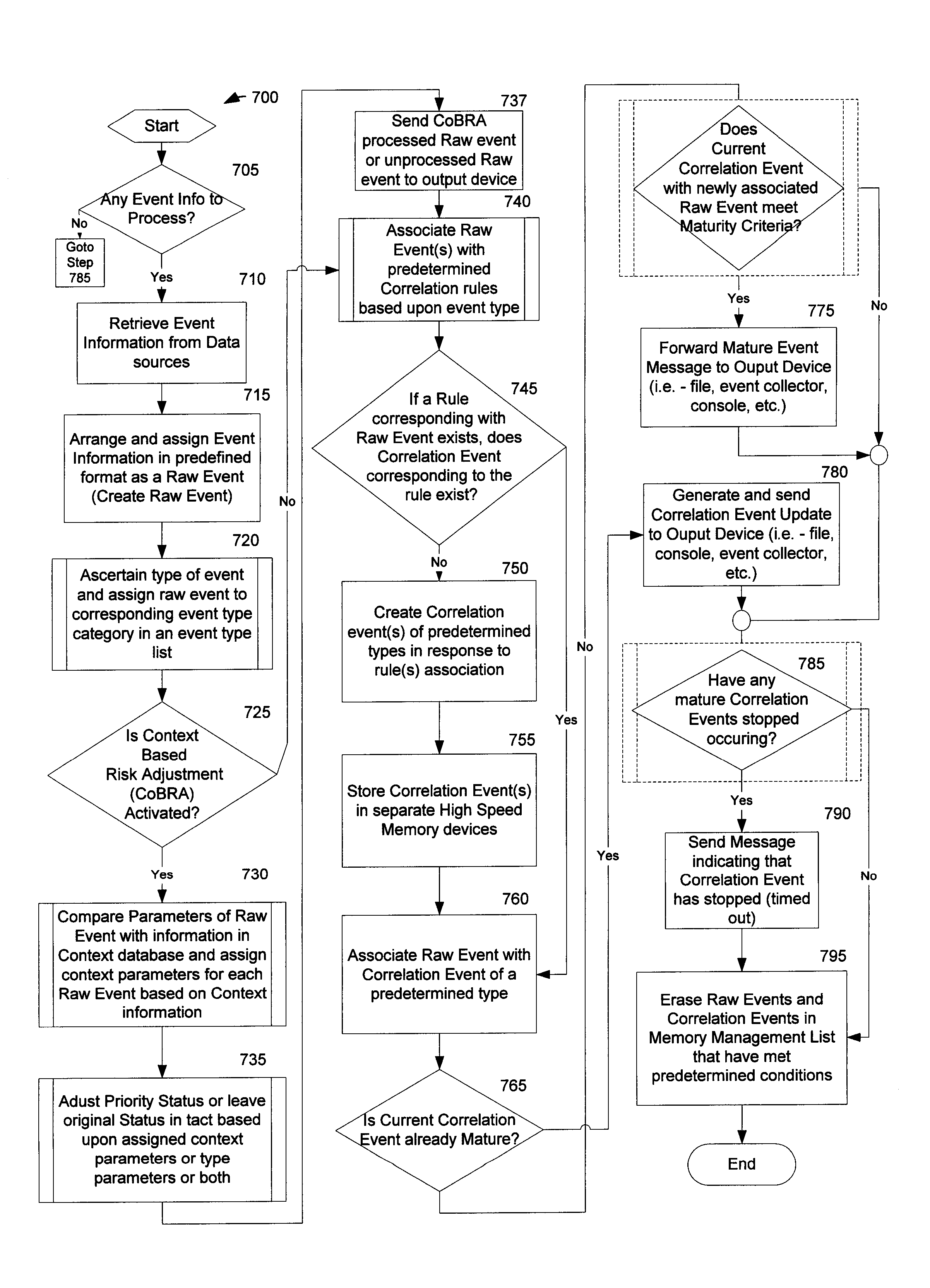
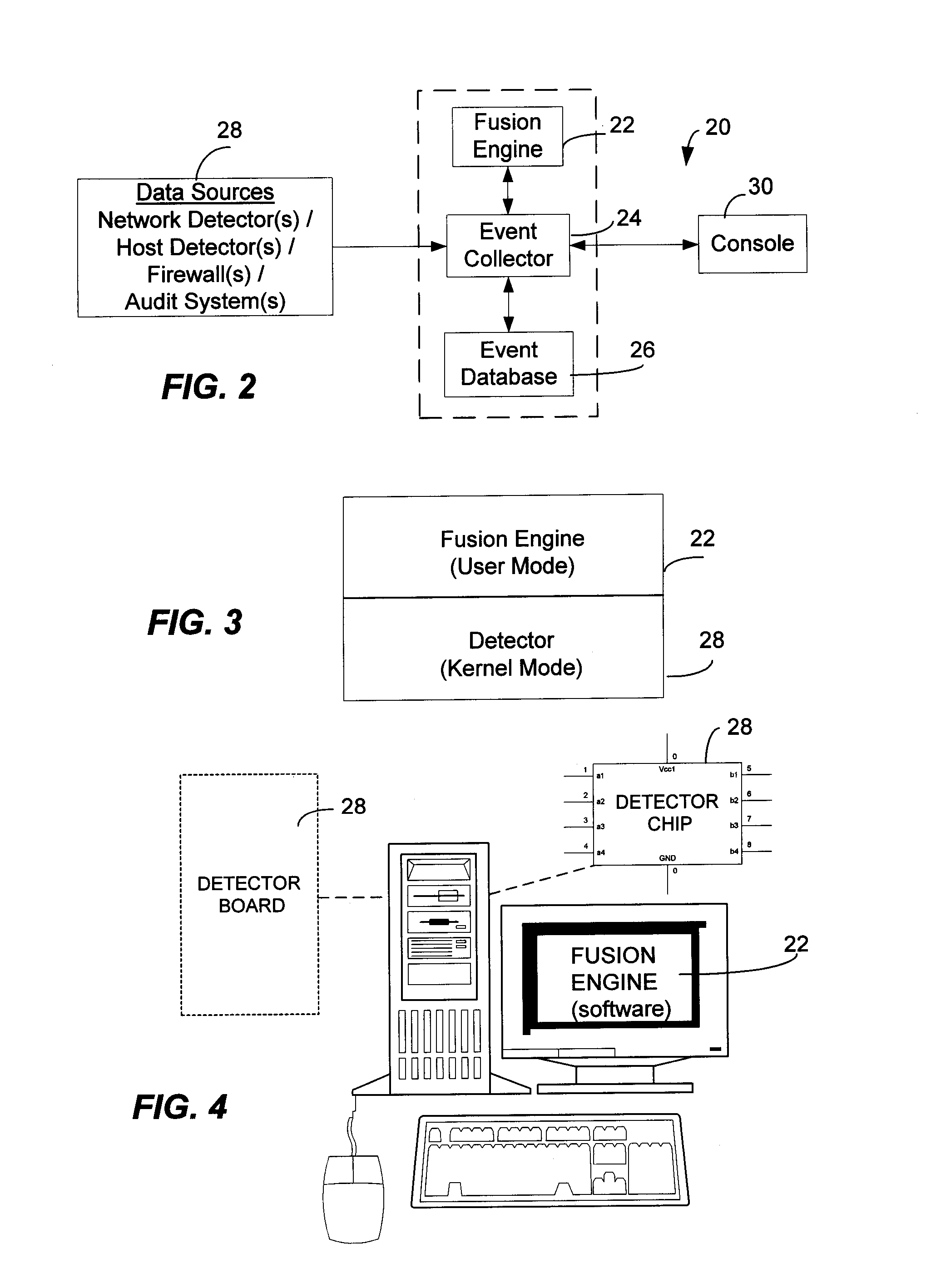
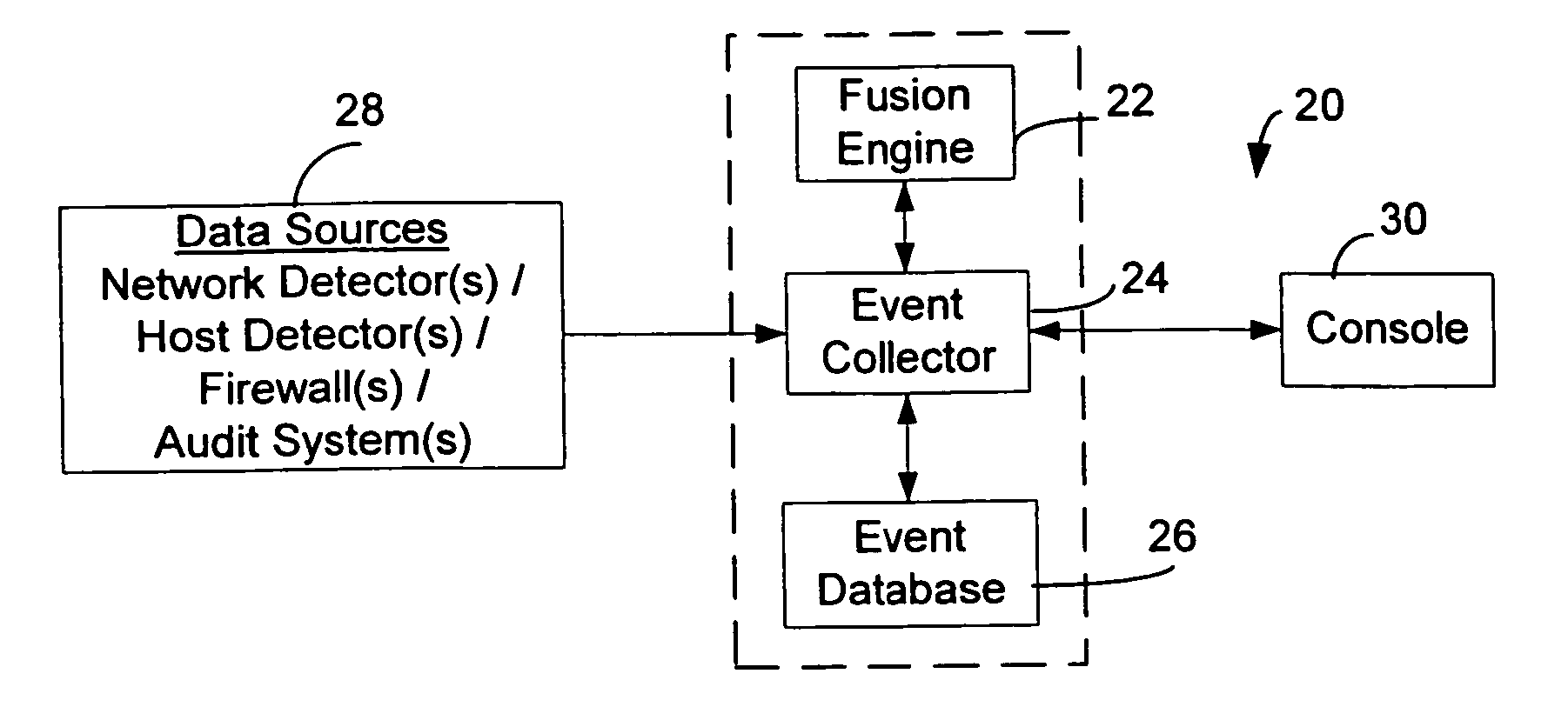
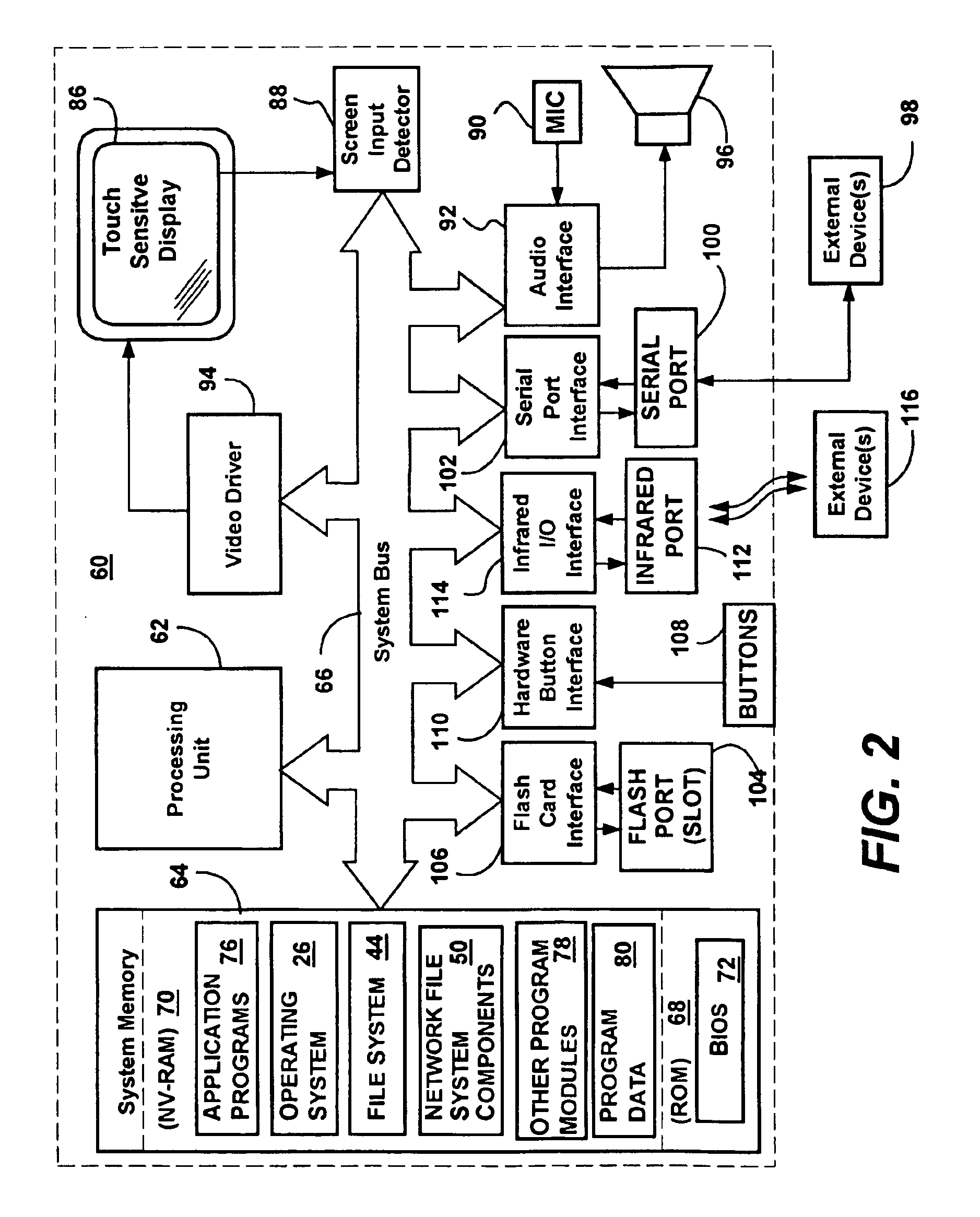
Method and System for Managing Computer Security Information
InactiveUS20020078381A1Efficient managementReduce processing speedMemory loss protectionDigital data processing detailsTraffic capacitySafety management systems
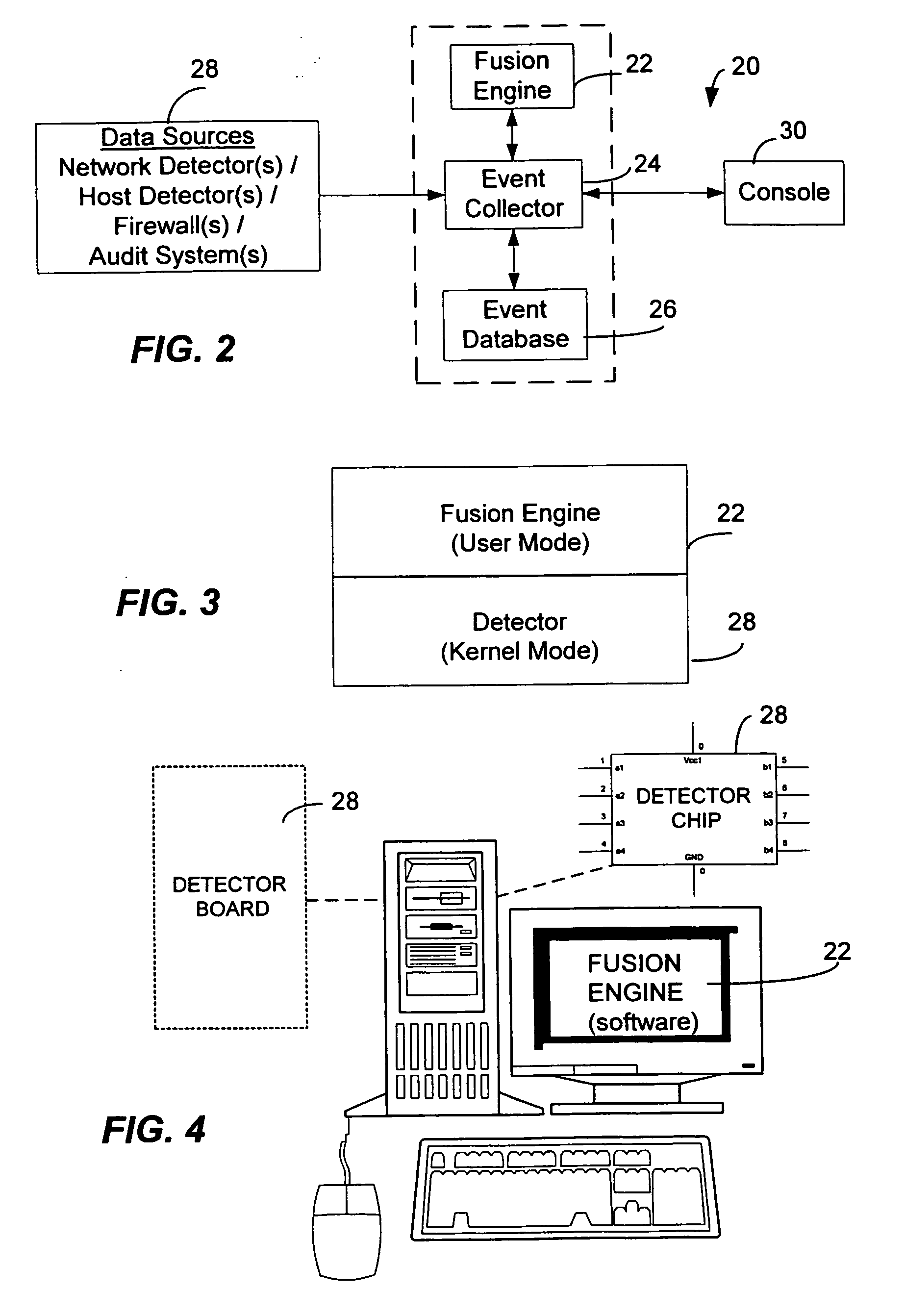
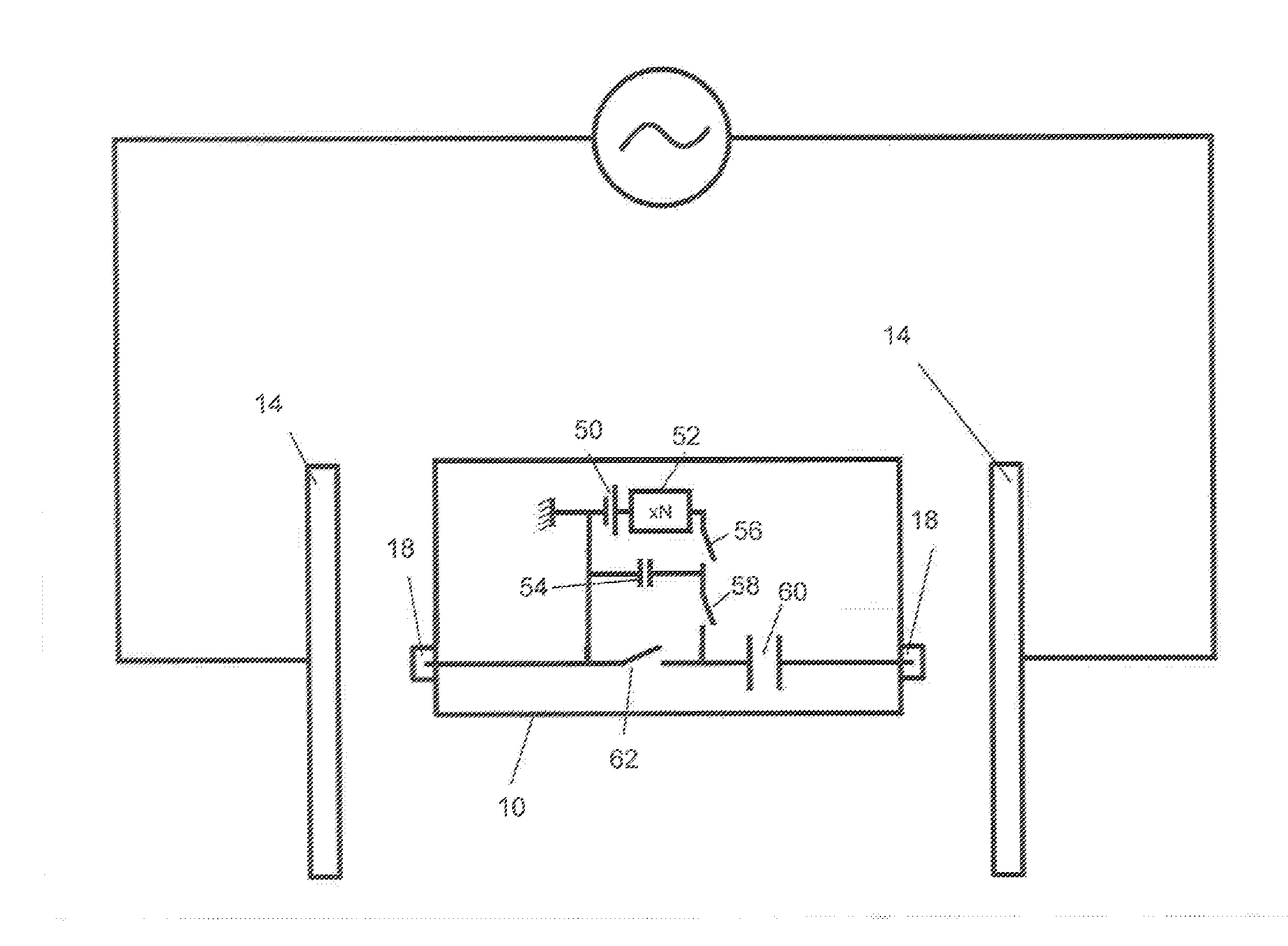
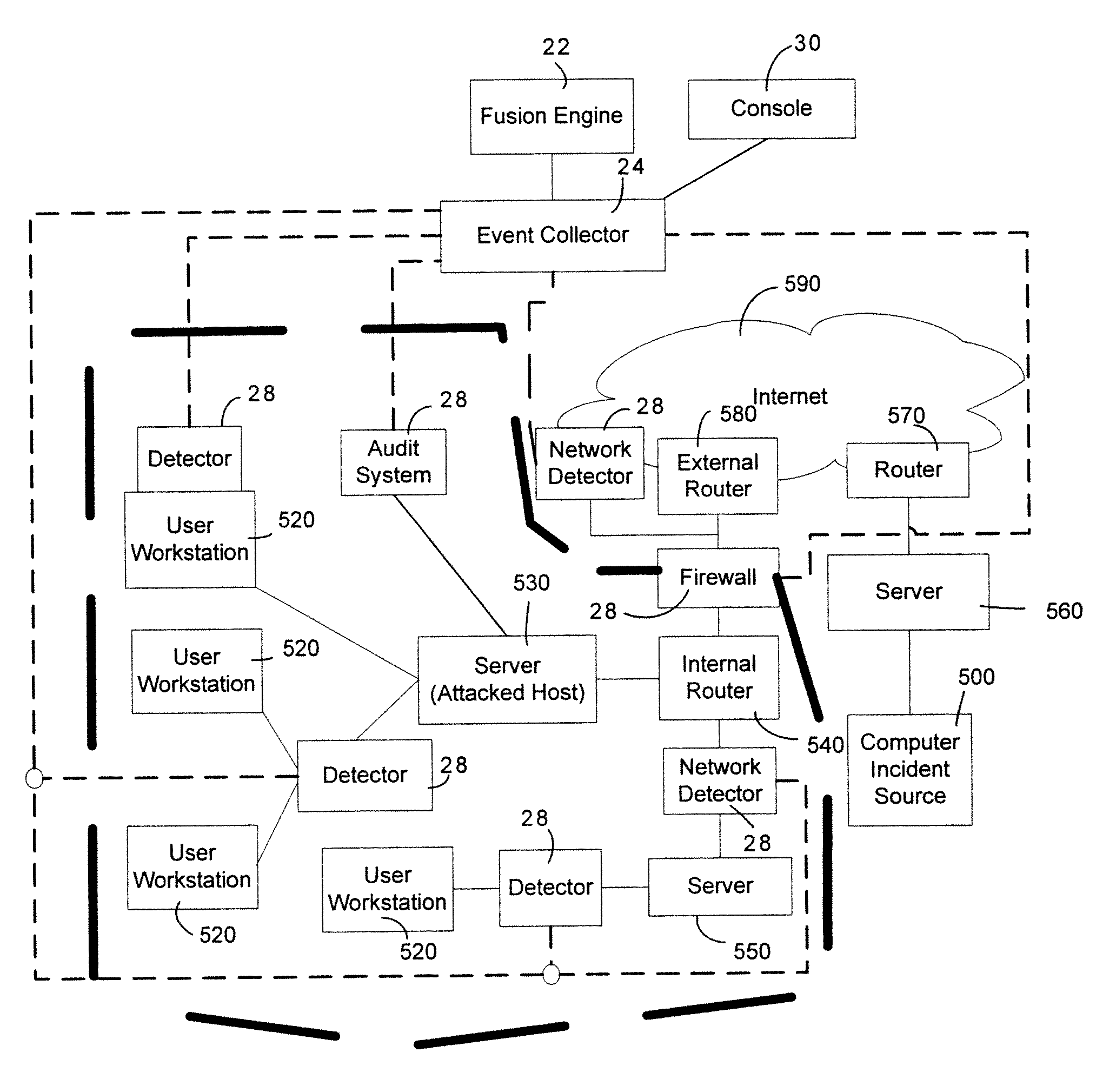
<heading lvl="0">Abstract of Disclosure< / heading> A security management system includes a fusion engine which "fuses" or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
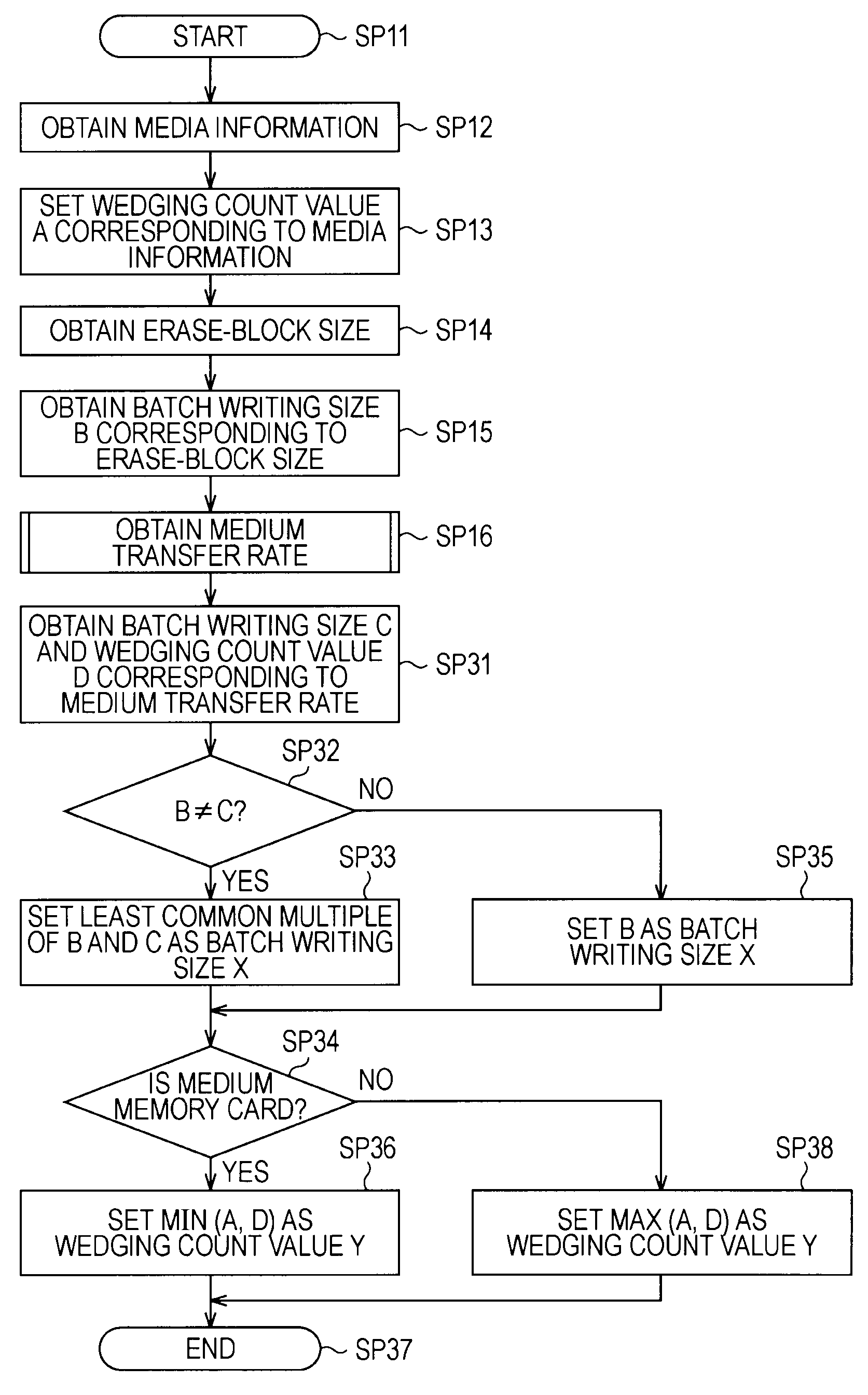
Recording apparatus, recording method, program for recording method, and storage medium that stores program for recording method
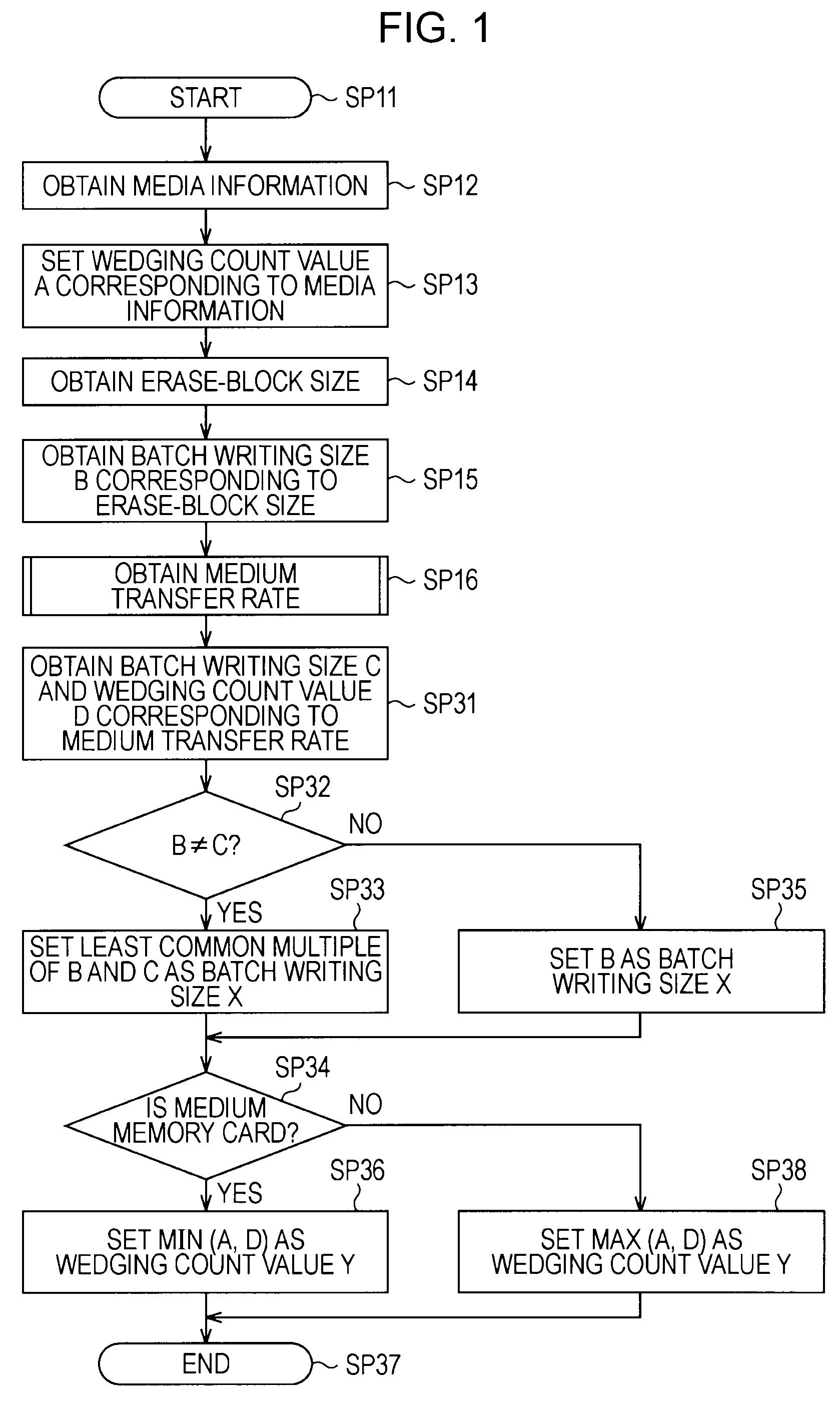
InactiveUS20090198889A1Suppress significant in serviceable lifeIncrease in sizeRecording carrier detailsInput/output to record carriersData recordingRecords management
A recording apparatus includes: a type detecting section that detects a type of storage medium; an erase-block size detecting section that detects an erase-block size of the storage medium; a recording section that records desired data to a data area in the storage medium and records management information of the data area to a management area in the storage medium; and a control section that controls the recording section by issuing a command to the recording section, on the basis of results of the detection. Each time a certain amount of data is recorded to the data area, the control section updates the management information in accordance with the recording, and when the storage medium is a storage medium in which recorded data is updated for each erase-block size, the control section increases the certain amount of data according to an increase in the erase-block size.
Owner:SONY CORP
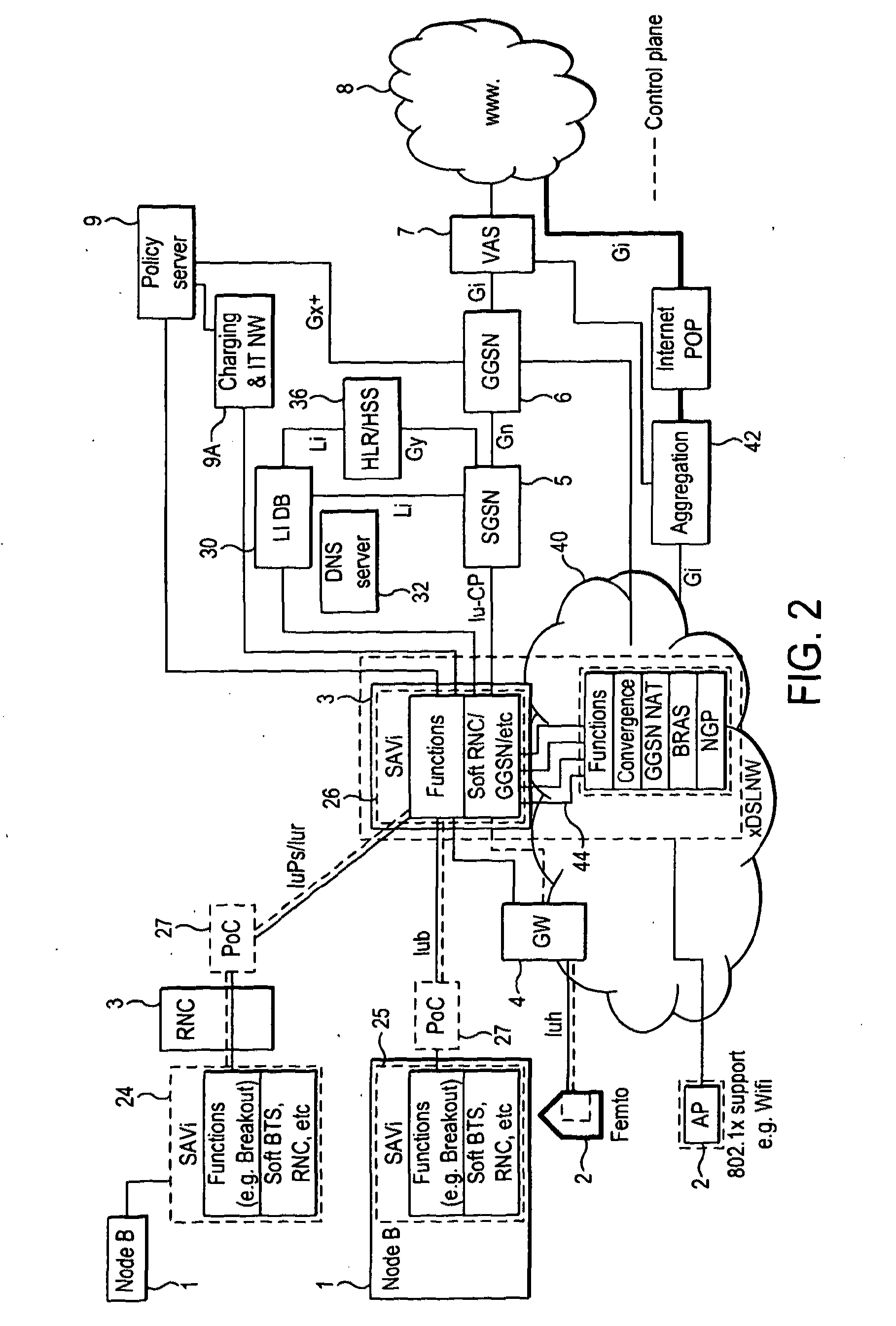
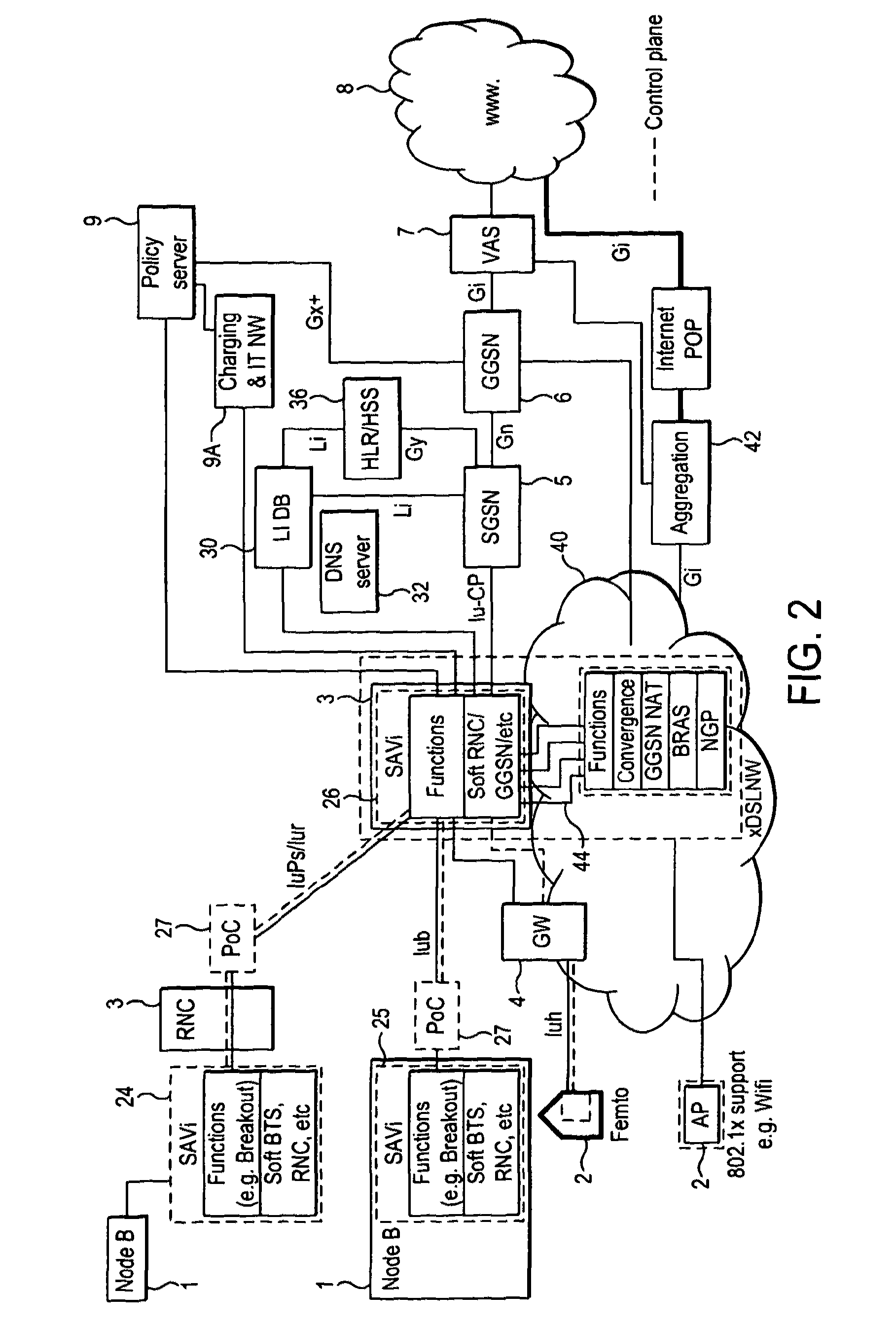
Telecommunication networks
ActiveUS20120064908A1High resolutionIncrease volumeAccounting/billing servicesNetwork traffic/resource managementAccess networkTelecommunications network
A mobile telecommunications network includes a core and a radio access network having a radio for wireless communication with mobile terminals registered with the network, wherein the radio access network includes a controller operable to control the use of network resources by the mobile terminals. The controller may include an application programming interface, API, which provides a consistent interface to a multiplicity of applications hosted on the control mean. The controller may be provided at an access node site and / or a gateway site.
Owner:VODAFONE IP LICENSING
Telecommunication networks
ActiveUS8639260B2Increase volumeReduce the amount requiredAccounting/billing servicesNetwork traffic/resource managementAccess networkTelecommunications network
A mobile telecommunications network includes a core and a radio access network having a radio for wireless communication with mobile terminals registered with the network, wherein the radio access network includes a controller operable to control the use of network resources by the mobile terminals. The controller may include an application programming interface, API, which provides a consistent interface to a multiplicity of applications hosted on the control mean. The controller may be provided at an access node site and / or a gateway site.
Owner:VODAFONE IP LICENSING
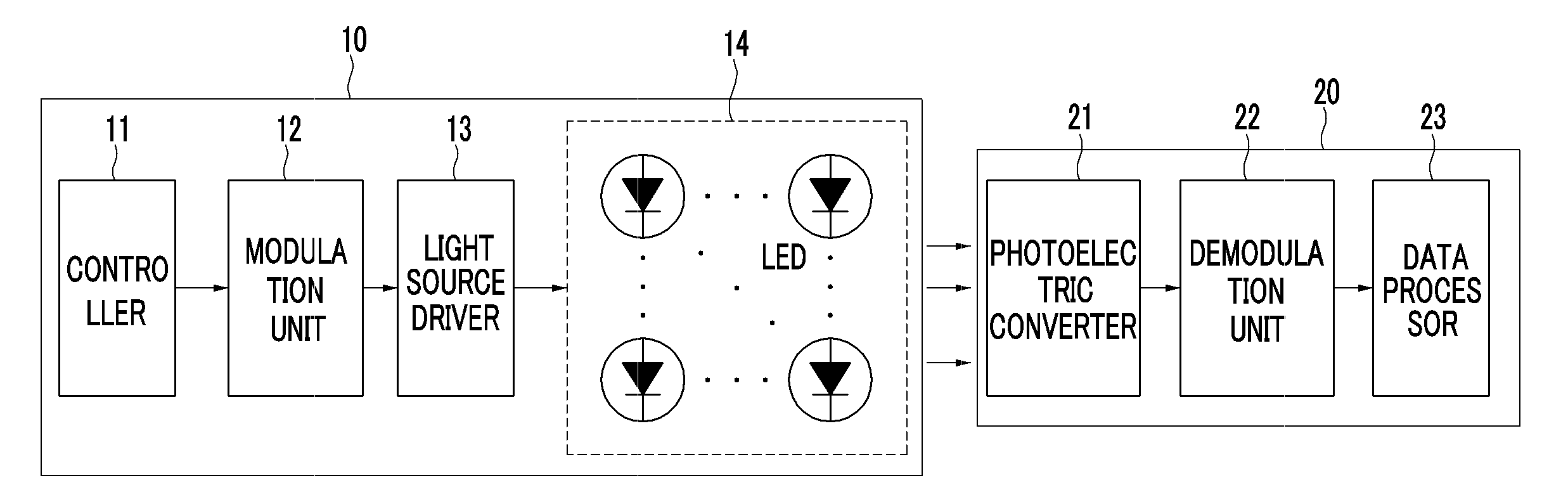
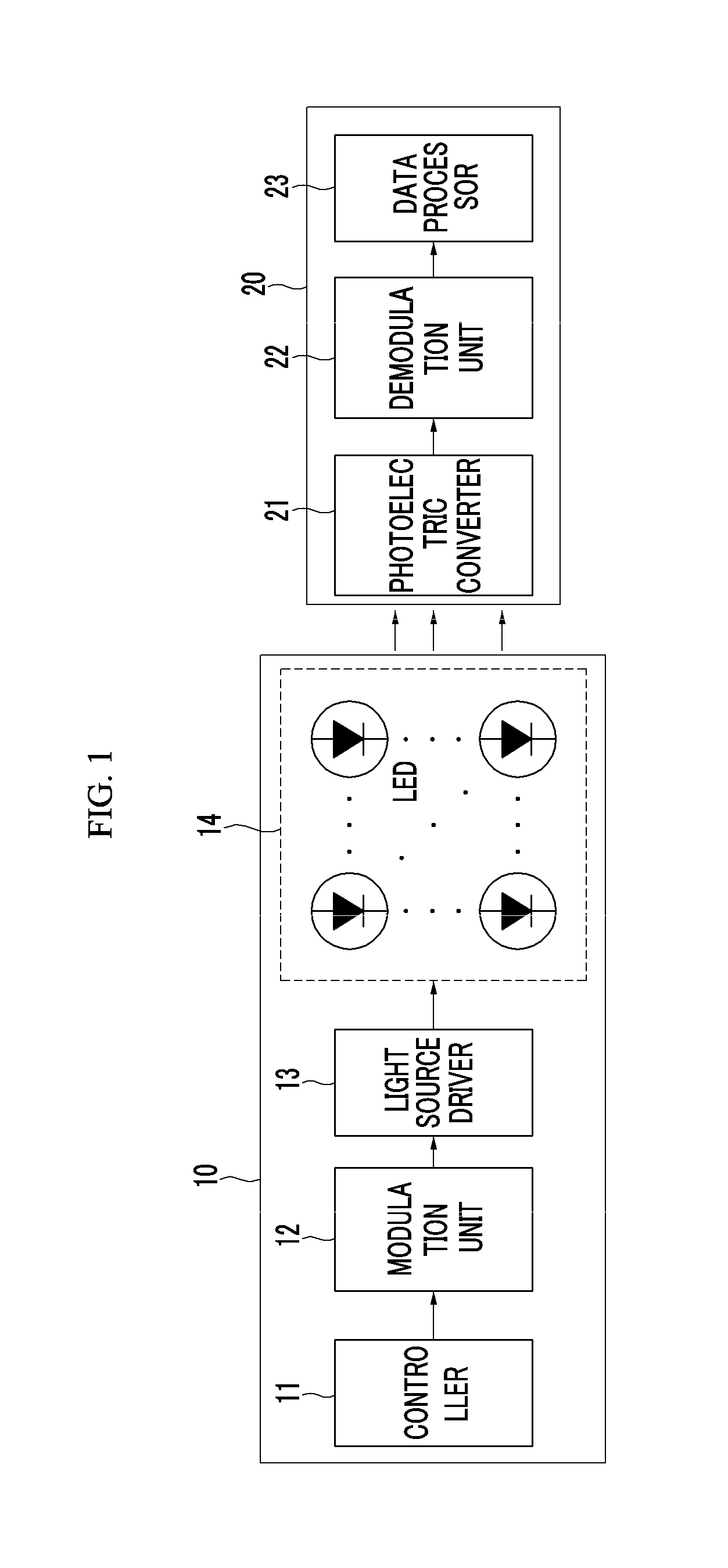
Method and apparatus for transmitting and receiving data using visible light communication
InactiveUS20120155889A1Increase amount of dataIncrease in information amountClose-range type systemsElectromagnetic transmittersCode bookImage sensor
A transmitting apparatus using visible light communication generates transmission data into a two-dimensional data code according to a predetermined code method between the transmitting apparatus and a receiving apparatus and transmits the two-dimensional data code through a plurality of light emitting diodes (LED) that are arranged in a two-dimensional form. Therefore, the receiving apparatus senses light from a plurality of LEDs as an image using an image sensor, demodulates the image into a two-dimensional data code, decodes the two-dimensional data code using a code book, and restores data.
Owner:ELECTRONICS & TELECOMM RES INST
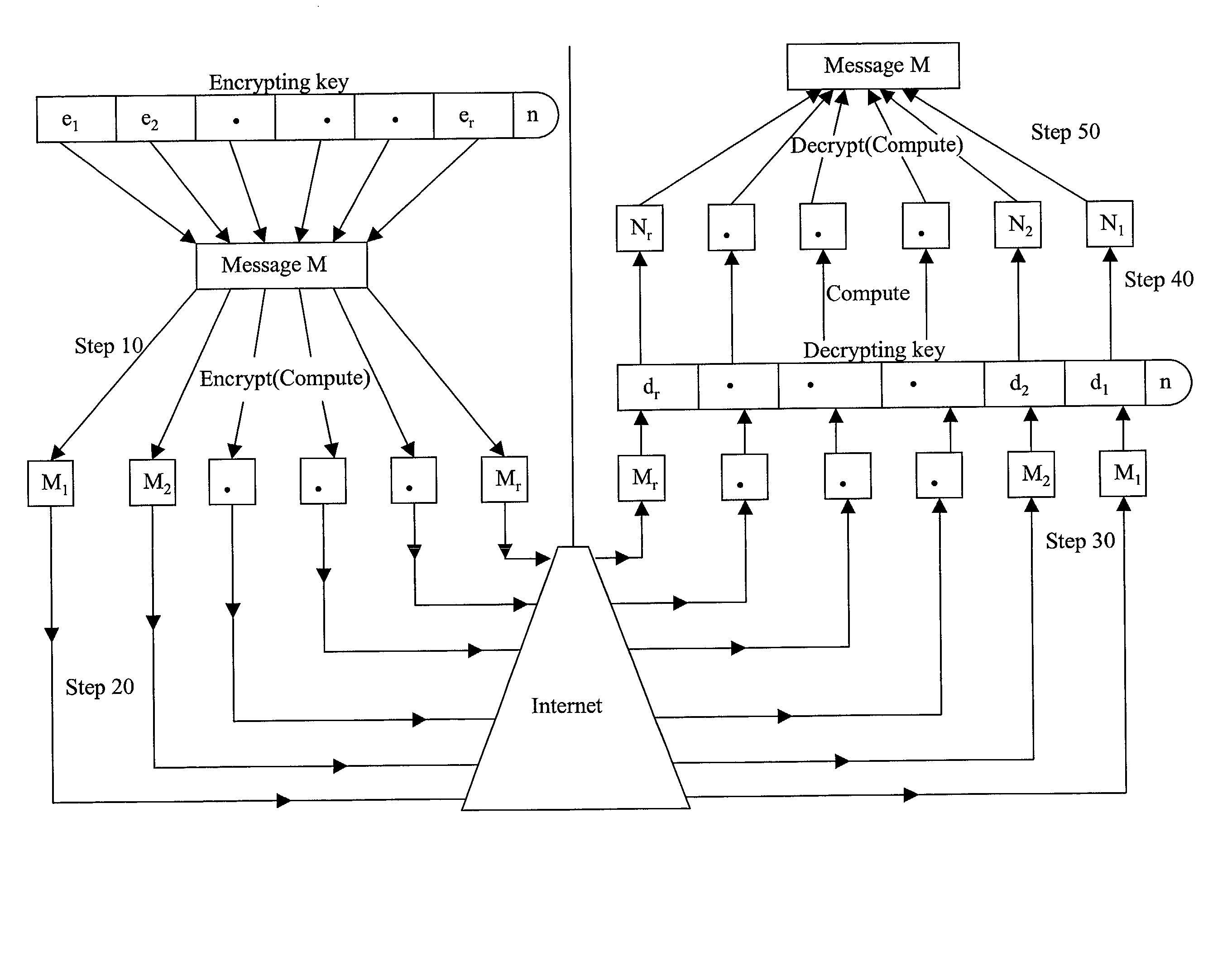
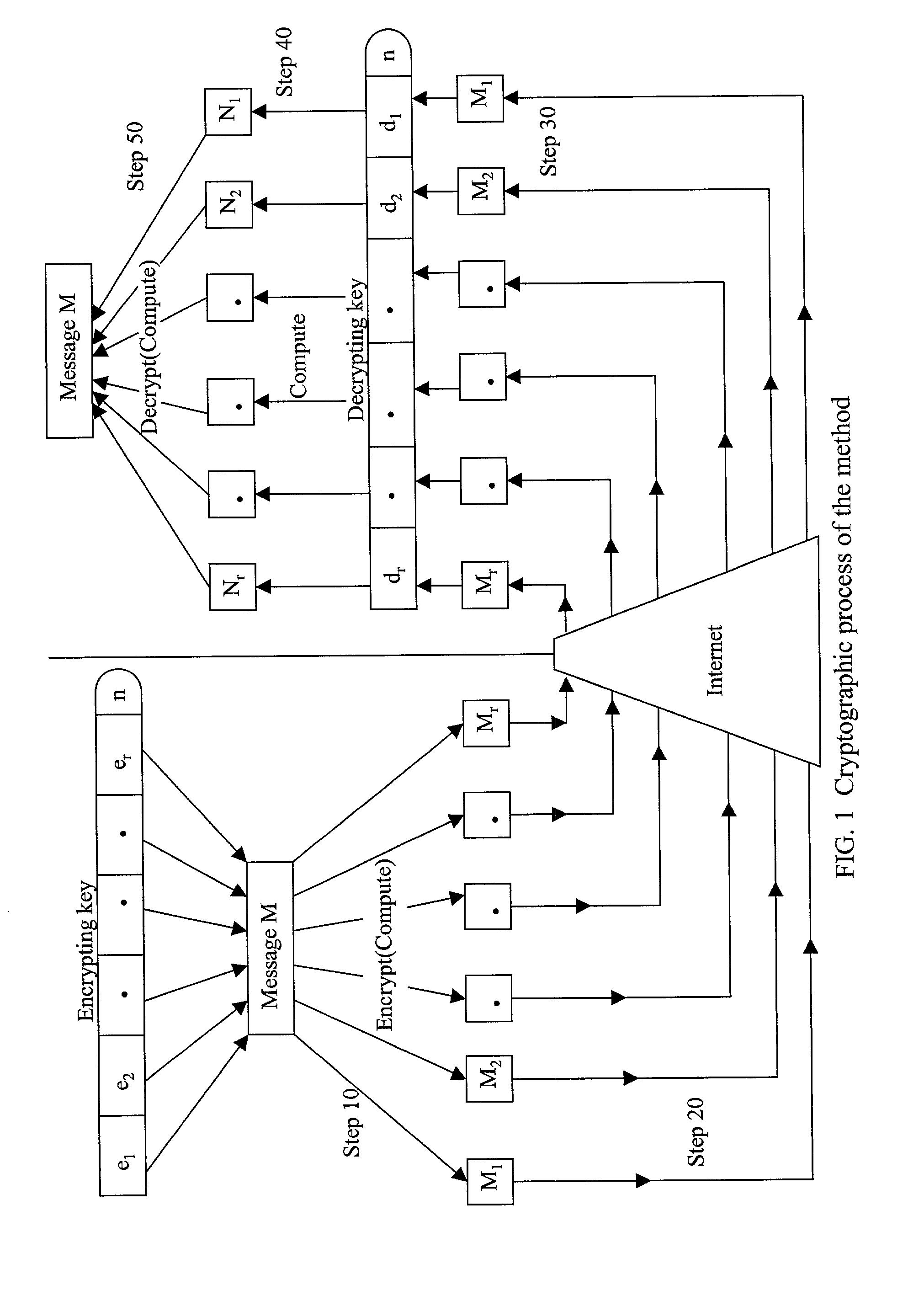
Absolute public key cryptographic system and method surviving private-key compromise with other advantages
InactiveUS20020186848A1Less powerful processorOvercomes shortcomingKey distribution for secure communicationPublic key for secure communicationEncryption systemTwo-way communication
Owner:KIOBA PROCESSING LLC
Transmission control method and system
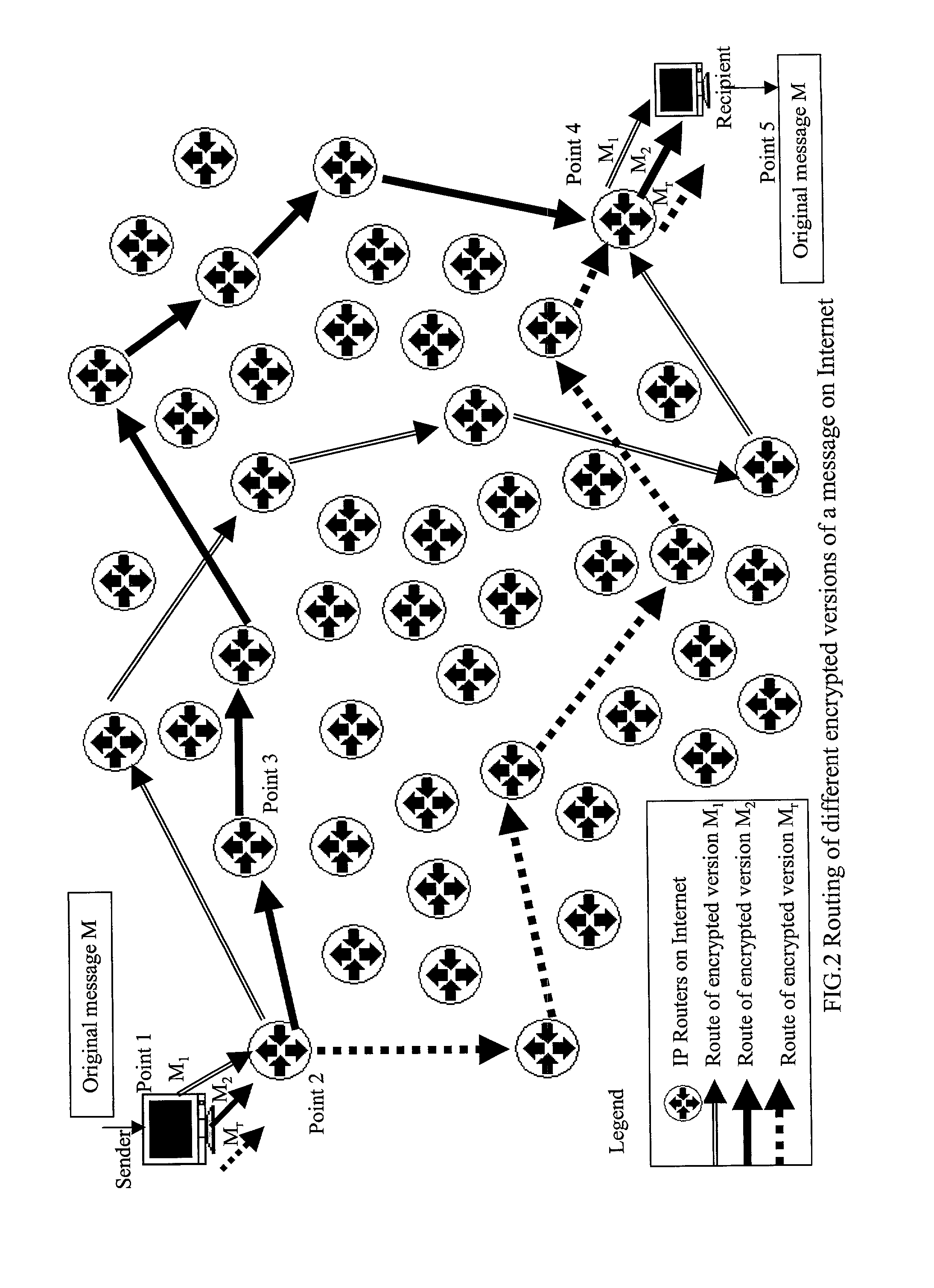
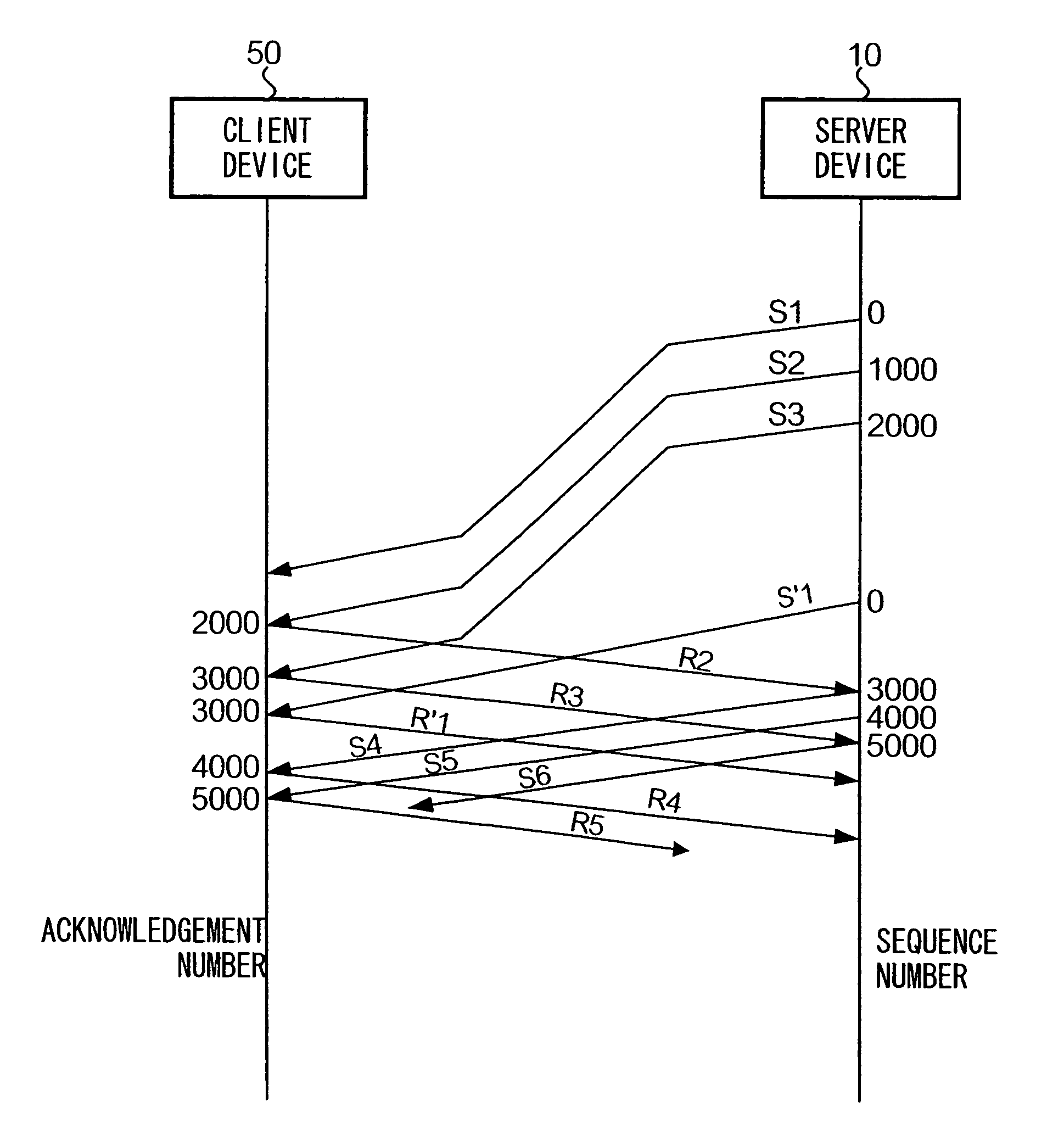
InactiveUS7505412B2Increasing data amount of dataUnnecessary transmission of data can be preventedError prevention/detection by using return channelFrequency-division multiplex detailsData segmentComputer science
Upon receiving an acknowledgement after retransmission of a data segment, an acknowledgement number contained in the acknowledgement is compared with an acknowledgment number expected to be contained in an acknowledgement pertaining to the retransmitted data segment. When the former is larger than the latter, it is determined that the acknowledgement pertains to a data segment that was originally transmitted.
Owner:NTT DOCOMO INC
Reducing the effects of noise in non-volatile memories through multiple reads
InactiveUS6621739B2Increase storage capacityReduce physical sizeRead-only memoriesDigital storageNormal modeOperation mode
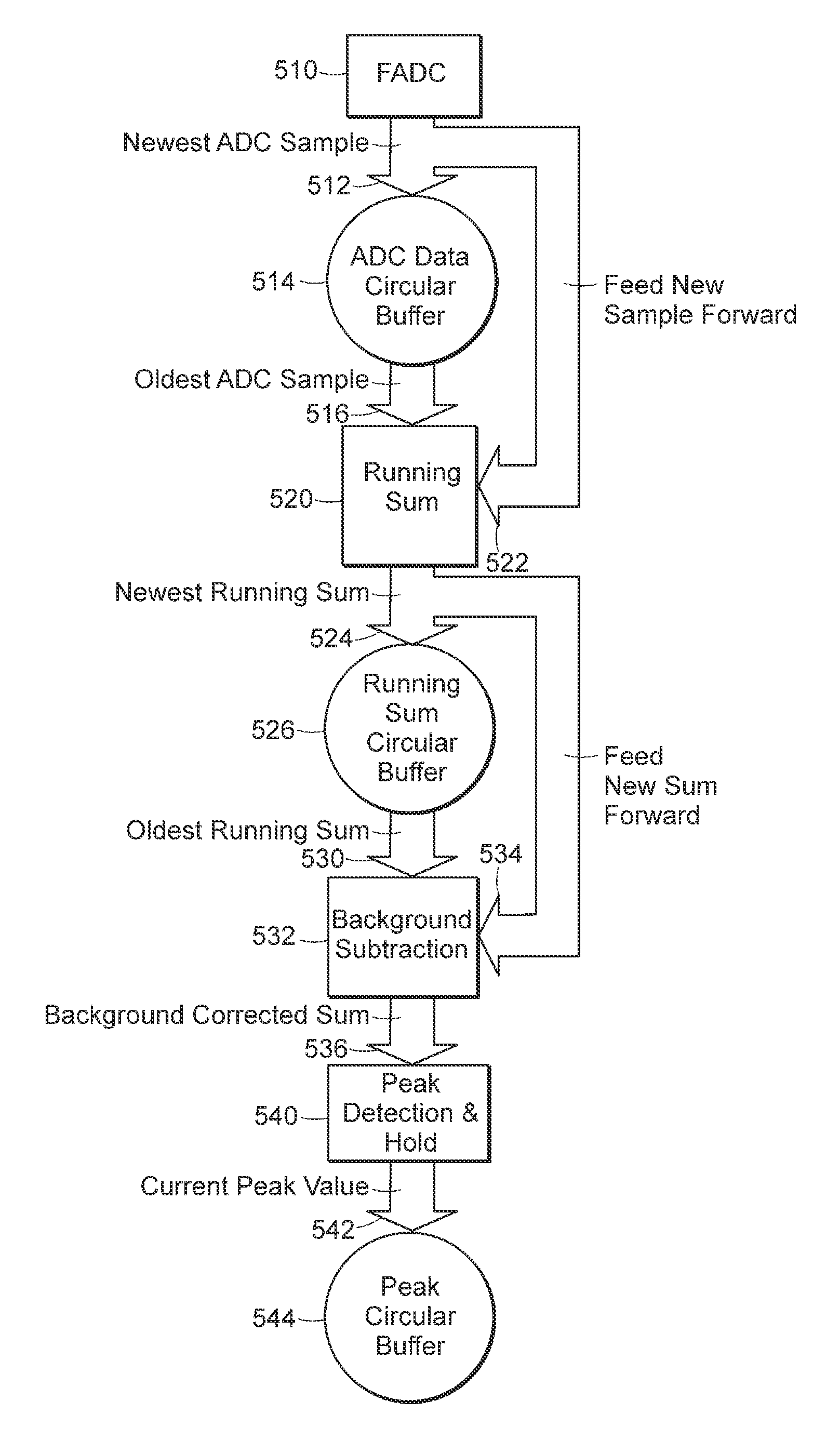
Storage elements are read multiple times and the results are accumulated and averaged for each storage element to reduce the effects of noise or other transients in the storage elements and associated circuits that may adversely affect the quality of the read. Several techniques may be employed, including: A full read and transfer of the data from the storage device to the controller device for each iteration, with averaging performed by the controller; a full read of the data for each iteration, with the averaging performed by the storage device, and no transfer to the controller until the final results are obtained; one full read followed by a number of faster re-reads exploiting the already established state information to avoid a full read, followed by an intelligent algorithm to guide the state at which the storage element is sensed. These techniques may be used as the normal mode of operation, or invoked upon exception condition, depending on the system characteristics. A similar form of signal averaging may be employed during the verify phase of programming. An embodiment of this technique would use a peak-detection scheme. In this scenario, several verify checks are performed at the state prior to deciding if the storage element has reached the target state. If some predetermined portion of the verifies fail, the storage element receives additional programming. These techniques allow the system to store more states per storage element in the presence of various sources of noise.
Owner:SANDISK TECH LLC
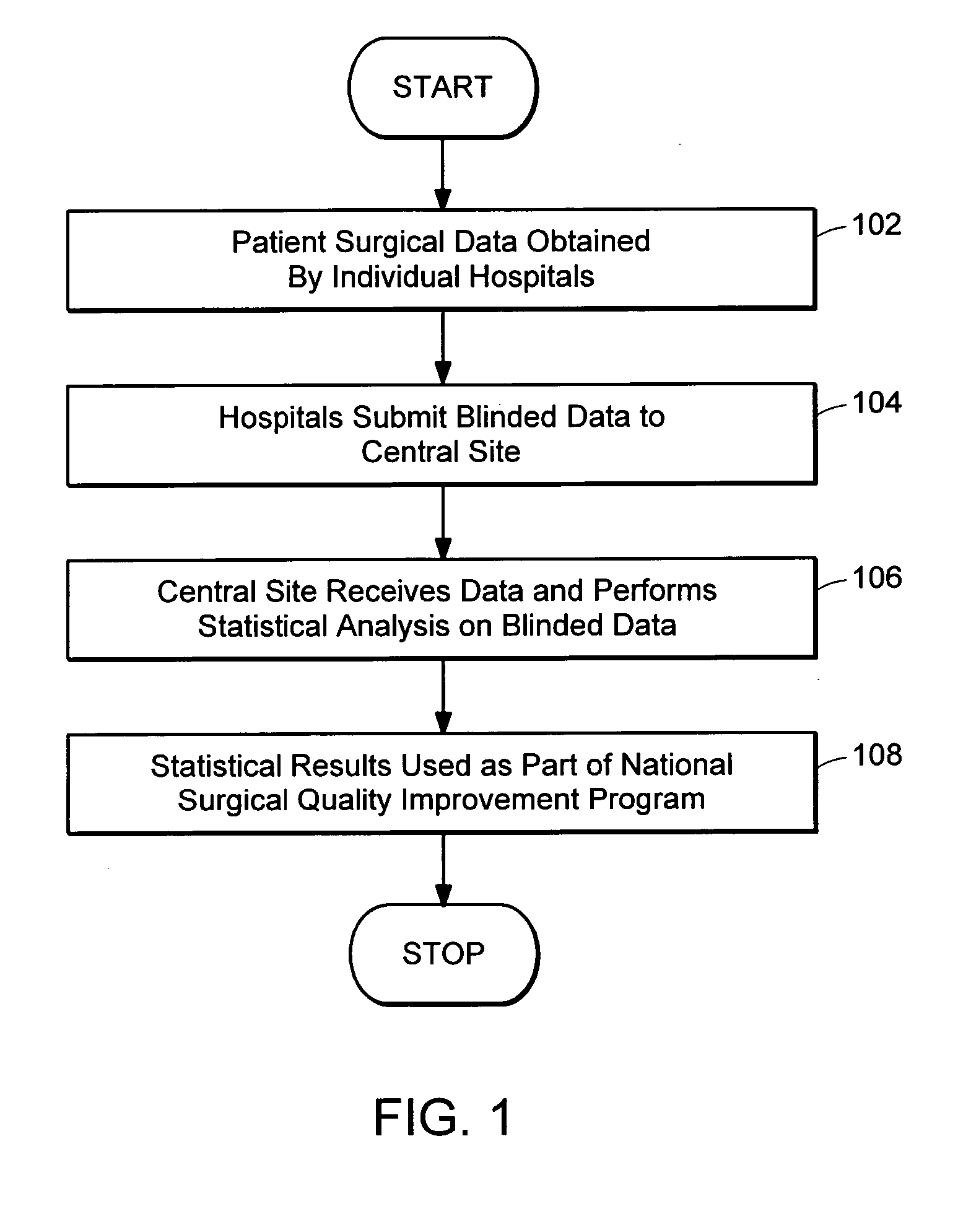
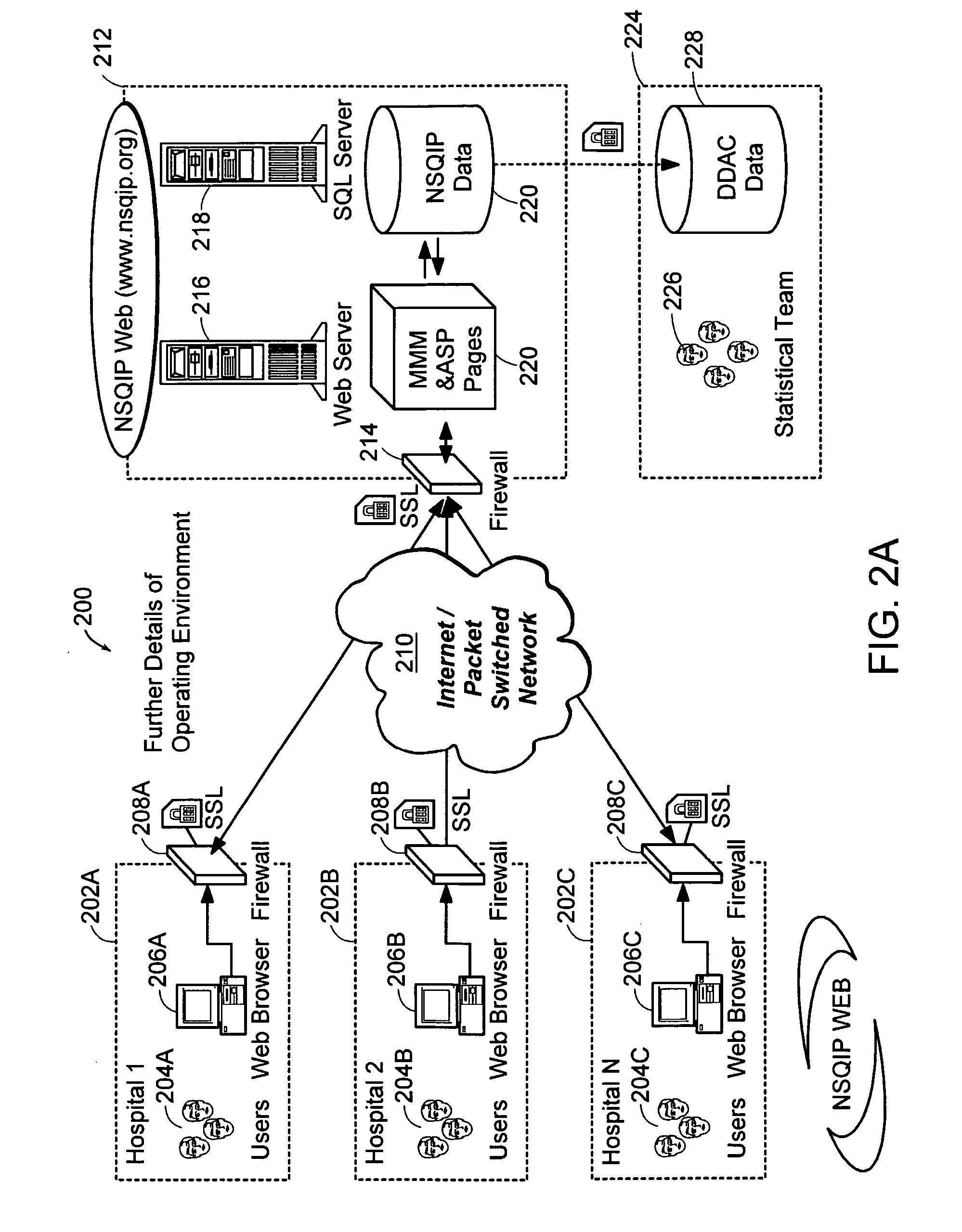
System and methods to collect, store, analyze, report, and present data
InactiveUS20050182655A1Great reliability of data collectionLow costMedical data miningData processing applicationsWeb siteMedicine
A system and method for collecting and processing surgical data as provided. Hospitals act as local sites and collect data associated with surgical procedures performed therein. The local sites send data to a central site which processes the data and provides recommendations back to the local sites. The recommendations are used by the local sites to improve surgical protocols and procedures.
Owner:QCMETRIX
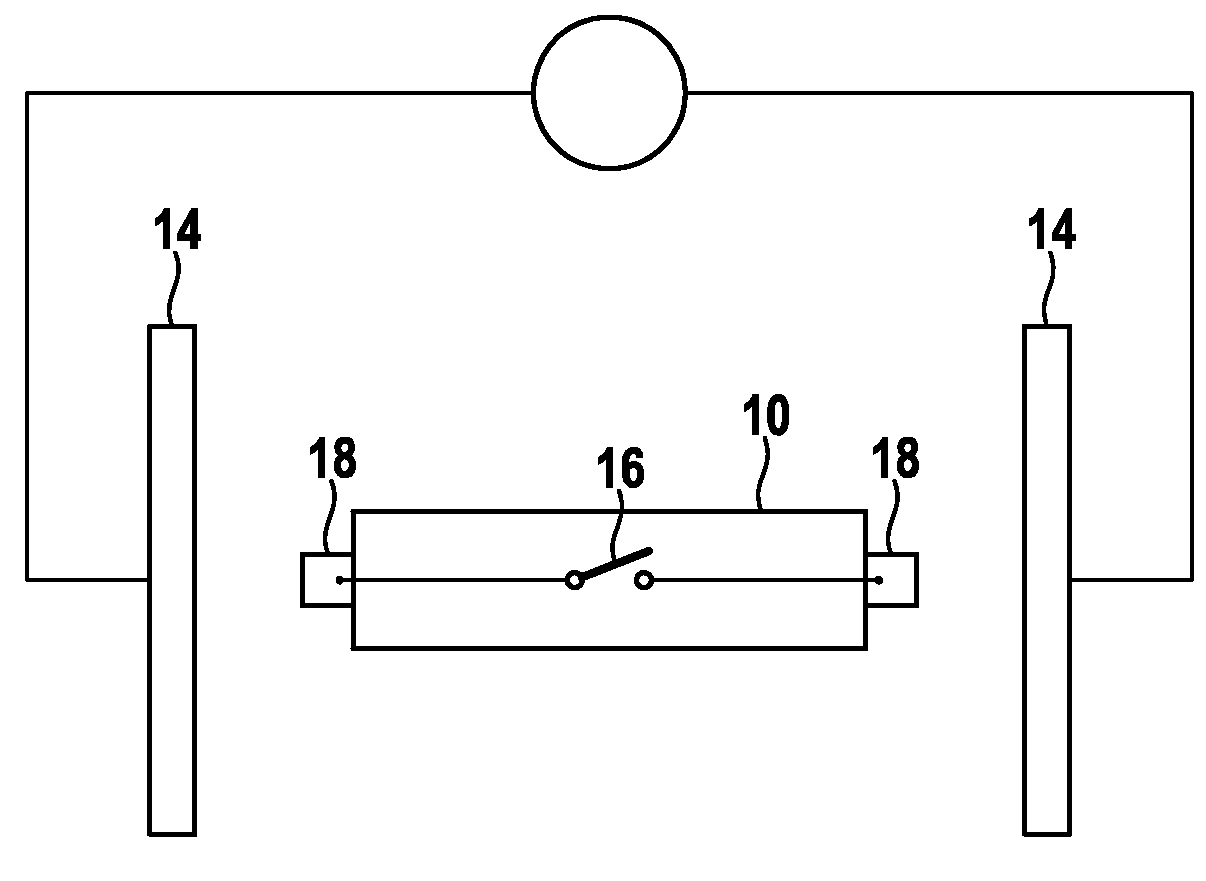
Method and system for managing computer security information
InactiveUS20060265746A1Efficient managementReduce processing speedMemory loss protectionError detection/correctionTraffic capacitySafety management systems
A security management system includes a fusion engine which “fuses” or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real- time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
Hard disk apparatus, medium, and collection of information
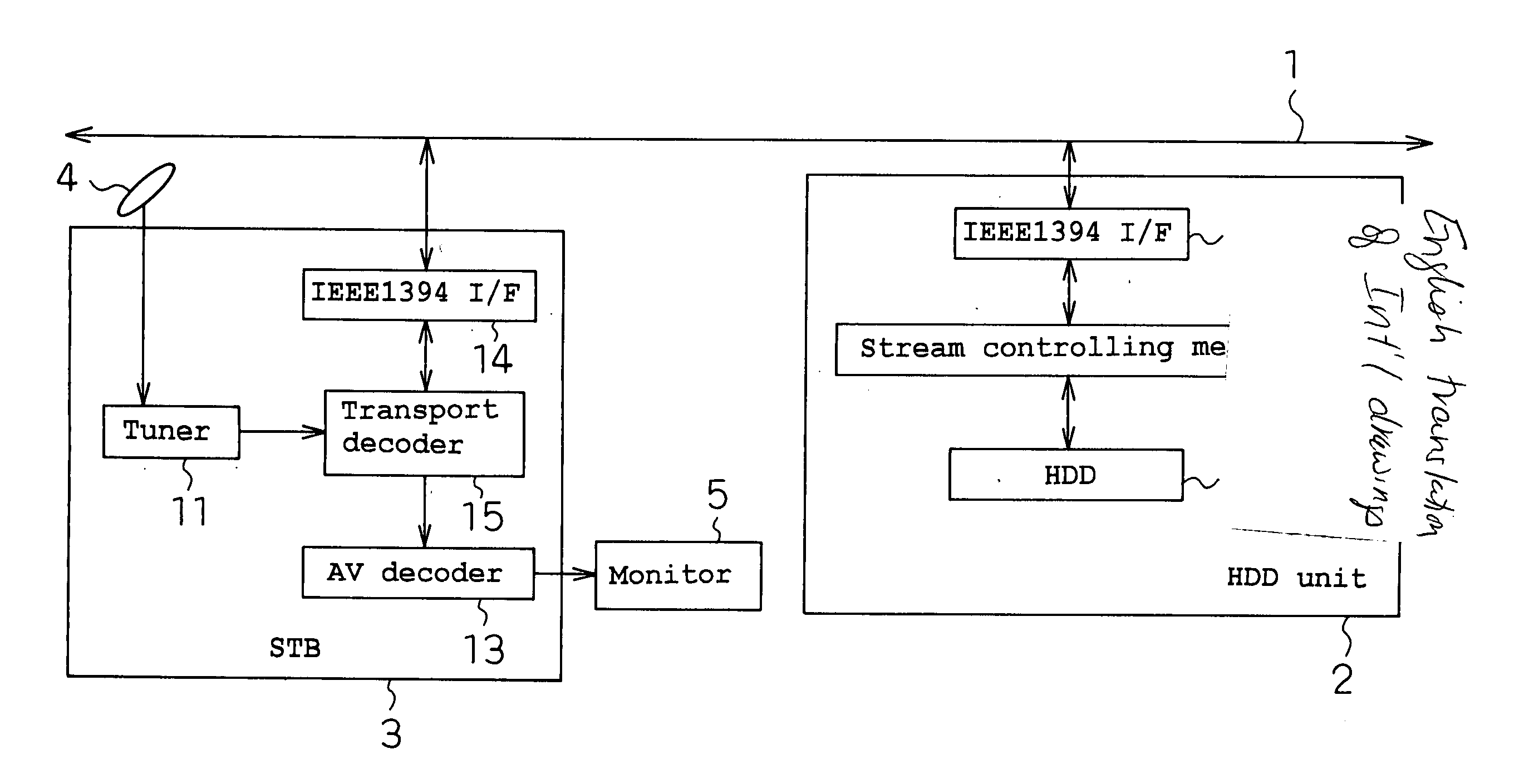
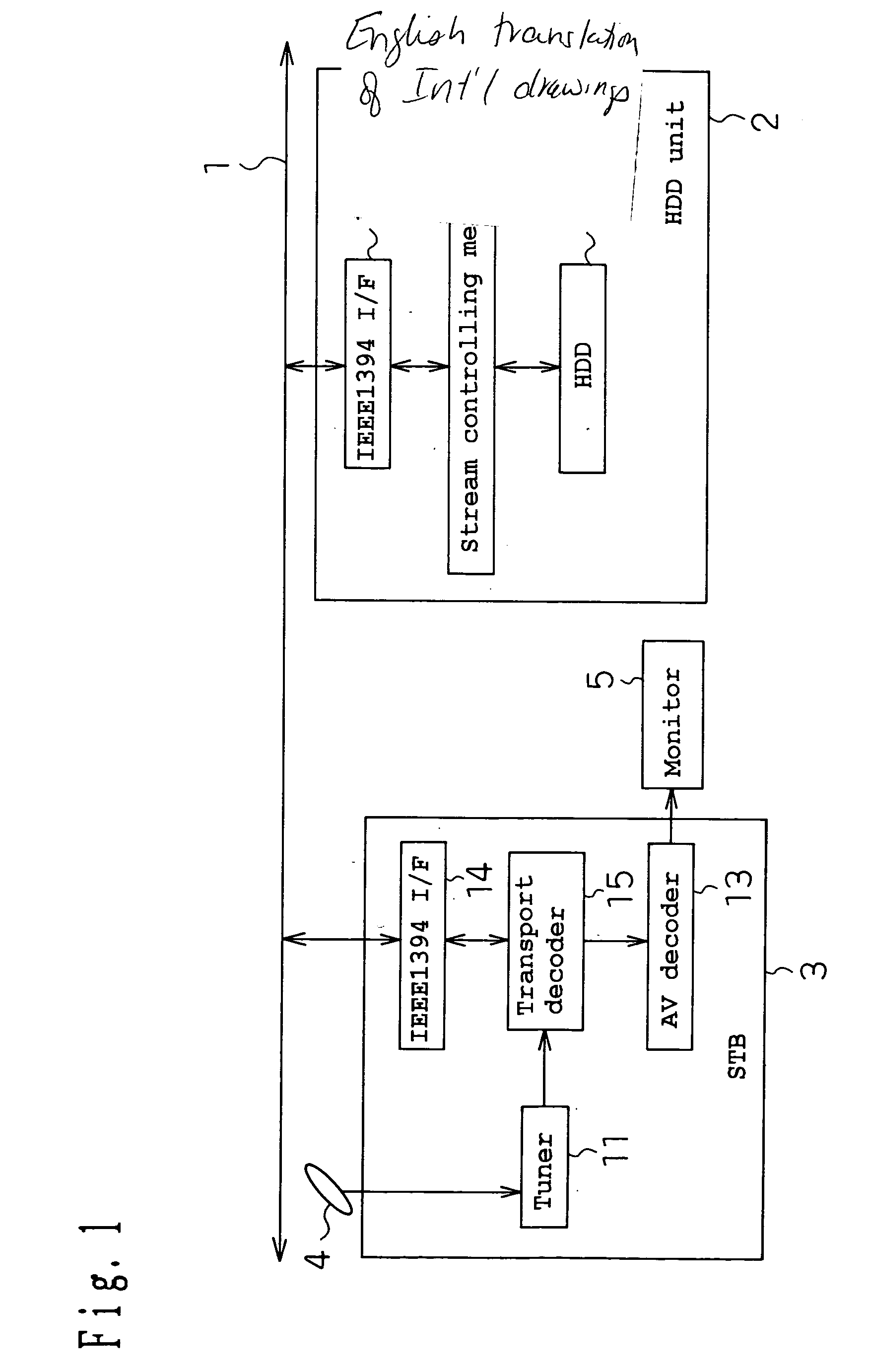
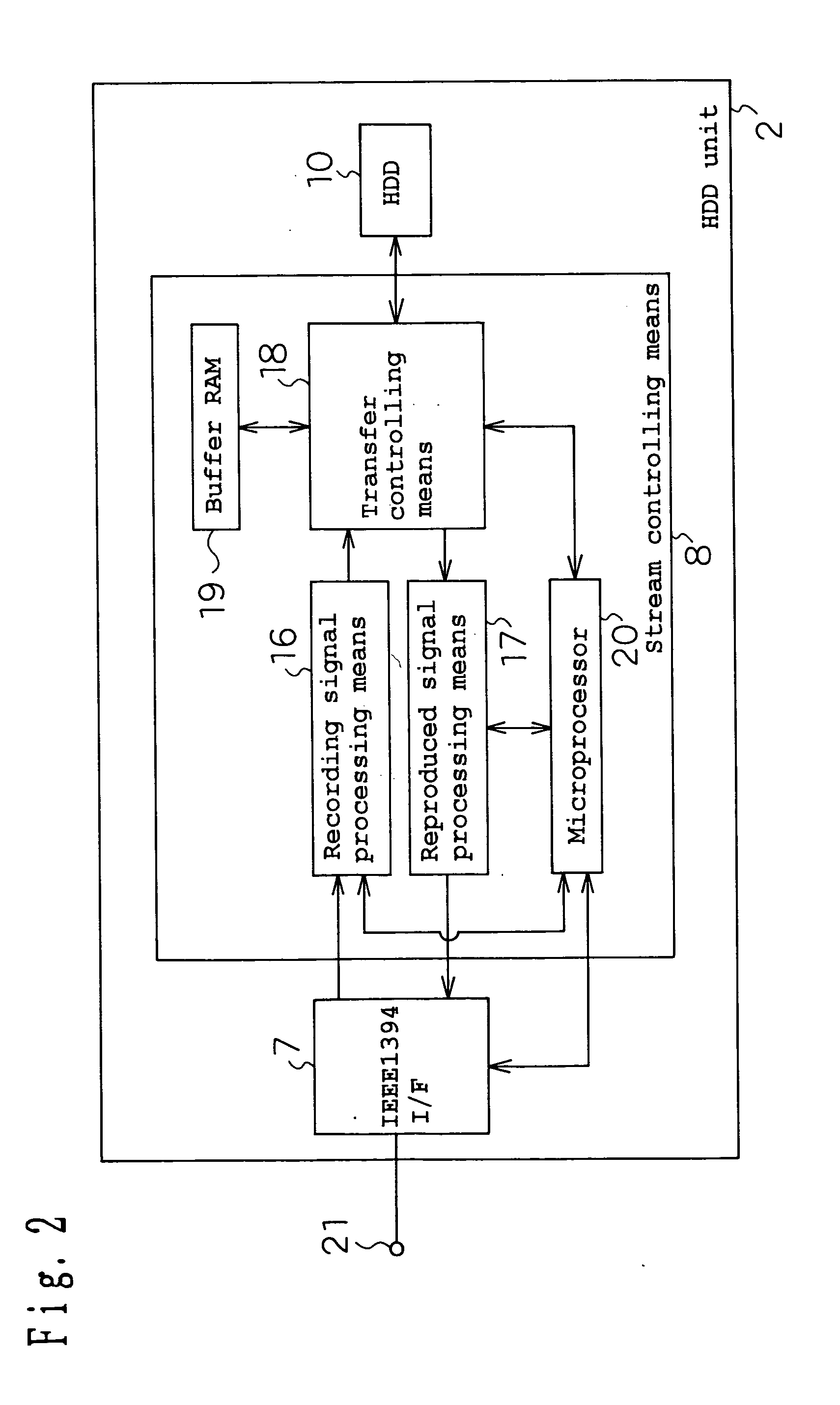
InactiveUS20040022526A1Increase the amount of dataAvoid idle timeTelevision system detailsDisc-shaped record carriersReproduction speedExecution unit
Alternation processes reduce the recording and reproducing speed of a hard disk apparatus. A hard disk apparatus comprising: an HDD 10 for recording AV data onto a hard disk; and stream controlling means 8 which is connected to the HDD 10 and thereby processes the signal of AV data transmitted from an IEEE1394 I / F 7 or the signal of AV data transmitted to the IEEE1394 I / F 7; whereby the hard disk apparatus can record and / or reproduce the AV data, wherein when AV data transfer is not normally completed for a disk access unit which is a minimum continuous unit in the access to the hard disk, an alternation process on a disk access unit basis is carried out so that another disk access unit is used hereafter in place of that disk access unit.
Owner:PANASONIC CORP
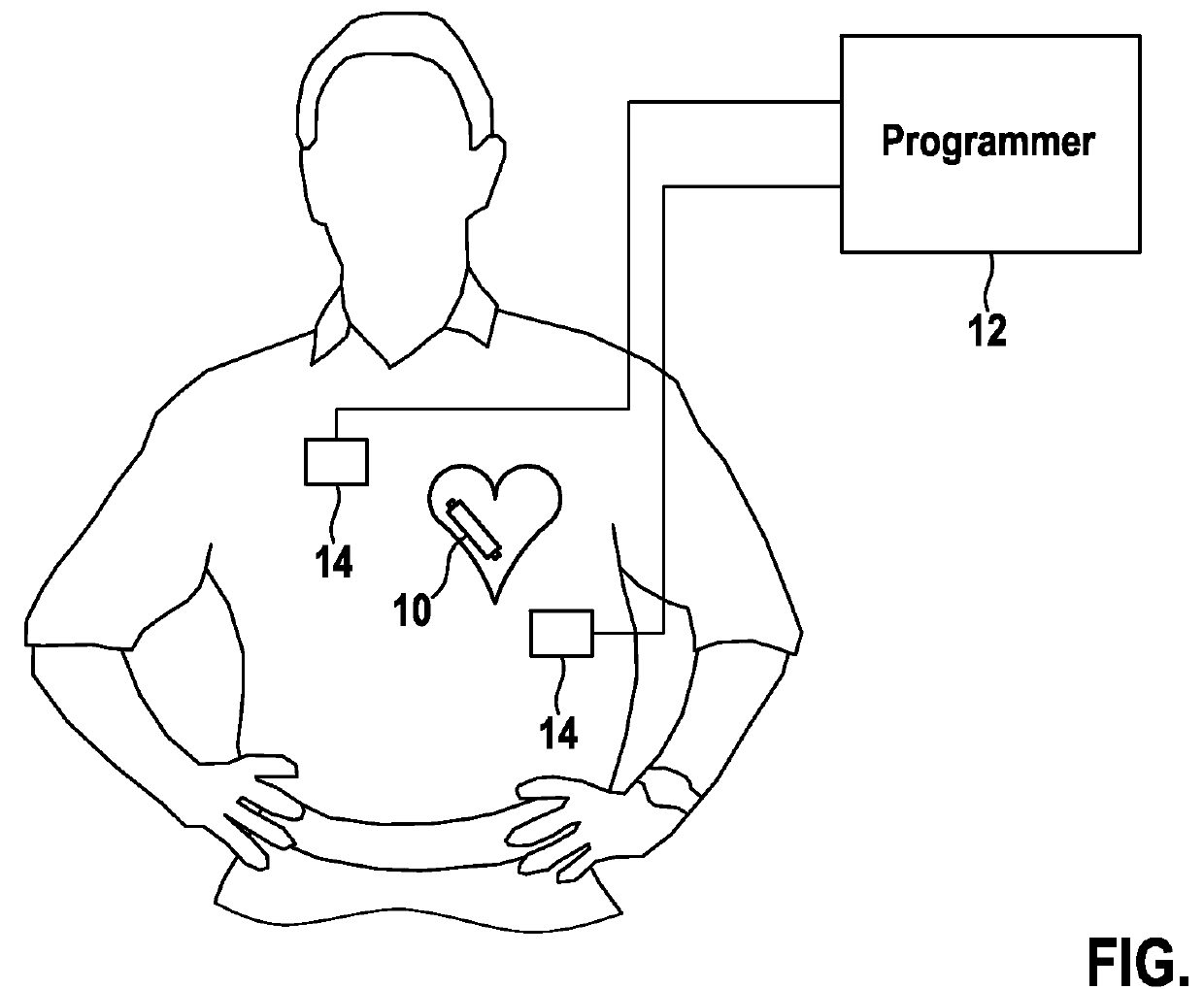
Implantable stimulation device, stimulation system and method for data communication
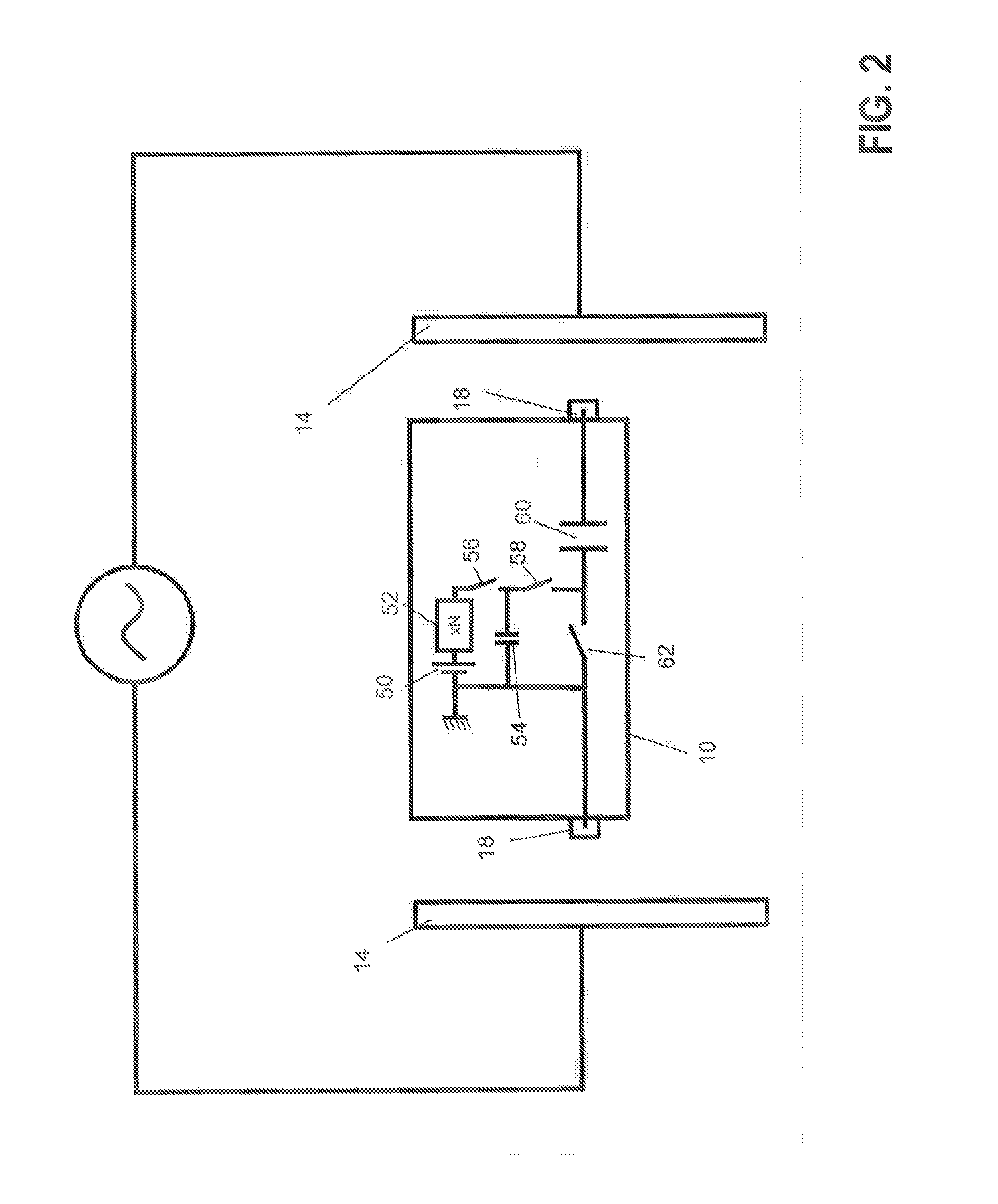
ActiveUS20140222098A1Minimizes battery drainIncrease the amount of dataHeart stimulatorsComputer moduleEngineering
An implantable stimulation device including a stimulation module and a data communication module. The stimulation device includes electrodes to delivery stimulation pulses, a voltage source, a DC-blocking capacitor and autoshort switch. The voltage source is connected to the electrodes via stimulation-pulse-switch(s) that controls delivery pacing pulses. The DC-blocking capacitor is connected with the voltage source and an electrode. The autoshort switch allows discharging of the DC-blocking capacitor via the electrodes when closed. The data communication module includes a data transmission control module connected to the autoshort switch and / or the at least one stimulation-pulse-switch, to alternatingly open and close the autoshort switch or the at least one stimulation-pulse-switch respectively, during an autoshort period following the delivery of a stimulation pulse or during a stimulation pulse period, respectively, to modulate an autoshort pulse or a stimulation pulse peak amplitude, respectively.
Owner:BIOTRONIK SE & CO KG
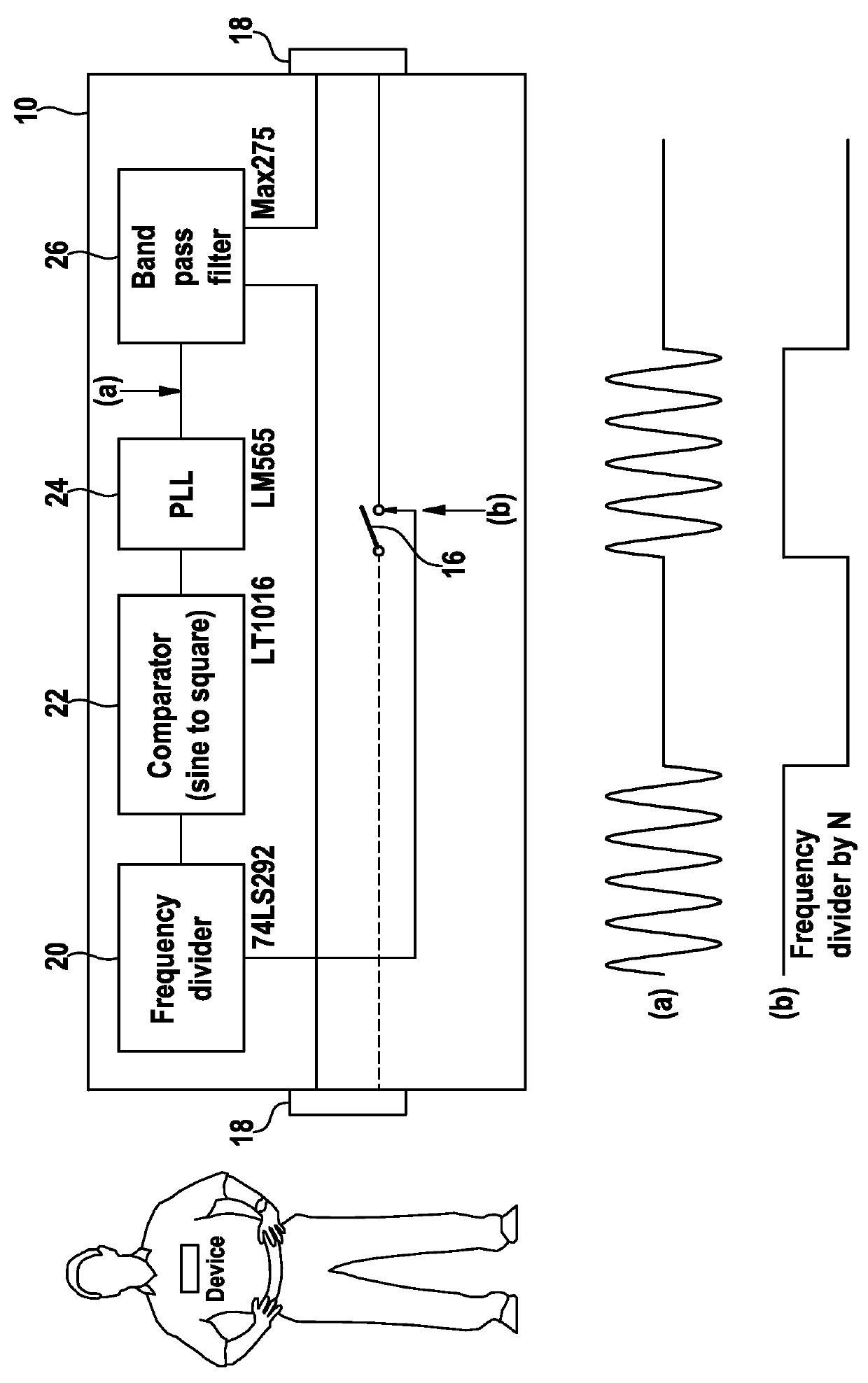
Method and System for Managing Computer Security Information
InactiveUS20100083382A1Reduce processing speedEasy to operateMemory loss protectionError detection/correctionTraffic capacitySafety management systems
A security management system includes a fusion engine which “fuses” or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:INT BUSINESS MASCH CORP
Communication System, Communication Apparatus and Method, and Computer Program
InactiveUS20090052902A1Increase the amount of dataIncrease volumeLine-of-sight transmissionClose-range type systemsComputer hardwareCommunications system
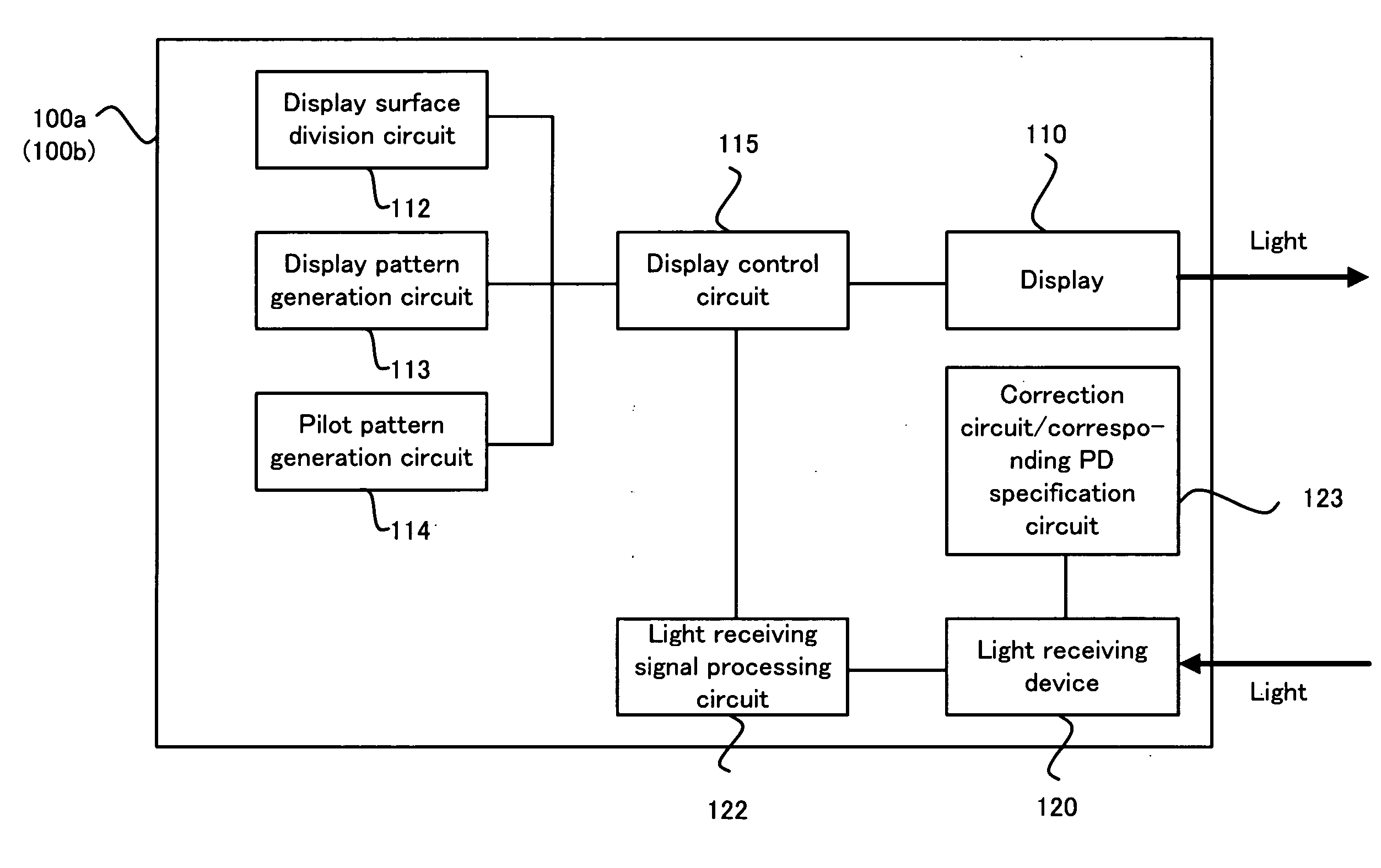
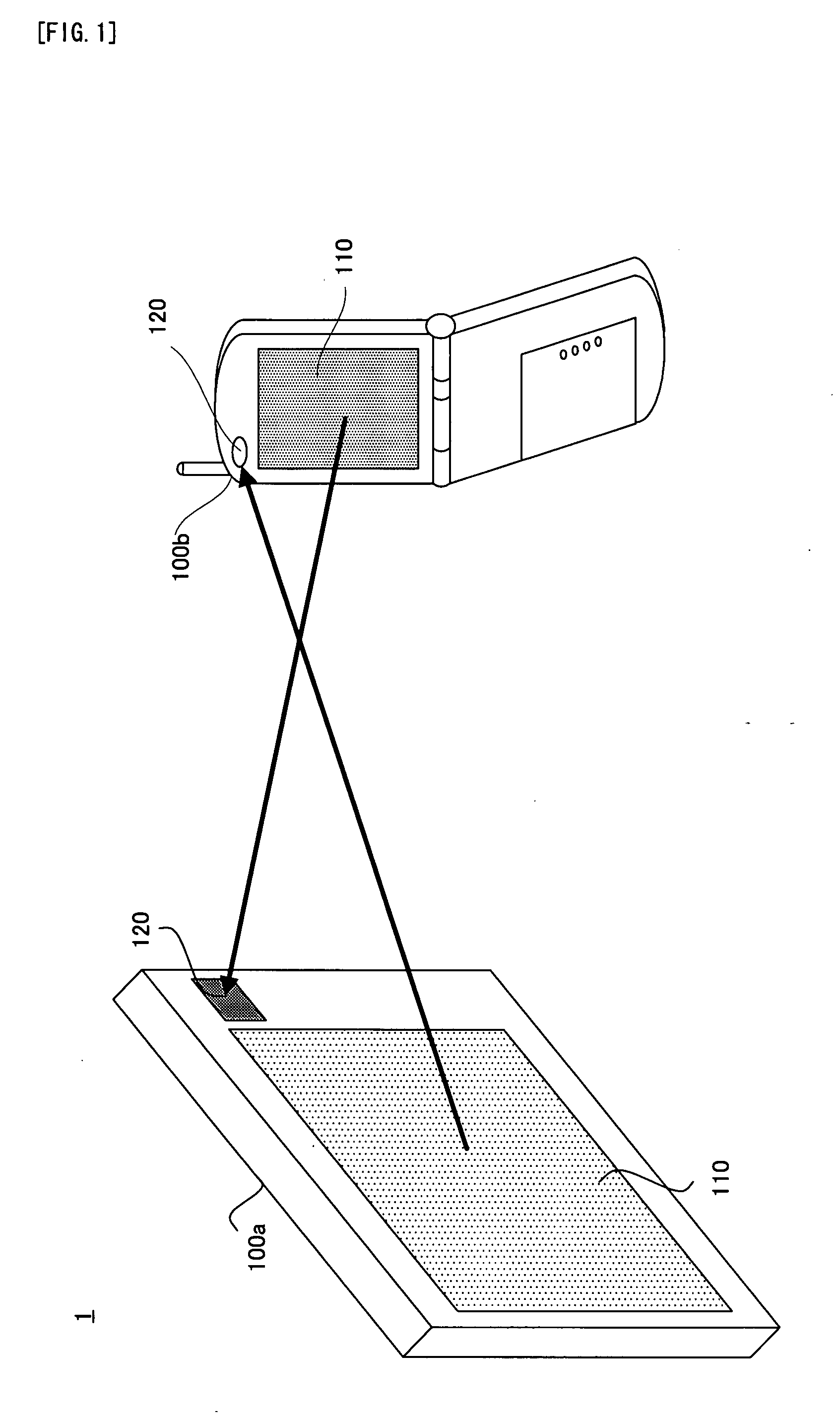
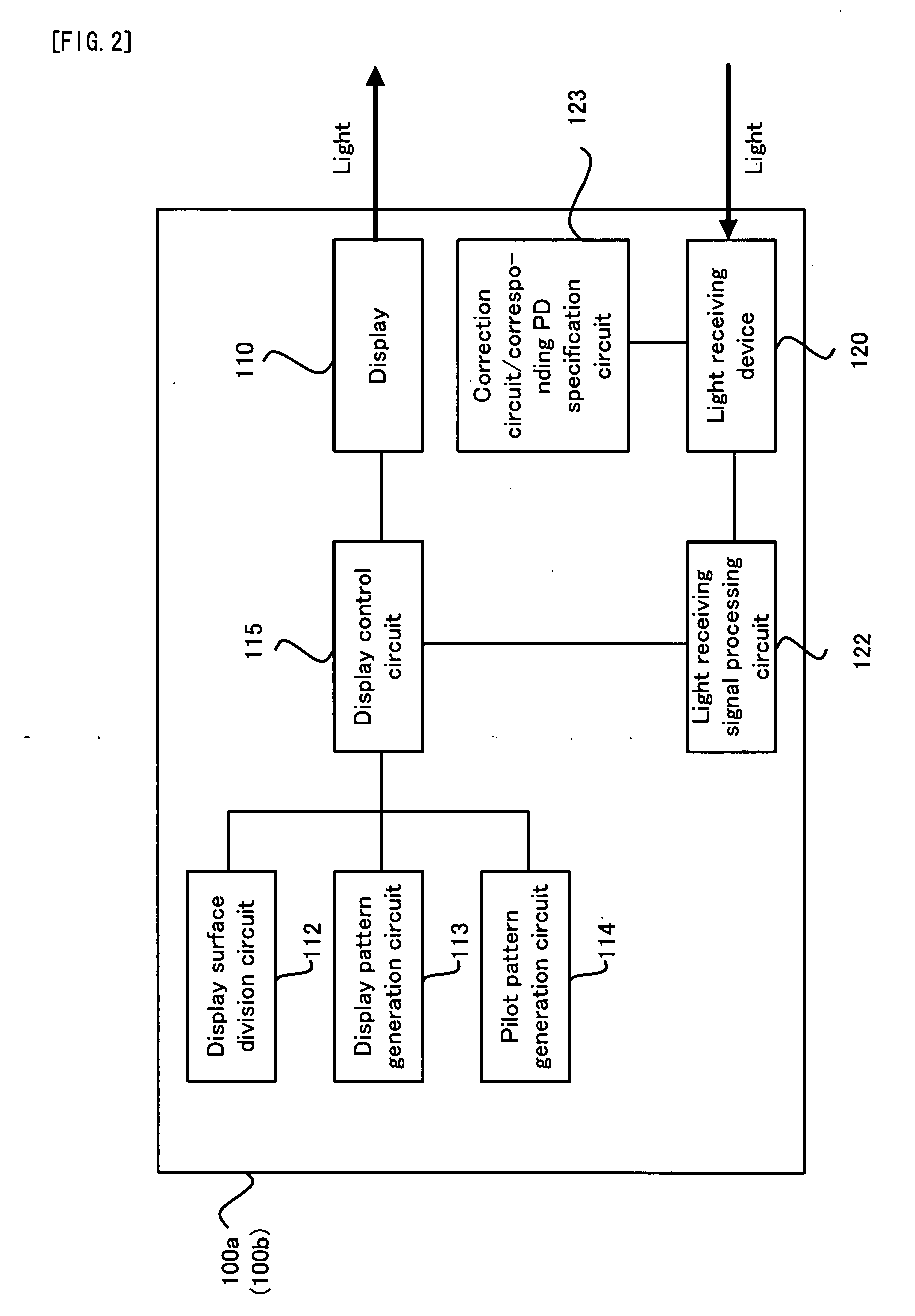
A communication system (1) is provided with: a first communication apparatus (100a); and a second communicating apparatus (100b), the first communicating apparatus is provided with: (i) a displaying device (110) which can perform high-speed modulation; (ii) a display dividing device (112) for dividing a display surface of the displaying device into a plurality of display blocks; and (iii) a controlling device (115) for controlling the displaying device to display a display pattern in each of the divided plurality of display blocks, the second communicating apparatus is provided with: (i) a light receiving device (120) for light-receiving the display pattern which is displayed on the displaying device; and (ii) an obtaining device (121) for obtaining the predetermined data on the basis of the light-received display pattern.
Owner:PIONEER CORP
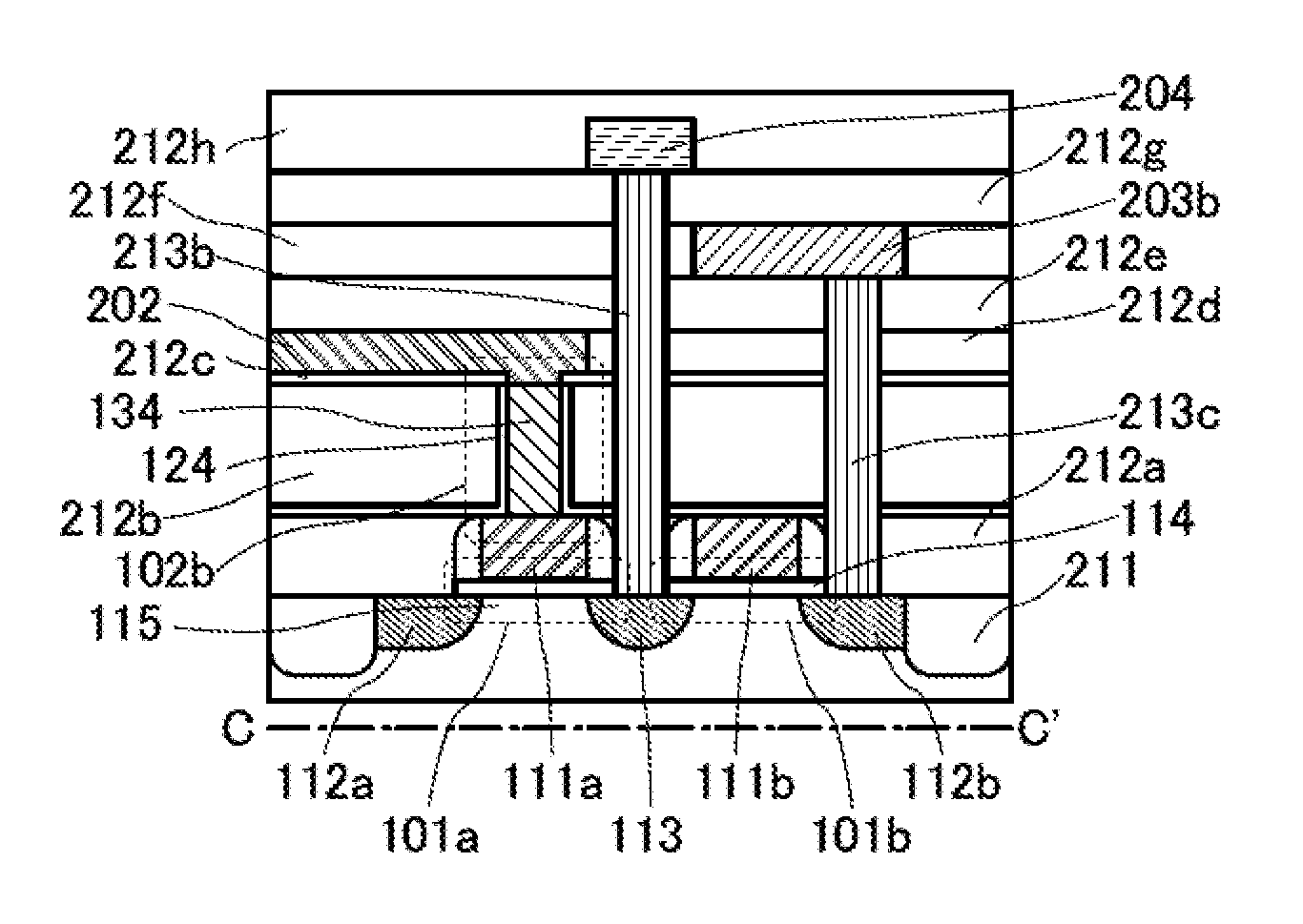
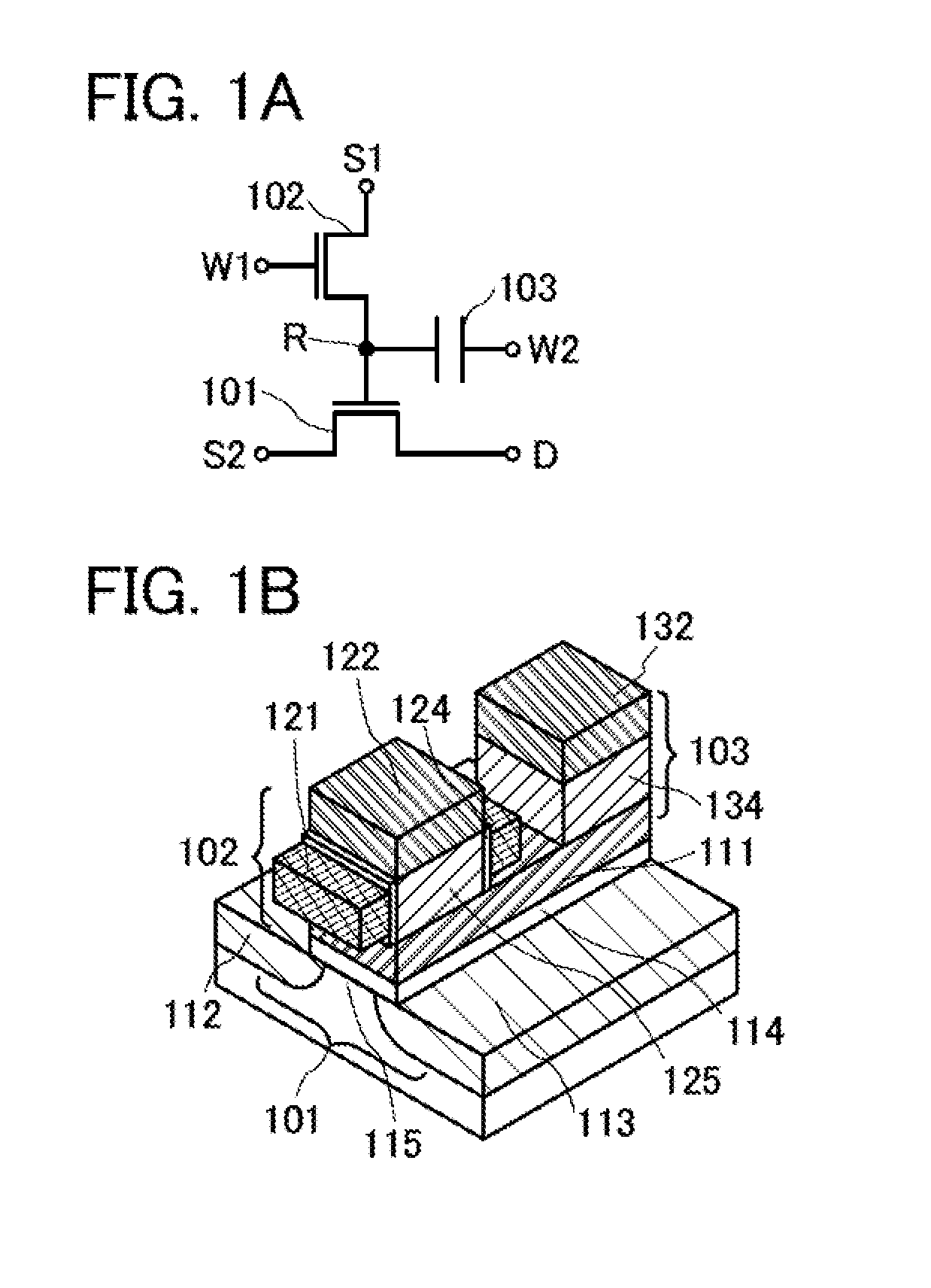
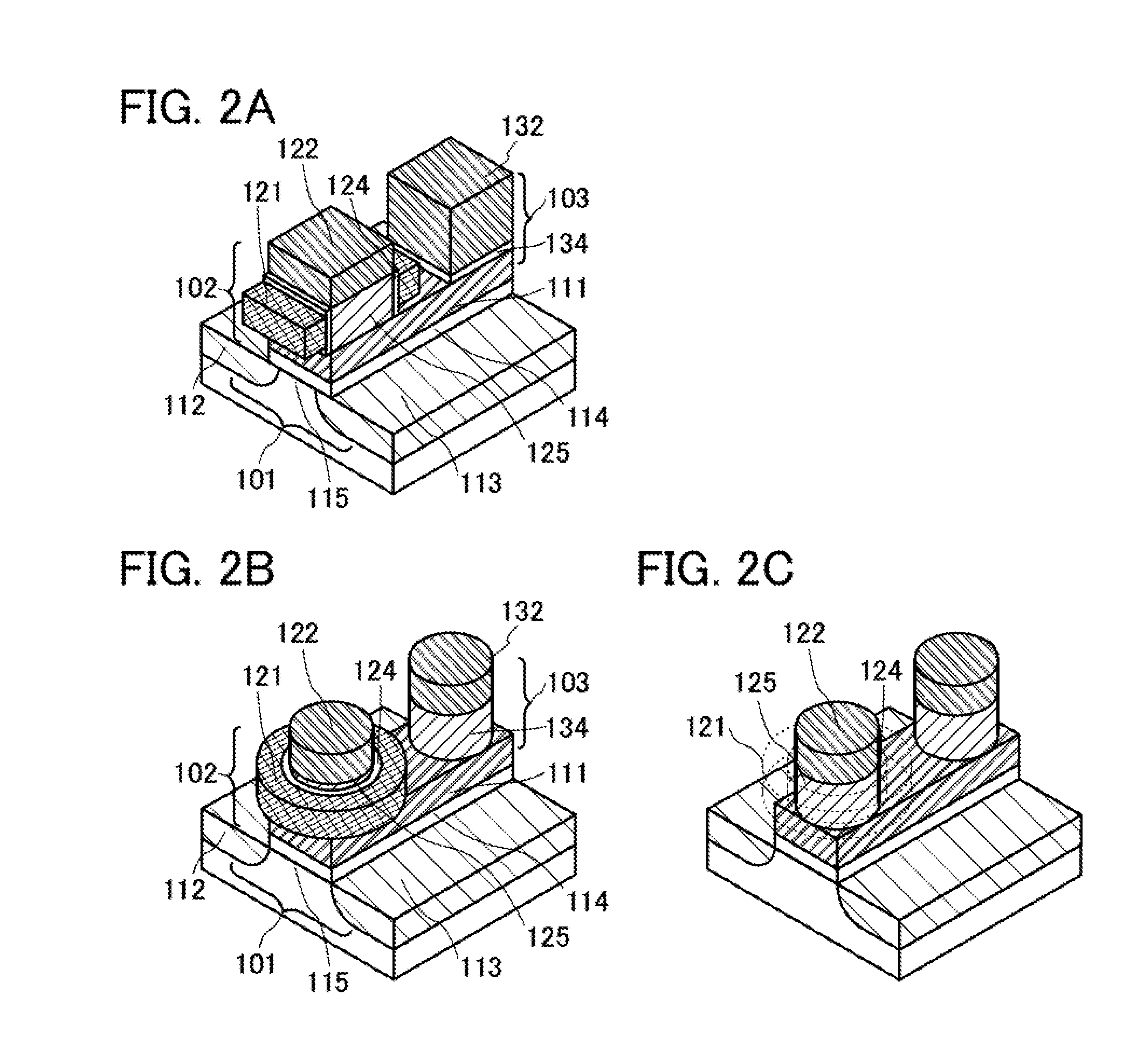
Semiconductor device
A semiconductor device is described, which includes a first transistor, a second transistor, and a capacitor. The second transistor and the capacitor are provided over the first transistor so as to overlap with a gate of the first transistor. A semiconductor layer of the second transistor and a dielectric layer of the capacitor are directly connected to the gate of the first transistor. The second transistor is a vertical transistor, where its channel direction is perpendicular to an upper surface of a semiconductor layer of the first transistor.
Owner:SEMICON ENERGY LAB CO LTD
Implantable medical device, medical system and method for data communication
ActiveUS9381365B2Little battery drain from the medical device's batteryIncrease the amount of dataHeart stimulatorsMedical deviceCommunication device
An implantable medical device including a data communication device that includes a device to alter and / or generate an oscillatory electric field imposed on body tissue surrounding the implantable medical device when the implantable medical device is in its implanted state. The device that alters an oscillatory electric field modulates an impedance of body tissue surrounding the implantable medical device when the implantable medical device is in its implanted state and within an oscillatory electric field. The device that alters an oscillatory electric field includes a device that generates an oscillatory electric field that is phase-synchronized with an oscillatory electric field imposed on body tissue surrounding the implantable medical device when the implantable medical device is in its implanted state.
Owner:BIOTRONIK SE & CO KG
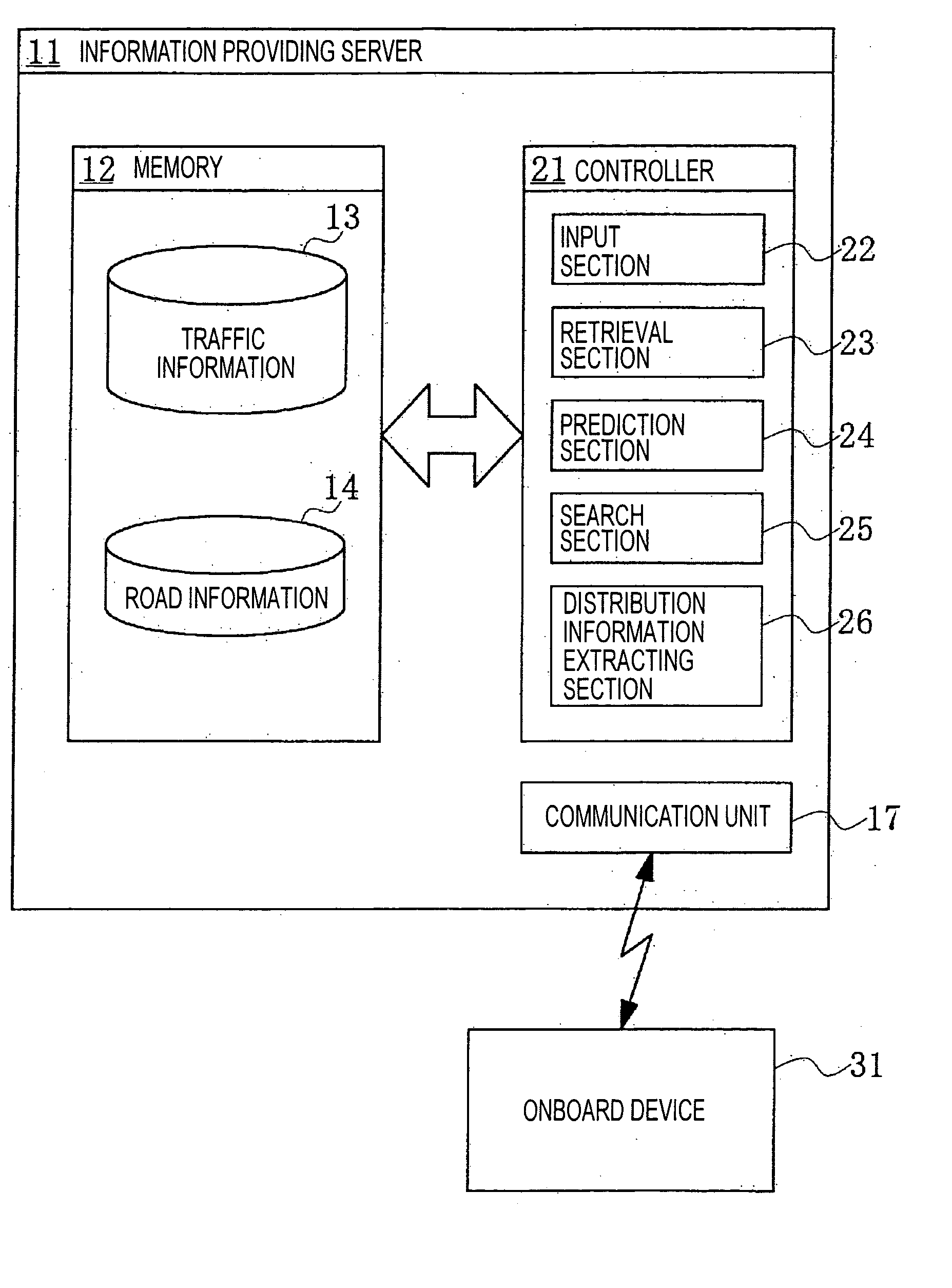
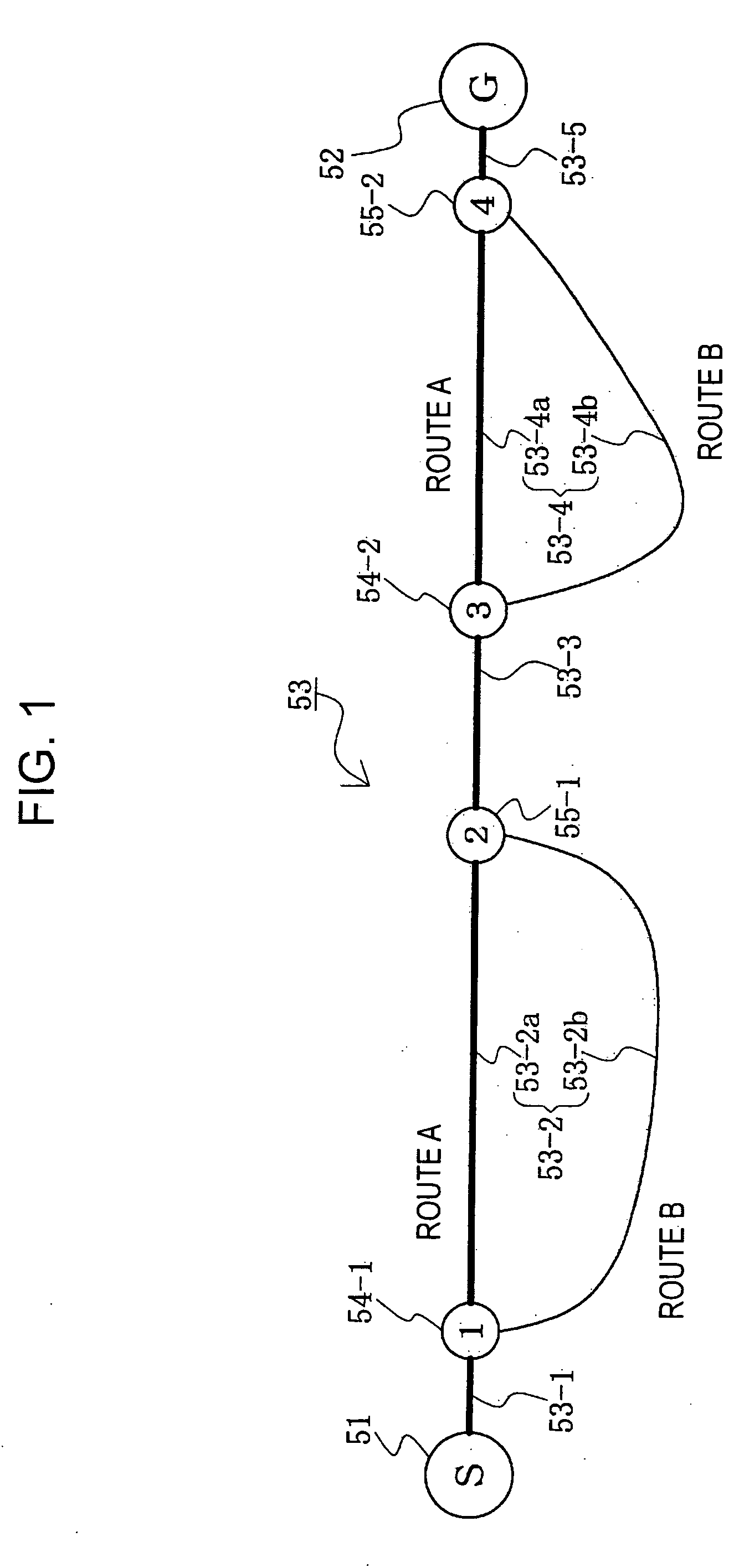
Navigation systems, methods, and programs
InactiveUS20050209772A1Effectively and efficiently distributes information usefulAvoid traffic jamsAnalogue computers for vehiclesInstruments for road network navigationRoute searchNavigation system
Navigation systems, methods, and programs store traffic information and crated prediction traffic information based on the stored traffic information. The systems, methods, and programs search a plurality of routes to a destination, each route including at least one link and calculate a predicted passage time of each link in each route. The systems, methods, and programs obtain, for each link, prediction traffic information at the predicted passage time, based on the created prediction traffic information and extract the obtained prediction traffic information pertinent to route-search-as information to be distributed, according to a predetermined order of priority.
Owner:AISIN AW CO LTD
Real-time expression recognition method based on multichannel parallel convolutional neural network (MPCNN)
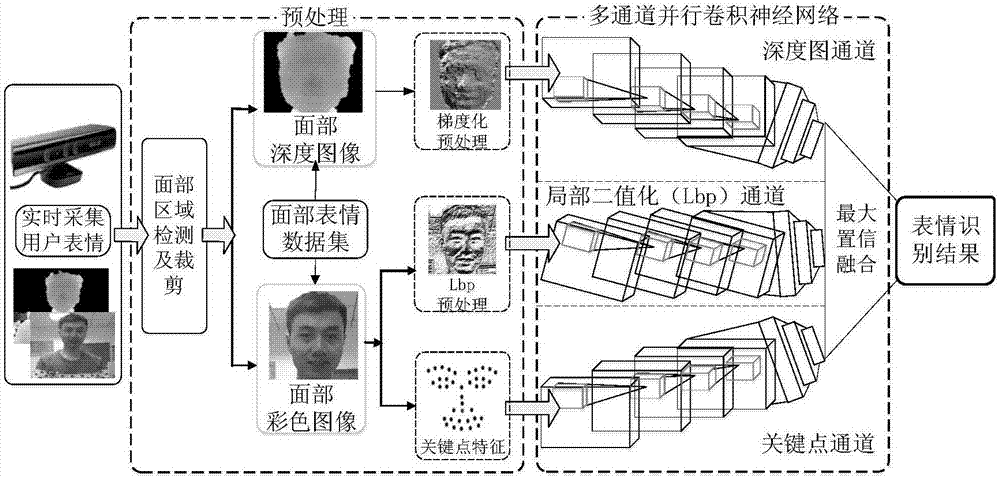
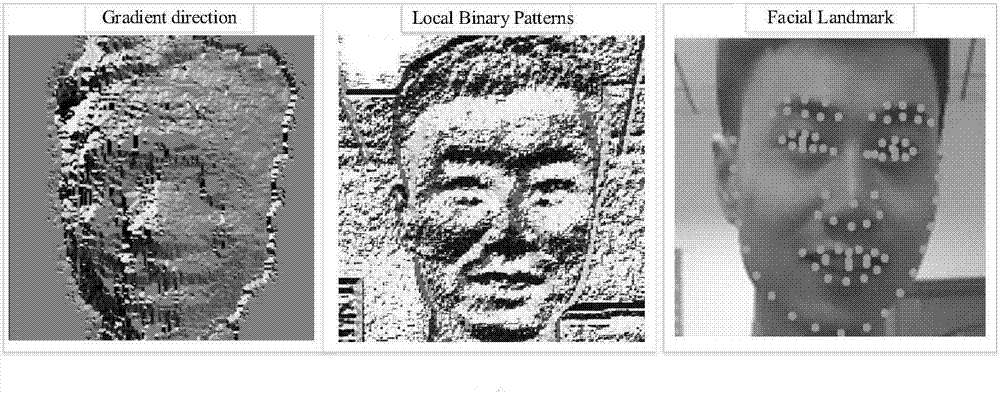
ActiveCN107491726AExpand data volumeImprove accuracyAcquiring/recognising facial featuresClassification resultFacial expression
The invention discloses a real-time expression recognition method based on a multichannel parallel convolutional neural network (MPCNN). The method comprises the steps of: extracting expression data, which contains RGB and Depth images, from a facial-expression data set; carrying out local binarization preprocessing (LBP) and facial-key-point extraction preprocessing on the color images, carrying out gradient preprocessing on the depth images, dividing the preprocessed images into two parts of a training set and a test set, and building the multichannel parallel convolutional neural network; sending the preprocessed images in the training set to the network for training to obtain depth channel, lbp channel and key-point channel recognition models which learn facial-expression outlines, stereoscopic distribution and key-point features; and adopting maximum confidence to fuse classification results of the three recognition models to obtain a final expression recognition model, and building a real-time expression recognition system. The method enhances the robustness of the recognition network, and effectively improves the performance of the real-time expression recognition system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Distributed secure data storage and transmission of streaming media content
InactiveUS20170048021A1Increase safetyHigh degree of safetyError preventionCode conversionDistributed securityMedia content
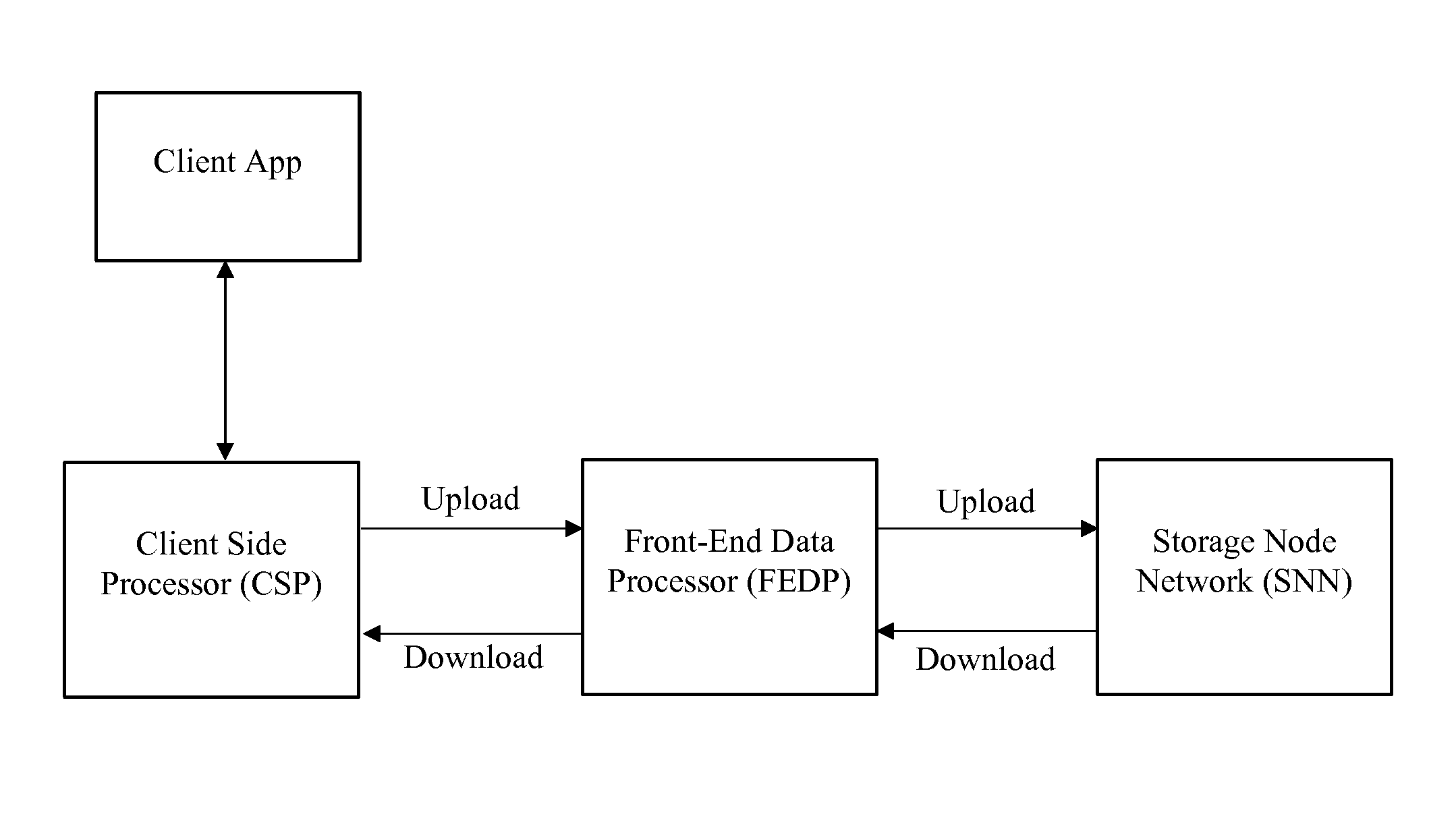
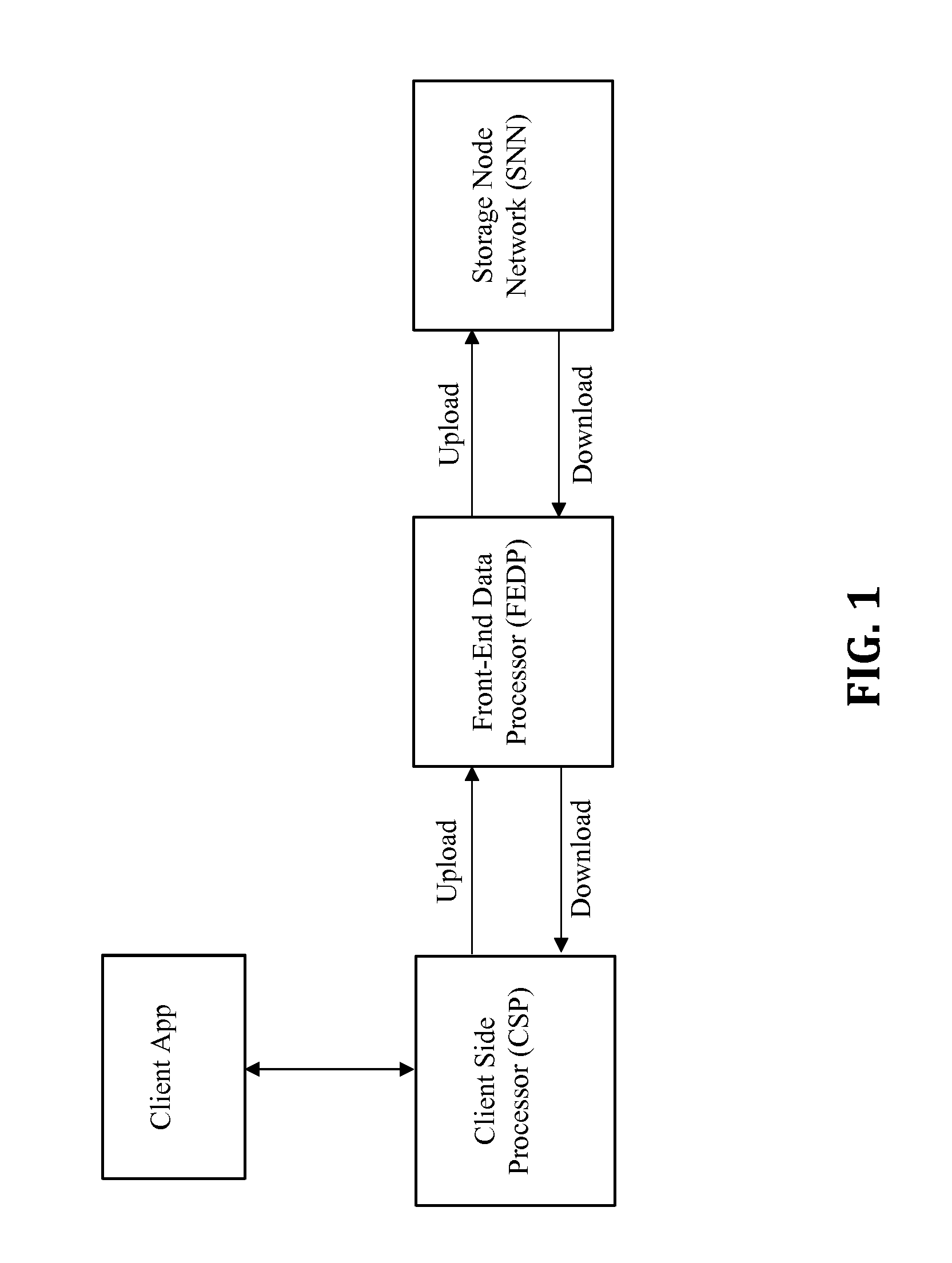
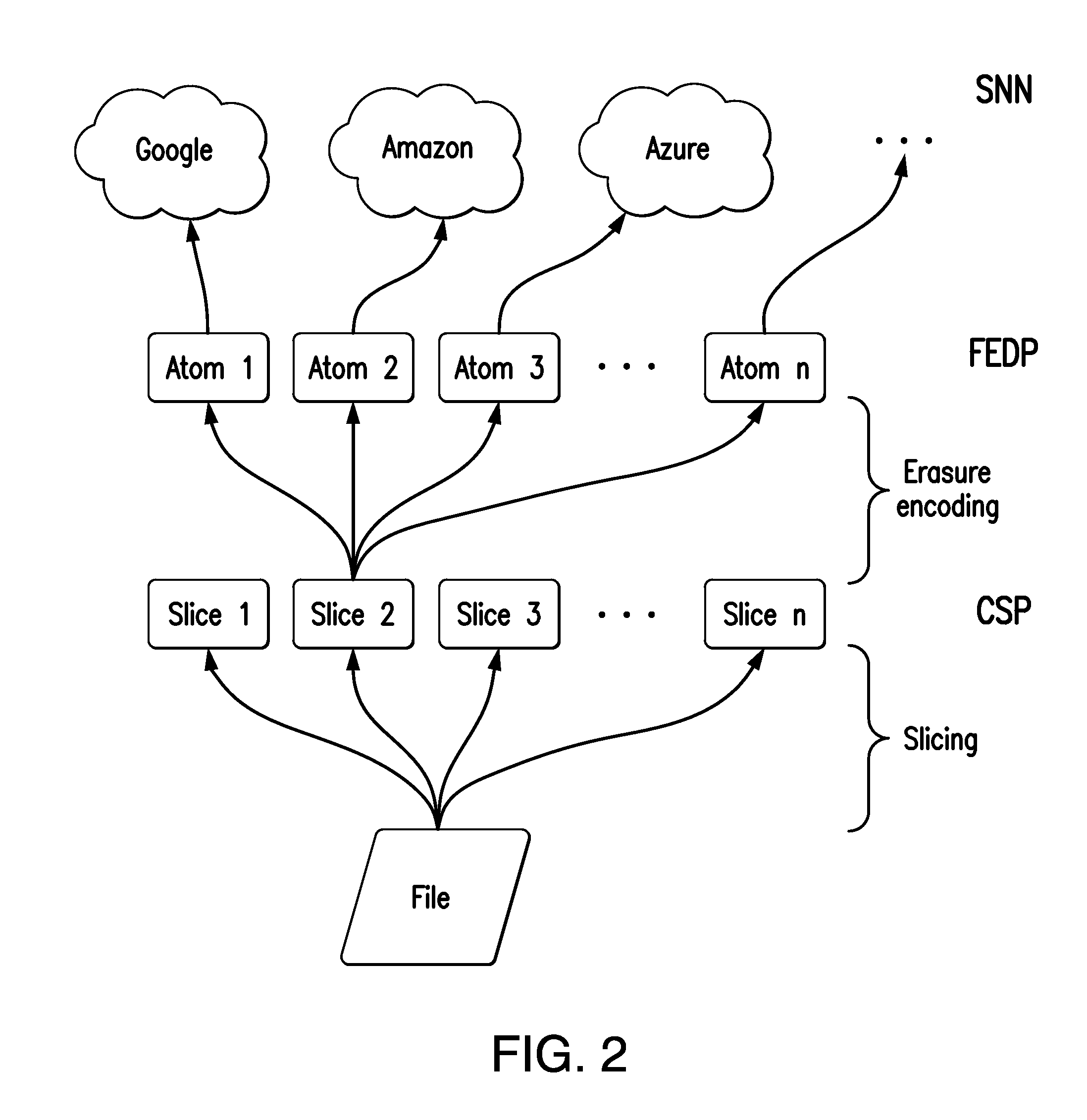
Disclosed is a method for the distributed storage and distribution of data. Original data is divided into fragments and erasure encoding is performed on it. The divided fragments are dispersedly stored on a plurality of storage mediums, preferably that are geographically remote from one another. When access to the data is requested, the fragments are transmitted through a network and reconstructed into the original data. In certain embodiments, the original data is media content which is steamed to a user from the distributed storage.
Owner:DATOMIA RES LABS OU
System and method for managing data from a flow analyzer
InactiveUS7274316B2Increase the number ofIncrease the amount of dataAnalogue/digital conversionElectric signal transmission systemsParallel computingData acquisition
Owner:LUMINEX
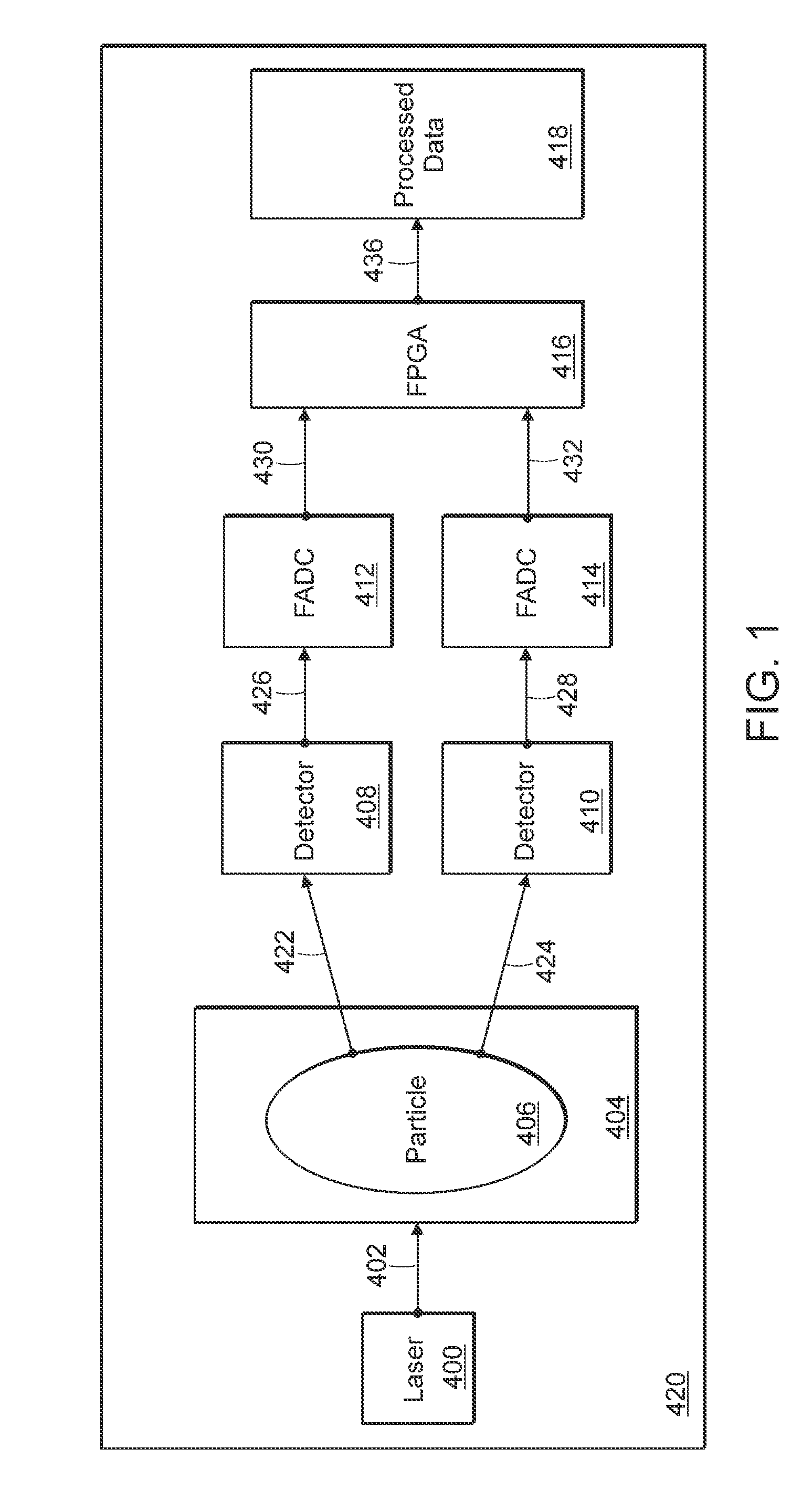
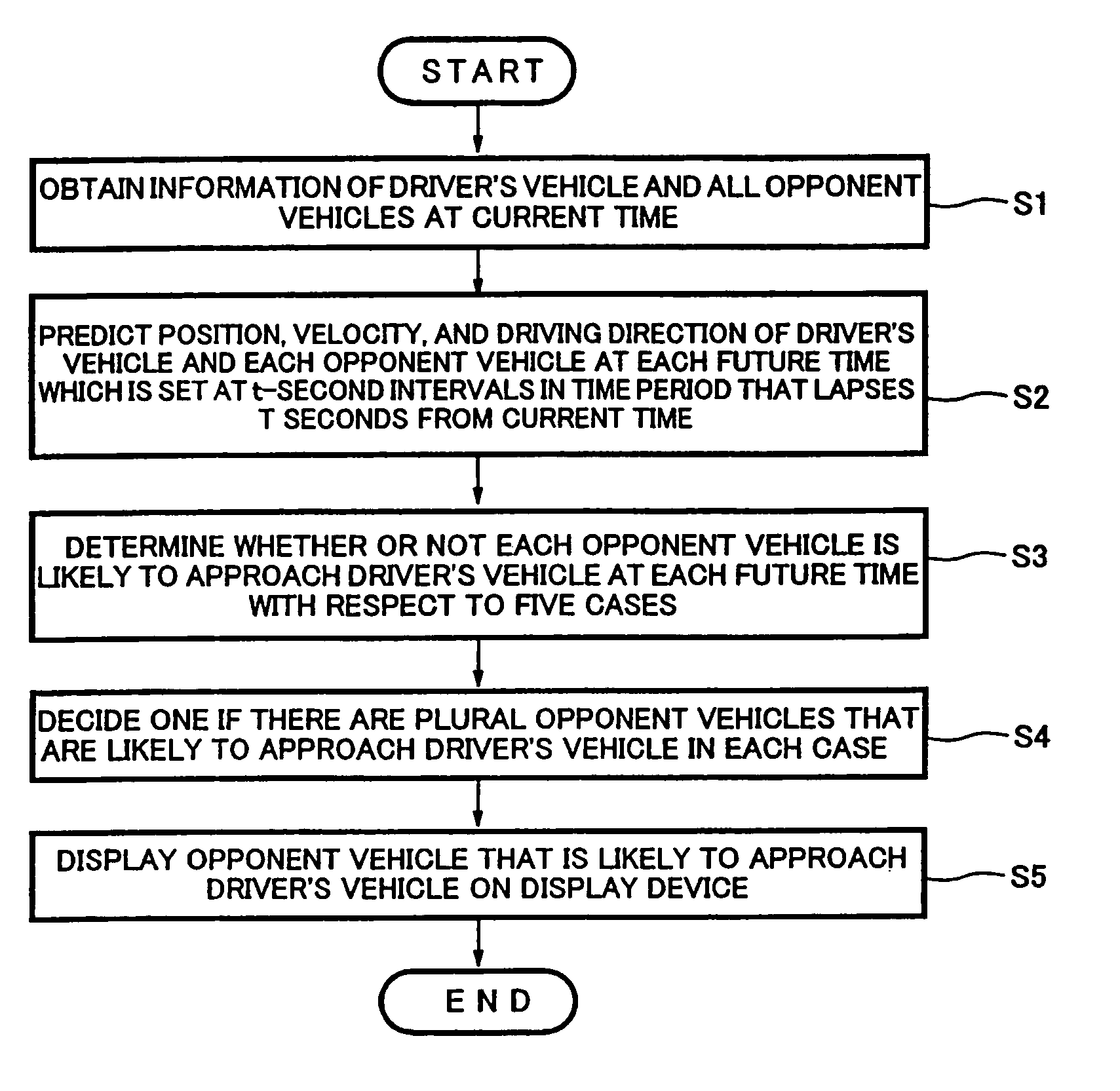
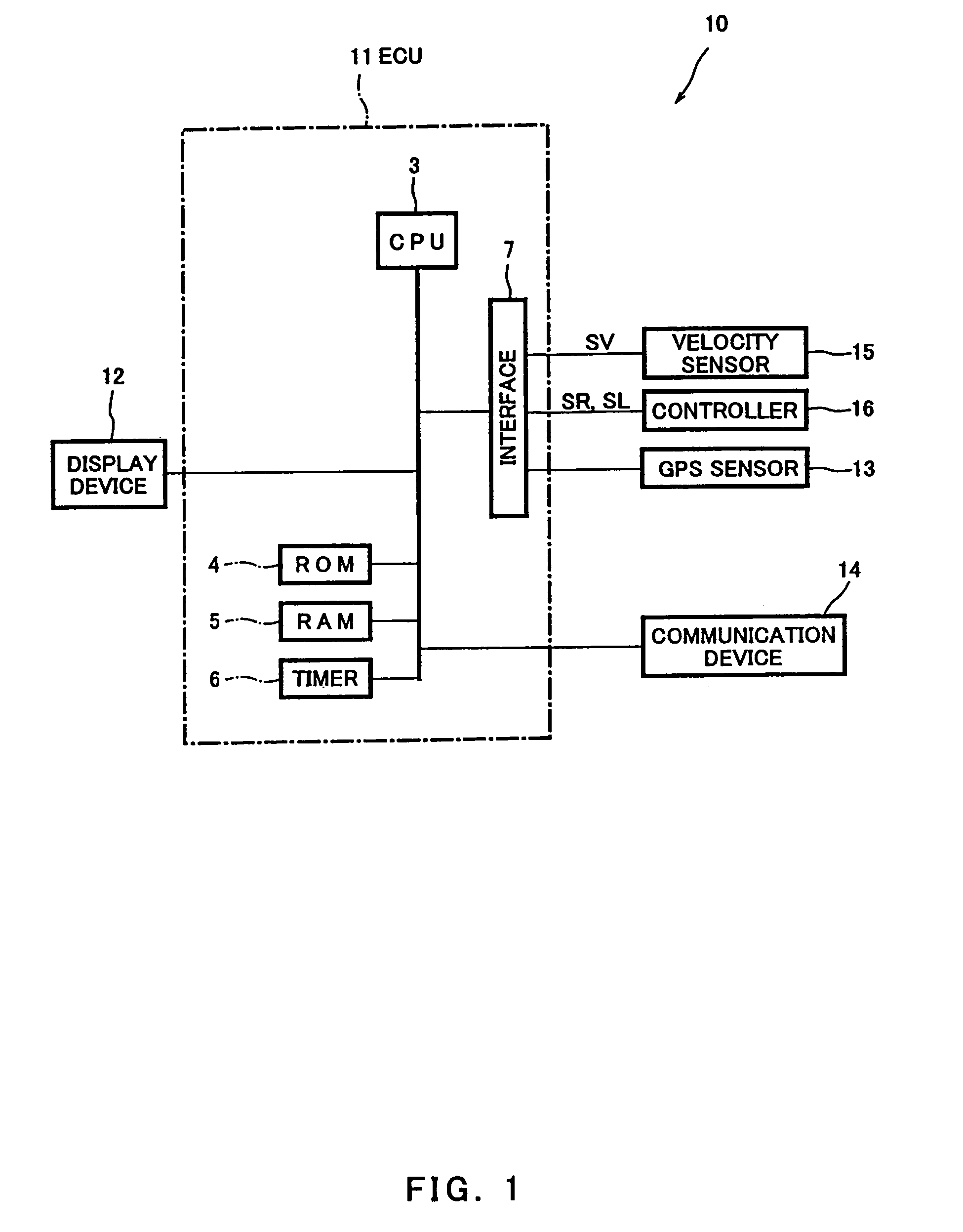
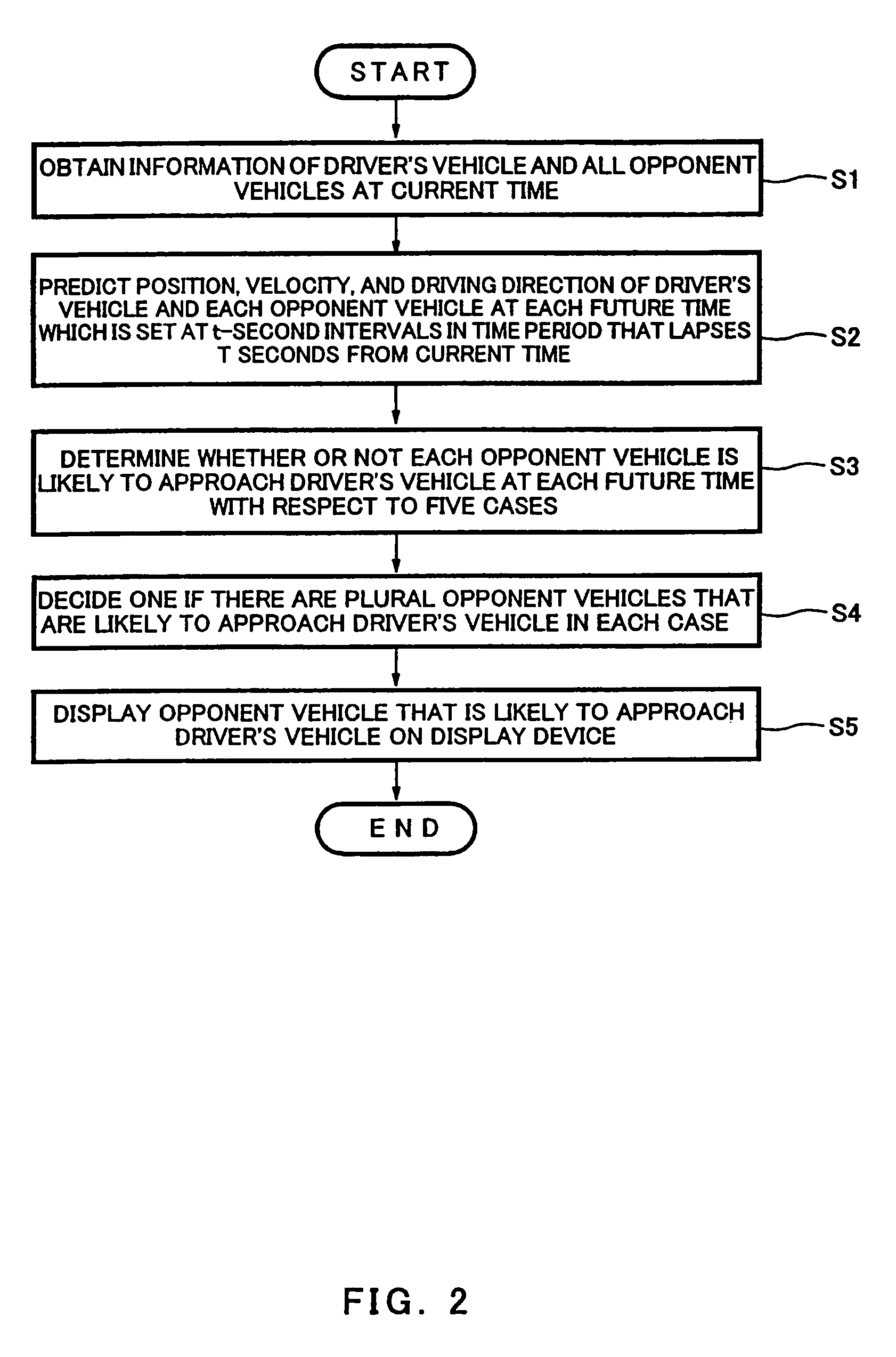
Information provision apparatus and driving assistance system using the same
InactiveUS7865310B2Increase the amount of dataEasy to identifyDigital data processing detailsAnti-collision systemsDriver/operatorEngineering
An information provision apparatus mounted in a driver's vehicle, including a vehicle approach determiner configured to execute a vehicle approach determination process to determine whether or not an opponent vehicle is likely to approach the driver's vehicle at a future time, based on driving information including information as to whether a blinker of the driver's vehicle is in an on-state or in an off-state at a current time, and driving information including information as to whether a blinker of the opponent vehicle is in an on-state or in an off-state, and a notification device configured to inform a driver driving the driver's vehicle of an opponent vehicle that is likely to approach the driver's vehicle.
Owner:KAWASAKI HEAVY IND LTD
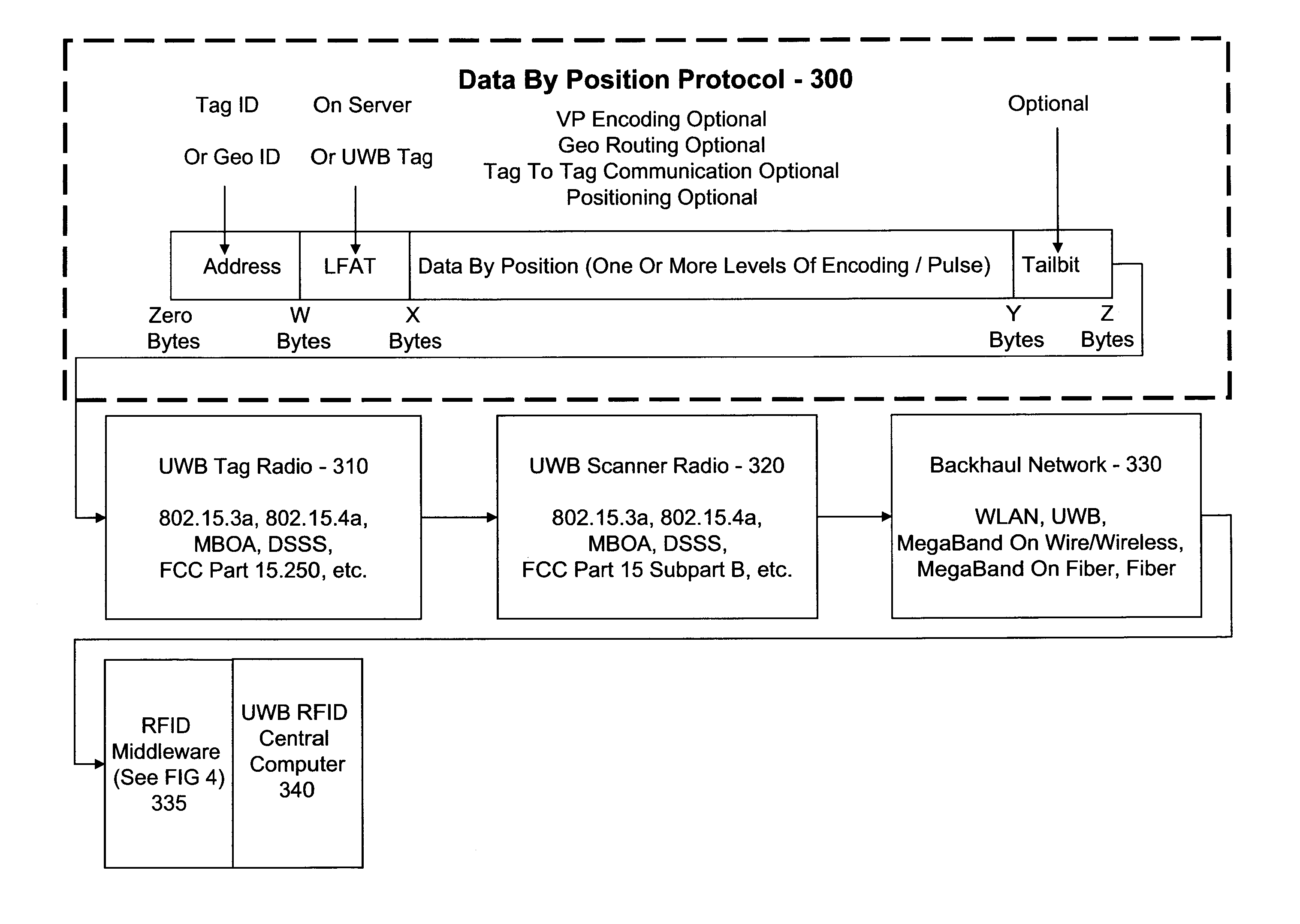
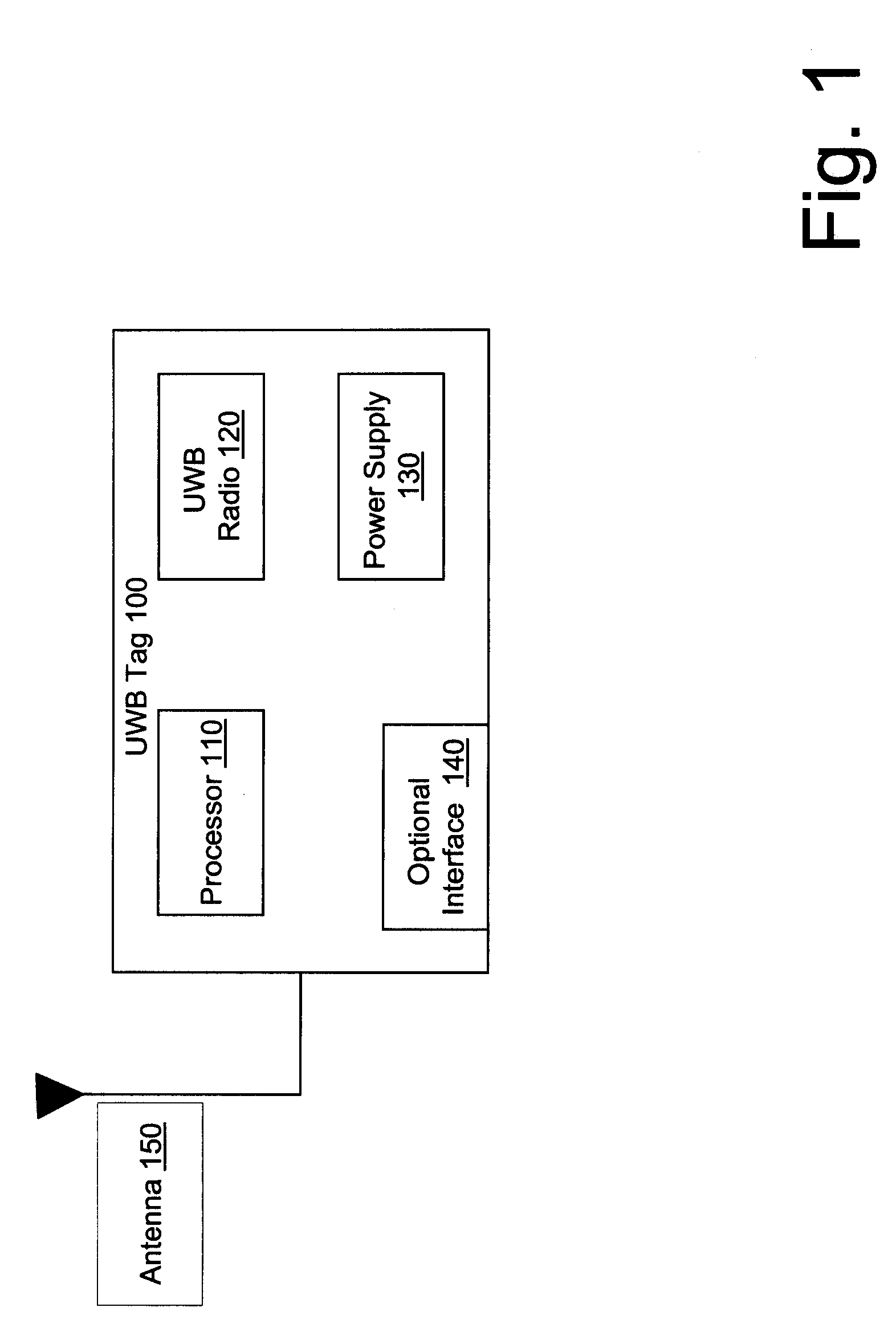
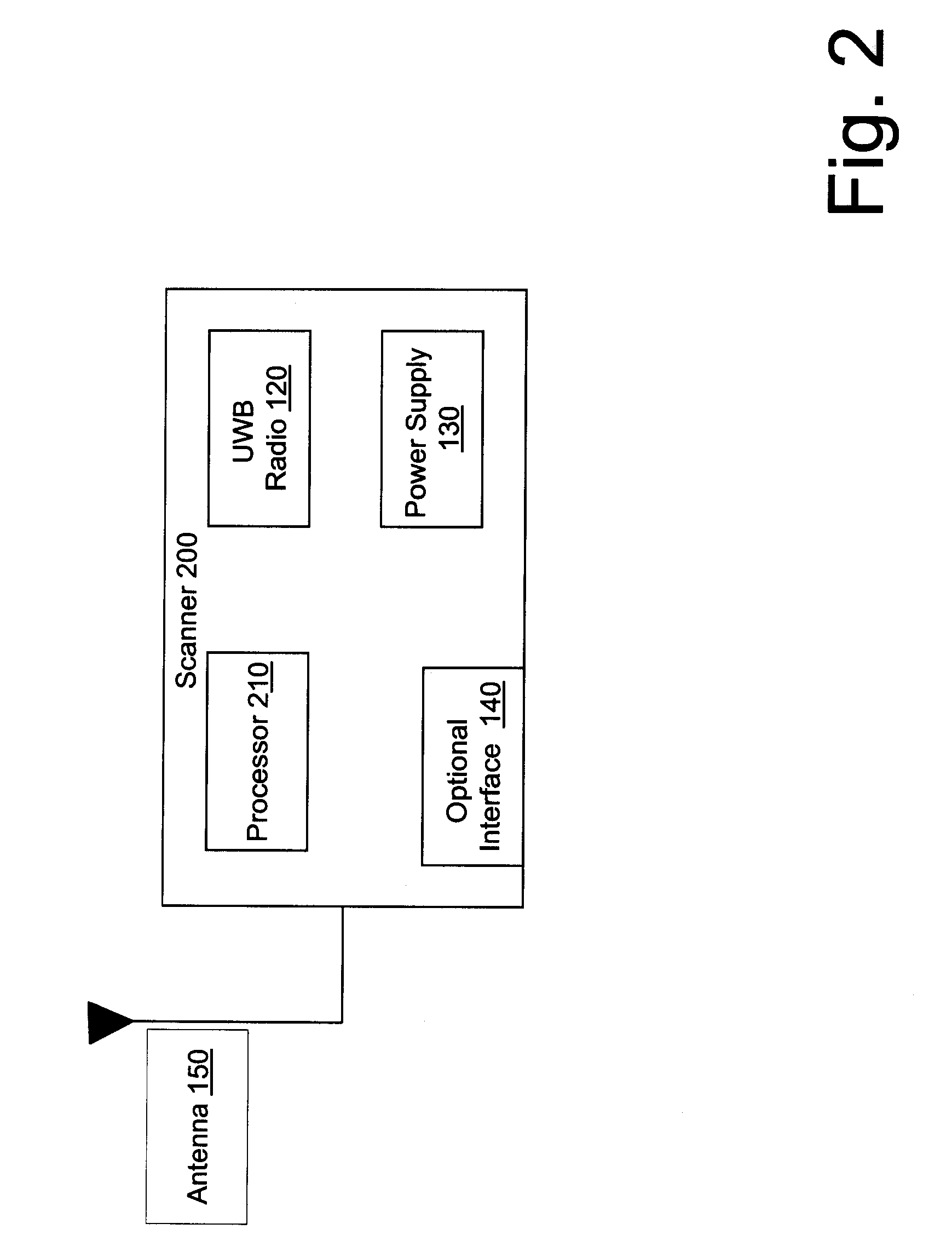
Ultra wideband radio frequency identification system, method, and apparatus
InactiveUS20070205867A1Electronics SimplifiedLow costSensing record carriersSubscribers indirect connectionComputer hardwareUltra-wideband
A method associated with a UWB RFID system provides for receiving a data transmission transmitted using UWB and accessing data within the data transmission using a communications protocol. An initial portion of the data transmission defines a structure of the data transmission such that subsequent data in the data transmission is directly accessible without additional decoding.
Owner:LIGHTWAVES SYST
Information processing device, information processing system, and program
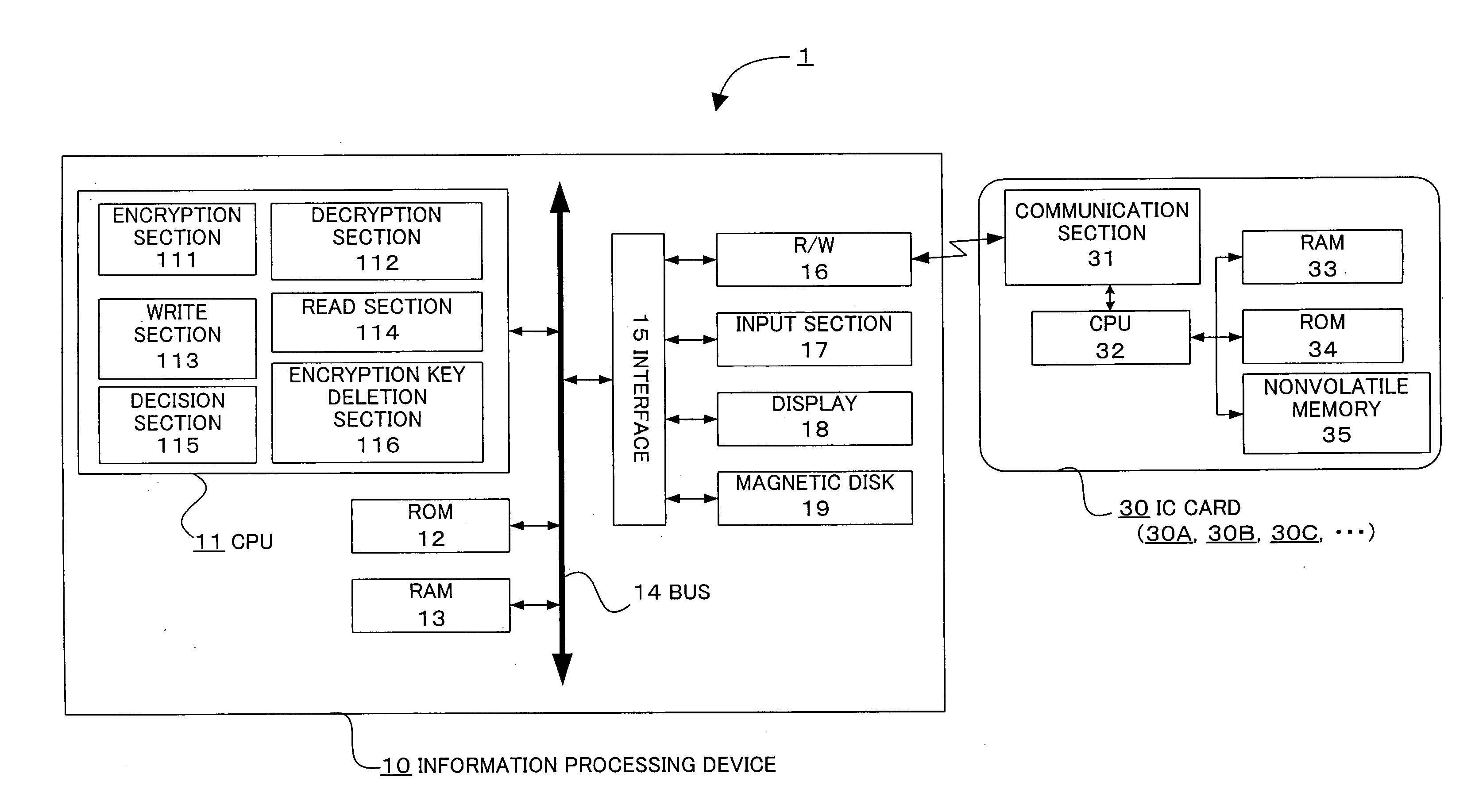
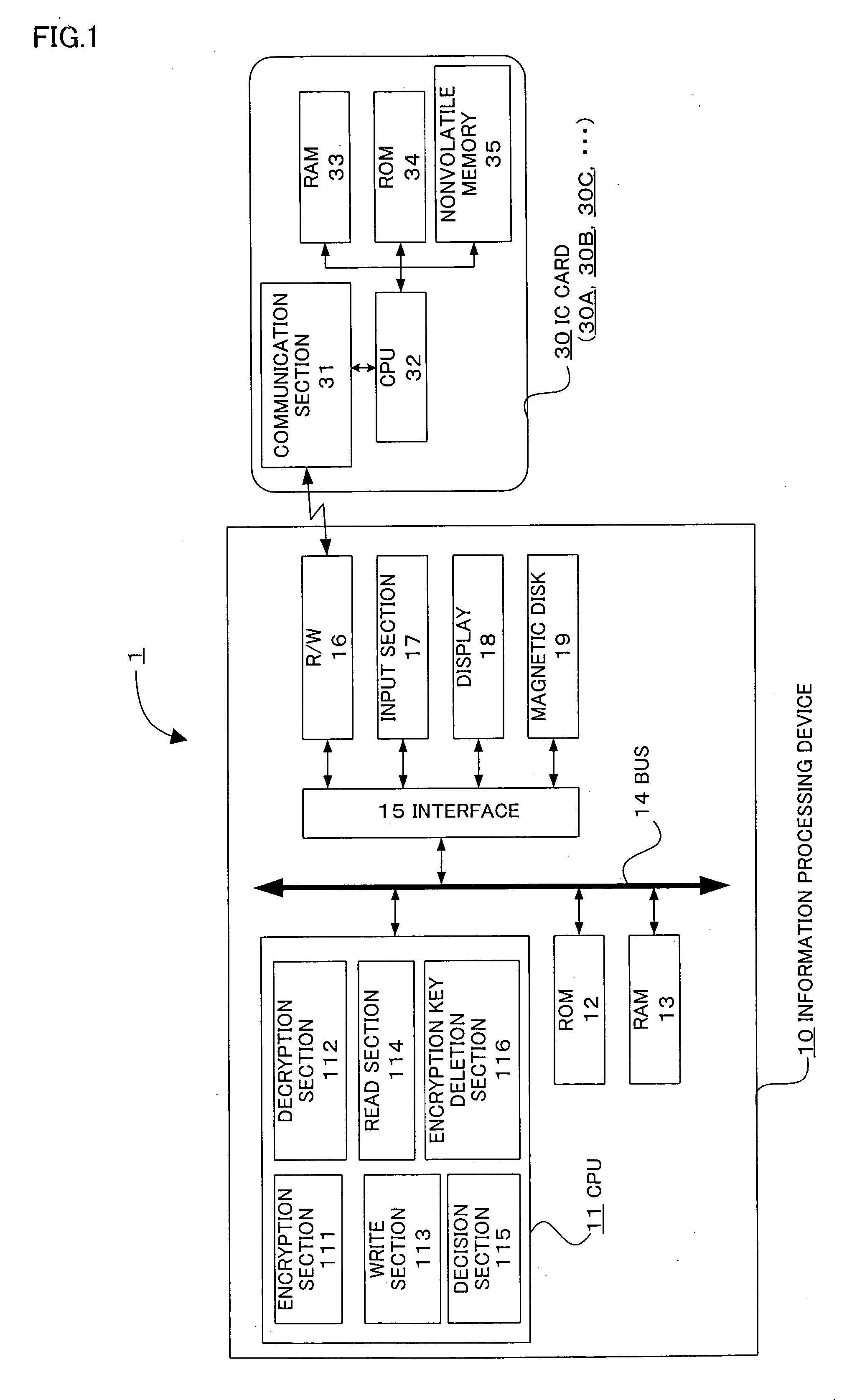
InactiveUS20060018484A1Eliminate the problemImprove securityKey distribution for secure communicationUnauthorized memory use protectionInformation processingPassword
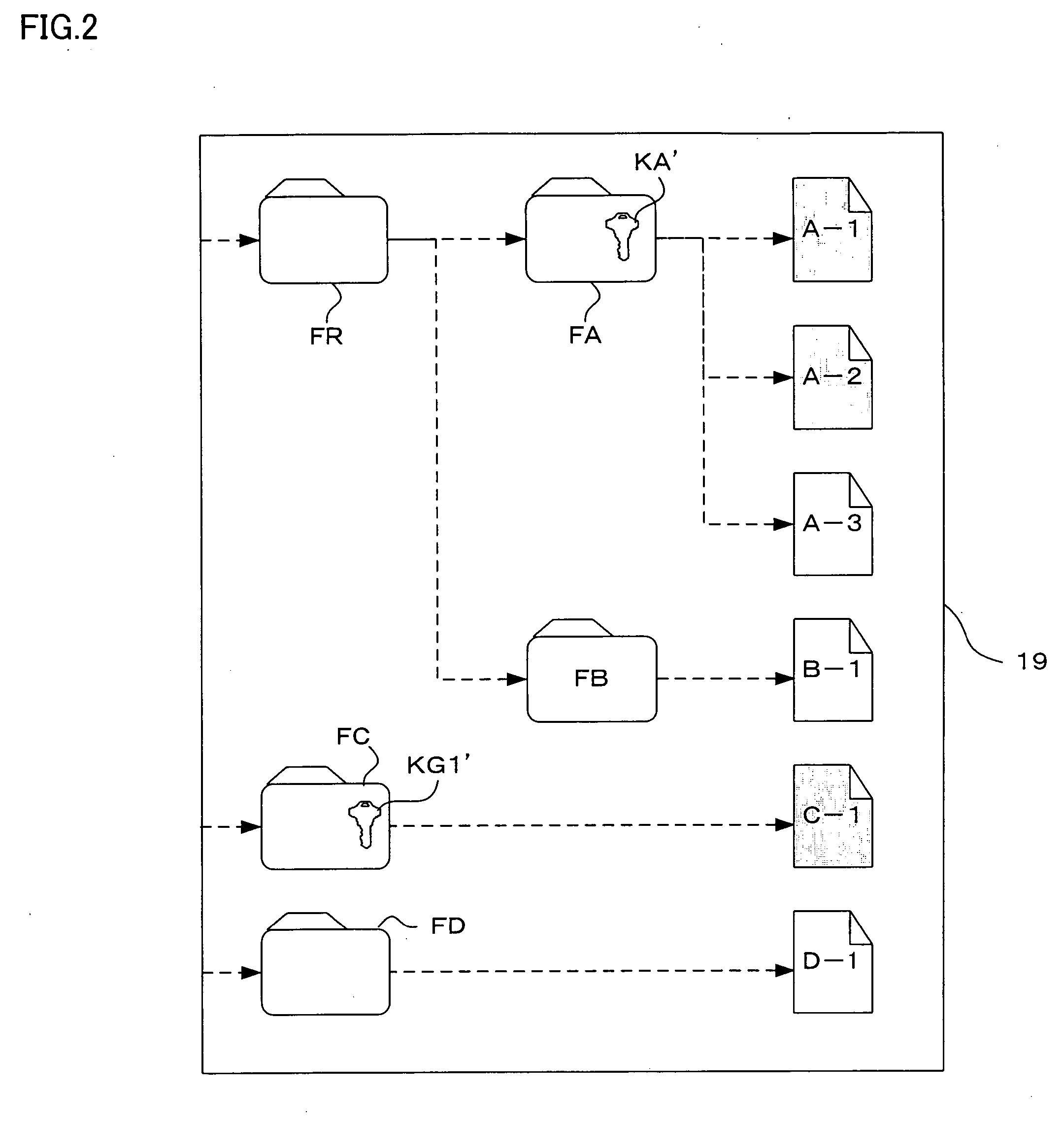
The present invention provides an information processing device, an information processing system, and a program capable of improving security and convenience. An information processing system (1) includes an IC card (30) which stores an encryption key and a registered password and allows the encryption key to be read when the IC card (30) has authenticated the user as an authorized user based on the registered password, and an information processing device (10) which stores folder information in which the folder name, path, and hash value of the encryption key are associated, when a request to save data in the folder has been issued from the user, decides whether or not an encryption key corresponding to the folder is included in the encryption key read from the IC card (30) based on the folder information, encrypts the request target data using the corresponding encryption key when the information processing device (10) has decided “YES”, and stores the encrypted data.
Owner:DAI NIPPON PRINTING CO LTD
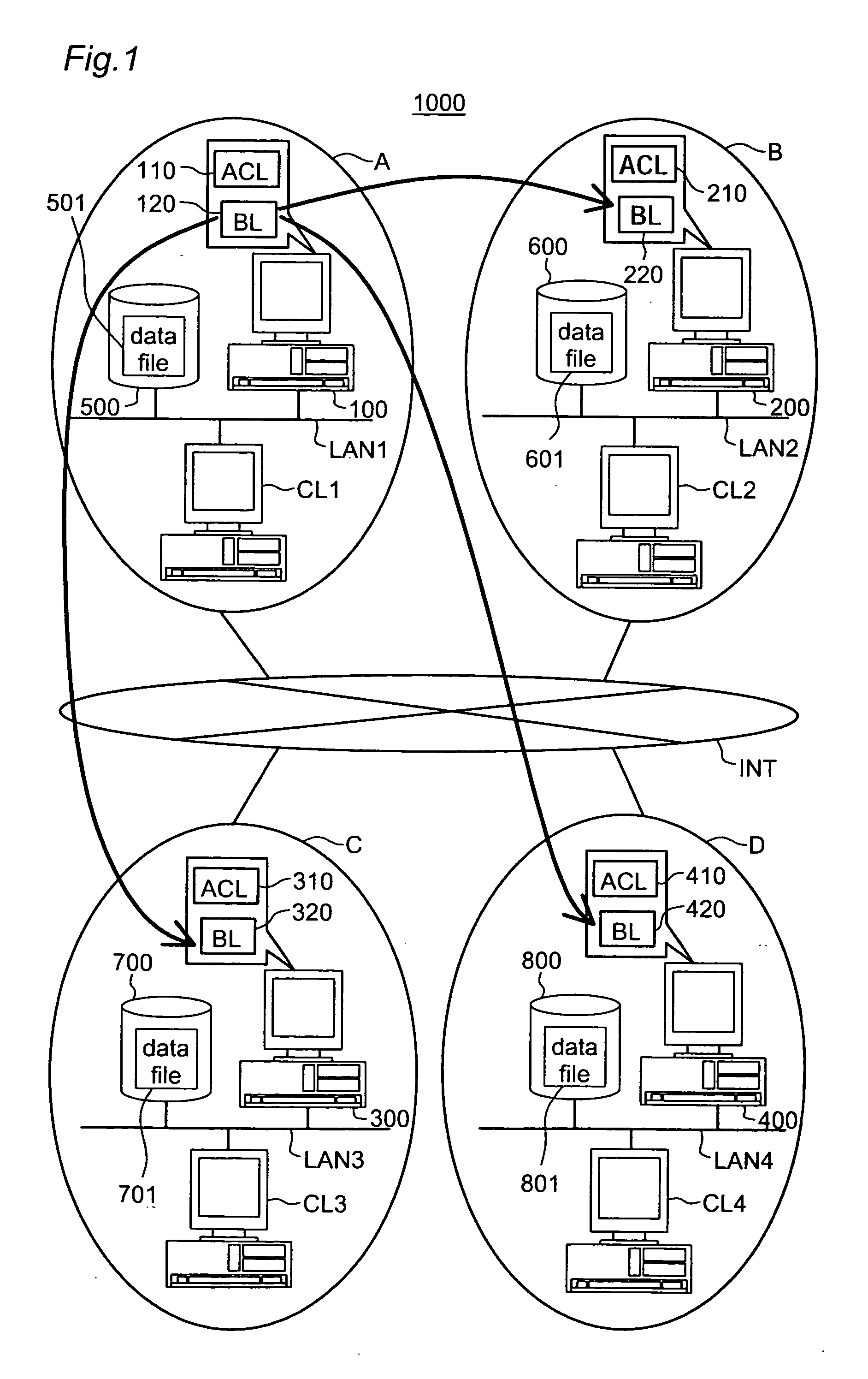
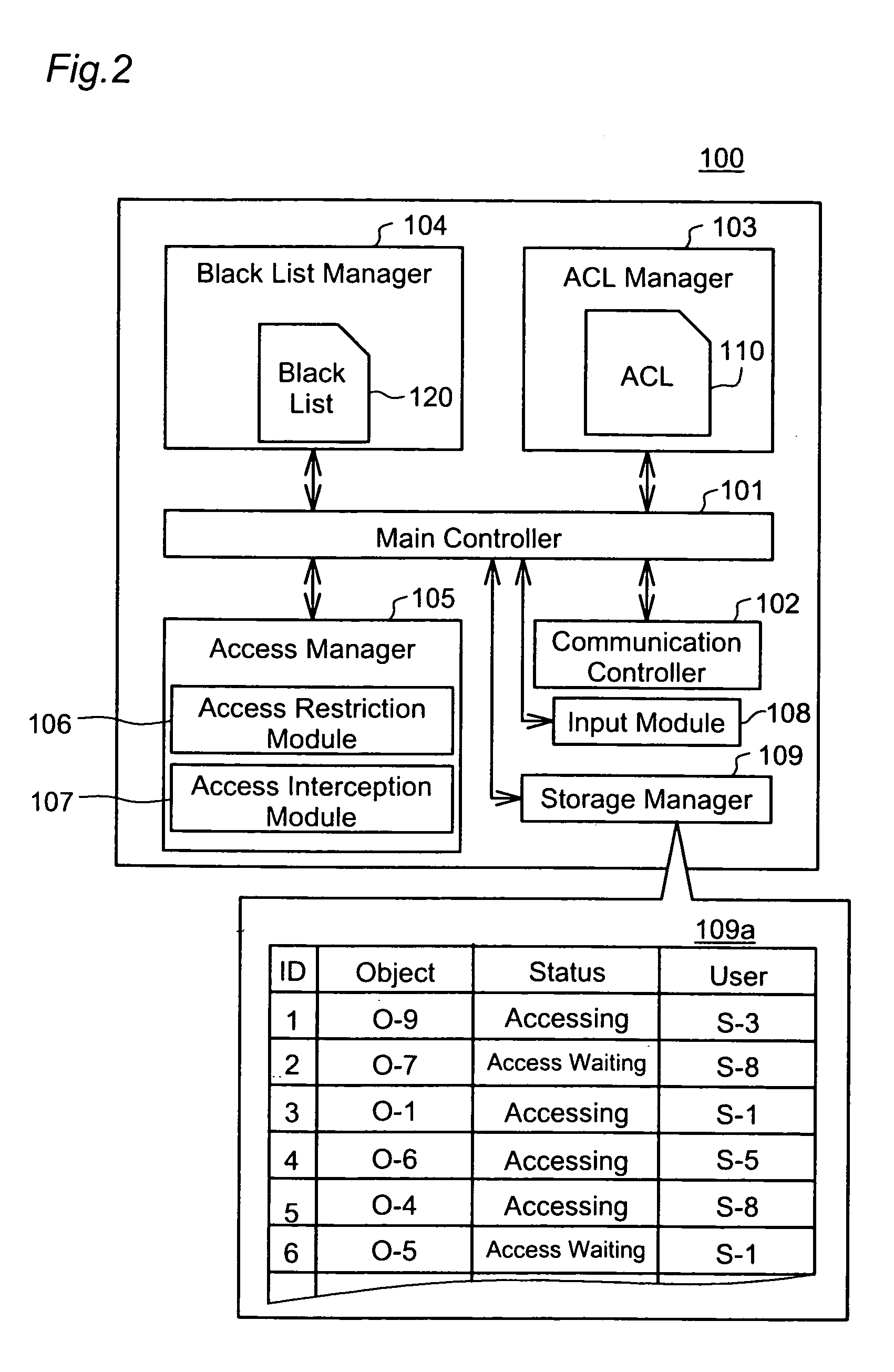
Emergency access interception according to black list
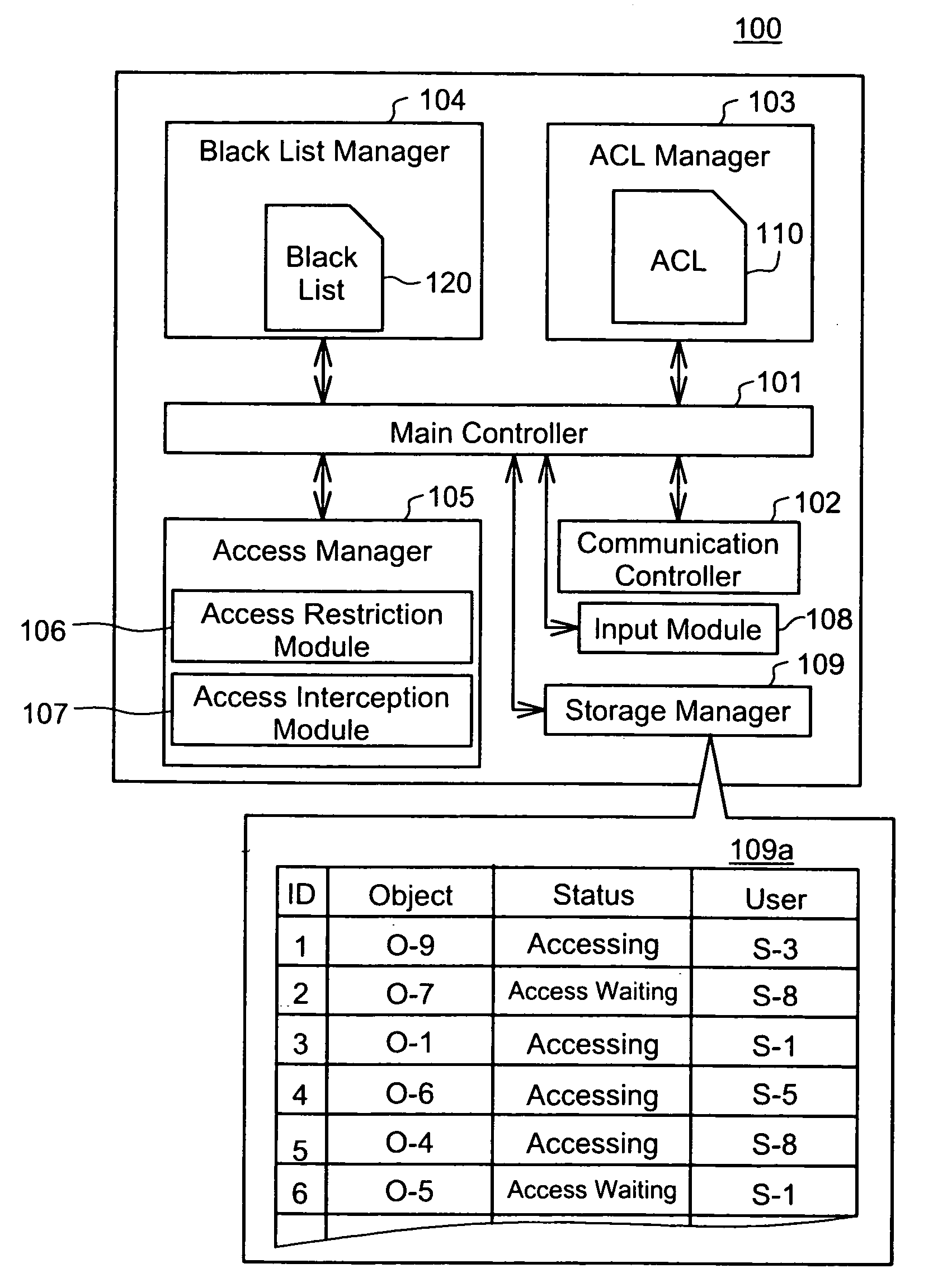
InactiveUS20050108257A1Increase the amount of dataKeep for a long timeDigital data processing detailsUnauthorized memory use protectionVLAN access control listBlack list
This invention addresses to execute an emergency access interception in a widely distributed environment. An access controller 100 manages an access control list (ACL) 110 recording access right to each object, and a black list (BL) 120 recording user information corresponding to the emergency access interception. The access controller 100 receives a request for authentication to access right and judges whether or not the access right is proper, first according to the BL 120 then ACL110. In case where the user information corresponding to the request is recorded in the BL 120, the access controller 100 sends out the user information to other access controllers and instructs them to register it in the black list. This invention effectively actualizes the emergency access interception under the widely distributed environment in case where the interception is required for any user.
Owner:GOOGLE LLC
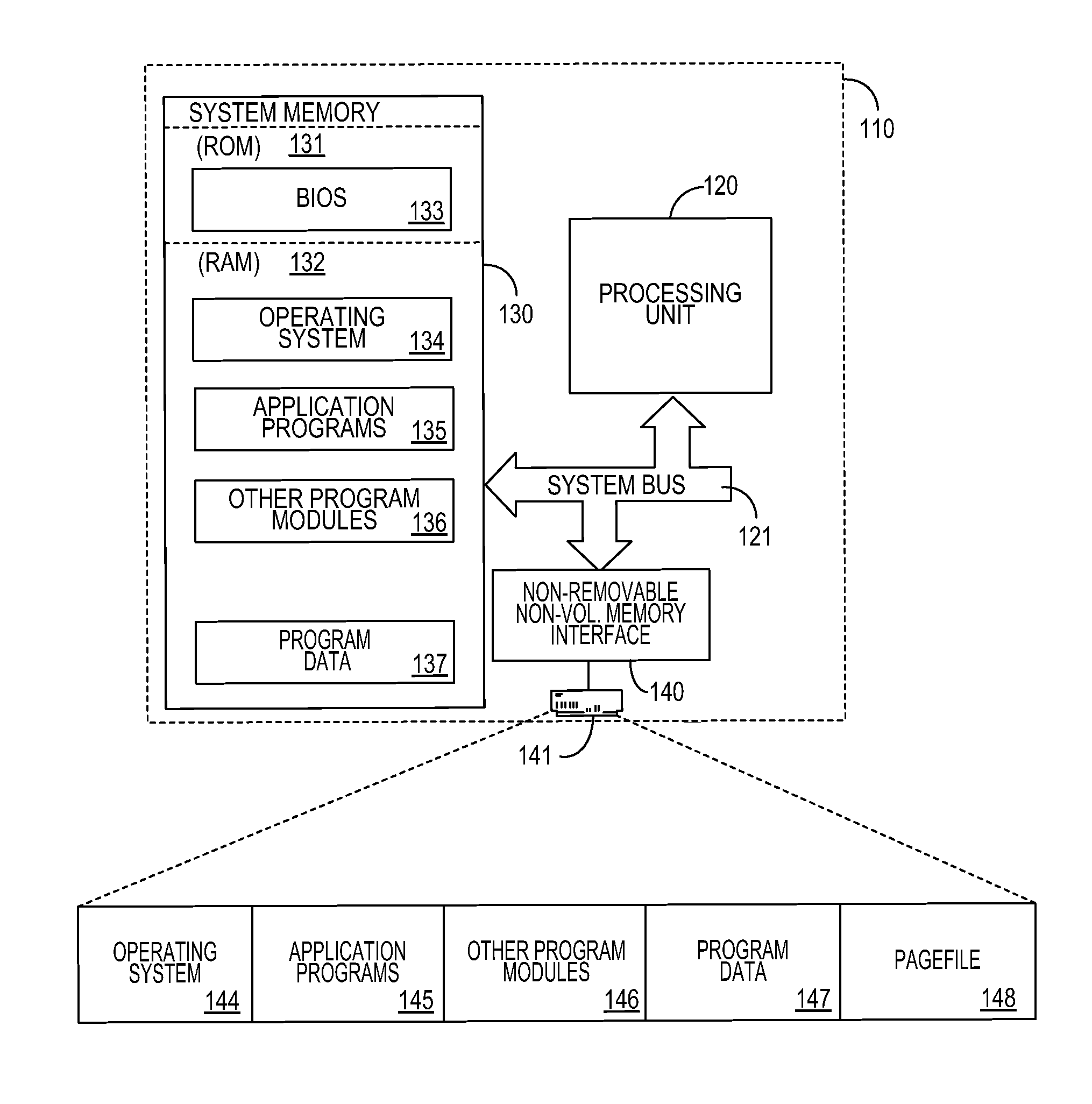
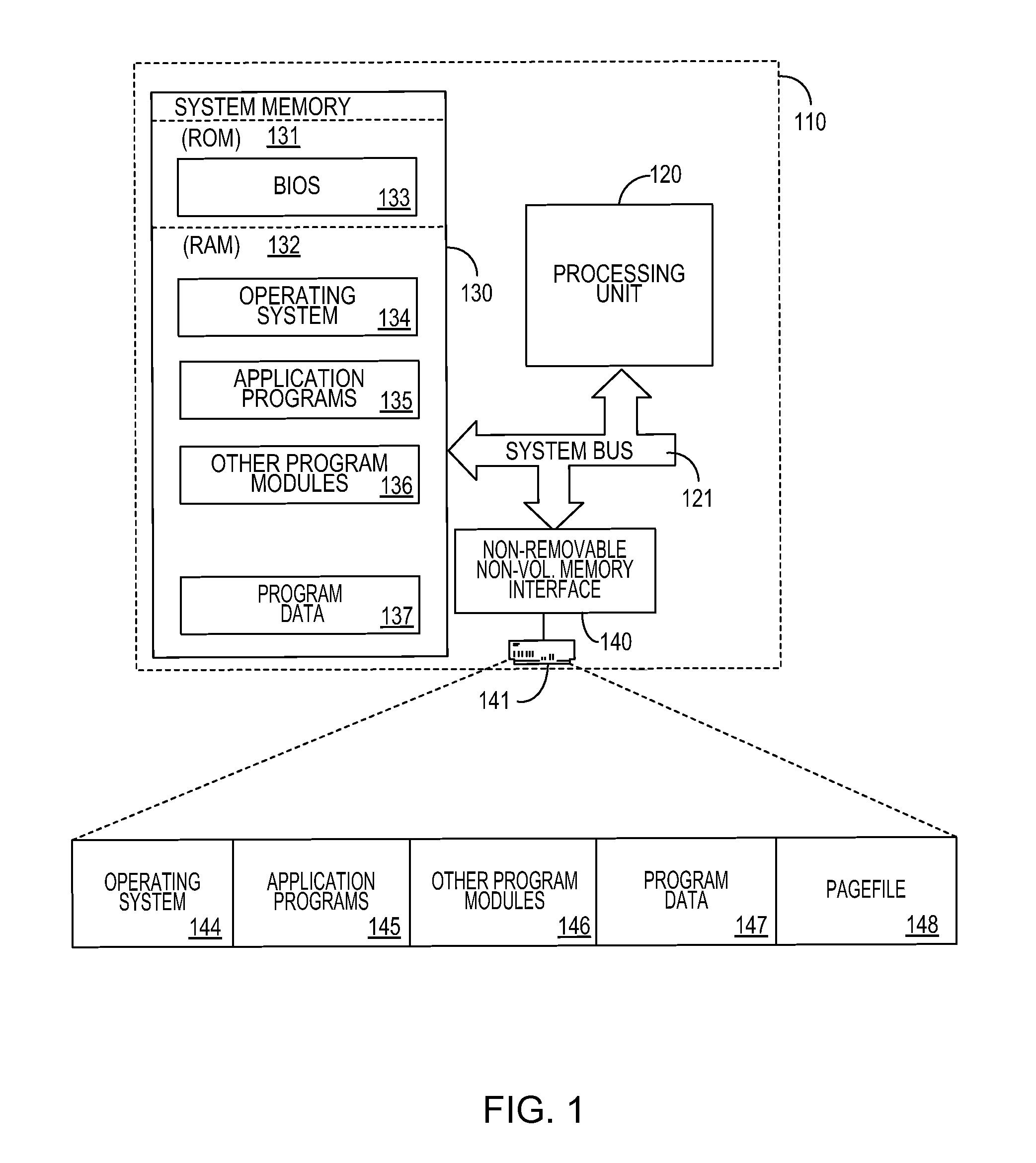
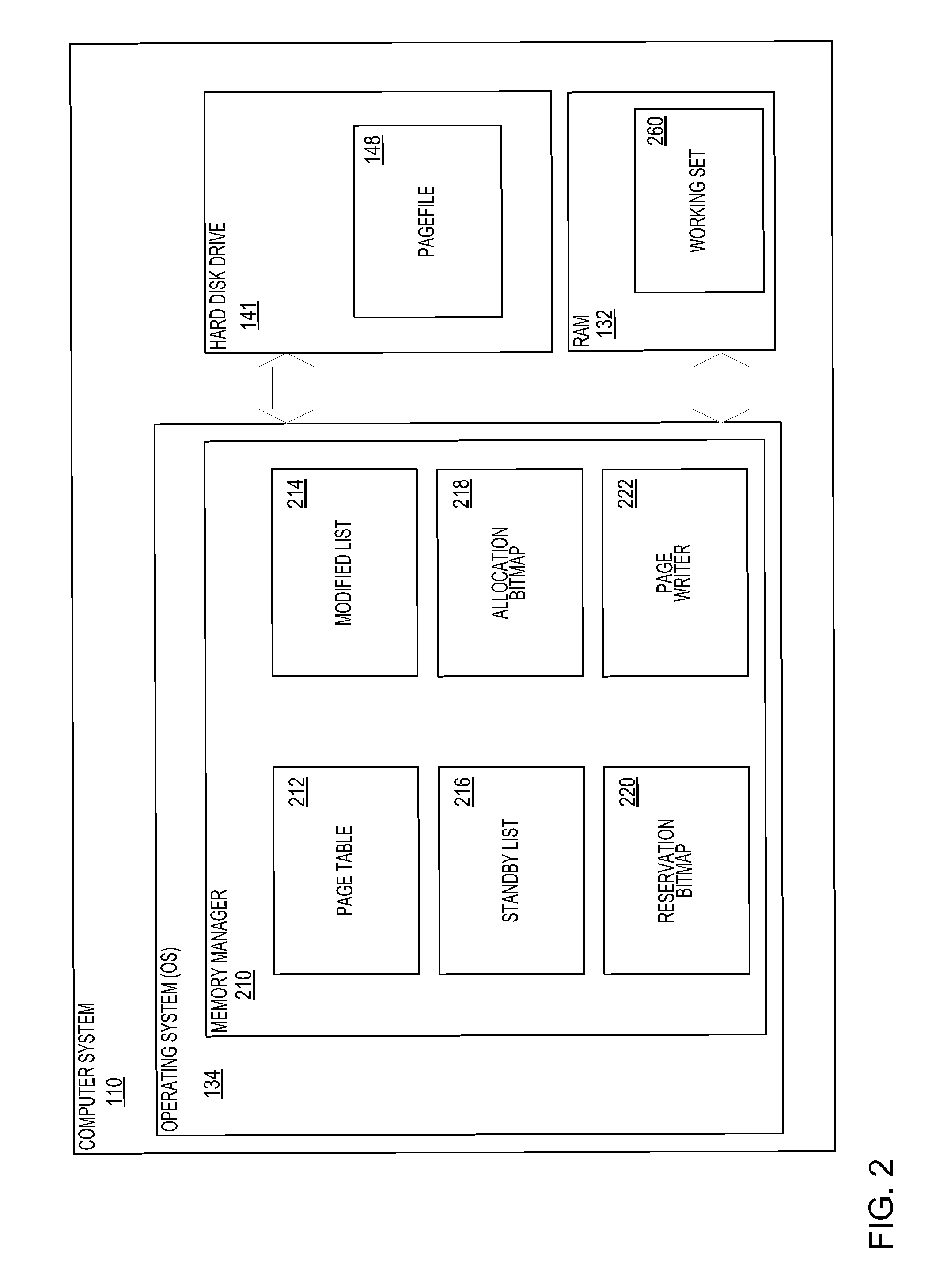
Pagefile reservations
ActiveUS20120233438A1Time inefficientSlow performanceMemory adressing/allocation/relocationMicro-instruction address formationVirtual memoryComputerized system
A system and method for maintaining a pagefile of a computer system using a technique of reserving portions of the pagefile for related memory pages. Pages near one another in a virtual memory space often store related information and it is therefore beneficial to ensure that they are stored near each other in the pagefile. This increases the speed of reading data out of the pagefile because total seek time of a disk drive that stores the pagefile may decrease when adjacent pages in a virtual memory address space are read back from the disk drive. By implementing a reservation system that allows related pages to be stored adjacent to one another, the efficiency of memory management to of the computer system is increased.
Owner:MICROSOFT TECH LICENSING LLC
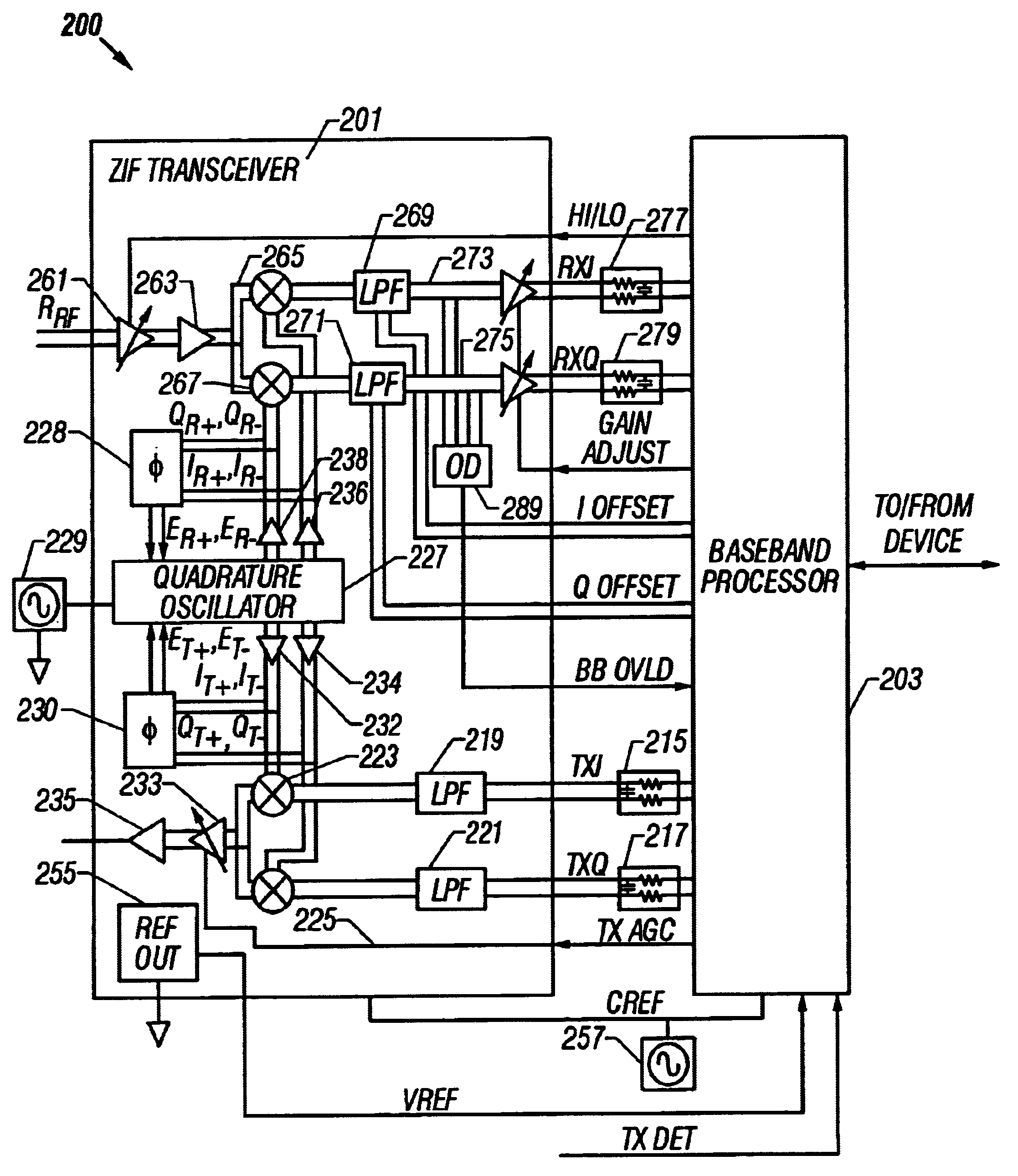
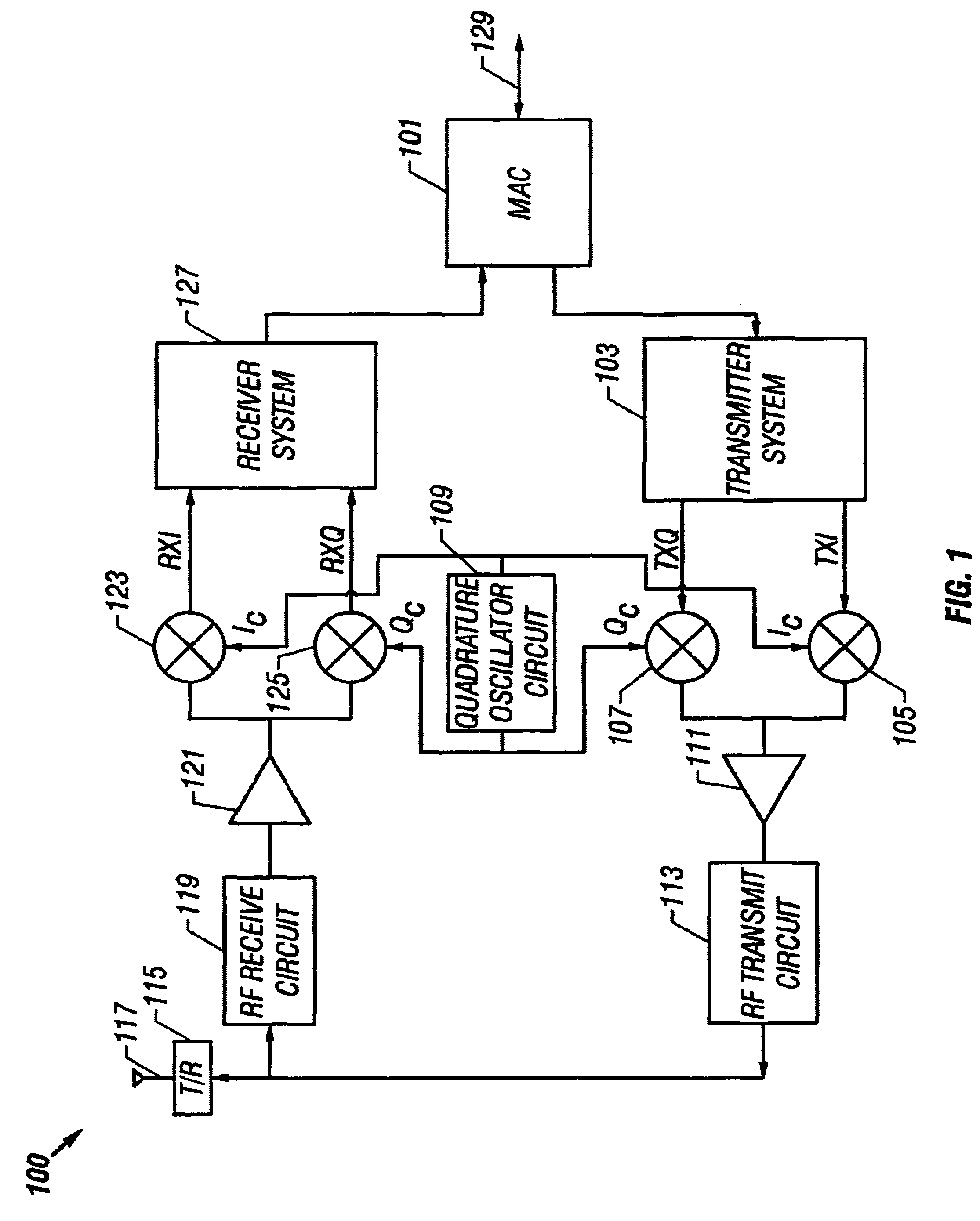
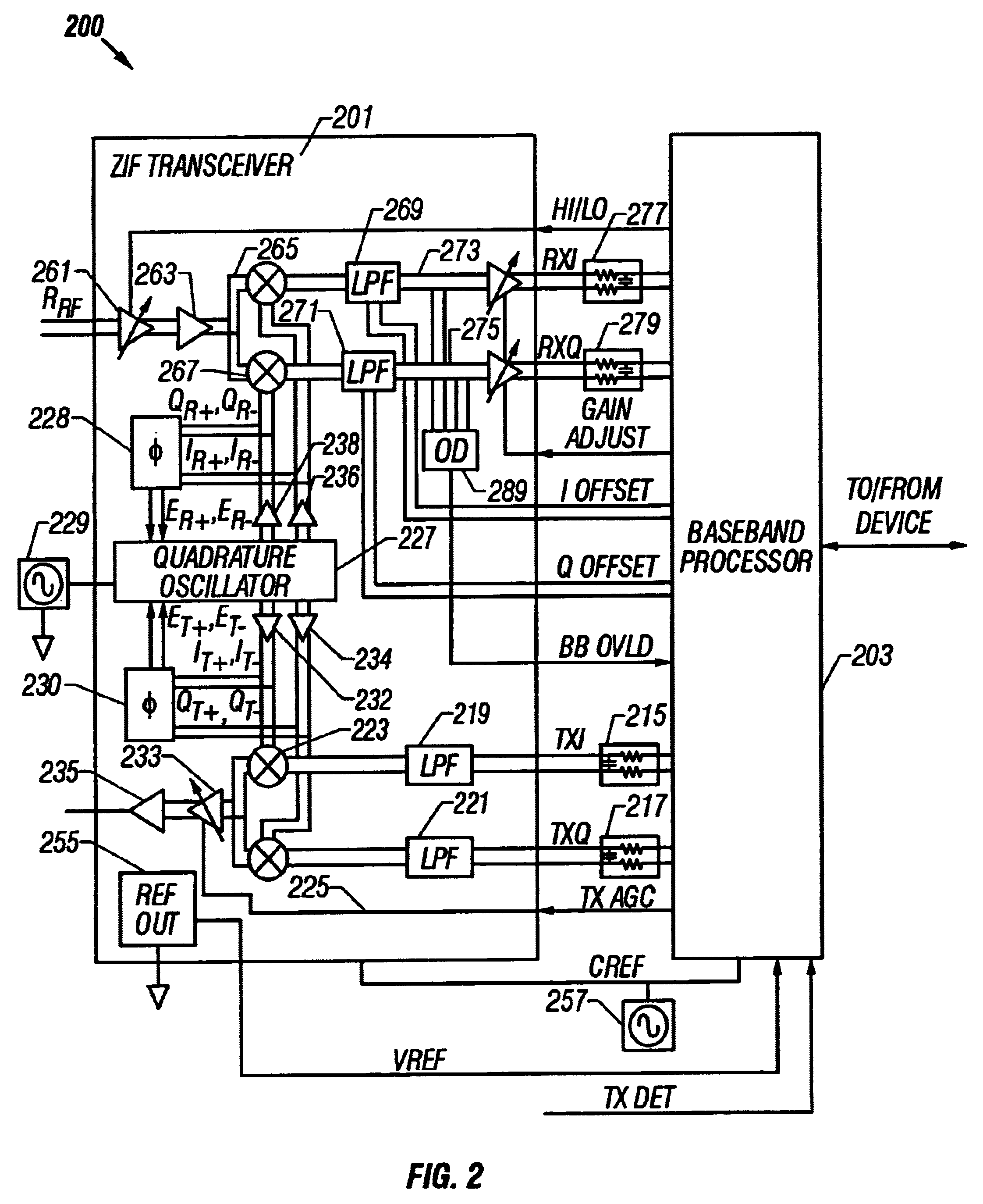
System and method for detecting and correcting phase error between differential signals
InactiveUS6674998B2Detect and reduce and otherwise eliminate phase errorIncrease the amount of dataPulse automatic controlGain controlDifferential signalingQuadrature oscillator
A phase error detector that detects phase error between differential signals. A quadrature oscillator provides in-phase (I) and quadrature phase (Q) differential carrier signals and receives a phase error signal from the phase error detector. The oscillator maintains a quarter cycle phase delay between the I and Q carrier signals based on the phase error signal. The phase error detector includes a summing network and first and second bipolar transistor mixer circuits. The summing network develops four sum signals by summing respective pairs of the differential components of the I and Q carrier signals. A bias circuit biases the transistors to turn on at positive base voltages. The mixer circuits may include filter capacitors so that the transistors are responsive to positive base voltages. The mixer circuits develop polarity signals based on the sum signals, and the resulting phase error signal is the differential of the polarity signals.
Owner:M RED INC
Flash memory system and programming method performed therein
InactiveUS7765359B2High bandwidthData augmentationProgram control using stored programsRead-only memoriesData recordingData storing
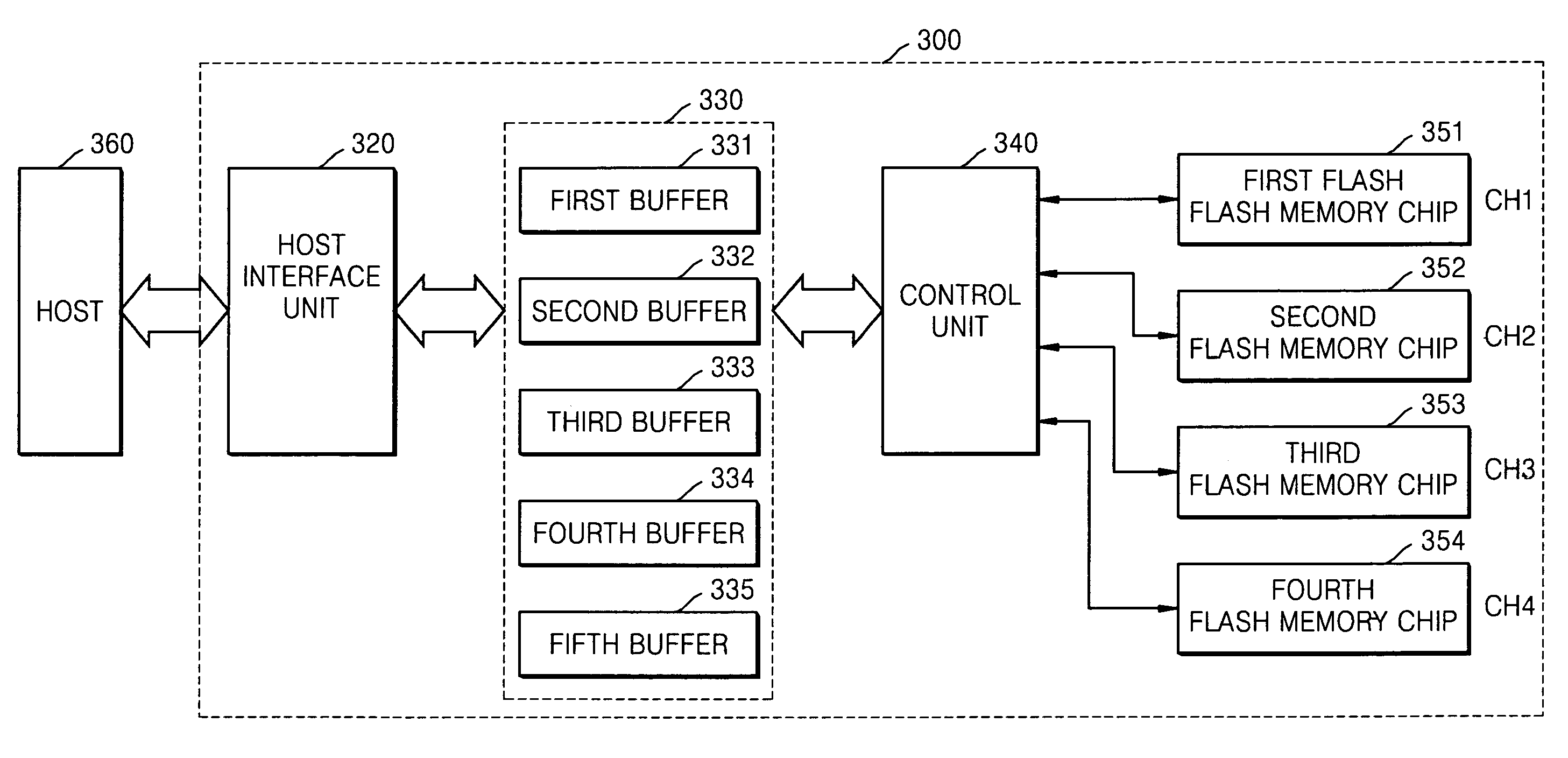
Provided are a flash memory system and a programming method performed in the flash memory system. The flash memory system includes a buffer unit including a plurality of buffers, and temporarily storing data transmitted by a host; a plurality of channel units each including at least one flash memory chip that includes a plurality of memory cell arrays; and a control unit which controls the data stored in the buffer unit to be sequentially transmitted to the channel units and the transmitted data to be recorded to the memory cell arrays of the flash memory chips in the channel units.
Owner:SAMSUNG ELECTRONICS CO LTD
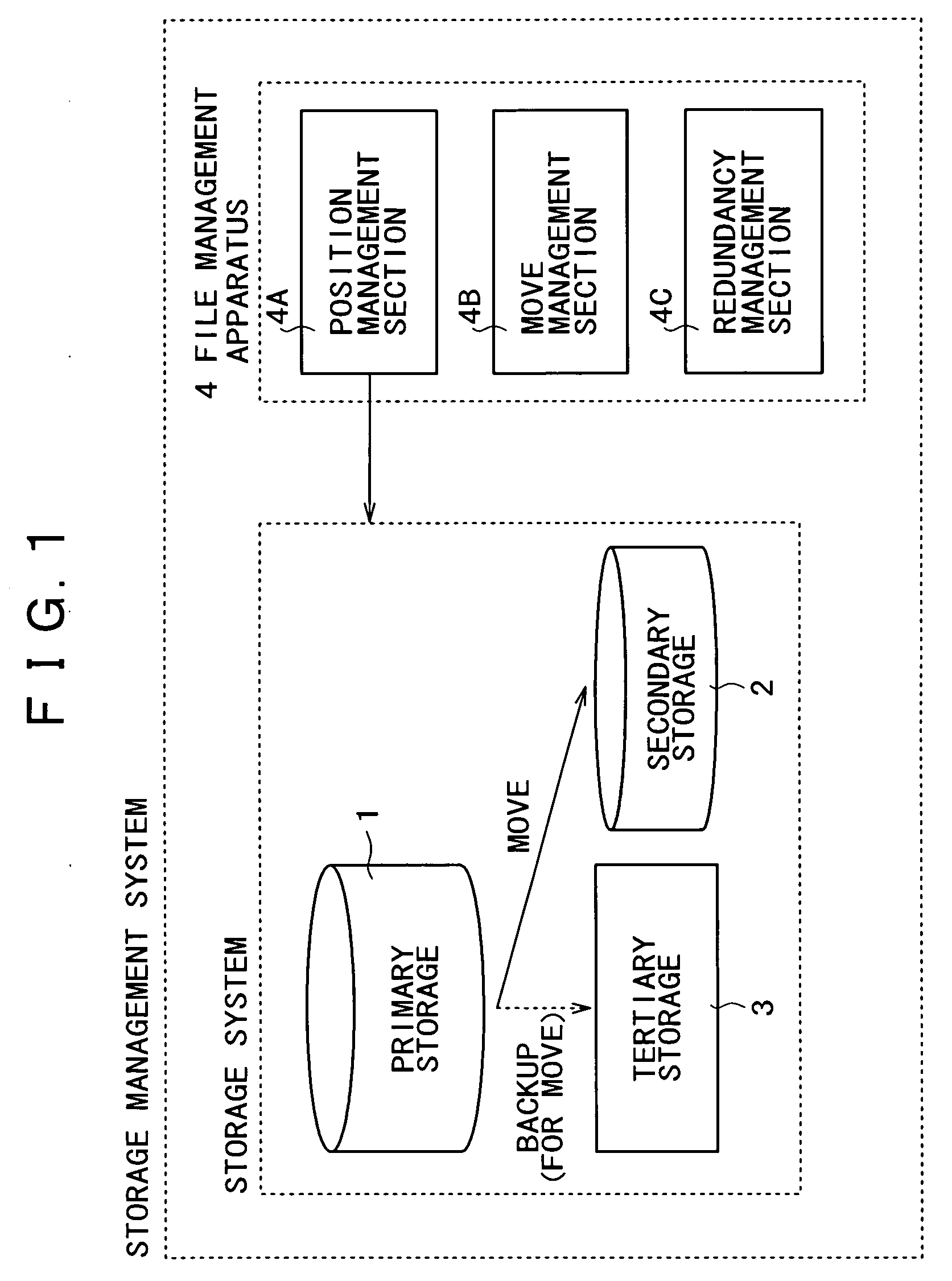
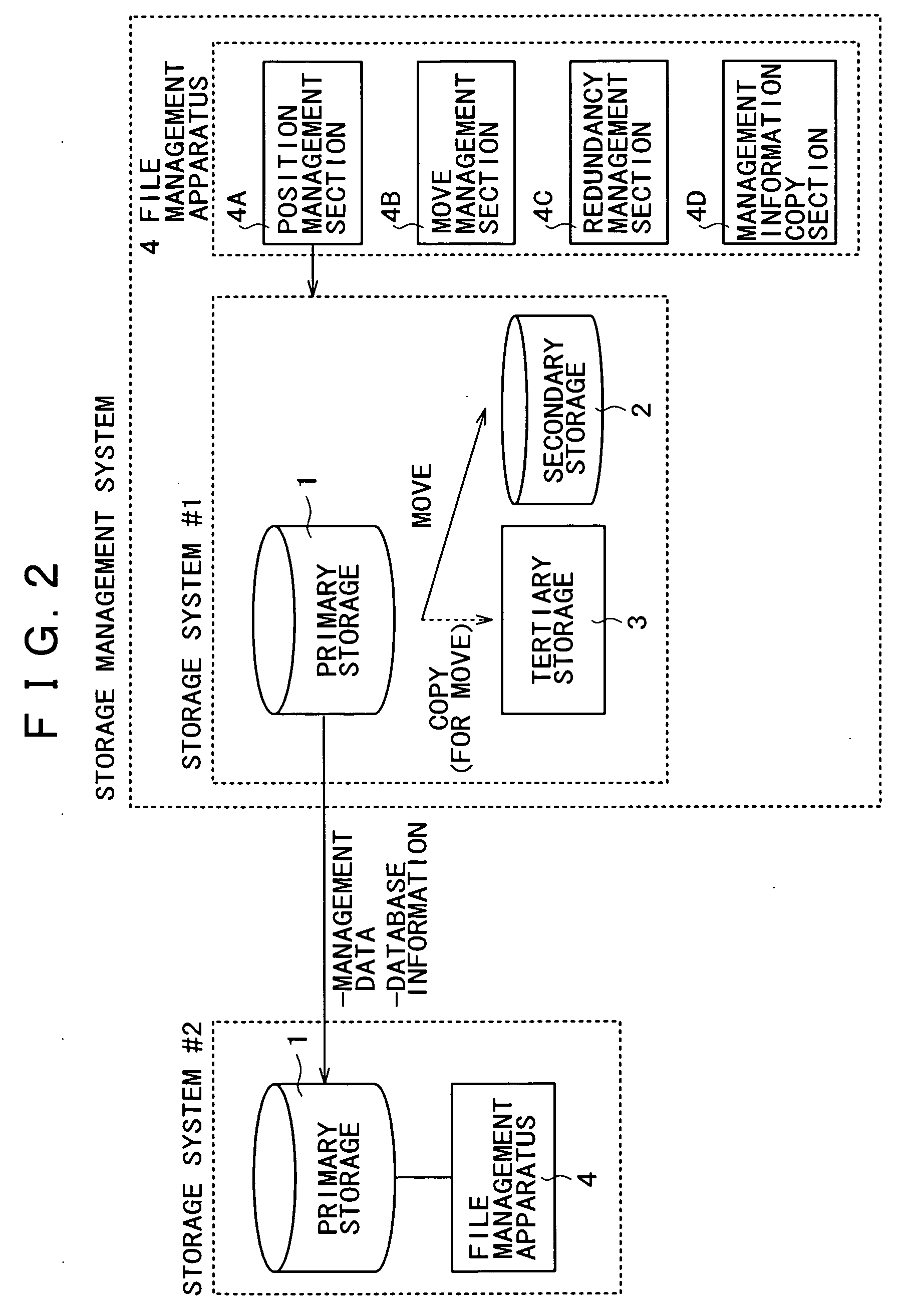
File management apparatus, storage management system, storage management method, program, and recording medium
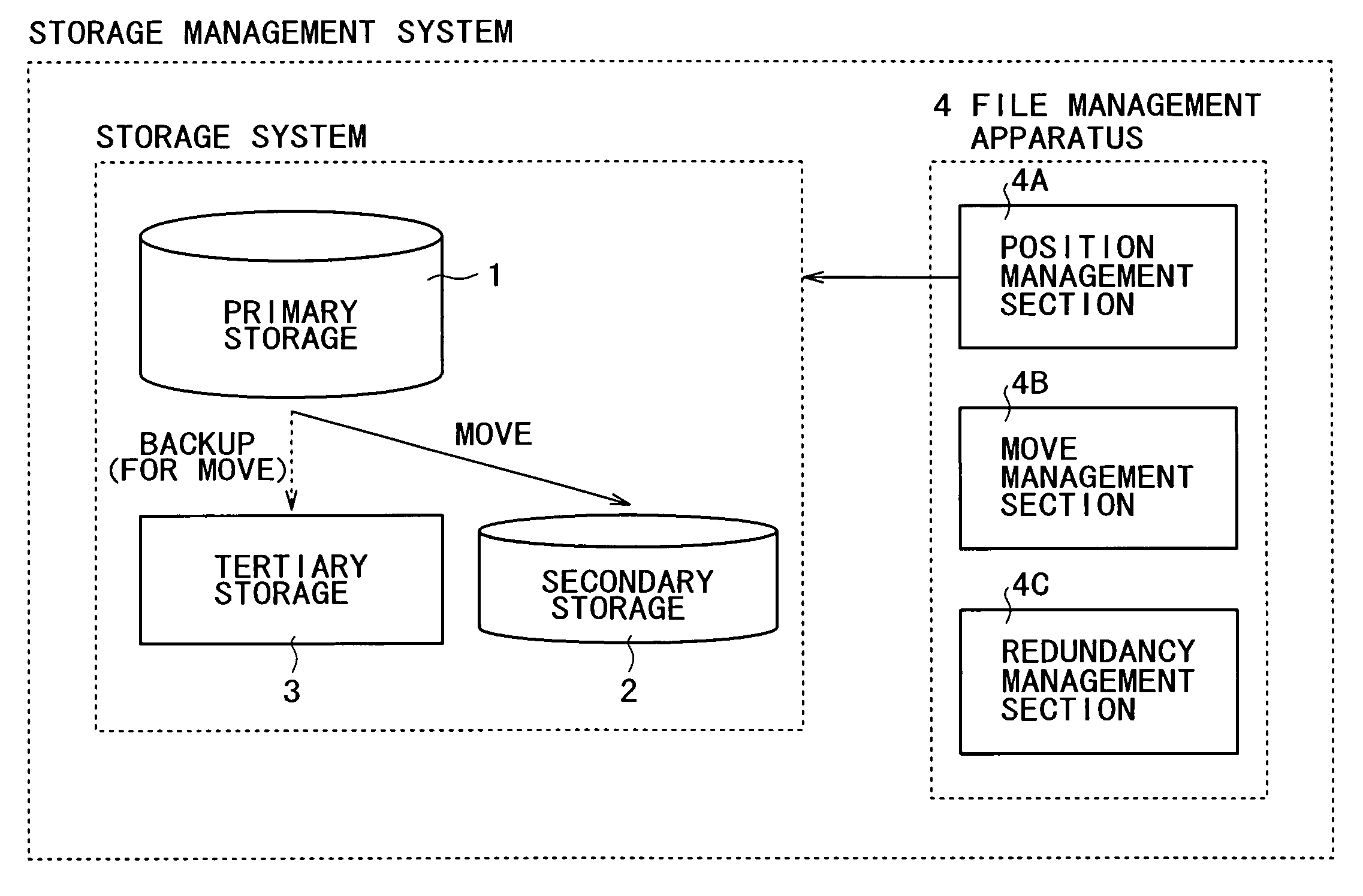
InactiveUS20050120058A1Improve reliabilityLow costDigital data information retrievalInput/output to record carriersFile systemStorage management
A storage system constructed by combining a plurality of types of storage media differing in physical properties is managed as a single virtual storage. Consequently, a single file is divided into actual data and the identification information for accessing the actual data and then the identification information for access is associated with a file system for management purposes. Further, files are managed in a layered manner, in accordance with use frequency categories to manage the move of files between the categories. When the actual data in a file is to be moved to a storage medium in a lower level category, the actual data is backed up on another storage medium in a still lower level category.
Owner:SONY CORP
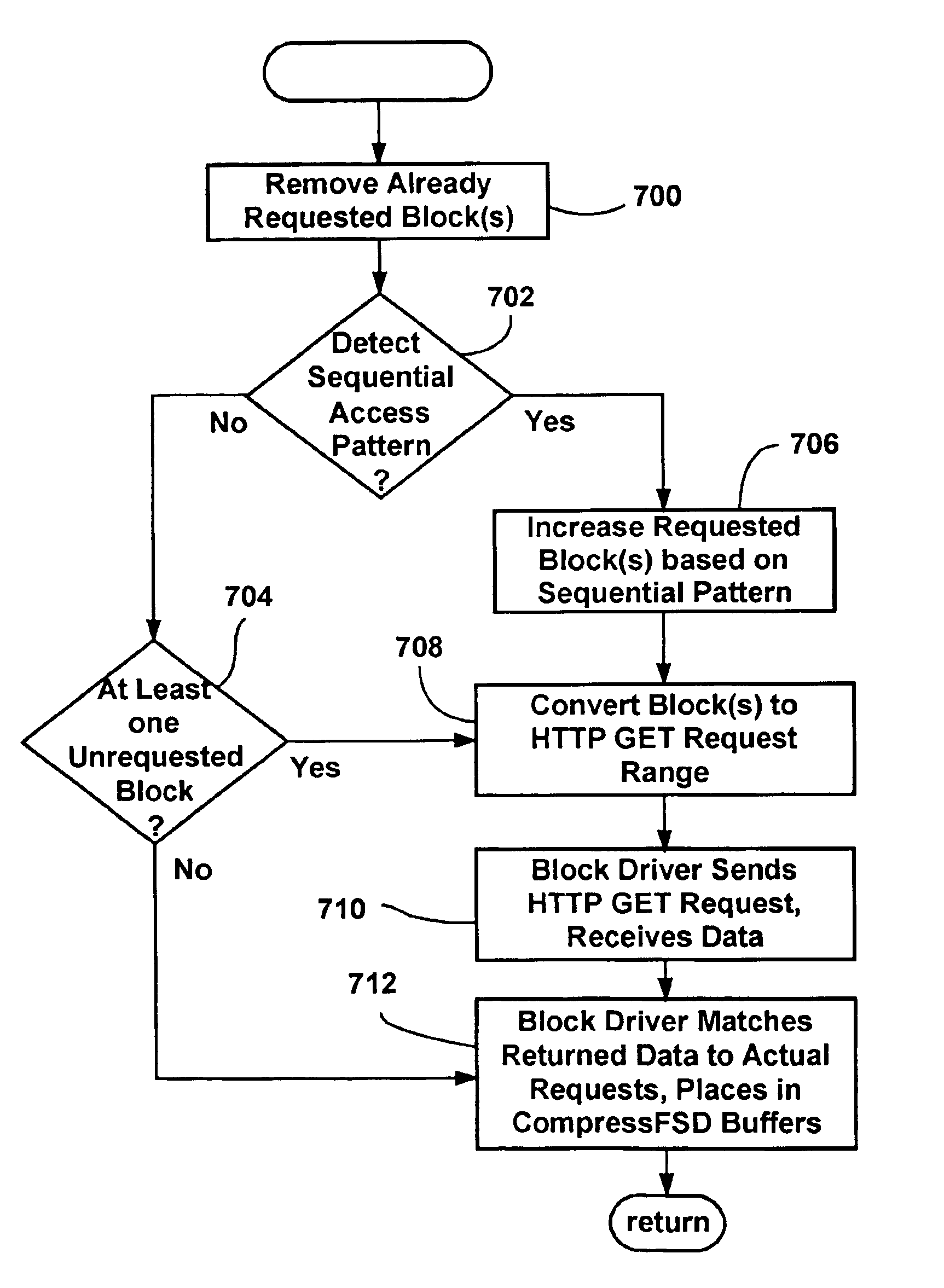
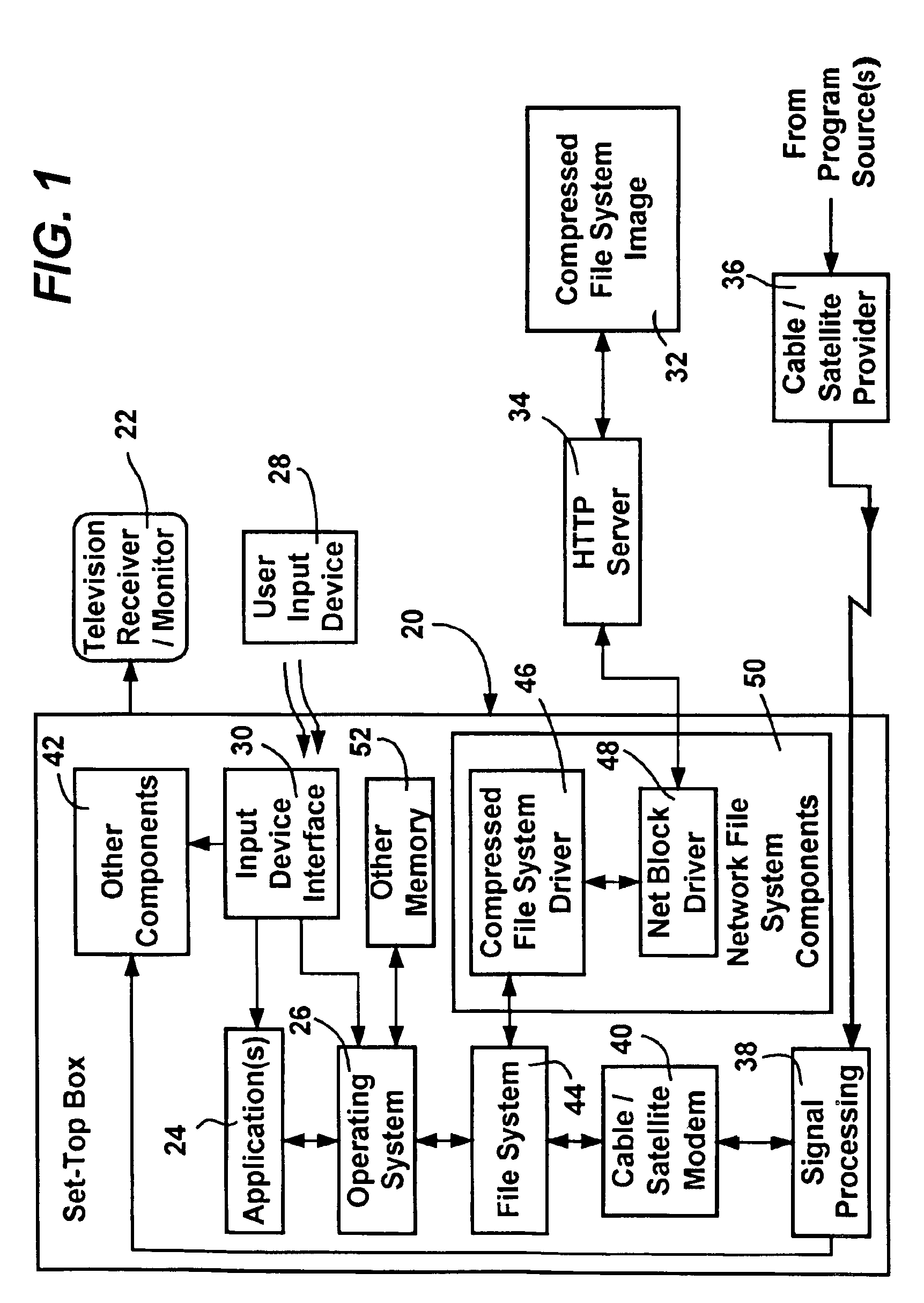
System and method for converting and reconverting between file system requests and access requests of a remote transfer protocol
InactiveUS6889256B1Minimized in sizeReduces seek requirementMultiple digital computer combinationsTransmissionTransmission protocolStreaming data
A method and system that combines efficient caching and buffering to provide a network file system, that may utilize data stored in one or more compressed image files of sequentially arranged byte stream data. As an application requests file opens and file reads of a file system, one or more drivers convert the block requests into HTTP: byte range requests or the like in order to retrieve the data from a remote server. As the data is received, it is reconverted and adjusted to match the application's request. Sequential block access patterns can be detected and used to request additional data in a single request, in anticipation of future block requests, thereby increasing efficiency. Local caching of received data, including caching after uncompressing received data that was compressed, further increases efficiency. A compressed file system format optimized for sequential access is also described that when used, further improves the efficient data access.
Owner:MICROSOFT TECH LICENSING LLC
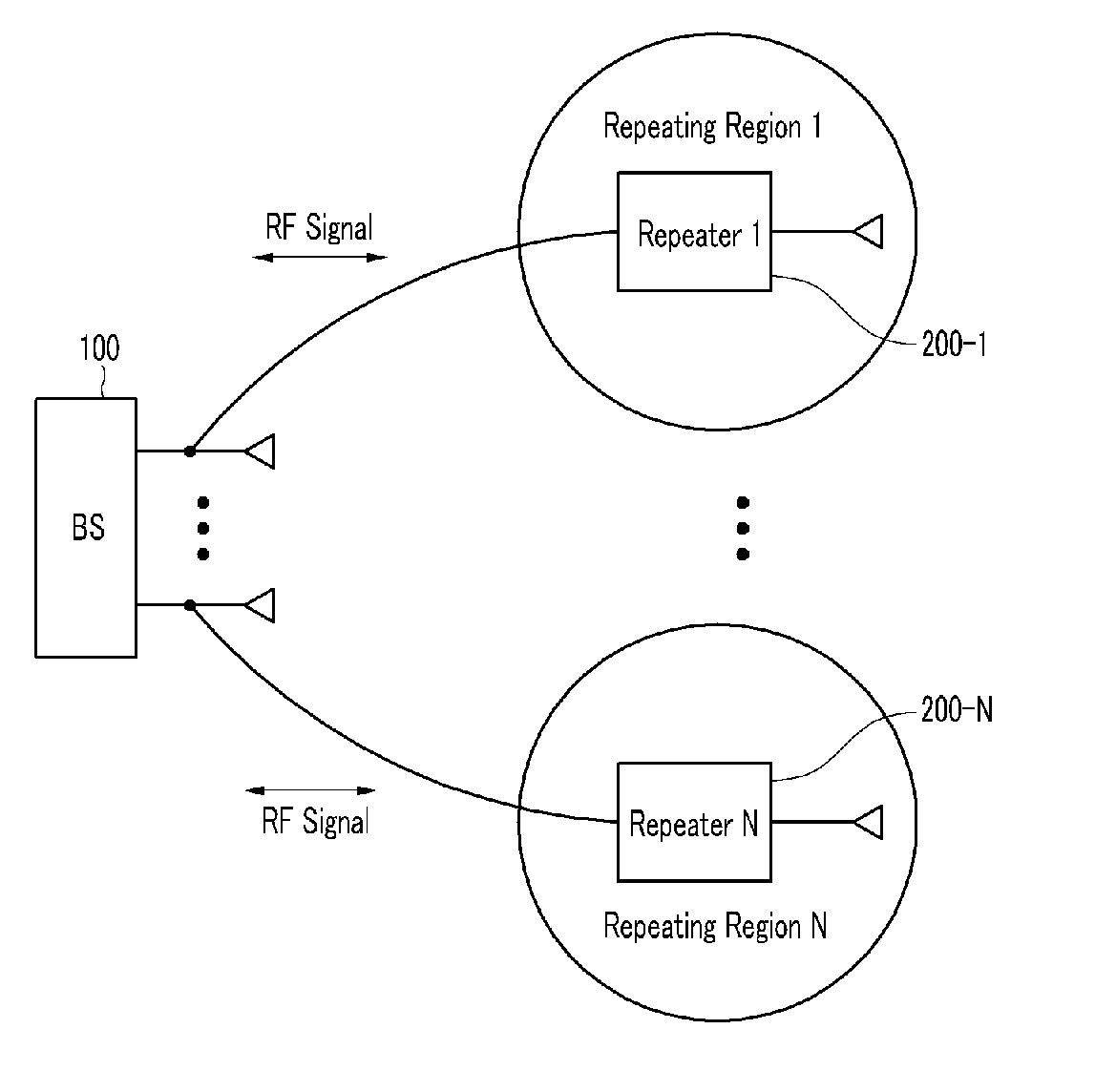
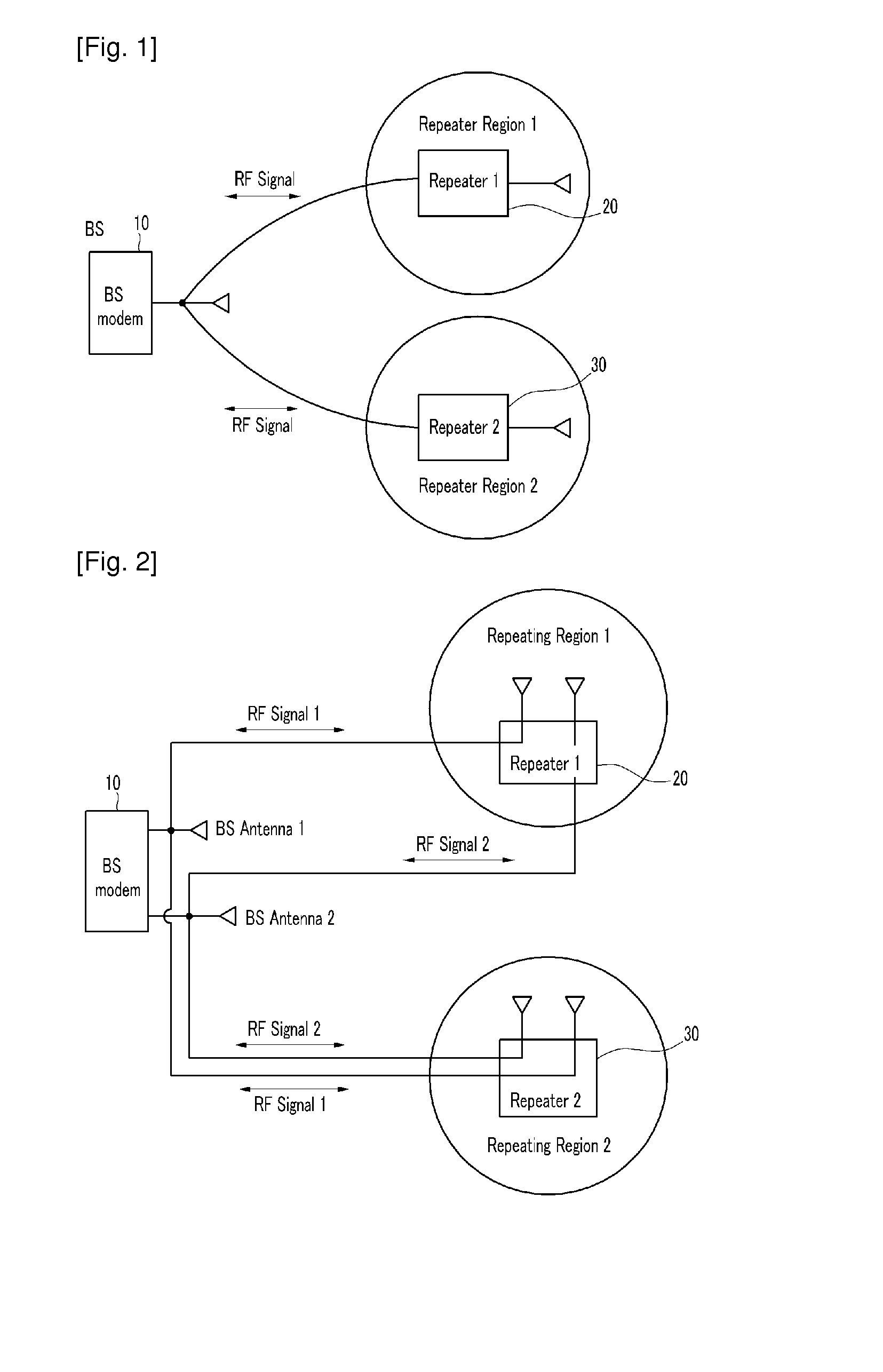
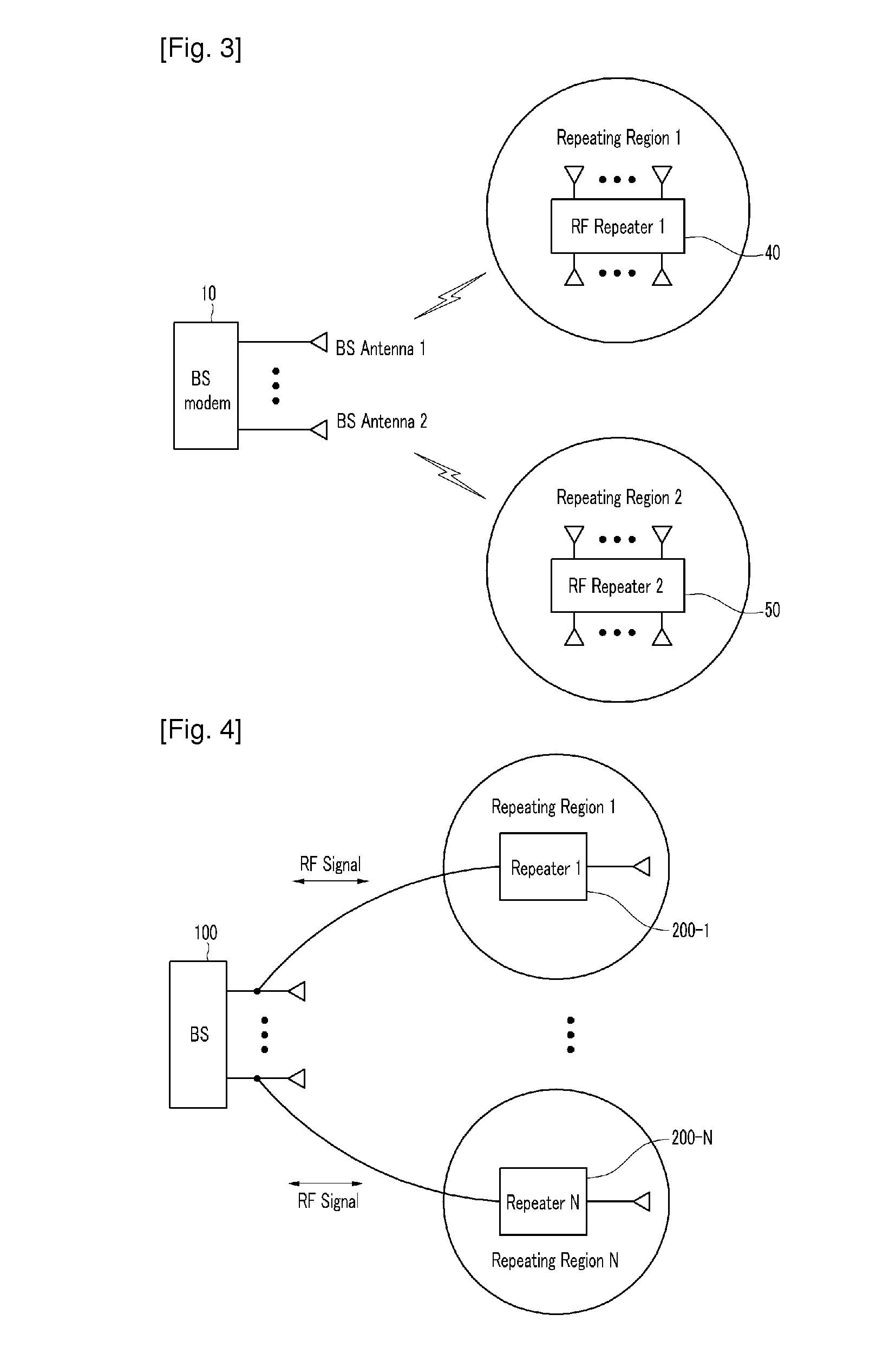
Method for connecting base station and repeater for spatial division multiple access and repeating method thereof
InactiveUS20100208776A1Increase capacityEasily transmitted/receivedRepeater/relay circuitsActive radio relay systemsData streamSpatial partition
The present invention relates to a method for connecting a base station and a repeater for a spatial division multiple access, and a repeating method thereof. In order to provide efficient spatial division by using a repeater, data streams are repeated by using a repeating system including at least one repeater for performing wireless communication with a terminal located in a repeating region controlled by using at least one repeating antenna and a base station including a plurality of base station antennas corresponding to the repeating antenna. In this instance, the terminal detects location information on the repeating region to which the terminal belongs by using the pilot signal transmitted by the base station or repeated by the repeater. Location information detected by the terminal is fed back to the base station so that the base station may use it for the spatial division multiple access for simultaneous transmission to many terminals. Therefore, the spatial division multiple access for increasing sector capacity by efficiently combining the base station including multiple antennas and the repeater is available.
Owner:ELECTRONICS & TELECOMM RES INST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com