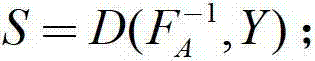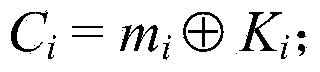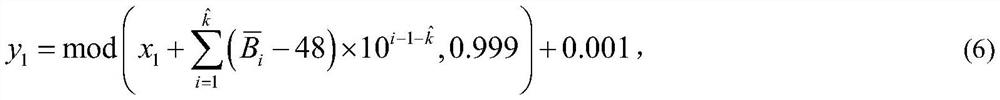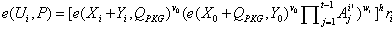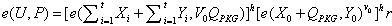Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42results about How to "Unforgeable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
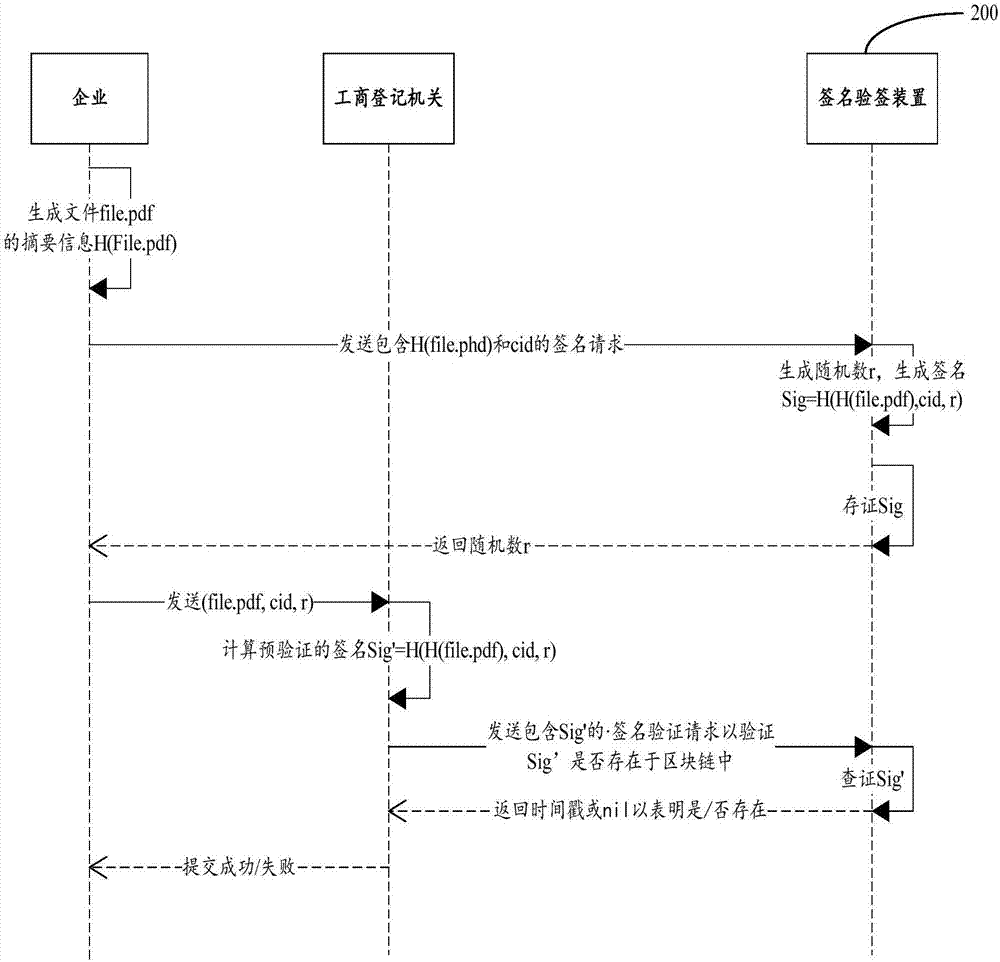
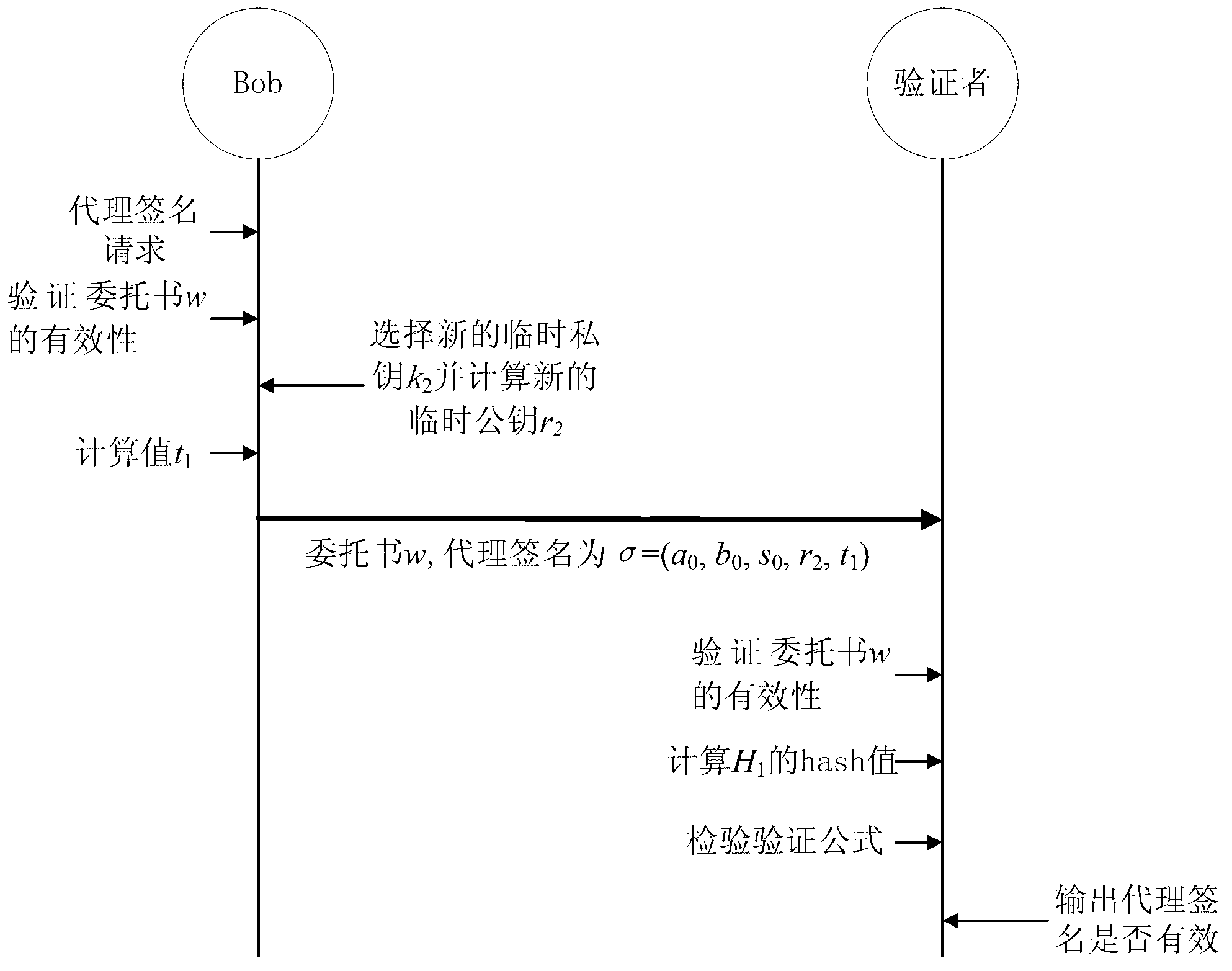
Signature verification method and device
ActiveCN107342867ALow costTamper proofKey distribution for secure communicationEncryption apparatus with shift registers/memoriesUSBComputer science
The invention discloses a signature verification method and a device. The signature verification method can include the following steps: receiving a signature request, wherein the signature request contains abstract information of a file and a sender identifier; generating a random number; generating a signature of the file according to a signature generation algorithm and based on the random number, the abstract information and the sender identifier; and saving the signature to a block chain, and returning the random number to a sender sending the signature request. Through the technical scheme of the invention, an electronic signature can be realized without a USB key.
Owner:深圳和信中欧科技有限公司
Certificateless multi-receiver signcryption method with multivariate-based cryptosystem
InactiveCN102811125APrivacy protectionImprove securityPublic key for secure communicationUser identity/authority verificationCiphertextConfidentiality
The invention discloses a certificateless multi-receiver signcryption method with a multivariate-based cryptosystem. The certificateless multi-receiver signcryption method is used for solving the technical problem of poor security of an existing certificateless signcryption method. The technical scheme includes that the method includes: firstly, using a key generation center to generate system parameters, and selecting a secure multivariable encryption algorithm to generate keys; and enabling a user U to obtain system private keys of the key generation center and generate the private keys to user keys prior to that a user Alice with the identity IDA sends signcryption messages to a user group L={ID1, ID2,...,IDt}, and accepting or refusing ciphertext sigma by means of un-signcryption. By the aid of the multivariate-based cryptosystem, high security of anti-quantum computation is achieved, and the certificateless multi-receiver signcryption method is still high in security facing attack of a quantum computer. Compared with the background art, the certificateless multi-receiver signcryption method is small in computation and high in security, has the advantages of completeness, confidentiality, unforgeability, forward security, backward security, receiver privacy protection and the like and is capable of resisting existing known attack.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Novel procuration signature and verification method based on integer factorization problems
InactiveCN103259662AShorten the lengthSmall amount of calculationUser identity/authority verificationHash functionDigital Signature Algorithm
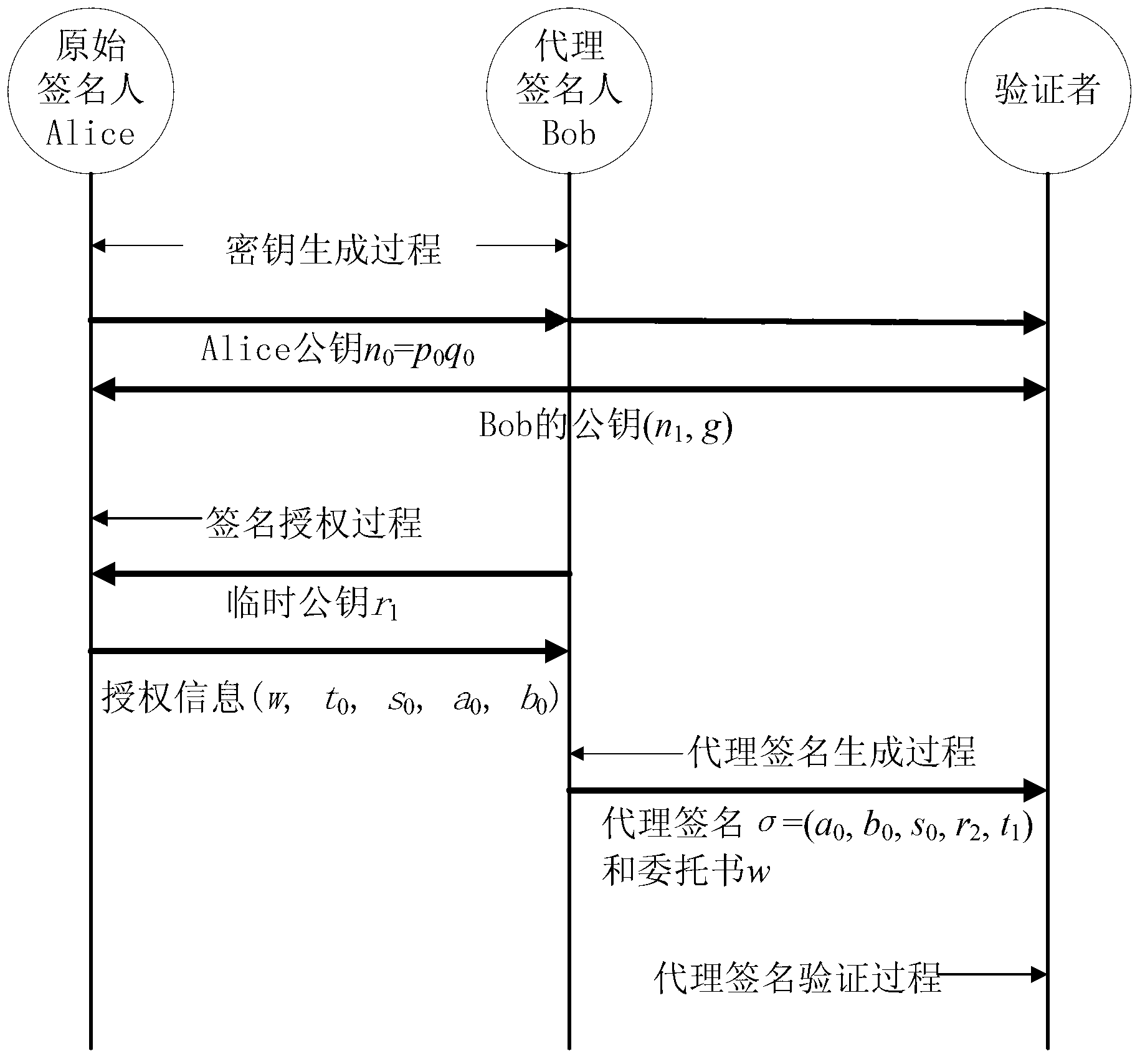
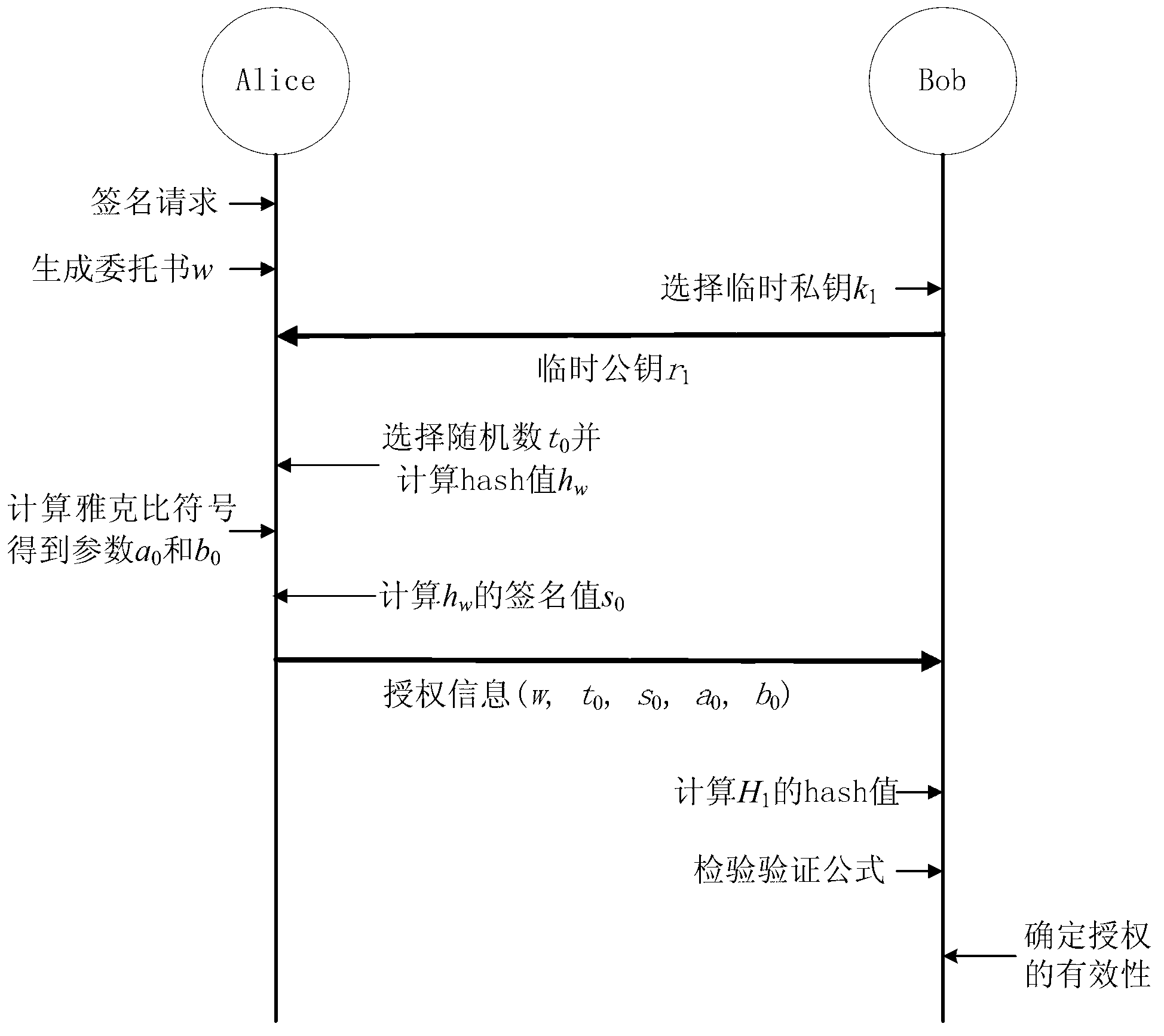
The invention discloses a novel procuration signature and verification method based on integer factorization problems. The novel procuration signature and verification method based on the integer factorization problems includes the steps: before a network operates, firstly generating personal public keys and private keys by original signature people and procuration signature people, and issuing the public keys; when signature requests are provided, generating authorization letters by the original signature people, and calculating signature authorization based on a chameleon hash function and an ordinary digital signature algorithm, sending the signature authorization to the procuration signature people, carrying out validity verification on the received signature authorization by the procuration signature people, if the signature authorization is effective, generating the procuration signature based on collision property of the chameleon hash function, and digital signature does not need to be carried out on information, when a verifier receives the authorization letters and the procuration signature, firstly, verifying whether the authorization letters are effective or not, after the authorization letters are verified to be effective, and then verifying validity of the procuration signature. According to the application of the novel procuration signature and verification method based on the integer factorization problems, processing efficiency of the procuration signature is high, and the length of the procuration signature is short. The novel procuration signature and verification method based on the integer factorization problems is suitable for environments such as mobile networks and the wireless networks where computing power and network bandwidth are limited.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
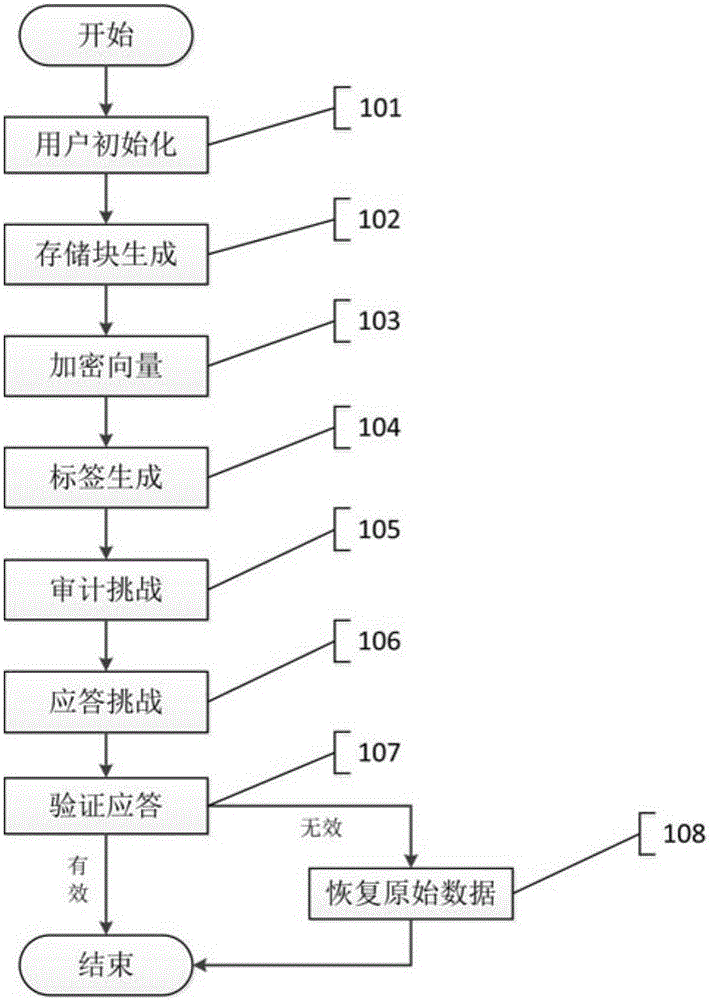
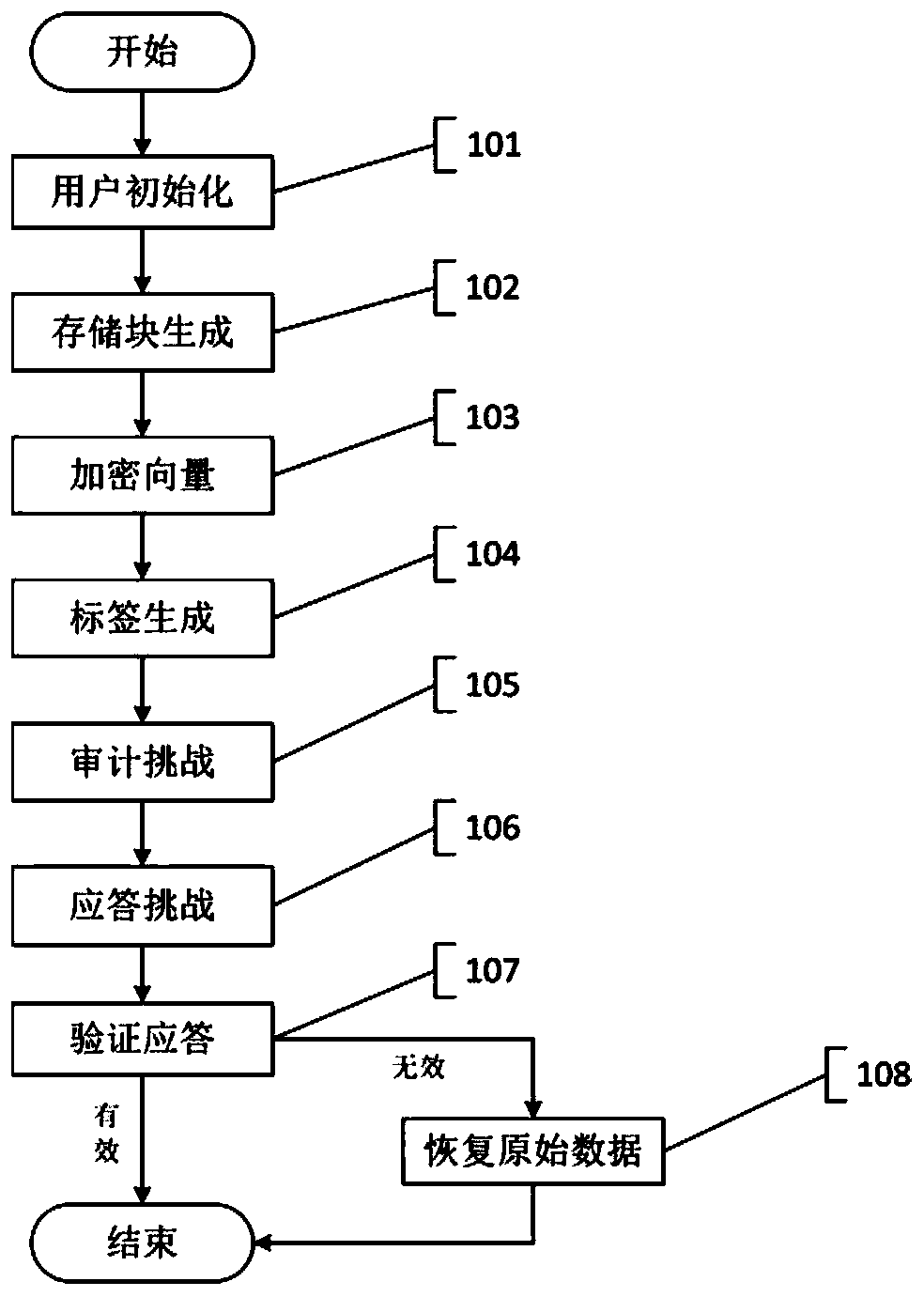
Cloud side data integrity verification and restoration method based on IDA
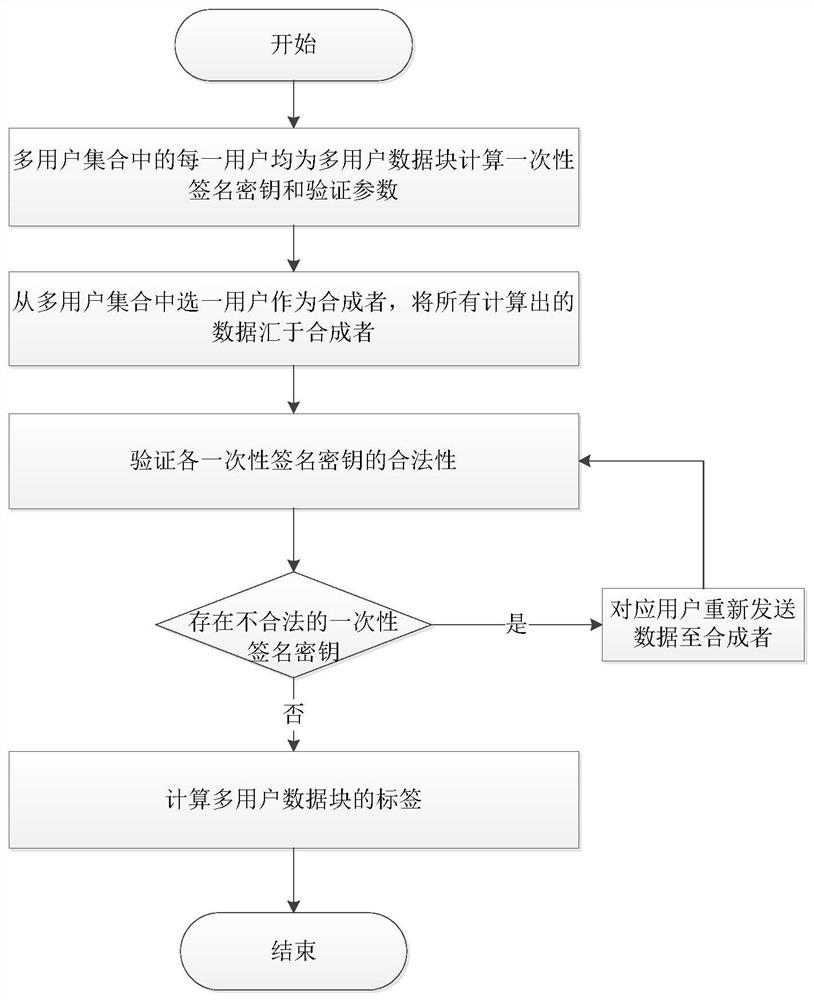
ActiveCN106650503AAchieve recoveryUnforgeableDigital data protectionTransmissionData integrityOriginal data
The invention discloses a cloud side data integrity verification and restoration method based on IDA. The method comprises the following steps of 1, user initialization; 2, storage block generation; 3, vector quantity encryption; 4, label generation; 5, challenging auditing; 6, challenging responding; 7, responding verification; 8, original data restoration. According to the scheme, an original file is encoded, and damaged data is completely restored on the basis of verifying cloud side data integrity. Meanwhile, under the condition of guaranteeing system safety, the complexity of completely verifying labels and restoring calculation is reduced, and the efficiency of the method is effectively improved.
Owner:NANJING UNIV OF SCI & TECH
A public key encryption method supporting multi-keyword search against keyword guess attack
InactiveCN109086615AUnforgeableOvercoming the Problem of Guessing AttacksDigital data protectionTransmissionThird partyCiphertext
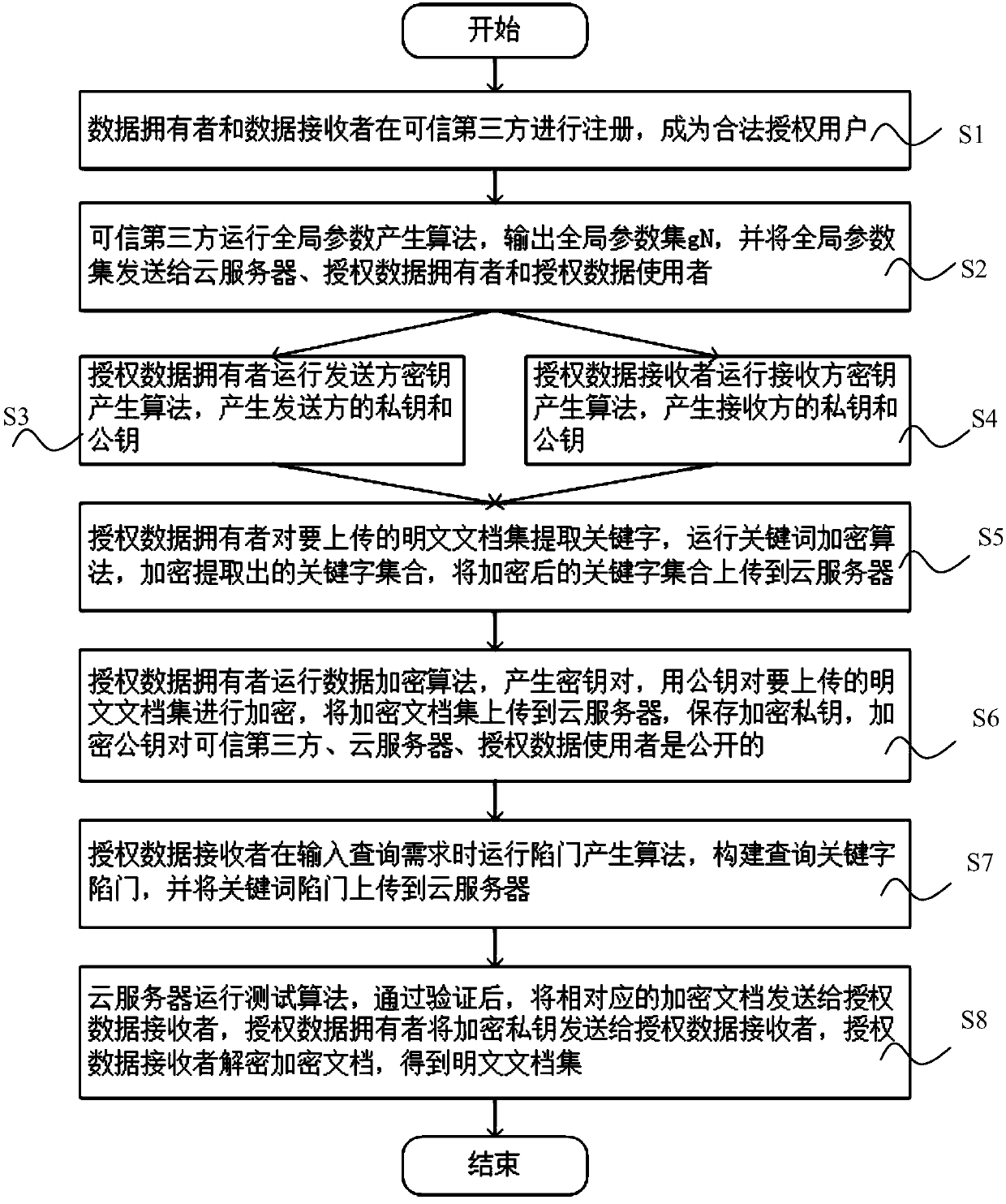
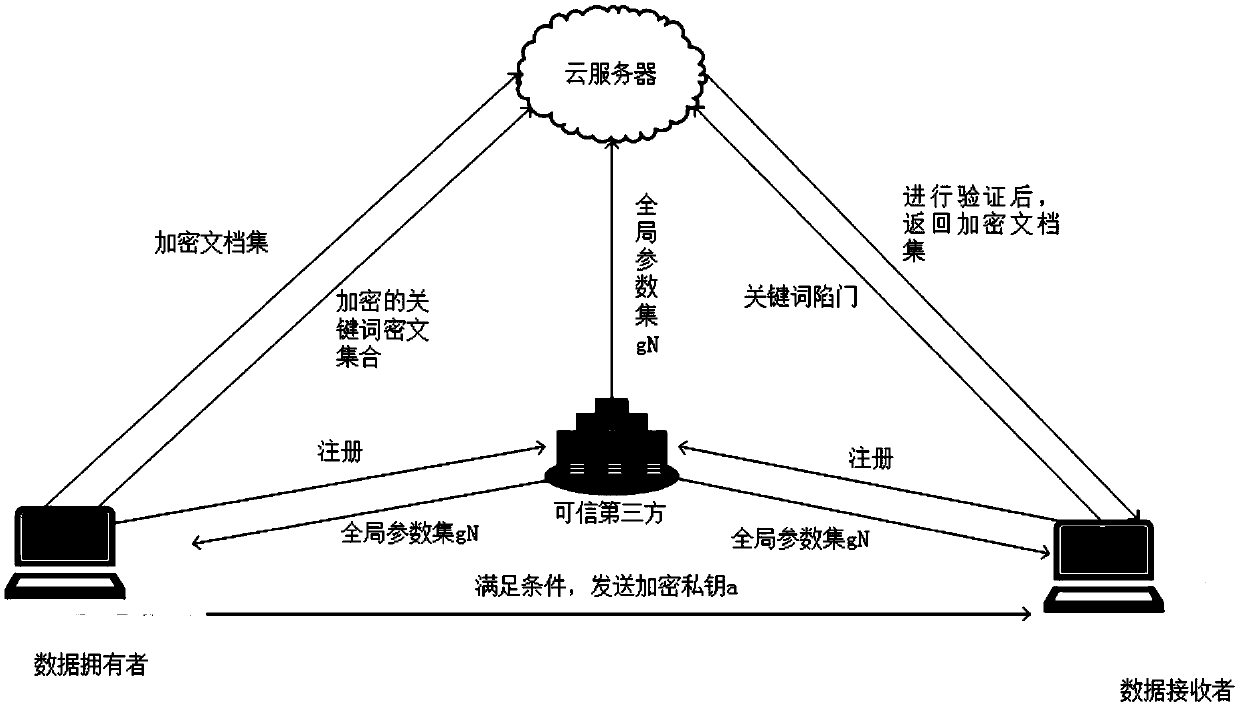
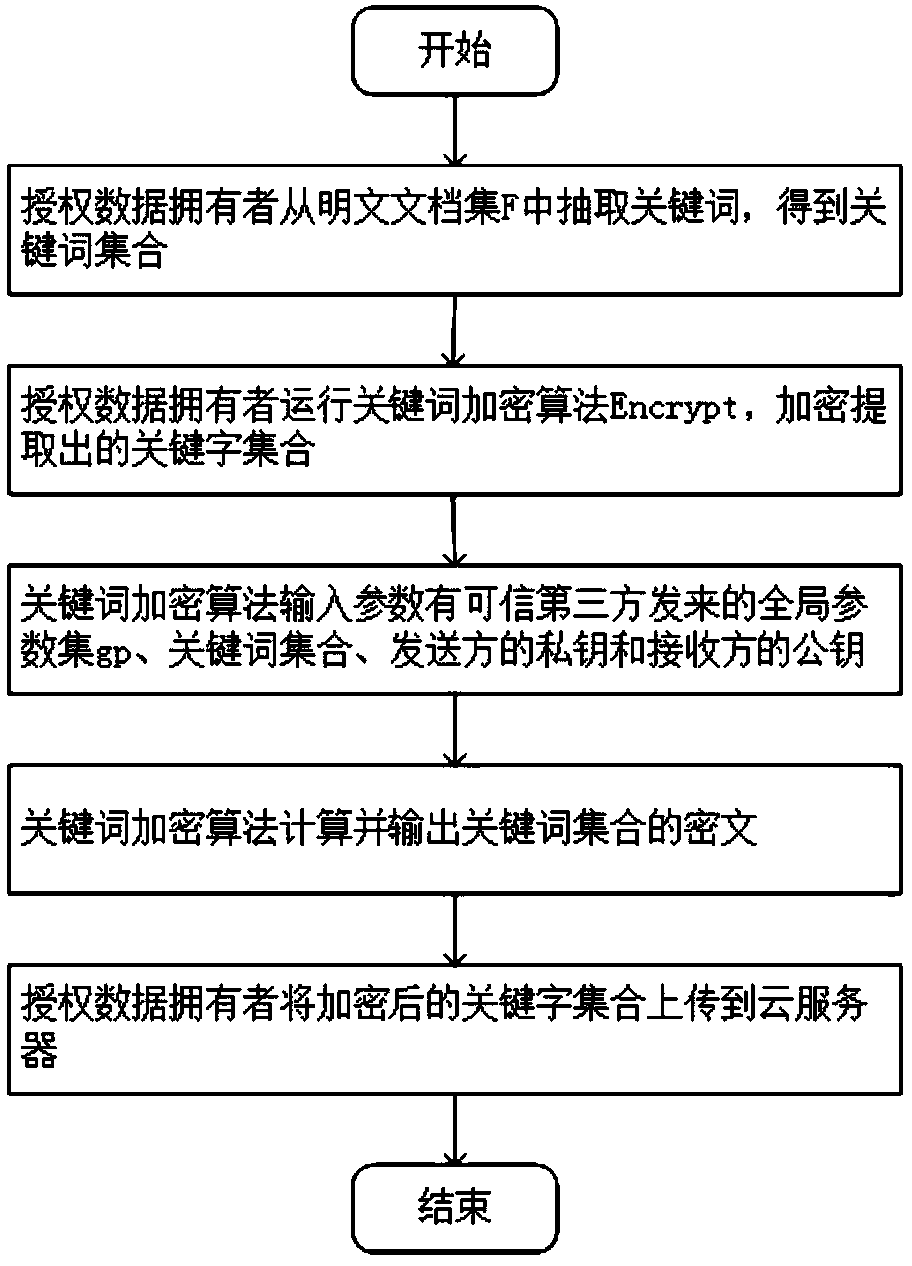
The invention discloses a public key encryption method for supporting multi-keyword search to resist the attack of keyword guess. The method comprises the following steps: a data owner and a data receiver are registered as a legal authorized user in a trusted third party; the trusted third party runs the global parameter generation algorithm, outputs the global parameter set and sends it to the cloud server, the authorized data owner and the authorized data receiver. The data owner receives the global parameter set and sends the encrypted document set and the keyword ciphertext to the cloud server. The data receiver receives the global parameter set, constructs the keyword trap according to the query sentence, and sends the keyword trap to the cloud server. The cloud server receives the global parameter set, encrypts the ciphertext document, the keyword ciphertext and the keyword trap, and returns the satisfied ciphertext document to the authorized data recipient by running the test algorithm verification. The invention effectively solves the problem of keyword guess attack, realizes keyword search, and has obvious advantages in computational efficiency and communication cost.
Owner:SHANGHAI MARITIME UNIVERSITY
Product traceability system
InactiveCN108319998APromote transparency and claritySupport rights protectionCo-operative working arrangementsCommerceProduct processingClient-side
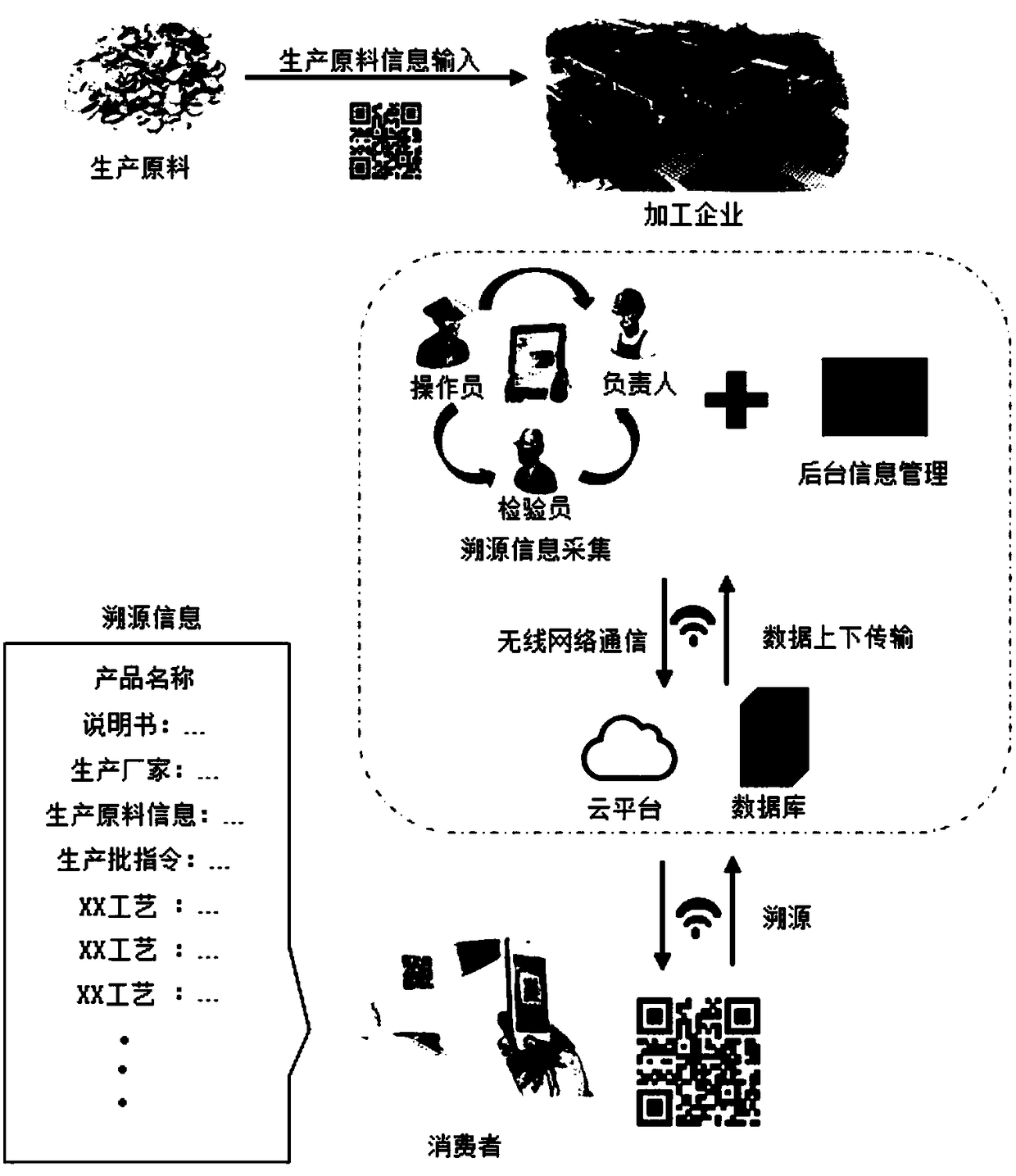
The invention discloses a product traceability system. The system comprises a traceability information acquisition client, a wireless communication module and a cloud platform; the cloud platform comprises a background information management module, a two-dimensional code generation module, a database and a traceability module; the background information management module enters product processingrelated information in advance; the traceability information acquisition client acquires traceability information and sends the traceability information to the cloud platform; the database is used for storing the traceability information of each process flow of a processing process and the traceability QR code labels of corresponding batch products; the traceability module is used for obtaining corresponding traceability information from the database according to the traceability QR code labels when receiving a traceability request sent by the scanning of the traceability QR codes by a user,and transmitting the traceability information to a user terminal; and therefore, traceability operation is completed. According to the product traceability system of the invention, a modern data storage transmission technology is additionally adopted on the basis of a product actual management process; and therefore, the requirements of safety management can be satisfied, the transparency and clearness of a production process can be promoted, and it is can be ensured that the traceability data of the whole process are authentic and unforgeable.
Owner:JIANGSU TIANZHAO PHARMA
Data processing method and electronic equipment
InactiveCN104915591AImprove securityIrreversibleDigital data authenticationDigital signatureData treatment
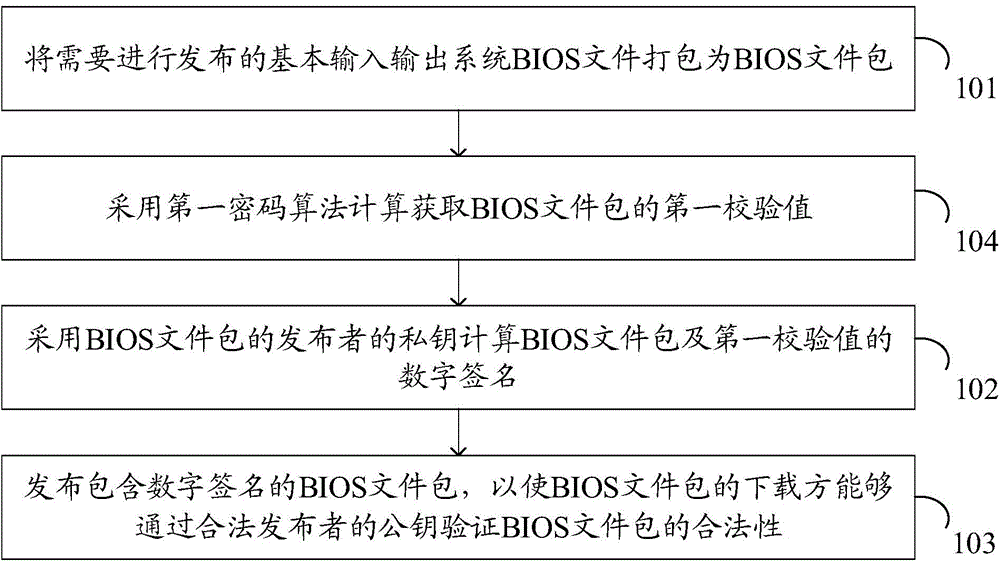
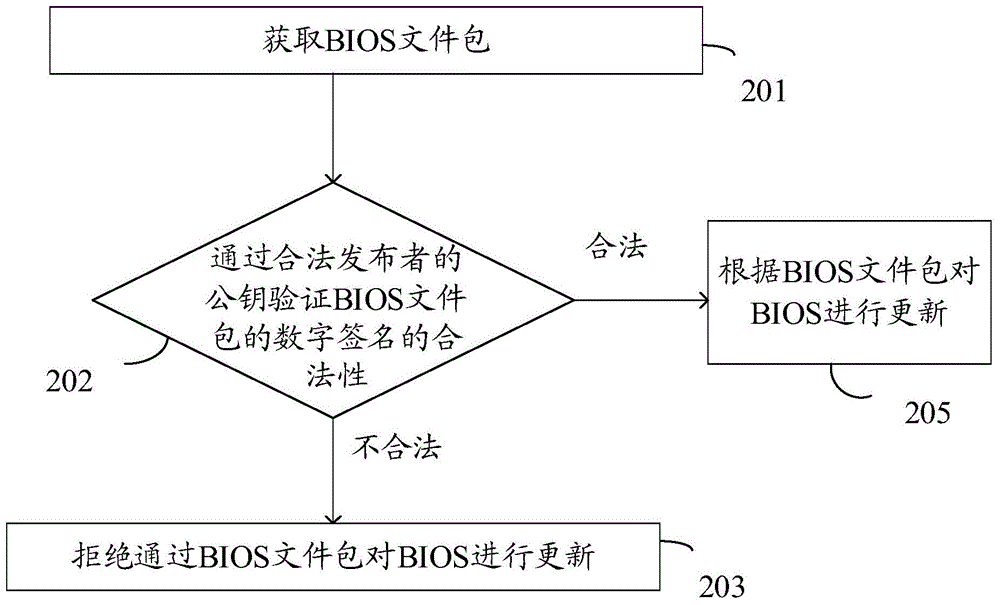
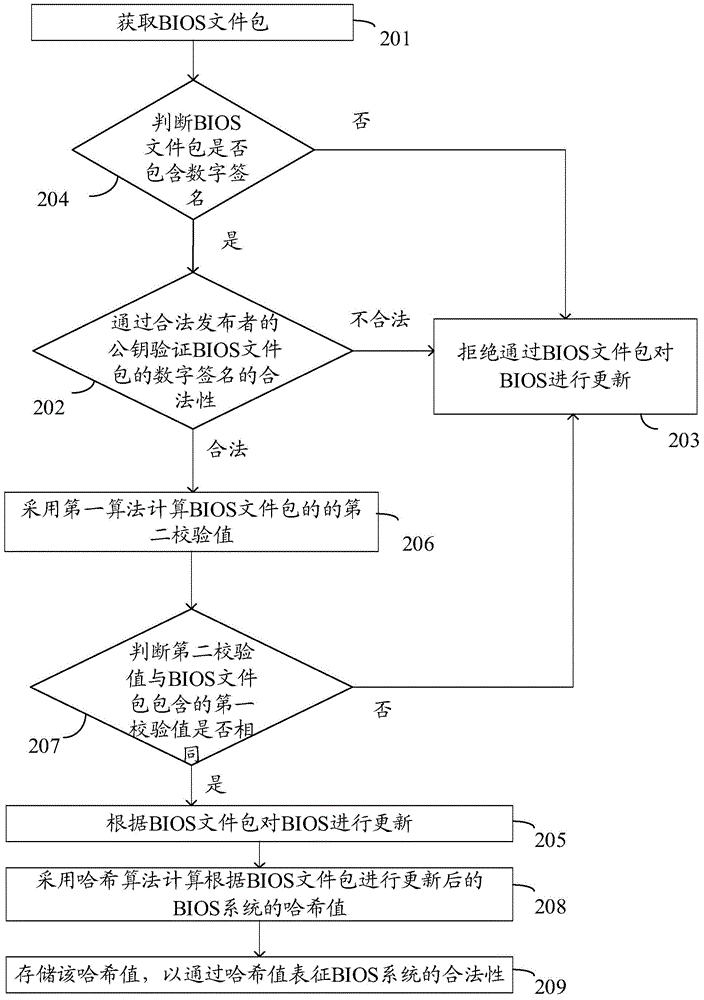
The invention discloses a data processing method and electronic equipment. The method is used for solving the technical problem that an existing BIOS updating security authentication mechanism cannot ensure the security of BIOS updating files. The method is applied to the electronic equipment with a BIOS. The method comprises the steps of obtaining a BIOS file package; verifying the legality of a digital signature of the BIOS file package through a public key of a legal publisher; if the verifying result shows that the digital signature of the BIOS file package is illegal, rejecting updating of the BIOS through the BIOS file package.
Owner:LENOVO (BEIJING) LTD
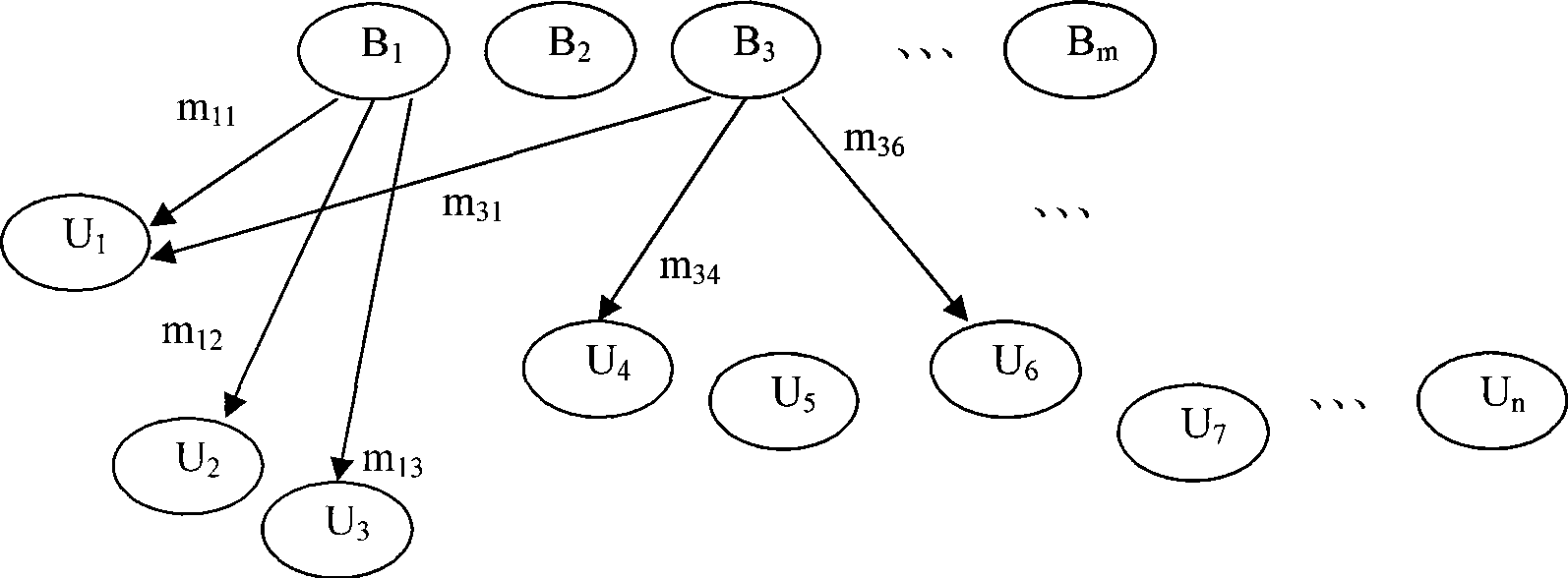
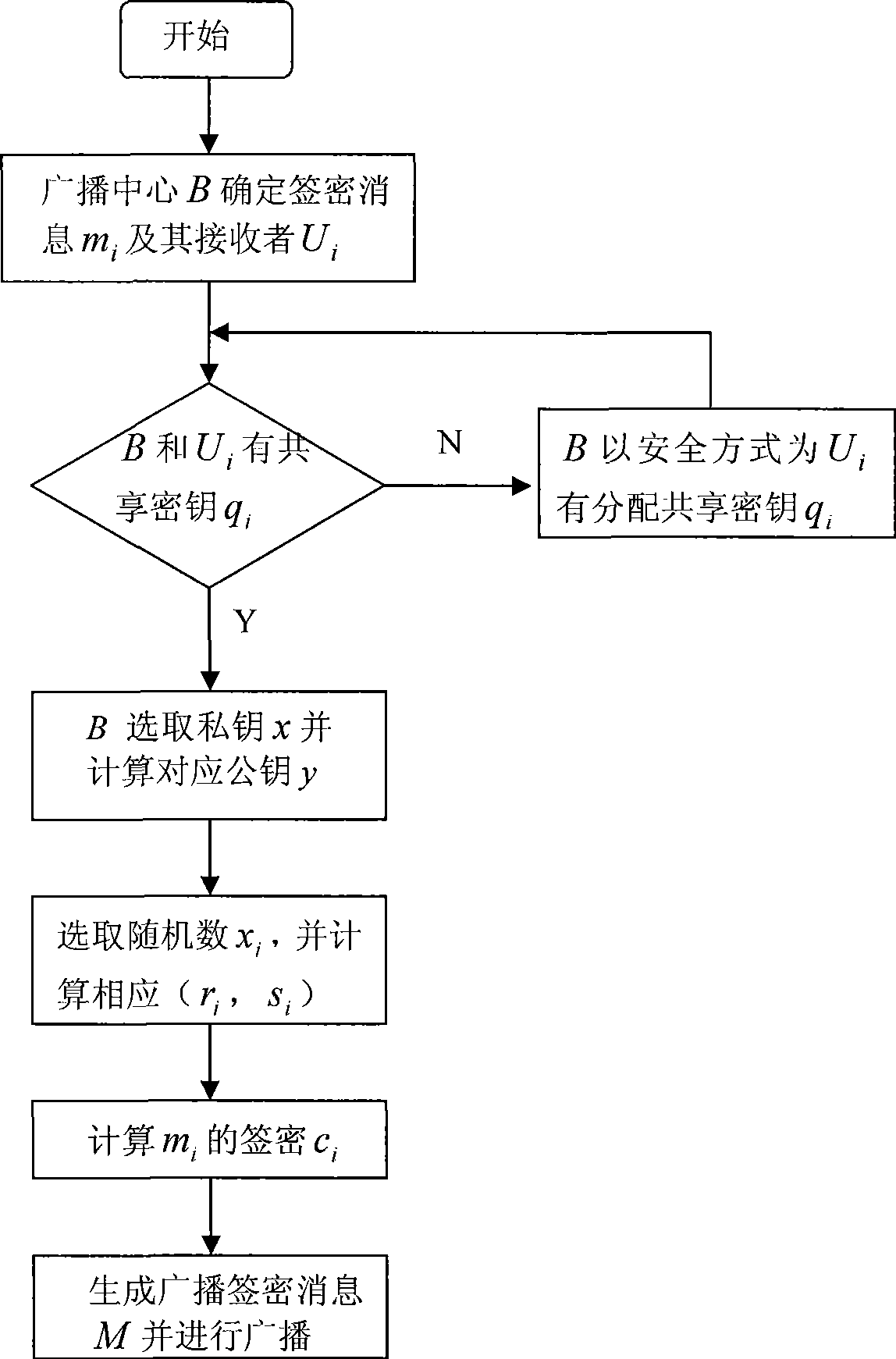
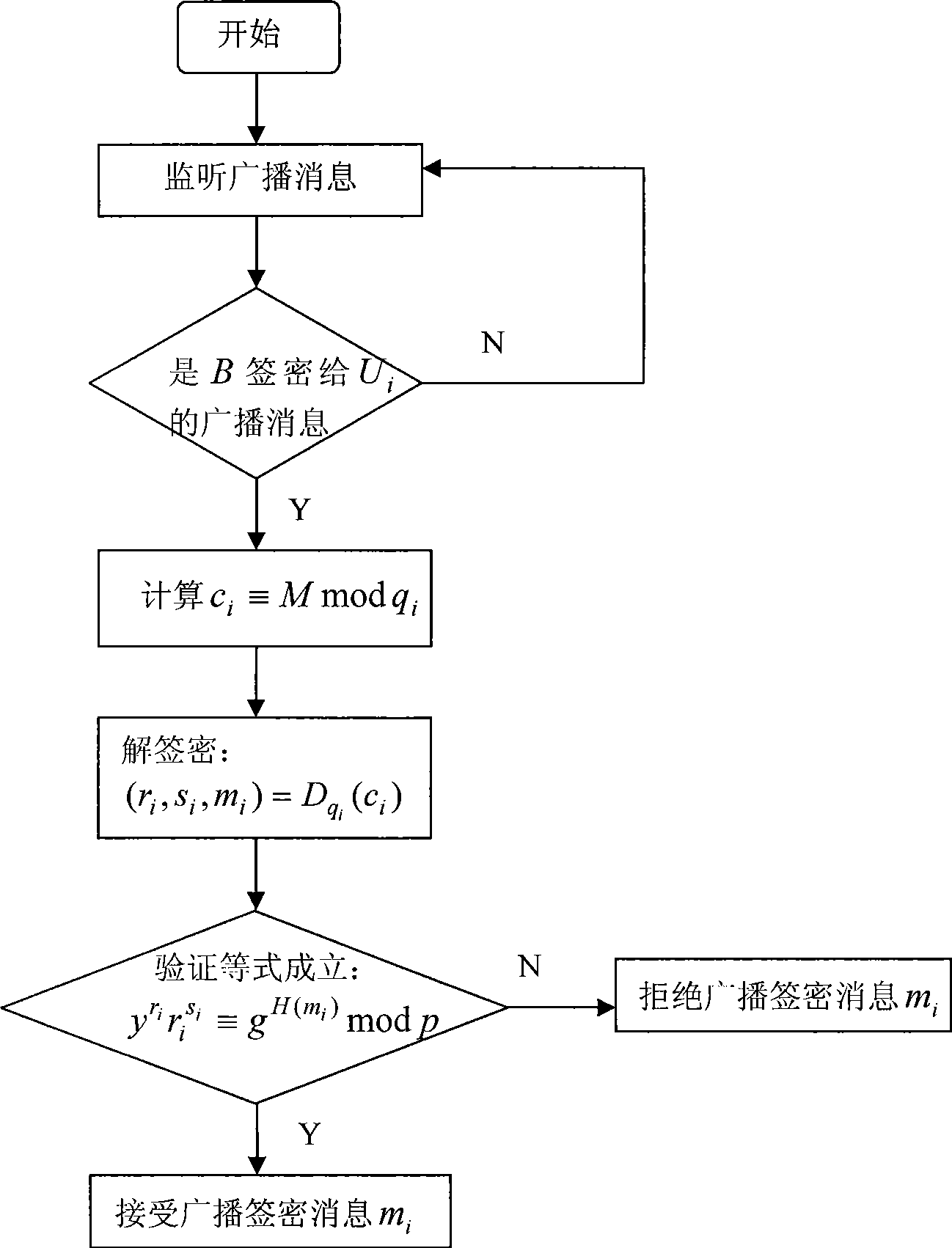
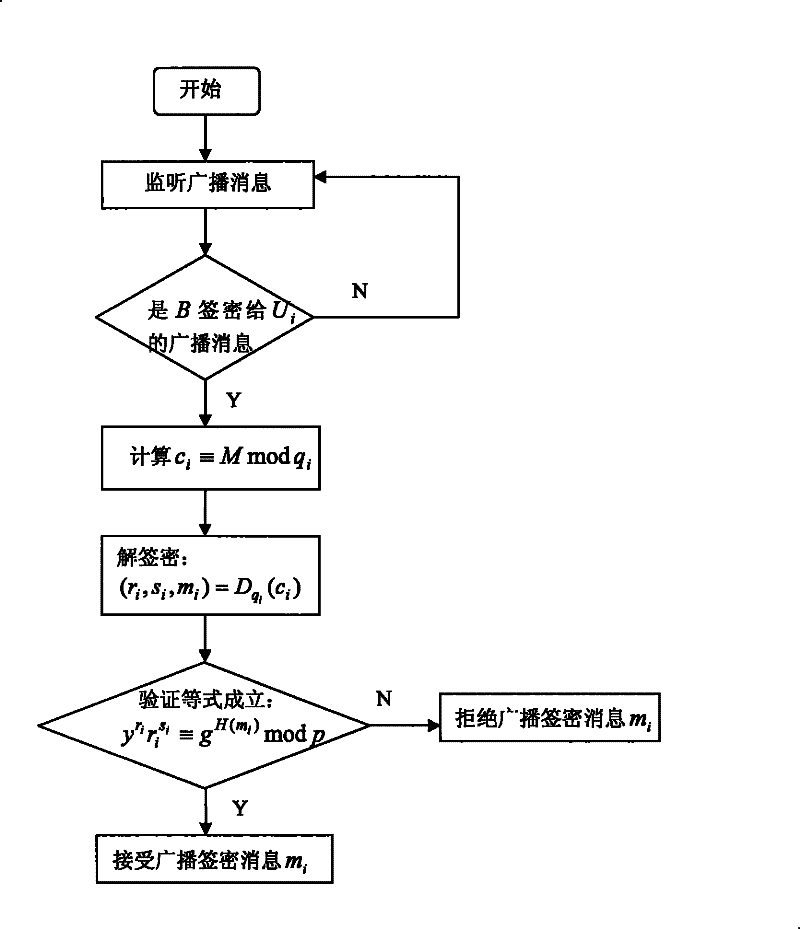
Authentication method by broadcast signature and ciphering
InactiveCN101505301AHigh strengthUnforgeableSpecial service provision for substationPublic key for secure communicationSigncryptionHigh intensity
The invention discloses a broadcast signcryption authentication method, which comprises the following steps that: 1) system parameters are set; 2) a broadcast center calculates public key signature according to the parameters, and uses a user secret key to encrypt message to be broadcasted; 3) the broadcast center broadcasts the encrypted message acquired in step 2) to a user group; and 4) the user receives the encrypted message broadcasted in the broadcast center, uses a private key to decrypt the signature and verifies the validity of the signature. The method carries out two-layer confidential encapsulation of signature and encryption for the message, and broadcasts and mass-sends different messages to a group of users in once broadcast; and only specific authorized users can receive the designated message; therefore, the method has high-strength information confidentiality, signcryption information unforgeability and signcryption information non-repudiation. The method can regulate legal user groups at any time according to actual demand, but does not need to newly distribute new shared secret keys, has high flexibility, can make full use of communication bandwidth, saves cost, and greatly improves the communication efficiency.
Owner:SHIJIAZHUANG RAILWAY INST
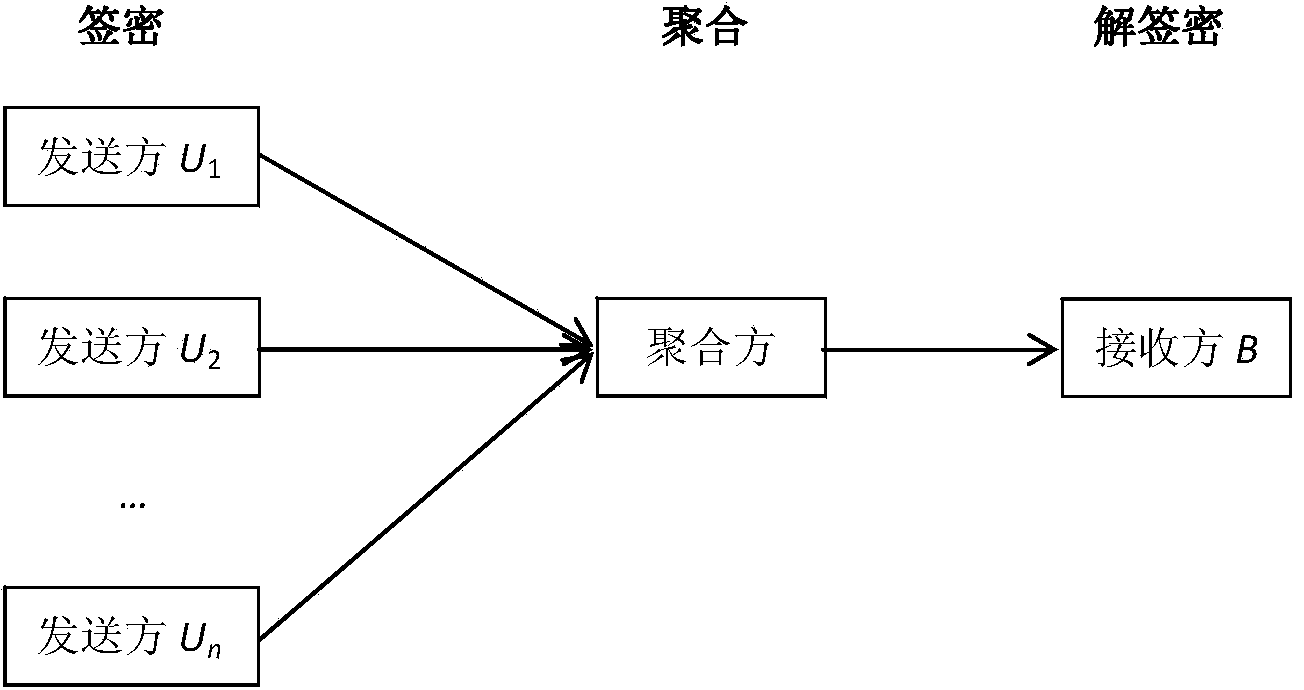
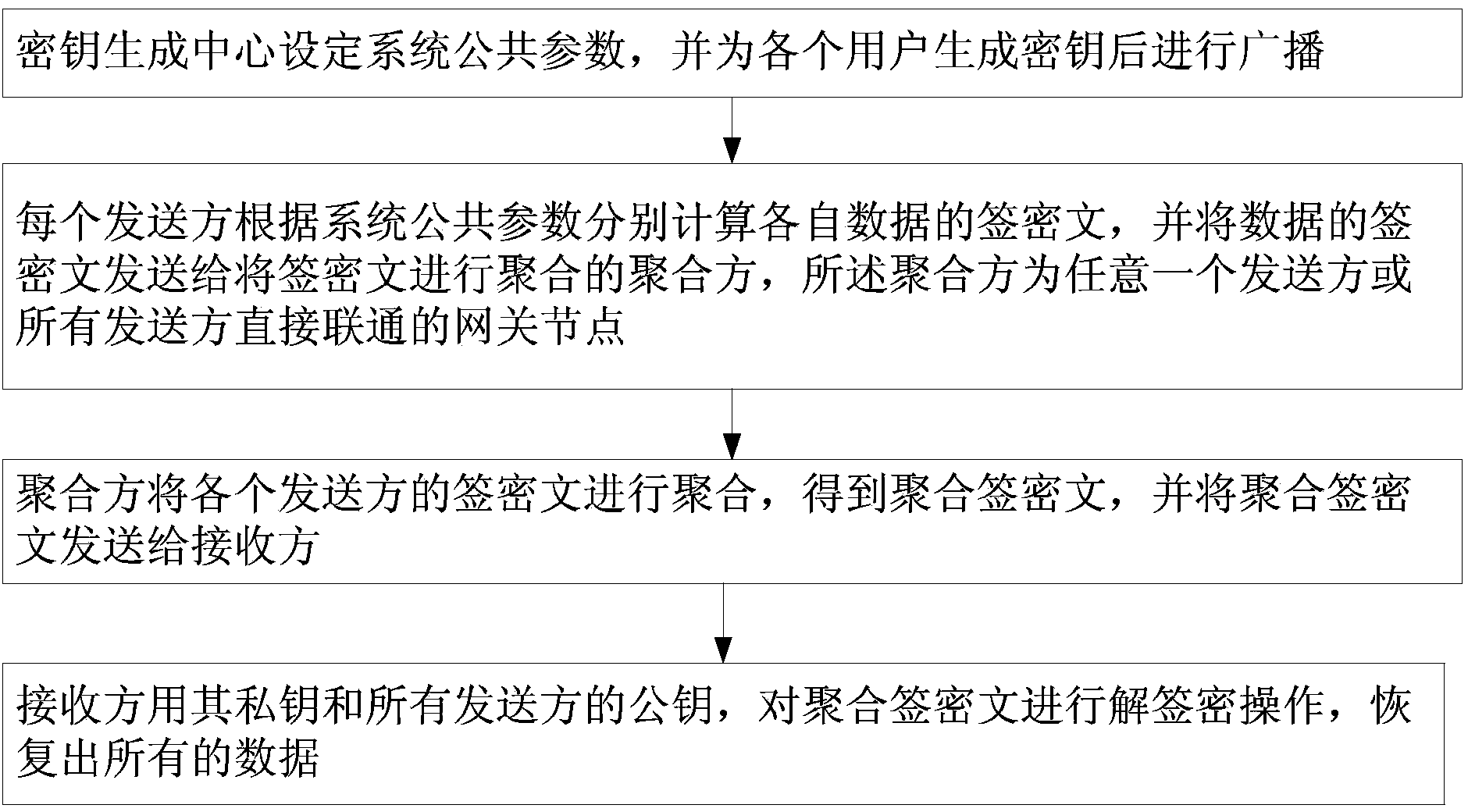
Identity based aggregate signcryption method
InactiveCN104113420AReduce the number of transfersShorten the lengthMultiple keys/algorithms usageUser identity/authority verificationCiphertextConfidentiality
The invention discloses an identify based aggregate signcryption method. The identify based aggregate signcryption method includes the following steps that (1) a key management center sets system public parameters and produces user keys; (2) each sending party signcrypts respective data to produce a signcryption text; (3) an aggregate party aggregates all signcryption texts to produce aggregated signcryption texts; (4) a receiving party verifies the aggregated signcryption texts. According to the identify based aggregate signcryption method, three parameters in the signcryption texts of each sending party are aggregated, and the data size of the entire signcryption texts is totally the same as that of a single signcryption text; meanwhile, the receiving party can achieve verification of all the signcryption texts only through once verification operation, and the calculated amount of the verification of all the signcryption texts is basically equivalent to that of the verification of the single signcryption text; confidentiality, integrality, and authentication can be simultaneously achieved in the aspect of safety; the defect of low efficiency caused by the fact that each sending party sends the signcryption texts and the receiving party verifies the signcryption texts one by one in traditional methods is overcome, and higher transmission efficiency and computational efficiency are achieved.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
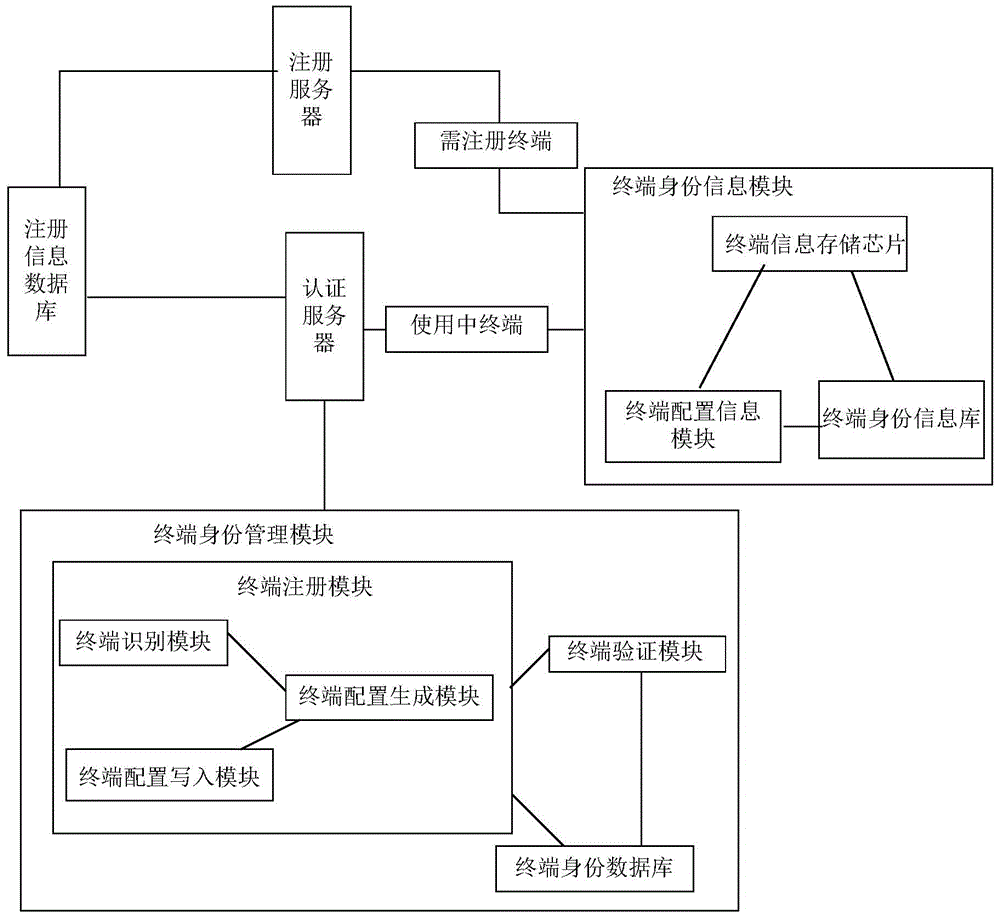
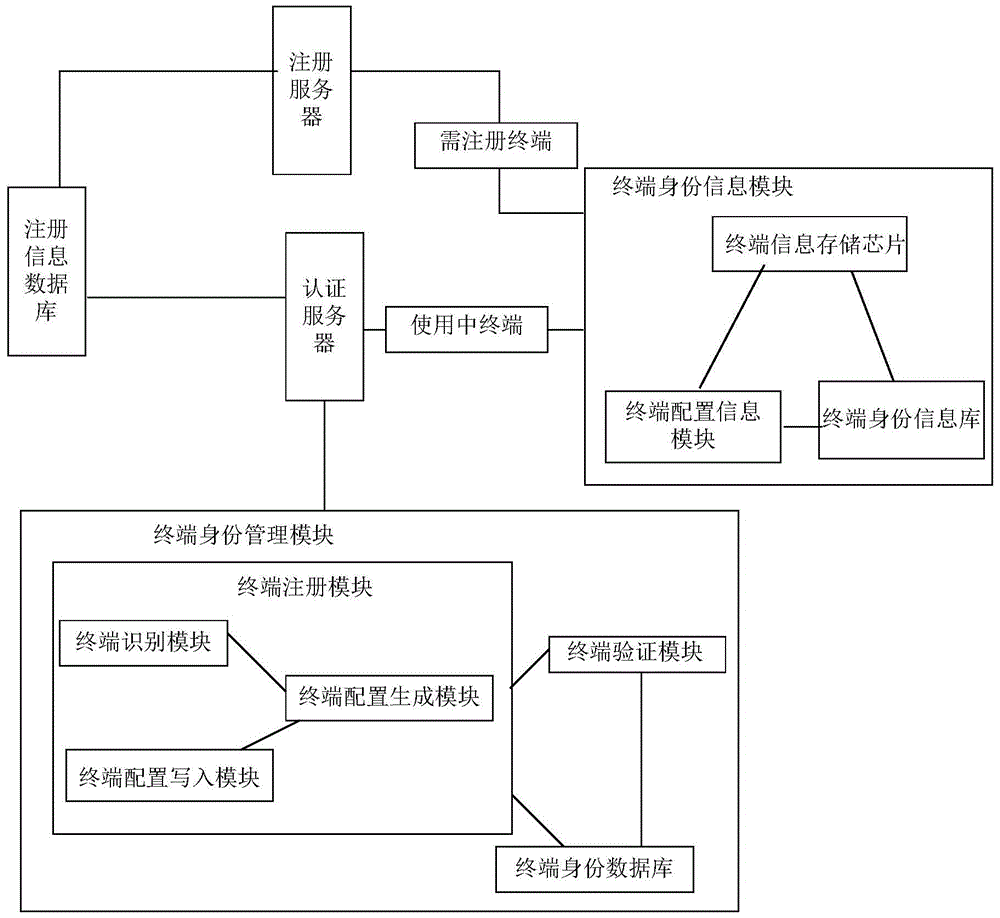
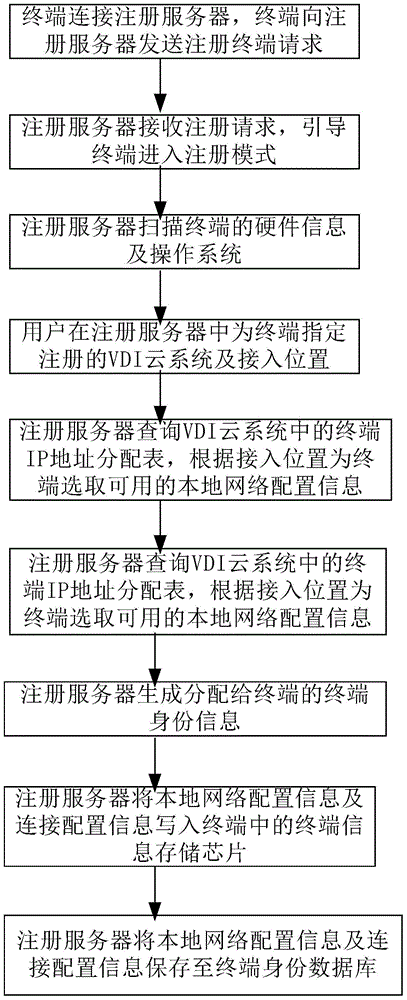
Registration system and registration method for full hardware terminal in cloud desktop system
The invention provides a registration system and a registration method for a full hardware terminal in a cloud desktop system. The registration system comprises a terminal identity information module, a terminal identity management module, a registration server and a registration information database; the terminal identity information module and the registration information database are both connected with the registration server; the terminal identity information module and the terminal identity management module are both connected with the registration information database; the terminal identity information module is positioned above terminal equipment, is composed of hardware of the terminal equipment as well as configuration and certification information stored inside the terminal equipment, and is used for authentication of the terminal equipment; the terminal identity management module is used for managing identity information, and is used for creating, registering, authenticating and managing terminal identity information. According to the system and the method provided by the invention, the registration of the terminal equipment and the storage of the configuration information of the terminal equipment are realized, so that the terminal equipment has unforgeability, and the safety and the reliability of the terminal equipment in the cloud desktop system are improved.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
Blockchain medical data management method based on distributed attribute signature and system
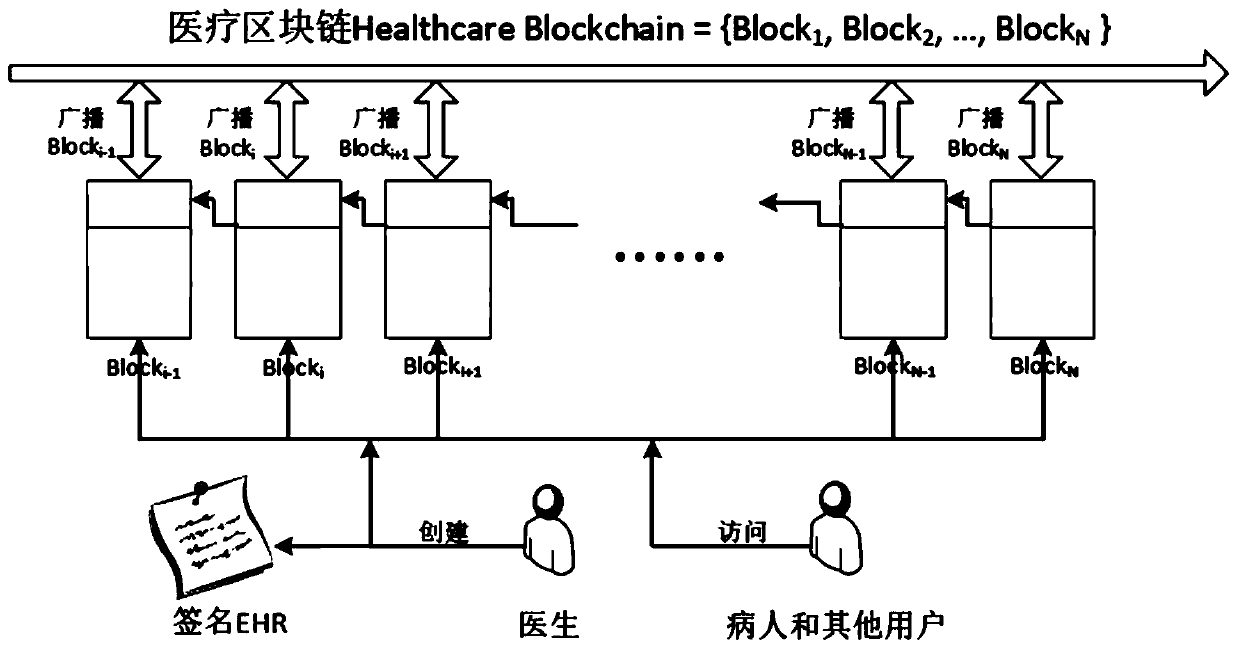
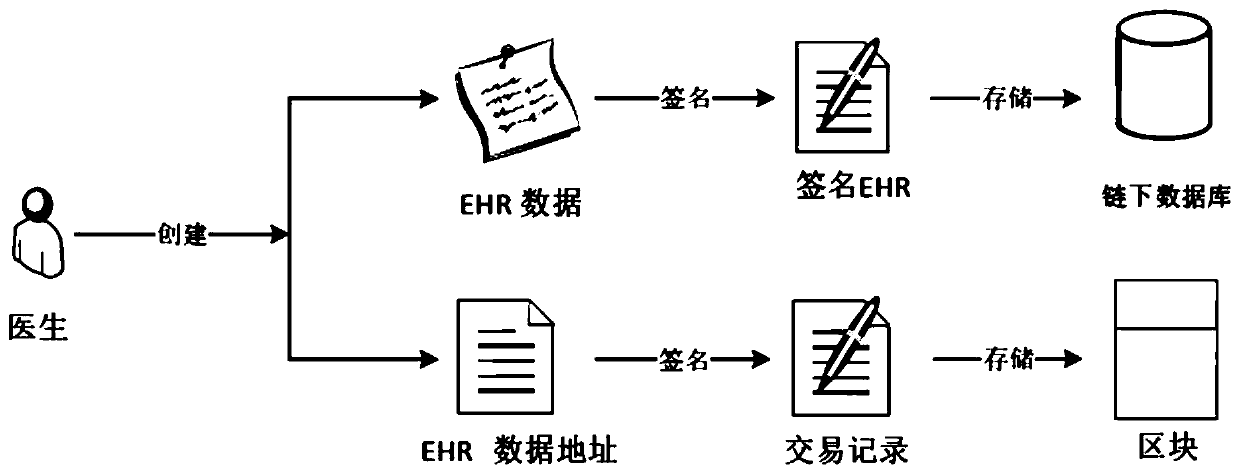
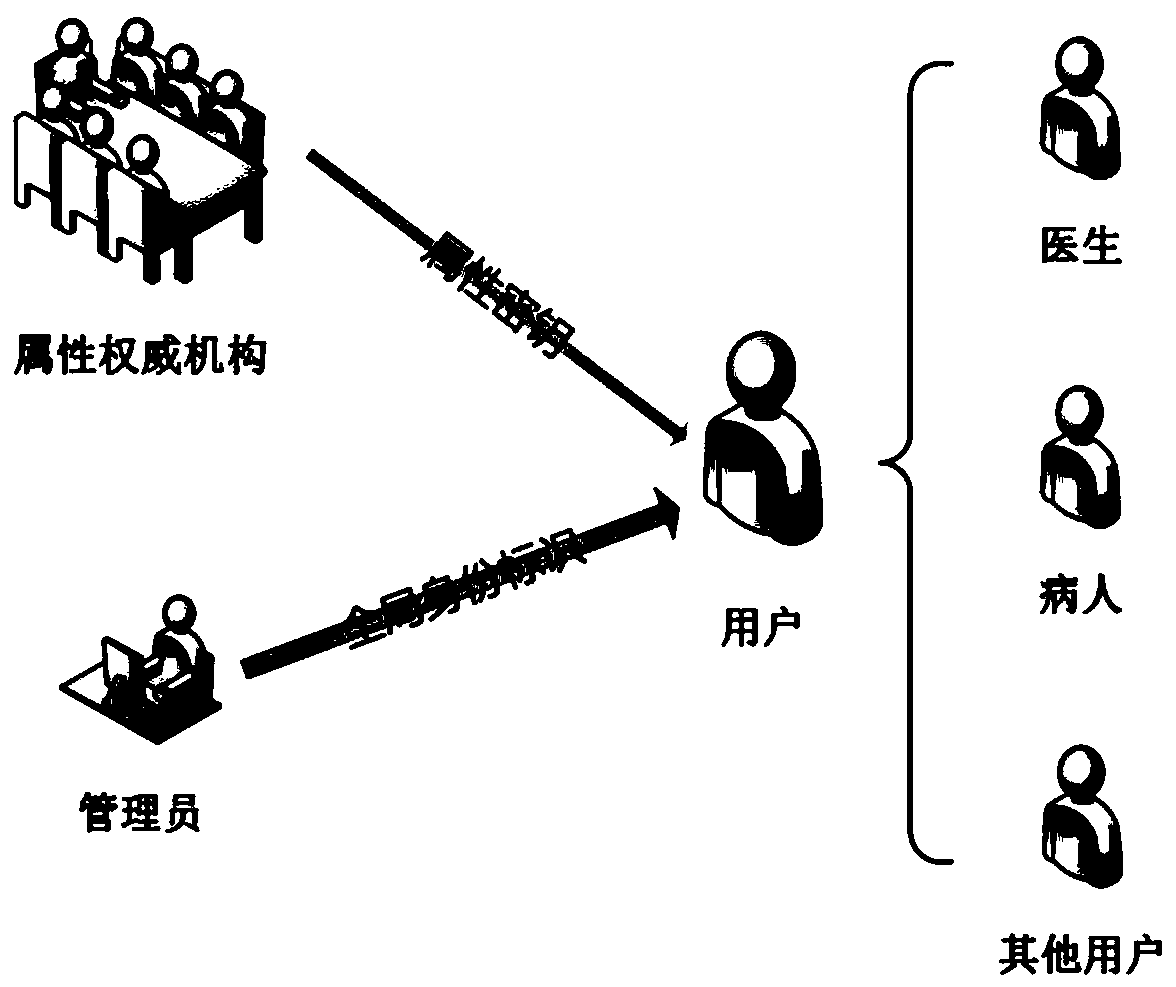
ActiveCN109979550AAttribute validationDo not reveal identityDigital data protectionPatient-specific dataHash functionFinancial transaction
The invention discloses a blockchain medical data management method based on distributed attribute signature and a system. The method comprises the following steps of S1, generating a global parameterof the distributed attribute signature and selecting a Hash function; S2, producing a signature secret key and a verification secret key which correspond with each attribute by each attribute authority mechanism; S3, generating a signature secret key set which corresponds with the global identity identification and the attribute set of a user by the user; S4, after generating EHR data by the user, storing the signature in an off-chain database, performing address signature on the HER data, and issuing the address signature in the blockchain; and S5, firstly verifying the signature attribute of the address which is stored in an on-line transaction by the user, and finding the EHR in the off-chain database through the address and verifying the attribute of a data signature person. The blockchain medical data management method and the system have advantages of protecting identity information of the signature person, realizing EHR data safe sharing over different CDO systems, and settlinga problem of blockchain storage capacity limitation through an on-chain and off-chain coordinated storage mode.
Owner:INST OF INFORMATION ENG CAS
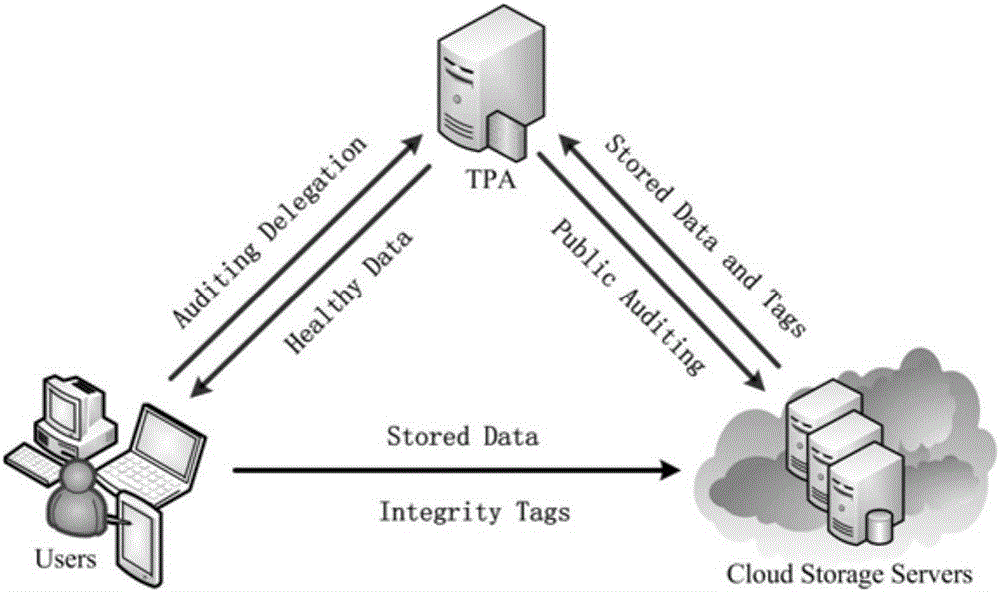
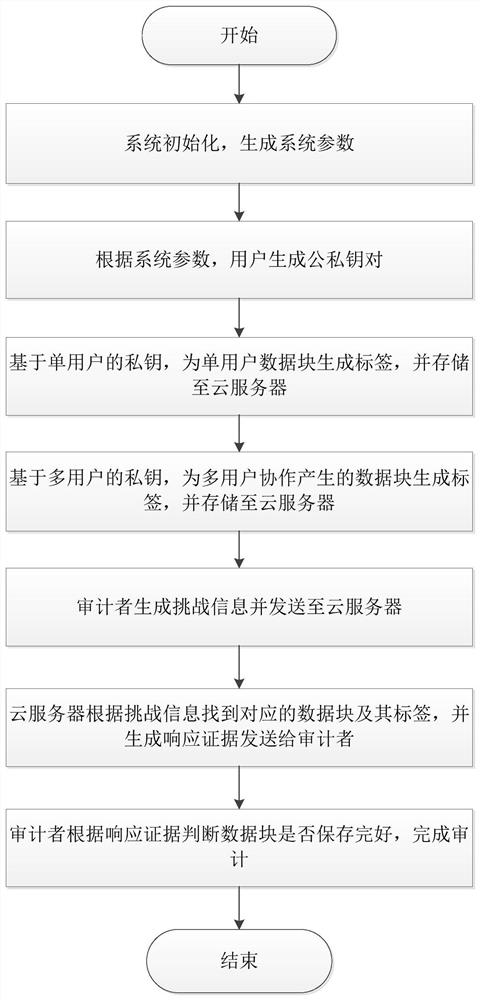
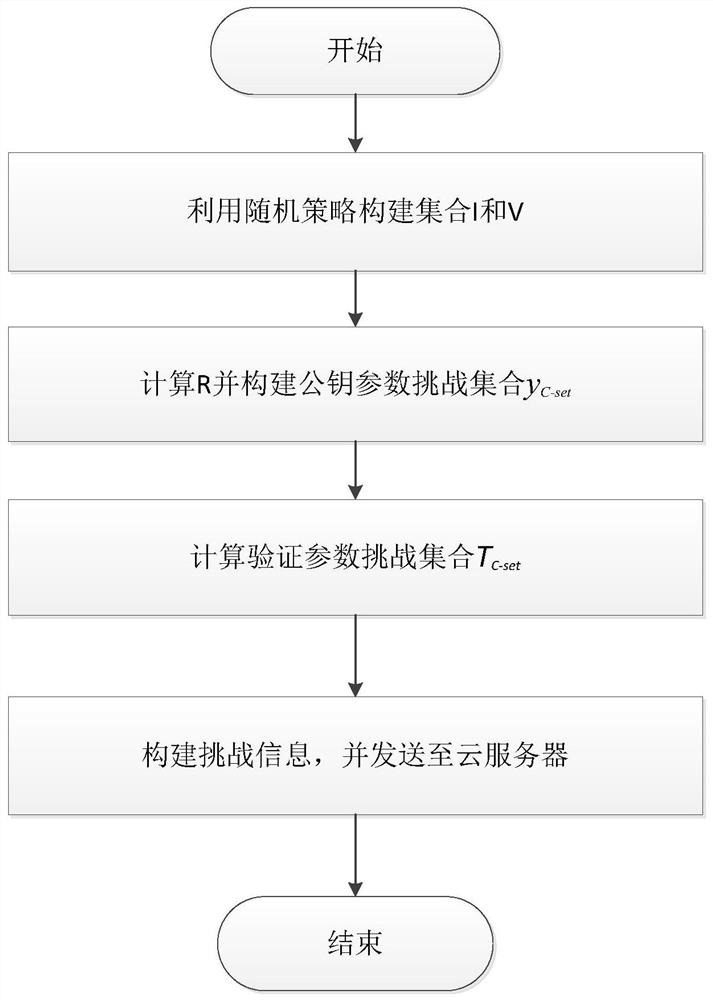
Public auditing method supporting composite data
ActiveCN111859030AUnforgeableSimultaneous auditingDigital data protectionOffice automationData privacy protectionEngineering
The invention discloses a public auditing method supporting composite data, and relates to the field of data security in cloud computing. The method comprises the following steps: generating a publicand private key pair according to system parameters; generating a label for a single-user data block based on a private key of the single-user public and private key pair, and storing the label to a cloud server; based on the private key of a multi-user public and private key pair, generating a label for a data block generated by multi-user cooperation, and storing the label to the cloud server; an auditor generating challenge information and sending the challenge information to the cloud server; the cloud server finding corresponding data blocks and labels thereof according to the challenge information, generating response evidences and sending the response evidences to the auditor; and the auditor judging whether the data blocks are well stored according to the response evidences to finish auditing. According to the method, the number of participating members is not limited when the multi-user data is generated, the single-user data and the multi-user data can be audited at the sametime, data privacy protection and identity privacy protection are achieved in the auditing process, and identity tracing of a data block generator is achieved.
Owner:SOUTHWEST JIAOTONG UNIV
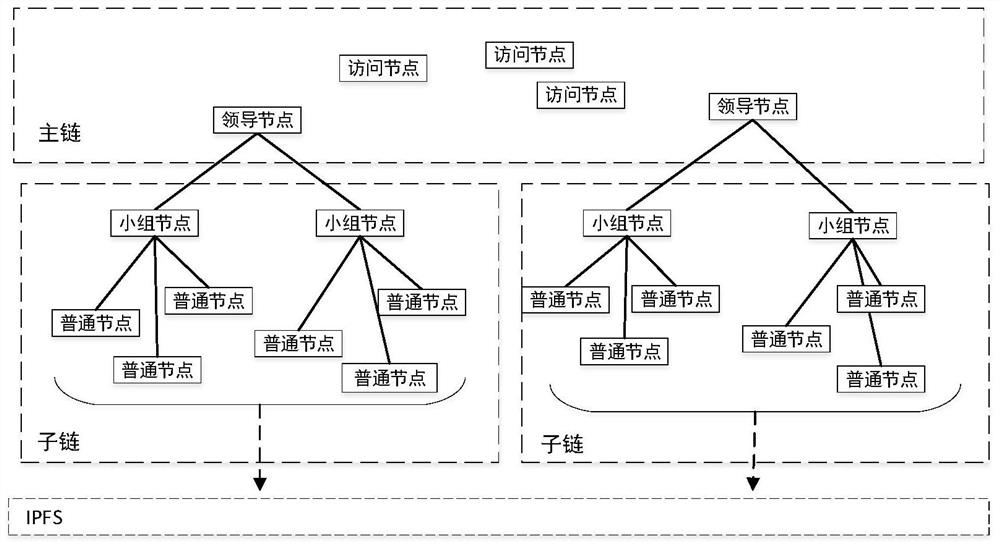
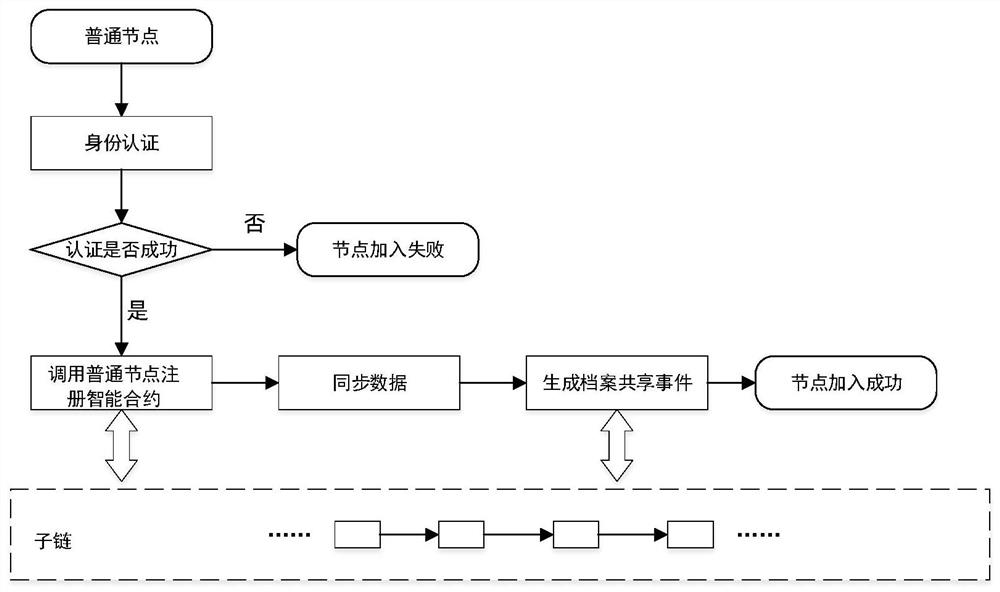
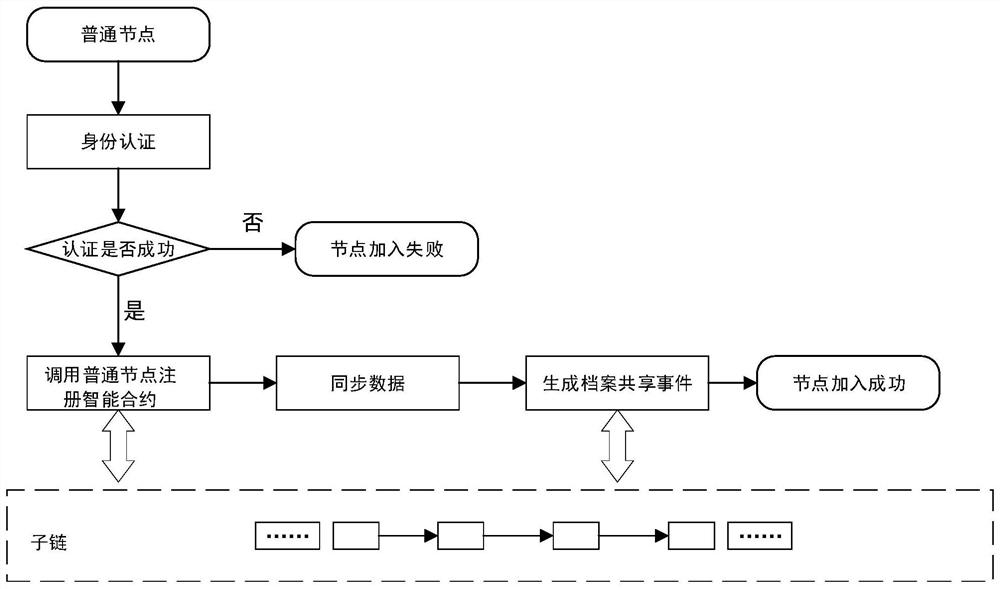
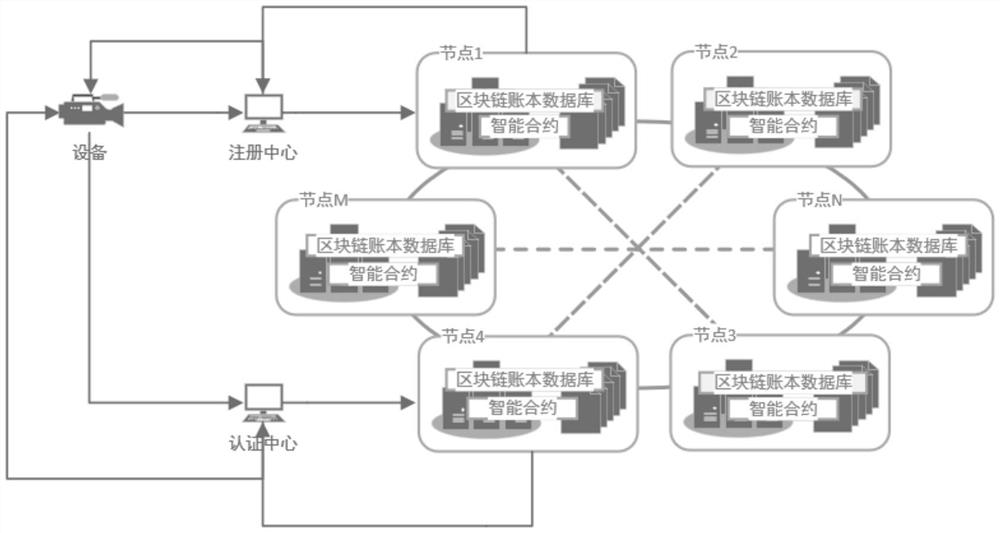
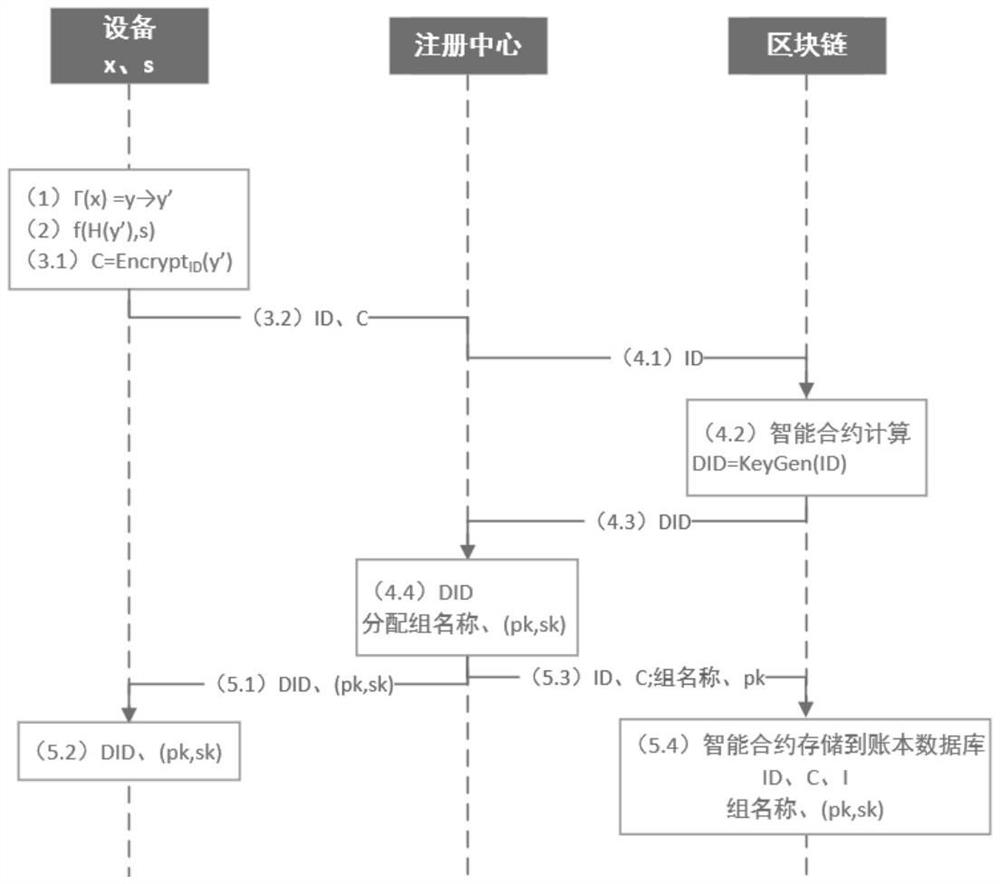
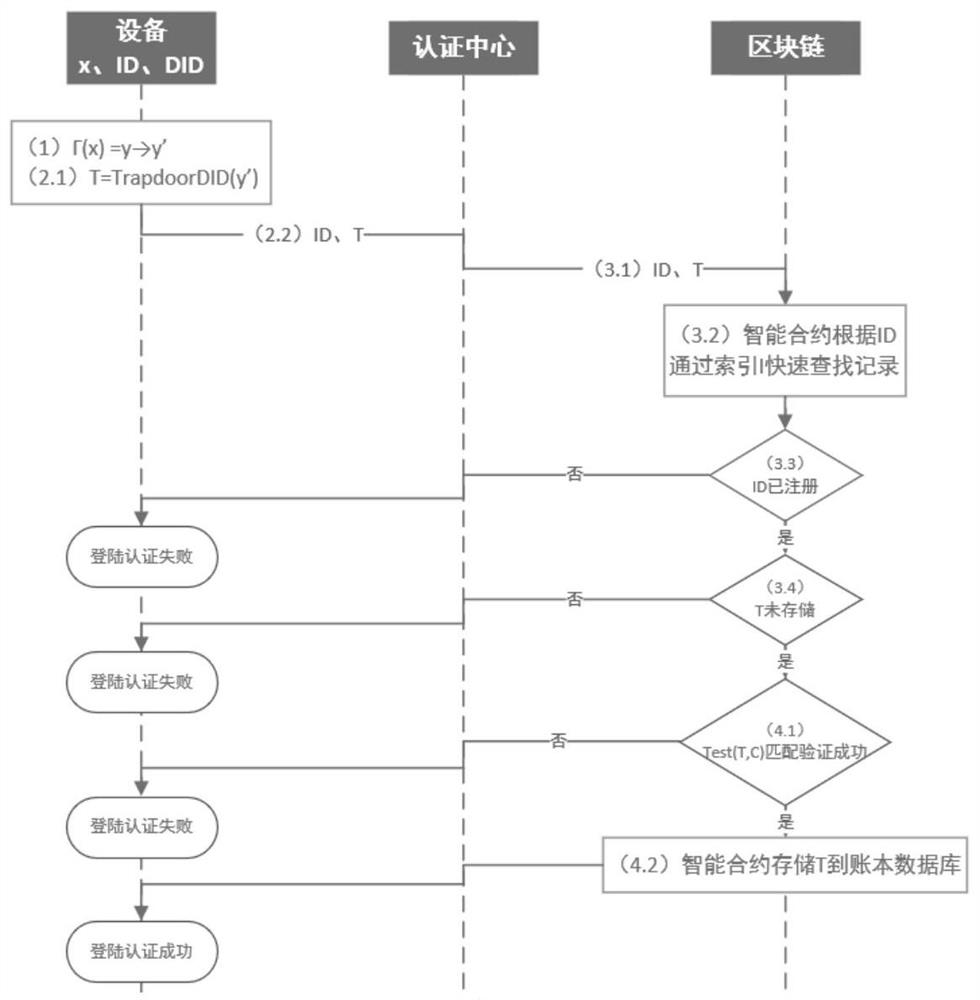
Archive secure storage and sharing system based on hybrid block chain and implementation method
ActiveCN112540957AAddress the right to knowSolve protection problemsDatabase distribution/replicationDigital data protectionThird partyPrivacy protection
The invention discloses an archive secure storage and sharing system based on a hybrid block chain and an implementation method, belongs to the field of archive sharing, and aims to solve the technical problem of how to realize archive privacy protection, prevent archives from forging and tampering, enable authorized access of the archives, and improve the archive sharing speed. According to the technical scheme, the system comprises a storage layer which is used for storing shared files and protecting the files against tampering, and adopts an IPFS; a sharing layer which is used for recordinggenerated transaction information, providing evidences for tracing of the file sharing process, automatically executing identity authentication and guaranteeing safe sharing of files under the condition that no third party participates, and comprises a multi-layer block chain model and an intelligent contract on a block chain; and a user layer which is used for managing, updating, checking and sharing files, and is composed of participants. The method specifically comprises the following steps: initializing; identity registration and authentication; encrypting and storing the archives; and archive sharing.
Owner:QILU UNIV OF TECH
Anti-counterfeiting system and anti-counterfeiting method based on random anti-counterfeiting marks
InactiveCN104794624AUnforgeableNon-repudiationCo-operative working arrangementsCharacter and pattern recognitionThird partyCommunications system
The invention relates to an anti-counterfeiting system and an anti-counterfeiting method based on random anti-counterfeiting marks. The anti-counterfeiting system comprises a server, a sampling device and an inspection device which are connected to one another through a communication system. The anti-counterfeiting marks cannot be counterfeited; by the anti-counterfeiting method, a manufacturer cannot deny if the manufacture transmits the anti-counterfeiting marks to a server; the system can track all operations on the anti-counterfeiting marks; each anti-counterfeiting mark is associated with a corresponding user or a corresponding factory; all operation records and related information of all the anti-counterfeiting marks can be audited and consulted; the anti-counterfeiting system runs in the server by a third party; and when the third part follows rules severely, the anti-counterfeiting marks cannot be counterfeited or denied through the anti-counterfeiting system, and the anti-counterfeiting cost is low.
Owner:石立公
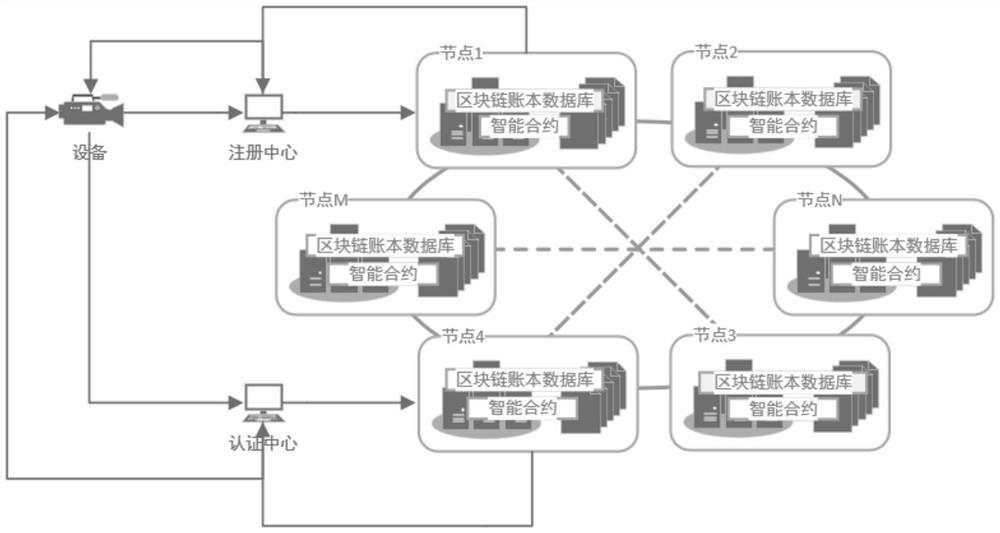
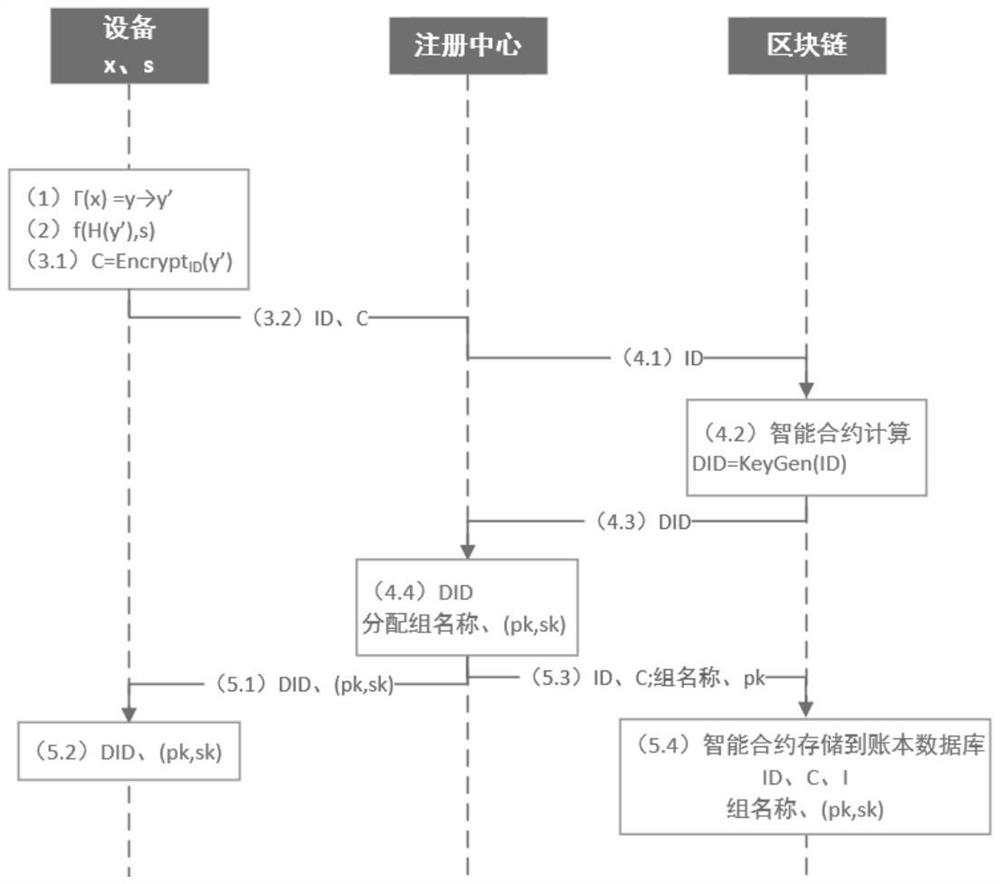
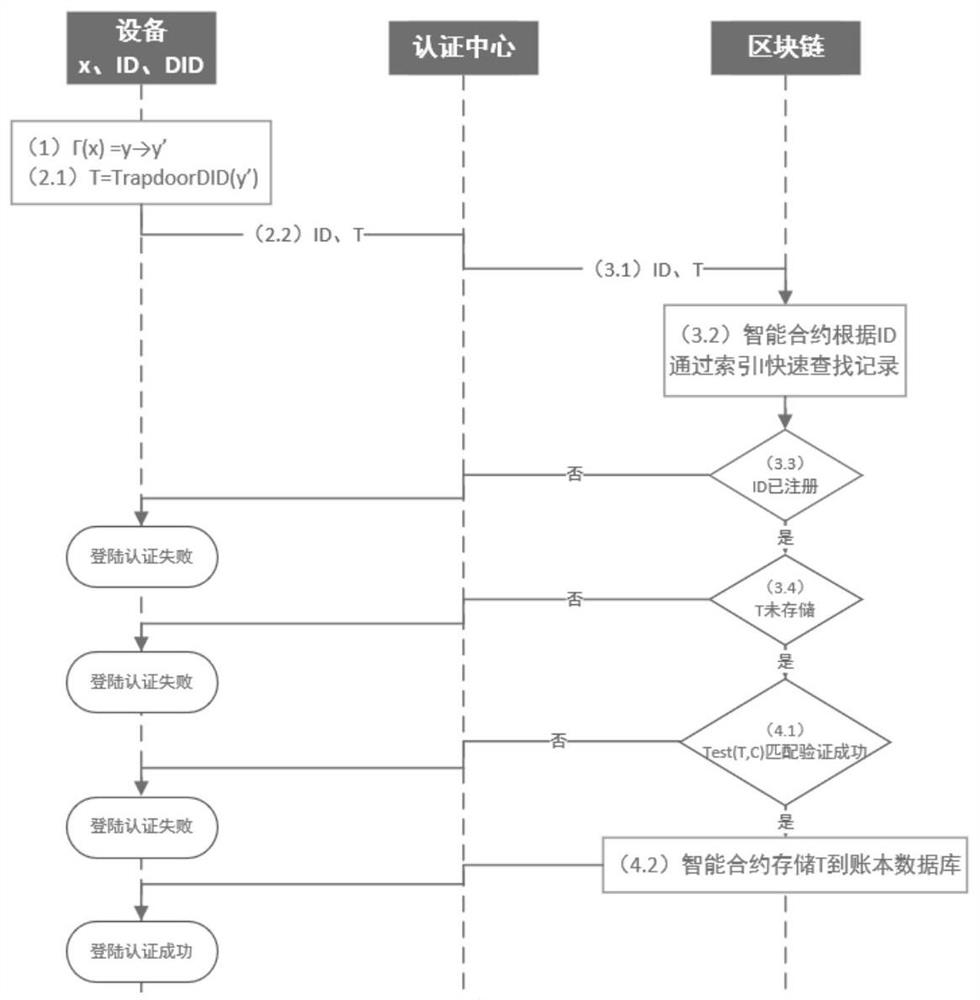
Intelligent Internet of Things equipment authentication method and system based on blockchain
ActiveCN113162768ACannot be tampered withUnforgeableKey distribution for secure communicationUser identity/authority verificationRing signatureCiphertext
The invention discloses an intelligent Internet of Things device authentication method and system based on a blockchain, and the method comprises the steps that equipment generates an identity label of the equipment based on a physical unclonable function, takes the identity label of the equipment as a public key of a searchable encryption algorithm, and generates a ciphertext; a registration center generates a private key of a searchable encryption algorithm corresponding to the equipment based on the smart contract and the distributed account book database, and distributes a public and private key pair of a group name and a ring signature algorithm to the equipment to complete registration of the equipment; an authentication center performs searchable encryption based on the identity label of the equipment by using an intelligent contract to realize personal login authentication of the equipment; and group login authentication of the equipment is realized based on a ring signature algorithm. According to the method, effective combined authentication can be implemented on the intelligent Internet of Things equipment, the intelligent contract is automatically executed, the problem of excessive resource consumption is reduced, the novel cryptographic algorithm is higher in calculation efficiency, and the safety of the system can be better ensured.
Owner:UNIV OF SCI & TECH BEIJING
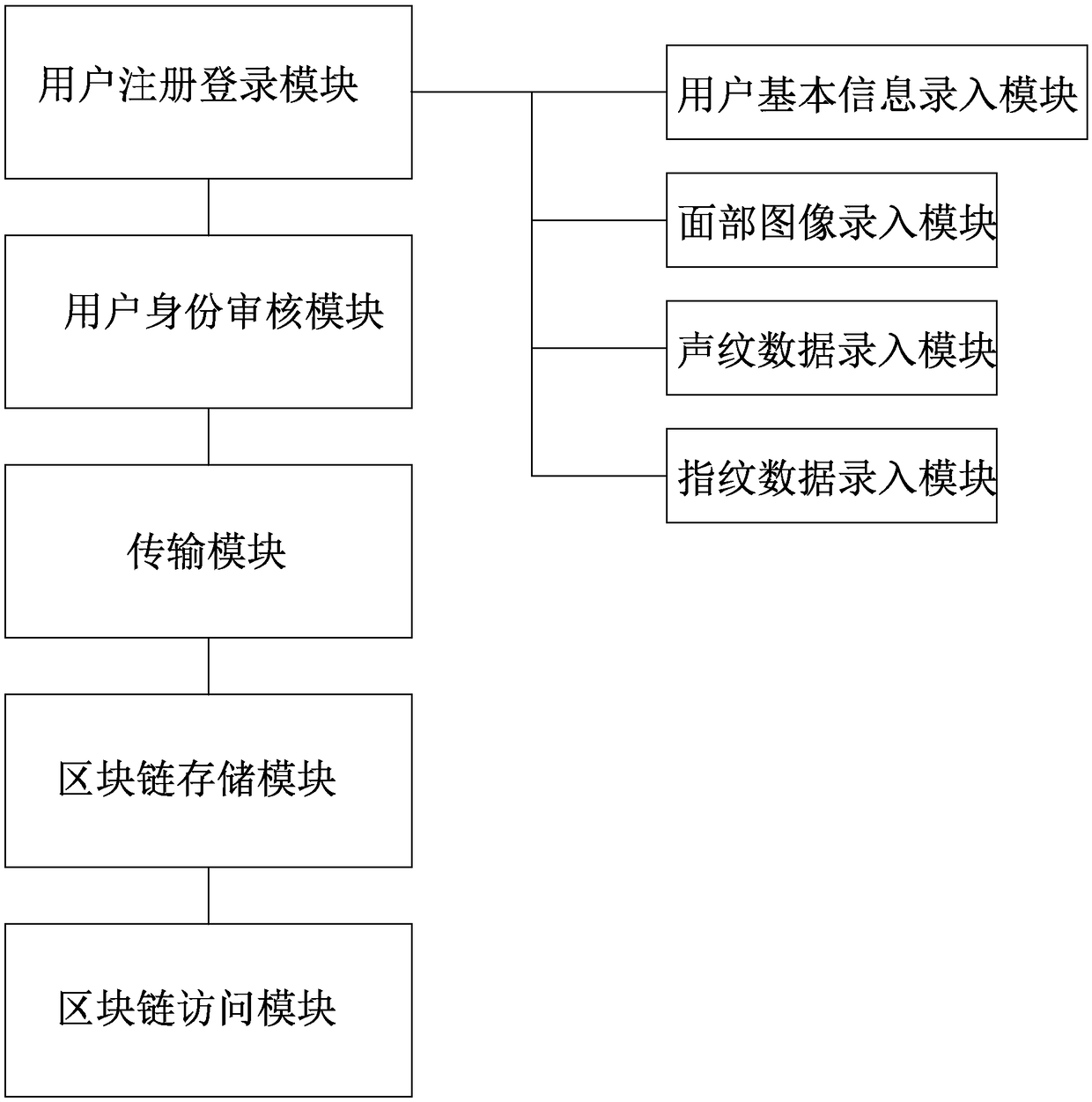
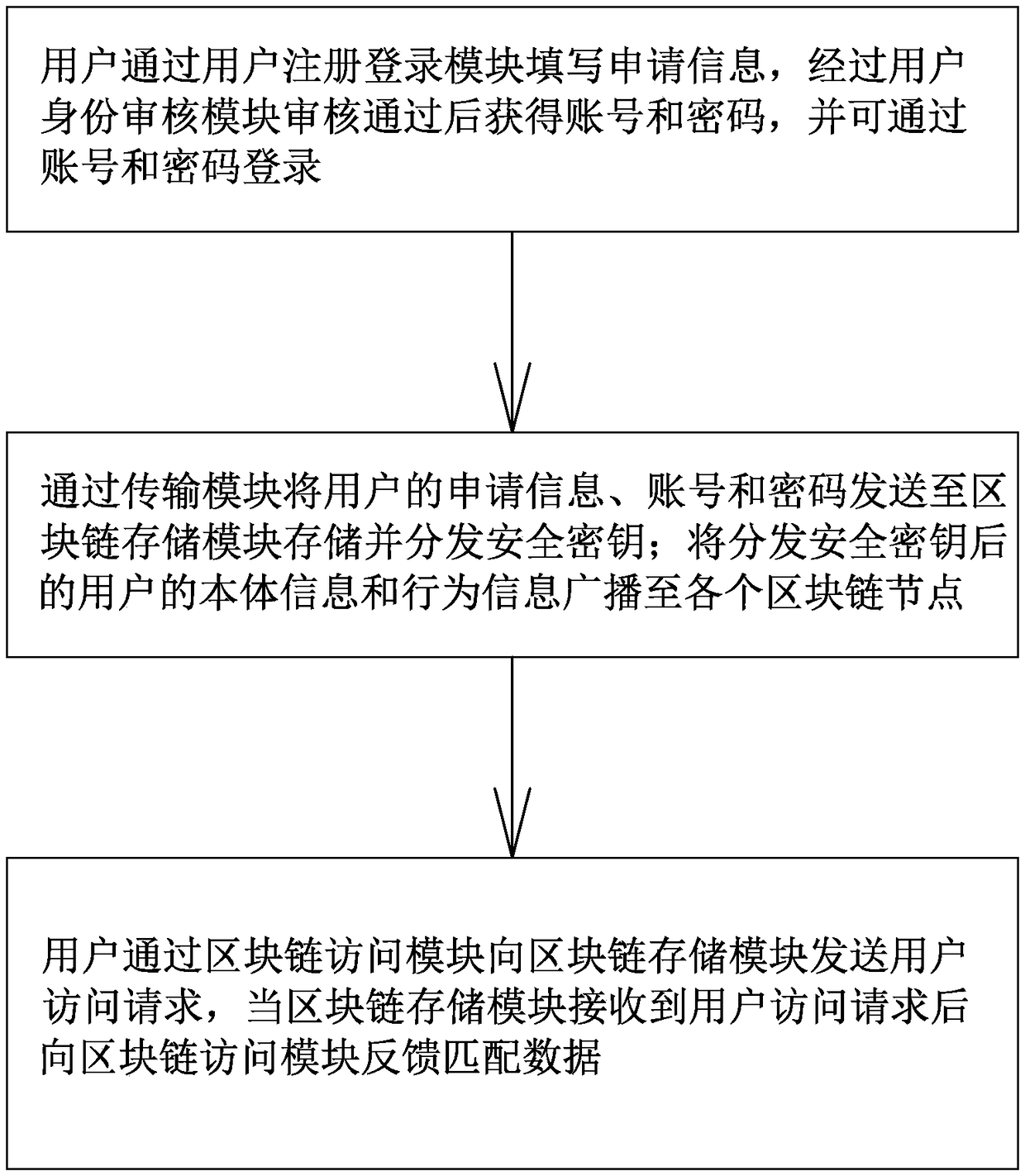
A user management system and a user management method
InactiveCN109271769ASafe storageUnforgeableFinanceDigital data authenticationComputer scienceUser management
The invention discloses a user management system, which is characterized in that the system comprises a user registration login module, a user identity audit module, a transmission module, a block chain storage module and a block chain access module. An object of the present invention is to provide a user management system and a user management method based on the user management system in order to overcome shortcomings in the prior art.
Owner:广东博商商业服务有限公司
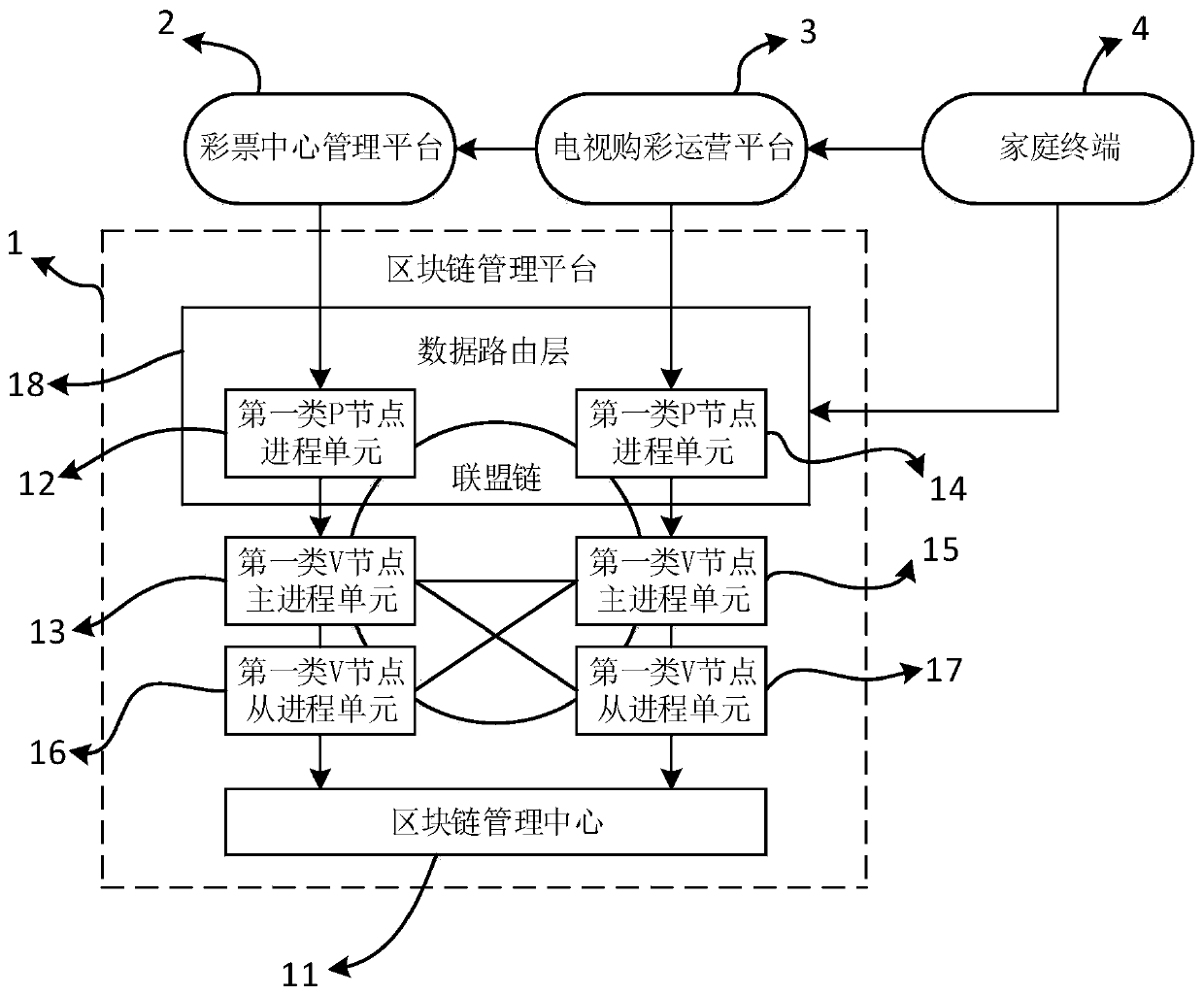
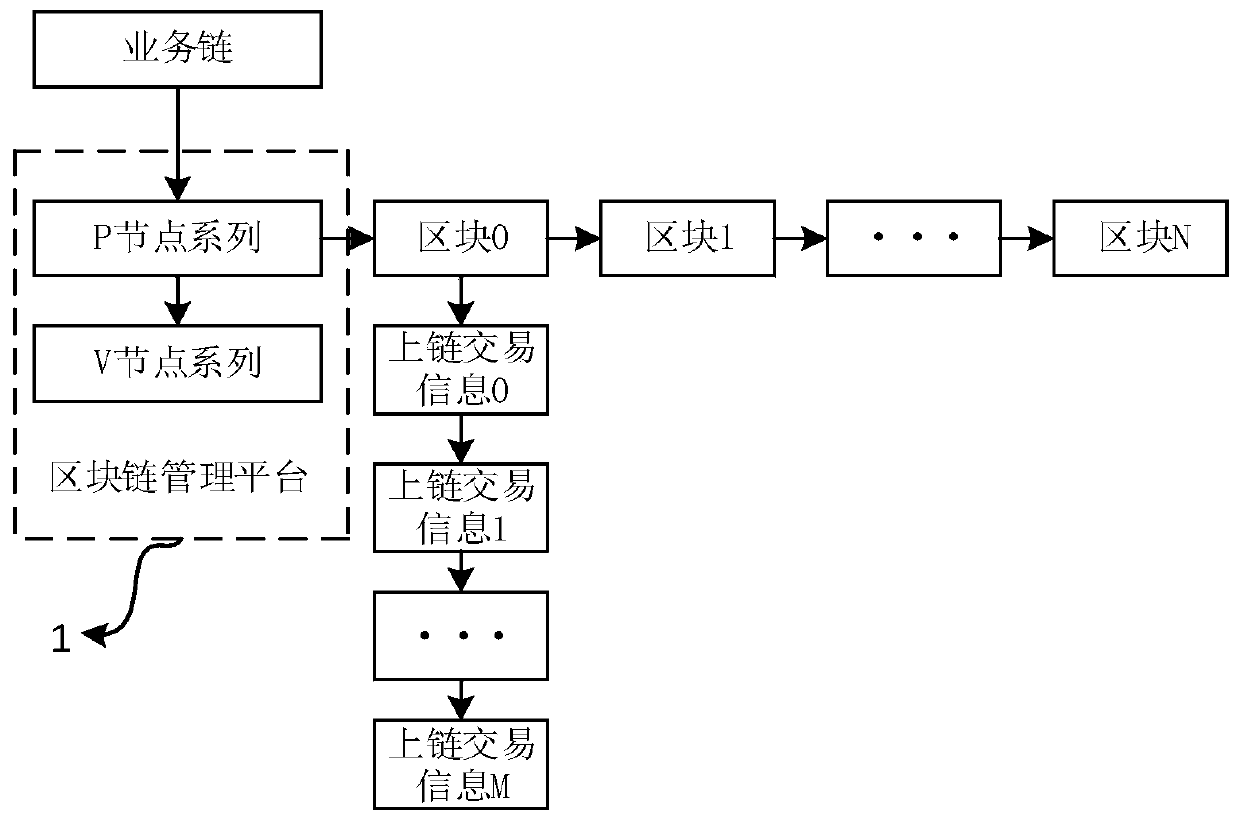
Blockchain television lottery buying system
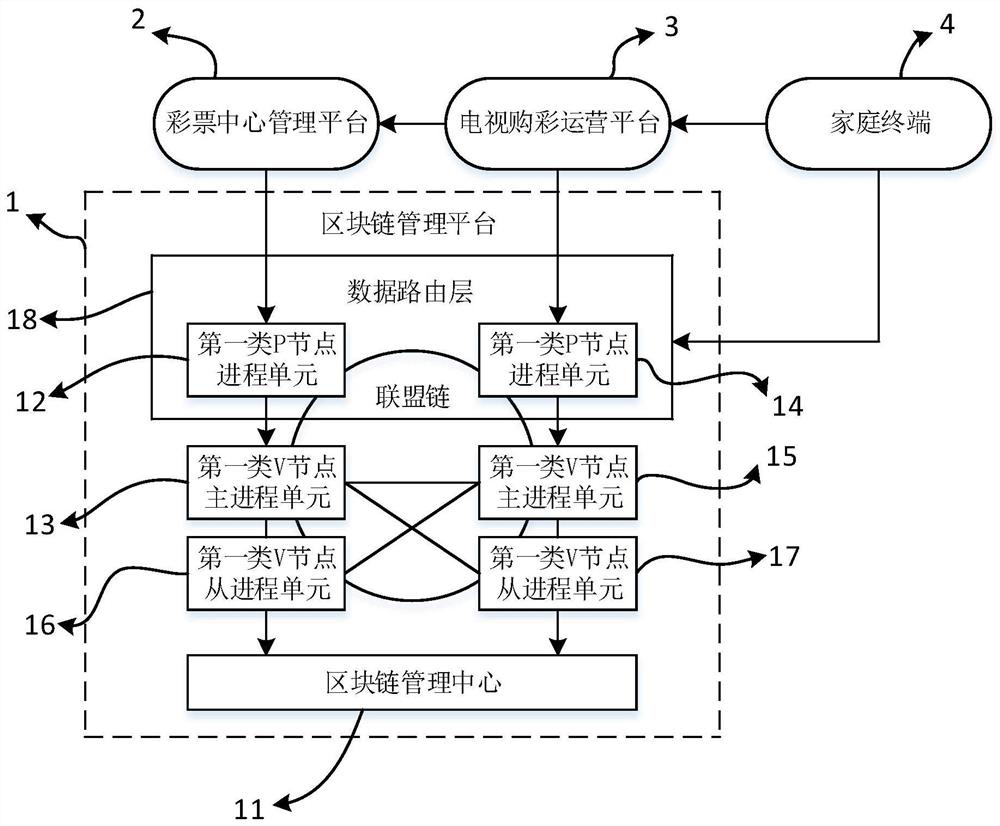
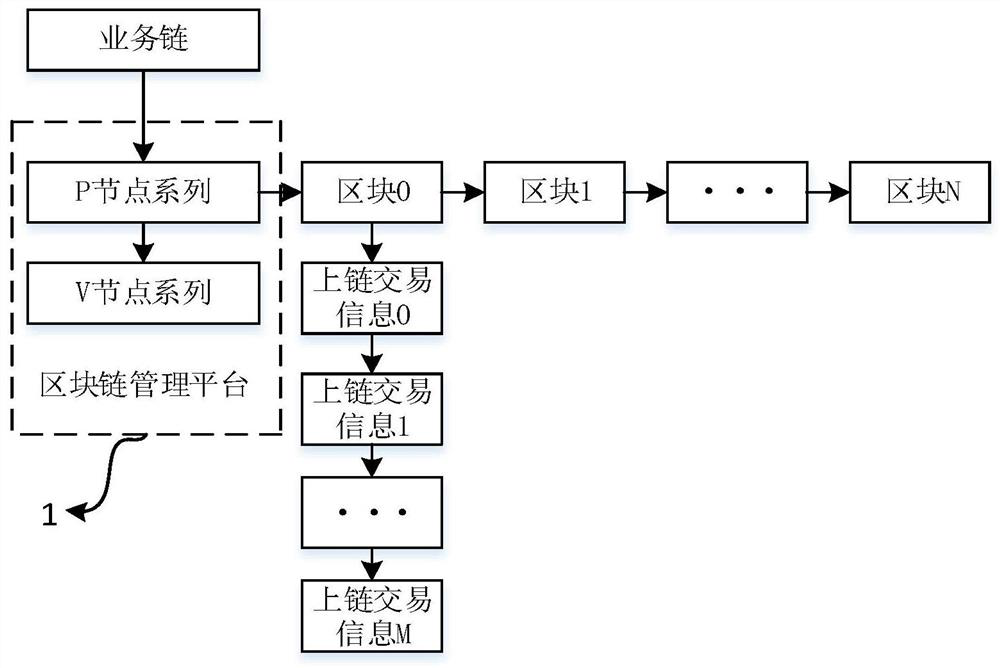
ActiveCN111353778AImprove reliabilityUnforgeableFinanceDigital data protectionBlockchainEngineering management
The invention discloses a blockchain television lottery buying system, belonging to the field of lottery buying systems, the blockchain television lottery buying system comprises a blockchain management platform for controlling and managing an alliance chain, a lottery center management platform, a television lottery buying operation platform and a home terminal, uplink transaction information uploaded by the lottery center management platform, the television lottery buying operation platform and the home terminal is stored in blocks of all nodes managed by the block chain management platformin a distributed mode, and block management of lottery transaction data is achieved. According to the blockchain television lottery buying system disclosed by the invention, a blockchain technology iseffectively combined with a television, so that a credibility lottery buying platform which cannot be forged, tampered and traceable is formed among a lottery buying operator, a lottery buying supervisor and a user.
Owner:广东南方新媒体股份有限公司
Random anti-counterfeiting mark-based anti-counterfeiting system and anti-counterfeiting method thereof
InactiveCN106066989AUnforgeableNon-repudiationCo-operative working arrangementsCharacter and pattern recognitionThird partyCommunications system
The invention relates to a random anti-counterfeiting mark-based anti-counterfeiting system and an anti-counterfeiting method thereof. The anti-counterfeiting system includes a server, sampling devices and inspection devices; the server, the sampling devices and the inspection devices are connected via a communication system. According to the system and method of the invention, used anti-counterfeiting marks are uncounterfeitable; with the support of the anti-counterfeiting method, once fabricators transmit the anti-counterfeiting marks to the server, the anti-counterfeiting marks cannot be denied; the system tracks and records all operations of the anti-counterfeiting marks; each anti-counterfeiting mark is associated with users / manufacturers; all operation records and related information thereof of all the anti-counterfeiting marks can be checked and verified; and the server is operated by a third party, and the third party strictly abides by rules. With the anti-counterfeiting system adopted, the anti-counterfeiting marks have uncounterfeitability and non-repudiation and are low in cost.
Owner:石立公
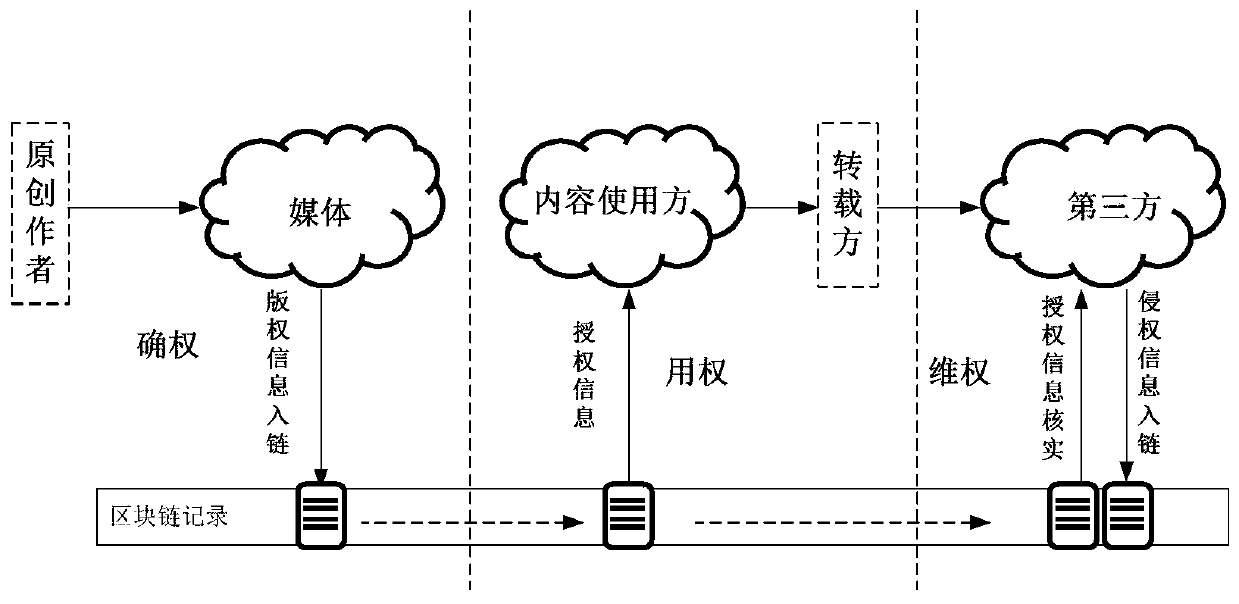
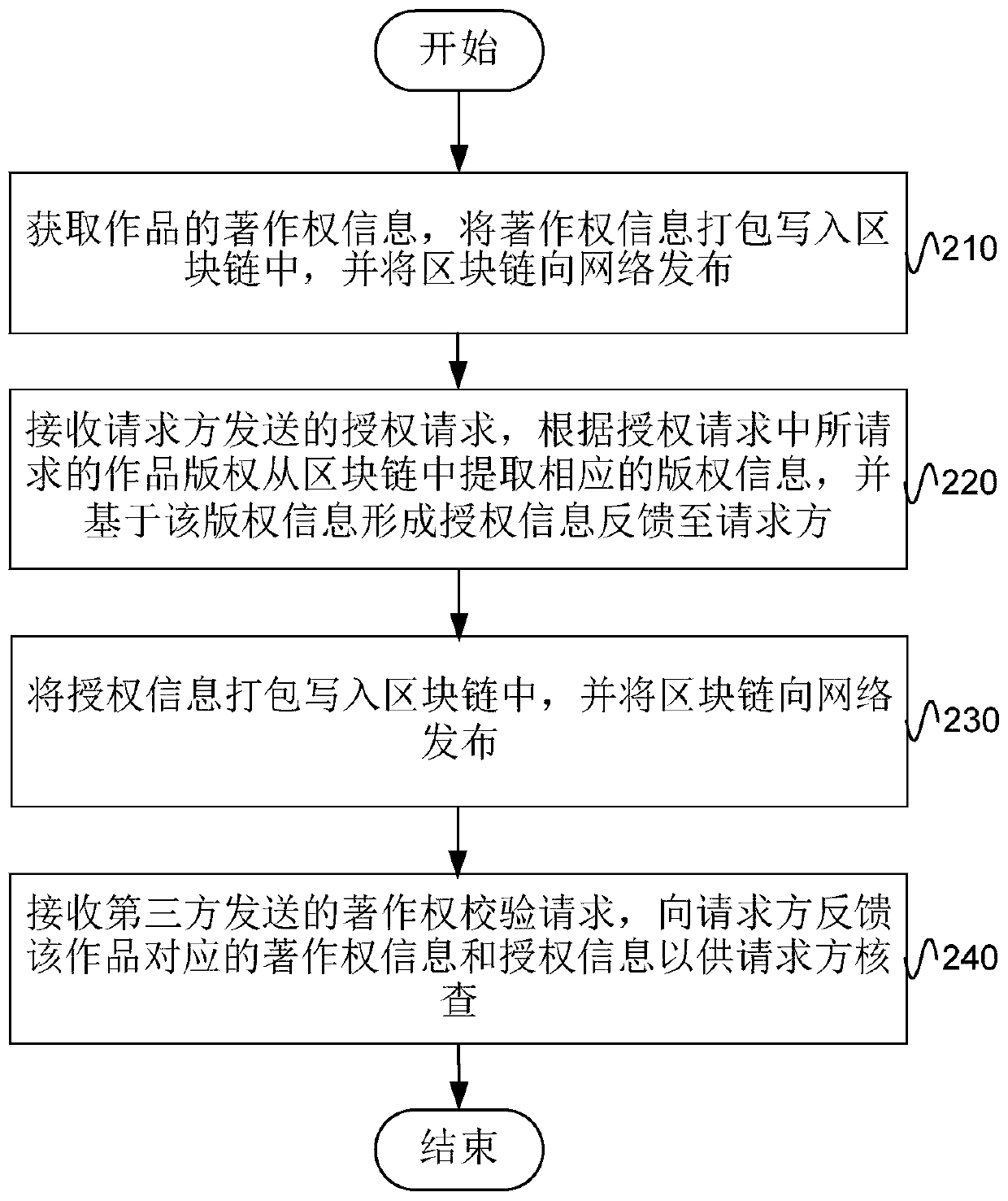
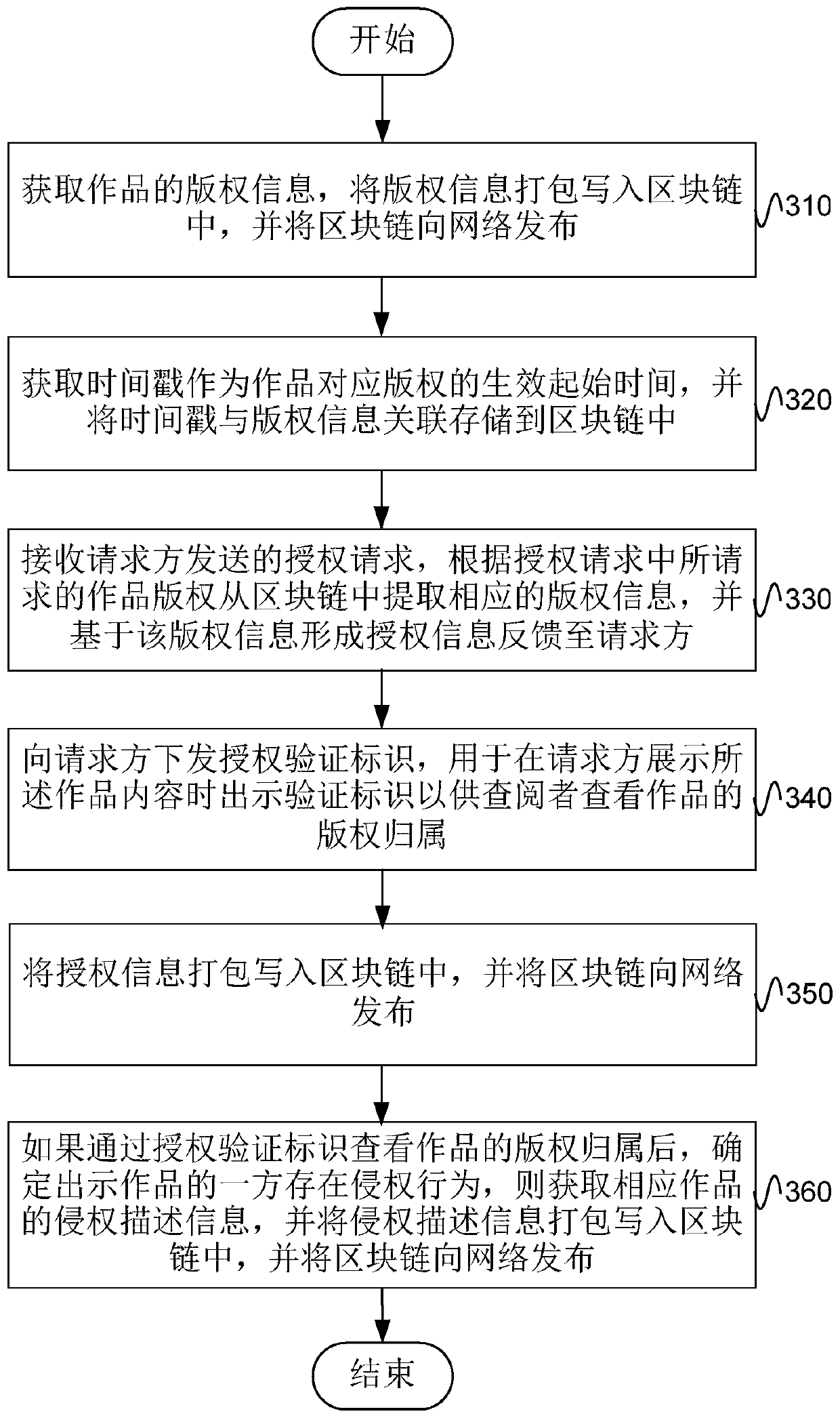
Copyright protection method, device and system based on blockchain technology
ActiveCN107659610BQuick confirmationGuaranteed unforgeableData processing applicationsTransmissionThird partyEngineering
The embodiment of the invention provides a copyright protection method, device and system based on block chain technology, and belongs to the field of the block chain technology. The method comprisesthe following steps: obtaining copyright information of works, packaging and writing the copyright information in a block chain, and issuing the block chain to a network; receiving an authorization request sent by a requester, extracting corresponding copyright information from the block chain according to the work copyright requested in the authorization request, forming authorization informationbased on the copyright information, and feeding back the authorization information to the requester; packaging and writing the authorization information in the block chain, and issuing the block chain to the network; receiving a copyright verification request sent by a third party, and feeding back the copyright information and the authorization information corresponding to the works according tothe works requested for checking in the copyright verification request for the check of the requester. The scheme of the embodiment of the invention can ensure quick verification of the copyright, and the right belonging is exact and can be checked at any time.
Owner:BEIJING RZXT TECH DEV CO LTD
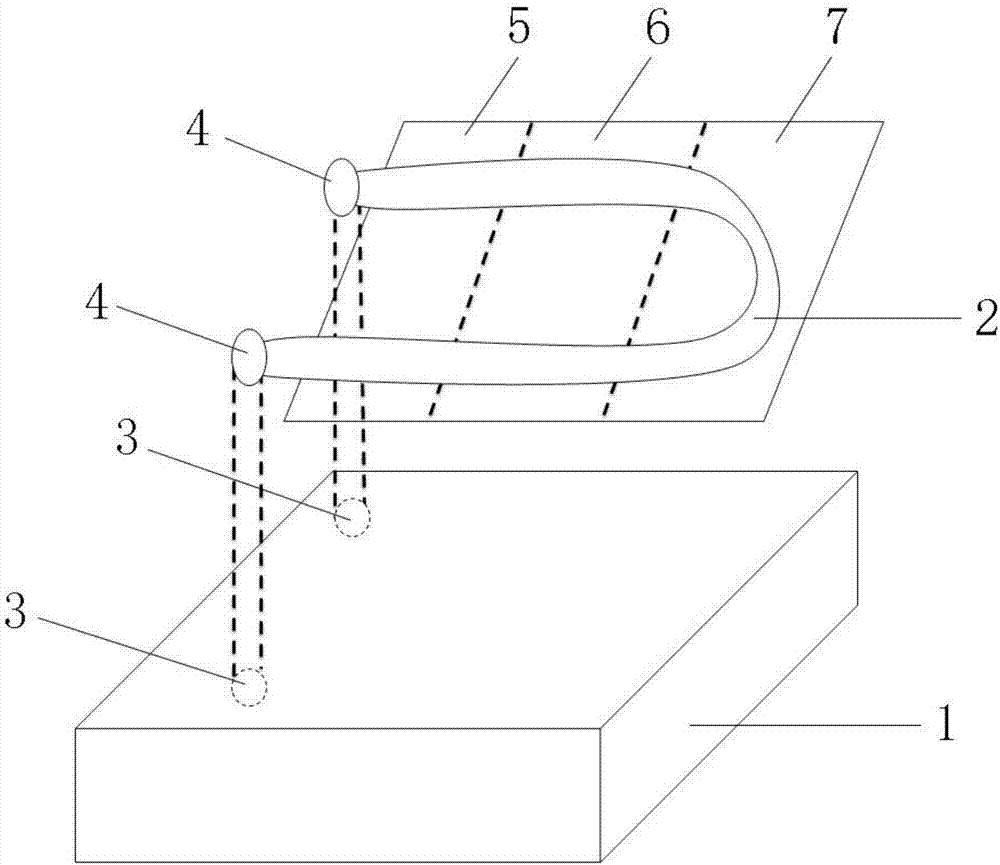
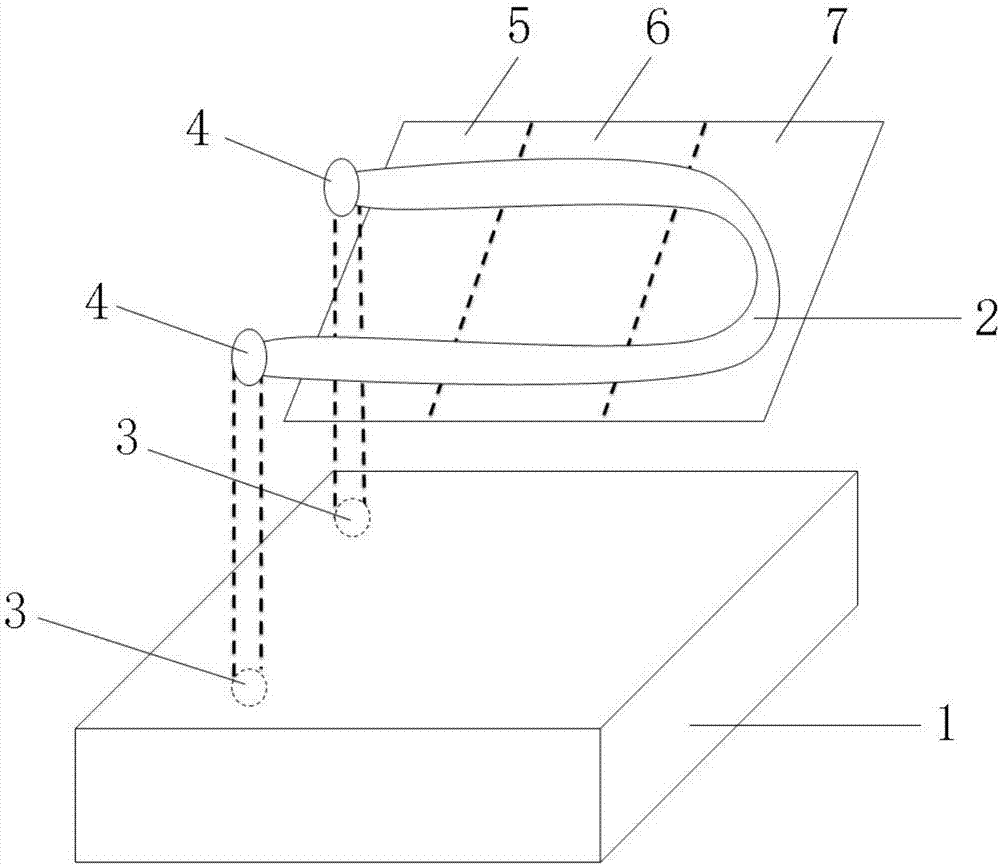
Anti-detachment alarming method of on-vehicle positioning equipment
InactiveCN108010238AUnforgeableNon-repeatableVehicle componentsBurglar alarm by hand-portable articles removalEngineeringDependability
The invention provides an anti-detachment alarming method of on-vehicle positioning equipment, wherein an inner switch circuit is arranged outside. A detachment action is associated with a switch circuit. Once a detachment action occurs, the switch circuit can be destroyed in one time, thereby triggering alarming. When the positioning equipment (1) is torn off, the rubber surface of a middle area(5) is adhered to a positioned vehicle. When a random welding point is broken or a metal conductive film (2) is torn off, the switch circuit is switched off, and hereon alarming is activated. Comparedwith the prior art, the anti-detachment alarming method is advantageous in that the reliability reaches 100%; once the equipment is detached, alarming is performed for sure; and furthermore the anti-detachment alarming method has benefits and effects of no counterfeiting and no repetition.
Owner:北京北科汇智软件技术有限公司
Method for preventing unlicensed driving and fatigue driving based on blockchain technology
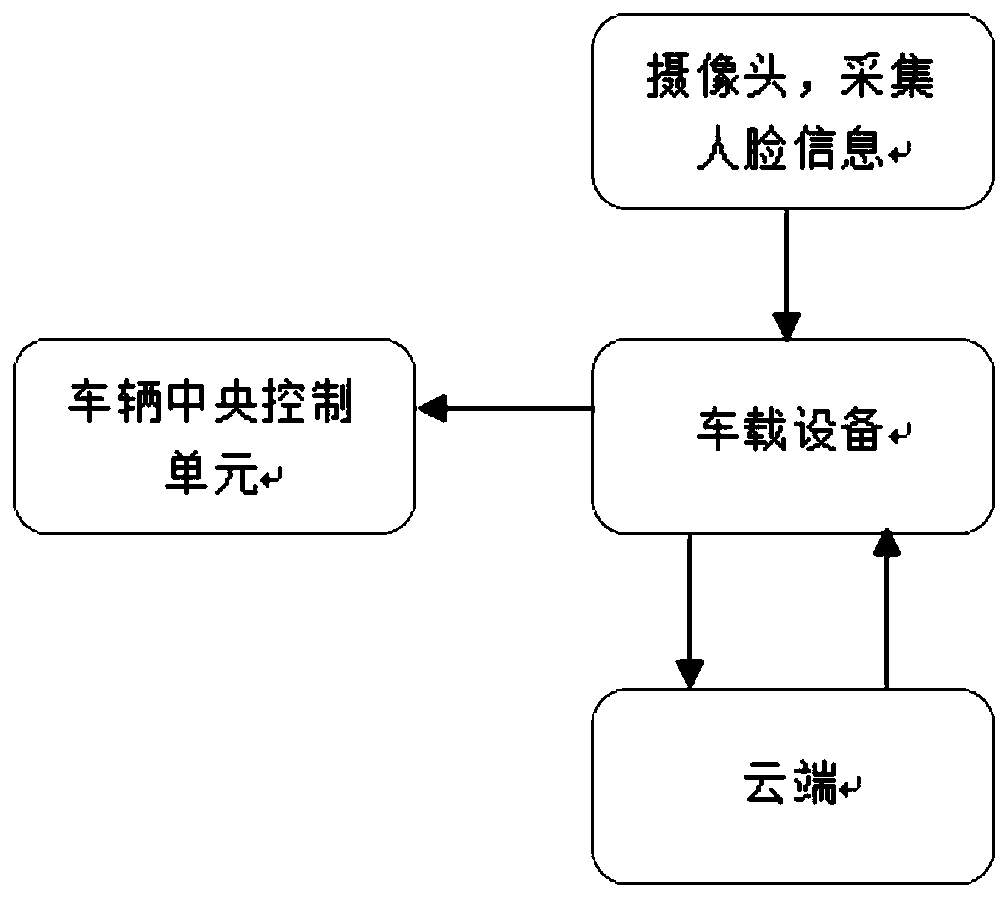
InactiveCN111540208AAlleviate resource pressureGuaranteed accuracyDetection of traffic movementCharacter and pattern recognitionDriver/operatorNerve network
The invention relates to the field of traffic safety. The invention specifically provides a method for preventing unlicensed driving and fatigue driving based on the blockchain technology. An information collection module collects face information of a driver entering a vehicle and transmits the collected face information to the vehicle-mounted device. On the one hand, the vehicle-mounted equipment preprocesses the collected face information, then transmits the face information to the cloud through the mobile network, compares the face information with a database of people with driving licenses in the cloud, and judges whether the vehicle is driven without the driving licenses; on the other hand, the vehicle-mounted equipment identifies the face information through the neural network, compares the face information with a preset threshold value, judges whether a fatigue driving phenomenon occurs in a vehicle operation driver or not, and gives an alarm. Compared with the prior art, the method can complete the dual control over fatigue driving and unlicensed driving, and the accuracy and uniqueness of information are guaranteed through the blockchain.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Database security audit record storage method
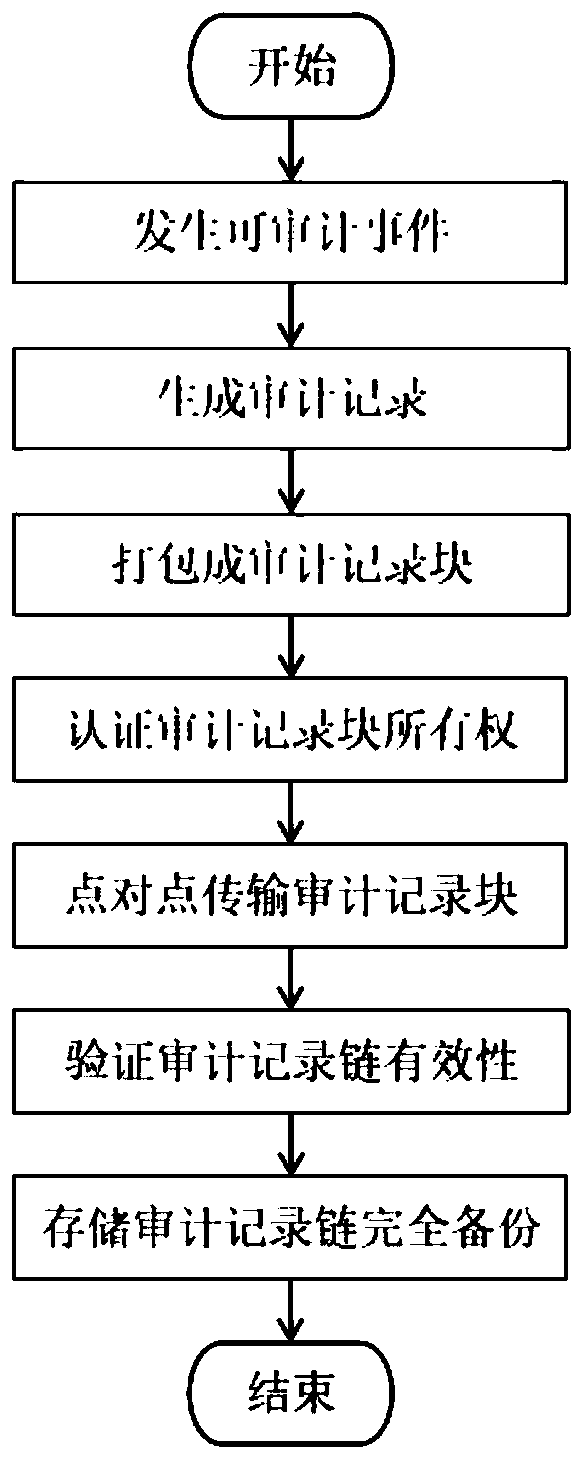
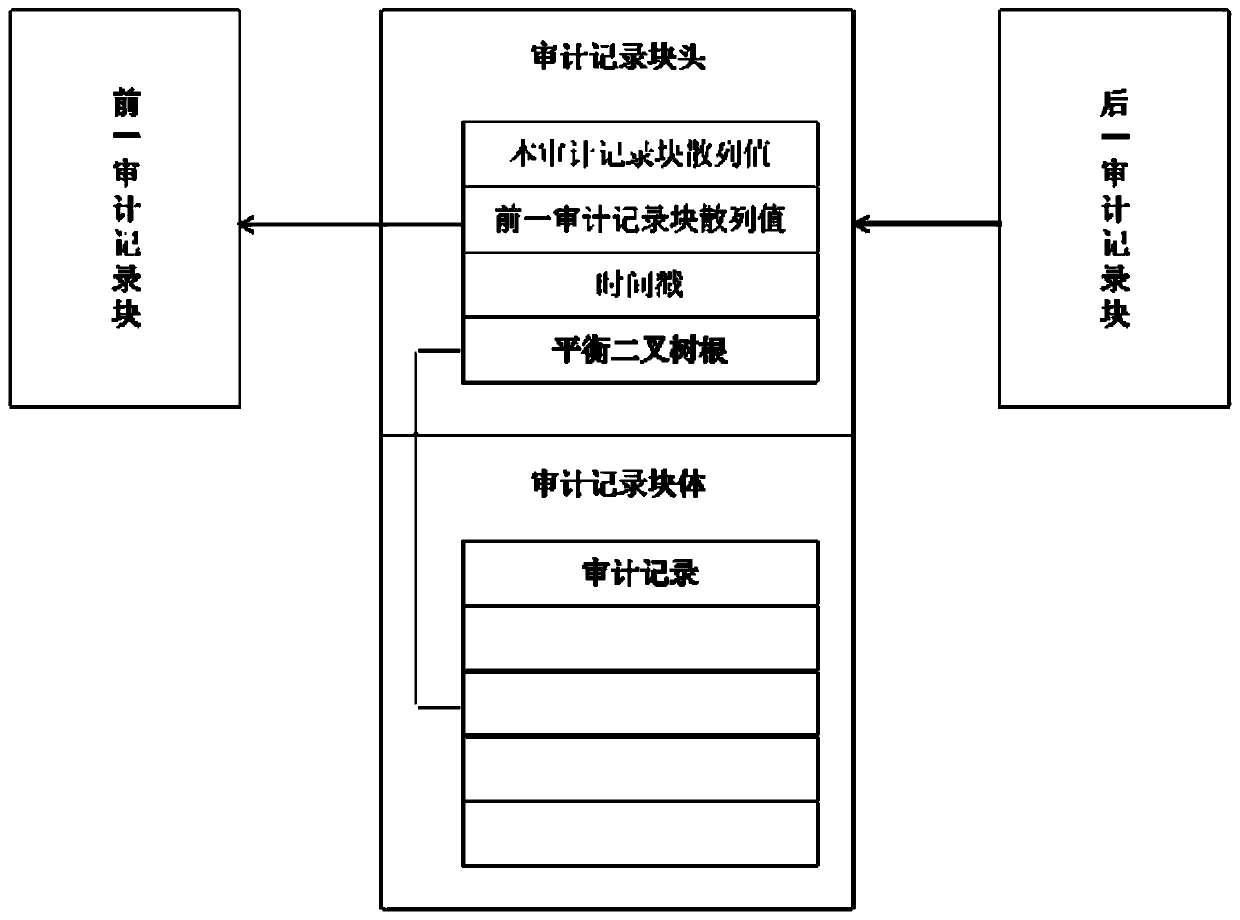
InactiveCN111143837AImplement storageUnforgeableError detection/correctionDigital data protectionPoint-to-Point ProtocolDatabase server
The invention provides a database security audit record storage method. The method comprises the following steps of S1 when a database server identifies an auditable event and generates a database security audit record, identifying the database security audit records by using the hash values to enable each database security audit record to correspond to a unique hash value; S2, packaging the plurality of database security audit records into a database security audit record block; and S3, performing encryption transmission on the database security audit record block by adopting a point-to-pointprotocol for directly performing network communication between the two nodes, and verifying the ownership of the database security audit record block. The method has the advantages that through an encryption mechanism and a consensus mechanism, the storage of the database security audit records is achieved in the point-to-point network, and it is guaranteed that the database security audit records cannot be tampered and forged.
Owner:TIANJIN NANKAI UNIV GENERAL DATA TECH
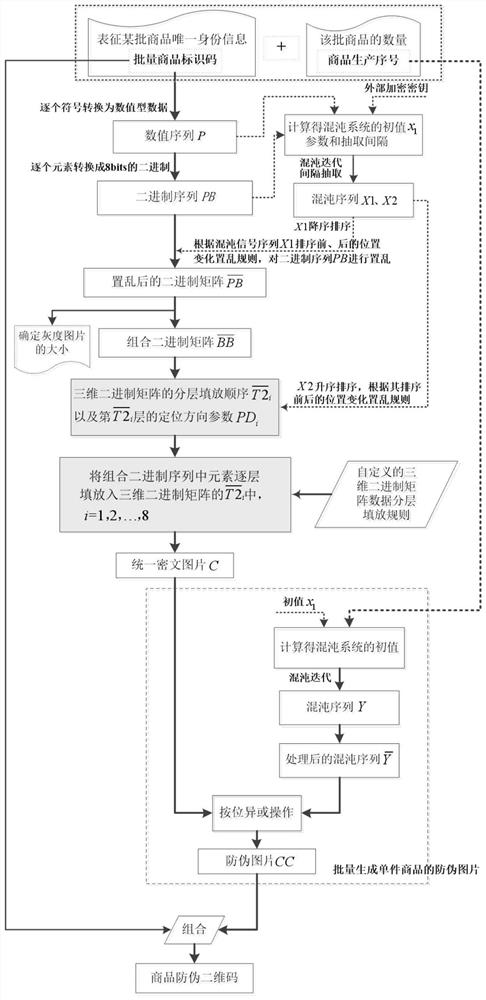
Commodity anti-counterfeiting code batch generation method based on character string-to-picture encryption
ActiveCN113935345AUniqueUnforgeableSecuring communication by chaotic signalsRecord carriers used with machinesAlgorithmCiphertext
The invention discloses a commodity anti-counterfeiting code batch generation method based on character string-to-picture encryption, and the method comprises the following steps: carrying out numeric data and 8-bit binary conversion of batch commodity identification codes representing the unique identity information of a certain batch of commodities, obtaining a binary sequence PB, and according to the number of the batch of commodities, obtaining the number of the batch of commodities, setting a commodity production serial number with a certain length; scrambling the sequence PB by using a chaotic signal, and filling layer by layer according to a self-defined three-dimensional binary matrix data hierarchical filling rule to generate a unified ciphertext picture; and generating different chaotic signals according to different production serial numbers of each commodity in the batch of commodities, and performing bitwise XOR operation on the chaotic signals and the unified ciphertext picture pixels in sequence, thereby generating anti-counterfeiting pictures of single commodities in batch, and further combining to generate the commodity anti-counterfeiting two-dimensional code. The commodity anti-counterfeiting code batch generation method provided by the invention is simple and feasible, has very high security and is not easy to crack, and the commodity anti-counterfeiting two-dimensional codes generated in batches have uniqueness and unforgeability.
Owner:NANTONG UNIVERSITY
A threshold proxy signature method without trusted pkg based on smart grid identity security
ActiveCN104079412BImprove execution efficiencyWith confidentialityUser identity/authority verificationPrecomputationIdentifiability
Provided is a trusted PKG-free threshold proxy signature method based on the identity safety of a smart power grid. According to the signature method, a signer interacts with a PKG and then obtains a private key pair (xid, yid) and a public key pair (Xid, Yid) of the PKG; proxy signers are authorized according to a verifiable secret sharing scheme, and it is supposed that P1, P2, ... , Pt are the t proxy signers, the t proxy signers will cooperate to generate a proxy signature of a message m; each proxy signer Pi generates a proxy signature part and sends the proxy signature part to a verifier C, and if all the proxy signature parts pass verification, the C combines the proxy signature parts into a valid threshold proxy signature. The method has higher execution efficiency due to many steps of precomputation and guarantees the security features of privacy, proxy protection, unforgeability, non-repudiation, strong identifiability and the like of the valid threshold proxy signature.
Owner:GANSU ELECTRIC POWER DESIGN INST
A Blockchain TV Lottery Buying System
ActiveCN111353778BUnforgeableImprove reliabilityFinanceDigital data protectionFinancial transactionOperations research
The invention discloses a blockchain TV lottery buying system, which belongs to the field of lottery buying systems. The blockchain TV lottery buying system includes a blockchain management platform for controlling and managing alliance chains, a lottery center management platform, and a TV lottery buying system. The operation platform and home terminal, the lottery center management platform, the TV lottery shopping operation platform and the on-chain transaction information uploaded by the home terminal are all stored in distributed storage in the block of all nodes managed by the blockchain management platform to realize the data of lottery transactions block management. The blockchain TV lottery purchasing system disclosed in the present invention effectively combines blockchain technology and TV to ensure that the lottery operator, the lottery supervisor and the user form an unforgeable, tamperable and traceable credibility lottery platform.
Owner:广东南方新媒体股份有限公司
Authentication method by broadcast signature and ciphering
InactiveCN101505301BHigh strengthUnforgeableSpecial service provision for substationPublic key for secure communicationSigncryptionHigh intensity
The invention discloses a broadcast signcryption authentication method, which comprises the following steps that: 1) system parameters are set; 2) a broadcast center calculates public key signature according to the parameters, and uses a user secret key to encrypt message to be broadcasted; 3) the broadcast center broadcasts the encrypted message acquired in step 2) to a user group; and 4) the user receives the encrypted message broadcasted in the broadcast center, uses a private key to decrypt the signature and verifies the validity of the signature. The method carries out two-layer confidential encapsulation of signature and encryption for the message, and broadcasts and mass-sends different messages to a group of users in once broadcast; and only specific authorized users can receive the designated message; therefore, the method has high-strength information confidentiality, signcryption information unforgeability and signcryption information non-repudiation. The method can regulate legal user groups at any time according to actual demand, but does not need to newly distribute new shared secret keys, has high flexibility, can make full use of communication bandwidth, saves cost, and greatly improves the communication efficiency.
Owner:SHIJIAZHUANG RAILWAY INST
ida-based cloud data integrity verification and recovery method
ActiveCN106650503BAchieve recoveryUnforgeableDigital data protectionTransmissionRecovery methodData integrity
The invention discloses a cloud side data integrity verification and restoration method based on IDA. The method comprises the following steps of 1, user initialization; 2, storage block generation; 3, vector quantity encryption; 4, label generation; 5, challenging auditing; 6, challenging responding; 7, responding verification; 8, original data restoration. According to the scheme, an original file is encoded, and damaged data is completely restored on the basis of verifying cloud side data integrity. Meanwhile, under the condition of guaranteeing system safety, the complexity of completely verifying labels and restoring calculation is reduced, and the efficiency of the method is effectively improved.
Owner:NANJING UNIV OF SCI & TECH
A blockchain-based smart IoT device authentication method and system
ActiveCN113162768BCannot be tampered withUnforgeableKey distribution for secure communicationUser identity/authority verificationRing signatureCiphertext
The invention discloses a blockchain-based intelligent IoT device authentication method and system. The method includes: the device generates its own identity mark based on a physical unclonable function, and uses the own identity mark as a public key of a searchable encryption algorithm , generate the ciphertext; the registration center generates the private key of the searchable encryption algorithm corresponding to the device based on the smart contract and the distributed ledger database, and assigns the group name and the public-private key pair of the ring signature algorithm to the device to complete the registration of the device; the certification center Using smart contracts, searchable encryption is performed based on the identity of the device to realize the personal login authentication of the device; and the group login authentication of the device is realized based on the ring signature algorithm. The invention can realize effective combined authentication for intelligent Internet of things equipment, automatic execution of intelligent contracts, reduce the problem of excessive resource consumption, and the new cryptographic algorithm has higher calculation efficiency and can ensure the security of the system.
Owner:UNIV OF SCI & TECH BEIJING
Registration system and registration method of all hardware terminals in cloud desktop system
The present invention provides a registration system and registration method for all hardware terminals in a cloud desktop system. The registration system includes a terminal identity information module, a terminal identity management module, a registration server, a registration information database, a terminal identity information module, and a registration information database Both are connected to the registration server, and the terminal identity information module and the terminal identity management module are connected to the registration information database; the terminal identity information module is located on the terminal device, which is composed of the hardware of the terminal device and internally stored configuration and authentication information, and is used for the terminal device. Identity verification; the terminal identity management module is used to manage terminal identity information, create, register, authenticate and manage terminal identity information. The invention registers the terminal equipment and stores the configuration information of the terminal equipment, makes the terminal equipment unforgeable, and improves the security and reliability of the terminal equipment in the cloud desktop system.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
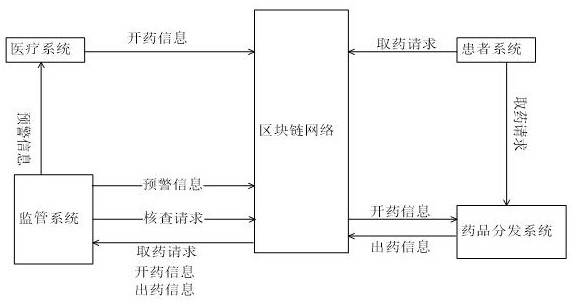
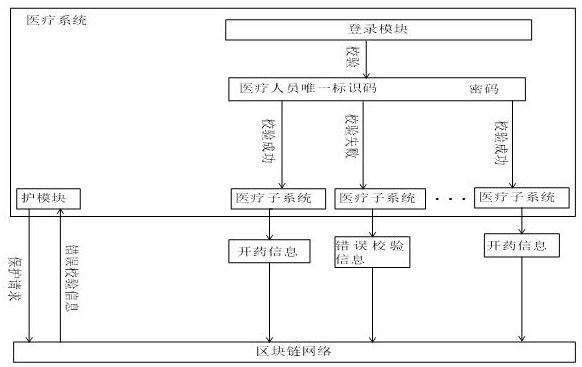
Medical system based on block chain
PendingCN111768849AIncrease credibilityAccurate recordHealthcare resources and facilitiesDistribution systemChain network
The invention provides a medical system based on a block chain. A medical system is used for generating prescription information and storing it in a block chain network. A drug distribution system isused for receiving a drug taking request to obtain prescription information from the block chain network, generating prescription information and storing the prescription information in the block chain network. A patient system is used for sending the drug taking request to the drug distribution system and storing the drug taking request in the block chain network. A supervision system is used forsending a verification request to the block chain network and obtaining the drug taking request, the prescription information and drug discharging information from the block chain network. The related information of doctors, patients and hospitals is accurately recorded, and the record has the characteristics of unforgeability, traceability, openness and transparency. Therefore, when doctors, patients and hospitals have disputes, the problems have traceability and the traceability results have high credibility. Through the supervision system, timely self-examination can be carried out to avoid the generation of erroneous information.
Owner:柴虎军
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com