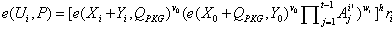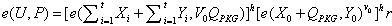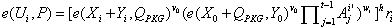A threshold proxy signature method without trusted pkg based on smart grid identity security
A proxy signature and smart grid technology, applied in the field of smart grid security data communication, can solve problems such as system disasters, threshold proxy signature key custody, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The threshold proxy signature method based on smart grid identity without trusted PKG provided by the present invention assumes that there are private key generation center PKG and original signer P in the system. 0 , proxy signer L={P 1 ,P 2 ,...,P n} and a verifier C, C is a member of the set L, C is responsible for verifying the validity of the personal proxy signatures of the members of the proxy group, and combining these effective personal proxy signatures into proxy signatures, set G 1 By PThe resulting cyclic additive group has order prime q ; G 2 are of the same order q The multiplicative cyclic group of ; bilinear maps e : G 1 x G 1 → G 2 ; The specific steps are as follows;
[0038] Step 1. System initialization: PKG randomly selects an integer s PKG ∈ , calculate the system public key Q PKG =s PKG P , and choose the following strong collision-free hash function H 1 :{0,1} * →G 1 , H 2 :{0,1} * → ; then the PKG will s PKG ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com