A blockchain-based smart IoT device authentication method and system
A technology of IoT devices and networking devices, applied in the field of IoT, can solve the problems of manpower password and certificate storage costs, low degree of automation of the authentication process, difficulty in certificate management, etc., to achieve strong security, save time, and reduce the amount of calculation Reduced effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
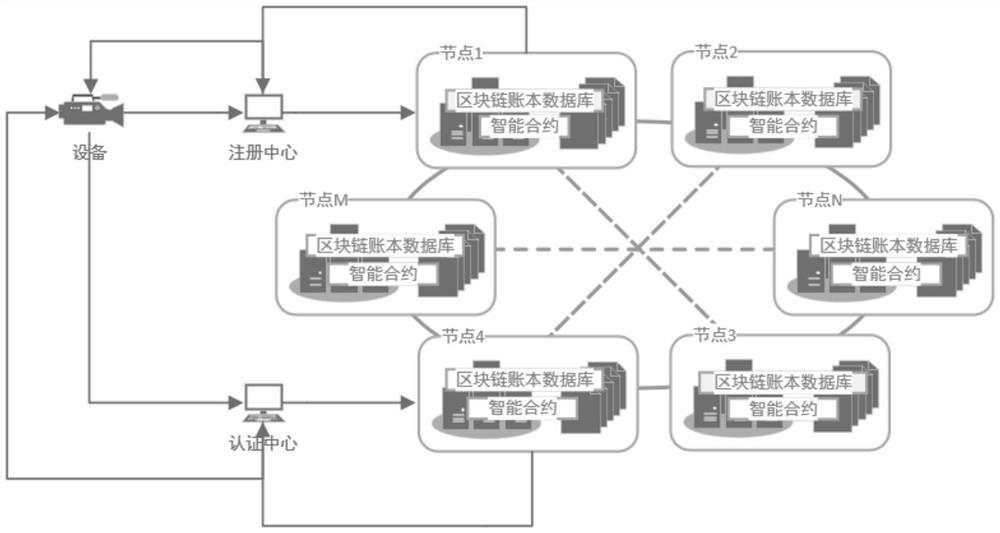
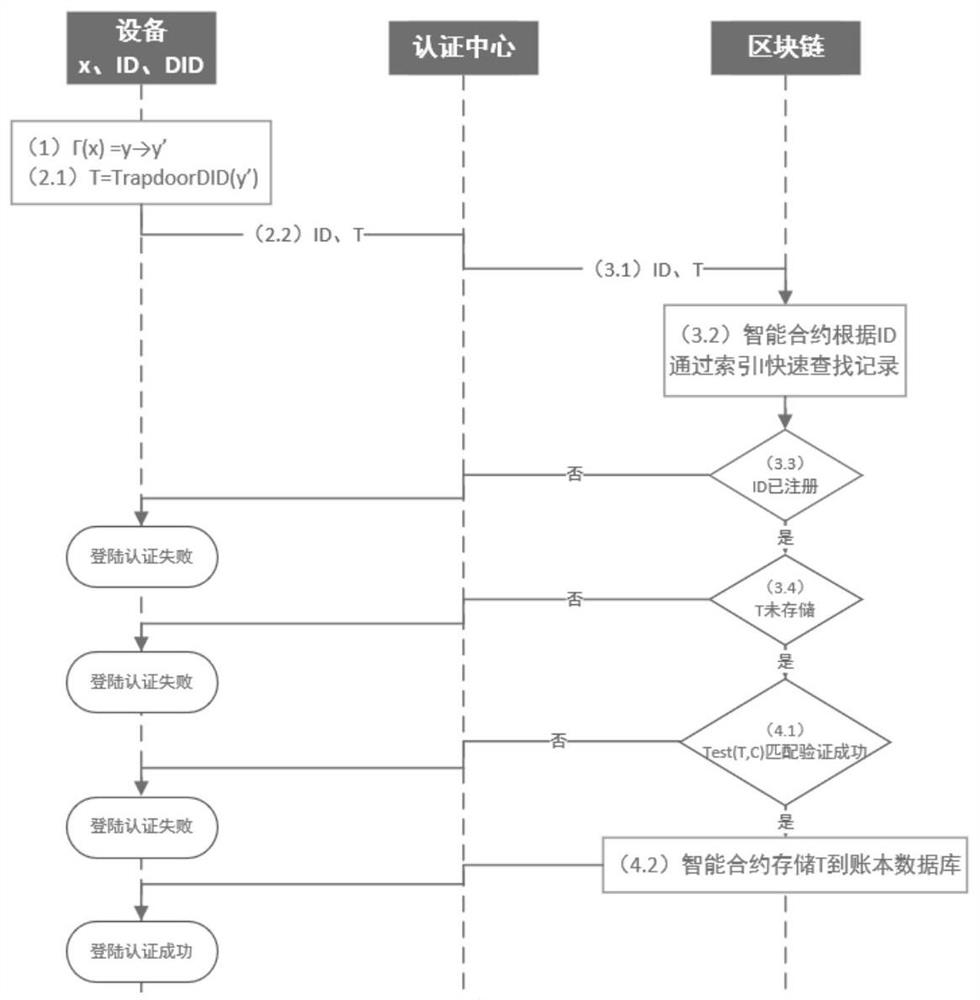
[0069] This embodiment provides a blockchain-based smart IoT device authentication method, which can be implemented by an electronic device, and the electronic device can be a terminal or a server. The model principle of this blockchain-based smart IoT device authentication method is as follows: figure 1 Specifically, the execution flow of the blockchain-based smart IoT device authentication method includes the following steps:
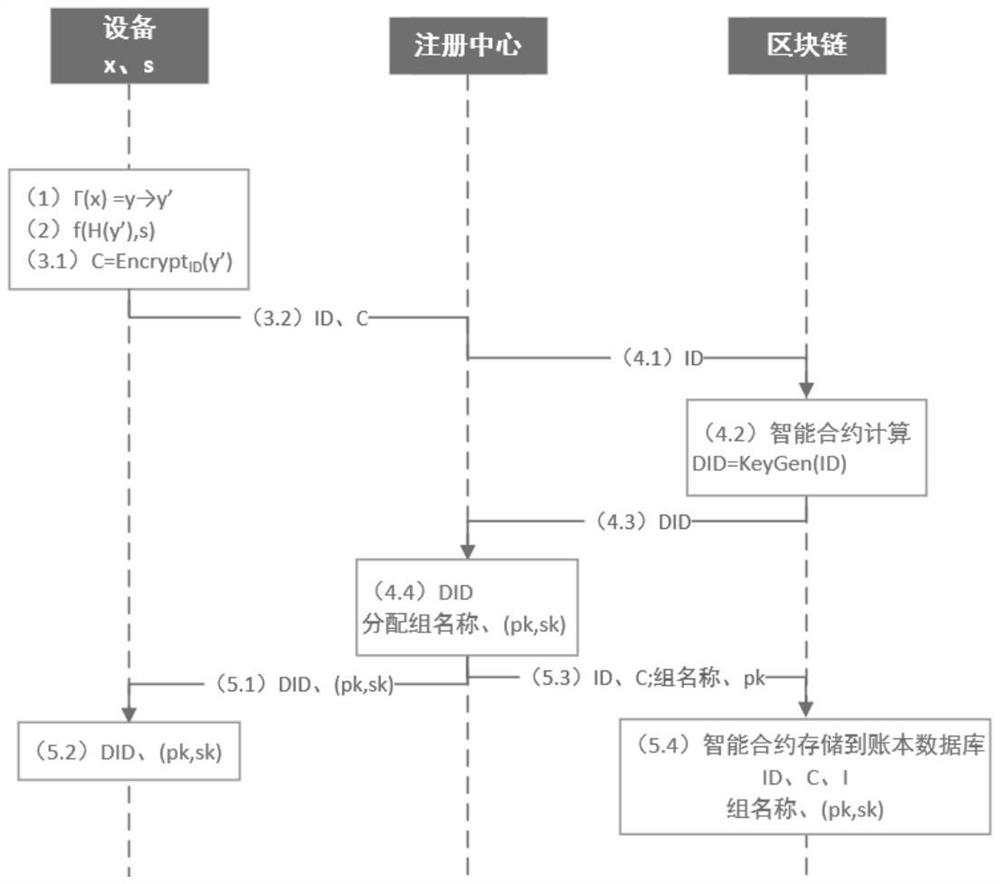
[0070] The IoT device generates its own identity based on the preset physical unclonable function, and uses its own identity as the public key of the searchable encryption algorithm, and generates the ciphertext through the searchable encryption algorithm;
[0071] The registry is based on blockchain-based smart contracts and distributed ledger databases, combined with the identity and ciphertext of the IoT devices, generates the private key of the searchable encryption algorithm corresponding to the IoT devices, and assigns group names and rings to t...
no. 2 example
[0103] This embodiment provides a blockchain-based authentication system for smart IoT devices, where the smart IoT device authentication system includes IoT devices, a registration center, and an authentication center; wherein,
[0104] The Internet of Things device is used to generate its own identity based on a preset physical unclonable function, and uses its own identity as the public key of the searchable encryption algorithm, generates ciphertext through the searchable encryption algorithm, and uses its own identity as the public key of the searchable encryption algorithm. The identification and ciphertext are sent to the said registration center;
[0105] The registration center is used for blockchain-based smart contracts and distributed ledger databases, and generates the private key of the searchable encryption algorithm corresponding to the IoT device in combination with the ID and ciphertext of the IoT device, and assigns a group to the IoT device. Name and public...
no. 3 example
[0109] This embodiment provides an electronic device, which includes a processor and a memory; wherein, at least one instruction is stored in the memory, and the instruction is loaded and executed by the processor to implement the method of the first embodiment.
[0110] The electronic device may vary greatly due to different configurations or performances, and may include one or more processors (central processing units, CPU) and one or more memories, wherein the memory stores at least one instruction, so The instructions are loaded by the processor and execute the above method.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com