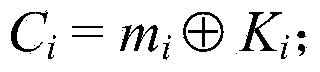Identity based aggregate signcryption method
A technology of identity and signcipher text, applied in the field of identity-based aggregated signcryption, which can solve the problems of poor scalability and achieve the effects of increasing processing speed, reducing length, and improving information transmission efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in detail below in conjunction with the accompanying drawings.
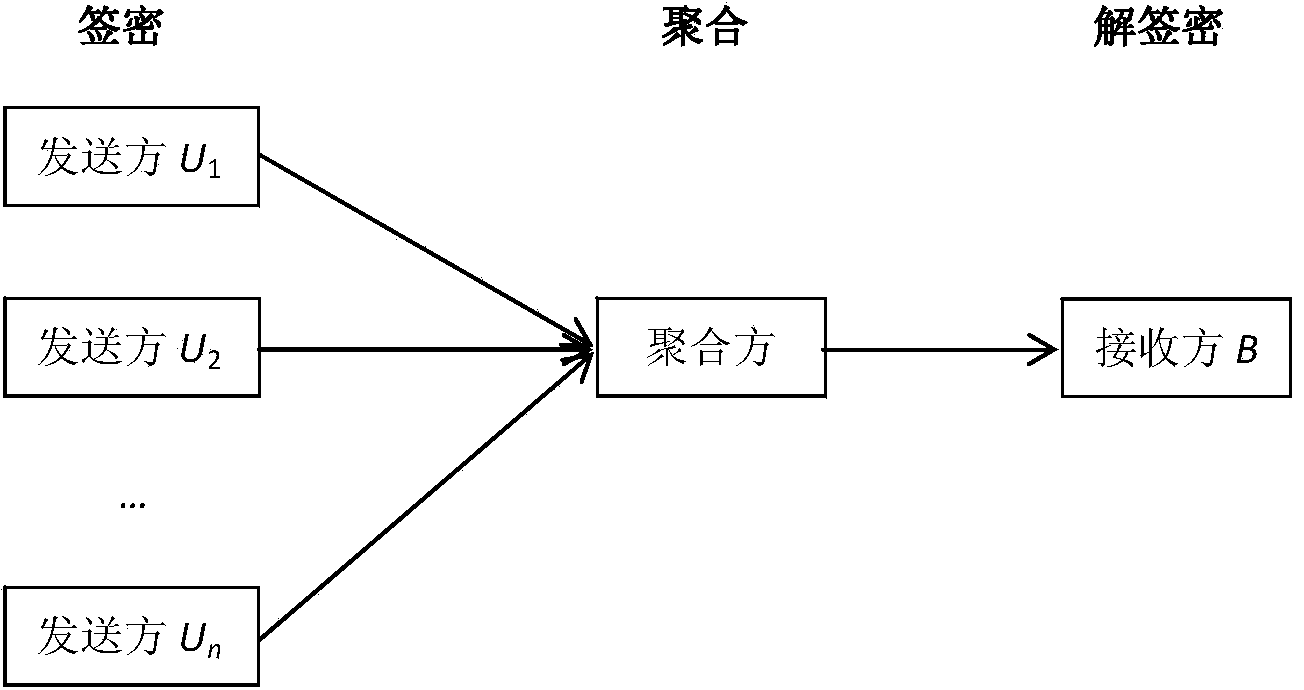
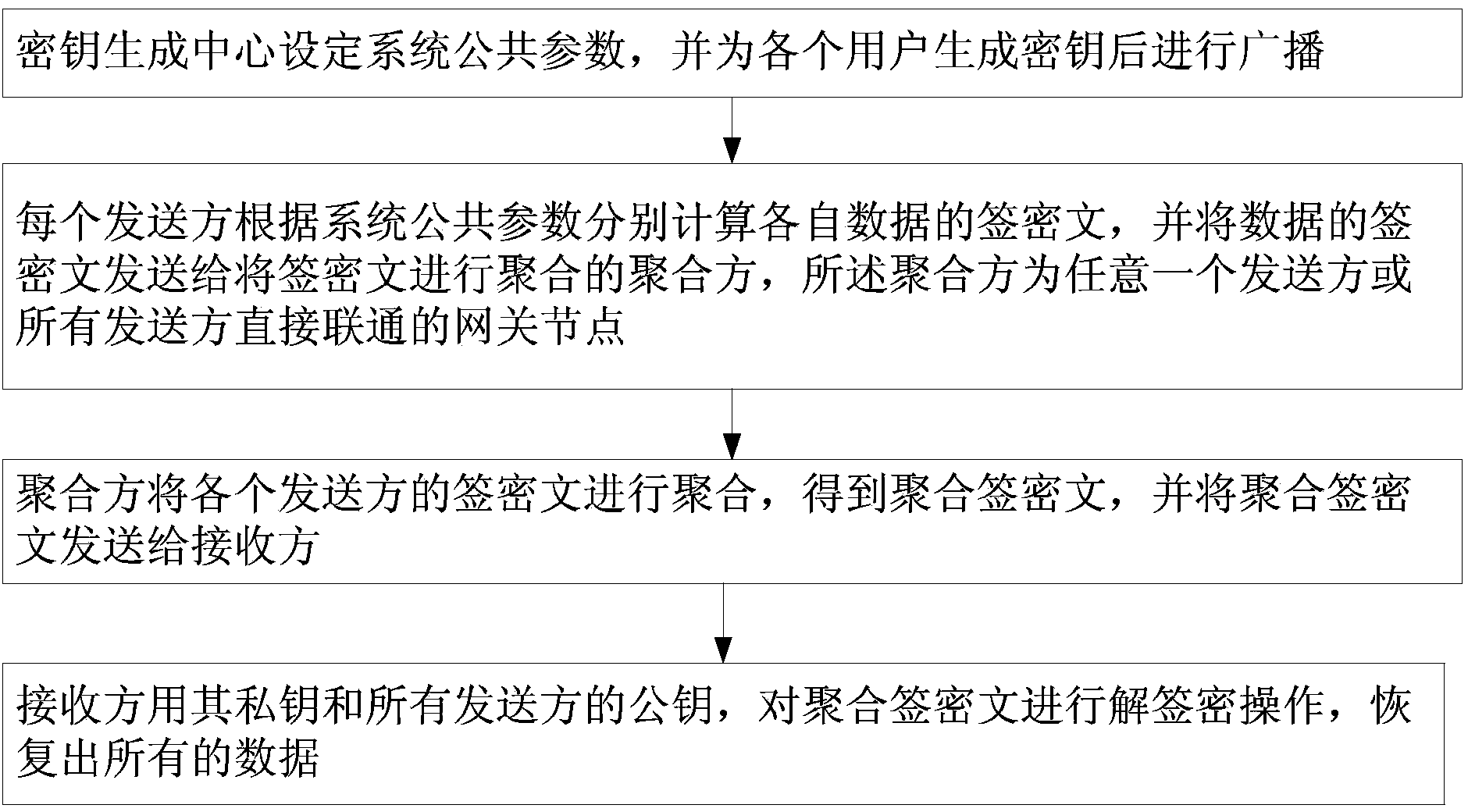
[0038] like figure 1 , 2 As shown, the present invention provides an identity-based aggregatable signcryption method. In the application scenario of the aggregatable signcryption method for signcryption, there are n peer-to-peer senders, and each sender is responsible for the corresponding plaintext message Independently generate signciphertext; have an aggregator responsible for aggregating signciphertext, and the aggregator can be undertaken by any sender, or by a gateway node that is directly connected to all senders; there is a receiver that receives all , and perform decryption, signcryption and verification operations on the aggregated signciphertext, including the following steps:
[0039] Step 1: The key generation center sets the public parameters of the system, and generates keys for each user before broadcasting;
[0040] (1) The key generation center s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com