Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
102results about How to "Suitable for deployment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
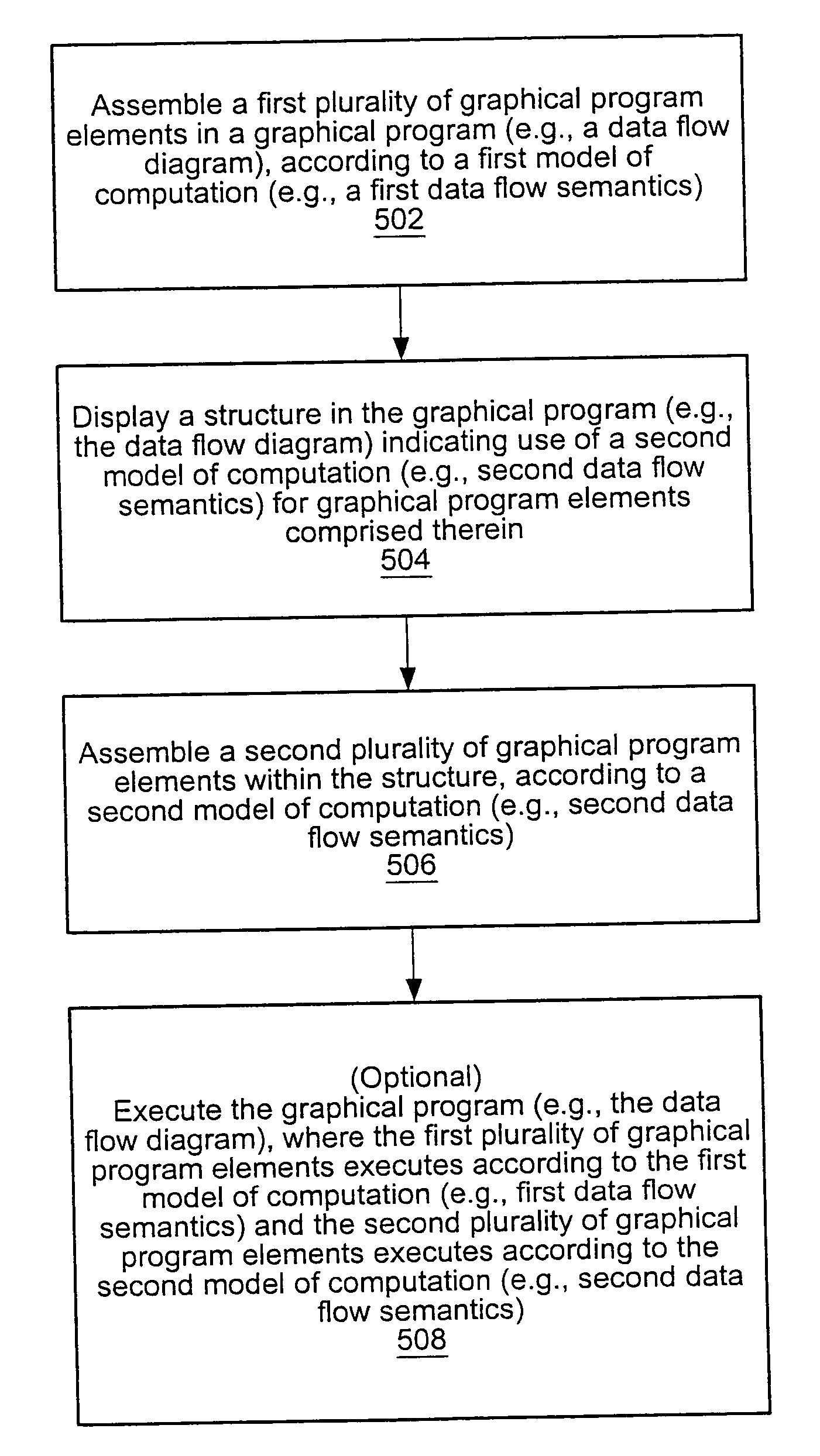
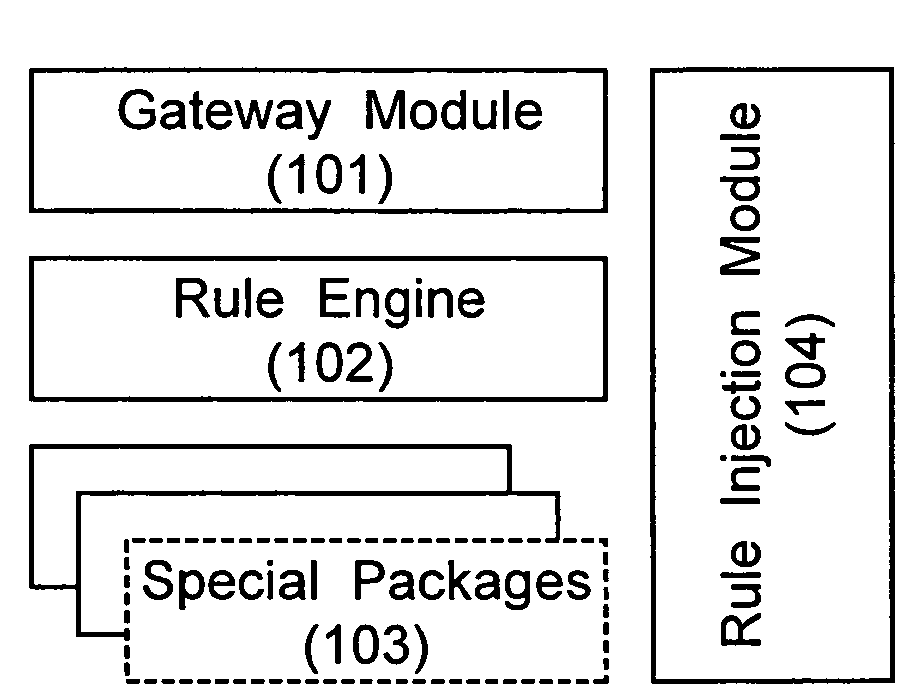
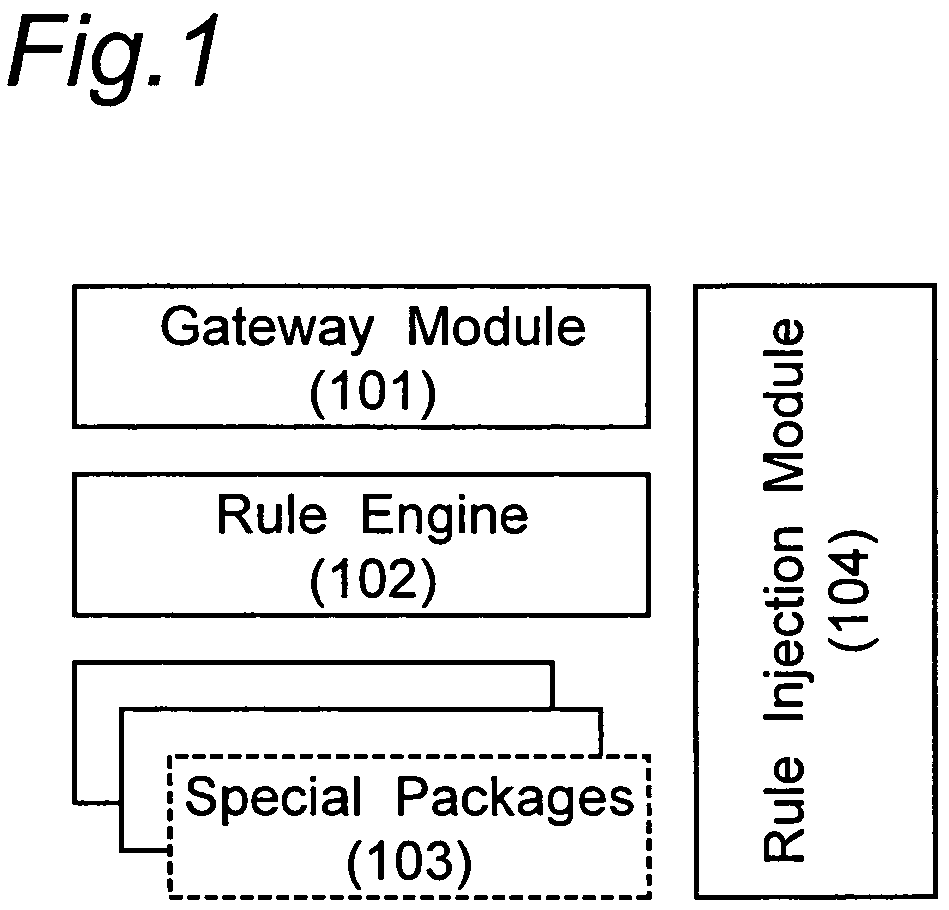
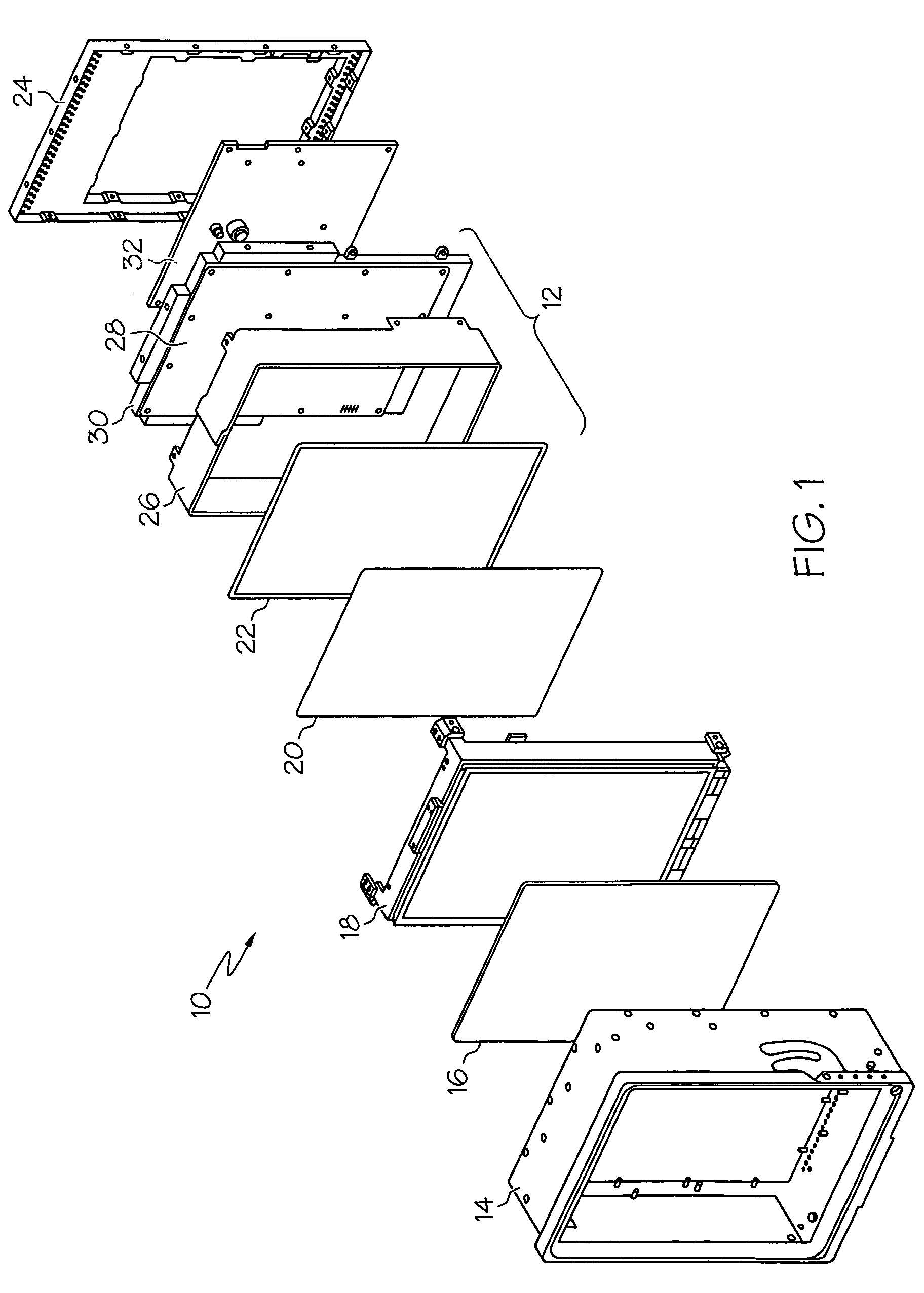
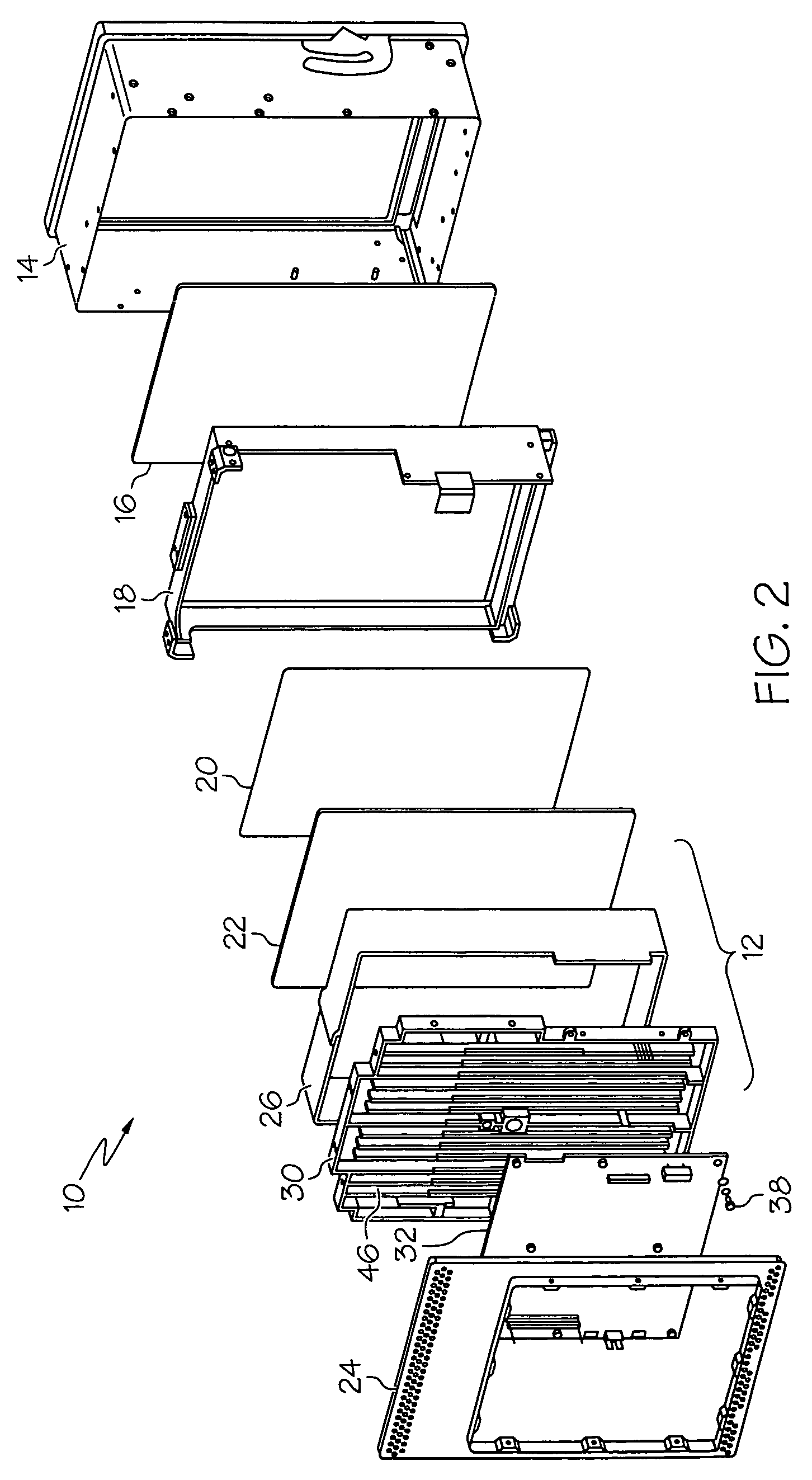
Creating and executing a graphical program with first model of computation that includes a structure supporting second model of computation
ActiveUS20050257195A1Suitable for deploymentVisual/graphical programmingSpecific program execution arrangementsMockupDataflow
System and method for creating and executing a graphical program. A first plurality of graphical program elements (GPEs) having a first model of computation (MoC), e.g., homogenous dataflow, are assembled in a graphical program in response to first input. A structure, including an interior portion, is displayed in the graphical program, indicating use of a second MoC, e.g., multi-rate dataflow, for GPEs within the interior portion. A second plurality of GPEs having the second MoC are assembled within the interior portion of the structure in response to second input. The second plurality of GPEs are converted into a new third plurality of GPEs having the first MoC, e.g., by parsing the second plurality of GPEs to determine multiple primitives according to the second MoC, determining the third plurality of GPEs based on the primitives, and assembling the third plurality of GPEs in the graphical program.
Owner:NATIONAL INSTRUMENTS
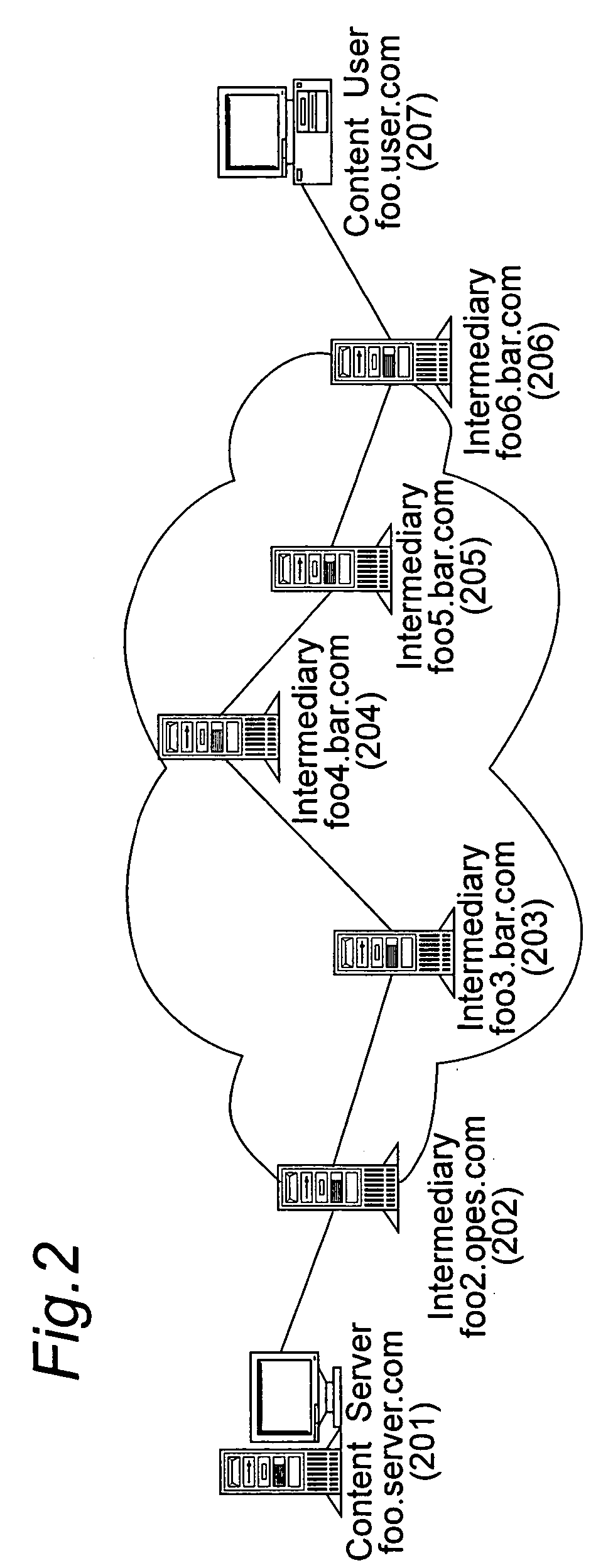
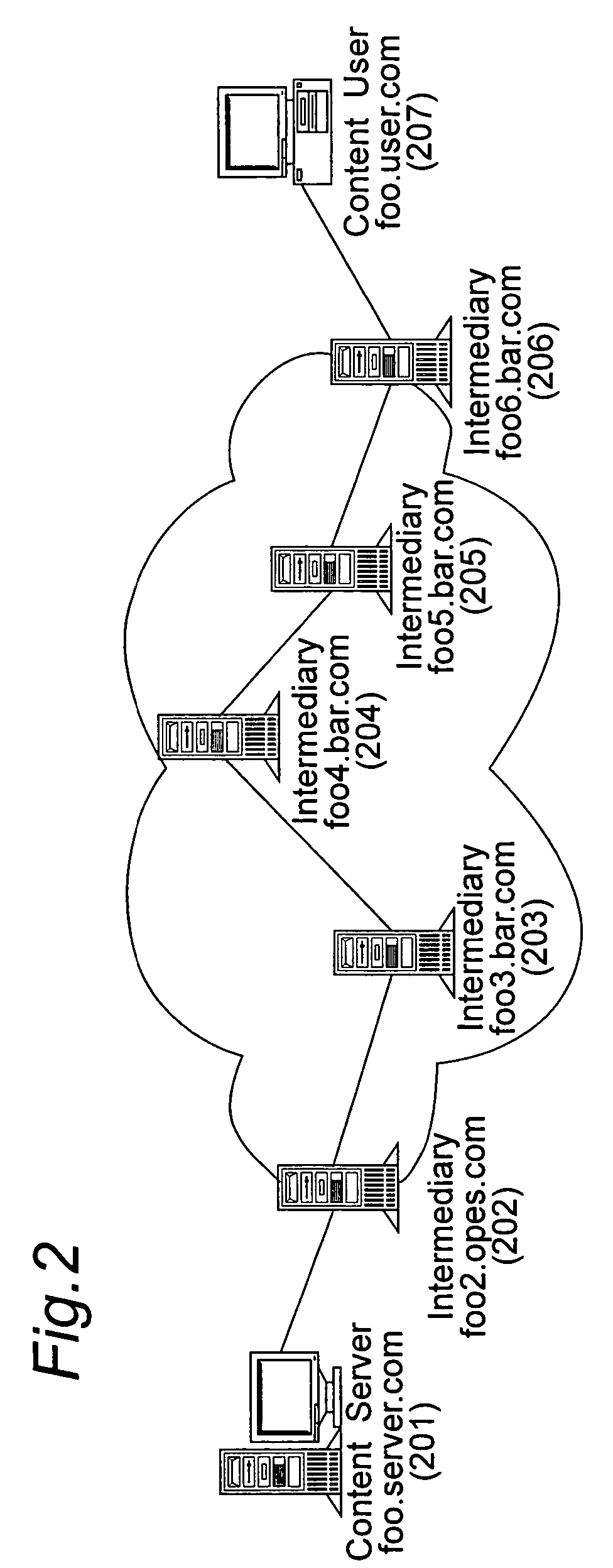
Method and apparatus for configuring and controlling network resources in content delivery with distributed rules
InactiveUS20050111467A1Easy to controlMost efficientData switching by path configurationSecuring communicationDistributed computingControl network
An intermediate network element deployed in a content delivery network is disclosed. The content delivery network cooperates its content delivery effort with other intermediate network element with similar capabilities. Distributing rules that govern the operations of the intermediate network element(s) are presented. These include the framework of the intermediate network element(s), the format of indicating part or whole of a rule specification to be distributed, the format of signatures for intermediate network elements to discover each other, the format of signaling other intermediate network elements that a rule is distributed to, and the method of determining the intermediate network element to distribute a rule to. In addition, authoring rules that are specific to real time streaming of contents are disclosed. A set of rule evaluation conditions are revealed that can be triggered based on different criteria during the streaming of real time contents. A set of parameters from which rules can be based on is disclosed.
Owner:PANASONIC CORP
Solar panel configurations
InactiveUS20120031470A1Easy to integrateMinimal trainingPhotovoltaic supportsSolar heating energyElectronic componentPolymer
The invention provides solar panel systems, which may be applied to surfaces such as residential rooftops. The invention also provides methods of installing solar panel systems. A solar panel system may comprise one or more module, which may comprise one or more solar panels and a rack. A solar panel may comprise a polymer, and may not comprise glass or a metal frame. The rack may include three footings and a plurality of adjustable fasteners that may enable the module to reside on an uneven surface. The rack may also include integrated electronic components and a microinverter. A module may yield a desired power output, and may generate performance monitoring data.
Owner:ARMAGEDDON ENERGY
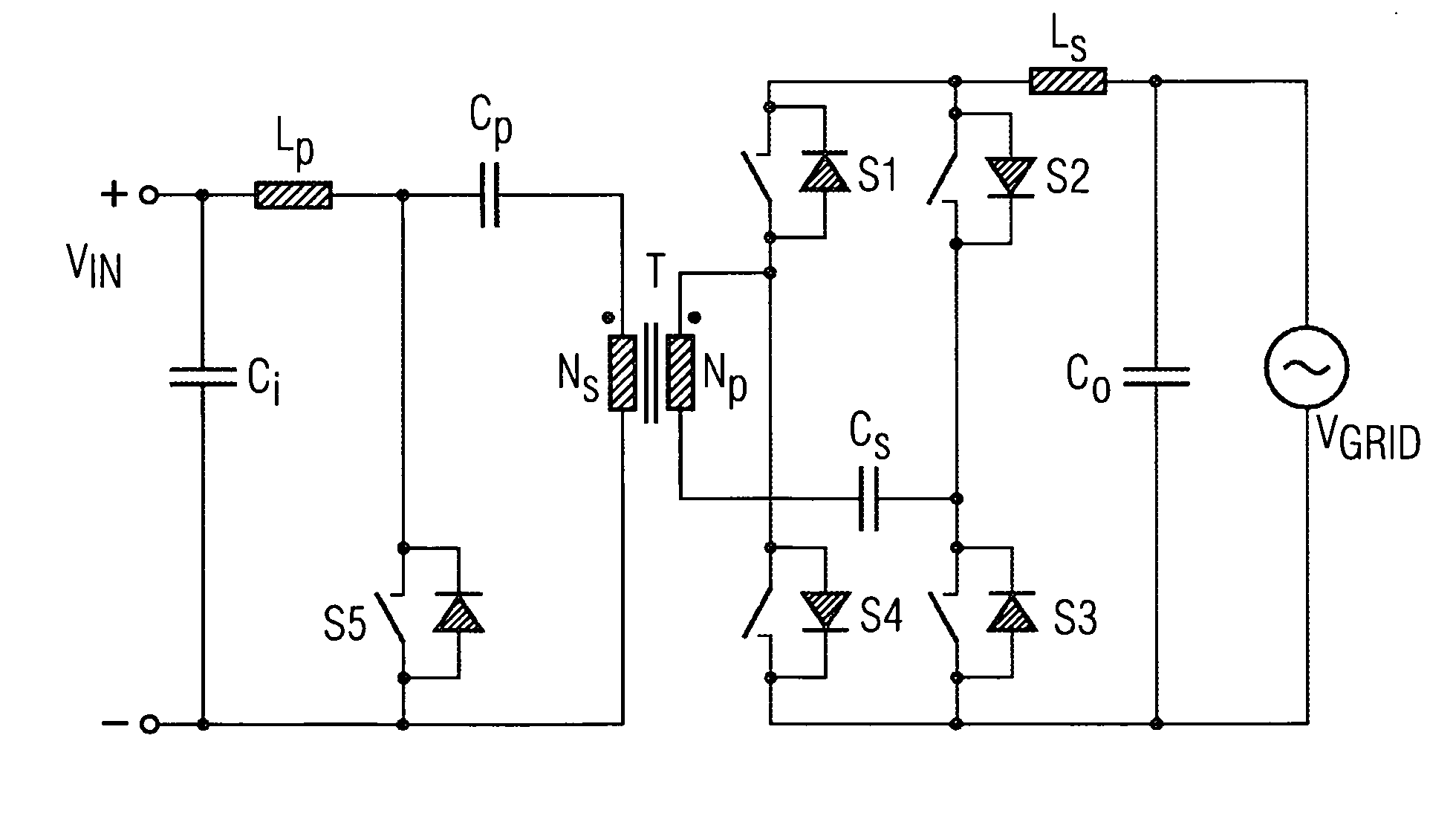
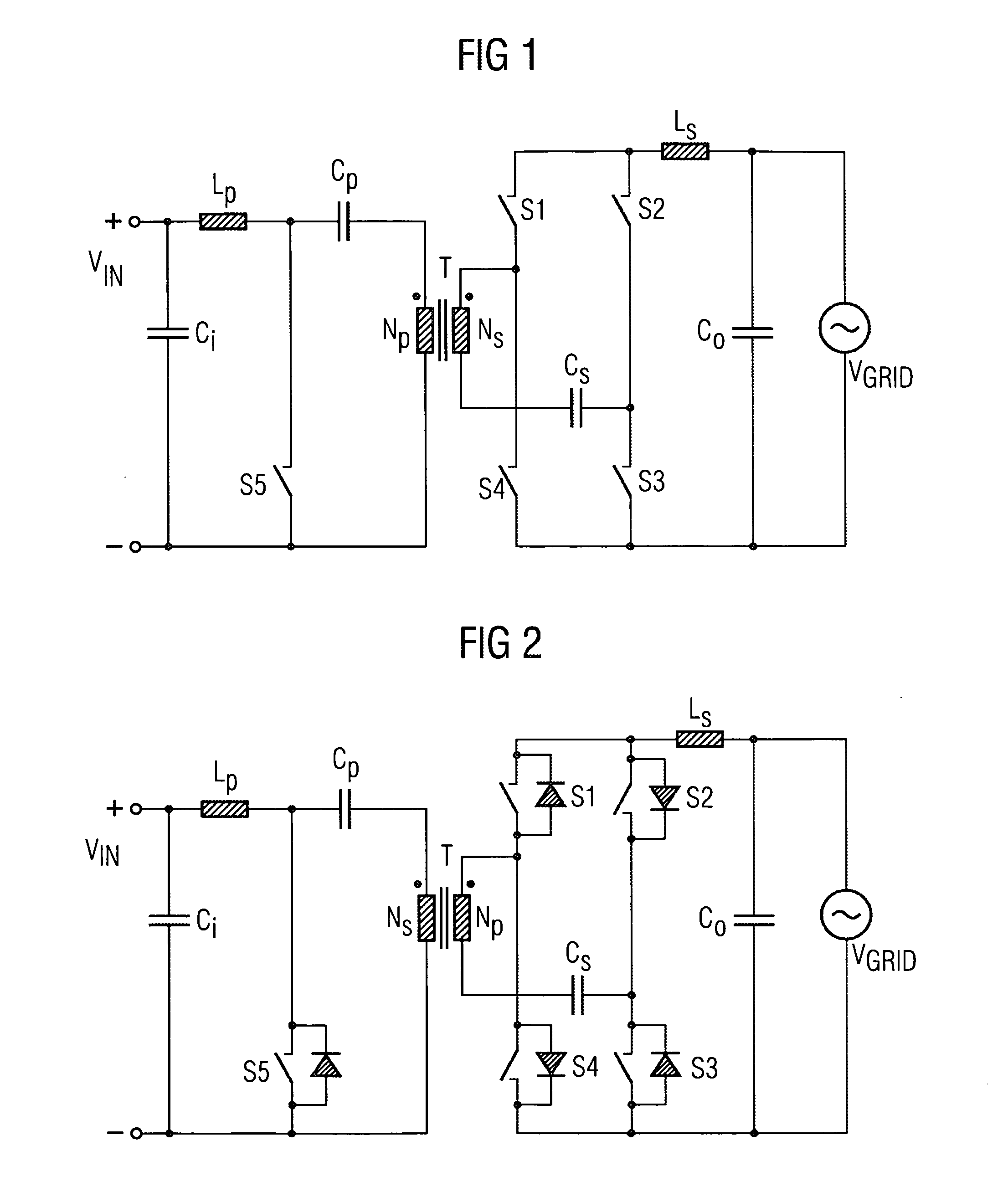
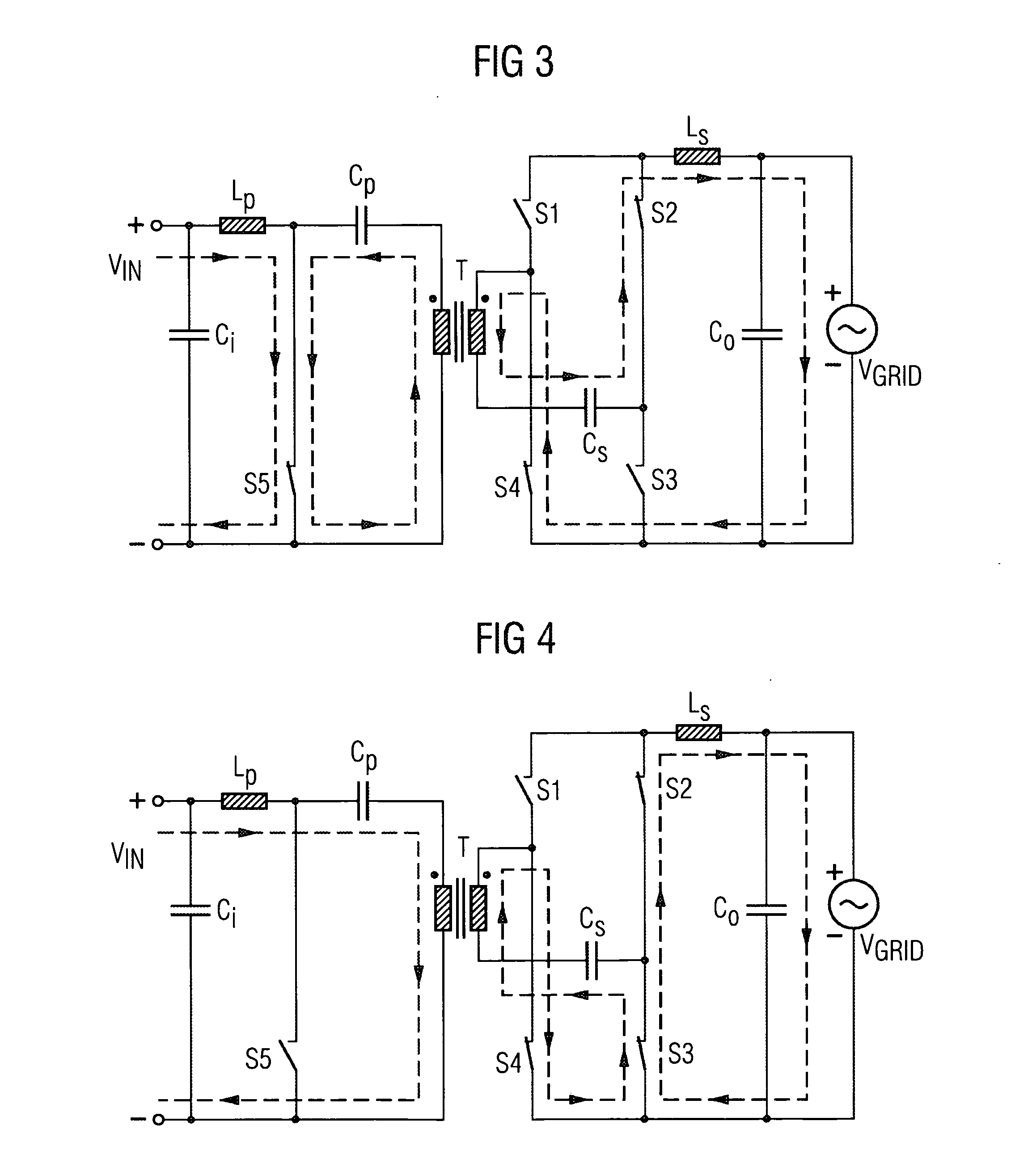
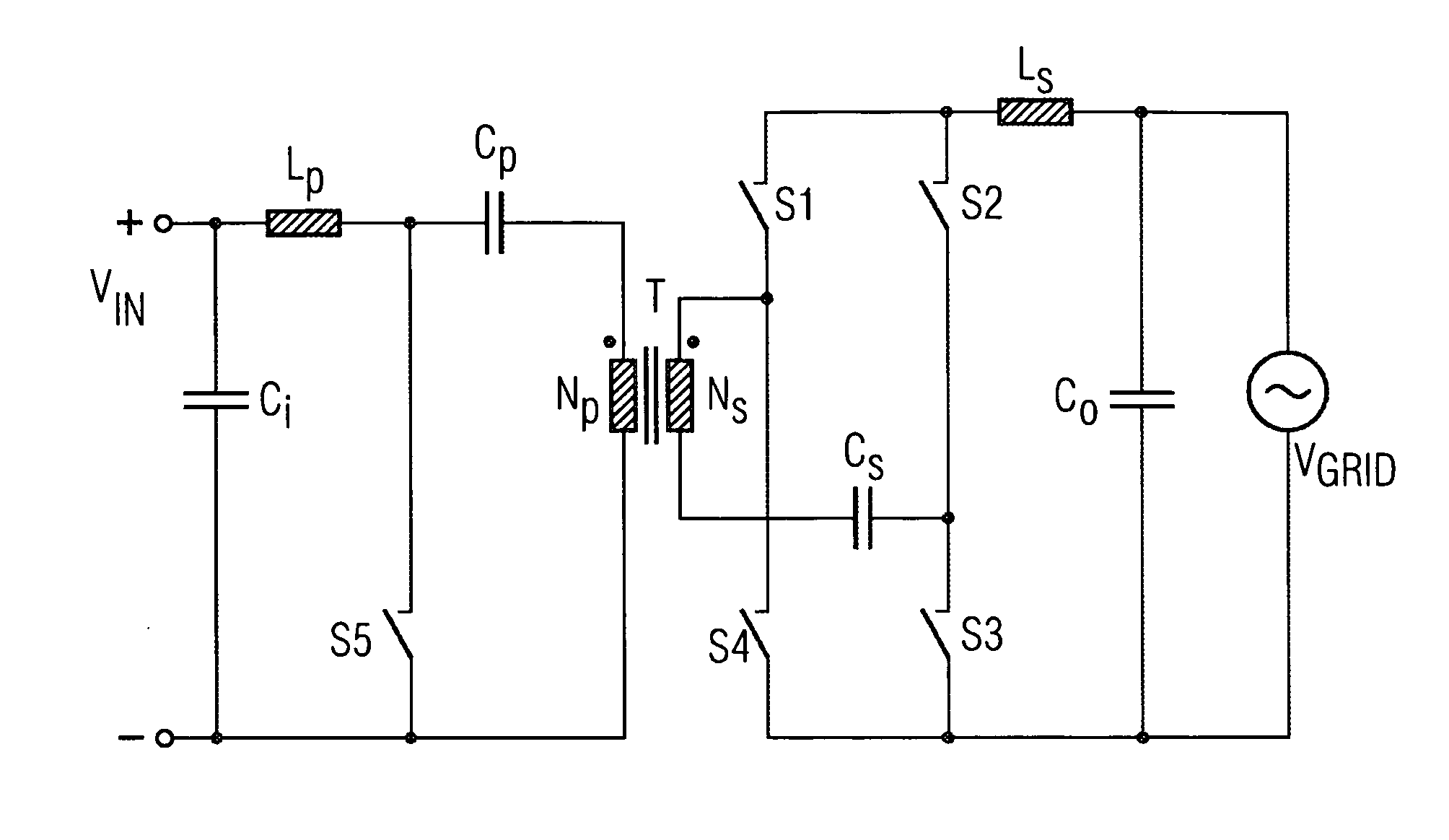
Inverter Circuit and Method for Operating the Inverter Circuit
InactiveUS20090251938A1Smaller and less expensive electrically isolatedLow costConversion with intermediate conversion to dcConversion using Cuk convertorsFull bridgeSecondary circuit
An inverter circuit having a primary circuit with a first choke for periodically connecting a primary winding to a DC voltage present at an input of the inverter circuit, a secondary circuit with a secondary winding, the secondary winding arranged in series with a first capacitor and connected via a full bridge consisting of four switching elements to a AC voltage present at an output of the inverter circuit via a second choke, and a transformer, wherein the primary circuit and the secondary circuit are electrically isolated by the transformer.
Owner:SIEMENS AG
Video monitoring system of full digitalized networking safe city
InactiveCN101742267ARealize digital networkingSave resourcesOptical transmission adaptationsClosed circuit television systemsVideo monitoringTransport system
The invention discloses a video monitoring system of a full digitalized networking safe city, and relates to a video monitoring system. The video monitoring system of the invention is composed of front-end equipment (100), a transmission network (200), a video monitoring management platform (300) and a user terminal (400), wherein the front-end equipment (100), the transmission network (200), the video monitoring management platform (300), the transmission network (200) and the user terminal (400) are communicated from back to forth in sequence; the front-end equipment (100) is the source of system monitoring information; the transmission network (200) is a medium for transmitting the system monitoring information; the video monitoring management platform (300) is a platform for system resource management, sharing and application; and the user terminal (400) is the object served by the system information. The video monitoring system of the invention realizes digital access of front-end monitory points, arranges monitory probes according to the logical relation of ring, lump, lattice and point, and is suitable for popularization in video monitoring applications in large-scale city.
Owner:武汉市公安科学技术研究所 +1
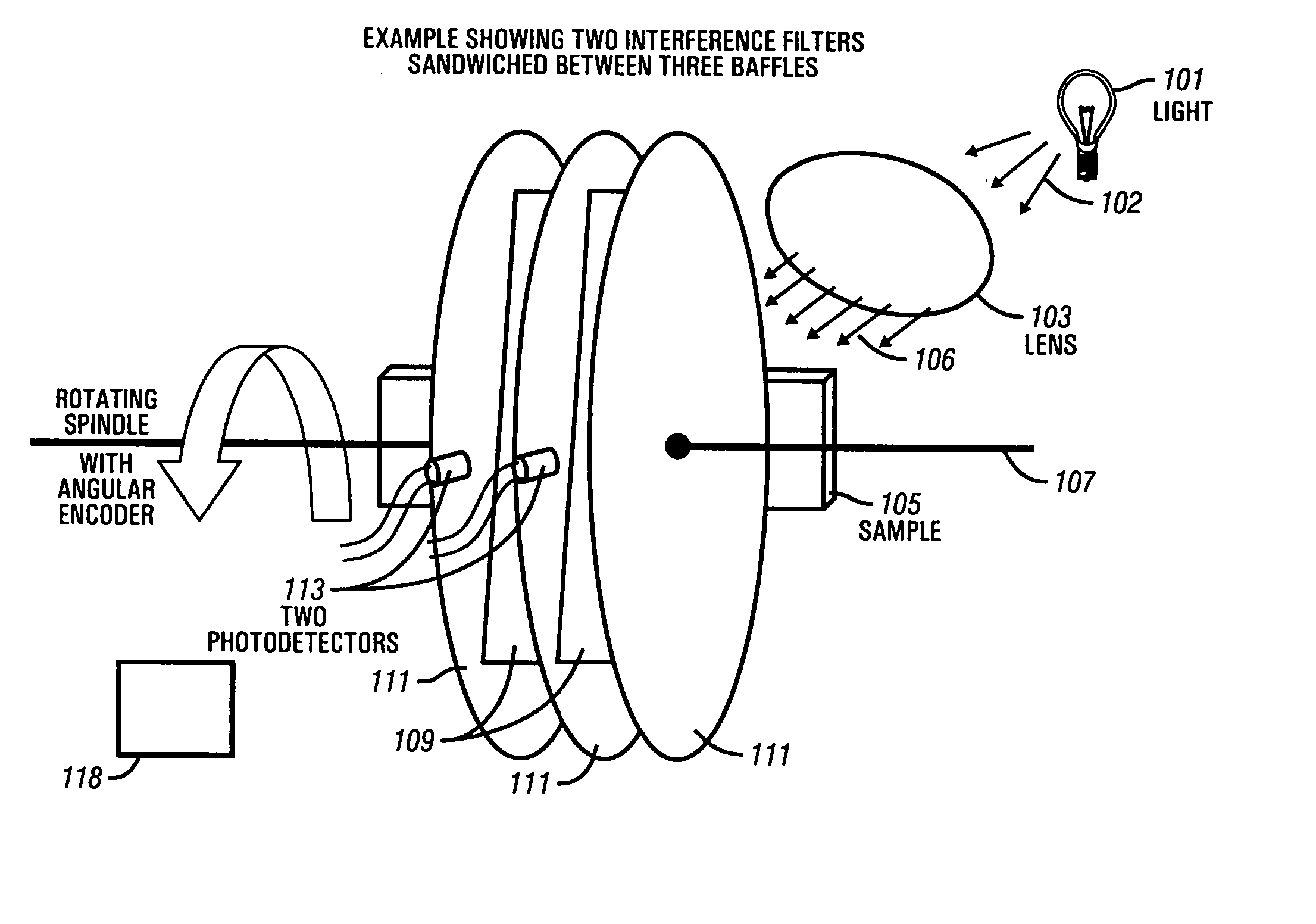
Method and apparatus for a high resolution downhole spectrometer
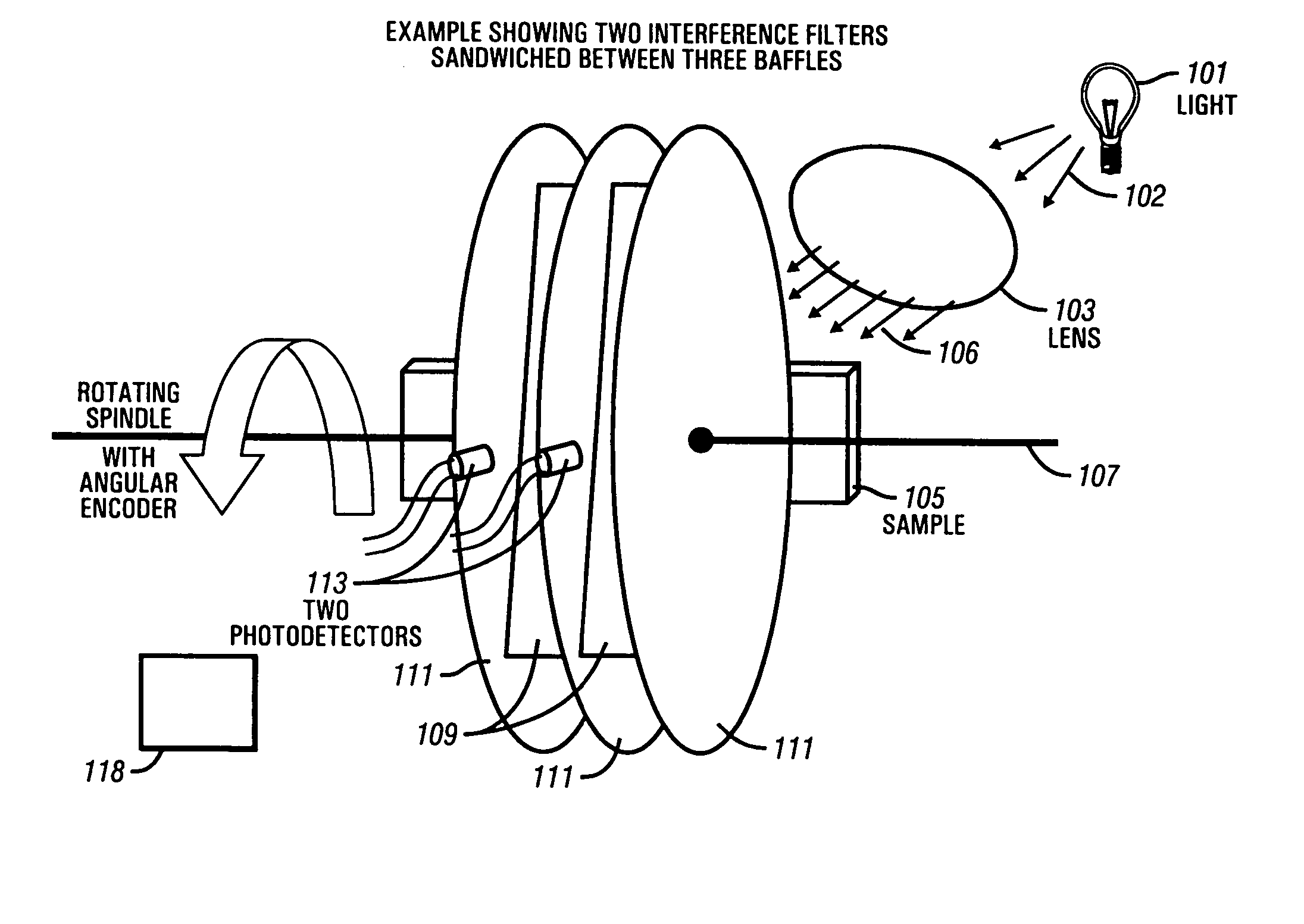
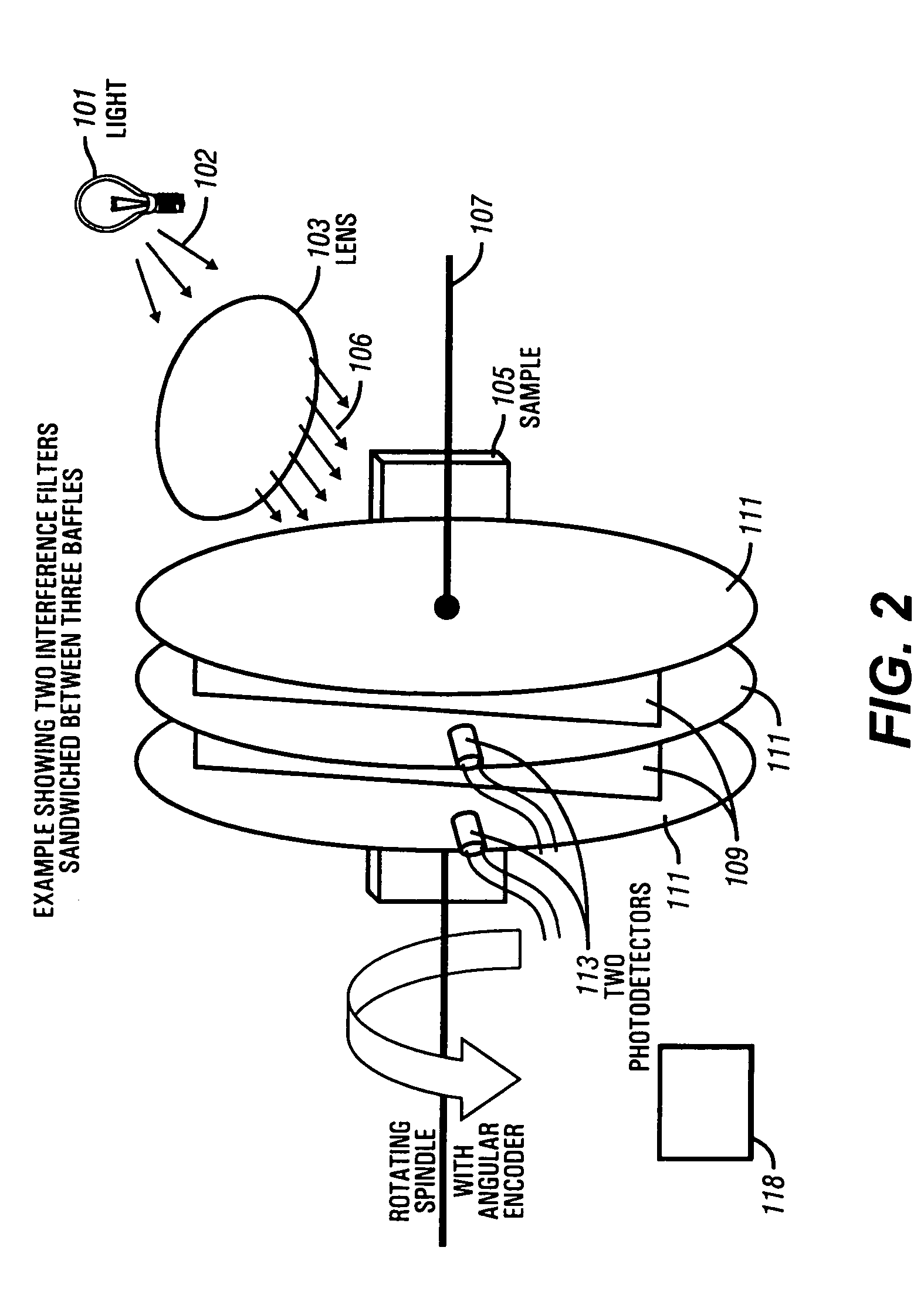
The present invention provides a simple, robust, and versatile high-resolution spectrometer that is suitable for downhole use. The present invention provides a method and apparatus incorporating a spinning, oscillating or stepping optical interference filter to change the angle at which light passes through the filters after passing through a sample under analysis downhole. As each filter is tilted, the color or wavelength of light passed by the filter changes. Black plates are placed between the filters to isolate each filter's photodiode. The spectrometer of the present invention is suitable for use with a wire line formation tester, such as the Baker Atlas Reservation Characterization Instrument to provide supplemental analysis and monitoring of sample clean up. The present invention is also suitable for deployment in a monitoring while drilling environment. The present invention provides a high resolution spectometer which enables quantification of a crude oil's percentage of aromatics, olefins, and saturates to estimate a sample's gas oil ratio (GOR). Gases such as CO2 are also detectable. The percentage of oil-based mud filtrate contamination in a crude oil sample can be estimated with the present invention by using a suitable training set and chemometrics, a neural network, or other type of correlation method.
Owner:BAKER HUGHES INC
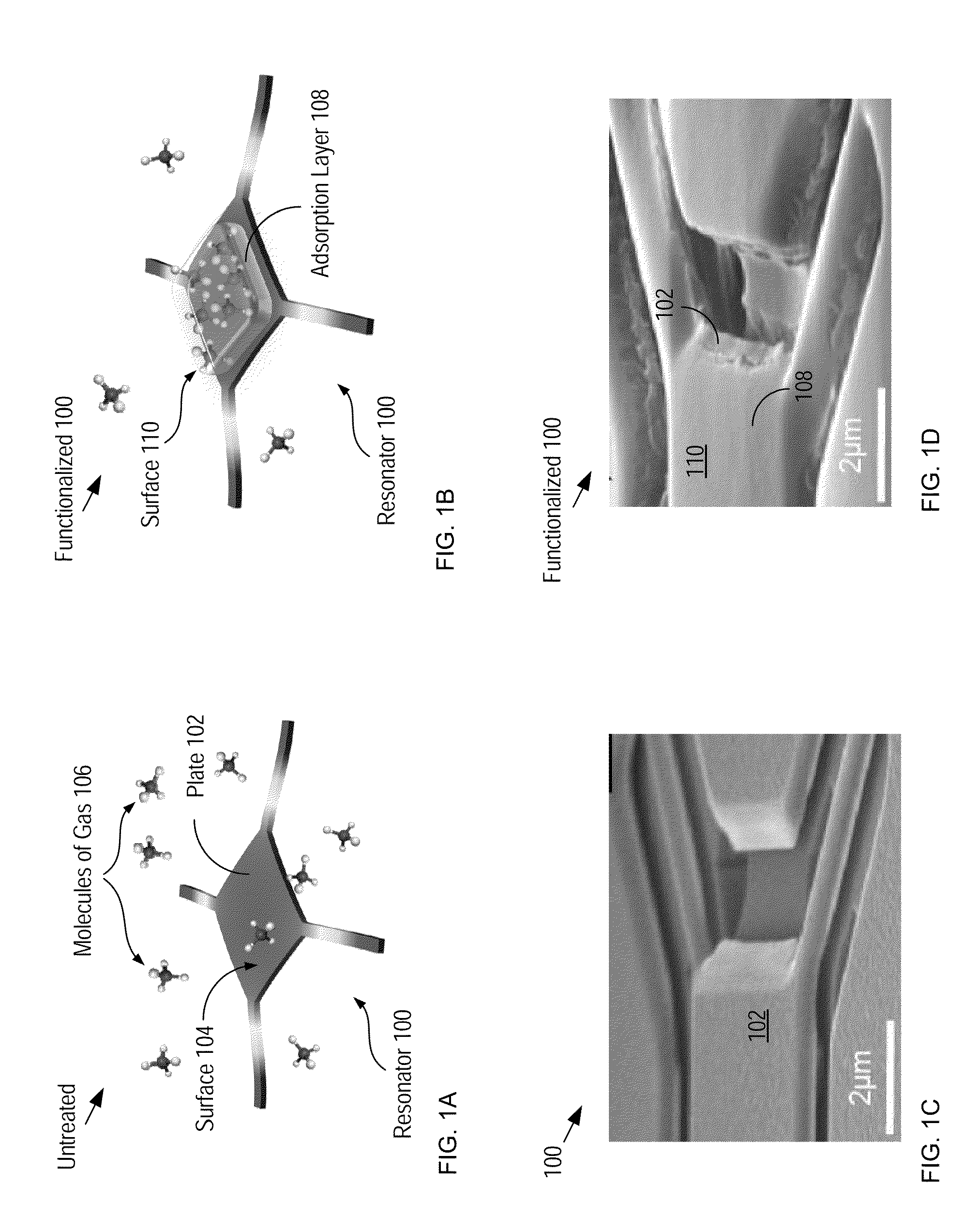
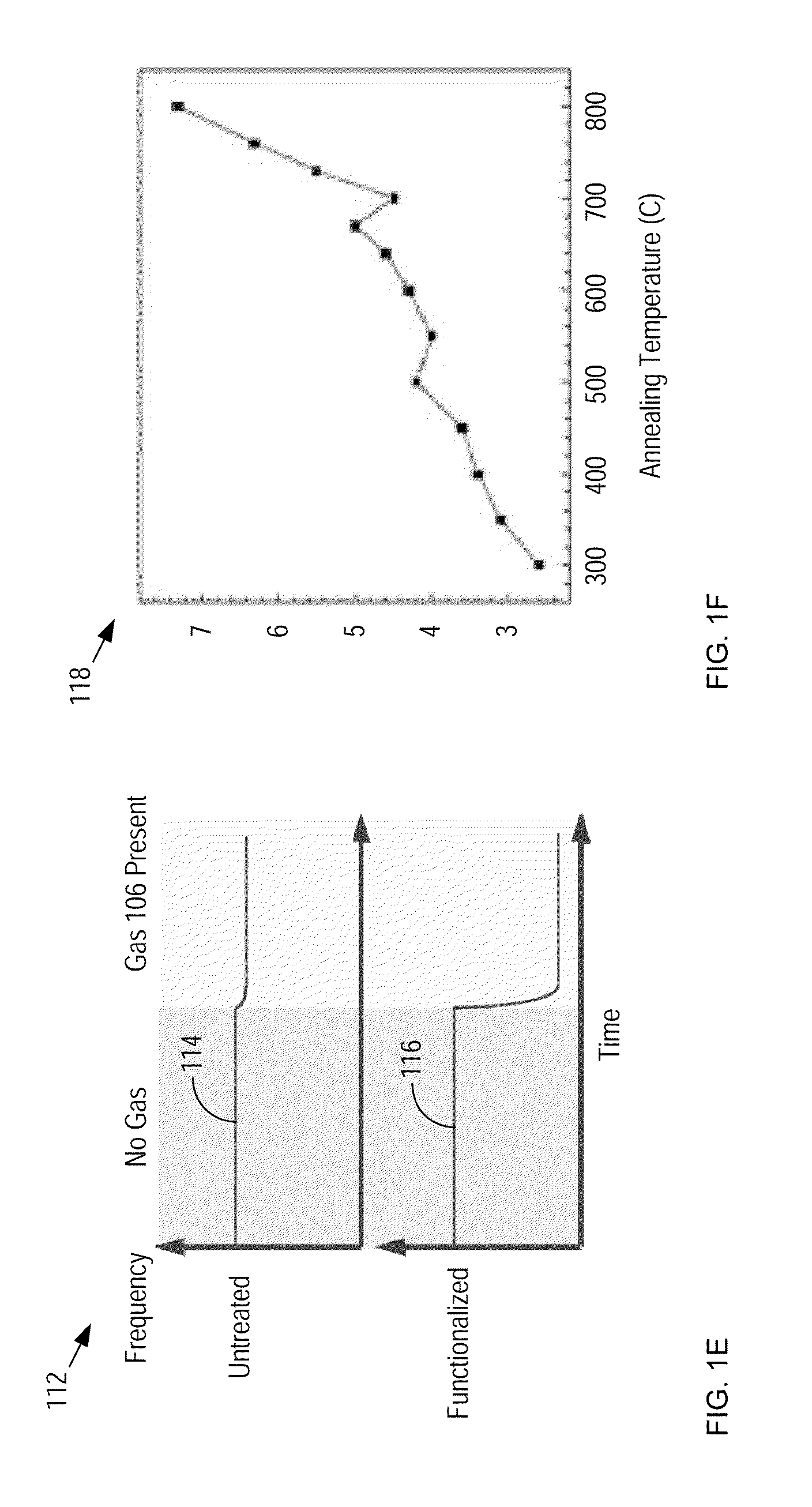
System for Detecting a Gas and Method Therefor
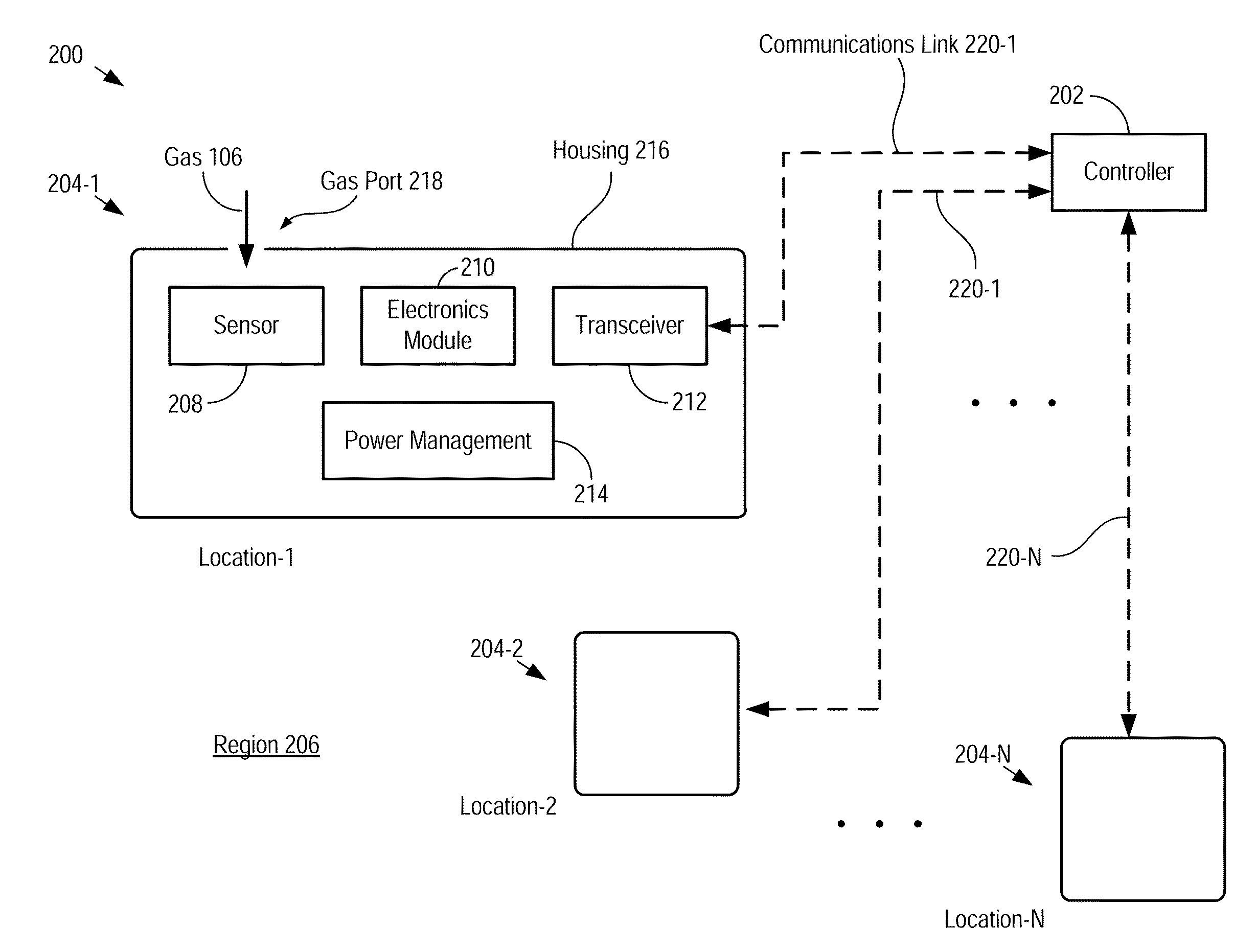
InactiveUS20160202225A1Low powerHigh sensitivityMaterial analysis using sonic/ultrasonic/infrasonic wavesMaterial thermal conductivityElectricityNanoparticle
An apparatus and method for detecting a gas with high sensitivity, high SNR, and low cost is disclosed. Embodiments of the present invention include sensor nodes that communicate with a common controller, where each sensor node includes a resonant sensor that comprises a resonator having a selectively chemisorptive layer disposed upon it. The chemisorptive layer is a nanoparticle-based layer that improves the trapping probability for target-gas molecules, thereby improving the correspondence of the resonance frequency of the resonator to the gas concentration in the atmosphere in which it resides, and improving the sensitivity of the resonant sensor as compared to prior-art resonant mass sensors. Measurement of an electrical parameter of the chemisorption layer can also be used as a secondary detection mode. By employing the chemisorptive layer as an efficient and selective mass-collection layer affords embodiments of the present invention improved noise immunity.
Owner:CASE WESTERN RESERVE UNIV
Apparatus for occluding body lumens
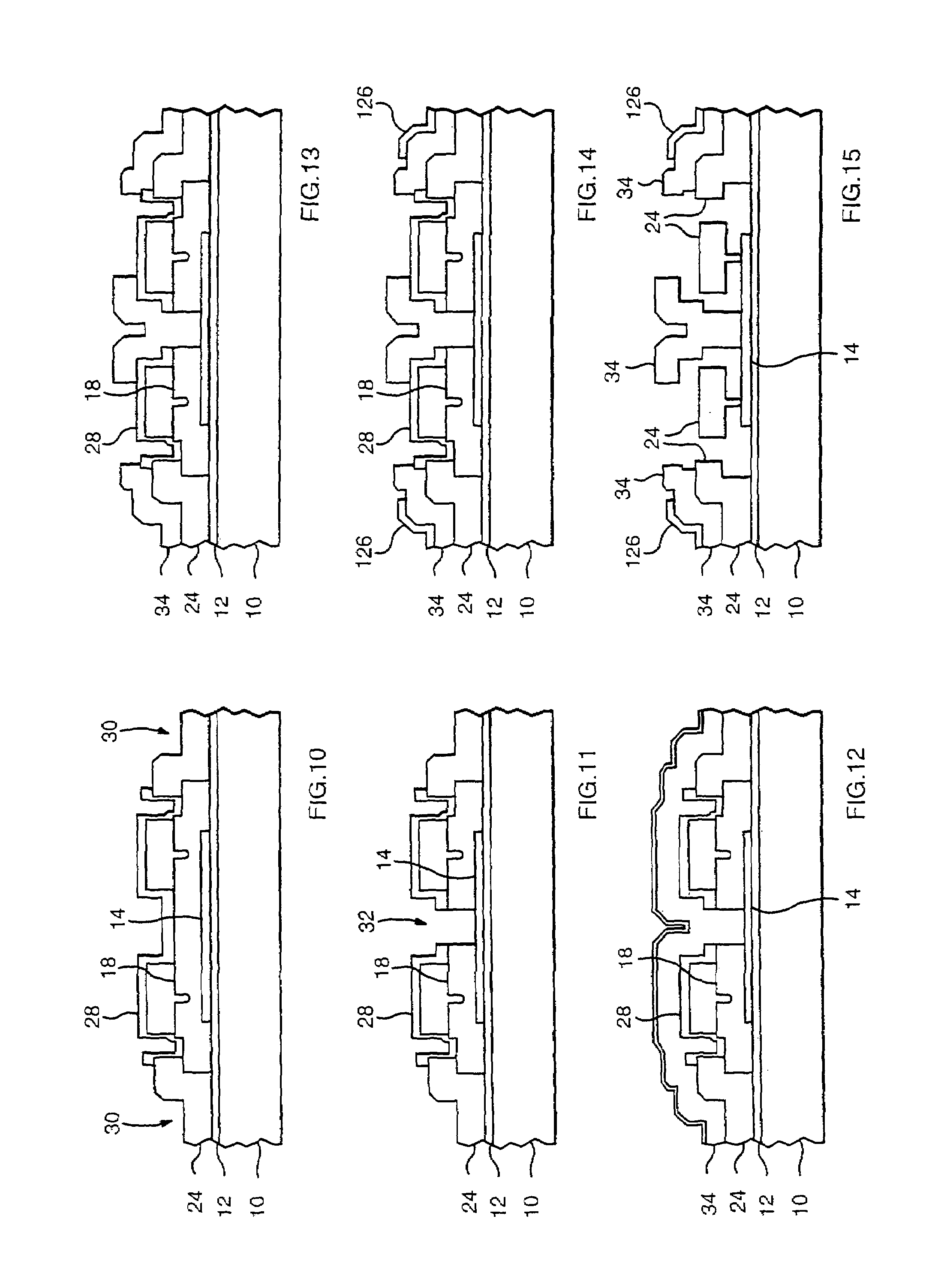
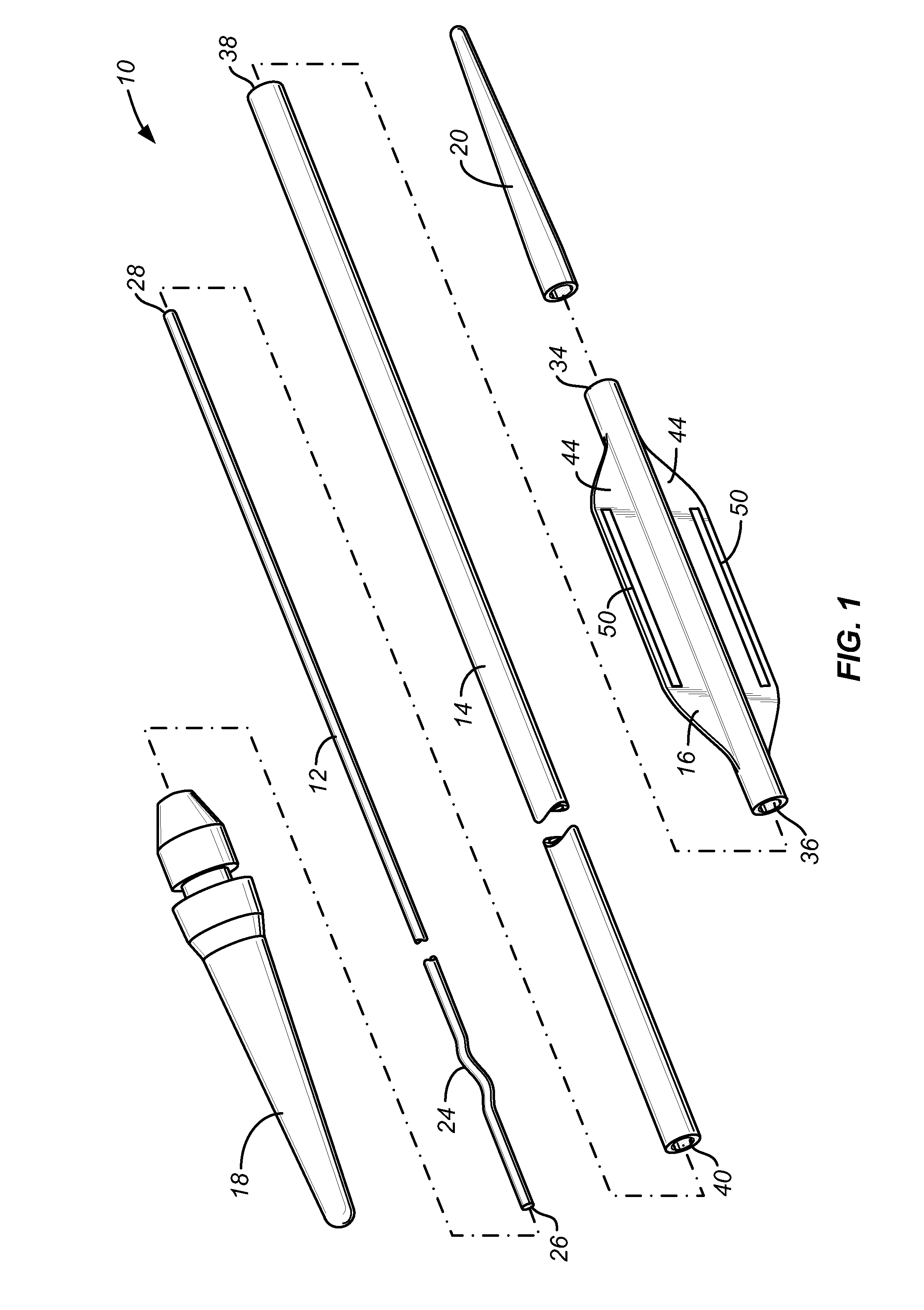
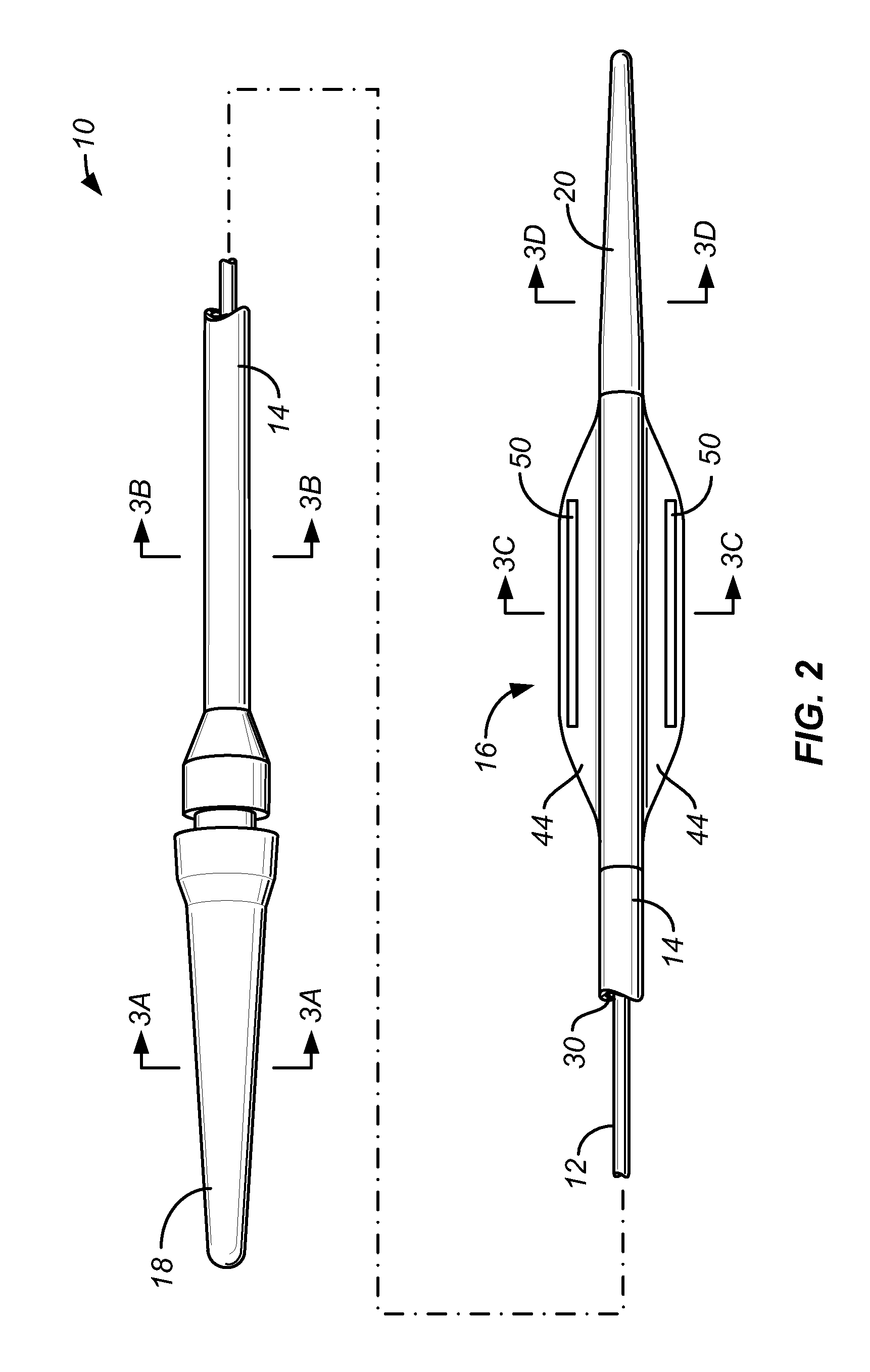
A luminal occlusion device comprises a tension member, an elongate shaft, and a flat film having an axial receptacle which is received over a distal portion of the tension member. The flat film has proximal and distal ends which are attached to the distal ends of the tension member and the elongate shaft, respectively. Thus, distal advancement of the tension member relative to the shaft will cause the flat film to assume a low profile configuration, while proximal retraction of the tension member relative to the elongate shaft will cause the flat film to assume a foreshortened, compacted configuration. The film usually includes one or more radioopaque markers which help shape the compacted film.
Owner:TAKAI HOSPITAL SUPPLY
Method and apparatus for a high resolution downhole spectrometer
InactiveUS20050018192A1Simple and robustHigh resolutionSurveyRadiation pyrometryGas oil ratioPhotodiode
The present invention provides a simple, robust, and versatile high-resolution spectrometer that is suitable for downhole use. The present invention provides a method and apparatus incorporating a spinning, oscillating or stepping optical interference filter to change the angle at which light passes through the filters after passing through a sample under analysis downhole. As each filter is tilted, the color or wavelength of light passed by the filter changes. Black plates are placed between the filters to isolate each filter's photodiode. The spectrometer of the present invention is suitable for use with a wire line formation tester, such as the Baker Atlas Reservation Characterization Instrument to provide supplemental analysis and monitoring of sample clean up. The present invention is also suitable for deployment in a monitoring while drilling environment. The present invention provides a high resolution spectometer which enables quantification of a crude oil's percentage of aromatics, olefins, and saturates to estimate a sample's gas oil ratio (GOR). Gases such as CO2 are also detectable. The percentage of oil-based mud filtrate contamination in a crude oil sample can be estimated with the present invention by using a suitable training set and chemometrics, a neural network, or other type of correlation method.
Owner:BAKER HUGHES INC
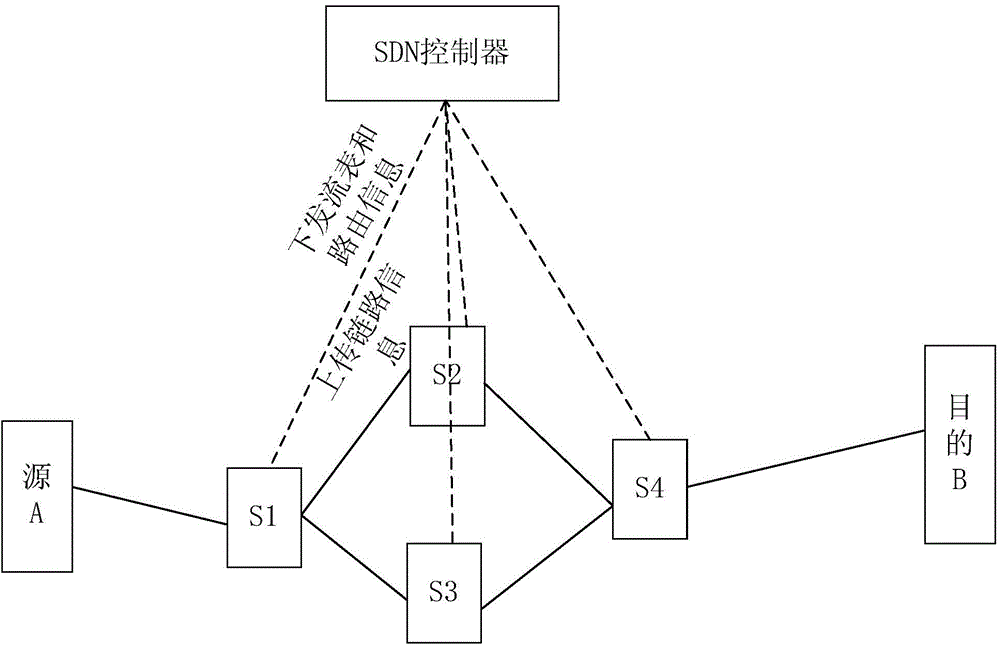
Route generating and coupling method and system of SDN
ActiveCN104901890ASolve the problem of slow convergenceSuitable for deploymentData switching networksHigh level techniquesRouting tableIp address
The invention provides a route generating and coupling method and system of an SDN. An SDN controller regularly obtains link state information and a network topology structure of the SDN; the SDN controller uniformly calculates route information and generates a flow table, a primary IP index routing table and a secondary IP index routing table of each SDN switch; and the SDN controller issues the corresponding flow table, the primary IP index routing table and a secondary IP index routing table corresponding to each SDN switch. In the coupling process, the flow table is searched according to a destination IP address and a mask of a message; the primary IP index routing table is searched according to the flow table; and the secondary IP index routing table is searched according to the flow table and the primary IP index routing table to obtain a corresponding interface and gateway. According to the invention, the generation of a route is integrally finished on the SDN controller, the route cost is used as a route selection basis, the method and the system are more suitable for a large-scale network, the network topology structure and the link state are dynamically monitored in real time, and the maintenance cost of the network is reduced.
Owner:湖州帷幄知识产权运营有限公司
Inverter circuit and method for operating the inverter circuit
InactiveUS8027179B2Smaller and less expensive electrically isolatedLow costConversion with intermediate conversion to dcConversion using Cuk convertorsElectricityPower inverter
An inverter circuit having a primary circuit with a first choke for periodically connecting a primary winding to a DC voltage present at an input of the inverter circuit, a secondary circuit with a secondary winding, the secondary winding arranged in series with a first capacitor and connected via a full bridge consisting of four switching elements to a AC voltage present at an output of the inverter circuit via a second choke, and a transformer, wherein the primary circuit and the secondary circuit are electrically isolated by the transformer.
Owner:SIEMENS AG
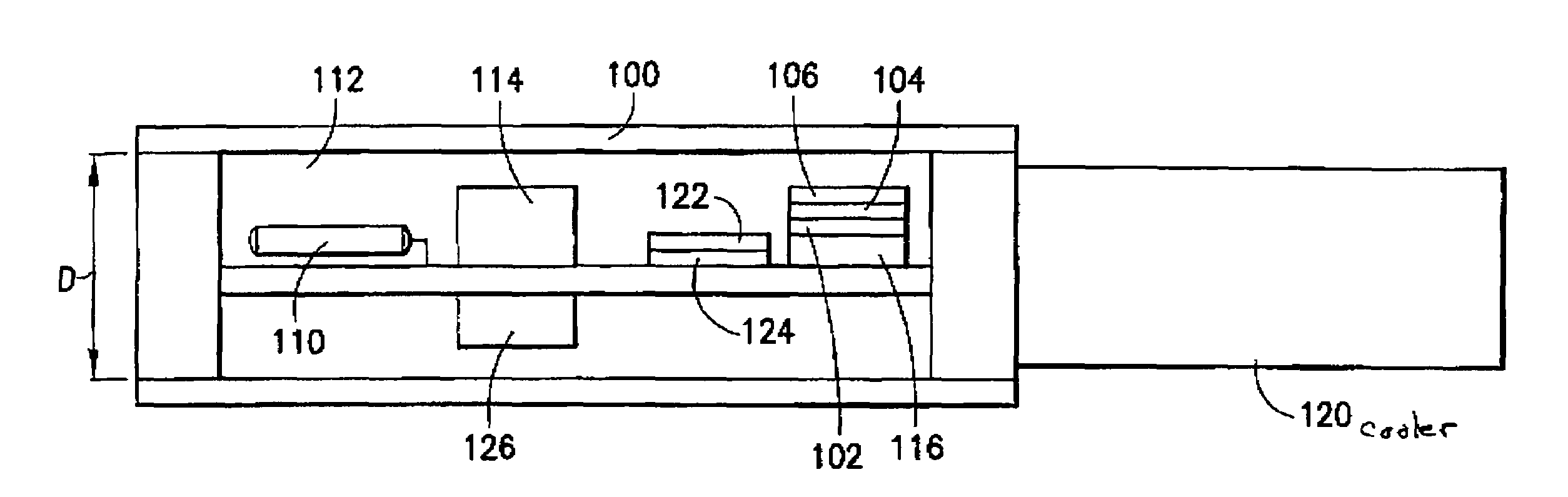
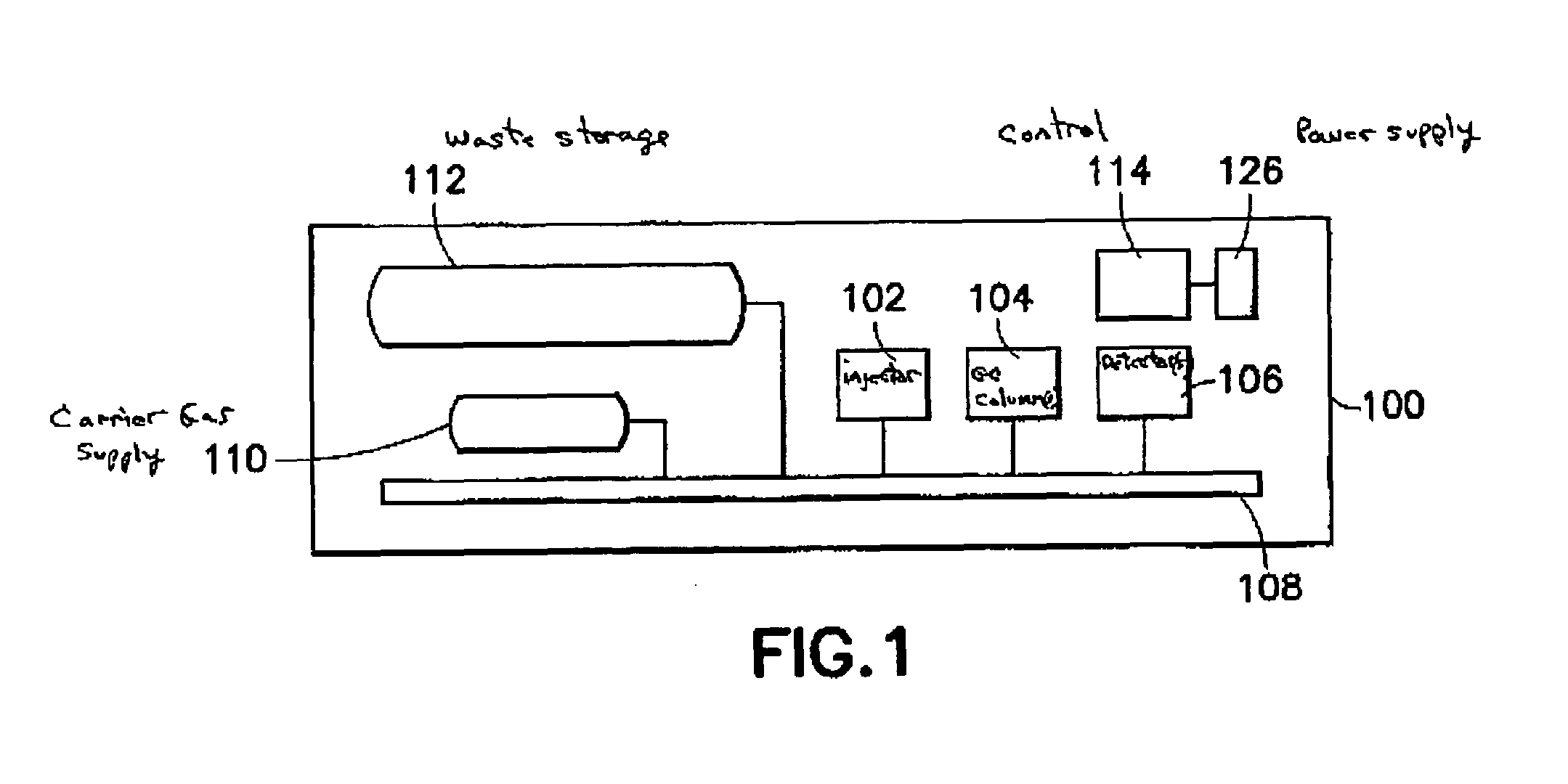
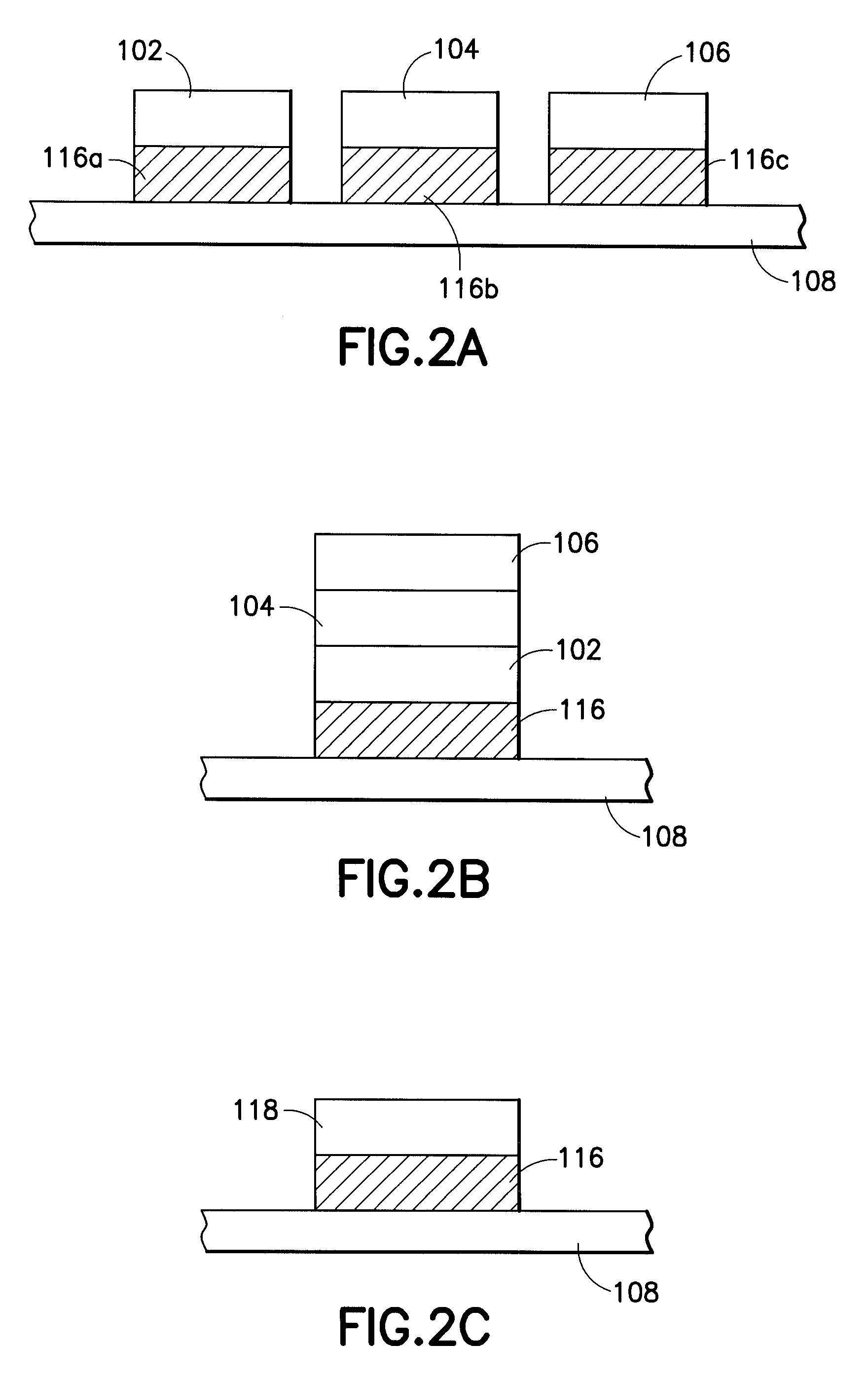
Gas chromatography system architecture
InactiveUS7600413B2Improve reliability and operabilityImproved thermal managementComponent separationLaboratory glasswaresDisposal wasteGas liquid chromatographic
A self-contained micro-scale gas chromatography system that includes a plurality of gas chromatography components arranged on a micro-fluidic platform with nearly zero dead volume “tubeless” fluidic connections for the gas chromatography components. The micro-fluidic platform includes a plurality of flow channels that provide fluid flow paths for a sample, carrier gas and waste gas through and among the micro-fluidic platform and the plurality of gas chromatography components. The system may also include an on-board supply of carrier gas and on-board waste management, as well as a thermal management scheme making the system suitable for use in oil and gas wells and also other remote environments.
Owner:SCHLUMBERGER TECH CORP
Method and apparatus for configuring and controlling network resources in content delivery with distributed rules
InactiveUS7734746B2Easy to controlMost efficientDigital computer detailsData switching networksDistributed computingControl network
An intermediate network element deployed in a content delivery network is disclosed. The content delivery network cooperates its content delivery effort with other intermediate network element with similar capabilities. Distributing rules that govern the operations of the intermediate network element(s) are presented. These include the framework of the intermediate network element(s), the format of indicating part or whole of a rule specification to be distributed, the format of signatures for intermediate network elements to discover each other, the format of signaling other intermediate network elements that a rule is distributed to, and the method of determining the intermediate network element to distribute a rule to. In addition, authoring rules that are specific to real time streaming of contents are disclosed. A set of rule evaluation conditions are revealed that can be triggered based on different criteria during the streaming of real time contents. A set of parameters from which rules can be based on is disclosed.
Owner:PANASONIC CORP
Display unit with an integrated backlight
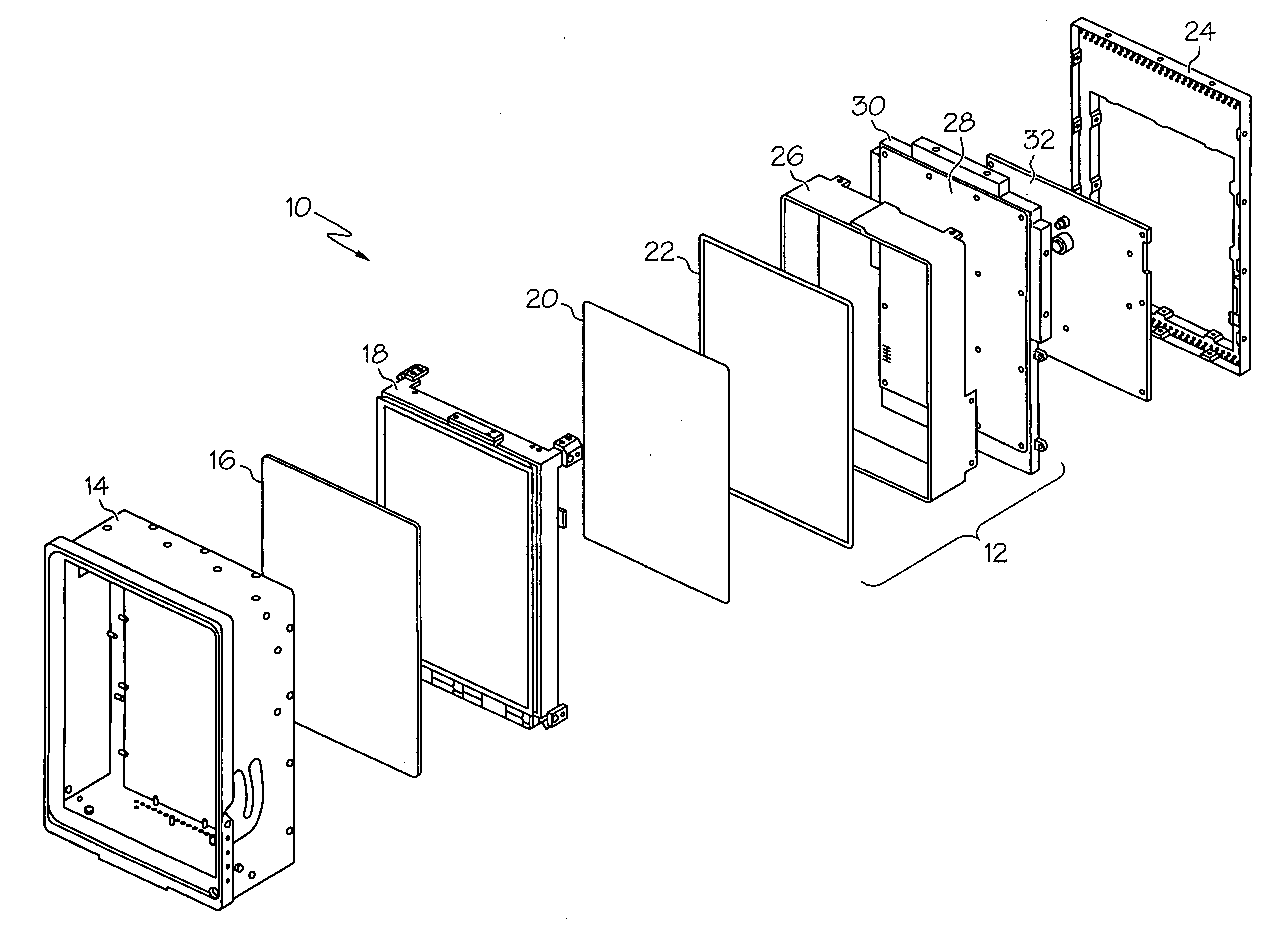
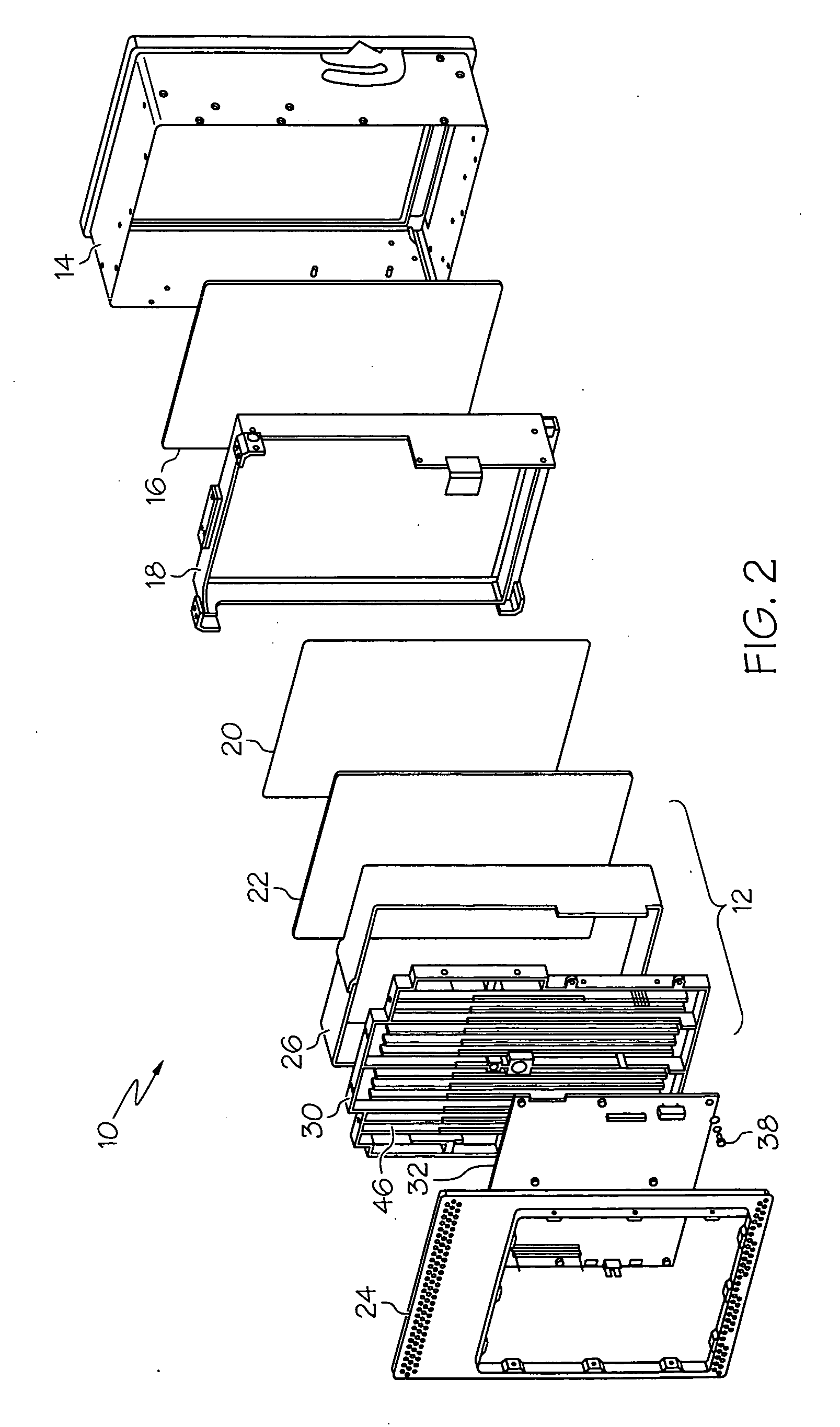
ActiveUS20110141389A1Effective coolingImprove performanceNon-linear opticsLiquid-crystal displayDisplay device
A display device includes an integrated liquid crystal display and a backlight unit. The liquid crystal display is provided with a backlight system that includes a light-emitting element positioned along one or more sides of the display. In order to efficiently distribute and dissipate the heat produced by the light-emitting element, the backlight cover can cover the light-emitting elements and the area over the liquid crystal display. For shielding, the backlight cover can separate the display from an electronic circuit assembly. The backlight cover may be made monolithically of a heat-conductive material such as aluminum, as well as an electro-conductive material for shielding. The backlight cover may also provide mechanical support for the display device and mounting features to ease assembly and mounting to a target location. Such a display device may be deployed on a vehicle, for instance, as part of a vehicle navigation, communication, and / or entertainment system.
Owner:HARMAN BECKER AUTOMOTIVE SYST
Unilateral thermal buckle beam actuator
InactiveUS7007471B2Reduce areaHigh strengthMechanical power devicesPiezoelectric/electrostrictive devicesLinear motionIn plane
A unilateral in-plane thermal buckle-beam microelectrical mechanical actuator is formed on a planar substrate of semiconductor material, for example. The actuator includes first and second anchors secured to the substrate and a floating shuttle positioned movably parallel to the substrate. Symmetric first and second sets of elongated thermal half-beams are secured between the floating shuttle and the respective first and second anchors. The first and second anchors and the first and second sets of thermal half-beams are positioned along one side of the floating shuttle. The half-beams are formed of semiconductor material, such as polysilicon. A current source directs electrical current through the thermal half beams via the anchors to impart thermal expansion of the thermal half-beams and hence linear motion of the floating center beam generally parallel to the substrate. A floating cold beam connected between the shuttle and the substrate constrains and amplifies the motion of the shuttle in a predefined direction.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus for occluding body lumens
InactiveUS20090018549A1Prevents accidental deploymentFacilitate manual deploymentDilatorsOcculdersDistal portionTension member
A luminal occlusion device comprises a tension member, an elongate shaft, and a flat film having an axial receptacle which is received over a distal portion of the tension member. The flat film has proximal and distal ends which are attached to the distal ends of the tension member and the elongate shaft, respectively. Thus, distal advancement of the tension member relative to the shaft will cause the flat film to assume a low profile configuration, while proximal retraction of the tension member relative to the elongate shaft will cause the flat film to assume a foreshortened, compacted configuration. The film usually includes one or more radioopaque markers which help shape the compacted film.
Owner:TAKAI HOSPITAL SUPPLY
Method for preventing campus network from virus attacks
InactiveCN101951367ALow costImprove efficiencyData switching by path configurationIp addressARP spoofing
The invention discloses a method for preventing a campus network from virus attacks, which comprises the following steps: (a) dividing a campus network into a plurality of VLANs; (b) bonding user IP address with network card MAC address; (c) adopting a double safety bonding mode of bonding the IP address of the host computer of a user and the MAC address of a network card on a core switch and bonding the MAC address of the network of the computer of the user and a switch port on an edge switch; and (d) making active defense on the basis of the MIB state library of network equipment. In the invention, the attacked terminal can be locked effectively, the attach of ARP on the port is blocked, and the ARP spoofing attack is prevented effectively; and the time of network administrators is saved greatly, the safety of a tested network section is protected by the combination with prevention measurements, and the normal operation of the campus network is protected effectively.
Owner:SUZHOU CHIEN SHIUNG INST OF TECH
Process for producing concentrated sea-buckthorn clear juice
The invention discloses a process for producing concentrated sea-buckthorn clear juice, which comprises the following steps of: crushing and squeezing the mature sea-buckthorn, adding water into the obtained juice, and fully stirring the juice to obtain primary turbid juice; sterilizing the primary turbid juice for 5 minutes at the high temperature of between 100 and 110 DEG C, cooling the sterilized juice to between 65 and 70 DEG C, separating the juice to obtain sea-buckthorn juice by using a centrifugal machine, then adding amylase, pectase and pear juice enzyme into the sea-buckthorn juice, and digesting the mixture at the constant temperature of between 50 and 55 DEG C to obtain secondary turbid juice; separating the supernate from the secondary turbid juice by centrifugation to obtain the sea-buckthorn clear juice; and filtering the sea-buckthorn clear juice to be clear by using a filter membrane, and concentrating the sea-buckthorn clear juice under vacuum to obtain the concentrated sea-buckthorn clear juice. The conditions adopted in the process are mild, pectin and starch which affect the clear juice are removed by combining ordered heating and cooling and enzymolysis, and the conditions of the whole process keep the nutrient components in the sea-buckthorn as much as possible and furthest reserve juice color and flavor.
Owner:合德堂食品工业(泾阳)有限公司
Production technique of concentrated clear persimmon juice
The invention discloses a production technique of concentrated clear persimmon juice. When being used for producing persimmon juice, the technique can concentratedly consume the raw material in a short time in the harvesting time of persimmon fruit, thereby enhancing economic value of persimmon. Orderly heating and cooling in combination with enzymolysis are used for removing pectin and starch which affect the clear juice, and the clear and bright juice is obtained through centrifugal separation. The low-temperature distillation is used for concentration in the concentration stage, thereby controlling the conditions in the whole technical process and maintaining the nutritional ingredients in fruit to the maximum, and the color and flavor of the fruit juice are maintained to the maximum.
Owner:合德堂食品工业(泾阳)有限公司
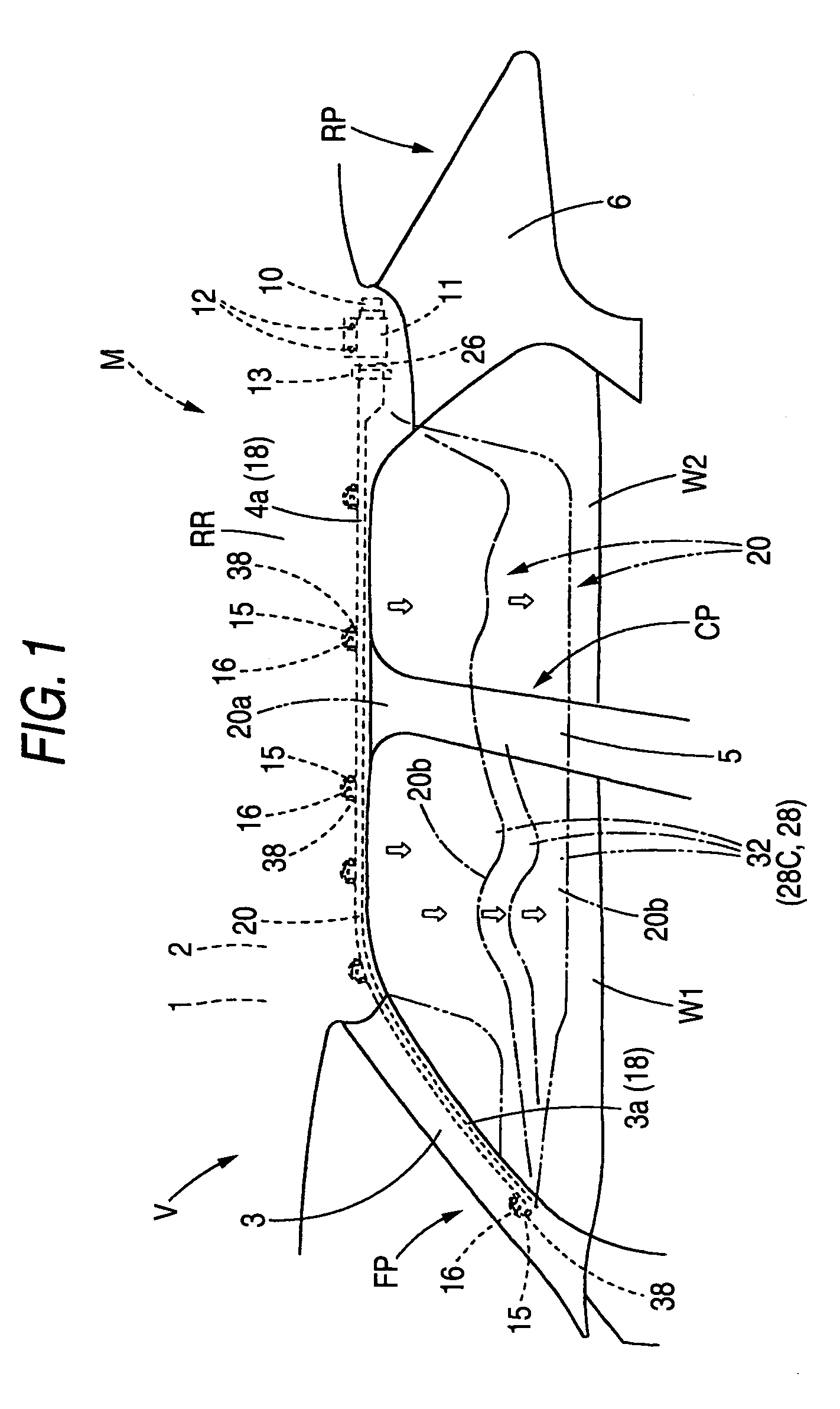
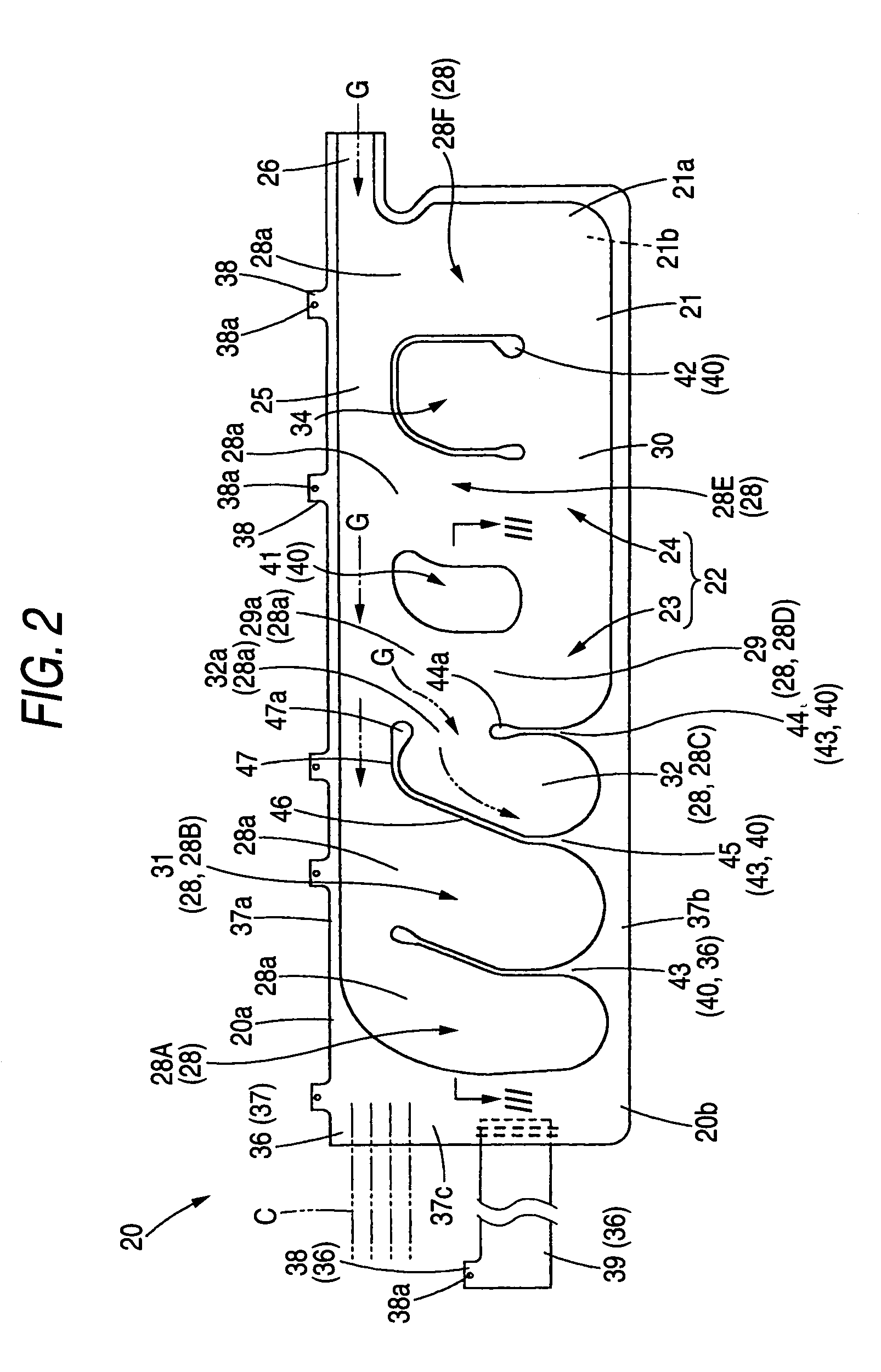
Airbag apparatus
InactiveUS7168735B2Suitable for deploymentRapid deploymentPedestrian/occupant safety arrangementEngineeringAirbag
Owner:TOYODA GOSEI CO LTD
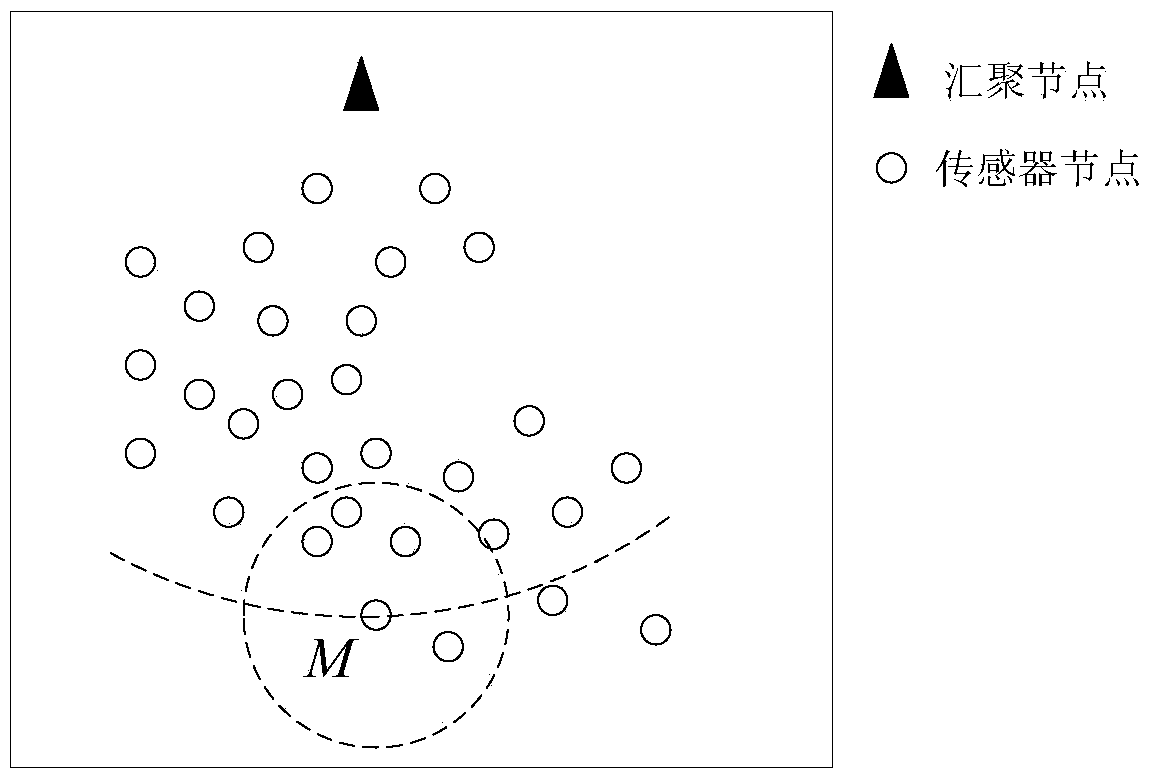
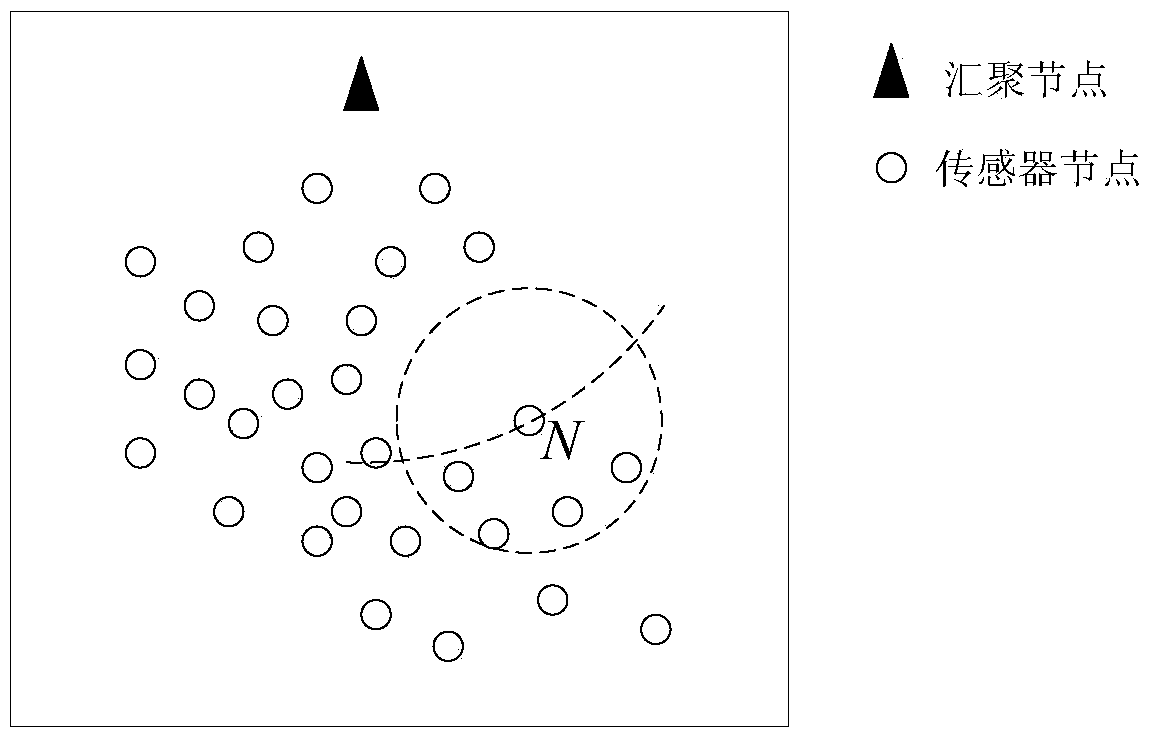
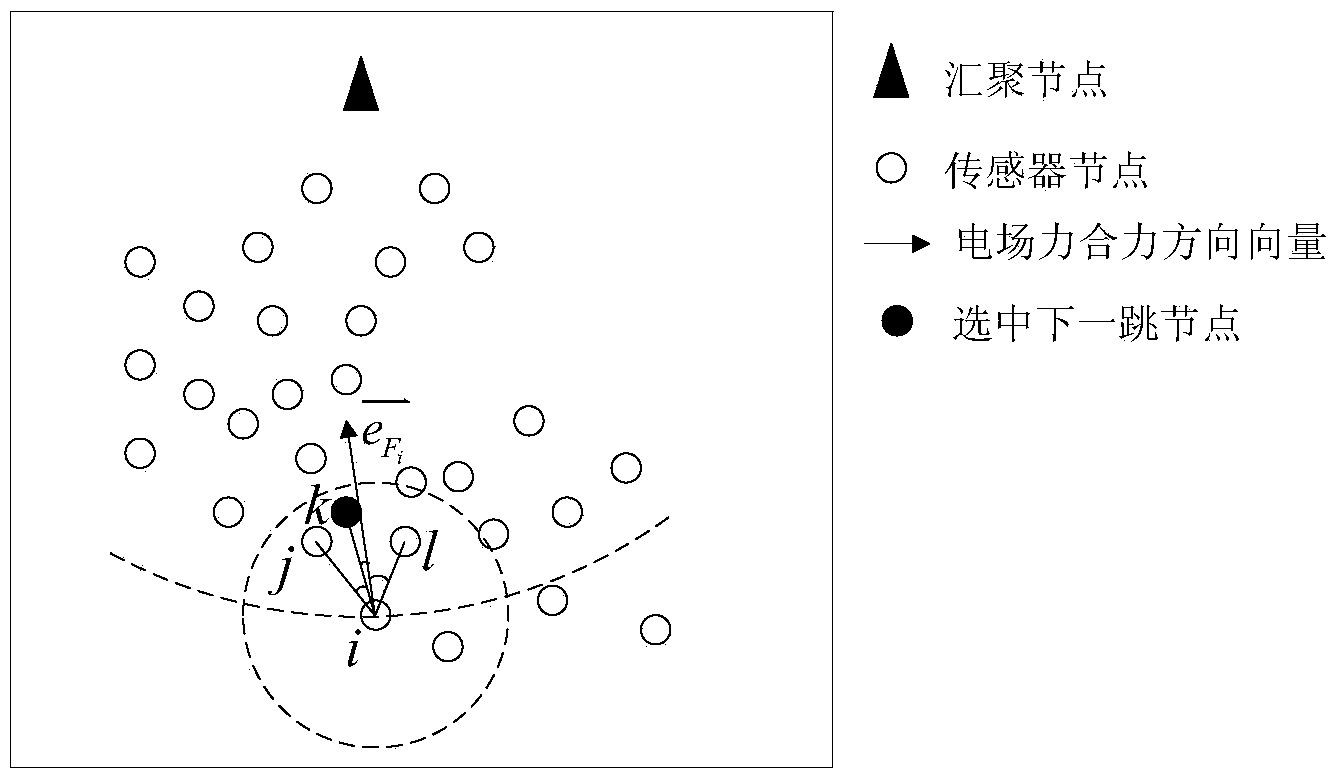
Wireless sensor network route method based on artificial potential field
ActiveCN103906166ASuitable for deploymentReduce overheadEnergy efficient ICTNetwork topologiesPotential fieldWireless sensor networking
The invention relates to a wireless sensor network route method based on an artificial potential field. The wireless sensor network route method includes the four steps of initializing, route building, route uploading and data transmitting. The problems that in the prior art, the route cost and the route energy consumption are large, and route selection does not have the load balancing function are solved, the calculation complexity is lowered, a large amount of route cost is avoided, the energy efficiency is improved, and the network load balancing function can be achieved.
Owner:韩小学
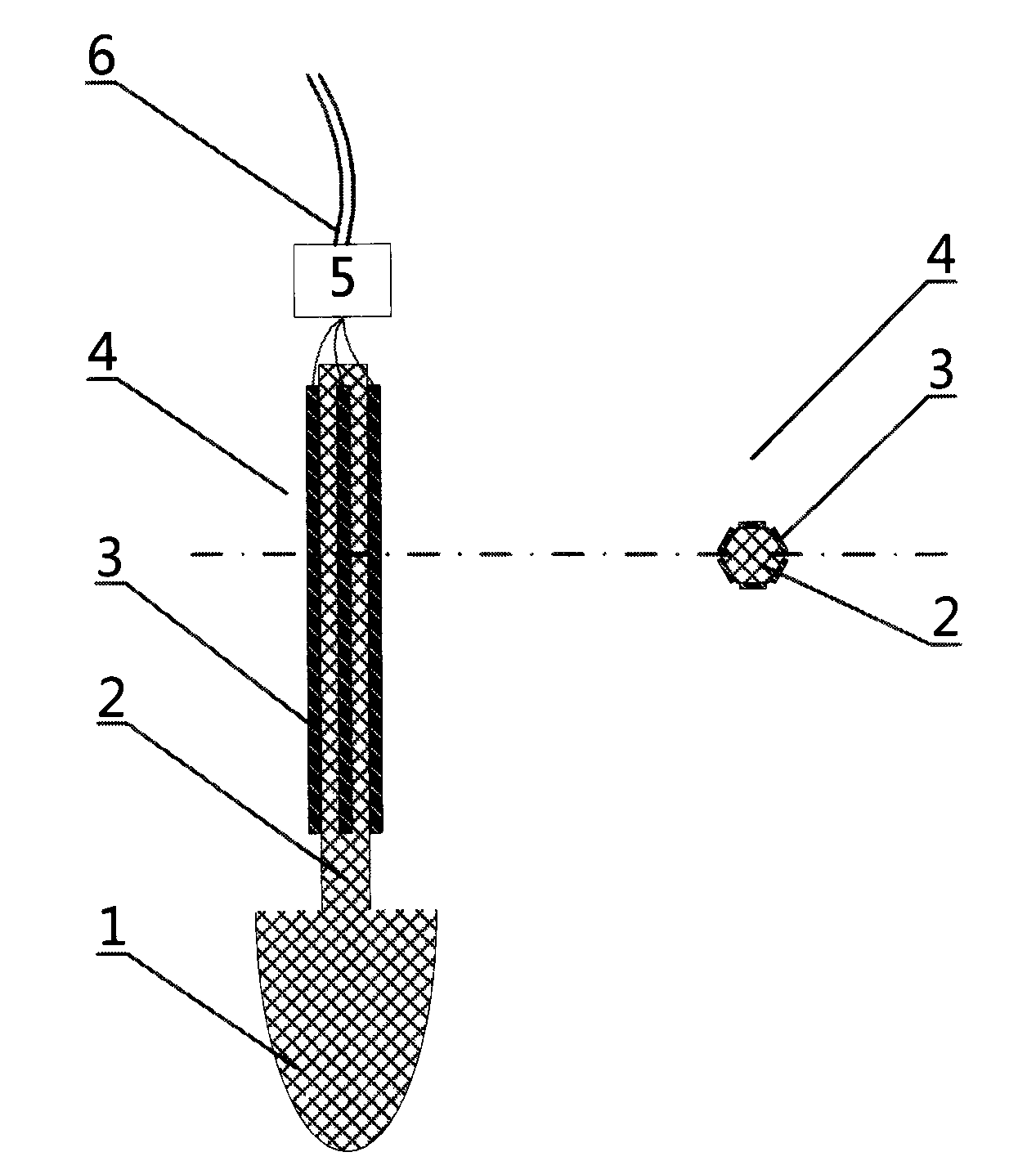
Violent earthquake gestation and imminent earthquake sound monitoring probe and circuit module structure
InactiveCN103353608AHigh sensitivityLarge dynamic rangeEarthquake measurementSeismic signal receiversElectricityBand shape
The invention discloses a violent earthquake gestation and imminent earthquake sound monitoring probe and a circuit module structure. The probe structure is directly coupled with a base rock through a taper microphone head and conducts an earthquake sound to a sound transmission rod which is directly connected with the probe structure. A band-shape piezoelectric film sensor which is pasted on a surface of the sound transmission rod converts an earthquake sound signal into an electrical signal. The sound transmission rod, a band-shape piezoelectric film sensor group and a processing circuit are packaged through using a glue, and are fixed and protected. Besides, a probe circuit module structure carries out backup on the captured earthquake sound signal from three hierarchies of a sensor unit, the processing circuit and a transmission process so that reliability of a whole circuit system is increased. The sensor adopts the piezoelectric film sensor. There are the advantages that sensitivity is high; a dynamic scope is large and a frequency response scope is large too. By using the above technical scheme, the probes can be densely arranged in the base rocks which are under 150 meters to 200 meters of an earthquake-prone belt in a large scale so that violent-earthquake imminent earthquake sound monitoring work can be performed reliably for a long time and with low cost.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
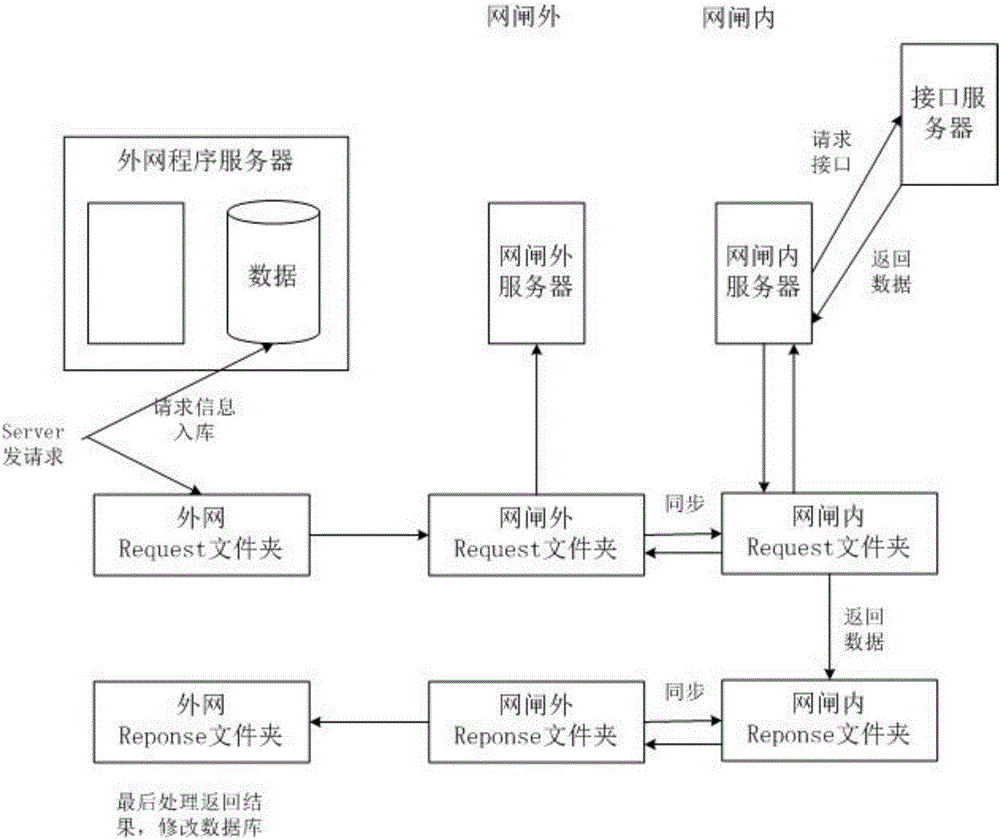
Network security system under mobile Internet environment
InactiveCN106230795AProtects against internal sabotage and external attacksReduce maintenance costsTransmissionSecurity arrangementService systemApplication server
The invention relates to a network security system under a mobile Internet environment, comprising a security isolation gap, an extranet application server, a gap external server, a gap internal server, and an interface server which is connected with a specific application service system and provides interface service. The extranet application server receives an access request of a user, transmits the access request among the gap external server, the gap internal server and the interface server through an inter-gap asynchronization and synchronization function, and gets returned data through the interface server. The returned data is transmitted among the gap internal server, the gap external server and the extranet application server the inter-gap asynchronization and synchronization function, and is returned to the user. The application service system is deployed through the security isolation gap to establish a perfect access control mechanism, and cross-operation-platform, cross-platform and cross-service-platform security access management strategies can be provided.
Owner:北京近颐科技有限公司
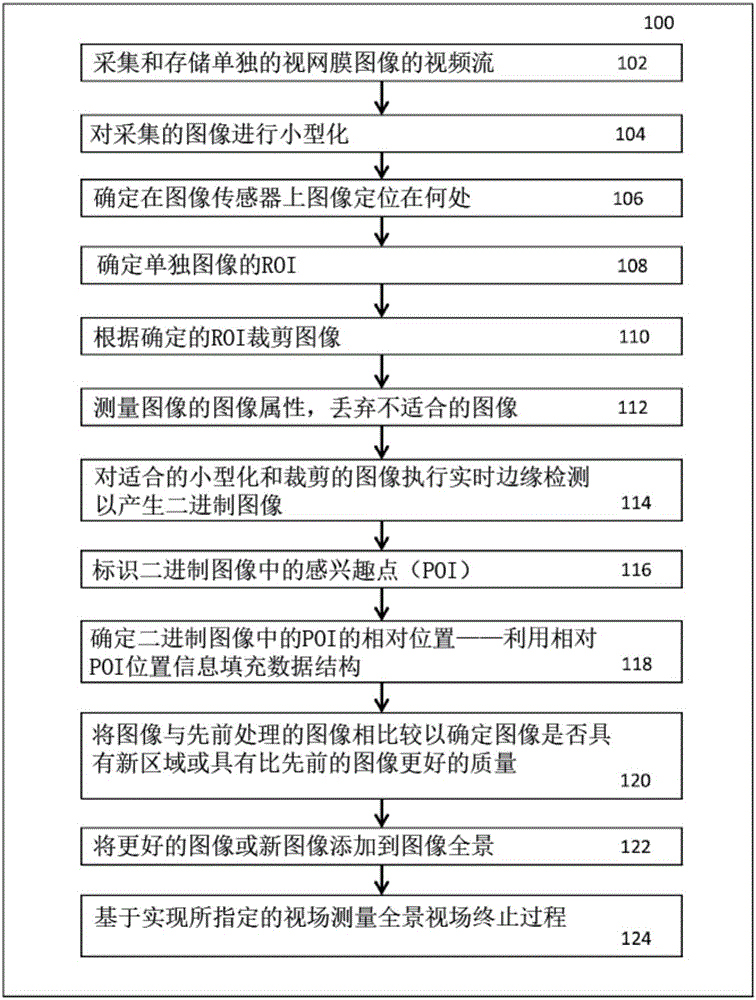
Wide field retinal image capture system and method
InactiveCN105934193AQuality improvementImprove usabilityImage enhancementTelevision system detailsDigital videoWide field
A method, system or apparatus for generating a wide field retinal image. System embodiments comprise a camera, which may be a smartphone camera and associated optics to capturing a digital video stream of individual retinal images and store the video stream of individual retinal images in a memory associated with the camera. The system or method then implements the steps of processing each retinal image and combining selected retinal images into a panorama in real time, during an ocular examination.
Owner:RSBV LLC
High efficiency backlight assembly for flat panel display assembly and method for the manufacture thereof
ActiveUS20100283933A1Improve reflectivitySuitable for deploymentVessels or leading-in conductors manufactureIlluminated signsElectricitySolder mask
A backlight assembly is provided for deployment within a flat panel display assembly. In one embodiment, the backlight assembly includes a printed wiring board (PWB), a casing sidewall, a plurality of light emitting diodes (LEDs), a reflective solder mask, and a first reflective silkscreen layer. The PWB includes a display-facing surface, and the casing sidewall disposed is around a peripheral portion of the PWB and cooperates with the display-facing surface to define a light cavity. The plurality of LEDs us electrically coupled to the PWB and illuminates the light cavity when energized. The reflective solder mask overlays the display-facing surface of the PWB, and the first reflective silkscreen layer overlays the reflective solder mask. The first reflective silkscreen layer cooperates with the reflective solder mask to increase the reflectivity of the light cavity over the visible color spectrum.
Owner:HONEYWELL INT INC
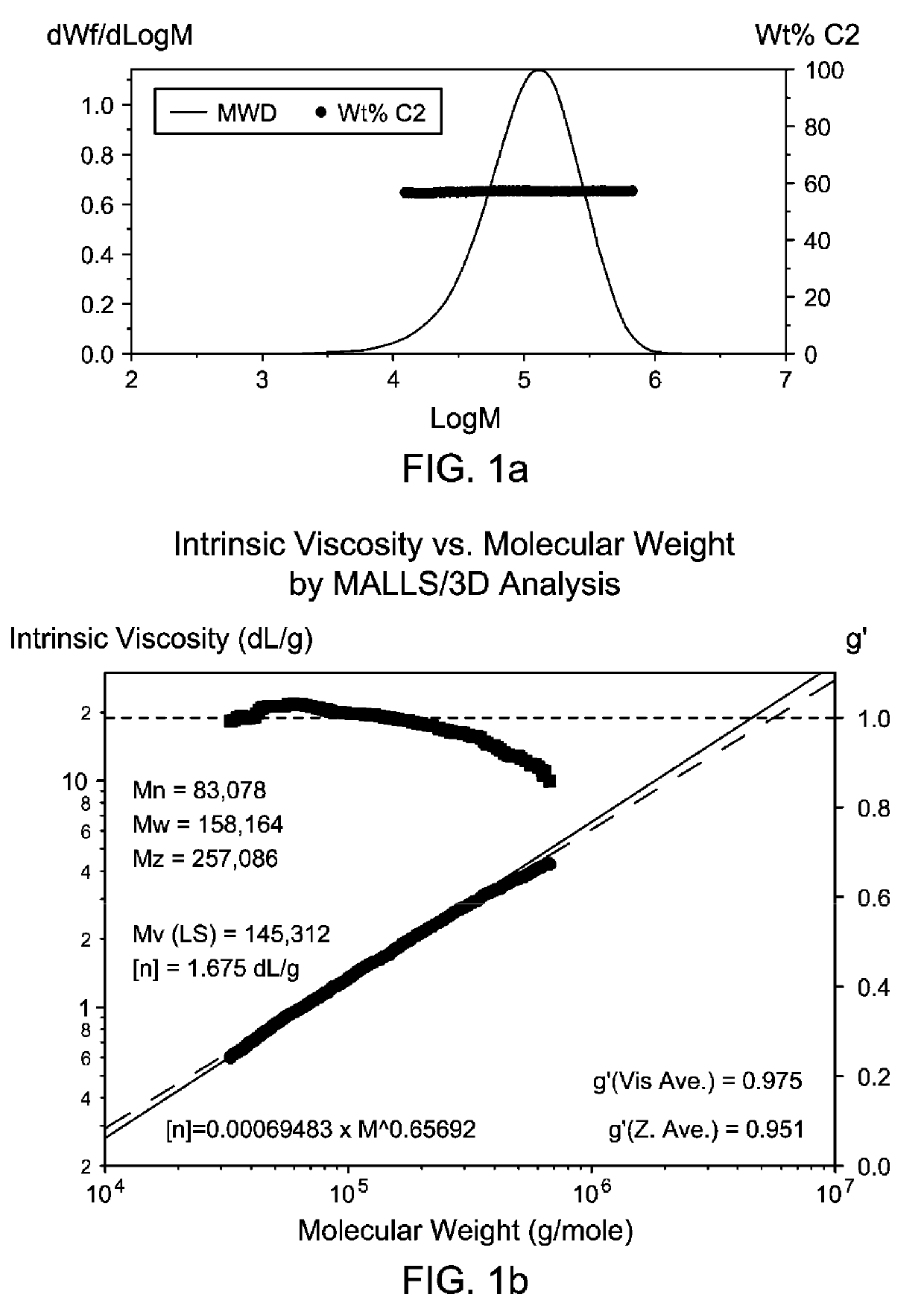
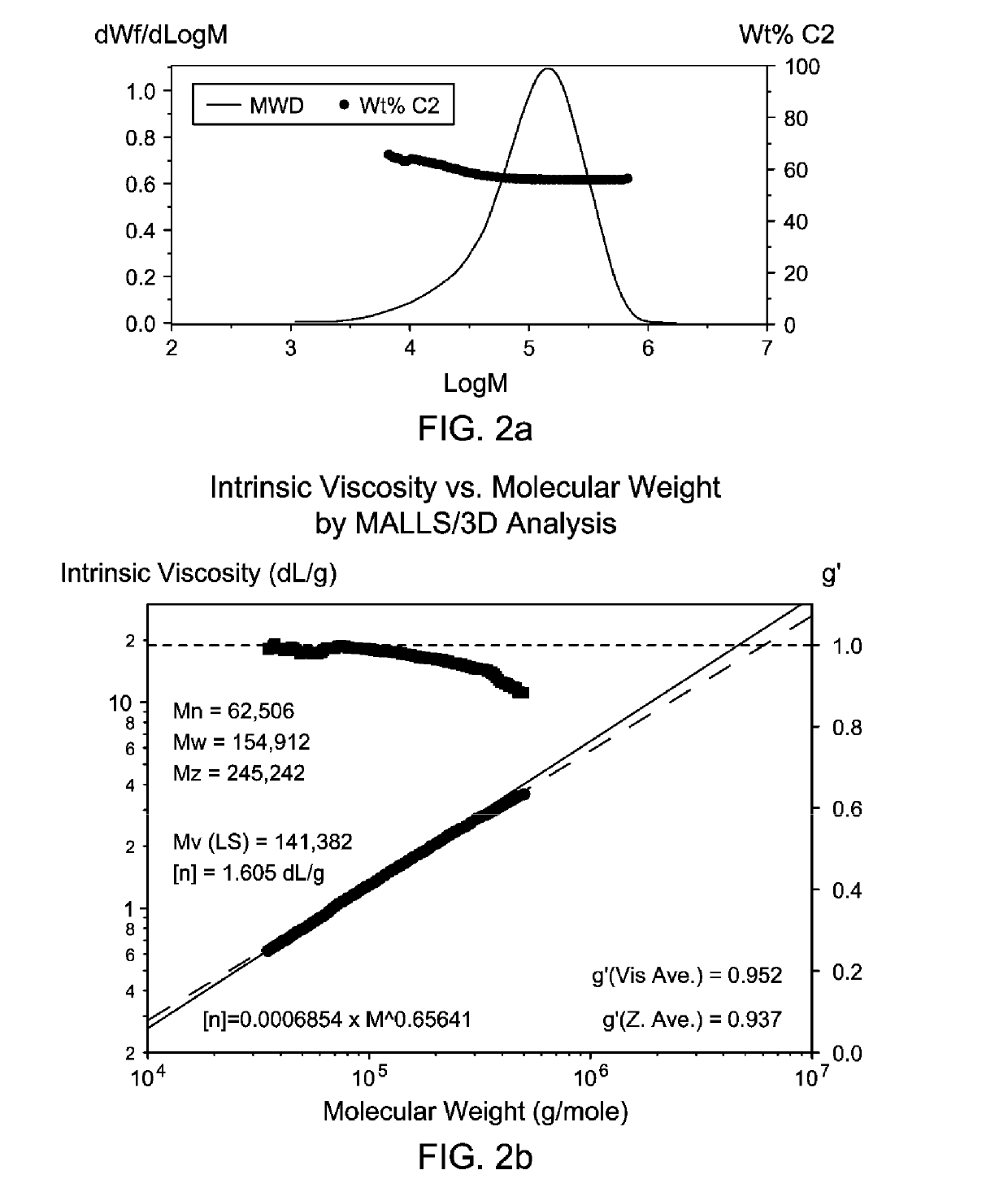
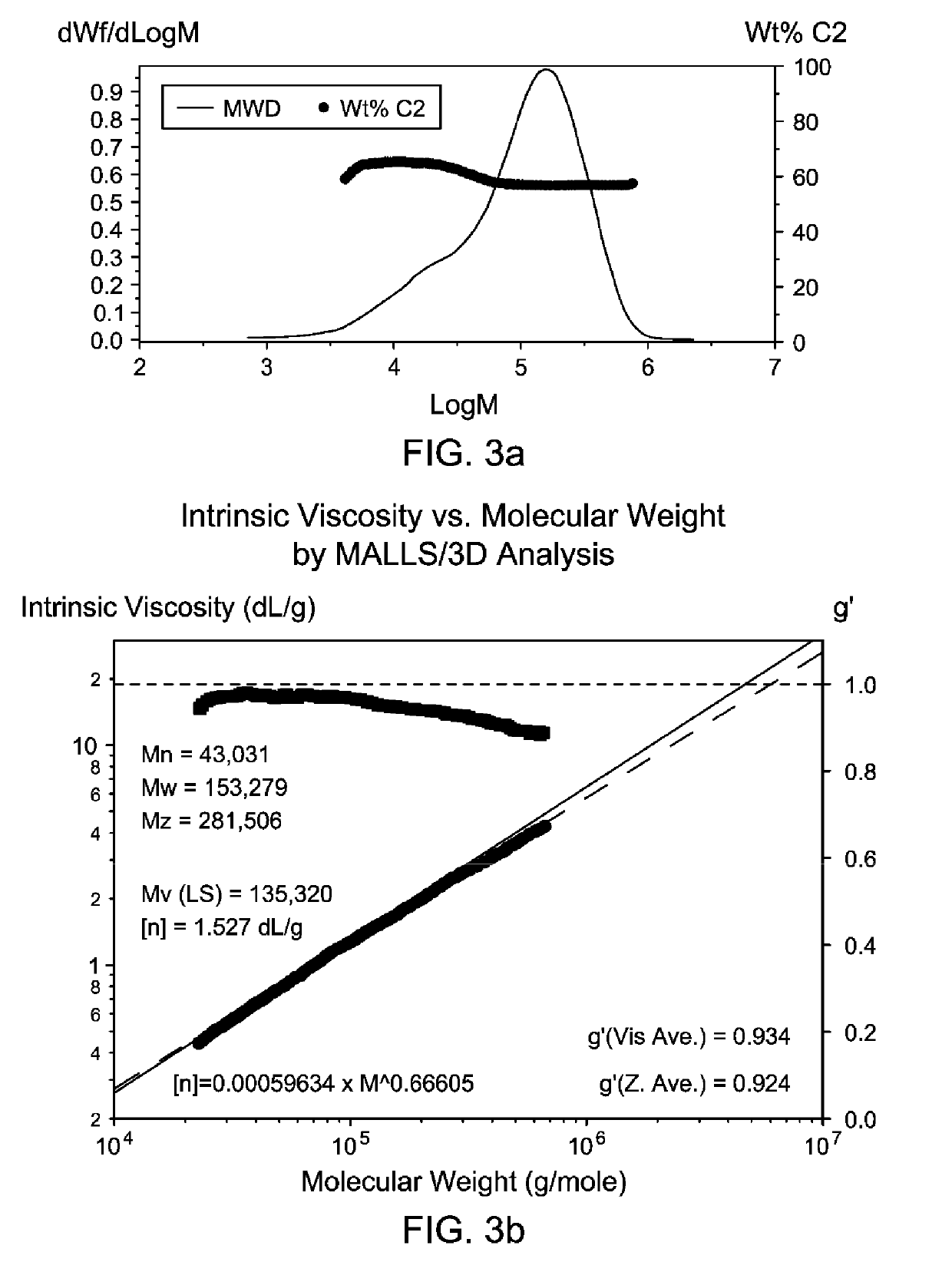
Lubricating Oil Compositions Comprising Dual Metallocene-Catalyzed Bimodal Copolymer Compositions Useful as Viscosity Modifiers
ActiveUS20190309236A1Maintain good propertiesSuitable for deploymentAdditivesPolymer sciencePtru catalyst
This application relates to copolymer compositions and copolymerization processes, as well as to lubricating oil compositions comprising such copolymer compositions as viscosity index improvers, and base oil. The copolymer compositions may be made using two different metallocene catalysts: one capable of producing high molecular weight copolymers; and one suitable for producing lower molecular weight copolymers having at least a portion of vinyl terminations, and the copolymer compositions produced thereby. Copolymer compositions may comprise (1) a first ethylene copolymer fraction having high molecular weight, exhibiting branching topology, and having relatively lower ethylene content (based on the weight of the first ethylene copolymer fraction); and (2) a second ethylene copolymer fraction having low molecular weight, exhibiting linear rheology, and having relatively higher ethylene content (based on the weight of the second ethylene copolymer fraction). Lubricating oil compositions comprising such copolymer compositions may exhibit superior viscosity properties.
Owner:EXXONMOBIL CHEM PAT INC
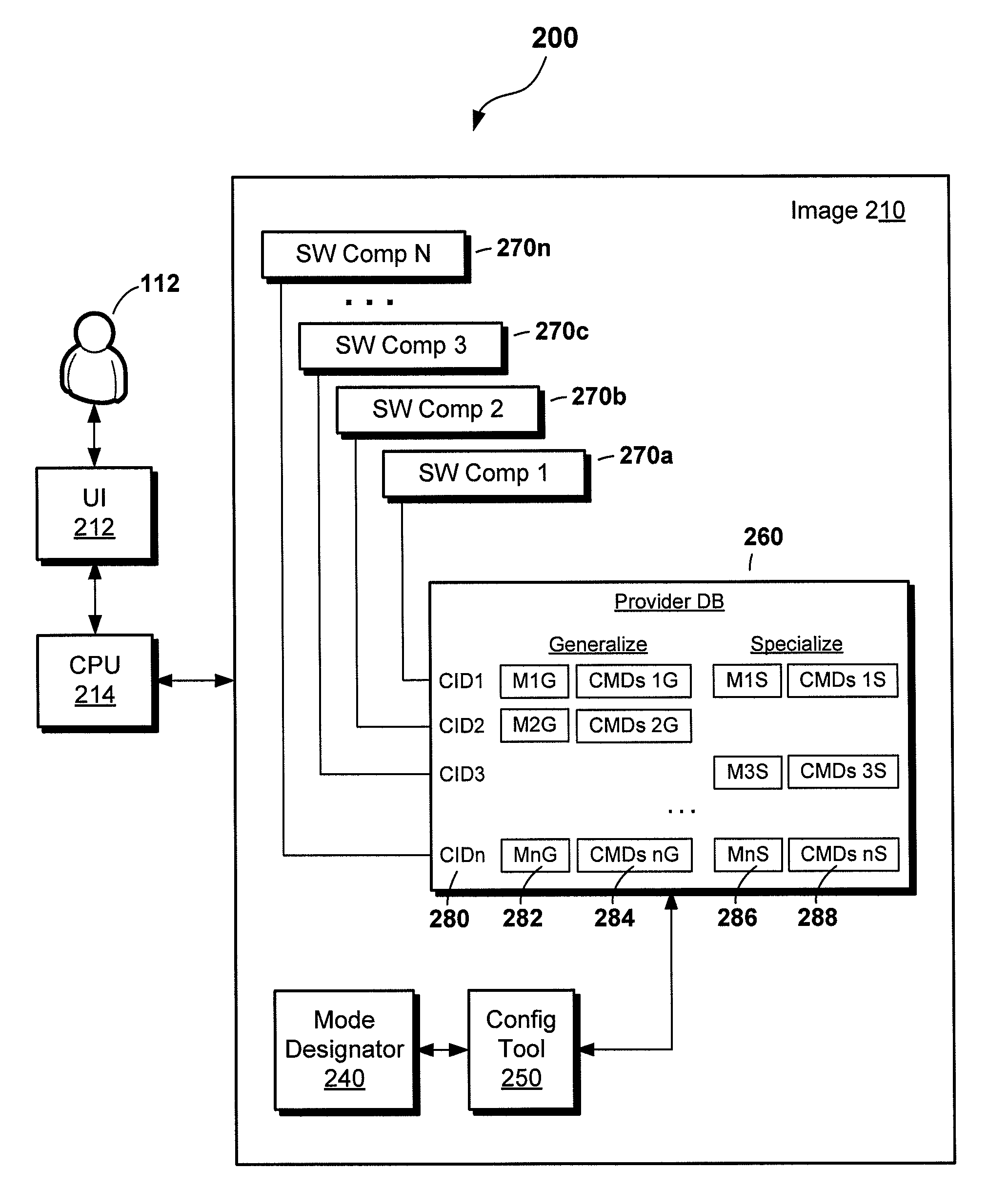
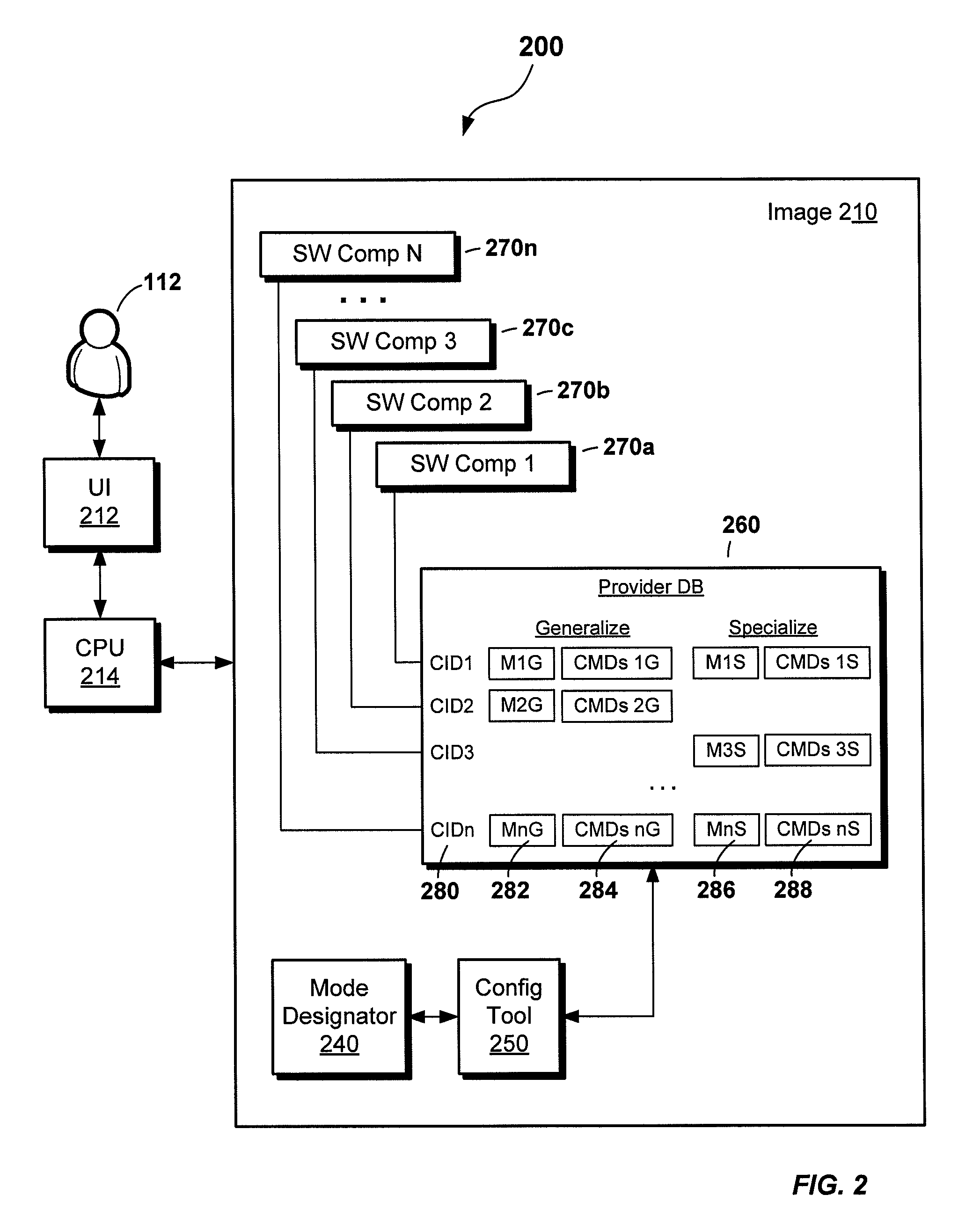
Customized computer image preparation and deployment including virtual machine mode
InactiveUS20120144390A1Shorten the timeSuitable for deploymentSoftware simulation/interpretation/emulationMemory systemsComputer hardwareTime efficient
A computer-implemented technique significantly reduces the time required to configure software images deployed from a golden reference machine to destination machines. Time is saved by applying a priori knowledge of the configuration of the intended destination machines and omitting normally run configuration steps known to be non-essential or irrelevant to the destination machines. This technique is particularly advantageous when the destination machines are virtual machines, as time-consuming commands for configuring hardware on the destination machines can be avoided.
Owner:MICROSOFT TECH LICENSING LLC
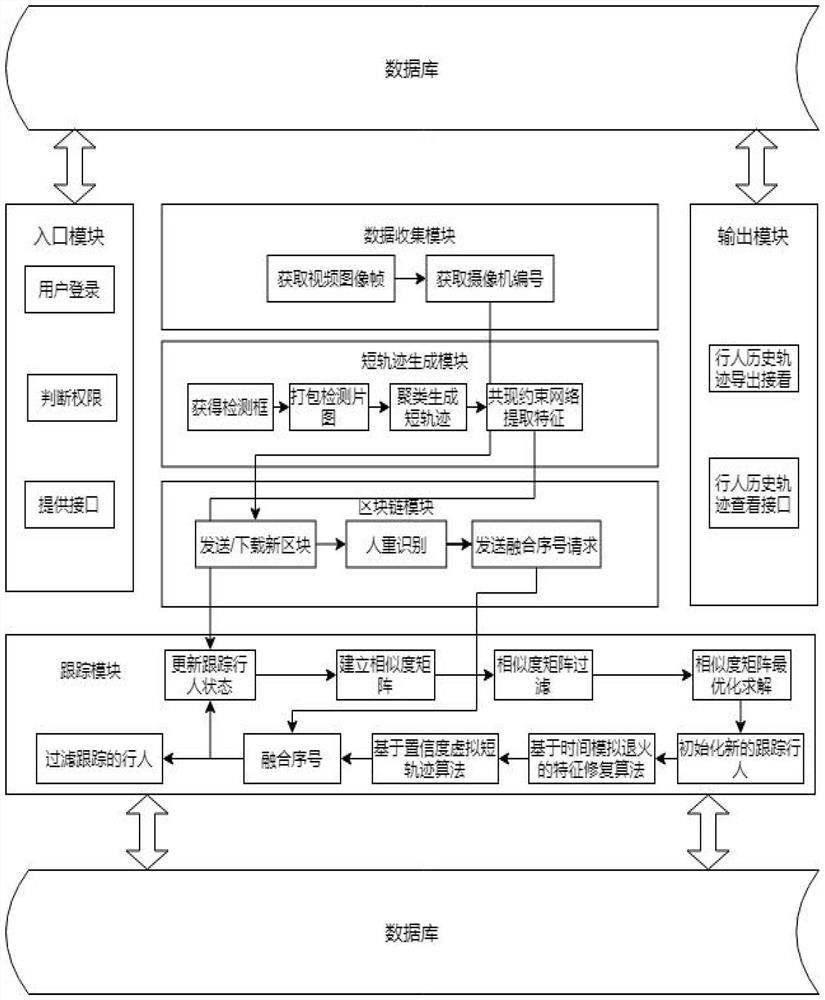
Cross-camera pedestrian tracking system and method based on block chain
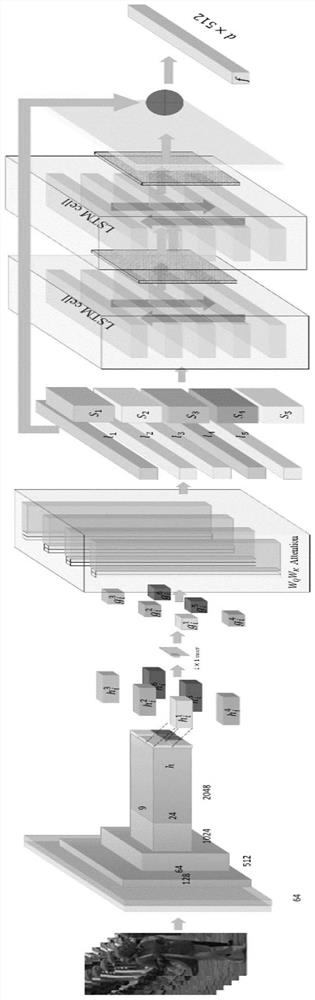
ActiveCN112131929AEasy to deployExact matchCharacter and pattern recognitionClosed circuit television systemsComputer graphics (images)Radiology
The invention relates to a cross-camera pedestrian tracking system and method based on a block chain. The cross-camera pedestrian tracking system comprises the following six modules: an entrance module, a data collection module, a short track generation module, a tracking module, an output module and a block chain sharing module. According to the invention, pedestrian tracking tasks and functionsdeployed at a camera end in a cross-camera scene are mainly completed. A user can utilize the system to complete tracking of pedestrians in a cross-camera monitoring scene, and consistency of pedestrian labels in the cross-camera monitoring scene is kept.
Owner:BEIHANG UNIV
Airbag apparatus
InactiveUS20060066081A1Suitable for deploymentRapid deploymentPedestrian/occupant safety arrangementEngineeringAirbag
A head protecting airbag is folded up to be housed at an upper part of a window of a vehicle so as to be deployed and inflated downward from the upper part of the window so as to cover an interior side of the window. In the airbag, a plurality of parallel cells adapted to be deployed and inflated by an inflating gas introduced thereinto are provided in parallel with each other below 10 a gas supply passage portion in which the inflating gas flows along a longitudinal direction. In a cell of the parallel cells so provided which is required to deploy quickly, of front and rear partitioning portions, a partitioning portion situated at an upstream side of the gas flowing in the gas supply passage portion is provided such that an end thereof which extends upward from a lower edge portion is disposed so as to form an inlet port between a distal end of a horizontal portion of a downstream side partitioning portion and itself.
Owner:TOYODA GOSEI CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com