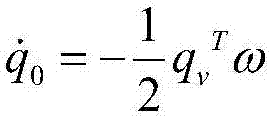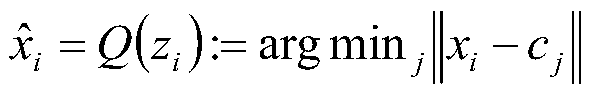Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
70results about How to "Reduced memory footprint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
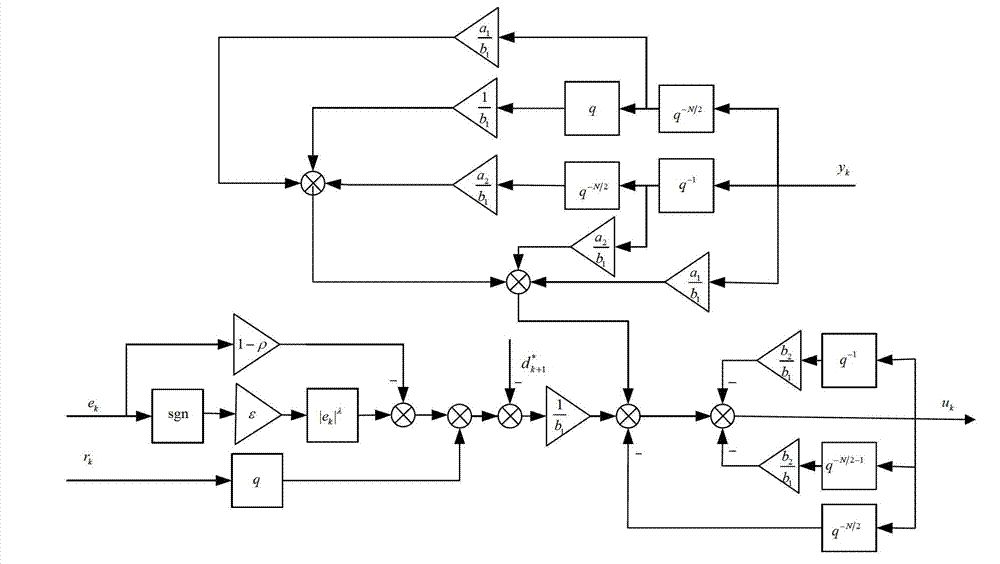
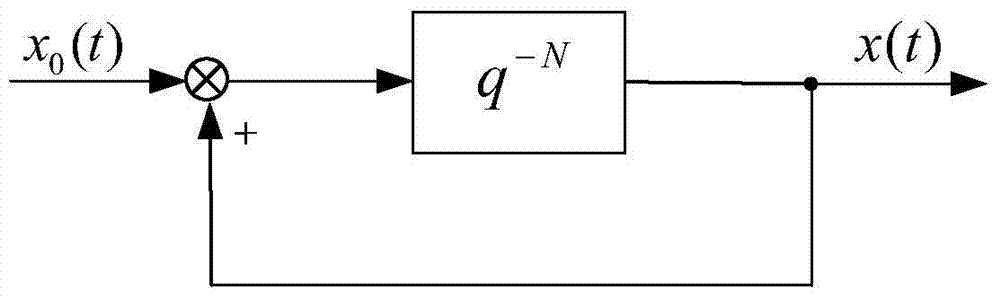
Half-cycle repetitive controller for position servo system
ActiveCN103048921AImplement trackingAchieve inhibitionElectric controllersInternal memoryDynamic equation
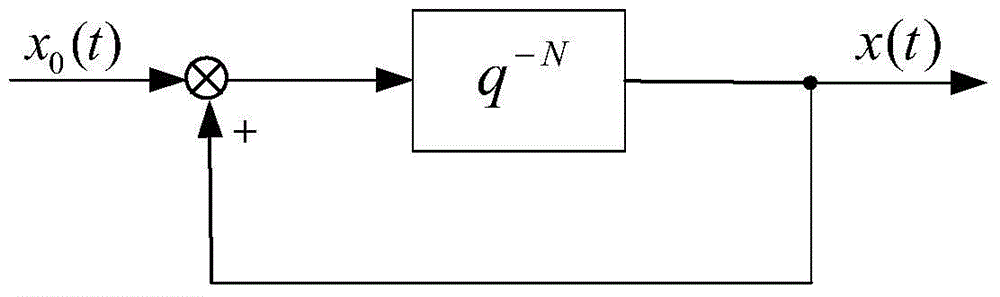
The invention discloses a half-cycle repetitive controller for a position servo system. Reference signals with half-cycle symmetry are set, a half-cycle feedback link is constructed, and an ideal error dynamic is formed according to a power attraction law; and according to an ideal error dynamic equation, an e / v signal conversion module is constructed, a signal obtained by calculating through the controller is used as control input of a controlled servo object, and the position servo system changes together with the reference signals by completely eliminating half-cycle symmetrical interference signals. By the half-cycle repetitive controller, the internal memory of the controller can be obviously reduced and the periodic interference is quickly and completely suppressed under the half-cycle symmetrical reference signals, and the half-cycle repetitive controller has high cost performance.
Owner:辽宁吉尔电子有限责任公司 +1
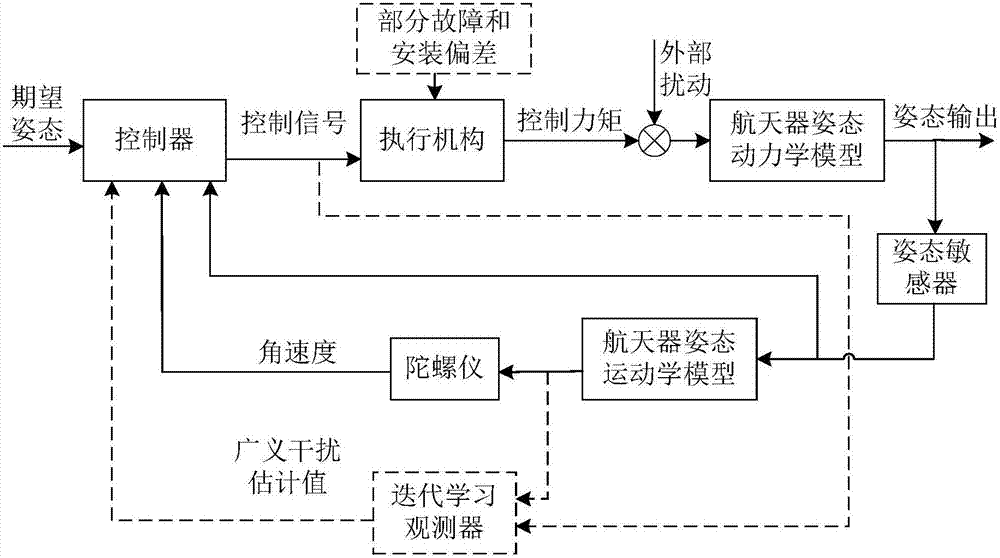
Spacecraft attitude fault-tolerant control method based on iterative-learning disturbance observer
ActiveCN107121961AImprove fault toleranceImprove robustnessProgramme controlCosmonautic vehiclesActive faultSpacecraft attitude control
The present invention relates to a spacecraft attitude fault-tolerant control method based on an iterative-learning disturbance observer. In order to solve the problem that actuator faults and external disturbances might occur during the attitude control process of the on-orbit operation of a spacecraft in the prior art, the invention provides an active fault-tolerant control method based on the iterative-learning observer. The method comprises the steps of firstly, establishing a dynamic model for the attitude control system of a spacecraft in considering the fault of an actuator in the attitude control system of the spacecraft and the external disturbance in the space of the spacecraft; secondly, estimating and designing a generalized disturbance torque of the iterative-learning disturbance observer composed of the actuator fault information and the external disturbance; finally, based on the estimated generalized interference, designing an active fault-tolerant controller. Based on the method, the stability of the attitude control system of the spacecraft, when the actuator of the spacecraft has a fault and the external disturbance exists in the space of the spacecraft, can be ensured. Meanwhile, the precision requirement of an actual control system is met. The method is strong in fault-tolerant ability and good in robustness for the external disturbance.
Owner:BEIHANG UNIV
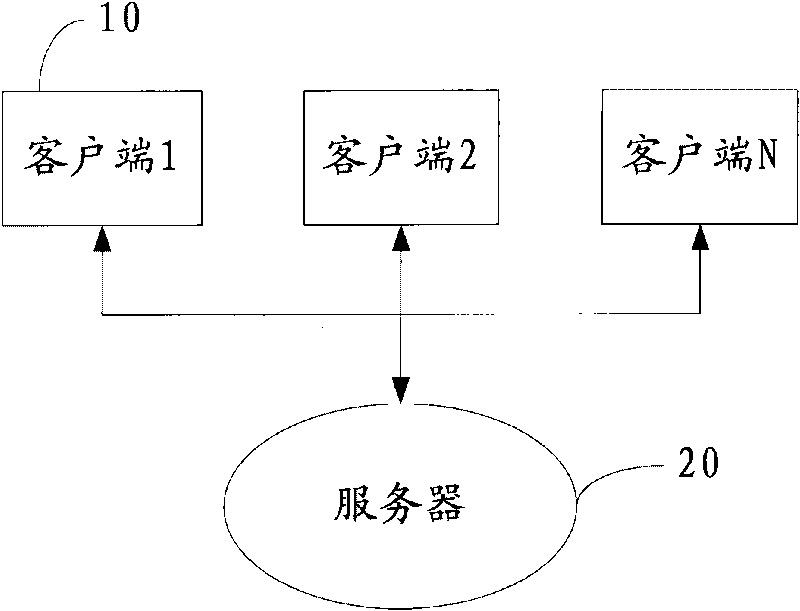
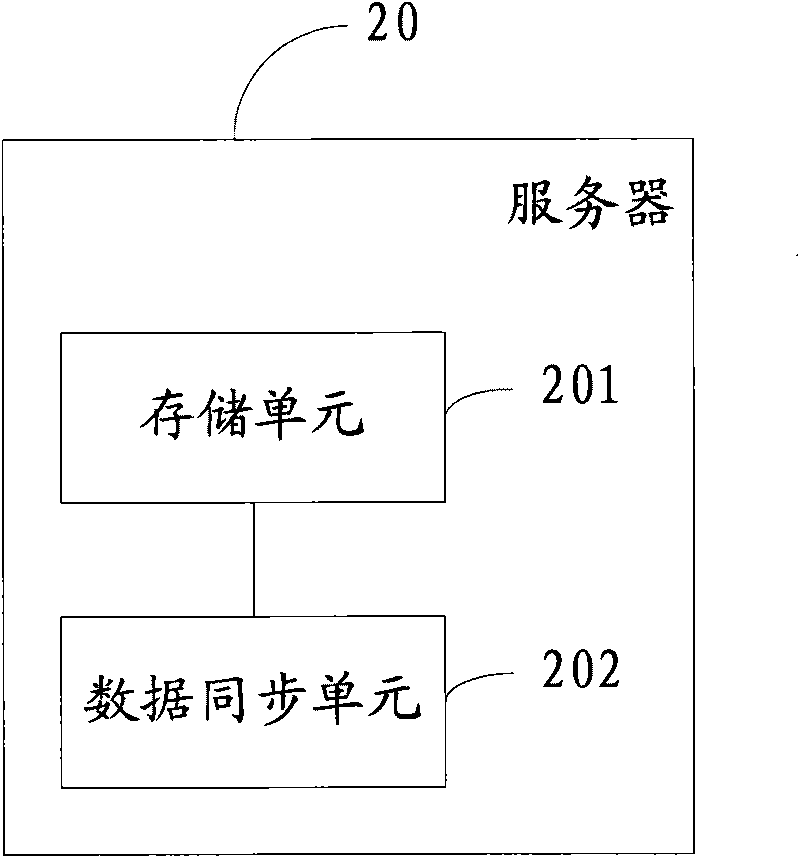
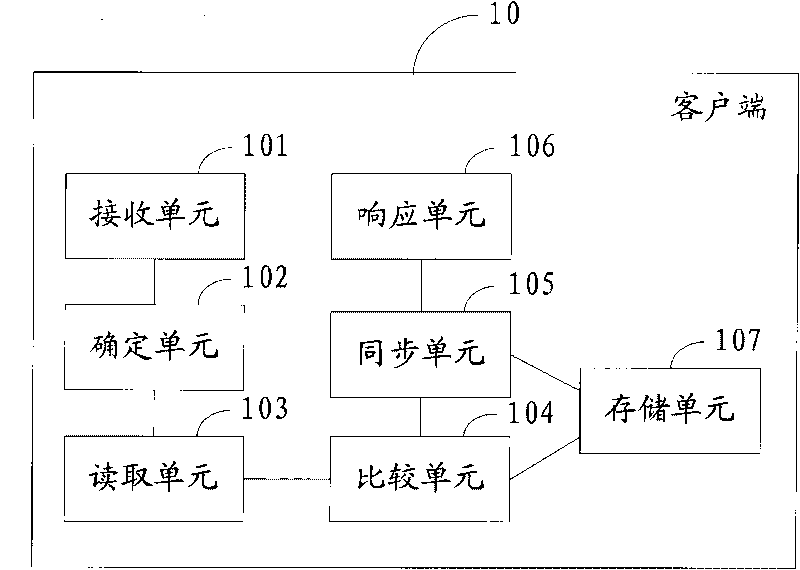
Method, system, client and server for realizing multi-client data synchronization
InactiveCN101741830AShorten the timeReduced memory footprintSynchronising arrangementData synchronizationMemory footprint
The invention discloses a method for realizing multi-client data synchronization. The method comprises the following steps that: a client receives an application request of a user, and determines the type of application data requested by the application request; according to the type of the application data, the client reads a last updating time T1 when the application data of the type is updated from a server; and the client compares the T1 with a last updating time T2 of the application data, of the type, stored by the client, synchronizes the application data of the type according to a comparison result, and responds to the application request according to the synchronized application data of the type. Correspondingly, the invention also discloses a client, a server and a system for realizing the multi-client data synchronization. The method, the system, the client and the server can ensure the data synchronization among a plurality of clients, and simultaneously, save time, reduce the occupation space of a memory of the system, and improve the performance of the system.
Owner:SHENZHEN LONG VISION
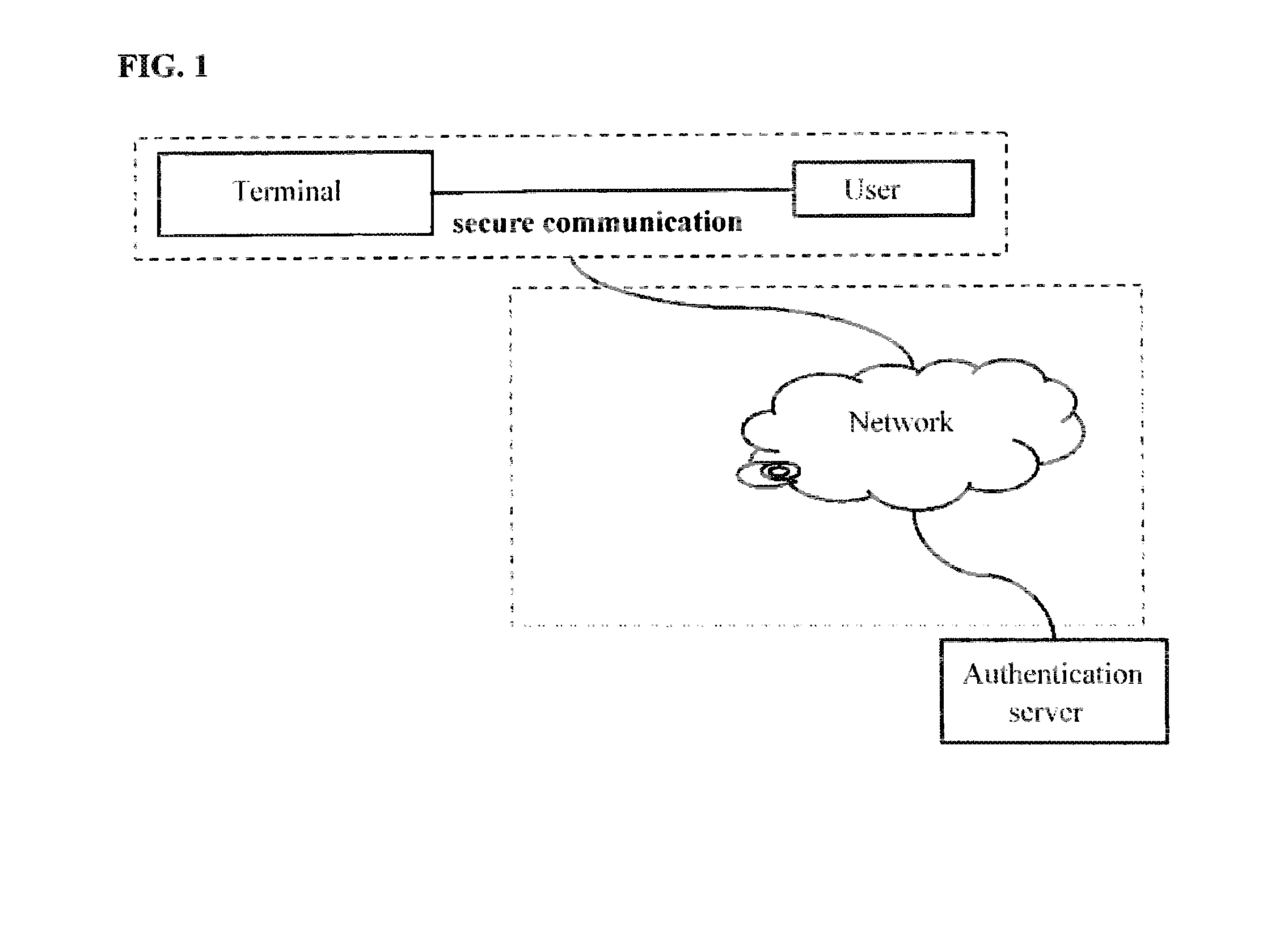
Authentication method and device using a single-use password including biometric image information
ActiveUS20140250517A1Improve reliabilityImprove stabilityImage analysisDigital data processing detailsComputer terminalIris image
The present invention relates to an authentication method and device using a single-use password generated from iris image information. The device comprises: a terminal and a server storing, in respective memories thereof, the iris image information for authentication; a camera attached to and installed on the device to capture the iris image information for authentication; the terminal, which generates the single-use password from the iris image information acquired through the camera, and transmits the single-use password to the server; and the server, which has a built-in algorithm for comparing and determining whether or not the single-use password transmitted from the terminal matches single-use password stored in the server.
Owner:IRITECH
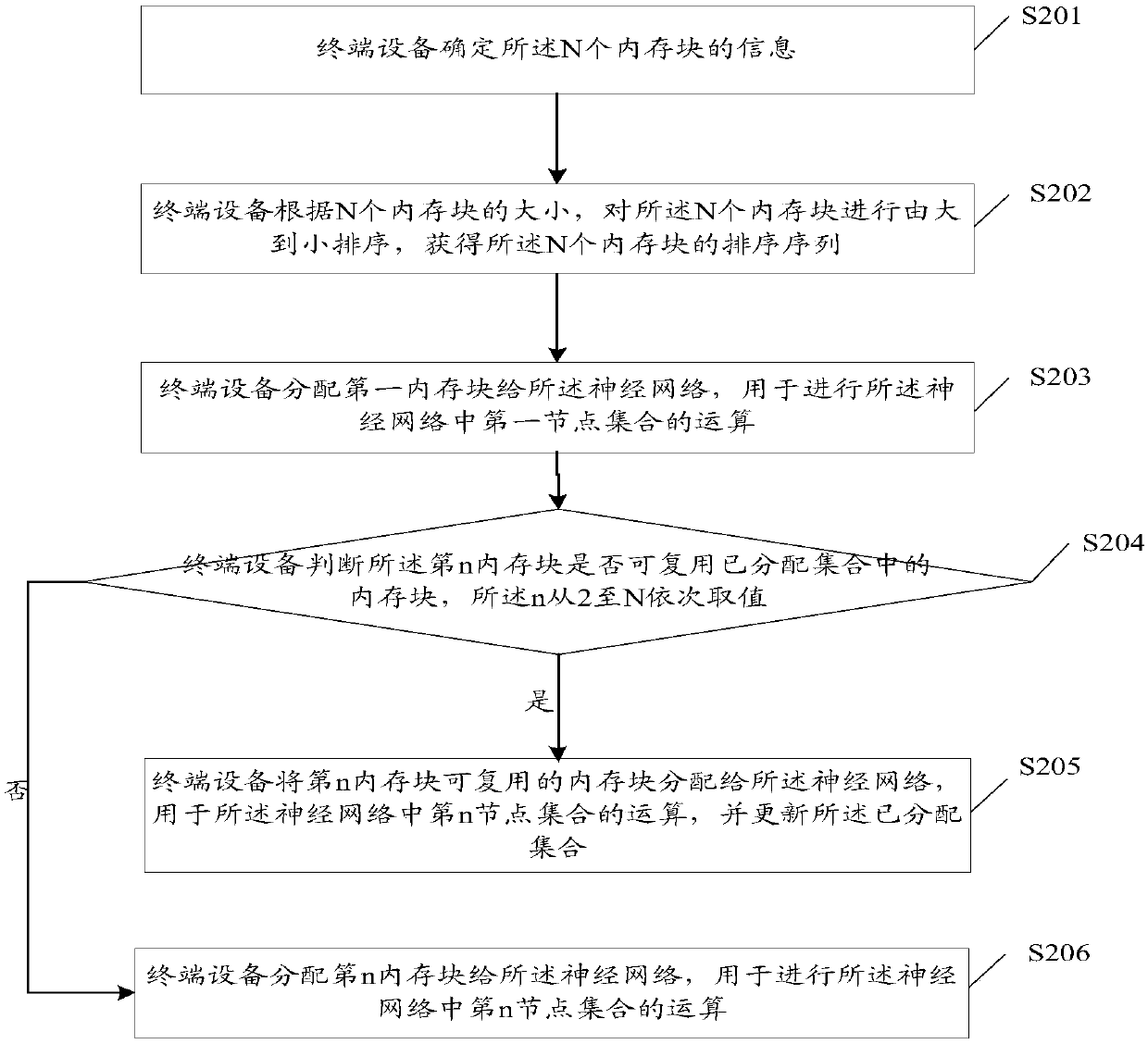
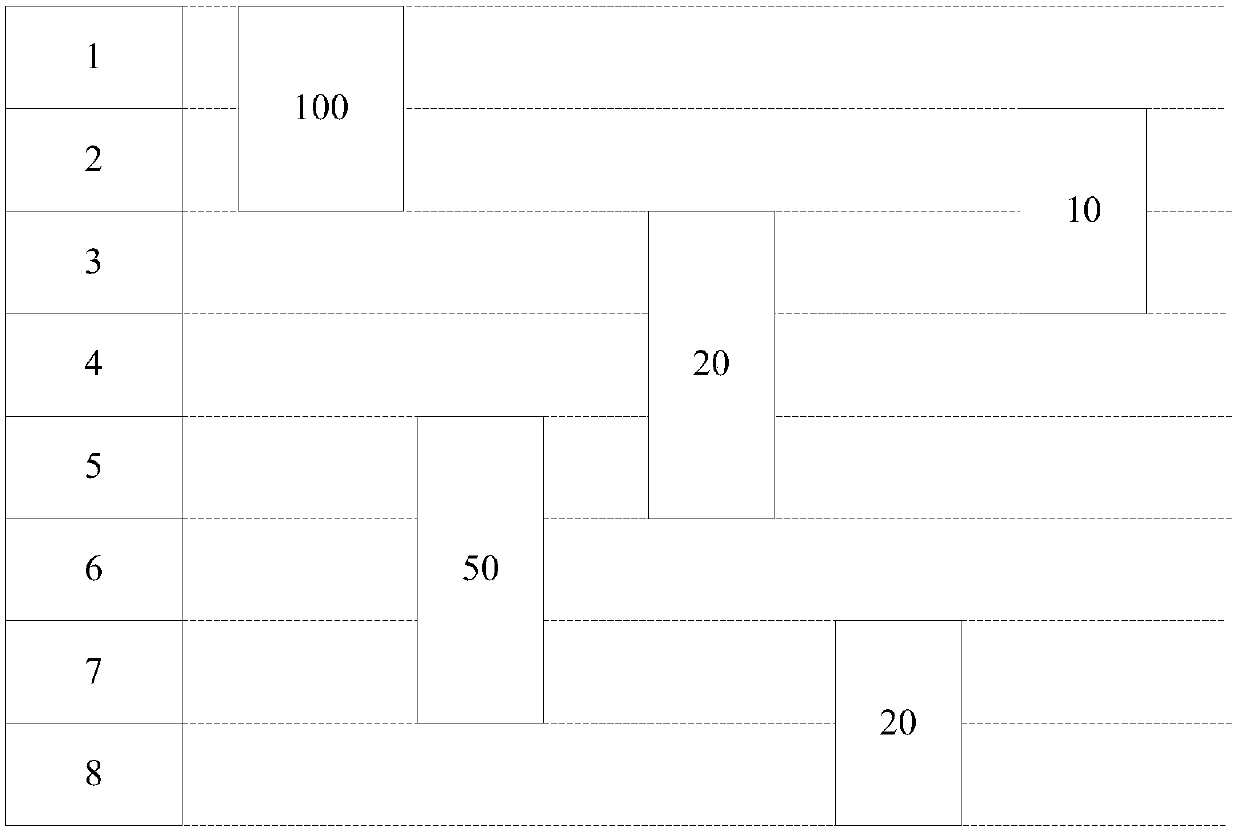
Memory allocation method and device of neural network
ActiveCN110597616AOptimize memory allocationReduced memory footprintMemory architecture accessing/allocationResource allocationParallel computingMemory block
The invention provides a memory allocation method and device for a neural network, and the neural network needs to occupy N memory blocks during operation, and the method comprises the following steps: determining the information of the N memory blocks; sorting the N memory blocks from large to small according to the sizes of the N memory blocks to obtain a sorting sequence of the N memory blocks;allocating a first memory block to the neural network for operation of a first node set in the neural network; judging whether the nth memory block can reuse the memory blocks in the allocated set ornot, wherein the allocated set comprises a memory block allocated to the neural network; and if the nth memory block can reuse the memory block in the allocated set, allocating the reusable memory block to the neural network for operation of an nth node set in the neural network, and updating the allocated set; and sequentially executing the judgment from n = 2 to n = N according to the sorting sequence. By adopting the method and the device provided by the invention, the memory allocation of the neural network can be optimized.
Owner:HUAWEI TECH CO LTD
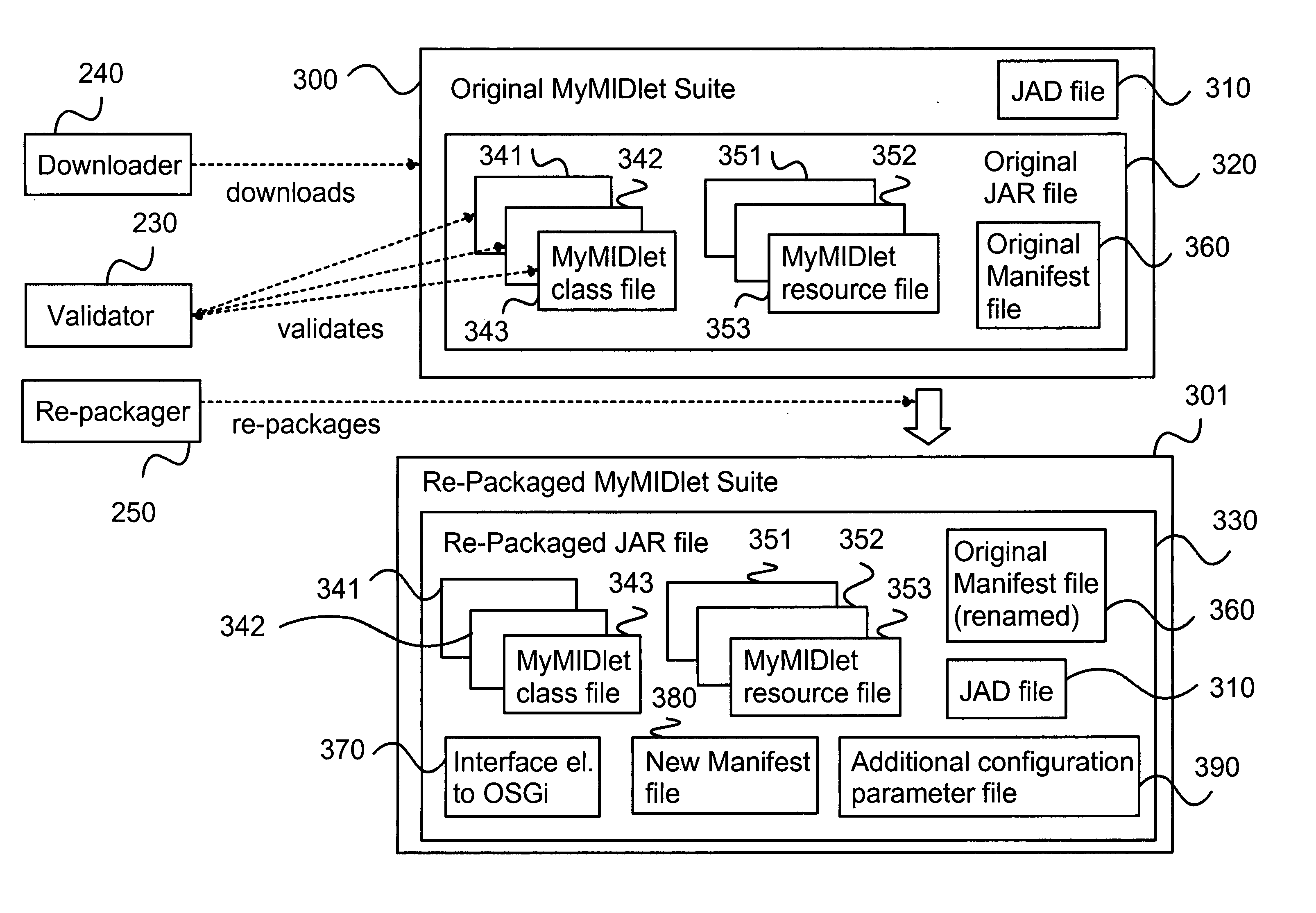
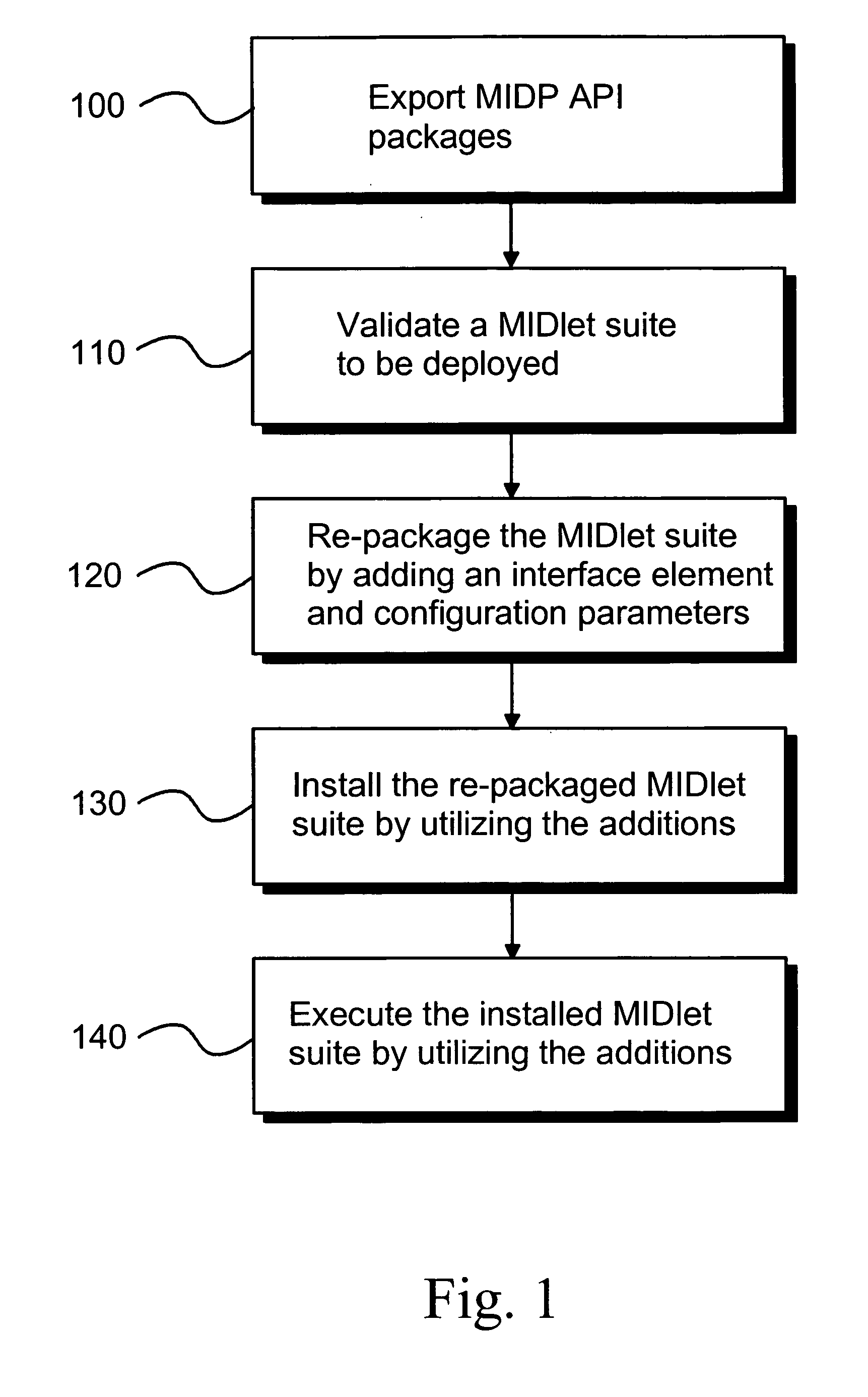
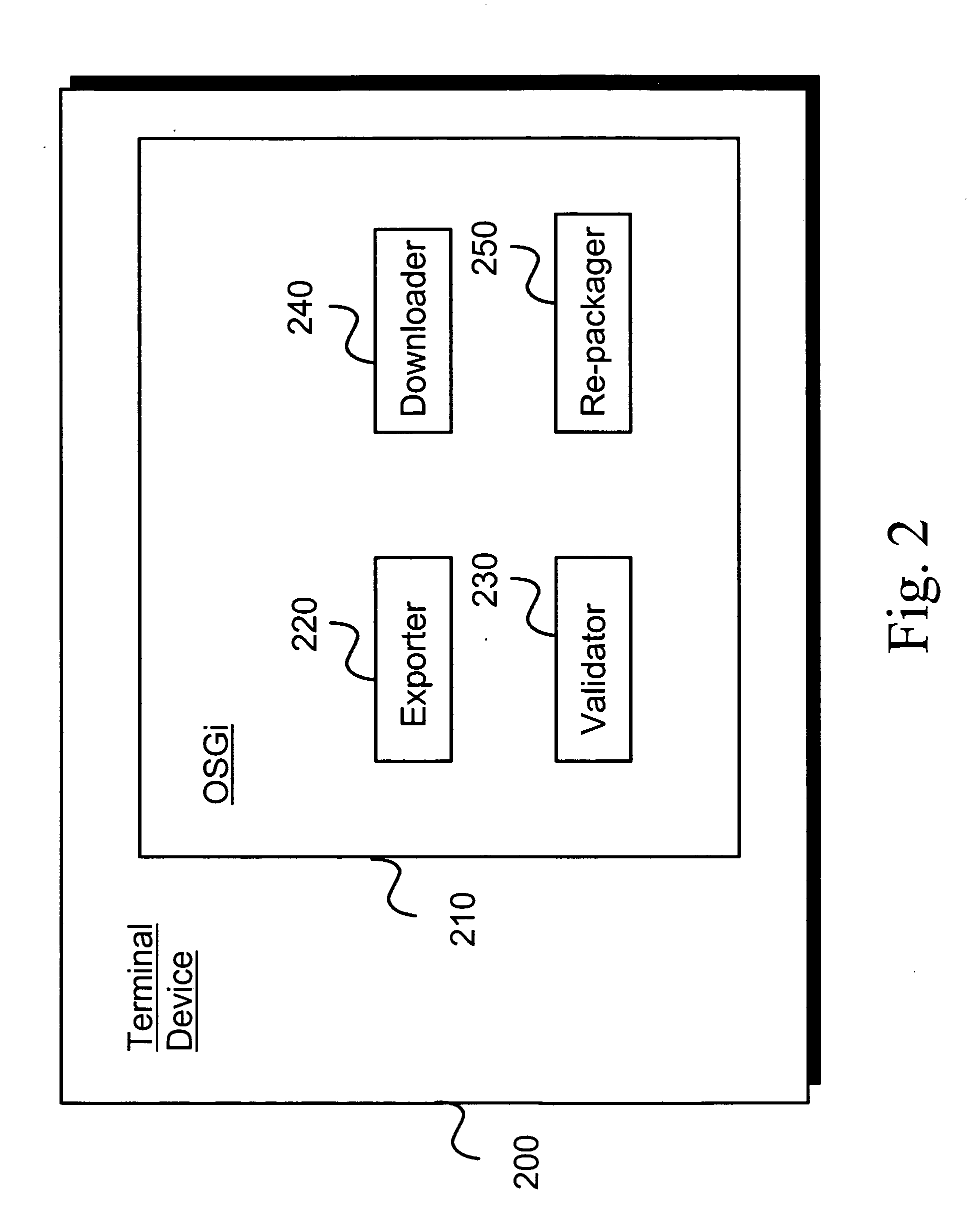
Managing midlet suites in OSGI environment
InactiveUS20060233126A1Reduced memory footprintLess user interactionRadio/inductive link selection arrangementsProgram loading/initiatingService gatewayComputer network
Owner:NOKIA CORP
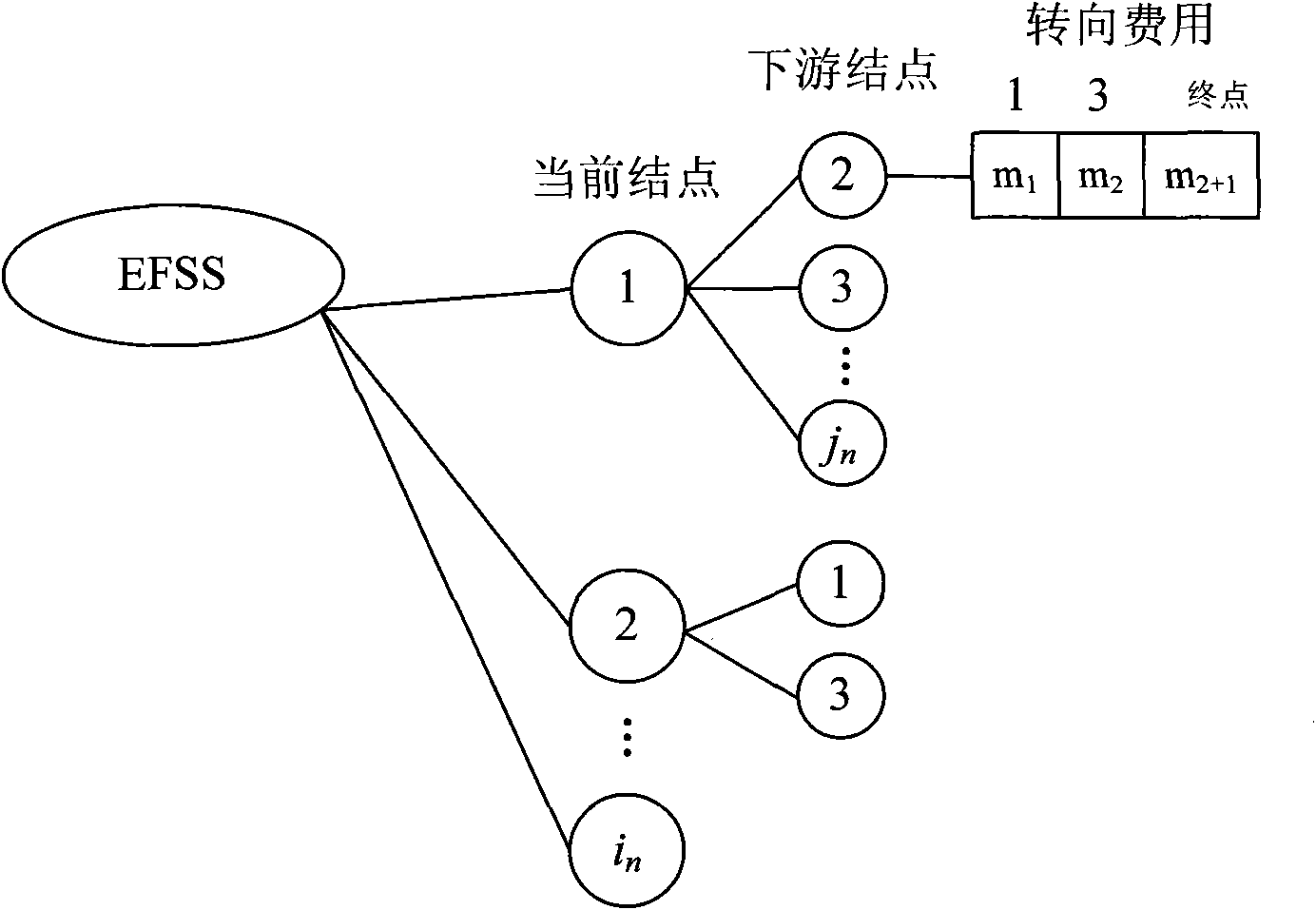
Shortest path labeling algorithm considering intersection turning
InactiveCN101571995AExcellent data storage spaceEasy to updateRoad vehicles traffic controlShortest-path treeShort path tree
The invention discloses a shortest path labeling algorithm considering intersection turning, which relates to improvement of a network representation method of the shortest path of a road. The algorithm comprises the following steps: generating a star-type data structure according to information on road section cost and intersection turning cost first; and establishing corresponding connections among a node, a road section and a turning according to the hierarchy of the data structure for the convenience of retrieving road network information by the shortest path algorithm. The steps of the shortest path labeling algorithm are basically same as that of the prior labeling algorithm, but during labeling in each step, the summation of a current node label, the downstream road section cost and the downstream node turning cost are calculated aiming to each turning behavior of a downstream node of the current node respectively, and the summation is compared with a shortest path label of a corresponding downstream node so as to update the label and finally generate a shortest path tree, thus the shortest path between a known starting point and a destination point is solved on the basis. The shortest path labeling algorithm occupies a small memory space, is convenient to update network information and makes clear about the difference among different turning movements.
Owner:SOUTHEAST UNIV
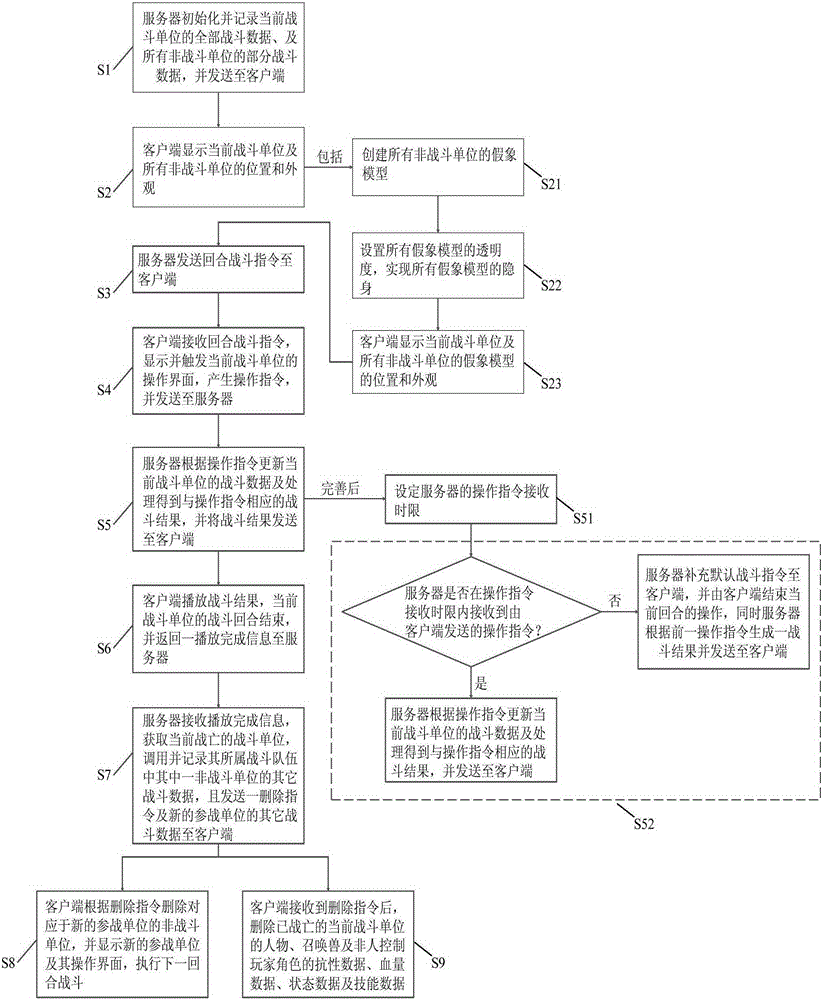
Data processing method and system of turn-based games, client end and server end
ActiveCN105338081AReduce data processing burdenIncrease processing rateSoftware designVideo gamesGame playerSkill sets
The invention relates to a data processing method and system of turn-based games, a client end and a server end. The method includes the following steps that: all combat data of current combat units and the position data and account data of non-combat units are only recorded through the server; the calculation of an operation sequence can be completed automatically according to operation instructions of the current combat units which are transmitted by a client end, combat results are obtained; and whether the other combat data such as blood, skills and states of the non-combat units are increased is decided according to the combat results. With the data processing method and system adopted, the quantity of data exchanged between the server and the client end can be decreased with normal proceeding of multi-turn combats ensured, and the data processing burden of the server can be reduced, and memory space in the server, which is occupied by the combat data of the non-combat units can be decreased, and therefore, the processing and response rate of the server can be increased, and experience of game players can be enhanced.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
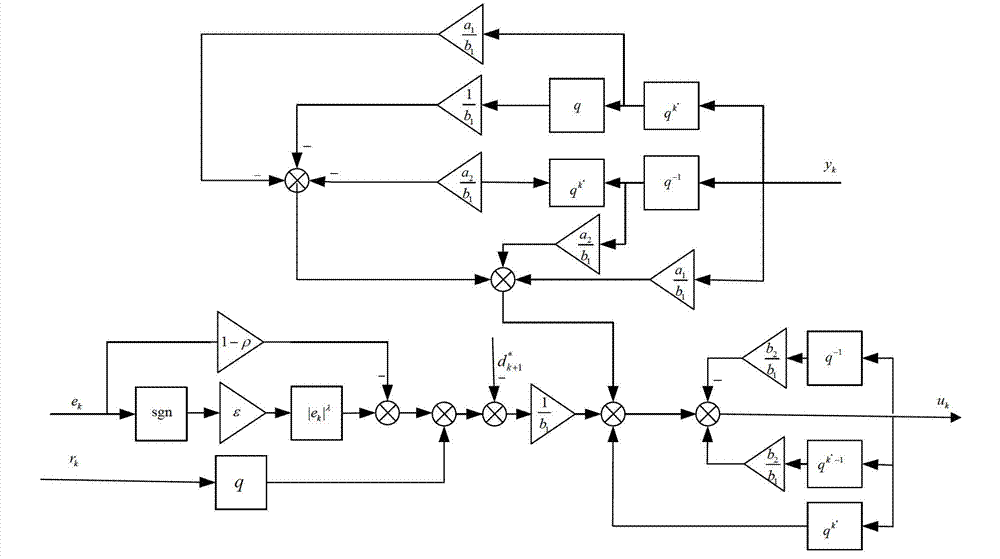
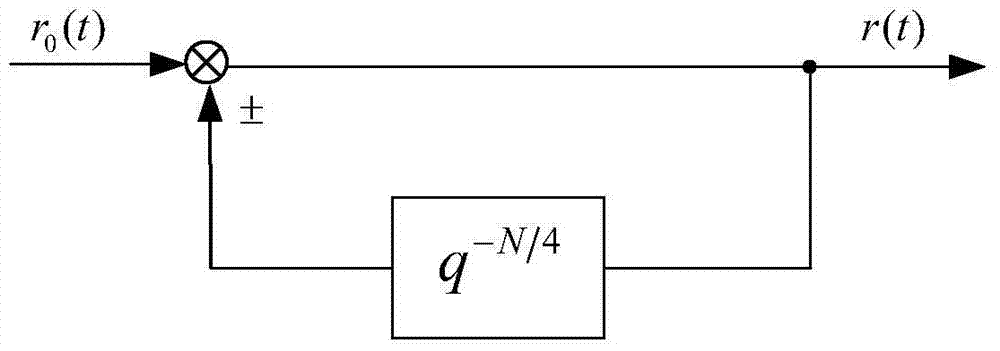
One-fourth period repetitive controller based on attractive rule
ActiveCN103605288ASmall footprintAchieve inhibitionAdaptive controlRepetitive controlSignal transition
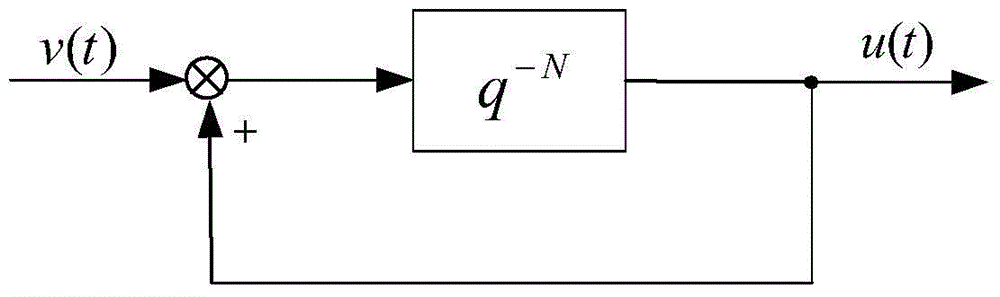
The invention discloses a one-fourth period repetitive controller based on the attractive rule. The one-fourth period repetitive controller comprises a giving link, a one-fourth period feedback link, an e / v signal transformation module and a subtraction / addition ring. The giving link generates a reference signal provided with one-fourth period symmetry; the one-fourth period feedback link is constructed; the e / v signal transformation module is constructed in dependence on the attractive rule, an output signal of the e / v signal transformation module is applied to the correction of the repetitive controller; then an output signal of the repetitive controller is worked out and taken as an input of a controlled object. A specific controller parameter setting operation can be carried out according to indexes of convergence performance of a representation system, and a monotone decreasing area, an absolute attraction layer and a steady-state error band boundary of a representation trace error convergence process are provided. A closed-loop system can completely eliminate one-fourth period symmetric interference signals, and the accurate control of the closed-loop system is achieved. By means of the time domain design of the one-fourth period repetitive controller, symmetric signal interference is effectively restrained, the control precision is improved, and the occupied space of a memory is remarkably reduced.
Owner:南京万枫电子科技有限公司
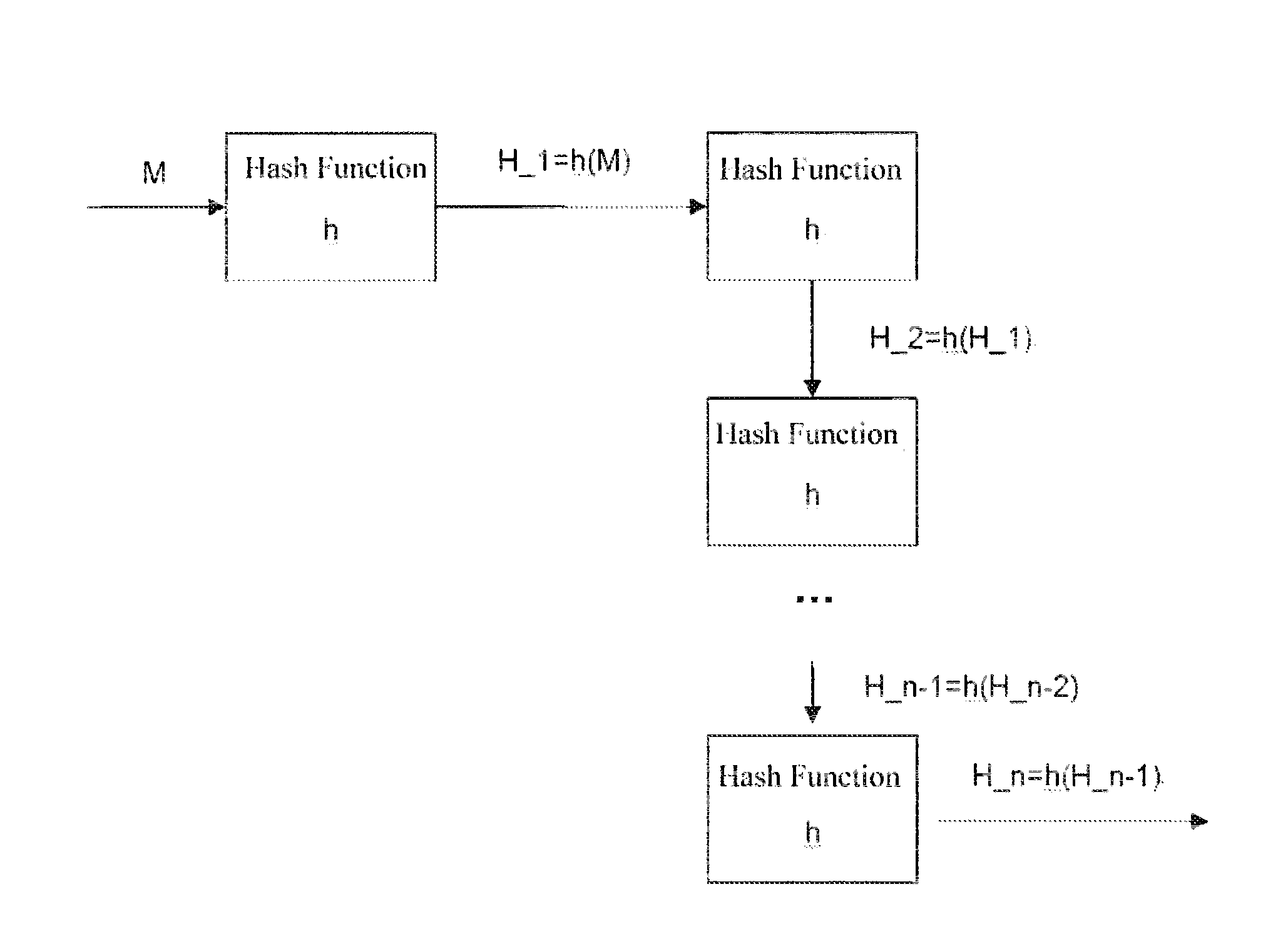
Variable length coding and decoding method and its coding and decoding device
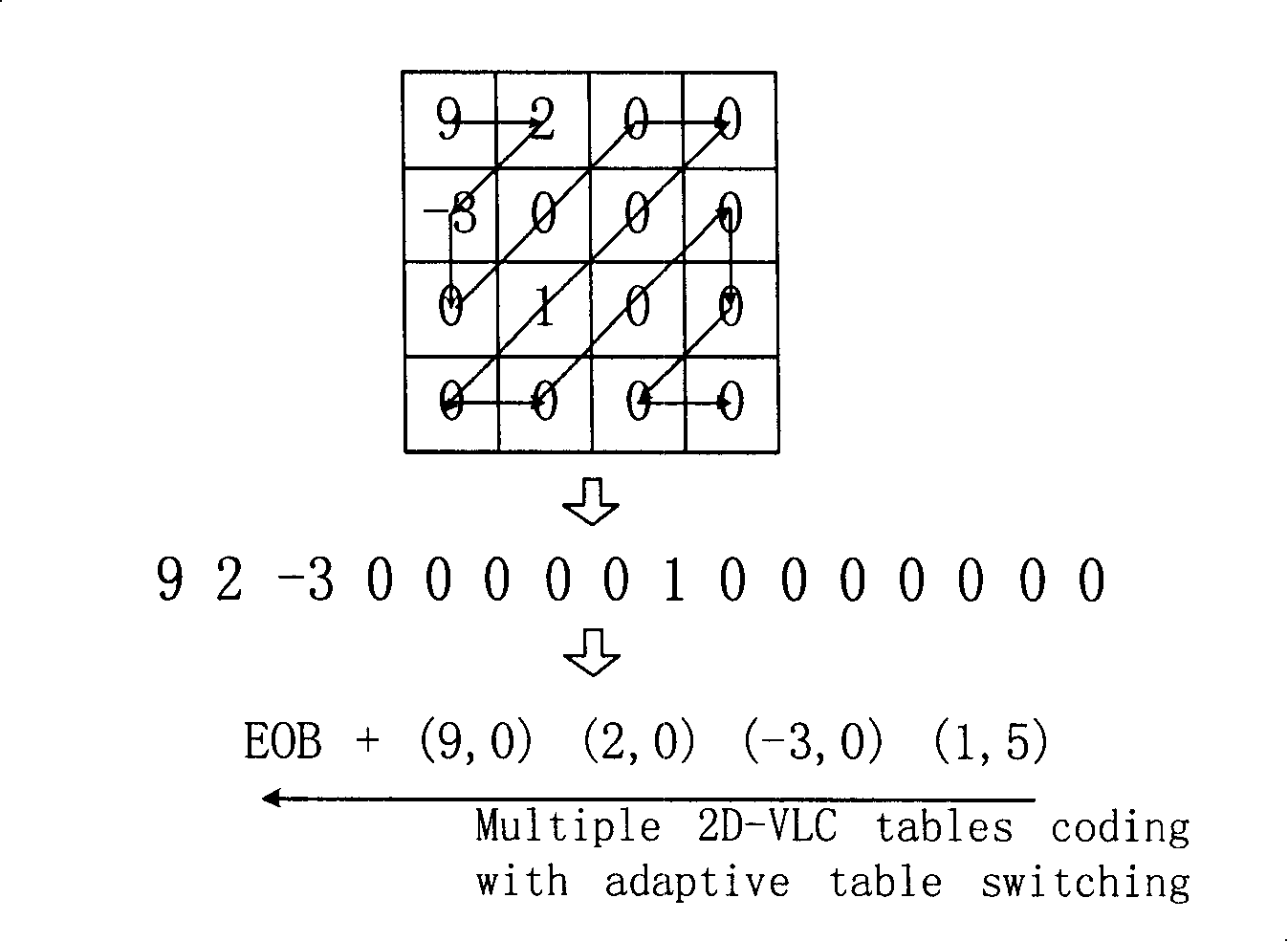
ActiveCN101198054AReduce code rateSave code streamCode conversionTelevision systemsRound complexityNonzero coefficients
The invention discloses a variable length coding method which comprises the following steps: nonzero coefficient number and number of coefficients the amplitude of which is larger than one in the prior block are computed; entry bit streams of the statistic nonzero coefficient number are coded; entry bit streams of various nonzero coefficient symbols in the prior block and corresponding zero coefficients before nonzero coefficients are coded; moreover, entry bit streams of the statistic number of coefficients the amplitude of which is larger than 1 are coded; entry bit streams of amplitudes of the corresponding nonzero coefficients in the prior block are coded. Correspondingly, the invention also discloses a corresponding variable length decoding method and a variable length codec. The invention can further improve coding efficiency of entropy coding and at the same time the coding process is based on a simpler code list structure, thereby complexity of switching computation is lowered and occupancy of memory space is reduced.
Owner:HONOR DEVICE CO LTD
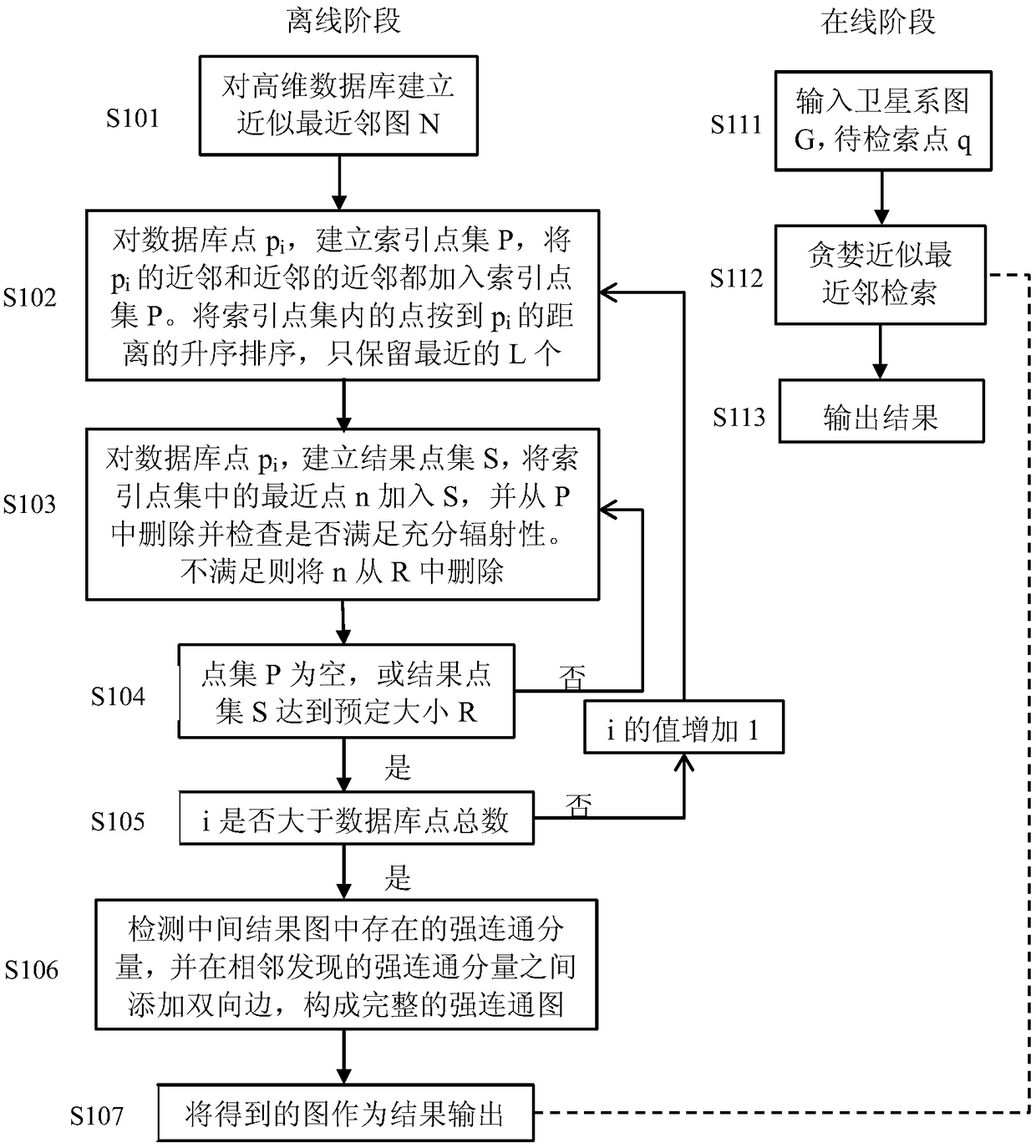
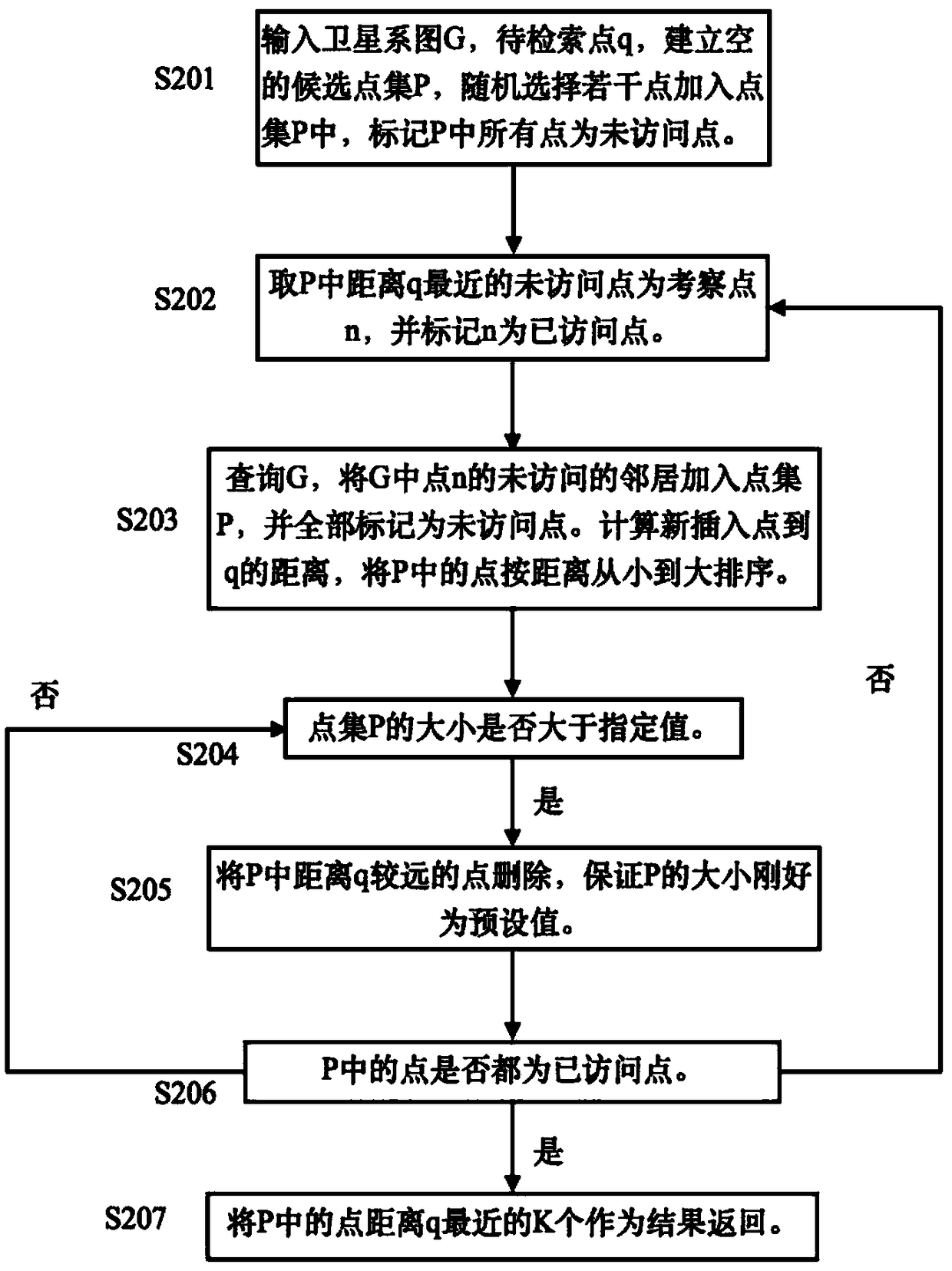
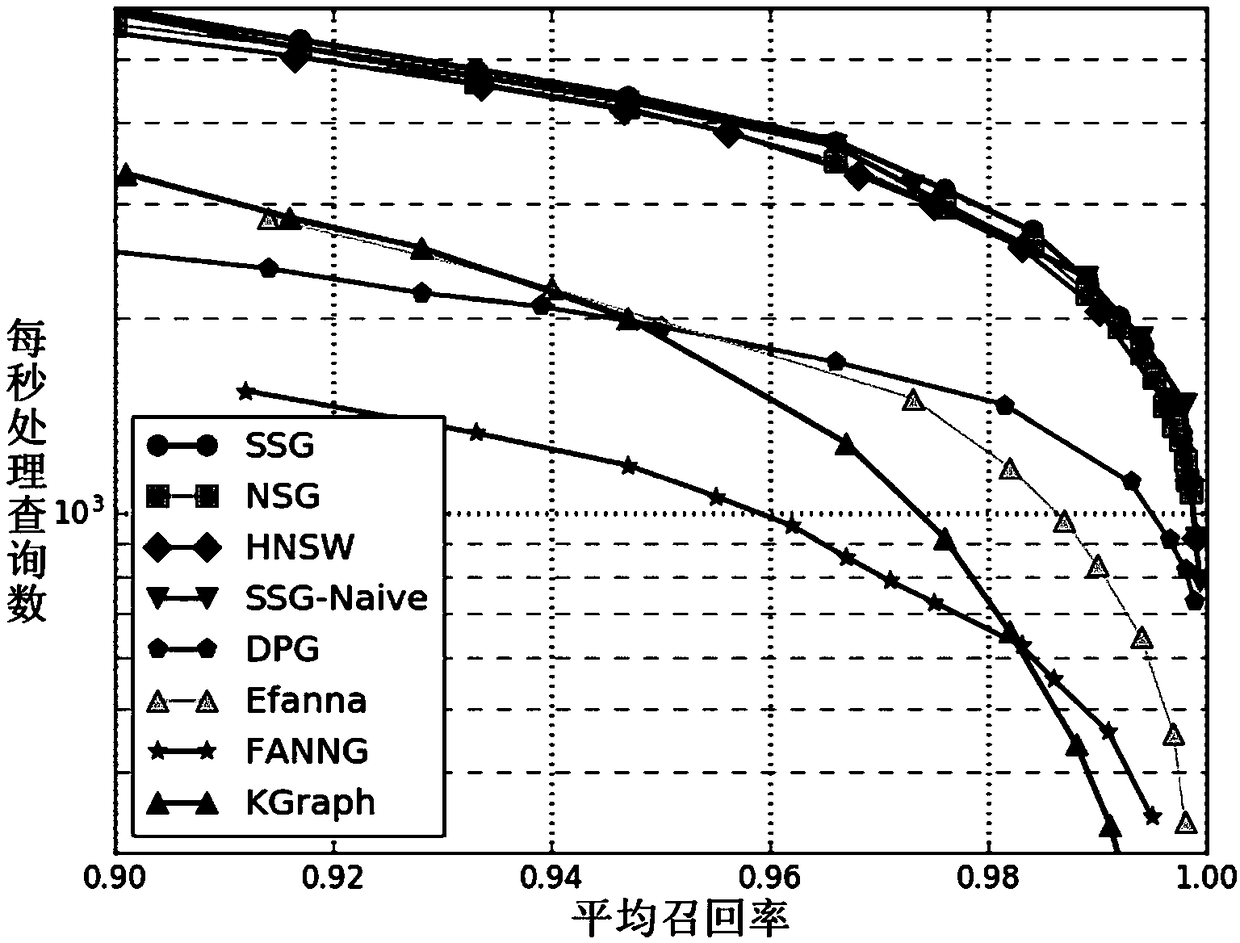
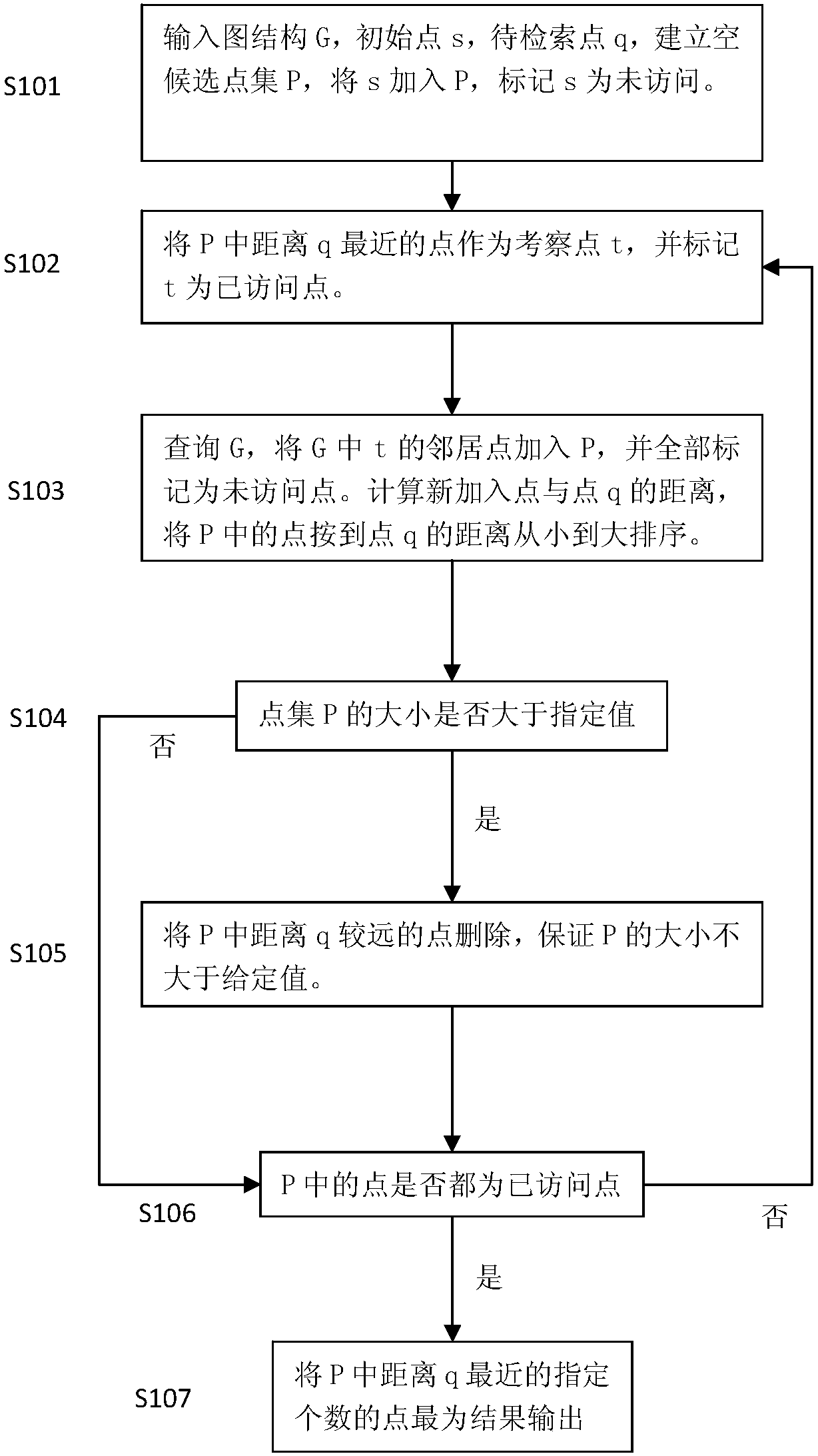
Approximate nearest neighbor retrieval method and retrieval system for high dimensional data based on satellite system diagram
InactiveCN108710626AShorten the timeImprove retrieval accuracySpecial data processing applicationsMemory footprintNear neighbor
The present invention discloses an approximate nearest neighbor retrieval method and retrieval system for high-dimensional data based on a satellite system diagram. The approximate nearest neighbor retrieval method for high-dimensional data based on the satellite system diagram comprises: (1) establishing a satellite system diagram for a high-dimensional database point set; (2) for to-be-retrievedpoints, randomly selecting a plurality of data points as a candidate point set, and performing greedy approximate nearest neighbor retrieval on the satellite system diagram; and (3) taking a given number of points in the obtained candidate point set as a result, namely, a nearest neighbor point set of the to-be-retrieved points. By virtue of the technical scheme of the present invention, logarithmic retrieval complexity can be achieved, so that not only the retrieval precision in a certain period of time can be greatly improved, but also the memory footprint and the time required for indexingduring retrieval can be greatly reduced.
Owner:ZHEJIANG UNIV
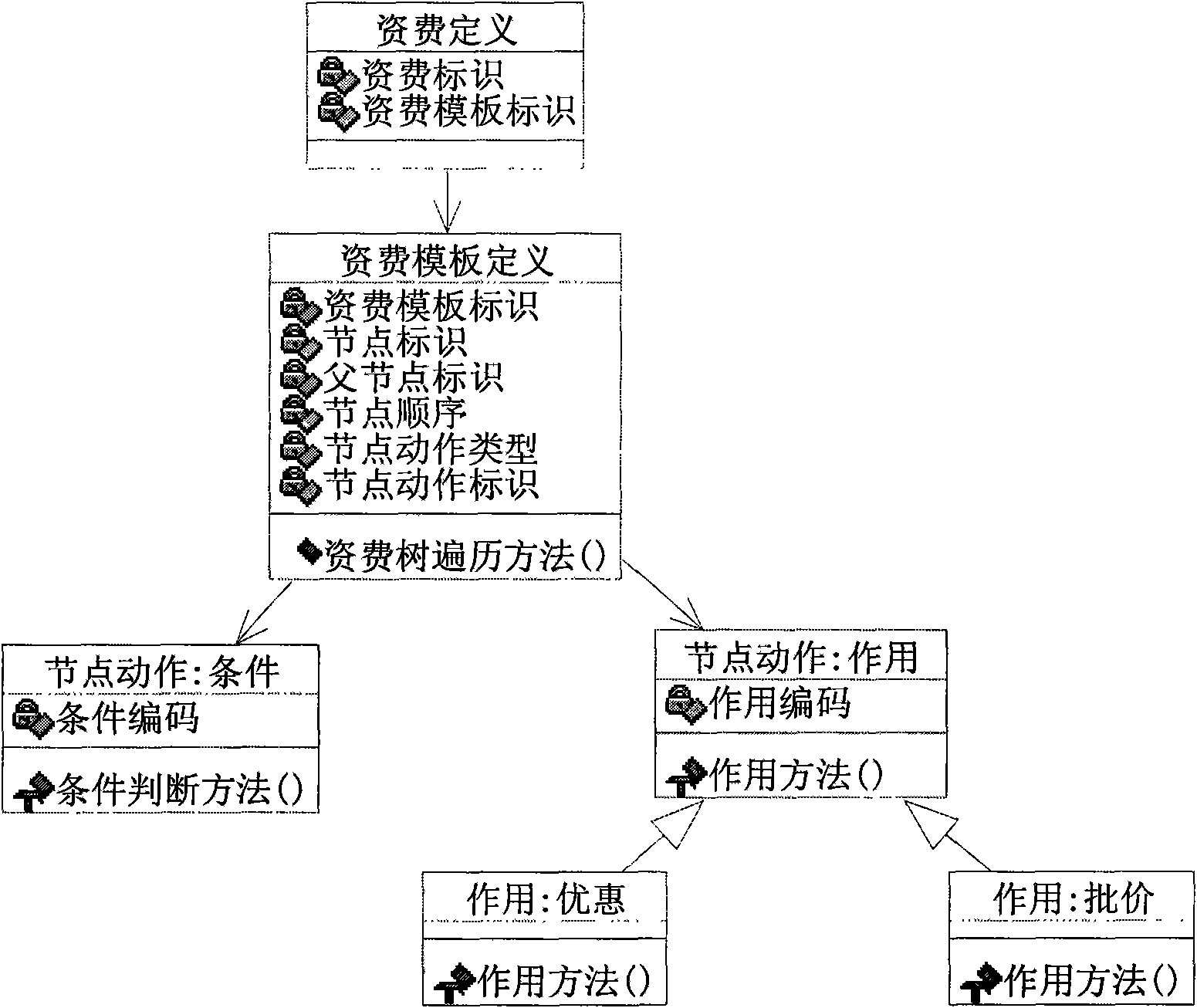
Tariff template tree setting method in charging account engine
InactiveCN101650723AEasy to traverseReduce occupancyWireless commuication servicesSpecial data processing applicationsComputer scienceDatabase
The invention relates to a tariff template tree setting method in a charging account engine: (1) a tariff constituent table is arranged, the tariff is described by a tree structure, every tariff is defined into a tariff tree, each tariff rule in the tariff is called into one node on the tariff tree; (2) a node action table is arranged, the tariff constituent table defines which actions form the tariff, and defines the execution sequence of the actions. The special actions related in the tariff constituent table are defined in the node action table; (3) a tariff instantiation parameter table isarranged; a tariff template is selected: suitable tariff template identification is chosen from the tariff constituent table; the parameters of the tariff template are instantiated; when determiningthe tariff template, firstly, determining which action values are likely to change; the process of the parameter instantiation of the tariff template is dynamically carried out in the ergodic processof the tariff tree.
Owner:LINKAGE SYST INTEGRATION
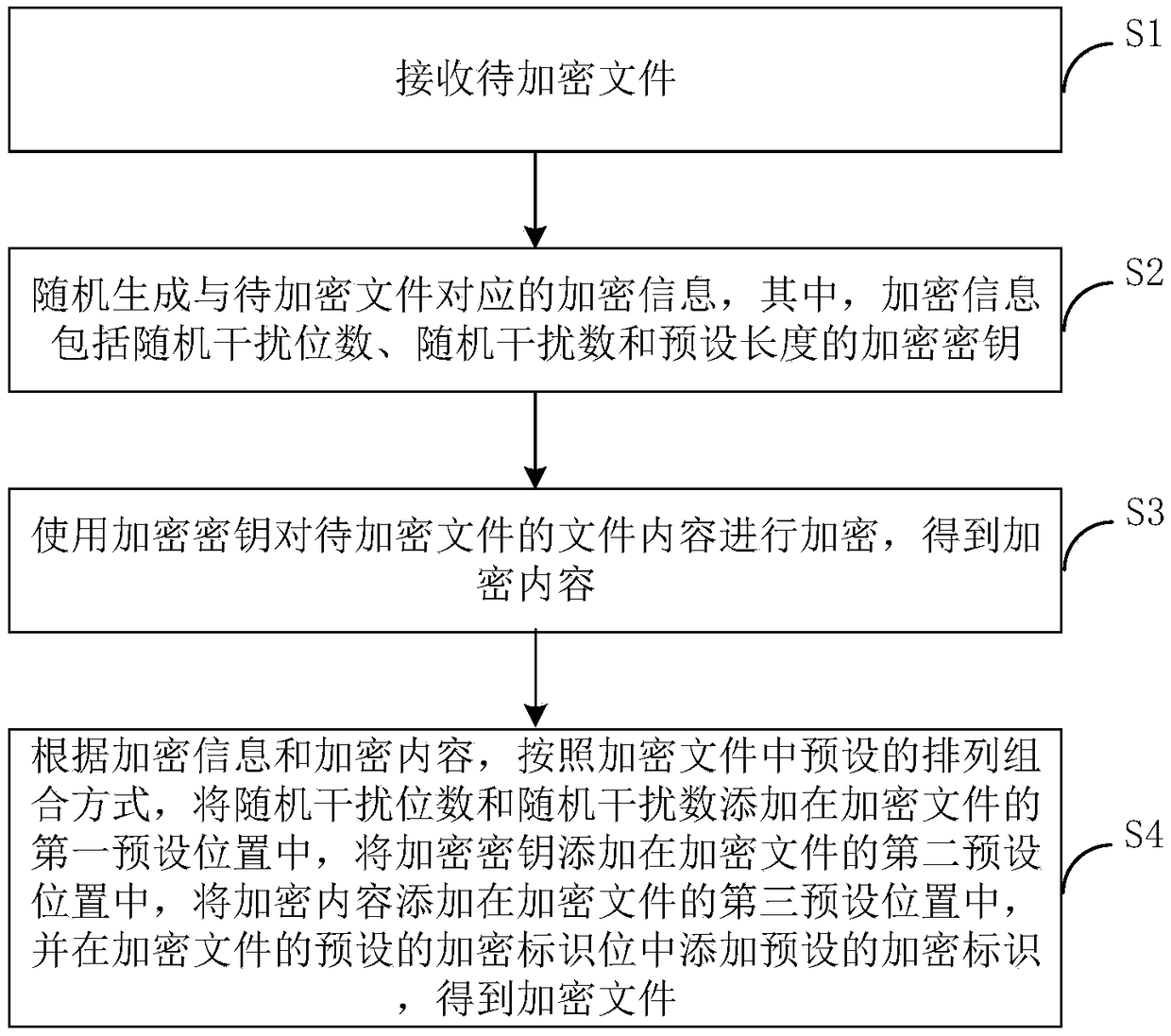
File protection method and device, computer device and storage medium
InactiveCN109218295AReduced memory footprintIncrease randomnessKey distribution for secure communicationStorage securityEncryption
The invention discloses a file protection method and device, a computer device and a storage medium. The method comprises receiving a file to be encrypted; generating at random encryption informationcorresponding to the file to be encrypted, wherein the encryption information comprises a random number of interference bits, a random interference number, and an encryption key of a preset length; encrypting the file content of the file to be encrypted by using the encryption key to obtain encrypted content; combining the encryption information and the encrypted content according to a preset permutation and combination manner and adding a preset encryption identifier to a preset encryption identifier bit to obtain an encrypted file. By encrypting and misaligning the content of the file, the content of the encrypted file is protected. An encryption algorithm is relatively simple and fast such that the memory storage space of the encrypted file can be reduced while file storage security isensured.
Owner:PING AN TECH (SHENZHEN) CO LTD
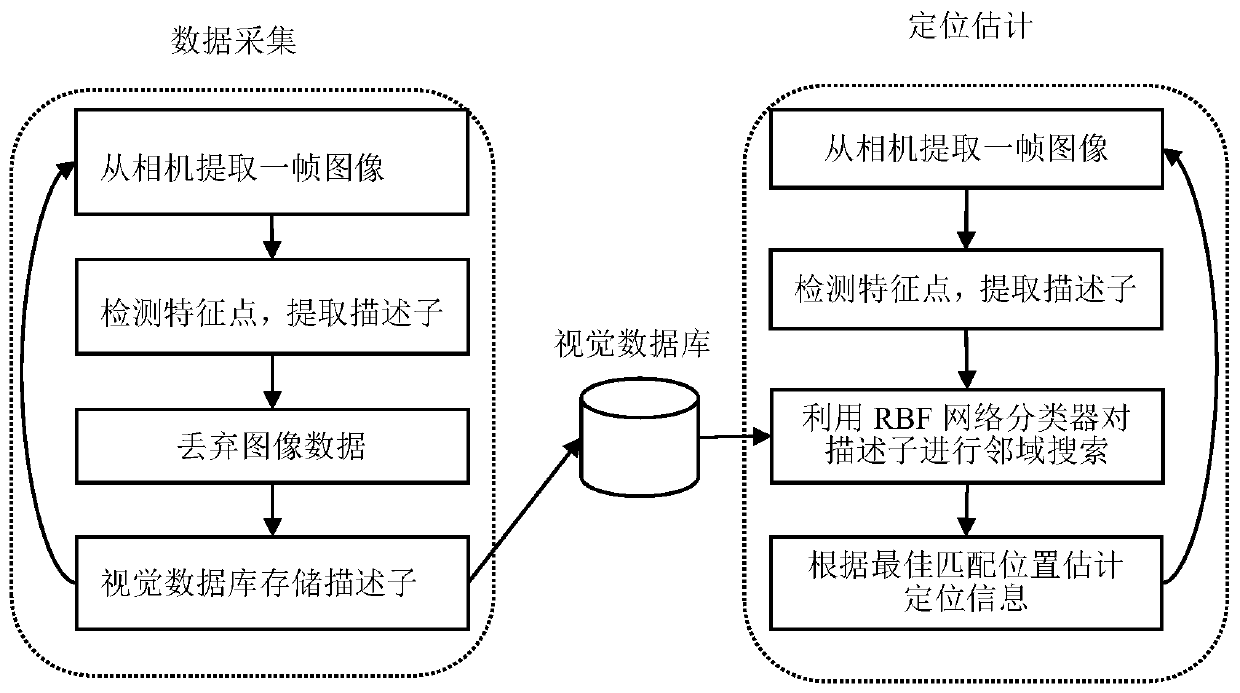
RBF-network-based visual navigation positioning method of unmanned aerial vehicle
ActiveCN110631588AReduced memory footprintBest match positionNavigational calculation instrumentsNeighborhood searchUncrewed vehicle
The invention discloses an RBF-network-based visual navigation positioning method of an unmanned aerial vehicle. When a GNSS signal is not lost, images are collected through a camera and image framesare extracted from the camera, feature points of all image are detected, descriptors are extracted, and feature point information of the images is reserved; the extracted descriptors of the image frames are processed repeatedly and descriptor information and the positioning information are stored into a visual database; when the GNSS signal is lost, shot images of the camera are extracted, descriptor extraction is performed, and an RBF network classifier is trained by using visual database information; and neighborhood searching is carried out on the generated descriptors according to the RBFnetwork classifier, an optimal matching position is estimated, and current positioning information is obtained based on recorded positioning information. According to the invention, the positioning and navigation processing of the unmanned aerial vehicle can be realized based on the constructed visual database while the GNSS signal is lost; and the visual database only stores feature point descriptor information of the images and the occupied space of a memory is small.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Applet application installation management method, device, equipment and system
ActiveCN111651734AGuaranteed legalityReduce application configuration timeProgram/content distribution protectionSoftware deploymentSoftware engineeringOperating system
The invention provides an installation management method, device, equipment and system for applet applications. According to the method, a applet application service with a plurality of applets can beprovided for hardware equipment; the equipment management platform can perform unified management on the hardware equipment installed with the applet application, the legality of the hardware equipment running the applet application is ensured, the hardware equipment does not need to adapt to environments of different applications, and applet services in the applet application can be changed at any time and do not depend on equipment upgrading.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
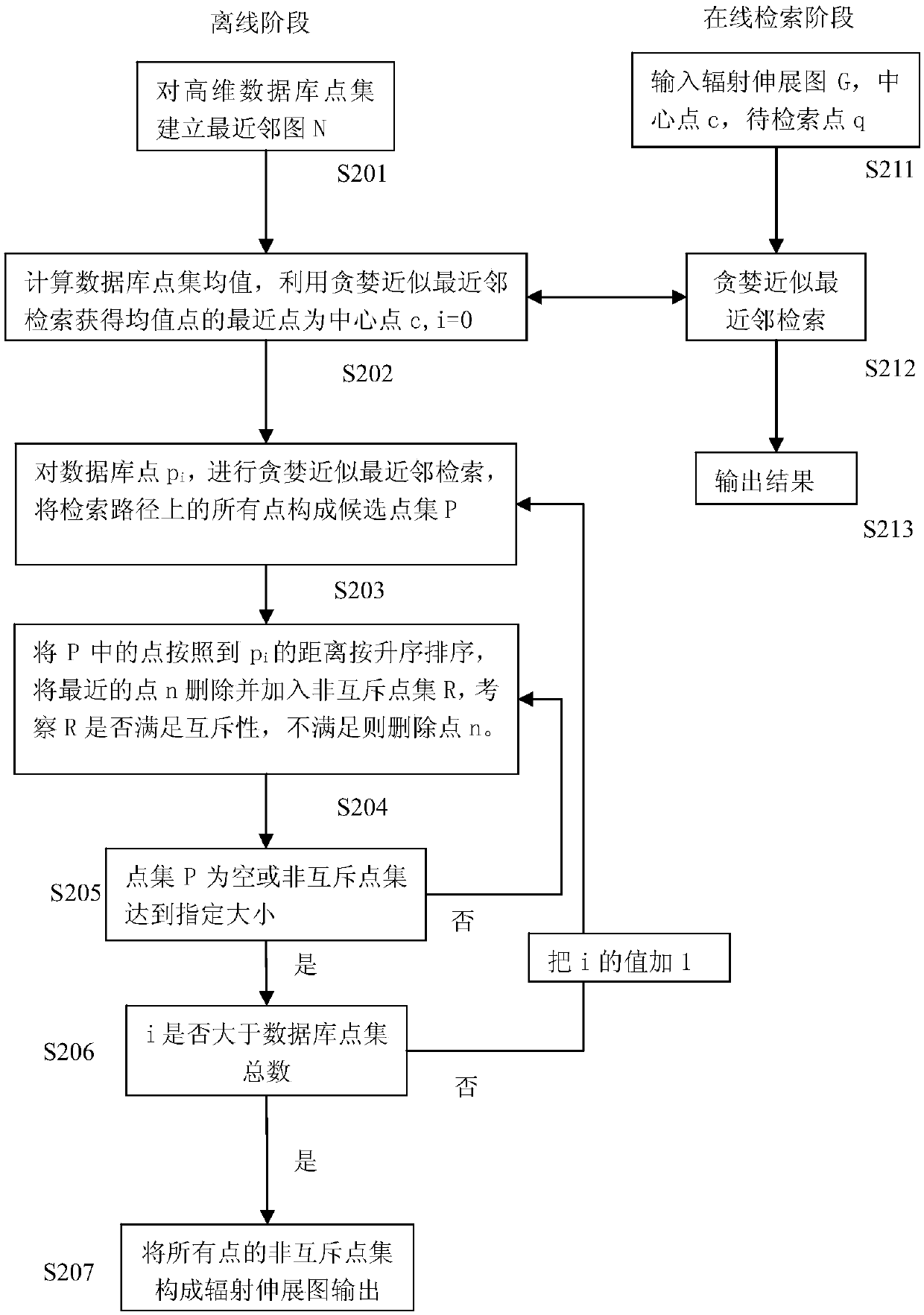
High-dimensional data approximate nearest neighbor retrieval method and system based on radiation stretching diagram
InactiveCN107729348AImprove retrieval accuracyReduced memory footprintOther databases queryingSpecial data processing applicationsPoint setNear neighbor
The invention discloses a high-dimensional data approximate nearest neighbor retrieval method and system based on a radiation stretching diagram. The retrieval method based on the radiation stretchingdiagram comprises the steps that 1, the radiation stretching diagram is established for a high-dimensional database point set; 2, for to-be-retrieved points, greedy approximate nearest neighbor retrieval is conducted on the radiation stretching diagram by starting from a center point of the radiation stretching diagram; 3, a given number of obtained points with concentrated candidate points serveas results, that is to say, a nearest neighbor point set of the to-be-retrieved points is obtained. Accordingly, the candidate nearest neighbor point set can have the exponential convergence speed, not only can the retrieval precision in a certain period of time be greatly improved, but also the memory occupied space in the retrieval process can be greatly reduced.
Owner:ZHEJIANG UNIV
Neural network operation device and method based on HMC
InactiveCN108256643AReduce power consumptionReduce wasteConcurrent instruction executionPower supply for data processingData transmissionMachine learning
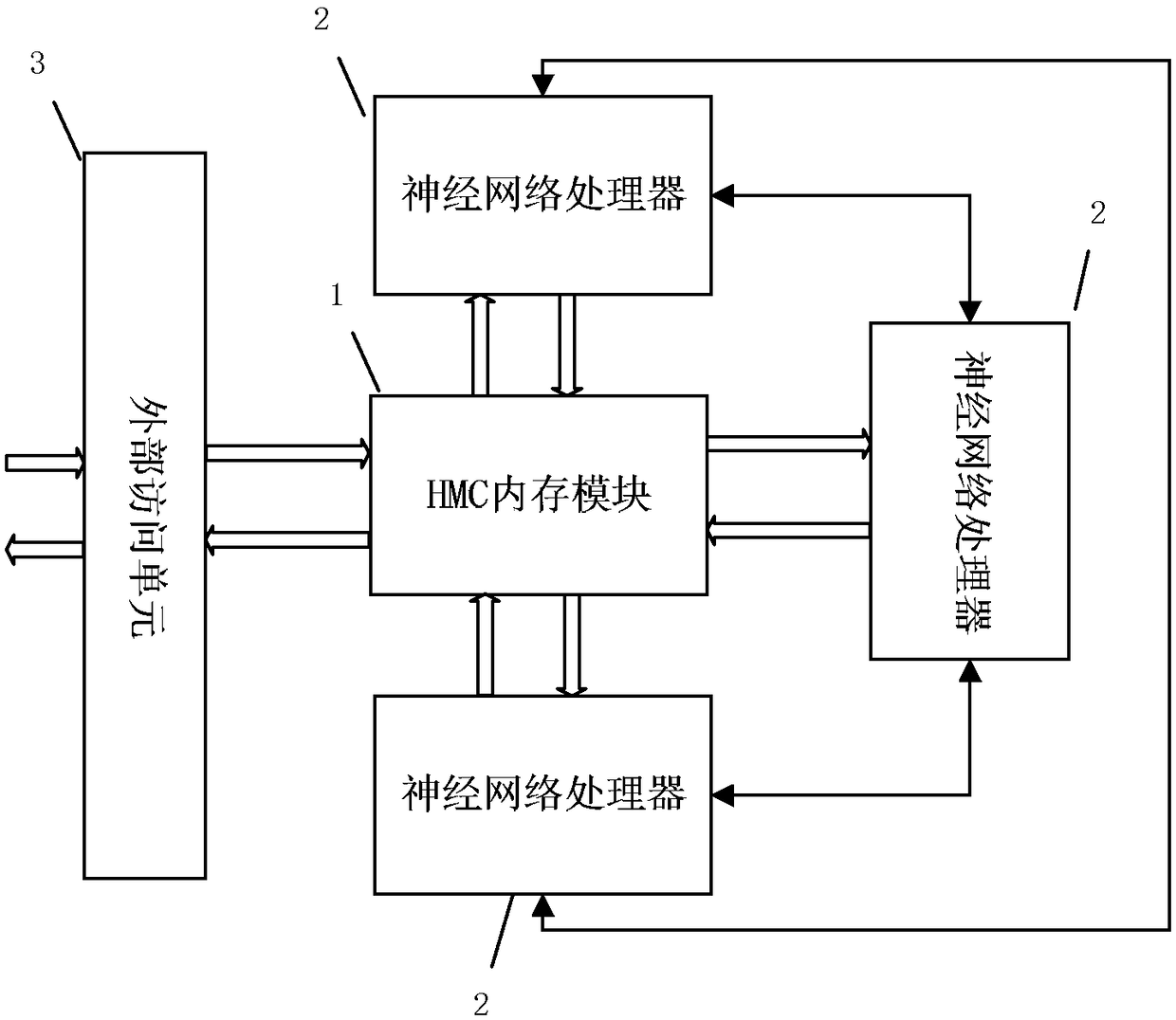
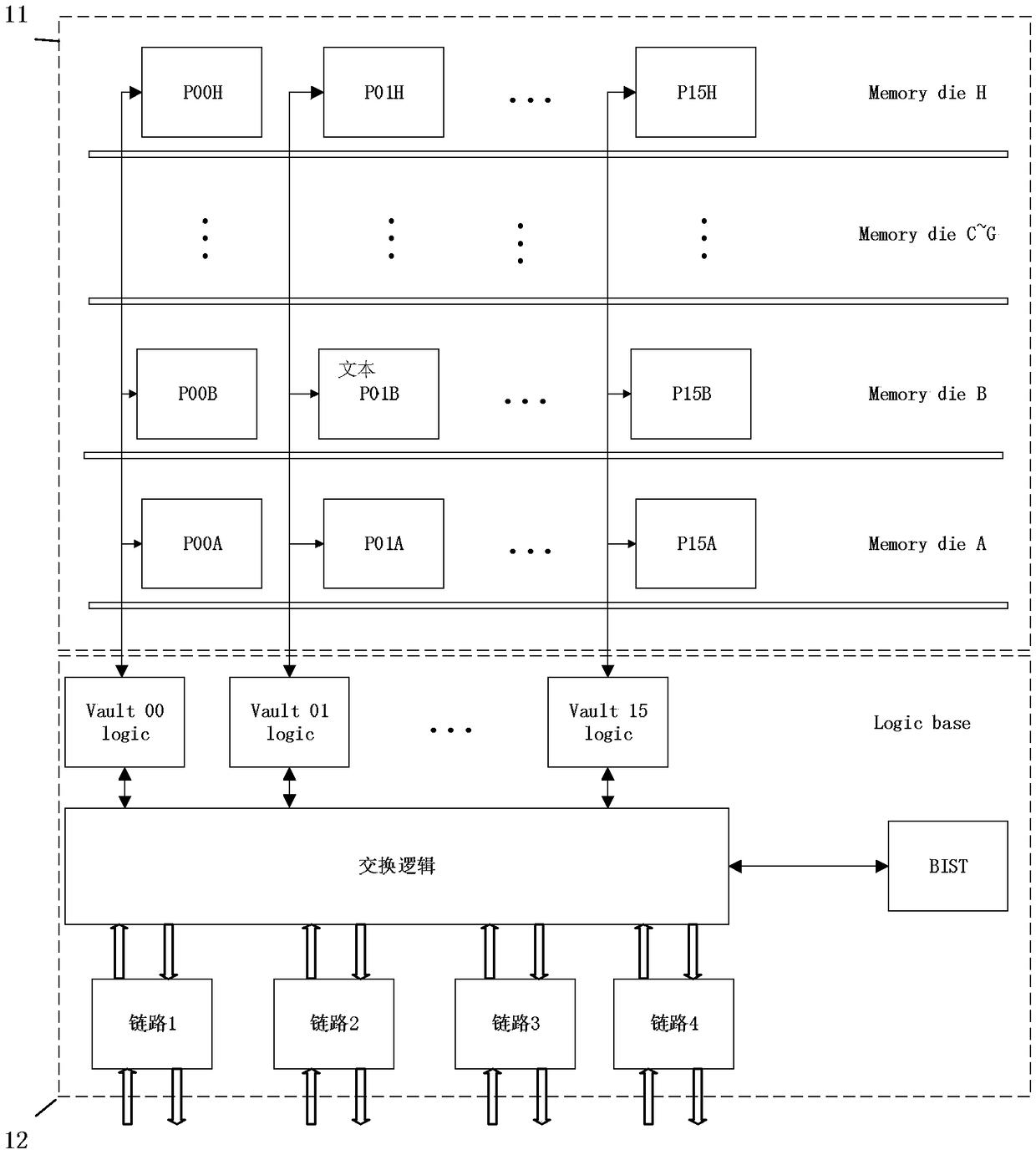
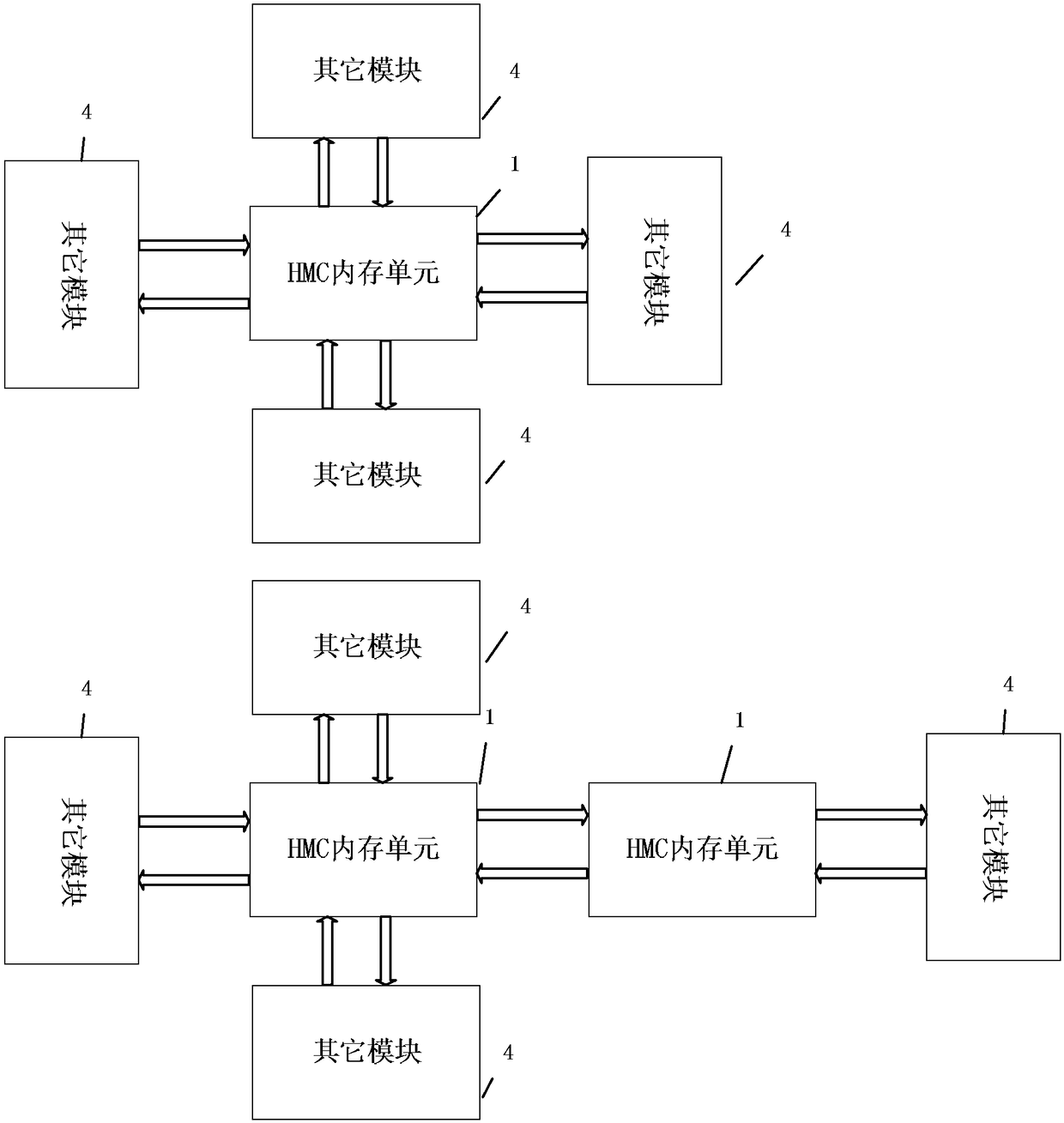
The invention provides a neural network operation device. The device comprises an HMC memory module, at least one neural network processor which is connected with the HMC memory module, and an external access unit. The neural network processor is used for acquiring data and instructions required for neural network operations from the HMC memory module, carrying out neural network partial operations, and writing the operation result back to the HMC memory module. The external access unit is connected with the HMC memory module, reads neural network instructions and data required for neural network operations from an external designated address, inputs the instructions and data into the HMC memory module, and outputs the neural network operation result from the HMC memory module to the external designated address space. The invention further provides a neural network operation method. According to the invention, the requirements for data transmission and storage in the operation processof the neural network operation device can be effectively met, and the device and method have the advantages of high memory utilization, low power consumption overhead, low cost and fast data transmission rate.
Owner:SHANGHAI CAMBRICON INFORMATION TECH CO LTD
Method and device of improving code execution performance
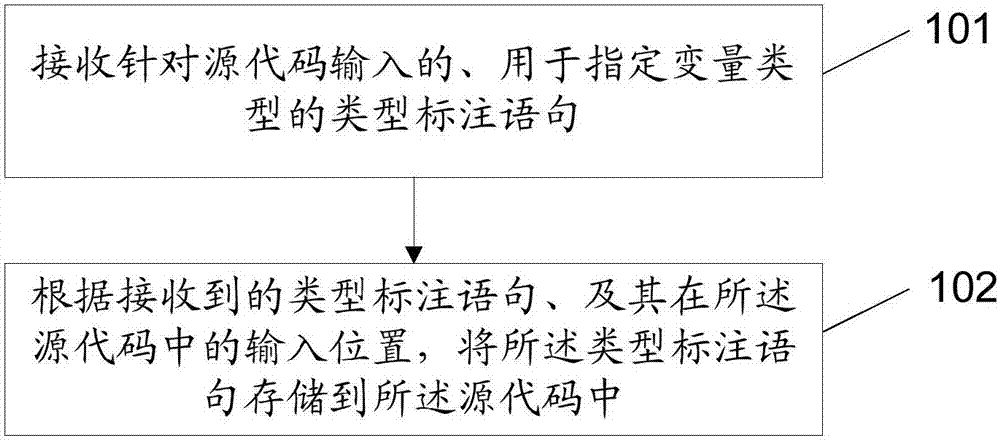
ActiveCN107515739AImprove executionReduced memory footprintSoftware engineeringSpecific program execution arrangementsSyntaxSource code
The application discloses a method and a device of improving code execution performance, and simultaneously discloses a method and a device of generating correspondence relationships of variable identifiers and types, and a method and a device used for generating source code containing type marking statements. The method of improving the code execution performance includes: acquiring the correspondence relationships which are pre-generated for the source code and of the variable identifiers and types; and compiling the source code, which is stored in a syntax tree format, according to the correspondence relationships to generate executable code after variable type limitation. By adopting the above-mentioned method, the variable types can be limited according to the pre-generated correspondence relationships when the source code is compiled, the executable code after variable type limitation can be generated, and thus memory space occupied by the executable code can be reduced; and processes of judgment for all the possible types are reduced, thus an execution rate of the executable code is also accordingly increased, and the overall execution performance is enabled to be improved.
Owner:BANMA ZHIXING NETWORK HONGKONG CO LTD
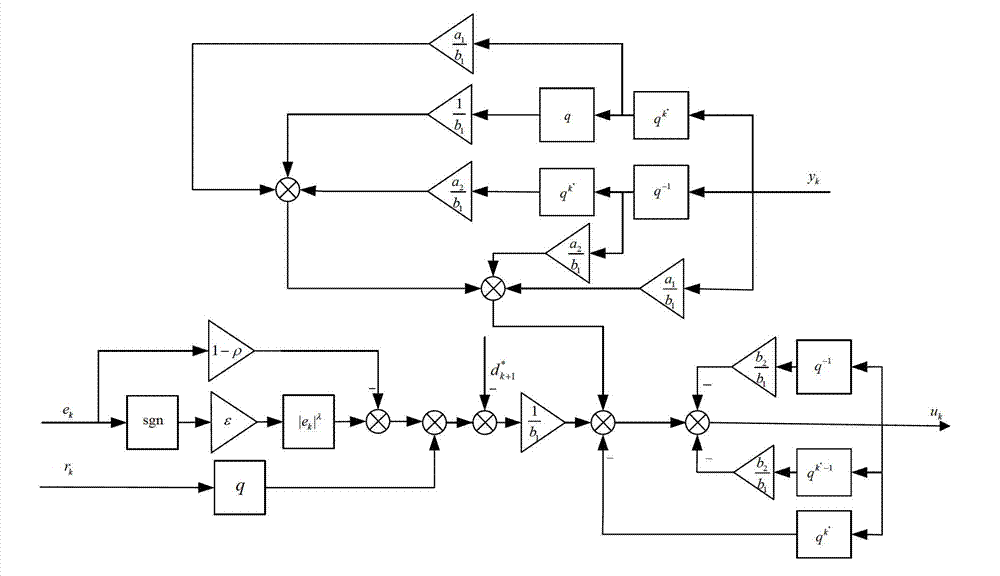
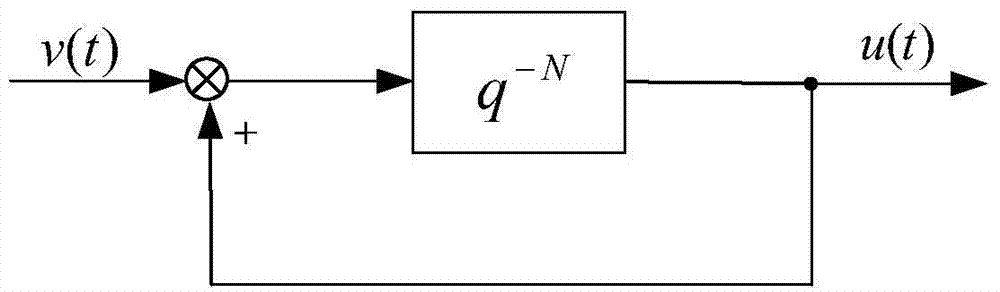
Quarter period repeated controller for converter
InactiveCN103812368AEasy to handleReduced memory footprintElectric controllersDc-ac conversion without reversalComputer moduleControl theory
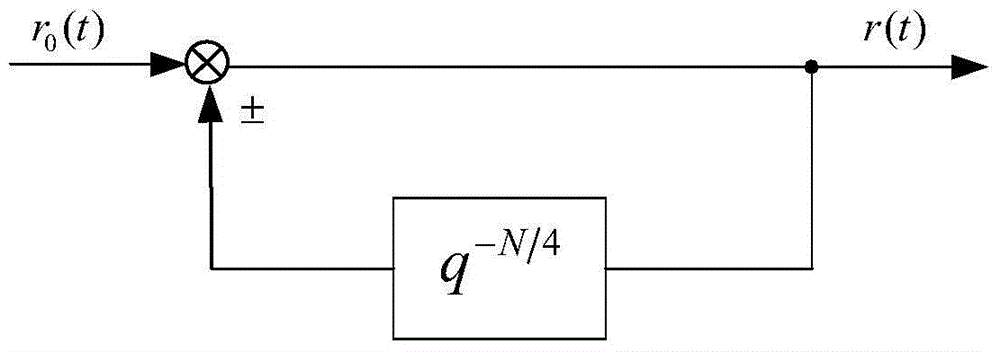
The invention discloses a quarter period repeated controller for a converter. In an existing repeated control technology, periodical external drive signals can be completely tracked or inhibited, and the front whole period of control and output signals can be stored. The controller comprises a given element, a periodical feedback element, and a signal transformation module and subtraction / addition element. A periodically symmetric reference signal is generated in the given element; the periodic feedback element is constructed; the signal conversion module is constructed according to the law of attraction, and the output signal of the signal conversion module is used for the allowance of the repeated controller; and the output signal of the repeated controller is served as the input of a controlled object. Specific controller parameter setting can be performed according to the index of the convergence performance of a representation system, and a monotone decreasing area, an absolute attraction layer and a steady state error boundary in the convergence process of representing tracking error can be provided. The quarter period repeated controller is capable of effectively restraining the symmetry signal interference, improving the control precision and greatly reducing memory usage.
Owner:NANTONG TAIYING NEW MATERIAL SCI & TECH CO LTD
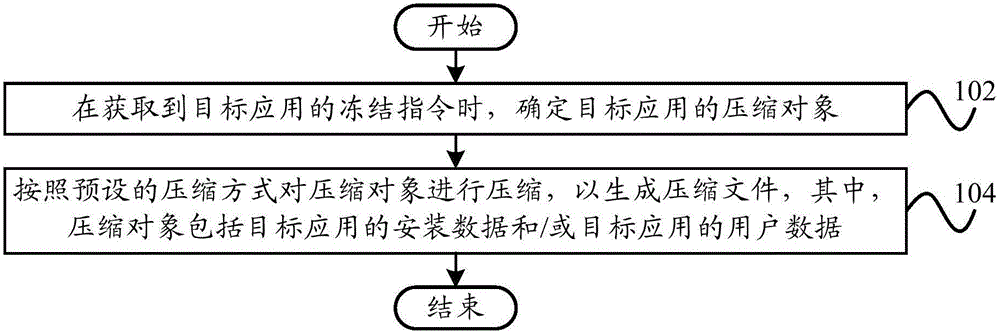
Freezing method and device of application programs and terminal
InactiveCN106201708AAchieve readMeet the needs of useResource allocationSpecial data processing applicationsMemory footprintComputer terminal
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
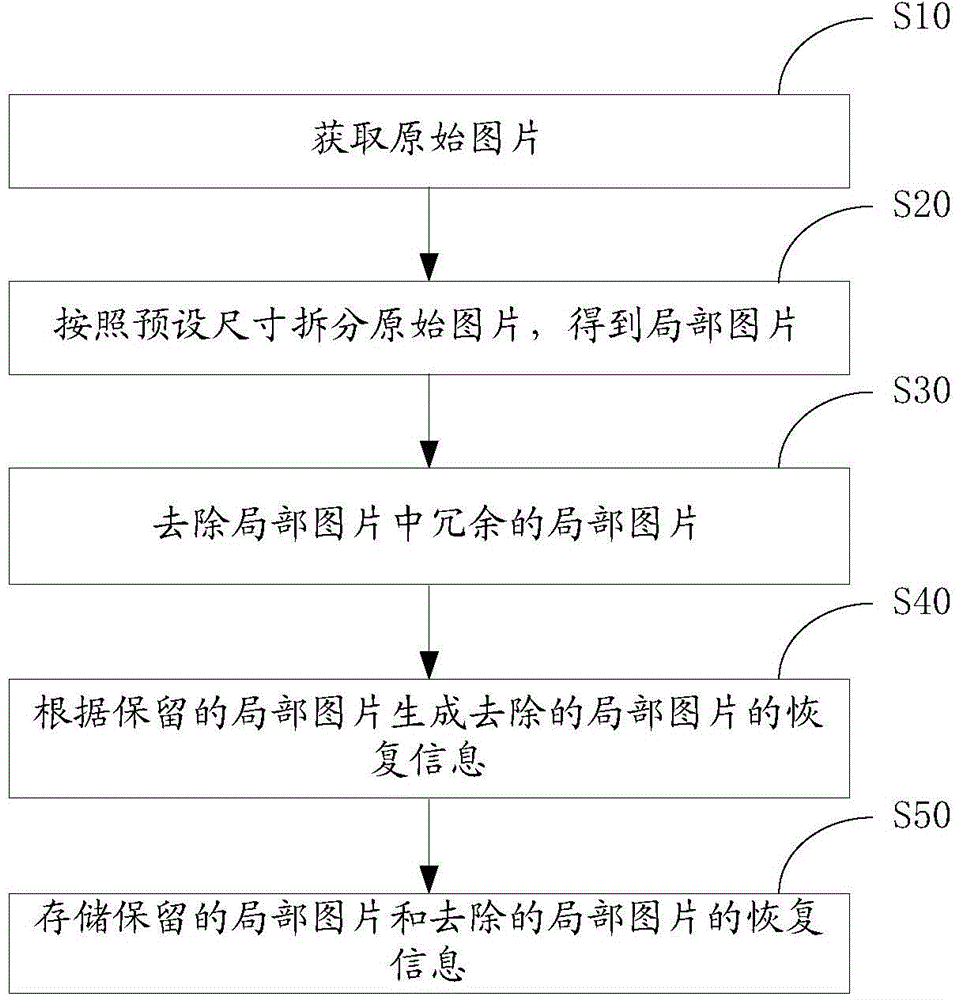
Image splitting method and device, image loading method and device
ActiveCN105023285AReduced memory footprintSave storage spaceImage enhancementImage codingPattern recognitionComputer graphics (images)
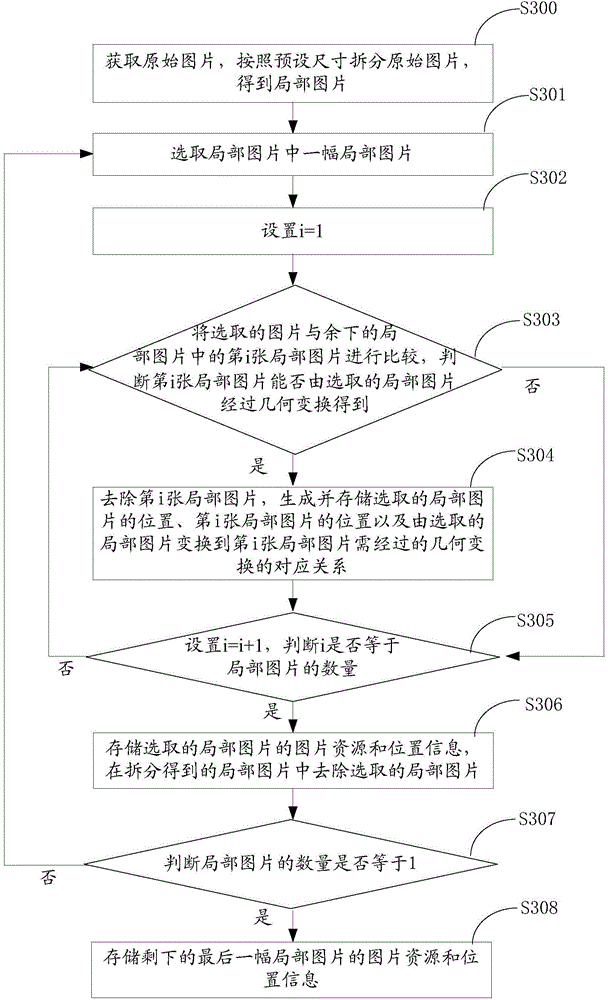
A picture splitting method includes: acquiring an original picture; splitting the original picture according to a preset size, to obtain partial pictures; removing a redundant partial picture in the partial pictures; generating restoration information of the removed partial picture according to a retained partial picture; and storing the retained partial picture and the restoration information. With the foregoing method, an original picture is split into partial pictures, a redundant partial picture is removed, restoration information of the removed partial picture is generated according to a retained partial picture, and the retained partial picture and the restoration information are stored. The file size of the retained partial picture is smaller than the file size of the original picture, which can reduce a storage space, and when the original picture needs to be loaded, it is feasible to load the retained partial picture only, and the removed partial picture is restored according to the restoration information, which can reduce a memory space occupied by picture loading.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Equipment management method, device and system, and storage medium
ActiveCN109032058AThe judgment result is accurateSmall amount of calculationProgramme control in sequence/logic controllersSingle typeComputer science
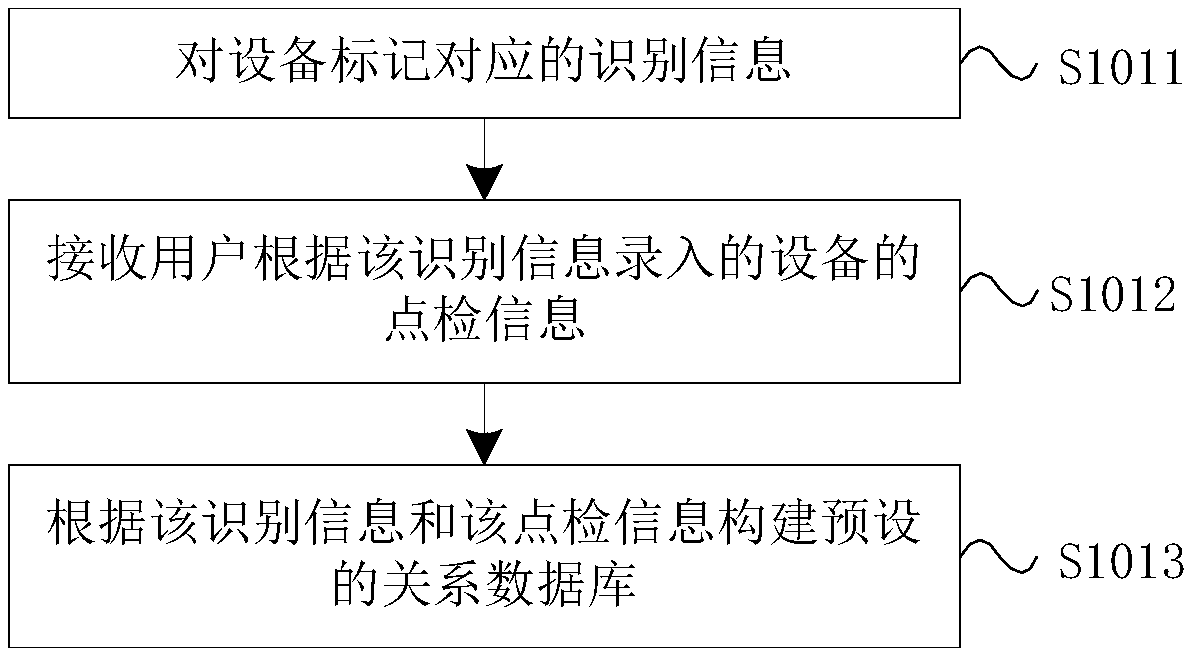
The invention provides an equipment management method, device and system, and a storage medium. The equipment management method comprises the following steps that: obtaining the point inspection information of equipment, judging whether the point inspection information is abnormal or not, when the point inspection information is abnormal, extracting the real-time operation data of the equipment atthe corresponding moment of the point inspection information, and judging the operation state of the equipment according to the point inspection information and the real-time operation data. Throughthe implementation of the invention, on one hand, the point inspection information and the real-time operation data of the equipment are combined to judge the operation state of the equipment. Compared with a way of managing the equipment only on the basis of a single type of data in the prior art, the equipment management method disclosed by the invention has an accurate judgment result. On the other hand, when the point inspection information is abnormal, the real-time operation data of the equipment is extracted, the real-time operation data does not need to be obtained all the time to carry out comparison and judgment, a calculated amount is reduced, and memory occupation space is saved.
Owner:HUADIAN HEAVY IND CO LTD
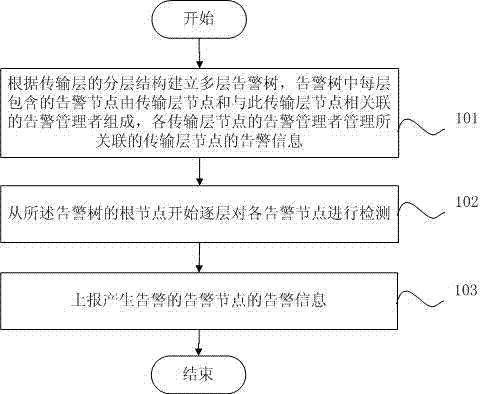
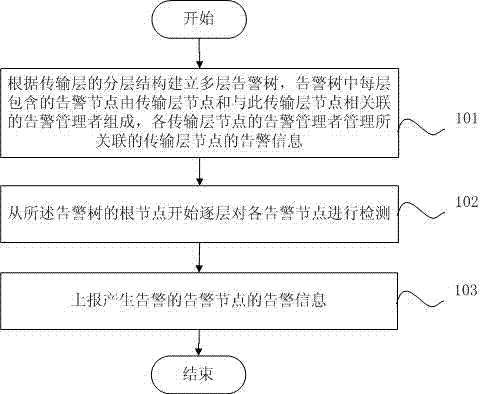
Method and equipment for alarming information processing report
InactiveCN102480374AReduce detection reporting timeReduce complexityData switching networksInternal memoryTransmission protocol
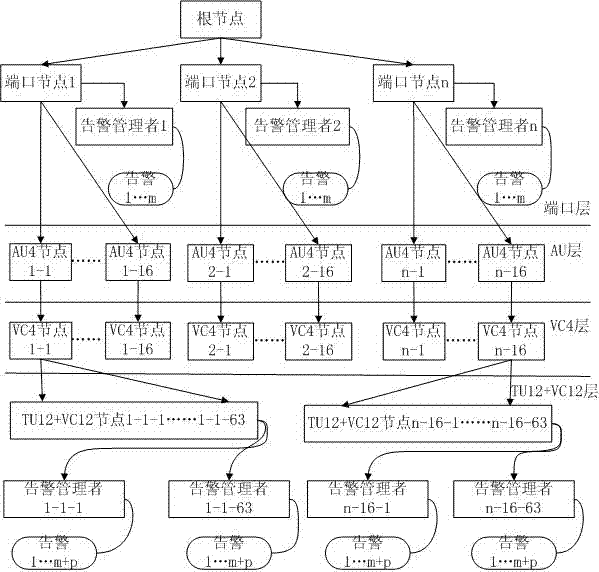
The invention discloses a method and equipment for alarming information processing report. The method includes firstly, setting up a multi-layer alarming tree according to a layered structure of a transmission layer, wherein each alarming node contained in each layer of the alarming tree consists of a transmission layer node and an alarming manager linked with the transmission layer node, and the alarming manager of each transmission layer node is used for managing alarming information of the transmission layer node linked with the alarming manager; and secondly, detecting the alarming nodes layer by layer from a root node of the alarming tree and reporting the alarming information of the alarming node generating alarms. The simplified alarming tree is set up according to the layered structure in the transmission protocol, the nodes are combined and integrally processed by means of the alarming manager linked with the nodes of each transmission layer, and thereby the alarming tree is simplified, occupied internal memory of the alarming tree is reduced, and alarm detection reporting time is shortened.
Owner:ZTE CORP
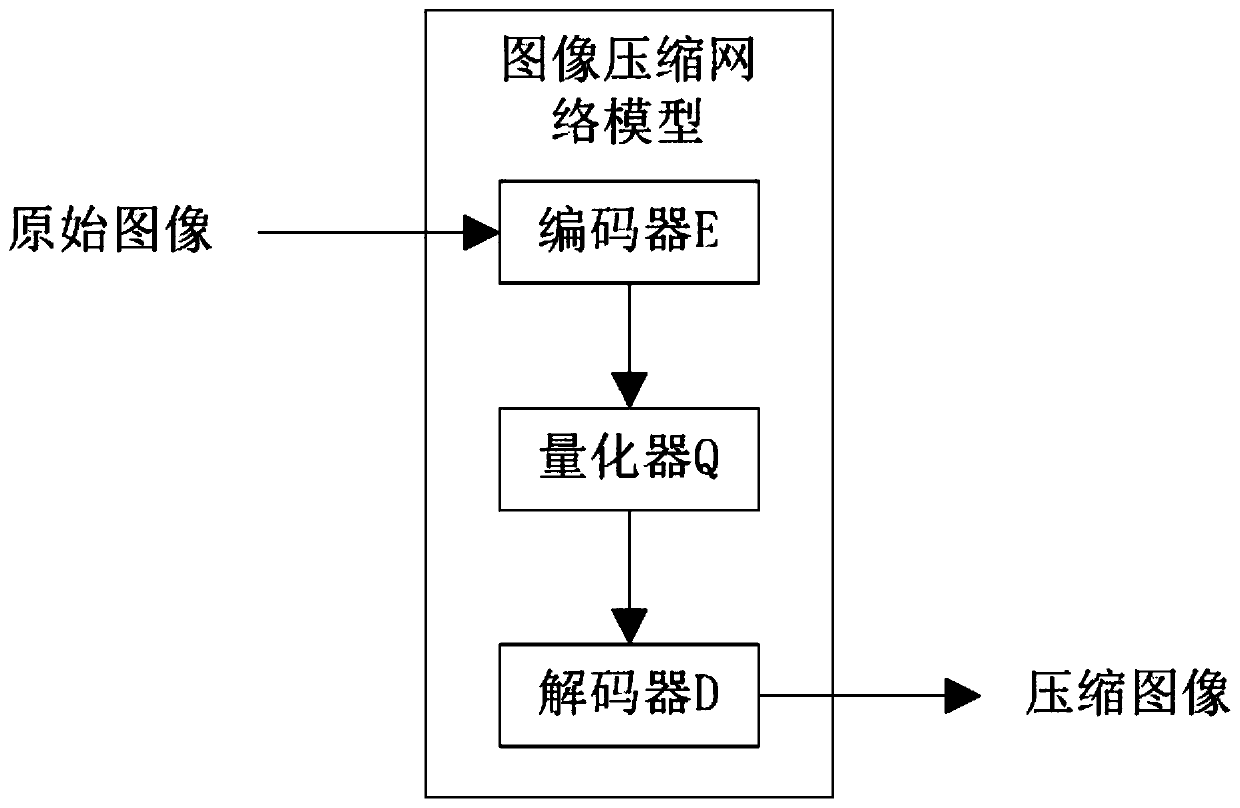
Deep learning-based image compression method applied to three-dimensional printing of furniture
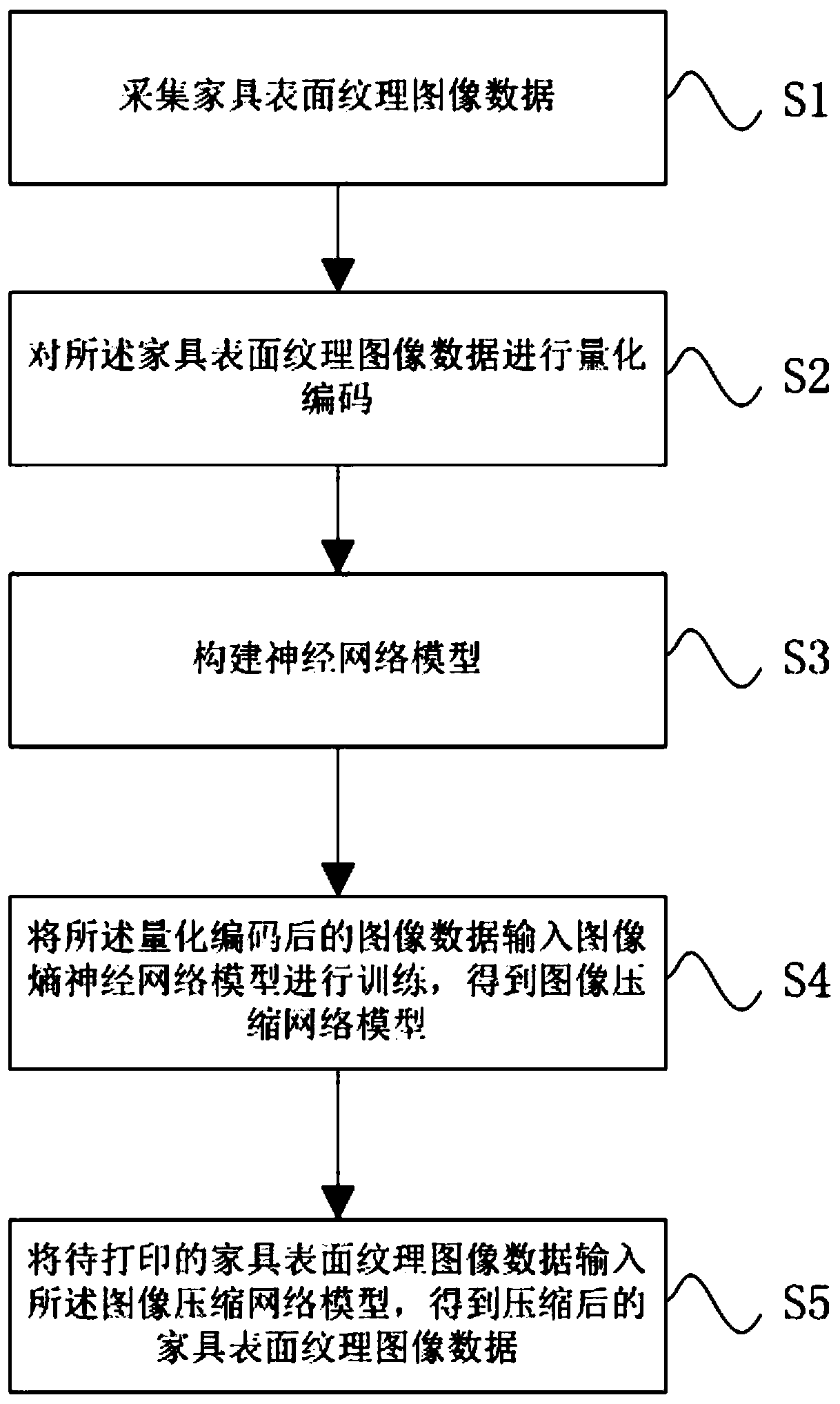
InactiveCN110084843AEfficient compressionCompressed deep learning worksAdditive manufacturing apparatusImage analysisPattern recognitionMean square
The invention discloses a deep learning-based image compression method applied to furniture three-dimensional printing. The method comprises the steps of collecting furniture surface texture image data; carrying out quantitative coding on the furniture surface texture image data; constructing an image entropy neural network model; inputting the quantized and encoded image data into an image entropy neural network model for training to obtain an image compression network model; inputting to-be-printed furniture surface texture image data into the image compression network model to obtain compressed furniture surface texture image data; and transmitting the compressed image data to a three-bit printer to perform decompression and printing processes. The neural network model can effectively compress the furniture texture image with rich structure information and unique geometric textures, and the mean square error between the original image and the decompressed image is reduced to the maximum extent; when the method is applied to three-dimensional printing of furniture, the occupied space of the memory can be effectively reduced, and the resolution of a printed image is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
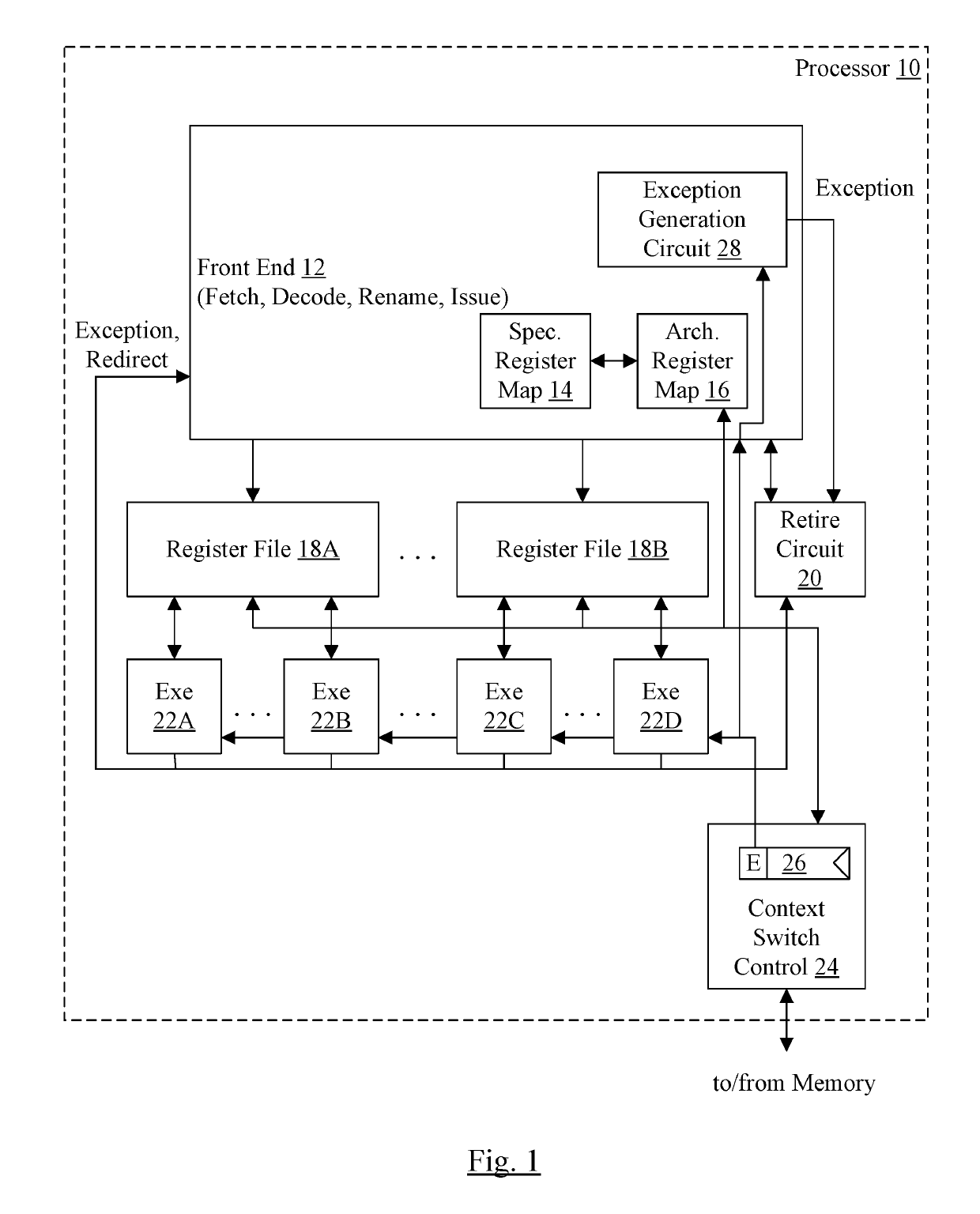
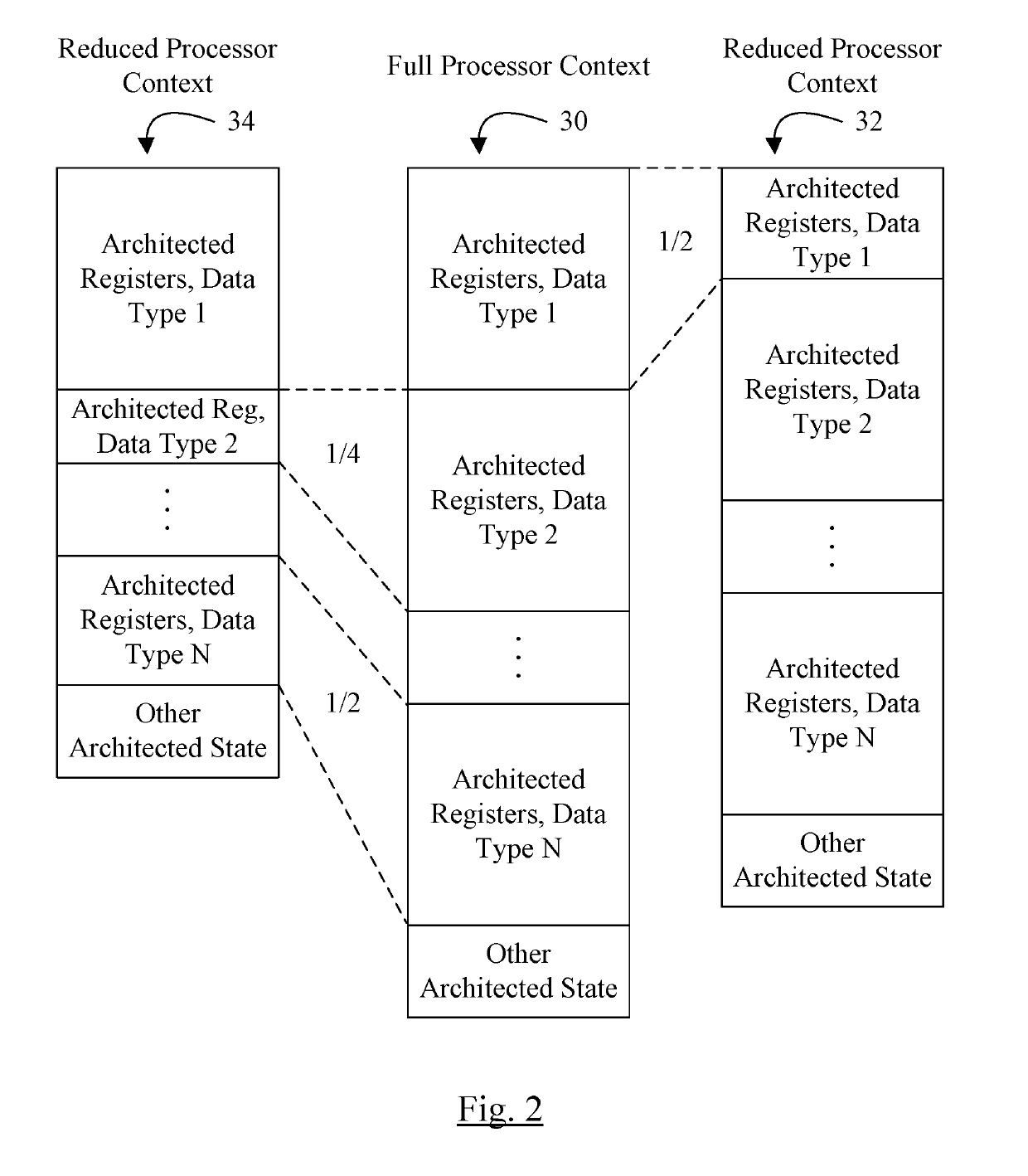
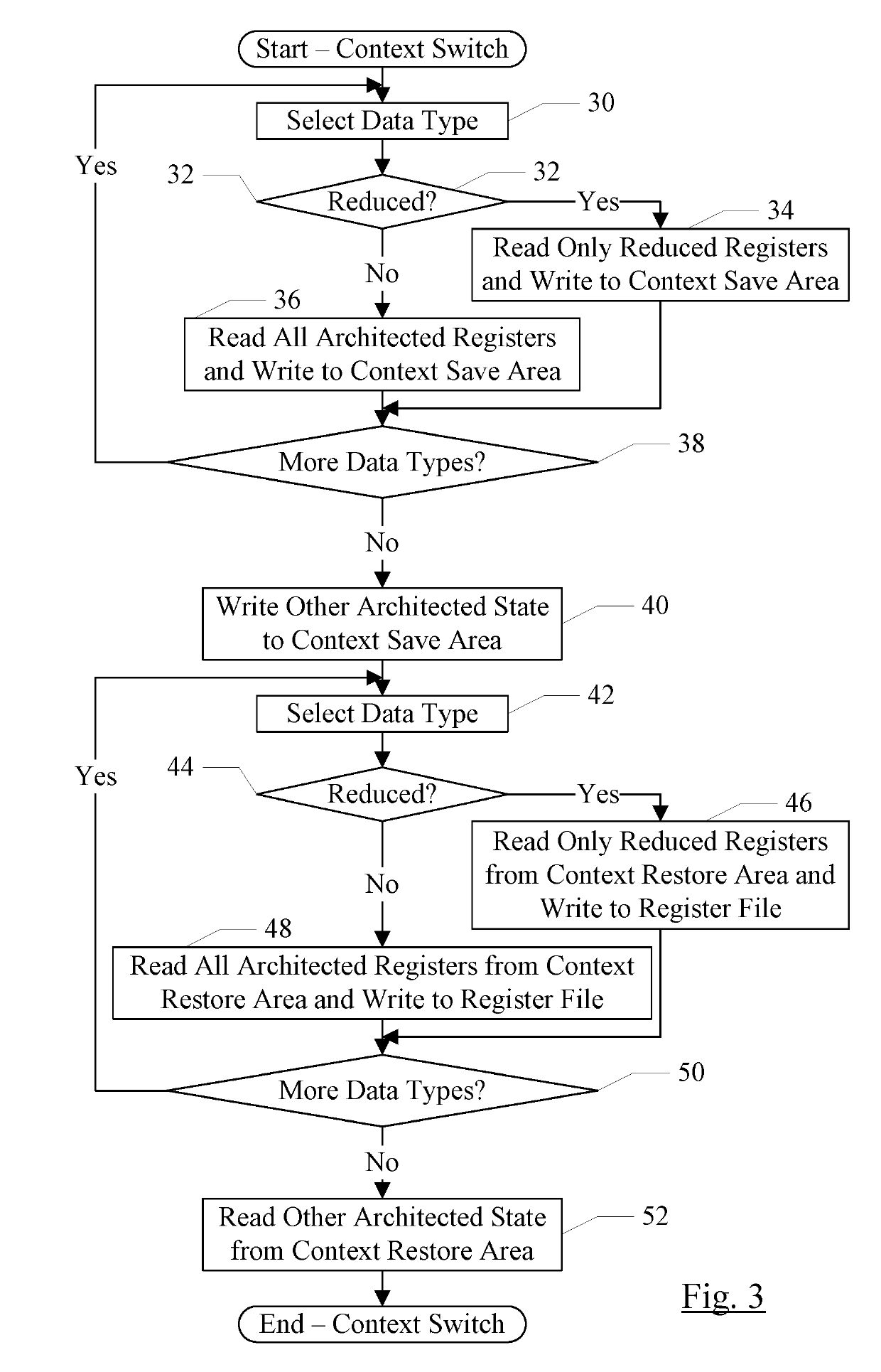
Context Switch Optimization
InactiveUS20190220417A1Reduced memory footprintIncrease performanceProgram initiation/switchingRegister arrangementsData typeRegister file
In an embodiment, a processor may include a register file including one or more sets of registers for one or more data types specified by the ISA implemented by the processor. The processor may have a processor mode in which the context is reduced, as compared to the full context. For example, for at least one of the data types, the registers included in the reduced context exclude one or more of the registers defined in the ISA for that data type. In an embodiment, one half or more of the registers for the data type may be excluded. When the processor is operating in a reduced context mode, the processor may detect instructions that use excluded registers, and may signal an exception for such instructions to prevent use of the excluded registers.
Owner:APPLE INC
Driving control method and device, intelligent robot and computer readable storage medium
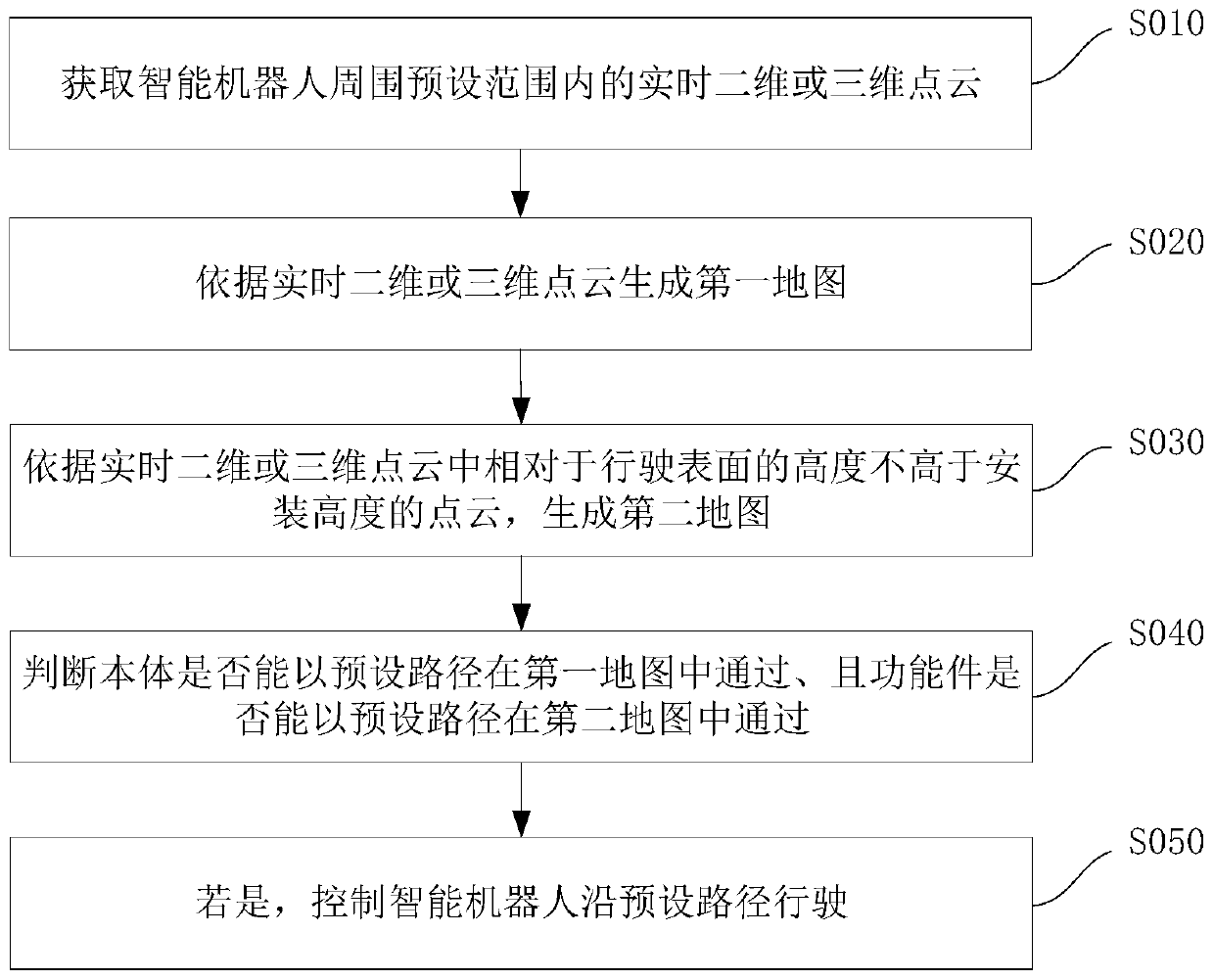
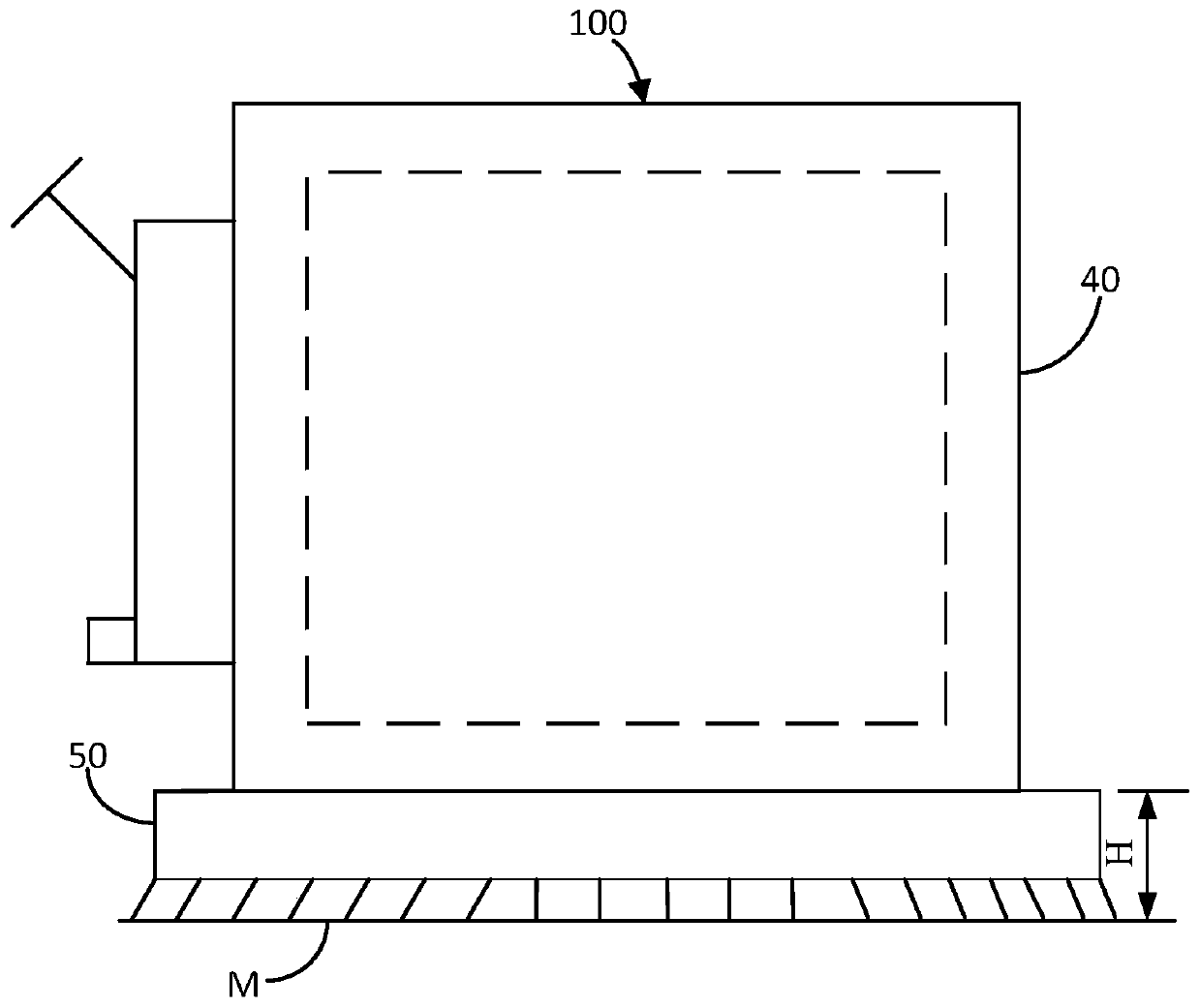
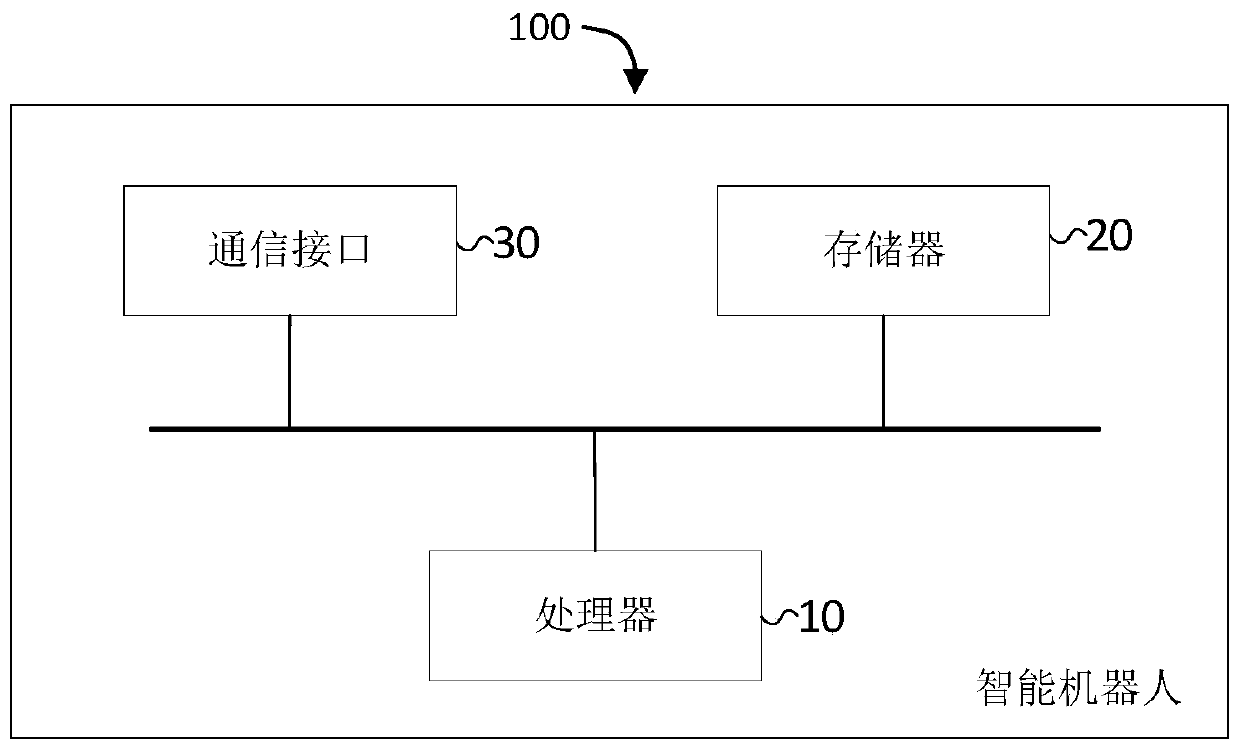
PendingCN111290393AIncreased driving areaQuality improvementGeographical information databasesSpecial data processing applicationsPoint cloudSimulation
The invention discloses a driving control method which is used for an intelligent robot. The intelligent robot comprises a body and a functional part installed on the body, wherein the functional partis installed at the installation height of the body. The driving control method comprises the steps of: acquiring real-time two-dimensional or three-dimensional point cloud in a preset range around the intelligent robot; generating a first map according to the real-time two-dimensional or three-dimensional point cloud; generating a second map according to the point cloud of which the heights relative to the driving surface are not higher than the mounting height in the real-time two-dimensional or three-dimensional point cloud; judging whether the body can pass through by taking a preset pathin the first map or not and whether the functional part can pass through by taking the preset path in the second map or not; and if so, controlling the intelligent robot to travel along the preset path. The invention further discloses a driving control device, an intelligent robot and a computer readable storage medium. Whether the body and the functional part can pass through the preset path ornot is judged by using the first map and the second map, so that the intelligent robot can avoid obstacles better, and the task completion quality of the intelligent robot is improved.
Owner:SHANGHAI GAOXIAN AUTOMATION TECH
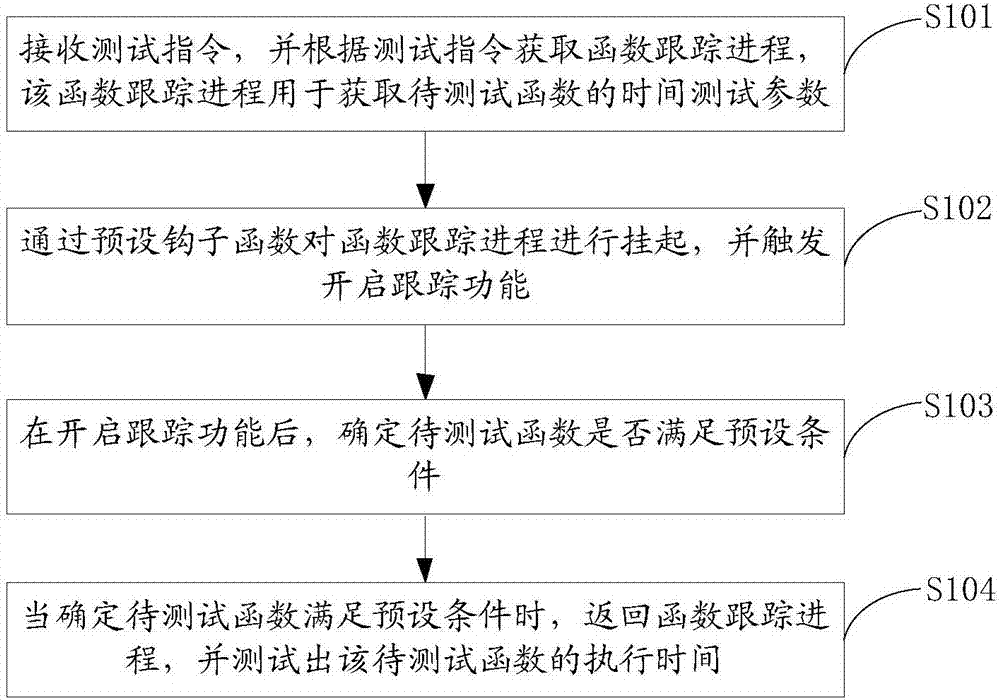
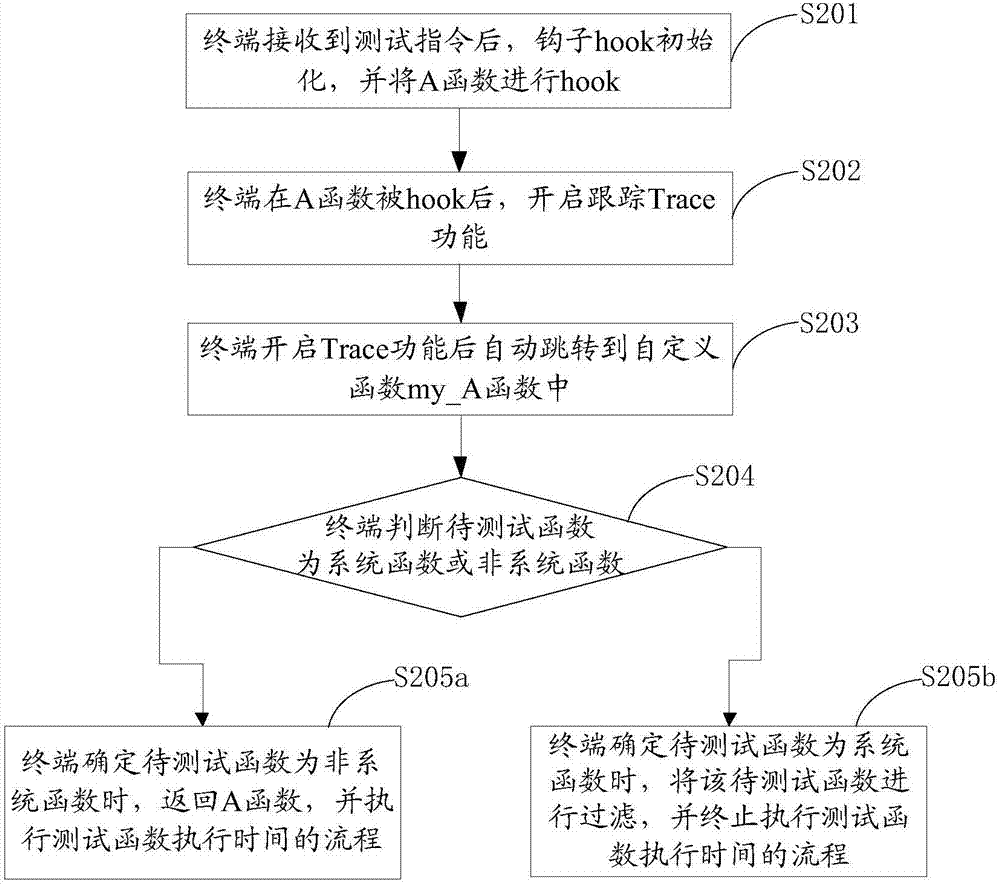
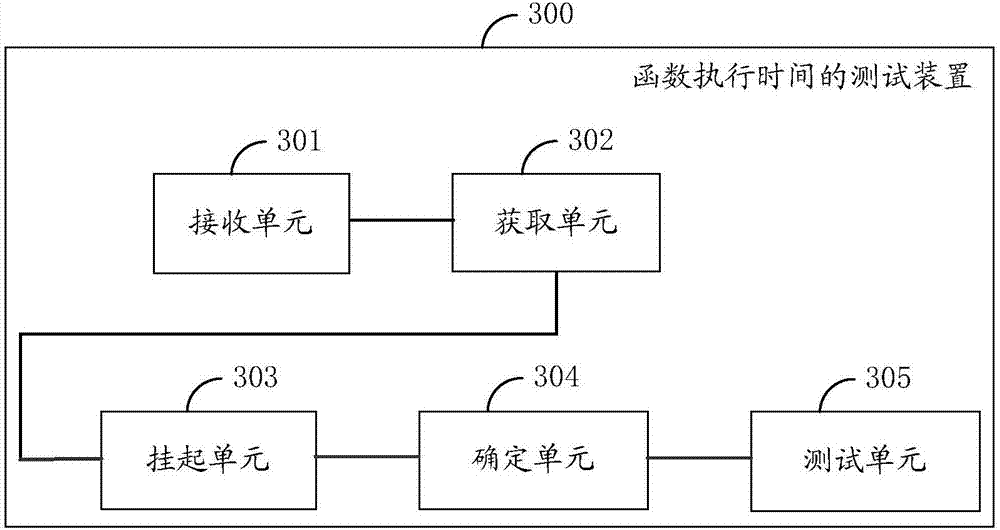
Function execution time testing method and device
ActiveCN107025173AReduced memory footprintReduce waste of resourcesSoftware testing/debuggingComputer hardwareReturn function
The invention discloses a function execution time testing method and device. The method comprises steps as follows: a test instruction is received, and a function tracking course is acquired according to the test instruction and is used for acquiring time test parameters of a to-be-tested function; the function tracking course is hung up by the aid of a preset hook function, and a tracking function is triggered to be enabled; after the tracking function is enabled, whether the to-be-tested function meets preset conditions is determined; when the to-be-tested function is determined to meet the preset conditions, the function tracking course is returned, and execution time of the to-be-tested function is tested. The function tracking course is hung up by the use of a hook, the execution path of the to-be-tested function is changed, after the tracking function is enabled, the to-be-tested function is judged firstly, logic for testing and recording function time consumption is executed only when the function meets preset conditions, thus, some useless function time consumption data can be filtered out, memory occupation space of the function time consumption data is greatly reduced, and system resource waste is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
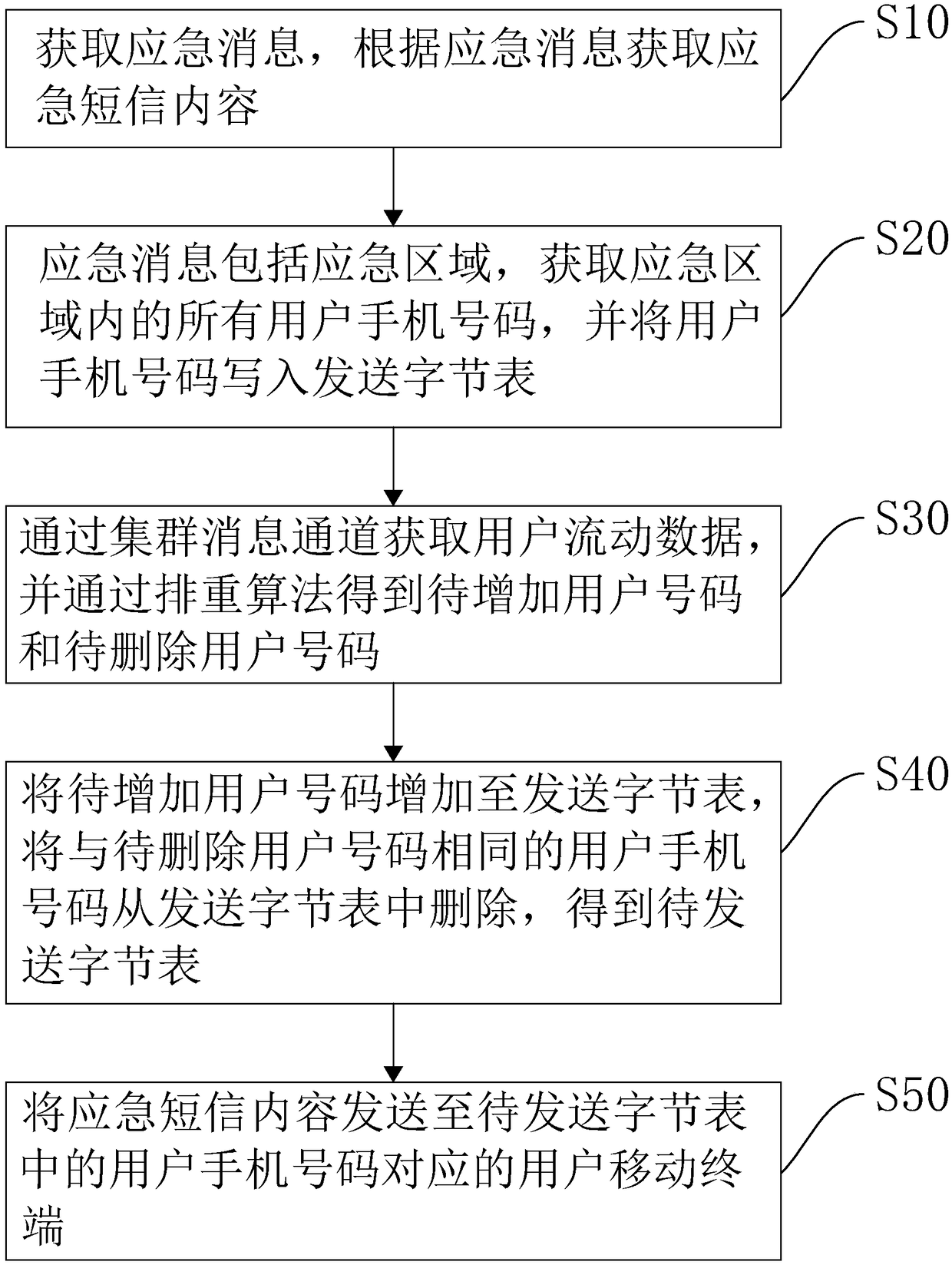
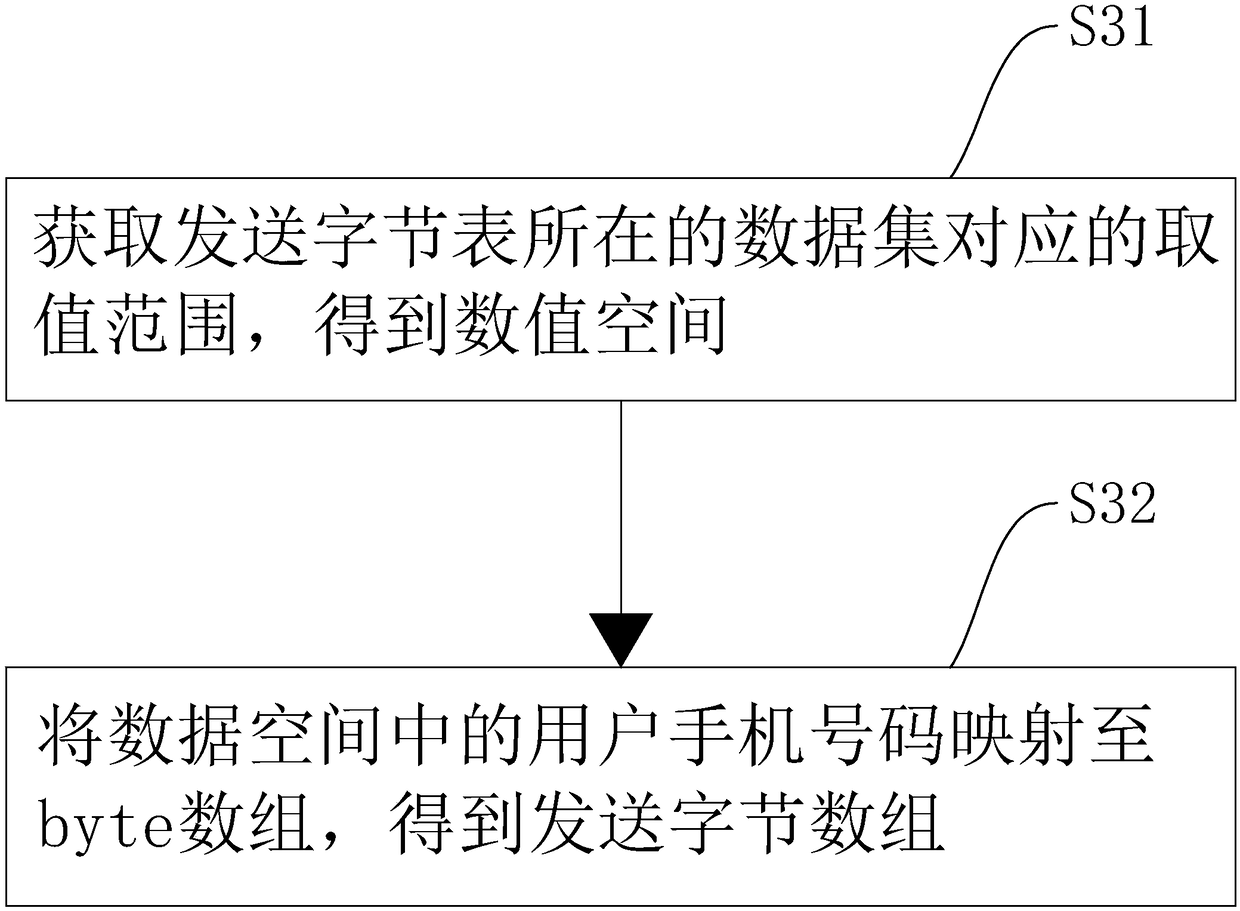
Short message group sending method and apparatus based on weighting algorithm, device and storage medium
ActiveCN109511094AReduced memory footprintImprove search efficiencyMessaging/mailboxes/announcementsMobile Telephone NumberOccupancy rate
The invention relates to the technical field of communication technology, and in particular, to a short message group sending method and apparatus based on a weighting algorithm, a device and a storage medium. The short message group sending method based on the weighting algorithm comprises the following steps: obtaining an emergency message, and obtaining emergency short message contents according to the emergency message; the emergency message comprising an emergency area, obtaining all user mobile phone numbers in the emergency area, and writing the user mobile phone numbers in a sending byte table; obtaining user mobile data through a cluster message channel, obtaining user numbers to be added and user numbers to be deleted through the weighting algorithm; adding the user numbers to beadded to the sending byte table, and deleting the user mobile phone numbers the as the user numbers to be deleted from the sending byte table to obtain a to-be-sent byte table; and sending the emergency short message contents to user mobile terminals corresponding to the user mobile phone numbers in the to-be-sent byte table. The short message group sending method and apparatus provided by the invention have the effects of improving the efficiency of searching for the user mobile phone numbers within a large-range area and reducing the memory occupancy rate.
Owner:广州市易杰数码科技有限公司
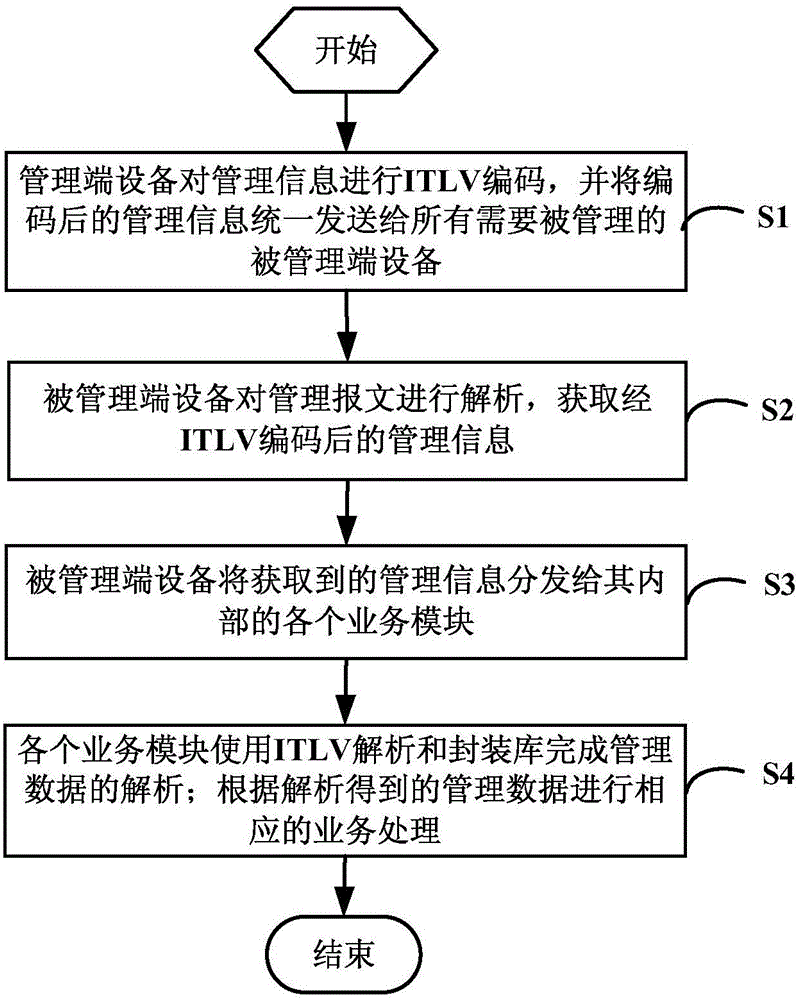
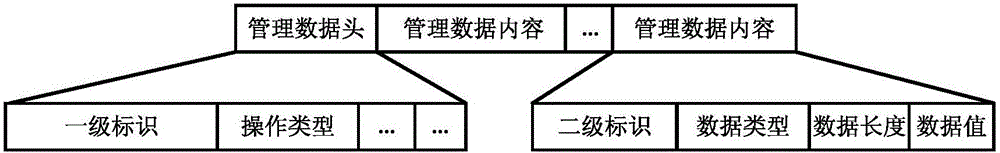
Method and system for carrying out coding transmission on management data
InactiveCN105978705ASimple codingEasy to operateError preventionData switching networksTerminal equipmentComputer module
The invention discloses a method and system for encoding and transmitting management data, and relates to the technical field of data communication. The method includes the following steps: the management device performs ITLV encoding on the management information, and uniformly sends the encoded management information to all managed devices that need to be managed; each managed device receives the information sent by the management device. After the management message, analyze the management message to obtain the management information encoded by ITLV; distribute the obtained management information to each internal business module; each business module completes the management data by using the ITLV parsing and packaging library analysis, and perform corresponding business processing according to the management data obtained from the analysis. The invention not only enables the management data to be directly identified and processed by the internal service modules of the equipment, and improves the system efficiency; but also the coding mode and the transmission mode are simple and easy to operate.
Owner:FENGHUO COMM SCI & TECH CO LTD
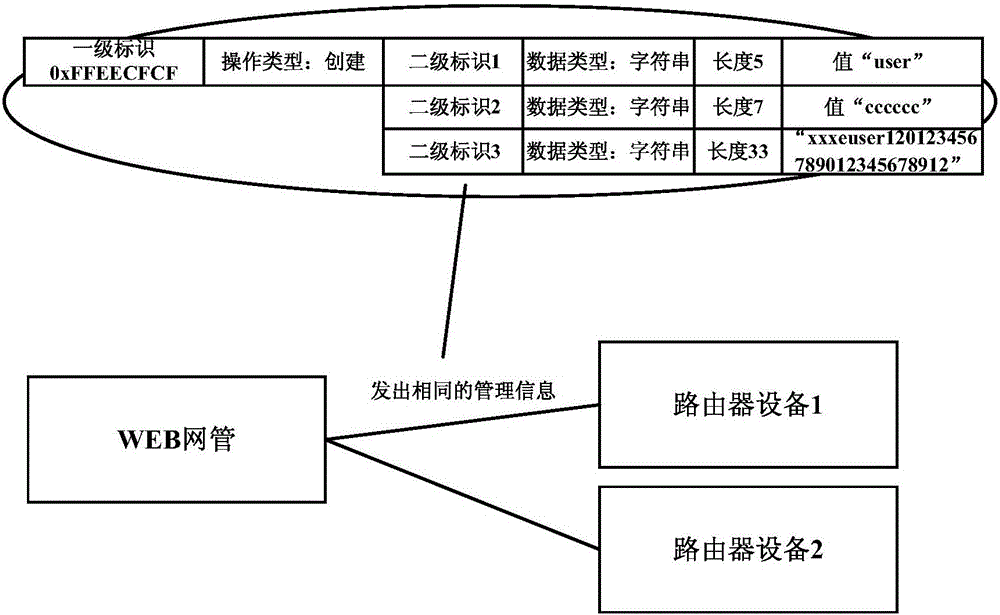
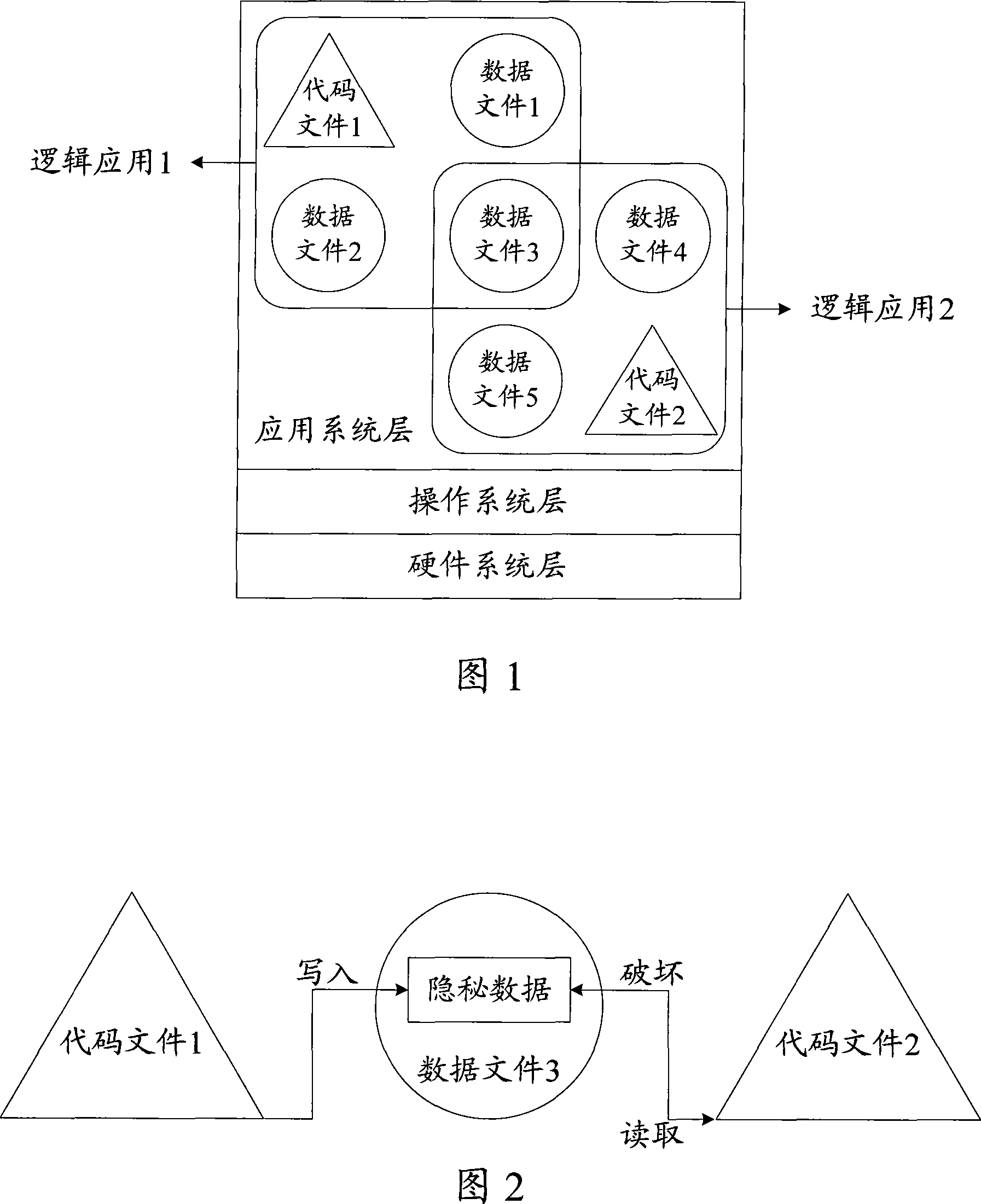
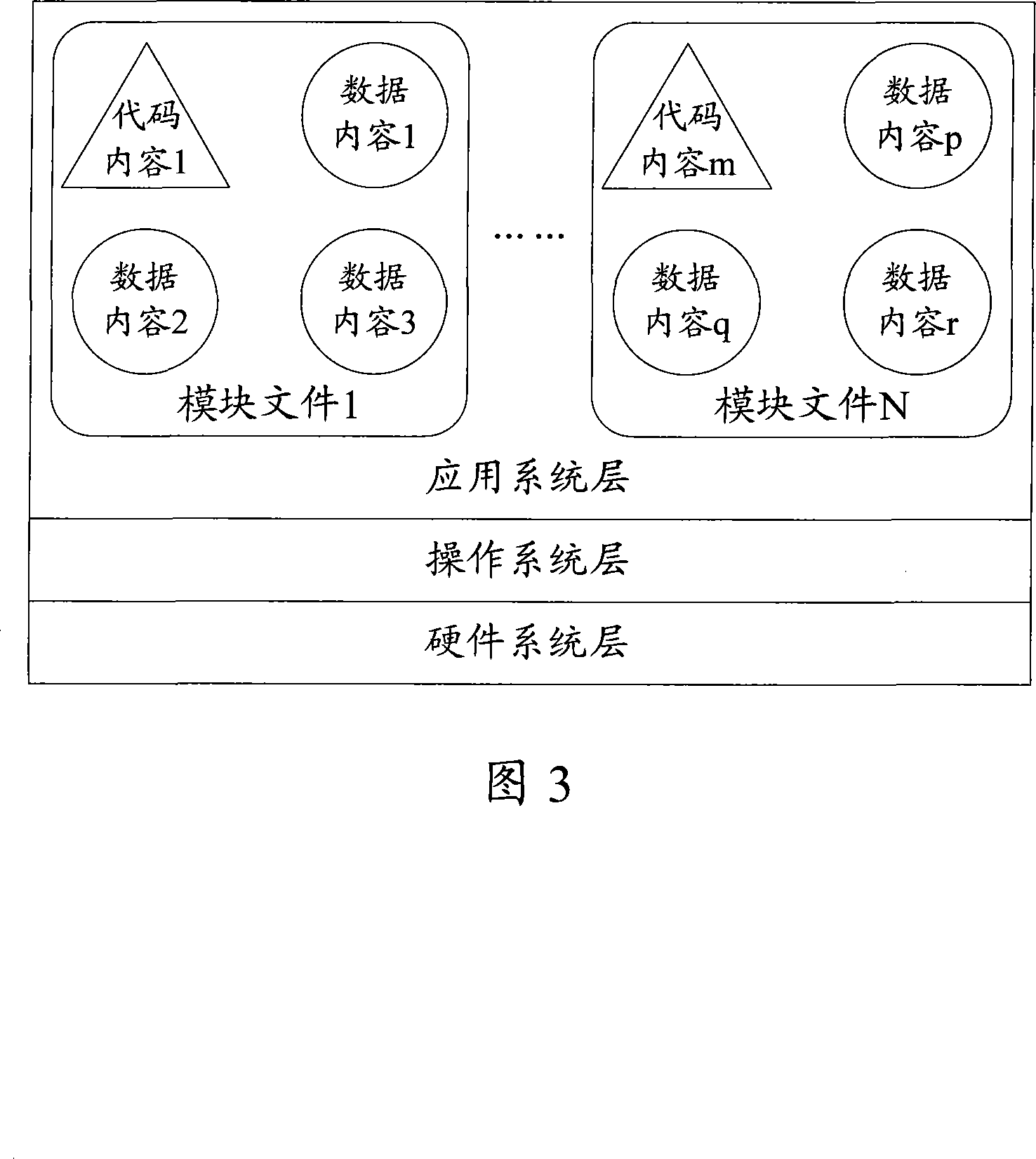
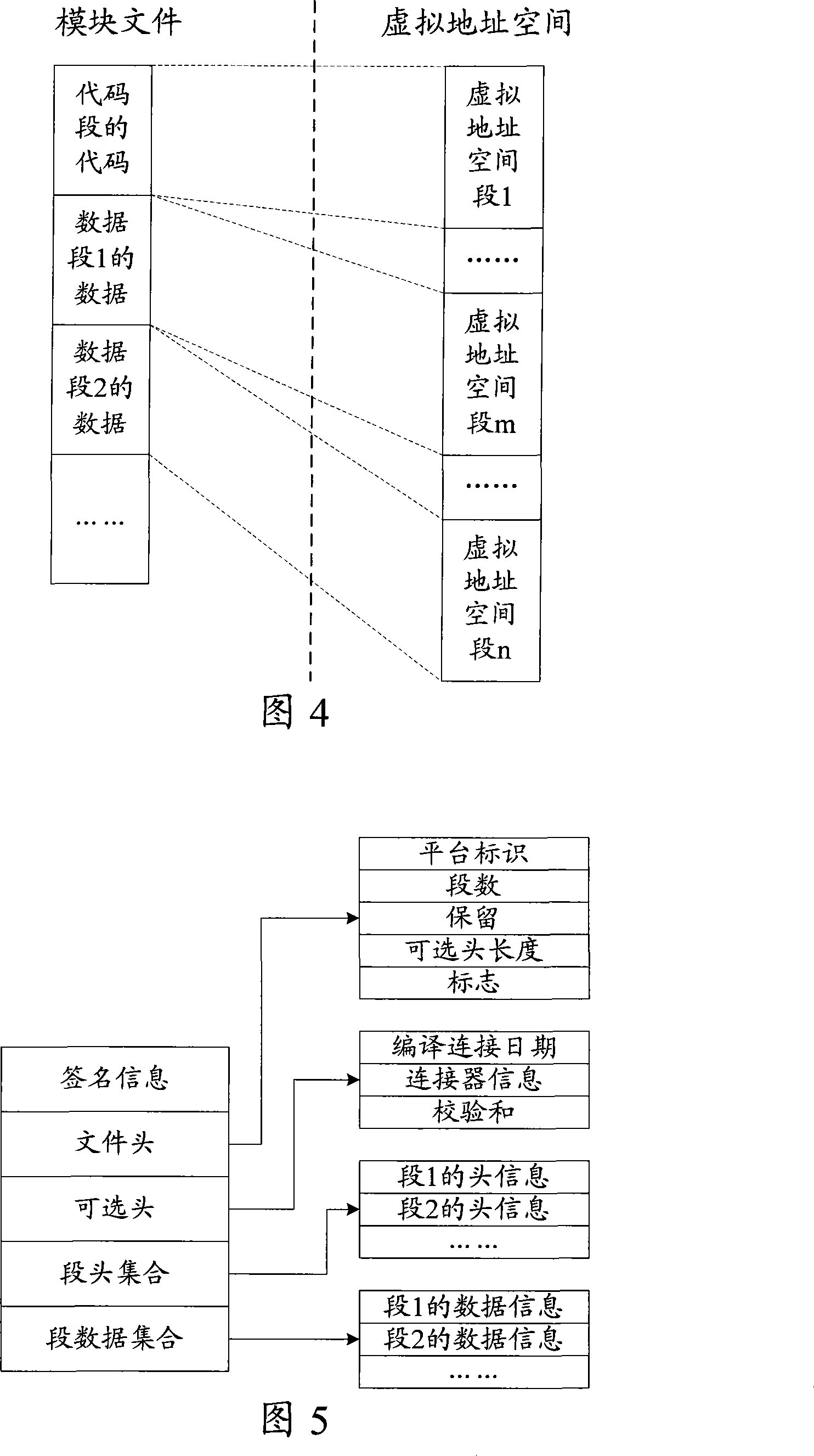
Information safety equipment and its file memory and access method
InactiveCN101196922AAvoid readingAvoid destructionSpecial data processing applicationsData segmentAccess method
The invention discloses a document store and access method in information security equipments. Code contents and data contents corresponding to the same application logic are respectively stored in a code segment and a data segment with the same module document and the code contents can only be used to access to the data contents in the data segment in the module document, therefore the code contents in each module document can not access to the data contents in other module documents to avoid that the code contents in other module documents read secret data in the module or damage the data contents in the module documents and improve the security of information security equipments. In addition, the invention does not need to set fussy addressing information in the code contents and read the data contents in a memory at first, thereby simplifying the compiling difficulty of the code contents and reducing the memory space occupied by executing code documents. The invention also discloses information security equipments which realize document store and access.
Owner:BEIJING SENSELOCK SOFTWARE TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com