Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
181results about How to "Reduce maintenance overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
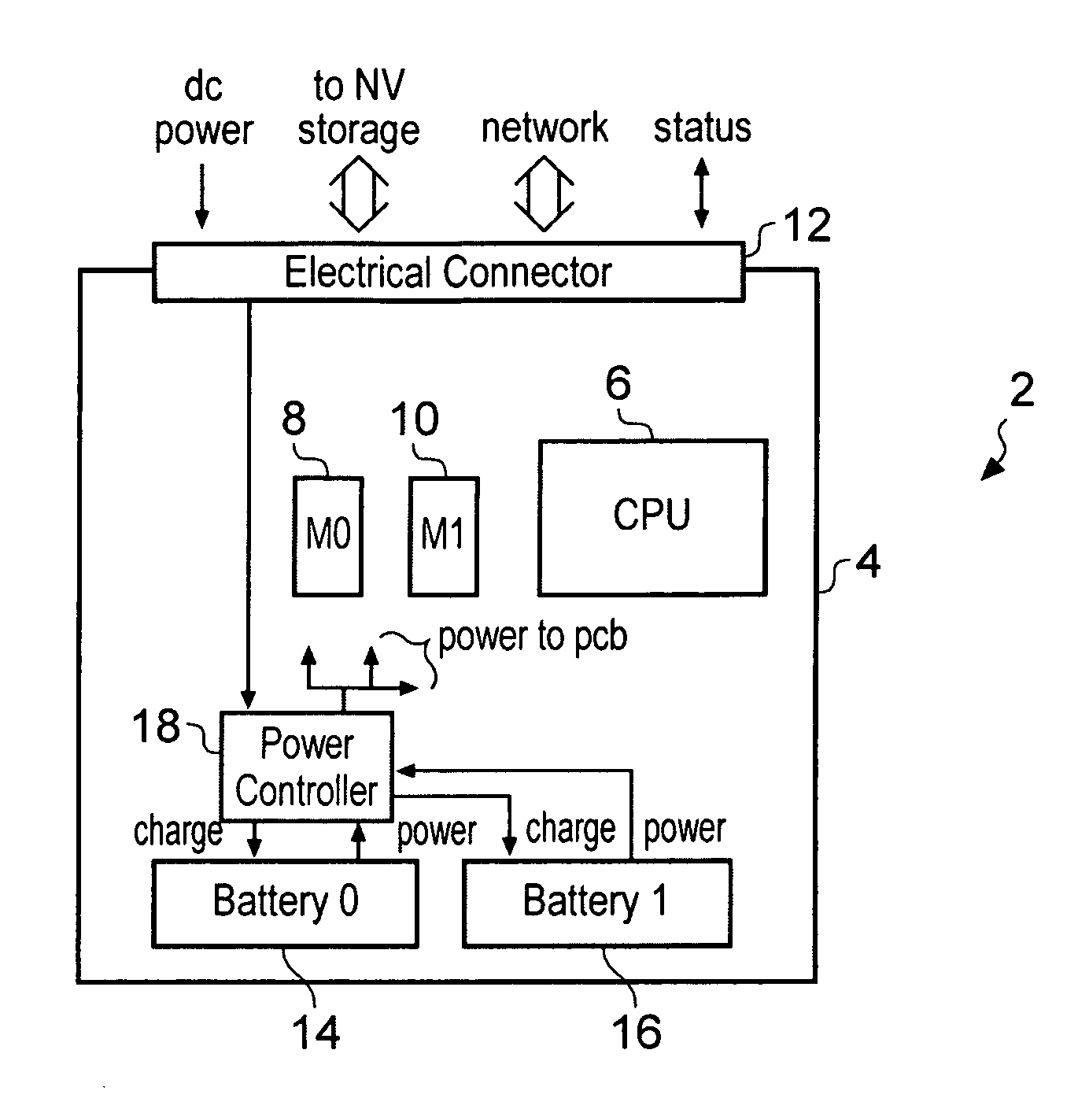
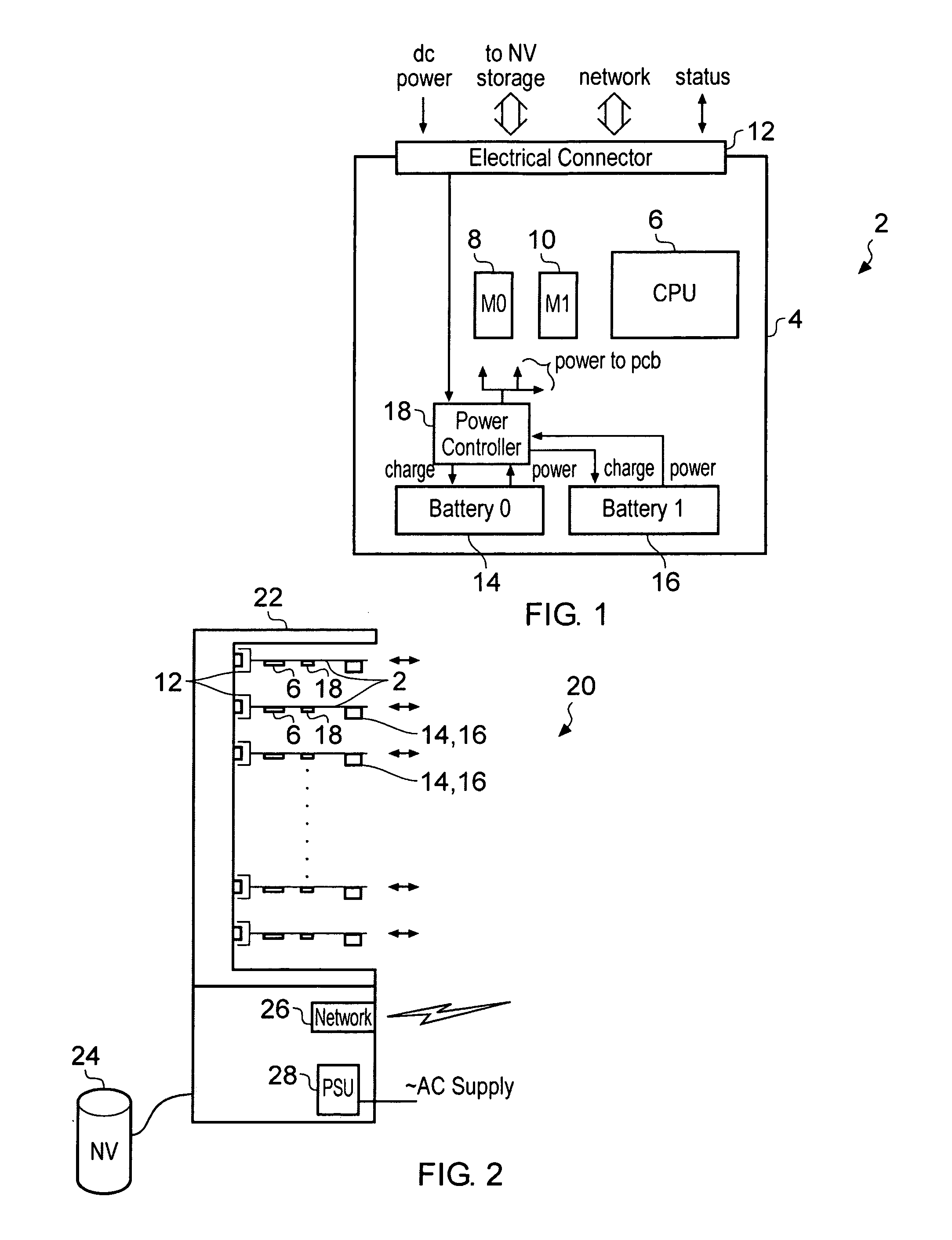
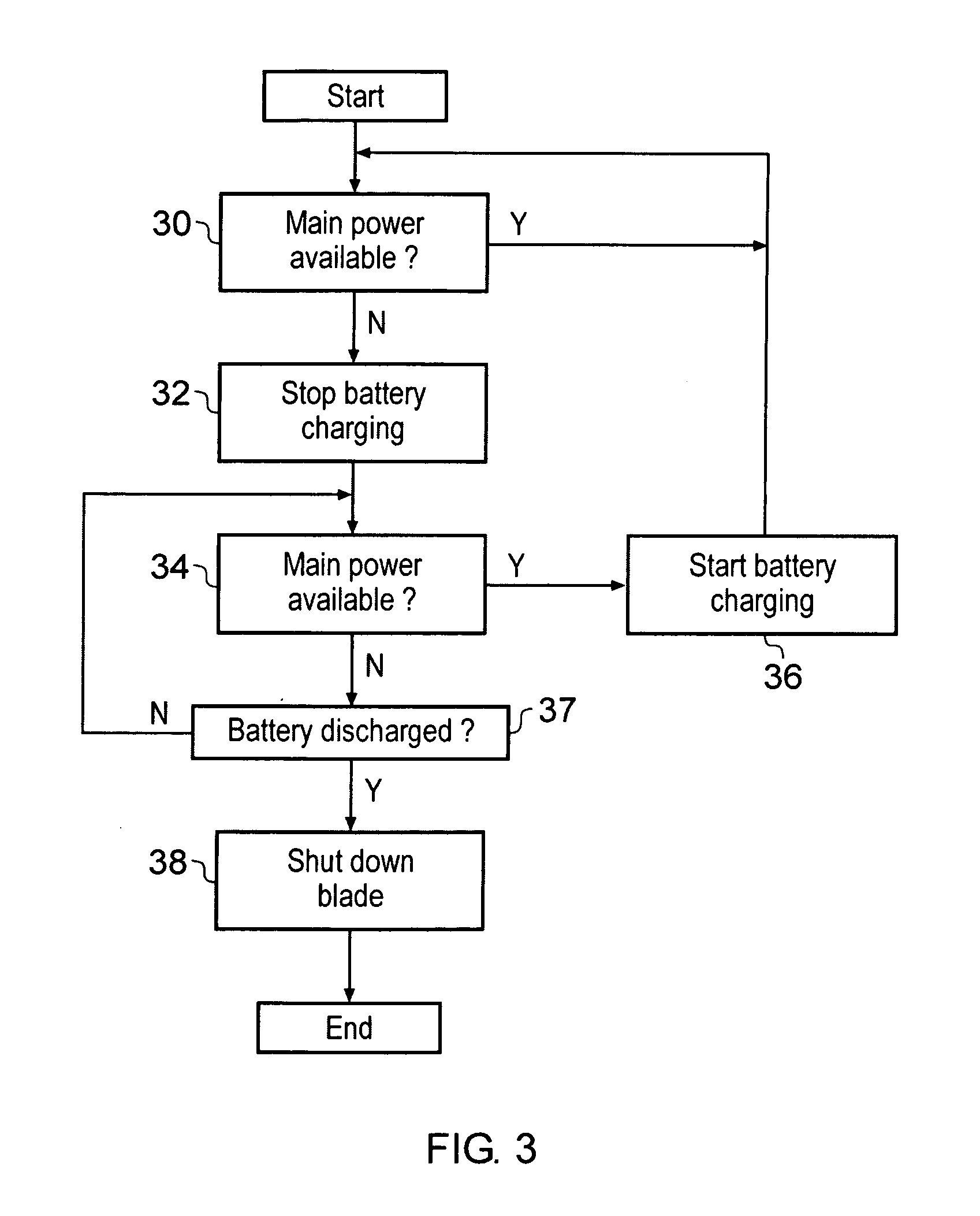
Blade server
InactiveUS20100299548A1Solve insufficient capacityMore power efficientHardware monitoringPower supply for data processingElectricityPower controller
A blade server 2 is provided with a processor 6 for executing program instructions and an electrical connector 12 for connecting to a blade enclosure 22. The blade server 2 also includes a power controller 18 connected to a plurality of power supply batteries 14, 16 which are provided on the blade server 2 itself. If the power controller 18 detects that the main power supply supplied via the electrical connector 12 has been interrupted, then a backup power supply to the processor is provided from the on-board power supply batteries 14, 16. The batteries 14, 16 on each blade are periodically discharged and recharged in turn to check their proper function.
Owner:ARM LTD
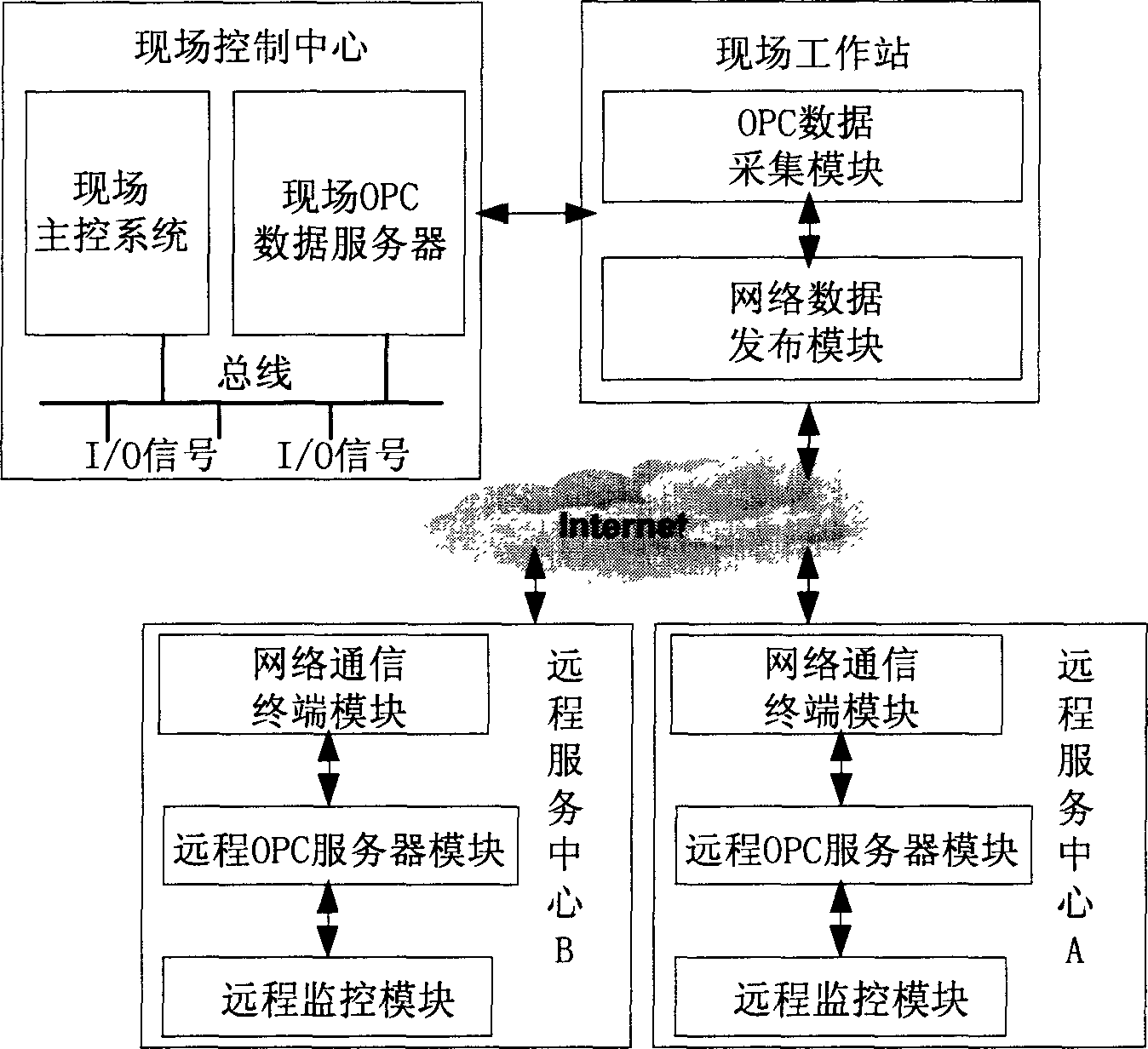
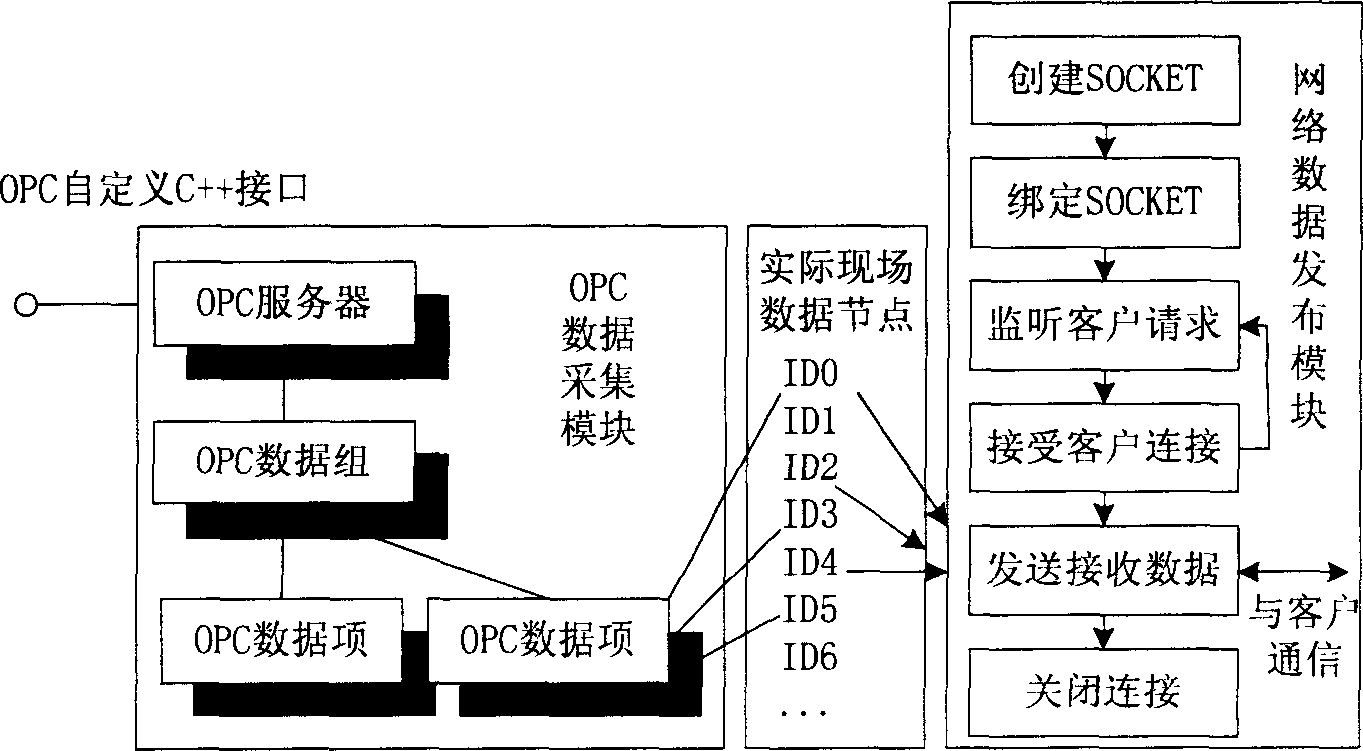
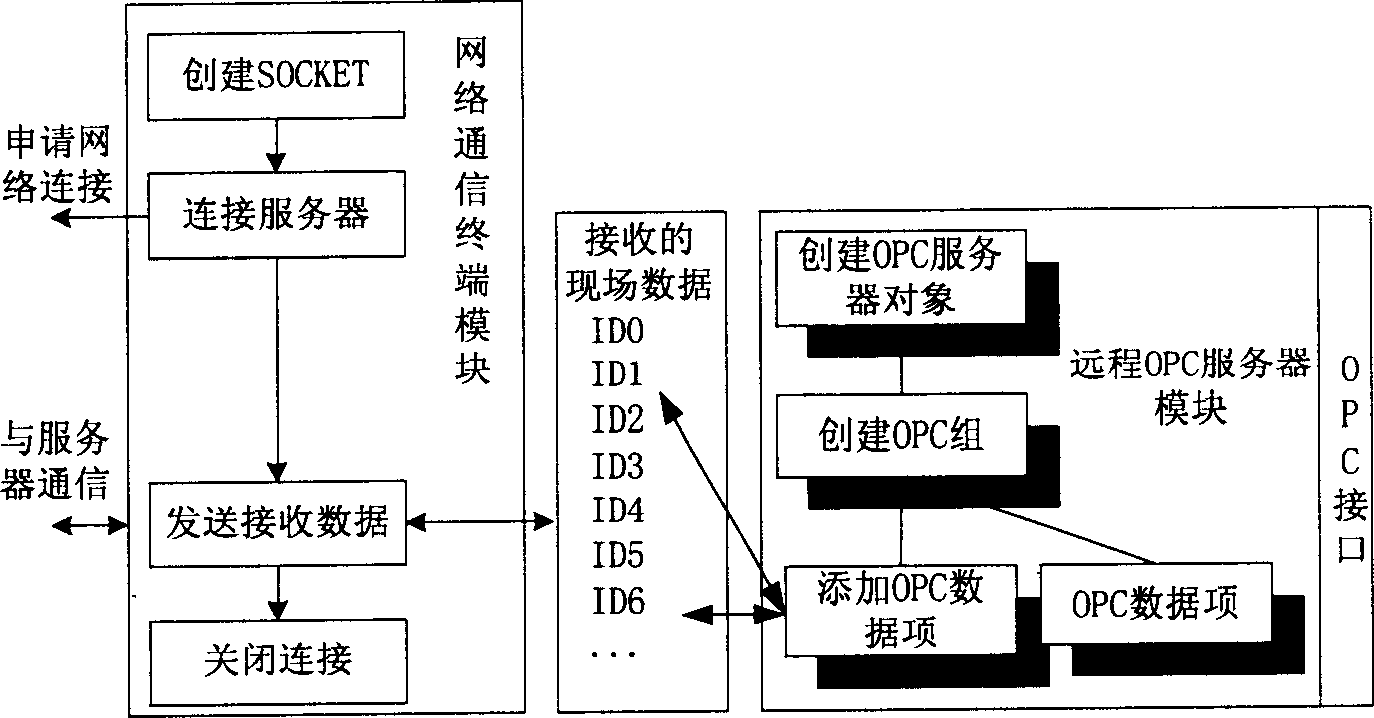
System accorded with OPC standard for monitoring remote configuration
InactiveCN1798141ATroubleshoot Remote TroubleshootingSolve problemsData switching networksTotal factory controlRemote controlData acquisition
The system includes a field working station and a remote service center. The field working station runs the OPC data collection module and the network data releasing module conforming to TCP / IP protocol by using the OPC data collection and network data releasing application program, and is connected to the field control center through OPC interface. The remote service center runs the network terminal module conforming to TCP / IP protocol, the remote OPC server module and the remote control module supporting OPC interface by using network terminal application program and the remote OPC service application program. The network communication terminal module receives the field data released by the network data releasing module, and then releases the received data to the remote OPC service module by which the data is transmitted to the remote monitoring module.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
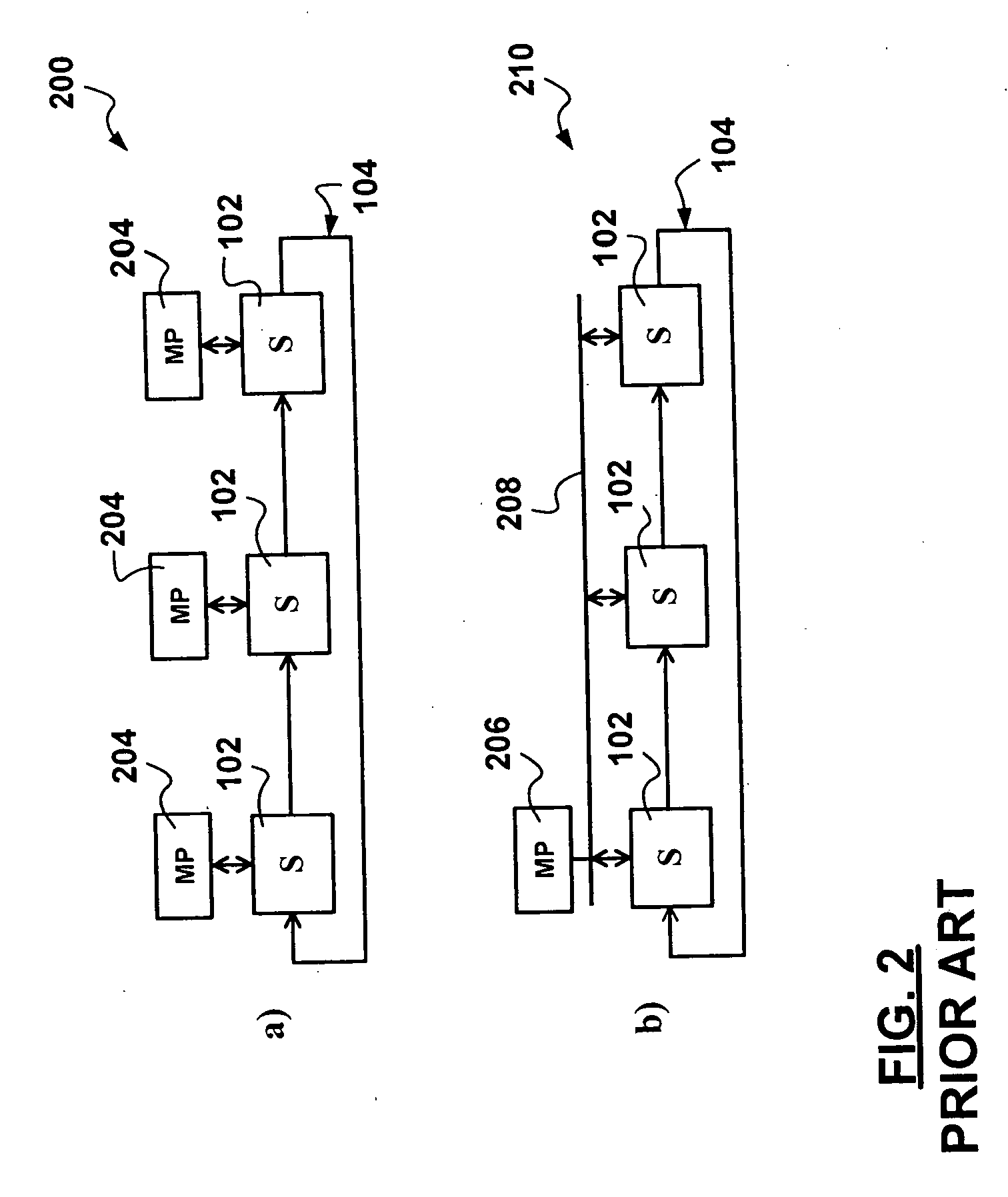
Remote control of a switching node in a stack of switching nodes
InactiveUS20060023640A1Reduce deploymentReduce configurationMultiplex system selection arrangementsData switching by path configurationExchange networkRemote control
A methods and apparatus for remote management of switching network nodes in a stack via in-band messaging are presented. Switching nodes in the stack default to reserved switching node identifiers and stacking ports default to a blocking state upon startup, restart, and reset. Each command frame received via a blocking state is forwarded to a command engine at each switching node and is acknowledged with the current switching node identifier. Each acknowledgement frame bearing the reserved network node identifier triggers configuration of the acknowledging switching node. Switching nodes and the management processor track interrupt state vectors regarding events. An interrupt acknowledgement process is employed to track raised interrupts. Configuration of switching node is performed via command frames transmitted by the management processor and destined to a command engine associated with the switching node. Services provided by the management processor are requested via control frames destined to the switching node to which the management processor is attached and destined to the management port thereof. The advantages are derived from engineered switching node deployments wherein an appropriate number of management processors, less than the number of switching nodes in the stack, are employed to provide services to corresponding switching nodes in the stack, based on processing, control, and configuration bandwidth requirements. The in-band configuration and control of the switching nodes in the stack reduce deployment, configuration, management, and maintenance overheads.
Owner:SYNAPTICS INC
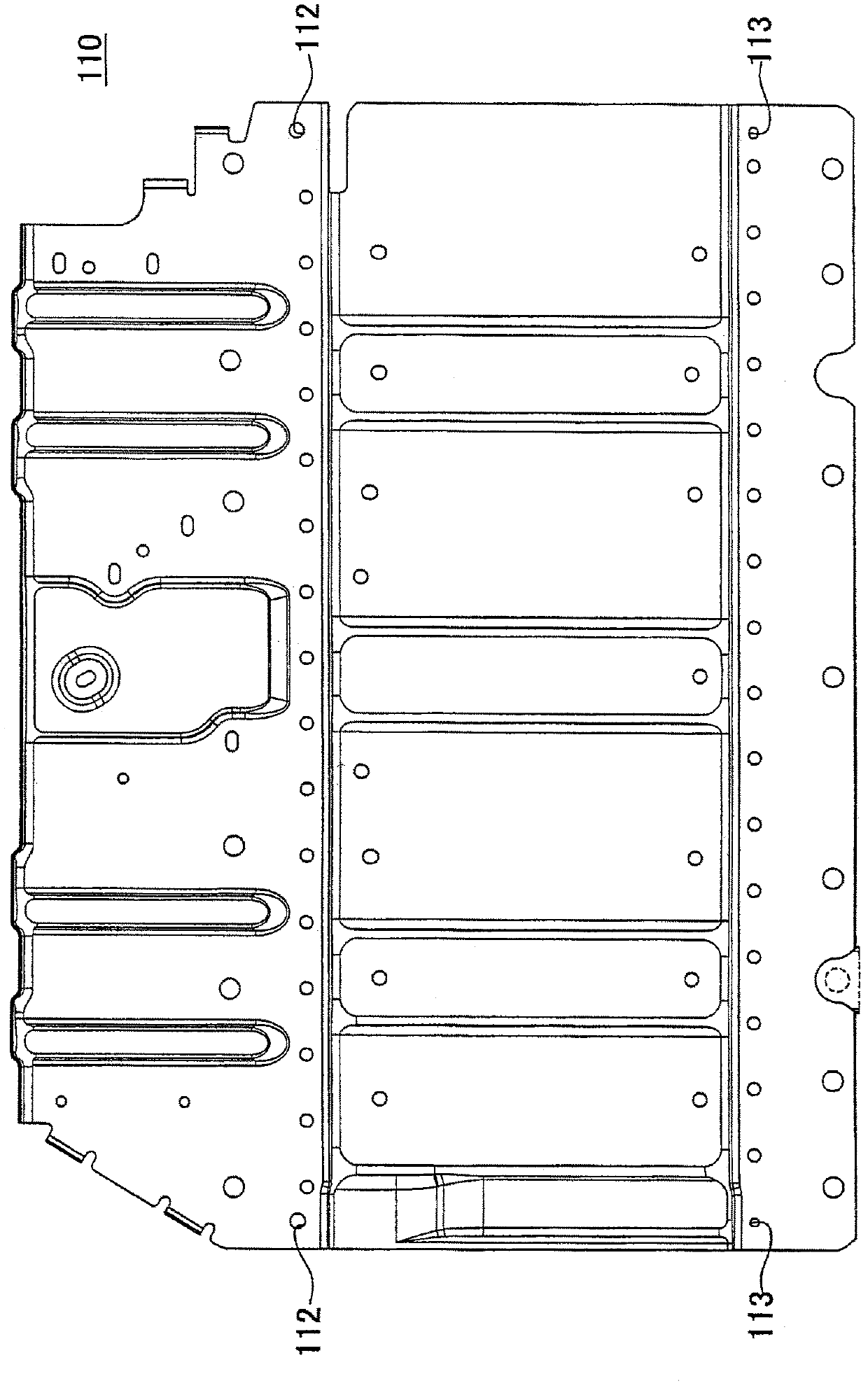
Assembly pallet for secondary battery and method for producing secondary battery
InactiveCN102893426AAct as a supportExtend your lifeSmall-sized cells cases/jacketsLarge-sized cells cases/jacketsBattery cellPallet
In order to provide an assembly palette for a secondary battery that can support plural types of secondary batteries, an assembly palette (200) for a secondary battery is used for a secondary battery having end plates (101) disposed on both ends of battery cells (103) that are lined up and a lower case (110) disposed on the bottom. This assembly palette (200) has a main positioning pin (201) and an auxiliary positioning pin (202) which determine the position of the end plates (101), seating face pins (203) that support the secondary battery stack assembly (105), and a base (210). The main positioning pin (201) is affixed to the base (210), and the auxiliary positioning pin (202) is held movably in the base (210).
Owner:TOYOTA JIDOSHA KK
Satellite network based on distributed-type SDN and construction method thereof
ActiveCN107294592ARealize Converged DeploymentReduce the burden onRadio transmissionData switching networksTotal delaySurvivability
Owner:DALIAN UNIVERSITY
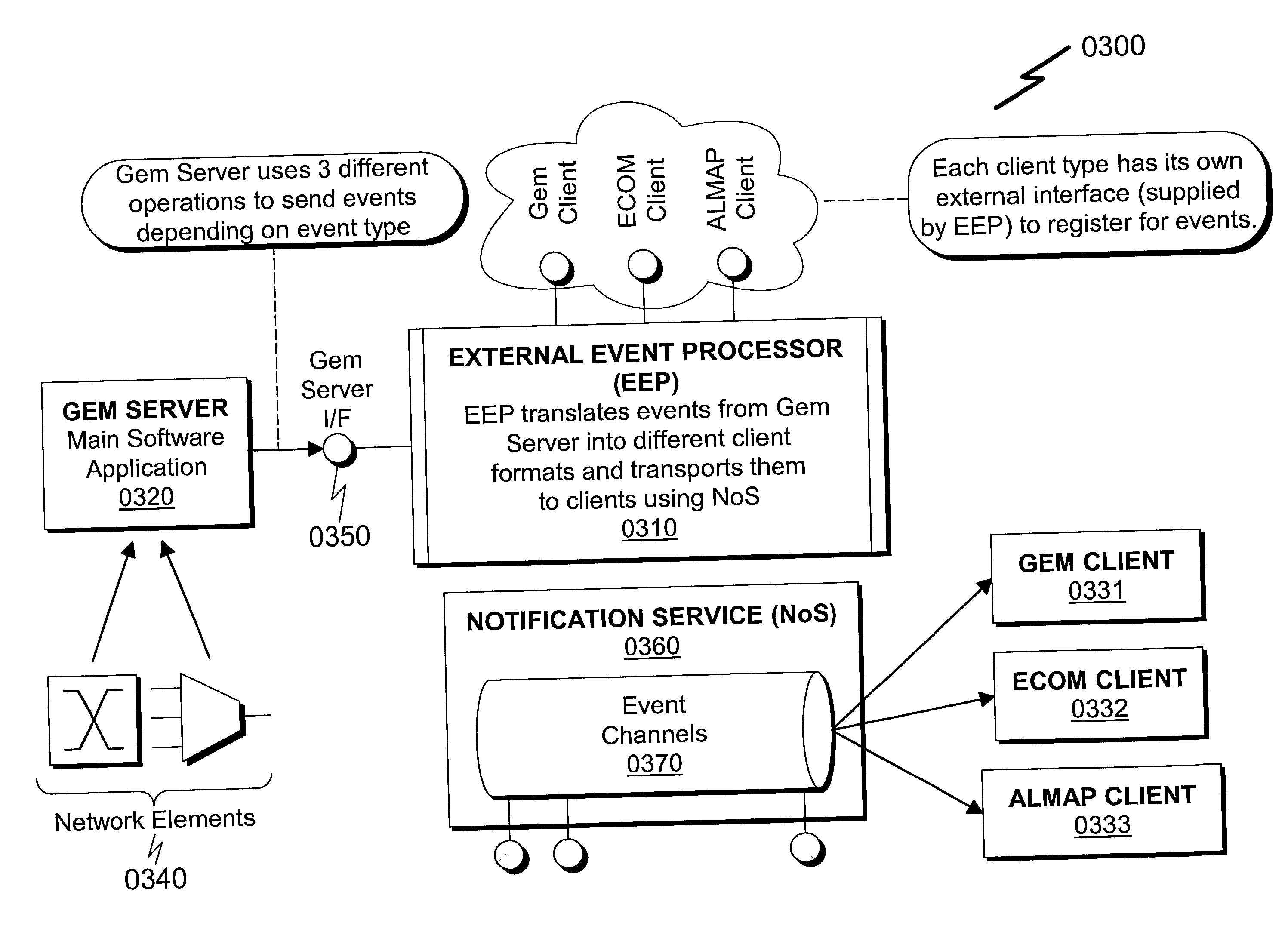
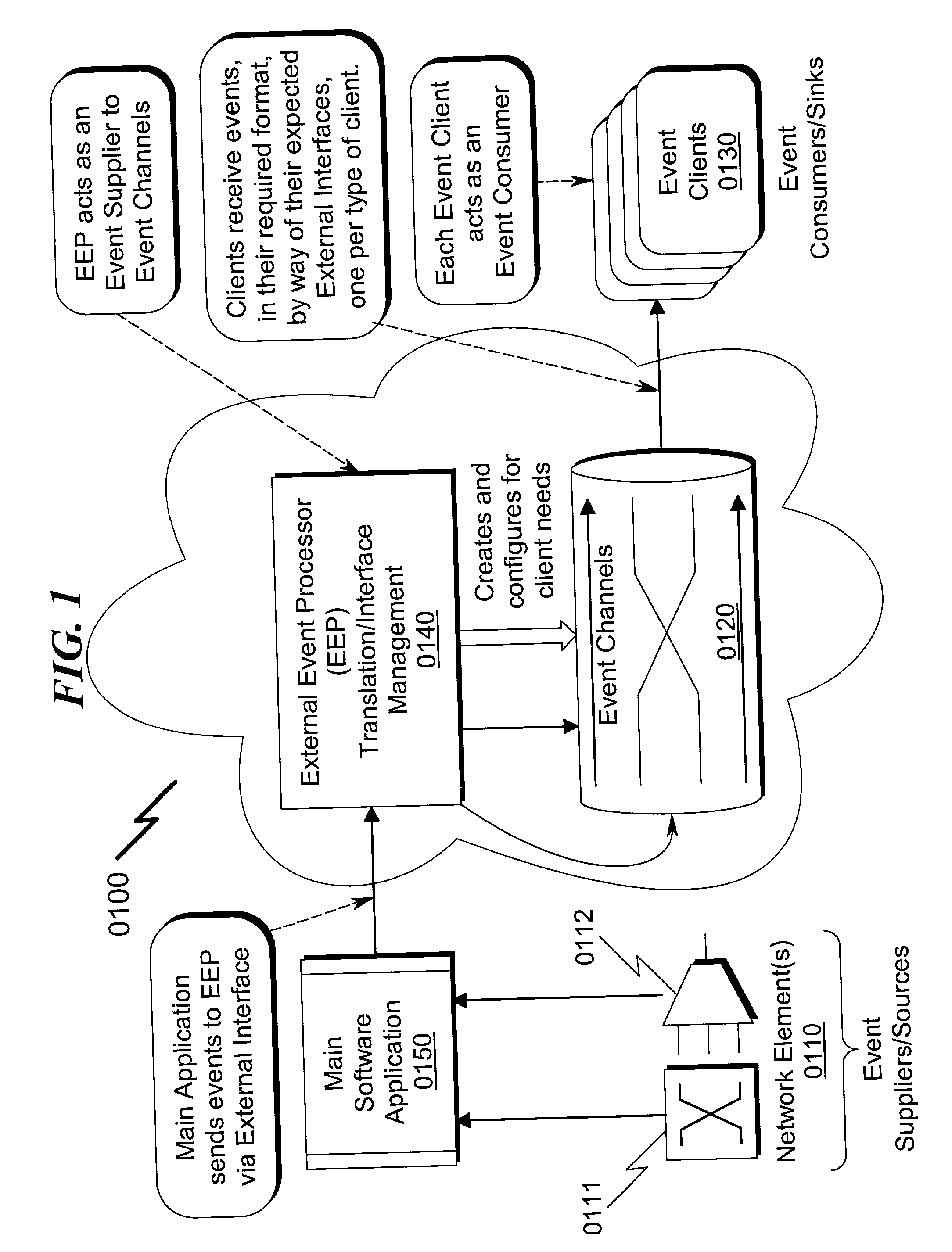
External event processor system and method
InactiveUS20030050983A1Avoid problemsLittle and no lossMultiprogramming arrangementsMultiple digital computer combinationsQuality of serviceComputer hardware
An External Event Processor (EEP) system and method incorporating a separate software component that permits reformatting of received events and transportation of these events to previously registered event consumers is disclosed. The present invention teaches creation of a separate software component to handle event processing and transportation, running within a separate software process. This separate software process has a remote interface utilized by a Network Management application to send events in their most basic form to the External Event Processor (EEP). Subsequently, the EEP performs all other functions that are necessary to convert the supplied even to the proper form and type required by the external event consumers. In addition, the EEP provides the event with Quality of Service (QoS) properties required by external consumers.
Owner:ALCATEL SOCIETE ANONYME
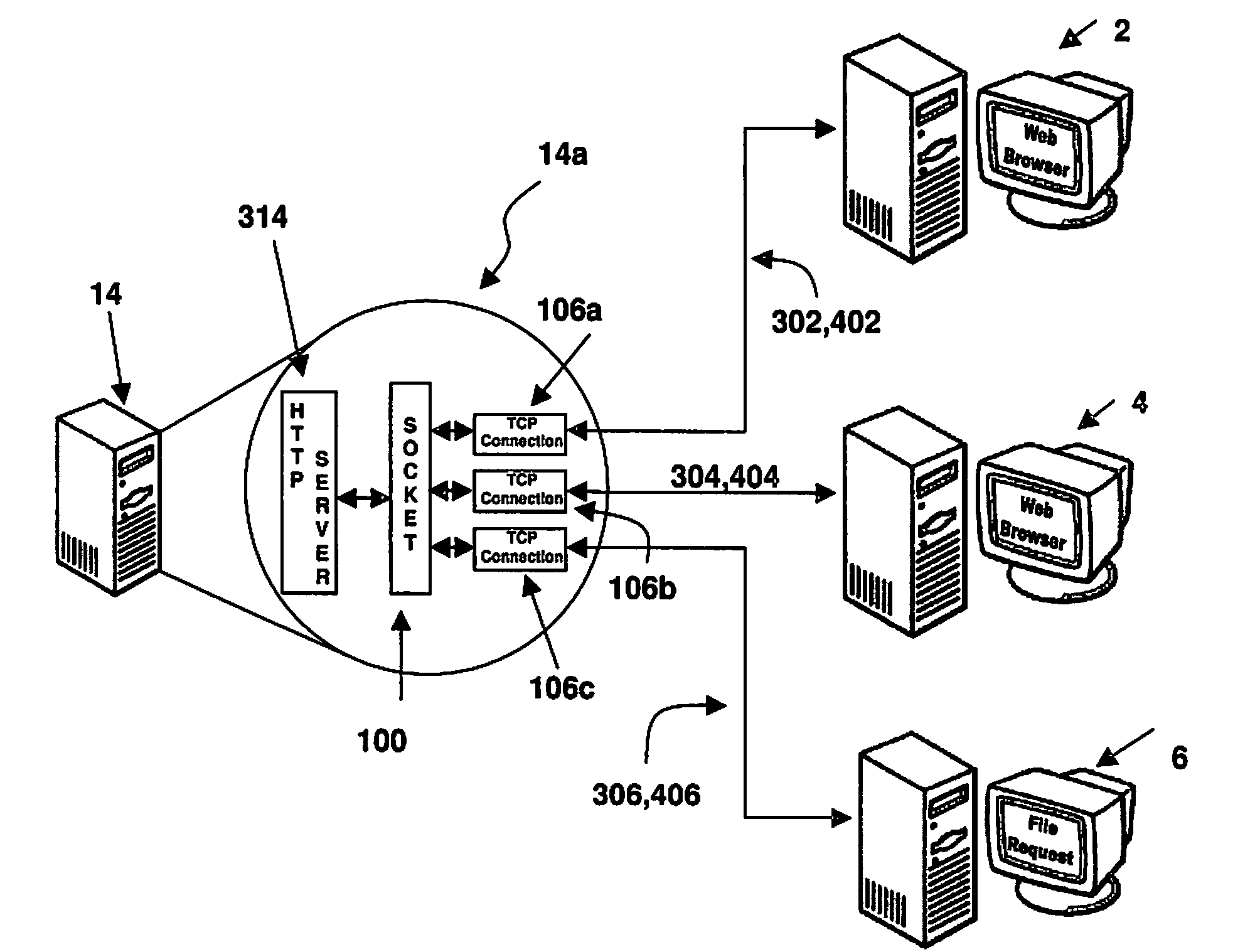
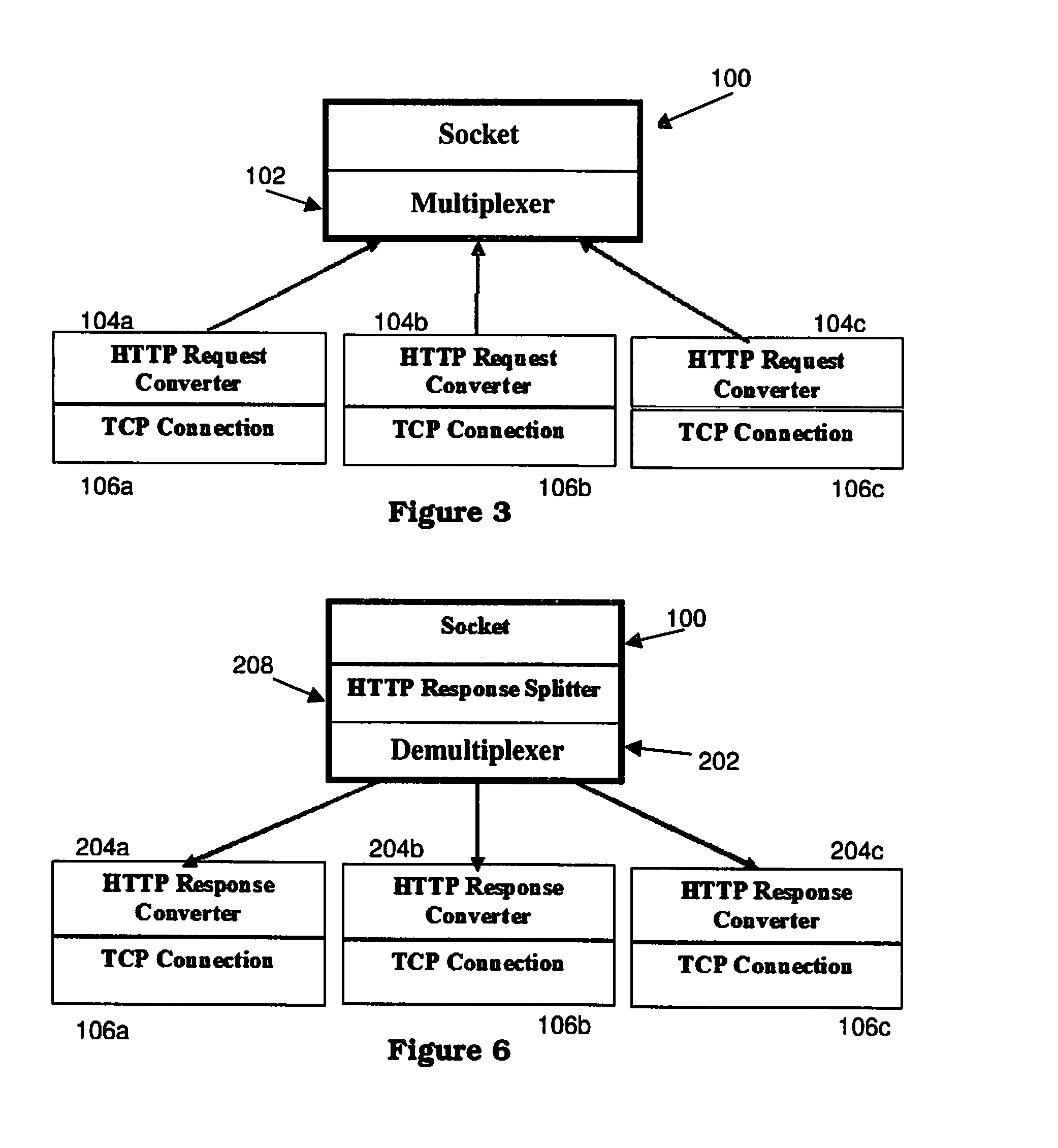
Multiplexing Multiple Client Connections in a Single Socket
InactiveUS20080114882A1Increase capacityAdding expenseMultiple digital computer combinationsTransmissionMultiplexingMultiplexer
An apparatus, program product and method allow for multiple connections to communicate with a server through a single socket without the need for a proxy. A plurality of client connections is associated with a socket. A multiplexer is utilized to multiplex in the socket a plurality of requests received from at least a subset of the plurality of client connections, and to demultiplex in the socket a plurality of responses to such requests and route the plurality of responses to the appropriate client connections.
Owner:IBM CORP
Message processing method and system for software-defined network
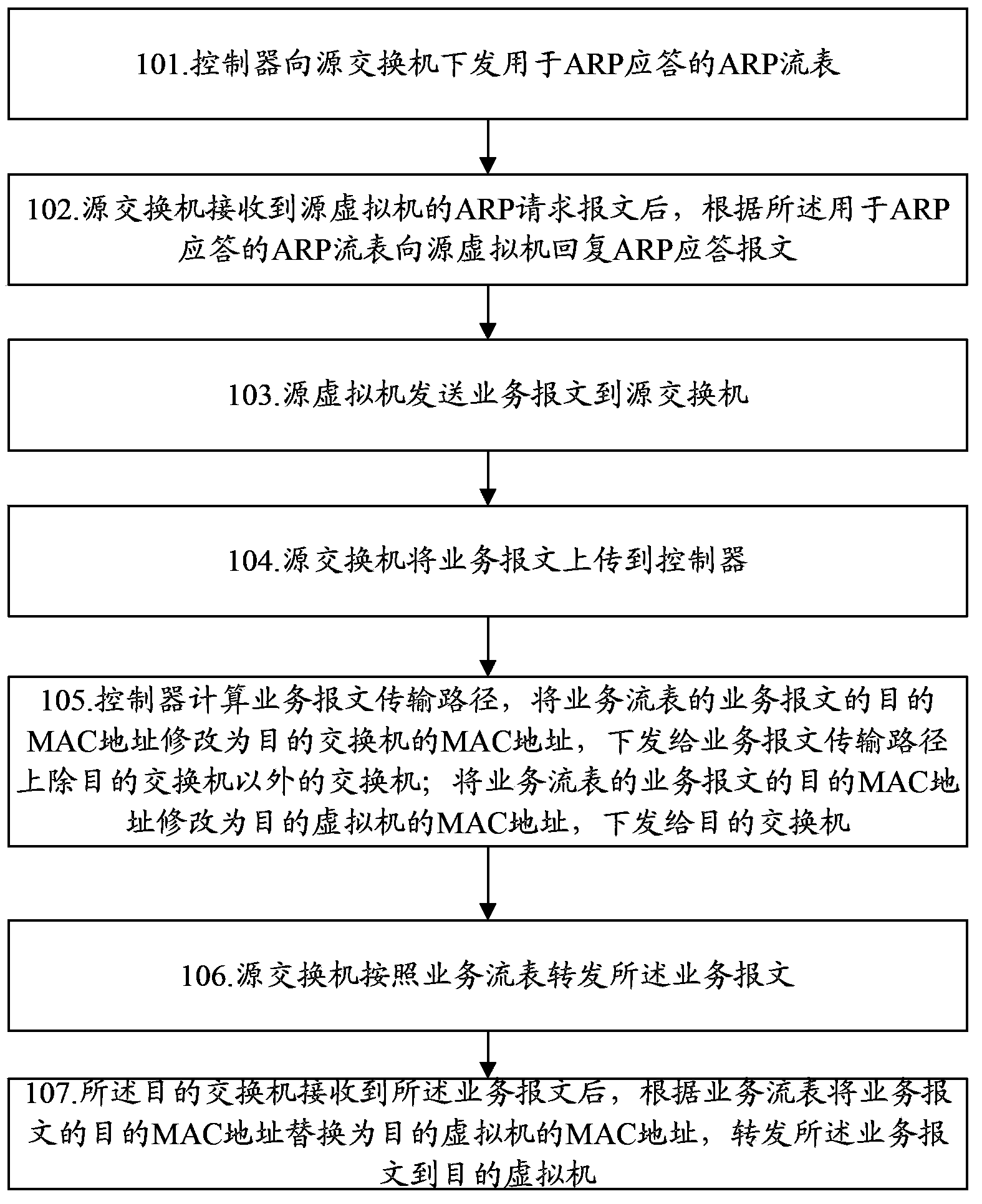
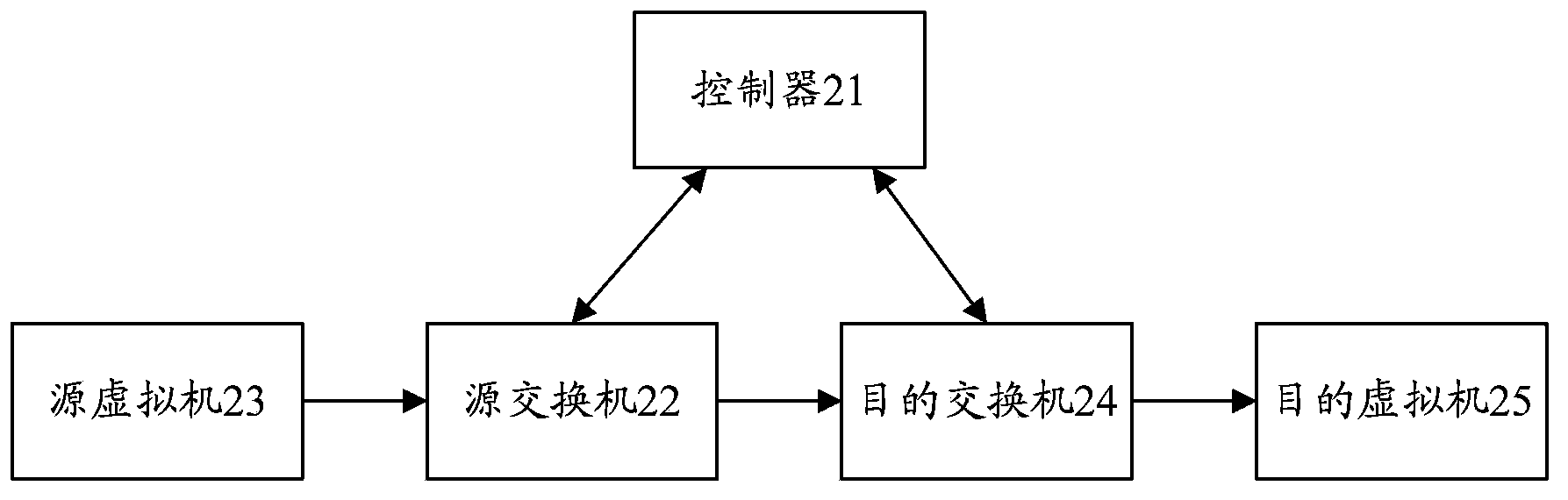
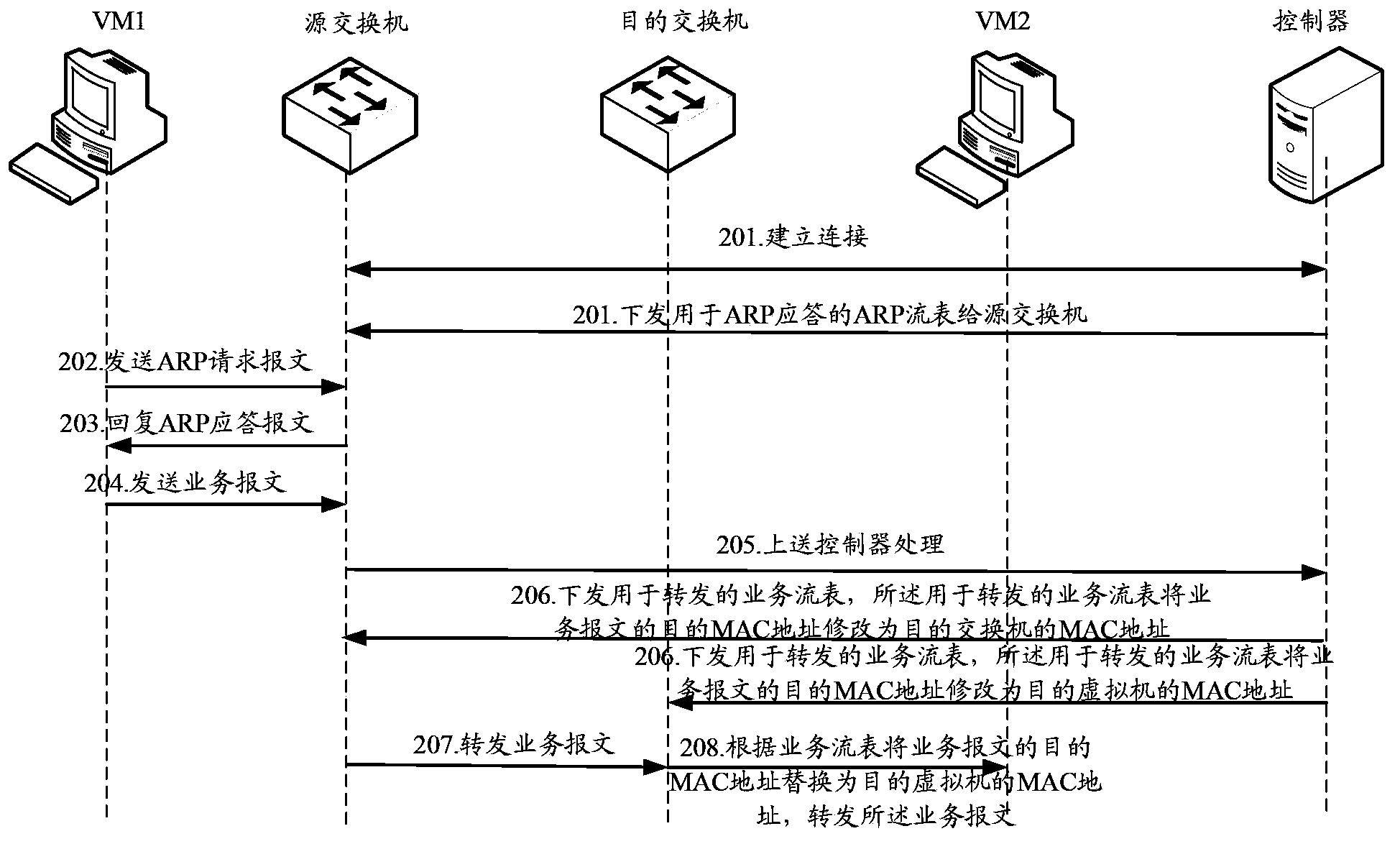
ActiveCN103905317AReduce maintenance overheadData switching networksService flowAddress Resolution Protocol
The invention discloses a message processing method for a software-defined network. A controller issues an ARP flow table for ARP responses to a source interchanger; the source interchanger returns ARP response messages to a source virtual machine according to the ARP flow table; the source virtual machine sends service messages to the source interchanger; the source interchanger uploads the service messages to the controller; the controller issues an MAC address service flow table with a target MAC address as a target interchanger to other interchangers excepts the target interchanger; a service flow table with the target MAC address as the MAC address of the target virtual machine is issued to the target interchanger; the source interchanger forwards the service messages according to the service flow table; the target interchanger forwards the service messages to the target virtual machine. The invention further discloses a message processing system for the software-defined network. Through the scheme of the message processing method and system for the software-defined network, maintenance expenses on the ARP flow table by the source interchanger can be reduced.
Owner:ZTE CORP
Data center, method for processing data and network controller
The invention discloses a data center, a method for processing data and a network controller. In the data center based on an SDN, a server generates a corresponding data packet according to protocols supported by the server; a switch receiving the data packet determines that the data packet is a first data packet in a data stream to which the data packet belongs, and the network controller generates a forwarding path according to the type of a data packet forwarding port; other data packets in the data stream to which the data packet belongs are forwarded through the generated forwarding path. According to the method, the type of the data stream is recognized according to the type of the data packet forwarding port, an optimal forwarding path suitable for the data stream is planned, different service grade qualities are matched for different data streams, the bottleneck of data transmission is avoided, and maintenance cost is reduced. Through the data center based on the SDN, the complexity of an original data center is lowered.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
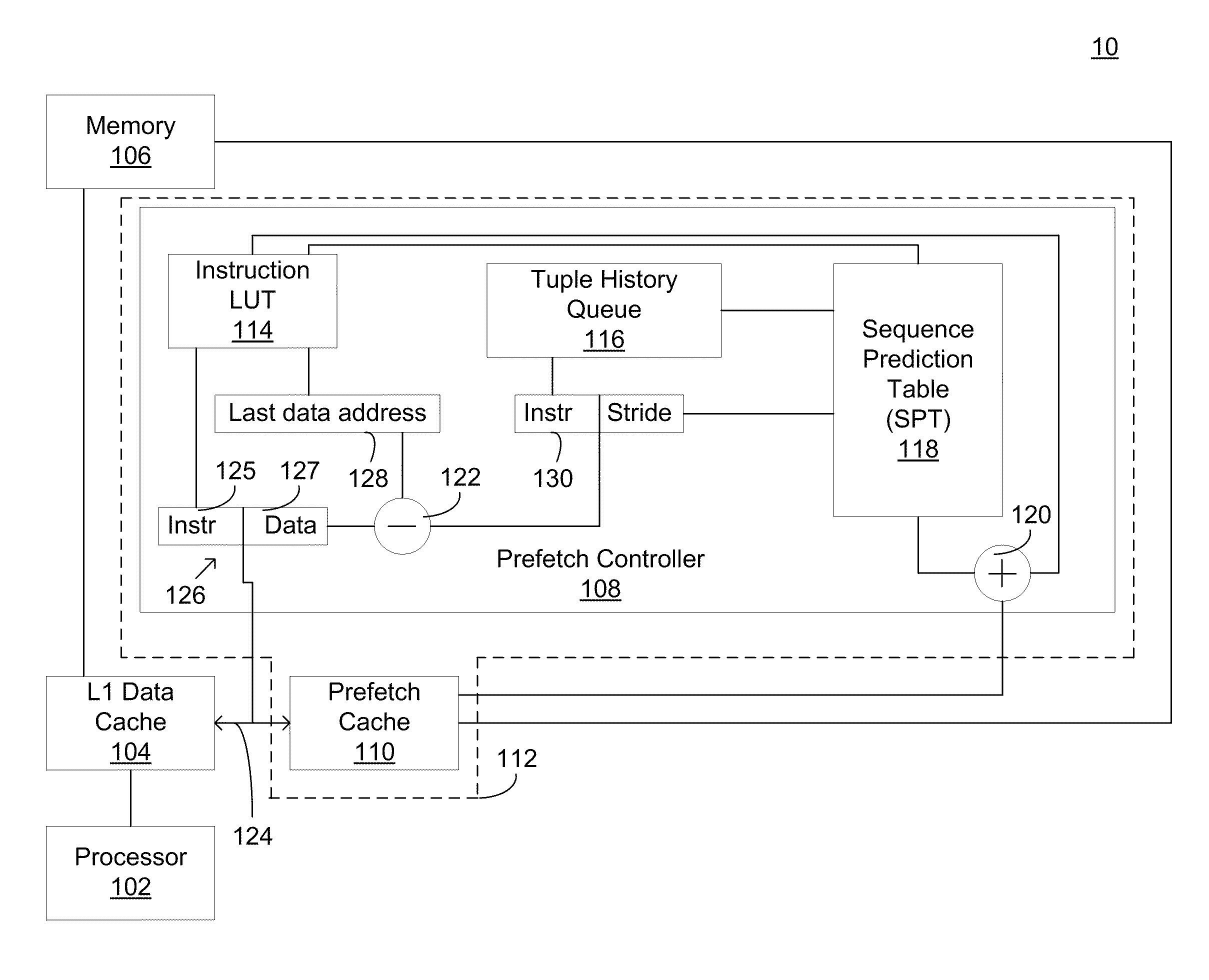
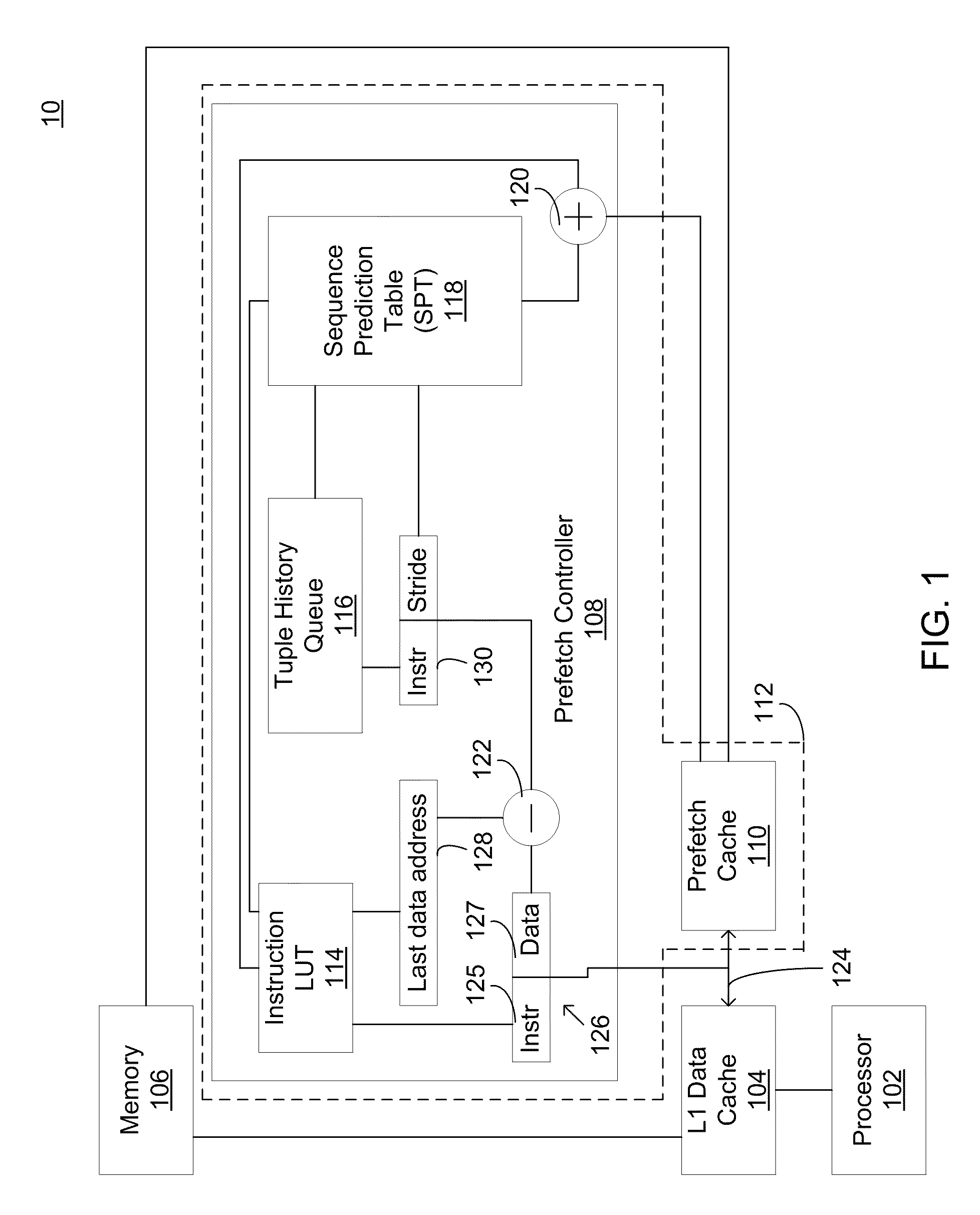
System and method for prefetching data
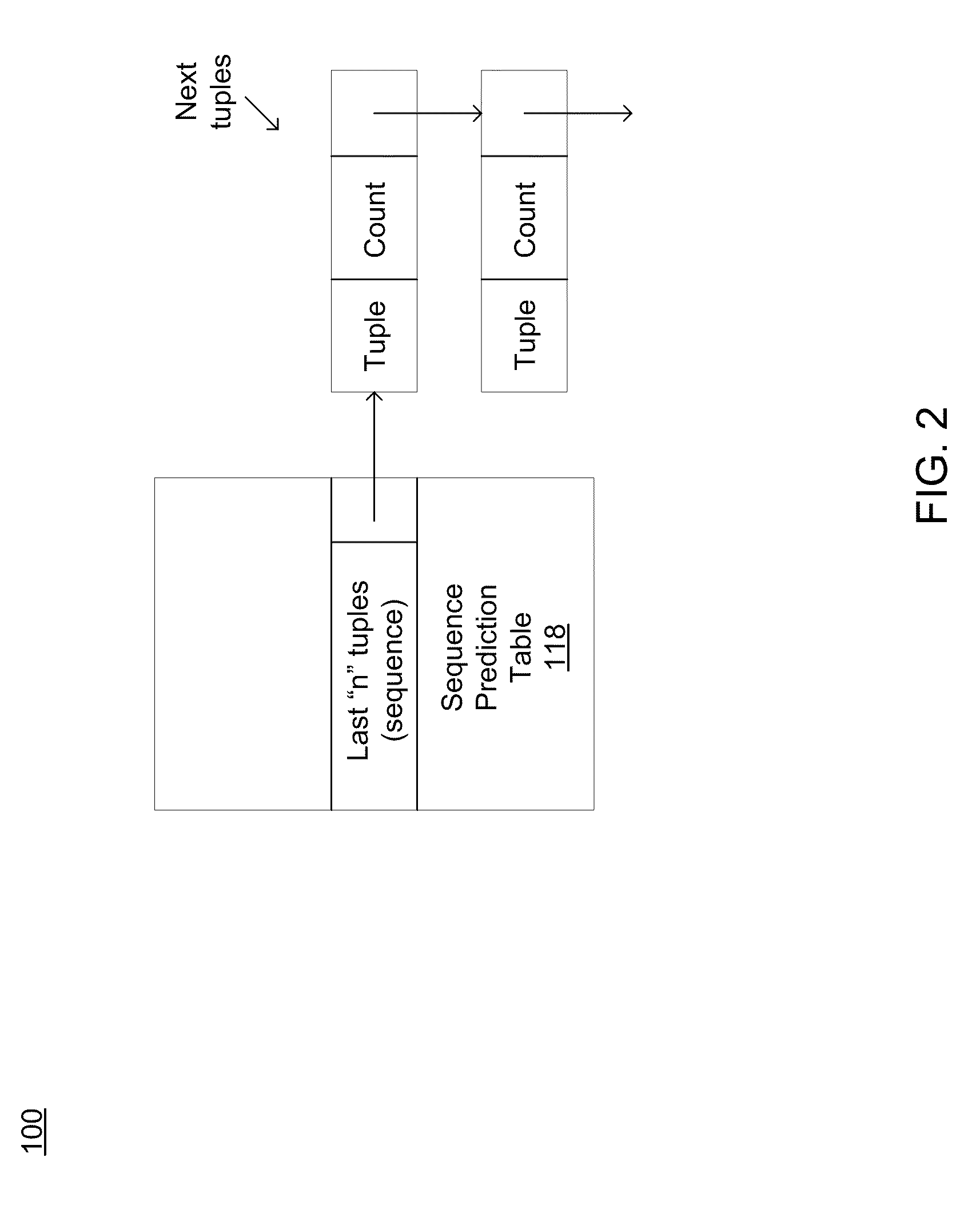
ActiveUS20100153653A1Accurate predictionReduce in quantityMemory architecture accessing/allocationMemory adressing/allocation/relocationMissing dataData access
The present disclosure is directed towards a prefetch controller configured to communicate with a prefetch cache in order to increase system performance. In some embodiments, the prefetch controller may include an instruction lookup table (ILT) configured to receive a first tuple including a first instruction ID and a first missed data address. The prefetch controller may further include a tuple history queue (THQ) configured to receive an instruction / stride tuple, the instruction / stride tuple generated by subtracting a last data access address from the first missed data address. The prefetch controller may further include a sequence prediction table (SPT) in communication with the tuple history queue (THQ) and the instruction lookup table. The prefetch controller may also include an adder in communication with the instruction lookup table (ILT) and the sequence prediction table (SPT) configured to generate a predicted prefetch address and to provide the predicted prefetch address to a prefetch cache. Numerous other embodiments are also within the scope of the present disclosure.
Owner:IBM CORP
Wireless local area network on-site bus network control station
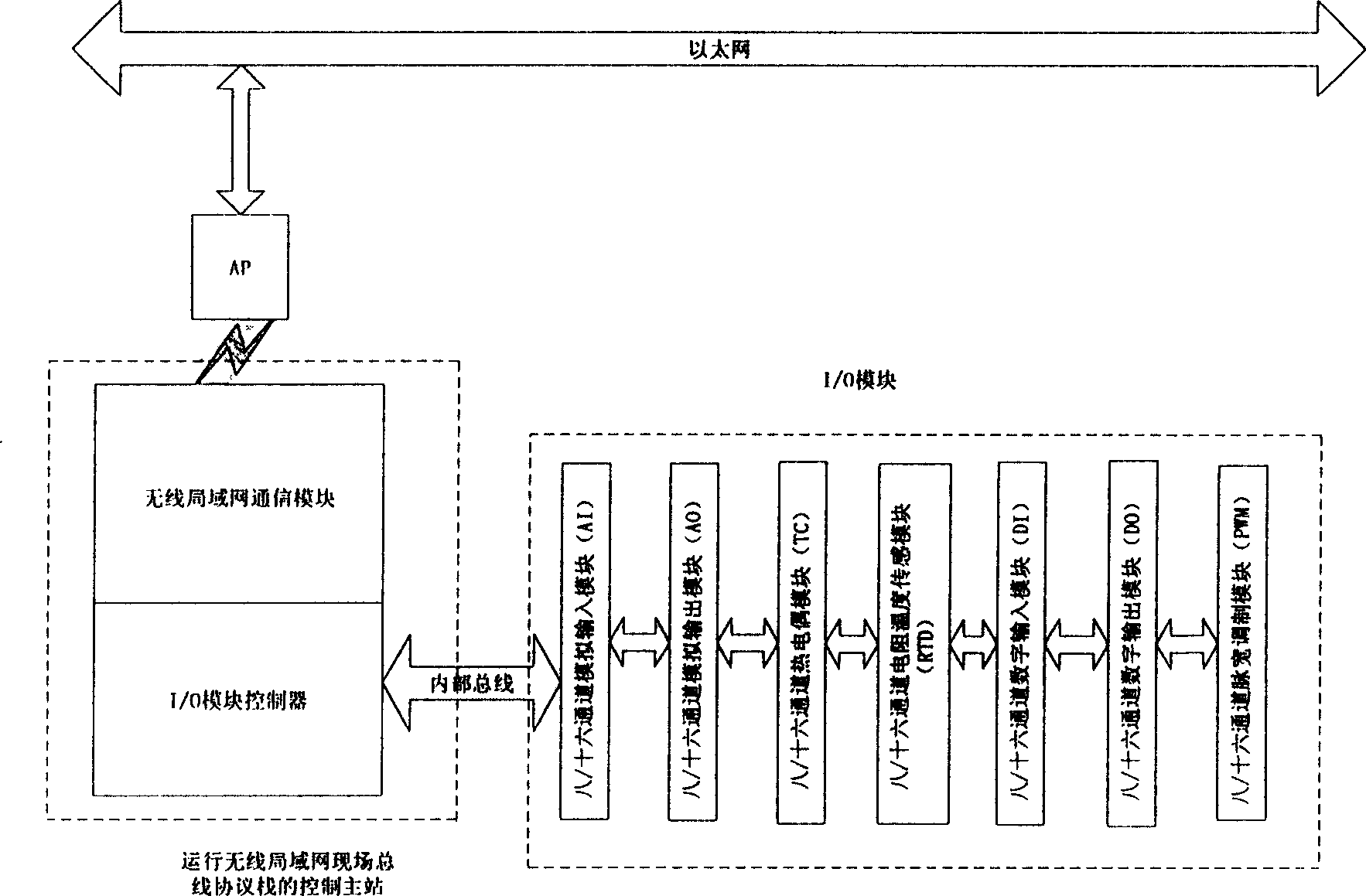
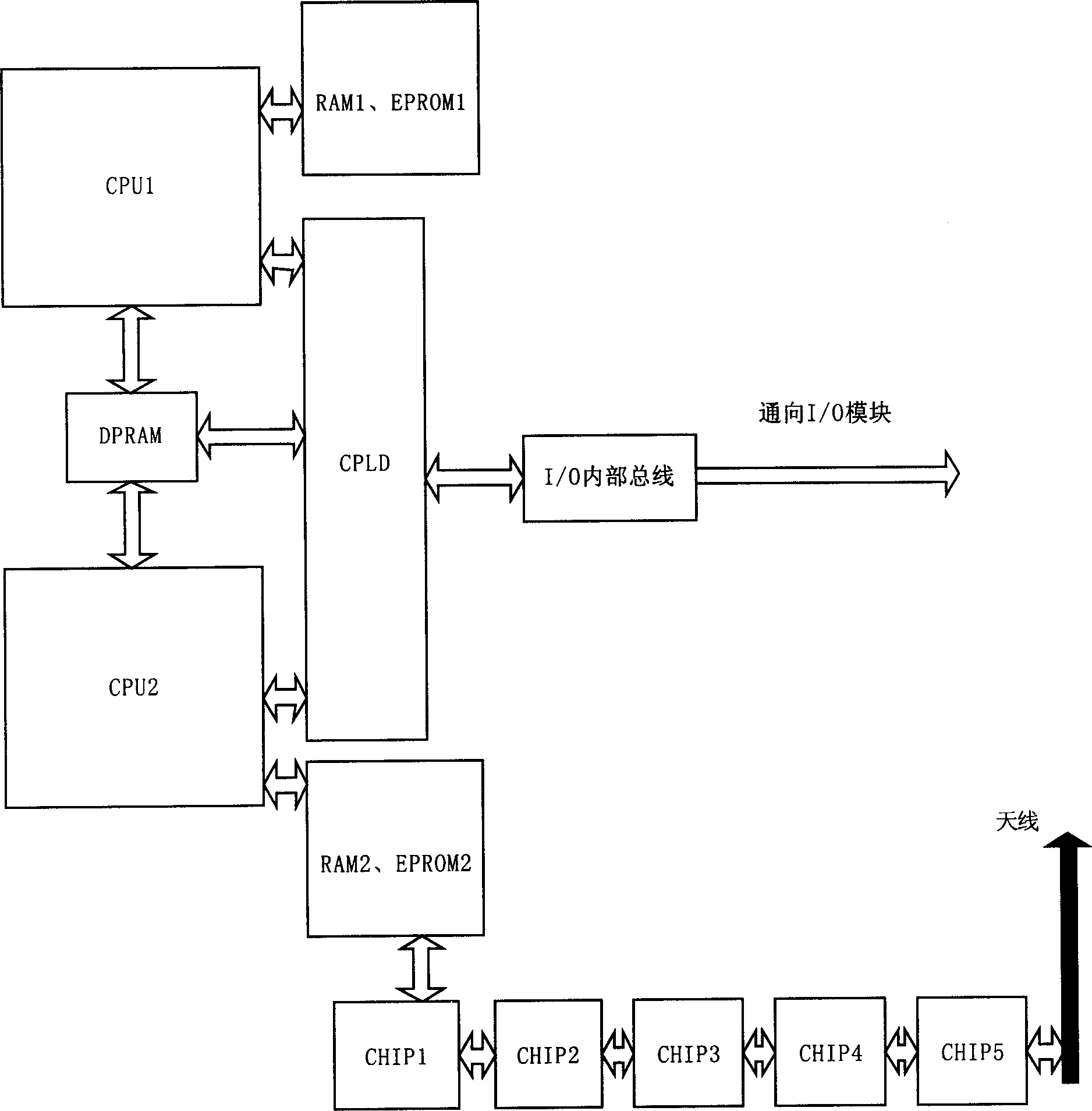
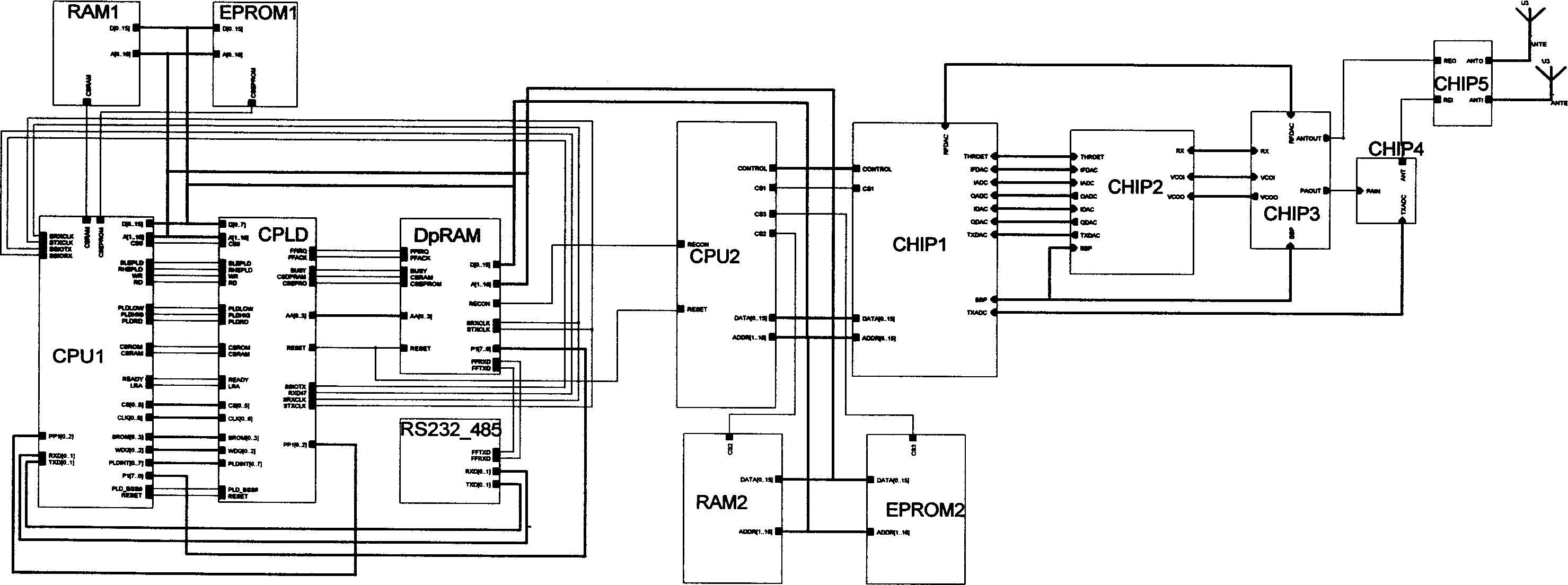
InactiveCN1567114ASupport hot swapSupport plug and play technologyTotal factory controlElectric digital data processingAutomatic controlDistributed structure
This invention relates to auto-control field, which in detail is used to a wireless LAN on-site bus net control station. It comprises main control station and I / O module, wherein, its main control station runs the wireless LAN on-site bus agreements and accomplishes the distribution I / O control through I / O module controller and receives and transmits data to Ethernet through wireless LAN transmission module. The I / O module is to accomplish the collection and conversion of the on-site signals. It is based on intelligence control device of the wireless Ethernet and turns the DCS total distributed system structure into new type of total distribution structure to completely distribute the control into the on site by network control station. This invention especially applies to old industry control system reconstruction to make it possible for old enterprises to enter the new time of on-site bus.
Owner:无锡中科泛在信息技术研发中心有限公司
Heterogeneous wireless network networking method based on calculation and processing
ActiveCN104053163AReduce construction costsReduce maintenance costsSpatial transmit diversityNetwork planningFrequency spectrumMacro base stations
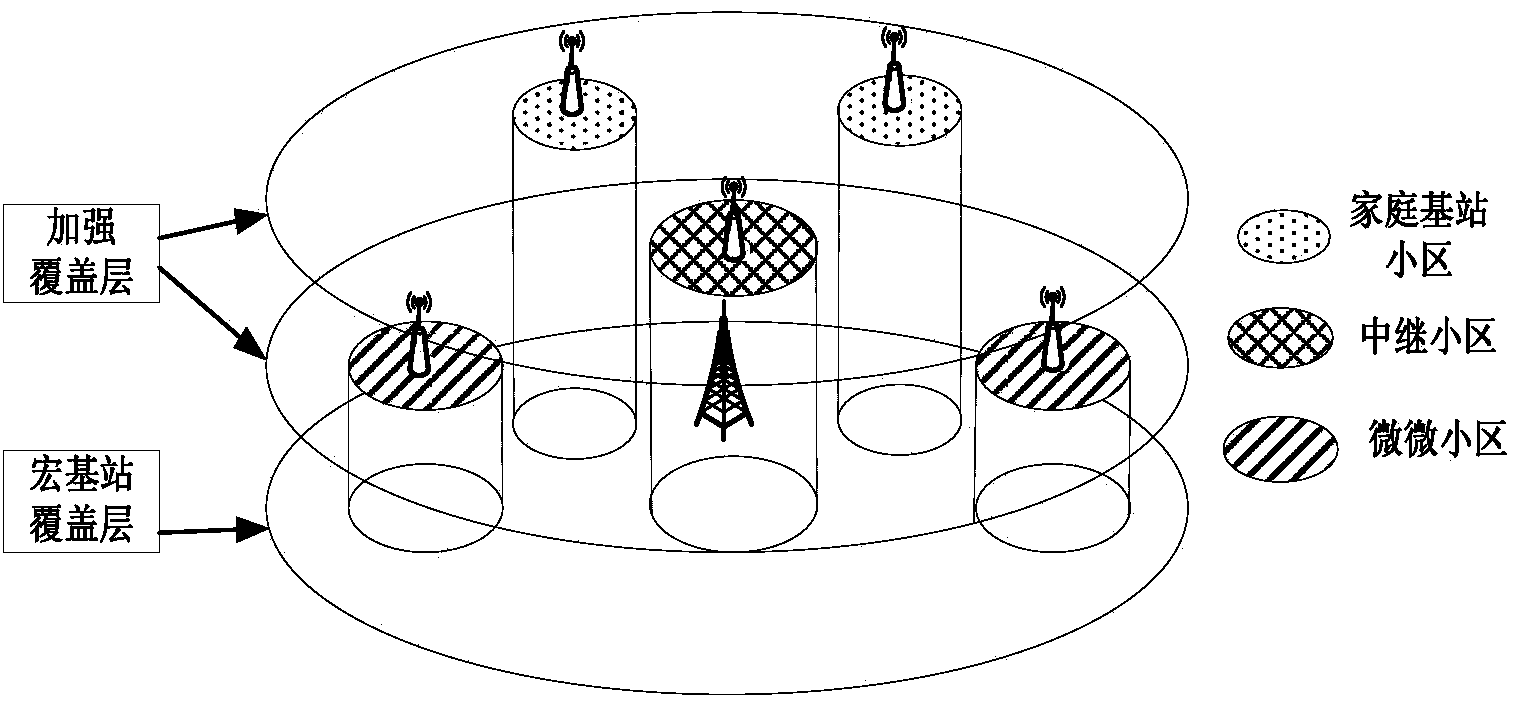
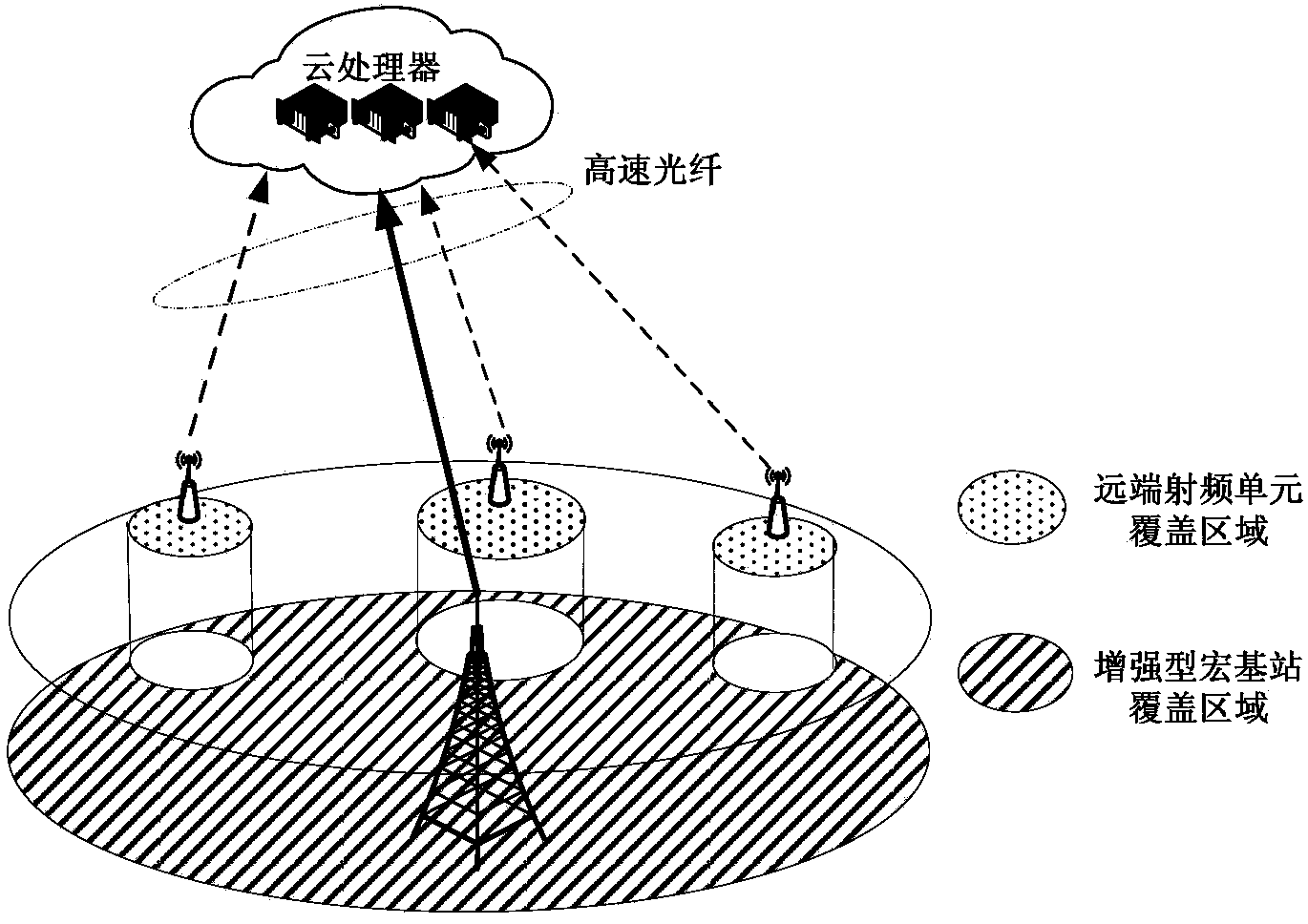
A heterogeneous wireless network networking method based on calculation and processing integrates features of a heterogeneous network and features of a cloud wireless access network, and a large-scale cooperative processing and multi-antenna technology is utilized for fully obtaining large-scale cooperative processing and calculation communication gains, reducing operating expenses, improving the network transmission frequency spectrum performance and reducing energy consumption. According to the heterogeneous wireless network networking method, a remote radio frequency unit is not directly connected with a fixed baseband processing unit, but the baseband processing unit and a wireless resource management unit of the remote radio frequency unit are both moved to a large-scale centralized processing server and are connected through a high-speed optical fiber. A traditional macro base station is upgraded to be a heterogeneous multi-antenna super base station to be in cooperative communication with the large-scale centralized processing server. The heterogeneous wireless network networking method based on calculation and processing is flexible in deployment and high in upgrading speed, the cost of constructing and maintaining the wireless access network by operators is lowered, and human intervention in network management is reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
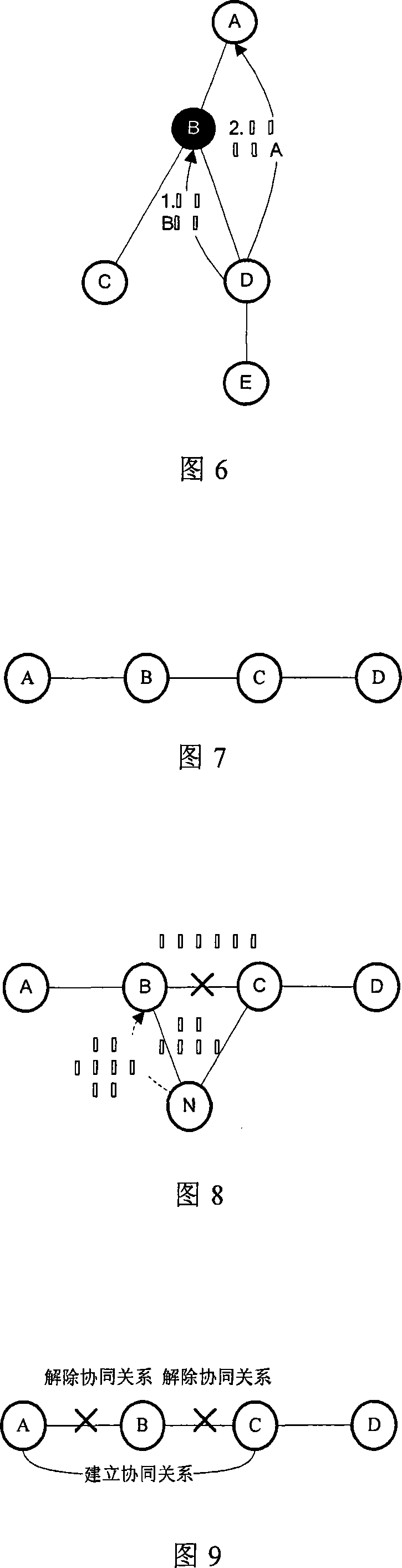
Maintenance method of service cooperated node organization structure in distributed environment
InactiveCN101247273AAvoid single point of failureAvoid problems in centralized control models such as performance bottlenecksData switching networksMaintainabilityStructure of Management Information
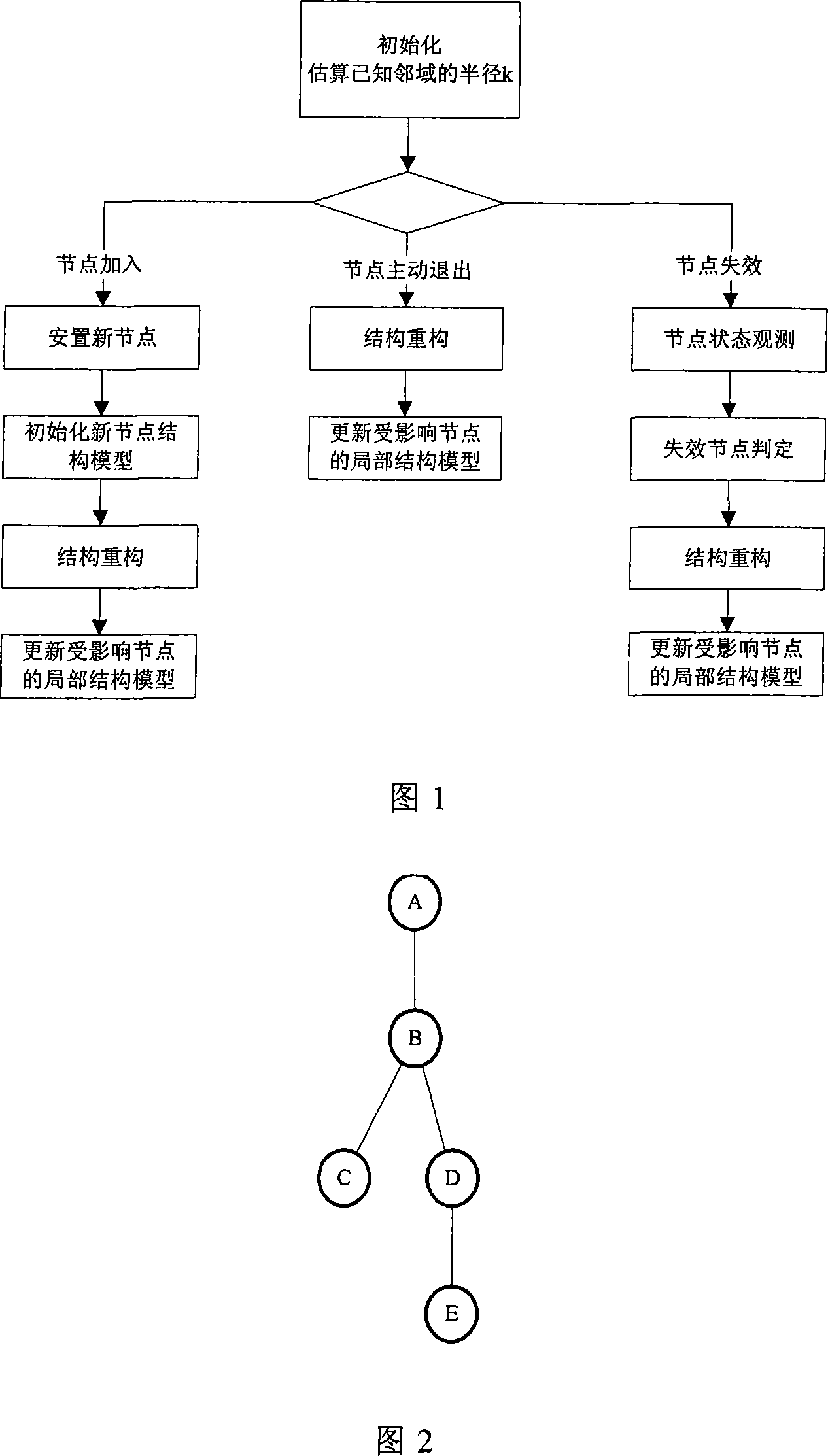
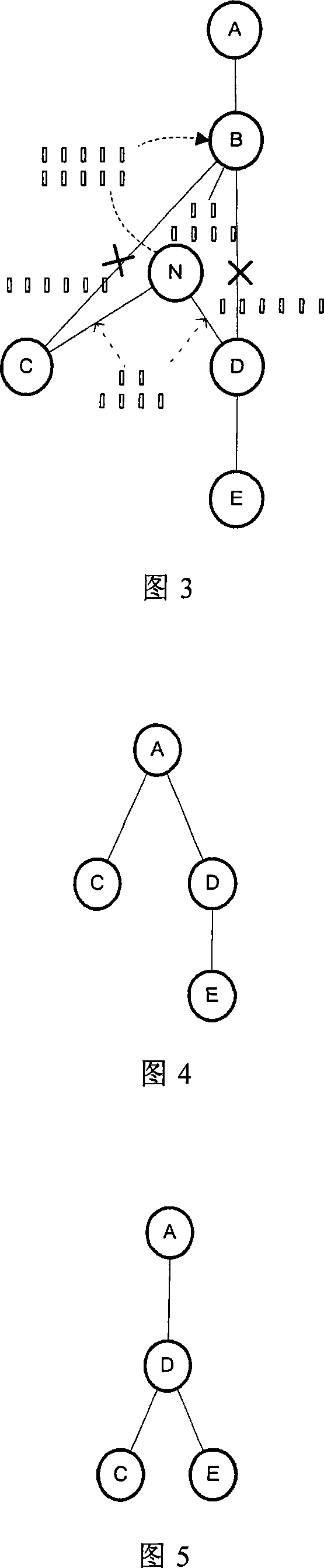
Step of maintenance method of service coordinated node structure in distributed surroundings is the following: (1) initialization, determining each node maintenance neighborhood scope according to computation method of maintainability probability; (2) executing maintenance for new node adding, node active quitting and node invalidation in the neighborhood scope; the steps (1) has three computation method of maintainability probability according to coordinated structure, three computation method is line shape, ring shape and tree structure. The present invention does not exist single point disabled problem, at the same time will not add network load pressure without over-great communications traffic.
Owner:BEIHANG UNIV
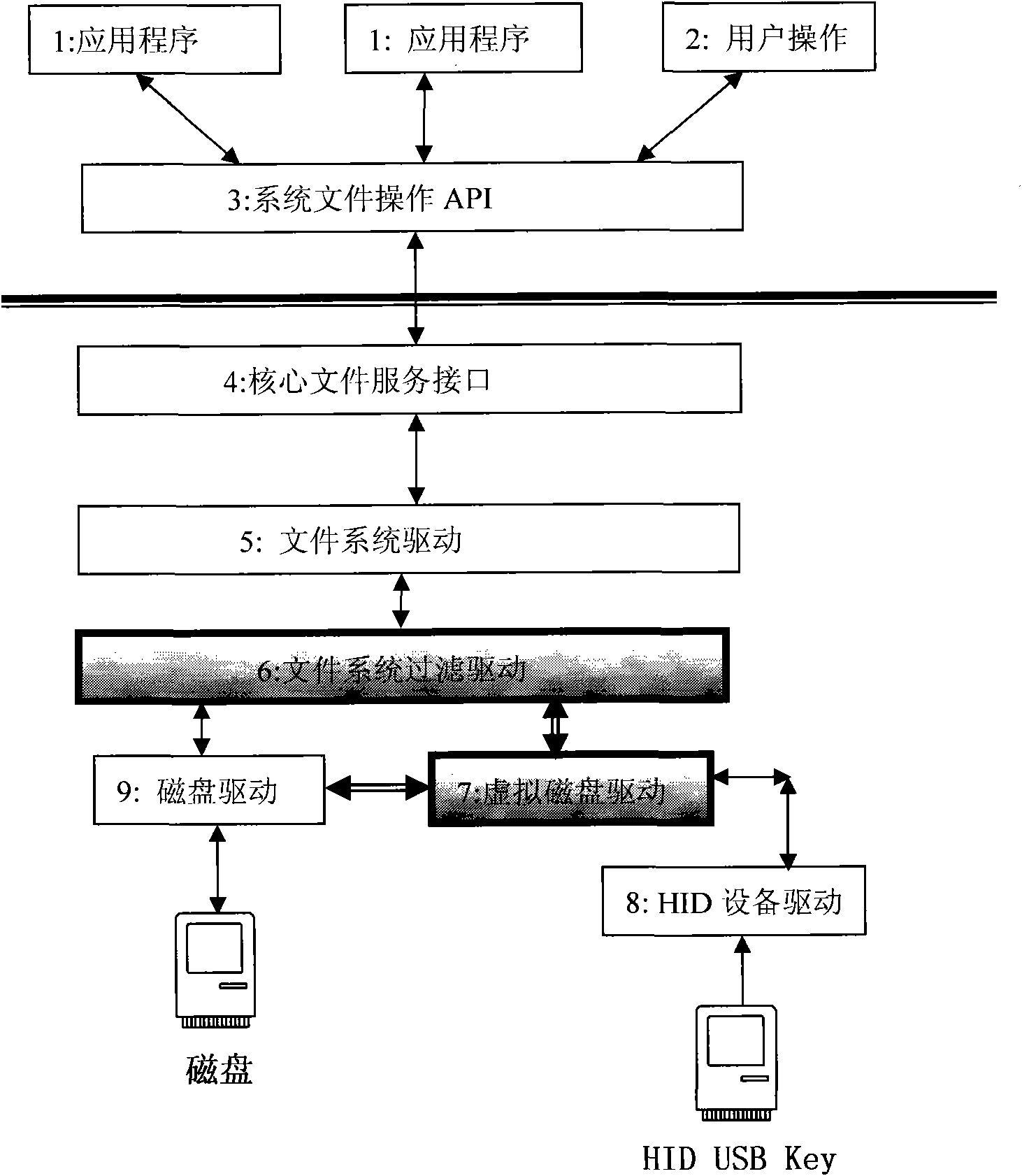
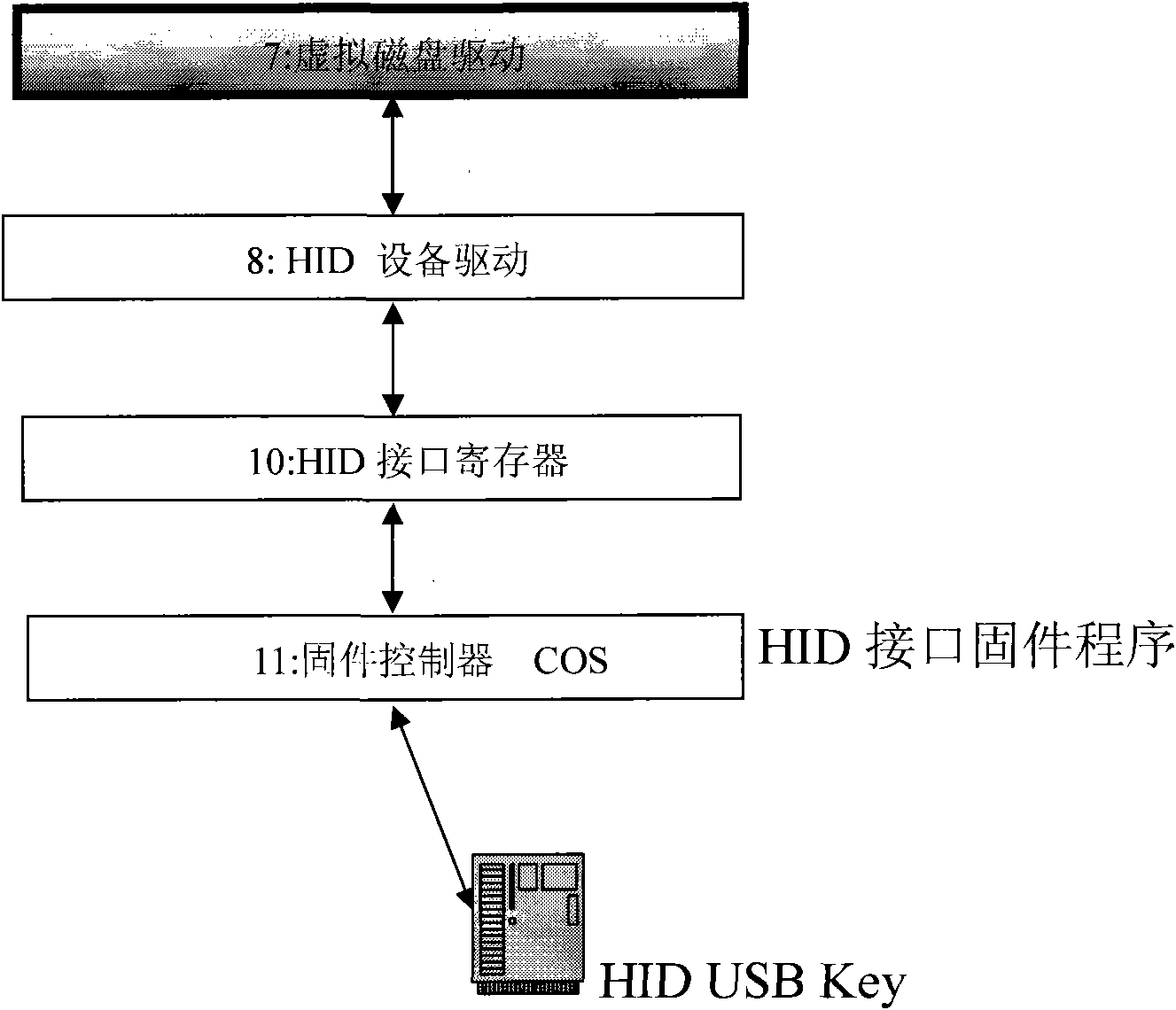
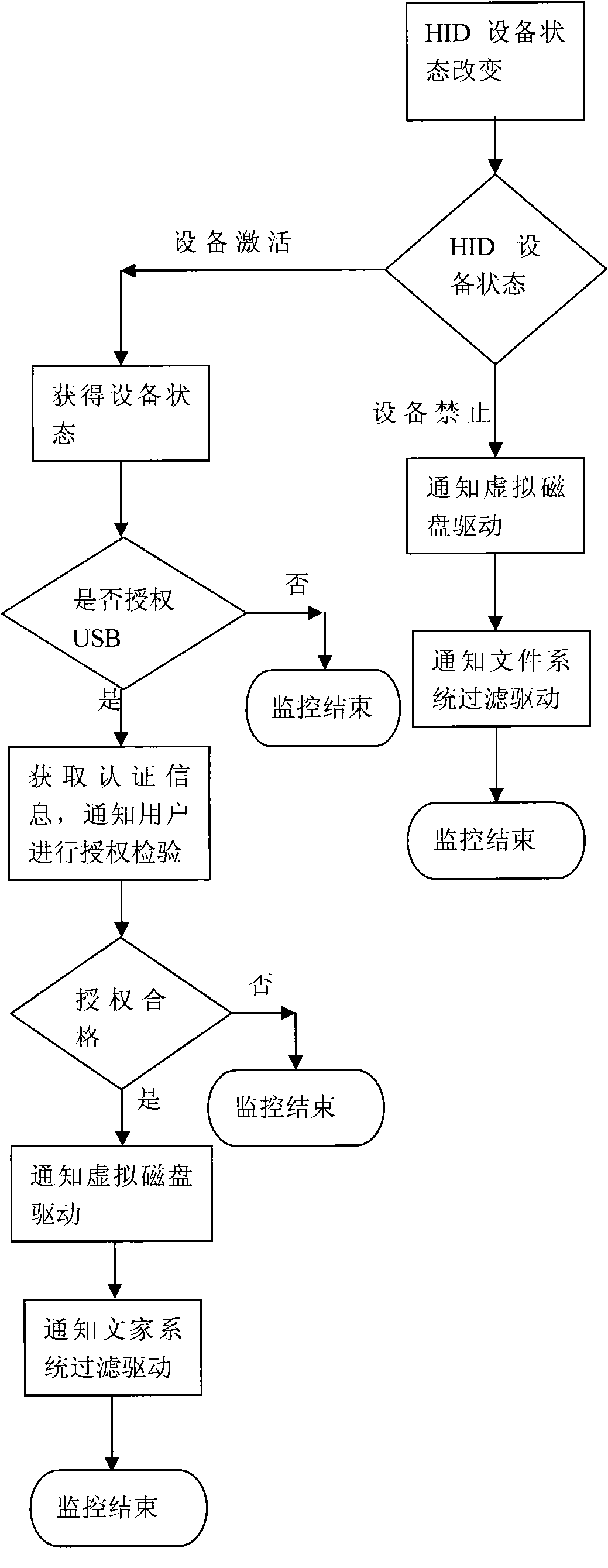
Realization method of data encryption in hard disk
InactiveCN102053925AReduce overheadReduce use costUnauthorized memory use protectionSpecial data processing applicationsFile systemHabit
The invention provides a realization method of data encryption in a hard disk, comprising the following steps: monitoring the status of a USB (universal serial bus) Key in real time, performing identity authentication by using an authorized USB Key and obtaining a secret key; storing the protected data in a protected catalog, mapping the space of the protected catalog into a virtual disc when the authorized authentication is successful, encrypting the data written into the disc and deciphering the data read from the disc; using an unprotected catalog as the common disc catalog; and hiding the virtual disc to prevent the access of the protected catalog and the protected data when the authorized USB Key is absent. The data stored in the virtual disc storage area of the protected catalog is encrypted forever, and is automatically decrypted in a memory when being used by a user. The method provided by the invention has the advantages that various discs and various file system can be supported, the traditional data use habit and application program behavior are not changed, and users do not need to purchase new disc devices.
Owner:许燕
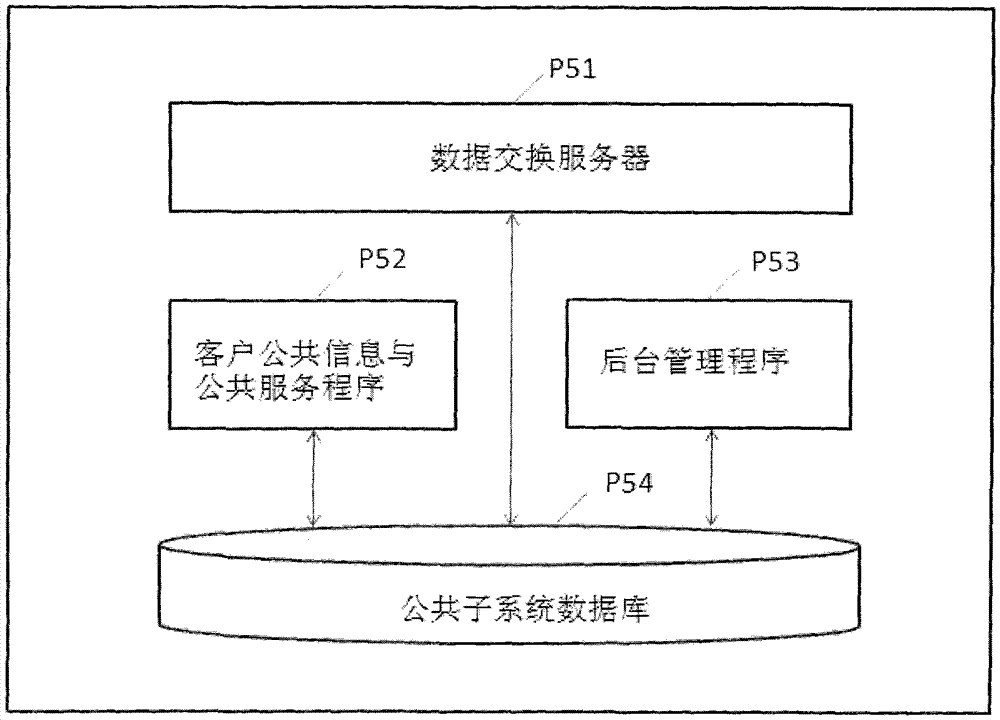
Method and system for accessing multiple subsystems and public subsystem with distributed storage personalized data through single APP program
InactiveCN103929473AImplement storageEnable secure storageTransmissionStructure of Management InformationOrganizational framework
The invention relates to a method and system for accessing multiple subsystems and a public subsystem with distributed storage personalized data through a single APP program. According to the method and system, in the interagency networking service system, the personalized data of clients are distributed and stored in different agency databases, independent management and safety of the data are ensured, a special service is provided, and agency subsystems are formed; public data and service are focused on the public subsystem, and public service extension, development and synergism are achieved; the agency subsystem and client access authentication information structures are planned, a client login access verification mirror image is generated on the public subsystem, the uniform mobile internet APP program (Client) is provided for the clients, the APP program interacts with an APP access centralized response server (Server), the APP access request is analyzed, client login access verification is conducted, personalized service client agency subsystems and a service content organizational framework are determined, personalized data are obtained and processed, the personalized and public service is provided, and the clients can synergistically access agency private systems and a public system.
Owner:冯力新 +1
Stamping device for inner strap
ActiveCN102211128AReduce maintenance overheadEasy to maintain and manageShaping toolsBeltsEngineeringMaterial supply
The invention provides a stamping device for an inner strap. The device comprises a pre-forming part, a hole detection part, a material supply part, a pattern forming part and a control part, wherein the pre-forming part comprises a piercing punch for forming position control holes on a processed plate at regular intervals, and a cutting punch for cutting off the processed plate with the position control holes according to set length; the hole detection part identifies the positions of the position control holes; the material supply part discontinuously supplies the processed plate according to the interval of the position control holes; the pattern forming part consists of a plurality of pattern stamping punches which are used for forming patterns on the processed plate supplied by the material supply part; and the control part controls to drive the material supply part and the pattern forming part based on the positions of the position control holes, which are detected by the hole detection part, and a forming program selected from pre-input forming programs for various forming types.
Owner:JIN YOUNG PRECISION MACHINE
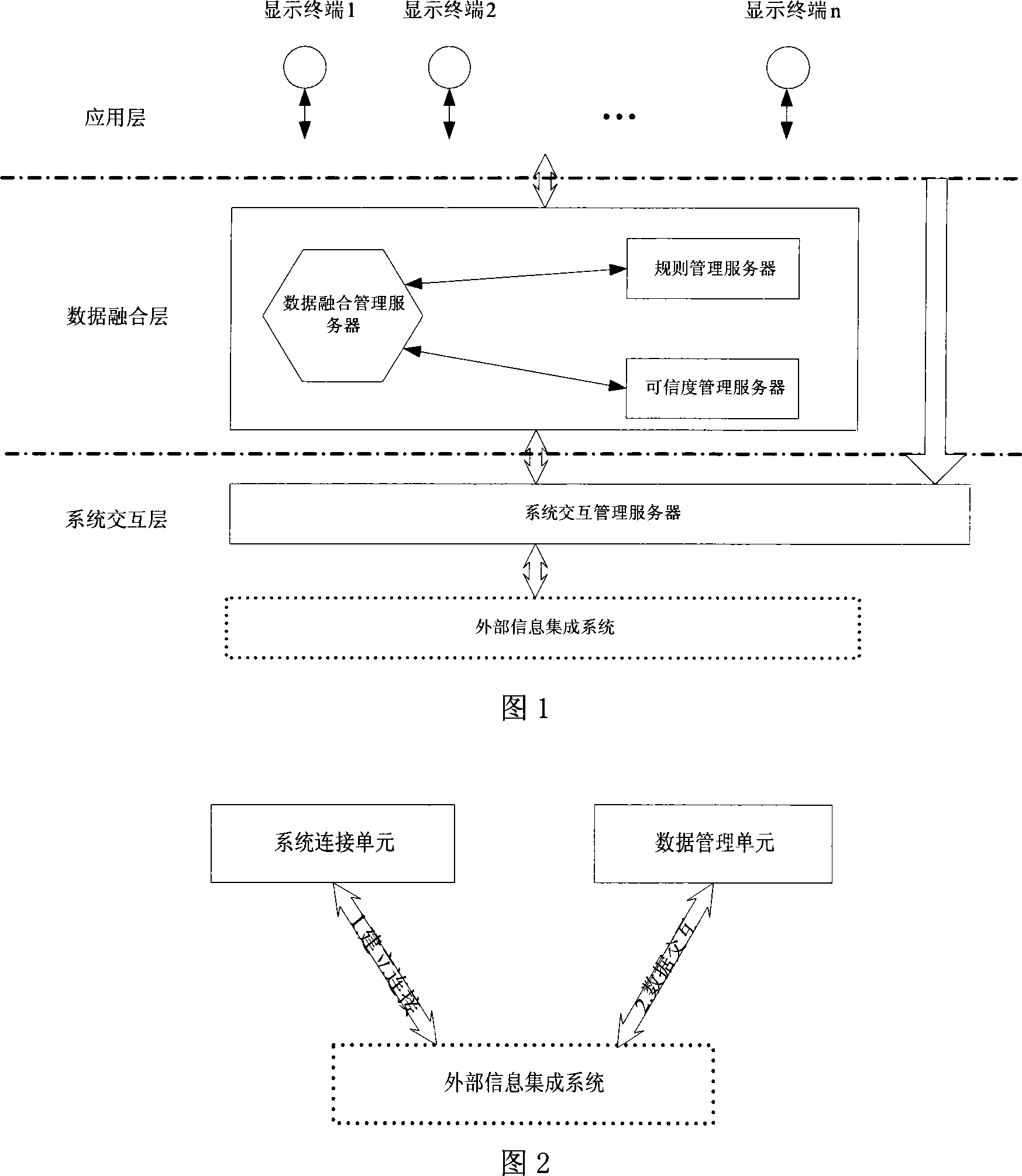
Multi-source data fusion system based on rule and certainty factor
InactiveCN101026627AImprove accuracyReduce overheadData switching detailsTelephonic communicationQuality of serviceRelevant information
The system includes system interaction management server (MS), certainty MS, data syncretizing MS, rule MS, display terminal. Connecting information integration system, the system interaction MS sands data to be interfused and relevant information to data syncretizing MS. data syncretizing MS syncretizes the inputted data through inference, and provides result for users through display terminal. In batch mode, user determines or further processes syncretized result. System returns final syncretized result back to external information integration system. Based on final syncretized result of system and QoS of each data sources in this syncretizing procedure, certainty MS modifies certainty of data sources. User can manage rule base in rule manager and certainty of each data source in data source certainty manager. Features are: legible modules, dynamic performance, generality and flexibility.
Owner:SHANGHAI JIAO TONG UNIV
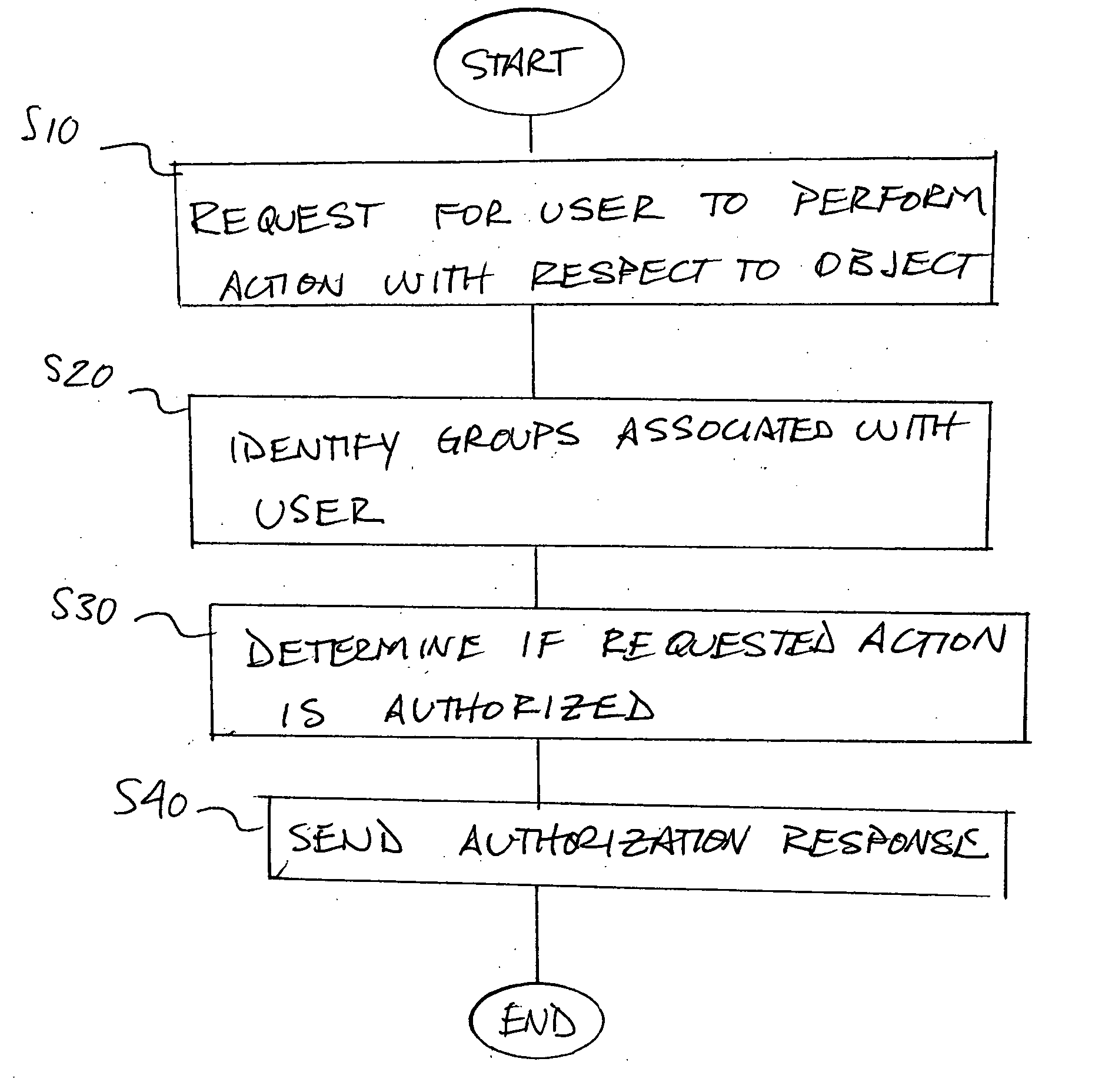
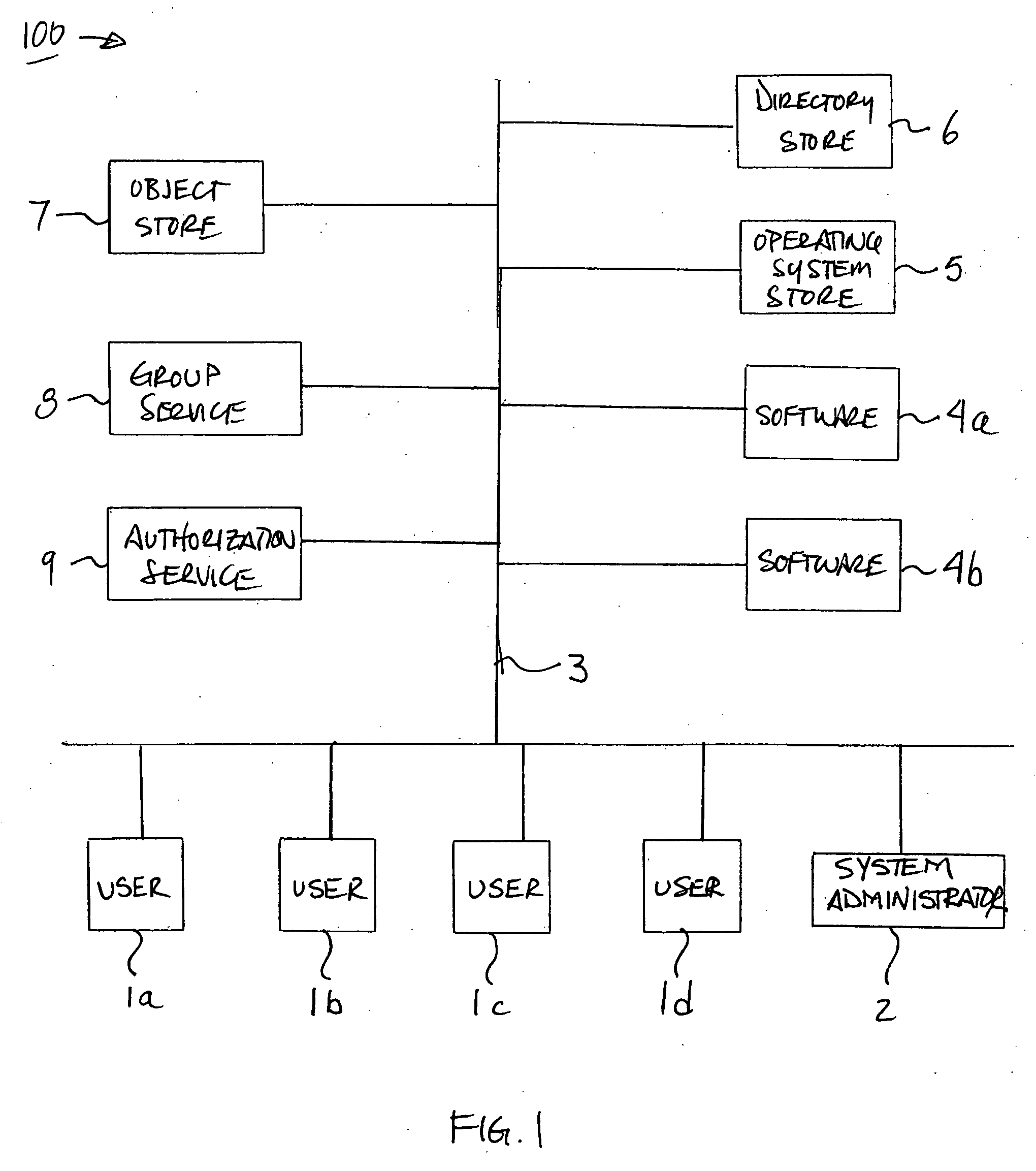
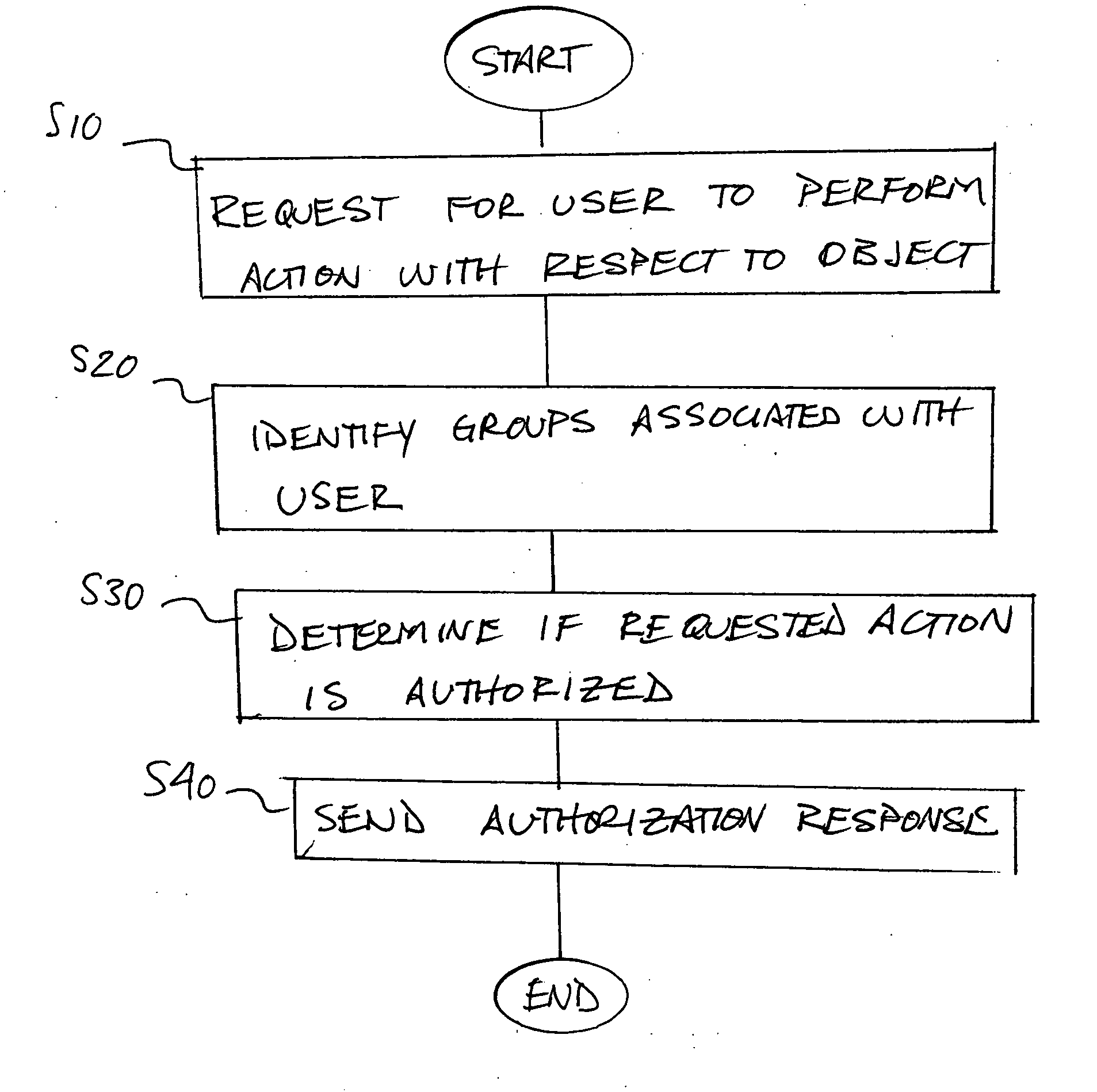
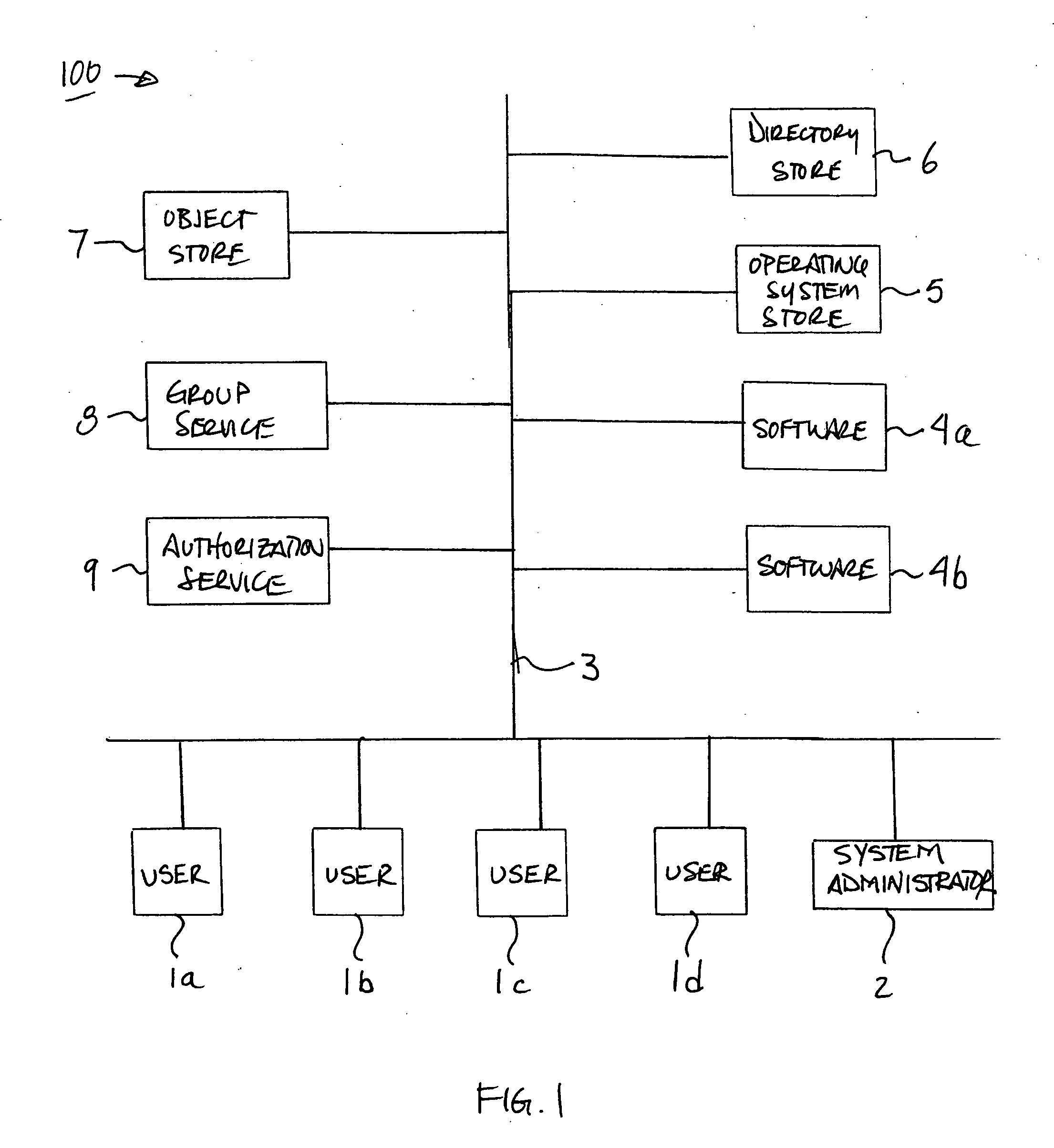
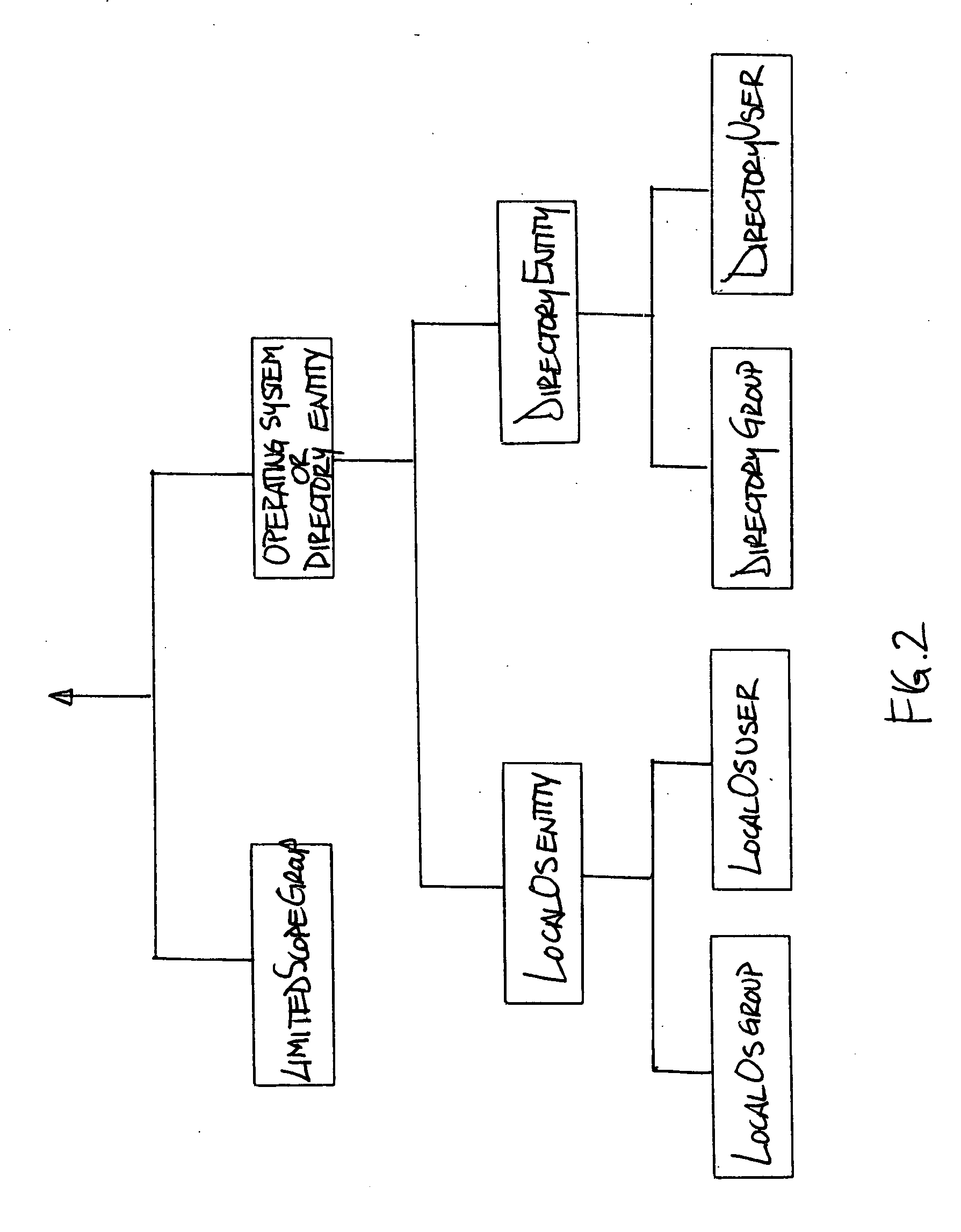
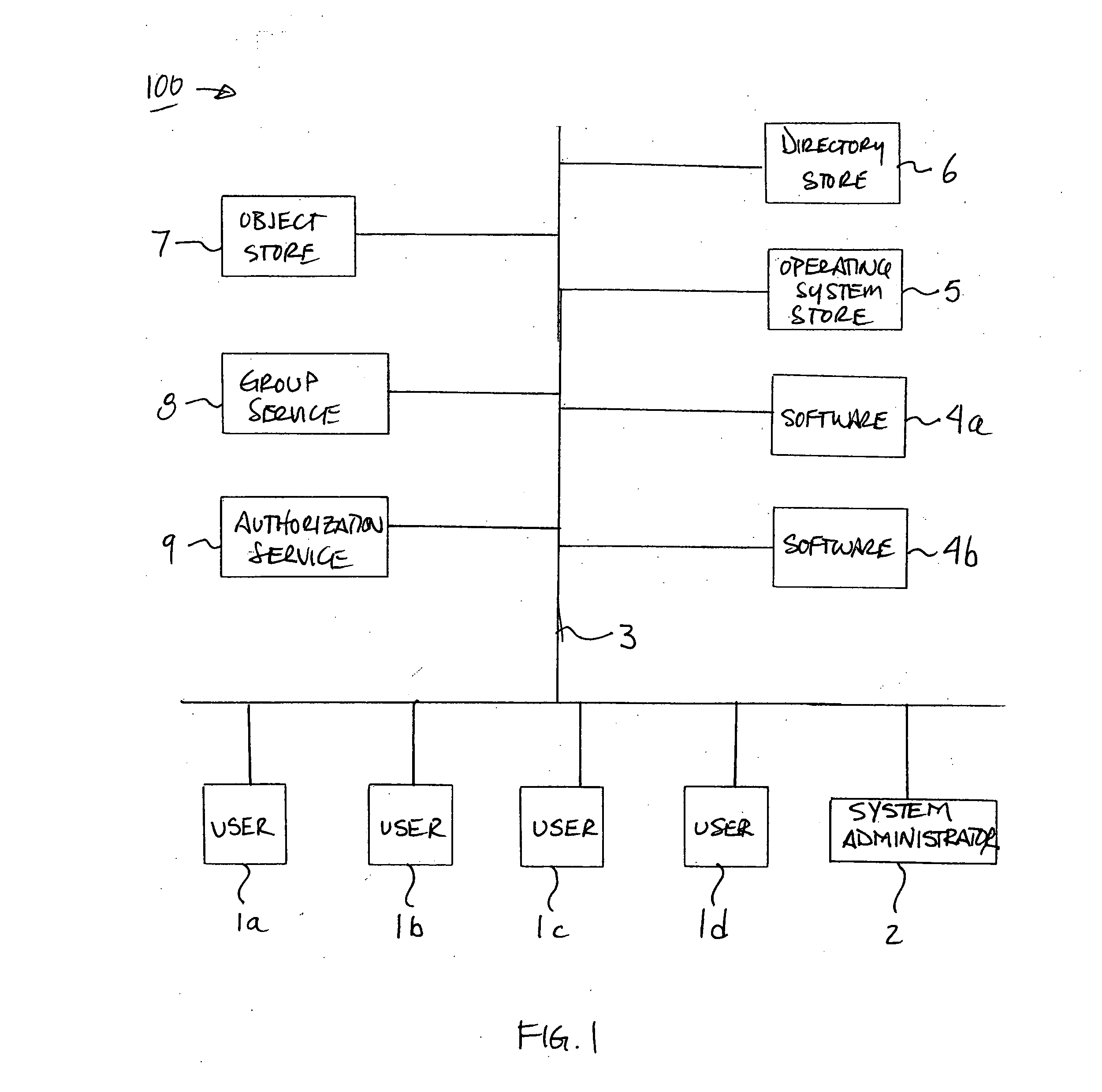
Method and apparatus for centralized security authorization mechanism
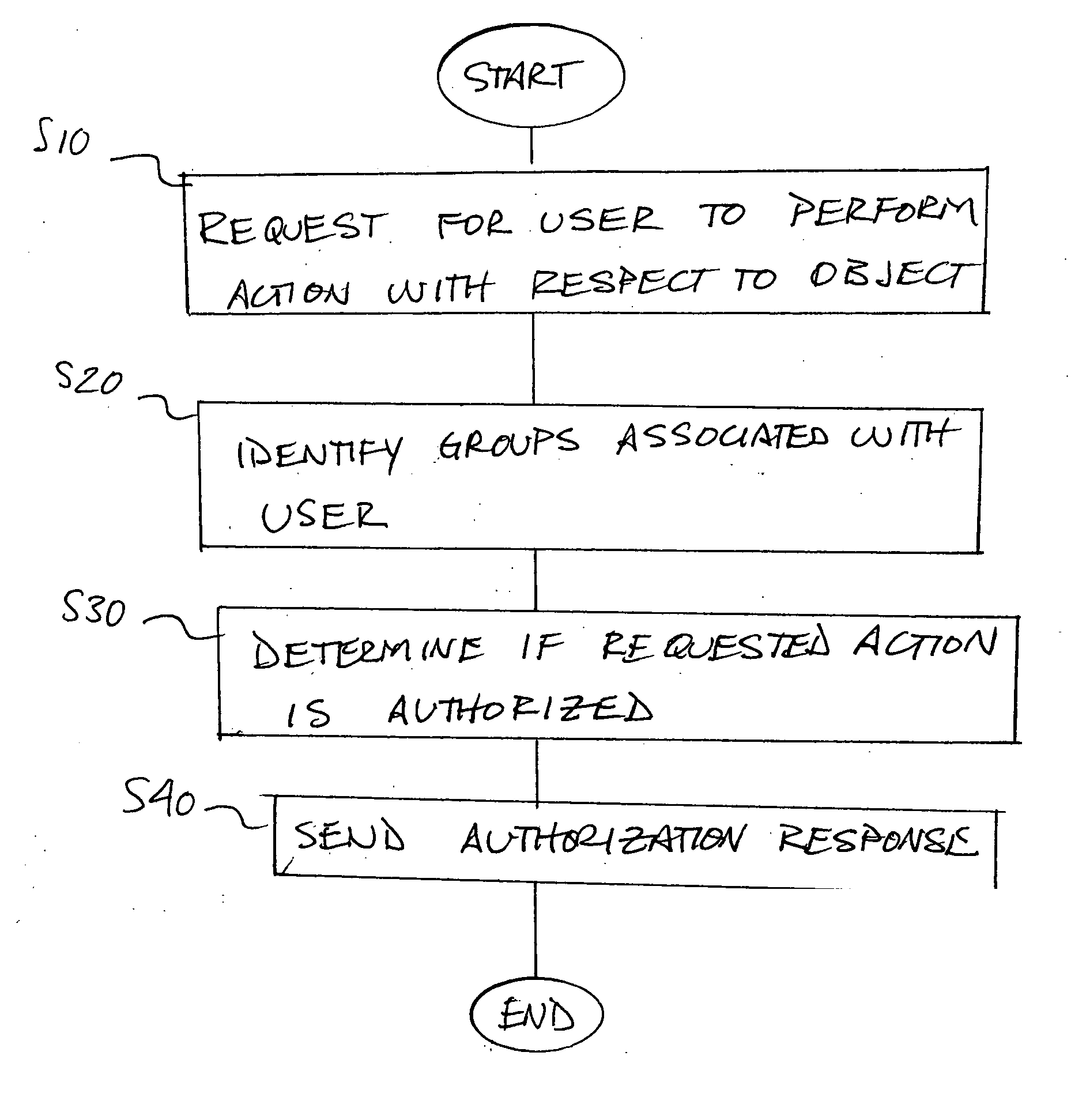
InactiveUS20060156020A1Quick identificationReduce the burden onComputer security arrangementsSecuring communicationAuthorizationSoftware
A method and apparatus for providing an extensible grouping mechanism for security applications for use in a computer system. Groups may be established and maintained by non-system administrators and used to control actions that are taken with respect to objects, such as files and other resources. The groups and associated security functions may be implemented across a plurality of different software products and optionally integrated into an existing security mechanism maintained by system administrators. Software products used in the system may be arranged to request authorization to perform requested actions with respect to objects access to which is not controlled by a systems administrator. Permission information used to determine the authorization for a user to perform a requested action may be stored for a plurality of software products in a common location.
Owner:MICROSOFT TECH LICENSING LLC
Blue tooth radio sensor
InactiveCN1617465AStrong opennessGuaranteed communication performanceNear-field systems using receiversLine sensorMultiple sensor
A blue-tooth wireless sensor includes a data collection module, a blue-tooth wireless moule further processing and transmitting data wirelessly, a program control module responsible for data collection, process and data communication with a level device. This device is mainly used in wireless data collection under industrial field control, it can set up connection and carry out data exchange with any device in conformity with blue-tooth wireless sensor stipulations and forms a wireless acess system with the level device by forming networks with multiple sensors to be used in many fields difficult of laying out cables.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Method and apparatus for maintaining routing information
ActiveUS20100281163A1Reduce inter-area routing table maintenance overheadEasy to processMultiple digital computer combinationsTransmissionPeer-to-peerManet routing
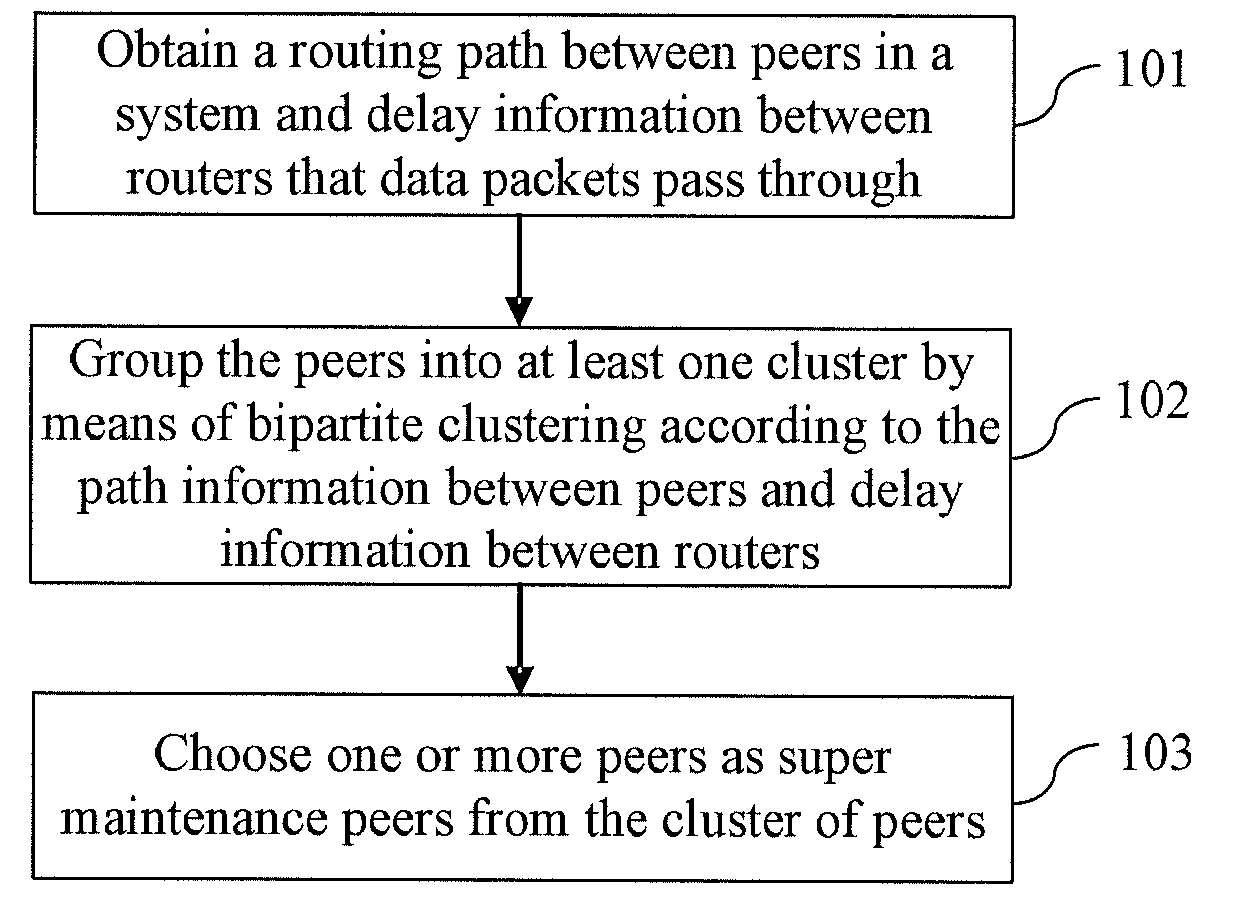
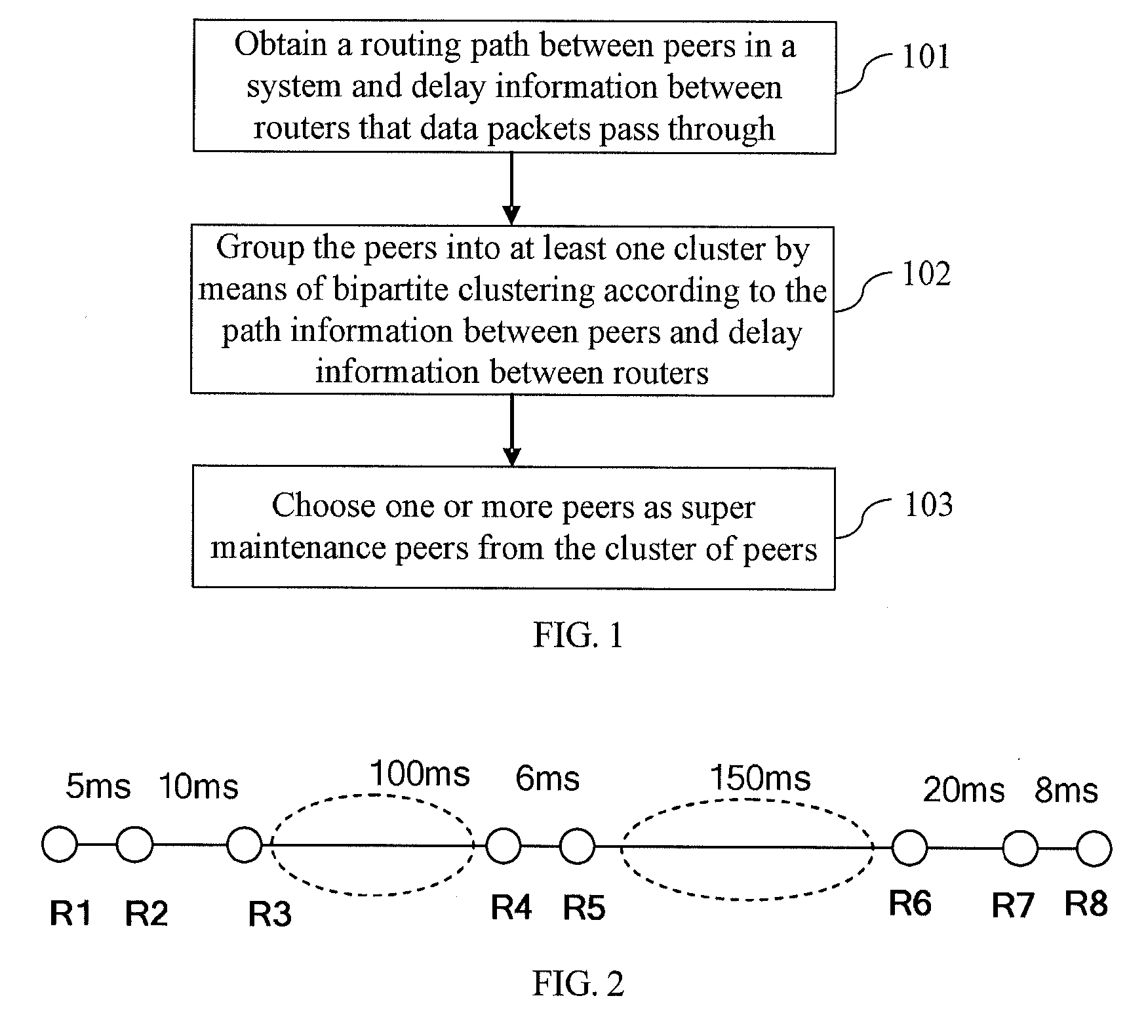
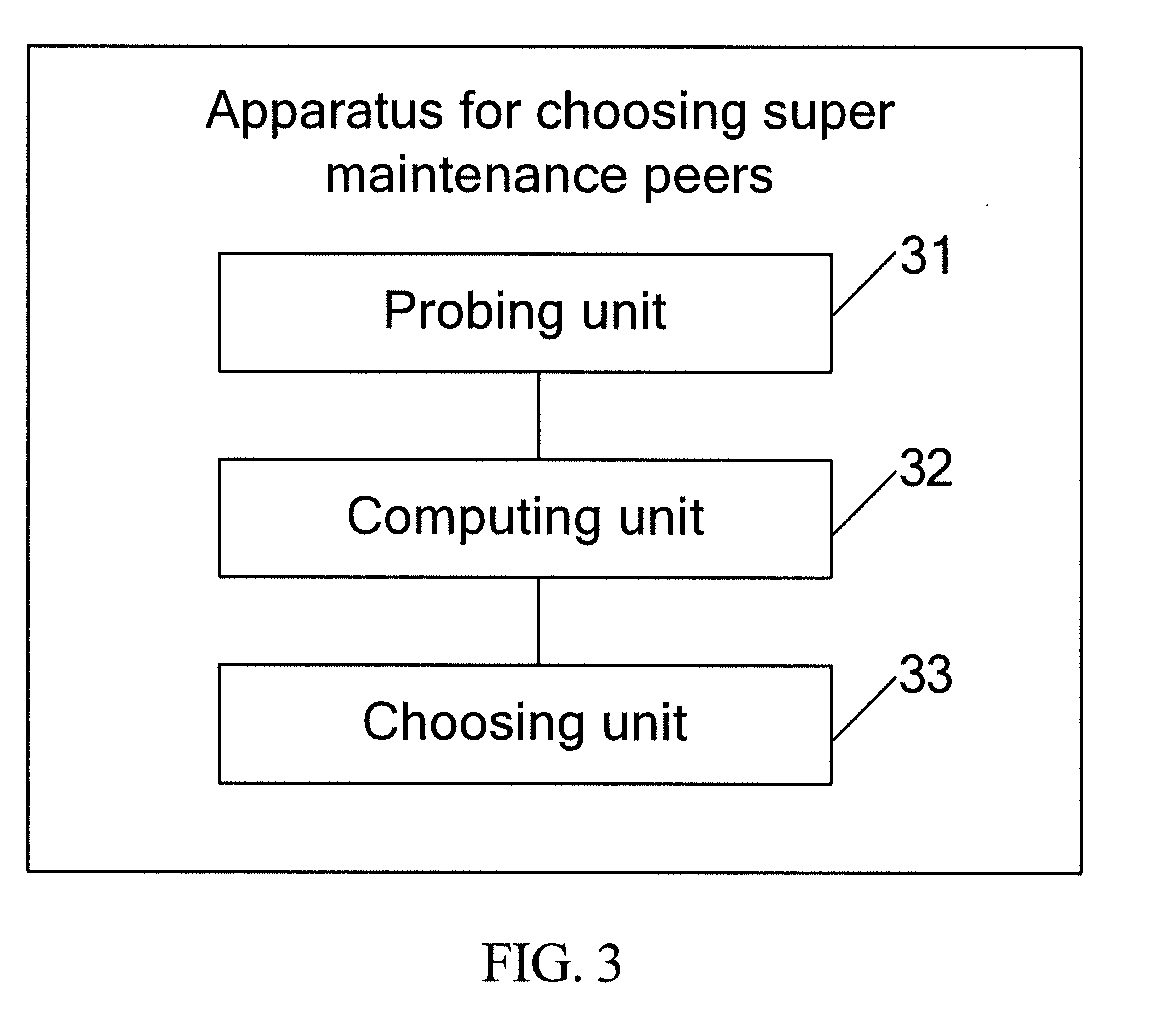
A method and apparatus for maintaining routing information in a Peer-to-Peer (P2P) network are provided. The method includes that: a super maintenance node receives routing update information of an ordinary node in its home area; the super maintenance node sends routing update information to super maintenance nodes in other network areas; the super maintenance nodes in other network areas notify ordinary nodes in their home network areas to update routing information. With the present invention, a node of strong processing capabilities at the network area border is chosen to act as a super maintenance node and other nodes as ordinary nodes; when a node joins or fails, an ordinary node sends detected routing update information only to the super maintenance node in the local network area; the super maintenance node then forwards the update information to super maintenance nodes in other network areas. Each super maintenance node notifies ordinary nodes in its home network area of the received routing update information.
Owner:HUAWEI TECH CO LTD
Self network organized and distance concerned multi-routing method for complete route information
InactiveCN1645838AQuick buildReduce maintenance overheadData switching networksNetwork packetWireless data
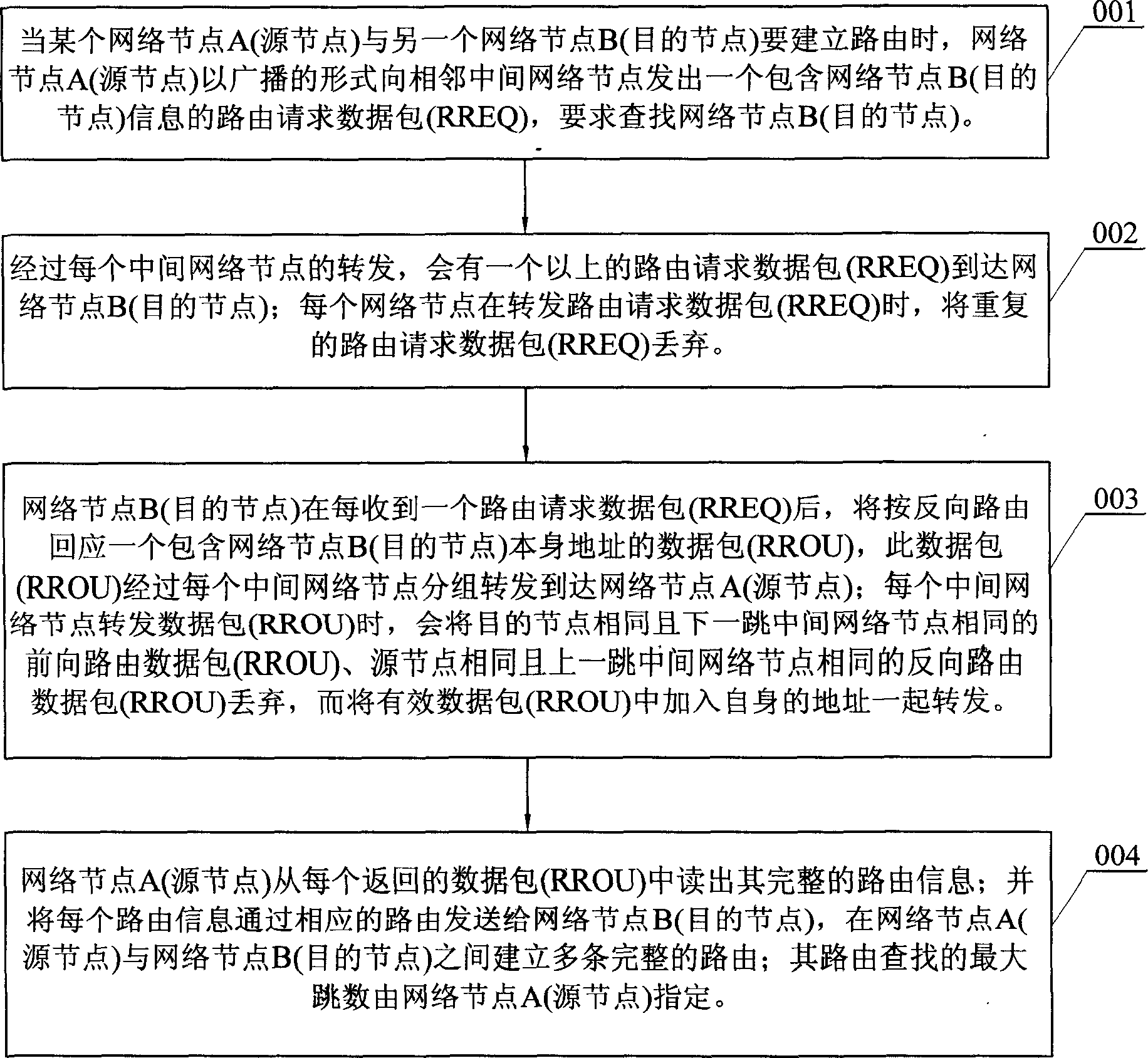
The method includes following steps: when node A (source node) and node B(destination node) needs to build up route, they send out a route-requested data package (RREQ)001 containing B message to the neighboring intermediate network node by using broadcast form; through retransmission of intermediate network node, more than one route-requested data package will arrive B 002; after B receives a route-requested data package, it responses a data package containing the address of B that is packetized and retransmitted to A 003 through intermediate network node; A reads out the whole route message from returned data package and sends the route message to B; multi whole routes are built up between the A and B.
Owner:HARBIN INST OF TECH
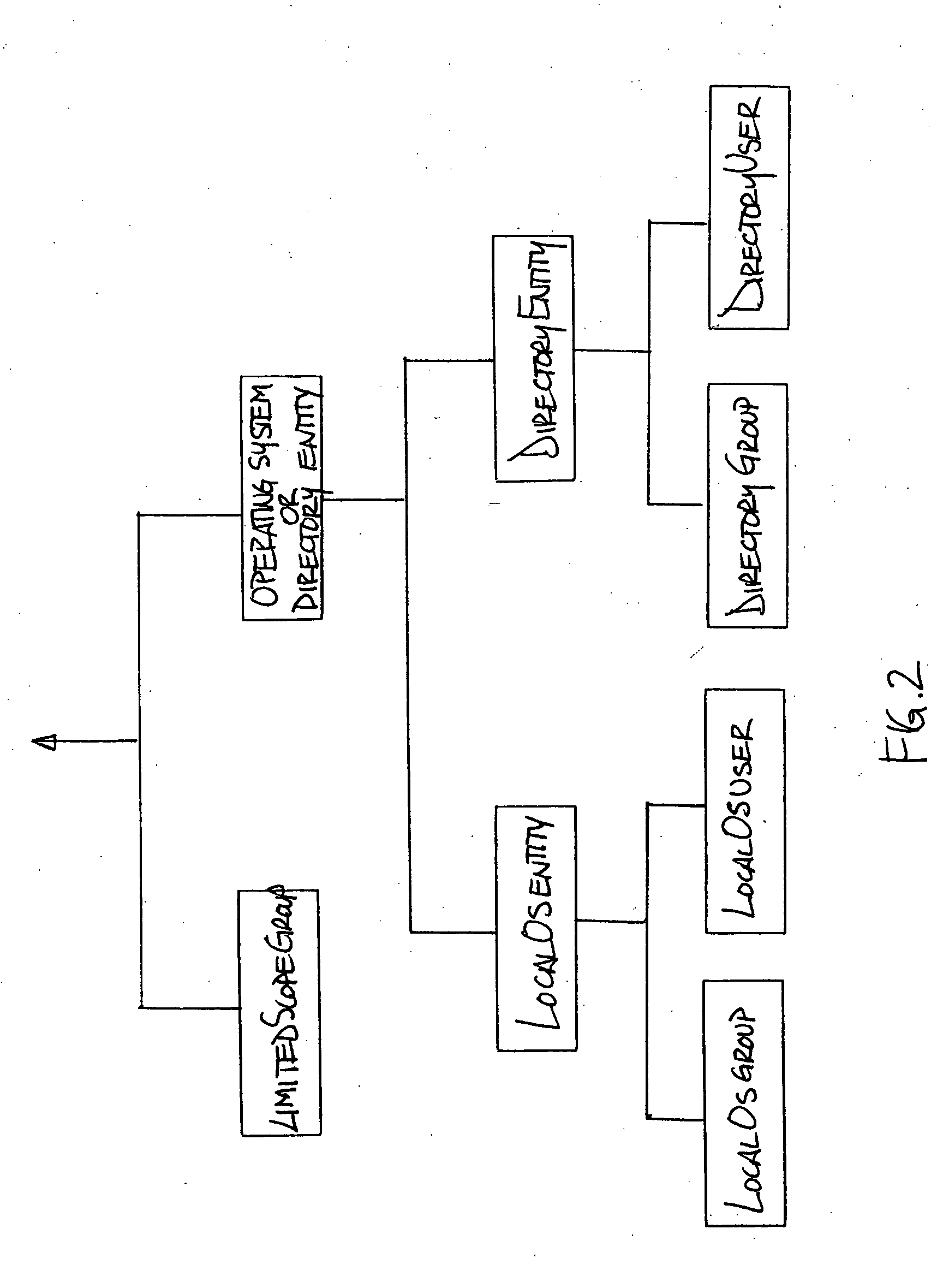
Method and apparatus for extensible security authorization grouping
InactiveUS20060156384A1Easy to adjustReduce maintenance overheadDigital data processing detailsUser identity/authority verificationAuthorizationSoftware
A method and apparatus for providing an extensible grouping mechanism for security applications for use in a computer system. Groups may be established and maintained by non-system administrators and used to control actions that are taken with respect to objects, such as files and other resources. The groups and associated security functions may be implemented across a plurality of different software products and optionally integrated into an existing security mechanism maintained by system administrators. Software products used in the system may be arranged to request authorization to perform requested actions with respect to objects access to which is not controlled by a systems administrator.
Owner:MICROSOFT TECH LICENSING LLC
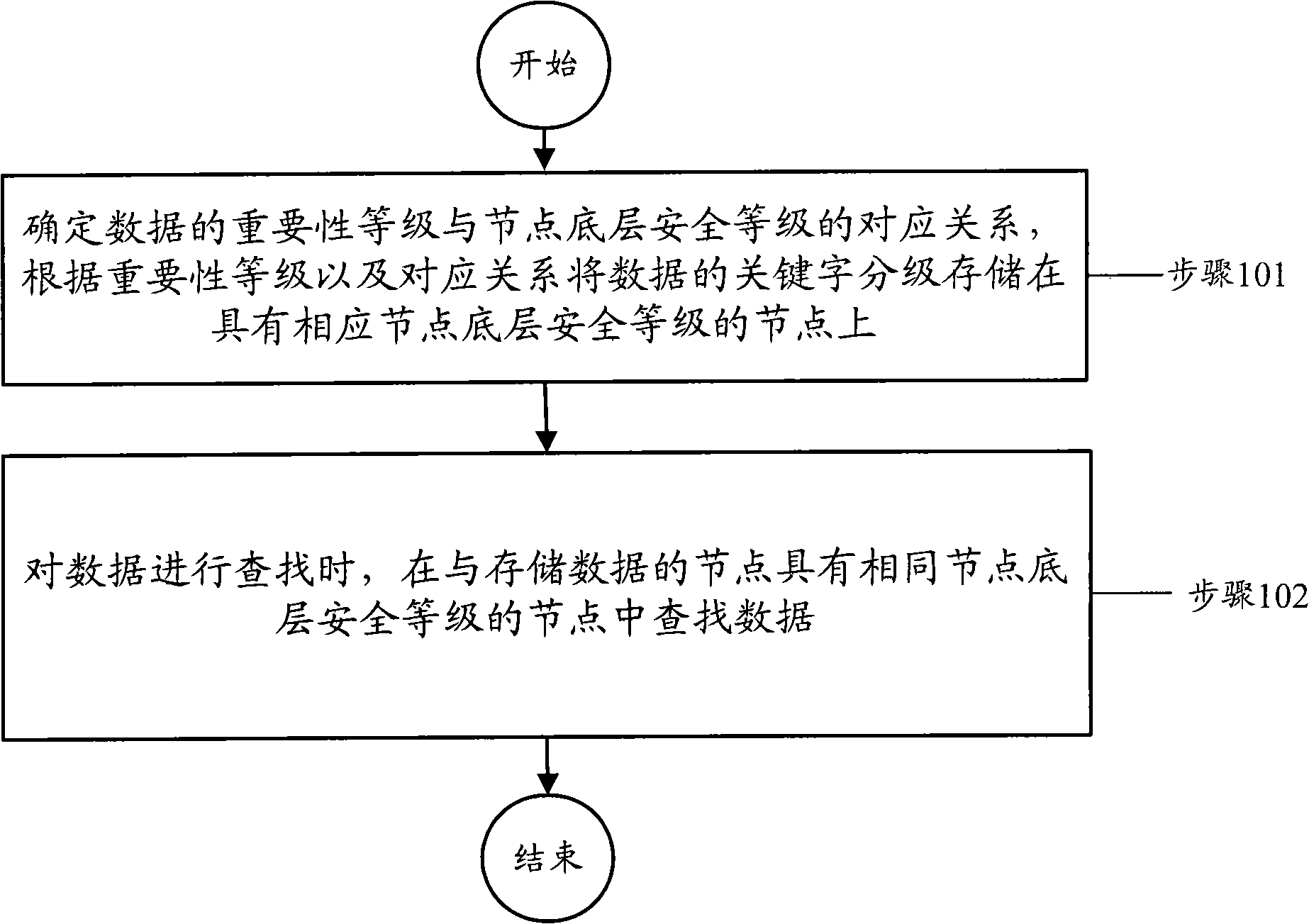
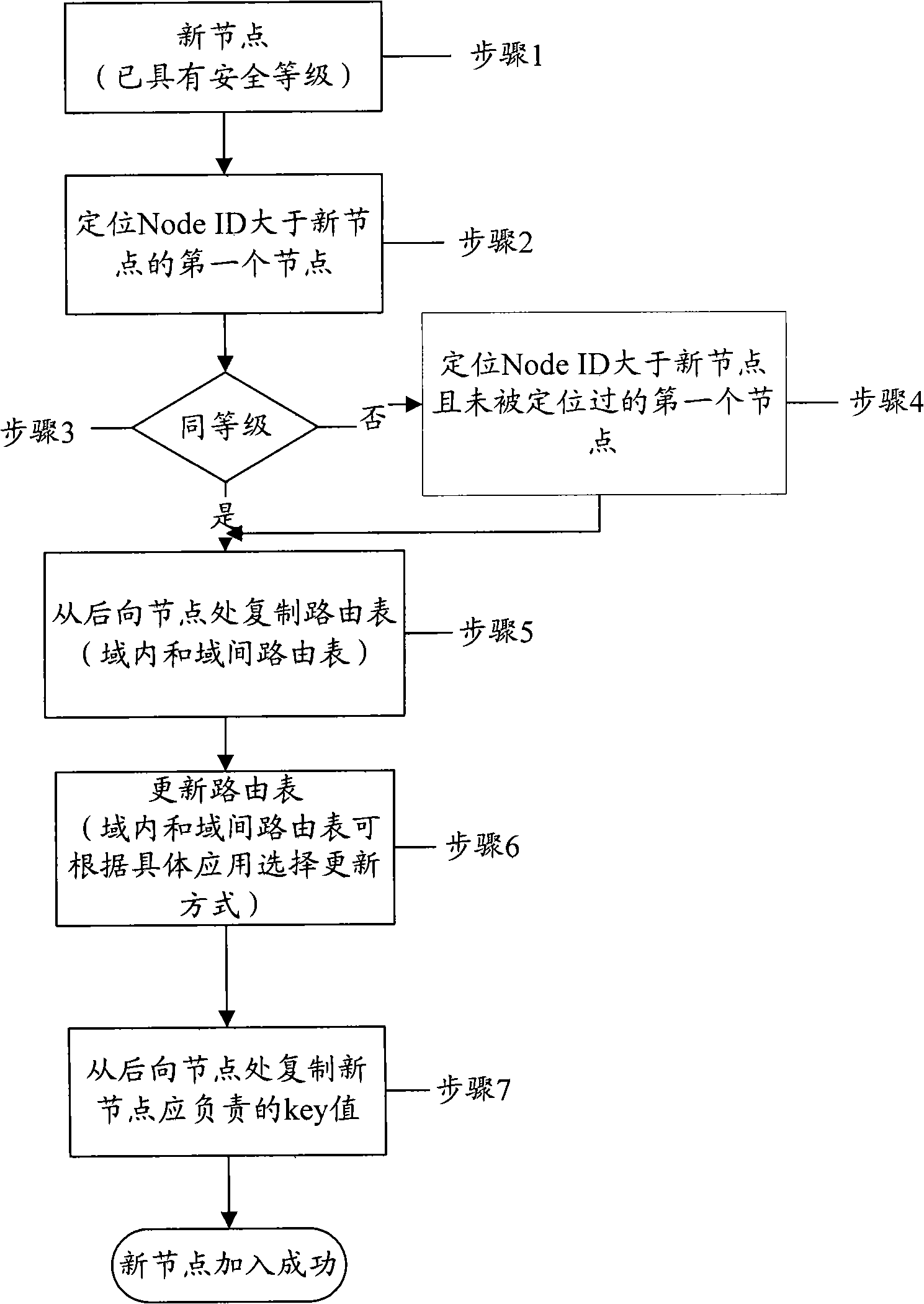
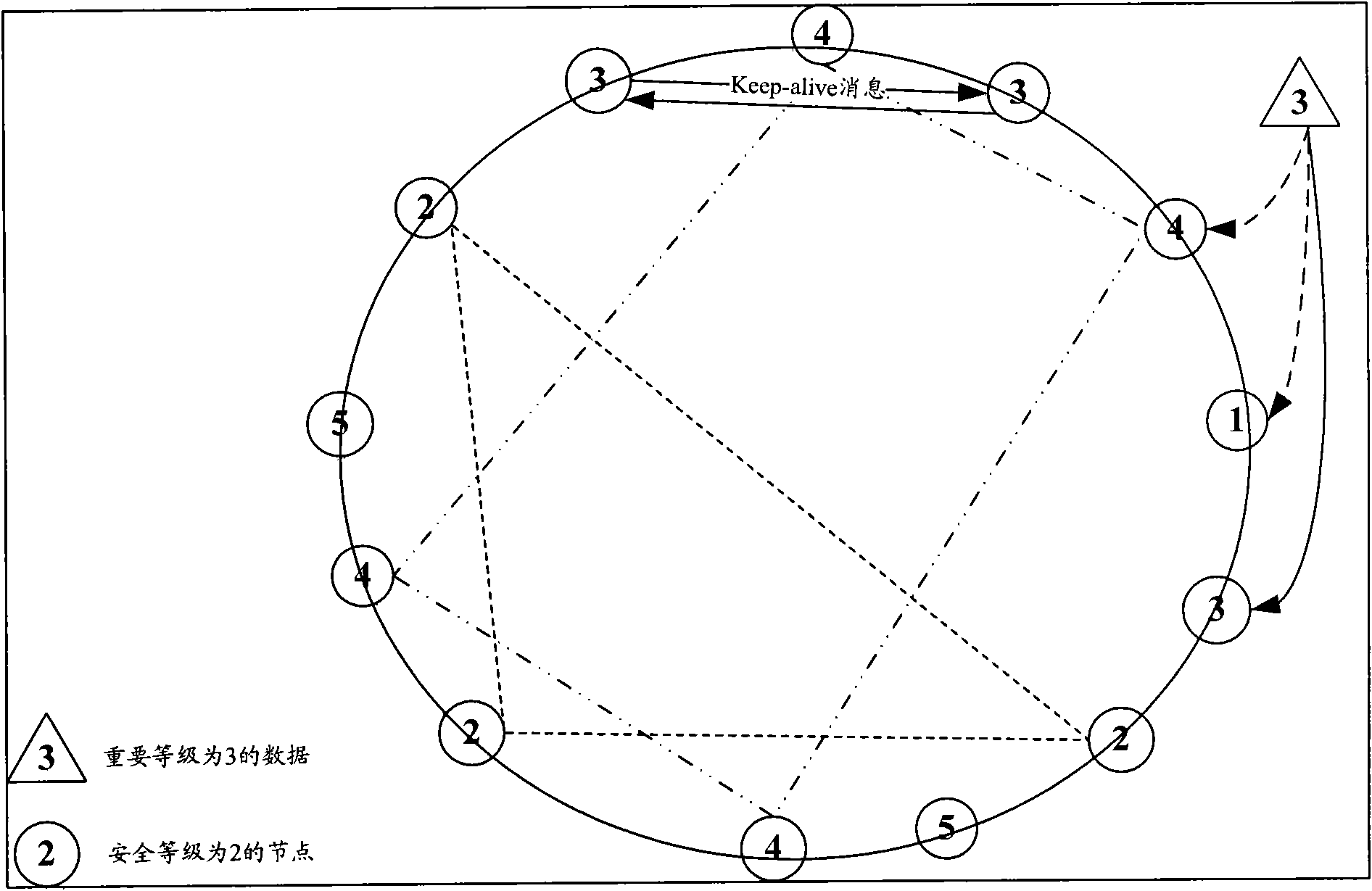
Method and node for storing and routing data on basis of node bottom layer security level
InactiveCN102487397ASimple structureReduce maintenance overheadData switching networksNetwork onSecurity level
The invention discloses a method and a node for storing and routing data in a peer-to-peer (P2P) network on the basis of the node bottom layer security level. The method comprises the following steps of: determining the corresponding relation between the importance level of the data and the node bottom layer security level, and storing the key word level of the data into the node with the corresponding node bottom layer security level according to the importance level and the corresponding relation; and when the data is searched, searching the data in nodes with the same node bottom layer security level as the node in which the data is stored.
Owner:艾欧特(沈阳)科技有限公司
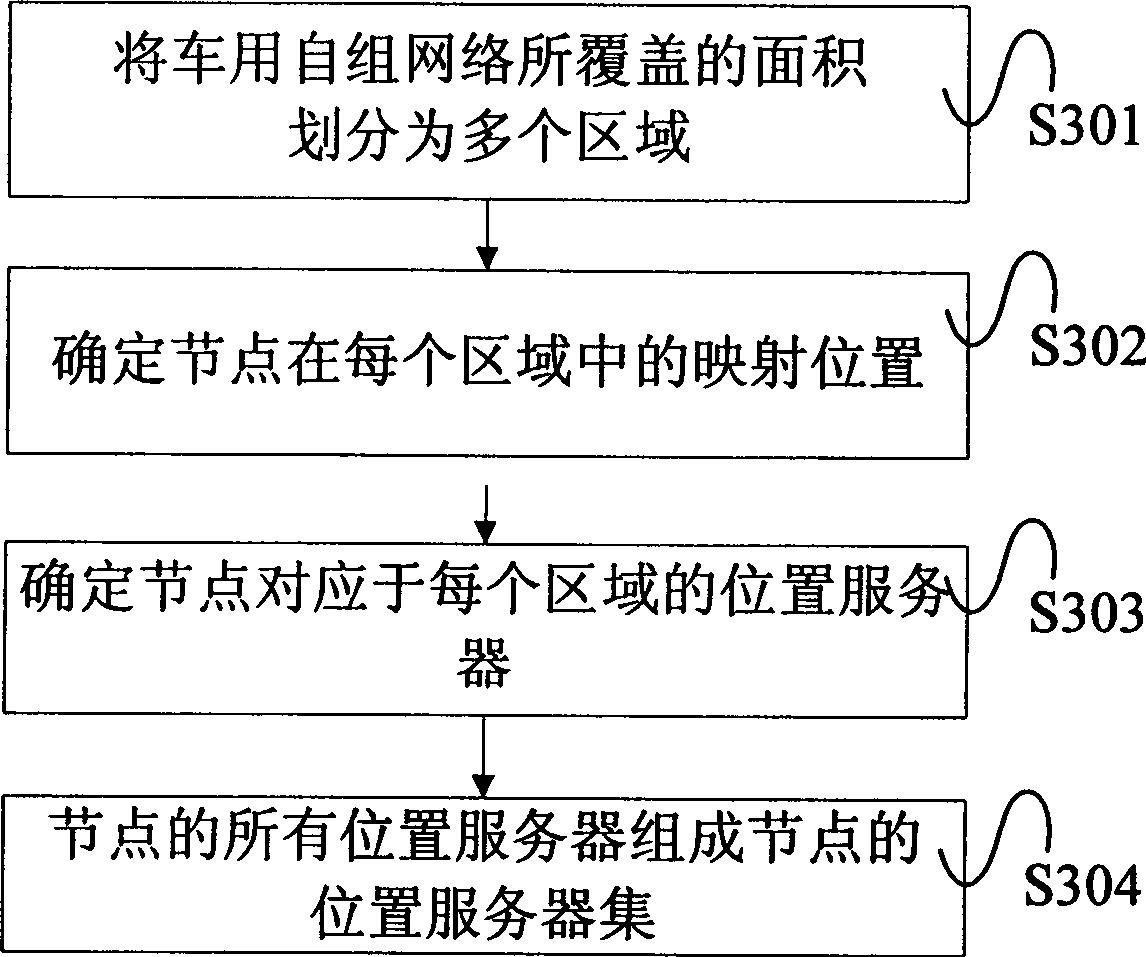
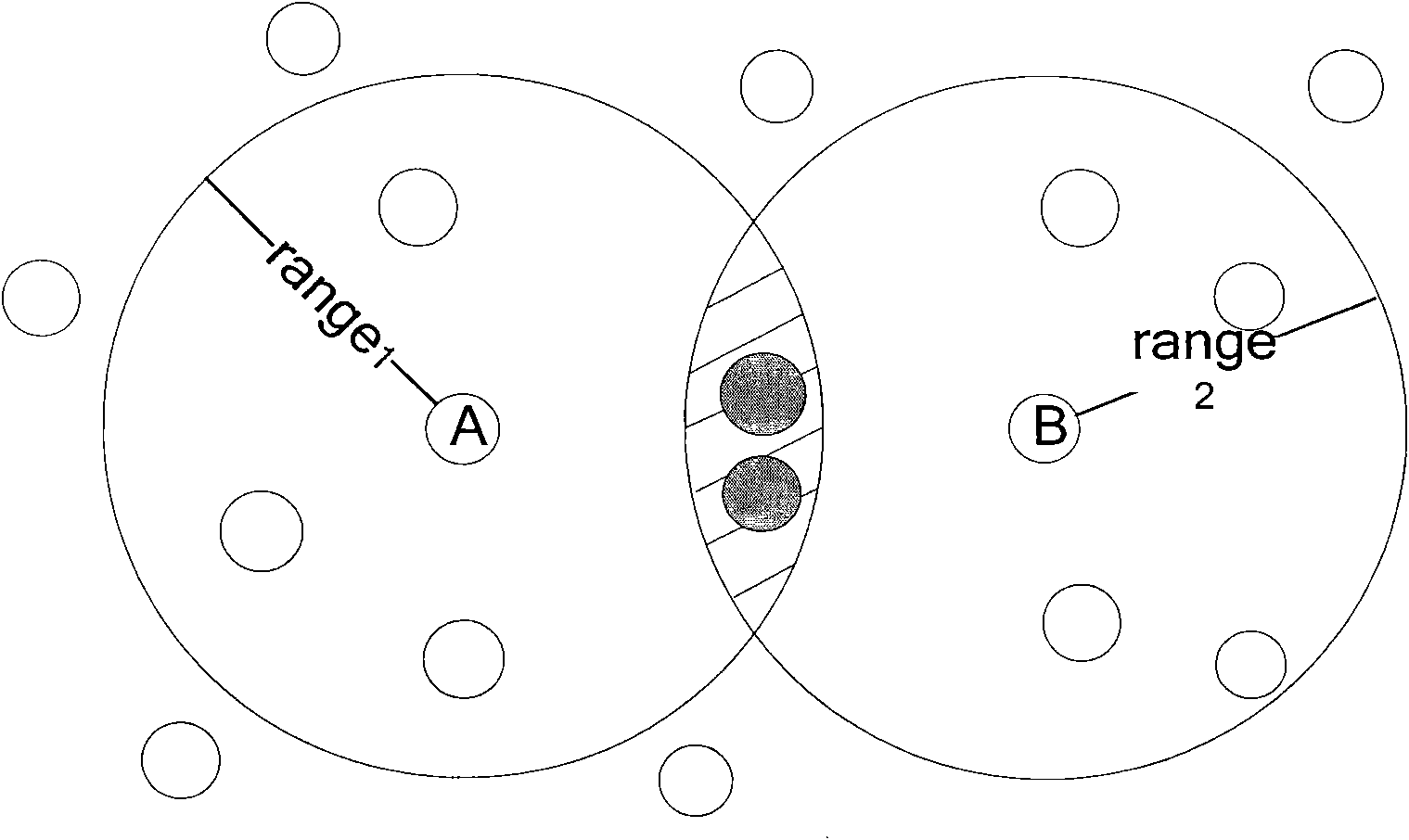
Method and system determining communication destination node position in automobile self-organized network
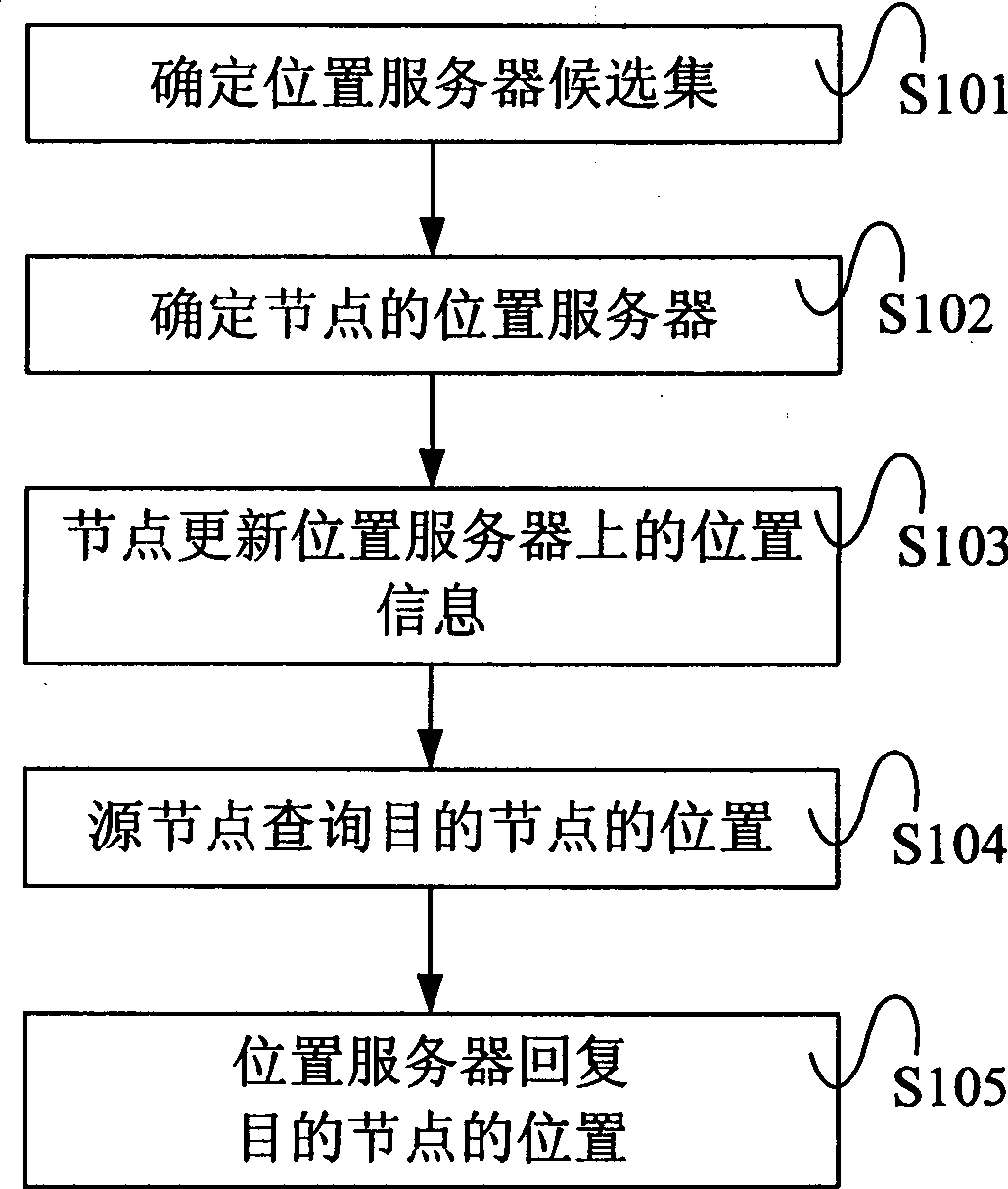
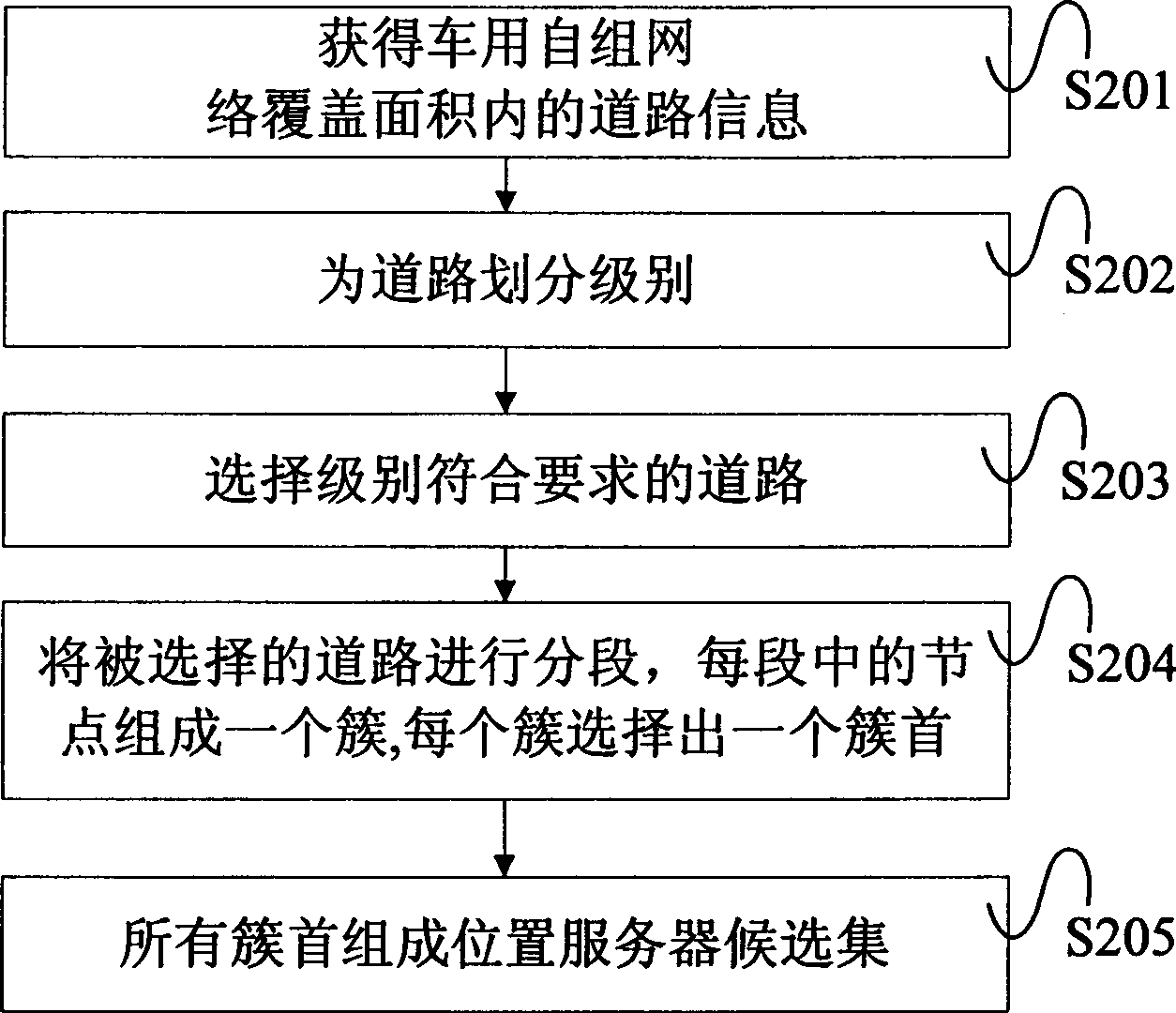
InactiveCN101364921AReduce the probability of invalidationImprove reliabilityBroadcast specific applicationsData switching by path configurationCommunication sourceSelf-organizing network
The invention relates to a method for determining the position of a communication destination node in a vehicle ad-hoc network and a system thereof. The method comprises the following steps: a path is selected in the vehicle ad-hoc network and divided into path sections, a node is selected from each path section, and all the selected nodes form a position server candidate generation; the vehicle ad-hoc network is divided into a plurality of regions, and a position server corresponding to each region is selected from the position server candidate generation for the nodes; position renewal messages are sent from the nodes to all or part of the position servers; a position server for the destination node is selected at the communication source node, and a position inquiry message is sent to the position server; the position server receives the position inquiry message, if the recorded position information meets the requirement, a reply to the position information is made, or else, the position inquiry message is forwarded to other position servers. The invention can improve the reliability of position service, and reduce the maintenance expense and the position inquiry delay.
Owner:烟台惠通网络技术有限公司
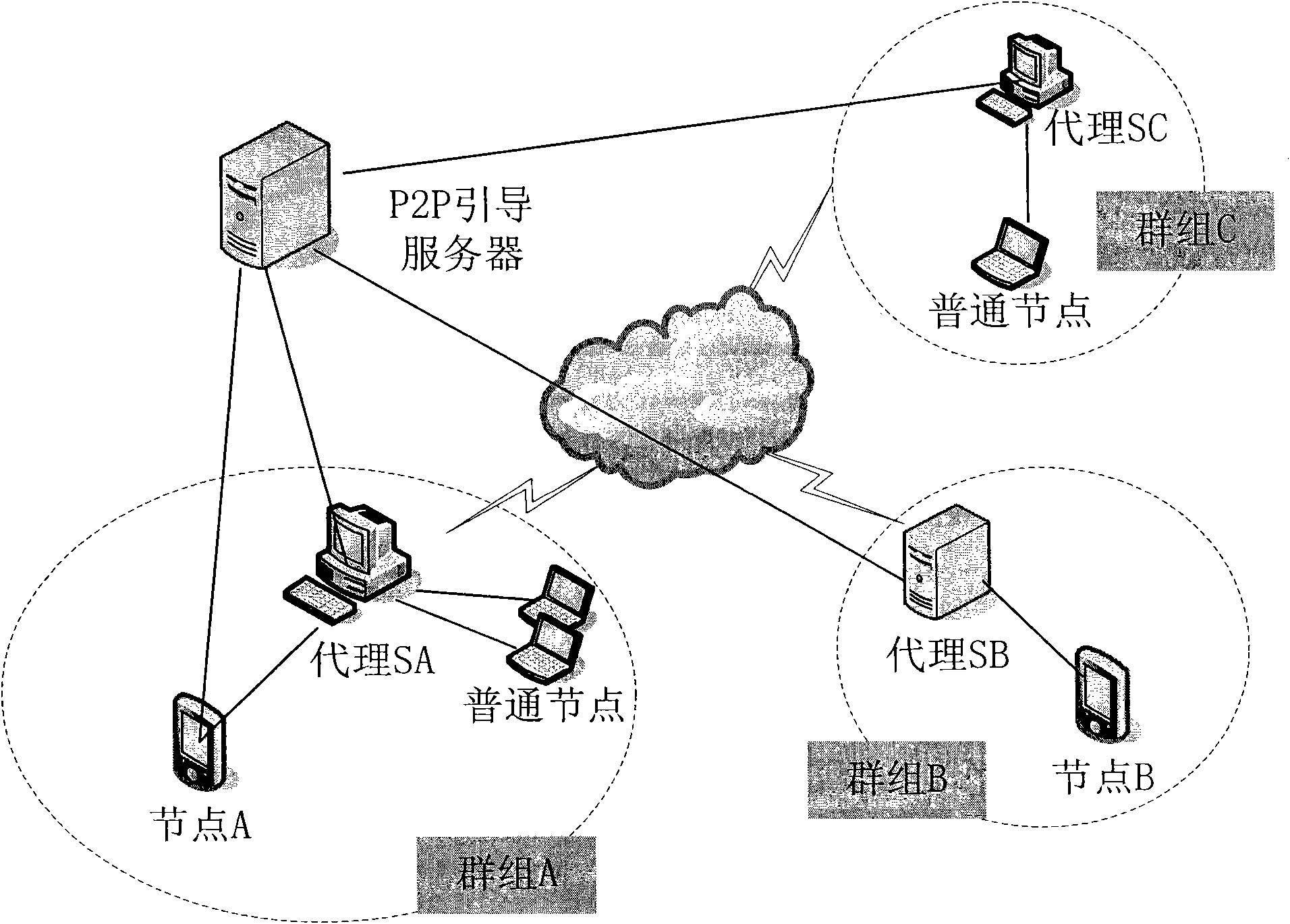
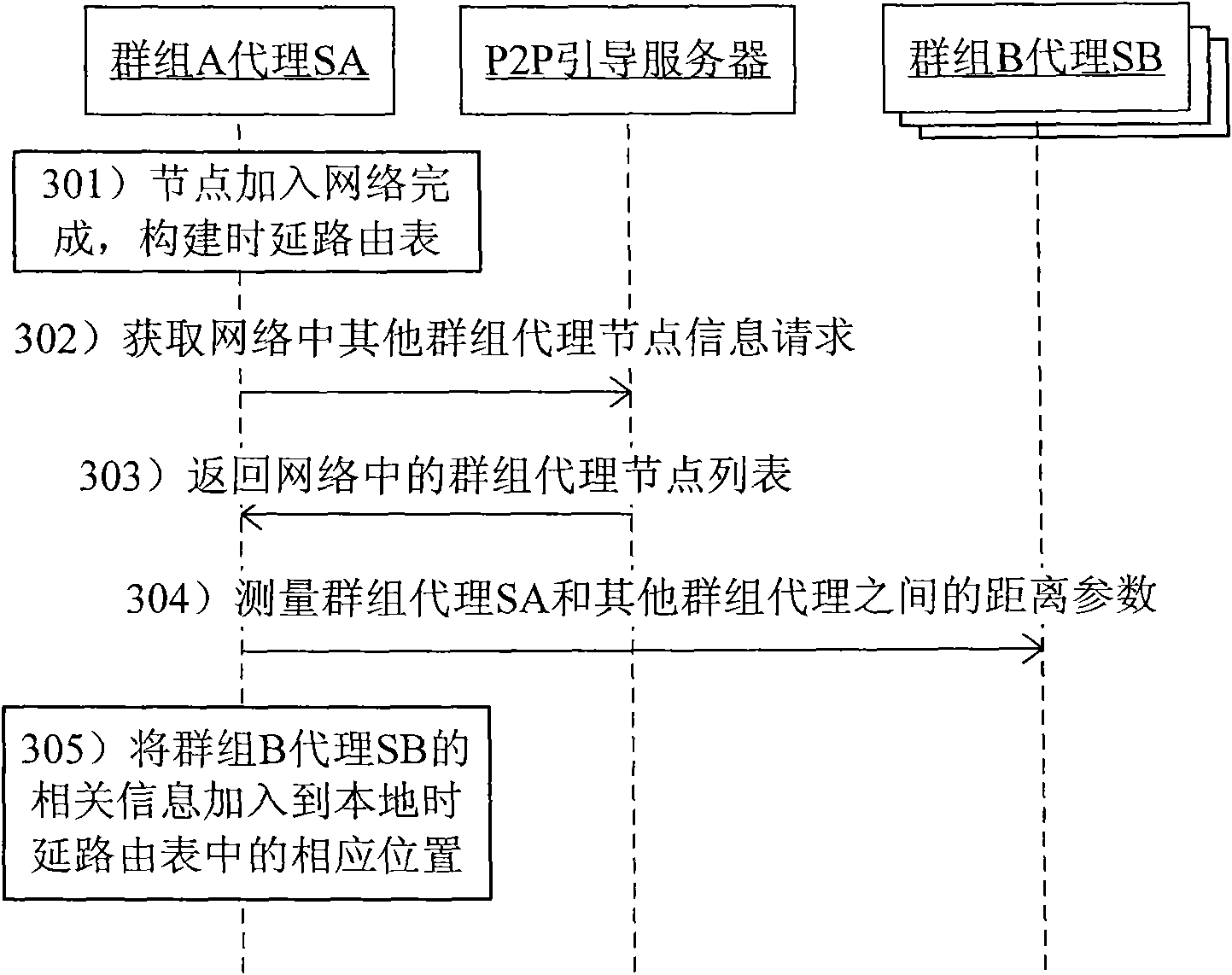
Method and system for selecting transit node of voice over internet protocol service in peer-to-peer network
InactiveCN102143290AReduce maintenance overheadInterconnection arrangementsTransmissionInternet protocol suiteTransit network
The invention discloses a method and a system for selecting a transit node of a voice over internet protocol service in a peer-to-peer network, wherein the method comprises the following steps of: setting the peer-to-peer network to comprise multiple groups, wherein each group comprises a group proxy node and one or more common nodes; and when the common nodes in the peer-to-peer network need the selection of the transit node, initiating a transit query request to the group proxy node of a per se ownership group, and selecting the transit node by the group proxy node. According to the method, the peer-to-peer is divided into multiple groups, and all member nodes in the groups perform transit node selection through the group proxy node, so the transit network maintenance cost is greatly reduced, and a more large-scale network can be supported.
Owner:ZTE CORP
Selection method of neighbor nodes related to physical topology in P2P system
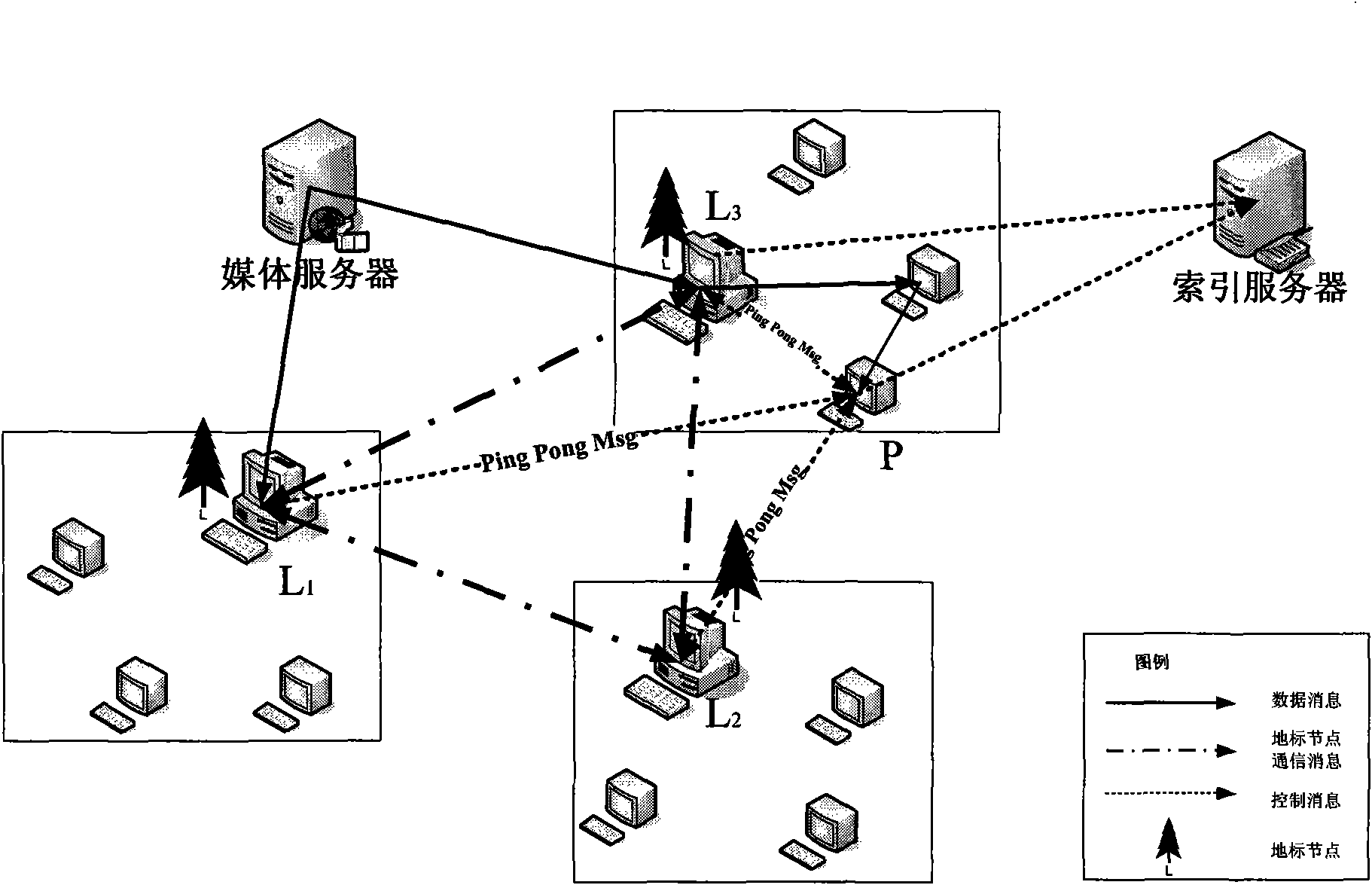
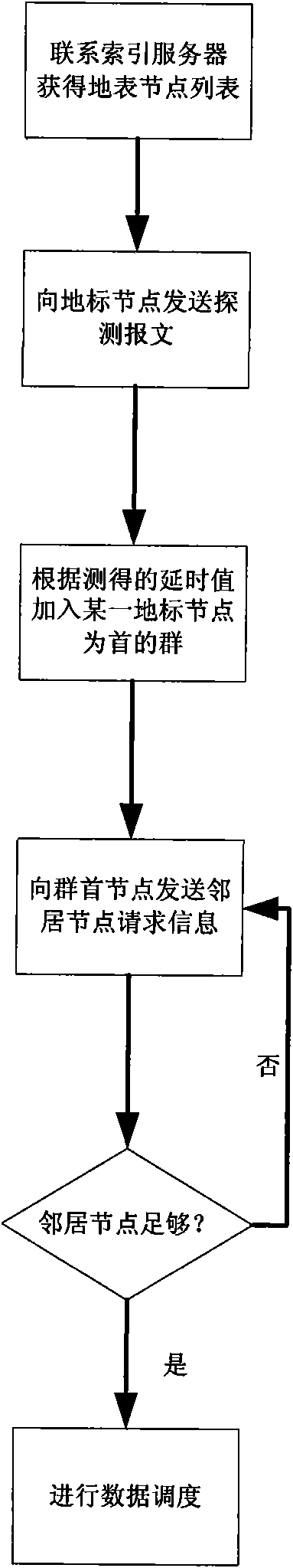
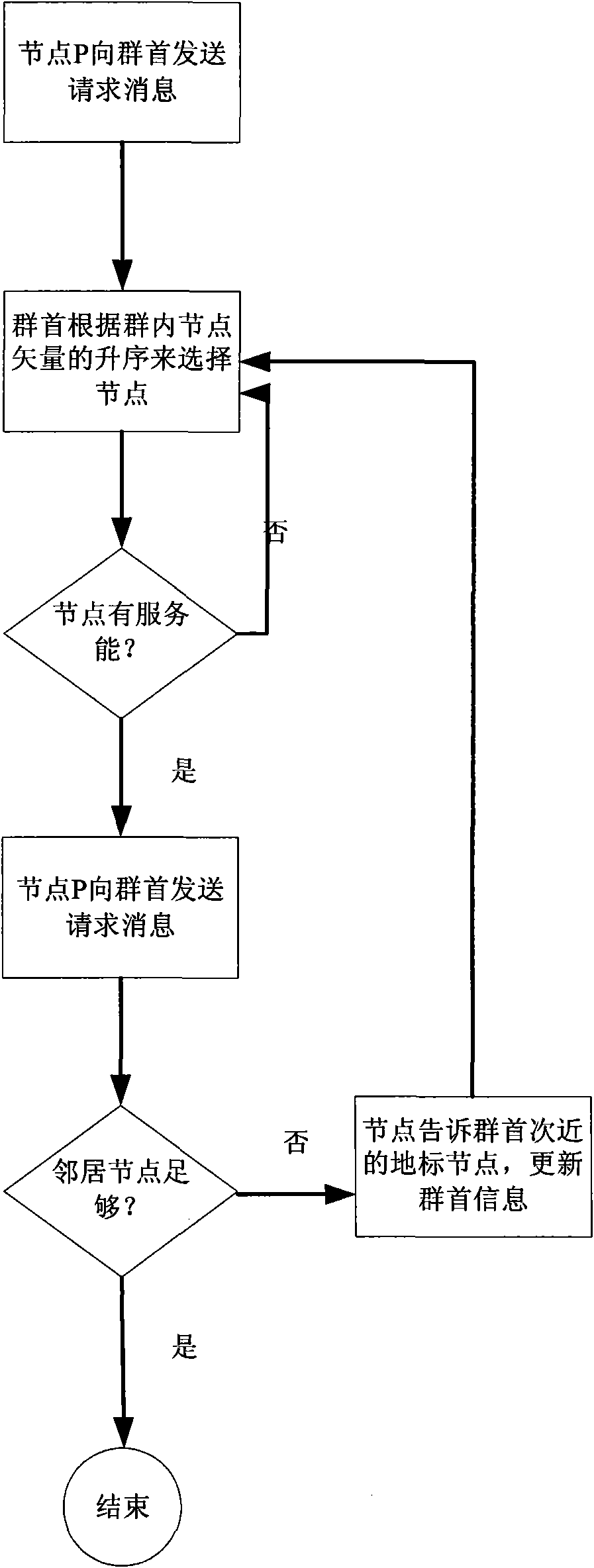
ActiveCN101645925AImprove exchange efficiencyRelieve pressureTransmissionDelayed timeData interchange
The invention relates to a selection method of neighbor nodes related to physical topology in a P2P system. The method comprises the following steps: 1) a group of landmark nodes is determined; 2) each landmark node is taken as a center to build a cluster, wherein, the cluster comprises cluster-head nodes and member nodes; the landmark nodes are cluster-head nodes, and delay time from the member nodes in the cluster to the cluster-head nodes is less than a predetermined threshold value; and the cluster-head nodes store an in-cluster delay table, and the in-cluster delay table records the delaytime from the member nodes in the cluster to the cluster-head nodes and sequentially arranges the delay time according to size of each delay time; 3) a certain solicited node requests a neighbor nodelist to the cluster-head nodes in the cluster of the node; and 4) the cluster-head nodes return the neighbor node list to the solicited node according to the in-cluster delay table. The method can help the P2P system improve data exchange efficiency, realize load balance and reduce maintenance expenditure.
Owner:ZHENGZHOU SEANET TECH CO LTD
Content security protection method of embedded television terminal system
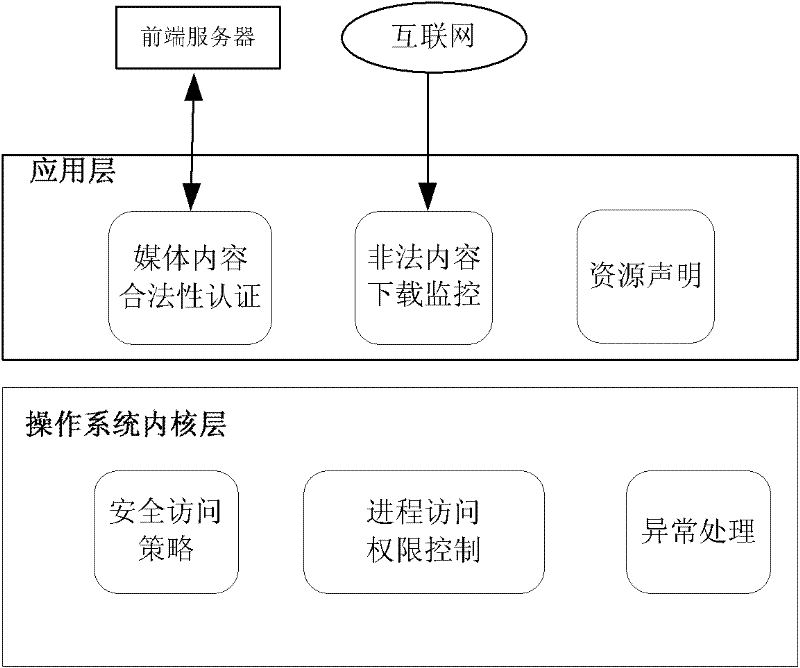
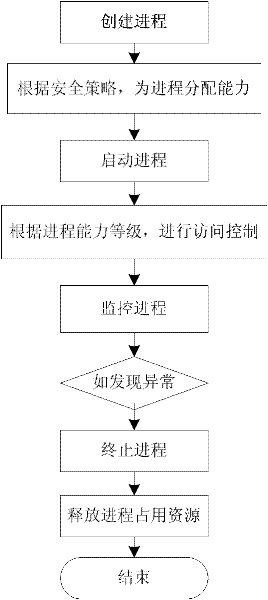
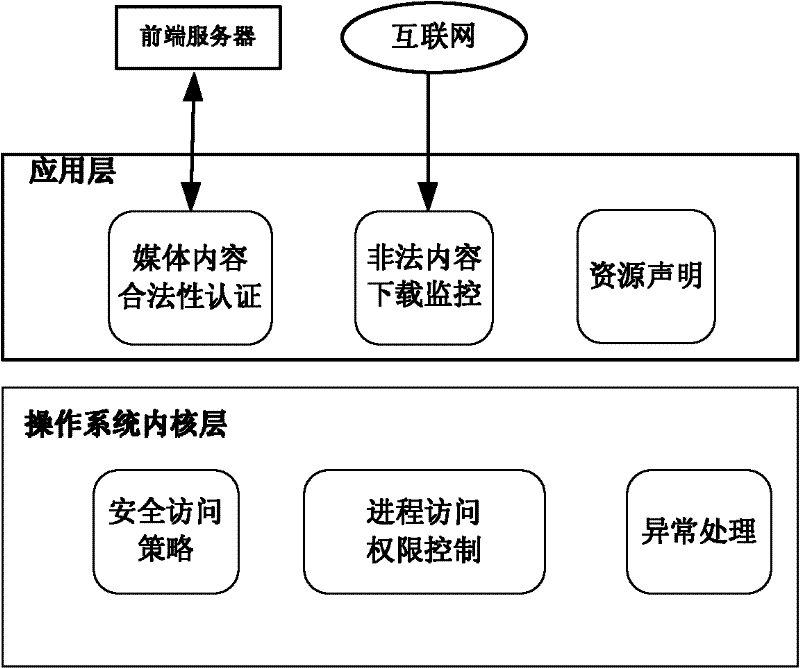
InactiveCN102547400AAvoid visitingPrevent tamperingComputer security arrangementsSelective content distributionOperational systemData integrity
The invention relates to a content security protection method of an embedded television terminal system. The method aims at attacks of illegal contents and malware, the real-time monitoring for the illegal contents and the proactive defense for malicious codes are ensured at a terminal, the presentation of the illegal contents and the damage for resource files of the system are prevented, and the content security control for the embedded television terminal is realized. The method comprises a TS (Transport Stream) content security mechanism based on digital watermarking, an external-network access restricting mechanism based on a resource declaration and a process access control mechanism, wherein the TS content security mechanism is that watermarking is added in a TS at the front end, the data flow is analyzed by the terminal through a corresponding digital watermarking algorithm, the measurement error of data integrity can be generated when the content is tampered or replaced, and then an application is stopped and closed; the external-network access restricting mechanism is that whether the application is allowed to access a network address or not is determined according to a white list used for maintaining a legal network address in the resource declaration; and the process access control mechanism is that the process of the embedded television terminal is defined through a security policy to control the access for the resource files in an operation system kernel layer.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Real-time wireless sensor network routing method supporting large-scale node application
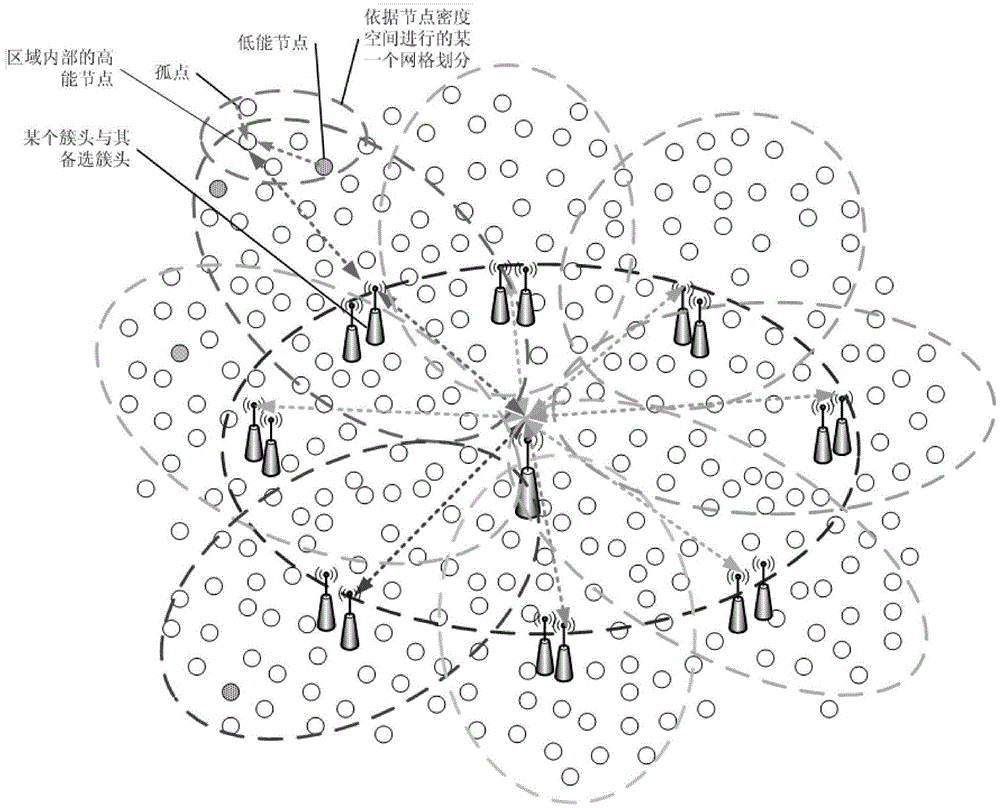
ActiveCN104684041AAvoid disasterReduce rebuild frequencyNetwork topologiesHigh level techniquesEnergy balancingMobile wireless sensor network
The invention relates to a real-time wireless sensor network routing method supporting large-scale node application. A network is constructed by combining a core cluster head routing mechanism and a flat routing mechanism, so that routing is determined by frequency, and is independent of a specific node; a cooperative processing strategy and an energy balancing strategy are adopted between the nodes; the network is divided into grids according to the space density of the nodes, and an isolated point reduction optimization measure is adopted. According to the method, inter-network cluster-based routing signal interference is reduced, the problem of network disasters caused by routing node failures is solved, the reconstruction frequency of network clusters can be maximally reduced, the maintenance overhead of the clusters is reduced, and the response real-time performance of the whole network is improved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
Method and apparatus for providing permission information in a security authorization mechanism
InactiveUS20060156021A1Quick identificationReduce the burden onComputer security arrangementsSecuring communicationAuthorizationDatabase
A method and apparatus for providing an extensible grouping mechanism for security applications for use in a computer system. Groups may be established and maintained by non-system administrators and used to control actions that are taken with respect to objects, such as files and other resources. The groups and associated security functions may be implemented across a plurality of different software products and optionally integrated into an existing security mechanism maintained by system administrators. Software products used in the system may be arranged to request authorization to perform requested actions with respect to objects access to which is not controlled by a systems administrator, and / or provide information specifying an object or object type and actions that are performable with respect to the object or object type by the respective software product.
Owner:MICROSOFT TECH LICENSING LLC
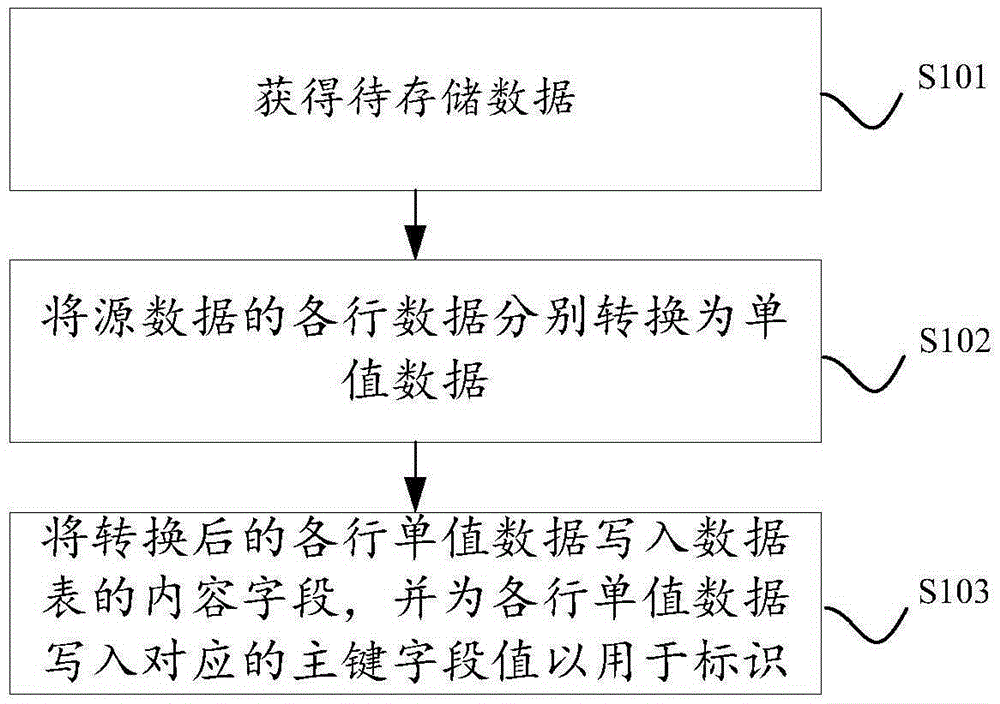
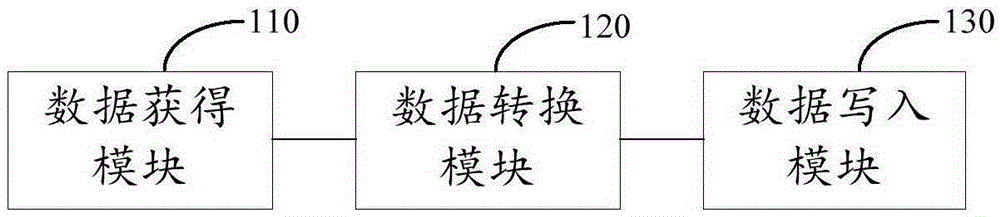
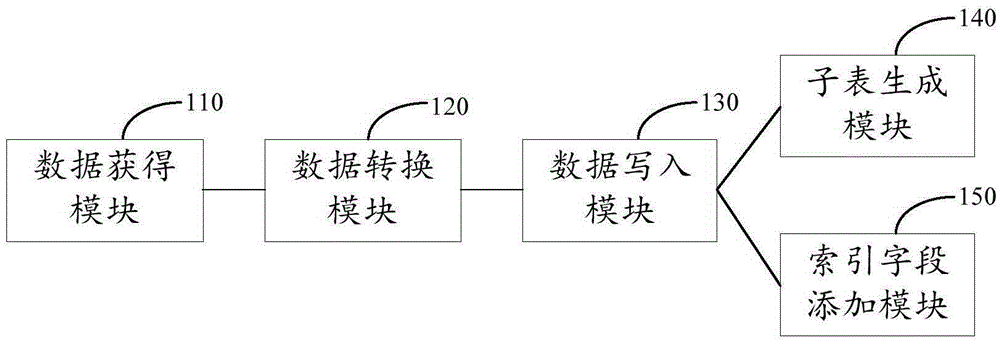
Data storage method and device
PendingCN106547786AReduce maintenance overheadReduced number of fieldsSpecial data processing applicationsData valueSource data
The invention discloses a data storage method and device. The data storage method and device are used for storing data of different structures into the same data table, and the data storage method comprises the steps of: acquiring source data to be stored; converting each row of data of the source data into single-value data respectively, wherein each single-value data value carries key value pair information of each column of the row of source data; writing each row of converted single-value data into a content field of the data table, and writing a corresponding main key field value for identifying for each row of single-value data. By adopting the solution, the data having different structures can be uniformly stored in the same data table, so that the overall maintenance overhead of data is effectively reduced. In addition, the quantity of fields to be processed practically in the data write process is obviously reduced, so that the storage and processing efficiency can be effectively improved.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com