Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Prevent data theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
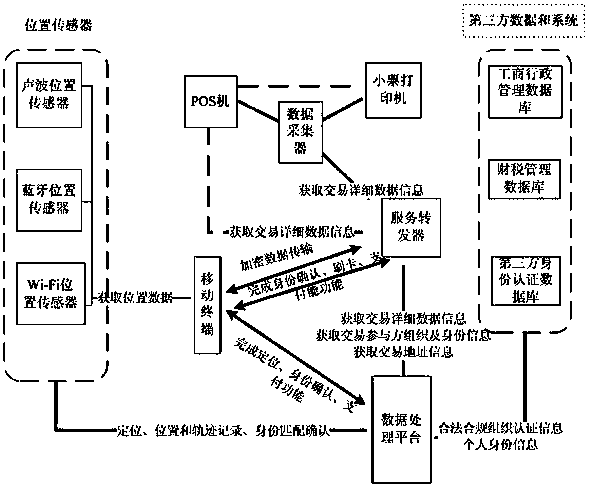
All-dimensional safety positioning trade information integration method
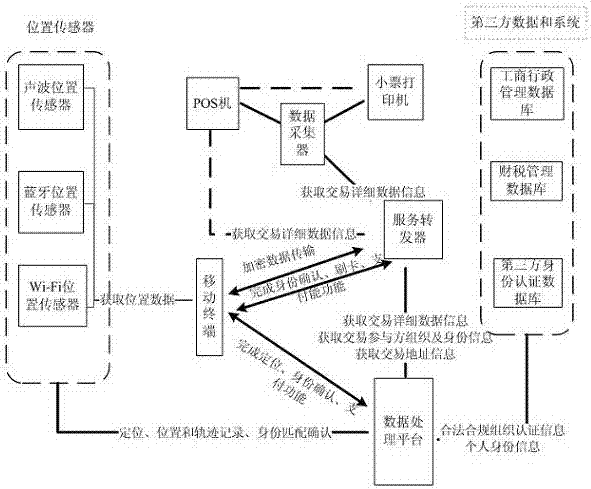
The invention relates to an all-dimensional safety positioning trade information integration method. Various kinds of correlation information, including seller information, buyer personal identity information, trade place information and trade content information, of true trades are obtained in real time to be transmitted to a data processing platform, the data processing platform obtains certified correlation information from third-party databases such as an industry and commerce administration database and a finance and taxation administration database, the obtained trade correlation information is compared and verified, and therefore whether a trade is legal, compliant and true or not can be comprehensively judged. According to the all-dimensional safety positioning trade information integration method, correlation data of the practically-generated trading activity can serve as basic data of finance and taxation collection administration, the collection data can be real and accurate, the trading activity is normalized, and cheating conditions of falsely invoicing and falsely declaring the trading data at present can be founded as early as possible and can be rapidly and accurately screened, so that the adaptation of the method will bring a transformation of a finance and taxation collection administration method.
Owner:北京数衍科技有限公司
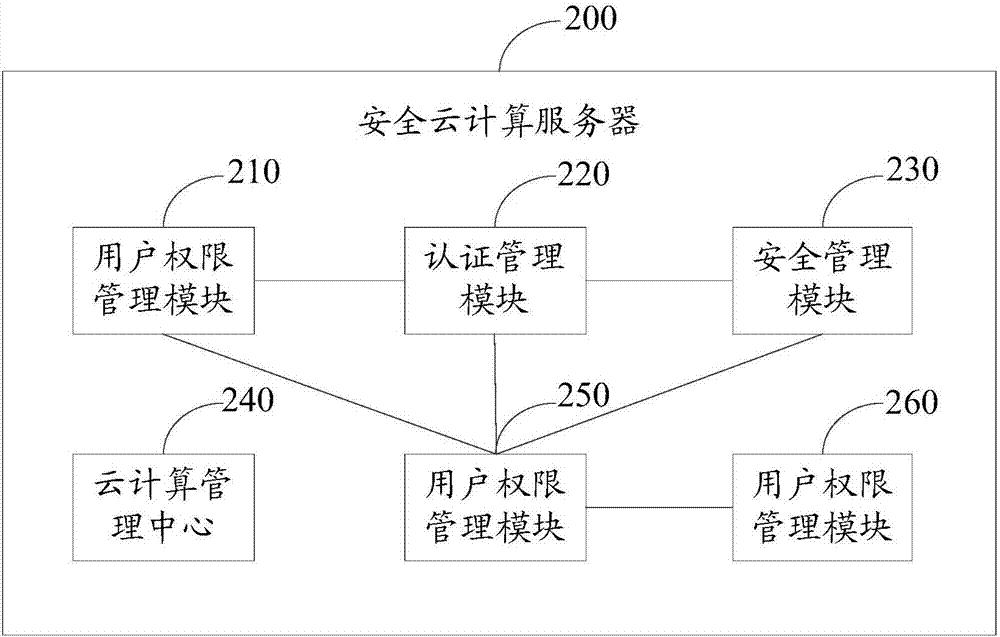
Secure cloud computing system
InactiveCN107197041AResolve the Leakage SituationAvoid lossDigital data protectionTransmissionData informationInformation security
The invention is applicable to the field of information security, and provides a secure cloud computing system. The secure cloud computing system comprises a cloud center, a secure cloud computing server and a proxy terminal, the cloud center is connected with the secure cloud computing server, the proxy terminal is installed on the secure cloud computing server and is in communication connection with the cloud center; a data storage form of three structures, namely, an independent database, an isolated database and a shared database, is adopted, the storage form can be selected according to the data security level, thereby not only saving resources and reducing the cost, but also providing effective security guarantee for the data storage; meanwhile, by means of the identity verification manner, the condition of user information leakage caused by the weak protection measure of the cloud computing terminal is effectively solved, the identity loss, data stealing, information loss and other potential safety hazards are prevented, and in the case of communication abnormality or network interruption, local terminal backup area data and local terminal backup area data and parameters can be used to prevent the loss of user data information in extreme cases.
Owner:SHENZHEN QIXIN GRP LLC
In-vehicle network safety communication system and method
ActiveCN110943957AGuaranteed to be legalEnsure safetyKey distribution for secure communicationSecure communicationNetwork connection
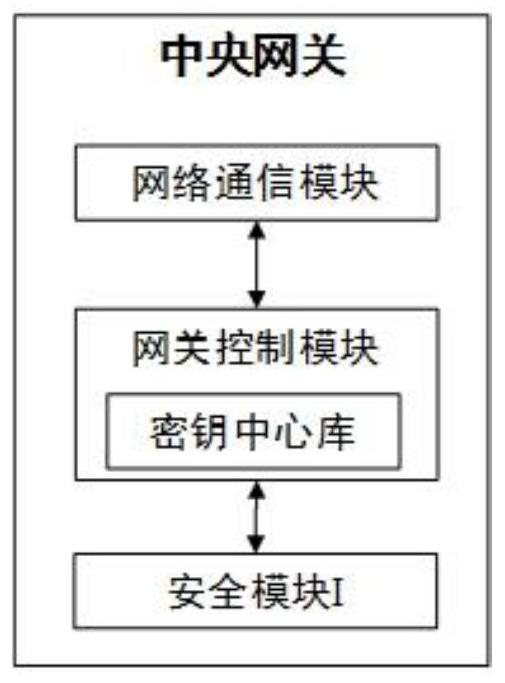
The invention provides an in-vehicle network safety communication system and method. The in-vehicle network safety communication system comprises a TSP platform, a central gateway, a domain controllerand ECU equipment. The TSP platform is connected with the central gateway through a network, the central gateway is connected with the one or more domain controllers through a network, and the domaincontrollers are connected with the one or more ECU devices through vehicle buses. The method comprises: after first identity authentication and key negotiation are carried out between the TSP platform and the central gateway, constructing a first secure channel, and the TSP platform carrying out encrypted communication with the central gateway through the first secure channel; performing second identity authentication and key distribution between the central gateway and the domain controller, and then constructing a second secure channel, wherein the central gateway performs encrypted communication with the domain controller through the second secure channel; and after third identity authentication and key distribution are carried out between the domain controller and the ECU equipment, constructing a third secure channel, and the domain controller carrying out encrypted communication with the ECU equipment through the third secure channel.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
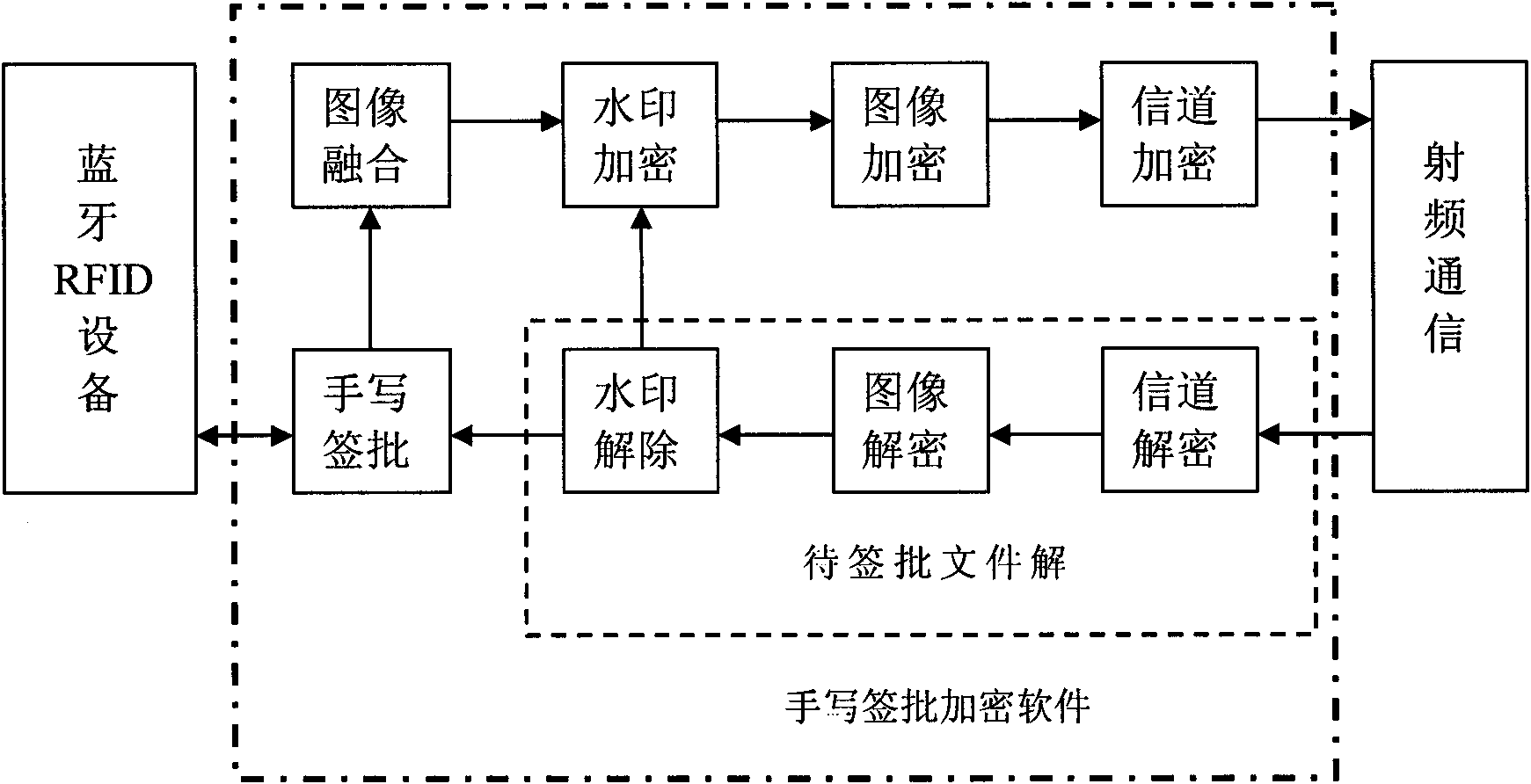
Encrypted writing signing mobile terminal
InactiveCN101872420AReduce the possibility of theftReduce lossesNear-field transmissionCharacter and pattern recognitionComputer moduleComputer terminal
The invention relates to an encrypted writing signing mobile terminal, comprising a display module, a writing input module, a control operation module and a communication module for data exchange. The display module, the writing input module and the communication are respectively connected with the control operation module. The encrypted writing signing mobile terminal also comprises a data processing module which comprises writing signing software, wherein the writing signing software can be executed by the control operation module to realize the writing signing function, and the data processing module is connected with the control operation module. The invention improves the automatic office level and efficiency of governments and enterprises, realizes the purpose that office business can be handled anywhere at any time, and reduces the carbon emission.
Owner:石明霞
Wireless network access method and wireless network access device
ActiveCN105163312APrevent access to wireless network problemsAvoid economic lossTransmissionSecurity arrangementTelecommunicationsSecurity level
The invention provides a wireless network access method and a wireless network access device. The wireless network access method comprises the following steps: receiving a query request which is sent by a wireless access point after an access password sent by the wireless access point to a terminal is verified to be correct, wherein the query request includes the terminal identifier, the wireless access point identifier and the request time; determining the security level of the terminal in a pre-established database according to the query request, wherein the terminal identifier, the wireless access point identifier, the request time and the correspondence between the terminal and the corresponding security level are stored in the database; and returning a response message corresponding to the security level to the wireless access point to enable the wireless access point to process a wireless access request according to the response message. Therefore, whether or not to allow a terminal to access a wireless network of the wireless access point can be determined according to the judged security level of the terminal, and a malicious terminal can be prevented from accessing a home wireless network.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
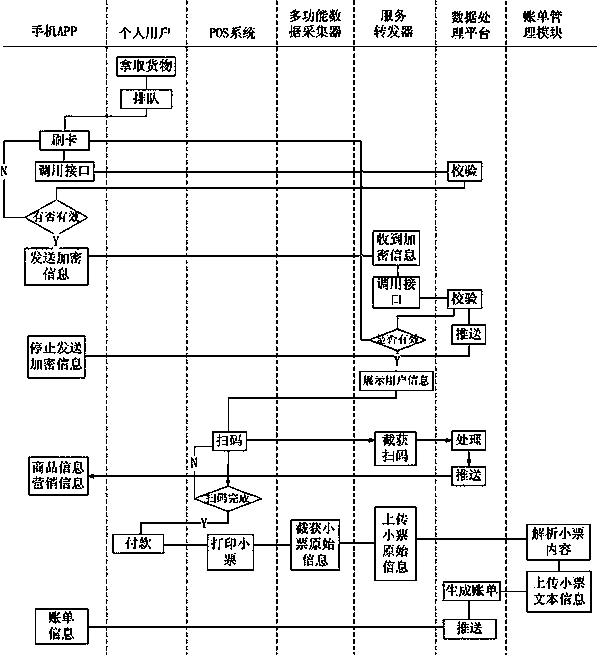
All-dimensional safety positioning trade information integration system
InactiveCN103778532AImprove abilitiesImprove the level ofBuying/selling/leasing transactionsPoint-of-sale network systemsPaymentTransaction data
The invention relates to an all-dimensional safety positioning trade information integration system which comprises a POS system, a service transponder and a data processing platform. The POS system is used for confirming trading payment, the service transponder is used for obtaining trading content information from the corresponding POS system and transmitting the trading content information and trading seller information to the data processing platform, and the data processing platform is used for accessing an industry and commerce administration database and a finance and taxation administration database, verifying the seller information and judging whether a trade is legal and compliant or not. According to the all-dimensional safety positioning trade information integration system, correlation data of the practically-generated trading activity can serve as basic data of finance and taxation collection administration, the collection data can be real and accurate, the trading activity is normalized, and cheating conditions of falsely invoicing and falsely declaring the trading data at present can be founded as early as possible and can be rapidly and accurately screened, so that the adaptation of the system will bring a transformation of a finance and taxation collection administration method.
Owner:北京购阿购技术服务有限公司
A method for developing application software
InactiveCN109375908ASpeed upShorten the timeSoftware designSoftware engineeringApplication software
A method for developing application software includes the following steps: S1: Firstly, economic information and technical information of software development required for software development are collected, S2: According to the collected information, analyze the collected information, S3: Information on page requirements for software development, The function requirement information and the component loading requirement information are coded, S4: the coded page requirement information, the function requirement information and the component loading requirement information data are integrated,S5: the developed software is tested, S6: the modified data is packaged into a software installation package for users to use. The design of the method is reasonable and convenient for the developmentof the software to be developed, which makes the software more matched with the industry to which the software belongs, facilitates the user to use the software, enhances the sense of experience of the user, and at the same time, the development speed is fast, the time is saved, and the work efficiency is improved.
Owner:华翕软件股份有限公司
External user login and backup system
ActiveCN101827090AImprove securityIntuitive monitoringTransmissionAuthentication serverVirtual computing
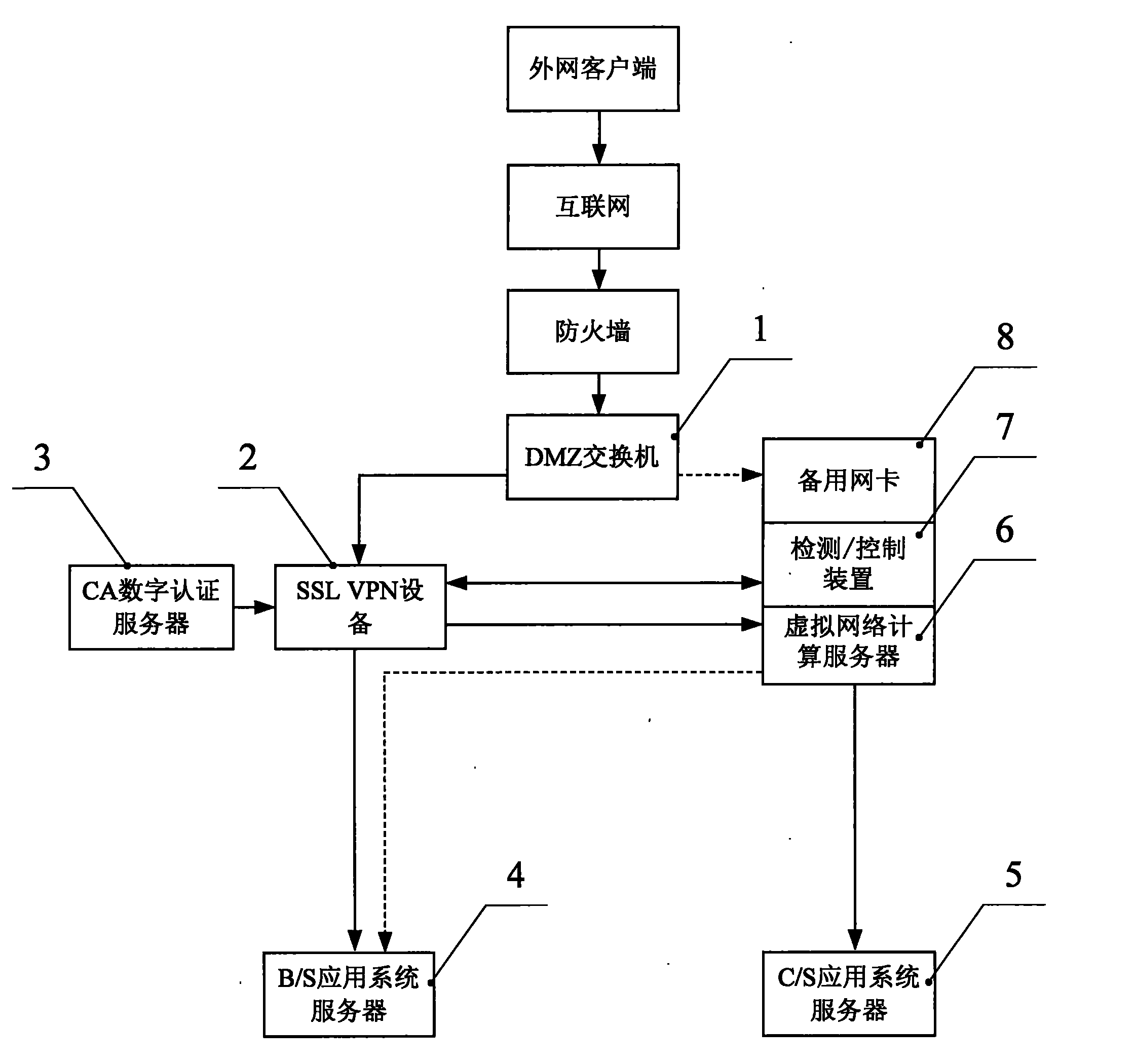
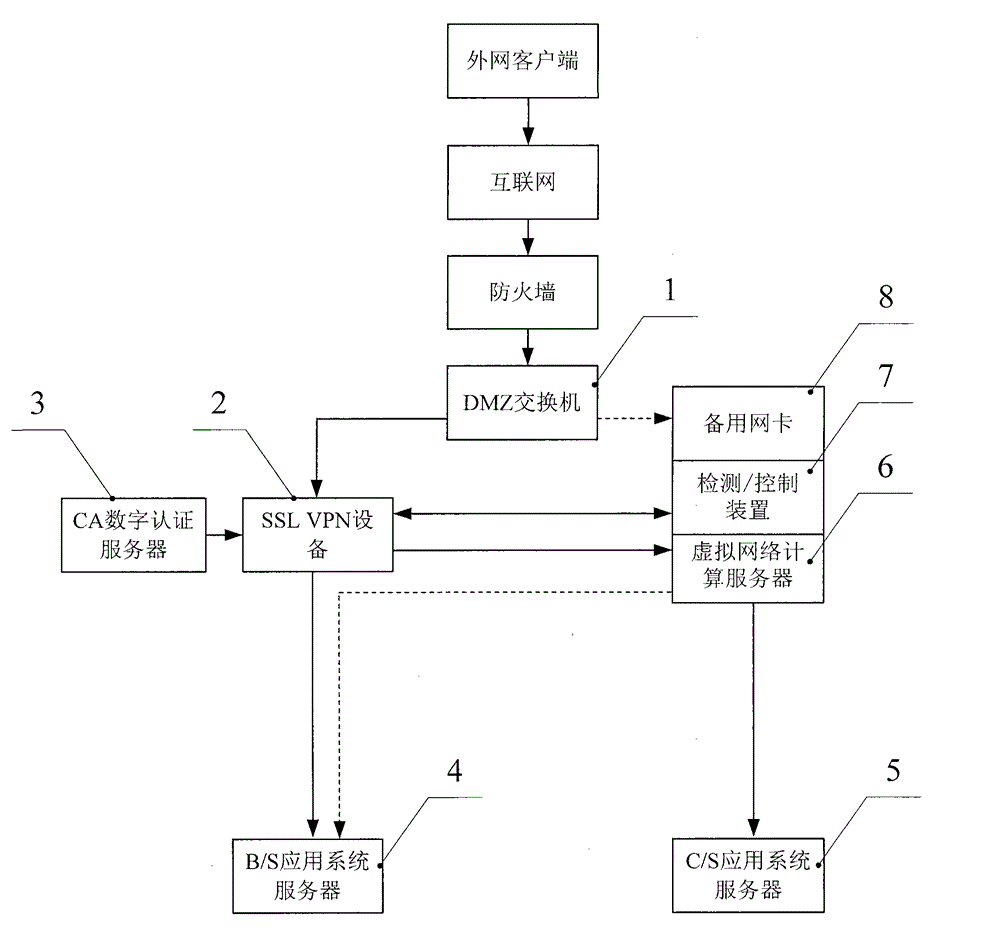
The invention relates to the technical field of SSL VPN, CA certification and virtual computing. Particularly, the invention relates to an external user registering system. The invention comprises a DMZ switch and SSL VPN equipment. The SSL VPN equipment is connected with the DMZ switch. The SSL VPN equipment is also connected with a B / S application system server; a CA digital certificate server is connected with the SSL VPN equipment; the virtual computing server is connected with the SSL VPN equipment. The virtual computing server is connected with a C / S application system server. The invention also comprises standby network card arranged on a virtual network computing server. The standby network card is connected with the DMZ switch. A monitoring / control device is arranged on the virtual network computing server. The virtual network computing server is also connected with the B / S application system server. In the application business of SSL VP, virtual network computing technology is adopted for backup. The monitoring / control device can switch over automatically so that the external user can login and visit internal network smoothly.
Owner:CHINA TOBACCO ZHEJIANG IND
Methods and systems for branch predictor
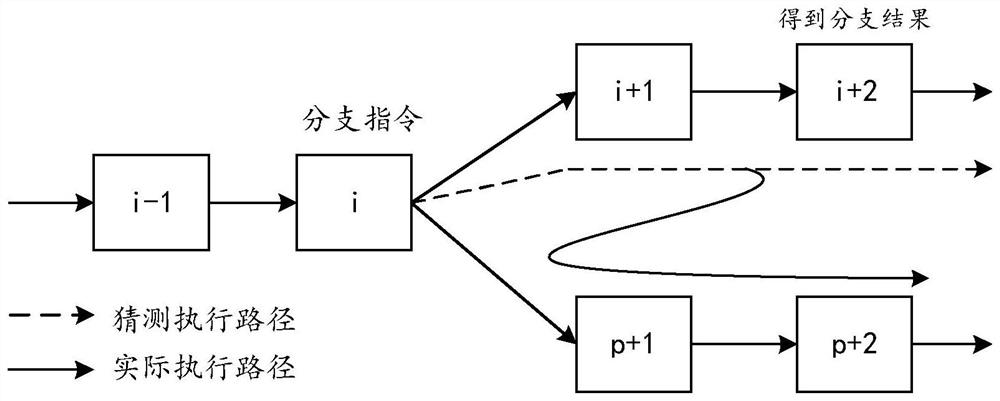
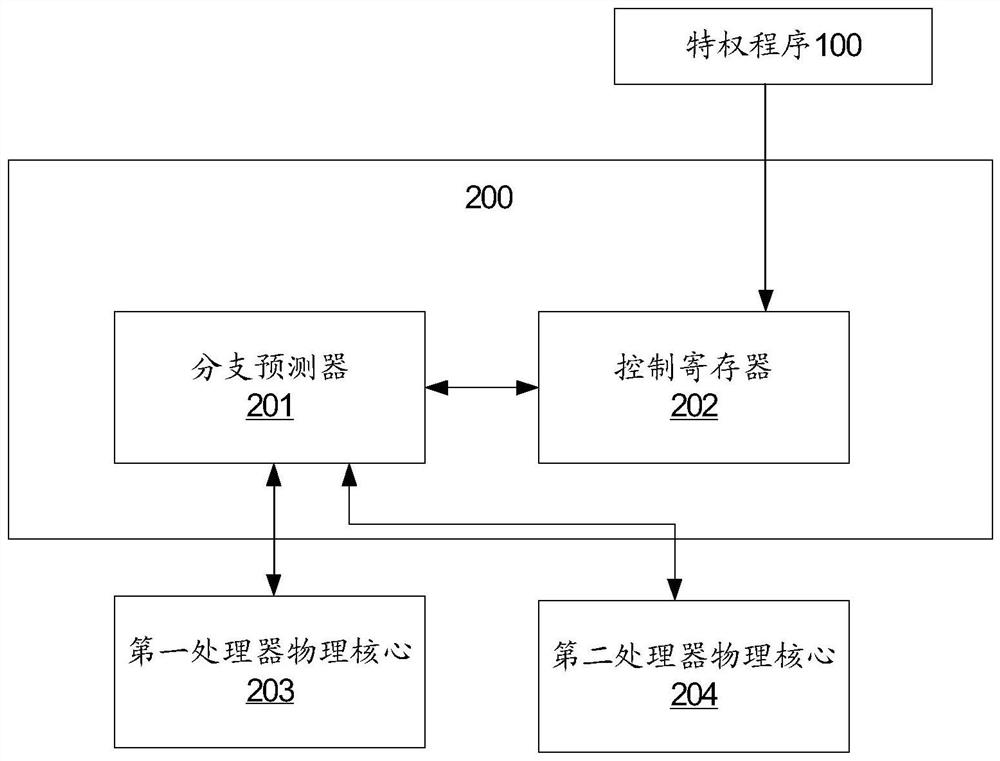
ActiveCN112035170AAvoid interferencePrevent data theftConcurrent instruction executionRecordComputer engineering
A method and system for a branch predictor shared by different processor logic cores of the same processor physical core is provided, the method comprising: in a case of enabling a flag function, adding a piece of branch prediction record information in response to one processor logic core, adding a flag indicating which processor logic core the branch prediction record information is added to theadded branch prediction record information; and when the branch predictor carries out branch prediction on a program executed on the first processor logic core, branch prediction record information added to the first processor logic core being determined according to the mark. Branch prediction is performed using only branch prediction record information added to the first processor logic core indicated by the flag.
Owner:HYGON INFORMATION TECH CO LTD
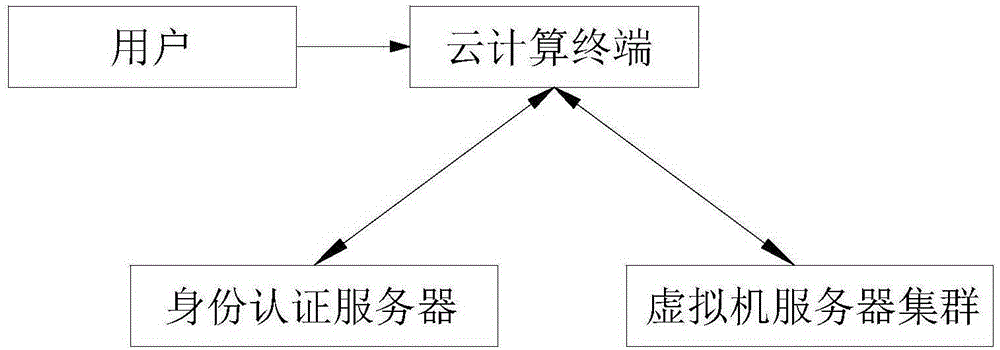
Cloud computing-based cloud authentication method and system
InactiveCN105208012AAvoid identity lossAvoid information that is not secure and cannot be kept privateTransmissionClient-sideVirtual machine
The invention relates to a cloud computing-based cloud authentication method. The method includes the following steps that: A, a cloud computing terminal generates a unique equipment serial number; B, the identity of a user is read, and an identity authentication server connected with the cloud computing terminal verifies the identity of the user, if the user does not exist, the cloud computing terminal restores initial settings, the method returns the step A; and the cloud computing terminal is connected with and starts a cloud virtual machine cluster server through a client end connection protocol; D, whether the cloud virtual machine cluster server is started normally is judged, if the cloud virtual machine cluster server is started normally, step F is executed, if the cloud virtual machine cluster server is started abnormally, step E is operated. With the cloud computing-based cloud authentication method of the invention adopted, the problem of user information weak caused by weak protective measures of the cloud computing terminal can be effectively solved, and potential safety hazards in various aspects, such as identity confidentiality loss, data interception and information loss can be effectively avoided; a complete cloud identity and cloud data trusted protection chain can be formed; and the problem of unsafety of information and the problem of incapability of realizing confidentiality of the information under a cloud computing environment can be effectively avoided.
Owner:WUHAN YUNTONG YINGFEI TECH CO LTD
Electronic storage device and data protection method thereof
InactiveCN103870766APrevent data theftDigital data protectionInternal/peripheral component protectionElectrical batteryProtection mechanism
The invention discloses an electronic storage device and a data protection method thereof. The electronic device is electrically connected with a host and used for storing data of the host. The date protection method comprises the following steps of: providing a standby battery which is arranged in the electronic storage device and used for providing electric power needed by operation of the electronic device when the host does not provide power for the electronic storage device; setting a time set value; transmitting a login event to the electronic device; judging whether the electronic storage device needs to protect the stored data in the electronic storage device according to the time set value and the login event through the electronic device, and if so, the electronic storage device protects the stored data. A protection mechanism of the electronic storage device can make judgments according to the time set value and the login event or according to whether the login event reaches a login failure threshold value so as to protect data stored in the electronic storage device from being stolen by others.
Owner:SHENXUN COMP KUNSHAN +1
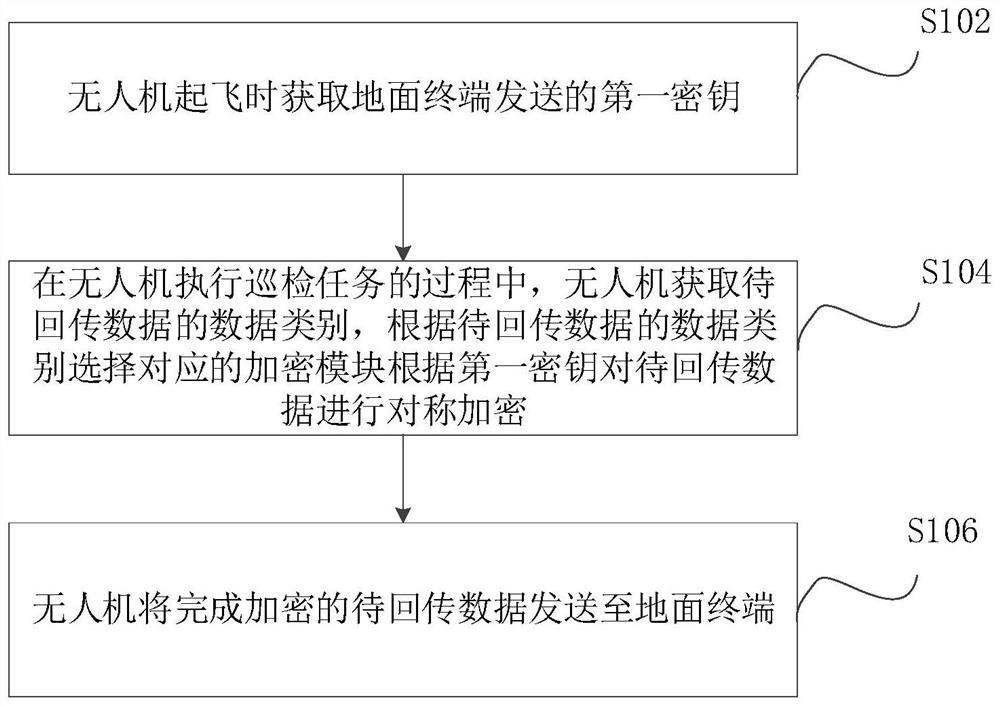
Unmanned aerial vehicle inspection system, encryption method thereof, unmanned aerial vehicle and ground terminal
PendingCN114726628APrevent data theftPrevent data from being tampered withKey distribution for secure communicationMultiple keys/algorithms usageUncrewed vehicleEncryption
The invention relates to an unmanned aerial vehicle inspection system, an encryption method thereof, an unmanned aerial vehicle and a ground terminal. The unmanned aerial vehicle inspection system comprises a ground terminal and at least one unmanned aerial vehicle. The encryption method comprises the steps of obtaining a first key sent by the ground terminal when the unmanned aerial vehicle takes off; in the process that the unmanned aerial vehicle executes the inspection task, the unmanned aerial vehicle obtains the data category of the to-be-returned data, and selects the corresponding encryption module according to the data category of the to-be-returned data to symmetrically encrypt the to-be-returned data according to the first key; and the unmanned aerial vehicle sends the symmetrically encrypted data to be returned to the ground terminal. According to the method, the security risks of data stealing, data tampering, identity counterfeiting and the like for the unmanned aerial vehicle inspection system can be avoided, and the data security of the unmanned aerial vehicle inspection system is greatly improved.
Owner:FOSHAN POWER SUPPLY BUREAU GUANGDONG POWER GRID
Trusted channel authentication system based on protection of sensitive data of evanescent members
ActiveCN113347213AAchieve protectionPrevent data theftDigital data protectionTransmissionAuthentication systemData security
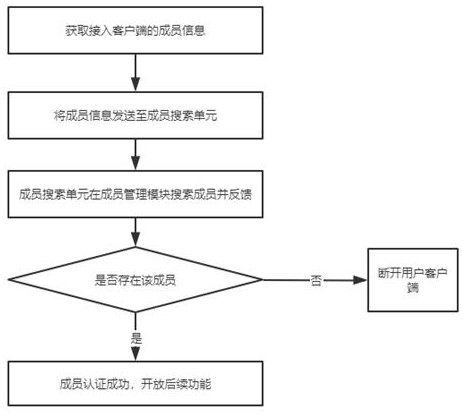
The invention provides a trusted channel authentication system based on protection of sensitive data of evanescent members, which comprises a member management module, a data management module, a trusted authentication module and a sensitive identification module, and is characterized in that the member management module is used for storing basic information of members and judging whether the members are evanescent or not; the data management module is used for storing data information of members, the credibility authentication module is used for acquiring the data information of the members and carrying out credibility authentication, and the sensitivity identification module is used for carrying out sensitivity identification on data items in the data information. The credible authentication module adopts an encryption protection mechanism when acquiring data, acquires a data storage code from the member management module as a certificate for acquiring the data from the data management module, and protects sensitive data of an evanescent user, so that the data security of the user is protected on the premise of ensuring the credible authentication function.
Owner:GLOBALTOUR GROUP LTD
Teaching information safety protection system based on cloud platform
ActiveCN111464543AImprove securityLess likely to leakTransmissionElectrical appliancesIntelligent NetworkThird party
The invention discloses a teaching information safety protection system based on a cloud platform, and particularly relates to the technical field of teaching information safety systems, which comprises a cloud platform, a system terminal and a plurality of personal modules. An intelligent gateway is connected between the cloud platform and the system terminal as well as the personal module, and the intelligent gateway is used for connecting the cloud platform and the system terminal with the personal module, carrying out data exchange and transmission and controlling connection and disconnection between the cloud platform and the system terminal; and each personal module is used for logging in the cloud platform and is configured with login identity verification including ID verification,fingerprint verification and face verification. A limited range is set for normal operation of the system. When a third party proves that the number of units is insufficient, corresponding data operation cannot be performed, so that the security of data in the system is improved.
Owner:HANGZHOU YUNTI TECH CO LTD
Authentication and key negotiation method and device, and storage medium
ActiveCN114726555AEnsure safetyPrevent data theftKey distribution for secure communicationUser identity/authority verificationPasswordTerminal equipment
Owner:南京易科腾信息技术有限公司
Wireless network access method and wireless network access device
ActiveCN105163312BPrevent access to wireless network problemsAvoid economic lossTransmissionSecurity arrangementSecurity levelWireless access point
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
External user login and backup system
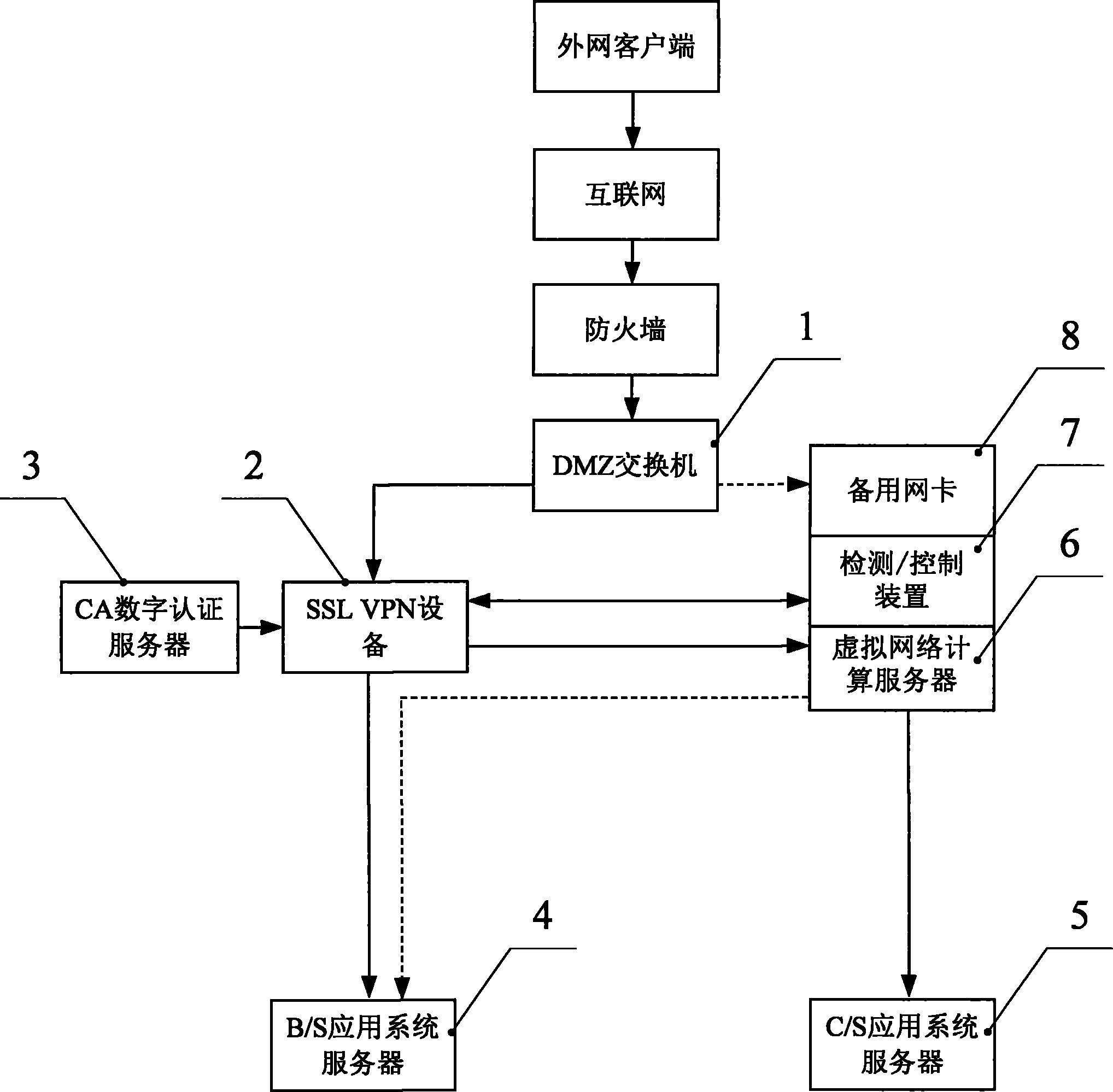
ActiveCN101827090BImprove securityIntuitive monitoringTransmissionAuthentication serverVirtual computing
The invention relates to the technical field of SSL VPN, CA certification and virtual computing. Particularly, the invention relates to an external user registering system. The invention comprises a DMZ switch and SSL VPN equipment. The SSL VPN equipment is connected with the DMZ switch. The SSL VPN equipment is also connected with a B / S application system server; a CA digital certificate server is connected with the SSL VPN equipment; the virtual computing server is connected with the SSL VPN equipment. The virtual computing server is connected with a C / S application system server. The invention also comprises standby network card arranged on a virtual network computing server. The standby network card is connected with the DMZ switch. A monitoring / control device is arranged on the virtual network computing server. The virtual network computing server is also connected with the B / S application system server. In the application business of SSL VP, virtual network computing technology is adopted for backup. The monitoring / control device can switch over automatically so that the external user can login and visit internal network smoothly.
Owner:CHINA TOBACCO ZHEJIANG IND
Comprehensive security positioning transaction information integration method
The invention relates to an all-dimensional safety positioning trade information integration method. Various kinds of correlation information, including seller information, buyer personal identity information, trade place information and trade content information, of true trades are obtained in real time to be transmitted to a data processing platform, the data processing platform obtains certified correlation information from third-party databases such as an industry and commerce administration database and a finance and taxation administration database, the obtained trade correlation information is compared and verified, and therefore whether a trade is legal, compliant and true or not can be comprehensively judged. According to the all-dimensional safety positioning trade information integration method, correlation data of the practically-generated trading activity can serve as basic data of finance and taxation collection administration, the collection data can be real and accurate, the trading activity is normalized, and cheating conditions of falsely invoicing and falsely declaring the trading data at present can be founded as early as possible and can be rapidly and accurately screened, so that the adaptation of the method will bring a transformation of a finance and taxation collection administration method.
Owner:北京数衍科技有限公司
A Trusted Channel Authentication System Based on Protecting Sensitive Data of Disappeared Members
ActiveCN113347213BAchieve protectionPrevent data theftDigital data protectionTransmissionData informationProtection mechanism
The invention provides a trusted channel authentication system based on protecting the sensitive data of vanished members, including a member management module, a data management module, a trusted authentication module and a sensitive identification module, the member management module is used to save the basic information of members and To judge whether a member disappears, the data management module is used to save the data information of the member, the trusted authentication module is used to obtain the data information of the member and perform credible authentication, and the sensitive identification module is used to check the data information of the member Sensitivity identification of data items. The trusted authentication module adopts an encryption protection mechanism when acquiring data, obtains the data storage code from the member management module as a credential for obtaining data from the data management module, and protects the sensitive data of the disappearing user, On the premise of ensuring the trusted authentication function, the user's data security is protected.
Owner:GLOBALTOUR GROUP LTD
An Encryption Method Based on rc4 Algorithm for Encryption of Code
ActiveCN107257282BProtection securityTaking into account efficiencyKey distribution for secure communicationUser identity/authority verificationRC4Algorithm
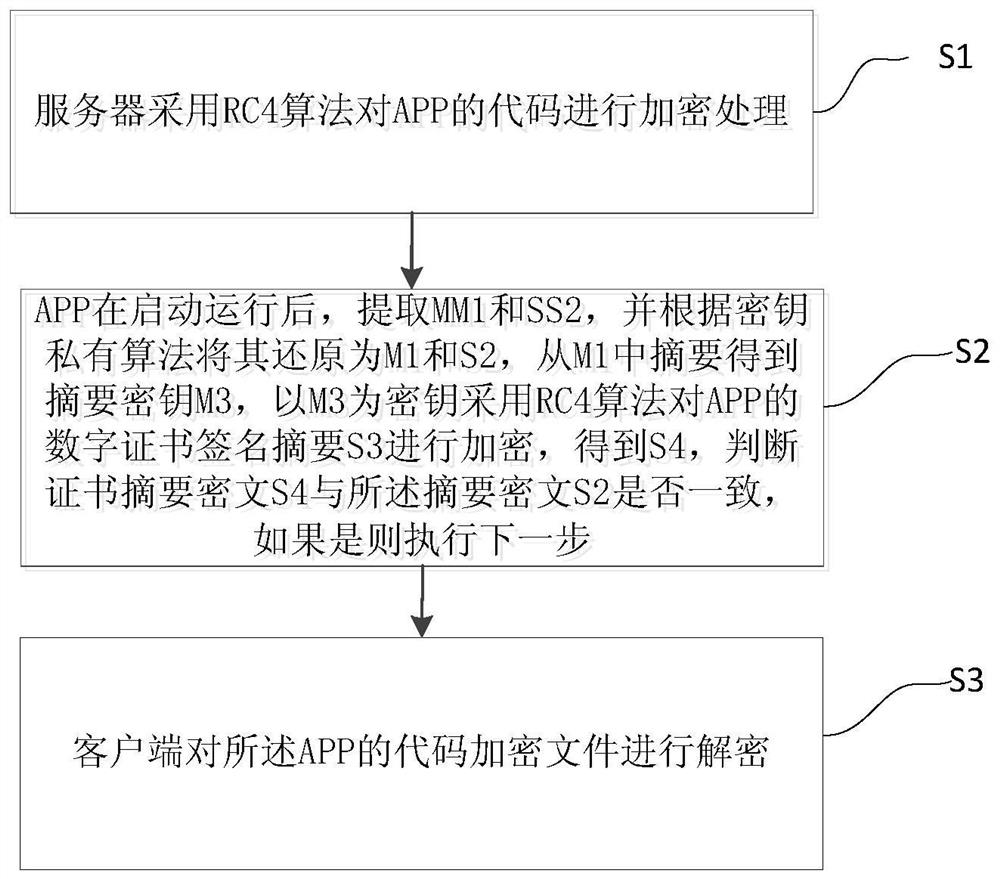
The invention provides an RC4 algorithm-based code full-packet encryption method. The method comprises the steps of subjecting the codes of an APP to encryption treatment by a server based on an RC4 algorithm; after the APP is started to run, extracting an MM1 and an SS2, and restoring the MM1 and the SS2 to a global ciphertext secret key M1 and an abstract ciphertext S2 based on a secret key private algorithm; obtaining an abstract secret key M3 from the abstract of the M1, and adopting the M3 as a secret key to encrypt the digital certificate signature digest S3 of the APP based on the RC4 algorithm so as to obtain a certificate abstract ciphertext S4; judging whether the certificate abstract ciphertext S4 is consistent with the abstract ciphertext S2 or not; and decrypting the code encryption file of the APP by a client. According to the invention, based on the combination of a standard RC4 symmetric encryption algorithm and a private key generation algorithm, the effects of high efficiency and good safety are achieved at the same time.
Owner:YONYOU NETWORK TECH CO LTD
Cloud data electronic information inquiry terminal
InactiveCN114611166AReduce brightnessPrevent data theftLighting elementsVolume/mass flow measurementComputer hardwarePoint light
Owner:杨艳
System and method for quickly exchanging data between networks
PendingCN114124416AEfficient data exchangeRaising Malicious Data TheftKey distribution for secure communicationMultiple keys/algorithms usageData packEncryption
Owner:CHINA AEROSPACE SYST ENG
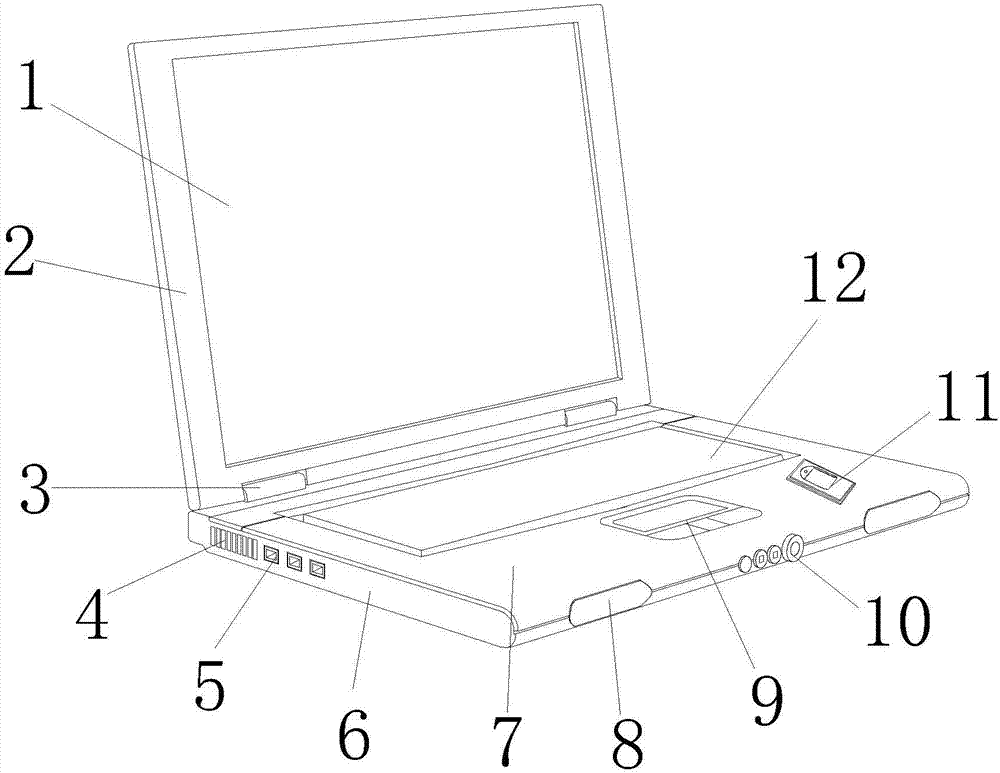
SDR (statistical data recorder)-based portable computer device
InactiveCN107247897AImprove securityPrevent Data TheftInternal/peripheral component protectionDigital data authenticationFingerprintRed light
The invention discloses a portable computer device based on SDR, the structure of which comprises a display screen, a cover plate, a hinge seat, a cooling hole, a USB socket, a body, a protective plate, a buckle, a mouse operation panel, a cover lock, and a fingerprint recognizer , keyboard, computer main board, the cover plate is hinged to the body through the hinge seat, the display screen is a square structure and installed in the middle of the cover plate, there are two hinge seats and are located on the same plane, and there are more than two cooling holes and are uniform Equidistantly arranged at the rear end on the left side of the body as an integral structure, the beneficial effect of the present invention is that a fingerprint reader is provided through its structure, and it is necessary to pass the fingerprint recognition disk inside the outer frame of the fingerprint reader mounting plate when in use. Carry out identification, and then make authentication on the identification board. When the identification is correct, the prompt light will light up green, and if the identification fails, the red light will light up, which can improve the security of the computer and prevent the data in the computer from being stolen.
Owner:广州市妙伊莲科技有限公司
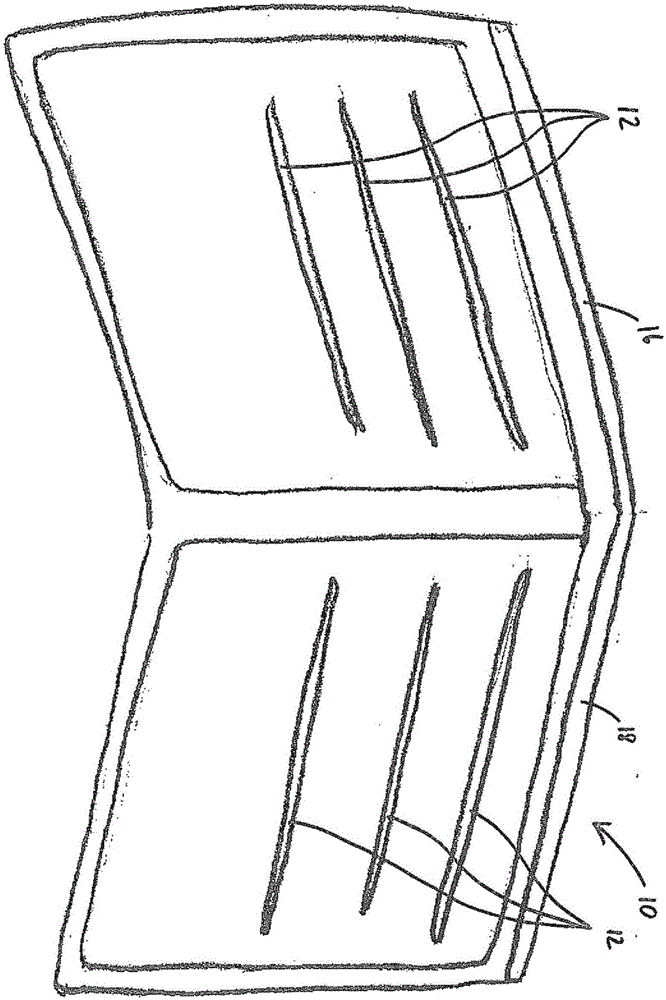
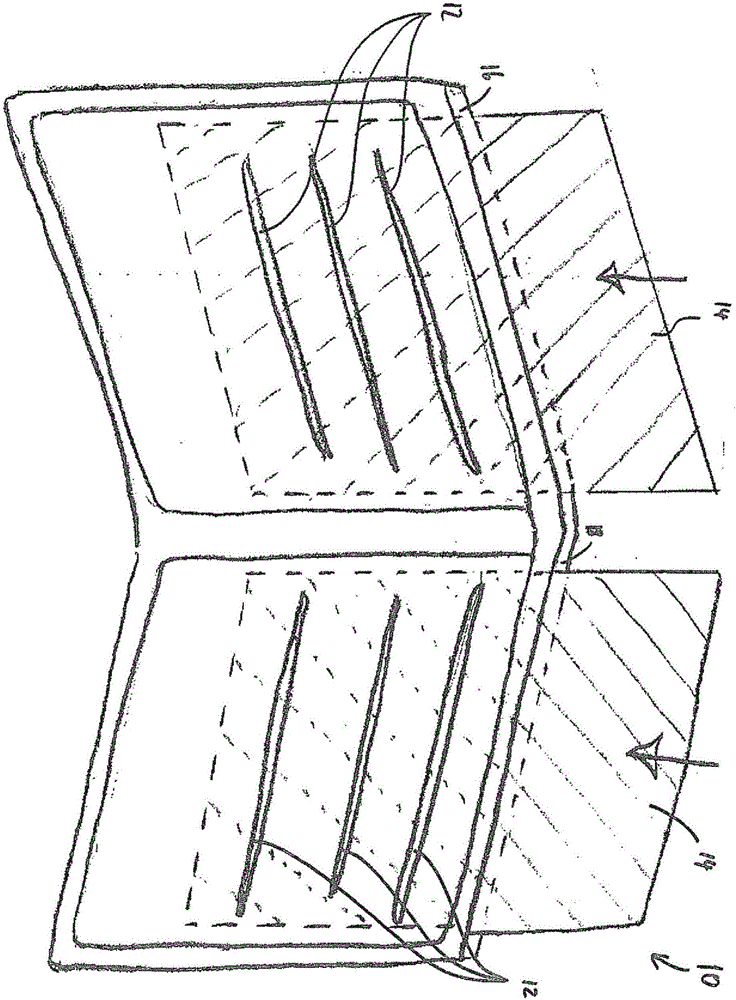
Device for preventing data theft, use of false identity, and fraud during contactless data transmission via electromagnetic radio waves
InactiveCN106575371AEasy to use and flexibleEasy to useRecord carriers used with machinesEngineeringData transmission
The application relates to a receptacle (10) comprising a plurality of inside pockets (12) for holding objects, each of which is equipped with an RFID or NFC chip. At least two surfaces (16) of the receptacle (10) which include at least one of the plurality of inside pockets (12) are provided with an electrically conductive layer (14) so that the at least one of the plurality of inside pockets (12) is shielded from electromagnetic radio waves by the at least two surfaces (16, 18).
Owner:马尔科・福西
Data security transmission method and system of embedded AI chip on edge side of unmanned aerial vehicle
ActiveCN113469139BImprove data exchange securityEnsure safetyCharacter and pattern recognitionDigital data protectionComputer architectureUnique identifier
The application provides a method and system for secure data transmission of an embedded AI chip on the edge side of a UAV. The embedded AI chip generates a first unique identifier corresponding to the embedded AI chip, and encrypts the first unique identifier to generate and identify it. string, and send the encrypted identification string to the server. The server obtains the program information of the embedded AI chip, generates the second unique identifier corresponding to the embedded AI chip, and compares the second unique identifier with the first unique identifier. If the comparison results are consistent, the verification is passed, and the server generates a dynamic The 3DES encryption key and dynamic 3DES decryption key are encapsulated into a response message and returned to the embedded AI chip. In this way, the embedded AI chip can use the dynamic 3DES encryption key and dynamic 3DES decryption key to encrypt or decrypt the data interacted with the server, thereby improving the security of data interaction between the drone and the server .
Owner:广州中科智云科技有限公司
A security communication system and method for in-vehicle network
ActiveCN110943957BGuaranteed to be legalEnsure safetyKey distribution for secure communicationNetwork connectionEngineering
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Data storage method, device and storage medium
ActiveCN111199044BGuarantee authenticityGuaranteed availabilityDigital data protectionTamper resistanceEngineering
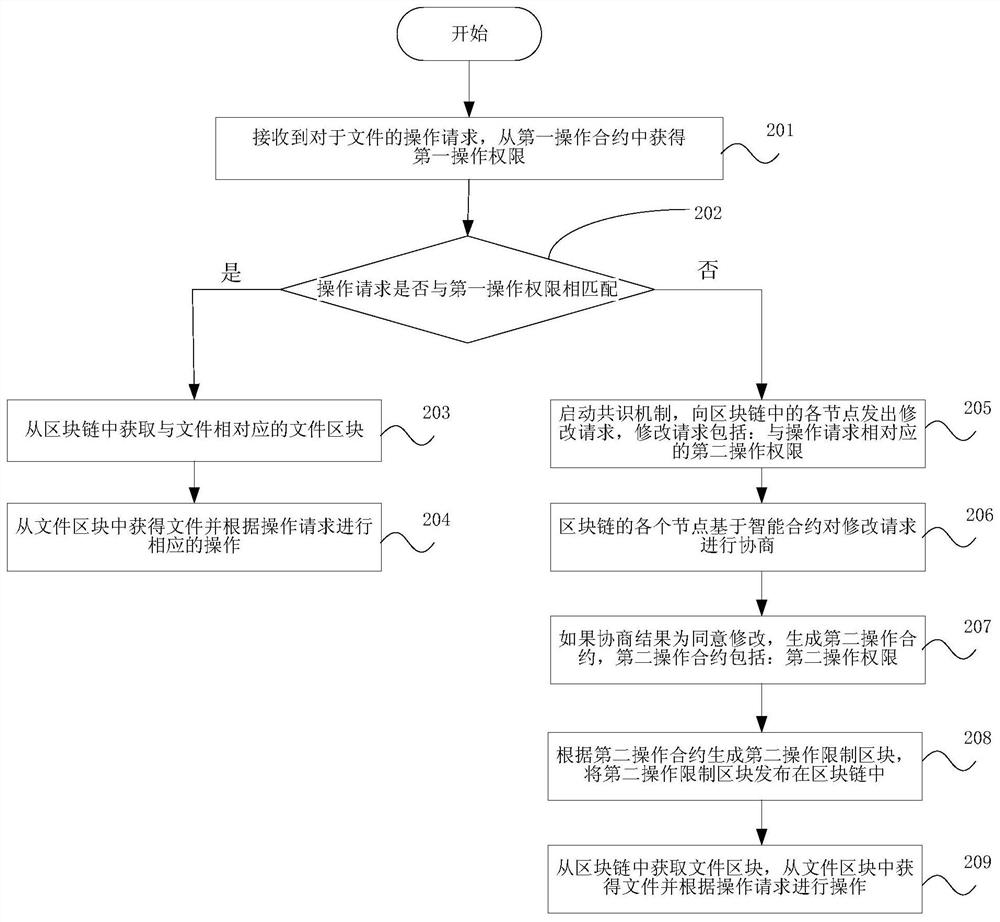
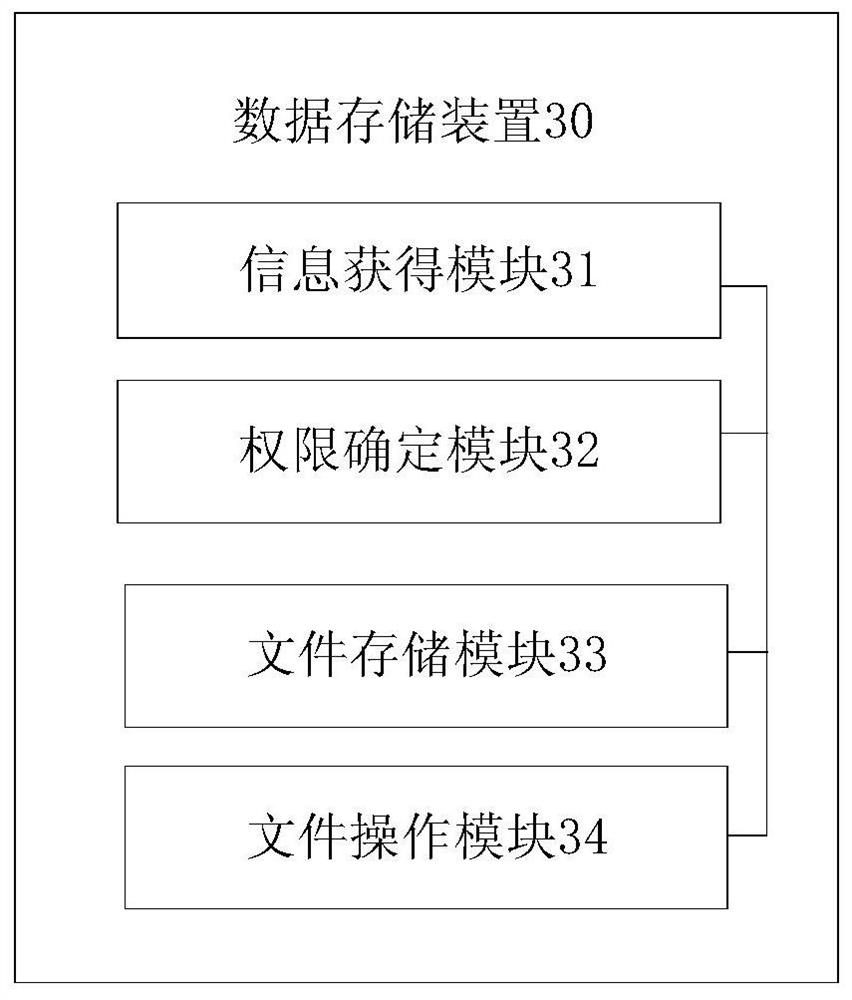
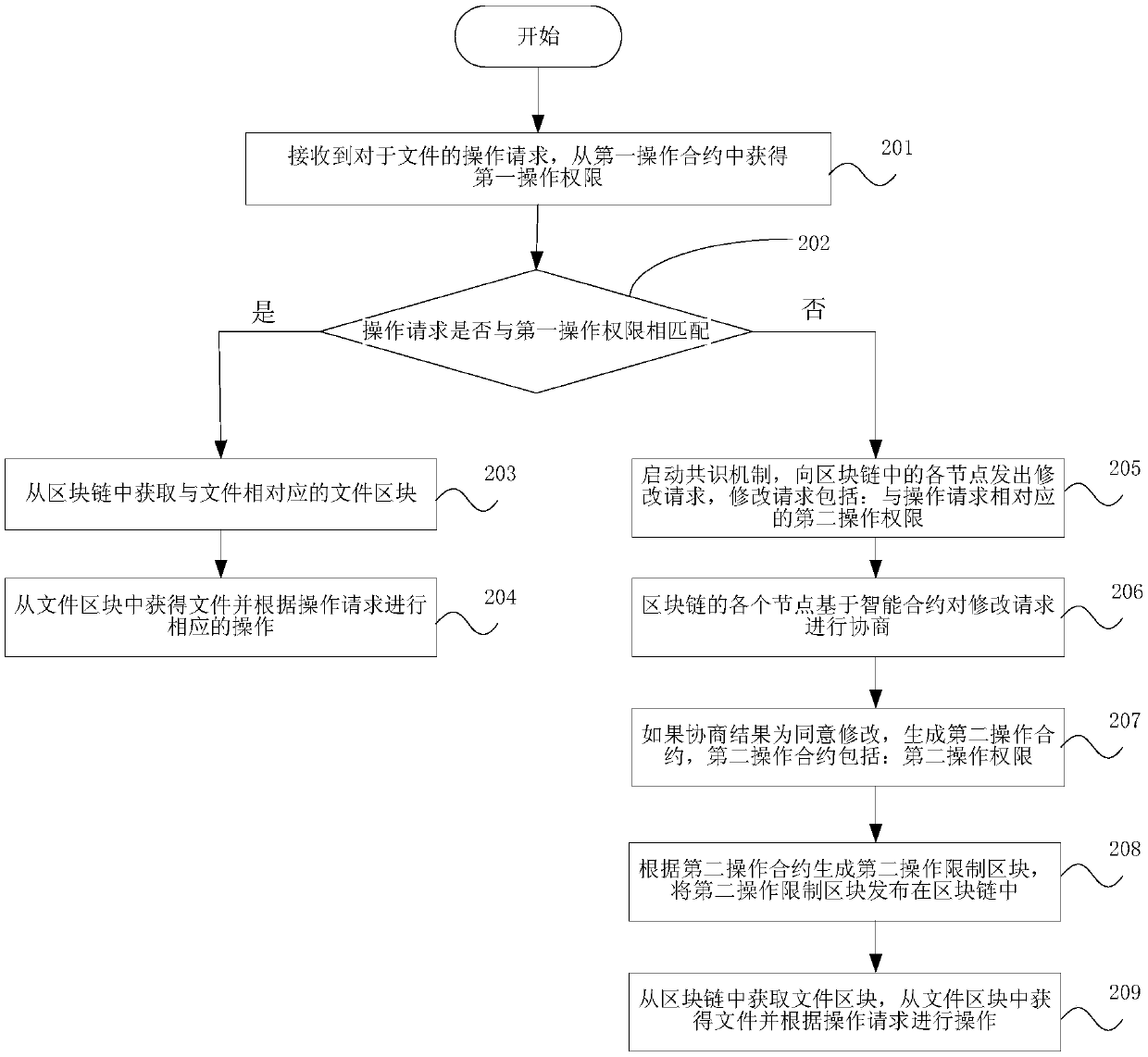
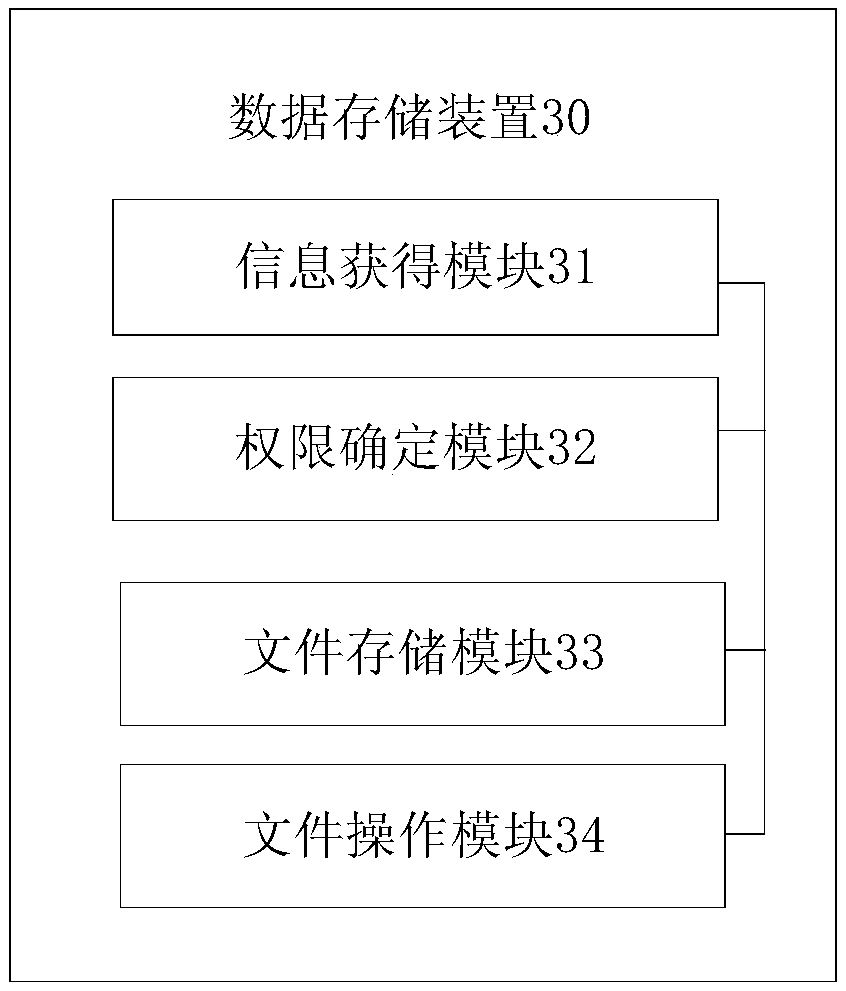
The present disclosure provides a data storage method, device, and storage medium, wherein the method includes: determining a first operation authority of a file based on file configuration information; generating a first operation contract corresponding to the file; wherein, the first operation contract includes: The first operation authority; store the file and generate the first operation restriction block according to the first operation contract, and publish the first operation restriction block in the block chain; obtain the first operation contract based on the first operation restriction block; The first operation authority is obtained in an operation contract, and the file is operated accordingly based on the first operation authority and the operation request. The disclosed method, device and storage medium utilize the tamper-proof feature of the block chain to store the operation authority for the file, and verify the operation based on the operation restriction block, so as to control the operation of all data and avoid data tampering , Data theft, effectively guaranteeing the authenticity and availability of stored files.
Owner:CHINA TELECOM CORP LTD
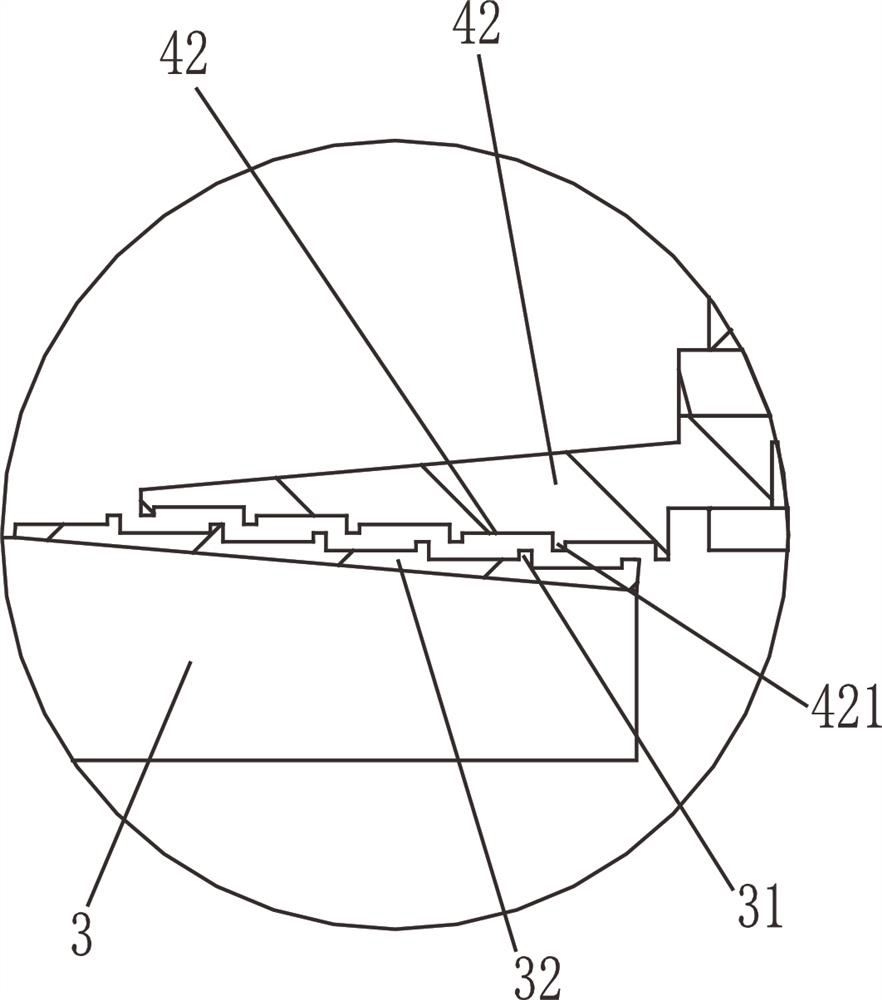
Data storage disk with anti-theft assembly
ActiveCN111967559APrevent Data TheftPrevent theftInternal/peripheral component protectionRecord carriers used with machinesStructural engineeringCard reader
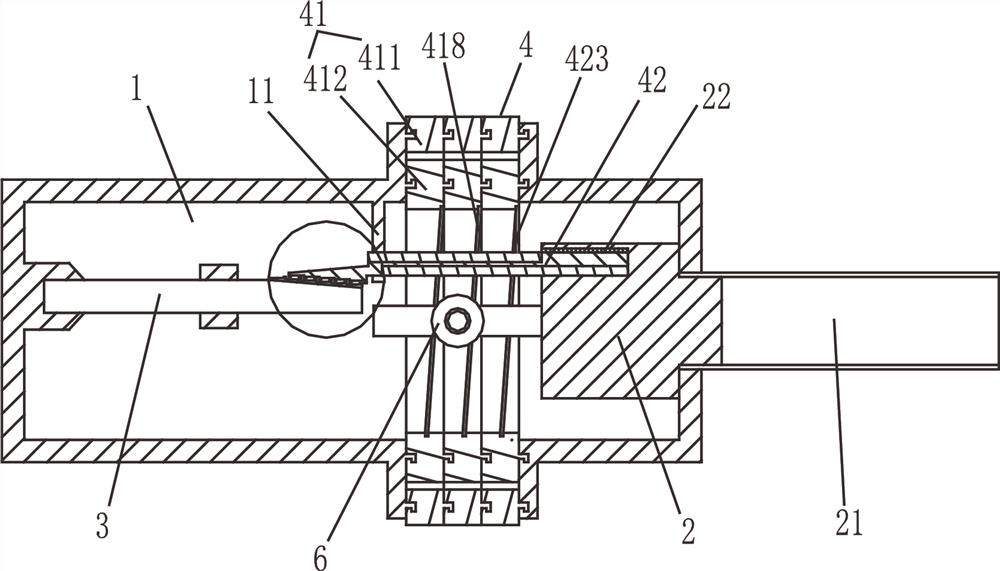
The invention discloses a data storage disk with an anti-theft assembly. The device comprises a shell, a card reader and an SD card, the card reader comprises a USB interface and an SD card slot. TheUSB interface extends out of one side of the shell; the anti-theft assembly comprises a plurality of lock sleeves and a plurality of conducting rods; the lock sleeve is rotationally connected with theshell; a spiral groove surrounding a circle is formed in each lock sleeve; a guide frame is arranged in the shell; a plurality of first guide holes are formed in the guide frame; a conducting rod isarranged in the first guide hole in a sliding manner; a guide block extending into the spiral groove is arranged on the conducting rod; one end of the conducting rod is always conductively connected with the contact part in the slot, a first contact is arranged on the SD card, a second contact is arranged at the other end of the conducting rod, axial alignment marks are arranged on the outer wallof the shell, a plurality of unlocking codes are arranged on the outer ring of the lock sleeve, and when the correct unlocking codes are aligned with the alignment marks, the first contact makes contact with the second contact for conduction. The data storage disk can effectively prevent data from being stolen.
Owner:杭州电子科技大学上虞科学与工程研究院有限公司 +1
A teaching information security protection system based on cloud platform
ActiveCN111464543BImprove securityLess likely to leakElectrical appliancesSecuring communicationIntelligent NetworkThird party
Owner:HANGZHOU YUNTI TECH CO LTD
Data storage method and device and storage medium
ActiveCN111199044APrevent data tamperingImprove safety and reliabilityDigital data protectionBlockchainTamper resistance
Owner:CHINA TELECOM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com