Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
147results about How to "Improve data integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
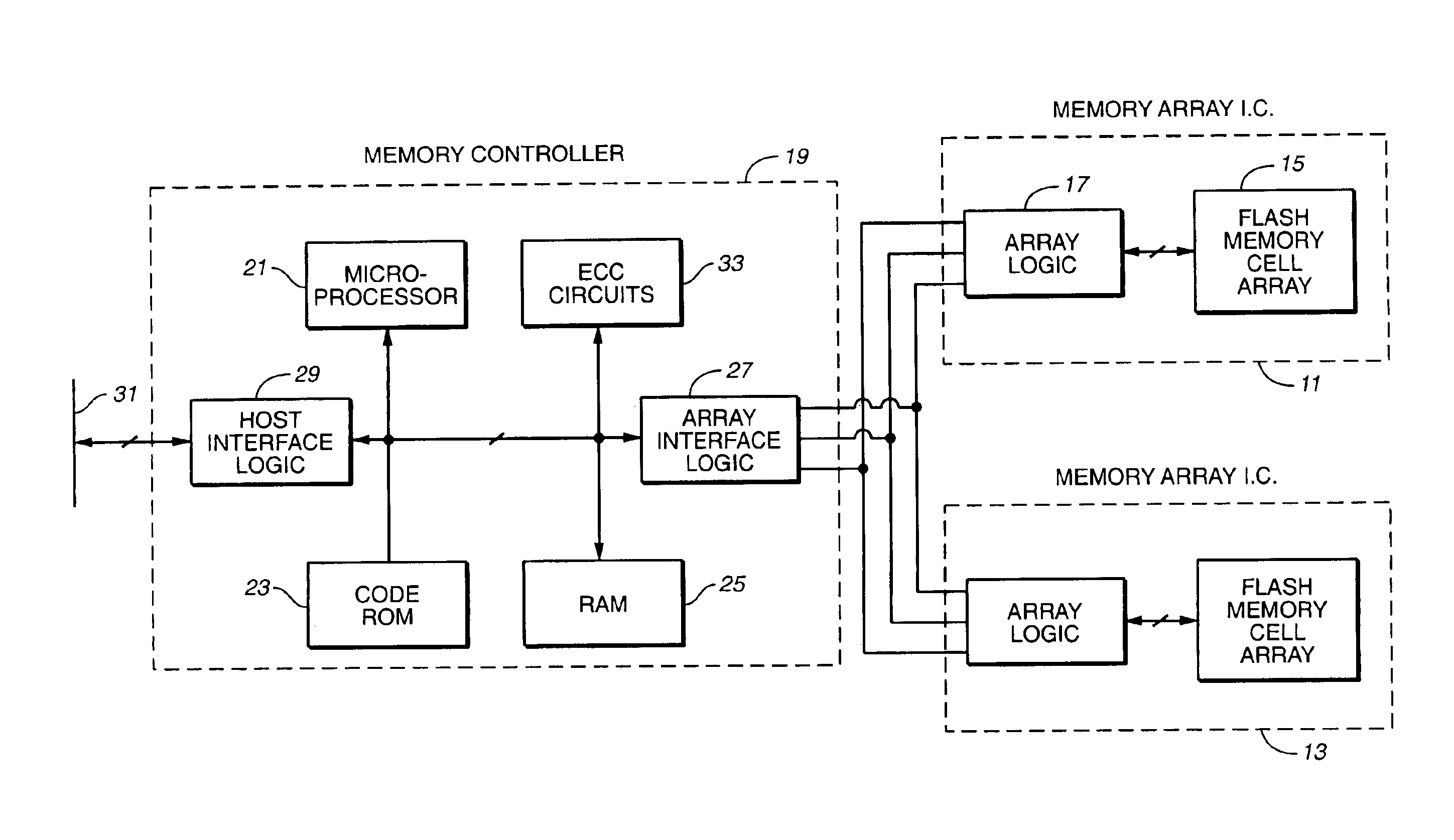
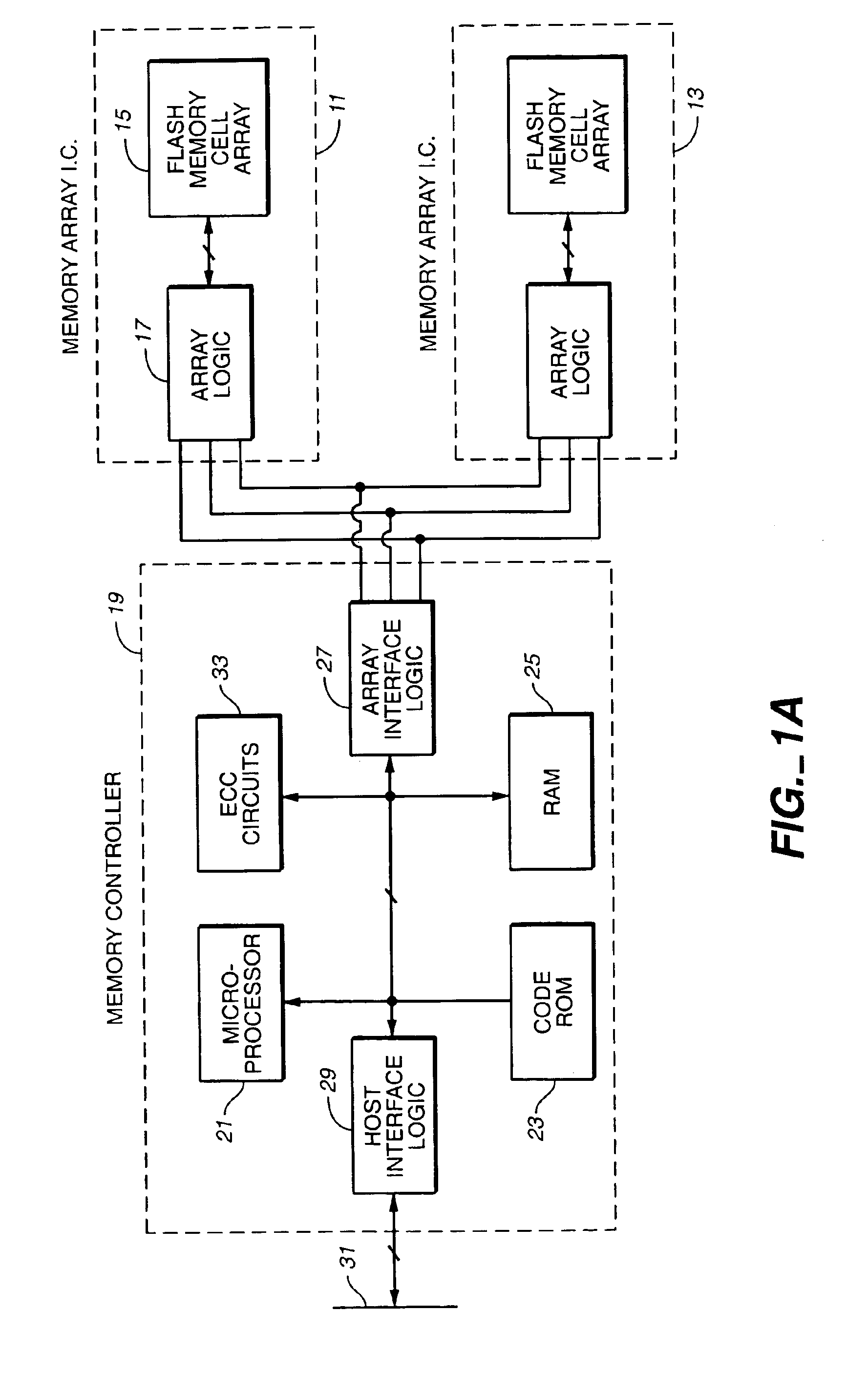
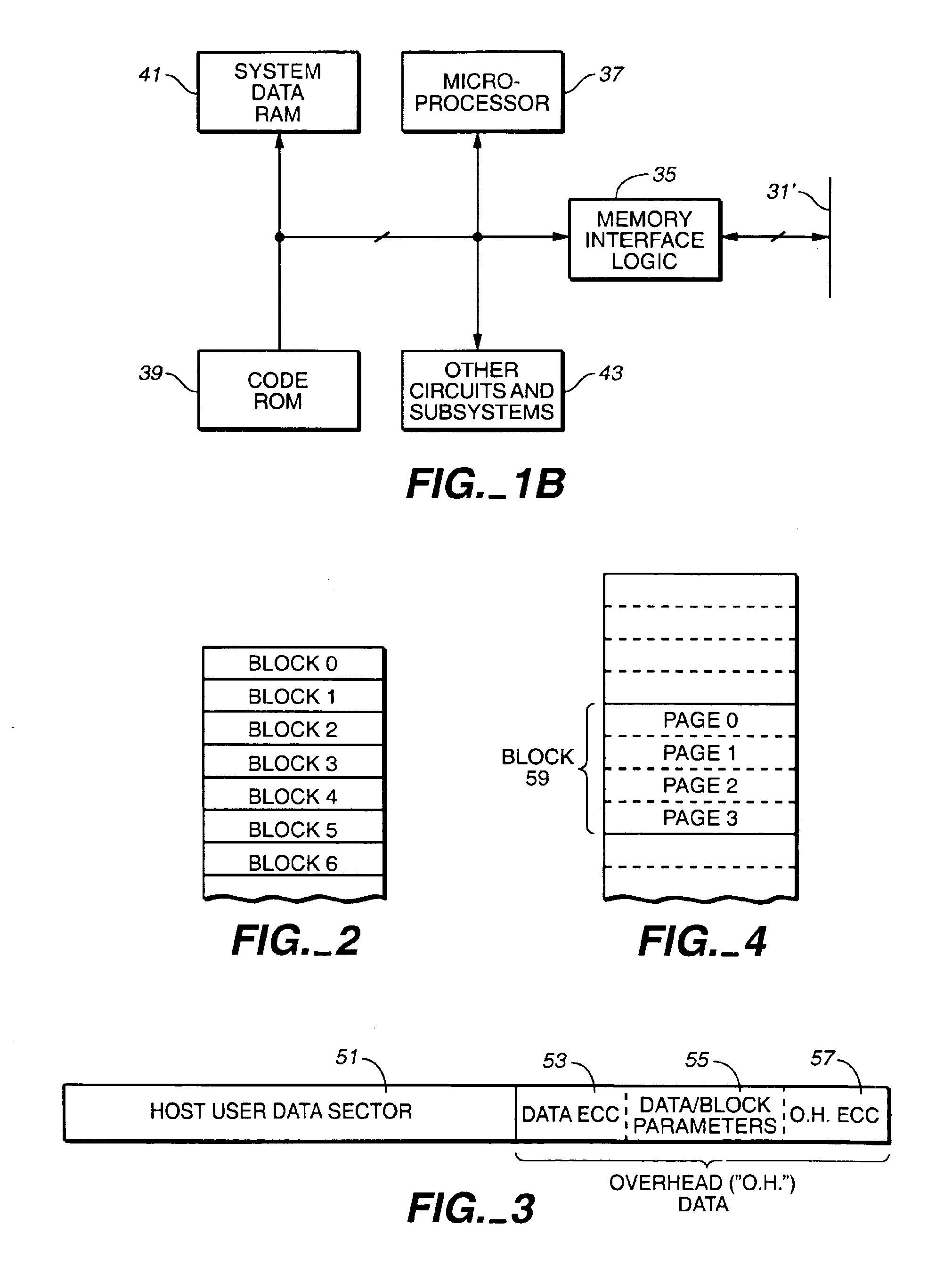
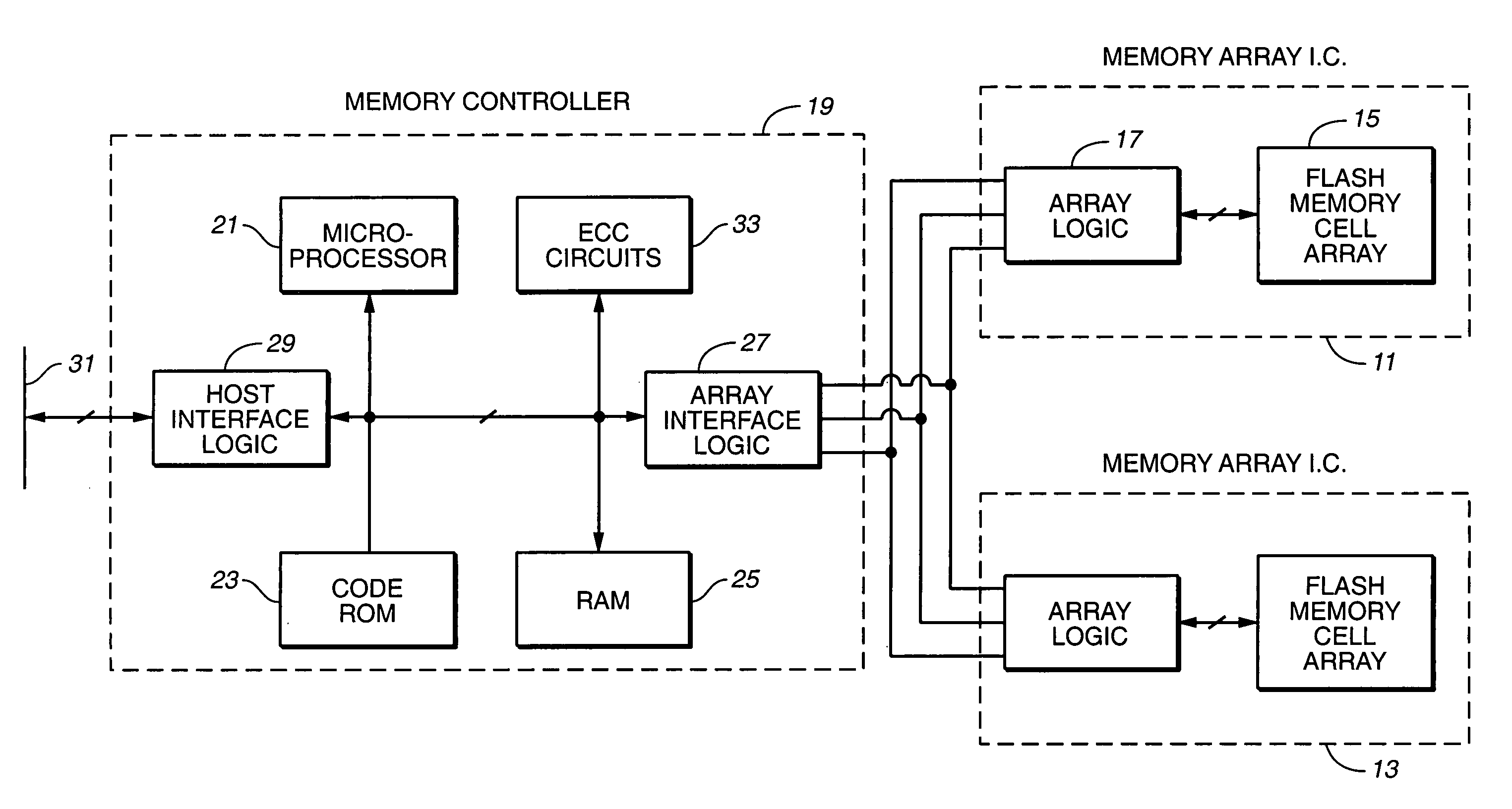
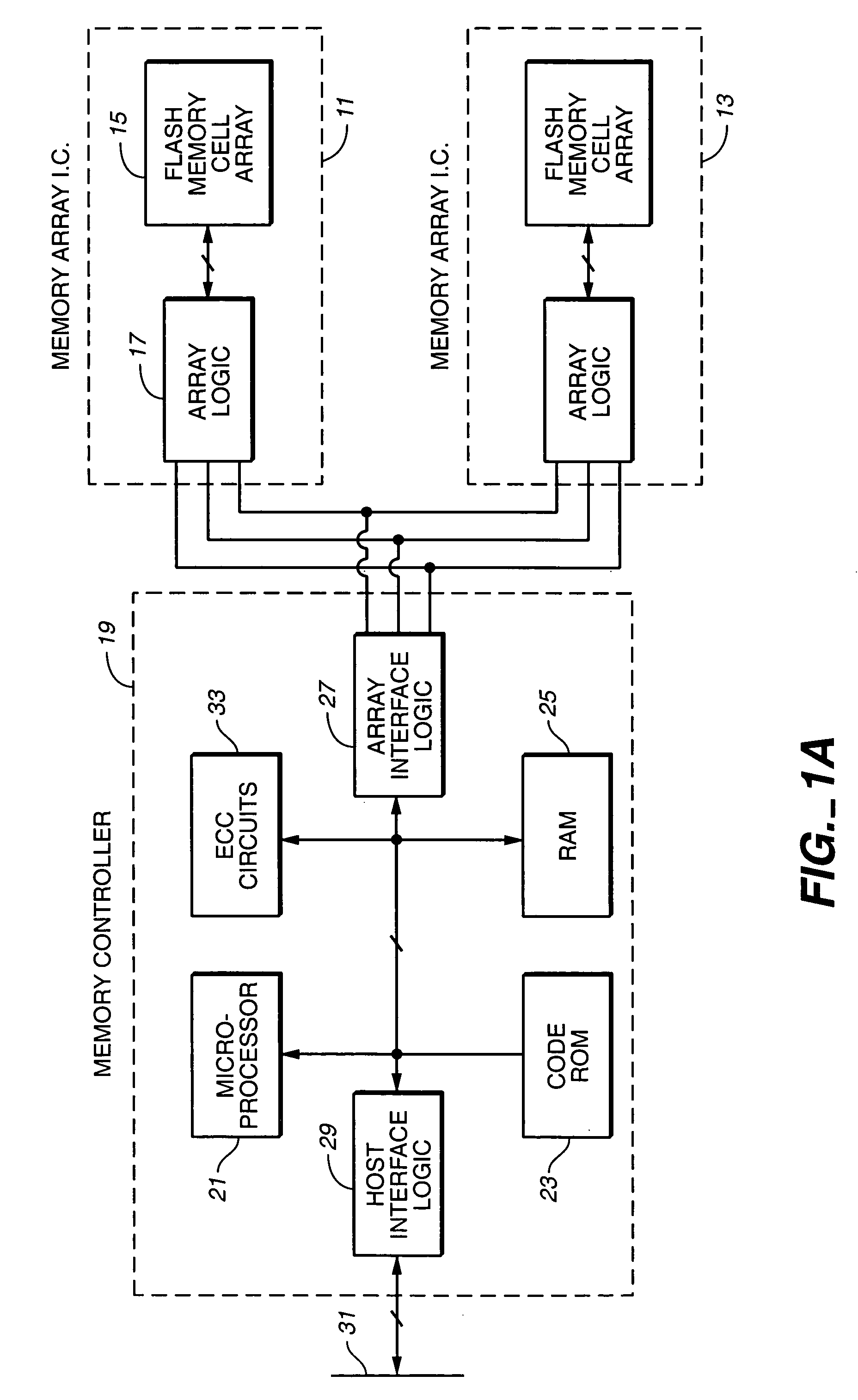
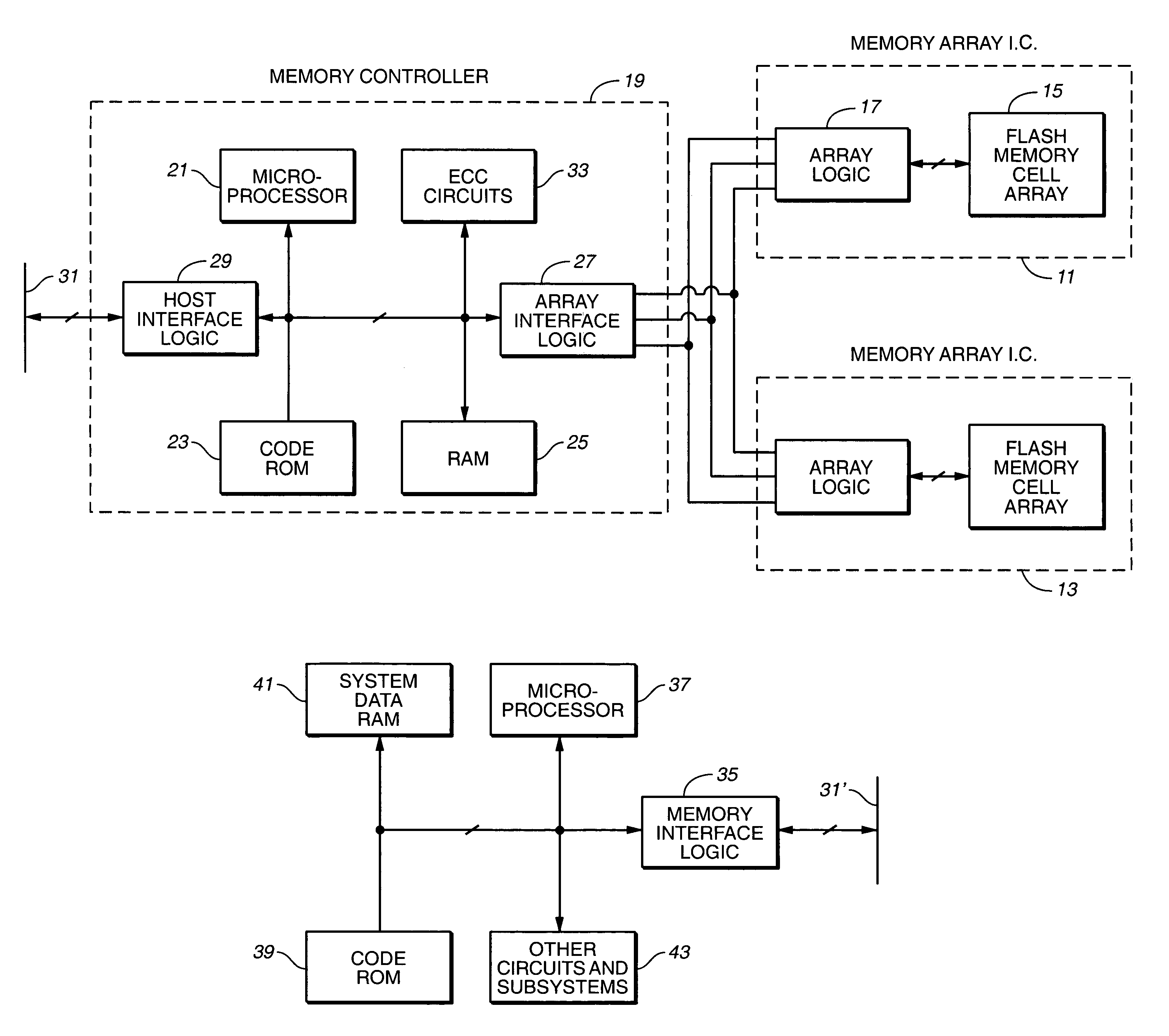
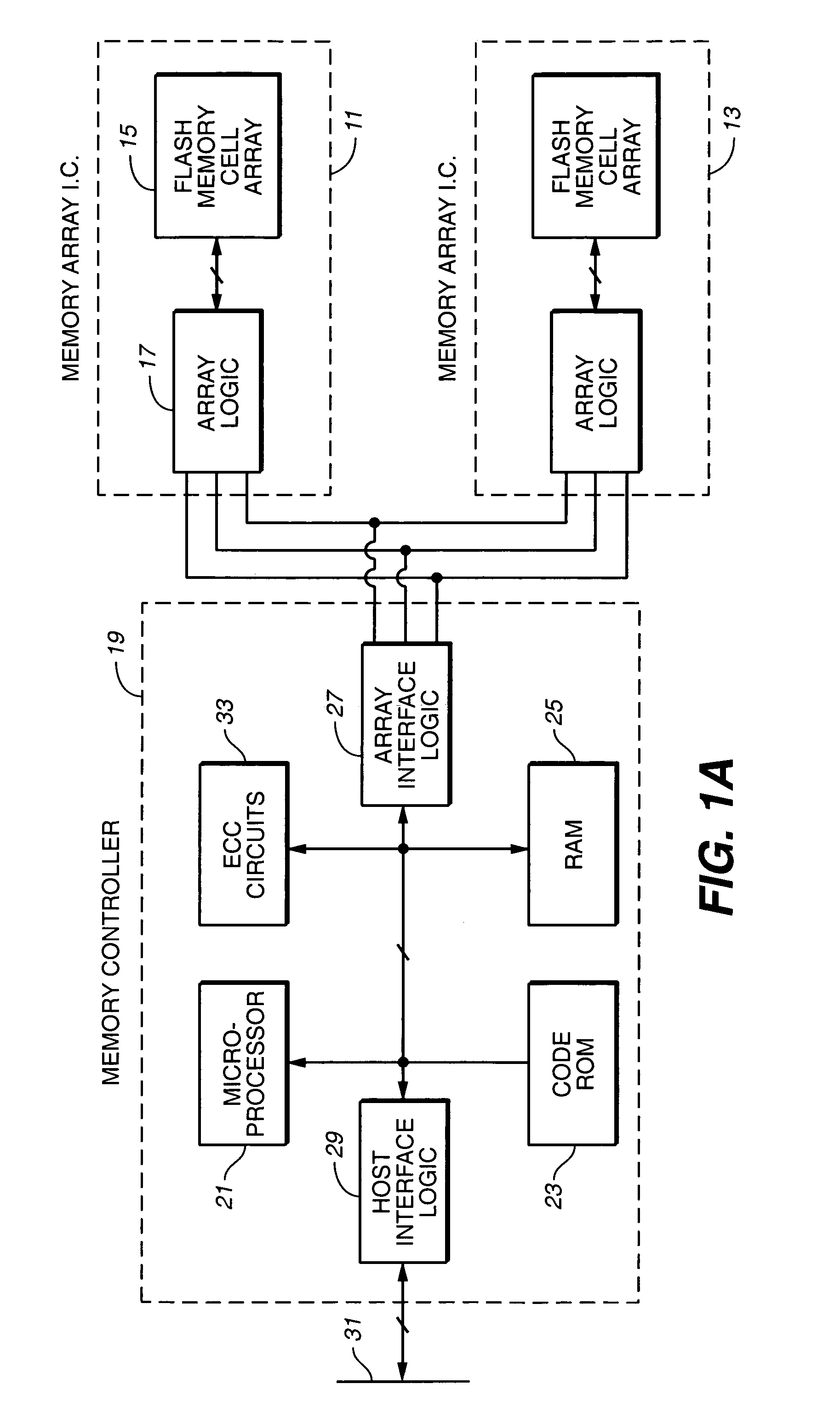
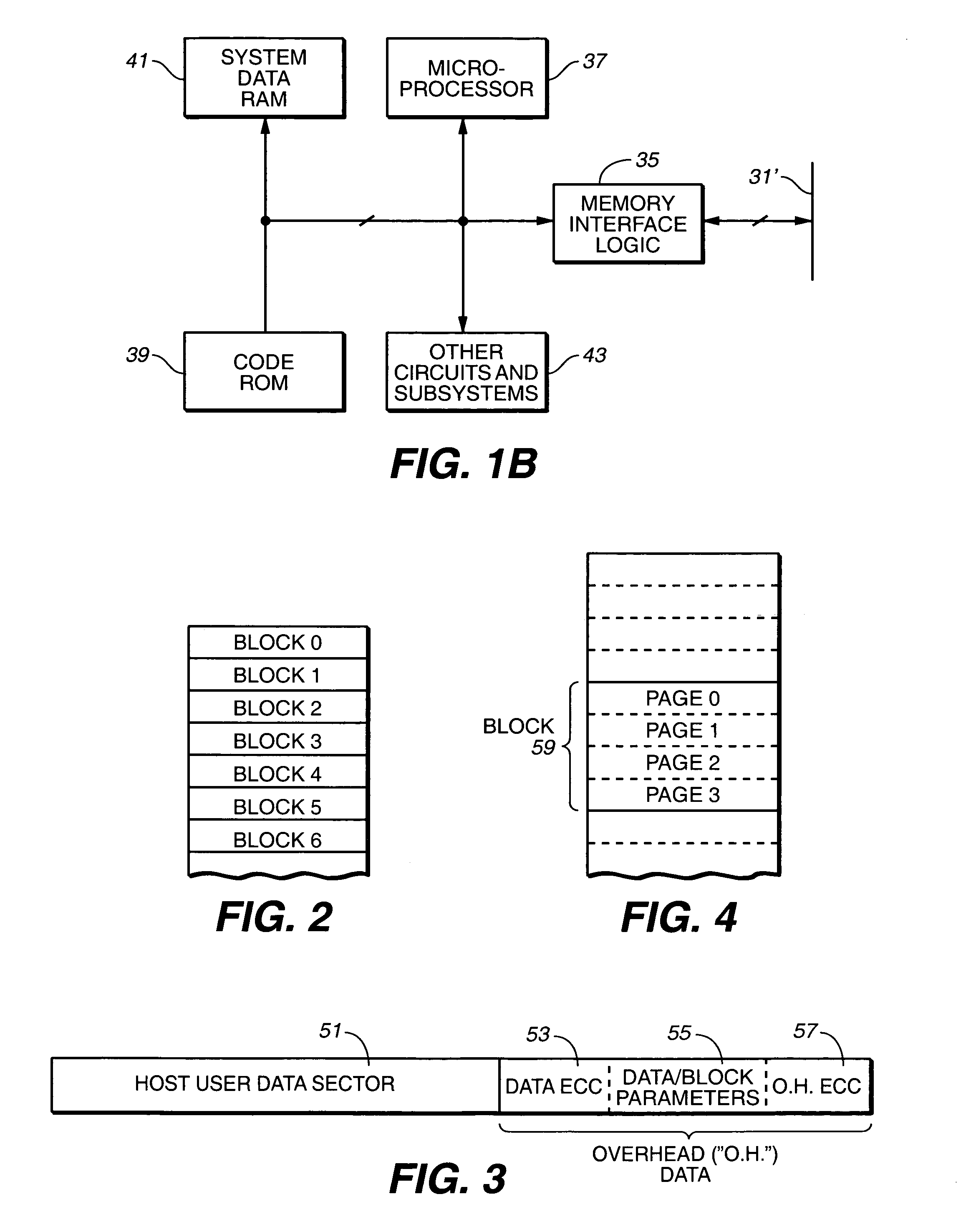
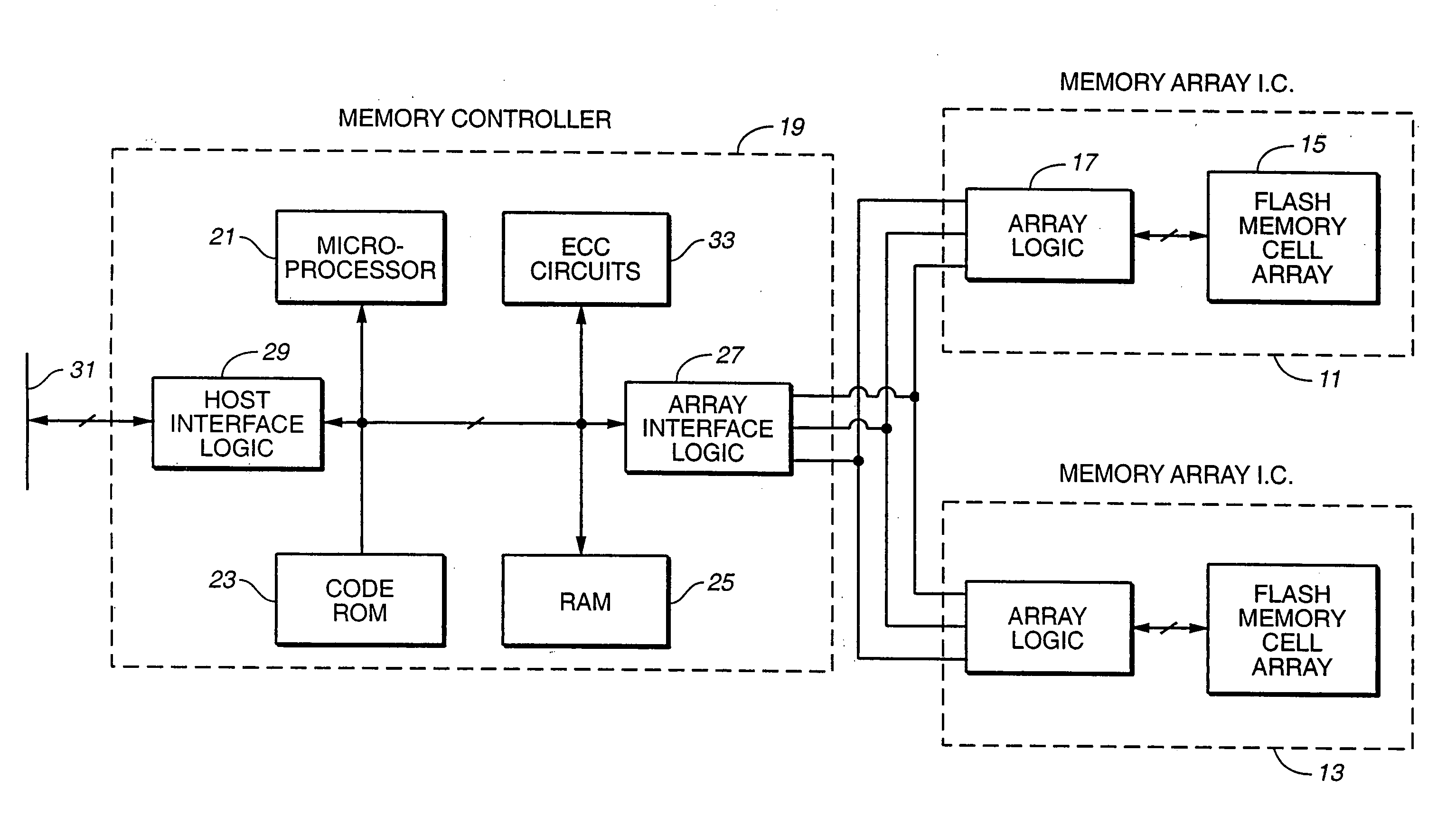
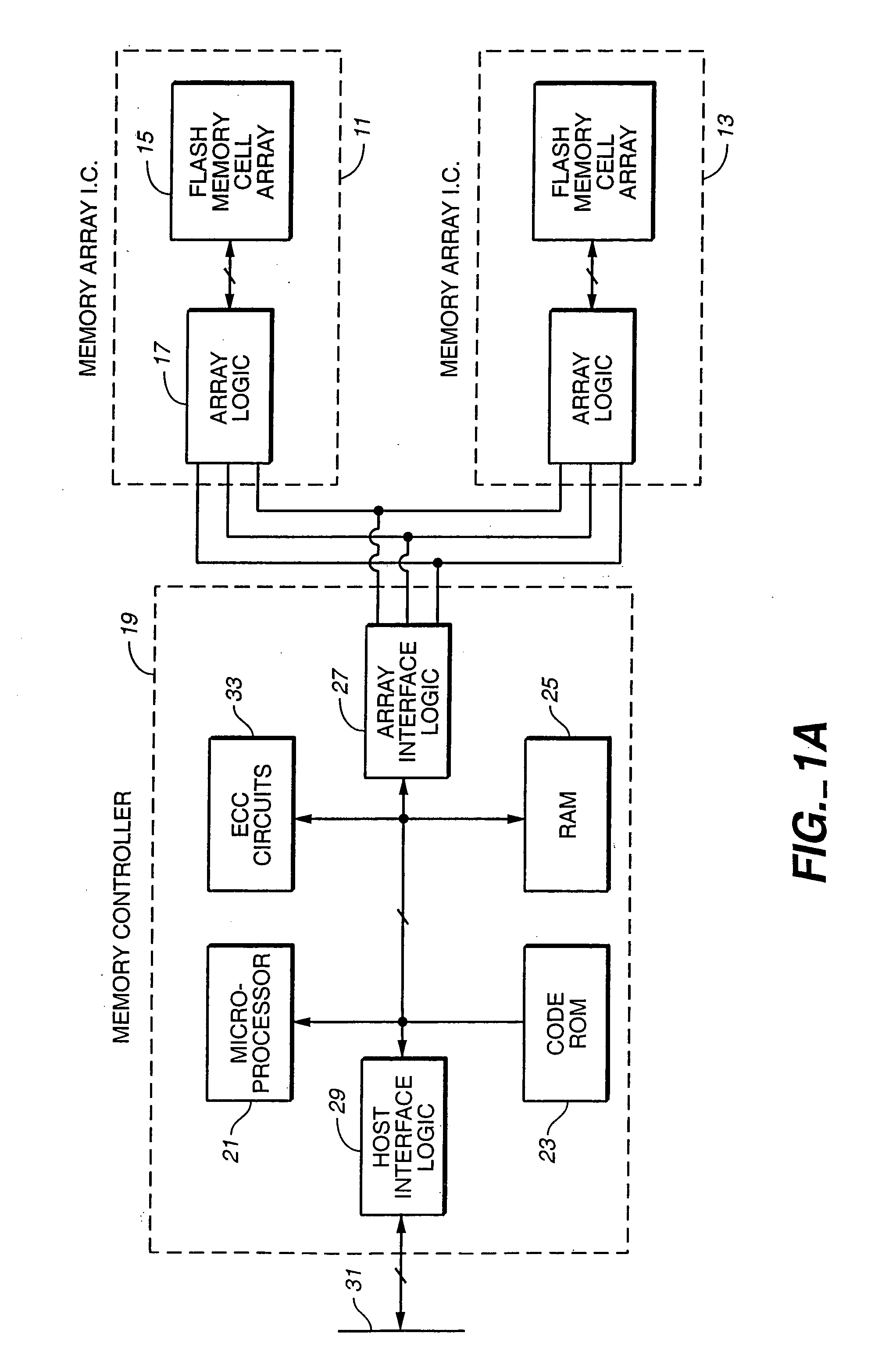
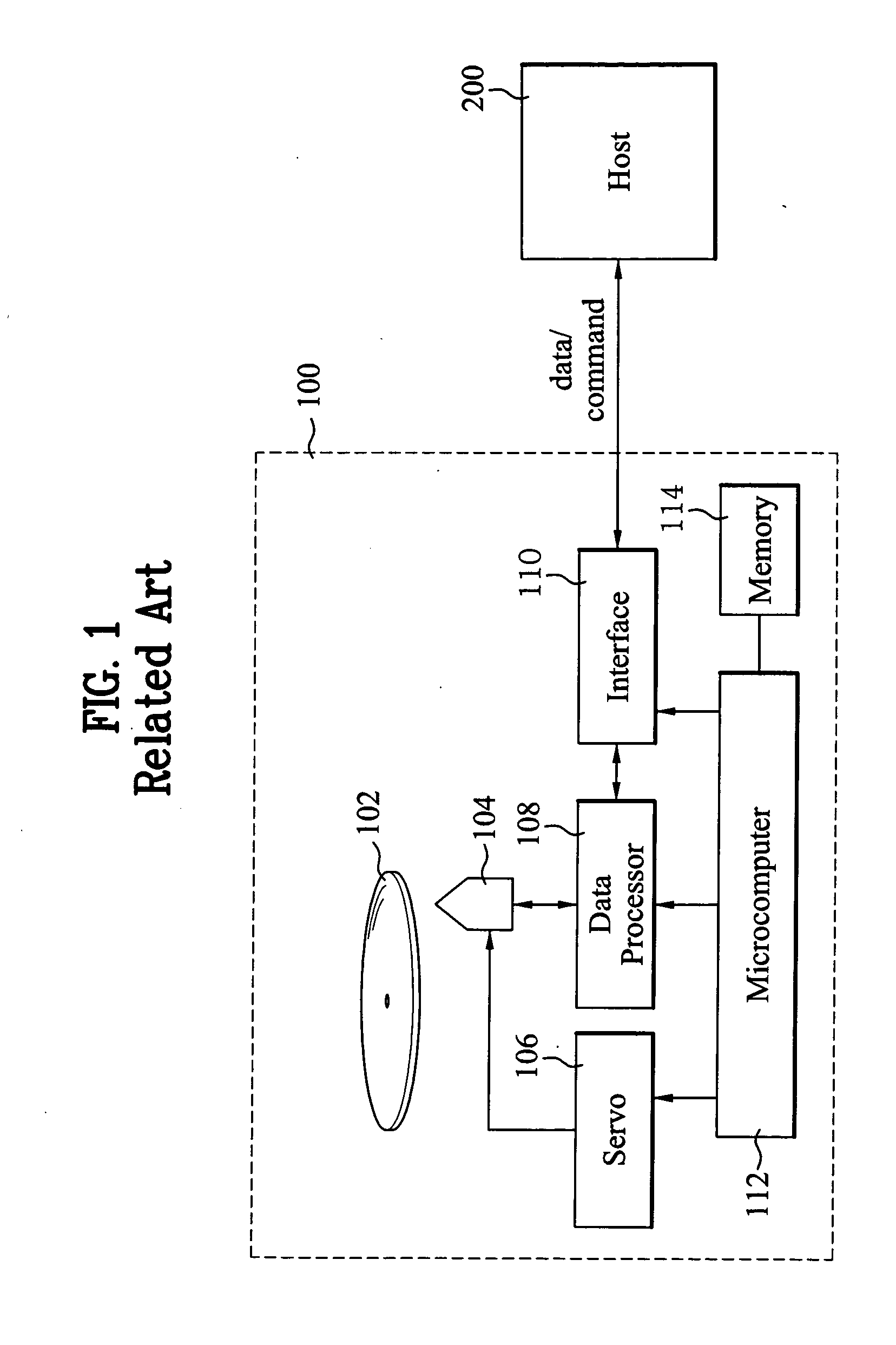
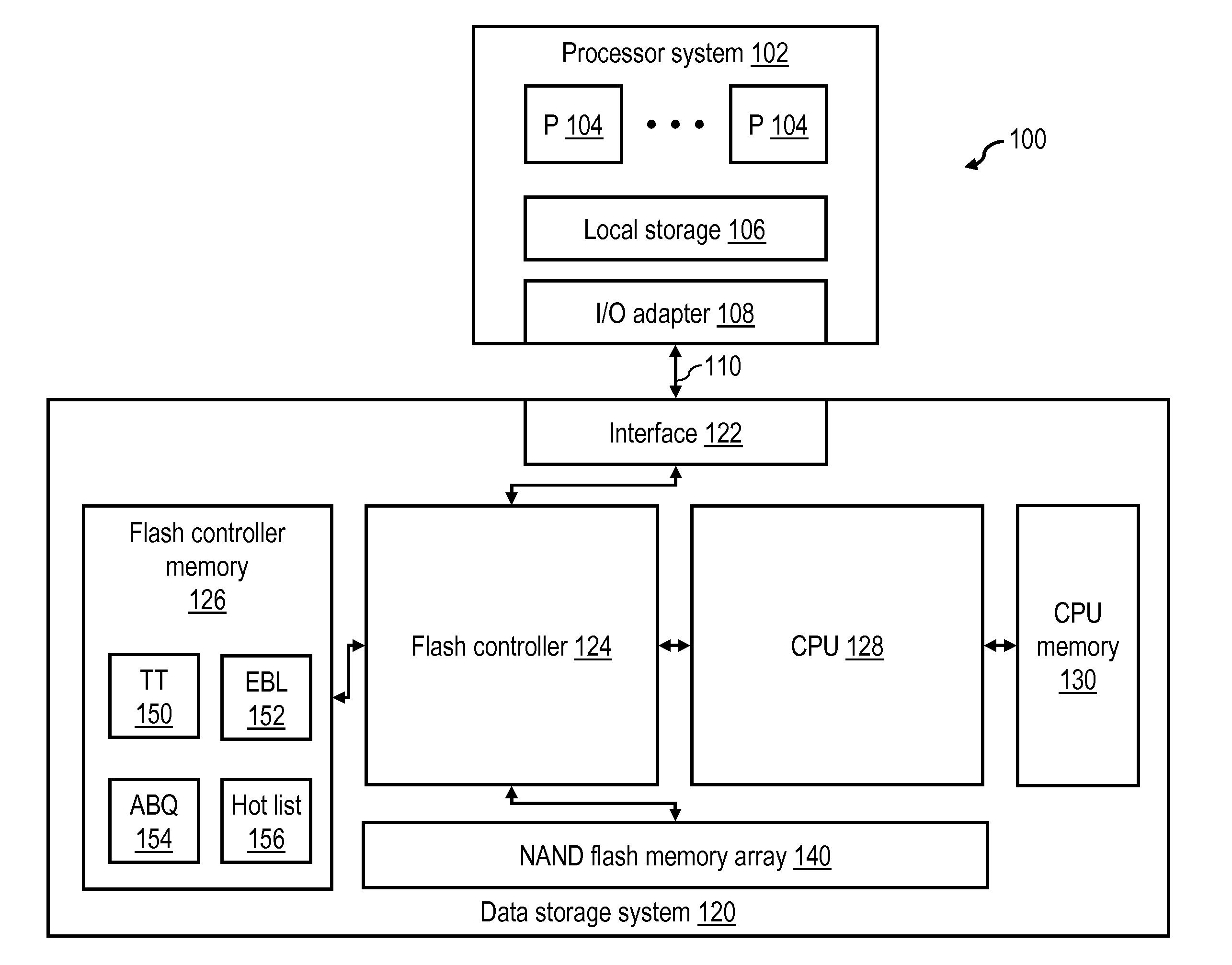
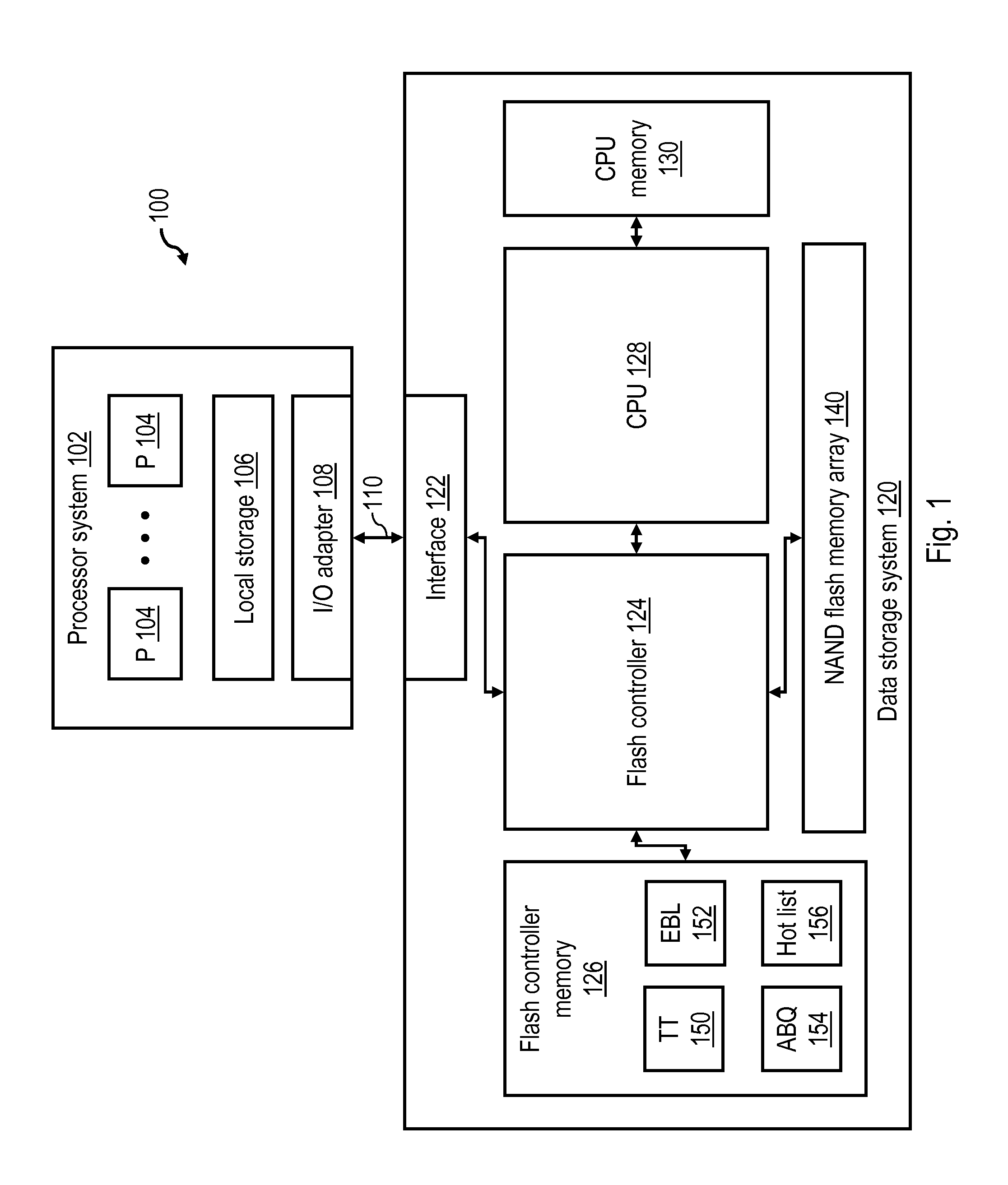
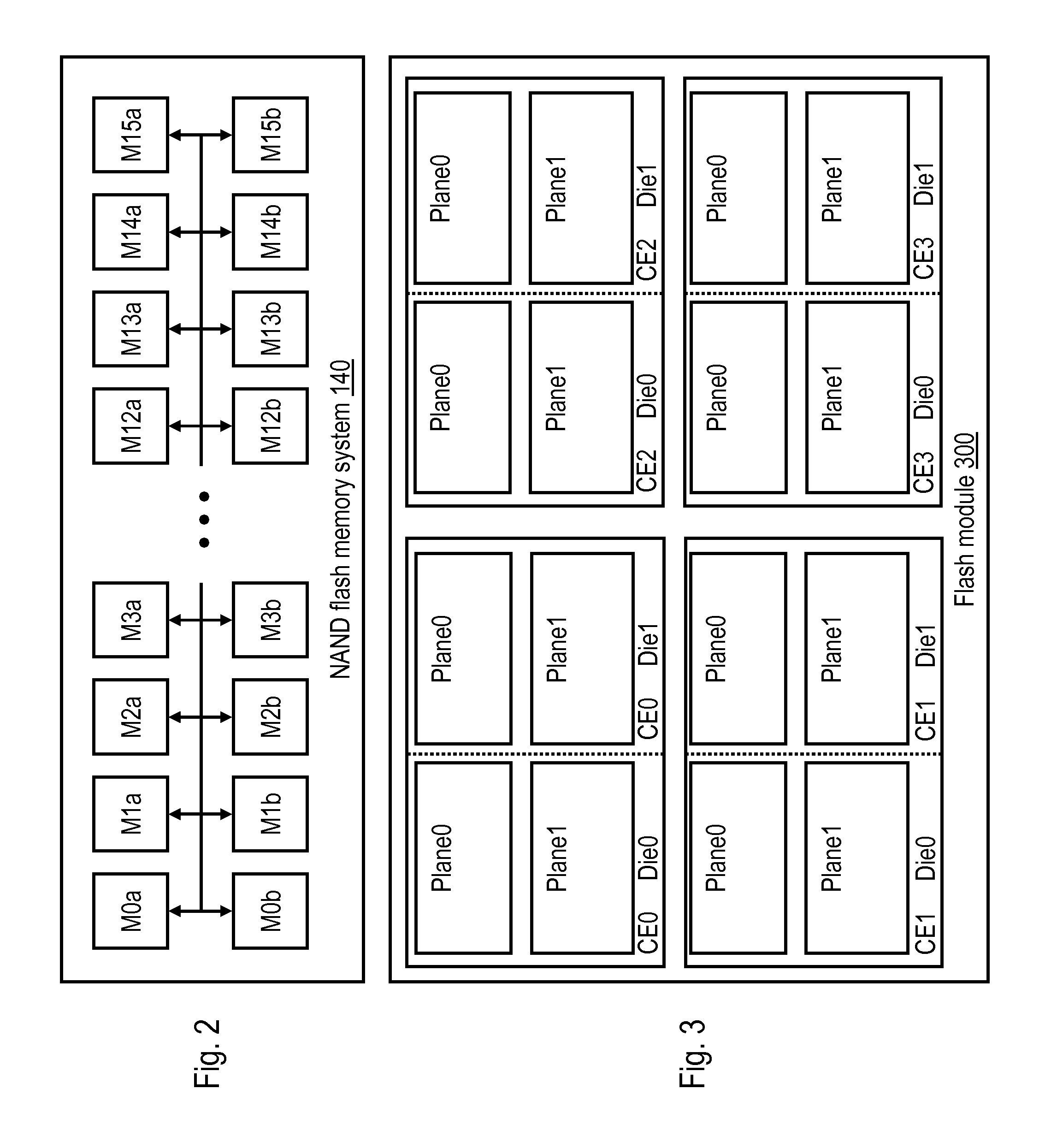
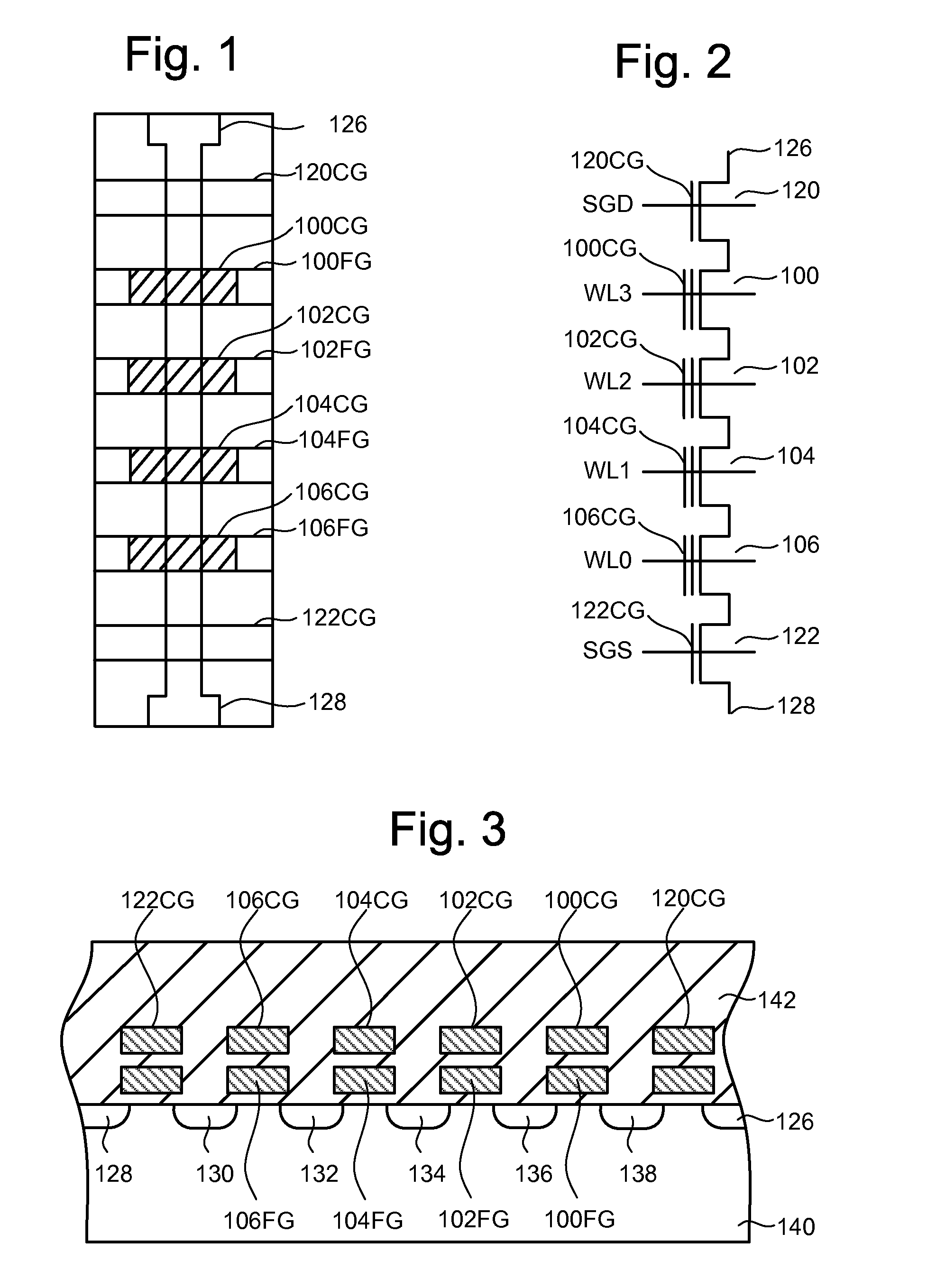
Flash memory data correction and scrub techniques
ActiveUS7012835B2Data disturbanceReduce storage dataMemory loss protectionRead-only memoriesData integrityData storing
In order to maintain the integrity of data stored in a flash memory that are susceptible to being disturbed by operations in adjacent regions of the memory, disturb events cause the data to be read, corrected and re-written before becoming so corrupted that valid data cannot be recovered. The sometimes conflicting needs to maintain data integrity and system performance are balanced by deferring execution of some of the corrective action when the memory system has other high priority operations to perform. In a memory system utilizing very large units of erase, the corrective process is executed in a manner that is consistent with efficiently rewriting an amount of data much less than the capacity of a unit of erase.
Owner:SANDISK TECH LLC
Flash memory data correction and scrub techniques
ActiveUS20050073884A1Data disturbanceReduce storage dataMemory loss protectionRead-only memoriesData integrityData storing
In order to maintain the integrity of data stored in a flash memory that are susceptible to being disturbed by operations in adjacent regions of the memory, disturb events cause the data to be read, corrected and re-written before becoming so corrupted that valid data cannot be recovered. The sometimes conflicting needs to maintain data integrity and system performance are balanced by deferring execution of some of the corrective action when the memory system has other high priority operations to perform. In a memory system utilizing very large units of erase, the corrective process is executed in a manner that is consistent with efficiently rewriting an amount of data much less than the capacity of a unit of erase.
Owner:SANDISK TECH LLC
Corrected data storage and handling methods
InactiveUS7173852B2Data disturbanceReduce storage dataRead-only memoriesDigital storageData integrityTime limit
In order to maintain the integrity of data stored in a flash memory that are susceptible to being disturbed by operations in adjacent regions of the memory, disturb events cause the data to be read, corrected and re-written before becoming so corrupted that valid data cannot be recovered. The sometimes conflicting needs to maintain data integrity and system performance are balanced by deferring execution of some of the corrective action when the memory system has other high priority operations to perform. In a memory system utilizing very large units of erase, the corrective process is executed in a manner that is consistent with efficiently rewriting an amount of data much less than the capacity of a unit of erase. Data is rewritten when severe errors are found during read operations. Portions of data are corrected and copied within the time limit for read operation. Corrected portions are written to dedicated blocks.
Owner:SANDISK TECH LLC
Corrected data storage and handling methods
ActiveUS20060039196A1Reduces store dataData disturbanceRead-only memoriesDigital storageReal-time computingTime limit
In order to maintain the integrity of data stored in a flash memory that are susceptible to being disturbed by operations in adjacent regions of the memory, disturb events cause the data to be read, corrected and re-written before becoming so corrupted that valid data cannot be recovered. The sometimes conflicting needs to maintain data integrity and system performance are balanced by deferring execution of some of the corrective action when the memory system has other high priority operations to perform. In a memory system utilizing very large units of erase, the corrective process is executed in a manner that is consistent with efficiently rewriting an amount of data much less than the capacity of a unit of erase. Data is rewritten when severe errors are found during read operations. Portions of data are corrected and copied within the time limit for read operation. Corrected portions are written to dedicated blocks.
Owner:SANDISK TECH LLC
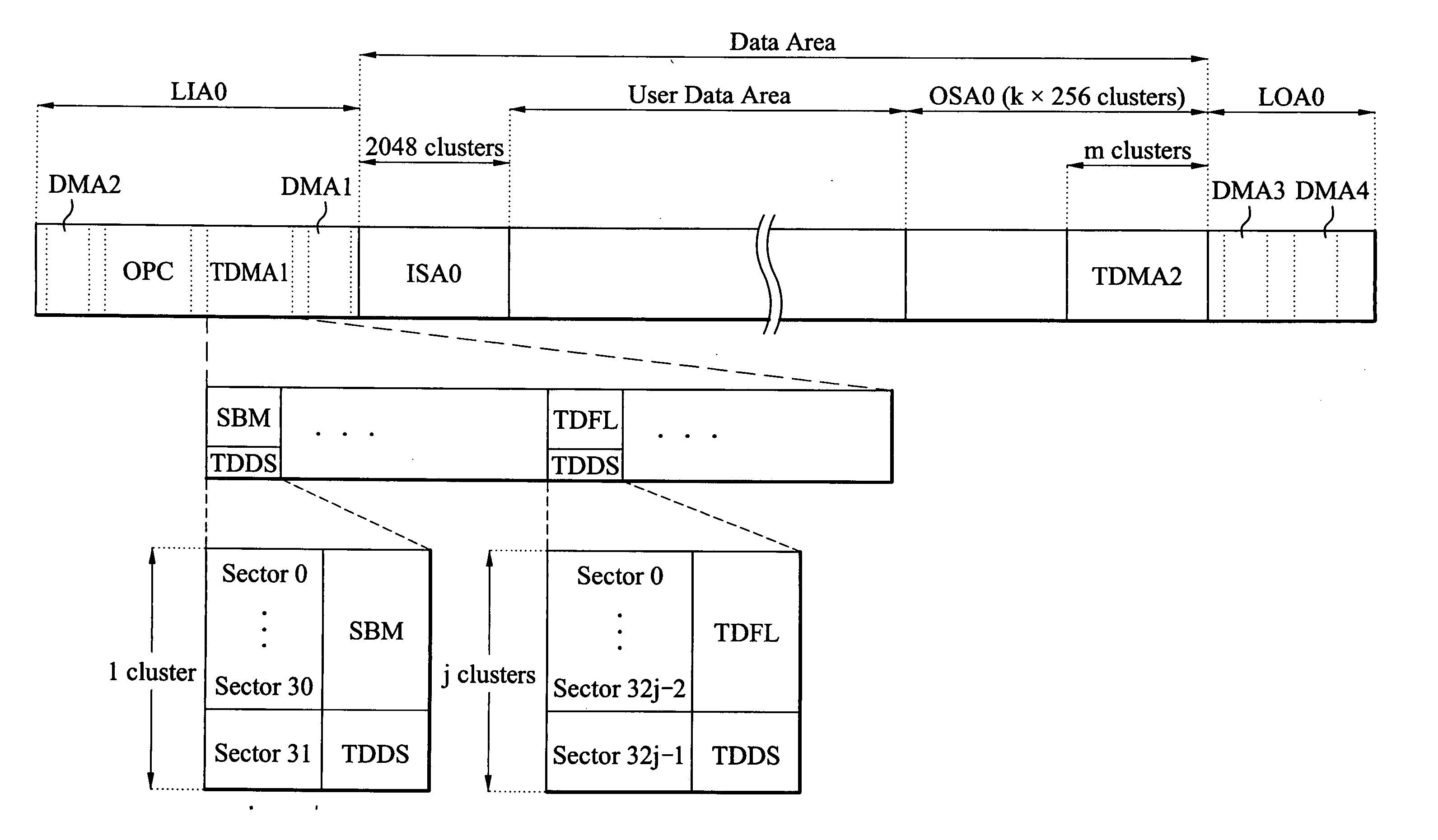
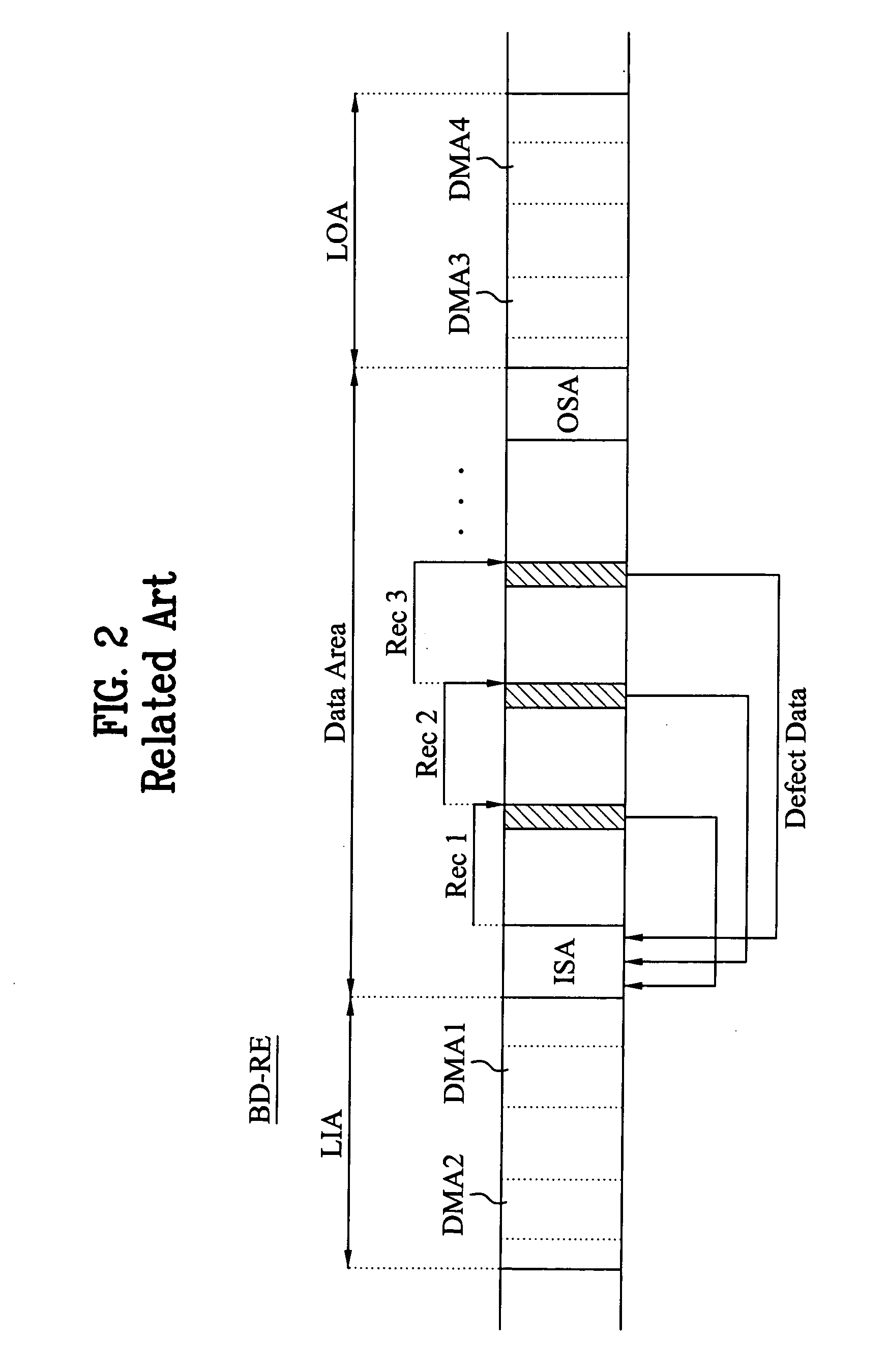
Method for recording on optical recording medium and apparatus using the same
ActiveUS20040174793A1Efficient managementImprove data integrityTelevision system detailsDisc-shaped record carriersInformation controlRecord status
A method and apparatus for recording on an optical recording medium, including the recording of management information, are described as a standard for the write-once Blu-ray disc. The management information is recorded in a management area of the disc, such as a temporary defect management area (TDMA), and includes record status information and update information. The record status information is a space bitmap (SBM) indicating whether a recording operation has been performed for a predetermined area of the disc, and the update information is SBM update information indicating whether the record status information is to be continuously managed. The SBM update information controls the state of an SBM-on / off function for each of a plurality of recording areas and may be in the form of either start position information and length information corresponding to the respective areas or an SBM update flag. The SBM update information is recorded in the TDMA and is stored in a memory of an optical disc recording / reproducing device for use during recording and reproducing operations. At the time of recording in the predetermined area, an SBM-on state enables a logical overwriting operation to be performed as necessary.
Owner:LG ELECTRONICS INC
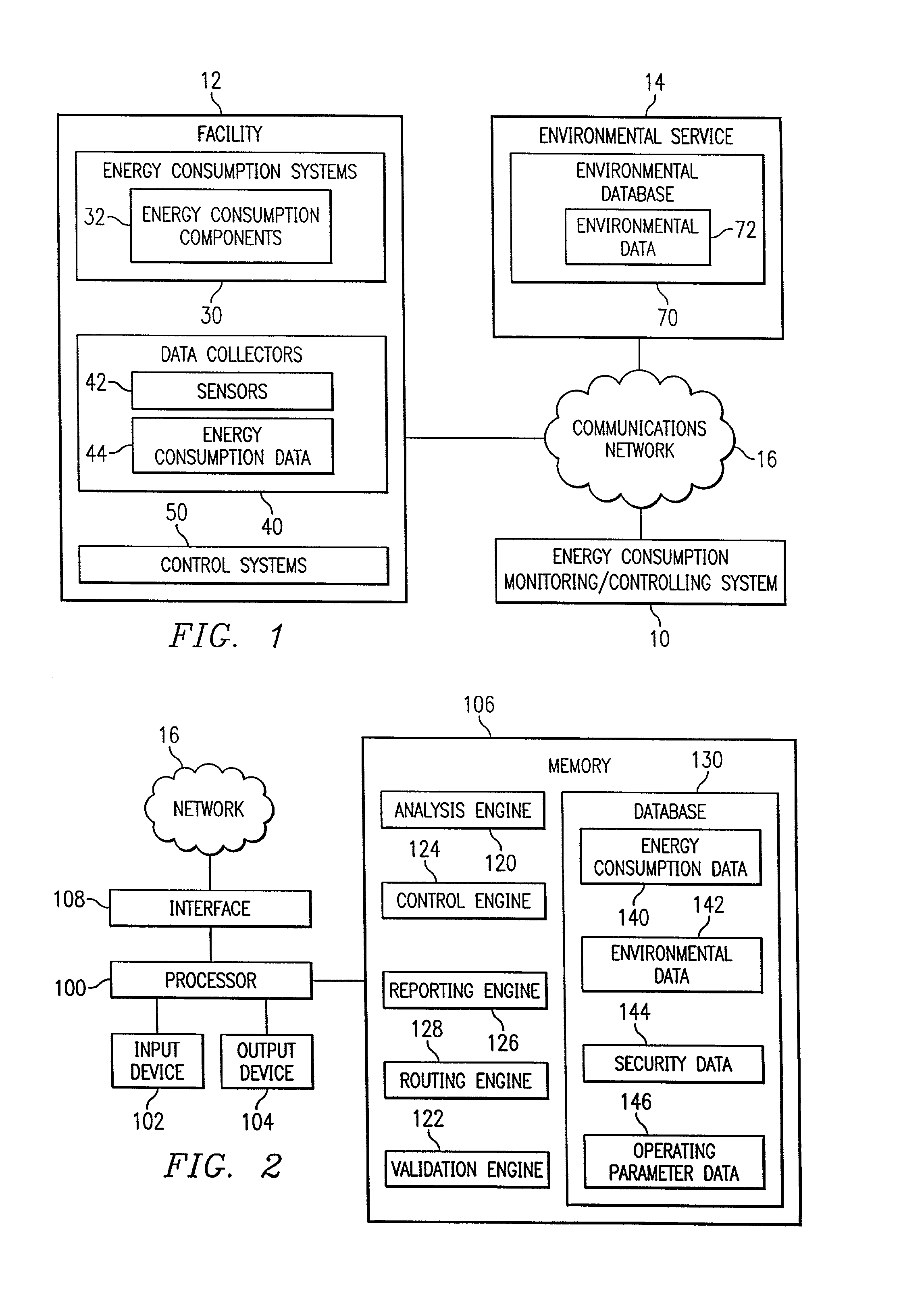
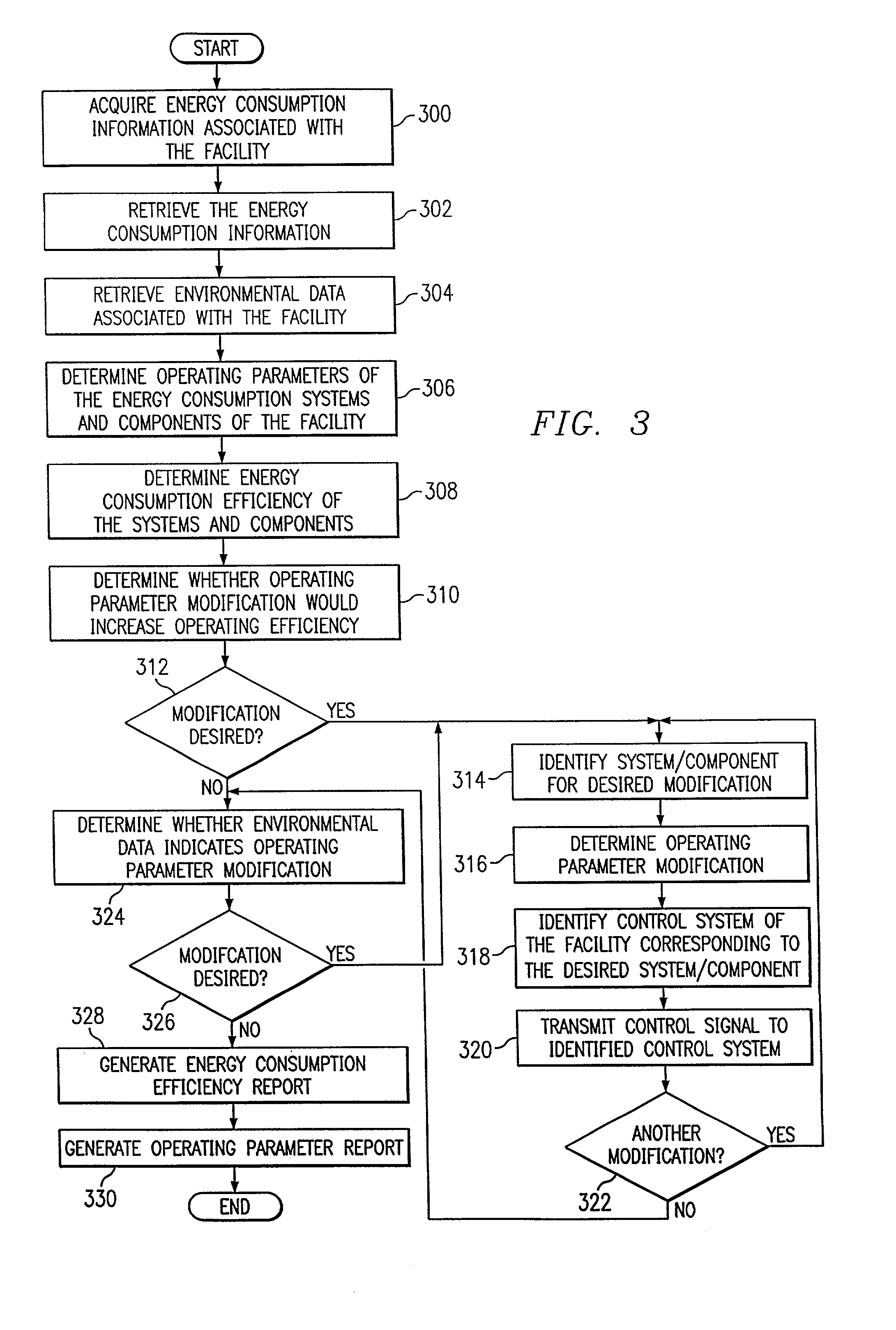
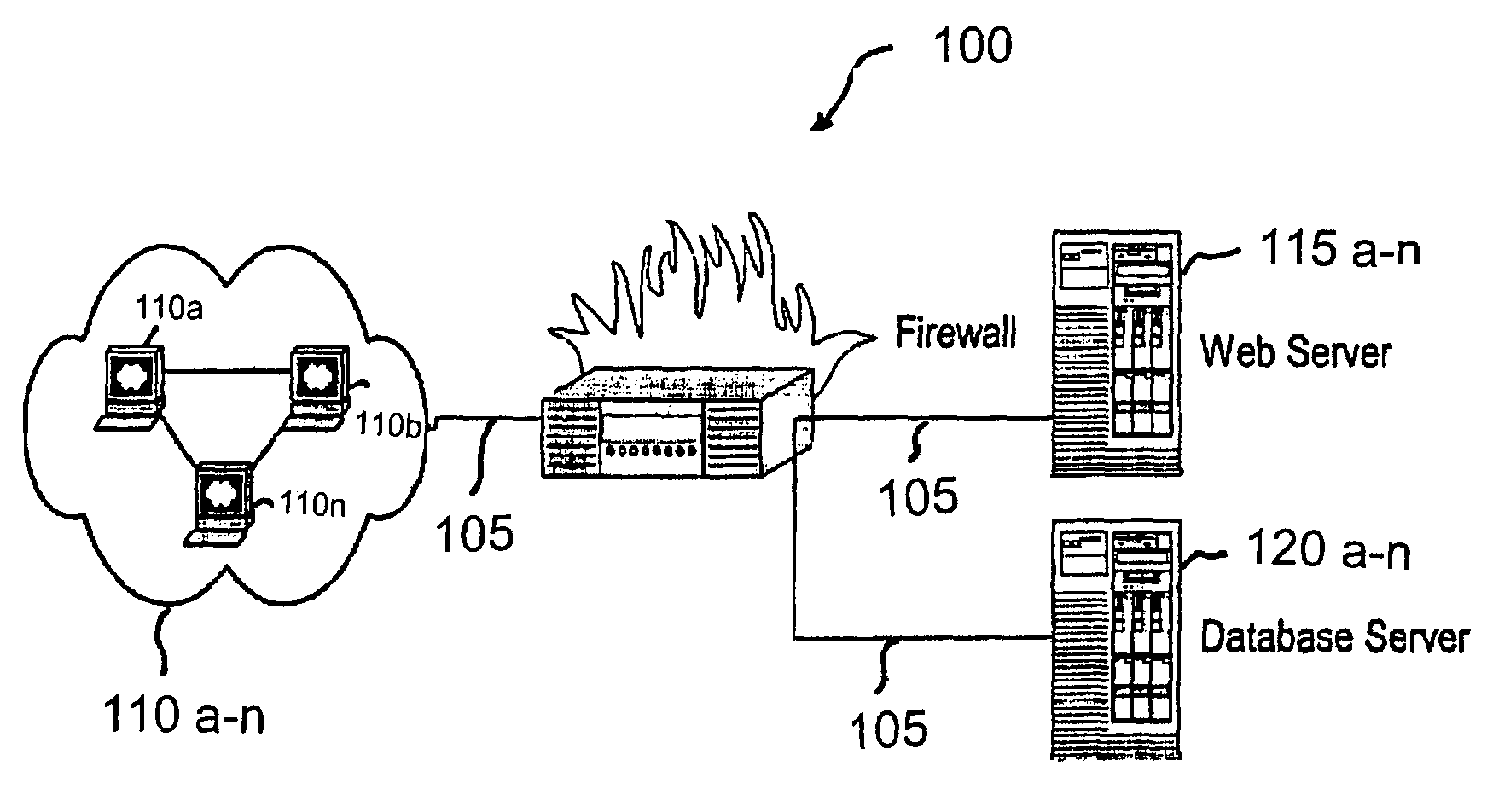
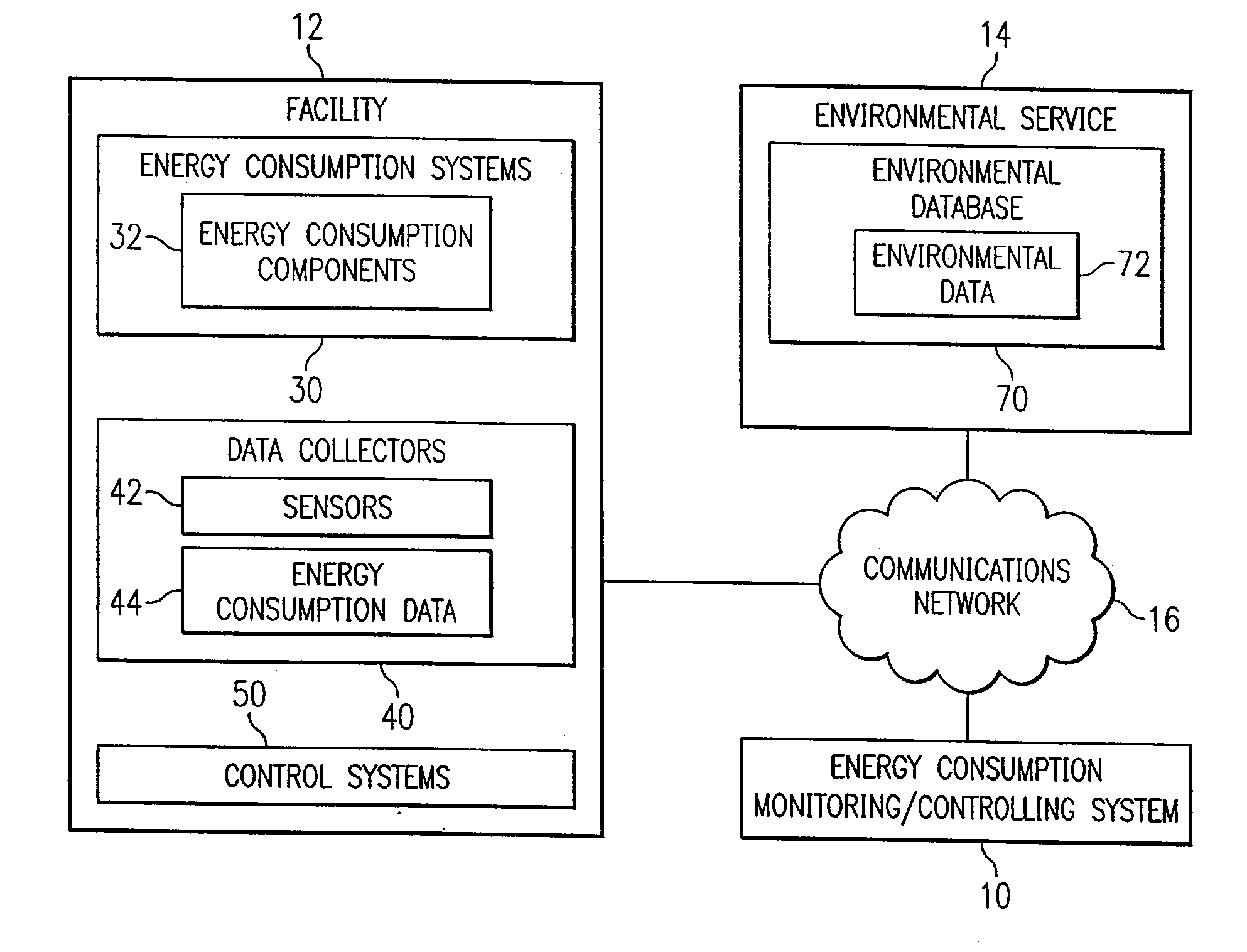
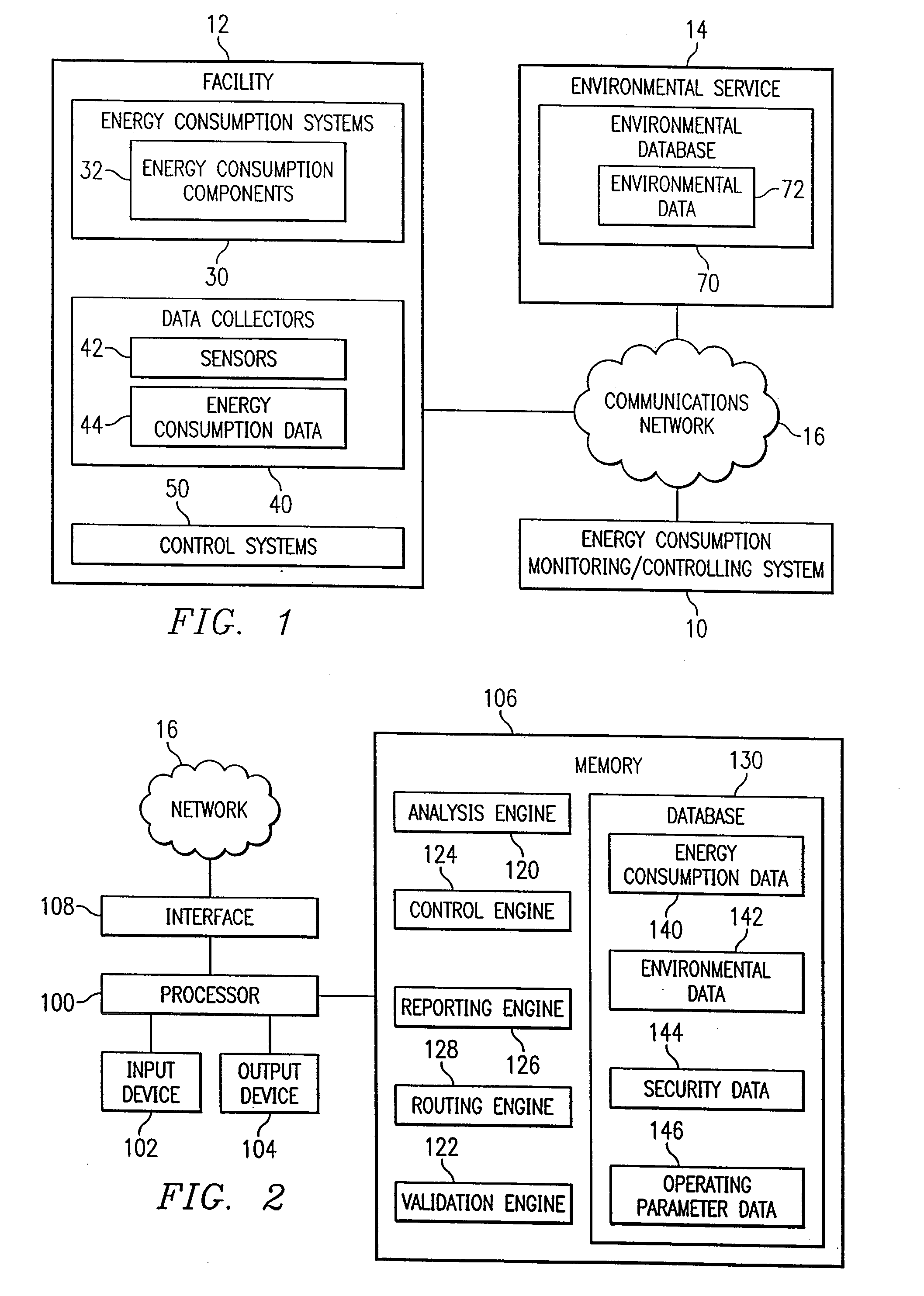
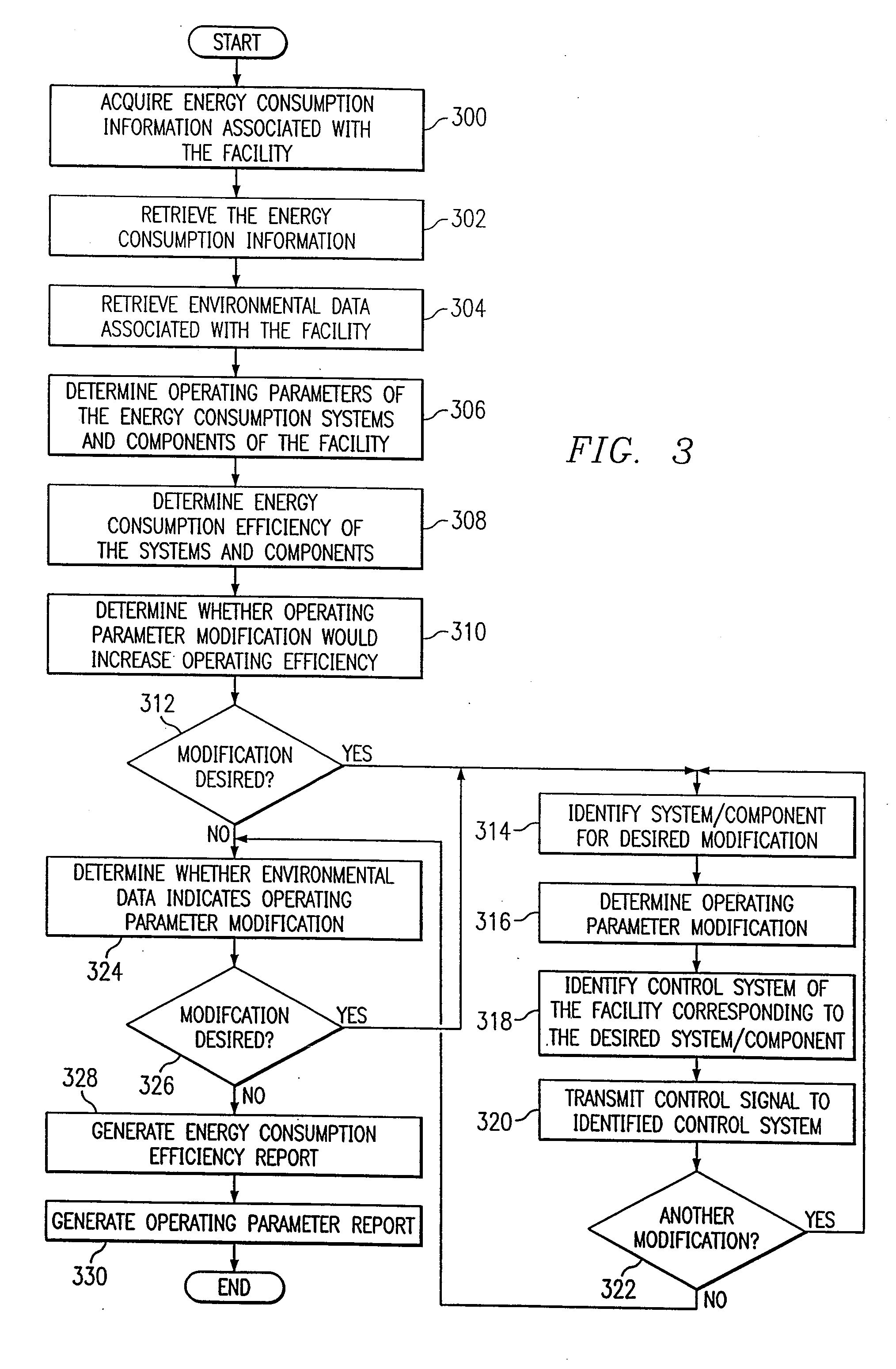
System and method for remote monitoring and controlling of facility energy consumption
InactiveUS7356548B1Increased energy consumption data integrityEnhanced energy consumption data acquisitionTransmissionSpecial data processing applicationsProcess engineeringEnergy expenditure
A method for remote monitoring and controlling of energy consumption of a facility includes receiving energy consumption data associated with the facility at a processor disposed remotely from the facility. The method also includes receiving environmental data associated with the facility. The method includes determining whether an operating parameter of an energy consumption system of the facility requires modification to increase efficiency using the energy consumption data and the environmental data. The method further includes automatically modifying the operating parameter of the energy consumption system corresponding to the required modification.
Owner:TEXAS A&M UNIVERSITY
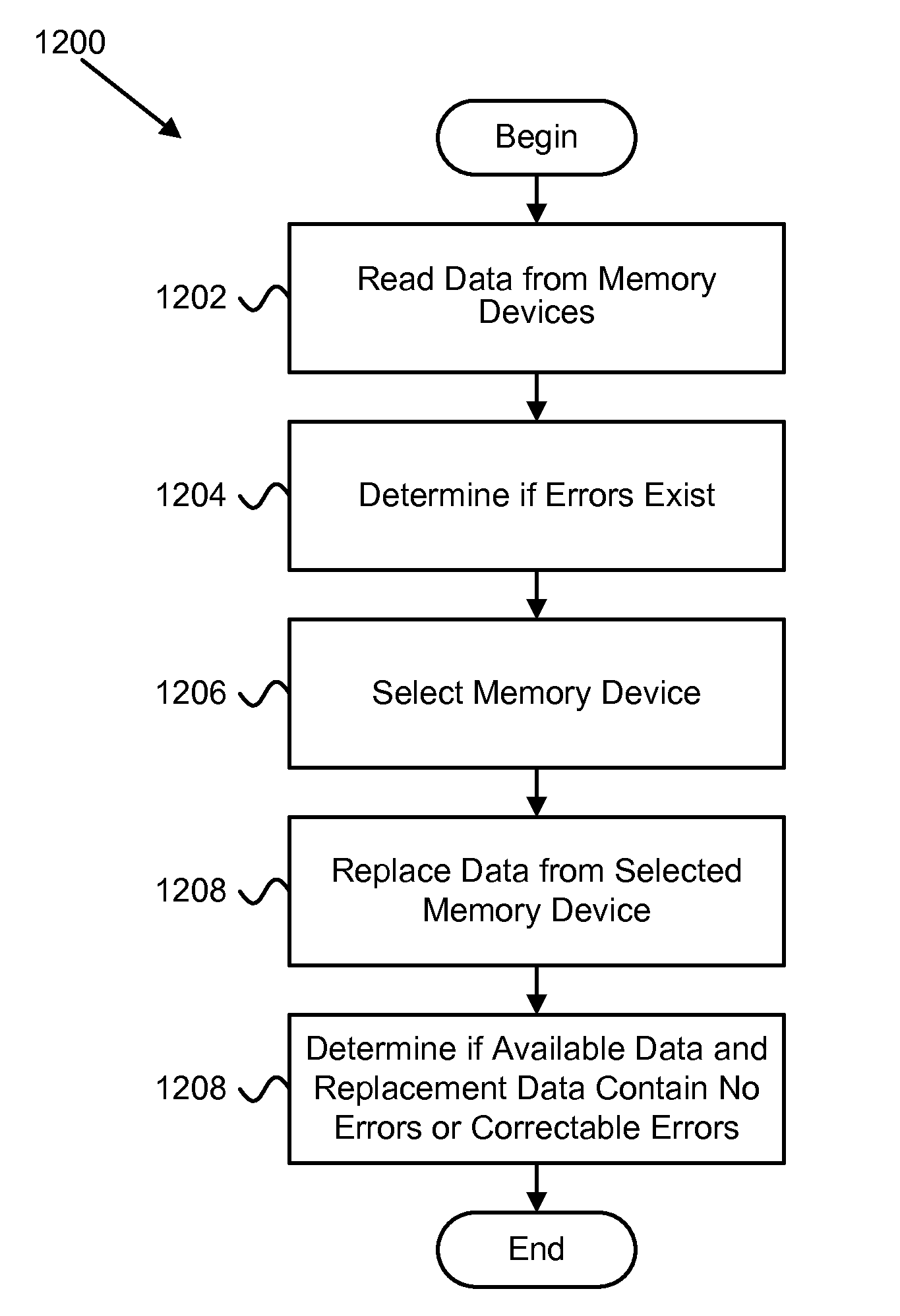
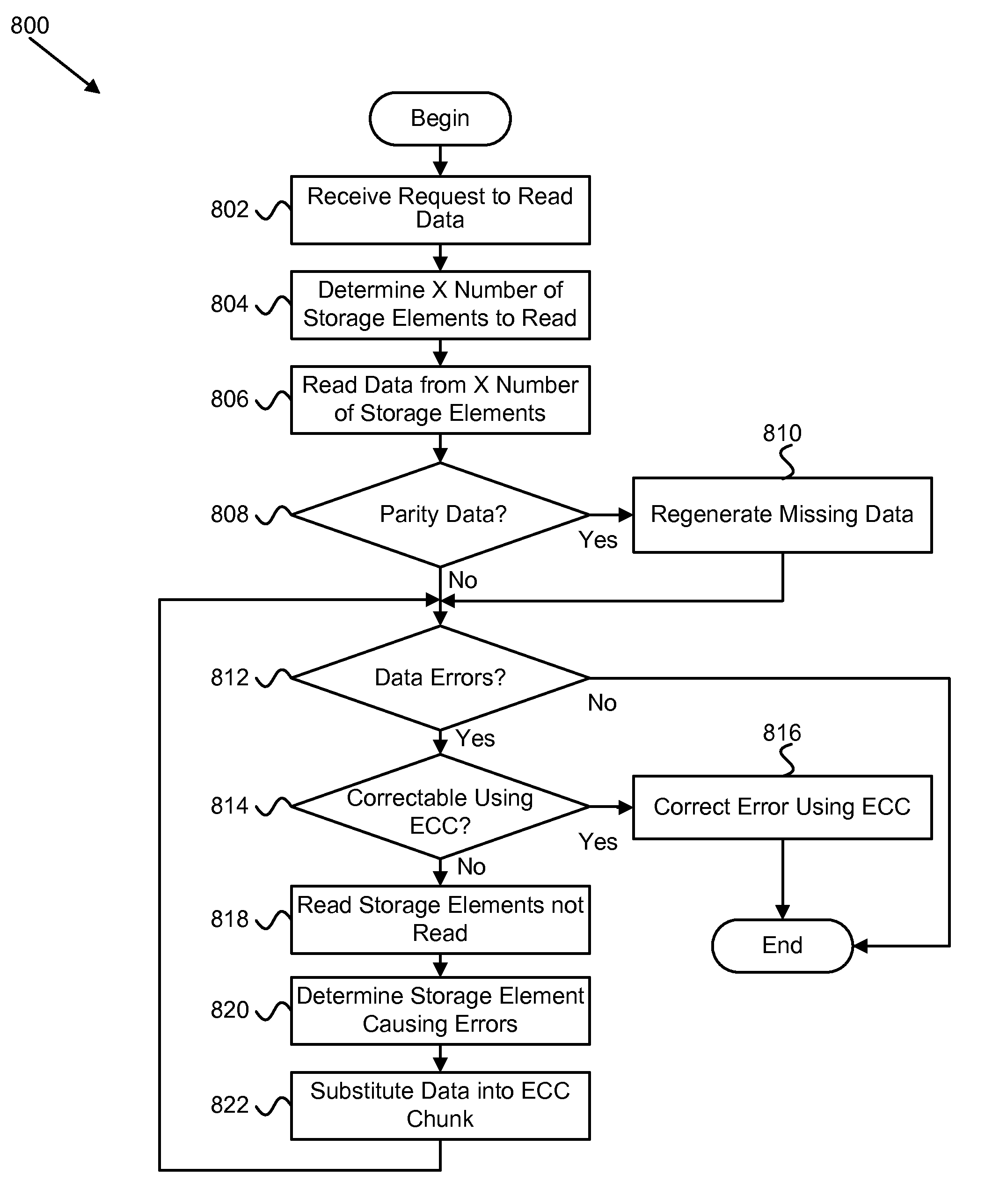
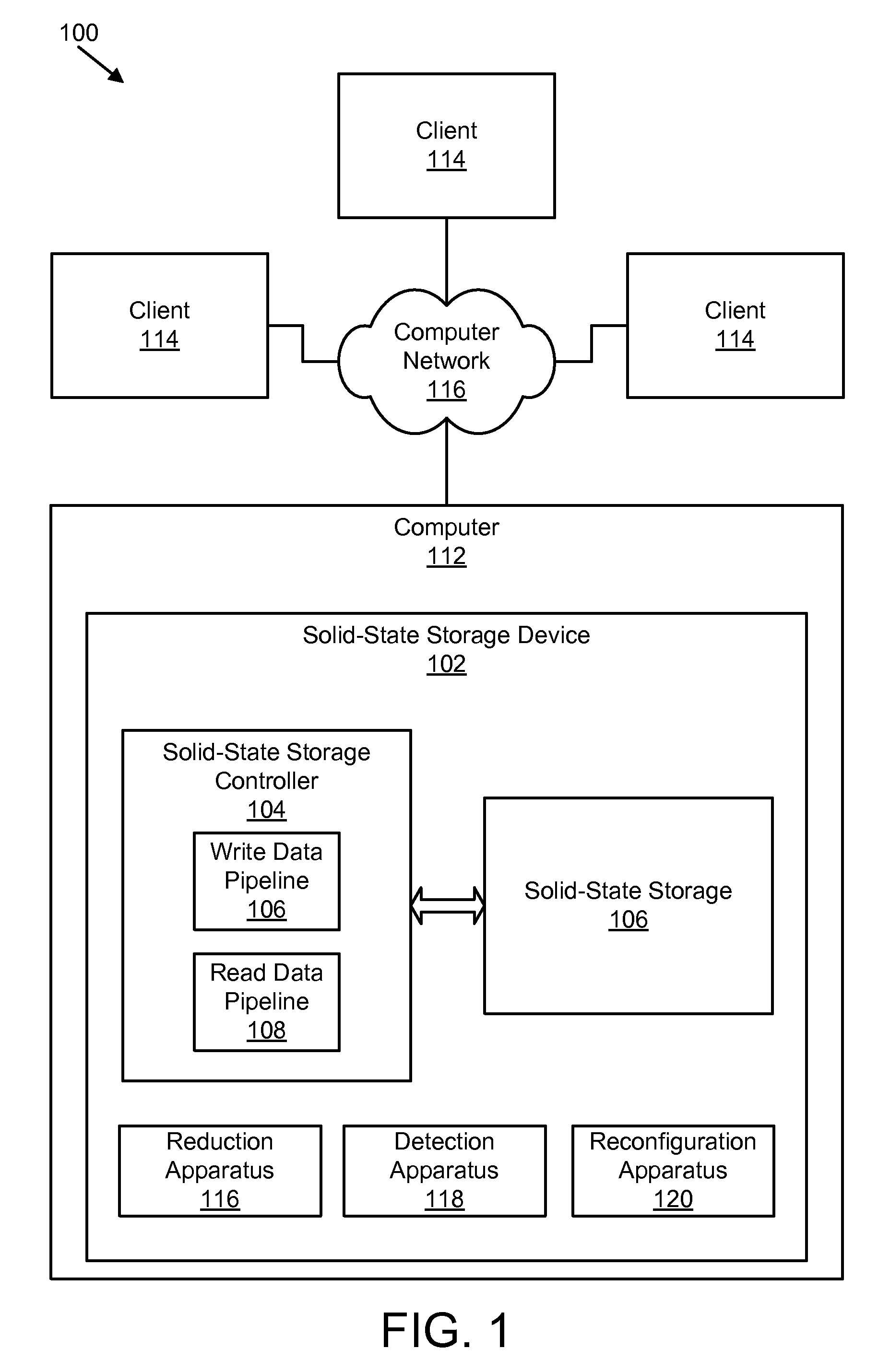
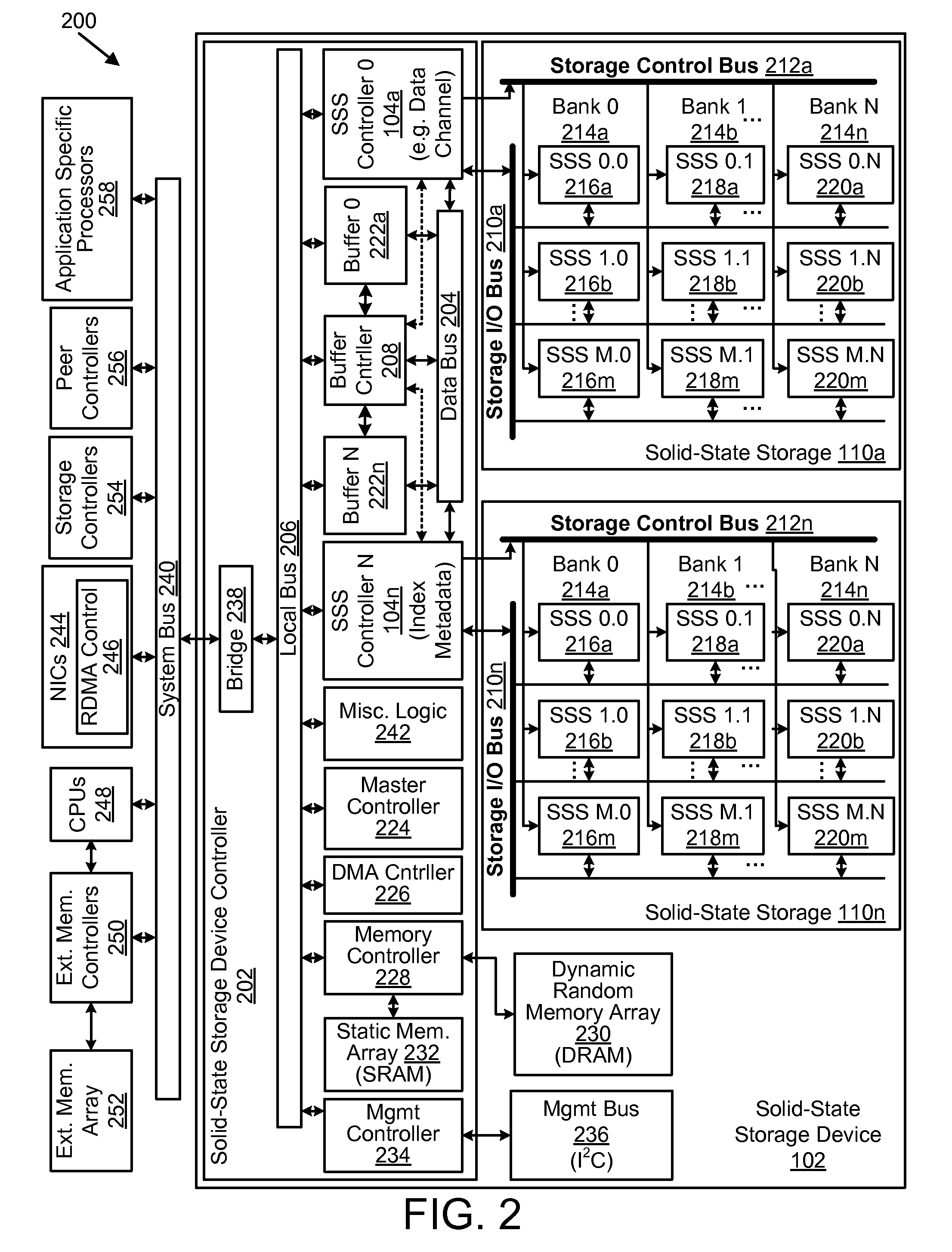
Apparatus, system, and method to increase data integrity in a redundant storage system
ActiveUS20100293440A1Improve data integrityReduce in quantityCode conversionNon-redundant fault processingMissing dataData integrity
An apparatus, system, and method are disclosed to increase data integrity in a redundant storage system. The receive module receives a read request to read data from a logical page spanning an array of N+P number of storage elements. The array of storage elements includes N number of the storage elements each storing a portion of an ECC chunk and P number of the storage elements storing parity data. The data read module reads data from at least a portion of a physical page on each of X number of storage elements of the N+P number of storage elements where X equals N. The regeneration module regenerates missing data. The ECC module determines if the read data and any regenerated missing data includes an error. The read data combined with any regenerated missing data includes the ECC chunk.
Owner:UNIFICATION TECH LLC
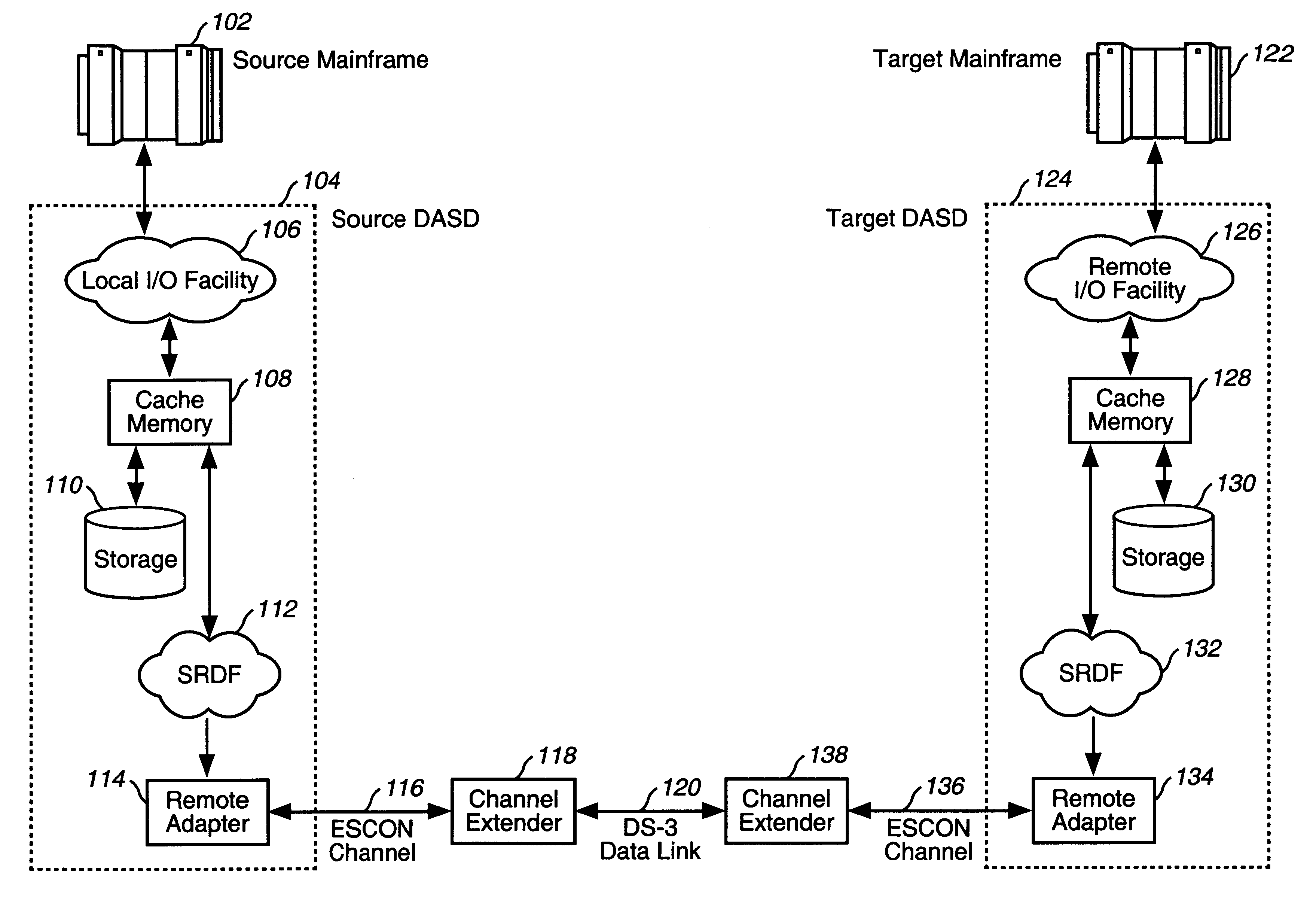
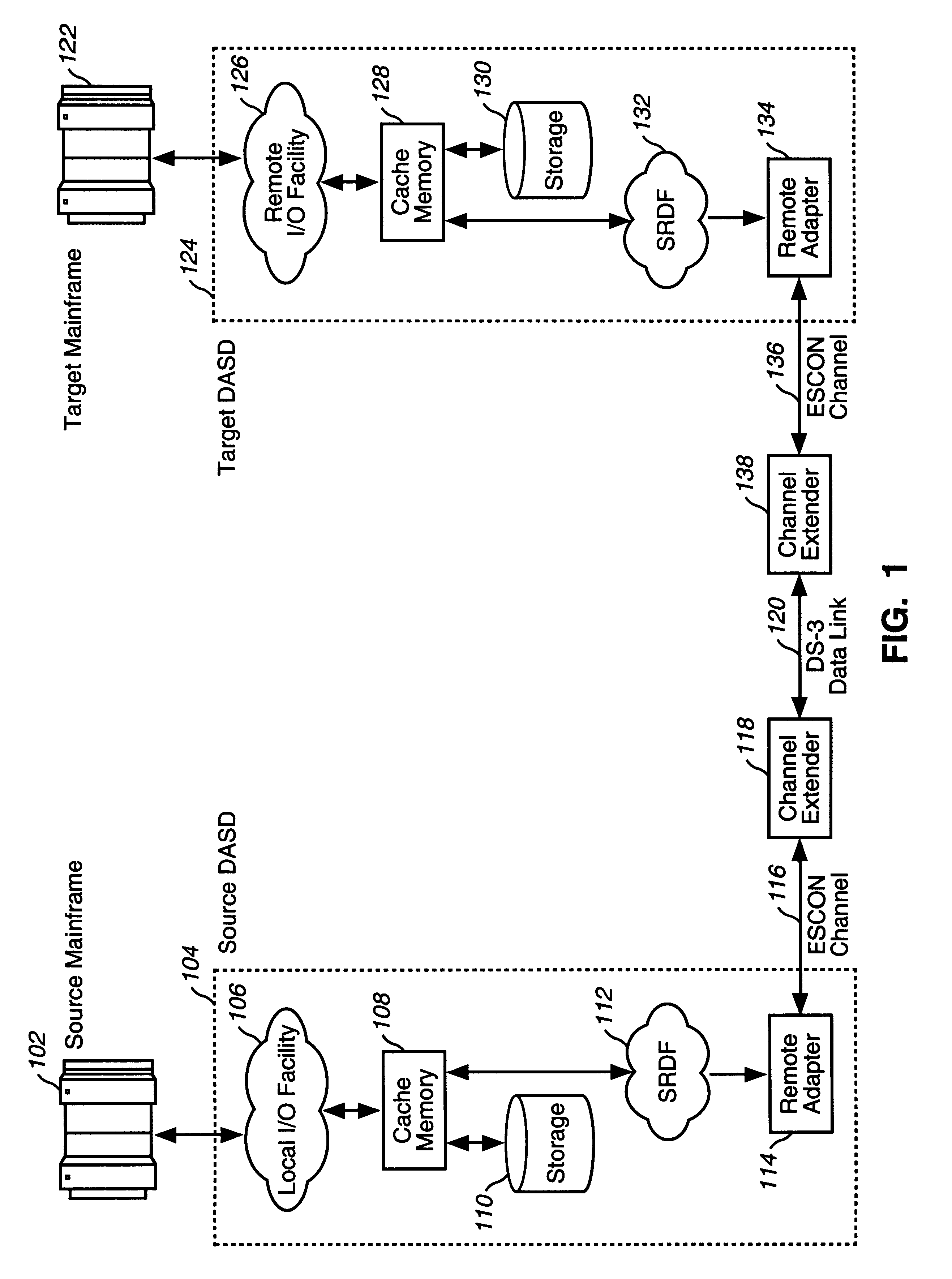
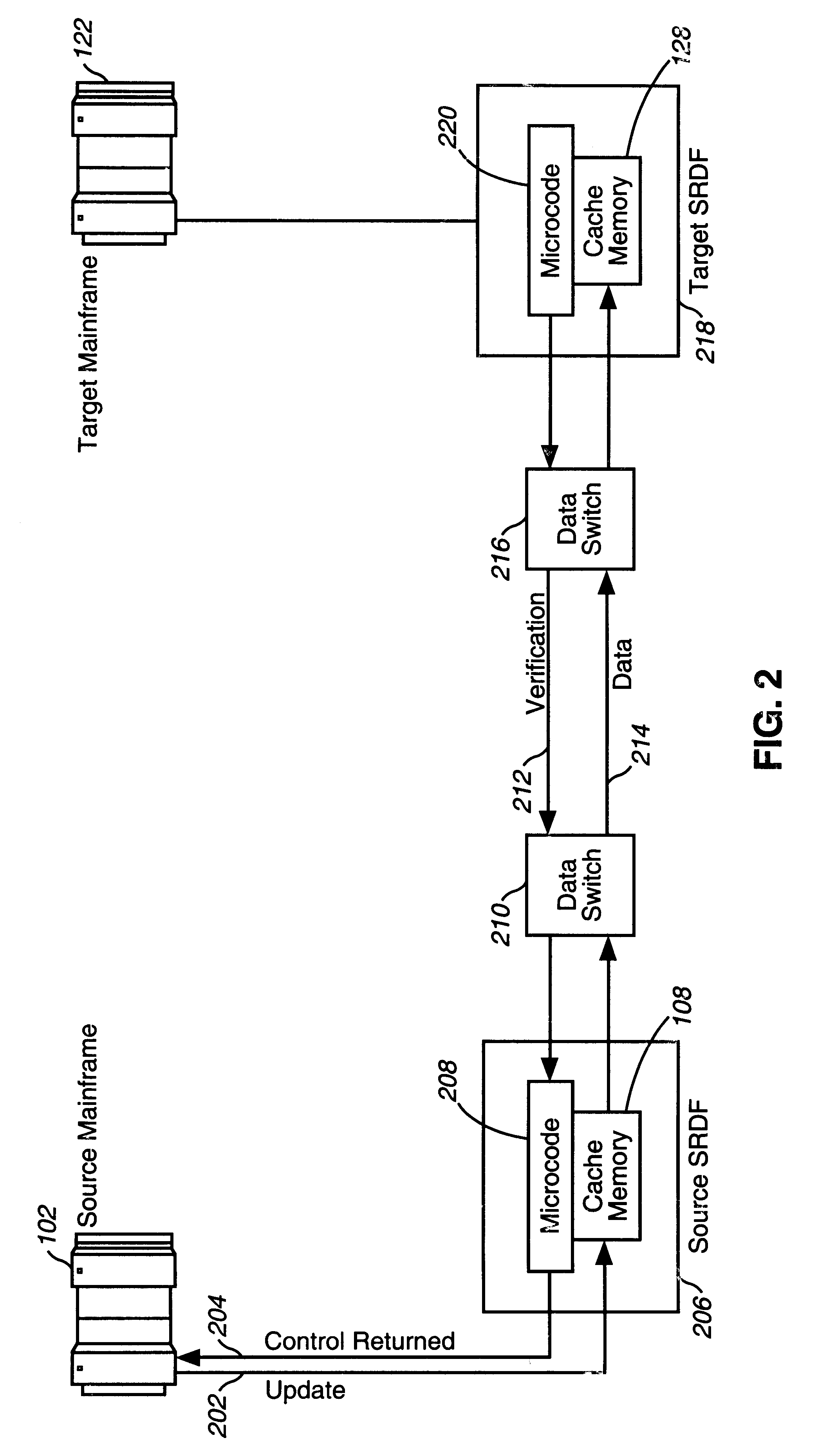
Data center migration method and system using data mirroring
InactiveUS6405294B1Save resource costLow costInput/output to record carriersRedundant operation error correctionSystem usageApplication software
A method and system for migrating computer applications and volumes of data from a source DASD connected to a source computer system to a target DASD connected to a target computer system. The method comprises ensuring data integrity on the source DASD, initiating one or more processes to mirror all data and all data updates from the source DASD to the target DASD, ensuring synchronization of data updates to the source DASD by the source computer system with data updates to the target DASD, deactivating all applications executing on the source computer system, mirroring one or more remaining data updates to the source DASD by the source computer system to the target DASD, disconnecting the source computer system and the source DASD from the target computer system and the target DASD; and bringing the target computer system and the applications executing on the target computer system on-line.
Owner:VERIZON PATENT & LICENSING INC
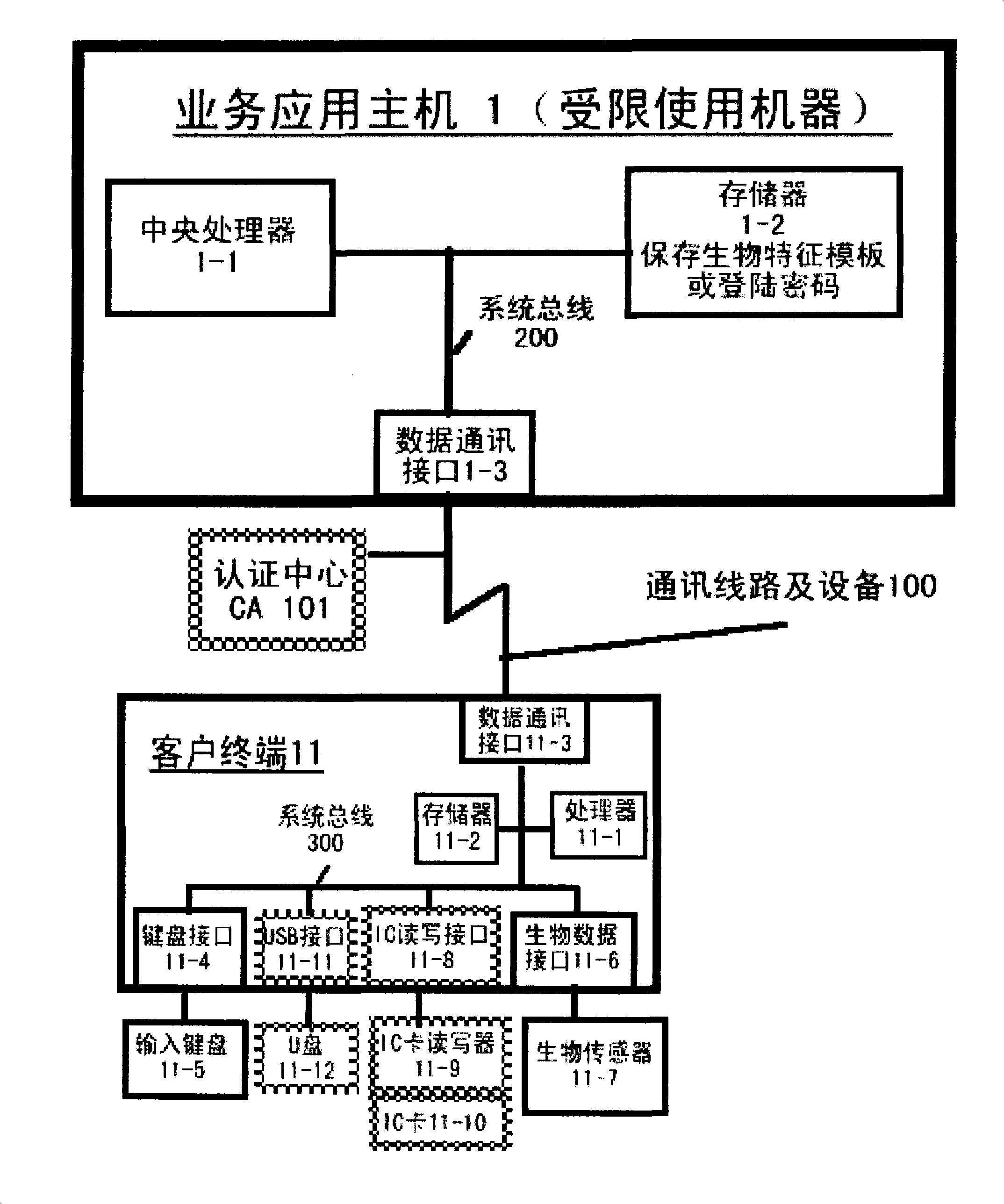
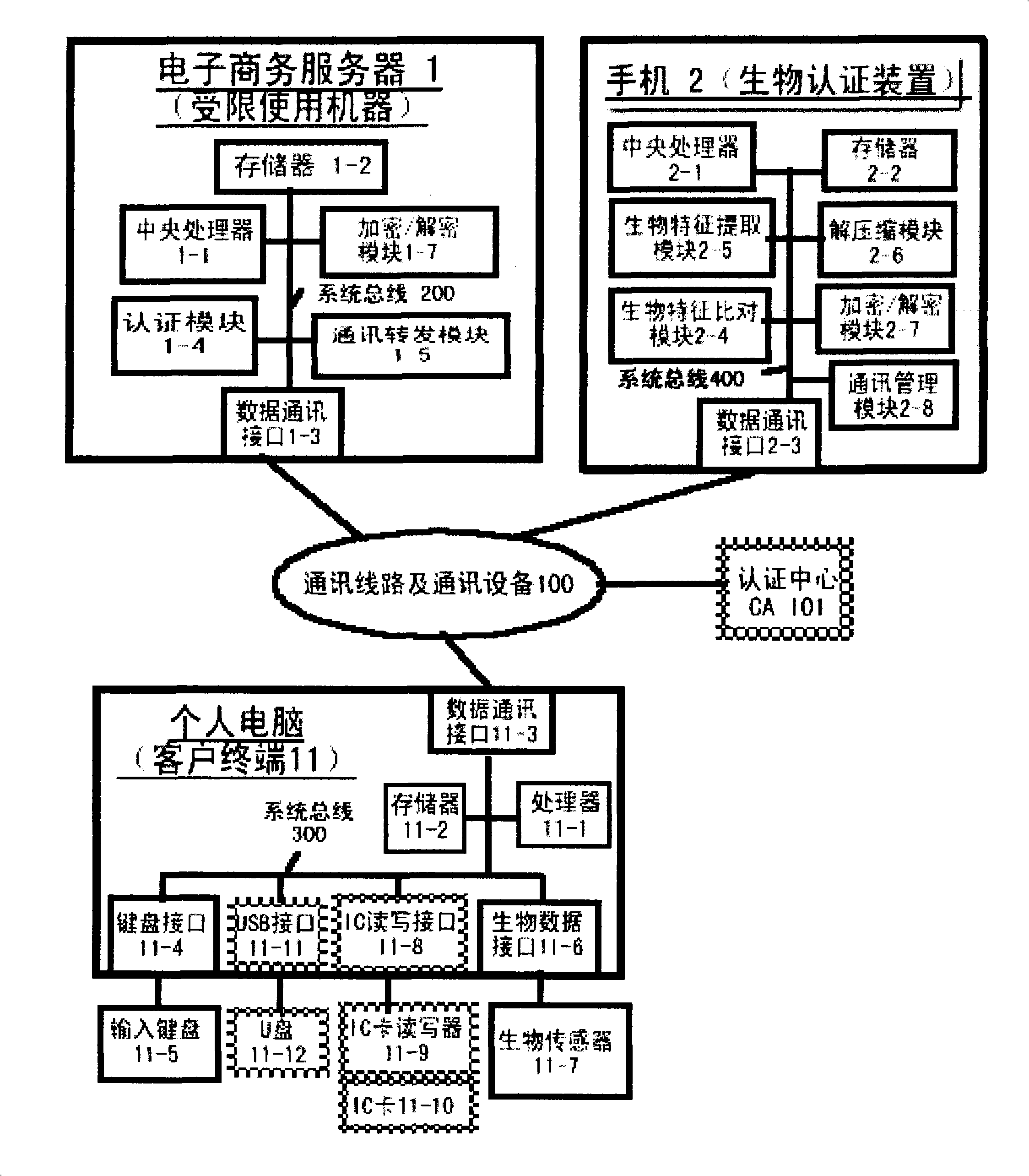
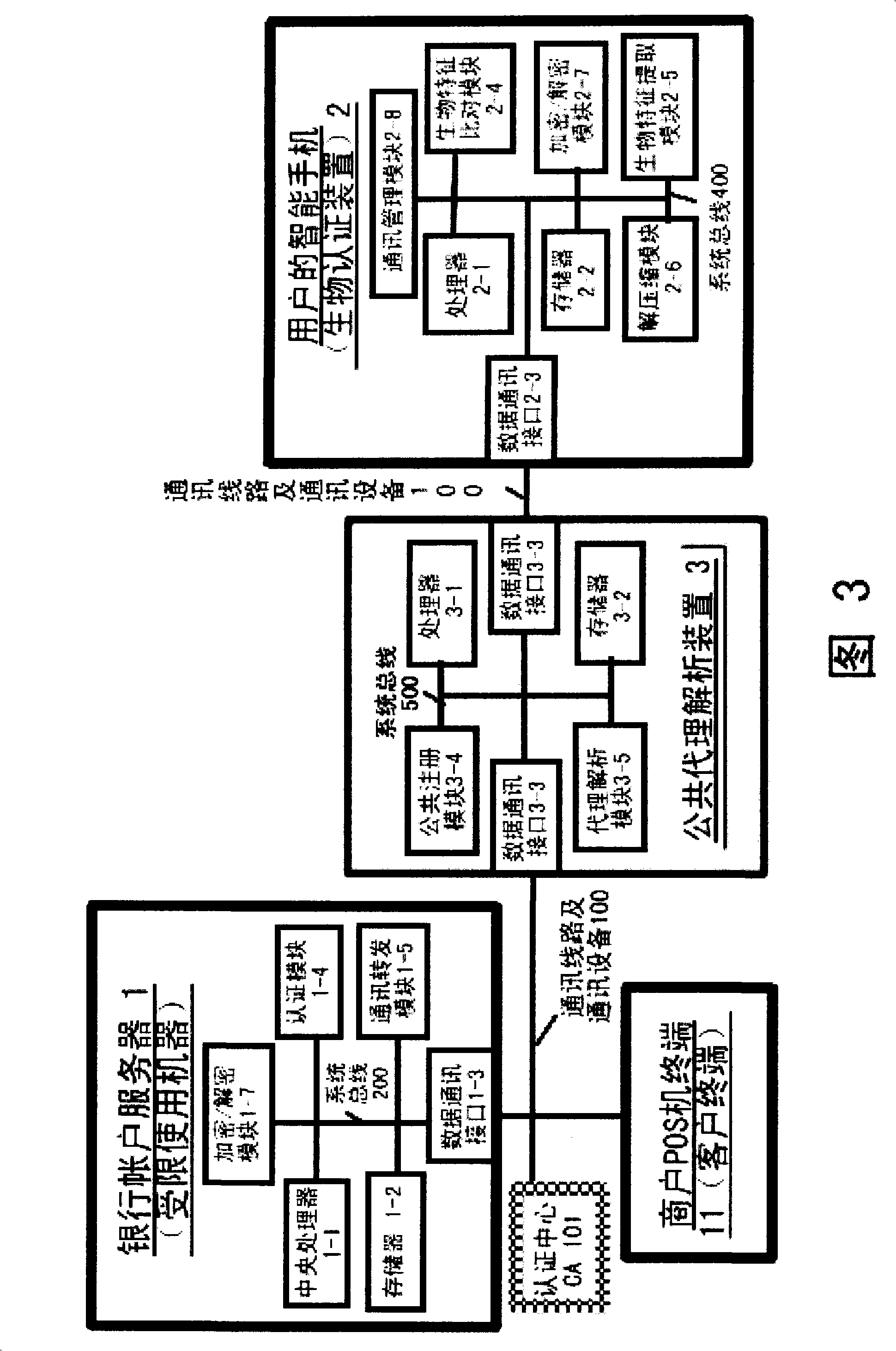
Authentication system based on biological characteristics and identification authentication method thereof
InactiveCN101330386AAttack is notAttacks are not directlyUser identity/authority verificationCharacter and pattern recognitionInternet privacyComputer terminal
The invention relates to an authentication system and an authentication method based on biological features. The method comprises the steps of conducting centralized storage and biological feature comparison operation for a large quantity of user biological feature templates according to user ID identifiers stored on a memory on a limited use machine and corresponding biding ID identifiers thereof on a biological authentication device of a digital processing terminal; separating the biological feature templates from the authentication function of the limited use machine; allocating to digital processing terminals (including PCs, notebooks or mobile phones, PDAs of users)of users as biological authentication device-storing the biological feature templates with decentralization and operating and processing biological features to be authenticated with decentralization so as to conduct comparison with the biological feature templates pre-stored on the respective digital processing terminals; feeding back comparison and verification results to the limited use machines; authorizing to conduct equal authentication of the biological authentication device ID identifier on the digital processing terminal for the corresponding binding user ID identifiers by the centralized authentication of the limited use machine according to the comparison verification result data.
Owner:刘洪利
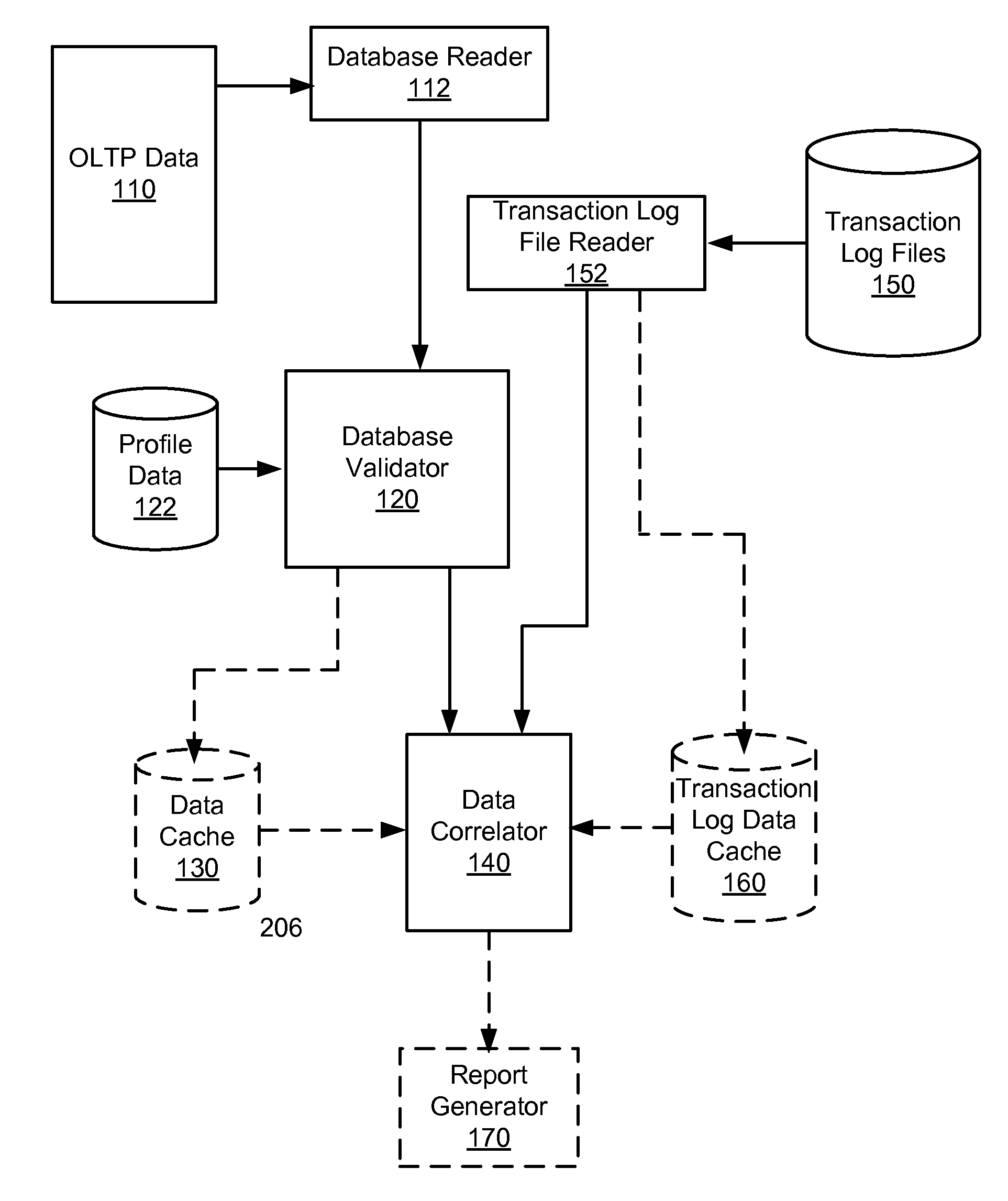
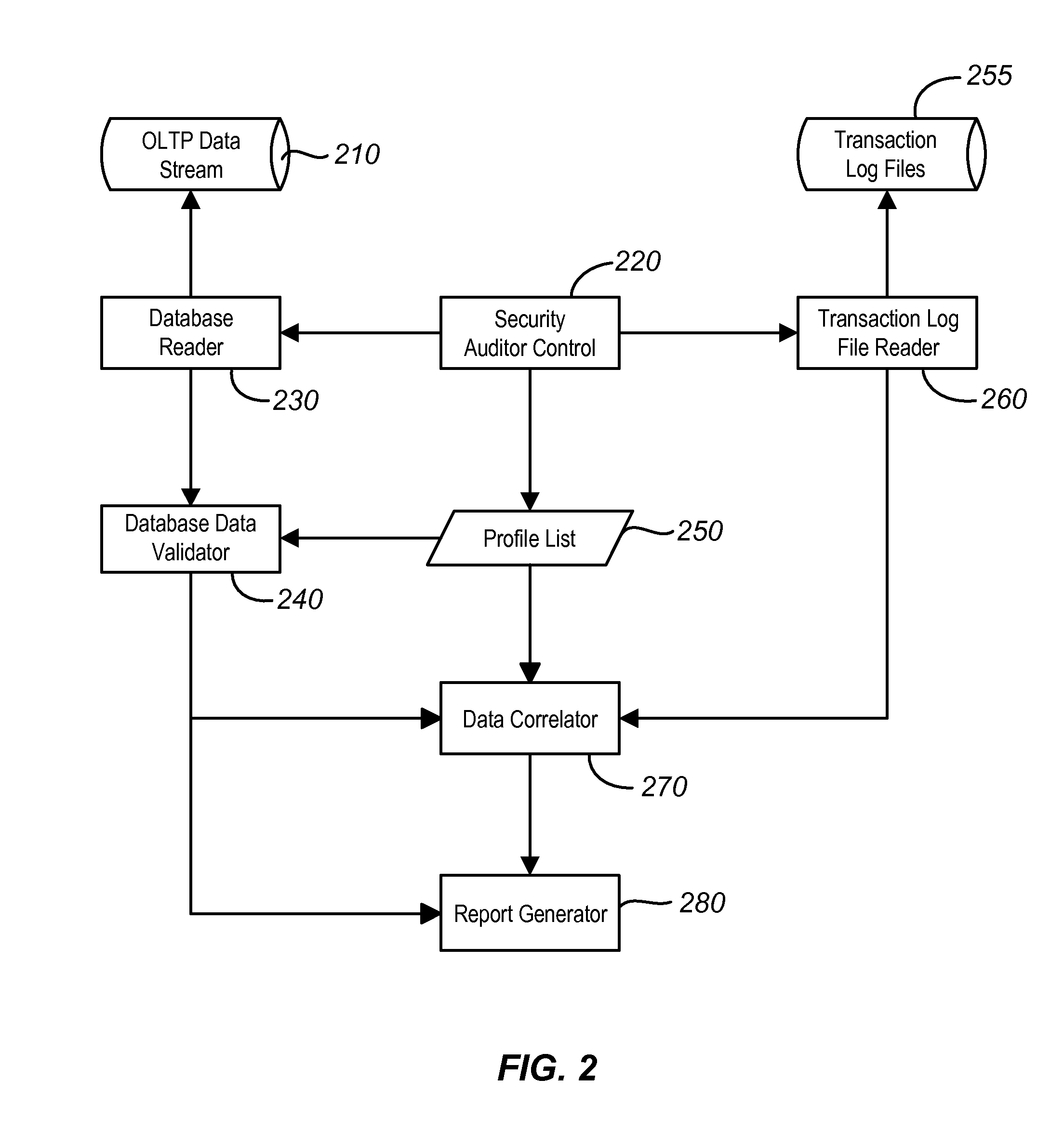
Method and system for auditing transaction data from database operations
ActiveUS20100318858A1Improve data integrityLimiting potential damageFault responseMemory adressing/allocation/relocationTransaction dataXML
A method for validating SRS registry transaction data includes receiving OLTP transaction data from a first database, parsing the OLTP transaction data, and comparing the parsed OLTP transaction data to one or more of a set of profiles. Each of the one or more of the set of profiles includes metadata in XML files. The method also includes caching the parsed OLTP transaction data in a first data cache, receiving log data associated with the OLTP transaction data; and caching the log data in a second data cache. The method further includes correlating the parsed transaction data cached in the first data cache with the log data cached in the second data cache.
Owner:VERISIGN
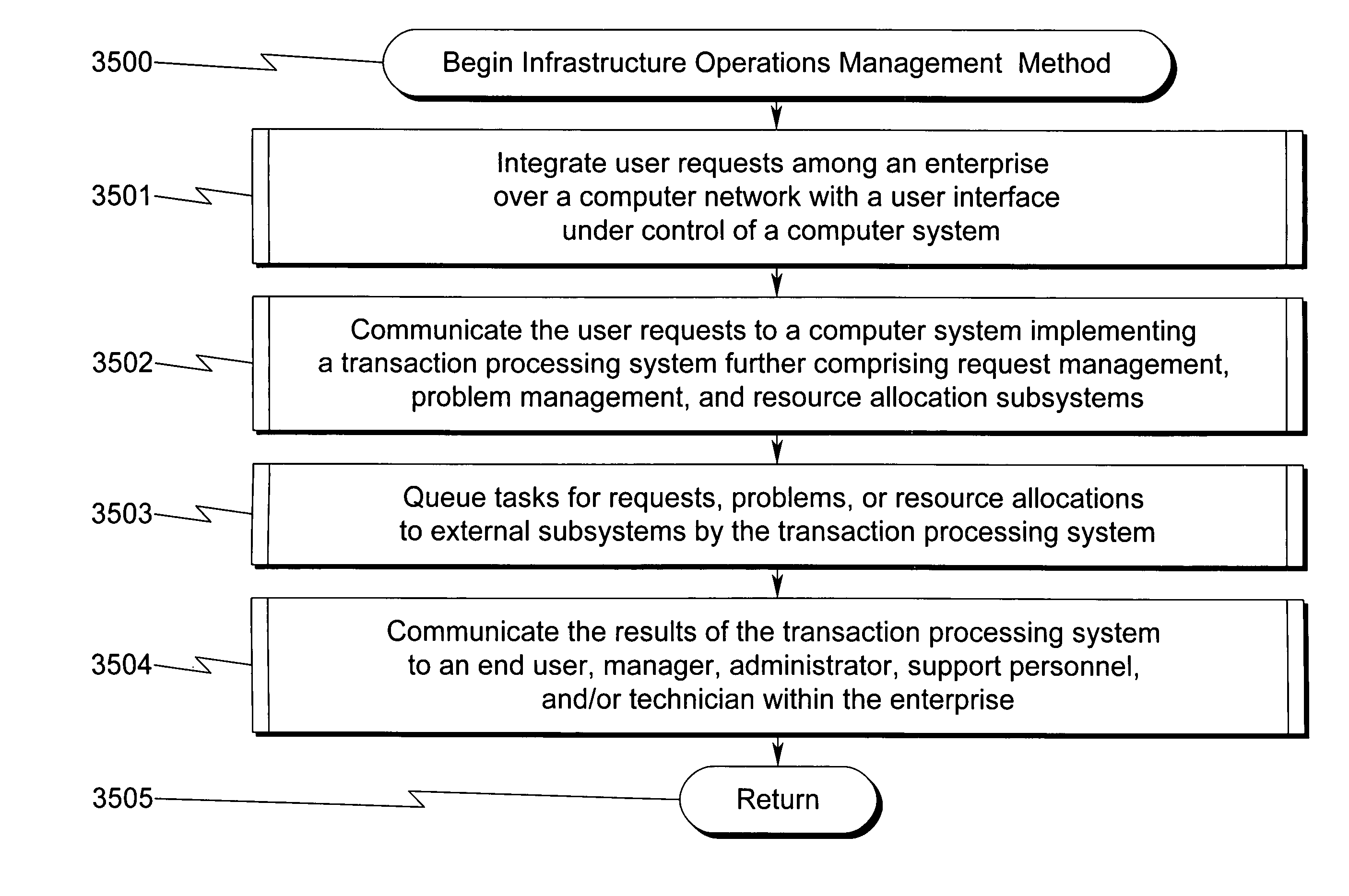
Integrated infrastructure operations management system and method
InactiveUS20100198651A1High data reliabilityReduce effortResourcesRelational databaseApplication software
A business computing system and method for integrated management of operations and infrastructure of a business is disclosed. The system architecture contains data stored in one or more relational databases, web-based, and / or non-web based user interfaces provided by an aggregation of software, automated processes, and a transaction processing system. A standardized interface is defined for modular components to be incorporated. A specialized business process description and control language is utilized to support flexibility, configuration, and modeling of processes. Persistent messaging is utilized for inter-process communication. Various other processes and components provide automation and integration with external systems / subsystems. The purpose of this combination of applications and business processes is to provide a robust and flexible enterprise management platform for managing infrastructure (including facilities, cabling, security, furniture, etc.) and information technology (IT) services (including network, voice, platform management, printing, etc.).
Owner:JOHNSON STEPHEN MICHAEL +1
Data entry, cross reference database and search systems and methods thereof
ActiveUS7225197B2Improve data integritySpeed efficientData processing applicationsDigital data processing detailsData integrityData field
A method and system unifying existing data of a target industry from existing sources of the data by designing a data model by applying varying data integrity methods to define characteristics, features and / or functions of items in the target industry as data elements, electronically reading, parsing and transforming data from existing electronic data sources of the target industry to input to the data model, designing user interfaces to the data model, the user interfaces corresponding to user segments of the target industry, and dynamically maintaining normalization of the data model according to the varying data integrity methods during any type of access to the data model by the user segments. A data entry access to the data model comprises dynamically constructing search indexes, each search index defined as a unique data field and a text searchable concatenation of other fields' data in any given data table of the data model.
Owner:ELECDECOM
System and Method for Remote Monitoring and Controlling of Facility Energy Consumption
InactiveUS20090012654A1Improve data integrityEasy access to dataMechanical power/torque controlLevel controlProcess engineeringEnergy expenditure
A method for remote monitoring and controlling of energy consumption of a facility includes receiving energy consumption data associated with the facility at a processor disposed remotely from the facility. The method also includes receiving environmental data associated with the facility. The method includes determining whether an operating parameter of an energy consumption system of the facility requires modification to increase efficiency using the energy consumption data and the environmental data. The method further includes automatically modifying the operating parameter of the energy consumption system corresponding to the required modification.
Owner:TEXAS A&M UNIVERSITY
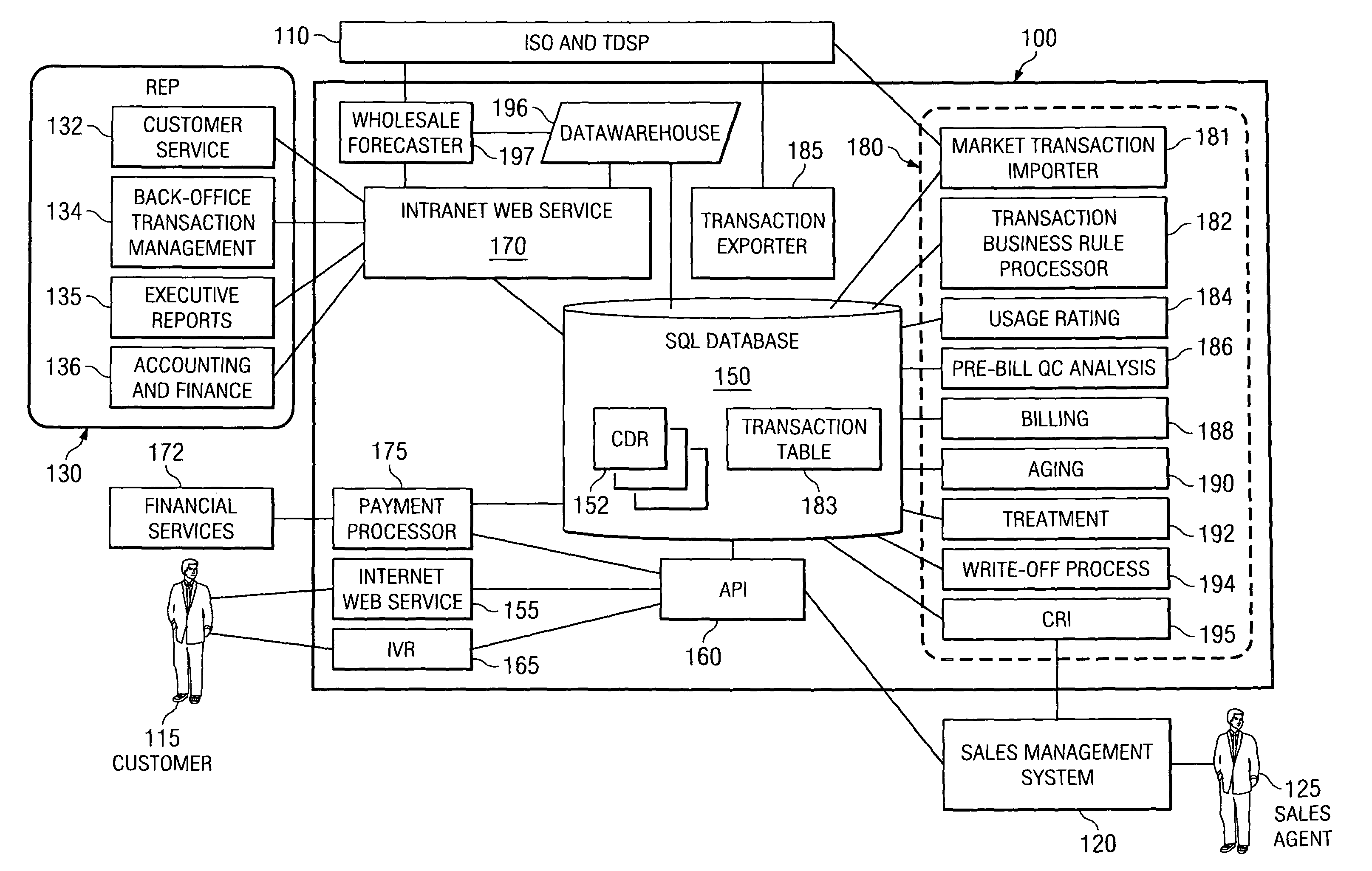
Energy distribution and marketing backoffice system and method
ActiveUS8442917B1Reduce human workload requirementLower requirementElectric devicesSpecial tariff metersWeb serviceInteractive voice response system
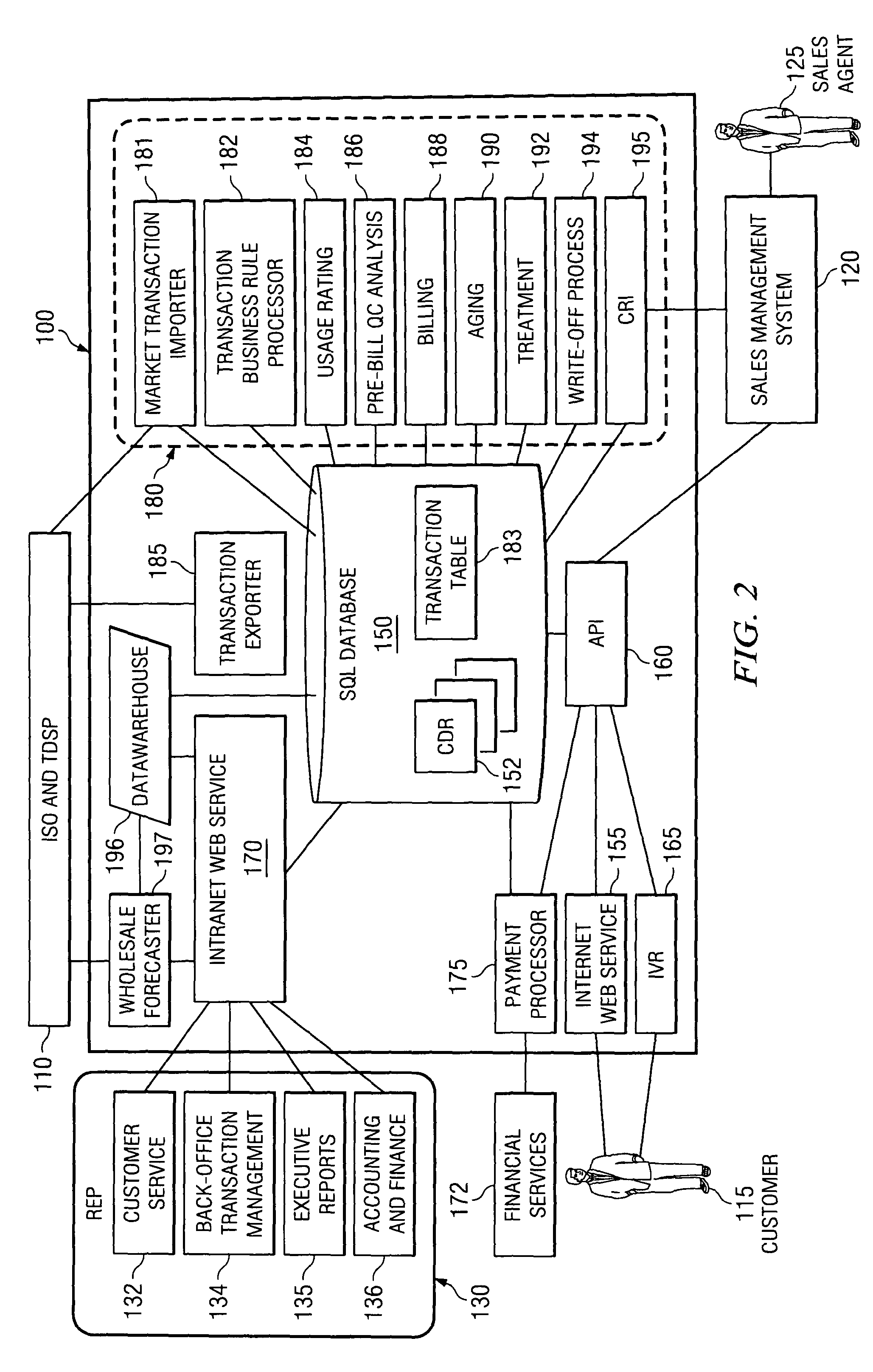
A retail energy provider system comprising a market transaction manager, business rules and requirements processor, usage rater, customer analysis and quality control auditor, customer billing processor and collection manager, customer payment processor, third party sales and marketing application programming interface, customer acquisition and residual income interface, having a wholesale forecaster, interactive voice response system, intranet web services, internet web services and network based external customer service and executive management systems and financial services functions, all said functions and systems interacting with a robust SQL database engine for which the novel database schema is taught herein.
Owner:BLUENET HLDG LLC
Apparatus, system, and method to increase data integrity in a redundant storage system
ActiveUS8281227B2Improve data integrityReduce in quantityCode conversionNon-redundant fault processingData integrityMissing data
Owner:UNIFICATION TECH LLC
Automated method for loan settlement
InactiveUS20020082984A1Reduce labor intensityReduce processFinanceSpecial data processing applicationsThe InternetComputer science
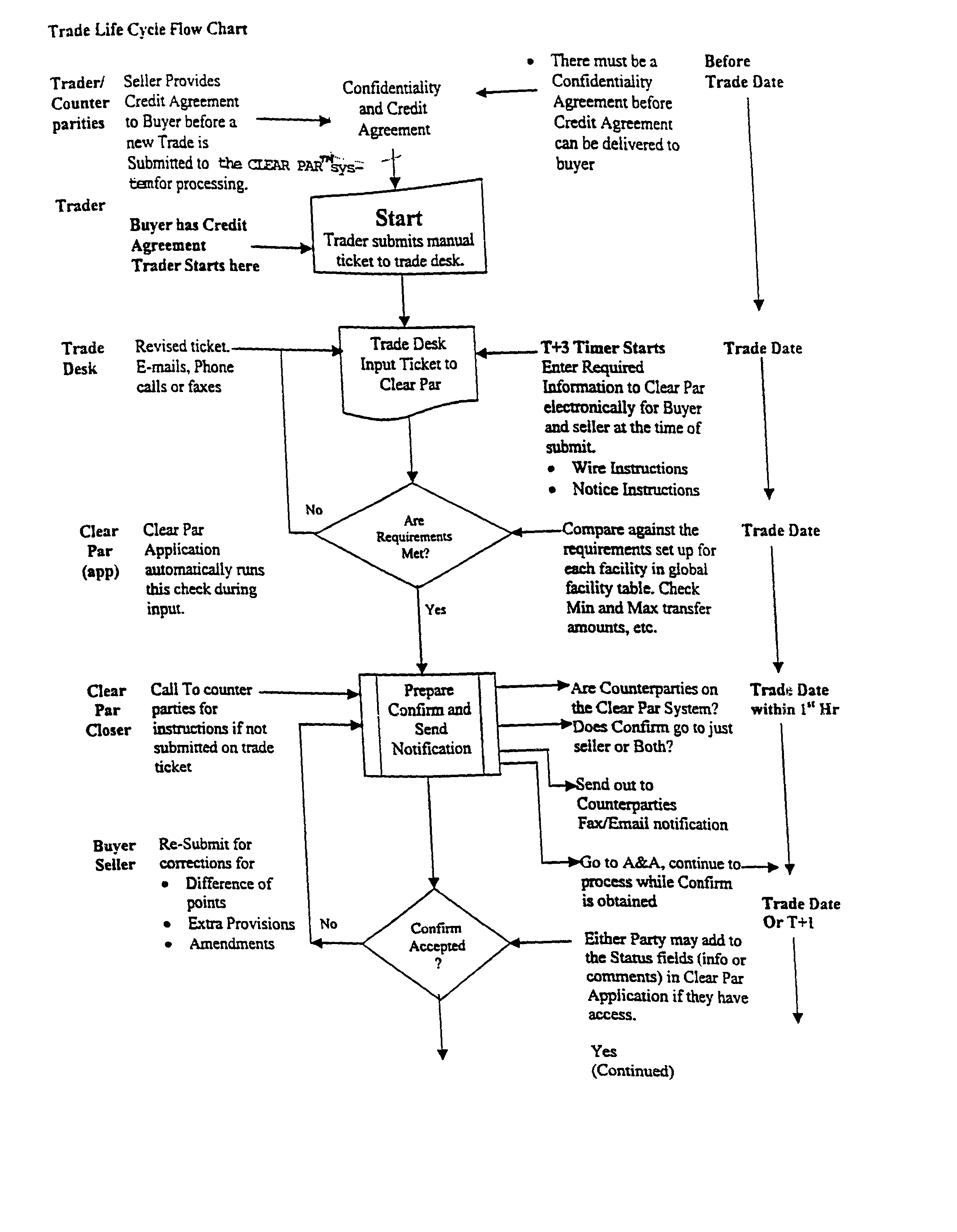
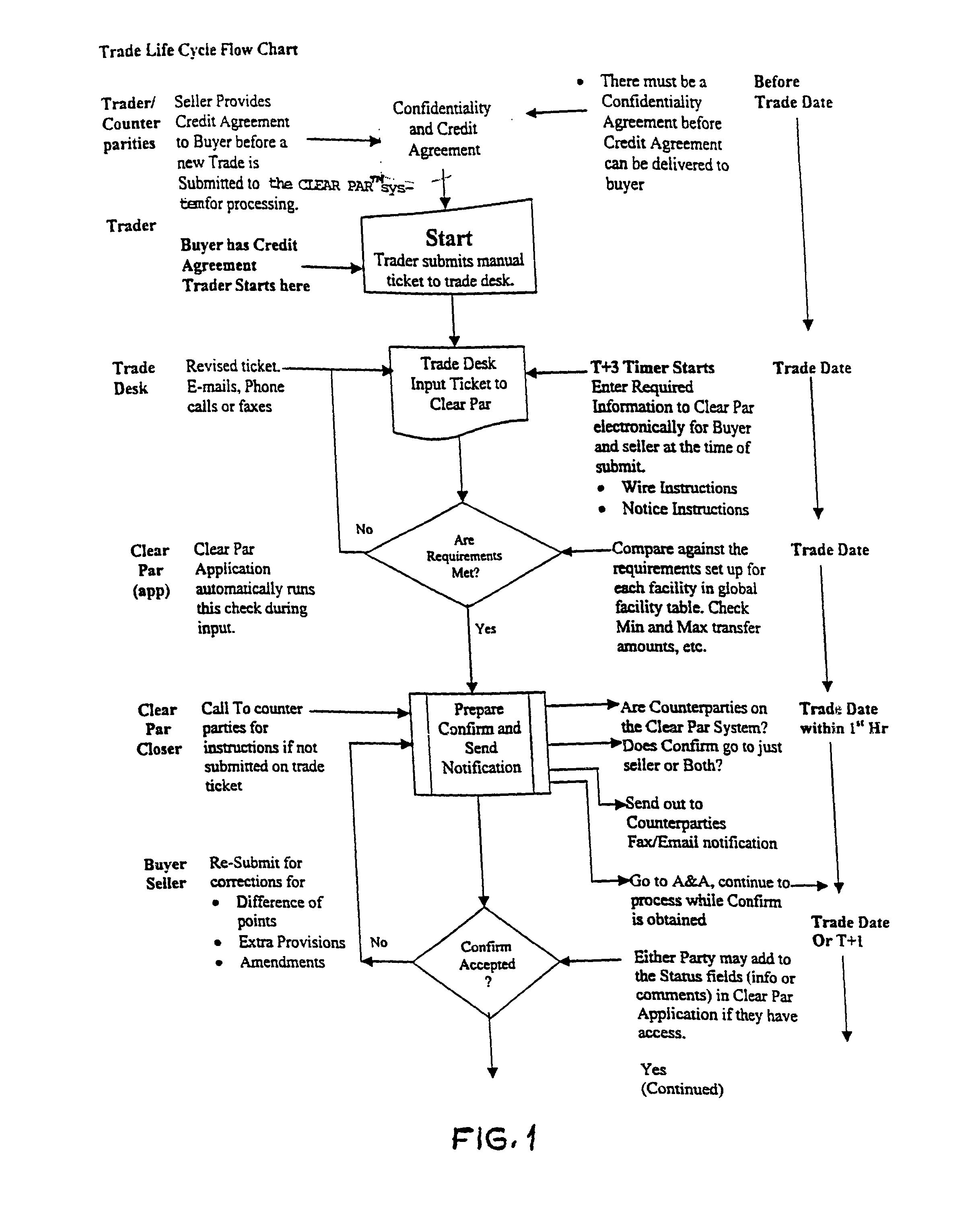
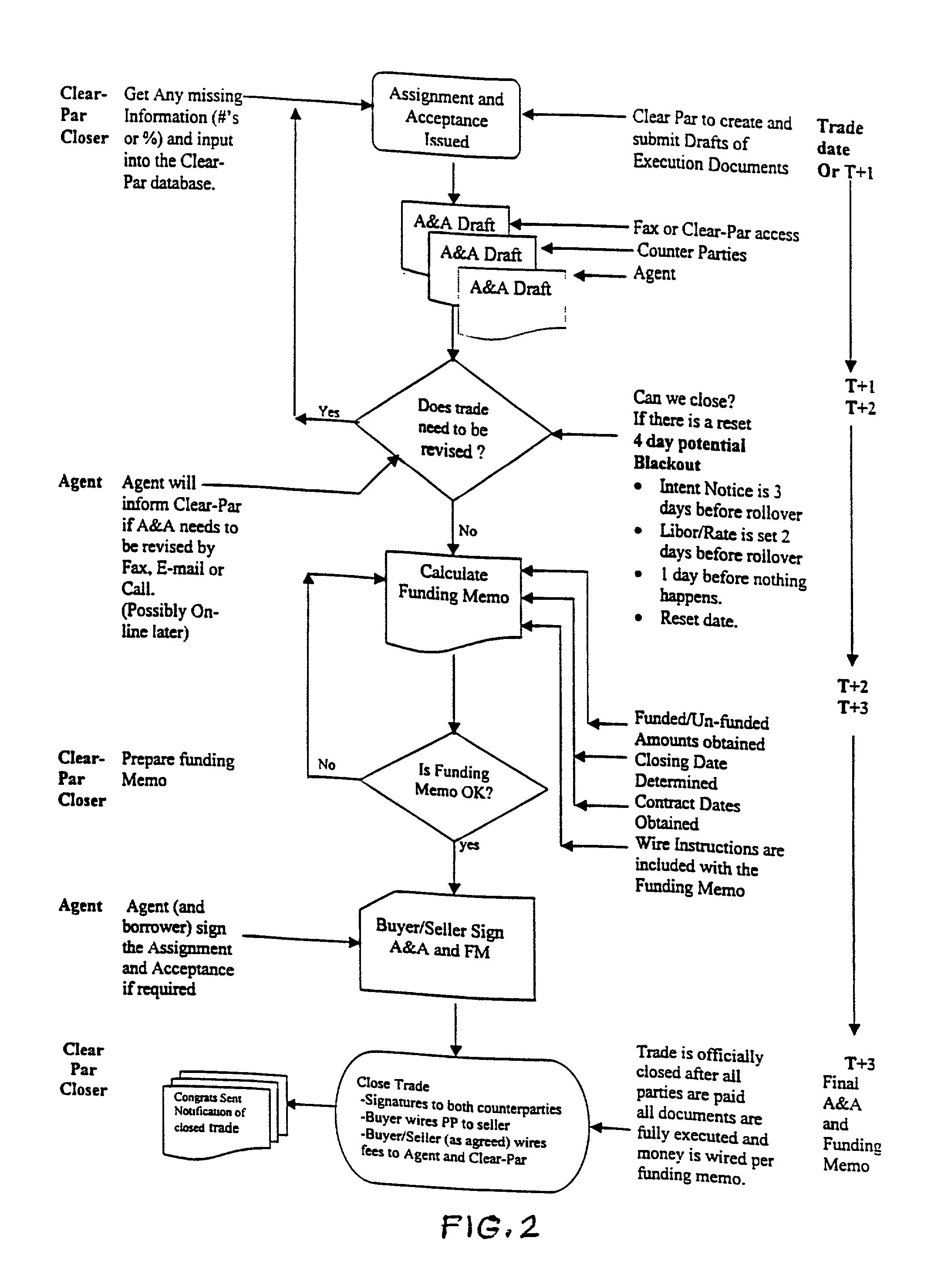
This method of loan settlement is accomplished by providing automated document production through the internet for all documents relating to a loan settlement, particularly a par loan trading settlement. Once the information is entered by the client and supplemented by the automated system, the system enables the buyer and the seller, on their business or home computers, to access such documents and information, immediately and in a secure and efficient manner. The system itself is accomplished easily by the use of state-of-the art hardware, software and internet links. The system expedites closing, and is used, as well, for settlement of original loans, and / or loans for distressed entities.
Owner:MARKIT NORTH AMERICA +1
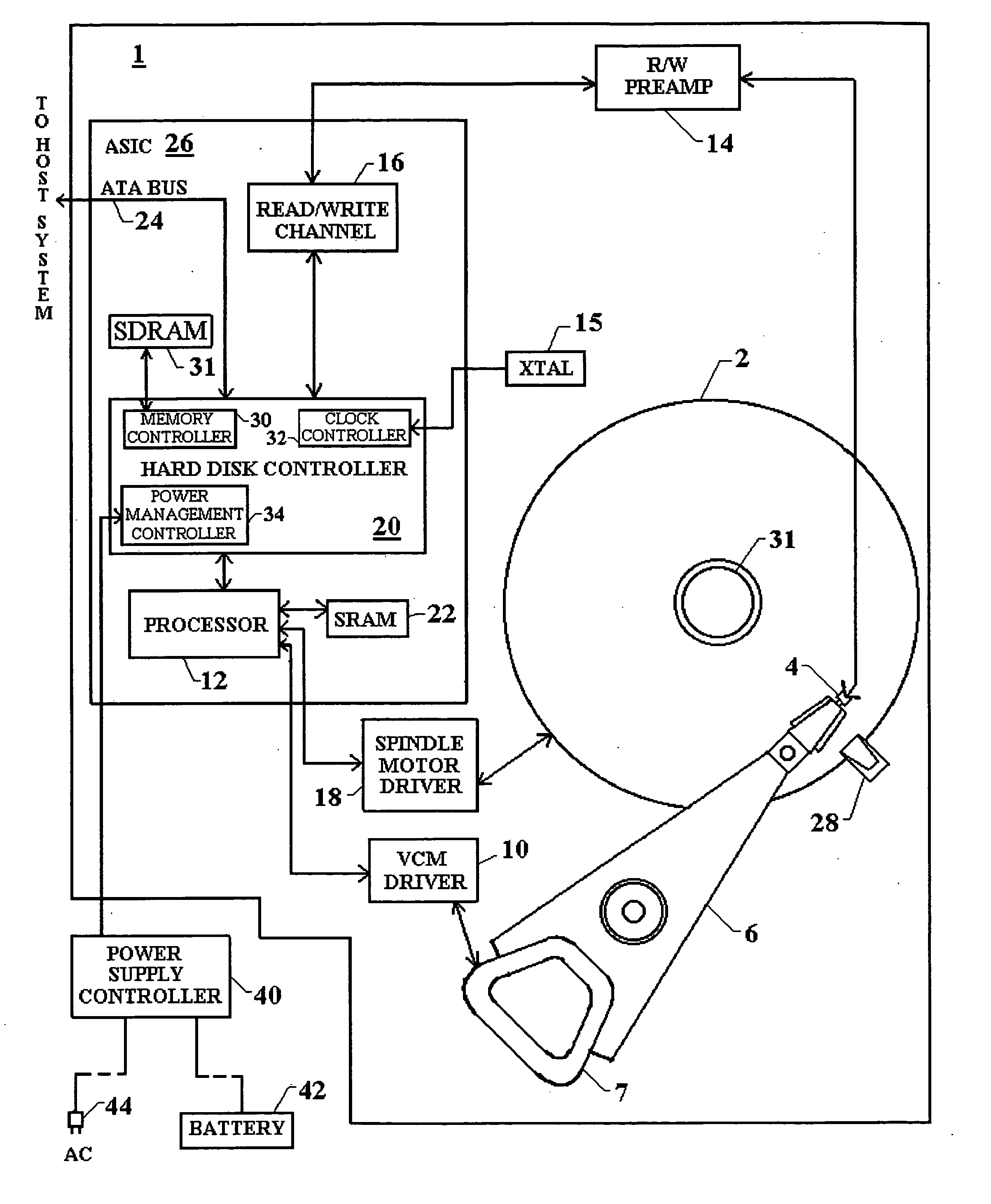
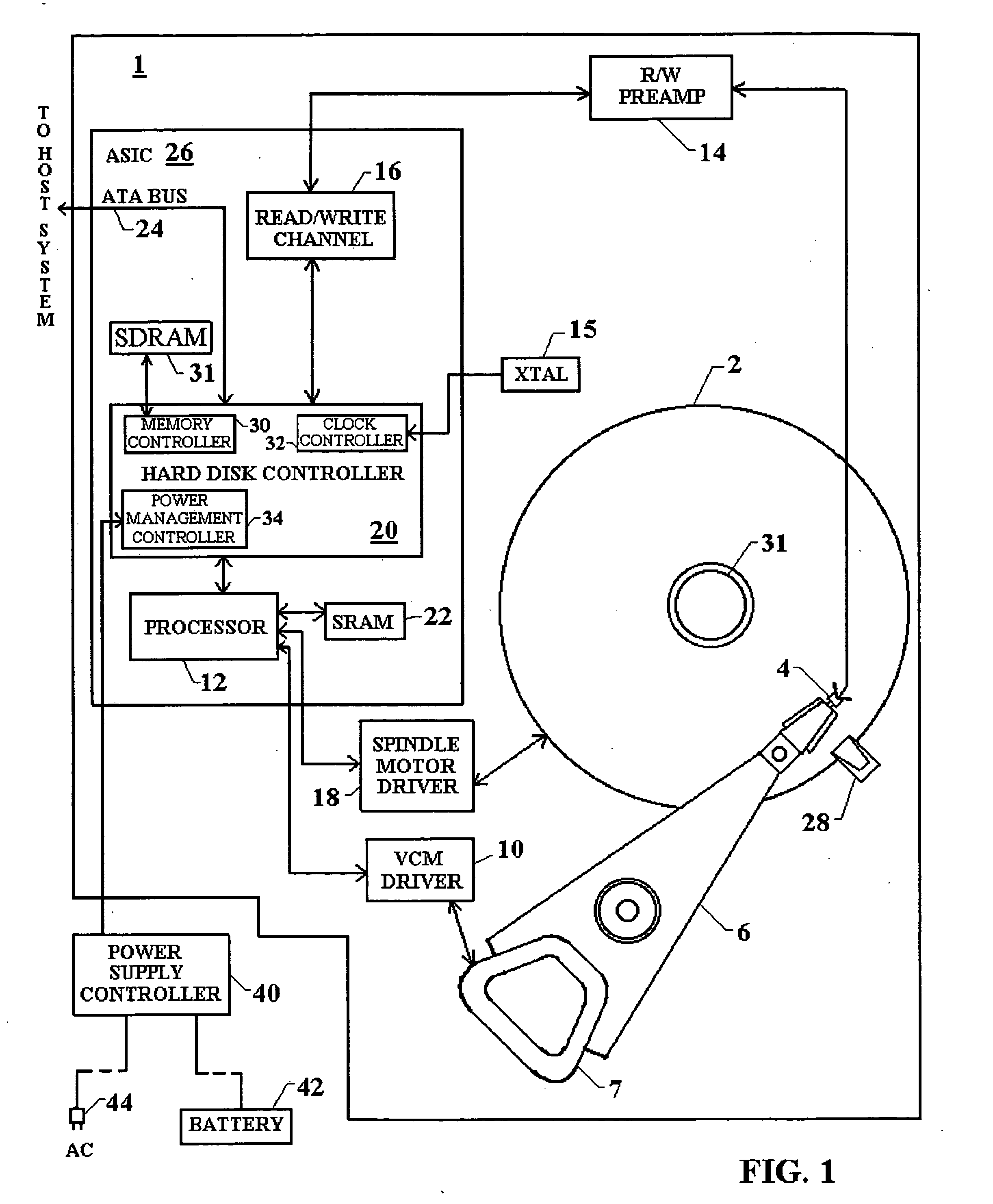
Stepping power consumption levels in a hard disk drive to maximize performance while minimizing power consumption
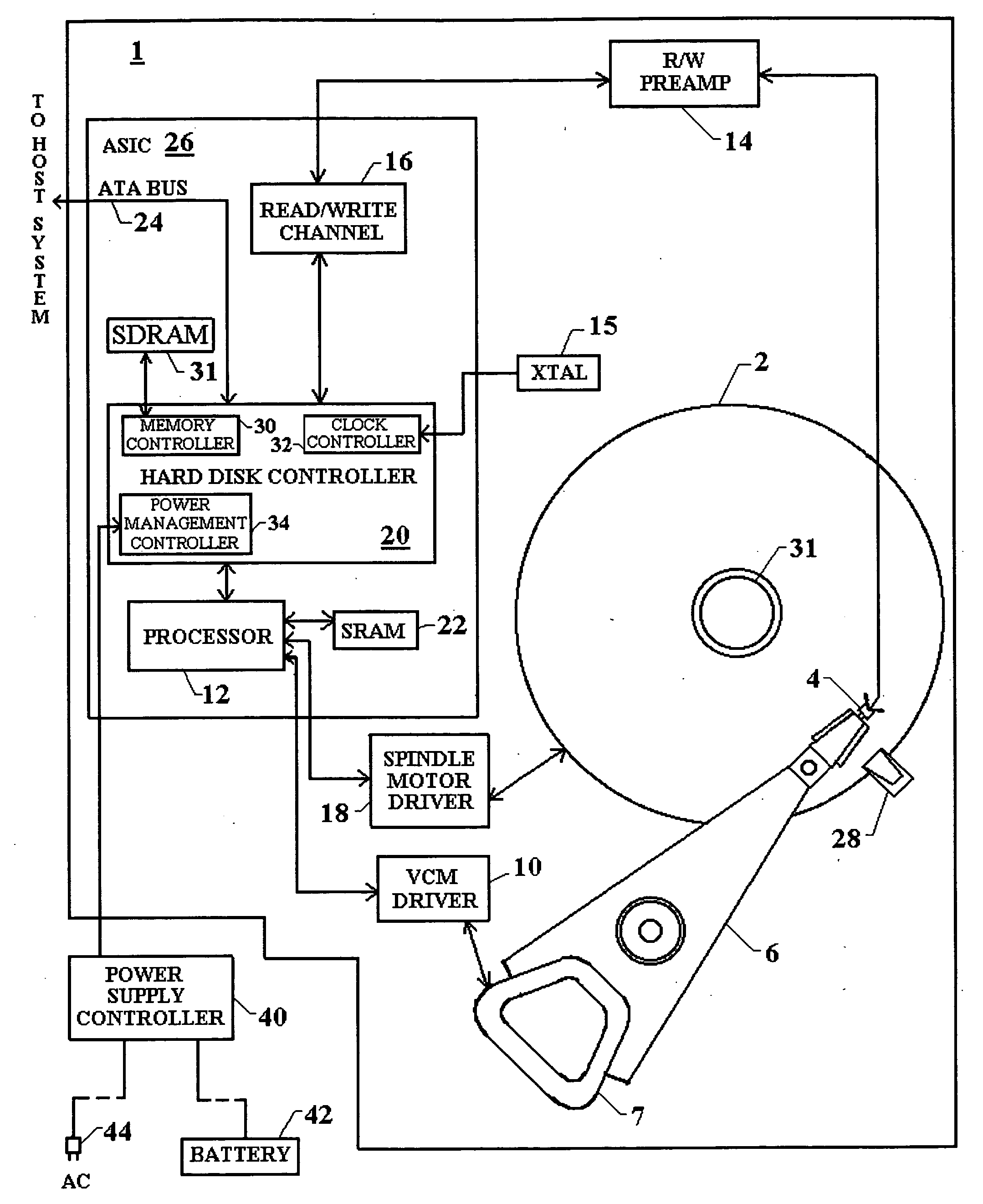
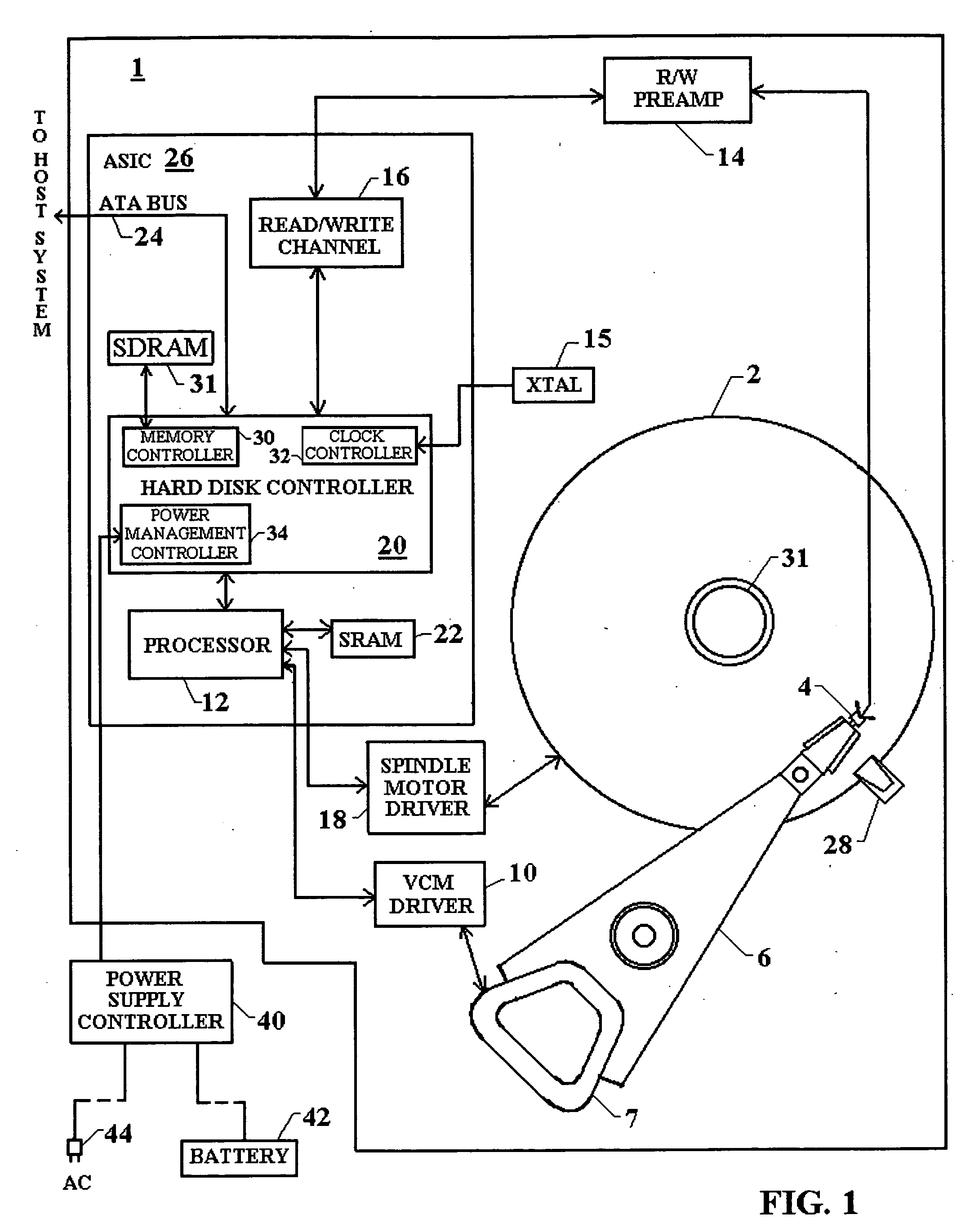
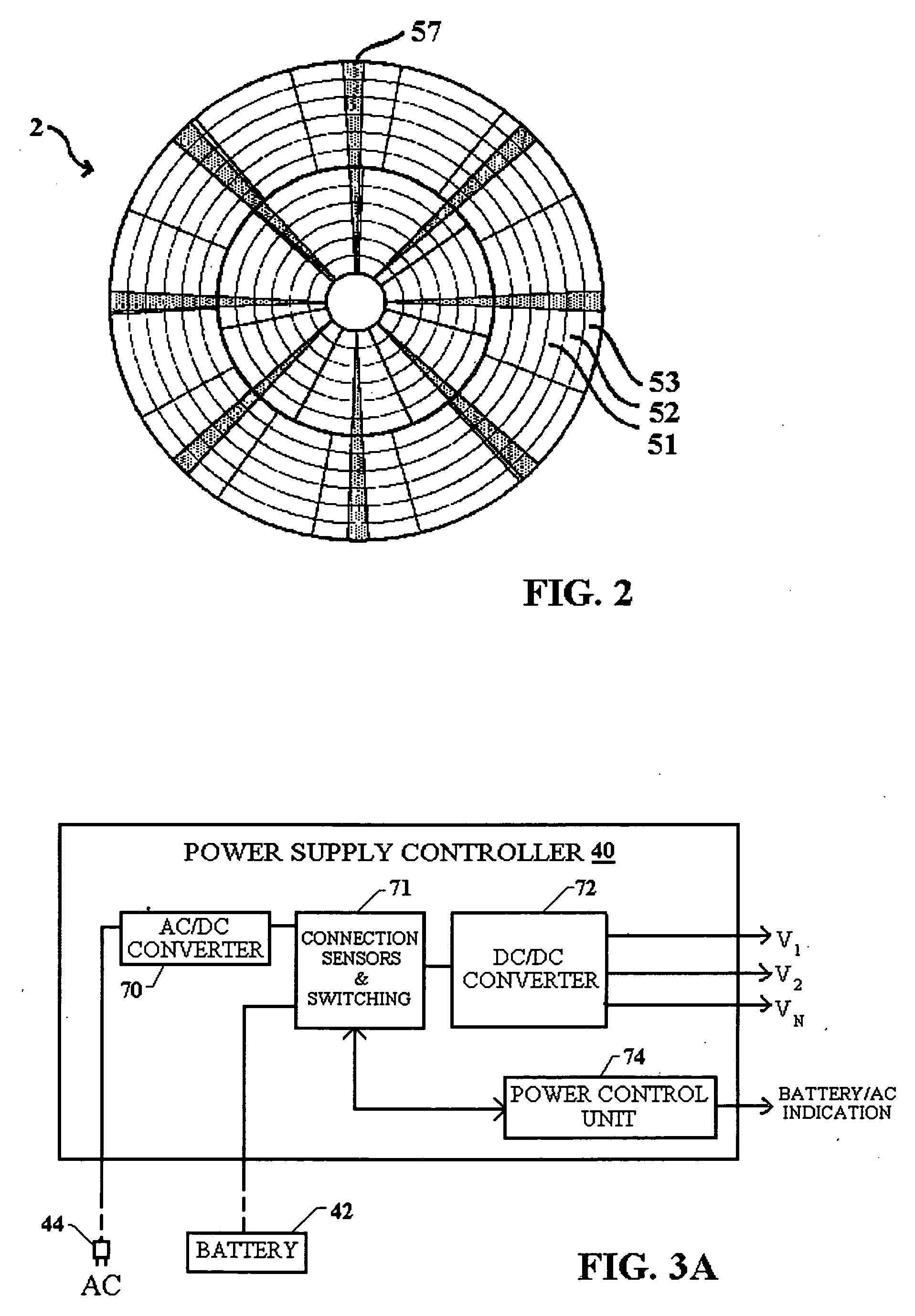
InactiveUS20050174678A1Improve life expectancyReduce switching frequencyRecord information storageCarrier speed control/regulation/indicationHard disc driveMemory interface
Attributes of a hard disk drive are stepped between different power consumption levels to optimize the trade-off between minimizing power consumption and maximizing performance depending on whether AC or battery power is used. One attribute is the clock speed which can be changed for a number of disk drive components including the processor, the external interface bus and the memory interface bus. The system power supply voltage can further be changed in a number of components integrated together on an application specific integrated circuit (ASIC). Further, spindle motor rotation speed can be changed, or the spindle motor spun-down. Further, actuator movement by the VCM can be controlled to provide faster movement during track seek operations when high performance is desired. Additionally, write-back caching parameters are adjusted based on the source of power for the hard drive, be it battery, AC power, or a combination.
Owner:PANASONIC CORP
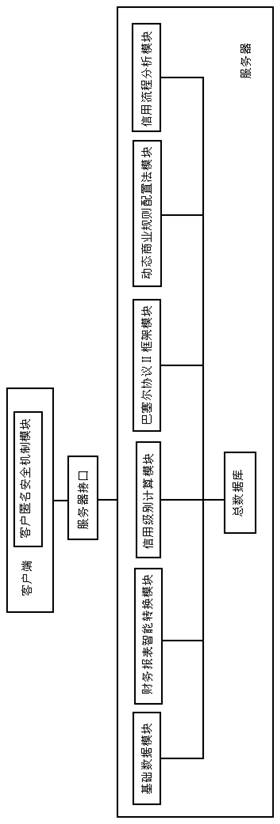
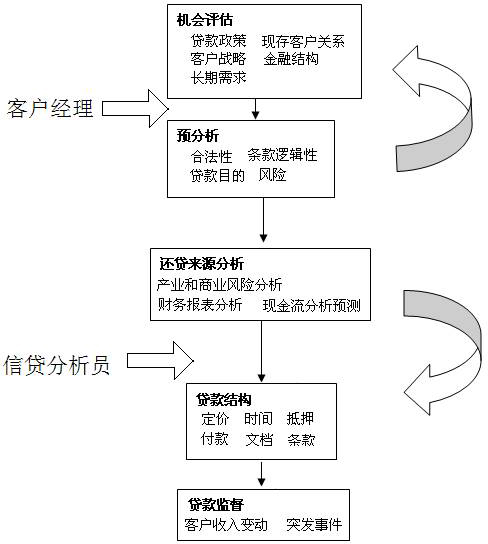
System for analyzing enterprise credit risk and application method thereof
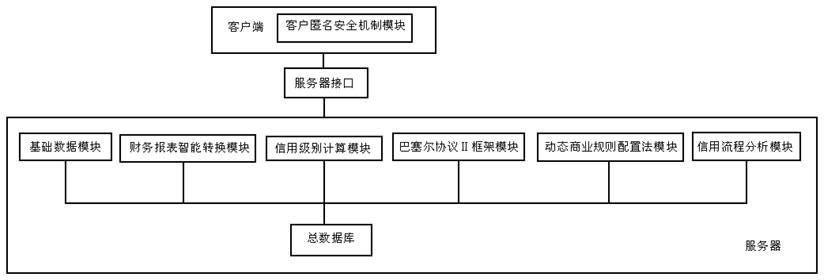
The invention relates to a global system for analyzing credit risk, comprising a client, a server and a general database, wherein the client is connected to the server through a server interface and is equipped with a client anonymous security mechanism module, and the server comprises a basic data module, an intelligent transition module of financial statements, a credit level calculating module, a Basel II frame module, a dynamic commercial-rule configuration-method module, a credit process analyzing module and the general database. Various modules are used to supply sufficient bases for final credit risk analysis, thereby improving accuracy of the analysis result. The method comprises the most comprehensive methods for analyzing enterprise credit, is able to carry out risk analysis for various financial lending institutions, and has a wide application scope.
Owner:钟文清
Broadcast encryption transmission method in network based on identification and centering on contents
InactiveCN103095710AImprove data integrityAchieve protectionSpecial service provision for substationPublic key for secure communicationData transmissionTransmission protocol
The invention discloses the technical field of network data transmission safety centering on contents and discloses a broadcast encryption transmission method in a network based on identification and centering on the contents. A content provider requests user identification through a broadcast interest package, a user can send identification information ID representing a public key to the content provider, the content provider uses a broadcast encryption algorithm based on the identification to encrypt plaintexts and then broadcasts the user, only a target user in user collection can decode the obtained plaintext contents, and the user collection can be composed of any user. When the user collection only has one user, a protocol is an end-to-end encryption transmission protocol. When the user collection has multiple users, the protocol is a broadcast encryption transmission protocol, and times of broadcast content encryption transmission are reduced. The method can enable the user identification to be added into the user collection to achieve content access controlling, and achieves data source authentication, data integrality and confidentiality protection based on an autograph of the identification and a broadcast encryption scheme.
Owner:BEIJING JIAOTONG UNIV
Programming non-volatile memory using a relaxed dwell time
InactiveUS20150161036A1Improve data integrityExtended service lifeMemory architecture accessing/allocationMemory adressing/allocation/relocationComputer architectureEngineering
In at least one embodiment, a data storage system includes a non-volatile memory array including a plurality of blocks of physical memory, each including multiple pages. The data storage system further includes a controller that maintains a data structure identifying blocks of physical memory in the memory array that currently do not store valid data. The controller, responsive to receipt of a write input / output operation (IOP) specifying an address and write data, selects a particular block from among the blocks identified in the data structure prior to a dwell time threshold for the particular block being satisfied, programs a page within the selected block with the write data, and associates the address with the selected block.
Owner:IBM CORP
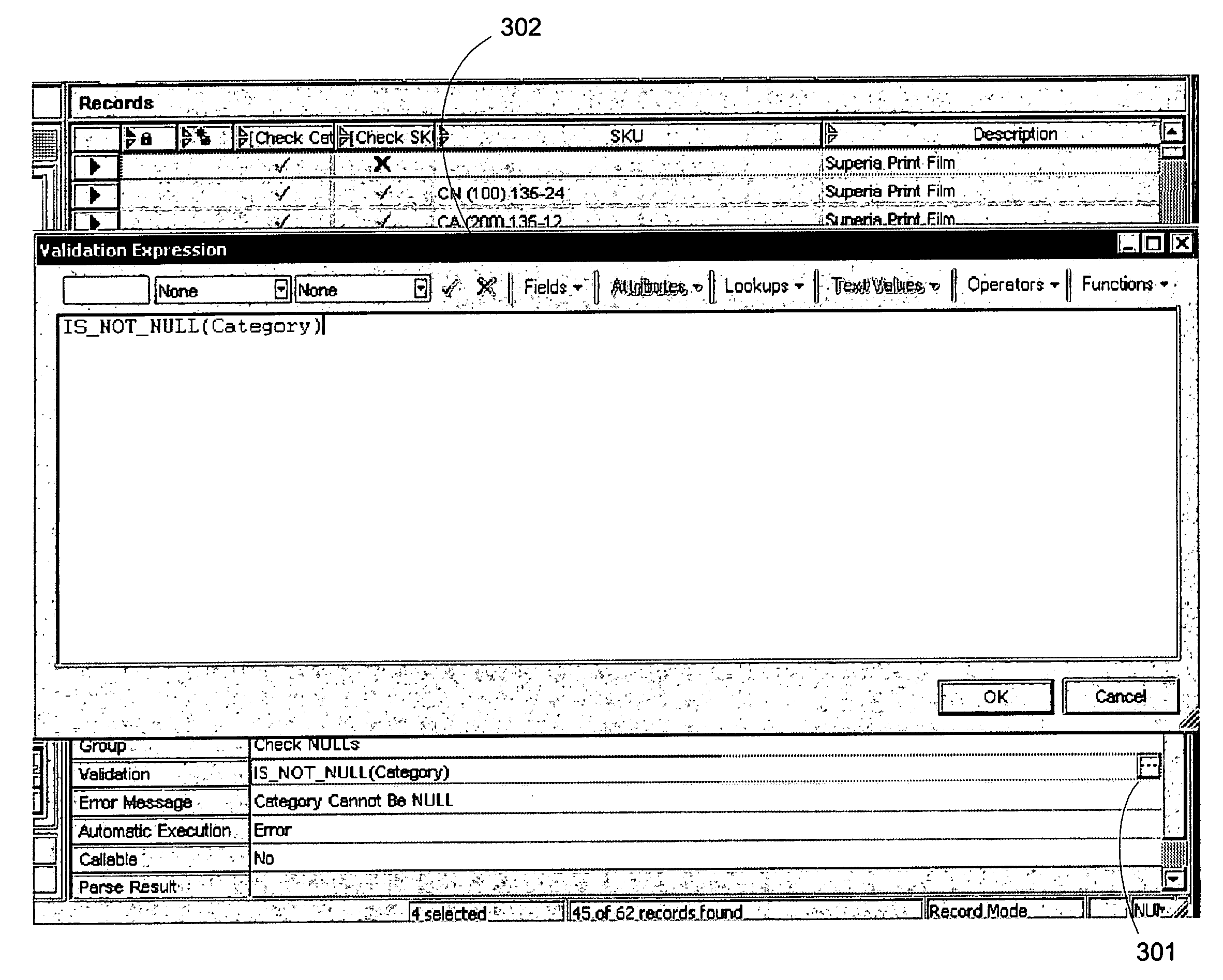
Method for generating properly formed expressions
ActiveUS20070027858A1Create quicklyImprove data integrityDigital data information retrievalDigital data processing detailsSyntaxSearch filter
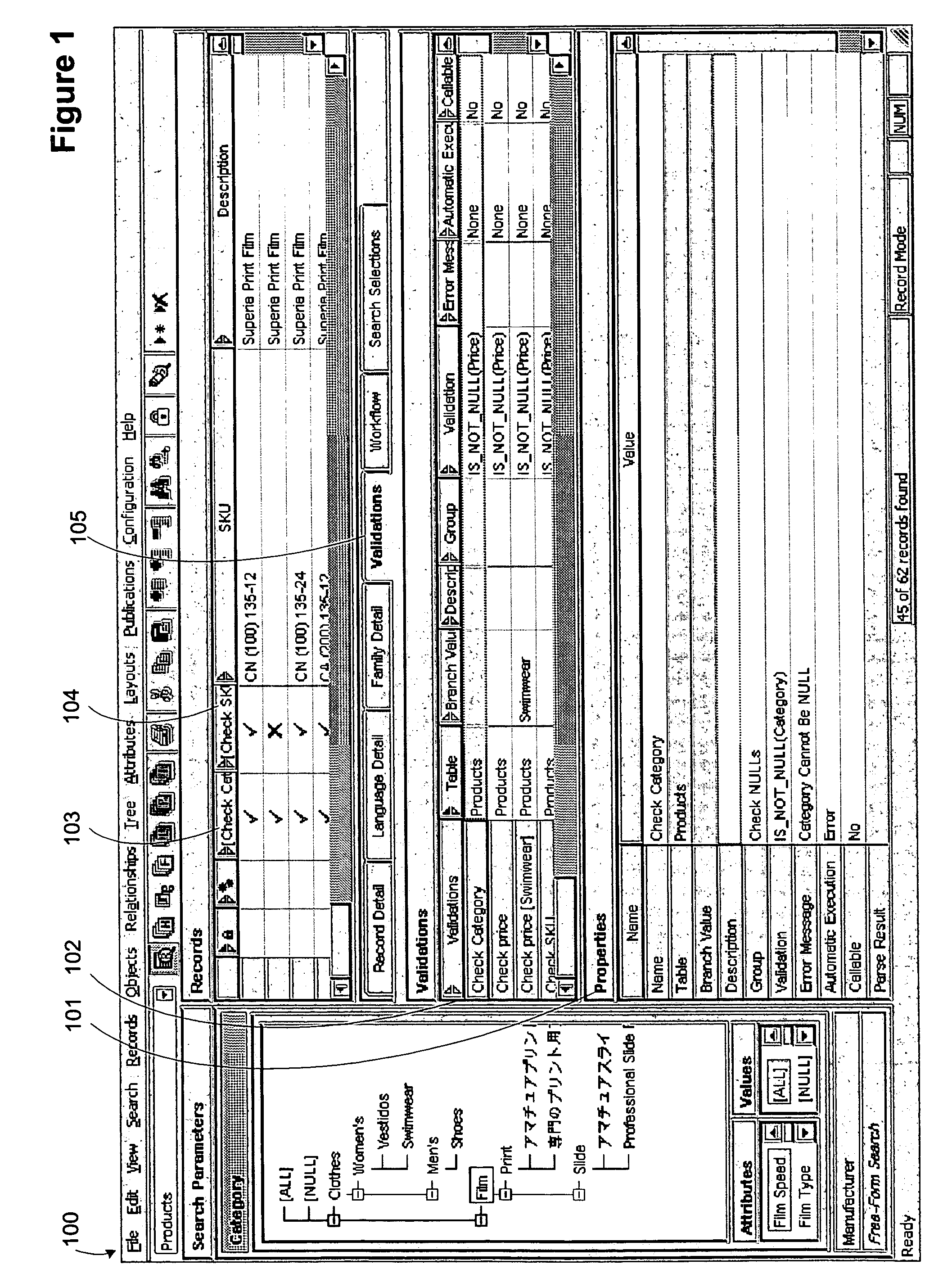
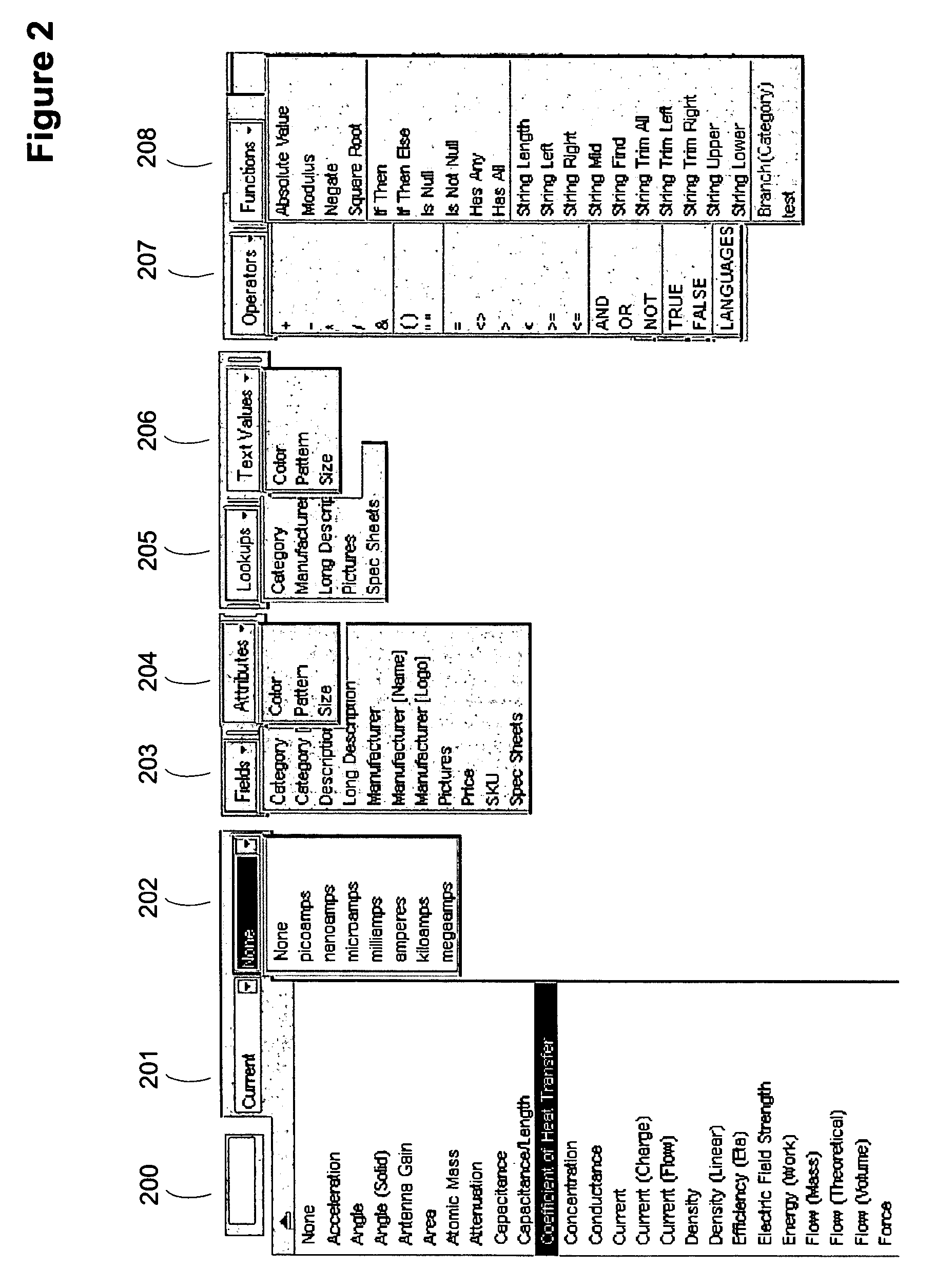
A method for generating properly formed expressions used as validation expressions and search filters for computer system database applications. One or more embodiments of the invention for example comprise an interface that assists users through the use of automatic tokenizing and / or pick lists of field names and fields values, including a measurement builder for entering legal tokenized measurement values with applicable units of measure. Embodiments of the invention allow knowledgeable users to rapidly create expressions to ensure that the legal syntax and semantics of an expression are not violated while providing the user with pick lists and measurement values within legal ranges and with applicable units of measure. Validations rules are generated and performed on desired records in a computer system database without requiring programs, scripts or queries to be written. A validation expression returns a Boolean result that signifies a success or failure result and may be performed manually or automatically.
Owner:SAP AG
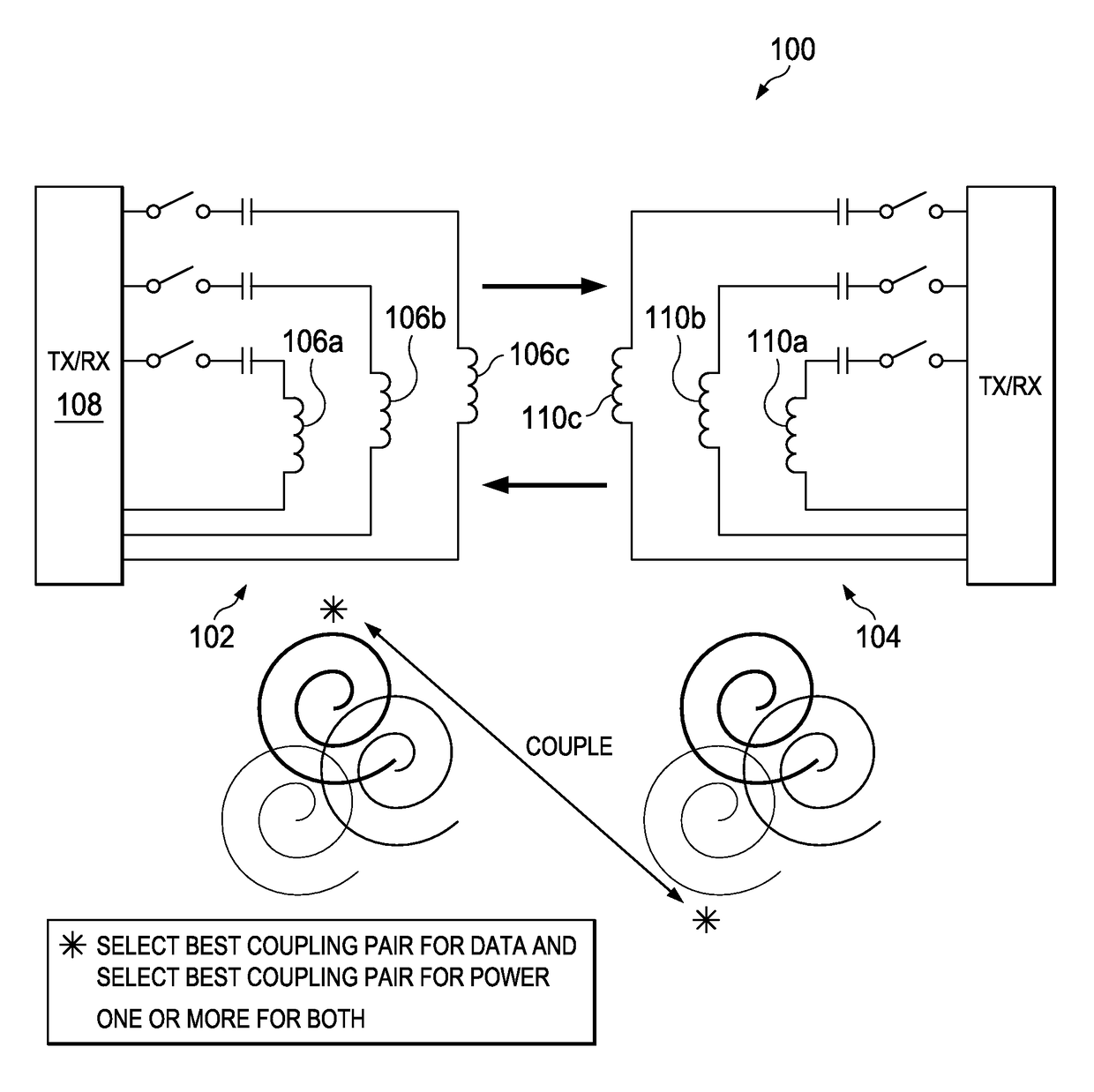
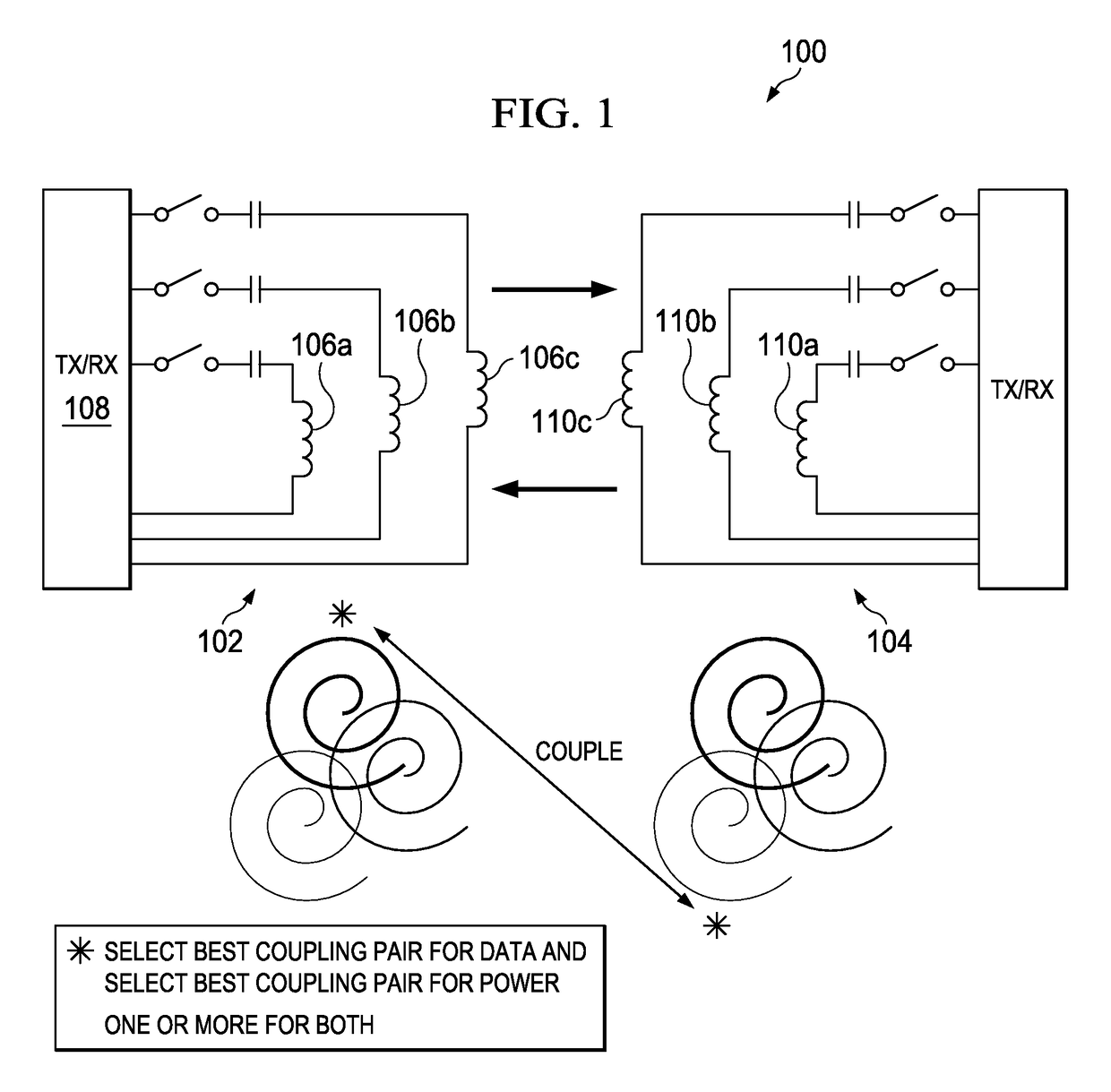
Multiple Coil System
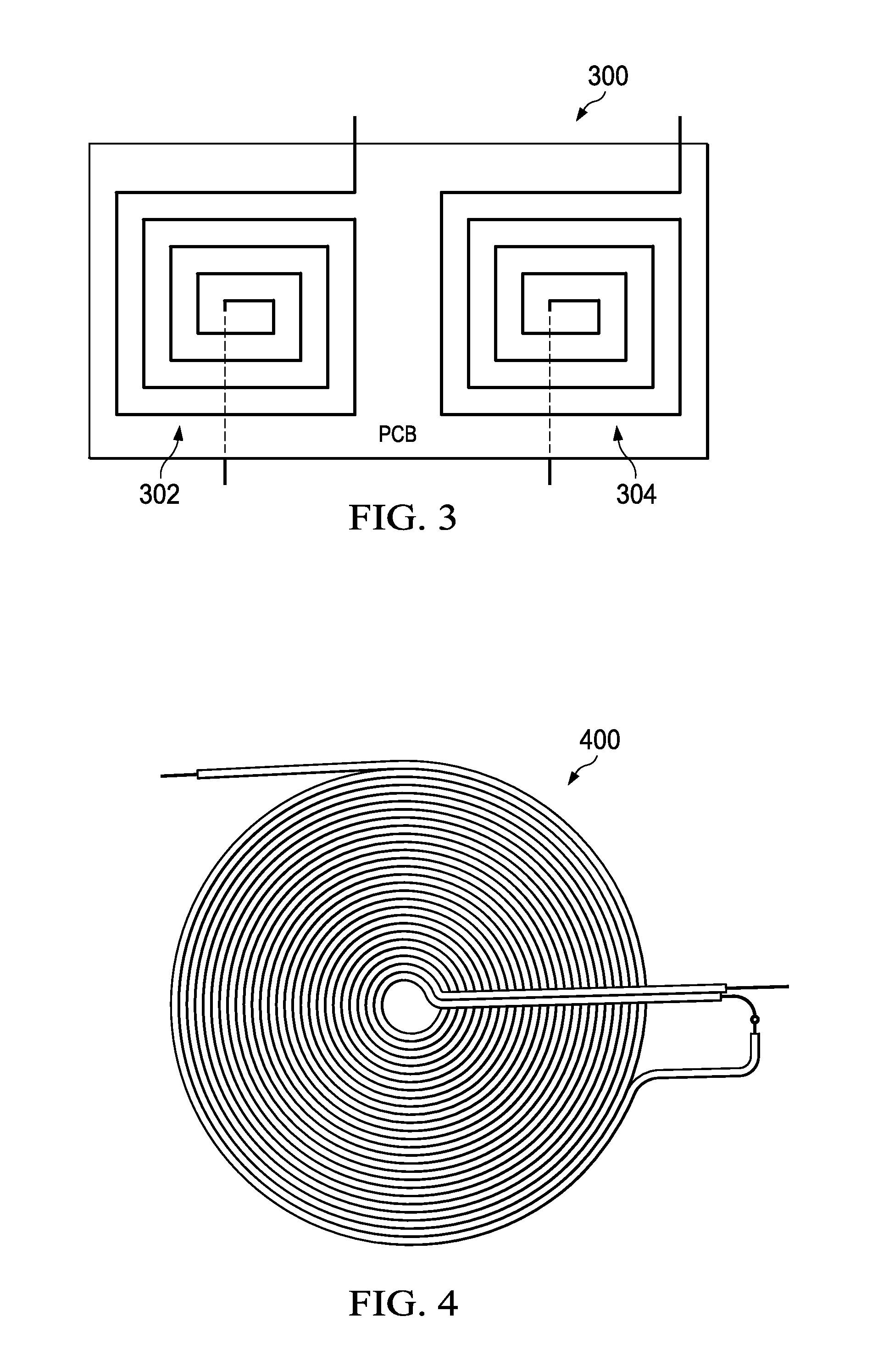
InactiveUS20120104999A1Increased form factorLow costNear-field transmissionTransformersInductorTransmitter
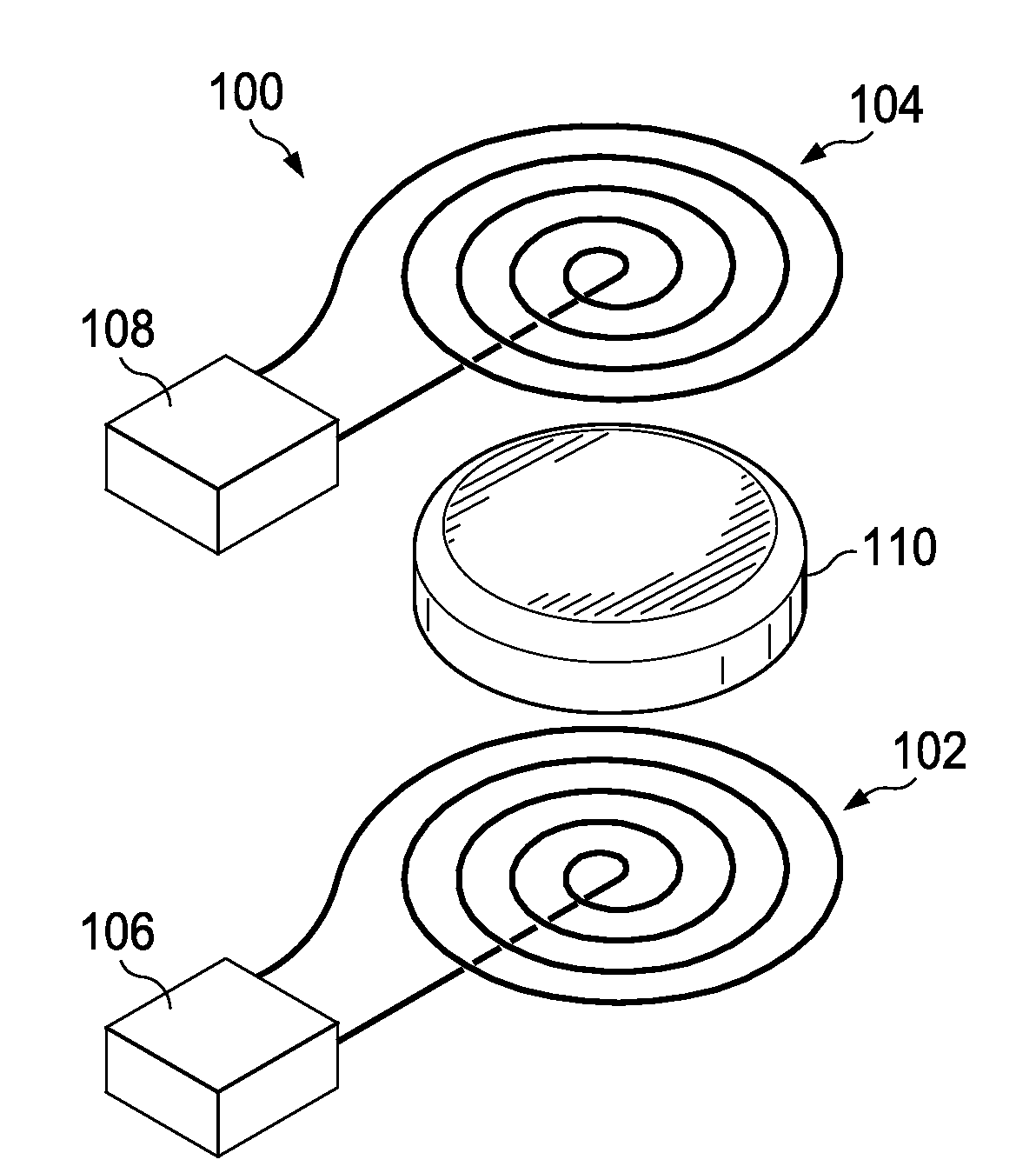
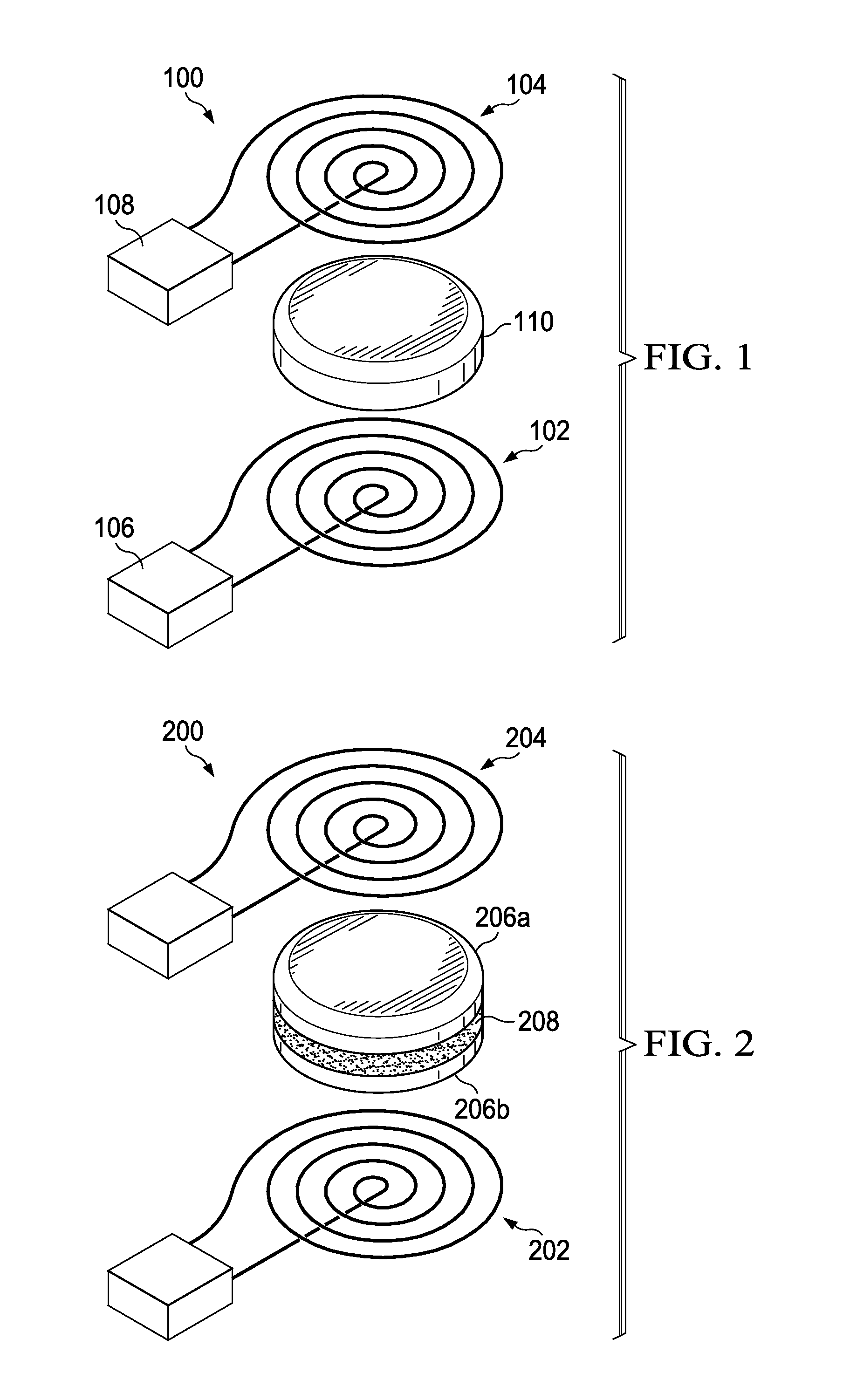
Multiple coil systems and methods are disclosed in which transmitter and receiver inductors, or coils, are coupled in a configuration for wirelessly transferring data and / or power among them. In preferred implementations, the systems and methods are used for transmitting both power and data using pairs of coupled coils. One preferred aspect of the invention is that the coils are not permanently affixed in physical proximity to one another, but can be moved and / or interchanged.
Owner:TRIUNE IP
Variable power consumption levels in a hard disk drive
InactiveUS20050144491A1Improve life expectancyReduce switching frequencyEnergy efficient ICTDisposition/mounting of recording headsHard disc driveMemory interface
Attributes of a hard disk drive are stepped between different power consumption levels to optimize the trade-off between minimizing power consumption and maximizing performance depending on whether AC or battery power is used. One attribute is the clock speed which can be changed for a number of disk drive components including the processor, the external interface bus and the memory interface bus. The system power supply voltage can further be changed in a number of components integrated together on an application specific integrated circuit (ASIC). Further, spindle motor rotation speed can be changed, or the spindle motor spun-down. Further, actuator movement by the VCM can be controlled to provide faster movement during track seek operations when high performance is desired. Additionally, write-back caching parameters are adjusted based on the source of power for the hard drive, be it battery, AC power, or a combination.
Owner:PANASONIC CORP
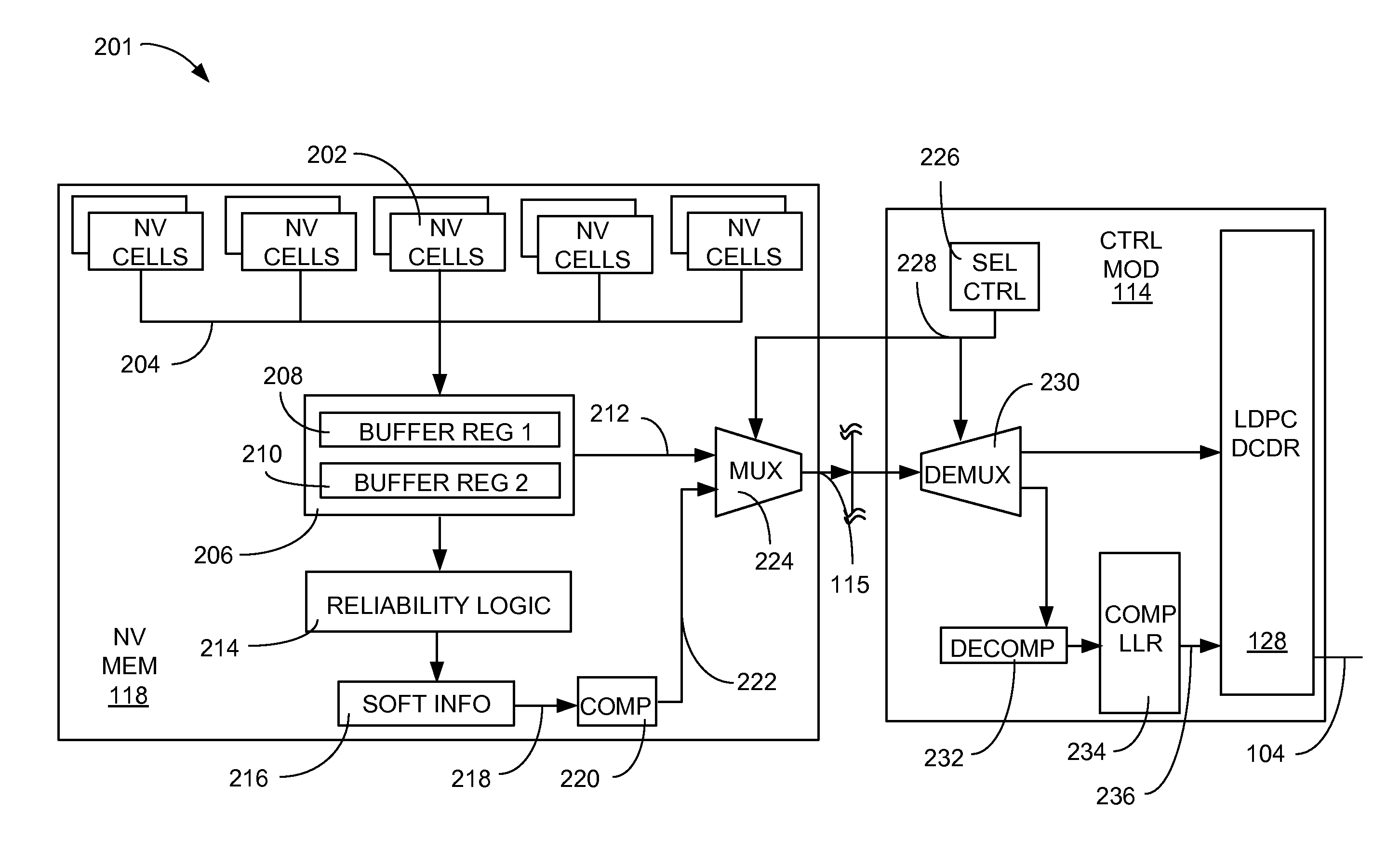
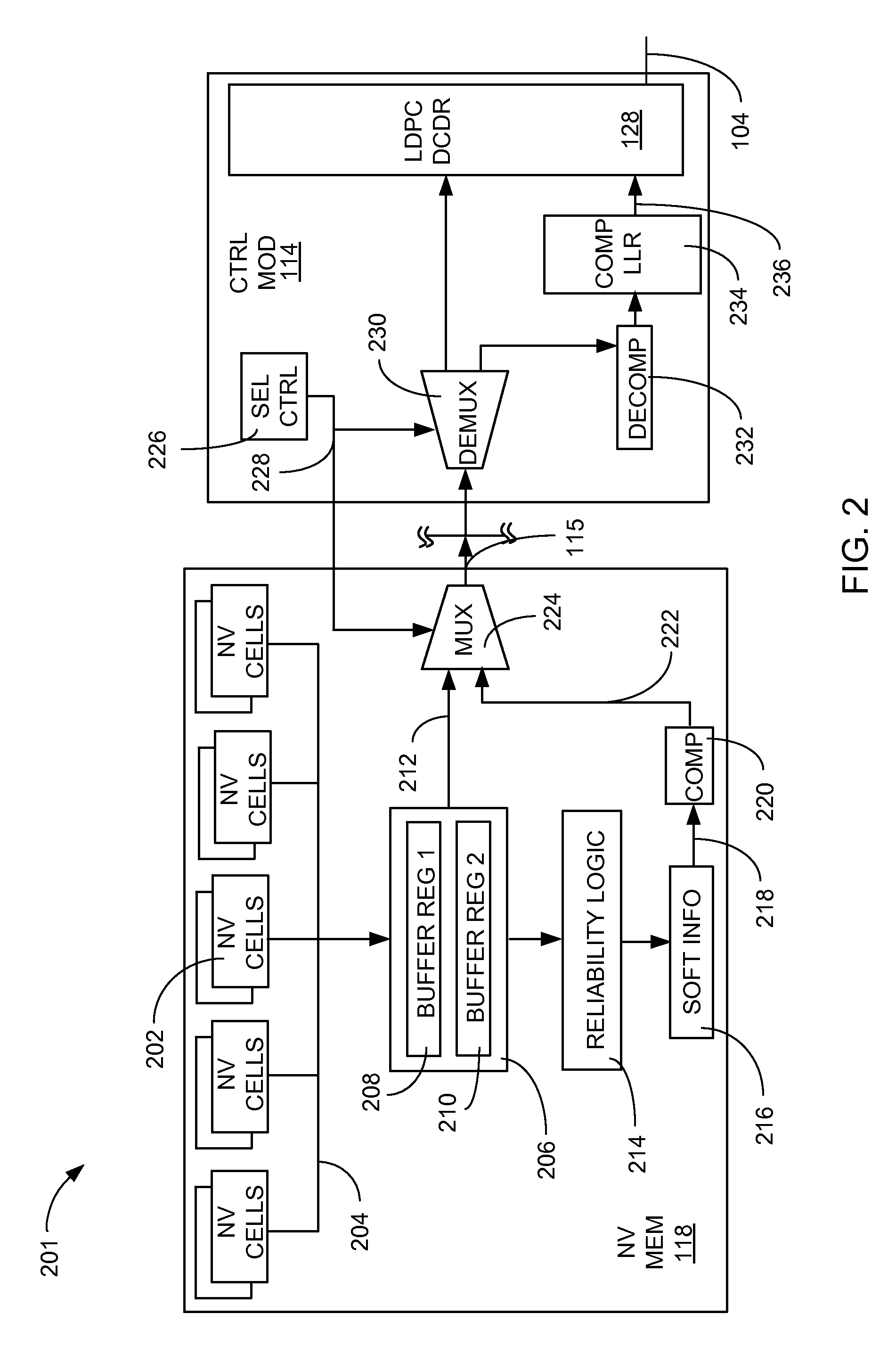
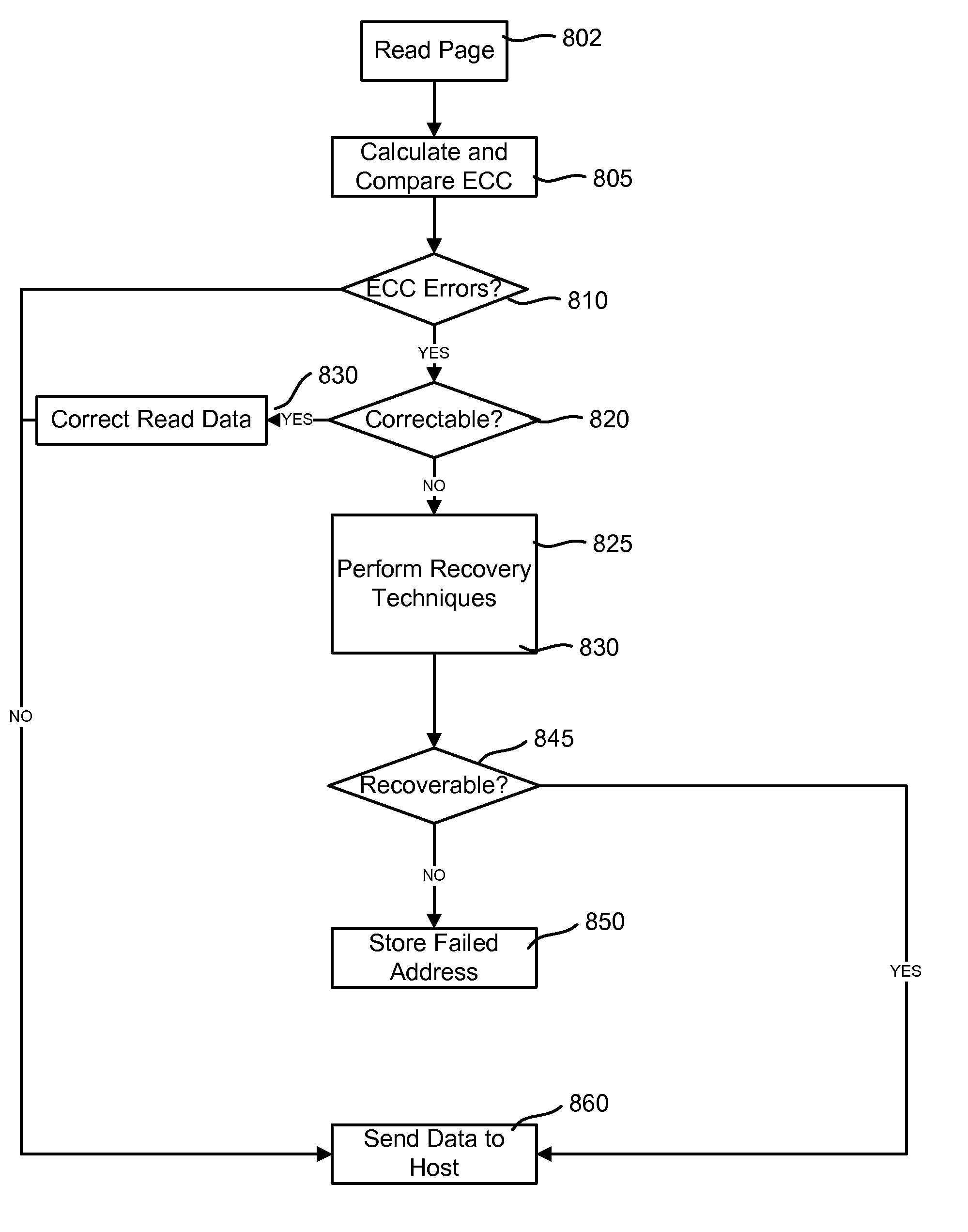
Method and system for improving data integrity in non-volatile storage
ActiveUS9214965B2Improve data integrityReduce the burden onCode conversionError correction/detection by combining multiple code structuresData integrityLow density
Owner:SANDISK TECH LLC
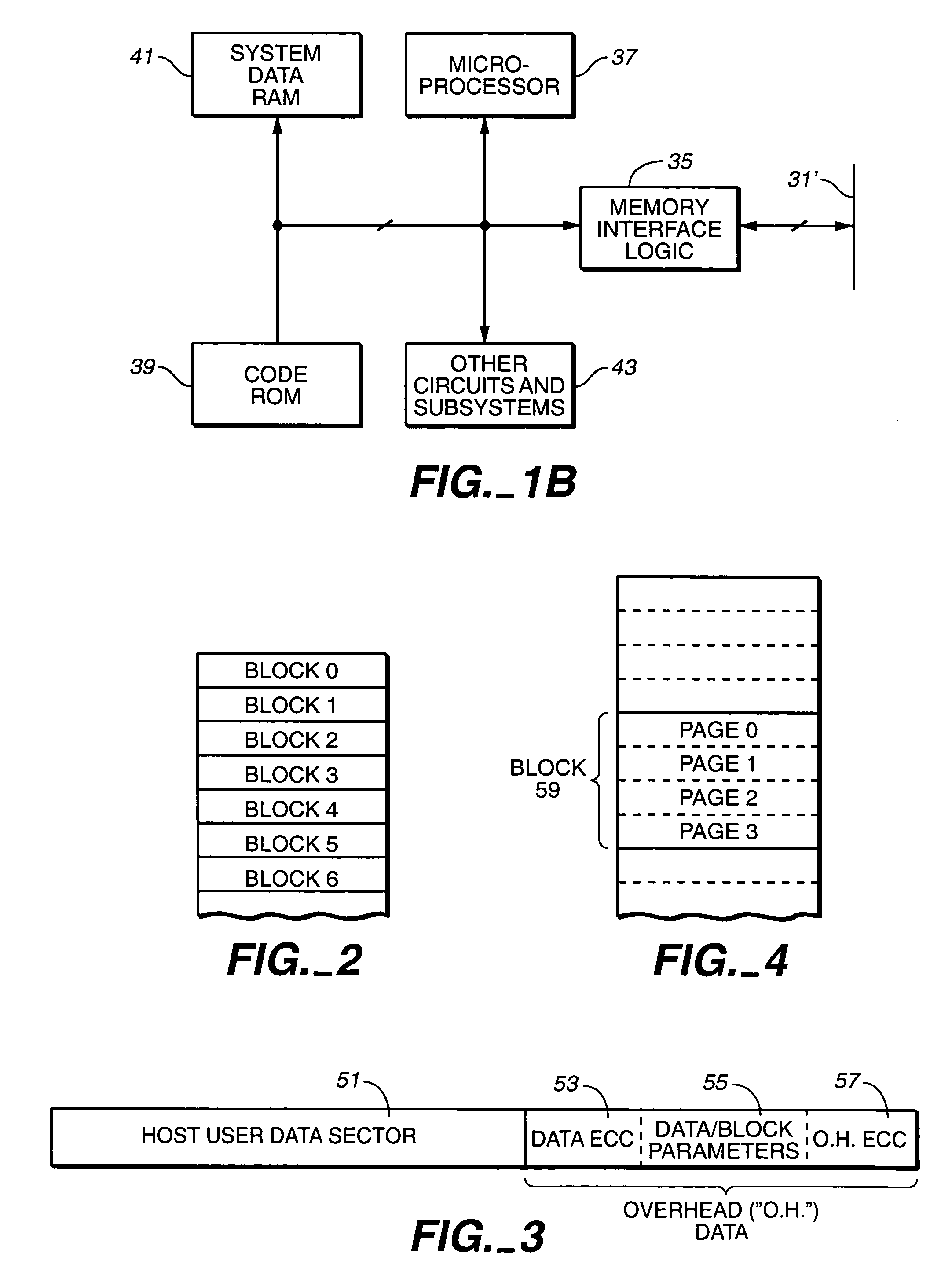
Page by page ecc variation in a memory device
A data structure for a memory device is provided. The device includes an array having a plurality of rows of storage elements divided into logical units composed of a plurality of data structures. The data structure includes a data sector including user data and user attribute data. The user attribute data includes error correction coding (ECC) for the user data. The user attribute data includes information for other sectors in the logical unit. The data sector is provided in one of the plurality of rows having a higher degree of data integrity than others of said plurality of rows.
Owner:SANDISK TECH LLC
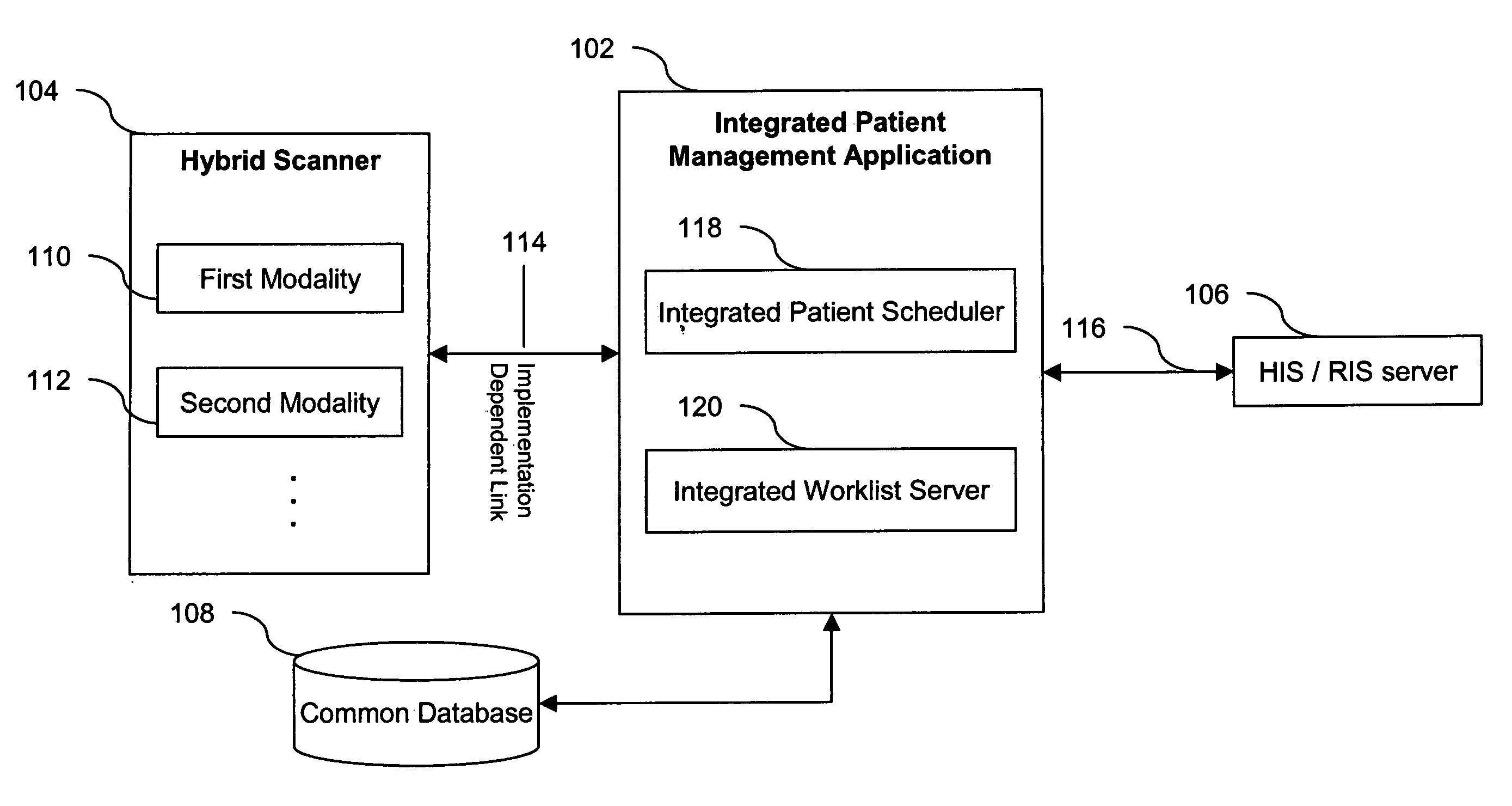
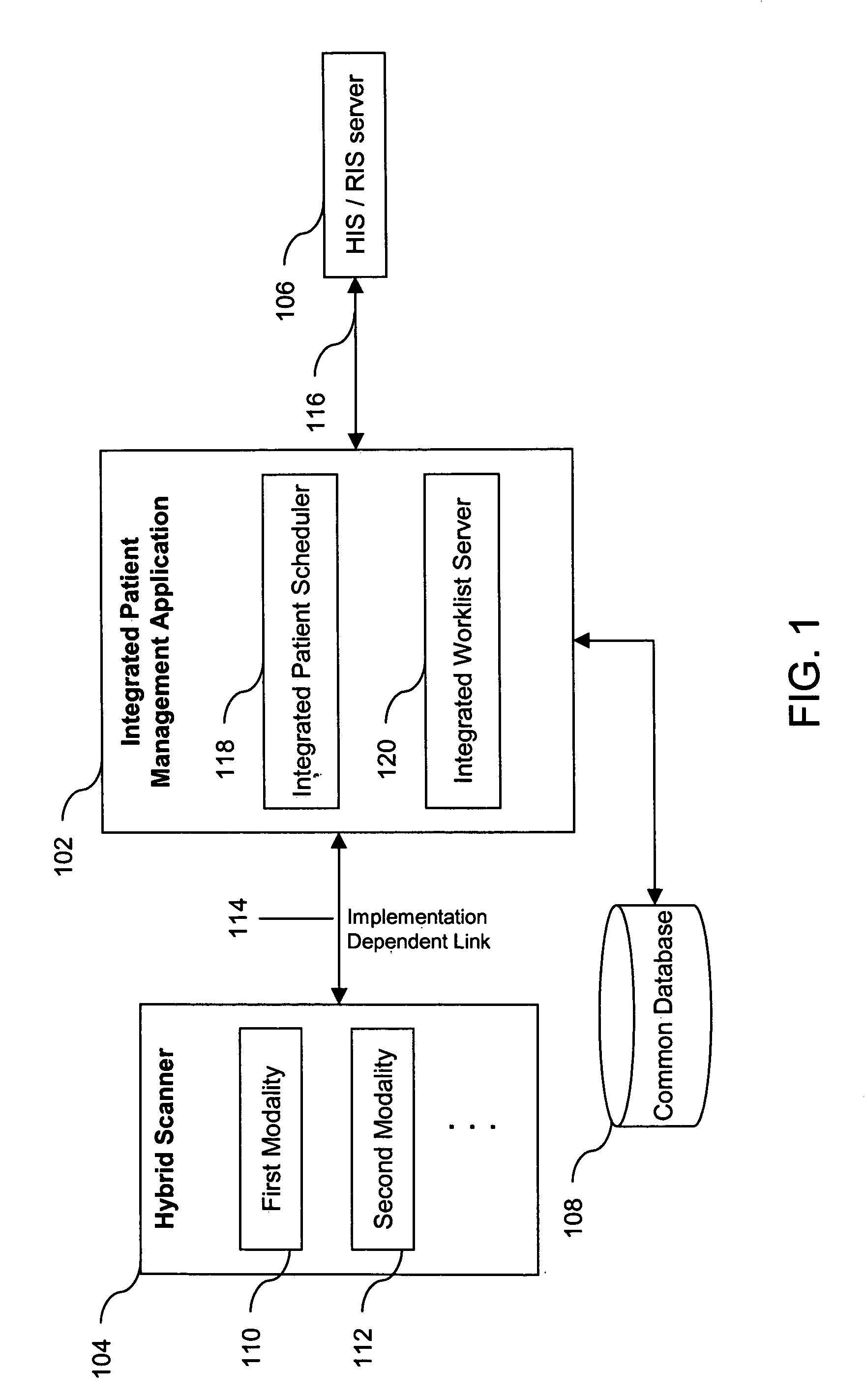
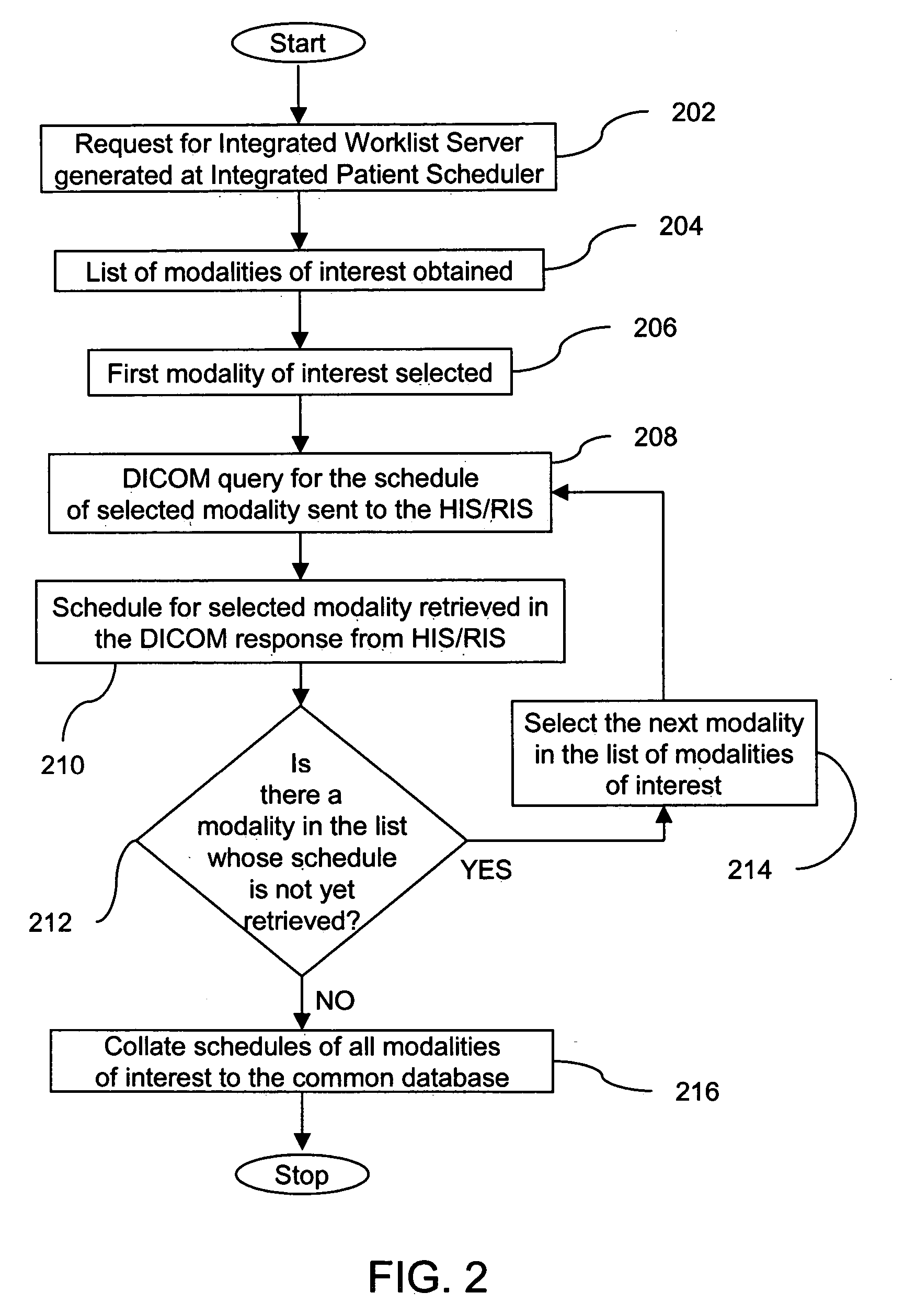
Method and system for managing modality worklists in hybrid scanners
InactiveUS20050206967A1Improve data integrityData conflictData processing applicationsRadiation/particle handlingData integrityData mining
A method and system for integrated modality worklists management for hybrid scanners is disclosed. The present invention retrieves schedules of multiple modalities in a hybrid scanner in response to a single action by the operator of the hybrid scanner, thereby improving operator efficiency. The retrieved schedules are collated and stored in a common database. The automated maintenance of a common database improves data integrity.
Owner:GENERAL ELECTRIC CO
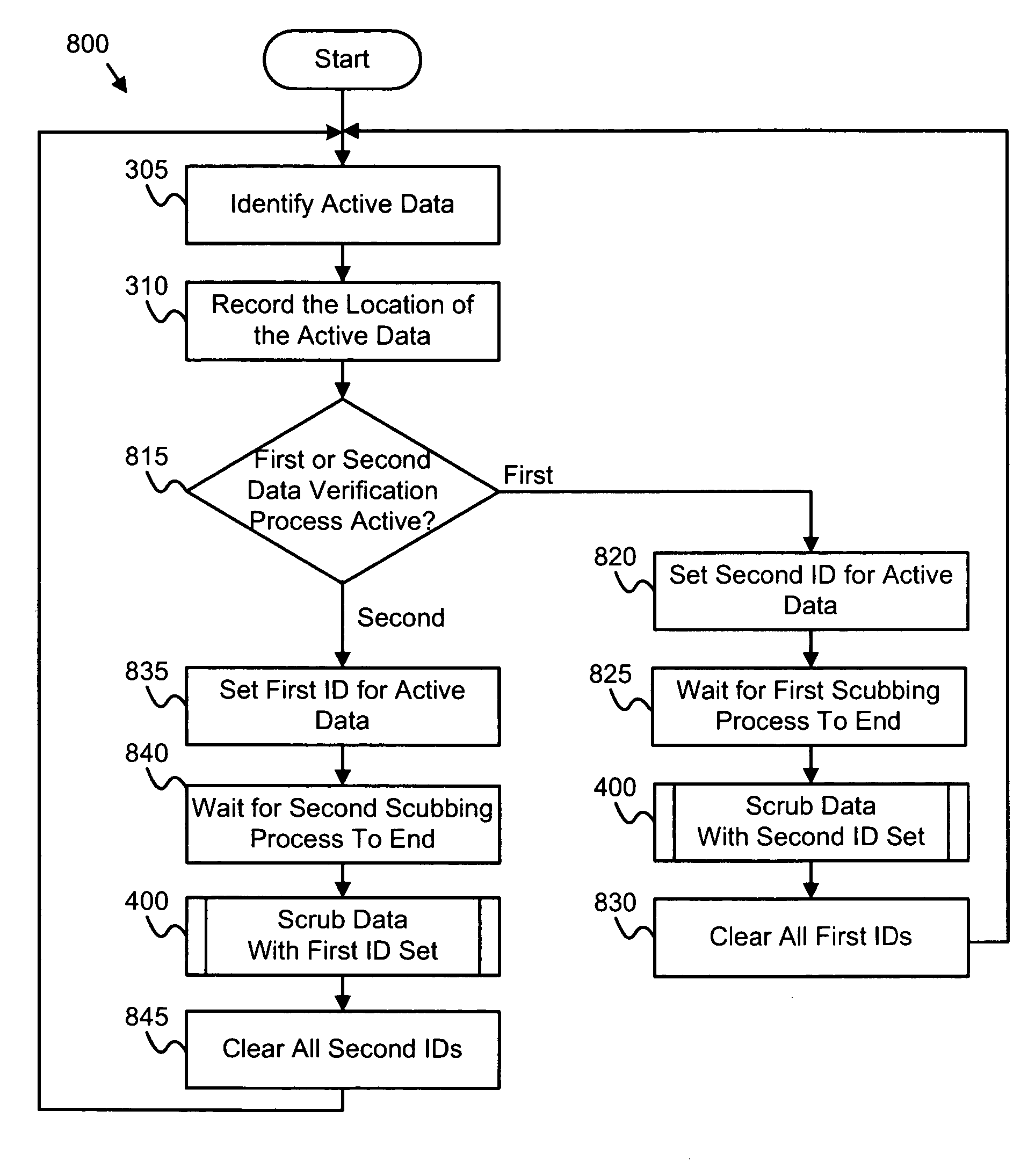
Apparatus, system, and method for active data verification in a storage system
InactiveUS7526686B2Low system requirementsShorten the timeError detection/correctionRedundant array of inexpensive disk systemsData segmentSource Data Verification
An apparatus, system and method of verifying data are provided. Active data are identified among data on a storage device, records the location of the active data, and the integrity of the active data are verified. In one embodiment, data in segments adjacent to the active data segments are also identified and verified for improved data reliability. The data verification may be used to increase data reliability with low system resource usage.
Owner:INT BUSINESS MASCH CORP
Multiple coil data transmission system
ActiveUS10079090B2Increase system bandwidthImprove data integrityNear-field transmissionTransformersTransport systemWireless transmission
Multiple coil systems and methods are disclosed in which transmitter and receiver inductors, or coils, are coupled in a configuration for wirelessly transferring data and / or power among them. In preferred implementations, the systems and methods are used for transmitting data using pairs of coupled coils. One preferred aspect of the invention is that the coils are not permanently affixed in physical proximity to one another, but can be moved and / or interchanged.
Owner:TRIUNE SYST LP
Computer-implemented method for deriving, translating, and using definitional expressions for data in a database
InactiveUS20100023481A1Maximum flexibilityMinimal maintenanceRelational databasesSpecial data processing applicationsDerived DataData mining
A computer-implemented method is disclosed for deriving definitional expressions for data in a database from membership abstractions, and for deriving membership abstractions from definitional expressions. Definitional expressions may be partially in a natural language. By automating the translation among definitional expressions and membership abstractions, definitional expressions may then be used as database commands for the purpose of query, data update, maintenance, and the like, and may also be used to provide users with a more readable and understandable definition of both stored and derived data (e.g., the result of an ad-hoc query or data modification).
Owner:MCGOVERAN DAVD O
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com