Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
56results about How to "Avoid conflict situations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
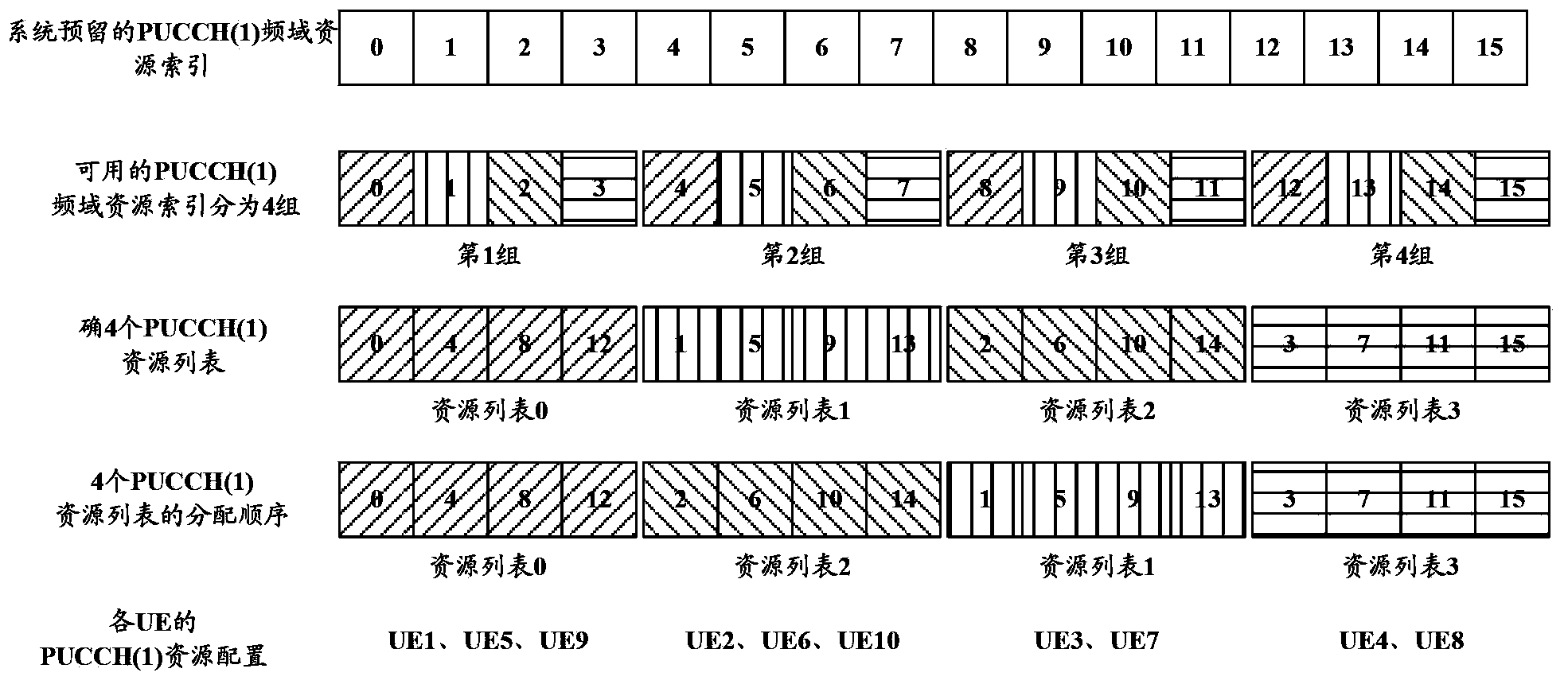
Uplink control channel resource allocating method in multi-antenna system and base station
ActiveCN104284424AReduce overheadAvoid conflict situationsWireless communicationControl channelBase station
The invention discloses an uplink control channel resource allocating method in a multi-antenna system and a base station, and relates to a communication technique. At least one resource list is determined according to frequency domain resources reserved by a system for an antenna port port1 based on channel selection in a physical uplink control format 1b; multiple pieces of UE are allowed to share one resource list when the resource lists are allocated to the UE in a cell so that cost of PUCCH resources can be reduced; meanwhile, the UE sharing the same resource list is scheduled in different ACK / NACK feedback windows and accordingly the situation that the ACK / NACK feedback resources of different pieces of UE collide is avoided.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method and device for automatic IP address detection
InactiveCN101175000AAvoid conflict situationsAvoid cumbersome problem-locating processesData switching networksIp addressNetwork addressing
The invention discloses a method which can detect IP address conflicts automatically. The method is concretely that a first terminal broadcasts ARP message to other terminals through a prearranged IP network address. The ARP message carries IP addresses to be detected. The ARP message is used in other terminals for judging whether the IP address of the ARP message is the same with the IP address to be detected. The first terminal receives the ARP response information sent by other terminals according to the judged results. The invention also discloses a device, which is used for detecting the IP address conflicts automatically. The invention still discloses a device which is used for helping detecting the IP address conflicts automatically. The invention judges the IP address conflicts through the ARP message and avoids the happening of the IP address conflicts from headstream. The method can be implemented under the condition of not influencing the network communication. Therefore, a trivial problem location process is avoided and a large quantity of maintenance cost is saved.
Owner:HUAWEI TECH CO LTD
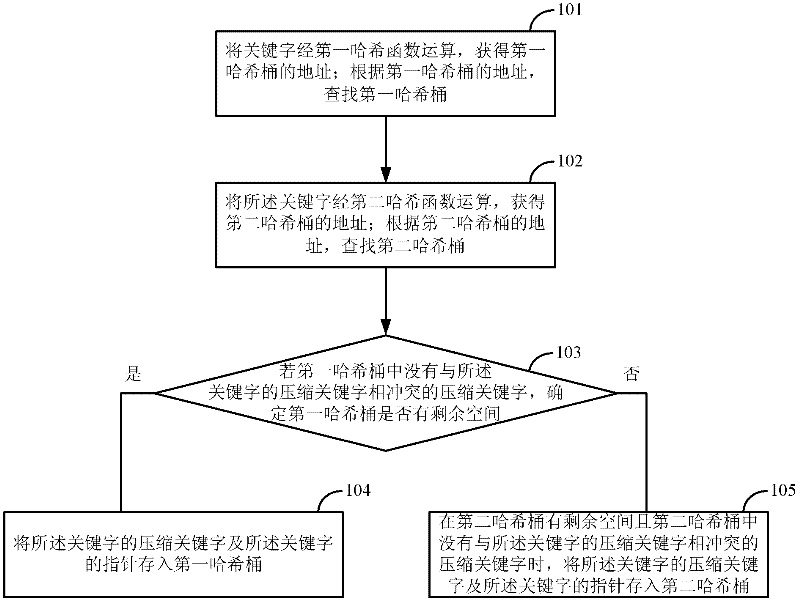
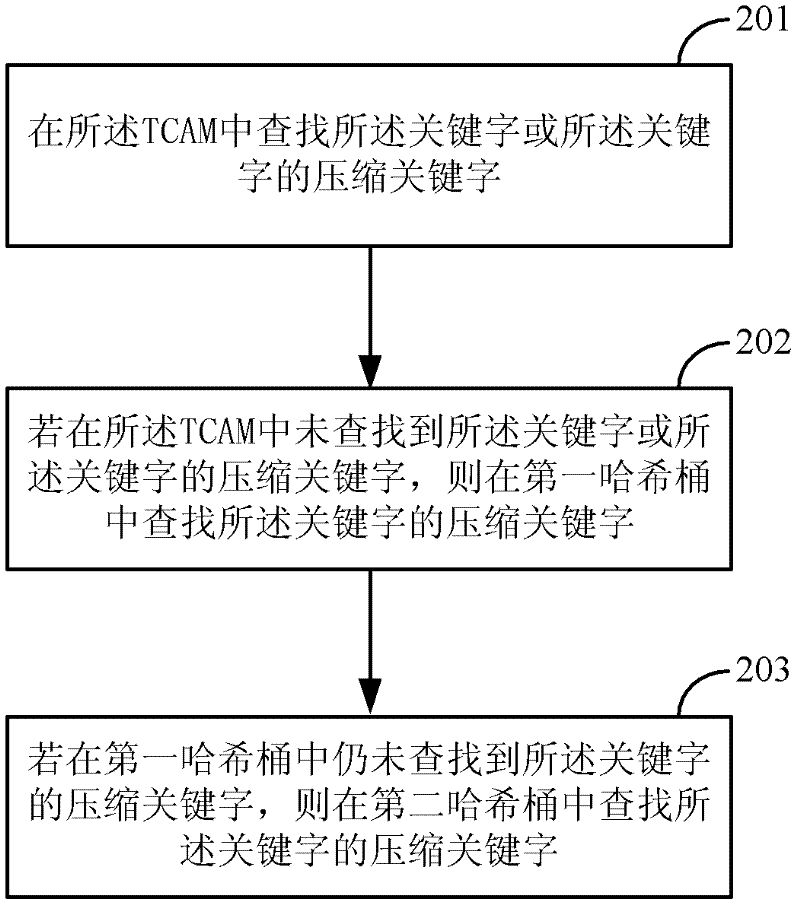
Method and device for storing and searching keyword
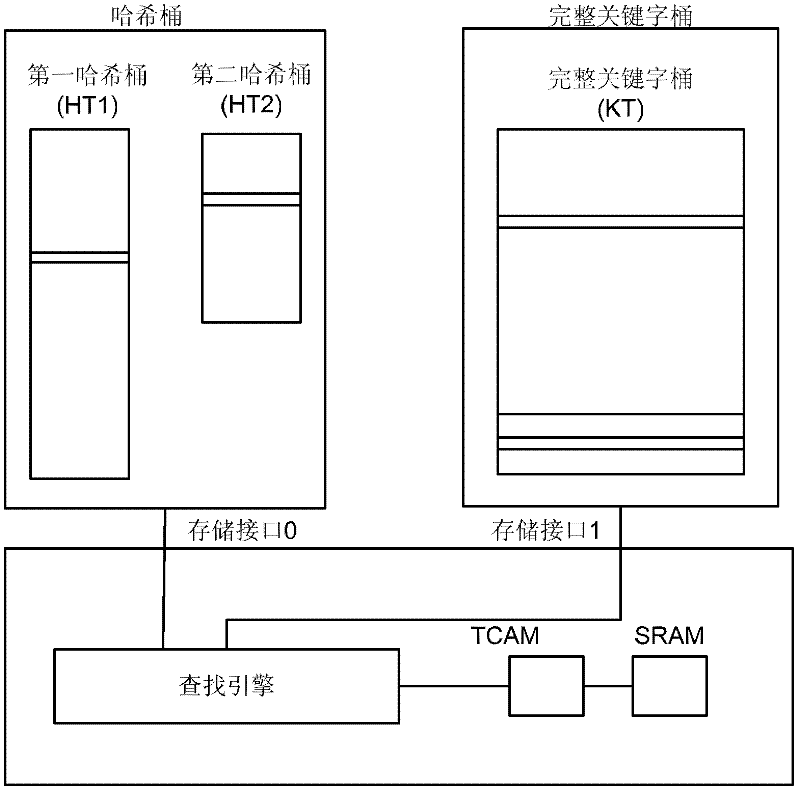
ActiveCN102232219AAvoid conflict situationsImprove memory utilizationDigital data information retrievalTransmissionHash functionTheoretical computer science
A method for storing keyword is disclosed, which includes: a keyword is operated respectively on the first and the second hash function in order to obtain the first and the second hash bucket addresses; the first and the second hash buckets are searched according to the first and the second hash bucket addresses; if no compressed keyword which conflicts with the compressed keyword of the keyword exists in the first hash bucket, the compressed keyword of the keyword and the pointer of the keyword are stored into the first hash bucket when the first hash bucket has remaining space; or the compressed keyword of the keyword and the pointer of the keyword are stored into the second hash bucket, when the first hash bucket has no remaining space and the second hash bucket has remaining space, and no compressed keyword which conflicts with the compressed keyword of the keyword exists in the second hash bucket. A method for searching keyword, a device for storing keyword and a device for searching keyword are also disclosed. The present invention enables increasing memory utilization ratio greatly and saving memory space and bandwidth.
Owner:HUAWEI TECH CO LTD
Method for uniformly maintaining access object information in information system and device thereof
ActiveCN101656720AAvoid conflict situationsRealize unified maintenanceUser identity/authority verificationSpecial data processing applicationsData formatDatabase
The invention relates to a method for uniformly maintaining access object information in an information system, comprising the following steps: collecting object attribute information of an access object of each application service system, wherein the object attribute information comprises entity information uniquely corresponding to the access object and authentication information when logging inthe application service system; removing redundant entity information from the object attribute information to obtain the entity information and the authentication information of the different accessobjects; building an entity mark which uniquely maps with the entity information and adopts an uniform data format; forming the entity mark, the entity information and the authentication information,which belong to the same access object, into a group of entity attribute information to be centrally memorized; and locating the entity attribute information of the access object for operating with amapping relation in the information system. The invention leads the entity attribute information which is located to operate the access object with the entity mark to uniformly maintain the access object information and be capable of synchronously updating the entity attribute information modified by the access object.
Owner:BEIJING WATCH DATA SYST
Data transmission method and system, terminal device and network side device
InactiveCN107018173AAvoid conflict situationsTime-division multiplexTransmissionTerminal equipmentEngineering
The invention discloses a data time sequence synchronization method and system in a communication network. The method comprises the steps of sending data to a terminal through a broadcast signal; and setting continuously countable fields as clock synchronization sources of communication terminals of the communication network in the broadcast signal. According to the method provided by the invention, the uploading data is set through utilization of a counting period of a counter, so the data of any period or any format can be uploaded, and a conflict problem is effectively solved. A device employing the data time sequence synchronization method in the communication network provided by the invention also has the same advantages.
Owner:HYTERA COMM CORP
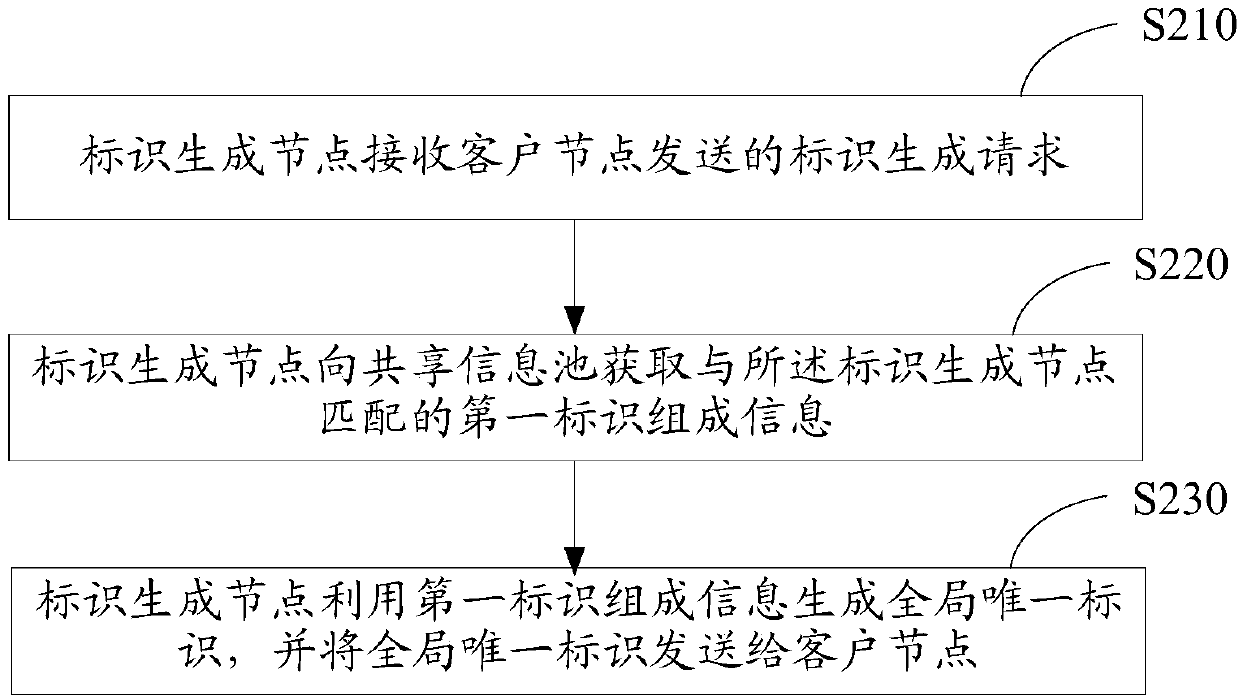
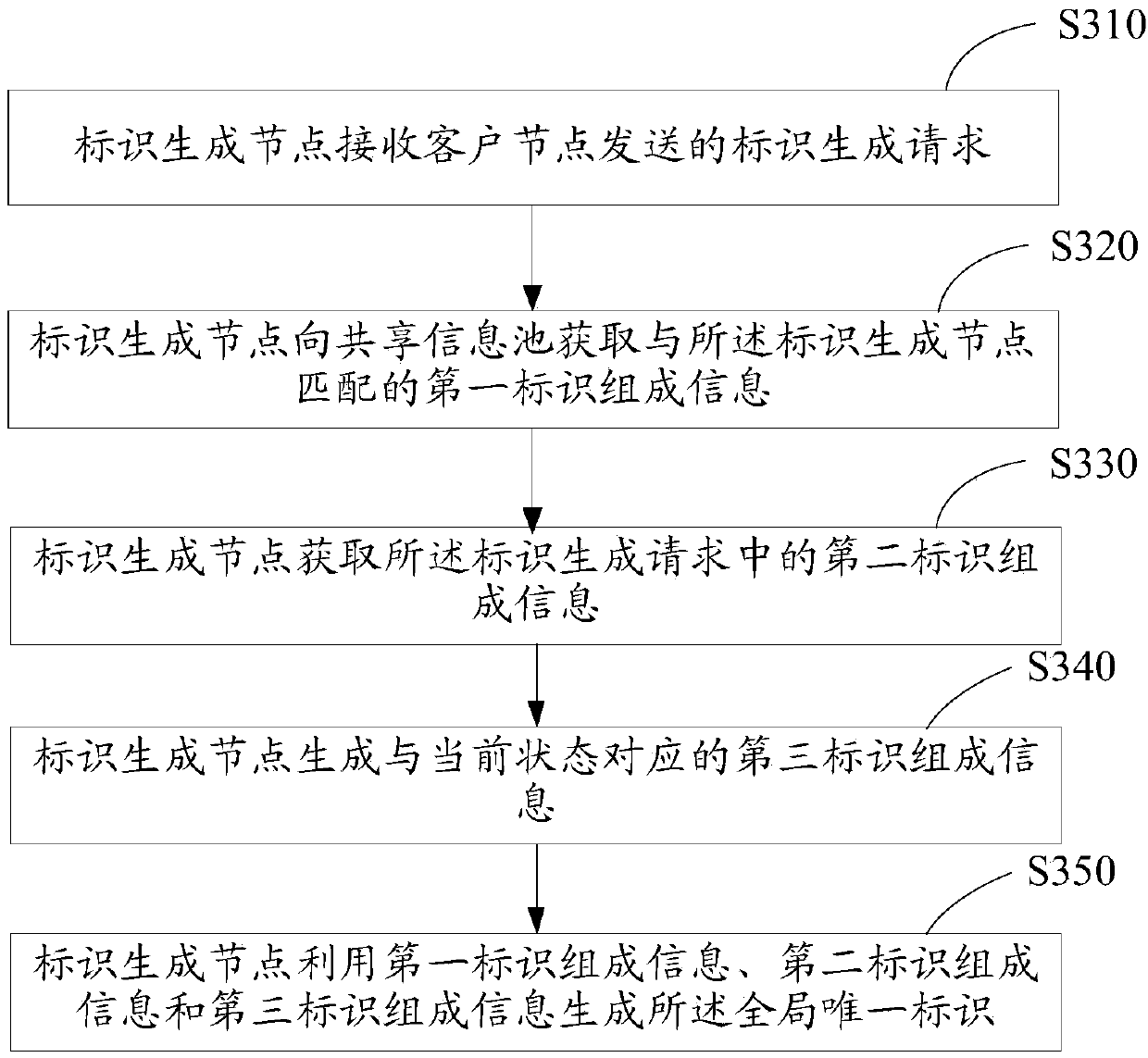
Identifier generation and management method, node, system and storage device
ActiveCN110636097AAvoid conflict situationsUniqueness guaranteedTransmissionUnique identifierUser identifier
The invention discloses an identifier generation and management method, a node, a system and a storage device. The method comprises the steps of enabling an identifier generation node to receive an identifier generation request sent by a client node; acquiring first identifier composition information matched with the identifier generation node from a shared information pool; and generating a globally unique identifier by using the first identifier composition information, and sending the globally unique identifier to the client node. According to the scheme, the uniqueness of the generated identifier can be ensured.
Owner:MASHANG CONSUMER FINANCE CO LTD
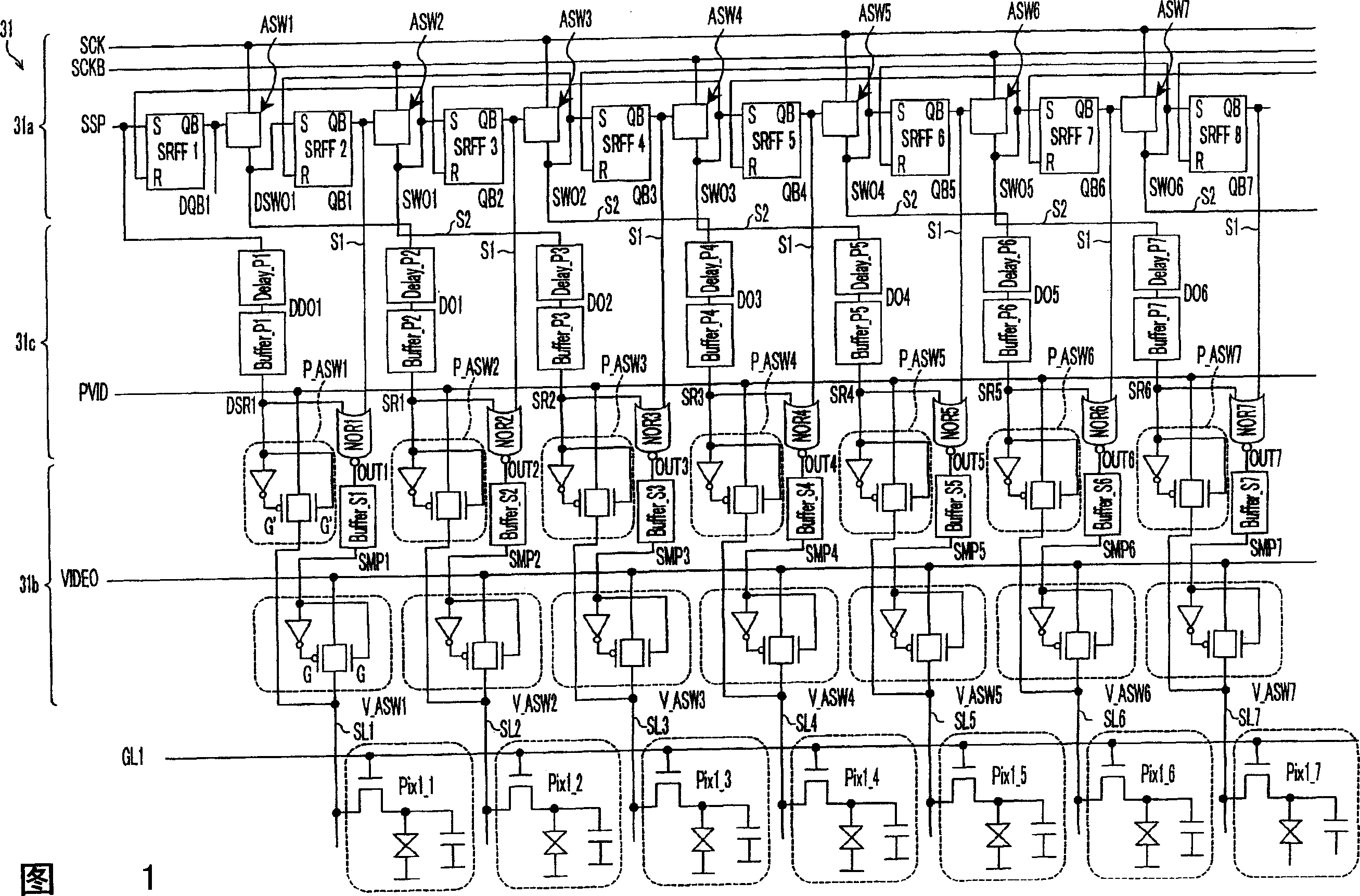
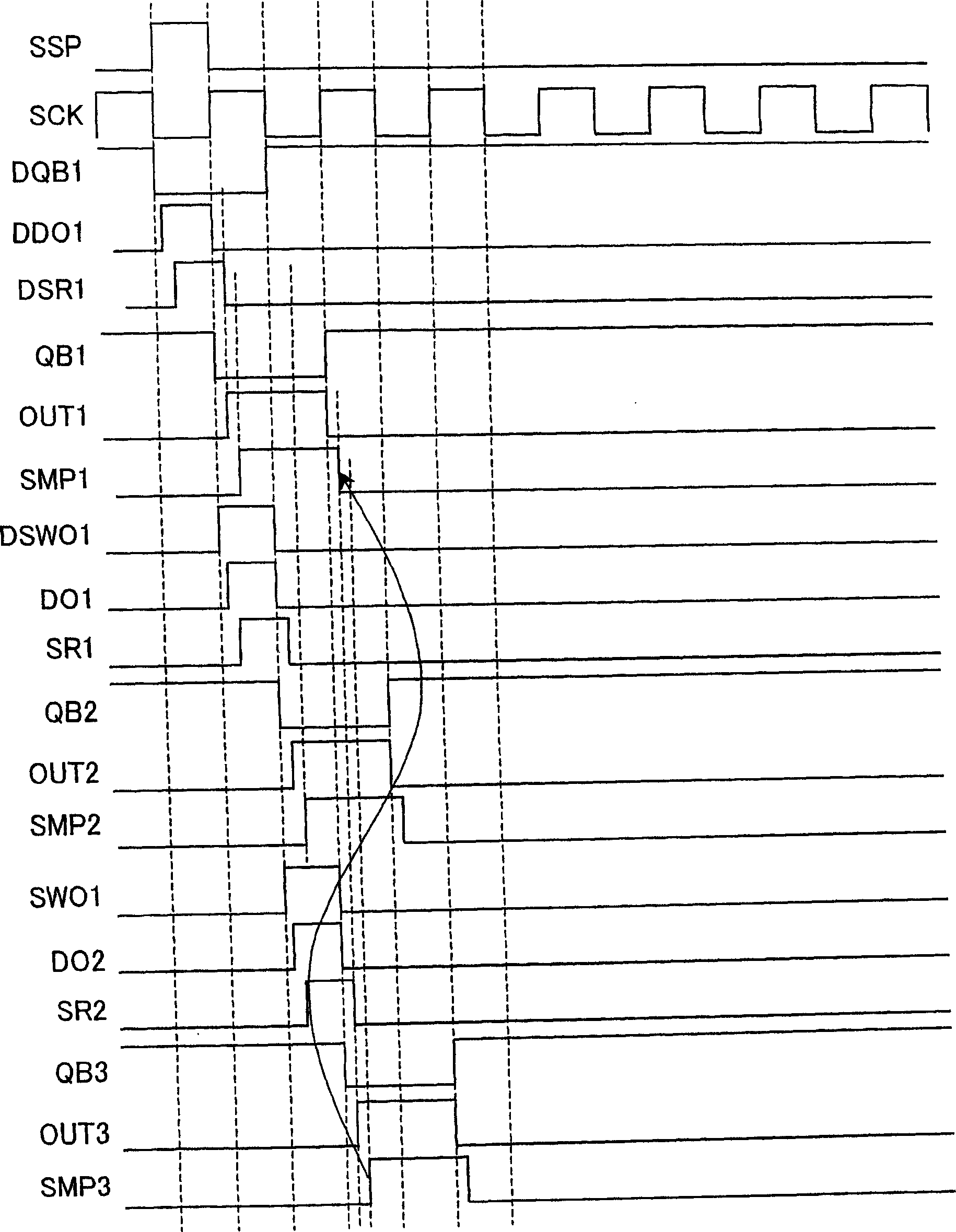
Display apparatus and driver circuit of display apparatus
InactiveCN1655224AAvoid conflict situationsImprove display uniformityBatteries circuit arrangementsStatic indicating devicesDriver circuitShift register
A driver circuit of a display apparatus is provided with a nor circuit in each output line of a timing pulse. To the nor circuit, inputted are a timing pulse to be supplied to the output line and a pre-charge pulse for pre-charging a data signal line SL to which a write signal is being inputted based on the timing pulse. With this structure, it is possible to realize a driver circuit storing a pre-charge circuit of a display apparatus, which can surely prevent a collision between a pre-charge potential and a potential of a video signal in a signal supply line when pre-charging the signal supply line from a pre-charge power supply of a small driving performance, while maintaining the number of stages in the shift register to be the required minimum number.
Owner:SHARP KK
Label synchronous control method concurrently operating multi-MPLS protocol in MPLS group network
InactiveCN1455568AAvoid conflict situationsSolve the problem of label synchronization controlData switching networksSelection arrangementsMessage queueSynchronous control
Owner:HUAWEI TECH CO LTD
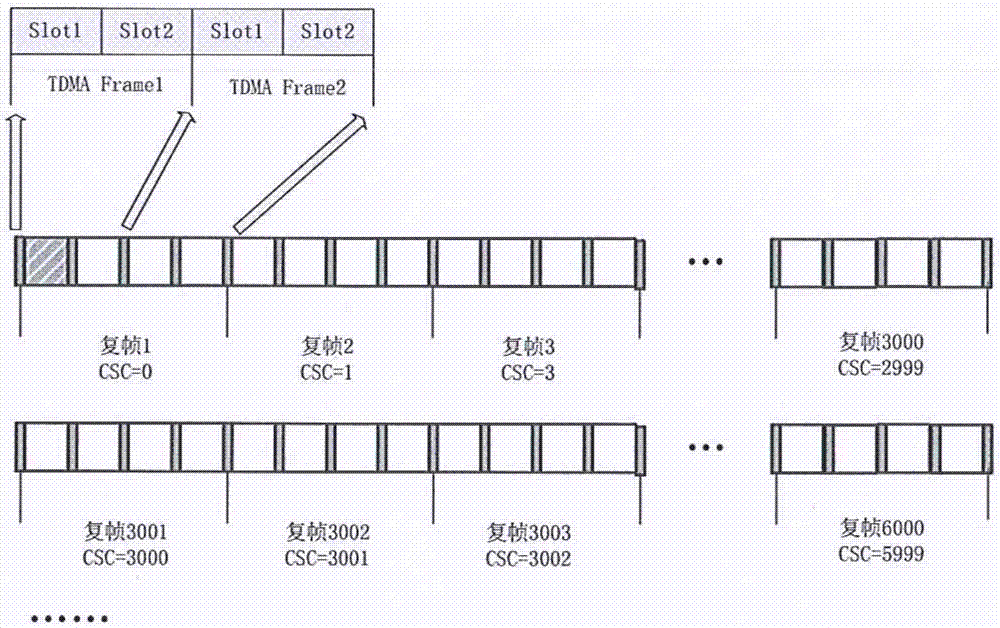
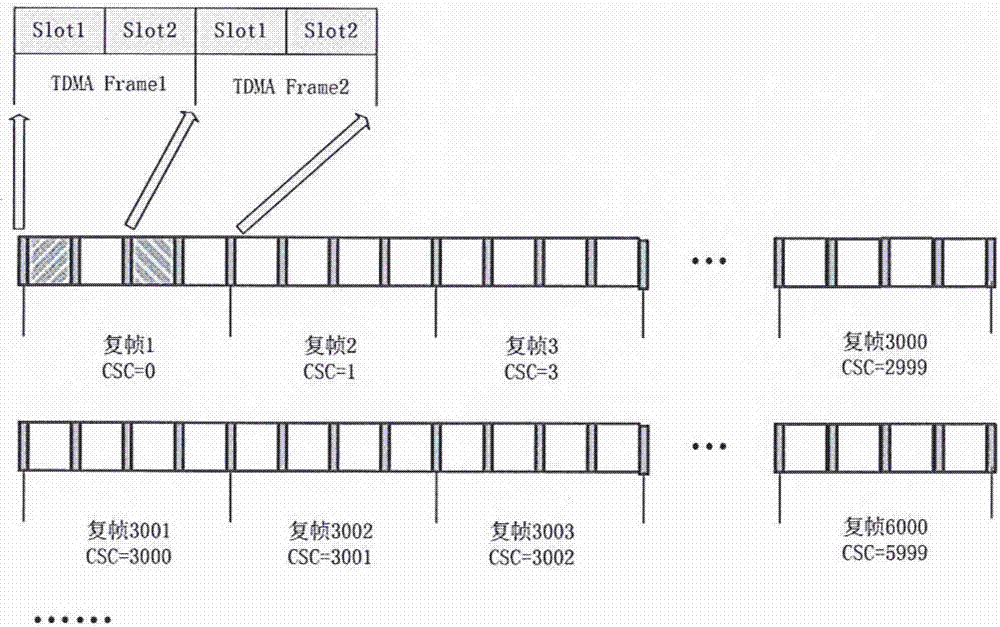
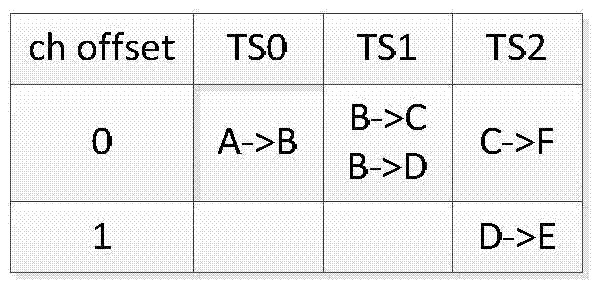
Channel and time slot scheduling method suitable for WIA-PA network
ActiveCN104754757AAvoid confictReliable operationNetwork topologiesResource distributionDistributed computing
The invention requests for protection of a channel and time slot scheduling method suitable for a WIA-PA network. The channel and time slot scheduling method includes that scheduling rules according to which channel and time slot scheduling is executed and a scheduling method meeting the scheduling rules are provided by combining actual WIA-PA network environment according to superframe structure of WIA-PA and characteristics of communication resource distribution; the scheduling rules include known conditions, hard conditions and scheduling priority which illustrate indicators in the scheduling method respectively; the scheduling method includes specifying scheduling of channels and time slot in a beacon state, a CAP state, an in-cluster communication stage and an inter-cluster communication stage in the WIA-PA superframe structure, and the method is used for scheduling the channels and the time slot of each equipment in the WIA-PA network; transmission of corresponding frames is arranged at corresponding stages according to the superframe structure of the WIA-PA, and all frames in the WIA-PA are ensured to be sent to a target node within a superframe period. By the channel and time slot scheduling method, scheduling of the channels and the time slot of the WIA-PA network is realized, the channels and the time slot are distributed for each equipment in the WIA-PA network, and requirements on time slot communication of the WIA-PA network are met.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
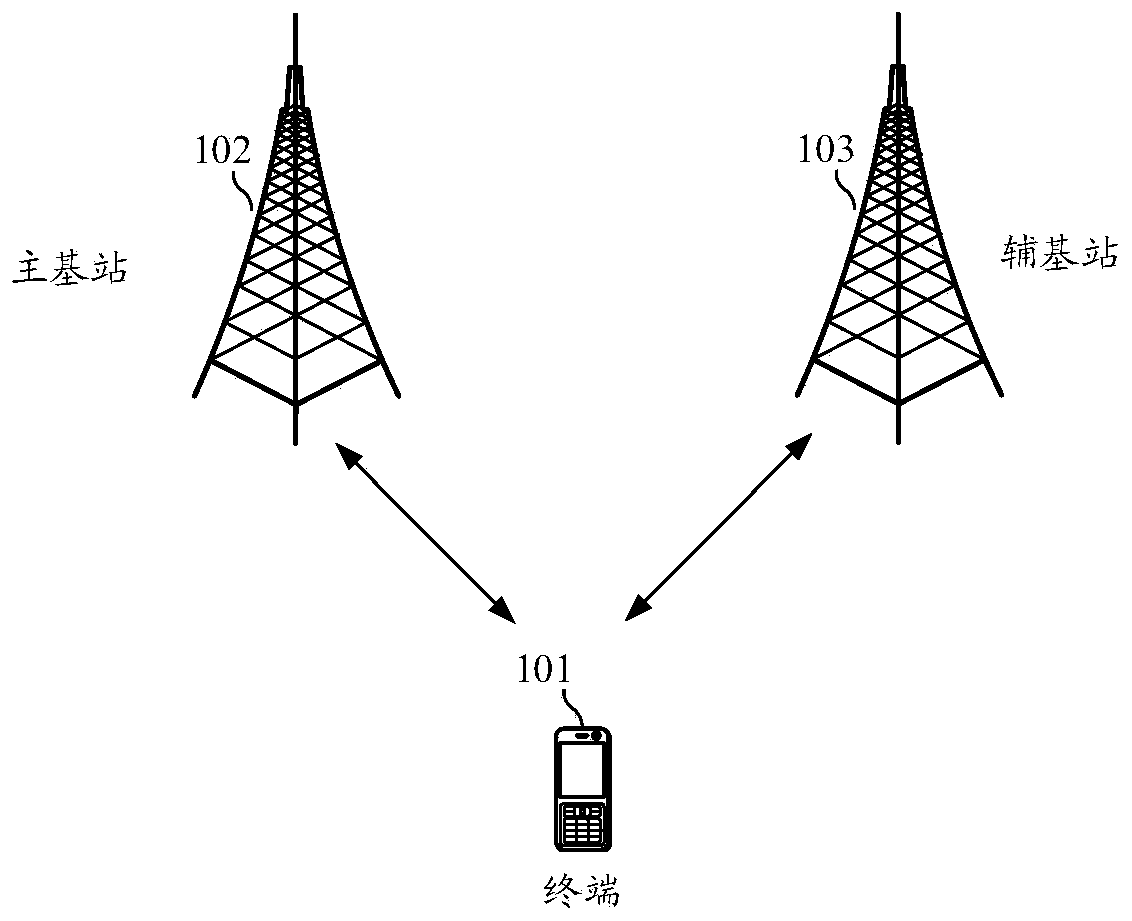
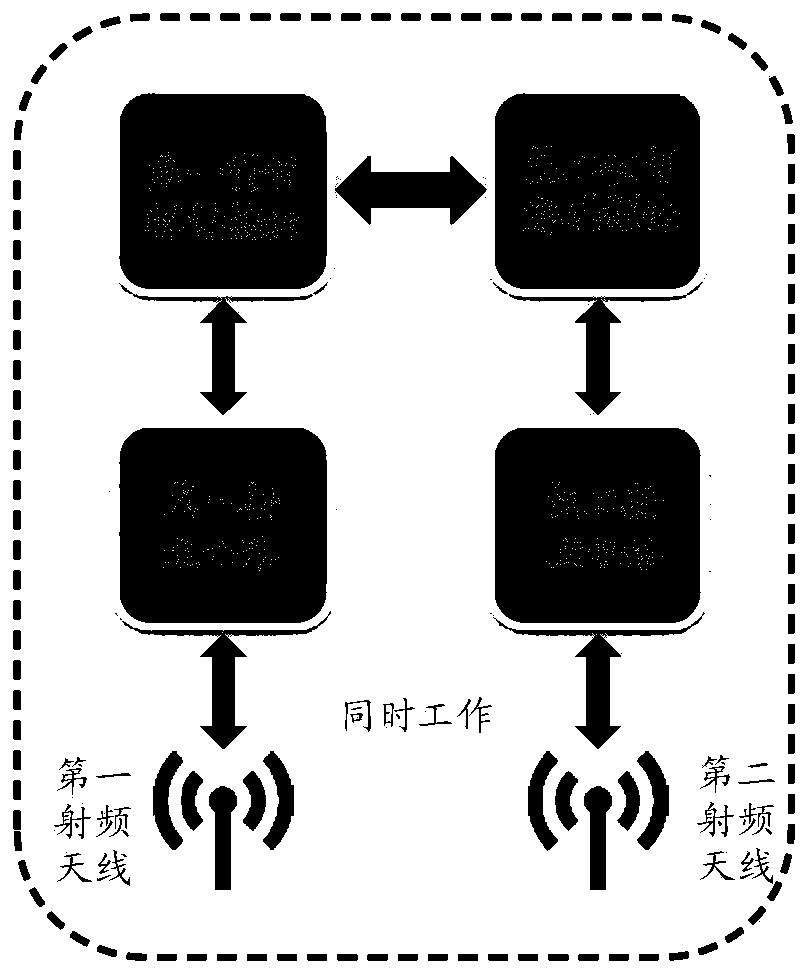
Antenna switching method and device, terminal and storage medium
ActiveCN110690910AAvoid conflict situationsGuaranteed success rateConnection managementTransmissionElectrical and Electronics engineeringReal-time computing
The embodiment of the invention discloses an antenna switching method and device, a terminal and a storage medium, the method is applied to a terminal with a dual-connection mode, and the terminal comprises a first antenna group and a second antenna group; the method comprises the following steps: acquiring performance parameters of at least two first antennas in a first antenna group and performance parameters of at least two second antennas in a second antenna group; performing performance sorting on the at least two first antennas to obtain a first antenna sequence, and performing performance sorting on the at least two second antennas to obtain a second antenna sequence; selecting a target first antenna and a target second antenna based on the first antenna sequence and the second antenna sequence, wherein the target first antenna and the target second antenna are different antennas. Thus, in the dual-connection mode, different target antennas can be selected for the first base station and the second base station, the conflict situation during antenna switching is avoided, and the success rate of antenna switching is ensured.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
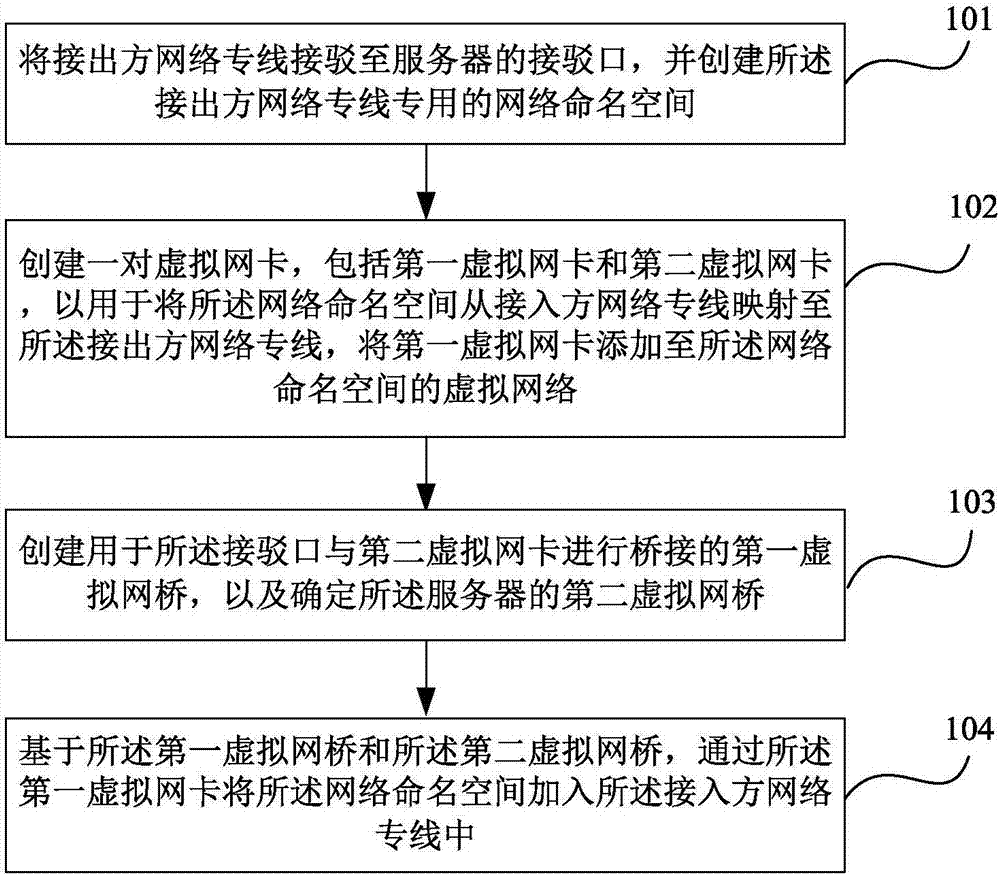
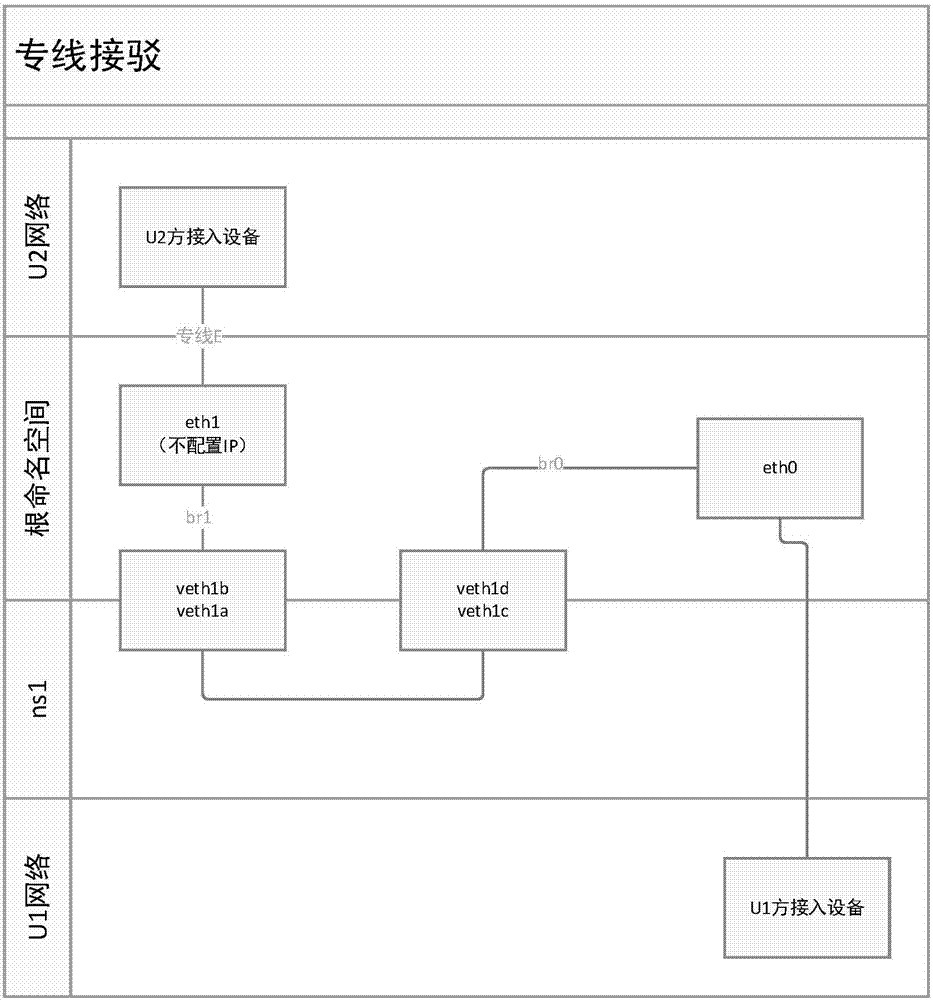
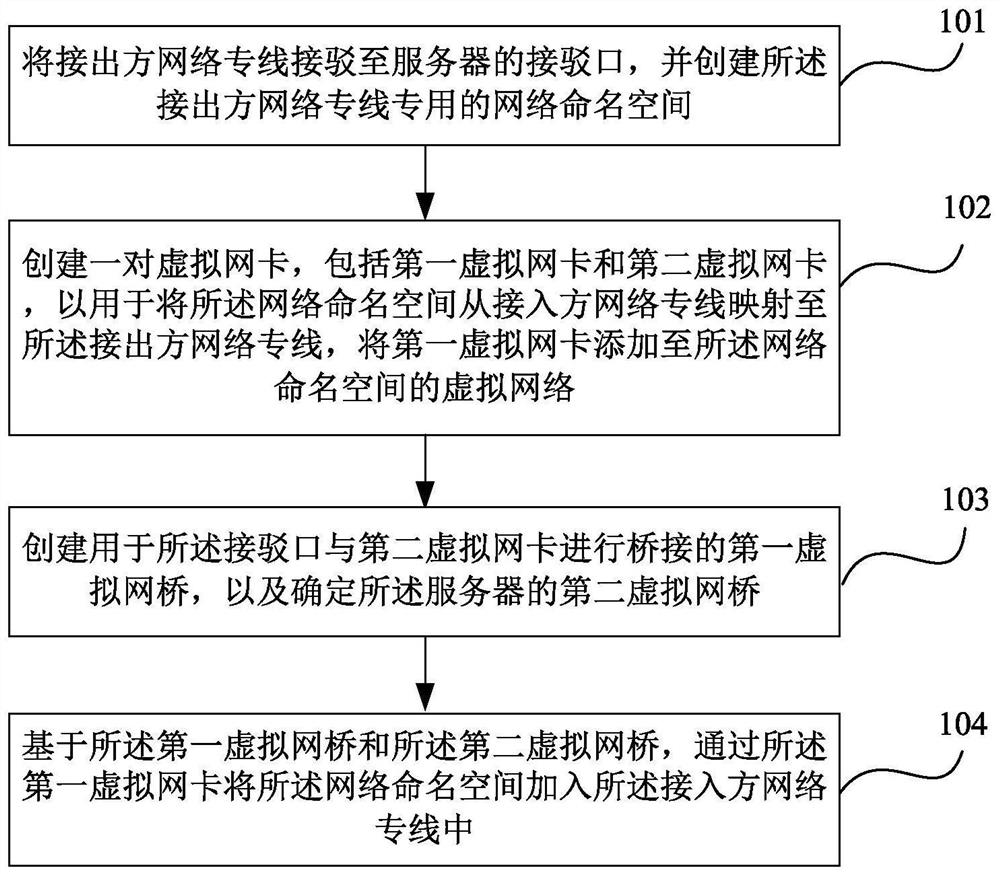
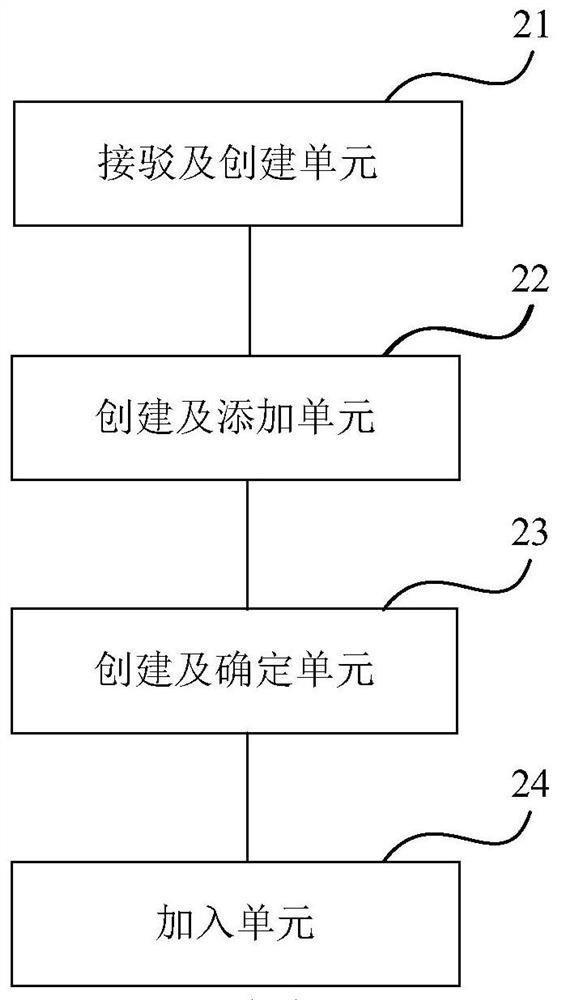
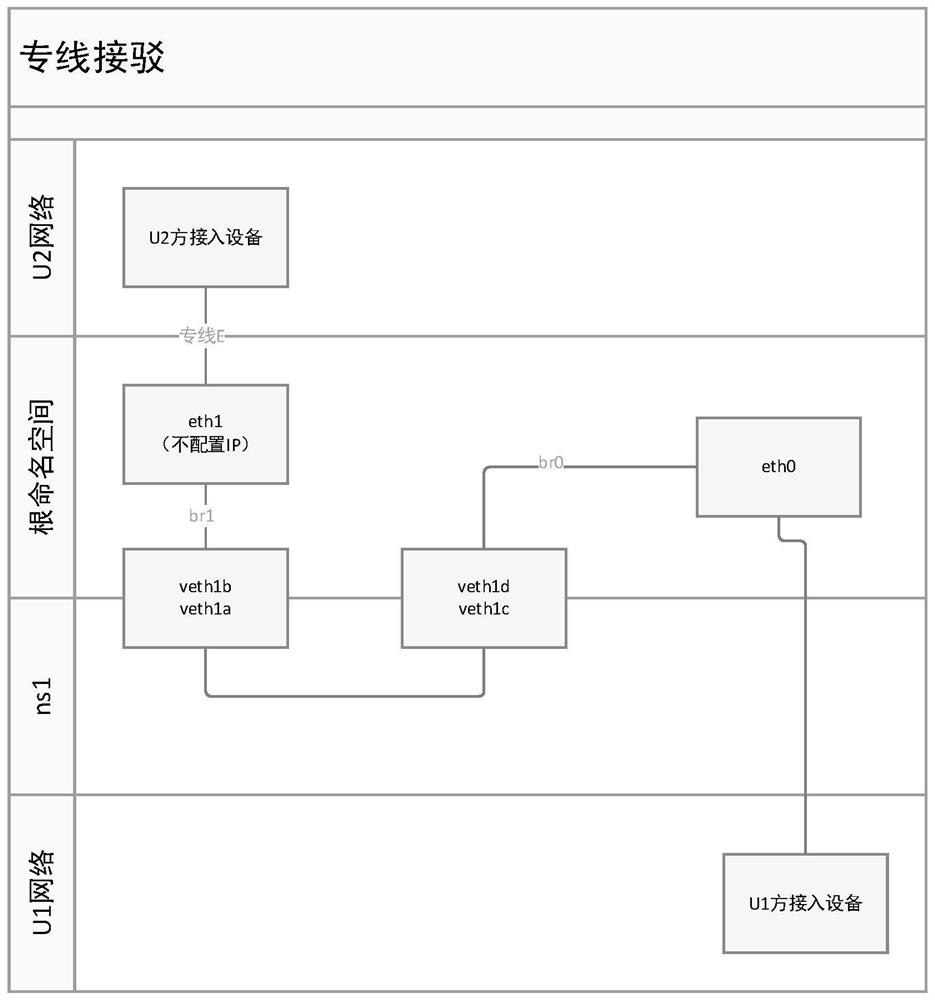
Dedicated network line connection method and device
An embodiment of the invention provides a dedicated network line connection method and device. The method comprises steps as follows: connecting a dedicated network line of a lead-out party to a connecting port of a server and creating dedicated network namespace for the dedicated network line of the lead-out party; creating a pair of virtual network cards including a first virtual network card and a second virtual network card to map the network namespace from a dedicated network line of a lead-in party to the dedicated network line of the lead-out party, adding the first virtual network cardto a virtual network of the network namespace; creating a first virtual network bridge for bridge connection of the connecting port and the second virtual network card to determine a second virtual network bridge of the server; and adding the network namespace to the dedicated network line of the lead-in party through the first virtual network card on the basis of the first virtual network bridgeand the second virtual network bridge. By means of the method and the device, the situation of conflict of network addresses is avoided, and use of dedicated hardware for connection is also avoided.
Owner:新浪财经移动网络科技(北京)有限公司
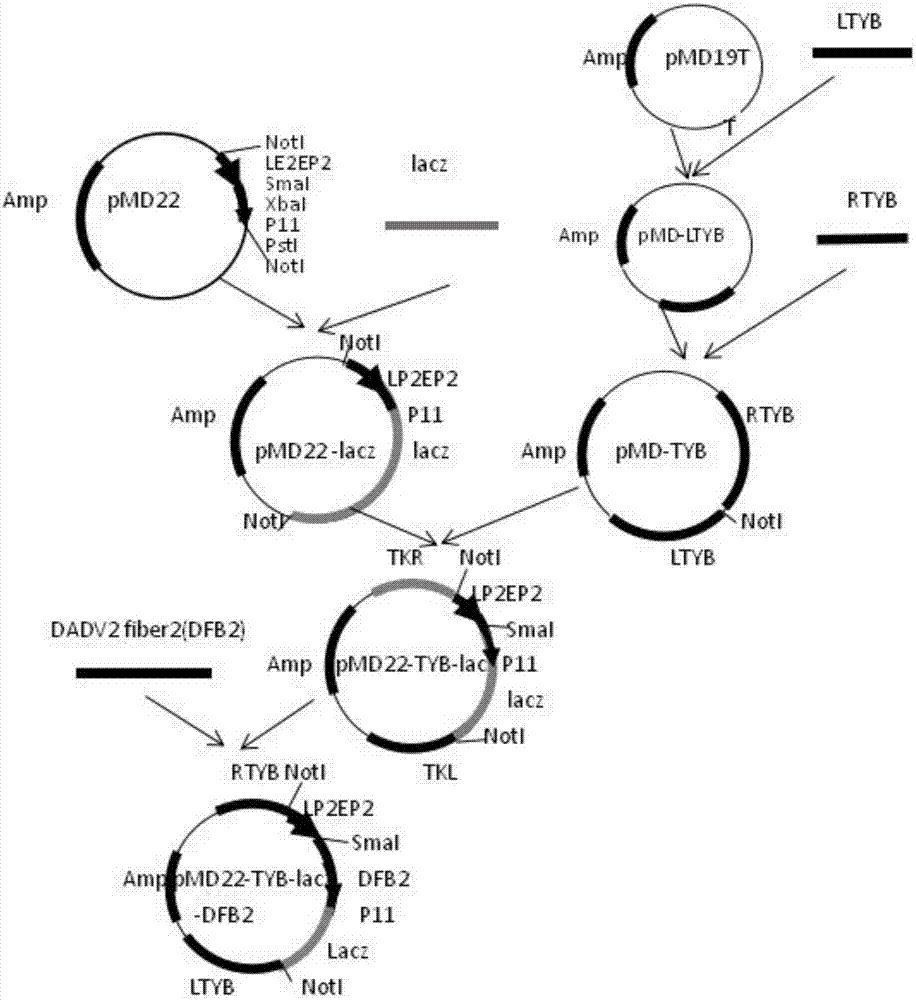
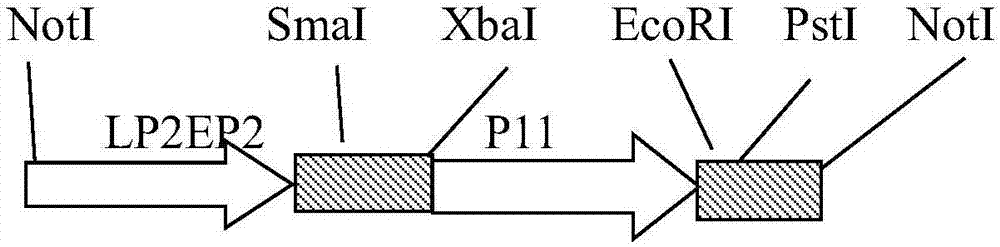
A recombinant fowlpox virus transfer vector expressing a duck adenovirus serotype-2 fiber2 gene, a constructing method thereof and applications of the transfer vector
ActiveCN107475297AAvoid conflict situationsImprove build efficiencyViral antigen ingredientsVirus peptidesGenetic engineeringLive vector vaccine
The invention belongs to the technical field of biology, and mainly relates to a recombinant fowlpox virus transfer vector expressing a duck adenovirus serotype-2 (DADV2) fiber2 gene, a constructing method thereof and applications of the transfer vector. According to the transfer vector, a DADV2 fiber2 gene promoted by a fowlpox-virus-containing early-late promoter LP2EP2, a lacz gene promoted by a P11 promoter, and fowlpox virus genome replicated non-essential fragments which are LTYB and RTYB used for homologous recombination are inserted in a TA cloning site of a pMD19T-Simple vector. The method includes constructing a plasmid pMD-TYB; constructing a plasmid pMD22; constructing a plasmid pMD22-lacz; constructing an intermediate vector pMD22-TYB-lacz; constructing the transfer vector pMD22-TYB-lacz-DFB2; and subjecting the transfer vector pMD22-TYB-lacz-DFB2 to effect verification. The recombinant fowlpox virus transfer vector constructed by the method lays a foundation for development of an efficient recombinant fowlpox virus genetic engineering living-vector vaccine expressing the duck adenovirus serotype-2.
Owner:WENS FOOD GRP CO LTD
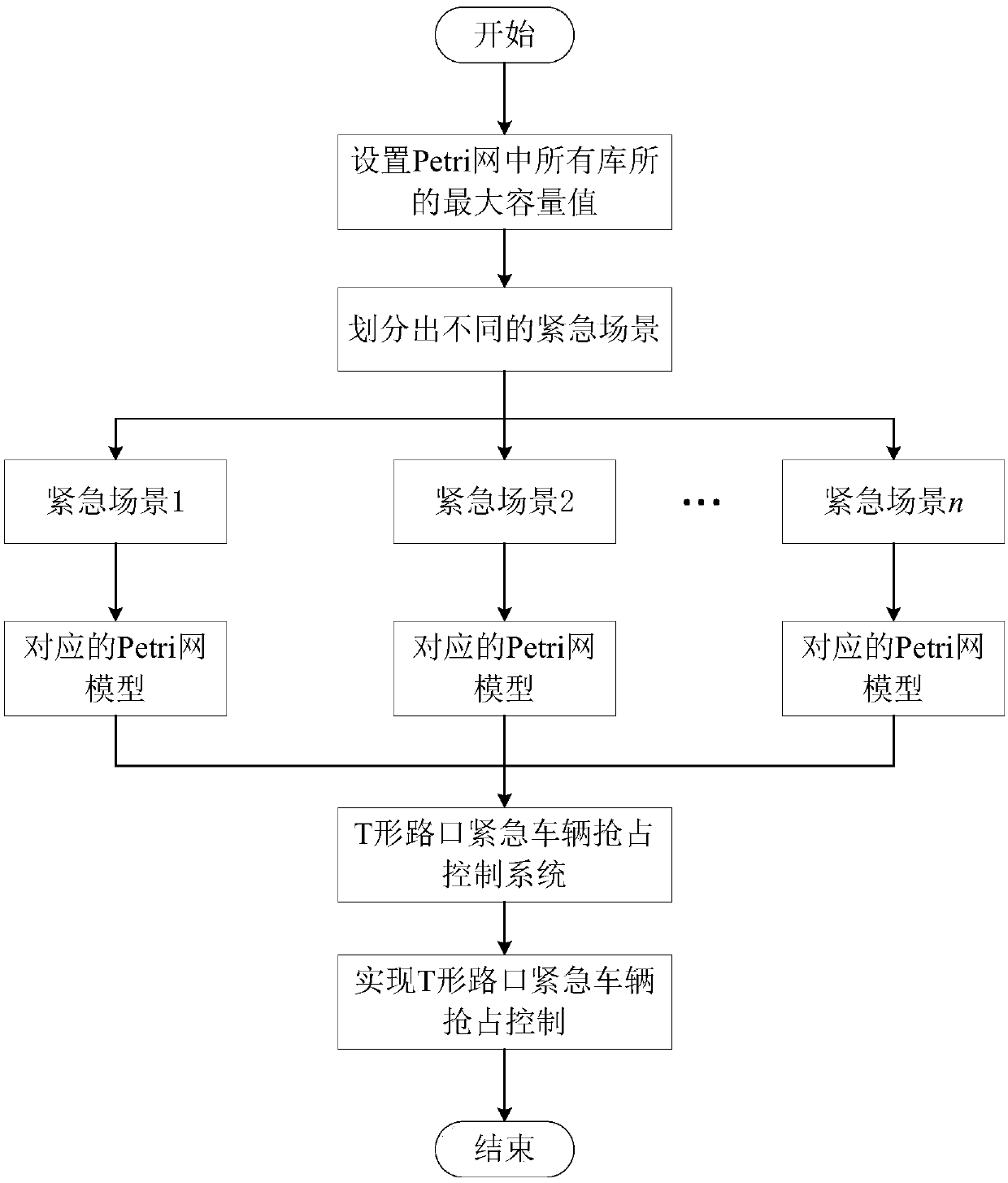
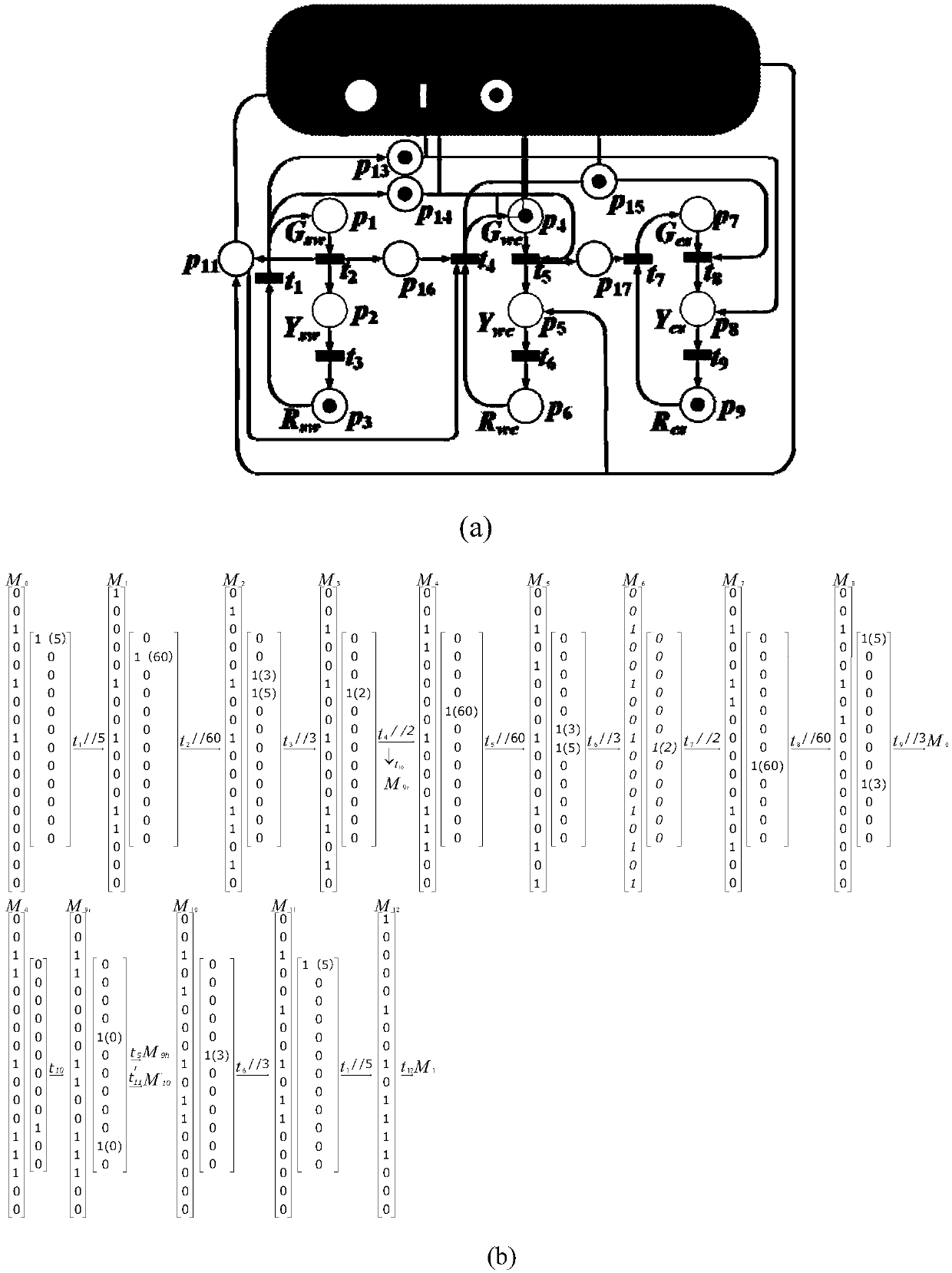
Preemption control method for emergency vehicles at T-junction based on timed Petri net
InactiveCN109598949AImprove traffic efficiencyReduce conflictControlling traffic signalsAnti-collision systemsControl systemThree-phase
The invention discloses a preemption control method for emergency vehicles at a T-junction based on a timed Petri net, which comprises the following steps: firstly, setting the maximum capacity valuesof all warehouses in the Petri net; then, obtaining different emergency scenes according to the traffic light state when the emergency vehicles arrive at the T-junction; then, establishing Petri netmodels corresponding to the different emergency scenes by using the timed Petri net; and finally, combining the Petri net models corresponding to the different emergency scenes to construct a preemption control system for emergency vehicles at a T-junction, which realizes the preemption control on emergency vehicles at T-junction. The method generates a collision-free preemption control system foremergency vehicles by taking a T-junction based on a three-phase control technology as an object and using the timed Petri net models as a modeling and analysis tool, can effectively avoid the collision of the emergency vehicles at the T-junction, improve the traffic efficiency of intersections, and effectively shorten the time required for emergency vehicles to reach the destination.
Owner:NANJING UNIV OF SCI & TECH
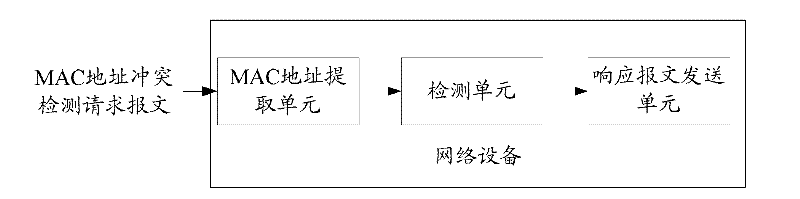
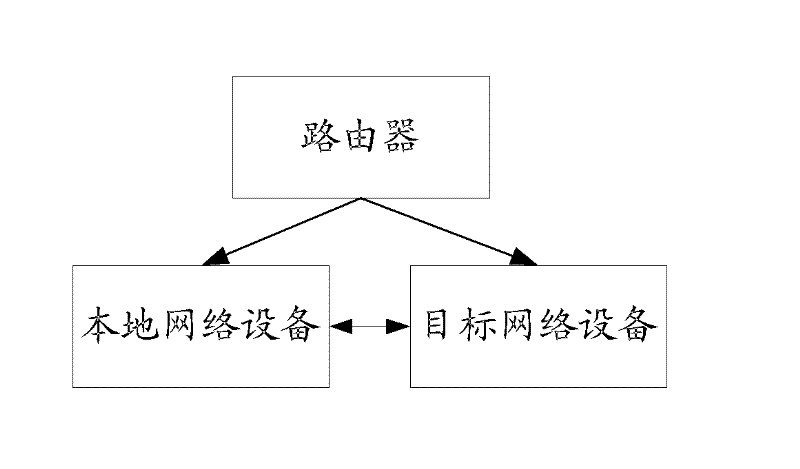
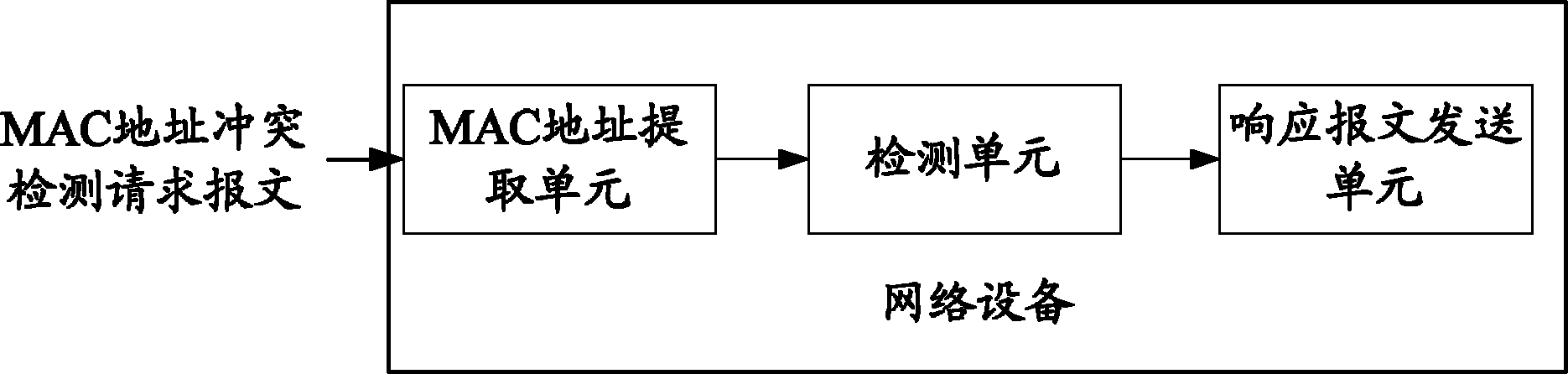
Medium/media access control address conflict detection method, device and system
ActiveCN102333134AAvoid conflict situationsEasy accessData switching networksMulticast addressNetwork attack
The invention provides a medium / media access control (MAC) address conflict detection method, which comprises that: before accessing a network, local network equipment transmits a MAC address conflict detection request message to a destination multicast address, wherein the request message carries a current MAC address of the network equipment; destination network equipment receiving the request message extracts the MAC address from the message request, detects the MAC address, and when judging that the extracted MAC address is the same as own MAC address, transmits a MAC address conflict detection response message to a requesting multicast address; and the local network equipment receiving the response message generates a new MAC address. The invention also discloses a MAC address conflict detection device and a MAC address conflict detection system. By the method, the device and the system, the occurrence of MAC address conflicts can be effectively avoided, the network equipment can be ensured to access the network normally, normal network service can be provided for a user, and risks in network attacks can be reduced.
Owner:ZTE CORP
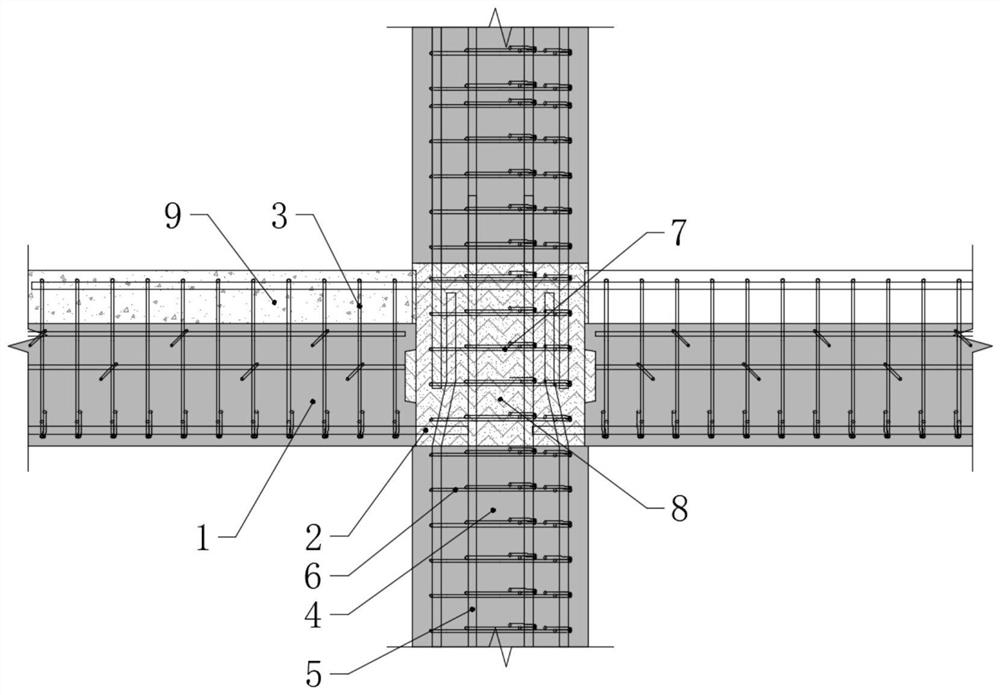
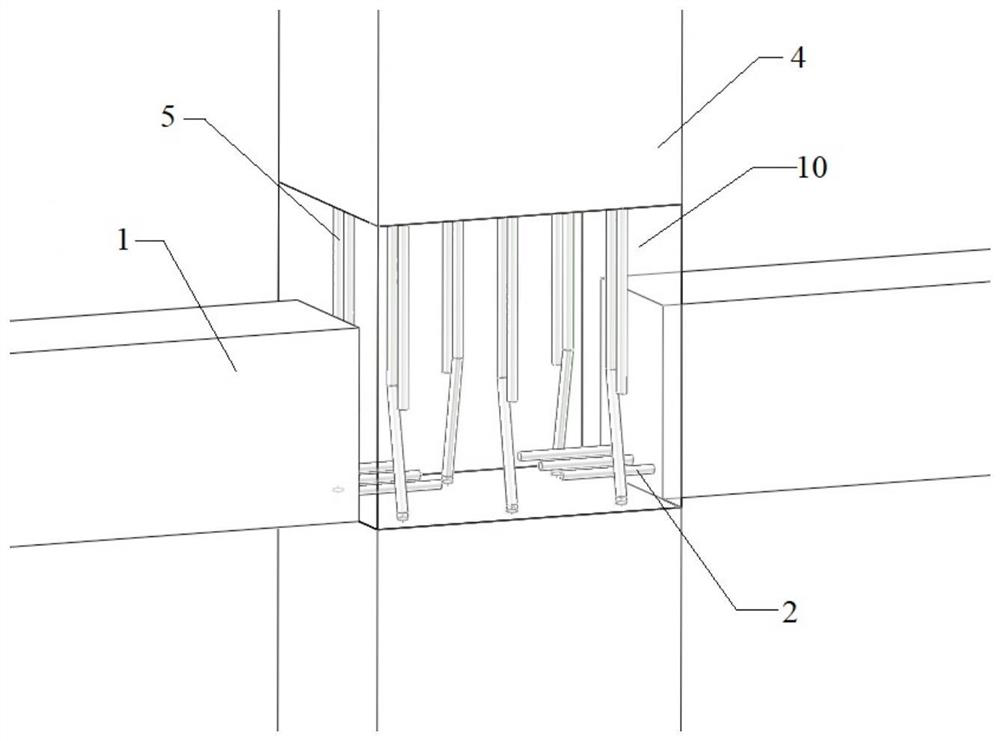
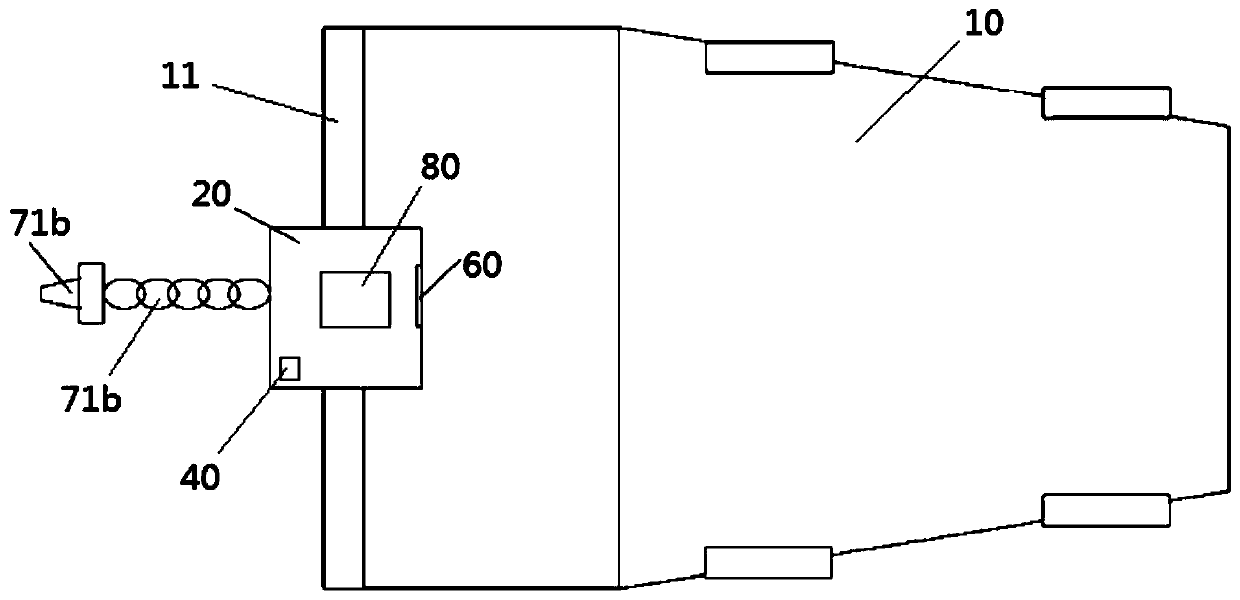
Fabricated beam-column connecting joint and construction method thereof
PendingCN113638491AActive connectionAvoid conflict situationsBuilding constructionsClassical mechanicsLap joint
The invention relates to a fabricated beam-column connecting joint and a construction method. The connecting joint comprises a prefabricated beam and a prefabricated column, wherein a joint core area is formed at the joint of the prefabricated beam and the prefabricated column, column longitudinal bars are arranged on the prefabricated column, the column longitudinal bars of the adjacent prefabricated columns are in lap joint in the joint core area, the prefabricated column is arranged in the joint core area, and a high-strength material is poured in the joint core area to form a post-pouring core area. Compared with the prior art, the connecting joint has the advantages of direct and reliable force transmission, convenience in construction and the like.
Owner:HUADONG BUILDING CO LTD OF CHINA CONSTR FIFTH ENG BUREAU +3
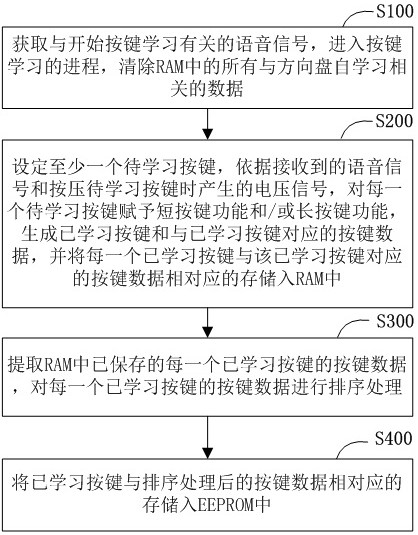
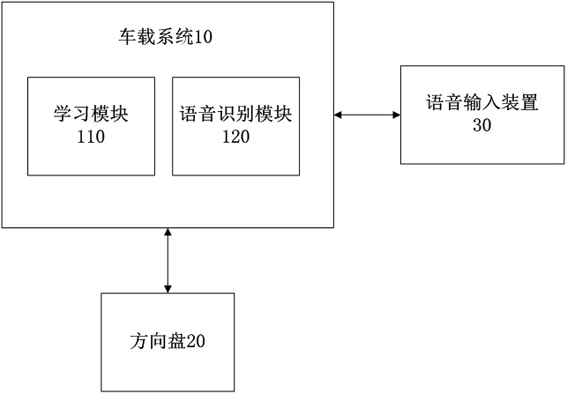
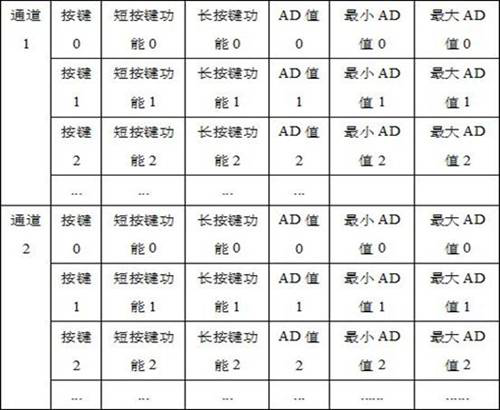
Self-learning method and self-learning system for steering wheel keys
ActiveCN111930247AQuality improvementReduce maintenance costsRedundant data error correctionInput/output processes for data processingHuman–machine interfaceSteering wheel
The invention relates to a self-learning method and a self-learning system for steering wheel keys, and a vehicle-mounted system realizes propulsion of a self-learning process according to a voice signal, transmitted by a voice input device, of a driver. The vehicle-mounted system binds and matches the short key function and / or the long key function with the voltage signal by acquiring the voltagesignal generated by pressing the physical key in a steering wheel by a driver, so that the custom endowing of the key function is realized. The vehicle-mounted system enables voltage signals betweenthe keys to be prevented from conflicting through error correction of the key data. The invention relates to the self-learning method and the self-learning system for steering wheel keys. Steering wheel difference points of all vehicle types are unified, differentiated software design does not need to be conducted for different vehicle types, the design work of a human-computer interface is simplified, steering wheel self-learning can adapt to the requirements of different vehicle types and different users, the software quality is improved, and the software cost is reduced.
Owner:宁波均胜新能源汽车技术有限公司 +1
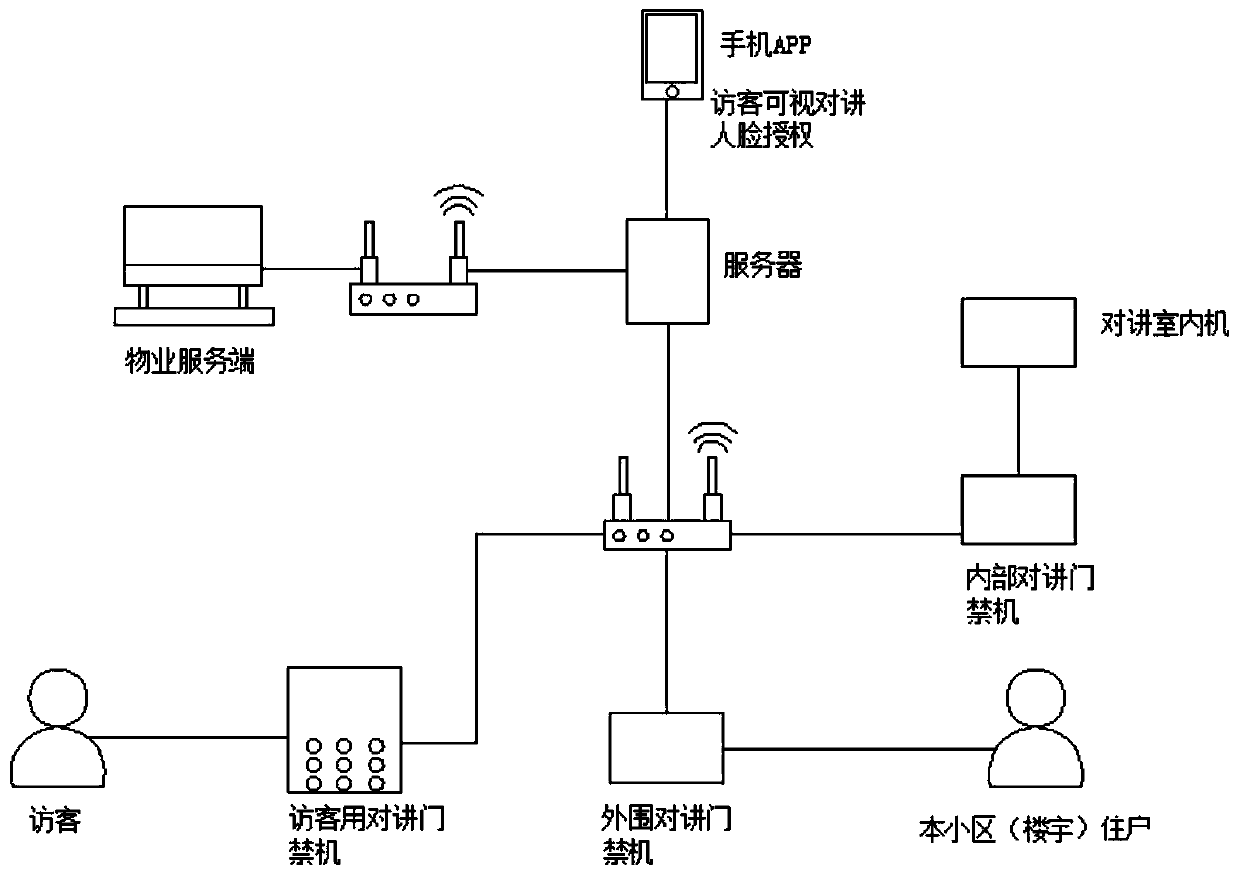
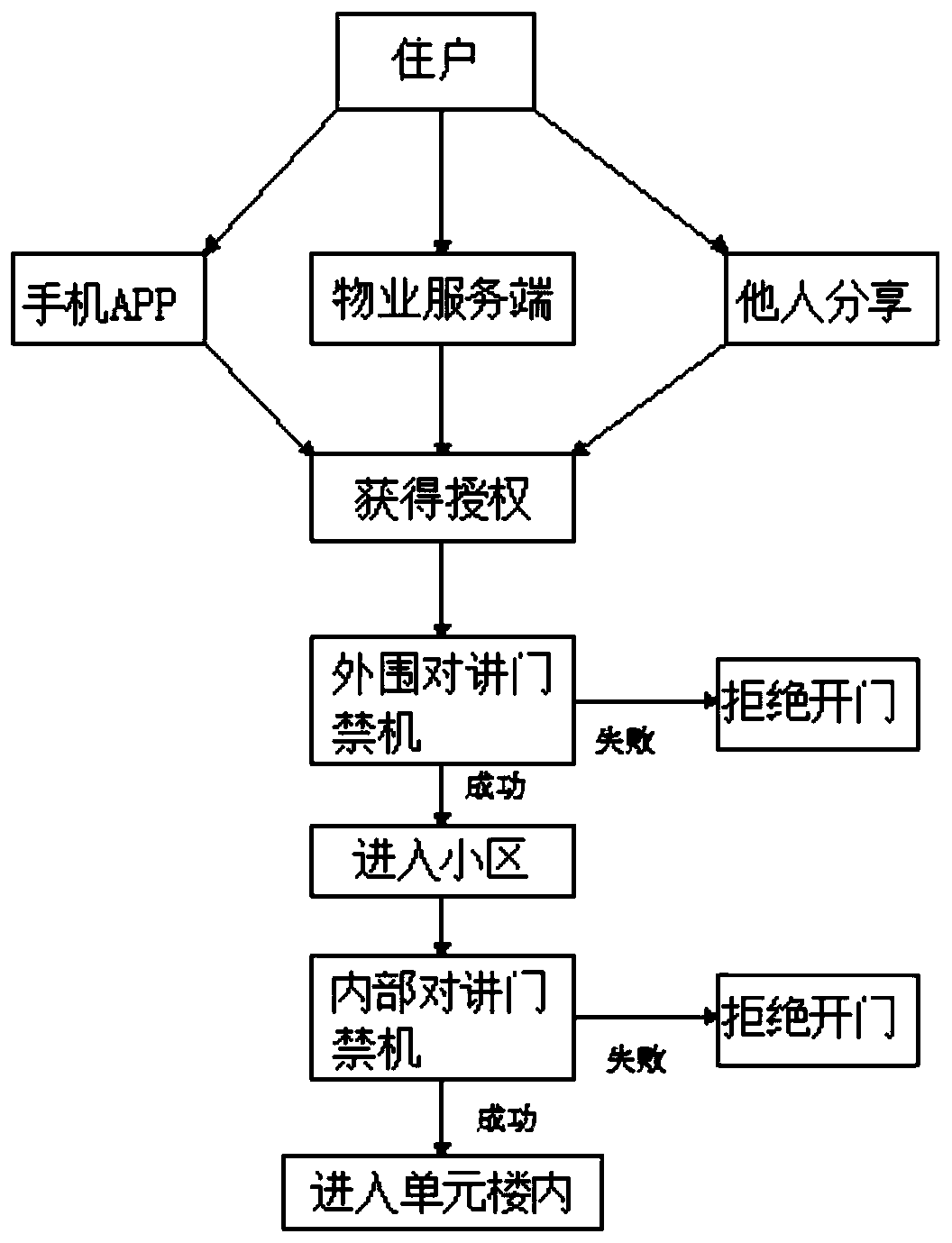
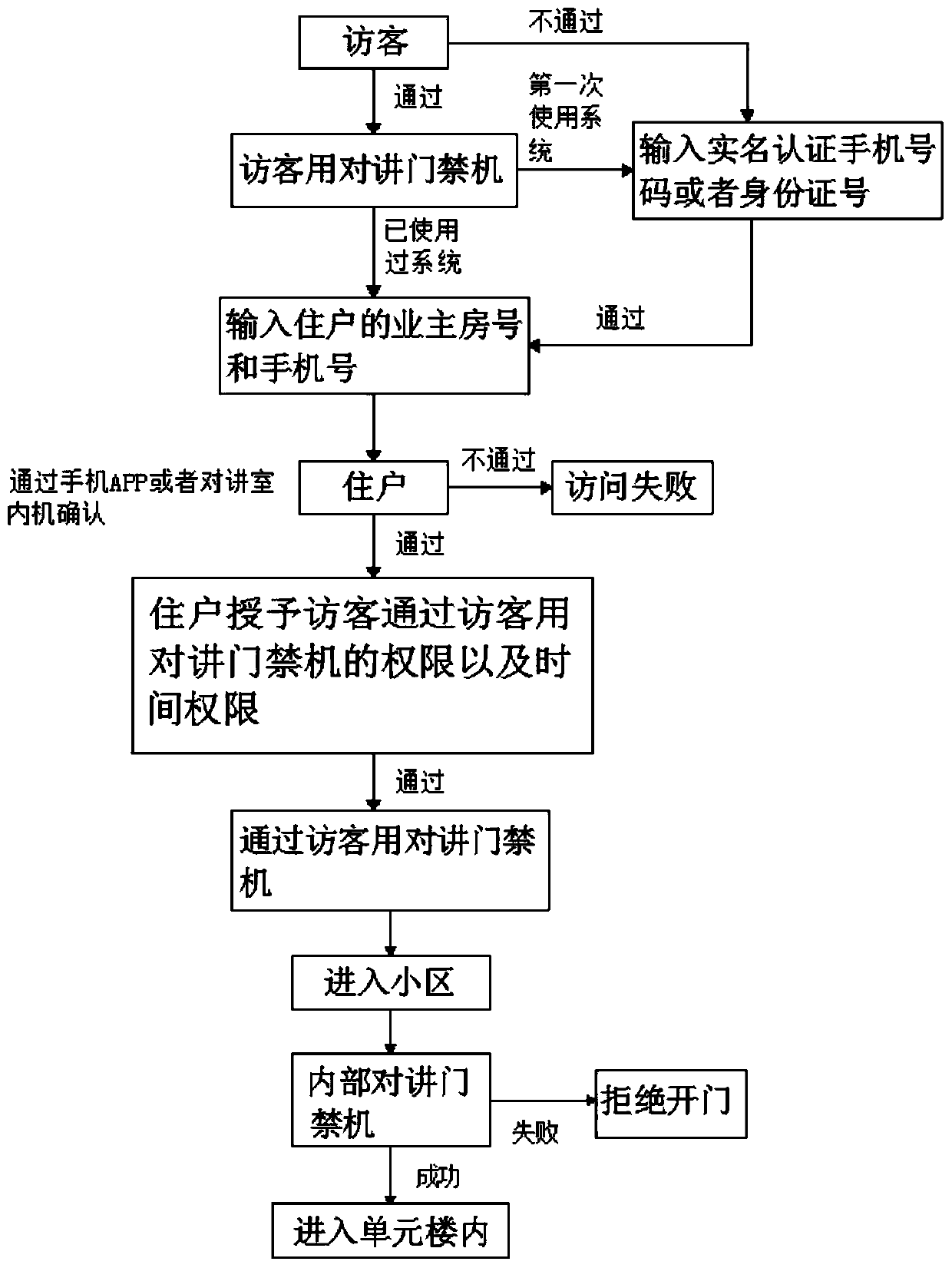
Visitor talkback access control system and use method thereof
InactiveCN110675534AValid confirmationAccurate confirmationIndividual entry/exit registersGuard - securityInternet privacy
The invention discloses a visitor talkback access control system and a use method thereof. The system includes a mobile phone APP, a server, a property service end, a talkback indoor machine, an internal talkback access control machine, a peripheral talkback access control machine and a talkback access control machine used by a visitor. According to the system, an identity of the visitor can be effectively confirmed because identity information of the visitor can be accurately confirmed by any of an identity card and a mobile phone number authenticated by a real name, and security is higher; the visitor information can be confirmed by a user and effectively recorded; an identity confirmation process is very simple, manual attendance is not required, massive labor fees are eliminated, and conflicts of manual registration with security staff are avoided; an entire visitor process is simplified, and a process is simple, secure and effective; and one-time authentication has lifelong validity, identity authentication is no longer required once the identity is authenticated in the system without limitation on times and places, and cases where identity authentication of existing systems is only valid currently and locally are completely avoided.
Owner:小控(杭州)科技有限公司
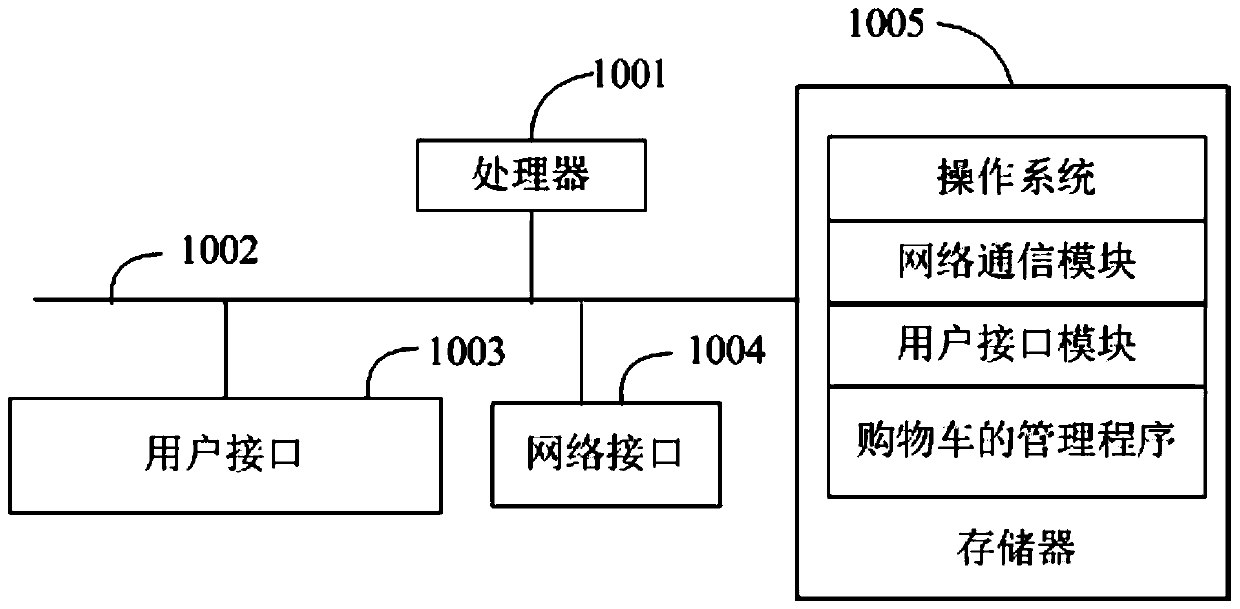
Shopping cart management system, method and equipment and readable storage medium
ActiveCN110555633ASimple and reliable management systemReduce operating costsIndividual entry/exit registersResourcesOperational costsEngineering
The invention relates to the field of smart retail, and discloses a shopping cart management system which comprises a shopping cart body, an intelligent electronic lock and a background server. The intelligent electronic lock is arranged on the shopping cart body and is in wireless connection with the background server; the intelligent electronic lock is provided with a mechanical switch, and after the intelligent electronic lock receives a trigger instruction generated by triggering the mechanical switch, the intelligent electronic lock generates mark information based on the trigger instruction and sends the mark information to the background server; and the background server generates prompt information based on the mark information and sends the prompt information to the correspondingunlocking terminal. The invention further discloses a shopping cart management method and equipment and a readable storage medium. The management system of the shopping carts is simple and reliable, the operation cost of the shopping carts is greatly saved, the shopping carts which are not returned in place cannot be missed as soon as the shopping carts are found by shopping mall workers, customers are automatically reminded and informed of non-return records, and the manpower communication cost is effectively saved.
Owner:WEBANK (CHINA)
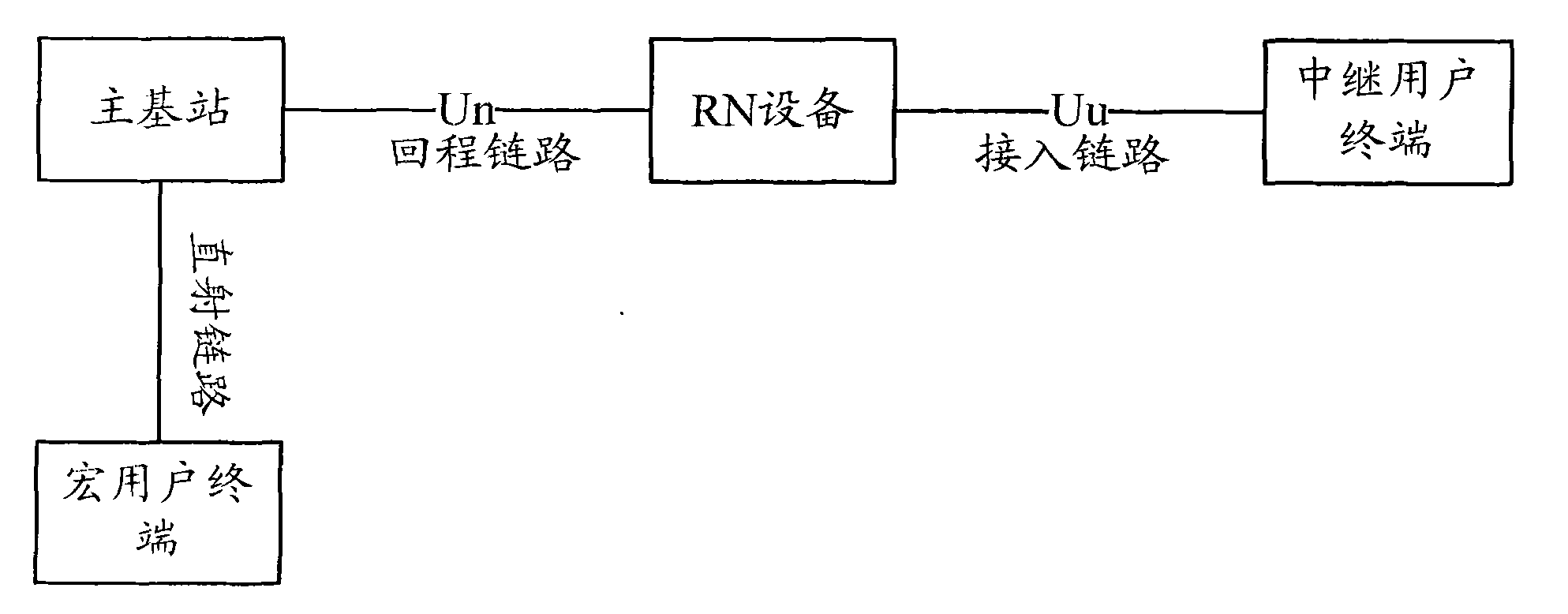
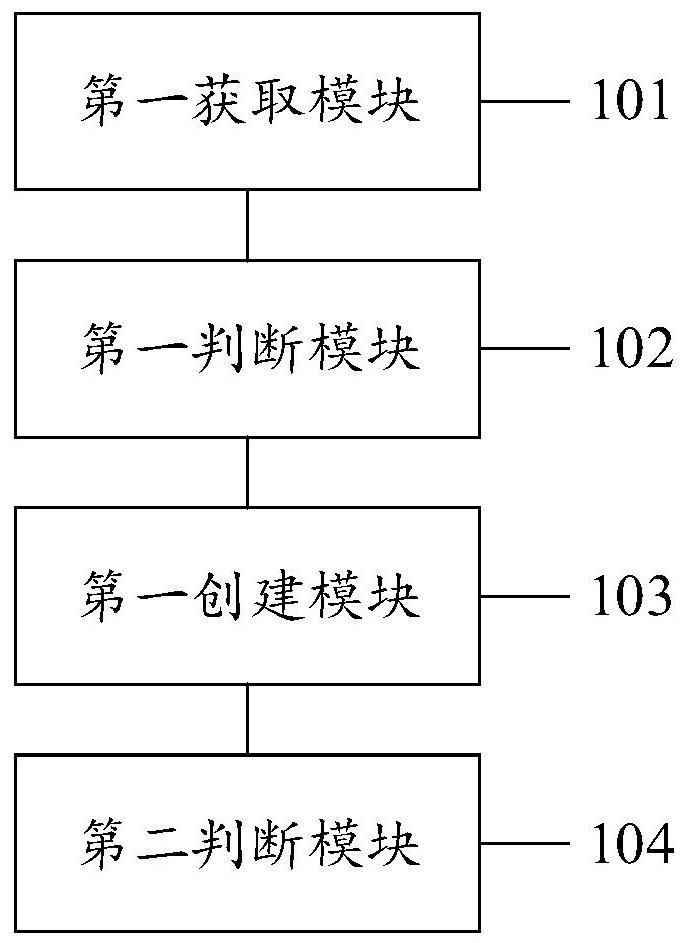
Method, system and equipment for allocating and determining cell identifiers
ActiveCN102378187AReduce the burden onAvoid conflict situationsNetwork planningNetwork data managementSystem maintenanceUser identifier
The embodiment of the invention relates to the technical field of wireless communication, in particular to a method, a system and equipment for allocating cell identifiers, and is used for solving the problem of increase of the maintenance cost of the system caused by cell identifier collision which possibly occurs during allocation of the cell identifiers to relay-node (RN) equipment in the prior art. The method provided by the embodiment of the invention comprises the following steps that: a base station determines the quantity of the cell identifiers which are required to be allocated to the RN equipment according to cell information which is received from the RN equipment,; the base station allocates the cell identifiers to the RN equipment according to the determined quantity, wherein each cell identifier uniquely identifies a cell; and the base station determines allocation information according to the allocated cell identifiers and sends the allocation information to the RN equipment. By allocating the cell identifiers to the RN equipment by using the base station, the collision of the cell identifiers which are allocated by the RN operation and maintenance (OAM) equipment of different manufacturers is avoided, allocation efficiency is improved, manual operation is avoided, and maintenance cost is reduced.
Owner:DATANG MOBILE COMM EQUIP CO LTD
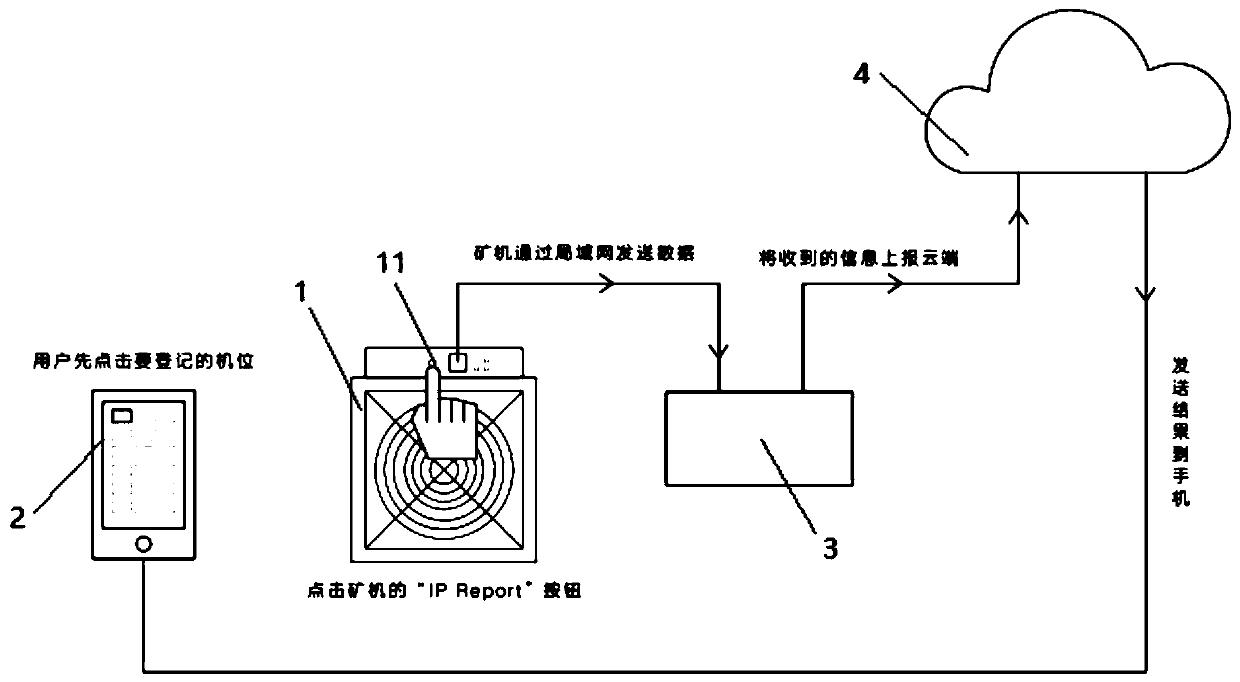
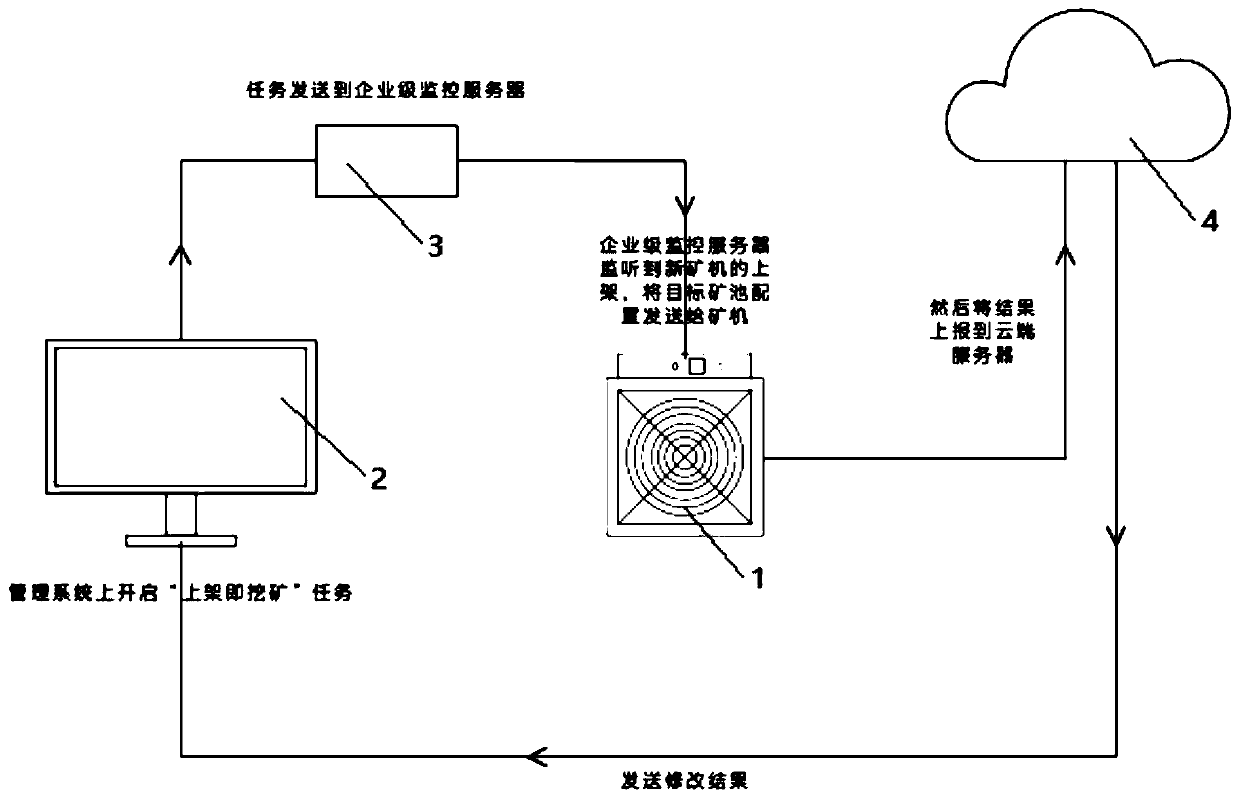
Dynamic network mine field management method and system
InactiveCN110380899AEfficient confirmationSave time and costData switching networksSite managementDynamical network
The invention relates to a dynamic network mine field management method and system. The method comprises: installing a local area network server in a mine field; configuring a target mine pool address; establishing an on-shelf mining task, and planning and monitoring an internet protocol address range; connecting the mine machine to a local area network of a mine field; arranging an ore pond of anore machine, and directly excavating ore; the mining machine sending a broadcast message in a local area network; the local area network server acquiring the broadcast message and uploading information contained in the broadcast message to a cloud server; the cloud server binding the information contained in the received broadcast message with the machine position information; the cloud server sending a binding result to the user terminal; transmitting the mine machine information in the mode that the mine machine publishes the broadcast message in the local area network, binding the mine machine and the machine position in cooperation with the cloud server, directly setting the mine pool configuration through the local area network server. The effect that the mine machine is erected, namely mining, can be achieved, the time cost for arranging the mine machine in a mine field is greatly reduced, and the mine field benefit is improved.
Owner:深圳市精一信息科技有限公司
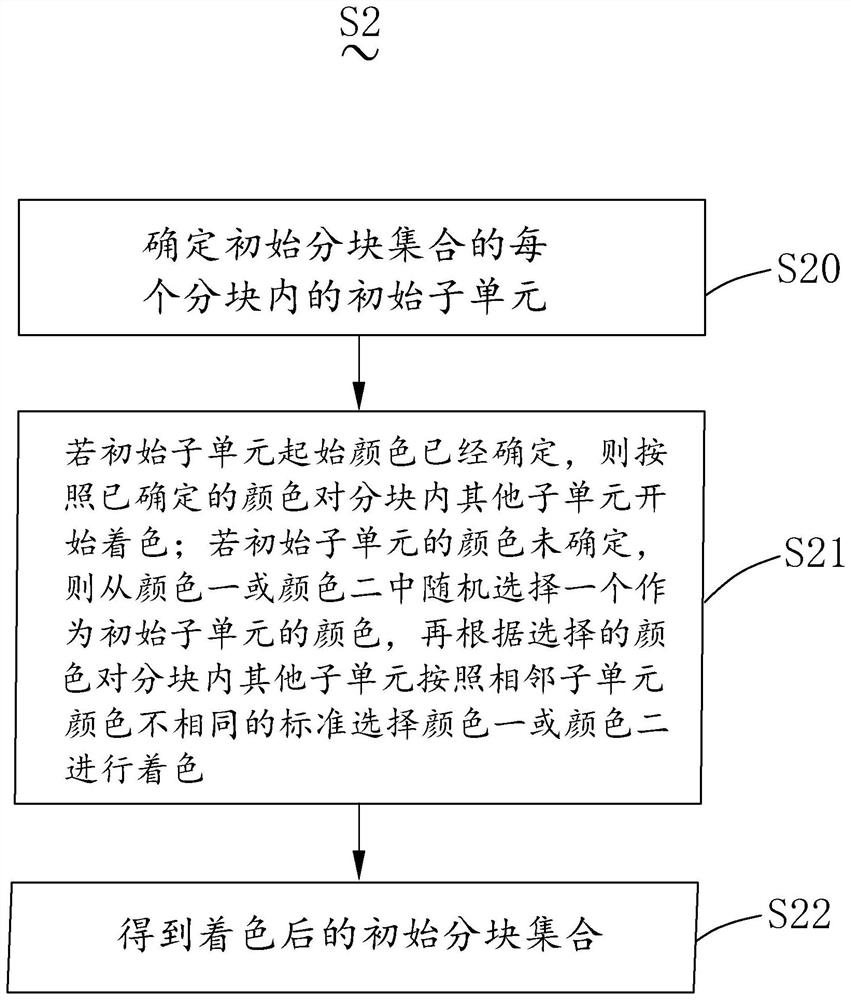
Method and device for solving mask coloring boundary conflict and computer equipment
PendingCN114638189AReduce wasteSave resourcesTexturing/coloringPhotomechanical exposure apparatusGraphicsAlgorithm
The invention relates to the technical field of photoetching, in particular to a method and device for solving coloring boundary conflicts and computer equipment, and the method comprises the following steps: S0, providing an initial mask pattern; the method comprises the steps that S1, an initial mask plate graph is divided into a plurality of blocks, each block comprises a plurality of subunits, and each block comprises an initial subunit and a key subunit; s2, selecting a predetermined area of the initial mask plate graph as an initial block set, the initial block set comprising at least one block, and coloring a subunit of each block in the initial block set through a preset coloring function to obtain a colored initial block set; and S3, coloring other blocks through the coloring function and the key subunit of each block in the initial block set after coloring to obtain a colored mask pattern. According to the method provided by the invention, the efficiency of solving the coloring boundary conflict problem is improved.
Owner:DONGFANG JINGYUAN ELECTRON LTD
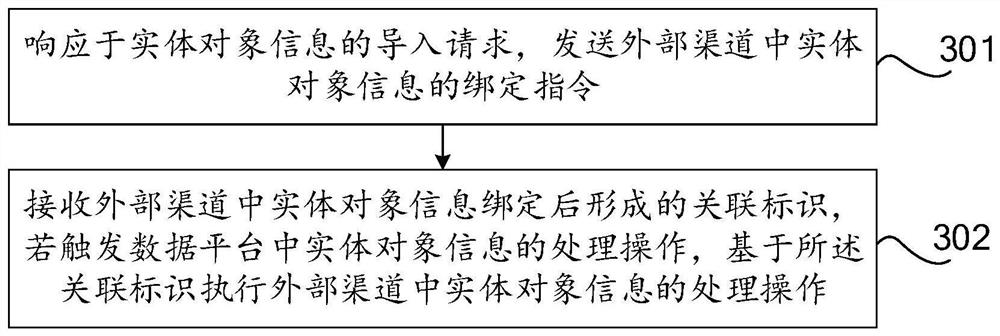
Information binding method, device and equipment
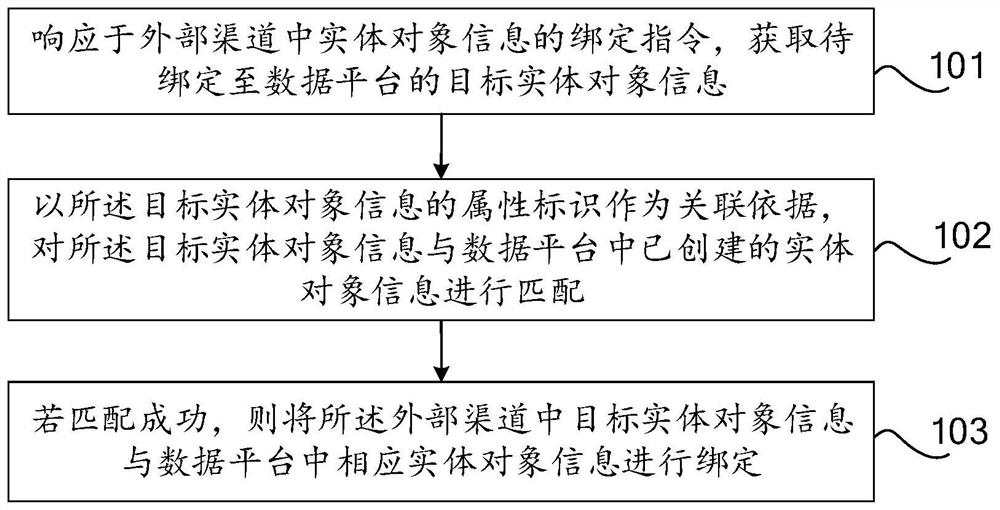
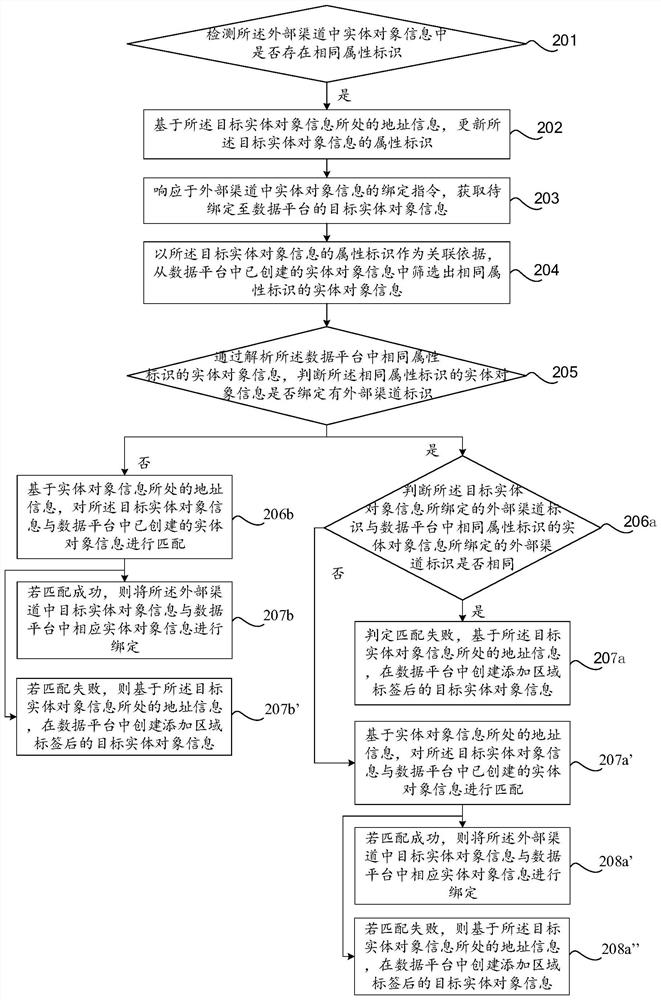
This application discloses an information binding method, device and equipment, which relate to the field of Internet technology, and can match and bind the information of entity objects settled in multiple channels and then import them into the data platform, so that the information of entity objects in the data platform is clear , to achieve efficient management of entity objects. The method includes: responding to the binding instruction of the entity object information in the external channel, obtaining the target entity object information to be bound to the data platform; using the attribute identification of the target entity object information as the association basis, and The information is matched with the created entity object information in the data platform; if the match is successful, the target entity object information in the external channel is bound with the corresponding entity object information in the data platform.
Owner:ZHEJIANG KOUBEI NETWORK TECH CO LTD
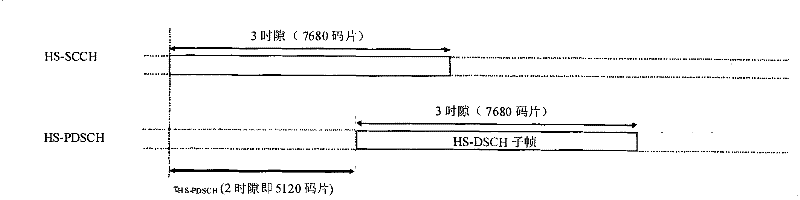
Blind test feedback of time division synchronous code division multiple access system and method for receiving same
ActiveCN101626583BAvoid conflict situationsReduce wasteRadio transmission for post communicationWireless communicationSystem capacityCode division multiple access
The invention relates to a time division synchronous code division multiple access system, and in particular discloses a blind test feedback of the time division synchronous code division multiple access system and a method for receiving the same. The method comprises the following steps that: configuring HS-SICH corresponding to pre-defining resources of the blind test on UE by a network, simultaneously setting the timing sequence relationship of the pre-defining resources and the HS-SICH, thereby avoiding the conflict between the pre-defining resources and the HS-SICH with current configuration, reducing the waste of signaling resources and improving system capacity. The HS-SICH which does not correspond to the HS-SCCH can be configured to correspond to the pre-defining resources of theblind test, or the HS-SICH also corresponds to the HS-SCCH while corresponding to the pre-defining resources of the blind test, the HS-SCCH is given up for scheduling, and the physical resources of the HS-SCCH given up is used for sending other data except the HS-SCCH.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
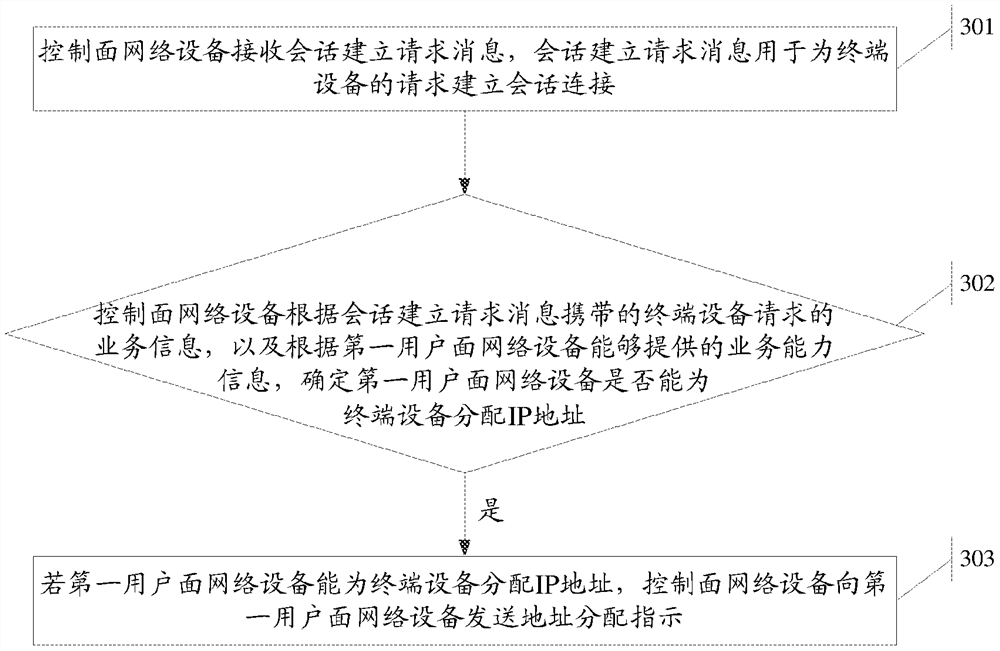
A method and device for allocating IP addresses
ActiveCN108476549BAvoid conflict situationsAssess restrictionConnection managementIp addressTerminal equipment
An IP address allocation method and device, used to solve the technical problem of IP address conflict caused when a control plane device and a user plane device assign an IP address to a UE at the same time; when the control plane network device receives a session establishment request message, it can determine the first Whether a user plane network device is capable of allocating an IP address for a terminal device, and if the first user plane network device is capable of allocating an IP address for a terminal device, the control plane network device may send an address allocation instruction to the first user plane network device, so that It can be clear which device is to allocate the IP address, avoiding two devices to allocate an IP address to a terminal device at the same time, thereby avoiding the situation of IP address conflict.
Owner:HUAWEI TECH CO LTD
Medium/media access control address conflict detection method, device and system
ActiveCN102333134BAvoid conflict situationsEasy accessData switching networksMulticast addressNetwork attack
The invention provides a medium / media access control (MAC) address conflict detection method, which comprises that: before accessing a network, local network equipment transmits a MAC address conflict detection request message to a destination multicast address, wherein the request message carries a current MAC address of the network equipment; destination network equipment receiving the request message extracts the MAC address from the message request, detects the MAC address, and when judging that the extracted MAC address is the same as own MAC address, transmits a MAC address conflict detection response message to a requesting multicast address; and the local network equipment receiving the response message generates a new MAC address. The invention also discloses a MAC address conflict detection device and a MAC address conflict detection system. By the method, the device and the system, the occurrence of MAC address conflicts can be effectively avoided, the network equipment can be ensured to access the network normally, normal network service can be provided for a user, and risks in network attacks can be reduced.
Owner:ZTE CORP
A method and device for network dedicated line connection
The embodiment of the present invention provides a method and device for connecting a dedicated network line. The method includes: connecting the outgoing network dedicated line to the connection port of the server, and creating a dedicated network namespace for the outgoing network dedicated line ; Create a pair of virtual network cards, including a first virtual network card and a second virtual network card, for mapping the network namespace from the network dedicated line of the receiving party to the network dedicated line of the receiving party, and adding the first virtual network card to The virtual network of the network namespace; creating a first virtual network bridge for bridging the port and the second virtual network card, and determining the second virtual network bridge of the server; based on the first virtual network The bridge and the second virtual network bridge add the network namespace to the private line of the access party through the first virtual network card. The present invention not only avoids the occurrence of network address conflicts, but also avoids the use of dedicated hardware for connection.
Owner:新浪财经移动网络科技(北京)有限公司
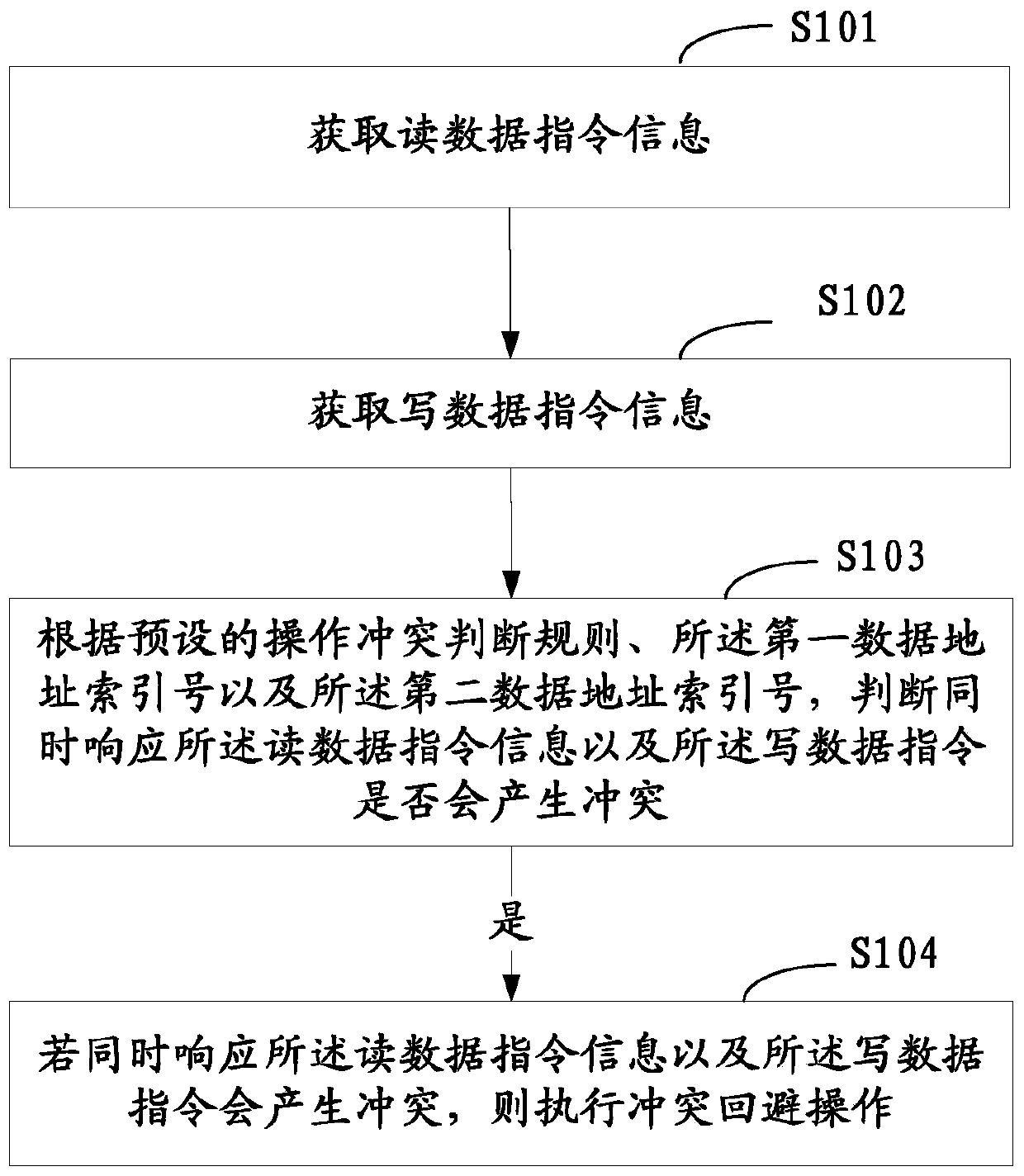
A method and device for reading and writing data
ActiveCN106933512BImprove processing efficiencyAvoid conflict situationsInput/output to record carriersSoftware engineeringInformation acquisition
The invention is applicable to the field of data processing technology and provides a data read-write method and equipment thereof. The method comprises the steps that data reading instruction information is acquired; data writing instruction information is acquired; whether a conflict will be generated when a response is made to the data reading instruction information and the data writing instruction information at the same time is judged according to preset operation conflict judgment rules, a first data address index number and a second data address index number; and if a conflict will be generated when a response is made to the data reading instruction information and the data writing instruction information at the same time, conflict avoiding operation is executed. By acquiring the data address index numbers in the data reading instruction information and the data writing instruction information in two processes, whether a conflict will be caused when a response is made to two instructions at the same time is judged, and therefore the problems that according to an existing computing equipment data processing technology, when read-write operation is performed on the same data region of a shared storage unit in different processes, operation exclusion will occur due to a lack of conflict avoiding rules, much time is wasted for making a new response to relevant read-write operation, and data processing efficiency is lowered are solved.
Owner:SHENZHEN YIHUA COMP +2
Self-learning method and self-learning system of steering wheel buttons
ActiveCN111930247BQuality improvementReduce maintenance costsRedundant data error correctionInput/output processes for data processingHuman–machine interfaceSoftware design
The application relates to a self-learning method and a self-learning system for steering wheel buttons. The vehicle-mounted system realizes the advancement of the self-learning process based on the driver's voice signal transmitted by a voice input device. The in-vehicle system obtains the voltage signal generated by the driver pressing the physical buttons on the steering wheel, so as to bundle and match the short button function and / or long button function with the voltage signal, realizing the custom assignment of button functions. The on-board system avoids conflicts between the voltage signals between the buttons by correcting the button data. The self-learning method and self-learning system of the steering wheel buttons involved in this application unifies the differences of the steering wheels of all models, does not need to do differentiated software design for different models, and simplifies the design of the man-machine interface at the same time, making the steering wheel self-learning It can adapt to the needs of different models and different users, which improves the quality of the software and reduces the cost of the software.
Owner:宁波均胜新能源汽车技术有限公司 +1
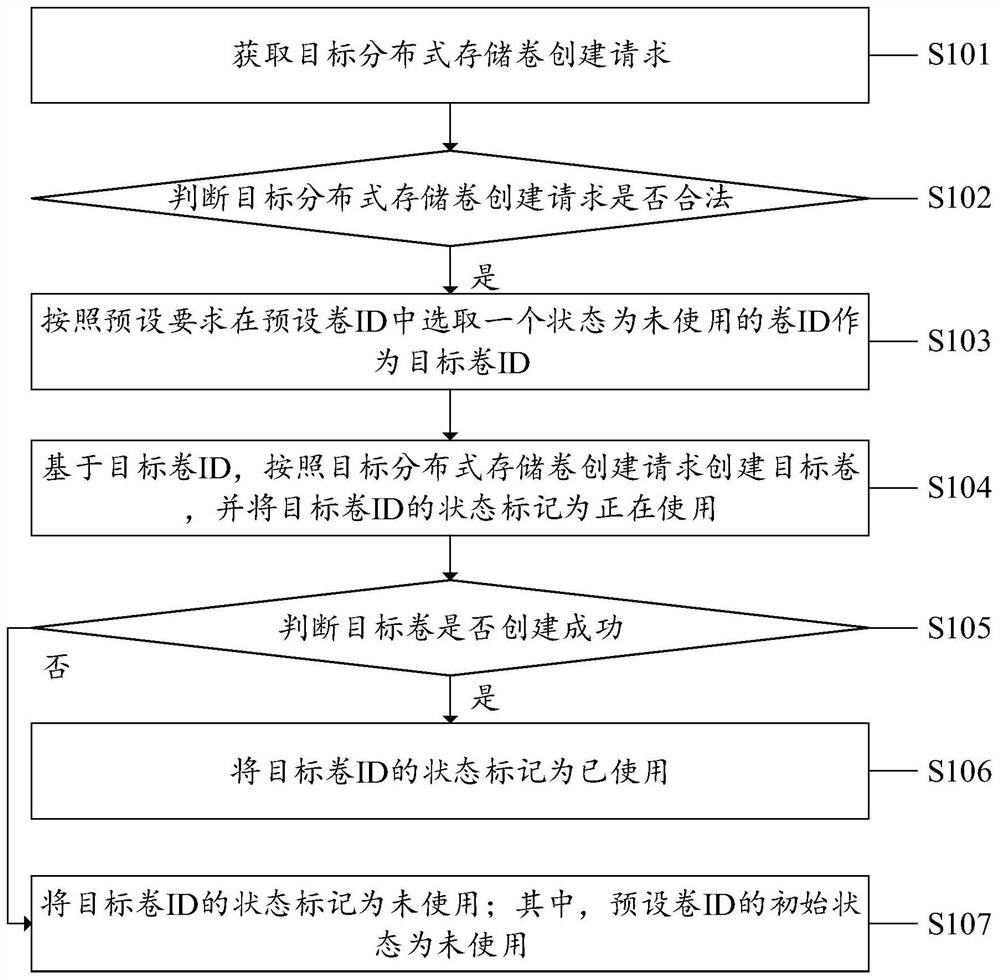
Distributed storage volume creation method, system and device and computer medium
ActiveCN111880742AIncrease success rateAvoid multiple use casesInput/output to record carriersDigital data information retrievalComputer hardwareTarget distribution
The invention discloses a distributed storage volume creation method, system and device and a computer medium. The method comprises the steps: obtaining a target distributed storage volume creation request; judging whether the target distributed storage volume creation request is legal or not; if the target distributed storage volume creation request is legal, selecting a volume ID in an unused state from preset volume IDs as a target volume ID according to a preset requirement; based on the target volume ID, creating a target volume according to the target distributed storage volume creationrequest, and marking the state of the target volume ID as an in-use state; judging whether the target volume is successfully created or not, and if the target volume is successfully created, marking the state of the target volume ID as a used state; if the target volume fails to be created, marking the state of the target volume ID as an unused state, wherein the initial state of the preset volumeID is unused. According to the volume creation method and device, the unused state, the in-use state and the used state are set for each volume ID, so the volume ID conflict condition is avoided, andthe volume creation success rate can be increased.
Owner:北京浪潮数据技术有限公司
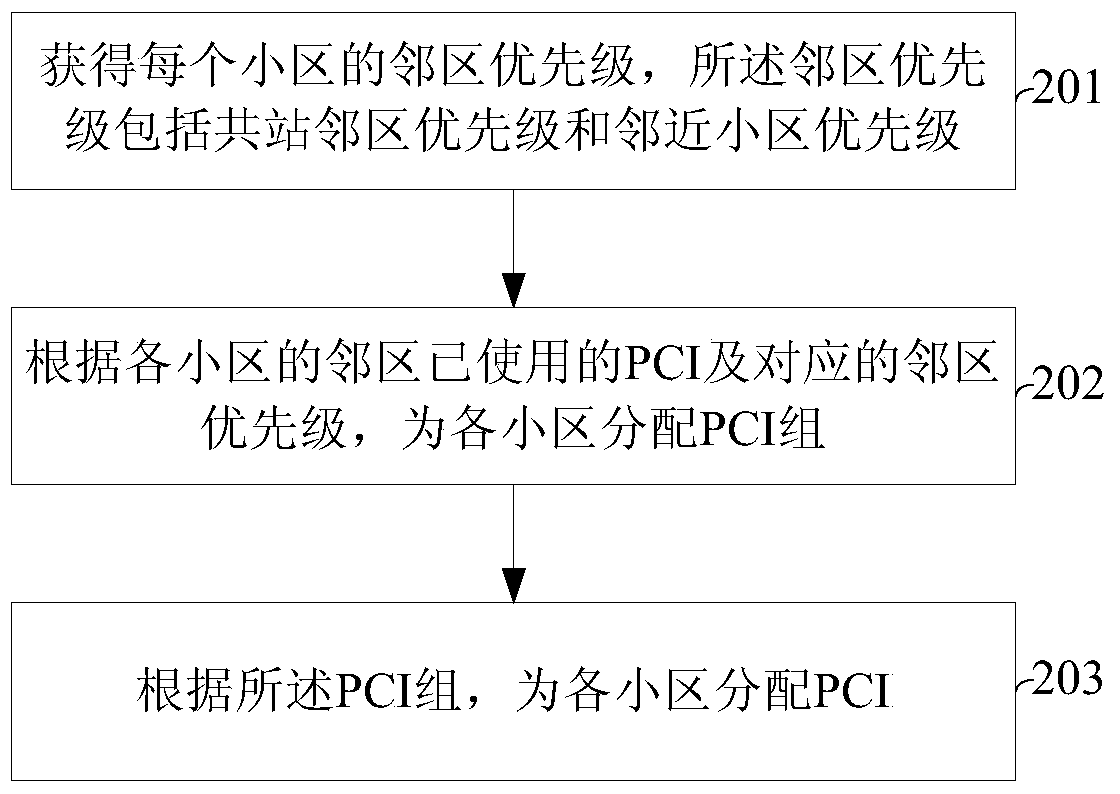
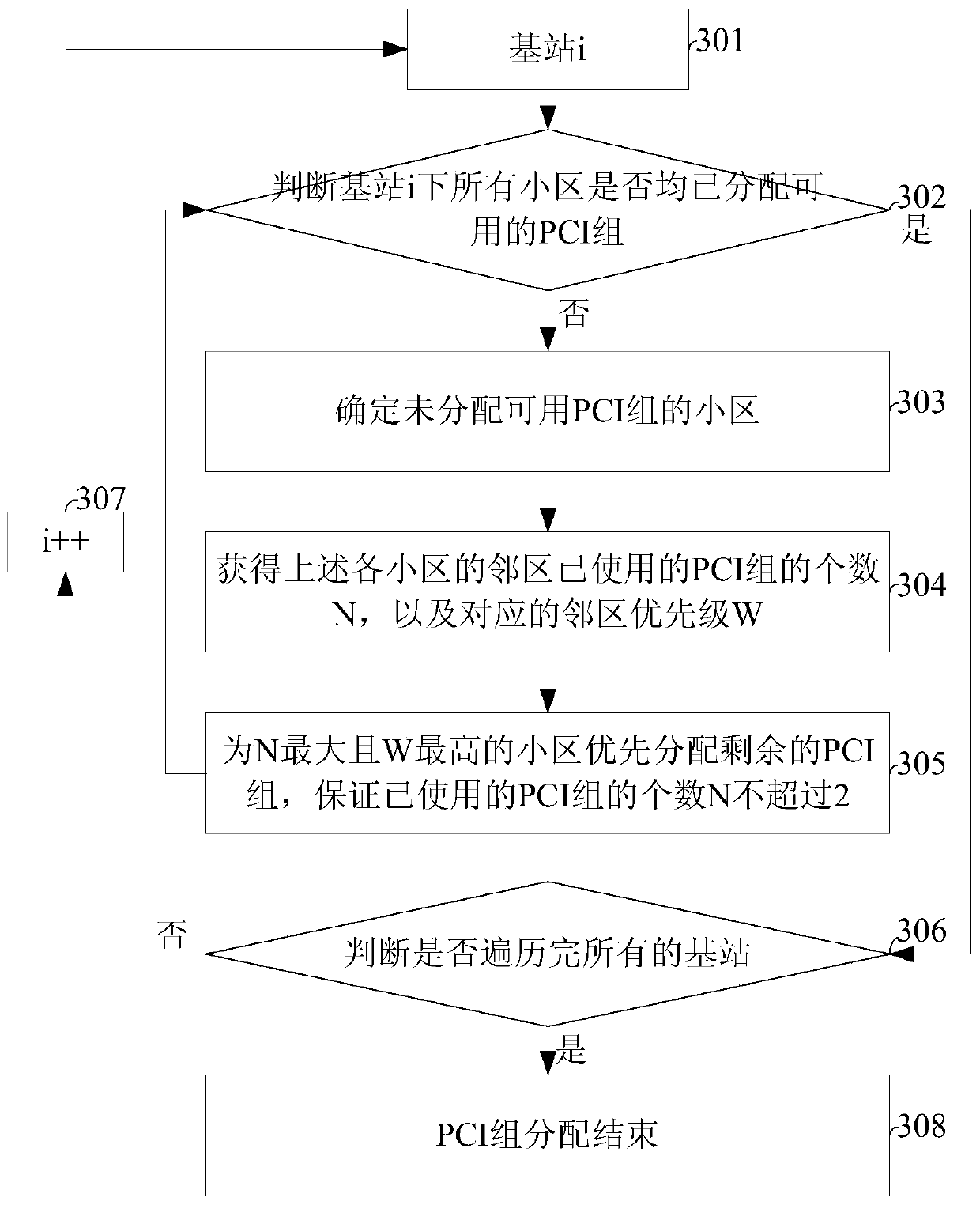
PCI planning method and device for multiple co-sited sectors
ActiveCN105992227BAvoid PCI Conflict SituationsAvoid conflict situationsNetwork traffic/resource managementNetwork planningComputer sciencePlanning method
The invention provides a PCI planning method for a plurality of co-site sectors. The method comprises the steps of acquiring the neighboring cell priorities of each cell, wherein the neighboring cell priorities are composed of a co-site neighboring cell priority and a neighboring cell priority; according to physical cell identifiers (PCI) adopted in the neighboring cells of each cell and the neighboring cell priorities, allocating a PCI set to each cell; according to the above PCI set, allocating PCIs to each cell. The invention also provides a PCI planning device for the plurality of co-site sectors. The device comprises a priority calculation module, a PCI set allocation module and a PCI allocation module. According to the technical scheme of the invention, the PCI conflicting phenomenon among a plurality of co-site sectors can be effectively avoided. Therefore, the method and the device can be applied to the PCI planning of various systems.
Owner:POTEVIO INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com