Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
185 results about "Pre-shared key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a pre-shared key (PSK) is a shared secret which was previously shared between the two parties using some secure channel before it needs to be used.
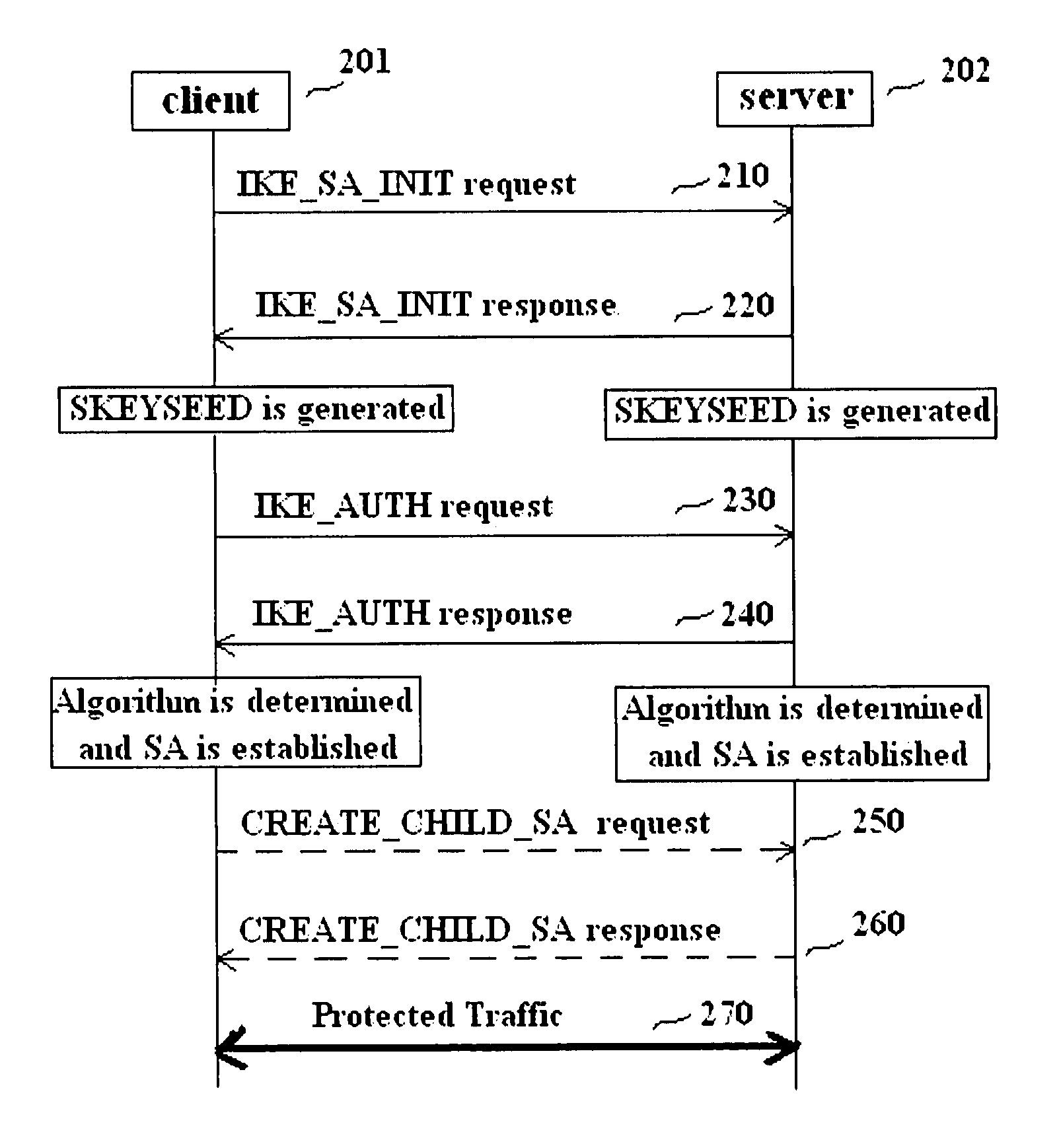
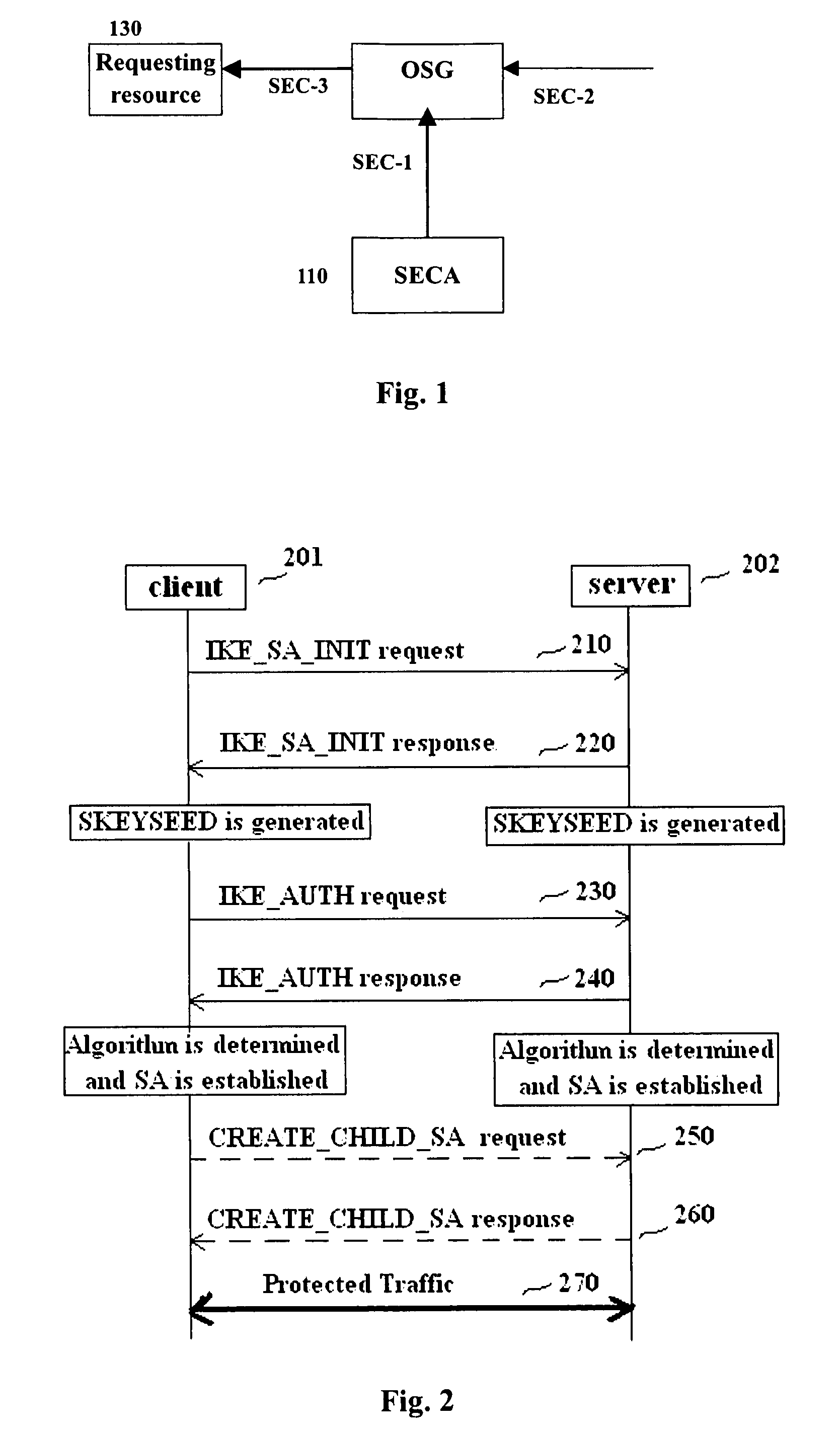
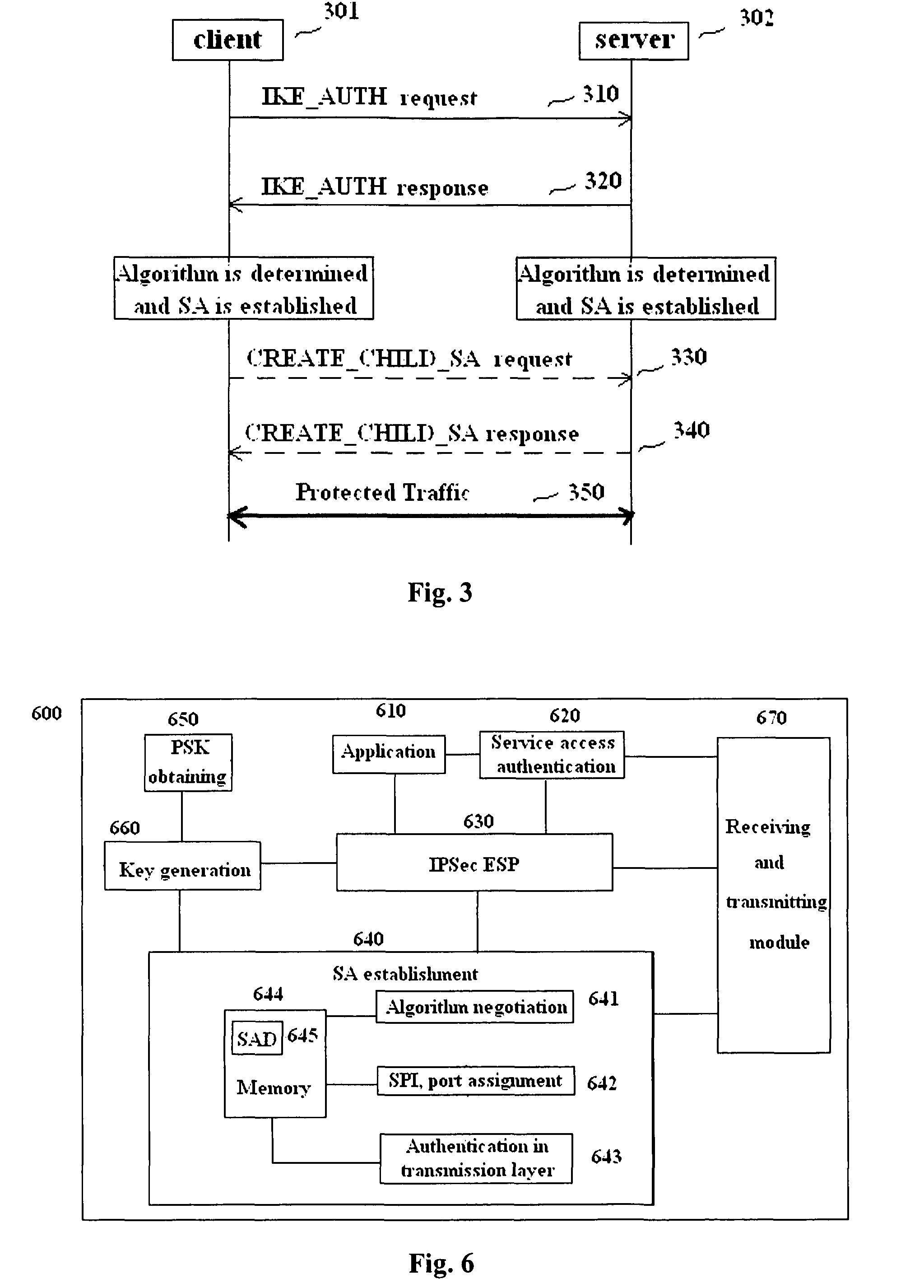
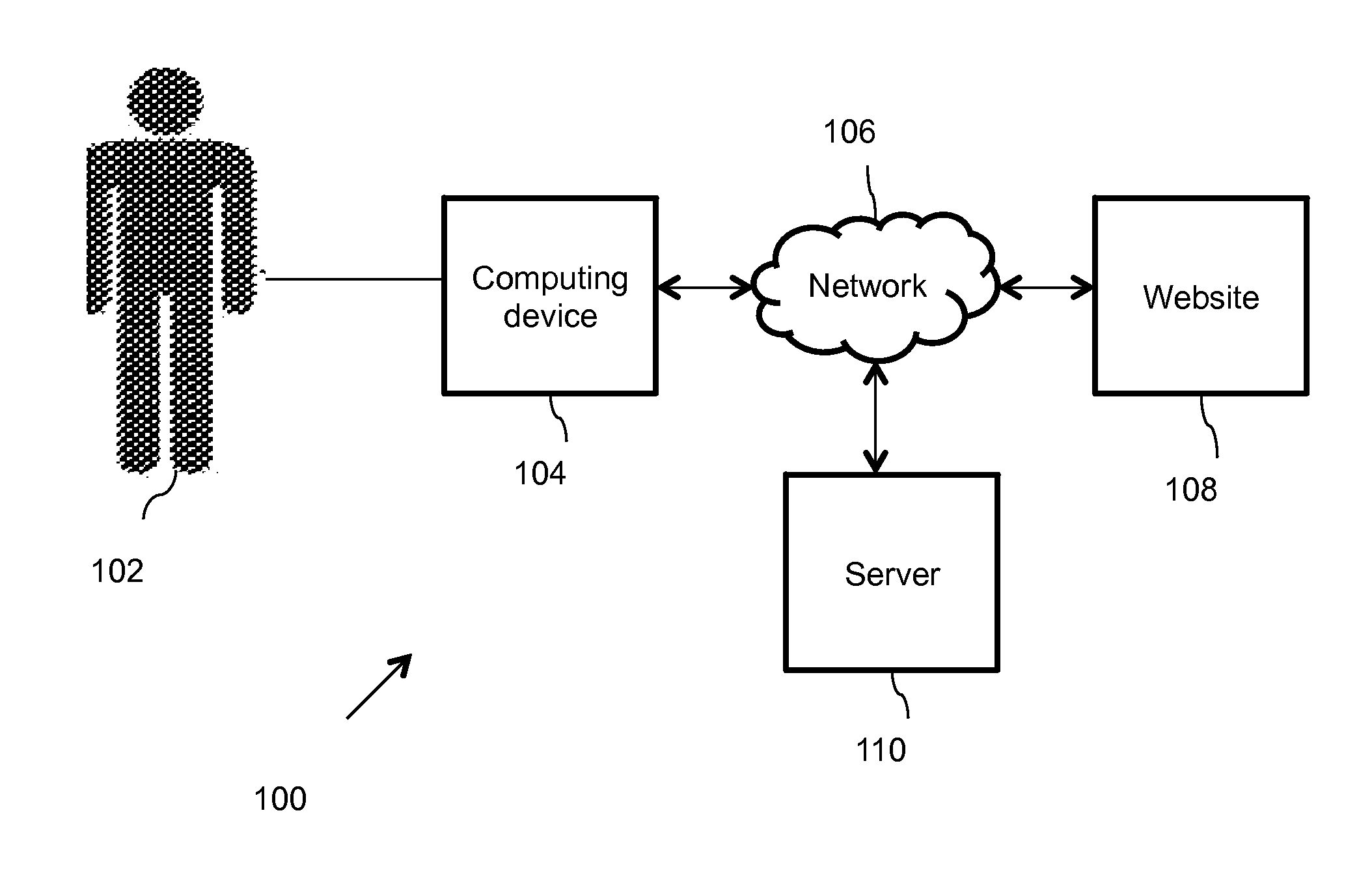
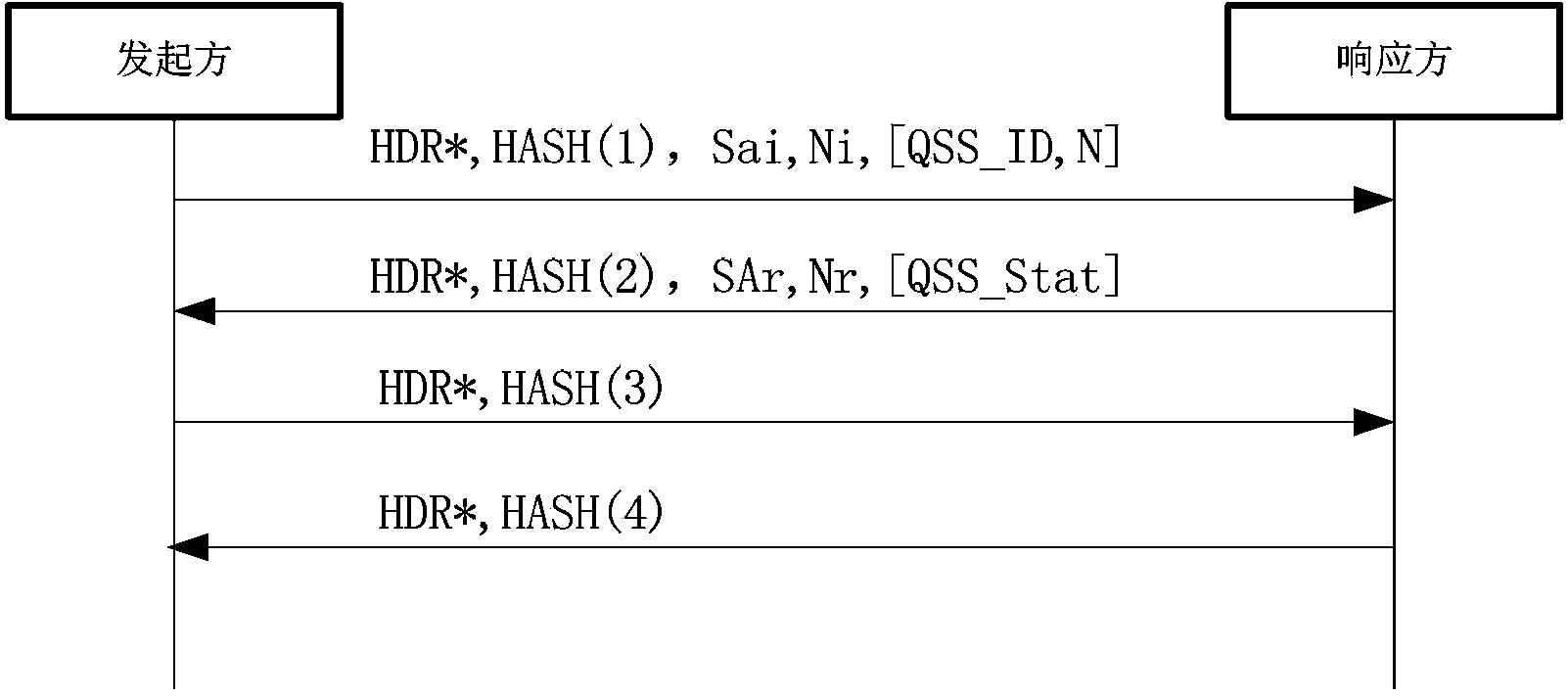
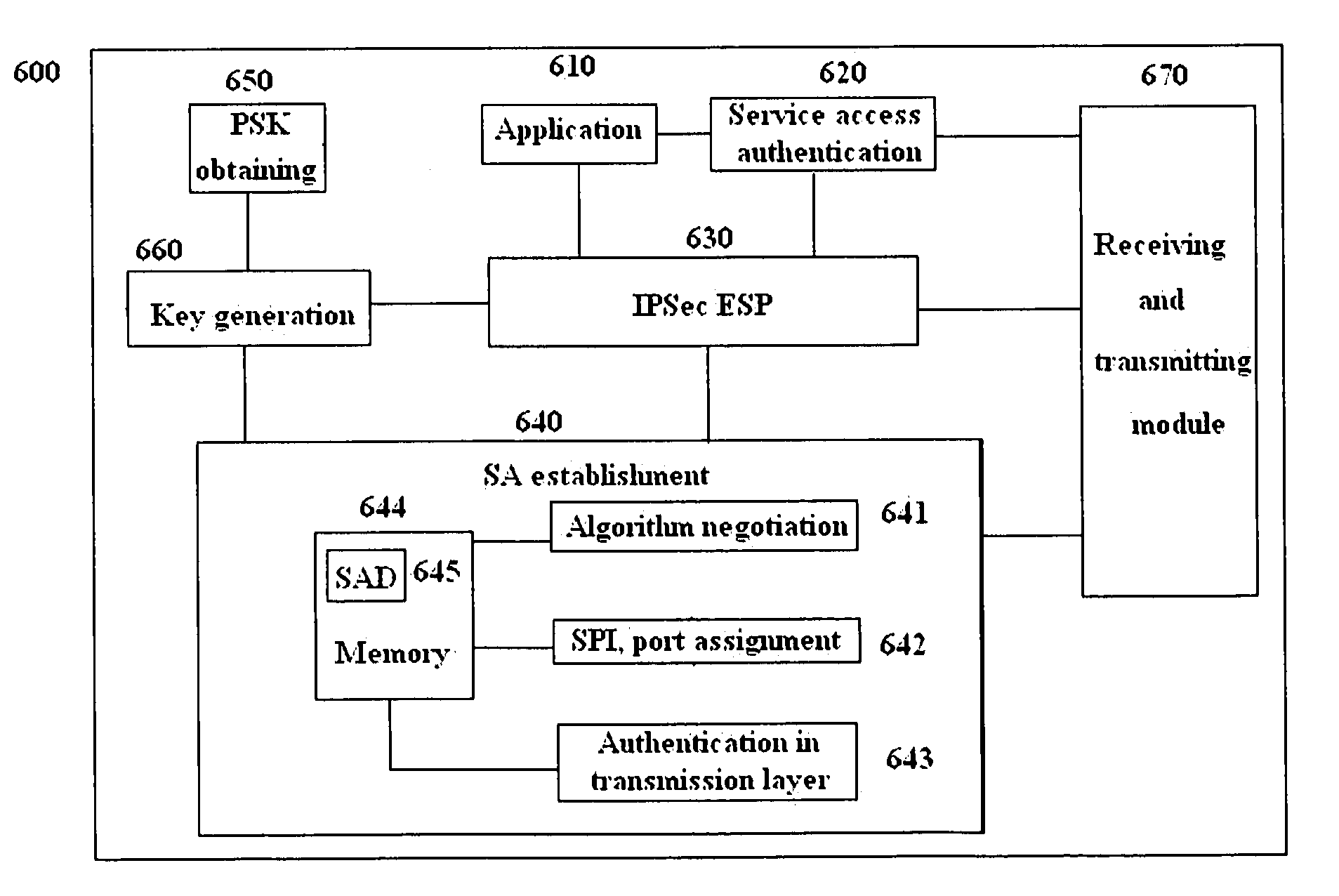
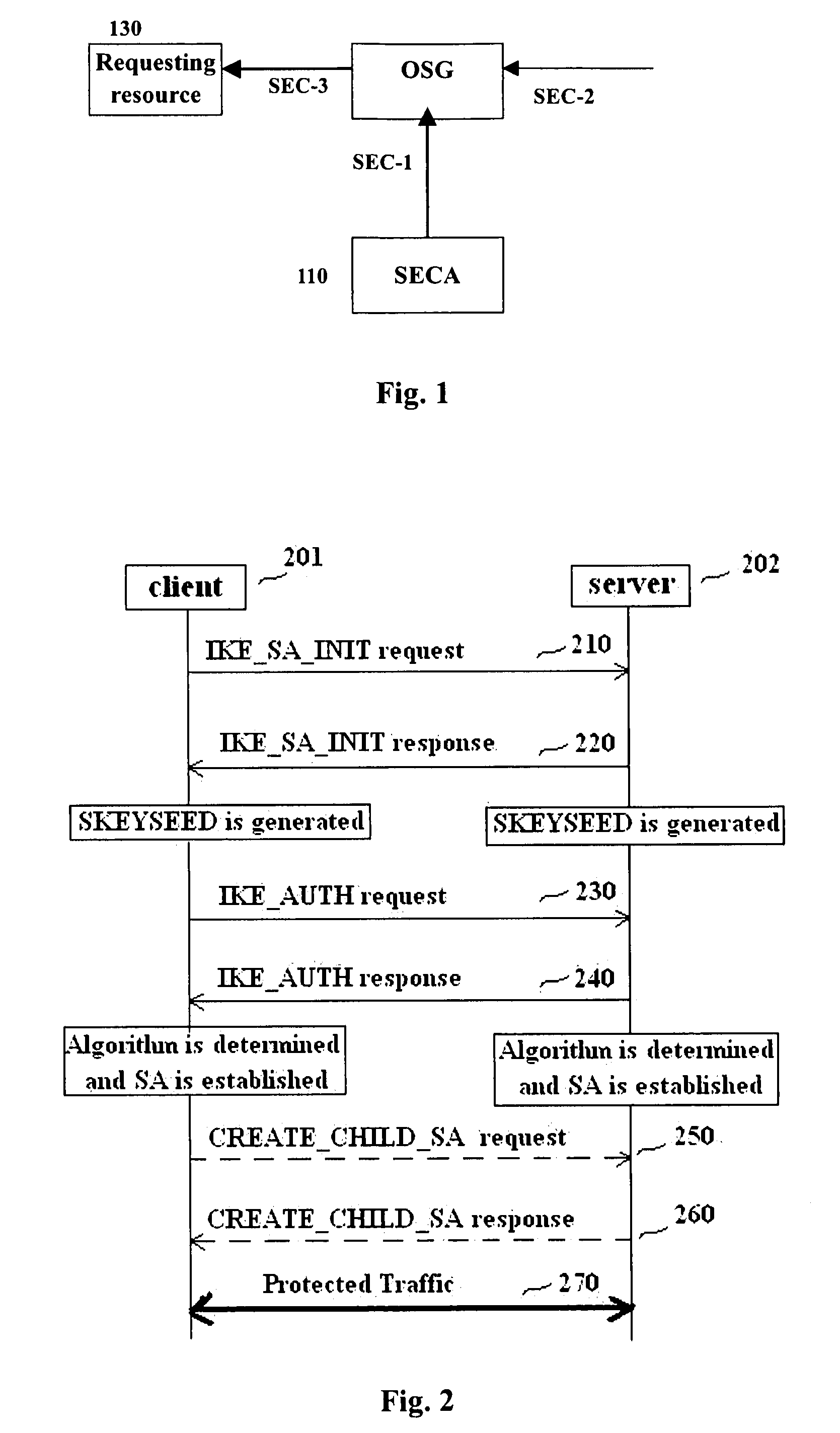
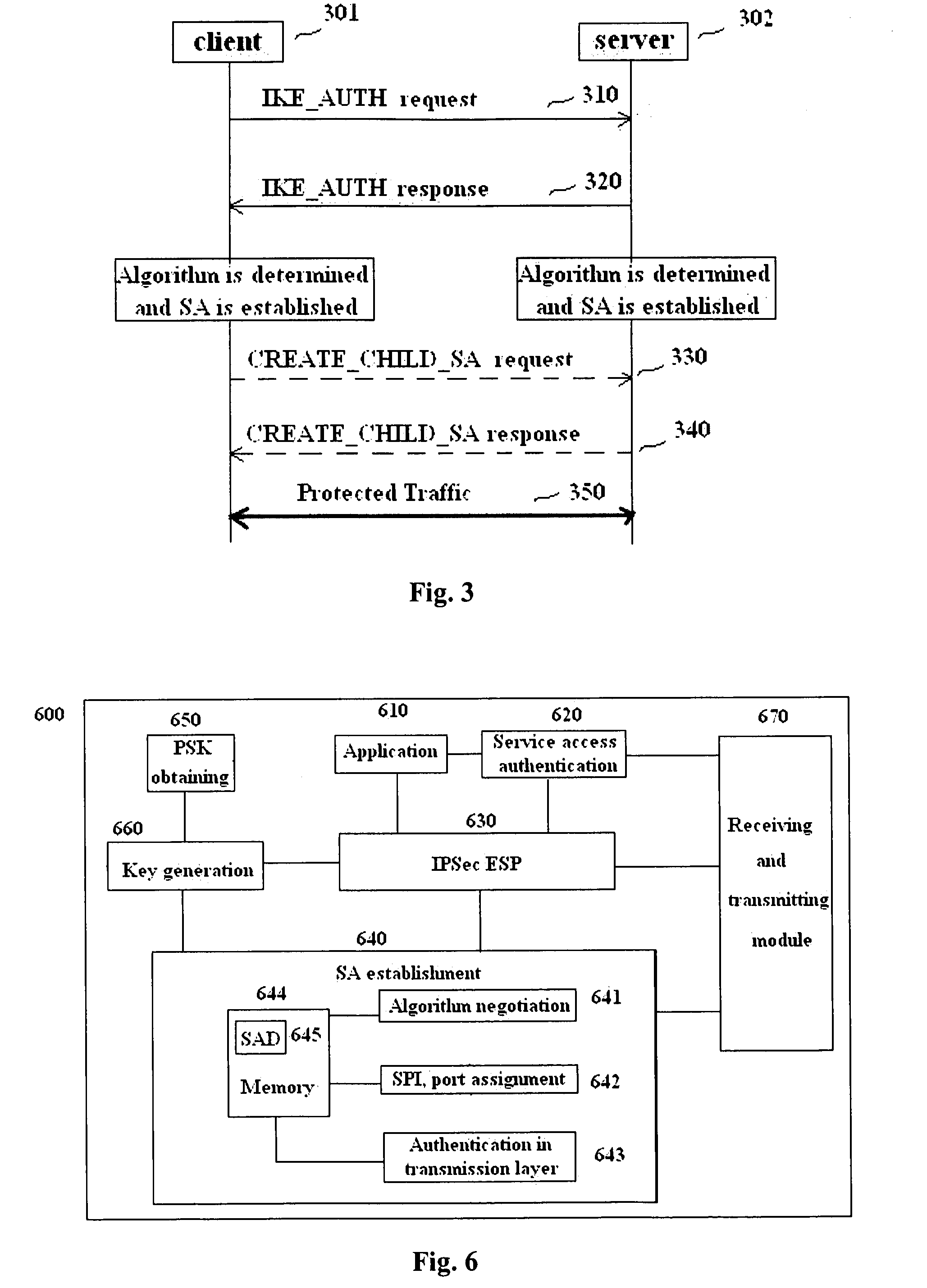
Methods and entities using IPSec ESP to support security functionality for UDP-based traffic
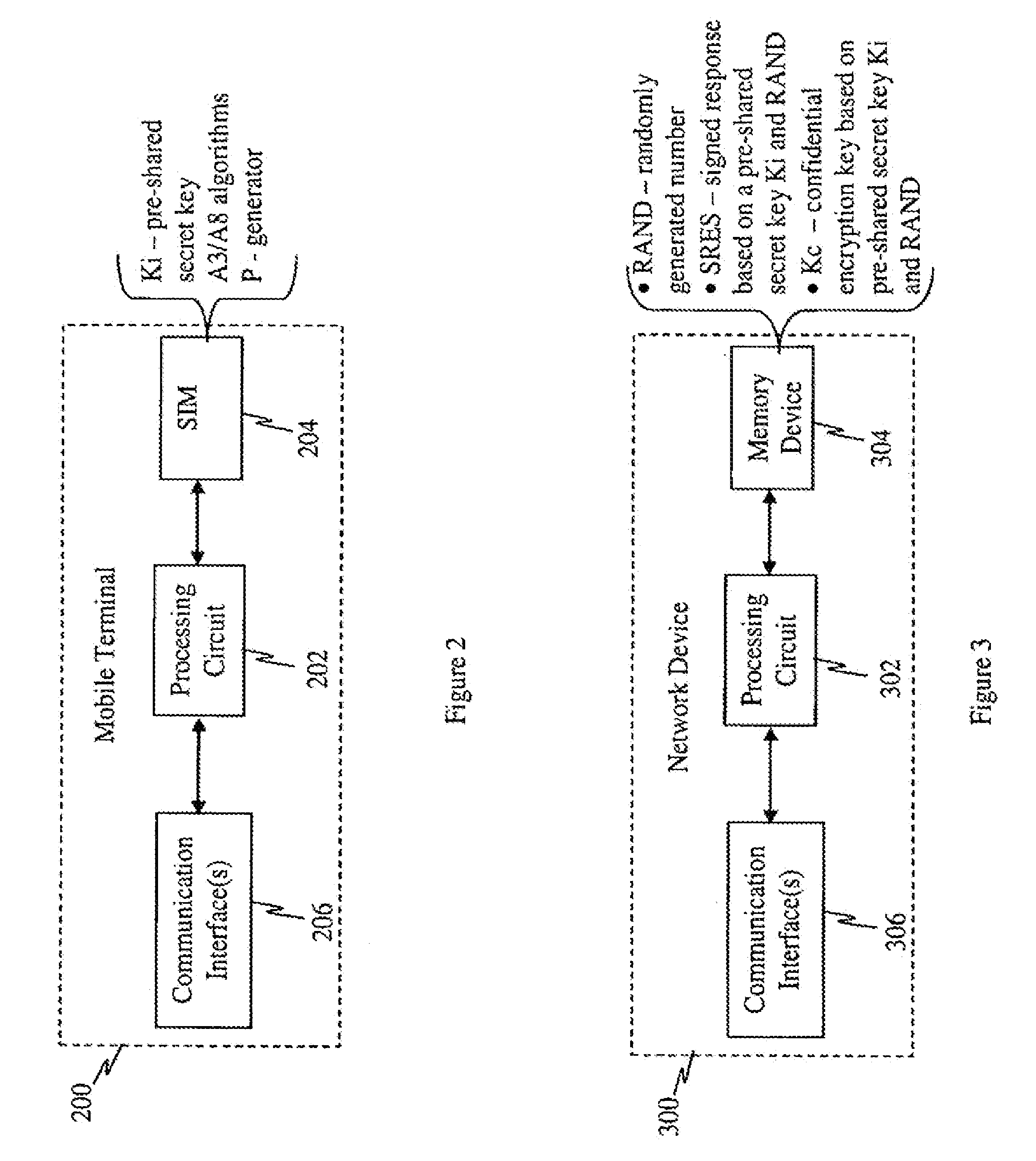
ActiveUS8639936B2Improve efficiencyOptimize procedureUser identity/authority verificationComputer security arrangementsTraffic capacityIPsec
Owner:ALCATEL LUCENT SAS
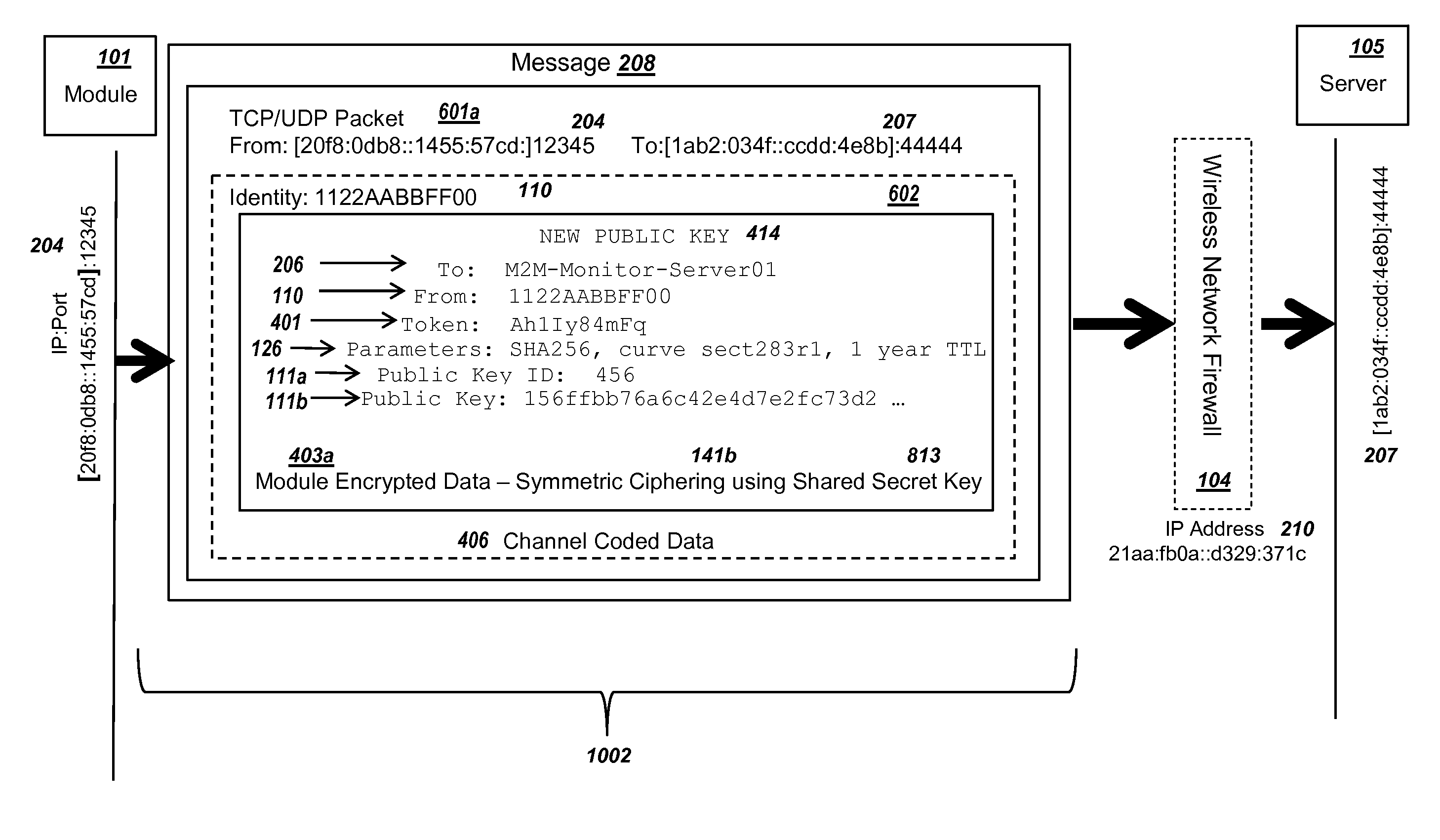
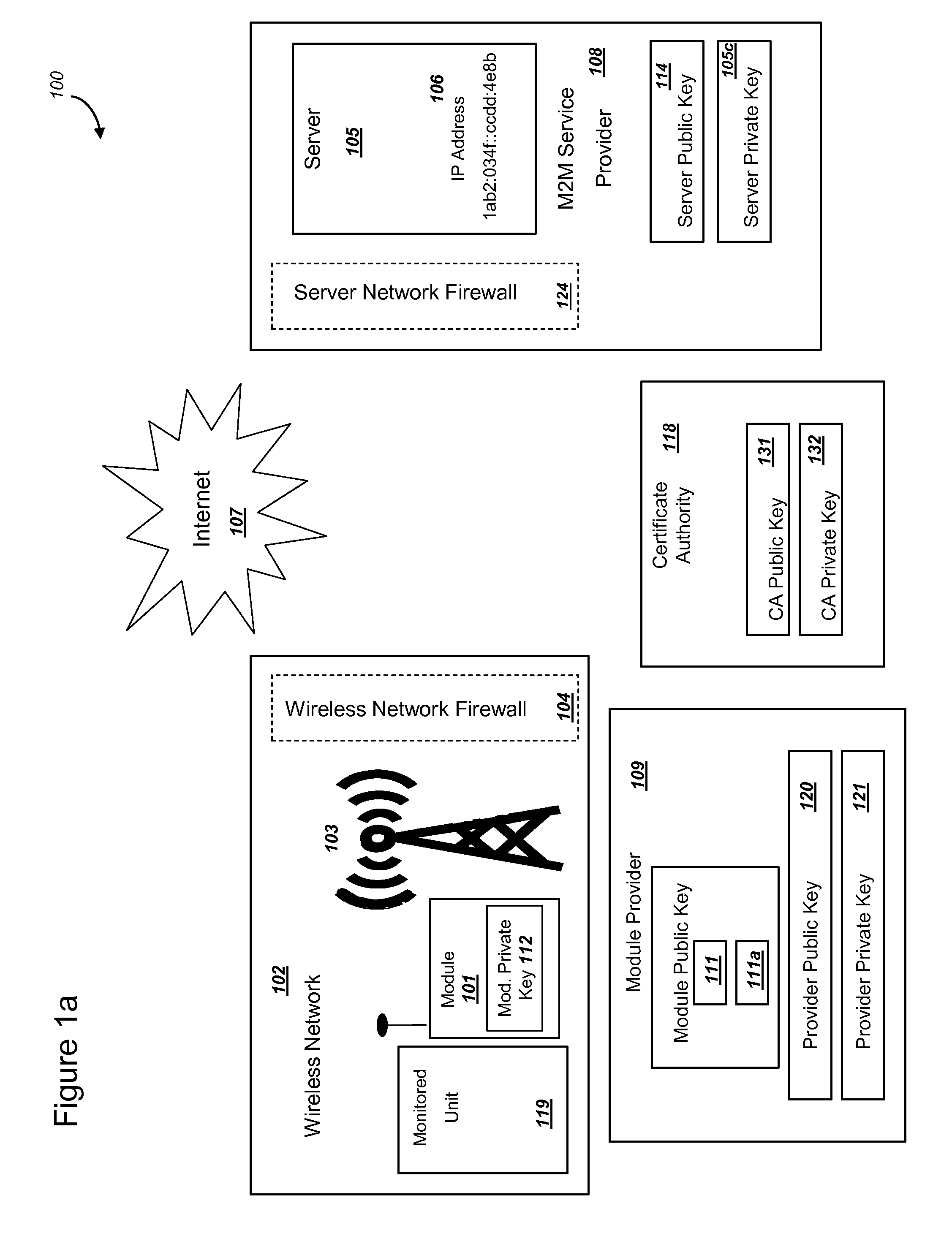
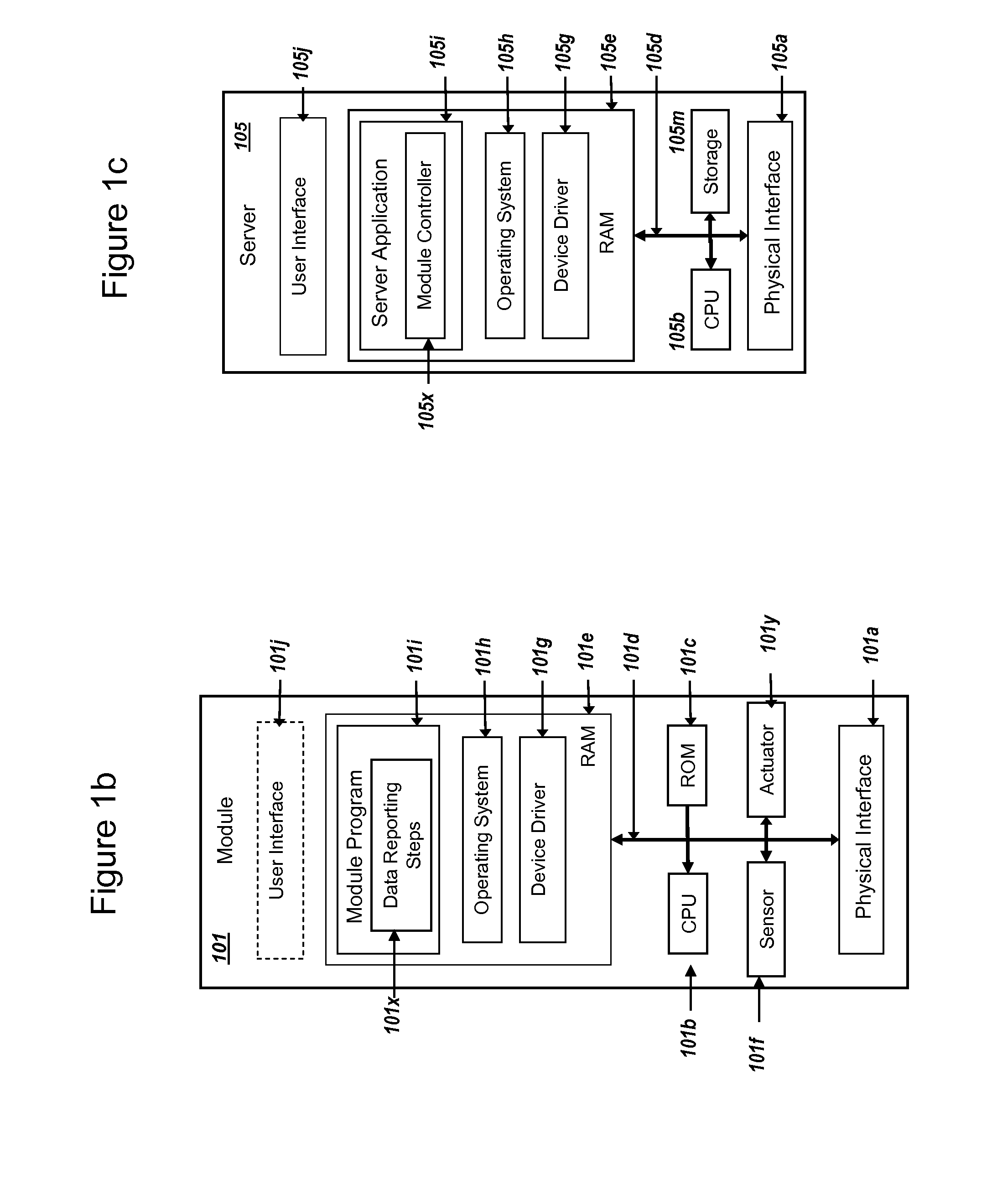
Secure PKI Communications for "Machine-to-Machine" Modules, including Key Derivation by Modules and Authenticating Public Keys
ActiveUS20150095648A1Extend battery lifeImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareDigital signature
Methods and systems are provided for efficient and secure “Machine-to-Machine” (M2M) between modules and servers. A module can communicate with a server by accessing the Internet, and the module can include a sensor and / or actuator. The module and server can utilize public key infrastructure (PKI) such as public keys to encrypt messages. The module and server can use private keys to generate digital signatures for datagrams sent and decrypt messages received. The module can internally derive pairs of private / public keys using cryptographic algorithms and a set of parameters. A server can use a shared secret key to authenticate the submission of derived public keys with an associated module identity. For the very first submission of a public key derived the module, the shared secret key can comprise a pre-shared secret key which can be loaded into the module using a pre-shared secret key code.
Owner:NETWORK 1 TECH +1
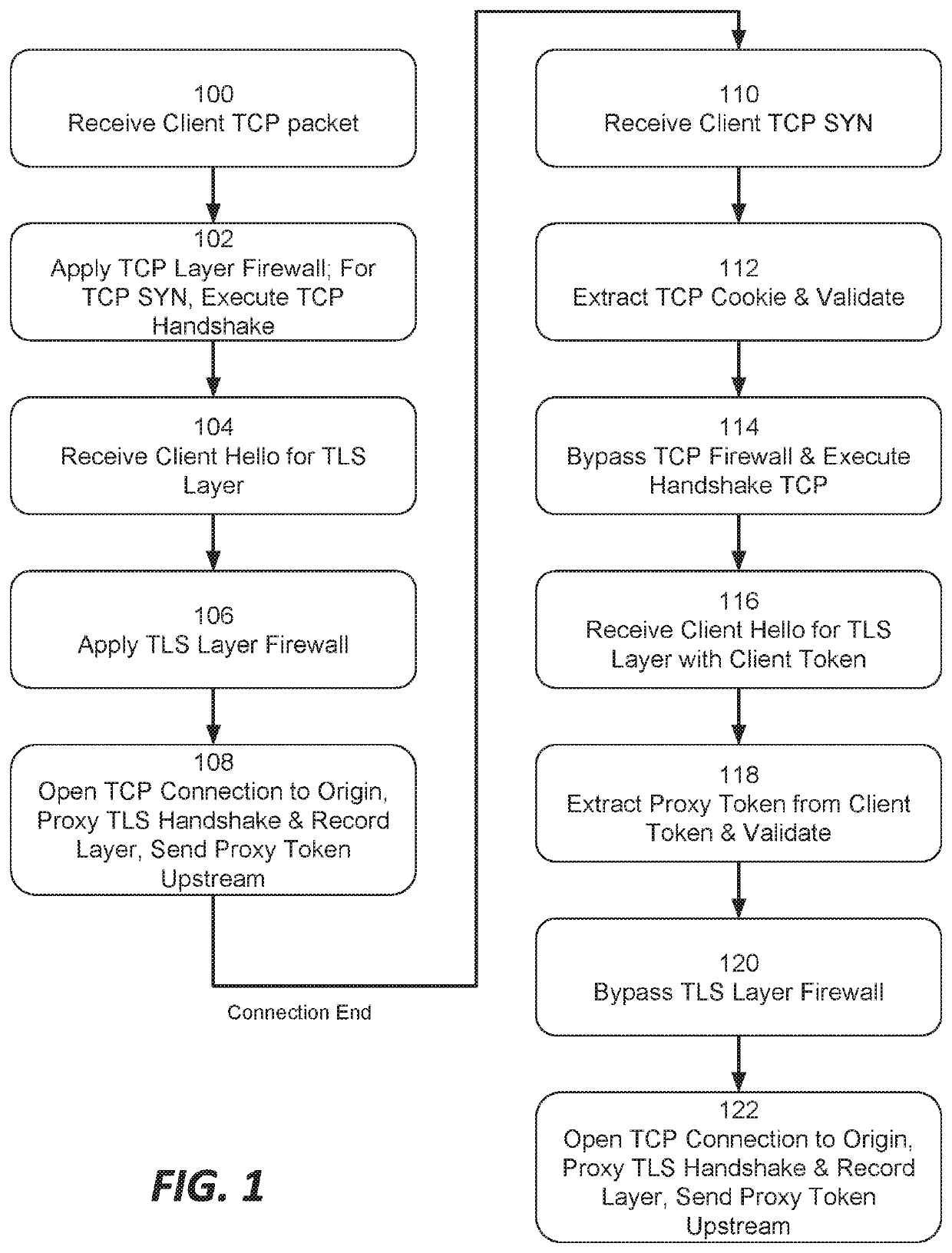
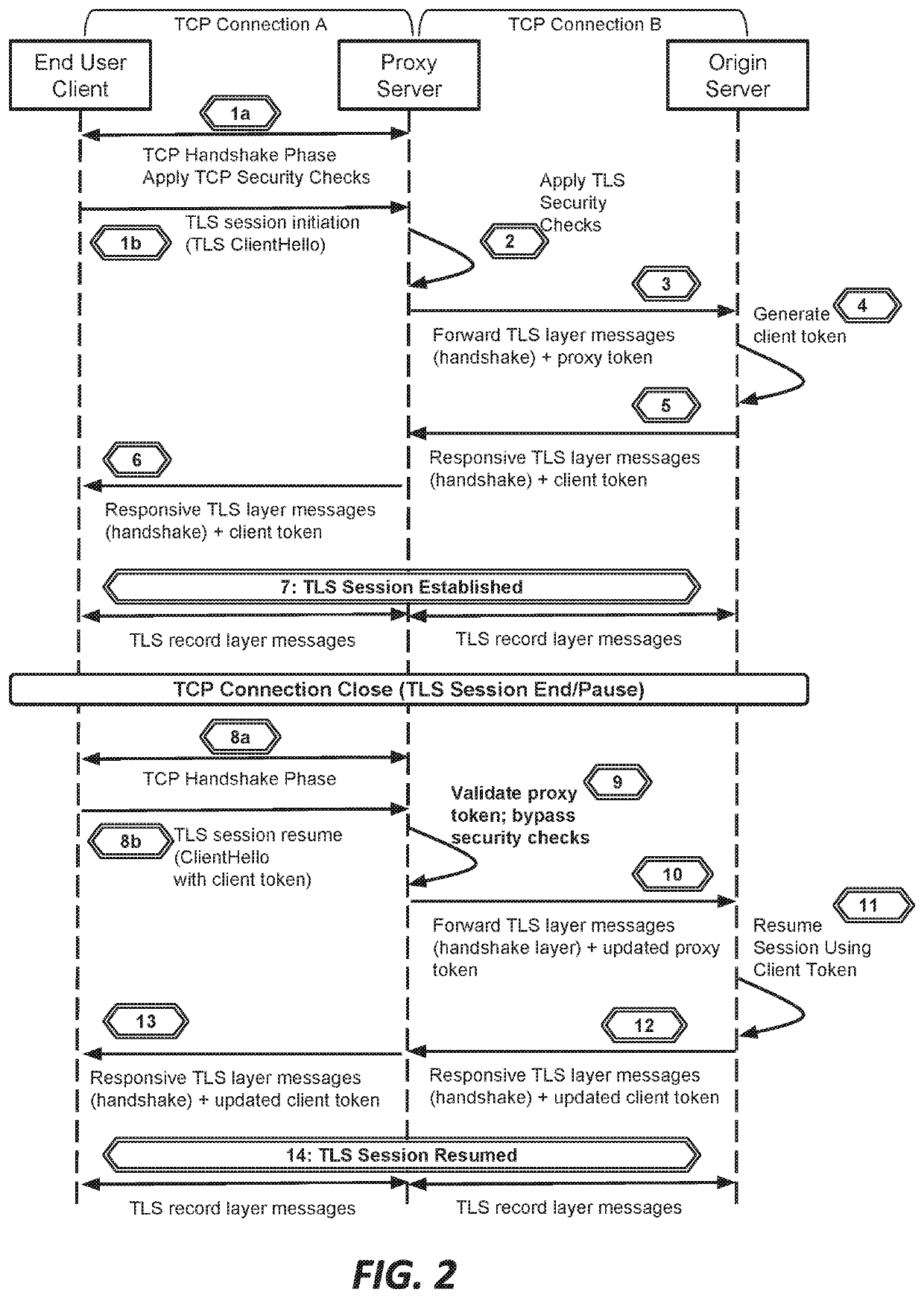
Systems and methods for proxying encrypted traffic to protect origin servers from internet threats
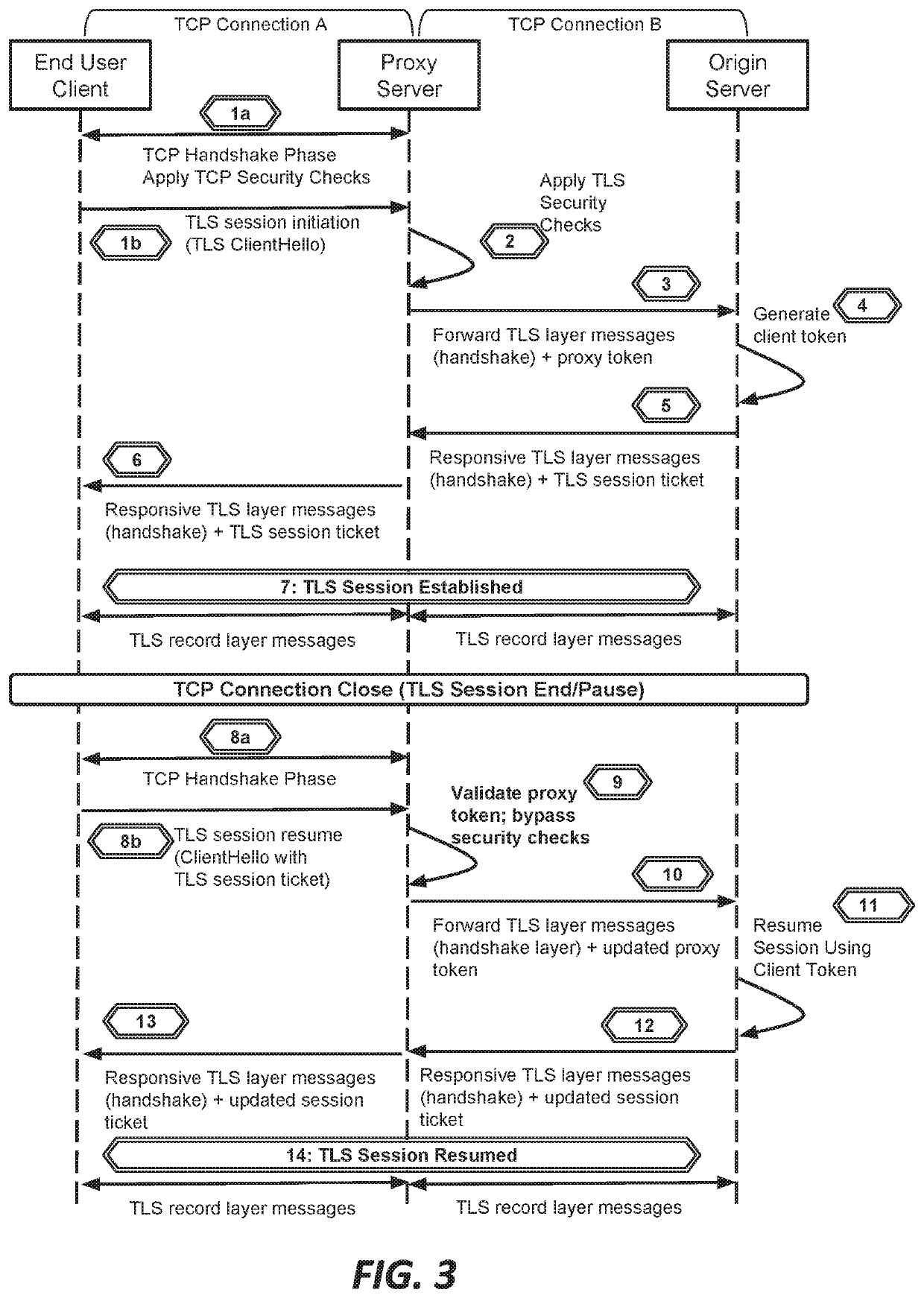
This document describes, among other things, systems and methods for more efficiently resuming a client-to-origin TLS session through a proxy layer that fronts the origin in order to provide network security services. At the time of an initial TLS handshake with an unknown client, for example, the proxy can perform a set of security checks. If the client passes the checks, the proxy can transmit a ‘proxy token’ upstream to the origin. The origin can incorporate this token into session state data which is passed back to and stored on the client, e.g., using a TLS session ticket extension field, pre-shared key extension field, or other field. On TLS session resumption, when the client sends the session state data, the proxy can recover its proxy token from the session state data, and upon successful validation, bypass security checks that it would otherwise perform against the client, thereby more efficiently handling known clients.
Owner:AKAMAI TECH INC
System and method for multiple virtual private network authentication schemes
InactiveUS6938155B2Multiple digital computer combinationsElectric digital data processingPrivate networkRemote system
A system and method for providing multiple virtual private networks from a computer system. The computer system communicates with a remote computer system in order to allow encrypted data traffic to flow between the respective systems. Two phases are used to authenticate the computer systems to one another. During the first phase, digital certificates or pre-shared keys are used to authenticate the computer systems. A phase 1 ID rules list contains authentication rules for local-remote computer pairs. During the second phase, a hash value is used to authenticate the computer systems and a security association payload is created. The remote system's IP address is used for connecting. The phase 1 ID rules list corresponds to one or more phase 2 ID rules lists. If the remote ID is not found in the phase 2 ID rules list, a default rule is used based upon the phase 1 ID rules list.
Owner:TREND MICRO INC
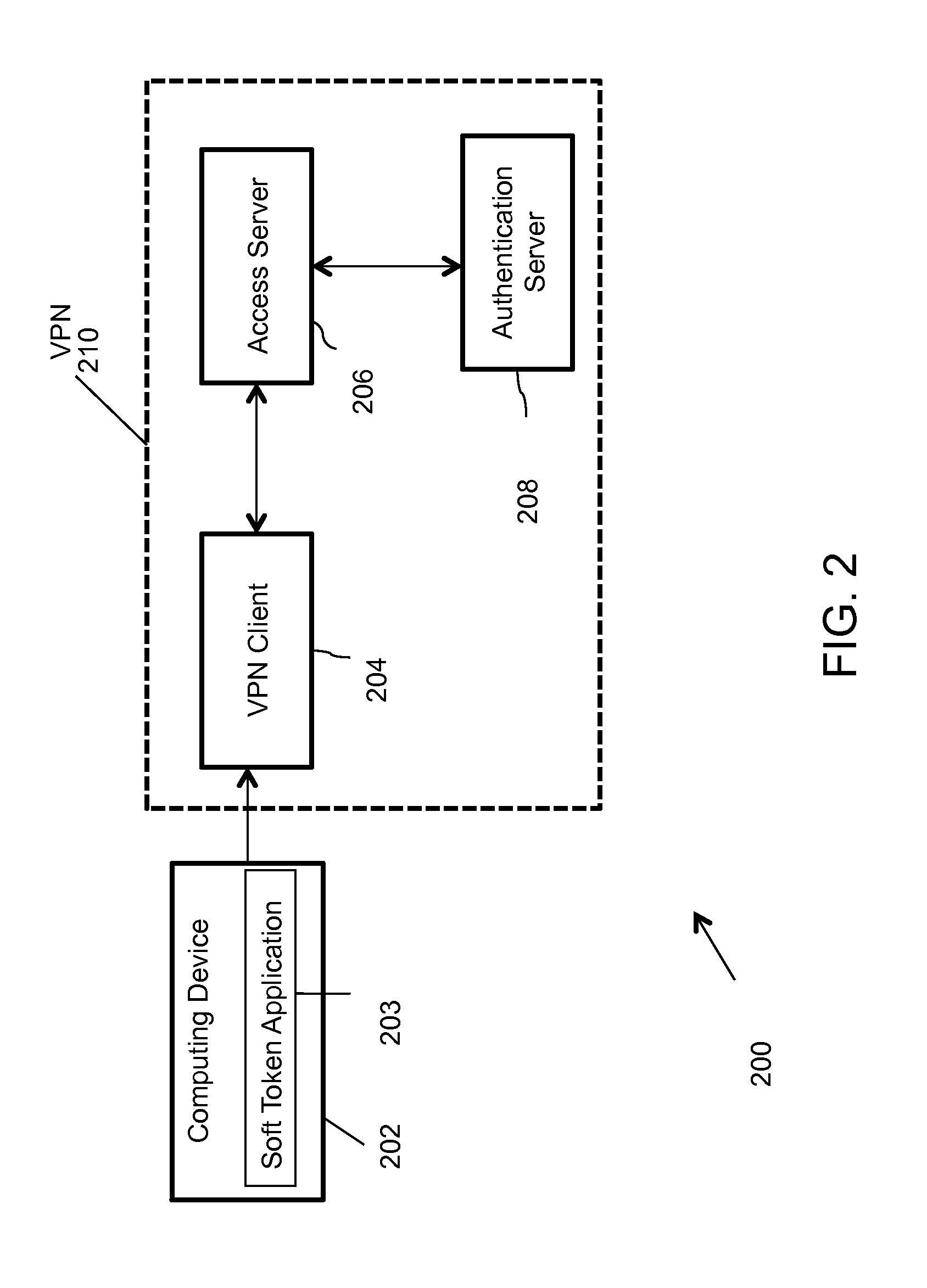
Soft token system
ActiveUS20140281506A1Multiple keys/algorithms usagePublic key for secure communicationMobile devicePre-shared key
Systems and methods for a secure soft token solution applicable to multiple platforms and usage scenarios are provided. According to one embodiment a method is provided for soft token management. A mobile device of a user of a secure network resource receives and installs a soft token application. A unique device ID of the mobile device is programmatically obtained by the soft token application. A seed for generating a soft token for accessing the secure network resource is requested by the soft token application. Responsive to receipt of the seed by the soft token application, the soft token is generated based on the seed and the soft token is bound to the mobile device by encrypting the seed with the unique device ID and a hardcoded pre-shared key.
Owner:FORTINET
Support of multiple pre-shared keys in access point
ActiveUS20100115278A1Significant user burdenLess riskPublic key for secure communicationUser identity/authority verificationClient-sideComputer science
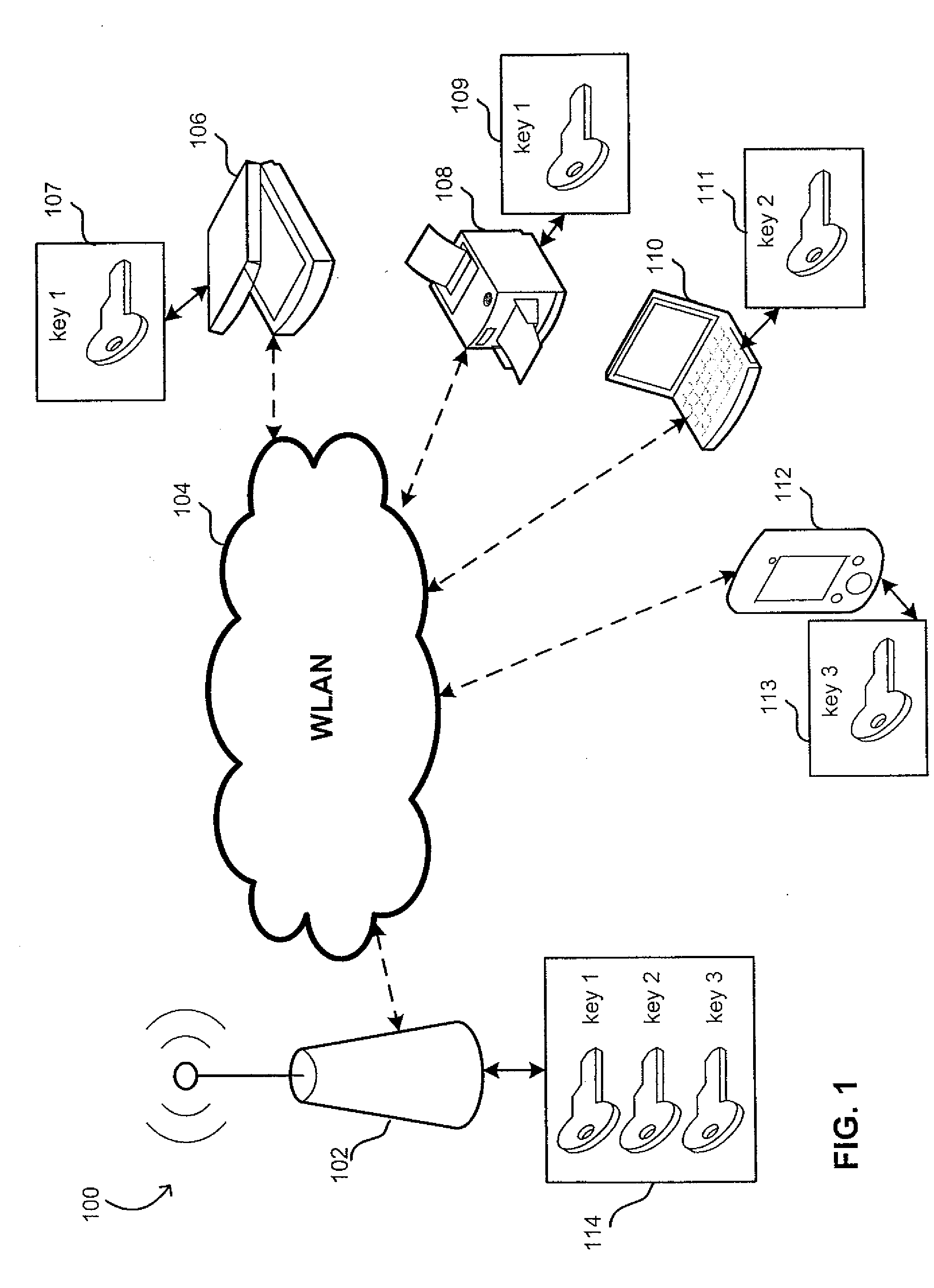
A method of operating an access point (AP) configured to support multiple pre-shared keys at a given time to authenticate its associated client devices. Each client device associated with the AP is provisioned with a key. To authenticate the client device tat attempts to connect to the AP, the AP determines which pre-shared key (PSK) of the multiple supported pre-shared keys (PSKs). if any, matches information including the key received from the client device. When the information matches, the client device is allowed to connect to the AP. Provisioning the AP with multiple PSKs allows selectively disconnecting associated client devices from the AP. The AP may be configured to support PSKs of different lifetime and complexity. Removing a PSK of the multiple PSKs supported by the AP and disconnecting a client device that uses this PSK does not disconnect other client devices using different keys to access the AP.
Owner:MICROSOFT TECH LICENSING LLC
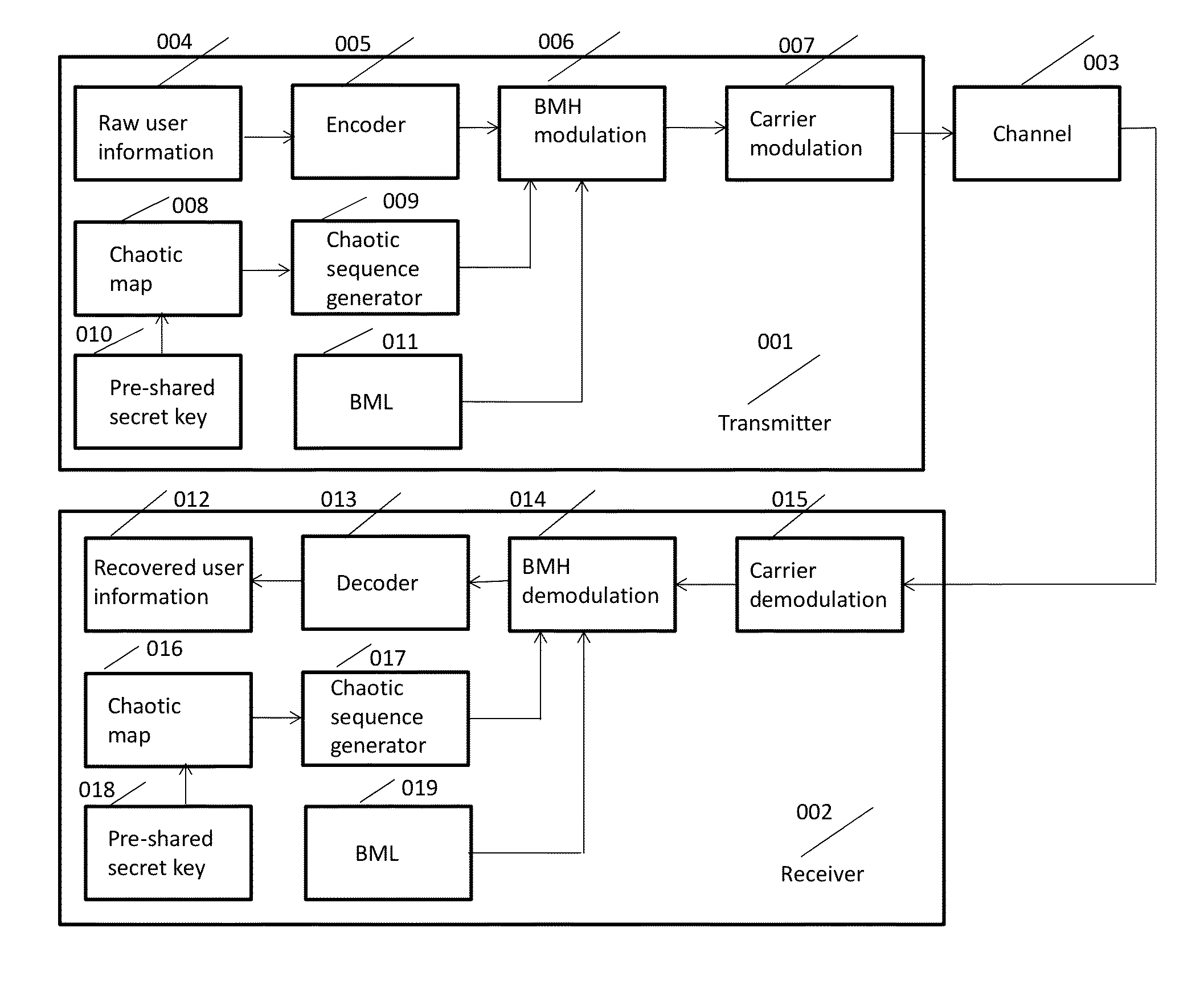
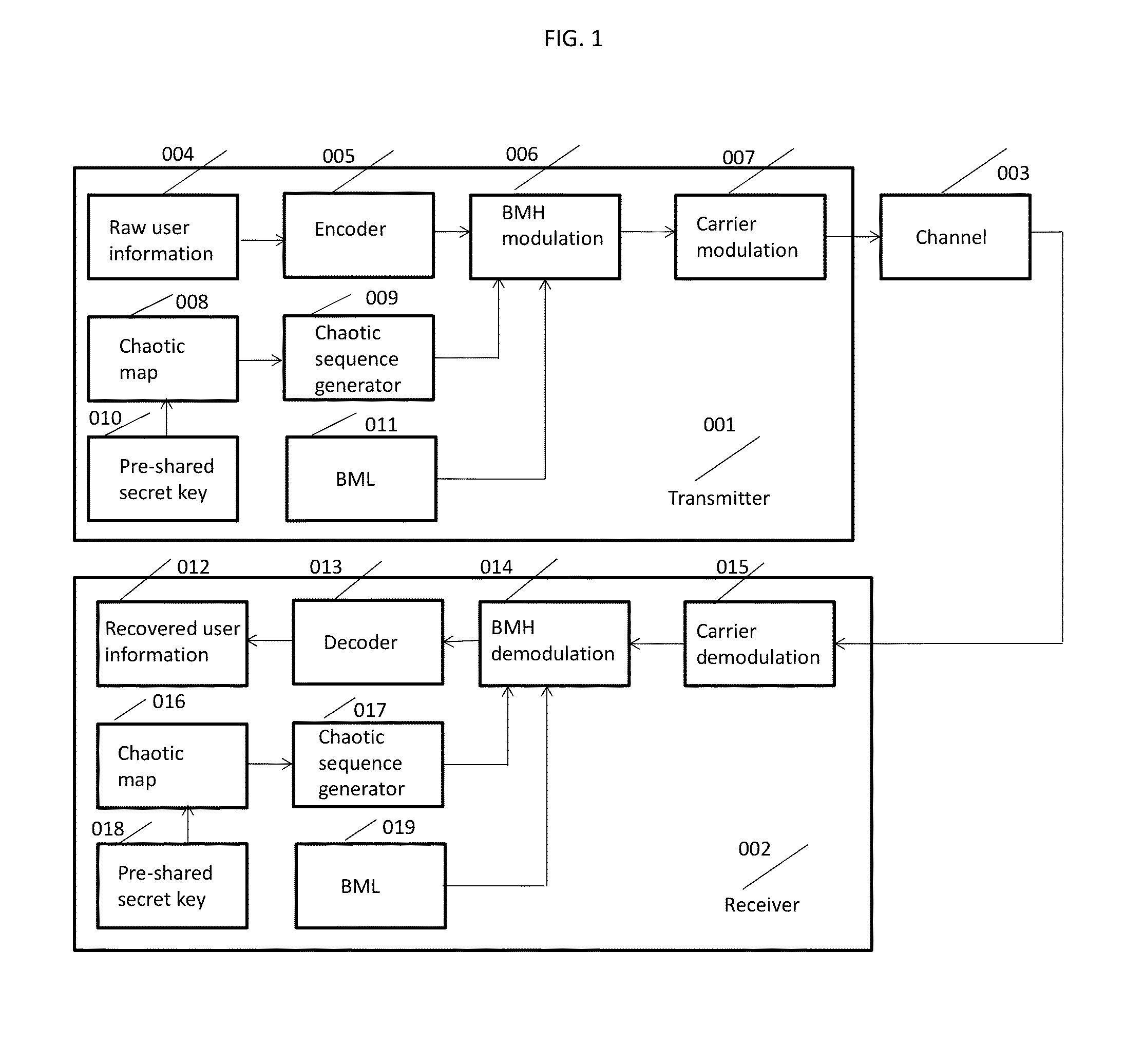
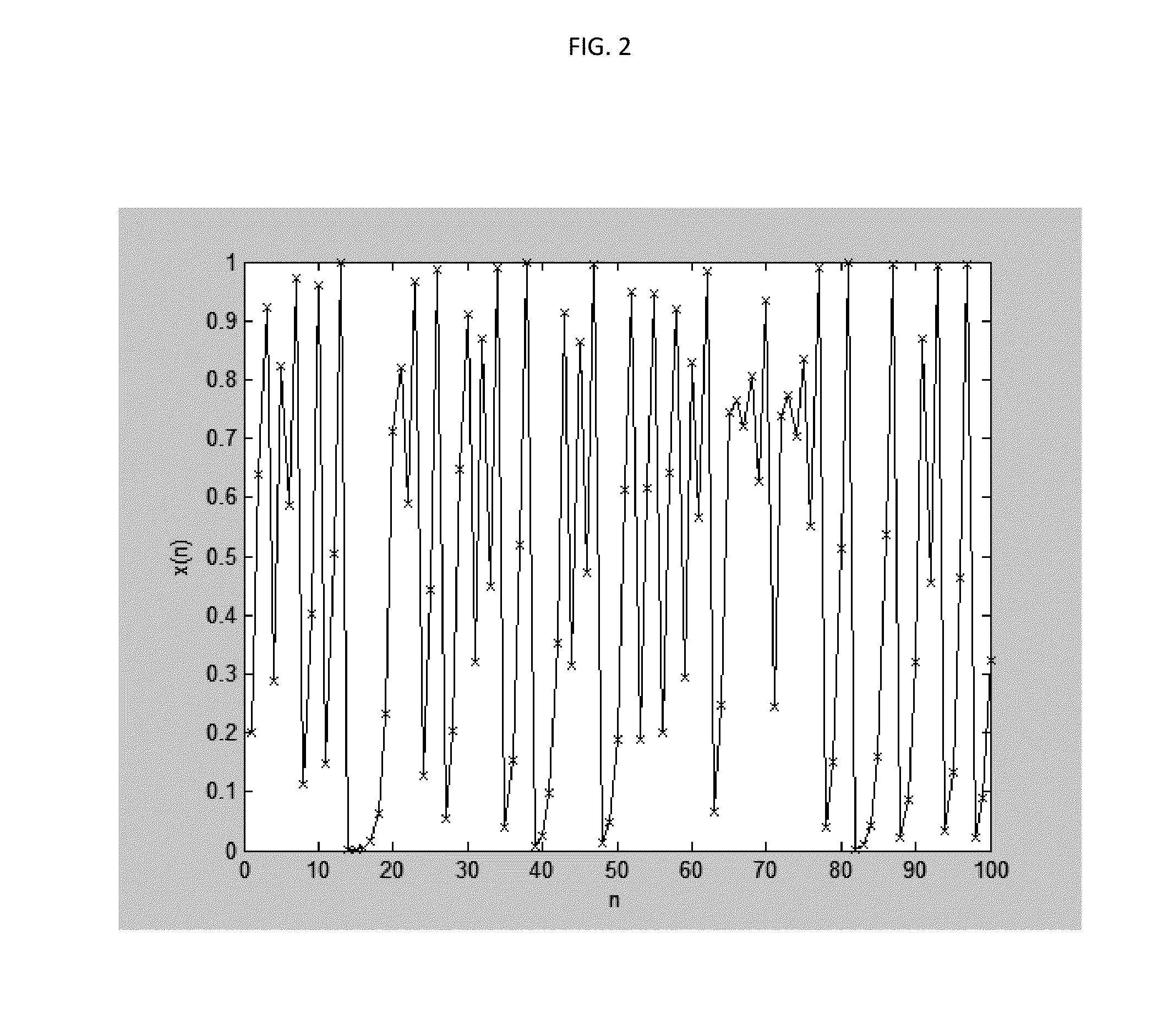
Chaotic Baseband Modulation Hopping Based Post-Quantum Physical-Layer Encryption
A post-quantum physical-layer encryption / decryption system based on chaotic Baseband Modulation Hopping (BMH). The baseband constellation, mapping, power level, and phase will vary symbol-by-symbol according to assigned random sequences. Pre-shared secret keys are used as the chaotic system parameters, initialization, and quantization parameters to generate the BMH codes. The BMH physical-layer encryption / decryption system can be combined with digital-domain based encryption algorithms such as AES, code-based post-quantum cryptography, and other physical-layer secure communication techniques such as Frequency Hopping (FH) and Direct Sequence Spread Spectrum (DSSS). It can also be combined with Quantum Key Distribution (QKD) to provide mutual authenticated key distribution. This invention can be applied to all kinds of communication systems including wireless (radio frequency, optical, quantum channel, sonar) and wire (optical fiber, power-line, telephone line, wire quantum channel, etc.), single carrier and multi-carrier, OFDM, MIMO channels.
Owner:LI WENHUA +1
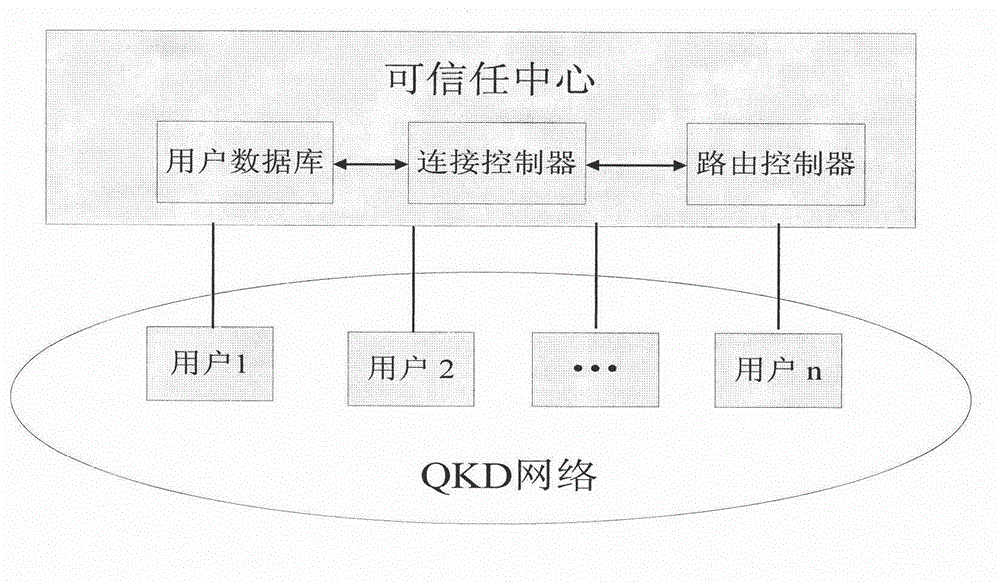
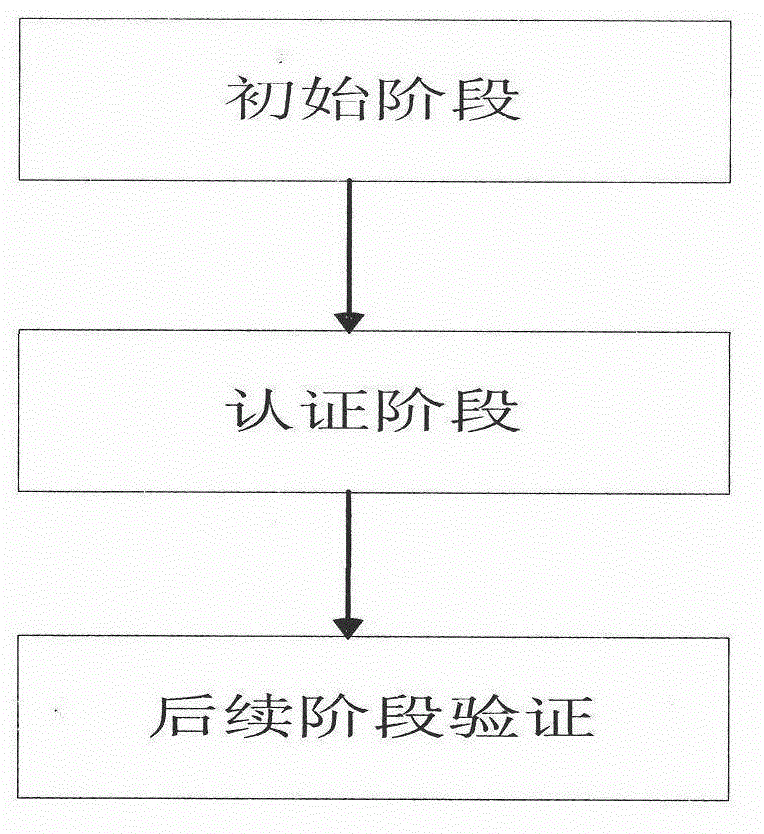
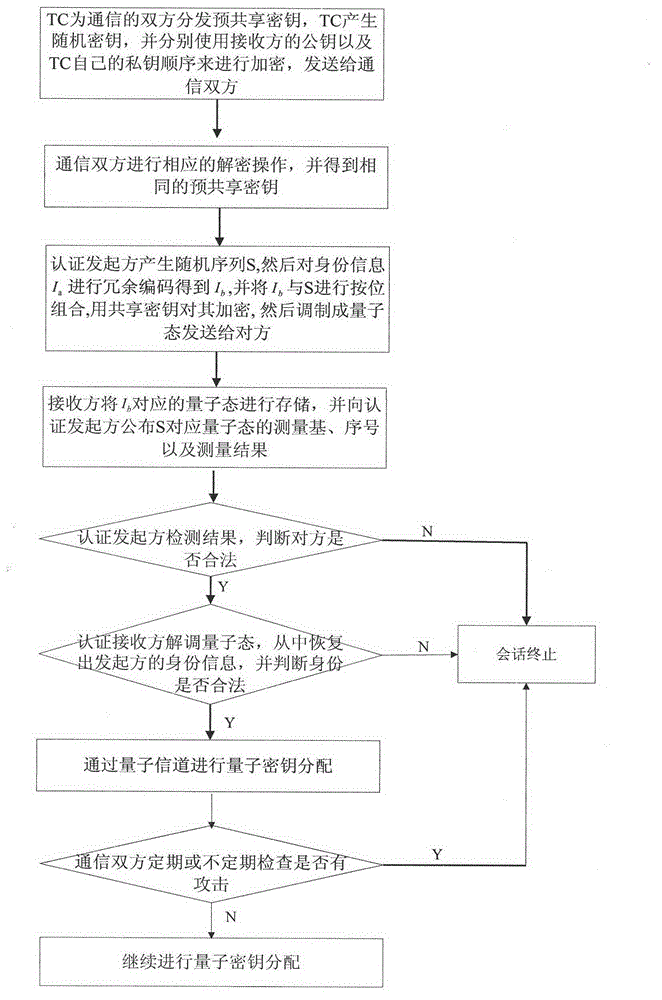
Model and method for user authentication for quantum key distribution network
ActiveCN102946313AAvoid Intermittent AttacksPrevent theftKey distribution for secure communicationUser identity/authority verificationCommunications securityMan-in-the-middle attack
The invention provides a model and a method for user authentication based on a trusted center in a quantum key distribution network, specifically, a user authentication model based on the trusted center is provided and an implementation method is described in detail, in order to realize the communication security between any two users in the network and prevent a man-in-the-middle attack. Based on the model, the invention further provides a method for user authentication, which comprises the following steps that: 1, any user requesting for communication in the network sends a connection request to the trusted center; 2, the trusted center sends a pre-shared key to the two communication parties respectively; 3, the two communication parties set up a quantum channel and are authenticated; and 4, the two parties are authenticated regularly or irregularly in the subsequent communication process. According to the invention, by fully considering the development status of the current quantum key distribution network and by combining with the actual requirement, a quantum communication channel can be set up securely between any two nodes in the network, so that the communication security between users can be realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
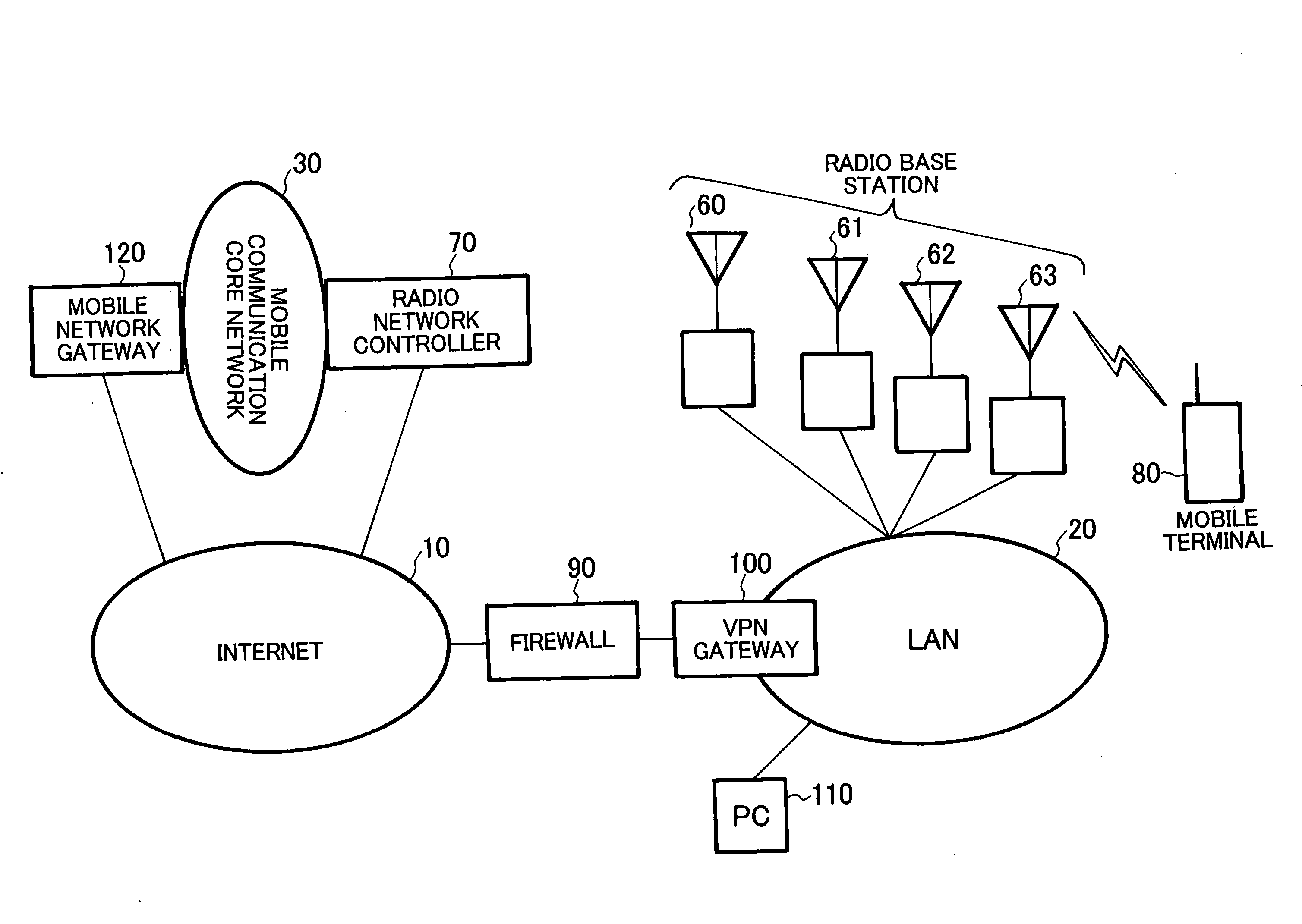
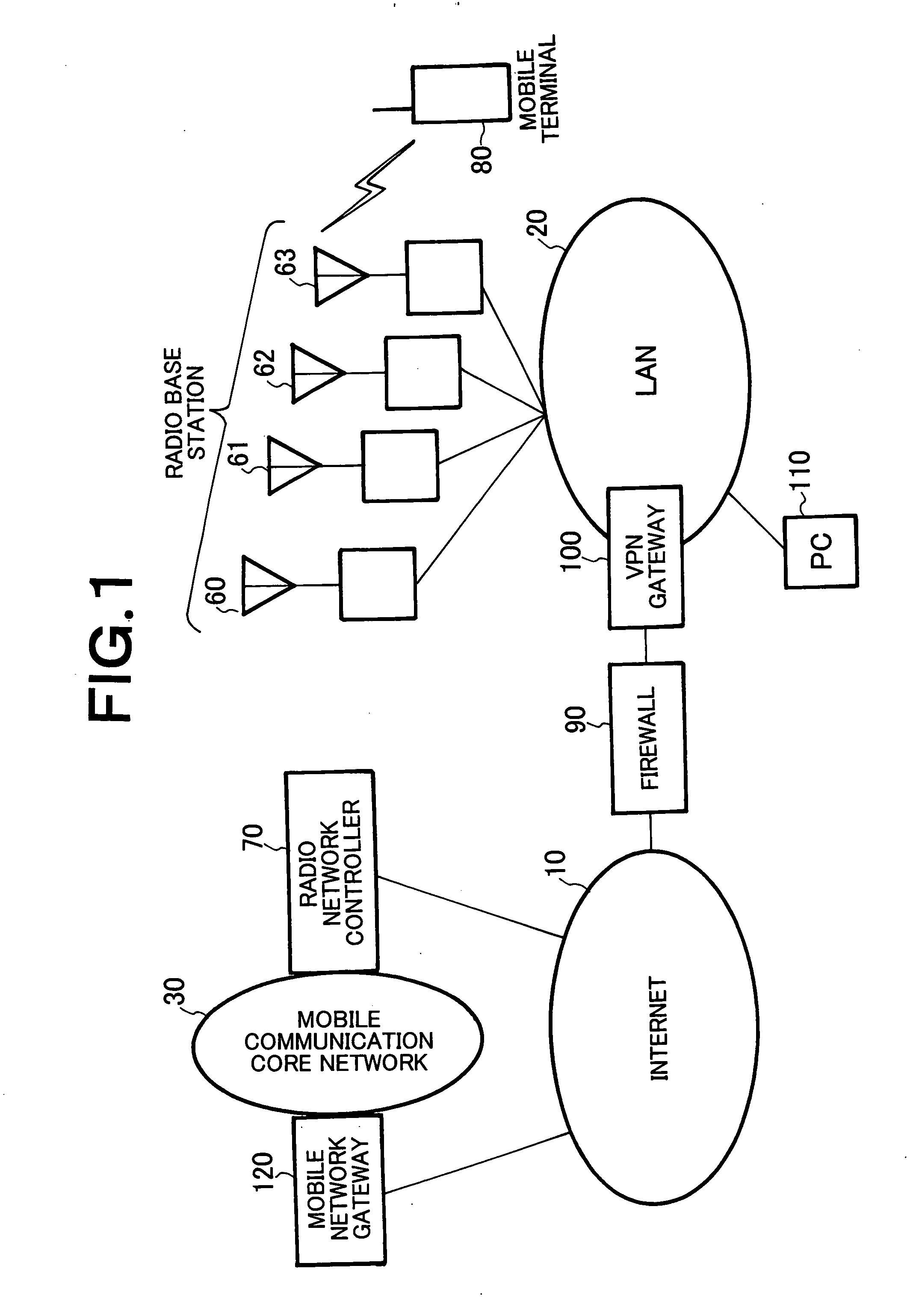
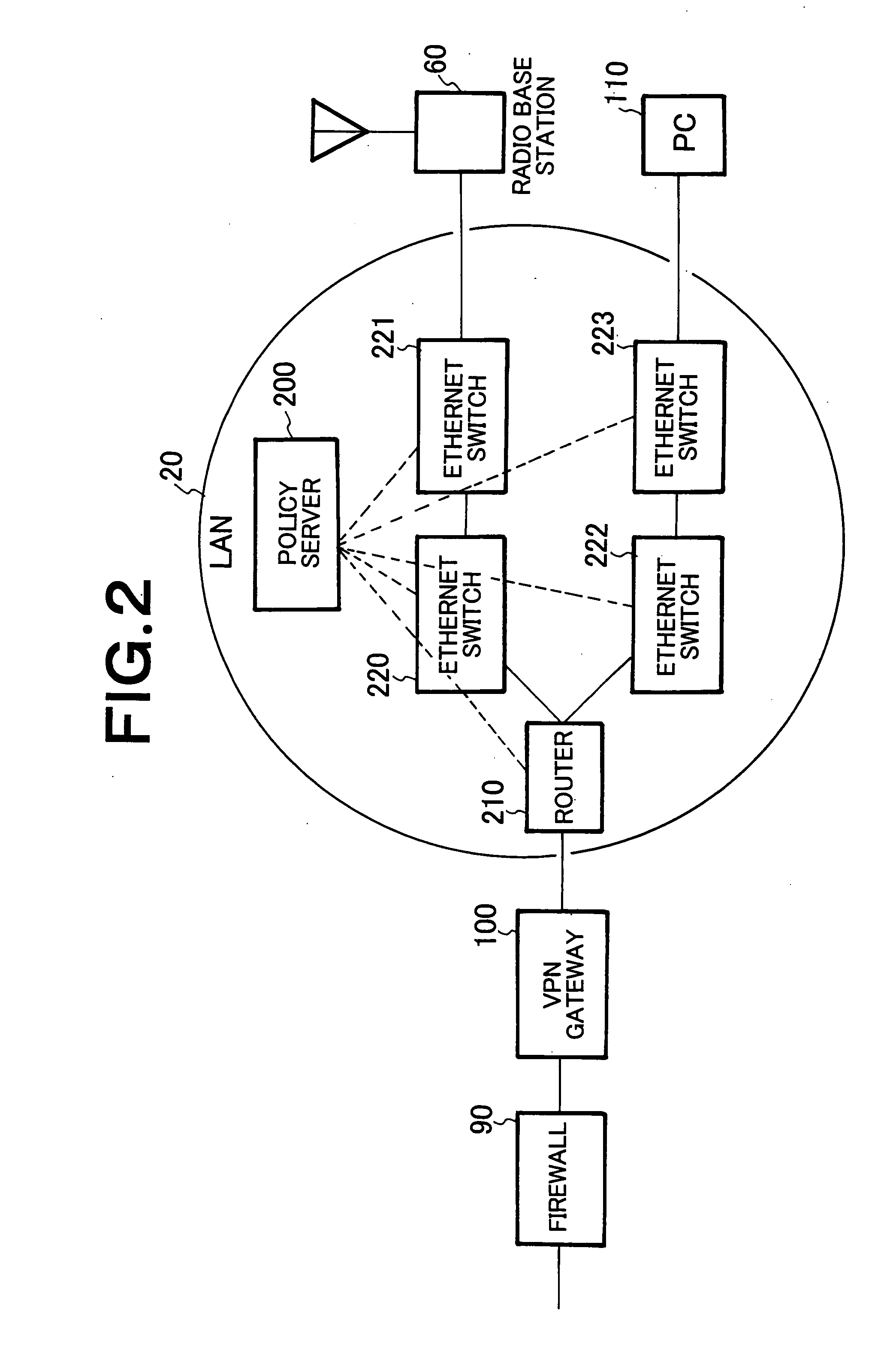
Mobile communication system using private network, relay node, and radio network controller
InactiveUS20070105549A1Avoid trafficEasy to operateNetwork traffic/resource managementNetwork topologiesRadio networksPrivate network
Upon receiving a mobile communication control signaling at the time when a mobile terminal 80 makes or receives a call, VPN gateway 100, which serves as a relay node, performs reception determination in cooperation with policy server 200 serving as a bandwidth control mechanism within LAN 20 which is a private network. When permitting the reception, the VPN gateway 100 provides a communication line to the mobile terminal 80 or a pre-shared key is dynamically generated between a radio base station and radio network controller 70, and the pre-shared key is notified to the VPN gateway 100 by the radio network controller 70.
Owner:NEC CORP
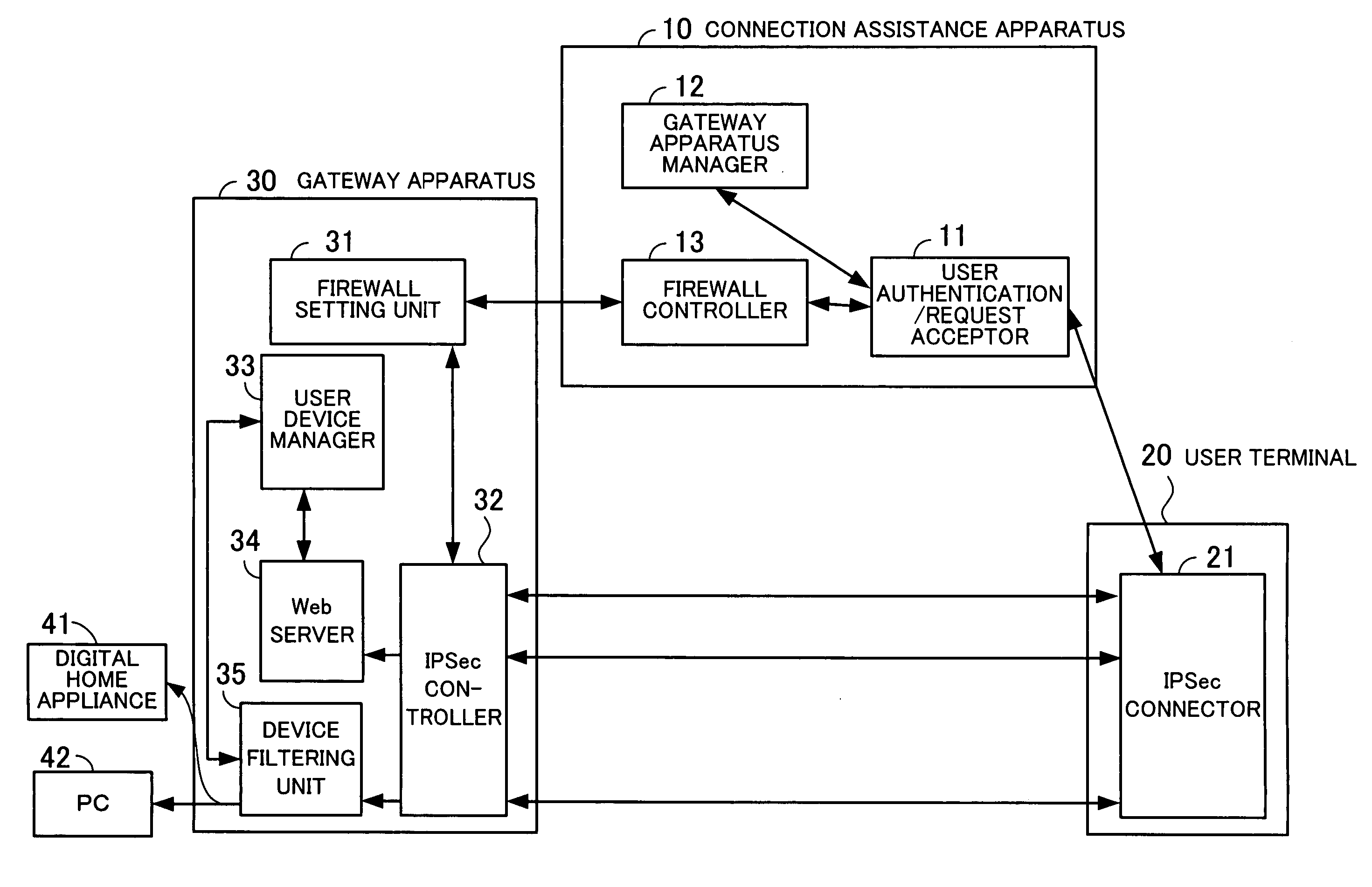
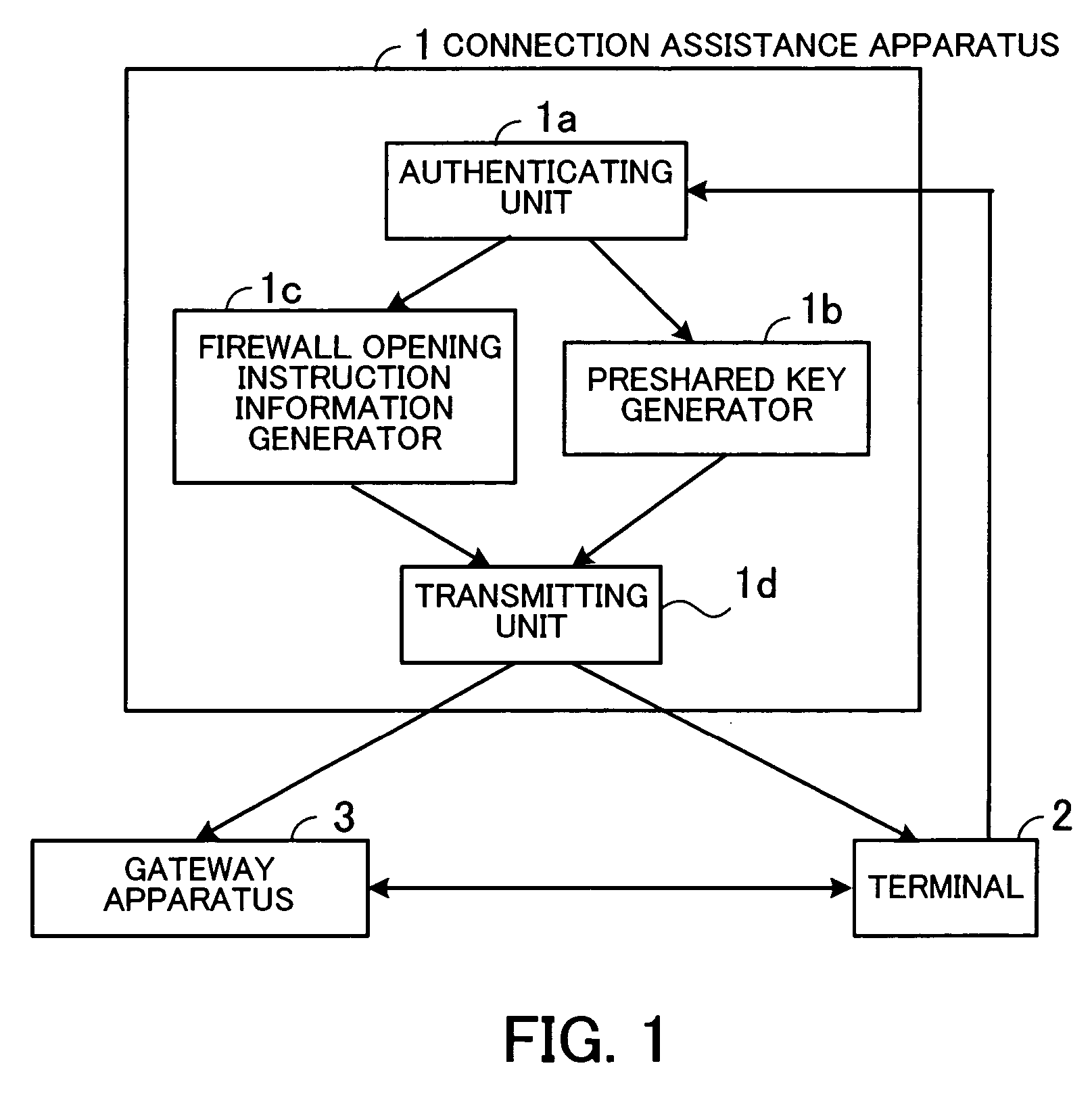
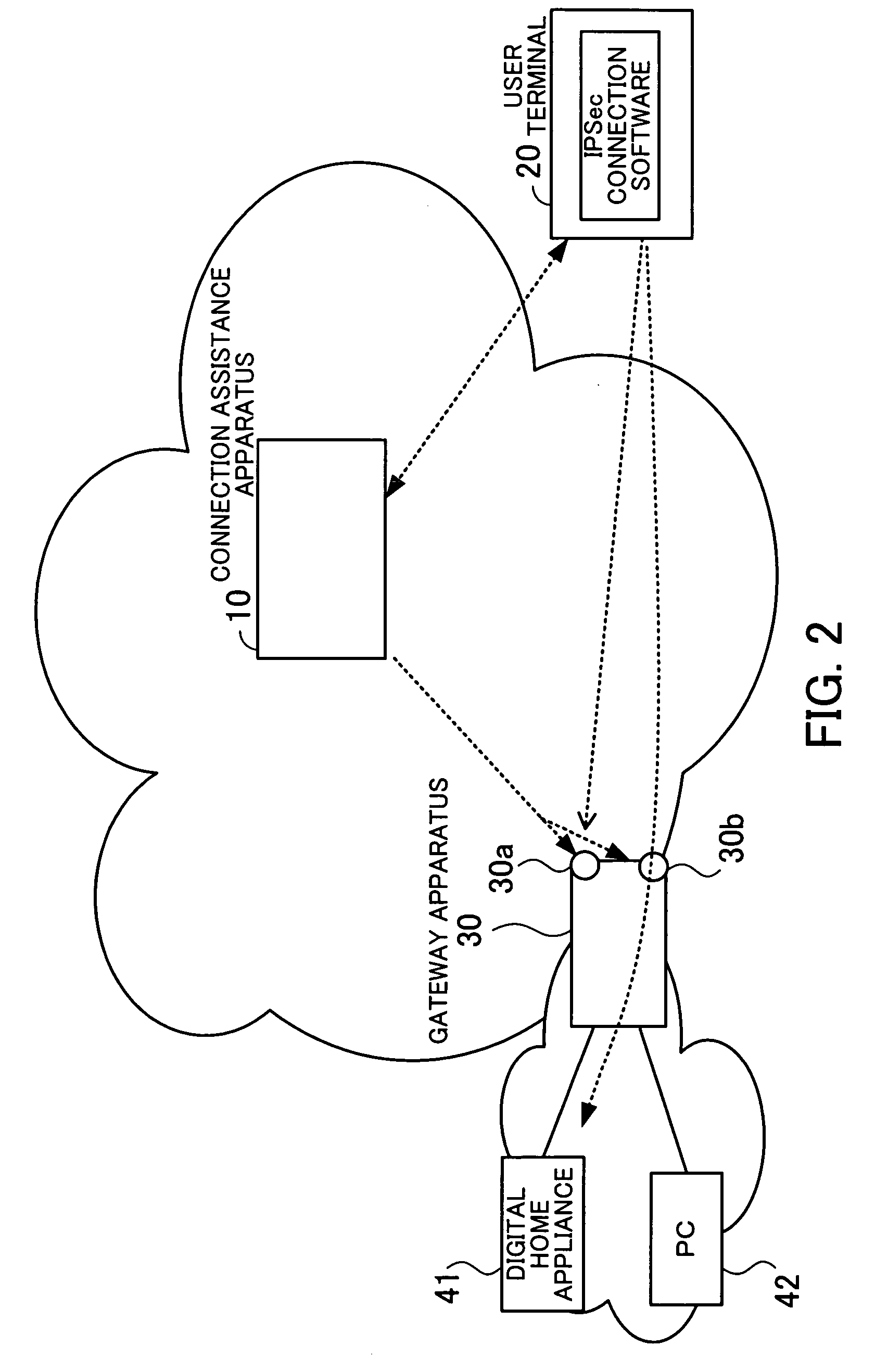
Connection assistance apparatus and gateway apparatus
InactiveUS20070079368A1Avoid performanceKey distribution for secure communicationDigital data processing detailsIPsecPre-shared key
A connection assistance apparatus avoids unauthorized access and DoS attacks, prevents a performance degradation from occurring, and does not need to recognize different connections to gateway apparatus. An authenticating unit authenticates the validity of a terminal by checking if the terminal is a valid terminal capable of communicating with a gateway apparatus according to IPSec in response to a request from a user who owns the terminal. If it is judged that the terminal is a valid terminal, then a preshared key generating unit generates a preshared key for the terminal and the gateway apparatus, and a firewall opening instruction information generating unit generates firewall opening instruction information to open a firewall of the gateway apparatus. A transmitting unit sends the preshared key to the terminal and the gateway apparatus and sends the firewall opening instruction information to the gateway apparatus.
Owner:FUJITSU LTD
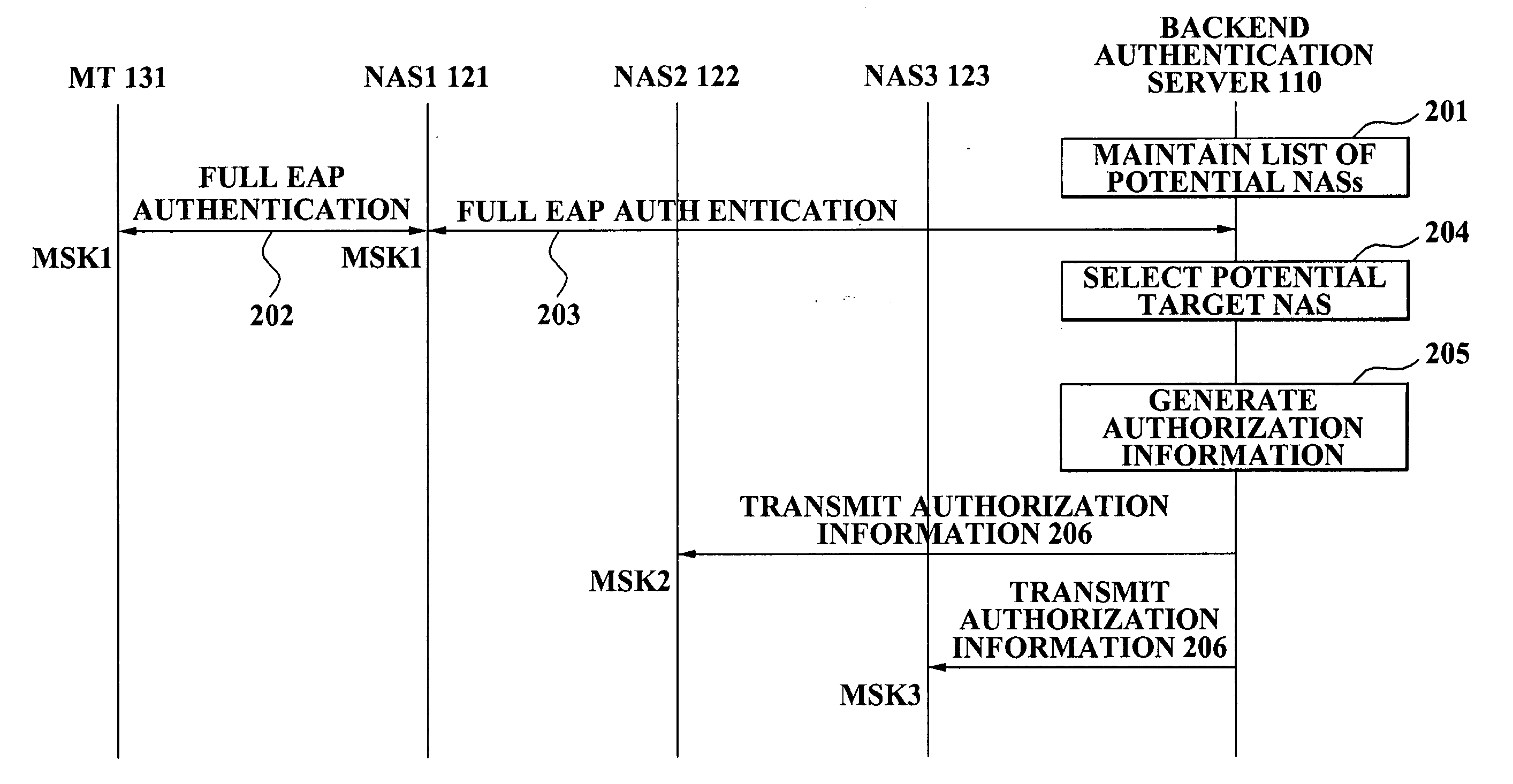
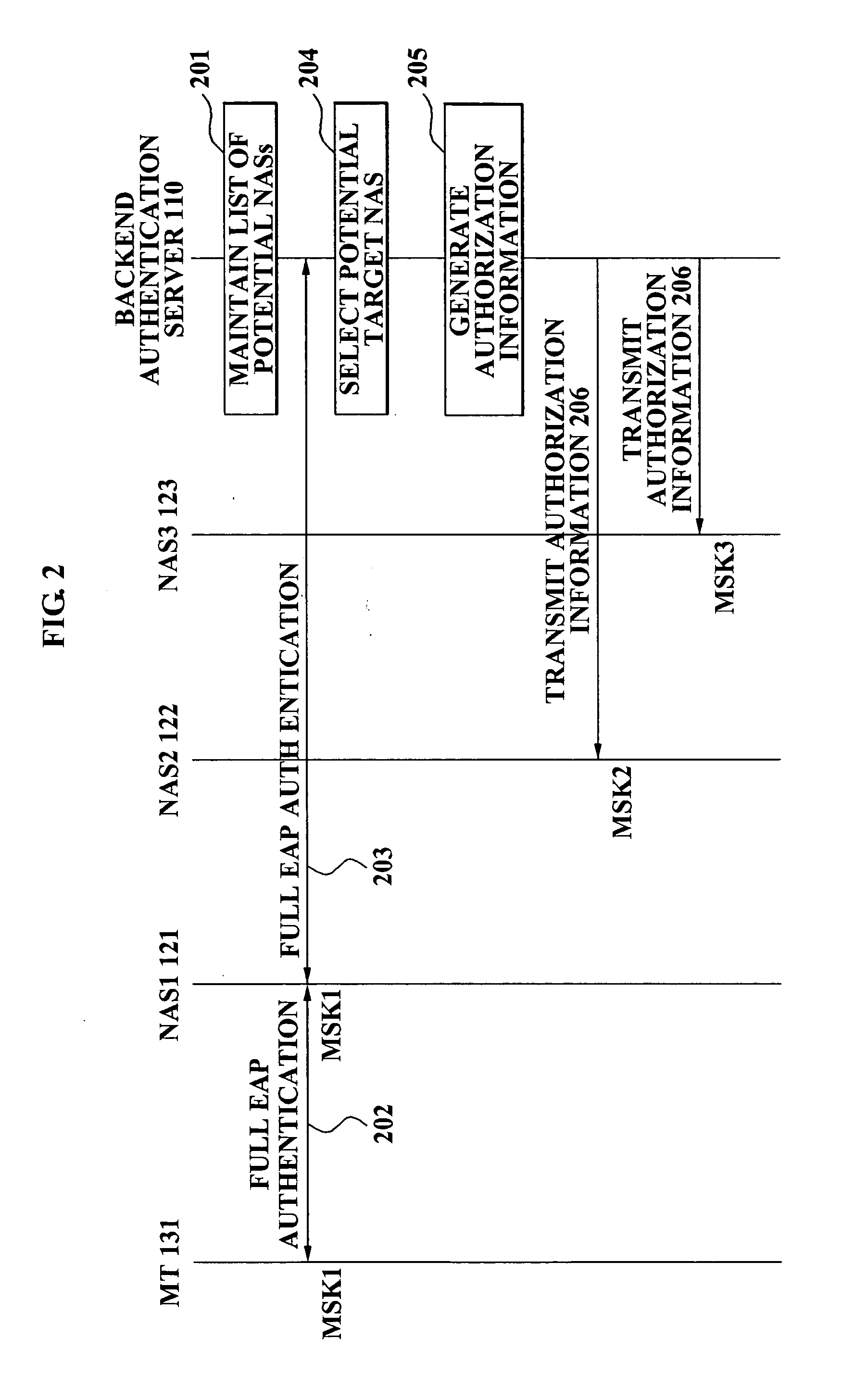
Method and apparatus for authenticating mobile terminal on handover
ActiveUS20070213033A1Reduce switching delayUnauthorised/fraudulent call preventionEavesdropping prevention circuitsNetwork access serverAuthentication server
A method and apparatus for authenticating a mobile terminal are provided. A list of potential Network Access Servers (NASs) corresponding to a NAS are maintained in a backend authentication server, authorization information corresponding to each of the potential NASs is transmitted, from the backend authentication server to each of the potential NASs, when the mobile terminal is authenticated via the NAS. The mobile terminal detects whether a new NAS is pre-authenticated, when the mobile terminal moves to a domain of the new NAS, the new NAS detects whether the mobile terminal is pre-authenticated, and the new NAS authenticates the mobile terminal via a Pre-Shared Key (PSK) method, when the mobile terminal and the new NAS are pre-authenticated.
Owner:SAMSUNG ELECTRONICS CO LTD
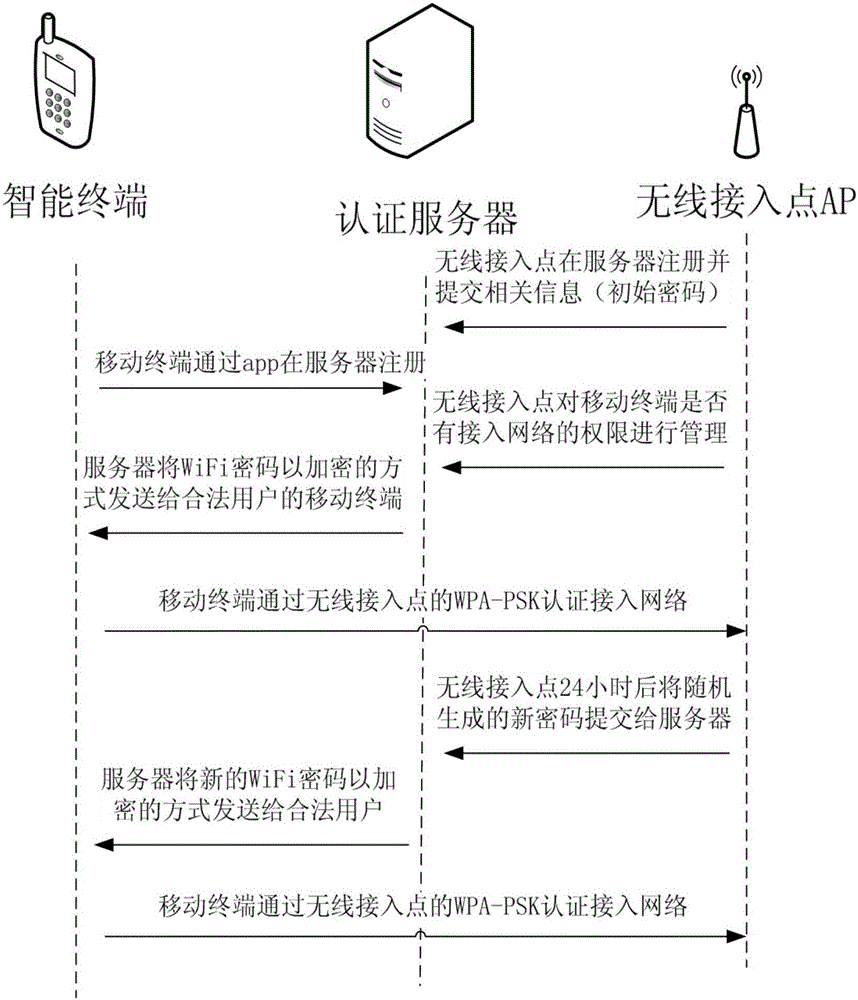
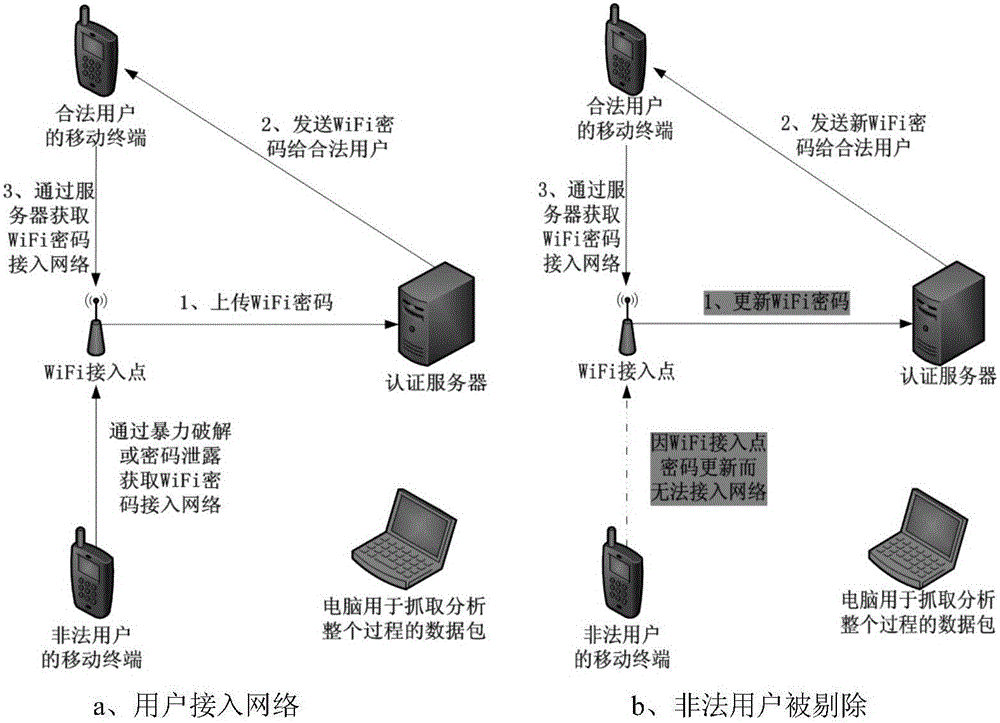
WiFi authentication system and method based on dynamic password
InactiveCN104994118AConsider operabilityTake security into considerationKey distribution for secure communicationSecurity arrangementWi-Fi Protected AccessRelevant information
The invention discloses a WiFi authentication system and method based on a dynamic password. A mobile terminal is arranged. The mobile terminal registers on a server; a wireless access point registers on an authentication server and submits relevant information; the wireless access point manages an authority to access or not access the network of the mobile terminal; the server sends a WiFi password to the mobile terminal of a legal user in an encryption manner; the mobile terminal passes Wi-Fi protected access pre-shared key (WPA PSK) authentication and accesses the network; 24 hours later, the wireless access point randomly generates a new strong password and submits the strong password to the authentication server; the server sends the new WiFi password to a legal user of the system in the encryption manner; and the mobile terminal of the legal user passes WPA PSK authentication and accesses the network. Through adoption of the system and method, problems of weak passwords and password leakage by insiders are solved, the digital dynamic password of very high security is adopted, and the password is updated and authenticated automatically, so that human factors are furthest reduced.
Owner:吴培希
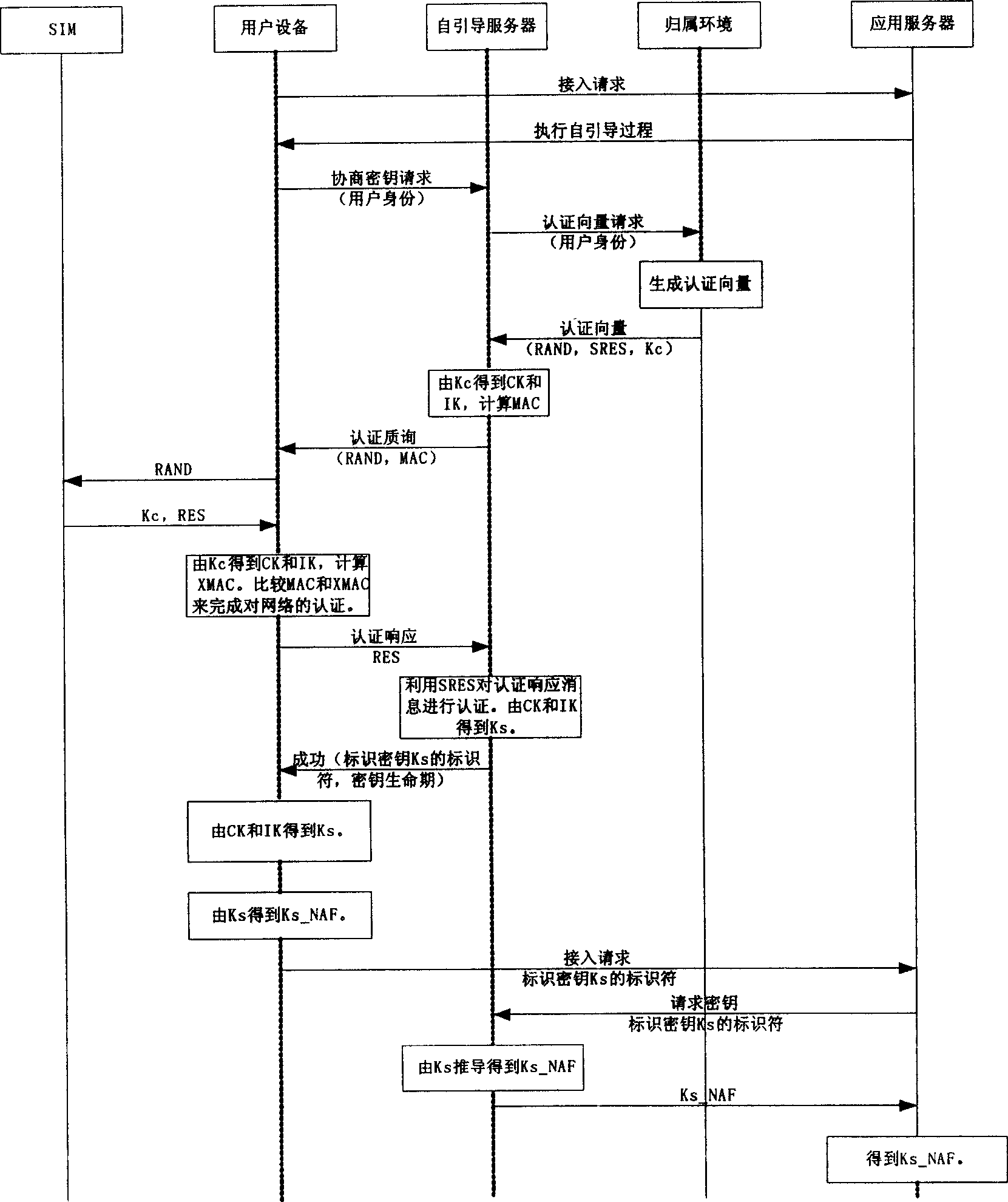
Method for negotiating about cipher key shared by users and application server
InactiveCN1697373AImplement two-way authenticationSynchronising transmission/receiving encryption devicesApplication serverAuthentication
Using cipher key Kc in triple of 2G authentication self-booted server deduces cipher key CK and IK useful for 3G. Using IK to calculate out MAC value, self-booted server sends MAC and RAND together to 2G users. Based on RAND, 2G users calculate out Kc. Using a method same as the way utilized by self-booted server to deduce cipher key CK and IK deduces out cipher key CK and IK from Kc. using IK calculates out value of XMAC. Comparing the received MAC with XMAC realizes authenticating network for user. The invention makes both of 2G users and 3G users possible to negotiate about sharing cipher key in advance with self-booted server as well as realizes bi-directional authentication between user and network.
Owner:ZTE CORP
Access authentication method and system in mobile communication network
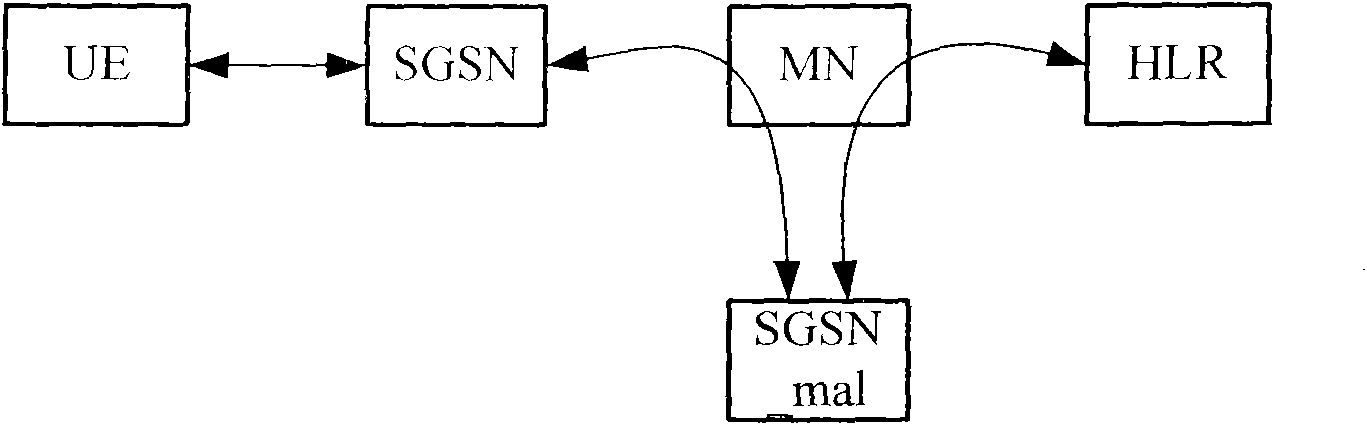
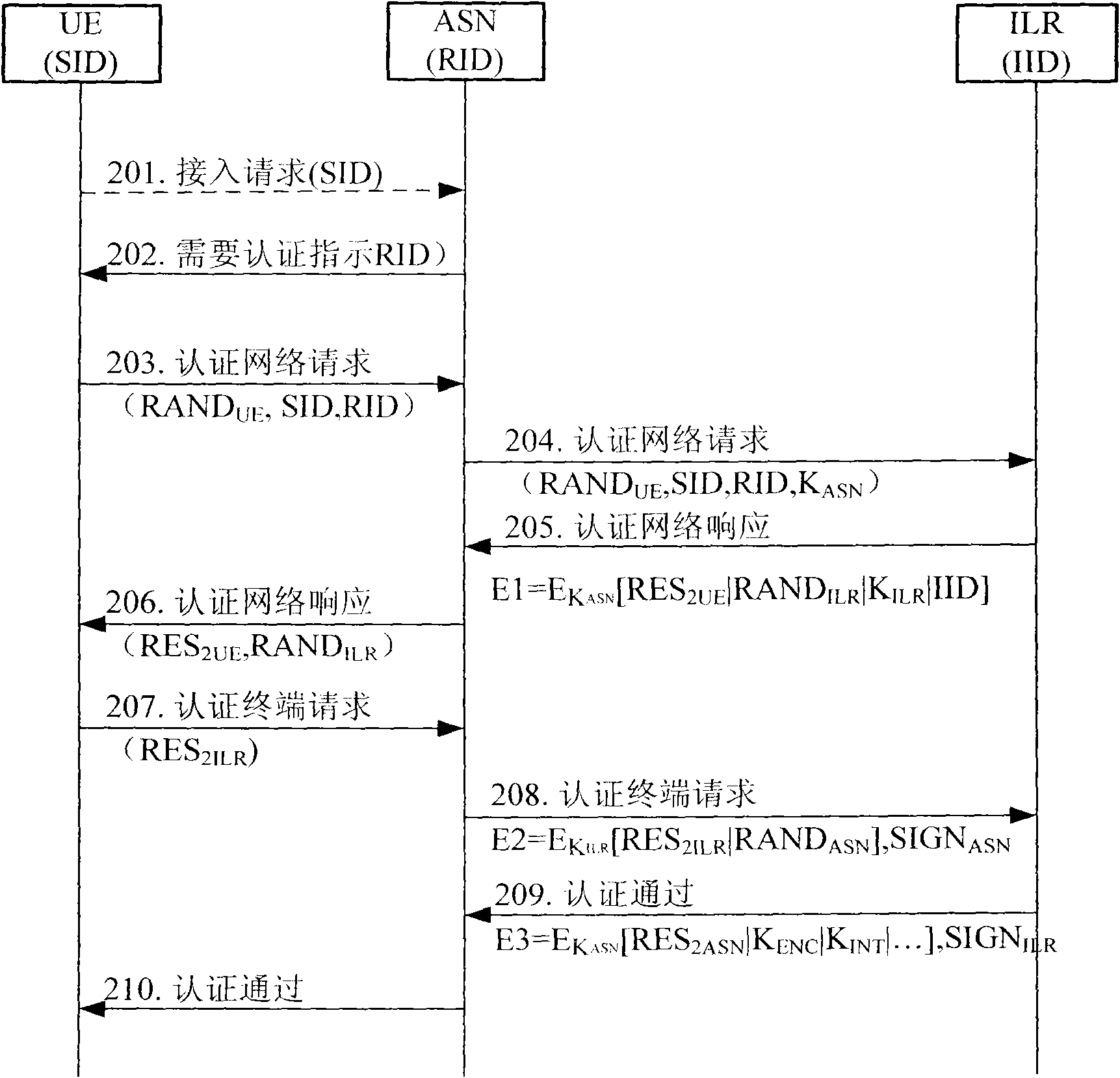
InactiveCN102036242AAvoid attackArrived without errorUser identity/authority verificationSecurity arrangementMan-in-the-middle attackDigest access authentication
The invention discloses an access authentication method in a mobile communication network. The method comprises the following steps that: a user terminal generates a random number RANDUE, and acquires a random number RANDILR generated by route identification (RID) and an identity location register (ILR) of an access service node (ASN) in a network when needing to perform authentication; the user terminal calculates to obtain an authentication result RES2ILR by using a pre-shared key K1 and sends the RES2ILR to the ASN; the ASN generates a random number RANDASN and sends the RES2ILR and the random number RANDASN to the ILR; and the ILR calculates to obtain an authentication result XRES2ILR by using the pre-shared key K1 and compares the XRES2ILR with the received RES2ILR; and if the XRES2ILR is consistent with the RES2ILR, the access authentication is successful. Correspondingly, the invention also provides a system for implementing the method. Through the method and the system, Man-in-the-Middle attacks caused by an unreliable network can be effectively avoided.
Owner:ZTE CORP
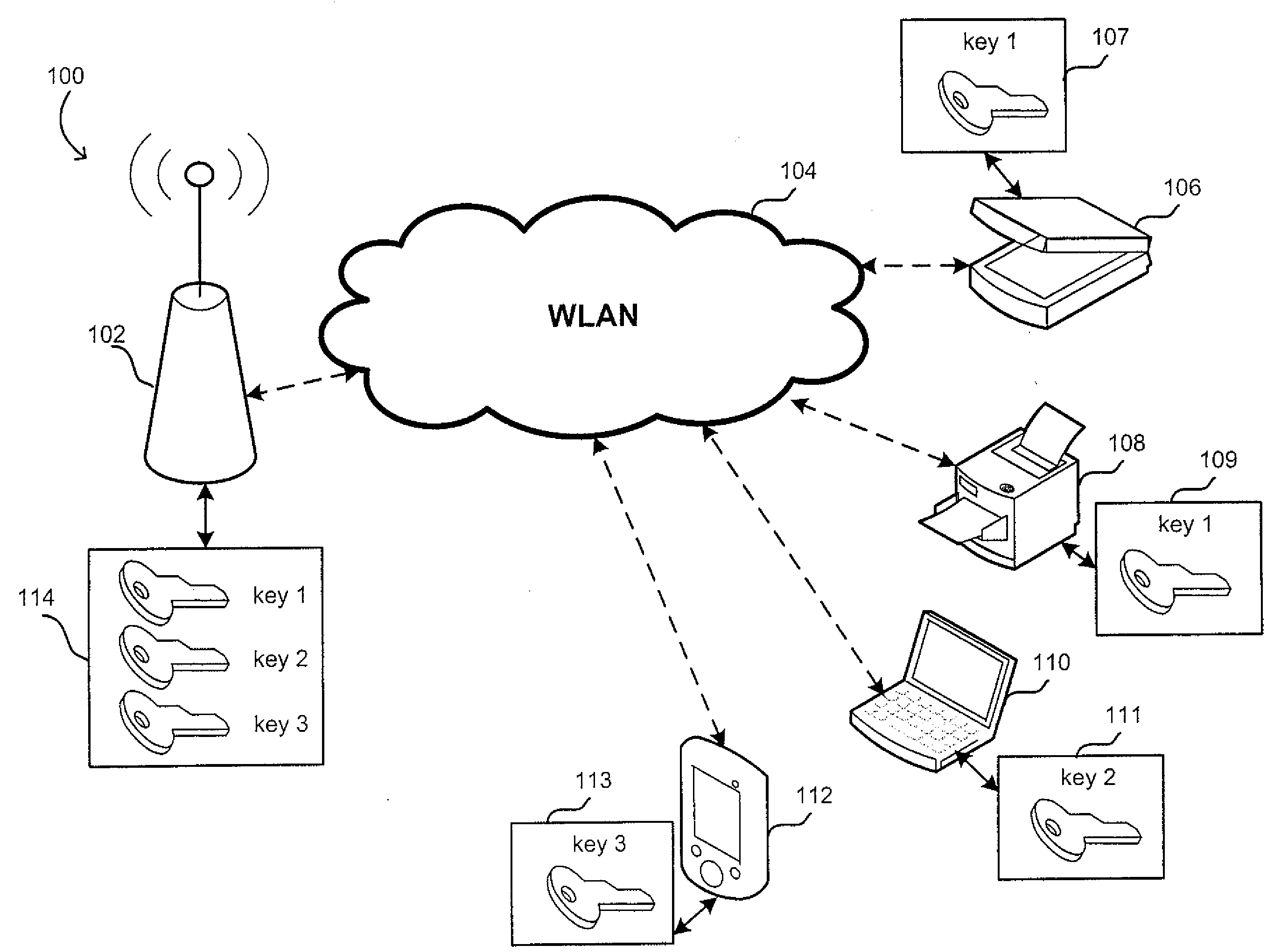
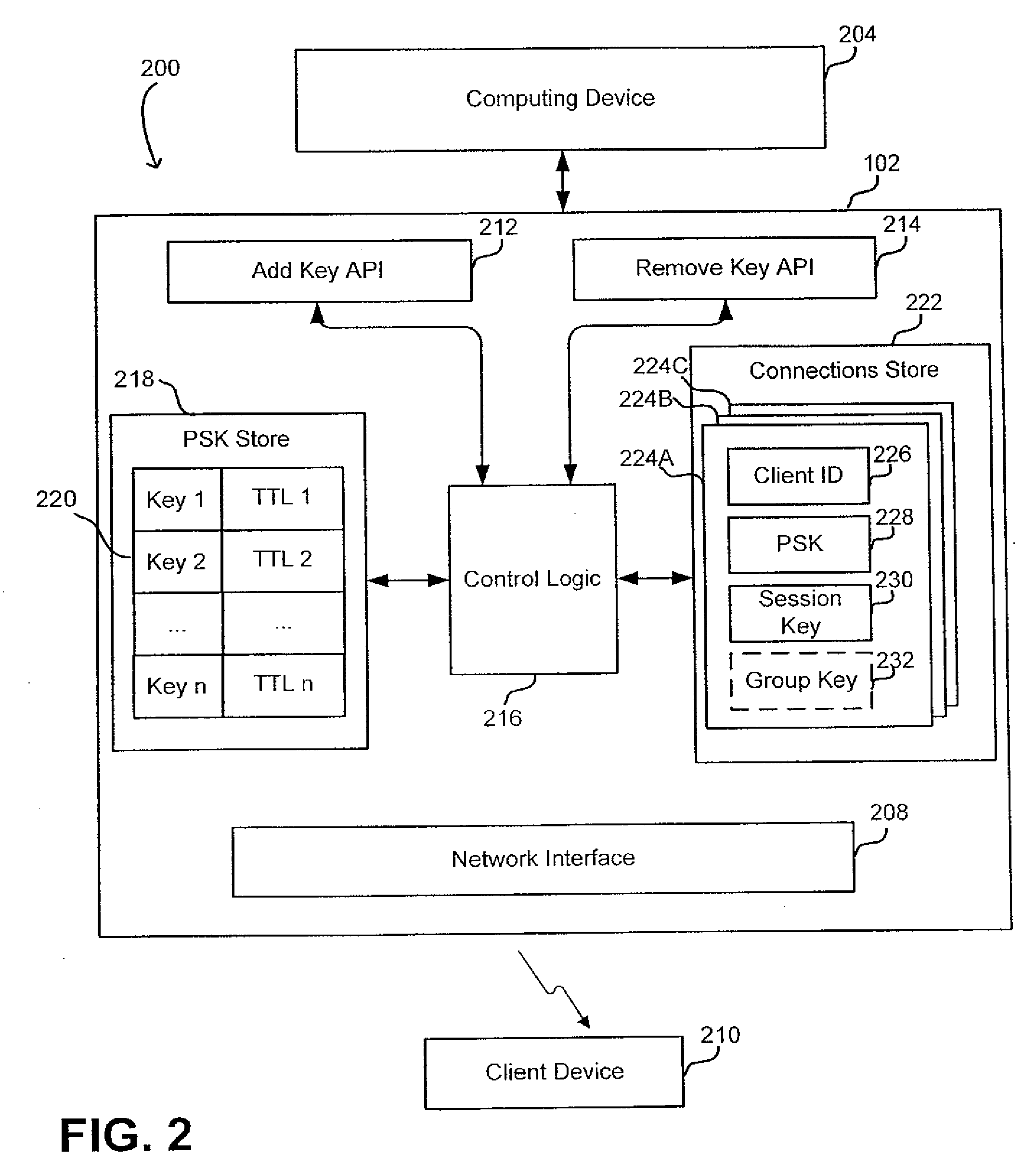
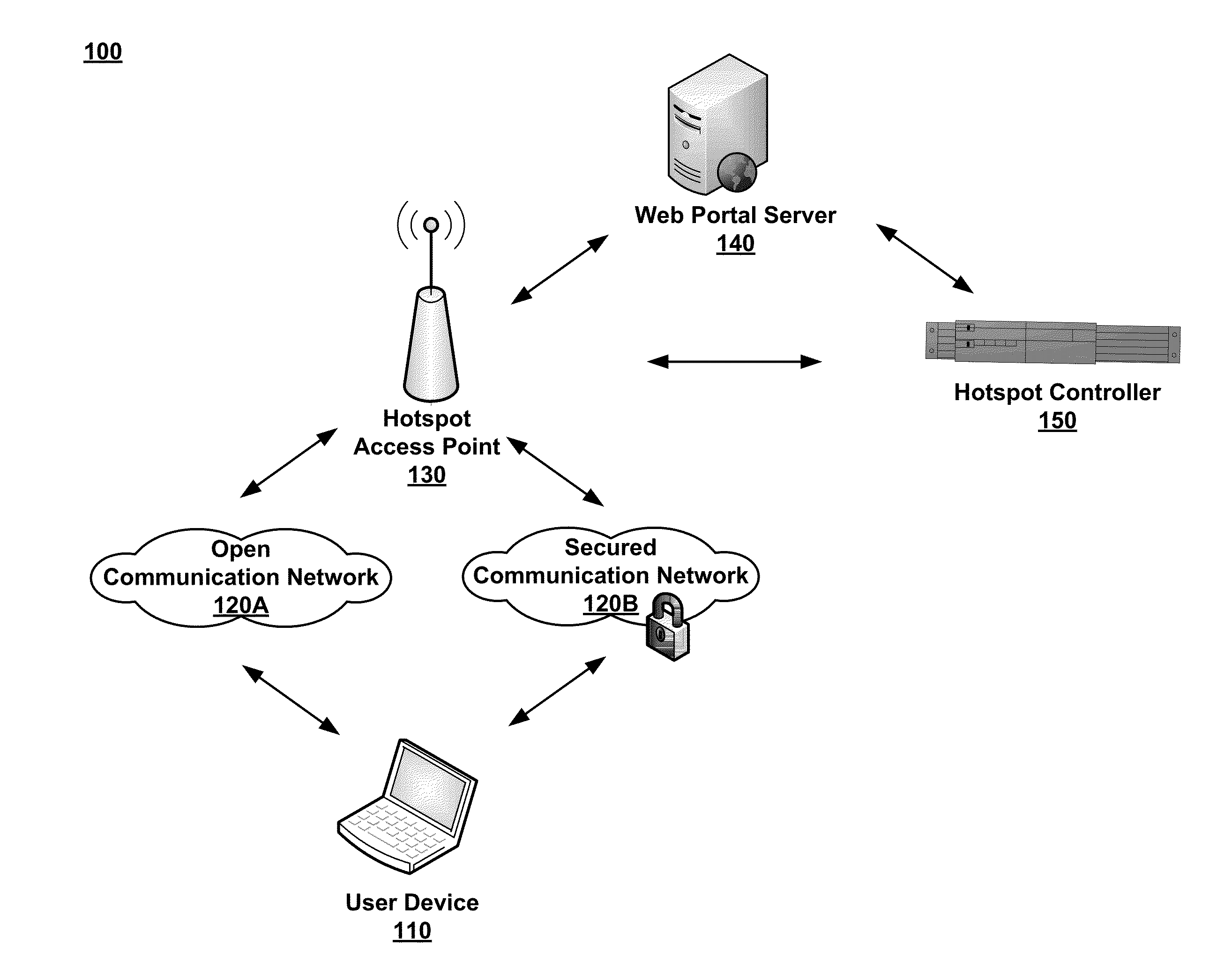
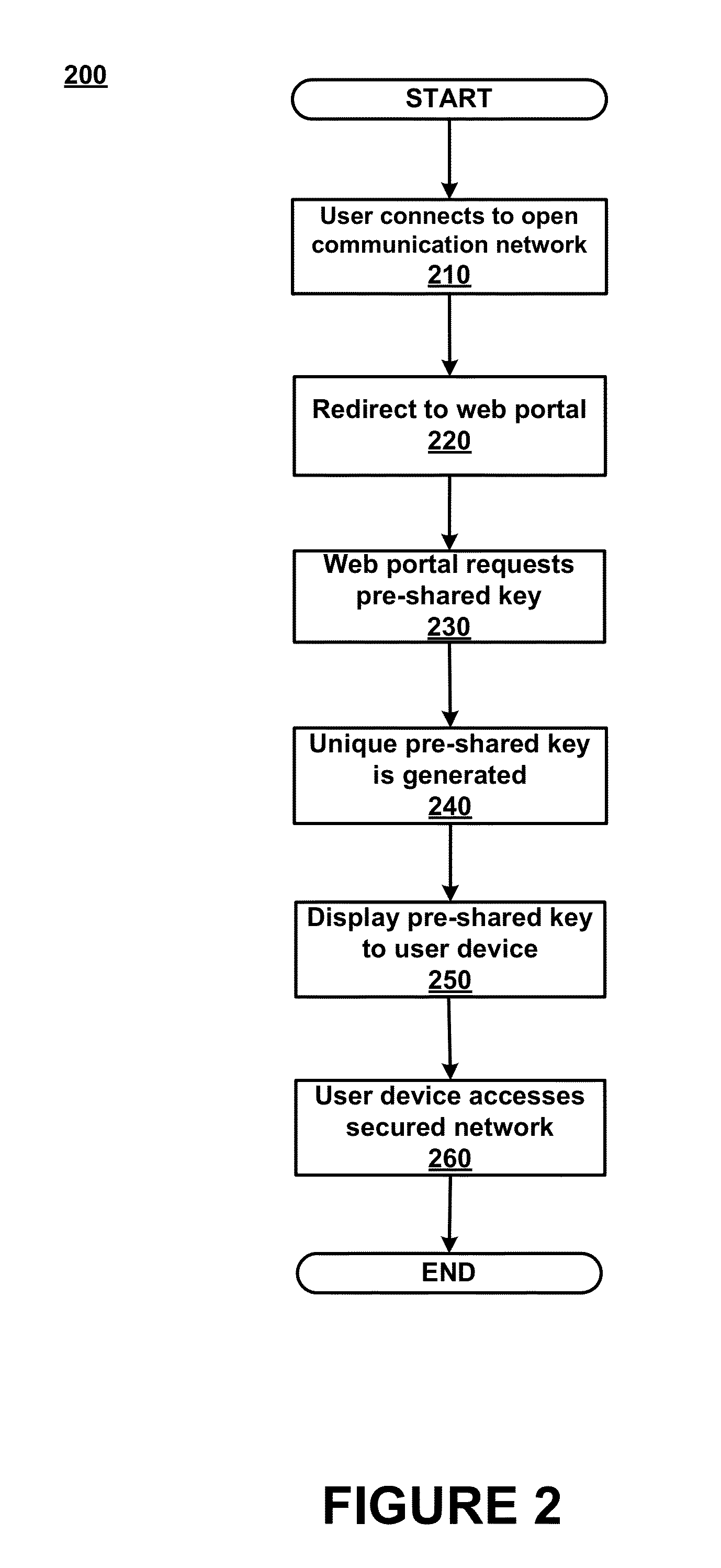
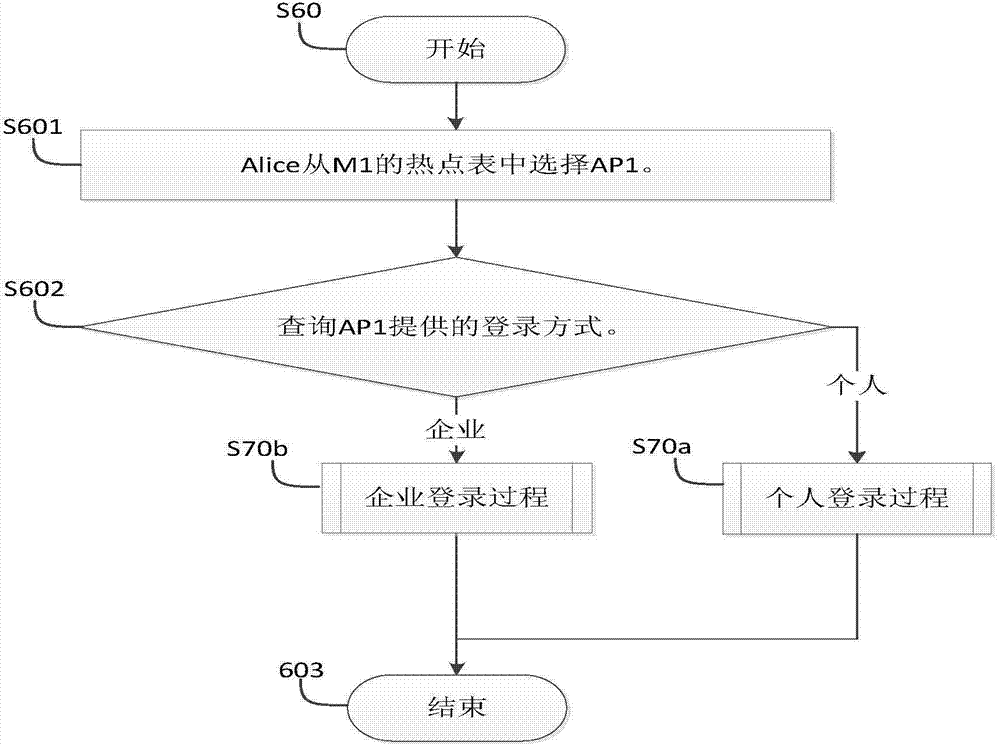
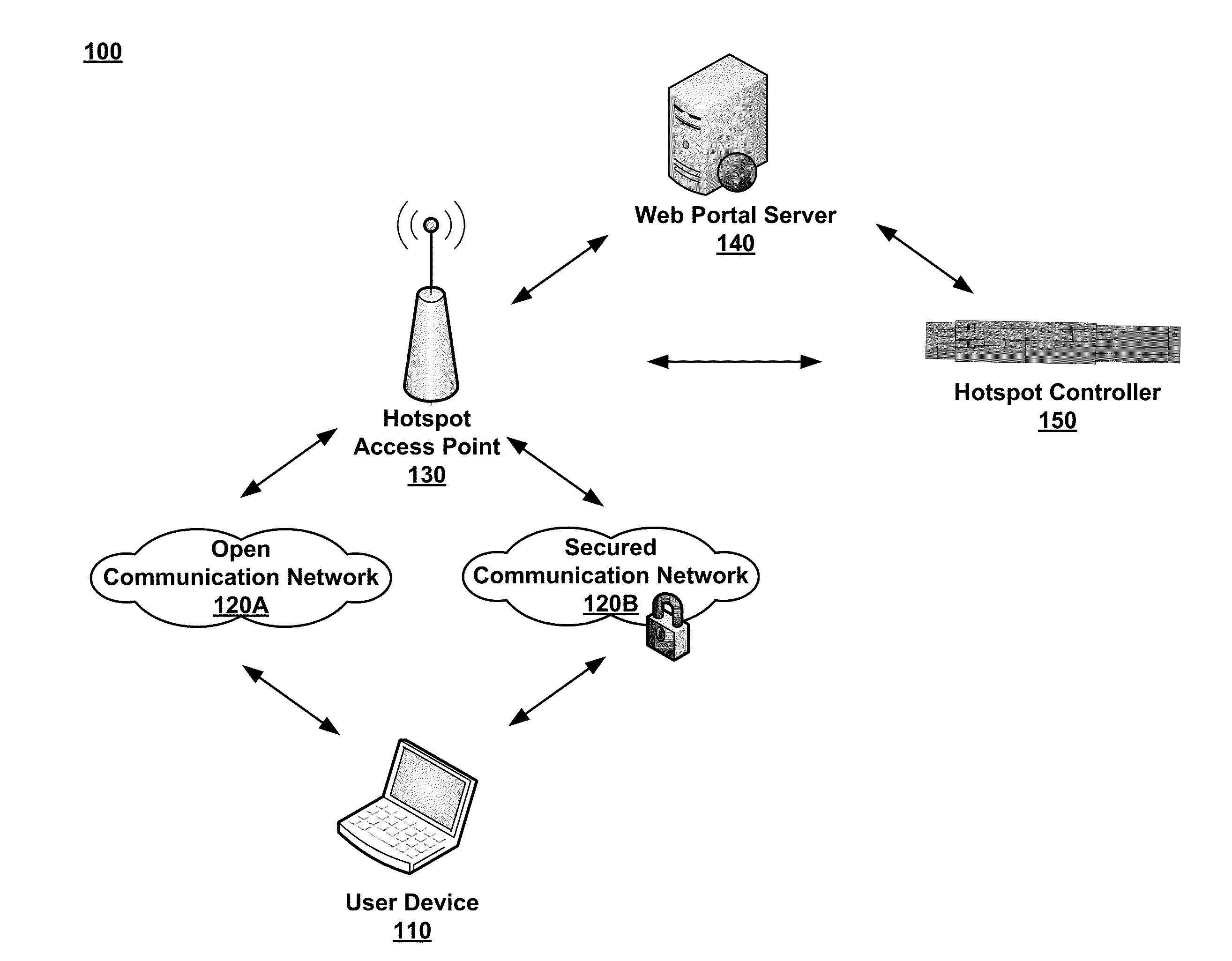
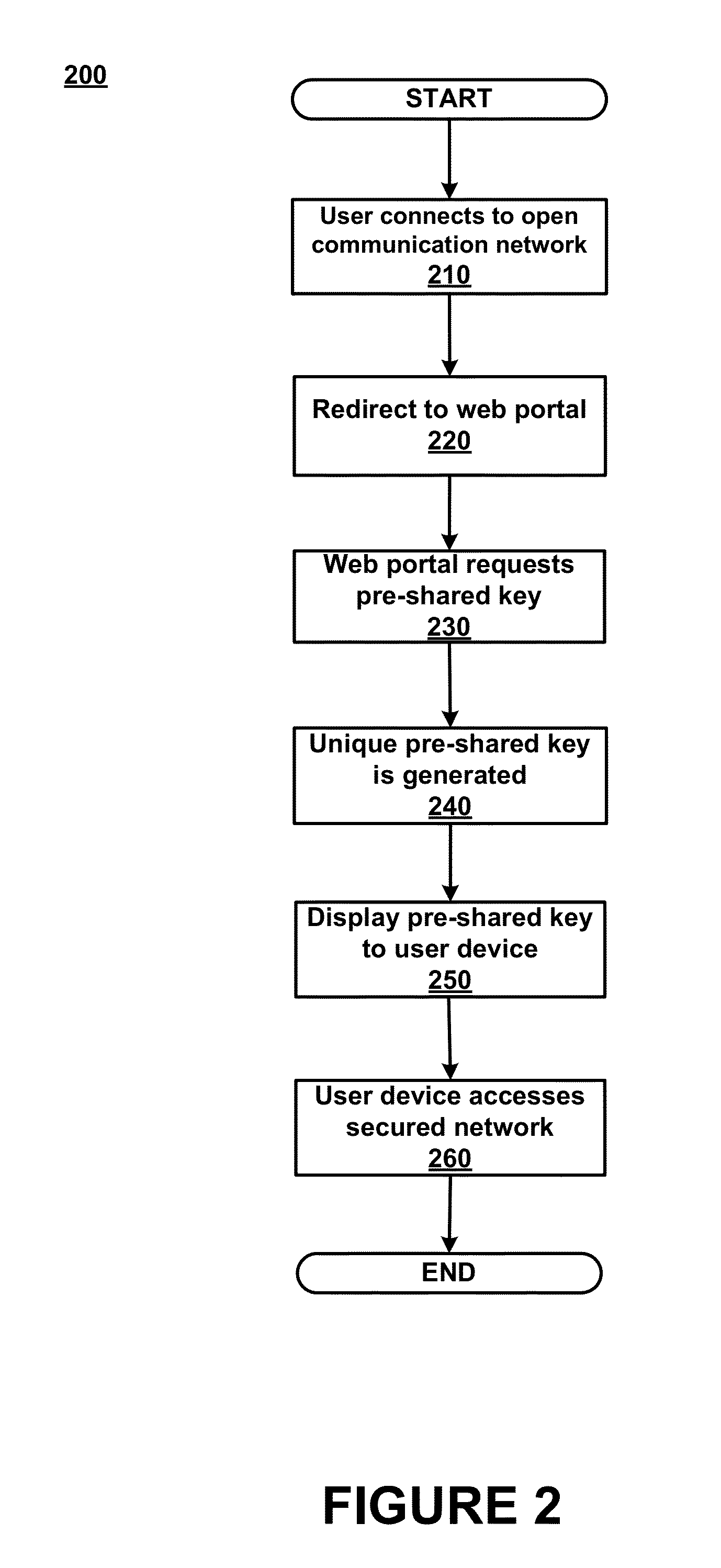
Dynamic PSK for Hotspots
ActiveUS20130212656A1Digital data processing detailsComputer security arrangementsComputer networkWeb page
Systems and methods for providing secured network access are provided. A user device located within range of a hotspot initiates a request sent via an open communication network associated with the hotspot. The request concerns secured network access at the hotspot by the user device. A unique pre-shared key is generated for the user device based on information in the received request and transmitted over the open communication network for display on a webpage accessible to the user device. The unique pre-shared key is stored in association with information regarding the user device. The user device may then use the unique pre-shared key in subsequent requests for secured network access.
Owner:ARRIS ENTERPRISES LLC
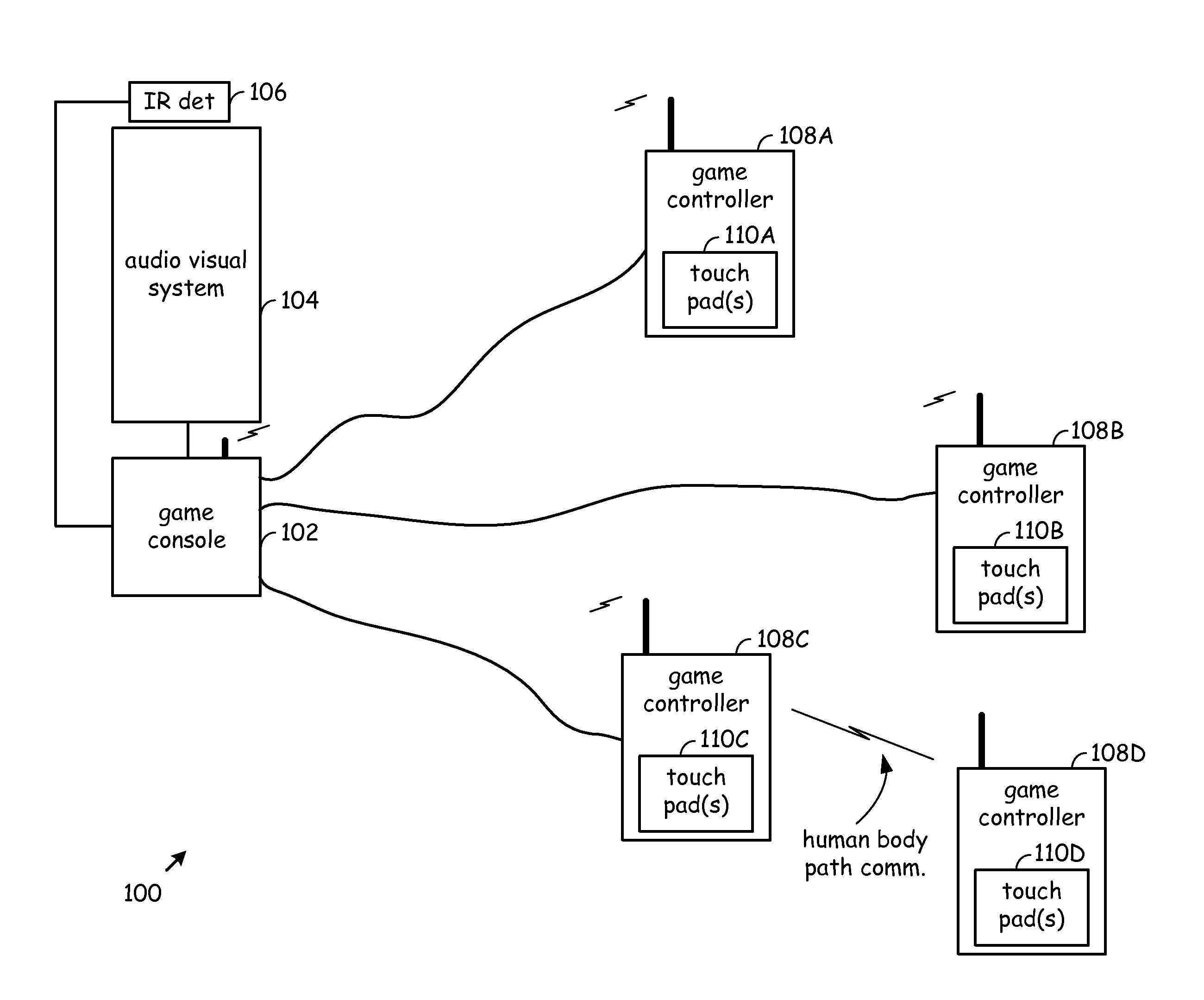
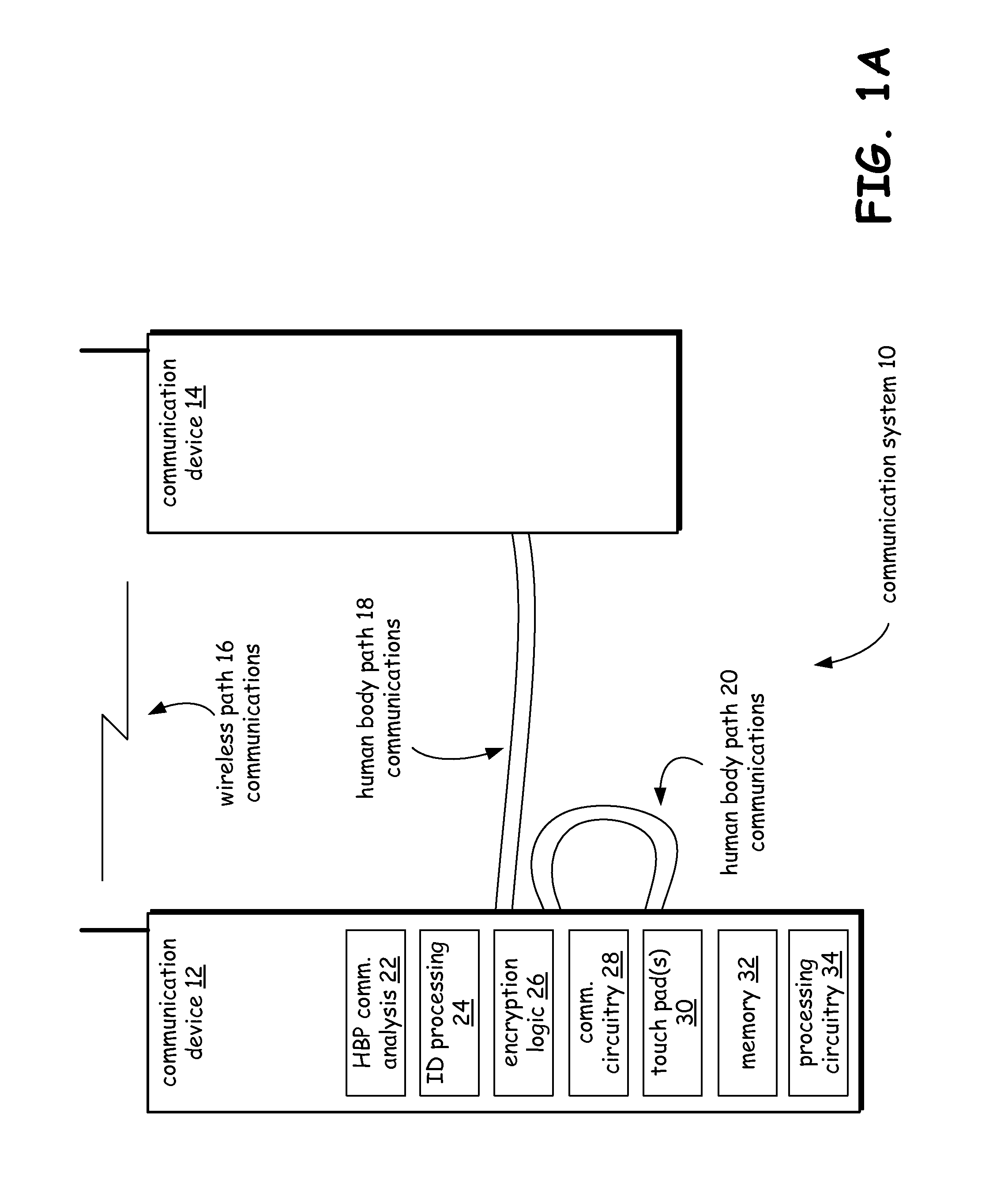
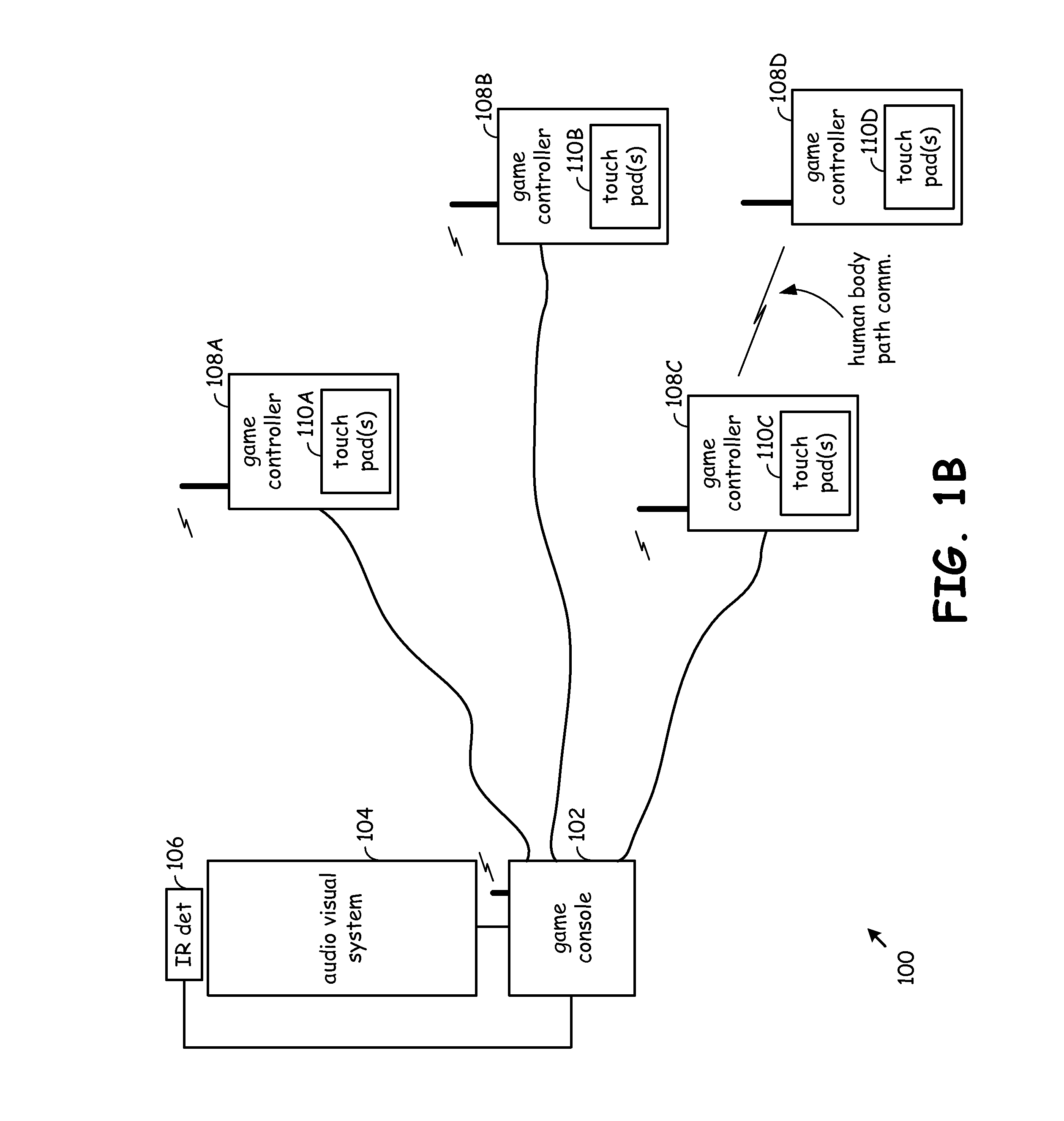
Device communications via intra-body communication path
A communication device that may comprise one of a cell phone or a game controller system that further includes a game console and a pair of game controllers that communicate via a human body path. Generally, the communication device communicates by way of a touch pad array through a human body path using capacitive coupling in one embodiment of the invention. Encryption parameters and user contact information may be exchanged through the human body path. For example, a pre-shared key may be transmitted through the human body path to support subsequent encrypted wireless communications. The touch pad array may be a part of a display of the communication device but is not required to be so.
Owner:AVAGO TECH INT SALES PTE LTD
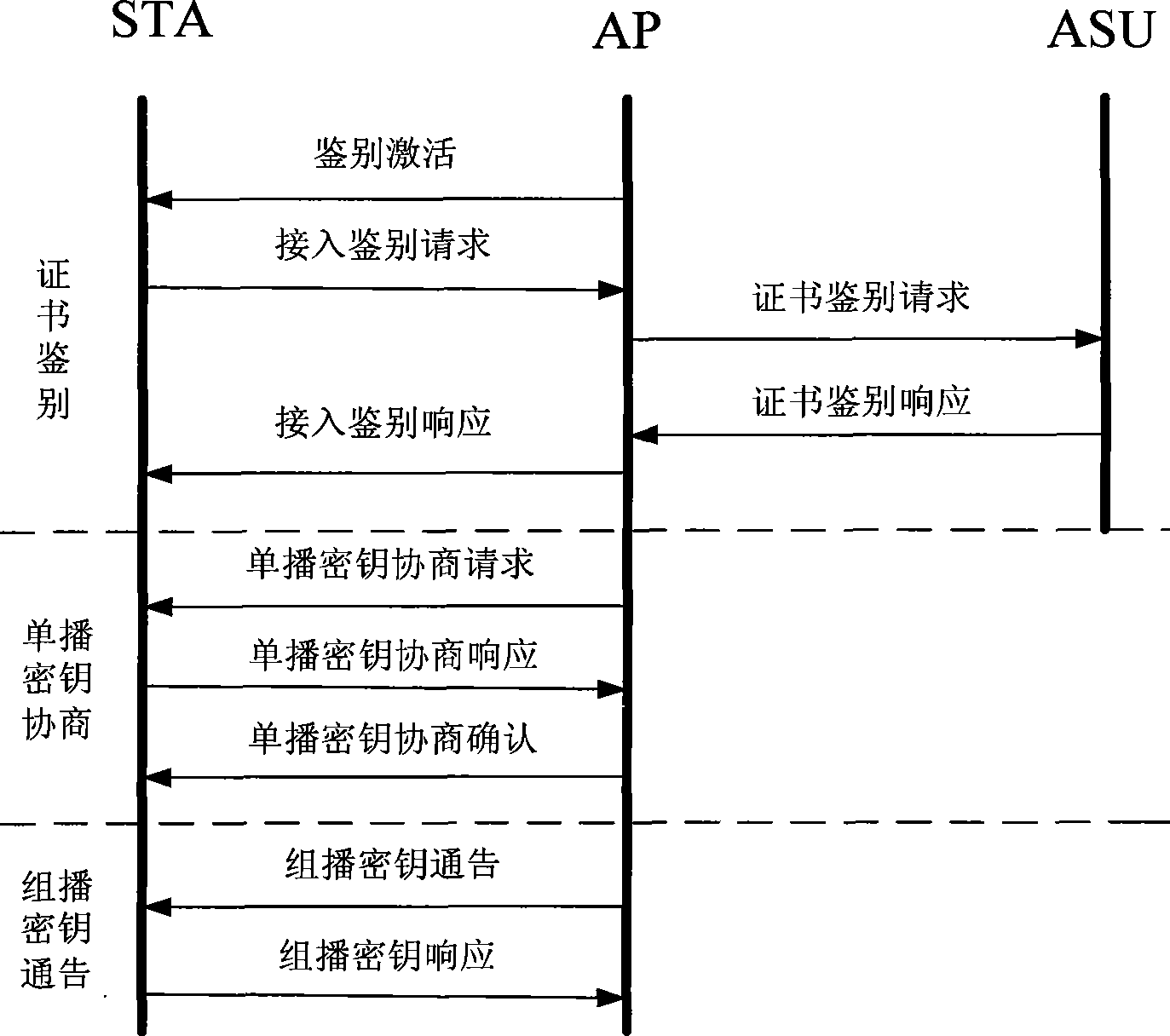
WAPI-XG1 access and fast switch authentication method
InactiveCN101420694AReduce complexitySolve the problem that fast switching is not supportedNetwork topologiesTransmissionClient-sideDictionary attack
The invention provides a method used for authentificating the access and quick switching over of WAPI-XG1, belonging to the field of wireless communication. The method comprises the steps as follows: an authentication protocol is accessed and used for establishing a connection between an STA and a first AP, the session key with the first AP is established, and keys used for quick switching over with an ASU are established; when the STA moves to the control domain of a second AP, a safety correlation establishing protocol and a unicall session key updating protocol under quick switching over are carried out. The method can solve the problems that the WAPI-XG1 can not support the quick switching over and the forward secrecy can not be ensured and the offline dictionary attack can not be resisted under a pre-shared key authentication mode; meanwhile, the method needs not change the authentication framework of the WAPI-XG1needs not changing, the two authentication modes based on the certificate and shared key are integrated into one authentication proposal; furthermore, when the switching over occurs on the client terminal, only the quick switching over safety correlation establishment protocol runs with the destination access point for the authentication mode based on the certificate, without re-authentication or pre-authentication.
Owner:TIANJIN POLYTECHNIC UNIV +1
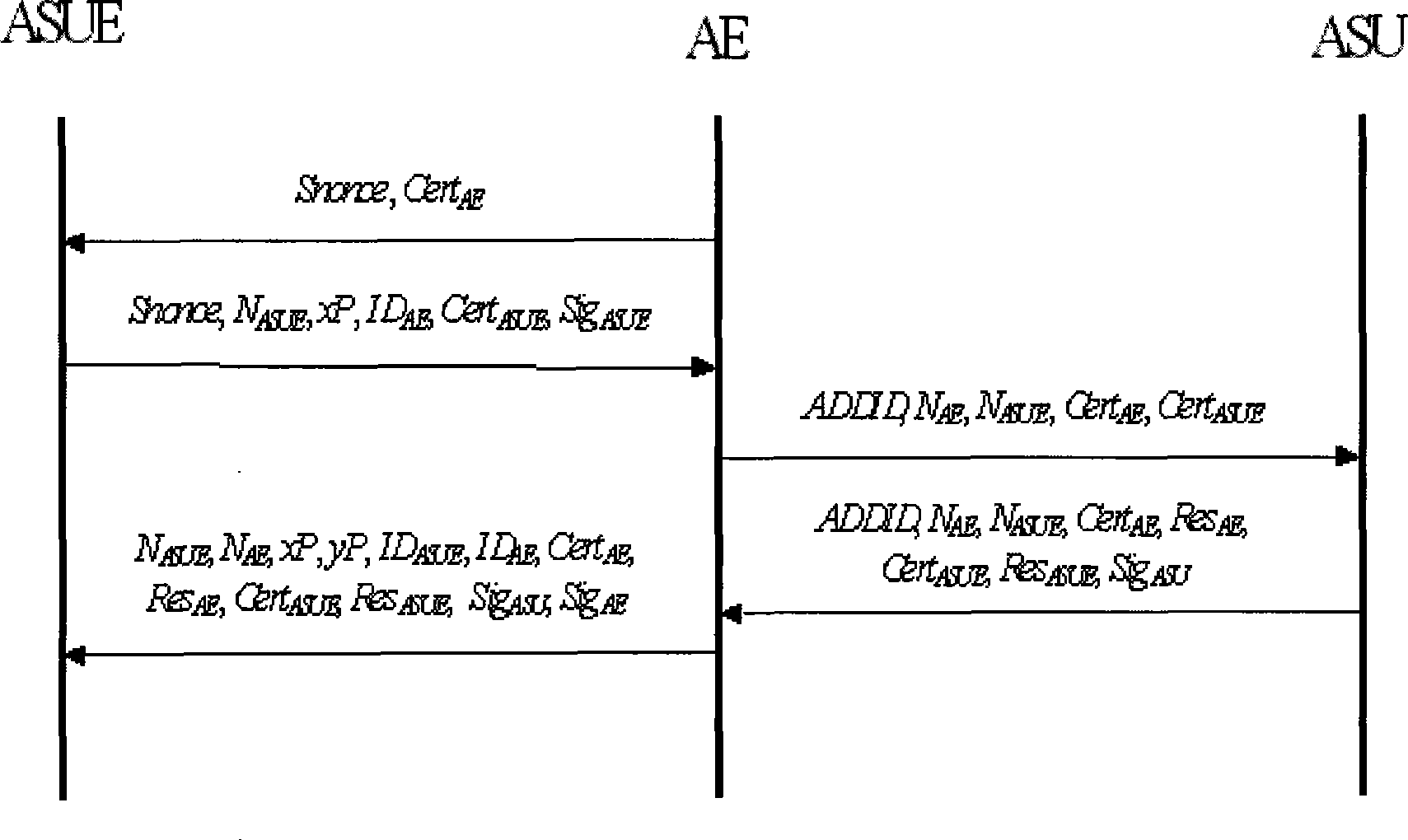
Method and system for using quantum cryptography in safe IP communication
ActiveCN103441839AImprove securityFix compatibility issuesKey distribution for secure communicationKey exchangeIPsec
The invention provides a method and system for using the quantum cryptography in safe IP communication. The method is on the basis of a framework defined by an ISAKMP and comprises the following steps that quantum keys are distributed and a shared secret is established; IQKE SA negotiation is conducted; IPSec SA negotiation is conducted; session keys are generated. According to an IQKE protocol defined by the method and system, the framework defined by the ISAKMP is adopted and is independent of a standard IKE protocol, the problem existing in the compatibility of the standard IKE protocol and a QKD system can be avoided so that the safety of the quantum keys generated by the IPSec through the QKD system can be enhanced; in addition, according to the IQKE protocol, the quantum keys generated by the QKD system are adopted and serve as pre-shared keys, so that the adoption of the typical key exchange algorithm is not needed and the complexity of key negotiation is reduced. QIKE and QKD can be conducted in parallel; according to the QKD system with the low speed, the key storage technology is adopted; according to the QKD system with the high speed, OTP encryption can be achieved, so that the unconditional safety is achieved. The method and system are significant for improvement of the safety of IP communication.
Owner:STATE GRID CORP OF CHINA +3
System and method for secured communication
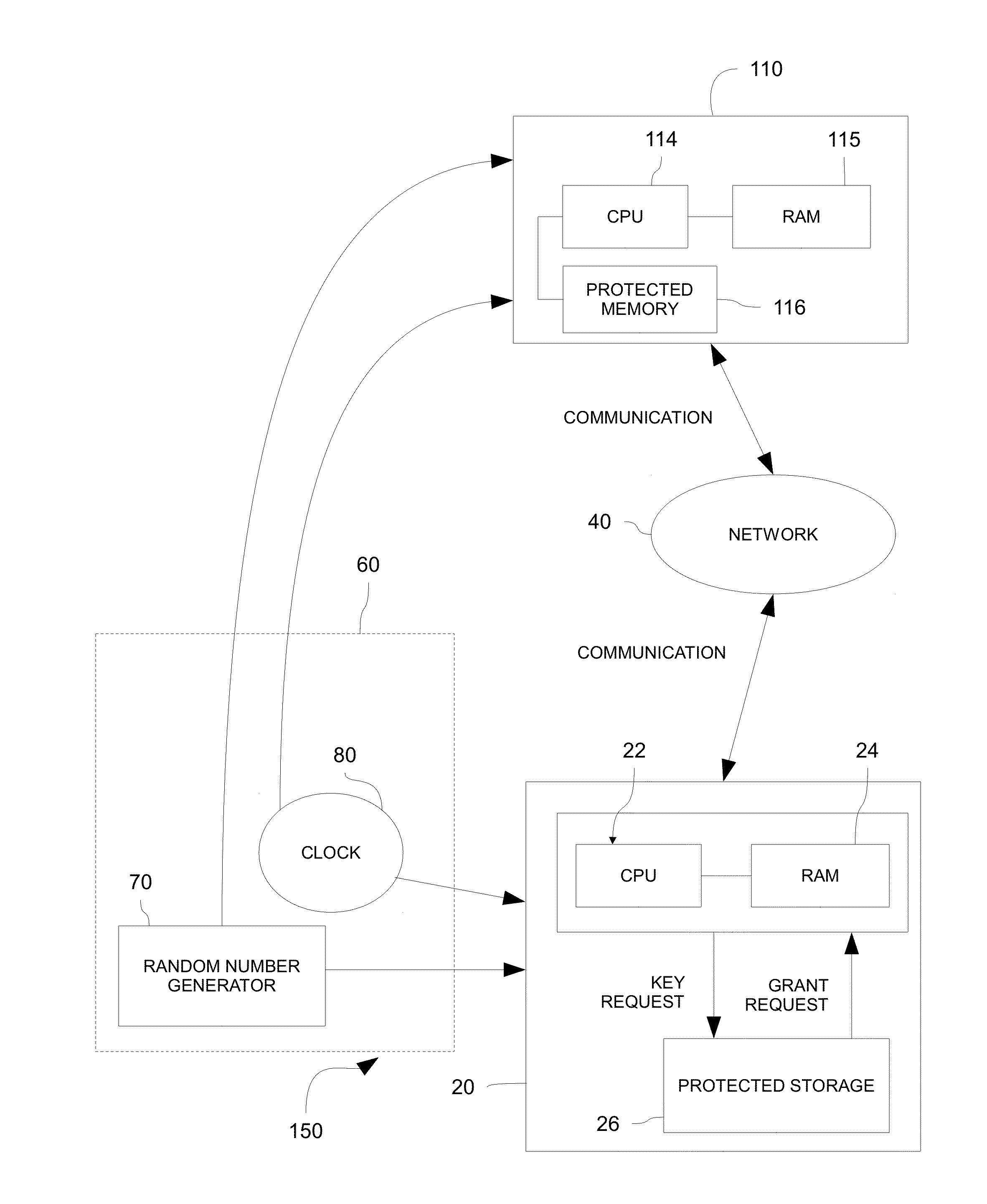
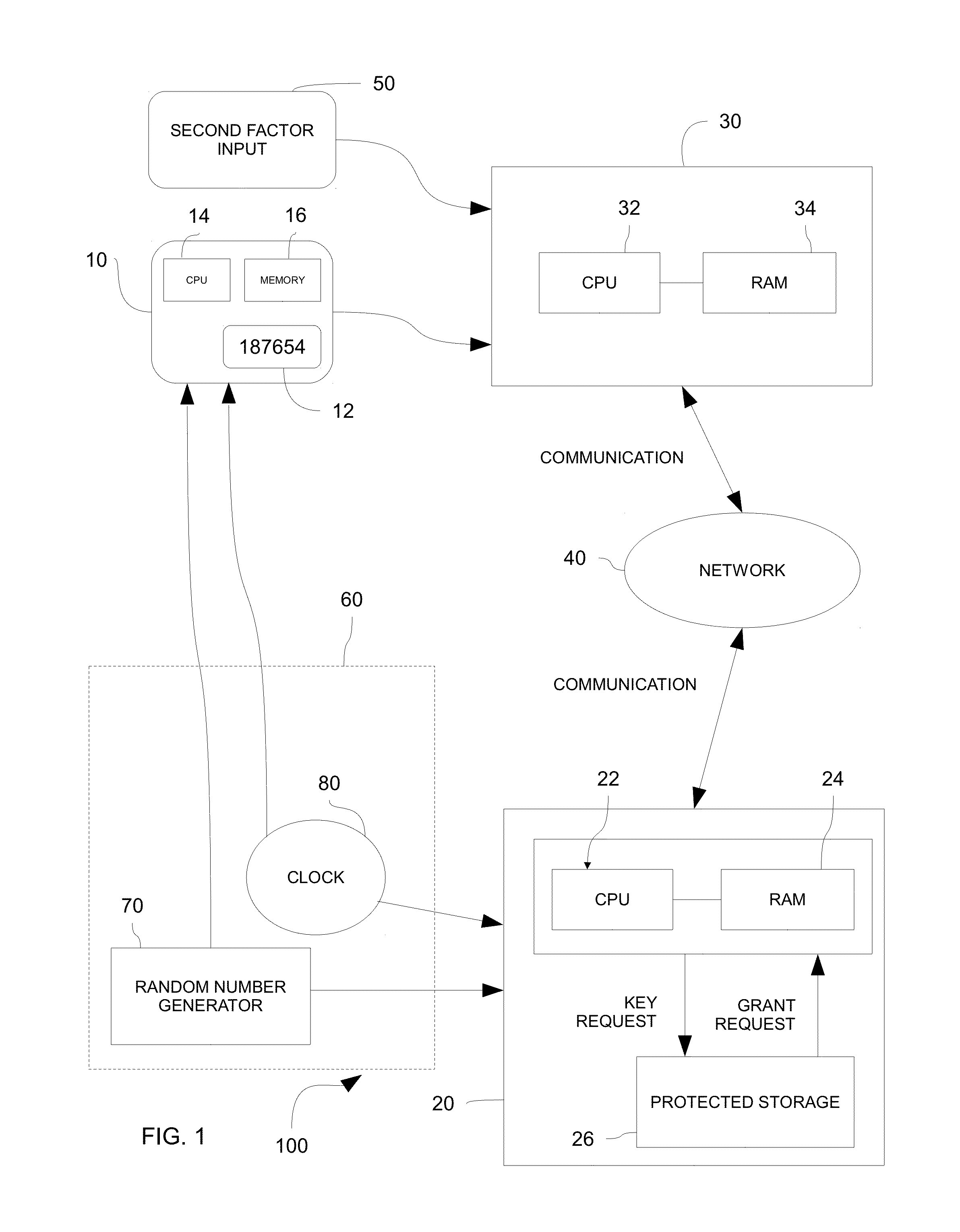
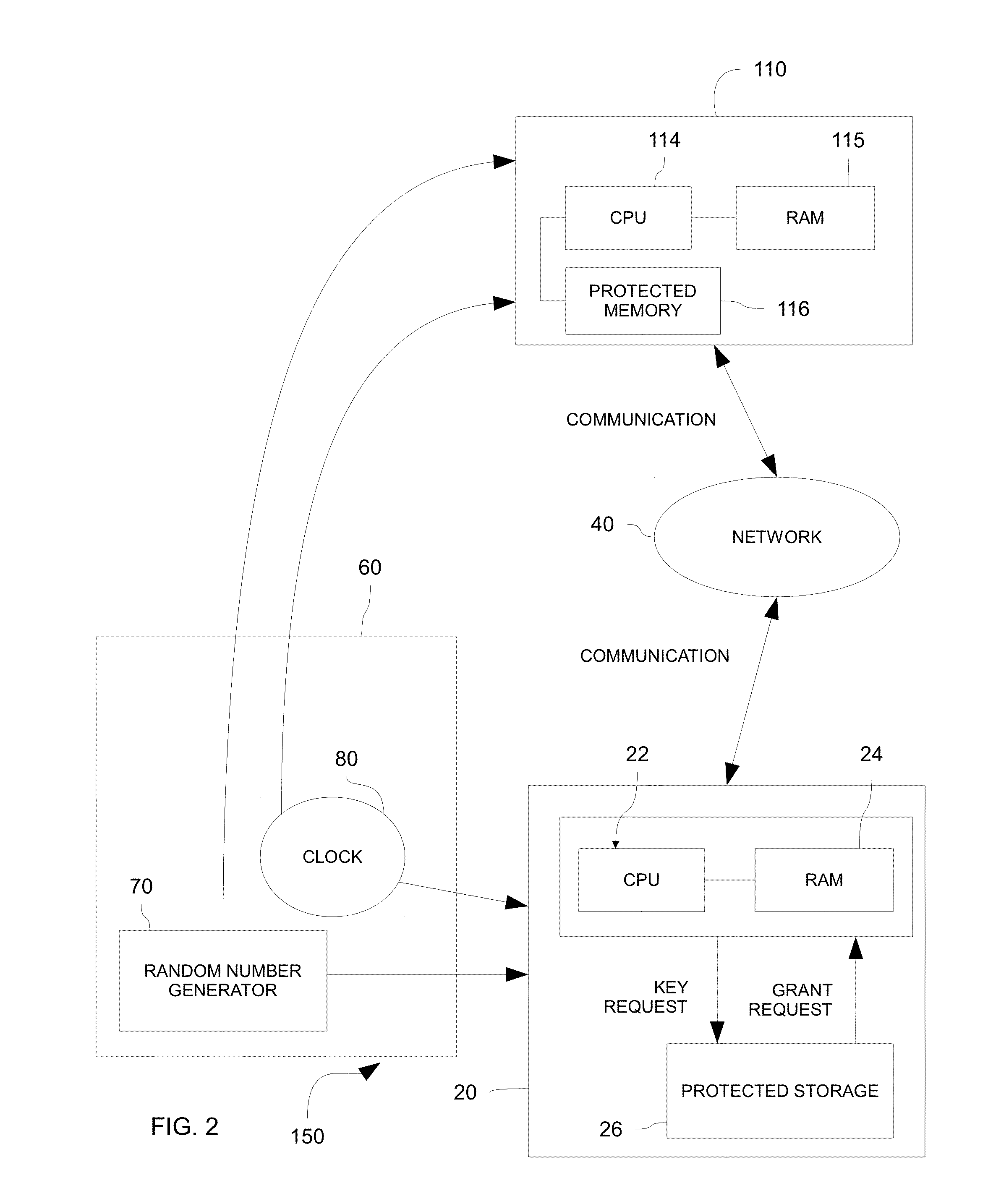
InactiveUS20150288517A1Avoid security threatsKey distribution for secure communicationSynchronising transmission/receiving encryption devicesSecure communicationCommunications system
Systems and methods for securely communicating with a server device are provided. Both the server device and a client device may be provided pre-shared keys, which may be based on a stream of random digits generated by a quantum random number generator. The client device may promote a new client-side key from among the pre-shared keys for use in secure communication with the server device in response to an event, such as a time-based event (e.g., passage of 30 seconds). The server device may be substantially synchronized with the client device such that a server-side key matches a client-side key being used to communicate securely with the server device.
Owner:UT BATTELLE LLC
Secure bootstrapping for wireless communications
ActiveUS7966000B2Unauthorised/fraudulent call preventionMultiple keys/algorithms usageKey exchangeChallenge response
A mutual authentication method is provided for securely agreeing application-security keys with mobile terminals supporting legacy Subscriber Identity Modules (e.g., GSM SIM and CDMA2000 R-UIM, which do not support 3G AKA mechanisms). A challenge-response key exchange is implemented between a bootstrapping server function (BSF) and mobile terminal (MT). The BSF generates an authentication challenge and sends it to the MT under a server-authenticated public key mechanism. The MT receives the challenge and determines whether it originates from the BSF based on a bootstrapping server certificate. The MT formulates a response to the authentication challenge based on keys derived from the authentication challenge and a pre-shared secret key. The BSF receives the authentication response and verifies whether it originates from the MT. Once verified, the BSF and MT independently calculate an application security key that the BSF sends to a requesting network application function to establish secure communications with the MT.
Owner:QUALCOMM INC
METHODS AND ENTITIES USING IPSec ESP TO SUPPORT SECURITY FUNCTIONALITY FOR UDP-BASED OMA ENABLES
ActiveUS20110016314A1Overhead traffic is decreasedEfficiently establishedUser identity/authority verificationSecurity arrangementIPsecClient-side
Methods in OMA SEC_CF for providing security services to traffic over UDP between a client and a server and the relevant entities are provided. A pre-shared key is pre-shared between the client and the server. A pair of IPSec ESP SAs between the client and the server is established without shared key negotiation, wherein traffic data cryptographic algorithms are determined. Traffic data security keys are derived from the pre-shared key via the determined traffic data cryptographic algorithms. Then, data of the traffic can be provided with security services with the traffic data security keys through use of IPSec ESP.
Owner:ALCATEL LUCENT SAS
Proxy method and system for secure wireless administration of managed entities
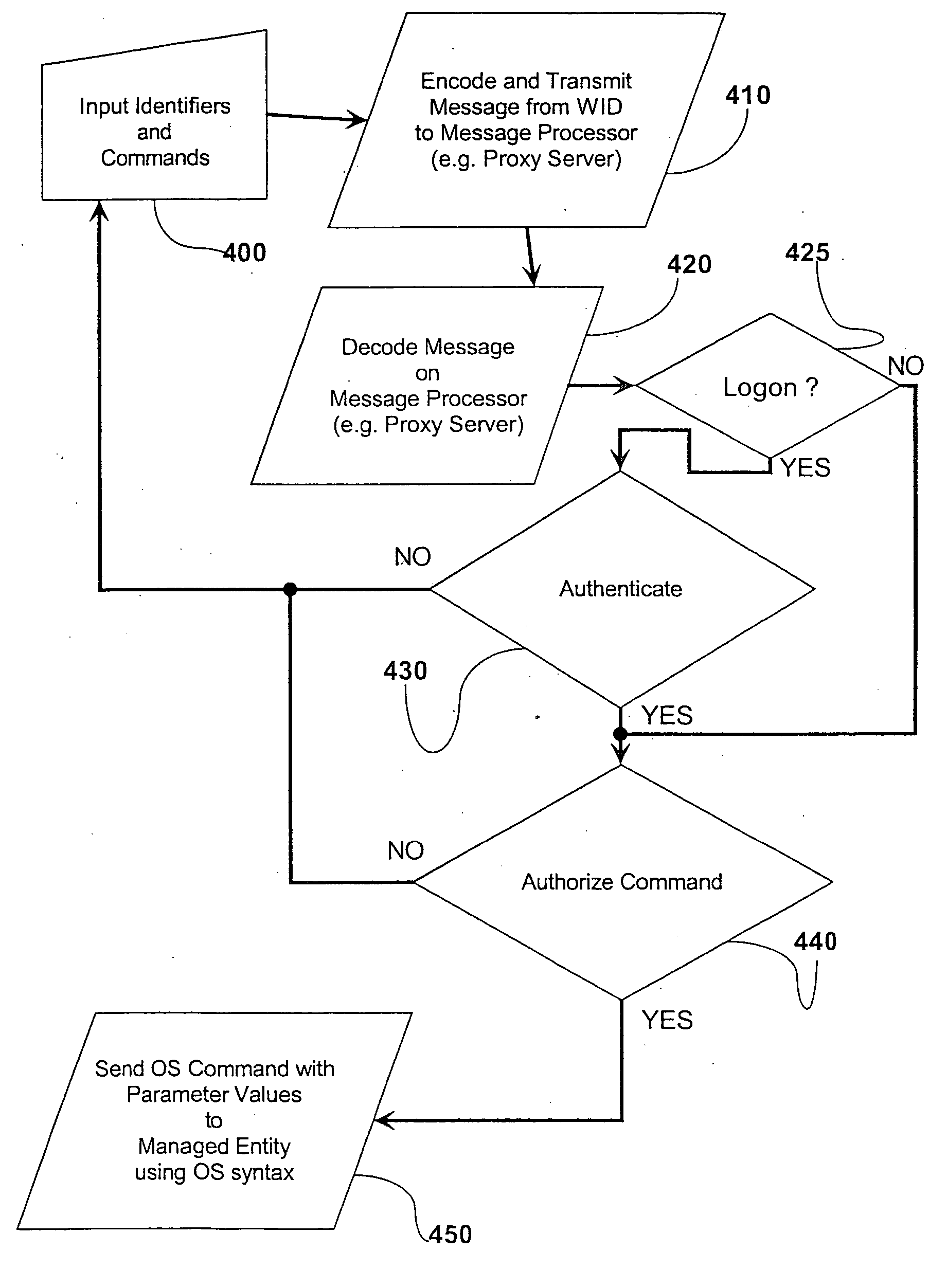
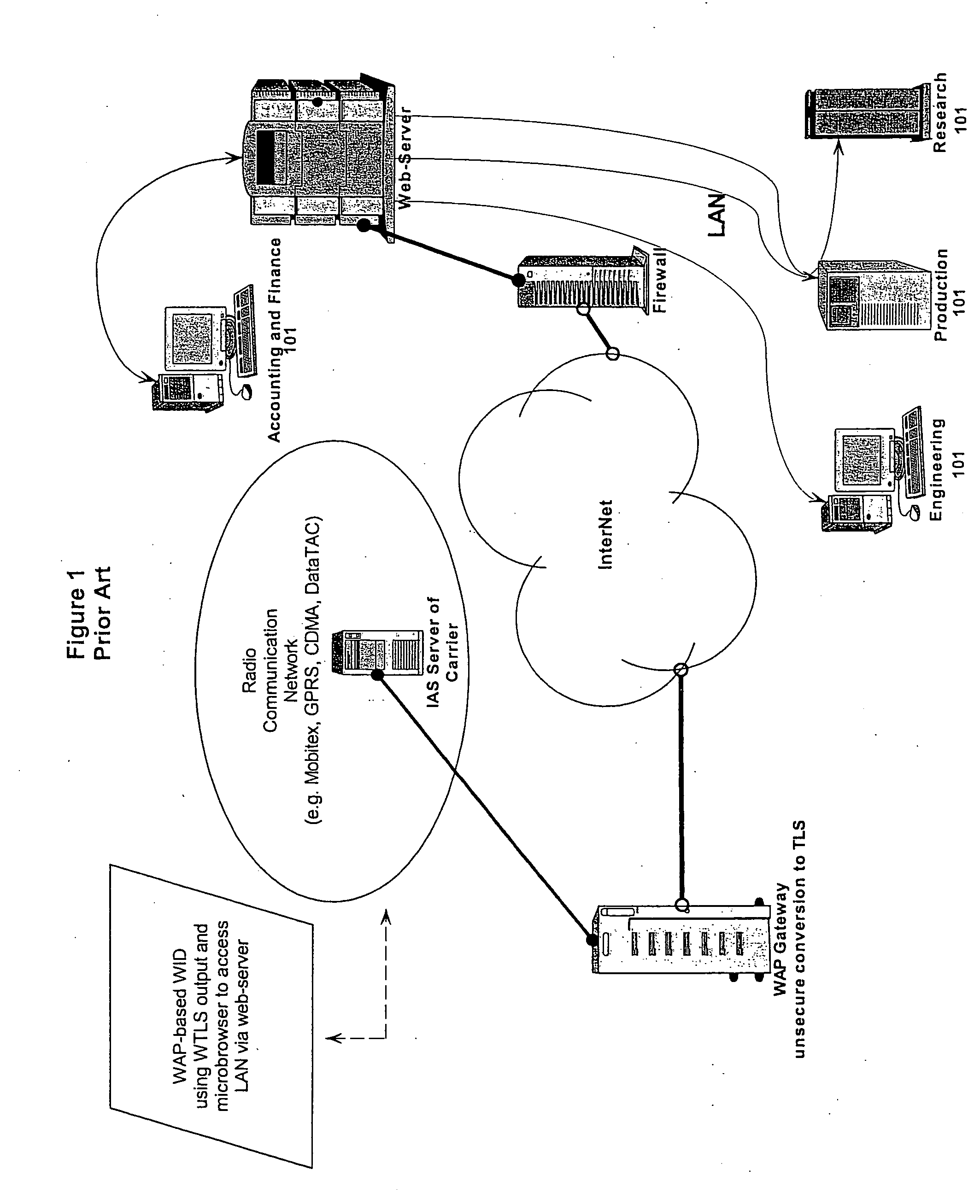
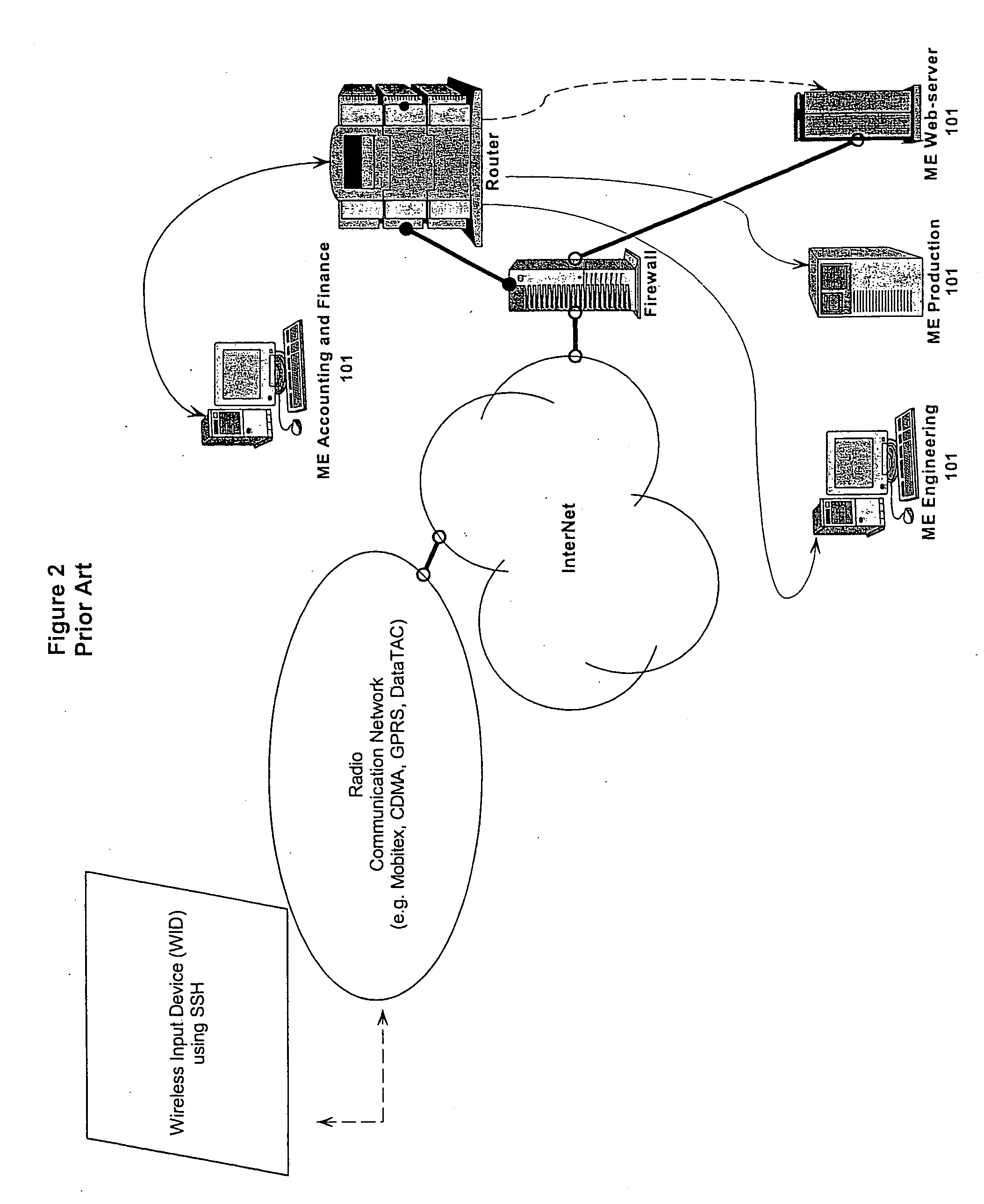
InactiveUS20060218402A1Reduce usageIncrease varietyKey distribution for secure communicationUser identity/authority verificationTraffic capacityWeb service
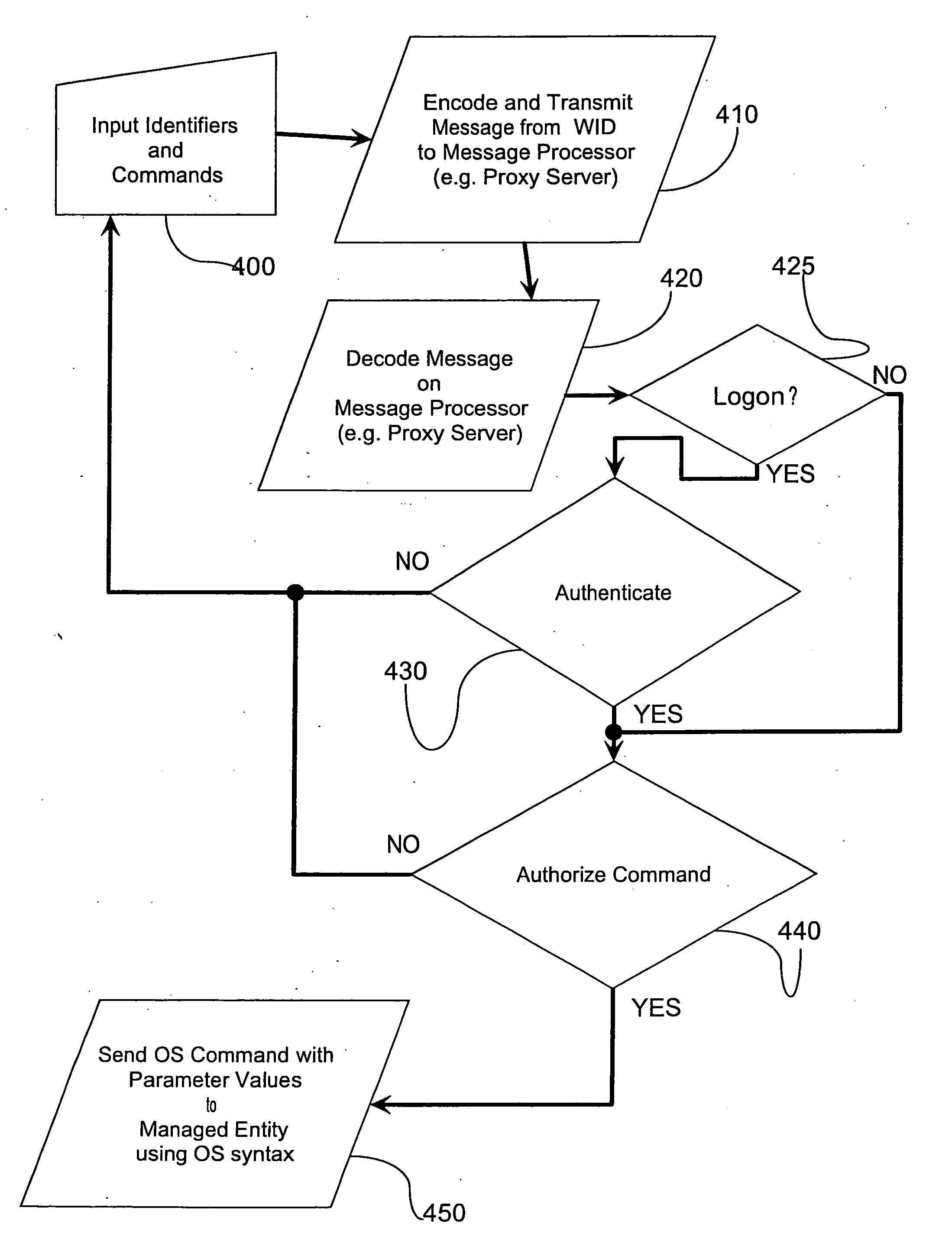
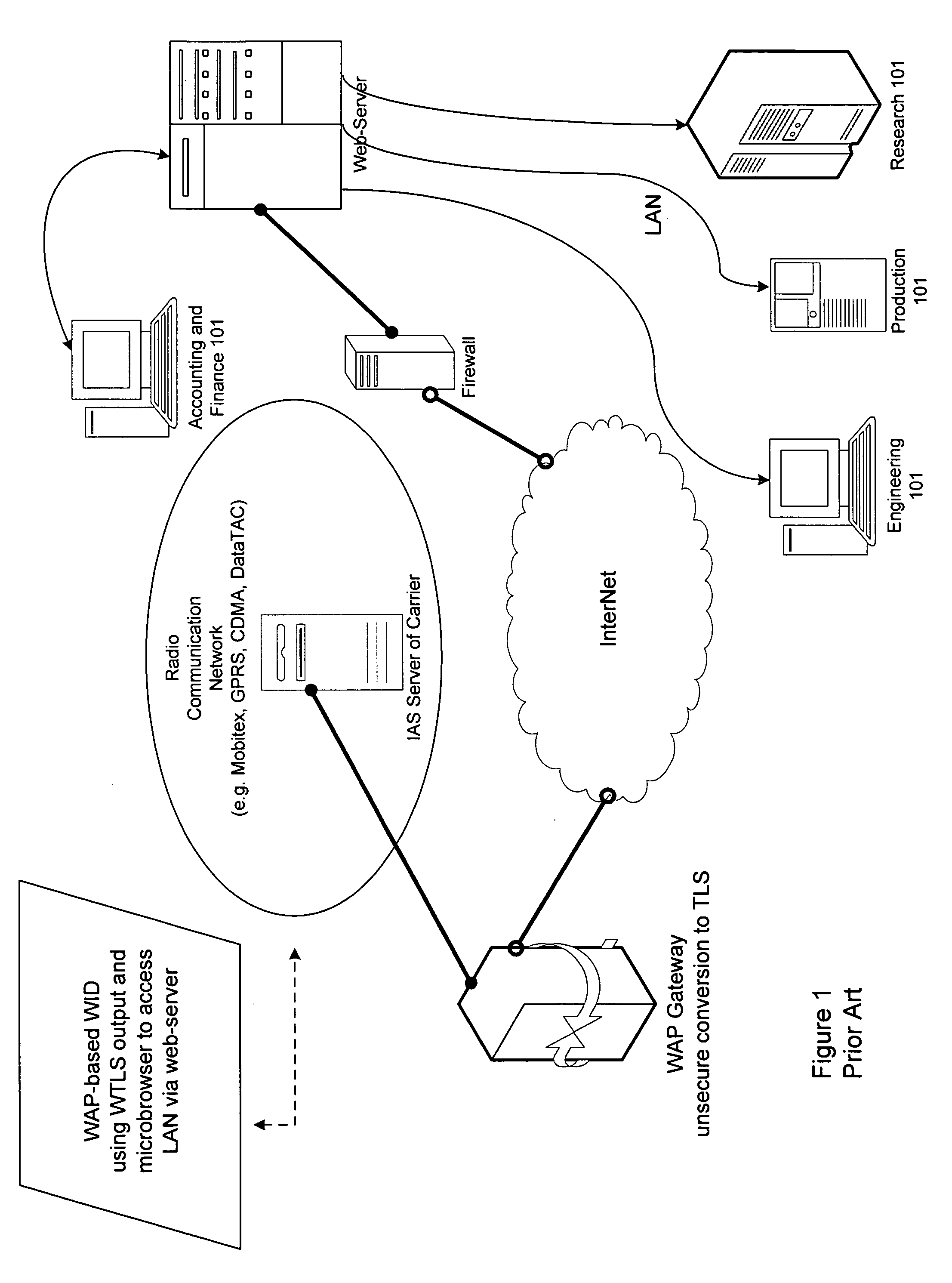
A method, system and apparatus are described for avoiding the use of a web-server or generic security when providing network administration services remotely to managed entities using wireless technology. Instead a true Proxy device, not operating as a web-server, is used to pre-process all command traffic from wireless input devices (WID). The intervention between the WID and the managed entities of the Proxy isolating the managed entities from the WID, enhanced by encoding using a novel messaging protocol, further enhanced by a novel security model based on multiple pre-shared keys and algorithms together with identifiers and passwords that are not transmitted, achieves several bandwidth and security advantages including the ability to deliver TELNET services across the Internet and behind a firewall.
Owner:VERTIV IT SYST INC
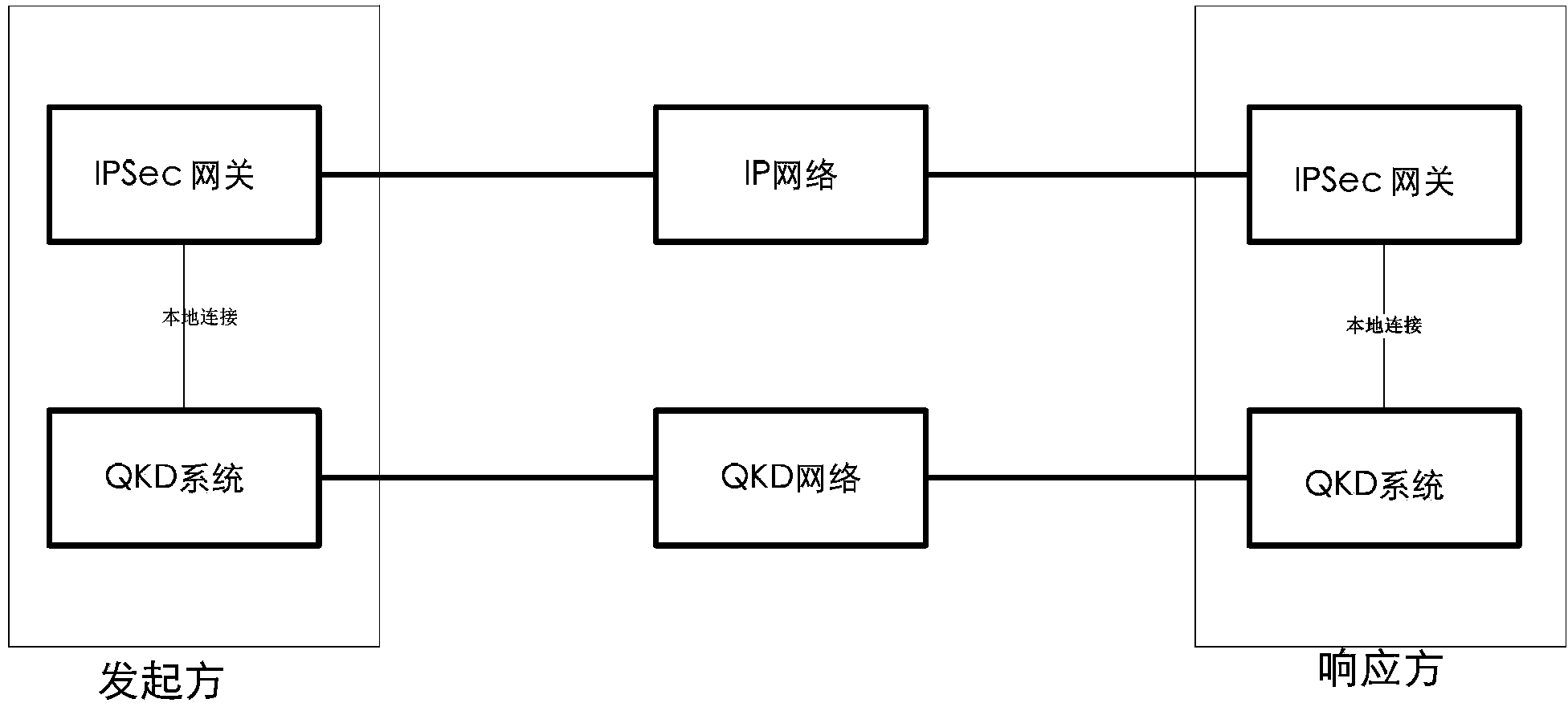
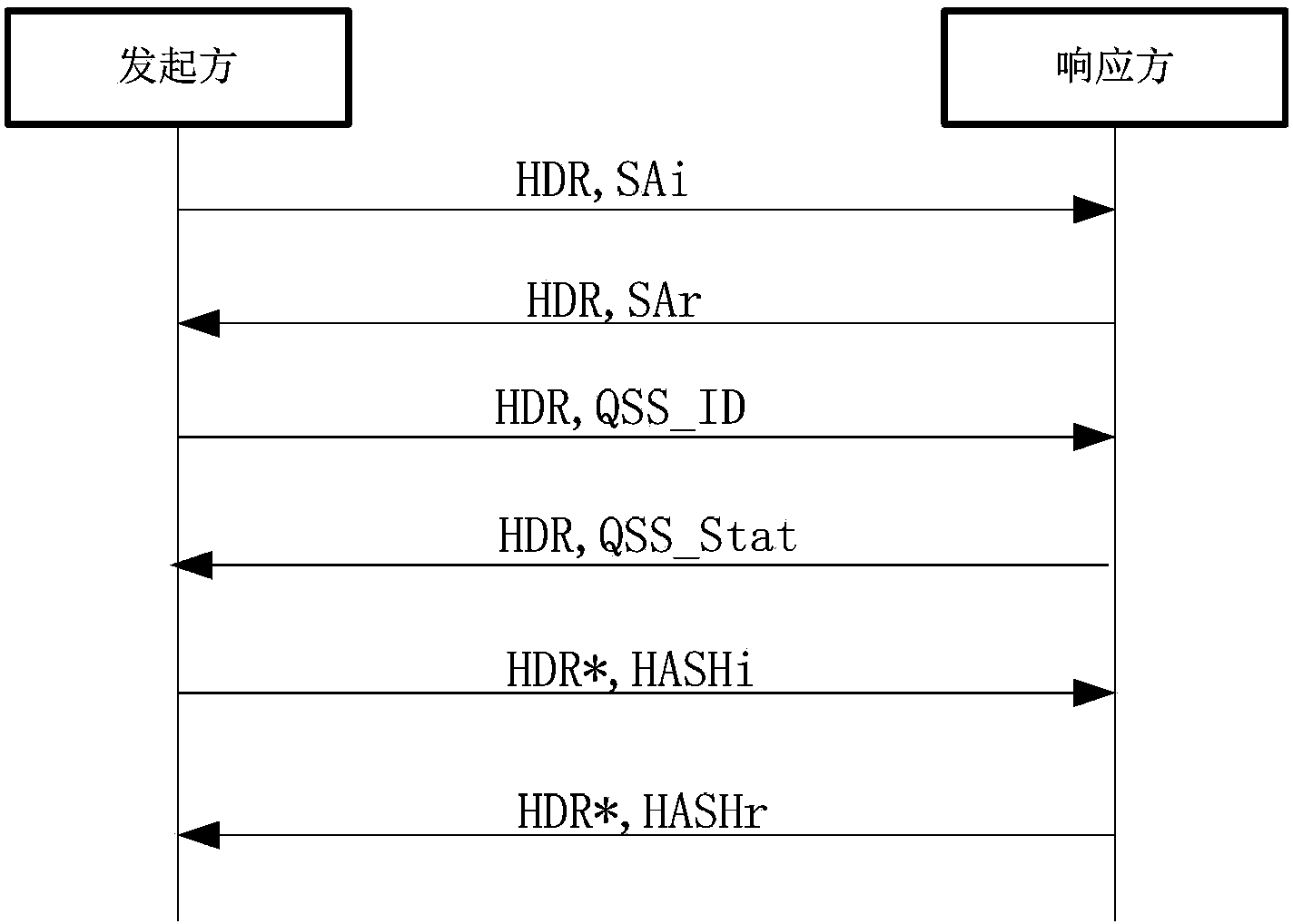
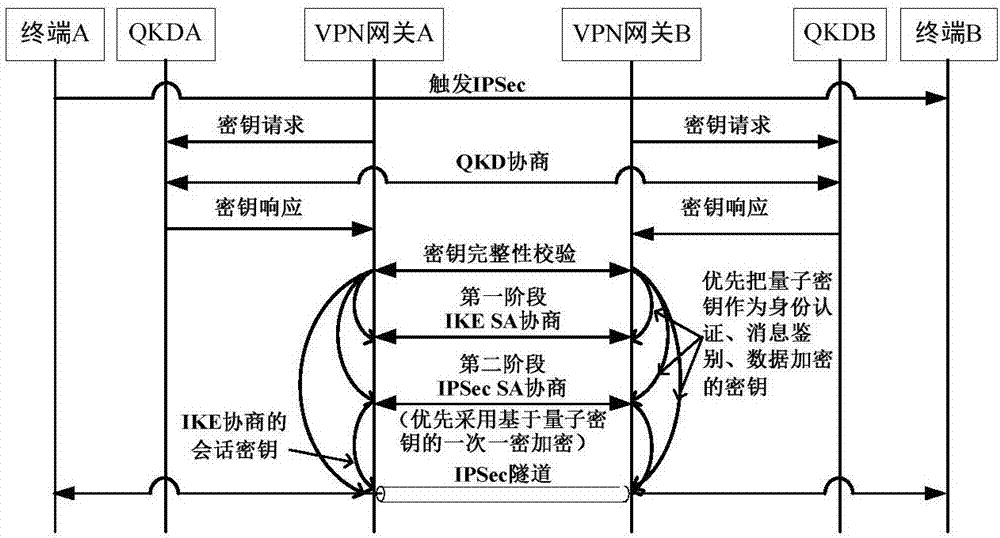
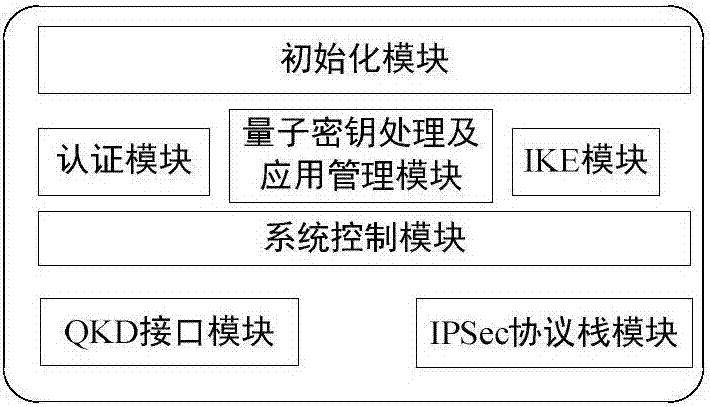
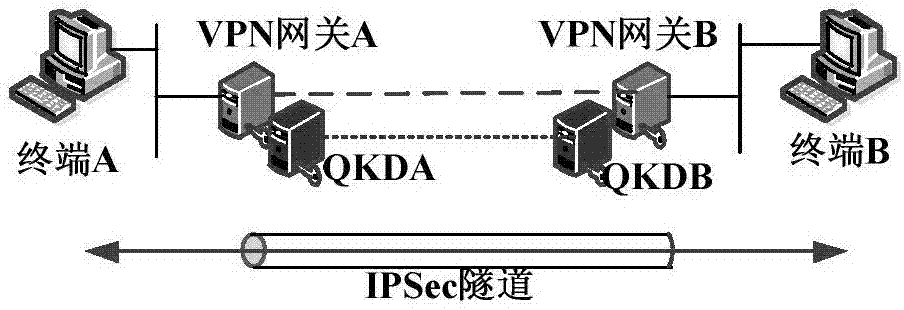
IPSec VPN method used for realizing quantum safety
ActiveCN107453869AImproving Quantum SecurityImplement converged applicationsKey distribution for secure communicationOne-time padQuantum
The invention discloses an IPSec VPN method used for realizing quantum safety. The method is characterized by adding a safe interface of QKD in an IPSec VPN gateway; adding a quantum key access and application mechanism in an IPSec VPN safety strategy; adding a one-time pad encryption option based on a quantum key in an IPSec encryption component and adding a strategy which preferentially adopts the quantum key as a pre-shared key, and adopts a session key of a data encryption algorithm and a shared key of an HMAC algorithm; and realizing fusion application of the QKD, quantum encryption and an IPSec protocol, and increasing quantum safety of identity authentication, message authentication and data encryption of an IPSec VPN system. The safety of the system is high, application access is flexible, and a good application prospect is possessed in fields of party, government, industrial control, finance, military and the like.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
WiFi hot spot safe login method and system
ActiveCN104735052AReduce leakageReduce the difficulty of implementationKey distribution for secure communicationUser identity/authority verificationPasswordThe Internet
The invention provides a WiFi hot spot safe login method and system. A label which is unique globally is embedded in an SSID of a hot spot, a server inquires description information of the hot spot with the label as a key clue, and a user identifies peripheral hot spots through the hot spot description information sent from the server; a contact relation is established between the user with the hot spot login request and owners of the hot spots so that the user can log into all the hot spots with the owners being the user or contacts of the user; the server located in the internet is maintained, a temporary key needed by the user in a personal login mode is generated through a pre-shared key, a terminal used by the user is in handshake communication with the hot spots through the temporary key distributed from the server, and the possibility of pre-shared key leakage or cracking is lowered. The user logs into the hot spots working in any login mode through an account number registered in the server and a password, the different login modes of the hot spots can be switched at will, and the whole switching process is transparent to the user.
Owner:SUN YAT SEN UNIV
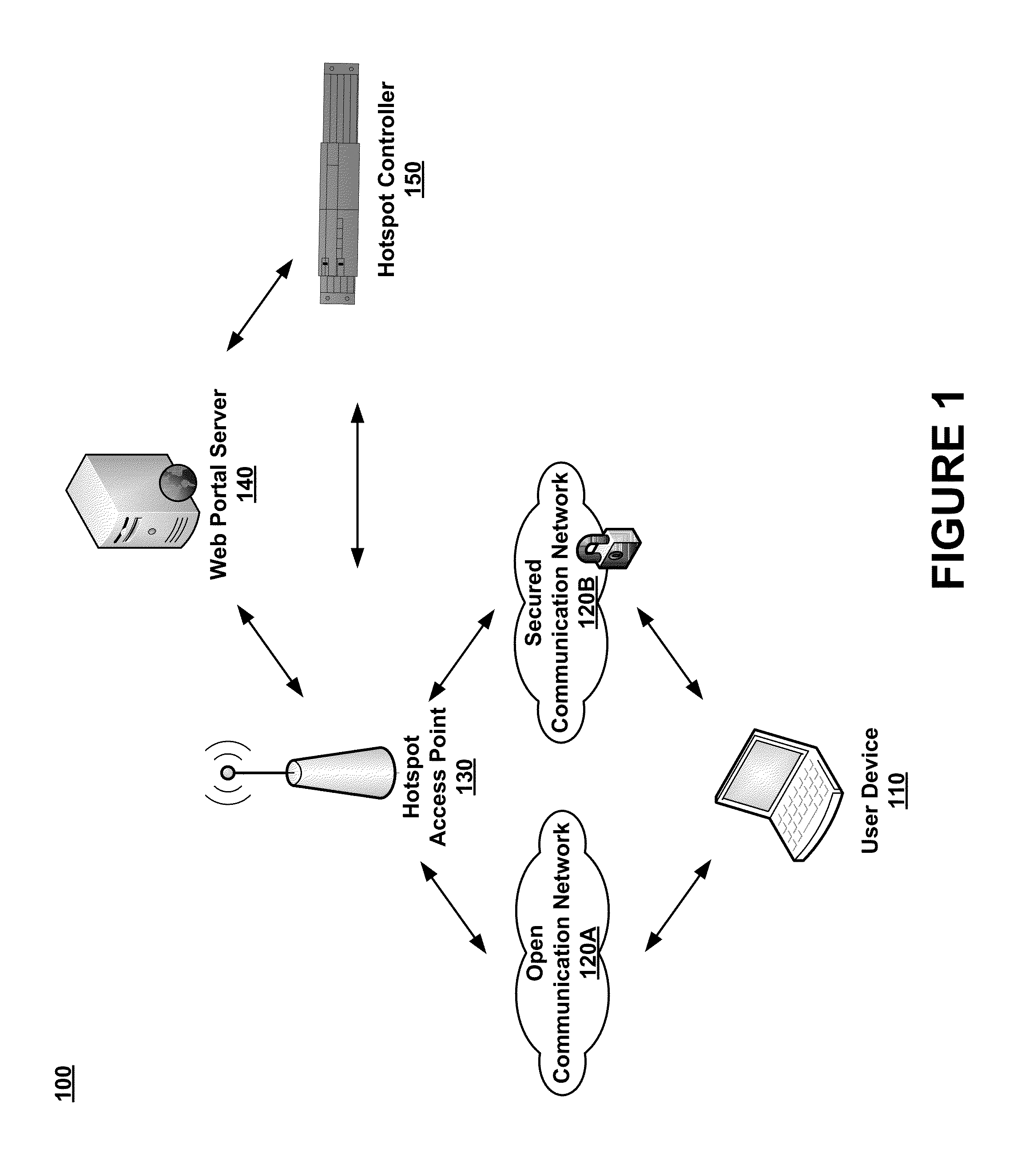
Dynamic PSK for hotspots
ActiveUS8756668B2Digital data processing detailsUser identity/authority verificationComputer networkWeb page
Systems and methods for providing secured network access are provided. A user device located within range of a hotspot initiates a request sent via an open communication network associated with the hotspot. The request concerns secured network access at the hotspot by the user device. A unique pre-shared key is generated for the user device based on information in the received request and transmitted over the open communication network for display on a webpage accessible to the user device. The unique pre-shared key is stored in association with information regarding the user device. The user device may then use the unique pre-shared key in subsequent requests for secured network access.
Owner:ARRIS ENTERPRISES LLC
Apparatus and method for managing stations associated with wpa-psk wireless network
ActiveUS20080044024A1Key distribution for secure communicationUser identity/authority verificationWi-FiTelecommunications
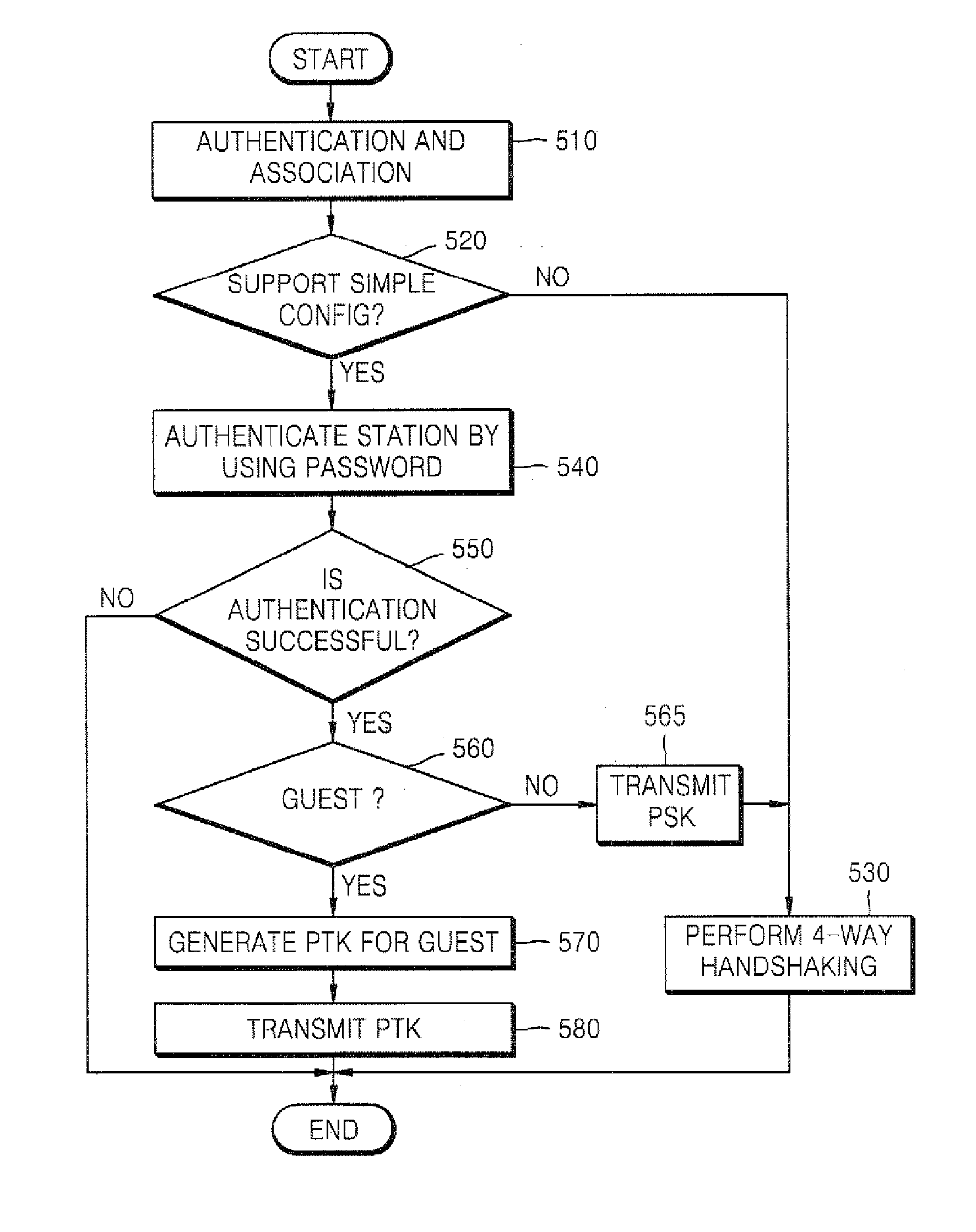
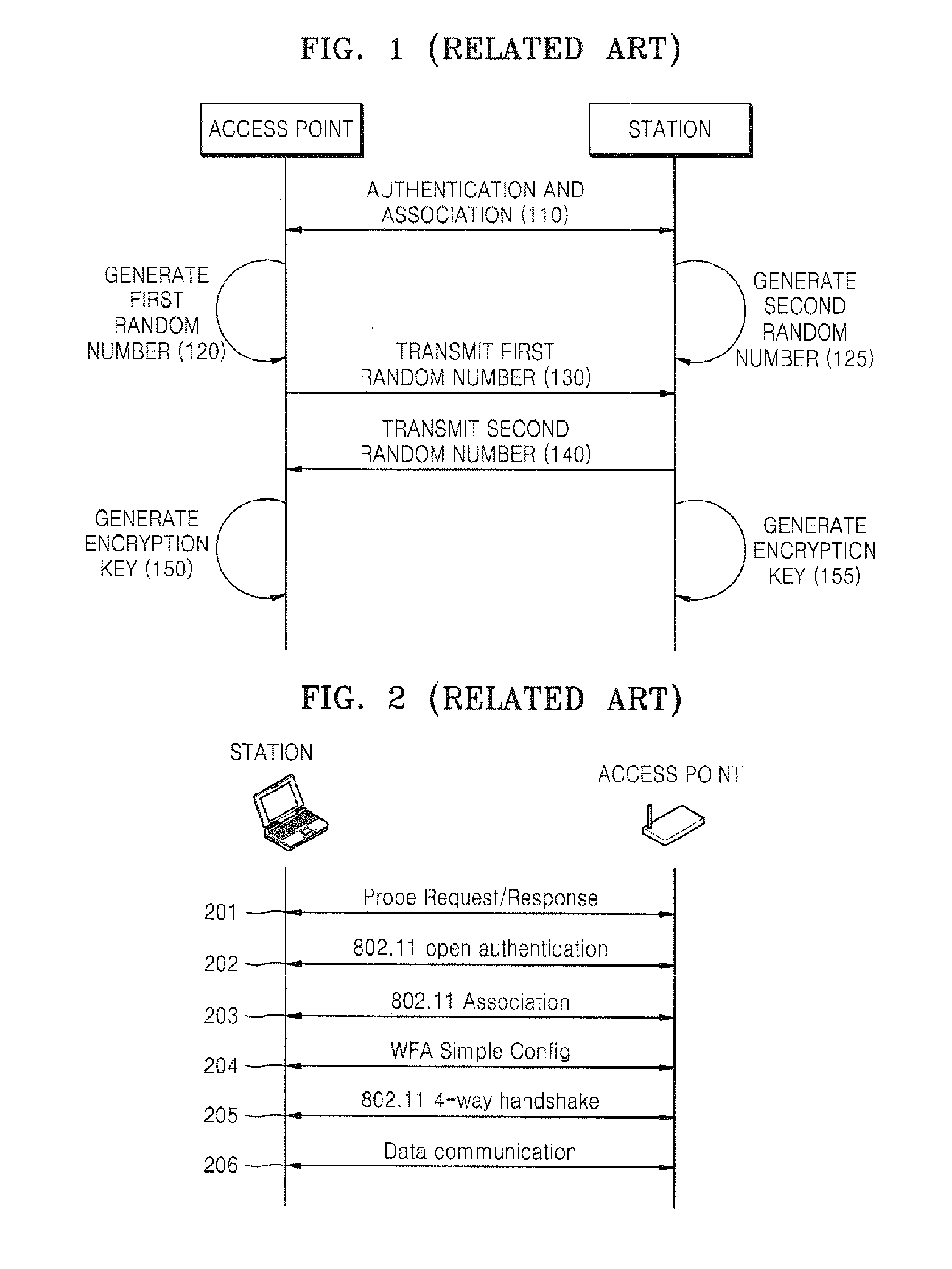
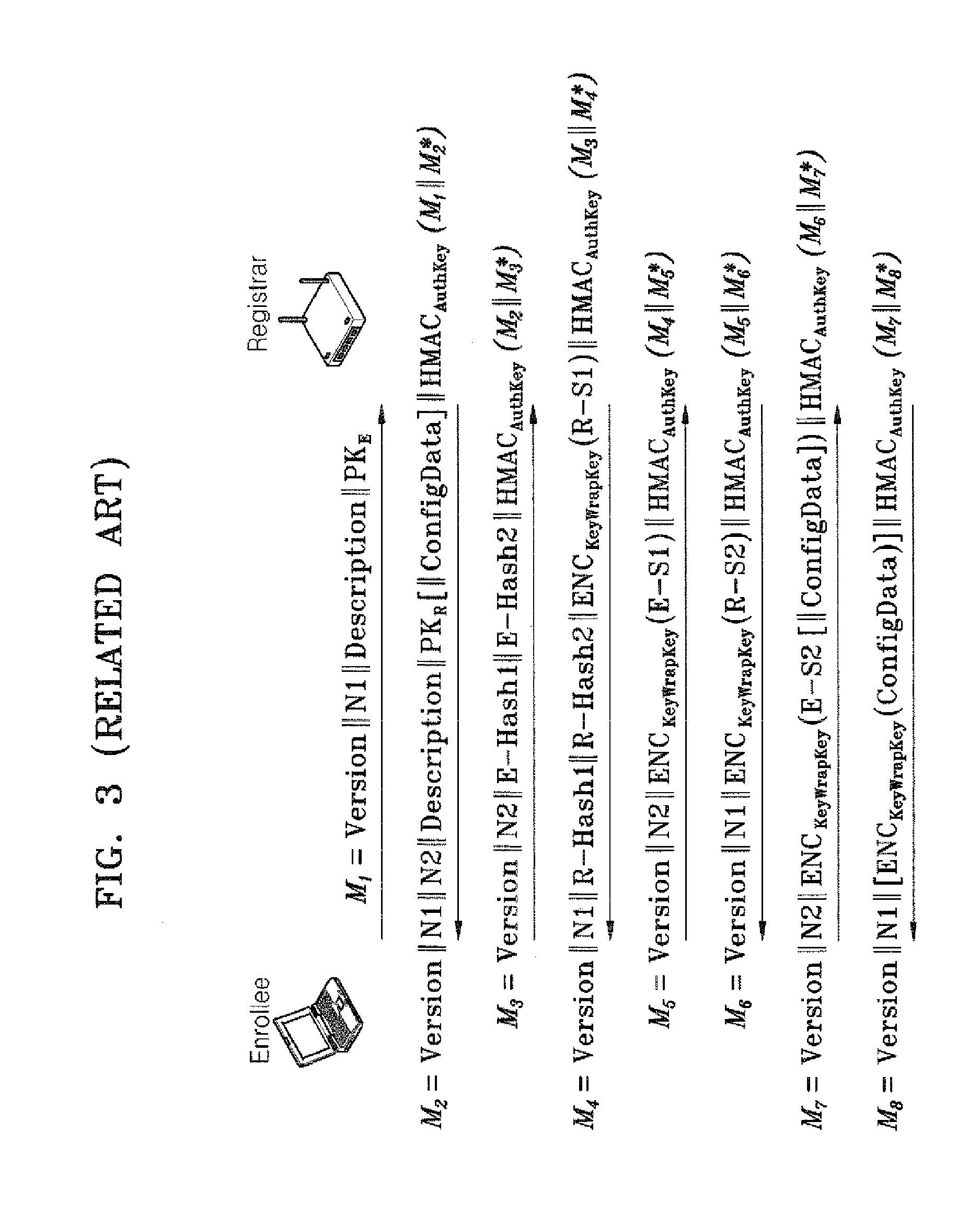
Provided are a method and apparatus for managing a station by providing an encrypted key to the station in a wireless network under a Wi-Fi Protected Pre-Shared Key (WPA-PSK) environment. In the method, a registrar determines whether a new station is a guest station, based on user input. If the new station is a guest station, the registrar includes a session key (and not a shared key) into an M8 message according to a Wi-Fi Alliance (WFA) Simple Config protocol and transmits the M8 message to the station. Accordingly, it is possible to permit a guest station to temporarily access the network without a user's management of information regarding the guest station.
Owner:SAMSUNG ELECTRONICS CO LTD
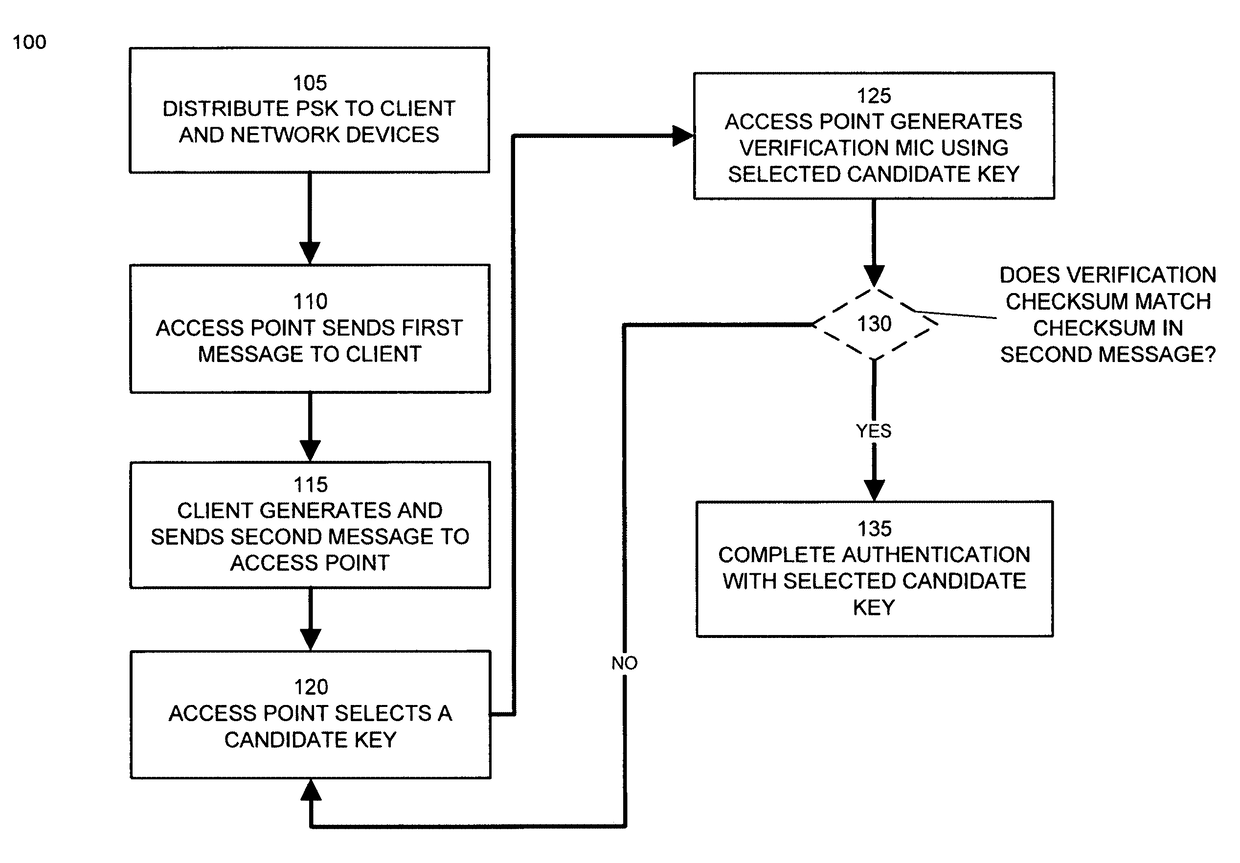
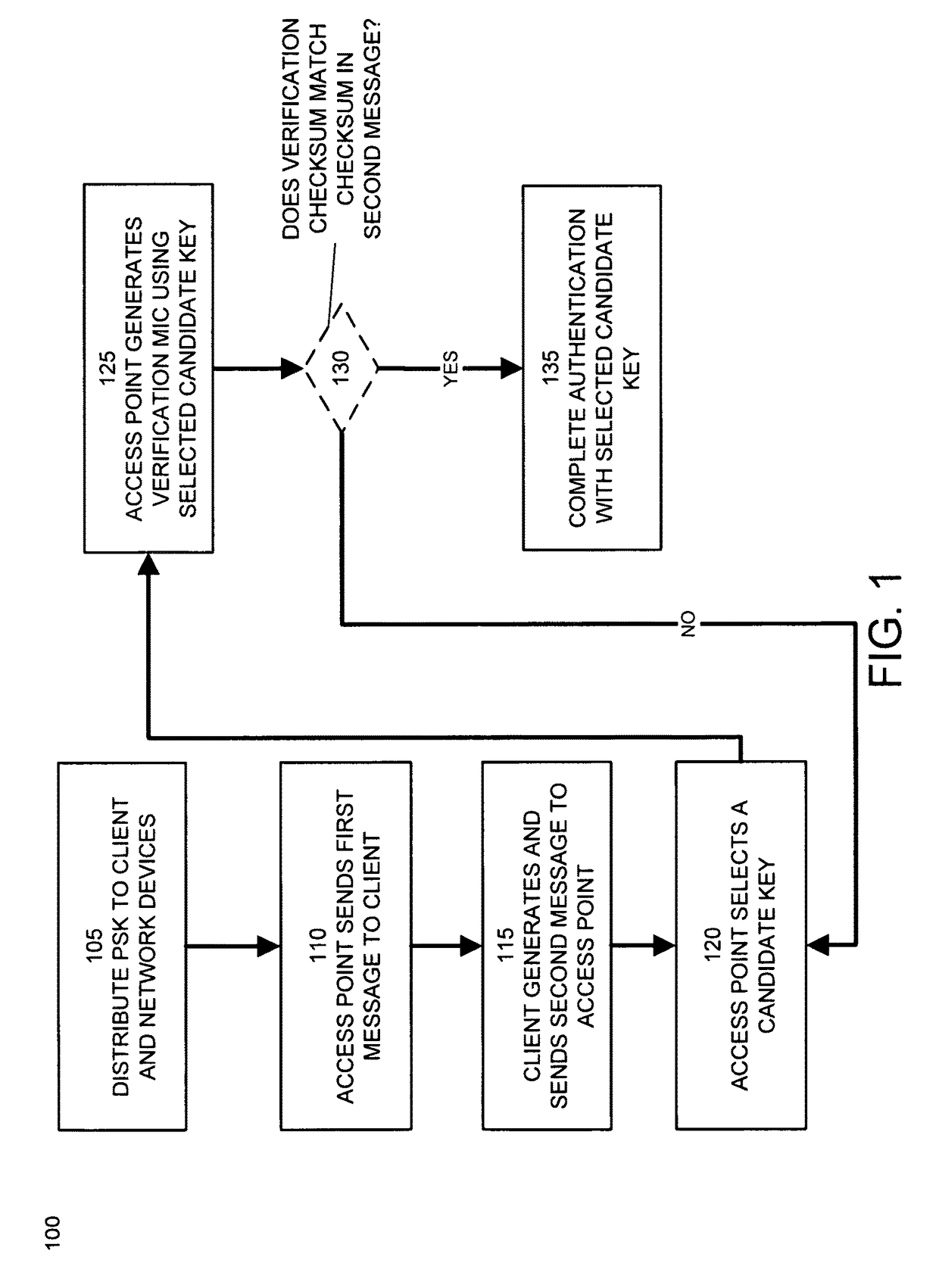
Exclusive preshared key authentication
ActiveUS9674892B1Same controlSame flexibilityUser identity/authority verificationSecurity arrangementNetwork connectionChecksum
Preshared keys are assigned to client devices, users, or user groups. The set of valid preshared keys or keys derived therefrom is distributed to network devices such as wireless access points. A client device attempts to establish a secure network connection with a network device using its assigned preshared key. A network device identifies the client device's preshared key by selecting a candidate key from its set of valid preshared keys. The network device determines a validation cryptographic checksum based on the selected candidate key. If the validation cryptographic checksum matches the client's cryptographic checksum, the network device establishes a secure network connection with the client device using this candidate key. If the validation cryptographic checksum does not match the cryptographic checksum provided by the client device, the network device repeats this comparison using different candidate keys selected from its set of valid preshared keys until a match is found.
Owner:EXTREME NETWORKS INC
Method for managing wireless multi-hop network key
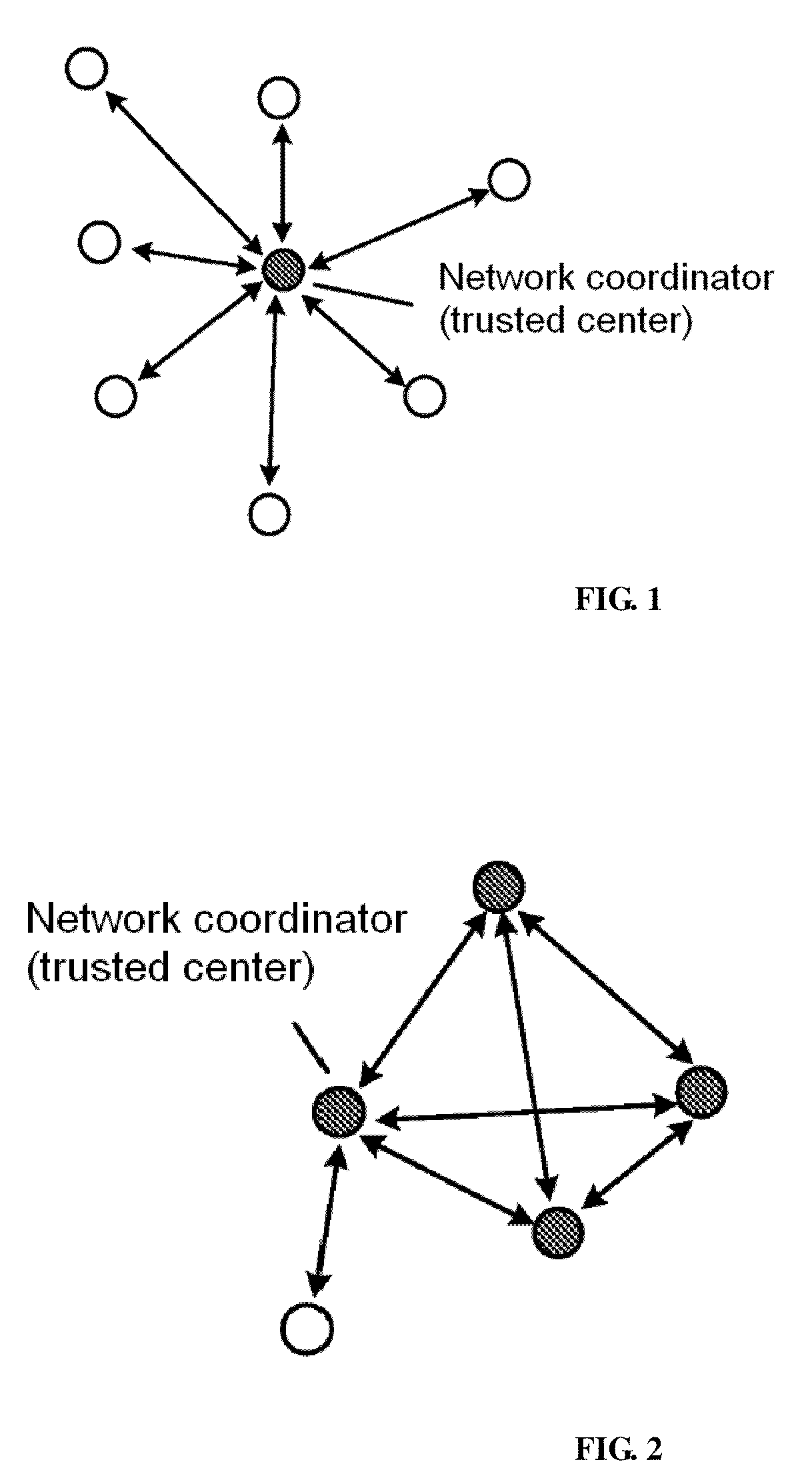
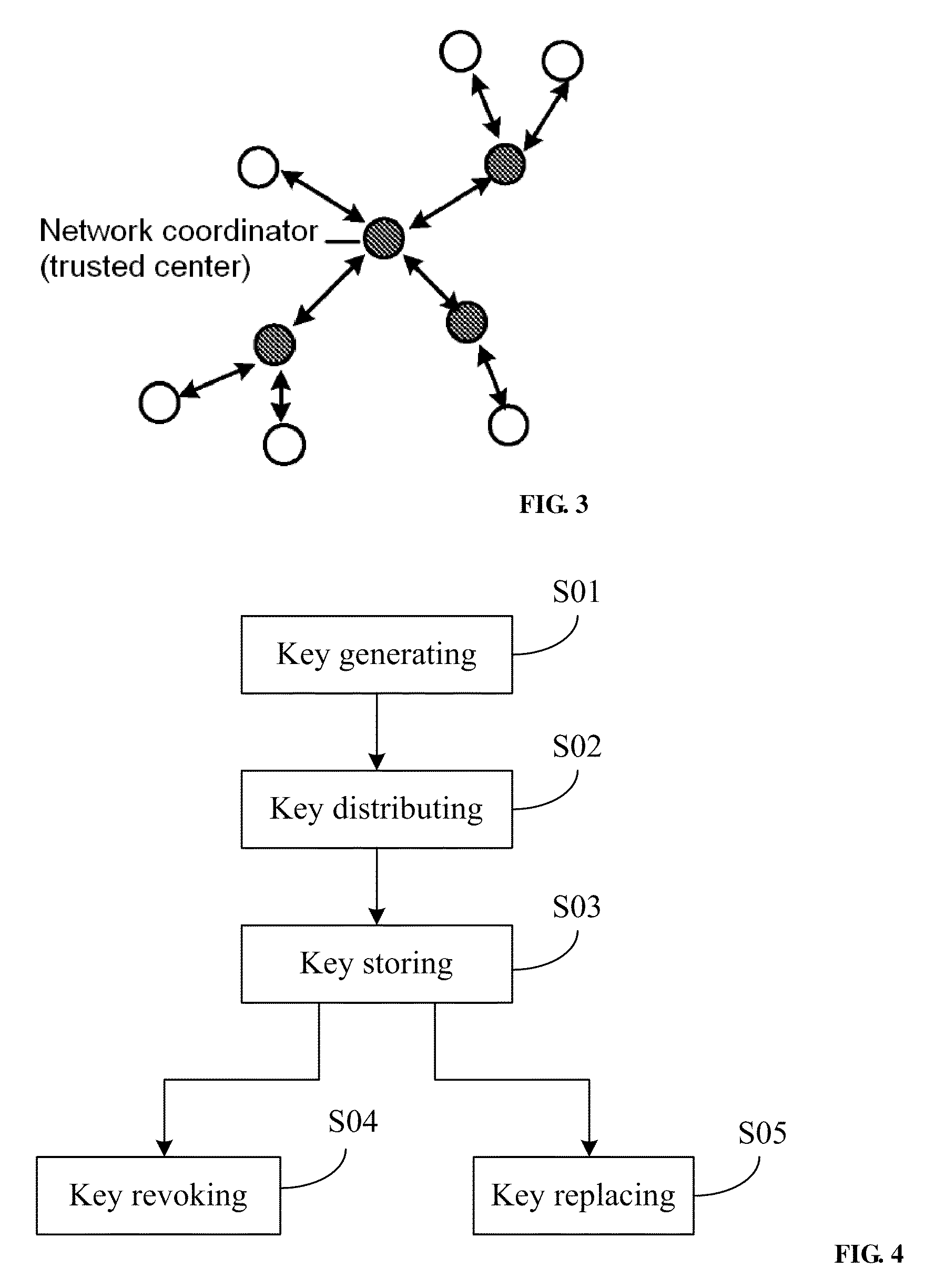
InactiveUS20100299519A1Improve securityImprove performancePublic key for secure communicationNetwork topologiesNetwork keyLarge networks
A method for managing wireless multi-hop network key is applicable to a security application protocol when a WAPI frame method (TePA, an access control method based on the ternary peer-to-peer identification) is applied in a concrete network containing a Wireless Local Area Network, a Wireless Metropolitan Area Network AN and a Wireless Personal Area Network. The key management method of the present invention includes the steps of key generation, key distribution, key storage, key modification and key revocation. The present invention solves the technical problems that the prior pre-share-key based key management method is not suitable for larger networks and the PKI-based key management method is not suitable for wireless multi-hop networks; the public-key system and the ternary structure are adopted, thereby the security and the performance of the wireless multi-hop networks are improved.
Owner:CHINA IWNCOMM
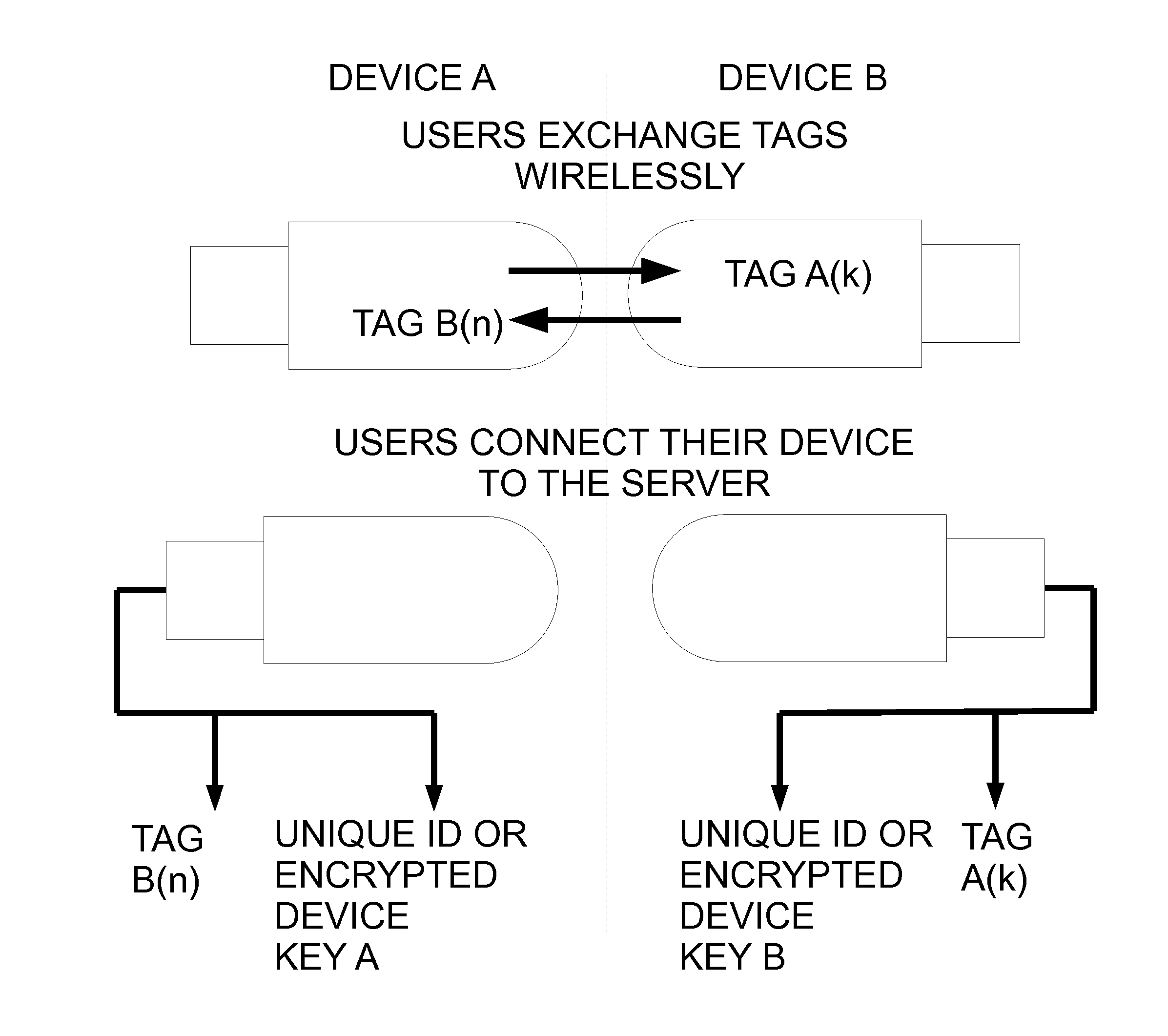
Electronic data sharing device and method of use
An electronic data sharing device configured to exchange a first tag with a corresponding tag from a further electronic data sharing device, wherein the first and second tags provide information that enables respective users of the electronic data sharing devices to share information via a server enabled internet-connected software system associated with the electronic data sharing devices, wherein the electronic data sharing device is either configured with a pre-shared key or is able to encrypt a session key, wherein the pre-shared key or session key are used to generate tags to ensure that: the electronic data sharing device and tags can only be made use of by the server.
Owner:BLENDOLOGY
Proxy method and system for secure wireless administration of managed entities
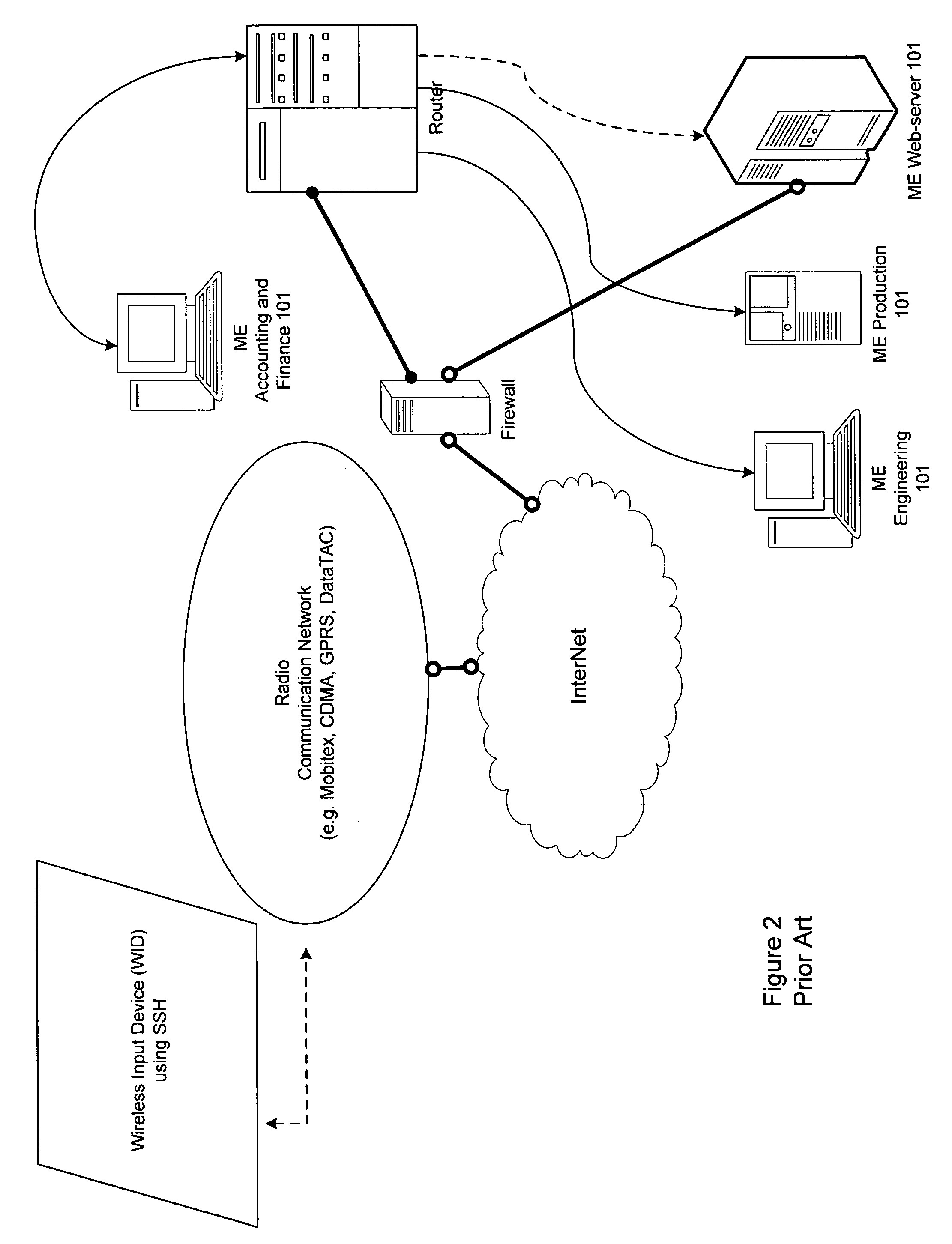
InactiveUS20060285692A1Reduce usageIncrease varietyKey distribution for secure communicationDigital data processing detailsWeb servicePassword
A method, system and apparatus are described for avoiding the use of a web-server or generic security when providing network administration services remotely to managed entities using wireless technology. Instead a true Proxy device, not operating as a web-server, is used to preprocess all command traffic from wireless input devices (WID). The intervention between the WID and the managed entities of the Proxy isolating the managed entities from the WID, enhanced by encoding using a novel messaging protocol, further enhanced by a novel security model based on multiple pre-shared keys and algorithms together with identifiers and passwords that are not transmitted, achieves several bandwidth and security advantages including the ability to deliver TELNET services across the Internet and behind a firewall.
Owner:AVOCENT HUNTSVILLE CORPORATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com