WiFi hot spot safe login method and system
A technology for secure login and login method, applied in the field of realizing terminal secure login to WiFi hotspots, which can solve the problems of protocol incompatibility, lack of security, and easy leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0129] The present invention will be further described below in conjunction with the accompanying drawings, but the embodiments of the present invention are not limited thereto.
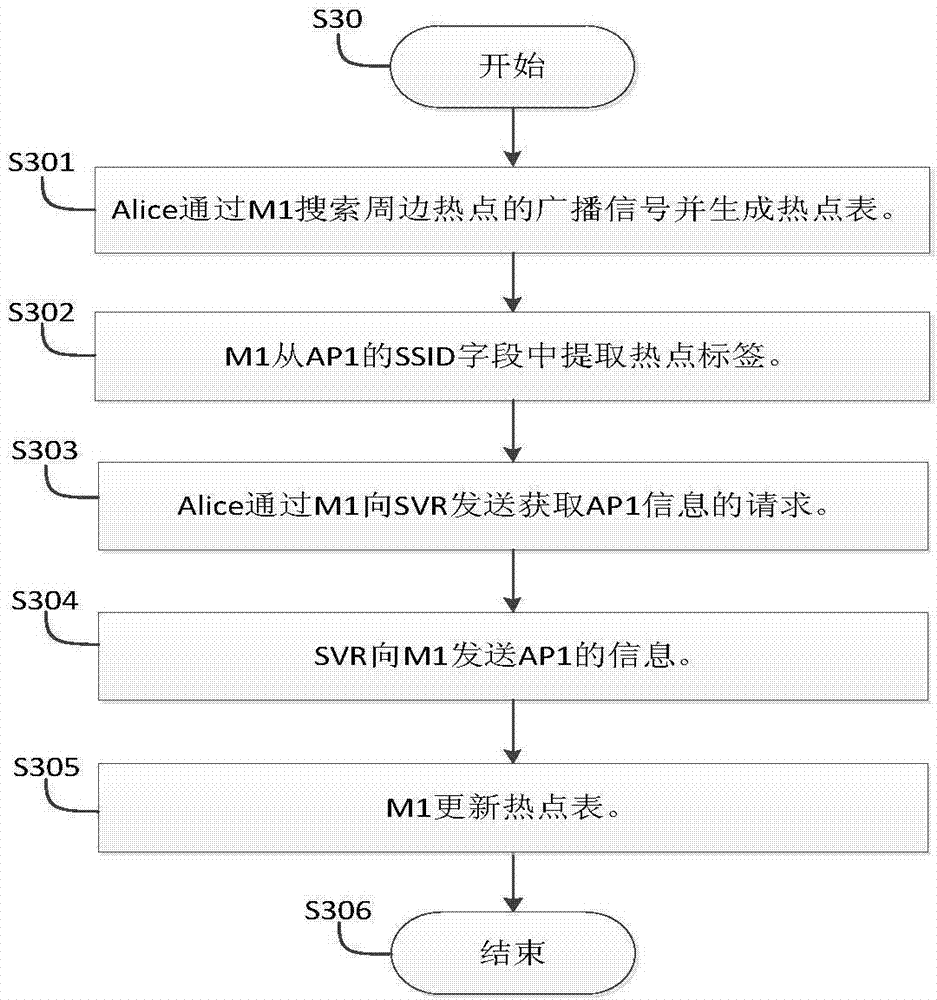
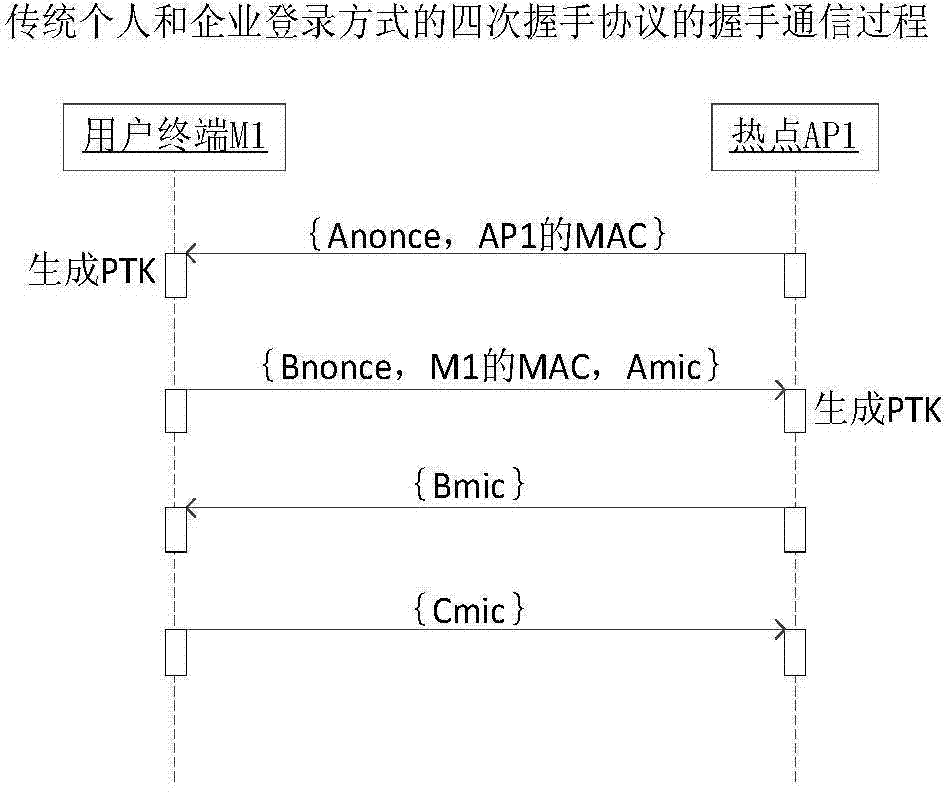
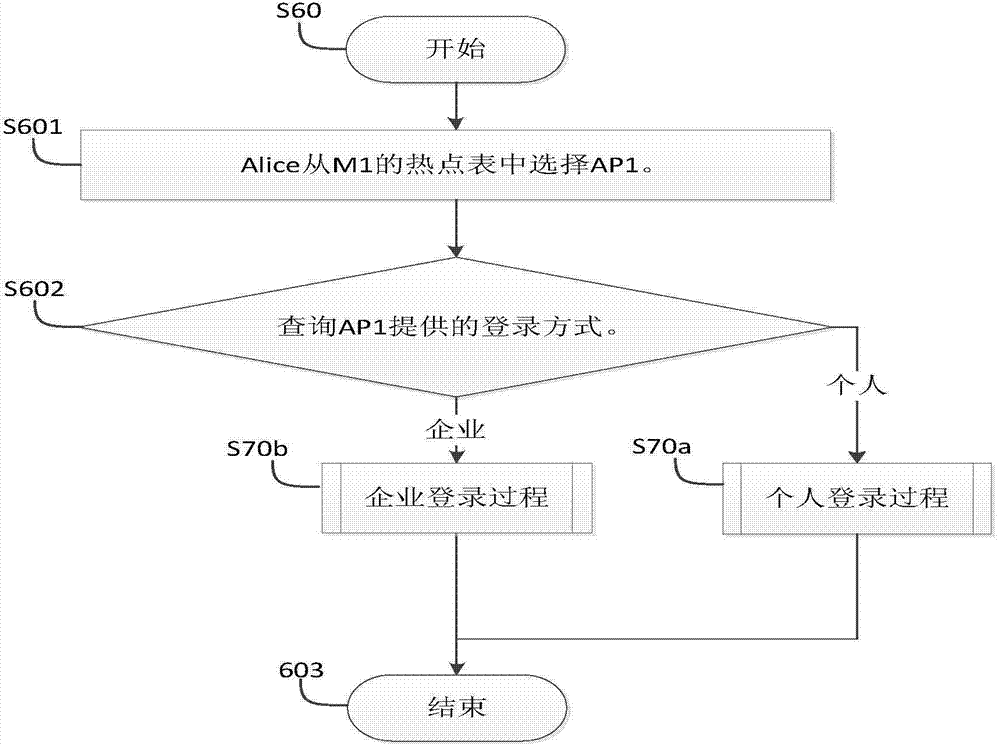
[0130] Such as figure 1 As shown, user Alice’s terminal M1 is located within the wireless and mobile signal coverage of hotspot AP1 and base station BS1, user Bob’s terminal M2 is located within the signal coverage of hotspot AP2 and base station BS2, Bob is an owner of hotspot AP1, and AP1’s None of the owners are Alice herself or her contacts.
[0131] In the login method, when users Alice and Bob are in a session with the server SVR, Alice requests the SVR to add Bob, the owner of the hotspot AP1, as a contact through the terminal M1. The process is as follows:
[0132] (1) User Alice selects hotspot AP1 from the hotspot list of terminal M1 and selects one of all non-contact owners of AP1, and then sends a request to add the owner as a contact to the server SVR through M1, and the request include...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com