Method and system for using quantum cryptography in safe IP communication
A technology of secure communication and quantum cryptography, which is applied in key distribution, can solve problems such as limited computing power in security and difficult security calculation index, and achieve unconditional security, resist high-performance computing attacks, and reduce complexity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be described in further detail below in conjunction with the accompanying drawings.
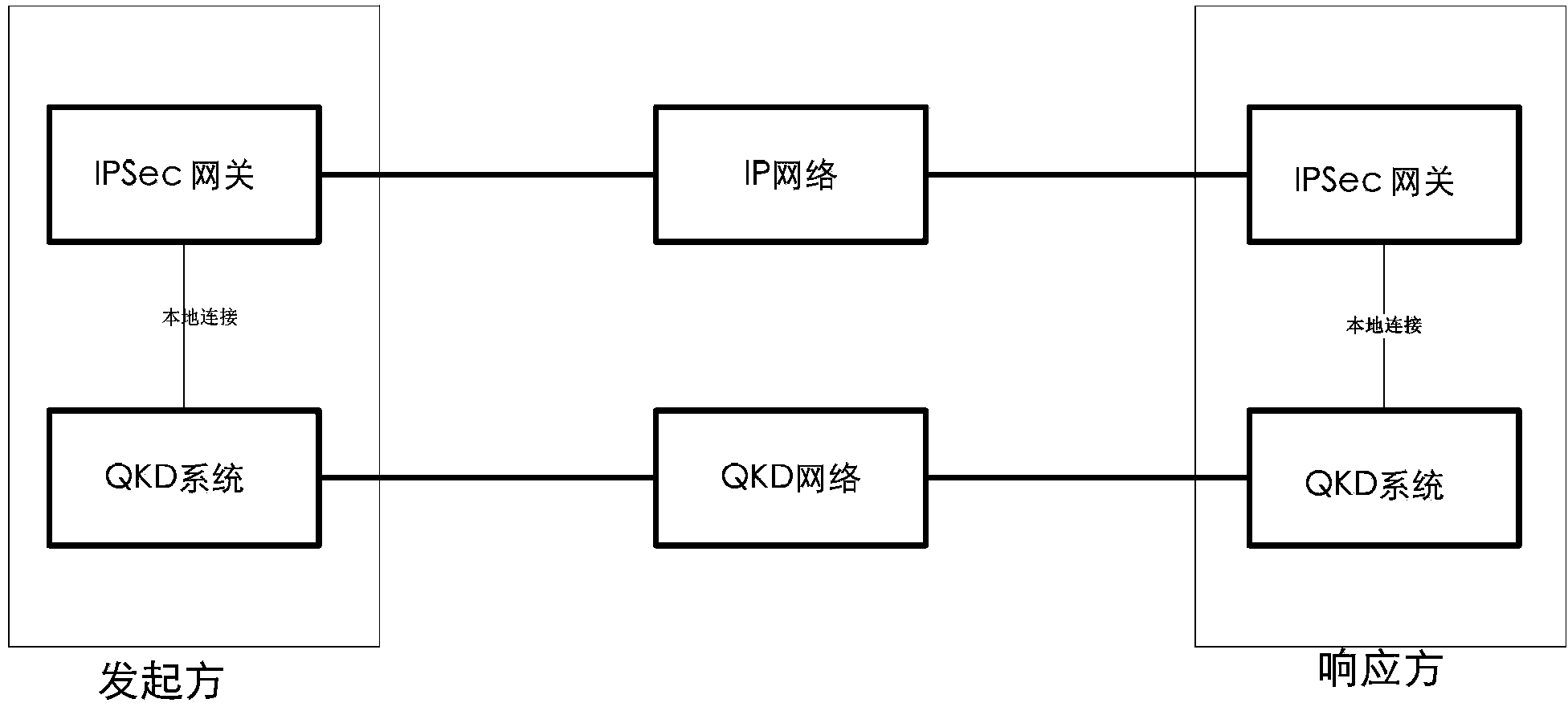
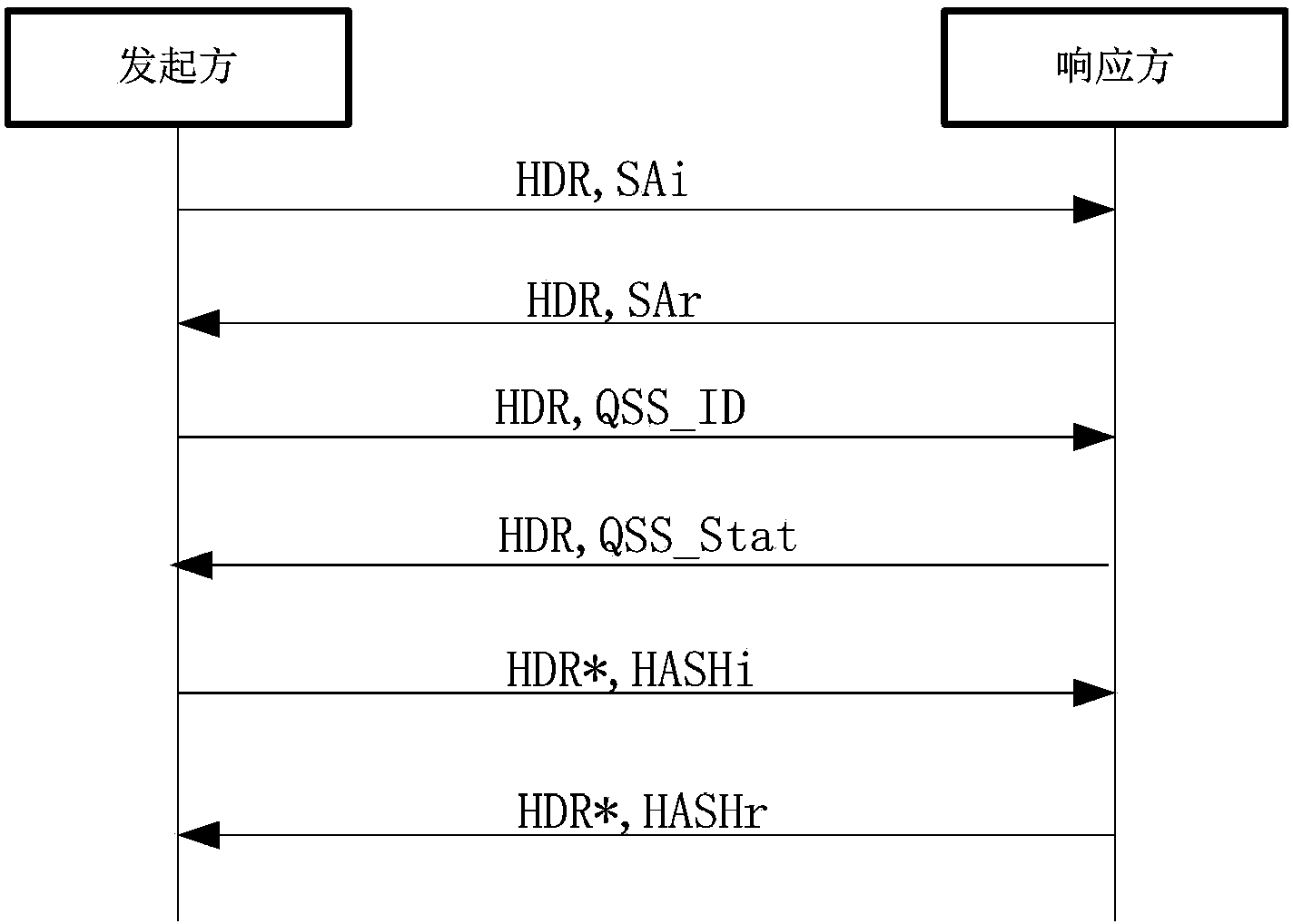
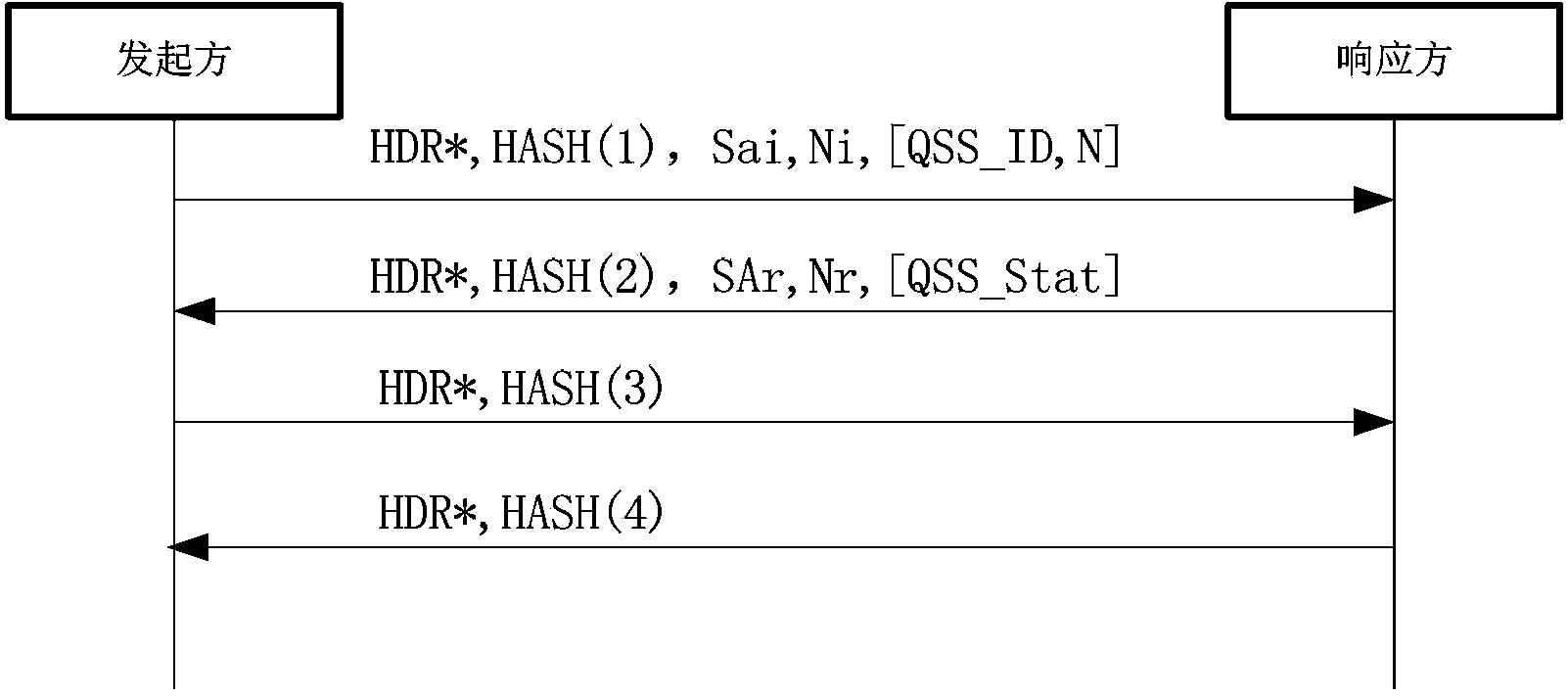
[0048]The invention proposes a key exchange method for enhancing the security of IP communication, the security of which does not depend on the complexity of calculation and can resist high-performance computing attacks. This method uses the framework defined by ISAKMP to establish the Internet Quantum Key Exchange Protocol (IQKE for short). Security is possible. The realization of the method of the present invention needs to establish at least two physically separated channels: one is a classical channel connecting IPSec gateways, and the other is a quantum channel connecting the QKD system. In addition, QKD devices need to be authenticated through classic channels to prevent man-in-the-middle attacks. The quantum key generated by the QKD system is injected into the IPSec gateway through the local connection. The key can be used for identity authentication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com