Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
76 results about "OpenID" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
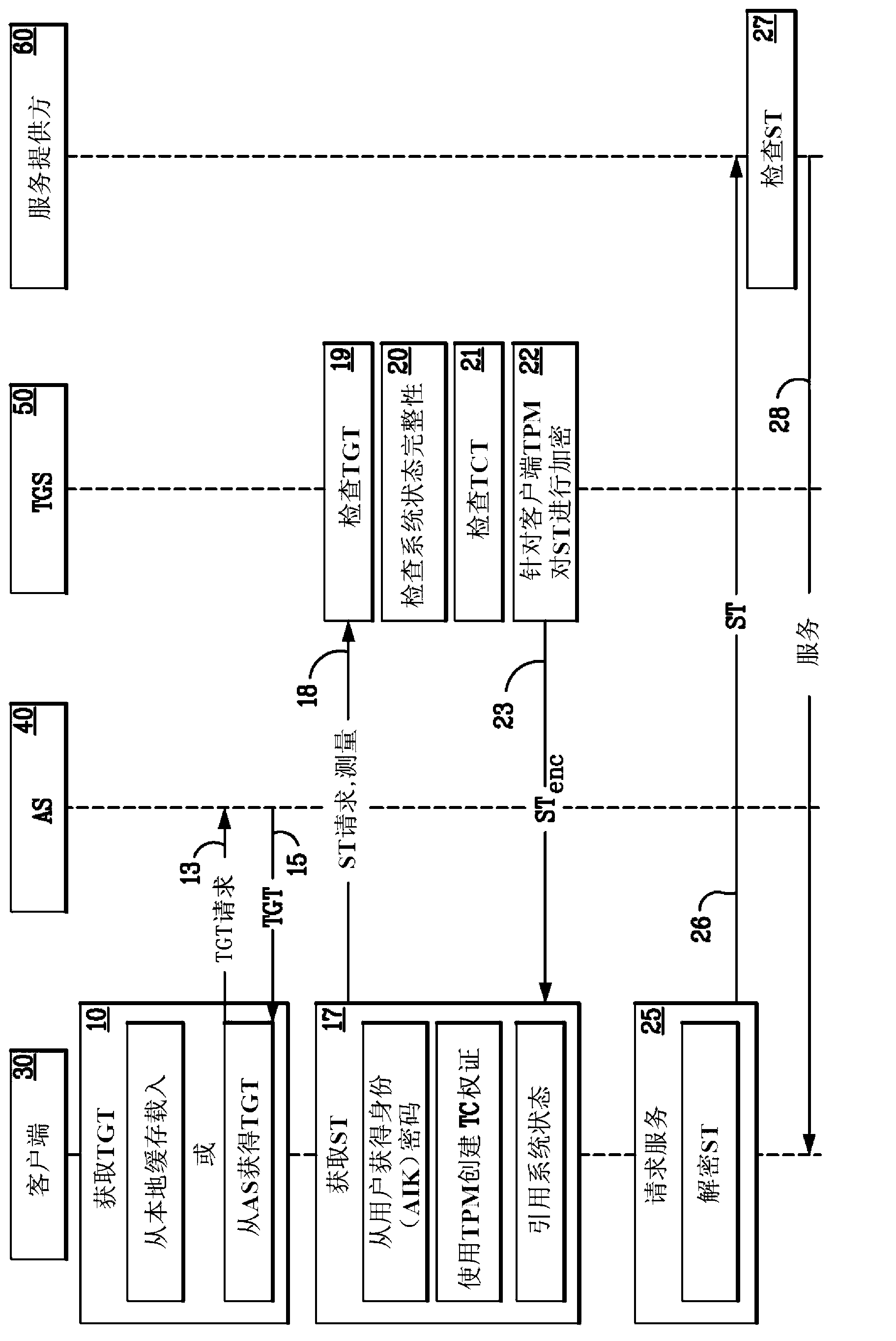
OpenID is an open standard and decentralized authentication protocol. Promoted by the non-profit OpenID Foundation, it allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party service, eliminating the need for webmasters to provide their own ad hoc login systems, and allowing users to log into multiple unrelated websites without having to have a separate identity and password for each.
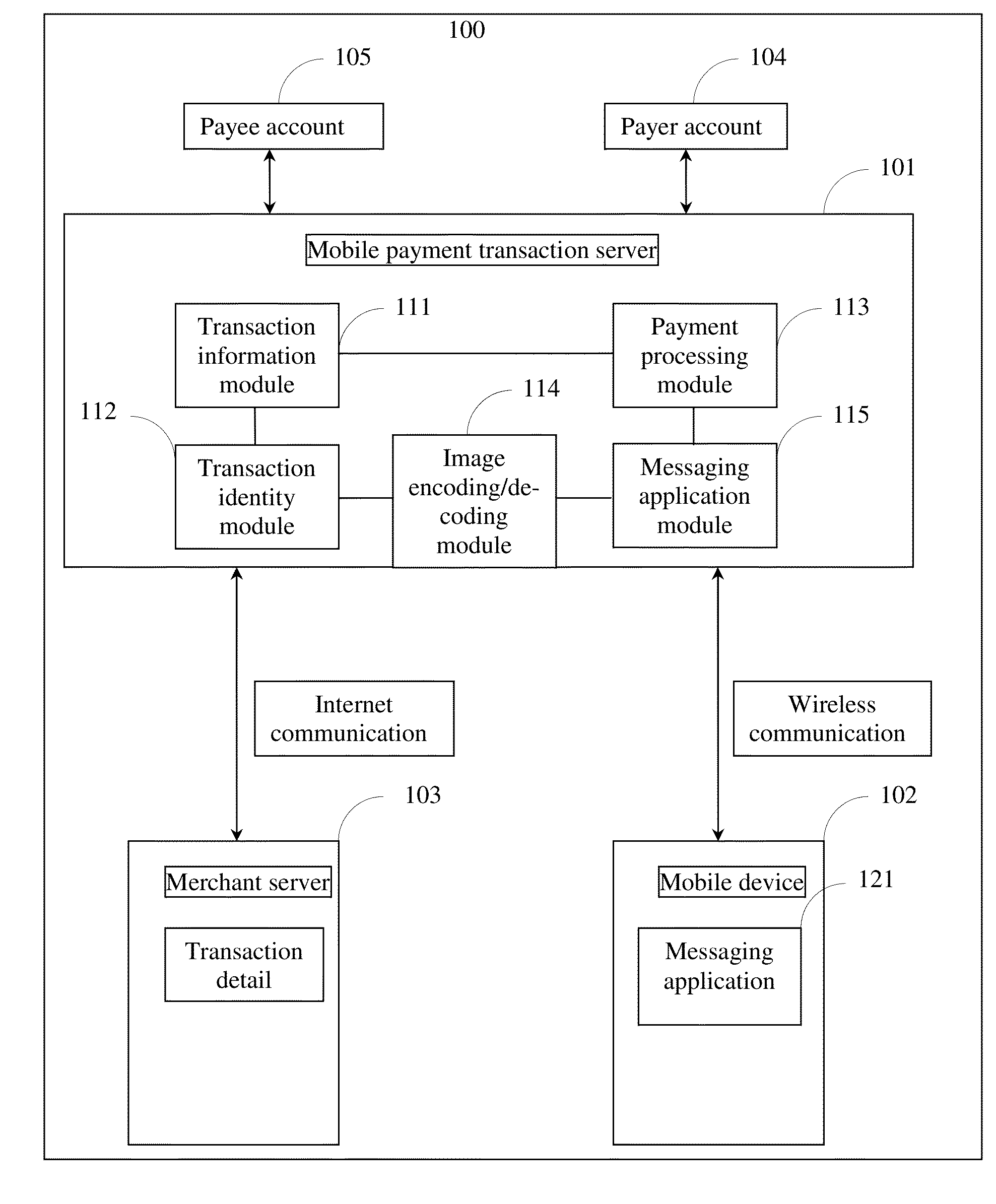
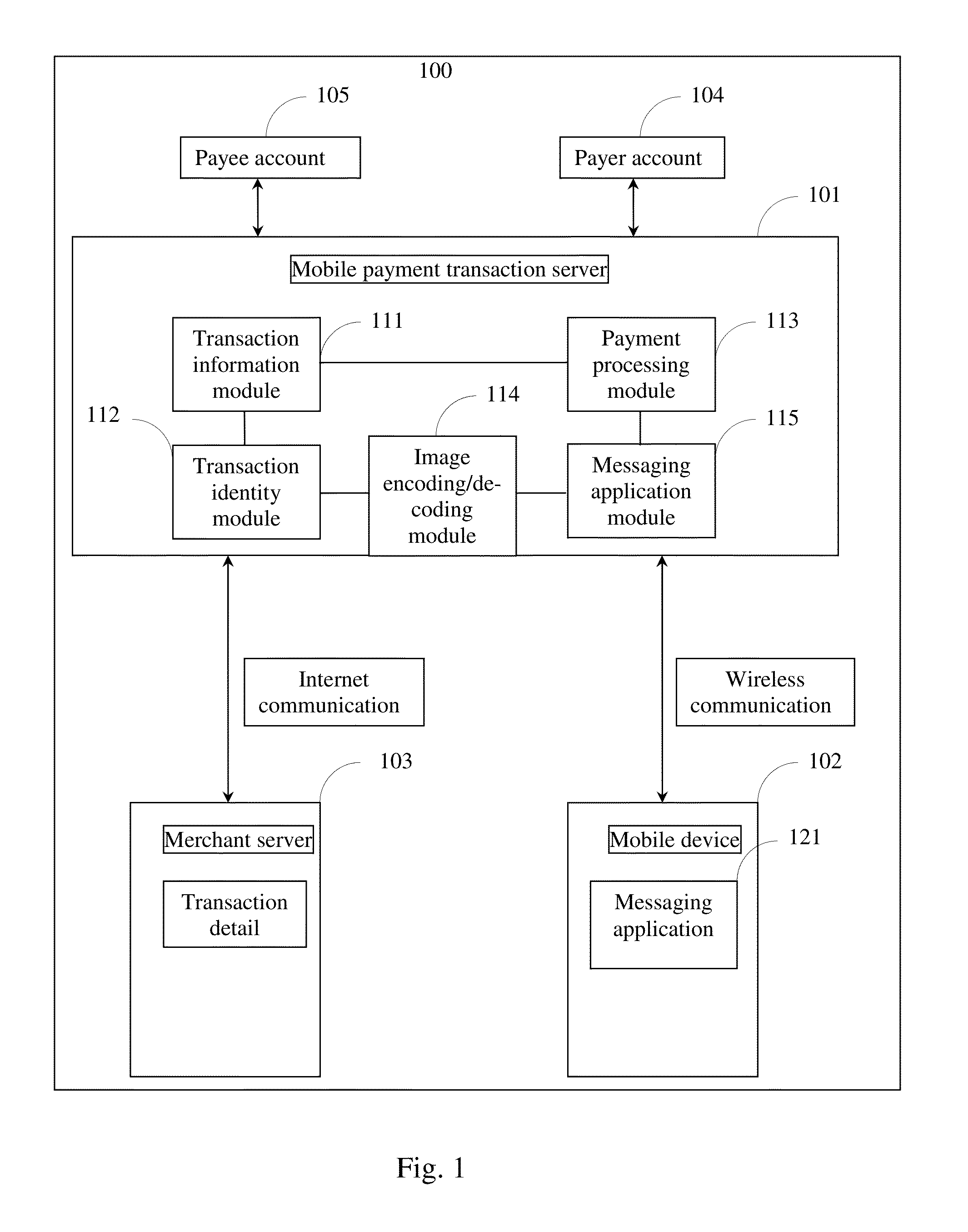
Method, device, server, and system for making payment with a messaging application on a mobile device
InactiveUS20140337207A1Improve user experienceFinanceProtocols using social networksPayment transactionApplication software
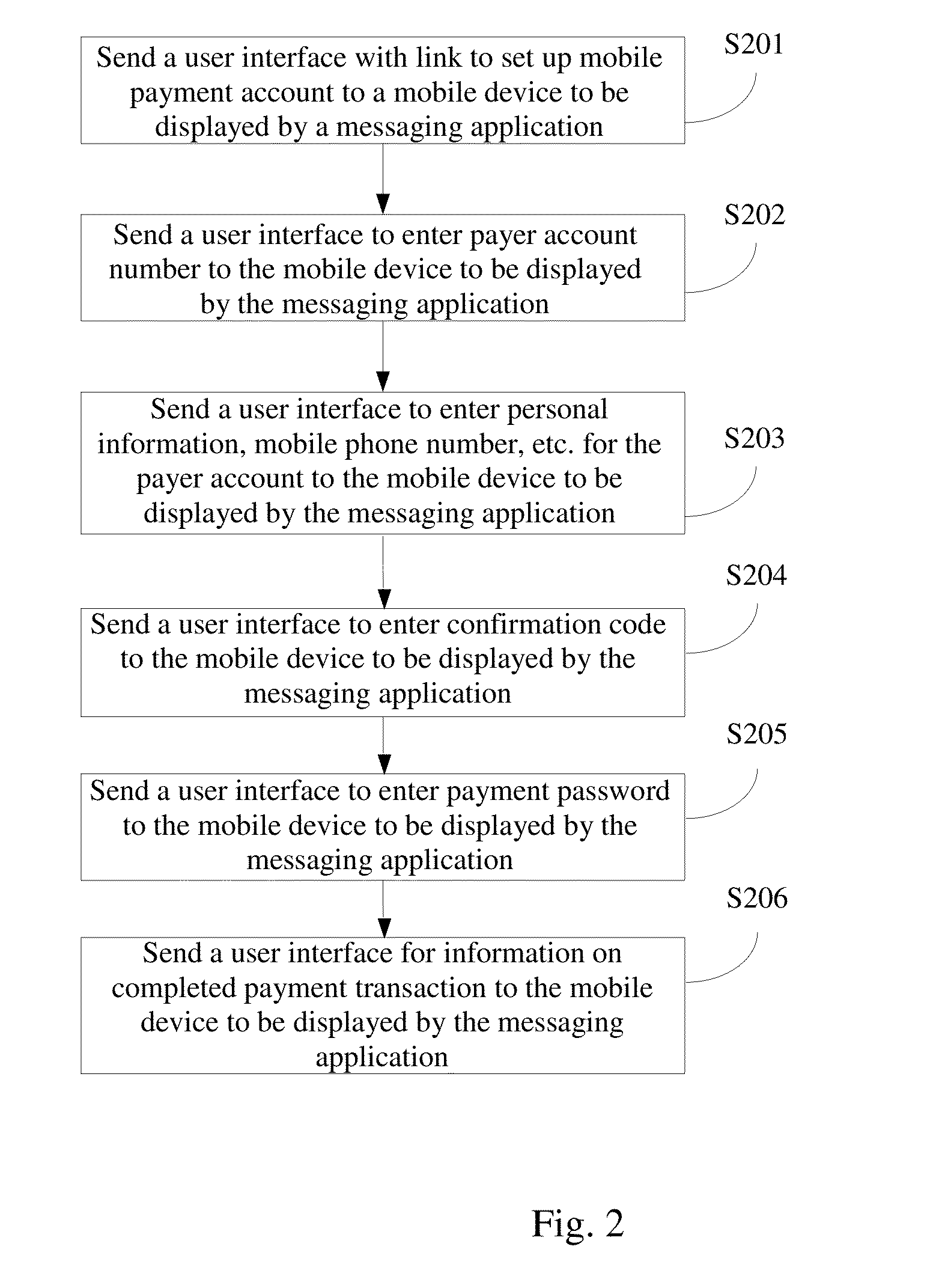
A first aspect of the present disclosure provides a device, server and system for making a payment from a messaging application on a mobile device. A second aspect of the disclosure provides a method of associating a payer account number with a mobile device. Further provided herein is a method of performing a payment transaction from a messaging application on a mobile device, wherein the payment transaction is initiated by a message or a 2D image from an OpenID with the messaging application, a 2D image from a website, or a mobile application from the merchant.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and apparatus for trusted federated identity management and data access authorization
InactiveCN102763111AUser identity/authority verificationPlatform integrity maintainanceTrusted Platform ModuleData access
Systems, methods, and instrumentalities are disclosed that may provide for integration of trusted OpenID (TOpenID) with OpenID. The authentication may be accomplished, in part, via Communications between a trusted ticket server on a UE and a network application function. The UE may retrieve platform validation data (e.g., from a trusted platform module on the UE). The UE may receive a platform verification in response to the platform validation data. The platform verification may indicate that the network application function has verified the platform validation data and the user. The platform verification may indicate that the platform validation data matches a previously generated reference value.
Owner:INTERDIGITAL PATENT HLDG INC
Authentication method and system for mobile subscribers
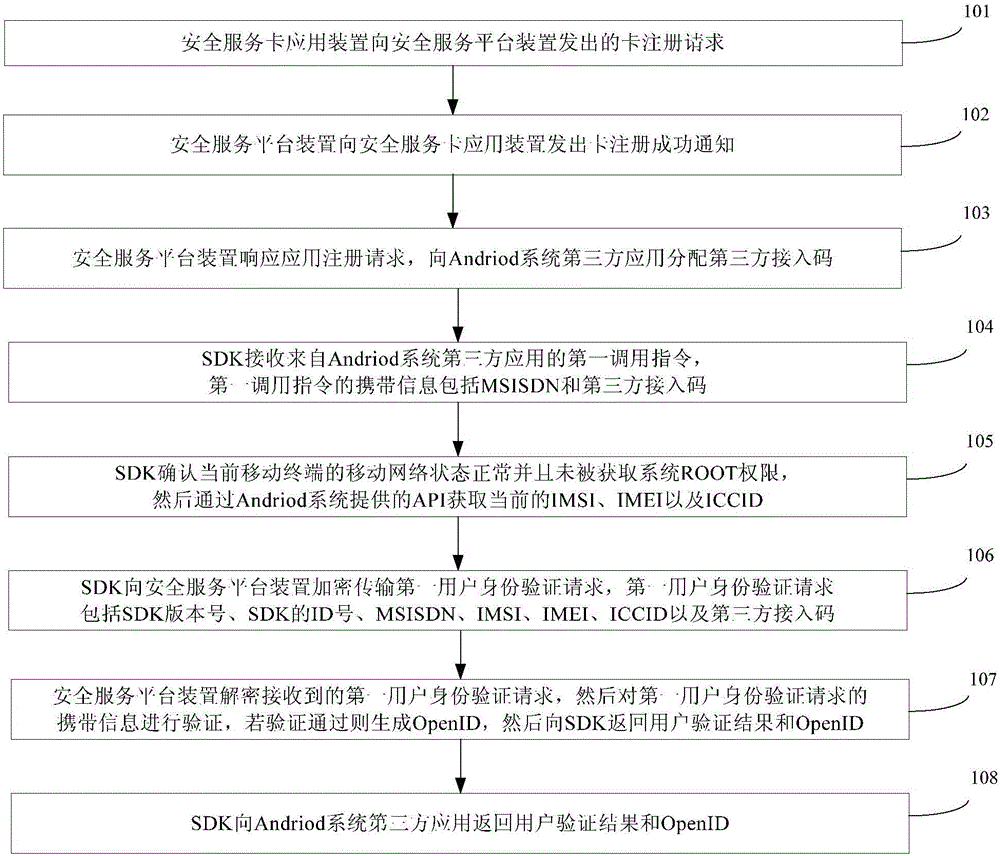
ActiveCN106304074AProtect personal privacy informationEasy to useSecurity arrangementInformation repositoryThird party
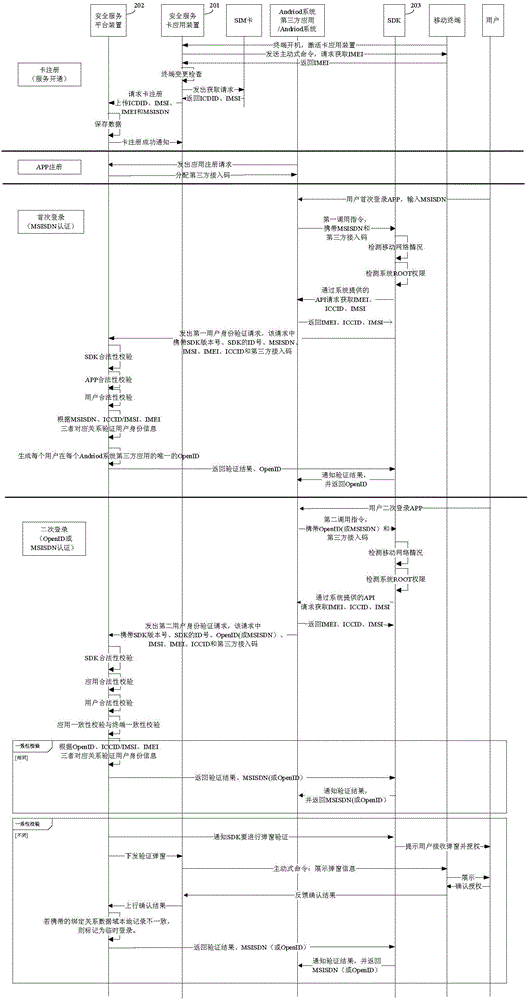
The invention provides an authentication method and system for mobile subscribers, which can realize the password-free registration and login and have advantages of convenience in use, high safety and low cost. The authentication method for the mobile subscribers of a third-party application of an Andriod system or an iOS system comprises the following steps: completing access registration of a third-party application on a safety service platform apparatus; and registering a safety service card application apparatus so as to establish a user information database; and when a user logs in at a first time, transmitting, by the safety service platform proxy apparatus SDK, a mobile phone number of a user to the safety service platform apparatus to perform the authentication, if the mobile phone number of the user passes the authentication, generating, by the safety service platform apparatus, an exclusive OpenID, and returning, by the safety service platform apparatus, a user authentication result and the OpenID to the third-party application by virtue of the SDK; and when the user logs in at a second time, transmitting, by the SDK, the OpenID to the safety service platform apparatus to perform the authentication, and if the OpenId passes the authentication, returning, by the safety service platform apparatus, the user authentication result and the user mobile phone number to the third-party application by virtue of the SDK.
Owner:尹子栋
Cloud-based biometric enrollment, identification and verification through identity providers
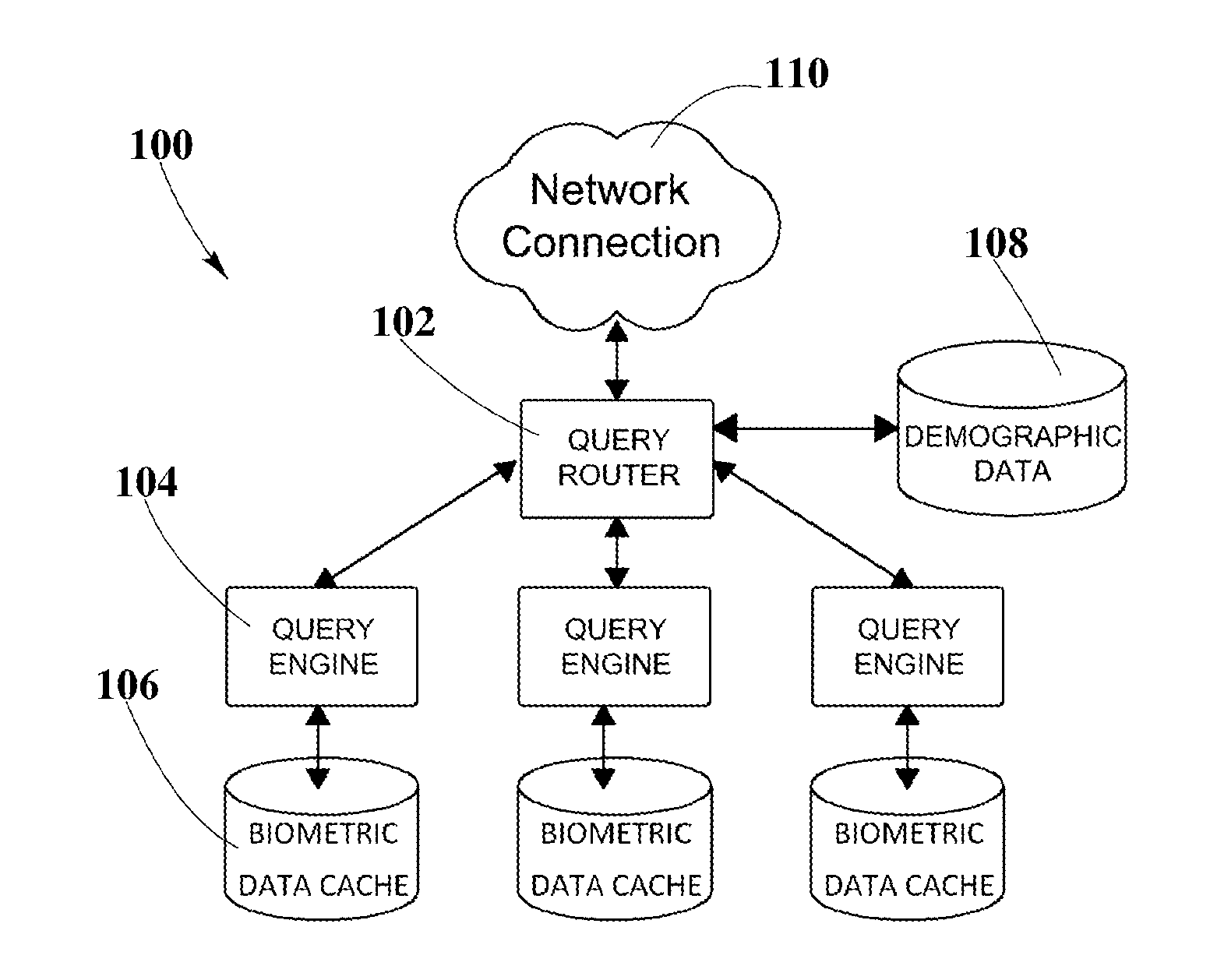
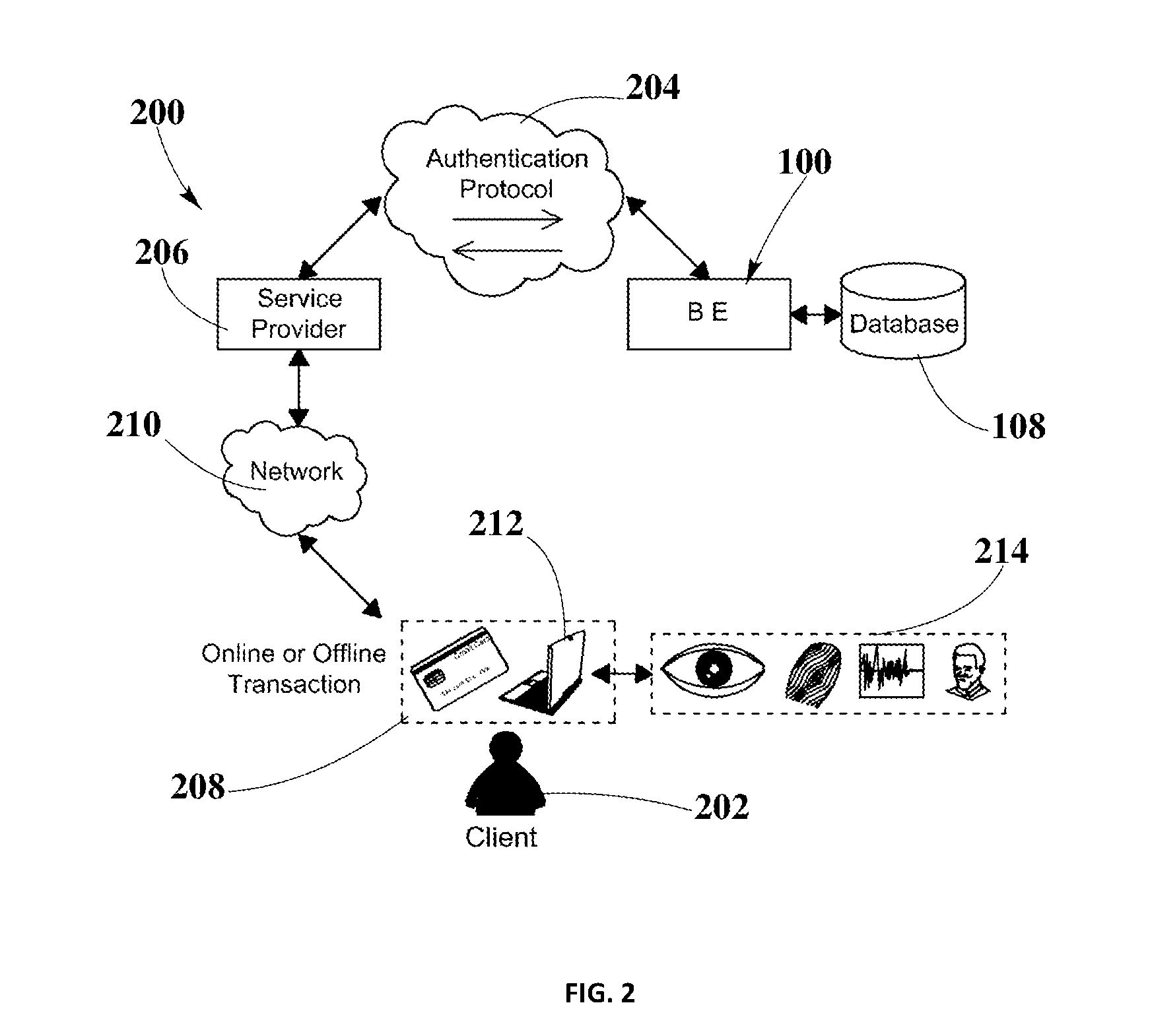
A system and method for cloud-based biometric enrollment, identification and verification are disclosed. More specifically, a cloud-based system and method is used for enrollment of biometric templates. An identity provider serves as an interface between a service provider and a biometric engine. Identity provider employs an open standards protocol such as Security Assertion Markup Language (SAML) or OpenID to exchange authentication data between the service provider and the biometric engine. Service provider employs embedded and / or externally attached hardware in client computing devices for capturing biometric probes and client identity information. Subsequently, biometric engine generates biometric templates from the captured biometric probes and enrolls biometric templates and client identity information for use in identification and authentication in a subsequent transaction.
Owner:IMAGEWARE SYST
Distributed identifier management
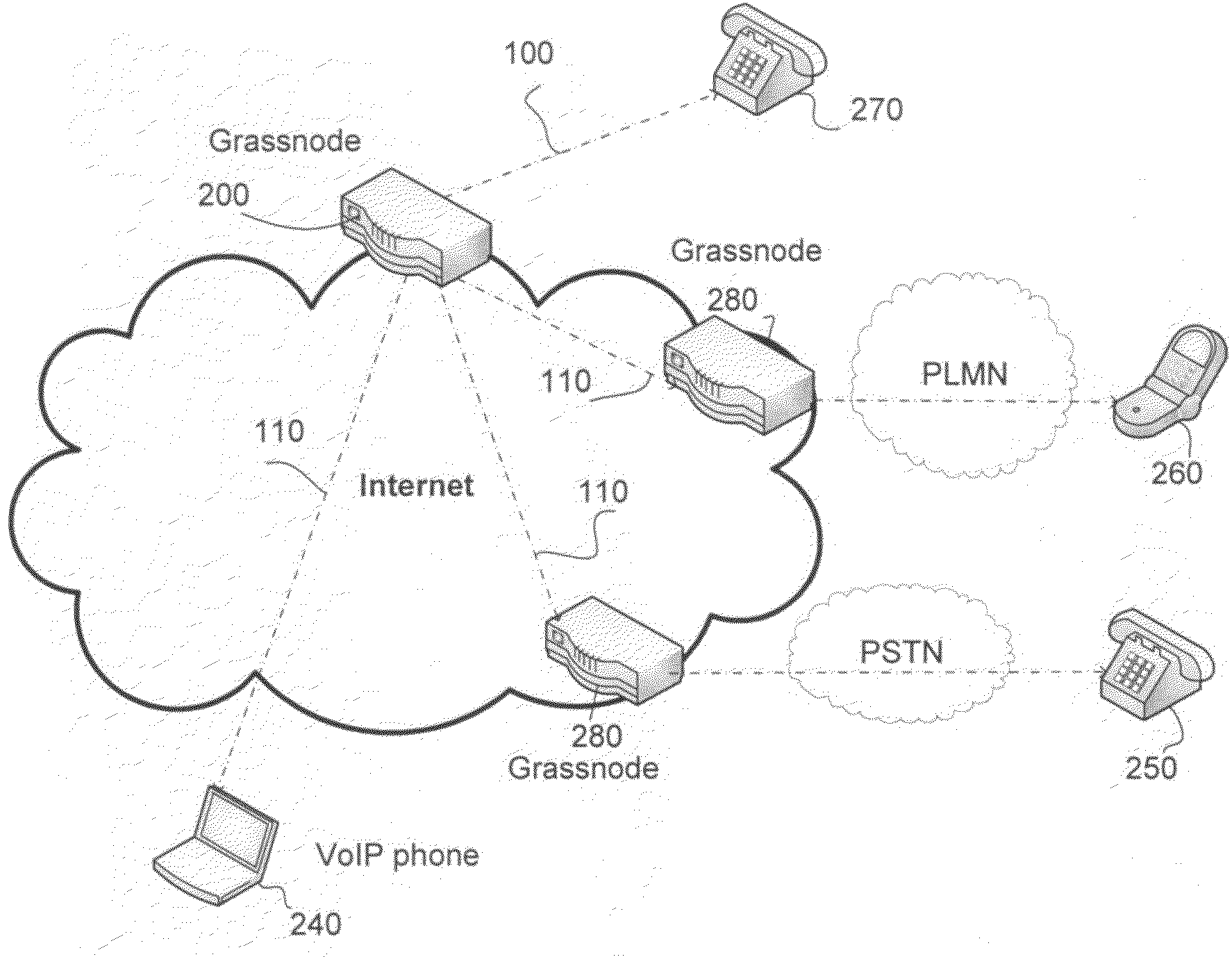
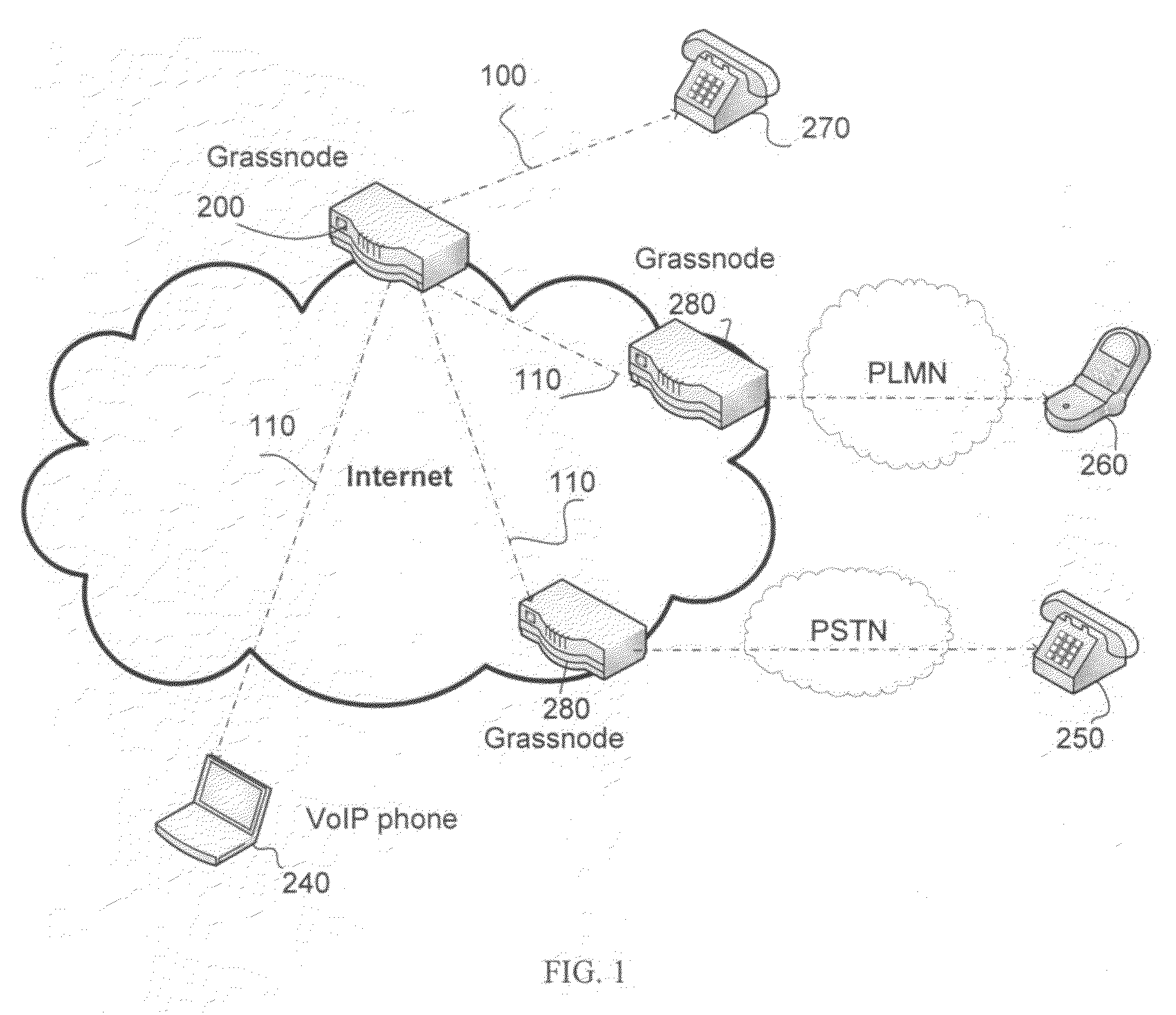
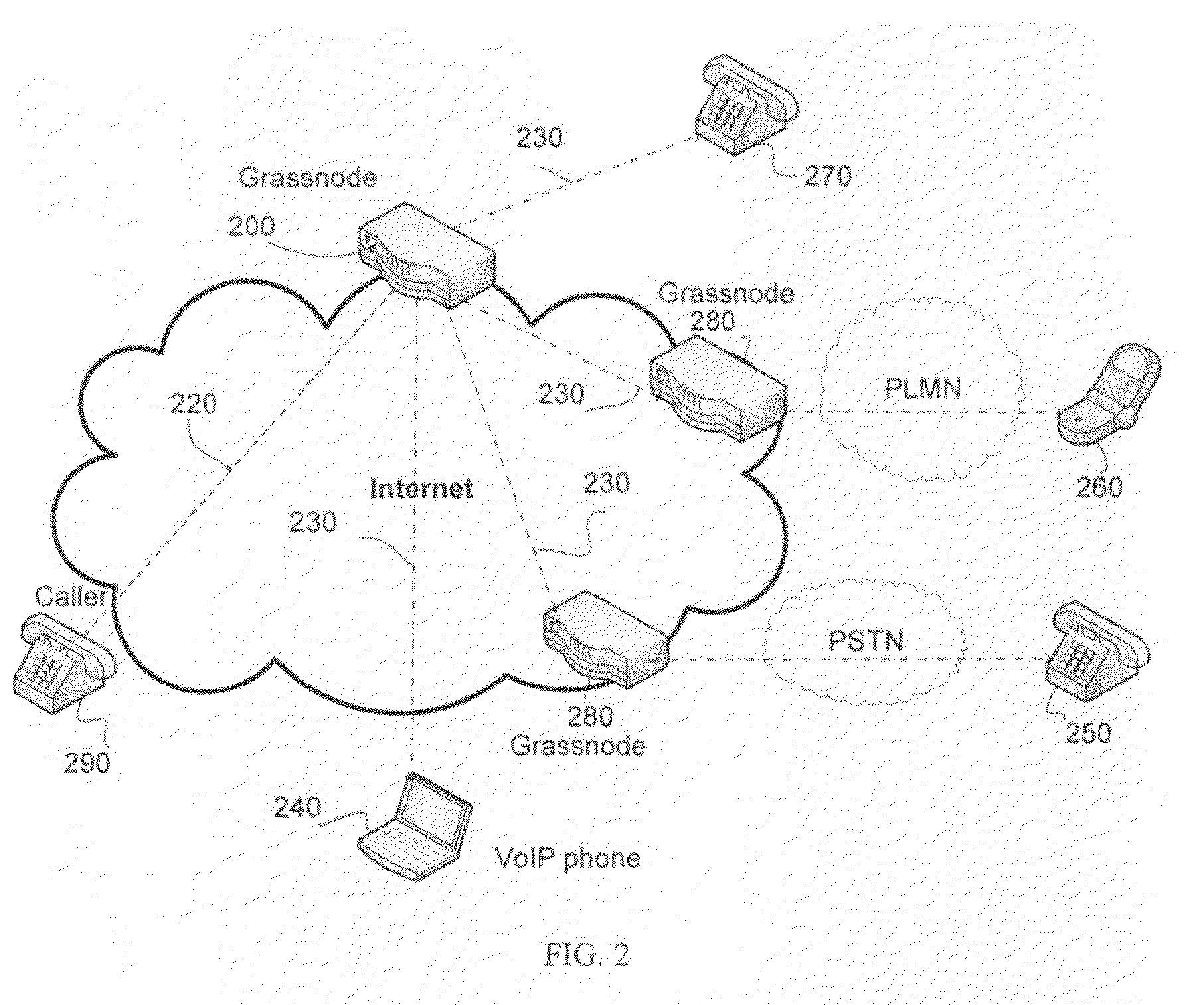
InactiveUS20090214018A1Scalable and fast accessMinimize calling chargeInterconnection arrangementsAutomatic exchangesUser identifierComputer science
An overlay network of volatile nodes, without centralized servers, using DHT-like search algorithms, is programmed to perform One-Number or One-ID services. A user's public number is either the PSTN or PLMN line that is connected to an overlay node, or a voice (or video) over IP number, which is serviced through the overlay. An overlay node is connected to the Internet, and may connect to a PSTN or PLMN phone line as well. The phone numbers allowed in the One-Number service is generally defined. The One-ID service architecture is based on user-proxy, and does not require social networking other one-ID protocols such as OpenID and protocols suites drafted by OASIS. The user-ID of such a One-ID service is not required to be globally unique while a mapping is used to transform a user-defined non-globally unique ID into a site-specific and site-unique ID.
Owner:GRASSTELL NETWORKS
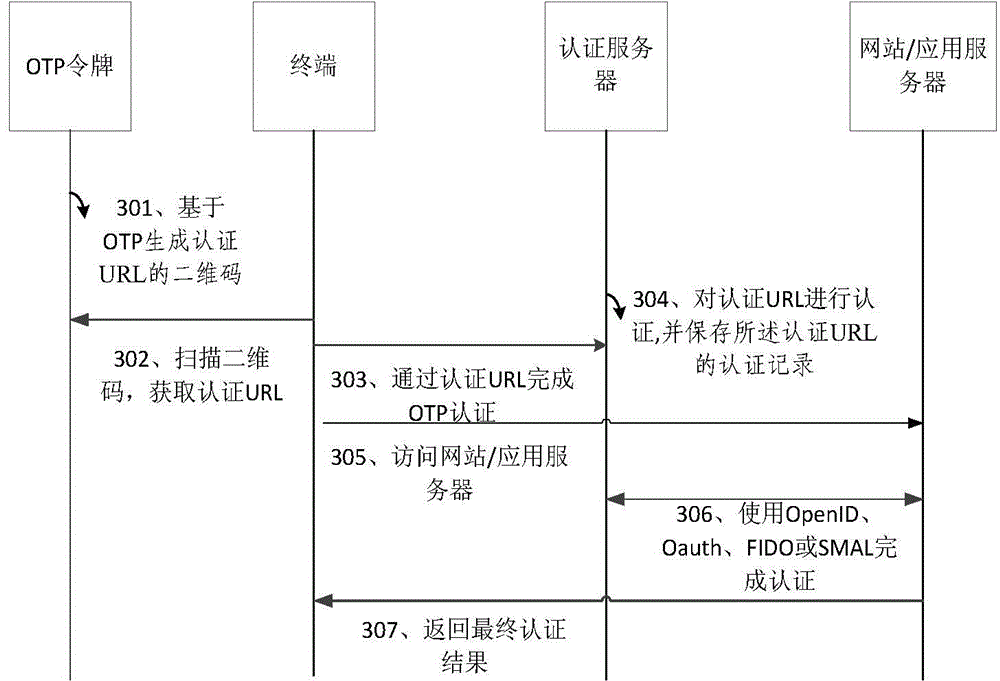
Identity authentication device and method of OTP (one time password) token-based equipment based on two-dimension codes
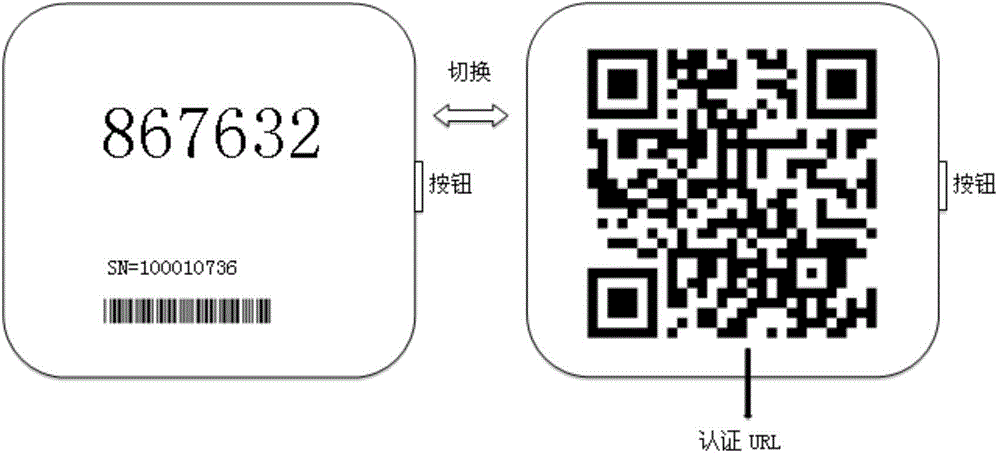
ActiveCN104601594AImprove experienceUser identity/authority verificationApplication serverAuthentication server
The invention discloses an identity authentication device and method of OTP (one time password) token-based equipment based on two-dimension codes. The identity authentication method includes that a terminal acquires authentication URL (uniform resource locator) by scanning the two-dimension codes on OTP tokens; the terminal transmits the authentication URL to an authentication server for authentication; when the terminal accesses a website supporting the authentication URL after authentication of the authentication server is passed, a website / application server acquires authentication records of the authentication URL in the authentication server through OpenID, Oauth, FIDO or SAML; the website / application server transmits authentication results to the terminal according to the authentication records of the authentication URL in the authentication server. By the identity authentication method, the integral authentication process does not need manually inputted dynamic passwords, and the problems that authentication process of manually inputted dynamic passwords is complicated and user experience is poor are solved.
Owner:BEIJING QIHOO TECH CO LTD
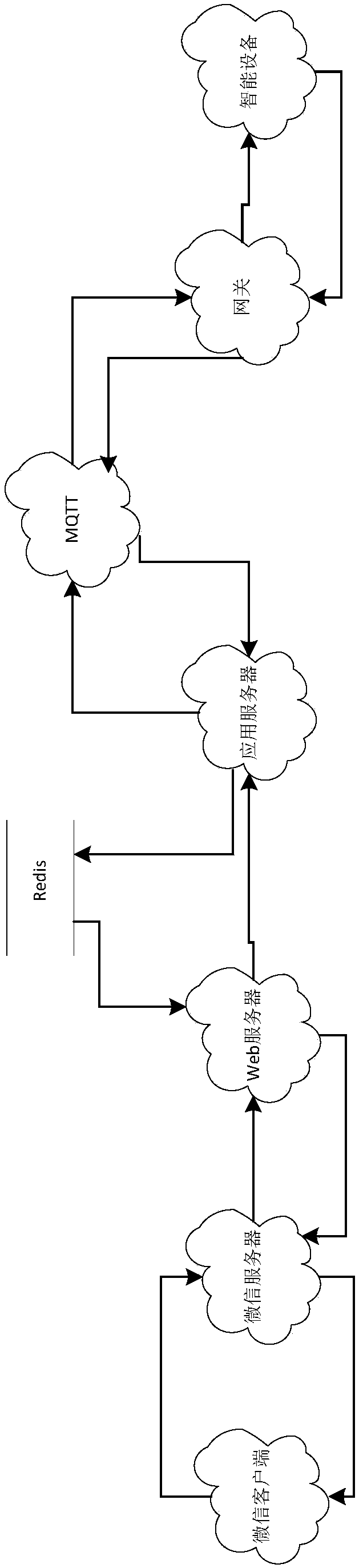
Smart home system
InactiveCN107623613AReduce labor maintenance costsData switching by path configurationPersonalizationSummary data
The invention provides a smart home system. The WeChat Openid of the WeChat is authorized to operate smart home appliances and to perform data query, a control mode is set and device control is performed, wherein an authorization two-dimensional code contains permissions and a gateway serial number, a WeChat server is used for receiving and processing information sent by a WeChat client, making response to the message of a public number and feeding back the message to the WeChat client, the functions of a Web server comprises device configuration query: providing gateway and device configuration for the client to generate a personalized interface; real-time data query: querying real-time data from a distributed cache; historical data query: querying historical data from the distributed cache; summarized data query: querying summarized data from the distributed cache; corresponding control instruction: making response to the user instruction to send the control instruction of the user to message-oriented middleware; and data cache service used for caching the data in a relation database in redis.
Owner:微赫智能科技(上海)有限公司
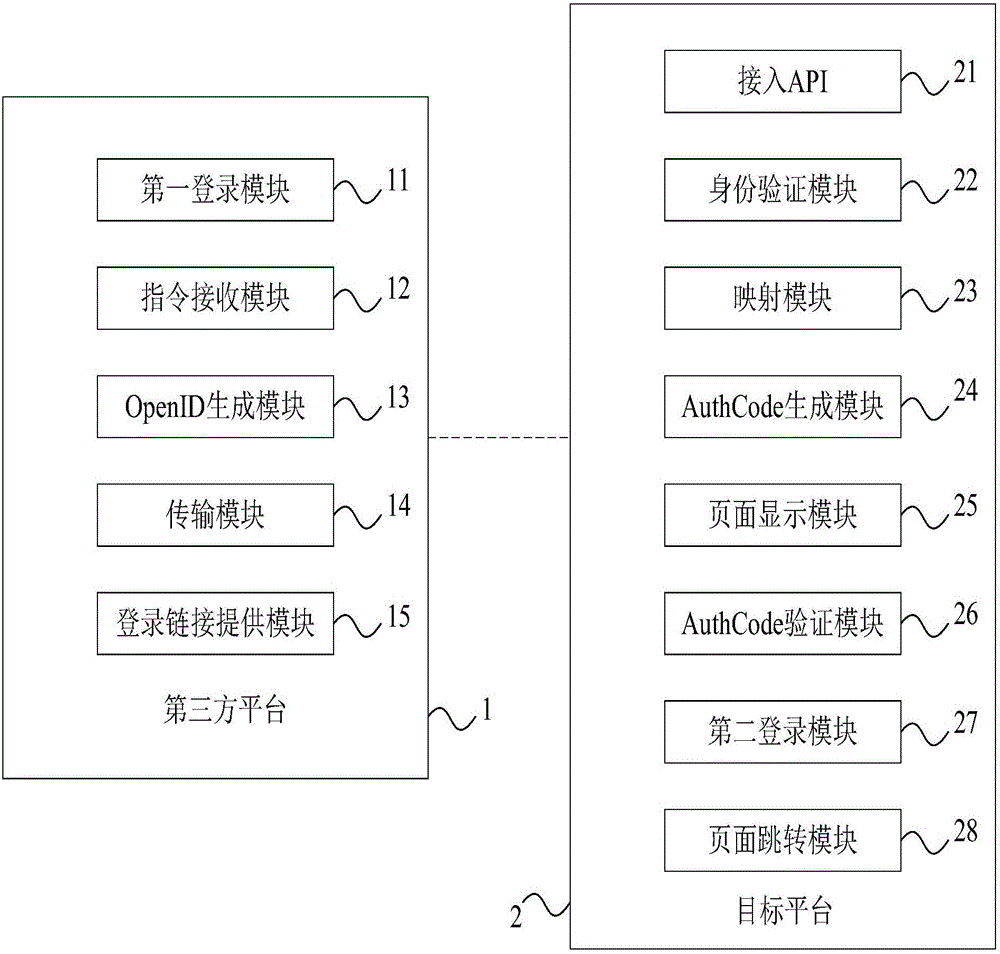
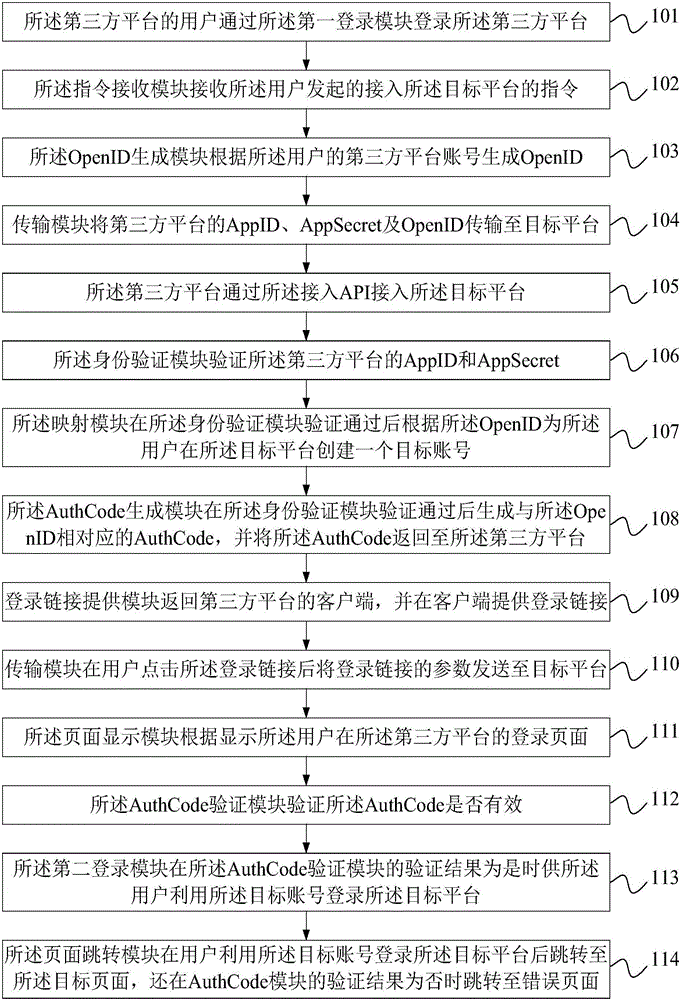
Authorization and authentication system and authorization and authentication method
The invention discloses an authorization and authentication system and an authorization and authentication method. The authorization and authentication system comprises a third-party platform and a target platform, wherein the third-party platform comprises a first login module for user login, an instruction receiving module for receiving an instruction initiated by a user, an OpenID generation module for generating an OpenID, and a transmission module for sending an AppID, an AppSecret and the OpenID; the target platform comprises an access API, an identity verification module for verification, a mapping module for creating a target account number, and an AuthCode generation module; the third-party platform comprises a login link providing module for providing a login link, and a transmission module for sending a login link parameter; and the target platform comprises a page display module for displaying the login page of the third-party platform, an AuthCode verification module, a second login module for a user to log in the target platform, and a page jumping module for jumping to the target page. According to the authorization and authentication system and the authorization and authentication method disclosed by the invention, the account number of the third-party platform can be rapidly accessed through a reverse proxy authorization method.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
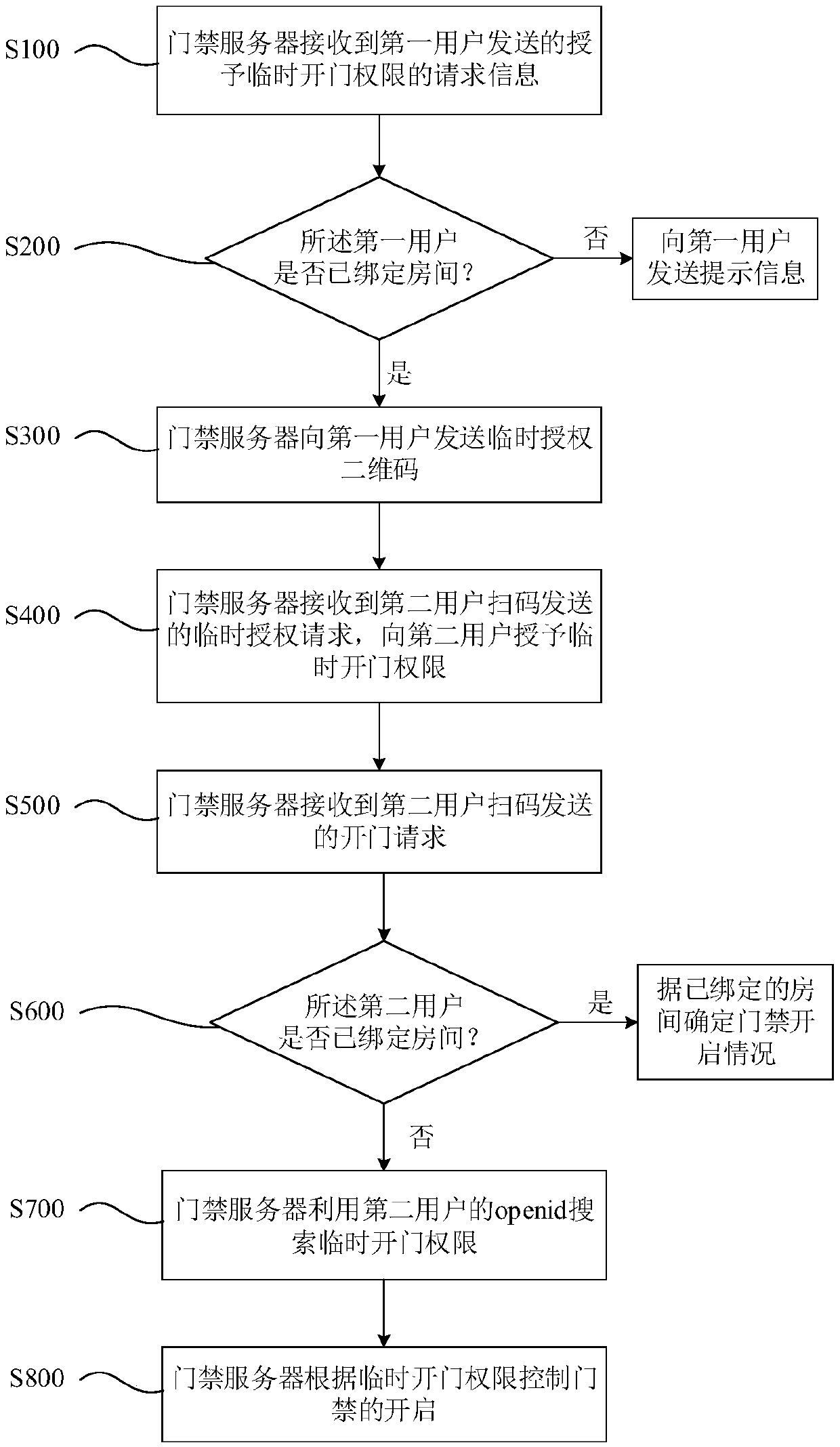
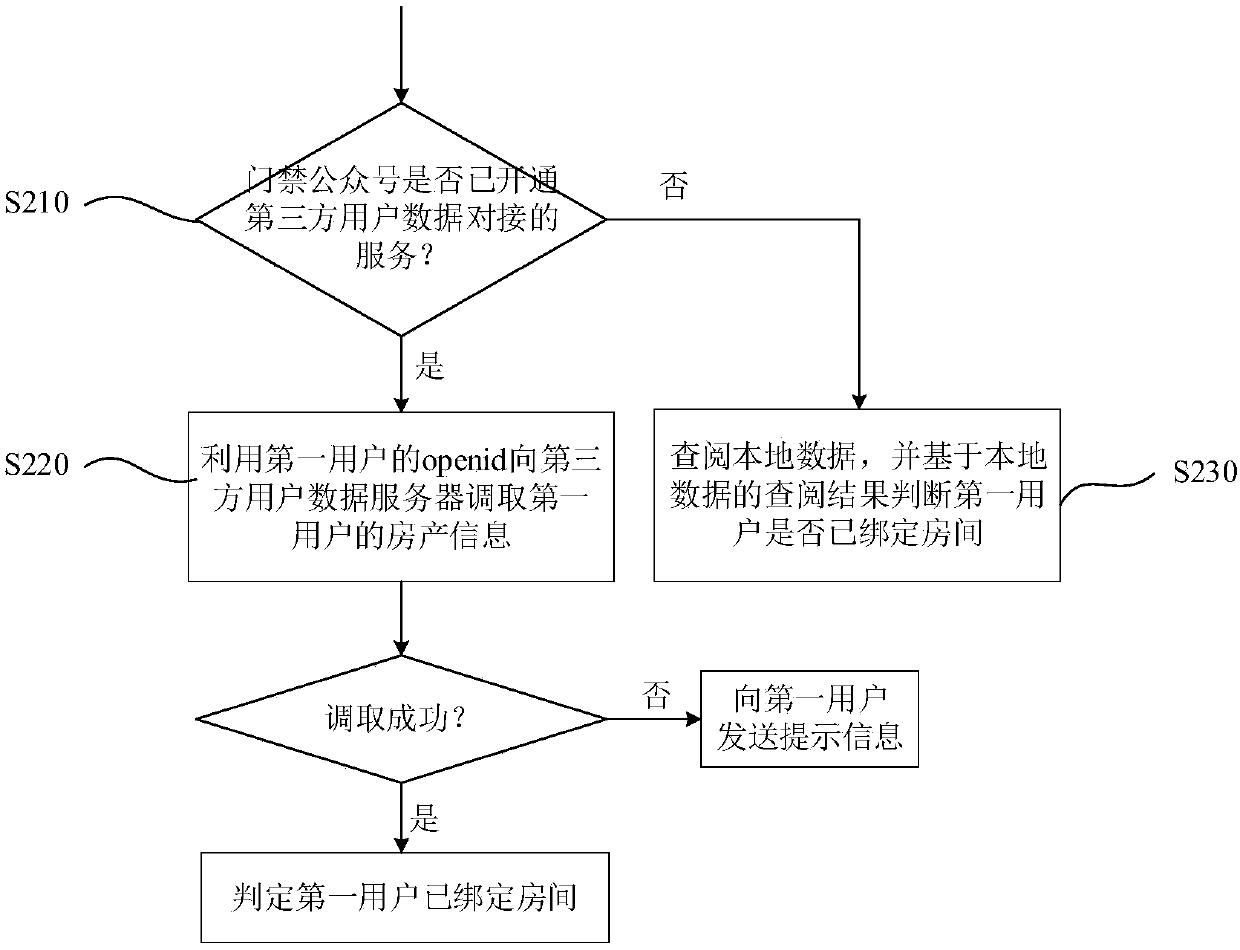
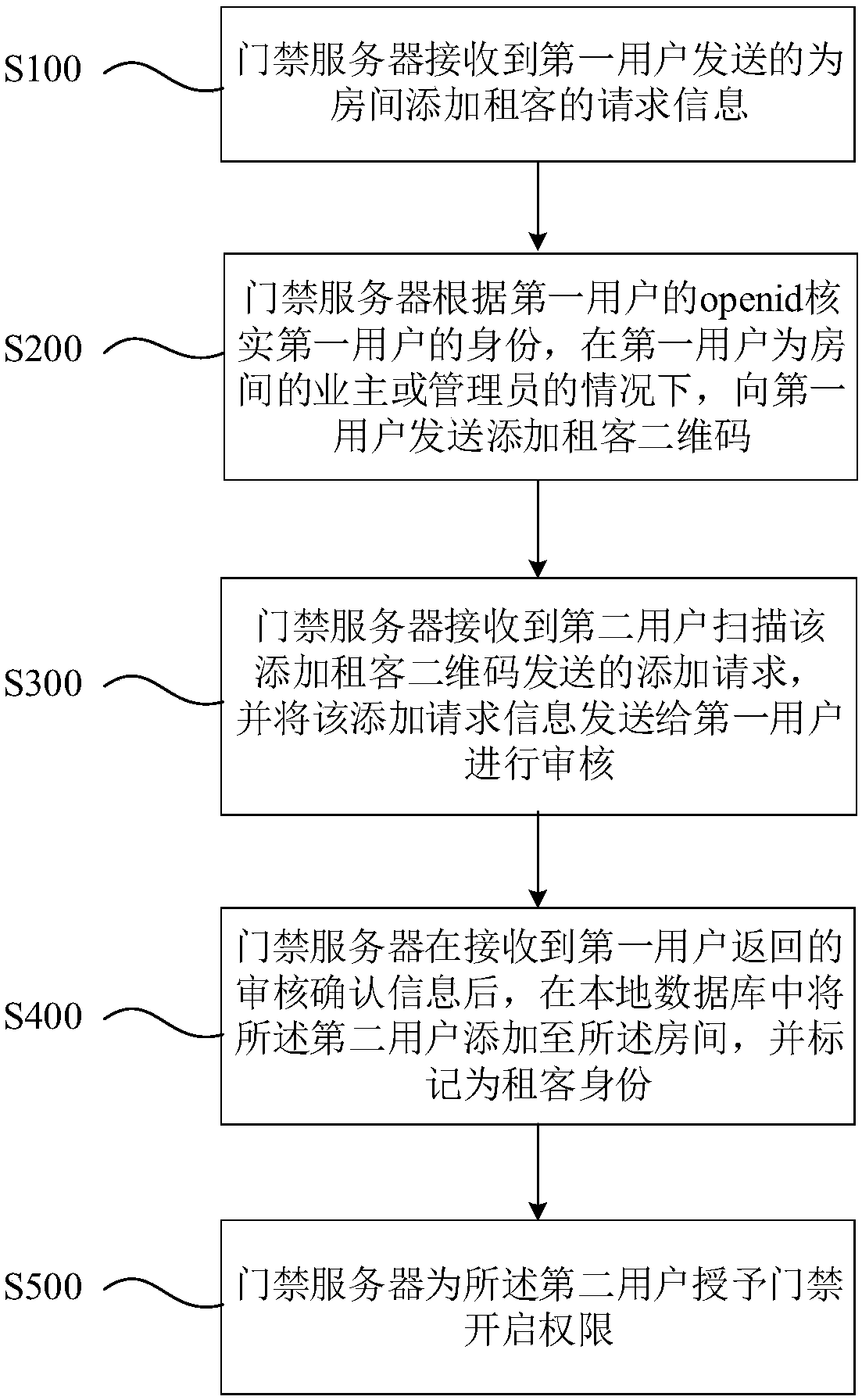
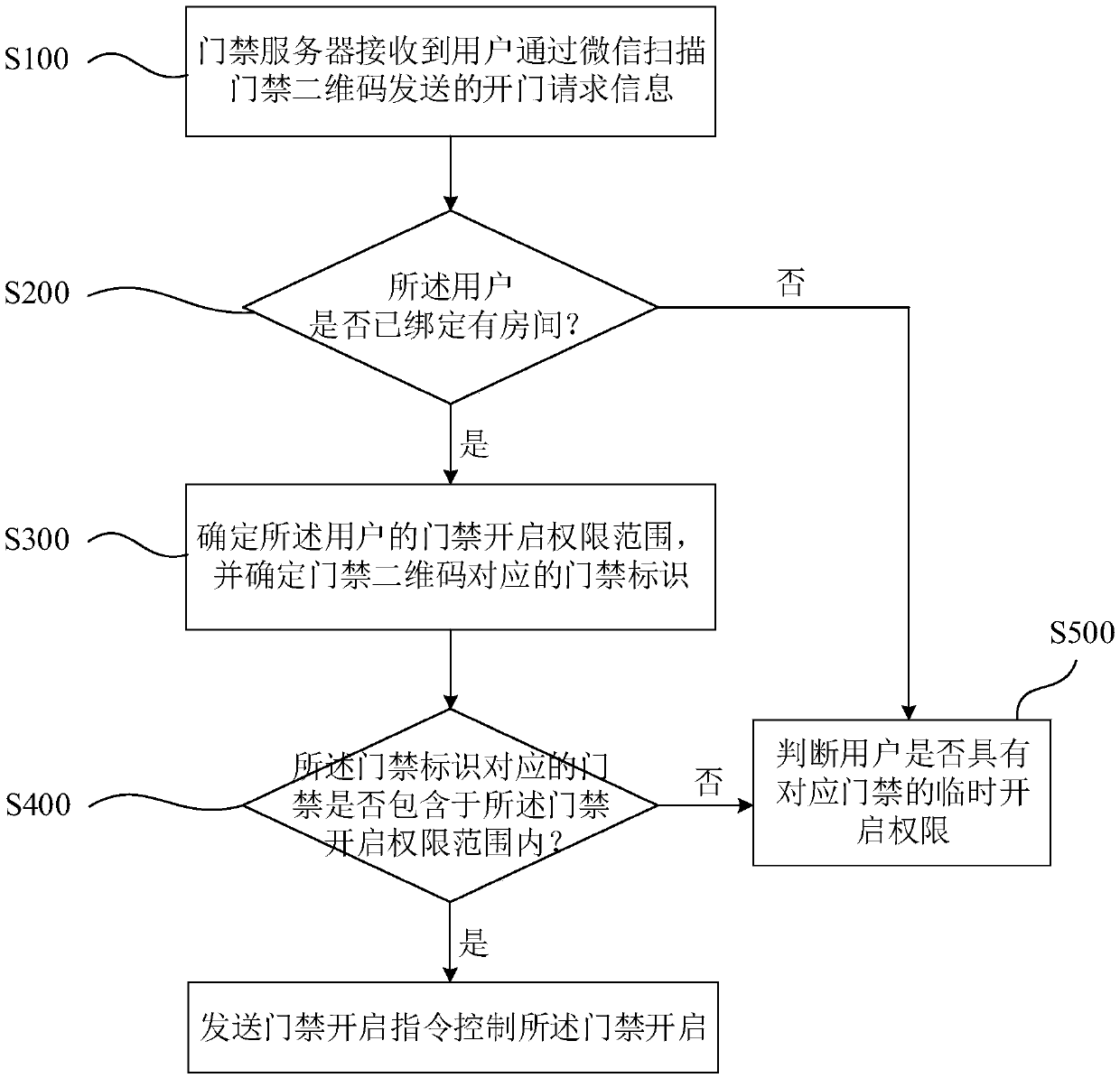
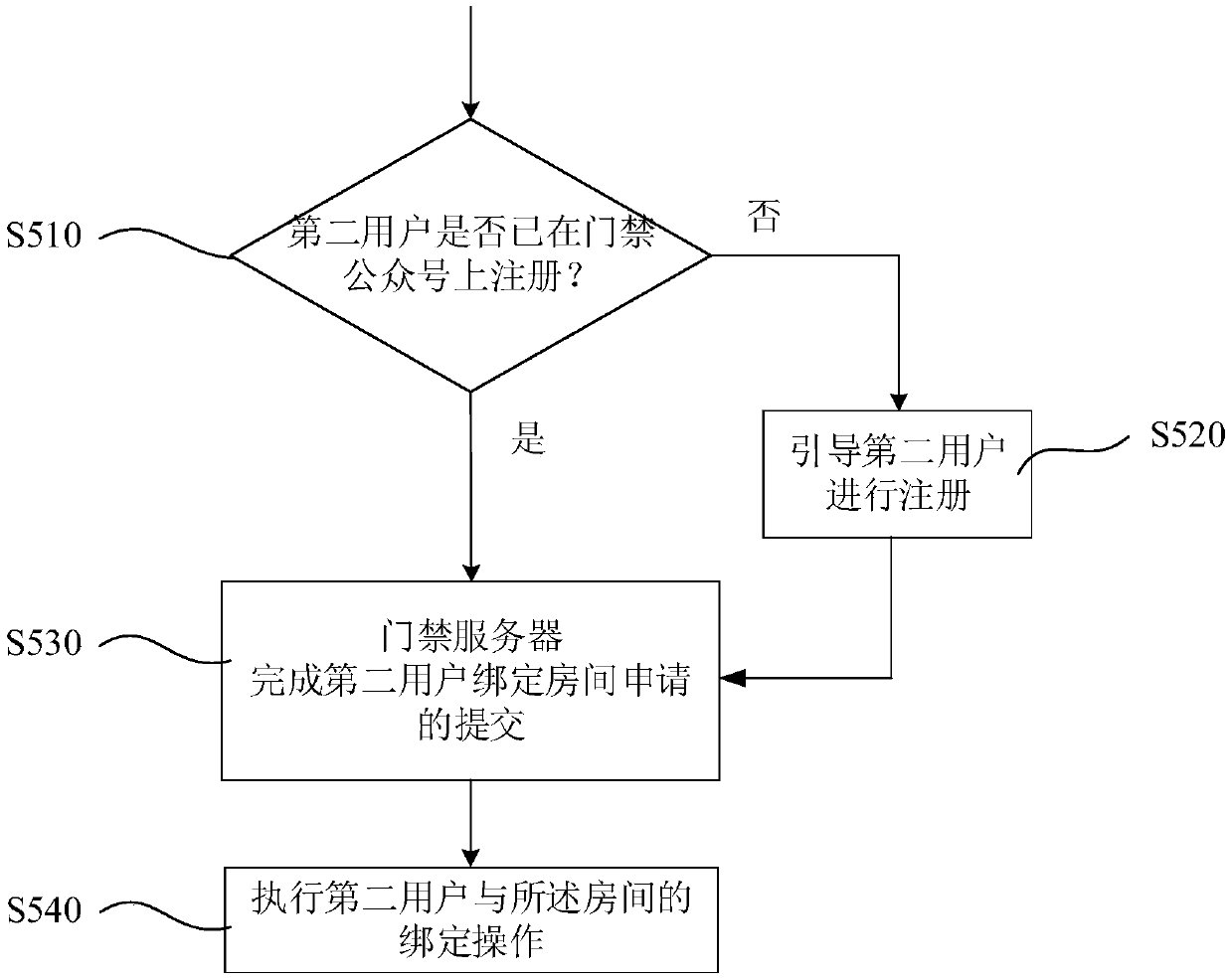
Openid-based temporary door opening authorization method
ActiveCN110021086AEasy to operateImprove efficiencyIndividual entry/exit registersAuthorizationDatabase
The invention discloses an openid-based temporary door opening authorization method. The method comprises steps: a door access server receives the request information sent by a first user for giving temporary door opening authorization; the door access server sends a temporary authorization two-dimensional code to the first user; the door access server receives a temporary authorization request sent by a second user through scanning the temporary authorization two-dimensional code and then gives temporary door opening authorization; the door access server receives door opening request information sent by the second user through scanning the door access two-dimensional code; the door access server uses the openid of the second user to search and acquire the temporary door opening authorization already given to the second user; and the door access server controls the door opening condition according to the room associated with the temporary door opening authorization. The door opening authorization can be conveniently given to a temporary visitor, an inhabitant does not need to input information manually, and the information of the temporary visitor can be protected against leakage.
Owner:深圳市微开互联科技有限公司
Code-scanning login method based on parameter-containing two-dimensional code of wechat official account
InactiveCN107480308AAuto FollowCo-operative working arrangementsData switching networksDimensional modelingMobile device
The invention discloses a code-scanning login method based on a parameter-containing two-dimensional code of a wechat official account. The method includes the following steps that 1, an application in a weak interaction terminal builds socket connection with a server terminal; 2, a server generates a unique socketId to return the unique socketId to the terminal through a communication channel; 3, the terminal obtains the socketId and the unique deviceId of equipment and requests the parameter-containing two-dimensional code from the server terminal; 4, the server terminal makes the socketId, and the deviceId bound with a scene Id of the two-dimensional code, stores the socketId and the deviceId into a database or a cache, and returns the parameter-containing two-dimensional code to the terminal; 5, a user uses the wechat for scanning the code; 6, the server terminal obtains a user code-scanning event parameter fed back by the wechat official account, the socketId is obtained from the code-scanning event parameter, according to the socketId and the deviceId bound with the scene Id, logged-in information and skip parameters are fed back to the terminal, and meanwhile, and according to the user openid in the code-scanning event parameter, operation prompt information is pushed to the user. The rapid login method is achieved, the user is guided to perform complex operation on a mobile phone and other mobile devices, and meanwhile the Wechat official account is automatically subscribed.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Data processing method, device and equipment
ActiveCN107196840AProtection securityPrivacy protectionData switching networksComputer hardwareComputer science
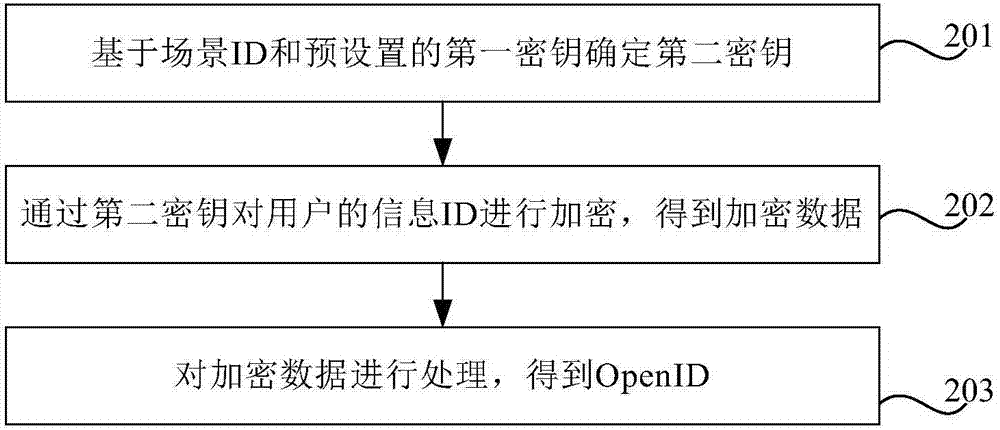
The invention discloses a data processing method, device and equipment. The method is applied to a server. The method comprises the steps that a second secret key is determined based on the scene ID and a preset first secret key; the information ID of the user is encrypted through the second secret key so as to obtain the encrypted data; and the encrypted data are processed so as to obtain OpenID. With application of the data processing method, device and equipment, the complexity and the security of encryption can be guaranteed, the corresponding OpenID of the information ID is ensured to be different under the same scene ID and thus the decryption difficulty can be increased.
Owner:蚂蚁(杭州)基金销售有限公司
WeChat applet and API security protection method and device, equipment and storage medium
InactiveCN110210203AGuaranteed legalityDigital data protectionDigital data authenticationAccess tokenOperating system
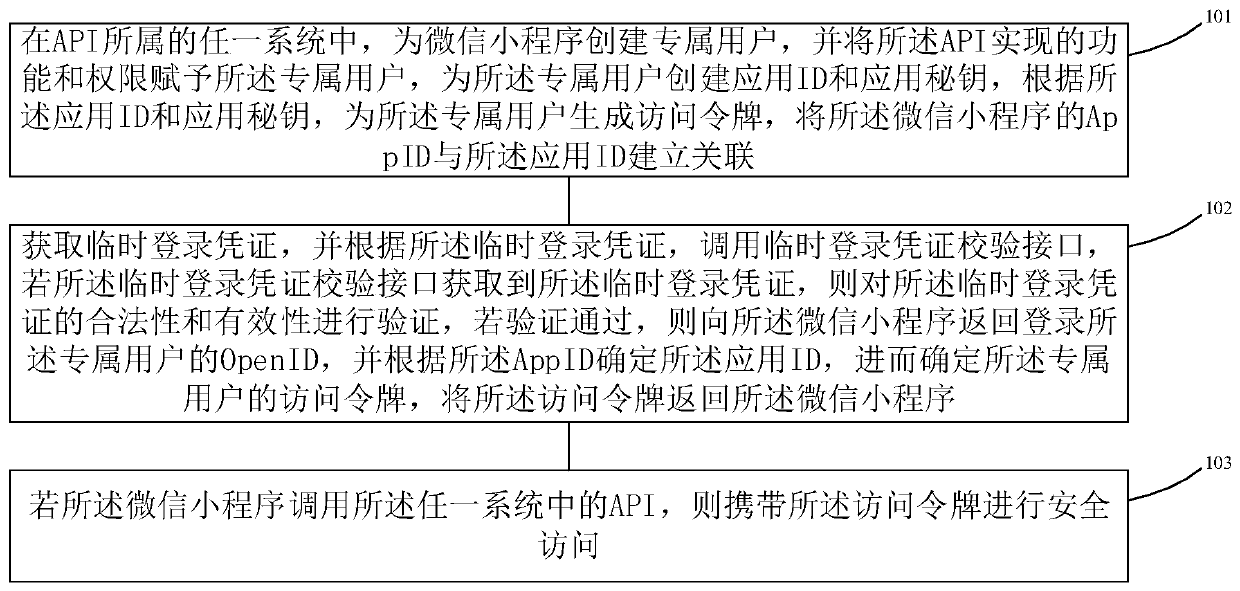
The embodiment of the invention provides a WeChat applet and API security protection method and equipment. The method comprises the following steps: in any system to which an API belongs, creating anexclusive user for a WeChat applet, endowing the exclusive user with functions and permissions realized by an API, creating an application ID and an application secret key for the exclusive user, generating an access token for the exclusive user, and correlating the AppID of the WeChat applet with the application ID; obtaining a temporary login certificate and calling a temporary login certificateverification interface, if the temporary login certificate verification interface obtains the temporary login certificate, verifying the legality and effectiveness of the temporary login certificate,if the verification is passed, returning the OpenID of the login special user, determining the application ID according to the AppID, determining the access token of the special user, and returning the access token; and if the WeChat applet calls the API in any system, enabling the WeChat applet to carry the access token to perform secure access. According to the method and the system, the methodof realizing the user permission in the system can be multiplexed, and the security of calling the API is ensured.
Owner:武汉神算云信息科技有限责任公司
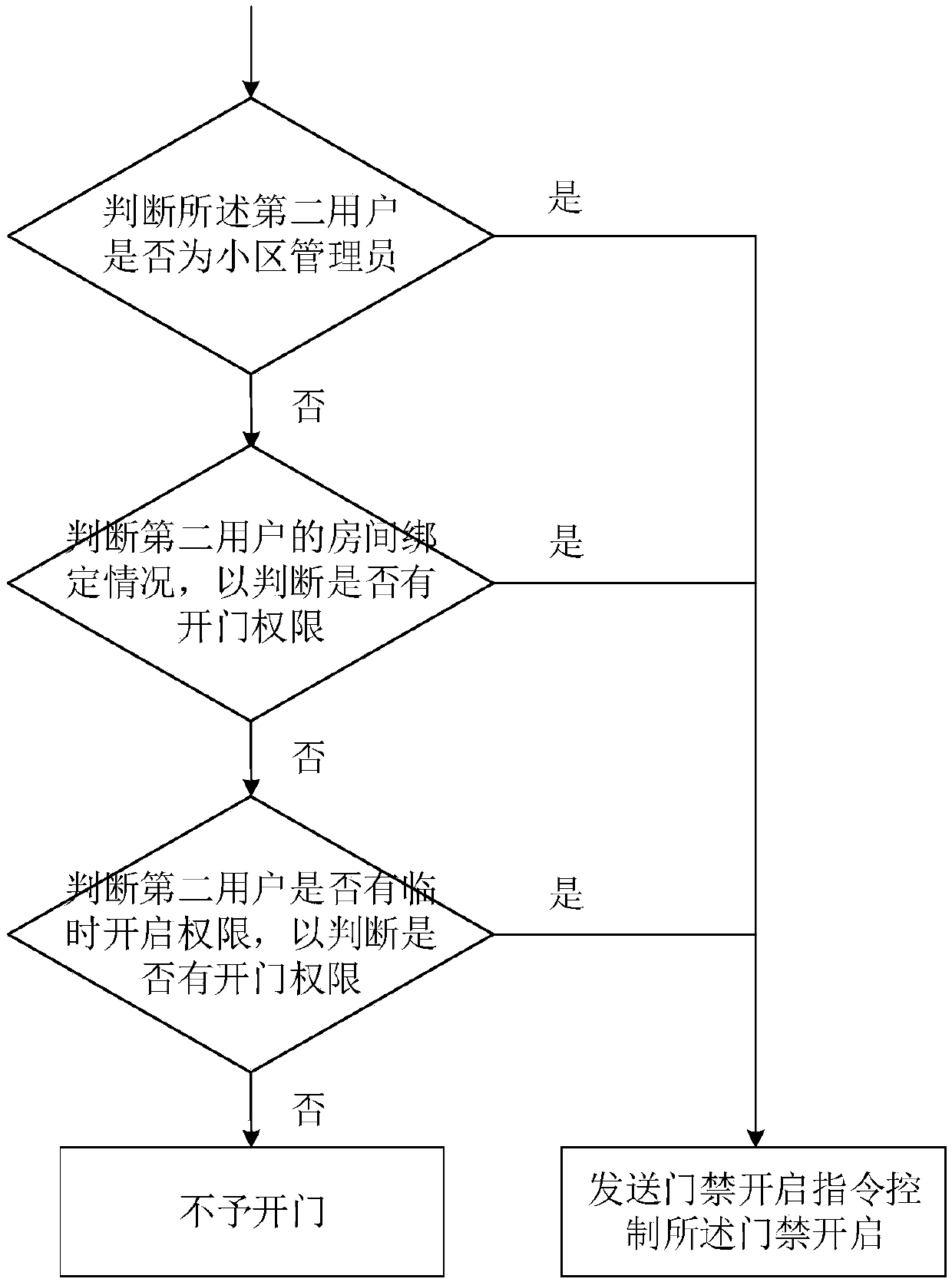
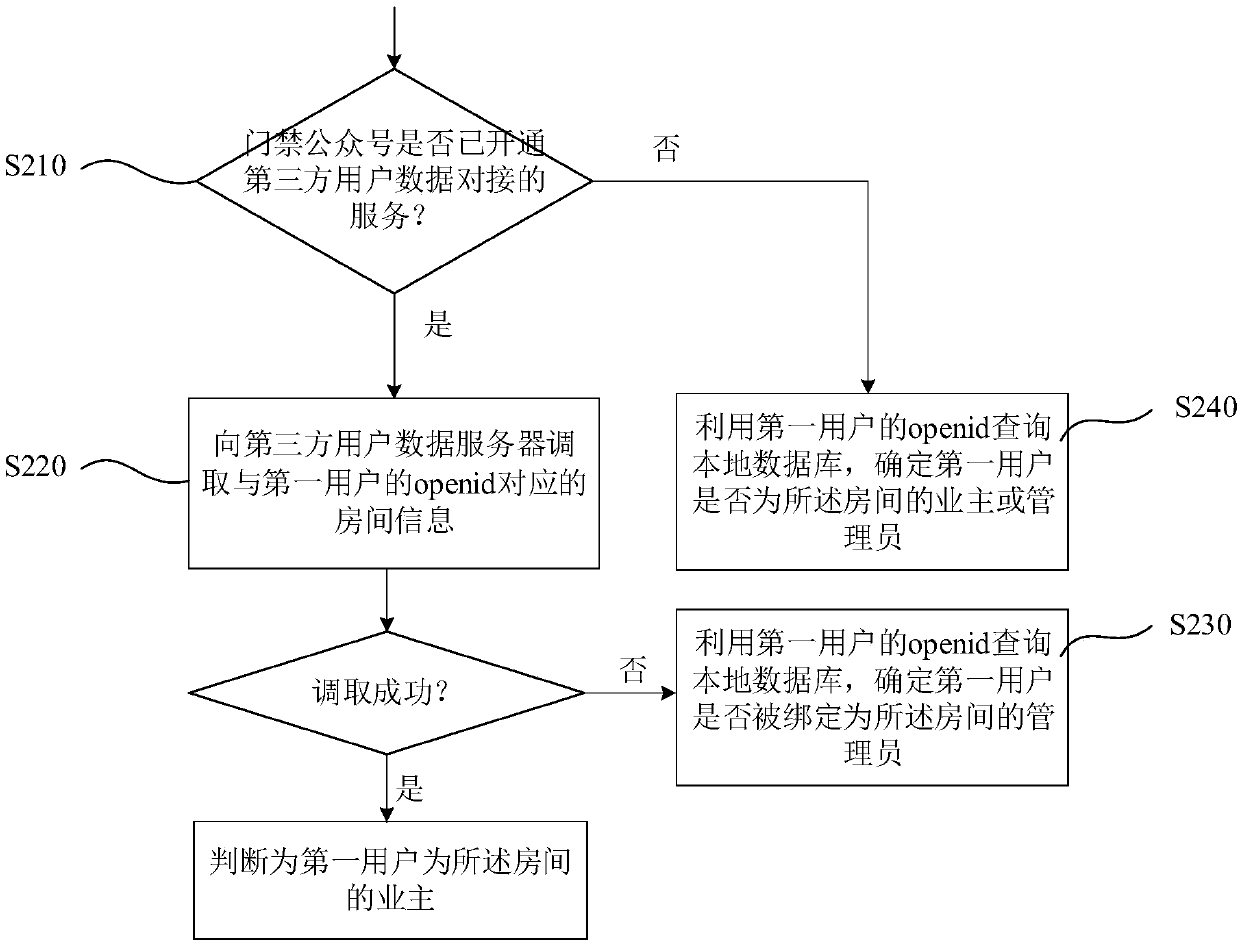
Openid-based tenant access control authority control method
ActiveCN110021092AImprove experienceEasy to operateIndividual entry/exit registersAuthority controlComputer access control
The invention discloses an openid-based tenant access control authority control method. The method comprises steps: an access control server receives the request information sent by a first user for adding a tenant to the room; the access control server verifies the identity of the first user according to the openid of the first user, and in a condition in which the first user is the owner or theadministrator of the room, a tenant adding two-dimensional code is sent to the first user; the access control server receives an adding request sent by a second user through scanning the tenant addingtwo-dimensional code, and the adding request information is sent to the first user for verification; after the access control server receives the verification confirmation information returned by thefirst user, the second user is added to the room and is marked as the tenant; and the access control server gives an access control permission to the second user. In the method, giving of opening permissions for multiple access control can be completed when the owner (or the administrator) and the tenant only need to simply operate for one time, and repeated operation for single access control isnot needed.
Owner:深圳市微开互联科技有限公司
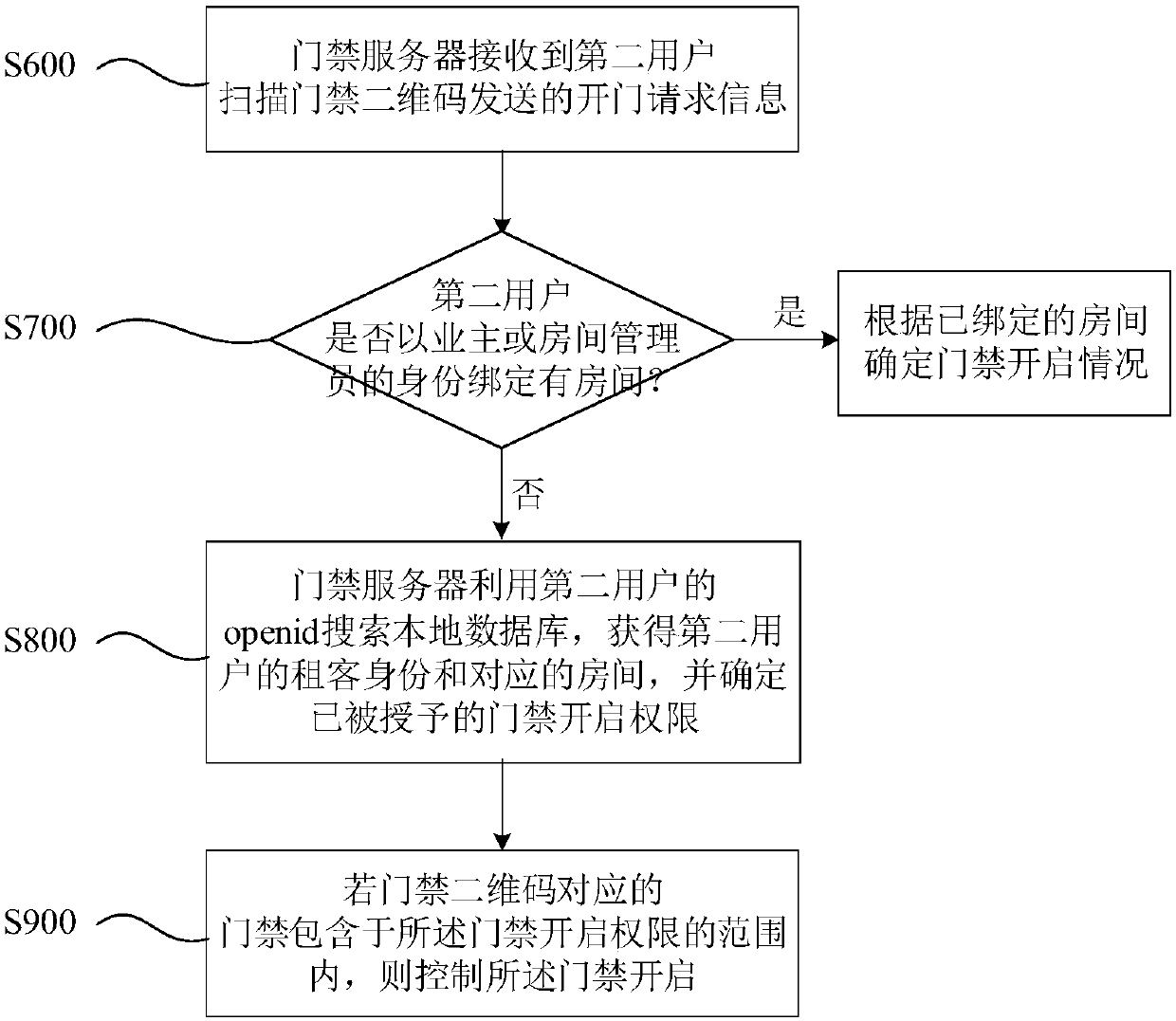
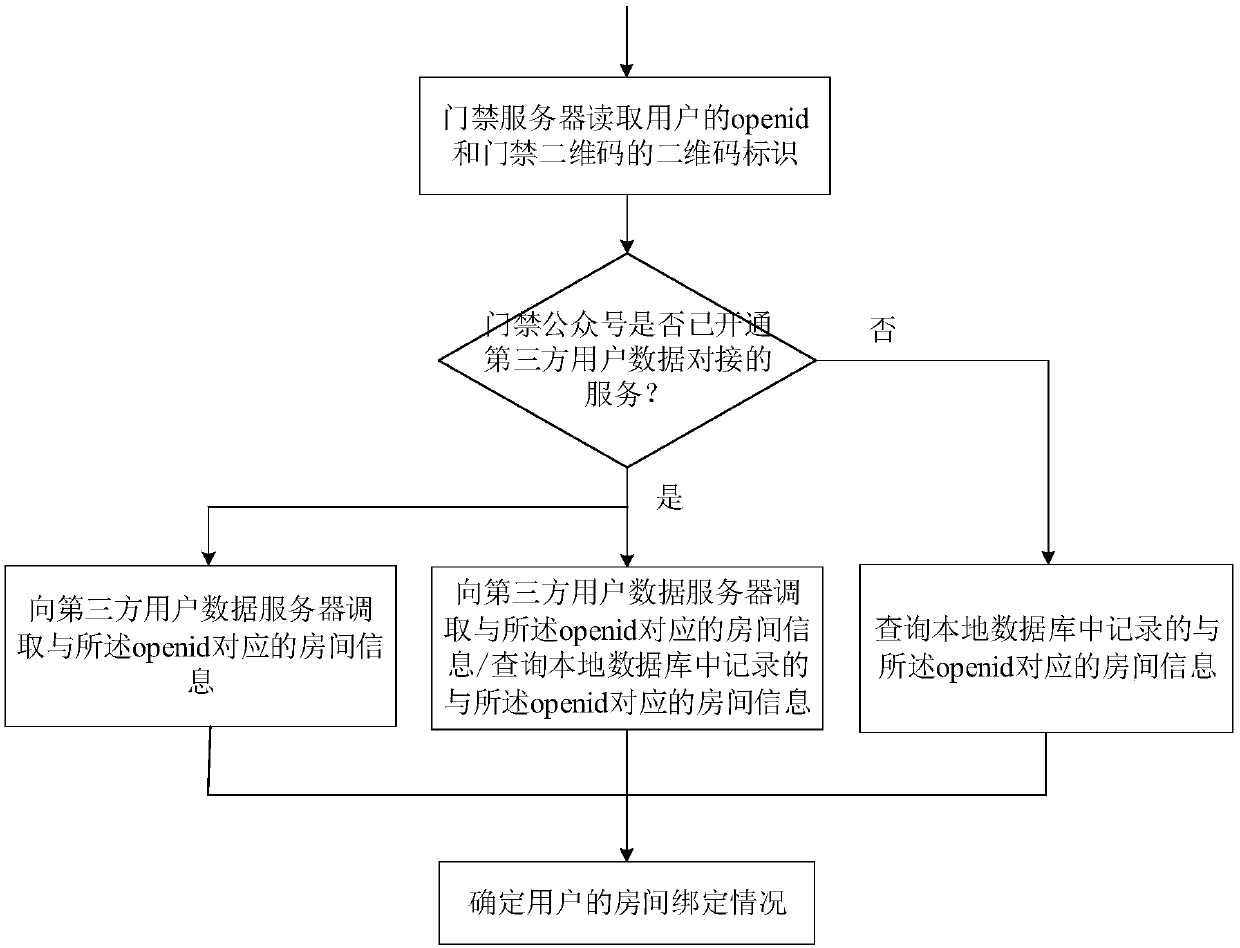
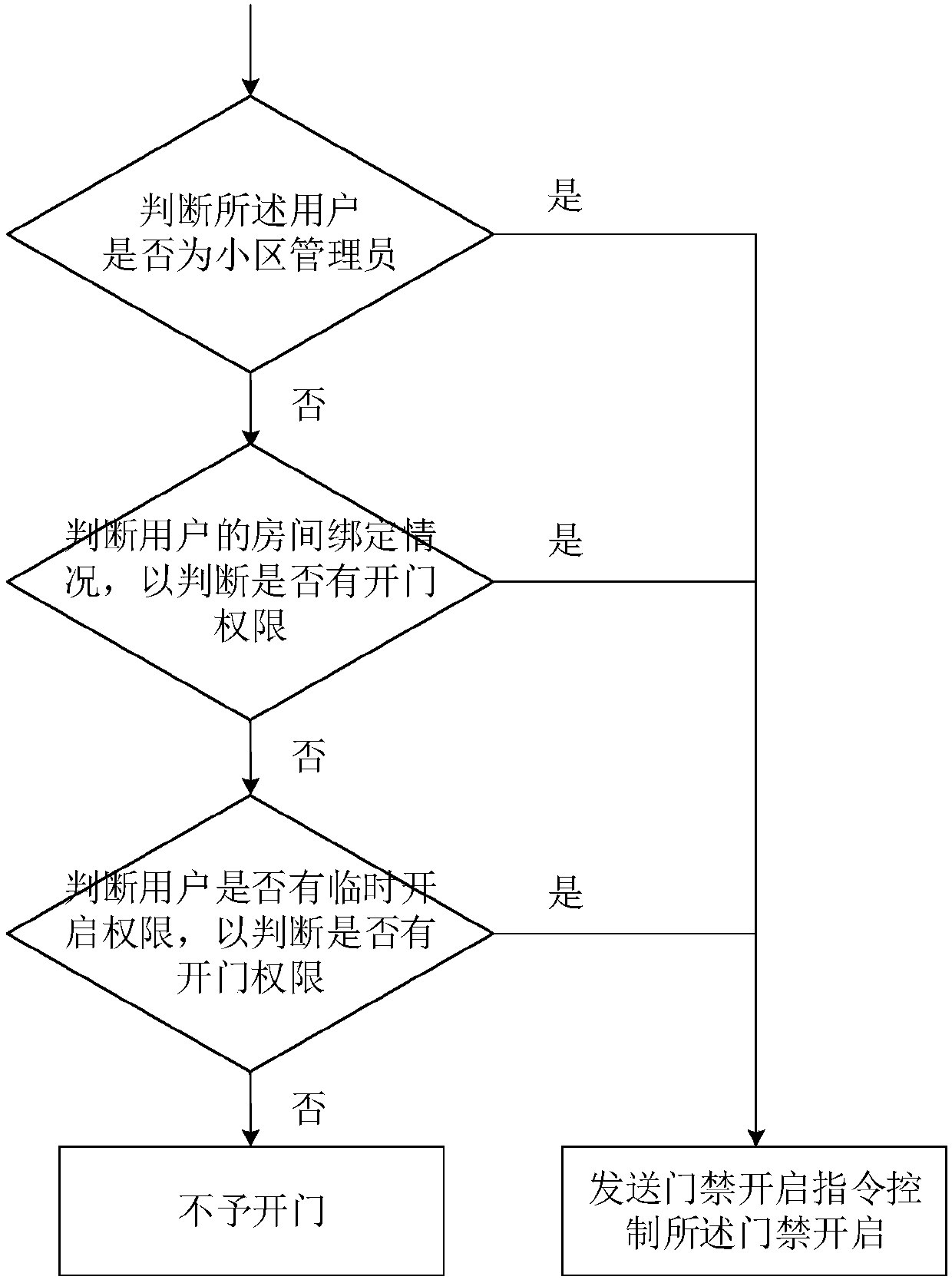
Openid-based access control method
ActiveCN110021093AProtection of personal informationHigh acceptanceIndividual entry/exit registersSensing by electromagnetic radiationAccess control matrixWorkload
The invention discloses an openid-based access control method. The method comprises steps: an access control server receives opening request information sent when a user scans an access control two-dimensional code; the access control server reads the openid of the user and the two-dimensional code identifier of the access control two-dimensional code, and according to the openid, whether the useris already bound with a room in the name of the homeowner or the family member on an access control official account; the access control server determines the access control opening permission rangeof the user according to the identifier of the room, and an access control identifier corresponding to the access control two-dimensional code is determined based on the two-dimensional code identifier; and the access control server determines whether the access control corresponding to the access control identifier is included in the access control opening permission range, and if yes, opening iscarried out. The association relationship between each access control and each user does not need to be stored, the data input workload and the data amount read by the access control server during the working process can be reduced obviously, the error probability in data input can be avoided, and the burden of the access control server is also lessened.
Owner:深圳市微开互联科技有限公司
Door opening system by code scanning parallel verification and method
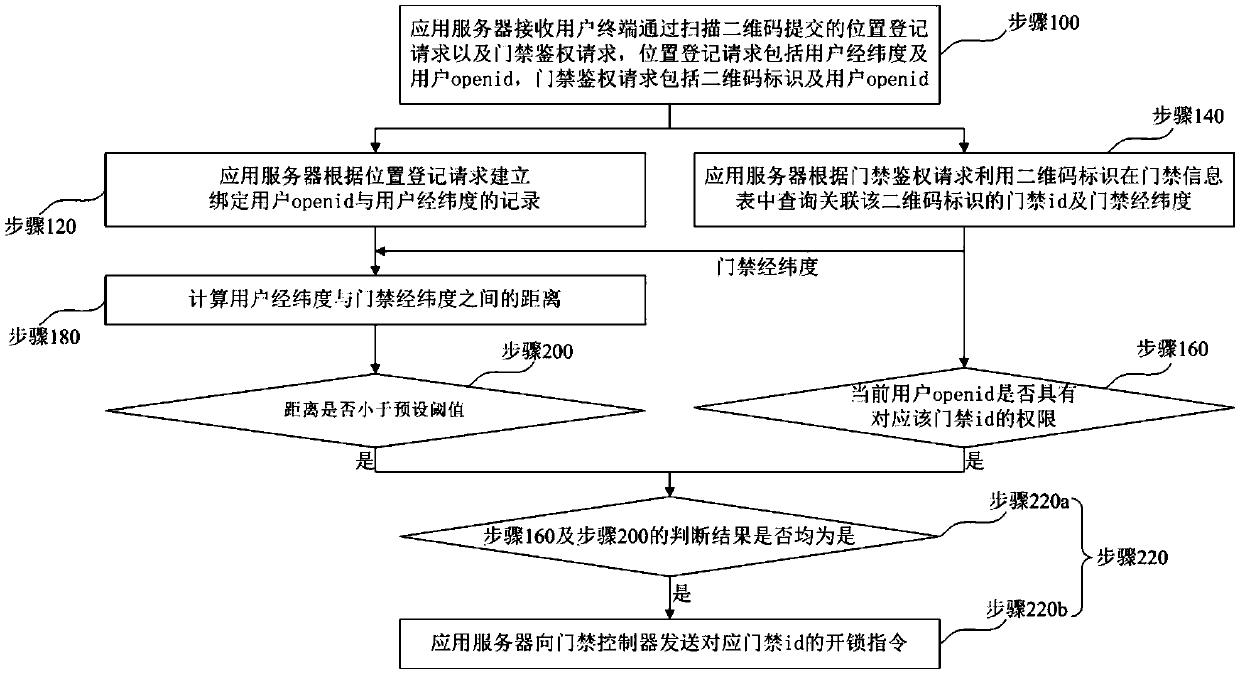
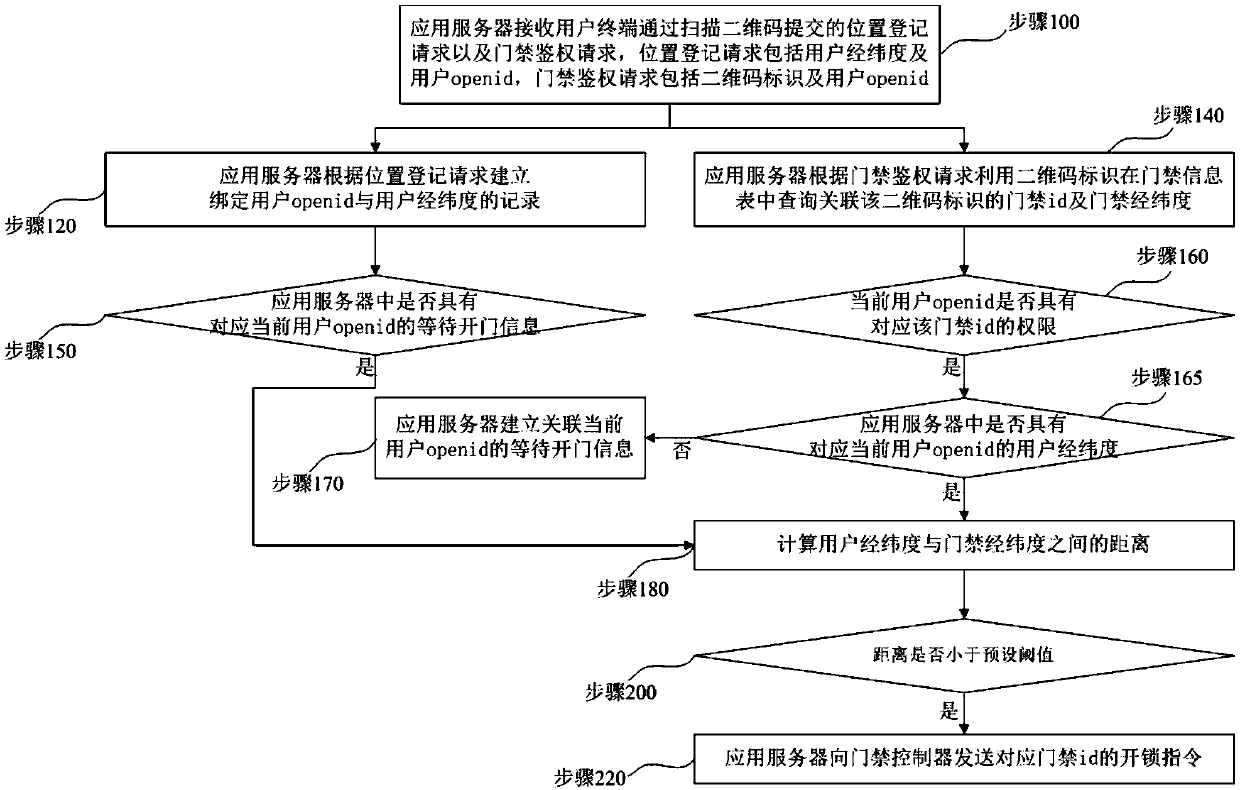
ActiveCN110021085AImprove experienceImprove securityIndividual entry/exit registersApplication serverLongitude
The invention relates to a door opening system by code scanning parallel verification and method. The system comprises an application server and an access controller, wherein the application server isconfigured to receive a location registration request and an access control authentication request submitted by a user terminal by scanning a two-dimensional code; a record of binding the user openidand latitude and longitude of the user is established according to the location registration request; an access control id and access control latitude and longitude related to the two-dimensional code identifier are queried according to the access control authentication request; whether the current user openid has an unlocking authority corresponding to the access control id is judged; the distance between latitude and longitude of the user and the access control latitude and longitude is calculated and whether the distance is smaller than a preset threshold is judged; and if the unlocking authority is achieved and the distance is smaller than the preset threshold, an unlocking instruction is sent. Apart from verification on the authority of the user during a door opening process, the position of the user when opening the door is subjected to distance judgment, code scanning for door opening can be carried out only when the position of the user is ensured to be in a specified positionrange, and the effect of enhancing the access control safety is achieved.
Owner:深圳市微开互联科技有限公司
WeChat door opening-based quick room binding method
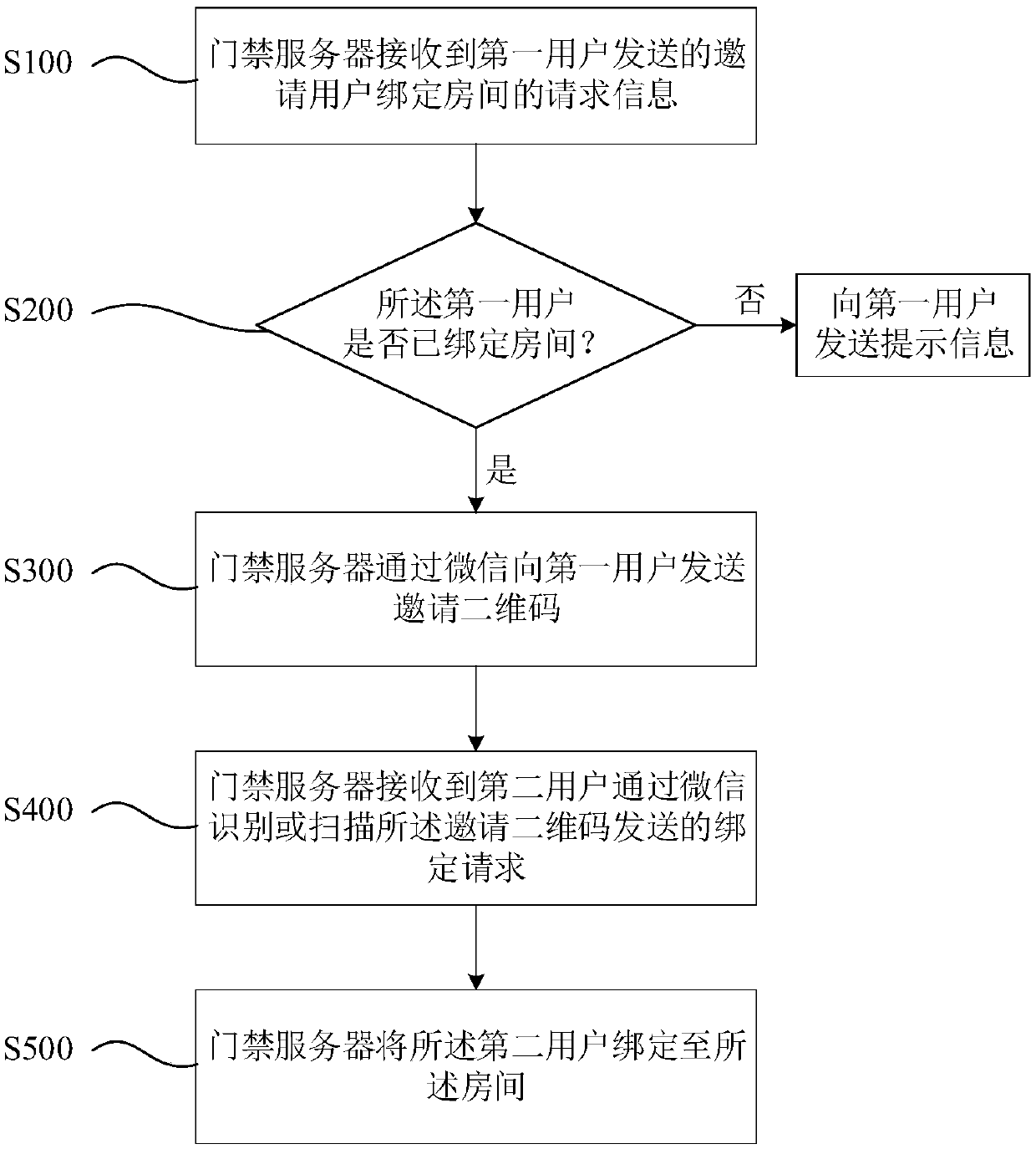
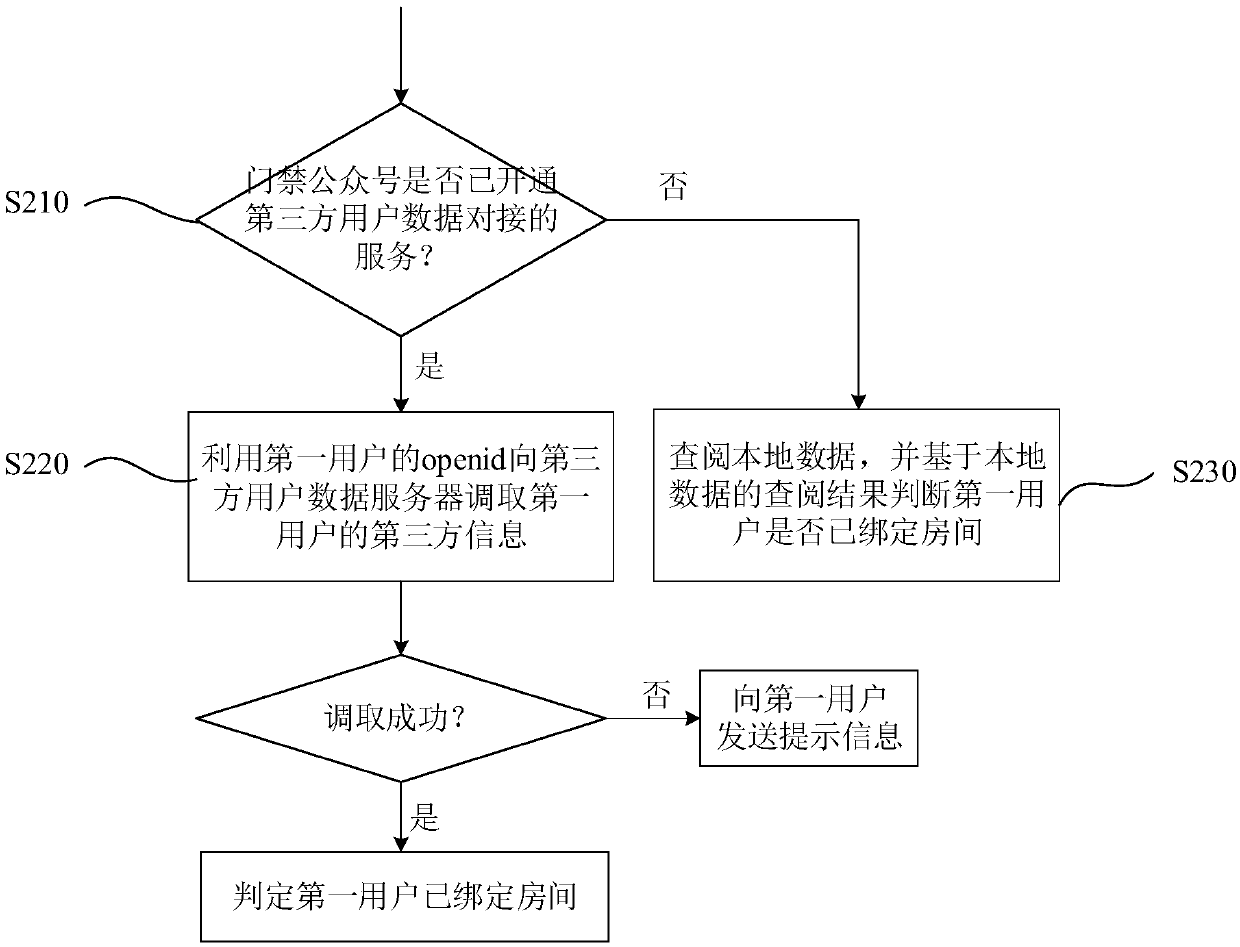
ActiveCN110021087AEasy to operateEliminate manual operationCo-operative working arrangementsIndividual entry/exit registersDatabaseAccess control
The invention discloses a WeChat door opening-based quick room binding method. The method comprises steps: S100, an access control server receives the request information sent by a first user to invite a user to bind a room, and the openid acquired when the first user logs into an access control official account is acquired; S300, the access control server sends an invitation two-dimensional codeto the first user, wherein the invitation two-dimensional code includes information about the room when the first user sends the request; S400, the access control server receives a binding request sent by a second user through WeChat recognition or invitation two-dimensional code scanning; and S500, the access control server binds the second user to the room and stores the binding relationship between the second user and the room to a database. The quick room binding method disclosed in the invention is extremely simple in operation process, eliminates various complicated manual operations, and can obviously improve the efficiency of binding a room.
Owner:深圳市微开互联科技有限公司
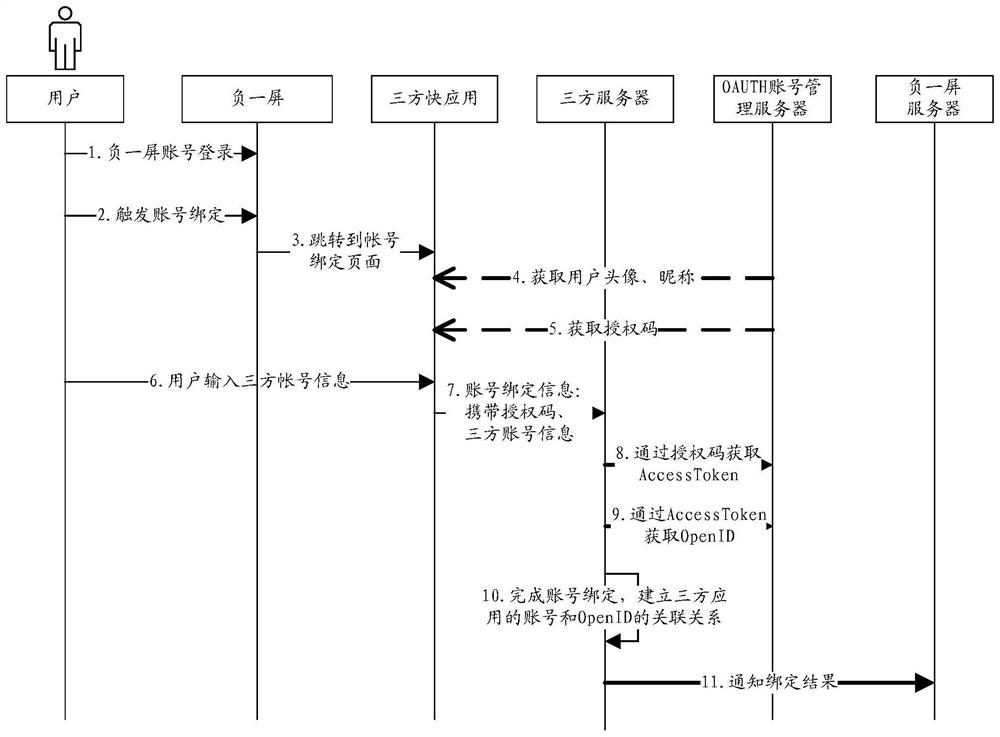
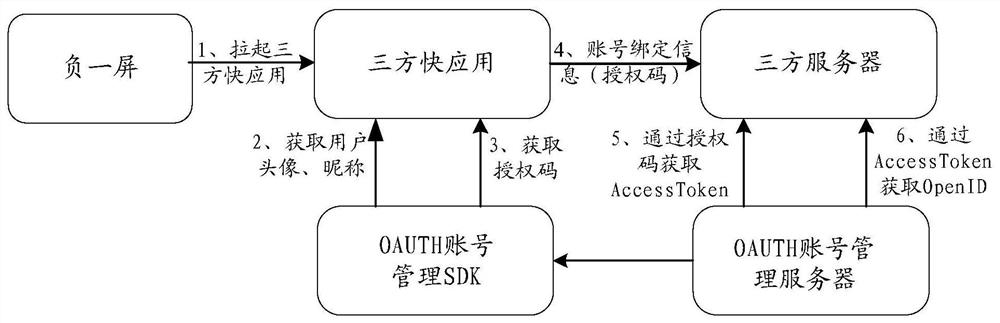
Account binding method, device and system
The embodiment of the invention provides an account binding method, device and system, and relates to the technical field of electronics. A secondary screen can replace a three-party fast application to obtain an OpenID corresponding to a user account of the secondary screen, so that binding of the user account of the three-party application and the user account of the secondary screen is achieved through the OpenID, the development workload of the three-party application is reduced, the account binding process of the three-party application and the secondary screen is simplified, and the account binding efficiency and flexibility are improved. According to the specific scheme, the electronic equipment logs in a user account of a first application; after a first preset operation of a user is detected, an OpenID corresponding to a user account of the first application is obtained through the first application, and the first preset operation is used for indicating to associate the second application with the first application; the OpenID and the identity information of the second application are sent to a server of the first application; and account binding success information is obtained from a server of the first application. The embodiment of the invention is used for account binding.
Owner:HUAWEI TECH CO LTD
A multi-application user unified authentication method based on a WeChat platform
InactiveCN109274579ARealize unified managementData switching networksDomain nameUniform resource locator
The method is a multi-application user unified authentication method based on a WeChat platform. The method comprises the following steps: a user visits a sub-website to initiate a request to a current proxy server; The proxy server receives the request and verifies the validity through the sub-website security authentication information. If the authentication is passed, sending an authorization request to the WeChat server; The WeChat server receives and processes the authorization request, and finally returns to the callback url set by the proxy server with the code code; The proxy server judges whether the code code is received or not, if not, ignores it. If a callback url returned to the subsite setting is received and security information authentication is performed; The subsite receives the information returned by the proxy server. The sub-website sends a request for obtaining user information to WeChat through the code code returned by WeChat and saves the request; The user visits another subsite of the corresponding domain name to obtain the value of the user unique information openid to determine whether or not the same user.
Owner:江苏龙虎网信息科技股份有限公司
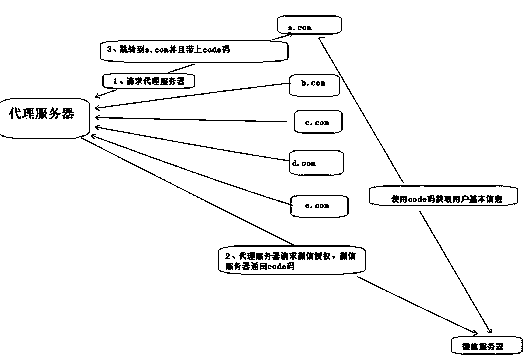
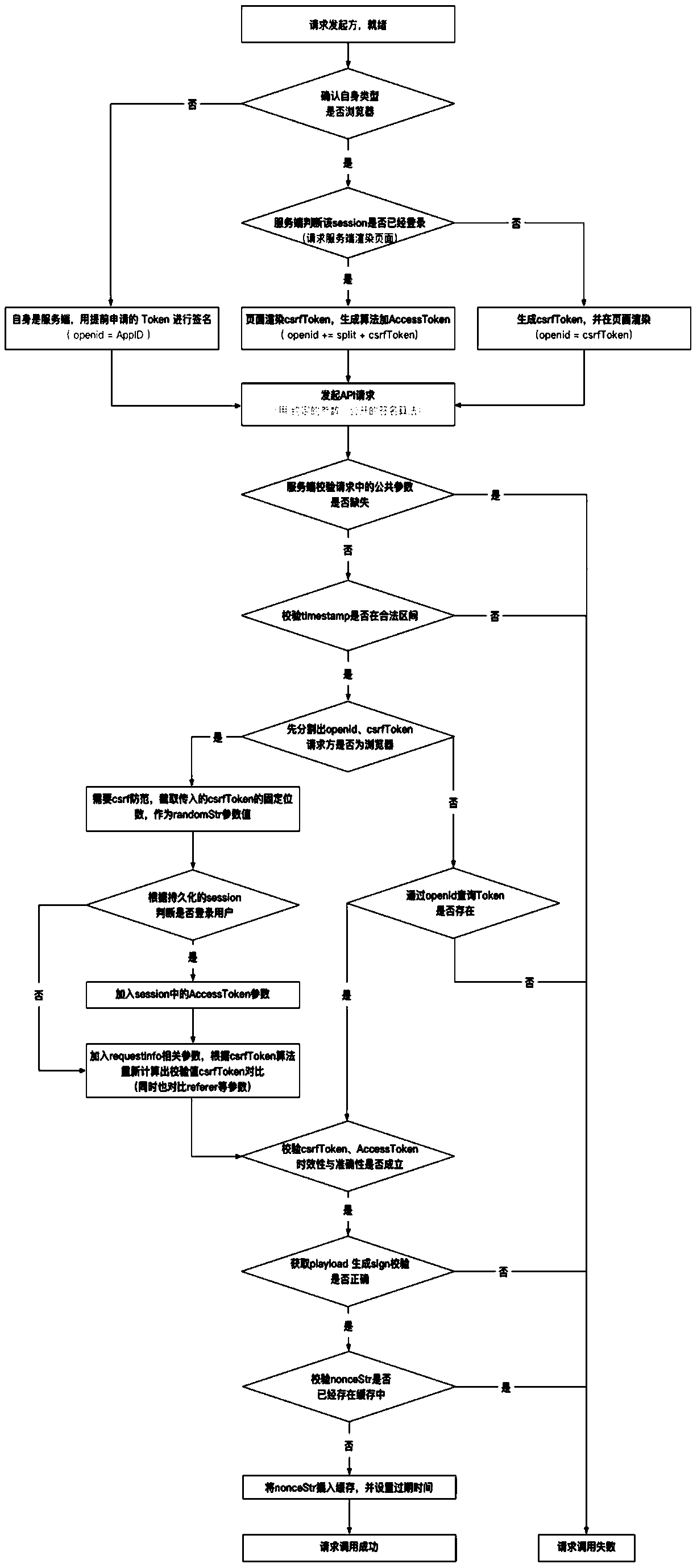
Web interface design method for preventing request message from being tampered, attacked and replayed
ActiveCN111447195APrevent tamperingSafe against CSRFUser identity/authority verificationTimestampEngineering
The invention discloses a web interface design method for preventing a request message from being tampered, attacked and replayed. The method specifically comprises the following steps: a server constructs a Token in combination with specific information, and issues the Token in advance if a caller is also the server; if the caller is a browser client, csrfToken is returned to; a public parametersignature algorithm and public parameters including nonceStr, openid, timestamp and token of the signature algorithm are appointed; an abstract service parameter, i.e., playload, which refers to a setof all service parameters is appointed; an API request is initiated; the legality of the request is verified according to the public parameters and the program in the request, and the verification flow priority following: parameter verification is the first, simple or complex operation is the second, and query cache delay is delayed. The method has the beneficial effects of ensuring no leakage even if the request is captured, preventing CSRF security of the browser and the server, preventing parameters from being tampered, and ensuring that the request is not replayed.
Owner:HANGZHOU QUWEI SCI & TECH
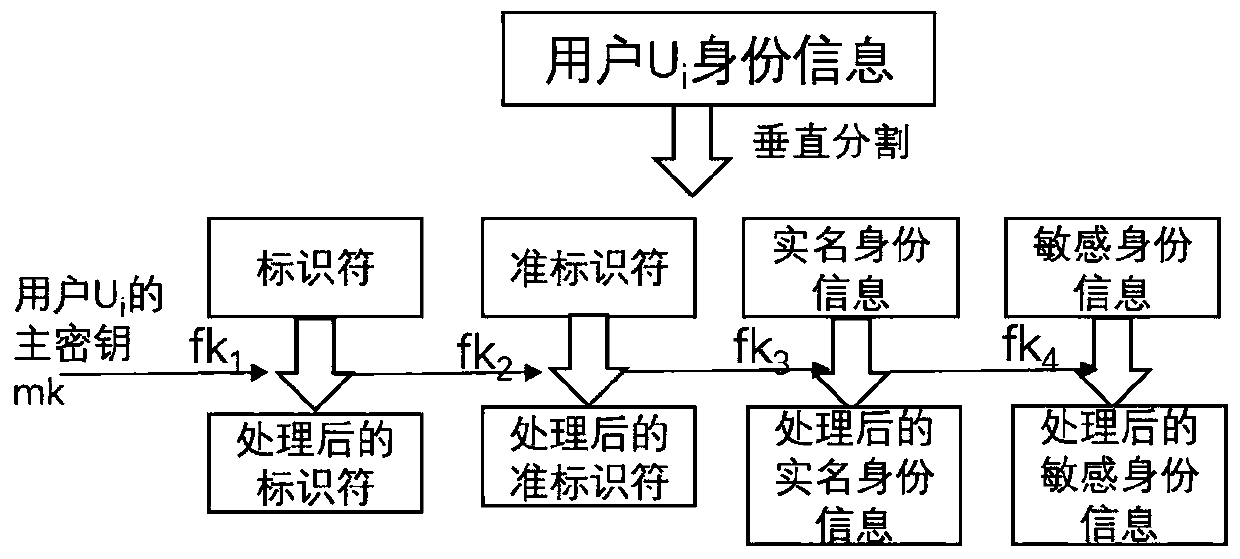
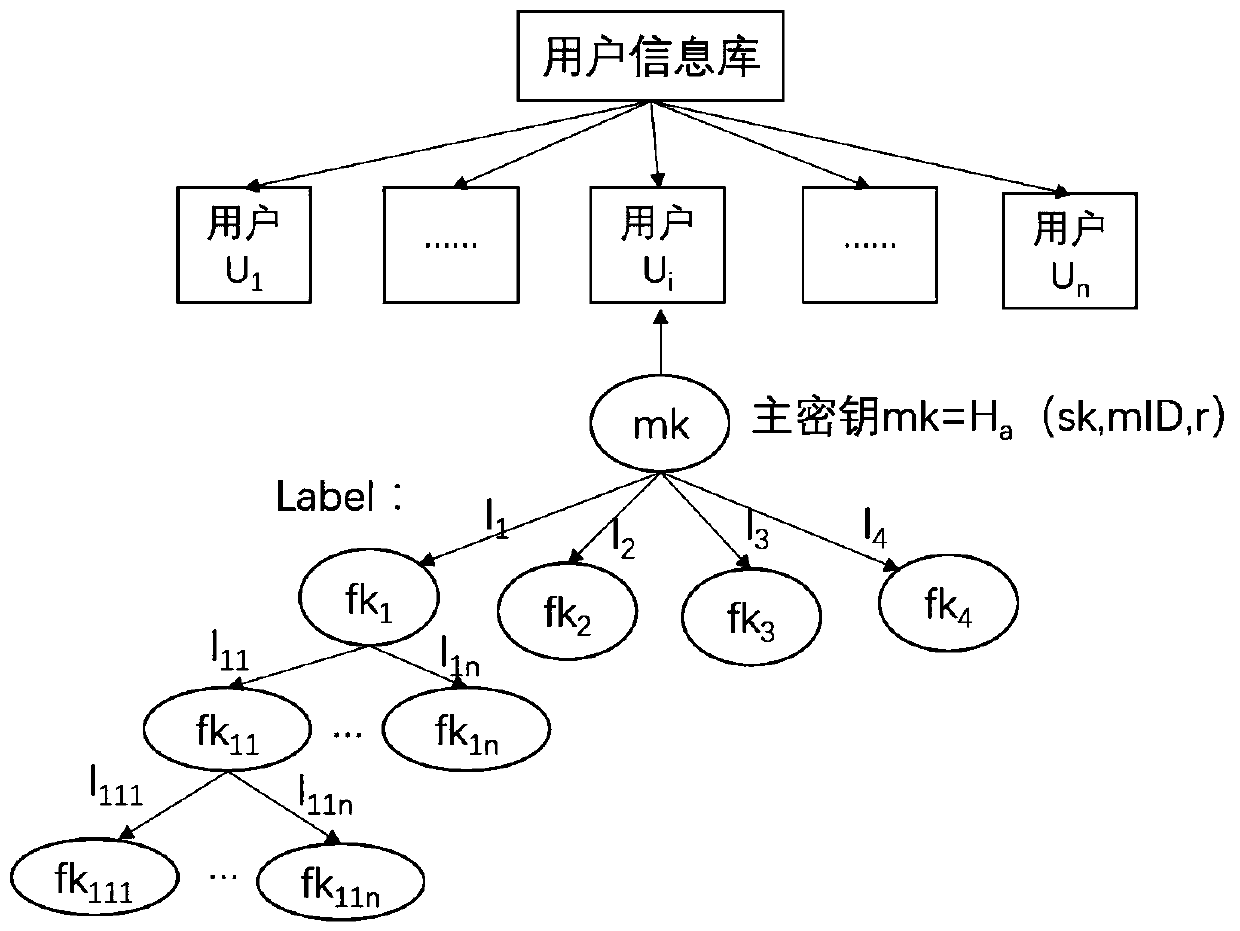
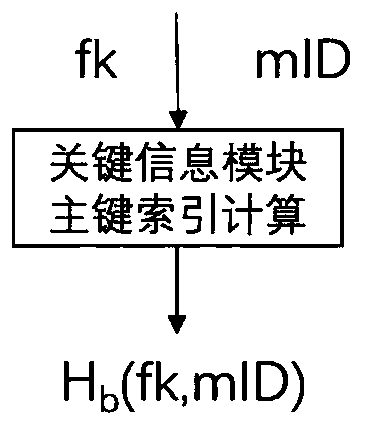
key information protection method and system based on an OpenID
ActiveCN109829333AEffectively control the spreadControl spreadDigital data protectionInformation repositoryPassword
The invention provides a key information protection method and system based on an OpenID., relating to identity authentication technology, Password technology, DATA DESENSITIZATION TECHNIQUES, the user key information is vertically segmented into identifiers; Quasi-identifier, According to the method, the real-name identity information and the sensitive information are classified into four types,the function key is adopted for protection and decentralized storage, the track information is encrypted, anti-association cutting, encryption, noise adding and other desensitization processing can becarried out on different types of key data, the privacy of a user can be effectively protected, and the risk of leakage of a user information base is greatly reduced.
Owner:INST OF INFORMATION ENG CAS
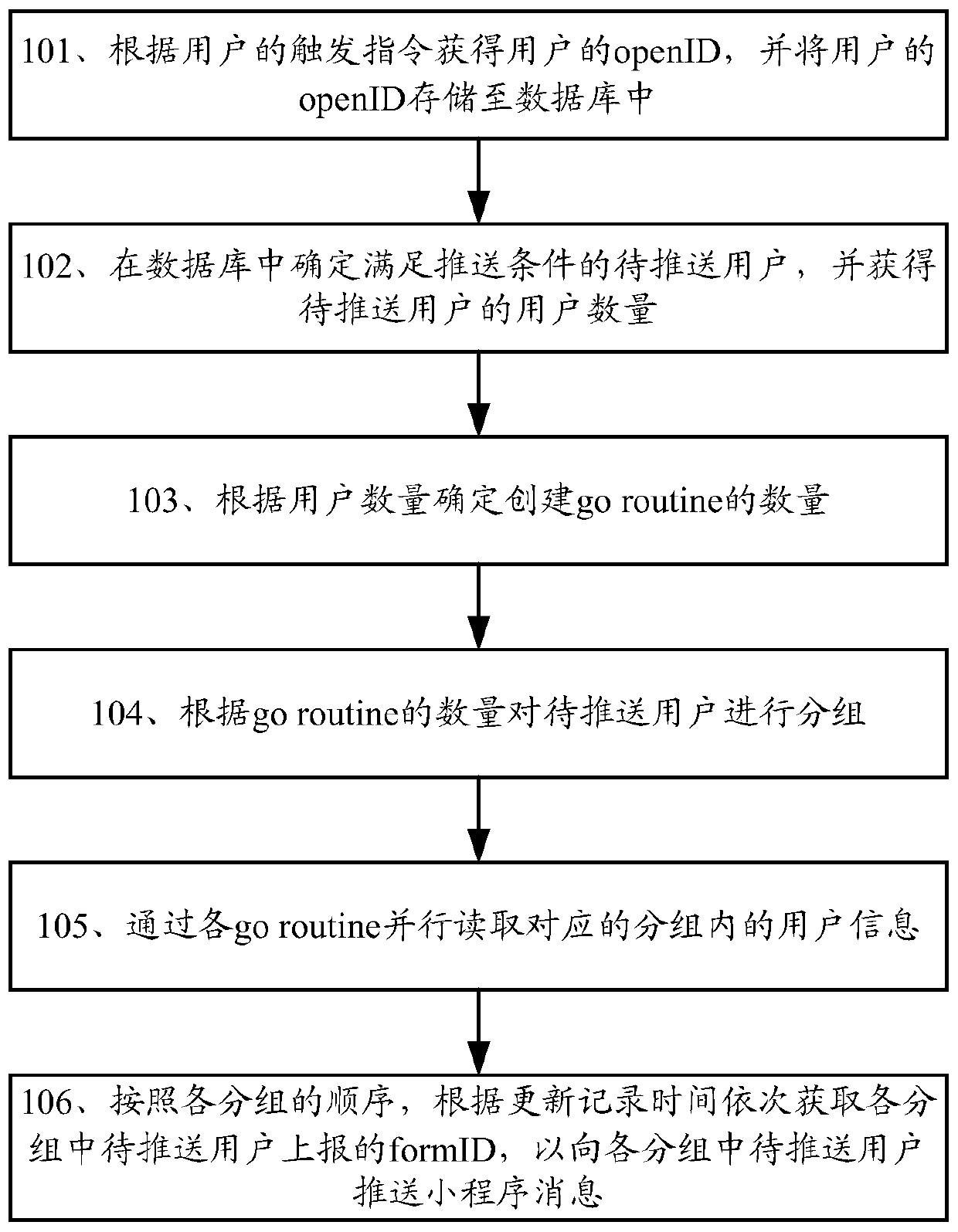
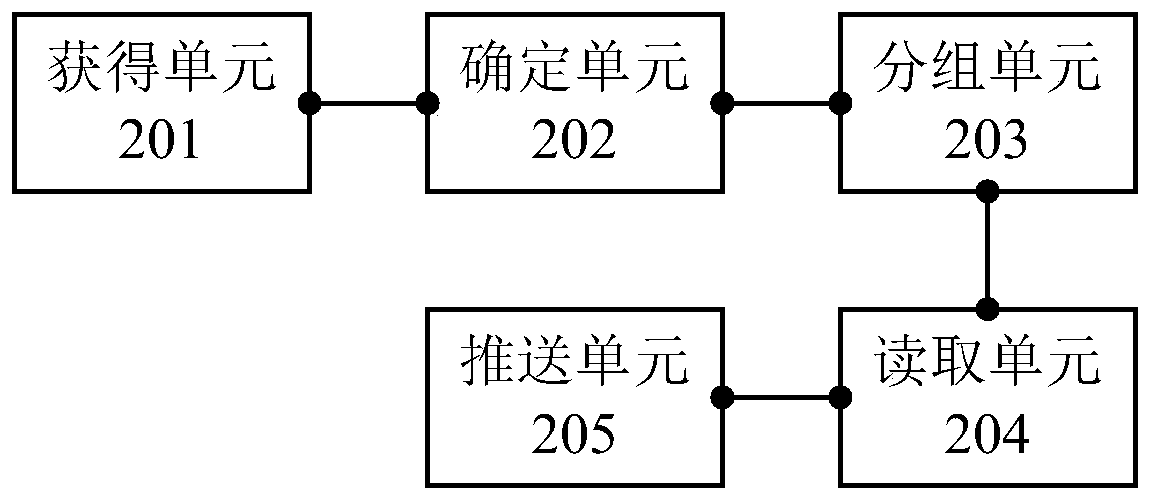
A method for pushing an applet message and a related device
The embodiment of the invention discloses a method for pushing an applet message and a related device, which are used for improving the applet message pushing efficiency. The method comprises: obtaining the openID of a user according to a trigger instruction of the user, storing the openID of the user in a database, whereinthe user and the openID of the user are in one-to-one correspondence; Determining to-be-pushed users meeting the pushing condition in a database, and obtaining the number of the users to be pushed; According to the number of the users, determining the number of created go routines; Grouping the to-be-pushed users according to the number of the go routines, each go routine corresponding to one group, and each group comprising at least one to-be-pushed user; Reading the user information in the corresponding group in parallel through each group, wherein the user information comprises the openID and the update record time of the to-be-pushed user; And according to the sequence of each group, sequentially obtaining the formID reported by the to-be-pushed user in each group according to the updating record time so as to push the small program message to the to-be-pushed user in each group.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Systems and methods of integrating openid with a telecommunications network
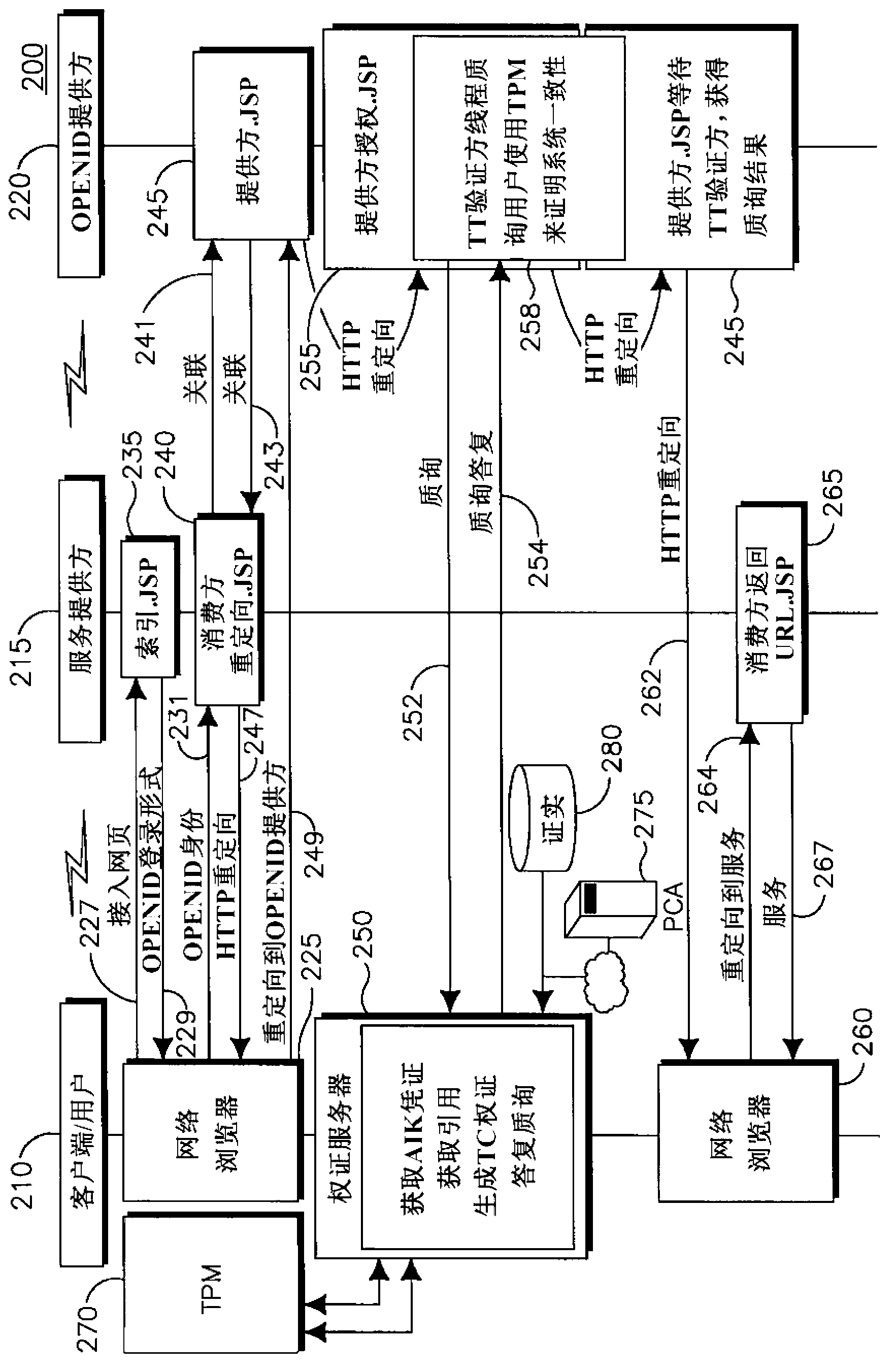
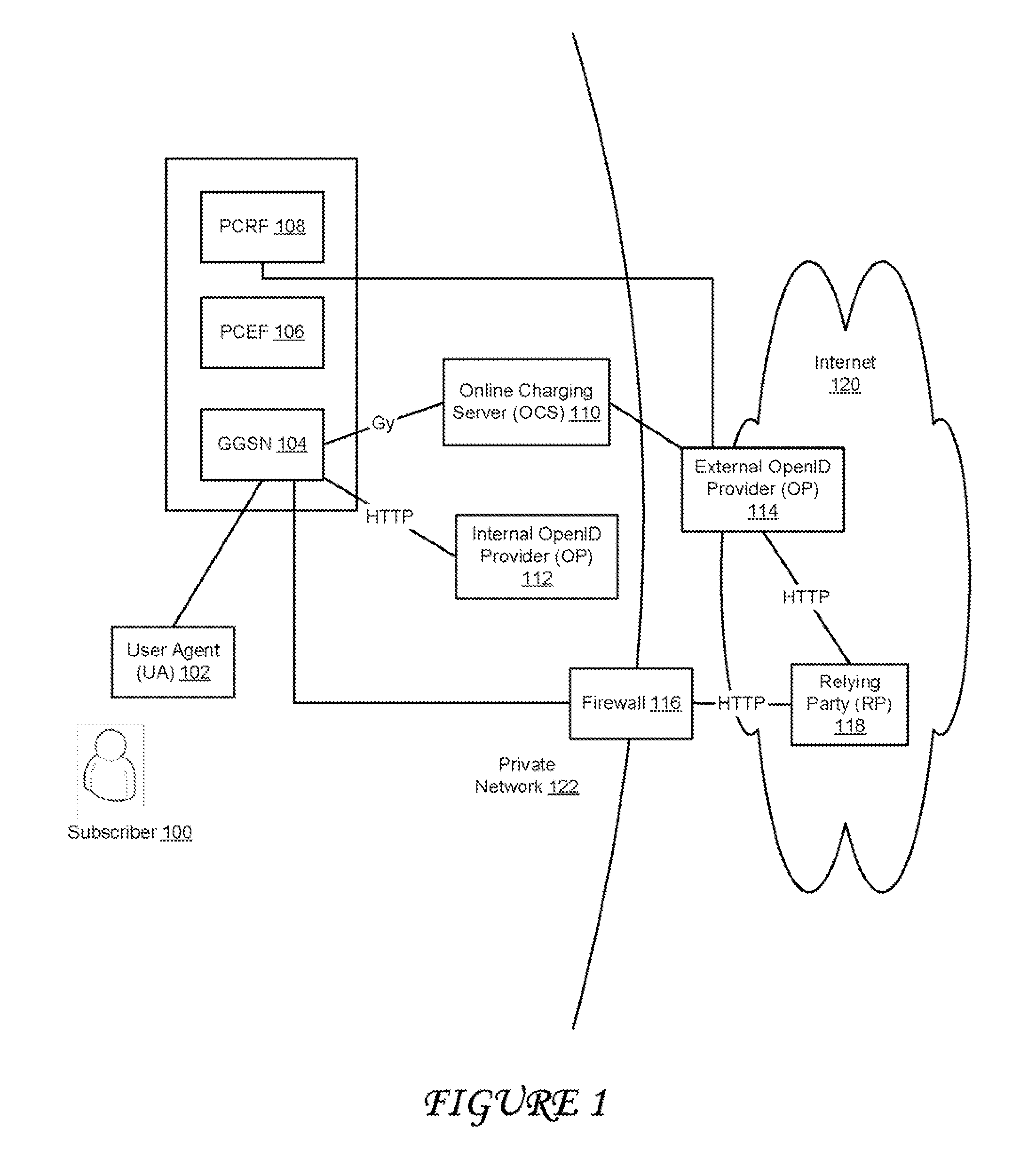
ActiveUS20120324558A1Digital data processing detailsUser identity/authority verificationTelecommunications linkTelecommunications network
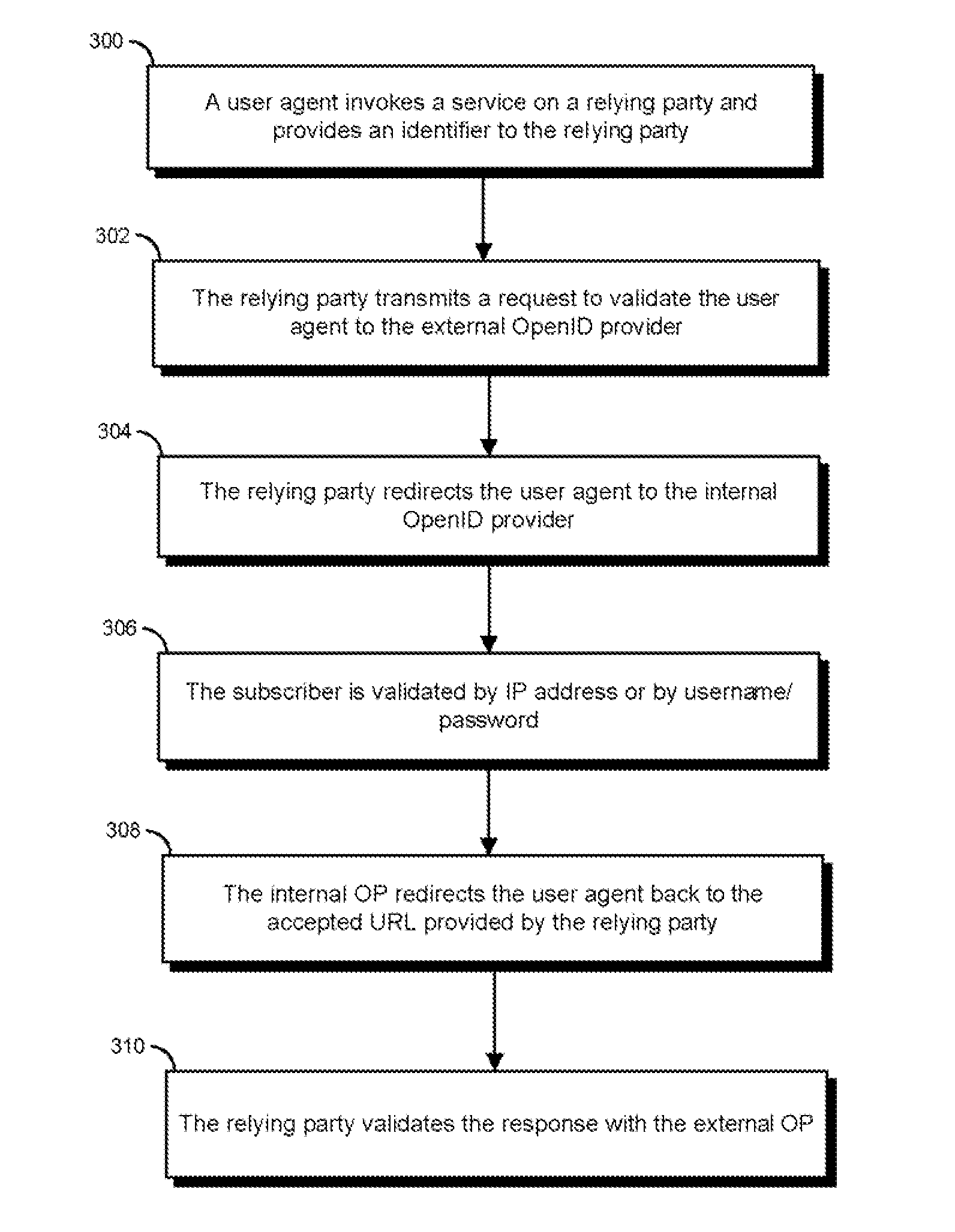
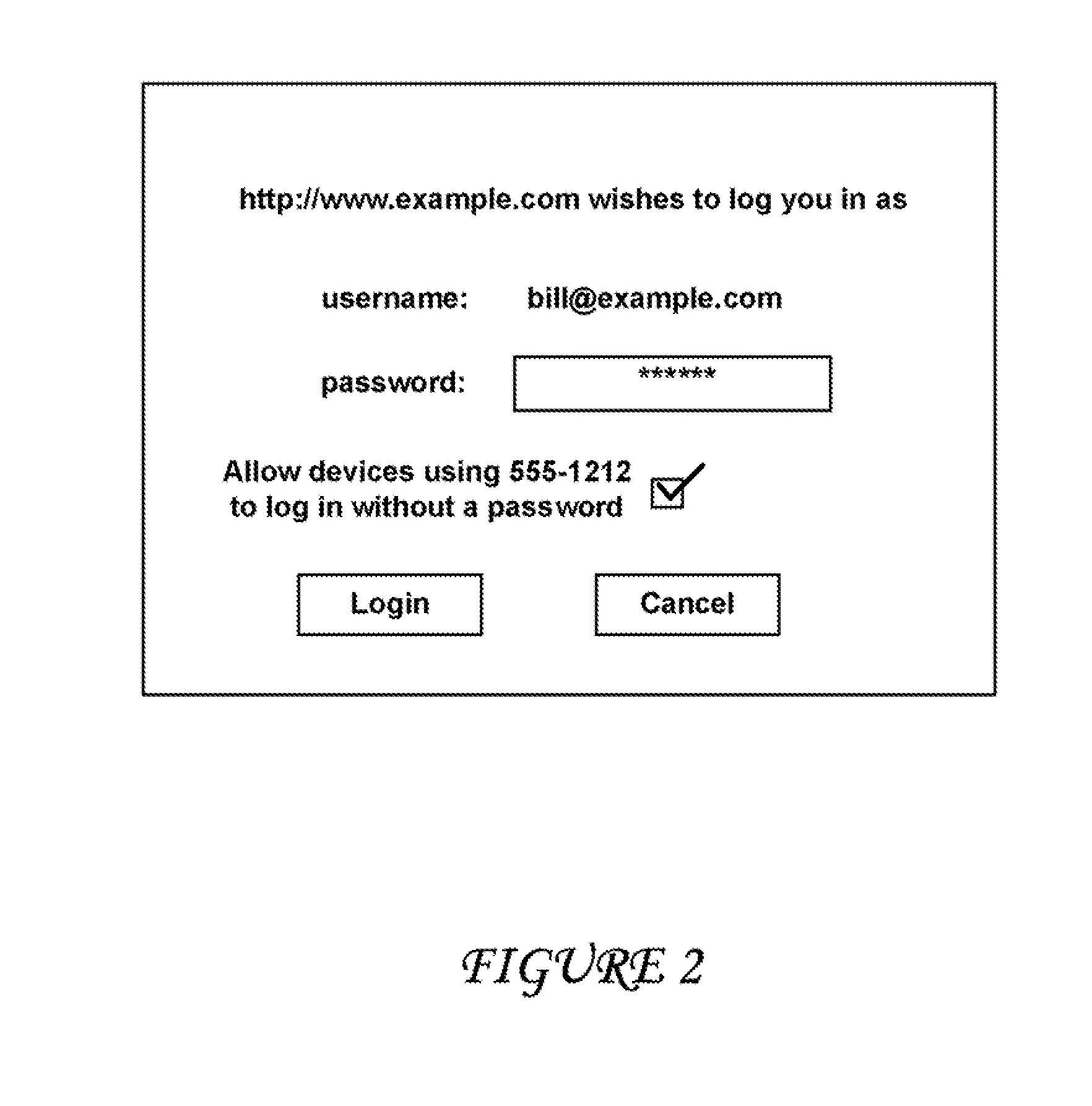
A solution is described which allows mobile devices to specify that certain sites are allowed to be logged into based on the device credentials alone. The solution integrates OpenID with a telecommunications network in order to verify the user's identity. This verification is based on the trust that the telecom carrier has to identify the subscriber at the GGSN. The solution splits the OpenID Provider (OP) into two systems—an internal OP and an external OP. The external OP can reside in the public network and can allow the user to authenticate with a password. The internal OP resides in the private network of the carrier and is directly connected to the GGSN such that it is only reachable from the GGSN.
Owner:ORACLE INT CORP
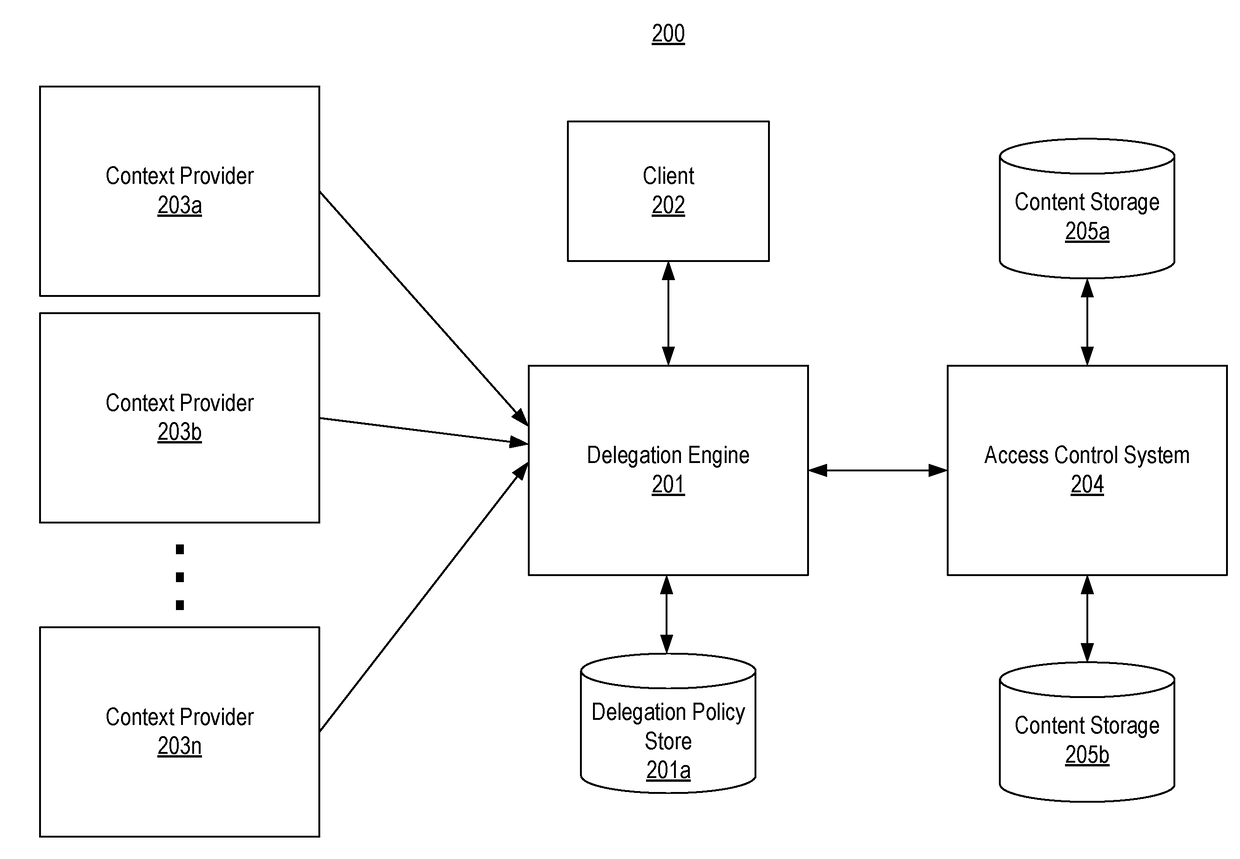
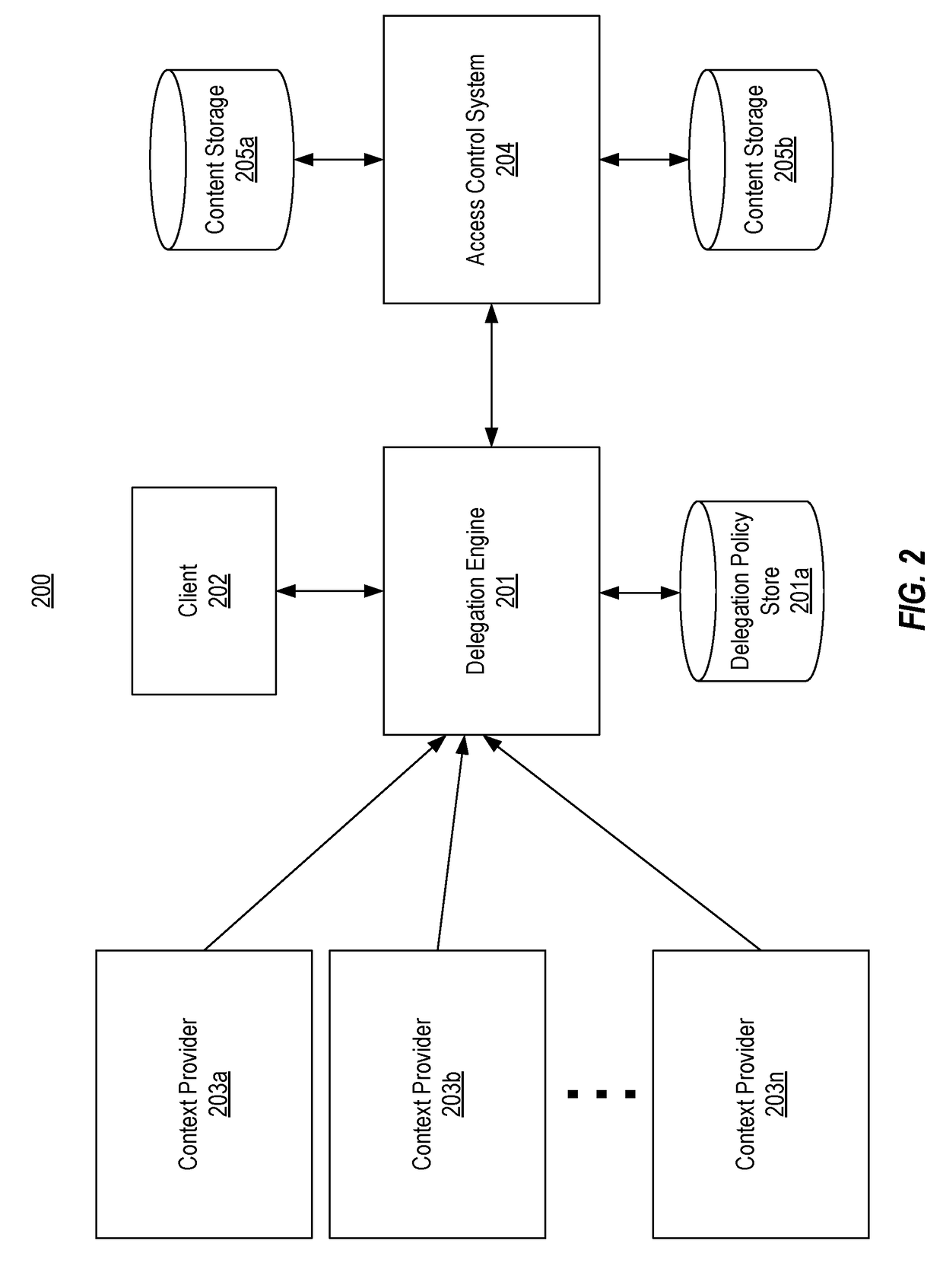
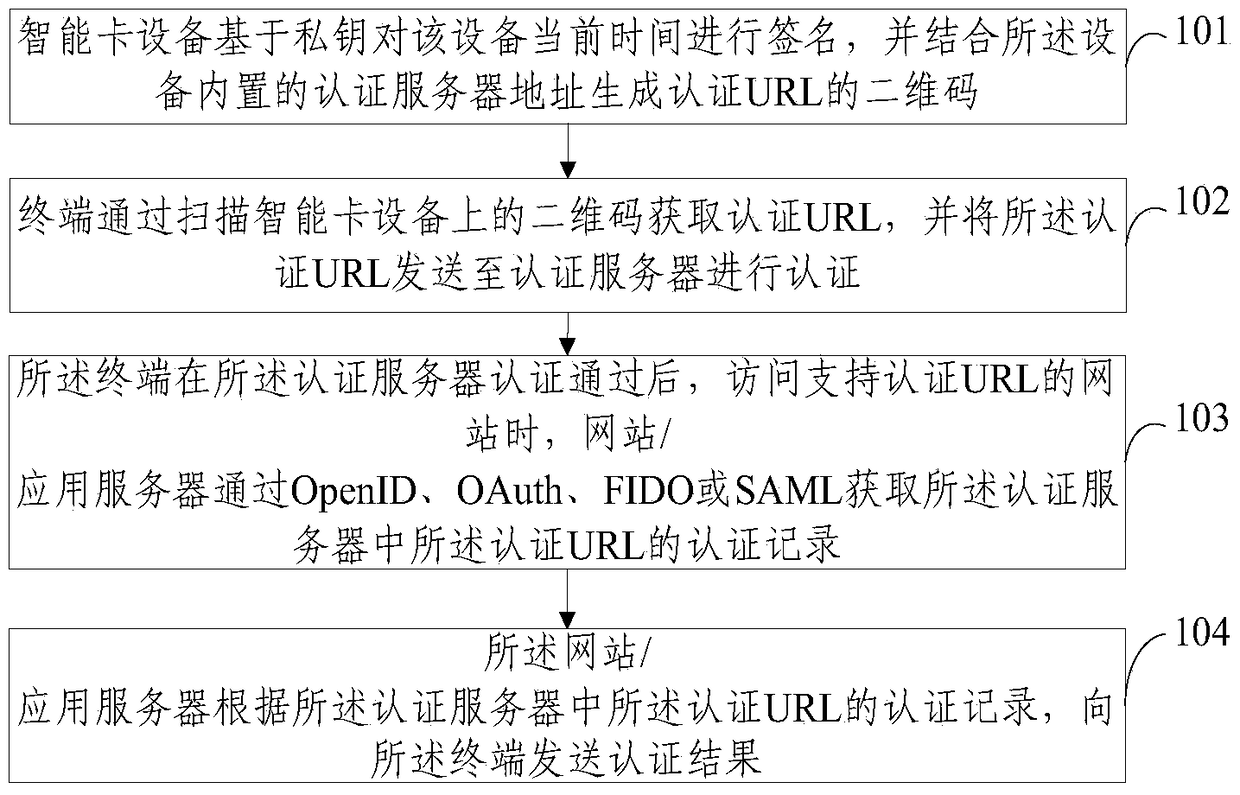
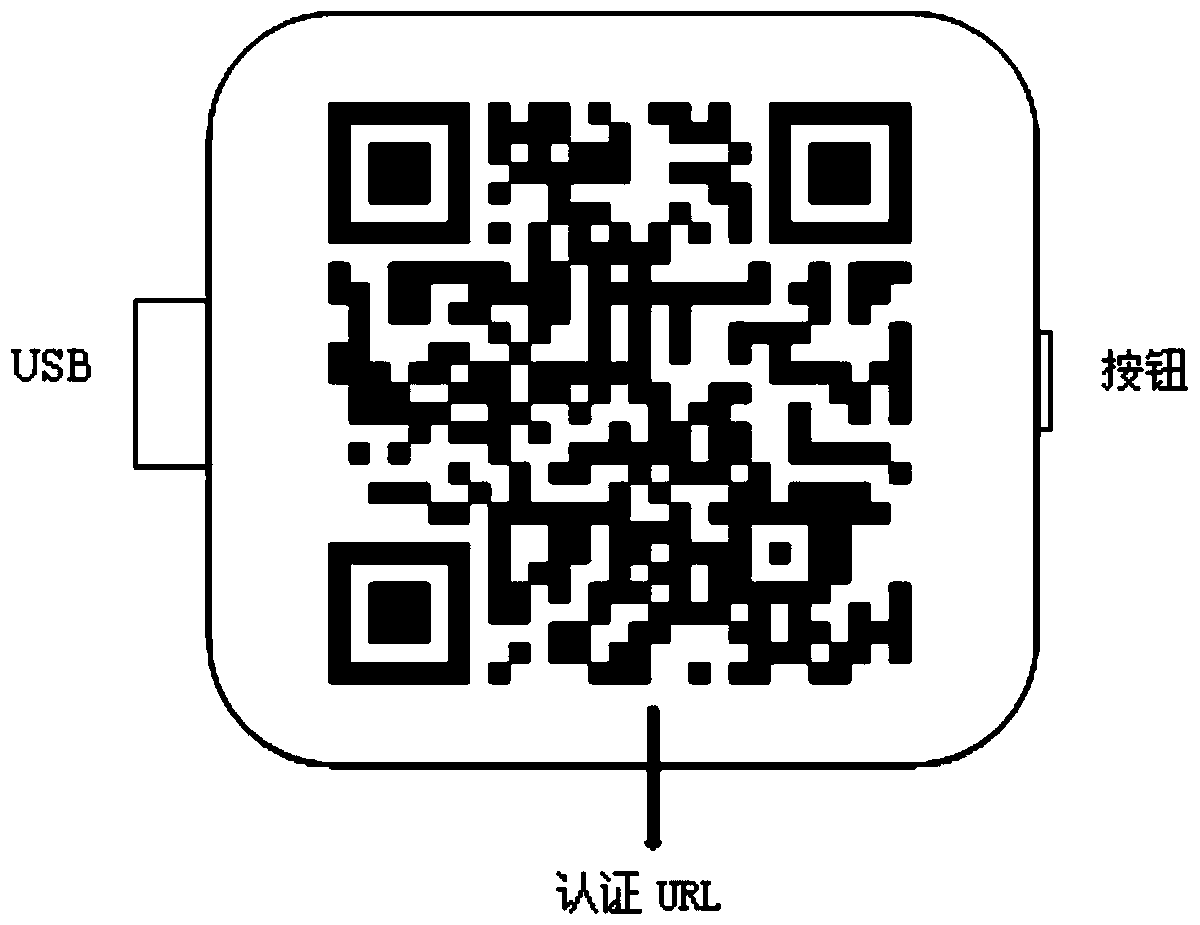
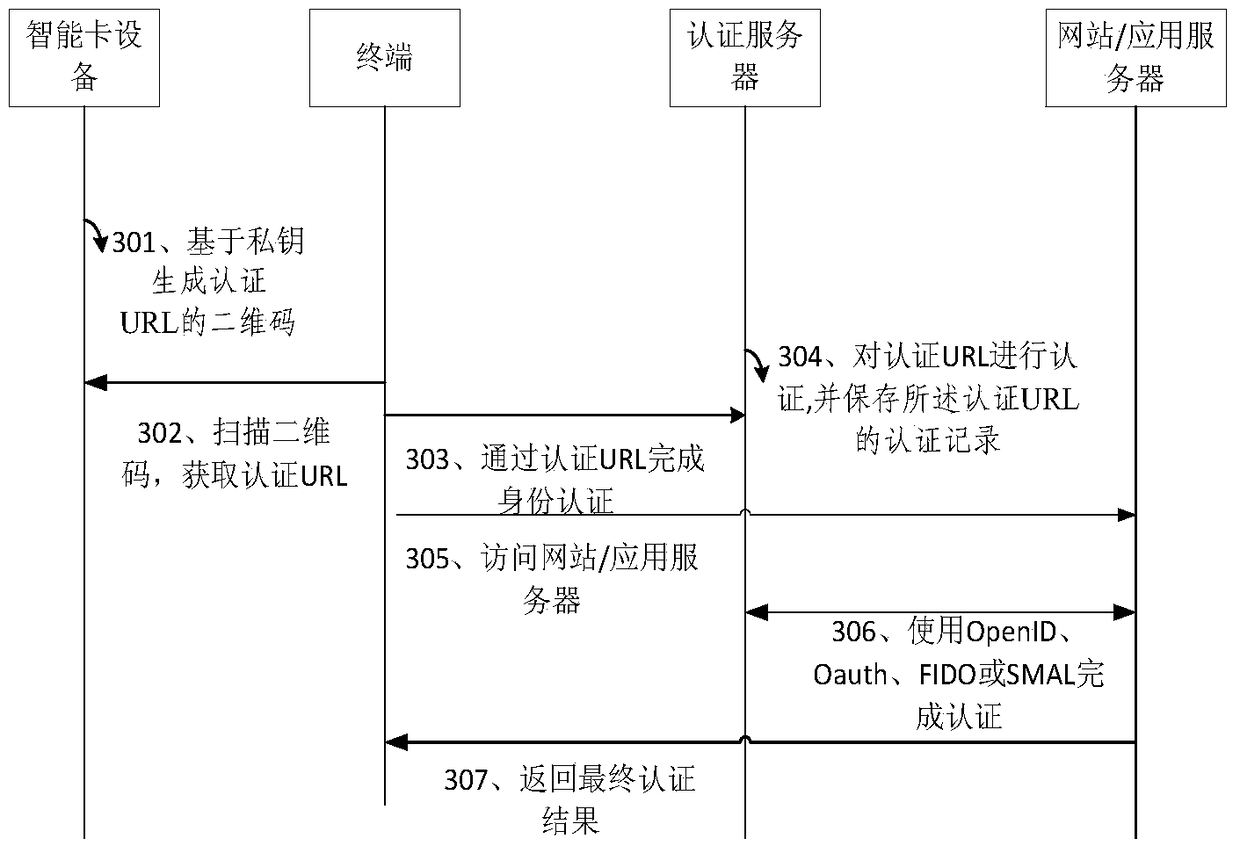
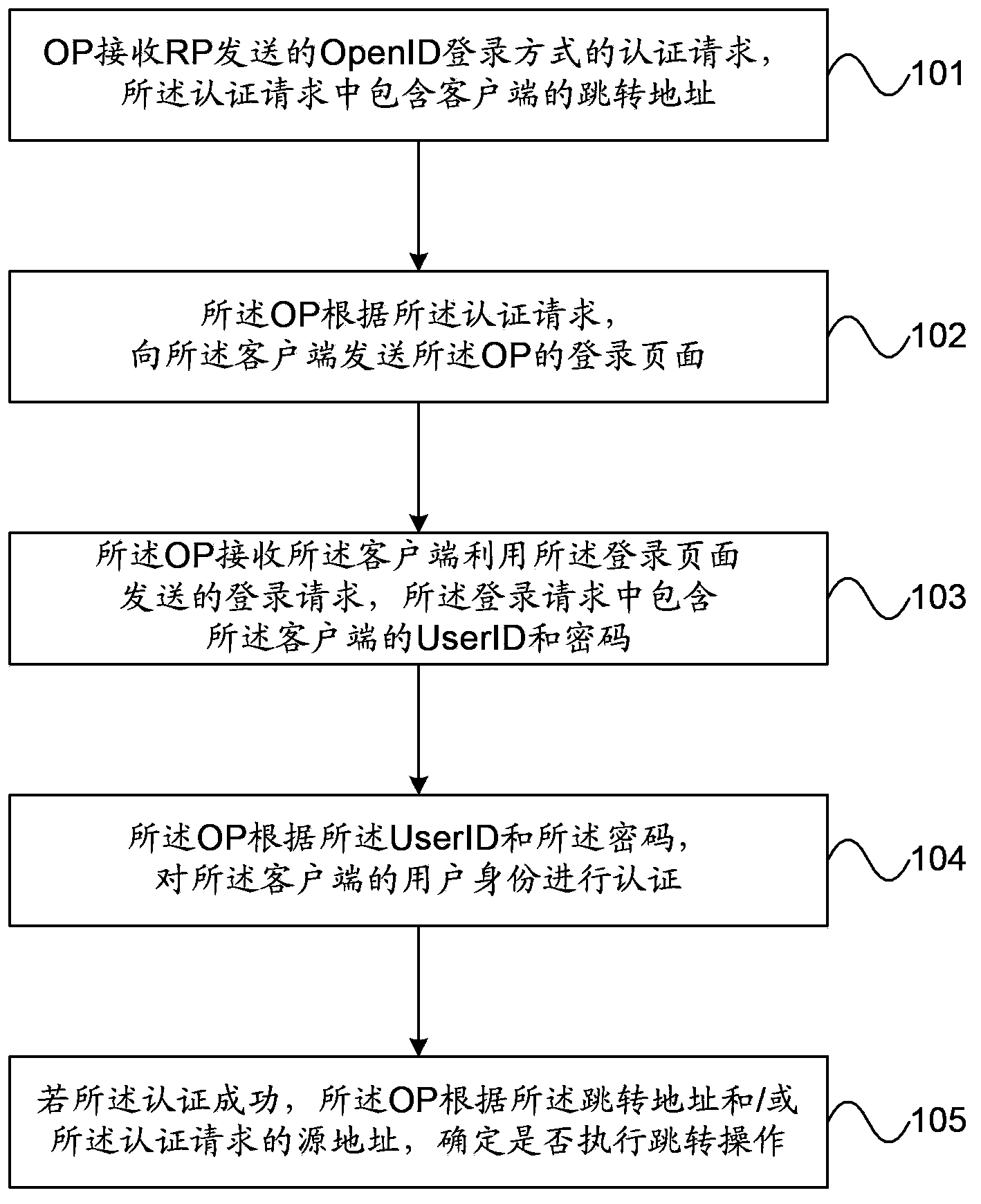
Context-aware delegation engine
A context-aware delegation engine can enable an account owner to identify granular criteria (or context) that will be used to determine what content a delegate will have access to. The account owner can therefore leverage a wide range of information to dynamically determine whether a delegate will receive access to particular content. The delegation engine can be configured to provide a delegation policy to be evaluated to determine whether a delegate should receive access to particular content. Such a delegation policy can be generated based on input provided by the delegator thereby providing the delegator with fine-grained control over which content will be accessible to a particular delegate. The delegation policy can be structured in accordance with an authorization protocol schema such as XACML, SAML, OAuth 2.0, OpenID, etc. to allow the evaluation of the delegation policy to be performed by a policy decision point in such authorization architectures.
Owner:QUEST SOFTWARE INC
Technology for WiFi network distribution and authentication of equipment through WeChat applet
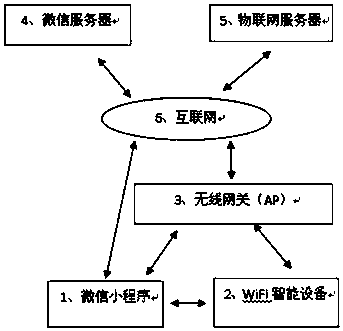
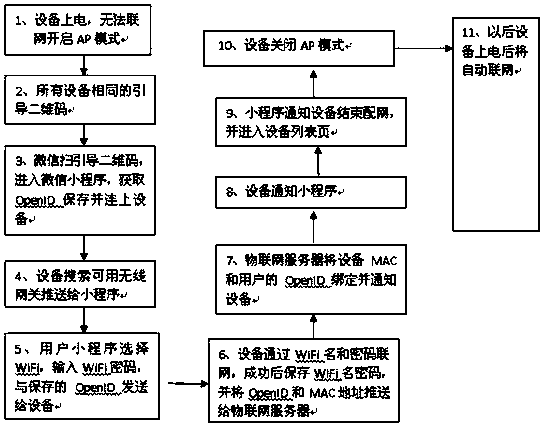
InactiveCN111556500AReduce the use effectEasy to operateAssess restrictionExecution for user interfacesWifi networkPassword
The invention discloses a technology for WiFi network distribution and authentication of equipment through a WeChat applet, and belongs to the technical field of Internet of Things. The method is characterized in that all devices use the same guide two-dimensional code. The method comprises the steps that 1, equipment is powered on to start an AP mode; 2, all equipment use the same guide two-dimensional code; 3, a user scans the two-dimensional code through WeChat to enter a WeChat applet, and the applet acquires the OpenID of the user, saves the OpenID and opens the WiFi of the mobile phone to be connected with the equipment; 4, the equipment searches nearby available WiFi and pushes the available WiFi to the applet; 5, the user selects a WiFi name in the applet, inputs a WiFi password, and pushes the WiFi password and the OpenID to the equipment; 6, the equipment is networked through the WiFi name and the password, the WiFi name and the password are stored after success, and the OpenID and the equipment Mac are pushed to the server; 7, the server binds the equipment Mac with the user OpenID and informs the equipment; 8, the equipment informs the small program of success; 9, the applet informs the equipment of ending and enters an equipment list page; 10, the equipment stops the AP mode; and 11, automatic networking is performed after the equipment is powered on.
Owner:南昌傲亚信息有限公司
System and method for managing user authority on basis of WeChat platforms
PendingCN108319847AImprove securityImprove stabilityDigital data authenticationData switching networksCode moduleExtensibility
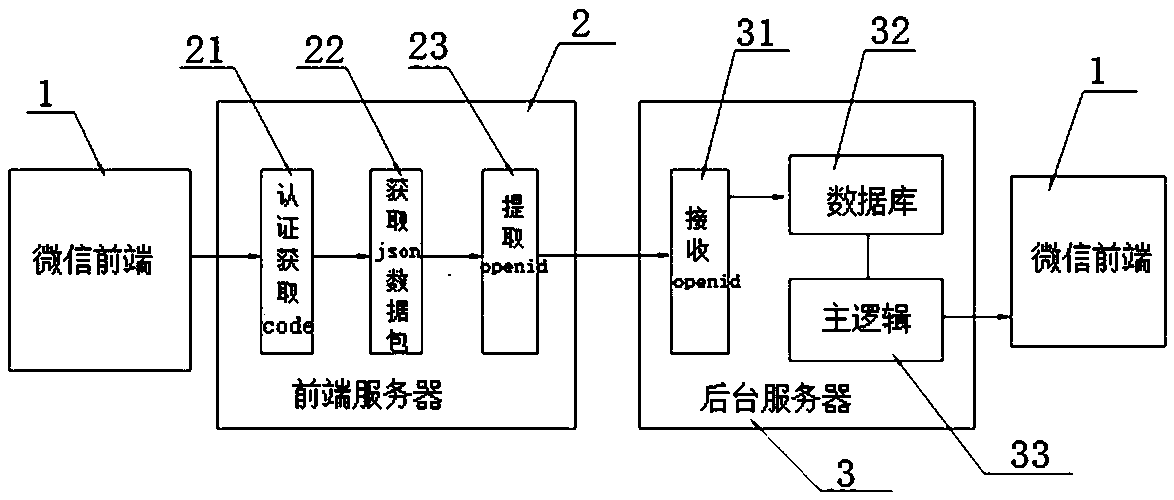
The invention relates to a system and a method for managing user authority on the basis of WeChat platforms. The system comprises a WeChat front end, a front-end server and a backstage server. The front-end server comprises an authentication acquisition code module, a json data packet acquisition module and an openid extraction module; the backstage server comprises a database, an openid receivingmodule and a main logic module; the authentication acquisition code module, the json data packet acquisition module and the openid extraction module are in unidirectional embedded unidirectional transmission logic relations with one another; the openid receiving module and the database are in unidirectional transmission relations with each other; duplex transmission is carried out between the database and the main logic module via data ports; the WeChat front end, the front-end server and the backstage server are connected with one another by wired networks or wireless networks. The system and the method for managing the user authority have the advantages that the system and the method are high in user authority management safety and stability, the servers are stable and are low in operation and maintenance costs, the system for managing the user authority can be easily and quickly constructed at a low cost, and modular programming is high in extensibility and compatibility.
Owner:FOSHAN POWER SUPPLY BUREAU GUANGDONG POWER GRID
Code scanning door opening system for distributed authorization architecture and door opening method
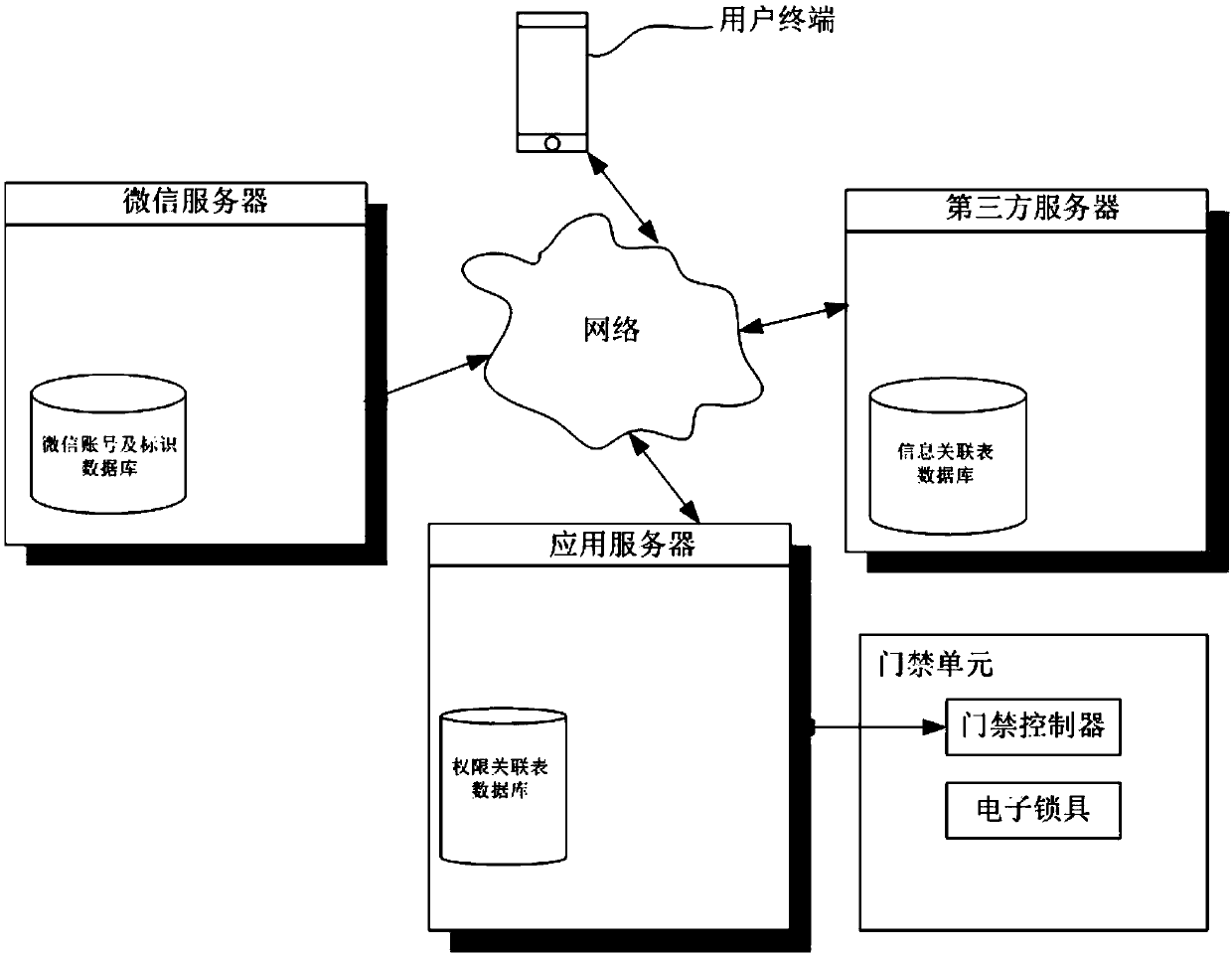
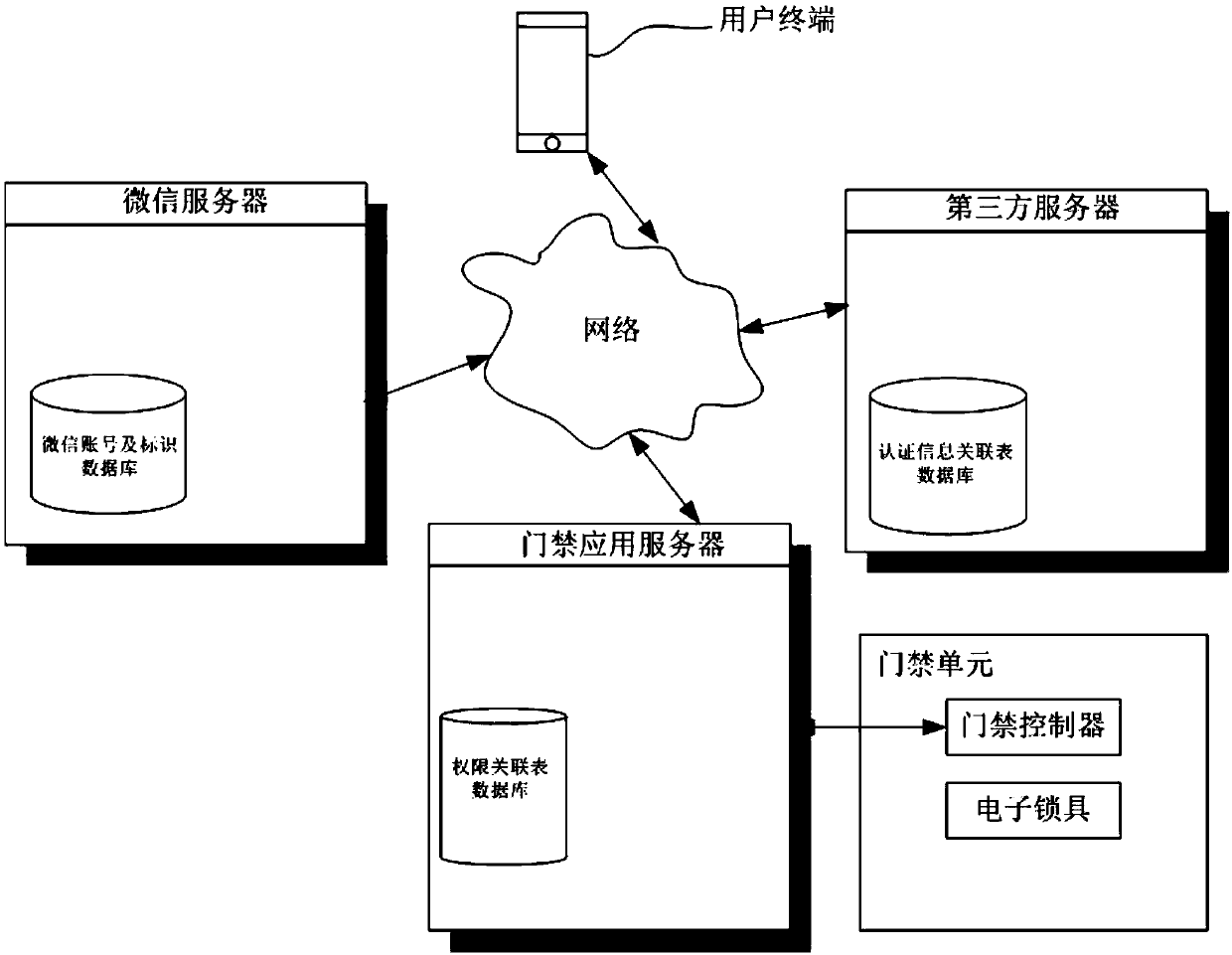
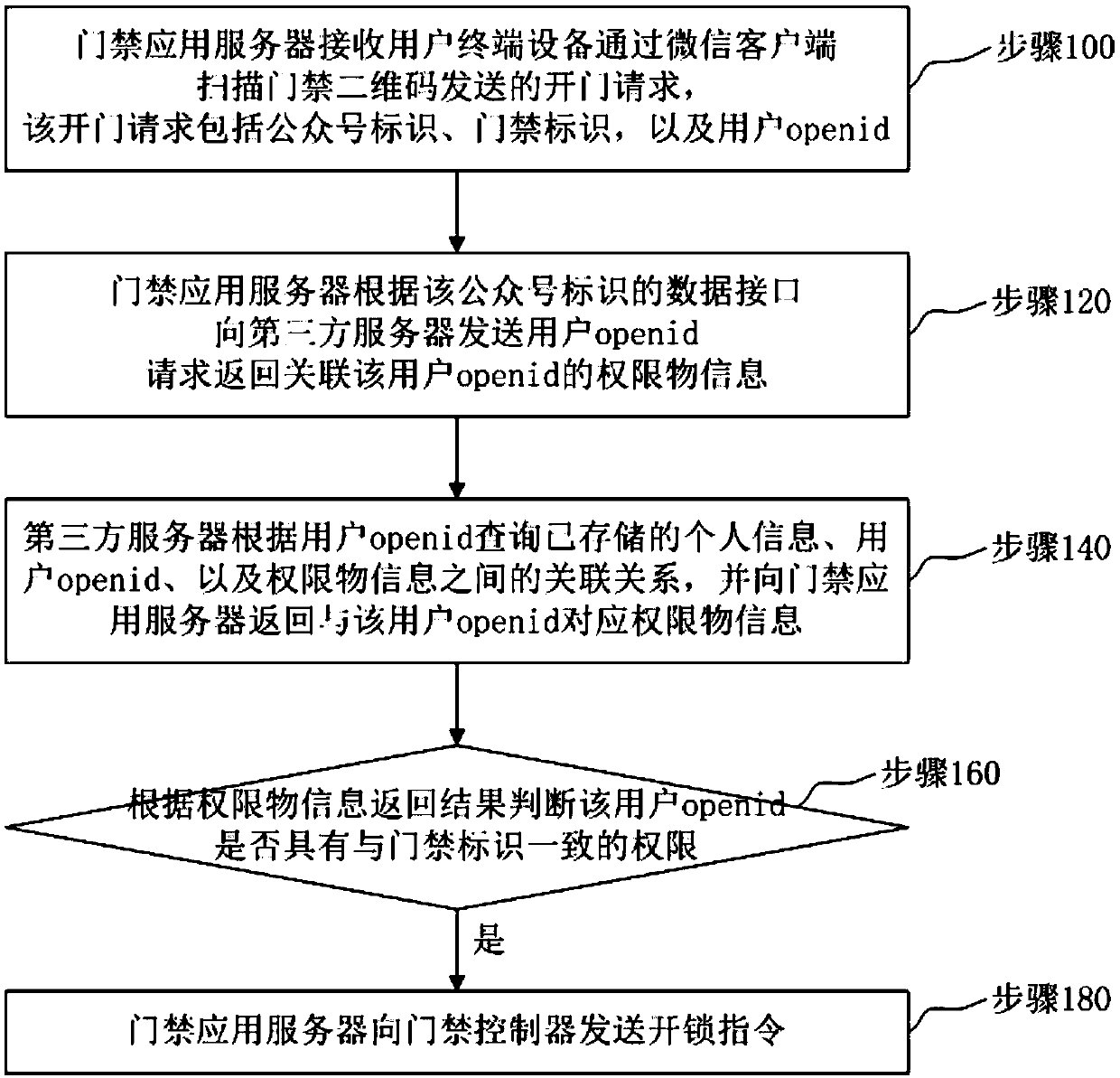
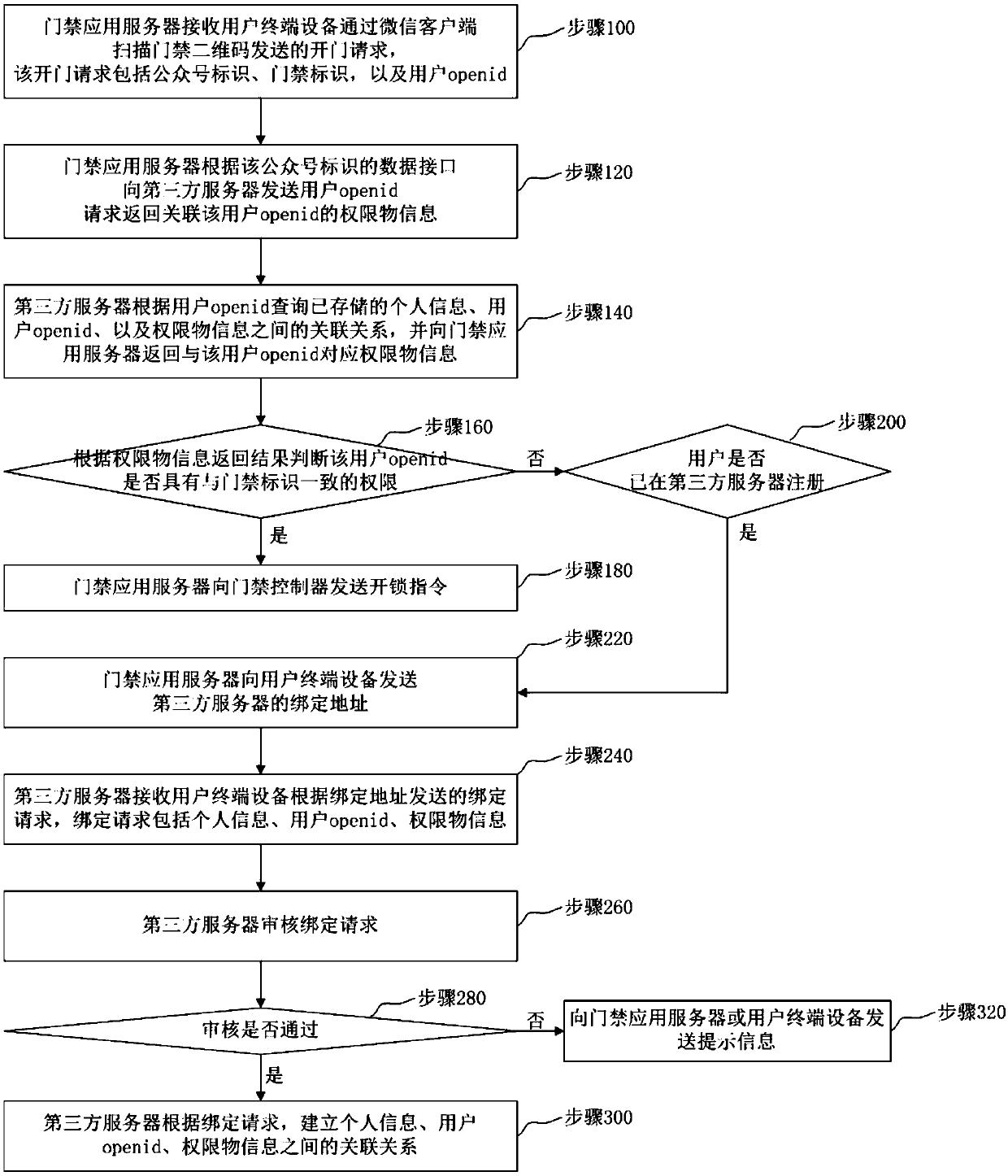
ActiveCN110021084ASpeed up deploymentImprove securityIndividual entry/exit registersThird partyApplication server
The invention relates to a code scanning door opening system for distributed authorization architecture and a door opening method. One part of data for implementing authentication is set on a third-party server, and the other part is set on an access control server. On the basis of the association among personal information already stored in the third-party server, the user openid and authority object information, the association between an authority object and an authority can be established on the access control application server at one time according to the existing logic, that is, establishment and maintenance of a complete authorization database on the access control application server for implementing authentication are not needed, the access control service deployment speed can beenhanced, and the user information security can also be enhanced. Besides, the information associated with the user in a door opening request sent by scanning of the user is the user openid rather than direct user information, the authority object information returned to the access control application server by the third-party server is also the same without direct user information, and further, the user information security is enhanced.
Owner:深圳市微开互联科技有限公司
Method and system for binding information system account and WeChat account
ActiveCN105306435AUniqueness guaranteedEnsure safetyData switching networksMobile Telephone NumberLibrary science
The invention relates to a method and a system for binding an information system account and a WeChat account. The method comprises the following steps of user information establishment, verification information generation, user information binding and binding verification feedback. According to the method and the system, a verification code matched with a mobile telephone number is taken as a second verification mark; the mobile telephone number and the verification code are utilized to carry out dual verification; and a WeChat OpenID is stored in an information system to identify which user of the information system is represented by the WeChat account interactive with the information system. The system comprises the following modules of a user establishment module, a verification information generation module, a user information binding module and a binding verification feedback module. The method and the system are convenient for information interaction and mutual operation between the information system account and the WeChat account.
Owner:XIAMEN KINGTOP INFORMATION TECH
Identity authentication device and method for smart card equipment based on two-dimensional code
ActiveCN104618117BImprove experienceUser identity/authority verificationRecord carriers used with machinesApplication serverSmart card
The invention discloses an identity authentication device and method of a smart card device based on a two-dimensional code. The method includes: the smart card device signs the current time of the device based on a private key, and generates a two-dimensional code of an authentication URL according to a built-in authentication server address. code; the terminal scans the QR code on the smart card device to obtain the authentication URL, and sends it to the authentication server for authentication; after the terminal is authenticated by the authentication server, when accessing a website that supports the authentication URL, the website / application server passes OpenID, OAuth, FIDO or SAML Obtain the authentication record of the authentication URL in the authentication server; the website / application server sends the authentication result to the terminal according to the authentication record. The method solves the problem that the smart card needs to communicate with the terminal through a USB or a card reader during use, and a driver is installed in the terminal, resulting in complicated use process and poor user experience.
Owner:BEIJING QIHOO TECH CO LTD
Third-party login method and device based on limited skip
InactiveCN103414696AImprove securityAvoiding the Problem with Phishing OperationsTransmissionThird partyStatus changed
The invention provides a third-party login method and device based on limited skip. According to the embodiment of the third-party login method, in an OpenID login mode, an OP does not directly carry out skip operation to enable a client to skip to an RP, but selectively carry out the skip operation according to a skip address and / or a source address of a certification request after the OP carries out successful certification on the user identity of the client. Therefore, the third-party login method and device can solve the problem in the prior art that a false RP carries out phishing operation due to the fact that the OP directly carries out the skip operation and enables the client to skip to the RP, and the safety of the OpenID login mode is improved.
Owner:BEIJING YINZHIBANG CULTURE TECH CO LTD
Mobile internet cross-platform user management method and apparatus
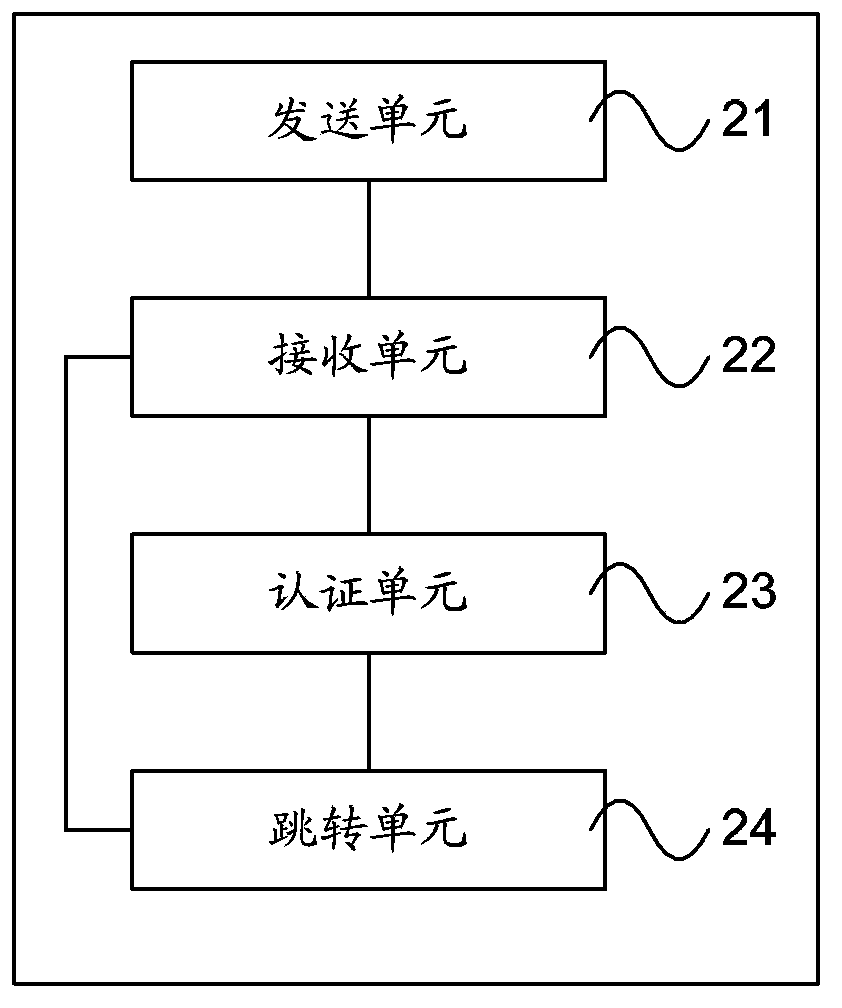
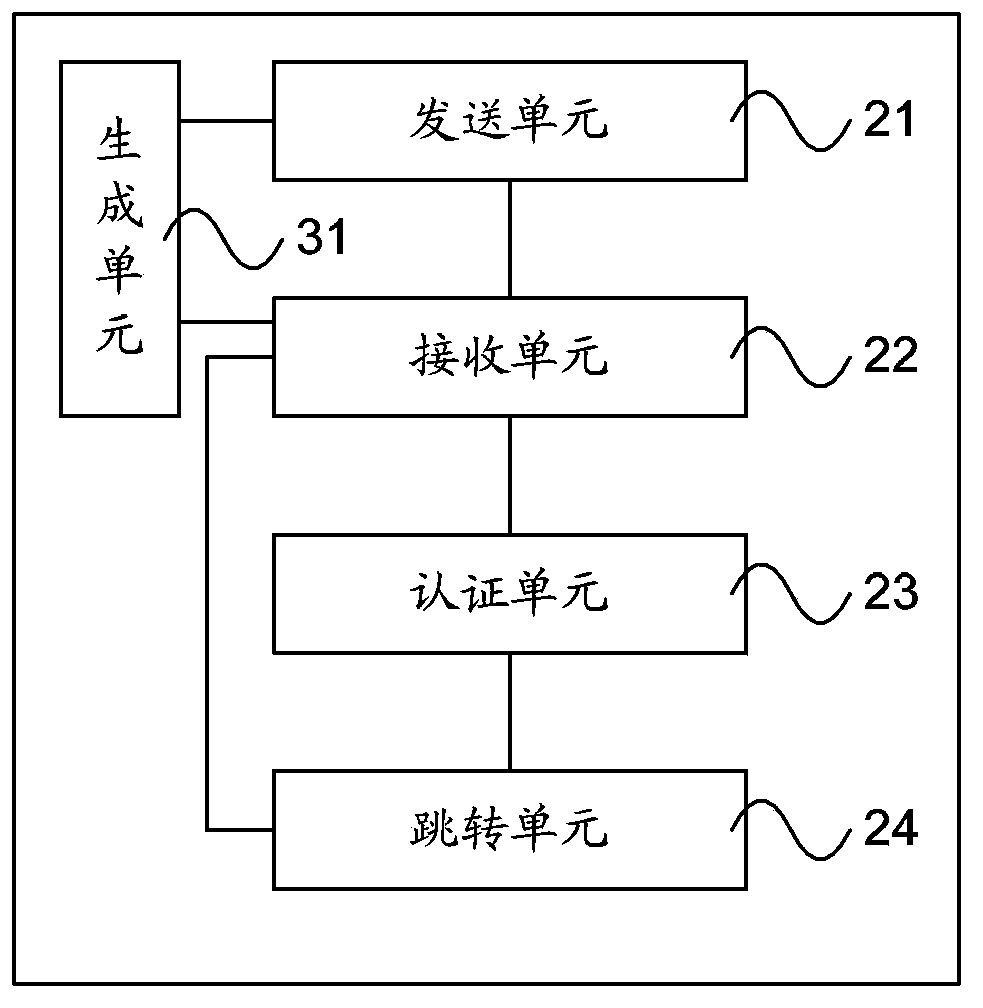
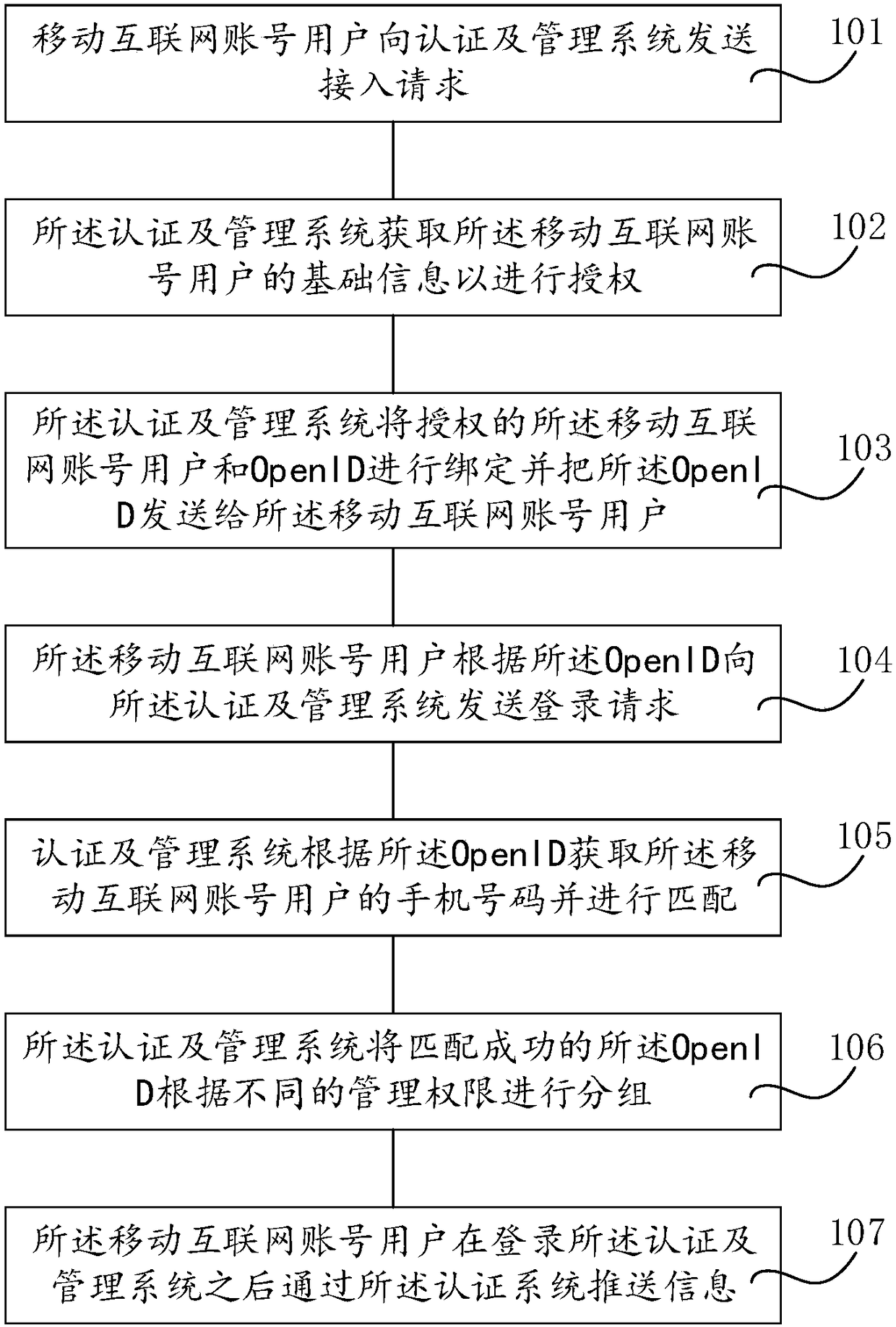
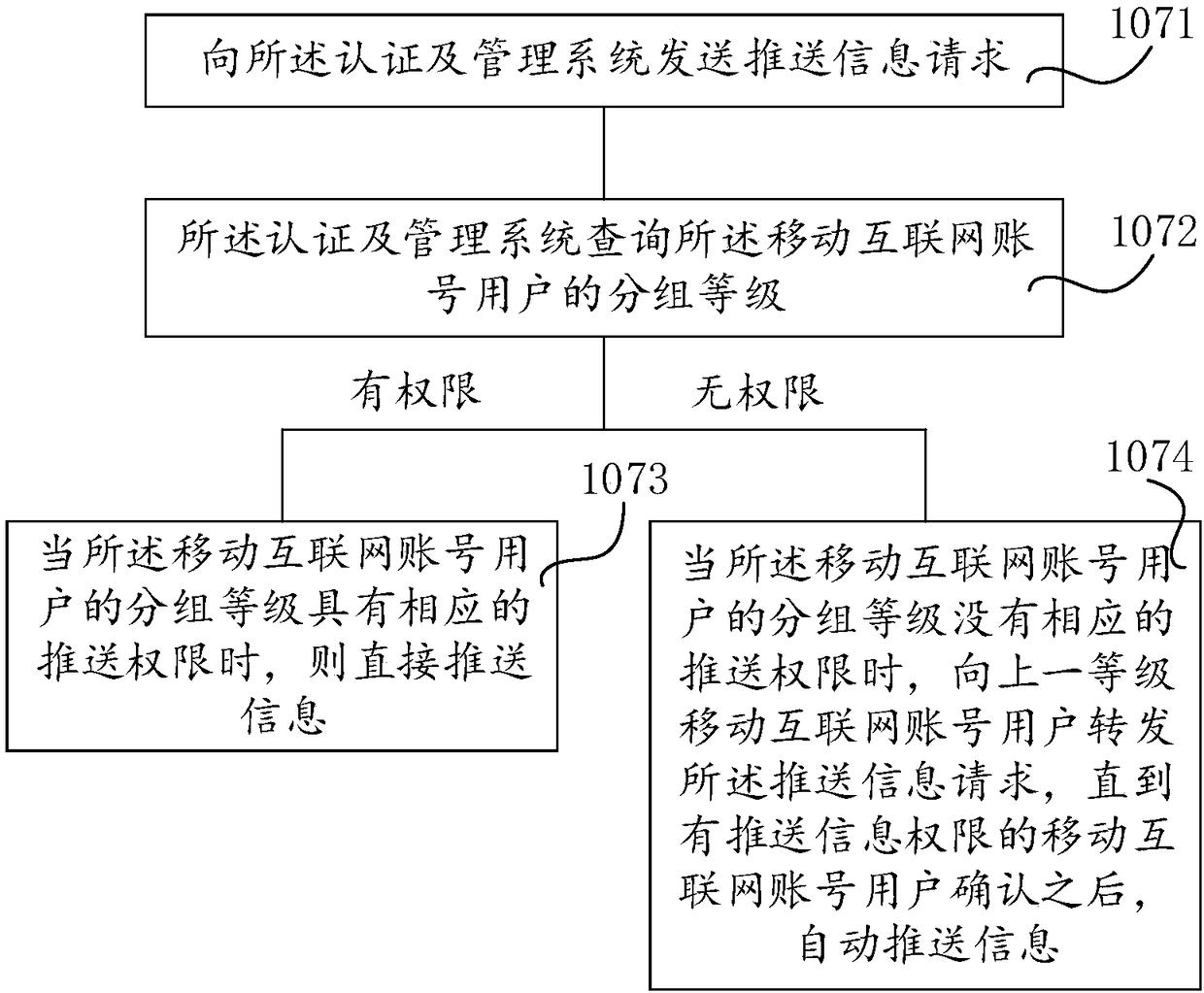
PendingCN108076130AImprove interoperabilityAvoid conflictData switching networksHigh level techniquesUser equipmentUser management
The invention relates to a mobile internet cross-platform user management method and apparatus. The apparatus comprises mobile internet account user equipment and an authentication and management system, wherein the mobile internet account user equipment is used for sending an access request to the authentication and management system, sending a login request to the authentication and management system according to OpenID, and pushing information through the authentication and management system after logging in the authentication and management system, wherein the authentication and managementsystem is used for obtaining basic information of the mobile internet account user equipment for authorization, binding an authorized mobile internet account user with the OpenID, sending the OpenIDto the mobile internet account user equipment, obtaining a mobile phone number of the mobile internet account user according to the OpenID, performing matching and grouping the successfully matched OpenID according to different management permissions.
Owner:北京微应软件科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com