Openid-based access control method
A technology of access control and control method, which is applied in the direction of electromagnetic radiation induction, instruments, and induction recording carriers, etc., can solve the problems of high server burden, affecting users' normal travel, and heavy input workload, so as to avoid data storage and The need for maintenance, saving storage and computing costs, and the effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
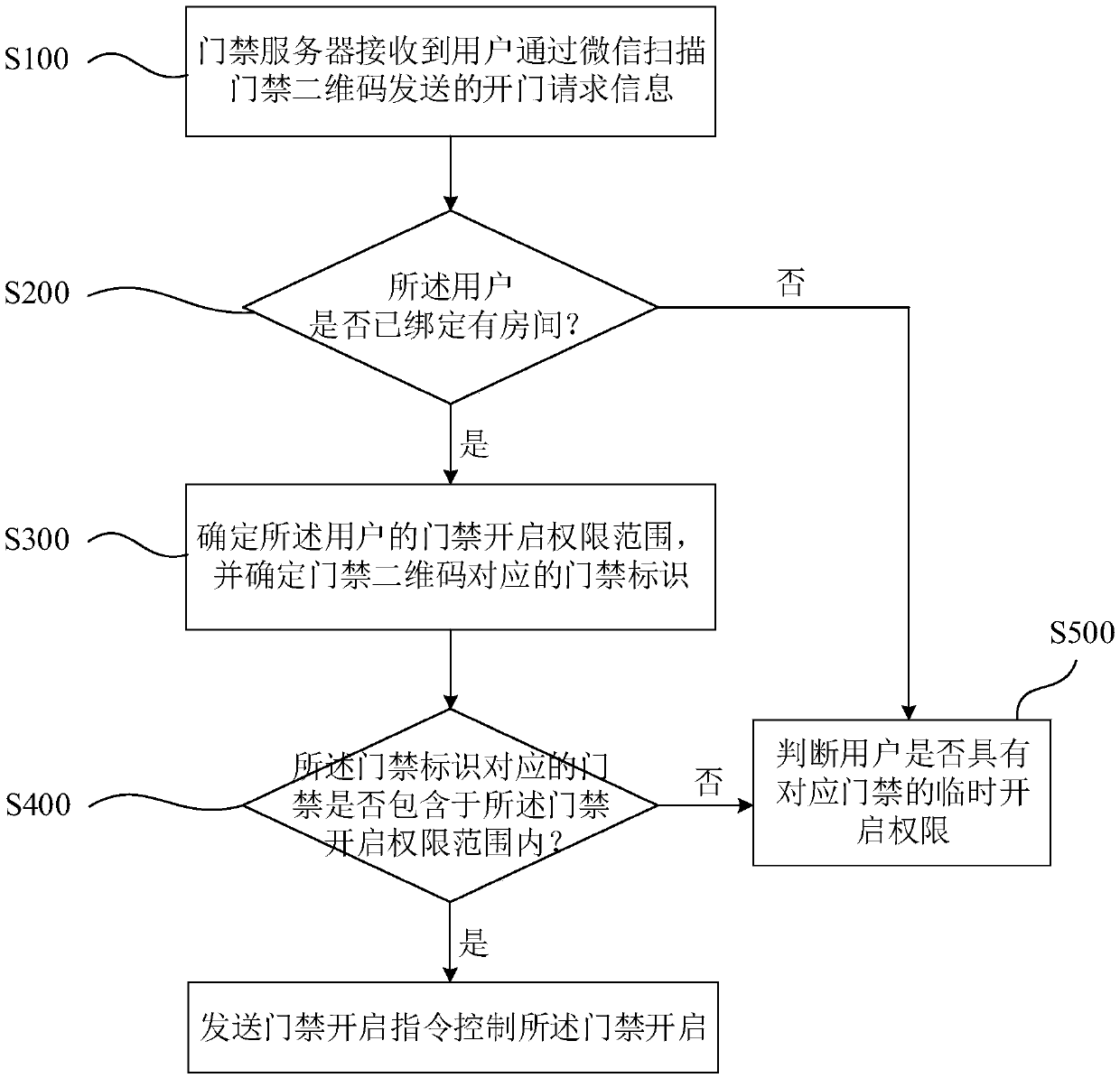
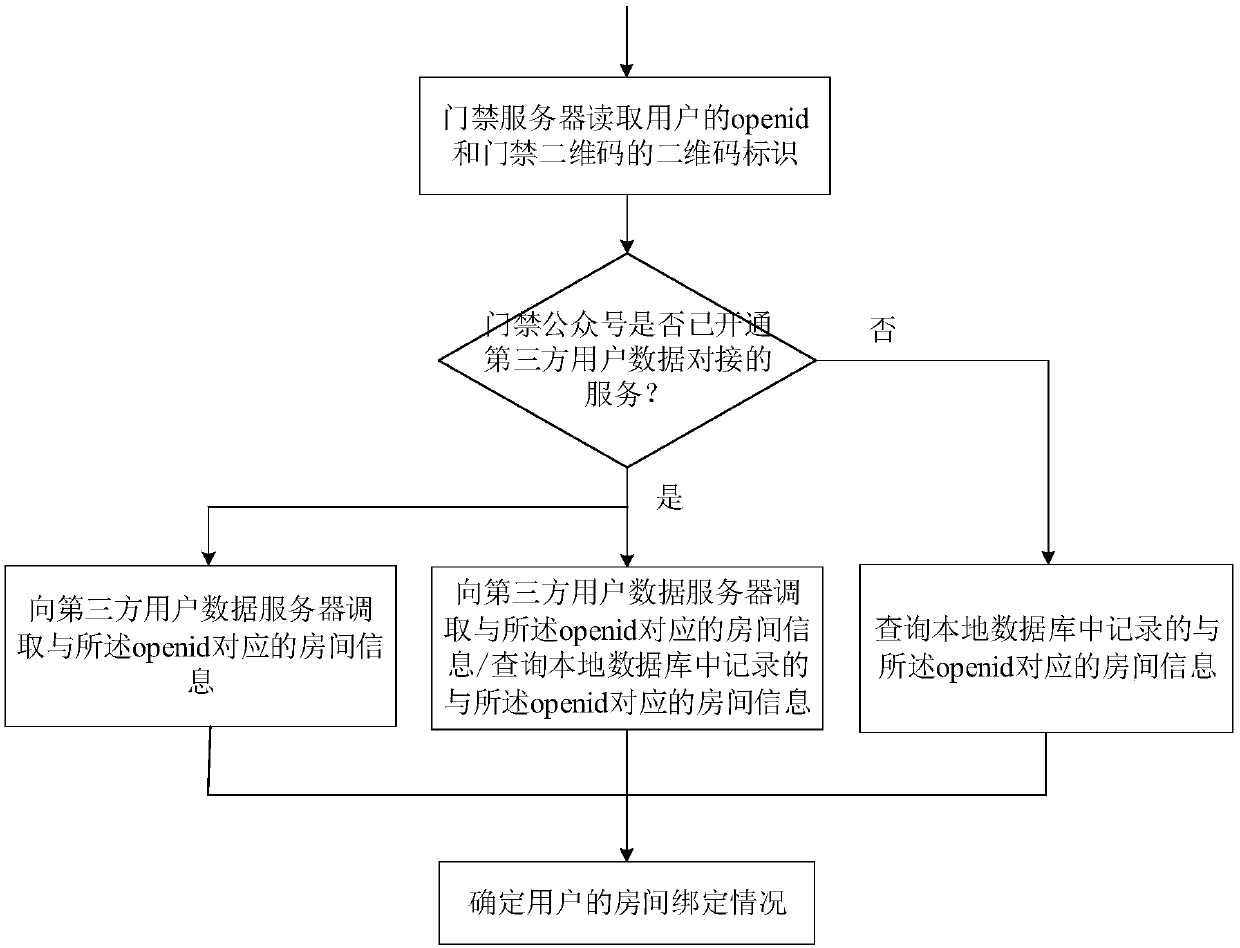
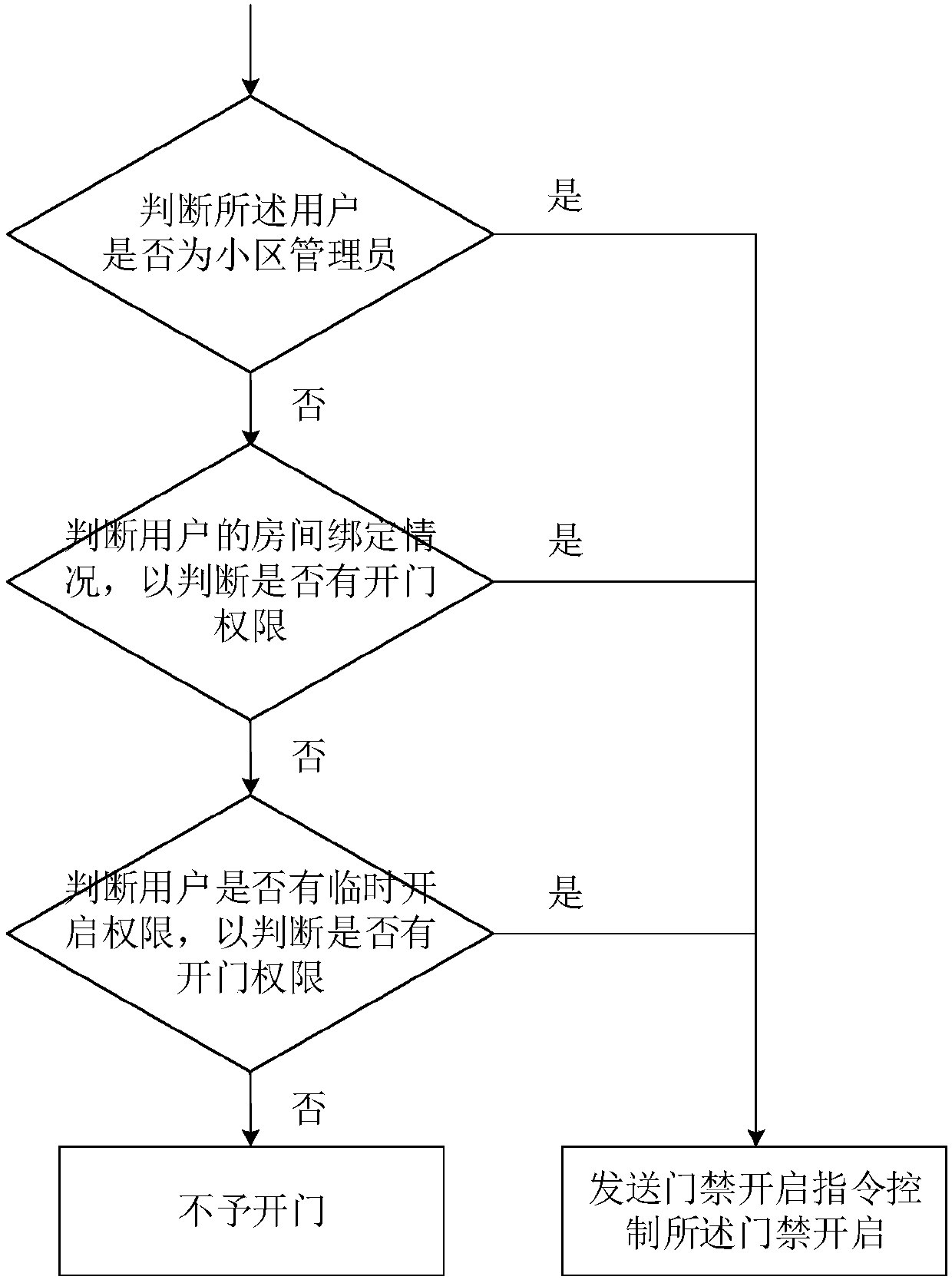
[0040] Aiming at the aforementioned problems existing in the WeChat door opening method of the prior art, the present invention provides an access control method based on openid, which can significantly simplify the amount of data read by the server when judging the authority to open the door, and at the same time is beneficial to protect user information. vent. The access control method of the present invention mainly judges whether the user has the right to open the corresponding access control according to the binding room situation of the user on the access control official account, and the amount of data read by the server is small and is not easy to make mistakes.
[0041]The room mentioned in the present invention should generally be understood as the smallest property right unit of a house, such as a house property in a residential area. However, in some cases, it can also be understood as a specific room in a property right unit, such as in an office building. One of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com