Method and apparatus for trusted federated identity management and data access authorization
A technology for data and wireless devices, applied in the field of trusted federated identity management and data access authorization and devices, and can solve security problems and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
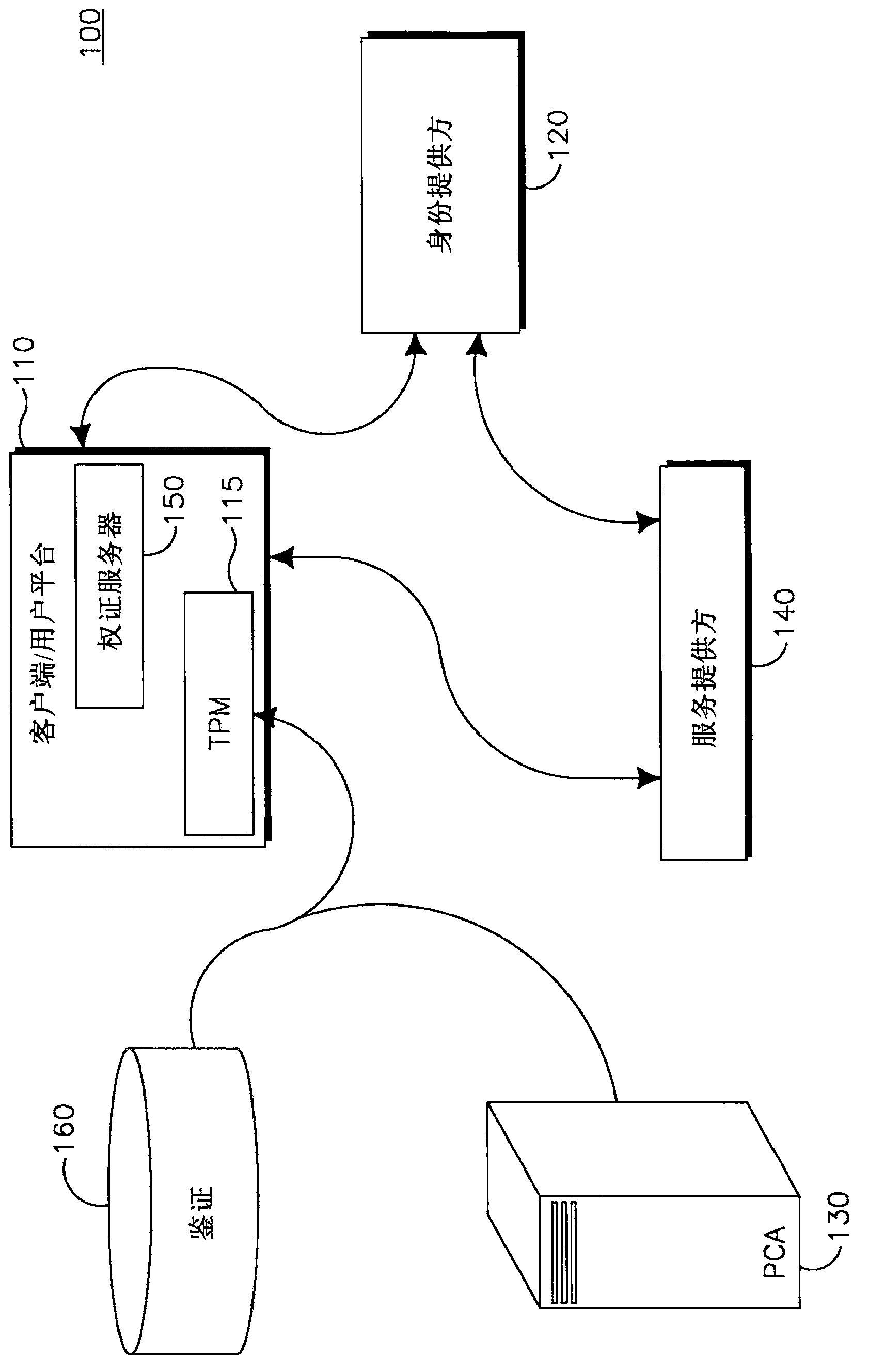
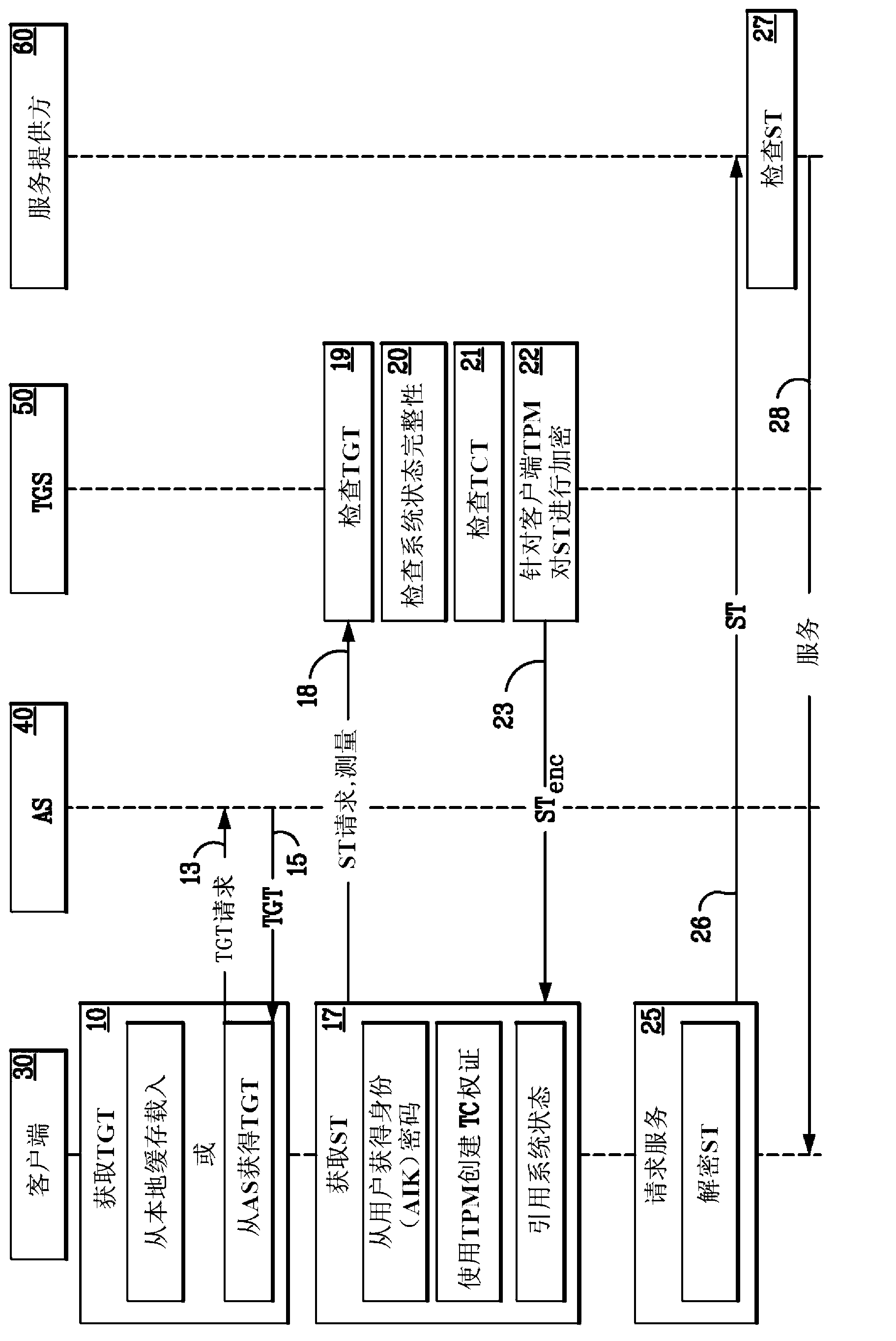
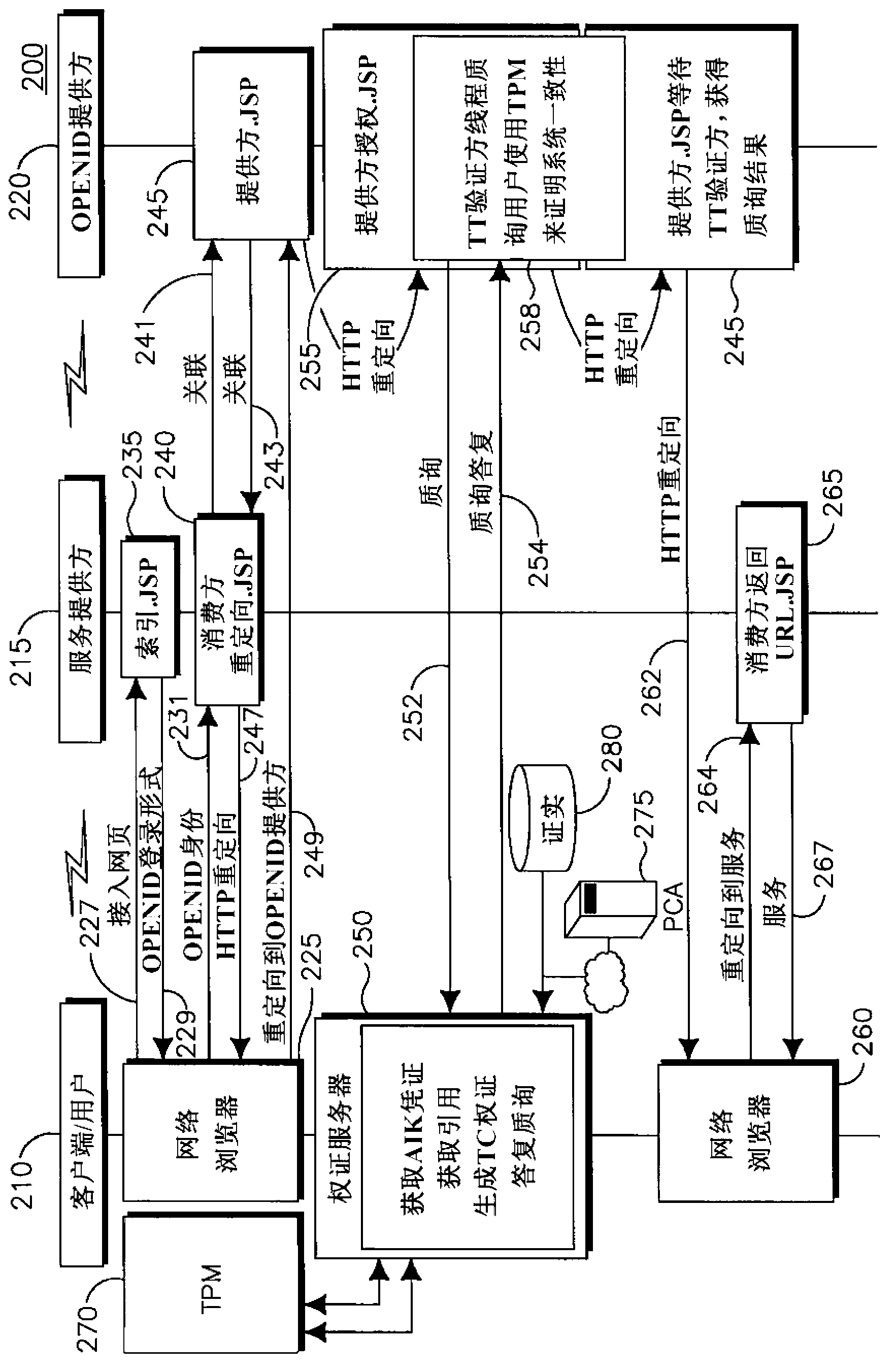
[0031] Figure 1-Figure 21 Example implementations may be made in which the disclosed systems, methods, and instrumentalities may be practiced. However, while the invention may be described in connection with example embodiments, it is not limited thereto, and it is to be understood that other embodiments may be utilized or modifications and modifications may be made to the described embodiments without departing from the invention. added to perform the same function of the present invention. Additionally, the figures may show call flows, which are for example purposes. It is understood that other implementations may be used. Also, the order of the streams can be changed appropriately. Also, streams can be omitted if not required, and additional streams can also be added.
[0032] The term "wireless transmit / receive unit (WTRU)" referred to below includes, but is not limited to, user equipment (UE), mobile station, fixed or mobile subscriber unit, pager, cellular telephone...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com