key information protection method and system based on an OpenID
A technology of key information and identity information, applied in the direction of digital data protection, etc., can solve the problems of identity information sensitivity, user privacy, life and property safety threats, etc., to ensure availability, reduce the risk of leakage and use, and prevent illegal trajectory information acquisition Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
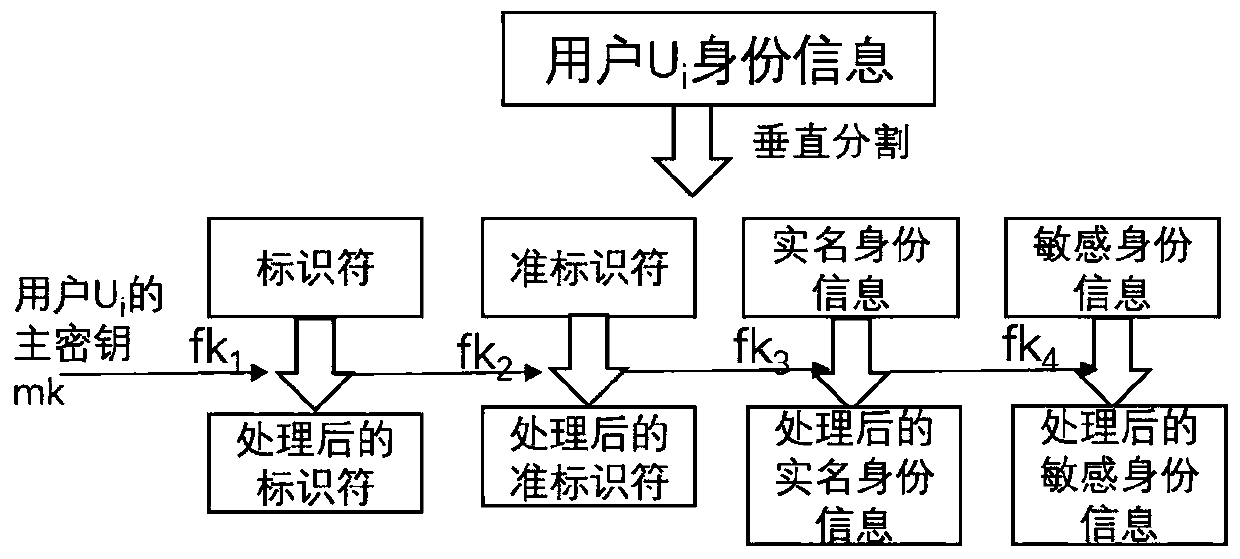
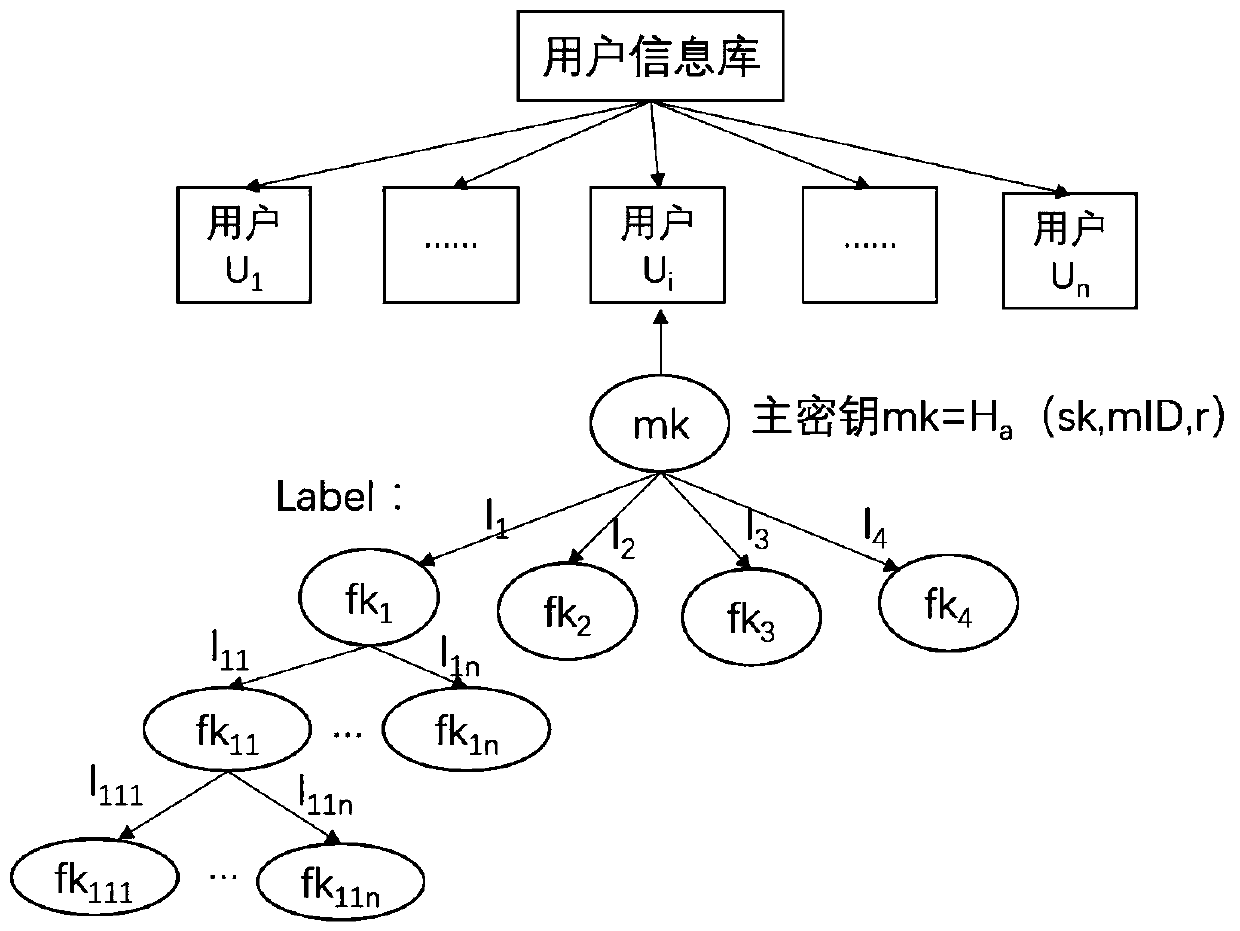
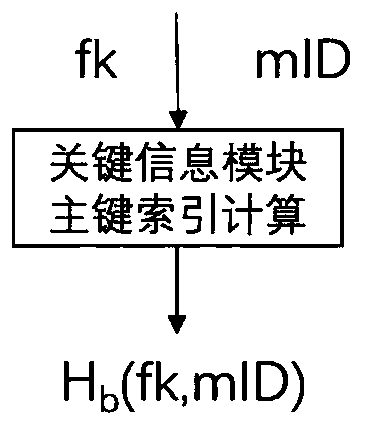
[0045] Before enumerating the embodiments, the method for protecting key information based on OpenID provided by the present invention is further explained. The present invention refers to the definition of personal information in national standards such as "Personal Information Security Requirements" and "Guide to De-identification of Personal Information", and divides user information maintained by identity service providers into five categories: identifiers, quasi-identifiers, and real-name identity information , Sensitive information and other information. The present invention protects the first four types of information as key user information. According to the four types of key information, the records in the user information database are vertically divid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com