Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
165 results about "Extended memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
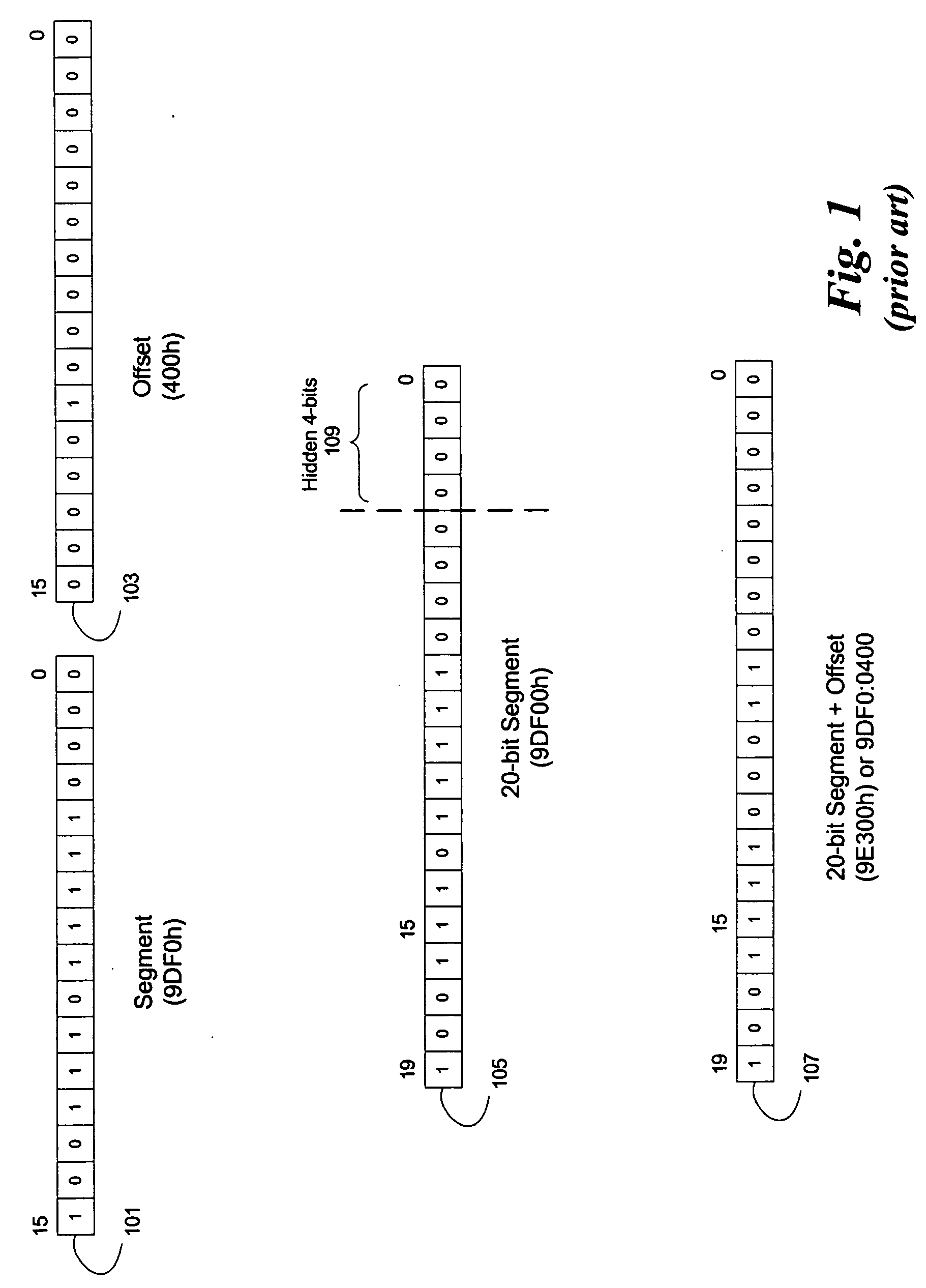
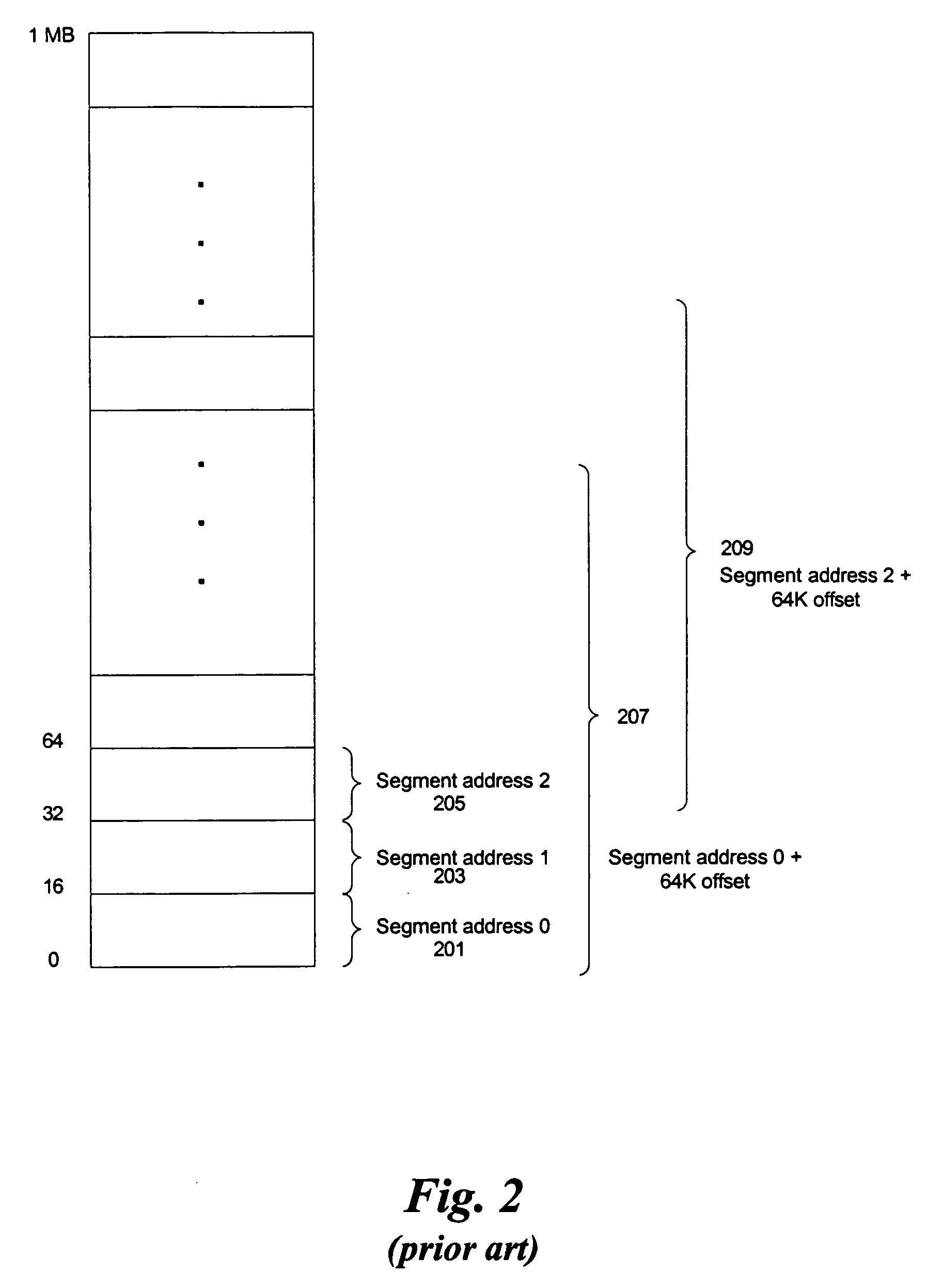
In DOS memory management, extended memory refers to memory above the first megabyte (2²⁰ bytes) of address space in an IBM PC or compatible with an 80286 or later processor. The term is mainly used under the DOS and Windows operating systems. DOS programs, running in real mode or virtual x86 mode, cannot directly access this memory, but are able to do so through an application programming interface called the eXtended Memory Specification (XMS). This API is implemented by a driver (such as HIMEM.SYS) or the operating system, which takes care of memory management and copying memory between conventional and extended memory, by temporarily switching the processor into protected mode. In this context the term "extended memory" may refer to either the whole of the extended memory or only the portion available through this API.
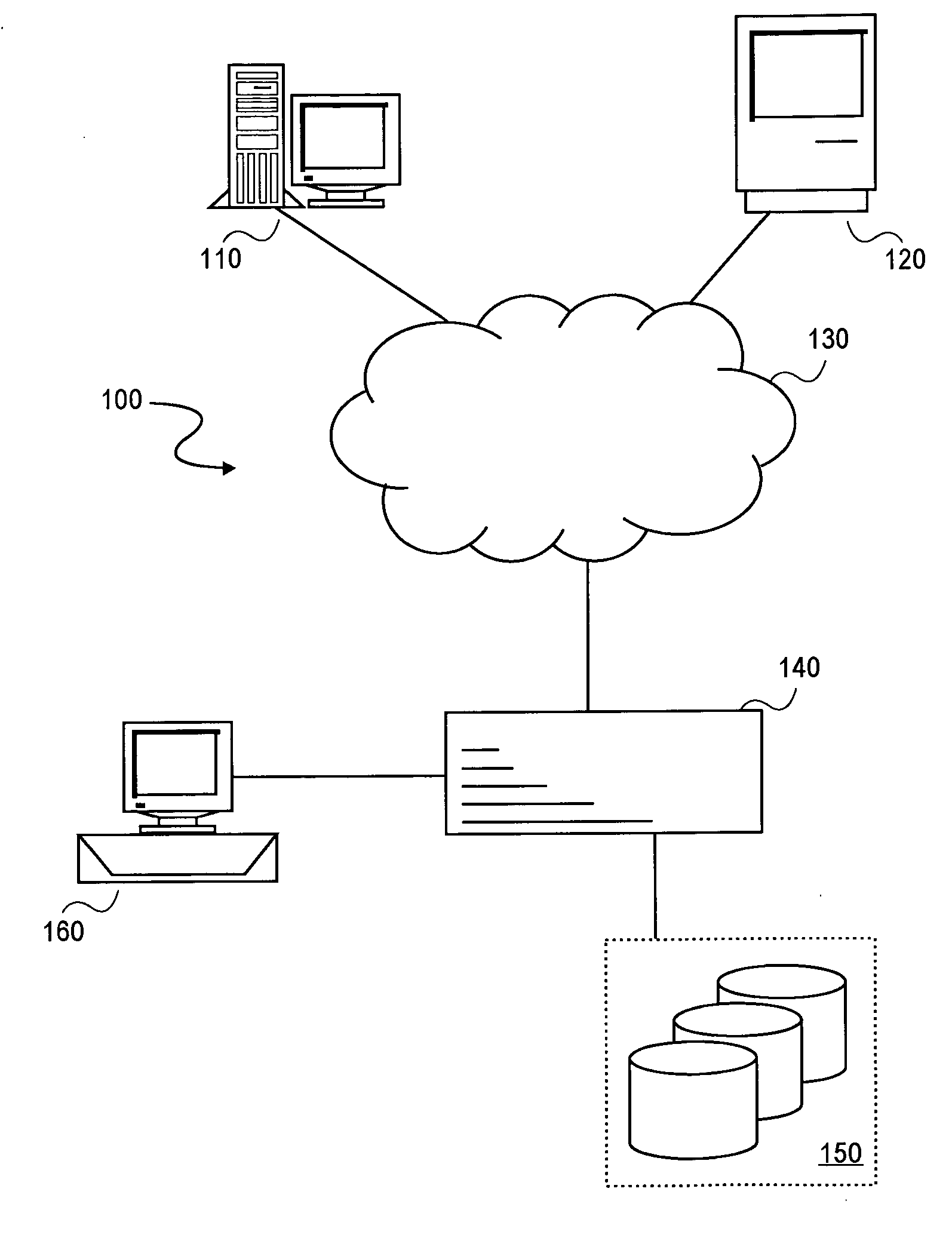
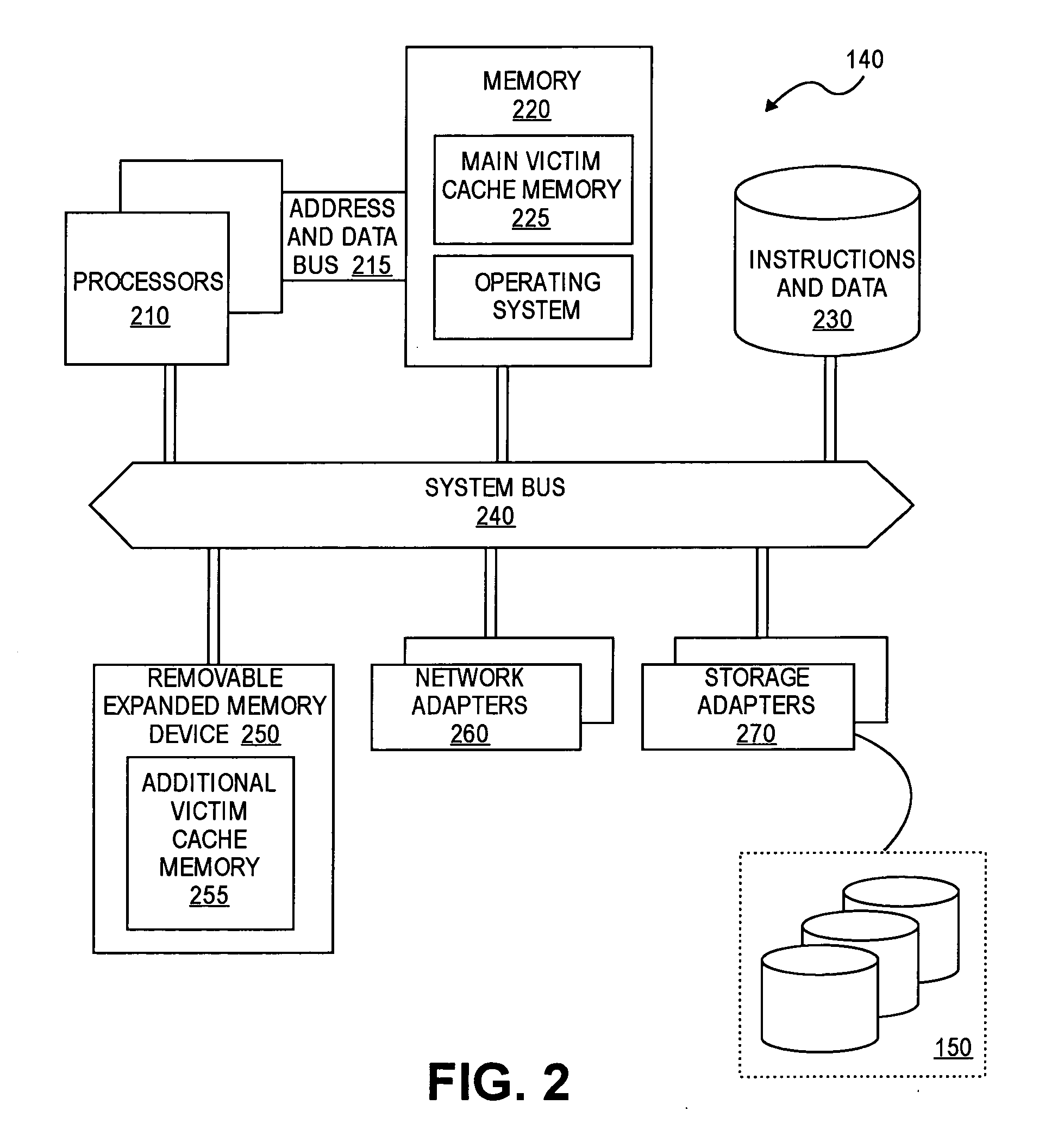
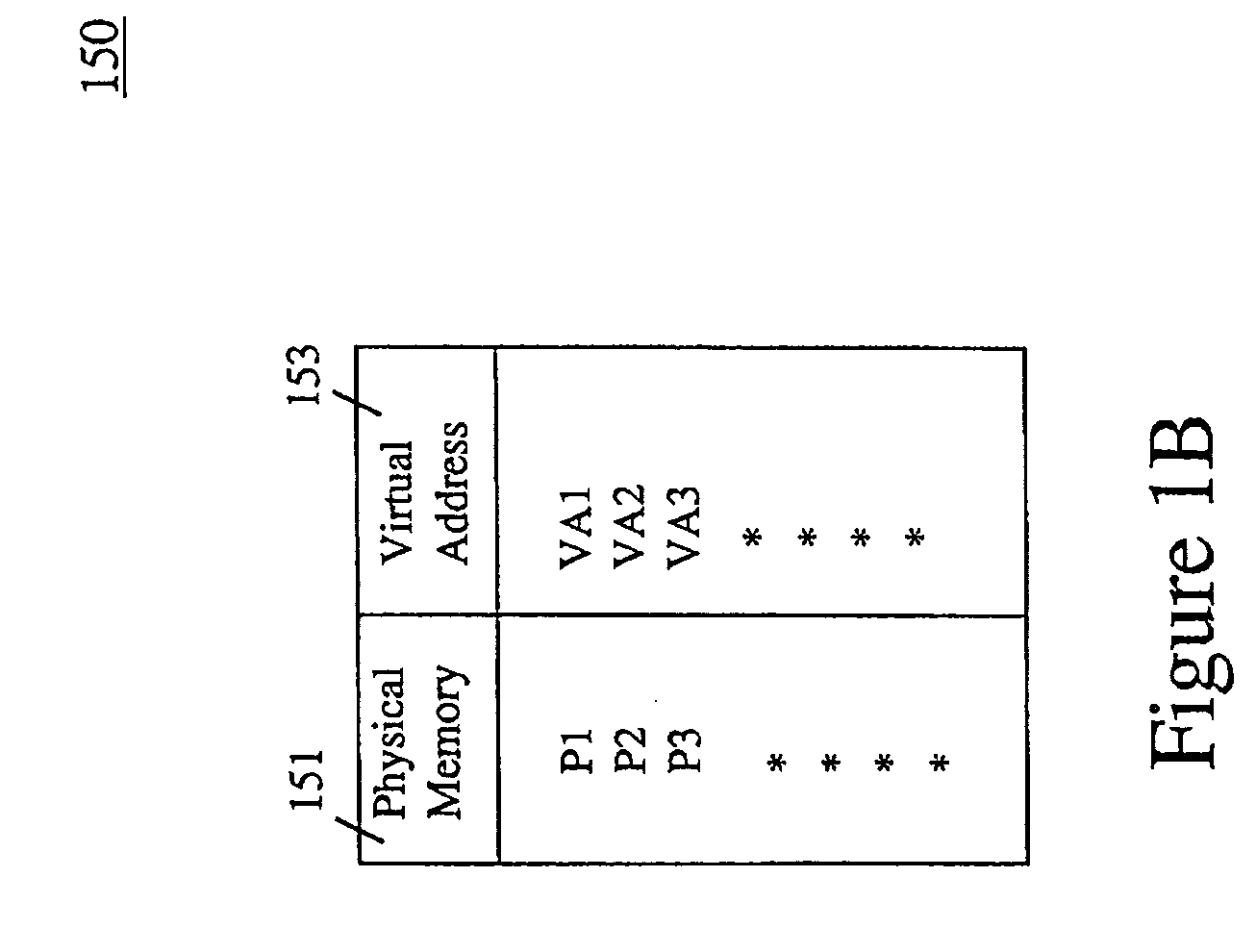
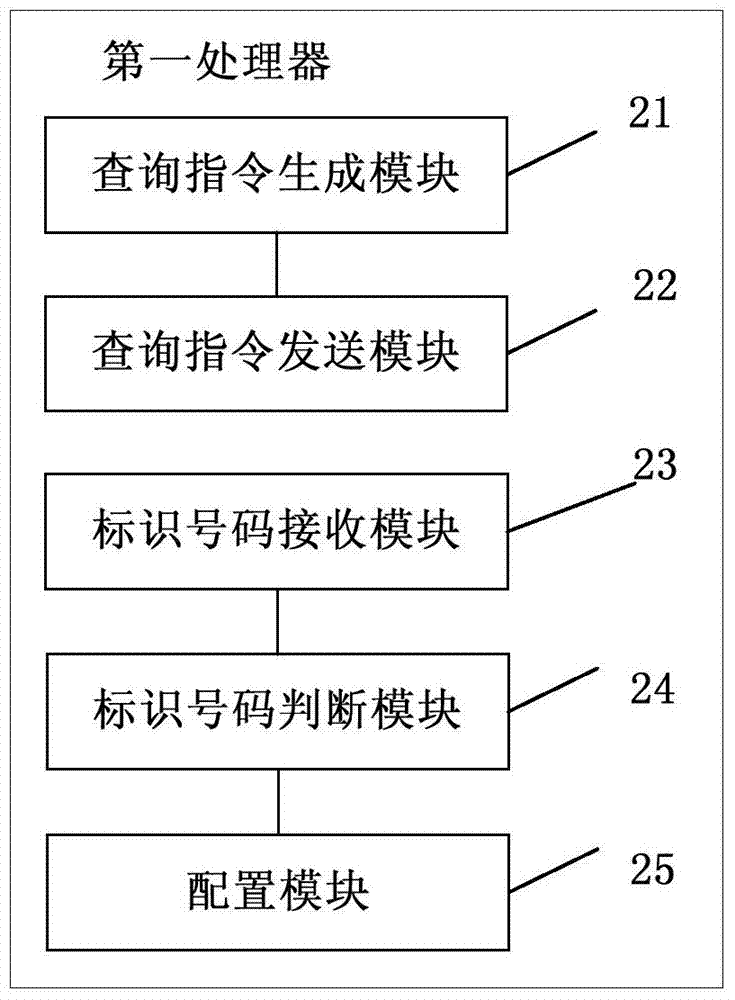
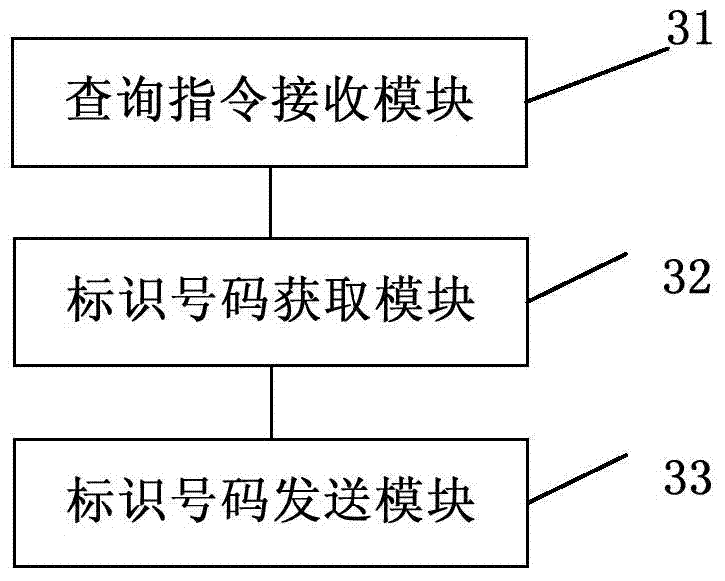
Database System Providing Methodology for Extended Memory Support
ActiveUS20050193160A1Memory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingVirtual address space
A database system providing methodology for extended memory support is described. In one embodiment, for example, a method is described for extended memory support in a database system having a primary cache, the method comprises steps of: creating a secondary cache in memory available to the database system; mapping a virtual address range to at least a portion of the secondary cache; when the primary cache is full, replacing pages from the primary cache using the secondary cache; in response to a request for a particular page, searching for the particular page in the secondary cache if the particular page is not found in the primary cache; if the particular page is found in the secondary cache, determining a virtual address in the secondary cache where the particular page resides based on the mapping; and swapping the particular page found in the secondary cache with a page in the primary cache, so as to replace a page in the primary cache with the particular page from the secondary cache.
Owner:SYBASE INC
Memory scrubbing of expanded memory
Embodiments of the invention include a memory device, such as a removable expanded memory card, having a host bus interface that allows a host to access a memory of the device. The memory device also includes memory scrubbing circuitry to read data stored at addresses in the memory and to identify single-bit errors and multiple-bit errors in the data read from the memory.
Owner:NETWORK APPLIANCE INC
High-density removable expansion module having I/O and second-level-removable expansion memory
InactiveUS20040048503A1Navigational calculation instrumentsIncorrect coupling preventionExpansion cardComputer architecture
The utility of portable computer hosts, such as PDAs (or hand-helds), is enhanced by methods and apparatus for removable expansion cards having application specific circuitry, a second-level-removable memory, and optional I / O, in a number of illustrative embodiments. In addition to providing greater expansion utility in a compact and low profile industrial design, the present invention permits memory configuration versatility for application specific expansion cards, permitting easy user field selection and upgrades of the memory used in conjunction with the expansion card. Finally, from a system perspective, the present invention enables increased parallelism and functionality previously not available to portable computer devices.
Owner:SOCKET MOBILE
Expandable memory for use with solid state systems and devices
ActiveUS20200089420A1Easy accessInput/output to record carriersInternal/peripheral component protectionSoftware engineeringTerm memory
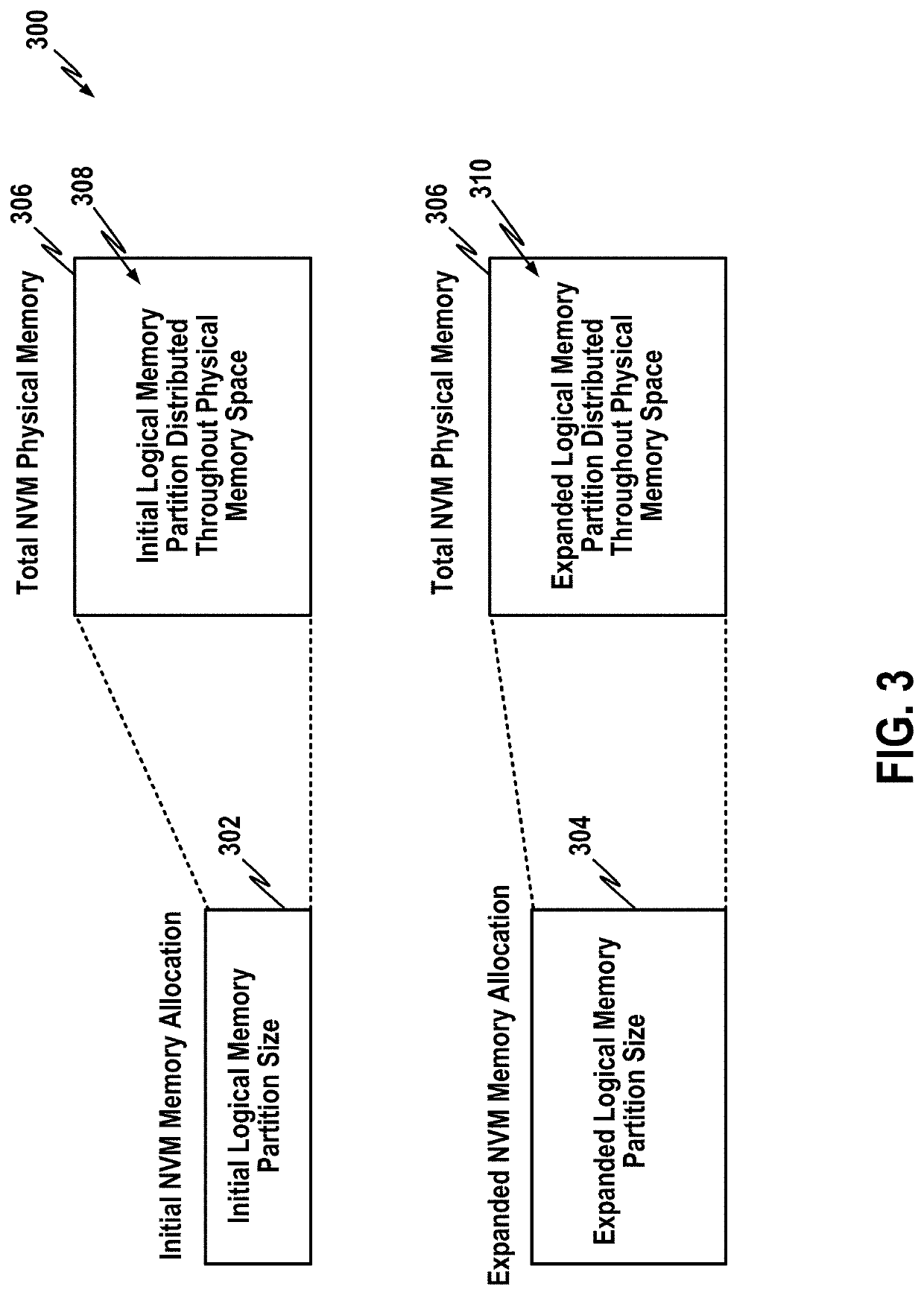
The present disclosure describes technologies and techniques for use by a data storage controller—such as a controller for use with a NAND or other non-volatile memory (NVM)—to provide a user-expandable memory space. In examples described herein, a customer may choose to purchase access to only a portion of the total available memory space of a consumer device, such as a smartphone. Later, the customer may expand the user-accessible memory space. In one example, the customer submits suitable payment via a communication network to a centralized authorization server, which returns an unlock key. Components within the data storage controller of the consumer device then use the key to unlock additional memory space within the device. In this manner, if the initial amount of memory the consumer paid for becomes full, the consumer may conveniently expand the amount of user-accessible memory.
Owner:WESTERN DIGITAL TECH INC
Method and system for extended memory with user mode input/output operations
ActiveUS20050256976A1Easy to operateEliminate needMemory adressing/allocation/relocationComputer security arrangementsMemory addressVirtual memory
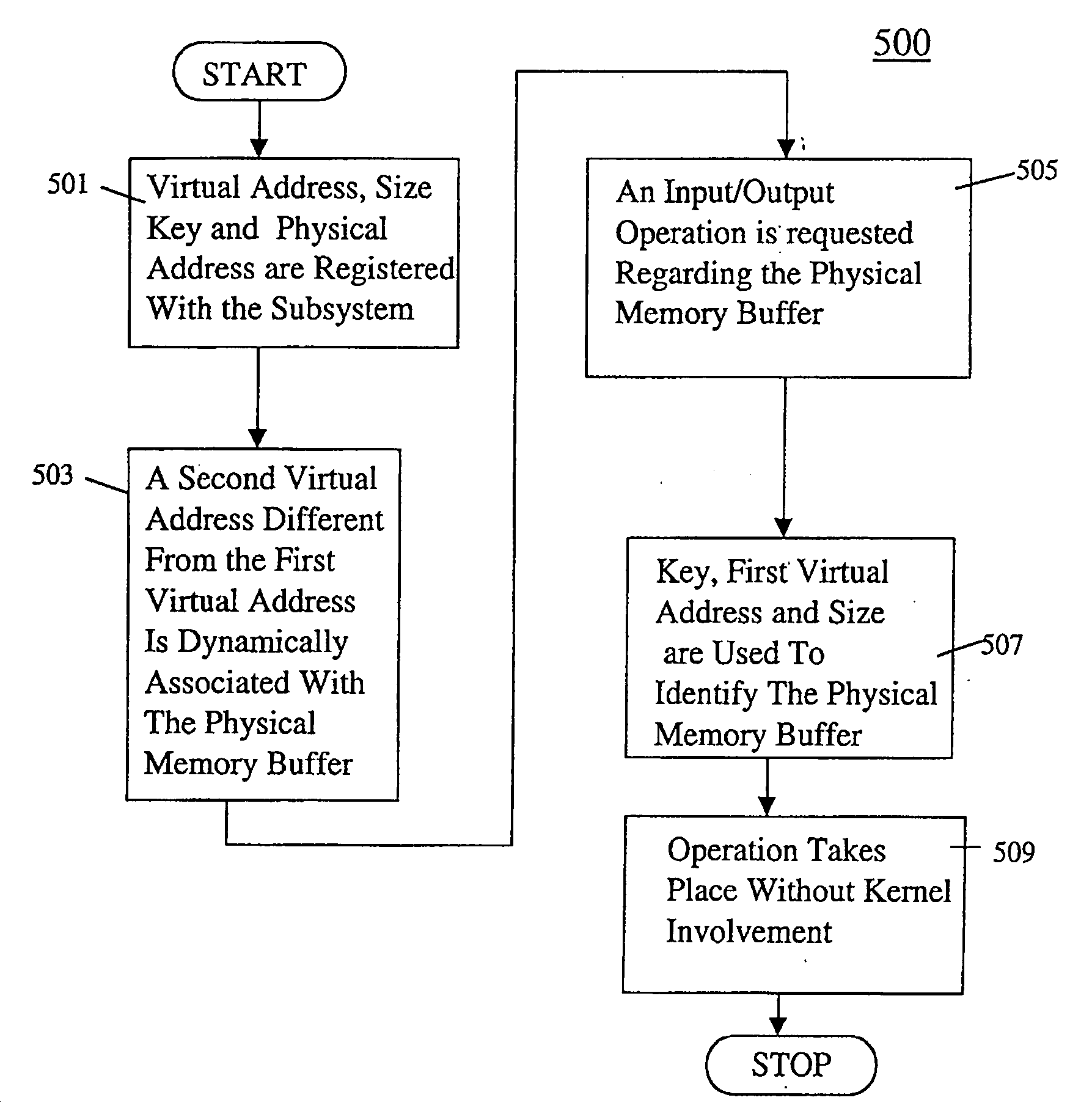
A computer system having a kernel for mapping virtual memory address space to physical memory address space. The computer system uses a method for performing an input / output operation. A physical memory buffer is registered with a subsystem, and the physical memory buffer is associated with a first virtual address, a size and a key. The physical memory buffer is dynamically associated with a second virtual address which is different from the first virtual address. As part of an application program an input / output operation is requested regarding the second virtual address. An application table is used to obtain the first virtual address, the key and the size. The first virtual address, the key and the size are supplied to the subsystem. The subsystem uses the first virtual address, the key and the size, to determine the physical memory buffer and performs an input / output operation using the physical memory buffer without intervention of the kernel.
Owner:ORACLE INT CORP
Memory module with integrated bus termination
A memory module includes a memory device, a connector, a plurality of lines coupling the memory device and the connector, and termination circuitry coupled to at least a subset of the lines. A method for terminating a memory bus includes providing at least two expansion sockets coupled to the memory bus; interfacing two expansion memory modules including termination circuitry with the expansion sockets; and disabling the termination circuitry for one of the expansion memory modules.
Owner:ROUND ROCK RES LLC
Extended peripheral battery pack for a tablet computer
InactiveUS20050213297A1Digital data processing detailsElectrical apparatus contructional detailsTablet computerEngineering
A device is provided which comprises an ultra thin extended battery pack (301). A incorporating a functional peripheral device (321) such as a DVD player, card reader, receiver and / or transmitter, or extended memory.
Owner:MOTION COMPUTING
Expandable memory for use with solid state systems and devices
ActiveUS10983715B2Input/output to record carriersInternal/peripheral component protectionSoftware engineeringTerm memory
The present disclosure describes technologies and techniques for use by a data storage controller—such as a controller for use with a NAND or other non-volatile memory (NVM)—to provide a user-expandable memory space. In examples described herein, a customer may choose to purchase access to only a portion of the total available memory space of a consumer device, such as a smartphone. Later, the customer may expand the user-accessible memory space. In one example, the customer submits suitable payment via a communication network to a centralized authorization server, which returns an unlock key. Components within the data storage controller of the consumer device then use the key to unlock additional memory space within the device. In this manner, if the initial amount of memory the consumer paid for becomes full, the consumer may conveniently expand the amount of user-accessible memory.
Owner:WESTERN DIGITAL TECH INC
Providing extended memory protection
InactiveUS20060225135A1Digital data processing detailsAnalogue secracy/subscription systemsTerm memoryMalware
In one embodiment, the present invention provides for extended memory protection for memory of a system. The embodiment includes a method for associating a protection indicator of a protection record maintained outside of an application's data space with a memory location, and preventing access to the memory location based on the status of the protection indicator. In such manner, more secure operation is provided, as malicious code or other malware is prevented from accessing protected memory locations. Other embodiments are described and claimed.
Owner:INTEL CORP
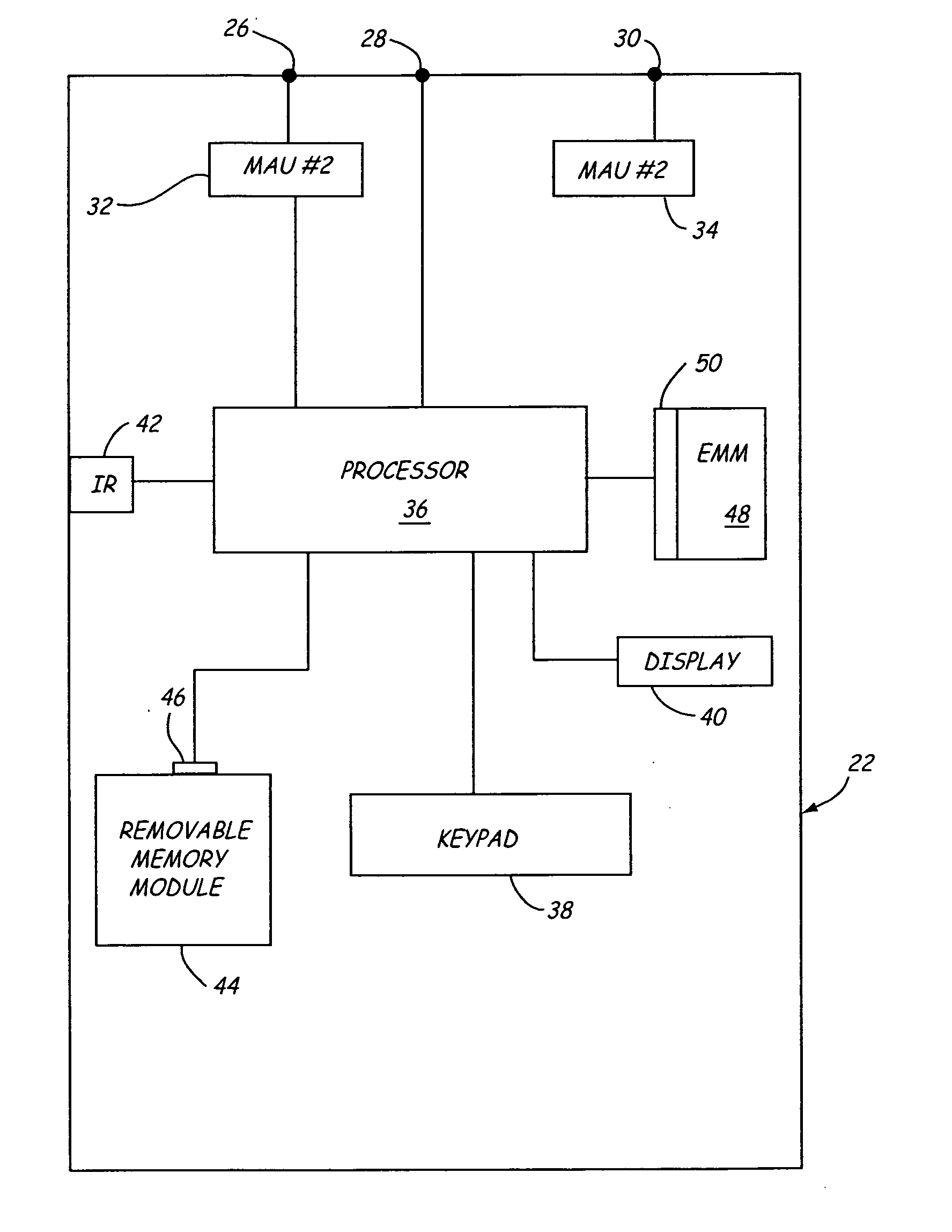
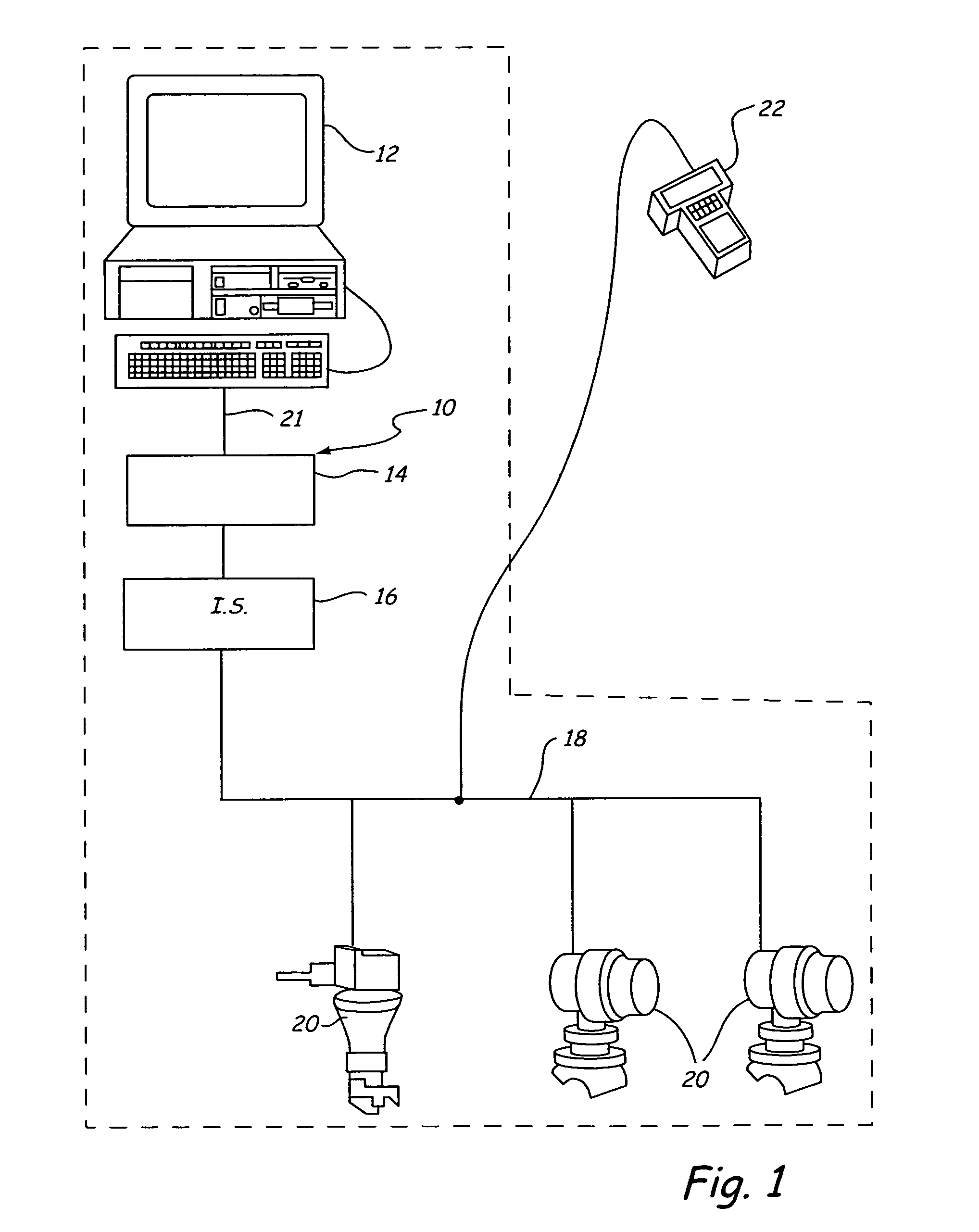
Field maintenance tool
An improved intrinsically safe field maintenance tool is provided. The tool is operable with process communication loops in accordance with a plurality of process industry standard protocols. Aspects of the invention include hardware features such as an infrared port; removable memory module; and an expansion memory module. Additional aspects of the invention include protocol-specific diagnostic methods executable with the improved intrinsically safe field maintenance tool.
Owner:FISHER-ROSEMOUNT SYST INC
A Program Upgrading Mechanism for Peripheral Devices Based on Microcontroller Without External Memory
ActiveCN102298526ARealize remote upgradeImprove versatilityProgram loading/initiatingMicrocontrollerCommunications system
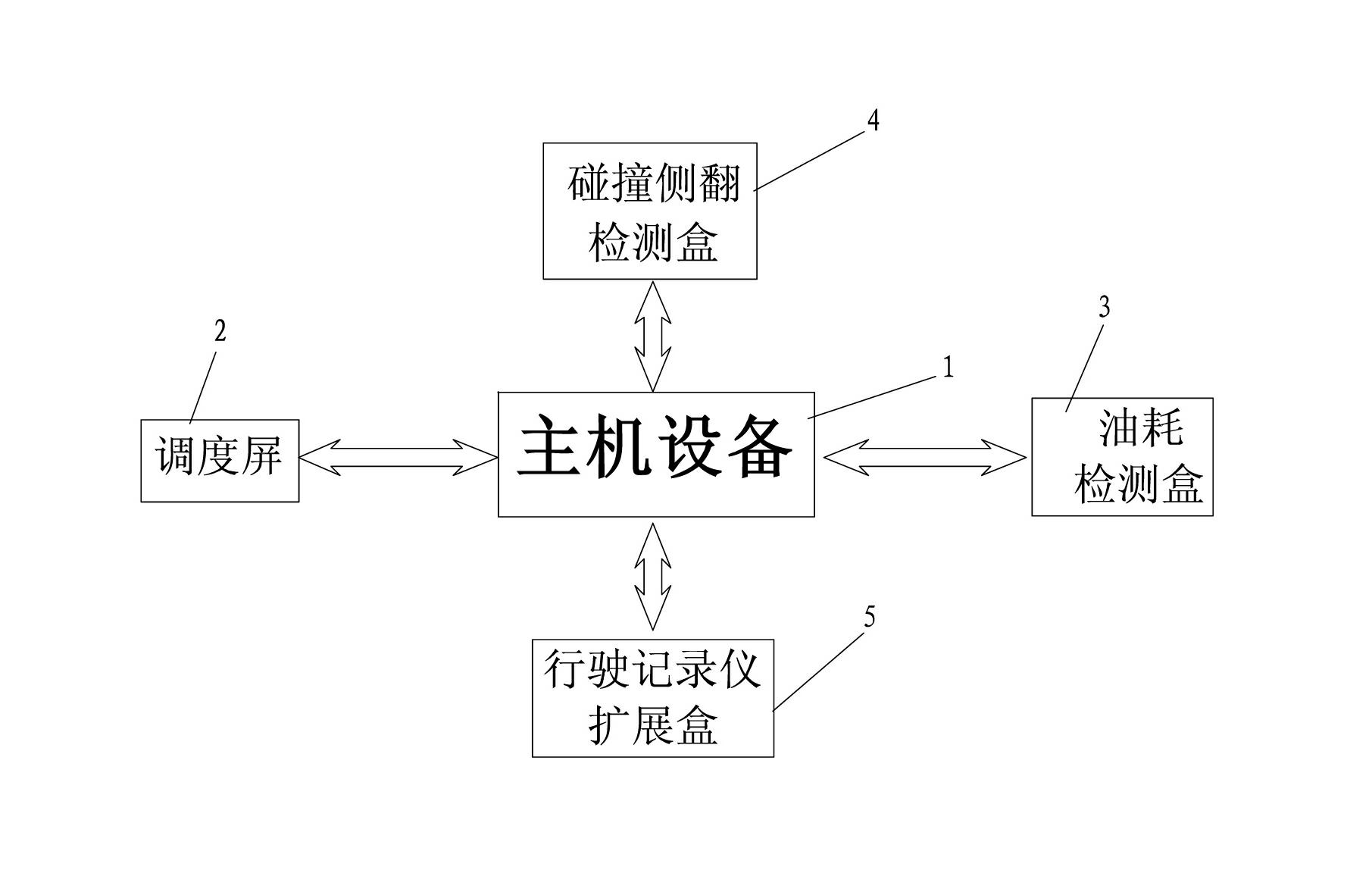
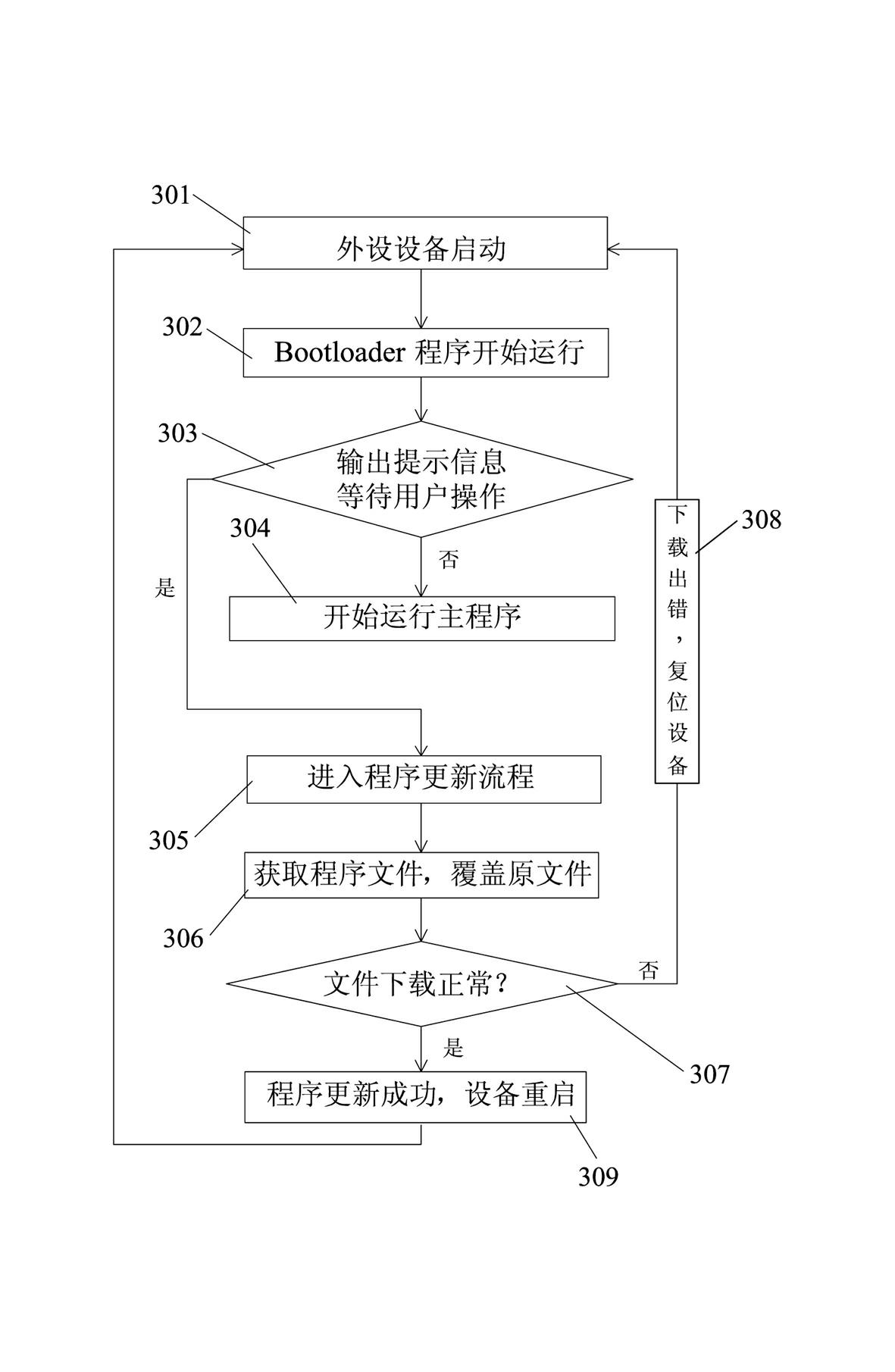
The invention provides a method for remotely upgrading the program of the peripheral equipment of a single-chip microcomputer without an externally expanded memory. A master-slave device communication system, including a host device and multiple peripheral devices, in which a stable communication is established between the host device and each peripheral device through physical means (such as RS-232 / RS-485 / CAN bus, etc.) Connection, and the program design of the peripheral device adopts the BootLoader program to guide the main program to start. With the help of the storage space of the host, the communication channel between the peripheral device and the host is used. The two parties communicate according to the agreement agreed in advance, and the host recognizes it. And be controlled to realize the remote upgrade of the peripheral device program. The advantage of adopting the present invention is that there is no need to make any changes to the host hardware and peripheral hardware, and the whole mechanism is completed through the interaction of software and protocols, which has good versatility and strong expandability.
Owner:XIAMEN YAXON NETWORKS CO LTD
Hash table-based and extended memory-based high-performance IPv6 address searching method
InactiveCN101827137AImprove search efficiencyAdd depthMemory adressing/allocation/relocationData switching networksExtensibilityProcess module
The invention discloses a hash table searching-based and extended memory searching-based IPv6 address searching scheme. A system comprises one searching classifier, one updating classifier, seven parallel hash processing units, six extended memory processing units, seven hash collision processing units and one priority comparing unit. The first six hash processing units are correlated with the corresponding extended memories in two stages and combined with the corresponding hash collision processing units to form six paths of processing modules; the seventh hash processing unit and the corresponding hash collision processing unit form one path of processing module; and the seven paths of modules searches the IPv6 address in parallel so as to determine the next hop of information. Due to the adoption of the method, the searching operation of the IPv6 address is finished in one to two storage periods in combination with the principle of hash searching and extended memory searching according to the distribution rule of the prefix of the IPv6 address. The method has high searching and updating performance and high extensibility, so that the method is a searching scheme suitable for the high-performance IPv6 router.
Owner:XIAN UNIV OF POSTS & TELECOMM
Memory-expandable electronic equipment and memory expanding method
InactiveCN102103470AStorage moreDon't worry about running out of memoryInput/output to record carriersMemory systemsComputer scienceElectronic equipment
The invention discloses a memory expanding method. The method comprises the following steps of: detecting whether a built-in expandable memory is newly inserted; if the built-in expandable memory is not newly inserted, performing storage and installation operation according to a default program of a processor; if the built-in expandable memory is newly inserted, judging whether the inserted built-in expandable memory is partitioned or not; if the built-in expandable memory is not partitioned, partitioning the built-in expandable memory into at least two subareas, wherein at least one subarea is used as a built-in expandable area for expanding a user area in the memory; and storing and installing files or application programs to the built-in expandable area. The invention also provides memory-expandable electronic equipment.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Memory extending system and memory extending method
ActiveCN103488436ALarge memory capacityAvoid the problem of redundant processing powerInput/output to record carriersComputer architectureQuick path interconnect
An embodiment of the invention discloses a memory extending system and a memory extending method. The system comprises processors, extended memories, extended chips and multiple processor installation positions, and a memory installation position is arranged at each process installation position; the processor installation positions are connected mutually through QPI (quick path interconnect) interfaces, at least one processor installation position is provided with a processor, and at least one of the rest installation positions serves as extended installation position; the extended chips are installed in the extended installation position; the extended memories are installed to the memory installation positions connected with the extended chips. The memory extending system has the advantages that the extended chips are mounted at other processor installation positions to replace the processors, and the existing processors are enabled to be capable of accessing the extended memories carried by the extended chips through the extended chips, so that memory capacity of the existing processors is increased on the condition that processing capacity is not improved, and the problem of processing capacity redundancy caused by the fact that memories are extended by adding processors in the prior art is solved.
Owner:XFUSION DIGITAL TECH CO LTD
Database system providing methodology for extended memory support
ActiveUS7421562B2Memory architecture accessing/allocationOperational speed enhancementParallel computingVirtual address space
A database system providing methodology for extended memory support is described. In one embodiment, for example, a method is described for extended memory support in a database system having a primary cache, the method comprises steps of: creating a secondary cache in memory available to the database system; mapping a virtual address range to at least a portion of the secondary cache; when the primary cache is full, replacing pages from the primary cache using the secondary cache; in response to a request for a particular page, searching for the particular page in the secondary cache if the particular page is not found in the primary cache; if the particular page is found in the secondary cache, determining a virtual address in the secondary cache where the particular page resides based on the mapping; and swapping the particular page found in the secondary cache with a page in the primary cache, so as to replace a page in the primary cache with the particular page from the secondary cache.
Owner:SYBASE INC
Methods and devices for encrypting and decrypting video file and mobile terminal
ActiveCN102867153AImprove securityImprove encryption efficiencyTelevision system detailsData processing applicationsComputer terminalEncryption
The invention discloses a method for encrypting a video file, a method for decrypting the video file, a device for encrypting the video file, a device for decrypting the video file, and a mobile terminal, and belongs to the field of mobile terminals. The method for encrypting the video file comprises the following steps of: acquiring the video file to be encrypted and a key; encrypting the video file to be encrypted by using the key to obtain an encrypted video file; acquiring a pre-scanned mobile terminal and partitions storing user data except hidden partitions in an extended memory on the mobile terminal; and determining a partition storing the video file to be encrypted in all the partitions, and moving the encrypted video file into a preset folder in the partition storing the video file to be encrypted. The method for decrypting the video file comprises the following steps of: acquiring a video file to be decrypted and the key; decrypting the video file to be decrypted by using the key to obtain a decrypted video file; and determining the storage position of the video file to be decrypted before encryption, and moving the decrypted video file to the storage position before encryption. The video file can be quickly encrypted.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
System and method for offering one or more drivers to run on the computer
In accordance with at least some embodiments of the invention, a computer-implemented method, and associated apparatus, comprises determining a configuration of a computer, comparing the computer's configuration to configuration information in a database, and based on the comparison, offering a user at least one driver from which to select for running on the computer. In accordance with other embodiments, a computer-implemented method, and associated apparatus, comprises, in response to a user selecting a software control, determining if extended memory exists above a maximum amount of memory permitted by an operating system, and if extended memory exists, automatically making accessible the extended memory.
Owner:HEWLETT PACKARD DEV CO LP
Apparatus and Method for Serving Digital Content Across Multiple Network Elements
InactiveUS20070260546A1Easy to scaleImprove abilitiesData processing applicationsComputer security arrangementsDigital contentClient-side
An apparatus and method use a scale out paradigm to spread digital content across multiple servers, which then deliver the content in parallel to a client. Spreading content over multiple servers allows easily expanding memory and I / O capabilities at a reasonable cost. The client includes a mechanism for receiving the content on multiple channels from multiple server computer systems, and for assembling the content into a single stream. The result is a system that may be easily scaled to provide digital content to an increasing number of users at a reasonable cost.
Owner:IBM CORP
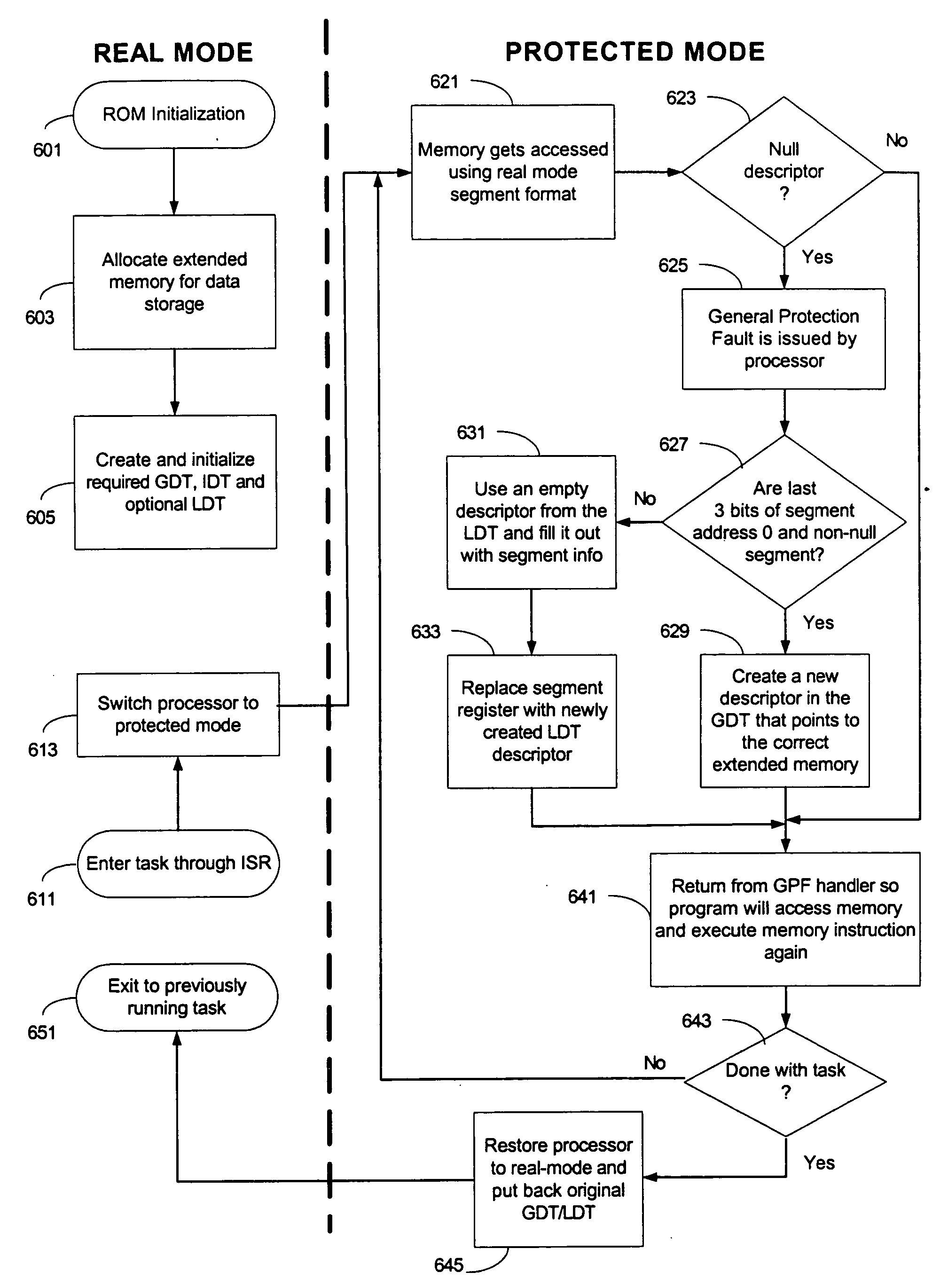
System and method for simulating real-mode memory access with access to extended memory
InactiveUS20060004982A1Memory adressing/allocation/relocationDigital computer detailsOption ROMParallel computing
In some embodiments, the invention involves a system and method relating to switching to protected mode to access extended memory while executing instruction code that is designed for real mode memory access. In at least one embodiment, the present invention is intended to enable complex option-ROM code to be executed during pre-boot without corrupting system memory used by the BIOS or other option-ROMs. Other embodiments are described and claimed.
Owner:INTEL CORP
Dirty word detection aid and using method thereof
InactiveCN101794576AReduce volumeEasy to carrySpeech recognitionData processing systemStatistical analysis
The invention discloses a dirty word detection aid, which comprises a portable terminal and a data processing system, wherein the portable terminal is provided with a voice acquisition unit and a voice recognition unit. The invention is characterized in that the voice acquisition unit and the voice recognition unit are used to realize the recognition function of dirty phases in the speech of a user, and the data processing system is used to realize the functions of data processing and software upgrade; and a CPU, an externally extended memory, an output display unit and a buzzer alarm circuit are arranged on the portable terminal. The using method of the dirty word detection aid is that dirty word information voice samples are established or upgraded first; then dirty word information detection is realized; and finally data statistical analysis is realized. The invention has the advantages that the volume of the product is small, the carrying is convenient, the time and the frequency of the dirty words used by the user can be recorded, the severity of the dirty words used by the user can be judged, and alarm prompt information is output to prompt the user to pay attention to words and deeds when the user uses the dirty words too frequently.
Owner:CHONGQING UNIV
Interleaver or deinterleaver method and device thereof based on block interleaver
ActiveCN101800619AReduce sizeIncrease bit widthError preventionError correction/detection using multiple parity bitsComputer architectureExtended memory
The invention relates to an interleaver or deinterleaver method and a device thereof based on a block interleaver, an interleaver or deinterleaver block is extended to a square, when a first time interleaver or deinterleaver is carried out by the method of writing by row and reading by column, then a second time interleaver or deinterleaver is carried out by the method of writing by column and reading by row, therefore, the second time writing and the first time reading are basically carried out at the same time in a same memory and the data which is not processed by the first time interleaver or deinterleaver is not washed off. The method is carried out all the time alternately, only an extended memory is needed to finish the interleaver / deinterleaver, thereby greatly reducing the size of the needed memory, meanwhile, a little buffer memory is added before the memory to increase the bit wide of the memory, thereby being convenient to process.
Owner:FUZHOU ROCKCHIP SEMICON
Method for simultaneously loading multiple FPGA using CPU
InactiveCN101165652AImprove loading speedImprove reliabilityProgram loading/initiatingProcessor registerAddress bus
The method is used in a system comprising one or more FPGAs and CPUs, and comprises: 1) generating a FPGA loading file by means of combining multi FPGA loading bit-stream files; 2) making logical expand for the address bus of the CPU to get the registers and latch units required by loading said multi FPGAs; 3) said CPUs reads said FPGA loading files and sends the files to the expending memory of said CPU; said CPU controls said register and latch units to generate the loading time sequence in order to make loading for one of multi FPGAs.
Owner:ZTE CORP
Indicator for forecasting shelf life of cold fresh pork
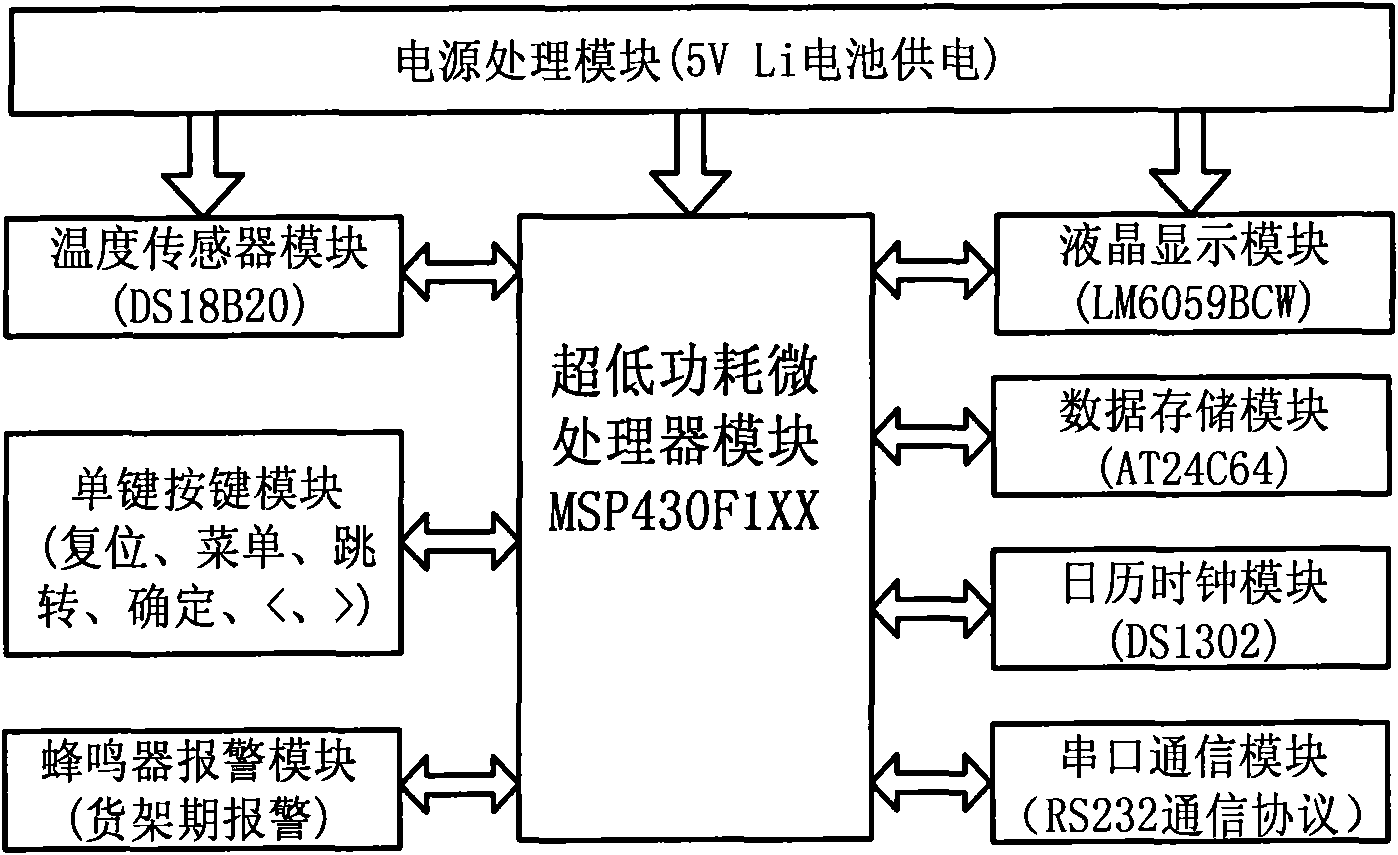
InactiveCN101769884AImprove completenessImprove utilization efficiencyThermometer detailsMaterial heat developmentEngineeringSerial port
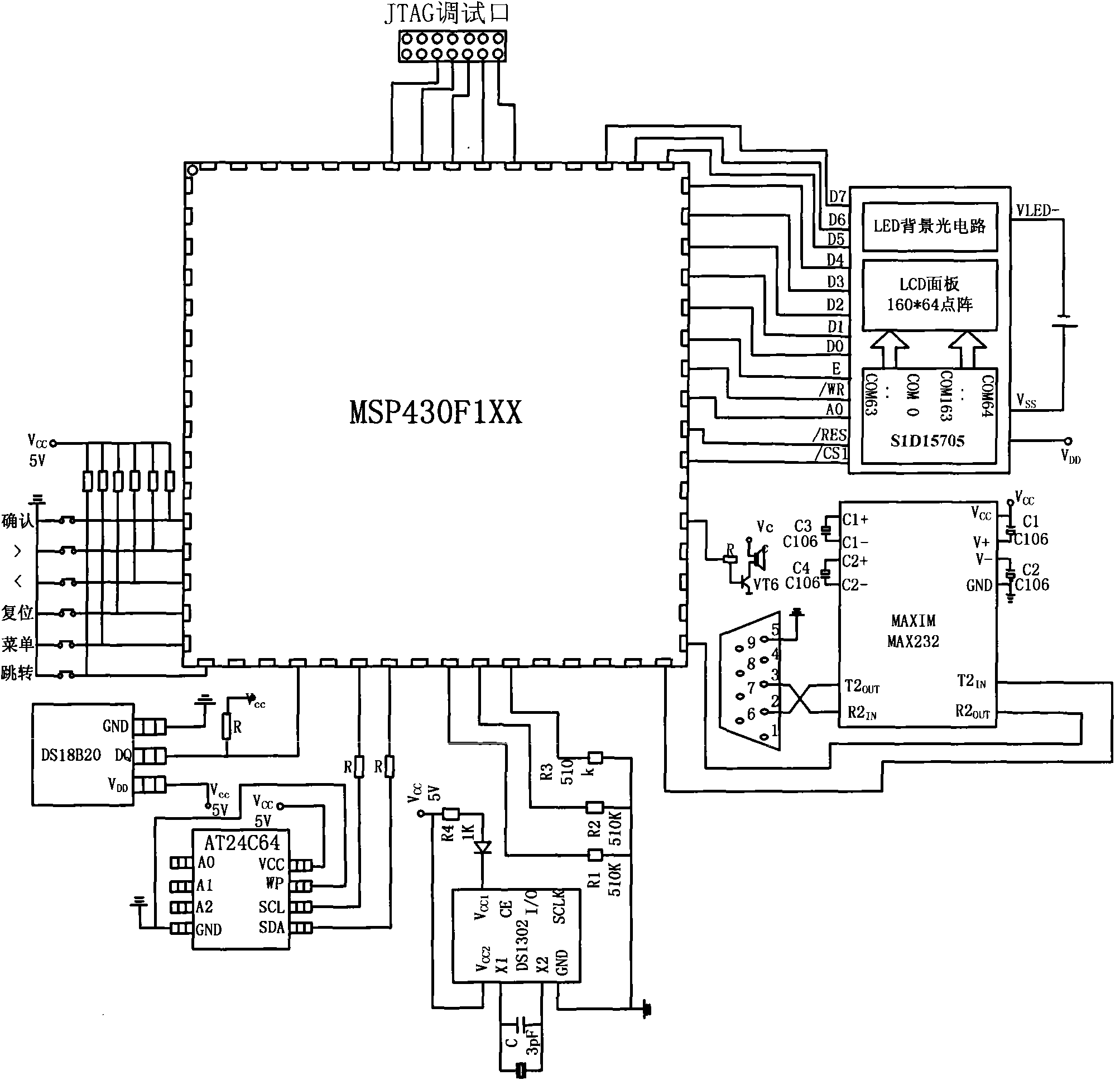
The invention relates to an indicator for forecasting the shelf life of cold fresh pork, belonging to the technical field of detecting the quality of the pork by acquiring the temperature of the pork. The indicator forecasts the shelf life of the pork by timely acquiring the temperature of the pork in the circulation process from output to sell. The indicator has small volume and convenient use, can be directly attached to the surface of the cold fresh pork, and timely updates and displays the temperature, the shelf life and the system time of the fresh pork. The indicator uses a high-precision temperature sensor DS18B20 to acquire the temperature of the surface of the cold fresh pork, transmits the temperature value to a micro controller MSP430F1XX through a data wire DQ, uses the controller to forecast the real-time shelf life based on the TTT theory of the temperature, and uses a liquid crystal display LM6059BCW to display real-time temperature, the shelf life, the system time and the food names. The system time, the real-time temperature and the shelf life are all memorized in an extended memory card every 1 hour, and can be transmitted to a computer through serial ports of the indicator as required by users. The indicator has high precision, low energy consumption, multiple functions and convenient operation, and effectively solves the problem for forecasting the shelf life of the cold fresh pork during circulating.
Owner:SHANGHAI OCEAN UNIV
Power jack for Zigbee-based wireless network technology
InactiveCN101262708AAvoid interferenceEasy to operateElectrically conductive connectionsTelemetry/telecontrol selection arrangementsRemote controlComputer module
A power socket based on Zigbee wireless network technology is provided by the invention, which comprises a socket and a remote control which is required for controlling the operation of the socket. The socket comprises a single chip microcomputer of the socket as well as a temperature sensing module, an overload protection module, a relay module, a write enable module which are respectively connected with the single chip microcomputer; the remote control comprises a single chip microcomputer as well as an RS232 serial communication module, an LCD display module, a keyboard input module, an extended memory module, a clock module and an alarm module which are respectively connected with the single chip microcomputer; the socket is controlled to be operated by the remote control and both are connected with each other by radio signals while the socket is connected on each electric appliance. The device of the invention has high intelligence and a plurality of functions can be realized, such as the self-adaptation to the Zigbee network, zoning management and control, time switching, overload and overheat protections, etc.
Owner:SHANDONG UNIV
Extended memory access method, device and system
ActiveCN106155577AMemory architecture accessing/allocationInput/output to record carriersAccess methodTime delays
The embodiment of the invention discloses an extended memory access method, device and system. The method includes the steps that N+1 memory access requests sent serially by a processor system of a computer are received, access addresses in all the memory access requests are different and point to the same physical address, the physical address is the storage address, on the extended memory, of data to be accessed, and N is an integer larger than or equal to one; when the first memory access request is received, a read request is sent to the extended memory, and specific response information is returned to the processor; in the process of reading the data to be accessed from the extended memory, each time one memory access request is received, within time delay specified in the memory bus protocol, specific response information is returned to the processor until the data to be accessed is written into a data buffer; then the data to be accessed is returned to the processor system.
Owner:HUAWEI TECH CO LTD +1
Data processing system and method based on data warehouse
InactiveCN103218415AImprove computing efficiencyFlexible extensionSpecial data processing applicationsData processing systemData warehouse
The invention discloses a data processing system and method based on a data warehouse. The data processing system comprises a temporary data model building unit, a screening and collecting unit and a loading unit, wherein the temporary data model building unit is used for dynamically building temporary data models according to the user input; the screening and collecting unit is used for screening and collecting data from the data warehouse according to the temporary data models; and the loading unit is used for loading the screened data into an extended memory system.
Owner:HOOLAI GAMES BEIJING TECH
Extended Memory Card and Manufacturing Method
InactiveUS20080248692A1Wave amplification devicesRecord carriers used with machinesControl storeData file
An embodiment of the present invention includes an extended memory card comprising memory circuitry, extended memory controller circuitry, a plurality of first format connection fingers, and a plurality of second format connection fingers. The memory circuitry is operable to store data files therein. The extended memory controller circuitry is operable to control data file storage and retrieval to and from the memory circuitry.The extended memory controller circuitry is further operable to control interface of the extended memory card through either the first format connection fingers or the second format connection fingers with a host device to transfer data files from the host device to be stored on the memory circuitry, and to retrieve data files from the memory circuitry to the host device.
Owner:SUPER TALENT ELECTRONICS
Code and thread differential addressing via multiplex page maps
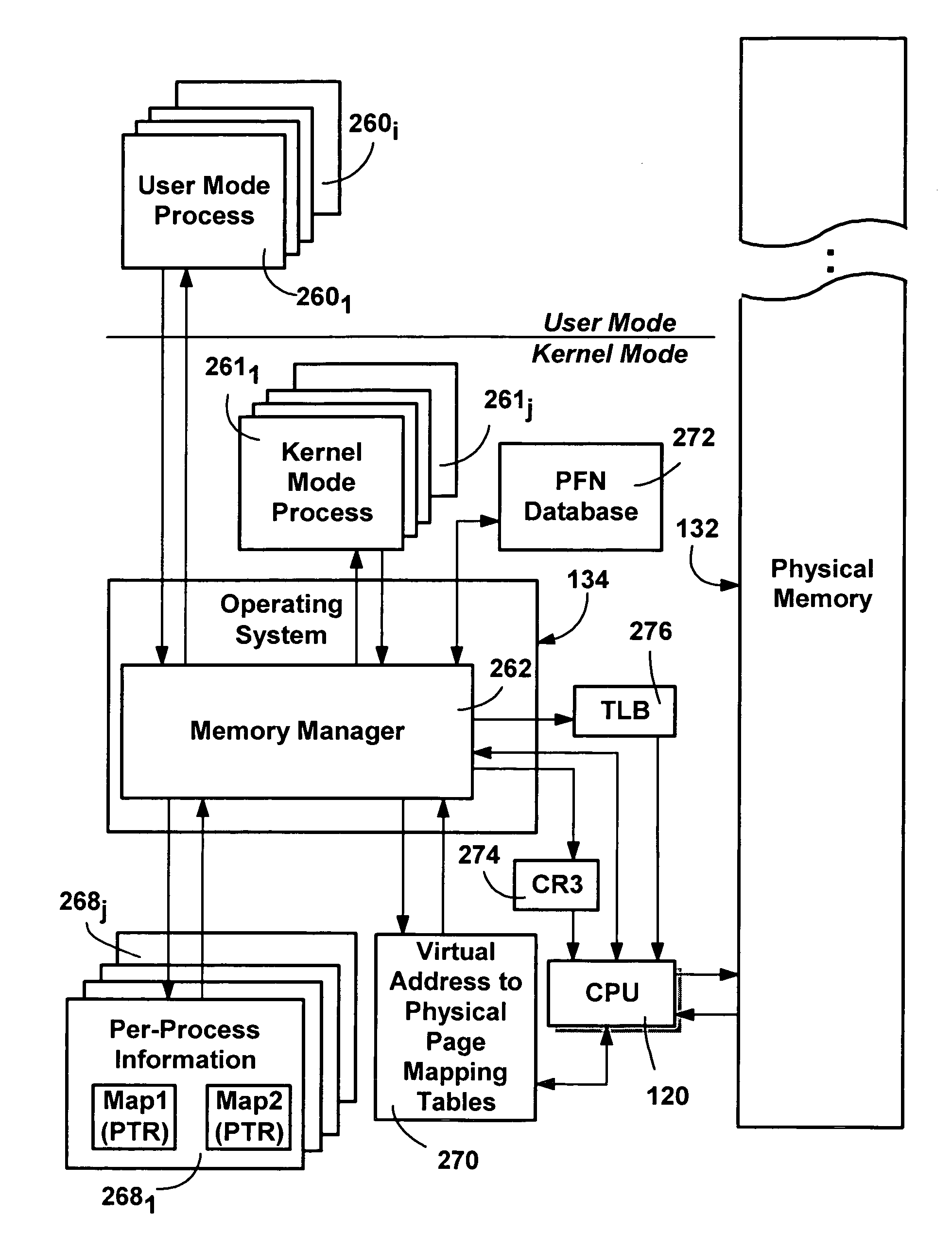
InactiveUS20060158690A1Facilitates expanded user mode memory addressingRemove changeSpecific access rightsVisual presentationMemory addressSingle process
Described is a system and method whereby processes may have multiple memory maps associated therewith to provide curtained memory and overcome other memory-related problems. Multiple maps are used to restrict memory access of existing code such as drivers, without changing that code, and without changing existing microprocessors. A thread of a process is associated with one memory map at a time, which by mapping to different memory locations, provides memory isolation without requiring a process switch. Memory isolation may be combined with controlled, closed memory map switching performed only by trusted code, to ensure that some protected memory is inaccessible to all but the trusted code (curtained memory). For example, the threads of the process may ordinarily run at one privilege level with a restricted map, with map switching is only allowed at a higher privilege level. As the threads run through code, the map may be appropriately changed on entering and leaving the trusted code, thus controlling what memory addresses are accessible based on what code is currently being executed. Map switching among multiple maps eliminates the need to change a process in order to access different memory, thereby allowing expanded memory addressing in a single process and isolating untrusted code run in process from certain memory of that process.
Owner:MICROSOFT TECH LICENSING LLC
Method for decoding and displaying digital broadcasting signals
InactiveUS6891894B1Television system scanning detailsPicture reproducers using cathode ray tubesDigital broadcastingComputer science
The present invention relates to a method for decoding and storing digital broadcasting signals which is capable of freely adjusting size and position of a broadcasting video window by preventing a frame buffer conflict between storing and fetching timing of the decoded data which can be occurred depending on the position and the size of the video window displayed on a screen, without expanding memory or upgrading speed of the decoder.
Owner:LG ELECTRONICS INC
Software upgrades from a printer module with on-board intelligence
An intelligent on-board monitoring system for replaceable module for a printing apparatus includes a memory element, an input for receiving information either from sensors on the replaceable module, or from the printing apparatus concerning printing operations performed, and a microprocessor connected to the memory for performing calculations upon data stored in the memory and upon the input information. By expanding this intelligent on-board monitoring system with expanded memory, either on board the replaceable module, or by way of network access, the capability to enable software upgrades is provided. The software upgrades may relate to the performance of the replaceable module or to the machine into which it is installed. These software upgrades may be accomplished without requiring computational resources of the printing apparatus itself and by proper scheduling without impacting customer machine utilization.
Owner:XEROX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com