Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
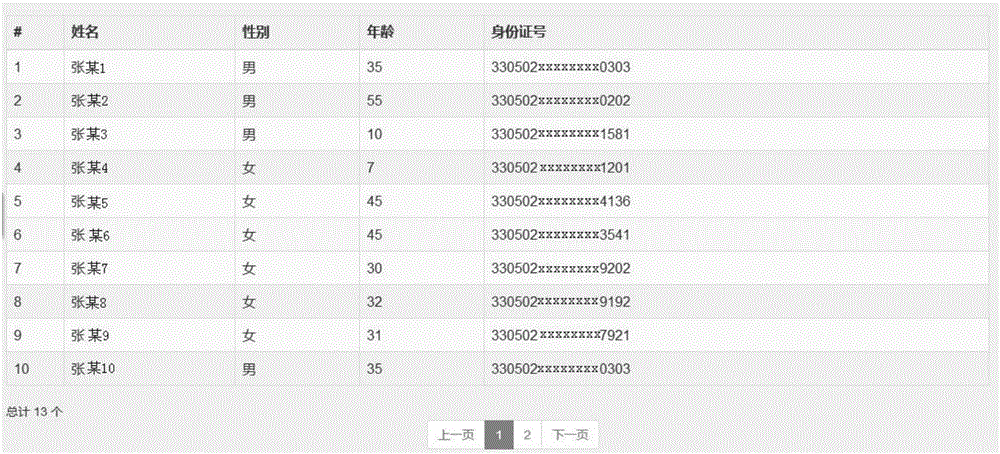
138 results about "Affiliation network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
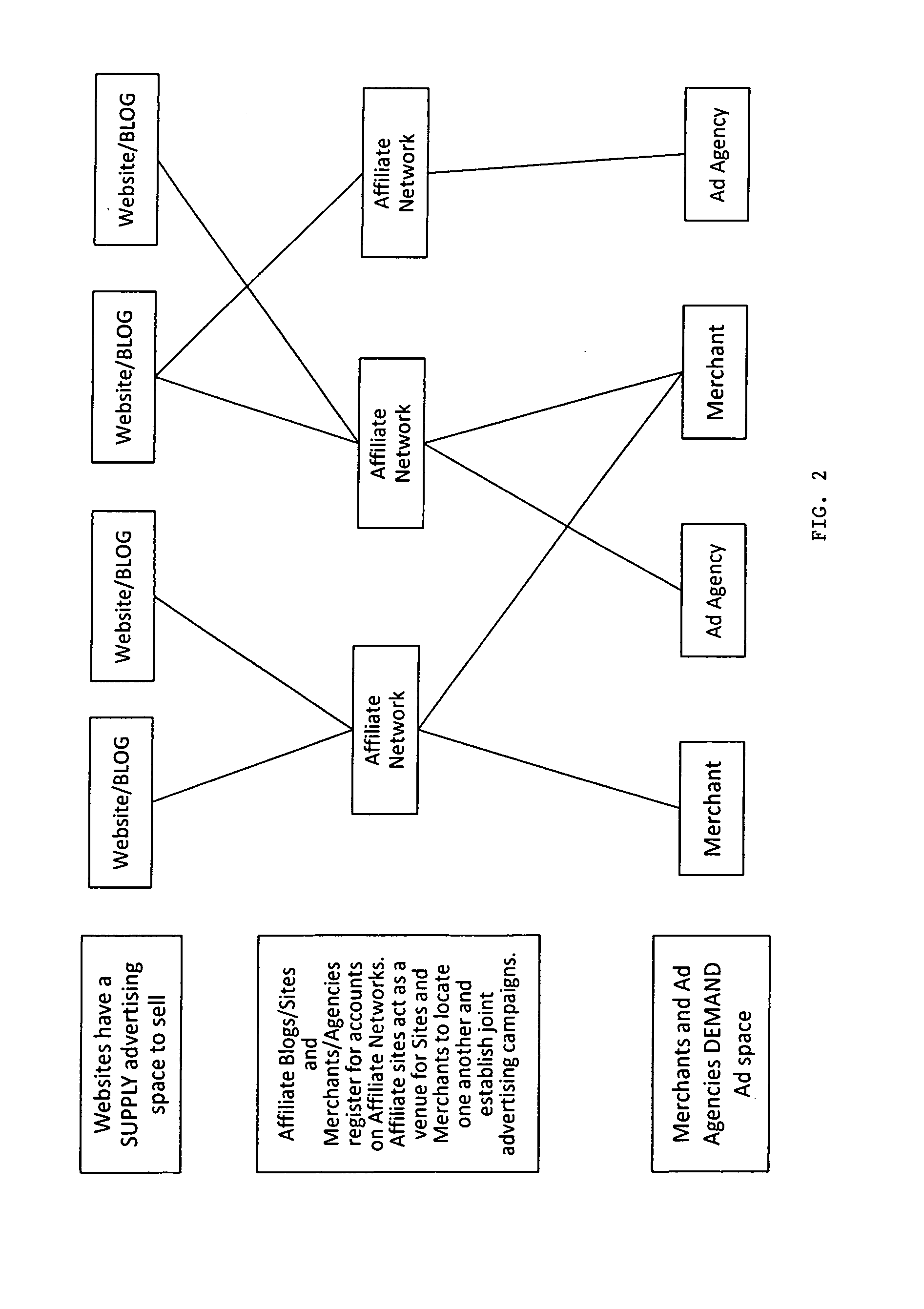
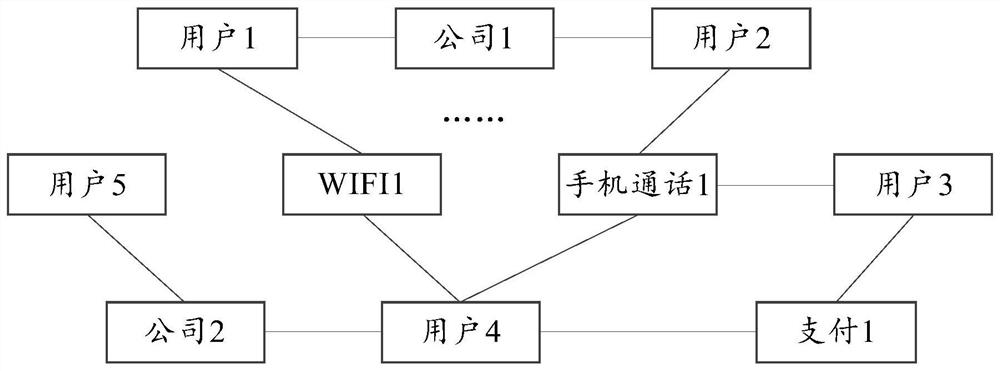
An affiliate network is a group of associated (or affiliated) companies that sometimes offer compatible or complementary products and will often pass leads to each other.
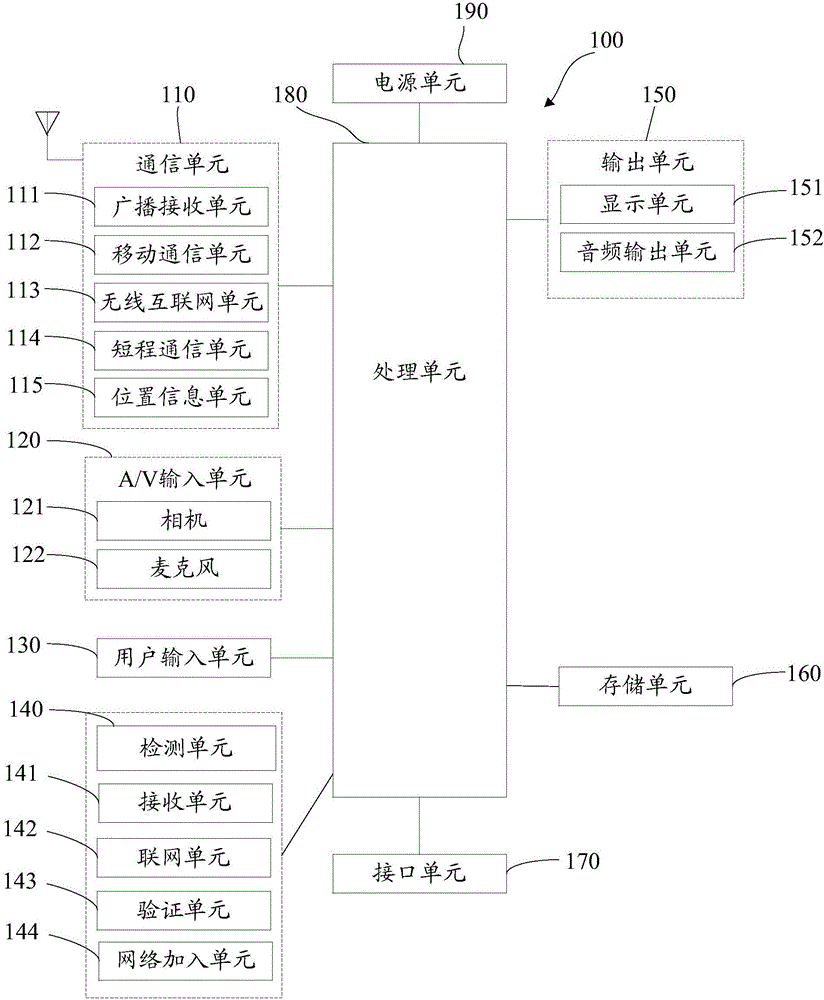
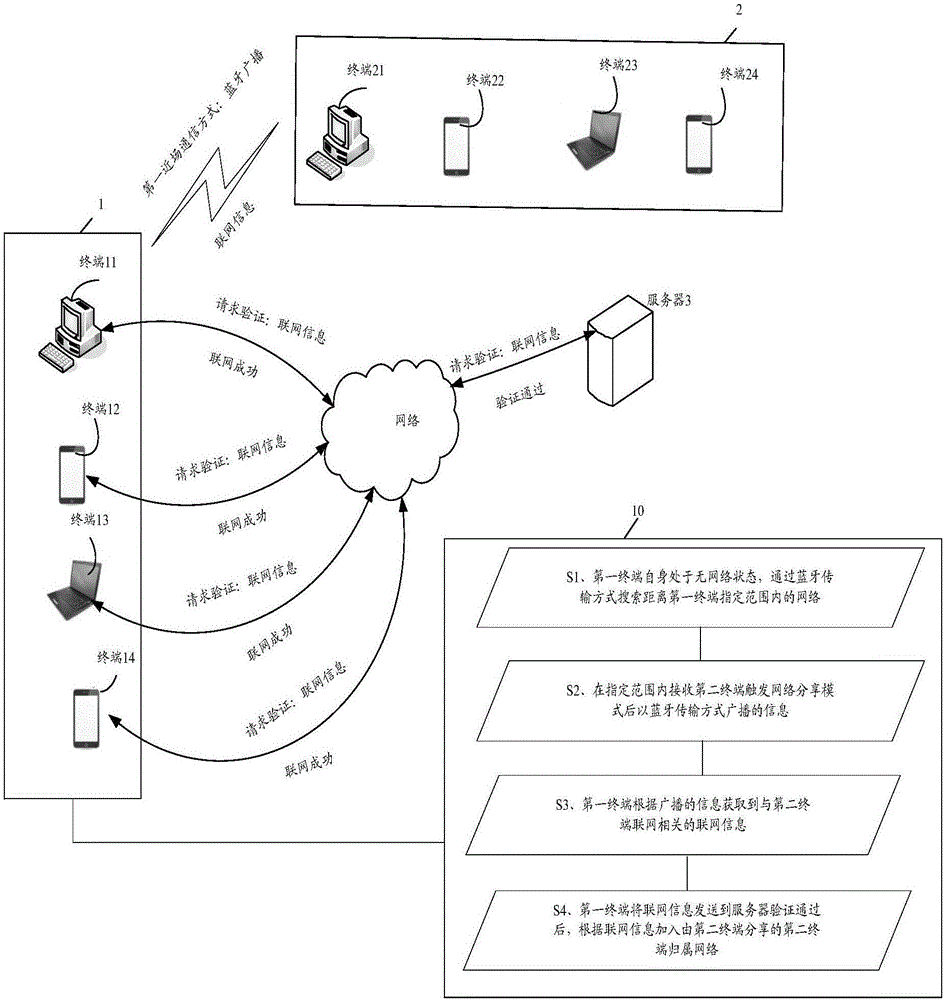
Networking information sharing method, first terminal and system
ActiveCN106817671ASave storage spaceAssess restrictionWireless commuication servicesInformation sharingNetwork connection
The invention discloses a networking information sharing method, a first terminal and a system. The method comprises the steps of detecting the current network connection condition by the first terminal; when the first terminal is in a network-free state, searching networks nearby the first terminal in the first near-field communication manner; receiving a broadcast message broadcasted nearby the first terminal in the first near-field communication manner, wherein the broadcast message is sent in the broadcasting form by a currently and successfully networked second terminal and the second terminal is triggered to be in the network sharing mode; acquiring the networking information related to the networking of the second terminal by the first terminal according to the broadcast message; sending the networking information to a server for verification; after the networking information passes the verification by the server, adding the networking information to the affiliation network of the second terminal shared by the second terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
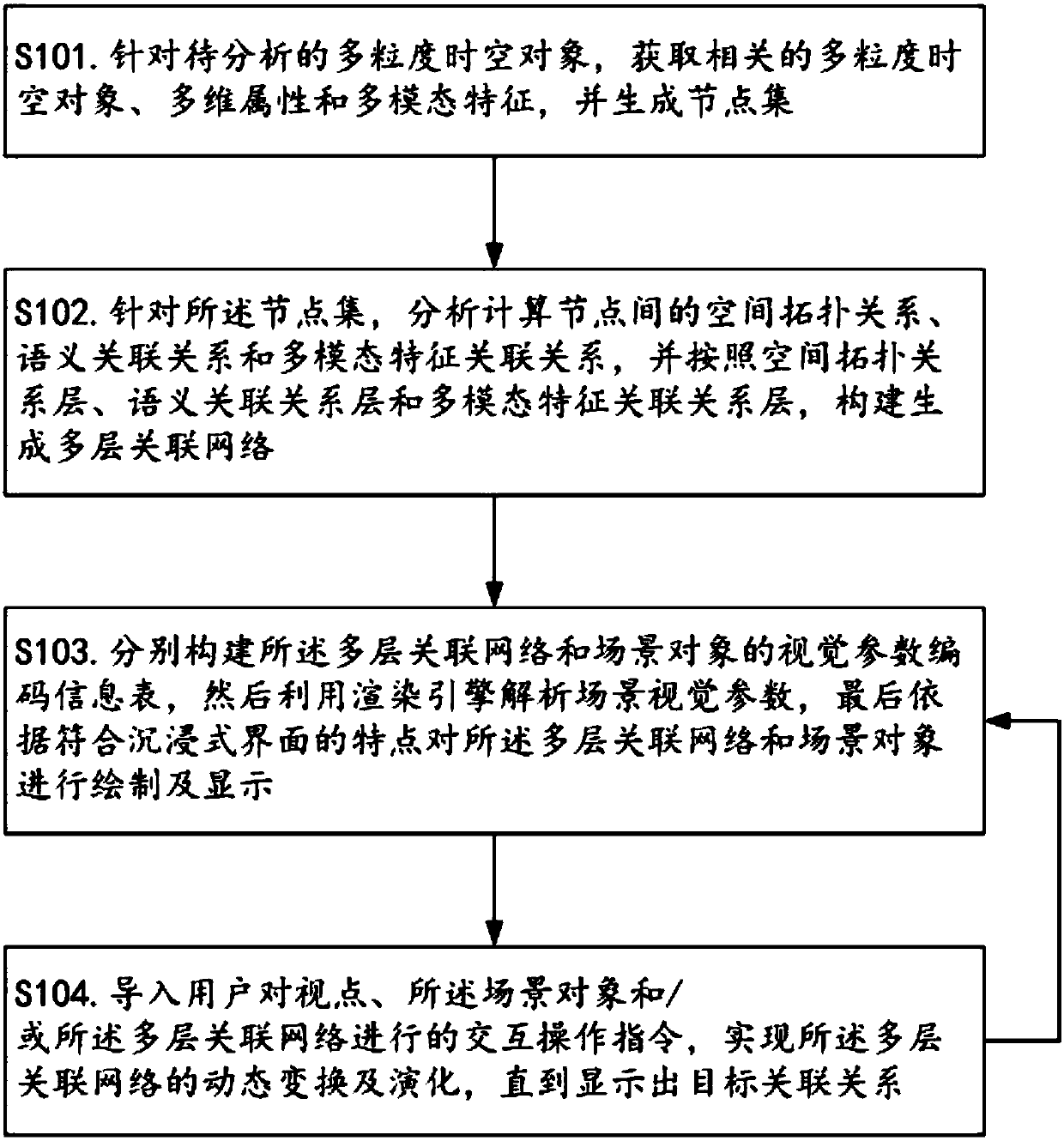
Immersive visual analysis method for spatio-temporal data on the basis of multilayer association network
InactiveCN108052580APromote progressImprove developmentGeographical information databasesOther databases browsing/visualisationNODALSpatial information systems
The invention relates to the technical field of geographic space information systems, and discloses an immersive visual analysis method for spatio-temporal data on the basis of a multilayer association network. The invention has the concept that: firstly, abstracting and extracting an object node related to a task from a scene; then, analyzing and calculating an association relationship among nodes, and carrying out hierarchical division on the association relationship among multi-granularity spatio-temporal objects; according to a spatial topological relationship, a semantic association relationship layer and a multi-modal characteristic association relationship layer, constructing a multilayer association network, and carrying out collaborative visual processing on the constructed multilayer association network and a scene; and finally, through a human-computer interaction operation, realizing a final purpose that inferential reasoning and discovery ability of a human brain can be combined and a potential and complex association relationship is assisted in discovery. Therefore, the method is favorable for people to quickly discover a new knowledge rule, and the progress and the development of human scientific knowledge are accelerated.
Owner:SOUTHWEST JIAOTONG UNIV +1
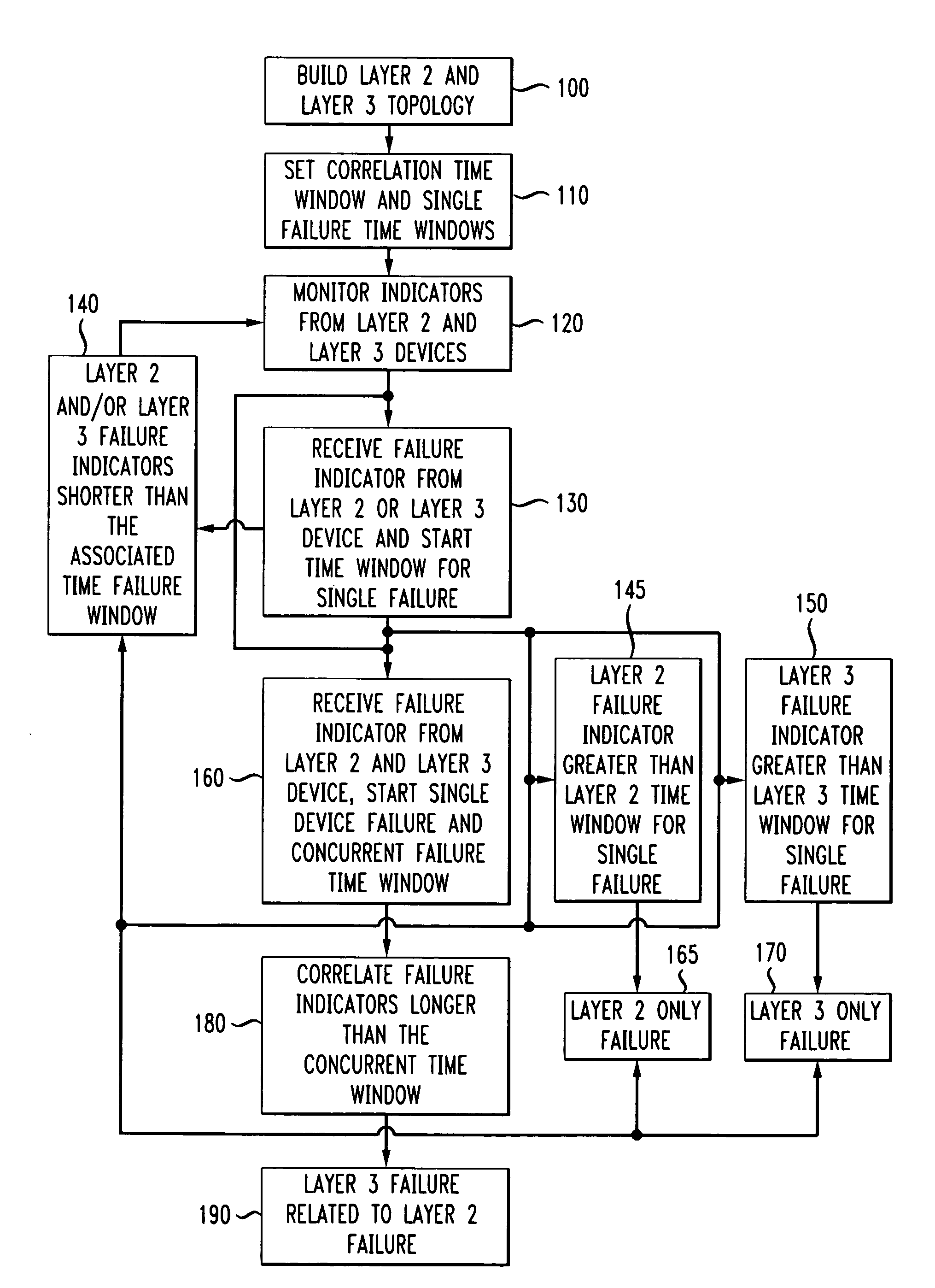
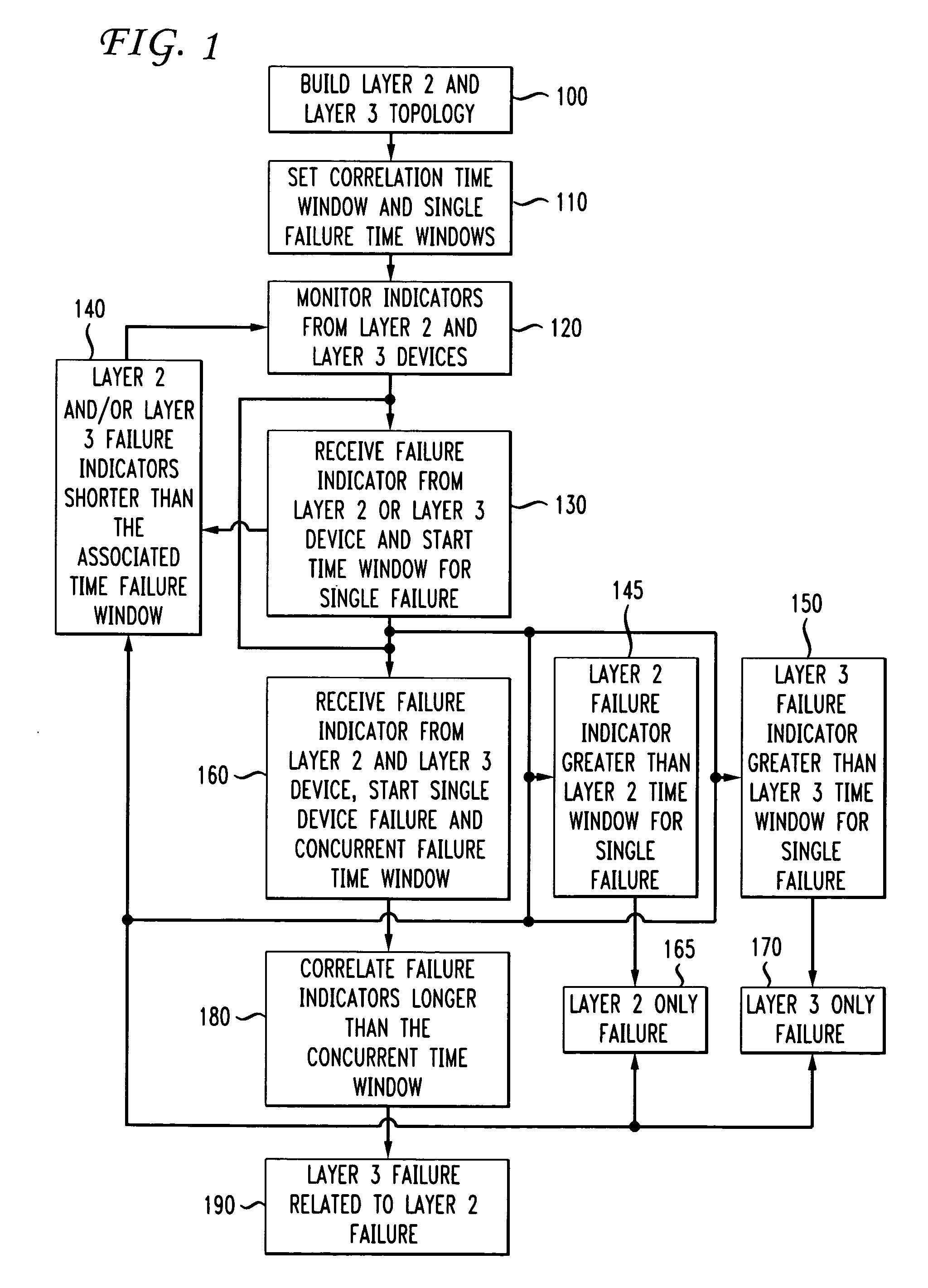
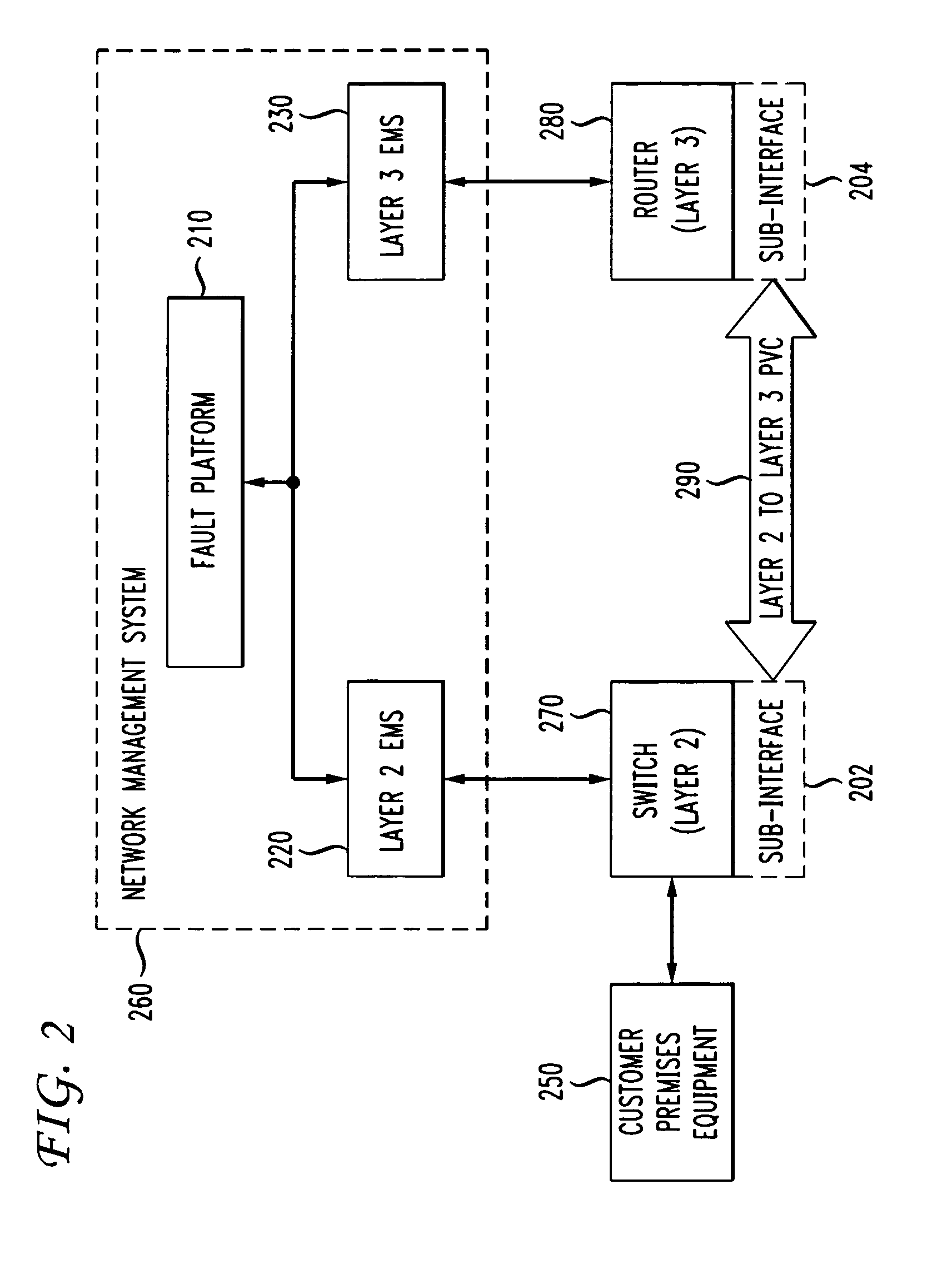
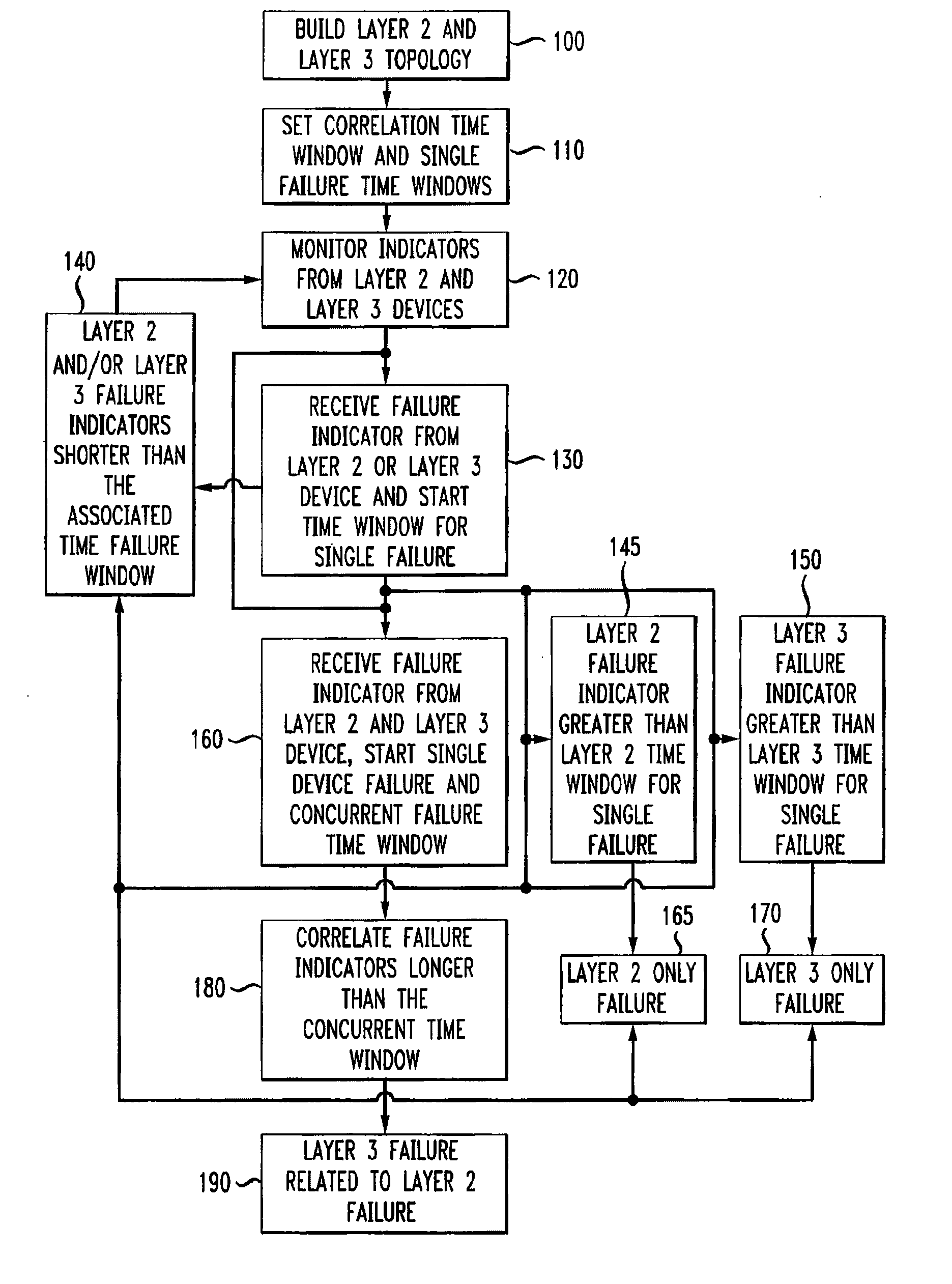
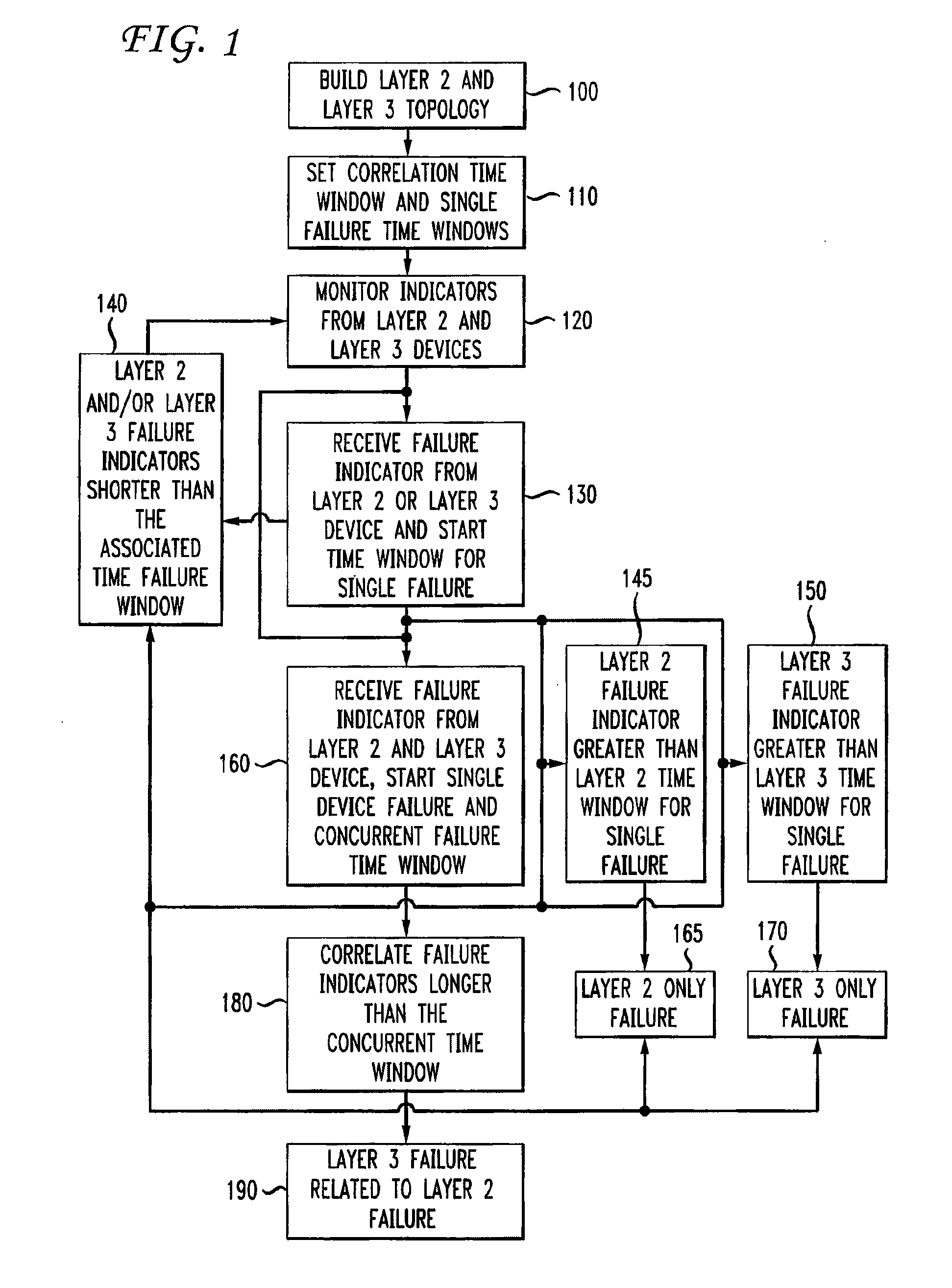
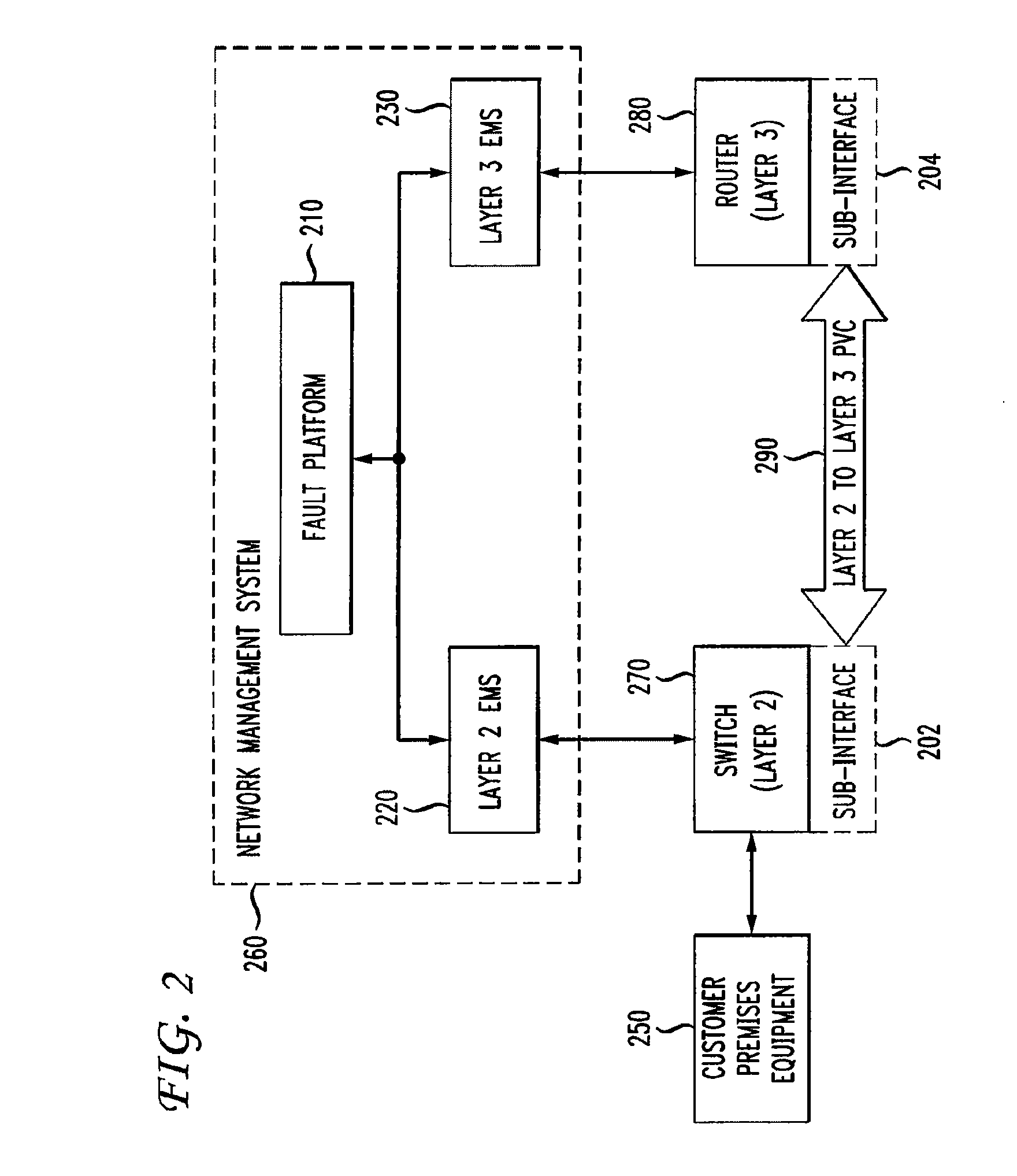
Automatic problem isolation for multi-layer network failures
ActiveUS7570580B1Valuable processing timeEliminate needError preventionTransmission systemsFault indicatorOpen Systems Interconnection
A method and apparatus includes automatically correlating indicators already generated by network components to detect and isolate failures that are caused by or related to network components operating on different layers of the open system interconnect (OSI) model. Failure indicators that persist for longer than a specified time window are automatically detected and correlated with one another based on a topology table. The method uses indicators already generated by the network components, obviating the need for software that typically resides on and consumes valuable processing time of network components.
Owner:ATLASSIAN US INC
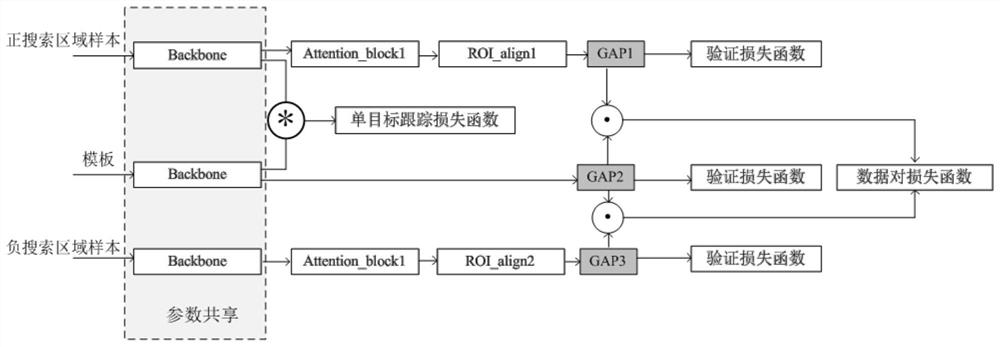
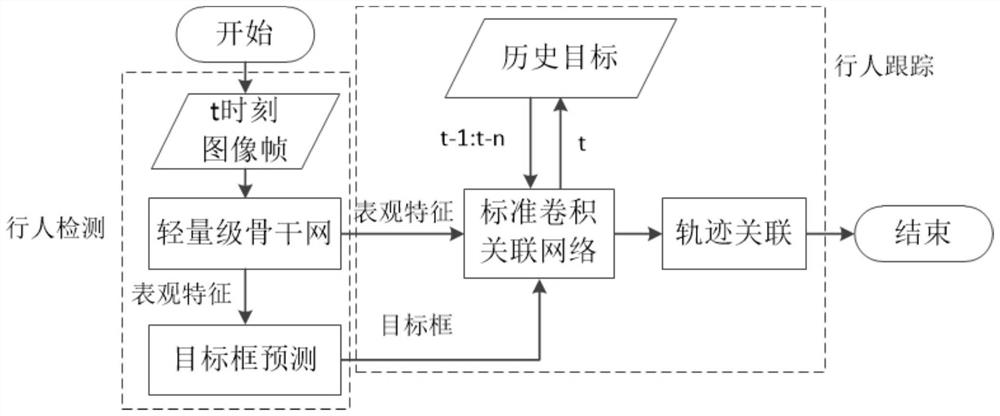
Pedestrian multi-target tracking method combining attention mechanism end-to-end training
PendingCN112560656AEnhance feature expressionImprove computing efficiencyImage analysisCharacter and pattern recognitionData setAlgorithm
The invention discloses a pedestrian multi-target tracking method combining attention mechanism end-to-end training, and the method comprises the steps of collecting a pedestrian data set of a video sequence with a label, employing a first frame real boundary frame of each video in the label as a template sample, cutting a positive search region sample in a second frame according to the center ofthe sample, and cutting out a negative search area sample in an area which is not the same kind of target; forming triple data input; extracting feature information of the sample by using a convolutional neural network; using an attention mechanism module for guiding the network model to tend to important feature information, and finally calculating similarity and data association. According to the invention, single-target tracking based on the twin network and the association network are integrated into a unified network structure, and the attention mechanism is combined to serve as meaningful feature information for network bias learning, so that the feature expression capability of a network model is improved, the calculation efficiency is improved, and the training process is simplified.
Owner:成都东方天呈智能科技有限公司
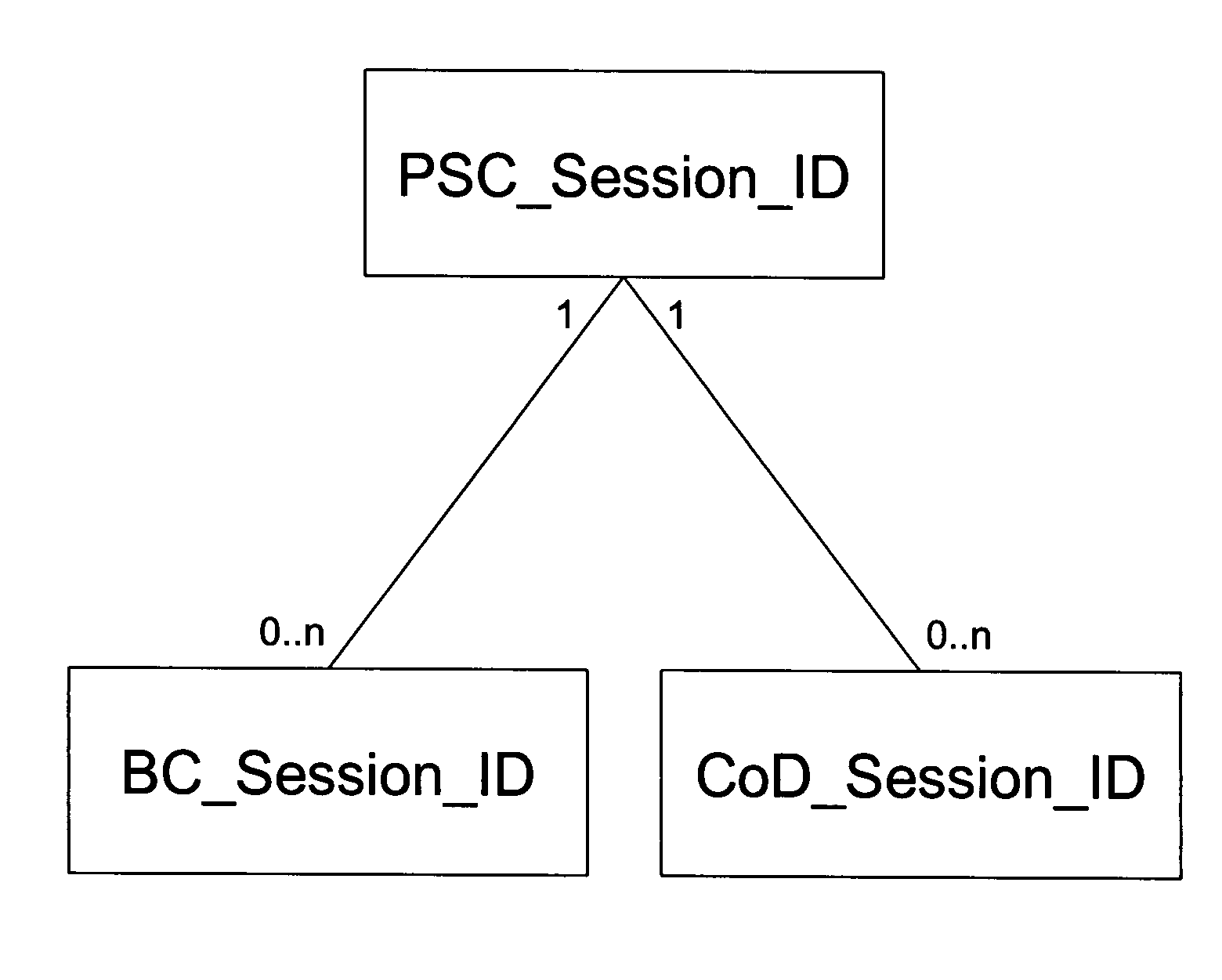
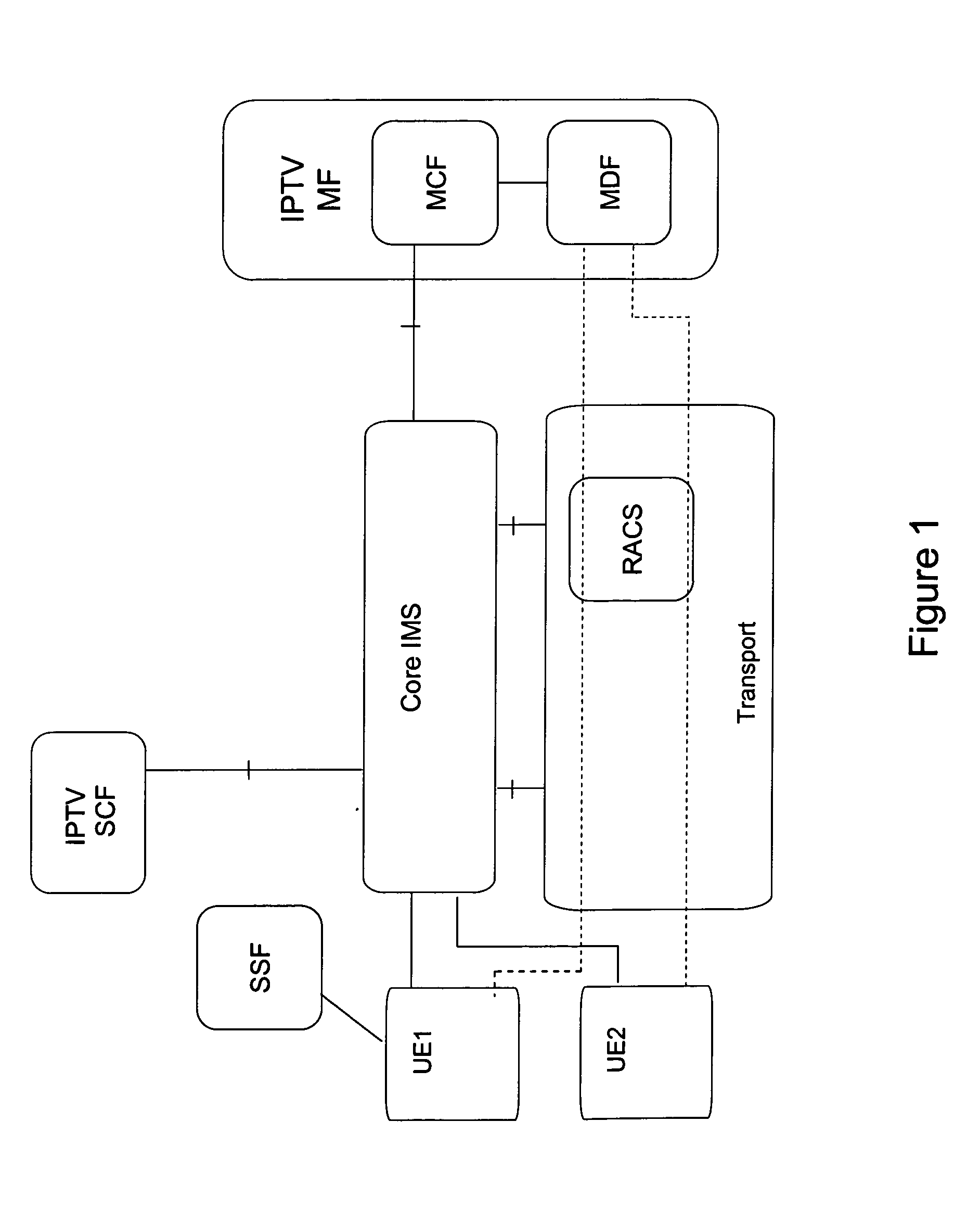
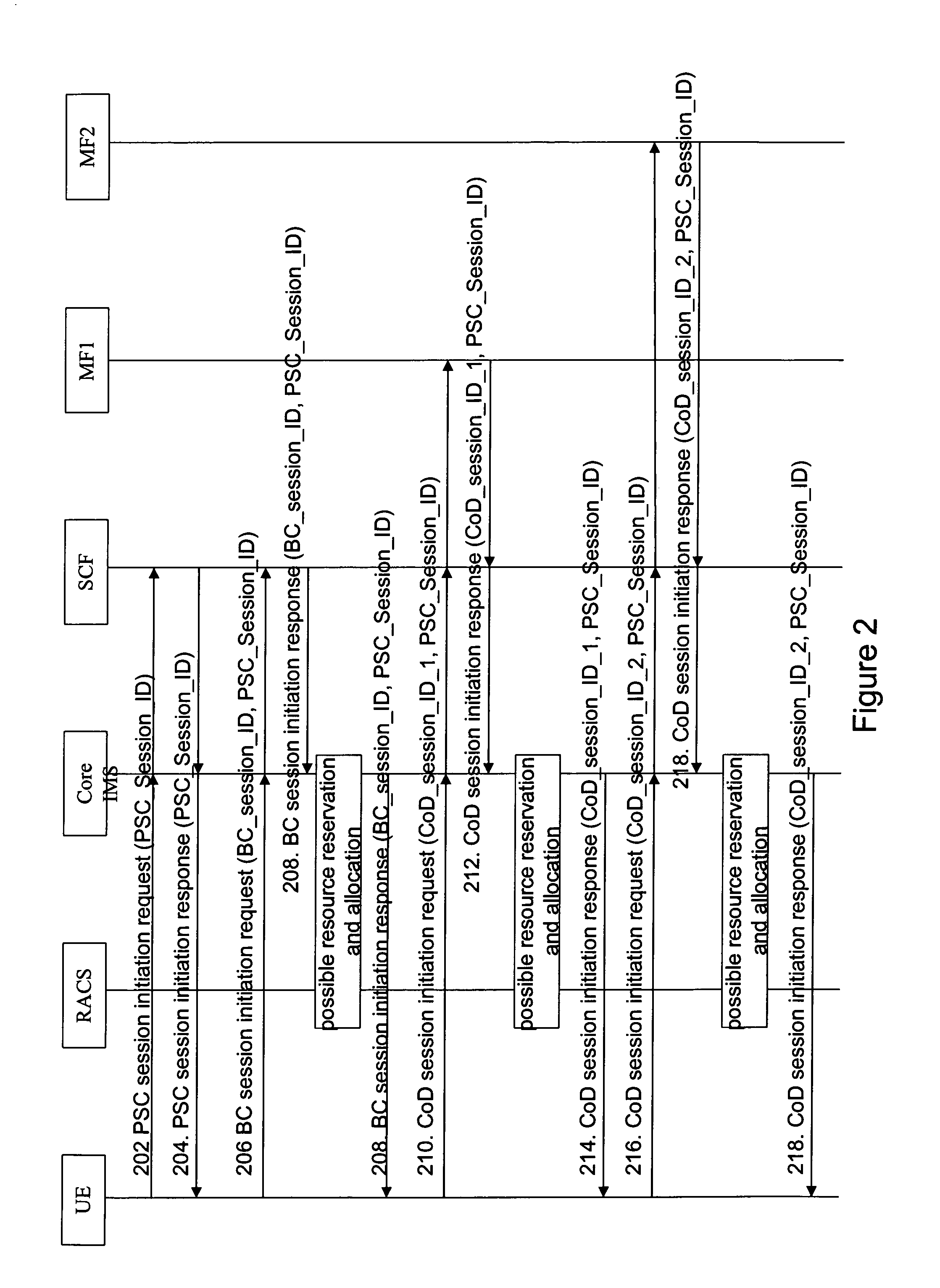
Managing Associated Sessions in a Network
ActiveUS20110276705A1EnhancedEasy to useMultiple digital computer combinationsTransmissionNetwork elementUser equipment
A method and a system for managing associated sessions in a network is described, wherein the network comprises a network element configured for managing associated sessions between the network and user equipment. The method comprises the steps of providing a composition session identifier for associating sessions in a network; exchanging the composition session identifier between a user equipment and the network element; and associating two or more sessions with the composition session identifier by exchanging the composition session identifier.
Owner:KONINK KPN NV
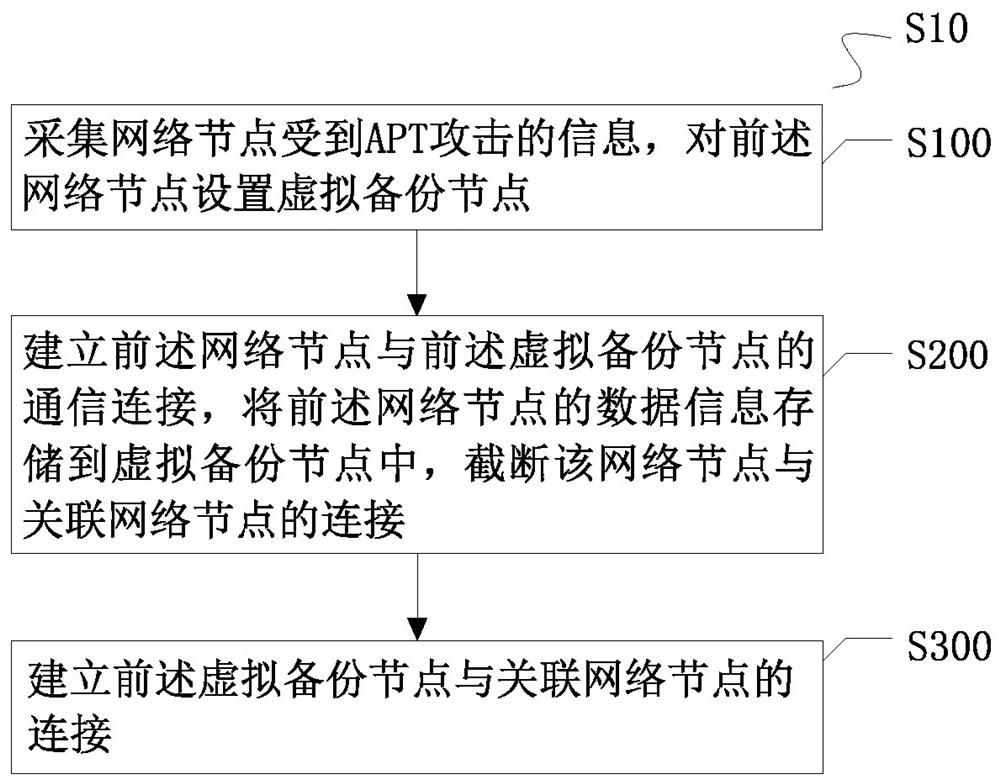
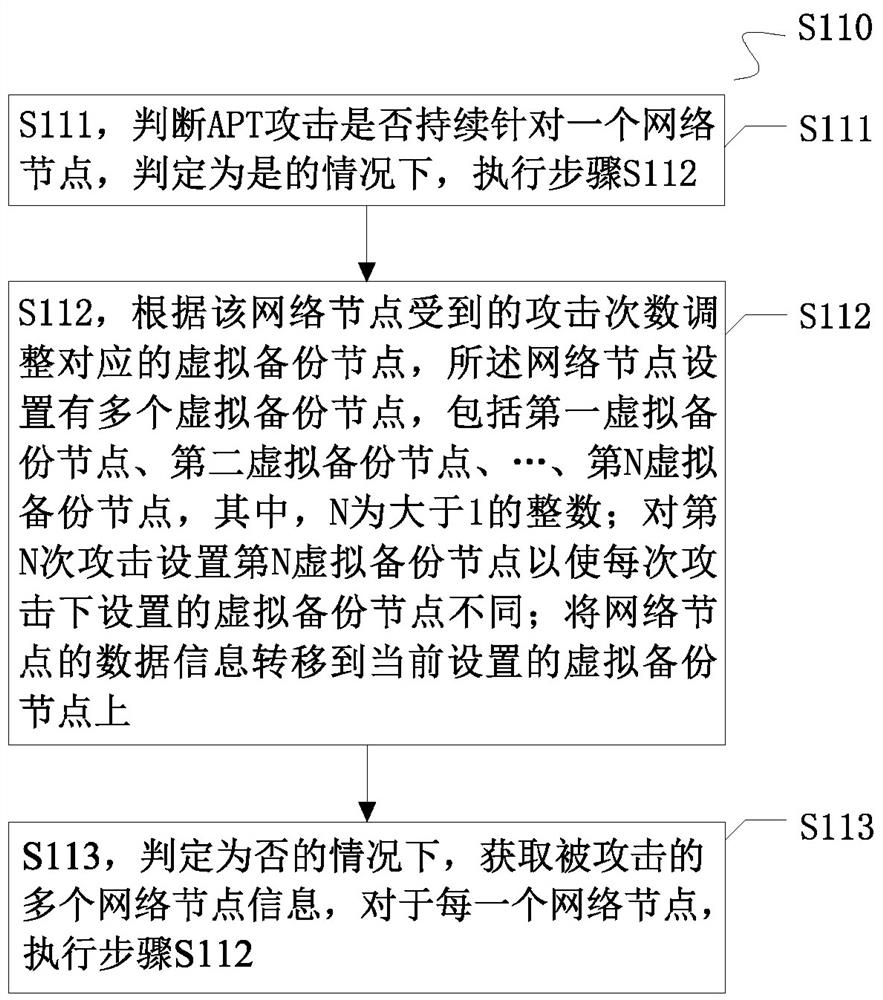
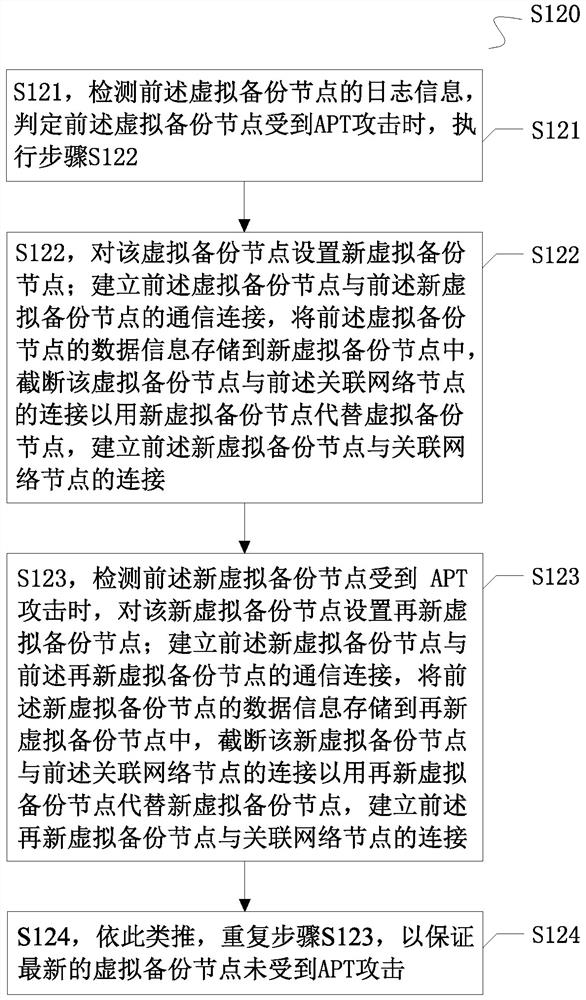
Situation awareness node defense method and system aiming at APT attack
ActiveCN113329029AChange the storage path in real timeImplement reverse traceabilityTransmissionPathPingInternet privacy
The invention provides a situation awareness node defense method and system for APT attacks, and relates to the technical field of network security. The node defense method comprises the following steps: collecting information that a network node is attacked by APT, and setting a virtual backup node for the network node; establishing a communication connection between the network node and the virtual backup node, storing the data information of the network node into the virtual backup node, and cutting off the connection between the network node and the associated network node; and establishing a connection between the virtual backup node and the associated network node. According to the method, the storage path of the data information is changed in real time based on the attack mode information in the network, so that an attacker is difficult to find the storage address of the data information to attack, and situation awareness system node defense is realized on the basis of ensuring normal communication of the whole network.
Owner:SHANGHAI NEWDON TECH CO LTD
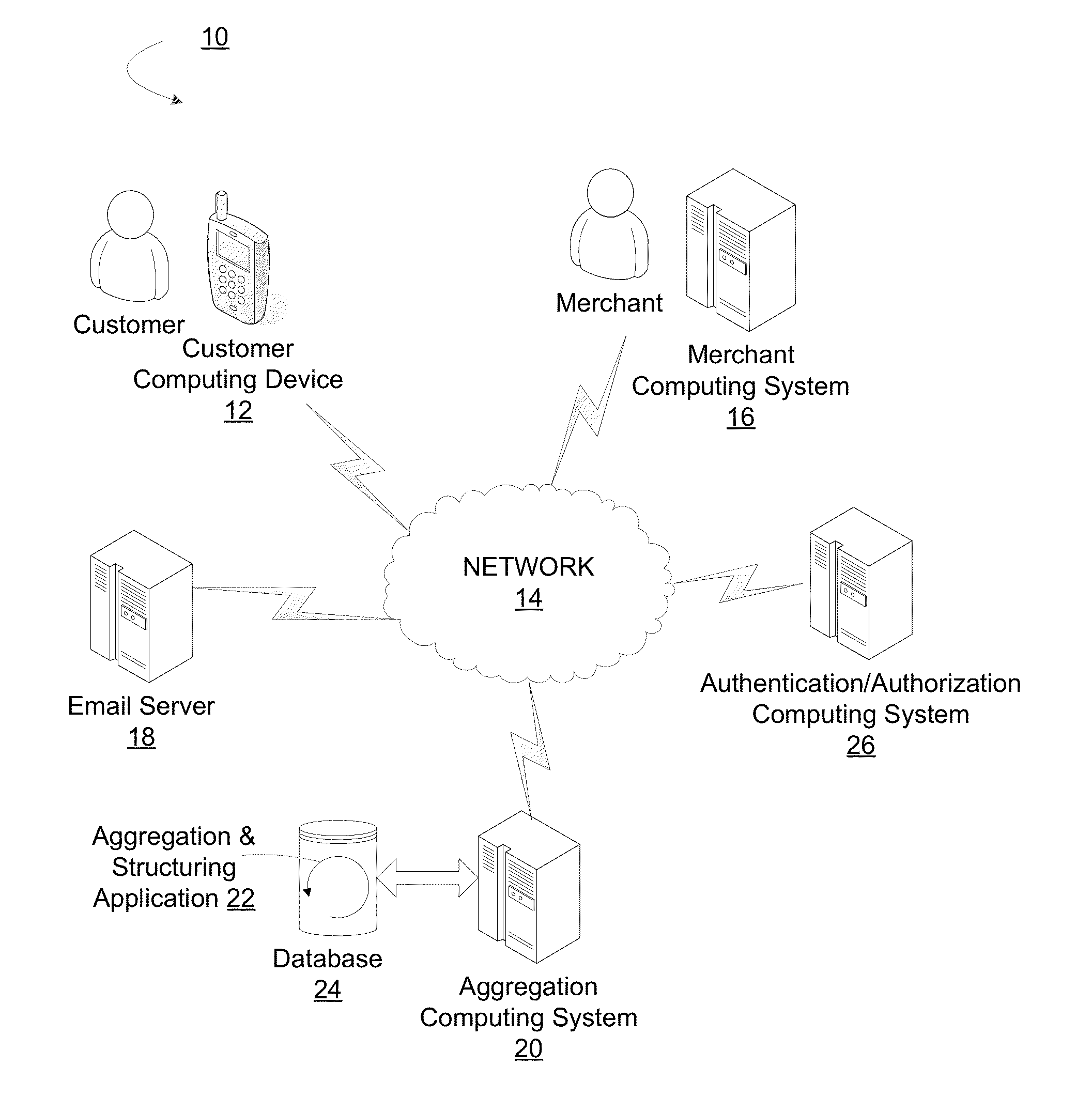
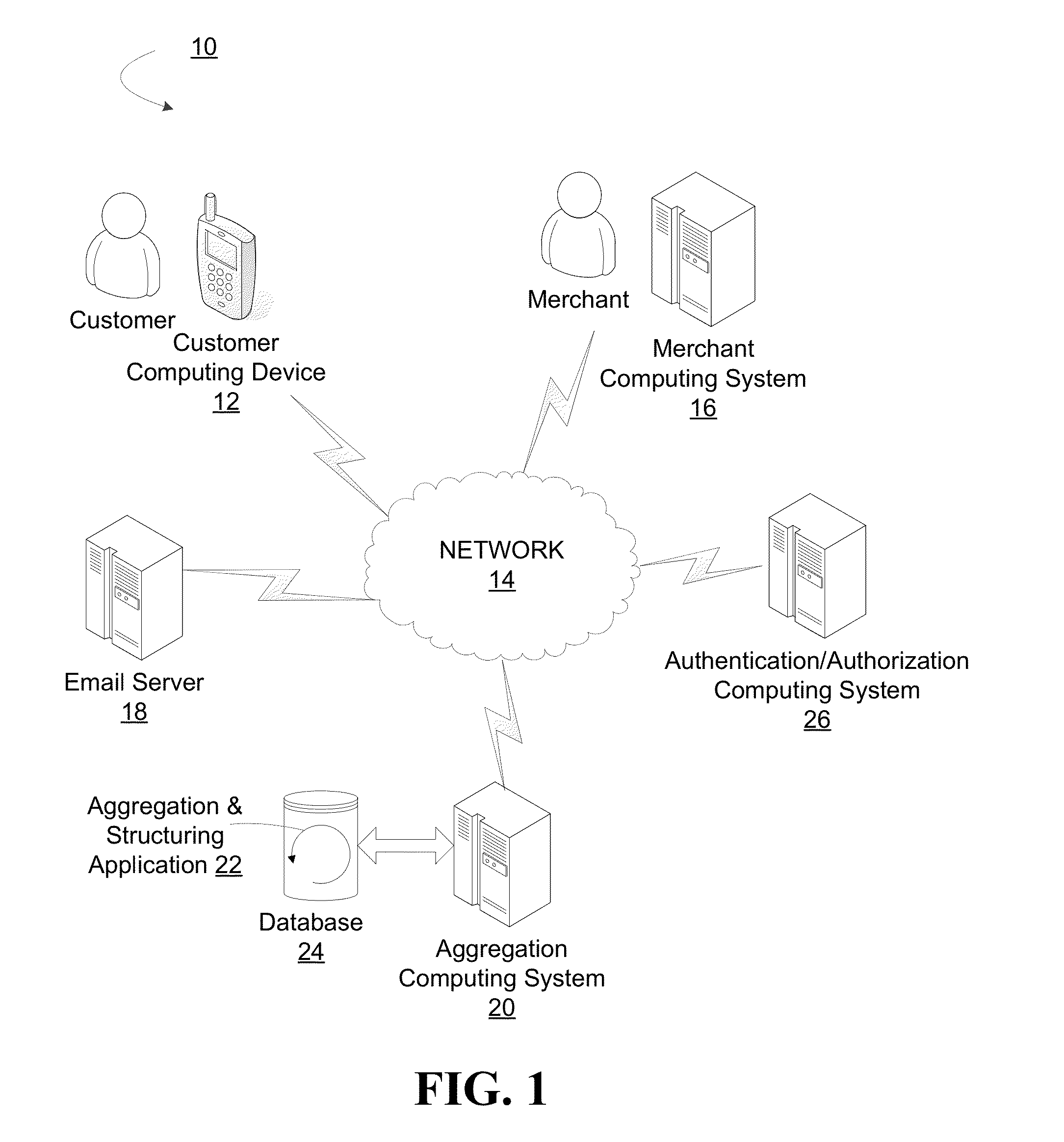
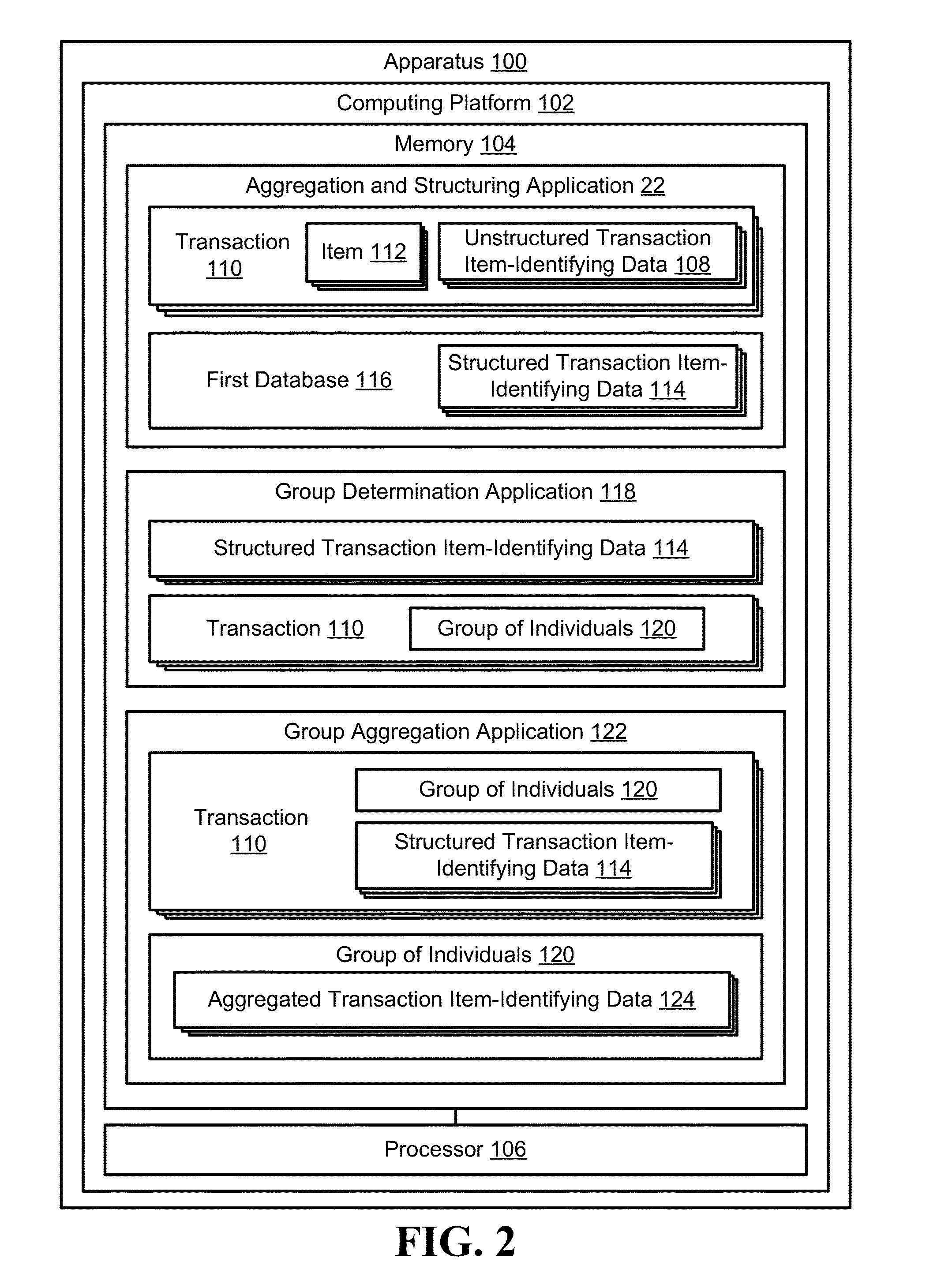
Aggregation of item-level transaction data for a group of individuals
Apparatus, methods, and computer program products are provided for that automatically identify transactions and / or items in a transaction that are associated with a group of individuals, such as a family, co-workers, a special interest group, a demographic group a social network group or the like. Once transactions and / or items in the transaction have been identified as being associated with the group, the transaction data associated with the transactions and / or the items in the transactions is aggregated and aggregated views of the data are made accessible to individuals in the group, such as through a financial institution financial management application, e.g., online or mobile banking application.
Owner:BANK OF AMERICA CORP
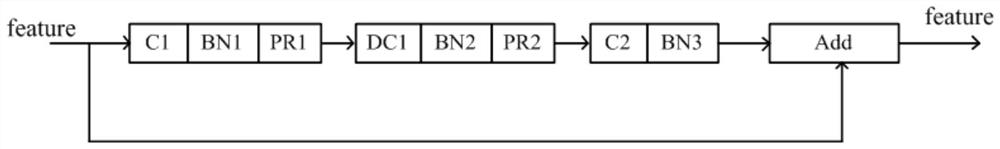
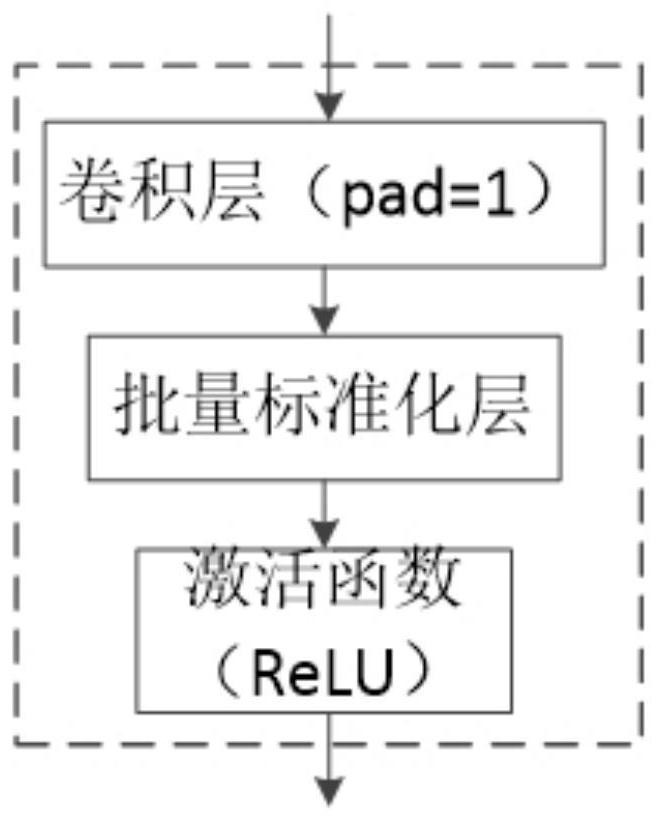
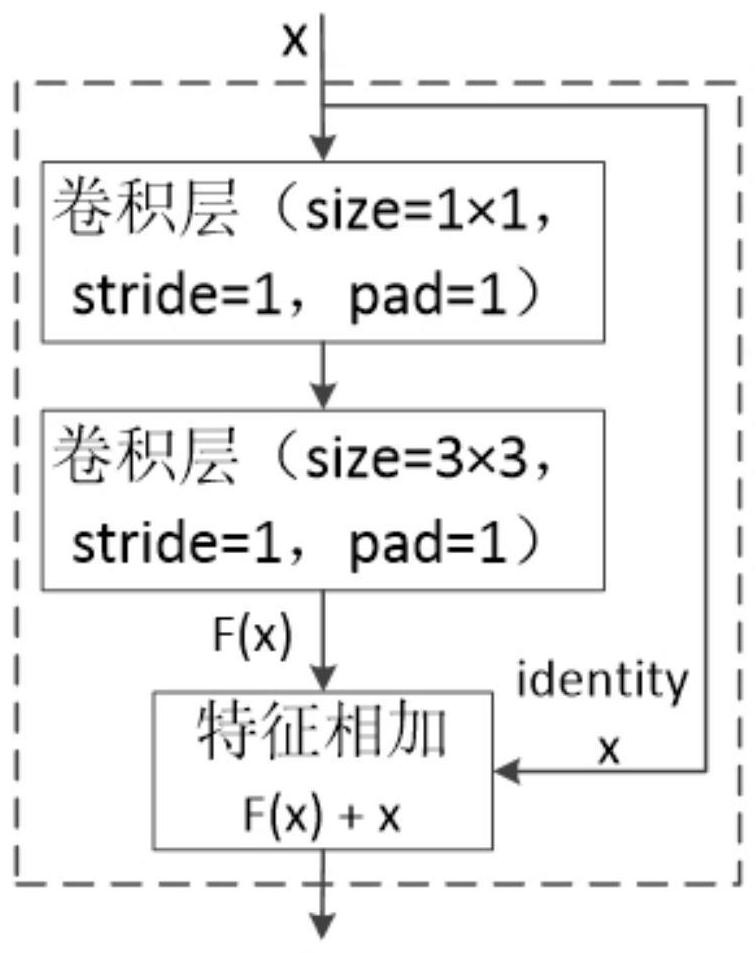
Pedestrian target tracking method based on convolution association network in automatic driving scene
ActiveCN111652903AMeet real-time requirementsReduce feature redundancy calculationsImage enhancementImage analysisPattern recognitionEngineering
The invention relates to a pedestrian target tracking method based on a convolutional association network in an automatic driving scene. Characteristics are shared by using a convolution association network and a lightweight target detection network, the relevance between the targets is captured, and then target tracking is achieved. The method specifically comprises the following steps: A1-1, obtaining a one-stage target detection model, performing down-sampling for five times in total; performing prediction on the feature maps of the last three scales; adopting a common convolution module except during first downsampling, replacing adopted models designed in a multi-scale downsampling module during subsequent four downsampling with separable convolution modules, performing target frame prediction on the models on a feature map of the last three downsampling, and finally forming a lightweight pedestrian target detection network is formed; A2-1, predicting a target incidence matrix toobtain a target incidence matrix; and A3-1, designing a pedestrian target tracking strategy through a convolutional association network, and finally obtaining a pedestrian associated target tracking result. The method can well adapt to an automatic driving scene in the aspects of tracking precision and speed.
Owner:CHONGQING UNIV OF TECH
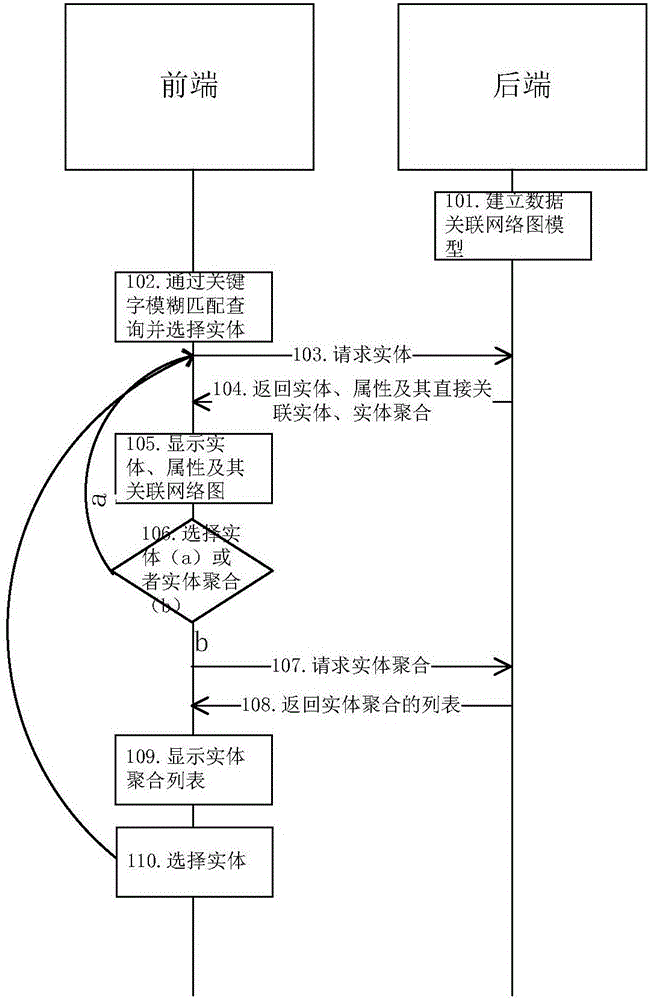
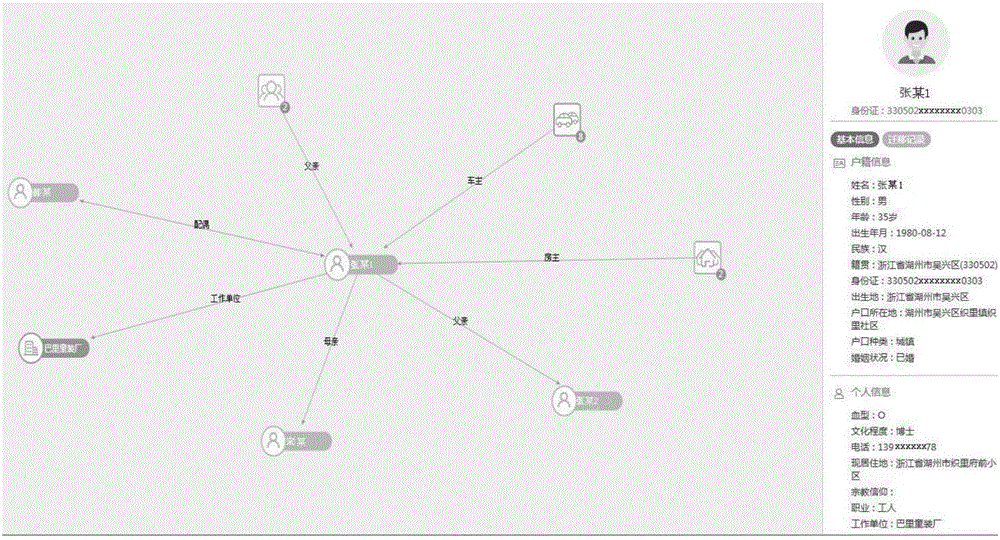
Representing method and system capable of dynamically expanding data associated network diagram
InactiveCN105824883AImprove visual effectsDrawing from basic elementsOther databases browsing/visualisationData feedDecision system
The invention relates to the field of data associated processing and data visualization, in particular to a representing method and system capable of dynamically expanding a data associated network diagram. The representing method comprises the following steps: establishing a data associated network model through the back end so as to respond to a request from the front end and return a result; according to a user's operation, generating an operating command and requesting the back end for data through the front end, and further drawing and updating the data associated network diagram according to the data associated network model after receiving data fed back by the back end, wherein the data associated network can be continuously and dynamically expanded under the operation of the user. According to the representing method and system capable of dynamically expanding the data associated network diagram, provided by the invention, an entity relationship network with infinitely many elements can be supported, and entities of different types, relationships and entity aggregations can be expanded; the representing method and system can further intuitively and friendly represent complex data associated diagrams, bring great convenience to data analysis personnel for work and can be applicable to a data analysis and assistance decision making system.
Owner:CETHIK GRP
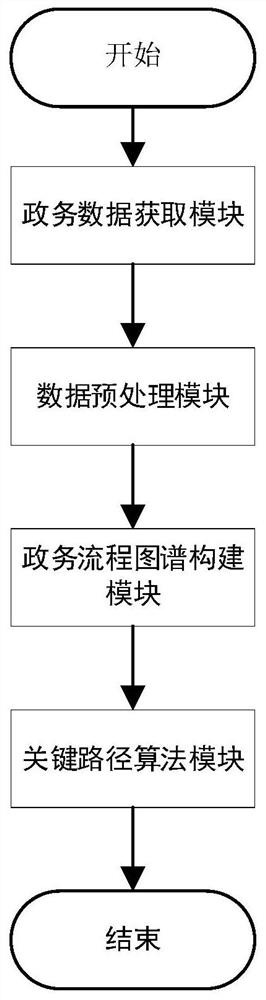
Key government affair process identification method and device based on item association network
ActiveCN111694963ASimplified government proceduresImprove work efficiencyOffice automationOther databases queryingProcess identificationProcess map
The invention provides a key government affair process identification method and device based on an item association network. The method comprises the following steps: 1) acquiring government affair data; 2) data preprocessing; 3) building a government affair process map; and 4) calculating a key path. In addition, the invention provides a set of system device for realizing the method. A large amount of government affair process data is effectively managed by constructing the government affair process map, the workload of manually carding government affair processes is reduced, a key handlingpath is obtained based on the map, a quick handling process is recommended to a handler, the handling time is shortened, and therefore the handling efficiency of the whole government affair departmentis indirectly improved. And a theoretical basis is provided for collaborative optimization among government departments and realization of integration and optimization of business handling links.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +2
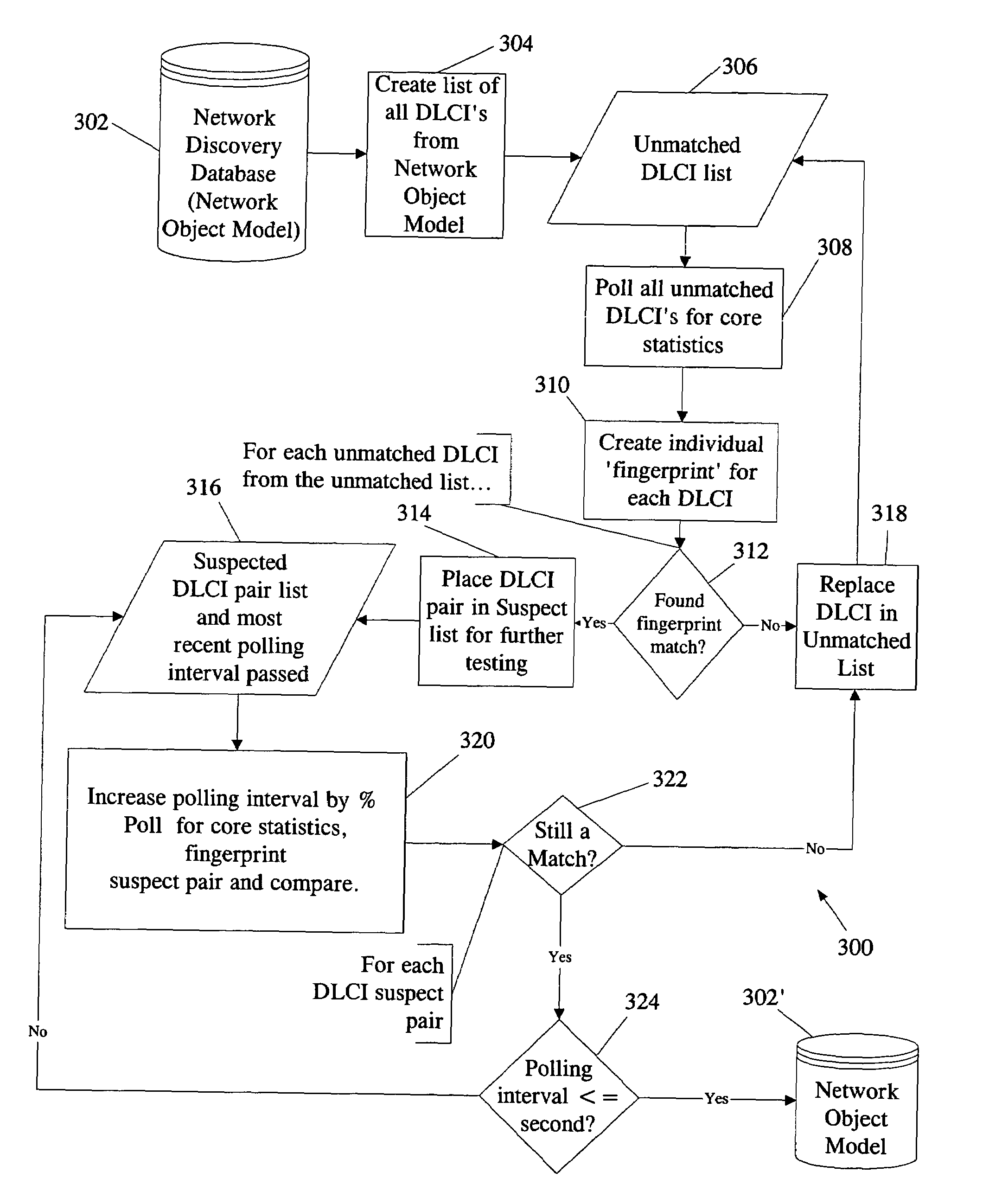
Method and apparatus for network analysis, such as analyzing and correlating identifiers of frame relay circuits in a network
InactiveUS7126964B1Reduce possibilityReduce time intervalError preventionFrequency-division multiplex detailsWeb environmentTelenet
A system, method or facility allow a user to analyze a telecommunications network having virtual private network segments, such as frame relay circuits, where standard network analysis tools fail to identify such circuits. The facility receives identifiers or addresses for such circuits and gathers statistical data with respect thereto. Based on such statistical data, the facility matches end points of the circuits with corresponding starting points. Thus, a network designer or manager may use standard and less expensive hardware in networks employing frame relay circuits, and other virtual private network segments, by employing the facility to fully document and verify the overall configuration of the network environment, without prior knowledge of the network's makeup.
Owner:MICROSOFT TECH LICENSING LLC
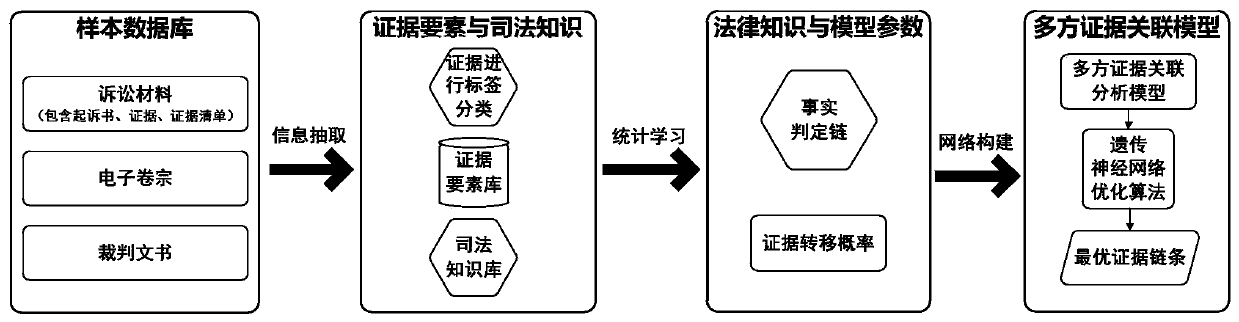
Multi-party evidence association model construction method based on Bayesian network and evidence chain extraction method and device
ActiveCN110674840AImprove the speed of association analysisHigh precisionCharacter and pattern recognitionGenetic algorithmsThird partyAssociation model
The invention provides a multi-party evidence association model construction method based on a Bayesian network and an evidence chain extraction method and device. The method comprises evidence network construction based on a fact judgment chain, evidence weight calculation and an evidence chain reasoning method based on a Bayesian network. Evidence sources are divided into original evidences, informed evidences, judicial expertise evidences, third-party evidences and the like. Firstly, a multi-party evidence association network is constructed, each evidence entity serves as a node in the network, and the correlation probability between the nodes in the network is calculated based on the association relationship between the evidence elements; then, based on the evidence type of the event judgment chain, a multi-party evidence association model based on the Bayesian network is constructed; and finally, the Bayesian network is optimized by adopting a genetic algorithm to obtain a credible evidence chain. According to the method, the evidence chain with the maximum credibility can be found from multiple sources, and judicial personnel are helped to screen the credible evidence chain from multi-party certification or contradictory evidences.
Owner:中国司法大数据研究院有限公司
Internet affiliate network marketing system and method with associated computer program
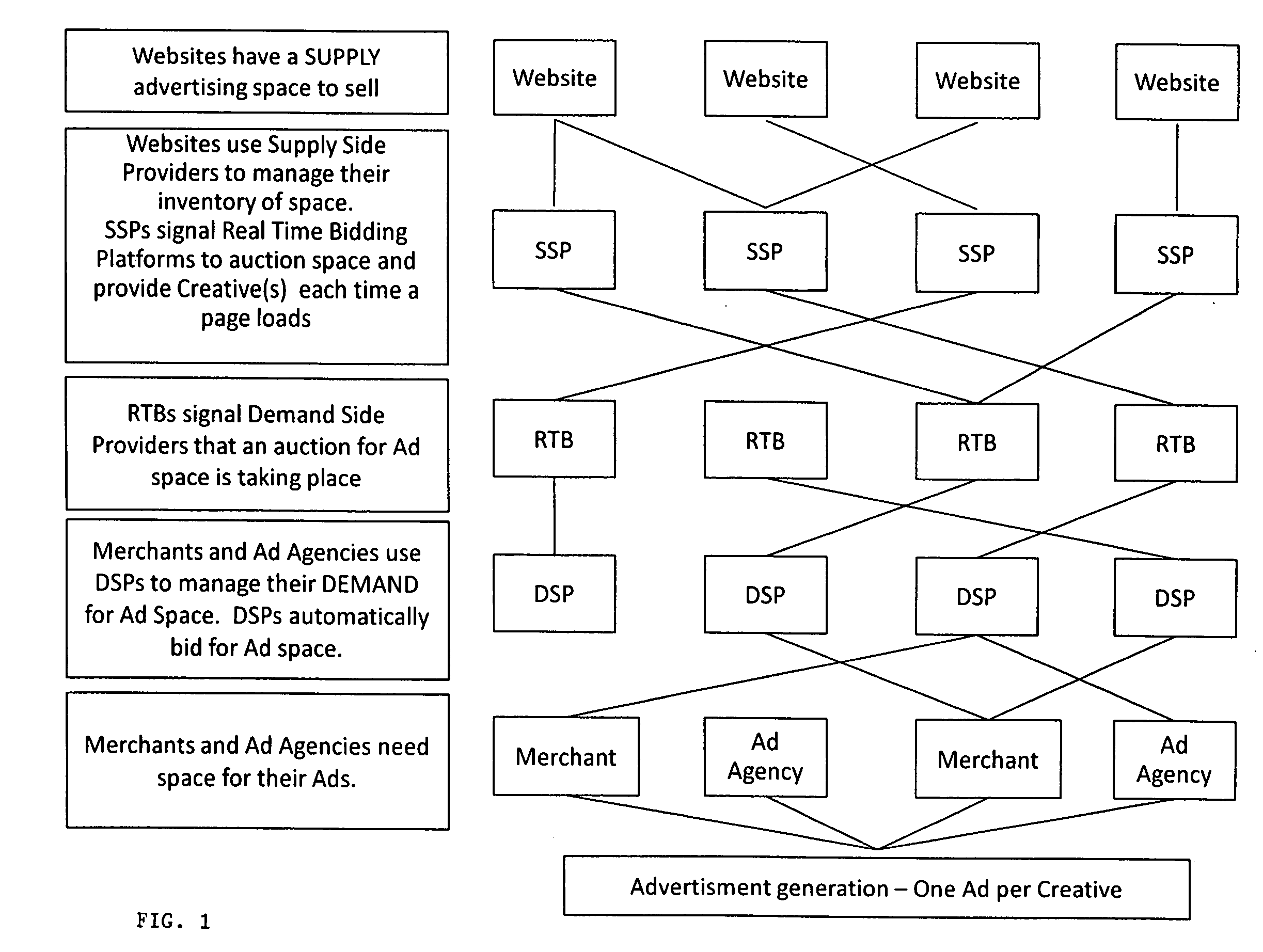
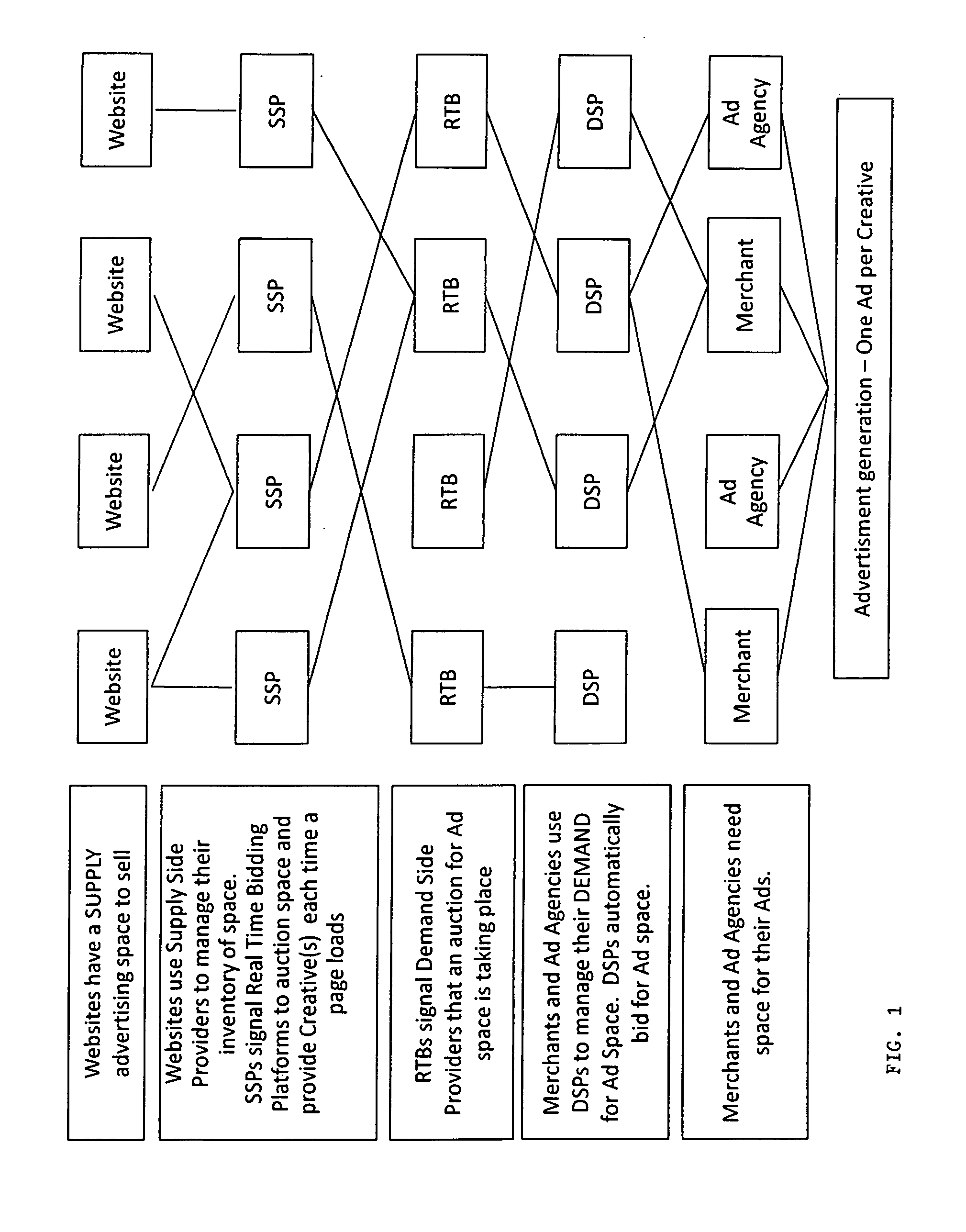
An Internet affiliate marketing method and associated computer program whereby a next generation affiliate network acts as an exchange for advertisers and merchants on one side and affiliates and next generation affiliates on the other. Affiliates and next generation affiliates sell content advertising in creatives to advertisers and merchants. Parties use this network to find each other, evaluate each other, and establish a purchase or advertising agreement using rewards. Creatives, using traditional advertising, familiar creative advertising, and combination advertising, are transmitted to the network website which posts them on selected social media sites. Parties accessing these sites are exposed to advertisers' and merchants' products appearing on creatives found therein. The network interfaces with enhanced capability supply-side platforms, real-time bidding platforms, and demand-side platforms that accommodate the new advertising concepts, familiar creative advertising and combination advertising.
Owner:SCALISE PETER
Automatic problem isolation for multi-layer network failures
ActiveUS20090290498A1Valuable processing timeEliminate needError preventionTransmission systemsOpen Systems InterconnectionEmbedded system
Owner:ATLASSIAN US INC
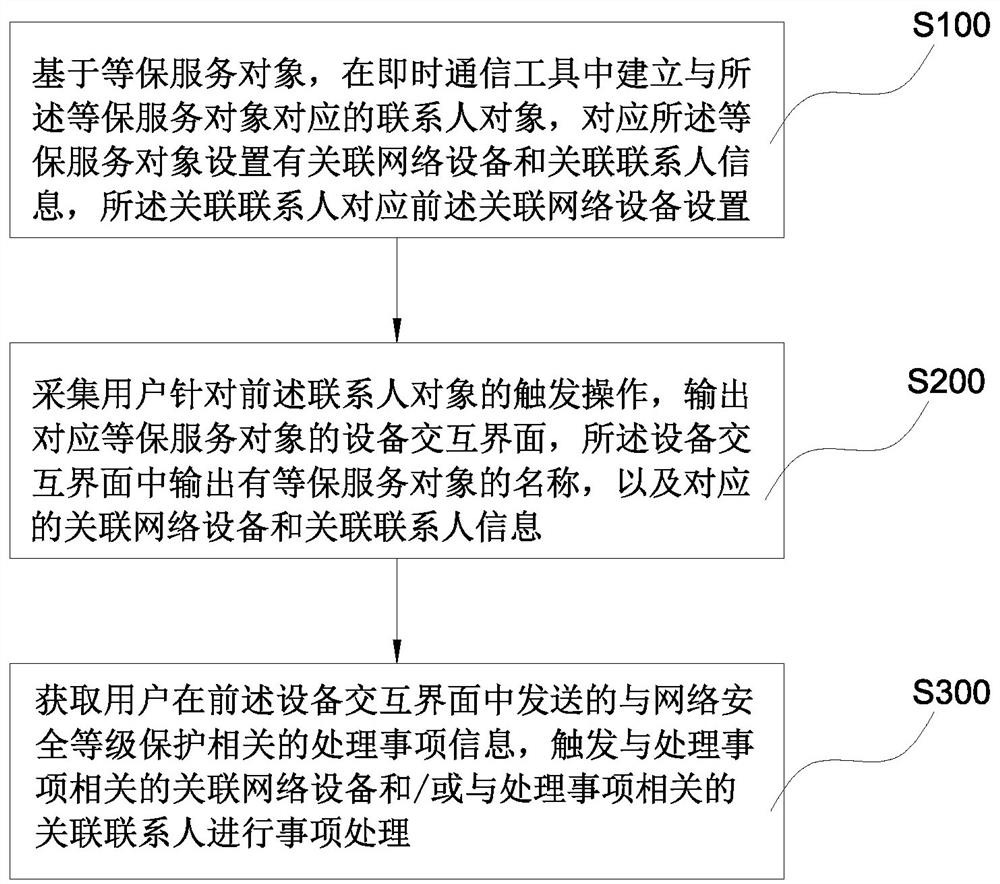
Intelligent information processing method and device in network security level protection
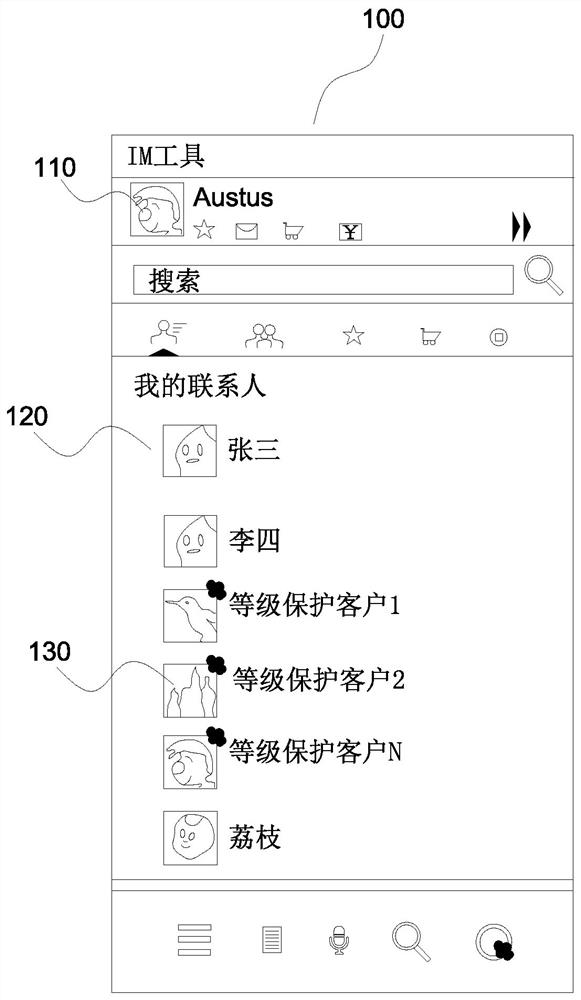
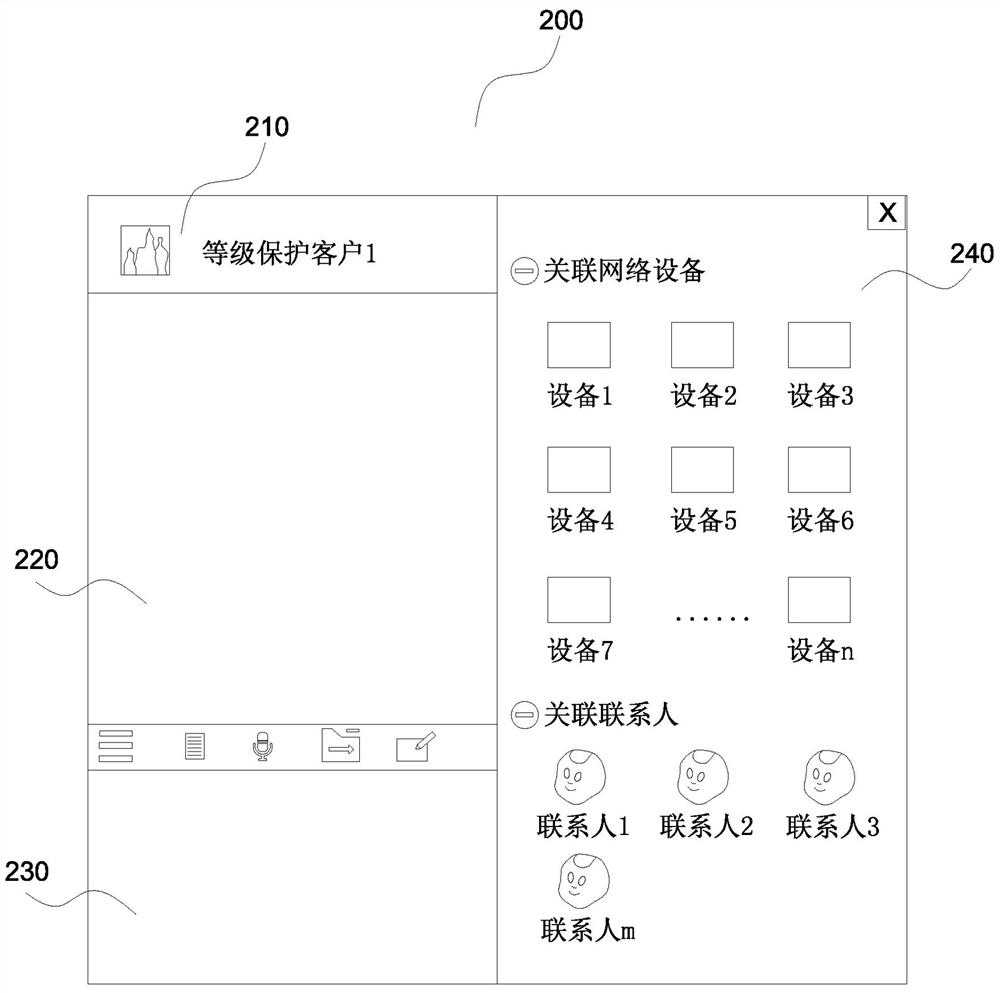
ActiveCN113055390AImprove processing efficiencyEasy accessSemantic analysisExecution for user interfacesInformation processingInteraction interface
The invention discloses an intelligent information processing method and device in network security level protection, and relates to the technical field of network information security. The method comprises the following steps: based on an insurance service object, establishing a contact object corresponding to the insurance service object in an instant messaging tool; collecting a trigger operation of a user for the contact object, outputting an equipment interaction interface corresponding to the insurance service object, and outputting associated network equipment and associated contact information in the equipment interaction interface; processing item information related to network security level protection and sent by the user in the equipment interaction interface is obtained, and associated network equipment related to processing items and / or associated contacts related to the processing items are / is triggered to carry out item processing. By utilizing the method and the device, the user can quickly obtain the equipment information and the contact information of the insurance service object, and the real-time interaction efficiency and the item processing efficiency with the insurance service object are remarkably improved.
Owner:SHANGHAI NEWDON TECH CO LTD
Automatic penetration test system based on AI
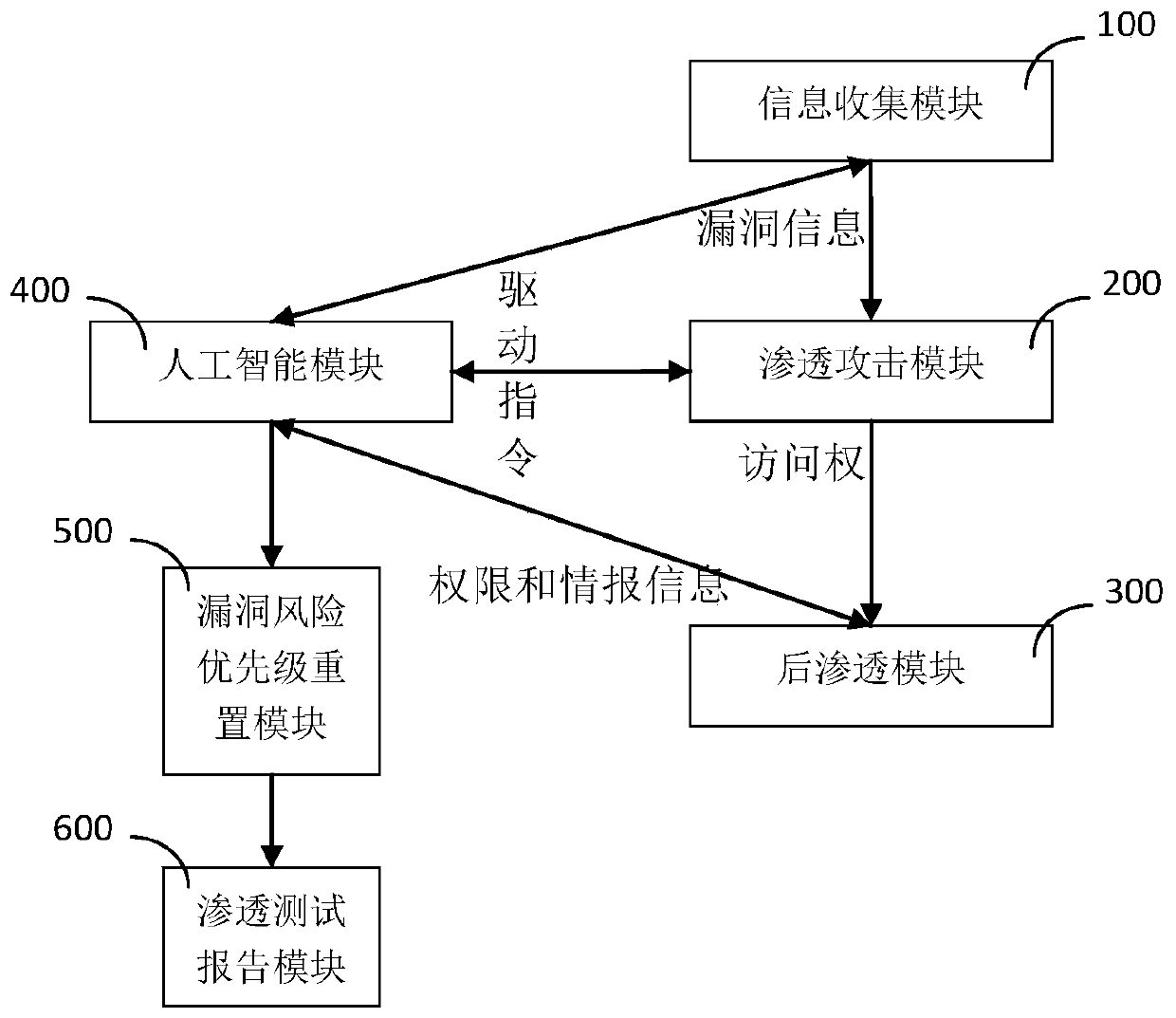
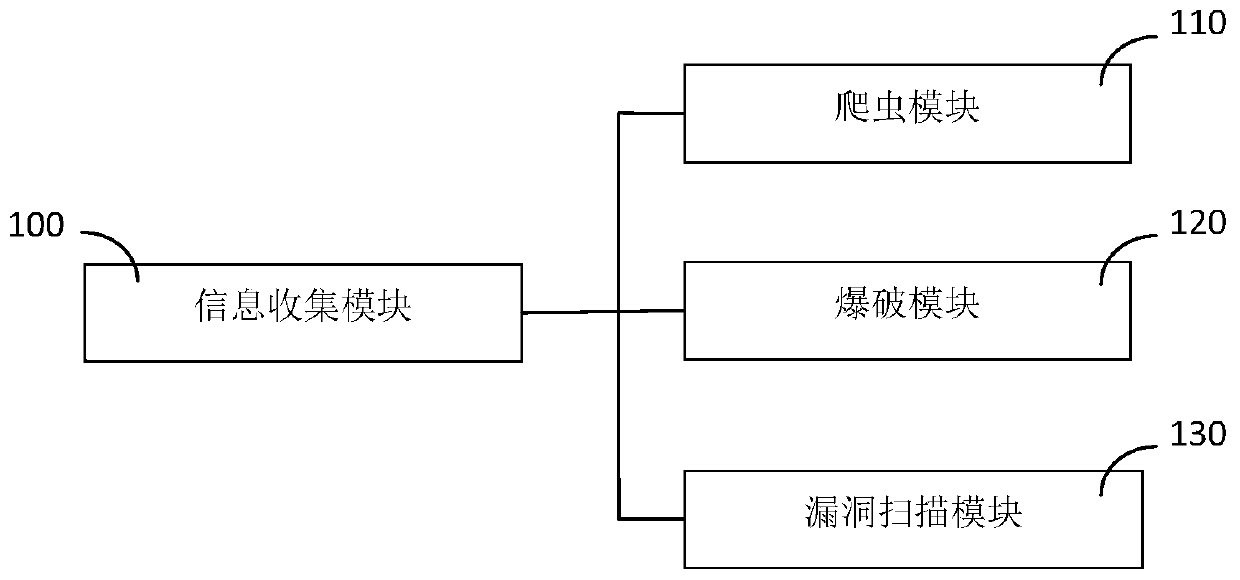
PendingCN111488587AStandardize Penetration Testing ServicesService level is stableWeb data indexingPlatform integrity maintainanceAttackEngineering
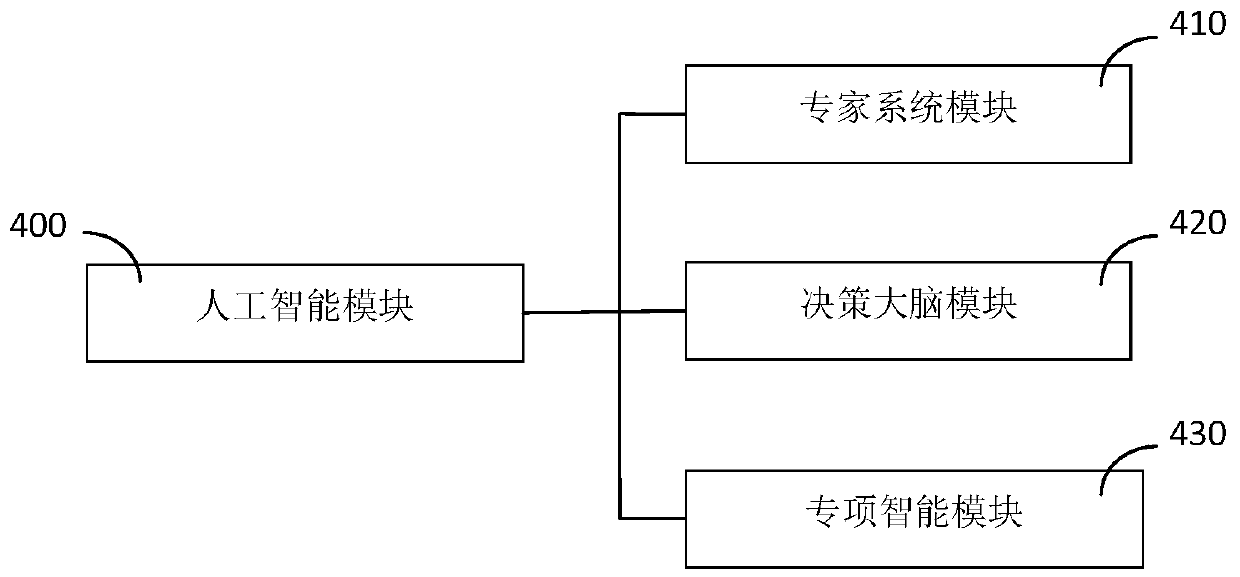
The invention discloses an automatic penetration test system based on AI. The automatic penetration test system includes an information collection module (100) which is used for collecting attack surfaces and intelligence information of network targets and analyzing vulnerabilities existing in the network targets to generate vulnerability information; a penetration attack module (200) which is used for utilizing the vulnerabilities and attacking the network targets to obtain access rights or information of the network targets.; a rear permeation module (300) which is used for carrying out right extraction and intelligence information extraction on the network target and carrying out detection and springboard attack on other objects in the network target association network; and an artificial intelligence module (400) which is used for generating an attack method according to the vulnerability information, the access right or information, the authority information and the intelligence information and generating a driving instruction according to the attack method. The AI-based automatic penetration test system provided by the invention can effectively improve the stability and efficiency of penetration test.
Owner:北京墨云科技有限公司
Natural scene text recognition method and system of multi-path parallel position association network
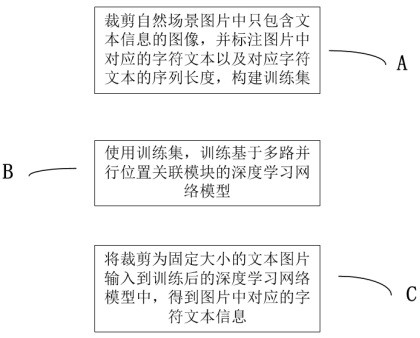
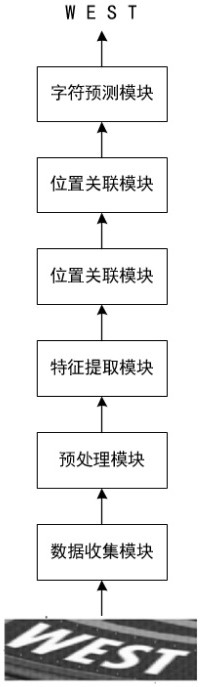
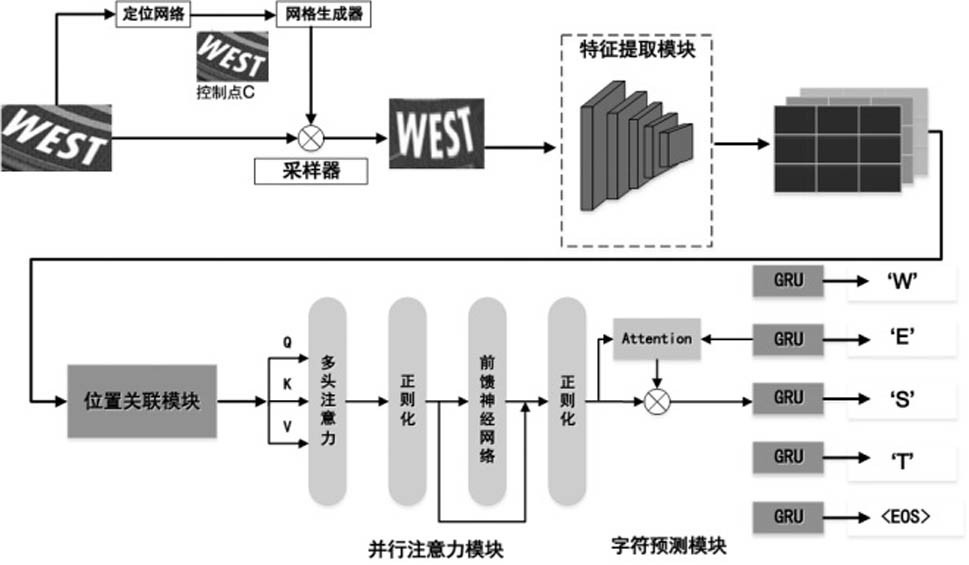
PendingCN114399757AImprove alignment accuracyImprove accuracyCharacter and pattern recognitionNeural architecturesText recognitionData set
The invention relates to a natural scene text recognition method and system for a multi-path parallel location-associated network. Comprising the following steps: step A, cutting an image only containing text information in a natural scene picture, labeling a corresponding text and a text length in the picture, and constructing a training data set S; step B, using the training set S to train a deep learning network model G based on multi-path parallel position association, wherein the deep learning network model G is used for identifying text information in a natural scene picture; and step C, inputting the text picture which is cut into a fixed size into the trained deep learning network model G to obtain corresponding target character text information in the picture. According to the invention, the text recognition accuracy can be effectively improved.
Owner:FUZHOU UNIV
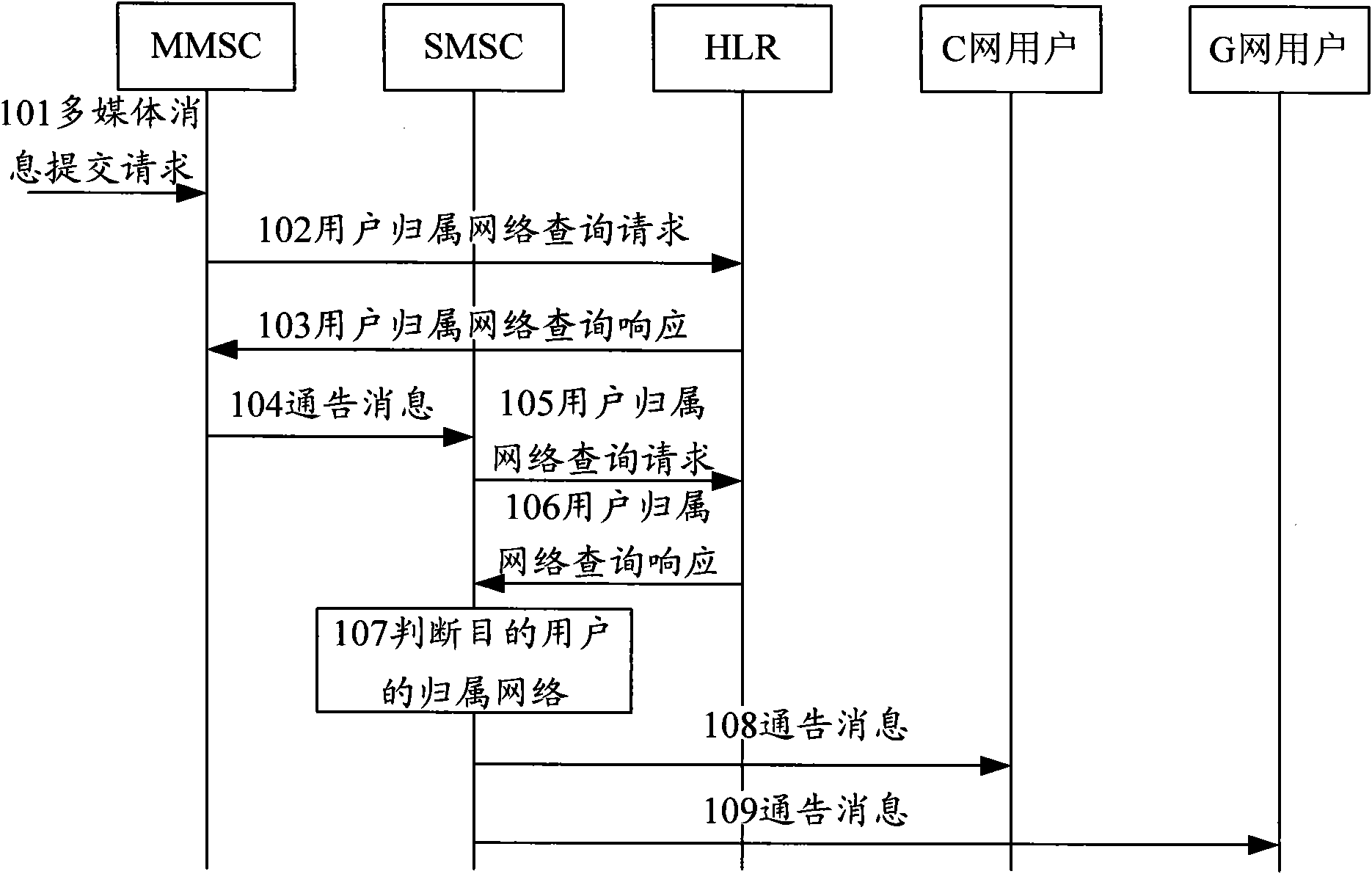
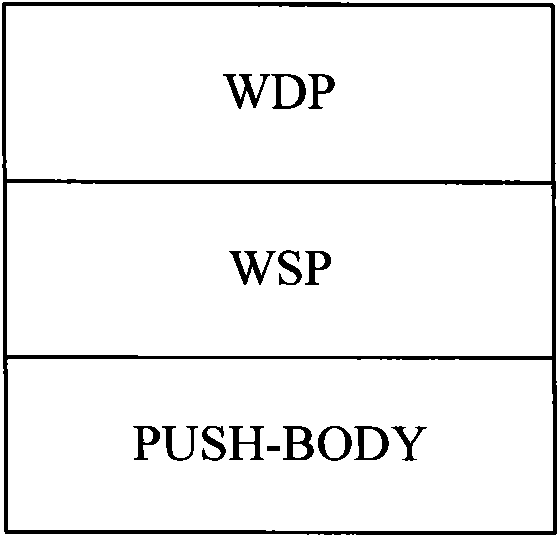
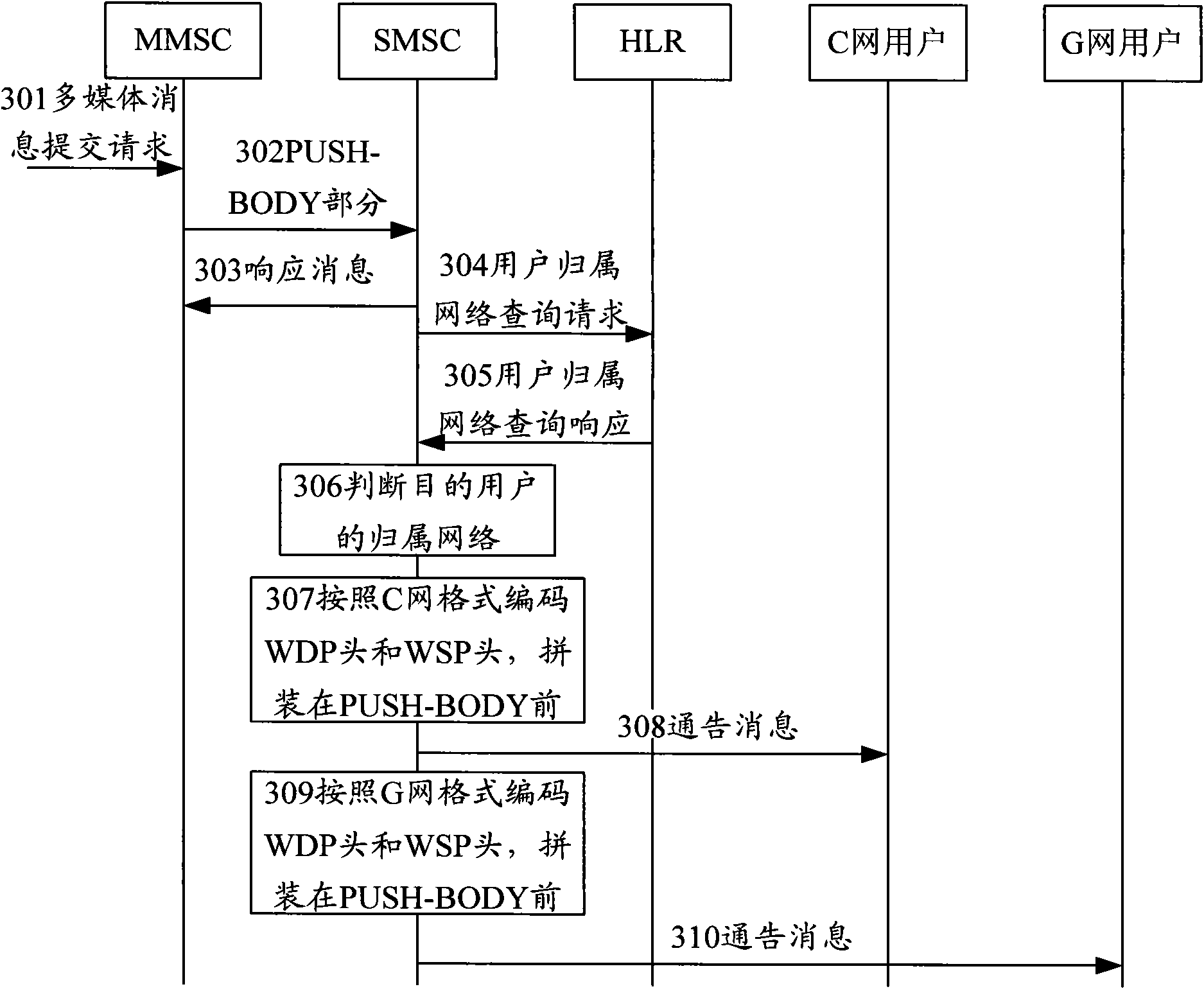
Method for assigning messages in multi-media messaging service and system
InactiveCN101895838AImprove processing efficiencyIncrease success rateInformation formatContent conversionComputer scienceMultimedia Messaging Service
The invention discloses a method for assigning messages in multi-media messaging services and a system, wherein the method comprises the following steps: coding the message content of messages at the time of assigning messages to users by a multi-media messaging service center (MMSC), and sending the message content to a short message center; and receiving the message content by the short message service center (SMSC ) before inquiring the affiliation network information of the users, coding the message heads of the messages in accordance with the affiliation network information, scrabbling the message heads and the message content into messages and then sending the scrabbled messages to the users. In the invention, a part of the codes of the messages in the multi-media messaging service are transformed from the MMSC to the SMSC; and the coding of the message heads and operations for assigning the messages can be completed after inquiring the affiliation network message of the users once by the SMSC, thereby being able to remove an interface between the MMSC and an HLR and reducing the whole message process.
Owner:ZTE CORP
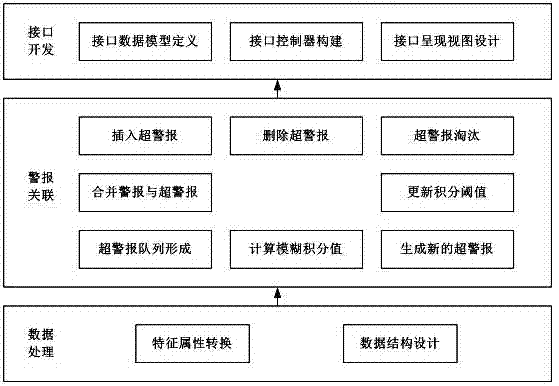
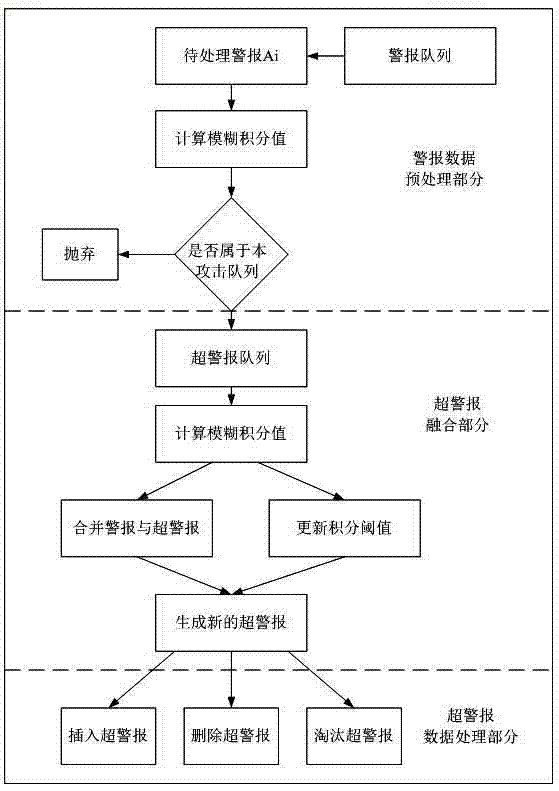
Multi-step attack alarm associated network service interface development method
InactiveCN104219253ASolve the large amount of dataSolve problems that are difficult to apply to smart terminalsTransmissionResource consumptionComputer module
The invention relates to a multi-step attack alarm associated network service interface development method, and belongs to the field of safety of network information. A data processing module, an alarm associating module and a network service interface developing module are provided aiming at the process design of the multi-step attack alarm associated network service interface development method; a fuzzy measured value is computed by fuzzy integral, an alarm is combined into a super alarm according to the measured value, a threshold value represented by an integral value is updated according to the combination situation of the alarms, and the support alarm is generated, weed out or deleted in a super alarm queue according to the integral value. The association of the alarms is achieved in a fuzzy integral manner, and distributed by the network service interface for being invoked. According to the method, the problems that a traditional intrusion detection system is large in system resource consumption and cannot be applicable to various terminals, in particular to mobile terminals, are overcome. Burdens of network safety staffs can be relieved, and protection to complex network attacks can be performed in a targeted manner.
Owner:JILIN UNIV
Ecological index efficiency evaluation method based on network analysis
The invention relates to an ecological index efficiency evaluation method based on network analysis. The method comprises the steps that a, according to the objective level and the content of a system to be evaluated, a to-be-evaluated ecological index system with a level structure is constructed; b, through literature research and expert consultation, a theoretical perfect standard ecological index system level network is constructed, and the index weight is calculated; c, a relevance network between the operation layers of two index systems is constructed; d, according to the relevance network, the index weight of the to-be-evaluated index system is calculated; and e, the coverage degree and the characterization degree of the to-be-evaluated index system are calculated. According to the invention, the science connection in the to-be-evaluated index system is explicated from the three aspects of the relevance, the coverage degree and the characterization degree; the application efficiency of an operation index is improved; the method can be applied to the efficiency evaluation of an index system related to ecological construction, such as the evaluation of an ecological province construction index system and other problems; and the method can be applied to the efficiency evaluation of other similar complex index systems, such as regional society, economic index evaluation and the like.
Owner:INST OF URBAN ENVIRONMENT CHINESE ACAD OF SCI
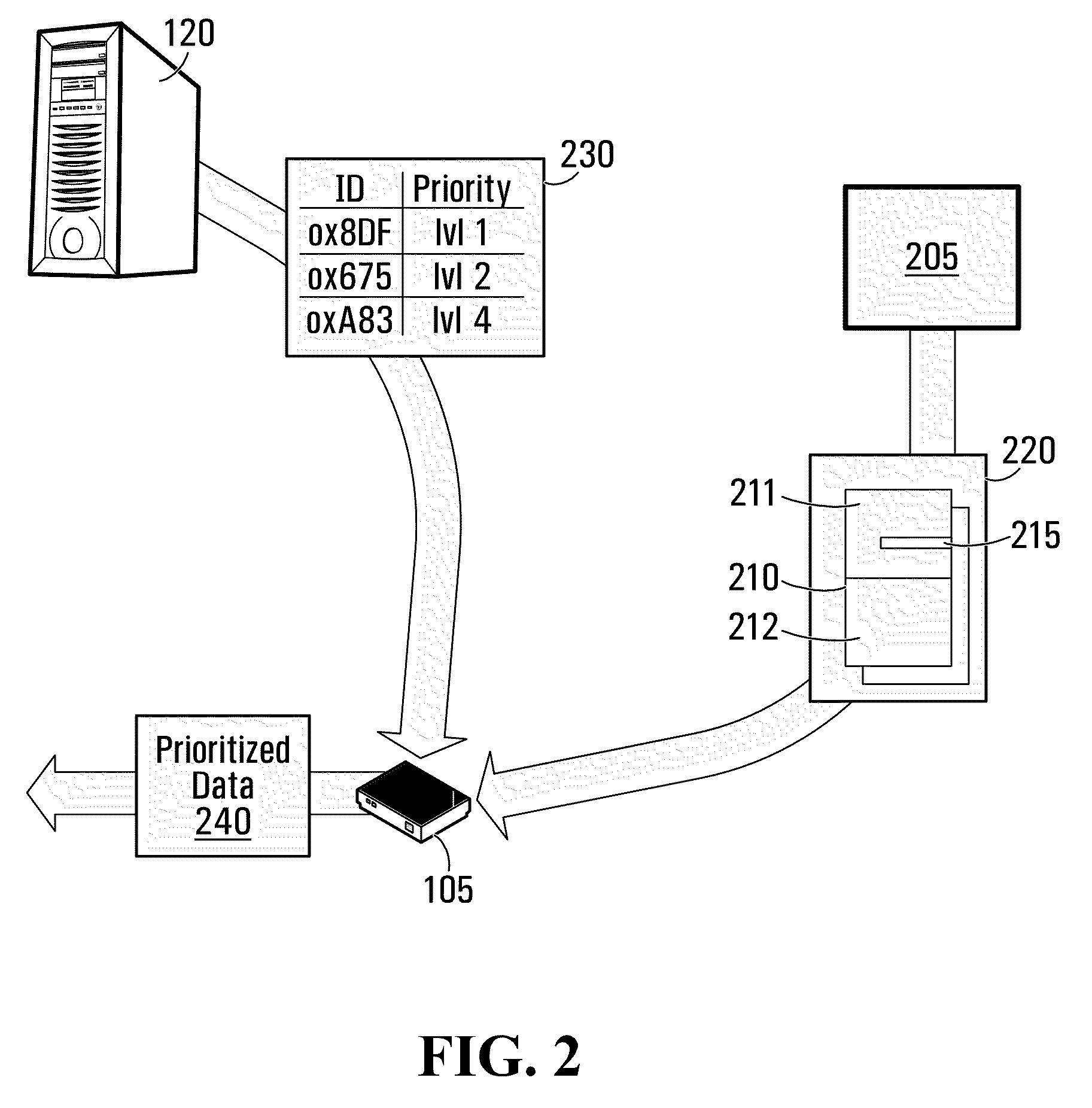
Differentiated priority level communication
Provided are methods, apparatuses and systems for providing prioritized data distribution at a customer premise. A network access component may receive priority information from a trusted source, the priority information being indicative of an association between at least one identifier and a respective priority level. The network component may determine a particular identifier associated with data received from a communication entity. The network access component may determine a particular priority level associated with the data based on the particular identifier and the priority information. The network component may also prioritize at least a portion of the data on a basis of the particular priority level.
Owner:BCE
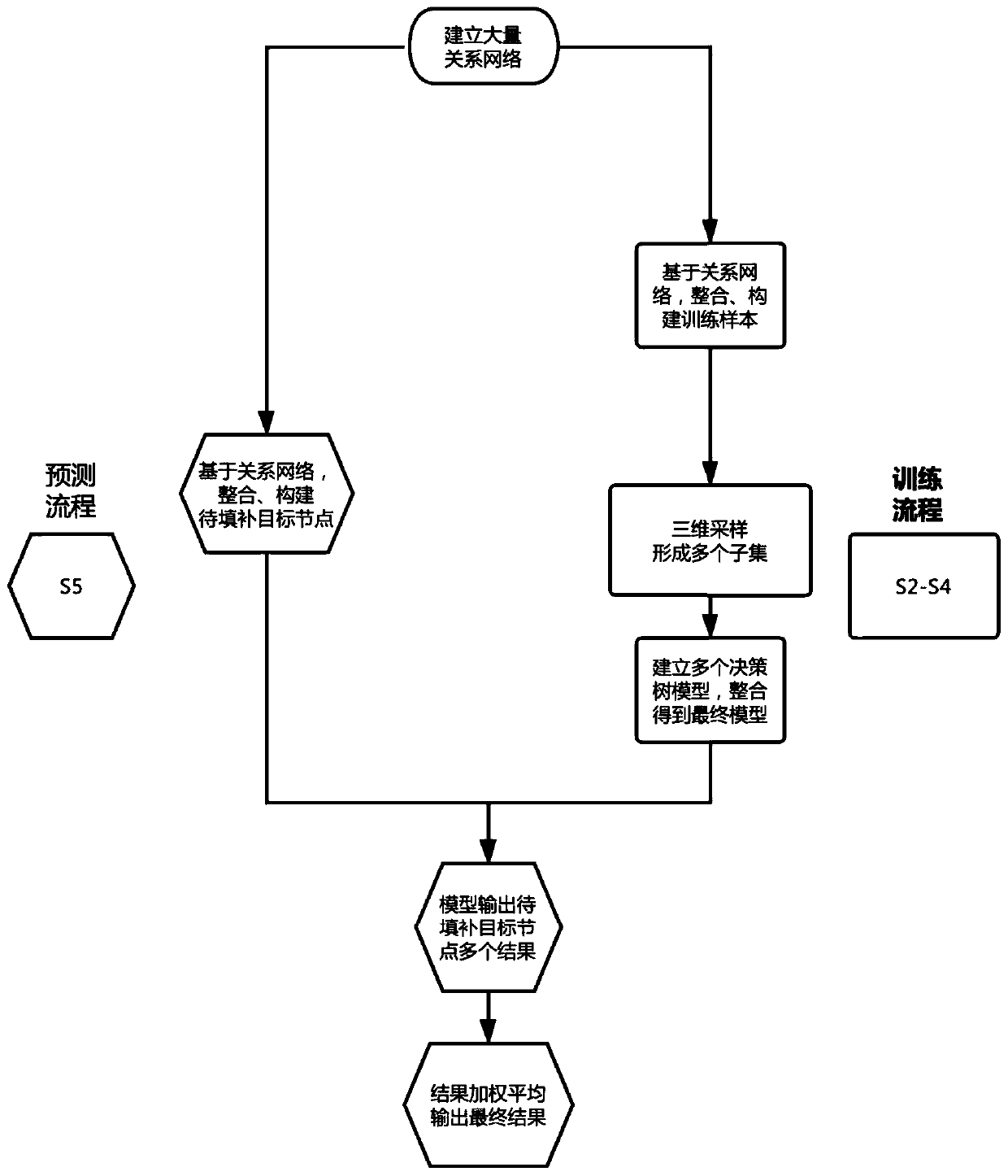
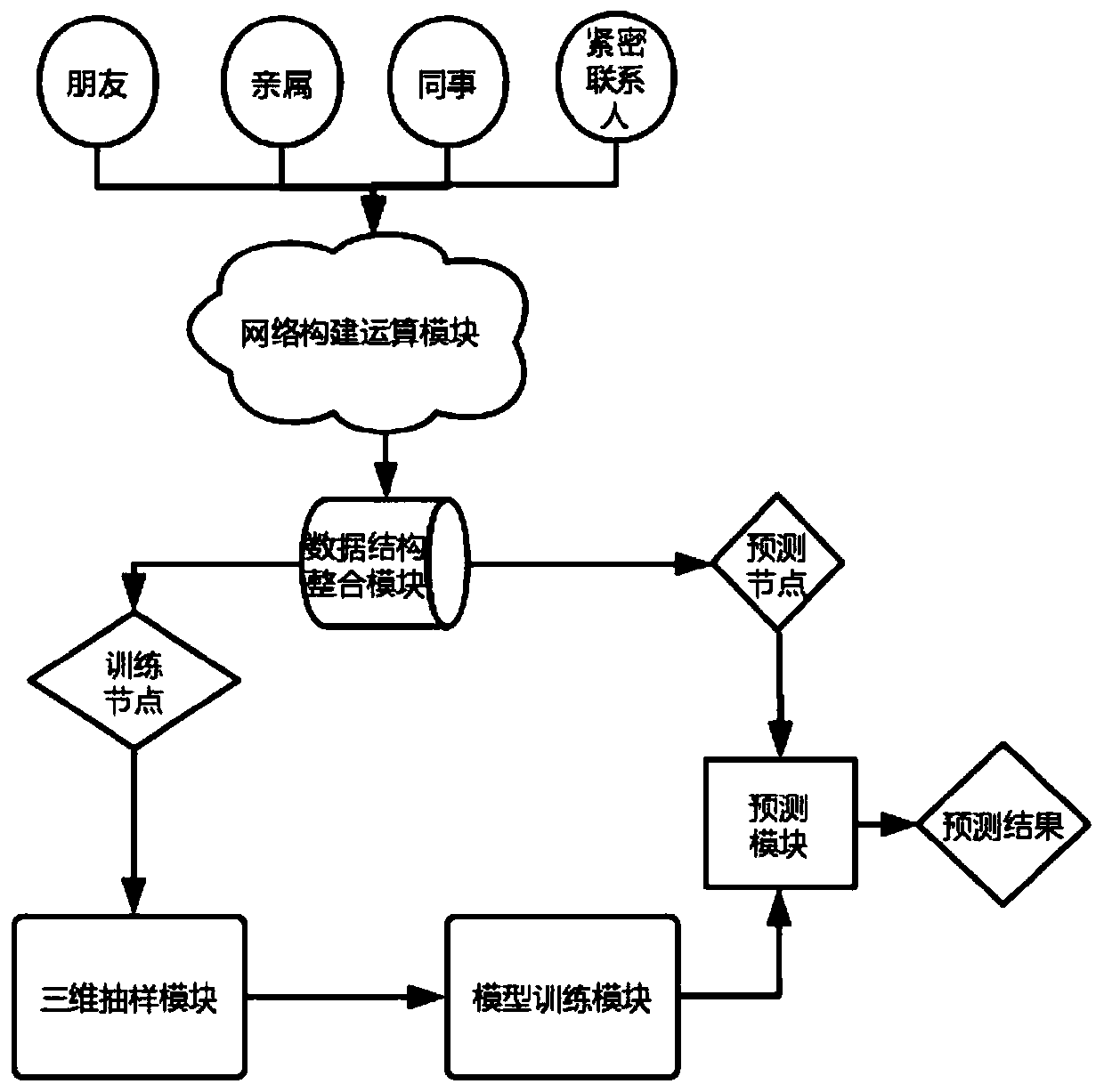
Target node key information filling method and system based on association network
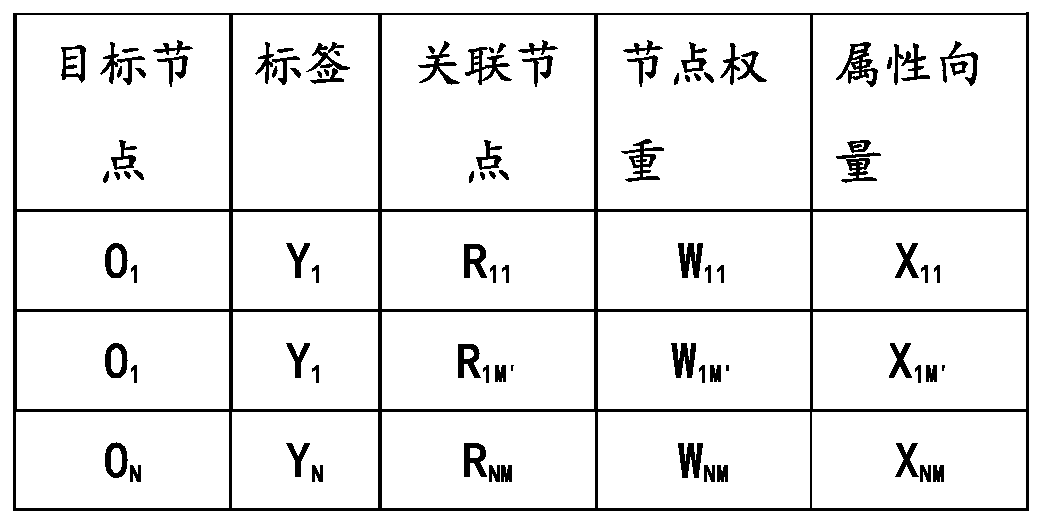
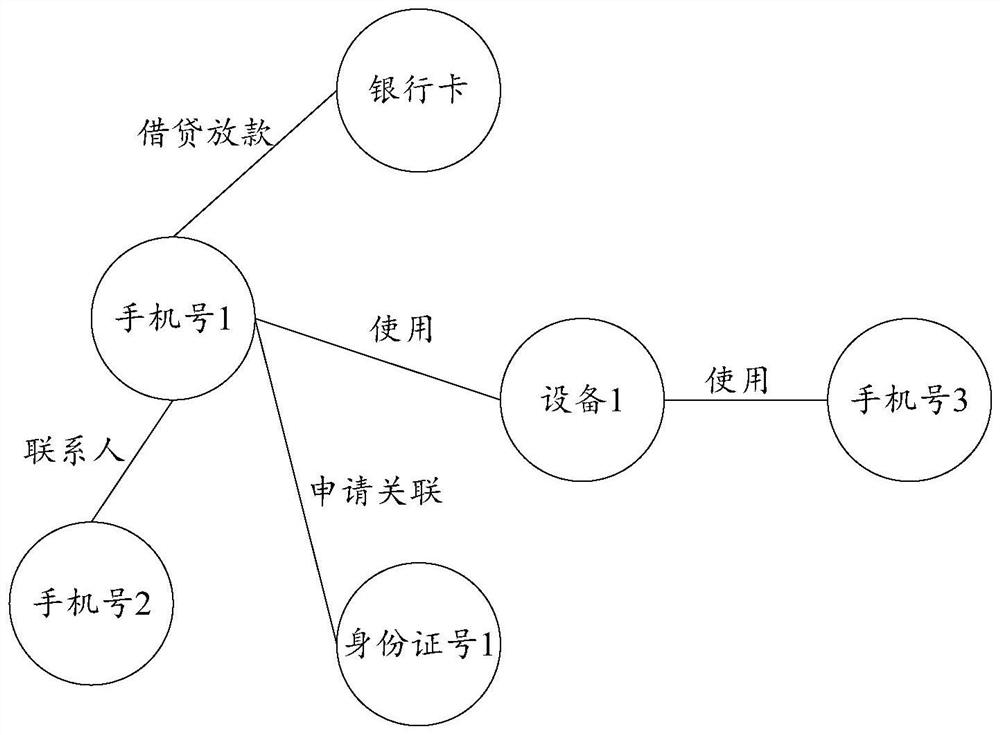
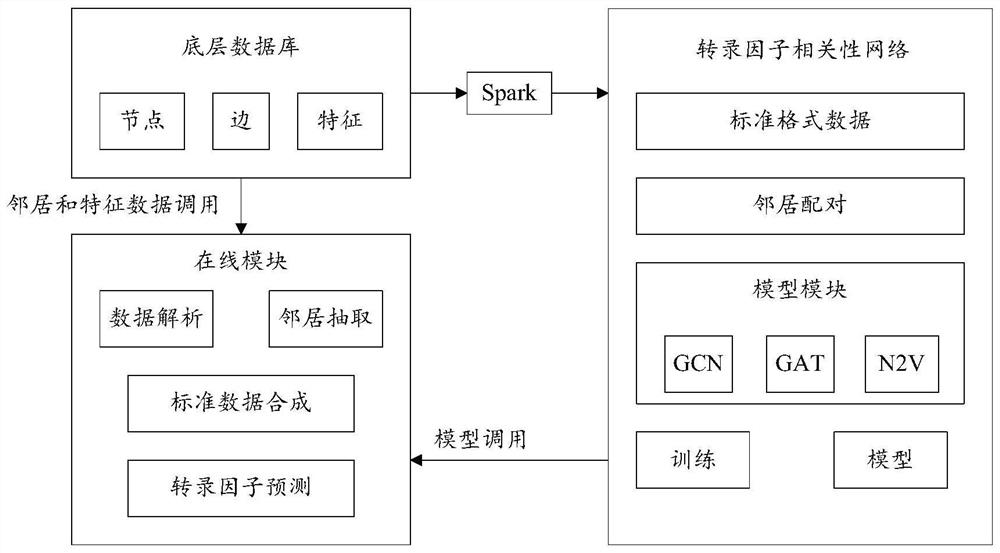
The invention discloses a target node key information filling method and system based on an association network, and belongs to the technical field of data mining, machine learning and graph theory. The problem of low accuracy of the filled key information of the target node in the prior art is solved. According to an application scene, the method comprises steps of establishing a relational network of a large number of nodes; based on network relation, obtaining an association network of a target node with key information, integrating the association network into a data structure comprising atarget node, a label, an association node, an association node weight and an attribute vector, performing multiple three-dimensional sampling on the data structure based on an improved random forestmethod to obtain a subset of a plurality of training decision trees, giving a plurality of decision trees to perform training, and performing integration after training to obtain a final model; and based on the associated nodes of the to-be-filled target node, performing prediction through the final model, and performing weighted average on multiple results after prediction to obtain final fillinginformation. The key information of the target node is filled based on the association network.
Owner:SICHUAN XW BANK CO LTD
Method and device for identifying risk user, storage medium and electronic device
PendingCN114782161AReduced rulemaking costsSolve the costFinanceNeural architecturesFeature extractionEngineering
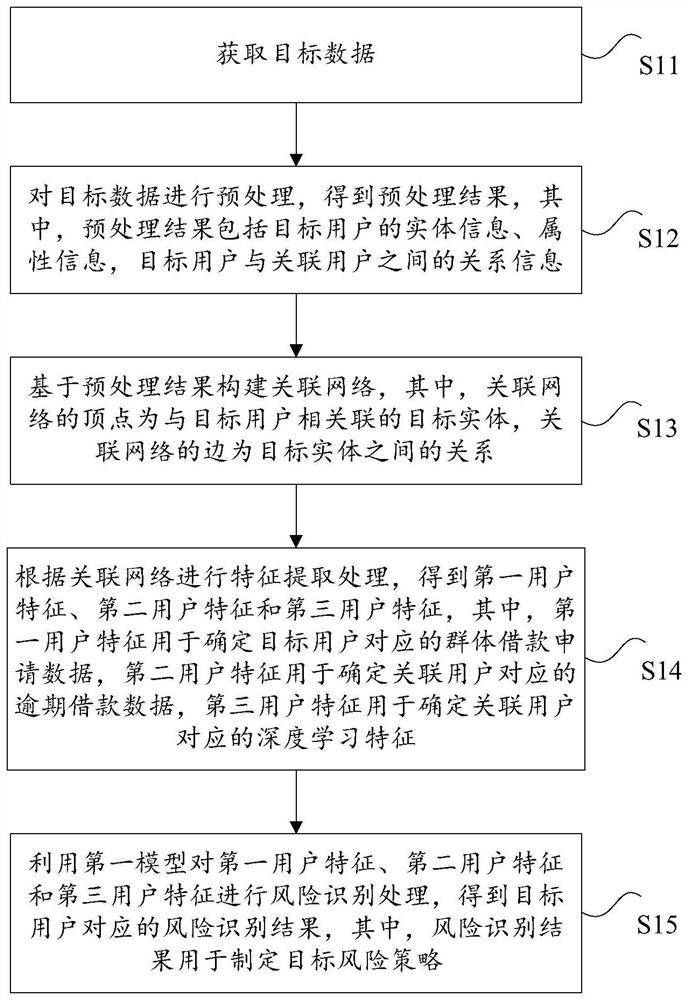
The invention discloses a method and device for identifying a risk user, a storage medium and an electronic device. The method comprises the following steps: acquiring target data; preprocessing the target data to obtain a preprocessing result; an association network is constructed based on the preprocessing result, the vertex of the association network is a target entity associated with the target user, and the edge of the association network is the relationship between the target entities; performing feature extraction processing according to the associated network to obtain a first user feature, a second user feature and a third user feature; and performing risk identification processing on the first user feature, the second user feature and the third user feature by using a first model to obtain a risk identification result corresponding to the target user, the risk identification result being used for formulating a target risk strategy. The technical problems that in the prior art, a method for identifying a risk user is high in rule making cost and poor in interpretability are solved.
Owner:度小满科技(北京)有限公司
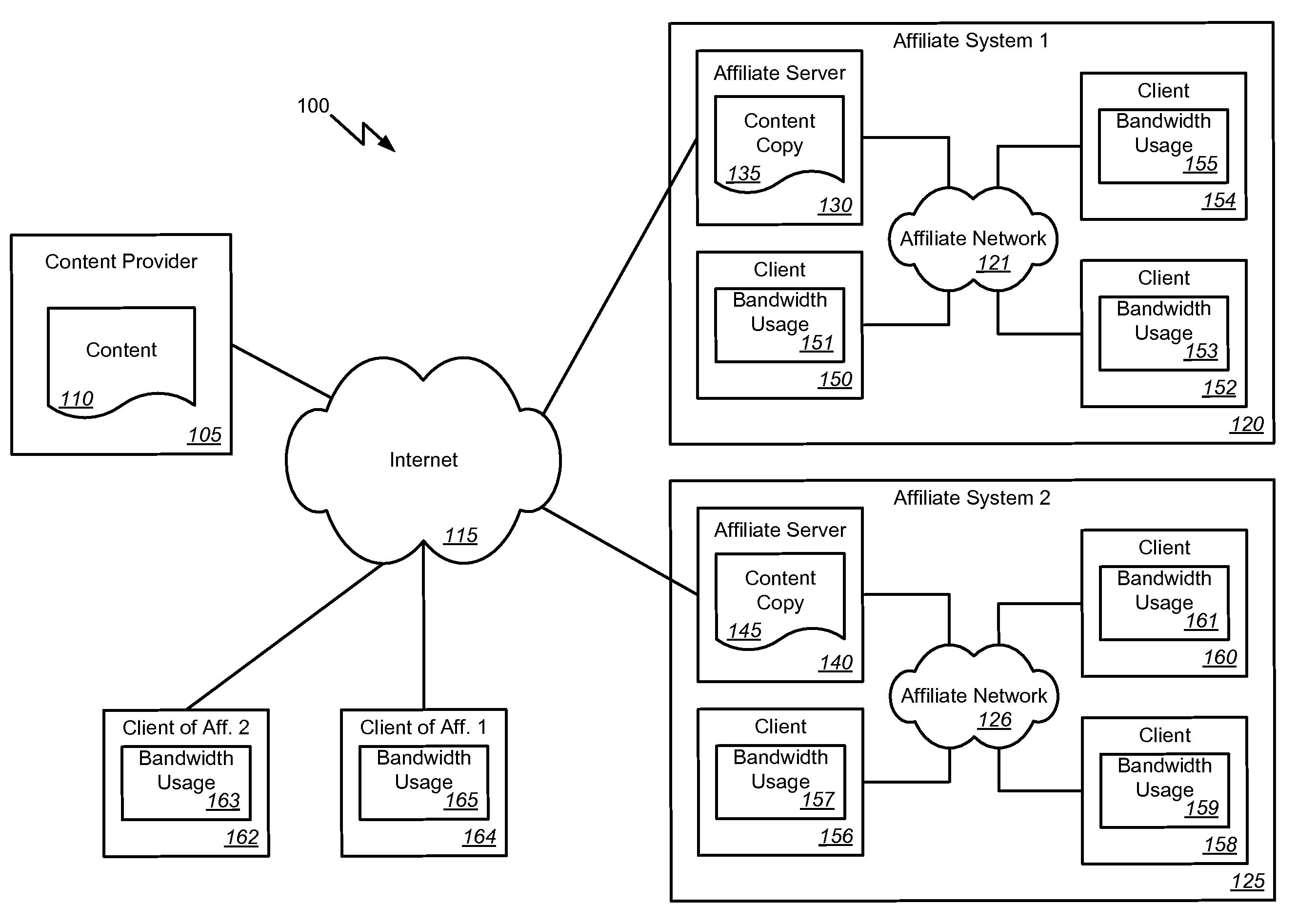
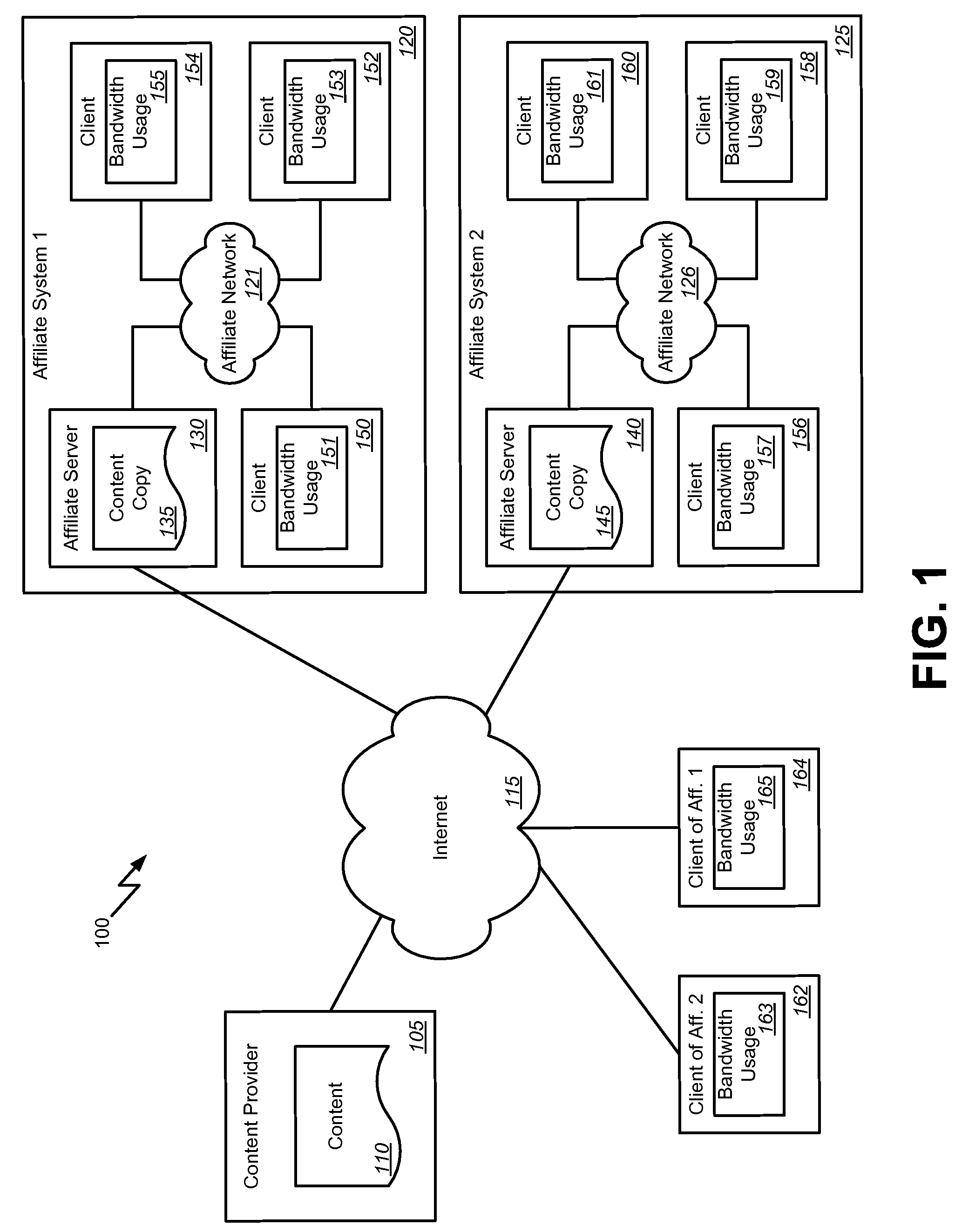
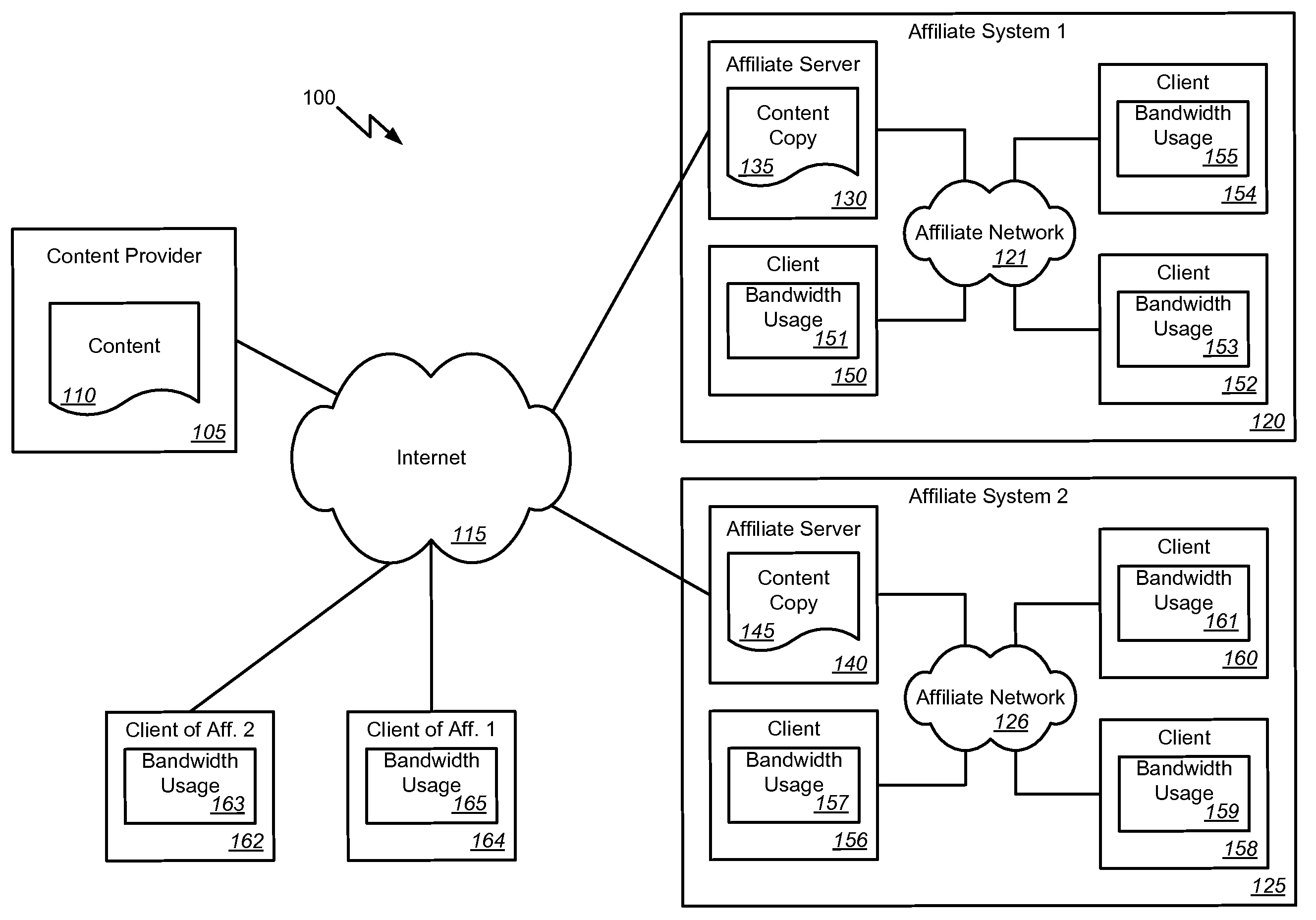
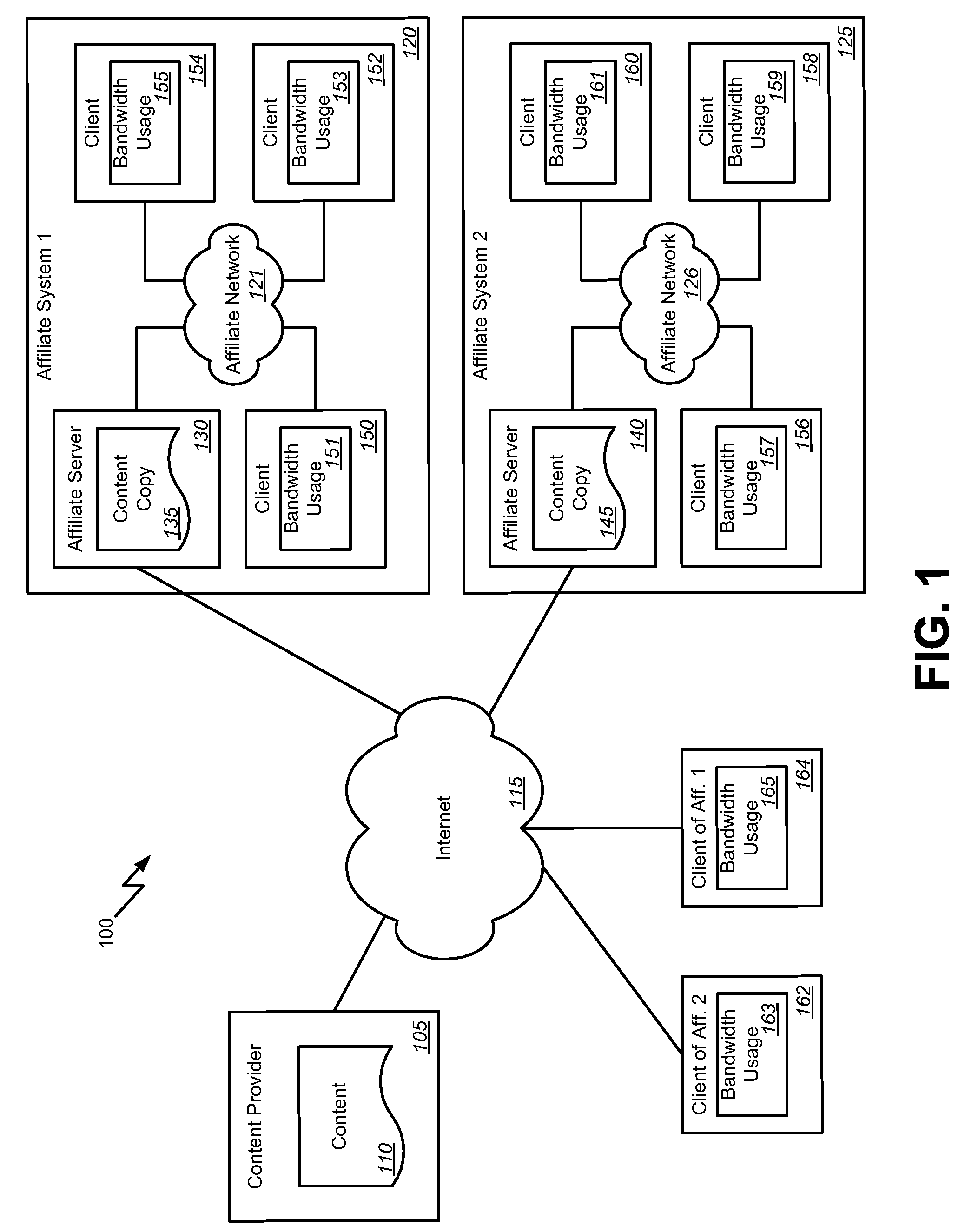
Affiliate bandwidth management
Methods, systems, and machine readable media are disclosed for managing bandwidth usage of a content provider. According to one embodiment, a system for managing bandwidth usage of a content provider can comprise a content provider system adapted to maintain and provide content and a first affiliate system comprising an affiliate network, an affiliate server communicatively coupled with the affiliate network, and a client. The client can be adapted to selectively request the content from either the content provider system or the affiliate server of the first affiliate system based on bandwidth costs for the content provider system.
Owner:STARZ ENTERTAINMENT GROUP
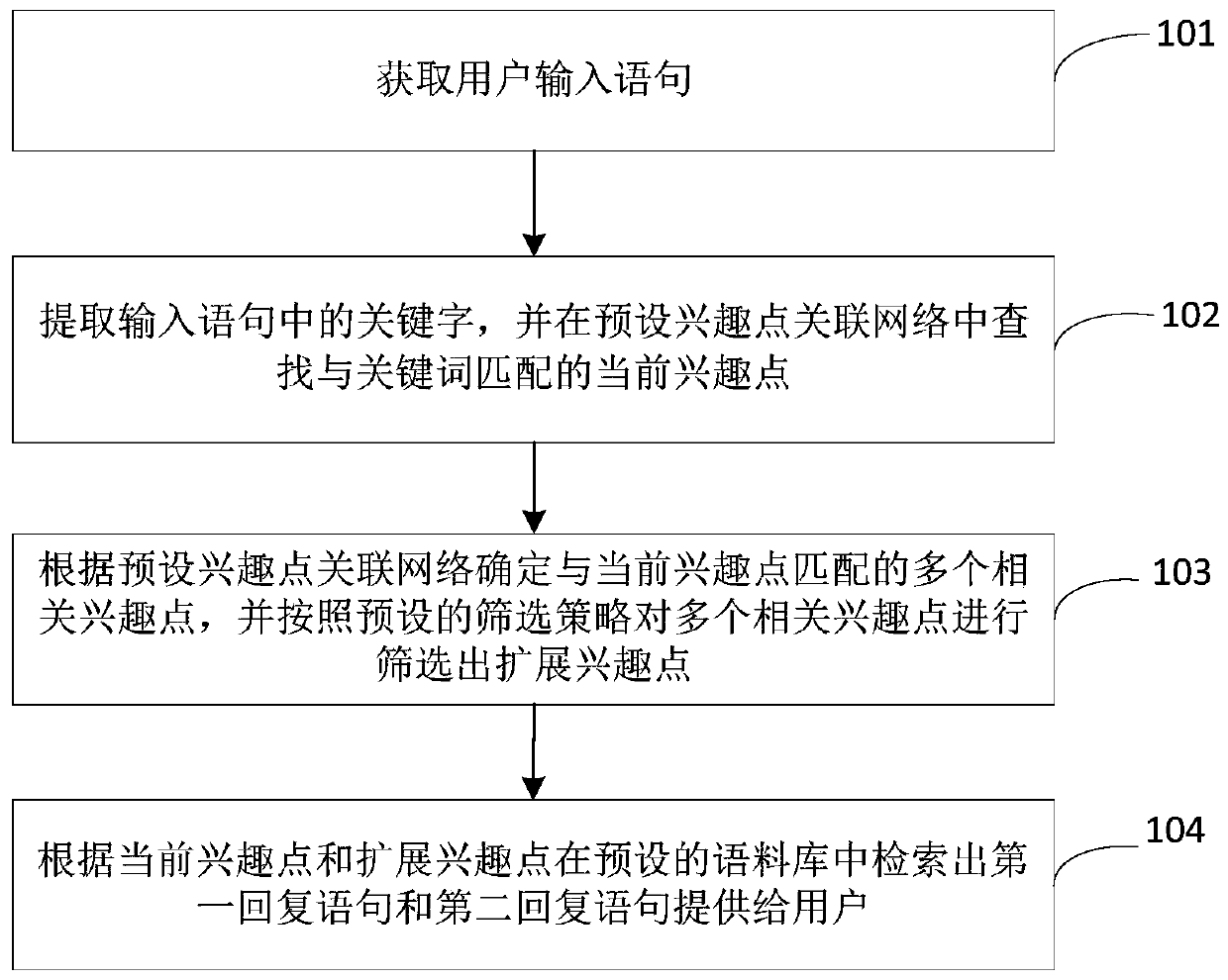
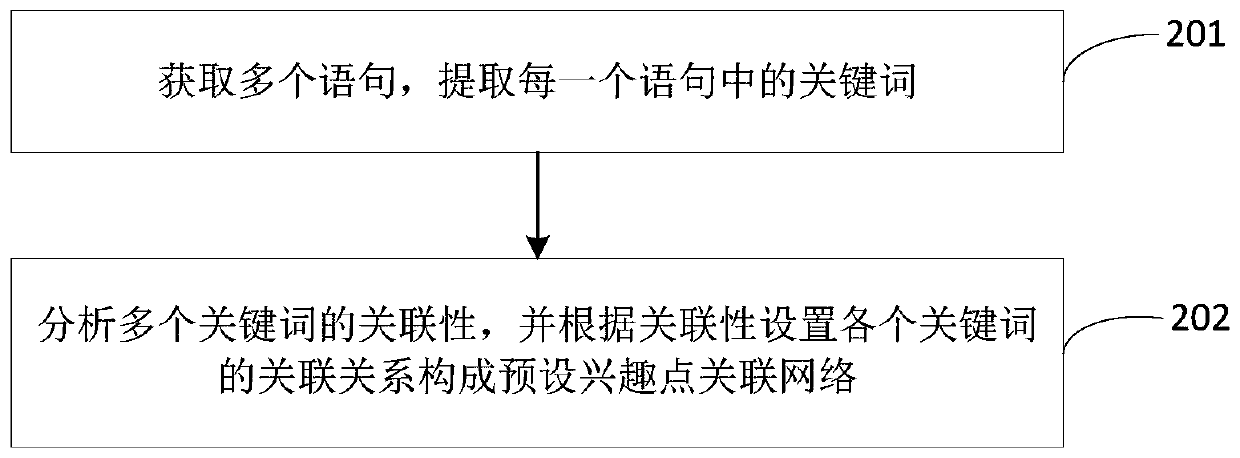
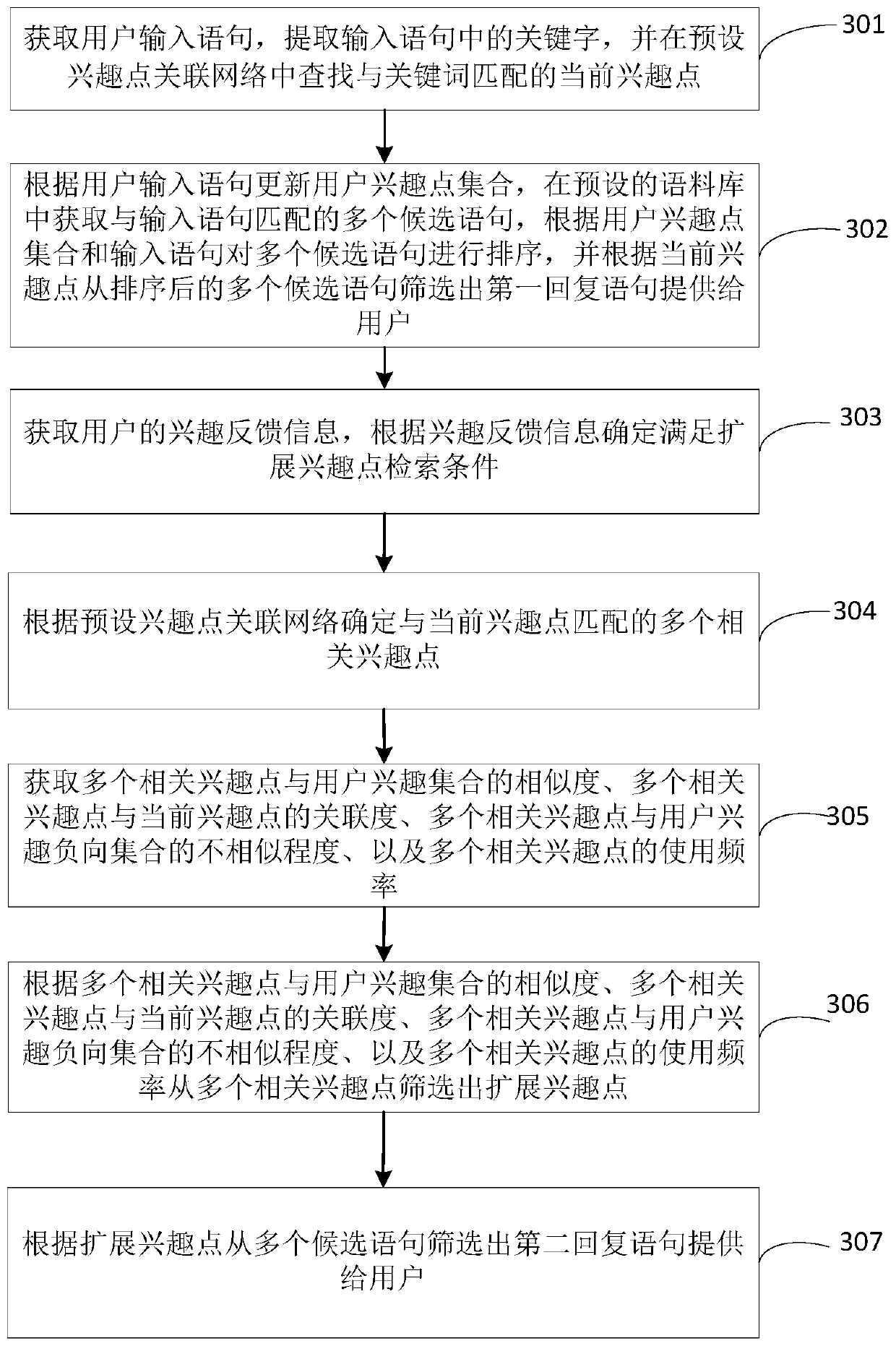
Statement recommendation method and device based on associated interest points
ActiveCN109977215AExpand interest profileImprove experienceNatural language translationDigital data information retrievalUser inputMan machine
The invention provides a statement recommendation method and device based on associated interest points, wherein the method comprises the steps of obtaining a statement inputted by a user; extractinga keyword in the inputted statement, and searching a current interest point matched with the keyword in a preset interest point association network; determining a plurality of related interest pointsmatched with the current interest point according to a preset interest point association network, and screening the plurality of related interest points according to a preset screening strategy to obtain the extended interest points; and retrieving the first reply statement and the second reply statement in a preset corpus according to the current interest point and the extended interest point, and providing the first reply statement and the second reply statement for the user. Therefore, the expanded interest points are guided through the association between the different interest points, then the reply sentences containing the expanded interest points are provided for the user, and the user interest point set is expanded based on the user feedback, the user interest portrait can be expanded more efficiently, the topic diversity in the man-machine conversation is improved, and the user experience is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Risk assessment method and device based on association network, equipment and storage medium
PendingCN112669143ASave storage spaceAccurate identificationFinanceNeural architecturesNetwork modelGoal node
The invention provides a risk assessment method and device based on an association network, equipment and a storage medium, and the method comprises the steps: obtaining a target community of a target node in the association network, wherein the target node is a node, corresponding to a to-be-assessed target object, in the association network, and the target community is composed of a plurality of nodes with the association degree greater than a preset value; acquiring community features of a target community, wherein the community features are determined based on the features of each node in the target community; inputting the community features and the first features into a risk assessment model to obtain a risk assessment result of the target object, wherein the risk assessment model is obtained by training based on a neural network model, Wherein the first feature is determined based on the features of the n-order neighbor nodes of the target node, so that the risk of the target object is comprehensively and accurately evaluated.
Owner:度小满科技(北京)有限公司
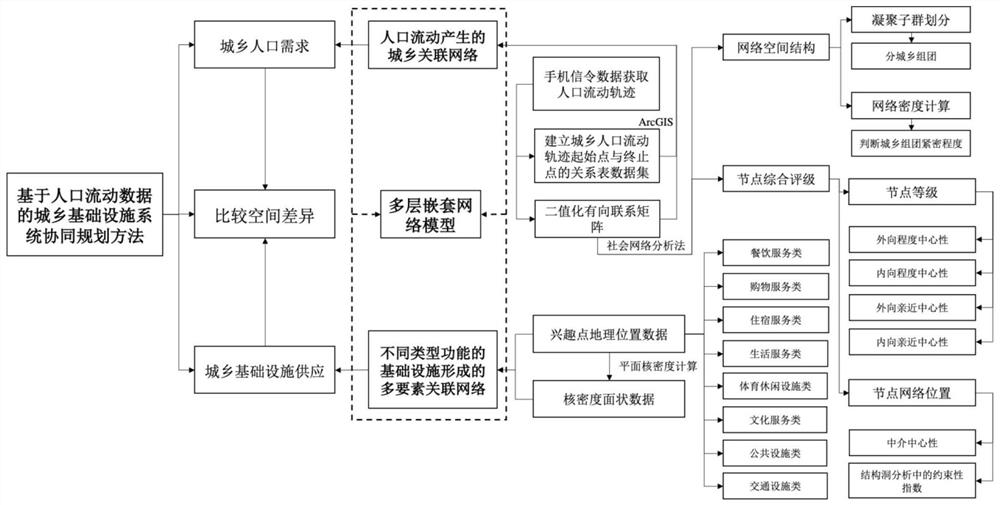
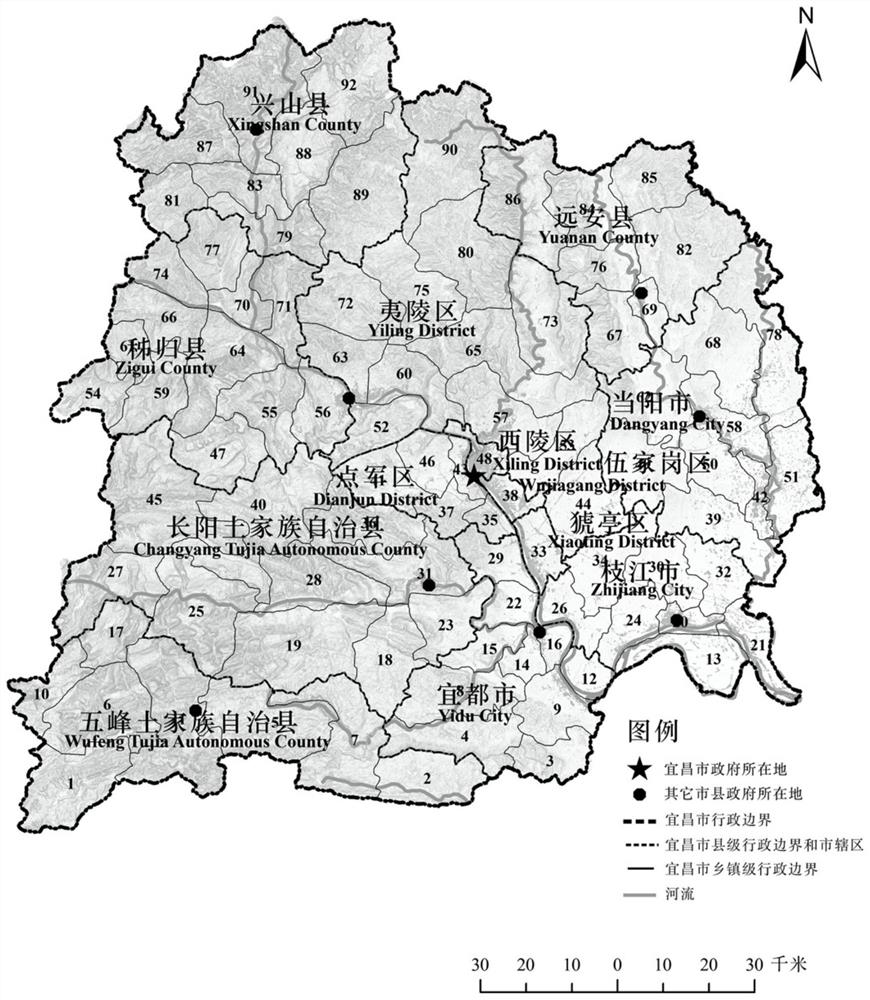
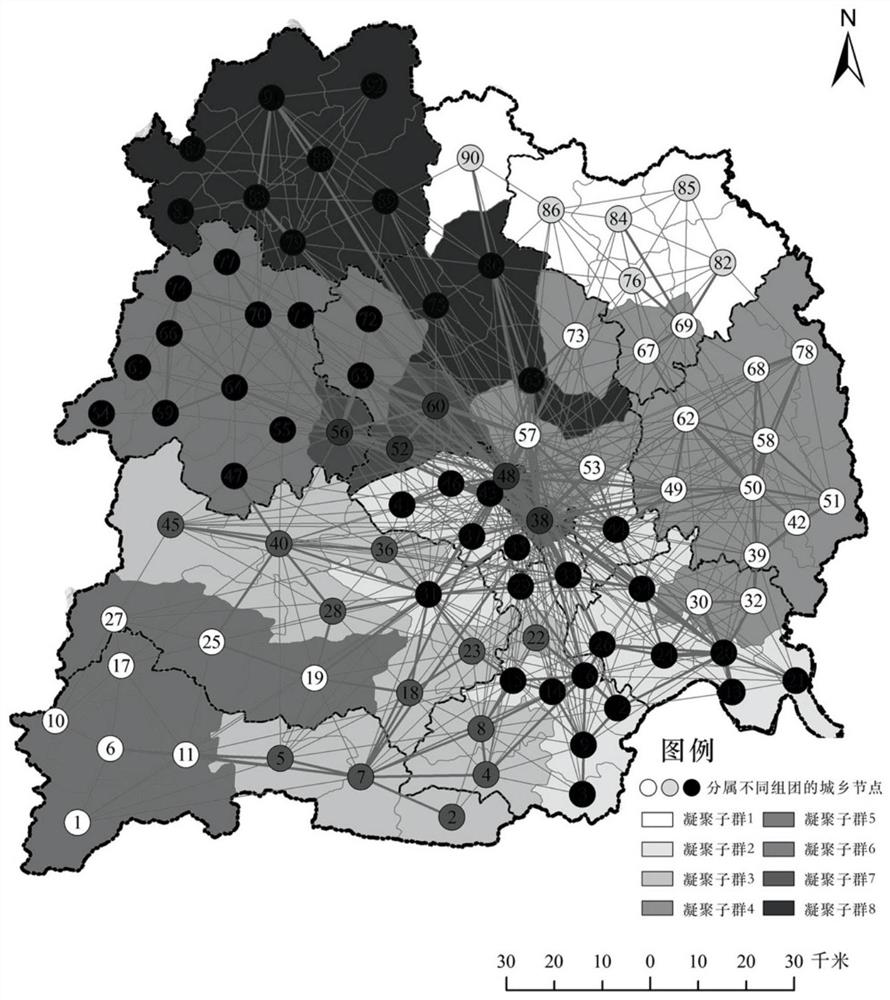
Urban and rural infrastructure system collaborative planning method based on population flow data
ActiveCN112990654APromote coordinated developmentGlobal pattern optimizationResourcesRural infrastructureComputer science
The invention discloses an urban and rural infrastructure system collaborative planning method based on population flow data, and the method comprises the steps: determining the grouping division, node levels and network positions of different urban and rural nodes through an urban and rural associated network established through the population flow data, comparing according to the current multi-element association network formed by the infrastructures with different types of functions to find the supply and demand difference between the urban and rural association network influencing the target decision and the current multi-element association network, and adjusting the spatial layout and configuration of the infrastructures in the multi-element association network, so as to match the node level and position in the urban and rural associated network, so that effective planning and reasonable adjustment of urban and rural infrastructure matching are realized, efficient and accurate resource configuration and global pattern optimization of infrastructure integration are realized, and a new planning means is provided for promoting urban and rural infrastructure integration and system collaborative development.
Owner:PEKING UNIV
Affiliate bandwidth management
ActiveUS20080320141A1Least bandwidth costDigital computer detailsTransmissionClient-sideBandwidth management
Methods, systems, and machine readable media are disclosed for managing bandwidth usage of a content provider. According to one embodiment, a system for managing bandwidth usage of a content provider can comprise a content provider system adapted to maintain and provide content and a first affiliate system comprising an affiliate network, an affiliate server communicatively coupled with the affiliate network, and a client. The client can be adapted to selectively request the content from either the content provider system or the affiliate server of the first affiliate system based on bandwidth costs for the content provider system.
Owner:STARZ ENTERTAINMENT GROUP
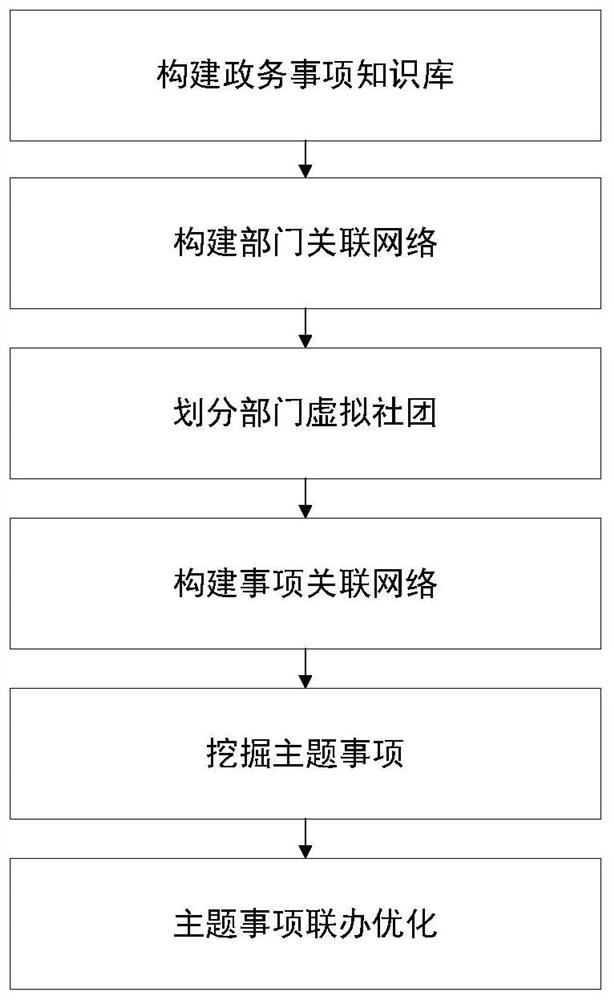
Government affair theme item joint handling method and system based on item association network
PendingCN111694878AHelp managementEliminate the "Information Island" problemRelational databasesData miningService efficiencyData mining
The invention provides a government affair theme item joint handling method based on an item association network. The government affair theme item joint handling method comprises the steps of 1) constructing a government affair item knowledge base; 2) constructing a department association network; 3) dividing department virtual communities; 4) constructing an item association network; 5) mining theme items; and 6) performing subject matter joint optimization. According to the invention, the strength of the association relationship between government departments is fully considered, the government departments are subjected to association clustering, the cooperation relationship between the departments is improved, and a theoretical basis is provided for the joint handling of the departments. Theme items are mined in department virtual communities with close association relationships, and theme item output is generated, so that the service efficiency of government departments is effectively improved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA +1
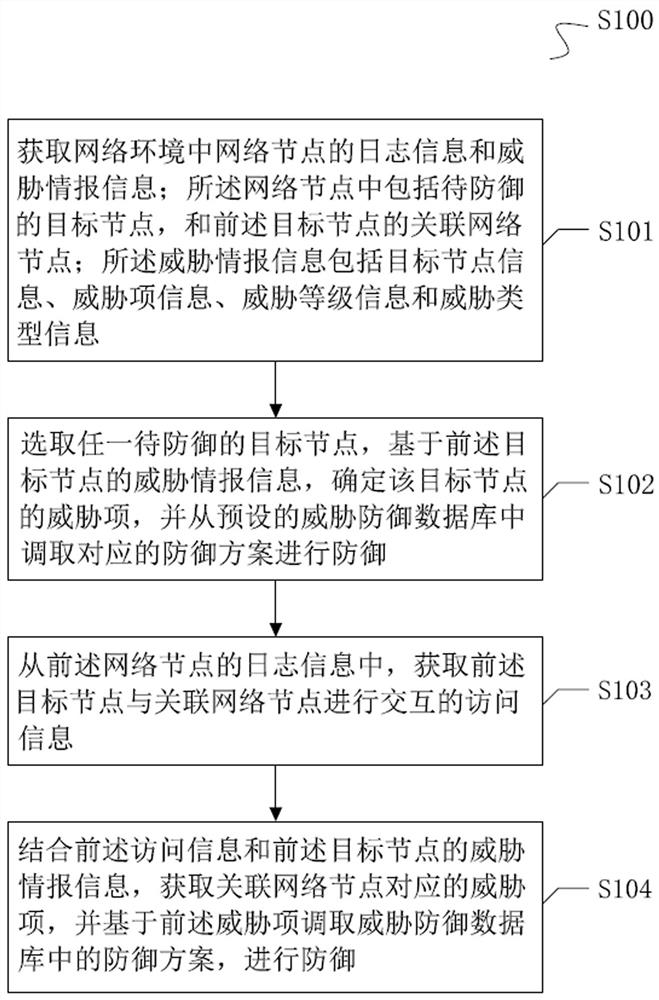
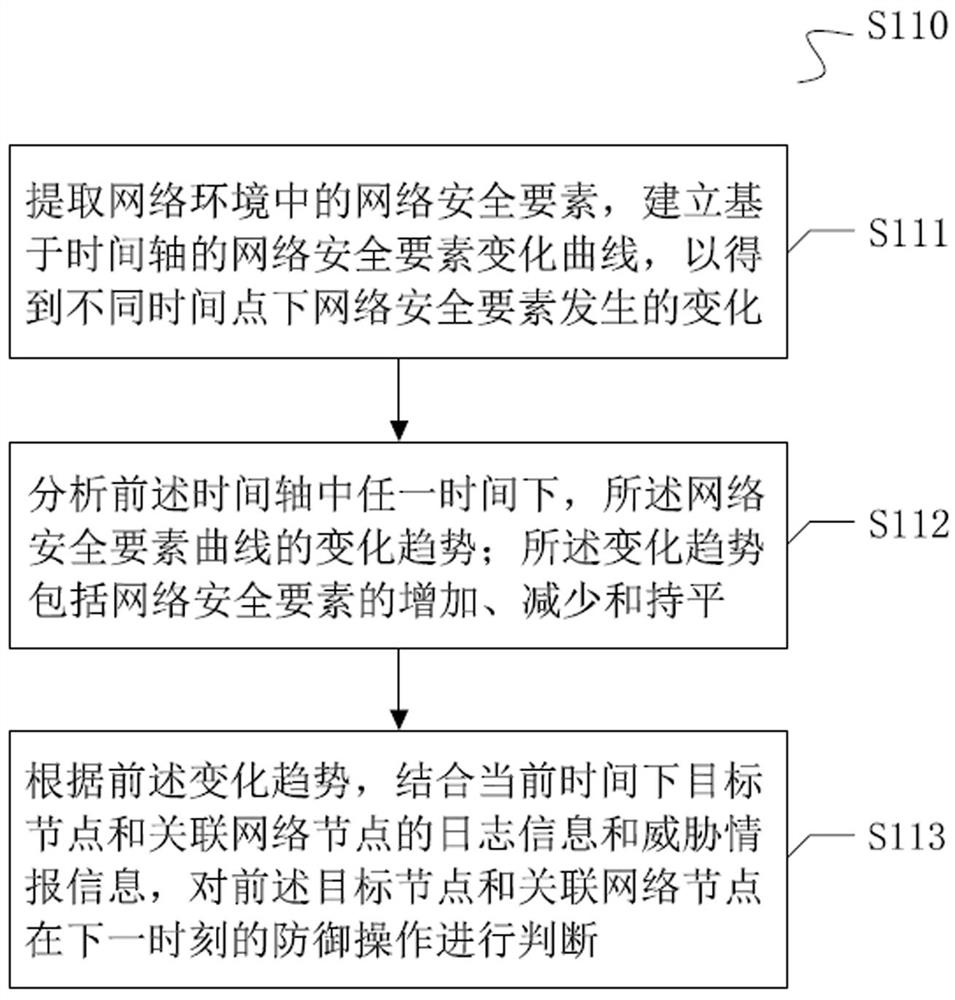
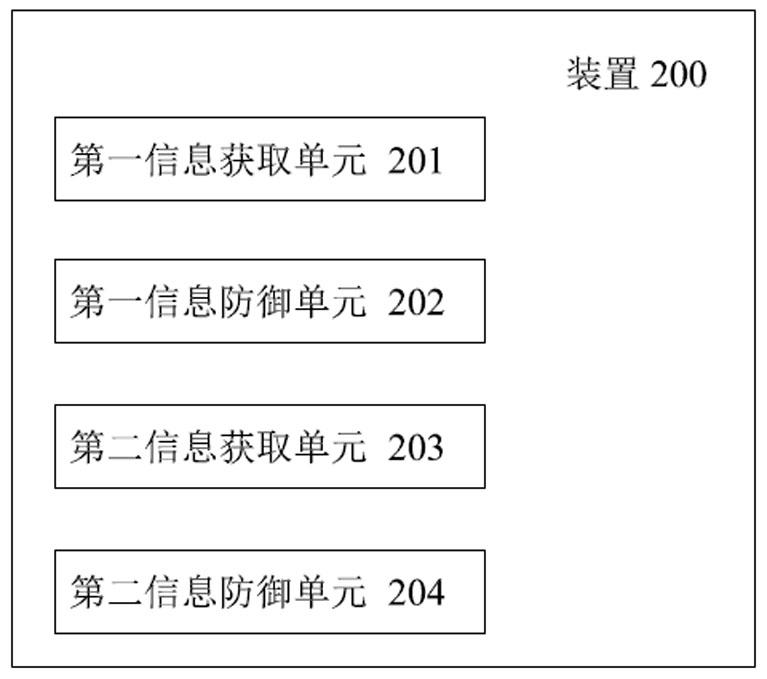
Defense method, device and system based on existing threats in target node
The invention provides a defense method, device and system based on an existing threat in a target node, and relates to the technical field of network security. The processing method comprises the following steps: acquiring log information and threat intelligence information of network nodes in a network environment; the network nodes comprise a to-be-defended target node and an associated network node; selecting any to-be-defended target node, determining a threat item of the target node based on the threat intelligence information of the target node, and calling a defense scheme for defense; obtaining access information of interaction between the target node and the associated network node from the log information of the network node; and in combination with the access information and the threat intelligence information of the target node, obtaining a threat item corresponding to the associated network node, and calling a defense scheme for defense. According to the method, the target node and the associated network node thereof are effectively defended by acquiring the log information and the threat intelligence information of the network node, so that resources consumed during network security defense are reduced.
Owner:SHANGHAI NEWDON TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com