Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
89results about How to "Save disk space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
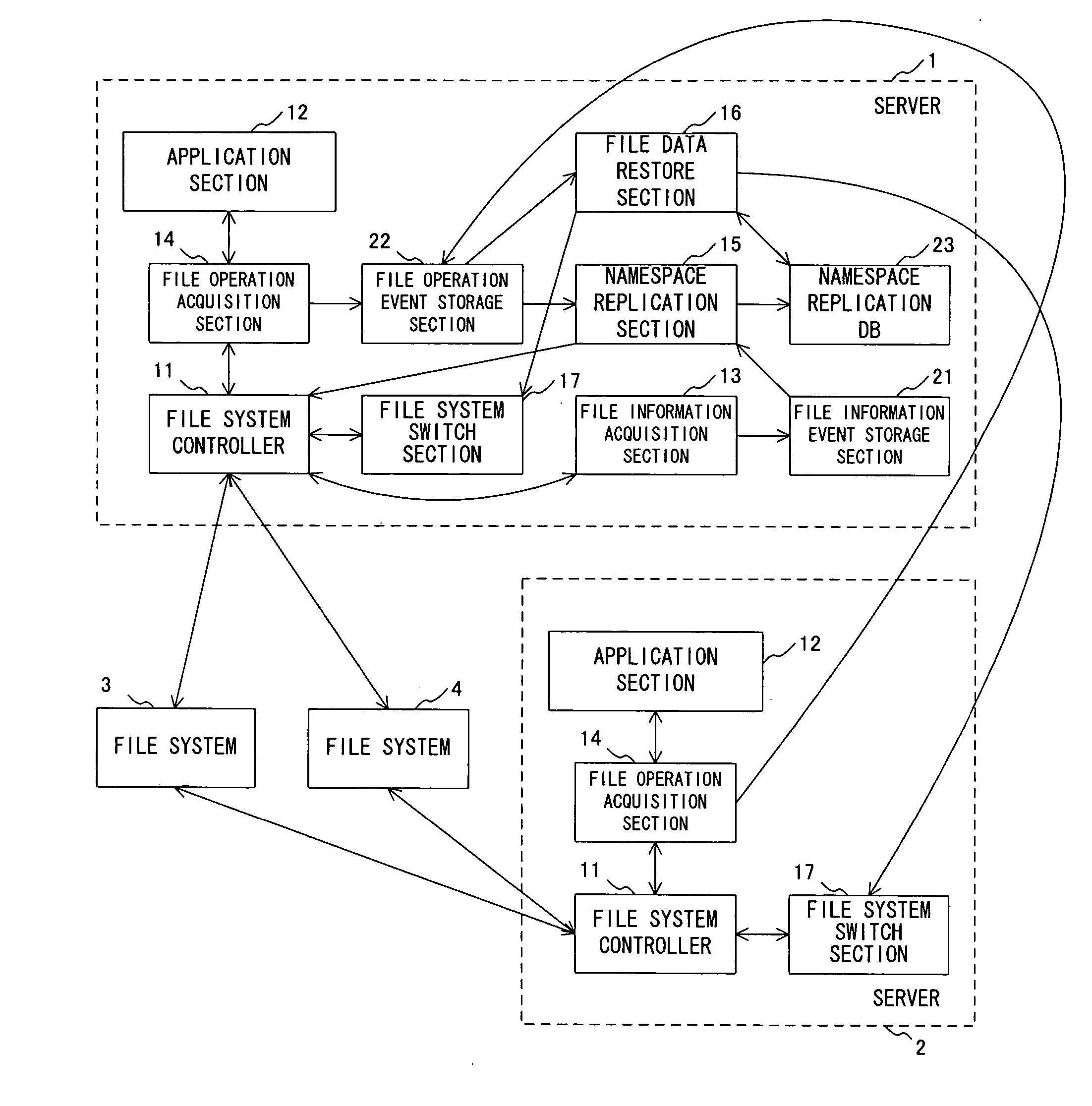
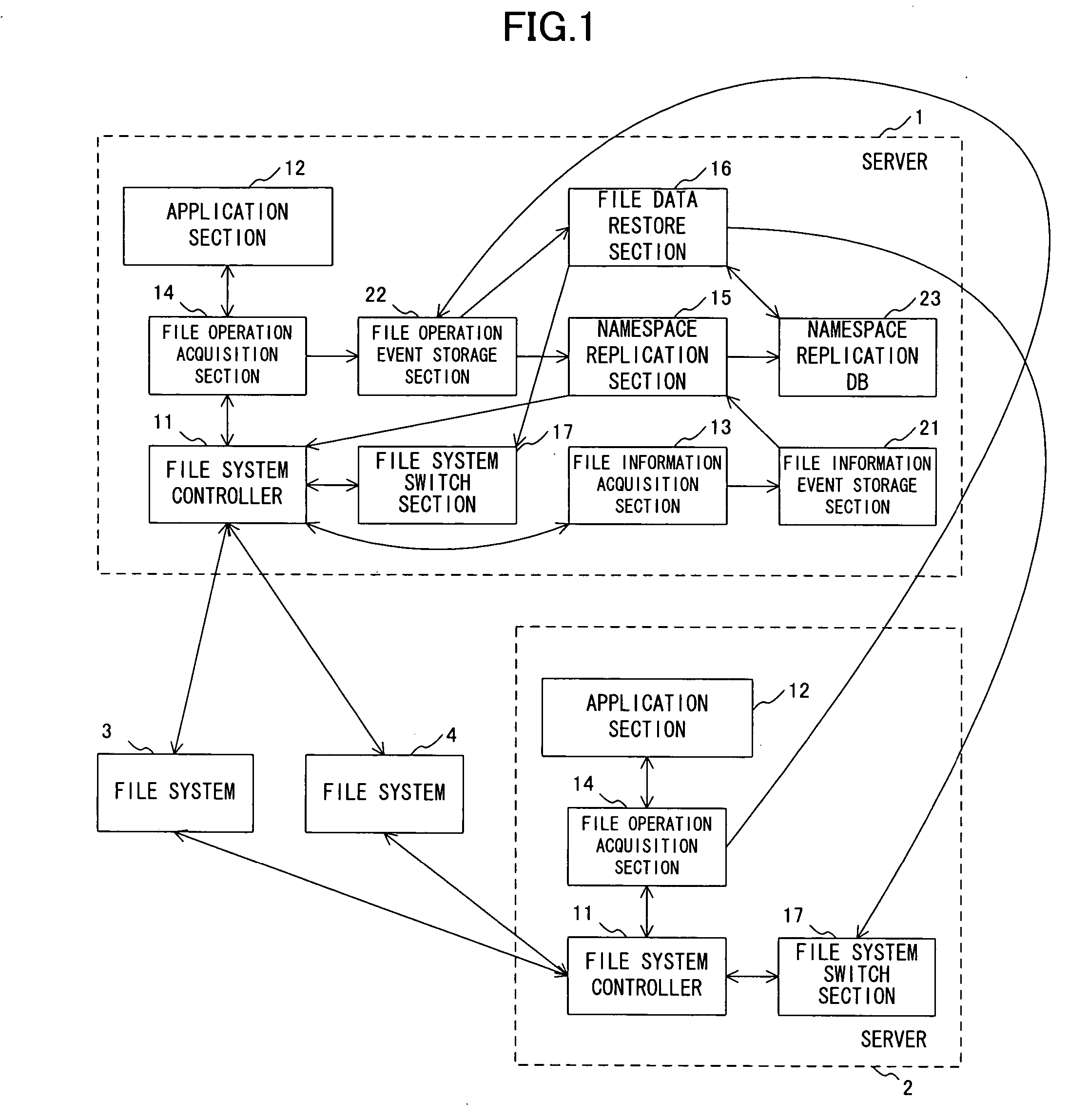
File management program, file management apparatus and file management method
InactiveUS20070038689A1Save disk spaceReduce spacingDigital data information retrievalData processing applicationsFile systemProcfs
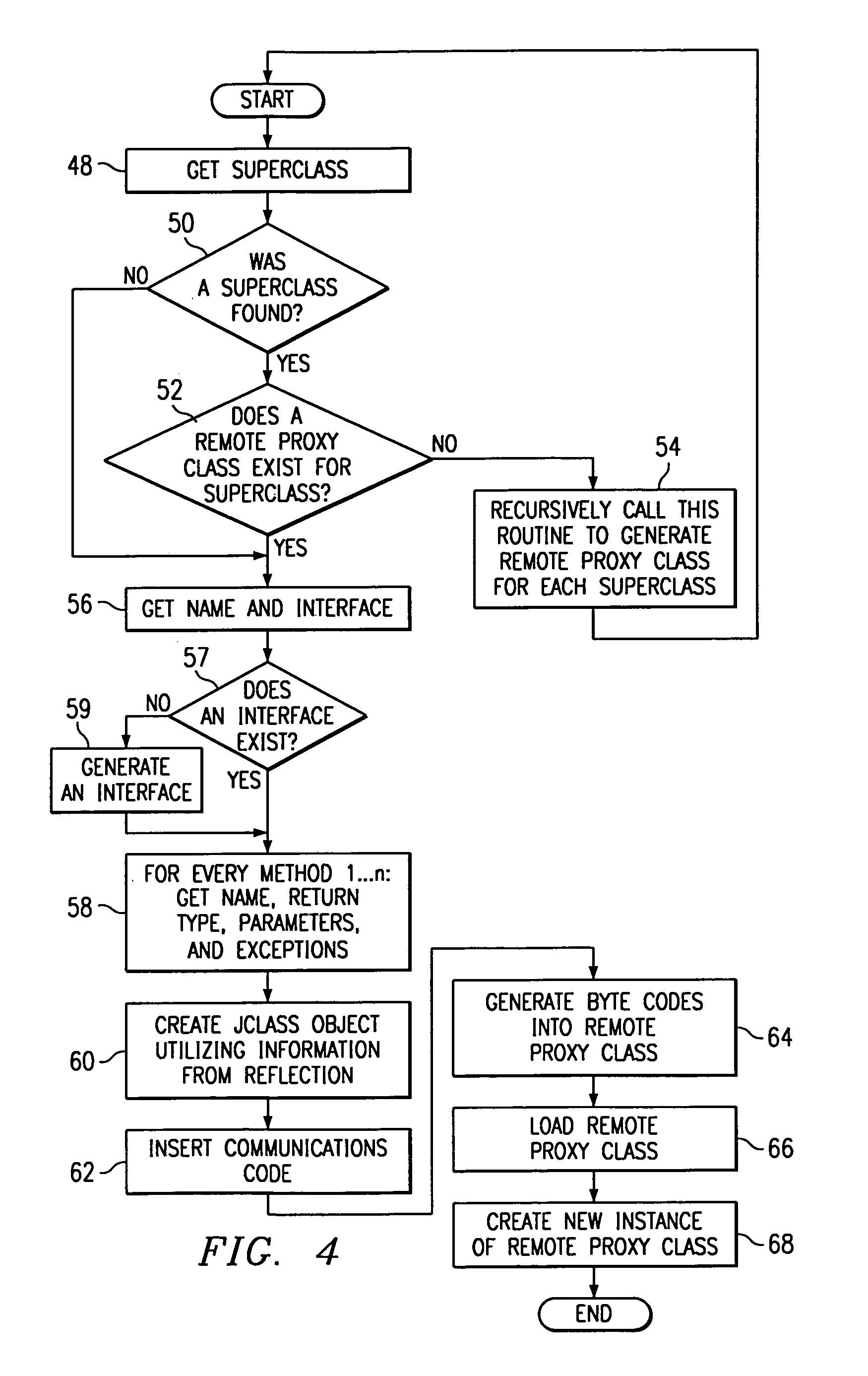
The present invention has been made to provide a file management program, a file management apparatus, and a file management method capable of migrating files between file systems while an application program is being run. A file management program allowing a computer to manage files on a plurality of file systems, the program allowing the computer to execute: a file information retrieve step that acquires the file information of source files on source file system and records the acquired file information as a file information event; a file operation trace step that acquires the information of file operation made for the source files and records the acquired file operation as a file operation event; and a namespace replication step that generates, based on the file information event and file operation event, a namespace replication database in which the namespace of the source files has been replicated logically.
Owner:FUJITSU LTD
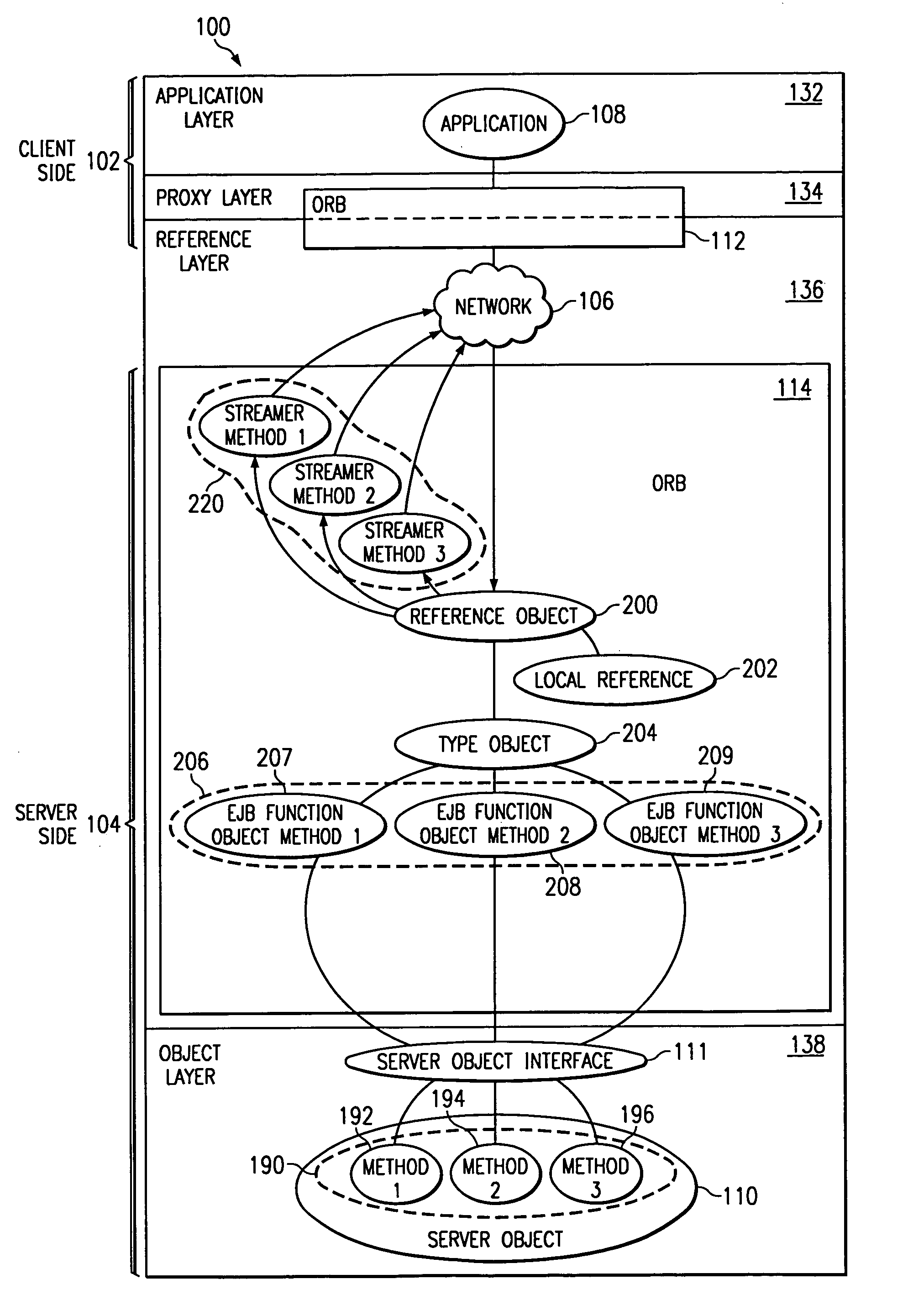
System and method for server-side communication support in a distributed computing environment
InactiveUS6951021B1Without incurring overheadSave disk spaceInterprogram communicationDistributed object oriented systemsDistributed Computing EnvironmentServer-side
A system for server-side communication support in a distributed computing environment is provided that includes a local reference (202) to a server object (110) on a server system (104). The local reference (202) provides a location of the server object (110) and a type of the server object (110). The local reference (202) resides within a server-side object request broker (114). A type object (204) is accessible by the local reference (202) using the type of the server object (110) from the local reference (202). The type object (204) represents a class of the server object (110). One or more specialized function objects (206) are linked to the type object (204) and correspond in number to one or more methods (190) of the server object (110). The one or more specialized function objects (206) provide wrapper functionality for each method (190) of the server object (110). Each specialized function object (206) provides access to a corresponding one of the one or more methods (190) of the server object (110).
Owner:INTELLECTUAL VENTURES ASSETS 119 LLC +1
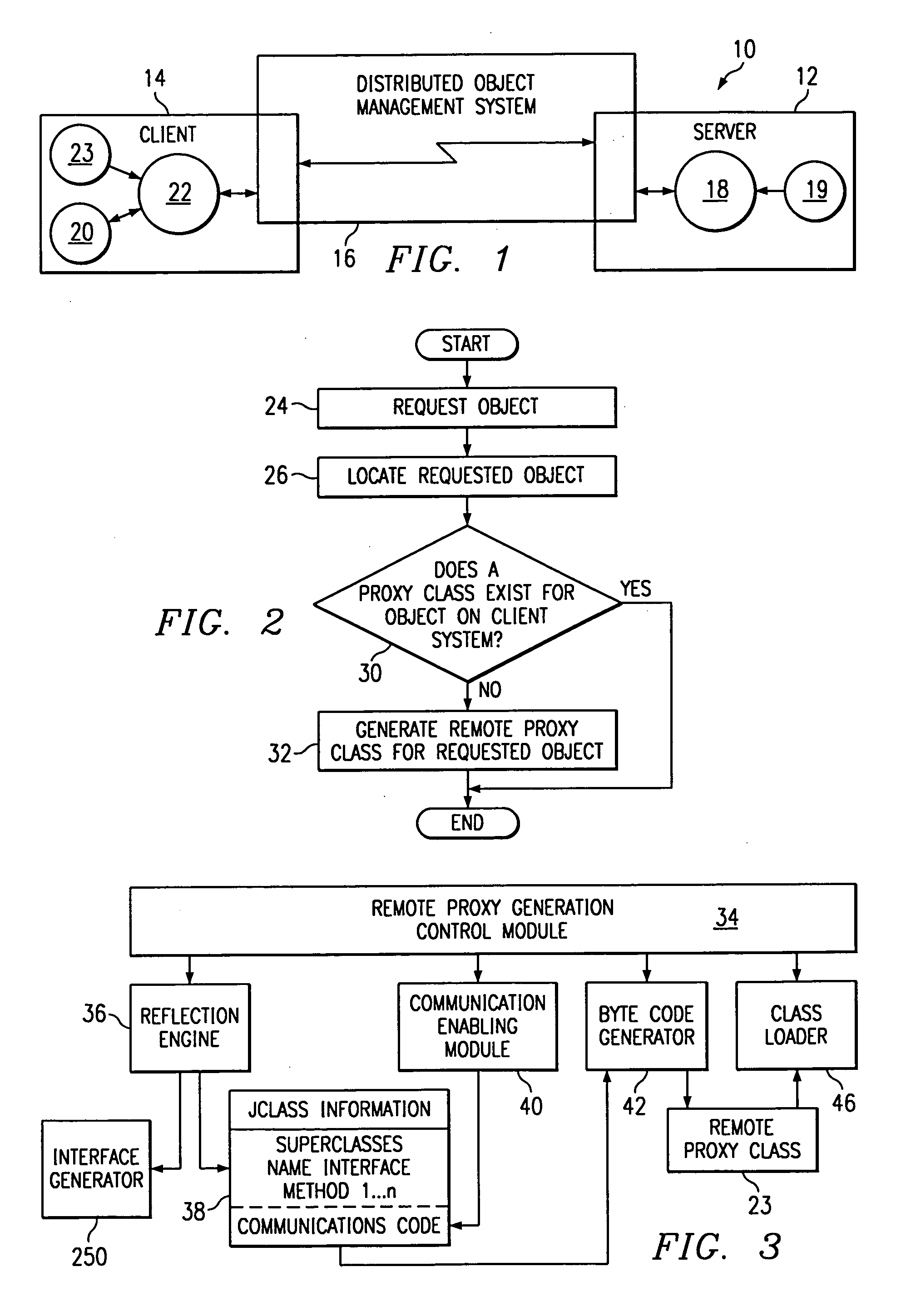
Log acquisition device and log acquisition method
InactiveCN101969386AReal-time deliveryRealize distributed collectionData switching networksServer logNetwork connection
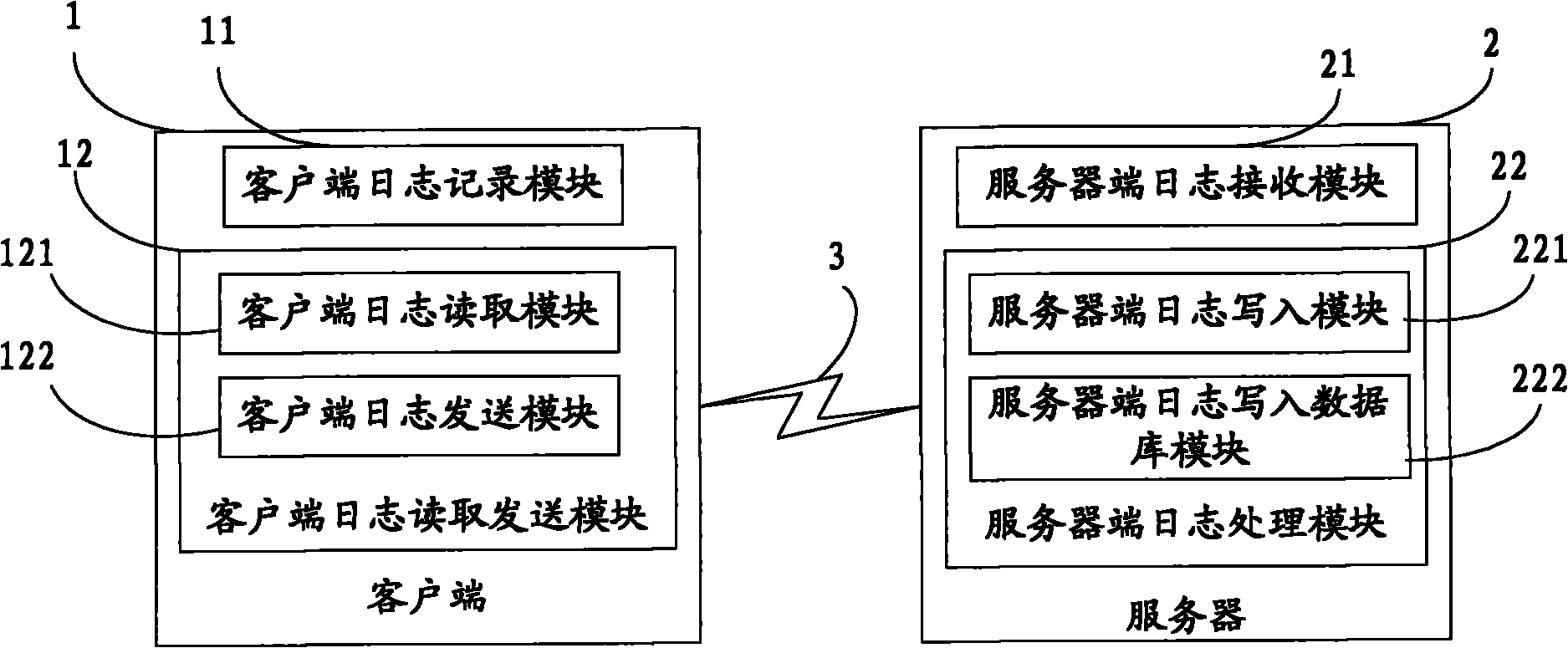
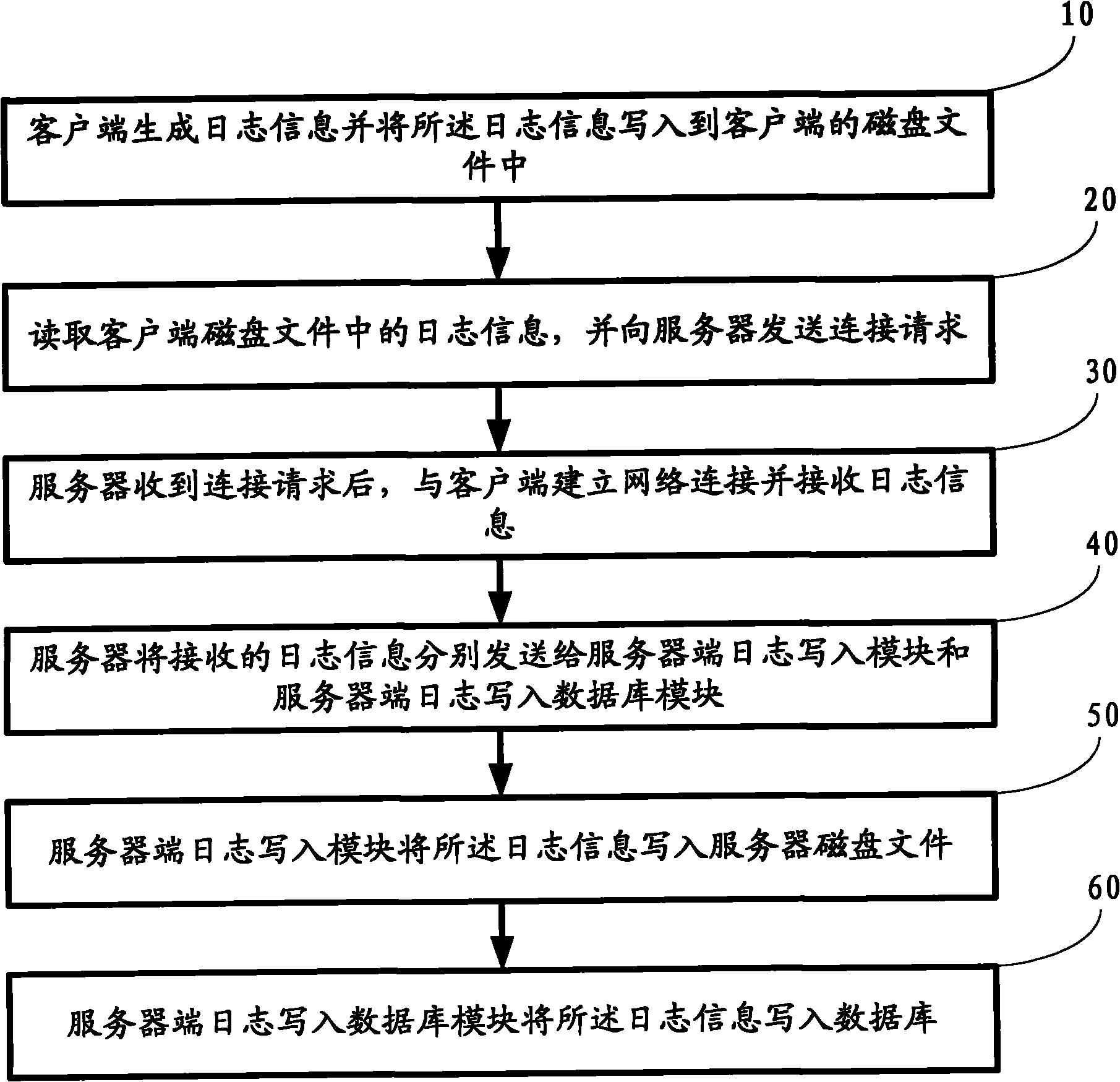
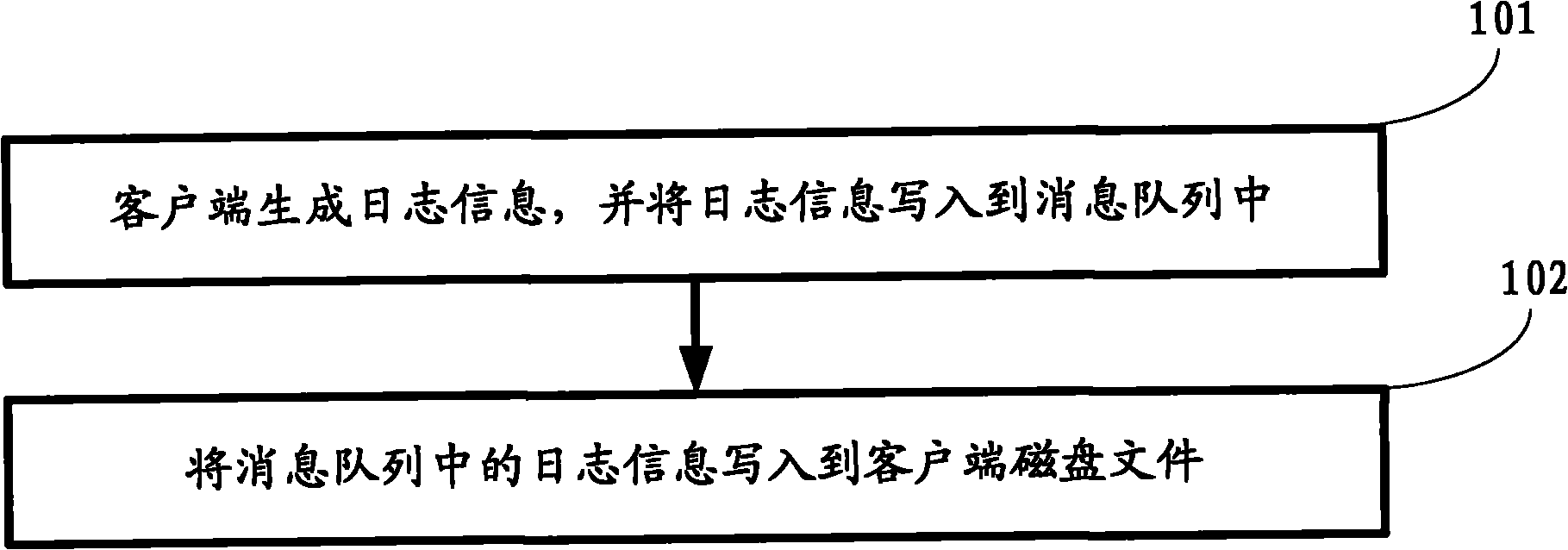
The invention relates to a log acquisition device and a log acquisition method. The device comprises at least one client for collecting logs and at least one server for recording the logs, wherein log information is transmitted between the client and the server through a network in real time. The method comprises that: the client generates the log information, writes the log information into a disk file of the client, reads the log information from the disk file of the client, and sends a connection request to the server; after receiving the request, the server establishes network connection with the client and receives the log information; the server sends the received log information to a server log writing module and a server log writing database module; the server log writing module writes the log information into the disk file of the server; and the server log writing database module writes the log information into the database. When the device and the method of the invention are used, the data analysis is more real-time, and the distributed acquisition of the logs is realized.
Owner:道有道科技集团股份公司 +1
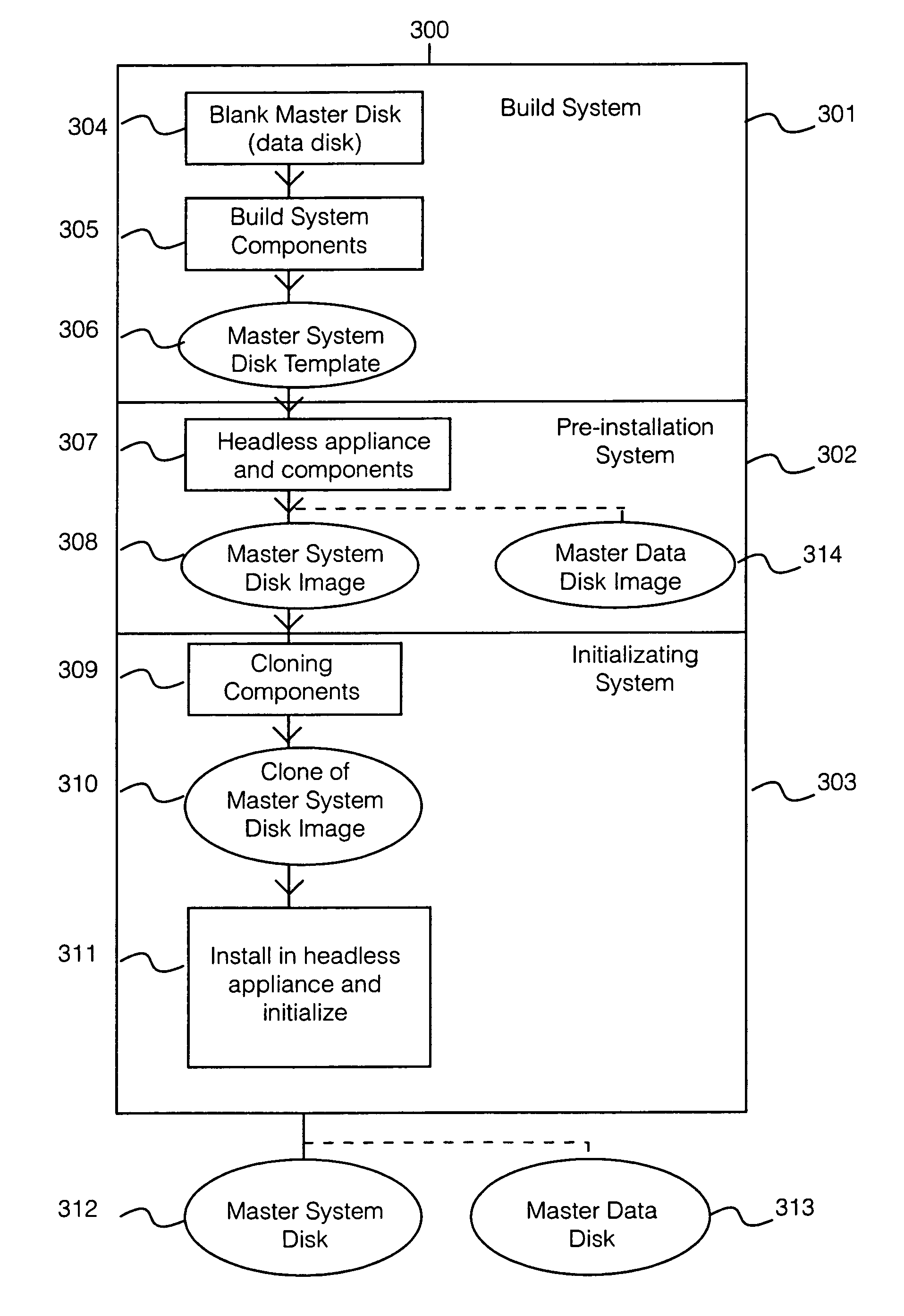
Method of manufacturing operating system master template, method of manufacturing a computer entity and product resulting therefrom, and method of producing a production version of an operating system
InactiveUS7000231B1Maximizing available disk spaceSpace maximizationError detection/correctionDigital computer detailsOperational systemManufacturing systems
A manufacturing system is disclosed for creating a master disk for producing clone copies installed on a plurality of production headless computer entities, said manufacturing system comprising: a build operating system, a set of primary operating system files, a set of emergency operating system files, a set of set-up files, a user interface and a data disk, wherein the manufacturing system creates a master system disk template from the data disk. The master system disk has not less than 3 operating systems, and the master manufacturing system is configured to initialize the master system disk.
Owner:HEWLETT PACKARD DEV CO LP
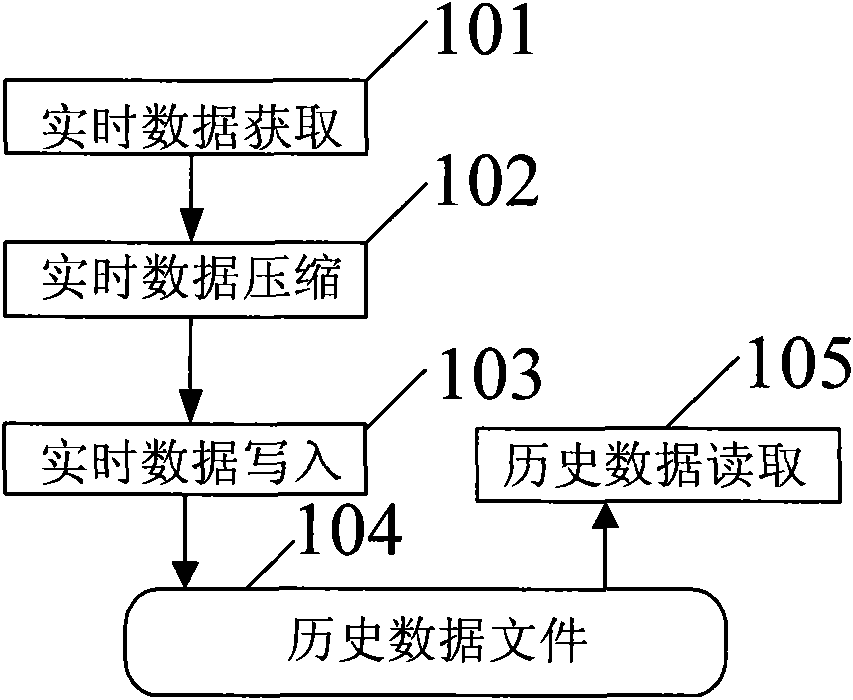
Establishing method for process control historical data file structure and data read-write method
ActiveCN102043795AReduce disk space usageSave disk spaceSpecial data processing applicationsData fileData compression
The invention discloses an establishing method for a process control historical data file structure, comprising the following steps: S1, establishing a file header, and writing file identification information into the file header; S2, establishing an index area, and dividing the index area into a measuring point description area and a data address area, wherein a data address in the data address area is an initial address of the historical data in a historical data file when fixed time duration data is written every time; S3, establishing a data area used for storing written measuring point historical data, wherein all data of each measuring point is stored on at least three continuous storage area. The invention further discloses a storage method and query method for process control historical data. In the invention, by data compression combined with a plurality of modes, the space of a magnetic disc can be greatly saved; the data storage speed is increased by adopting modes of blockwriting and memory mapping; and the data reading speed is greatly improved by modes of continuous storage, fast search and block reading of single measuring point data.
Owner:SHANGHAI XINHUA CONTROL TECH GROUP
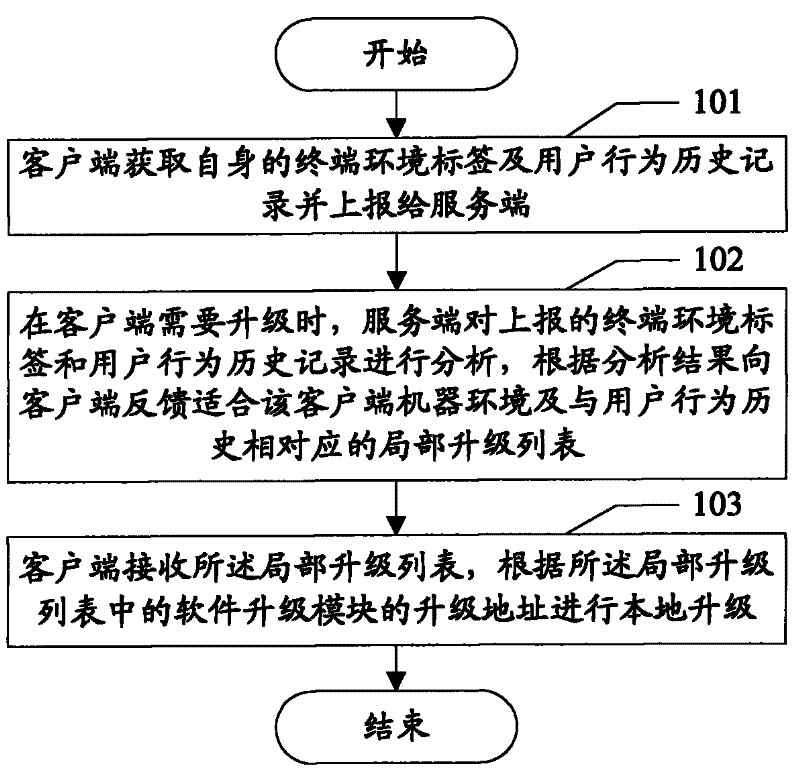
Software upgrading method and system
InactiveCN102236563ASave disk spaceSave network bandwidthProgram loading/initiatingTransmissionSoftware engineeringClient-side
The invention discloses a software upgrading method and a software upgrading system, which are used for solving the technical problem that a user machine environment and a user behavior history are not taken into account in the conventional software upgrading method to cause the wasting of a disk space and network bandwidth. In the method and the system, the user machine environment and user behavior historical records are collected, a server generates a local upgrading list for client software according to the machine environment with the client software and the behavior likes and dislikes of a user, and the client software is only required to download a software upgrading module suitable for the client software per se according to the local upgrading list for upgrading. By the technical scheme provided by the invention, not only the disk space and the network bandwidth are saved for the user, but also user experiences are improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
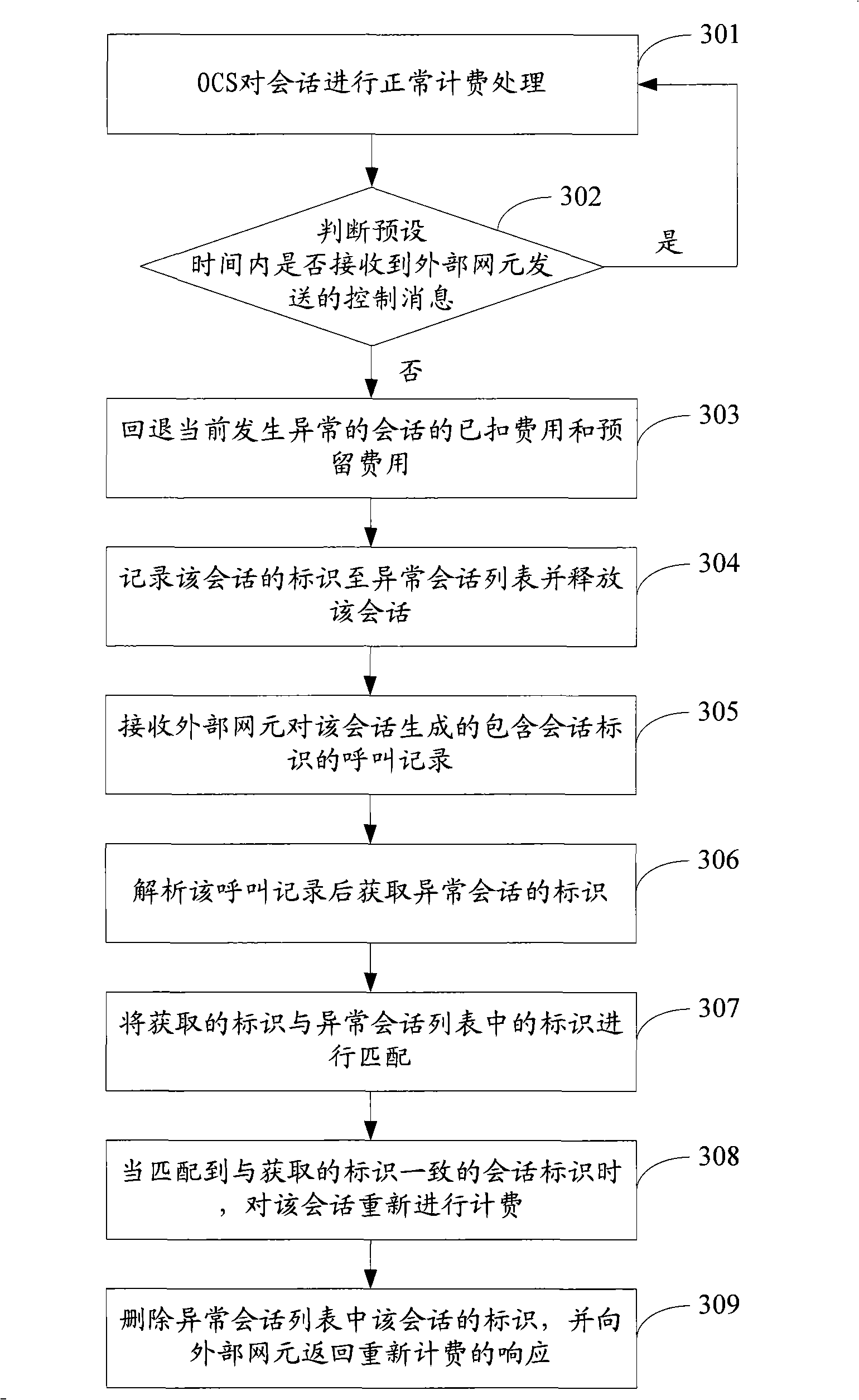
Billing processing method, system and online billing system
ActiveCN101267480AAccurate billingSave processing resourcesMetering/charging/biilling arrangementsTelephonic communicationHandling systemComputer science
The invention discloses a charging processing method, comprising the following steps: when a charging processing of a conversion has abnormal changes, an OCS receives the calling record generated by an external network element, which includes the label of the conversion; and re-charging is carried out on the conversion according to the label in the calling record. The invention also discloses a charging processing system and the on-line charging system OSC. In the embodiment of the invention, a calling record is generated only for conversion having abnormal changes, in no need of generating CDR for all conversions, thus saving the processing resources of the external network element and saving disk space for storing the CDS; since the OCS can re-charge for the conversion having abnormal changes, the loss caused by directly drawback of deducted fee and reserved fee is reduced, thus realizing precise charging when a conversion has abnormal changes.
Owner:HUAWEI TECH CO LTD
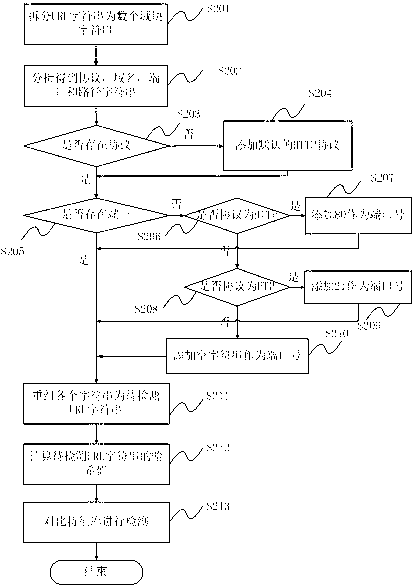
Formalization detection method and system for malicious URL (uniform resource locator)
ActiveCN102843271AImprove the detection rateGood detection rateData switching networksSoftware engineeringFeature data
The invention discloses a formalization detection method for a malicious URL (uniform resource locator). The formalization detection method comprises the following steps of: splitting the URL to be detected into syntactic element character strings according to a URL syntactic structure on the basis of the standard of RFC (request for comments); extracting designated character strings from the character strings obtained by splitting; performing completing treatment on the non-existent character strings; reordering the character strings obtained after completing treatment to obtain a new URL, and calculating the hash value of the new URL; and traversing a malicious URL feature library, and performing contrast detection on feature data in the malicious URL feature library and the hash value of the URL to be detected. The invention further discloses a formalization detection system for the malicious URL. The technical scheme disclosed by the invention can be effectively used against the variability in the formats of the URL; and compared with the traditional URL detection method, the detection rate against the malicious URL which often changes the format is higher, and a single feature can also be adopted for corresponding to multiple format variants of the malicious URL, so that the volume of a virus feature library required for the detection method is smaller, and the space of a memory and a magnetic disk can be further saved.
Owner:HARBIN ANTIY TECH
Recording method and profiling method for play-on-demand program
InactiveCN101489103AReduce disk array I/O operationsImprove performanceTelevision system detailsColor television detailsComputer hardwareTime segment
The invention discloses a recording method of a recording video-on-demand business and an archiving method applying to an Internet Protocol Television (IPTV) business system which provides a Time-Shifted Television and a Television On Demand business. The IPTV business system real-timely records the video of a time-shifted channel and fragment stores according to the video recording of the TSTV business and a storage mode, and deletes the fragment when the storage time period of the fragment is longer than a presetting time period; the IPTV business system receives a recording request of the TVOD business, parses the time-shifted channel and a time segment where the request recording video content is, if the time length of the time segment is shorter than the presetting storage time length, queries whether the stored recording content contains the video content after the time segment reaches over, if so, returns a successfully recorded response to a recording request sender. The method uses the TSTV recording content to implement the recording of the TVOD, saves the recording magnetic array space. Furthermore, the invention also provides the method for implementing a TVOD archiving assignment by using the TSTV recording content.
Owner:ZTE CORP
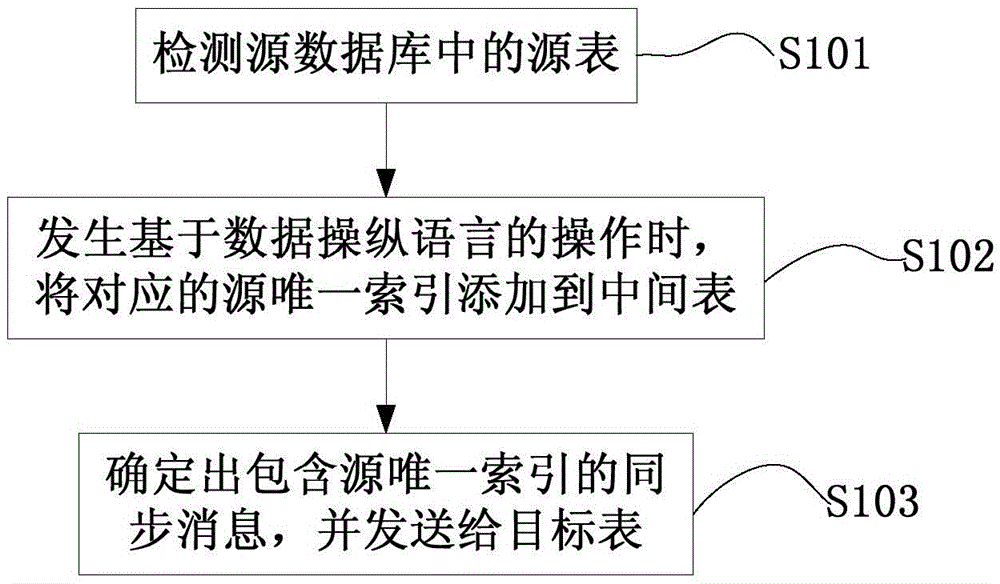
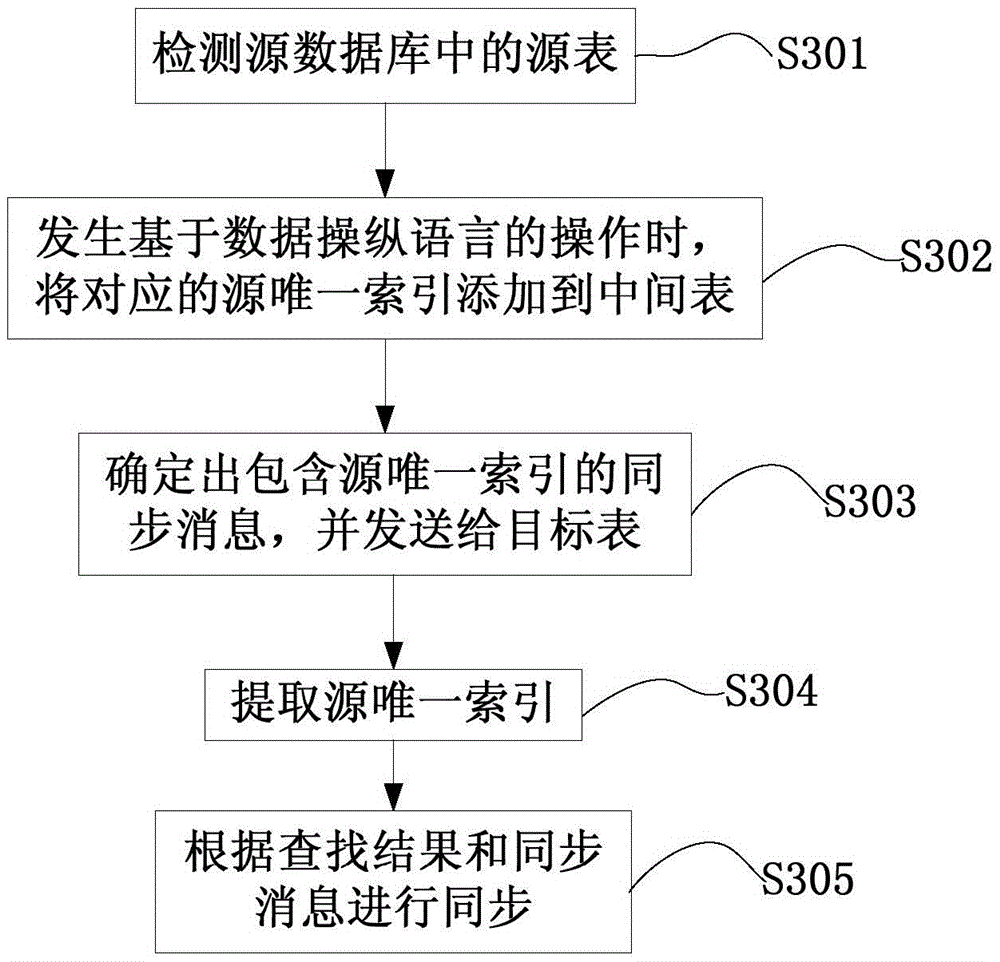
Database synchronization method and system, source data and target data synchronization device
InactiveCN106682002AGuaranteed performanceSave disk spaceSpecial data processing applicationsSource dataData manipulation language
The invention provides a synchronization device for source data and target data and a database synchronization method and system. Through monitoring source tables in source database, the source unique index of the source data in the source table based on the operation of the data manipulation language is added to the intermediate table corresponding to the source table; after satisfying the synchronization conditions, relevant source data to be synchronized in the source table is searched based on the source unique index recorded in the intermediate table and a synchronization message carrying the source unique index is sent to a target in the target library corresponding to the source table; searching and synchronization are carried out in the target table according to the synchronization message. The synchronization process does not need to be done in archive mode, which guarantees the performance of database and saves disk space.
Owner:ZTE CORP
System, device and method for filtering warning information
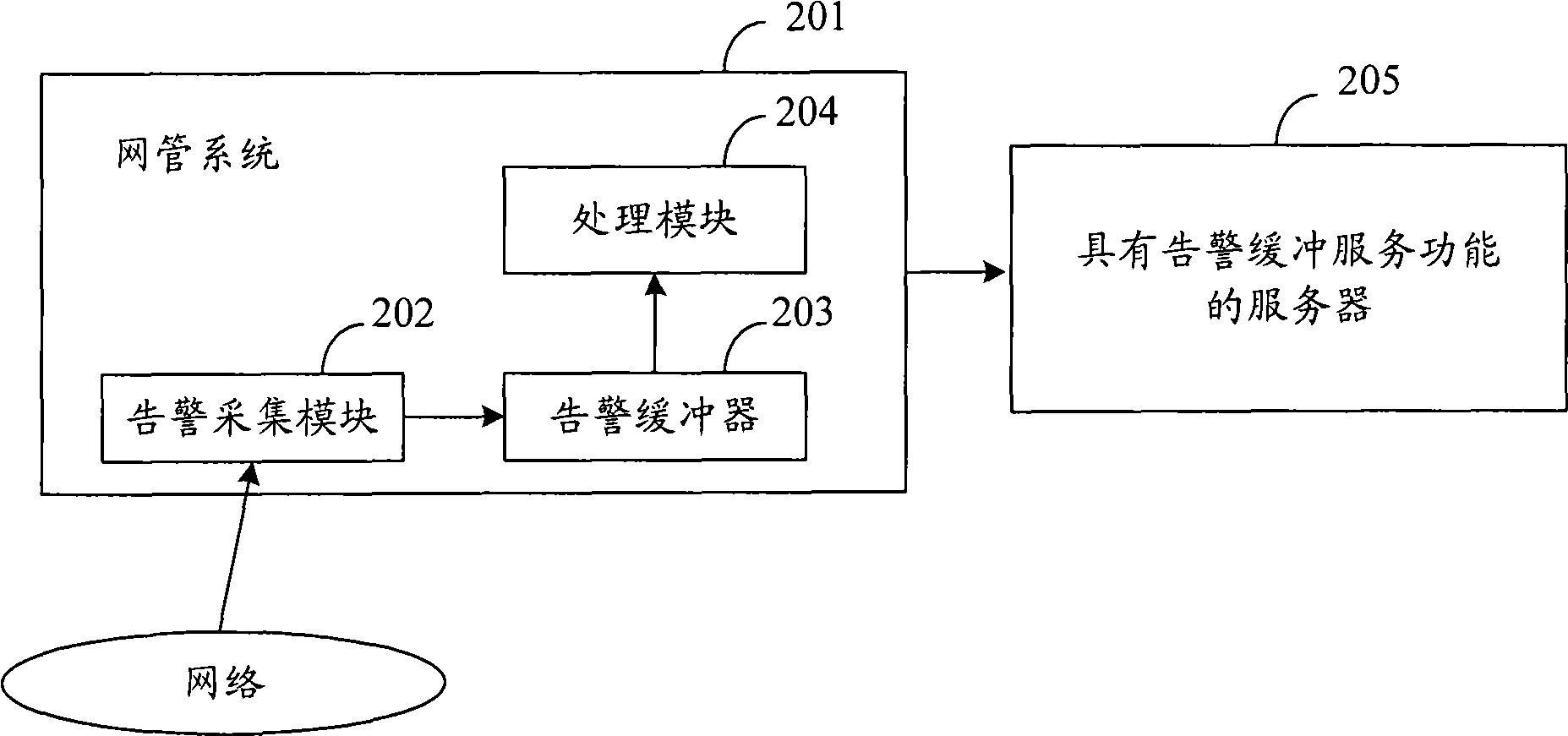
ActiveCN101547113AReduce shockReduce the number of alertsSupervisory/monitoring/testing arrangementsData switching networksNetwork managementComputer science
The invention discloses a system, a device and a method for filtering warning information used for a network management system; the warning information filtering system comprises a warning acquisition module, a warning filtering module, a warning buffer and a warning processing module, wherein the warning acquisition module is used for acquiring and sending the warning information to the warning filtering module; the warning filtering module is used for storing the received warning information; if warning disappearing information is received and then warning generation information with same warning is received in the set time, the warning generation information and the warning appearing information which have the same warning are deleted; the warning buffer is used for buffering the warning information filtered by the warning filtering module; and the warning processing module is used for extracting the warning information from the warning buffer and processing the warning information. The technical proposal can effectively reduce the warning number needing buffering, thus reduce the disk space used for storing the warning, reduce the impact of warning storm on CPU and improve the utilization ratio of the system.
Owner:ZTE CORP
Data storage system and method
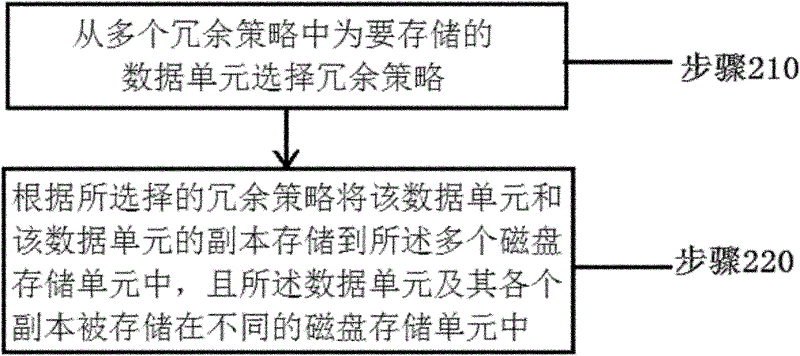
InactiveCN102622184AGuaranteed safetySave disk spaceInput/output to record carriersControl cellEngineering
The invention provides a data storage system and a method for storing data by using the system. The system comprises a plurality of disk storage units, a redundant strategy database and a storage control unit. The data storage method and the system select redundant strategies respectively according to different data units, save disk spaces on the basis of system safety guarantee, further improve system performance, and reduce operation cost successfully.
Owner:北京东方广视科技股份有限公司
A method and a device for realizing cloud storage
InactiveCN104519078AImprove real-time performanceIncrease flexibilityTransmissionFile synchronizationData synchronization
The disclosure relates to a method and a device for realizing cloud storage. The method comprises: receiving cloud storage strategies that are set by a user according to data synchronization requirement, wherein, the cloud storage strategies comprise mapping of a specified attribute file; monitoring operation from the user on a file of a client end in real time; in the case that the user executes, at the local client end, operation of creation, modification, or deletion on the file meeting the cloud storage strategies, executing corresponding operation on a file in a cloud storage server; and in the case that the user executes, at the local client end, the operation of deletion on the file meeting the cloud storage strategies, determining whether a strategy corresponding to the operation of deletion is removed from the cloud storage strategies according to the data synchronization requirement, and updating the cloud storage strategies in the case that the strategy corresponding to the operation of deletion is removed from the cloud storage strategies. The method and the device for realizing cloud storage can synchronize the specified files at different directories onto the cloud storage server without constructing the local virtual disks.
Owner:CHINA TELECOM CORP LTD
Real-time monitoring system and method suitable for mobile health care
ActiveCN104055500ASave disk spaceReduce hardware requirementsSensorsBlood characterising devicesMonitoring dataLocal area network
The invention discloses a real-time monitoring system and method suitable for mobile health care. The system comprises a monitor, a data acquisition terminal, a database server, an observing relay server and an observing terminal. The method is an asynchronous real-time monitoring method, and comprises a step of requesting real-time monitoring through the observing terminal and a step of requesting to check history data. The monitor, the data acquisition terminal, the observing relay server, the observing terminal and the database server are connected to the Internet or a local area network, and share one database server with a plurality of hospitals, a plurality of areas and even the whole country, so that share of patient monitoring data is realized, the observing terminal only requests current real-time data while requesting real-time monitoring data without requesting history real-time data, real-time data are only requested when a real-time data duration is greater than a buffering duration, the transmission data size of real-time data is reduced, and the stable transmission of real-time data is ensured; history data are transmitted after being compressed, so that the network transmission data size is reduced, and the network pressure is lowered.
Owner:CONTEC MEDICAL SYST
Method and device for assessing safety of application program
ActiveCN104850775ASave disk spaceUser identity/authority verificationDigital data authenticationInformation findingComputer terminal
The invention discloses a method and a device for assessing safety of an application program, wherein the method comprises the steps as follows: a feature server receiving a request of a first feature terminal for assessing the safety of the application program; transmitting an acquisition request for an executable file corresponding to the application program to at least one second feature terminal, wherein the acquisition request carries unique identification information of the application program, the executable file stores operation behavior of the application program during operation, and the feature server is a server for performing safety management on the first feature terminal and the second feature terminal based on an internal network; finding the executable file corresponding to the application program according to the unique identification information, and assessing the safety of the application program according to the executable file. According to the method and the device of the invention, the terminal does not need to upload the executable file of the application program safety of which is unknown, and the executable file only needs to be uploaded when required, thereby saving network bandwidth resources and disk space of a server.
Owner:BEIJING QIANXIN TECH
Search system index switching method and search system
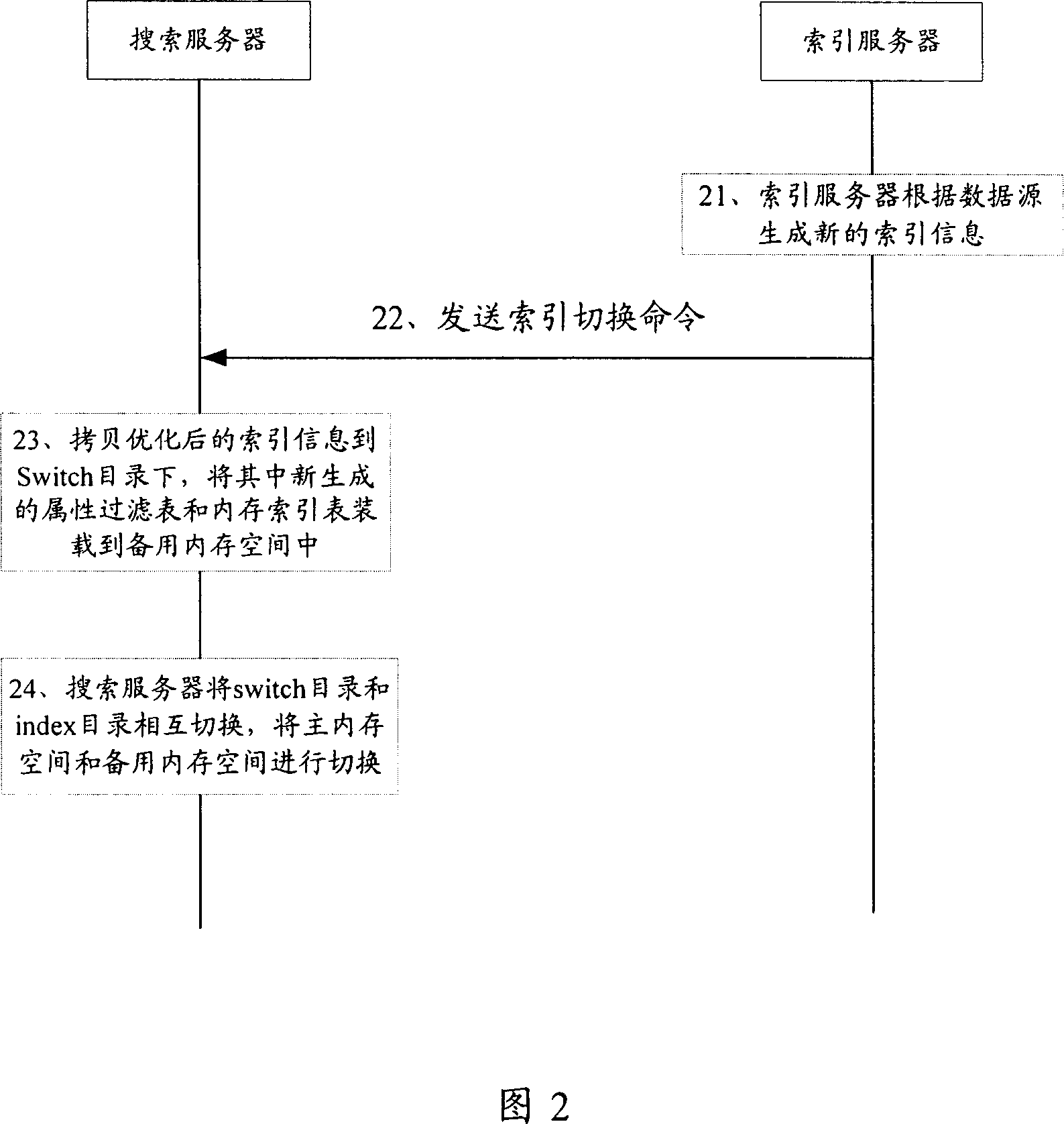
ActiveCN1975717AShorten the timeThe search service does not affectSpecial data processing applicationsIndexing ServiceBackup
The invention opens an index switching method in search system. The searching servers reserves main directories and backup directories, main memory space and backup memory space to load index information. Search servers perform searching according to the index in main directories and memory space. In the index switching, the new index information produced by search servers are stored in backup directories as well as backup memory space. Then exchange data between main directories and backup directories; exchange data between main memory and backup memory. The invention also opens a searching system based on described method, which including index server, transit server and search server.
Owner:SHENZHEN SHI JI GUANG SU INFORMATION TECH
Medical imaging system and method
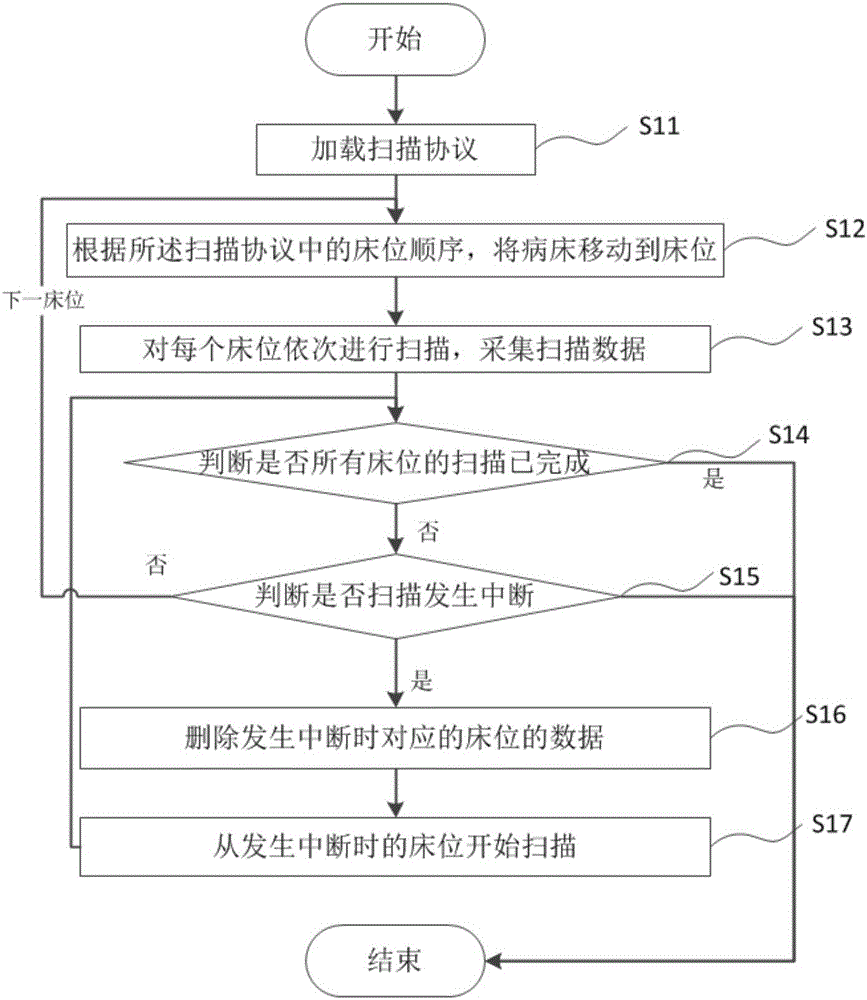
InactiveCN105796122AReduce the burden onAvoid rescanningRadiation diagnostics testing/calibrationDiagnostic recording/measuringComputer moduleMedical imaging
The invention discloses a medical imaging system which comprises an examination module, a control module and a data collection module. The examination module is used for loading a scanning protocol; the control module is used for controlling the examination module to scan a bed according to the scanning protocol based on a scanning request given by the examination module and controlling the data collection module to collect scanned data; after scanning is interrupted, the control module is used for controlling the data collection module to delete the bed collected data of the bed where interruption happens and controlling the examination module to start scanning from the bed where the interruption happens. The invention further discloses a medical imaging method. When scanning is recovered after being interrupted, the scanning is started from the bed where interruption happens, thus, repeated scanning caused by the situation that scanning should be started from the first bed after being interrupted in the prior art is avoided, scanning time can be saved, the burden on a patient can be reduced, and hardware disk space can be saved.
Owner:SHANGHAI UNITED IMAGING HEALTHCARE
Method and system of cloud workflow scheduling in container environment
InactiveCN109639791AMonitor performanceReduce sizeEncryption apparatus with shift registers/memoriesData switching networksCloud workflowMirror image
The invention belongs to the technical field of cloud workflow scheduling in container environments, and discloses a method and a system of cloud workflow scheduling in a container environment. The system of cloud workflow scheduling in the container environment includes a resource acquisition module, a container performance monitoring module, a main control module, a resource allocation module, adata mirror image optimization module, an allocation report module, a data storage module and a display module. According to the system, container performance can be monitored through the container performance monitoring module while performance of a server can be simply and conveniently monitored, error warnings can be generated, and a method of visually presenting parameters through forms of graphs and tables can be implemented; at the same time, a mirror image is enabled to still ensure good re-editability after packaging and publishing through the data mirror image optimization module; and all file drives of existing Docker are supported, and through firstly containerizing a local mirror image and then carrying out exporting after abridging processing, no specific file drive is depended on.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
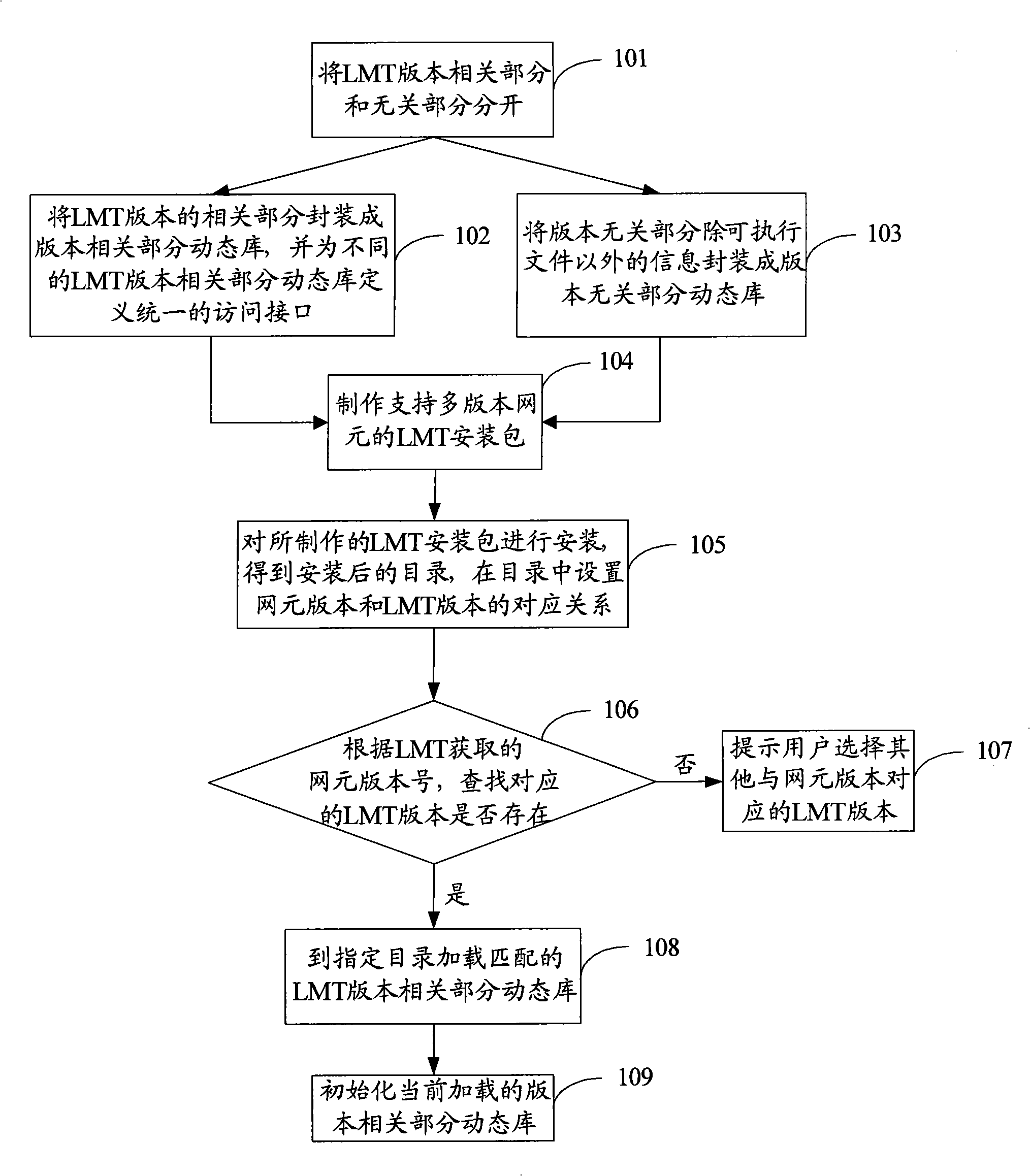
Method and device for implementing local maintenance terminal management multi-version network element
InactiveCN101272279ASave disk spaceShorten the timeData switching networksSoftware engineeringNetwork element
The invention discloses a method for realizing the management of multi-version network elements at local maintenance terminal. The method comprises the steps that: the content of the local maintenance terminal (LMT) is divided into version relevant part and version irrelevant part according to service relativities thereof, and the LMT version relevant parts are packaged into dynamic library of version relevant parts; and the LMT installation package supporting multi-version network elements is divided, made and installed according to the LMT version, and the corresponding relationship between network element version and the LMT version is arranged in an installed list; when the LMT is accessed to a network element, the LMT can automatically acquire the version number of the present network element and automatically upload the dynamic library of version relevant part of LMT version corresponding to the network element version according to the version number of the network element. The invention also discloses a device for realizing the management of multi-version network elements at local maintenance terminal. By adopting the method and the device of the invention, the LMT version and the network element version can be self adapting and disc space occupied by the LMT version can be saved.
Owner:沈春梅
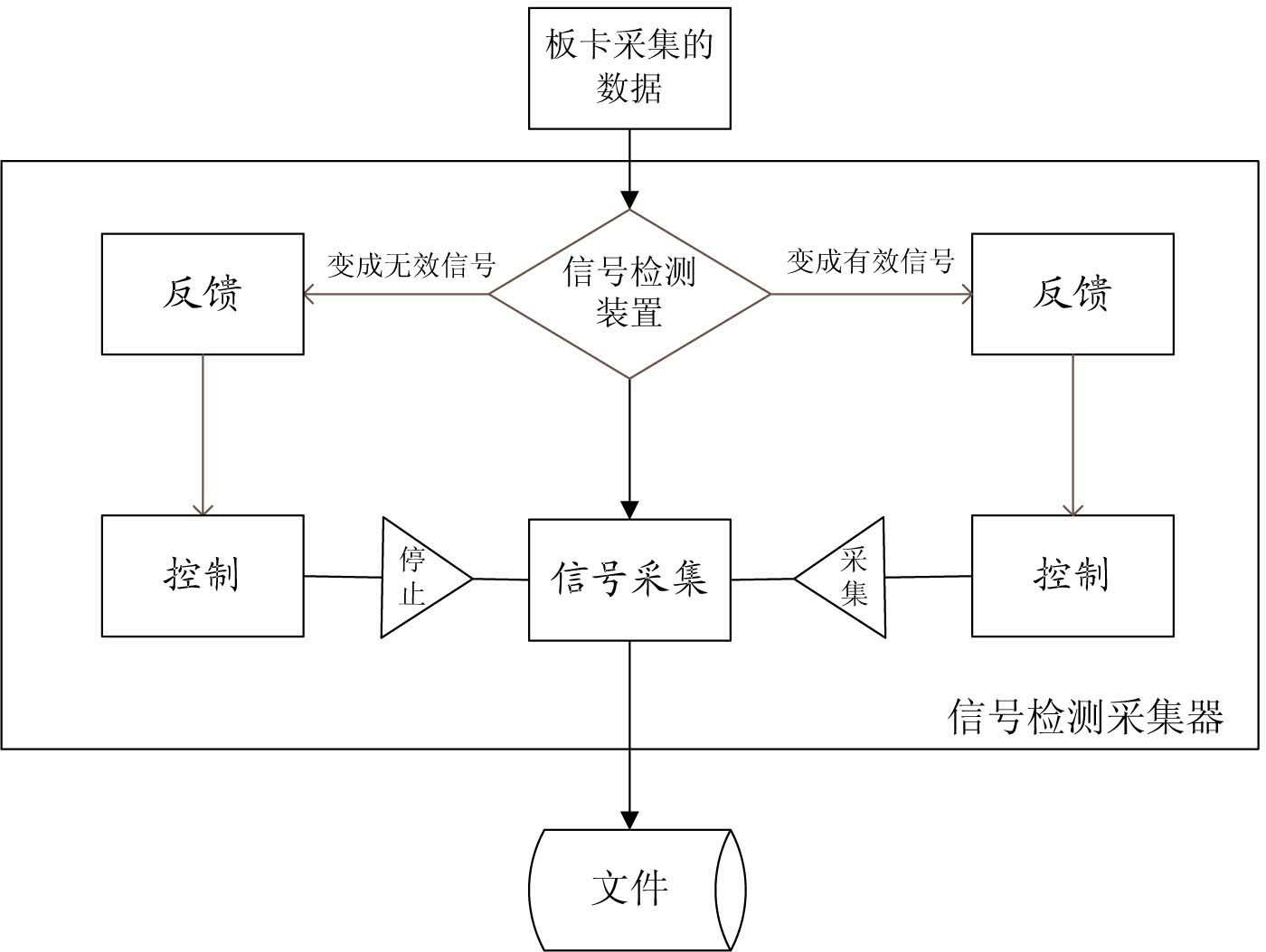
Method for automatically detecting real-time signals or streams to realize full-automatic recording
ActiveCN102098450AShort manufacturing cycleSave manpower and material resourcesTelevision system detailsColor television detailsMaterial resourcesComputer science
The invention relates to a method for automatically detecting real-time signals or streams to realize full-automatic recording. The hardware used in the method comprises an acquisition private line, a board card connected with a signal acquisition line and a signal detection acquisition equipment, wherein, the board card is connected with a signal acquisition server in an insertion manner; and the signal detection acquisition equipment is arranged on the signal acquisition server and comprises a signal detection device, a feedback device, a control device and an acquisition device. The methodcomprises the following steps: a signal receiving step, a caching step, a signal detection step, a feedback step, a control step and a signal acquisition step. In the invention, the signal detection device is adopted to judge which are the effective signals or streams, or ineffective signals or streams through the detection of the received signals or streams; the materials are selectively acquired, and a great quantity of manpower and material resources are saved, thus leading that the collecting and editing personnel are liberated from the annoying material selection work without any technical content, saving a large amount of disk space and shortening the programming period.
Owner:BEIJING DAYANG TECH DEV
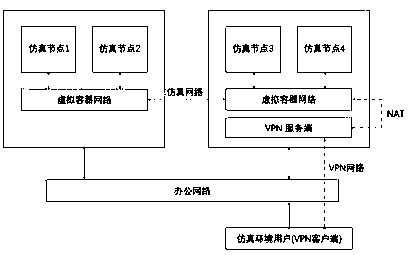
Production environment simulation method based on container
ActiveCN110572484AEasy to integrateNetwork emulationNetworks interconnectionVirtualizationIp address
A production environment simulation method based on a container comprises the following steps: manufacturing a container basic mirror image according to an operating system and a middleware assembly of a terminal user; deploying a container service and a container virtualization network component on a plurality of machines, and creating one or more virtual networks corresponding to the network ofthe terminal user in the container virtualization network component; according to the node deployment condition of the terminal user site, creating containers one to one, wherein host names and IP addresses of the containers are consistent with the terminal user site; deploying a VPN server on any machine, creating an independent VPN network, and establishing NAT forwarding from the VPN network tothe virtual container network; and installing a VPN client on a terminal user computer, connecting the VPN client to the VPN server in the step s4, setting a local router, and pointing the route of the virtual container network to the VPN server. Environment simulation is realized based on a container technology, the cost is reduced, and the software delivery efficiency is improved.
Owner:WHALE CLOUD TECH CO LTD
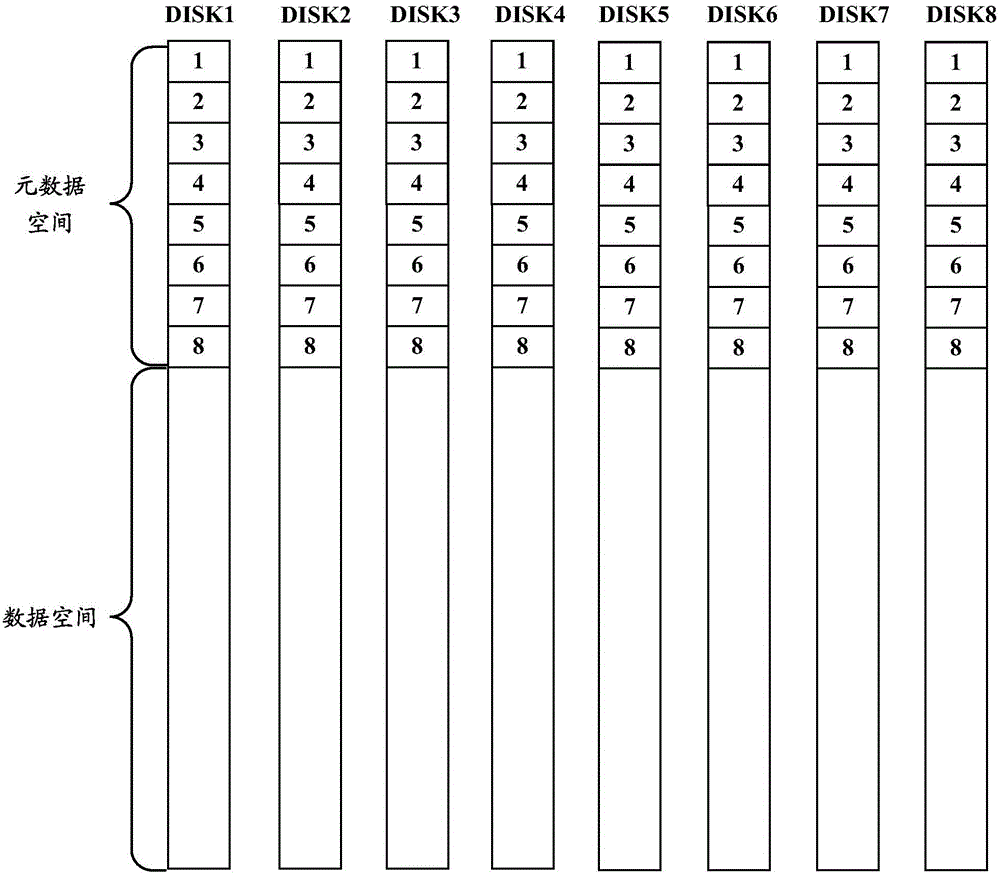
Metadata storage method and apparatus
ActiveCN106095330AImprove operational efficiencyEasy to operateInput/output to record carriersRAIDMetadata
The invention provides a metadata storage method and apparatus. The method and the apparatus are applied to an RAID comprising N member disks; and the redundancy degree of the RAID is M, wherein N is greater than M. The method comprises the steps of maintaining a mapping relationship between the member disks and storage regions, wherein for each member disk, L member disks are selected from the N member disks, one storage region is selected from each member disk of the L member disks, the mapping relationship between the member disks and the selected L storage regions is maintained, L is greater than M and less than or equal to N, and the L storage regions are arranged in a metadata space of each member disk; and querying the L storage regions corresponding to the member disk by utilizing the mapping relationship when metadata of the member disk needs to be stored, and storing the metadata in the L storage regions. Through the technical scheme provided by the method and the apparatus, the storage space of the disk can be saved, the space utilization rate can be increased, the metadata operation efficiency and performance can be improved, and the updating speed and efficiency are high.
Owner:MACROSAN TECH
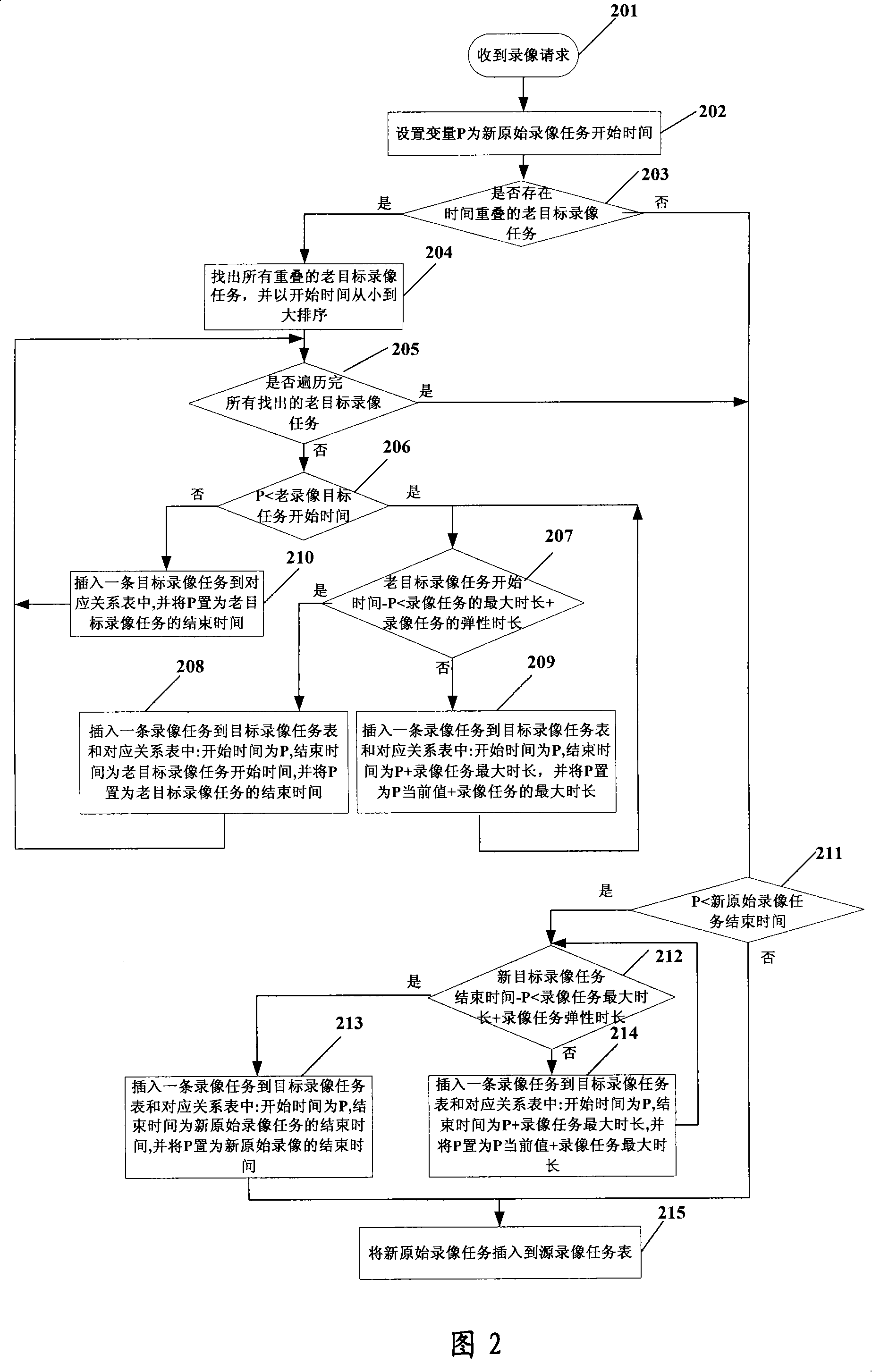
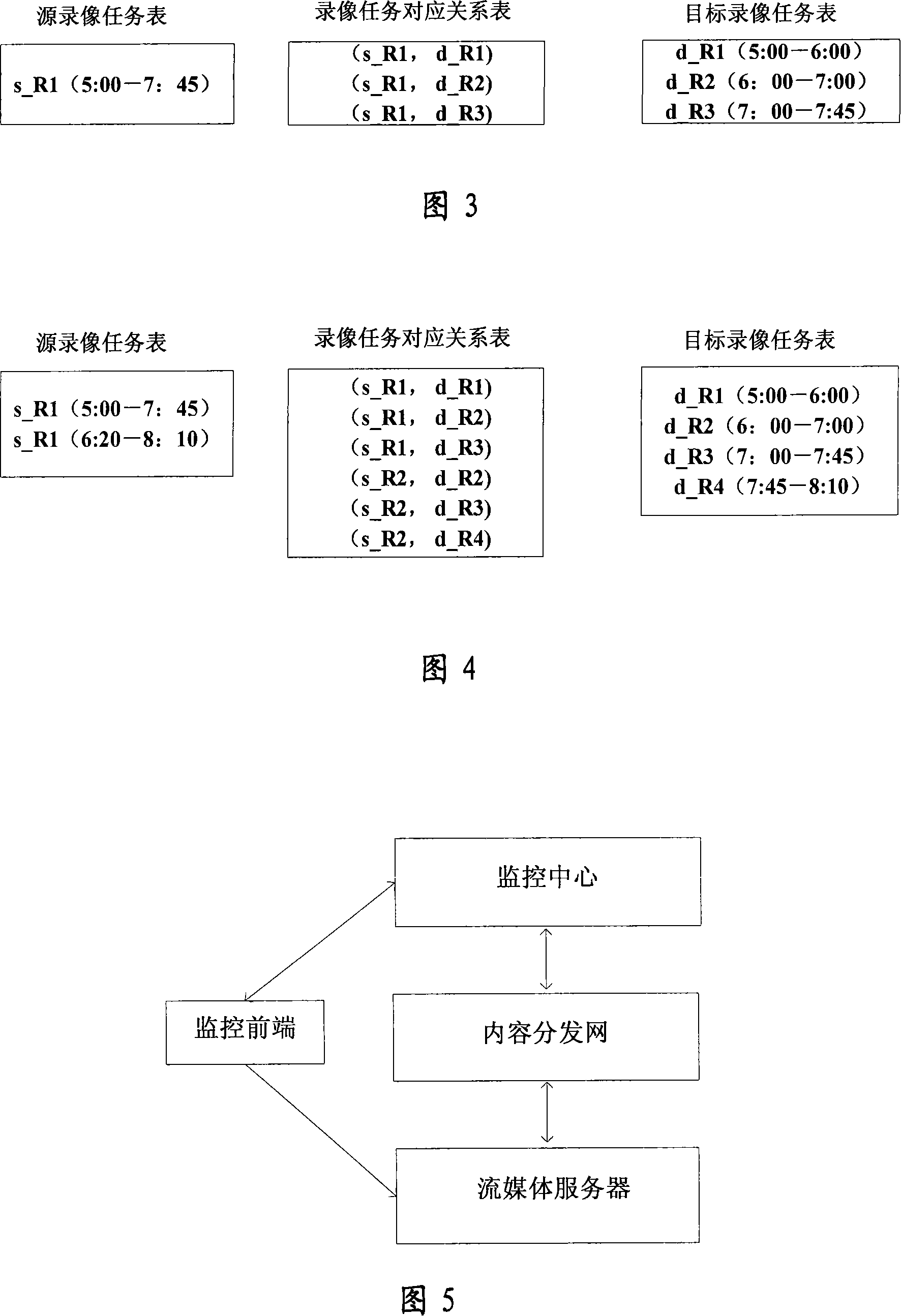
Method and system for preventing video recording from overlapping in Global E-eye system
InactiveCN101227597ASave disk spaceImprove performanceTelevision system detailsColor television detailsContent distributionMedia server
The invention discloses a method of preventing video overlapping in the global eye system, which is pre-provided with a source-video task list, a target video task list and a corresponding relation list, the method comprises the following steps: a content distribution network compares a new original video task received from a monitoring center with an old target video task stored in the target task list, when the existence of an old target video task is overlapped or part-overlapped with a new original video task in the video recording time is confirmed, the new original video task is separated into at least one target video task and then is inserted into the target video task list and the corresponding relation list; scanning the to-be-distribute target video task in the target video task list at predetermined time, and distributing the to-be-distribute target video task to a streaming media server in advance; the streaming media server starts to order according to the videos which gets from the content distribution network, obtains a code current from the terminal of the monitoring, and stores the code current on a magnetic matrix of the streaming media server. The invention successfully avoids detect of repeat-recording in a streaming media server.
Owner:ZTE CORP
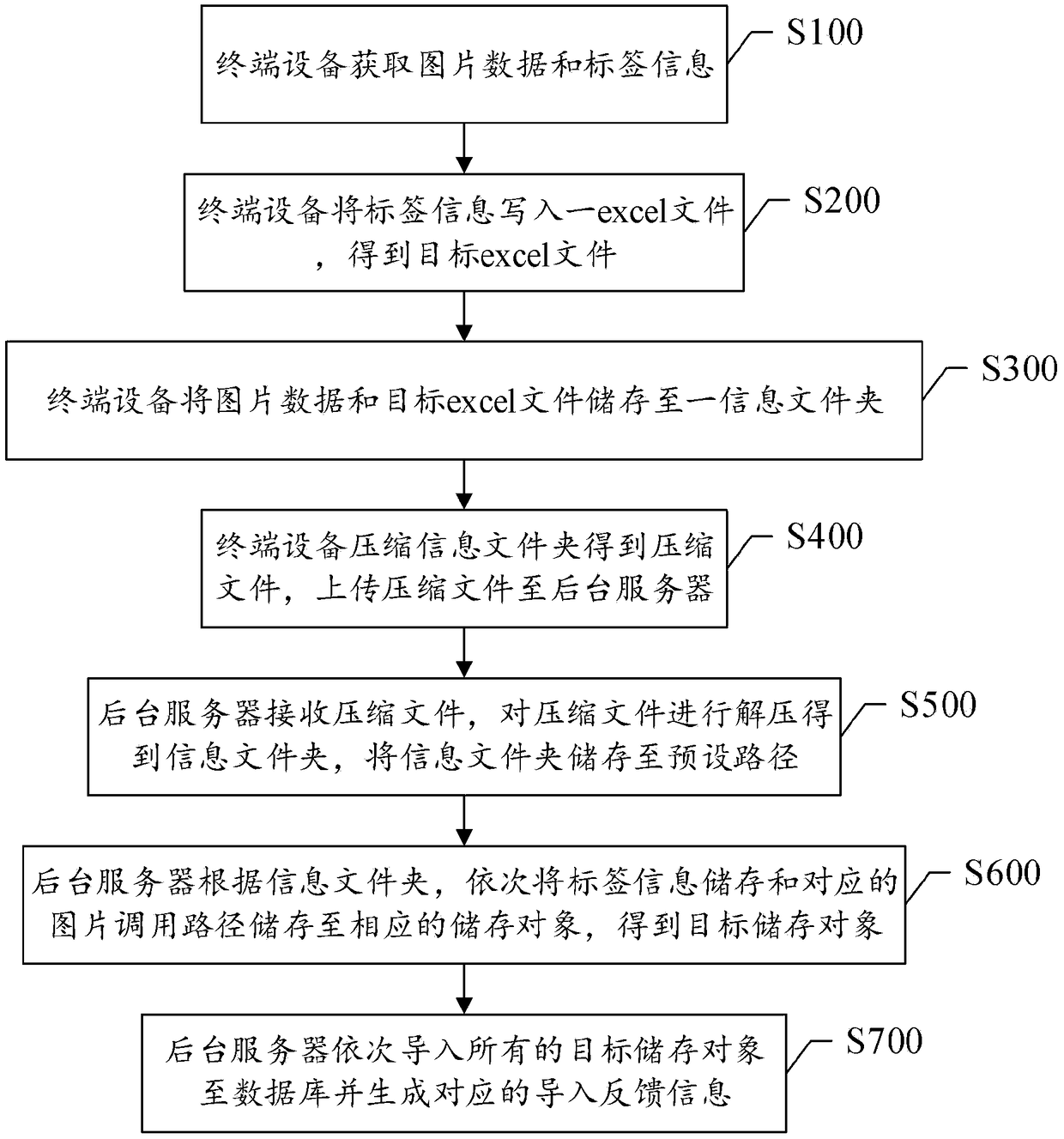
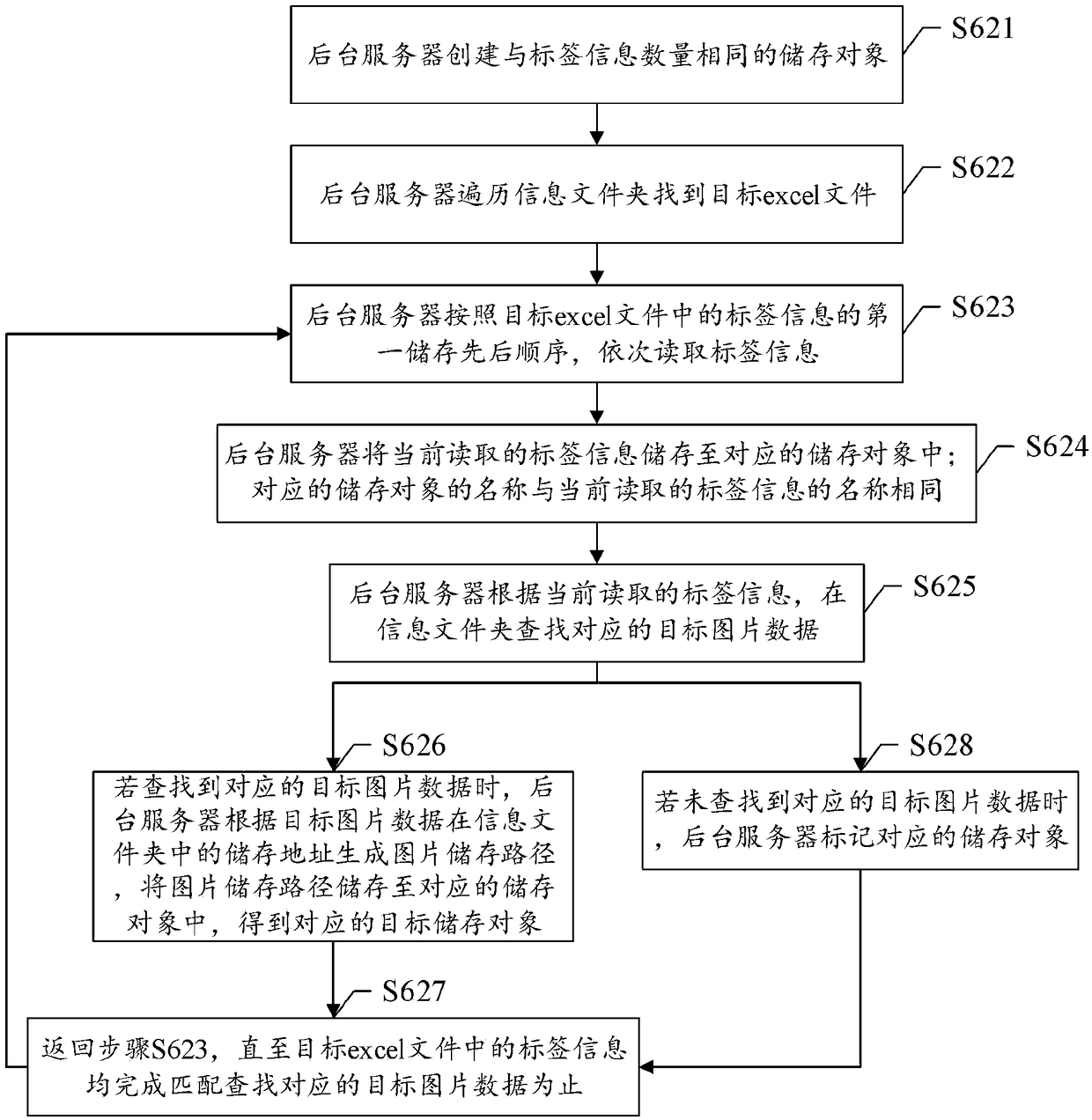
Splicing method and system of picture data and label information
InactiveCN108829736AReduce manual workloadSave disk spaceSpecial data processing applicationsObject storeOccupancy rate
The invention discloses a splicing method and system of picture data and label information. The method includes: acquiring the picture data and the label information by terminal equipment; writing thelabel information into an excel file to obtain a target excel file; storing the picture data and the target excel file to an information folder by the terminal equipment; compressing the informationfolder to obtain a compressed file, and uploading the compressed file to a background server; receiving the compressed file by the background server, decompressing the compressed file to obtain the information folder, and storing the information folder to a preset path; sequentially storing the label information and corresponding picture calling paths to corresponding storage objects according tothe information folder to obtain target storage objects, wherein the target storage objects store the label information and the corresponding picture calling paths; and sequentially importing all thetarget storage objects into a database, and generating corresponding import feedback information. The method reduces labor and a disk occupancy rate, and reduces an error rate.
Owner:SICHUAN FEIXUN INFORMATION TECH CO LTD
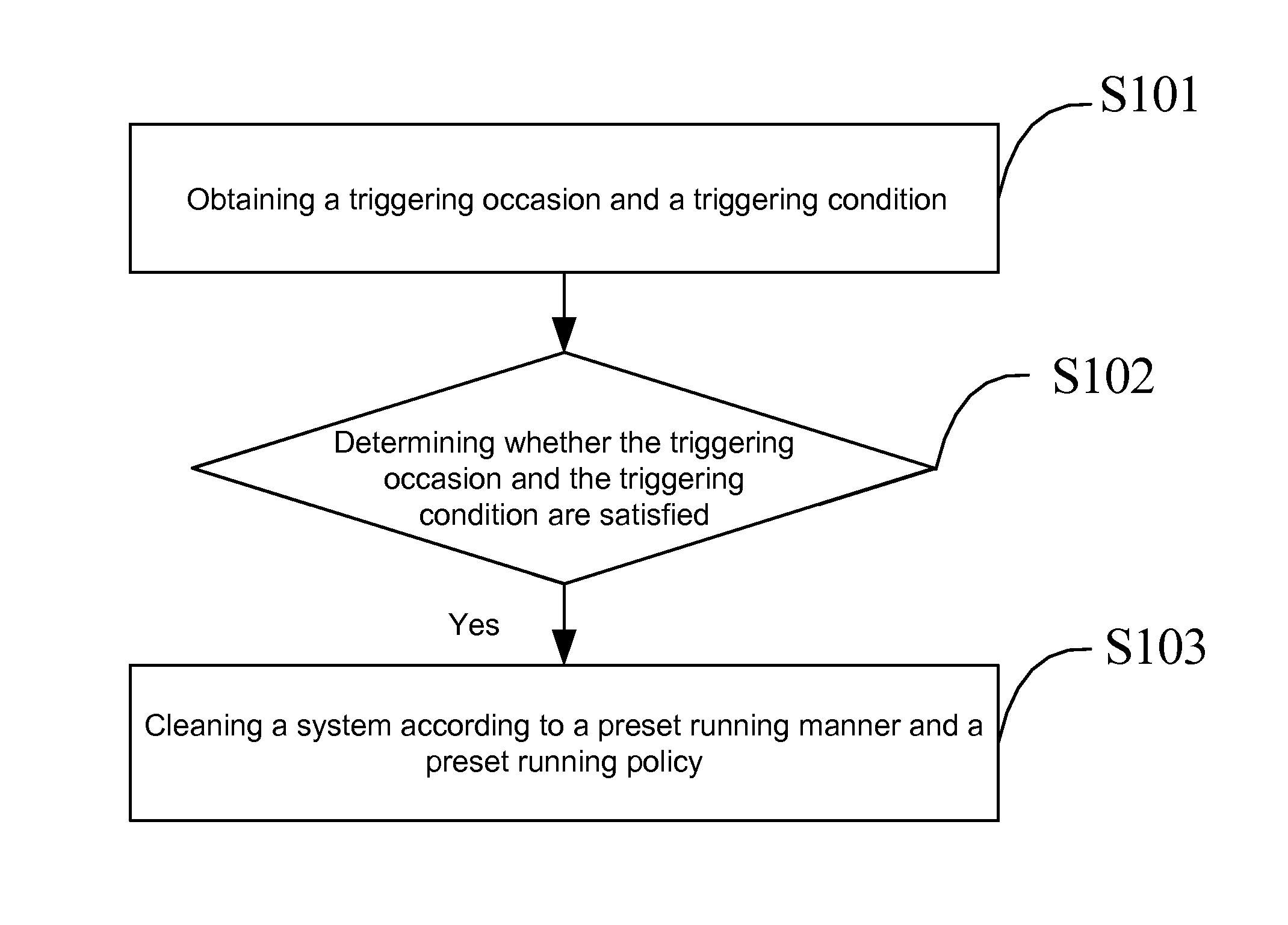
Method and apparatus for automatic system cleaning, and storage medium
ActiveUS20140089355A1Save disk spaceImprove system performanceMemory adressing/allocation/relocationFile/folder operationsEngineering
The invention relates to a method and an apparatus for automatic system cleaning, and a storage medium. The method includes obtaining a triggering occasion and a triggering condition which are selected by a user; determining whether the triggering occasion and the triggering condition are satisfied; and if yes, cleaning a system according to a preset running manner and a preset running policy. Through combination of system cleaning functions and scheduled task functions, and expansion of existing triggering conditions of a tasks scheduler, a user can self-define a triggering occasion, a triggering condition, a running manner and a running policy of system cleaning. When the triggering occasion and the triggering condition designated by the user are satisfied, system cleaning is automatically performed according to the selected running manner and policy, thereby improving the system performance and the system cleaning efficiency, and protecting the computer security and the individual privacy.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and device for processing SWF (Shock Wave Flash) separation encryption in batches
InactiveCN103226673ASave disk spaceImprove encryption efficiencyDigital data protectionProgram/content distribution protectionShock waveClient-side
The invention provides a method and device for processing SWF (Shock Wave Flash) separation encryption in batches. The method comprises the following steps: obtaining source SWF files uploaded by a client in batches; sequentially analyzing the source SWF files and obtaining a file header of the source SWF files; loading a binary stream including a key code in the file header in a binary stream manner, converting the source SWF files into a first intermediate file with a non-SWF format, and combining and loading the first intermediate file and a second intermediate file including a key corresponding to the key code into encrypted SWF files; and sending each encrypted SWF file to the client. Through encrypting the plurality of SWF files in batches, the encryption efficiency is greatly improved, and encryption software does not need to be downloaded, so that the disk capacity of the client is saved.
Owner:4399 NETWORK
System and method for automatically constructing modules based on software code
InactiveCN107357583ASave disk spaceShorten the timeModel driven codeSpecific program execution arrangementsModularityTime-Consuming
The invention relates to a system and method for automatically constructing modules based on a software code. Through modularized storage of the software code and identity information of a relied module, when the code is automatically constructed, the modules with the specific quantity can be constructed only, the software code and a target file generated by construction are stored according to the modules respectively, it is guaranteed that the identity information of all the relied modules is correct, when an automatic constructing server constructs the specific modules, identity information configuration files of the modules relied by the modules can be correctly read, and the relied targets can be correctly downloaded. Through the adoption of the system and method for automatically constructing the modules based on the software code, the disk space of an automatic constructing platform is saved, the time consumed by automatic construction triggered by module code submitting is further drastically shortened, and real-time automatic construction on the server which is not prominent in performance is more easily achieved.
Owner:SHANGHAI GONGJIN COMM TECH
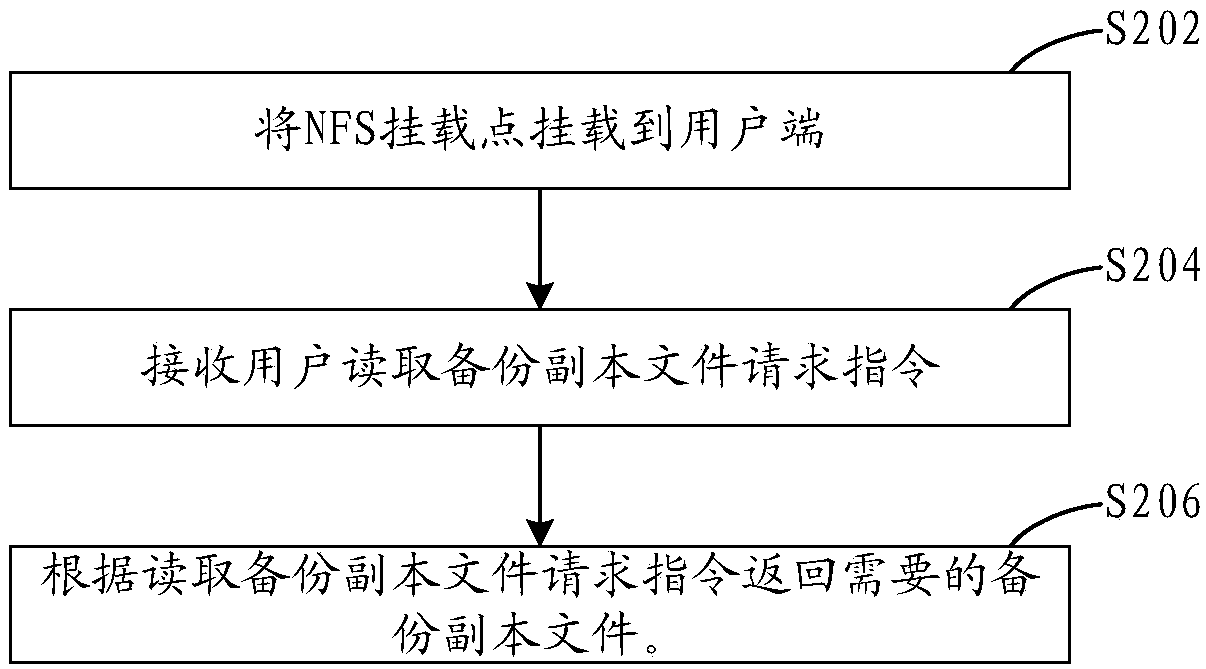
File mounting recovery method
ActiveCN108205482AImprove recovery efficiencySave disk spaceRedundant operation error correctionRecovery methodVirtual file system
The invention relates to a file mounting recovery method. According to the method, a file recovery request of a user is received; a backup copy file needing to be recovered is determined according tothe file recovery request of the user; the backup copy file is parsed to generate a virtual file system; and a layer of the virtual file system is exported as an NFS mounting point, and the needed backup copy file is recovered from the NFS mounting point. Therefore, the file recovery method, a file recovery device, computer equipment and a storage medium reduce file recovery time, improve file recovery efficiency, save disk space, and solve a case where the user fails to recover the file due to insufficient disk space.
Owner:广州鼎甲计算机科技有限公司
Data backup method and device and data restoration method and device
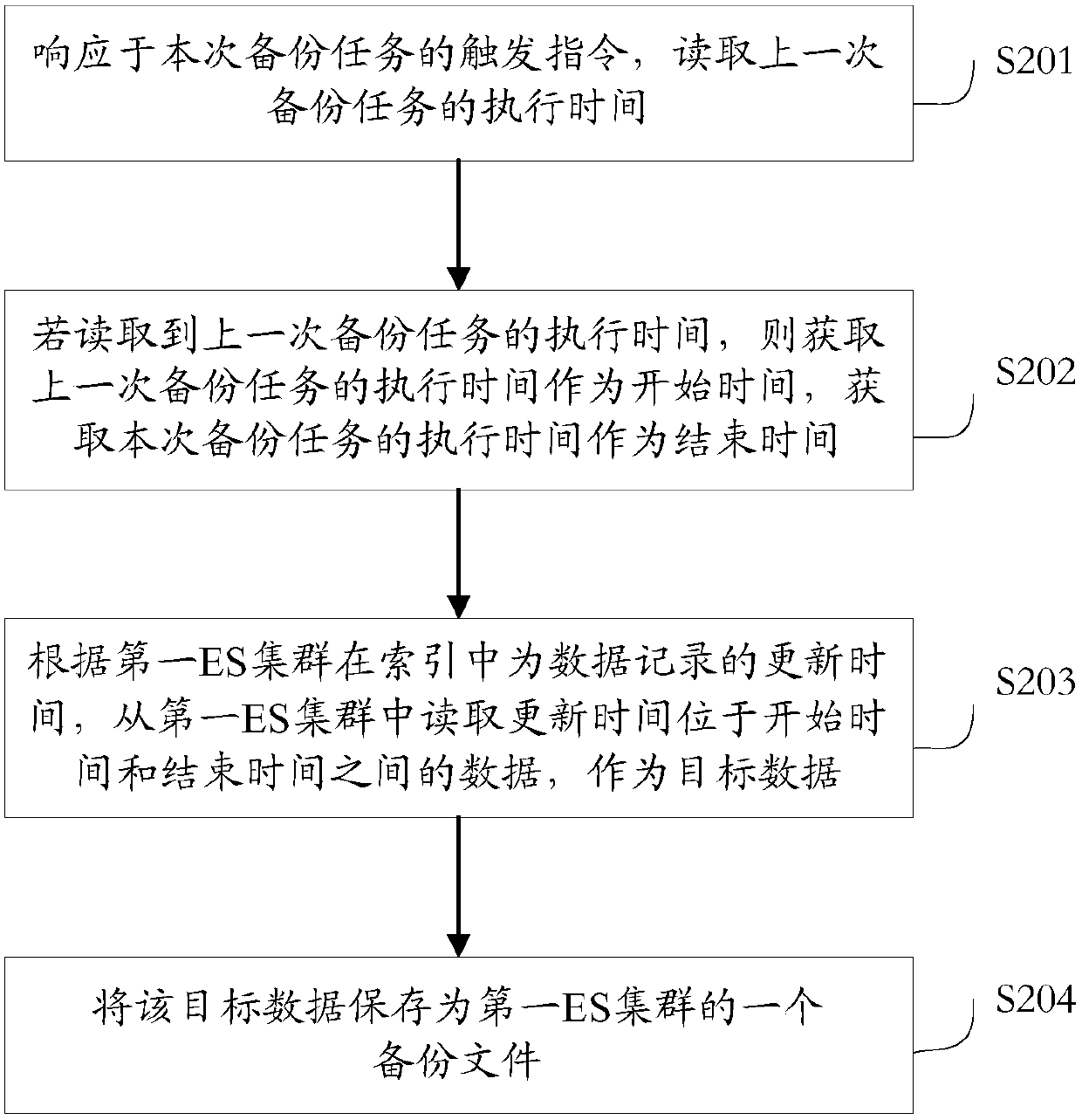
ActiveCN109558270AImplement incremental backupsAvoid duplicate backupsTransmissionRedundant operation error correctionStart timeRestoration method
The embodiment of the invention discloses a data backup method and device and a data restoration method and device, wherein the execution time of the previous backup task is taken as the starting time, and the execution time of the backup task is taken as the ending time. According to the updating time recorded in the index of the ElasticSearch cluster, the data updated between the starting time and the ending time are found out, and therefore only the found data are backed up, so that by recording updating time for data in an index of an ElasticSearch cluster and recording execution time of each backup task, the ElasticSearch cluster can realize incremental backup, the repeated backup of the same data is avoided, the backup efficiency is improved, and the disk space occupied by backup issaved.
Owner:BEIJING GRIDSUM TECH CO LTD
Method of manufacturing an engraved plate
InactiveCN101117041AShorten the timeSave disk spacePattern printingPlate printingGratingMarine engineering
Owner:KBA NOTASYS SA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com