Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
46results about How to "Reduce the number of alerts" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
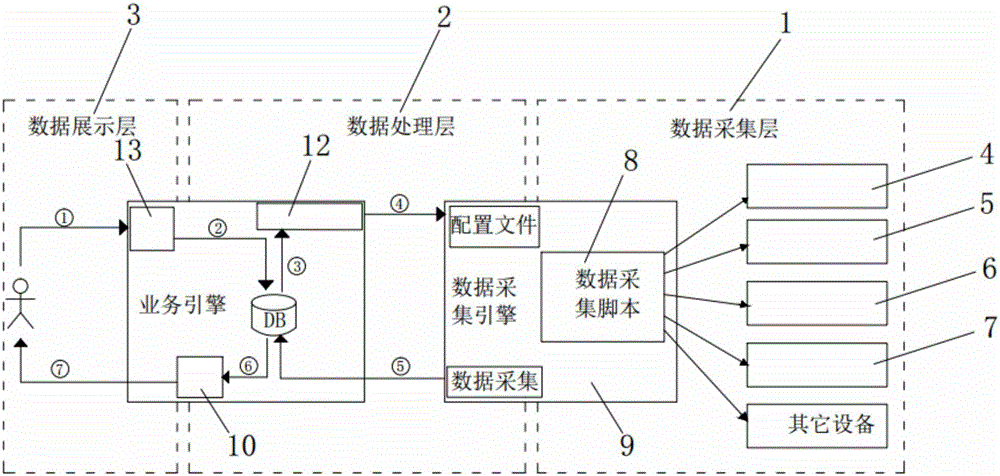
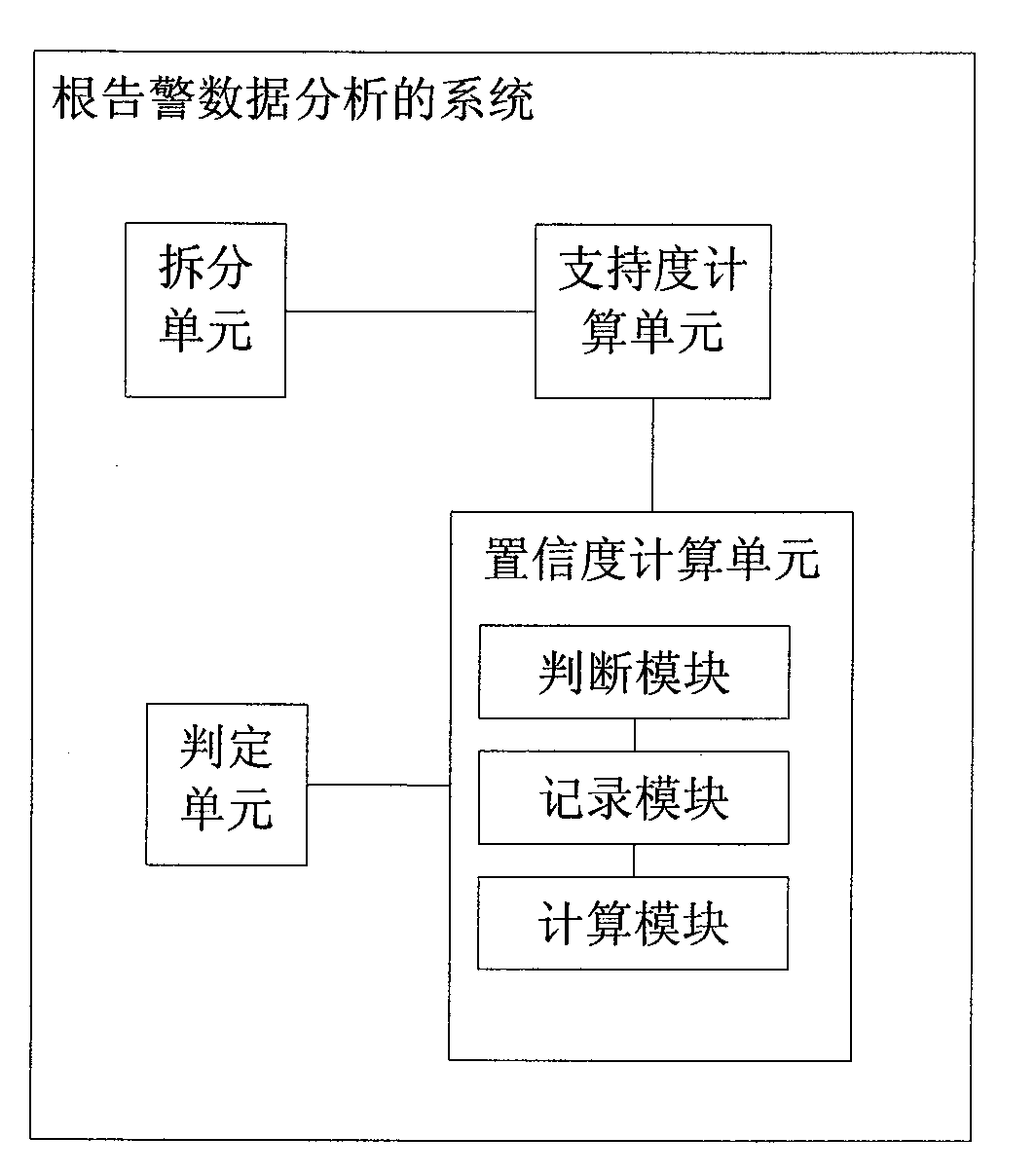
Comprehensive device monitoring system architecture
InactiveCN106487585AQuick searchLabor savingData switching networksIntegrated monitoringFile transmission
The invention discloses comprehensive device monitoring system architecture. The comprehensive device monitoring system architecture comprises a data collection layer, a data processing layer and a data presentation layer; the data collection layer comprises a data collection engine and a data collection script and monitors the automatic generation of a configuration file; the data processing layer comprises a CMDB library data processing module, a business engine, a data collection engine monitoring configuration file transmission module, a collected transmission module of a data collection engine and a business engine and an analyzing and processing module of alarm data; the comprehensive device monitoring system architecture disclosed by the invention has a large alarm data size, thereby requiring a good alarm collection processing means to ensure the instantaneity; as the definitions of alarm fields of different industries and manufacturers are different, a large amount of works are required to trim the alarms; a flat management structure collectively processes the alarms in the industries on the basis of standardization of the alarms, thereby requiring an extract alarm association and preprocessing rule; and the incidence relation among the alarms, the IT resources and business is confirmed, and a model of alarm influence analysis is established.
Owner:深圳市思博创科技有限公司
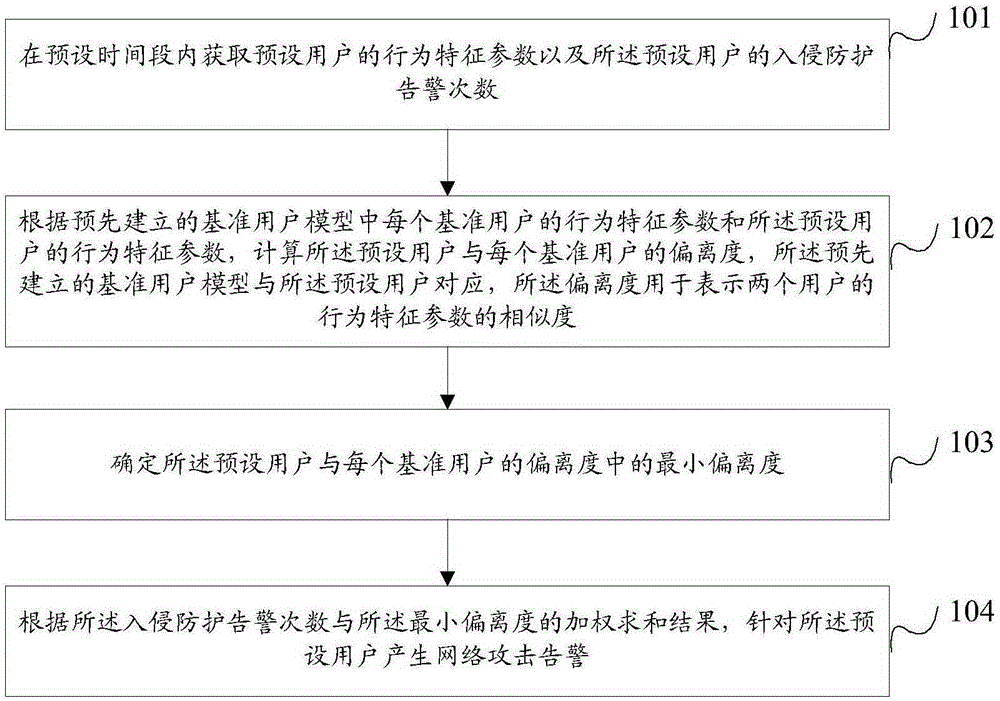
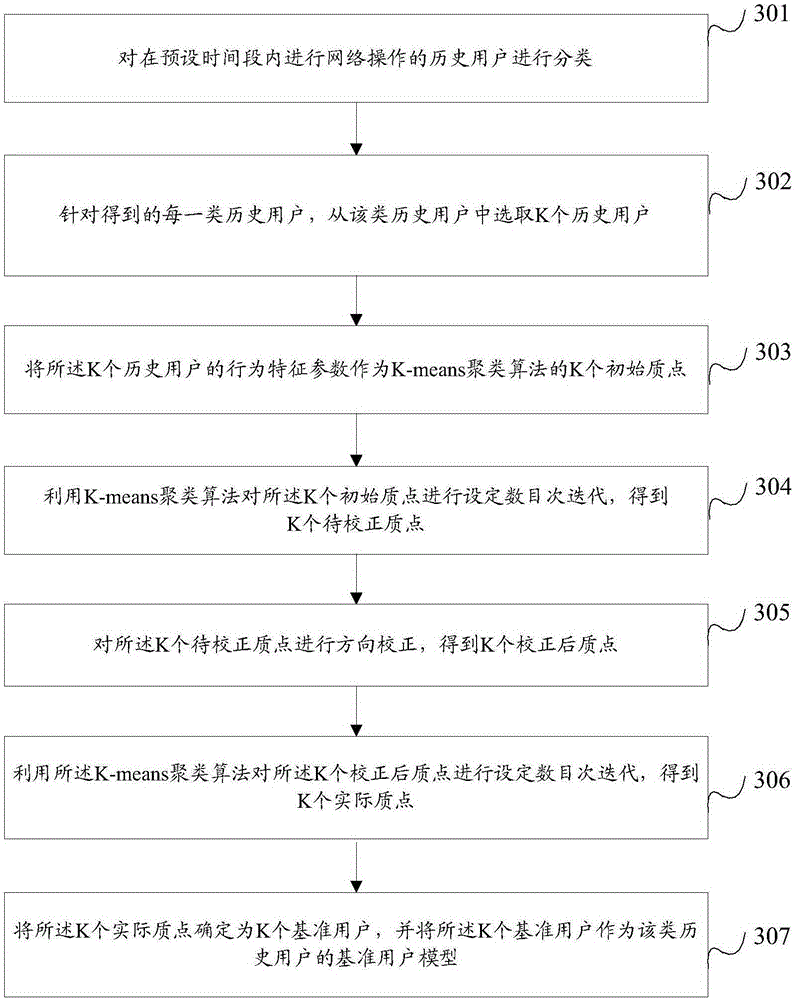
Network attack detection method and device
ActiveCN105208040ATo achieve the purpose of network attack detectionSmall amount of calculationData switching networksTime segmentMinimum deviation
The invention provides a network attack detection method and device. The method includes the steps that behavior characteristic parameters of a preset user and the number of intrusion prevention alarming times of the preset user are obtained in a preset period of time; the deviation degree of the preset user and each standard user is calculated according to behavior characteristic parameters of each standard user in a pre-built standard user model and the behavior characteristic parameters of the preset user, the pre-built standard user model corresponds to the preset user, and the deviation degree is used for representing the similarity of the behavior characteristic parameters of two users; the minimum deviation degree in the deviation degrees of the preset user and the standard users is determined; according to a weighted summation result of the number of intrusion prevention alarming times and the minimum deviation degree, network attack warning is generated for the preset user. The method and device can reduce the number of warning times and improve the effective rate of warning.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +2
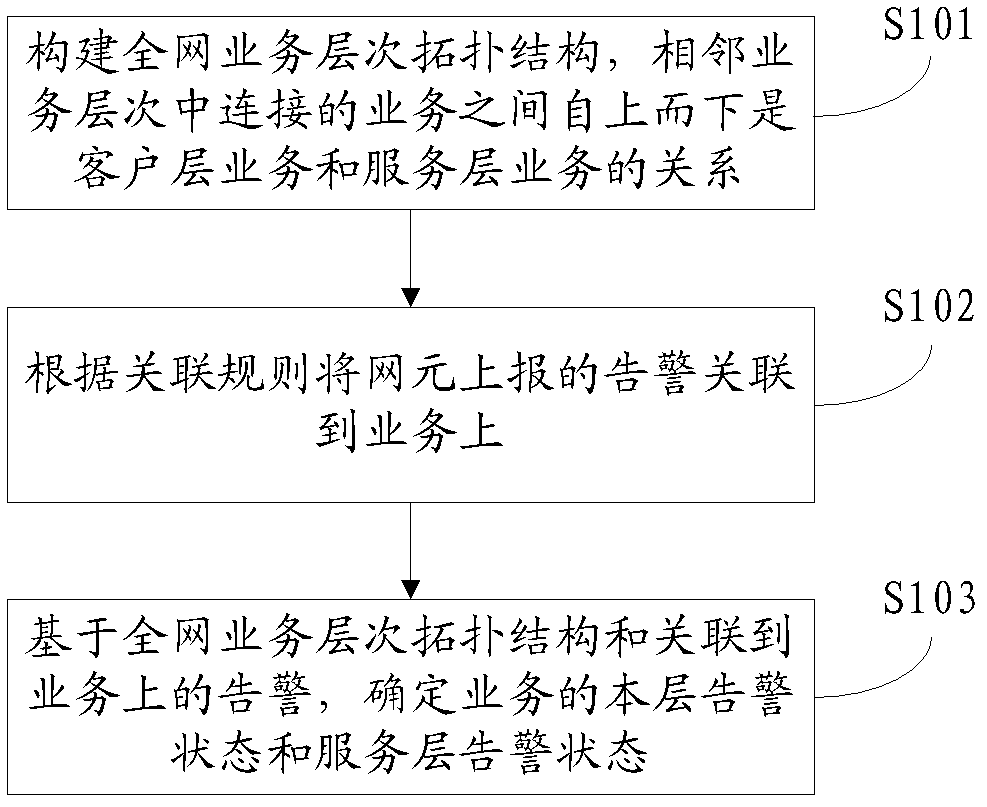
Method for correlation analysis of layer network alarm with business and device thereof
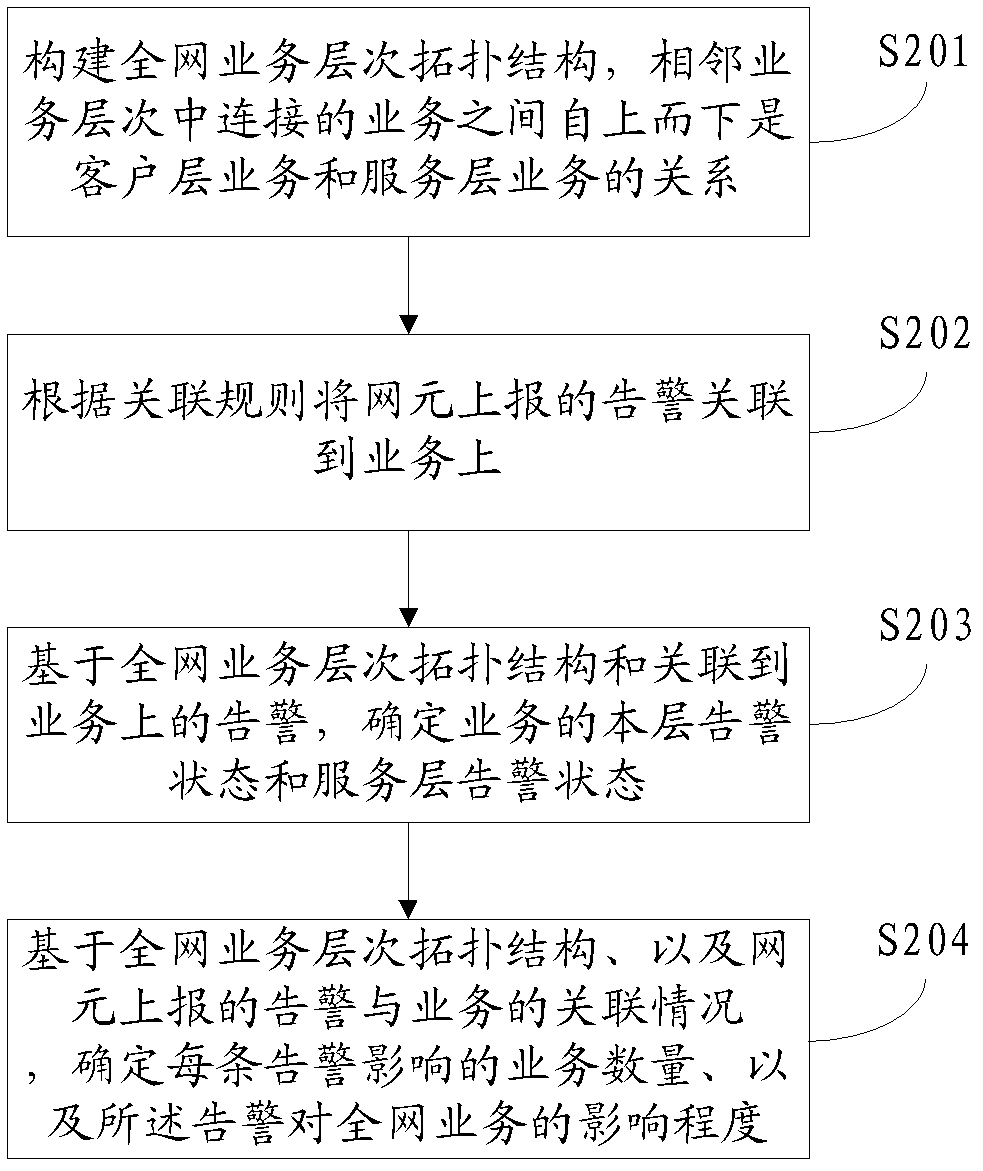
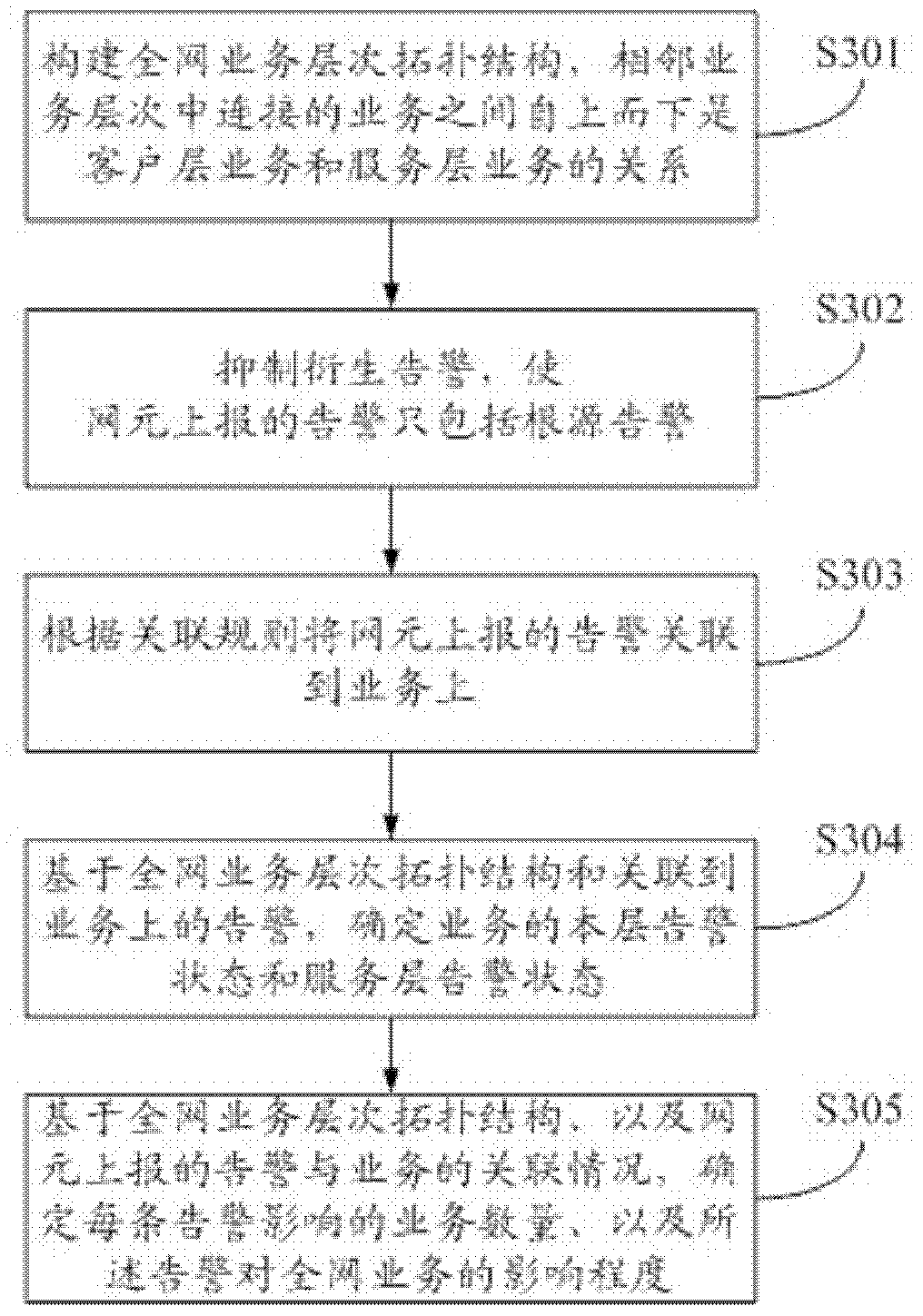
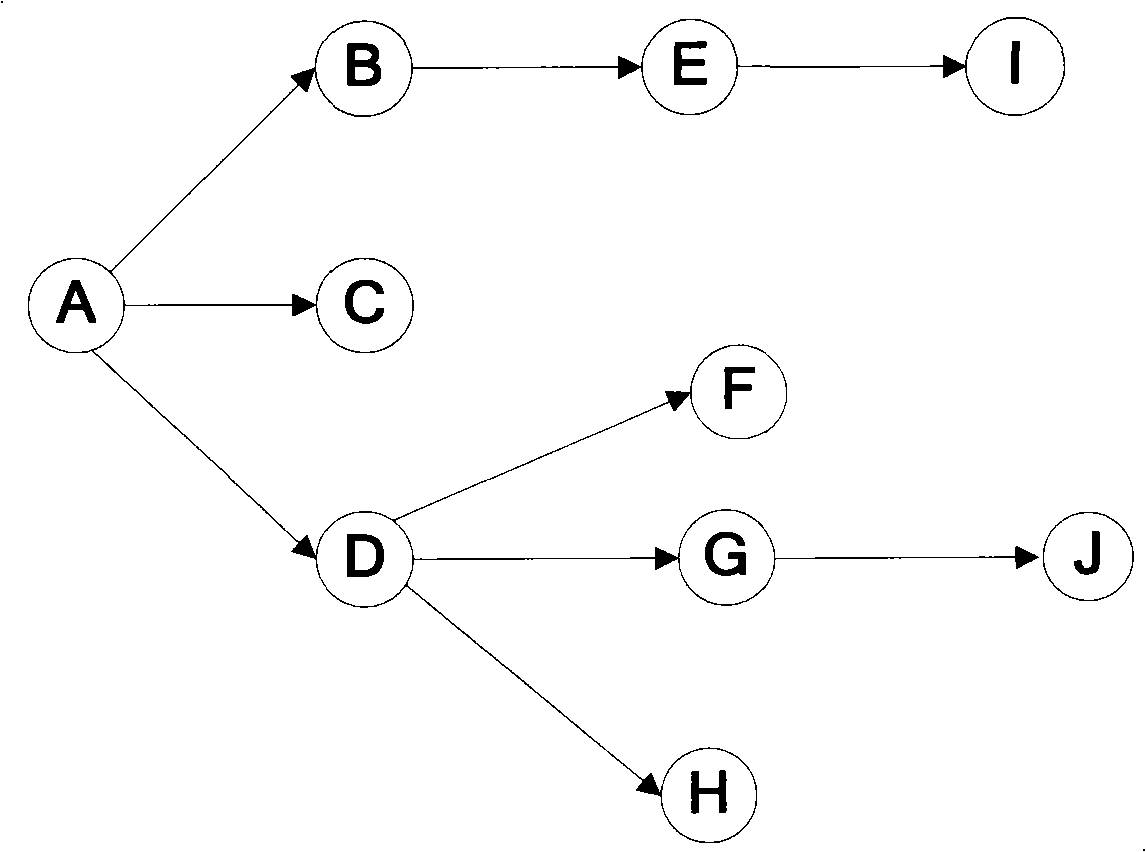
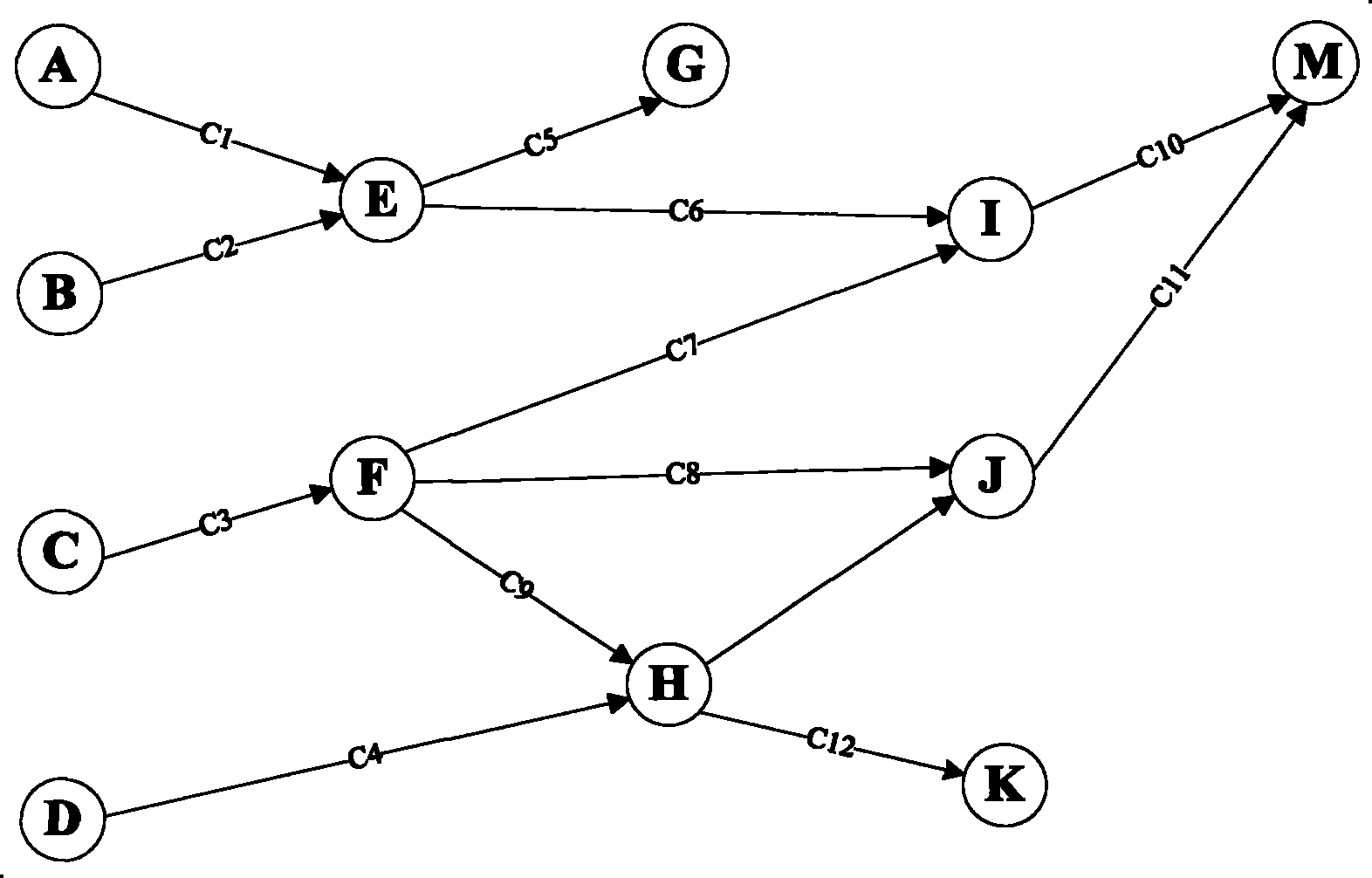
ActiveCN103378980AReduce the number of alertsEffective positioningData switching networksNetwork managementCorrelation analysis
Disclosed are a method and apparatus for correlation analysis of layered network alarms and services, wherein the method including: constructing the whole network service layer topology structure, where the relationships of connected services in adjacent service layers are client layer service and server layer service from top to down; relating alarms reported by network elements to services according to correlation rules; on the basis of the whole network service layer topology structure and alarms related to services, determining local layer alarm status and server layer alarm status of the services. This invention enables network management system to obtain local layer alarm status and server layer status according to the relationships of alarms reported by network elements and services on the network elements and further to estimate the number of services affected by alarms and the influence degree, thereby analyzing service fault status, accelerating the positioning of critical network failure and reducing operation and maintenance cost. This invention makes the positioning of critical network failure more efficient by suppressing derivative alarms, decreasing the number of alarms reported by network elements and filtering out more important alarms.
Owner:HENAN VALLEY INNOVATION NETWORK TECH
Alarm processing method and alarm management system
InactiveCN102111788AReduce redundancyImprove efficiencyWireless communicationAlarm managementAlarm correlation
The invention discloses an alarm processing method and an alarm management system. The method comprises the following steps of: pre-establishing a correlation relation among a plurality of alarms and a condition for the correlation relation in the alarm management system; after the alarm management system receives one of the alarms, shielding the alarm if the alarm is judged to be a sub-alarm of the other alarms received by the alarm management system according to the locally-stored correlation relation and if the condition for the correlation relation between the alarm and the other alarms is met, otherwise, not shielding. The system arranged in network element equipment comprises a storage unit, a receiving unit and a judging unit. In the invention, according to the characteristics of correlation and derivability of the respective alarms, an alarm correlation report decision device is implemented, a source alarm is reported preferentially, the correlation for a derivative alarm is shielded, the redundancy of alarm information can be reduced effectively and the quantity of the alarms can be reduced greatly; moreover, the source information of a fault is highlighted and the efficiency of problem positioning is improved.
Owner:ZTE CORP
System, device and method for filtering warning information
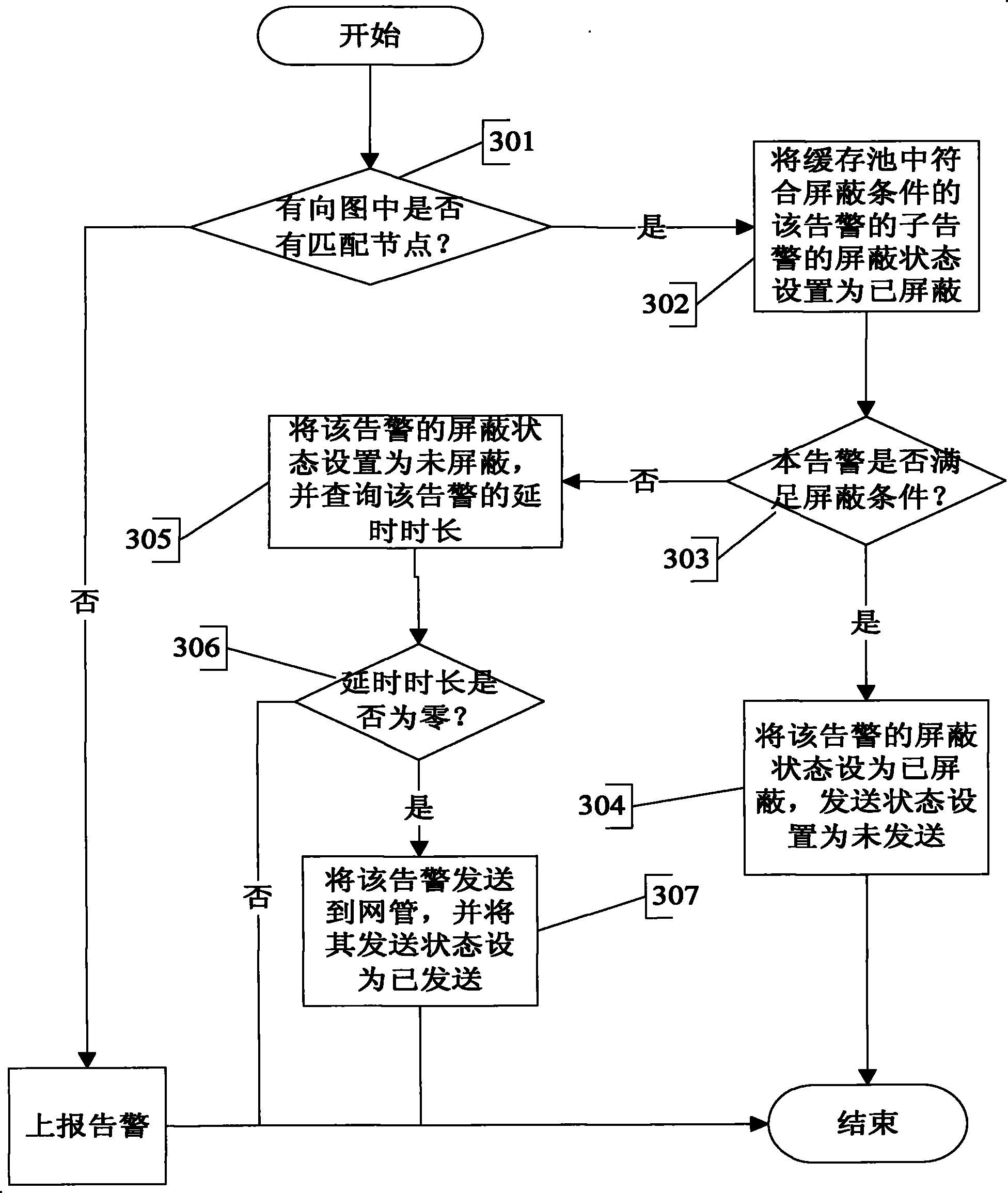
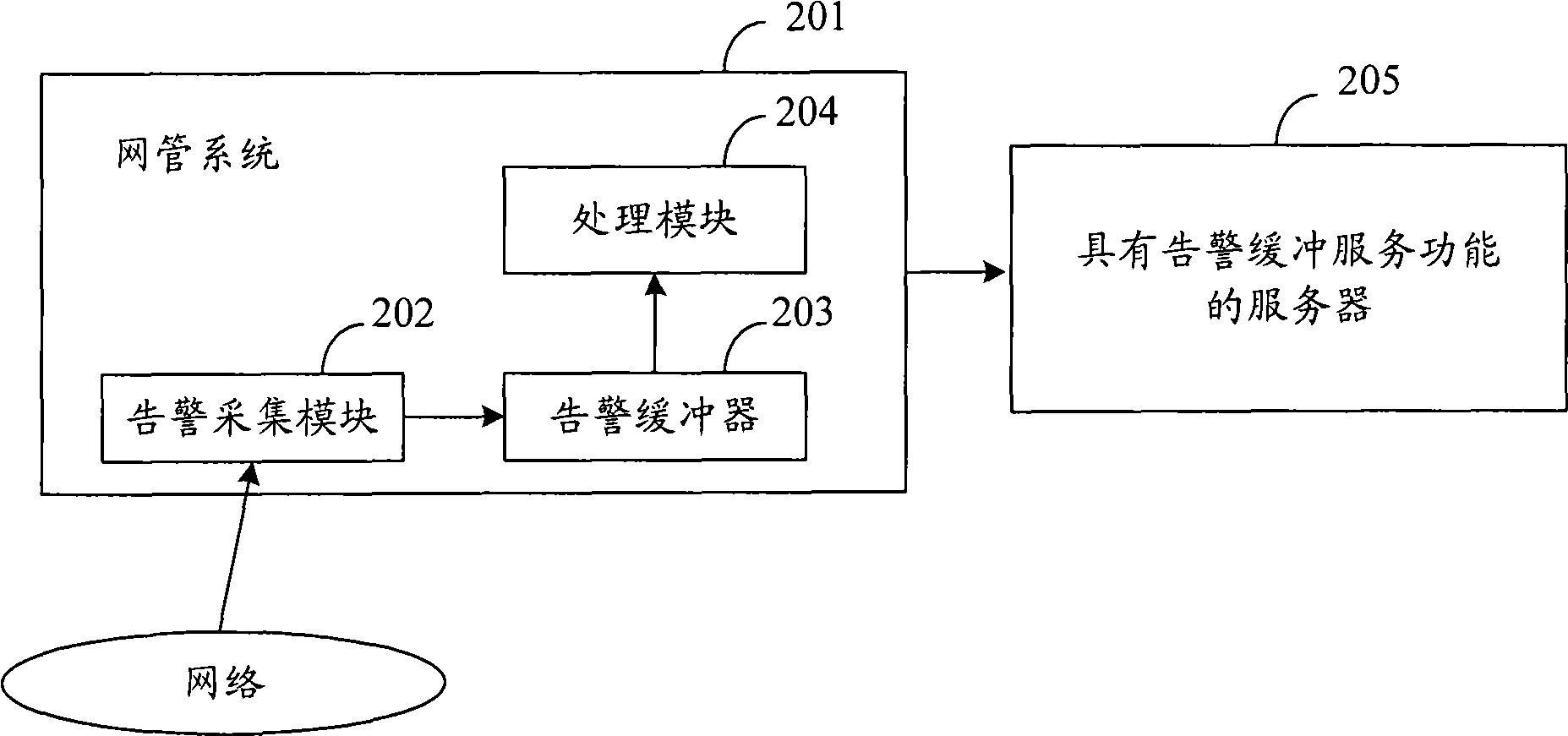
ActiveCN101547113AReduce shockReduce the number of alertsSupervisory/monitoring/testing arrangementsData switching networksNetwork managementComputer science
The invention discloses a system, a device and a method for filtering warning information used for a network management system; the warning information filtering system comprises a warning acquisition module, a warning filtering module, a warning buffer and a warning processing module, wherein the warning acquisition module is used for acquiring and sending the warning information to the warning filtering module; the warning filtering module is used for storing the received warning information; if warning disappearing information is received and then warning generation information with same warning is received in the set time, the warning generation information and the warning appearing information which have the same warning are deleted; the warning buffer is used for buffering the warning information filtered by the warning filtering module; and the warning processing module is used for extracting the warning information from the warning buffer and processing the warning information. The technical proposal can effectively reduce the warning number needing buffering, thus reduce the disk space used for storing the warning, reduce the impact of warning storm on CPU and improve the utilization ratio of the system.
Owner:ZTE CORP
Fault detection method and device for big data cluster
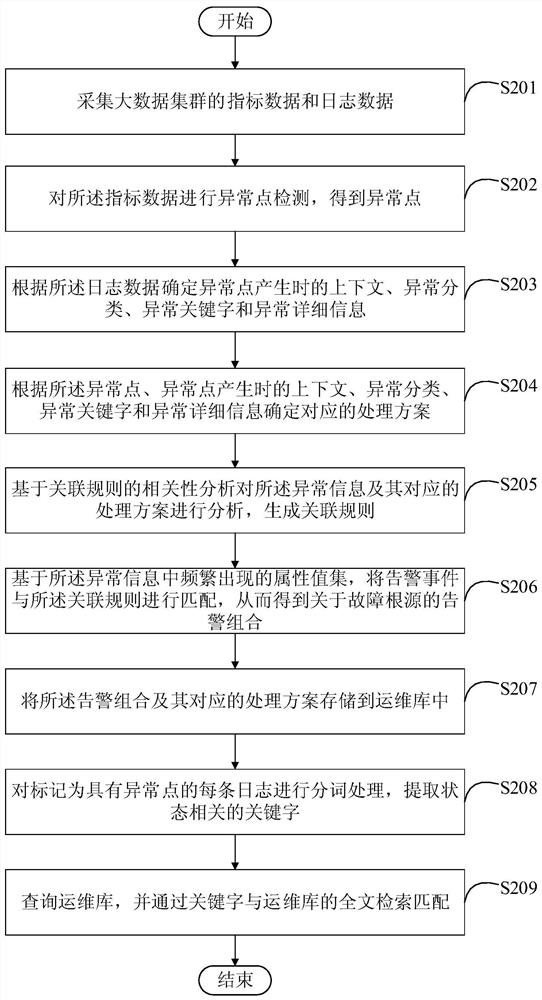
PendingCN111984499AAvoid submersionReduce the number of alertsHardware monitoringMachine learningData setEngineering
The invention discloses a fault detection method and device for a big data cluster, and relates to the technical field of computers. A specific embodiment of the method comprises the steps of collecting index data and log data of a big data cluster; determining abnormal information and a corresponding processing scheme according to the index data and the log data; performing machine learning on the abnormal information and the corresponding processing scheme, and storing a learning result into an operation and maintenance library; and performing fault detection on the big data cluster based ona learning result in the operation and maintenance library. According to the embodiment, the technical problems of difficult fault source detection and high operation and maintenance cost can be solved.
Owner:CHINA CONSTRUCTION BANK
Method and device for updating configuration management databases
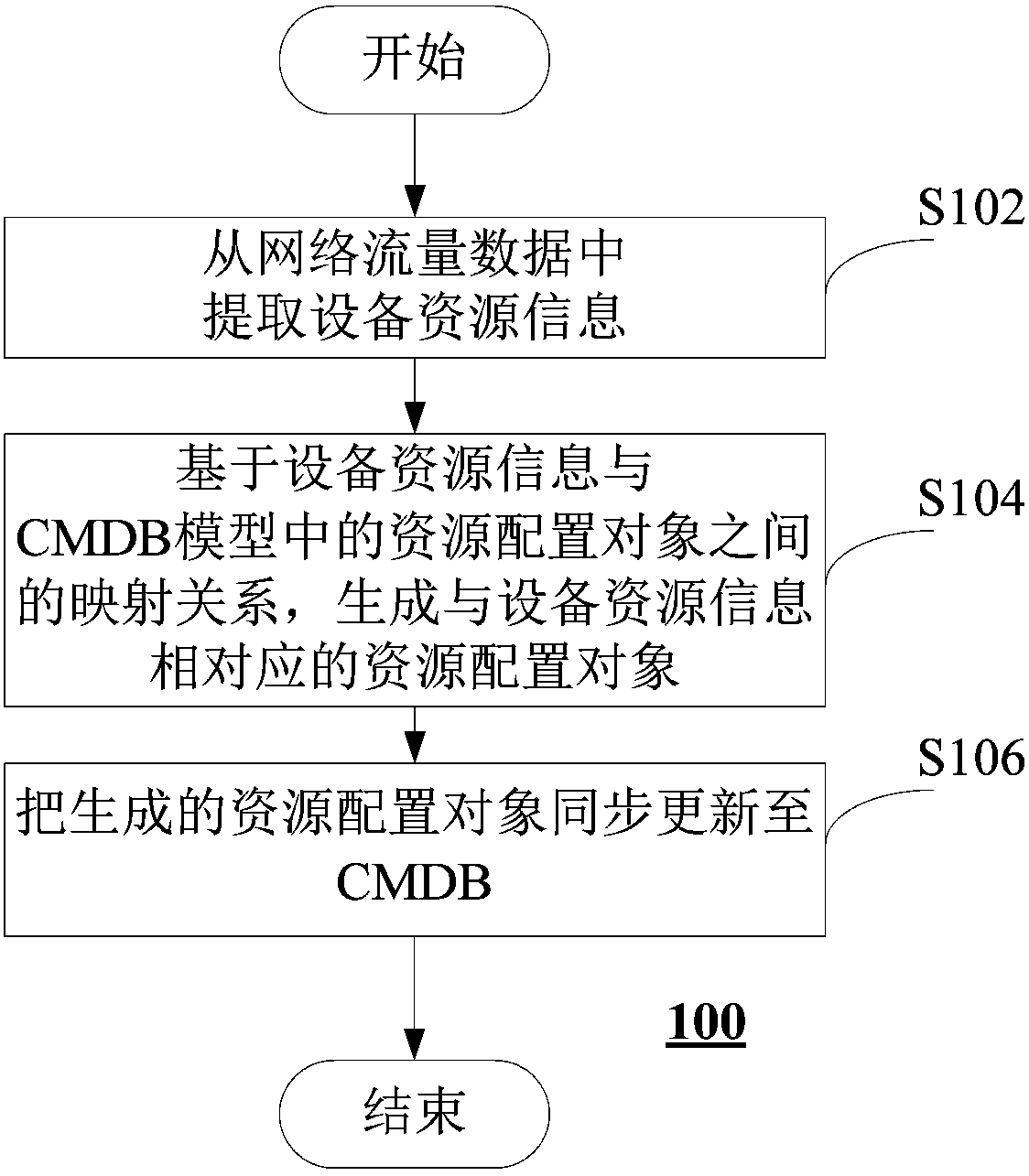
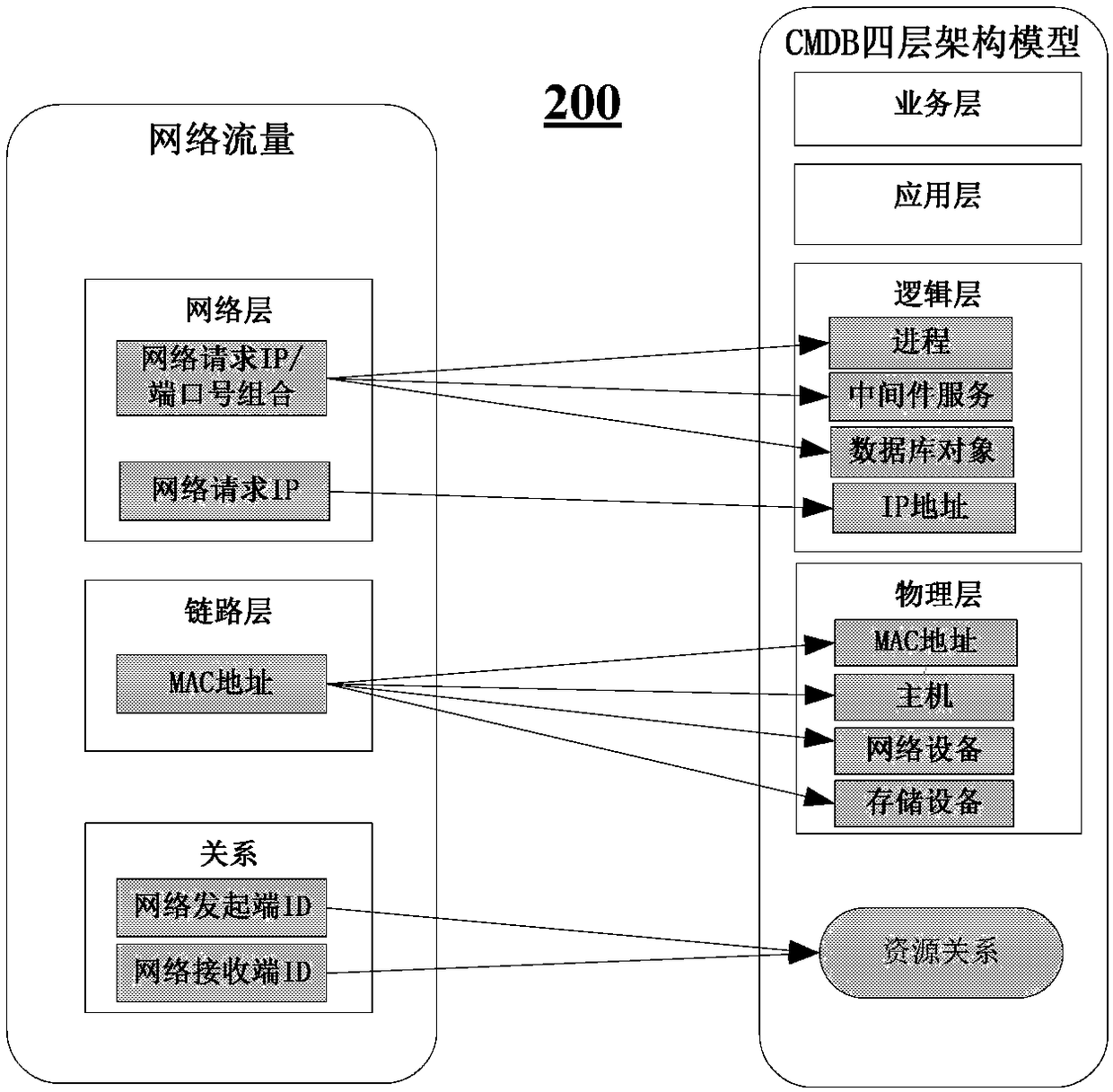
ActiveCN108205569AImprove consumer service capabilitiesSolve the problem of automatic managementSpecial data processing applicationsDatabase design/maintainanceResource informationPhysical layer
The invention provides a method and device for updating configuration management databases. The method comprises the following steps of: extracting equipment resource information from network flow data; generating a resource configuration object corresponding to the equipment resource information on the basis of a mapping relationship between equipment resource information and resource configuration objects in a CMDB model, wherein the resource configuration objects comprises resource objects and resource relationship objects of physical layer and a logic layer in the CMDB model; and synchronously updating the generated resource configuration object to the CMDB model. According to the method, a network flow system is combined with automatic CMDB resource management, so that the automatic CMDB resource management problems are solved, and dynamic updating and maintenance of CMDB resources and relationships are realized.
Owner:SHANXI CHINA MOBILE COMM CORP +1
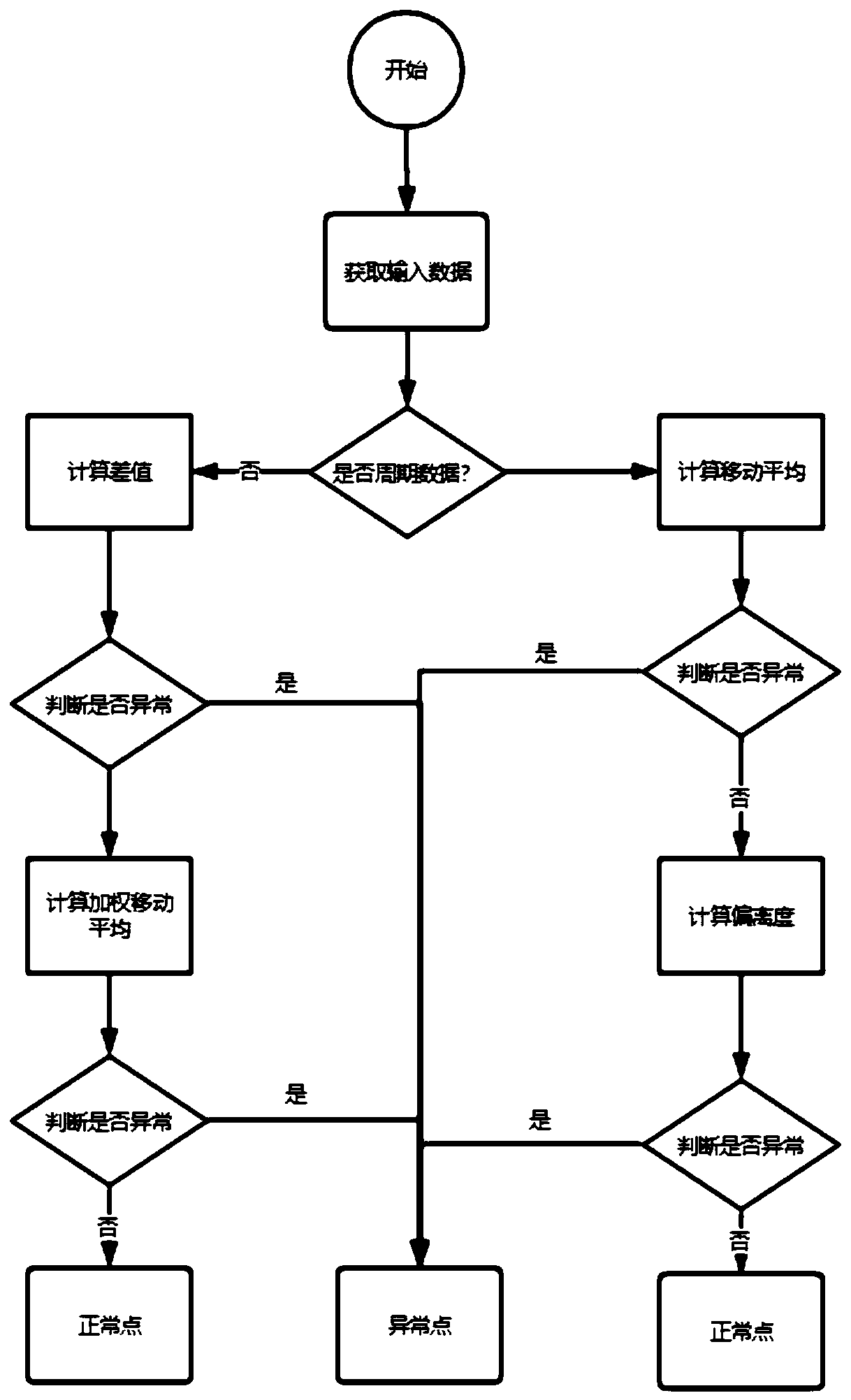
Abnormity detection system based on time sequence data in cloud environment
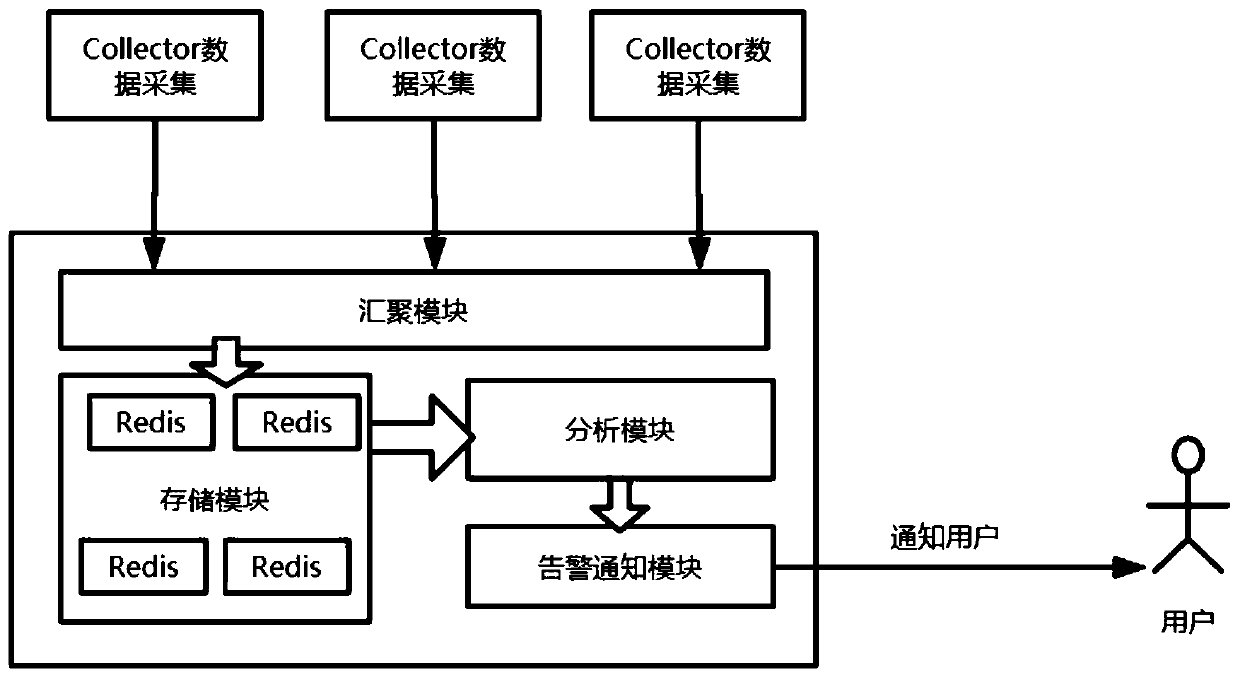
InactiveCN110213125AImprove operation and maintenance efficiencyAdaptableData switching networksDynamic modelsAnomaly detection
The invention relates to an abnormity detection system based on time sequence data in a cloud environment. The system comprises the following modules: a Collector data acquisition module, a data storage module, an Analyst analysis module and an alarm notification module. The Collector data collection module collects service index data of a device where the Collector data collection module is located at regular time and transmits the service index data to the data storage module through the convergence module. The storage module is used for storing time sequence data and transmitting the data to the analysis module, and the Analyst analyzer module is used for analyzing the time sequence data and pushing a notification message to a user rate through the alarm notification module. According to the scheme, the dynamic model is established through an algorithm to carry out abnormal detection, the operation and maintenance efficiency of the data center is improved, and the system is suitablefor centralized operation environments such as enterprise private clouds and data centers and does not depend on fixed empirical threshold setting. The monitoring system and the dynamic algorithm provided by the invention are used for detecting abnormities, so that the stiff setting of regularized alarms can be avoided.
Owner:南京维拓科技股份有限公司
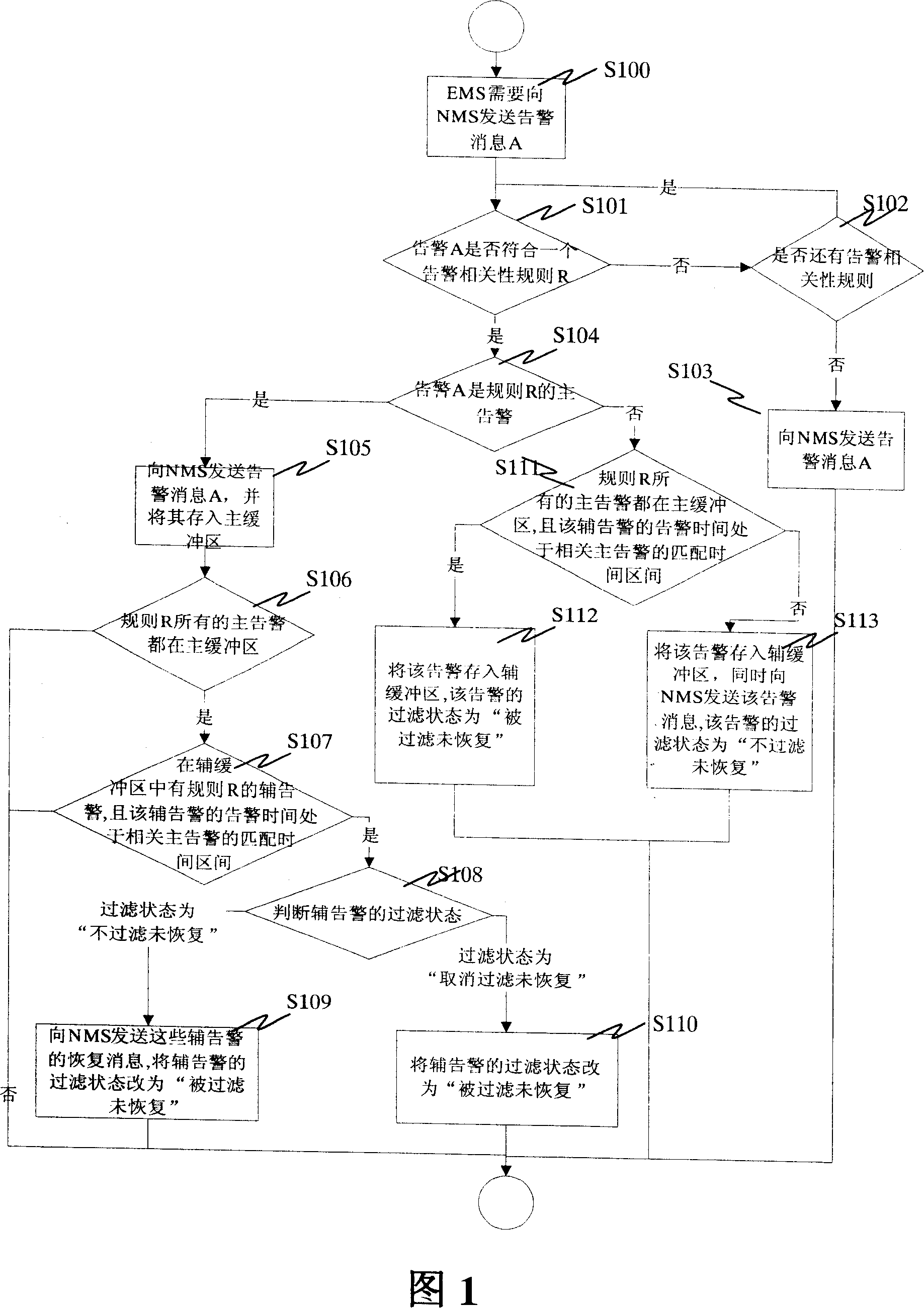
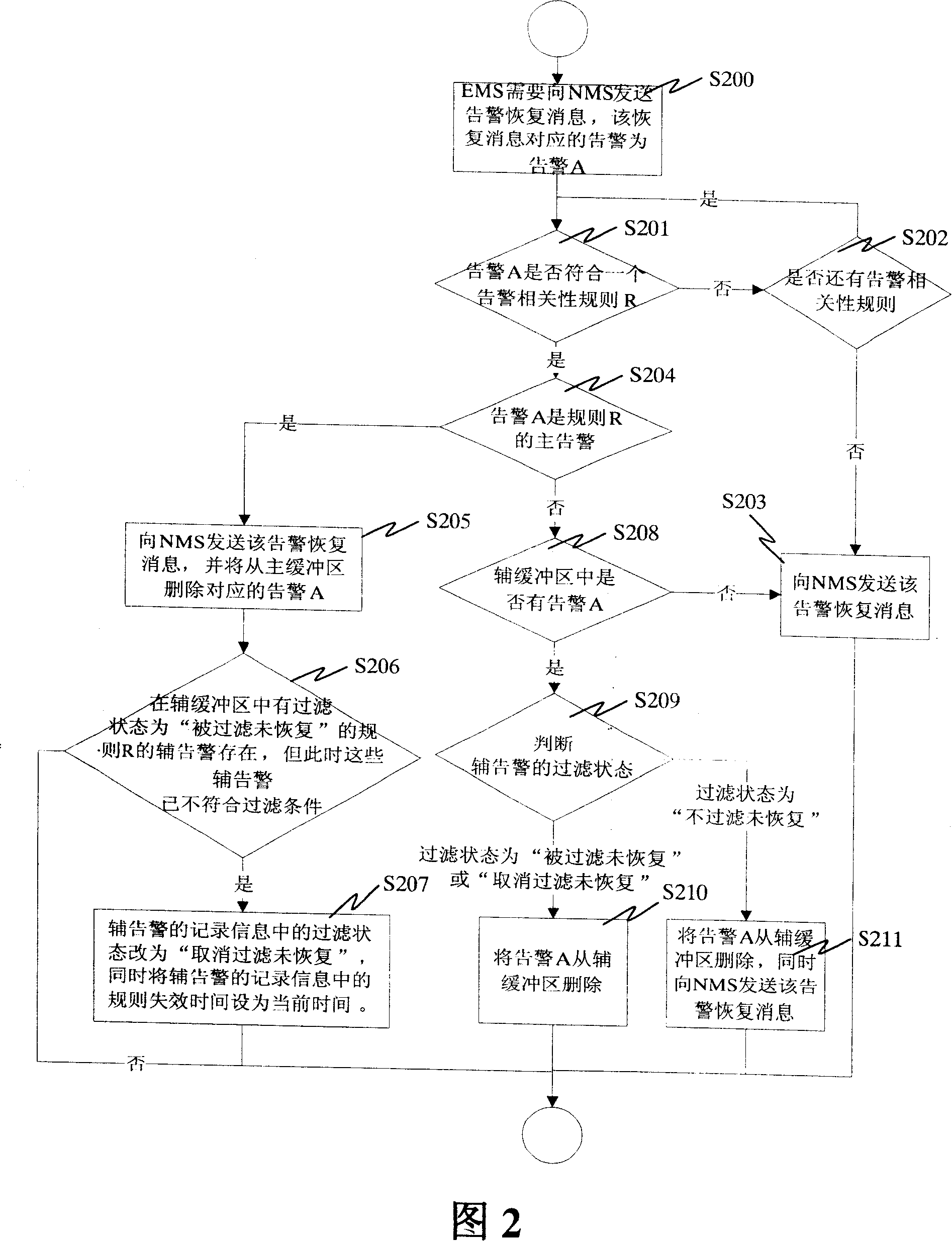
Method for filtering alarm between network management system and network element management system
InactiveCN101047535AReduce the number of alertsReduce the burden onData switching networksAlarm messageNetwork management
A method for making filter alarm between network management system and network element management system includes setting alarm correlation rule including master alarm and auxiliary alarm for network element management system by network management system, judging whether alarm message required to be sent by network element management system is master alarm or auxiliary alarm according to alarm correlation rule, sending alarm message to network management system if it is master alarm or otherwise filtering off said alarm message and not sending it to network management system.
Owner:ZTE CORP
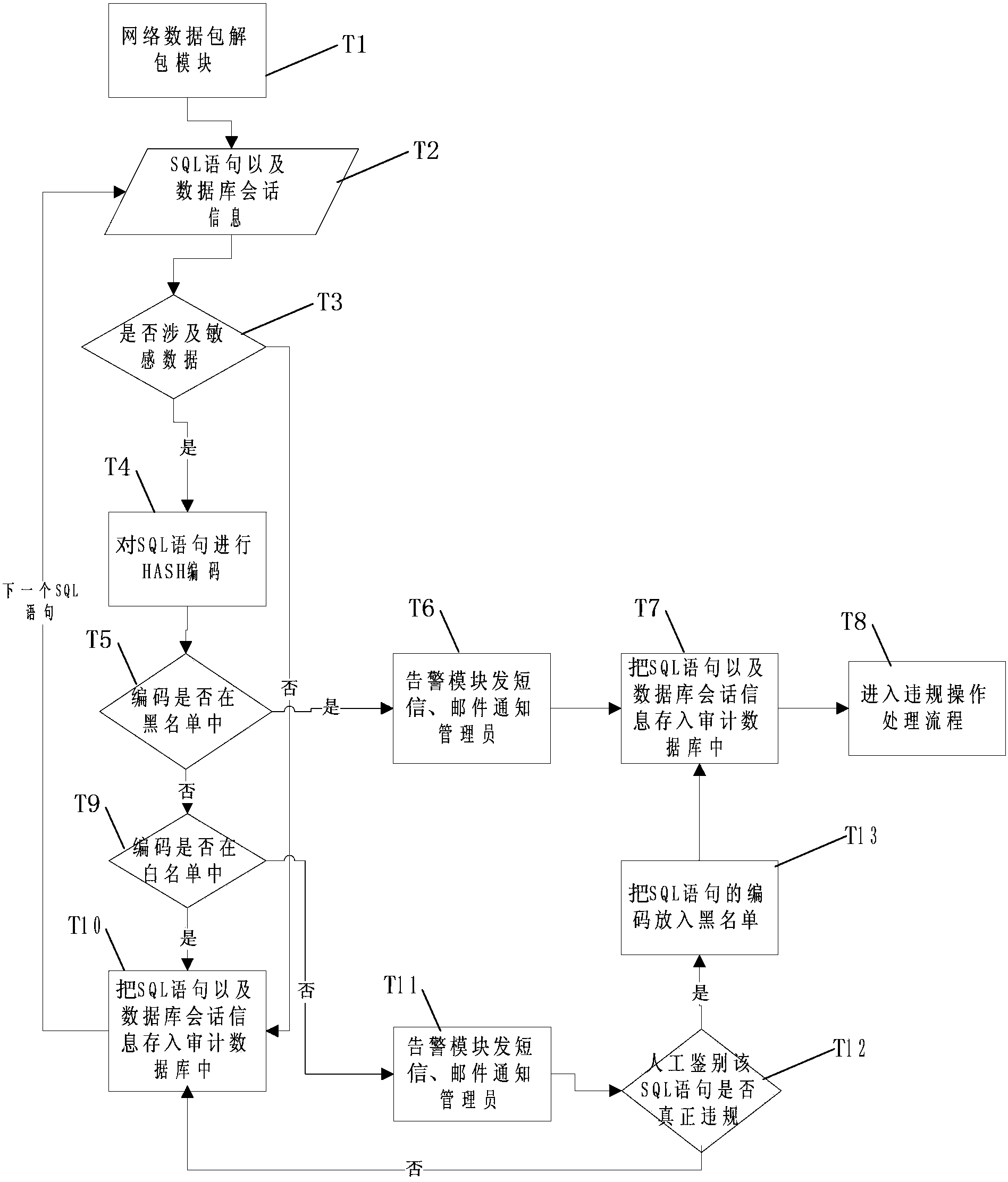
Method for quickly testing compliance by database auditing system
ActiveCN103365963AQuick filterReduce daily workloadSpecial data processing applicationsDatabaseRoutine work
The invention discloses a method for quickly testing compliance by a database auditing system. According to the invention, a 'black and white list' mode is introduced into database auditing products, so that the database auditing system is enabled to quickly screen out suspicious data from massive information, the number of alarm per day is effectively reduced, and the daily work burden of administrators is greatly reduced.
Owner:赛姆科技(广东)有限公司
Method for uploading alarm quantity information to network management system by network element management system
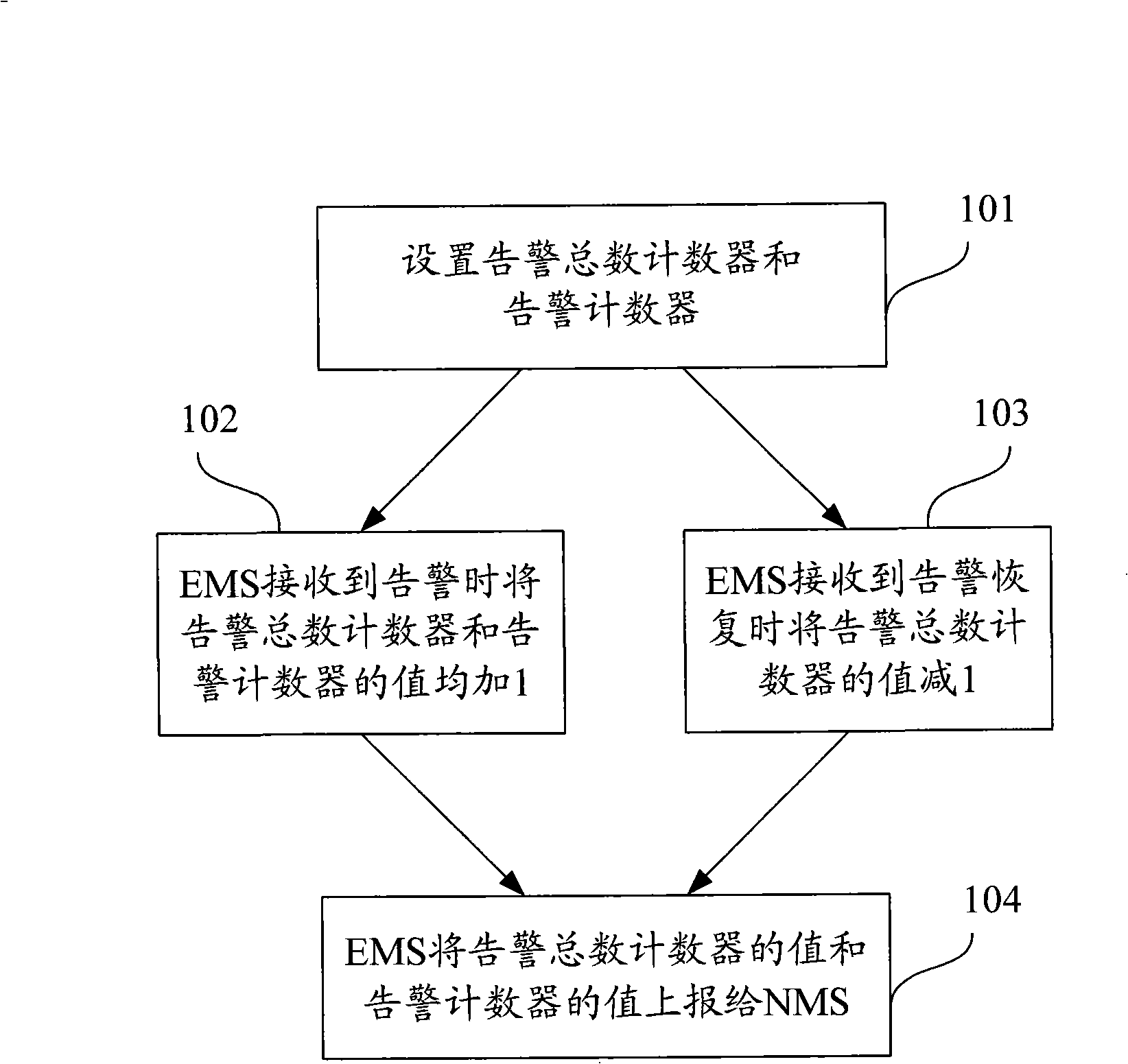
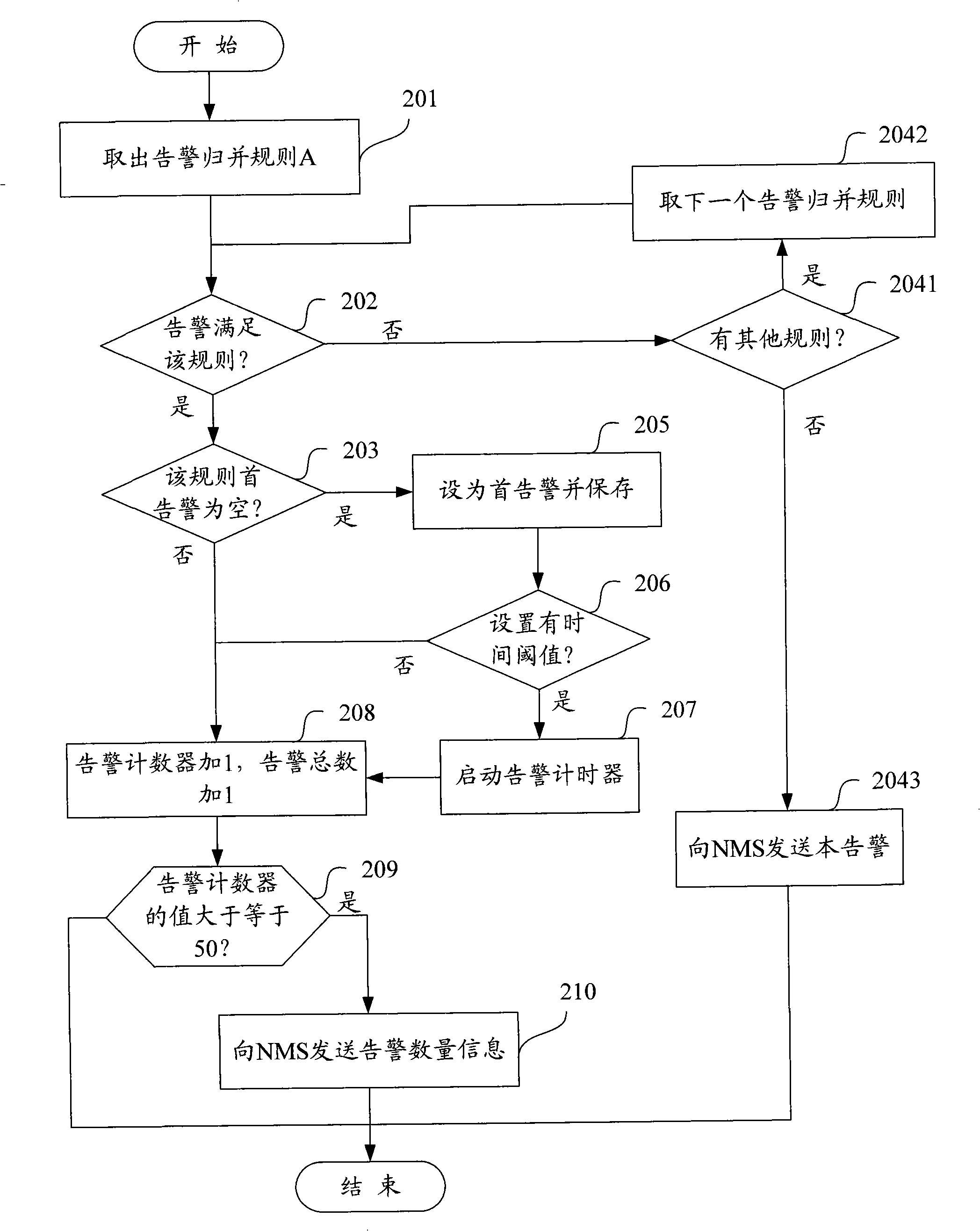
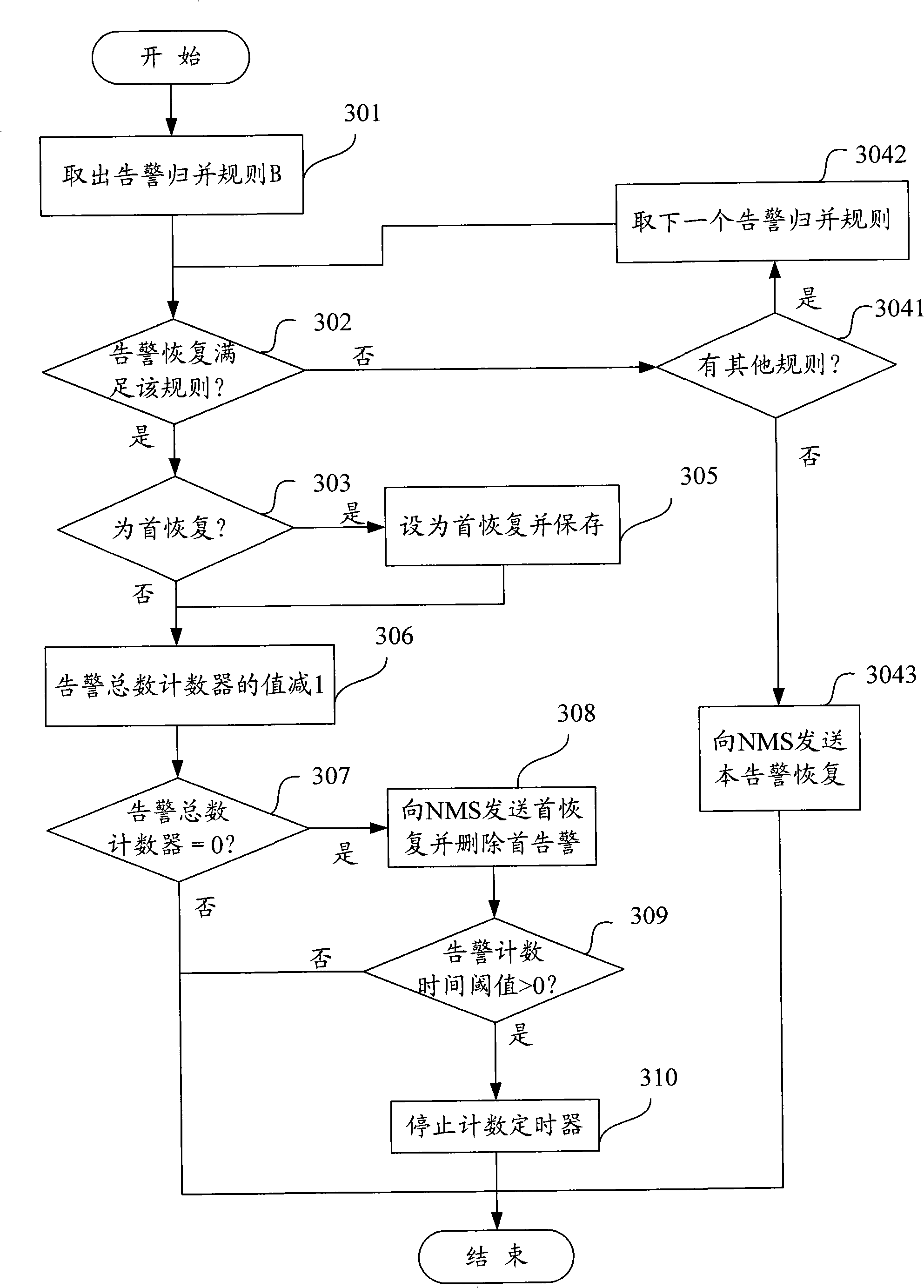
ActiveCN101360313AReduce the number of alertsEasy accessRadio/inductive link selection arrangementsData switching networksNetwork managementManagement system
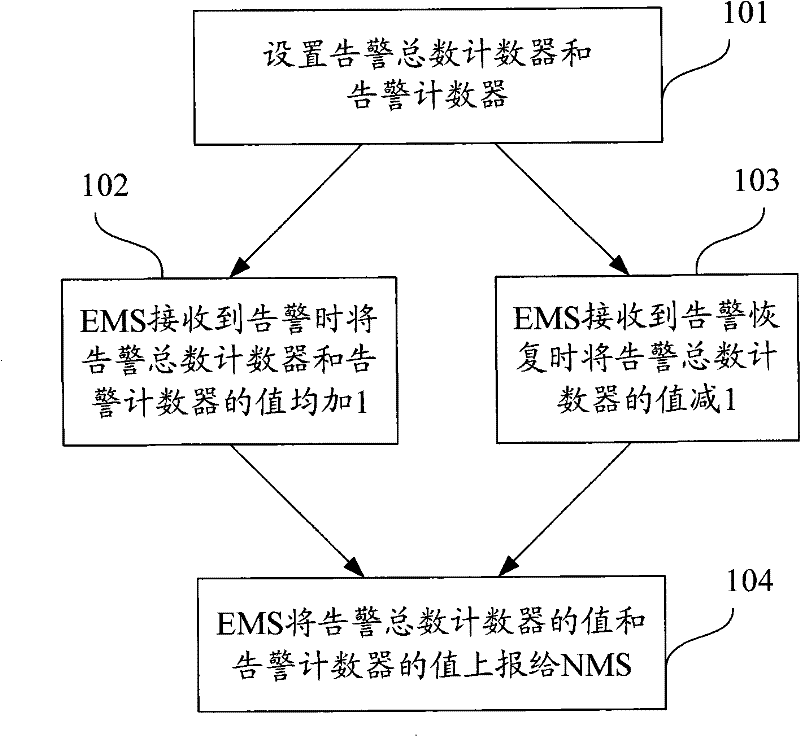
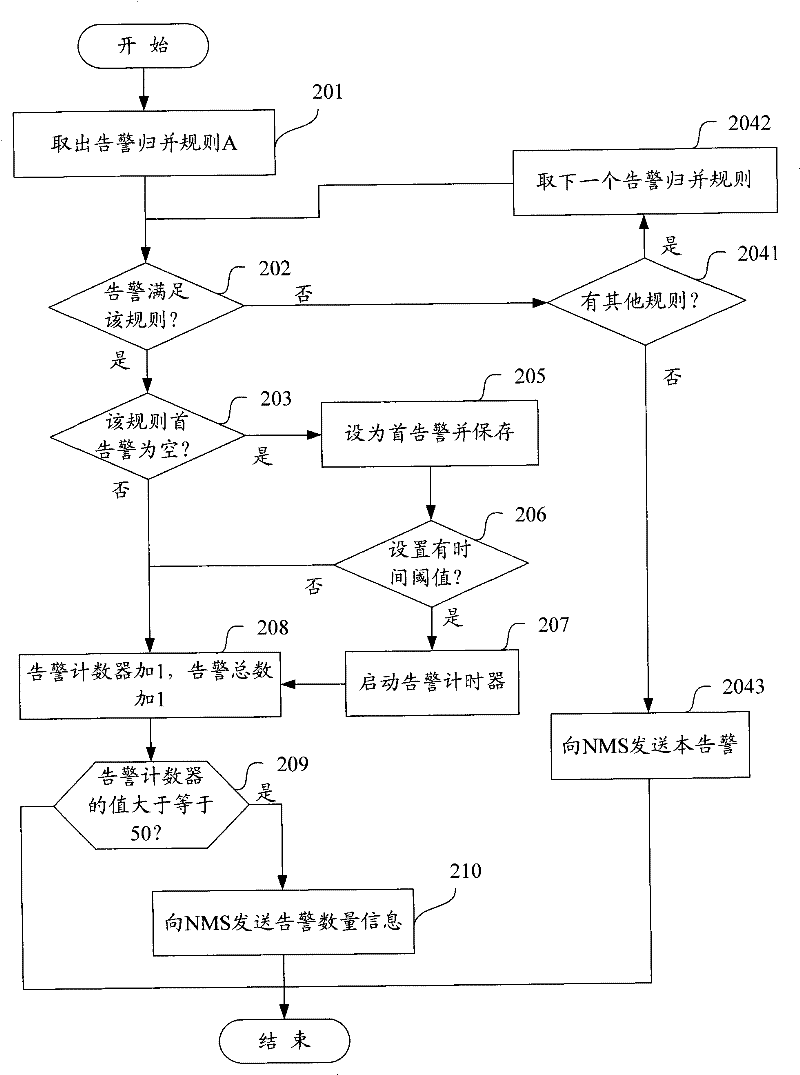
The invention discloses a method of a network element management system reporting the warning number message to a network management system, which aims at reporting the warning occurrence number message and reducing the warning number at the same time. The method is characterized in recoding the warning occurrence total number which is received by the network element management system, and the warning number which is received in a time interval; wherein, the warning occurrence total number is the unrestored warning total number which is received by the network element management system; the network element management system takes the warning occurrence total number and the warning number as the content of warning number message to report to the network management system. By adopting the method provided by the invention, the EMS can report the warning number message to the NMS while reduce the warning number at the same time, thus facilitate the NMS to obtain more warning related messages, and also facilitate the management and maintenance work of the managers.
Owner:OPEN INVENTION NEWTORK LLC
System for realizing monitoring system business logic online modification
ActiveCN105915381AReduce the number of alertsImprove operational efficiencyData switching networksElectricityMonitoring system
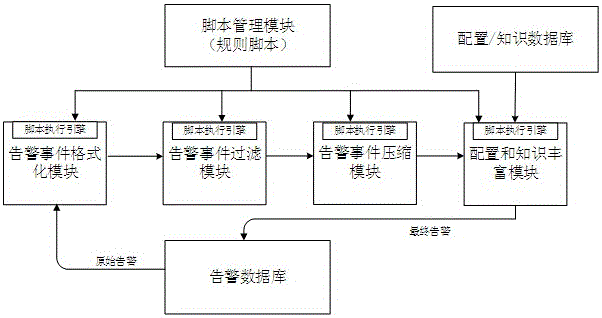
The invention discloses a system for realizing monitoring system business logic online modification. The system comprises an alarm event formatting module which is electrically connected with a script management module and an alarm database; an alarm event filtering module which is electrically connected with the script management module, the alarm event formatting module and an alarm event compression module; the alarm event compression module which is electrically connected with the script management module, the alarm event filtering module and a configuration and knowledge enriching module; the configuration and knowledge enriching module which is electrically connected with the script management module, the alarm event compression module, a configuration and knowledge database and the alarm database; and the script management module which is electrically connected with the alarm event formatting module, the alarm event filtering module, the alarm event compression module and the configuration and knowledge enriching module. The technical problems of extra development cost caused by business logic modification and shutdown of a business system caused by delayed discovery of alarm and fault processing in the shutdown period of a monitoring system can be solved.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
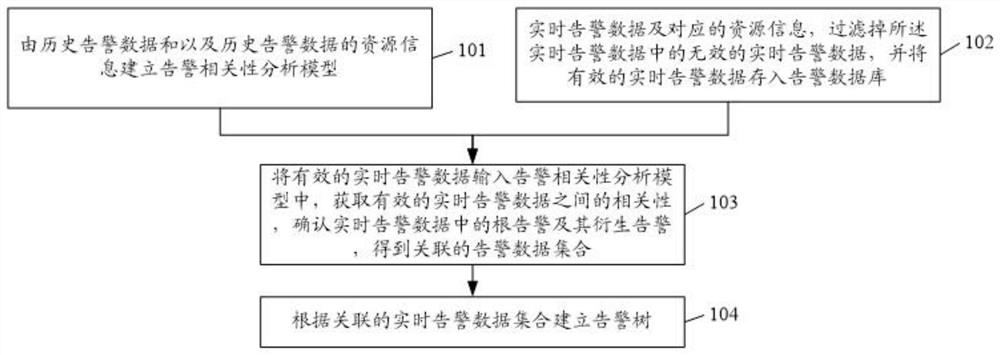
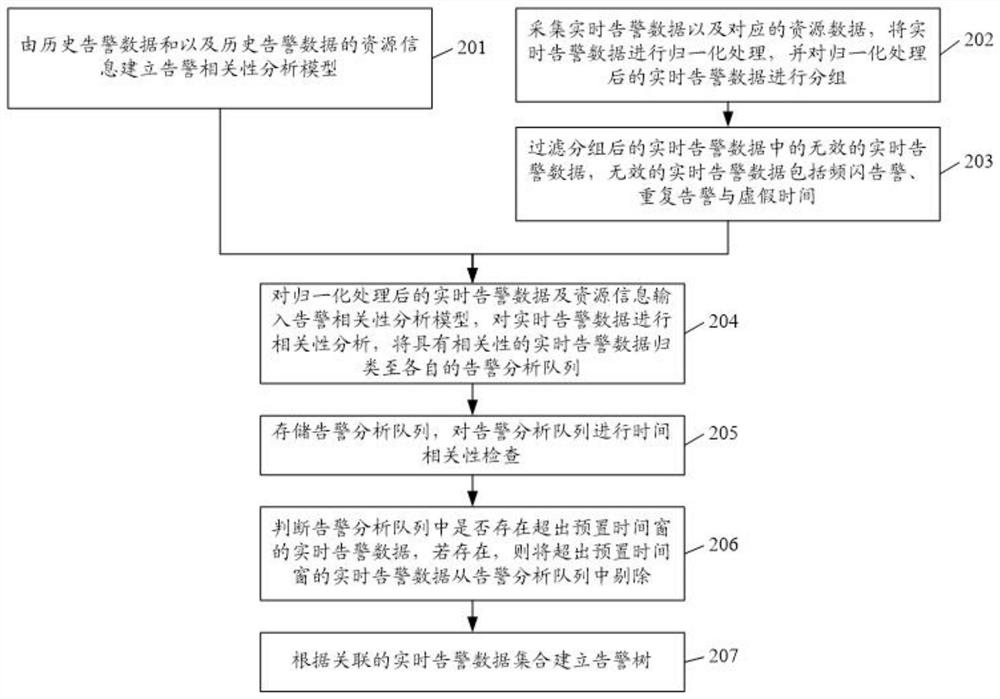
Root alarm analysis and identification method and device
ActiveCN112787860AReduce manual analysis processRapid positioningData switching networksData setResource information
The invention discloses a root alarm analysis and identification method and device. The method comprises the following steps: establishing an alarm correlation analysis model according to historical alarm data and resource information of the historical alarm data; collecting real-time alarm data and corresponding resource information, filtering invalid real-time alarm data in the real-time alarm data, and storing the valid real-time alarm data into an alarm database; inputting the effective real-time alarm data into the alarm correlation analysis model, obtaining the correlation between the effective real-time alarm data, confirming a root alarm and a derivative alarm thereof in the real-time alarm data, and obtaining an associated alarm data set; and establishing an alarm tree according to the associated real-time alarm data set. According to the method, the alarm set with the incidence relation is analyzed, and the root alarm in the alarm set is confirmed, so that maintenance personnel can quickly position and remove faults.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD
Ship network real-time abnormity detection method based on programmable data plane
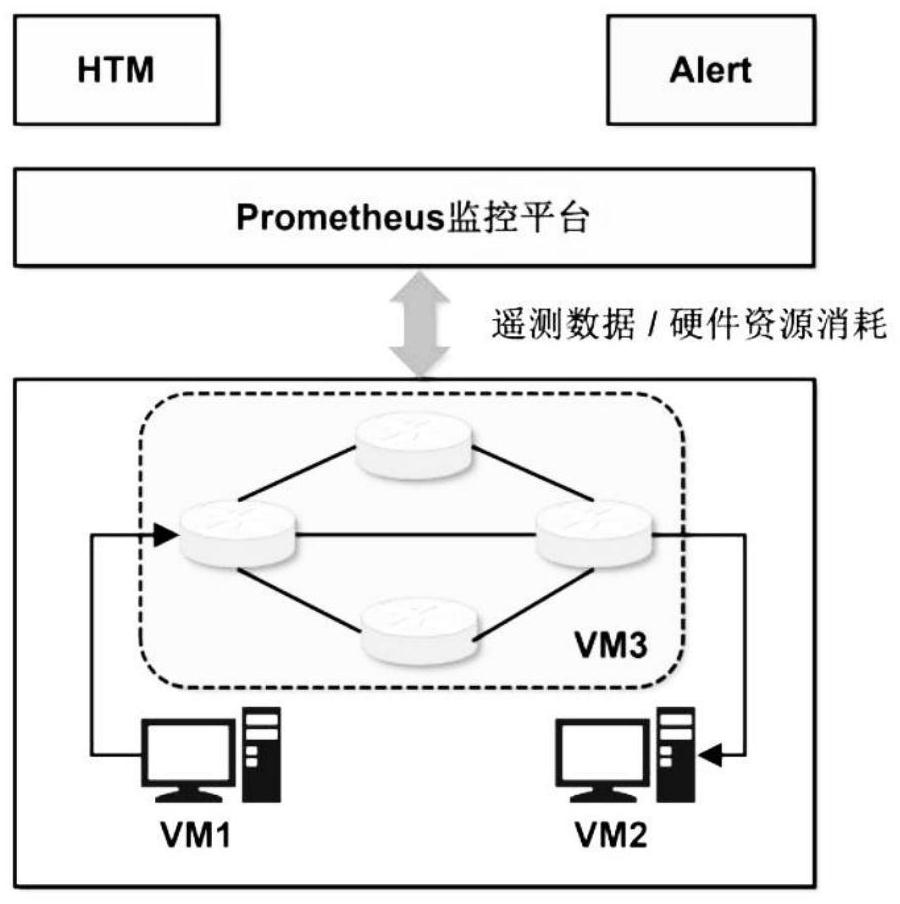
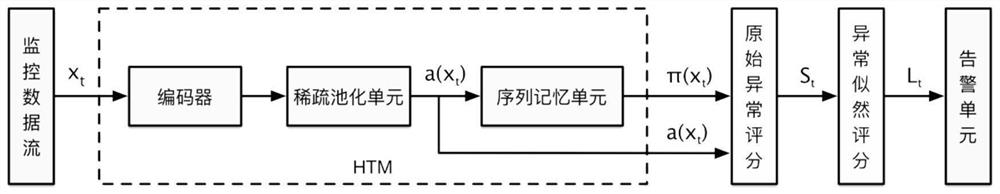
ActiveCN111884874AReduce the number of alertsData switching networksComplex mathematical operationsData entrySequencing data
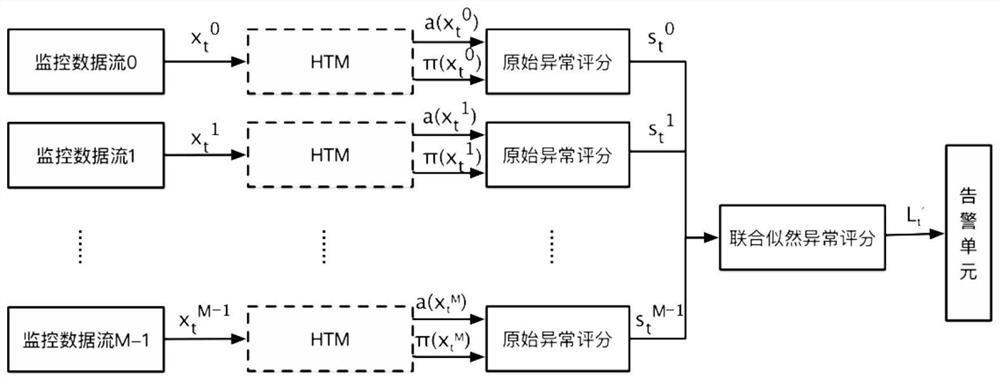
The invention discloses a ship network real-time abnormity detection method based on a programmable data plane. The method comprises the following steps: 1) collecting network state data of each nodei in a network; 2) at each time point t, inputting the sequence data of the network state data into a hierarchical memory network HTM to obtain a prediction error; 3) taking the distribution of the original prediction error as a measure, calculating the likelihood value of the abnormal degree by using the distribution, and judging whether to trigger an abnormal alarm; 4) in multivariable joint anomaly detection, decomposing the input into a plurality of sub-modules according to the number of parameters, and obtaining a global metric through joint likelihood anomaly score calculation to represent an abnormity likelihood score of the whole system; and 5) carrying out joint estimation on the distribution of the original abnormity scores of the plurality of detection systems, and judging whether to trigger an anomaly alarm. The invention provides the abnormity detection method capable of quantitatively evaluating the abnormity degree of a network.
Owner:CHINA SHIP DEV & DESIGN CENT
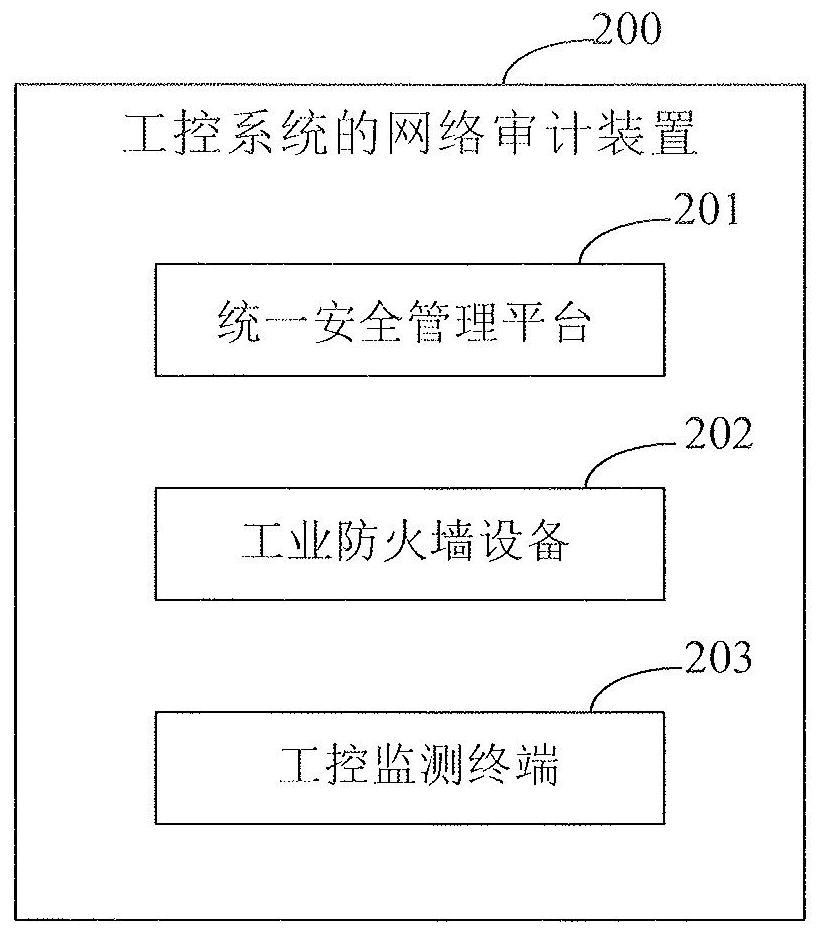
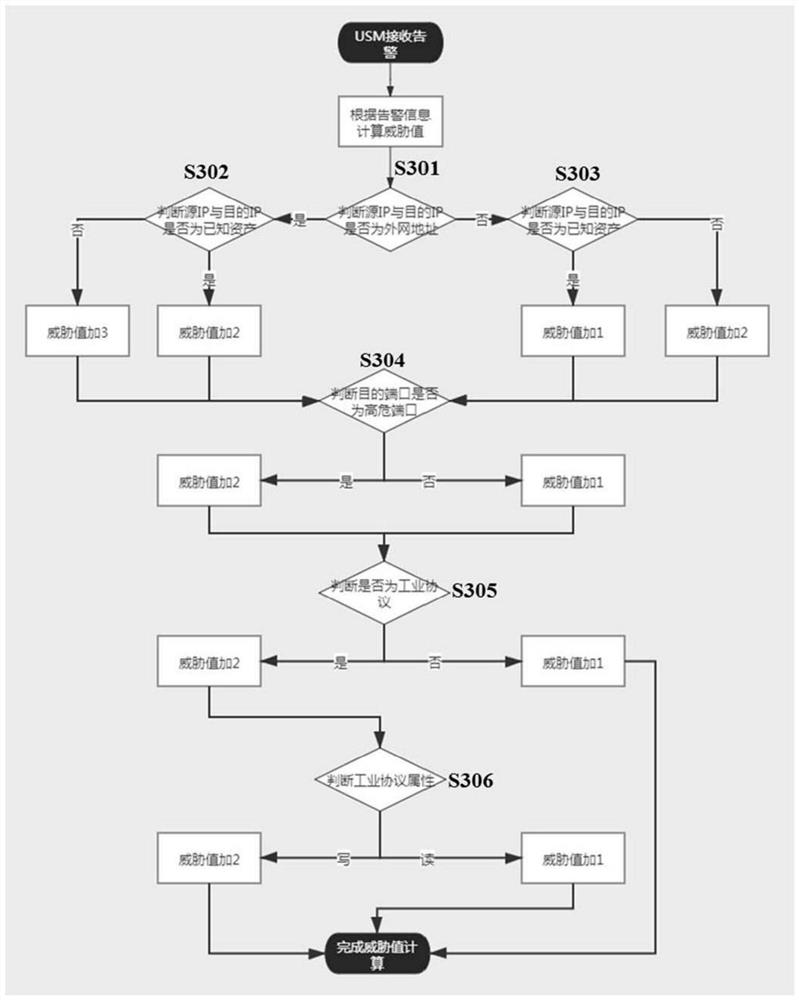
Network auditing method and device of industrial control system
The invention discloses a network auditing method and device of an industrial control system, and relates to the technical field of industrial automation control. One specific embodiment of the methodcomprises the following steps: industrial firewall equipment and an industrial control monitoring terminal being used for identifying and alarming, putting the identified alarms into a filter table,receiving each alarm in the filter table by a unified security management platform, and for each alarm, obtaining a total threat value of each alarm according to a threat value list pre-stored in theunified security management platform; and determining the threat level of each alarm based on the acquired total threat value of each alarm, and determining the display of the alarm according to the determined threat level. According to the embodiment, high-risk alarm identification can be carried out on the alarm information generated by violation of the white list rule, a large number of high-risk alarms caused by incomplete white list learning data are avoided, the number of the high-risk alarms is reduced, and a user can process the high-risk alarms conveniently and preferentially.
Owner:GUIZHOU QIANYUAN POWER CO LTD +1
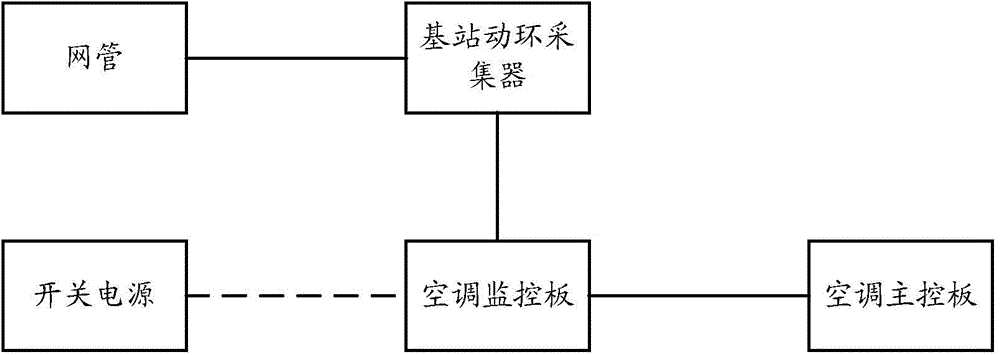
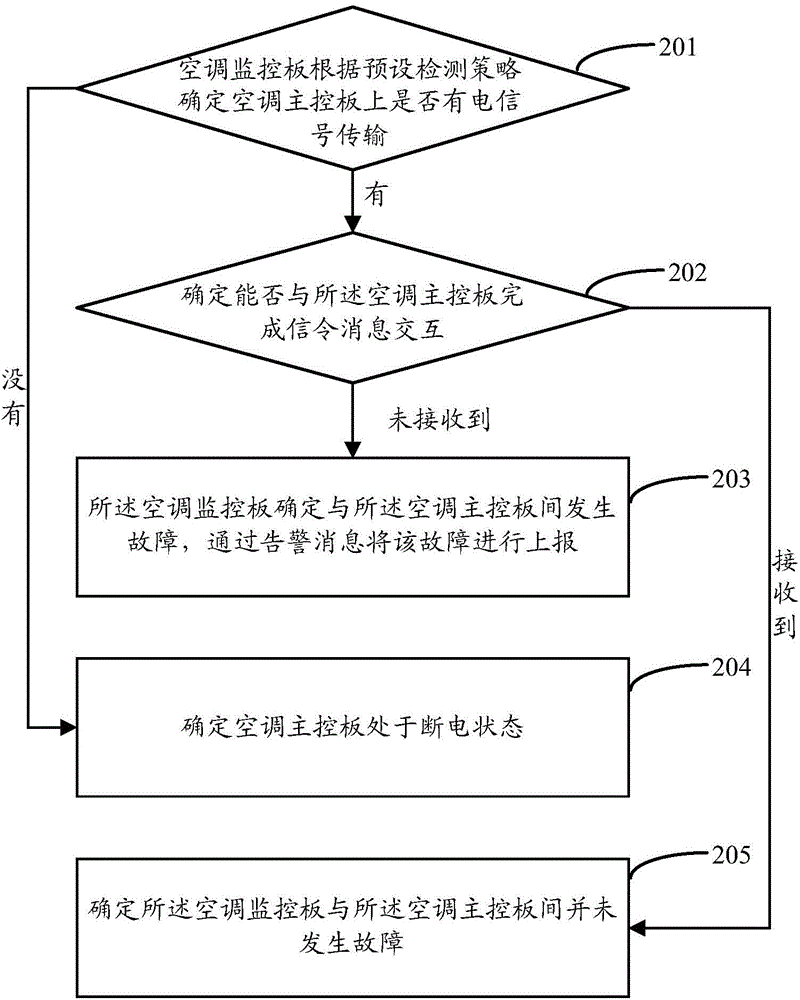
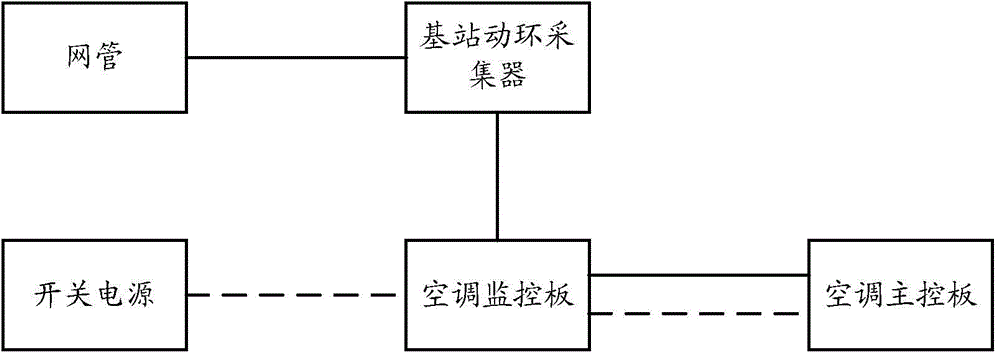
Air conditioner power supply state alarm detection method and device
InactiveCN105319452ASolve the problem of rising maintenance costsImprove maintenance efficiencyElectrical testingAlarm messageElectric signal
The invention discloses an air conditioner power supply state alarm detection method and device. The method is used for an air conditioner monitor plate and comprises determining whether an electric signal is transmitted in an air conditioner main control board according to a preset detection strategy; when determining that the electric signal is transmitted in the air conditioner main control board, determining whether the air conditioner monitor plate can realize signaling information interaction with the air conditioner main control board; and when determining that the air conditioner monitor plate cannot realize signaling information interaction with the air conditioner main control board, determining that fault is caused between the air conditioner monitor plate and the air conditioner main control board, and reporting the fault through an alarm message. Through the scheme above, the problem that in the prior art, since power failure of an air conditioner is often erroneously assumed to be caused by communication failure between the air conditioner monitor plate and the air conditioner main control board, and wrong fault warning is given, the maintenance cost is improved is solved, thereby reducing unnecessary alarming times, improving air conditioner maintenance efficiency and reducing base station maintenance cost.
Owner:CHINA MOBILE GROUP ZHEJIANG
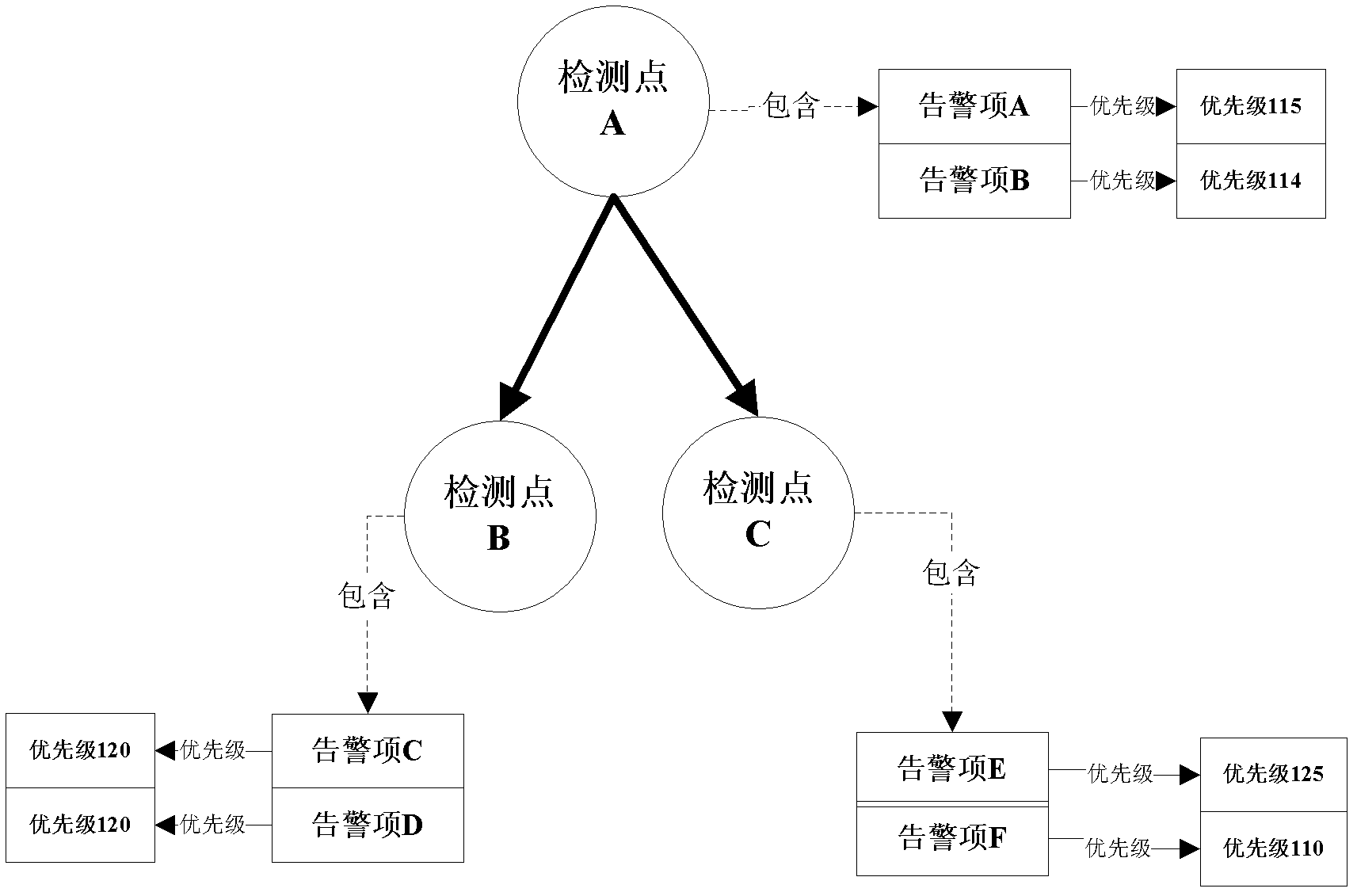
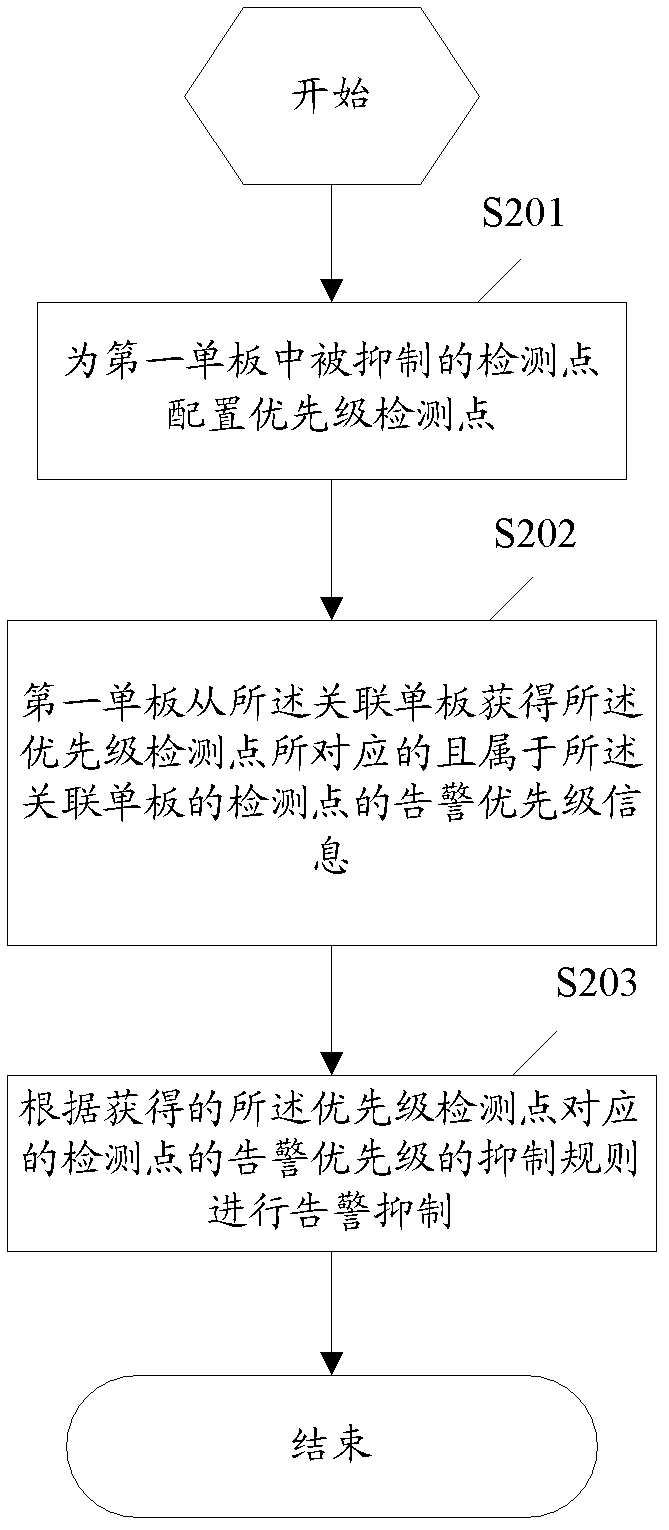
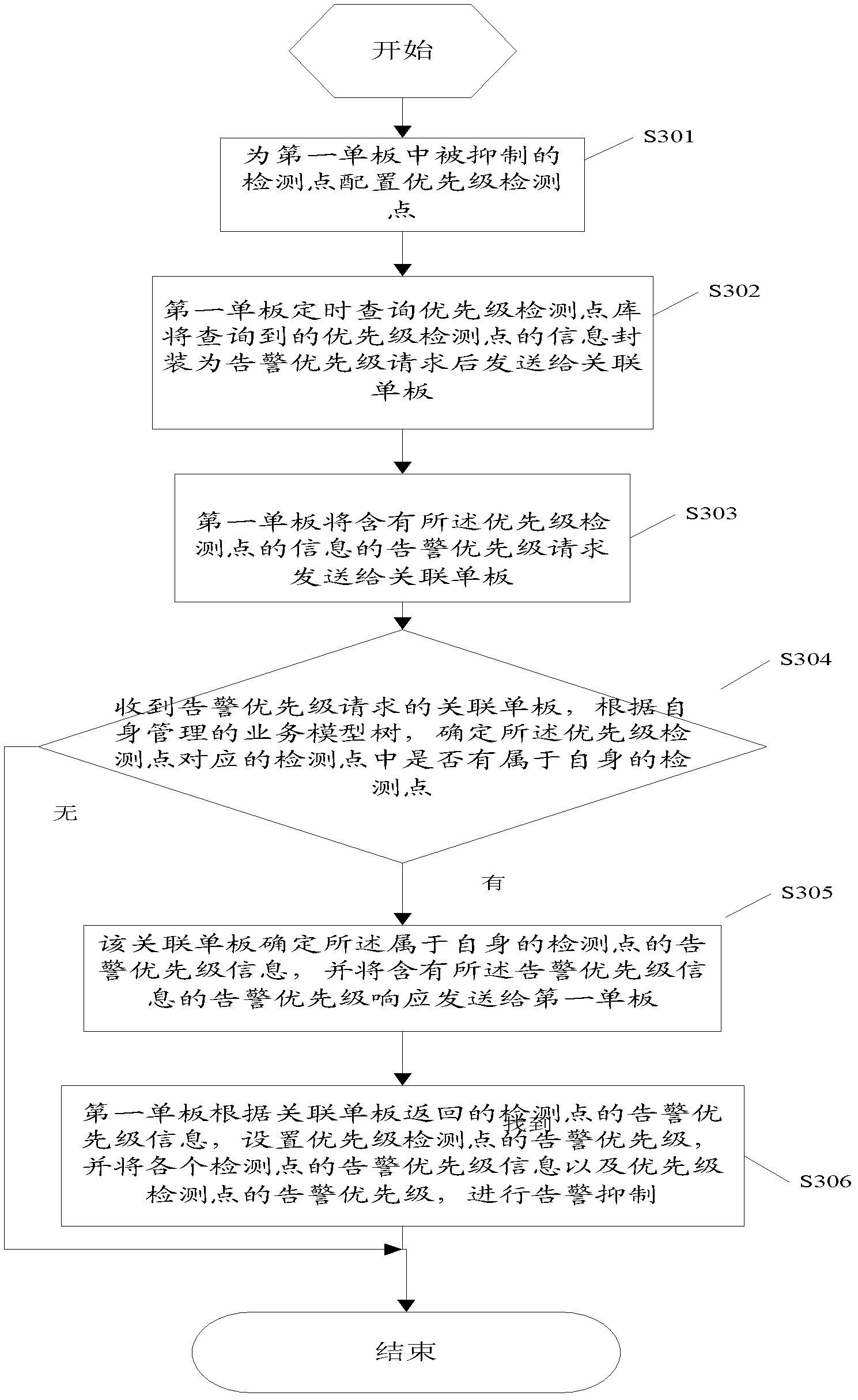
Method and system for suppressing inter-plate alarming priority
InactiveCN102843254AReduce the number of alertsImprove the efficiency of finding root cause alarmsHardware monitoringData switching networksSingle plateComputer science
The invention discloses a method for suppressing inter-plate alarming priority, solving the problems that the primary alarming cannot be distinguished via a user due to a large number of alarming when alarming information is sent via a plurality of single plates under one fault once PTN (Packet Transport Network) equipment is in fault. The method comprises the steps as follows: configuring a priority detecting point to a detecting point suppressed in a first single plate, wherein each priority detecting point is corresponding to a related detecting point, and at least one related detecting point is distributed on a related single plate; acquiring alarming priority information corresponding to the priority detecting point from the related single plate, wherein the alarming priority information belongs to the detecting point of the related single plate; and suppressing the alarming based on suppressing rules on the alarming priority of the detecting point corresponding to the obtained priority detecting point. The invention also provides a system for suppressing the inter-plate alarming priority. According to the method and system provided by the invention, the inter-plate suppressing is carried out, therefore, the alarming information is reduced, and the alarming processing efficiency is improved.
Owner:ZTE CORP
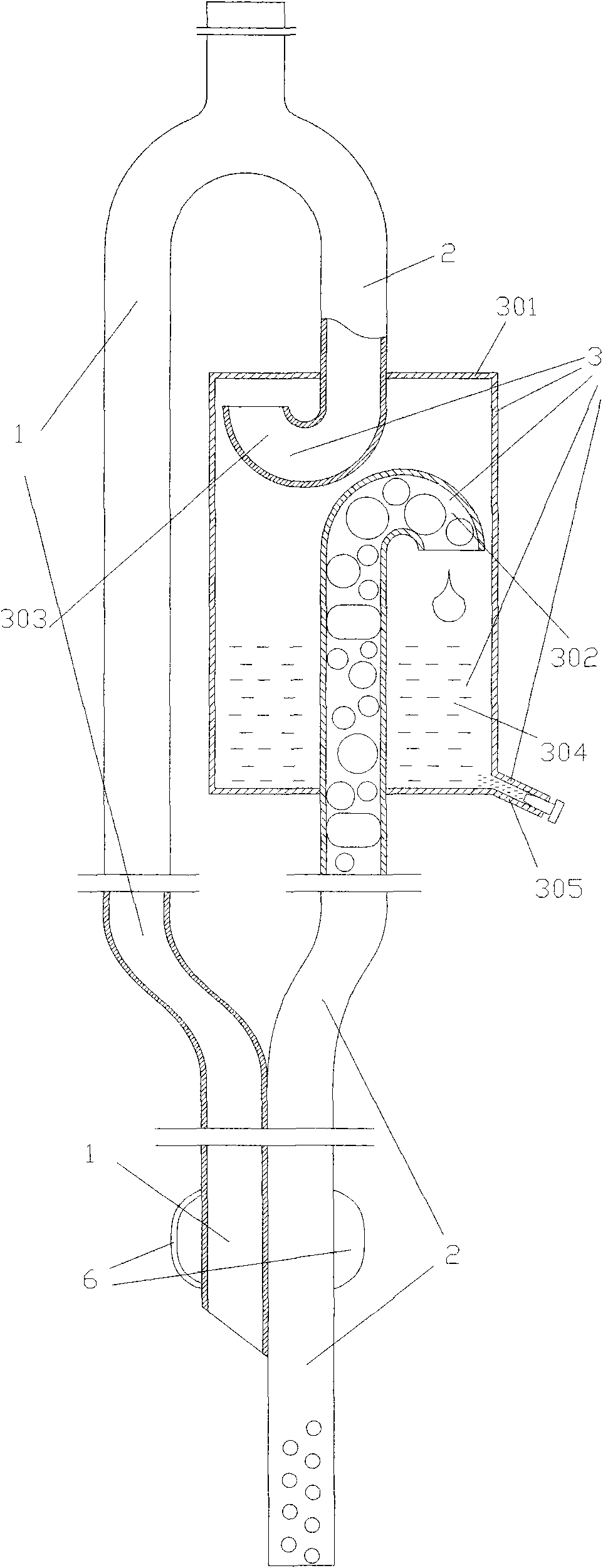
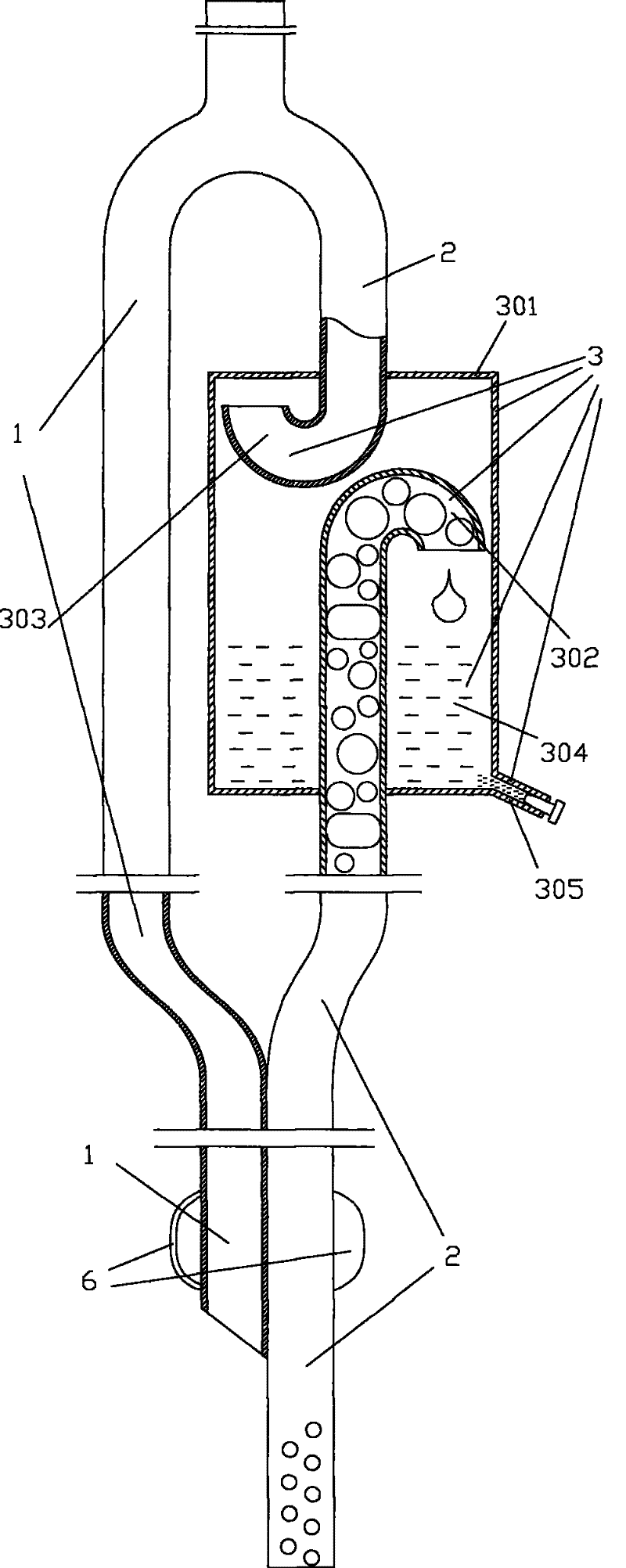
Tracheal cannula with function of automatically eliminating phlegm and automatic phlegm eliminating system using same
The invention discloses a tracheal cannula with function of automatically eliminating phlegm, which comprises two ventilation ducts, namely an air inlet and outlet duct (1) and a special exhaust duct(2); and the special exhaust duct (2) is provided with a phlegm eliminating device (3). The invention also discloses an automatic phlegm eliminating system comprising the tracheal cannula with the function of automatically eliminating phlegm. The air inlet and outlet duct (1) and / or the special exhaust duct (2) of the tracheal cannula with the function of automatically eliminating phlegm are respectively connected with a respirator (5) or are integrated into a common duct and then connected with the respirator (5). The tracheal cannula has the function of automatically sucking the phlegm, greatly lightens the work load of medical care personnel, reduces the alarm frequency of an artificial respirator, relieves the pain of the patient due to phlegm sucking, and has low cost and great marketand social values.
Owner:刘春江
Abnormity detection method and system based on self-adversarial variational auto-encoder
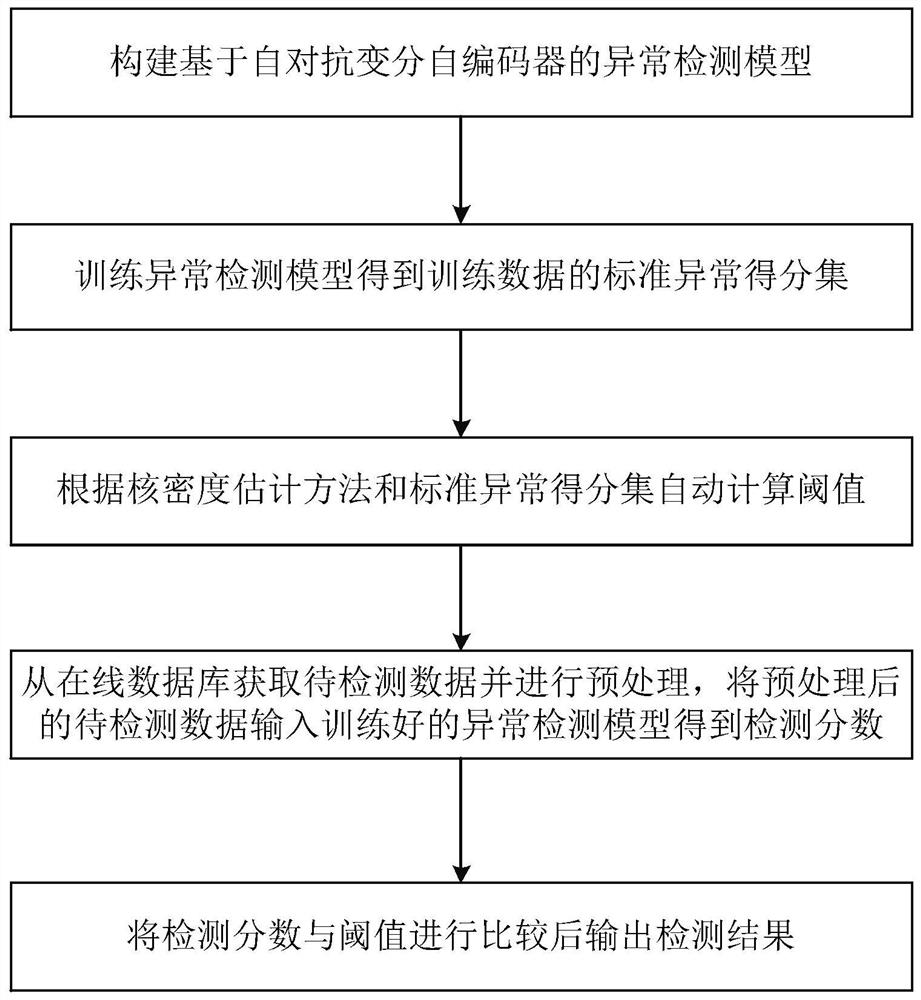
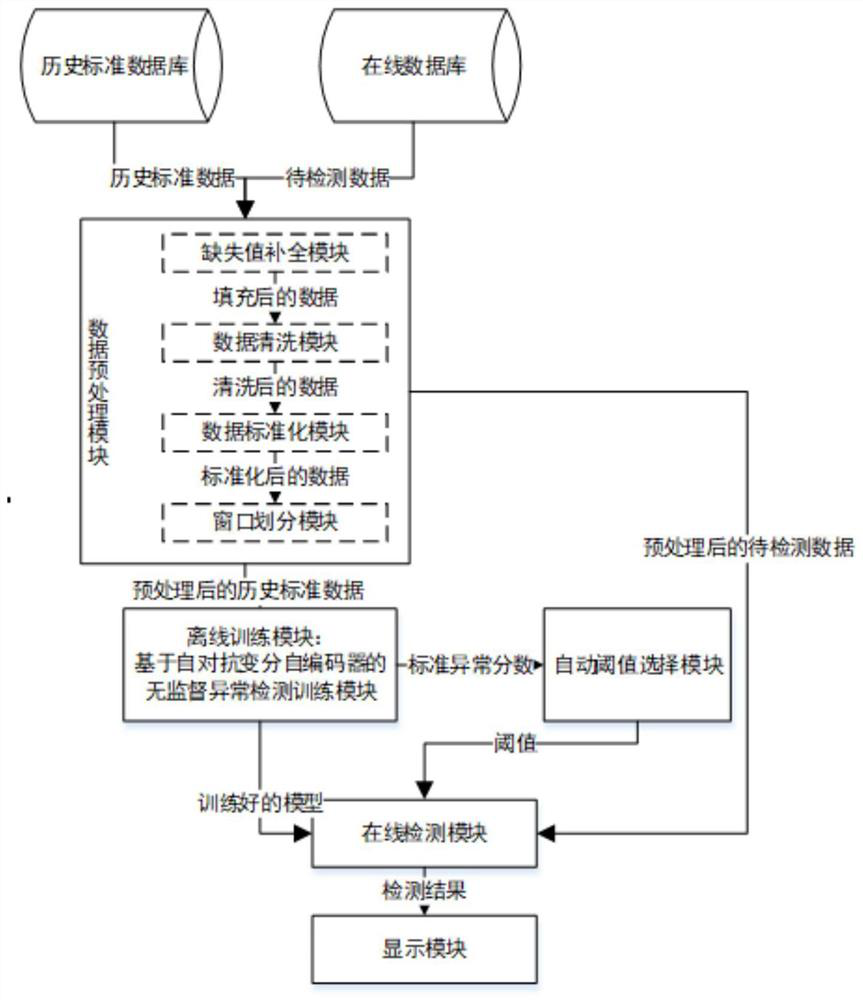
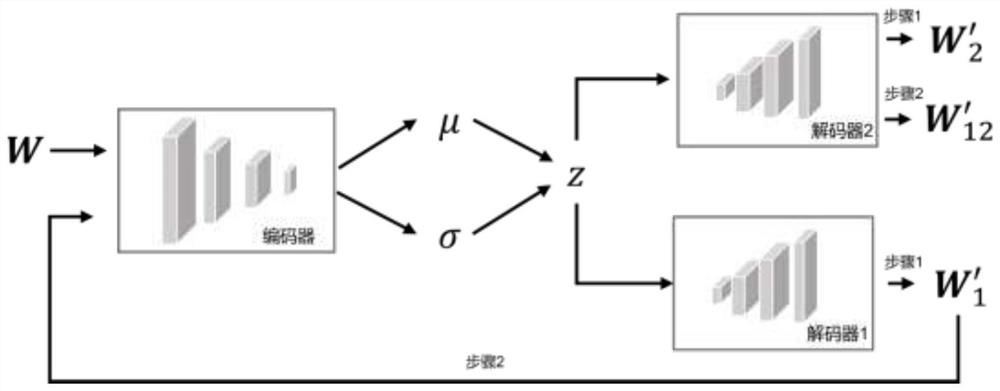
PendingCN114707577AHigh precisionMake up for limitationsCharacter and pattern recognitionNeural architecturesAlgorithmAnomaly detection
The invention belongs to the field of anomaly detection, and particularly relates to an anomaly detection method and system based on a self-adversarial variational auto-encoder, and the method comprises the steps: constructing an anomaly detection model based on the self-adversarial variational auto-encoder, training the anomaly detection model, and obtaining a standard anomaly score set of training data, automatically calculating a threshold value according to a kernel density estimation method and the standard anomaly score set, obtaining to-be-detected data from the online database, preprocessing the to-be-detected data, inputting the preprocessed to-be-detected data into the trained anomaly detection model to obtain a detection score, comparing the detection score with the threshold value, and outputting a detection result; according to the method, the advantages of an unsupervised anomaly detection method based on a variational auto-encoder and adversarial training are combined, the limitation of each technology is made up, the anomaly detection accuracy is improved, and the problem that the false alarm rate or the missing report rate is high due to a fixed threshold value method is effectively relieved by designing an automatic threshold value selection module.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Alarm intelligent analysis and display method
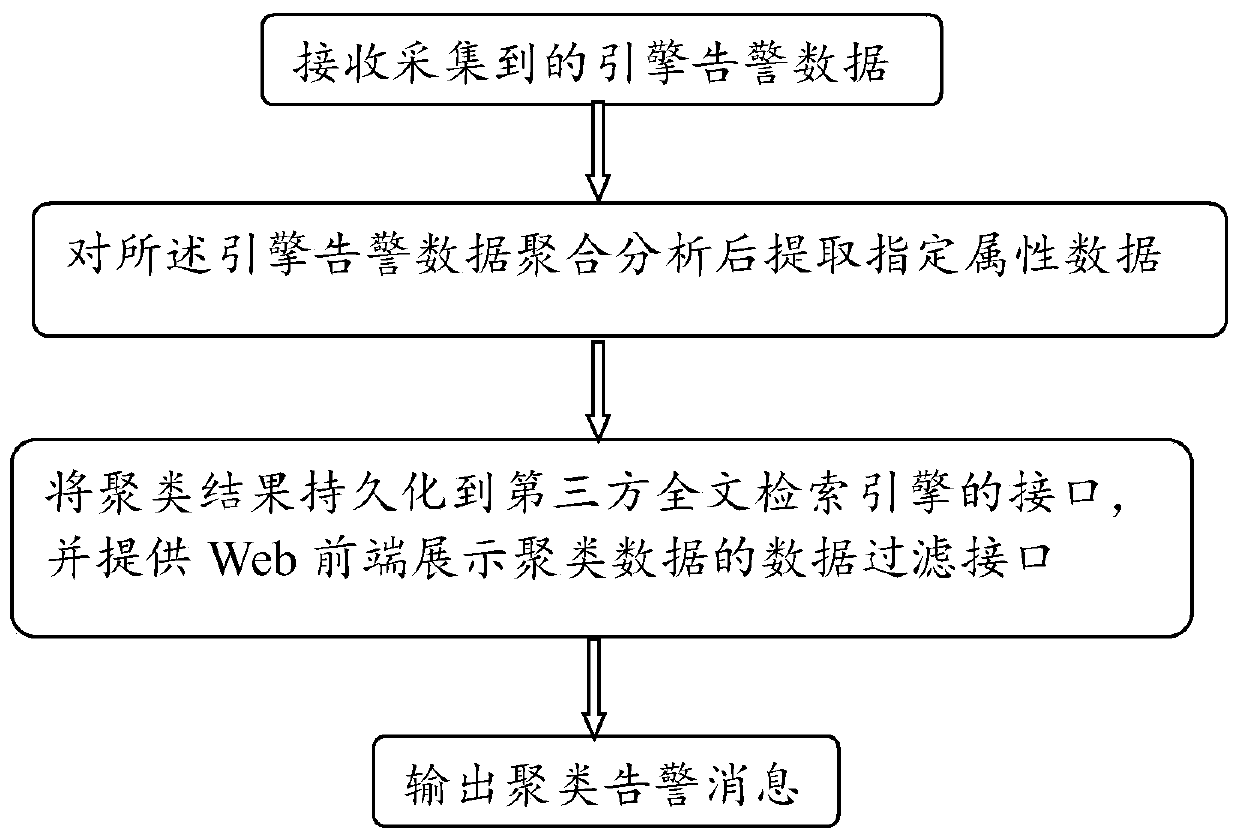
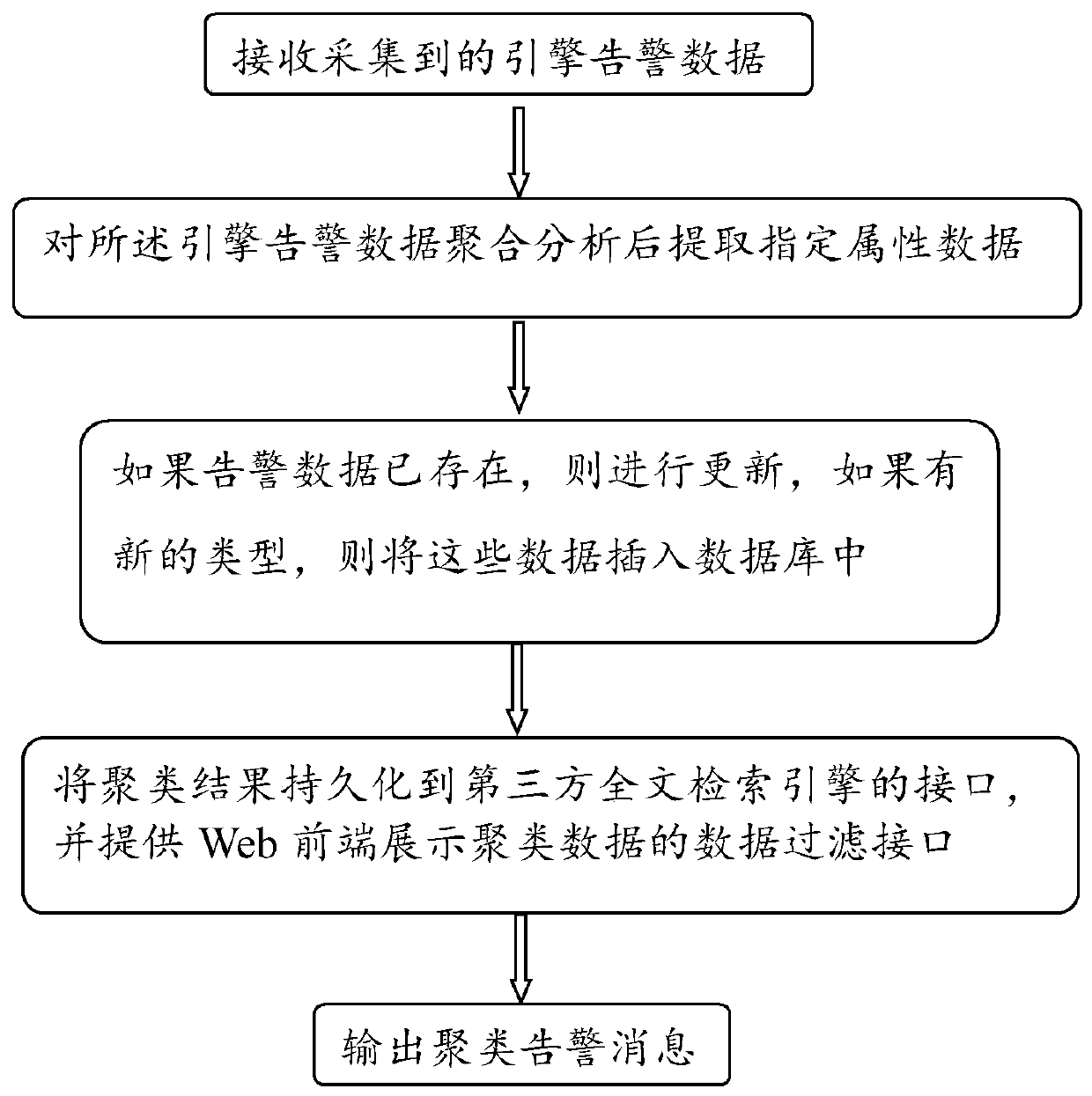
The invention relates to the technical field of Internet and multimedia, and provides an alarm intelligent analysis and display method which is characterized by comprising the following steps of Step1, receiving the collected engine alarm data; step2, after the aggregation analysis is conducted on the engine alarm data, extracting the specified attribute data; step3, persisting the clustering result to an interface of a third-party full-text retrieval engine, and providing a data filtering interface for displaying the clustering data at a Web front end; and step 4, outputting a clustering alarm message.
Owner:HANGZHOU GUYI NETWORK TECH CO LTD
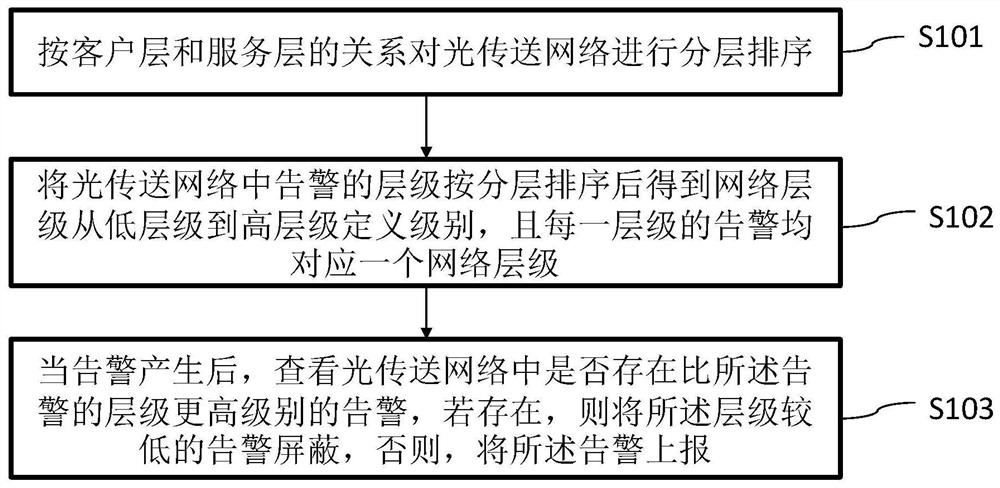
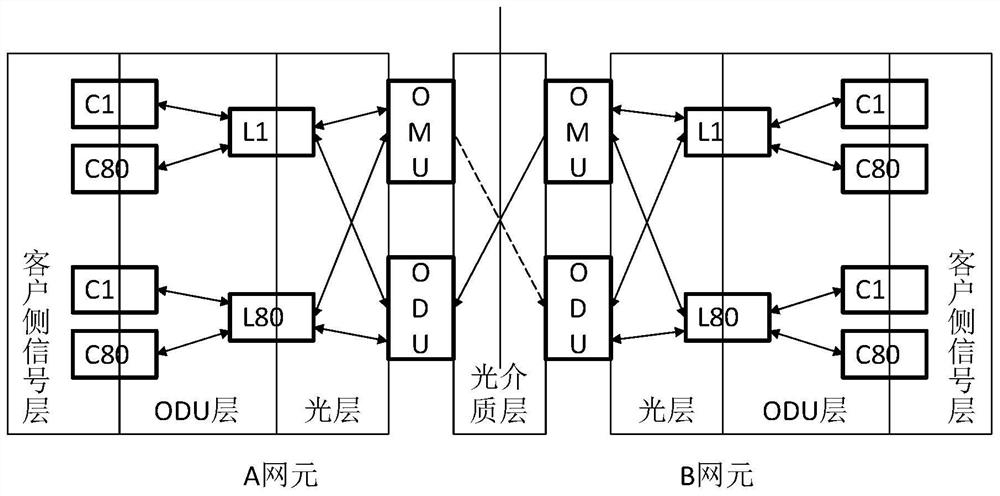
Optical transport network alarm processing method and device, terminal equipment and storage medium
InactiveCN112995800AReduce technical ability requirementsEasy maintenanceMultiplex system selection arrangementsTransmission monitoring/testing/fault-measurement systemsTerminal equipmentNetwork management
The invention provides an optical transport network alarm processing method and device, terminal equipment and a storage medium, and the processing method comprises the steps: carrying out the hierarchical sorting of an optical transport network according to the relation between a customer layer and a service layer; sorting the levels of the alarms in the optical transport network according to the levels to obtain network levels which are defined from a low level to a high level, wherein the alarms of each level correspond to one network level; after the alarm is generated, checking whether an alarm of which the level is higher than that of the alarm exists in the optical transport network, if so, shielding the alarm, and otherwise, reporting the alarm. According to the embodiment of the invention, invalid alarms are directly shielded, and the problem that the number of reported alarms is too large at one time is solved; the reported alarm is closely related to the fault, so the fault positioning efficiency is improved; meanwhile, all judgment operations are calculated by the network management server, and results are directly given, so the requirement on the technical capability of maintenance personnel is lowered, and the optical transmission network is easier to maintain.
Owner:ZTE CORP
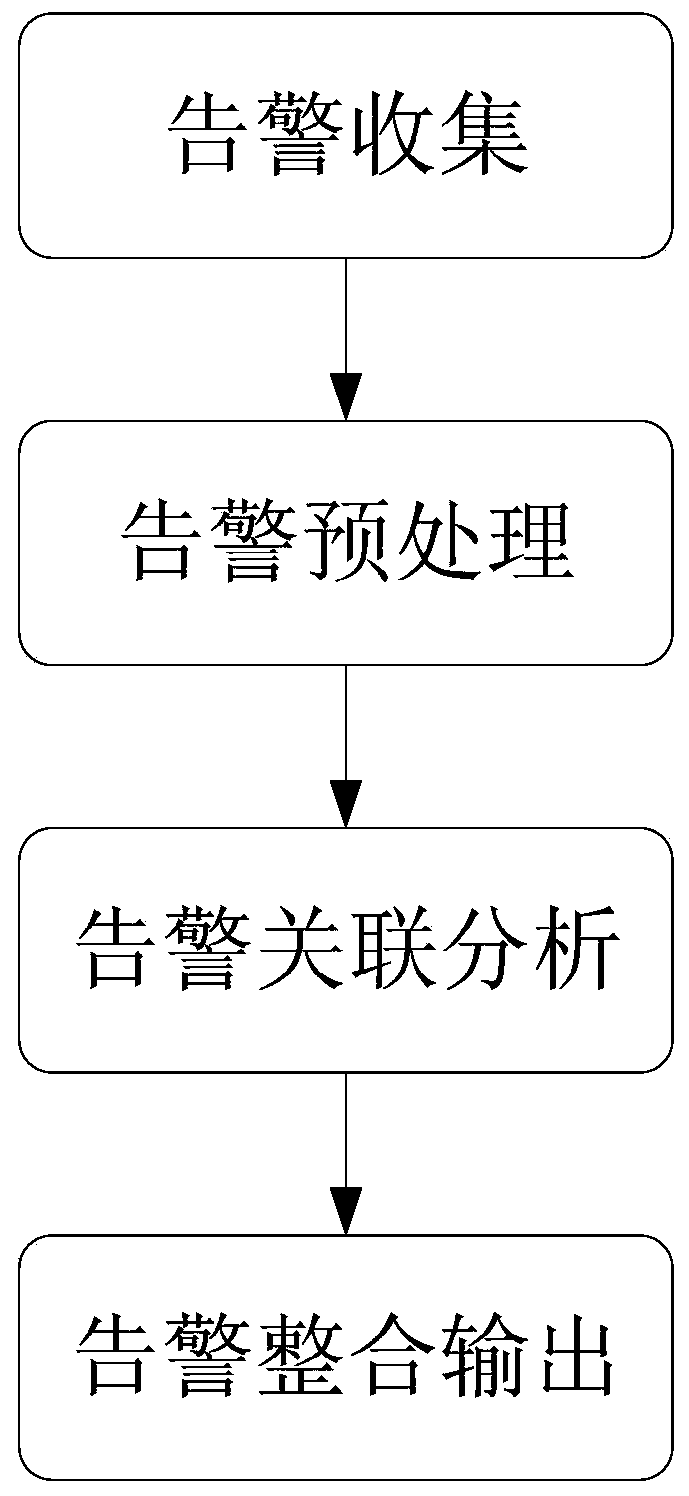
Alarm fusion system and method based on data center anomaly monitoring
ActiveCN110399278AReduce redundancyReduce the number of alertsHardware monitoringInformation technology support systemData centerData source
The invention provides an alarm fusion method based on data center anomaly monitoring. The alarm fusion method comprises the following steps: S1, alarm collection: collecting alarm information from each data source monitored by a whole operation and maintenance system in a series of time windows; S2, alarm preprocessing: carrying out redundancy elimination operation on the collected alarm information, and extracting key alarm information in the collected alarm information; S3, alarm association analysis: discovering association rules of the preprocessed alarm information according to a certainalgorithm; and S4, alarm integration and output: performing de-duplication and integration operation on the newly arrived alarm information within a certain time according to the association rule ofthe alarm information discovered in the step S3, and outputting the alarm information to a database. According to the invention, redundant information in the alarm information can be eliminated. The alarm information with a causal relationship is fused, so that the workload and the working difficulty of operation and maintenance personnel are reduced. The operation and maintenance cost is reduced.
Owner:JIANGSU R & D CENTER FOR INTERNET OF THINGS
Alarm Correlation Analysis Method Based on Knowledge Base
ActiveCN104021195BReduce work intensityRapid positioningSpecial data processing applicationsReal time analysisTree shaped
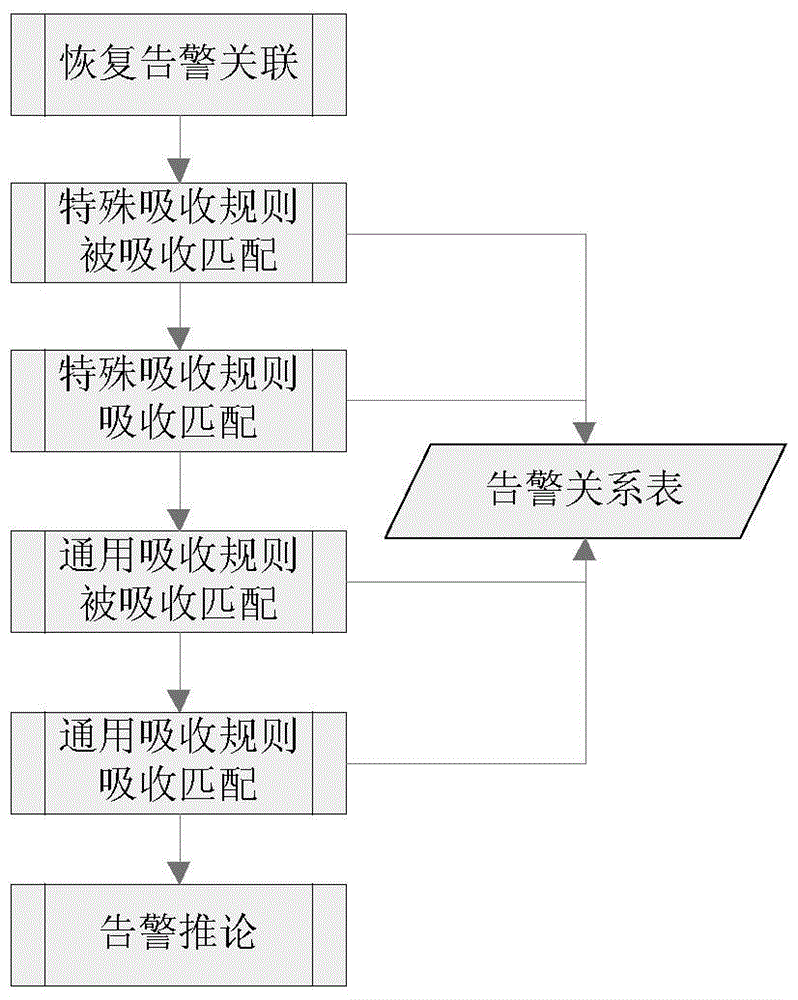
The invention provides a warning association analysis method based on a knowledge base. The method includes the steps that 1, warning information existing in a warning bus is acquired; 2, warning absorption association analysis is conducted on the warning information, and a root warning is obtained; 3, warning deduction association analysis is conducted on the warning information, and a new warning is deducted to serve as a root warning; 4, the result obtained after association analysis is identified in the warning bus in a association identifier setting mode; 5, after the root warning is determined, automatic confirmation is conducted on sub-warnings, and all the relevant sub-warnings are closed synchronously as along as the root warning is closed. According to the warning association analysis method, real-time rule match is conducted on multiple warnings in the warning bus according to the association rules of warning absorption and warning deduction stored in the knowledge base, the absorption relation and the deduction relation are built in sequence to form a tree-shaped structure, so that the root warning is analyzed in real time, the derivative warnings are absorbed, or a new warning is obtained according to the existing warning deduction.
Owner:TRAVELSKY
Method for uploading alarm quantity information to network management system by network element management system
InactiveCN101360313BReduce the number of alertsEasy accessData switching networksWireless communicationNetwork managementComputer science
The invention discloses a method of a network element management system reporting the warning number message to a network management system, which aims at reporting the warning occurrence number message and reducing the warning number at the same time. The method is characterized in recoding the warning occurrence total number which is received by the network element management system, and the warning number which is received in a time interval; wherein, the warning occurrence total number is the unrestored warning total number which is received by the network element management system; the network element management system takes the warning occurrence total number and the warning number as the content of warning number message to report to the network management system. By adopting the method provided by the invention, the EMS can report the warning number message to the NMS while reduce the warning number at the same time, thus facilitate the NMS to obtain more warning related messages, and also facilitate the management and maintenance work of the managers.
Owner:OPEN INVENTION NEWTORK LLC
Alarm information processing method and system
ActiveCN101651576BReduce workloadImprove timelinessData switching networksSpecial data processing applicationsInformation processingTopology information
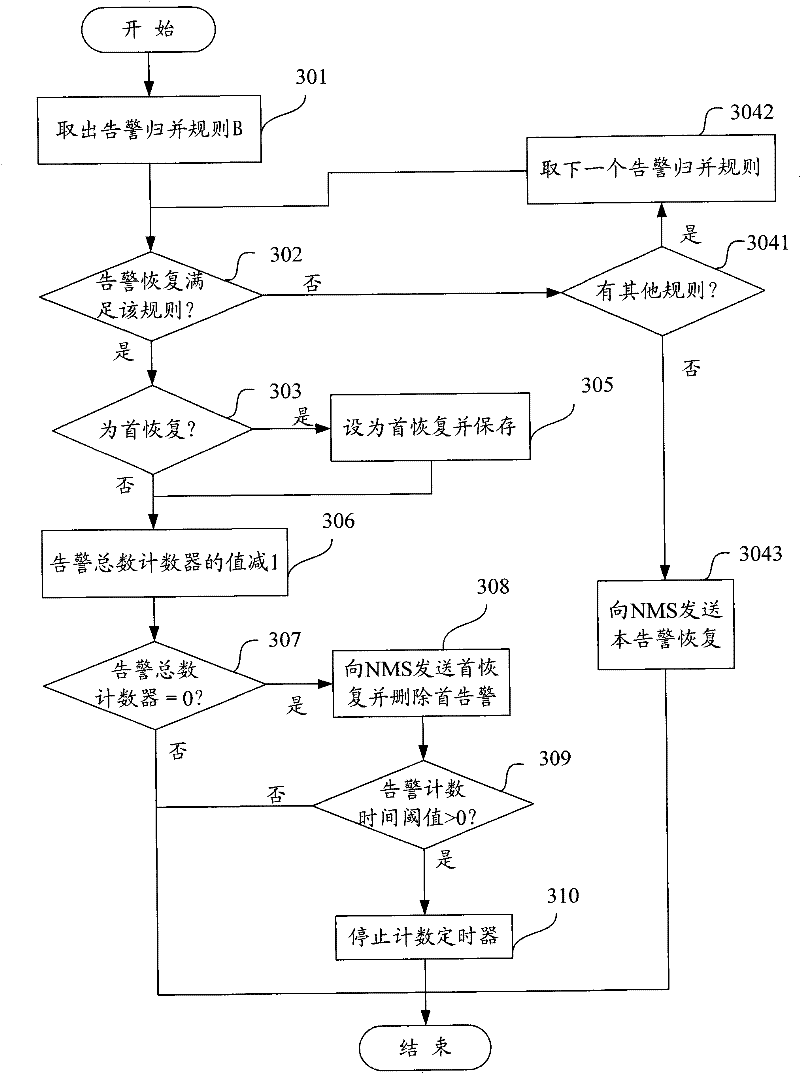
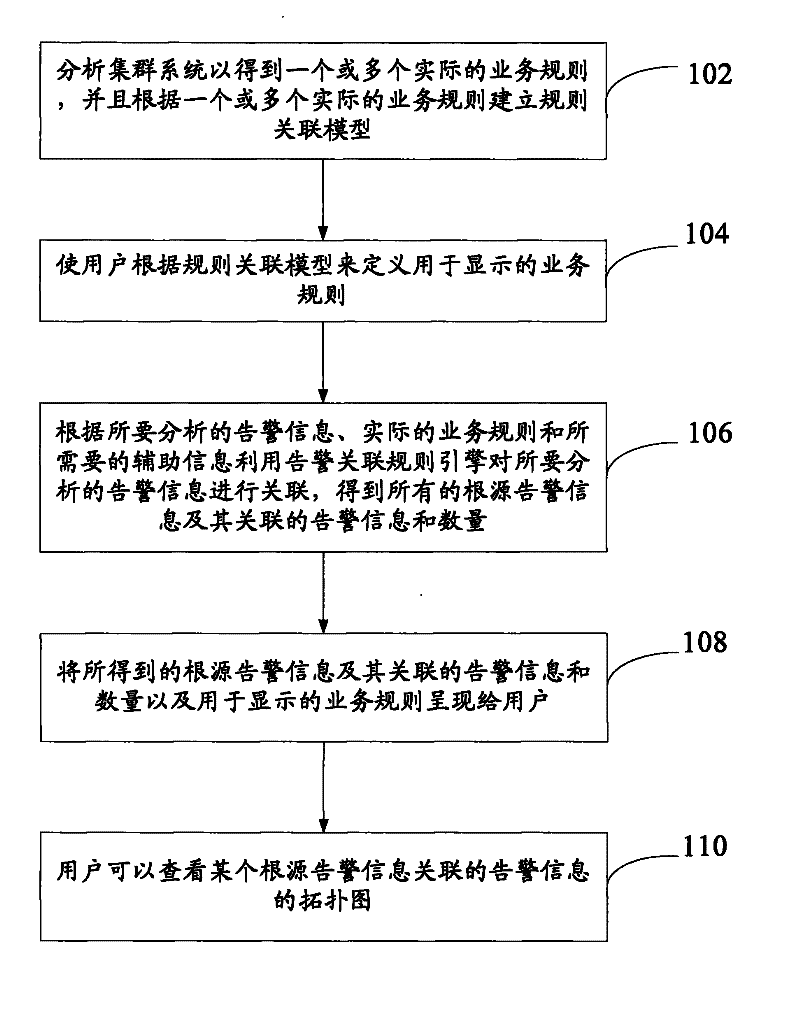
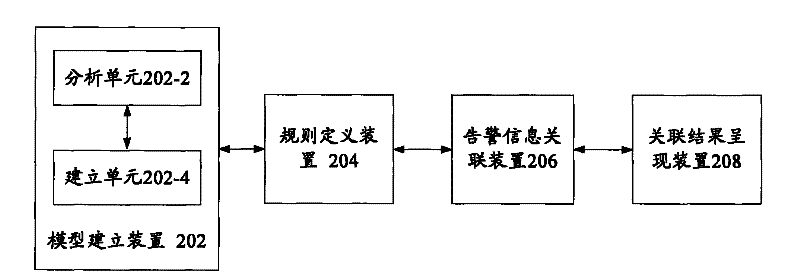
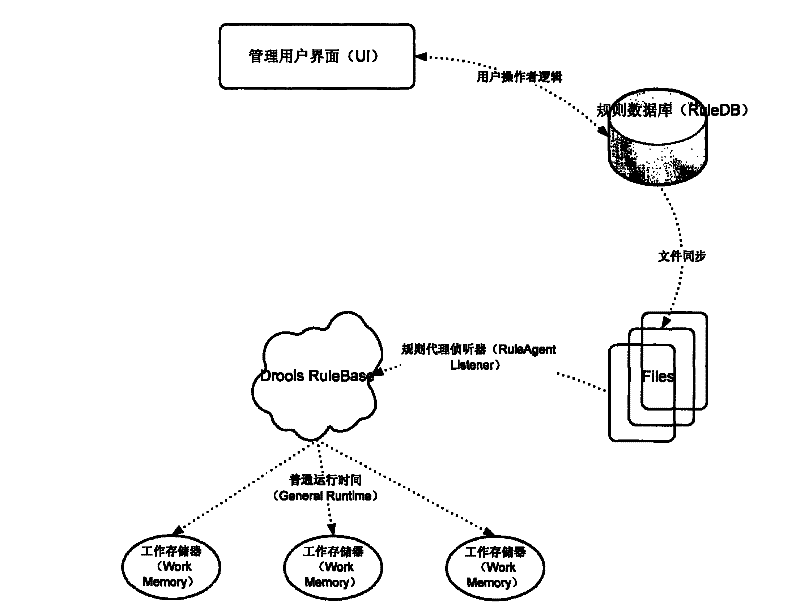
The present invention provides a method and device for processing alarm information, wherein the method for processing alarm information includes: analyzing the cluster system to obtain one or more actual business rules, and establishing a rule association model according to one or more actual business rules; Users define the business rules for display according to the rule association model, where the business rules for display correspond to and synchronize with the actual business rules; obtain the alarm information to be analyzed and the required auxiliary information, and according to the Alarm information, actual business rules and required auxiliary information use the alarm correlation rule engine to correlate the alarm information to be analyzed to obtain all root alarm information and its associated alarm information and quantity; combine the obtained root alarm information and The associated alarm information and quantity, as well as the business rules for display are presented to the user, and the user can also view the topology map of the alarm information associated with a certain root alarm information.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Tracheal cannula with function of automatically eliminating phlegm and automatic phlegm eliminating system using same
The invention discloses a tracheal cannula with function of automatically eliminating phlegm, which comprises two ventilation ducts, namely an air inlet and outlet duct (1) and a special exhaust duct (2); and the special exhaust duct (2) is provided with a phlegm eliminating device (3). The invention also discloses an automatic phlegm eliminating system comprising the tracheal cannula with the function of automatically eliminating phlegm. The air inlet and outlet duct (1) and / or the special exhaust duct (2) of the tracheal cannula with the function of automatically eliminating phlegm are respectively connected with a respirator (5) or are integrated into a common duct and then connected with the respirator (5). The tracheal cannula has the function of automatically sucking the phlegm, greatly lightens the work load of medical care personnel, reduces the alarm frequency of an artificial respirator, relieves the pain of the patient due to phlegm sucking, and has low cost and great market and social values.
Owner:刘春江
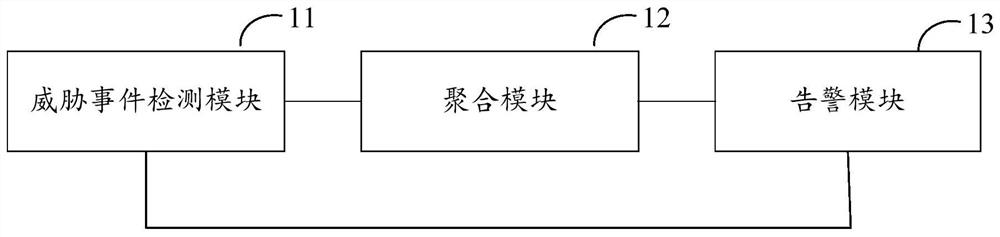
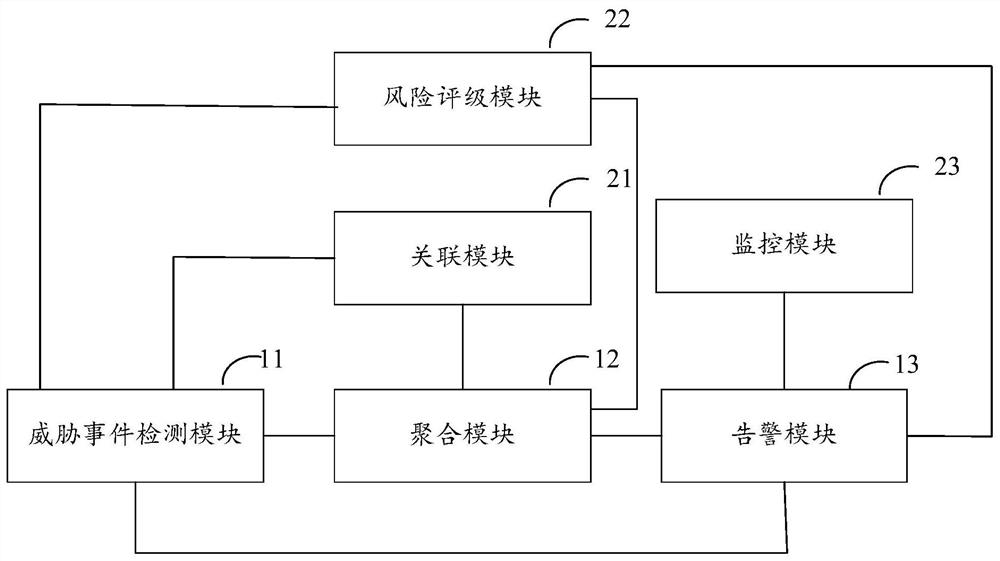
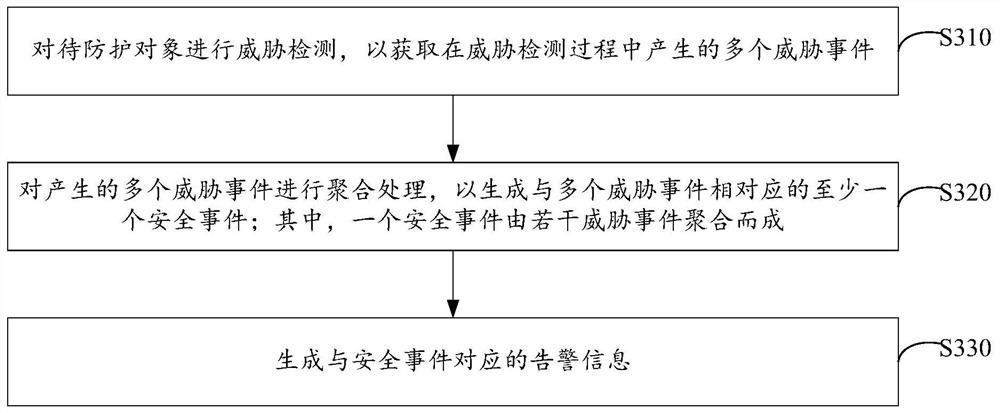
Safety protection system and method
PendingCN113127855AImprove processing efficiencyRealize effective protectionPlatform integrity maintainanceReal-time computingSystems engineering
The invention discloses a safety protection system and method. The system comprises: a threat event detection module which is suitable for carrying out threat detection on a to-be-protected object so as to obtain a plurality of threat events generated in the threat detection process; an aggregation module which is suitable for performing aggregation processing on the plurality of generated threat events so as to generate at least one security event corresponding to the plurality of threat events, wherein one security event is formed by aggregating a plurality of threat events; and an alarm module which is suitable for generating alarm information corresponding to the security event. By adopting the scheme, the closed-loop processing of the threat event can be realized, the processing efficiency is improved, and the effective protection of the security protection object is realized; moreover, according to the scheme, the number of events to be processed and the number of alarms can be greatly reduced through aggregation processing of the threat events, and the processing precision is further improved on the basis of saving system resources and improving the processing efficiency.
Owner:苏州三六零智能安全科技有限公司
Unsupervised KPI Anomaly Detection Method Based on Serialized Autoencoder
ActiveCN113204590BImprove accuracyStrong explainabilityDigital data information retrievalCharacter and pattern recognitionAnomaly detectionThresholding
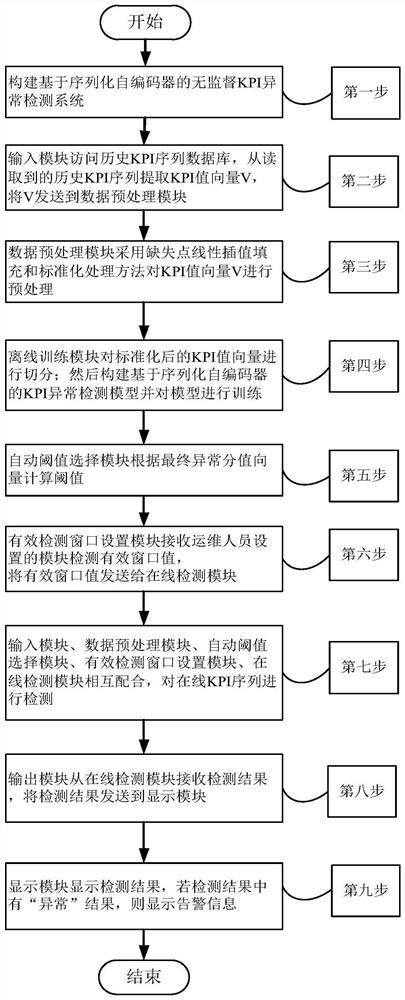
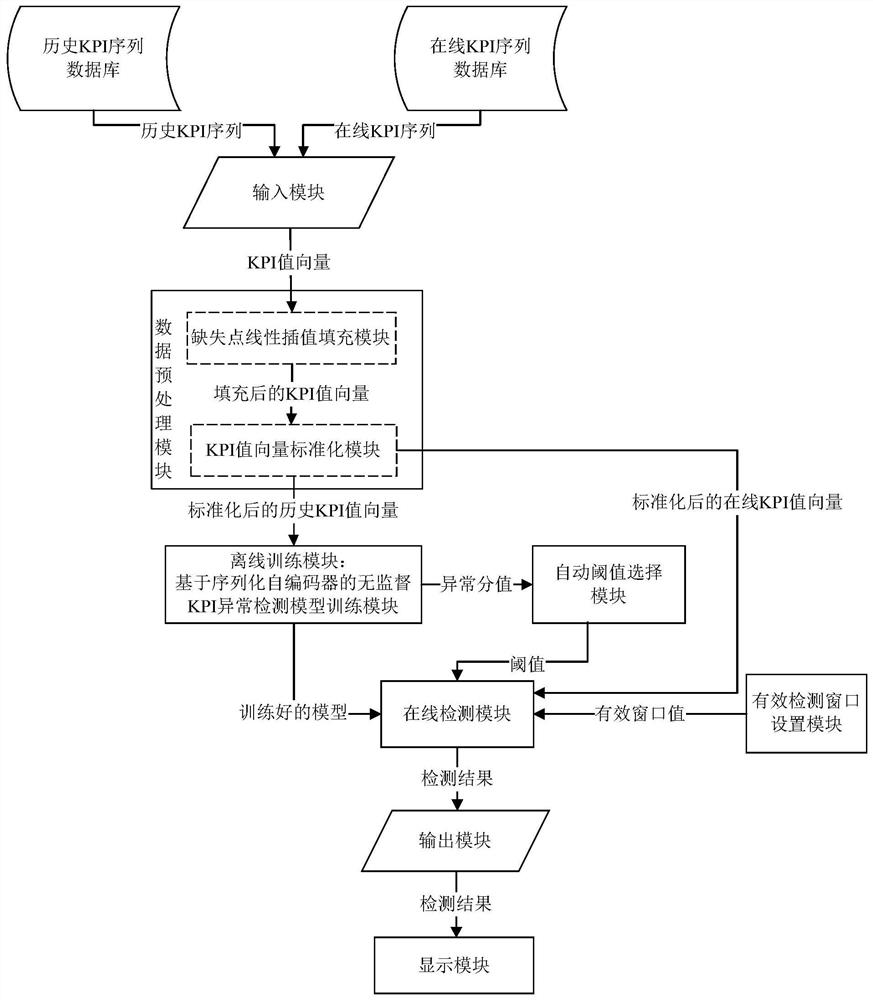
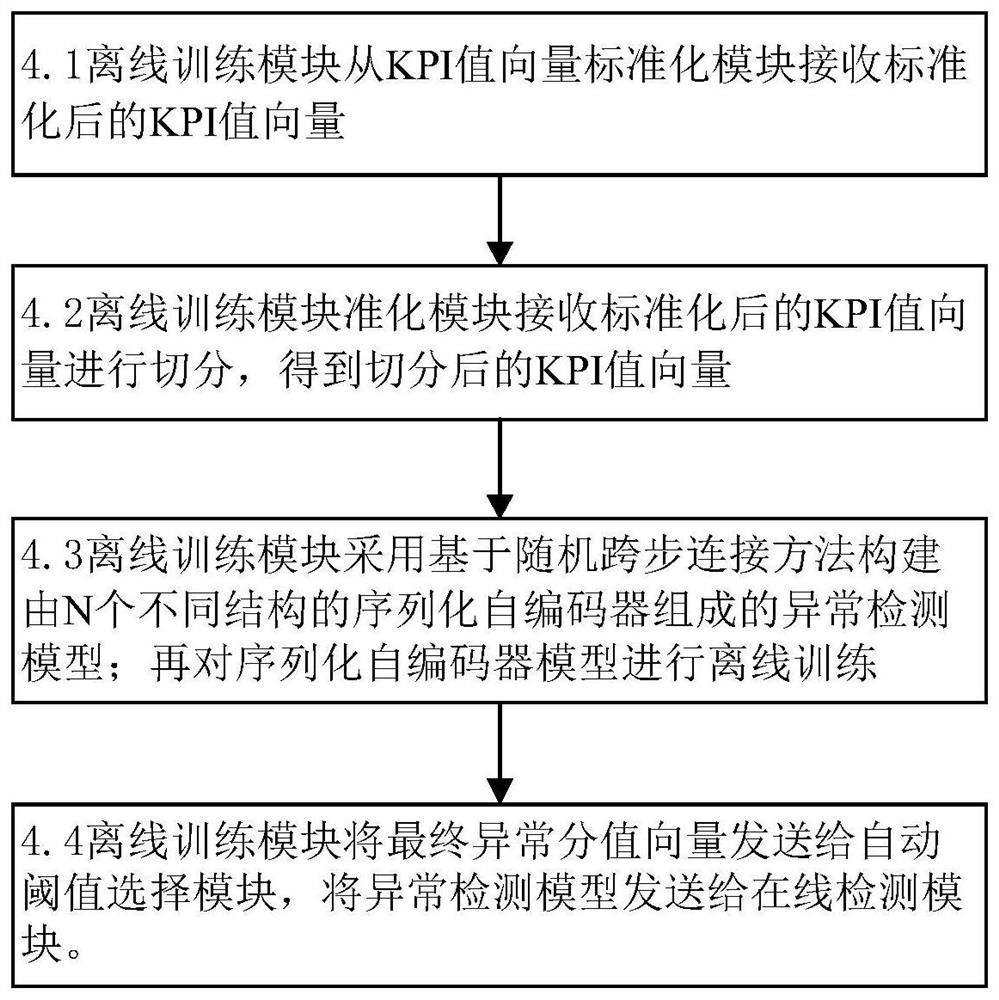
The invention discloses an unsupervised KPI anomaly detection method based on a serialized autoencoder, aiming at improving the accuracy and robustness of KPI anomaly detection. The technical solution is to build an unsupervised KPI anomaly detection system based on a serialized autoencoder; the input module extracts the KPI value vector; the data preprocessing module preprocesses the KPI value vector; the offline training module splits the standardized KPI value vector , build an anomaly detection model and train the model; the automatic threshold selection module calculates the threshold; the effective detection window setting module obtains the effective window value; the input module, the data preprocessing module, the automatic threshold selection module, the effective detection window setting module, and the online detection module Cooperate with each other to detect the online KPI sequence and obtain the detection result; the display module displays the detection result. The invention can solve the problems of high false positive rate and false negative rate, and effectively improve the accuracy rate of KPI abnormal detection.
Owner:NAT UNIV OF DEFENSE TECH
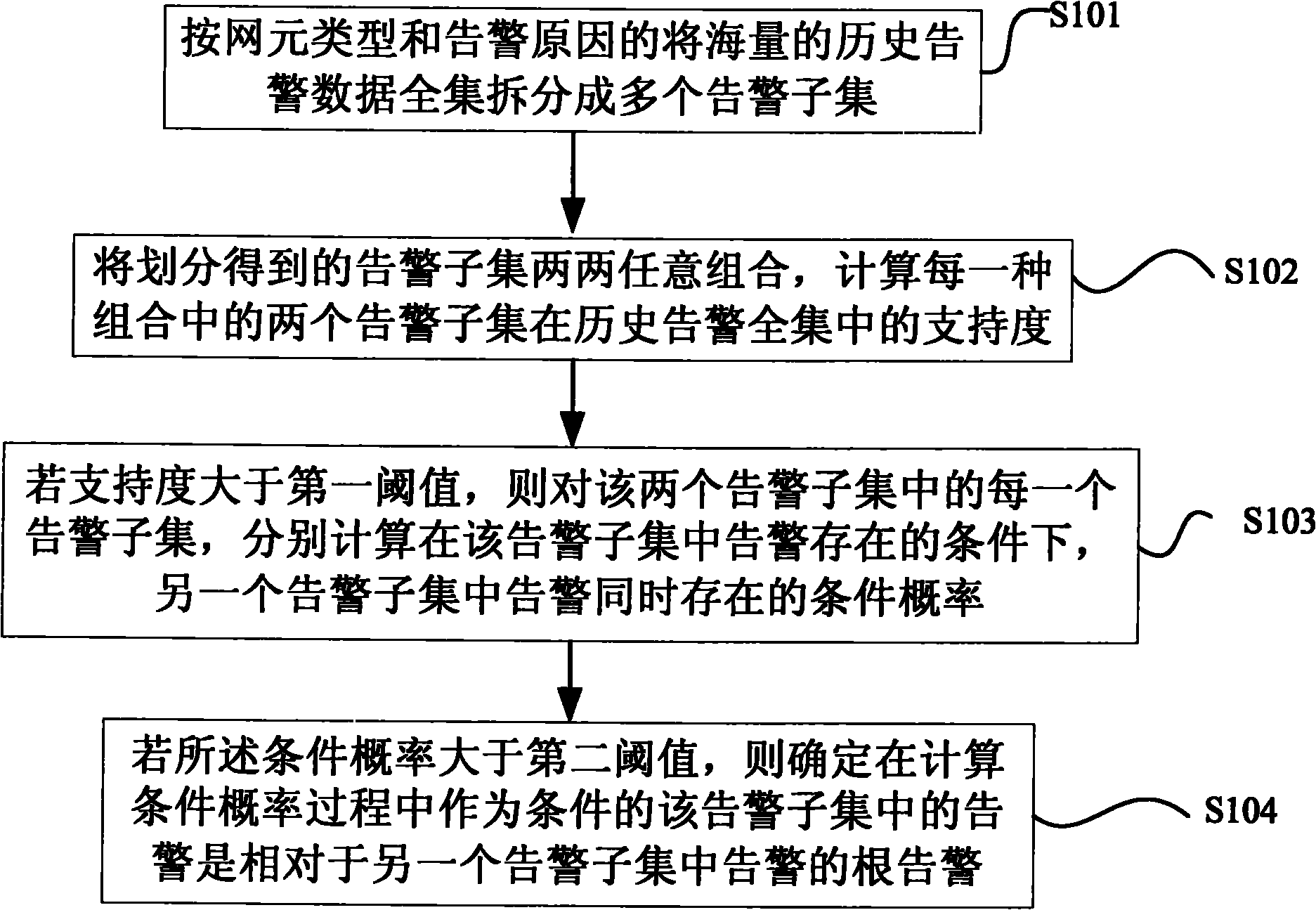
Root alarm data analysis method and system
InactiveCN101997709BPrecise positioningImplement auto-discoveryData switching networksAnalysis methodConditional probability
A method for analyzing alarm data and a system thereof are disclosed. The method, which is applied in a system having a peer-to-peer model indicating connection relation of network elements, includes: dividing a complete dataset of historical alarms into a plurality of alarm subsets according to network element types and alarm reasons (S101); combining any two divided alarm subsets, and calculating support degree of two alarm subsets in each kind of combination within the complete dataset of historical alarms (S102); if the support degree larger than a first threshold, according to each alarm subset of these two alarm subsets, calculating conditional probabilities of present of alarms in another alarm subsets in the simultaneous present of alarms in each alarm subset, respectively (S103); if the conditional probability larger than a second threshold, determining that alarms in the alarm subset, which function as conditions, are root alarms with respect to alarms in another alarm subsets (S104).
Owner:ZTE CORP
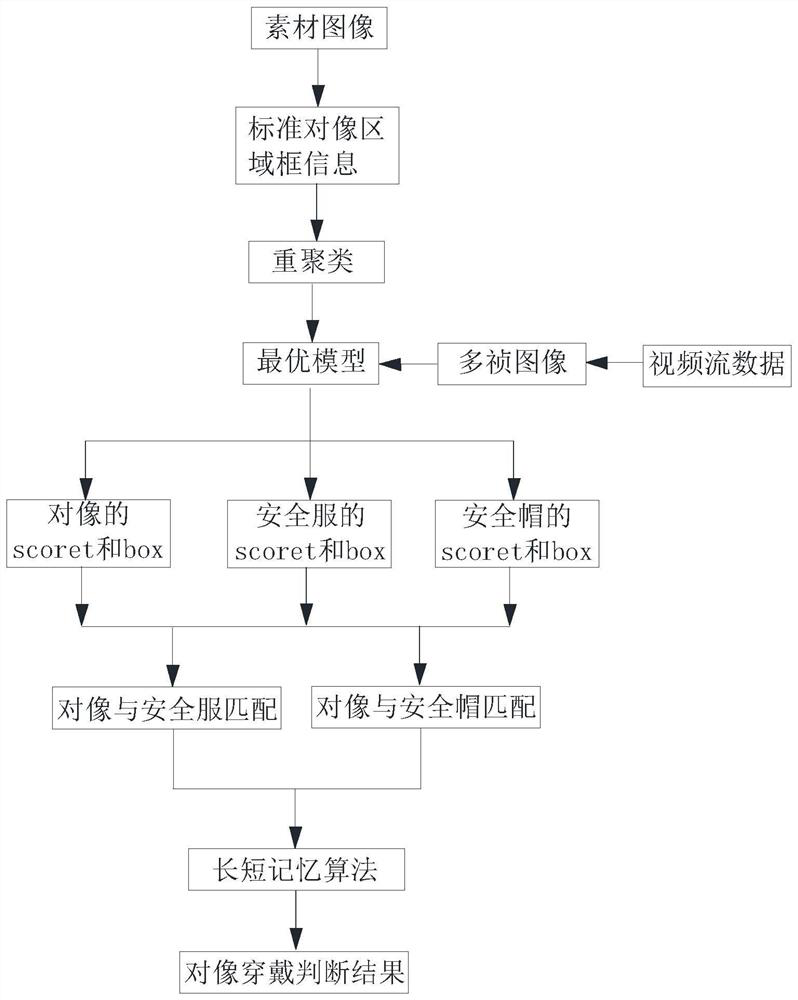
A method for identifying safety wearing conditions
ActiveCN112257620BAvoid false detectionReduce the number of alertsBiometric pattern recognitionNeural architecturesSimulationStream data
A safety wearing situation recognition method, through six steps, can obtain the wearing judgment result of an object within a time period according to the collected video stream data. The present invention uses the long-short memory algorithm to activate the long-memory algorithm structure or the short-memory algorithm structure correspondingly according to the wearing situation of the object within a period of time, so as to avoid errors caused by target deformation, sudden movement, background clutter, occlusion, video frame loss, etc. Inspection, missed inspection of safety clothing and helmets. The number of alarms generated by false detection and missed detection of safety clothing and helmets is greatly reduced, and the alarm information is output reasonably, which has the advantage of accurate judgment.
Owner:GUANGZHOU HUAWEI TOMORROW SOFTWARE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com