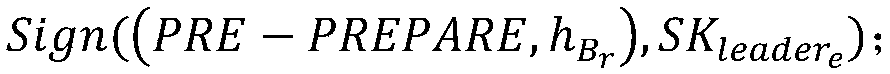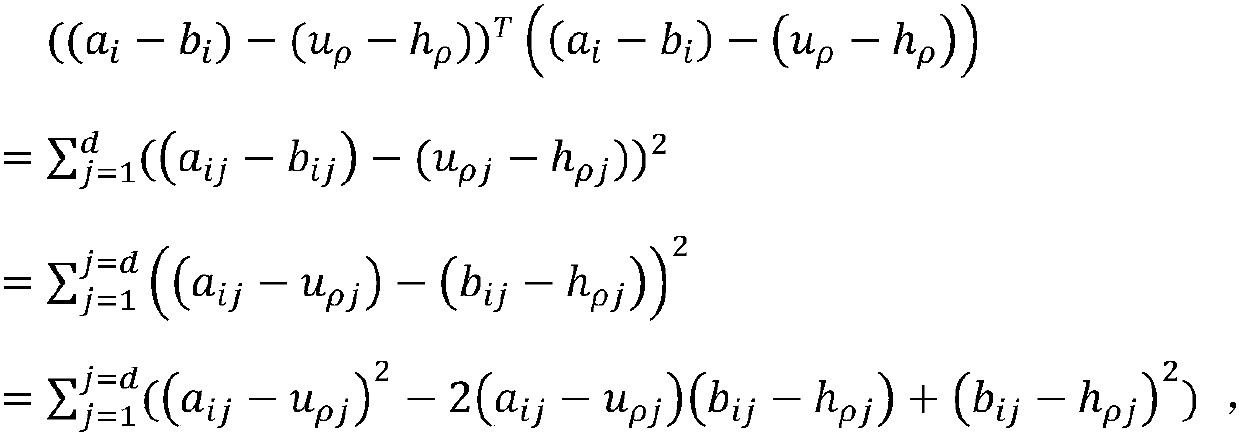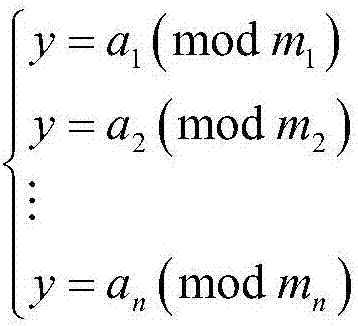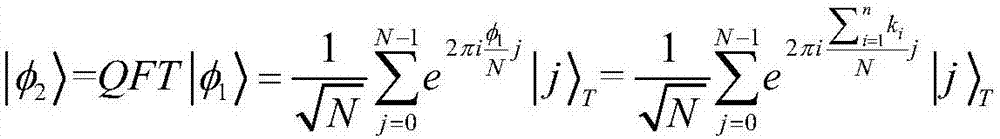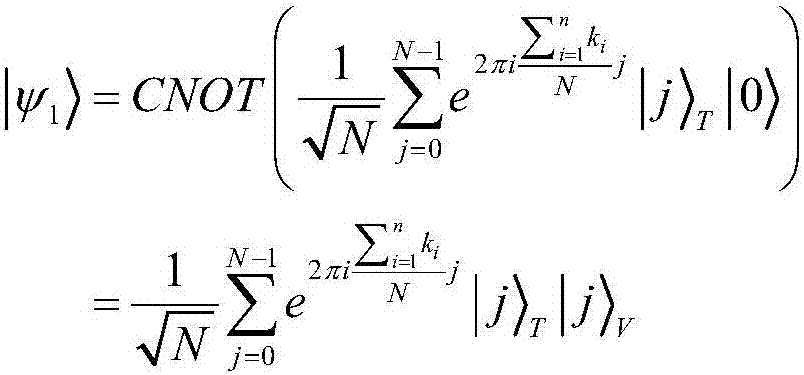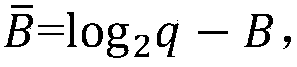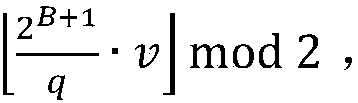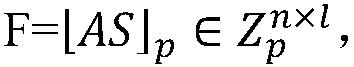Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
61results about How to "Reduce Communication Complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
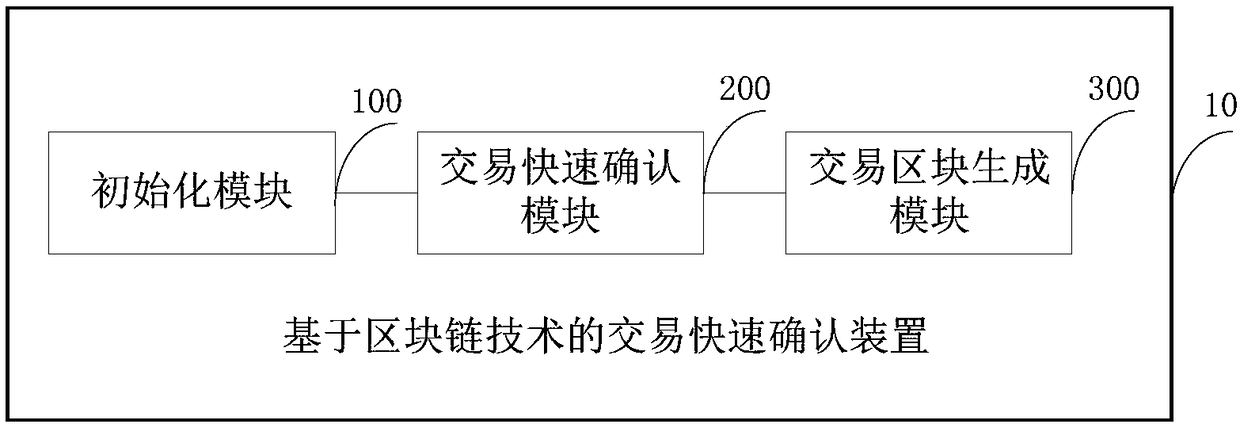
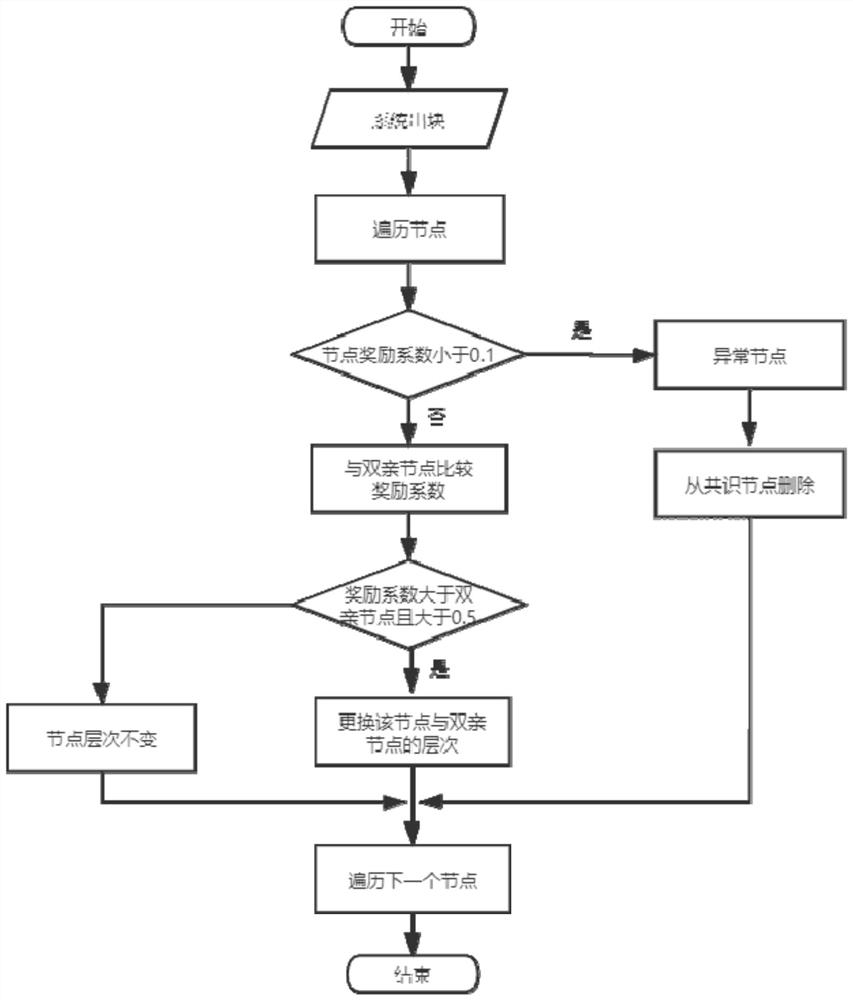
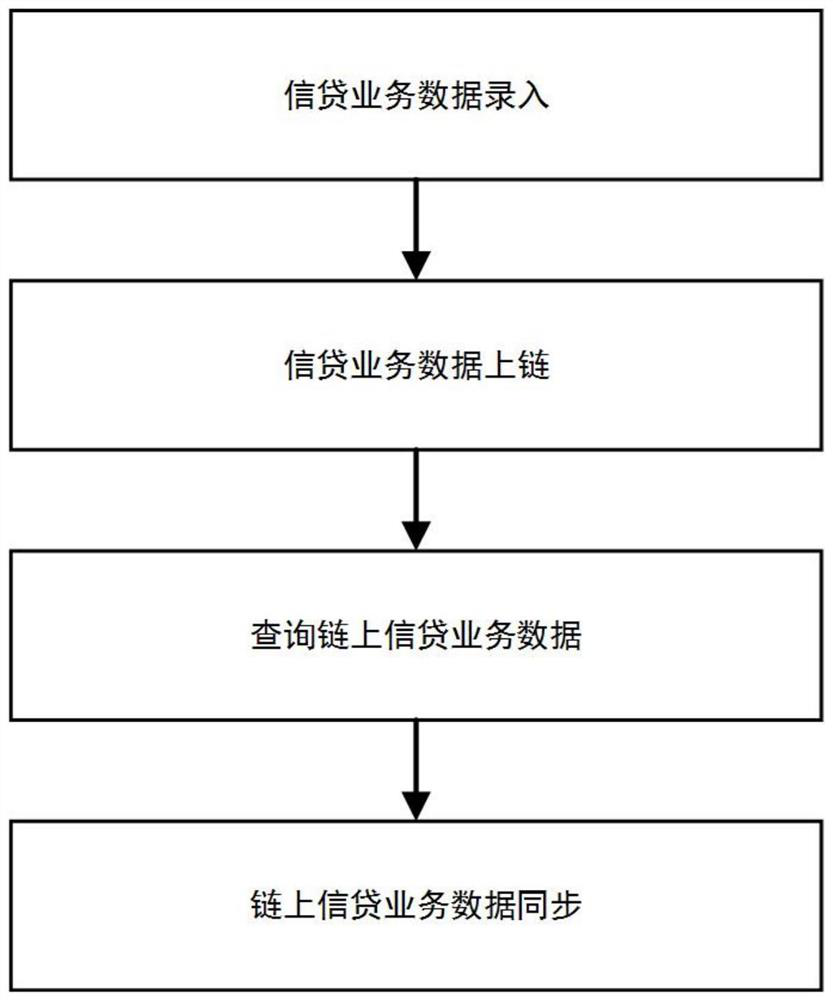
Fast transaction confirmation method and device based on block chain technology
ActiveCN109360100ARealize immutabilityQuick responseFinancePayment protocolsFinancial transactionOperating system
The invention discloses a transaction quick confirmation method and device based on a block chain technology, wherein, the method comprises the following steps: step S1, confirming the node identity and electing a consensus committee and a committee leader; S2, submitting the transaction to the committee, so that the committee leader initiates a round of BLS aggregation signatures for the transaction, and broadcasting the total signatures for the transaction on the whole network to quickly confirm the transaction; Step S3, packaging and summarizing the confirmed transactions by the committee leader, forming a current round block by the transaction package, the transaction proof, the previous block hash and the current unspent transaction pool, sending the current round block and the blockhash value to the members of the committee, and operating the consensus within the committee to generate a new block. The method can realize the fast confirmation of the transaction, and effectively improves the practicability and reliability of the transaction, which is simple and easy to realize.
Owner:UNIONTECH SOFTWARE TECH CO LTD
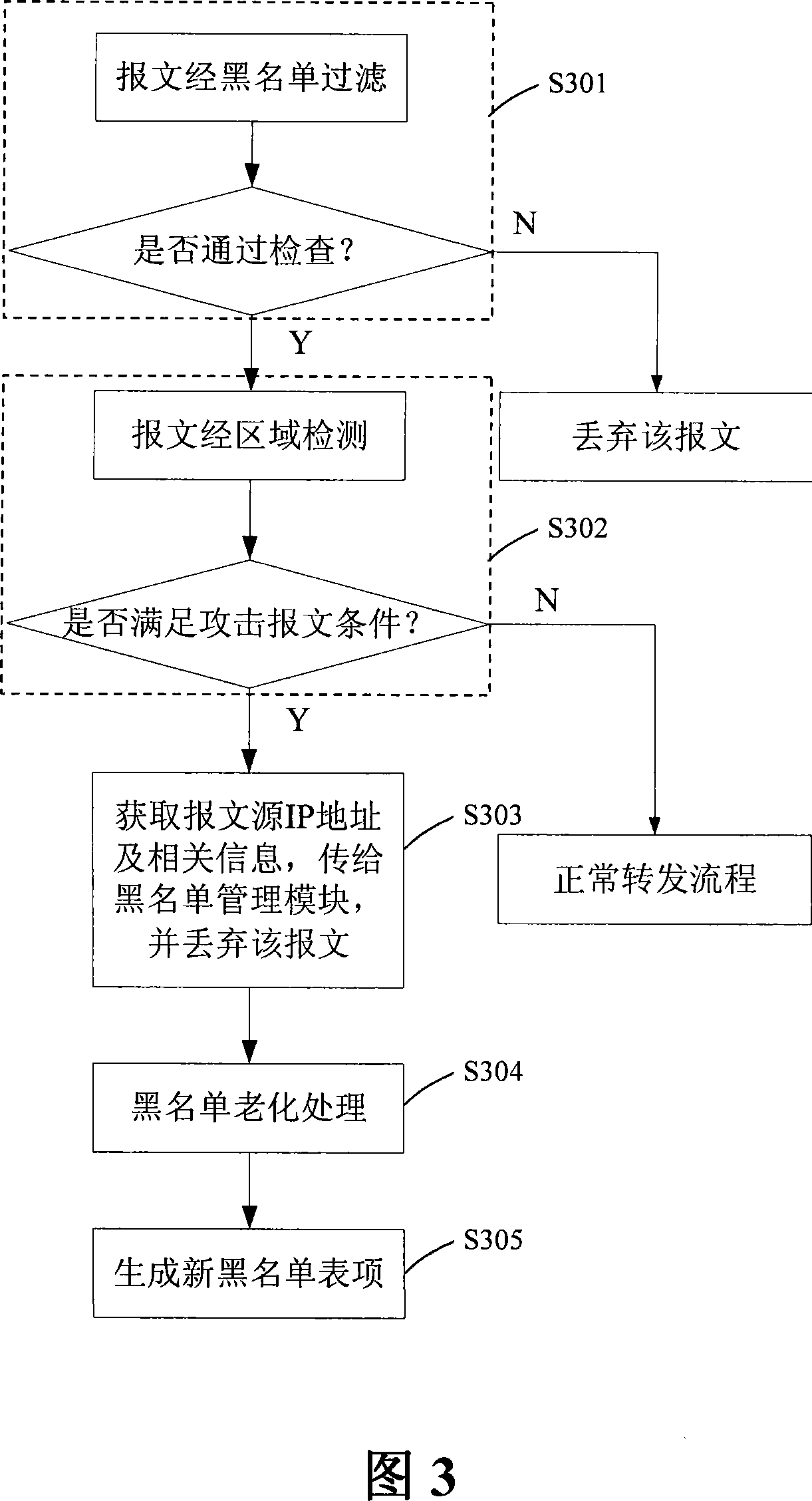
A blacklist real time management method and device
InactiveCN101188612AImprove securityImprove real-time performanceData switching networksSpecial data processing applicationsCommunications systemReal time management
The invention discloses a method for real-time blacklist management and the device thereof, wherein, the method comprise the following steps: step one, a transmission module sends detected message information with attack signature to a blacklist management module, and discards the message; step two, the blacklist management module searches all the blacklist list items in the blacklist, deletes aged blacklist list items, and adds the information into the blacklist list items. The invention adopts a module optimization treatment mode, obtains technical and security progresses, and truly achieves the effect of the real-time blacklist management. No information interaction exists between the modules, therefore the designs in the modules are required to be compactor and more logical, thereby the real time and the stability of the blacklist management are better, and the security of a communication system is higher.
Owner:ZTE CORP
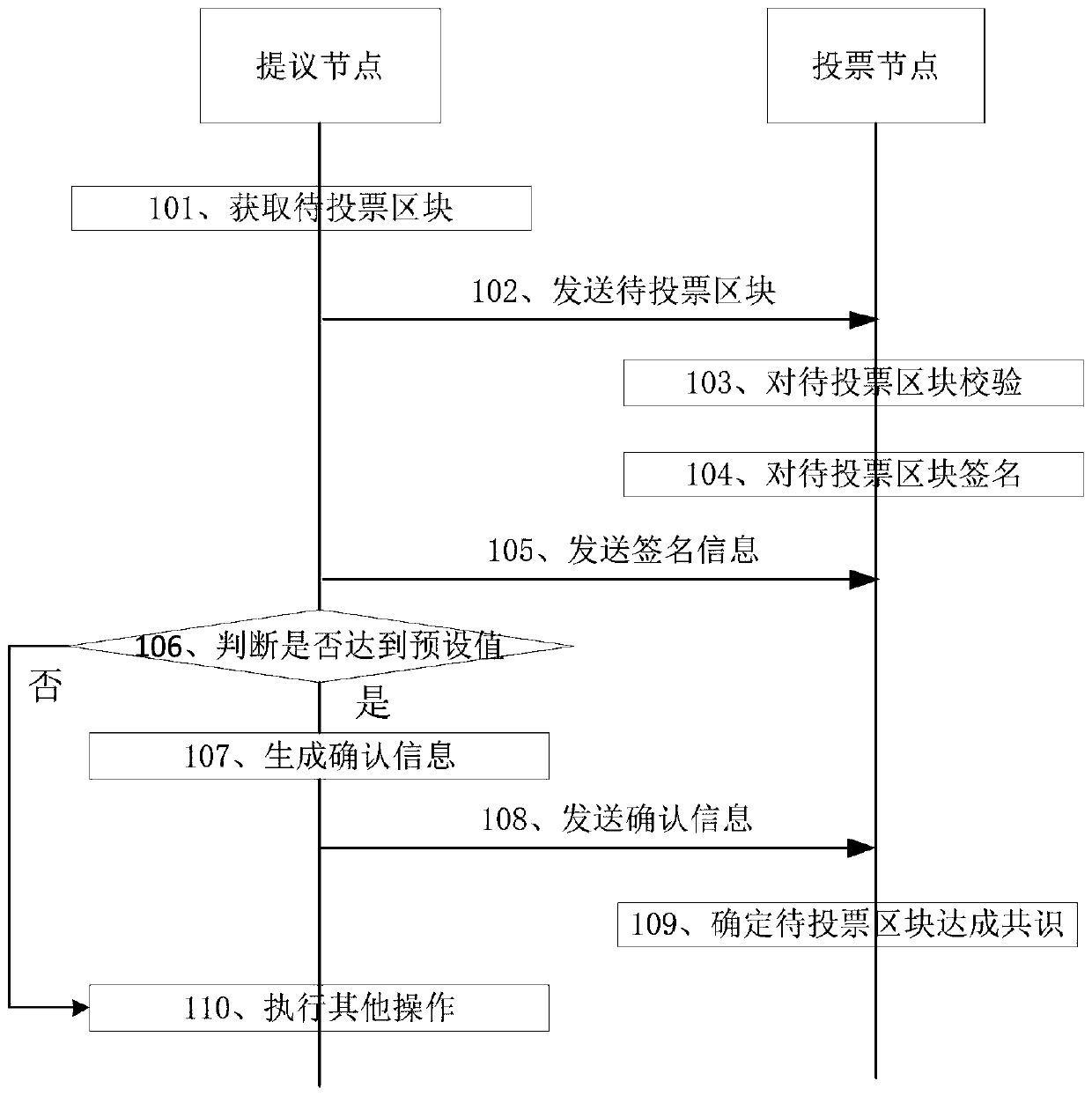
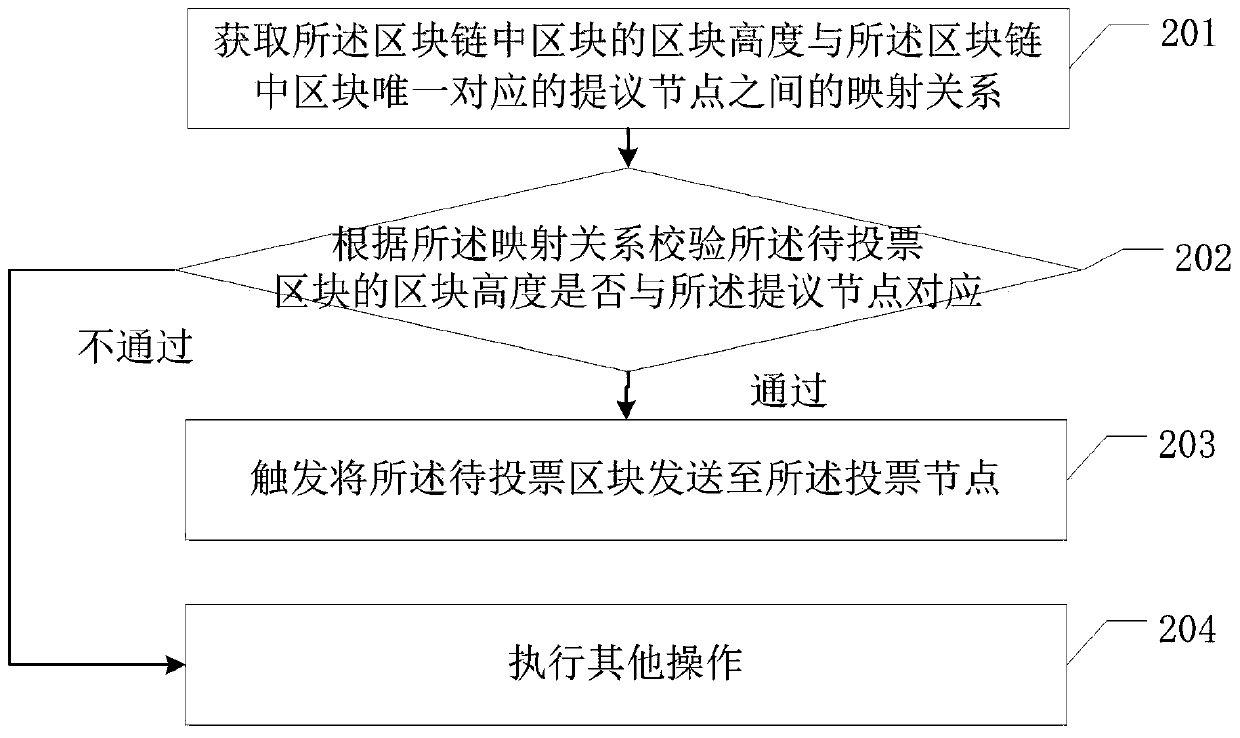
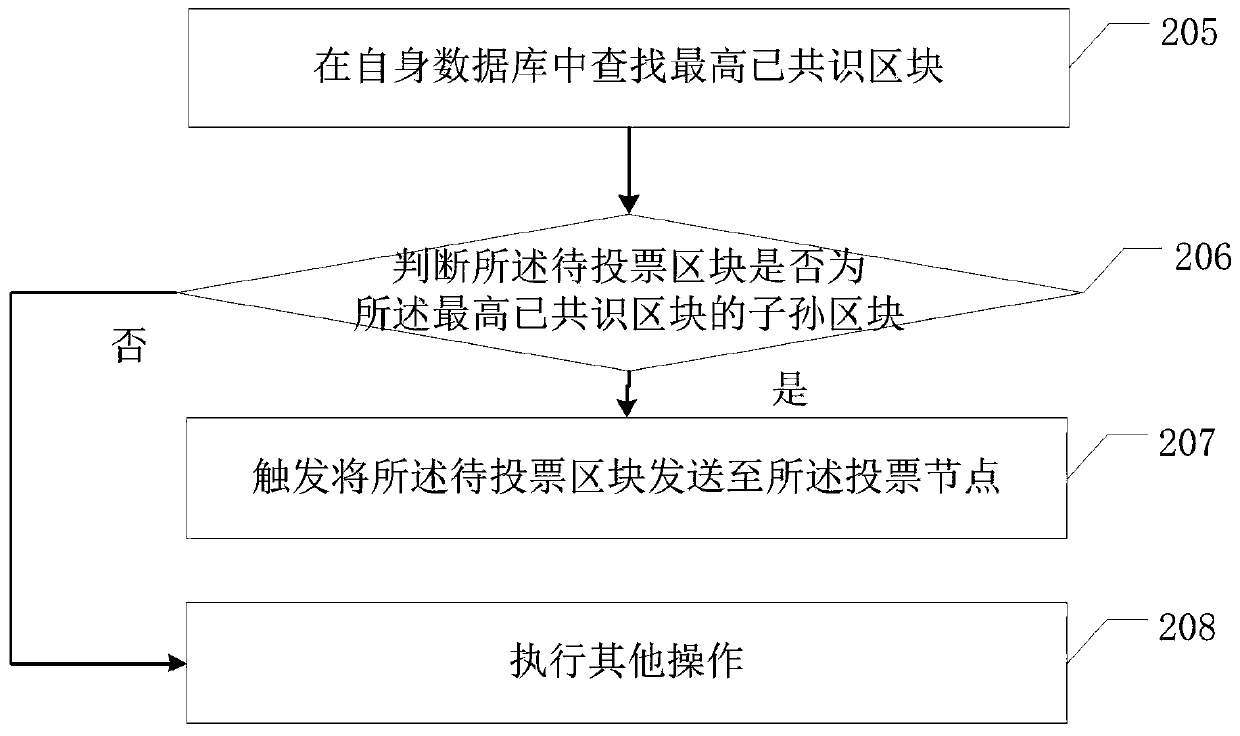
Consensus method of block chain data and related equipment
ActiveCN110288479AReduce Communication ComplexityImprove securityFinanceEnergy efficient computingBlockchainComputer security
The embodiment of the invention discloses a block chain data consensus method and related equipment thereof, which are used for reducing the communication complexity of block chain consensus. The method comprises the steps of a proposal node obtaining a to-be-voted block; sending the to-be-voted block to the voting node; receiving signature information sent by the voting node, wherein the signature information is used for indicating that the voting node successfully verifies the to-be-voted block; judging whether the number of the signature information received within preset time reaches a preset value or not; if yes, confirming information is generated according to the signature information, and the confirming information indicating that the to-be-voted block is a block achieving consensus; and sending the confirmation information to the voting node, so that the voting node determines the to-be-voted block as a block achieving consensus. The proposal node and the voting node in the block chain realize the consensus of the block to be voted through the signature information and the confirmation information, so that the communication complexity of the block chain consensus is effectively reduced.
Owner:SHENZHEN THUNDER NETWORK TECH +1
High-efficiency asynchronous Byzantine consensus method with low communication complexity and network communication platform
ActiveCN110022216ALower performance requirementsReduce storage performance requirementsUser identity/authority verificationCommunication with homomorphic encryptionCommunication complexityChain network
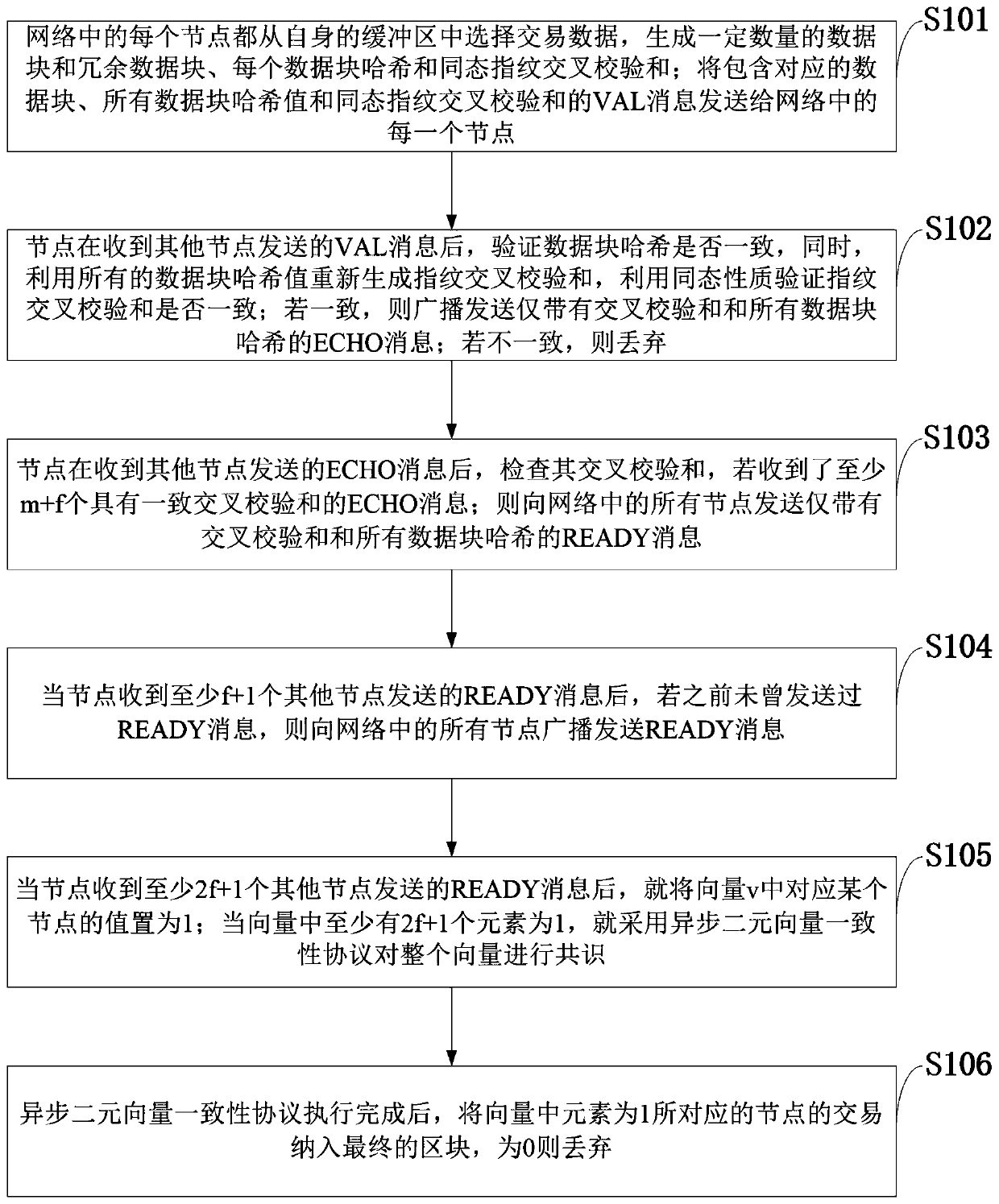
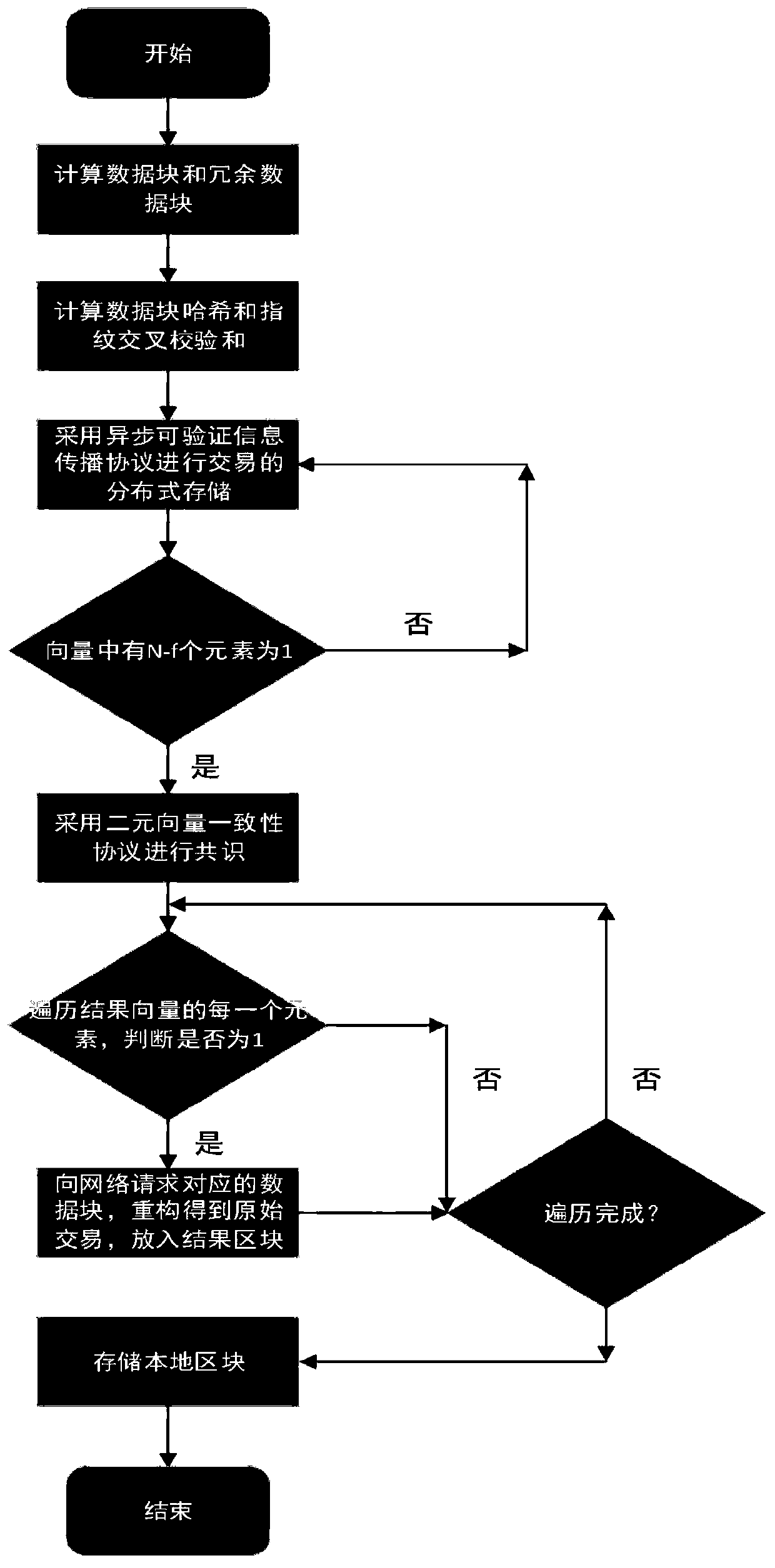
The invention belongs to the technical field of block chain network communication, and discloses a high-efficiency asynchronous Byzantine consensus method with low communication complexity and a network communication platform. A node in a network calculates transaction data blocks, redundant data blocks, a data block hash and a fingerprint cross checksum, and sends related data to each node in thenetwork by using an asynchronous verifiable information transmission protocol. After the nodes confirm that the transactions broadcast and sent by some nodes are correctly stored in the network, a binary vector consistency protocol is executed, and consensus is carried out on the transactions; and the node requests a specific data block from the network and reconstructs to obtain original transaction data. According to the invention, the problem of high communication complexity based on an erasure code protocol in the prior art is solved, and the throughput of the algorithm is improved; a binary vector consistency protocol is adopted, the defect that an original protocol can only consensus transactions broadcasted by a single node each time is overcome, the complexity of algorithm messages is reduced, the worst time complexity of an algorithm is optimized, and the high efficiency of the algorithm is guaranteed.
Owner:XIAN XIDIAN BLOCKCHAIN TECH CO LTD +1
The invention discloses a pPrivacy information protection method based on k-means clustering
ActiveCN109615021AEnsure safetyImprove securityCharacter and pattern recognitionDigital data protectionPlaintextData information
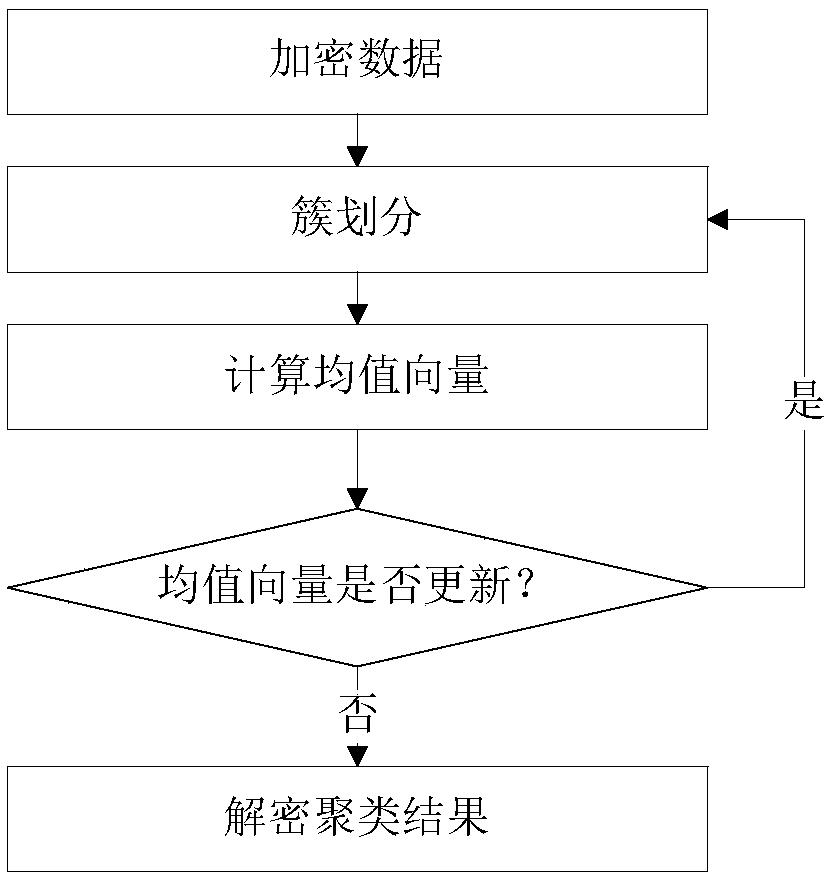
The invention belongs to the field of machine learning. The invention, and relates to a privacy information protection method based on k-means clustering. A linear homomorphic encryption algorithm LHE is combined with an addition homomorphic encryption algorithm Paillier to encrypt data; T; the method comprises the steps of obtaining ciphertext data through a cloud server, performing k-means clustering on the ciphertext data by utilizing a computing service provided by the cloud server to obtain a ciphertext clustering result, and decrypting the ciphertext clustering result by a client to obtain a plaintext clustering result. According to the invention, t, the cloud server does not obtain any privacy information of the user; t; the privacy information security of the user is ensured whilethe clustering algorithm is realized; I; in the data analysis process, data information is not leaked, t, the safety of user data is effectively improved, t, the communication traffic between the client side and the cloud server side is greatly reduced, t, the communication cost is reduced, t, the machine learning efficiency is improved, and the method is more suitable for being applied to an actual scene.
Owner:JINAN UNIVERSITY
A secure multi-party computing method and device
ActiveCN109446828AReduce the number of interactionsReduce Communication ComplexityDigital data protectionInformation securitySecure multi-party computation
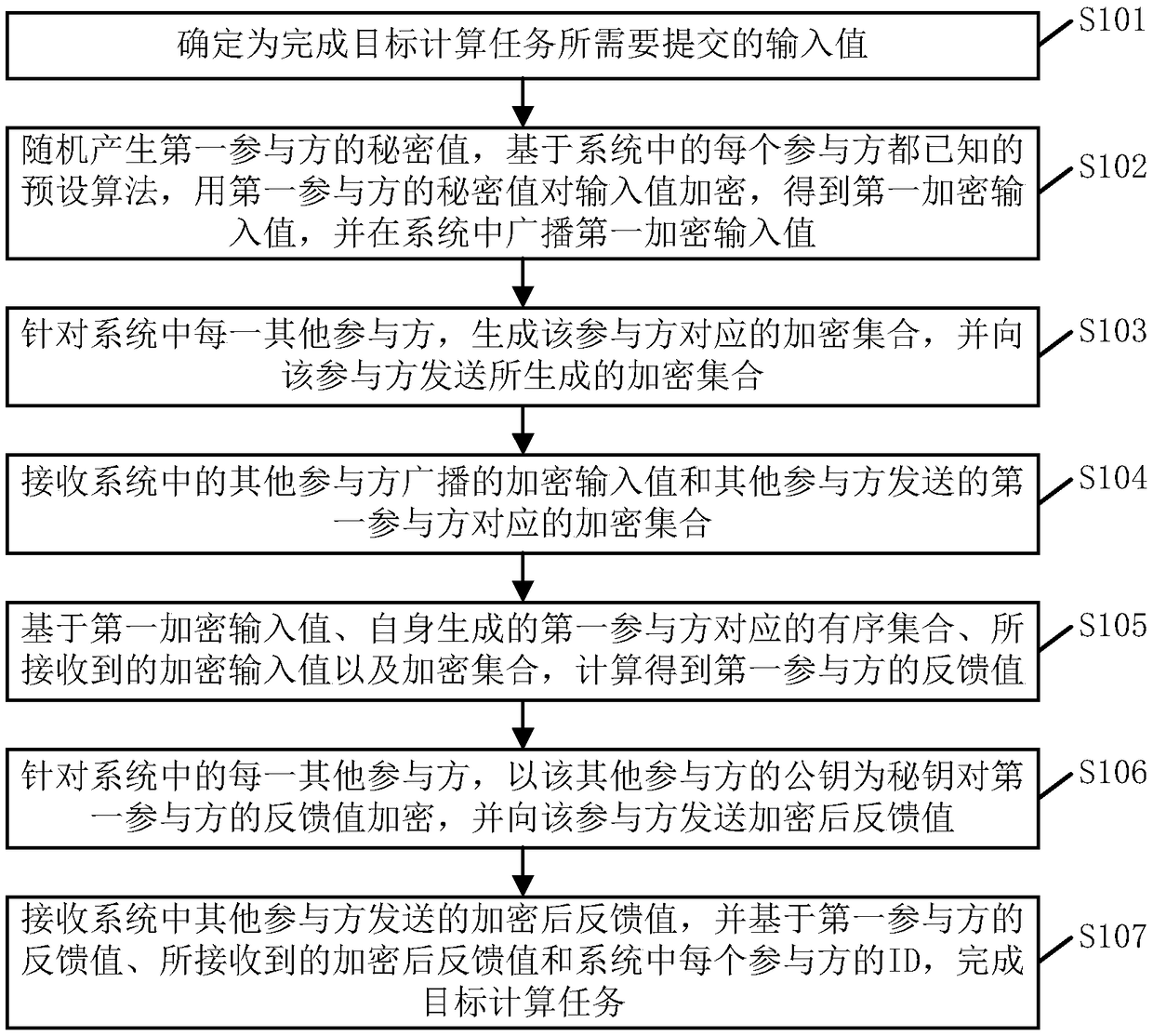
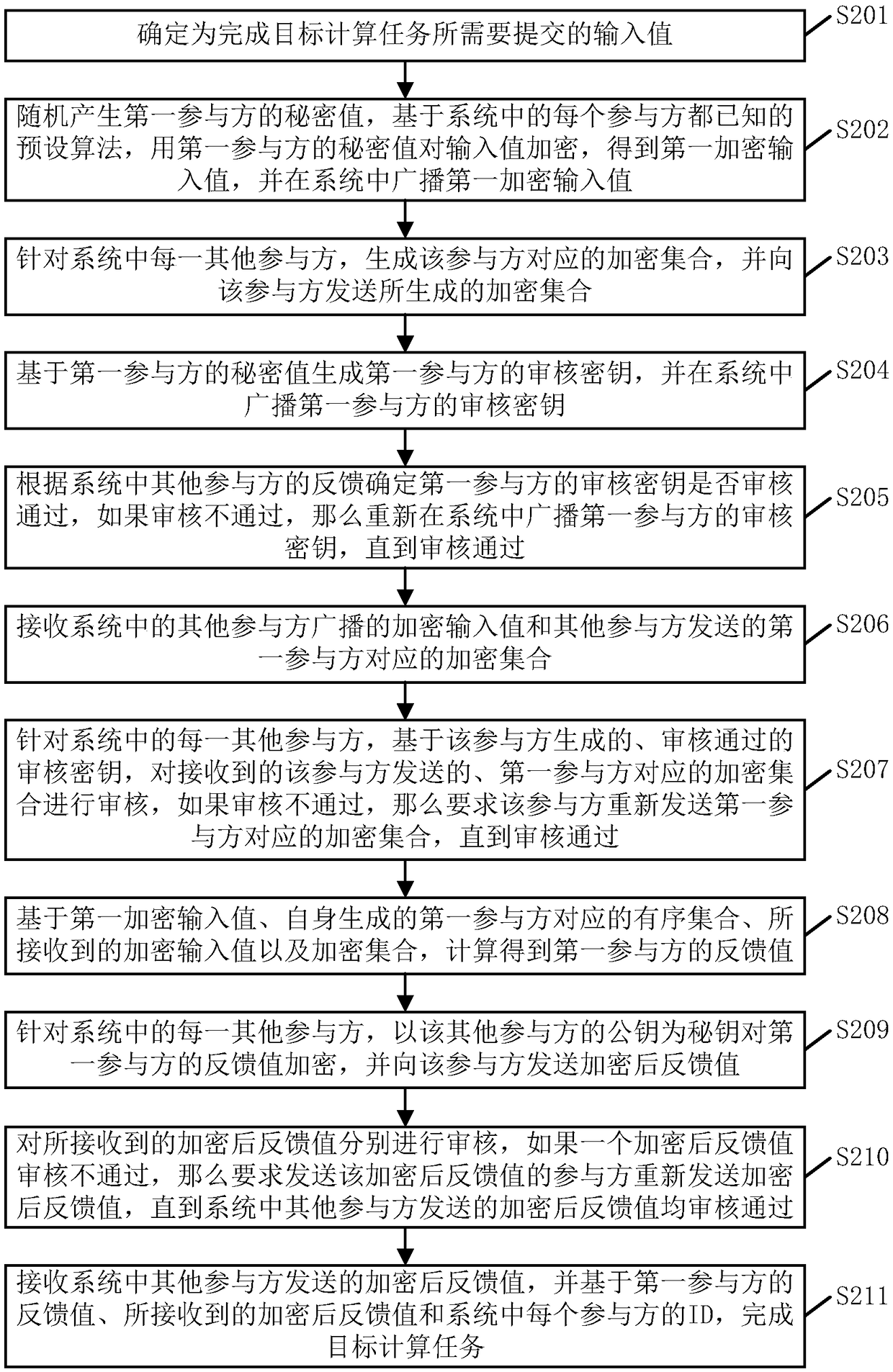
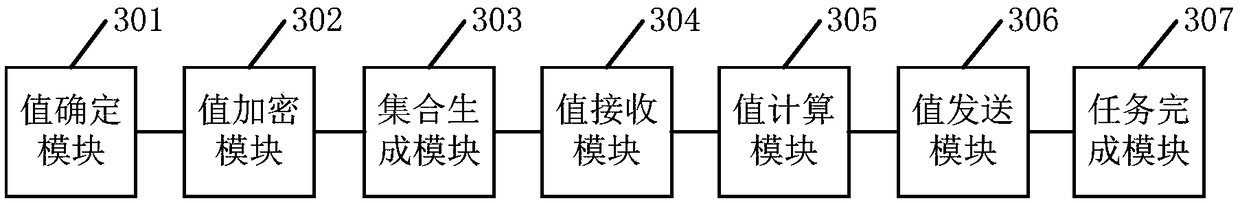
The embodiment of the invention provides a secure multi-party computing method and device, and relates to the technical field of information security, and the method is applied to any participant in asecure multi-party computing system, and comprises the following steps of determining an input value required to be submitted for completing a target computing task; randomly generating a secret value, encrypting the input value by using the secret value, and broadcasting the encrypted input value in the system; generating an encryption set corresponding to other participants, and sending the encryption set to the other participants; receiving an encryption input value and an encryption set broadcasted by other participants; based on the encryption input value and the encryption set, calculating to obtain a feedback value; encrypting the feedback value by using public keys of other participants, and sending the encrypted feedback value to the participants; and receiving the encrypted feedback value sent by other participants, and completing the target calculation task based on the encrypted feedback value and the ID of each participant in the system. By applying the scheme provided bythe embodiment of the invention, the communication complexity of secure multi-party calculation can be reduced, and the communication resources are saved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
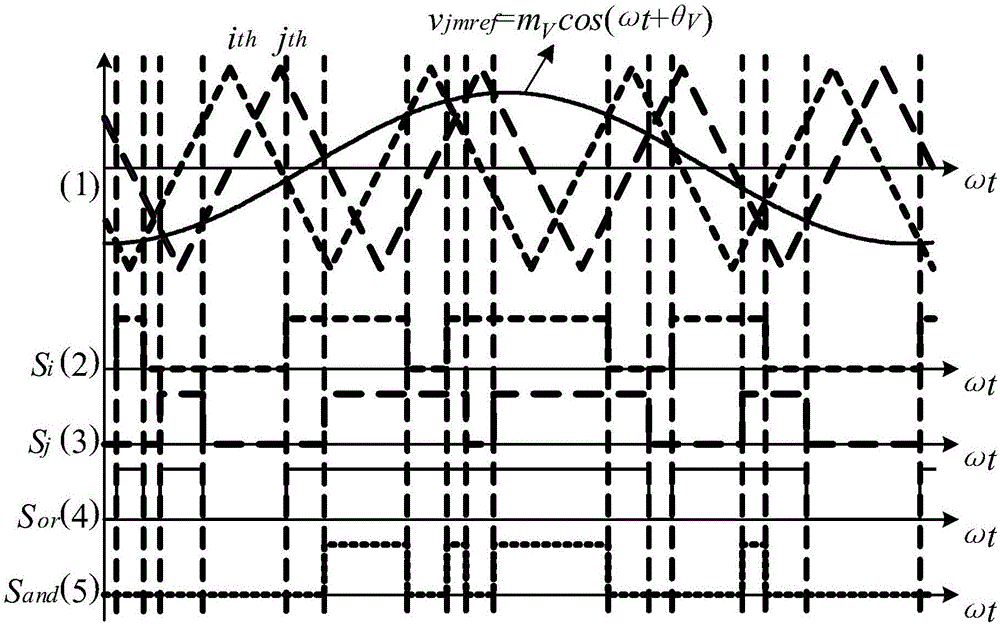
MMC capacitor voltage equalization control method based on driving signal logic processing
ActiveCN105915089ALow costReduce Communication ComplexityAc-dc conversionCapacitor voltageHemt circuits
The present invention discloses an MMC capacitor voltage equalization control method based on driving signal logic processing. The method comprises: (1) collecting the current capacitor voltage values of submodules; (2) ranking the current capacitor voltage values of the submodules; (3) grouping and calculating the capacitor voltage difference values according to the ranking of the submodules.; and (4) performing logic processing of the original driving signals and distributing driving signals again for the submodules according to the grouping and the voltage difference values. The MMC capacitor voltage equalization control method based on a driving signal logic processing is low in real-time requirement, saved in the calculation resource of a controller and easy to be applied to a large-scale MMC system, does not need the detection of the leg current so as to reduce the communication complexity of the system and reduce the cost of partial current sensors, and does not need the addition of the hardware circuit so as to avoid extra system cost. Under the control of the MMC capacitor voltage equalization control method based on the driving signal logic processing, all the submodules share the same switch frequency and the switch stress, and the switch frequency is low so as to facilitate system thermal design, effectively recover from the capacitor voltage unbalance and improve the system reliability.
Owner:ZHEJIANG UNIV
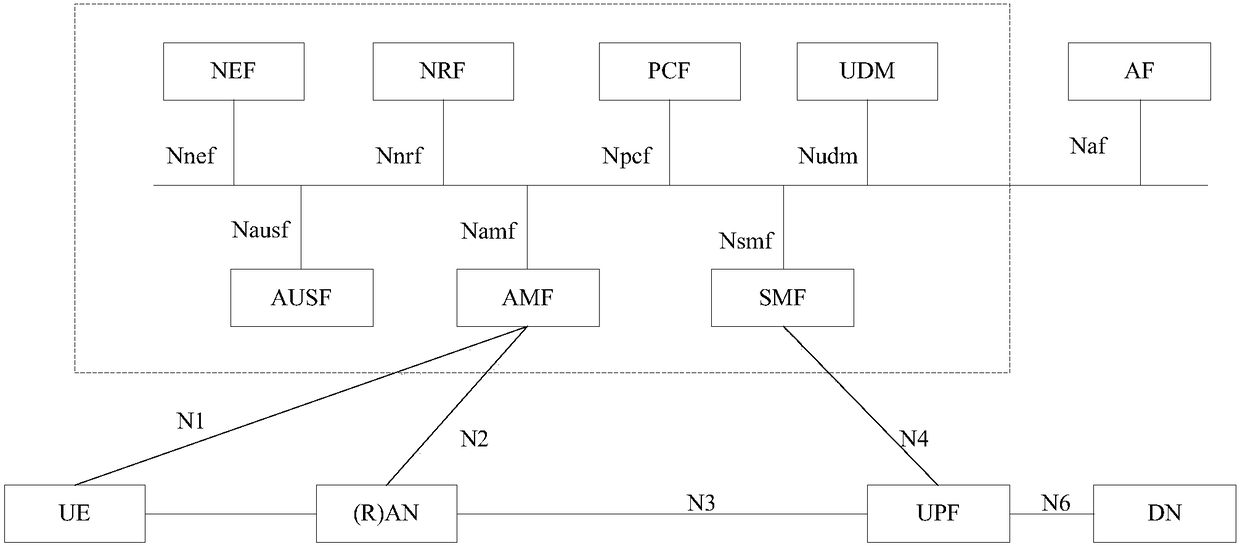
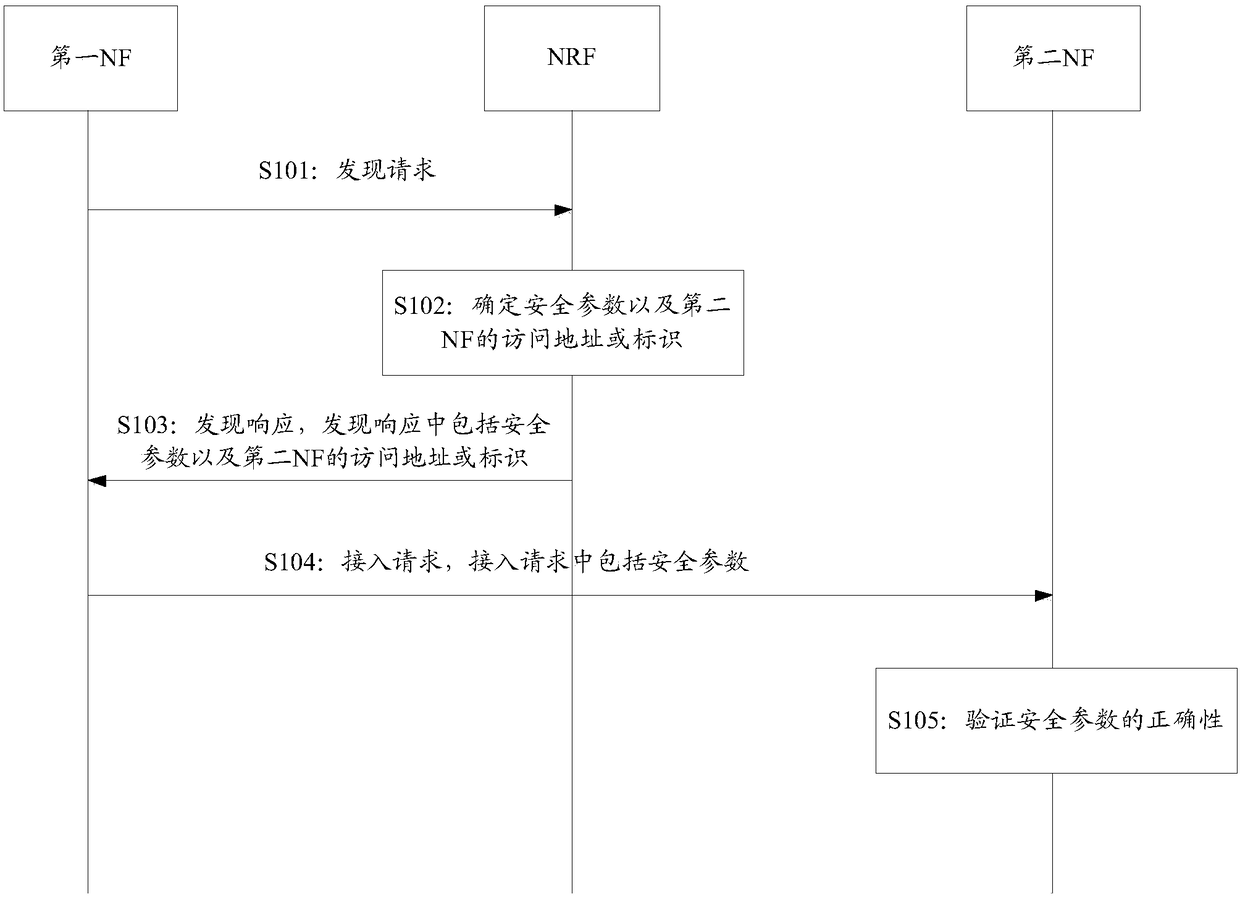
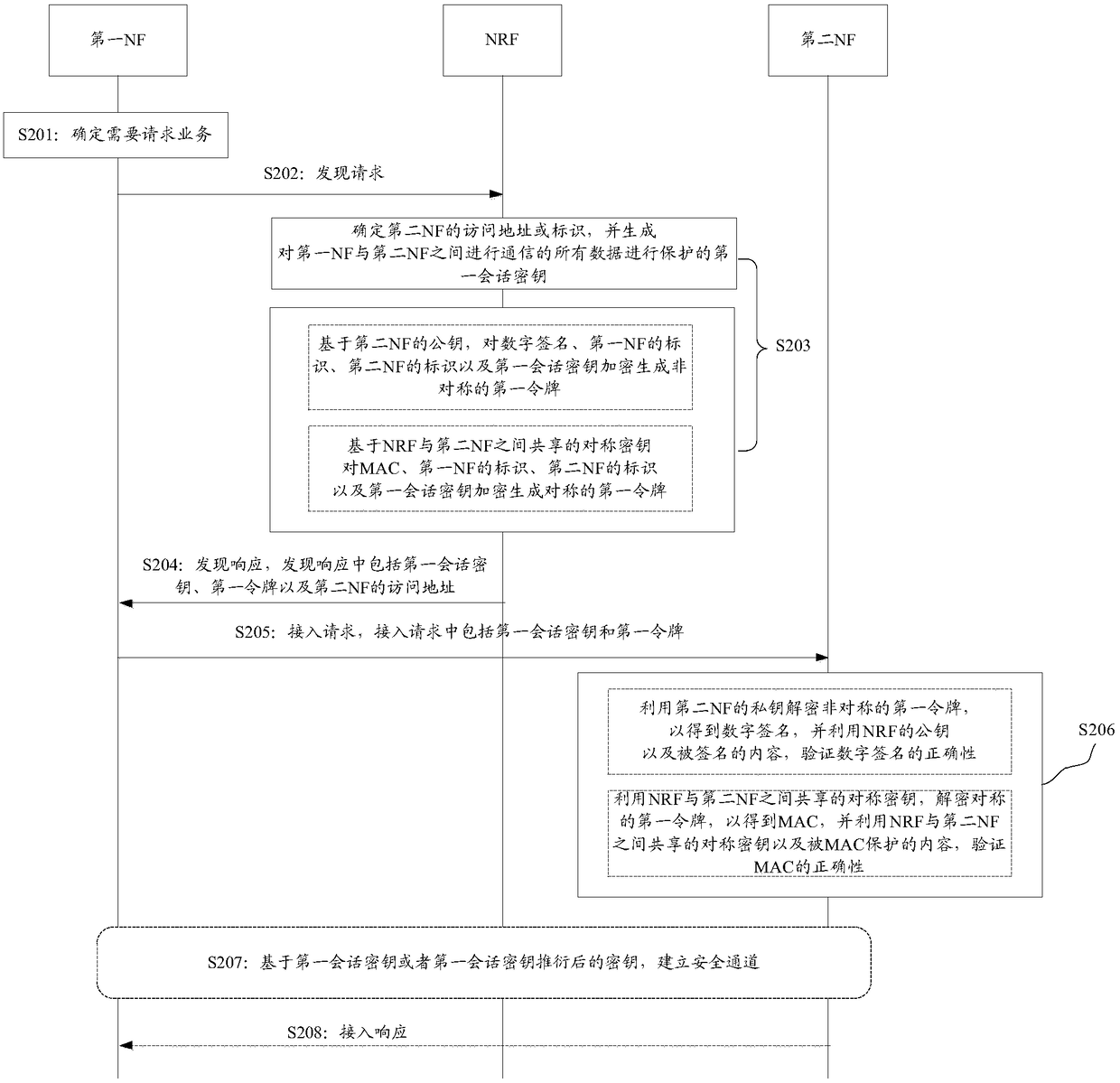
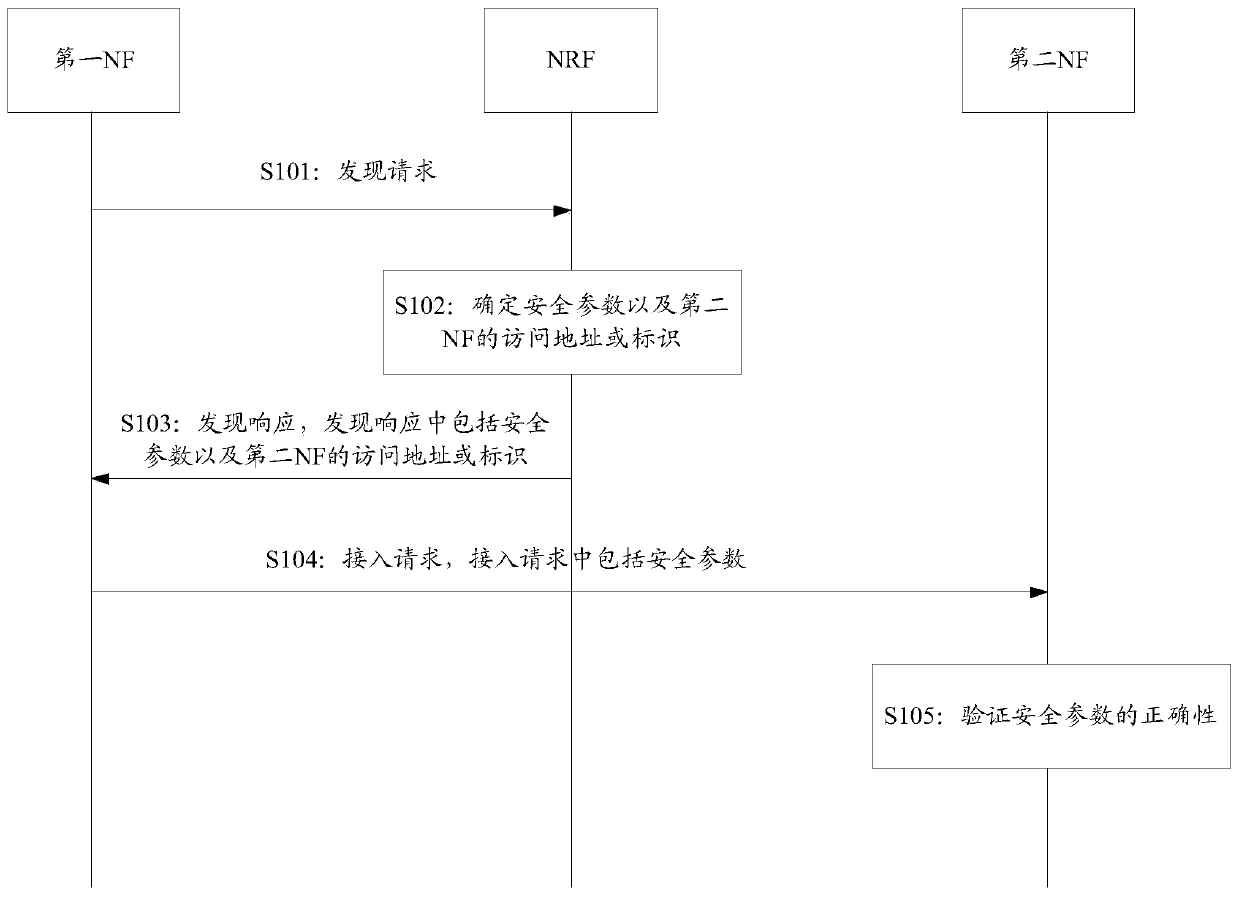
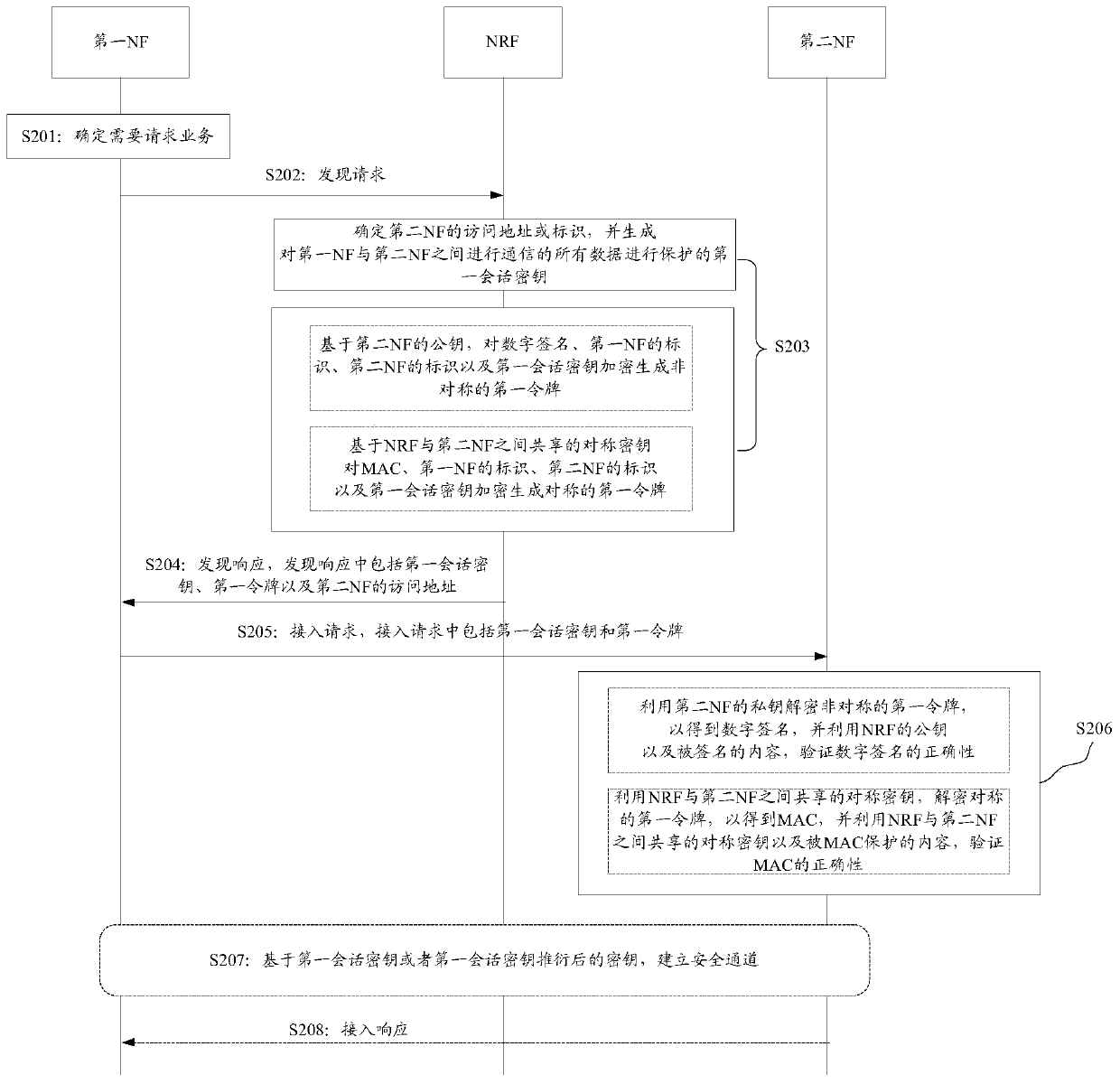
Discovery method and device based on servitization architecture
PendingCN109428875AReduce the number of communicationsReduce Communication ComplexityUser identity/authority verificationSecurity arrangementCommunication complexityFunctional networks
The application provides a discovery method and device based on a servitization architecture. In the method, a control network element sends a discovery response to a first functional network element,and the discovery response comprises a determined safety parameter and an access address or an identifier of a second functional network element; the first functional network element receives the discovery response sent by the control network element and sends an access request to the second functional network element according to the address or the identifier of the second functional network element, which is included in the discovery response, and the access request comprises the received safety parameter; and the second functional network element receives the access request sent by the first functional network element, verifies correctness of the safety parameter and determines whether the access request is authorized by the first functional network element on the basis of correctnessof the safety parameter. By the discovery method and device provided by the application, communication times can be reduced to a certain degree, and communication complexity is reduced.
Owner:HUAWEI TECH CO LTD
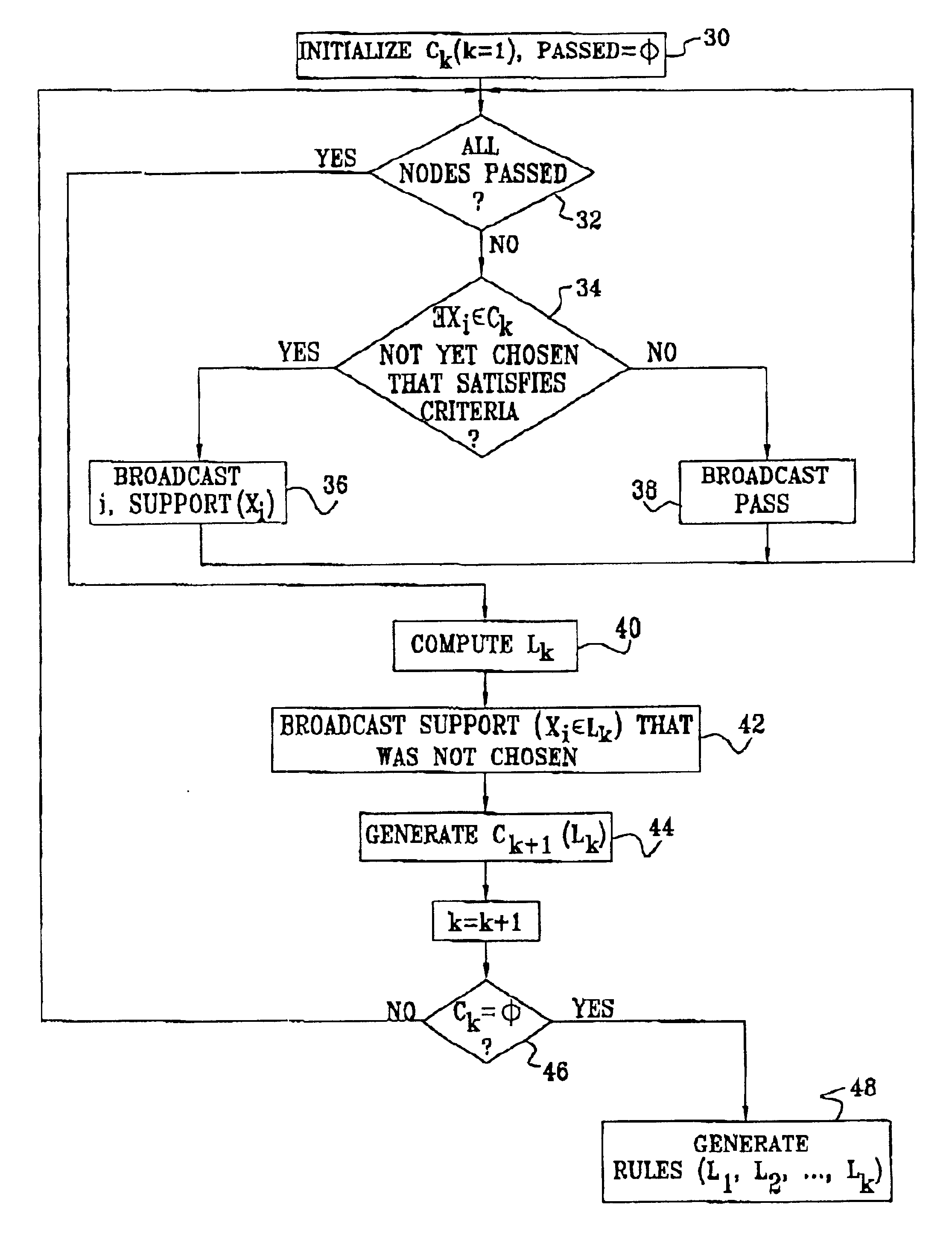
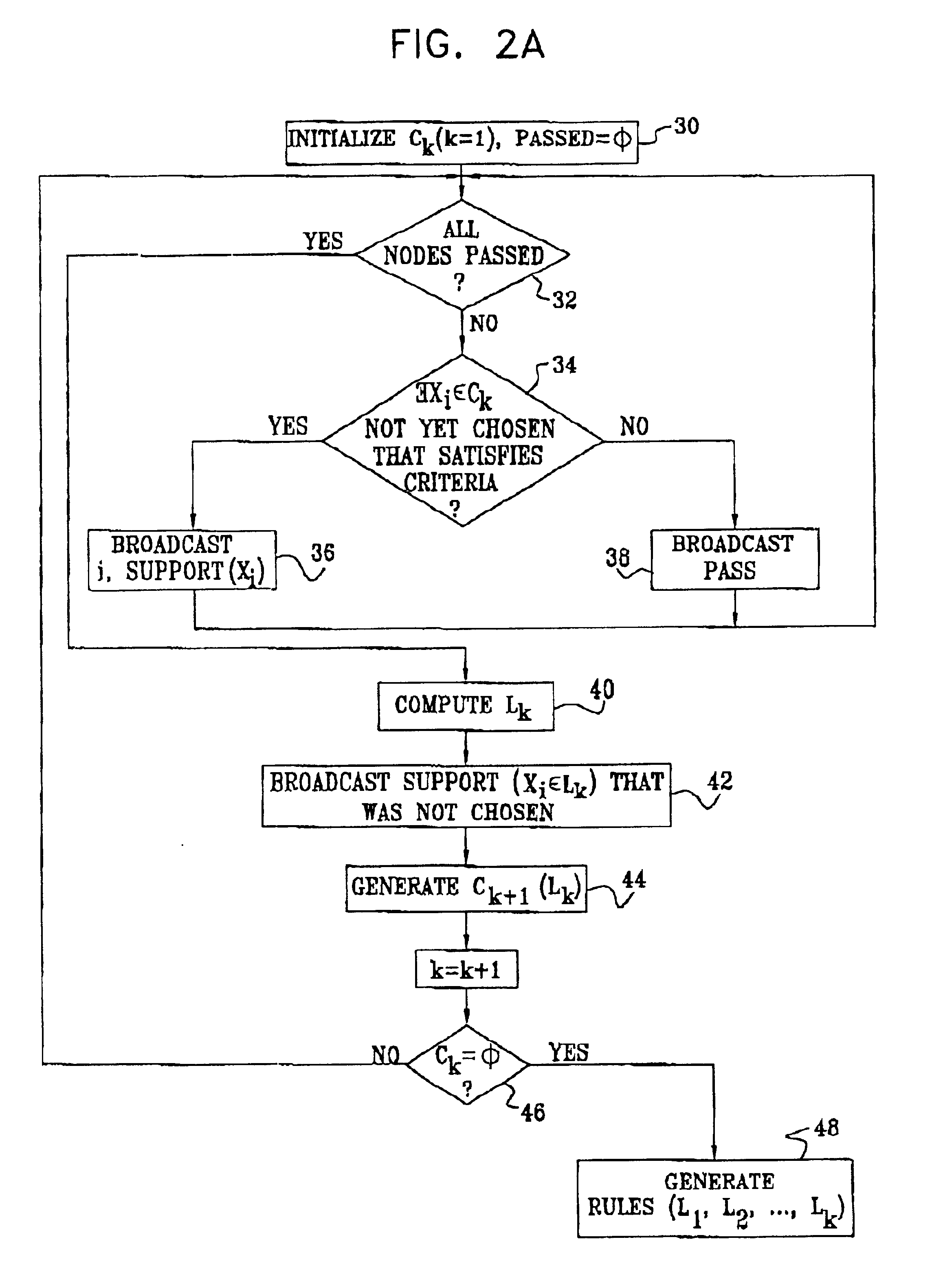
Distributed mining of association rules
ActiveUS6952693B2Reduce Communication ComplexityReduce communicationData processing applicationsMultiple digital computer combinationsData miningDistributed mining
A method for mining association rules in a database that is divided into multiple partitions associated with respective computing nodes. The method includes transmitting messages among the nodes with respect to local support of an itemset in the respective partitions of the database. Responsive to the messages transmitted by a subset of the nodes, the itemset is determined to be globally frequent in the database before the nodes outside the subset have transmitted the messages with respect to the local support of the itemset in their respective partitions. An association rule is computed with respect to the itemset, responsive to having determined the itemset to be globally frequent.
Owner:TECHNION RES & DEV FOUND LTD
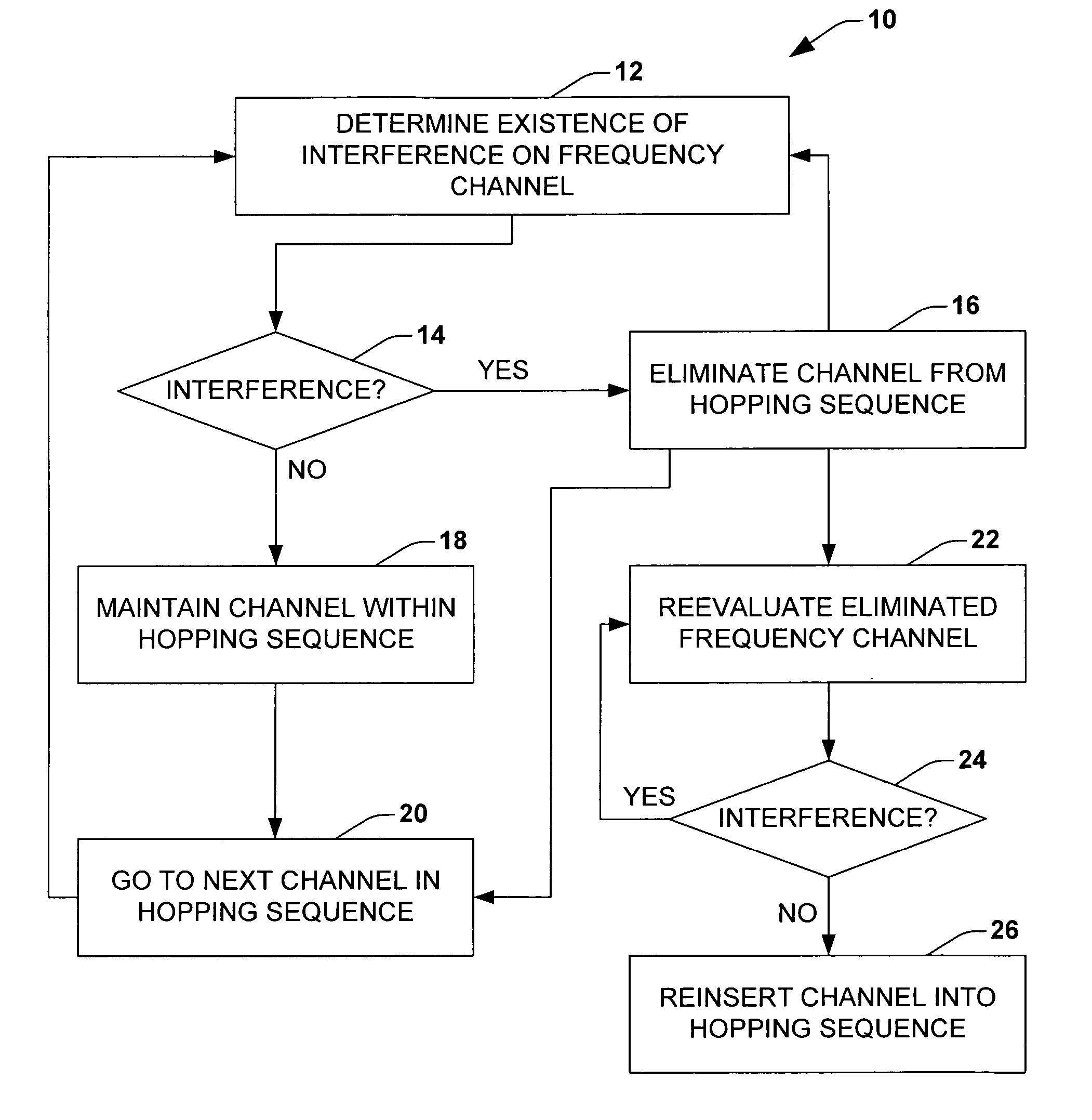
Frequency channel selection in a data transmission method which uses a frequency hopping method
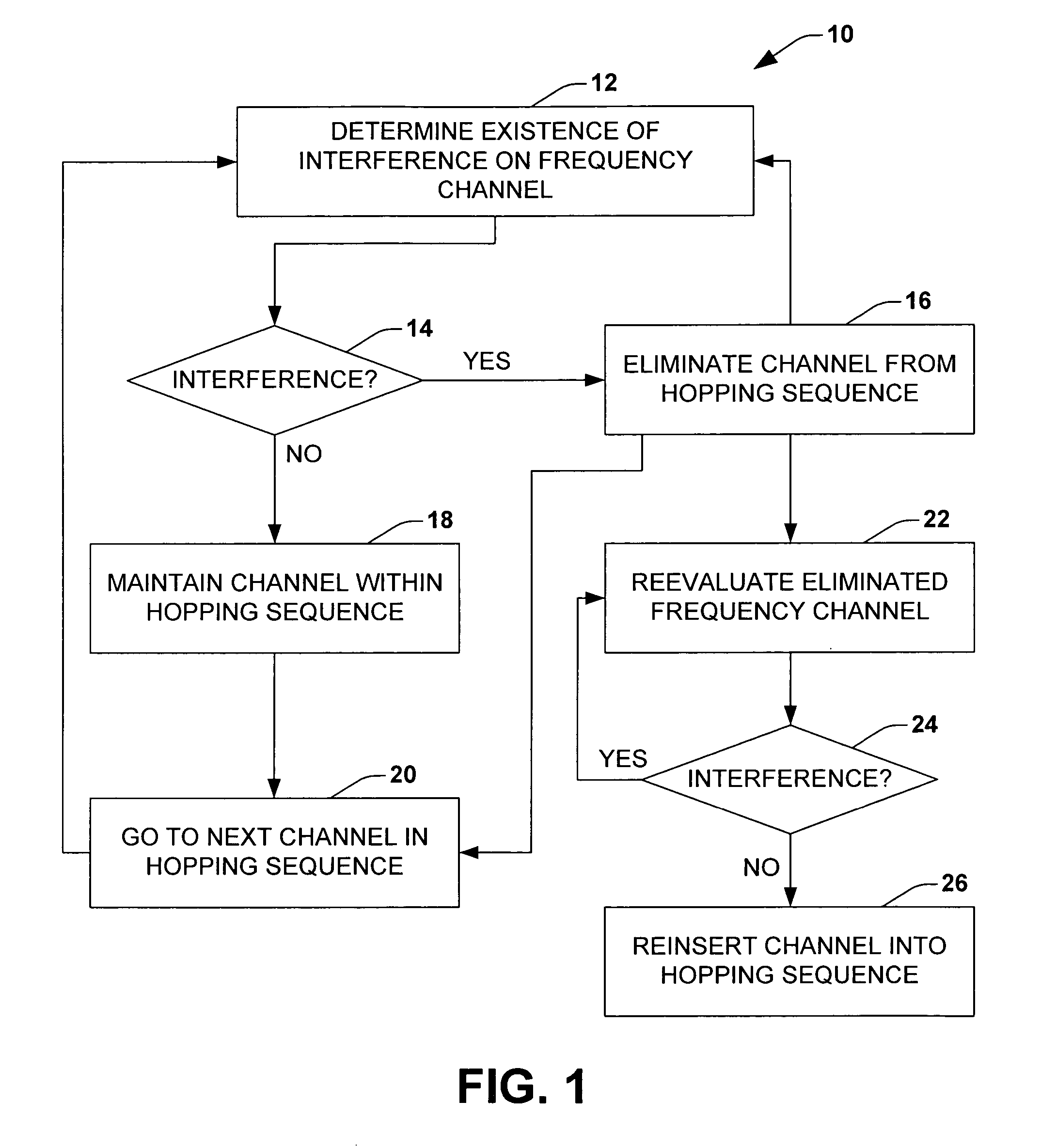
InactiveUS7773660B2Reduce reciprocal impairment of transmission qualityReduce Communication ComplexityWireless commuication servicesTransmissionData transmissionEngineering
Frequency channel selection in a data transmission method uses a frequency hopping method. In a first method step, interference in a frequency channel is determined by detecting multiple erroneous transmissions in the frequency channel, and the frequency channel with interference is then eliminated from the frequency hopping sequence. In a second method step, the strength of external signals is measured within the frequency range of an eliminated frequency channel with interference, and the frequency channel is reinserted into the frequency hopping sequence if the strength is below a prescribed threshold value.
Owner:INTEL CORP
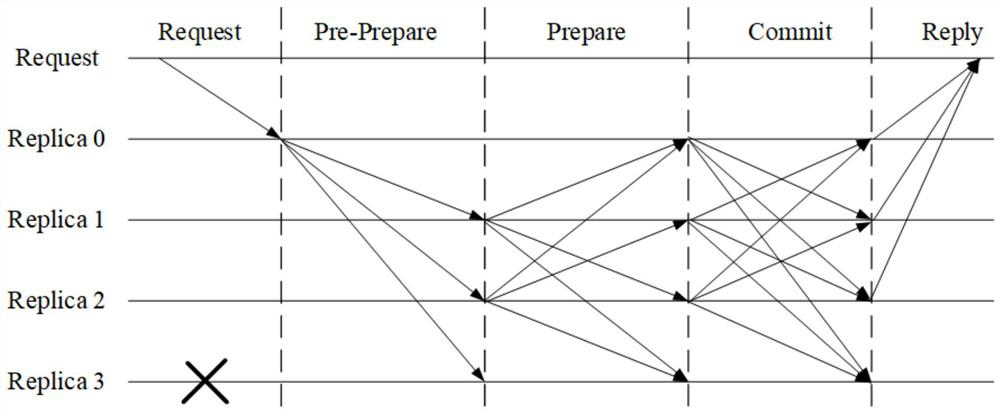
Optimized and improved block chain PBFT consensus method
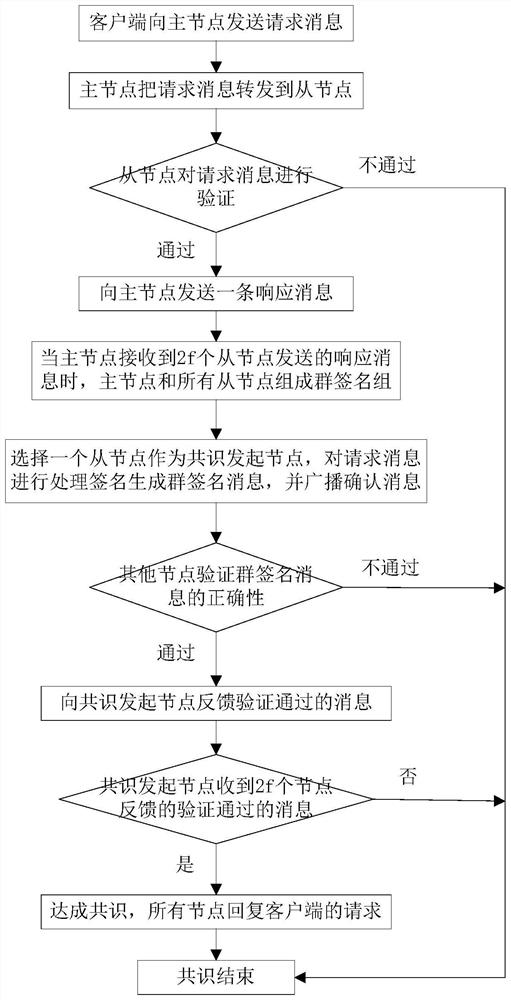
ActiveCN111865918AReduce Communication ComplexityKey distribution for secure communicationUser identity/authority verificationChain networkCommunication complexity
The invention provides an optimized and improved block chain PBFT consensus method. The method comprises the following steps: S1, sending a request message to a main node of a block chain network; S2,forwarding the request message to a slave node of the blockchain network; S3, enabling the slave node to verify the request message; S4, when the master node receives response messages sent by the 2fslave nodes, enabling the master node and all the slave nodes to form a group signature group, and acting the master node as a group administrator; S5, selecting a slave node as a consensus initiating node, processing and signing the request message to generate a group signature message, and broadcasting an acknowledgement message; S6, verifying the correctness of the group signature message by other nodes; and S7, if the consensus initiating node receives the verification passing messages fed back by the 2f nodes, showing that the consensus is reached, and all the nodes reply to the requestof the client. The invention provides an optimized and improved block chain PBFT consensus method, and solves the problem that the communication complexity of a current PBFT algorithm is too high.
Owner:GUANGDONG UNIV OF TECH
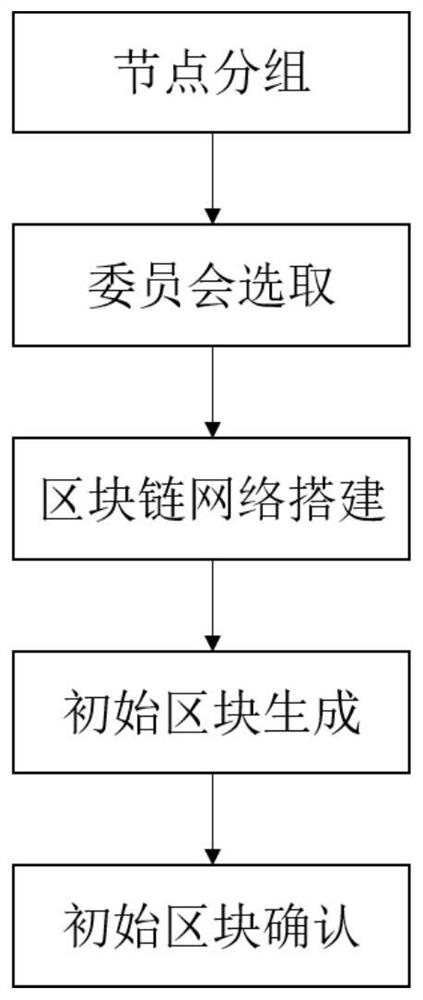
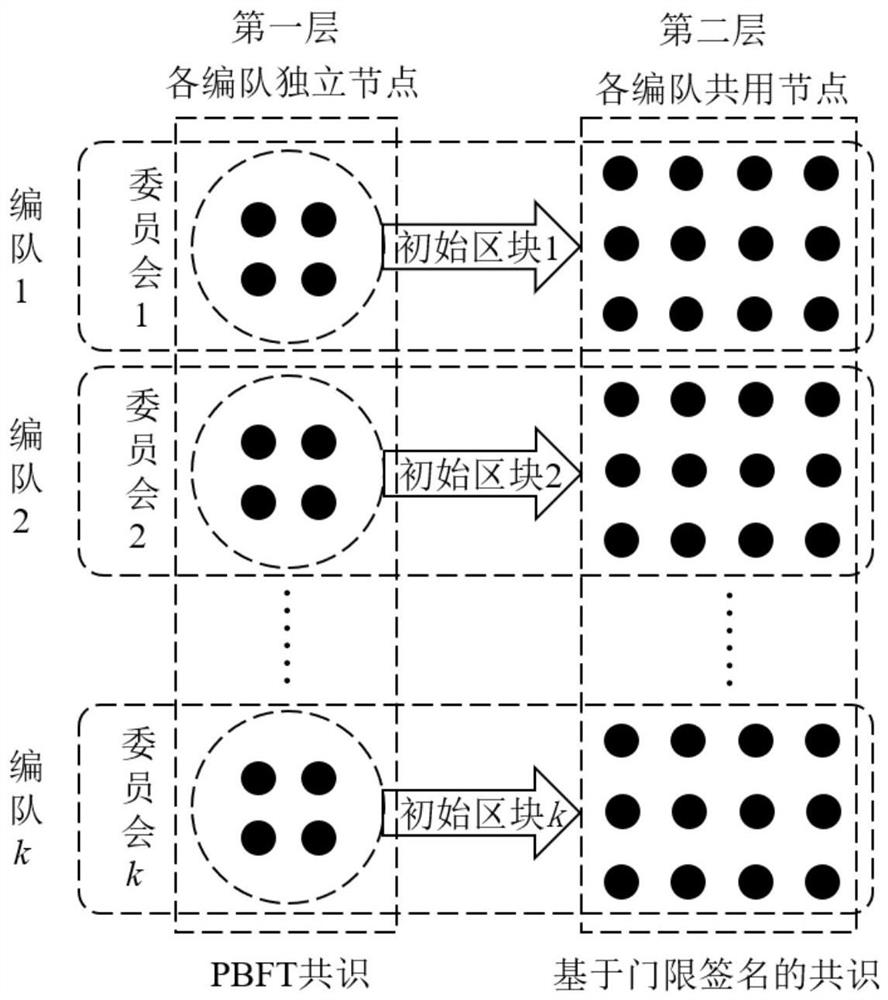
Double-layer grouping Byzantine fault-tolerant consensus method and system
PendingCN113642019AReduce Communication ComplexityReduce the number of communicationsDigital data protectionDigital data authenticationChain networkCommunication complexity
The invention discloses a double-layer grouping Byzantine fault-tolerant consensus method and system. The method comprises the following steps: S1, determining node groups; S2, for each group of nodes, selecting a part of nodes from the nodes as committee nodes, forming committee of the group, taking the remaining nodes except the committee nodes as common nodes, and selecting a main node of each group from the committee nodes; S3, building a block chain network; S4, if a certain group of committee receives a proposal request, the main node of the group generating a block according to the proposal request and sending the block to other committee nodes of the group for a first round of consensus, and if the first round of consensus passes, generating an initial block and sending the initial block to the common node of each group; and S5, performing a second round of consensus on the initial block by the common node of each group, and if the second round of consensus is passed, chaining the initial block and storing the initial block in a local account book. According to the method, a double-layer grouping consensus structure is adopted, and the system robustness is improved on the premise that low communication complexity is guaranteed.
Owner:NAT UNIV OF DEFENSE TECH
Block chain layered excitation consensus algorithm
ActiveCN112769580AReduce Communication ComplexityHigh rewardSpecial service provision for substationDatabase distribution/replicationEngineeringConsensus
The invention is suitable for the technical field of blockchain application, and provides a block chain hierarchical excitation consensus algorithm. According to the blockchain layered incentive consensus algorithm, the tree communication network topology is adopted, when nodes transmit data, messages do not need to be broadcasted to other nodes through a P2P network every time, the messages are sent to other nodes after being processed by parent nodes or child nodes, and the tree communication network topology is benefited; and the communication complexity of the system is greatly reduced. The consensus algorithm comprises a consensus node dynamic spanning tree algorithm and a corresponding reward mechanism, the traditional PBFT consensus algorithm lacks the corresponding reward mechanism, and the nodes need to pay computing power and bandwidth when participating in the consensus, so the nodes lack the power of participating in the consensus. The consensus node excites and encourages the node to participate in the consensus honest, and obtains higher rewards by keeping correct data consensus, and the core purpose is to enable the node to participate in the consensus and transmit correct messages according to rules.
Owner:GUANGDONG OCEAN UNIVERSITY +1
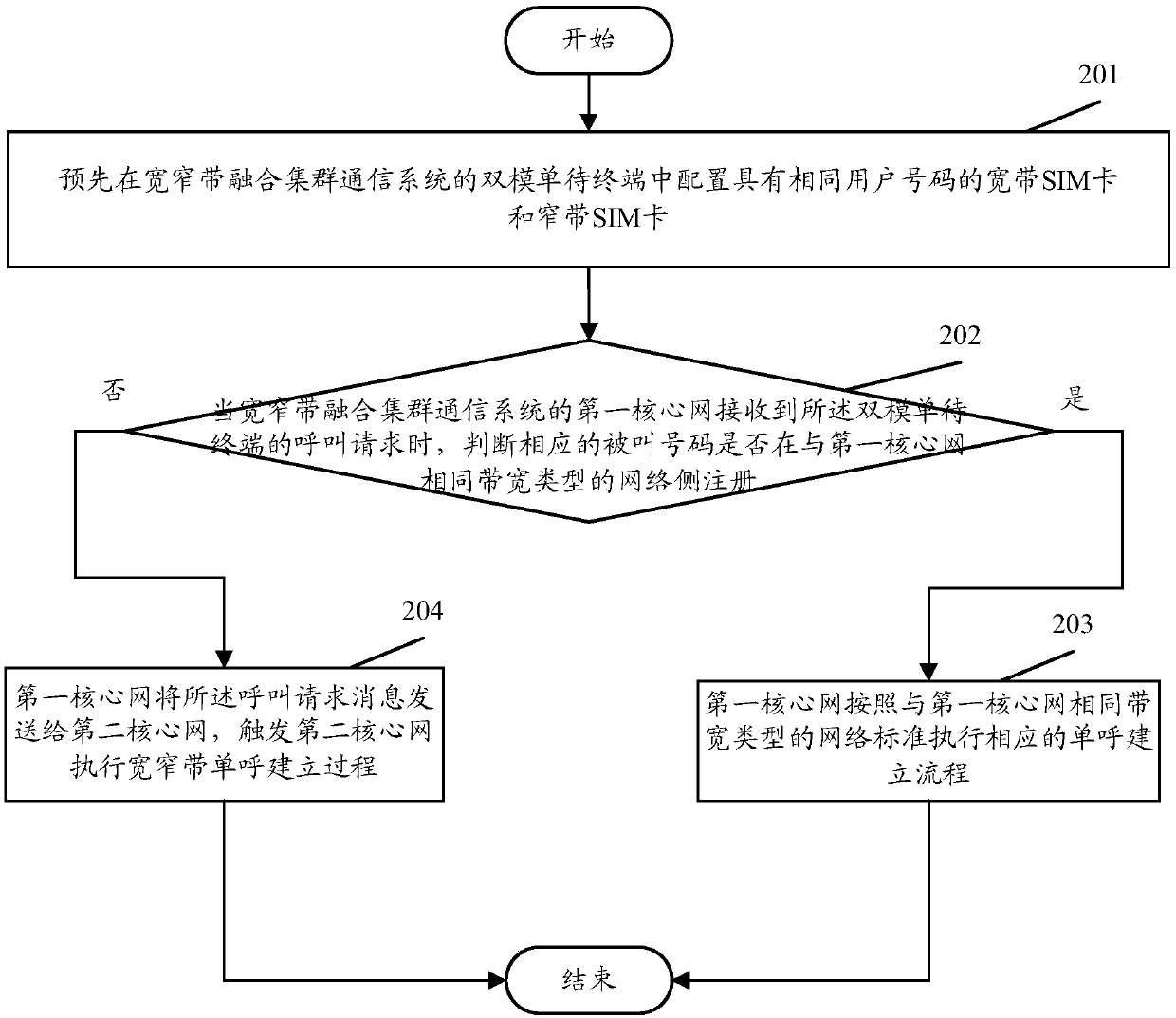
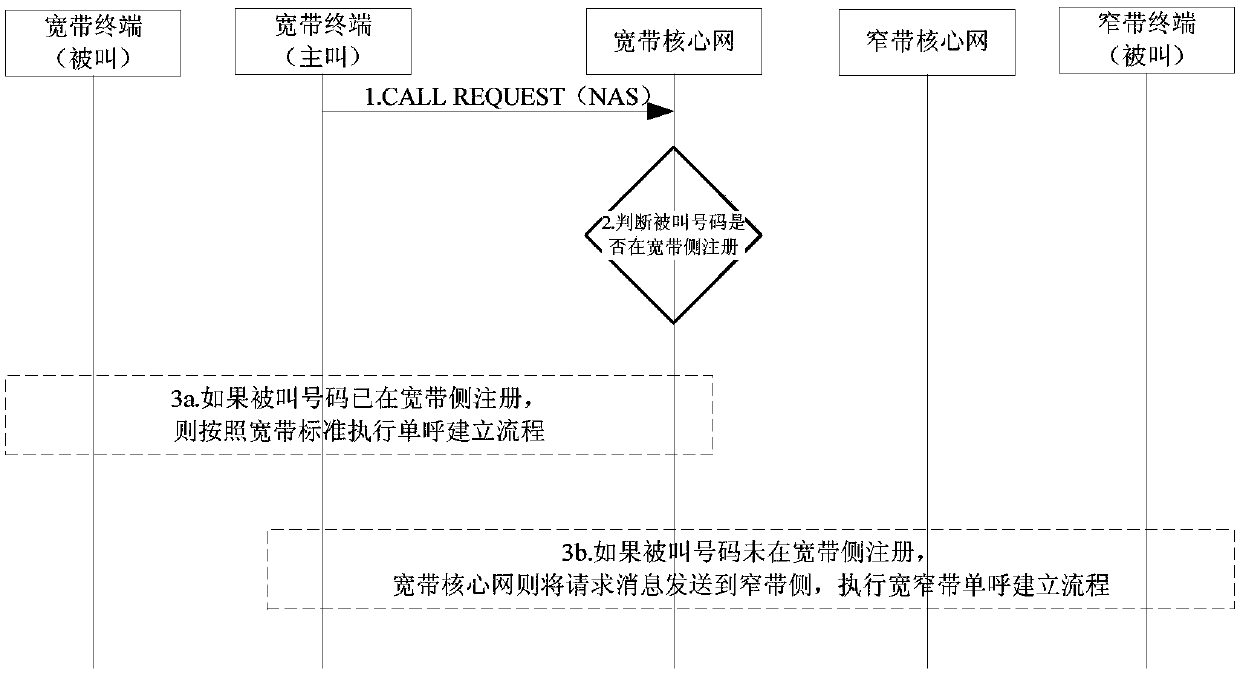
Communication method and system of dual-mode single-standby terminal
ActiveCN110392354AReduce Communication ComplexityEasy to implementNetwork topologiesCommmunication supplementary servicesCommunication complexityBroadband
The invention discloses a communication method and system of a dual-mode single-standby terminal. The method comprises the following steps: configuring a broadband SIM card and a narrowband SIM card with the same user number in the dual-mode single-standby terminal of a broadband and narrowband converged trunking communication system in advance; when the first core network receives a call requestof the dual-mode single-standby terminal, judging whether a corresponding called number is registered on a network side with the same bandwidth type as the first core network or not, and if so, executing a corresponding single call establishment process according to a network standard with the same bandwidth type as the first core network; otherwise, the first core network sends the call request message to a second core network, the second core network is triggered to execute a broadband and narrowband single call establishment process, and when the first core network is a broadband core network, the second core network is a narrowband core network; and when the first core network is the narrowband core network, the second core network is the broadband core network. By adopting the methodand the system, the communication complexity of the dual-mode single-standby terminal can be effectively reduced, and the method and the system are easy to implement.
Owner:POTEVIO INFORMATION TECH
Mobile quantum voting method based on Chinese remainder theorem
ActiveCN108010178APrevent secondary voting attacksReduce consumptionVoting apparatusChinese remainder theoremQuantum state
The invention discloses a mobile quantum voting method based on Chinese remainder theorem, which is characterized in that a supervisor, a teller and a plurality of voters exist. A quantum state is prepared by the supervisor, moreover, the quantum state is divided into two, one part of quantum bits are sent to the voters to serve as quantum votes, and the other part of the quantum bits are sent tothe teller to serve as vote-checking certificates; each voter performs voting operation on the same quantum vote, the quantum votes are sent to the teller for counting and verification after all voting operations are complete, and ultimately, voting results of all the voters are obtained. The objective of the invention is to solve the problem that conventional mobile voting cannot resist secondaryvoting attacks of dishonest voters and the problem that excessive quantum resource is consumed by conventional distributive voting, and the security of voting operation is enhanced.
Owner:ANHUI UNIVERSITY
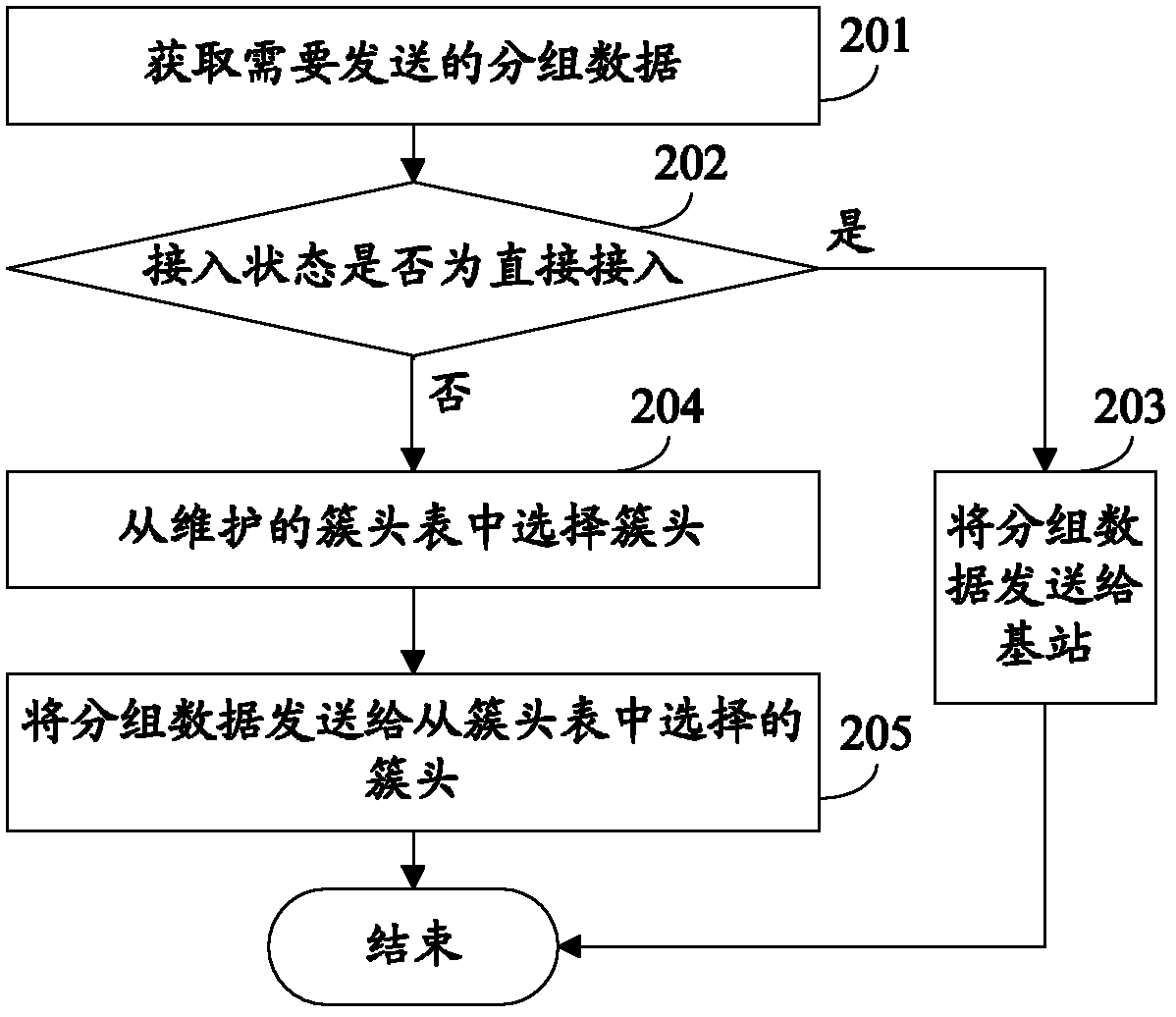
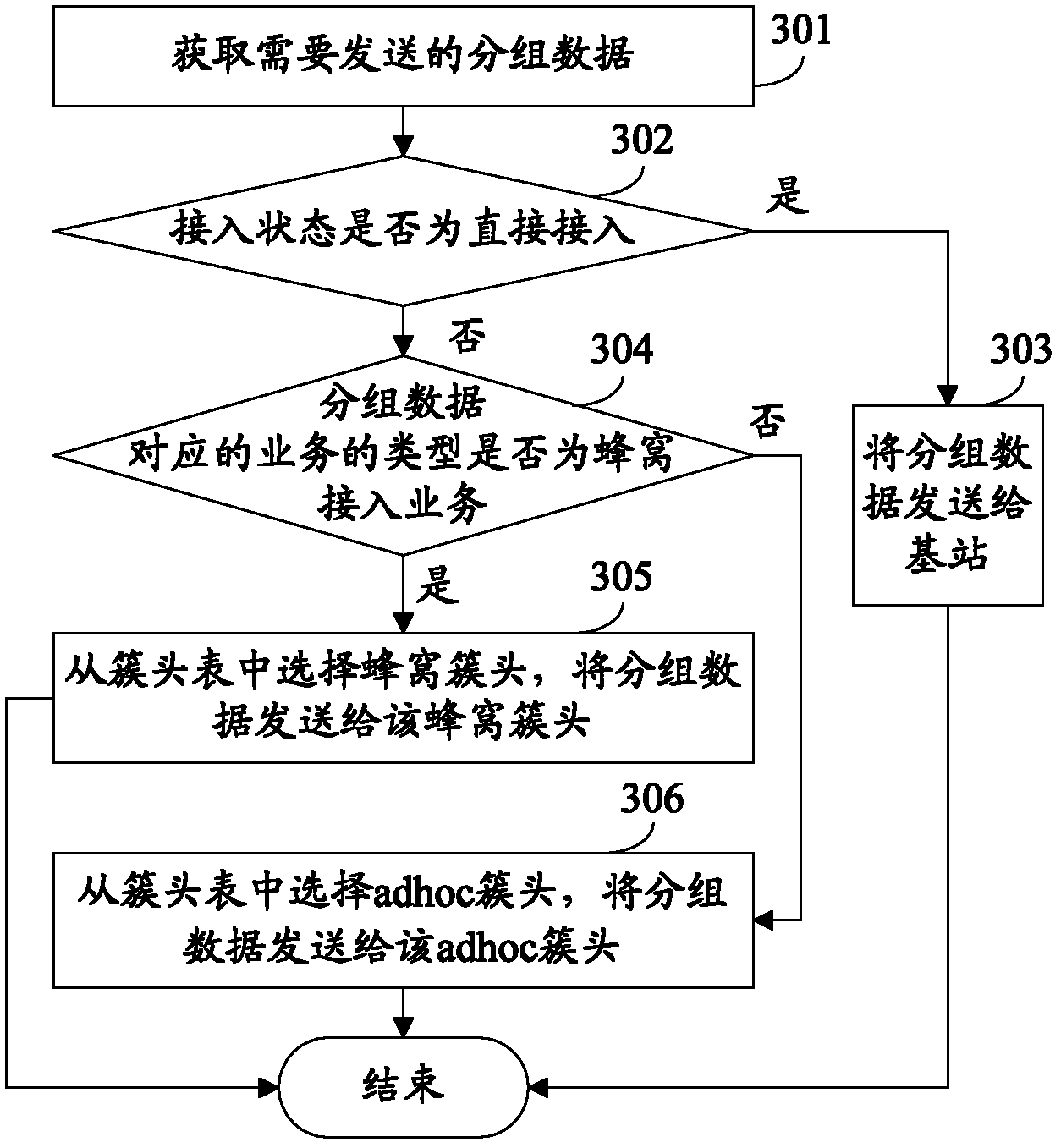
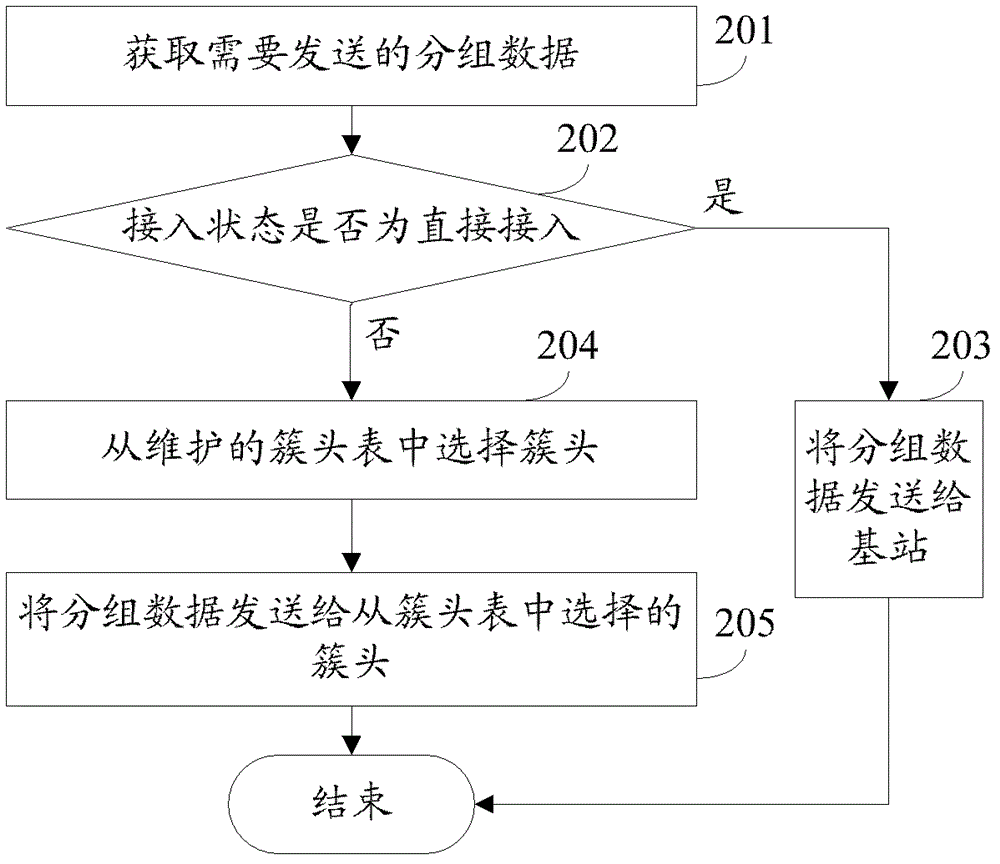
Grouped data sending method, base station and terminal
ActiveCN102630097AReduce resource overheadReduce Communication ComplexityWireless communicationInterface selectionBase station
The invention relates to a grouped data sending method, which comprises the following steps of: receiving grouped data comprising an identifier of a target terminal from a source terminal; finding out whether a path reaching the target terminal exists in a routing cache list; if finding out the path reaching the target terminal exists, carrying out interface selection; and forwarding the grouped data through a selected interface according to the found path. The invention further relates to another two grouped data sending methods corresponding to the grouped data sending method, and a terminal and a base station corresponding to the grouped data sending method. By adoption of the grouped data sending method, the base station and the terminal disclosed by the invention, link treatment can be carried out at the terminal.
Owner:HUAWEI TECH CO LTD
Block chain witness consensus method, system, equipment and storage medium based on Byzantine fault tolerance
ActiveCN114090693AReduce Communication ComplexitySolve the problem of bifurcationDatabase distribution/replicationEnergy efficient computingByzantine fault toleranceEngineering
The invention provides a block chain witness consensus method based on Byzantine fault tolerance, which is characterized in that a packaging node and a witness node are arranged, and the consensus method comprises the following steps: S1, the packaging node packages to generate a block and broadcasts the block; S2, the witness node carries out voting broadcasting and counting; S3, a main chain is confirmed according to a rule; in the step S2, all witness nodes are in any block height, and voting broadcast is only carried out once. The invention further provides a block chain witness consensus system and equipment based on Byzantine fault tolerance and a storage medium. According to the invention, the communication complexity of the consensus network is greatly reduced, the problem of chain bifurcation is still well solved, and the consistency and activity are fully ensured. Meanwhile, the method can be used for identifying the attacking nodes in the consensus network.
Owner:安徽中科晶格技术有限公司
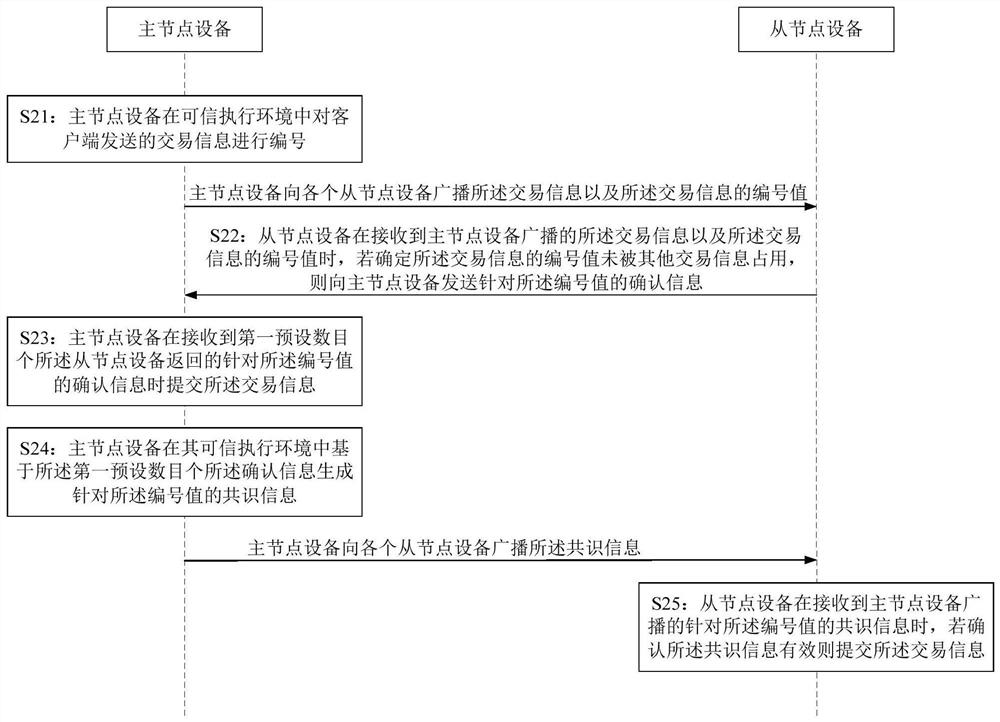
Consensus method of distributed node equipment, node equipment and distributed network
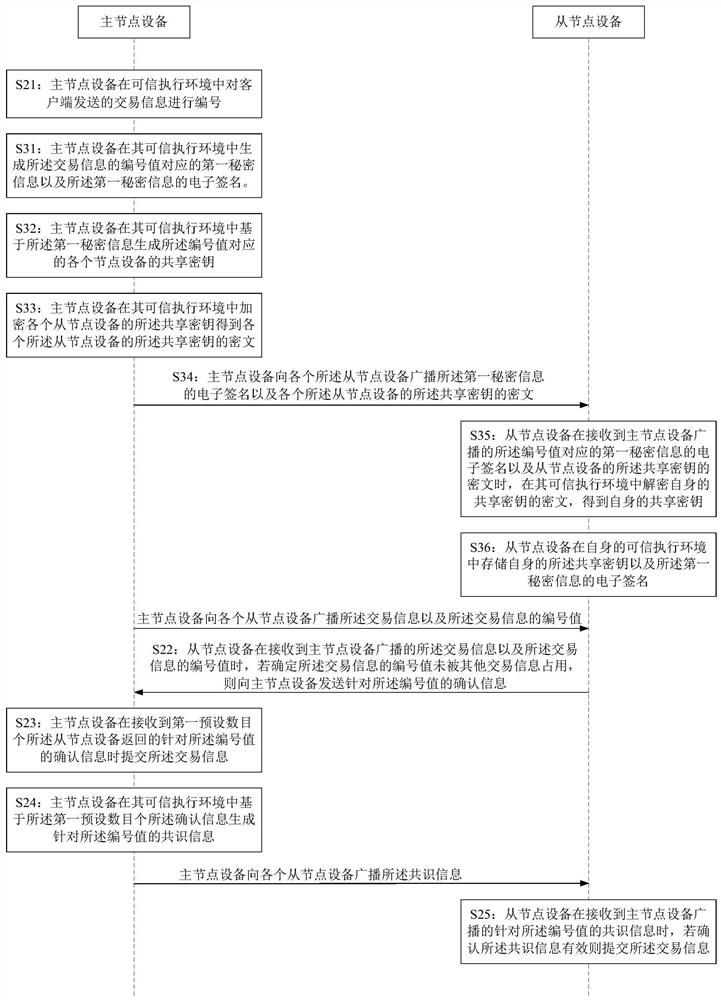
ActiveCN112865959AReduce Communication ComplexityAvoid evil situationsSpecial service provision for substationKey distribution for secure communicationComputer networkEngineering
The invention is suitable for the technical field of distributed networks, and provides a consensus method of distributed node equipment, node equipment, a distributed network and a medium. The consensus method comprises the following steps: numbering transaction information sent by a client in a trusted execution environment, broadcasting the transaction information and the number value of the transaction information to each slave node device; submitting the transaction information when confirmation information for the number value returned by the first preset number of slave node devices is received; generating the confirmation information when the slave node equipment determines that the serial number value of the transaction information is not occupied by other transaction information; generating consensus information for the number value based on a first preset number of pieces of confirmation information in the trusted execution environment, and broadcasting the consensus information to each slave node device, wherein the consensus information is used for indicating the slave node equipment to submit the transaction information after the slave node equipment confirms that the consensus information is valid, the communication complexity is low, and the situation that nodes are disable in the consensus process can be avoided.
Owner:HANGZHOU QULIAN TECH CO LTD
Cross-chain consensus architecture and method for treating chain by chain
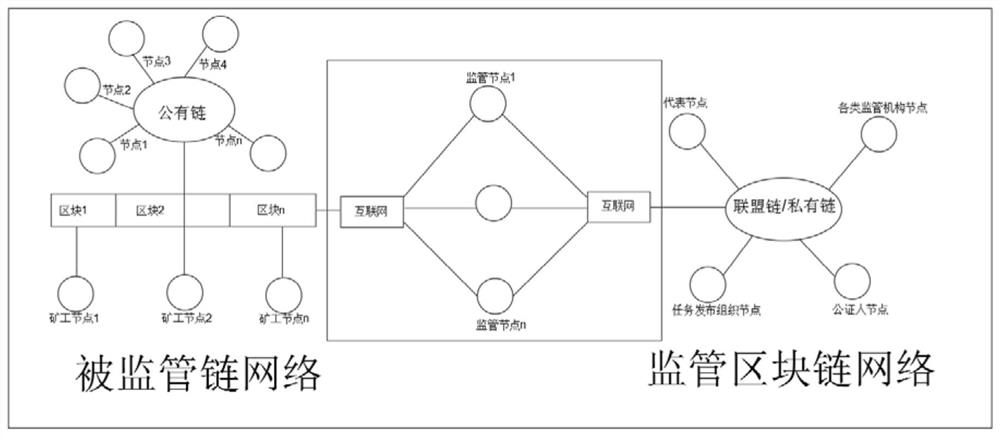
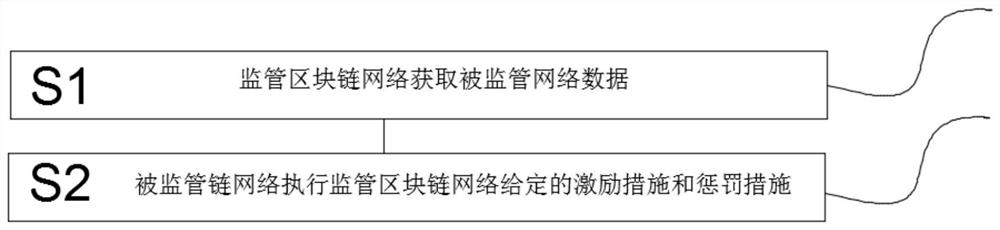
InactiveCN112788119AEffective monitoringReduce Communication ComplexityData switching networksData connectionData management
The invention provides a cross-chain consensus architecture and method for treating a chain with a chain, wherein the cross-chain consensus architecture comprises a supervision module, a communication module, a data module and a reward and punishment module; the supervision module is used for supervising a network, the communication module is used for data communication, the data module is used for data management and control, and the reward and punishment module is used for executing reward and punishment measures. The data module is in data connection with the supervision module through the communication module, and the reward and punishment module is in data connection with the monitoring module through the communication module. According to the invention, three functional requirements in total in two aspects of a chain control chain supervision mode can be supported, namely, the supervision block chain network is supported to acquire data of the supervised chain network, the supervised chain network is supported to execute excitation measures given by the supervision block chain network, and the supervised chain network is supported to execute punishment measures given by the supervision block chain network; therefore, a core solution of the vacancy of the chain supervision field is filled, the communication complexity is relatively low, and the safety, the expansibility and the efficiency are ensured.
Owner:HAINAN UNIVERSITY +1
Web end visual development method and system and storage medium
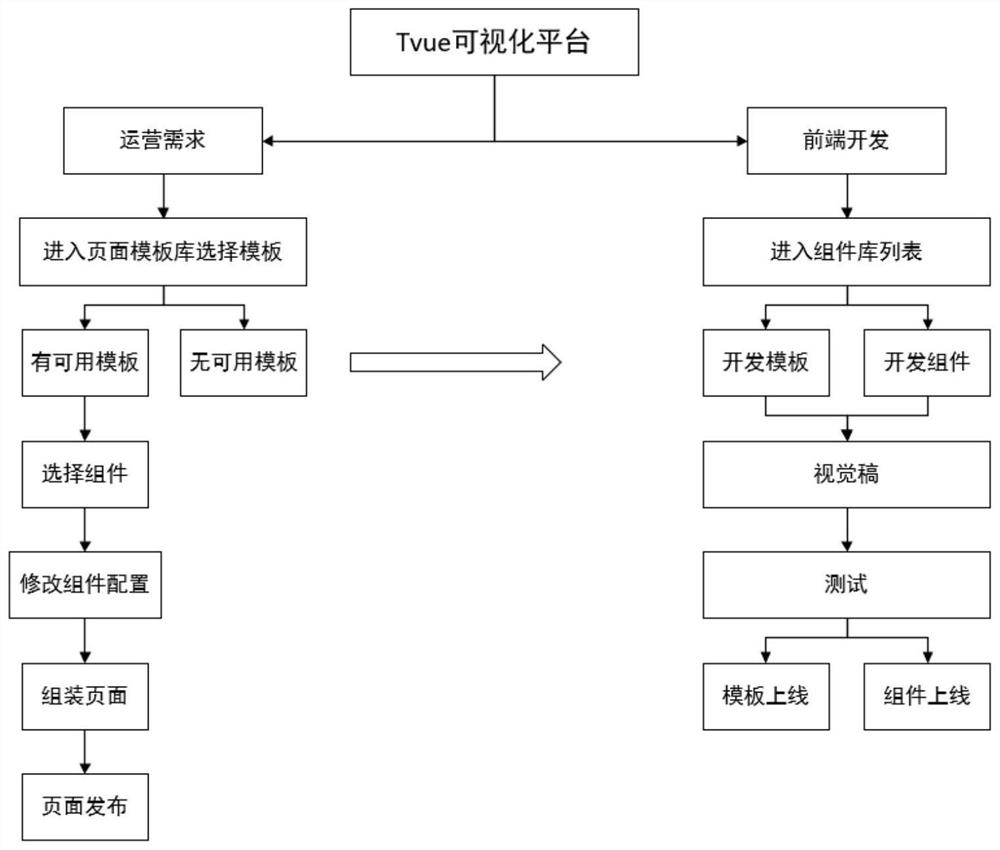
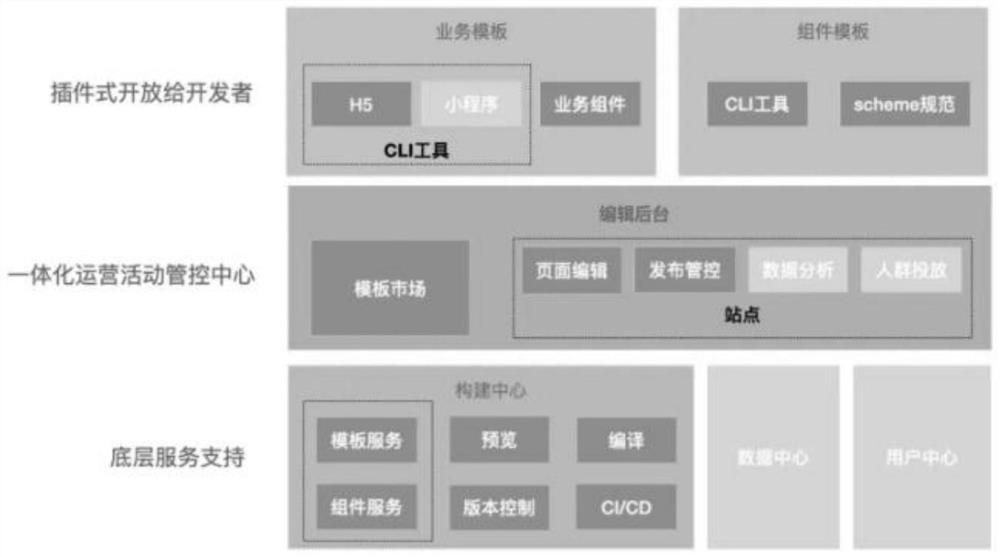
PendingCN114138256AProfessionalism requires low skillWrite less codeVisual/graphical programmingWebsite content managementSoftware engineeringDatabase
The invention discloses a Web end visual development method, relates to the technical field of Web end visualization, solves the technical problem of low development efficiency, and comprises the following steps: creating a service development platform, and integrating a vue whole-family bucket, an scss preprocessor, a cli tool, a schema specification and an npm component library package as a basic base to carry out development services; an online operation control center module is created, the online operation control center module comprises a background application list, a template market and an online editor, application templates of various application scenes are stored in the template market, the online editor is used for a user to select components in a component library to customize application components, and the background application list is used for displaying the use state of each application; creating an underlying service storage support module for storing the application developed by the user into a database; and during development, a user selects a proper application template in a template market according to a development task or makes an application component through an online editor, and issues the application component. The invention further discloses a Web end visual development system and a storage medium.
Owner:GUANGDONG ESHORE TECH
Discovery method and device based on servitization architecture
ActiveCN110474875AReduce the number of communicationsReduce Communication ComplexityUser identity/authority verificationSecurity arrangementSecurity parameterFunctional network
The invention provides a discovery method and a device based on a servitization architecture, and the method comprises the steps: enabling a control network element to transmit a discovery response toa first function network element, and enabling the discovery response to comprise a determined safety parameter and an access address or identification of a second function network element. And the first functional network element receives a discovery response sent by the control network element, sends an access request to the second functional network element according to the address or identifier of the second functional network element included in the discovery response, and includes the received security parameter in the access request. And the second functional network element receives the access request sent by the first functional network element, verifies the correctness of the security parameter, and determines whether the access request is authorized by the first functional network element based on the correctness of the security parameter. According to the method, the communication frequency can be reduced to a certain extent, and the communication complexity is reduced.
Owner:HUAWEI TECH CO LTD
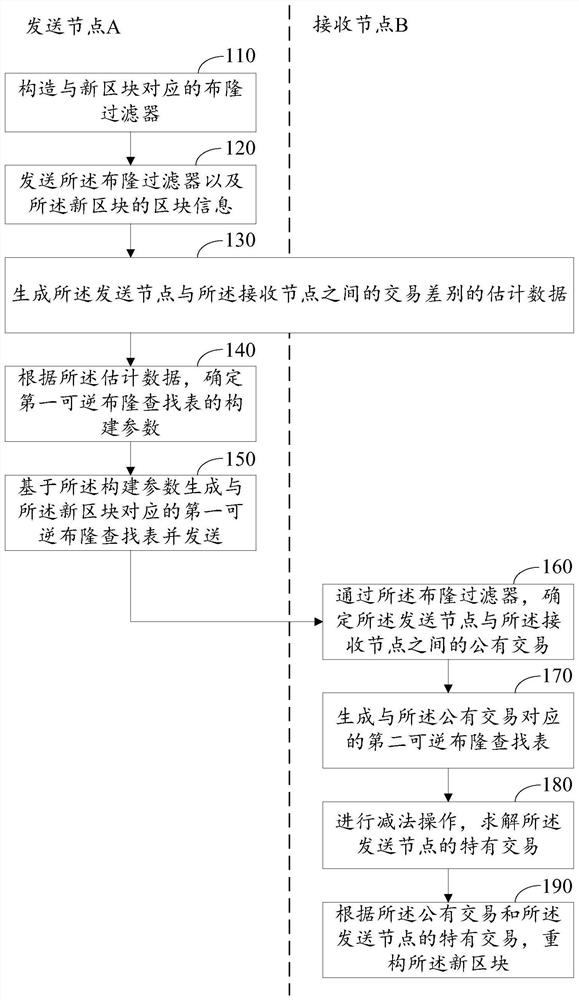
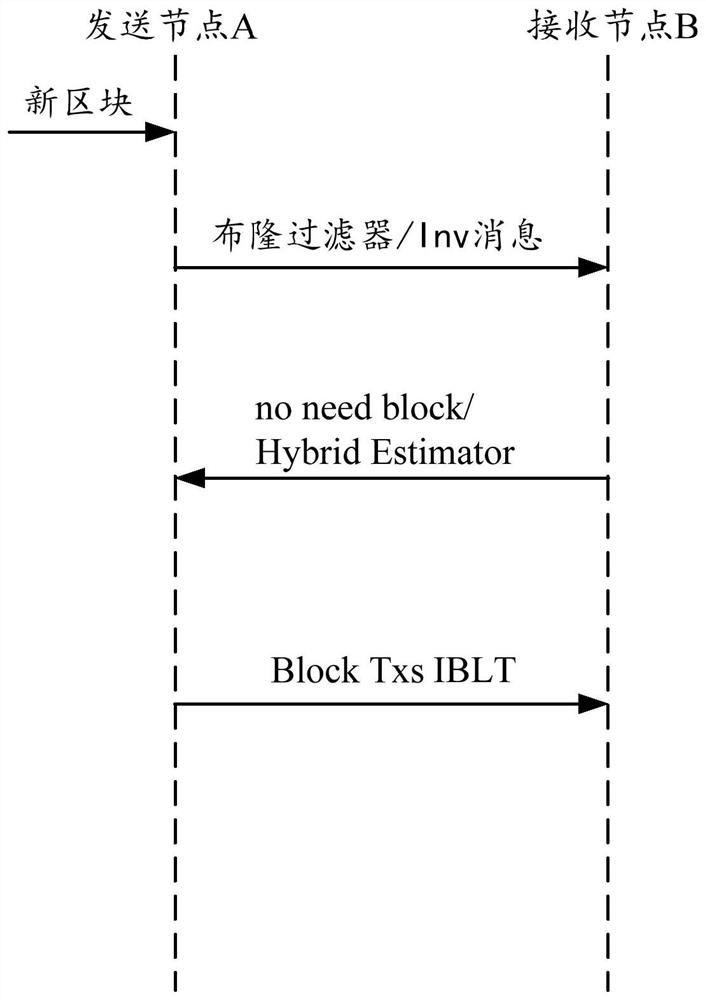
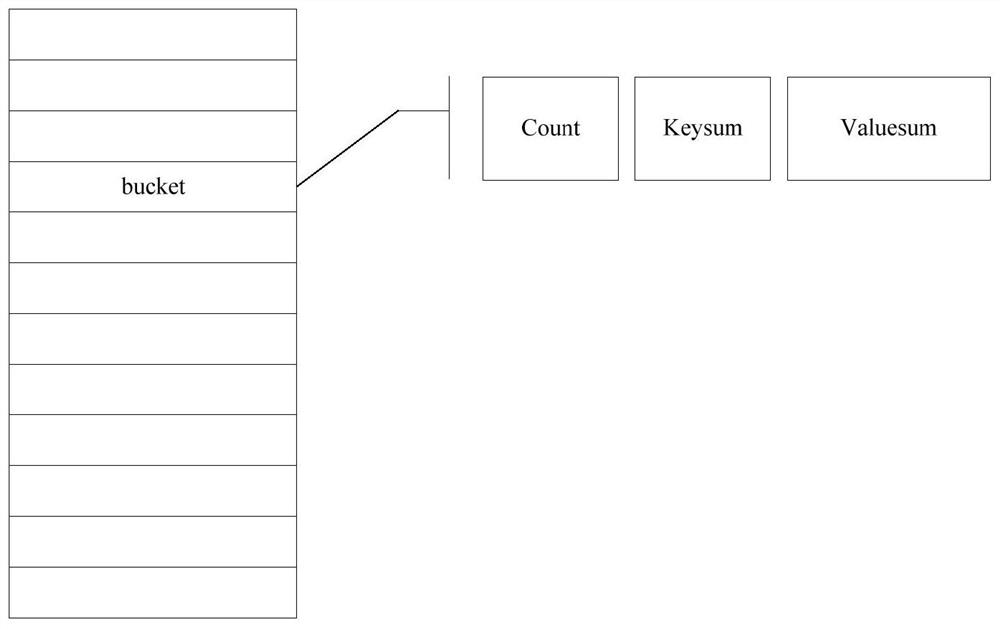
Block data transmission method and device, electronic equipment and nonvolatile computer storage medium
ActiveCN111667264AAvoid secondary communicationControlling the probability of inversion failureFinancePayment protocolsData transmissionComputer hardware
The embodiment of the invention relates to a block data transmission method and device, electronic equipment and a nonvolatile computer storage medium. The block data transmission method comprises thefollowing steps: constructing a Bloom filter; sending the block information of the Bloom filter and the new block; generating estimated data of the transaction difference between the sending node andthe receiving node; generating a first reversible Bloom lookup table corresponding to the new block according to the estimation data; determining a public transaction between the sending node and thereceiving node through the Bloom filter, and constructing a second reversible Bloom lookup table corresponding to the public transaction; and performing subtraction operation on the first reversibleBloom lookup table and the second reversible Bloom lookup table, solving a specific transaction of the sending node, and reconstructing a block according to the specific transaction. According to theblock data transmission method, estimation data of transaction difference between a sending node and a receiving node is given in advance, so that the size of a reversible Bloom lookup table can be reasonably selected, and the probability of inverse solution failure can be controlled.
Owner:深圳启元信息服务有限公司
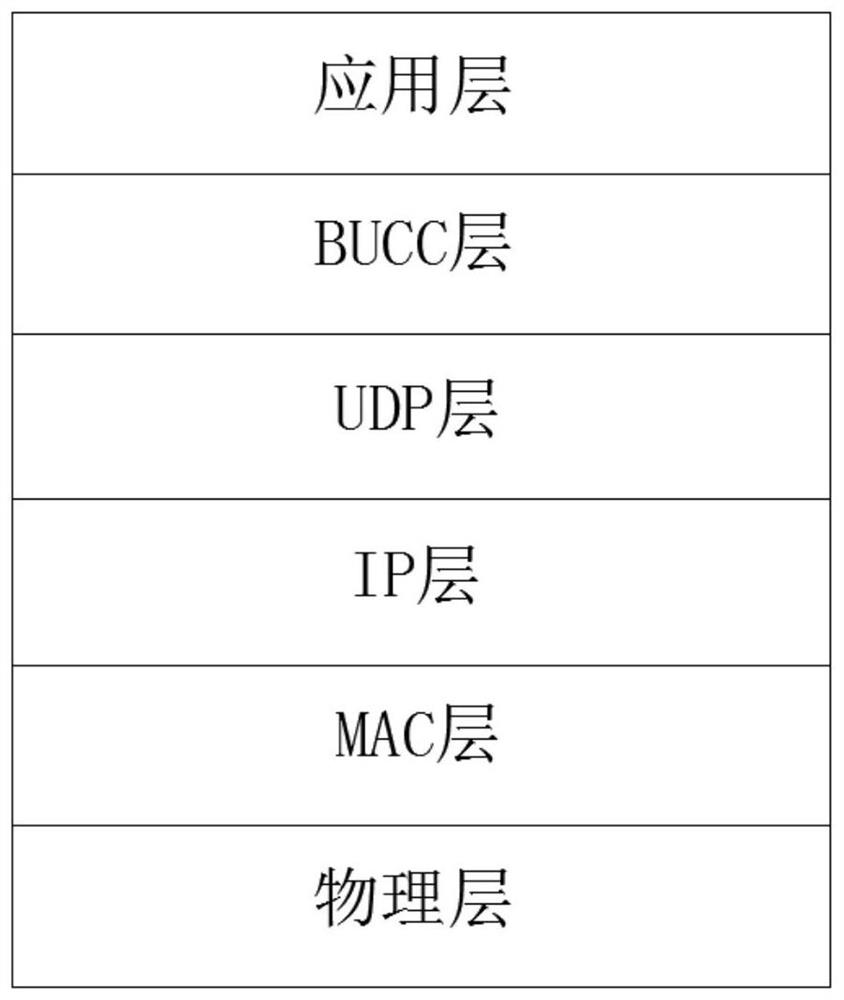
Terminal management communication protocol architecture of enterprise network
ActiveCN112468513AGood communication foundationReduce communication resource consumptionData switching networksData packMessage type
The invention discloses a terminal management communication protocol architecture of an enterprise network, which comprises an application layer, a transmission layer, a network layer, a medium accesscontrol layer and a physical layer, and a reliable connection layer based on a user data packet protocol is configured between the application layer and the transmission layer. The beneficial effectsare that the protocol provided by the invention is designed for the complexity of internal terminal management of an enterprise network, and the unique message format is set for the type and importance of communication data of the management end and the terminal, thereby well adapting to various data messages when the management end issues a strategy and the terminal reports log data; and different BUCC message types can be selected according to the importance of data messages, so that a good communication basis is provided for communication of application data.
Owner:南京中孚信息技术有限公司
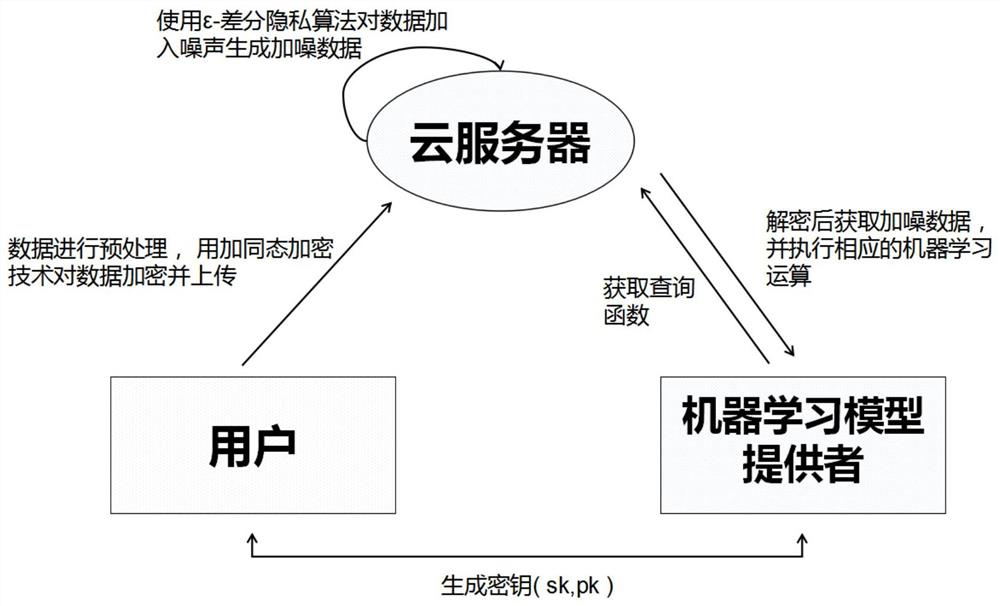
A security outsourcing machine learning method based on differential privacy
ActiveCN110059501BAvoid security issuesIntegrity is not affectedDigital data protectionData providerDifferential privacy
Owner:GUANGZHOU UNIVERSITY
An application-based block chain fragmentation method and device
ActiveCN108881274BImprove acceleration performanceMaintain securityFinanceTransmissionOperating systemBlockchain
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD +1
Quantum-resisting secret key negotiation method
ActiveCN108270562AReduce Communication ComplexityNo reduction lossKey distribution for secure communicationCryptographic attack countermeasuresAttack strategyComputer science
The invention discloses a quantum-resisting secret key negotiation method. A communication party Alice selects a matrix S including n rows and l columns, and F is calculated and sent to a communication party Bob; after that Bob receives the F, a matrix S' including l rows and n columns and a matrix y including n rows and l columns are selected, and W' is calculated; Bob calculates a matrix D' including l rows and l columns and calculates C; and Bob sends B' and C to the Alice. According to the received B' and C, Alice calculates D and km=rec(D, C). According to the method of the invention, theerror probability of negotiation is zero, present quantum attacks and other attack strategies can be resisted, the operation efficiency and practicality are high, the method is easy to enforce, and the method can be integrated to TLS protocols.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Grouped data sending method, base station and terminal
ActiveCN102630097BReduce resource overheadReduce Communication ComplexityWireless communicationComputer terminalInterface selection
Owner:HUAWEI TECH CO LTD
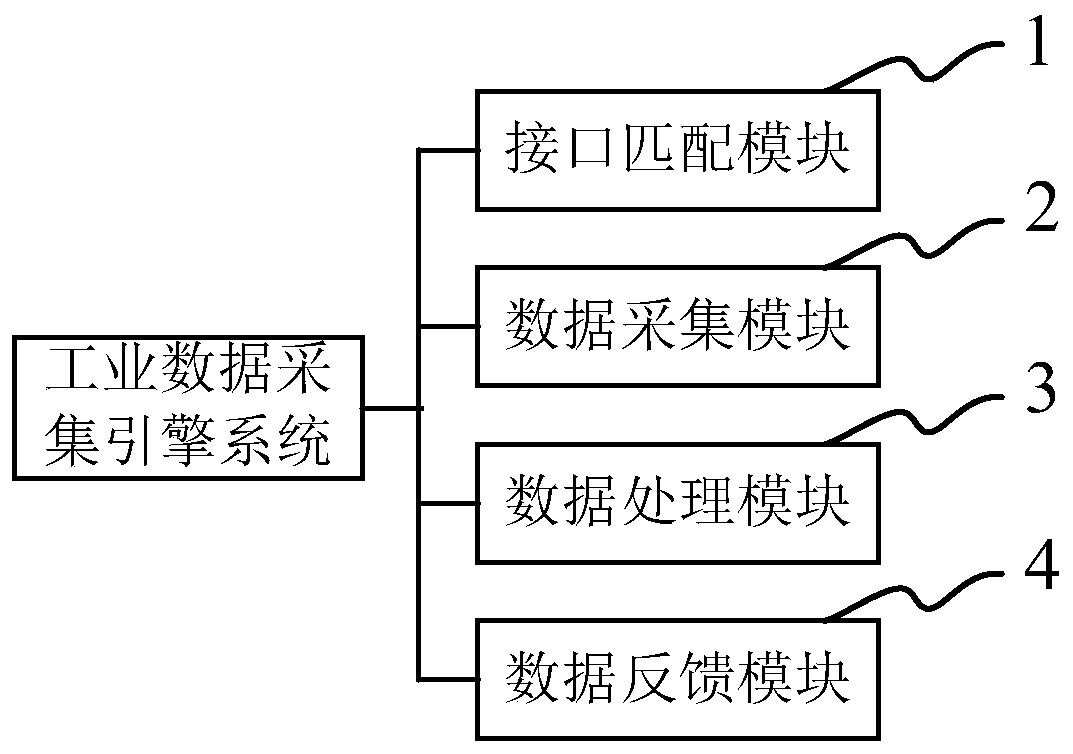
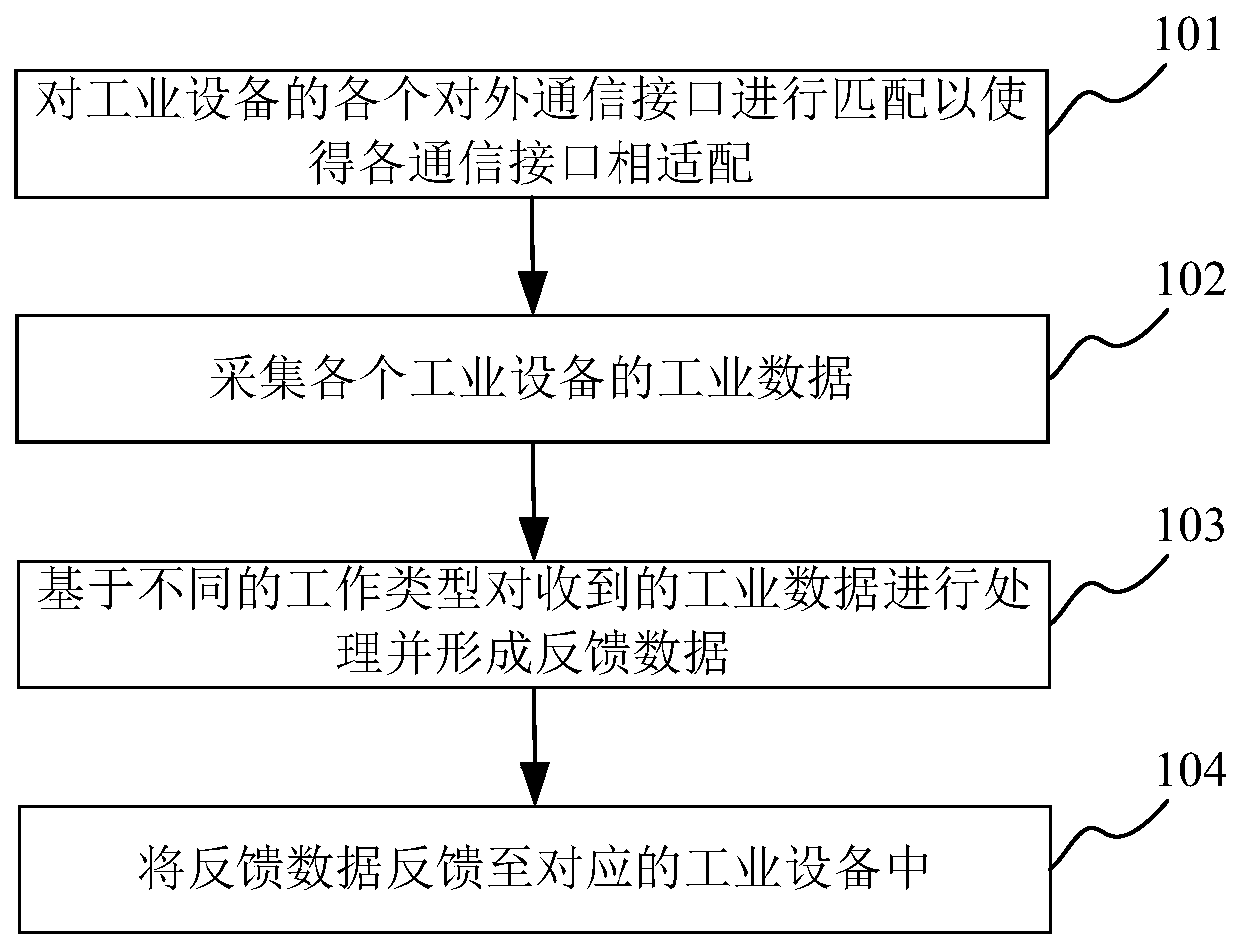
An industrial data acquisition engine system and method
InactiveCN109787972AAvoid isolationReduce the number of programsTransmissionCommunication interfaceData acquisition
The invention discloses an industrial data acquisition engine system and method. The system comprises an interface matching module, a data acquisition module, a data processing module and a data feedback module, The interface matching module is used for matching each external communication interface of the industrial equipment to enable each communication interface to be adaptive; The data acquisition module is used for acquiring industrial data of each industrial device; The processing module is used for processing the received industrial data based on different working types and forming feedback data; And the data feedback module is used for feeding back the feedback data to the corresponding industrial equipment. Through interface matching, data interface programs and data processing programs of an industrial field are greatly reduced, and meanwhile multiple devices can be intelligently combined to work cooperatively. The program is reduced, so that the IT operation and maintenanceefficiency is improved; And the devices work cooperatively, so that the intercommunication and interconnection of the information islands and the devices are broken through, and more possibilities areprovided for on-site intelligent scenes.
Owner:上海因致信息科技有限公司
Credit risk control method based on block chain technology
PendingCN112837141AOptimize the consensus processGuaranteed stabilityFinanceDatabase distribution/replicationRisk ControlBusiness development
The invention provides a credit risk control method based on a block chain technology. The method comprises a credit risk control step based on the block chain technology: synchronizing customer credit information and blacklist information on a block chain, carrying out credit rating on a customer, carrying out credit granting on the customer according to the credit rating, and carrying out credit business development according to credit granting. According to the method, the consensus process is improved, and the stability of external service of the block chain system during node failure and main switching is guaranteed. And meanwhile, by reducing unnecessary signature verification, the consensus process is simplified, the communication complexity is reduced, and the consensus efficiency and expansibility are effectively improved.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Multi-cell MIMO system uplink signal detection method based on constellation structure
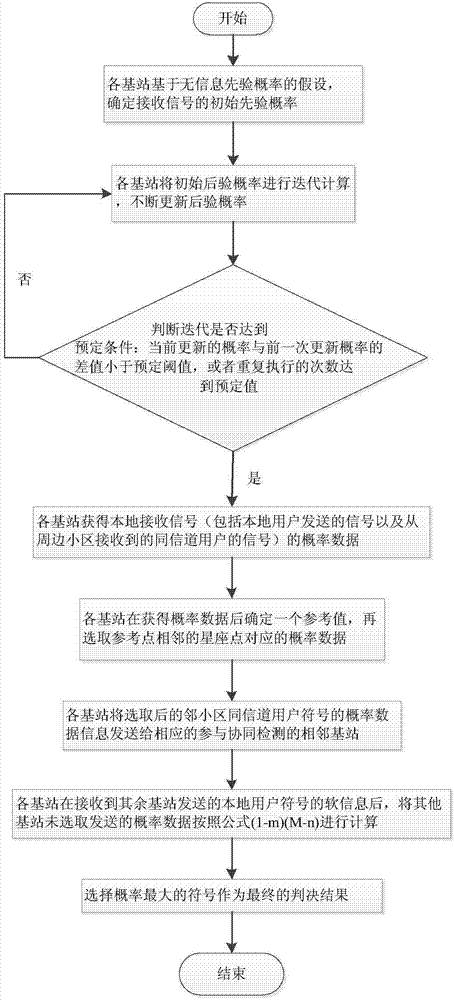
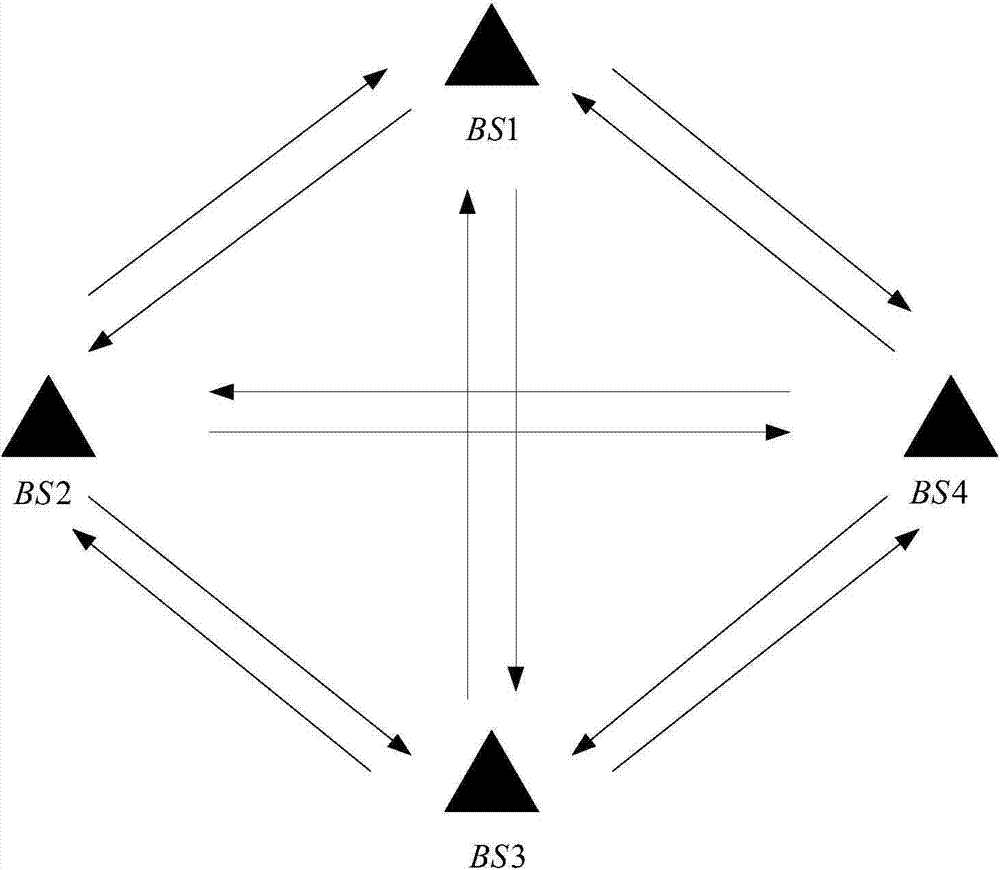
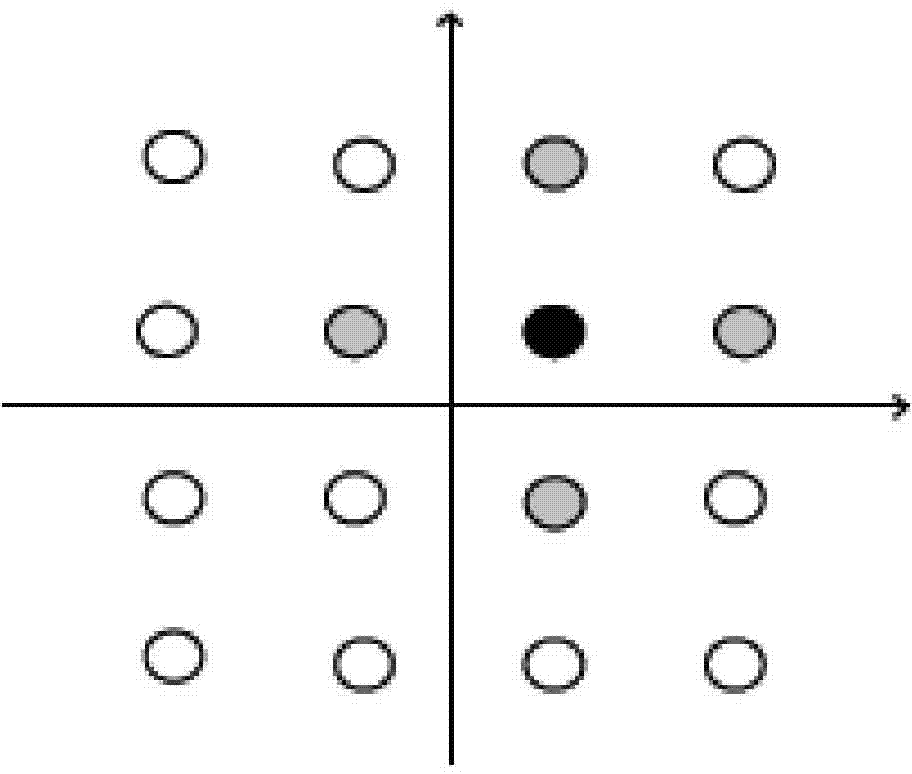
ActiveCN104852784AReduce the amount of interactionReduce Communication ComplexityTransmitter/receiver shaping networksForward error control useComputer scienceSoft information
The invention discloses a multi-cell MIMO system uplink signal detection method based on a constellation structure. The method includes the following steps: each base station detects all signals, obtains the posterior probability of all symbols of each base station, and selects the constellation point in each constellation diagram which corresponds to the maximum posterior probability data as a reference point of the whole constellation diagram; each base station selects posterior probability data of the reference point and an adjacent constellation point in the constellation diagram, and the selected posterior probability data of the constellation point are sent to a corresponding adjacent base station which participates in cooperative detection; after receiving soft information of local user symbols sent by another base station, each base station calculates posterior probability data that are not selected to send by other base station; and each base station performs soft merging on processed complete probability data, calculates the posterior probability of symbols sent by users of the cell, and selects the symbol with a maximum probability as a final detection result. The method provided by the invention can effectively reduce complexity of uplink baseband signal detection in a multi-cell MIMO system.
Owner:ZHEJIANG SCI-TECH UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com