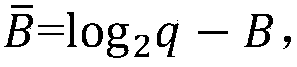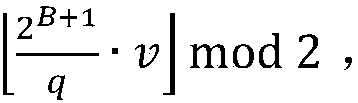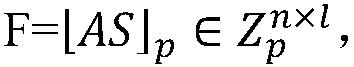Quantum-resisting secret key negotiation method
A technology of quantum key negotiation and key, applied in key distribution, which can solve the problem of no quantum attack, difficulty, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below through specific embodiments and accompanying drawings.
[0046] 1. Symbol description and suggested parameters
[0047] 1) Z q and Z p , respectively expressed as the interval and set of integers.
[0048] 2) Matrix is a public parameter shared by both communication parties, where Represents a collection of matrices, the matrix in the matrix collection is a matrix of n rows and n columns, and the elements of the matrix belong to Z q .
[0049] 3) Represents a collection of n-dimensional vectors, where each vector has n-h 0 components and h non-zero components, these non-zero components are taken from {±1}, where n is consistent with n in the matrix A in 2) above of. Represents a collection of n×l matrices, where each column of the matrix belongs to The n here is consistent with the n in the ring R in the following 6).
[0050] 4) {0,1} n Represents a set of n-dimensional vectors, each element in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com