Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
44results about How to "Meet deployment needs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Well pattern rebuilding method and device for water-injection development of old oil field
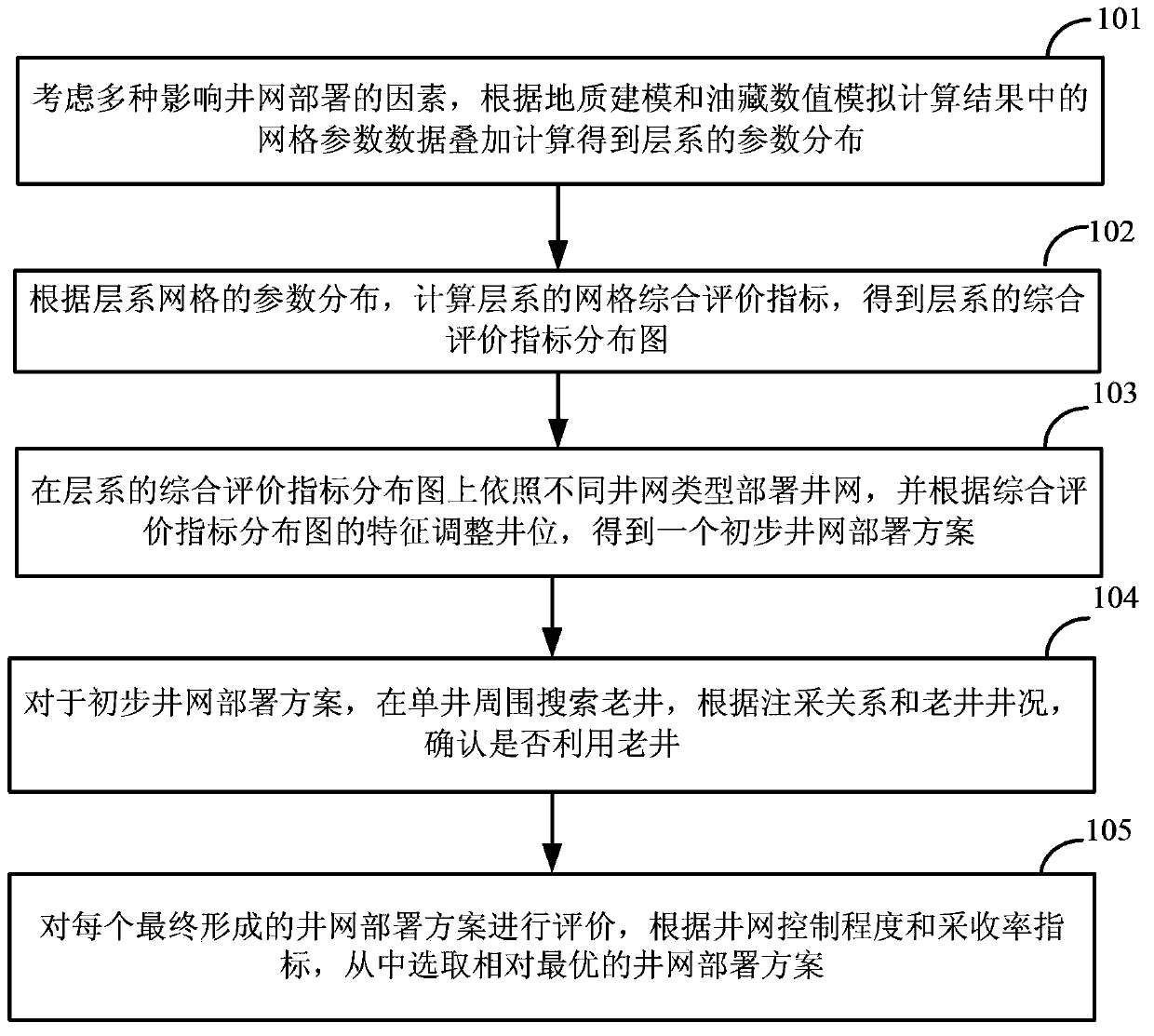
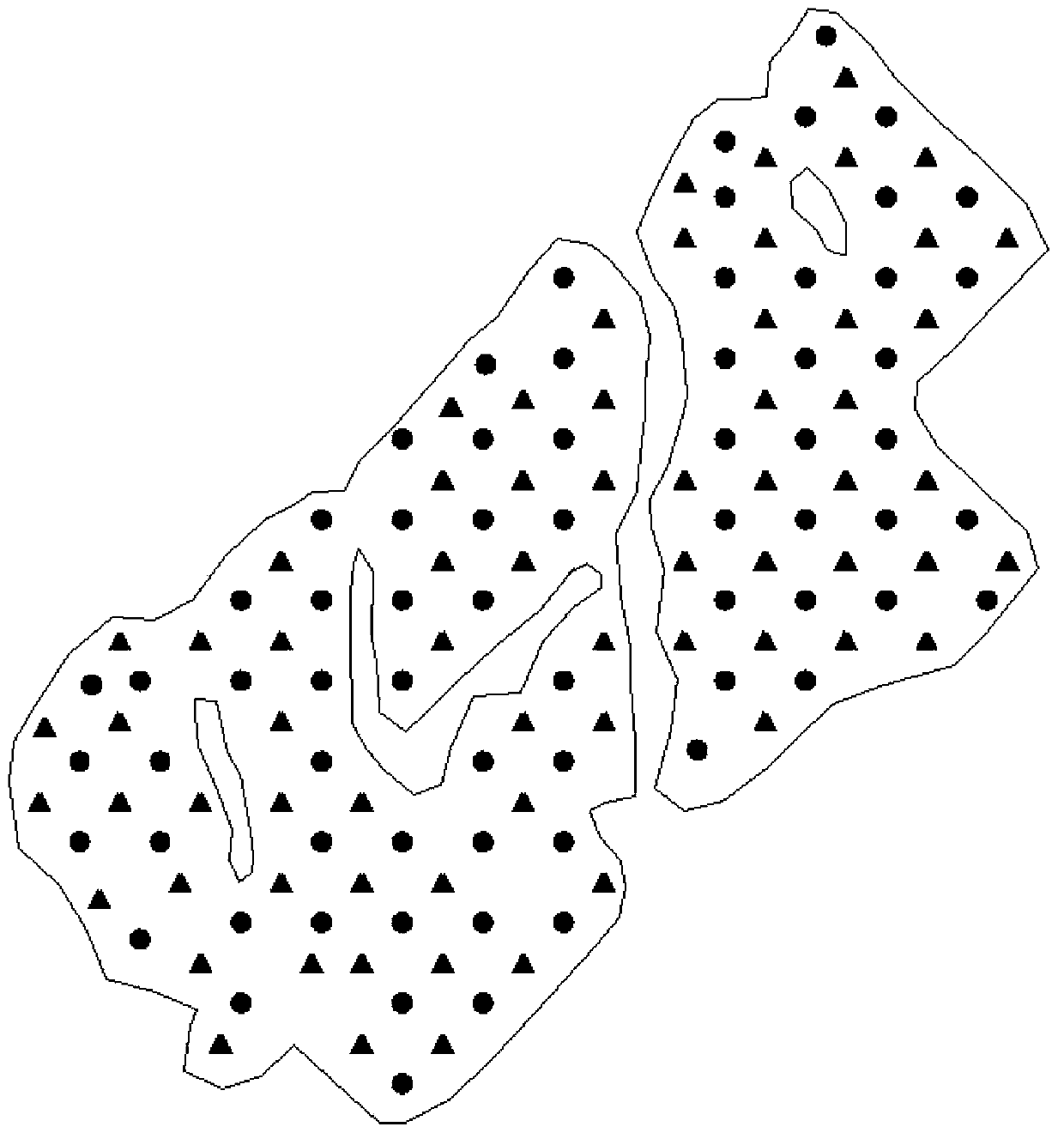
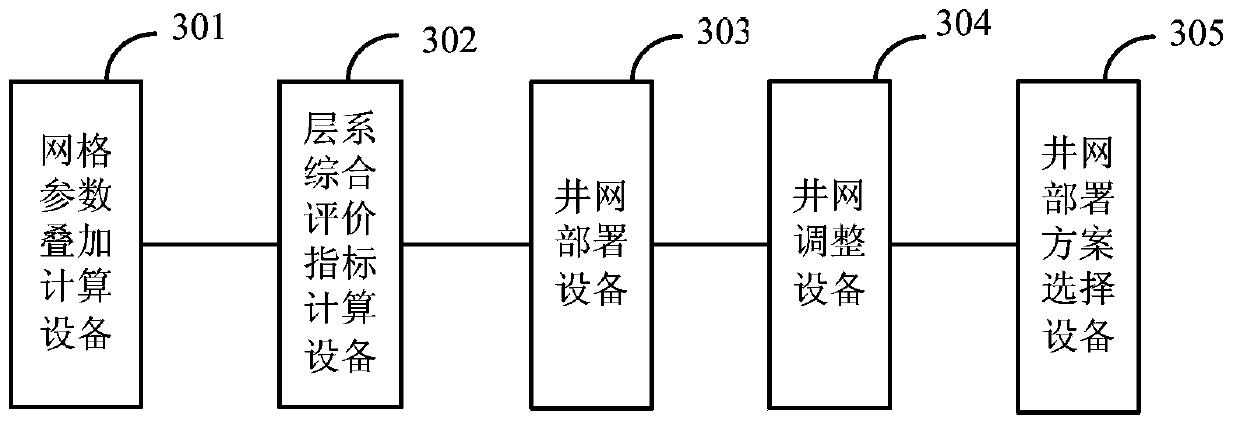
The invention discloses a well pattern rebuilding method and device for the water-injection development of an old oil field. The method comprises the steps that various factors for influencing well pattern arrangement are taken into account, and mesh parameter data in geologic modeling and numerical reservoir simulation computed results are stacked and computed to obtain parameter distribution of series of strata; the mesh comprehensive evaluation index of the series of strata is computed, and a comprehensive evaluation index distribution diagram of the series of strata is obtained; well patterns are arranged on the comprehensive evaluation index distribution diagram of the series of strata according to different well pattern types, well positions are adjusted according to the characteristics of the comprehensive evaluation index distribution diagram, and initial well pattern arrangement schemes are obtained; for each initial well pattern arrangement scheme, old wells are searched for around the signal wells, and whether the oil wells are utilized is determined according to well conditions and an injection-production relationship; each well pattern arrangement scheme formed finally is evaluated, and the relatively-optimal well pattern arrangement scheme is selected according to the well pattern control degree and a recovery efficiency index. The well pattern rebuilding method and device for the water-injection development of the old oil field can meet the well pattern arrangement requirements of old oil fields in the secondary development process.
Owner:PETROCHINA CO LTD
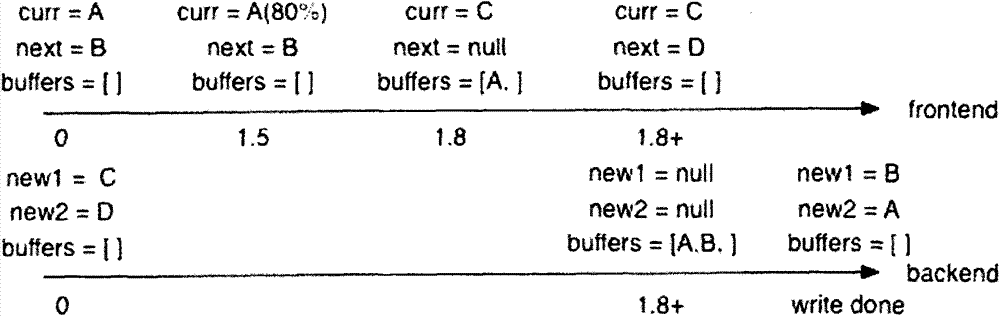
Efficient multi-thread log writing-in method
InactiveCN103885726ANo noticeable loss of performanceNoticeable loss of performanceInput/output to record carriersHardware monitoringSoftware engineeringLog data
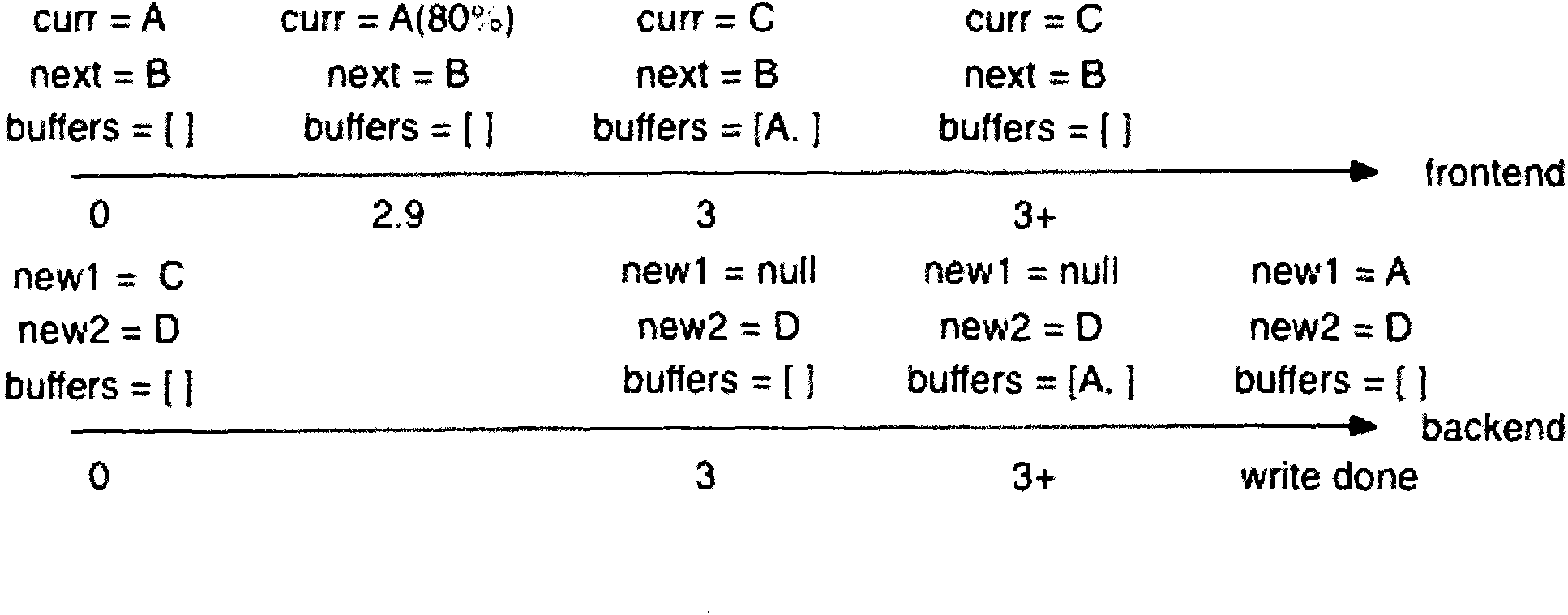
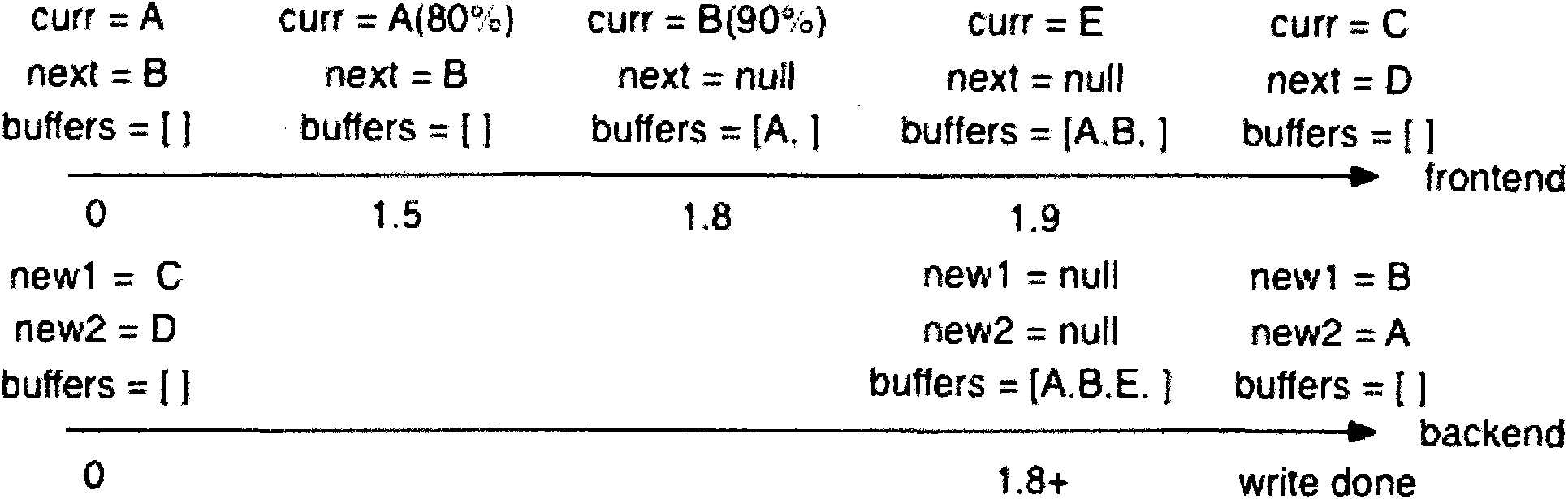
The invention relates to an efficient multi-thread log writing-in method. An interface used for an application program, a front terminal for generating log information and a rear terminal responsible for writing the log information into a local file are used. The efficient multi-thread log writing-in method includes the steps that (1) buffering regions of the front terminal and buffering regions of the rear terminal are initialized, (2) the front terminal is responsible for filling the buffering regions of the front terminal with the log information, (3) the rear terminal writes log data of the buffering regions of the rear terminal into the local file, (4) after the buffering regions of the front terminal are filled through writing, the buffering regions of the front terminal and the buffering regions of the rear terminal are exchanged, the rear terminal writes the data of the buffering regions of the rear terminal into the local file, the front terminal fills the buffering regions of the front terminal with the new log information, and the steps are circularly executed in this way. According to the efficient multi-thread log writing-in method, obvious performance losses can be avoided when thousands of logs are written per second, the scene that a large number of log data are generated through one course can be dealt with, normal executing flow is not blocked, and lock contention in a multi-thread program is avoided.
Owner:EASTLAND DIGITAL CORP
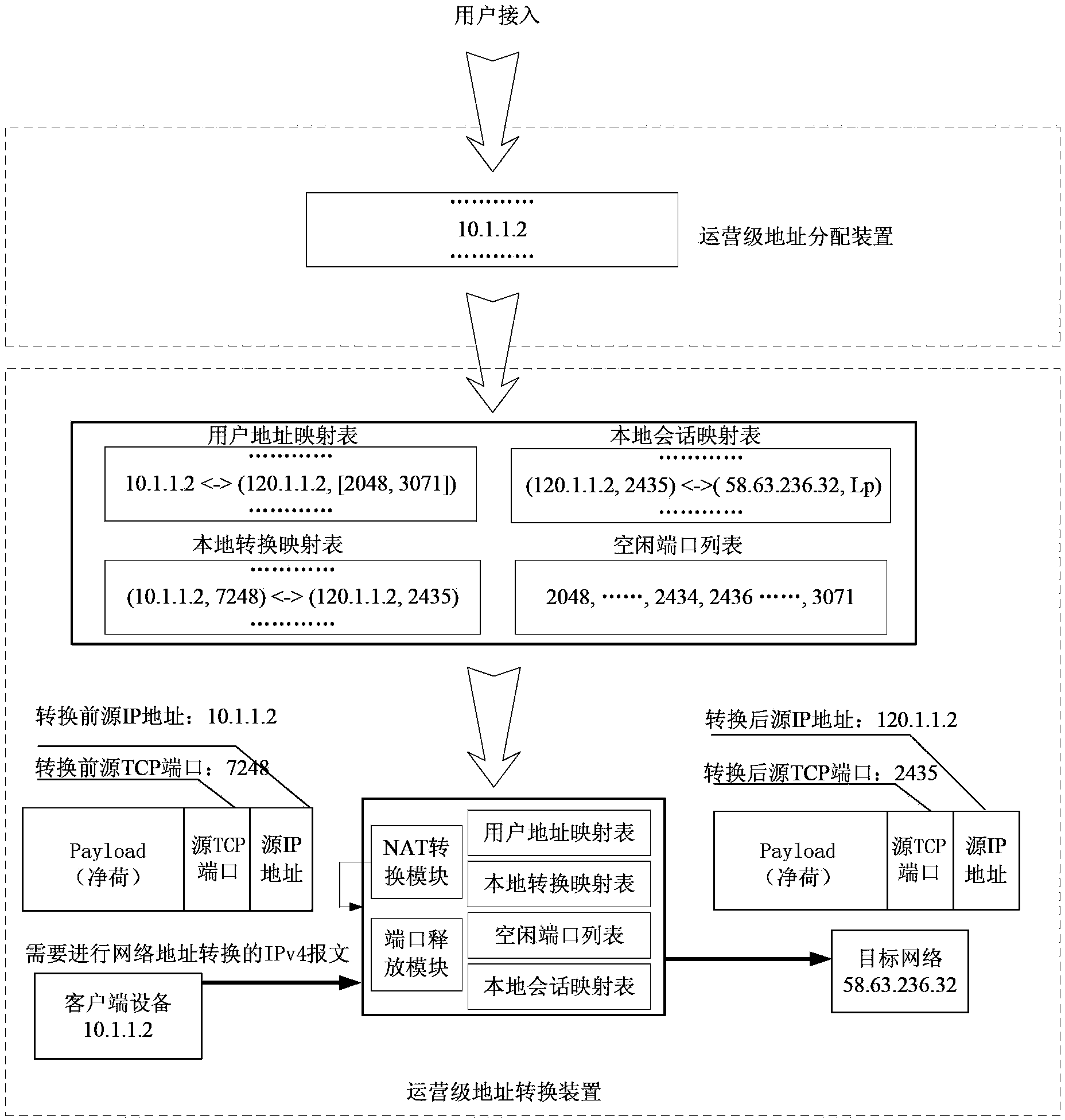
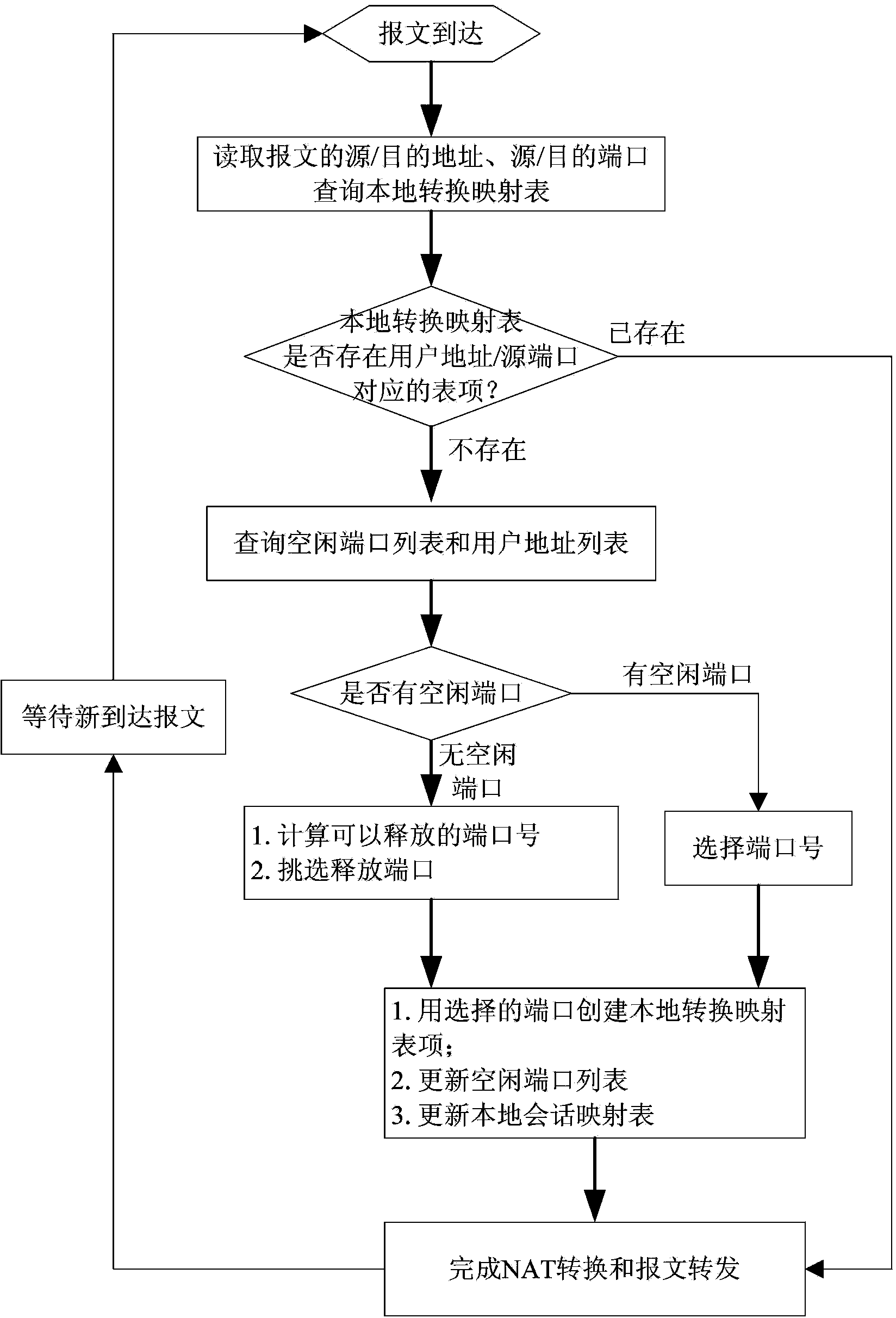
Method for releasing port of carrier-grade network address translation equipment
ActiveCN102882992AMeet deployment needsImprove efficiencyTransmissionCarrier gradeNetwork address translation
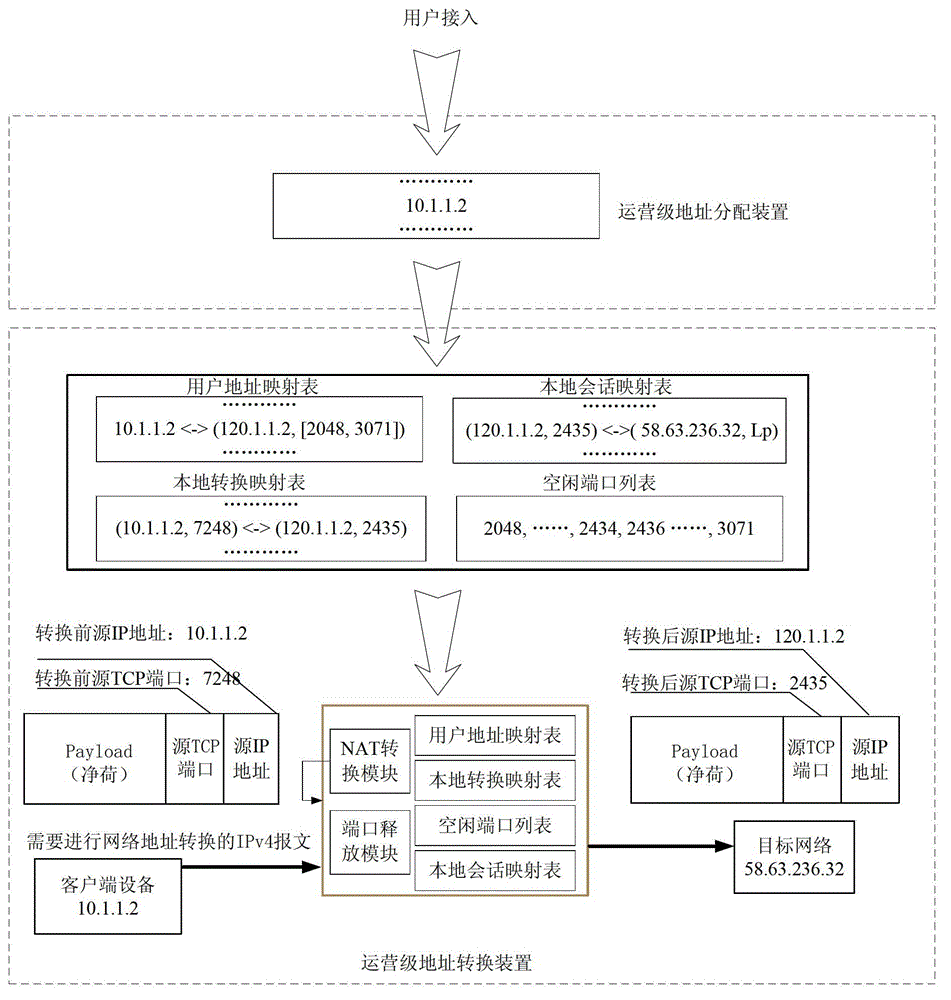
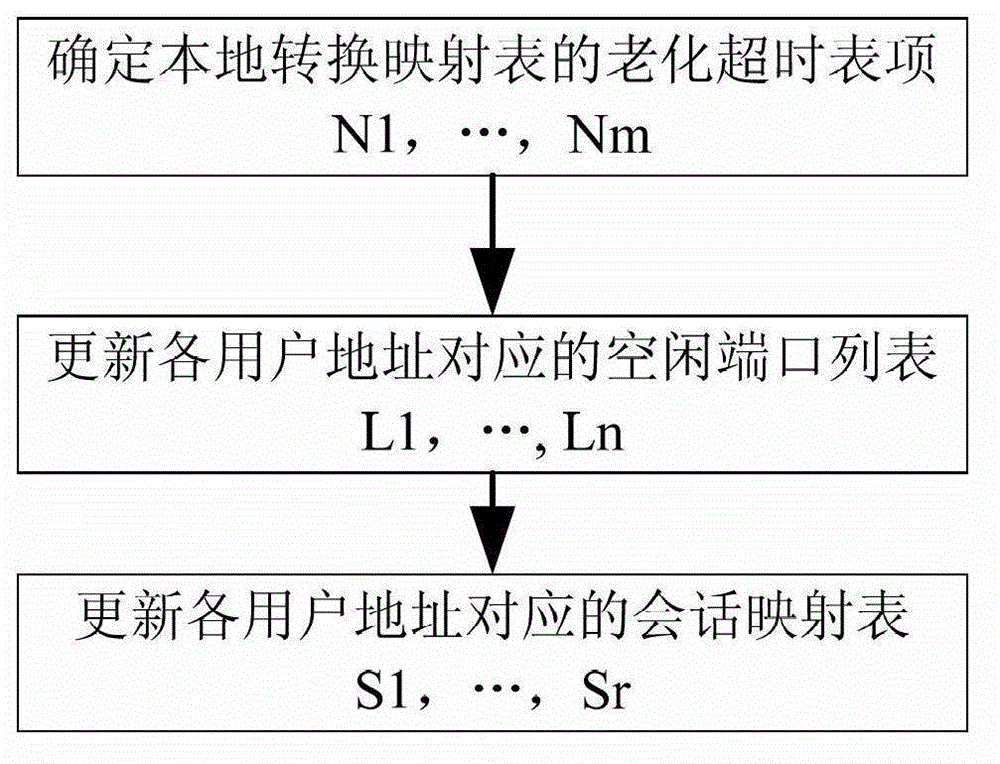
The invention discloses a method for releasing a port of carrier-grade network address translation equipment. According to the method, a carrier-grade network address translation device is involved; the carrier-grade network address translation device comprises a network address translation module, a port release module, a user address mapping table, a local translation mapping table, an idle port list and a local session mapping table; the carrier-grade network address translation device releases the port according to the occupation situation of the port accessed by a user; and the carrier-grade network address translation device executes the following steps on an arrived message: (a) inquiring the local translation mapping table; (b) inquiring the user address mapping table; (c) releasing the port; and (d) processing the local session mapping table.
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
Improved reinforced immune algorithm-based agricultural internet-of-things resource allocation method
ActiveCN107730393AMeet deployment needsThere are many deployment objectsLogisticsGenetic algorithmsLocal optimumSelf adaptivity
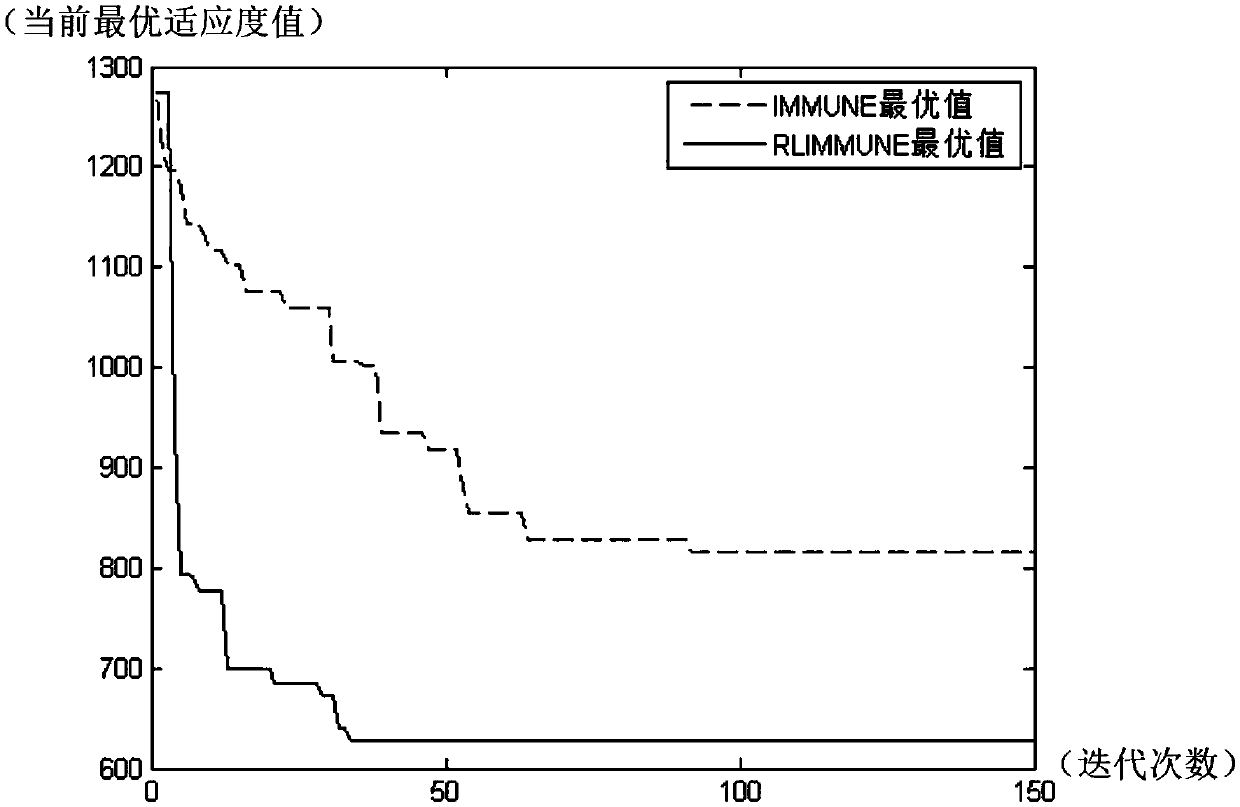
The invention relates to an improved reinforced immune algorithm-based agricultural internet-of-things resource allocation method. Related information of resource demand points and supply points in agriculture is obtained by adopting an internet-of-things technology, and the supply points perform efficient resource allocation on the demand points through allocation vehicles by utilizing an improved reinforced immune algorithm; and the improved reinforced immune algorithm is an algorithm obtained after an immune algorithm is improved by utilizing a reinforcement learning thought, the improvement refers to the initialization of a Q table according to the distances between the resource supply points and demand points where the vehicles are located, the Q table is updated according to an antibody with a minimum fitness value currently in each iteration, mutation of the antibody is guided by using the current Q table in a mutation stage, and meanwhile, when the Q table is continuously updated in the same position, the Q table is adjusted to escape from local optimum. The method has the characteristics of strong learning capability, high self-adaptivity, numerous allocation objects and high response speed.
Owner:DONGHUA UNIV
Application framework deployment method, apparatus and system, and cloud platform
InactiveCN108196764AReduce the difficulty of deploymentReduce the difficulty of operation and maintenanceSoftware deploymentInput/output processes for data processingTerminal equipmentOperating system
Embodiments of the invention provide an application framework deployment method, apparatus and system, and a cloud platform. The method comprises the steps of receiving a framework configuration filegenerated according to application components in an initial application framework and sent by a terminal device; analyzing the framework configuration file to obtain a relationship among the application components; and according to the relationship among the application components, packaging the application components in the framework configuration file to generate an application framework file comprising multiple configuration interfaces. Therefore, the application framework deployment and maintenance difficulty can be effectively lowered; and the application framework deployment demands in different business scenes can be met.
Owner:CHINAUMS
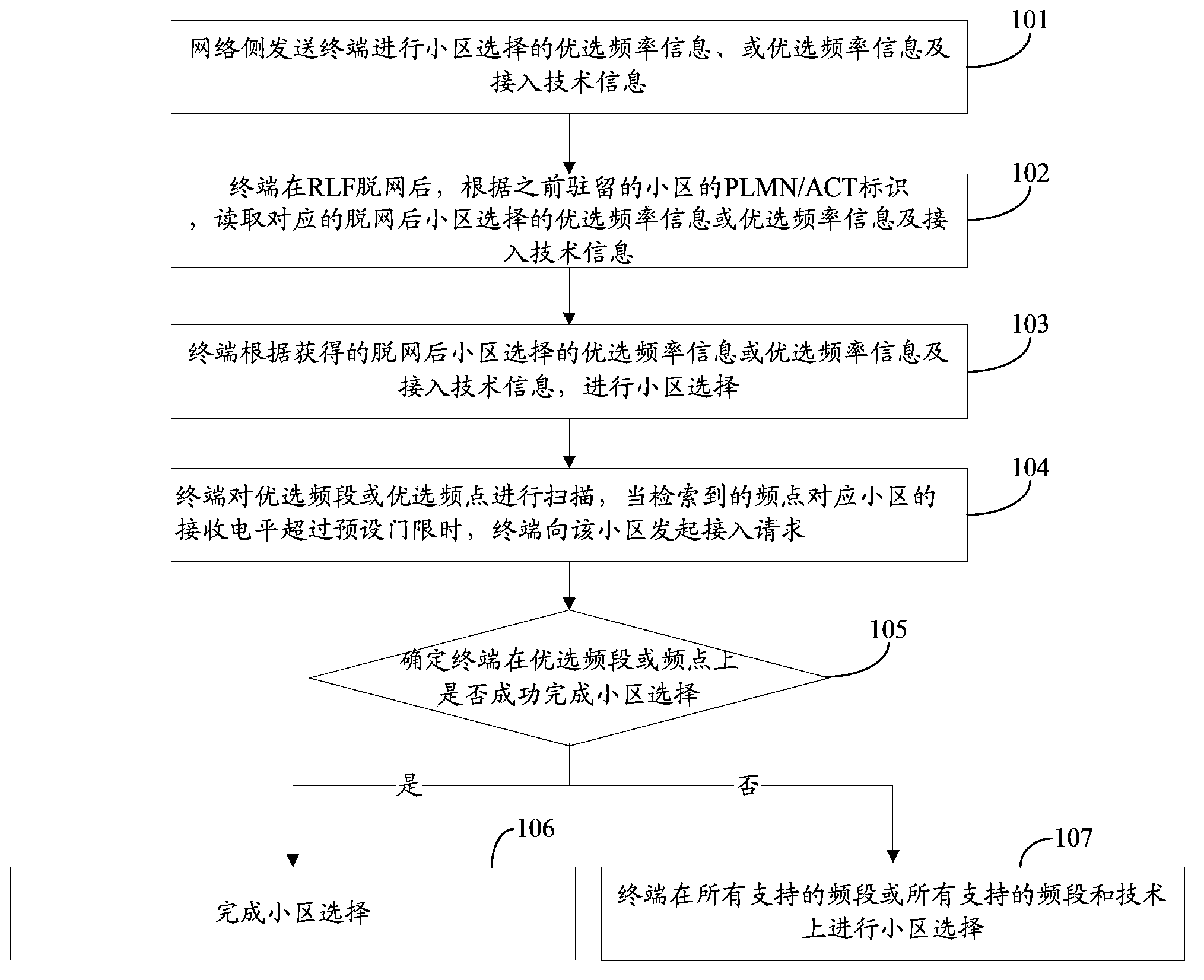
Method and device for cell selection information sending and configuration and cell selection method
ActiveCN103582084AReduce latencyMeet deployment needsAssess restrictionConnection managementTime delaysCell selection
The invention discloses a method for cell selection information sending. The method includes the steps that a network side sending terminal obtains preferred frequency information or preferred frequency information and access technology information for cell selection. The invention further discloses a configuration method of the cell selection information, wherein the method includes the step of directly configuring the preferred frequency information or the preferred frequency information and the ACT information in the sending terminal for cell selection. The invention also discloses a device for achieving the preceding methods and a cell selection method. The preferred frequency information or the preferred frequency information and the access technology information which can be accessed after the terminal is off line are configured in the terminal or sent to the terminal through a network side. Therefore, after the terminal is off line, cell searching can be carried out according the configured preferred frequency information of the terminal, once a cell corresponding to preferred frequency is searched, access can be achieved, and time delay is greatly reduced when the cell is accessed again.
Owner:CHINA MOBILE COMM GRP CO LTD
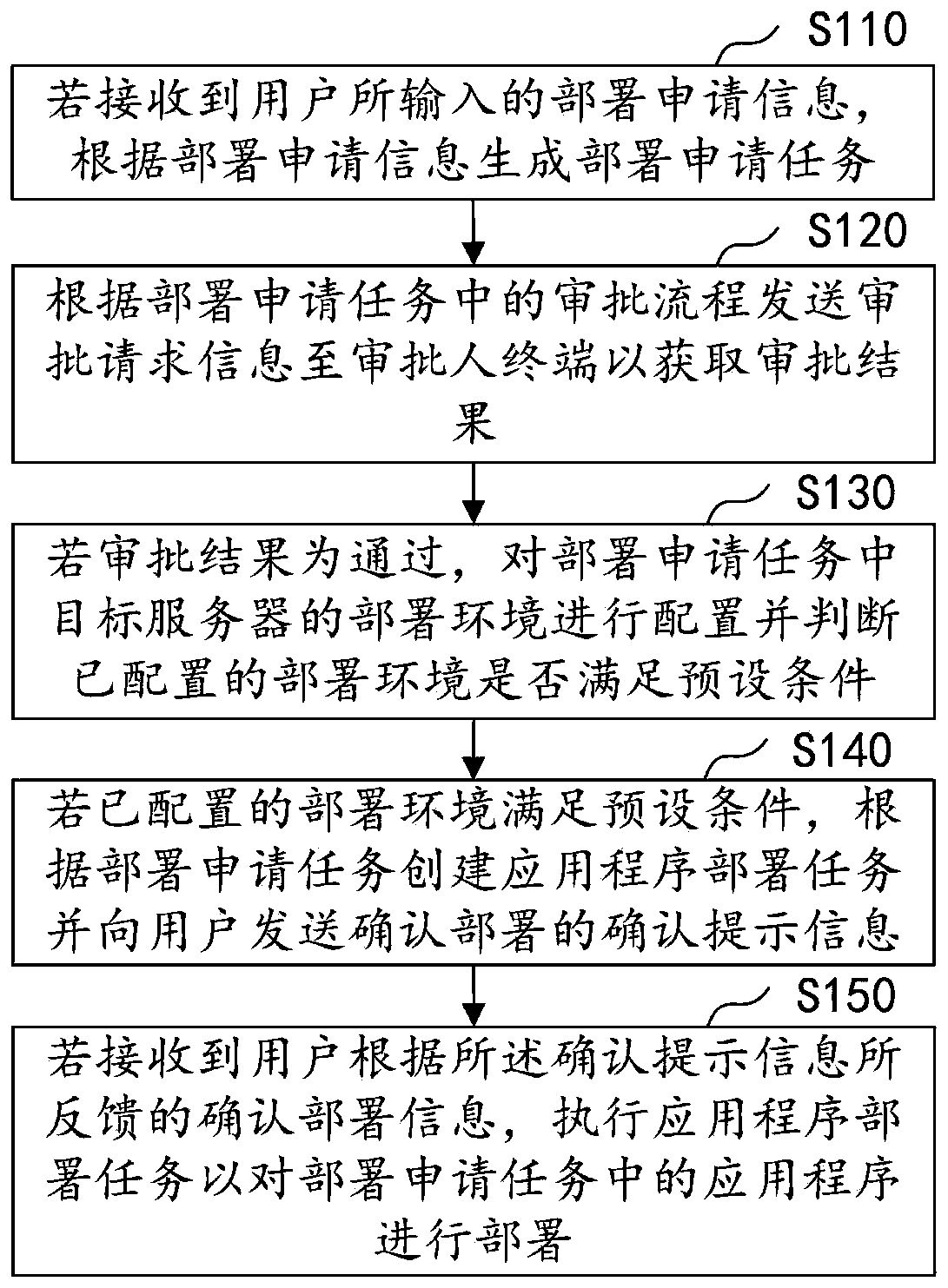
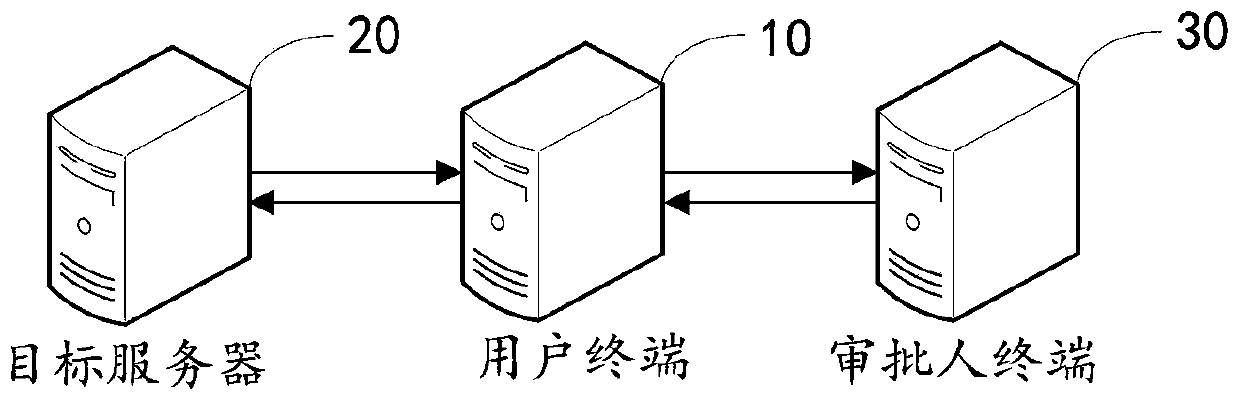
Application deployment method and device, computer equipment and storage medium
PendingCN109901842AImprove applicabilityFlexible configurationSoftware maintainance/managementSoftware deploymentProcess optimizationSoftware engineering
The invention discloses an application deployment method and device, computer equipment and a storage medium. The method comprises: if deployment application information input by a user is received, generating a deployment application task according to the deployment application information; According to an approval process in the deployment application task, sending approval request information to an approver terminal to obtain an approval result; If the approval result is passed, configuring a deployment environment of a target server in the deployment application task and judging whether the configured deployment environment meets a preset condition or not; If the configured deployment environment satisfies a preset condition, creating an application deployment task according to the deployment application task and sending confirmation prompt information for confirming deployment to the user; And if deployment confirmation information fed back by the user according to the confirmation prompt information is received, executing an application deployment task to deploy the application. Based on the publishing process optimization technology, the deployment application task can be flexibly configured to meet various deployment requirements.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Asymmetric cryptographic terminal based on quantum random number, communication system and method
InactiveCN110611572AImprove securityTo achieve the effect of security encryptionKey distribution for secure communicationUser identity/authority verificationNon symmetricCommunications system
The invention discloses an asymmetric cryptographic terminal based on a quantum random number, a communication system comprising a plurality of asymmetric cryptographic terminals, and a secret communication method for performing secret communication by using the asymmetric cryptographic terminals. The cryptographic terminal comprises a quantum random number generator and a key generator, wherein the quantum random number generator is used for generating and outputting two quantum random numbers; the key generator is used for firstly segmenting and truncating the two quantum random numbers intotwo groups of random number sequences with the same length, and then converting the two groups of random number sequences into a group of private keys and a group of public keys which are paired witheach other by using a private key algorithm and a public key algorithm respectively; and the asymmetric cryptographic terminal performs encryption, decryption, signature and signature verification according to the private key and the public key which are paired with each other. The password terminal is simple in algorithm and high in secret key updating frequency, and digital signature service and data encryption and decryption service can be provided at the same time in the communication process.
Owner:HENGTONG QASKY QUANTUM INFORMATION RES INST CO LTD
Resource scheduling system, method, and storage medium under space-based cloud calculation architecture
ActiveCN110753107AMeet deployment needsRealize unified schedulingResource allocationTransmissionDynamical networkResource scheduling
The invention provides a resource scheduling system, a method and a readable storage medium under a space-based cloud calculation architecture. The scheduling system comprises a scheduler, a network topology database, a hardware information database and an affinity rule database. A scheduling object of the scheduling system is a space-based service deployed in the form of a container. The action nodes of the scheduling system comprise space-based edge clouds and heterogeneous resource nodes in a fog satellite cluster. Three deployment schemes are designed for the physical position of the scheduling system, and one of the three deployment schemes is selected. According to the invention, unified scheduling of space-based cloud heterogeneous resources and fog heterogeneous resources can be realized. The historical scheduling data can be utilized by the scheduling, and the scheduling method has adaptability to a dynamic network and can meet deployment requirements of various space-based applications.
Owner:TECH & ENG CENT FOR SPACE UTILIZATION CHINESE ACAD OF SCI
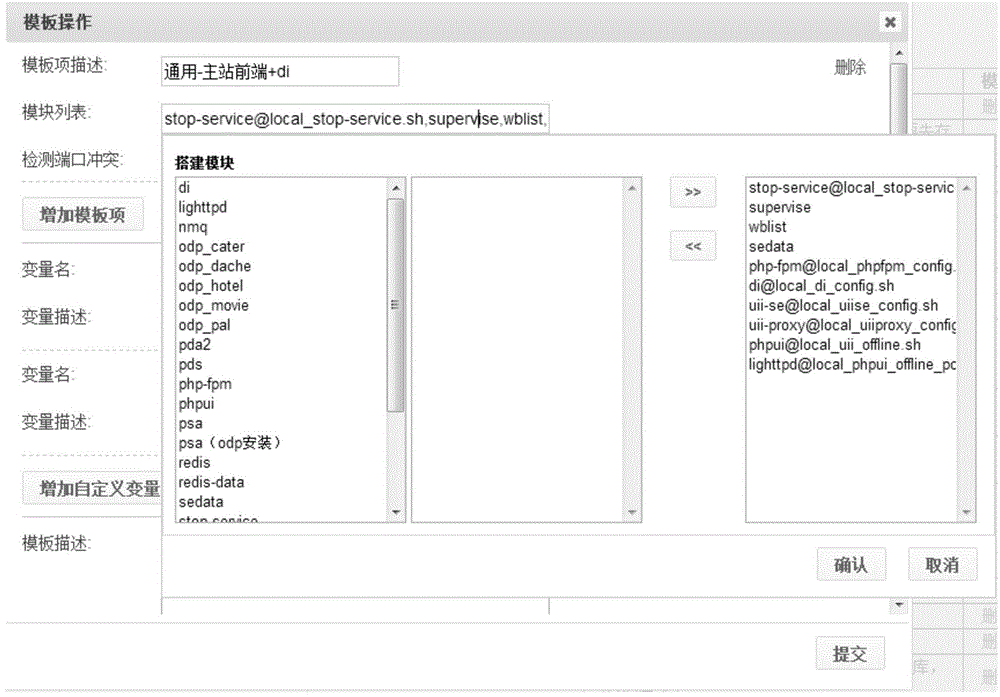
Environment deployment method and device
ActiveCN104090799AImprove reusabilityLess modification and reconfigurationProgram loading/initiatingSoftware engineeringHost machine
The embodiment of the invention provides an environment deployment method. The environment deployment method includes the steps that according to an environment template and click positions on the environment template, a module to be deployed in application, central control machine information of the module to be deployed and behavior commands of the module to be deployed are obtained; input destination host information is obtained; according to the module to be deployed, the central control machine information of the module to be deployed, the behavior commands of the module to be deployed and the destination host information, environment information in the application is obtained and used for achieving environment deployment of the application. The embodiment of the invention further provides an environment deployment device. According to the technical scheme, the efficiency of environment deployment can be improved, and cost of environment deployment can be lowered.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Design method enabling main board to be resistant to corrosion at high temperature
InactiveCN104199513AMeet deployment needsReduce PUE indexDigital data processing detailsFresh airLayout
The invention provides a design method enabling a main board to be resistant to corrosion at high temperature, and belongs to the field of server main boards. The design method mainly comprises the steps of (1) layout of a PCBA, (2) design of a machine case structure, (3) selection of materials of a PCB and materials used in elements, and (4) spraying of tri-proof paint and corrosion-resistance testing. By modifying the layout of a system, introducing NP-175FM / NPGN-170 materials and optimizing the materials of the elements, the main board can be used in a fresh air refrigerating station, the PUE index is effectively lowered, stable operation at 40 DEG C is realized, performance can be kept at 45 DEG C, and the MTBF time can reach five years. Signals keep stable at high temperature, and insertionLOSS and impedance are effectively controlled.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Latex paint coating material color matching device
InactiveCN110721628ASimple structureWide range of adaptationTransportation and packagingMixer accessoriesDrive motorEngineering
The invention discloses a latex paint coating material color matching device, and belongs to the field of color matching. In the prior art, the latex paint color matching device cannot conduct color recognition and movement. A purpose of the invention is to solve the problems in the prior art. According to the latex paint coating material color matching device, four driving motors are used for driving four material storage cylinders; a single chip microcomputer is used for carrying out driving control on a stirring motor; the stirring motor is used for carrying out driving control on a stirring cylinder; the single chip microcomputer is further used for sending a recognition command to a color control recognizer; a color recognizer is used for recognizing the color of the to-be-sprayed area of a wall surface according to the received recognition command and sending a recognition result to the single chip microcomputer; and the single chip microcomputer outputs four matching commands according to the color data of the non-spraying area of the wall surface and the recognition result of the color recognizer, and the four matching commands are used for controlling the four driving motors respectively, so that the material storage cylinders corresponding to the four driving motors quantitatively output latex paint coating materials with corresponding colors into the one stirring cylinder. The latex paint coating material color matching device of the invention is mainly used for household spraying.
Owner:HARBIN INST OF TECH
Automatic deployment method and system for large-scale test bed nodes
InactiveCN111786810AImprove formation efficiencyReduce sizeData switching networksNetwork testingHostname
The invention discloses an automatic deployment method and system for large-scale test bed nodes. The method comprises the following steps: 1) setting a terminal deployment process on a deployment machine; (2) by the terminal deployment process, splitting the hard disk mirror image reduction / cloning task based on the Clonezilla into independent sub-tasks taking a host as a unit, and sending the independent sub-tasks to a Clonezilla sub-process; splitting a customized network batch deployment task based on Cobbler into independent sub-tasks taking a host as a unit, and sending the independent sub-tasks to a Cobbler sub-process; 3) by the two sub-processes, generating a configuration file for each node to be deployed according to the distributed independent sub-tasks; 4) acquiring the configuration file from the deployment machine by the node to be deployed, restoring or installing the automatic system, and then modifying the name of the host, adding a new user and modifying the scene network information according to the configuration file, and 5) constructing an independent network by each deployed node according to the structure topological graph of a target network test bed scene.
Owner:INST OF INFORMATION ENG CAS
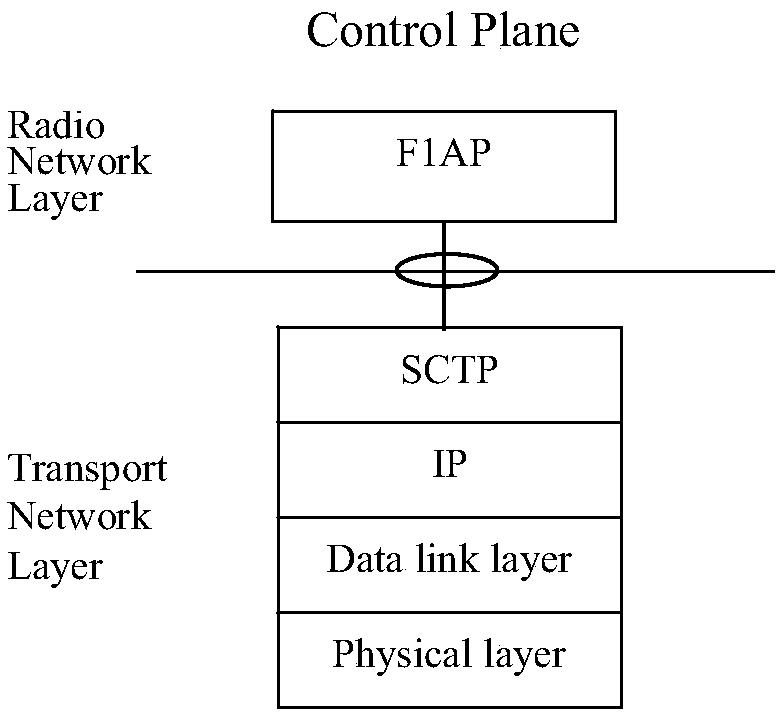
Connection processing method and equipment
ActiveCN109688631AMeet deployment needsConnection managementTransmissionVirtualizationBusiness requirements
The embodiment of the invention provides a connection processing method and equipment. The method includes the following steps: determining one or more TNL addresses of a CU; and establishing a plurality of TNL connections between a DU and the CU according to the one or more TNL addresses. Since the plurality of TNL connections are established between the CU and the DU, the deployment requirementsof the 5G CU in a cloud platform virtualization environment in the future can be met, and users can select CU equipment with different TNL addresses according to business requirements.
Owner:CHINA MOBILE COMM LTD RES INST +1
Resource allocation scheme generation method and device, equipment and storage medium
PendingCN113919699AFast shippingReasonable transportationResourcesLogisticsManagement unitKnowledge graph
The invention relates to the field of artificial intelligence, and provides a resource allocation scheme generation method and device, equipment and a storage medium, and the method comprises the steps: obtaining a first position of a to-be-allocated point, and obtaining a first knowledge graph corresponding to the to-be-allocated point according to the first position; obtaining an allocation demand, and determining whether a first management unit corresponding to the allocation demand meets the allocation demand in the first knowledge graph, wherein the allocation demand comprises one or more allocation resources; if not, obtaining a superior knowledge graph of the first knowledge graph until the obtained superior knowledge graph meets the deployment requirement; determining the transportation time of each allocation resource in the allocation demand from the corresponding management unit to the first position based on the superior knowledge graph; and determining a deployment scheme of the deployment demand according to the transportation time. Through the method provided by the invention, the allocation scheme can be quickly generated for resource transportation.
Owner:PINGAN INT SMART CITY TECH CO LTD
Wireless metropolitan area network (MAN) safe access method
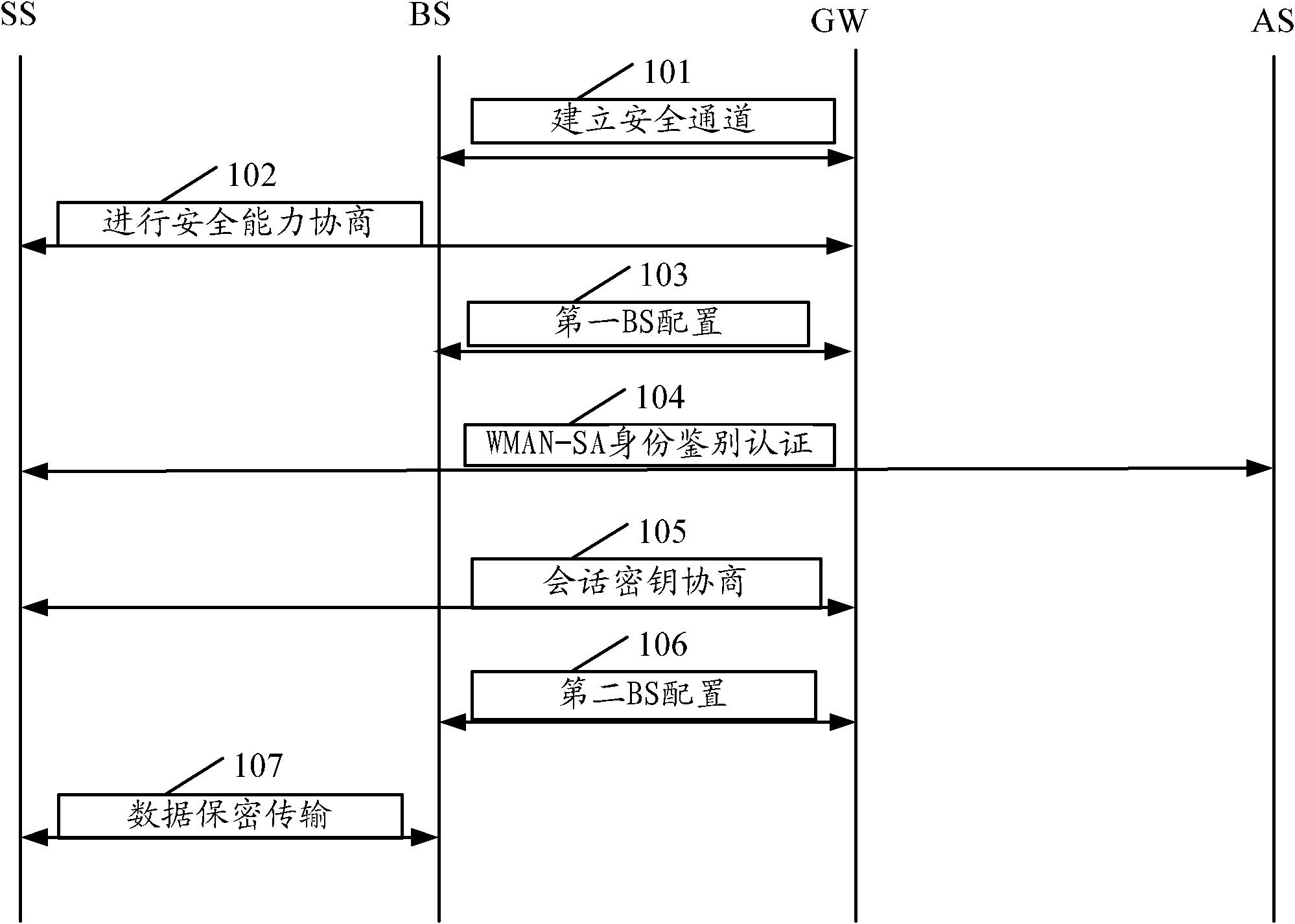
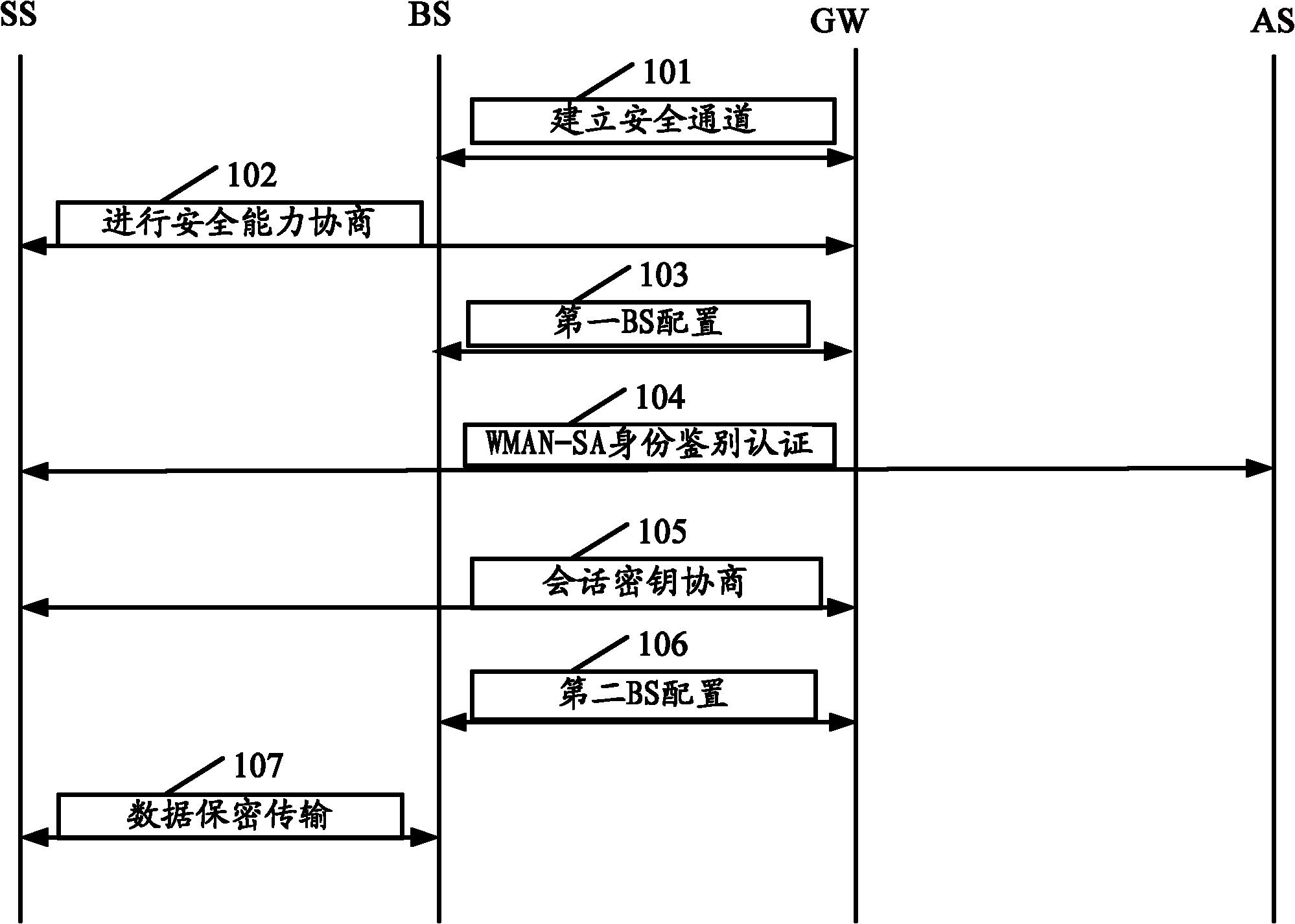
InactiveCN102006587AMeet deployment needsNetwork traffic/resource managementSecurity arrangementAccess methodWireless metropolitan area network
The invention discloses a wireless metropolitan area network (MAN) safe access method, comprising the steps of: completing security capability negotiation between a GW (Gateway) and an SS (Subscriber Station); performing first configuration on a BS (Base Station) by the GW, and closing a controlled port corresponding to the SS by the BS; completing an identity authentication based on WMAN-SA (Wireless Metropolitan Area Network-Security Access) by the GW, the SS and an AS (Authentication Server); negotiating to obtain a session key TEK (Traffic Encryption Key) by the GW and the SS; performing second configuration on the BS by the GW, and opening the controlled port corresponding to the SS by the BS; and encrypting and deciphering business data by using the TEK by the GW. In the invention, the access GW is used for controlling and managing the WMAN-SA of the BS, which can meet the requirement on large-scale deployment of the WMAN-SA.
Owner:GCI SCI & TECH
Workpiece fixing platform for machining
InactiveCN107253065AAchieving universal fixationAvoid the trouble of separately equipped with a dedicated fixed platformLarge fixed membersProduction lineThrust bearing
The invention discloses a workpiece fixing platform for mechanical processing, which comprises a support seat, at least four support rods are arranged at the lower end of the support seat, and an adjustment seat is installed on the lower end of the support rod through the fixing seat, and the lower end of the support seat A lifting device is provided, and the upper end of the lifting device is equipped with a support platform through a thrust bearing, and a ring gear is installed between the support platform and the support seat, which can meet various processing and positioning requirements of various workpieces, and realize the positioning of the workpiece. Universal fixation, and multiple devices of this type can be used to coordinately fix the same workpiece to achieve stable fixation of large-volume plates and rods, thereby avoiding the trouble of separately equipped with a dedicated fixing platform for each large-volume workpiece, and the device’s The location can be freely configured, so that it can be used in conjunction with different processing machines, which meets the deployment needs of different production lines and has high practical value.
Owner:蒋娟丽
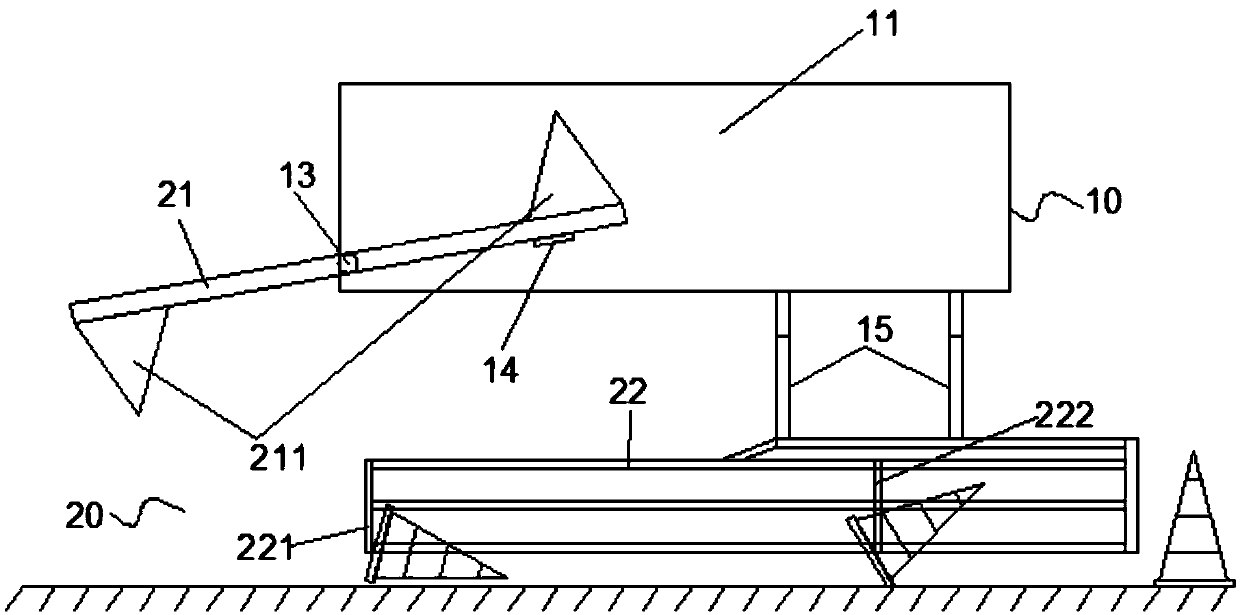
Vehicle-mounted traffic cone automatic laying device
InactiveCN111119092ASimple structureEasy to operateTraffic signalsRoad signsStructural engineeringRoad surface
The invention relates to a vehicle-mounted traffic cone automatic laying device. By ingeniously arranging a turnover plate, a preparation position elastic piece and a guide frame, after the traffic cone is located on the conical protrusion on the turnover plate, the turnover plate breaks through the limitation of the preparation position elastic piece due to the gravity effect of the traffic coneto rotate, and the traffic cone is transversely arranged on the road surface after the separation limiting effect of the guide frame; along with the continuous advancing of the vehicle, the supportinglimit of the guide frame reaches the position of the traffic cone and acts on the base of the traffic cone to erect the traffic cone. The device is simple in structure and convenient to operate; meanwhile, the vehicle-mounted traffic cone automatic laying device can directly utilize an old engineering vehicle and carry out equipment installation on the old engineering vehicle, equipment construction of related units does not need to be occupied, and the vehicle-mounted traffic cone automatic laying device is easier to popularize.
Owner:江门市新会区智华科技服务有限公司
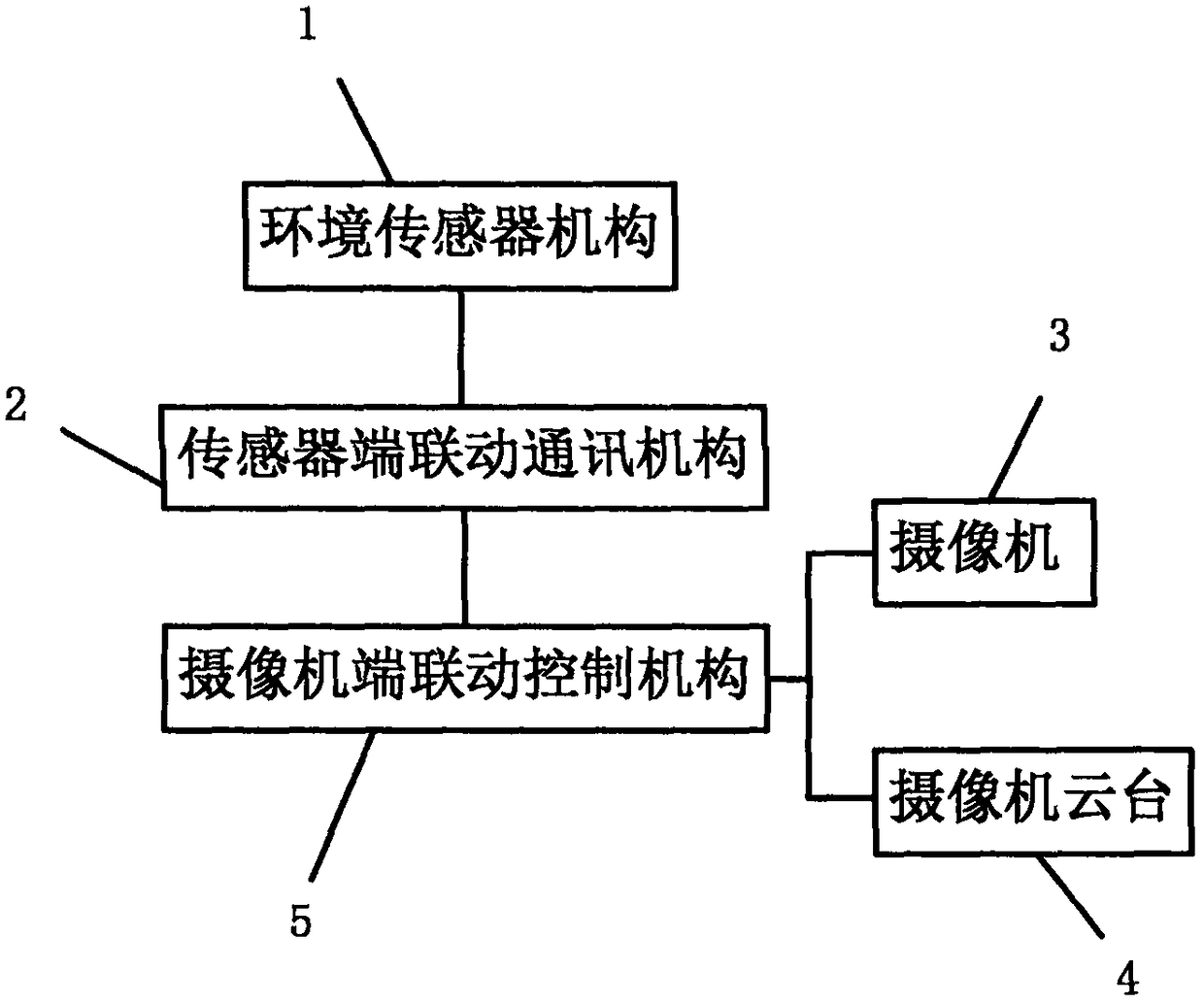
Linkage camera expansion device and method of controlling the same
InactiveCN108270957ARealize linkageComply with different environmental requirementsTelevision system detailsColor television detailsAlarm signalVideo camera
A ganged camera expansion device includes an environmental sensor mechanism for sensing an environmental condition and outputting an alarm signal for detection data that exceeds a threshold; a sensorend linkage communication mechanism for requesting motion information from the linkage camera, ie, requesting the camera to steer to the sensor control position for operation or the camera to resume shipping status; a camera for capturing video or images; a camera cloud stage for controlling the direction taken by the camera; the camera end linkage control mechanism controls the camera to take a corresponding capture action based on the request at the sensor end. A control method of the above-described linkage camera expansion device is also disclosed. The present invention is able to improvethe deficiencies of the prior art, and may enable proactive tracking and picture taking of environmental anomalies, enabling intelligent monitoring.
Owner:BEIJING HITARGET TECH CO LTD
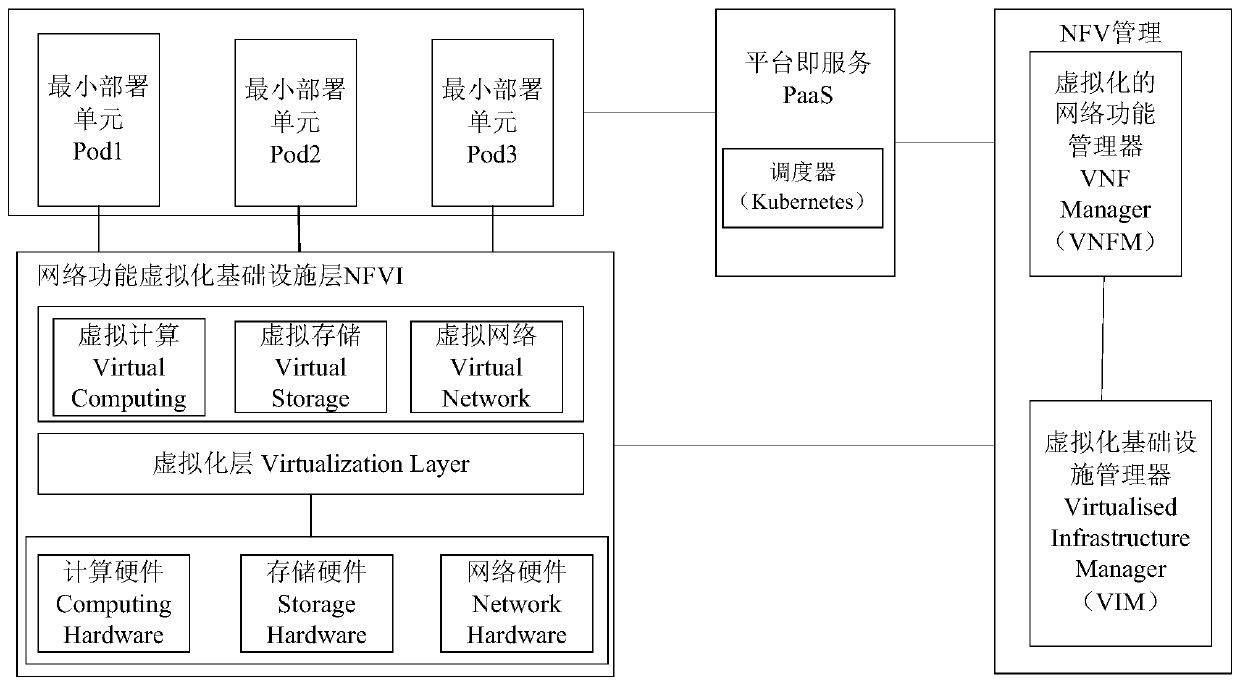
Scheduling management method and device for network function virtualization (NFV) architecture
ActiveCN111526168AMeet scheduling needsMeet deployment needsTransmissionSoftware simulation/interpretation/emulationVirtualizationDistributed computing
The embodiment of the invention discloses a scheduling management method and device for a network function virtualization (NFV) architecture. According to the method, scheduling management equipment sets corresponding VM tags for VMs according to HOST to which the VMs belong, division of the VMs can be achieved through the VM tags of the VMs, and under the condition, the VMs located in the same HOST are of the same type; then, the scheduling management equipment determines that the first VM is migrated from the first HOST to the second HOST; and the VM label of the first VM is updated to the second HOST, a scheduler is triggerred in the NFV architecture; the scheduler determines whether a first Pod in a first VM meets a deployment demand or not; if not, the scheduler schedules the first Pod to the second VM of the first HOST, so that after the first VM migrates, the first Pod is still deployed in the first HOST, the deployment requirement of the first Pod is met, and the scheduling requirement of the Pod in the HOST is met.
Owner:HUAWEI TECH CO LTD
An Efficient Multithreaded Log Writing Method
InactiveCN103885726BNo noticeable loss of performanceNoticeable loss of performanceInput/output to record carriersHardware monitoringComputer scienceLog data
Owner:EASTLAND DIGITAL CORP
Electric vehicle charging demand prediction method and device
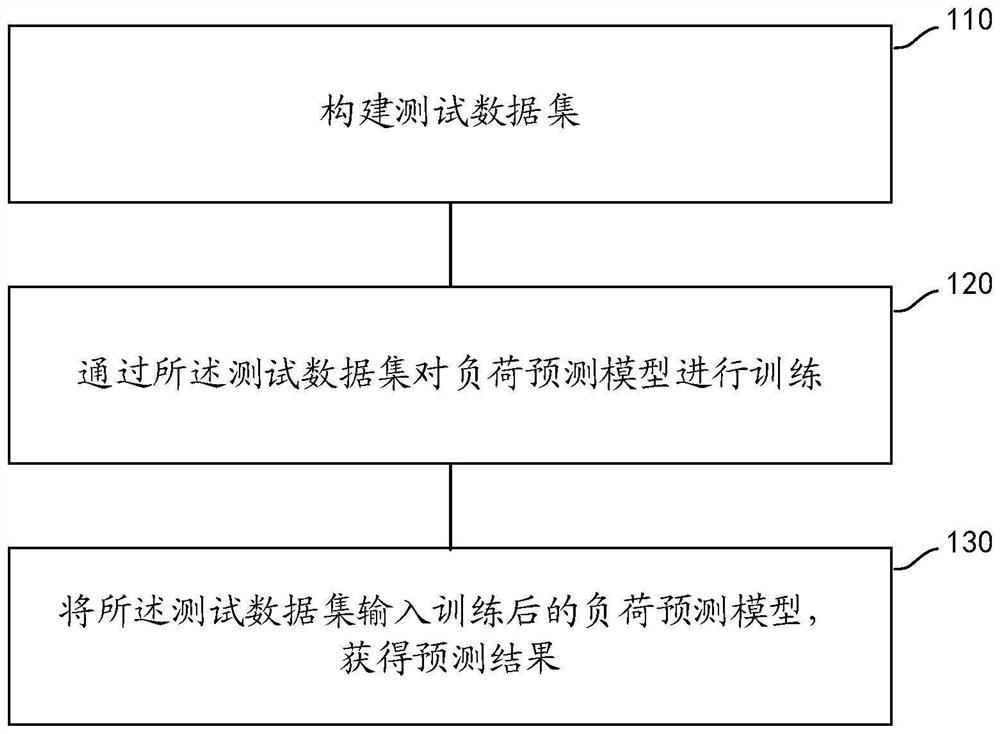
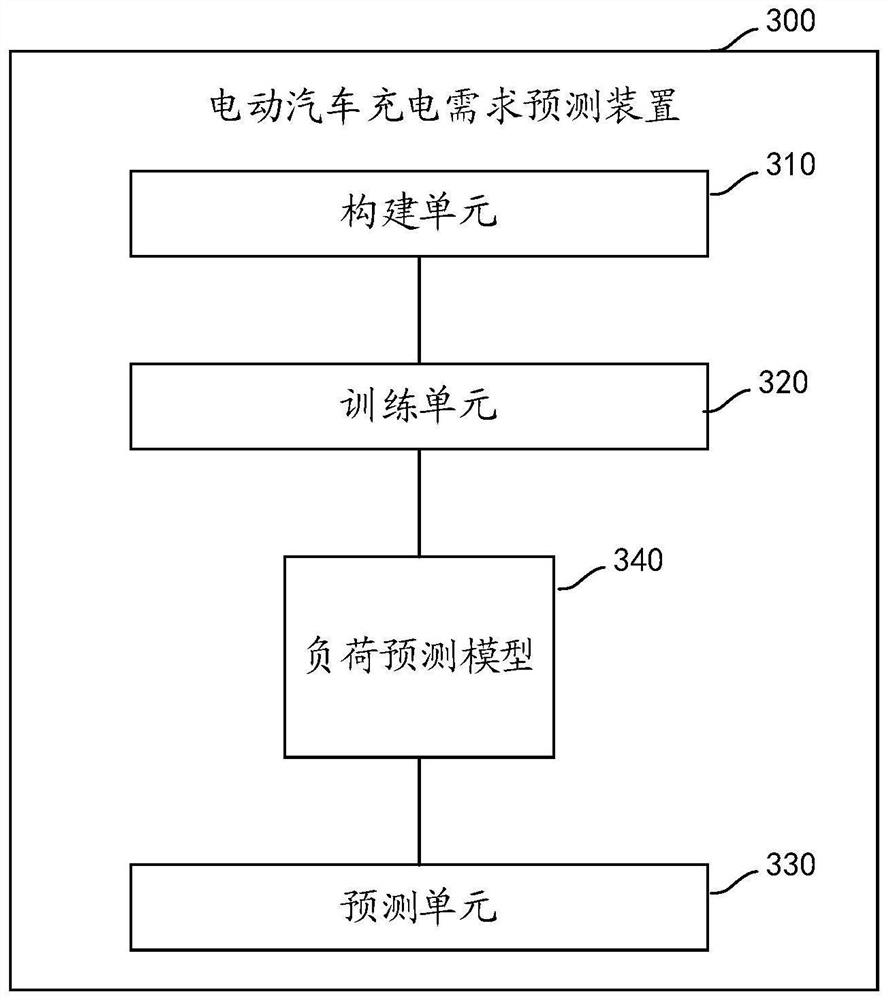
PendingCN114331542AImprove operational efficiencyWith intelligent upgrade spaceNeural architecturesMarketingData setSimulation
The embodiment of the invention provides an electric vehicle charging demand prediction method and device which are applied to an electric vehicle charging demand prediction server. The method comprises the following steps: constructing a test data set; training a load prediction model through the test data set; and inputting the test data set into the trained load prediction model to obtain a prediction result. According to the deep neural network electric vehicle charging demand prediction method based on improved probability sparse self-attention and comparative learning, the problems that the long-term demand prediction error is large and extra information correction is needed can be solved; the method can meet the deployment requirements of mobile terminal use, edge equipment operation, remote area local area network, network security limitation and other scenes, especially can be deployed in a charging station energy storage system or even in a charging pile to independently operate, provides a more accurate prediction result and a more flexible deployment mode, and enables an existing charging station to have an intelligent upgrading space.
Owner:智光研究院(广州)有限公司
Security access method for wireless metropolitan area network
InactiveCN102036237ARealize centralized controlRealize managementSecurity arrangementAccess methodWireless metropolitan area network
The invention discloses a security access method for a wireless metropolitan area network. The method comprises the following steps of: establishing a security channel between a base station (BS) and a gateway (GW) and negotiating to acquire a channel encryption key (CEK) and a channel integrity key (CIK); performing security capability negotiation by using the GW and a subscriber station (SS); performing first configuration on BS by using the GW and closing a controlled port corresponding to the SS by using the BS; finishing a wireless metropolitan area network-security access (WMAN-SA)-based identity authentication protocol by using the GW, the SS and an authentication server (AS); negotiating a traffic encryption key (TEK) by using the GW and the SS; performing second configuration on the BS by using the GW, transmitting TEK to the BS through a second BS configuration request message, and opening the controlled port corresponding to the SS by using the BS; and encrypting and decrypting service data by using the BS through the TEK. In the method, WMAN-SA of the BS is controlled and managed by using an access gateway (GW), so large-scale allocation requirement of the WMAN-SA can be met.
Owner:GCI SCI & TECH
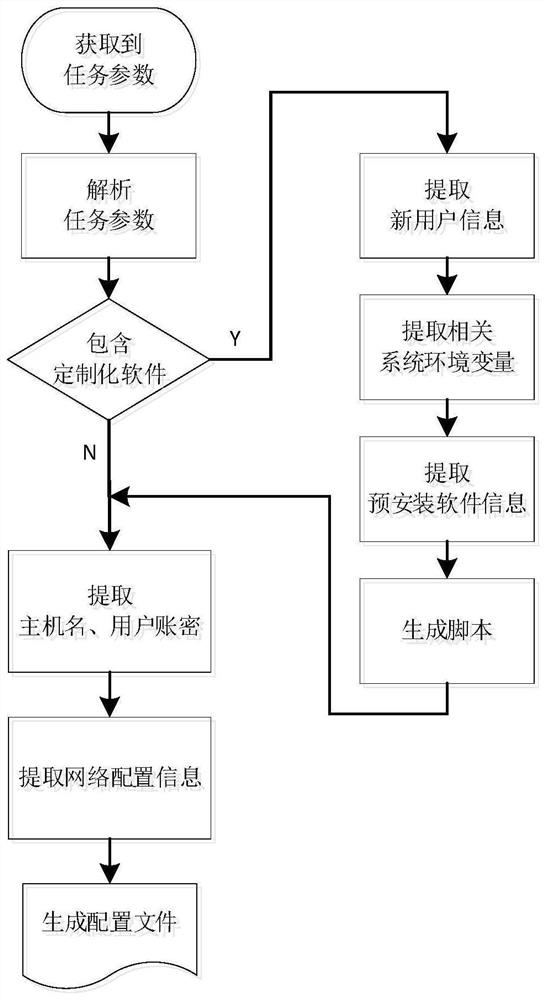
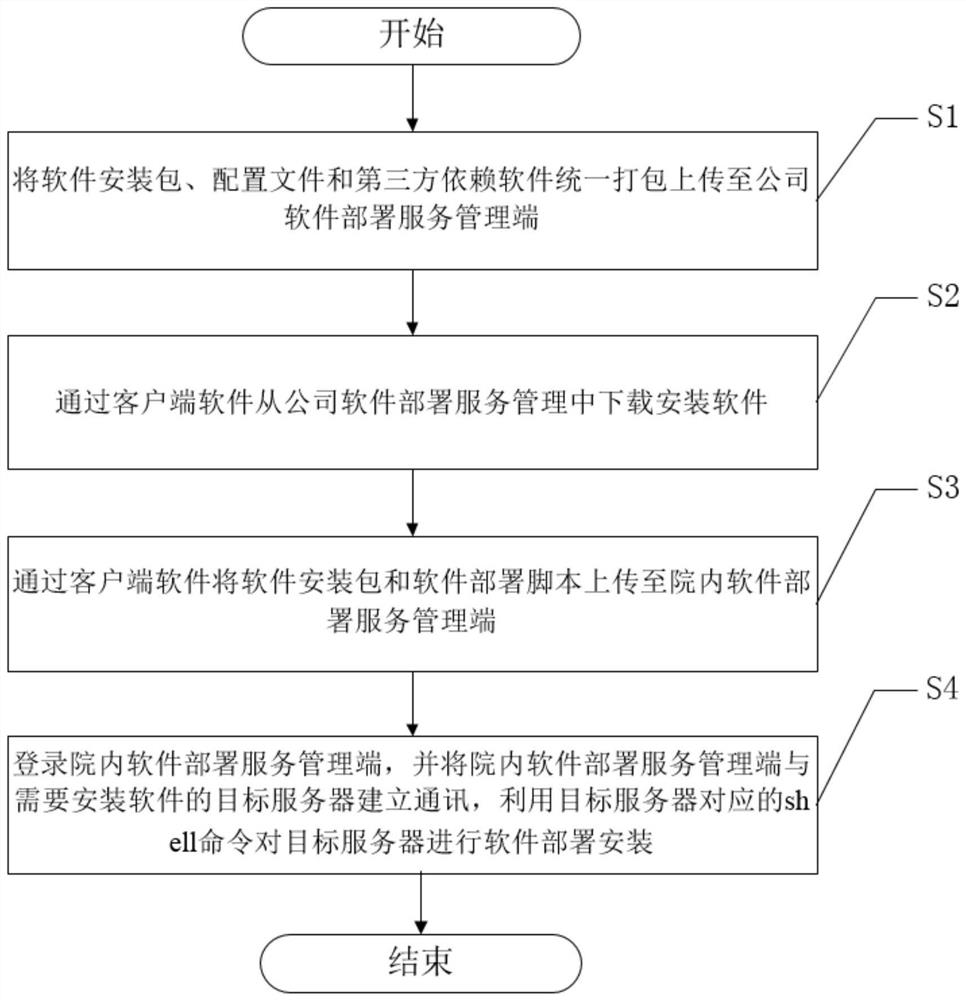
Hospital software automatic deployment method based on data elements
ActiveCN114816452AImprove the efficiency of deployment operation and maintenanceSolve the problem of offline installation and deploymentVersion controlMedical equipmentThird partyHospital network
The invention discloses a hospital software automatic deployment method based on data elements, which belongs to the technical field of software deployment, and comprises the following steps: S1, uniformly packaging and uploading a software installation package, a configuration file and third-party dependent software to a company software deployment service management end; s2, downloading installation software from company software deployment service management; s3, uploading the software installation package and the software deployment script to an in-hospital software deployment service management end through client software; and S4, logging in the in-hospital software deployment service management terminal, establishing communication between the in-hospital software deployment service management terminal and a target server needing software installation, and performing software deployment and installation on the target server by using a shell command corresponding to the target server. In a hospital network environment, compared with the prior art, the method has the advantages that the deployment operation and maintenance efficiency of field implementation personnel can be improved, and the problem of offline installation and deployment of Linux software is effectively solved.
Owner:成都瑞华康源科技有限公司 +1
Well pattern reconstruction method and device for water injection development old oilfield
The invention discloses a well pattern rebuilding method and device for the water-injection development of an old oil field. The method comprises the steps that various factors for influencing well pattern arrangement are taken into account, and mesh parameter data in geologic modeling and numerical reservoir simulation computed results are stacked and computed to obtain parameter distribution of series of strata; the mesh comprehensive evaluation index of the series of strata is computed, and a comprehensive evaluation index distribution diagram of the series of strata is obtained; well patterns are arranged on the comprehensive evaluation index distribution diagram of the series of strata according to different well pattern types, well positions are adjusted according to the characteristics of the comprehensive evaluation index distribution diagram, and initial well pattern arrangement schemes are obtained; for each initial well pattern arrangement scheme, old wells are searched for around the signal wells, and whether the oil wells are utilized is determined according to well conditions and an injection-production relationship; each well pattern arrangement scheme formed finally is evaluated, and the relatively-optimal well pattern arrangement scheme is selected according to the well pattern control degree and a recovery efficiency index. The well pattern rebuilding method and device for the water-injection development of the old oil field can meet the well pattern arrangement requirements of old oil fields in the secondary development process.
Owner:PETROCHINA CO LTD
Method for modifying BIOS configuration options in ARM server based on CentOS in-band
PendingCN112506574AMeet deployment needsImplement automated query modificationBootstrappingNetwork bootingConfiguration item
The invention discloses a method for modifying BIOS configuration options in an ARM server based on CentOS in-band, and the method realizes query and modification of configuration items in a configuration file by utilizing an out-of-band command terminal configuration tool, a CentOS system of the ARM server, a BIOS configuration query tool and a BIOS configuration modification tool, realizes queryand modification of the network boot startup sequence by utilizing the startup sequence read-write tool, realizes automatic query and modification of the BIOS configuration items of the ARM server, facilitates large-scale use of firmware BIOS deployment servers, and meets the deployment requirements of large-scale deployment and automatic operation and maintenance of ARM server clusters. In addition, the invention further provides a device and equipment for modifying BIOS configuration options in the ARM server based on CentOS in-band, and a readable storage medium, and the technical effect of the device and equipment corresponds to the technical effect of the method.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Method for releasing port of carrier-grade network address translation equipment
ActiveCN102882992BMeet deployment needsImprove efficiencyTransmissionCarrier gradeNetwork address translation
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
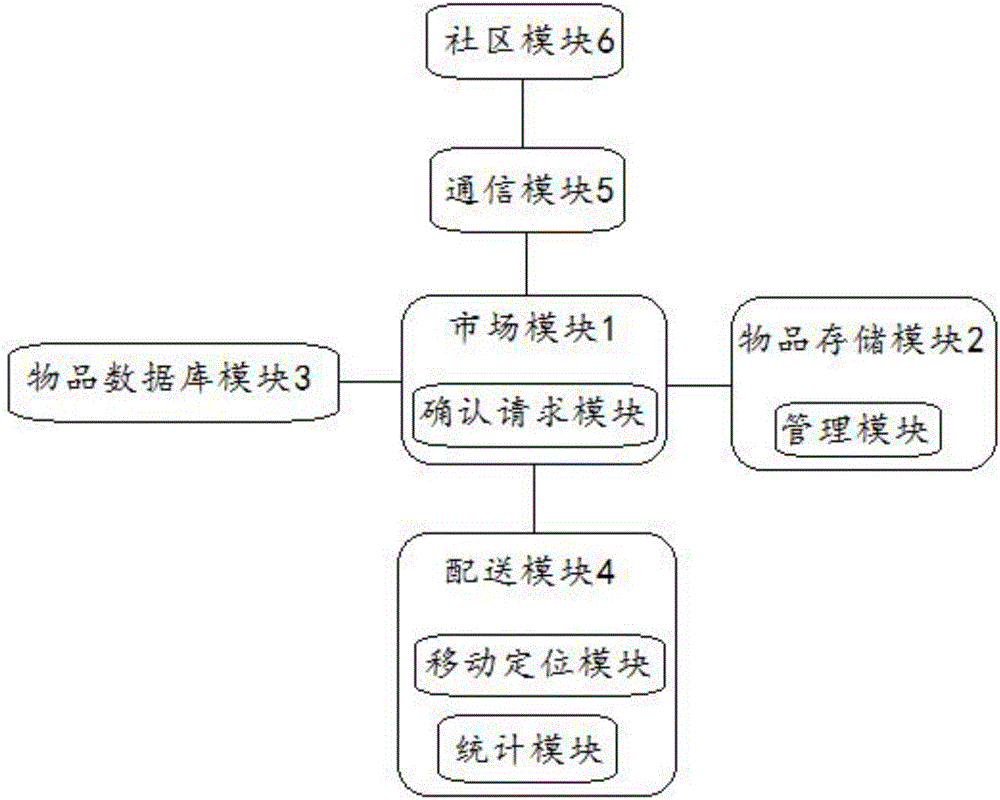
Integrated system for distributing goods on community life markets
InactiveCN106779521AMeet deployment needsMaster real-time operation statusLogisticsIntegrated systemsTransport engineering
The invention discloses an integrated system for distributing goods on community life markets. The system comprises a market module, a goods storage module, a goods database module, a distribution module and a community module, wherein the market module is used for sending goods required by a community life market and receiving a goods distribution request from the community module through a communication module; the market module is used for sending a goods distribution instruction to the goods storage module and the distribution module; the goods storage module is used for allotting distributed goods after receiving the distribution instruction; and the distribution module is used for distributing distribution vehicles adapted to the distributed goods after receiving the distribution instruction. According to the system disclosed by the invention, the market module, the goods storage module, the goods database module, the distribution module and the community module are matched in real time, so that the real-time operation conditions of goods transportation vehicles can be correctly grasped, and the goods requirements and goods transportation states of the community life markets can be correctly and timely grasped, thereby satisfying the deployment requirements of the community life markets.
Owner:安徽云匠信息科技有限公司
Wireless metropolitan area network (MAN) safe access method
InactiveCN102006587BMeet deployment needsNetwork traffic/resource managementSecurity arrangementAccess methodWireless metropolitan area network
The invention discloses a wireless metropolitan area network (MAN) safe access method, comprising the steps of: completing security capability negotiation between a GW (Gateway) and an SS (Subscriber Station); performing first configuration on a BS (Base Station) by the GW, and closing a controlled port corresponding to the SS by the BS; completing an identity authentication based on WMAN-SA (Wireless Metropolitan Area Network-Security Access) by the GW, the SS and an AS (Authentication Server); negotiating to obtain a session key TEK (Traffic Encryption Key) by the GW and the SS; performing second configuration on the BS by the GW, and opening the controlled port corresponding to the SS by the BS; and encrypting and deciphering business data by using the TEK by the GW. In the invention, the access GW is used for controlling and managing the WMAN-SA of the BS, which can meet the requirement on large-scale deployment of the WMAN-SA.
Owner:GCI SCI & TECH
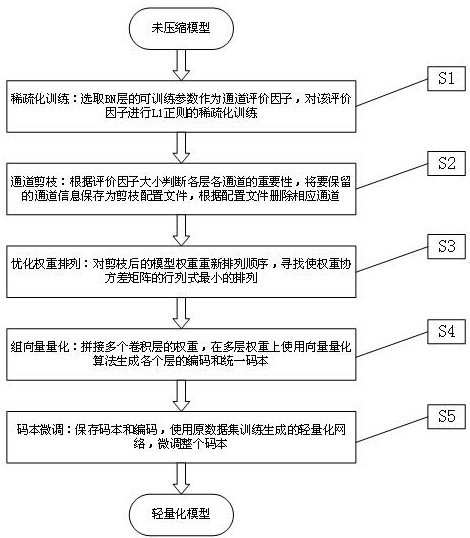
Depth model compression method for edge device multi-layer shared codebook vector quantization
PendingCN114781639AMeet deployment needsGuaranteed accuracyNeural architecturesNeural learning methodsTheoretical computer scienceNetwork model
The invention relates to a deep neural network model compression method, in particular to a depth model compression method for edge device multi-layer shared codebook vector quantization, which comprises five steps of sparse training, channel pruning, weight arrangement optimization, group vector quantization and codebook fine tuning. And sparse training: carrying out sparse training on each channel evaluation factor. And channel pruning: pruning the channels with low importance from the model. And weight arrangement optimization: carrying out weight optimization arrangement on the network model with a small size after channel pruning. And group vector quantization: implementing the pruned model to generate a lightweight network model. And codebook fine tuning: the lightweight model recovers the precision of the model. The method is used for compressing a network model with a large cloud size and a complex structure to obtain a lightweight model convenient for edge deployment, and the model deployment requirement under the condition that edge equipment computing power resources and storage resources are limited is met. Requirements of the model on storage space and computing power are effectively reduced, and the utilization rate of computing power resources and storage resources of edge devices is maximized.
Owner:SHENYANG INSTITUTE OF CHEMICAL TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com