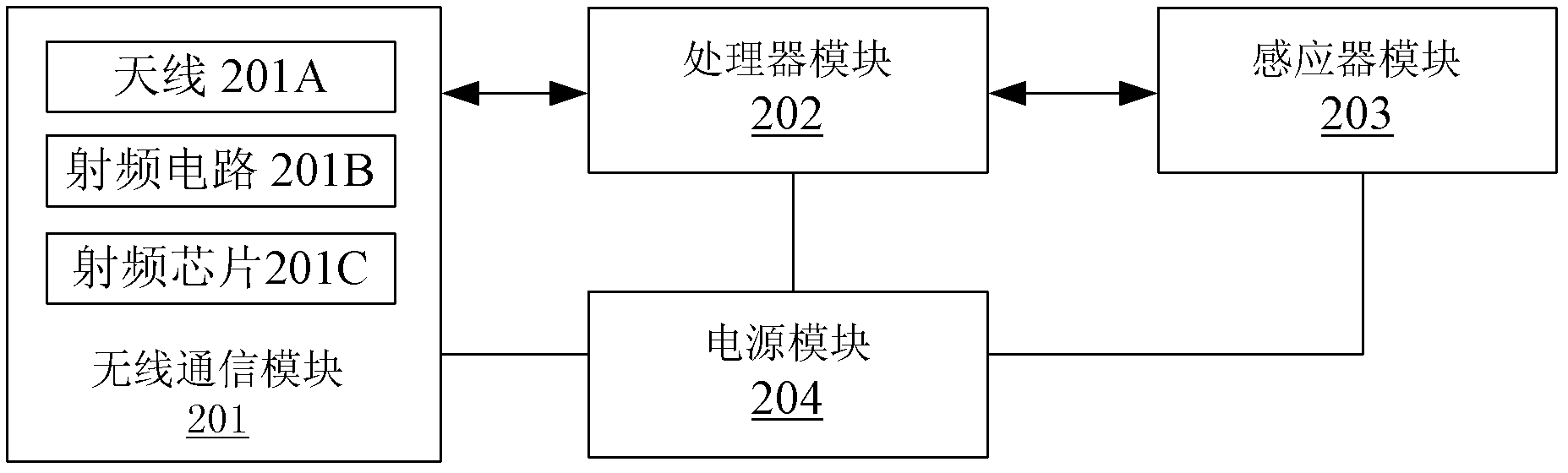
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
103 results about "Wireless metropolitan area network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
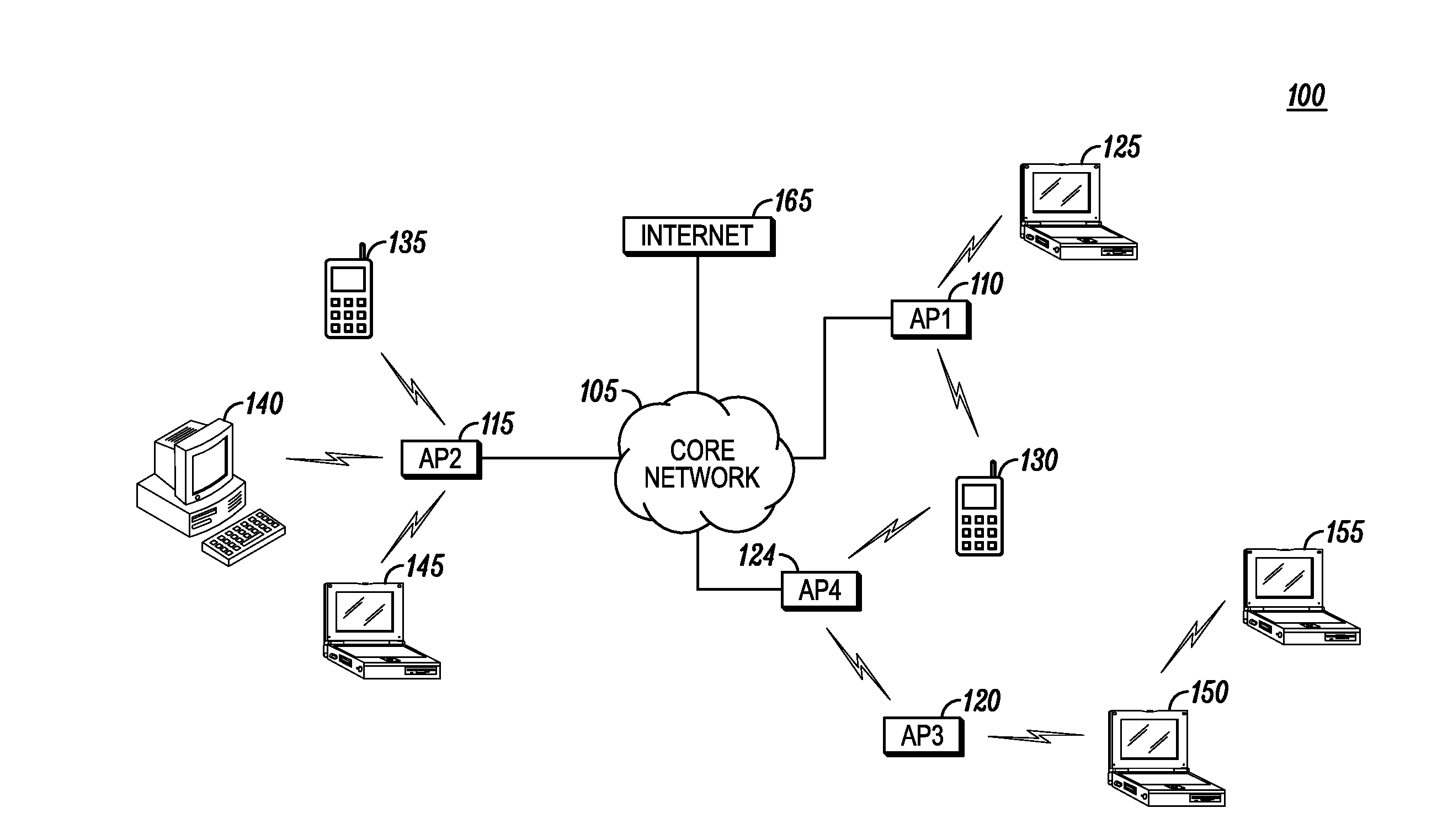
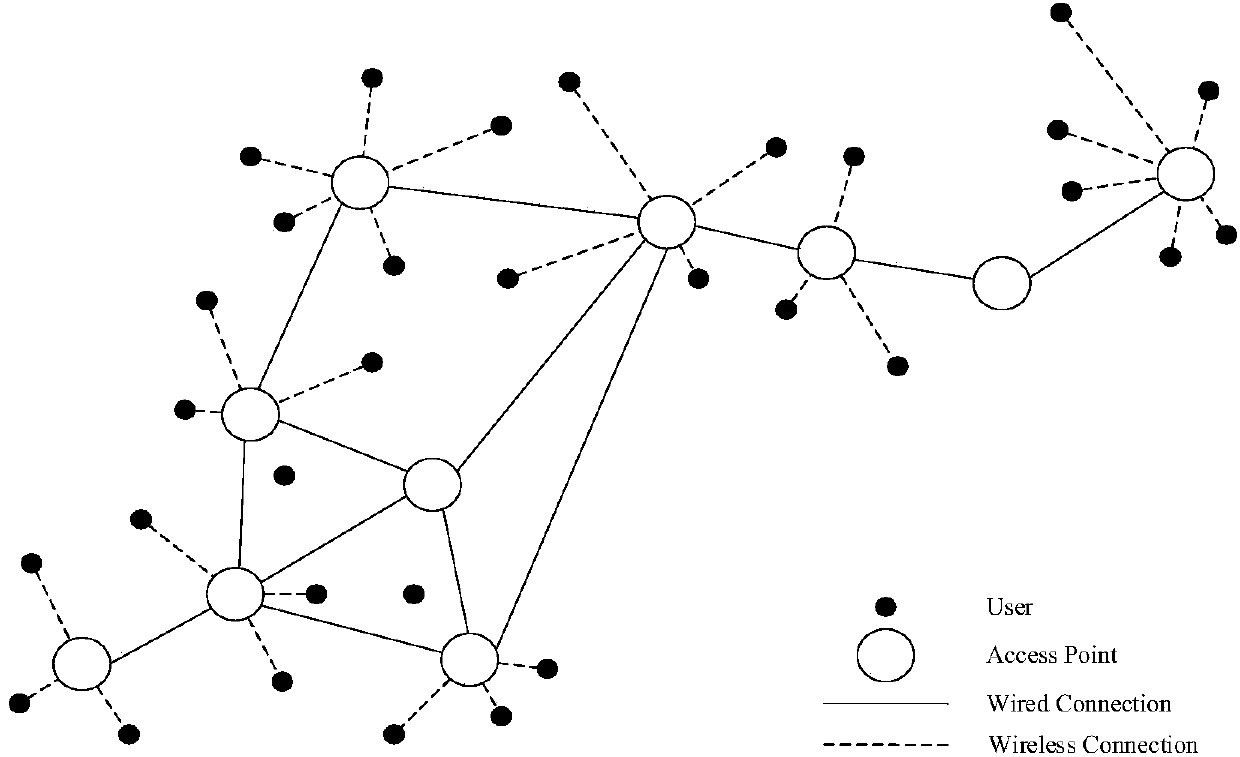
Wireless metropolitan area network. A wireless metropolitan area network (WMAN) is a form of wireless networking that has an intended coverage area — a range — of approximately the size of a city. A WMAN spans a larger area than a wireless local area network (WLAN) but smaller than a wireless wide area network (WWAN).
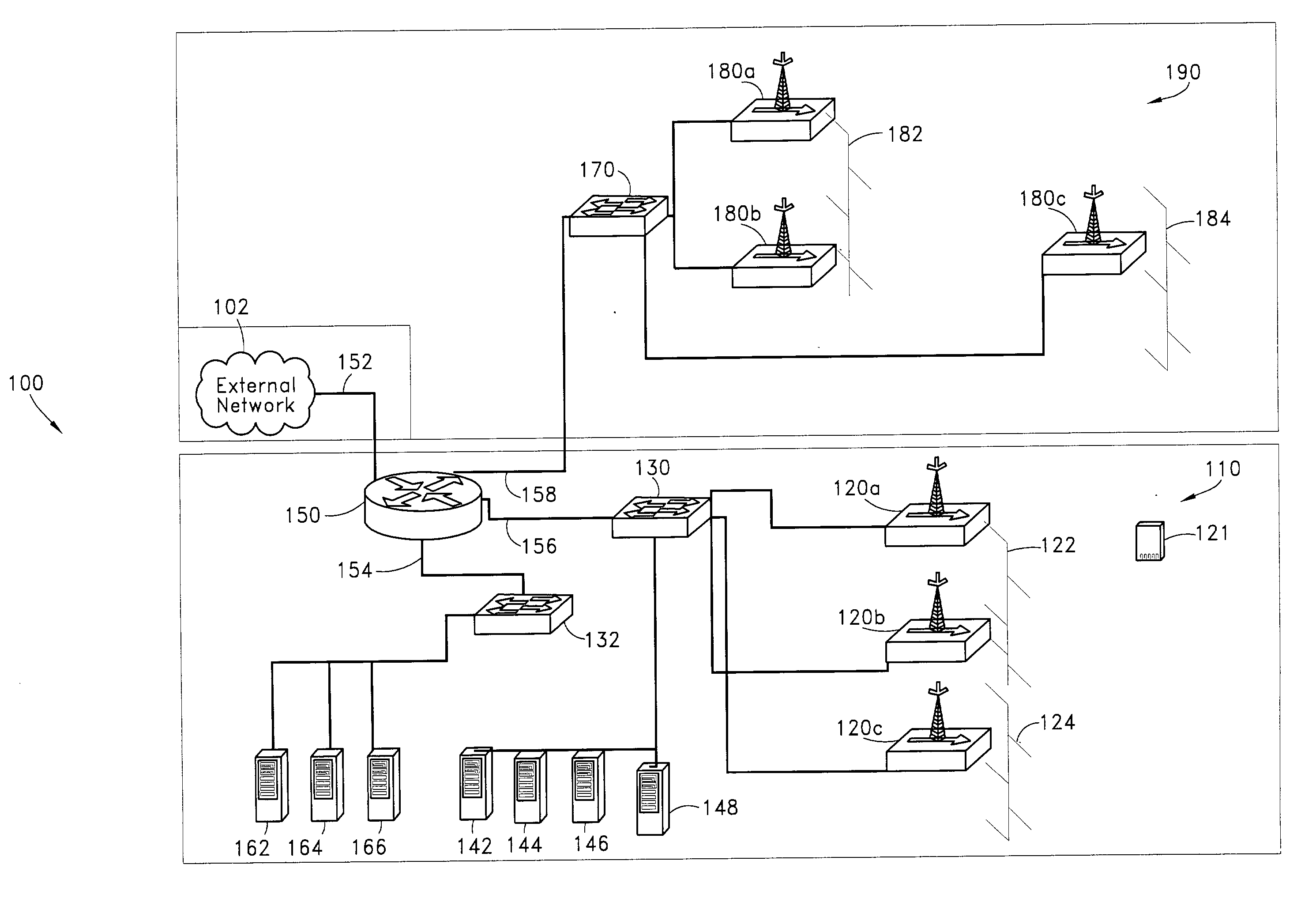
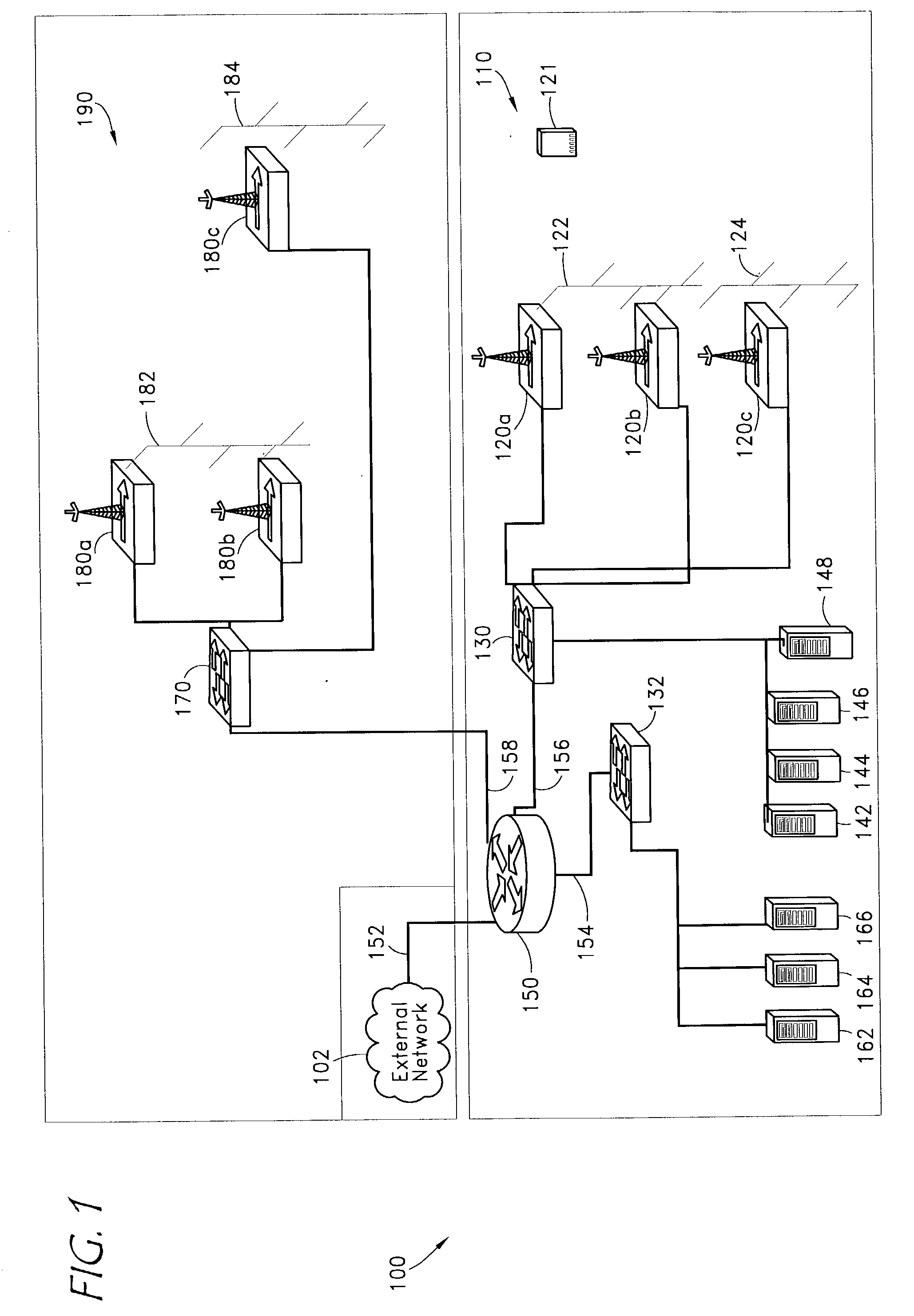
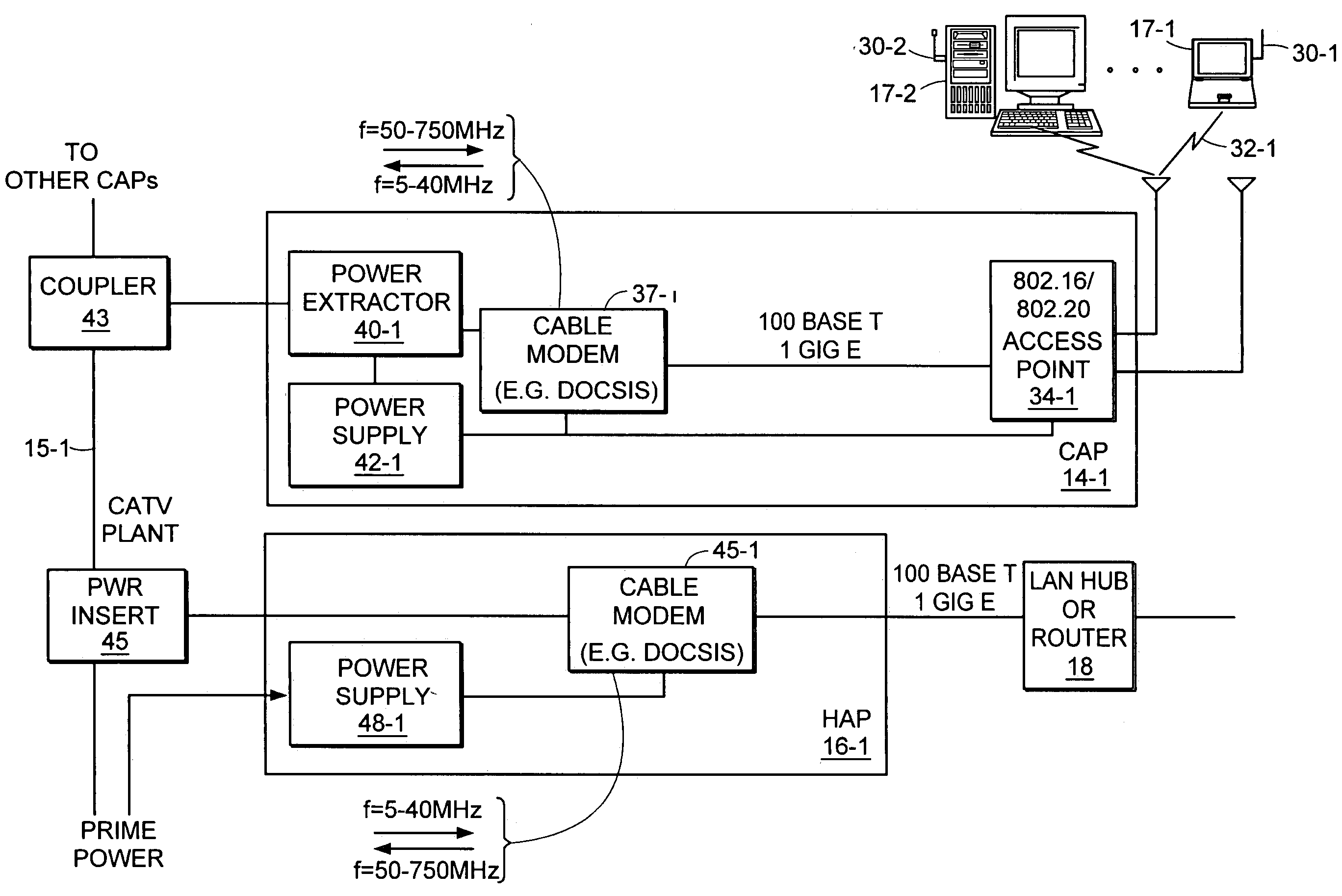
Device and Network Capable of Mobile Device Management
InactiveUS20080062900A1Radio transmissionData switching networksComputer hardwareWireless metropolitan area network
A method and system for interfacing to an electronic device is disclosed. At least one server may be used to manage an electronic device over a wireless metropolitan area network. Accordingly, the electronic device, which may be a mobile device, may be activated over-the-air. The electronic device may be minimally provisioned to allow initiation of the activation process. As part of activation, the servers can provision the electronic device and download applications that the electronic device needs for services that a user of the electronic device subscribed to. The services can then be enabled on the electronic device.
Owner:HEWLETT PACKARD DEV CO LP
Array structure for the application to wireless switch of WLAN and wman
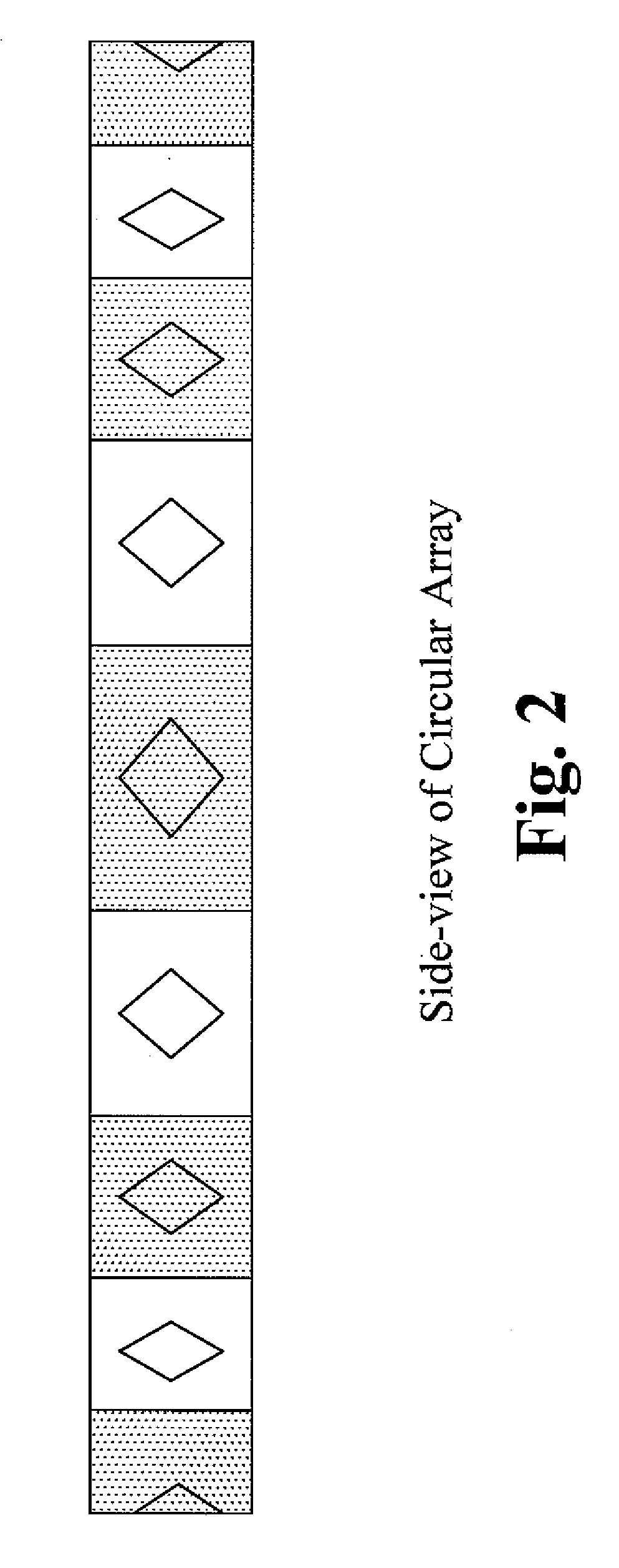
InactiveUS20070257858A1Improve efficiencyLow budgetIndoor communication adaptationIndividually energised antenna arraysArea networkArray data structure
The present invention provides an antenna array structure which includes multiple array elements, and the antenna array structure is using for the application of the WLAN (wireless local area network) or WMAN (wireless metro area network.) Furthermore, the array elements of the present invention are phased arrays or attenuated arrays, and when configuration with different type of the array element is used, the corresponding BFN (beam forming network) can also be implemented in various possibilities. With all the configuration of the present invention, the manufacturers can have a stable array structure for their applications.
Owner:ACCTON TECHNOLOGY CORPORATION
Wireless metropolitan area network system and method
InactiveUS20040022222A1Network topologiesTime-division multiplexAccess networkWireless metropolitan area network
A system and method are disclosed for providing a high speed wireless network. In one embodiment, a network is configured in a star configuration having a single router at the center. A Metropolitan Access Network (MAN) is configured with a plurality of access points that provide a wireless interface using defined physical layer and Media Access Control (MAC) layer. Packet data delivered to and from the access points are connected to the single router using a plurality of layer two links, which may include point to point links and packet switches. All links within the network operate at layer two or below and do not modify the packet data. The single router at the center of the MAN star network uses layer three information to direct packets between Local Area Networks (LANs) or sub-networks connected to different ports on the router.
Owner:VUIT
Method and apparatus for transporting ethernet data packets via radio frames in a wireless metropolitan area network
InactiveUS6907048B1Improve efficiencyElectric/magnetic signal storageRadio/inductive link selection arrangementsTransceiverWireless transceiver
Method and apparatus for transporting Ethernet data packets via radio frames in a wireless metropolitan area network. A terminal includes a data packet receiver for receiving data packets for communication over a wireless link wherein not every data packet has a same length; a data packet formatting apparatus for formatting the data packets according to radio frames wherein the radio frames each have a same length and wherein the data packets are formatted into the radio frames such that boundaries for the data packets are not necessarily aligned with boundaries for the radio frames; and a wireless transceiver for communicating the radio frames over the wireless link. The packets can be Fast Ethernet packets. The terminal does not convert the Ethernet data packets into a telephony communication protocol or into an asynchronous transfer mode (ATM) protocol prior to communication of the radio frames over the wireless link. The terminal can include a data packet synchronizer for synchronizing the data packets to a clock signal associated with the radio frames. The data packets can be time-division multiplexed into the radio frames. According to another aspect, a method of transporting Ethernet data packets via radio frames includes steps of receiving Ethernet data packets wherein each data packet includes a preamble and a start-of-frame delimiter, stripping off the preamble and start-of-frame delimiter, formatting the packet data according to radio frames, including appending a synch field to the packet data, and appending a length field to the packet data.
Owner:SAMSUNG ELECTRONICS CO LTD
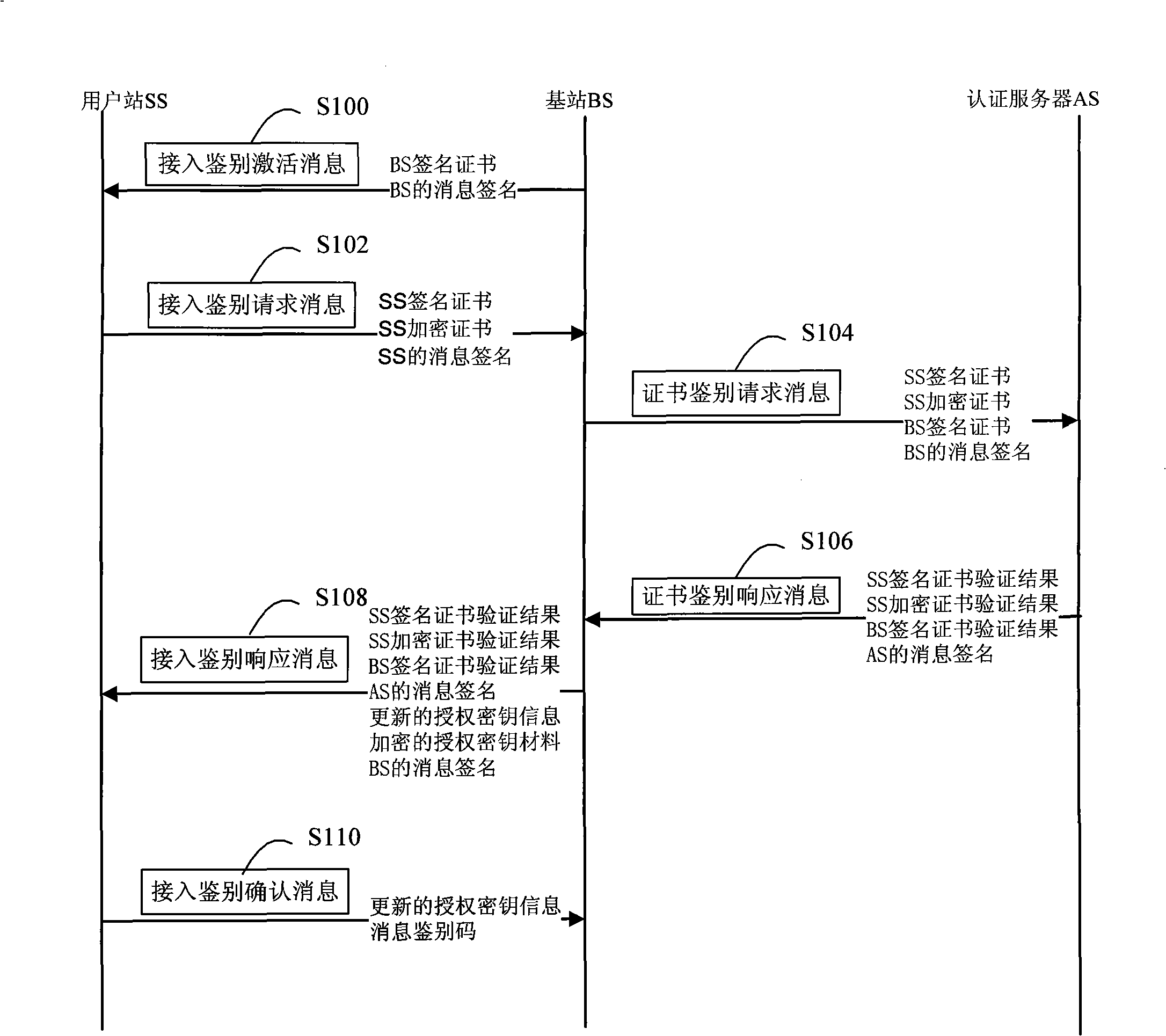
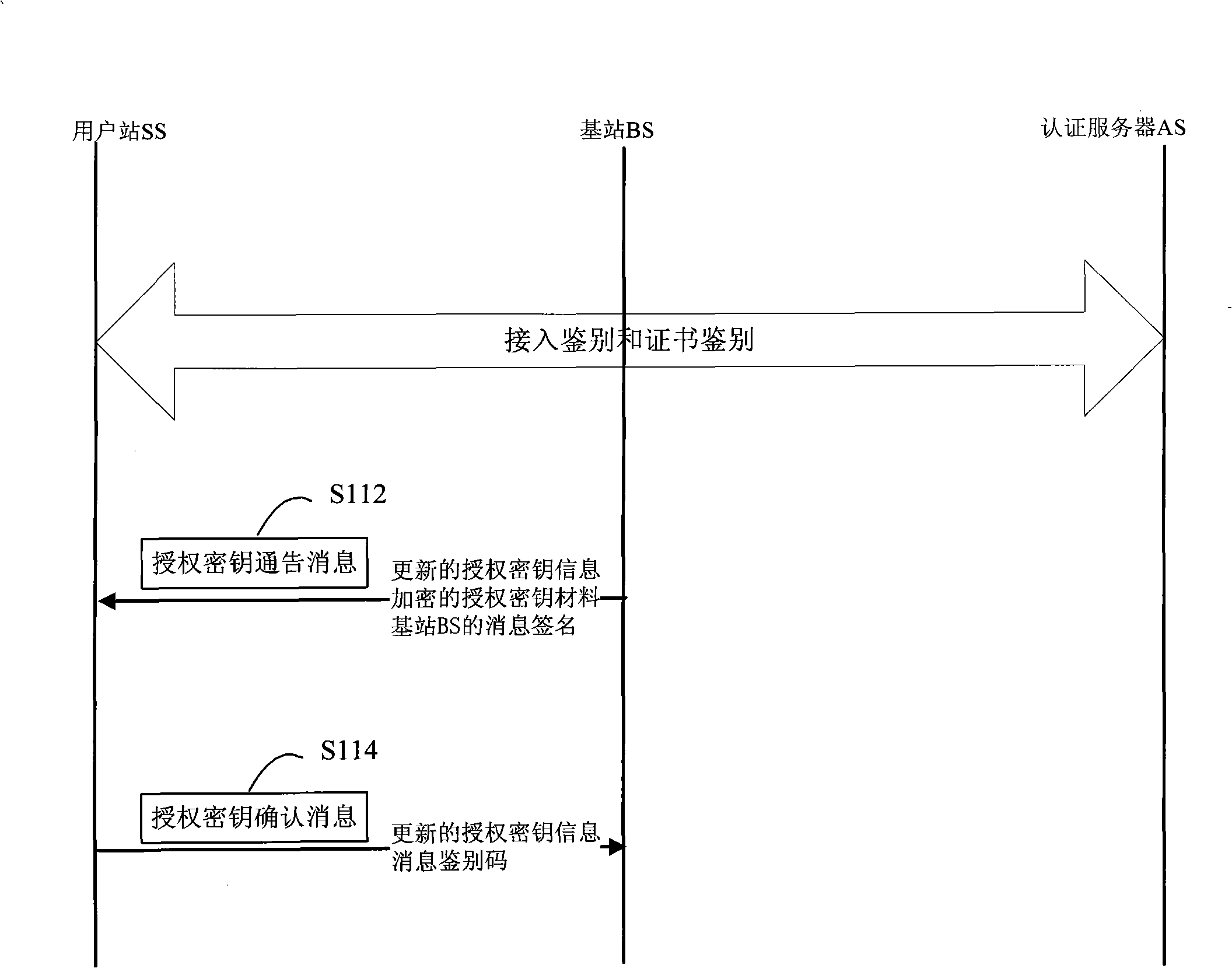
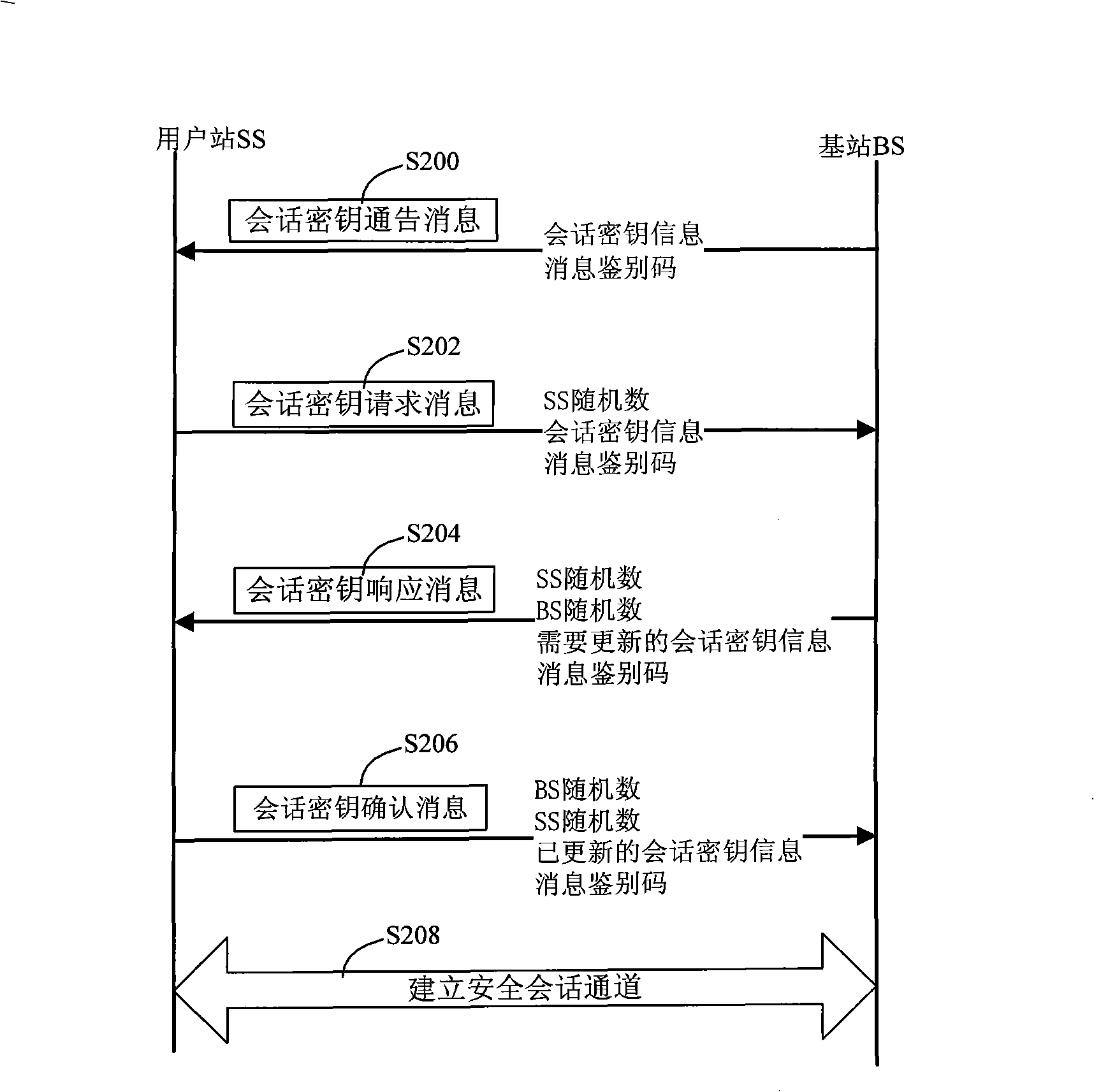
Safety access method of wireless metropolitan area network
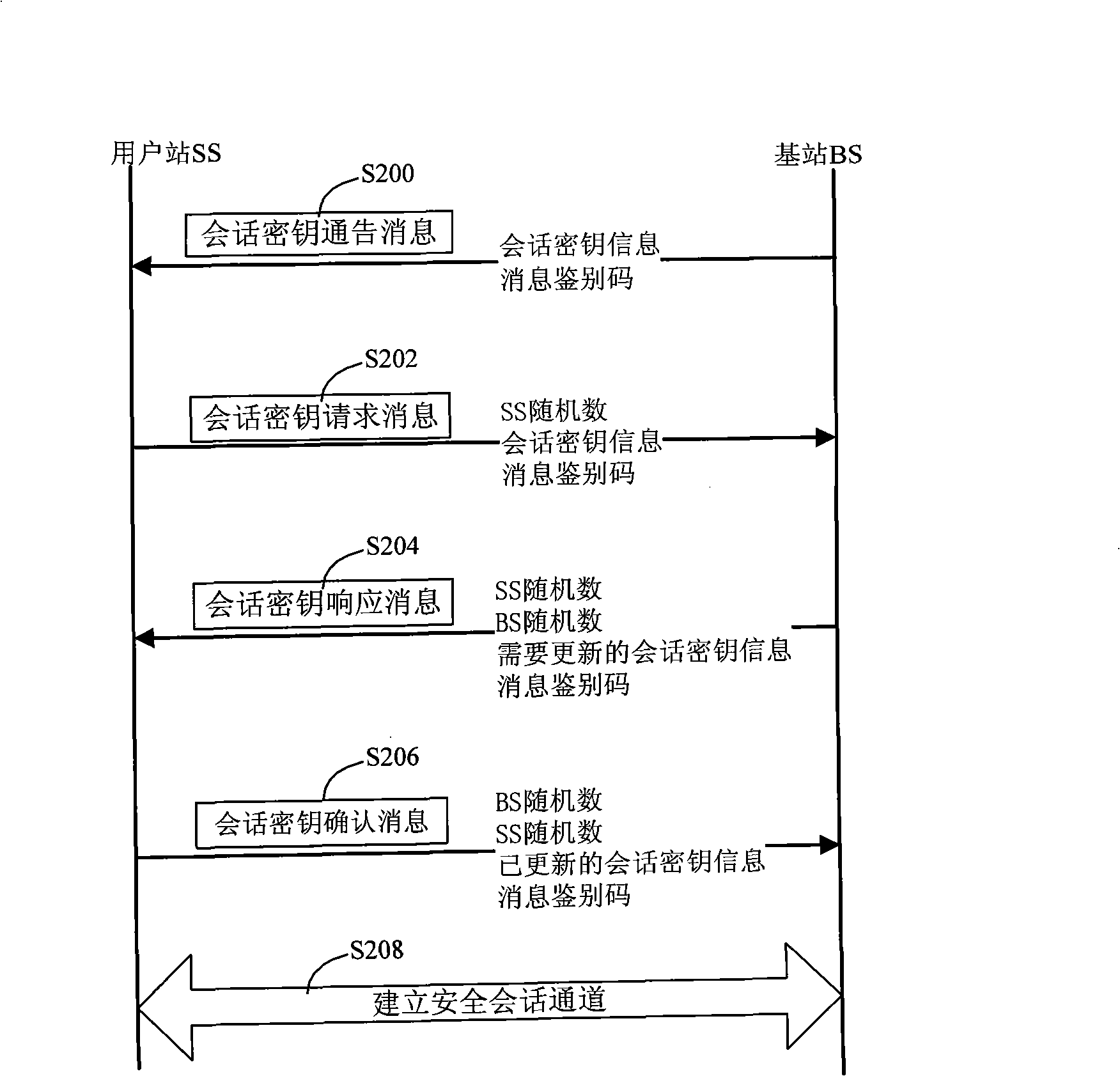
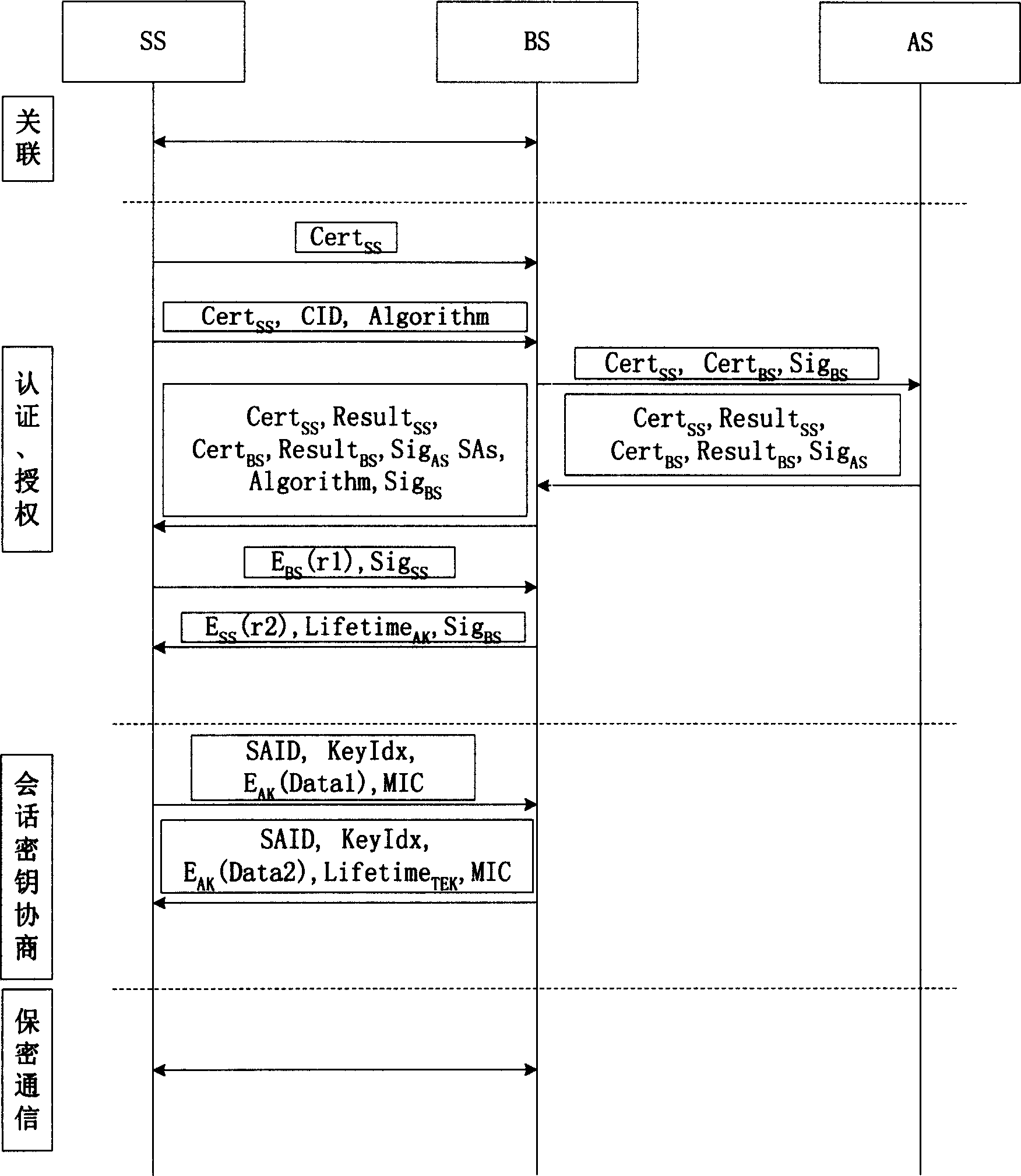
InactiveCN101272301AIncrease load capacityAvoid consumptionKey distribution for secure communicationUser identity/authority verificationAccess methodWireless metropolitan area network
The invention relates to a secure access method for the wireless metropolitan area network which comprises an identification-authentication step and a session-key consultation step. The identification-authentication step comprises: a base station (BS) sends an activating message for access identification to a subscriber station (SS); the SS sends a request message for access identification to the BS; if the SS which sends the request message for access identification has been sent with the activating message for access identification, the BS sends a request message for certificate identification to an authentication server (AS) and then the AS sends a response message for certificate authentication to the BS which then verifies the legitimacy of the SS according to the response message for certificate authentication; if the SS is legal, an access identification response message is sent to the SS which then verifies the legitimacy of the BS according to the access identification response message; if the BS is legal, following steps are continued. The BS of the proposal of the invention only handles the request message for access identification of the SS to which an 'activating message for access identification' has been sent, thus effectively avoiding DOS attacks or DDOS attacks, realizing the identification and authentication of the SS and the BS and increasing the security.
Owner:GCI SCI & TECH
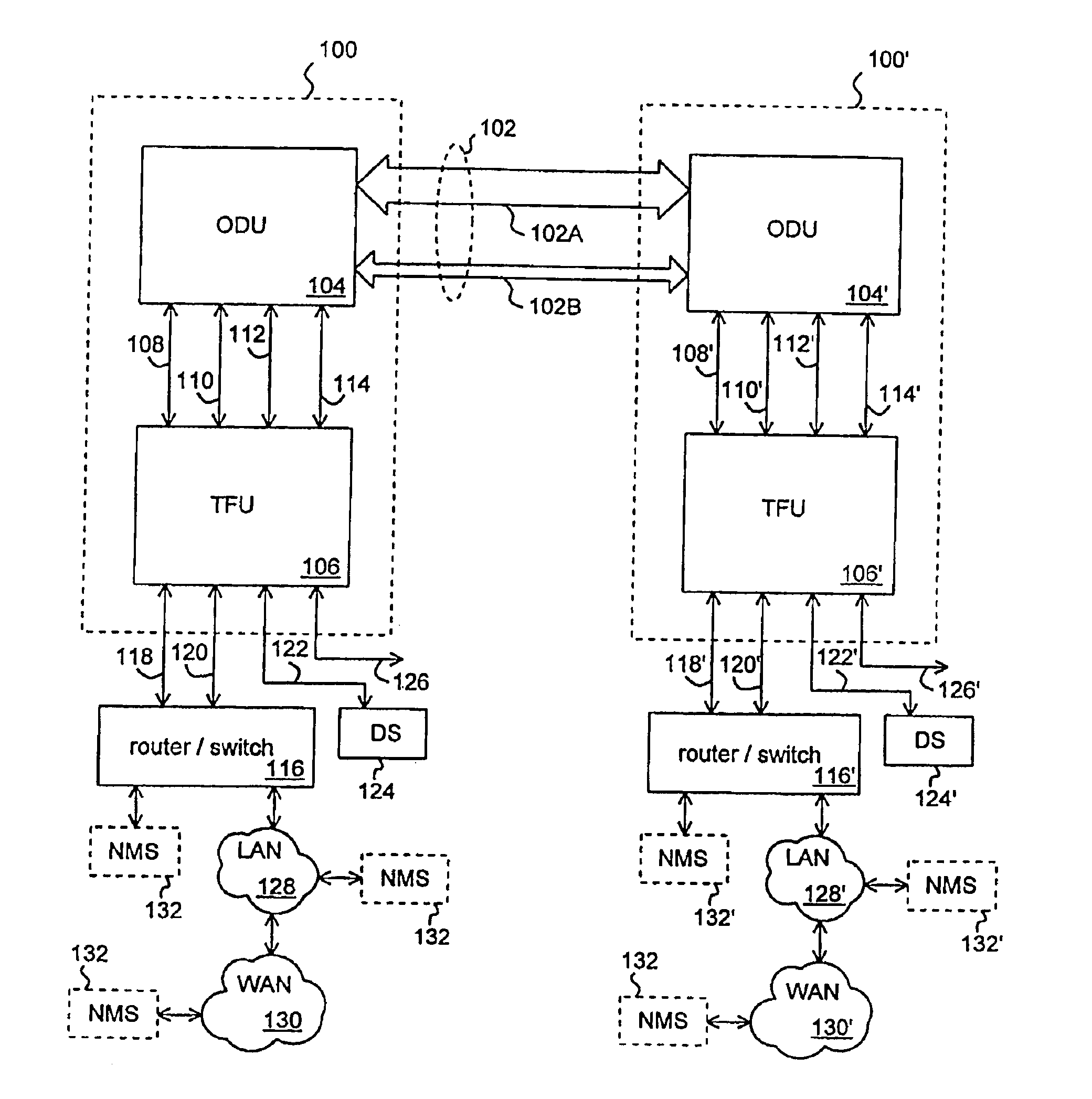
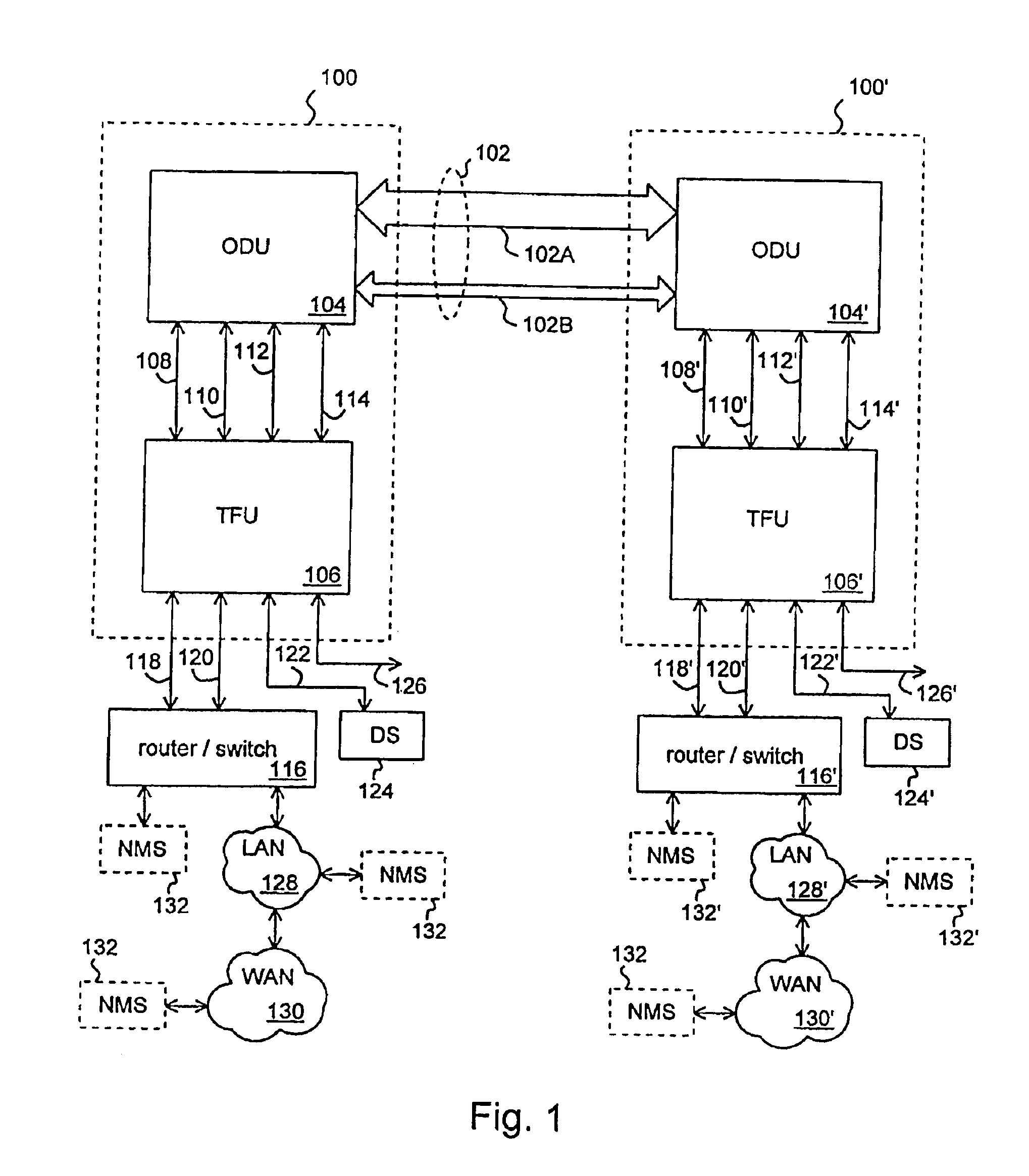
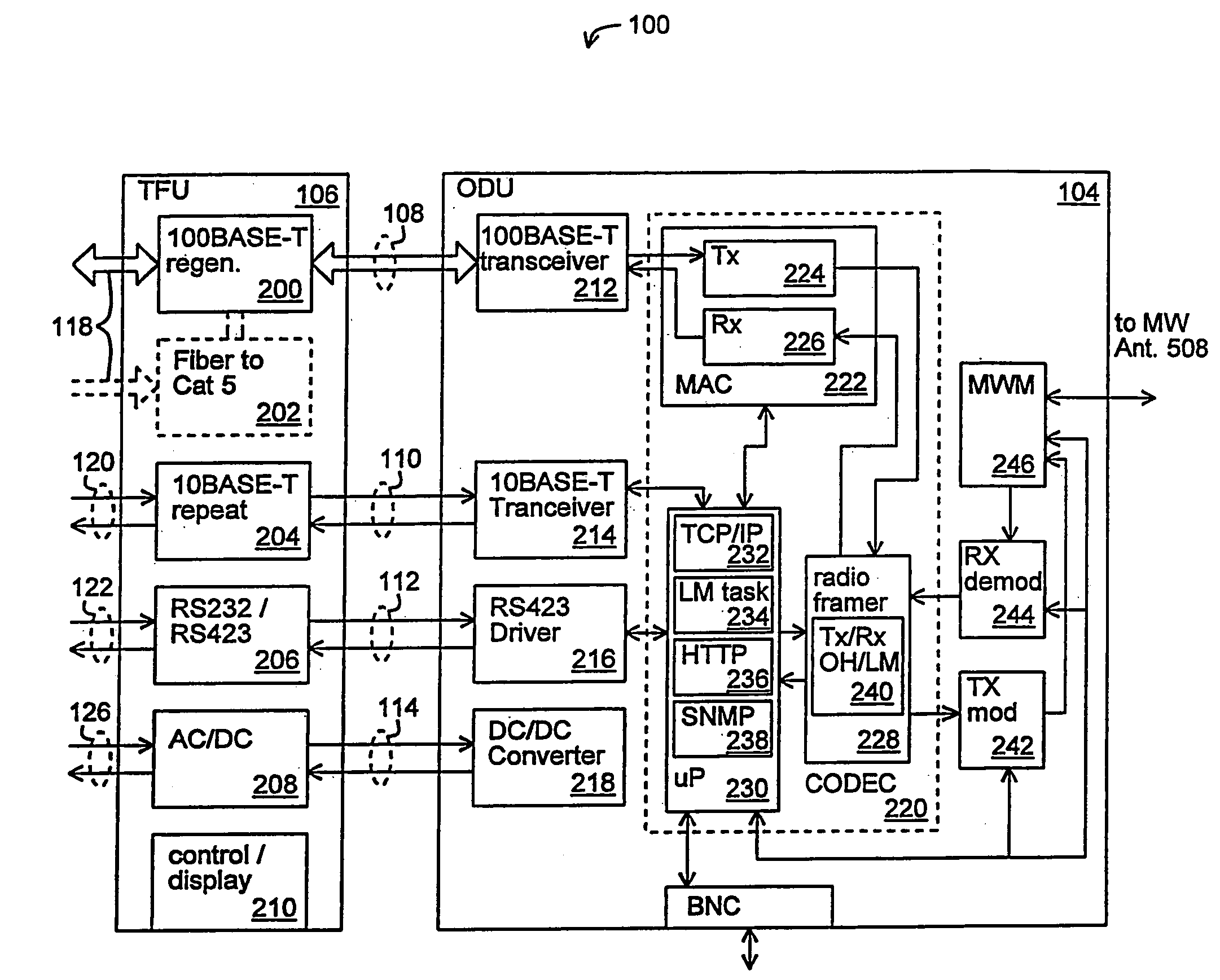
Method and apparatus for baseband transmission between a top floor unit and an outdoor unit in a terminal for a wireless metropolitan area network
InactiveUS6985451B1InexpensiveInexpensive twisted pair cablingFrequency-division multiplex detailsTime-division multiplexMicrowaveElectrical conductor
A method and apparatus for baseband transmission between a top floor unit and an outdoor unit in a terminal for a wireless metropolitan area network. A terminal for a wireless link in a metropolitan area network includes an extender device (e.g. a top floor unit) for receiving data packets from a computer network coupled to the extender device and for forwarding the data packets, and a broadcast device (e.g. an outdoor unit) coupled to the extender device for receiving the data packets from the extender device according to baseband transmission and having a wireless transceiver for communicating the data packets over the wireless link. The terminal can include a cable coupled between the extender device and the broadcast device wherein the cable comprises a twisted pair of conductors for providing the data packets from the extender device to the broadcast device. The twisted pair of conductors can be a Category 5 twisted pair of conductors. Thee broadcast device can include a microwave antenna coupled to the wireless transceiver; and a housing coupled to the microwave antenna for enclosing the wireless transceiver.
Owner:SPARKMOTION
Array structure for the application to wireless switch of WLAN and WMAN
InactiveUS7567213B2Improve efficiencyLow budgetIndoor communication adaptationIndividually energised antenna arraysArea networkWireless metropolitan area network
The present invention provides an antenna array structure which includes multiple array elements, and the antenna array structure is using for the application of the WLAN (wireless local area network) or WMAN (wireless metro area network.) Furthermore, the array elements of the present invention are phased arrays or attenuated arrays, and when configuration with different type of the array element is used, the corresponding BFN (beam forming network) can also be implemented in various possibilities. With all the configuration of the present invention, the manufacturers can have a stable array structure for their applications.
Owner:ACCTON TECHNOLOGY CORPORATION
Safety access method of wireless metropolitan area network
InactiveCN101272616AReduces the possibility of crackingRealize AuthenticationUser identity/authority verificationRadio/inductive link selection arrangementsDigest access authenticationAccess method
The invention relates to a method for safe accessing of a wireless metropolitan area network, which comprises an authenticating step and a session key negotiating step. The authenticating step comprises that: a subscriber station SS sends a request message for access authentication to a base station BS; the BS sends a request message for certificate authentication to an authentication server AS; the AS verifies the request message for certificate authentication and sends a response message for certificate authentication to the BS; the BS verifies the validity of the identity of the SS according to the response message for certificate authentication; if the SS is valid, the BS sends the response message for access authentication to the SS; the SS verifies the validity of the BS according to the response message for access authentication; if the BS is valid, the SS uses the encryption certificate key of the SS to decrypt the material of authentication key. The SS signing certificate in the proposal is used for stating the identity and the SS encrypting certificate is used for encrypting and decrypting the material of authentication key so as to reduce the risk that the key is decrypted; through verifying the certificates of the BS and the SS by the AS, authentication for the subscriber station SS and the base station BS is realized and security level is improved.
Owner:GCI SCI & TECH
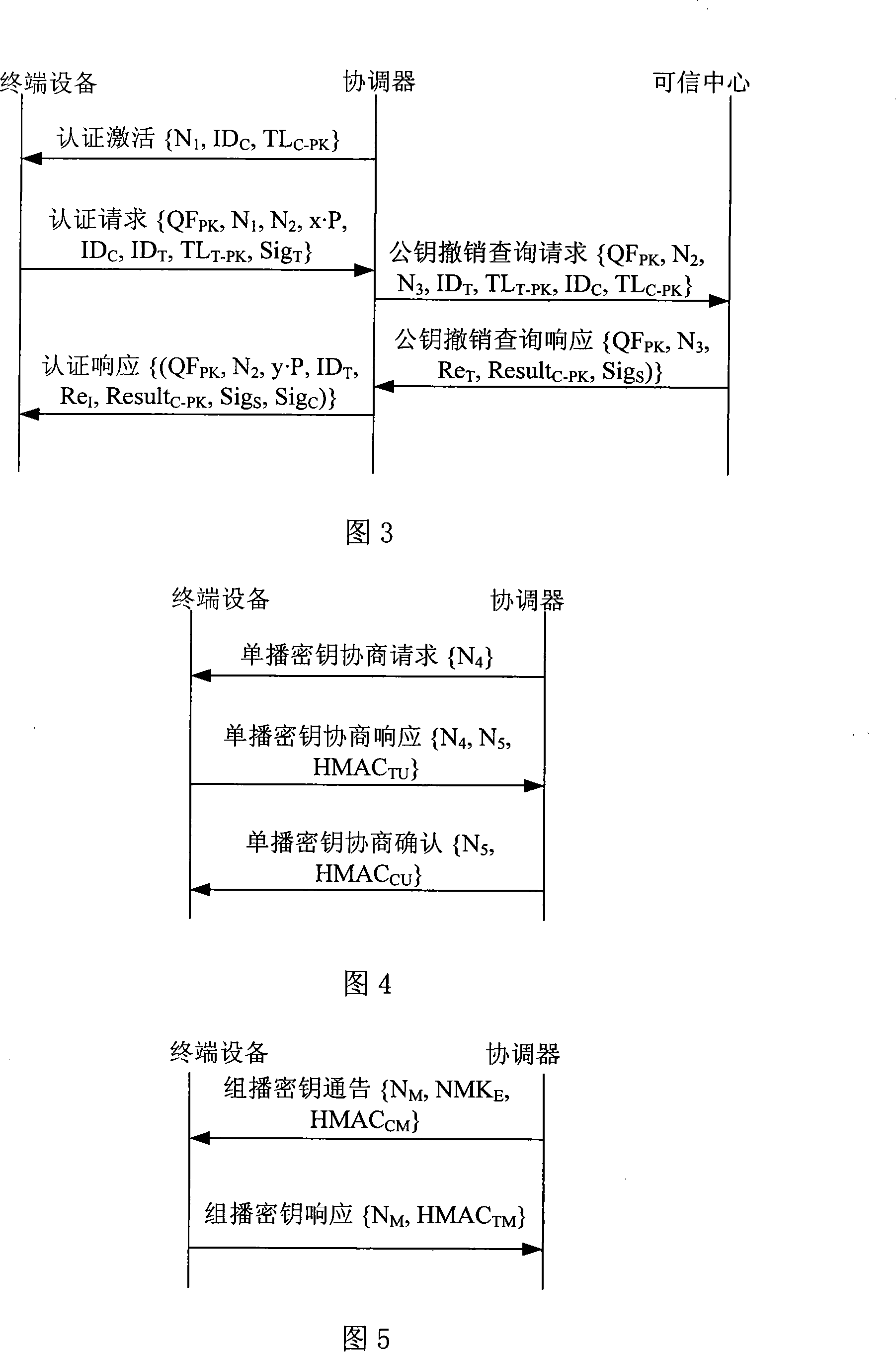
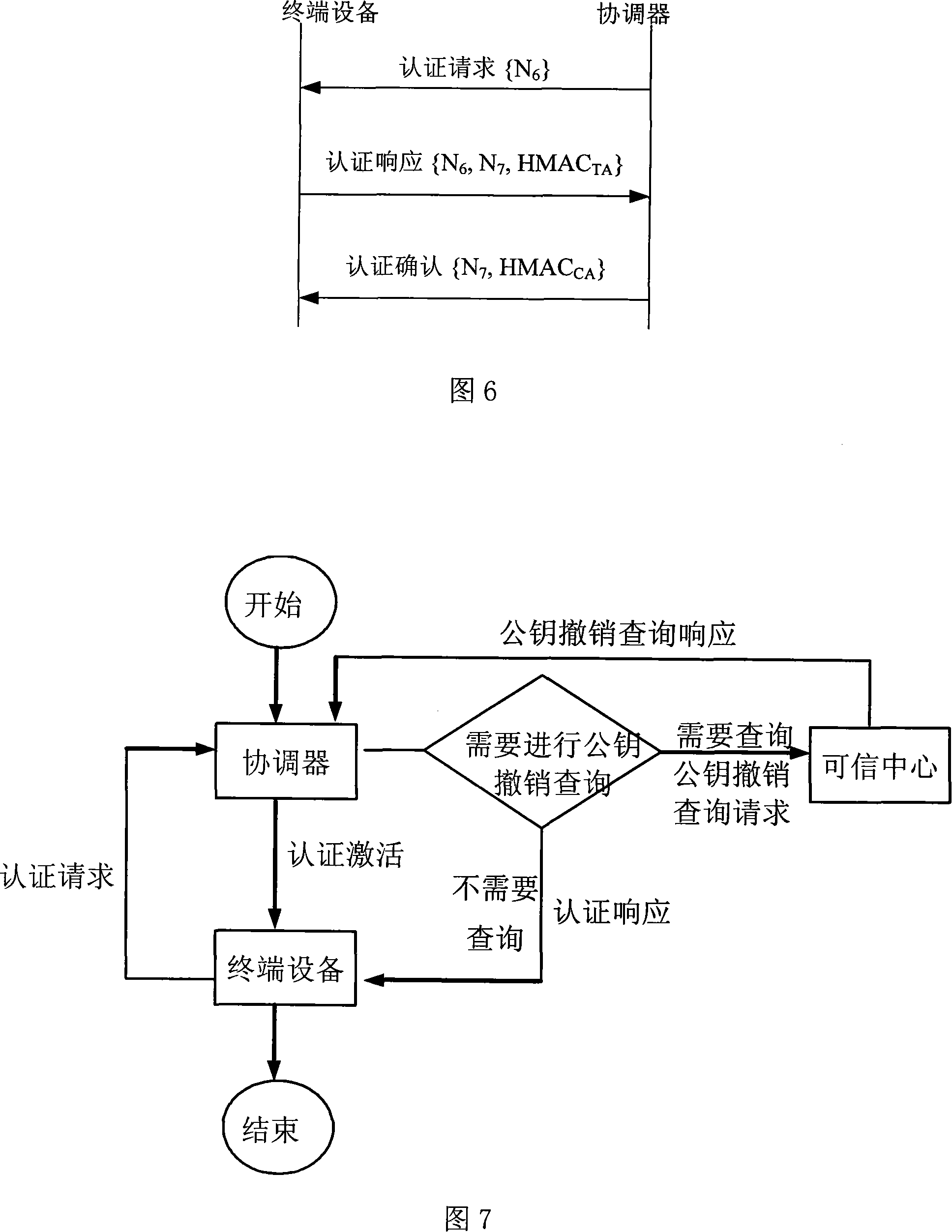
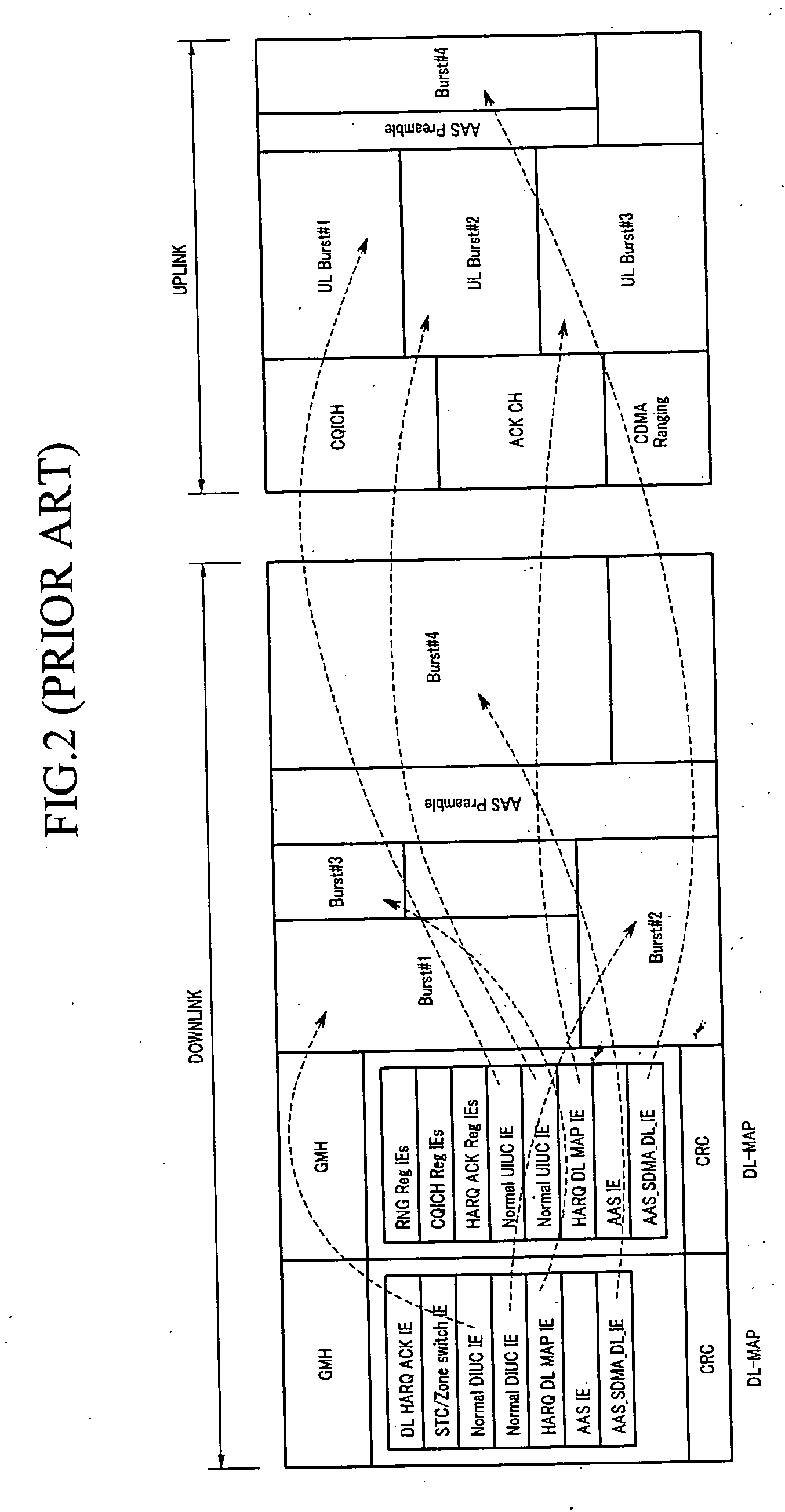
Authentication accessing method of wireless multi-hop network
InactiveCN101232378AImprove securityImprove performanceKey distribution for secure communicationPublic key for secure communicationAccess methodBeacon frame
The invention relates to an authentication access method of a wireless multi-hop network. The invention is applicable to the safety application protocol of the WAPI framework method (TePA, the access control method which is based on the triple peer-to-peer identification) during the application on the specific network which includes a wireless LAN, a wireless MAN and a wireless PAN. A terminal equipment and a coordinator have the port control ability, the terminal equipment selects the authentication and key management suit and sends the connection request to command the coordinator after the broadcast beacon frame of the coordinator, the coordinator carries out the authentication together with the terminal equipment according to the selected authentication and key management suit by the terminal equipment, the connection response command is sent to the terminal equipment after the finish of the authentication; the terminal equipment and the coordinator carries out the control to the ports according to the authentication result, so as to realize the authentication access of the wireless multi-hop network. The invention solves the technical problem of the safety hidden trouble of the prior authentication method of the wireless multi-hop network.
Owner:CHINA IWNCOMM
Architecture for signal distribution in wireless data networks
InactiveUS7359392B2Remove complexityLow costBroadband local area networksBroadcast transmission systemsWireless mesh networkWireless metropolitan area network
A distribution network for coupling wireless signals between an internetworking device and a plurality of remotely located access points to provide wireless service within a geographic coverage area composed of microcells. The distribution network makes use of available transport cabling. Examples of such wireless signals include wireless metropolitan area network signals and mobile broadband wireless network signals.
Owner:COMMSCOPE TECH LLC
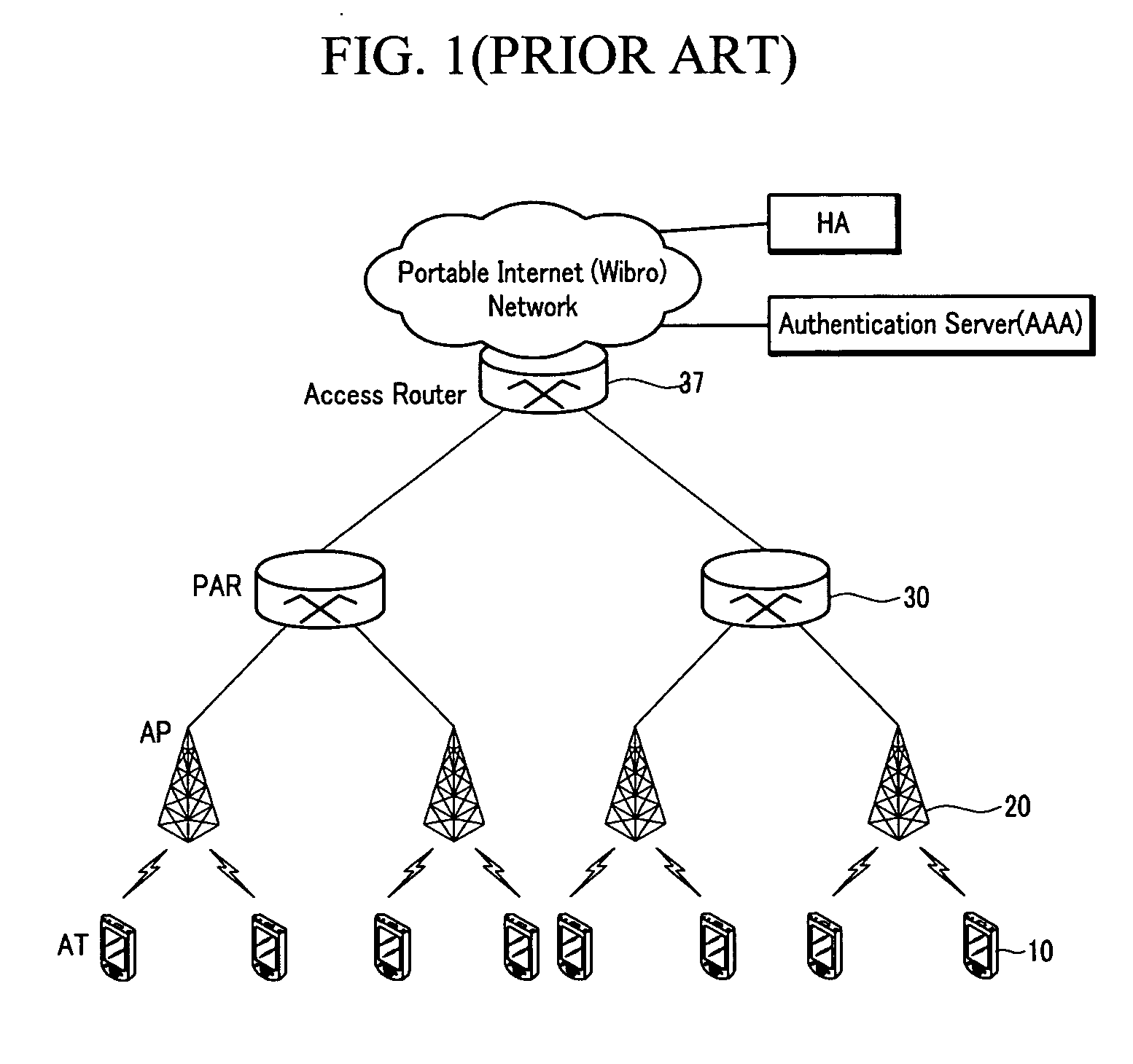
Apparatus and method for downlink packet scheduling in base station of a portable internet system
InactiveUS20070121636A1Improve fairnessImprove system efficiencyTime-division multiplexData switching by path configurationNetwork connectionPacket scheduling
In a base station of an IEEE 802.16 Wireless MAN-based portable Internet system, a forward packet scheduling method and apparatus is provided. The portable Internet system portable Internet service includes a user terminal AT for providing a portable Internet service, a base station AP for supporting an inter-user terminal wireless access and network connection, and a packet access router PAR for performing a mobility control and packet routing function of each user terminal AT. The forward packet scheduler includes a packet-based subsidiary scheduling part for considering a real-time service and a user-based scheduling part for ensuring fairness and increasing system efficiency (throughput). After finishing the 2-step scheduling, the generated frame data are transmitted though a physical layer to a wireless user terminal. Therefore, with such a structure, the forward packet scheduling method may guarantee a maximum of system efficiency and fairness according to each user's QoS requirements, and may also guarantee a delay performance for a real-time service.
Owner:SAMSUNG ELECTRONICS CO LTD +4
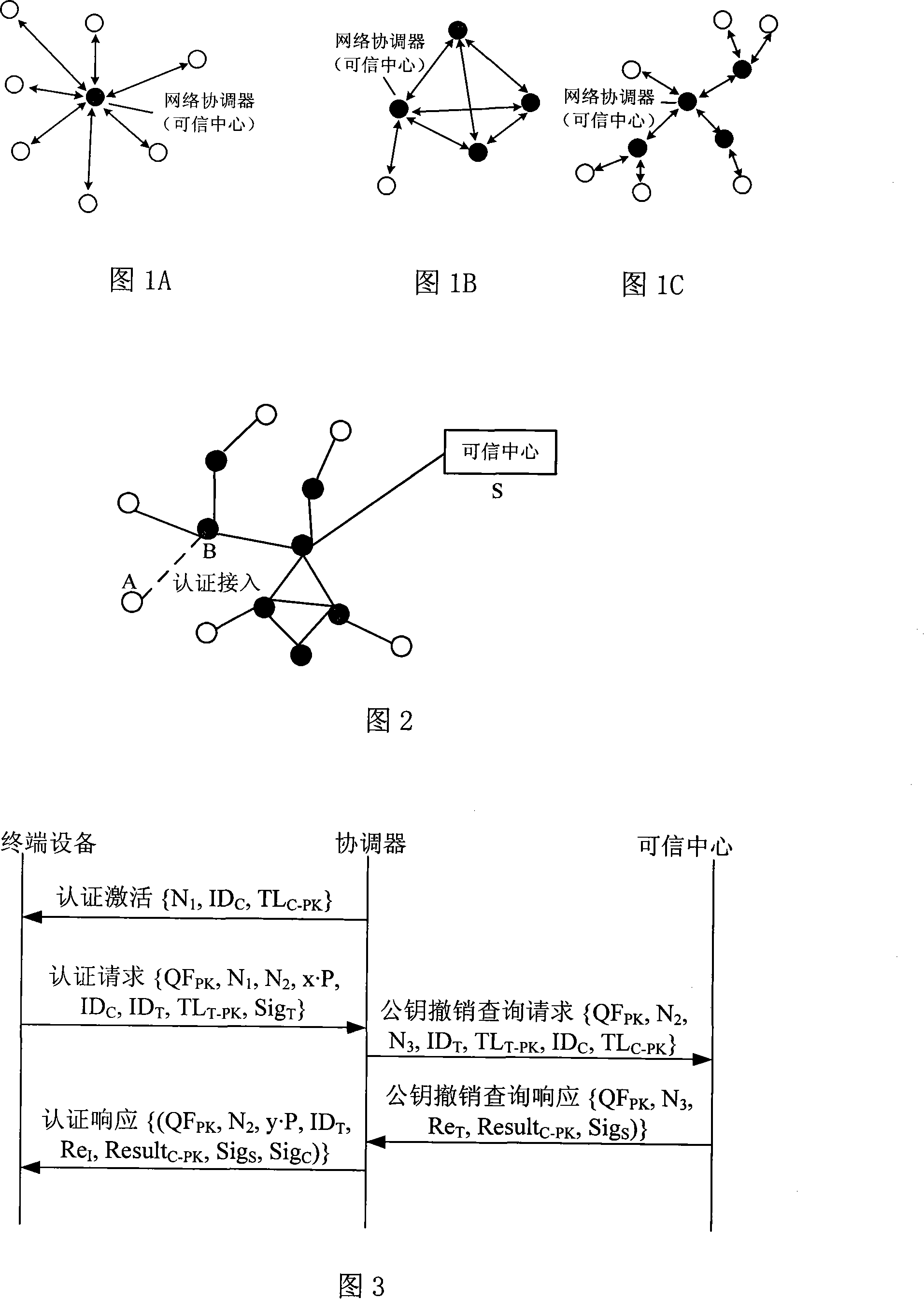
Wireless multi-hop network authentication access method based on ID
InactiveCN101222772AImprove securityImprove performanceUser identity/authority verificationNetwork topologiesCommunications securityAccess method
The invention provides an access authentication method in ID based wireless multi-hop network, which is applicable to the security application protocol when WAPI frame method (TePA, an access control method based on triplet peer authentication) is applied on specific network including wireless local area network, wireless metropolitan area network and wireless personal area networks. The methods comprises the following steps that: a non-controlled port and a controlled port are defined; a coordinator transmits a beacon frame; a terminal equipment sends a command for connection request; the coordination conducts authentication with the terminal equipment; after the authentication is successful, the coordinator opens the controlled port and sends a connection response command; the terminal equipments receive the connection response commands and opens the controlled ports so as to get access to the network. The method of the invention solves the technical problem that the prior wireless multi-hop network has safety hidden danger in access authentication method and ensures the communication security between the terminal equipment and the coordinator.
Owner:CHINA IWNCOMM
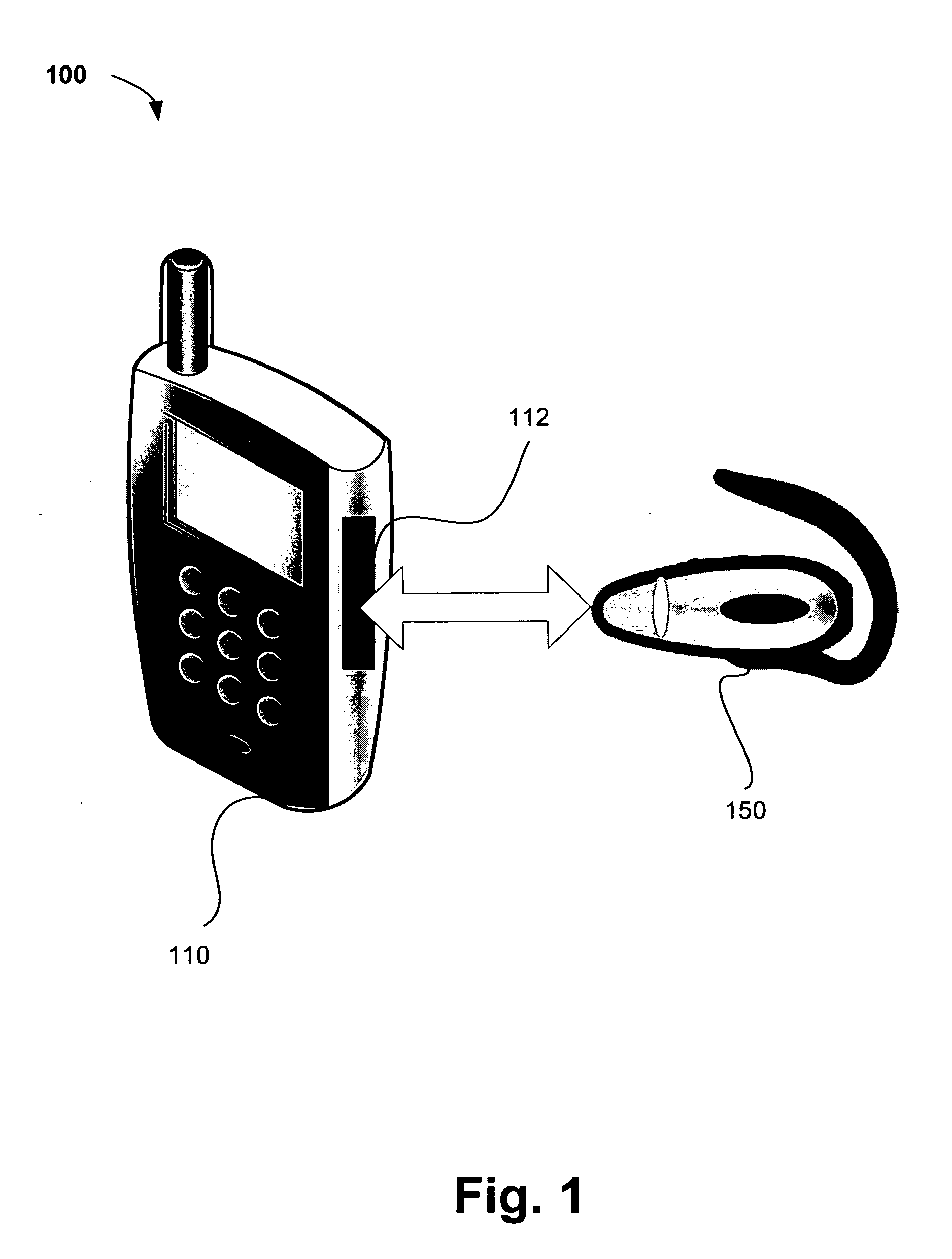
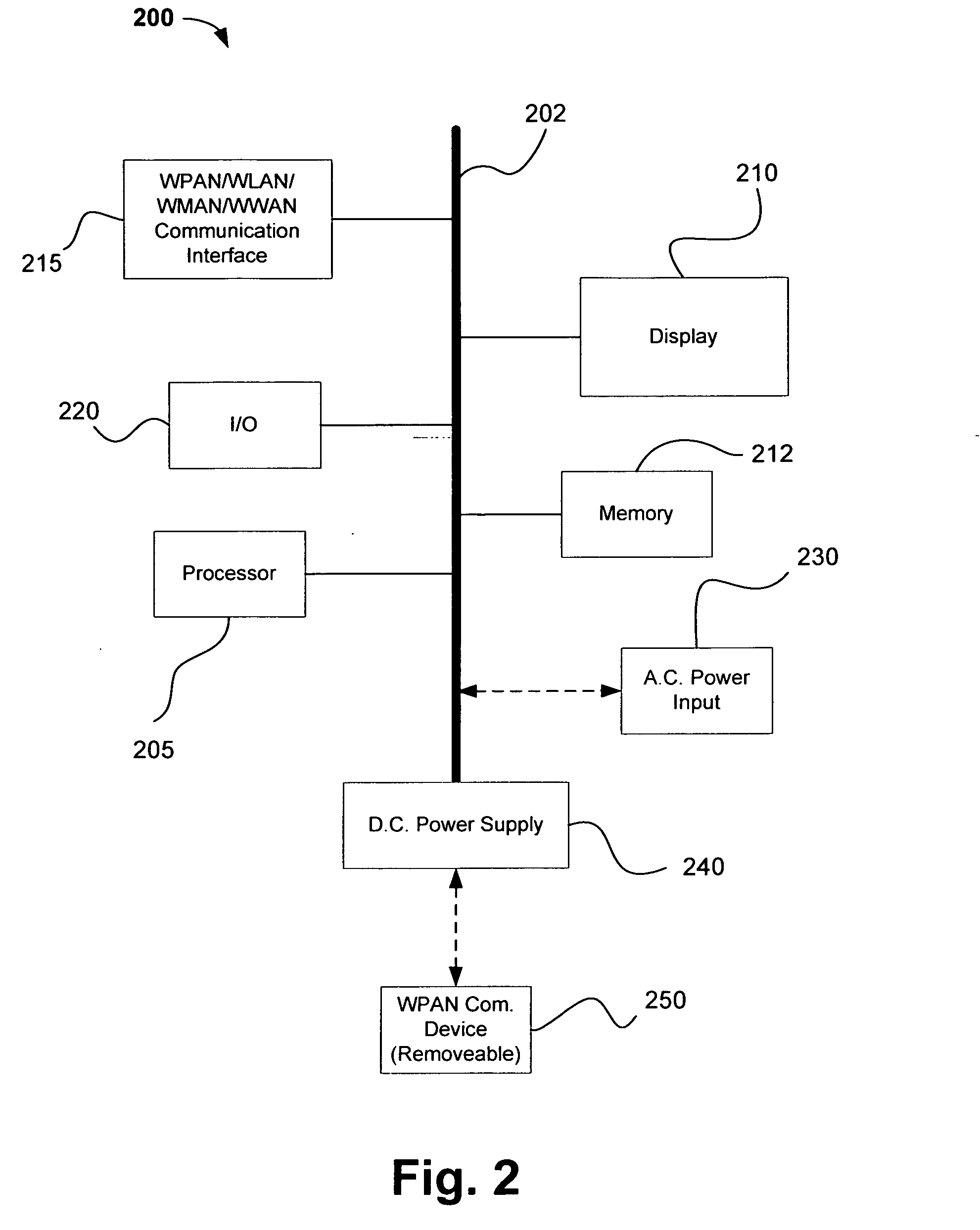
Portable communication device with detachable wireless headset
InactiveUS20080132168A1Devices with bluetooth interfacesSubstation equipmentWireless metropolitan area networkHeadphones
A portable communication device such a mobile phone is disclosed which may be configured to communicate using a wireless personal area network (WPAN) protocol and one or more wireless local area network (WLAN), wireless metropolitan area network (WMAN) or wireless wide area network (WWAN) protocols. The portable communication device includes a port to store and / or charge a separate WPAN device such as a wireless headset and in certain embodiments, the port may charge a battery of wireless headset so that both the portable communication device and wireless headset may be carried as an integrated single unit and / or charged using a single charging cord. Additional embodiments and variations are also disclosed.
Owner:INTEL CORP
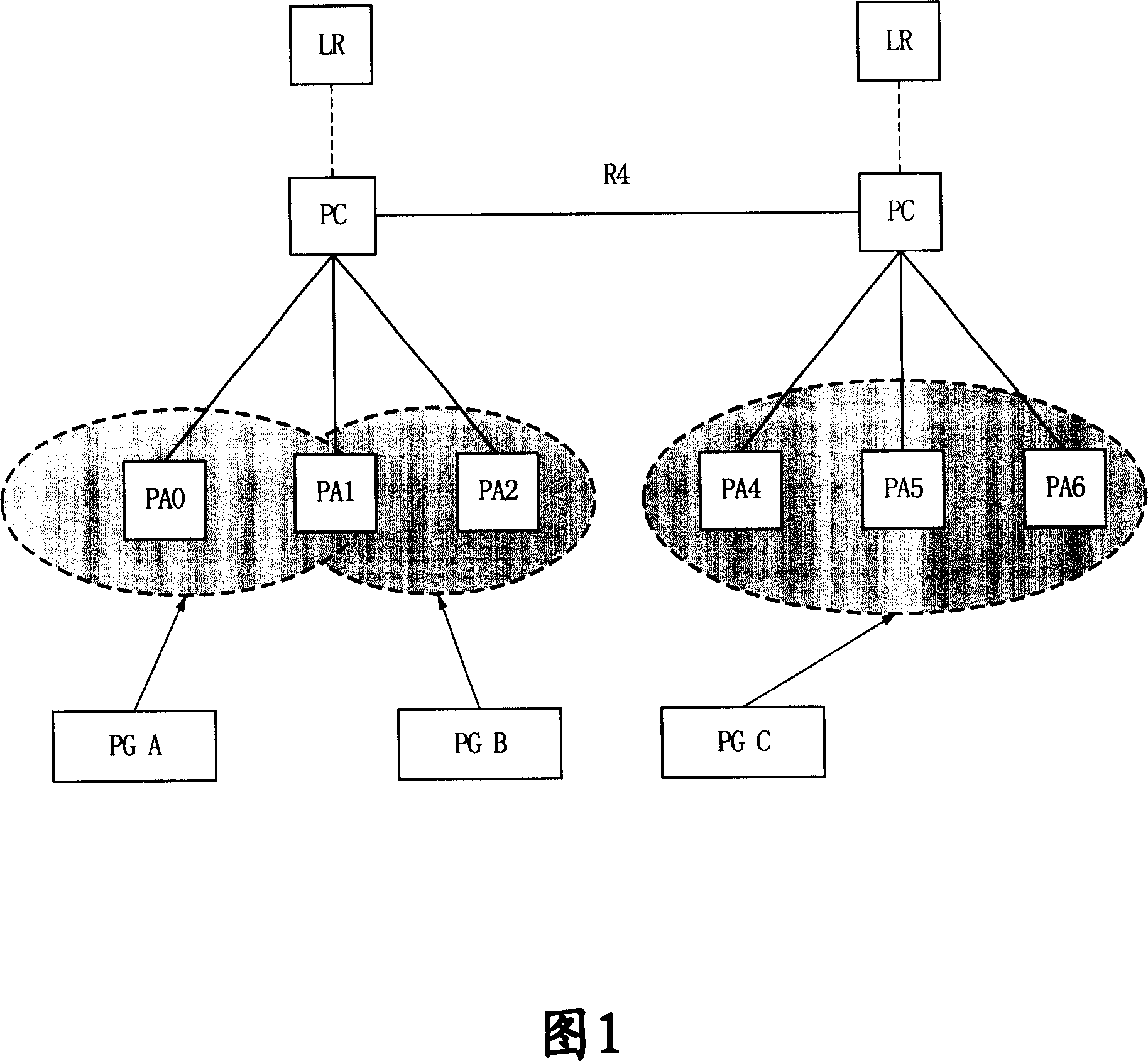
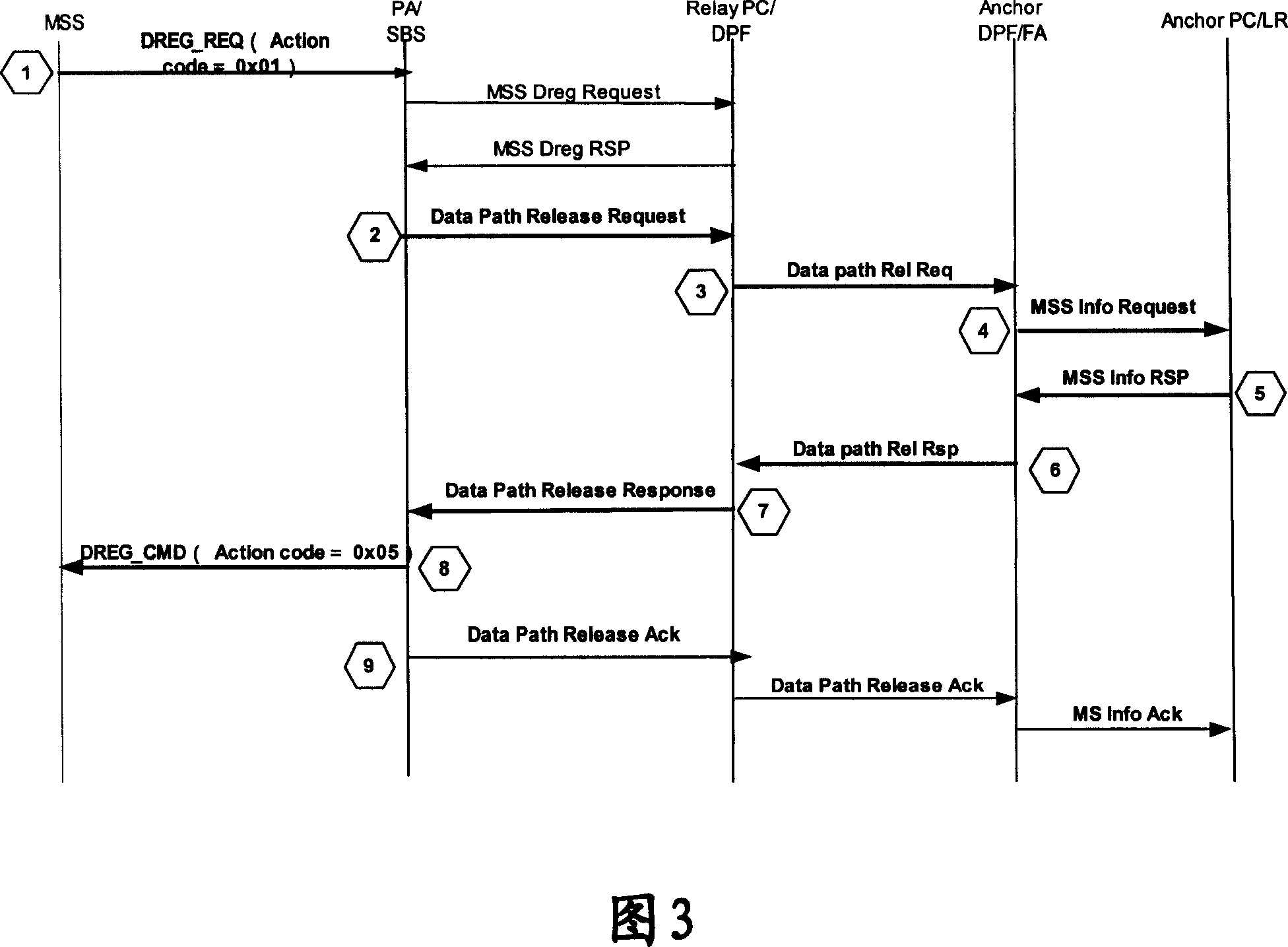
Method for terminal to enter into idle mode in wireless city domain network
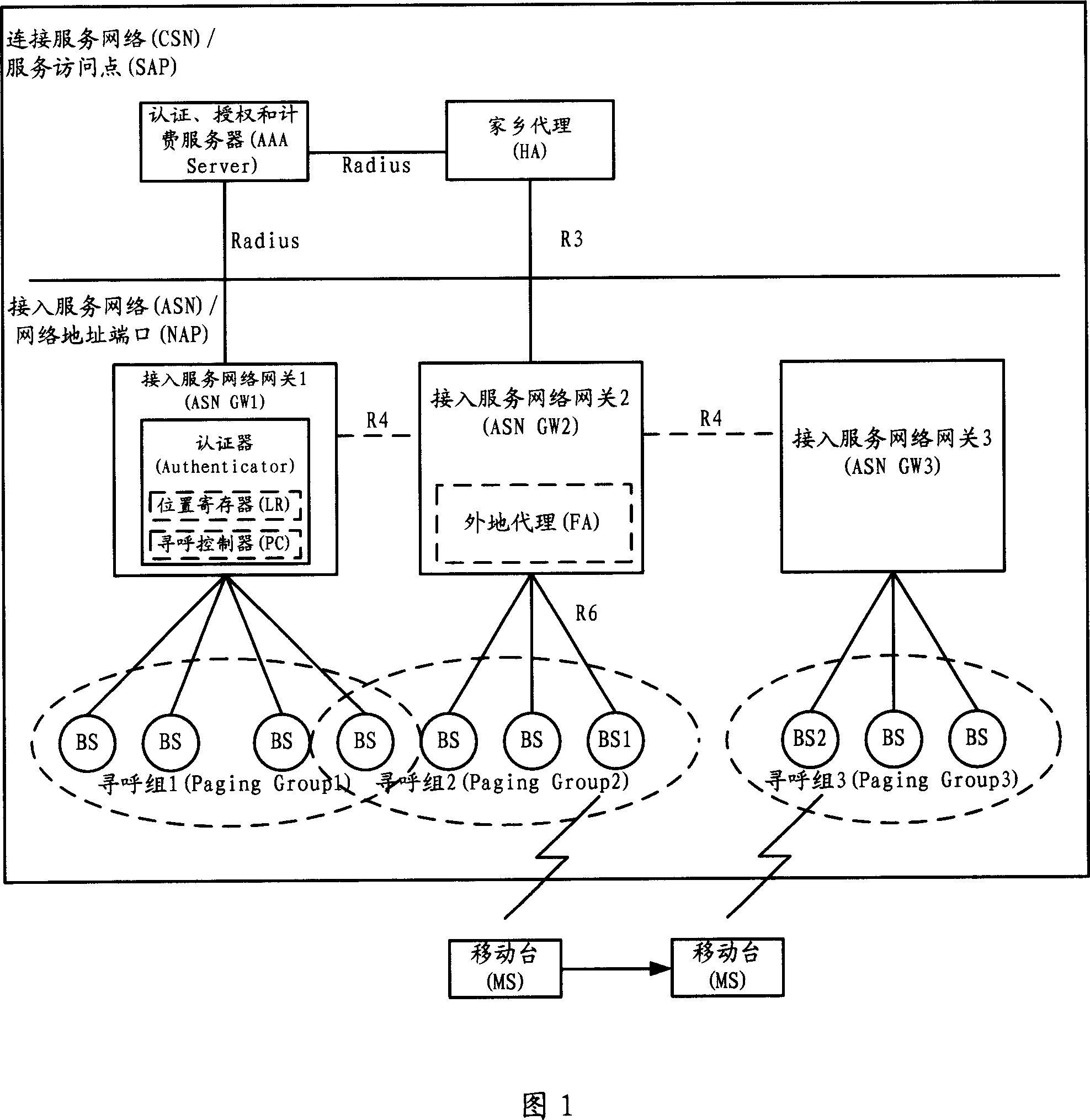
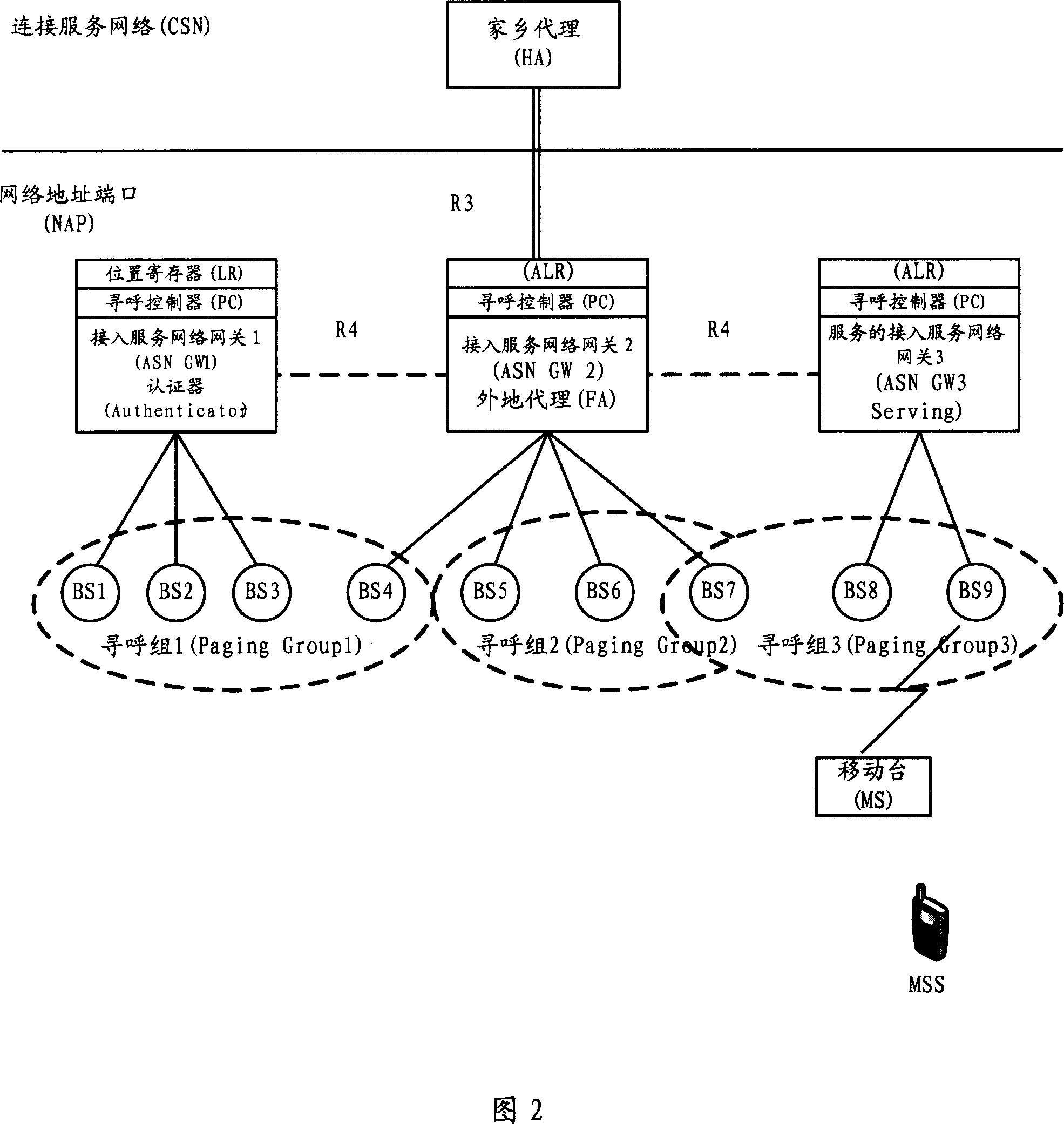
ActiveCN101064722APerfect processComplete and stable processConnection managementData switching by path configurationProcessor registerWireless metropolitan area network
The invention provides a method for the terminal in the wireless LAN entering the leisure mode, it includes following steps: a. the moving terminal sends the requirement for entering the idle mode to the base station BS / paging agent PA; b. said BS / PA response the requirement sent by the moving terminal, the drop point PC determines to allow the moving terminal entering the leisure mode, and informs the data path to release the link of moving terminal; c. after the link of moving terminal is released, BS / PA send deleted registration message which shows the location is refreshed successfully to the moving terminal; d. BS / PA sends the confirmed messages to the further agent FA, and the FA sends the message to the drop point paging controller PC / location register LR, and saves the context ofmoving terminal to refresh the data. The invention increases the integrality and stability for the moving terminal entering the idle mode.
Owner:HUAWEI TECH CO LTD
Method for managing wireless multi-hop network key
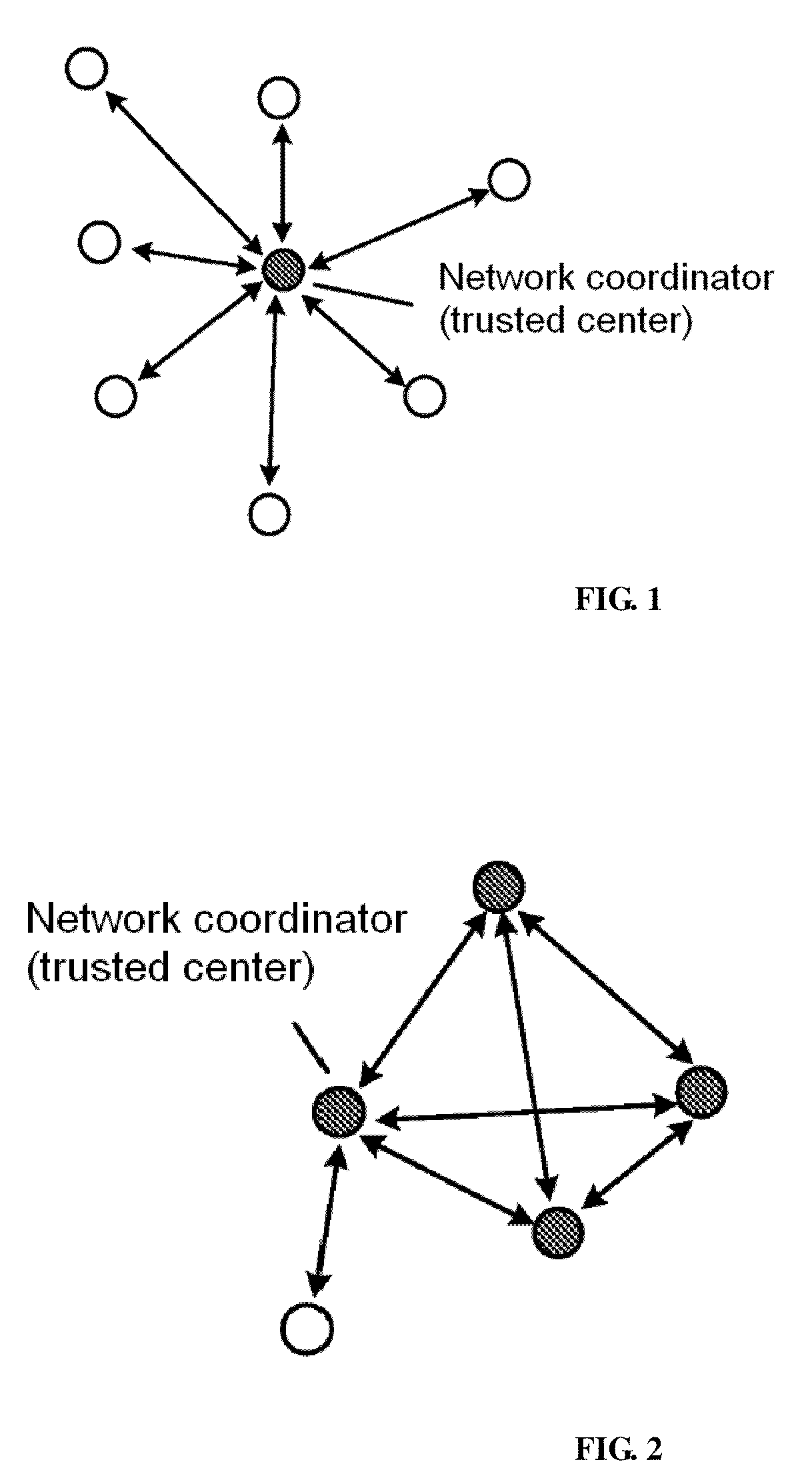
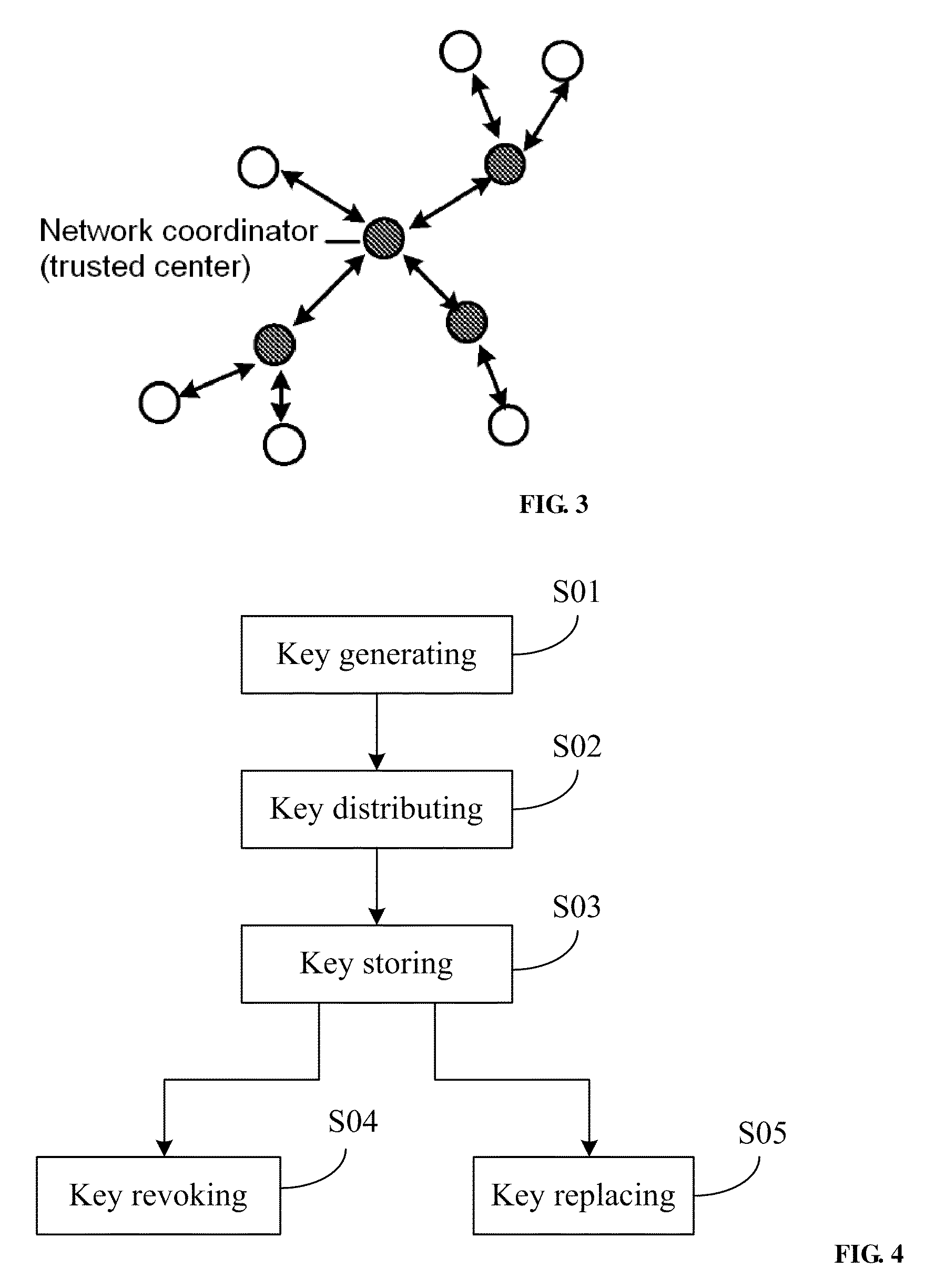
InactiveUS20100299519A1Improve securityImprove performancePublic key for secure communicationNetwork topologiesNetwork keyLarge networks
A method for managing wireless multi-hop network key is applicable to a security application protocol when a WAPI frame method (TePA, an access control method based on the ternary peer-to-peer identification) is applied in a concrete network containing a Wireless Local Area Network, a Wireless Metropolitan Area Network AN and a Wireless Personal Area Network. The key management method of the present invention includes the steps of key generation, key distribution, key storage, key modification and key revocation. The present invention solves the technical problems that the prior pre-share-key based key management method is not suitable for larger networks and the PKI-based key management method is not suitable for wireless multi-hop networks; the public-key system and the ternary structure are adopted, thereby the security and the performance of the wireless multi-hop networks are improved.
Owner:CHINA IWNCOMM
Method for increasing radio city area network safety
InactiveCN1588842ASatisfy functionFulfil requirementsSynchronising transmission/receiving encryption devicesUser identity/authority verificationWireless metropolitan area networkCity area
Owner:CHINA IWNCOMM
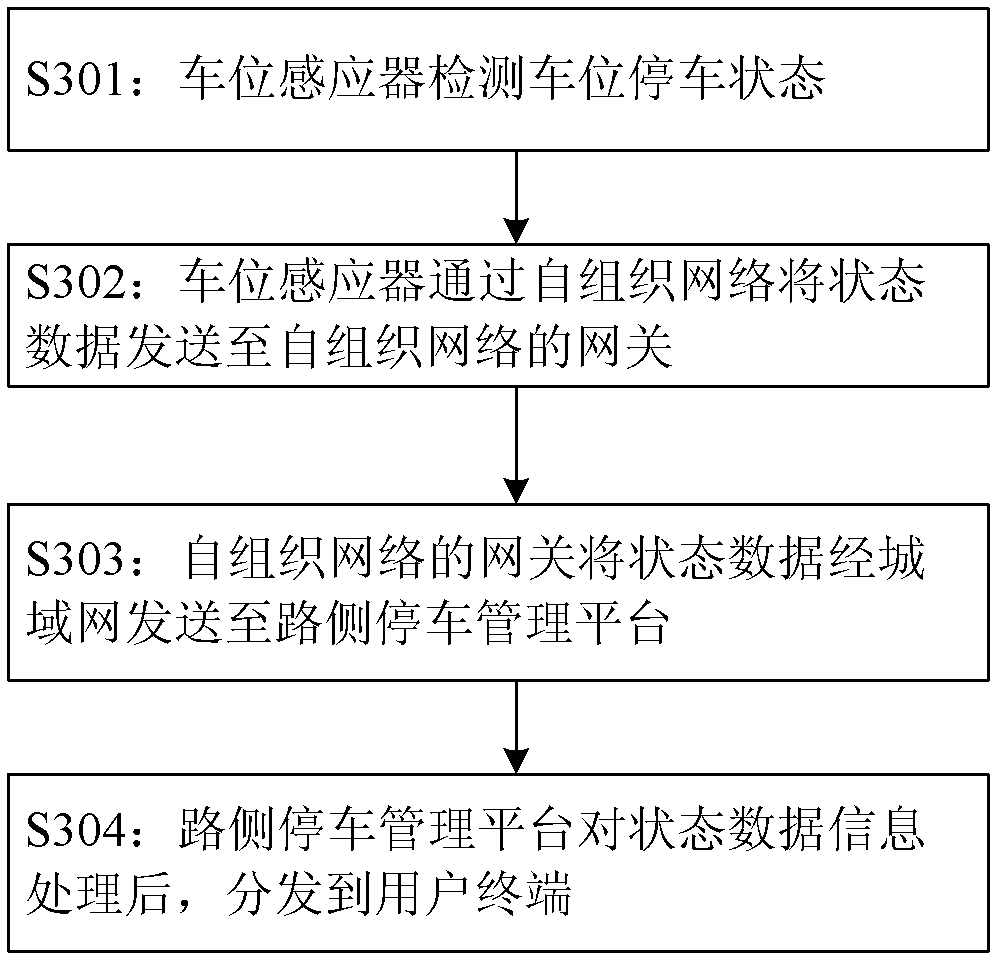
Roadside parking intelligence management system based on wireless sensor network technology and method thereof
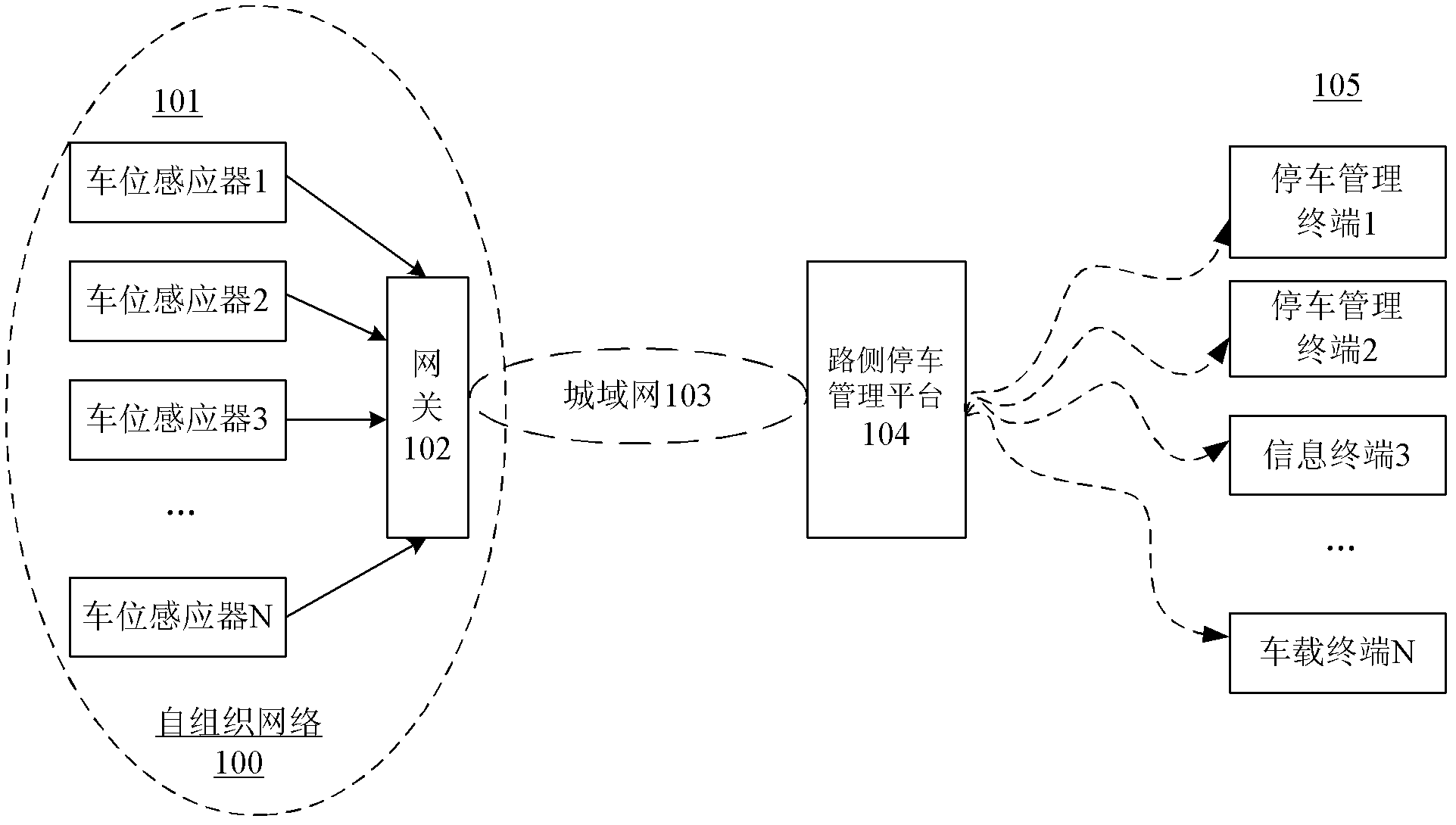
InactiveCN102722996AIndication of parksing free spacesNetwork topologiesData informationWireless metropolitan area network
The invention discloses a roadside parking intelligence management system and a realization method thereof. The system comprises a plurality of parking stall sensors (101), a self-organizing network gateway (102), a wireless metropolitan area network (103) and a roadside parking management platform (104). The parking stall sensors and the gateway (102) form a self-organizing network. The parking stall sensors (101) is used to sense a parking state of the parking stall and send parking state information to the gateway (102) of the self-organizing network by using the self-organizing network. The gateway (102) is used to send received parking state data of the parking stall sensors (101) to the roadside parking management platform (104) through the wireless metropolitan area network (103). The roadside parking management platform (104) is used to manage parking stall data information. According to the invention, through the parking stall sensors, the parking stall state information can be acquired in real time and can be timely reported to the roadside parking management platform so that high-efficient and accurate management is realized.
Owner:BEIJING LOIT TECH
Wireless multi-hop network key management method based on ID
InactiveCN101222325AImprove securityImprove performanceKey distribution for secure communicationPublic key for secure communicationStructure of Management InformationNetwork key
The invention discloses an ID-based wireless multi-hop network key management method which is applicable to a safety application protocol when a WAPI frame method (TePA, an access control method based on the ternary peer-to-peer identification) is applied in a concrete network containing a WLAN, a WMAN and a WPAN. The key management method of the invention comprises the steps of key generation, key distribution, key storage, key modification and key revocation. The invention solves the technical problems that the prior pre-share-key based key management method is not suitable for larger networks and the PKI-based key management method is not suitable for wireless multi-hop networks; the public-key system and the ternary structure are adopted, thereby improving the security and the performance of the wireless multi-hop networks.
Owner:CHINA IWNCOMM
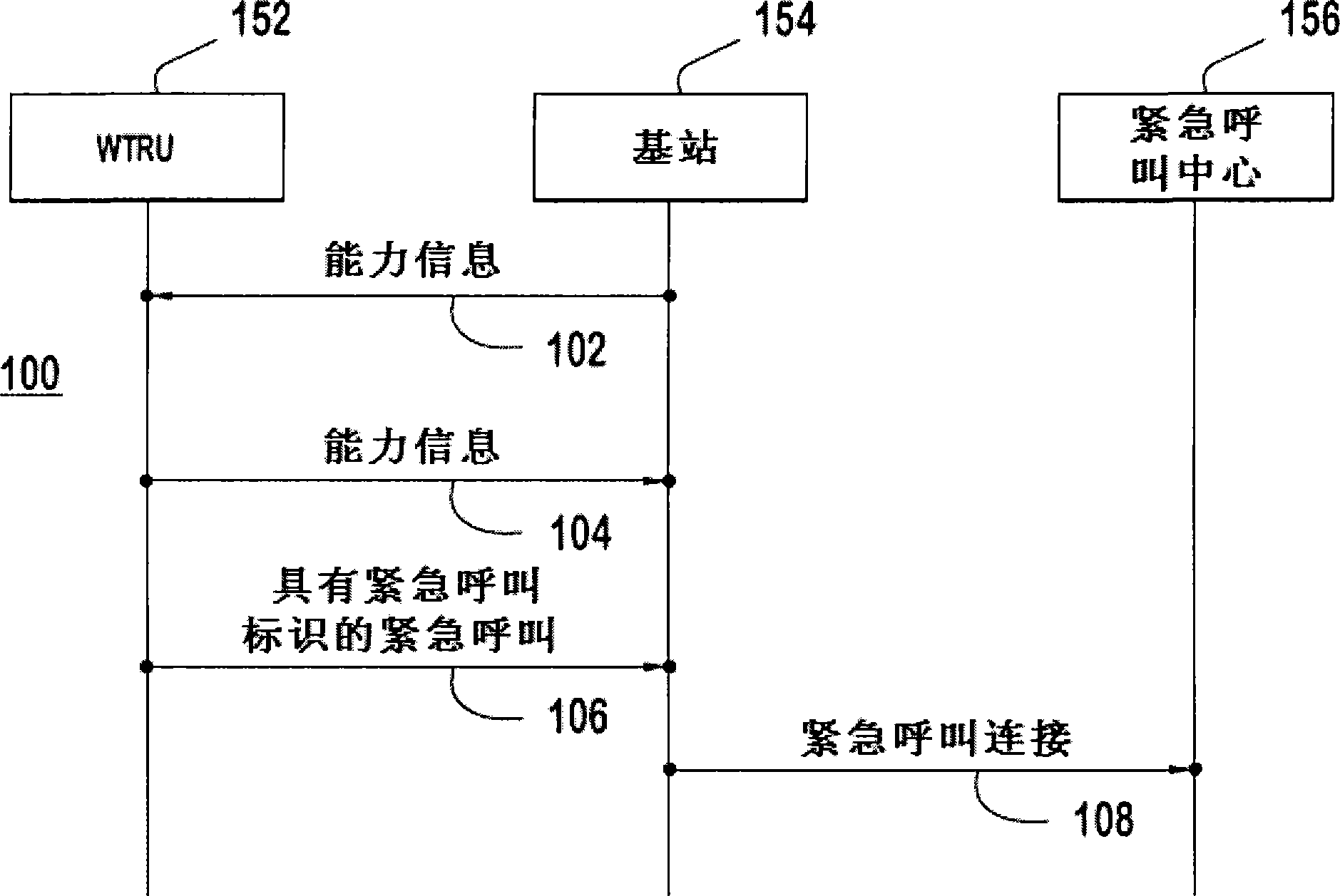
Method and apparatus for supporting an emergency call in a wireless metropolitan area network
InactiveCN101444118AEmergency connection handlingAssess restrictionCommunications systemWireless metropolitan area network
A method and apparatus for supporting an emergency call in a wireless communication system including a wireless metropolitan area network (WMAN) are disclosed. A wireless transmit / receive unit (WTRU) sends an emergency call message to a base station of the WMAN to make an emergency call along with an emergency call indication. The base station then admits the emergency call with or without performing a security procedure and connects the WTRU to an emergency call center. The base station and the WTRU may communicate capability information regarding support of emergency calls. Location information of the WTRU is also forwarded to the emergency call center. The base station may work as a proxy for the WTRU if the WTRU does not have all the required functionalities to complete the emergency call. The WTRU may be a multi-mode WTRU capable of communicating with two or more radio access networks (RANs).
Owner:INTERDIGITAL TECH CORP
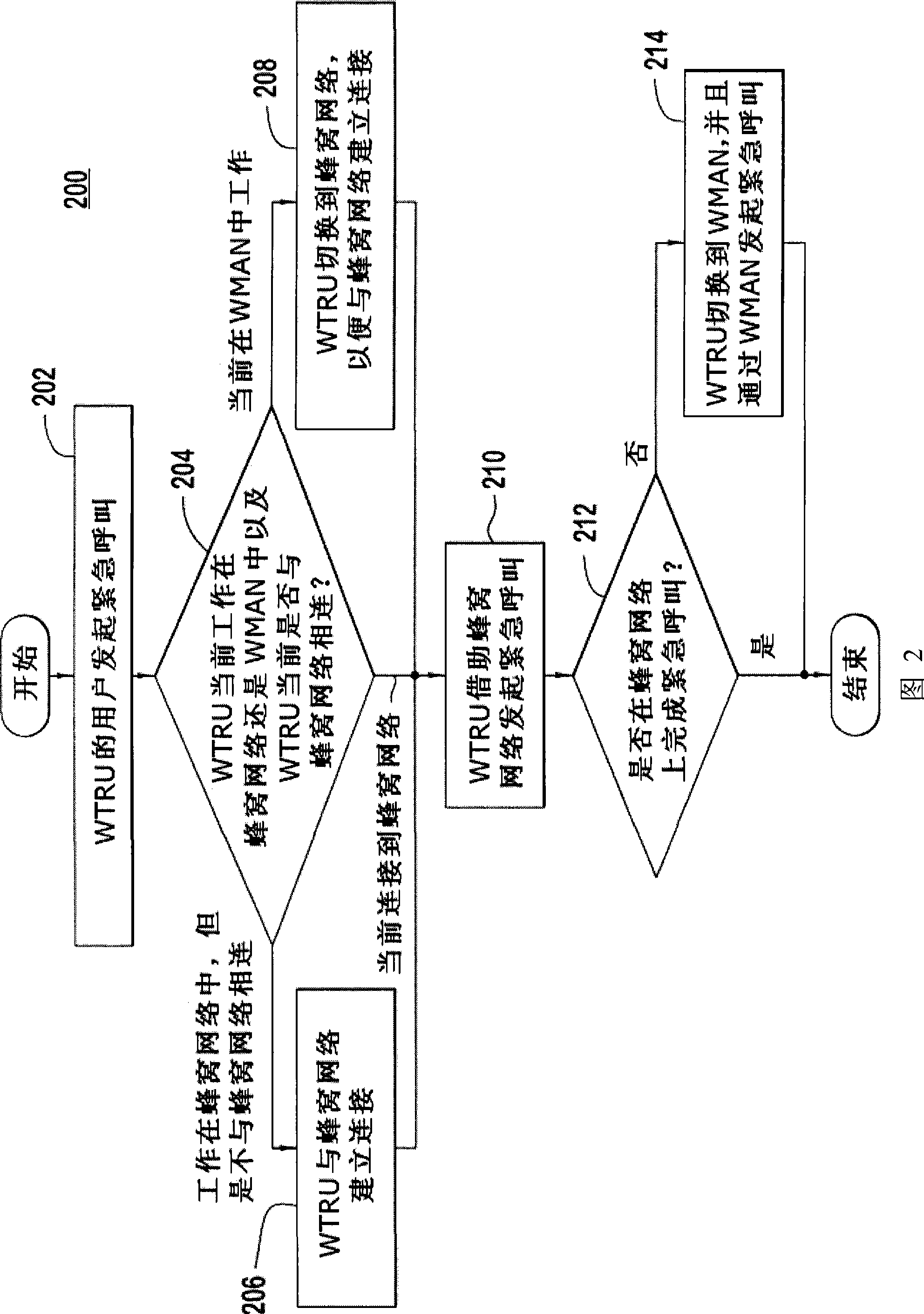
Method and apparatus for facilitating a fast handoff in a wireless metropolitan area network
ActiveUS20070280176A1Connection managementRadio/inductive link selection arrangementsWireless metropolitan area networkComputer science
A method and apparatus for facilitating a fast handoff for subscribers in a Wireless Metropolitan Area Network (WMAN) by establishing a hard association with a first entity by sending a hard association request to the first entity and receiving a hard association response in response to the hard association request and establishing a pending association with a second entity by sending a pending association request to a second entity and receiving a pending association response from the second entity. In one embodiment, the pending association with the second entity may be converted to a hard association.
Owner:MOTOROLA SOLUTIONS INC
Network access authentication and authorization method and an authorization key updating method
ActiveUS20100009656A1Avoid a lotSimple calculationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsWireless metropolitan area networkBroadband
A network access authentication and authorization method includes the steps of: constructing an access and authorization request packet; constructing a certificate authentication request packet, constructing a certificate authentication response packet; constructing an access and authorization response packet; constructing an access and authorization acknowledgement packet. And an authorization key updating method includes the steps of: constructing an access and authorization request packet; constructing an access and authorization response packet; constructing an access and authorization acknowledgement packet. The invention resolves the security problem that a mobile terminal accesses a base station in the wideband wireless multimedia network, and realizes both bi-directional identity authentication of a mobile terminal and a base station and unidirectional identity authentication from a base station to a mobile terminal. The authorization key negotiation calculation is simple, and the key management is simply realized by using message acknowledgement manner. The invention is applied to the wired network and the wireless network, such as the wireless local area network, the wireless metropolitan area network, and the broadband wireless multimedia network etc.
Owner:CHINA IWNCOMM
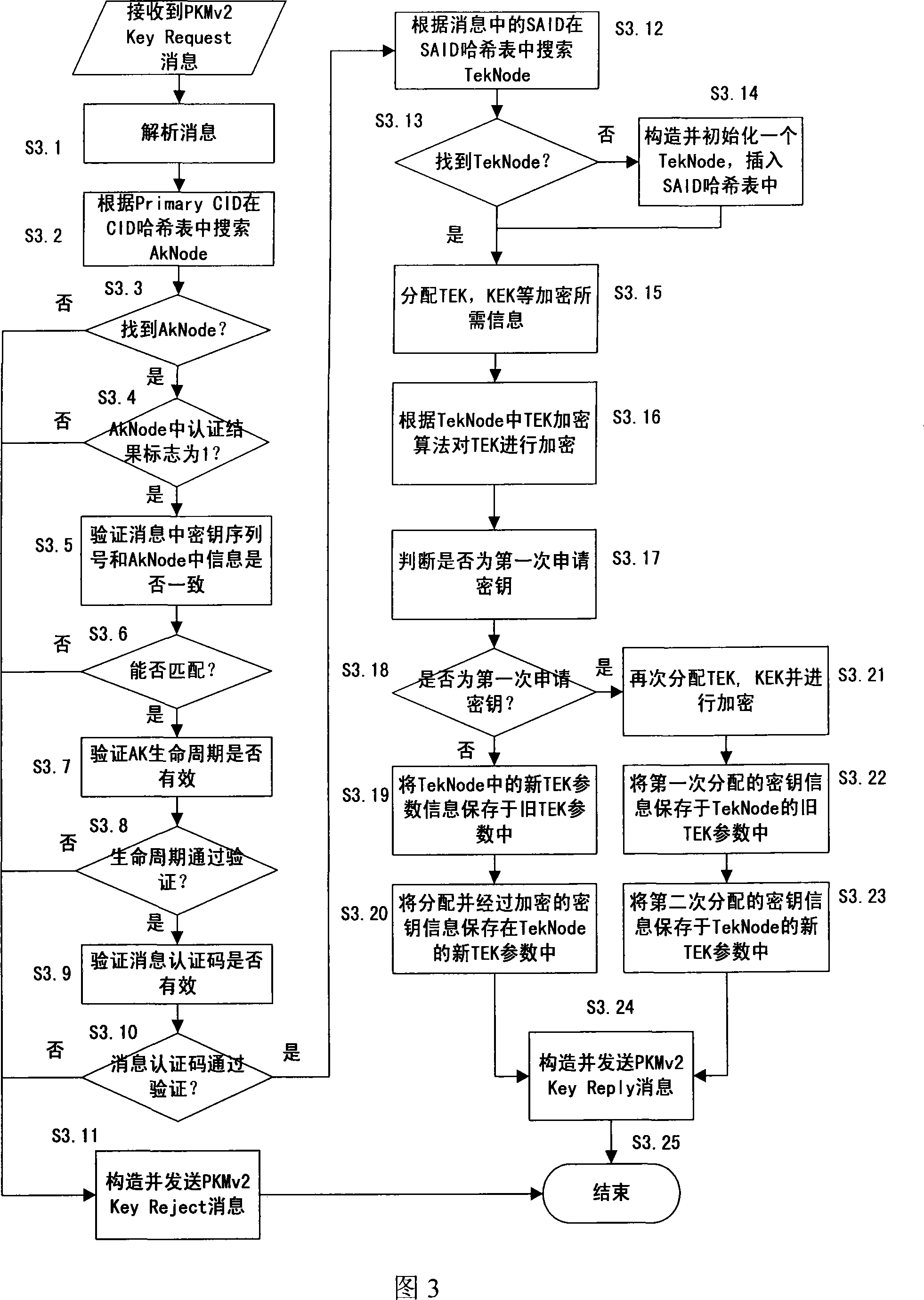
An organization structure and maintenance method of security context in media accessing control system
ActiveCN101217364AAchieve maintenanceImprove maintenance efficiencyKey distribution for secure communicationRadio/inductive link selection arrangementsService flowControl system
The invention discloses a safe context organizing structure and a maintaining method in broadband wireless metropolitan area network base station medium accessed to a control system. The organizing structure comprises a connection identifiers hashtable which is used for managing the context of authorization keys and a safety association identifying hashtable which is used for managing the context of communication secret keys. The maintaining method operates on the connection identifiers hashtable and the safety association identifying hashtable respectively when can authenticate the expandable authentication agreement to terminals, when in the process of safety association-communication encryption secret key shaking hands and when terminals distributes secret keys and create service flow. The invention can realize the organization and maintenance of safety context and high-speed searching. When terminals are in large number and the data amount is large, the maintaining efficiency of data can be improved to a large extent.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Beep-page method in wireless city region network
InactiveCN1921684AOptimize and perfect divisionOptimize and improve the paging processRadio/inductive link selection arrangementsNetwork data managementWireless metropolitan area networkBase station
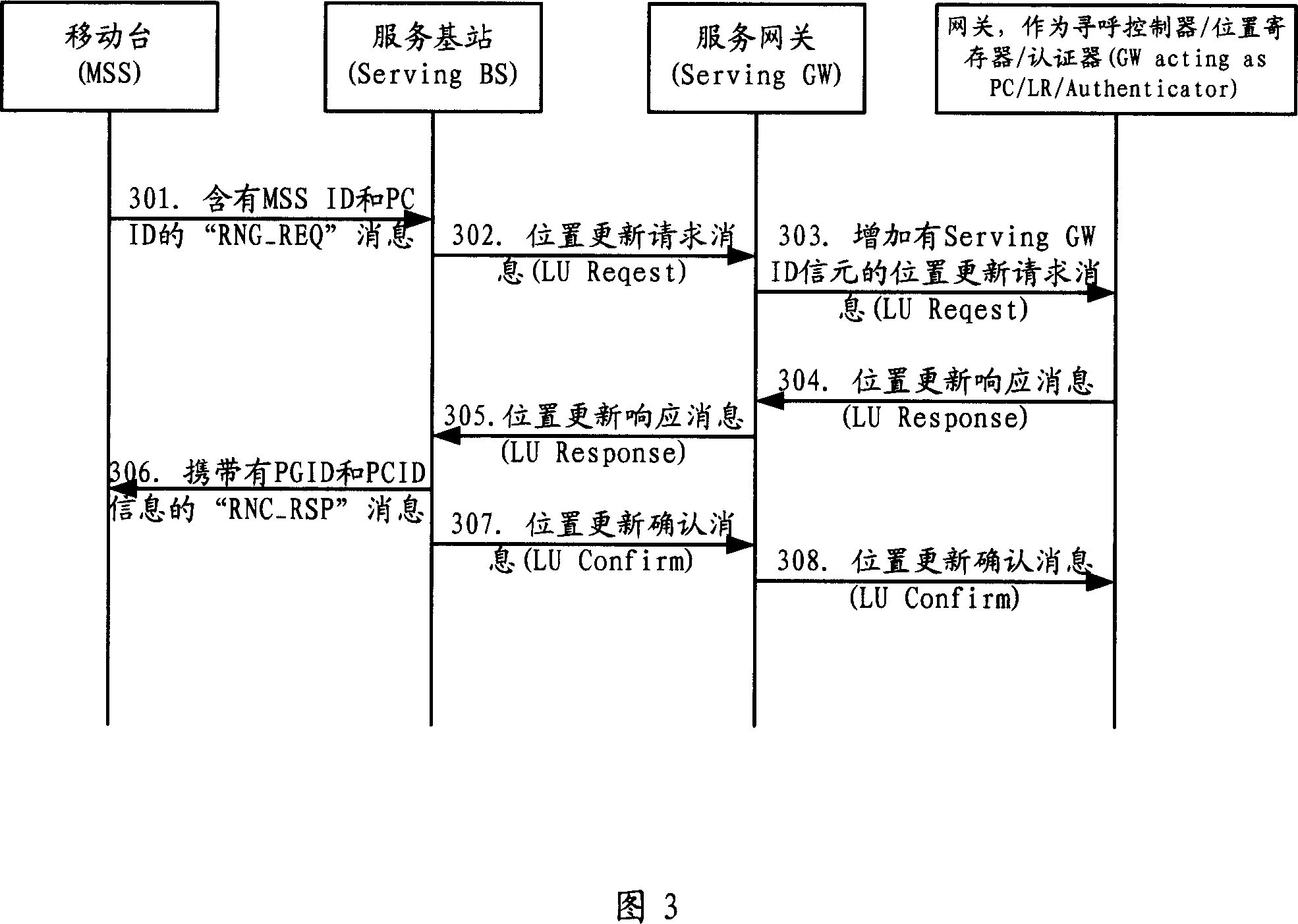
The invention relates to a page method of wireless city network, to reduce the maintenance, page range and number. Wherein, it limits the range of page group in one ASN GW; the Serving GW adds itself mark when transferring the position refresh message of base station; PC / LR receives said position refresh message and records the relationship between page group and Serving GW; when paging, based on said relationship, only sending page message to relative Serving GW.
Owner:HUAWEI TECH CO LTD
Multicast key management method for wireless city region network
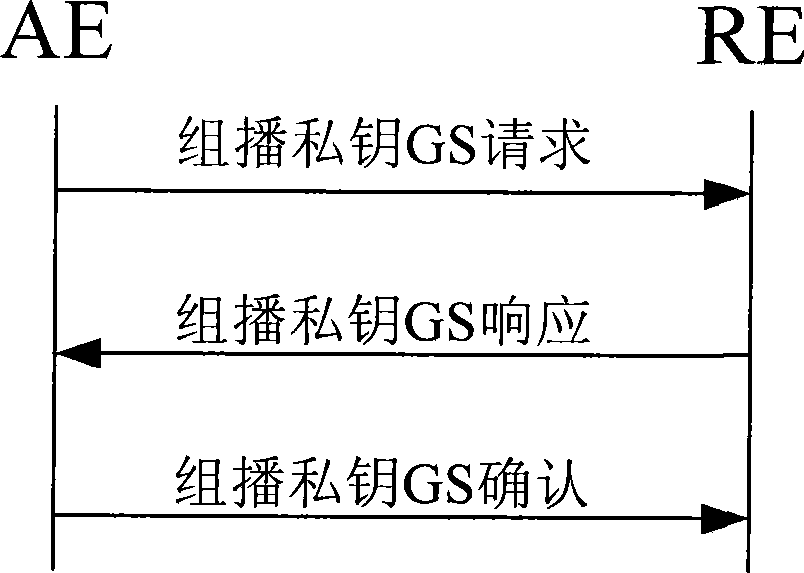
InactiveCN101364865AImprove securityTake advantage ofSpecial service provision for substationKey distribution for secure communicationWireless metropolitan area networkBroadcasting
The invention relates to a multicast key management method of wireless metropolitan area network. The method comprises the following steps: (1) distribution of multicast private keys: (1.1) transmitting a multicast private key request grouping from a requester entities to a responder entities, (1.2) transmitting a multicast private key response grouping from the responder entities to the requester entities, and (1.3) transmitting a multicast private key confirm grouping from the requester entities to the responder entities; and (2) distribution or updating of encrypted keys of the multicast private keys; (2.1) broadcasting the encrypted keys broadcasting grouping of the multicast private keys by the responder entities to all of the requester entities, and (2.2) deciphering the encrypted keys of the multicast private keys from the encrypted keys broadcasting grouping of the multicast private keys by the requester entities. The multicast key management method solves the problems of the poor key safety and low updating efficiency of the multicast keys of the multicast key management of the wireless metropolitan area network.
Owner:CHINA IWNCOMM
Combined narrowband interference detection, elimination and channel estimation method based on continuous cyclic shift training sequence in OFDM system
ActiveCN105897643AThe impact of reducing the estimated qualityAccurate detectionMulti-frequency code systemsSequence designEstimation methods
The present invention relates to a combined narrowband interference detection, elimination and channel estimation method based on a continuous cyclic shift training sequence in an OFDM system. On the condition of using two OFDM symbol training sequences to carry out the channel estimation, the method utilizes a signal detection and estimation technology and a training sequence design technology to realize the asynchronous narrowband interference detection, estimation and elimination, is applied to a the OFDM systems existing the narrowband interference, such as a wireless local area network IEEE802.11a, a wireless metropolitan area network WiMAX IEEE 802.16e, etc., realizes the accurate estimation and elimination of an asynchronous narrowband signal while realizing the interference robustness detection, and enables the training sequence auxiliary channel estimation performance on an interference condition to be improved effectively.
Owner:NAT UNIV OF DEFENSE TECH
Curb-side parking fee management system and method based on wireless metropolitan area network and POS terminal
InactiveCN101667305AInnovation of technical ideasKey Technology InnovationTicket-issuing apparatusApparatus for meter-controlled dispensingWireless metropolitan area networkComputer terminal
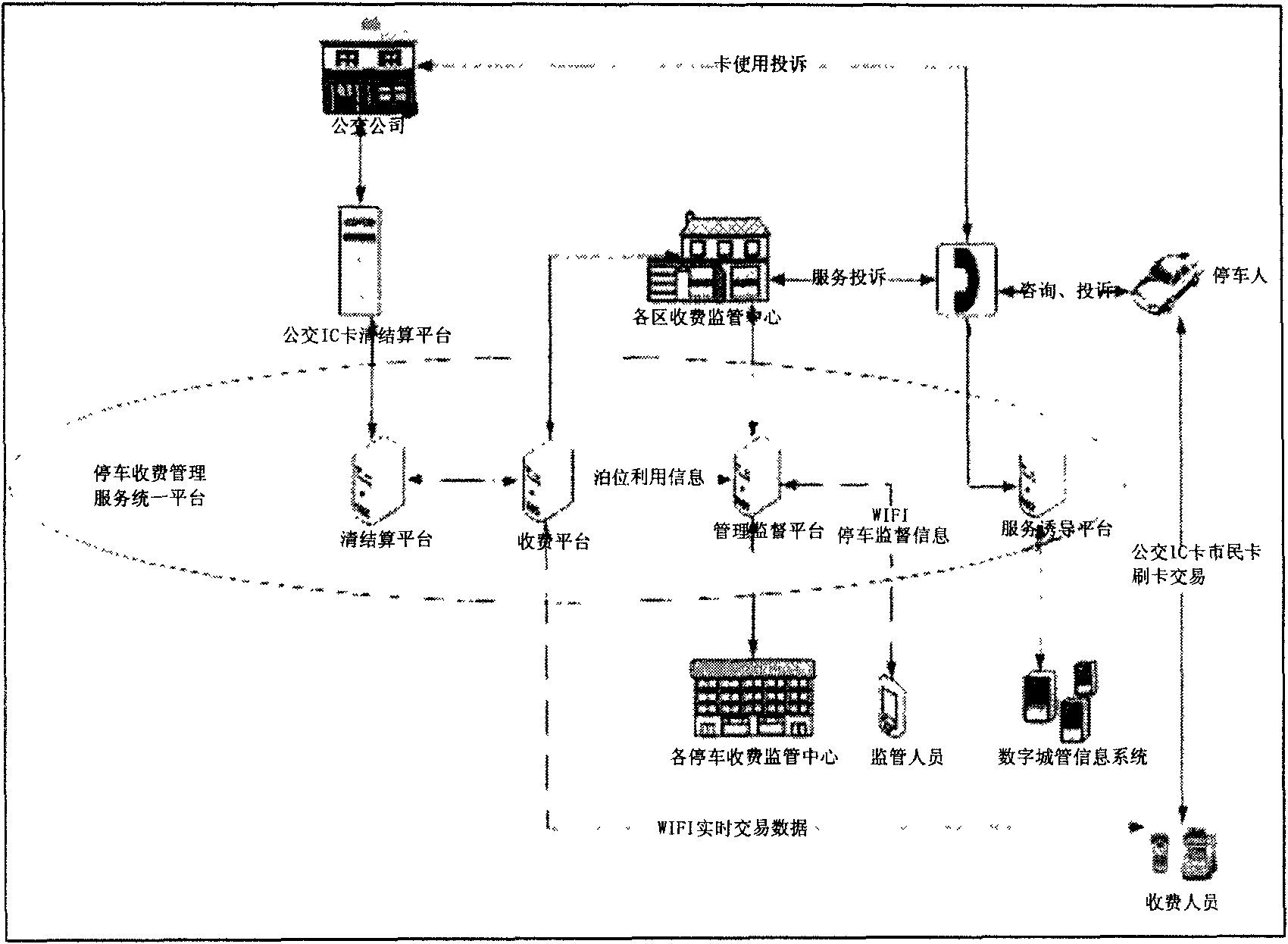
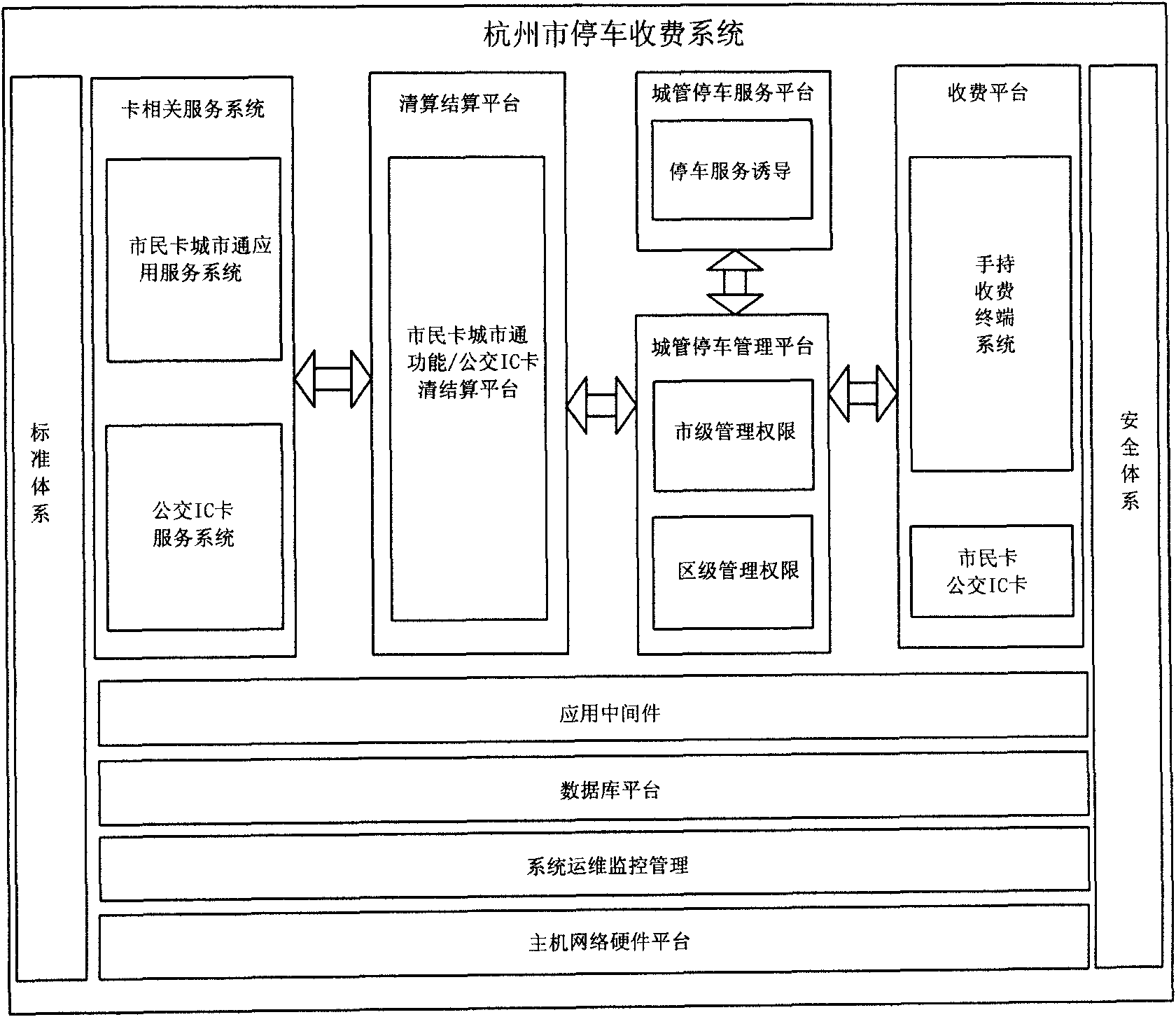
The invention discloses a curb-side parking fee management system and a method based on a wireless metropolitan area network and a POS terminal. The system at least consists of a parking fee management platform, a handheld automatic charging POS machine and a communication network, and a parking fee management service unified platform comprises a clearing platform, a charging platform, a management supervising platform and a service inducing platform. The method comprises the following steps of downloading the fee rate of a parking lot, collecting the parking information, uploading the parkinginformation to the parking fee management platform in real time by the communication network, charging the corresponding fee from a parker, and uploading the charging information to the parking fee management platform in real time through the wireless metropolitan area network. The invention integrates, innovates and utilizes the WIFI, handheld POS machine and IT information technology to comprehensively monitor personnel, data and finance, and creates an all-round service platform which integrates four functions of the parking management, the fee clearing, the information supervision and theinduction service.
Owner:杭州市人民政府城市管理办公室 +1
Electric transmission line real-time video condition monitoring system based on wireless communication
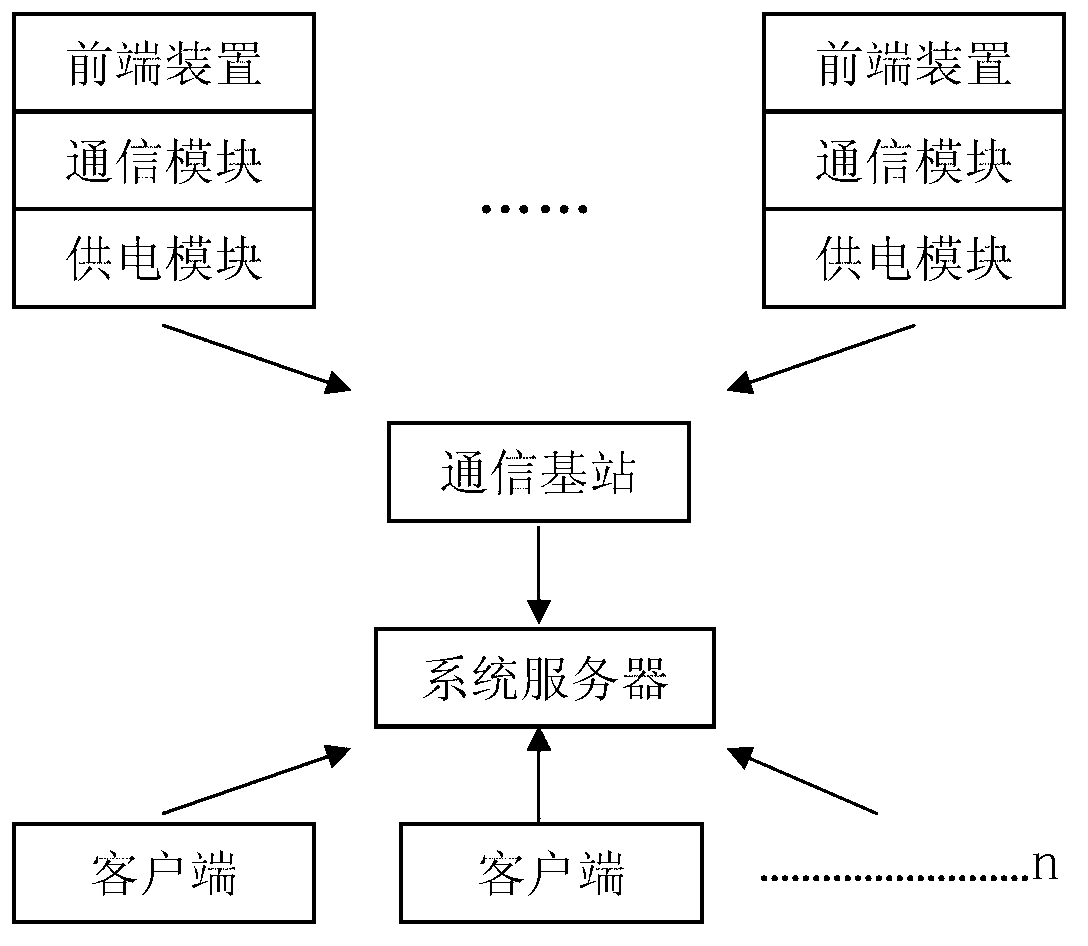
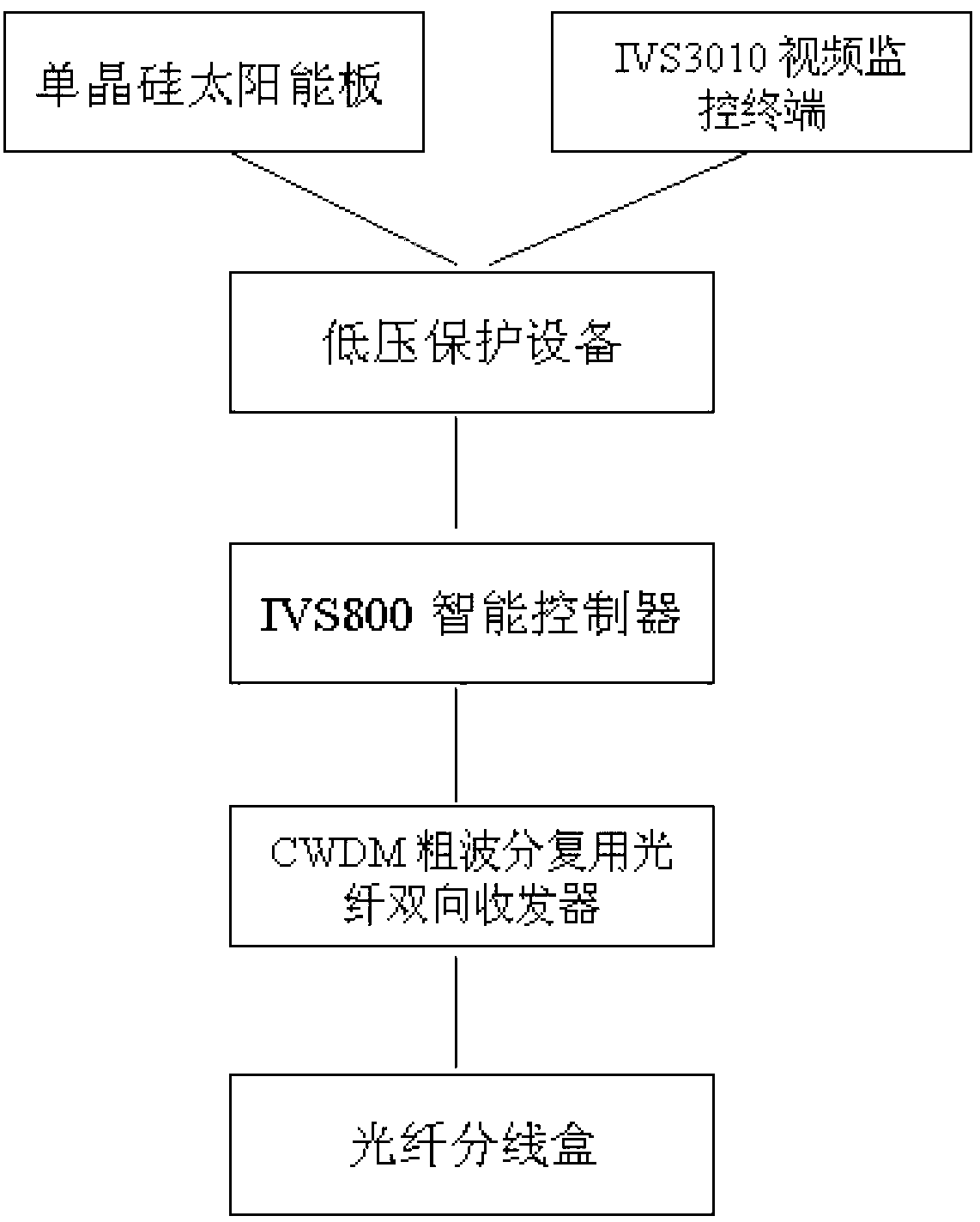
InactiveCN103022932AHigh bandwidthImprove securityClosed circuit television systemsApparatus for overhead lines/cablesEngineeringAdaptive capacity
The invention discloses an electric transmission line real-time video condition monitoring system based on wireless communication. The system comprises a plurality of front end monitoring devices, a communication module and a power supply module, the front end monitoring devices are installed on electric transmission line poles and towers, the communication module and the power supply module are connected with the front end monitoring devices, the front end monitoring devices transmit image video information collected through an optical ground wire (OPGW) optical fiber and a wireless metropolitan area network 802.16 protocol to a communication base station, the communication base station transmits the information to a system server, the server checks and browses a current real-time monitoring state through a client, and transmission line states are checked through rotation and focal distances of a pan-tilt remote control camera, so that electric transmission line video states are real-timely monitored. The system uses the OPGW optical fiber for transmission so that the network bandwidth is large and safety is high; and a wireless metropolitan area network technology is used for performing wireless extension so that the system can be used in mountain areas, and the system has the advantages of being high in safety, comprehensiveness, real-time performance and adaptive capacity.
Owner:BAOJI POWER SUPPLY BUREAU +1
Synchronization method for multiple low-power launching pads leaded by high-power launching pad
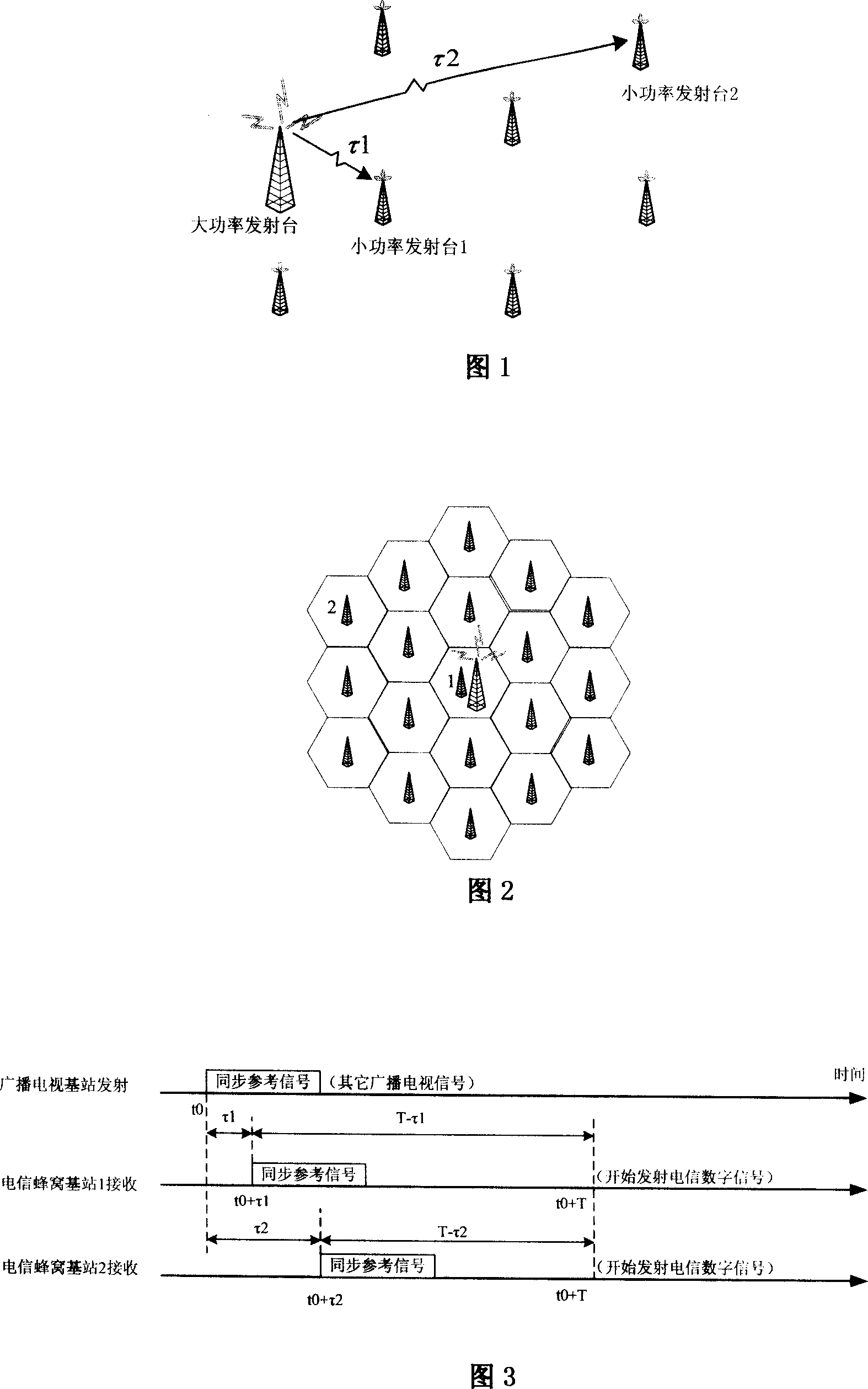
ActiveCN101154990AResolve synchronizationLow costSynchronisation signal speed/phase controlRadio transmission for post communicationCommunications systemTransmission time delay
The present invention relates to a method for synchronizing a plurality of low-power sending stations which are dominated by a high-power sending station, each low-power sending station receives the reference synchronizing signal transmitted by the high-power sending station, does synchronizing according to the synchronizing signal and respectively compensates the signal transmission time delay. The high-power sending station can be broadcasting television base station and the low-power sending station can be one or a plurality of base stations selected from wireless metropolitan area network cellular base station, wireless local area network base station and wireless personal area network. The present invention settles the problem of synchronizing the considerable sending stations and can be widely used in the wireless communication system that needs to be done with network synchronizing, and reduces the cost of realizing the network synchronizing.
Owner:SHANGHAI RES CENT FOR WIRELESS TECH
Interworking system and method between mobile communication network and wireless metropolitan area network
InactiveCN1874287AEasy to useLow costNetworks interconnectionWireless metropolitan area networkProxy server
Owner:ZTE CORP
Task scheduling method based on micro-cloud load balancing in wireless metropolitan area network
ActiveCN109639833AShort response timeImprove experienceData switching networksWireless metropolitan area networkBalance strategy
The invention discloses a task scheduling method based on micro-cloud load balancing in a wireless metropolitan area network. According to the method, how to unload tasks and dispatch the tasks to reasonable micro-clouds is considered, so that a system delay is shortened. For solving the problem of optimization of response time of the micro-cloud tasks in a wireless metropolitan area network environment, an algorithm thought of micro-cloud load balancing is introduced, and a micro-cloud load balancing strategy is provided, thereby shortening average response time of the micro-cloud tasks as much as possible under the condition of meeting multiple constraints in the network. According to the strategy, unique characteristics of the wireless metropolitan area network and micro-cloud task unloading are fully considered; and firstly, the micro-clouds of the network are classified, then expected values of input / output task quantities of the micro-clouds are calculated, and finally minimum-cost maximum flow meeting the constraints is found in a flow network so as to execute all the tasks in the network. The method has positive effects in shortening user task response time and improving user experience.
Owner:FUJIAN NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com