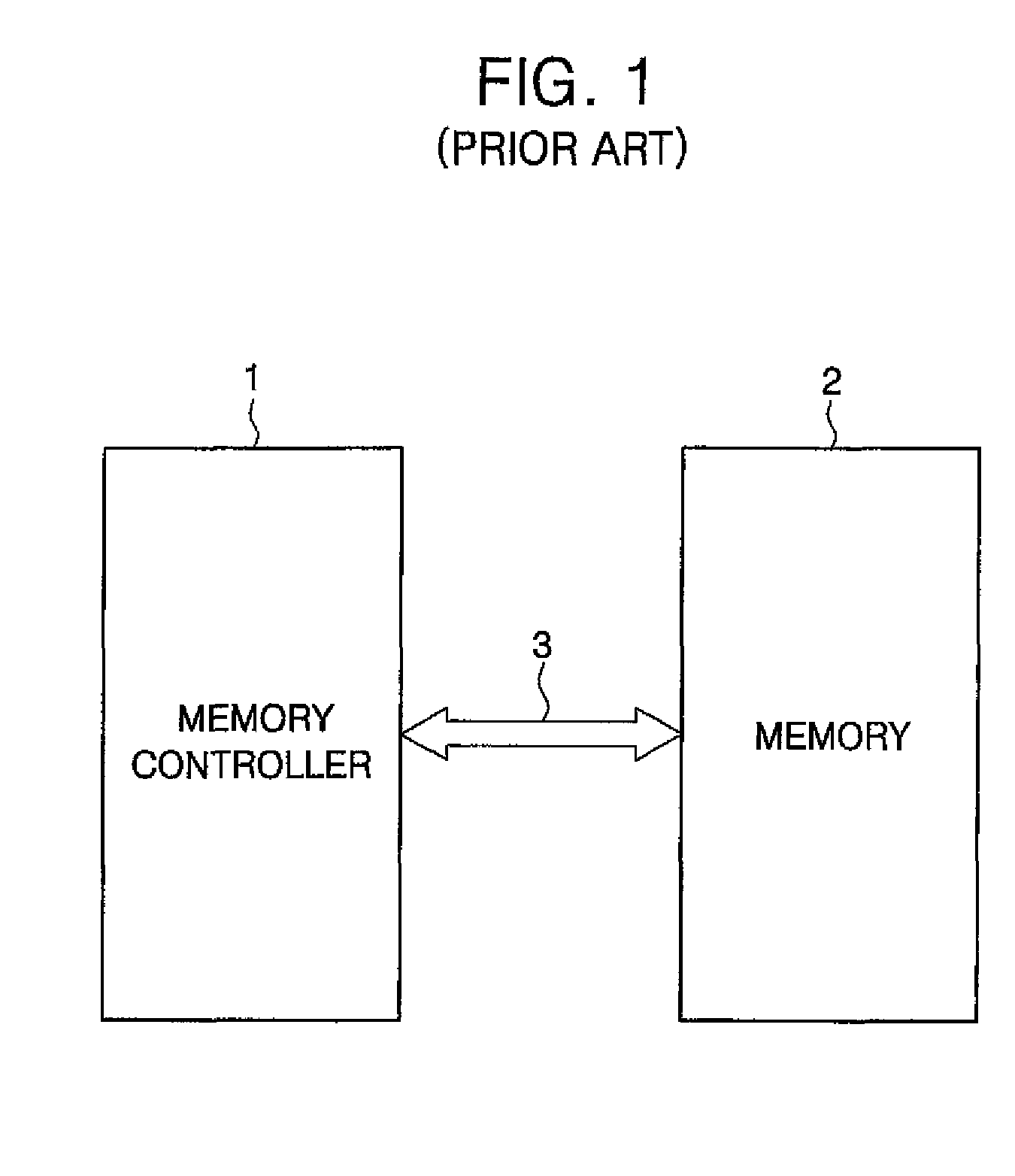
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40results about How to "Ensure data integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
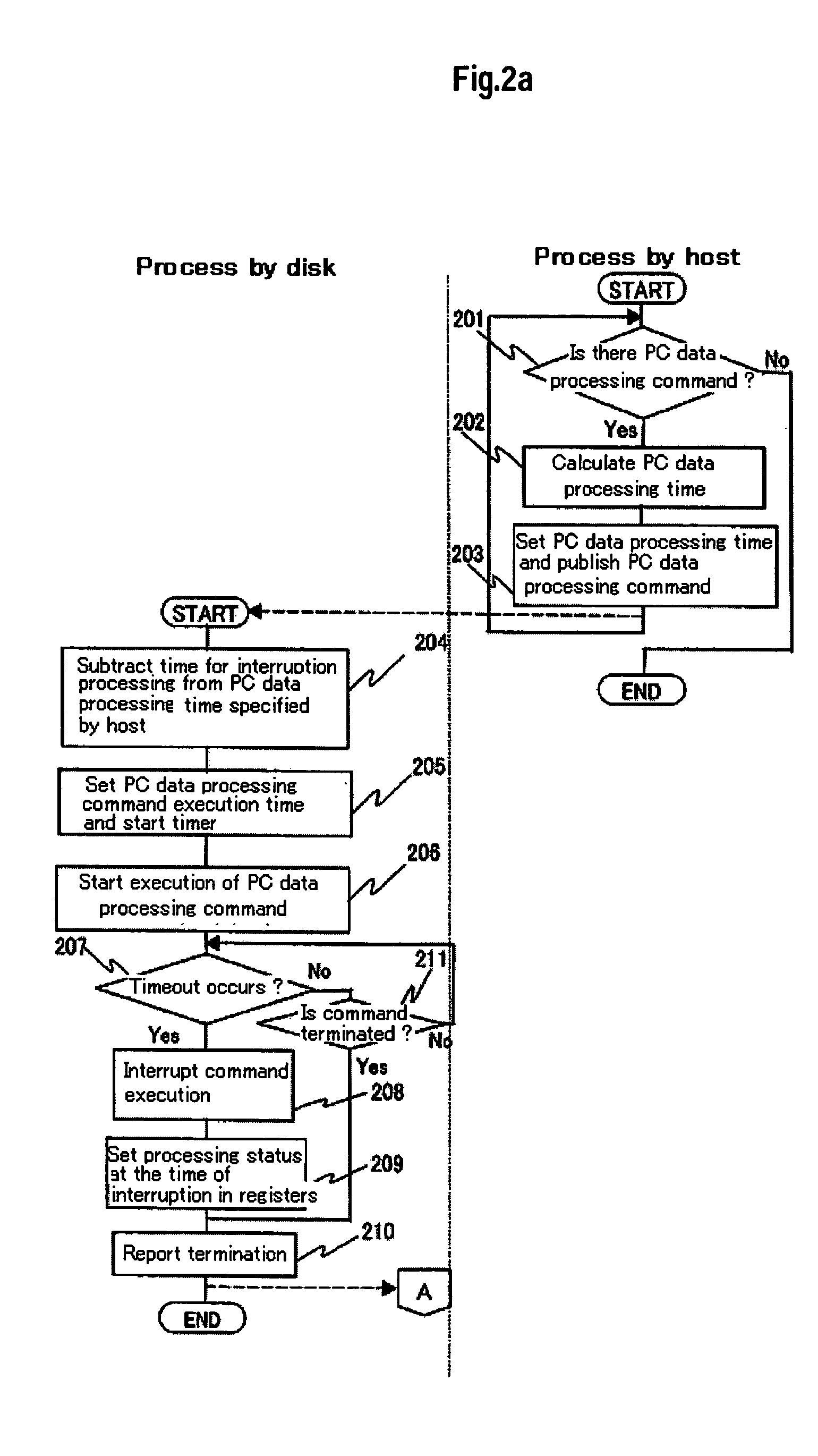
Method of enabling a wireless information device to access data services
InactiveUS20050154796A1Ensure data integrityEasy to orderBroadcast service distributionSubstation equipmentInformation deviceWeather data
A method of providing data to a wireless information device, in which data supplied from a remote service provider is represented by an icon which is (a) automatically displayed within an application running on the device, and which (b) changes if the data alters, in order to alert the user to new data or to represent that new data. For example, a weather icon could be displayed in a calendar application if the device is being supplied or can access weather data. The weather icon changes dynamically to represent the weather on the particular day in the calendar; perhaps tomorrow's predicated weather
Owner:SYMBIAN LTD
Ensuring data integrity in network memory
ActiveUS7571344B2Avoid and limit transmissionReduce network trafficError detection/correctionNetwork connectionsCommunication interfaceData integrity
A first appliance for ensuring data integrity in network memory is disclosed. The first appliance includes a processor and a communications interface that communicates over a communication network with a second appliance of the network memory. The processor determines whether reconciliation between a first peer state information in the first appliance and a second peer state information in the second appliance is needed. The first peer state information and the second peer state information track the status of data in the network memory. The processor determines an action to reconcile the first peer state information with the second peer state information based on a positive determination that the reconciliation is needed. The processor then performs the action to reconcile the first peer state information with the second peer state information.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
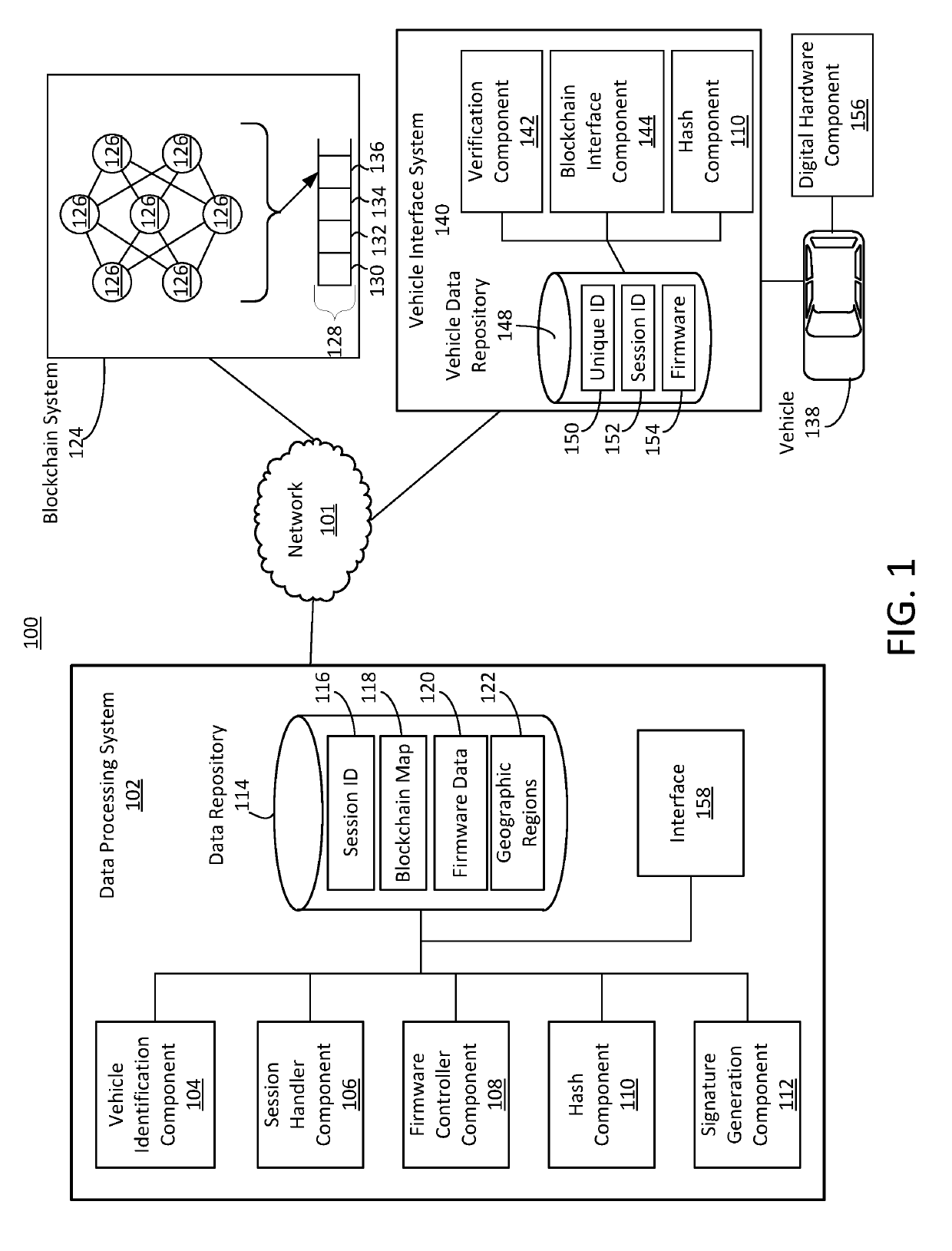
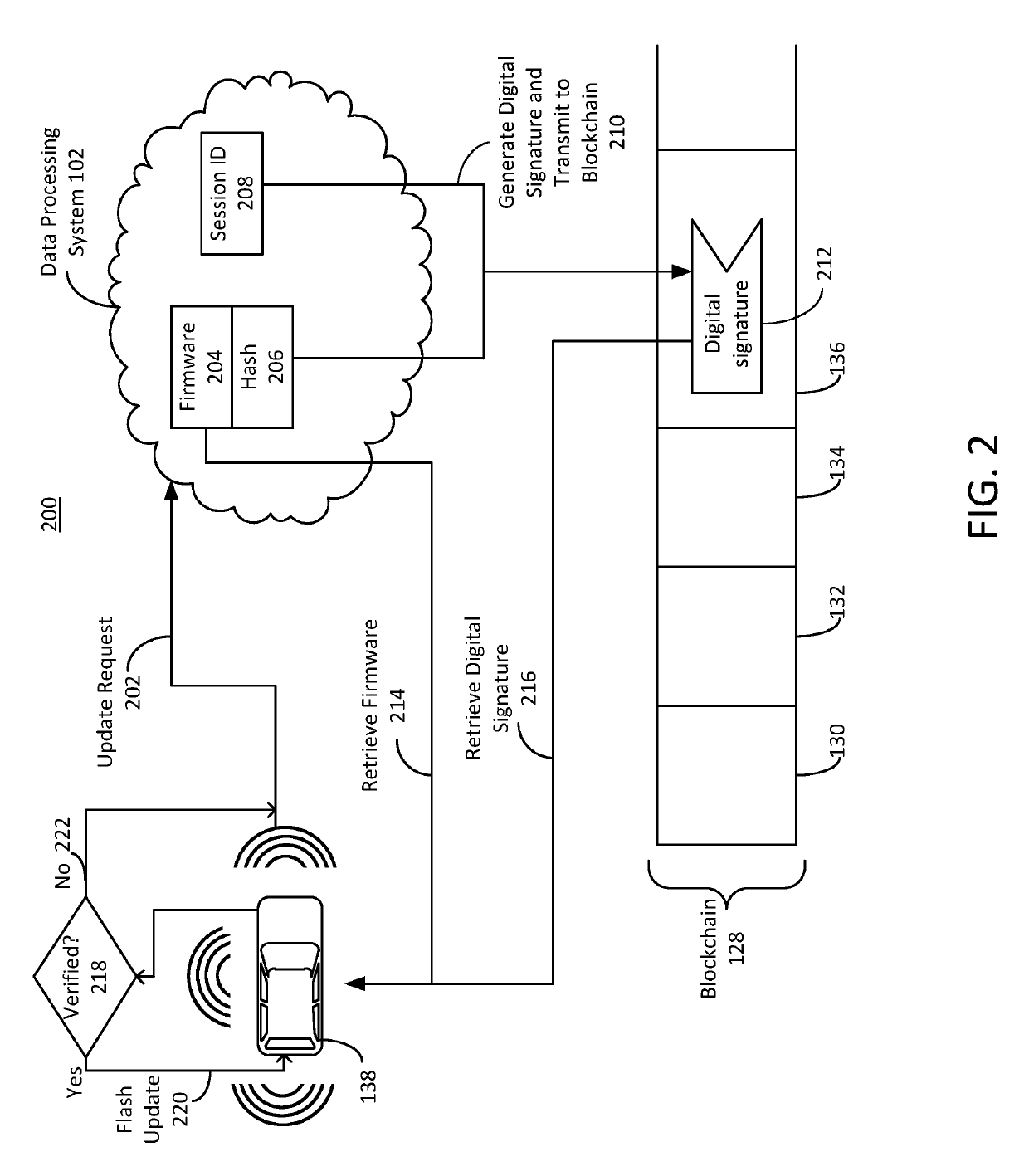
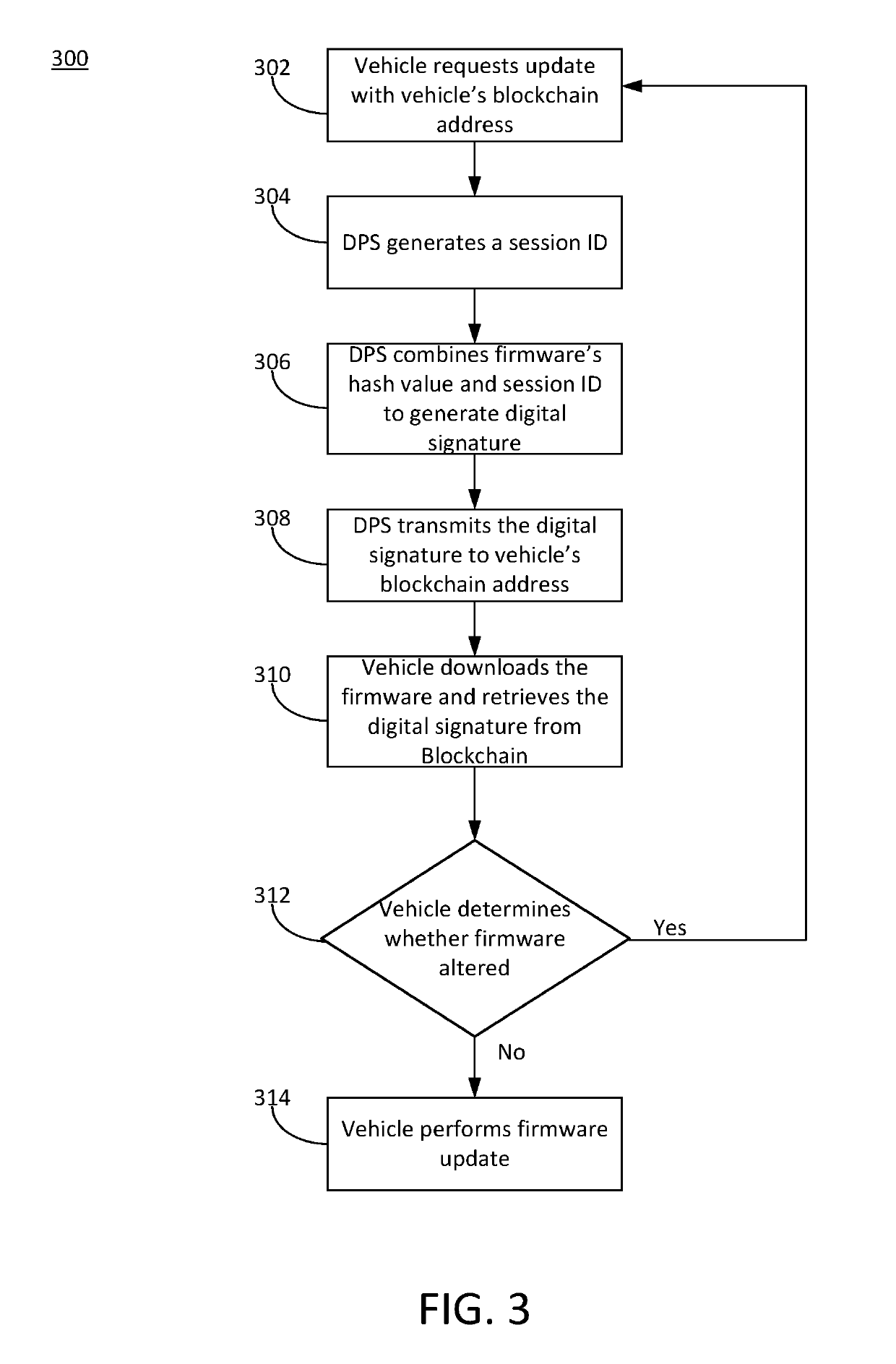
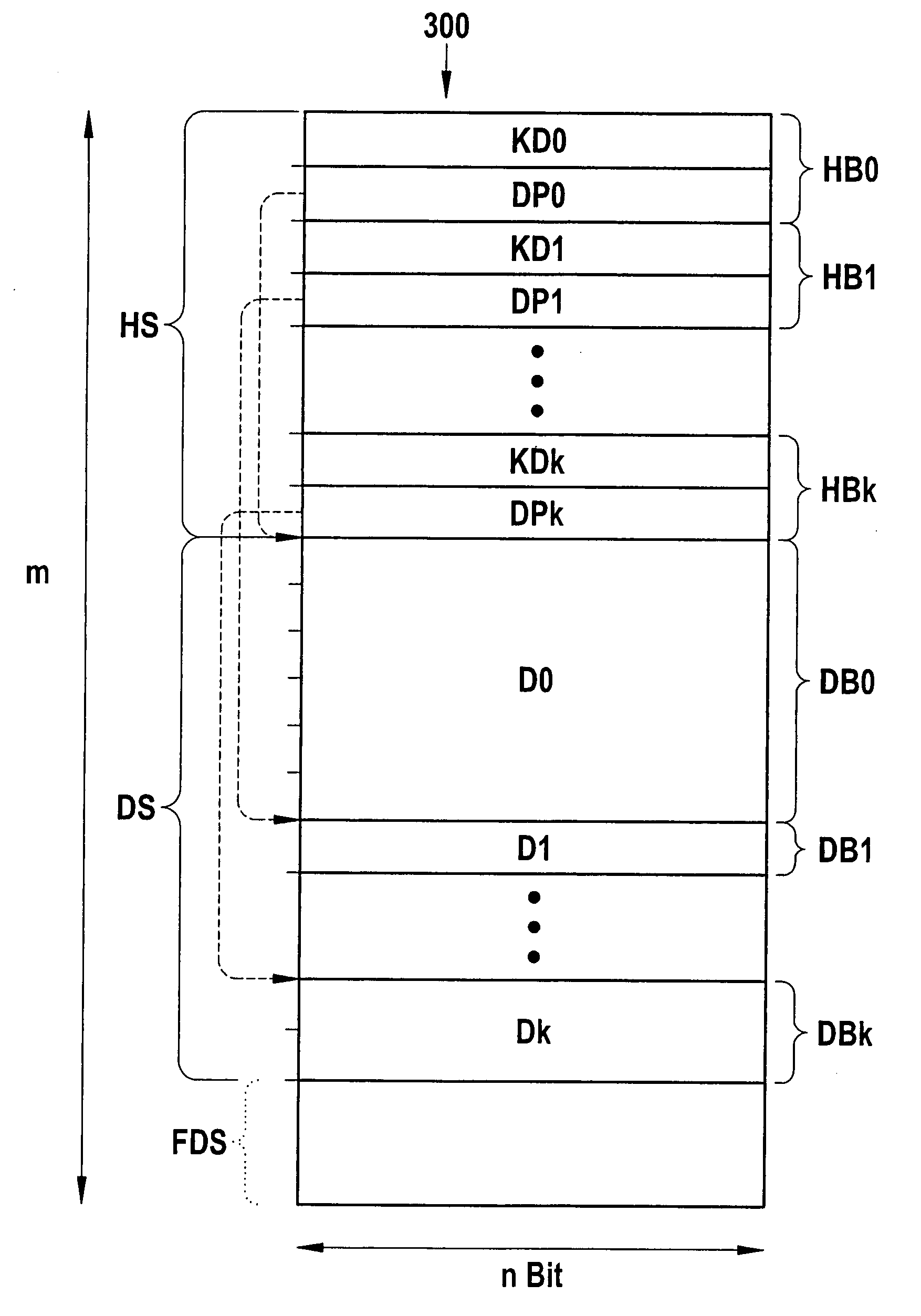
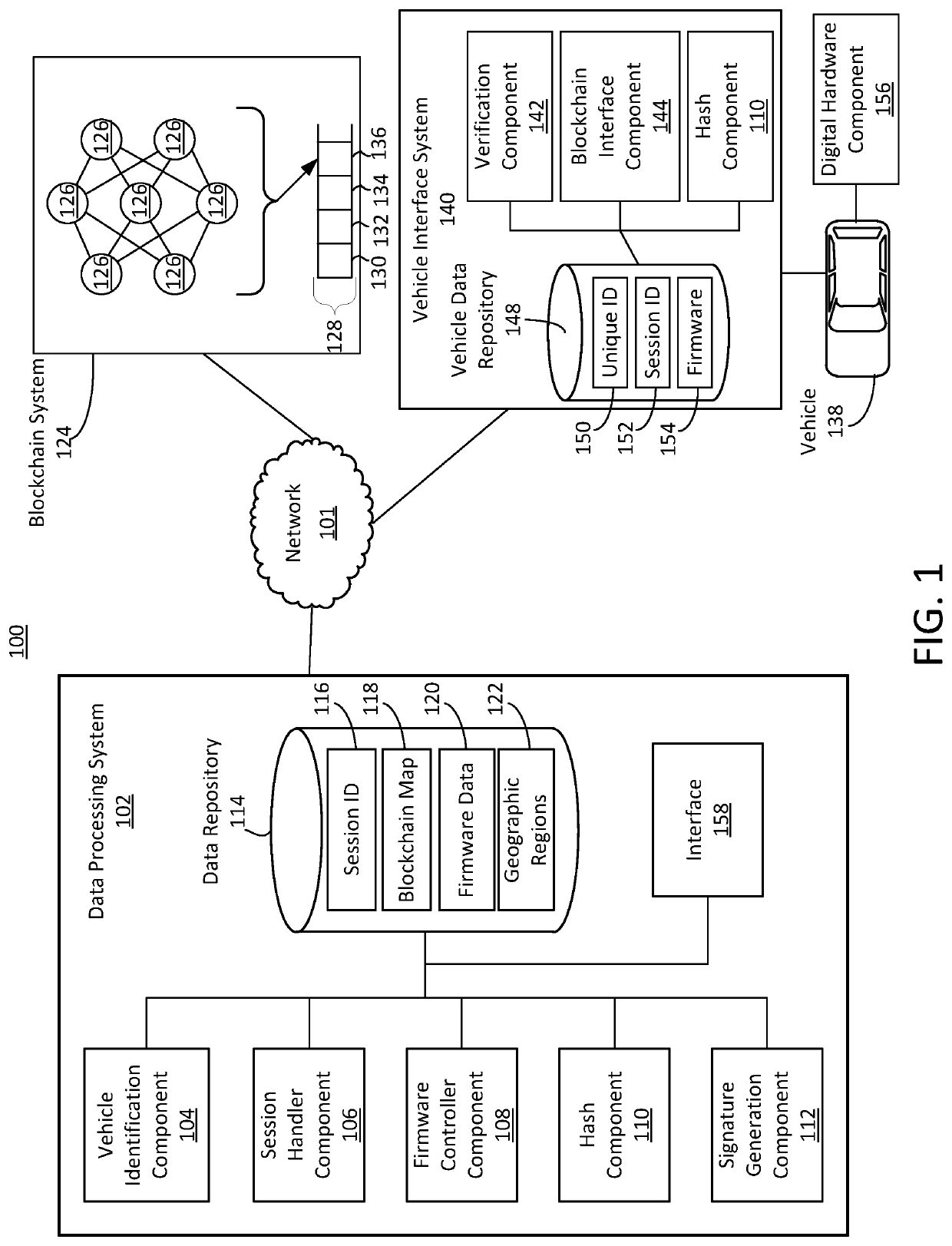
Secure firmware updates for remote vehicles
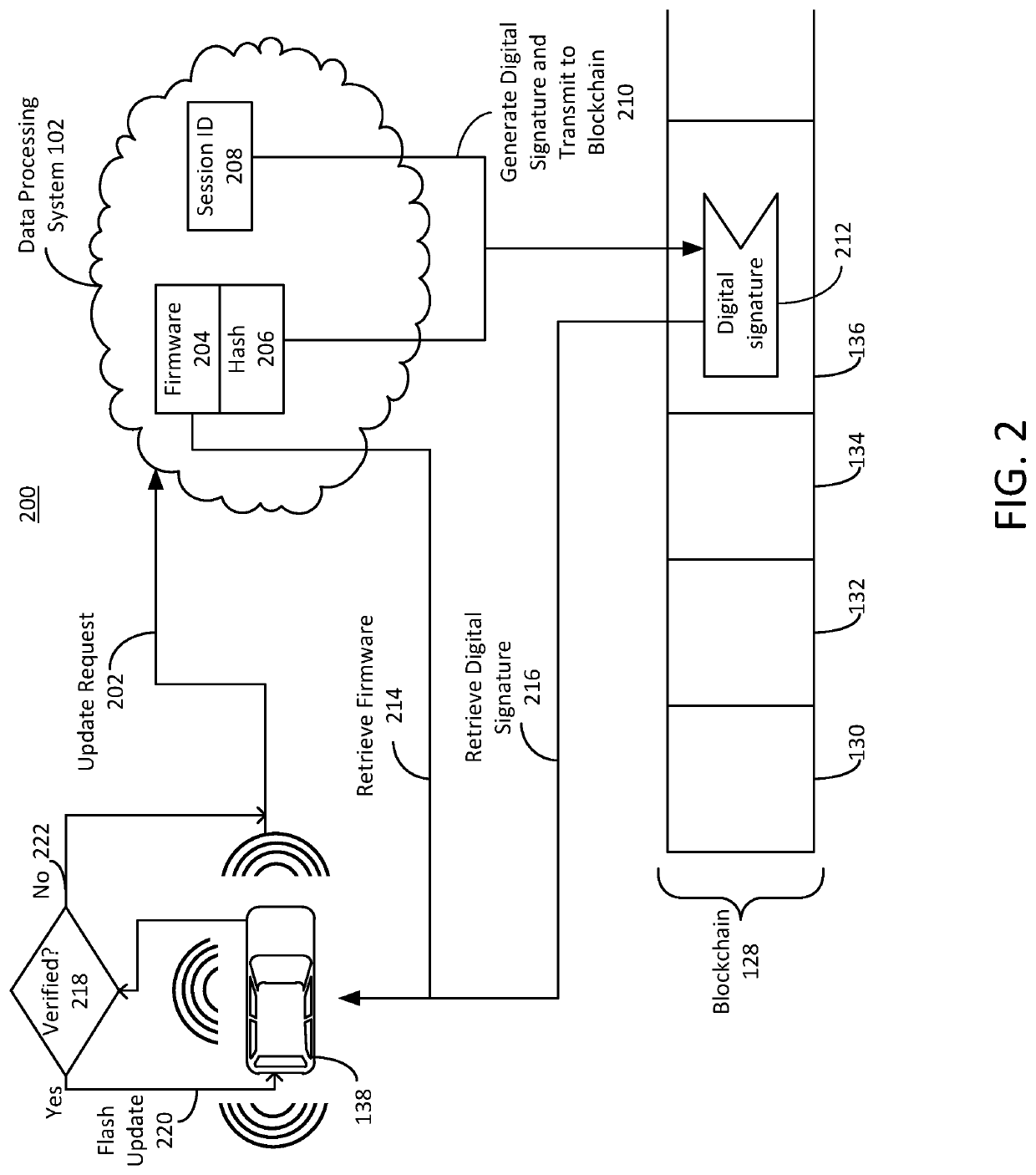
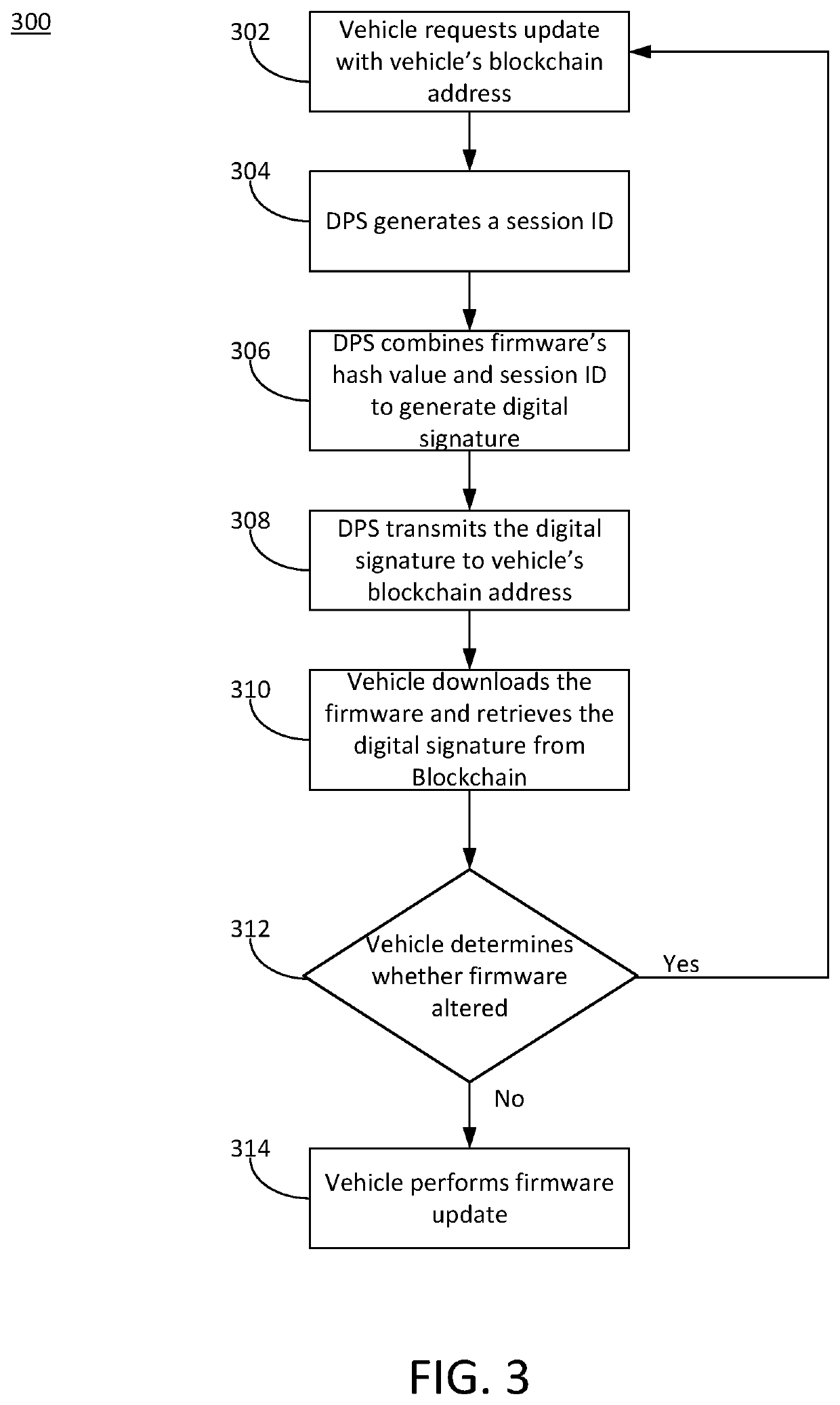
ActiveUS10447483B1Function increaseEfficiently securely transferEncryption apparatus with shift registers/memoriesUser identity/authority verificationData processing systemDigital signature
Systems and methods of secure firmware updates on remote vehicles are provided. The system receives a request from a vehicle for an update to vehicle firmware, and identifies a blockchain address for the vehicle. The system generates a session identifier and identifies a firmware update file. The system generates a digital signature based on a combination of the session identifier and a first hash value of the firmware update file. The system provides, for storage in a block at the blockchain address, the digital signature. The system transmits the session identifier to the vehicle. The system transfers the firmware update file to the vehicle. The vehicle verifies the firmware update file using the digital signature retrieved from the block at the blockchain address, a second hash value of the firmware update file received from the data processing system, and the session identifier received from the data processing system.
Owner:CHONGQING JINKANG NEW ENERGY VEHICLE CO LTD +1
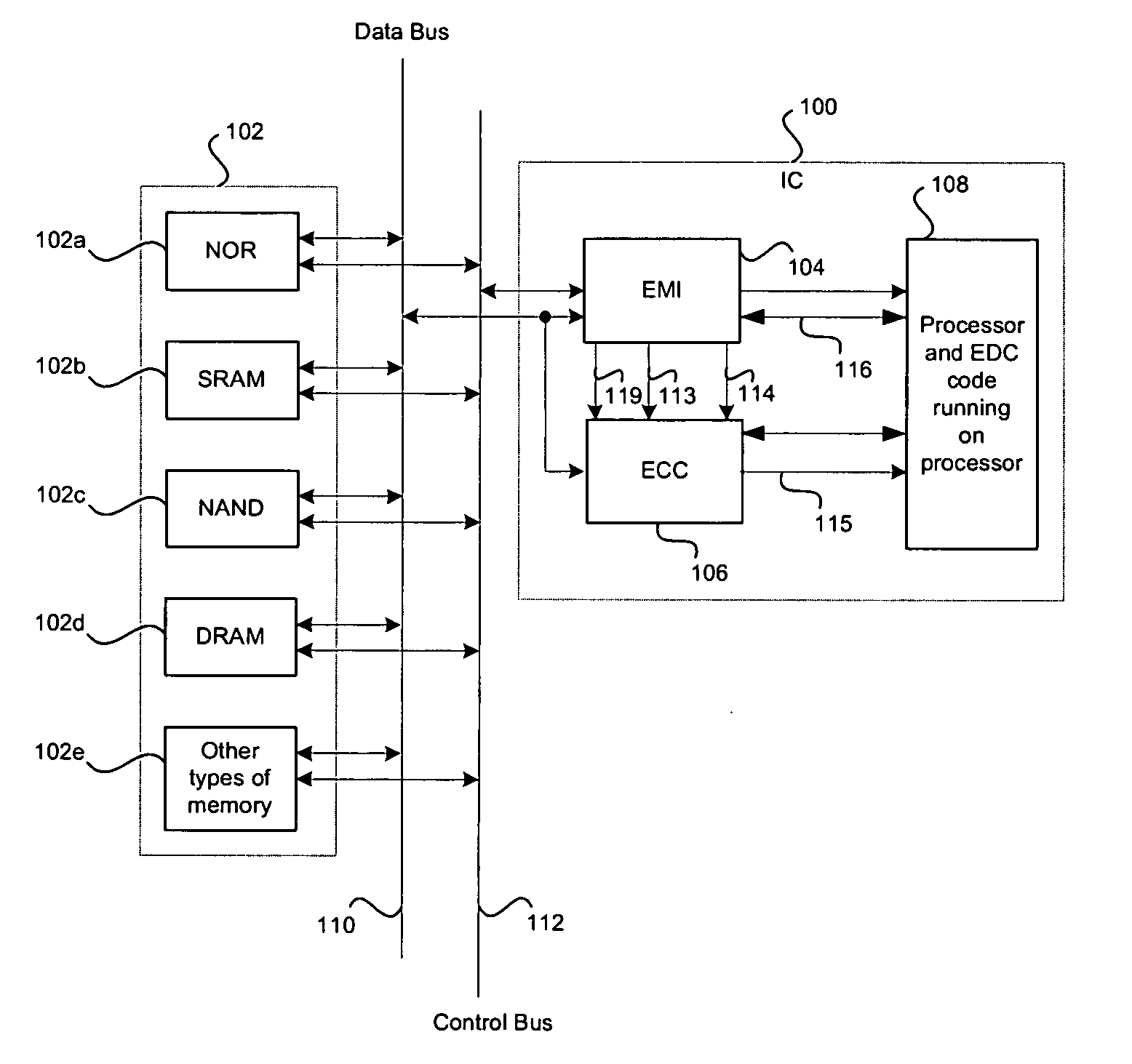
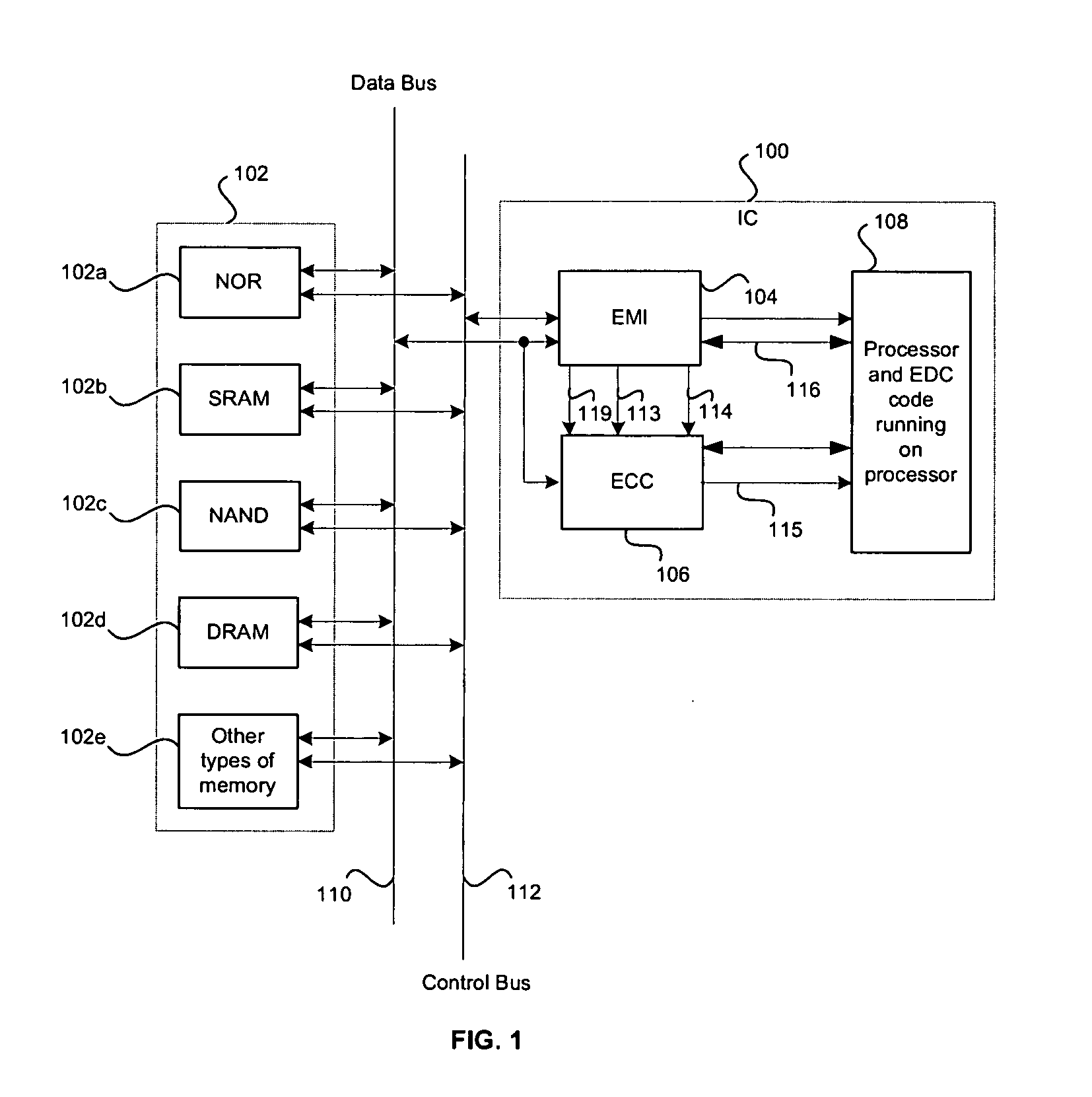
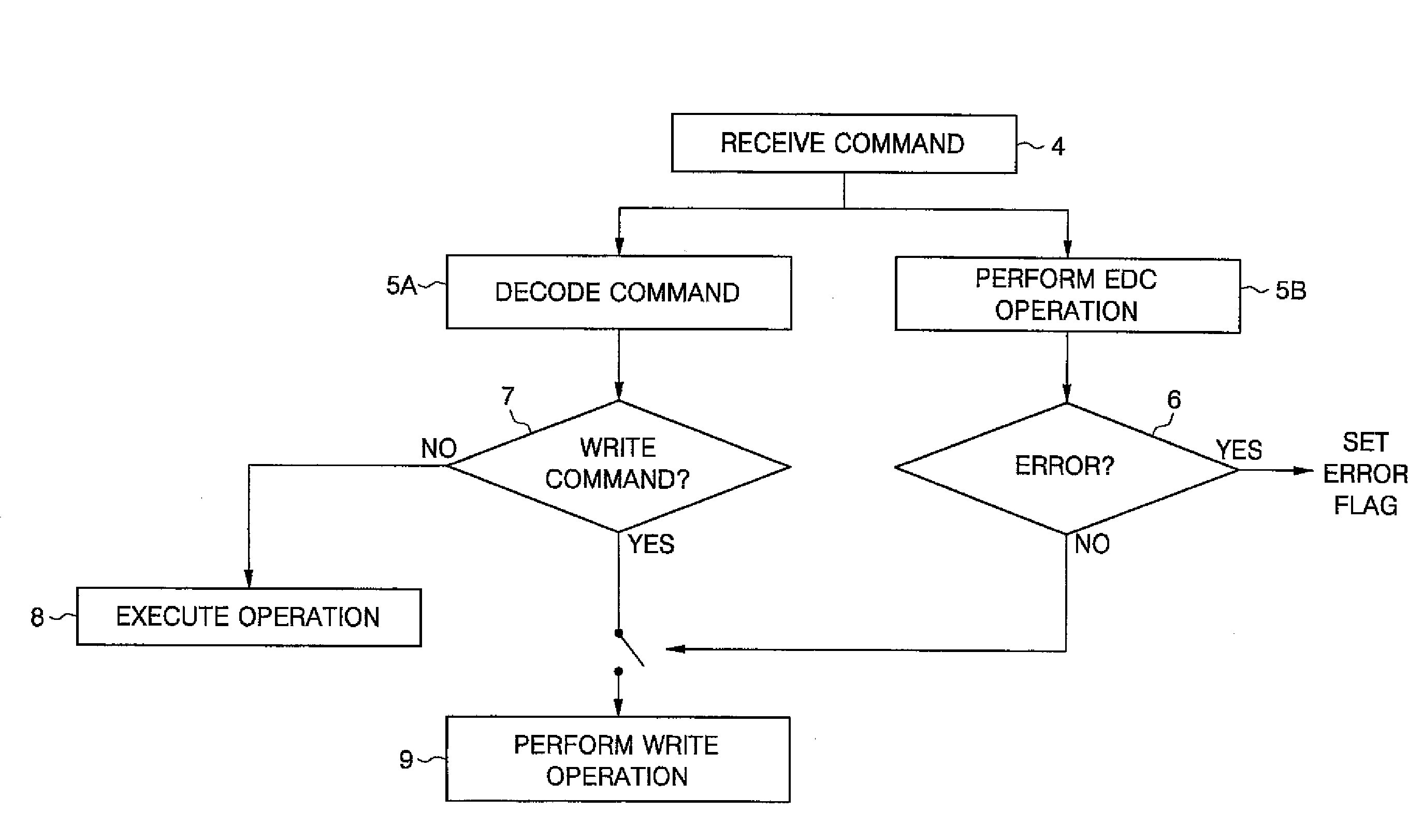
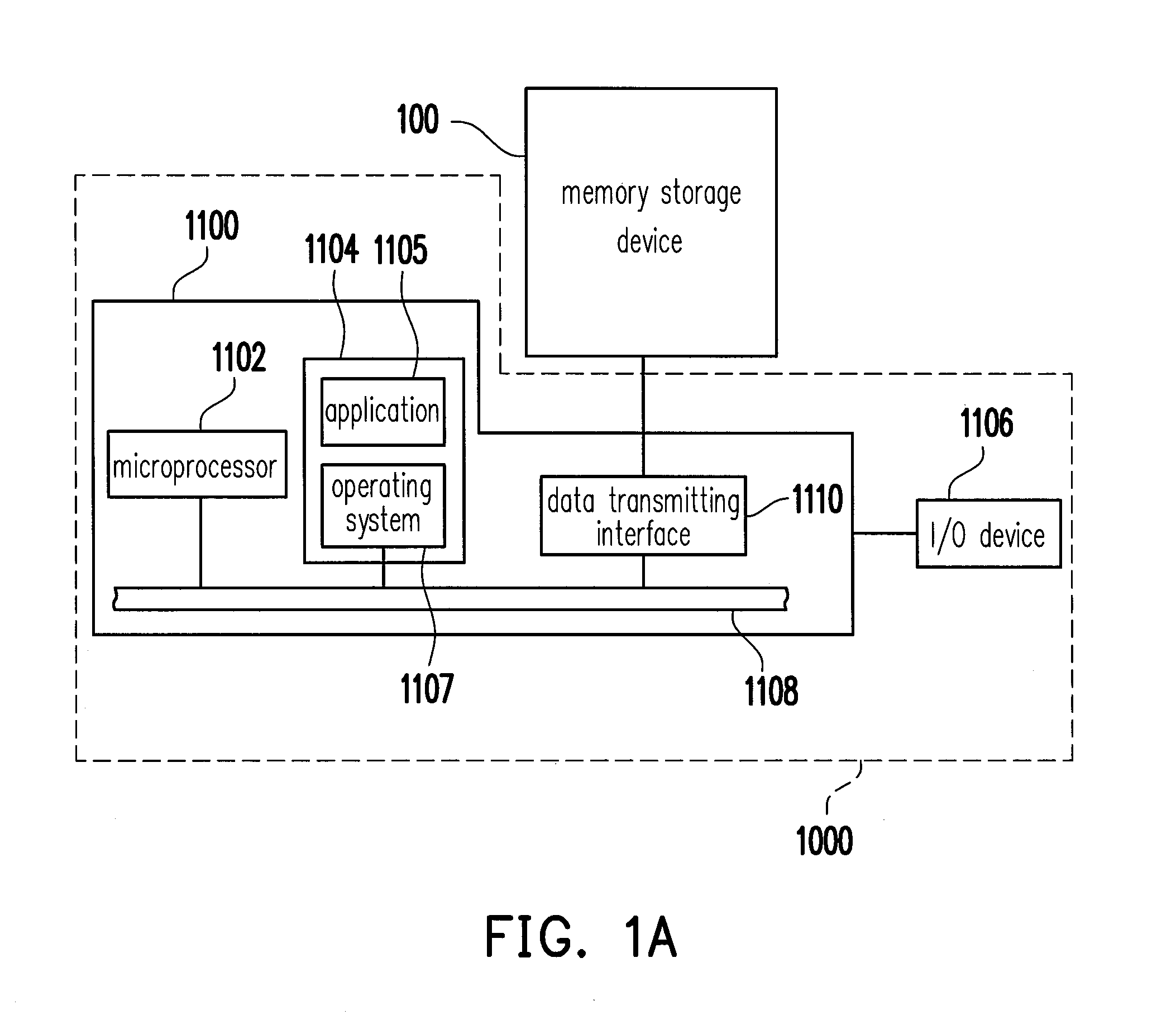
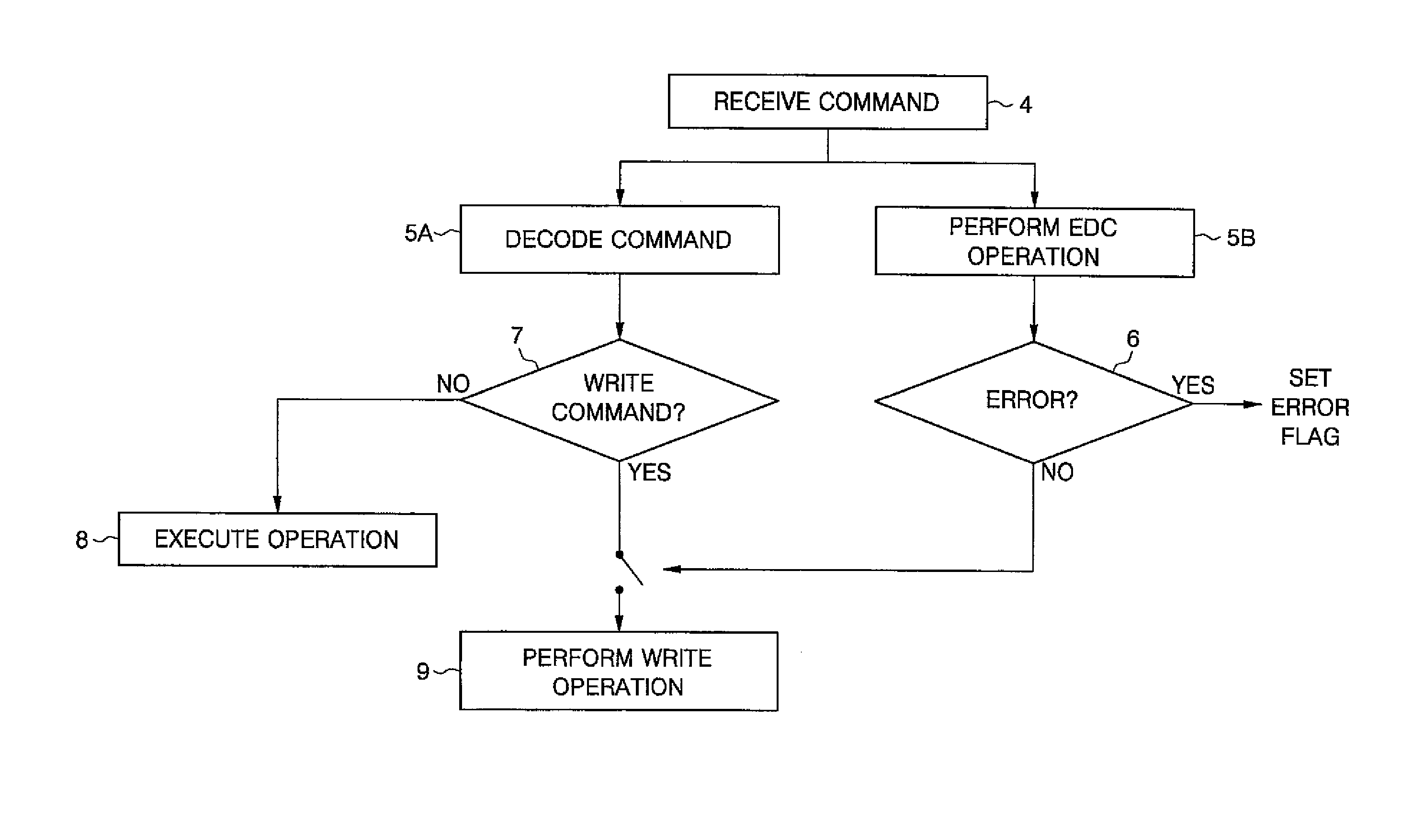
Memory system and command handling method
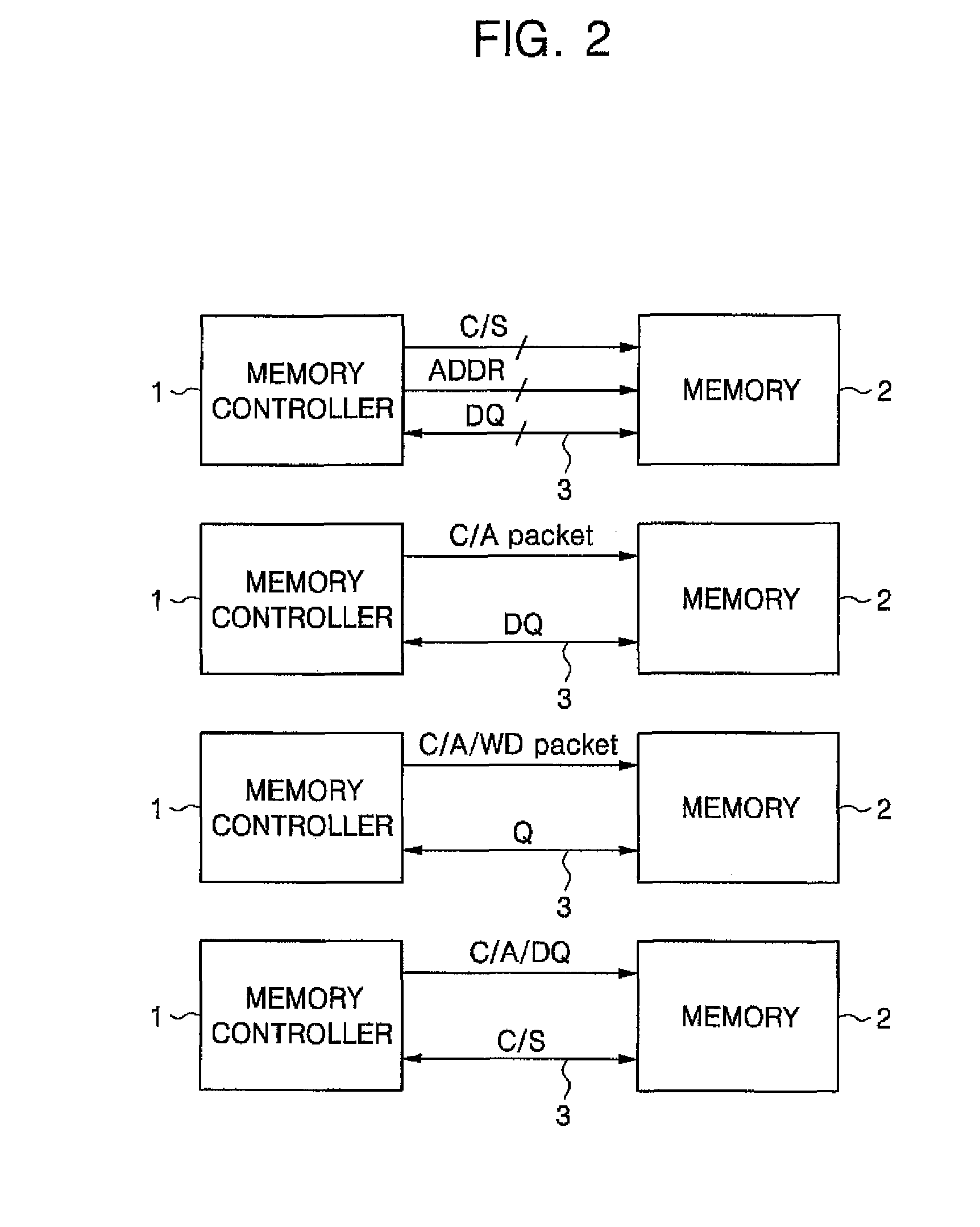
ActiveUS20080195922A1Potent inhibitionEnsure data integrityCode conversionCoding detailsTerm memoryMemory controller
A memory system including a memory controller and a memory and a related method are disclosed. The method includes communicating a command and error detection / correction (EDC) data associated with the command from the memory controller to the memory, decoding the command and executing an EDC operation related to the EDC data in parallel, and if the command is a write command, delaying execution of a write operation indicated by the write command until completion of the EDC operation, else immediately executing an operation indicated by the command without regard to completion of the EDC operation.
Owner:SAMSUNG ELECTRONICS CO LTD
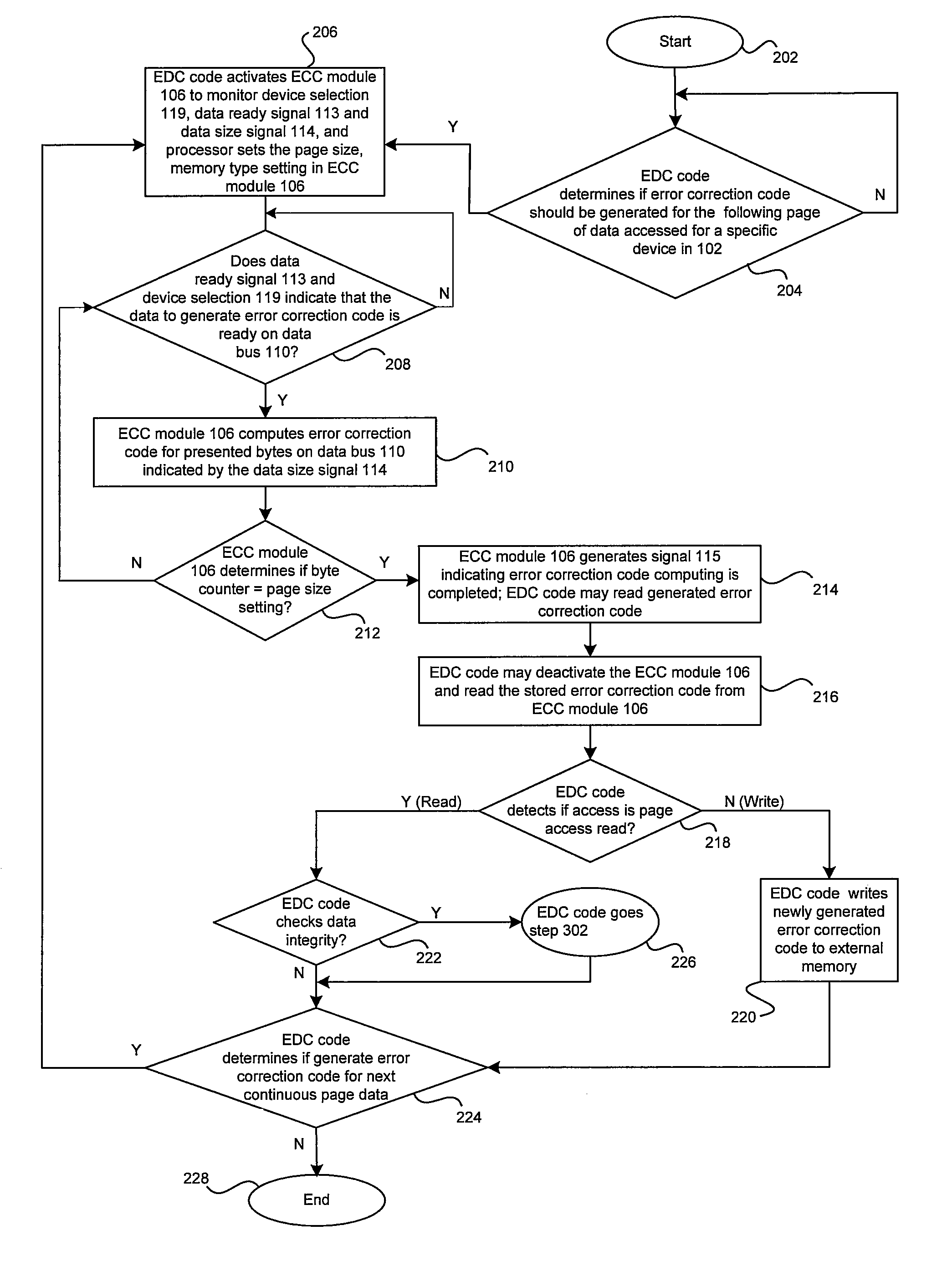
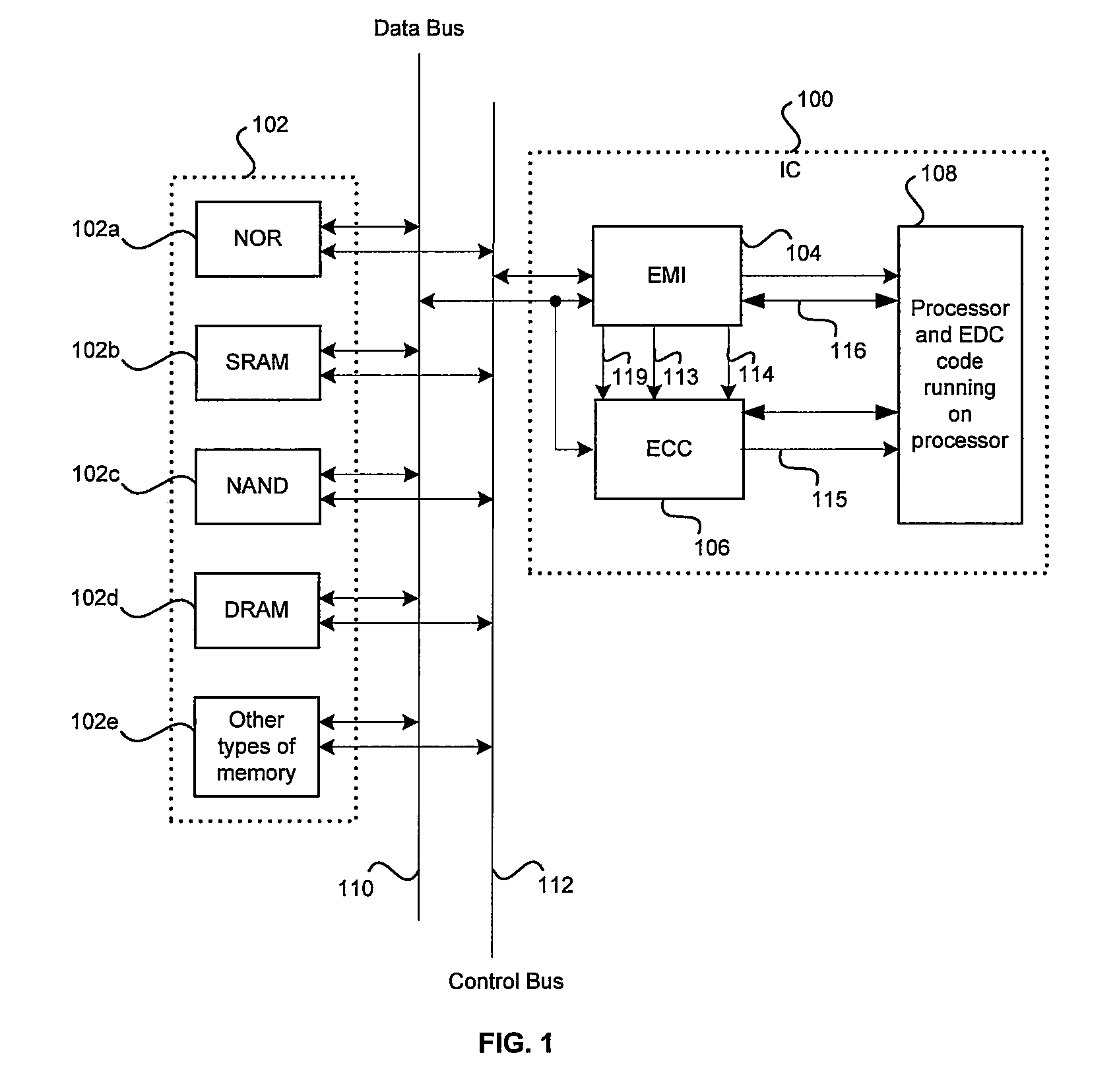
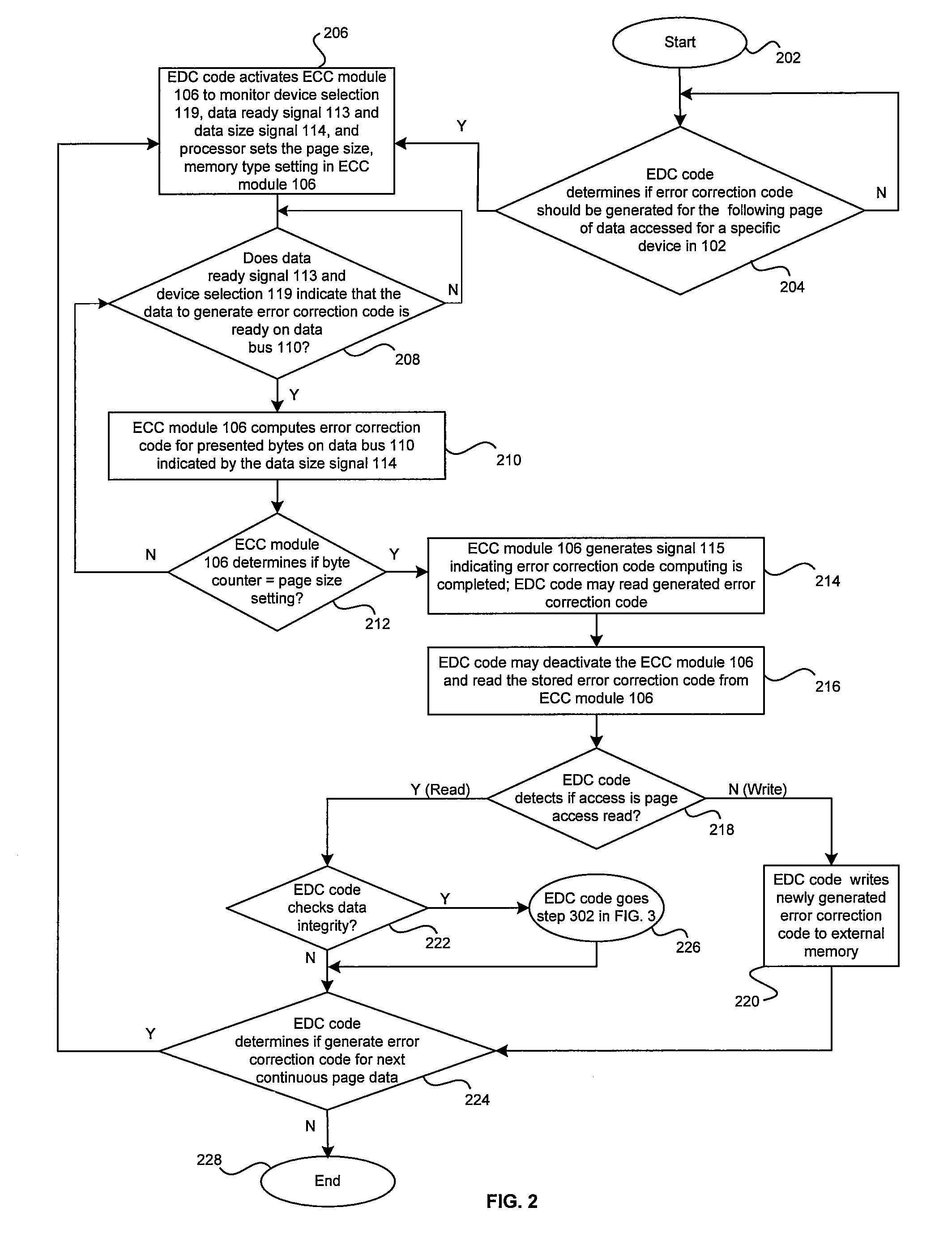
Method and system for detecting and correcting errors while accessing memory devices in microprocessor systems
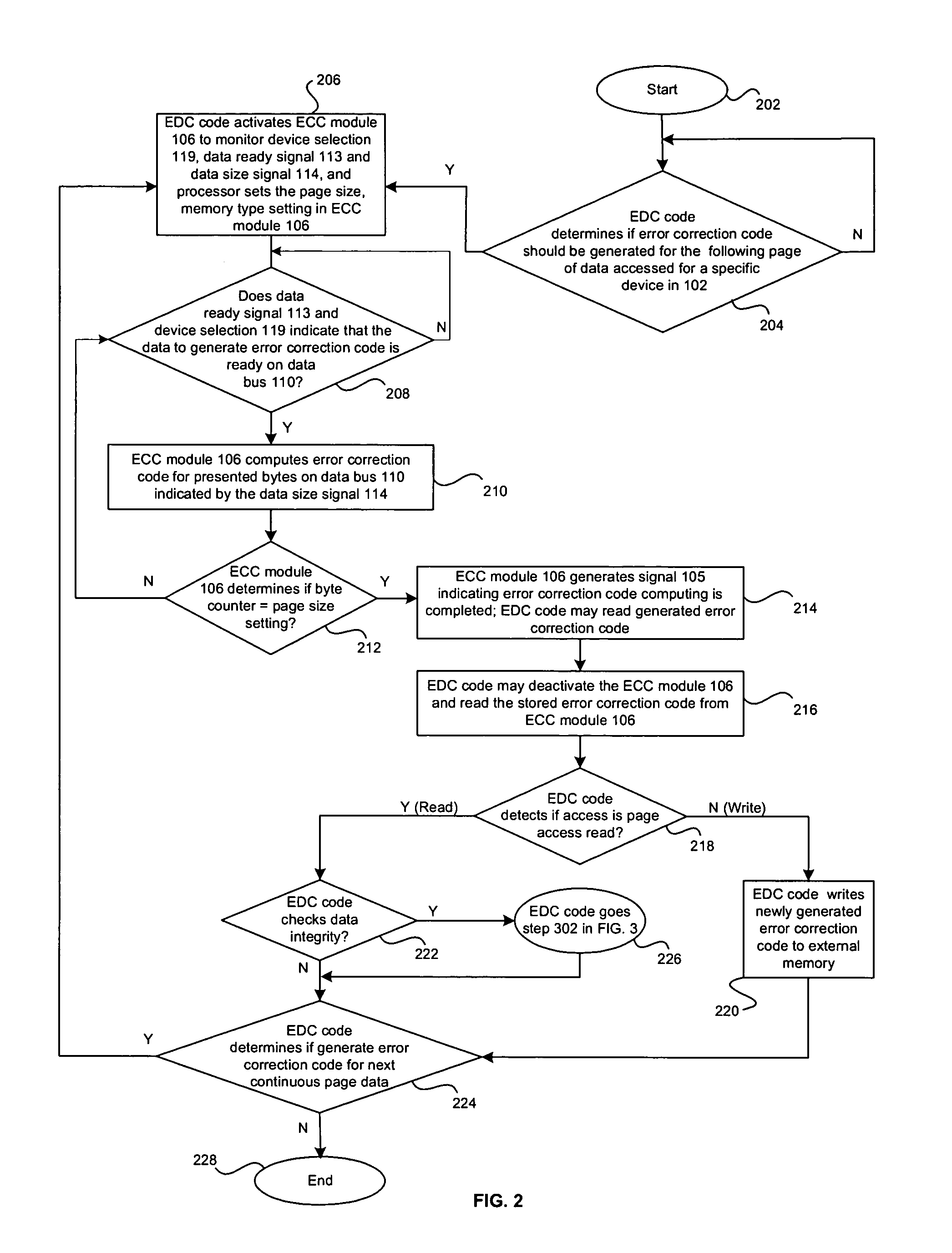
InactiveUS20050283650A1Ensure data integrityError detection/correctionStatic storageData processing systemData integrity
A method and system for ensuring data integrity in a data processing system may comprise monitoring when data for a specified device is available for error correction code generation, and receiving a first indication of the specified device, a second indication of the data, and a third indication of a size of the data during the monitoring. A new error correction code may be generated in hardware for the data based on the indicated size of the data and an indication may be provided to signal when generation of the new error correction code for a specified number of accesses for at least a portion of the data is complete. Detected errors may be corrected in software based on the newly generated error correction code. The first indication may be a device selection signal and the error correction code generation may be enabled or disabled via an enable signal.
Owner:AVAGO TECH INT SALES PTE LTD
Method and apparatus for ensuring the integrity of a downloaded data set
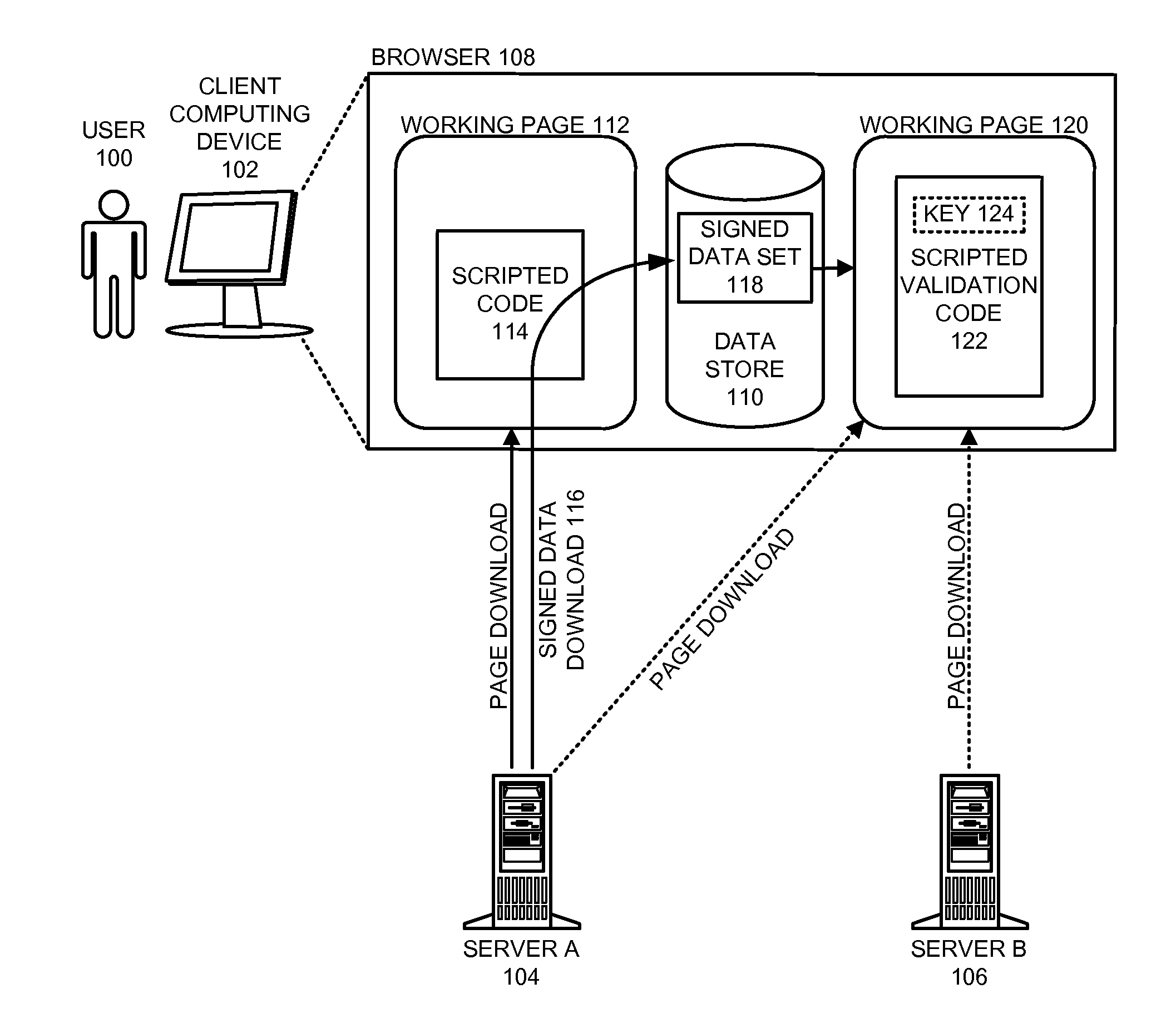
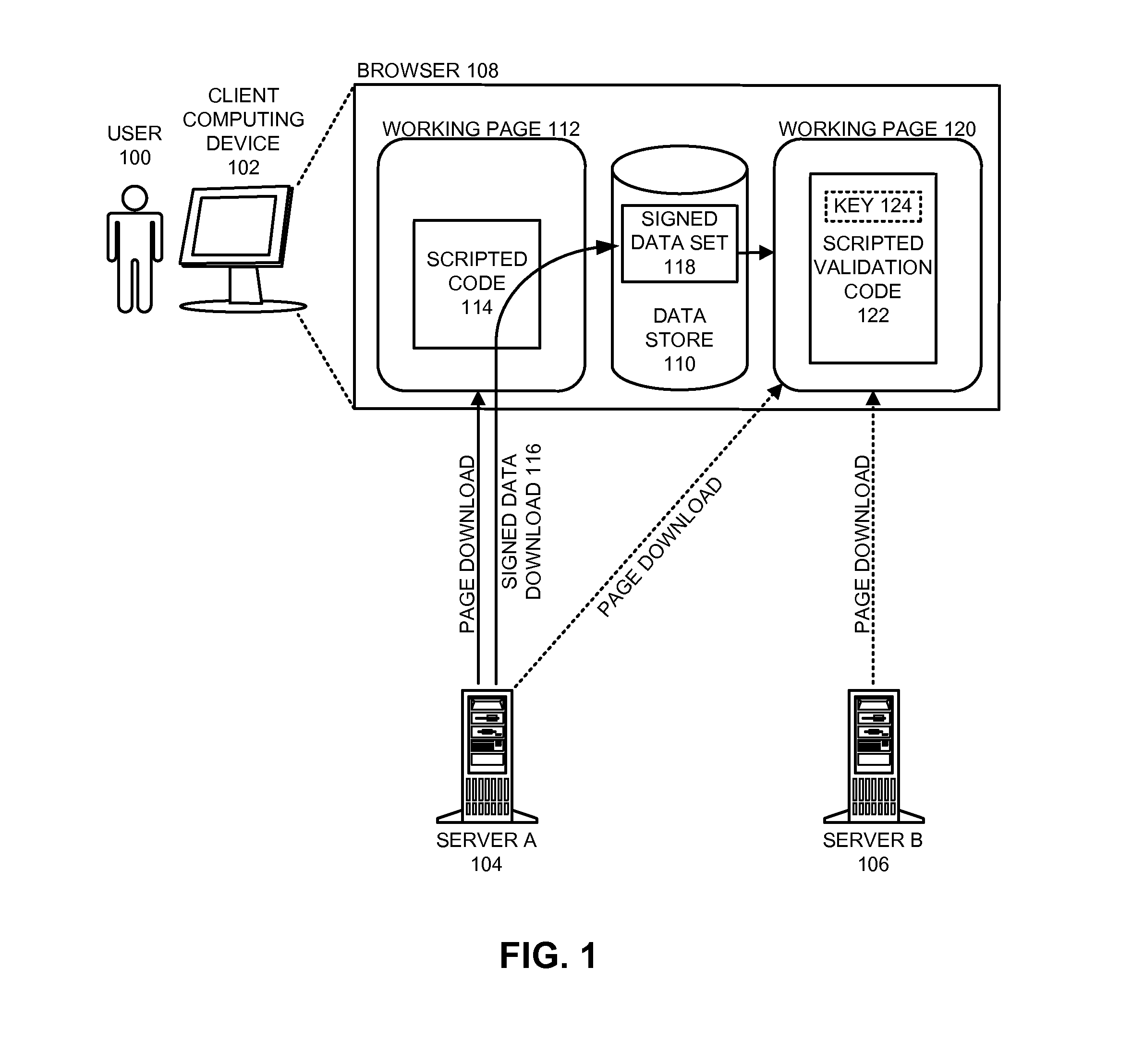
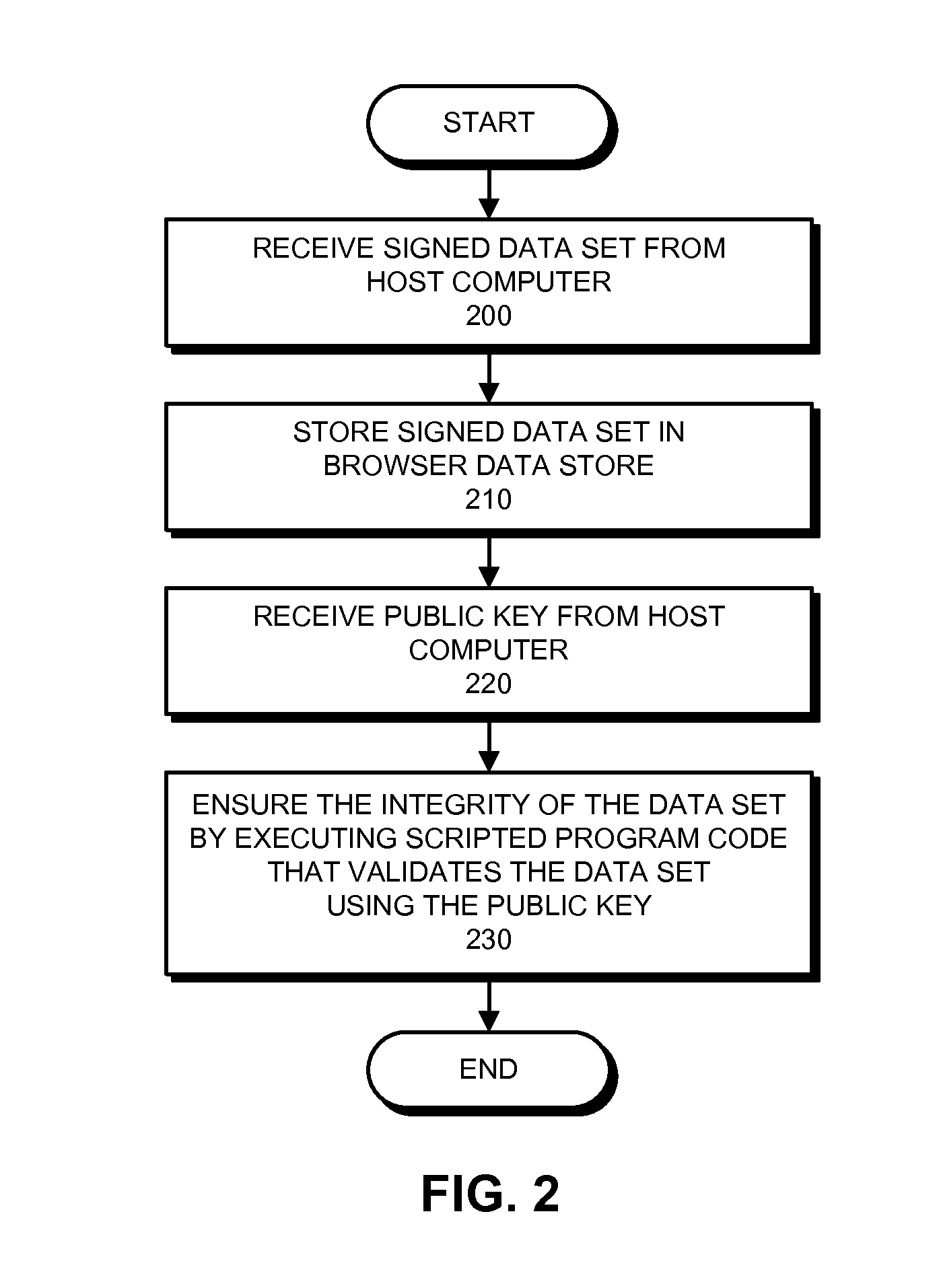
InactiveUS20120198234A1Reduce browser application delayEnsure data integrityUser identity/authority verificationData setData storing
The disclosed embodiments provide a system that ensures the integrity of a downloaded data set. During operation, a browser application executing on a computing device receives a data set that was signed using the private key of a host computer. The browser application stores this signed data set in a browser data store. Subsequently, the browser application also receives a public key from the host computer (e.g., while accessing a web page associated with the signed data set). The browser application ensures the integrity of the data set by executing scripted program code that: uses the public key to decode the signature for the data set; calculates a hash value for the signed data set; and compares the decoded signature with the hash value to validate the data set.
Owner:INTUIT INC
Computer System and Method for Comparing Output Signals
ActiveUS20130060526A1Less-expensiveHigh level of safety criticalityDigital computer detailsNuclear monitoringComputerized systemEngineering
A computer system includes at least two COTS processor cores and an evaluating device connected to the at least two COTS processor cores for evaluating output signals output by means of the at least two COTS processor cores. The evaluating device includes a comparator for pair-wise comparison of the respective generated output signals with each other. The comparator also outputs a comparison signal corresponding to the respective comparison of the output signals.
Owner:HENSOLDT SENSORS GMBH
Method and Apparatus for Accessing Data of a Message Memory of a Communication Module
ActiveUS20080282041A1Increase transfer speedAssure integrity of dataTransmissionMemory systemsShadow memoryData input
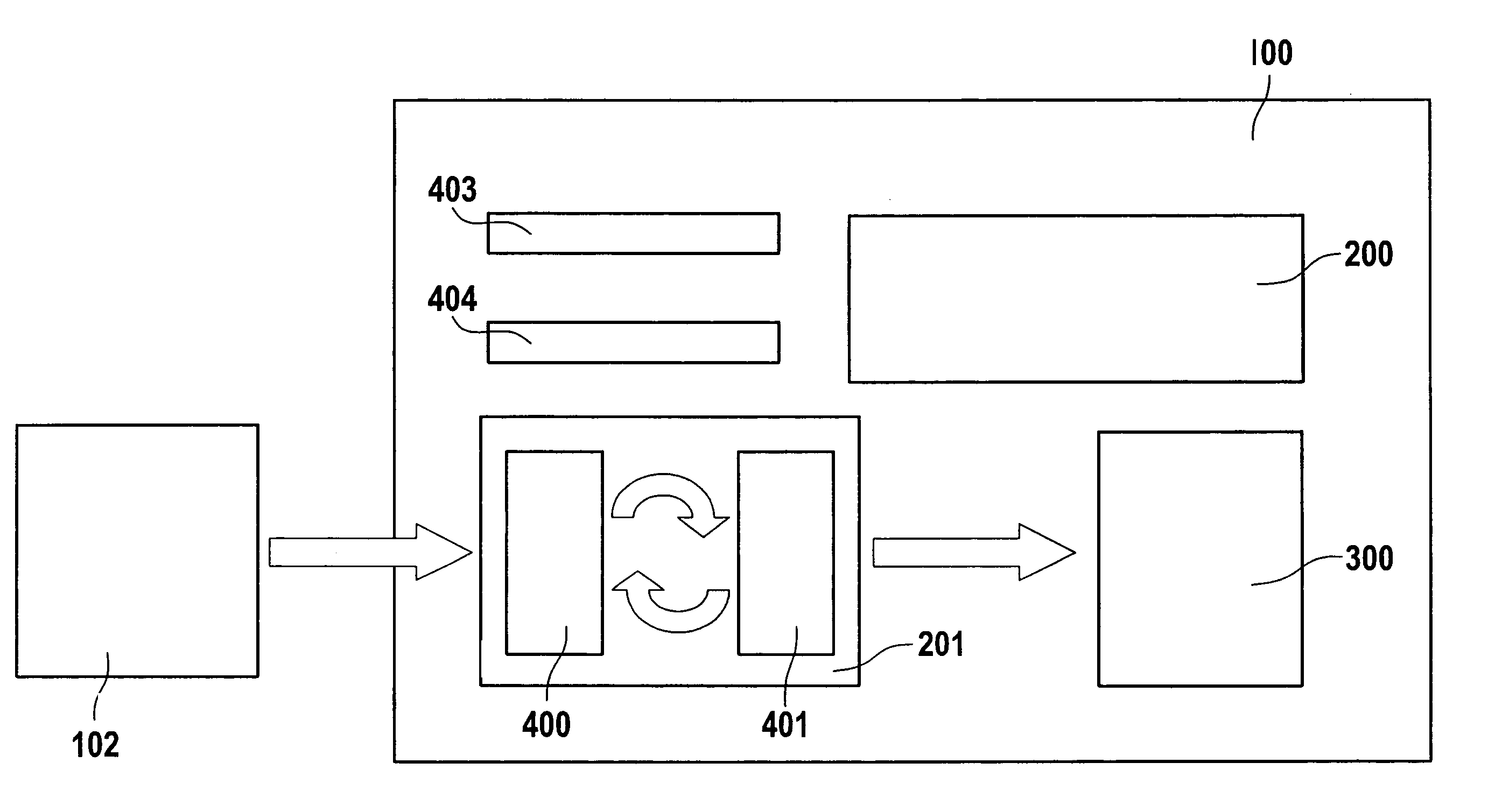
A method and an apparatus for accessing data of a message memory of a communication module by inputting or outputting data into or from the message memory, the message memory being connected to a buffer memory assemblage and the data being transferred to the message memory or from the message memory, the buffer memory assemblage having an input buffer memory in the first transfer direction and an output buffer memory in the second transfer direction; and the input buffer memory and the output buffer memory each being divided into a partial buffer memory and a shadow memory, the following steps being performed in each transfer direction: inputting data into the respective partial buffer memory, and transposing access to the partial buffer memory and shadow memory, so that subsequent data can be inputted into the shadow memory while the previously inputted data are already being outputted from the partial buffer memory in the stipulated transfer direction.
Owner:ROBERT BOSCH GMBH
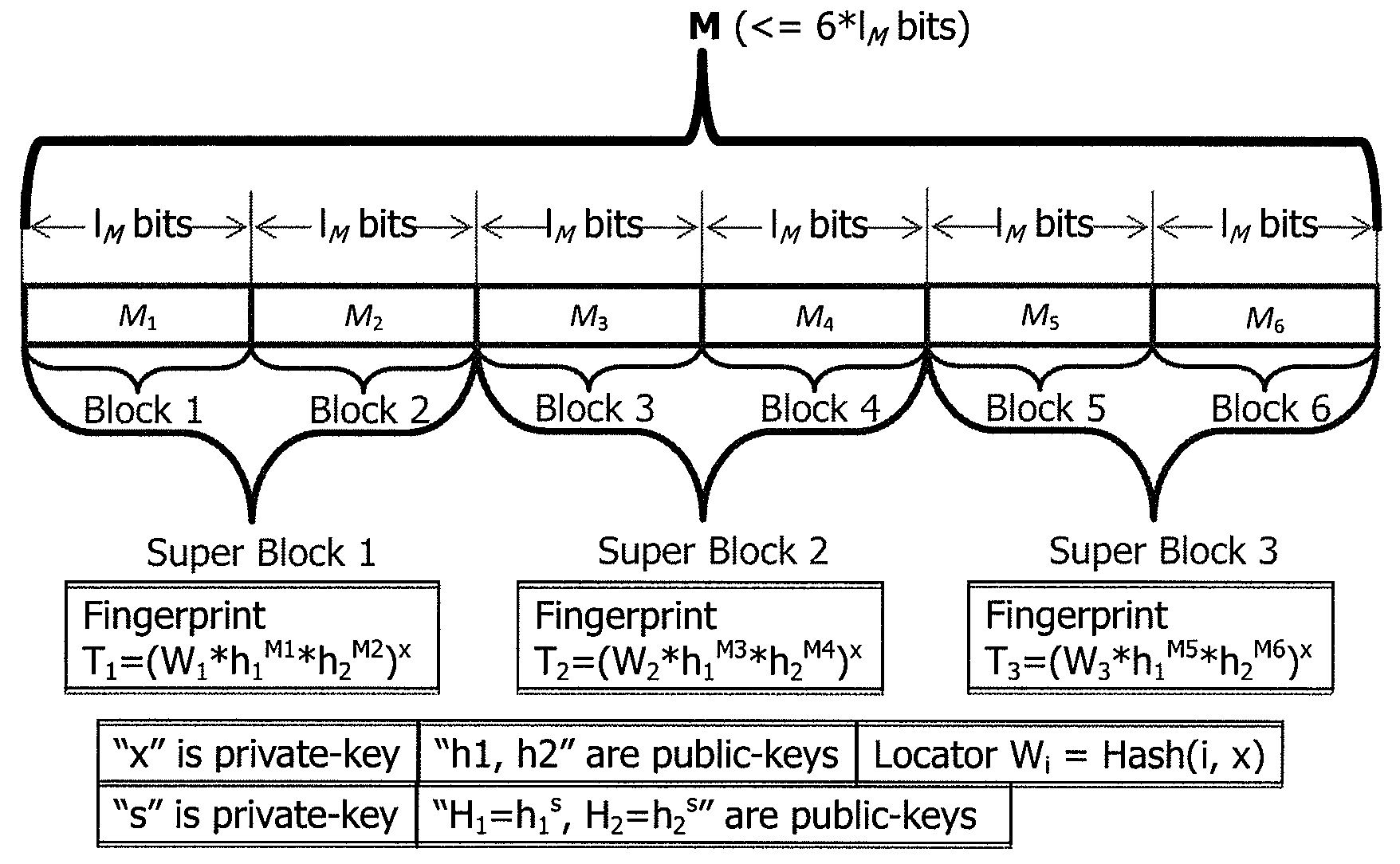
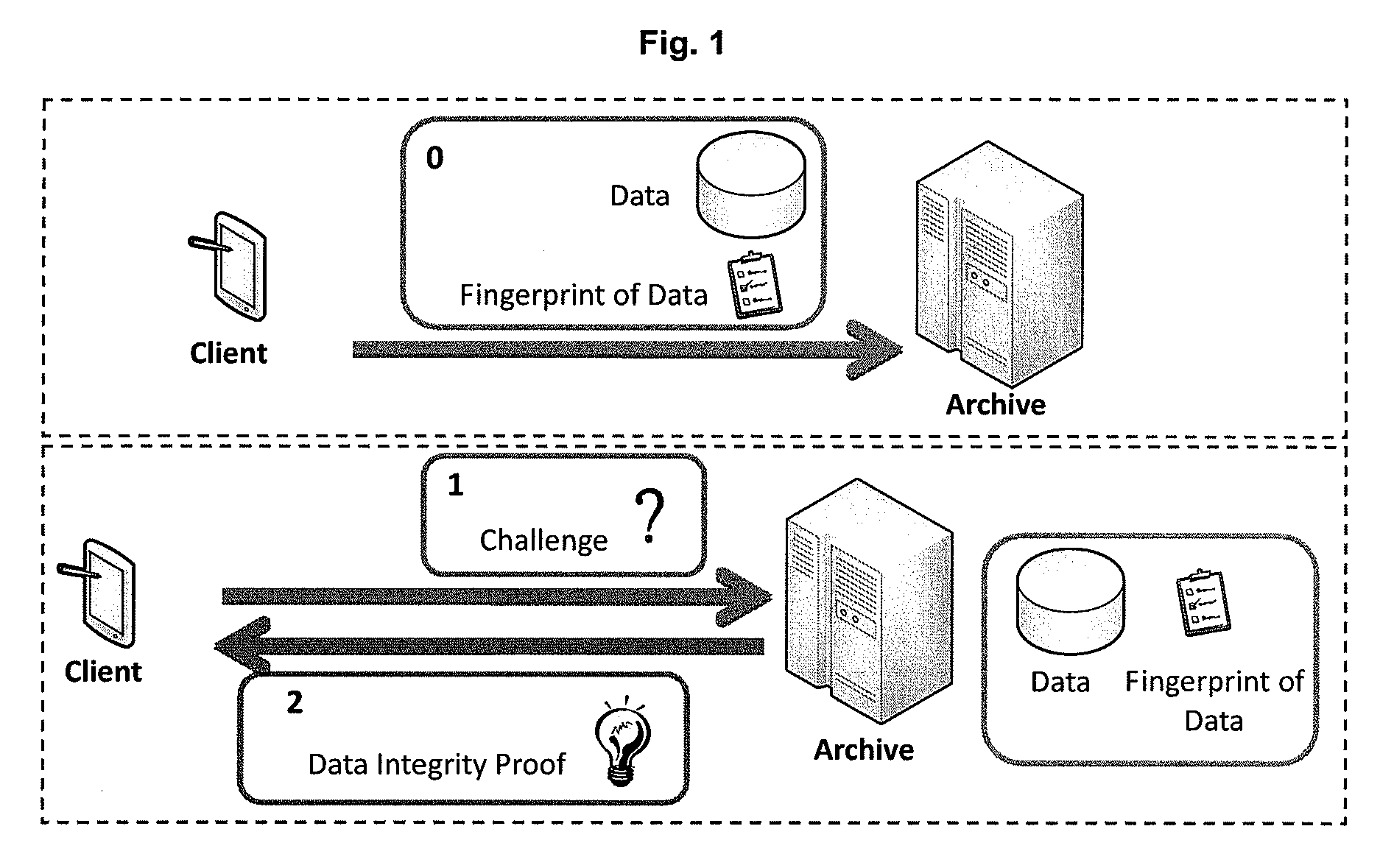
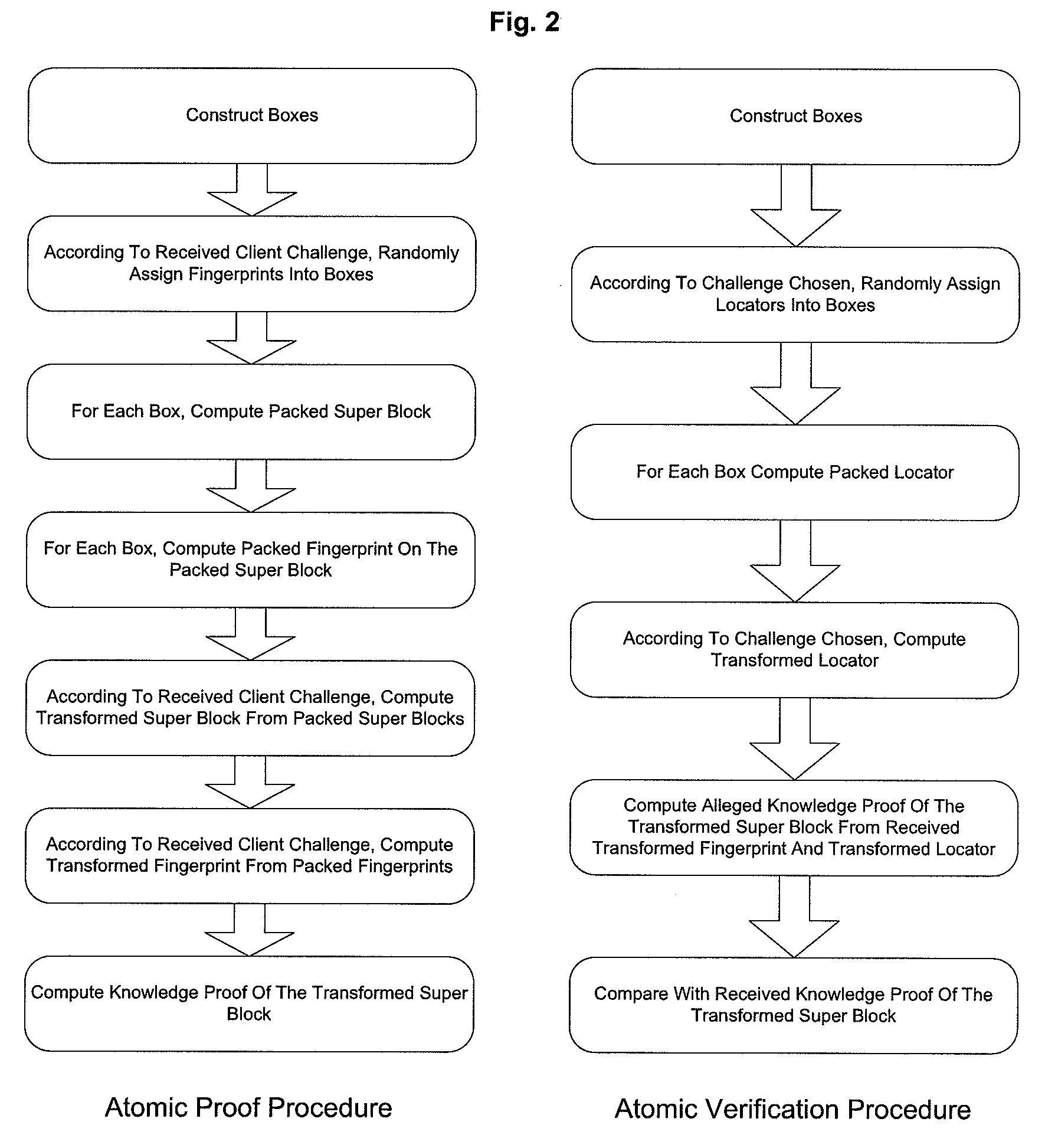
Provable data integrity verifying method, apparatuses and system
InactiveUS20090171878A1Ensure data integritySame sizeUser identity/authority verificationComputer security arrangementsComputer hardwareData integrity
The present invention proposes a Provable Data Integrity (PDI) verifying method, in which data are firstly fingerprinted at a client, and the fingerprints are sent to an archive along with the data; when necessary, the client sends a “challenge” to the archive so as to determine the integrity of the data, and the archive proves the integrity of the data by using the received fingerprints; and finally, the client verifies the integrity of the data based on the output from the archive in response to the “challenge”.
Owner:NEC (CHINA) CO LTD
Method and system for detecting and correcting errors while accessing memory devices in microprocessor systems
InactiveUS7334179B2Ensure data integrityError detection/correctionStatic storageData processing systemData integrity
A method and system for ensuring data integrity in a data processing system may comprise monitoring when data for a specified device is available for error correction code generation, and receiving a first indication of the specified device, a second indication of the data, and a third indication of a size of the data during the monitoring. A new error correction code may be generated in hardware for the data based on the indicated size of the data and an indication may be provided to signal when generation of the new error correction code for a specified number of accesses for at least a portion of the data is complete. Detected errors may be corrected in software based on the newly generated error correction code. The first indication may be a device selection signal and the error correction code generation may be enabled or disabled via an enable signal.
Owner:AVAGO TECH INT SALES PTE LTD
Flexray Communication Module
InactiveUS20080140949A1Flexible configurationOptimizationMultiple digital computer combinationsMemory systemsComputer scienceReal-time computing
A FlexRay communication module for coupling a FlexRay communication connection to a subscriber, associated with the FlexRay communication module, in a FlexRay network over which messages are transferred, the FlexRay communication module including a first assemblage for storing at least a portion of the transferred messages, and a second assemblage for connecting the first assemblage to the subscriber, and a third assemblage for connecting the FlexRay communication connection to the first assemblage.
Owner:ROBERT BOSCH GMBH
Secure firmware updates for remote vehicles
InactiveUS20190394046A1Function increaseEfficiently securely transferEncryption apparatus with shift registers/memoriesUser identity/authority verificationData processing systemDigital signature
Systems and methods of secure firmware updates on remote vehicles are provided. The system receives a request from a vehicle for an update to vehicle firmware, and identifies a blockchain address for the vehicle. The system generates a session identifier and identifies a firmware update file. The system generates a digital signature based on a combination of the session identifier and a first hash value of the firmware update file. The system provides, for storage in a block at the blockchain address, the digital signature. The system transmits the session identifier to the vehicle. The system transfers the firmware update file to the vehicle. The vehicle verifies the firmware update file using the digital signature retrieved from the block at the blockchain address, a second hash value of the firmware update file received from the data processing system, and the session identifier received from the data processing system.
Owner:CHONGQING JINKANG NEW ENERGY VEHICLE CO LTD +1
Recovery and relocation of a distributed name service in a cluster filesystem
ActiveUS7593968B2Promote recoveryEnsure data integrityData processing applicationsTransmissionStorage area networkFile system
A cluster of computer system nodes share direct read / write access to storage devices via a storage area network using a cluster filesystem. During relocation of a server for a distributed name service and recovery of a cluster, entries related to the distributed name service for filesystems is updated. During relocation, a new server for a filesystem informs all nodes in the cluster of the new server's location. During recovery, a process executing on each node deletes entries related to the distributed name service for any filesystem that does not have a server in the recovering cluster.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Method for automatically establishing Ethernet communication safety rules
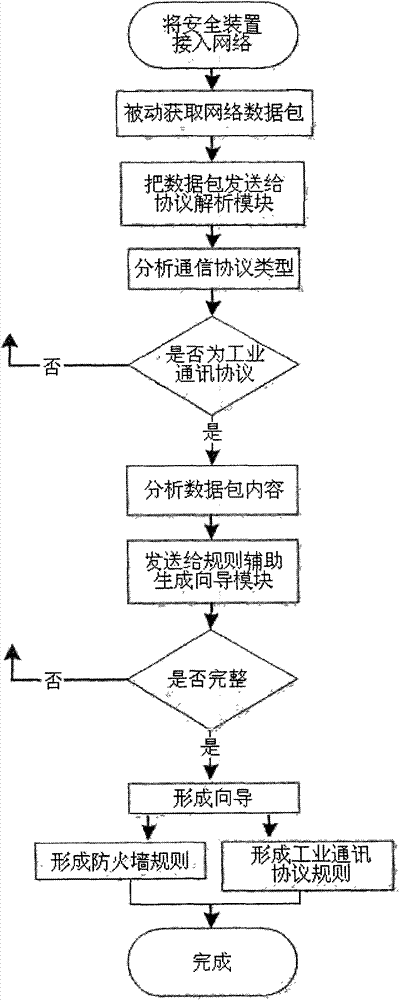
The invention relates to a method for automatically establishing an Ethernet communication safety rule. The steps are as follows: 1, a safety device is connected to a network; 2, the safety device acquires a data packet in the Ethernet passively; 3, the safety device sends the acquired data packet to a protocol analysis module; 4, the protocol analysis module analyzes the content of the data packet, acquires information of the type of a communication protocol, and determines whether the communication protocol is an industrial communication protocol or not; 5, if the communication protocol is the industrial communication protocol, key information in the data packet is analyzed and extracted; 6, the extracted information is sent to a rule auxiliary generation guide module; and 7, the rule auxiliary generation guide module receives the information and forms the safety rule after judging the information is complete. The method provided by the invention form the safety rule according to data information in actual communication, enables setting of the safety rule to be targeted, not missing and convenient for labor saving, and ensures the real-time performance of transmission and the integrity of data in an industrial network.
Owner:BEIJING LIKONG HUACON TECH
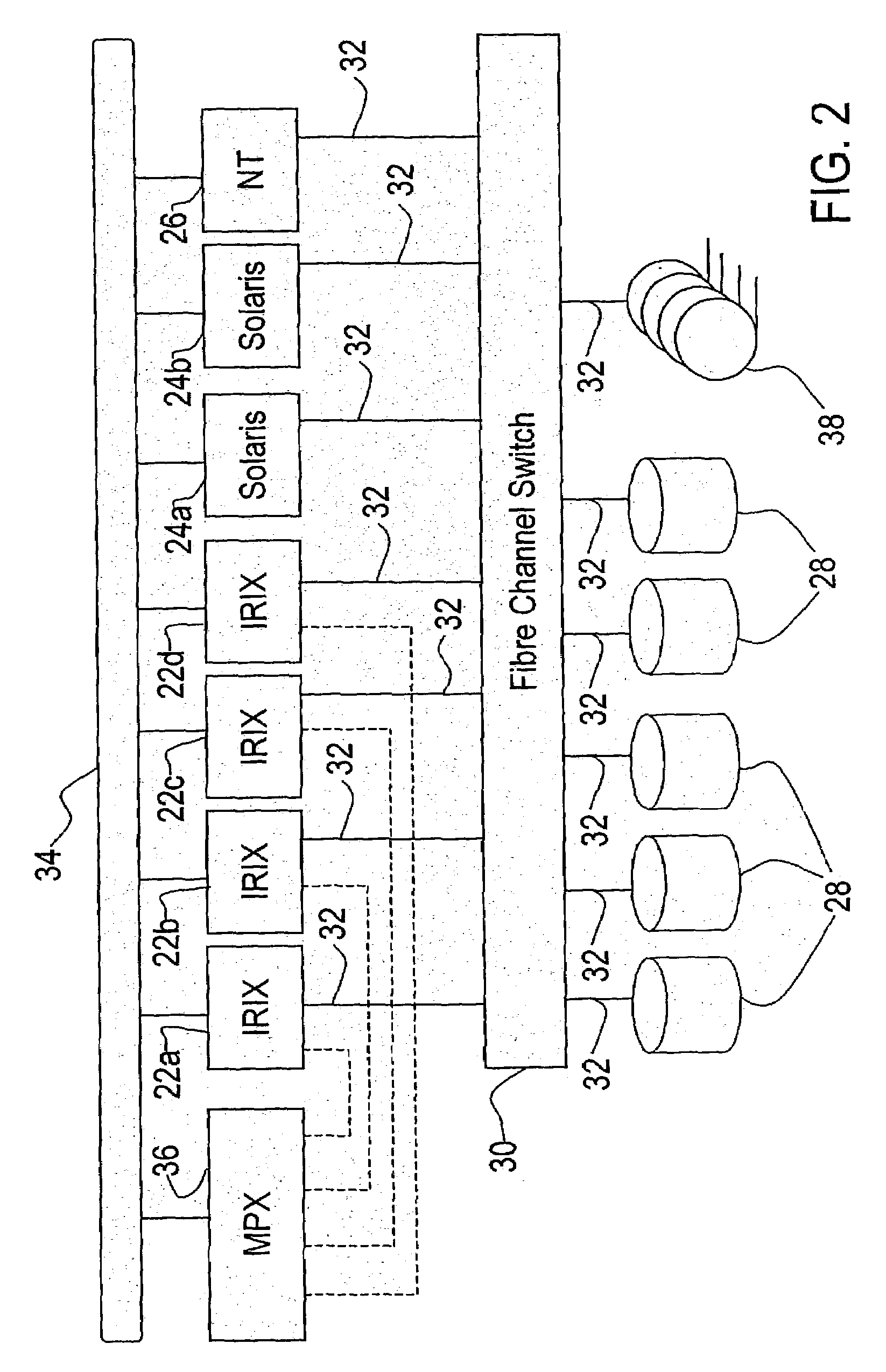
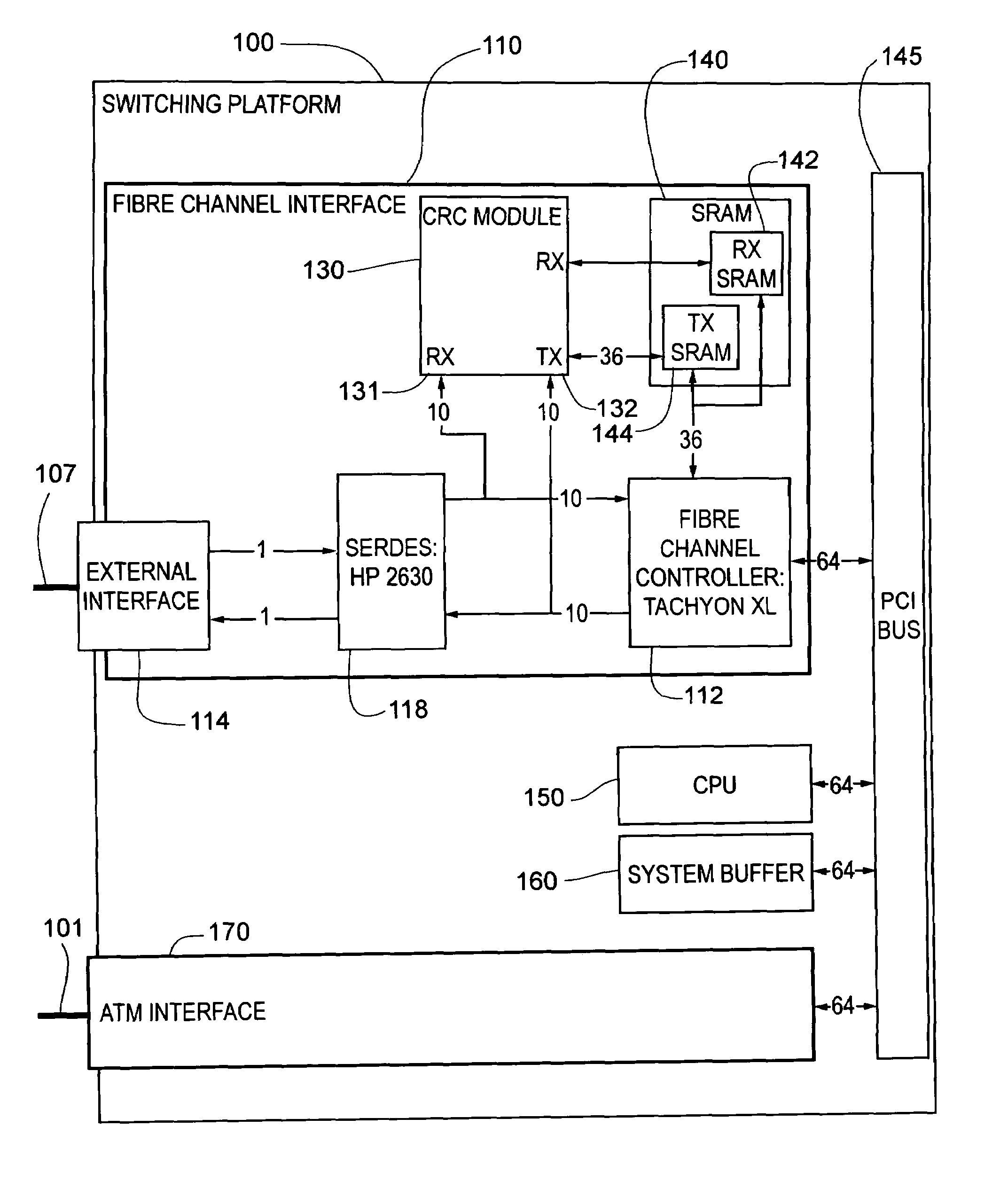
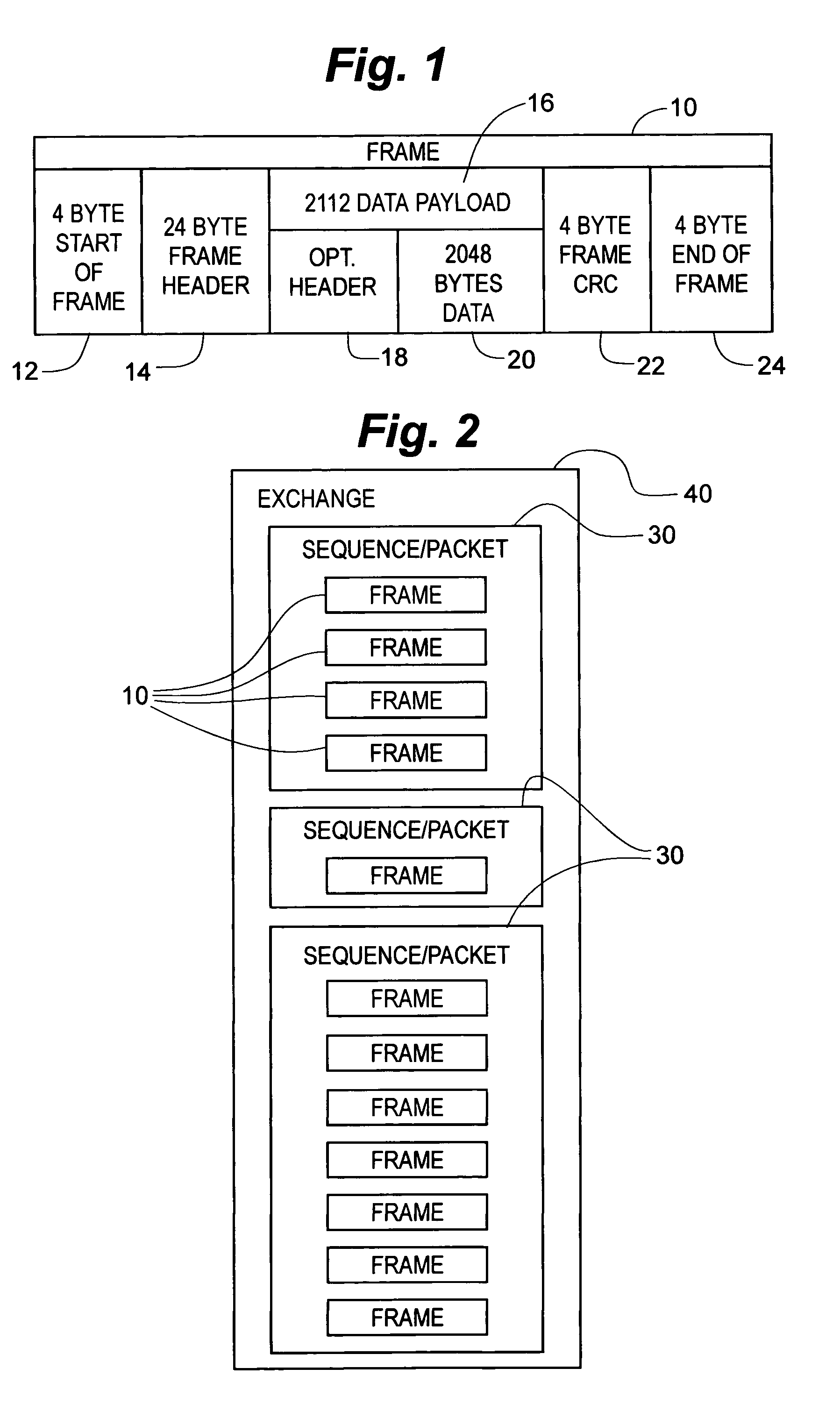
Frame-level fibre channel CRC on switching platform
InactiveUS7391723B2Ensure data integrityError preventionFrequency-division multiplex detailsSequencing dataSingle frame
A method and apparatus is presented for performing a sequence-level CRC calculation on fiber channel communications within a switching platform domain. A CRC generator searches the data communication for frames that contain the type of data for which a sequence-level CRC is desired, such as for a sequence containing SCSI data. If found, and the type of data allows multiple frames per sequence, the present invention creates a CRC value for the sequence. An intermediate CRC value is stored in a queue to allow the simultaneous calculation of sequence level CRC values for multiple frames. With inbound data, the sequence-level CRC is appended to the end of the sequence data. With outbound data, the calculated value is compared with the appended, expected value, With single-frame fiber channel protocols, the frame-level CRC value is obtained directly from the frames entering the switching platform domain. This value is placed in a local queue, from which it is appended to the data payload by a processor for transmission within the switching platform. When the single frame is leaving the switching platform domain, the flow of data leaving the switching platform domain is monitored and the frame-level CRC value calculated by the fiber channel controller is replaced with the original frame-level CRC value.
Owner:MCDATA SERVICES CORP
Transistor constructions and electronic devices
InactiveUS20050247982A1Increase charge storagePower efficient and fastTransistorSolid-state devicesSingle crystalSilicon oxide
The invention includes a non-volatile memory cell comprising a field effect transistor construction having a body region within a crystalline material. The body region includes a charge trapping region. The memory cell can be TFT-SOI based, and can be supported by a substrate selected from a diverse assortment of materials. The top portion of the substrate can be a conductive layer separated from the memory device by the SOI-oxide insulator film. The charge trapping region can be, for example, silicon enriched silicon nitride or silicon enriched silicon oxide. The crystalline material can include silicon and germanium. The transistor comprises first and second diffusion regions within the body region, and also comprises a channel region between the first and second diffusion regions. The entirety of the body region within the crystalline material can be within a single crystal of the material.
Owner:MICRON TECH INC
Memory system and command handling method
ActiveUS20080195914A1Potent inhibitionEnsure data integrityError detection/correctionCode conversionTerm memoryMemory controller
A memory system including a memory controller and a memory and a related method are disclosed. The method includes communicating a command and error detection / correction (EDC) data associated with the command from the memory controller to the memory, decoding the command and executing an EDC operation related to the EDC data in parallel, and if the command is a write command, delaying execution of a write operation indicated by the write command until completion of the EDC operation, else immediately executing an operation indicated by the command without regard to completion of the EDC operation.
Owner:SAMSUNG ELECTRONICS CO LTD
Data transmitting method, memory controller and data transmitting system
ActiveUS20140181324A1Increasing amount of data transmittedEnsure integrityInput/output to record carriersMemory systemsNetwork packetControl store
A data transmitting method for a memory controller is provided. A host system executes threads to transmit commands through a human interface device (HID) interface. The method includes: receiving a command packet from the host system; executing an operation corresponding to a command according to the command packet to generate responding data, which is divided into at least one responding data packet by the memory controller; transmitting a responding packet and the responding data packet to the host system by the memory controller; determining if one of the at least one responding data packet is lost according to the responding packet by the host system; if a responding data packet is lost, transmitting a retransmitting packet to the memory controller by the host system to request the memory controller to retransmit the lost responding data packet. Accordingly, the data transmission amount is improved, and the integrity of data is ensured.
Owner:PHISON ELECTRONICS
Memory system and command handling method
ActiveUS8020068B2Potent inhibitionEnsure data integrityCode conversionCoding detailsTerm memoryMemory controller
Owner:SAMSUNG ELECTRONICS CO LTD
Computer system and method for comparing output signals
ActiveUS9612922B2Less expensiveImprove security levelDigital computer detailsNuclear monitoringComputerized systemEngineering
A computer system includes at least two COTS processor cores and an evaluating device connected to the at least two COTS processor cores for evaluating output signals output by means of the at least two COTS processor cores. The evaluating device includes a comparator for pair-wise comparison of the respective generated output signals with each other. The comparator also outputs a comparison signal corresponding to the respective comparison of the output signals.
Owner:HENSOLDT SENSORS GMBH
Method for processing bad block in redundant array of independent disks
InactiveUS20100251013A1Ensure data integrityDirect deletion of the damaged disk can be avoidedMemory systemsRedundant hardware error correctionLocal memoriesBackup software
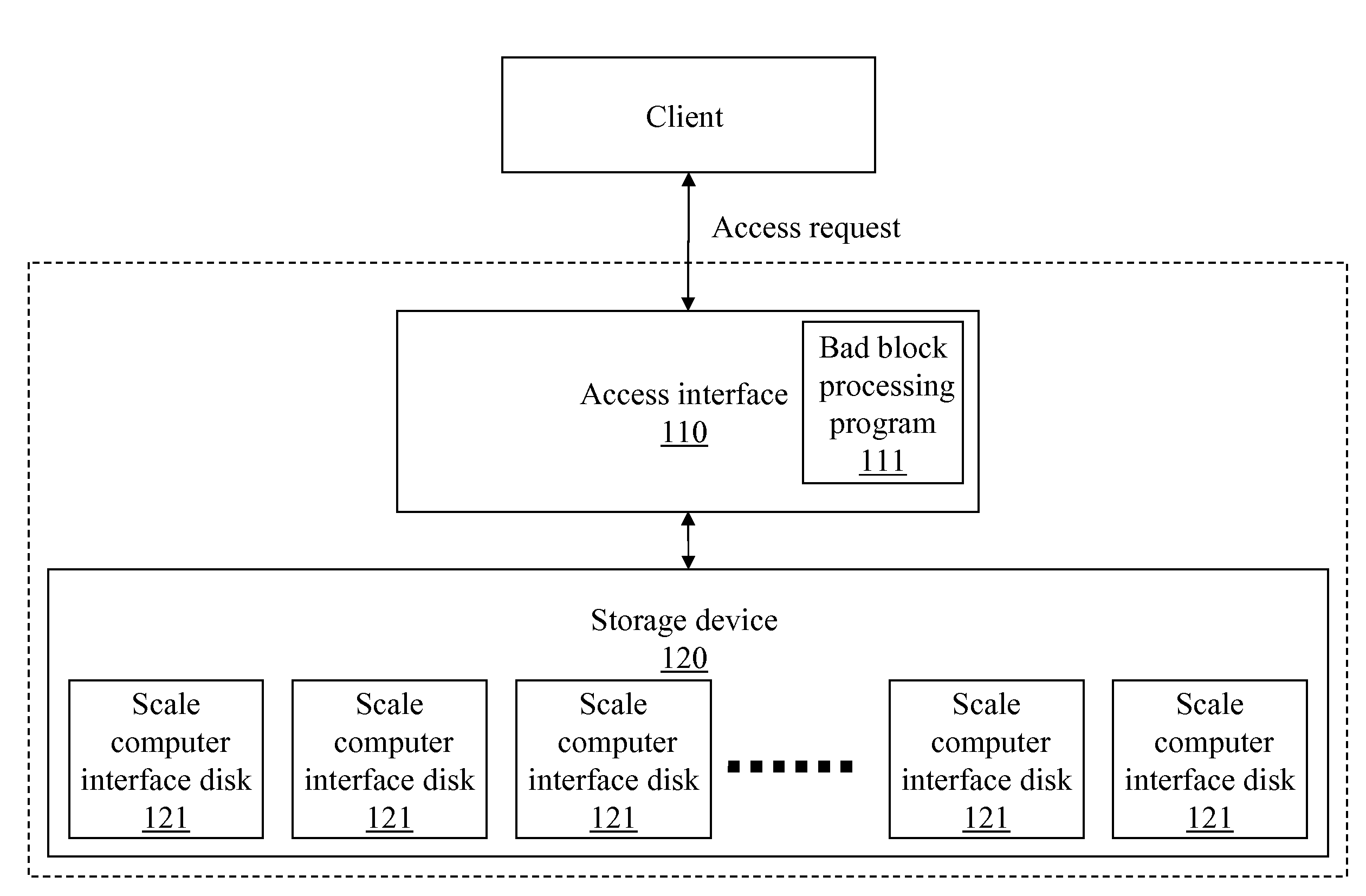
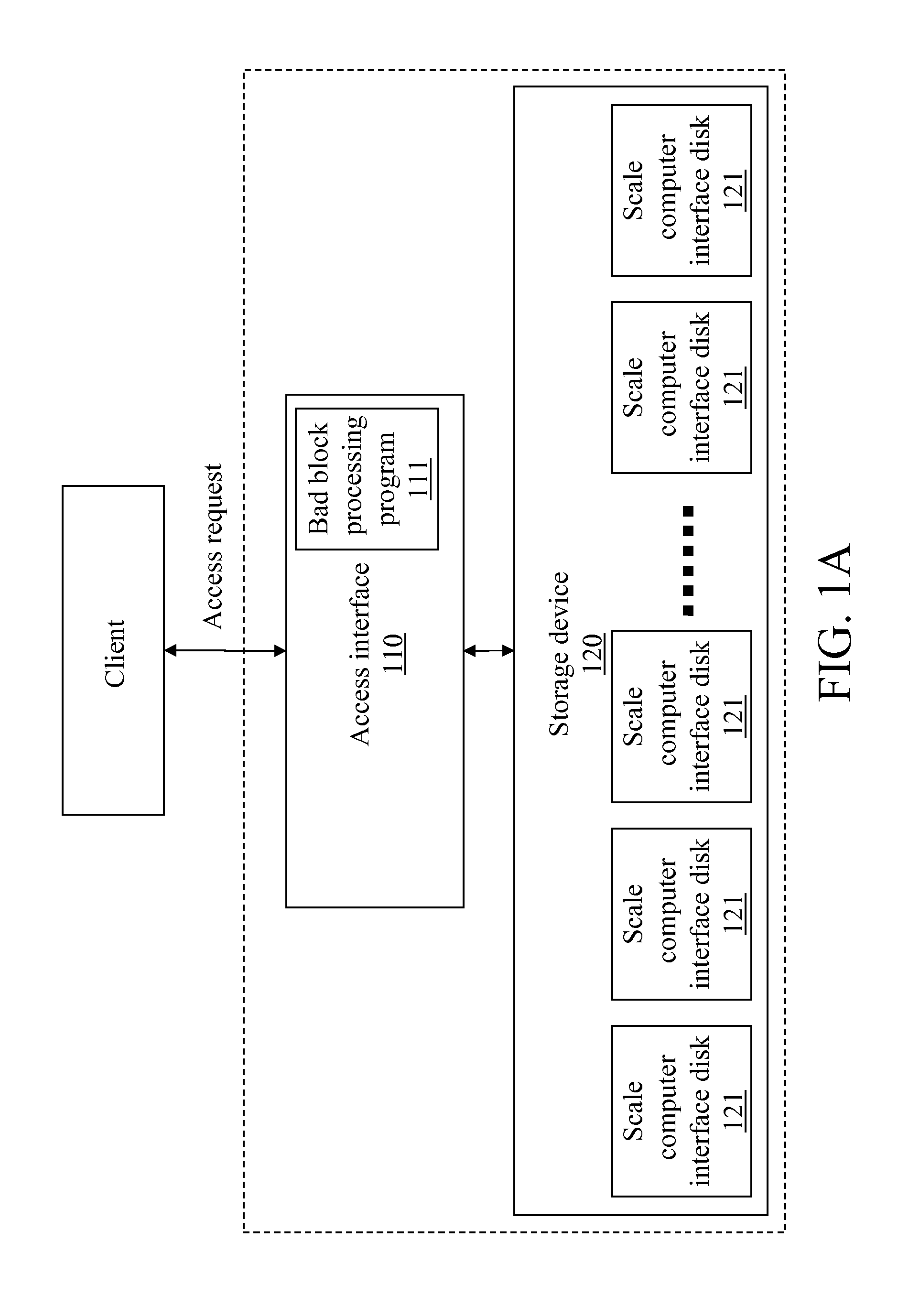
A method for processing a bad block in a redundant array of independent disks (RAID) is presented, which is characterized by a software RAID constructed by a scale computer interface disk, and adapted to backup data in a bad block in the software RAID. The method includes invoking an access error program to intercept an access instruction for a data block in the software RAID when the data block is a bad block; searching a disk number and a logical block address of the data block in the software RAID according to the access instruction; selecting the scale computer interface disk; and mapping data stored in the data block, the disk number, and the logical block address to a reserved local memory of the scale computer interface disk. Through the above steps, the data in the bad block can be mapped to a normal block, thus maintaining the data integrity.
Owner:INVENTEC CORP
Method and apparatus for accessing data of a message memory of a communication module
ActiveUS8095740B2Increase transfer speedAssure integrity of dataMultiple digital computer combinationsNetwork connectionsShadow memoryData input
A method and an apparatus for accessing data of a message memory of a communication module by inputting or outputting data into or from the message memory, the message memory being connected to a buffer memory assemblage and the data being transferred to the message memory or from the message memory, the buffer memory assemblage having an input buffer memory in the first transfer direction and an output buffer memory in the second transfer direction; and the input buffer memory and the output buffer memory each being divided into a partial buffer memory and a shadow memory, the following steps being performed in each transfer direction: inputting data into the respective partial buffer memory, and transposing access to the partial buffer memory and shadow memory, so that subsequent data can be inputted into the shadow memory while the previously inputted data are already being outputted from the partial buffer memory in the stipulated transfer direction.
Owner:ROBERT BOSCH GMBH
Information storage method and apparatus, storage medium and electronic device
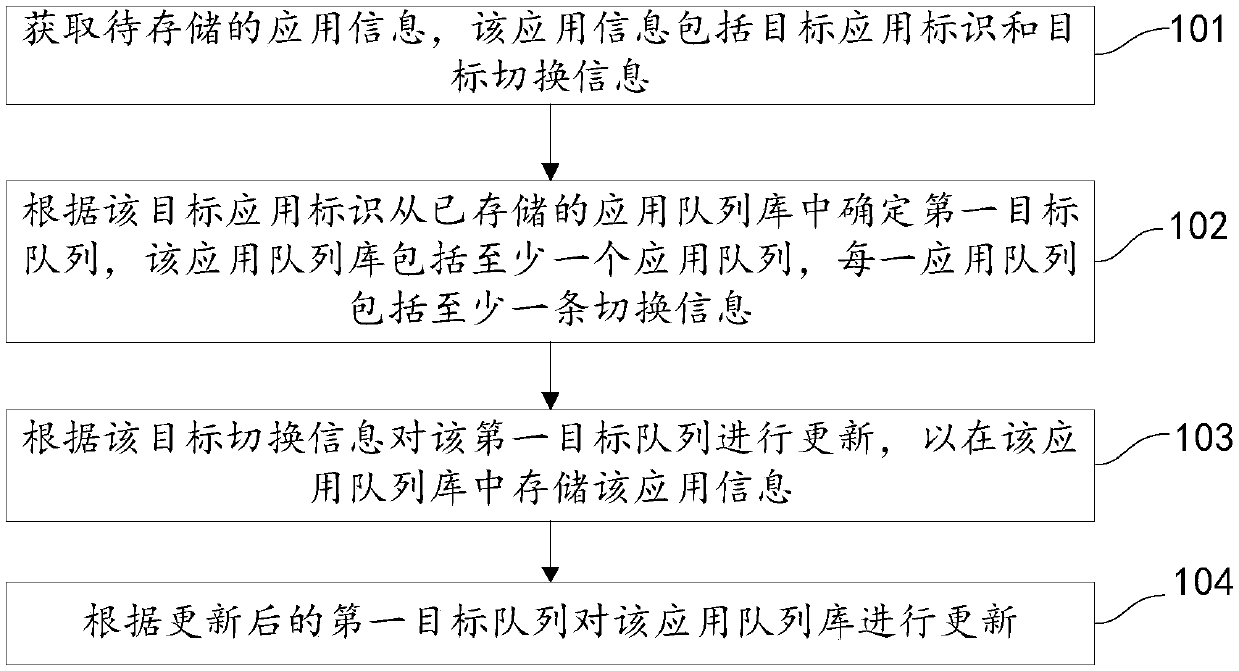
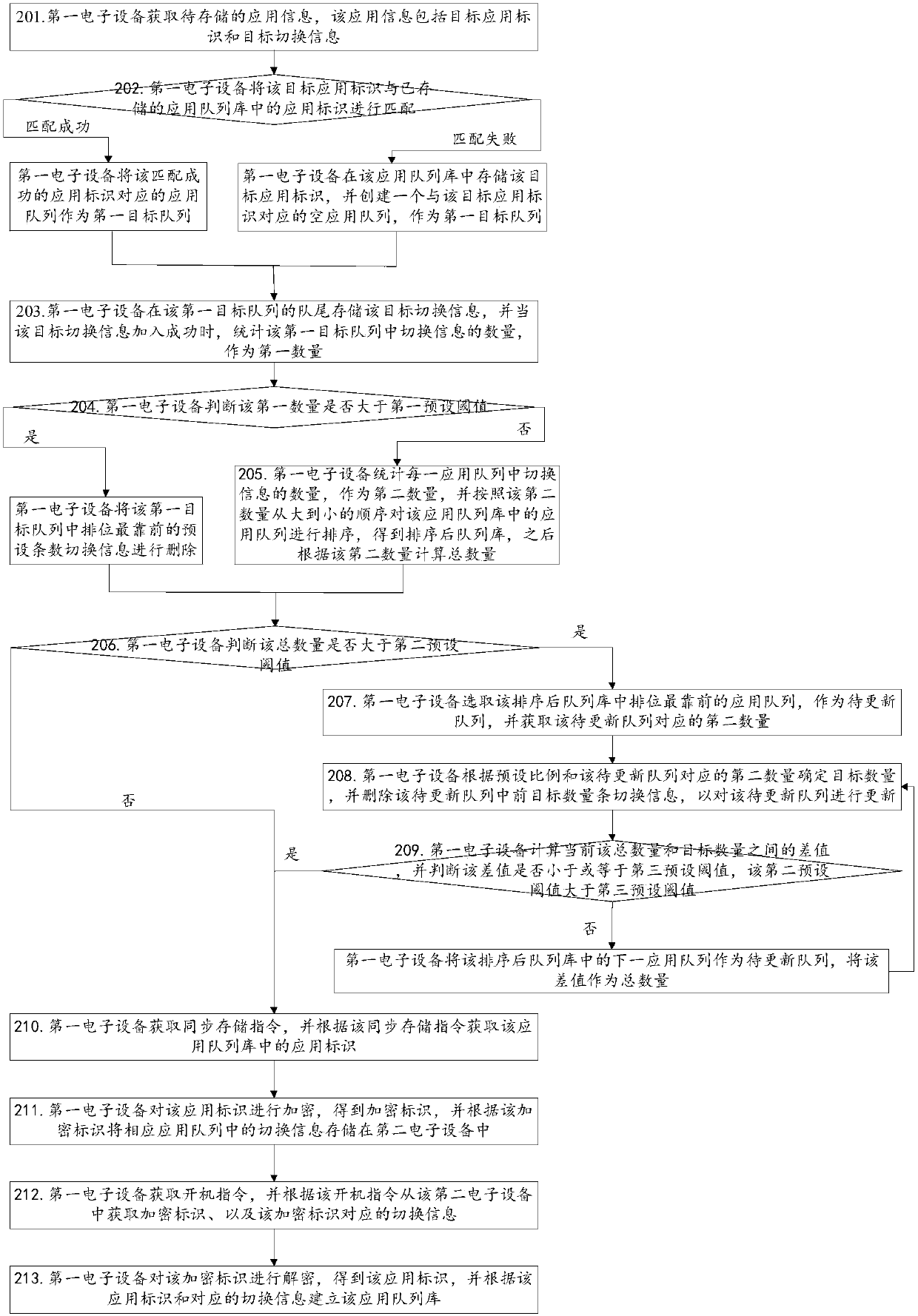
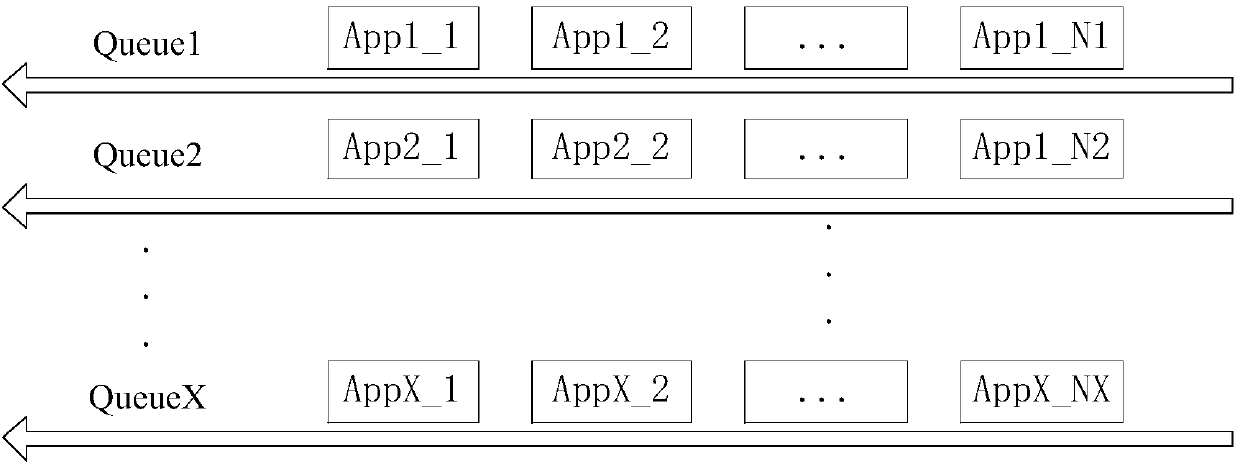
ActiveCN107943562AEnsure data integrityReduce memory usageInput/output to record carriersHardware monitoringMemory footprintStorage effect
The invention discloses an information storage method and apparatus, a storage medium and an electronic device. The information storage method is applied to a first electronic device. The method comprises the steps of obtaining to-be-stored application information, wherein the application information comprises a target application identifier and target switching information; according to the target application identifier, determining a first target queue in a stored application queue library, wherein the application queue library comprises at least one application queue, and each application queue comprises at least one piece of switching information; according to target switching information, updating the first target queue, thereby storing the application information in the application queue library; and according to the updated first target queue, updating the application queue library. Therefore, the system memory occupation can be reduced; the data comprehensiveness of the application information can be ensured; the method is simple; and the storage effect is good.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
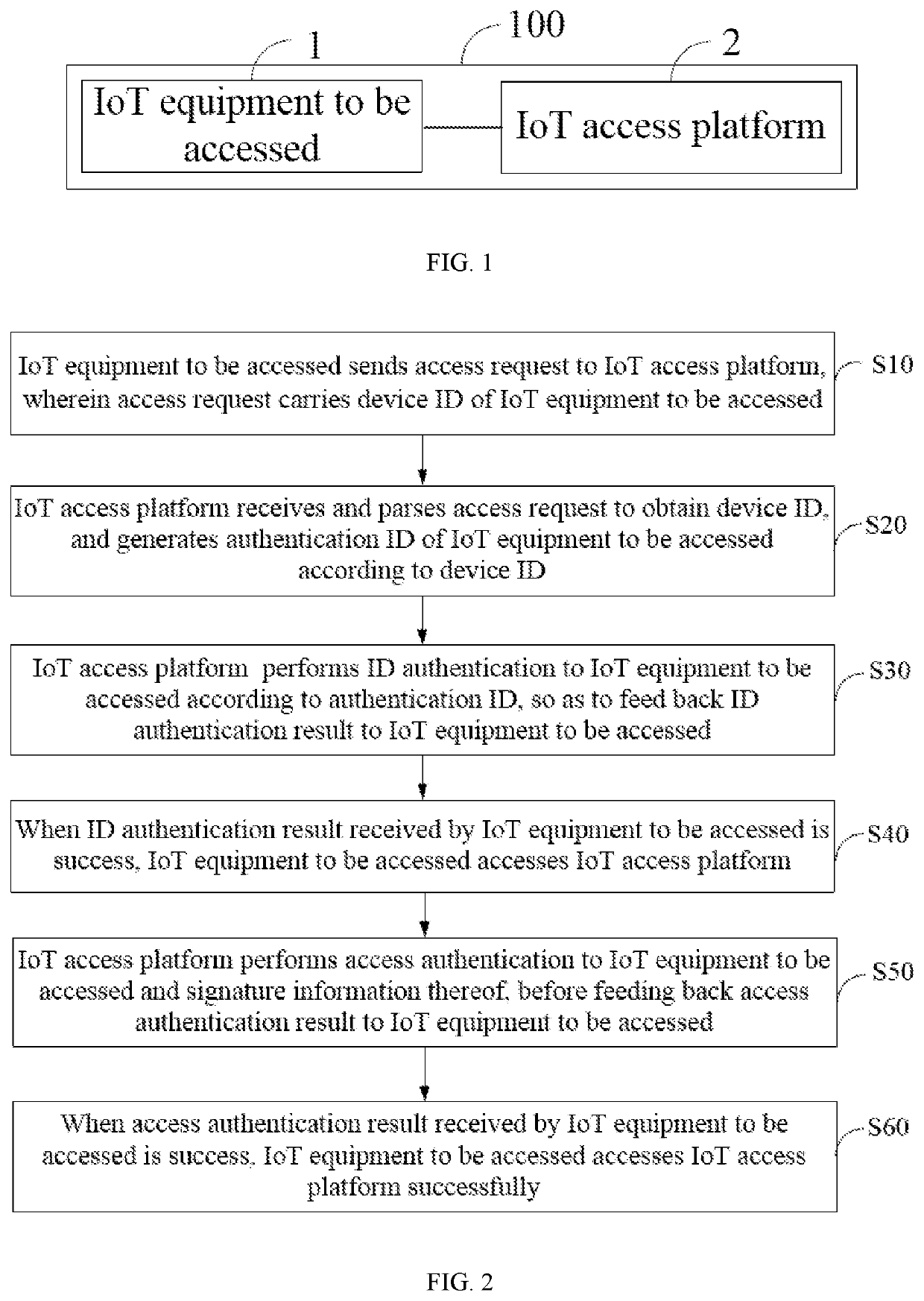
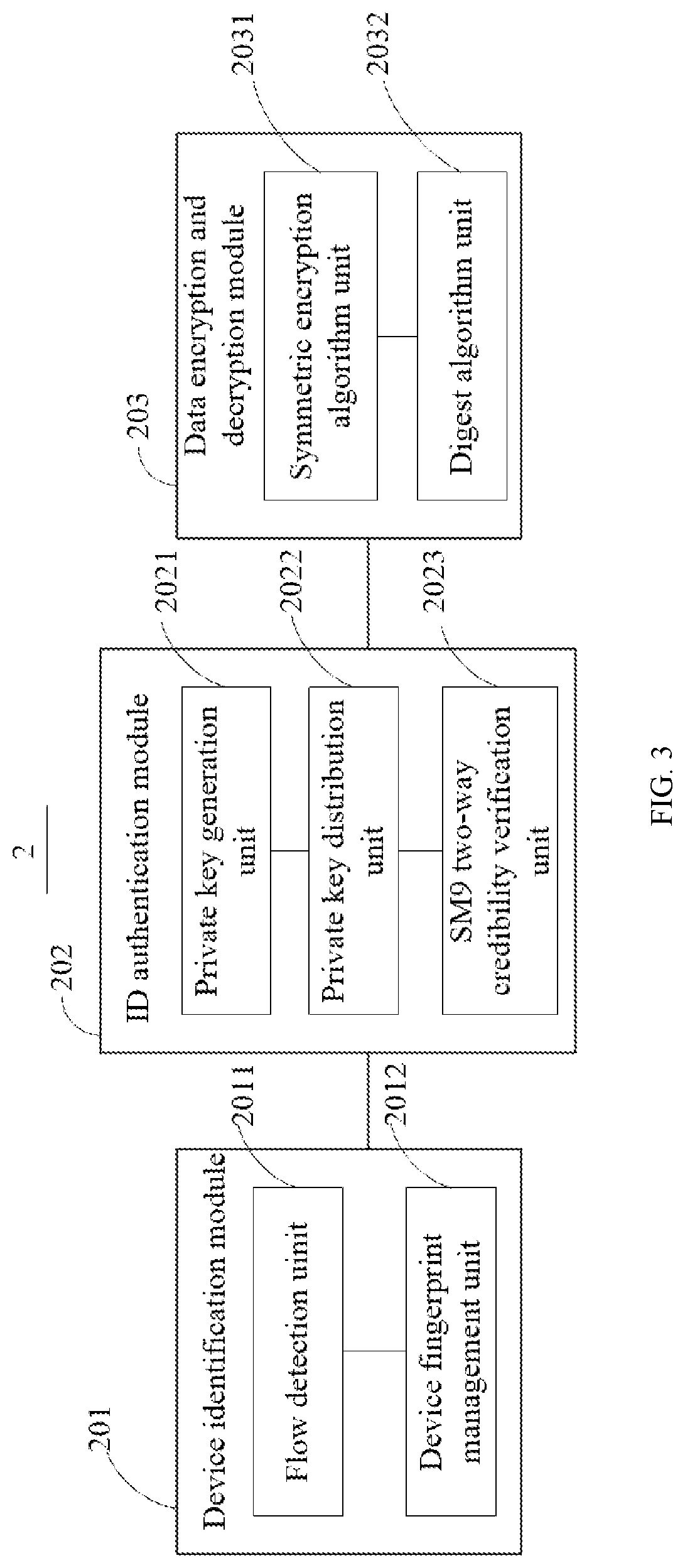
Access method and system of internet of things equipment based on 5g, and storage medium
ActiveUS20220312208A1Improve securityEnsure data integrityAssess restrictionSecurity arrangementData integrityAccess method
A 5G-based Internet of Things device access method and system, and storage medium. Method includes steps that IoT access platform generates authentication identification of to-be-accessed IoT device according to device identification of to-be-accessed IoT device, and carries out identity authentication of to-be-accessed IoT device through authentication identification, and identity authentication result is sent to to-be-accessed IoT device so when identity authentication result received by to-be-accessed IoT device is that identity authentication is passed, to-be-accessed IoT device accesses IoT access platform and performs encrypted data communication. Method is advantaged in that legal identity of to-be-accessed IoT equipment is verified by taking equipment fingerprint as authentication identifier, and data integrity of to-be-accessed IoT equipment is ensured through access authentication, so illegal terminal is prevented from accessing IoT access platform, and security of data transmission is improved.
Owner:SHENZHEN GAS CORP +1
Method for securing data and device for implementing the same
ActiveUS8103933B2Ensure data integrityReduce memory capacityAmplifier modifications to reduce noise influenceError detection/correctionComputer hardwareData integrity
A method and system to ensure the integrity of data in a data-processing device, a data packet is read from a memory and checked to determine whether the data packet is an existing code word of a predefined first code, and if the data packet is an existing code word, the data packet is accepted as intact, and if the data packet is not an existing code word, at least one data block of an error-correcting second code that overlaps with the read data packet is ascertained, and an error is searched for in the data packet using the second code, and the data packet is corrected on the basis of the result of the search, and the corrected data packet is accepted as intact.
Owner:ROBERT BOSCH GMBH
FlexRay communication module
InactiveUS7769906B2Ensure data integrityIncrease flexibilityMultiple digital computer combinationsElectric digital data processingReal-time computing
A FlexRay communication module for coupling a FlexRay communication connection to a subscriber, associated with the FlexRay communication module, in a FlexRay network over which messages are transferred, the FlexRay communication module including a first assemblage for storing at least a portion of the transferred messages, and a second assemblage for connecting the first assemblage to the subscriber, and a third assemblage for connecting the FlexRay communication connection to the first assemblage.
Owner:ROBERT BOSCH GMBH
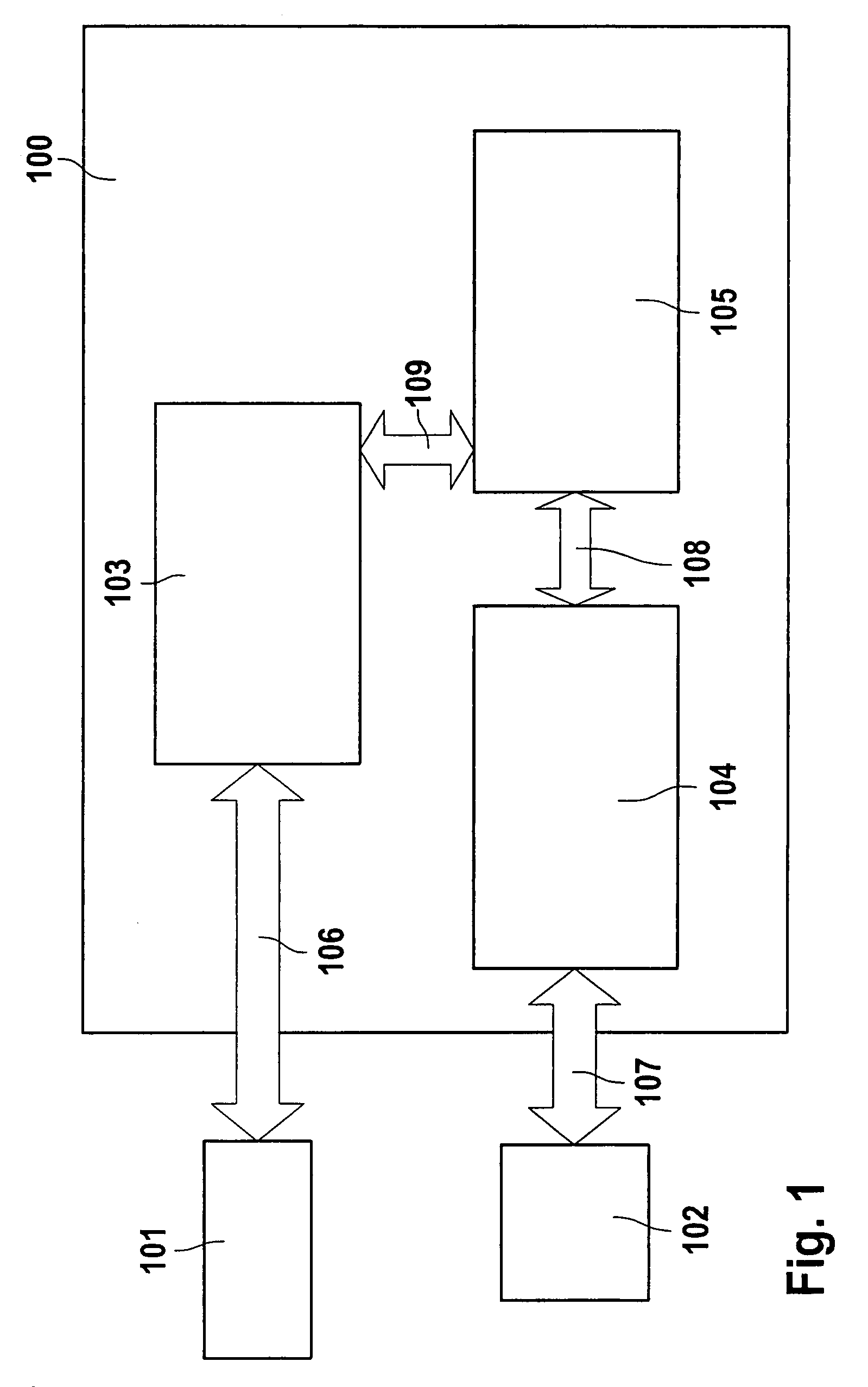
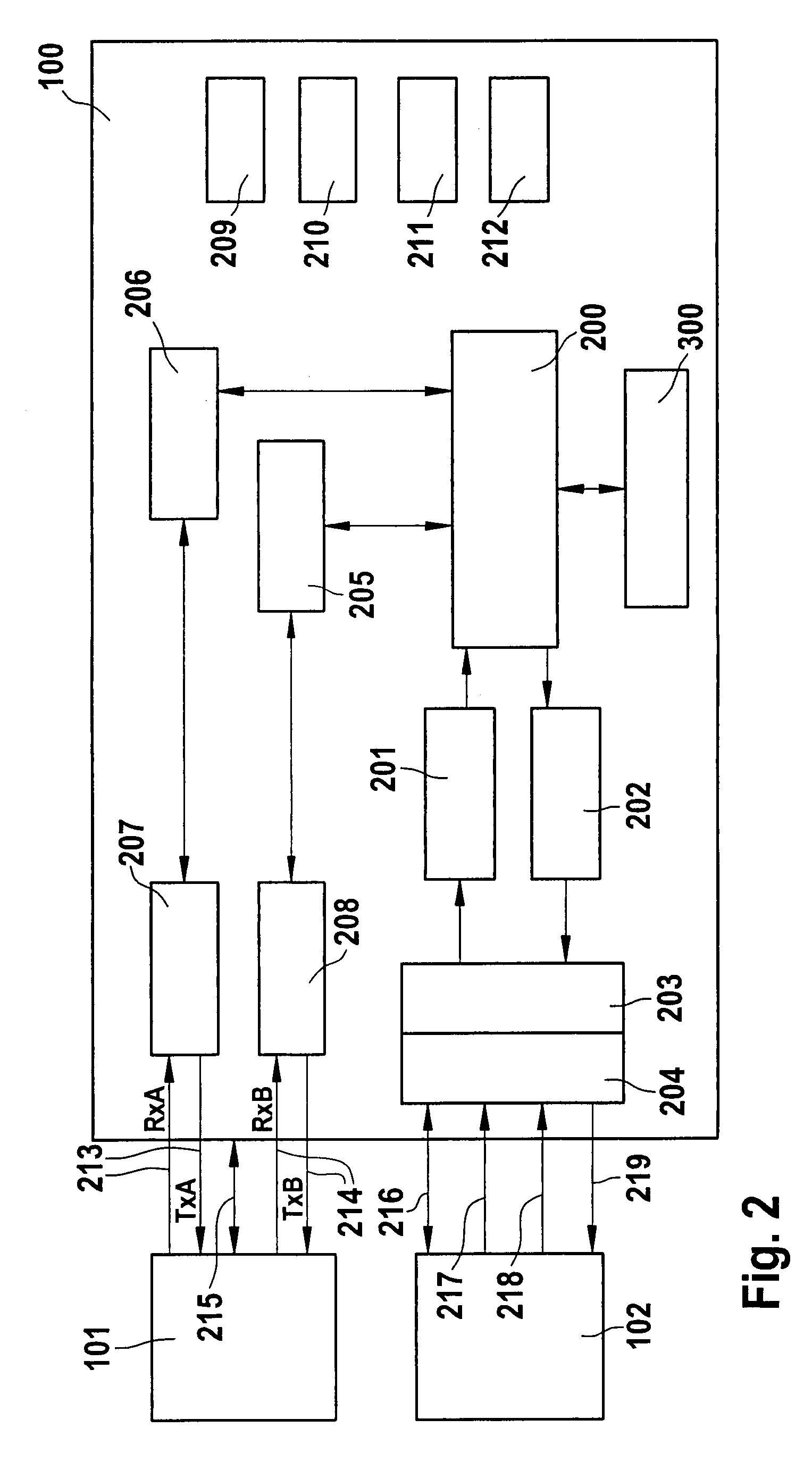
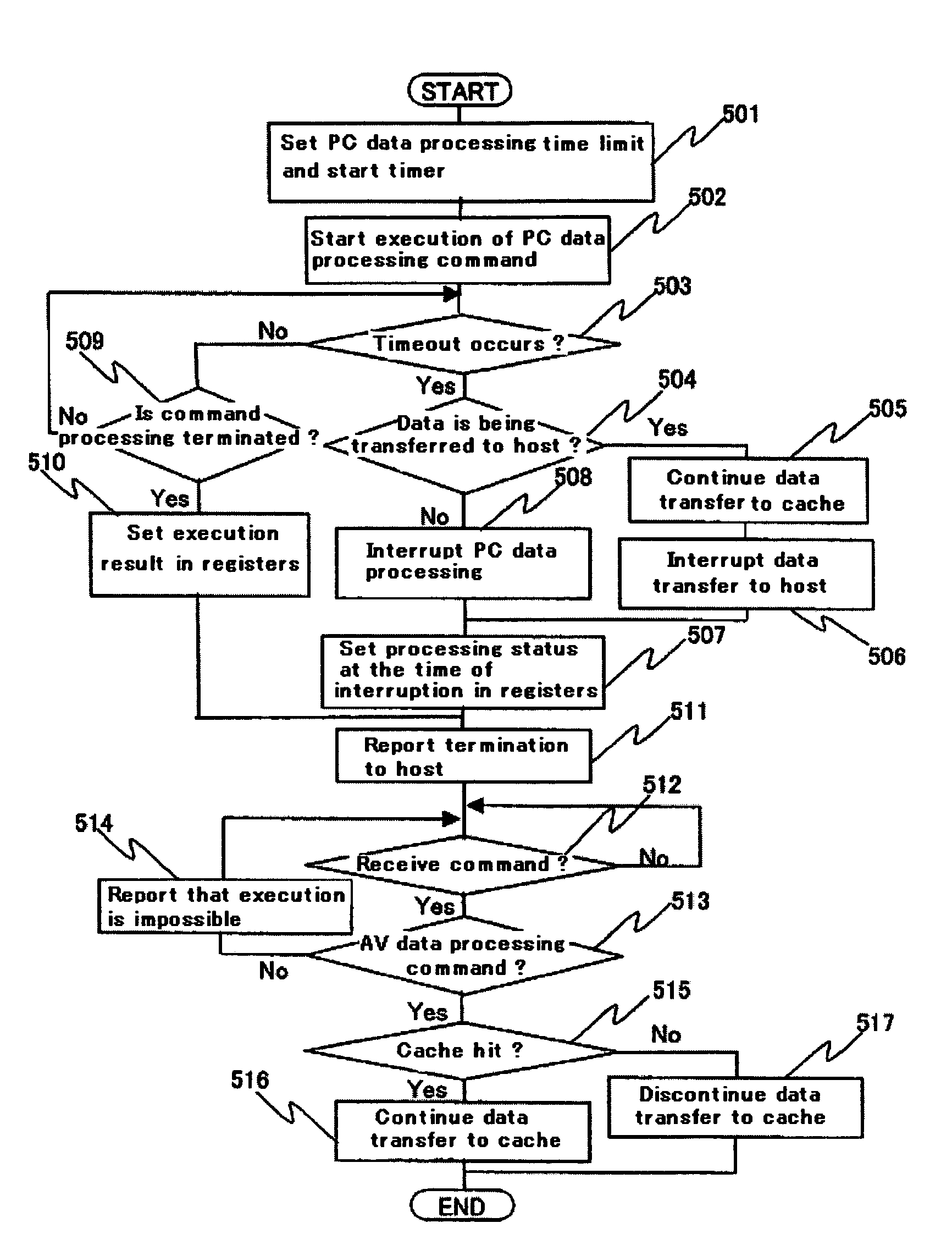
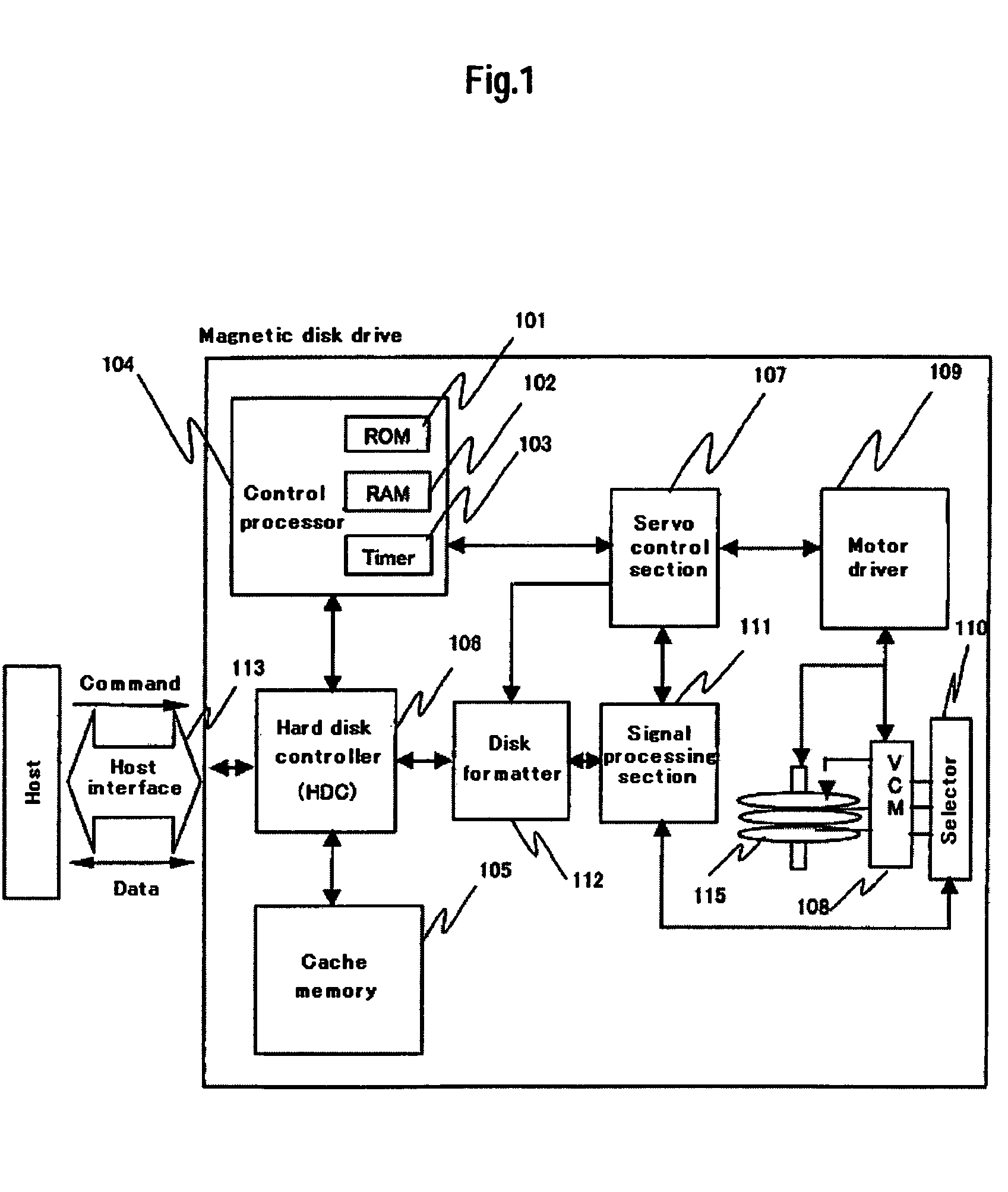
Disk drive and method for performing realtime processing and non-realtime processing simultaneously
InactiveUS7461219B2Efficient executionEnsure data integrityInput/output to record carriersFilamentary/web record carriersData integrityTime limit
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV
Method and System for Classifying Networked Devices
InactiveUS20070299957A1Ensure data integrityEnsure safetyError detection/correctionDigital data processing detailsSystems designData integrity
The present invention is a method of creating and assigning a class of storage that is defined by the customer at initialization, such that specific object code is assigned to and used by the devices in a class of storage and such that the devices themselves are grouped according to class of storage. This method provides the customer with greater system design flexibility over conventional naming standards and also provides greater data integrity and security. The method of the present invention includes the steps of assigning a class of storage label, storing the class of storage label, determining whether the device is the correct class of storage for the assigned sub-device group, delivering an error message if the class of storage is incorrect, and assigning the device to a sub-device group, if the class of storage is correct.
Owner:XYRATEX TECH LTD
Medical record sharing method and system based on zero trust principle and block chain technology
PendingCN114567491AEnsure encryptionAddressing Security-Related VulnerabilitiesUser identity/authority verificationDigital data authenticationMedical recordData transmission
The invention discloses a medical record sharing method and system based on a zero-trust principle and a block chain technology, the block chain technology is used for recording and auditing each transaction in data storage and transmission, the invariability of a block chain is used for ensuring the data security and integrity, security addition is performed based on the zero-trust principle, and the data security and integrity are ensured. It is ensured that the medical record data is encrypted, and only the user and the device which are authenticated can interact with the network. The method can solve many data security related vulnerabilities, and has good performance in the aspect of solving medical data transmission and storage problems.
Owner:北京雁翎网卫智能科技有限公司
Symmetrical clock distribution in multi-stage high speed data conversion circuits
InactiveUS7319706B2Reduce skewIncrease speedSynchronisation information channelsTime-division multiplexStream dataComputer science
The present invention provides a high speed bit stream data conversion circuit that includes input ports to receive first bit streams at a first bit rate. Data conversion circuits receive the first bit streams and produce second bit stream(s), wherein the number and bit rate of the first and second bit stream(s) differ. Symmetrical pathways transport the first bit streams from the input ports to the data conversion circuits, wherein their transmission time(s) are substantially equal. A clock distribution circuit receives and symmetrically distributes a clock signal to data conversion circuits. A central trunk coupled to the clock port and located between a first pair of circuit pathways with paired branches that extend from the trunk and that couple to the data conversion circuits make up the clock distribution circuit. The distributed data clock signal latches data in data conversion circuits from the first to the second bit stream(s).
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com