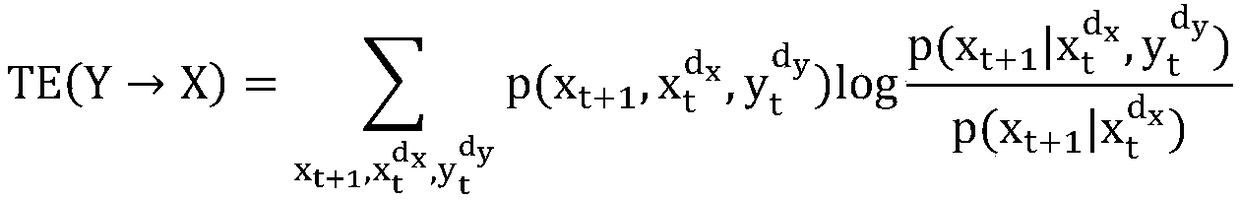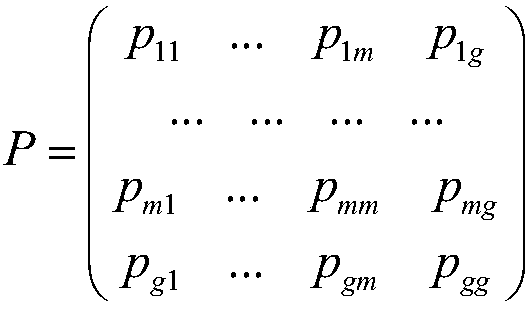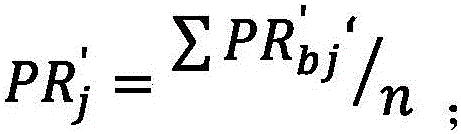Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
89 results about "Spread Networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Spread Networks is a company founded by Dan Spivey and backed by James L. Barksdale (former CEO of Netscape Communications Corporation) that claims to offer Internet connectivity between Chicago and New York City at ultra-low latency (i.e. speeds that are very close to the speed of light), high bandwidth, and high reliability, using dark fiber. Its customers are primarily firms engaged in high-frequency trading, where small reductions in latency are important to the extent that they help one close trades before one's competitors.
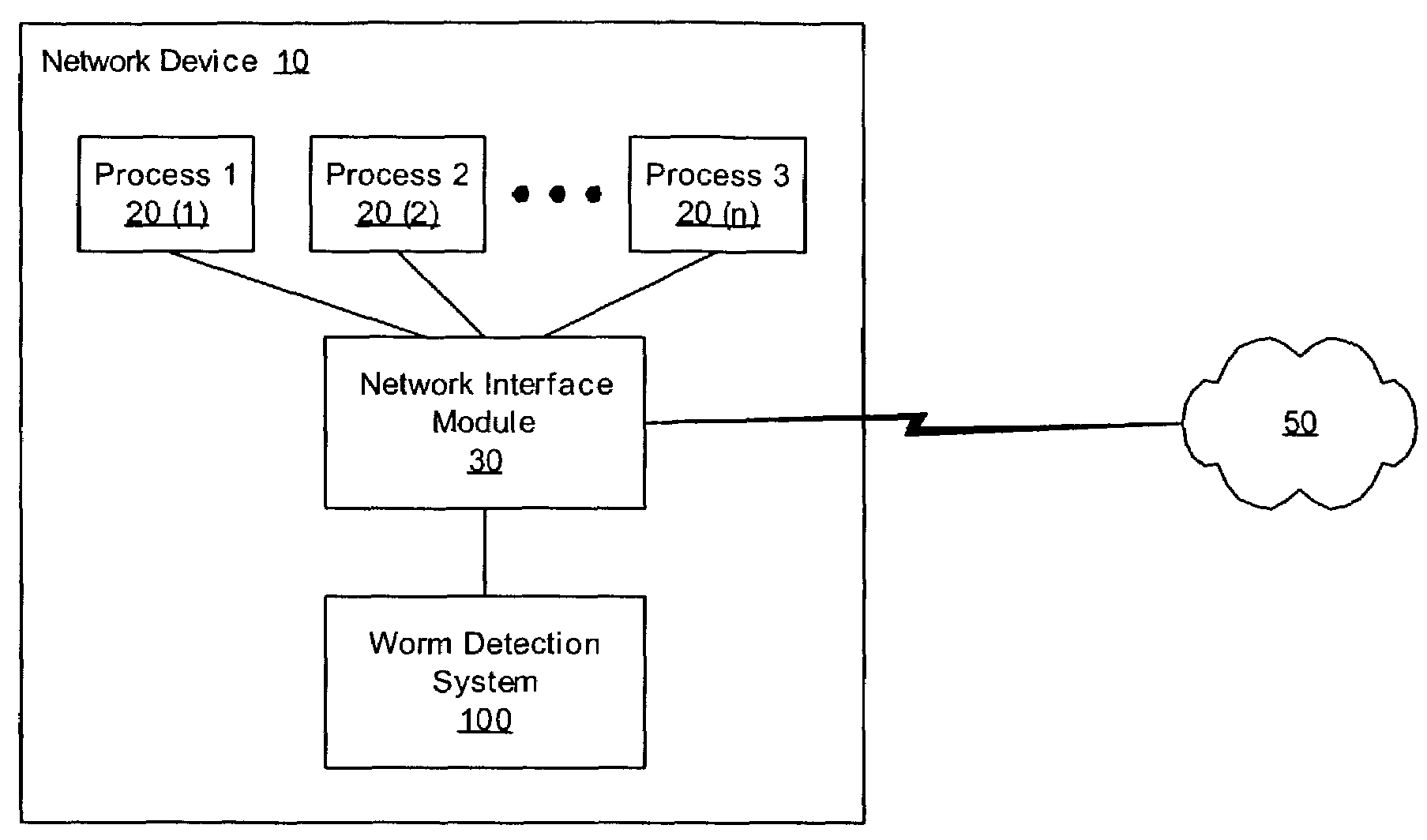
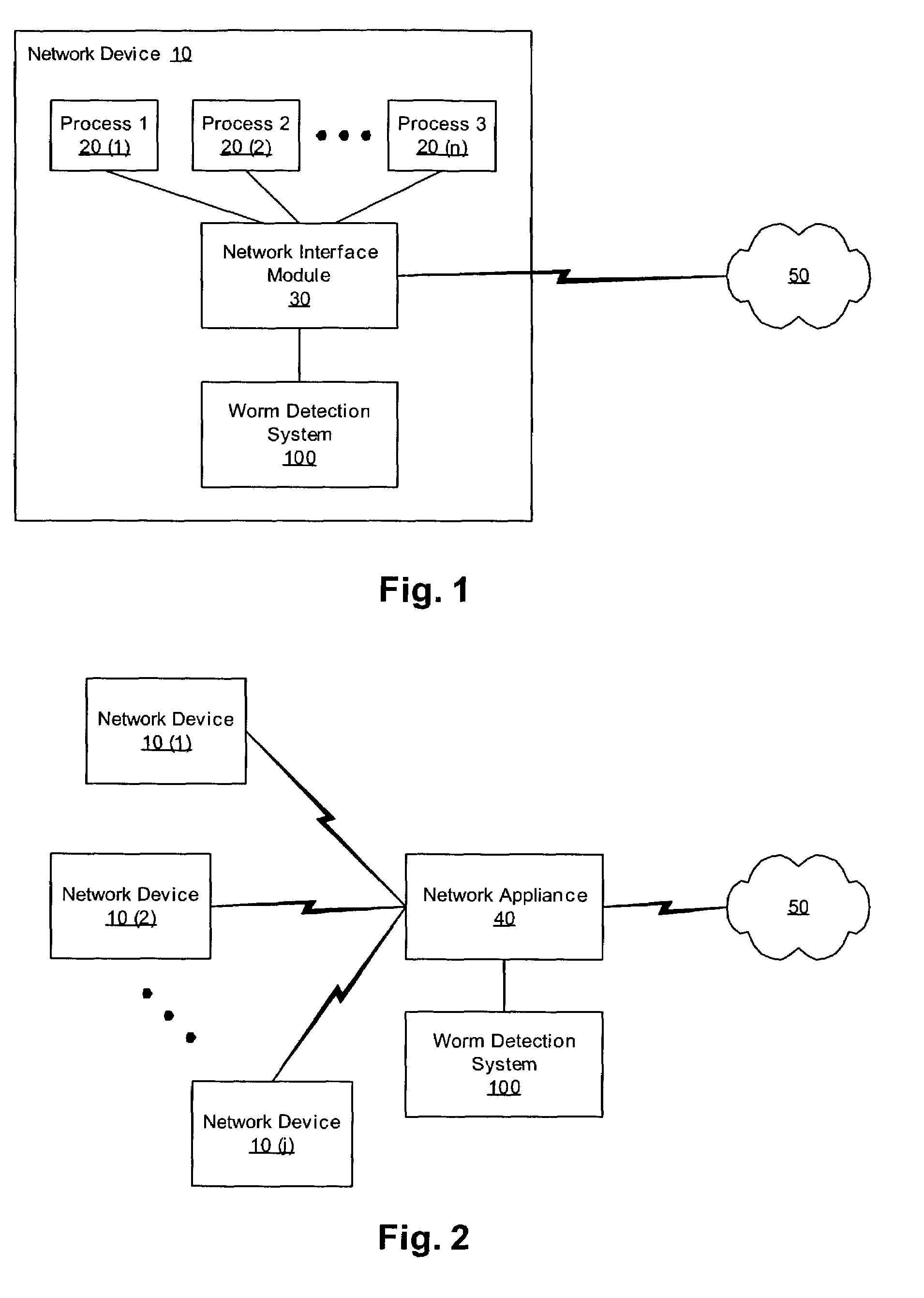
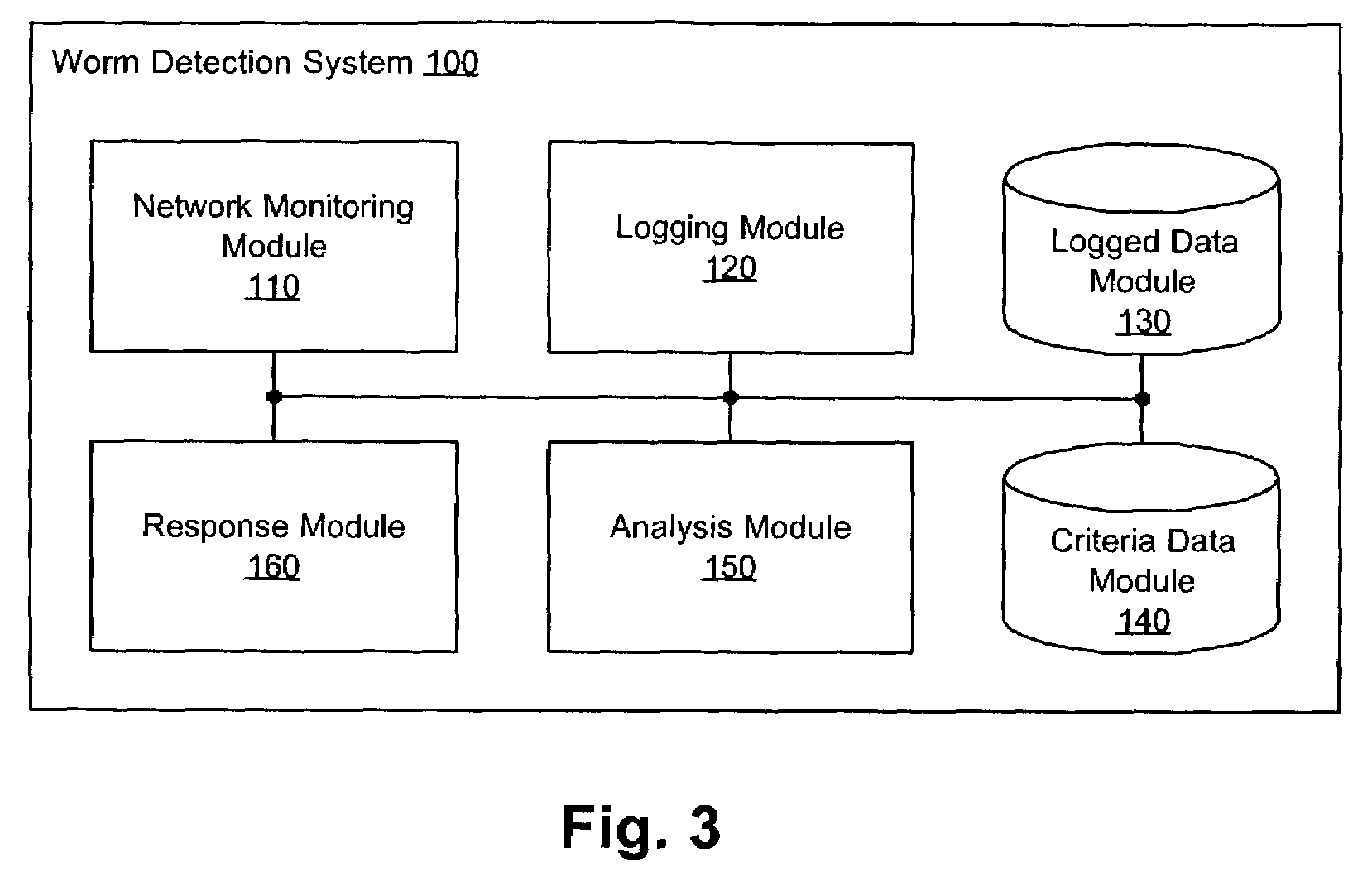
Heuristic detection and termination of fast spreading network worm attacks
Methods, apparati, and computer program products for detecting and responding to fast-spreading network worm attacks include a network monitoring module (110), which observes (205) failed network connection attempts from multiple sources. A logging module (120) logs (220) the failed connection attempts. An analysis module (150) uses the logged data on the failed connection attempts to determine (225) whether a sources is infected with a worm using a set of threshold criteria. The threshold criteria indicate whether a source's failed connection attempts are non-normal. In one embodiment, a response module (160) responds (240) to the computer worm by, e.g., alerting a user or system administrator, terminating an infected process (20), or terminating the infected source's network access.
Owner:CA TECH INC
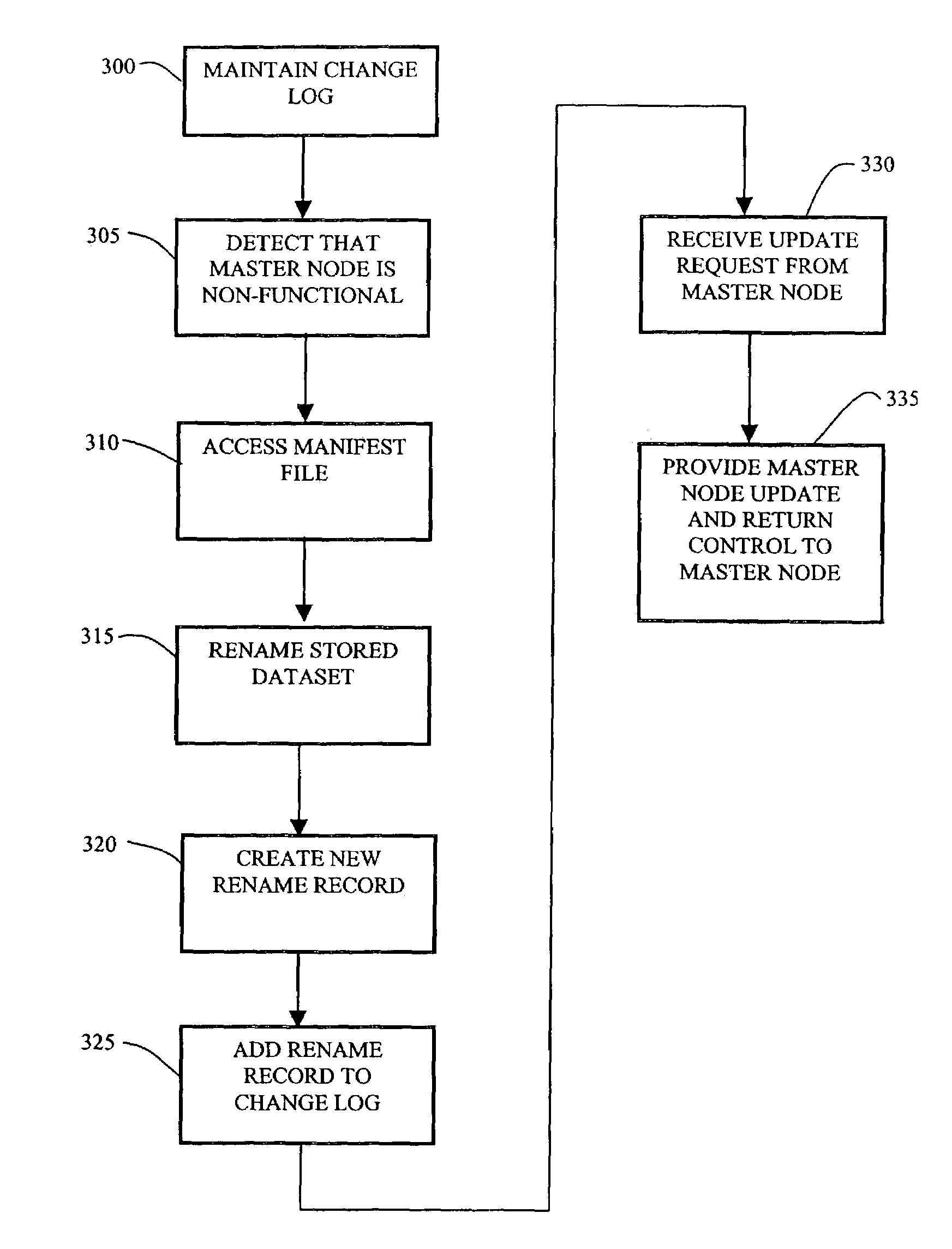
Method and apparatus for efficient propagation of large datasets under failure conditions
InactiveUS7158985B1Efficiently and accurately propagating dataset changes among nodesEffective maintenanceData processing applicationsDigital data processing detailsData setDistributed computing
A network of nodes caches replicated datasets in which dataset changes are efficiently propagated as a set of changes even under failure conditions. A master node and a plurality of subordinate nodes in the network each maintain a copy of the dataset and a change log storing change events in the dataset in that node. The change log further includes a rename chain having a plurality of linked rename records created in response to a new master gaining control of the dataset. The master node computes and propagates dataset changes to the subordinate nodes as a set of change events. If the master node fails, one of the subordinate nodes becomes temporary master and continues to propagate dataset changes using its dataset and its change log in response to update requests from other nodes where the update request contains information from the change log of the requestor node.
Owner:CISCO TECH INC
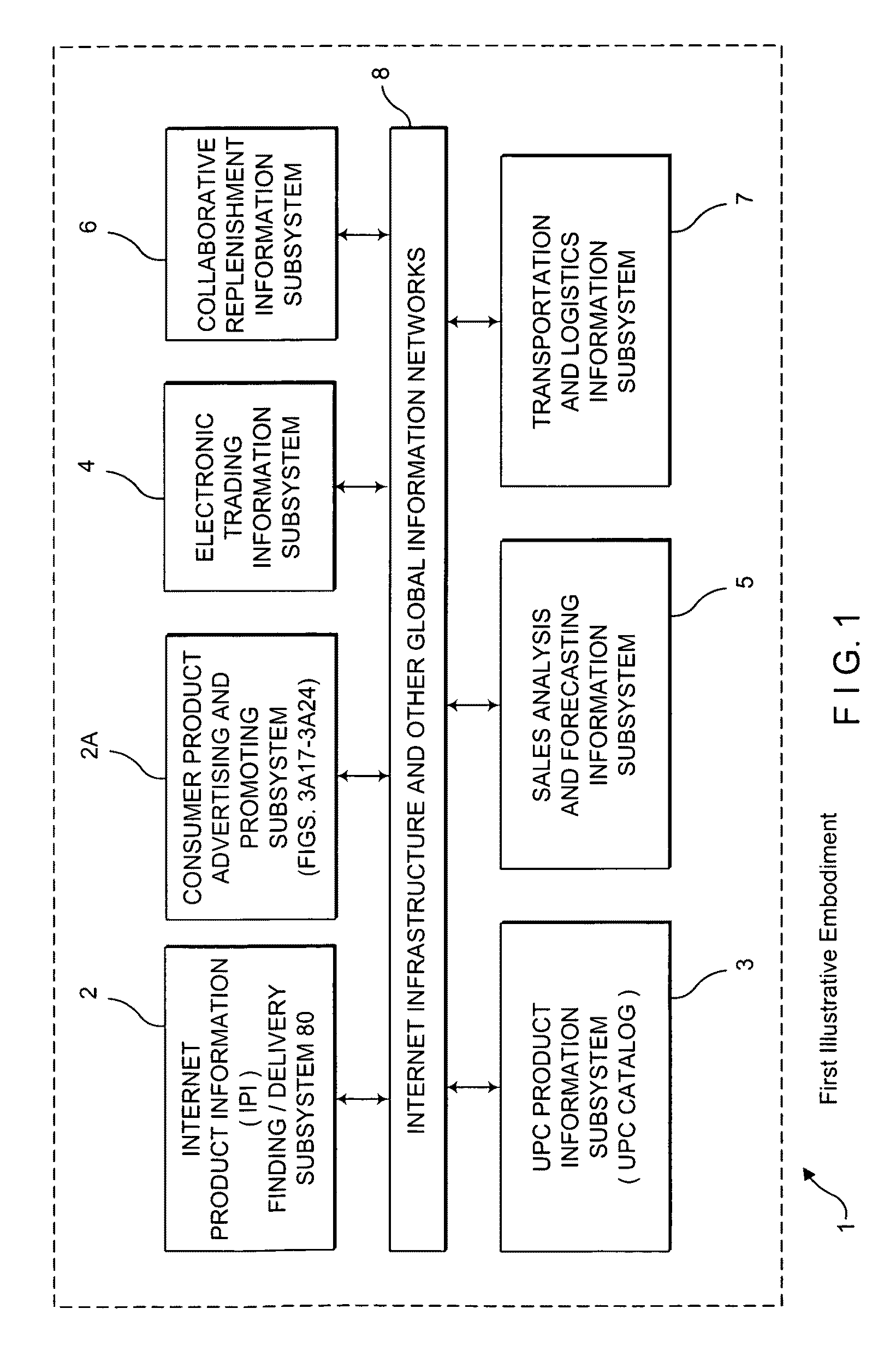
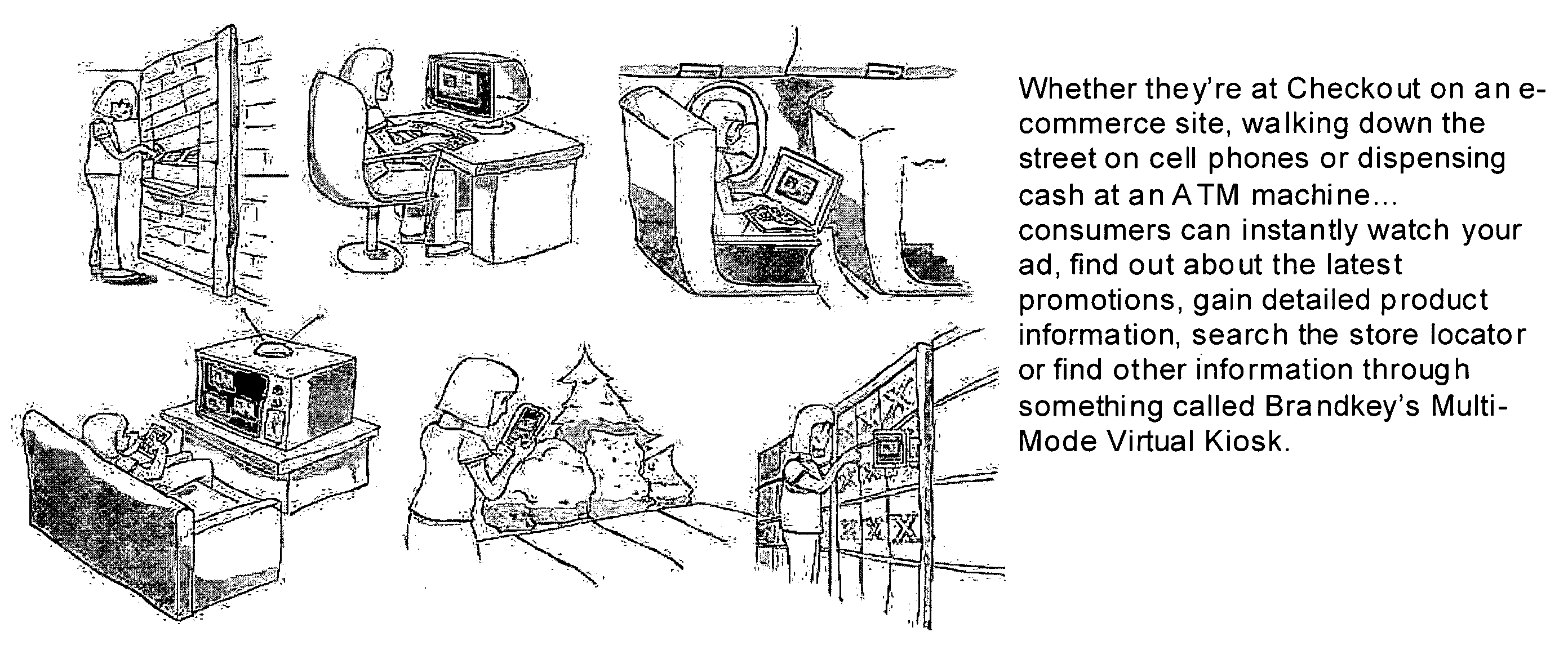
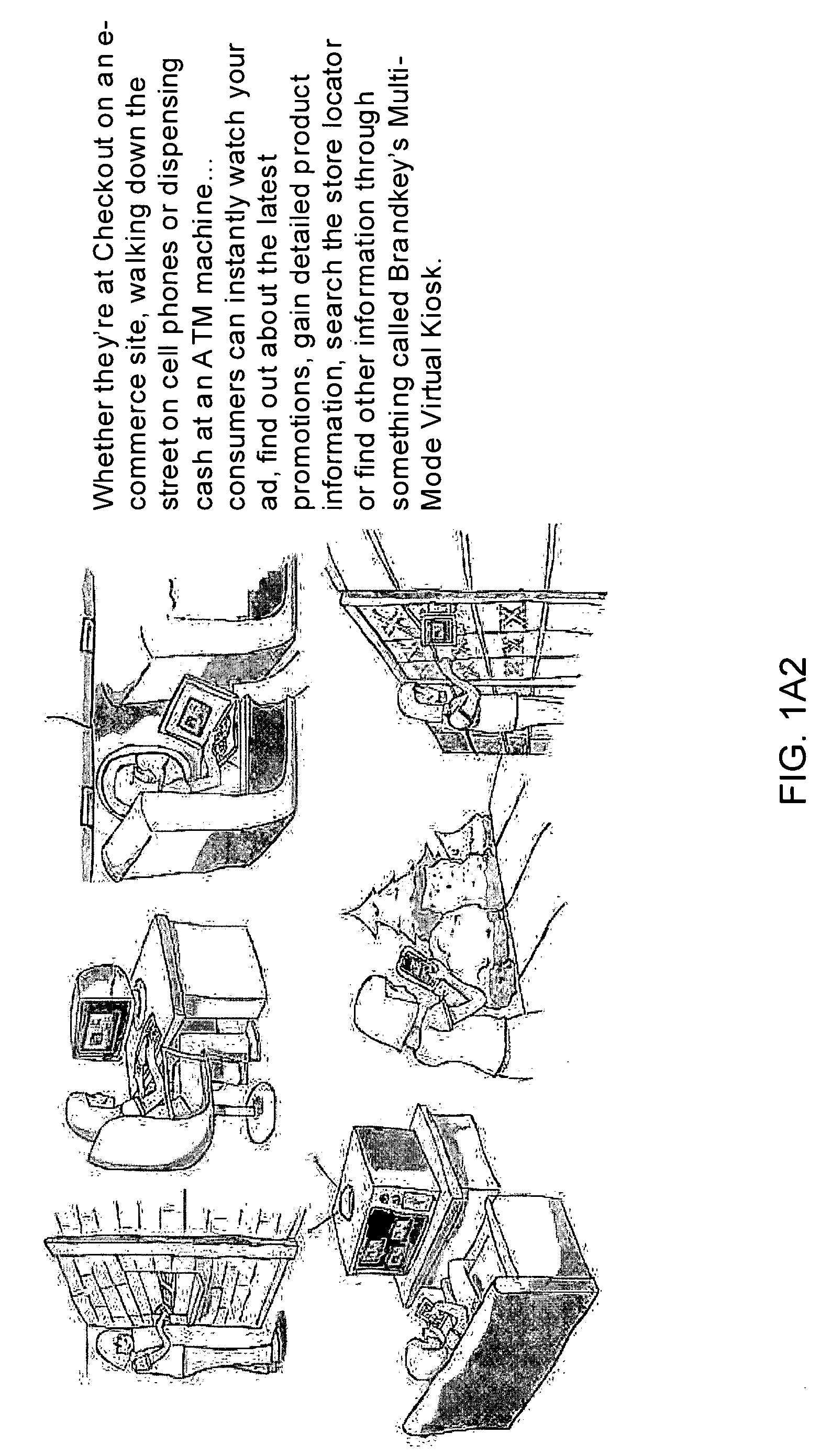
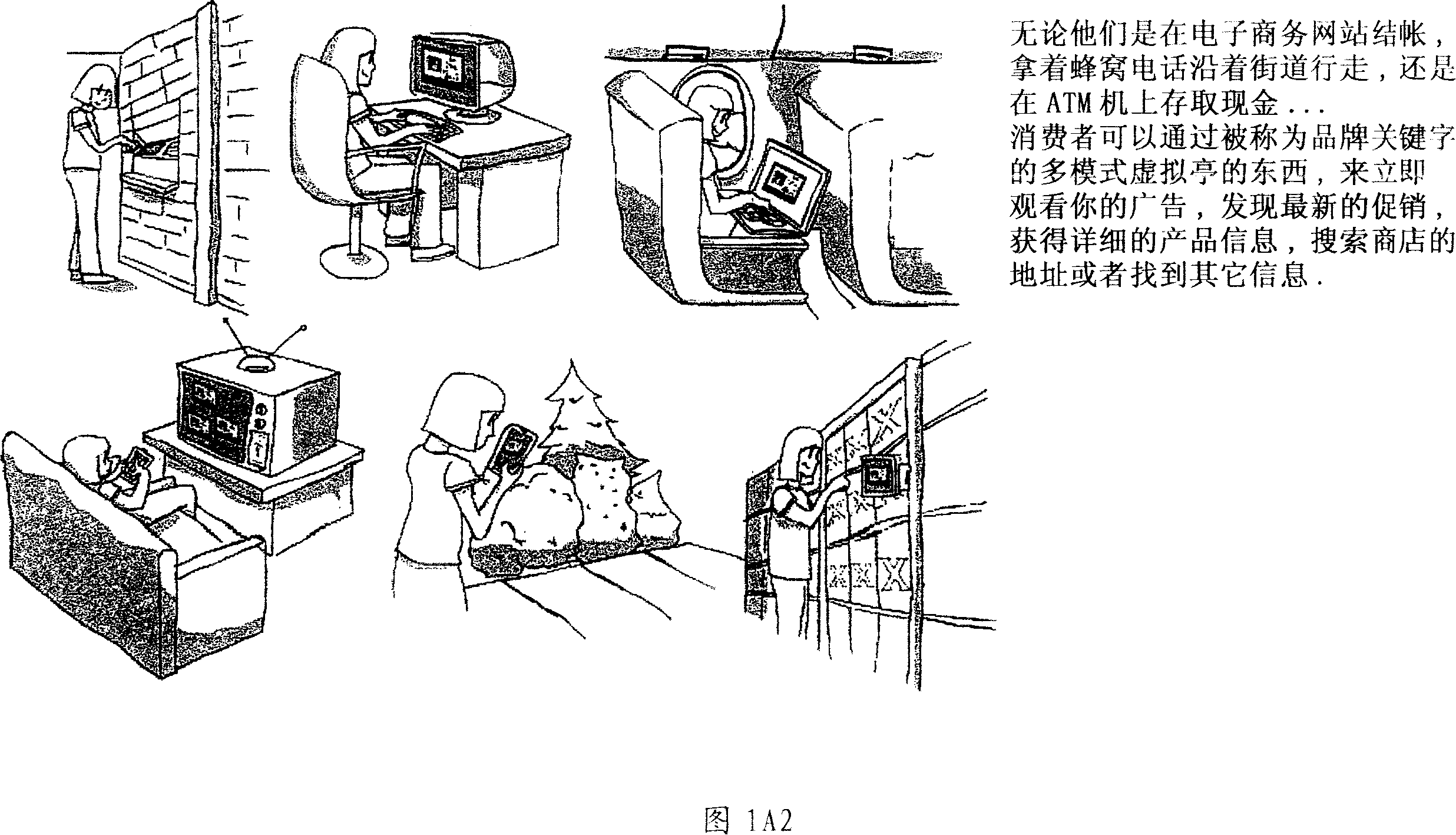
Inernet-based brand marketing communication network for enabling commission-based e-commerce transactions along the fabric of the world wide web (WWW) using server-side driven multi-mode virtual kiosks (MMVKs)
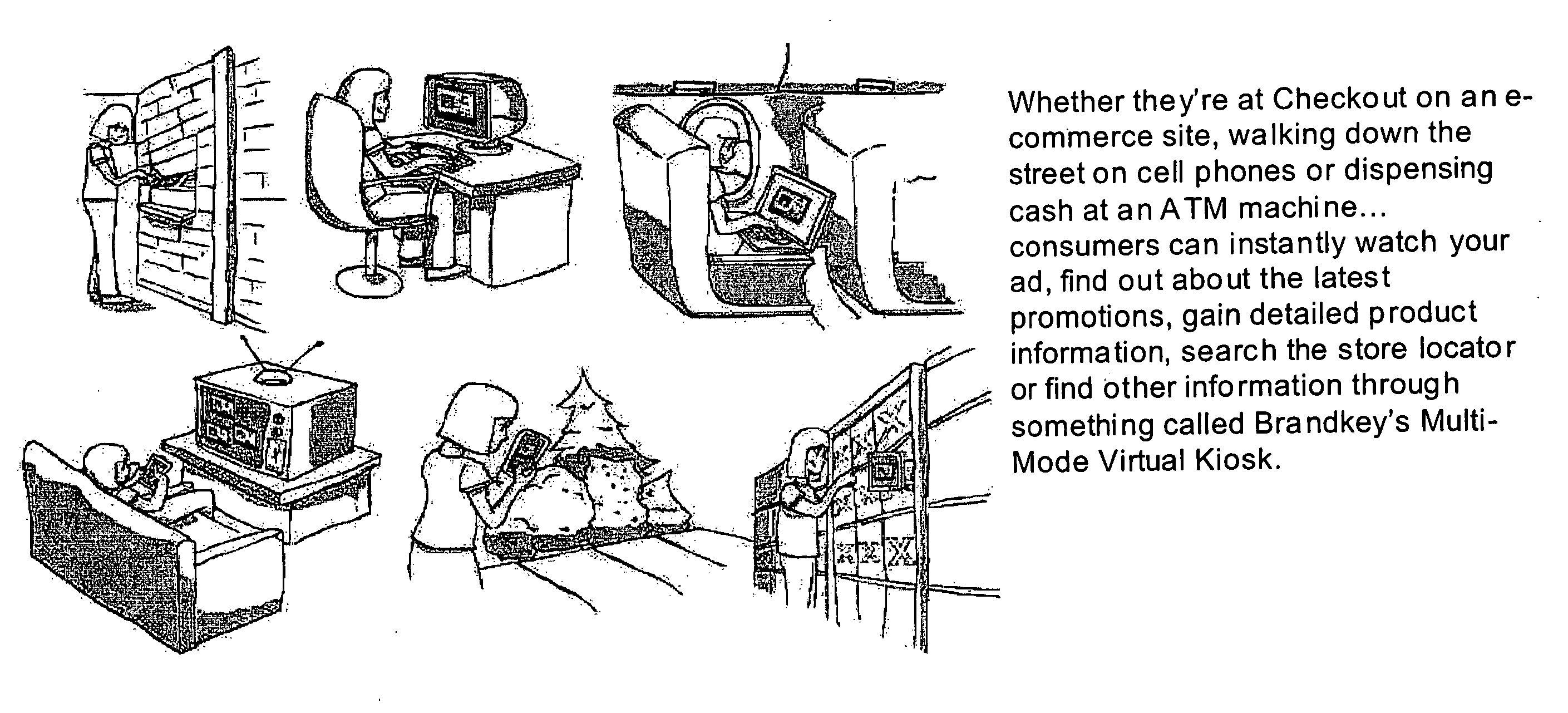
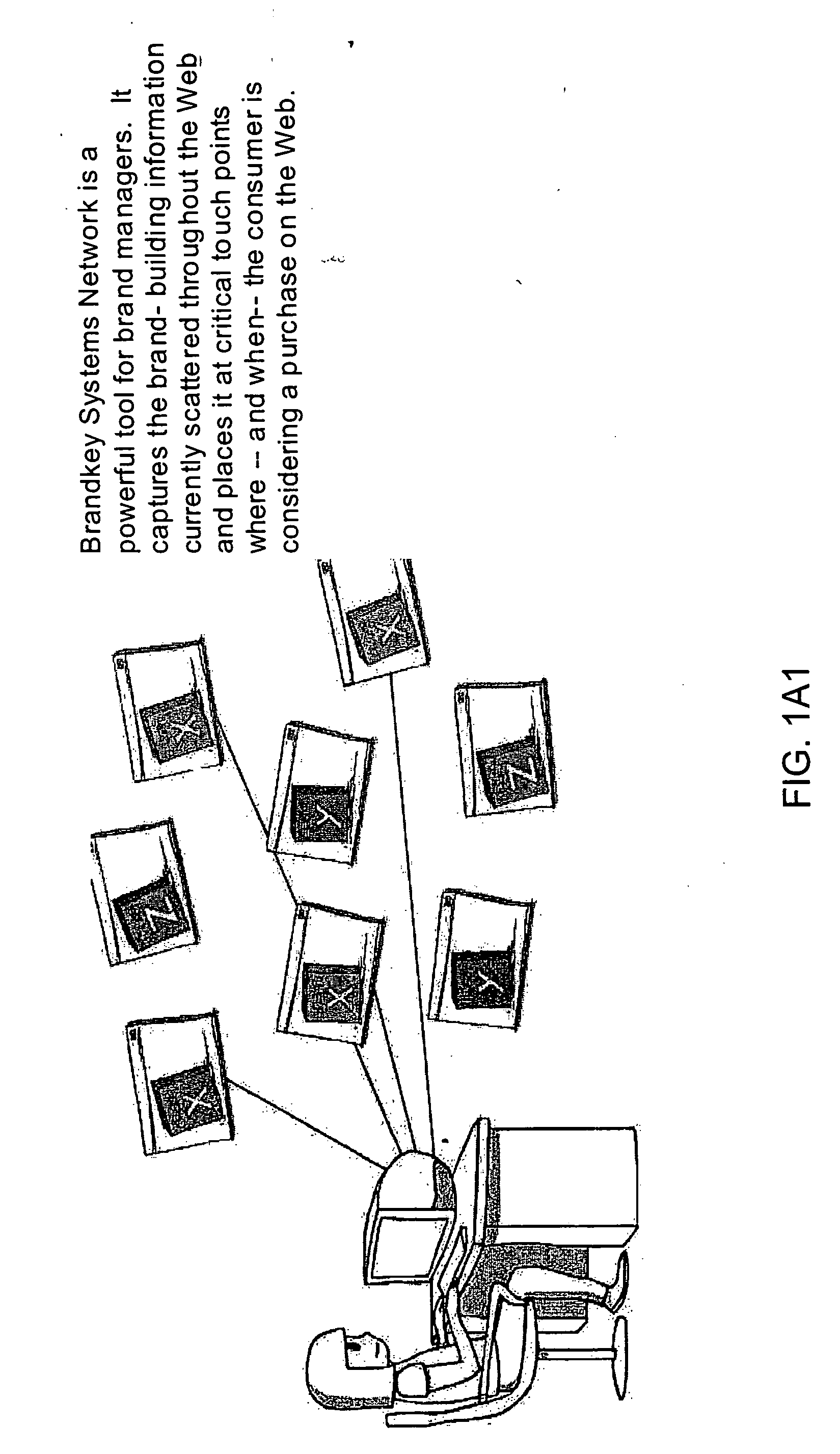
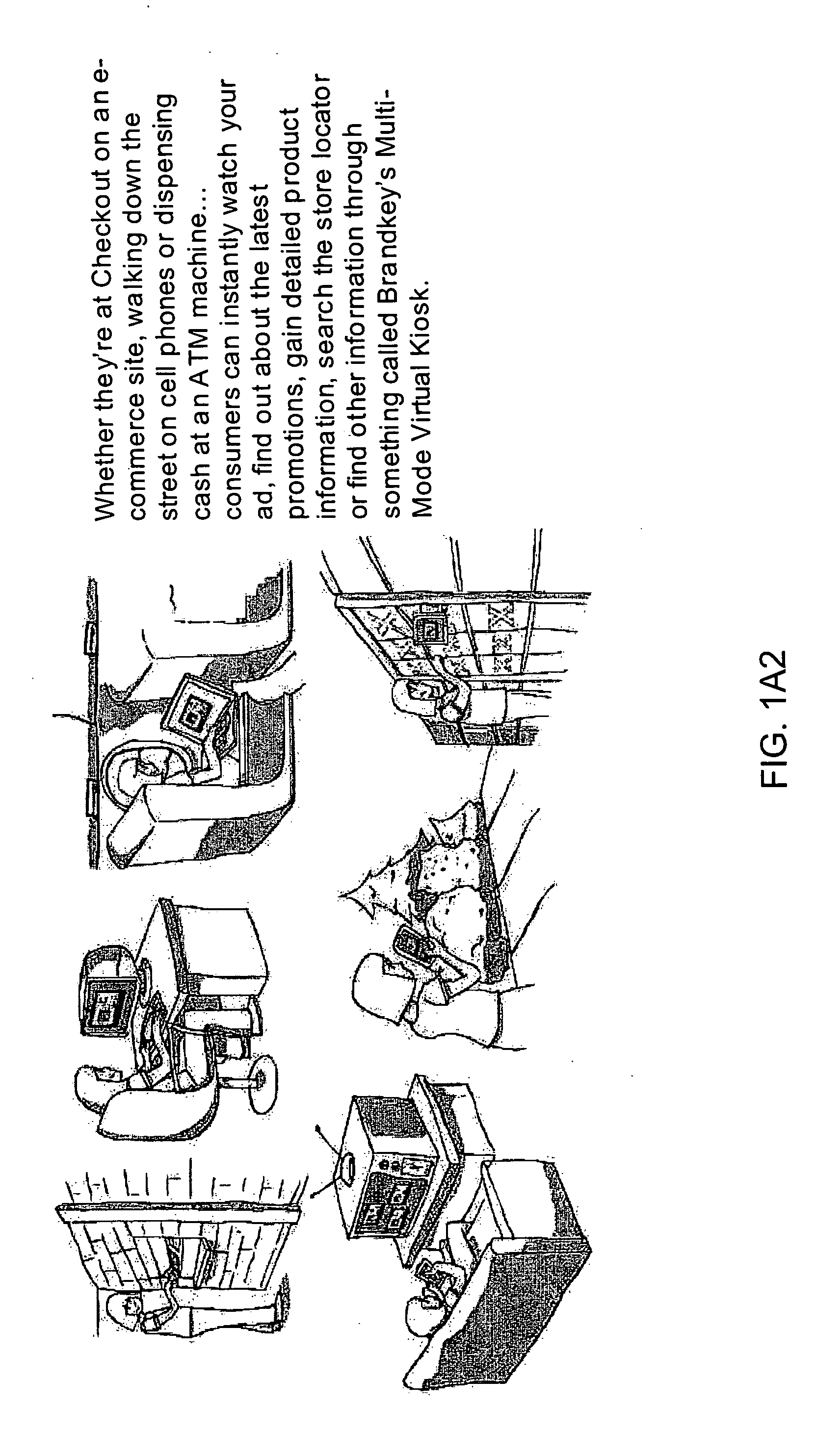
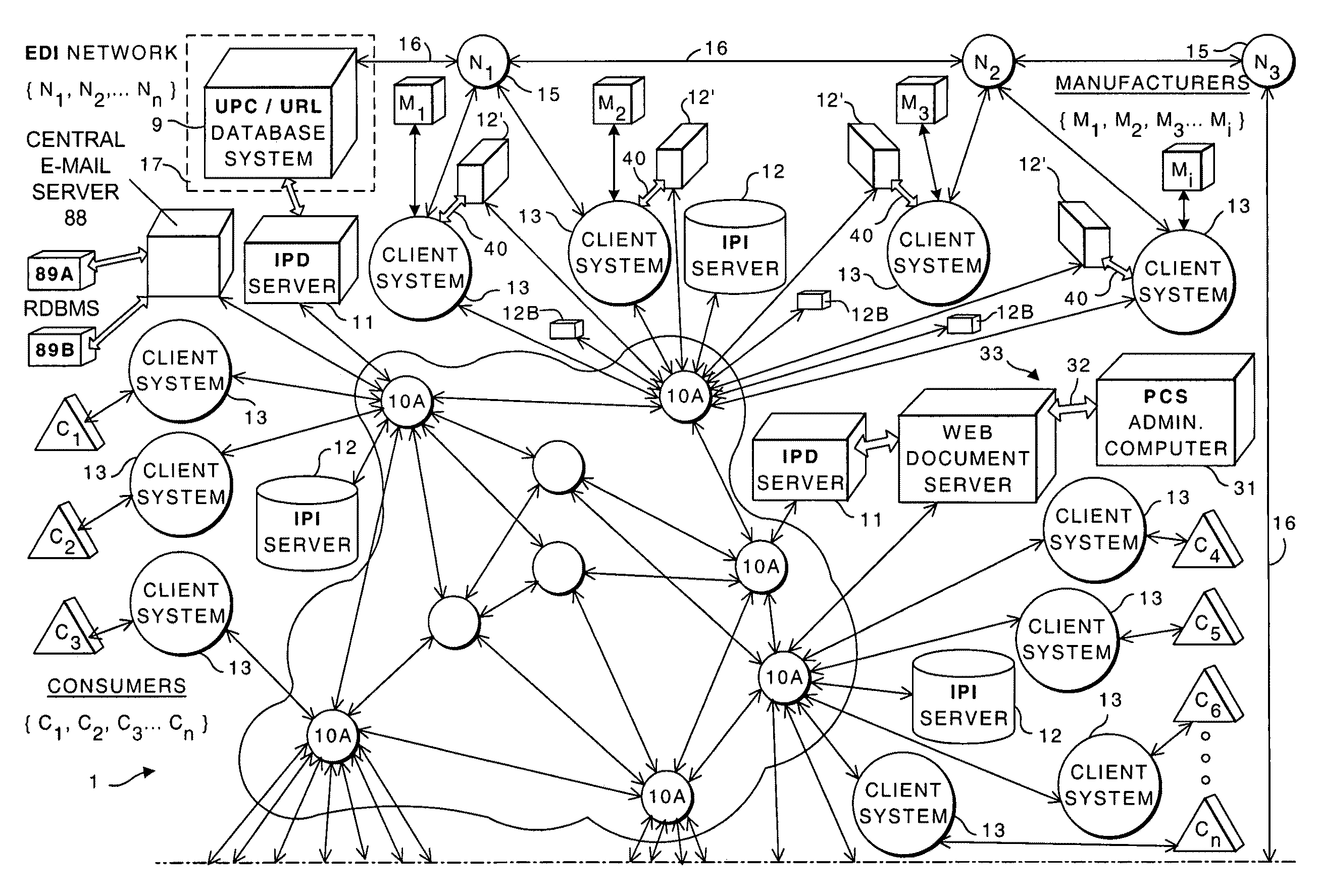
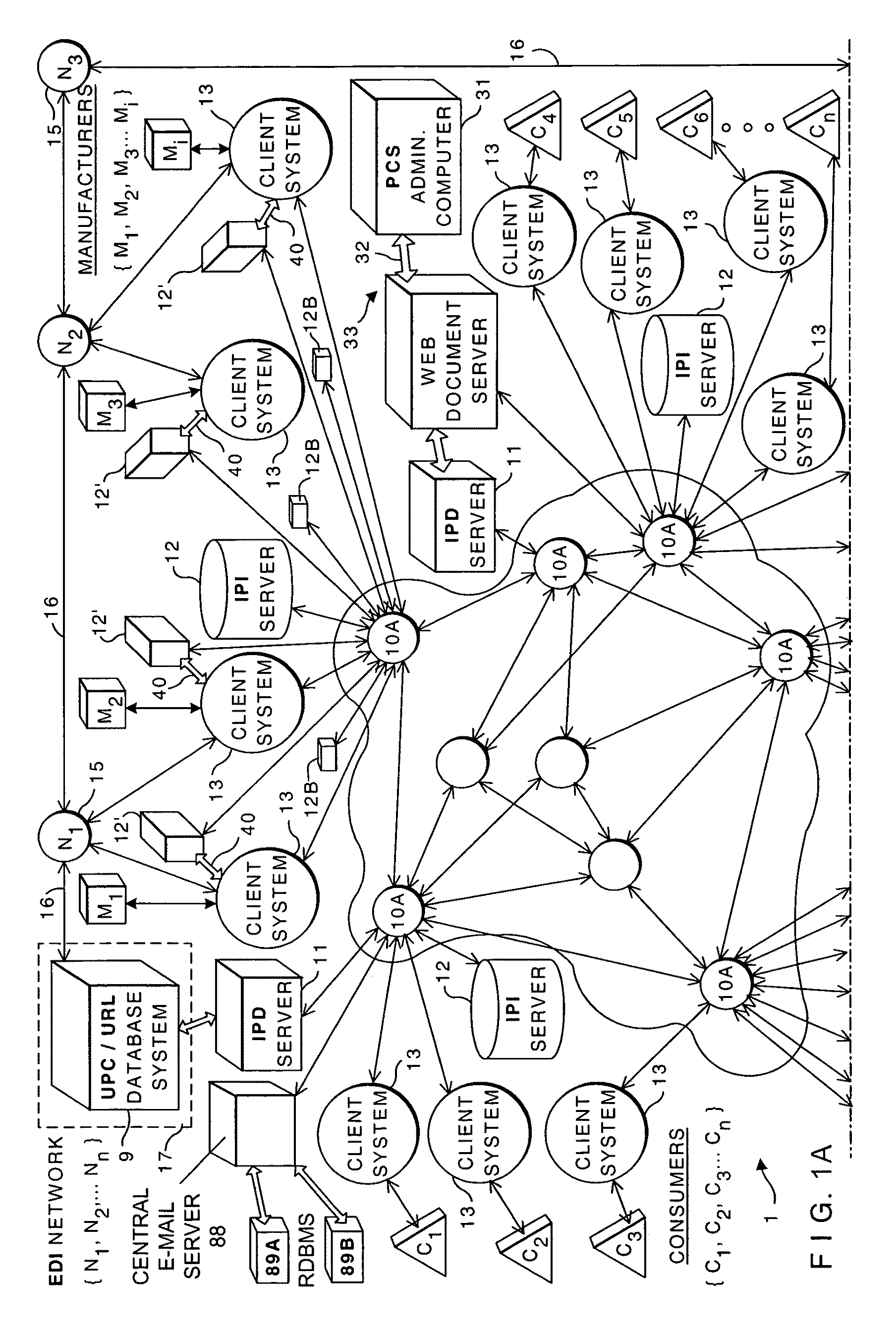
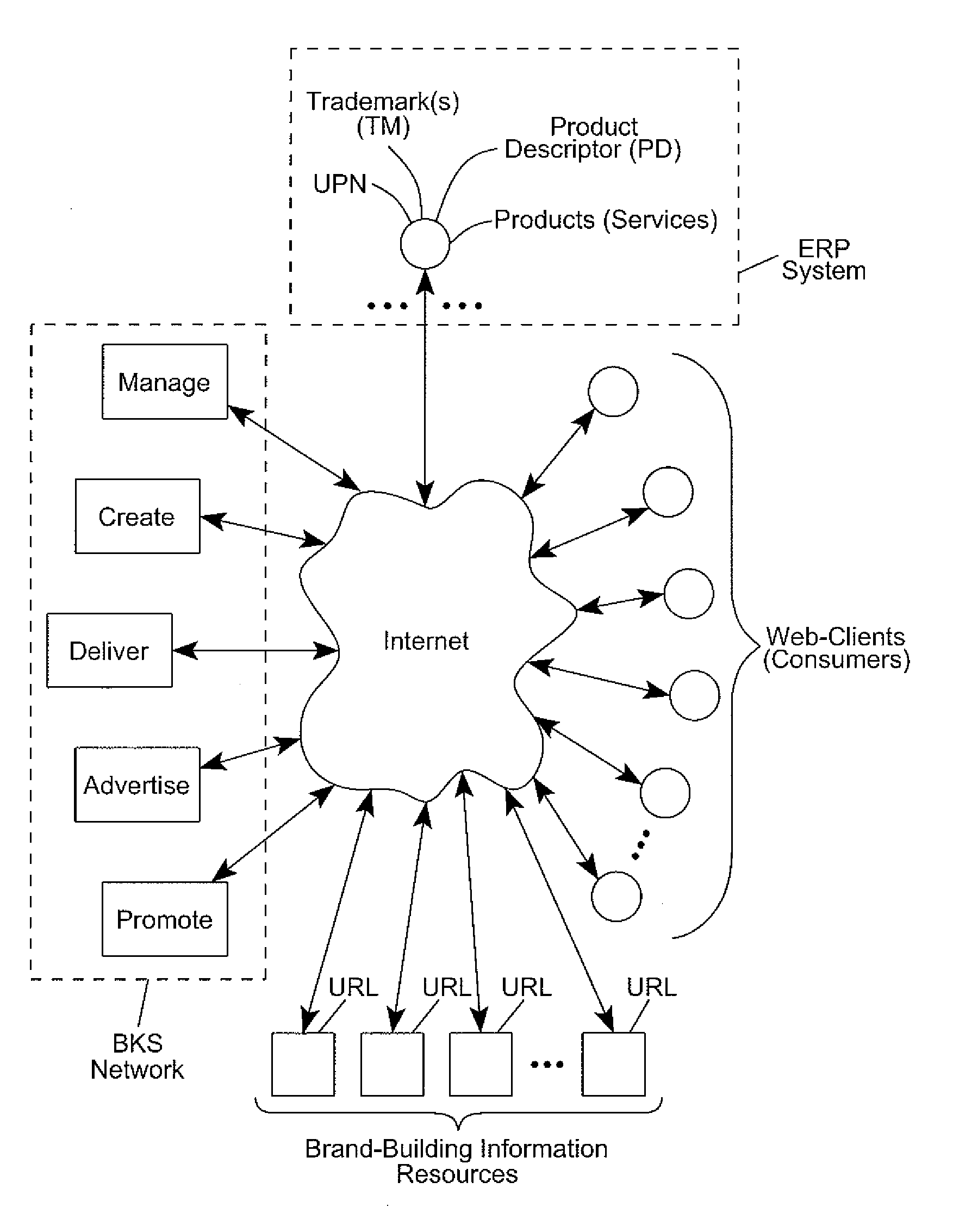
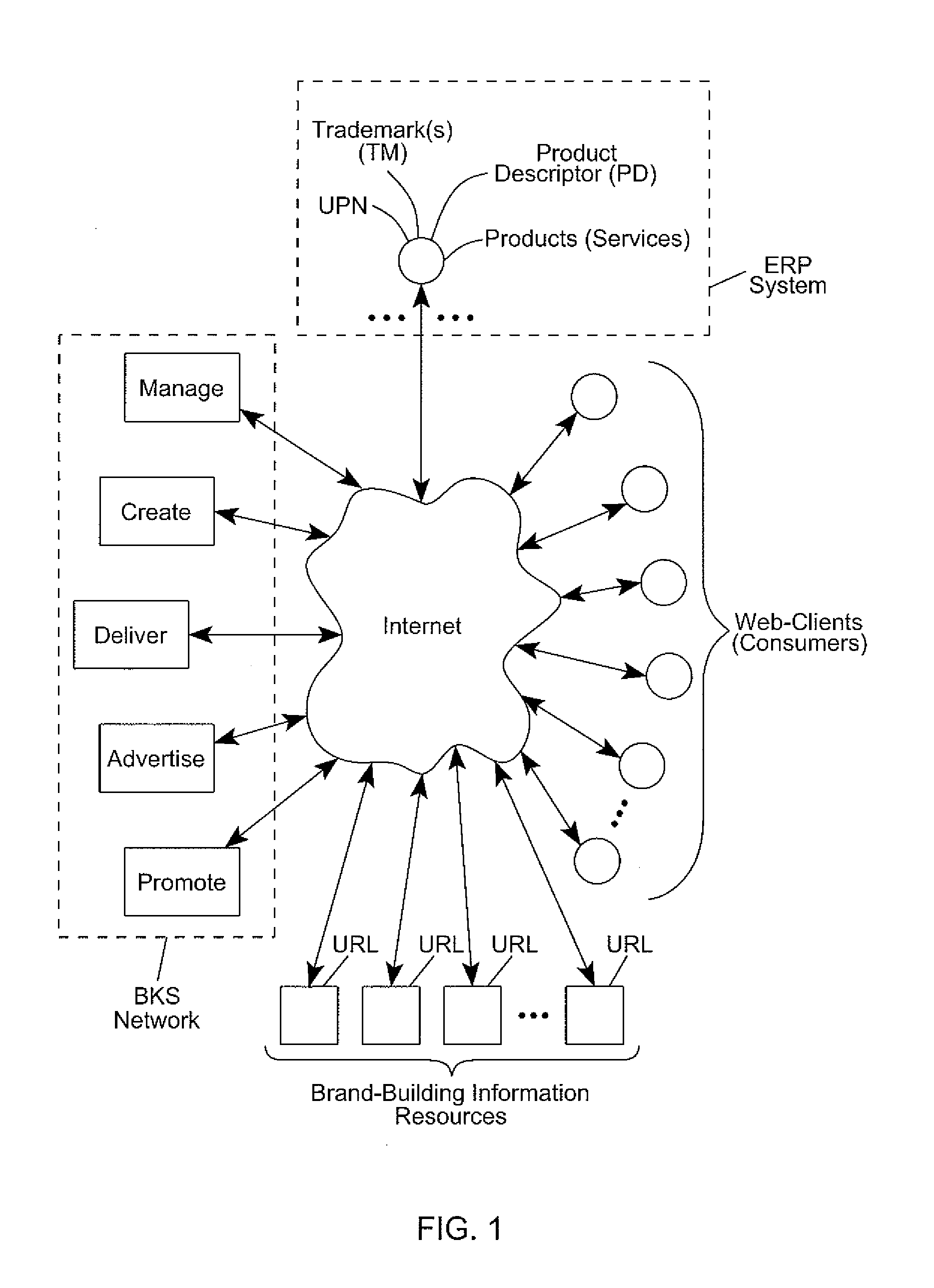
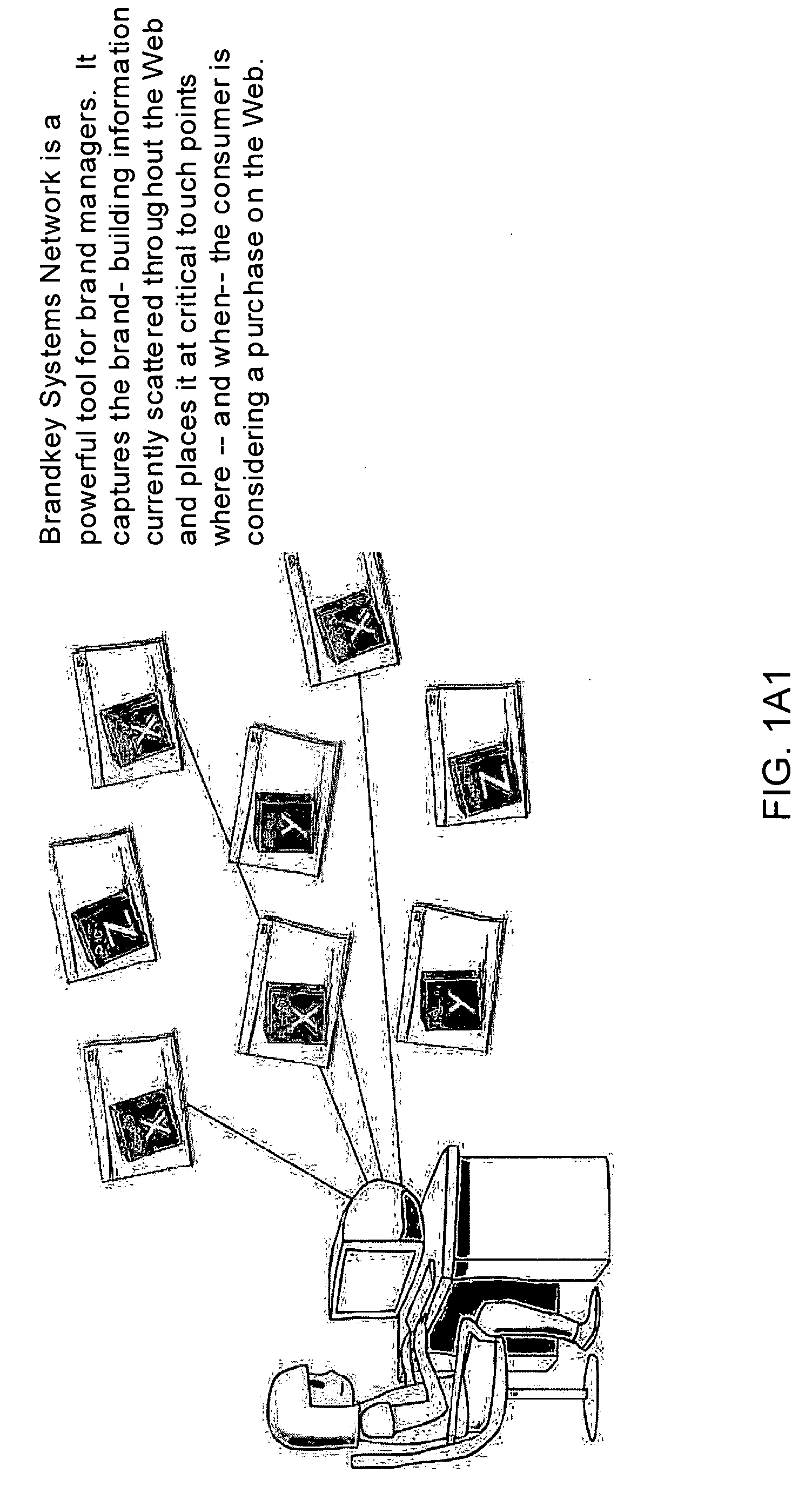
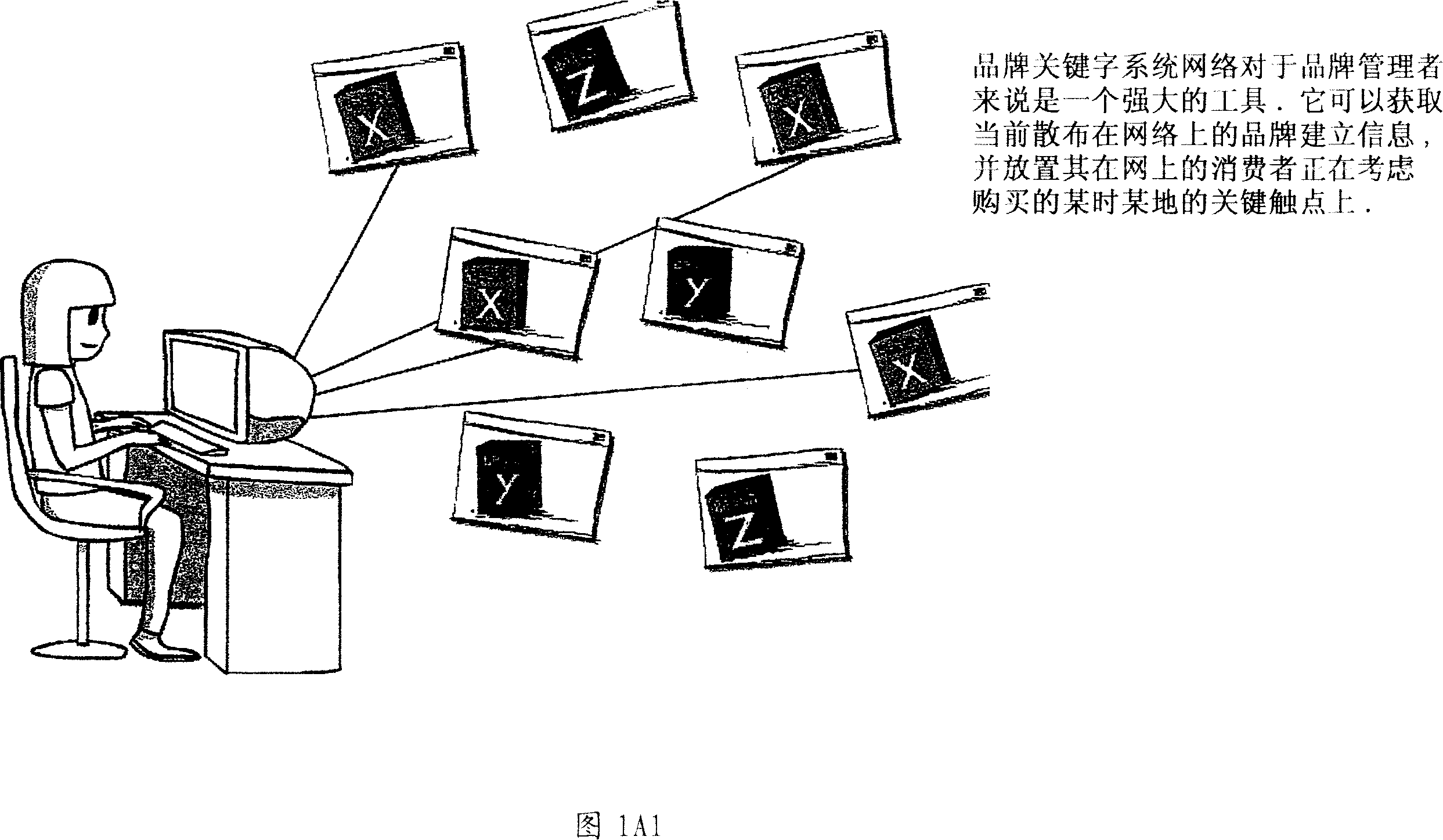
Internet-based Enterprise-Level Brand Management And Marketing Communication Network based on an innovative brand command, control and communication architecture (BC3), which gives brand owners complete command and control over the wide range of brand-building assets, messaging and promotions scattered throughout the Web, and how they are communicated to directly consumers at diverse Web touch points, with the efficiency and automation of supply-chain management solutions. The Network supports the deployment, installation and remote programming of brand-building server-side driven Multi-Mode Virtual Kiosks on the World Wide Web (WWW), and provide brand managers, their agents and online trading partners the power to build stronger online brands, drive sales and eliminate existing friction in the retail chain through a collaborative carrier-class, indutrial-strength e-marketing communication network.
Owner:BKS NETWORKS
Internet-based product brand marketing communication network configured to allow members of a product brand management team to communicate directly with consumers browsing HTML-encoded pages at an electronic commerce (EC) enabled web-site along the fabric of the world wide web (WWW), using programable multi-mode virtual kiosks (MMVKS) driven by server-side components and managed by product brand management team members
An Internet-based product brand marketing communication network allowing members of a consumer product brand management team to communicate directly with consumers present at HTML-encoded pages of an electronic commerce (EC) enabled Web-site along fabric of the World Wide Web (WWW), using programmable Multi-Mode Virtual Kiosks (MMVKs) driven by server-side components and managed by product brand management team members and / or authorized parties. When a consumer's Web browser encounters an MMVK tag along the WWW, the MMVK is generated and automatically plays through its display modes, inviting and allowing the consumer to review and interact with advertising spots, promotional spots, and brand information resources displayed within the GUI of the MMVK, along the fabric of the WWW where the MMVK has been installed. Web-based subsystems are provided for programming these display modes.
Owner:PERKOWSKI THOMAS J
Using transactions to compute and propagate network forwarding state
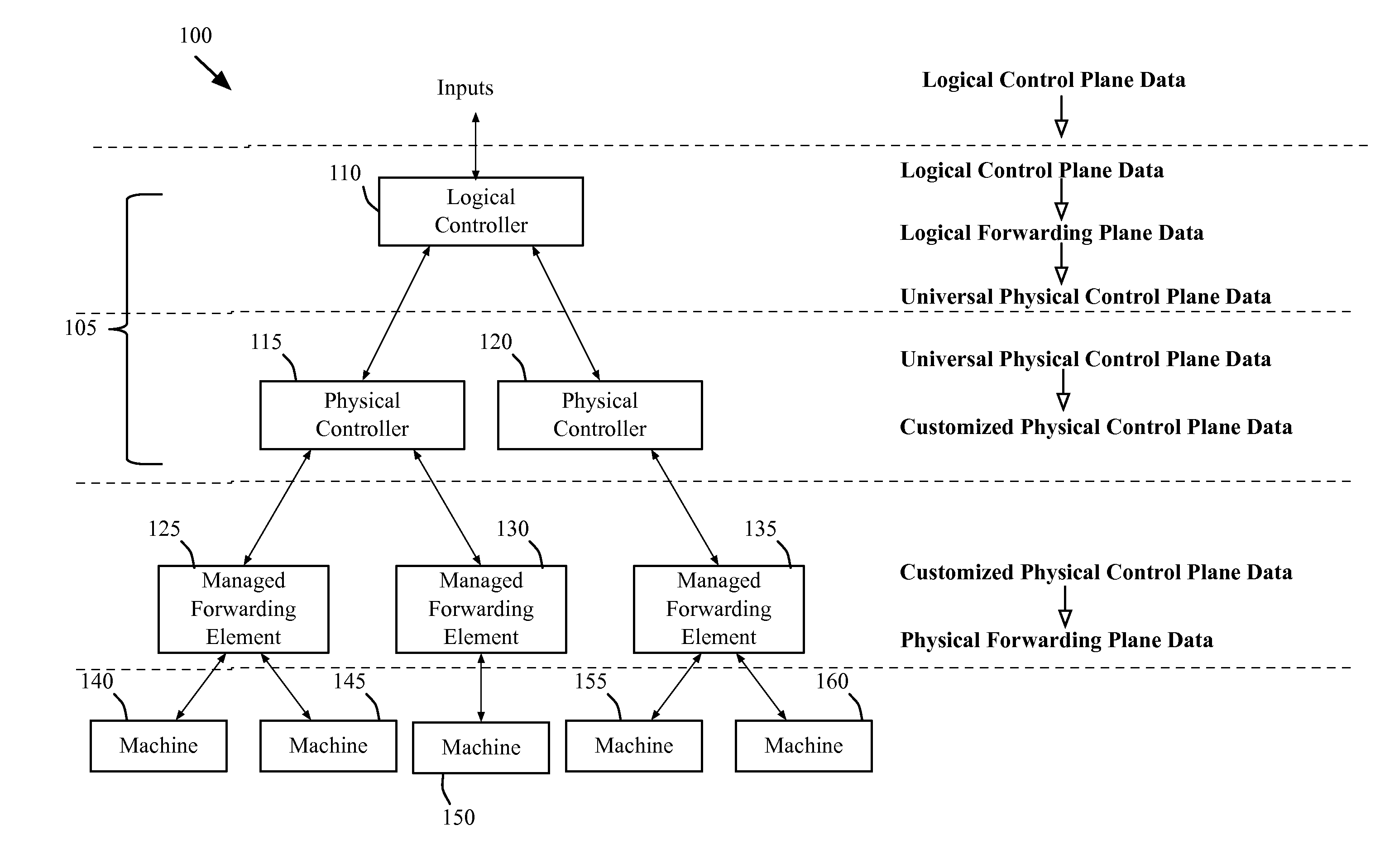
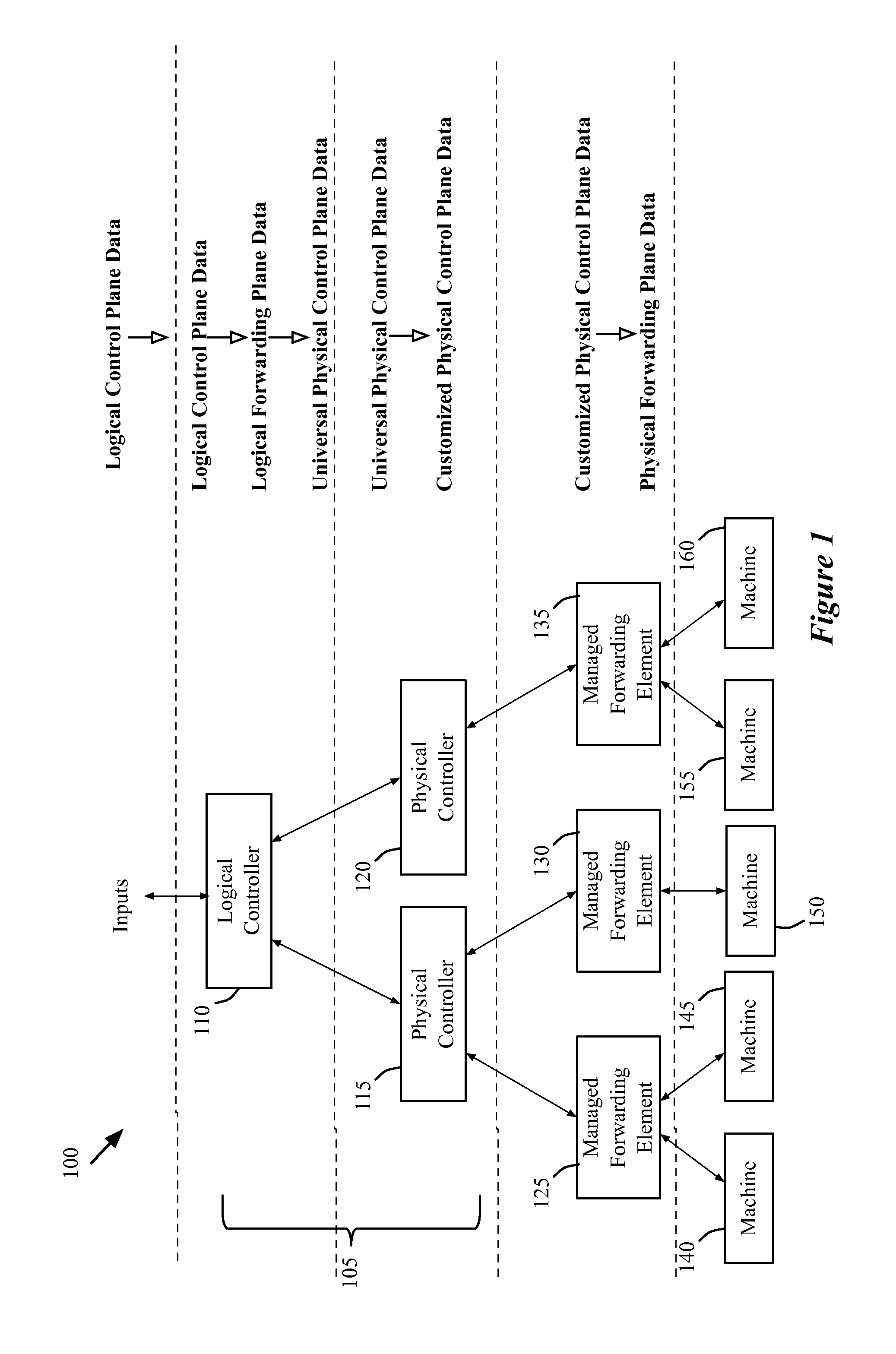
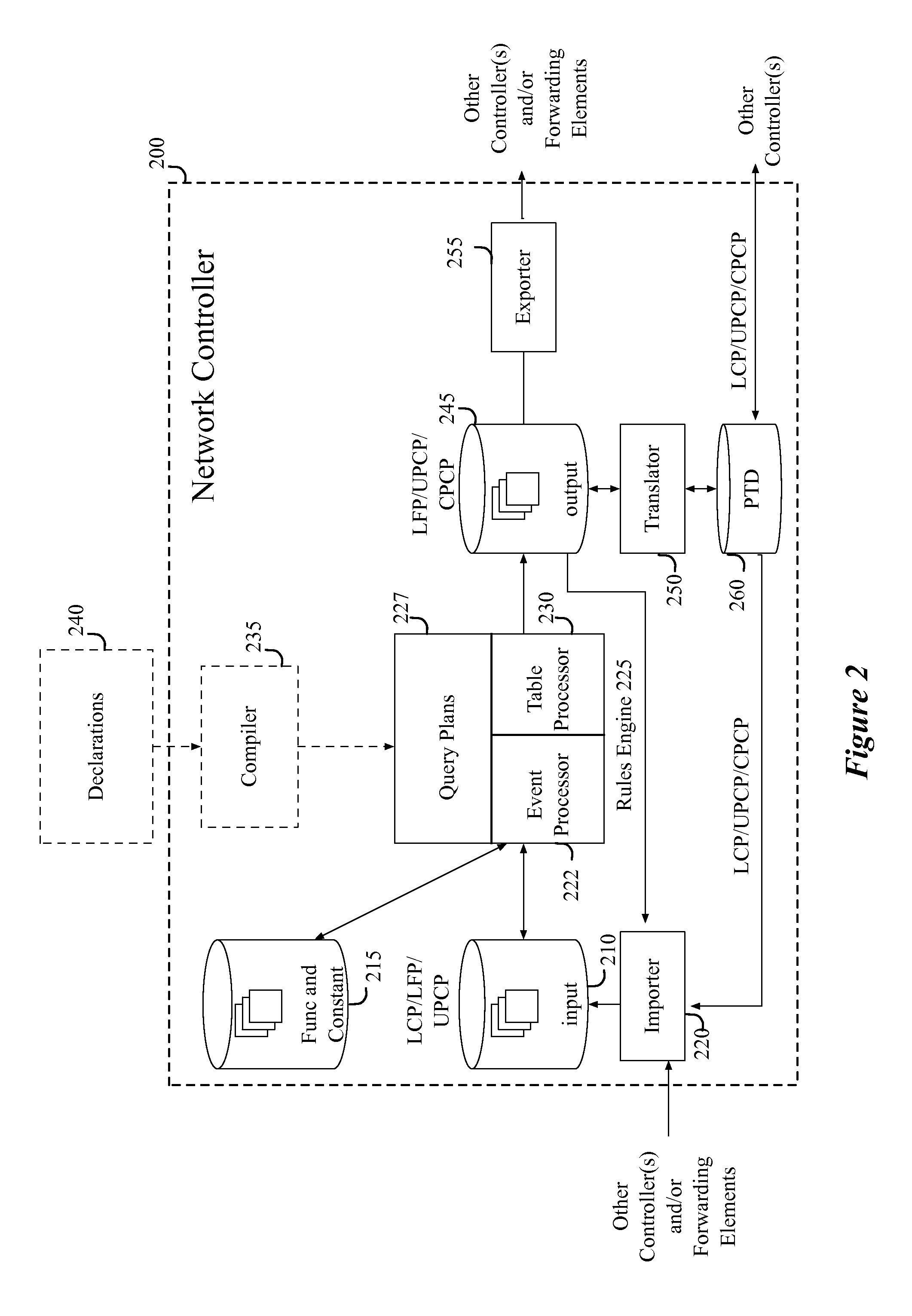
For a controller for managing a network comprising several managed forwarding elements that forward data in the network, a method for configuring a managed forwarding element is described. The method generates a first set of flow entries for defining forwarding behaviors of the managed forwarding element based on a current network policy for a logical network implemented in the several managed forwarding elements. The method sends the first set of flow entries to the managed forwarding element in order for the managed forwarding element to forward data that the managed forwarding element directly receives from an end machine based on the current network policy. The method generates a second set of flow entries for modifying forwarding behaviors of the managed forwarding element based on a new network policy for the logical network. The method sends the second set of flow entries to the managed forwarding element in order for the managed forwarding element to forward the data based on the new network policy.
Owner:NICIRA
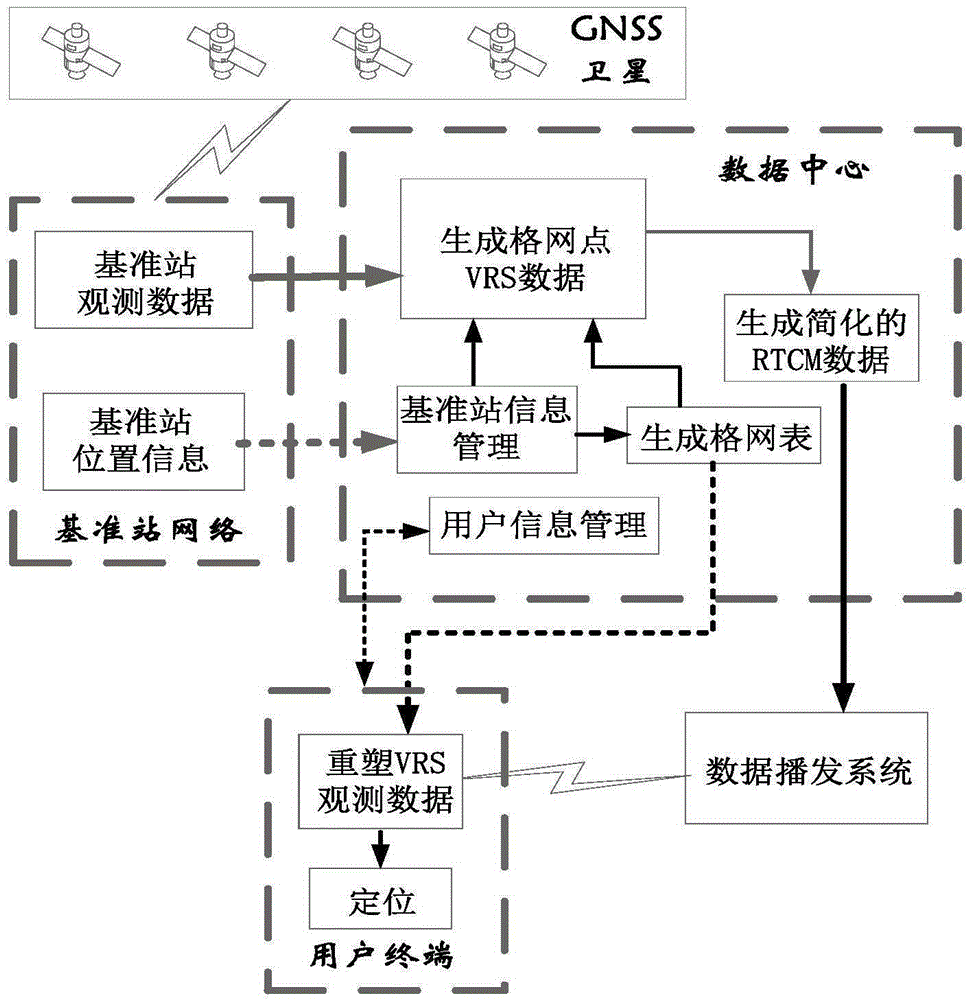
Broadcast-type network RTK positioning technology
ActiveCN106569239ARealize high-precision real-time positioningMeet high-precision real-time positioningSatellite radio beaconingData centerObservation data
The invention provides a broadcast-type network RTK positioning technology, and the technology comprises the steps: determining a virtual reference station position through grid dividing; calculating the observation data of the virtual reference station position; enabling a data center to broadcast differential correction number information to users through a unidirectional communication network; enabling a user terminal to receive a grid table and the observation data of the corresponding virtual reference station position, reforming the RTCM format of data of VRS data, and calculating a positioning results. The technology accords with the VRS data processing principle, employs the conventional GNSS reference station facility, just carries out proper modification of data processing software and data calculating software in moving station equipment, can achieve the centimeter-level real-time positioning, and can be widely used in many industries because the technology is small in introduction investment, is high in adaptability, is good in privacy and is infinite in number of users.
Owner:唐颖哲
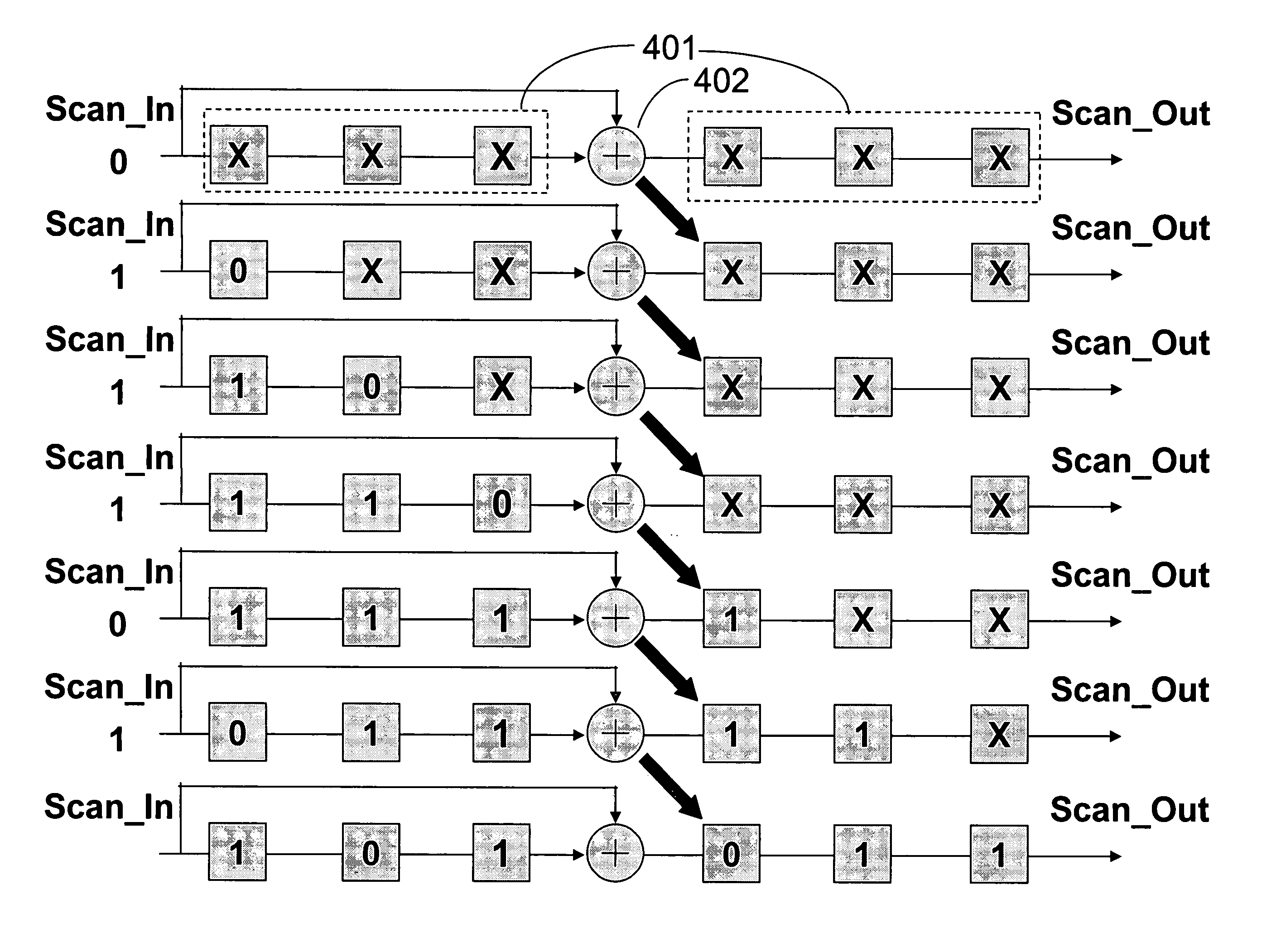
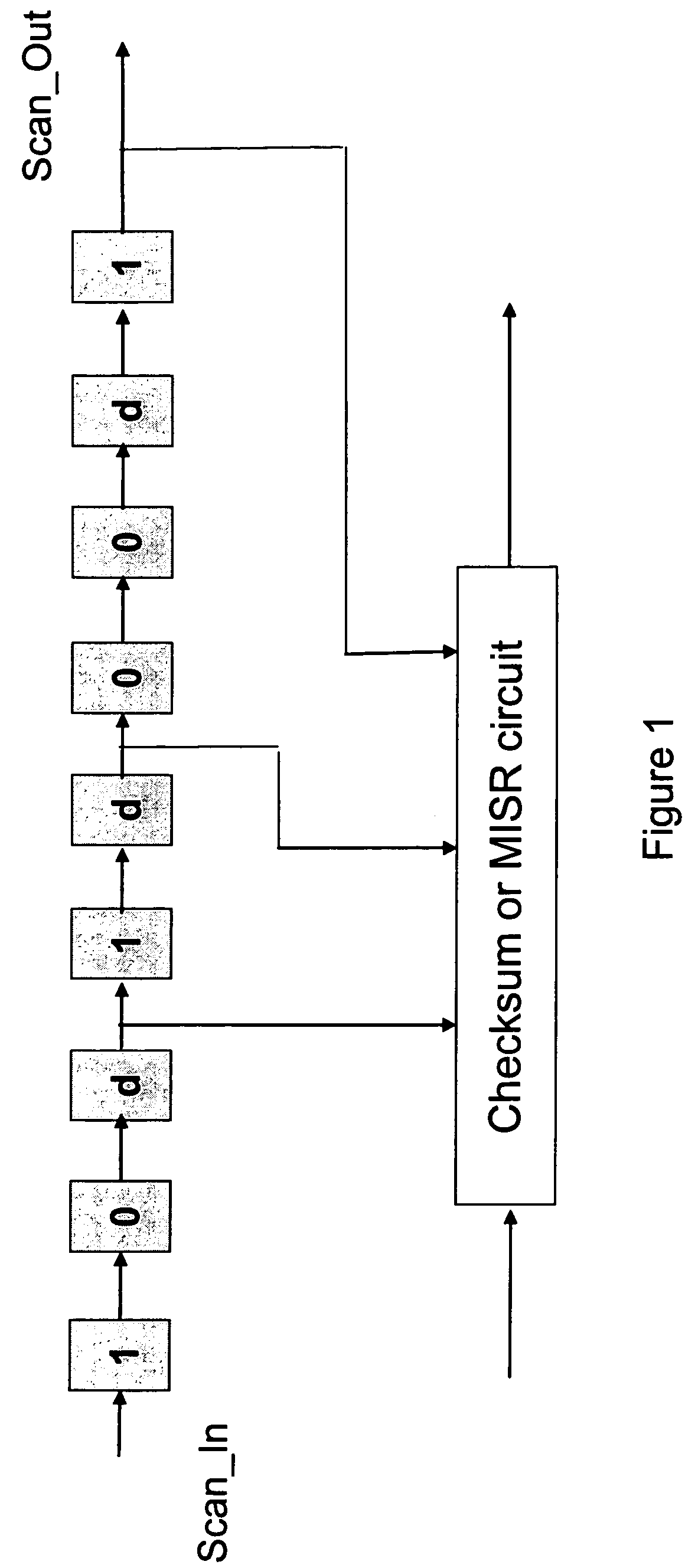
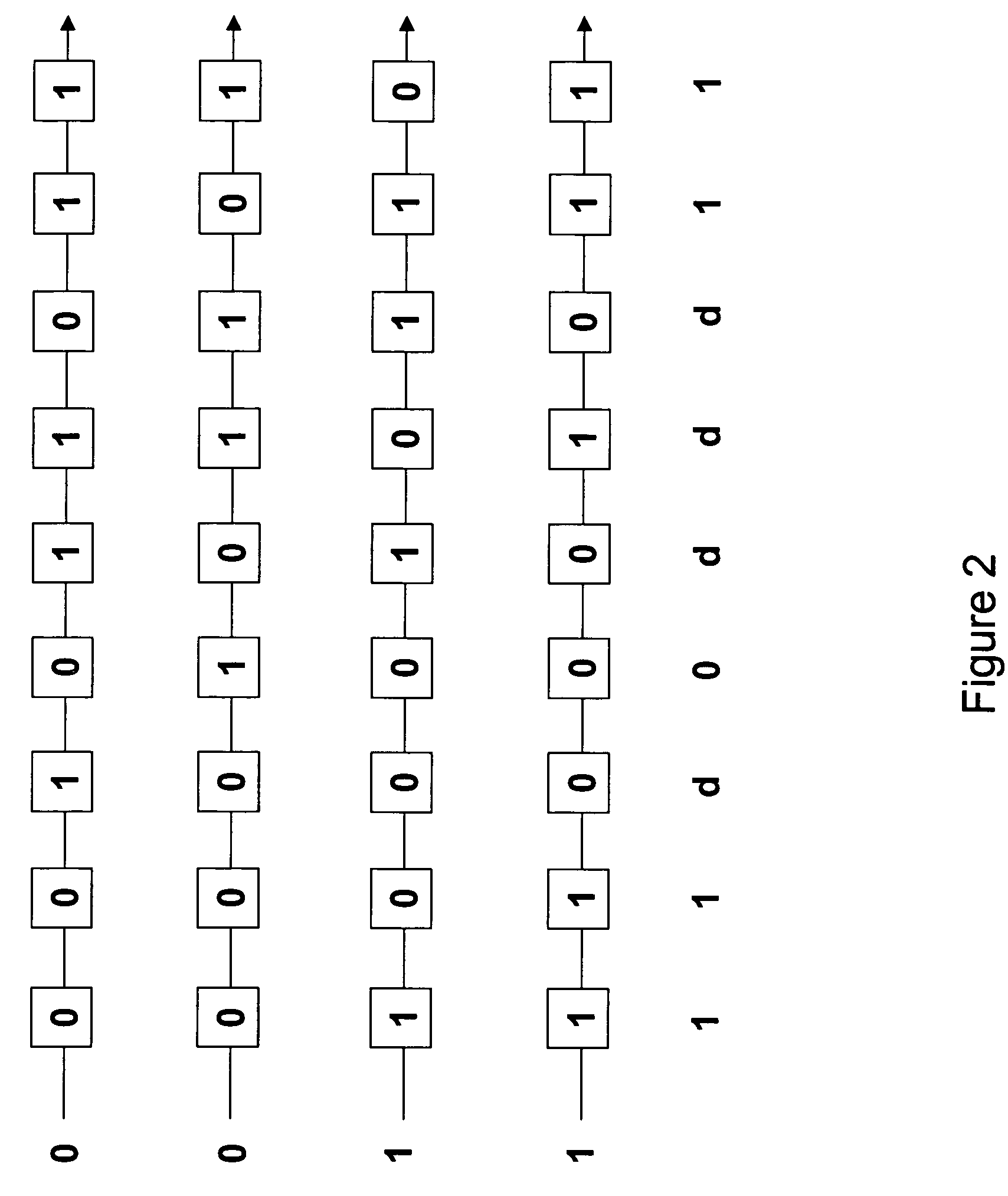
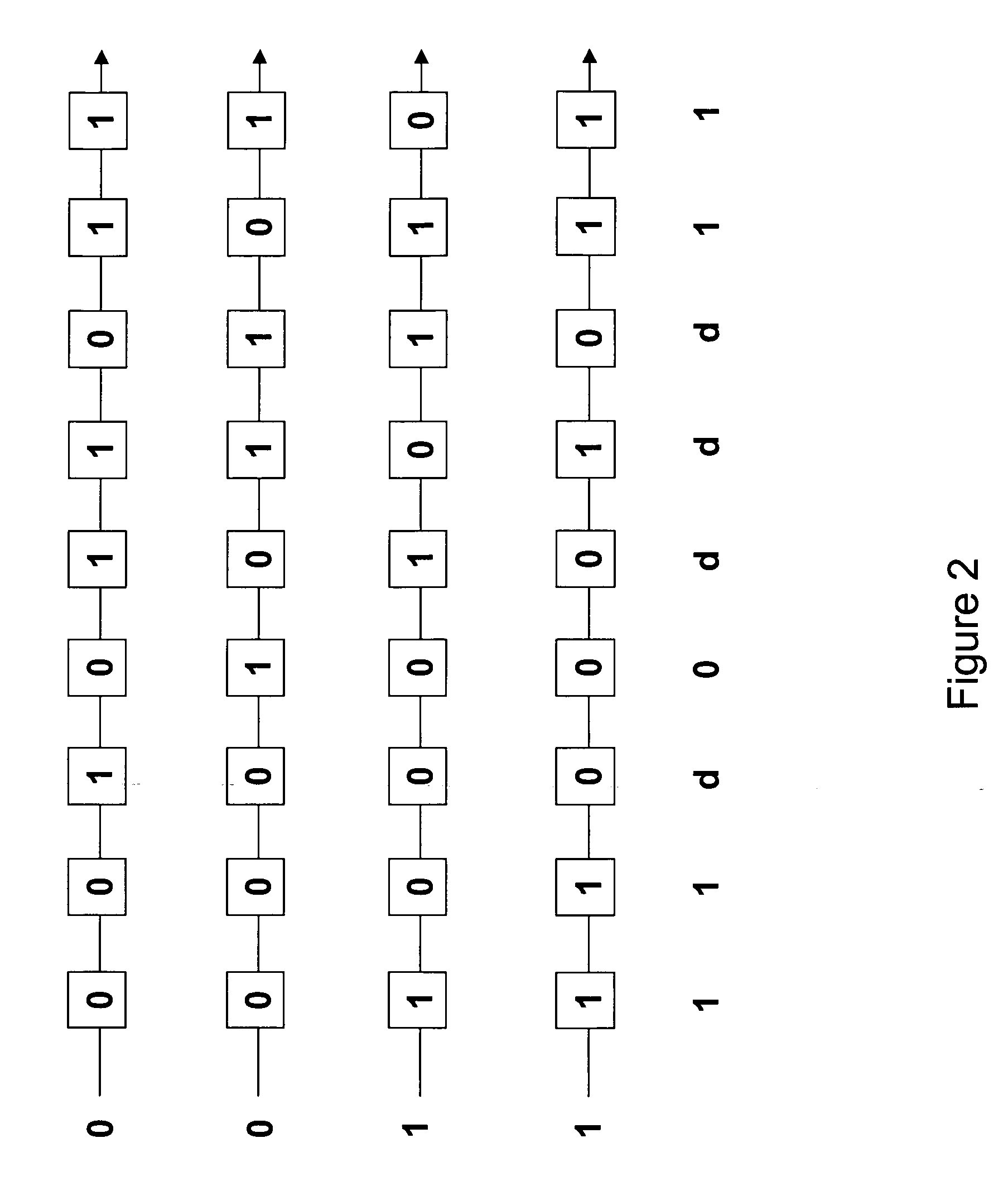
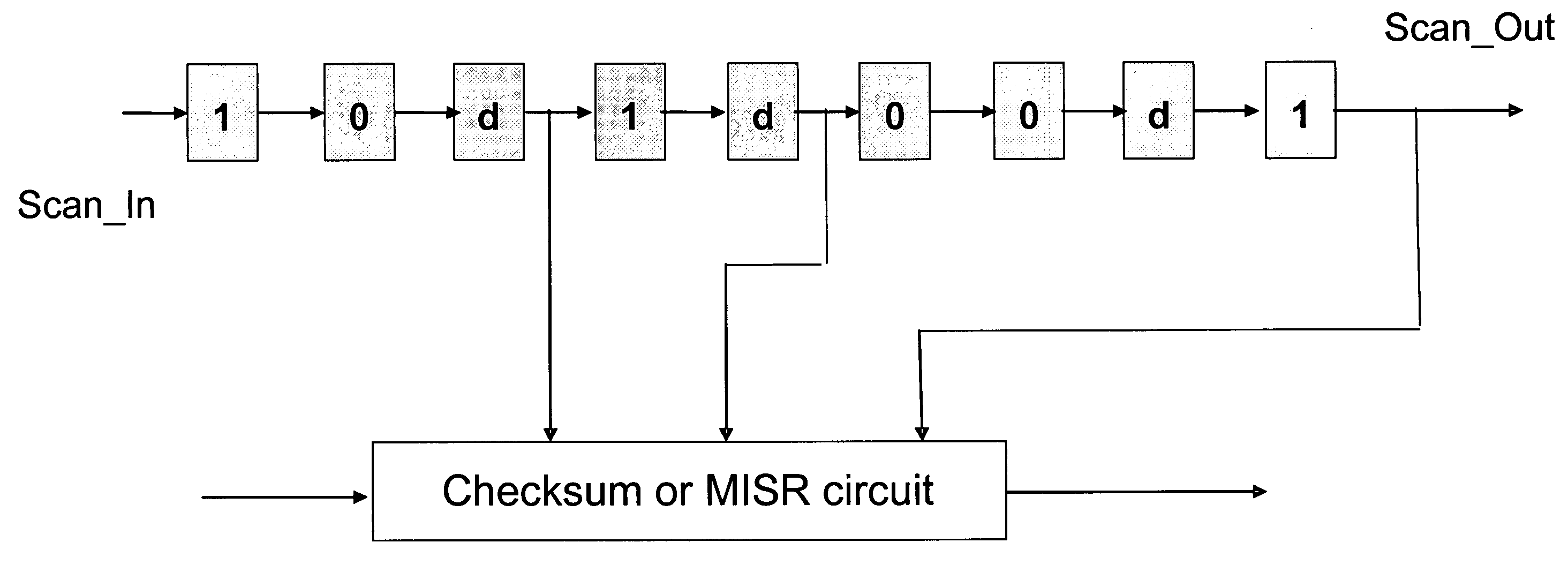
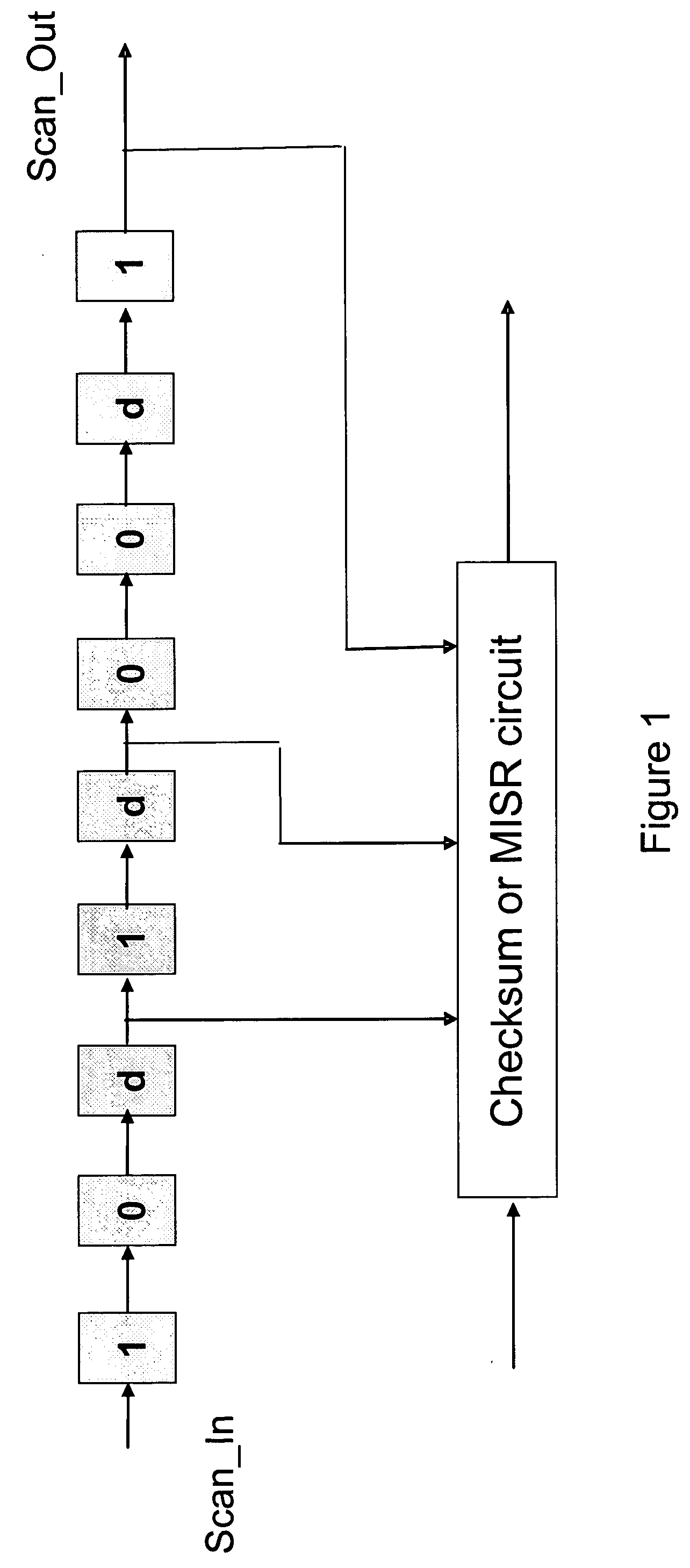
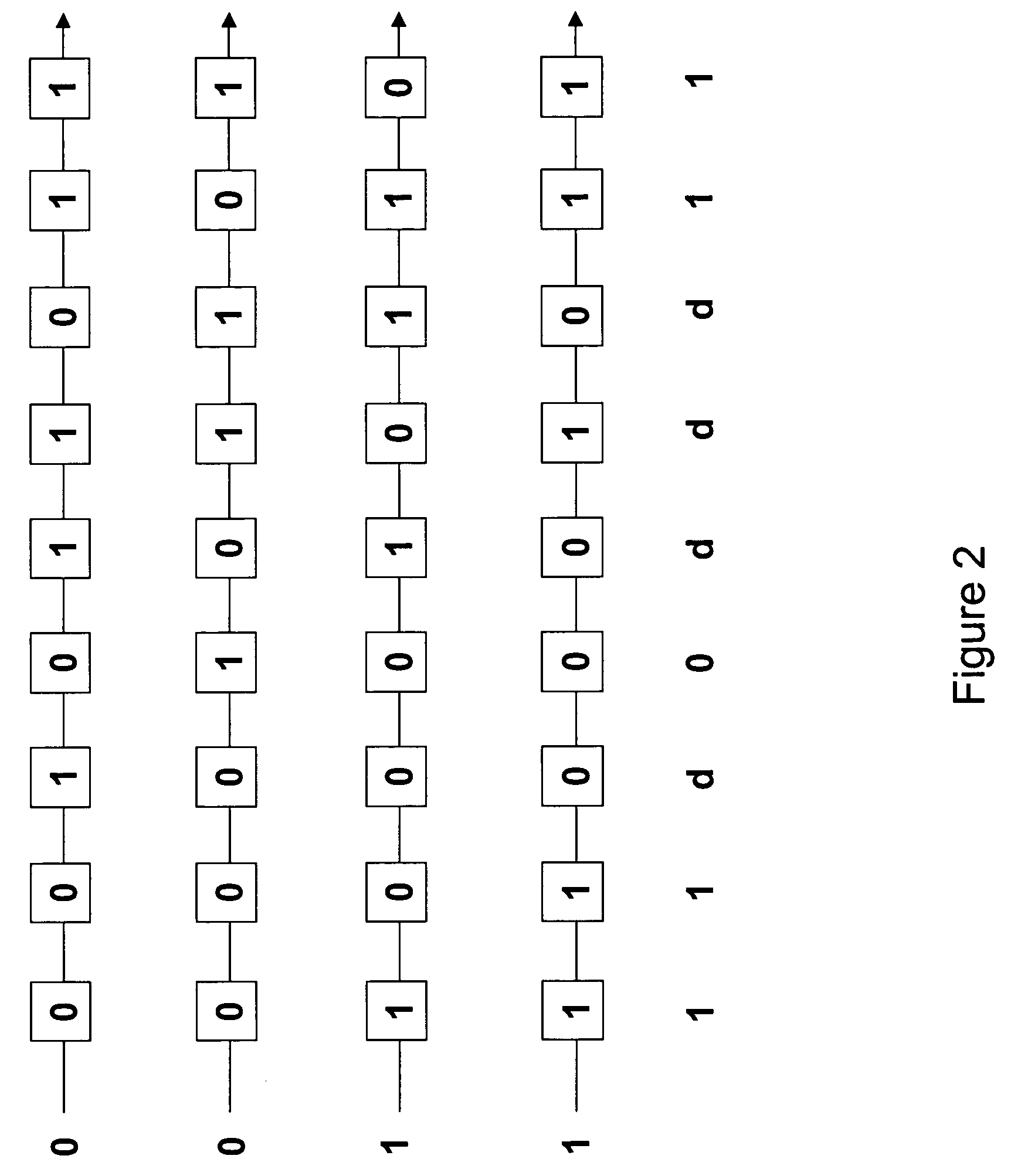
Accelerated scan circuitry and method for reducing scan test data volume and execution time
InactiveUS7197681B2Shorten the timeReduce volumeElectronic circuit testingError detection/correctionCouplingControl signal
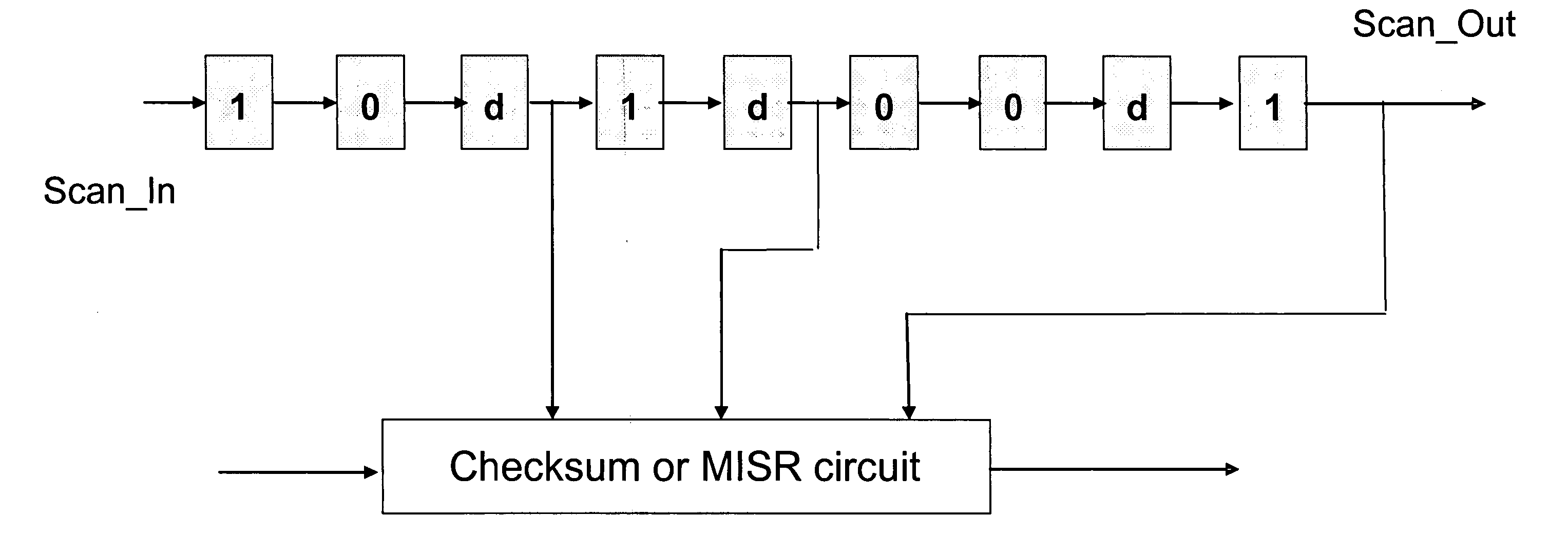
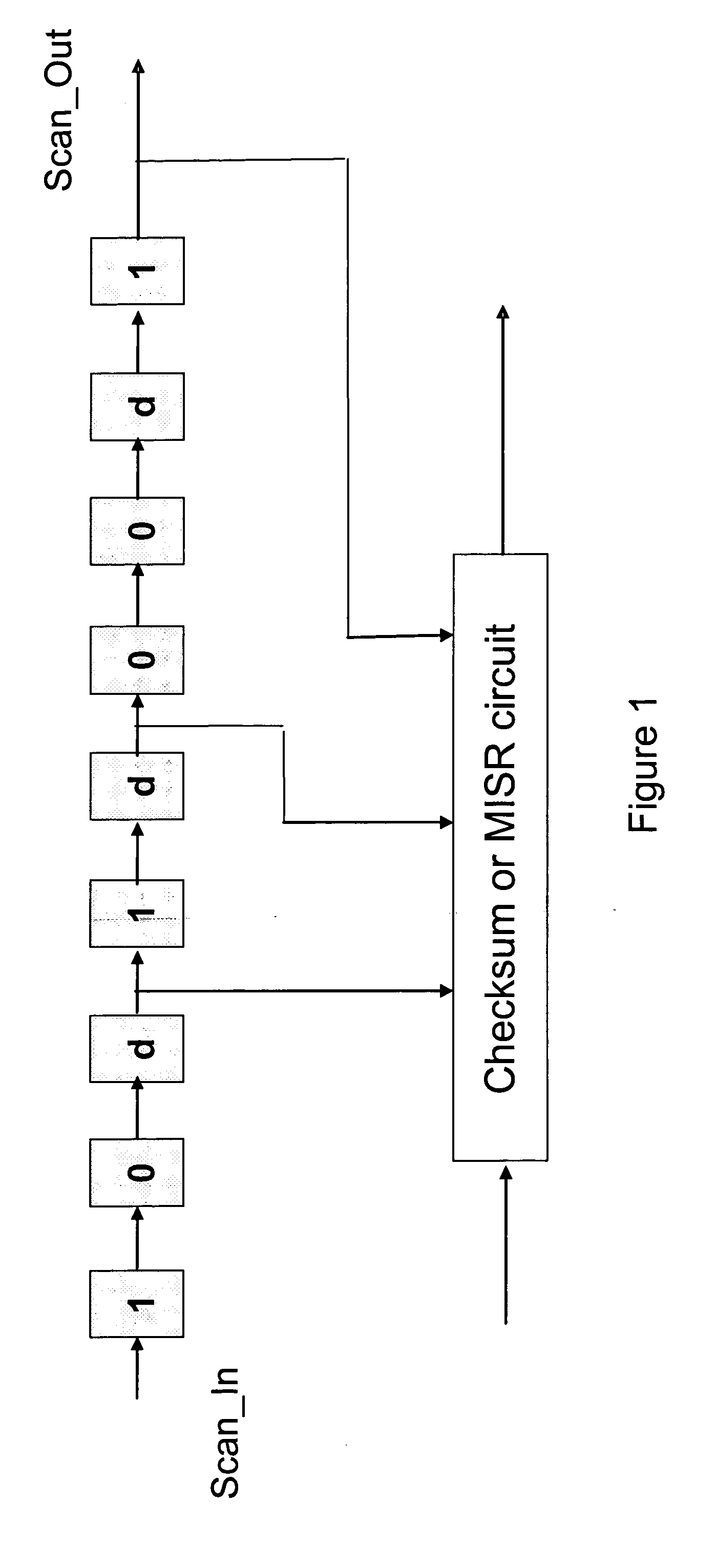
An architecture and methodology for test data compression using combinational functions to provide serial coupling between consecutive segments of a scan-chain are described. Compressed serial-scan sequences are derived starting from scan state identifying desired Care_In values and using symbolic computations iteratively in order to determine the necessary previous scan-chain state until computed previous scan-chain state matches given known starting scan-chain state. A novel design for a new flip-flop is also presented that allows implementing scan-chains that can be easily started and stopped without requiring an additional control signal. Extensions of the architecture and methodology are discussed to handle unknown (X) values in scan-chains, proper clocking of compressed data into multiple scan-chains, the use of a data-spreading network and the use of a pseudo-random signal generator to feed the segmented scan-chains in order to implement Built In Self Test (BIST).
Owner:AMERICAN PATENTS LLC +1
Method and System For Managing Data and Organizational Constraints
InactiveUS20080256099A1Clear separationUnprecedented level of flexibilityOffice automationSpecial data processing applicationsRelation (database)Data mining
A method and system for managing data and organizational constraints is provided. Data is collected and stored as records in a database and multi-dimensional matrices known as parameters are associated with each of the sets of records. The parameters are then processed using various formulae and functions and the results of the processing are kept separate from the parameters themselves allowing for a flexible and fast response to any change in any of the parameters. The dimensions of each parameter are defined to include zero or more properties configured to access the multi-dimensional matrices and each parameter is defined in relation to each of the dimensions of the parameter. The set of dependencies among the parameters form part of a large constraint propagation network so that any change to a value of one of the parameters will be propagated throughout the network.
Owner:STERNA TECH 2005
Distributed system and method for the detection of eThreats
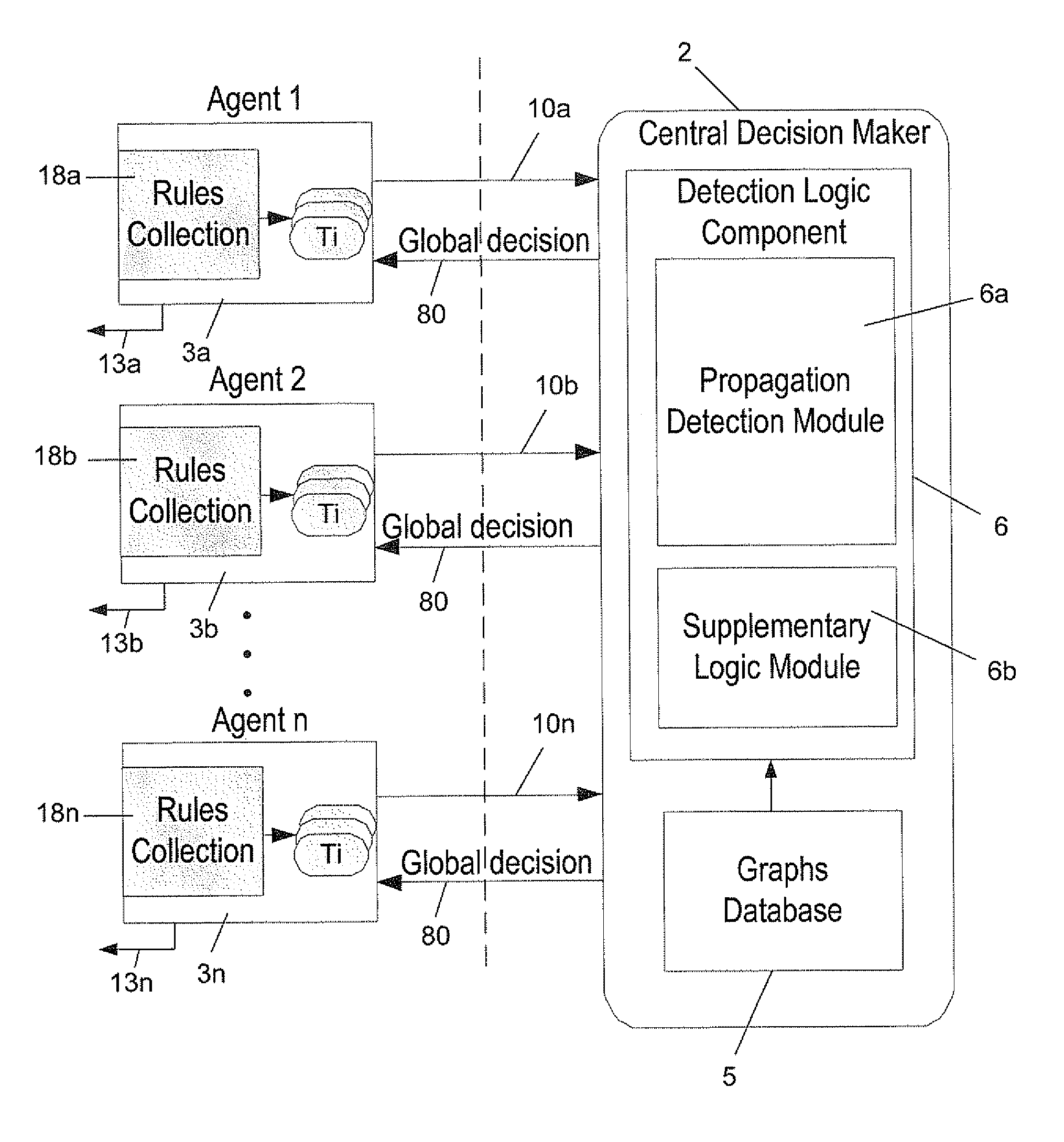
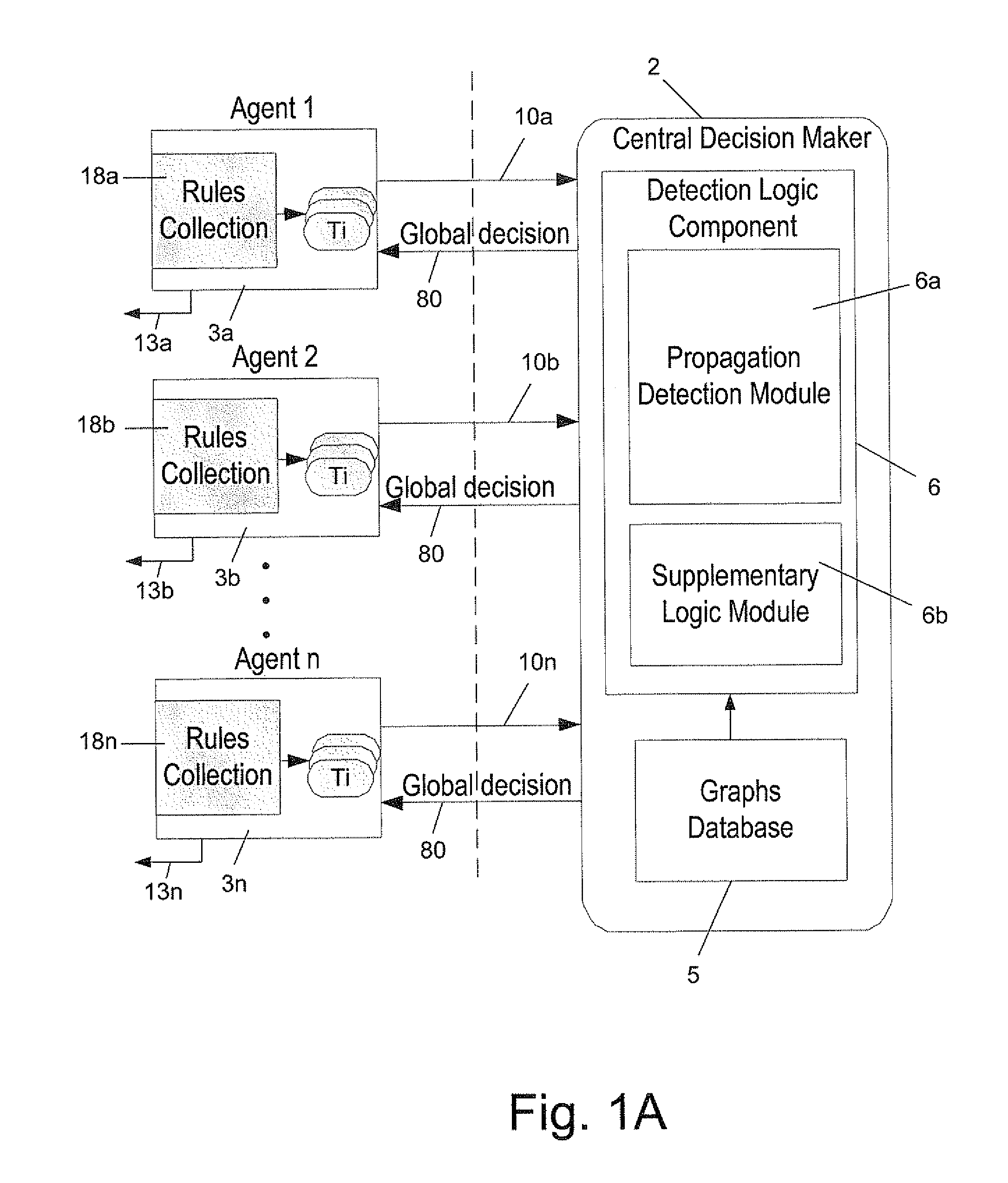
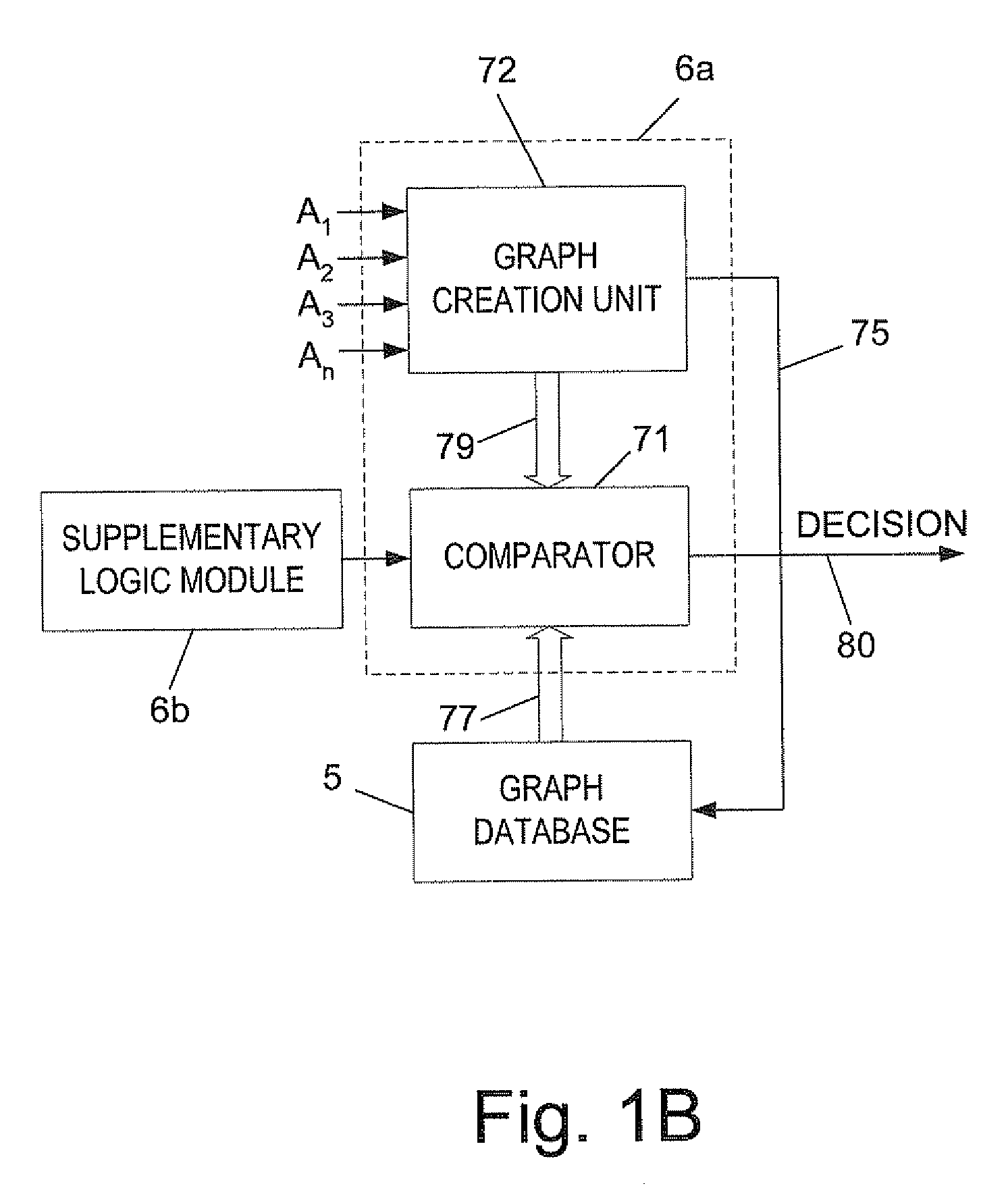
The invention relates to a distributed system for detecting eThreats that propagate in a network, which comprises: (a) graphs database storing at least one propagation graph, each graph describing the typical propagation over time of one eThreat class or a legitimate executable class within the network; (b) plurality of agents that are distributed in corresponding plurality of hosts within the network, each of said agents continuously monitoring the corresponding host and reporting to a Central Decision Maker (CDM) the identity of any new suspected executable, and the time in which said suspected executable has been first detected by said agent; (c) a CDM for: (c.1) receiving all said reports from said plurality of agents; (c.2) creating from said reports for each suspected executable a corresponding propagation graph which reflects the propagation characteristics over time of said suspected executable within the network, and (c.3) comparing each of said created graphs with said stored at least one propagation graph; (c.4) upon finding a similarity above a predefined threshold between a created graph and one of the stored graphs, concluding respectively that said executable belongs to the class as defined by said stored graph; and (c.5) conveying said conclusion to said agents, for optionally taking an appropriate action.
Owner:DEUTSCHE TELEKOM AG
Internet-based brand marketing communication network for managing and delivering brand marketing communications to consumers using multi-mode virtual kiosks (MMVKS) establishing virtual brand marketing communication channels between brand management team memmbers and consumers present in e-commerce enabled market space where the MMVKS are installed
InactiveUS20080015937A1Efficient managementAdvertisementsApparatus for meter-controlled dispensingMarket placeThe Internet
An Internet-based brand marketing communication network for managing and delivering brand marketing communications to consumers using server-side driven multi-mode virtual kiosks (MMVKs) that are created, deployed, and managed using a novel suite of Web-based marketing communication services. For each consumer product registered on the network, a MMVK is created, deployed and installed, so as to establish a virtual brand marketing communication channel between brand management team members and consumers present in e-commerce (EC) enabled market space at the point of MMVK installation in EC-enabled market space, including EC-enabled WWW-sites, EC-enabled stores, EC-enabled online product catalogs, and wherever else consumers are considering the purchase of products on the World Wide Web (WWW). By virtue of the network of the present invention, consumer product brand management teams can choreograph and control the delivery of brand experience consumers have with their products in EC-enabled market space, so as to communicate brand value, deliver service and provide decision support, while helping retailers build their brands, reduce overhead, and drive sales.
Owner:BKS NETWORKS
Internet-based brand management and marketing communication network
Internet-based Enterprise-Level Brand Management And Marketing Communication Network based on an innovative brand command, control and communication architecture (BC3), which gives brand owners complete command and control over the wide range of brand-building assets, messaging and promotions scattered throughout the Web, and how they are communicated to directly consumers at diverse Web touch points, with the efficiency and automation of supply-chain management solutions. The Network supports the deployment, installation and remote programming of brand-building server-side driven Multi-Mode Virtual Kiosks on the World Wide Web (WWW), and provide brand managers, their agents and online trading partners the power to build stronger online brands, drive sales and eliminate existing friction in the retail chain through a collaborative carrier-class, industrial-strength e-marketing communication network.
Owner:IPF
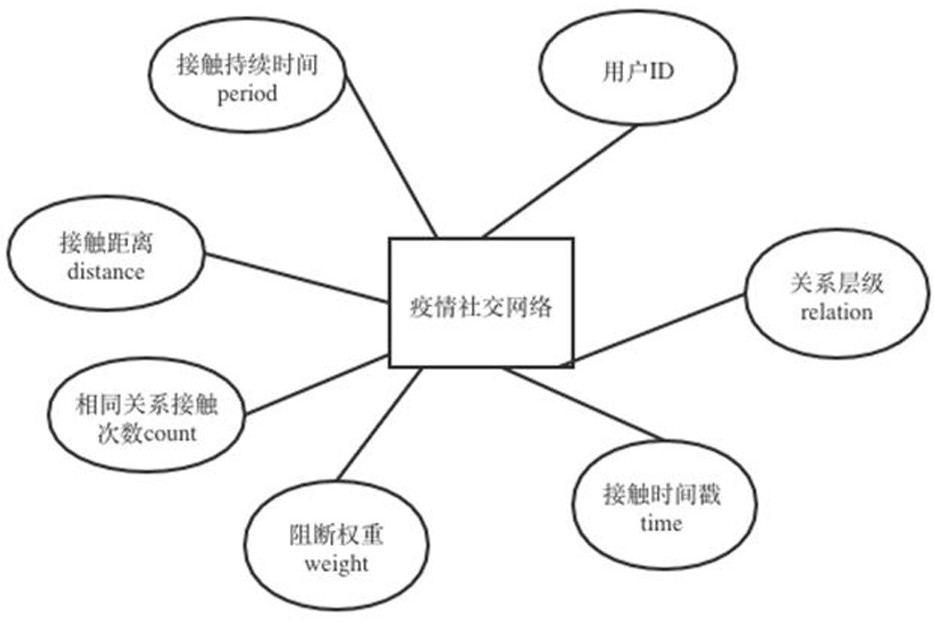
Short-distance epidemic situation propagation network construction method based on Bluetooth scanning
ActiveCN112203229AHighlight substantive featuresSignificantly progressiveParticular environment based servicesLocation information based serviceInformatizationData field
The invention discloses a short-distance epidemic situation tracking method based on Bluetooth scanning and a social topology network, or is understood as a propagation network construction method. According to the invention, real contact crowd information is acquired by using app-based registration binding of a user mobile phone, a bracelet and other devices and using an MAC address or a UUID scanned by Bluetooth, and contact information including indexes, contact timestamps, contact times, contact duration, contact strength, RSSI and other data fields are set in a back-end server. The contact information is visualized into a social network graph which is of a point-line topological structure and is used for displaying contact relationship between personnel at the front-end platform of the disease control center, so that real-time visual monitoring of the disease control center on the health condition of regional personnel and the contact condition between the regional personnel is realized, and an objective reference standard is provided for epidemic situation tracking of the disease control center; the method can be applied to epidemic situation tracking of various types of infectious diseases including but not limited to new coronal pneumonia and the like, and serves as an informatization auxiliary tool for disease control work.
Owner:中科苏州智能计算技术研究院
Method for optimizing memory controller configuration in multi-core processors using fitness metrics and channel loads
ActiveUS8407167B1Genetic modelsDigital computer detailsTraffic capacityStructure of Management Information
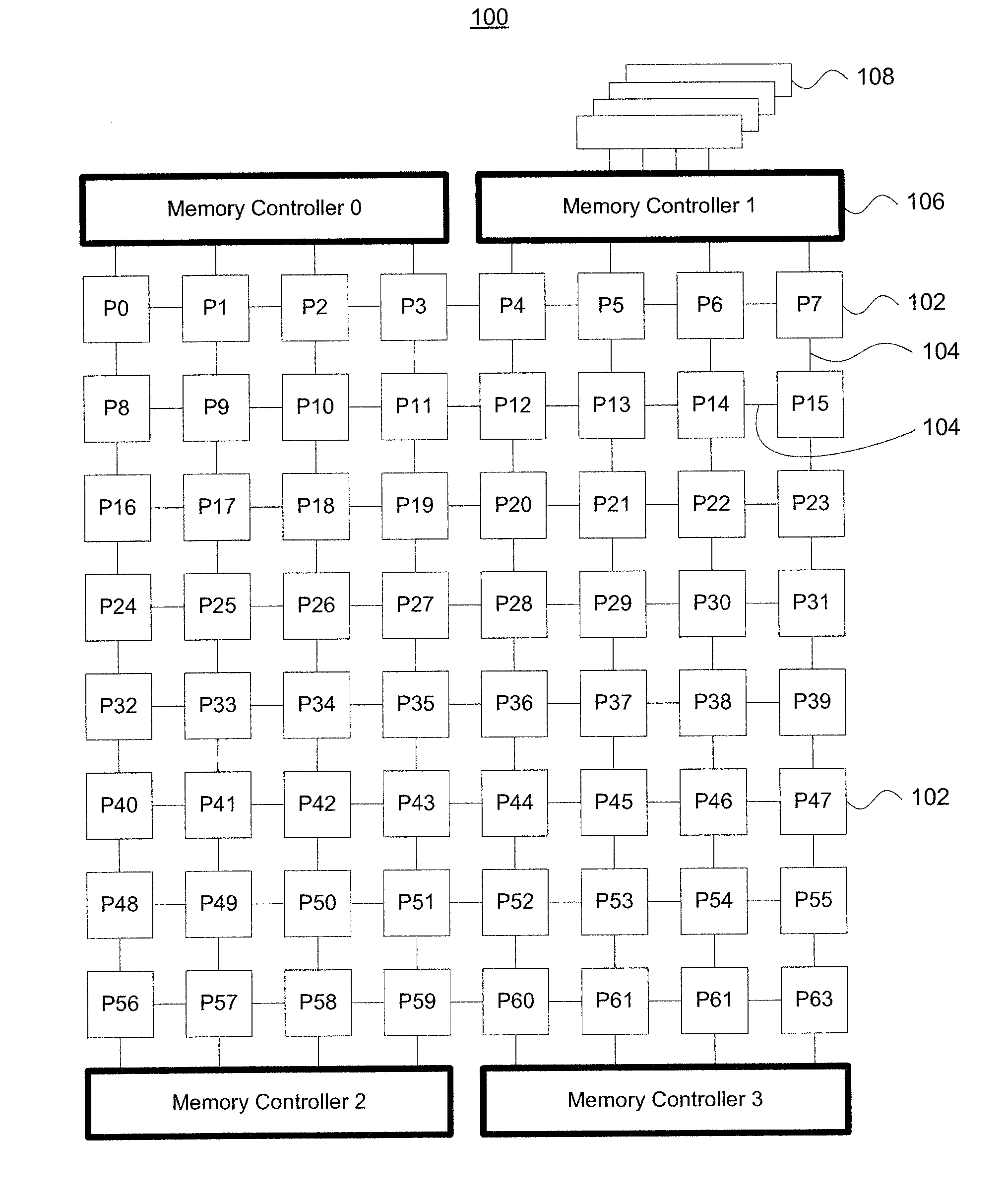
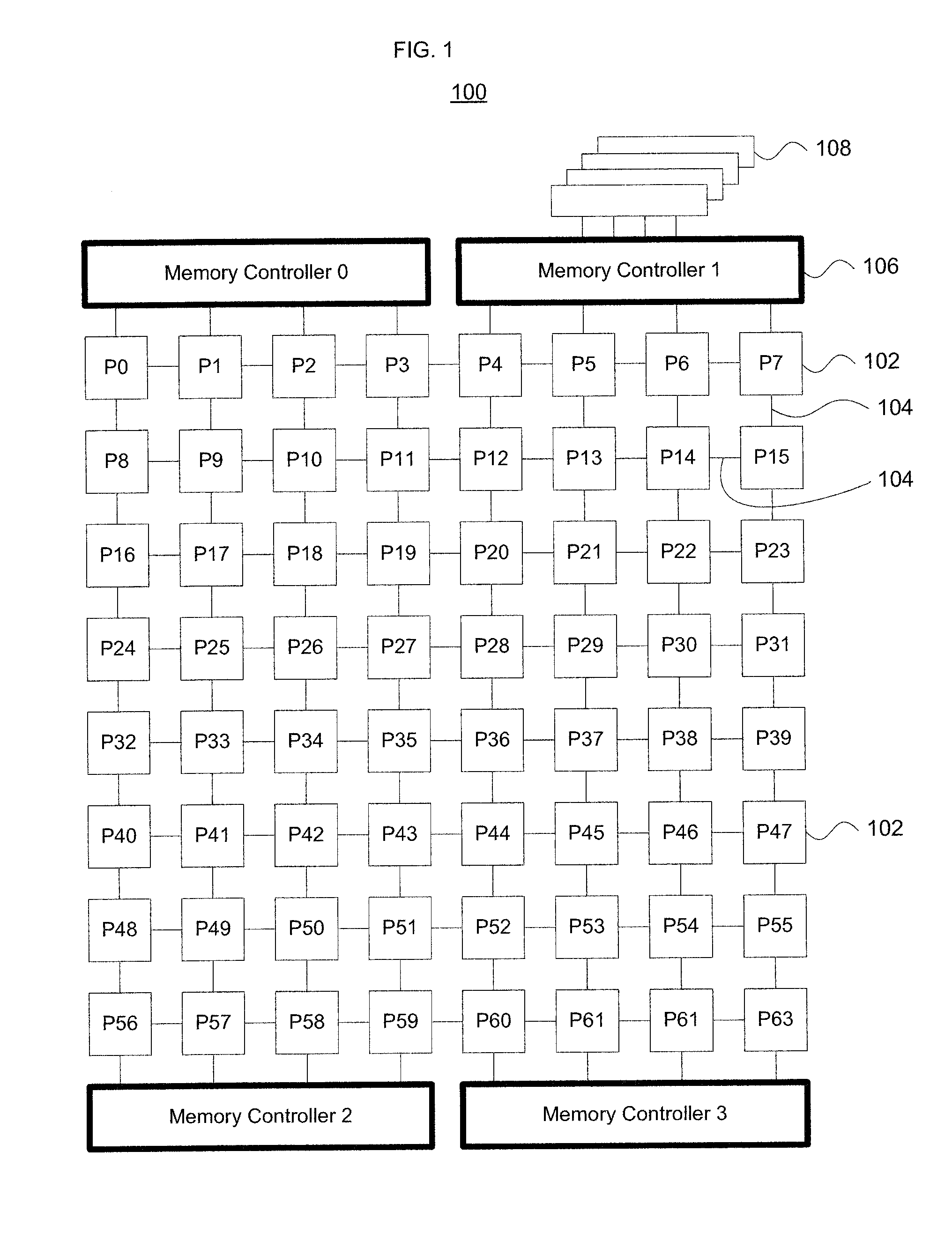
The location of the memory controllers within the on-chip fabric of multiprocessor architectures plays a central role in latency bandwidth characteristics of the processor-to-memory traffic. Intelligent placement substantially reduces the maximum channel load depending on the specific memory controller configuration selected. A variety of simulation techniques are used along and in combination to determine optimal memory controller arrangements. Diamond-type and diagonal X-type memory controller configurations that spread network traffic across all rows and columns in a multiprocessor array substantially improve over other arrangements. Such placements reduce interconnect latency by an average of 10% for real workloads, and the small number of memory controllers relative to the number of on-chip cores opens up a rich design space to optimize latency and bandwidth characteristics of the on-chip network.
Owner:GOOGLE LLC
Accelerated scan circuitry and method for reducing scan test data volume and execution time
InactiveUS20050154948A1Shorten the timeReduce volumeElectronic circuit testingError detection/correctionCouplingControl signal
An architecture and methodology for test data compression using combinational functions to provide serial coupling between consecutive segments of a scan-chain are described. Compressed serial-scan sequences are derived starting from scan state identifying desired Care_In values and using symbolic computations iteratively in order to determine the necessary previous scan-chain state until computed previous scan-chain state matches given known starting scan-chain state. A novel design for a new flip-flop is also presented that allows implementing scan-chains that can be easily started and stopped without requiring an additional control signal. Extensions of the architecture and methodology are discussed to handle unknown (X) values in scan-chains, proper clocking of compressed data into multiple scan-chains, the use of a data-spreading network and the use of a pseudo-random signal generator to feed the segmented scan-chains in order to implement Built In Self Test (BIST).
Owner:AMERICAN PATENTS LLC
Accelerated scan circuitry and method for reducing scan test data volume and execution time
InactiveUS20050028060A1Avoid excessive data volumeReduce the numberElectronic circuit testingError detection/correctionCouplingControl signal
An architecture and methodology for test data compression using combinational functions to provide serial coupling between consecutive segments of a scan-chain are described. Compressed serial-scan sequences are derived starting from scan state identifying desired Care_In values and using symbolic computations iteratively in order to determine the necessary previous scan-chain state until computed previous scan-chain state matches given known starting scan-chain state. A novel design for a new flip-flop is also presented that allows implementing scan-chains that can be easily started and stopped without requiring an additional control signal. Extensions of the architecture and methodology are discussed to handle unknown (X) values in scan-chains, proper clocking of compressed data into multiple scan-chains, the use of a data-spreading network and the use of a pseudo-random signal generator to feed the segmented scan-chains in order to implement Built In Self Test (BIST).
Owner:INTELLECTUAL VENTURES I LLC +1
Friend recommendation method based on friend relationship spread in social network
ActiveCN103345513AAccurate Dating BehaviorPredicting Dating BehaviorSpecial data processing applicationsRecommendation serviceSocial behavior
The invention relates to a friend recommendation method based on friend relationship spread in a social network, and belongs to the technical field of computer data mining. The method includes the steps that a potential friend relationship spread network is created for each self node; in each time period, a social behavior probability generative model is built, wherein social behaviors are perceived by interests, candidate middlemen and candidate interest fields are updated in an iterative mode, and the side-to-side weight in the potential friend relationship spread network is set according to the iterative result; as for each self node, the probability of choosing every friend to be the middleman is calculated on the partial layer of the potential friend relationship spread network in a random walking mode, the probability of choosing every node to be new friends is calculated on the whole layer of the potential friend relationship spread network in a random walking mode, and then the new friends with the largest probability are added in a recommended friend list. By constructing the potential friend relationship spread network, reasons and the structure of the social network are deeply analyzed from the angle of user behaviors, and then accurate friend recommendation services are provided.
Owner:TSINGHUA UNIV
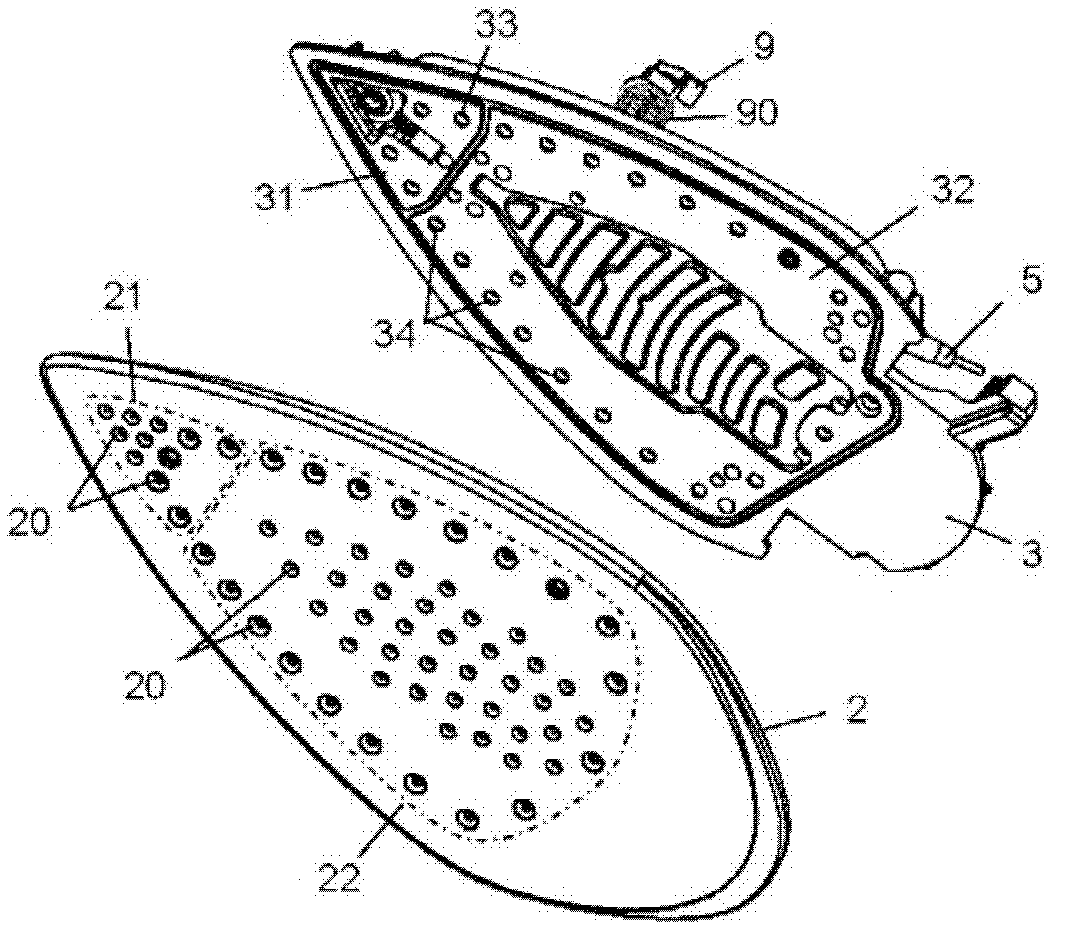
Steam iron comprising a soleplate including at least one first group and one second group of steam outlet holes
ActiveCN102644191AReduce the risk of condensationHand ironTextiles and paperEngineeringSpread Networks
The invention relates to a steam iron (1) which comprises a soleplate (2). The soleplate (2) at least comprises steam outlet holes (20) of a first group and a second group. The iron (1) comprises a steam distribution device which comprises a device (7) for blocking or reducing steam flows directed towards the steam outlet holes in the second group. The device (7) for blocking or reducing steam flows directed towards the steam outlet holes (20) in the second group is equipped inside the steam distribution chamber (6) the bottom of which is composed of a closing lid of a base plate (3). The distribution chamber (6) comprises at least one supply hole (42) equipped inside the lid and directed towards a pipeline connected with the steam entering pipeline integrated on the base plate (3); and at least one discharge hole equipped inside the lid and directed towards a steam spreading network facing the steam outlet holes in the second group.
Owner:SEB SA
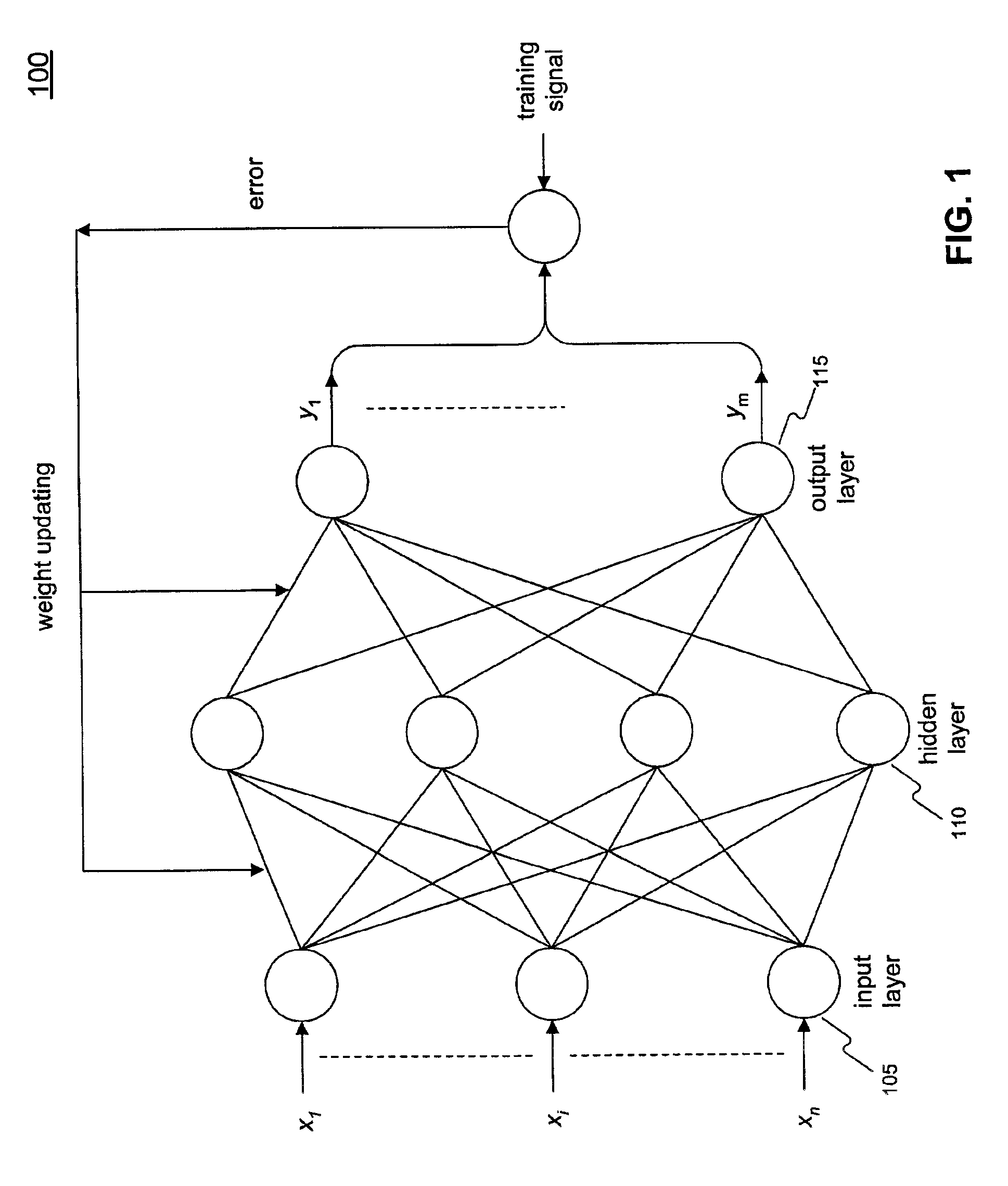
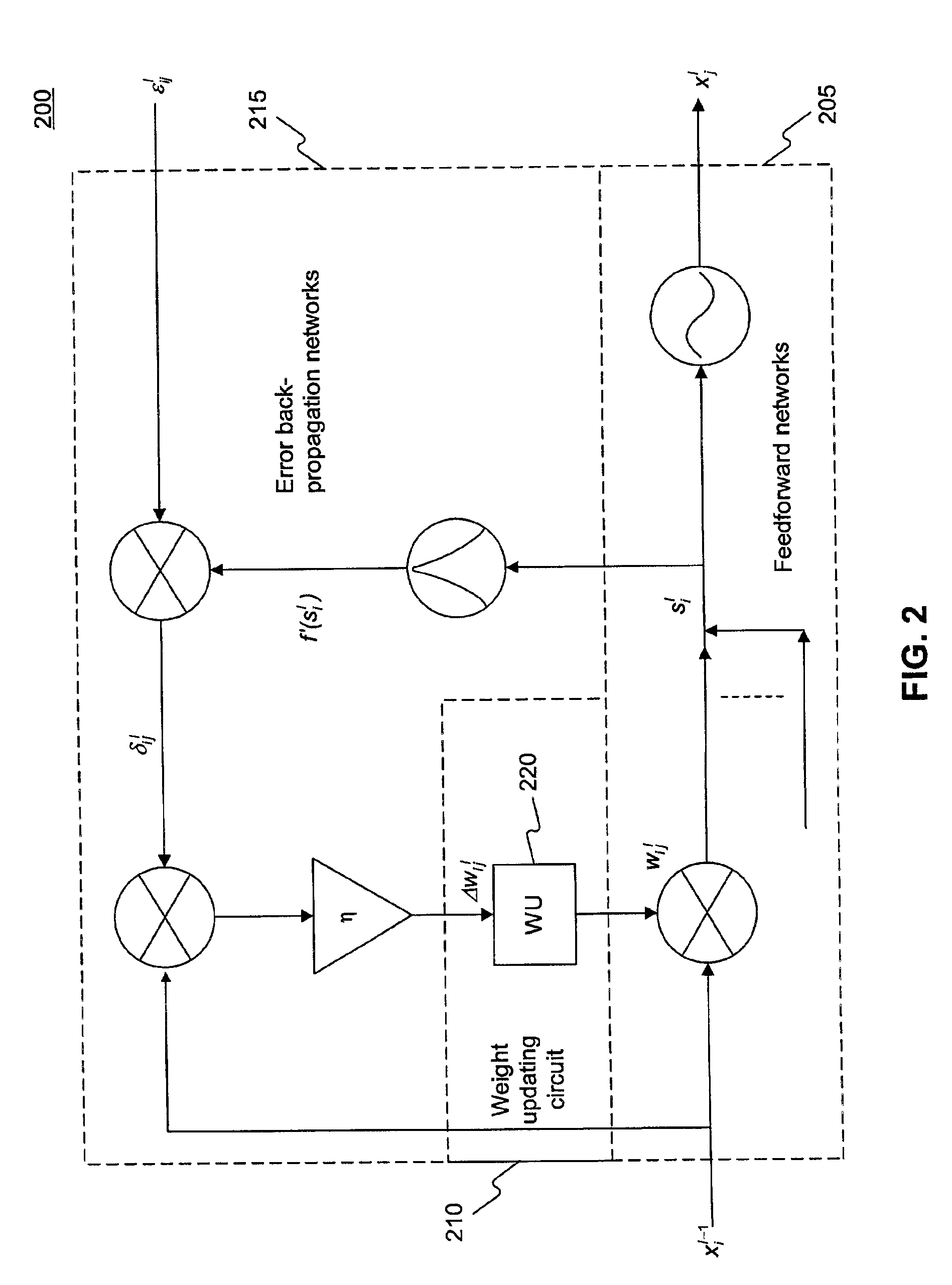
Back-propagation neural network with enhanced neuron characteristics
ActiveUS6876989B2Improve featuresAvoid problemsDigital computer detailsDigital dataActivation functionNeural network system
A neural network system includes a feedforward network comprising at least one neuron circuit for producing an activation function and a first derivative of the activation function and a weight updating circuit for producing updated weights to the feedforward network. The system also includes an error back-propagation network for receiving the first derivative of the activation function and to provide weight change data information to the weight updating circuit.
Owner:WINBOND ELECTRONICS CORP
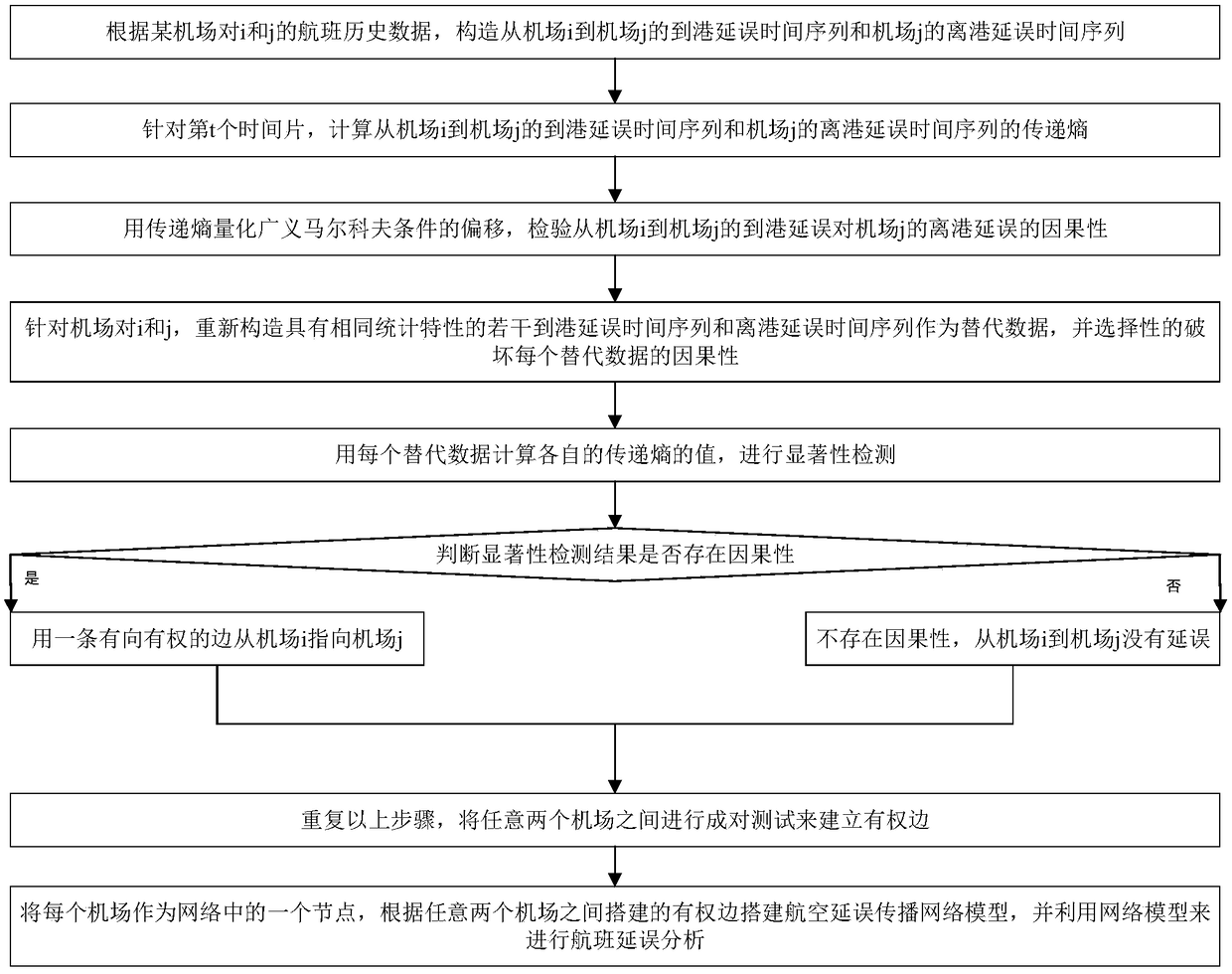
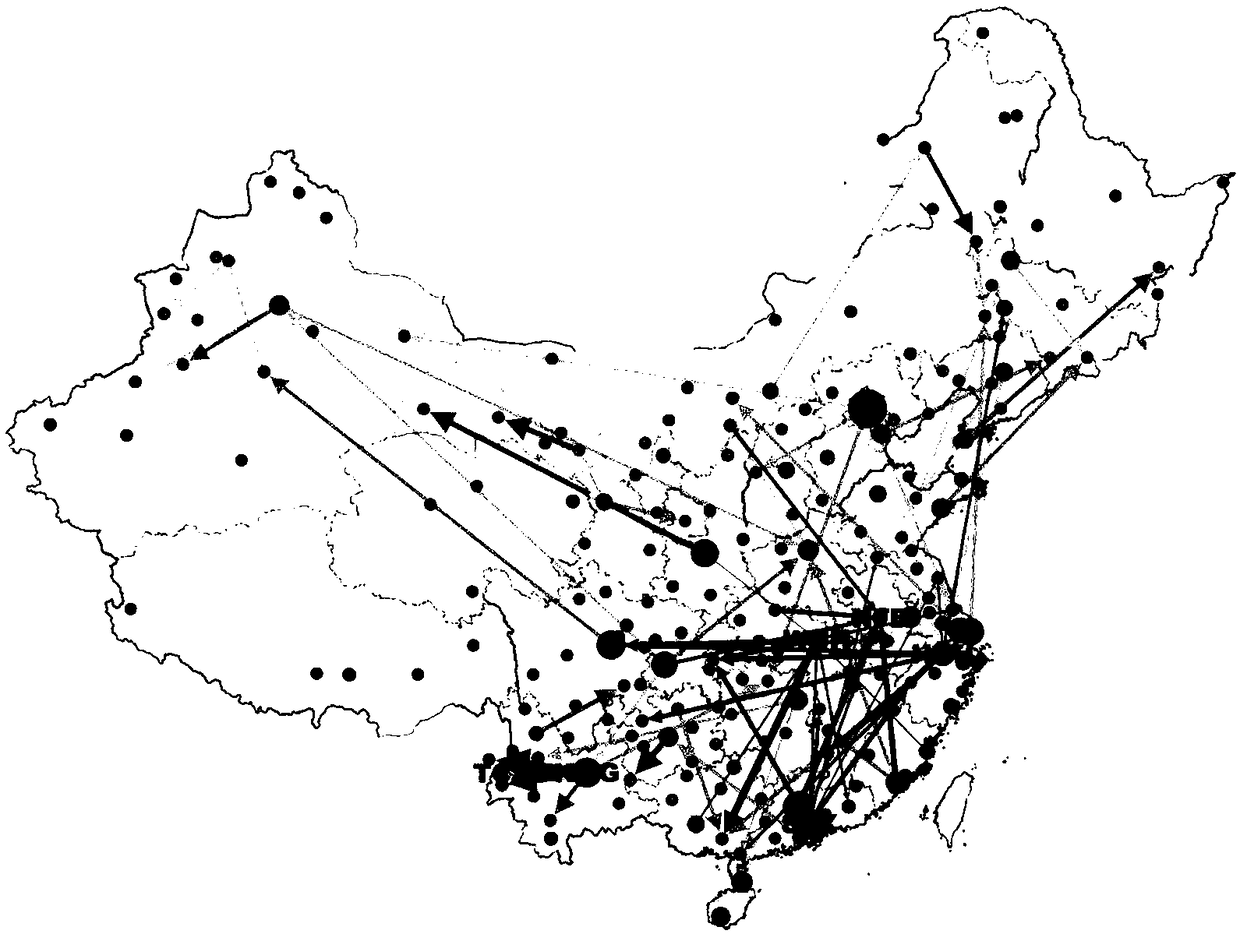
A quantitative analysis method of aviation delay propagation
The invention discloses a quantitative analysis method of aviation delay propagation, belonging to the technical field of aviation delay analysis. Firstly, the arrival delay time series from airport ito airport j and the departure delay time series of airport j are constructed, and the transfer entropy TE (Y(right arrow)X) of the t-th time slice is calculated to quantify the shift of the generalized Markov condition, and the causality of arrival delay to departure delay is tested. Then several arrival delay time series and departure delay time series with the same statistical characteristicsare reconstructed as substitute data, and the causality of each substitute data is destroyed; the transfer entropy (TE) is calculated with the substitute data, and the significance test is carried out. Pairs of tests are conducted between any two airports to establish the weighted edge, build the network model of aviation delay propagation, and use the network model to analyze flight delay. The invention only needs to analyze the causality between the delay time series, and can quantitatively calculate the delay propagation situation between the airports.
Owner:BEIHANG UNIV
Deep attention rumor identification method and device based on ternary features
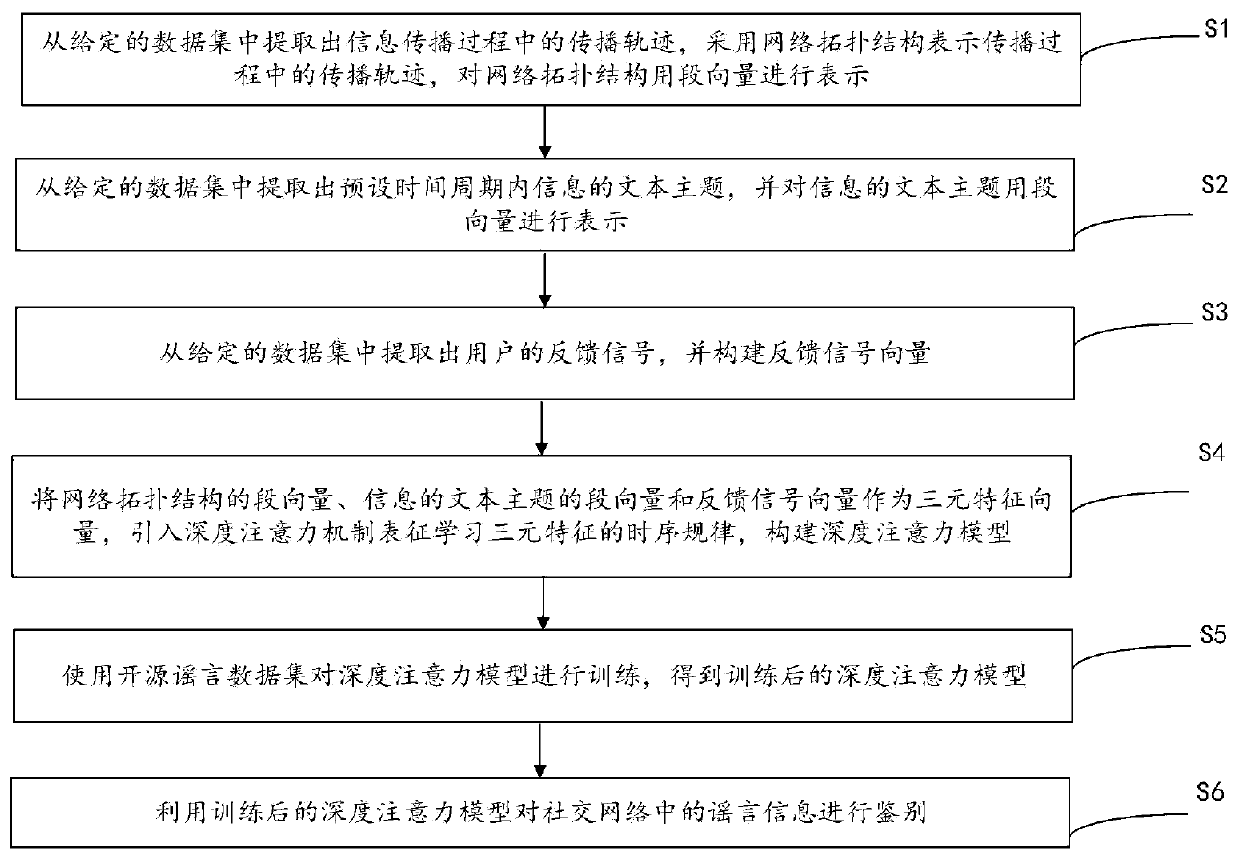
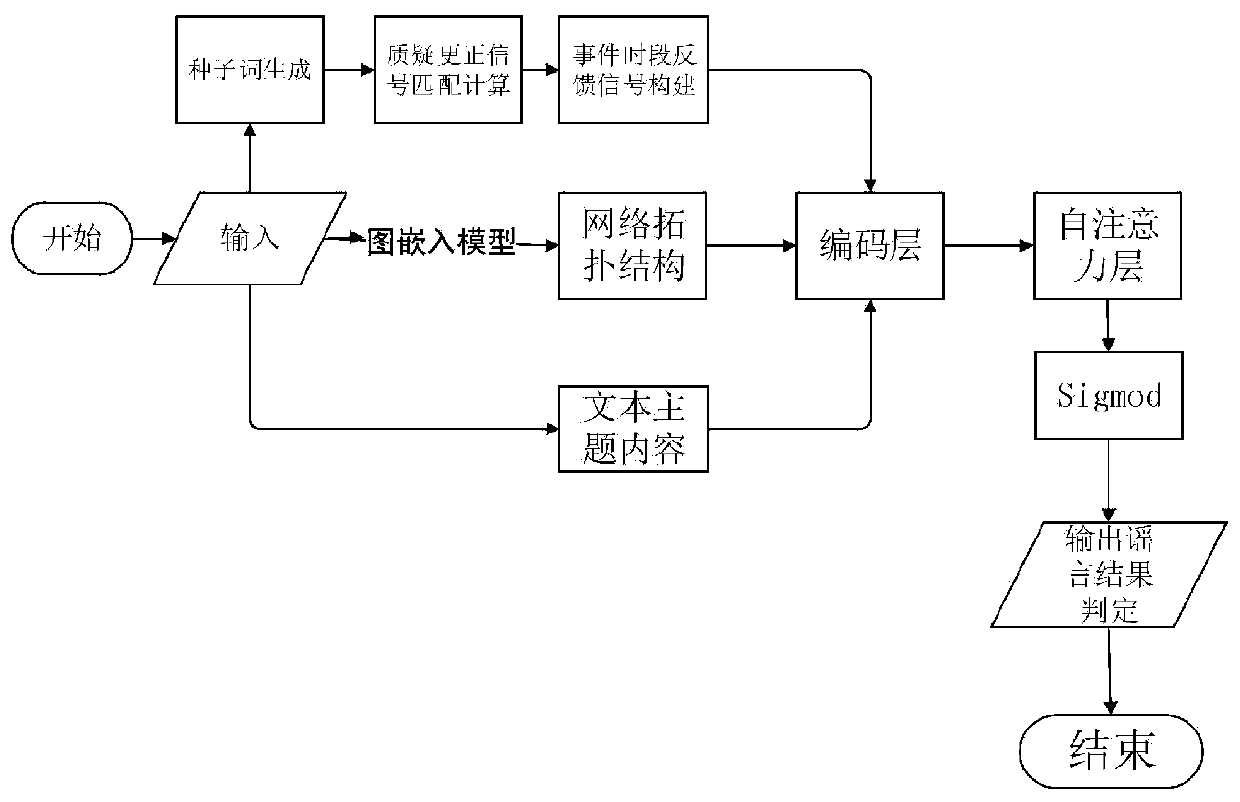
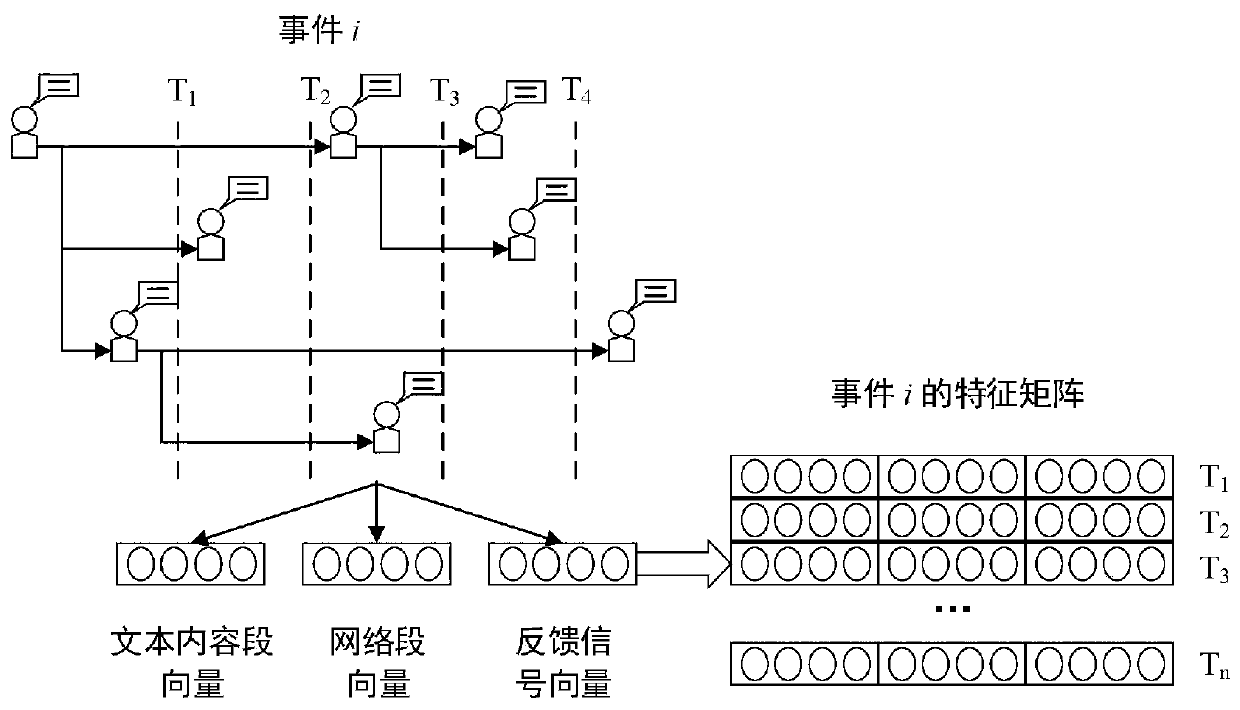
ActiveCN111008337ARealize authenticationOvercome the defect of single featureText database queryingSpecial data processing applicationsData setEngineering
The invention discloses a deep attention rumor identification method and device based on ternary features. A public social network platform rumor identification data set is adopted to extract text content of the information in the time period, propagation trajectory of events, the feedback signal of the user as the ternary features, and an improved biased random walk algorithm based on space-timestructure similarity and node measurement is provided for distributed representation learning of the nodes; an improved vectorization method of a propagation network node and an explicit vector representation method of a network topology structure are used for mapping the network topology structure from high dimension to low dimension representation, a time sequence identification method based onself-attention is adopted, and the feasibility of the method on a real world data set is verified. According to the method, rumor information can be effectively identified and the identification accuracy is improved.
Owner:WUHAN UNIV
Computer virus spreading source tracing method based on complex network
InactiveCN106599691AImprove securityRich defense systemPlatform integrity maintainanceSource tracingVirus
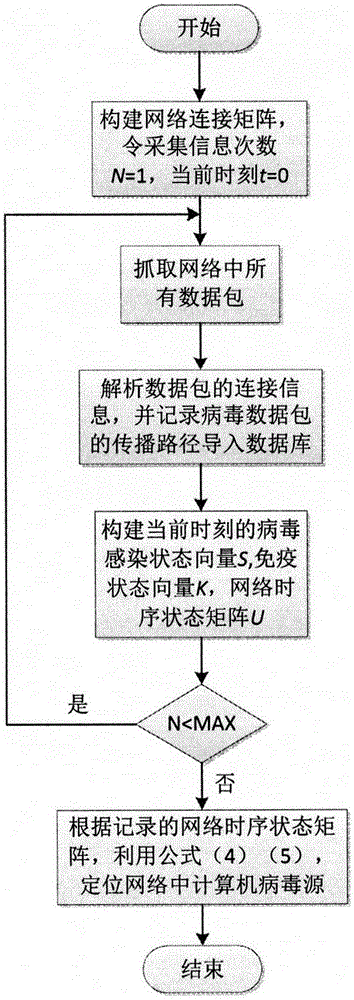
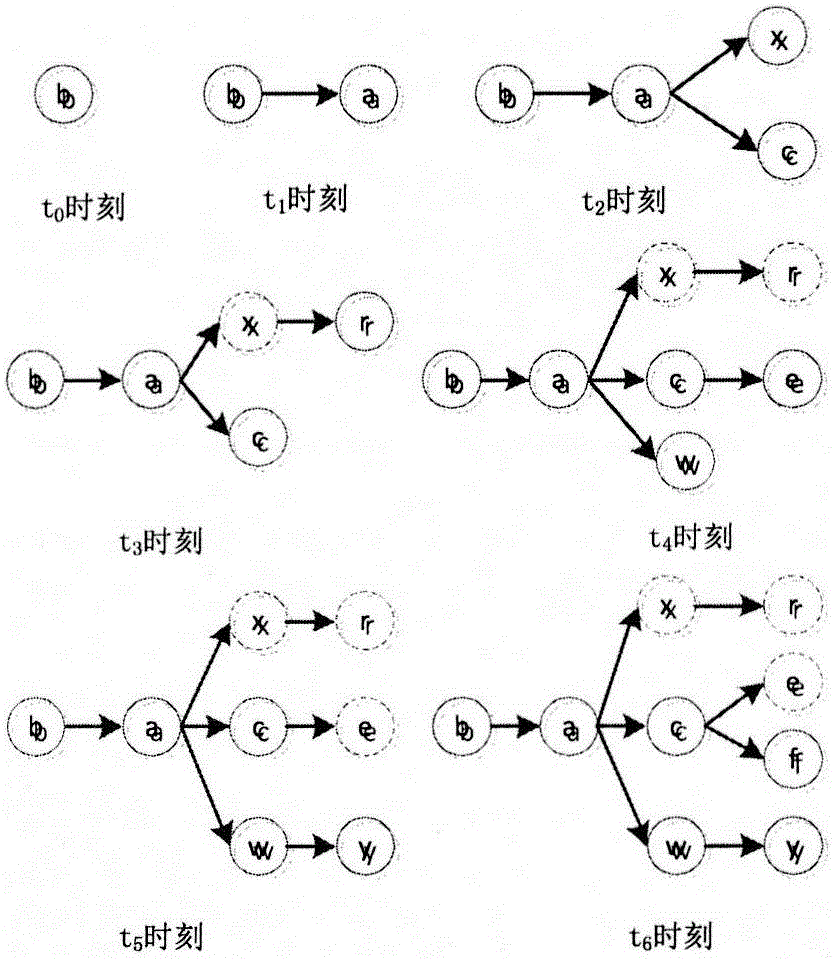
The invention discloses a computer virus spreading source tracing method based on a complex network, and relates to the technical field of computer virus network spreading. The source tracing method comprises the following steps: (1) building a computer virus spreading network diagram; (2) building a virus infection state vector; (3) building an immune state vector; and (4) building a network time sequence state matrix. Through adoption of the computer virus spreading source tracing method based on the complex network, an effective strategy is provided for the control of computer virus spreading; a computer virus defense system is further enriched; and the security of a computer is improved.
Owner:贾志娟
Instrument management informatization platform system and control method
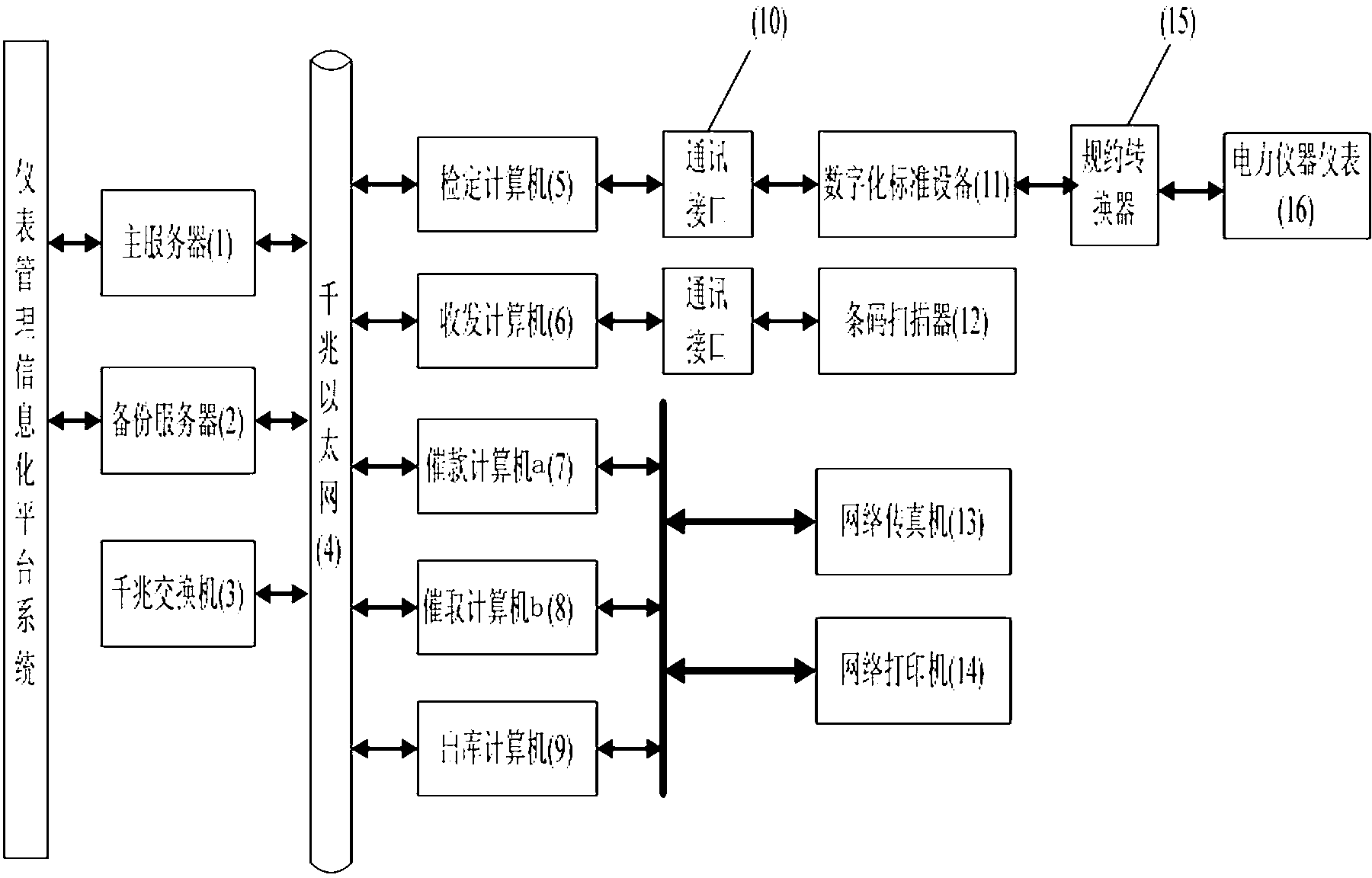
The invention relates to an instrument management informatization platform system, and particularly relates to an instrument management informatization platform system and a control method. A hardware part of the instrument management informatization platform system comprises a master server, a backup server, a kilomega switch, a gigabit ethernet, a verification computer, a dispatching computer, a payment computer a, a payment computer b, a delivery computer, a communication interface, a digitalized standard device, a bar code scanner, a network fax machine, a network printer, a protocol converter, and a power instrument meter, wherein the master server and the backup server form a redundant system; the gigabit Ethernet is used as a communication network; and the verification computer, the dispatching computer, the payment computer a, the payment computer b and the delivery computer at the terminal of the instrument management informatization platform system running at the server side are respectively connected through a network switch. The accuracy of a verification department management system can be ensured, and the instrument management informatization platform system has significant characteristics of being efficient, safe, and simple and feasible to operate.
Owner:LIAONING ELECTRIC POWER COMPANY LIMITED POWER SCI RES INSTION +3
Method and device for spreading network route to remote network using IPScc
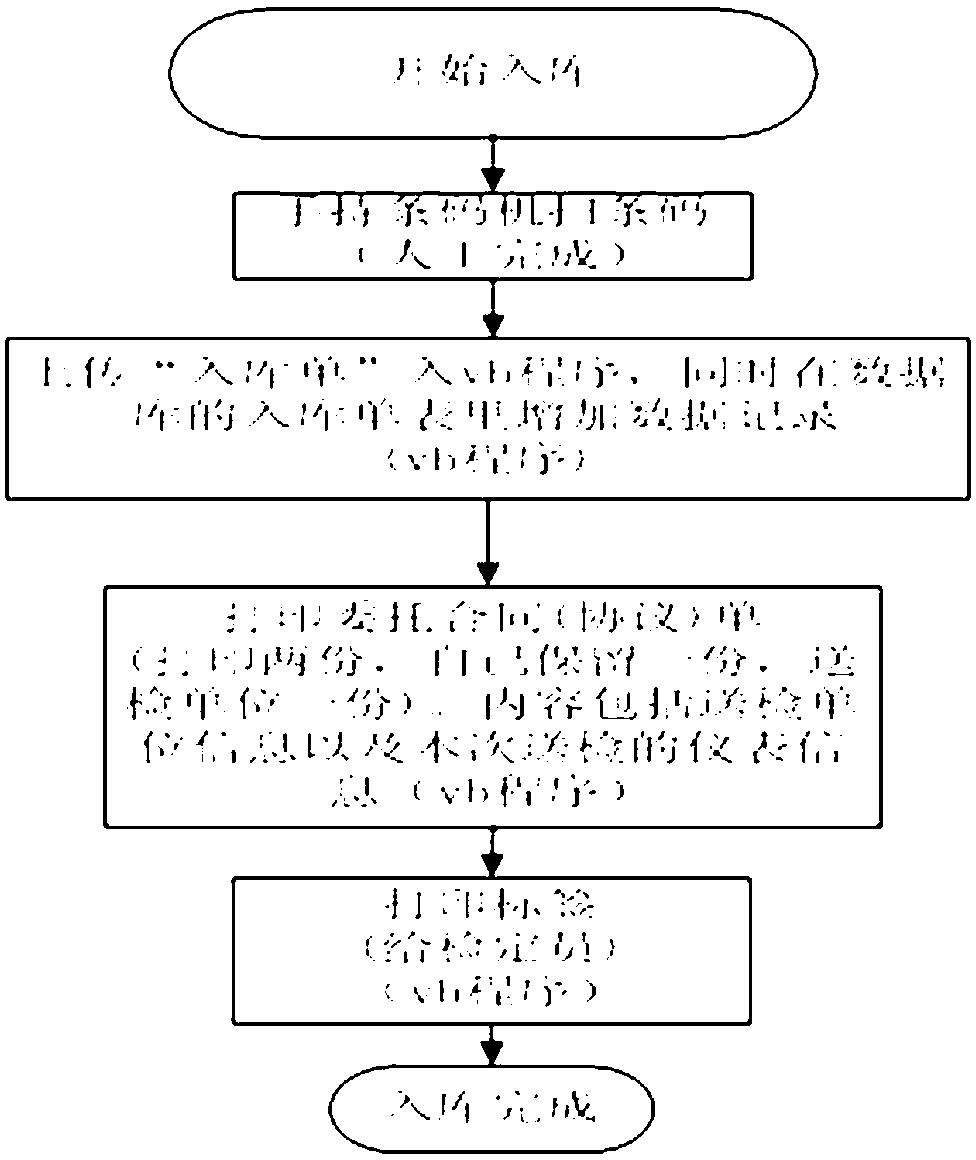
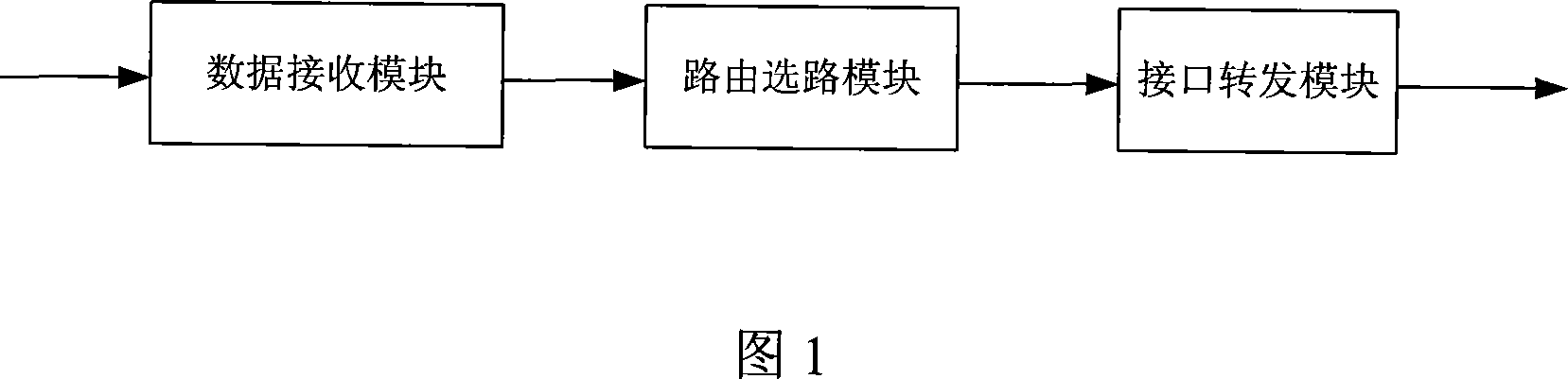
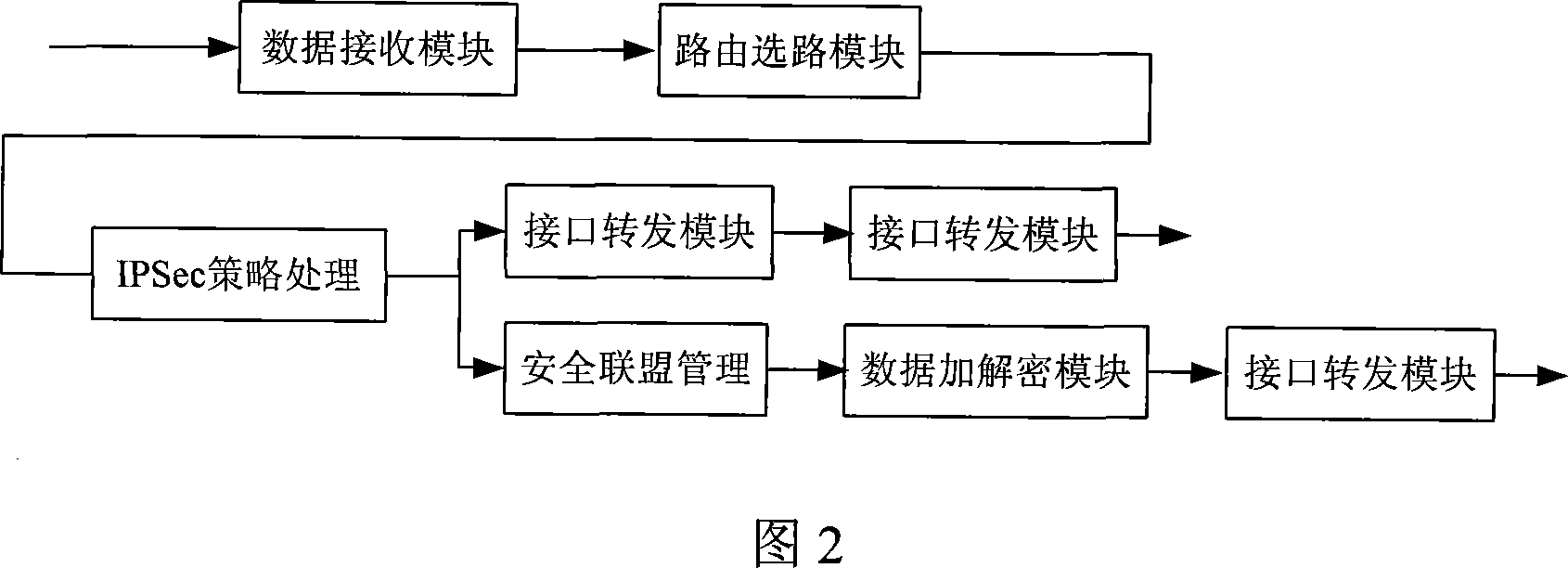
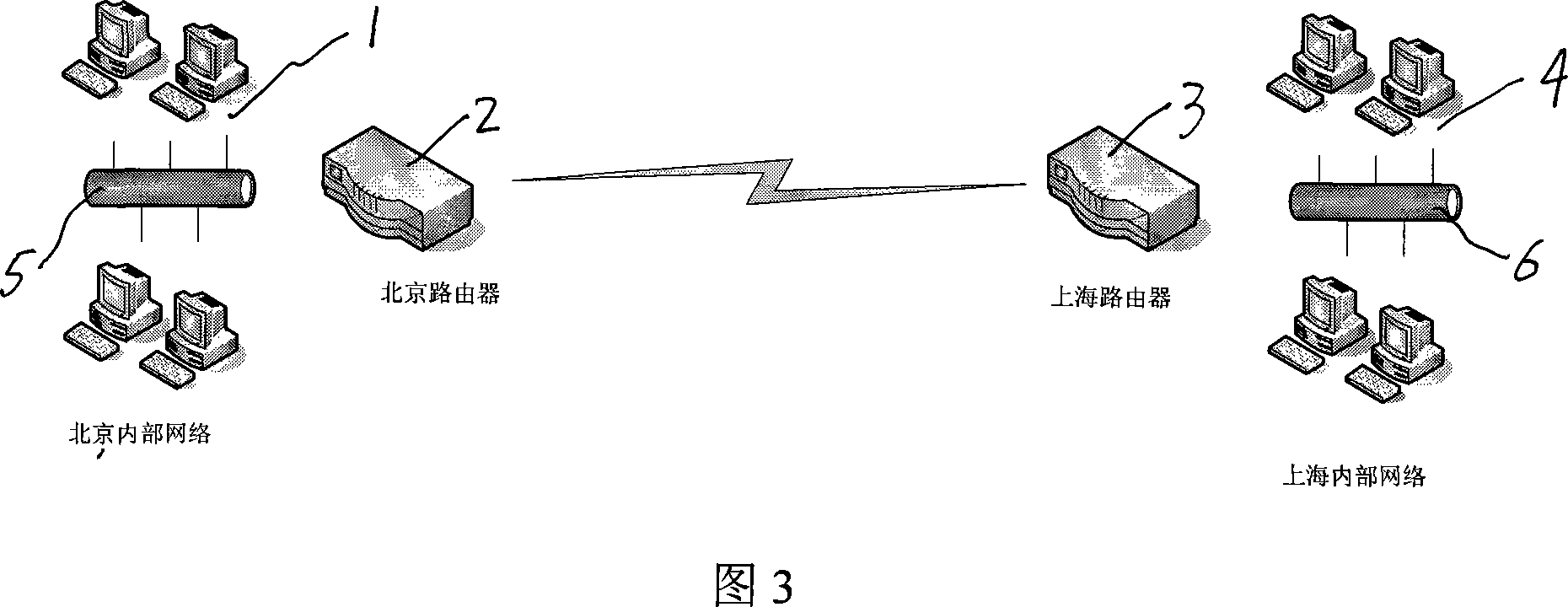
The method comprises: by expanding the route table of the security gateway, adding a tunnel virtual network interface supporting tunnel ID option and tunnel state option into network system; according to the tunnel virtual network interface selected by route, getting the tunnel ID, and according to the tunnel ID, getting the security association; making encryption and package process. By the invention, each branch LAN can be interconnected through route.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC
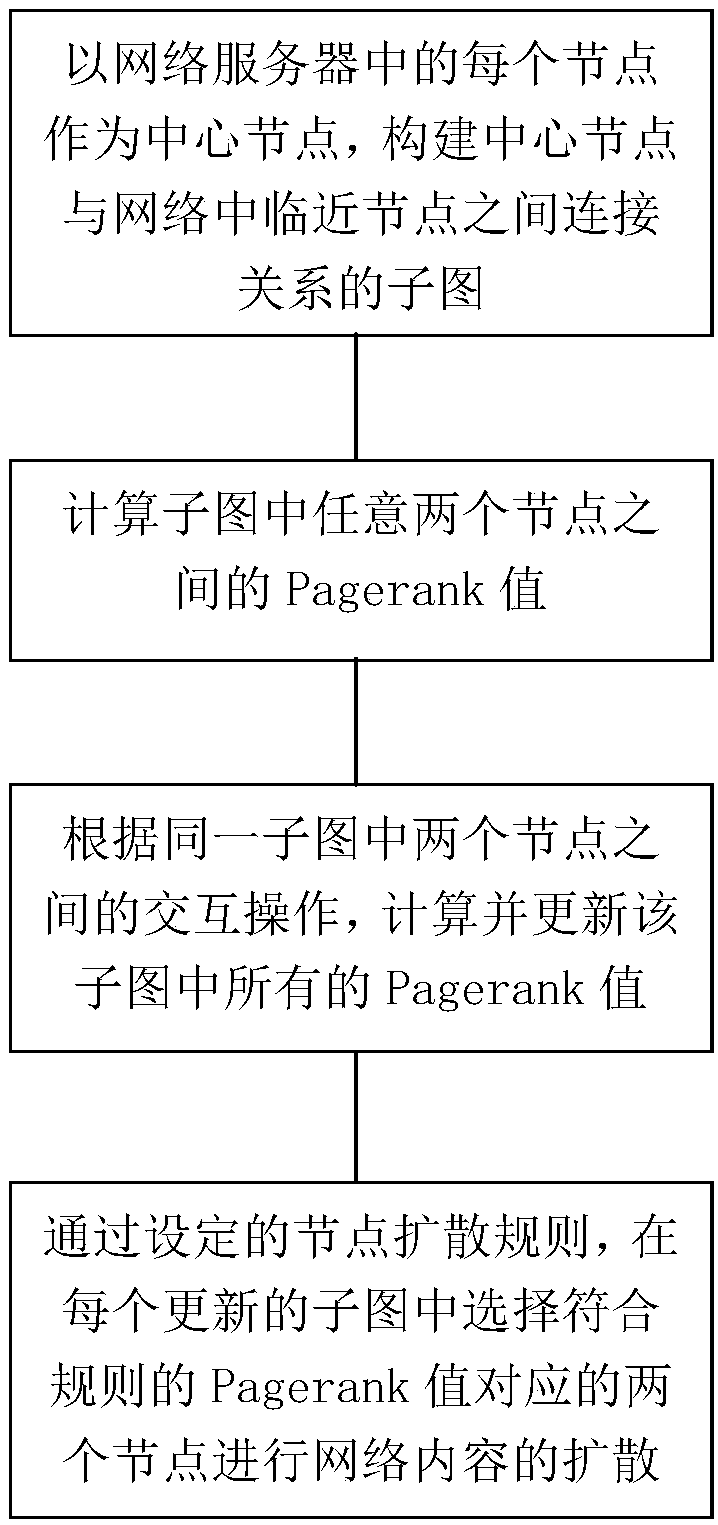
Network content spreading method based on network node distributed Pagerank
ActiveCN108512765AMitigating problems that are too different from the actual situationImprove performanceData switching networksRelation graphGlobal information
The invention provides a network content spreading method based on network node distributed Pagerank. The method comprises the steps that 1, by taking each node in a network server as a center node, asubgraph of the connecting relation between the center node and network adjacent nodes is constructed; 2, Pagerank values between any two nodes in the subgraphs are calculated; 3, according to an interaction operation between two nodes in the same subgraph, all the Pagerank values in the subgraph are calculated and updated; and 4, according to a set node spreading rule, two nodes corresponding tothe Pagerank value confirming to the rule are selected from each updated subgraph to spread network content. According to the network content spreading method, by setting one node which represents all other global information in each node neighbor connection relation graph to continuously iterate to gradually approach global information, the problem that the difference between a local model and the actual condition is too great is solved, and the content spreading performance is improved.
Owner:ZHENGZHOU SEANET TECH CO LTD
Inter cut prevention method for terrestrial digital television
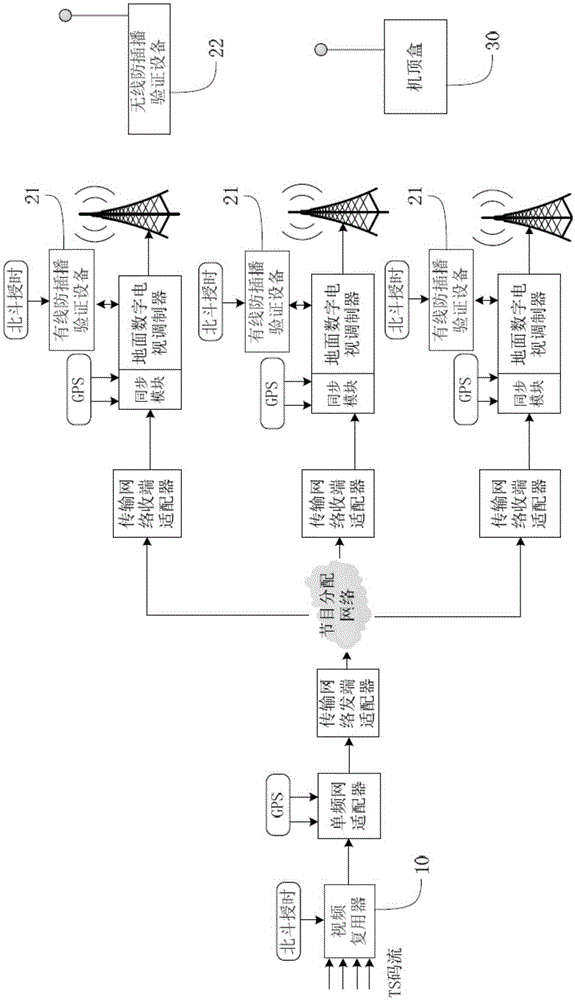
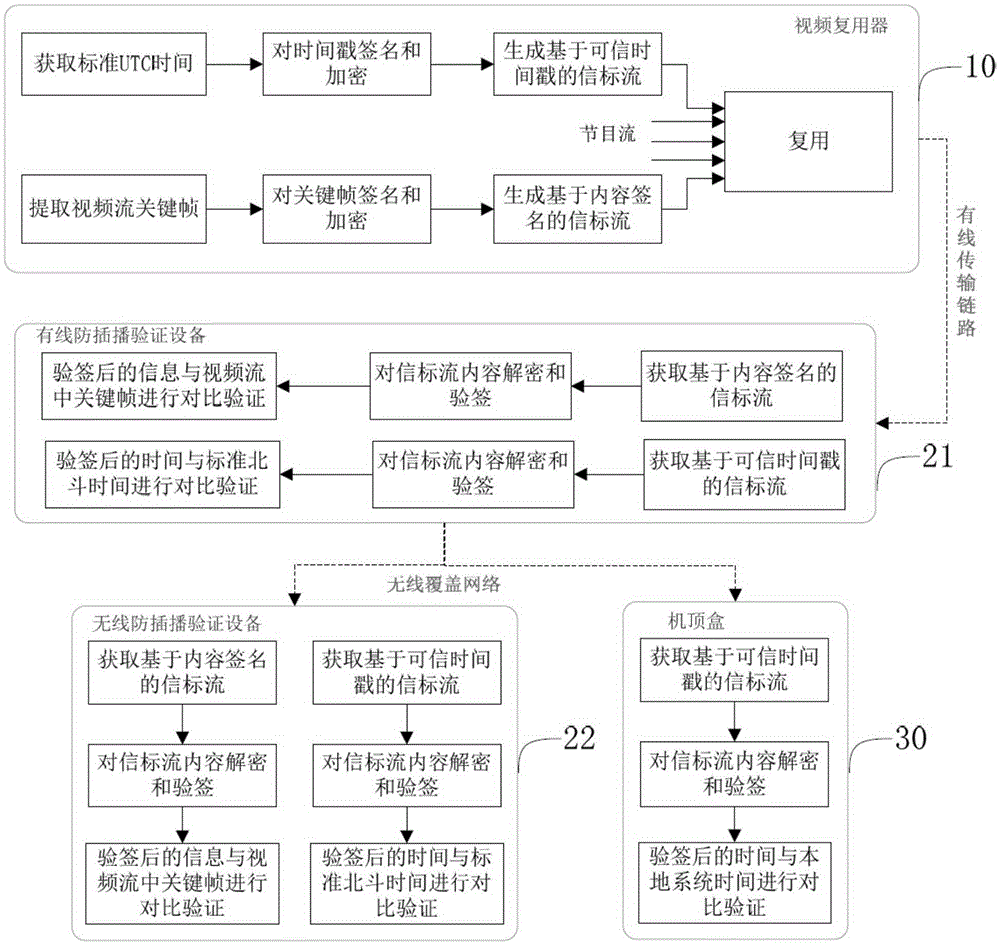
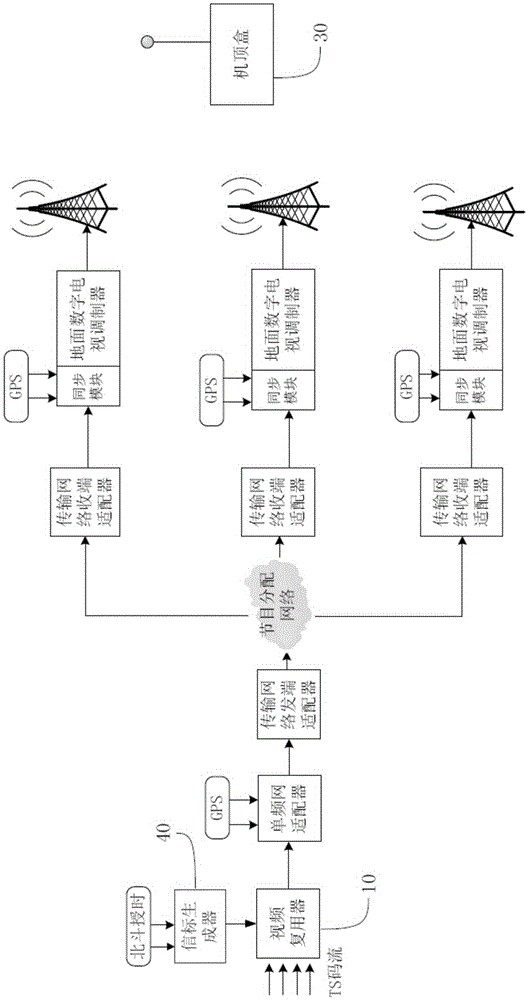
InactiveCN105307054ARapid deploymentSimple configurationSelective content distributionTimestampTime delays
The invention discloses an inter cut prevention method for a terrestrial digital television. The inter cut prevention method comprises the following steps: a first step, a beacon flow generator in a transmitting terminal device obtains a standard UTC time through a built-in Beidou time service module at first, and then carries out signature and encryption processing on a timestamp to generate an inter cut prevention beacon flow based on a credible timestamp; a second step, a video multiplexer in the transmitting terminal device integrates the inter cut prevention beacon flow with other program beacon flows and then transmits the same to a receiving end terminal through a transmission link; and a third step, a set-top box in the receiving end terminal obtains the inter cut prevention beacon flow based on the credible timestamp, decrypts and verifies the inter cut prevention beacon flow based on the credible timestamp, compares a local system time with a decrypted and verified timestamp, if the time delay exceeds a preset threshold, the set-top box has an inter cut attack and stops playing; and otherwise, the set-top box normally plays the program. The inter cut prevention method for the terrestrial digital television disclosed by the invention is used for protecting the security of a communication network of the digital television and preventing inter cut of illegal signals.
Owner:CHENGDU SANLING KAITIAN COMM IND
Complex electronic system fault diagnosis method based on fault propagation network
ActiveCN111444035ASolve the problem of fault diagnosis modelingImprove fault diagnosis abilityFault responseInformation technology support systemElectronic systemsDirected graph
The invention discloses a complex electronic system fault diagnosis method based on a fault propagation network, and the method comprises the steps: building a fault propagation directed graph of a complex electronic system through employing a graph theory, and achieving the storage and hierarchical optimization of the fault propagation directed graph through employing a matrix theory; simplifyingthe fault propagation network according to the fault phenomenon nodes; establishing a candidate fault source set by calculating the information output intensity and the working intensity of the nodes; and finally, calculating the comprehensive influence degree of the fault source by using an entropy weight method so as to determine a fault source therefrom. According to the invention, a fault propagation network is established based on a physical structure of a complex electronic system; the modeling problem of fault diagnosis of a complex electronic system is solved; design indexes such as the information output quantity and the fault-free working time of system components are utilized to solve the quantification problem of the system fault propagation influence relation, meanwhile, dependence on fault historical data is avoided, a fault source can be rapidly recognized and positioned, and the fault diagnosis capacity of a complex electronic system is improved.
Owner:XIJING UNIV
Prediction method, device and equipment for stability condition of public opinion propagation
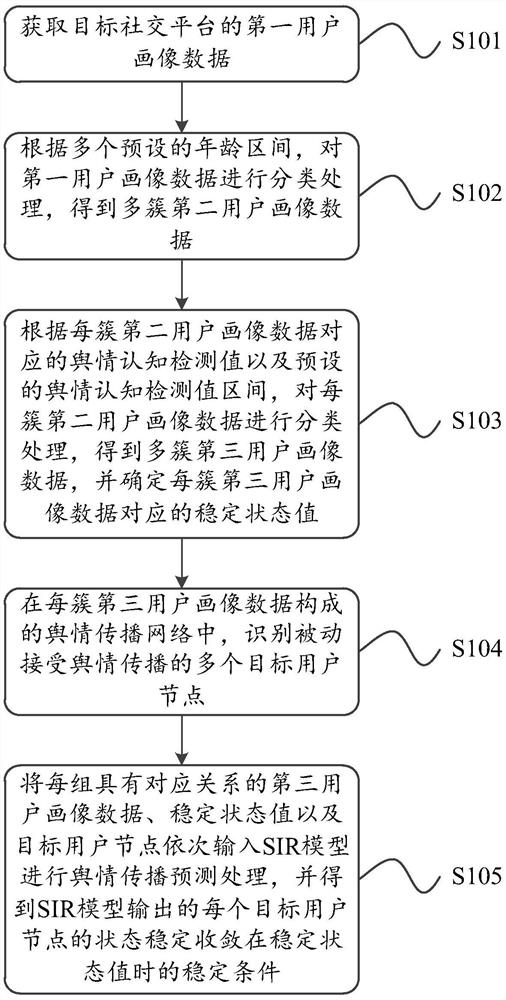
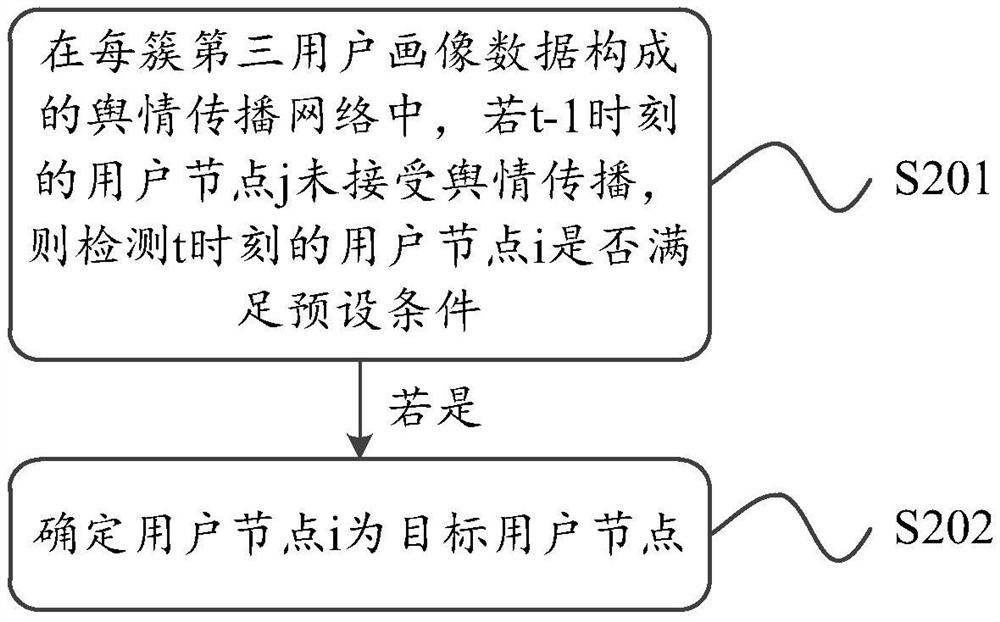
ActiveCN111966920AStable dynamic characteristicsGuaranteed experienceSpecial data processing applicationsText database clustering/classificationEngineeringData mining
The invention provides a prediction method, device and equipment for stability condition of public opinion propagation. The prediction method, device and equipment are used for accurately judging thepublic opinion propagation stability conditions in a target social platform. The method comprises the steps of obtaining first user portrait data of a target social platform; according to a pluralityof preset age intervals, performing classification processing on the first user portrait data to obtain a plurality of clusters of second user portrait data; according to the public opinion cognitiondetection value and a preset public opinion cognition detection value interval, performing classification processing on each cluster of second user portrait data to obtain multiple clusters of third user portrait data, and determining a corresponding stable state value; in a public opinion propagation network formed by each cluster of third user portrait data, identifying a plurality of target user nodes passively receiving public opinion propagation; and sequentially inputting each group of third user portrait data with the corresponding relationship, the stable state value and the target user node into the SIR model, and obtaining a stable condition when the state of each target user node is stably converged at the stable state value.
Owner:JIANGHAN UNIVERSITY
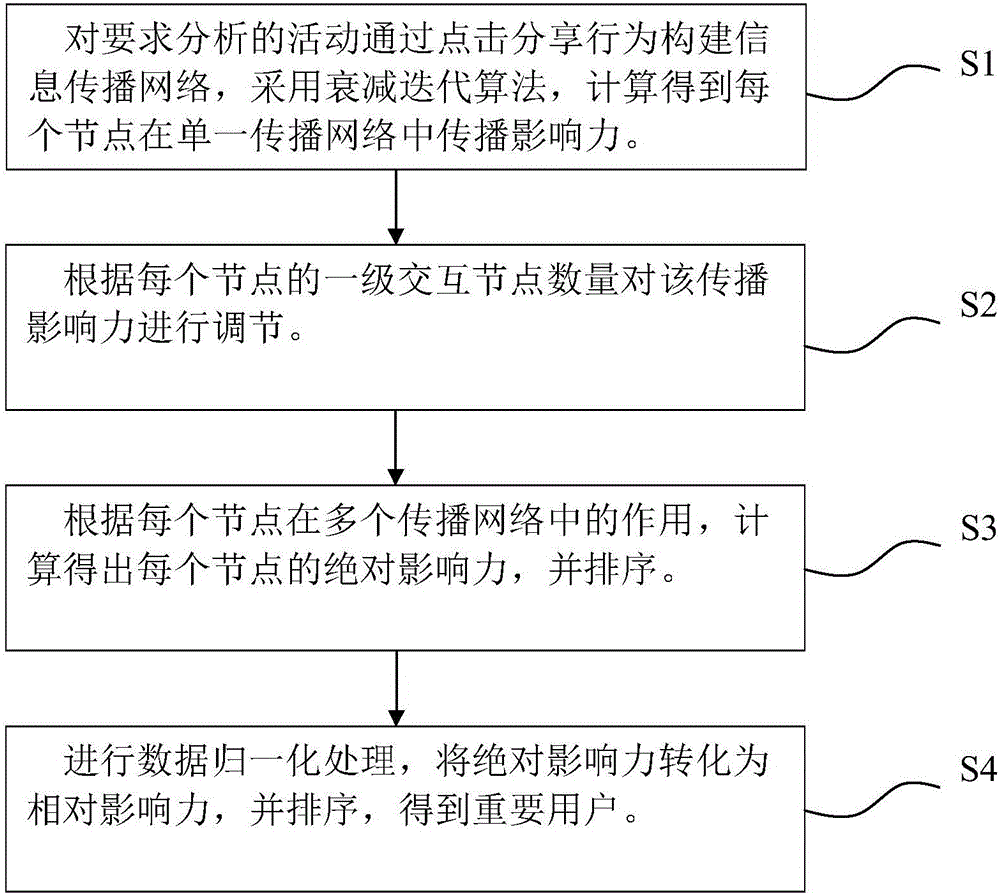
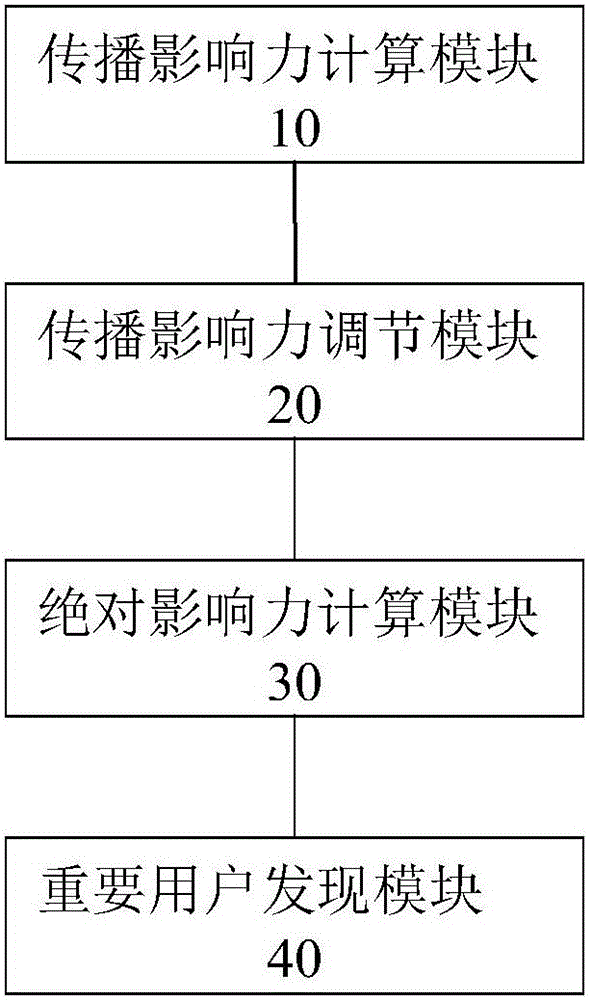
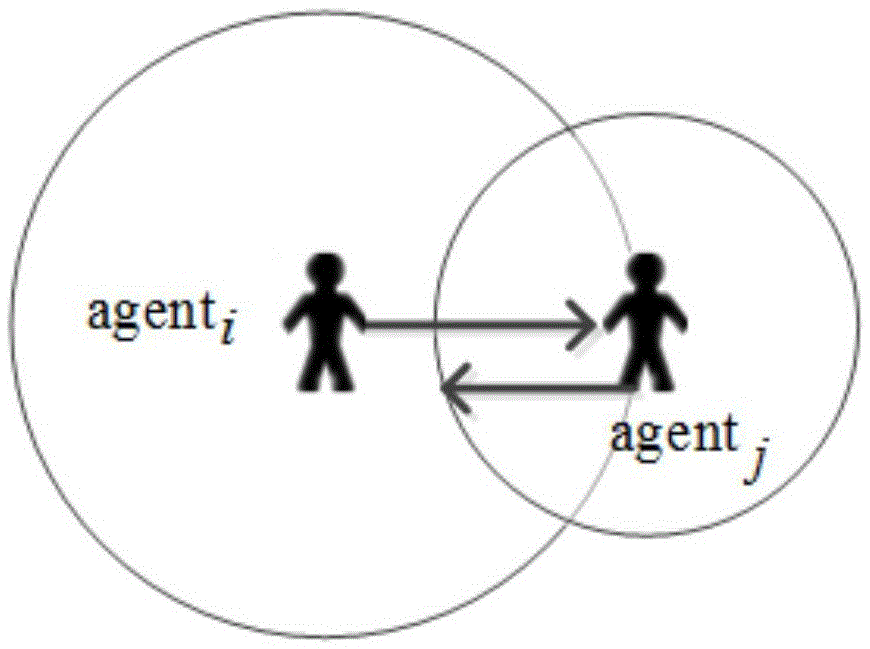
Method and device for discovering important users on the basis of spreading networks
ActiveCN105956925ACalculation speedImprove accuracyData processing applicationsNODALPagerank algorithm
The invention belongs to the technical field of social spreading analysis and specifically relates to a method and device for discovering important users on the basis of spreading networks. The method comprises a step 1 of constructing information spreading networks for activities required to be analyzed by means of clicking and sharing behaviors, and computing the spreading influence of each node in a single spreading network; a step 2 of regulating the spreading influence according to the number of primary interactive nodes of each node; a step 3 of computing the absolute influence of each node according to the effect of each node in multiple spreading networks and ordering the absolute influence; and a step 4 of normalizing data, transforming the absolute influence into relative influence, and ordering the relative influence to obtain the important users. The method prevents a possibility that a Pagerank algorithm plunges into an end node, increases computation speed, avoids a possibility of excessive iteration, comprehensively takes account of the effects of the node in multiple networks, and improves accuracy.
Owner:时趣互动(北京)科技有限公司
Agent social circle network based modeling simulation method for universal multi-language competition model
InactiveCN105550167AData processing applicationsNatural language data processingSocial circleMulti language
The invention relates to an agent social circle network based modeling simulation method for a universal multi-language competition model, belonging to the field of computer simulation. According to the method, the number of agents in the social circle is set, and a population proportion of a single language, status of three groups of languages, small, medium and large social radiuses, individual migration proportion, birth rate and death rate are set; agents establish a social network by use of a social circle principle according to respectivesocial radius; in the established network, individuals perform language communication through learning and forgetting, and children inherit the language from parents; the dynamism of the social network is depicted according to introduced individual migration proportion, birth rate and death rate; and modeling and simulation are performed on language competition spread by use of the established social circle network. According to the method, characteristics of the dynamic language spread network can be represented correctly, social network based quantitative explanation of multi-language evolution can be offered, and the model frame provides a feasible new method for further research of multi-language competition.
Owner:KUNMING UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com