Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
115 results about "Copying mechanism" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the study of scale-free networks, a copying mechanism is a process by which such a network can form and grow, by means of repeated steps in which nodes are duplicated with mutations from existing nodes. Several variations of copying mechanisms have been studied. In the general copying model, a growing network starts as a small initial graph and, at each time step, a new vertex is added with a given number k of new outgoing edges. As a result of a stochastic selection, the neighbors of the new vertex are either chosen randomly among the existing vertices, or one existing vertex is randomly selected and k of its neighbors are ‘copied’ as heads of the new edges.
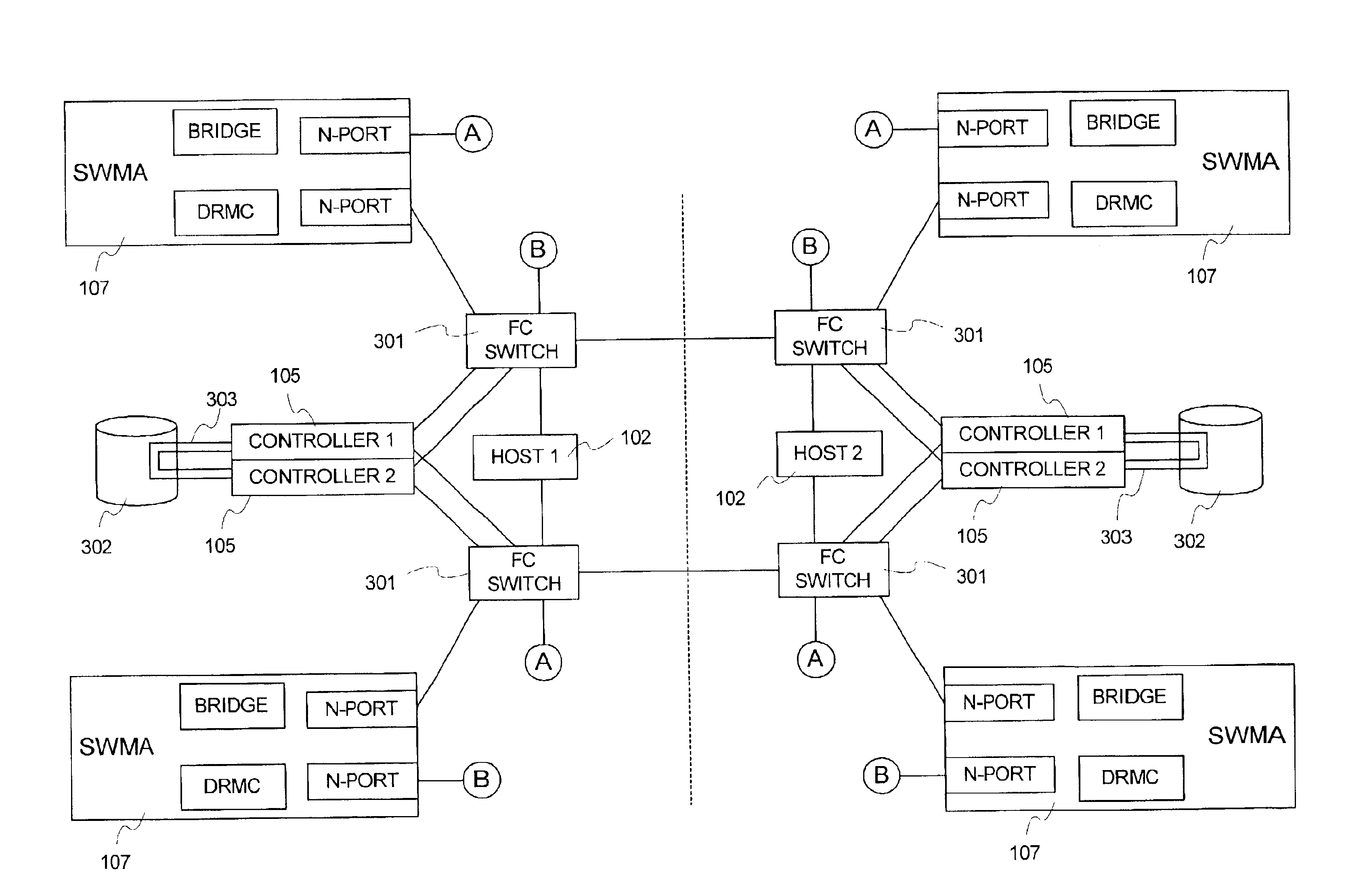
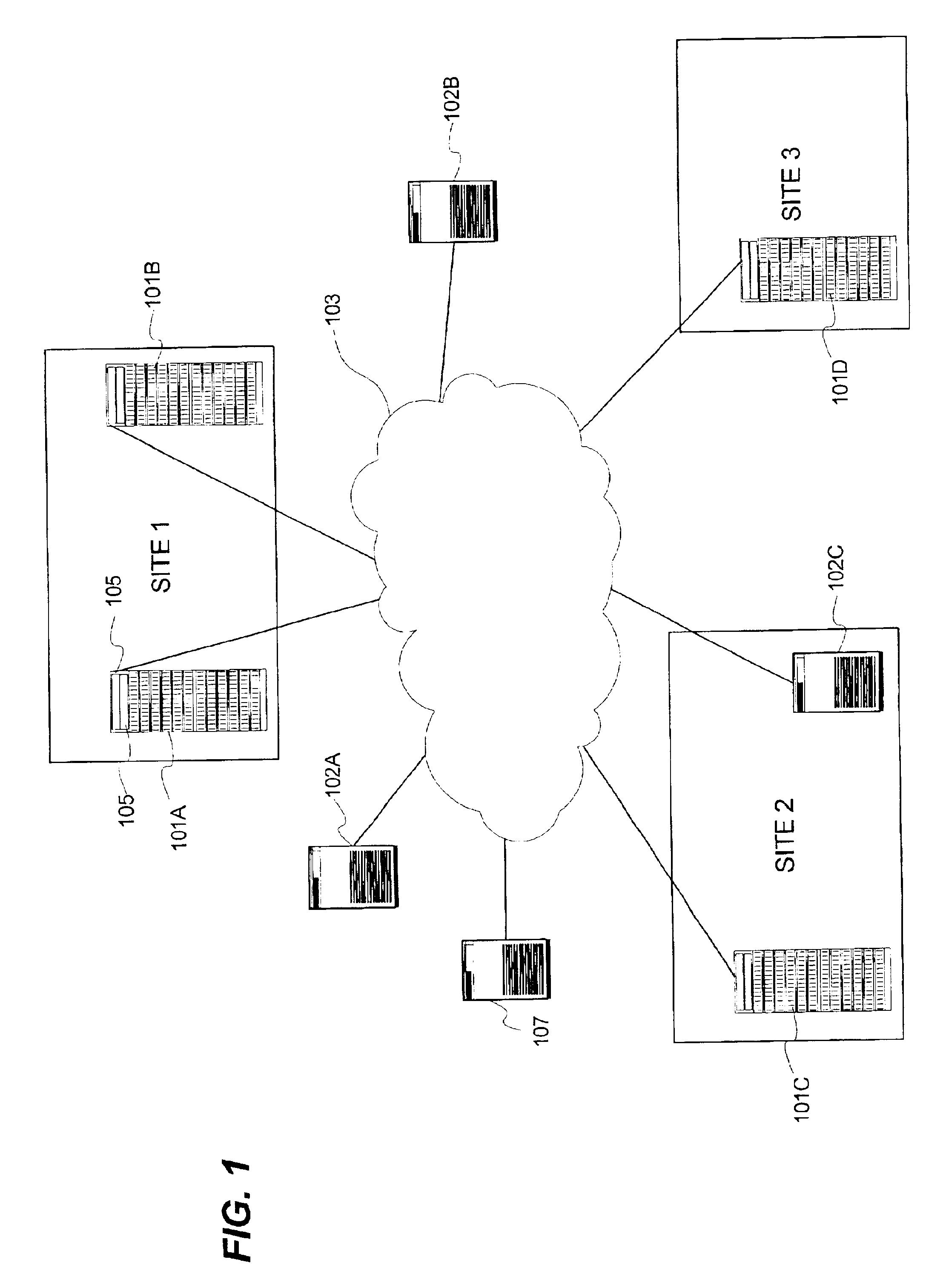
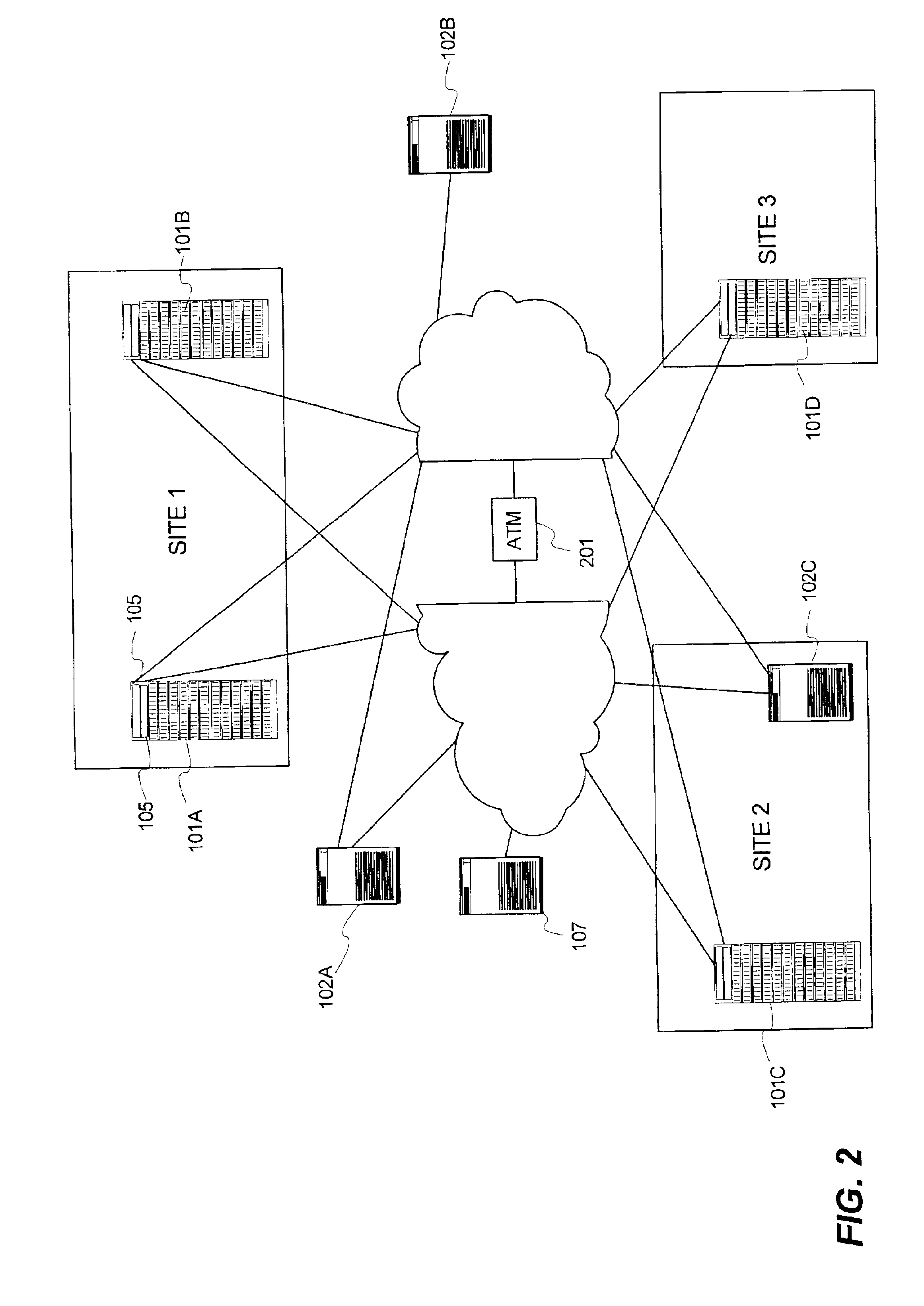
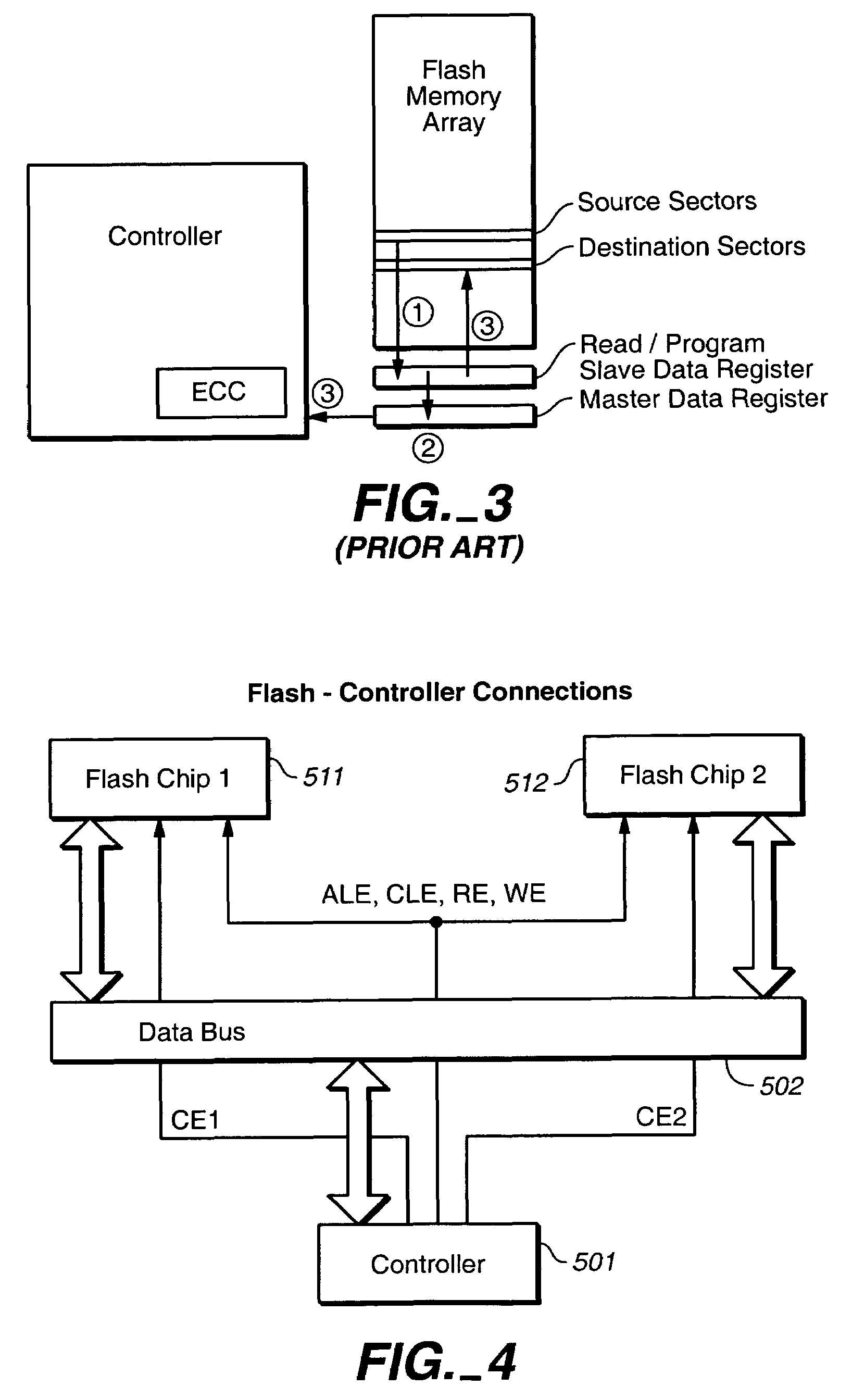
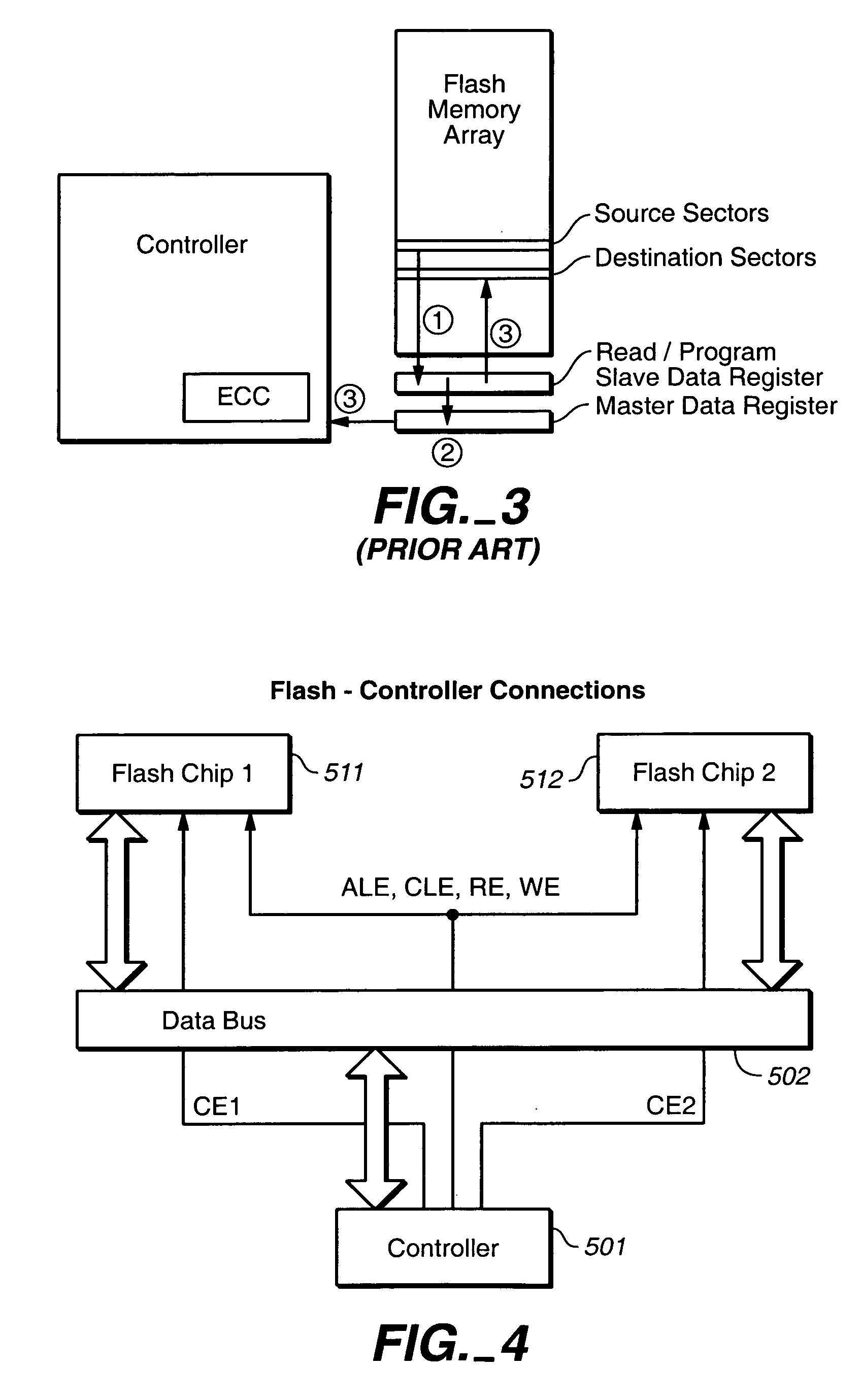
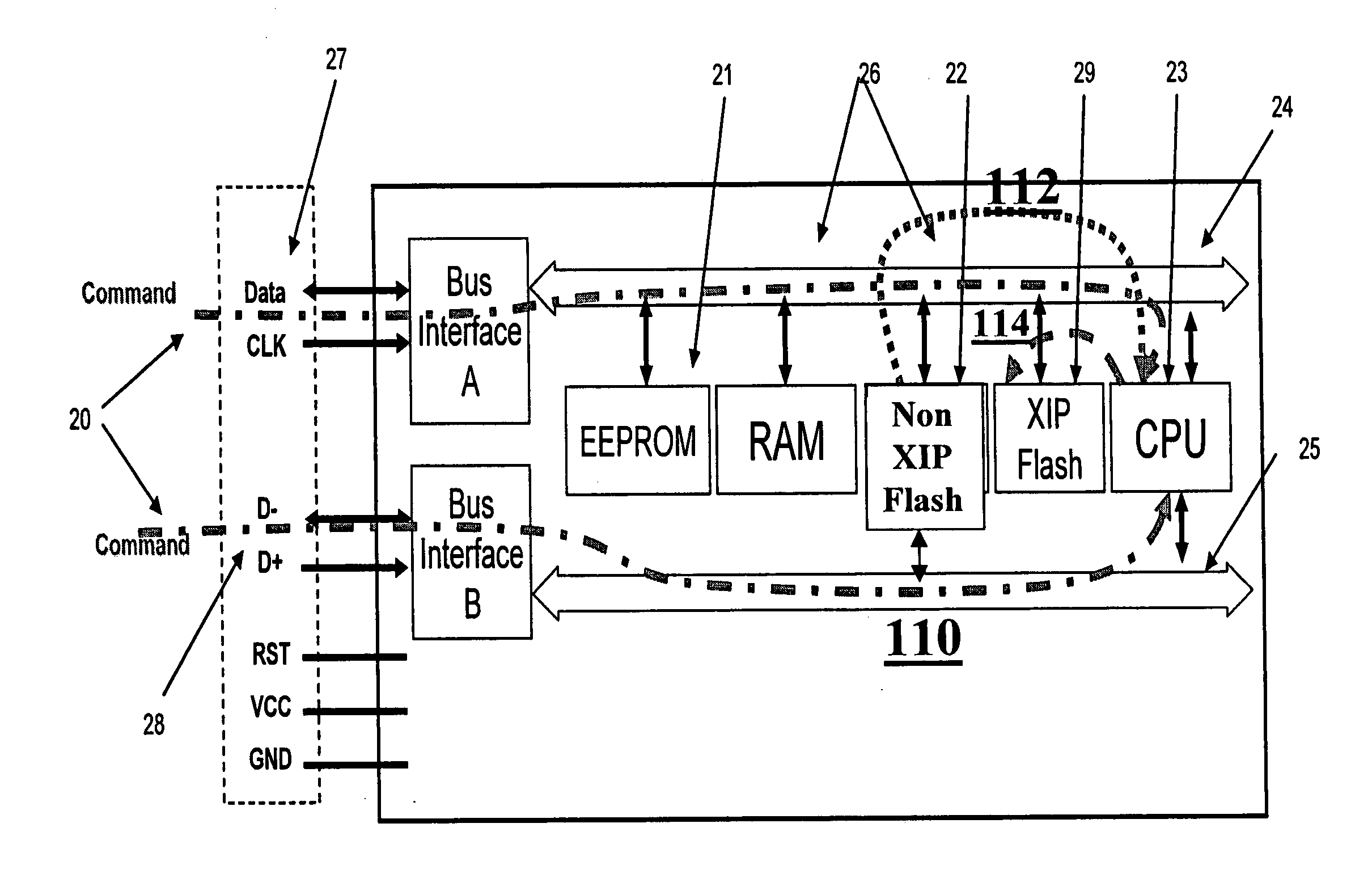
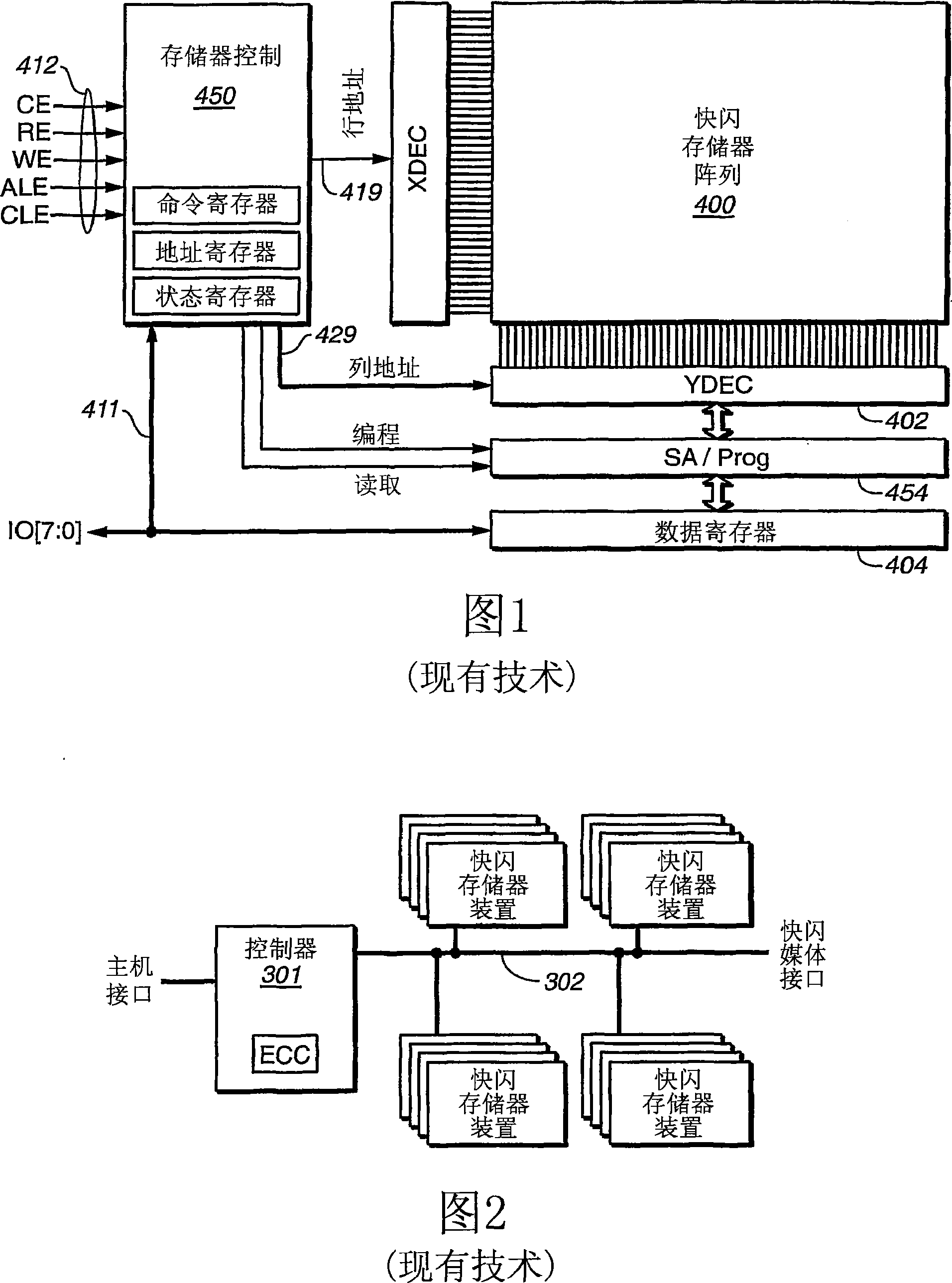
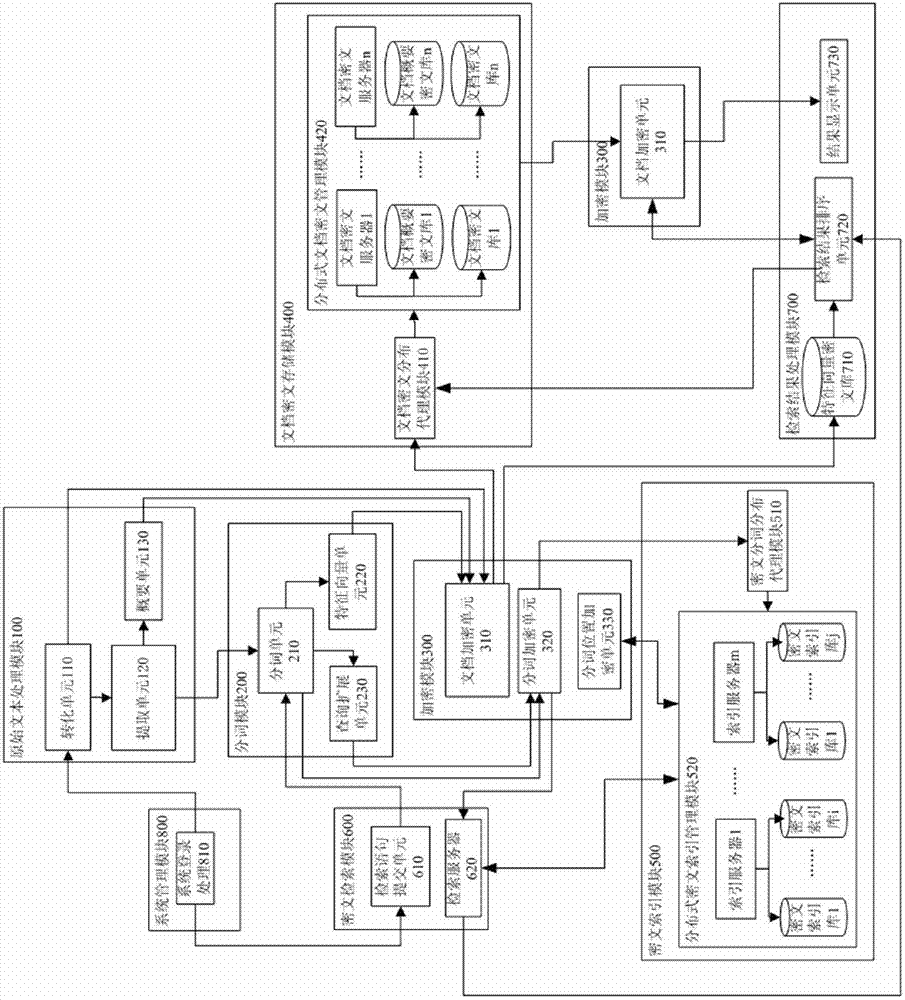
Flexible data replication mechanism
InactiveUS6947981B2Data processing applicationsDigital computer detailsControl storeCopying mechanism
A data replication management (DRM) architecture comprising a plurality of storage cells interconnected by a fabric. Flexibility in connectivity is provided by configuring each storage cell port to the fabric to handle both host data access requests and DRM traffic. Each storage cell comprises one or more storage controllers that can be connected to the fabric in any combination. Processes executing in the storage controller find a path to a desired destination storage cell. The discovery algorithm implements a link service that exchanges information related to DRM between the storage controllers. The DRM architecture is symmetric and peer cooperative such that each controller and storage cell can function as a source and a destination of replicated data. The DRM architecture supports parallel and serial “fan-out” to multiple destinations, whereby the multiple storage cells may implement data replicas.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Off-chip data relocation
ActiveUS7409473B2Reduce frequencyEasy to operateRead-only memoriesDigital storageComputer hardwareData set
The on-chip copy process is extended so that the data may be copied between two blocks that may be on different chips, different planes on the same chip, or the same plane of the same chip. More specifically, the methods described here provide a single data copying mechanism that allows data to be copied between any two locations in a memory system. An exemplary embodiment uses an EDO-type timing. According to another aspect, selected portions of the relocated data, such as chosen words in a transferred page, can be updated in the controller on the fly. In addition to transferring a data set directly from a read buffer of a source array to a write buffer of a destination array, the data set can concurrently be copied, if desired, into the controller where an error detection and correction operation can be performed on it.
Owner:SANDISK TECH LLC
Off-chip data relocation
ActiveUS20060136687A1Reduce frequencyEasy to operateMemory loss protectionRead-only memoriesComputer hardwareData set
The on-chip copy process is extended so that the data may be copied between two blocks that may be on different chips, different planes on the same chip, or the same plane of the same chip. More specifically, the methods described here provide a single data copying mechanism that allows data to be copied between any two locations in a memory system. An exemplary embodiment uses an EDO-type timing. According to another aspect, selected portions of the relocated data, such as chosen words in a transferred page, can be updated in the controller on the fly. In addition to transferring a data set directly from a read buffer of a source array to a write buffer of a destination array, the data set can concurrently be copied, if desired, into the controller where an error detection and correction operation can be performed on it.
Owner:SANDISK TECH LLC
Flexible data replication mechanism
Owner:LUBBERS CLARK +6
Message processing method, server cluster and message processing system
The application provides a message processing method, a server cluster and a message processing system. The server cluster comprises multiple queue servers. When writing a request message sent by a first client into a target log file, a target queue server triggers backup queue servers in the server cluster to synchronize the target log file. When the backup queue servers push the synchronization request message to corresponding backup message queues, the backup queue servers feed backup completion information back to the target queue server. After receiving a first preset number of pieces of backup completion information, the target queue server pushes the request message to a target message queue for storage, and feeds success response information for the request message back to the first client. Thus, the production reliability and storage reliability of the request message are ensured. Moreover, as a multi-copy mechanism is adopted, the reliability and availability of the system are guaranteed under the condition that the target queue server is in abnormal operation.
Owner:TENCENT TECH (SHENZHEN) CO LTD
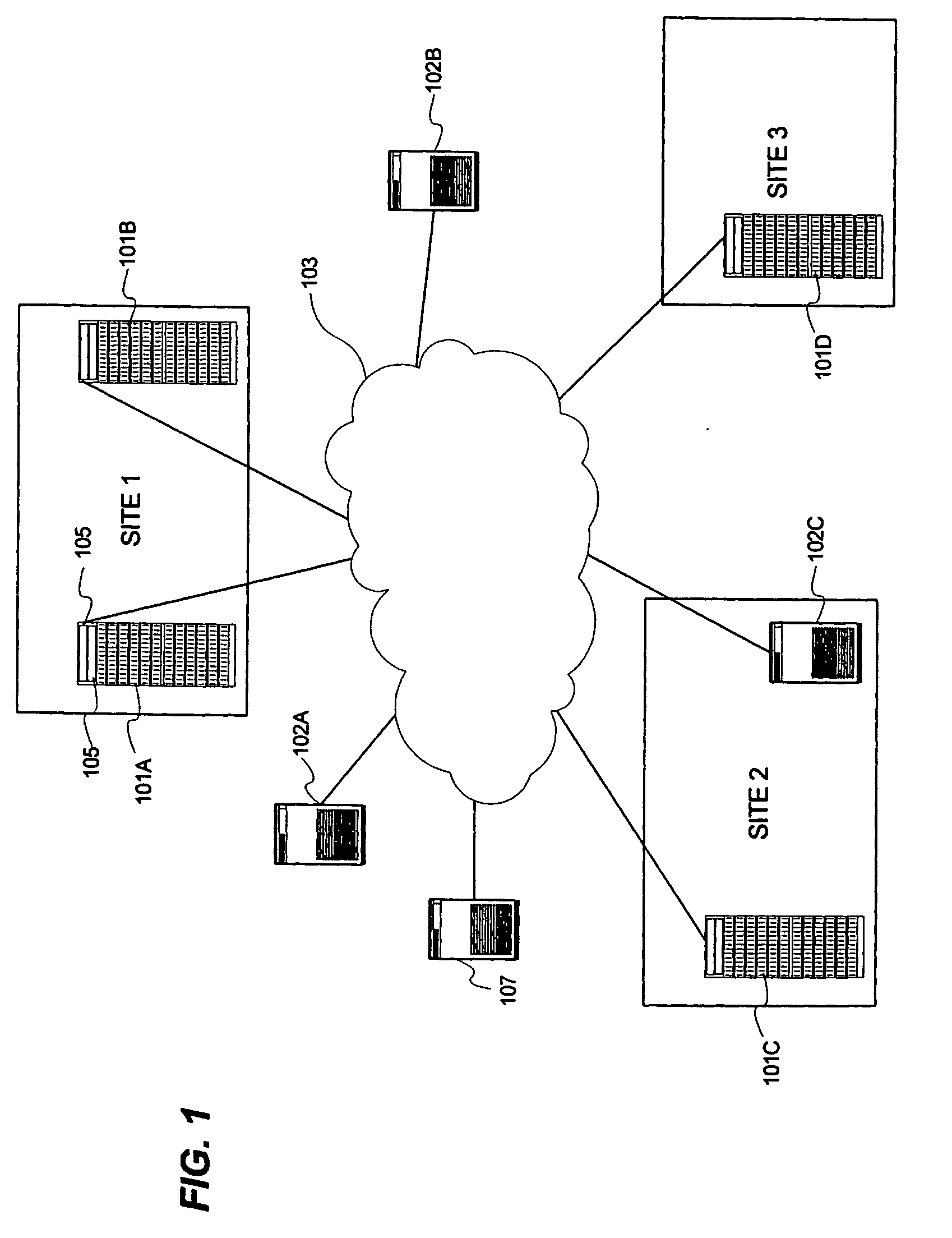
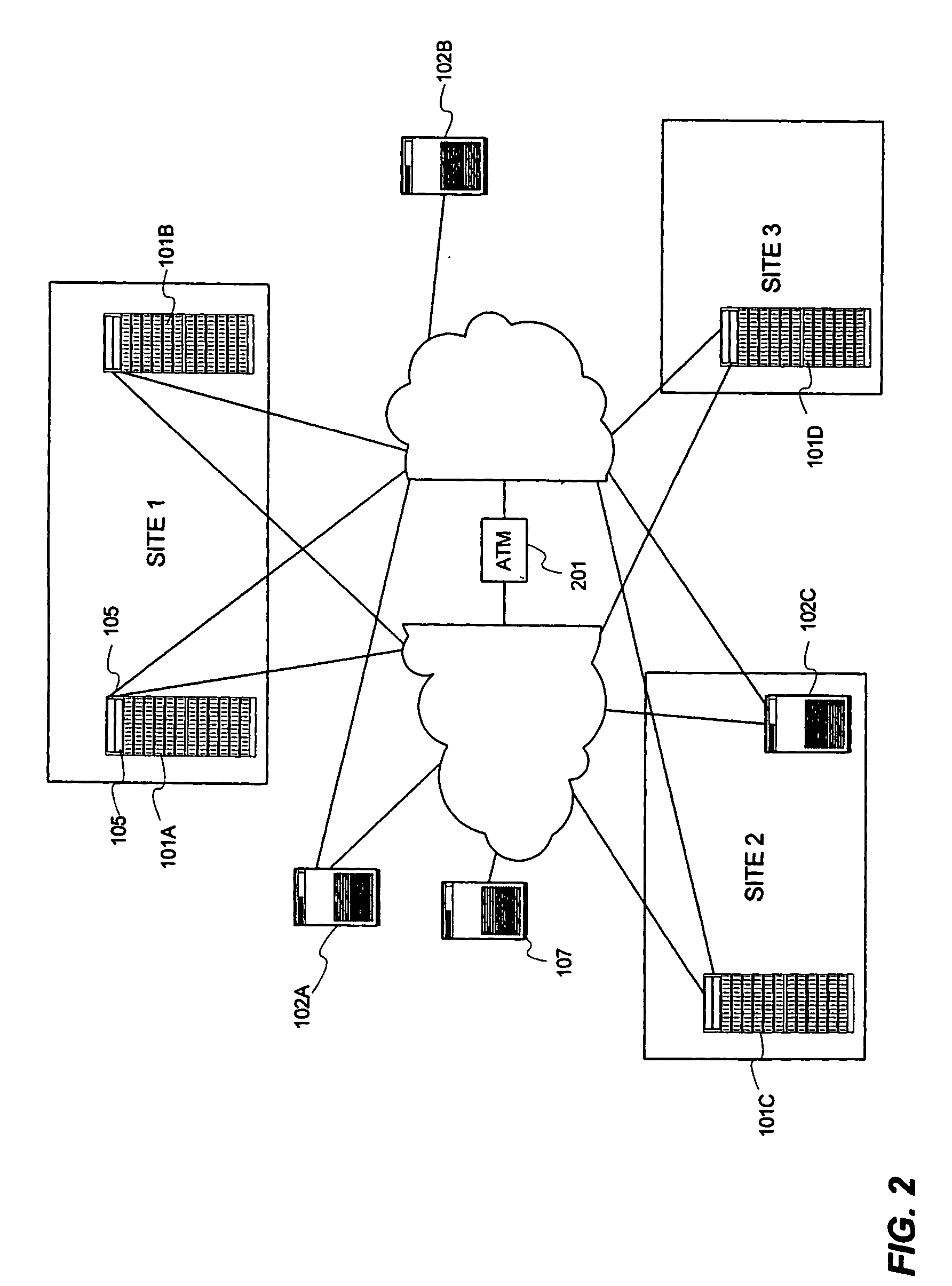
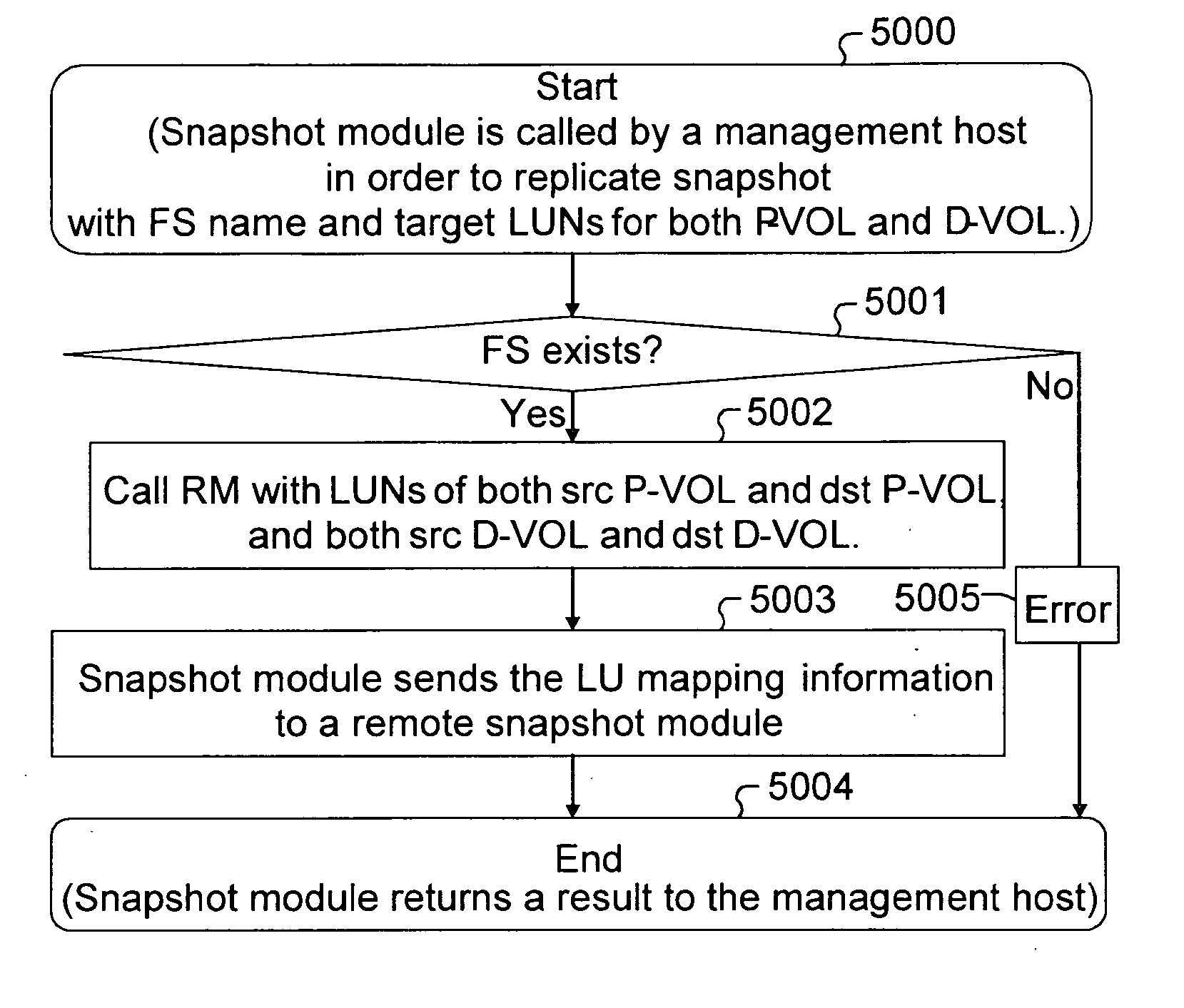
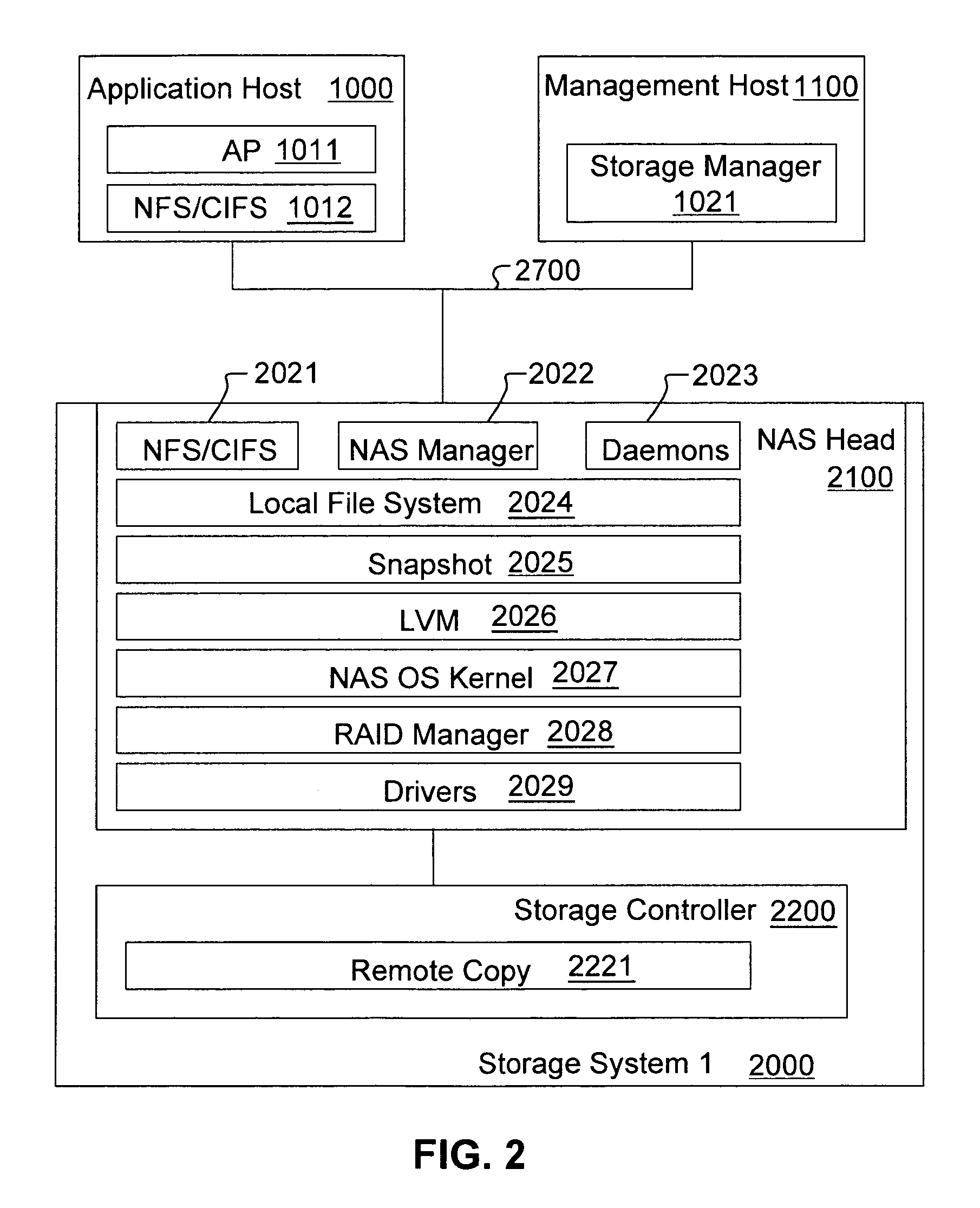
Method for replicating snapshot volumes between storage systems
An apparatus, system, and method for replicating a snapshot volume in a first storage system to a second storage system includes mapping information corresponding to data in the first storage system that is transferred from the first storage system to the second storage system so that a file system in the second storage system can mount the data after replication. Replication of the snapshot volume can be accomplished using a remote copy mechanism. The snapshot volume can be obtained from a primary source volume P-VOL and a differential source volume D-VOL. If the corresponding destination volumes are not known, a search is conducted to locate appropriate volumes in the second storage system. Mapping information regarding these destination volumes is utilized to enable the file system in the second storage system to mount the replicated snapshot volume.
Owner:HITACHI LTD
Storage device
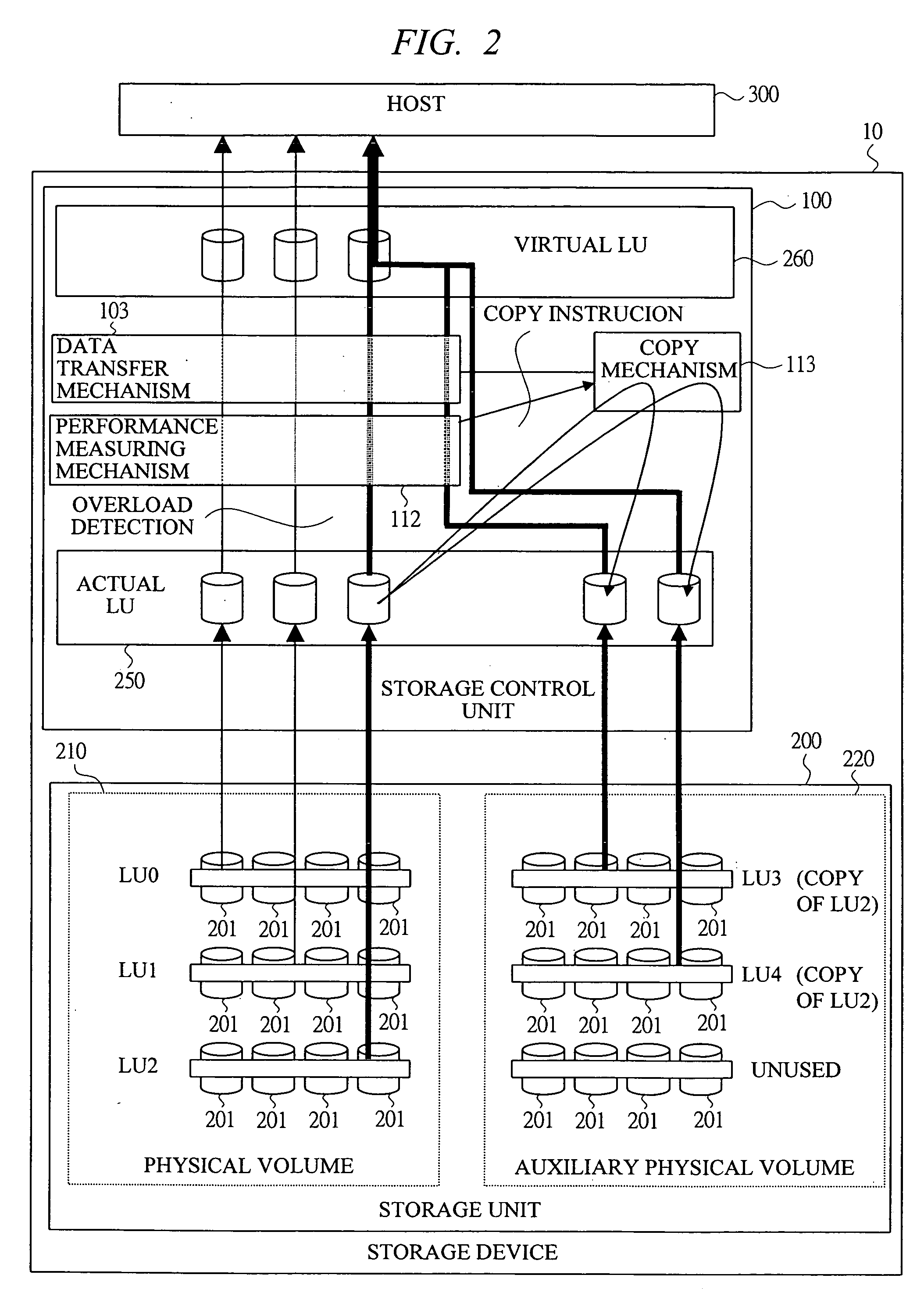
InactiveUS20060031648A1Flexible useMinimal costMemory loss protectionError detection/correctionComputer hardwareCopying mechanism
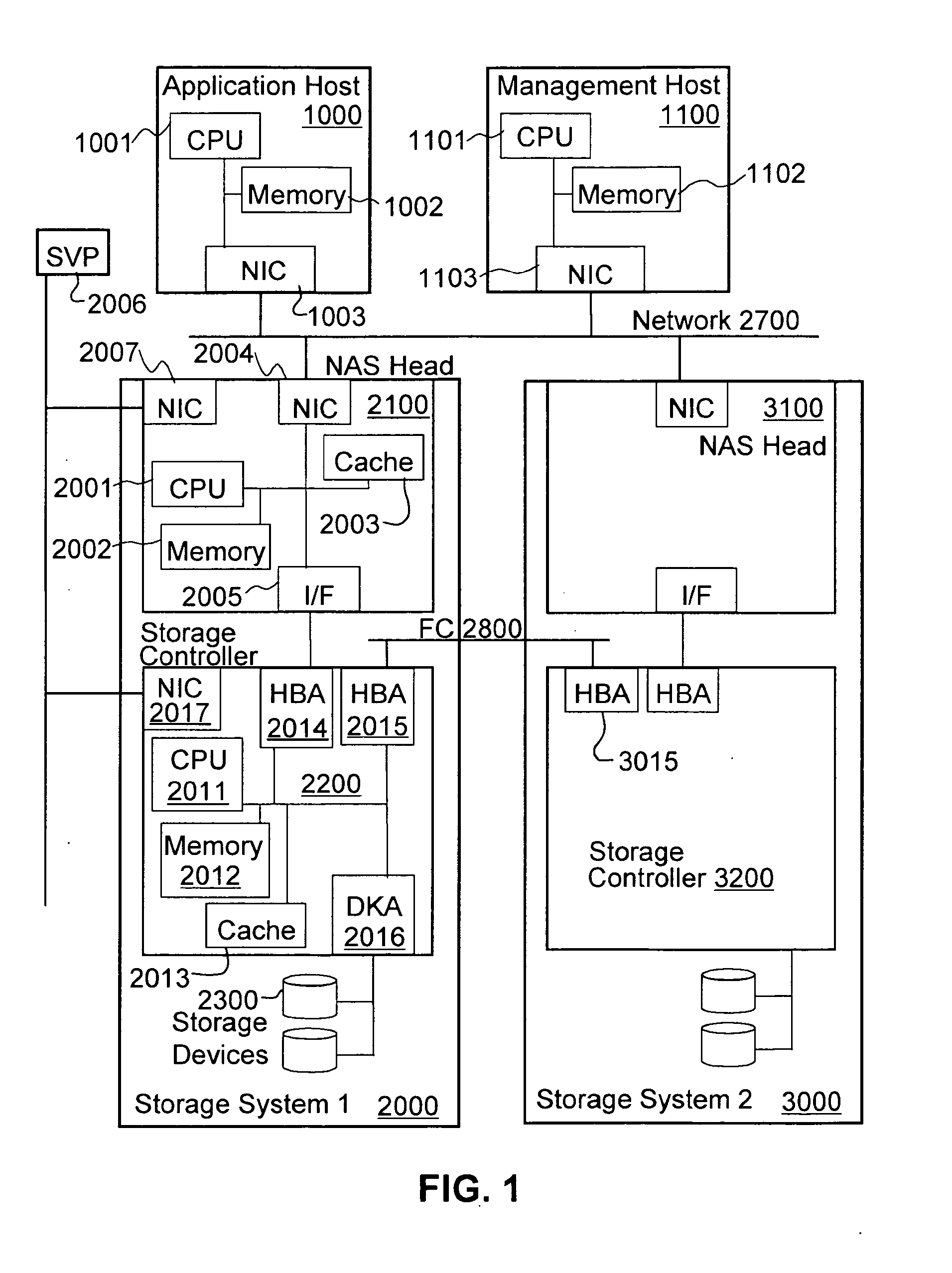
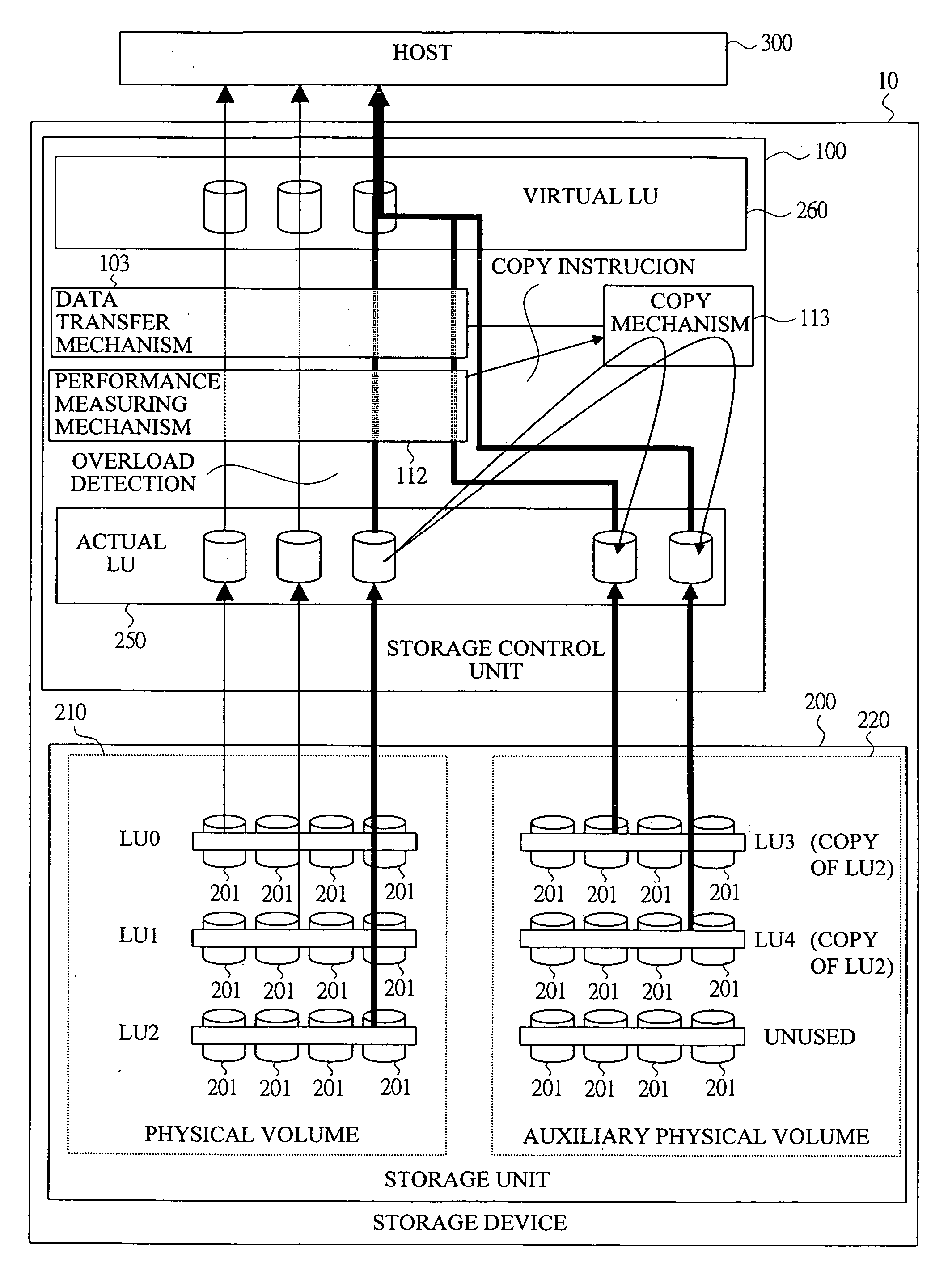
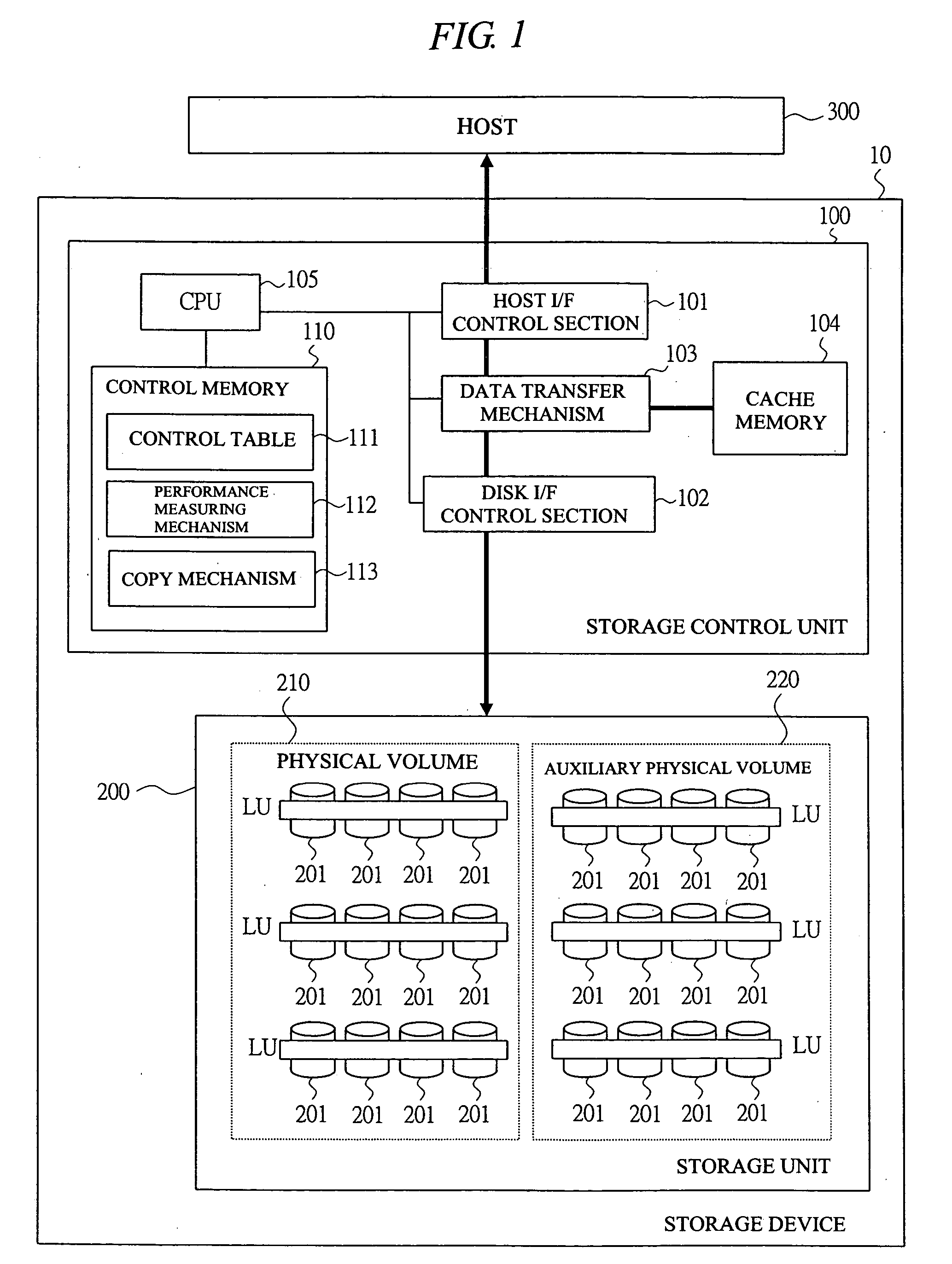
A storage device can flexibly apply a dynamic load distribution and a performance expansion to an unexpected peak performance demand changing in a time sequence such as a web server and a contents delivery at the minimum cost. In the storage device, a load condition of a logical volume is measured by a performance measuring mechanism based on a data and command processing amounts transferred by a data transfer mechanism, and contents of the logical volume set in the physical volume are copied to a logical volume set in the auxiliary logical volume by a copy mechanism based on a measurement result of the performance measuring mechanism, and the logical volume set in the auxiliary physical volume copied by the copy mechanism and the logical volume set in the physical volume serving as a copy source are provided as one virtual logical volume in a host, thereby distributing a load from the host.
Owner:HITACHI LTD
A text summarization model generation algorithm that fuses information selection and semantic association
ActiveCN109145105AReduce generationImprove semantic relevanceSemantic analysisSpecial data processing applicationsCopying mechanismSemantic association
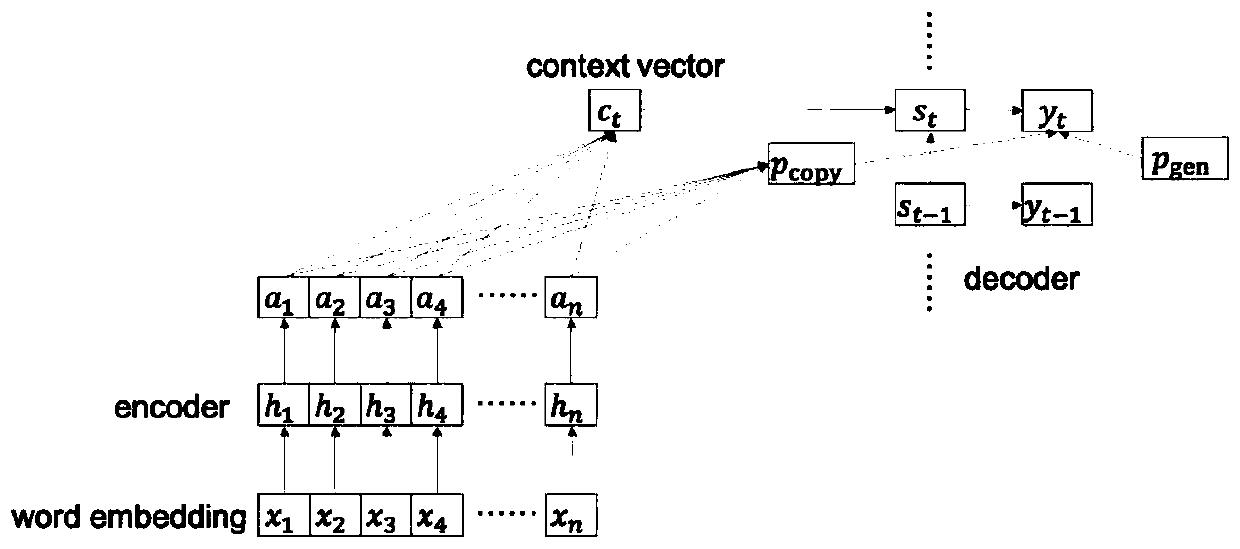
The invention relates to a text abstract model generation algorithm for fusing information selection and semantic association. Firstly, based on the Decoder model, the attention mechanism is combinedto obtain enough information of input sequence. Secondly, a copy mechanism and a coverage mechanism are used to solve the problem of non-login words and clause repetition in summary generation. Then aselective network is designed to encode the original text twice to filter the redundant information. Finally, by comparing the semantic relevance of the original text and the abstract, the semantic relevance of the abstract can be corrected, and the semantic relevance of the abstract and the original text can be enhanced.
Owner:FUZHOU UNIV
Intel e1000 zero copy method
The invention relates to a transmitting method of the data communication in a computer and is a method of direct communication through the user applying procedure and network card hardware driving procedure. The kernel and the applying layer procedure commonly share one ring-shaped memory buffering district, the memory buffering district is divided into a number of slots (can also be regarded as array which can buffer store a number of messages), and each slot buffer stores one message. The network card driving adopts a DMA method to write message into a buffering district; and the applying layer space reads data from the buffering district. When a socket connector is used for controlling the connector using zero copying mechanism, e1000 receiving message driving starts to write date into the ring-shaped buffering district, the up layer applying can directly visit the data in the ring-shaped buffering district after the socket mechanism binding the connector and getting the mapped memory.
Owner:莱克斯科技(北京)有限公司
Large scale integrated circuit test data and method for testing power consumption cooperate optimization
InactiveCN101158706AReduce test power consumptionGuaranteed reliabilityElectronic circuit testingTest powerTest set
The invention relates to a method collaborating and optimizing the test data and the power consumption of testing large scale integrated circuits. The method relates to the technical field of the large scale integrated circuits and is proposed to resolve the problem that in the prior art of SOC test, no method is available to effectively reduce the test data and the power consumption of test at the same time. The method has the following steps: the compatibility of scanning units of the circuit is analyzed and accordingly the scanning units are classified into three categories; each category of scanning units are connected respectively, and a scanning chain with copying mechanism is built; a set of test vector is adjusted according to the new scanning chain structure; the test set is compressed by the method based on the compression of repeated data and a compressed test set TE is acquired. When in the testing process, the compressed data is fully recovered by a decompression circuit to be tested. The invention discloses a design method for the testability of integrated circuits, and reduces the power consumption of circuits in the testing process, thus ensuring the reliability and testability; furthermore, the invention can effectively reduce the quantity of test data, shorten the test process, and lessen the number of ATE channels.
Owner:HARBIN INST OF TECH
Loading internal applications on a smartcard
ActiveUS20060214005A1High write/erase performanceReducing or eliminating the circuitous copying of codeAcutation objectsLink editingCopying mechanismSmart card
Portable smartcard devices, methods of executing program code using smartcard devices, and computer readable storage media including instructions for smartcard devices are provided. According to some embodiments, the presently disclosed smartcard device includes an interface for presenting smartcard functionality to a host system and for receiving a program execution command from the host system, non-volatile memory, executable memory, a copying mechanism such as an internal copying mechanism for copying program code from the non-volatile memory to the executable memory, and a program execution mechanism for executing the program code. Appropriate interfaces include but are not limited to ISO 7816 compatible interfaces, USB interfaces, and MMC interfaces. In some embodiments, the smartcard functionality includes SIM functionality and / or USIM functionality. Optionally, execution of the program code commences when only a portion of the copied executable code resides in the executable memory. A method of delivering pre-loaded protected executable code to smartcard users is disclosed.
Owner:WESTERN DIGITAL ISRAEL LTD
Method for replicating snapshot volumes between storage systems
An apparatus, system, and method for replicating a snapshot volume in a first storage system to a second storage system includes mapping information corresponding to data in the first storage system that is transferred from the first storage system to the second storage system so that a file system in the second storage system can mount the data after replication. Replication of the snapshot volume can be accomplished using a remote copy mechanism. The snapshot volume can be obtained from a primary source volume P-VOL and a differential source volume D-VOL. If the corresponding destination volumes are not known, a search is conducted to locate appropriate volumes in the second storage system. Mapping information regarding these destination volumes is utilized to enable the file system in the second storage system to mount the replicated snapshot volume.
Owner:HITACHI LTD
Docker container-oriented online migration system implementation and optimization method
ActiveCN110119377ARealize online migrationGuaranteed reliabilityFile system administrationSoftware simulation/interpretation/emulationFile systemCopying mechanism
The invention provides an online migration system implementation and optimization method for a Docker container. The online migration system realization and optimization method at least comprises thefollowing steps: determining an integrated collection mechanism of mirror image layer data based on different container file systems and parent-child relationships between mirror image layers thereofso as to complete integrated collection of the mirror image layer data; determining the latest version of the mirror image layer data based on a Diff command between the parent mirror image layer andthe child mirror image layer, and realizing transmission of the latest version of the mirror image layer data between the source machine container and the target machine container to complete iteration synchronization of the mirror image layer data; realizing iterative synchronization of memory in accordance with the implementation of the Pre-Copy mechanism; and executing container recovery operation of the target machine container under the condition that the iteration synchronization of the mirror image layer data and the memory is completed.
Owner:HUAZHONG UNIV OF SCI & TECH
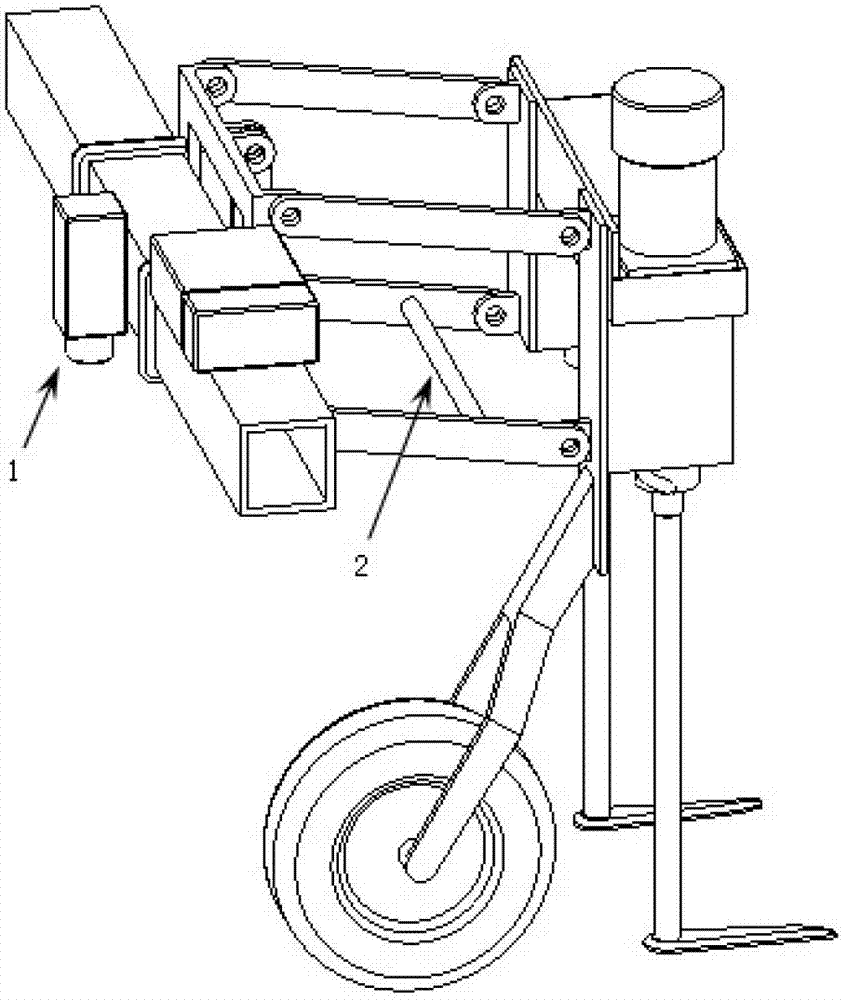
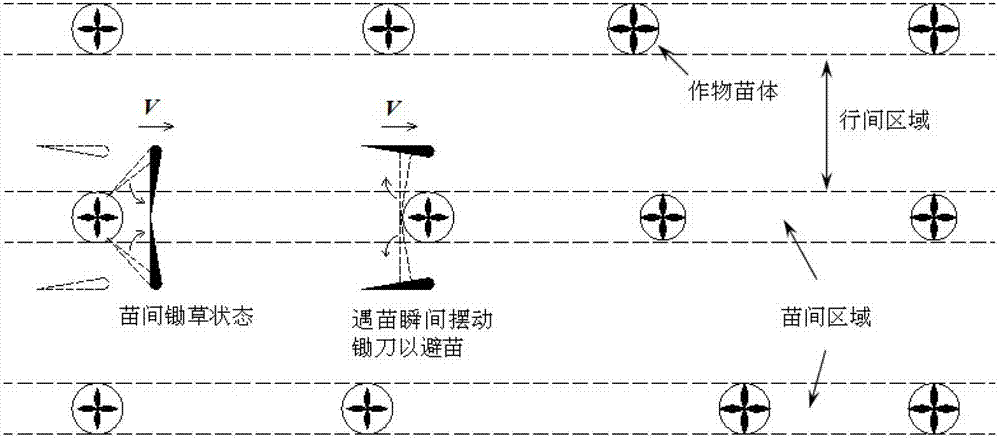
Swinging type intelligent inter-seedling hoeing machine and tool unit
InactiveCN103081597AEffective excisionQuickly avoid seedlingsSoil-working equipmentsMachine visionControl system
The invention relates to fine work agricultural equipment, in particular to a swinging type intelligent inter-seedling hoeing machine and tool unit. The swinging type intelligent inter-seedling hoeing machine and tool unit comprises a machine vision servo control system, a swinging type inter-seedling hoeing system and a ground copying mechanism. According to the swinging type intelligent inter-seedling hoeing machine and tool unit, the seedling damaging rate is greatly reduced, and mechanized elimination of inter-seedling weeds is achieved without plant seedlings damaged.
Owner:CHINA AGRI UNIV
Handhold wide-narrow row rice transplanting machine with seedling box partition plates of unequal spaces
InactiveCN101803502ARealize wide and narrow row transplanting operationReduce design costTransplantingDrive wheelCopying mechanism
The invention discloses a handhold wide-narrow row rice transplanting machine with seedling box partition plates of unequal spaces. The rice transplanting machine comprises an engine, a ground copying mechanism, two driving wheel systems, a seedling claw moving mechanism, a seedling box moving mechanism and a handhold operating system. The seedling box with partition plates of unequal spaces of the invention only needs one set of screw shaft mechanism for feeding the seedling transversely when the ratio of the spaces of the wide and narrow rows of the rice transplanting machine is not integral multiple, thereby greatly simplifying the seedling feeding mechanism. The screw shaft mechanism for feeding the seedling transversely of the invention is the same as that of the rice transplanting machine of equal space in terms of principle and structure so as to greatly reduce the design and manufacturing costs of the wide-narrow row rice transplanting machine; and because the size and shape of the middle partition plate of the seedling box are the same as those of other partition plates, the cost for manufacturing the partition plate mould is reduced.
Owner:ZHEJIANG SCI-TECH UNIV
Data relocation in a memory system
The on-chip copy process is extended so that the data may be copied between two blocks that may be on different chips, different planes on the same chip, or the same plane of the same chip. More specifically, the methods described here provide a single data copying mechanism that allows data to be copied between any two locations in a memory system. An exemplary embodiment uses an EDO-type timing. According to another aspect, selected portions of the relocated data, such as chosen words in a transferred page, can be updated in the controller on the fly. In addition to transferring a data set directly from a read buffer of a source array to a write buffer of a destination array, the data set can concurrently be copied, if desired, into the controller where an error detection and correction operation can be performed on it.
Owner:SANDISK CORP
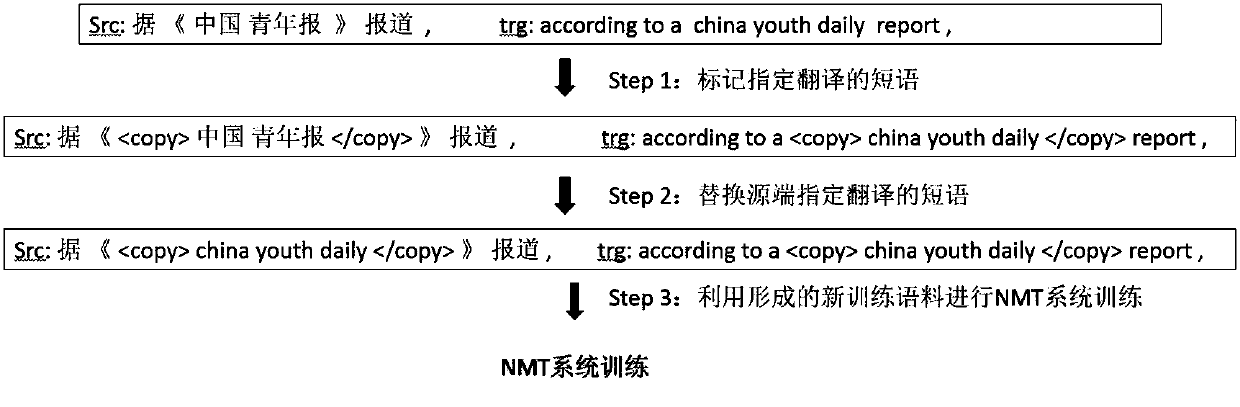
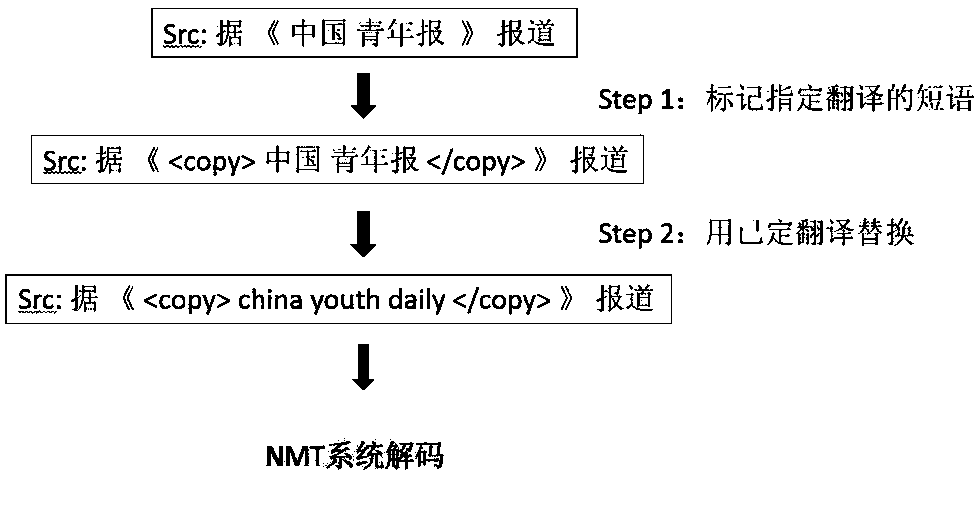
Neutral machine translation method with copy mechanism
ActiveCN108132932AAchieve replicationEnsure consistencyNatural language translationSpecial data processing applicationsEncoder decoderCopying mechanism
The invention relates to a neutral machine translation method with a copy mechanism. The method is applied to an NMT model based on an attention mechanism and adopting an encoder-decoder framework. The method includes the steps that source phrases needing to be translated specifically and corresponding target phrases are marked in a source language and a target language in original training sentences; the source phrases, needing to be translated specifically, in the source language in the original training sentences are replaced with the corresponding target phrases in the target language in the original training sentences; the processed original training sentences are subjected to training of an NMT system; phrases needing to be translated specifically are marked in the to-be-translated source sentences. By means of the neutral machine translation method with the copy mechanism, specific phrases such as person names, place names, mechanism names and brand names can be well translated,the method can be compatible with any corpus processing technology, the translation effect is further improved, the structure of the NMT system does not need to be changed, and the method can be conveniently applied to any NMT system.
Owner:SUZHOU UNIV
Loading internal applications on a smartcard
ActiveUS7243856B2Reducing or eliminating the circuitous copying of codeEliminate needAcutation objectsLink editingCopying mechanismSmart card
Portable smartcard devices, methods of executing program code using smartcard devices, and computer readable storage media including instructions for smartcard devices are provided. According to some embodiments, the presently disclosed smartcard device includes an interface for presenting smartcard functionality to a host system and for receiving a program execution command from the host system, non-volatile memory, executable memory, a copying mechanism such as an internal copying mechanism for copying program code from the non-volatile memory to the executable memory, and a program execution mechanism for executing the program code. Appropriate interfaces include but are not limited to ISO 7816 compatible interfaces, USB interfaces, and MMC interfaces. In some embodiments, the smartcard functionality includes SIM functionality and / or USIM functionality. Optionally, execution of the program code commences when only a portion of the copied executable code resides in the executable memory. A method of delivering pre-loaded protected executable code to smartcard users is disclosed.
Owner:WESTERN DIGITAL ISRAEL LTD
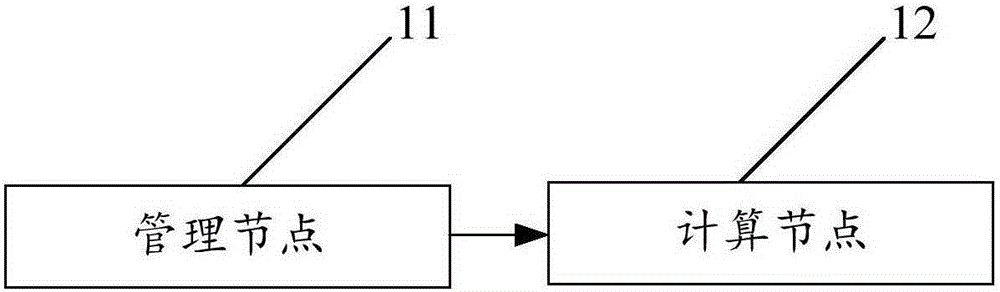
Memory system
InactiveCN105224256AProcessing speedShorten the timeInput/output to record carriersSpecial data processing applicationsCopying mechanismPerformance computing
The present invention discloses a memory system. The memory system comprises a management node and at least one computing node, wherein the management node comprises a shared directory; the shared directory is shared to each computing node via NFS (Network File System); the shared directory is mounted in each of the computing node; and each of the computing node stores calculation log information generated in operation of high-performance computing of FVCOM into the shared directory, or reads the needed calculation log information in the shared directory. Compared to the prior art, the memory system provided by the application does not need to store the generated calculation log information into a storage node of a copy mechanism and perform other calculations, but directly stores the calculation log information in the shared directory shared by the NFS and reads the needed calculation log information in the shared directory, thereby significantly increasing processing speed of the calculation log information, further shortening time and improving system performance.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
System and method for operating system image provisioning in a utility computing environment
A technique to provision an OS image during a boot-up of a computing server in a utility computing environment using disk array's inherent raw concurrent multi-disk copy mechanism. In one example embodiment, this is achieved by forming a pool of OS image boot-up disks in a disk array using the disk array's internal disk copy routine. An OS image boot-up disk is assigned from the pool of OS image boot-up disks to the computing server upon receiving a request from the computing server. The OS image is then received from the assigned OS image boot-up disk. The computing server then boots-up using the received OS image and runs one or more applications residing in the computing server.
Owner:VALTRUS INNOVATIONS LTD +1
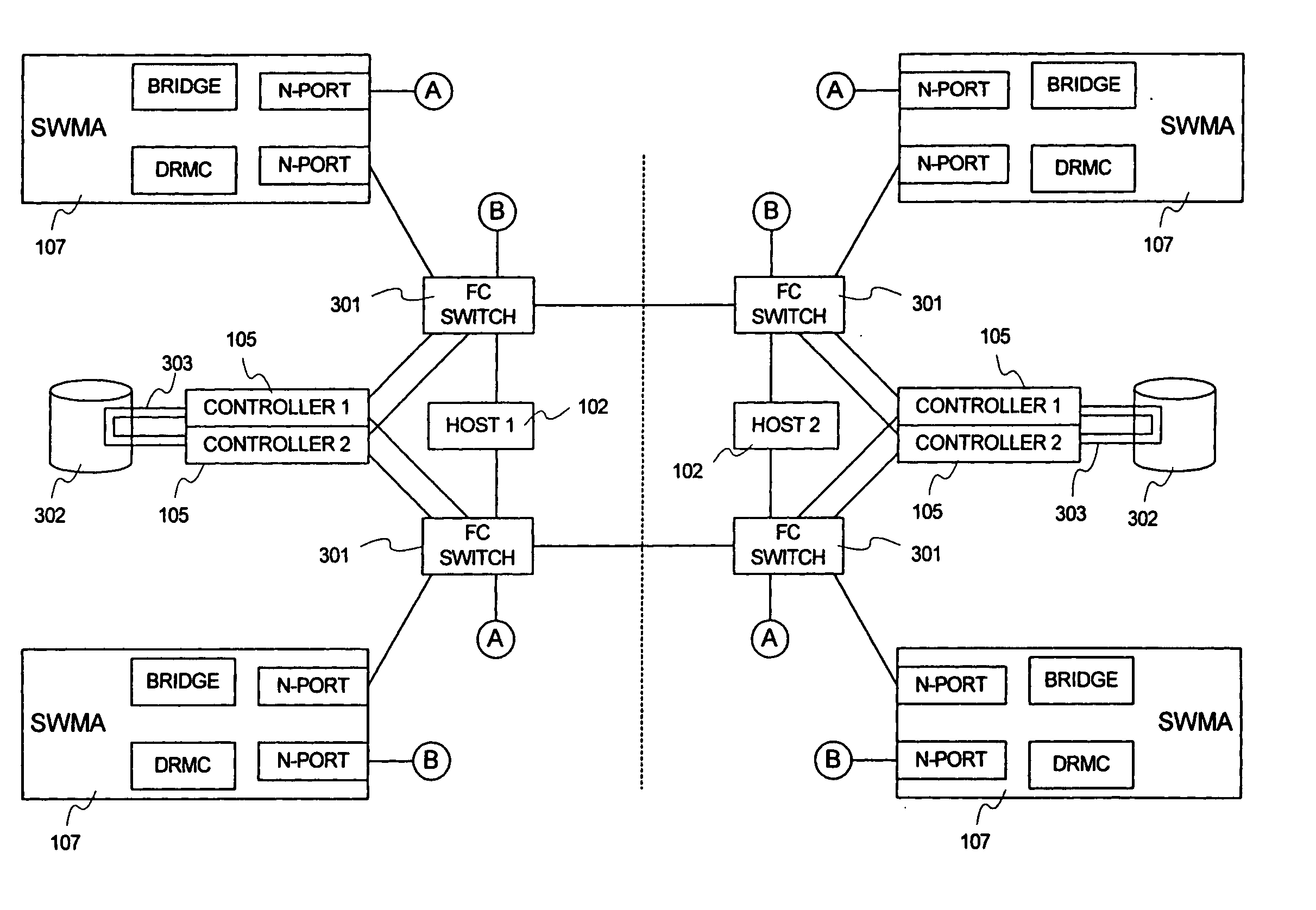
Reliable replication mechanisms based on active-passive hfi protocols built on top of non-reliable multicast fabric implementations
ActiveUS20170093756A1Special service provision for substationSignal allocationCopying mechanismReliable multicast
Methods, apparatus, and systems for reliable replication mechanisms based on active-passive HFI protocols build on top of non-reliable multicast fabric implementations. Under a first hardware-based scheme, a reliable replication mechanism is (primarily) implemented via Host Fabric Interfaces (HFIs) coupled to (or integrated in) nodes coupled to a non-reliable fabric. Under this approach, the HFIs take an active role in ensuring reliable delivery of multicast messages to each of multiple target nodes. Under a second hybrid software / hardware scheme, software running on nodes is responsible for determining whether target nodes have confirmed delivery of multicast messages and sending retry messages for cases in which delivery is not acknowledged within a timeout period. At the same time, the HFIs on the target nodes are responsible for generating reply messages containing acknowledgements rather than software running on the target nodes.
Owner:INTEL CORP
Interplant monomer between ridges with bidirectional profile modeling function
InactiveCN101248716ADoes not affect growthDoes not affect harvestSpadesSoil-working equipmentsCopying mechanismAgricultural engineering
An inter-planting and seeding single body with bilateral copying function belongs to agricultural machinery. A vertical four-bar copying mechanism is hinged on a horizontal four-bar copying mechanism; a single body beam frame is welded and hinged on the vertical four-bar copying mechanism; an assembly of fertilizer can and fertilizer feed, an assembly of seed can and seeding mechanism, a drive ground wheel, a welded fertilizer pipe mounting frame, a deep soil loosening and covering spade and a press wheel are welded and mounted on the single body beam frame; a rigid fertilizer pipe and a rigid seed spout are mounted on the welded fertilizer pipe mounting frame in an inserted manner; a fertilizer and seed furrow opener is mounted on the rigid fertilizer pipe. The single body is particularly applicable to winter wheat inter-planting and fertilizing operations in the fields where leguminous crops are still unripe and have not been harvested yet, thereby satisfying the operation of winter wheat production in extremely code regions. The single body is characterized in novel structure, good operational quality, reliable use, high efficiency and strong adaptability.
Owner:NORTHEAST AGRICULTURAL UNIVERSITY
Apparatus and method for implementing dynamic structure level pointers
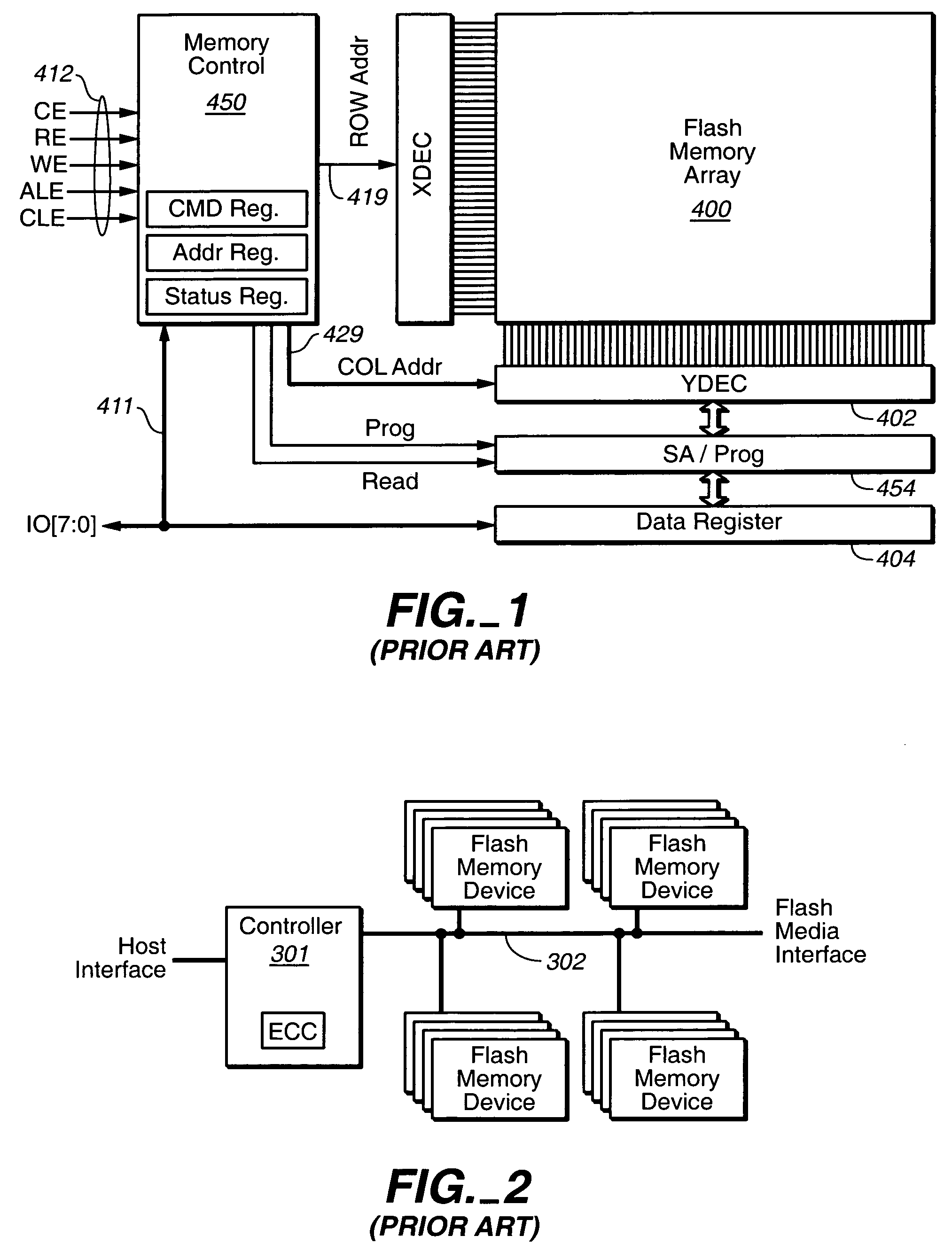
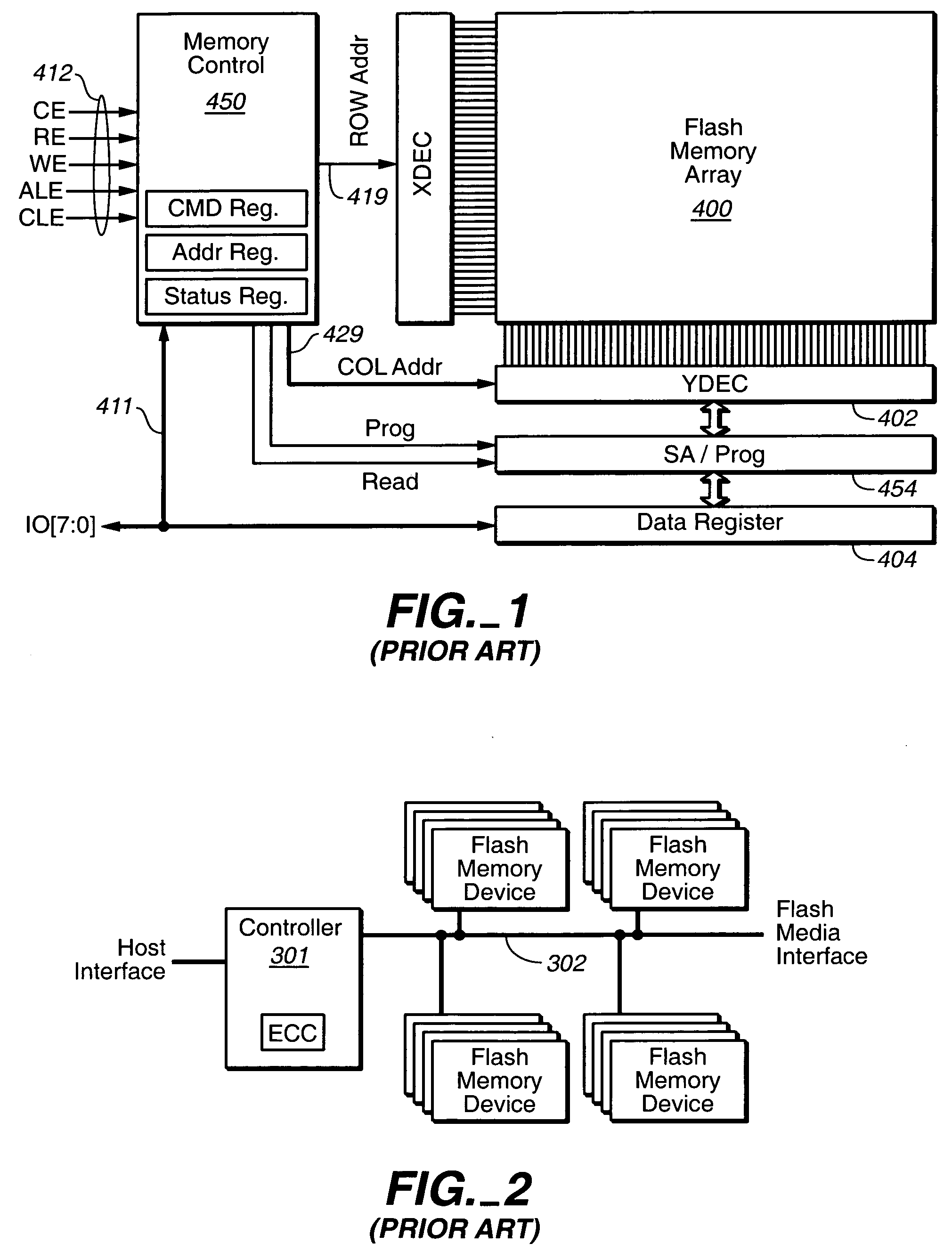
InactiveUS7073038B2Data processing applicationsInput/output to record carriersLevel structureCopying mechanism
An apparatus and method for implementing structure level pointers in a data storage system are provided. With the apparatus and method, a compound pointer system is provided in which fixed level pointers are augmented with associated pointers to metadata describing lower level structures. The companion metadata describes these lower level structures in a manner independent of the actual data stored within the lower level structures. With such an enhanced compound pointer system, an instant copy mechanism can process the pointers to the underlying structures and take instant copies of much finer detail. This allows individual records of data to be represented by the pointer system without having the overhead of carrying a pointer to all the individual records. The instant copy mechanism not only copies the fixed level pointers, but resolves the companion pointers to individual subsets of a general granularity for the instances of the instant copy domains.
Owner:ORACLE INT CORP
Data compression engine and method used for big data storage system
ActiveCN107463606ALower latencyReduce in quantityFile access structuresSpecial data processing applicationsData compressionDistributed File System
The invention puts forward a data compression engine and method used for a big data storage system. An access popular degree level to which each small file belongs is judged by aiming at mass small files in an HDFS (Hadoop Distributed File System), and a metadata table copy mechanism and a retrieval process number mechanism corresponding to each access popular degree level are set, wherein the small file with a high popular degree level is not compressed and combined; the small file with a medium popular degree level is imported and combined but is not compressed; and the small file with a low popular degree level is imported, combined and compressed, the small file of the same source are combined into a bigger file structure, and data compression is carried out. In addition, a resident access task is established by aiming at the small file with the high popular degree level, and therefore, a low efficiency phenomenon brought in a way that the access task is frequently set and recovered is avoided.
Owner:ZHEJIANG LISHI TECH
Anti-copy method for embedded device program
ActiveCN105260627AAchieve protectionSimple methodProgram/content distribution protectionPasswordCopying mechanism
The invention relates to an anti-copy method for an embedded device program. The method comprises: firstly, storing an embedded device ID and License information in a hidden region, and reading device ID information to an RAM region from the hidden region after the device program performs authorization; secondly, calculating the License information according to the read device ID information and an authorization algorithm; and finally, comparing the calculated License information with the License information in the hidden region, and if the calculated License information is the same as the License information in the hidden region, the program entering a running state, or otherwise, performing authorization requesting. According to the method, the ID and the License are stored in the hidden region and technically protected, and the program is subjected to authorization management through the ID and the License; and the program stealer does not have a password, so that the hidden region cannot be accessed, data copy also cannot be realized, and further the program is protected. The method is simple and feasible, and can effectively protect an authorization process only by processing a storage mechanism of the ID and the License information without the need for complex encryption and decryption of the algorithm and addition of an anti-copy mechanism in a process and a thread.
Owner:XUJI GRP +3
Neural problem generation method for improving correlation
ActiveCN110263143AHigh overlapImprove relevanceDigital data information retrievalNatural language data processingAlgorithmCopying mechanism
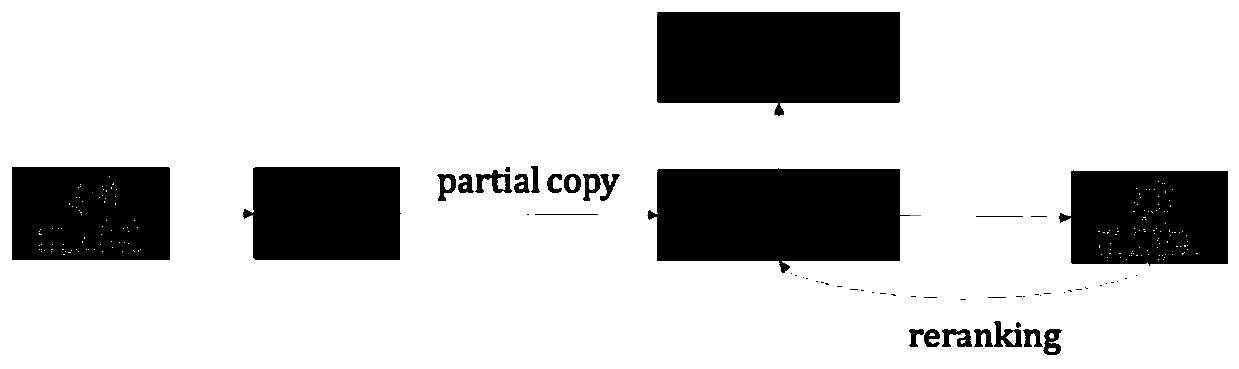
The invention discloses a neural problem generation method for improving correlation. The neural problem generation method for improving correlation comprises the steps: enabling a QG model based on seq2seq to be composed of an encoder layer and a decoder layer, and adding an attention mechanism and a copy mechanism; and providing a partial copy mechanism based on character overlapping. The method has the beneficial effects that through a partial copy mechanism based on the character overlap degree, the word level and the input document in the generated problem have higher overlap degree and correlation. Through a QA model-based reordering mechanism, higher scores can be given to the generated candidate questions with better quality, and the common questions difficult to answer can be filtered out.
Owner:SUZHOU UNIV
Coating unit and pattern correcting device equipped therewith
InactiveCN102049366ASpeed up the descentLiquid surface applicatorsSemiconductor/solid-state device manufacturingCopying mechanismBiomedical engineering
The invention provides a coating unit and a pattern correcting device equipped with the coating unit, wherein the yielding of a pre-sprayed member and the decrease of a coating element are quickly performed by a simple structure.The coating unit (19) comprises a driving device (47).A pre-sprayed board (36) is inserted between a coating part (20) and a substrate (1) by the driving device (47) during the pre-spraying operation.When the pre-spraying operation is finished, the pre-sprayed board (36) yields out of the intermediate of the coating part (20) and the substrate (1).The coating unit also comprises an X table (43) (copying mechanism).The coating part (20) is lifted along with the insertion of the pre-sprayed board (36) and is lowered along with the yielding of the pre-sprayed board (36) by the X table (43).Therefore, the yielding of the pre-sprayed member and the decrease of the coating element are quickly performed by a simple structure.
Owner:NTN CORP
Repressive force control apparatus for wheeled repression device
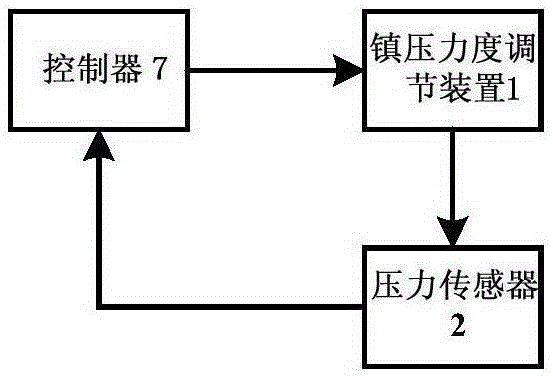
InactiveCN105165186AEnsure consistencyPlantingFurrow making/coveringHydraulic cylinderCopying mechanism
The present invention discloses a repressive force control apparatus for wheeled repression device. The control apparatus comprises a pressure sensor, a controller, and a repressive force adjustment device comprising a solenoid valve and a hydraulic oil cylinder. The control apparatus can solve the problems of poor repressive force consistency and uneasy control of the adjustment of poor repressive force value due to poor adaptability of mechanical copying mechanism to earth surface irregularities.
Owner:BEIJING RES CENT OF INTELLIGENT EQUIP FOR AGRI
Safety overlay network constructing method of ciphertext full text search system and corresponding full text search method
ActiveCN102855292ASafe and efficient dynamic updateSafe and efficient creationSpecial data processing applicationsFull text searchCiphertext
The invention relates to a safety overlay network constructing method of ciphertext full text search system and a corresponding full text search method. The invention initially provides a safety overlay network concept used for peer-to-peer full test search, solves the problems of distribution, storage and search of massive ciphertext data index files under the premise that recall ratio and precision ratio are not influenced, realizes storage and search of massive data to peer-to-peer nodes of a distributed P2P (peer-to-peer) network and introduces an index file duplicate copying mechanism based on a pivot node, wherein the mechanism ensures that resource can be rapidly obtained by searches in different directions by virtue of a duplicate of the pivot node without increasing occupation of network bandwidth, so that the safety overlay network constructing method and the corresponding full text search method disclosed by the invention are more applicable to peer-to-peer full text search when information amount is large, and efficiency of full text search under the peer-to-peer network environment is further improved.
Owner:GUANGXI UNIV
Milling machine for shaft lever of camshaft of general machinery
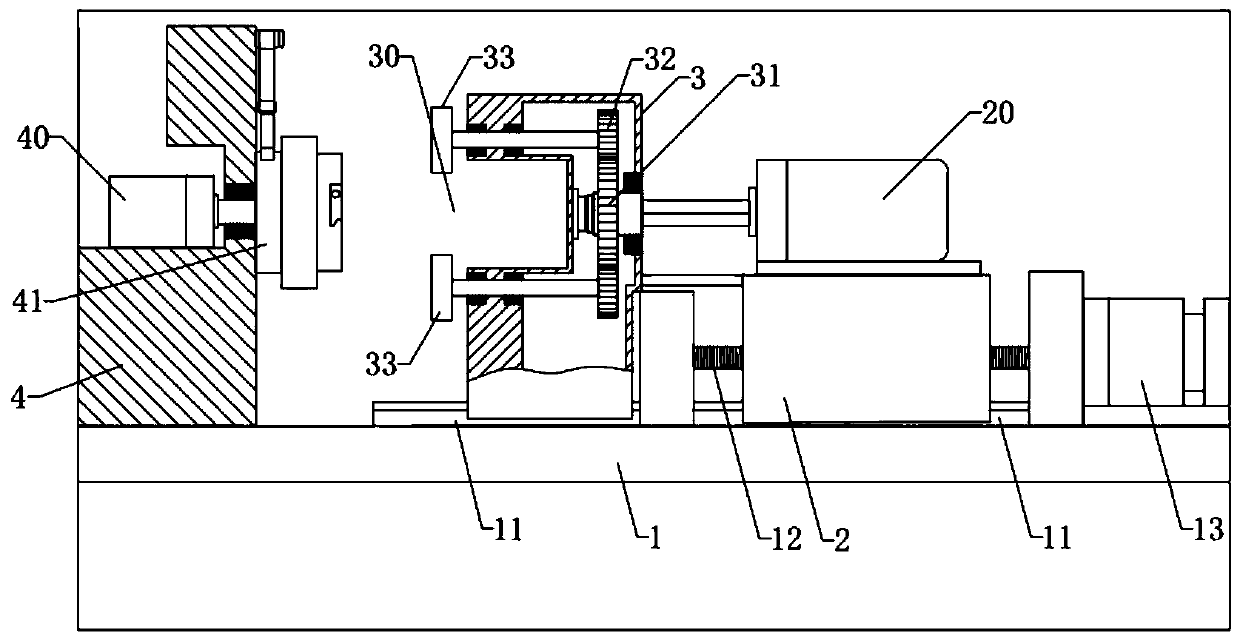
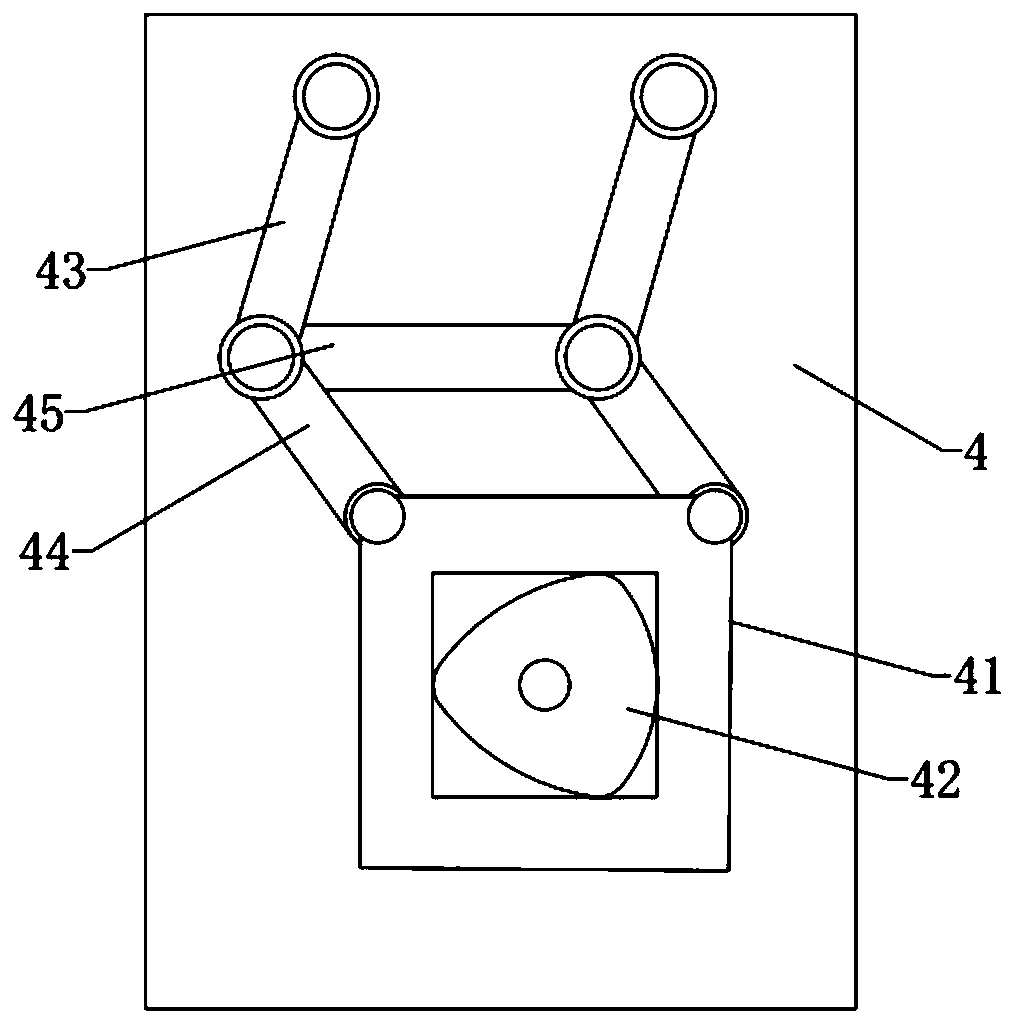
InactiveCN110576208AReduce wear rateReduce the number of round tripsCopying process control systemsMilling equipment detailsMilling cutterCopying mechanism
The invention relates to the technical field of machining equipment, in particular to a milling machine for a shaft lever of a camshaft of general machinery. The milling machine comprises a machine table and a worktable fixed to the machine table. A slide is movably connected to the machine table through a translation mechanism, a main motor is fixed to the slide, the main motor is connected to atool assembly, the tool assembly comprises a plurality of milling cutters driven by the main motor, and the milling cutters are arranged in a polygonal shape; the worktable is connected to a workpieceseat through a copying mechanism, the copying mechanism can drive the workpiece seat to move along a polygonal path, the workpiece seat is connected to a clamping seat, a plurality of clamping holesfor clamping camshafts are formed in the clamping seat, and the clamping holes as with the milling cutters are arranged in a polygonal shape. According to the scheme, the camshafts move along the polygonal path and lean against the milling cutters in the moving process to be milled, so that the camshafts can be machined at one time, and therefore, a problem of manual misoperation and high structural wear as a result of many roundtripping numbers of times of tool feeding and tool retracting in shaft lever milling in the prior art is solved.
Owner:重庆九方铸造有限责任公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com