Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "Compliance analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Compliance analysis involves auditing, organizing, and processing information and documents in order to ensure legal compliance. Potential job titles in the compliance analysis field include paralegal, occupational health and safety specialist, and building inspector.
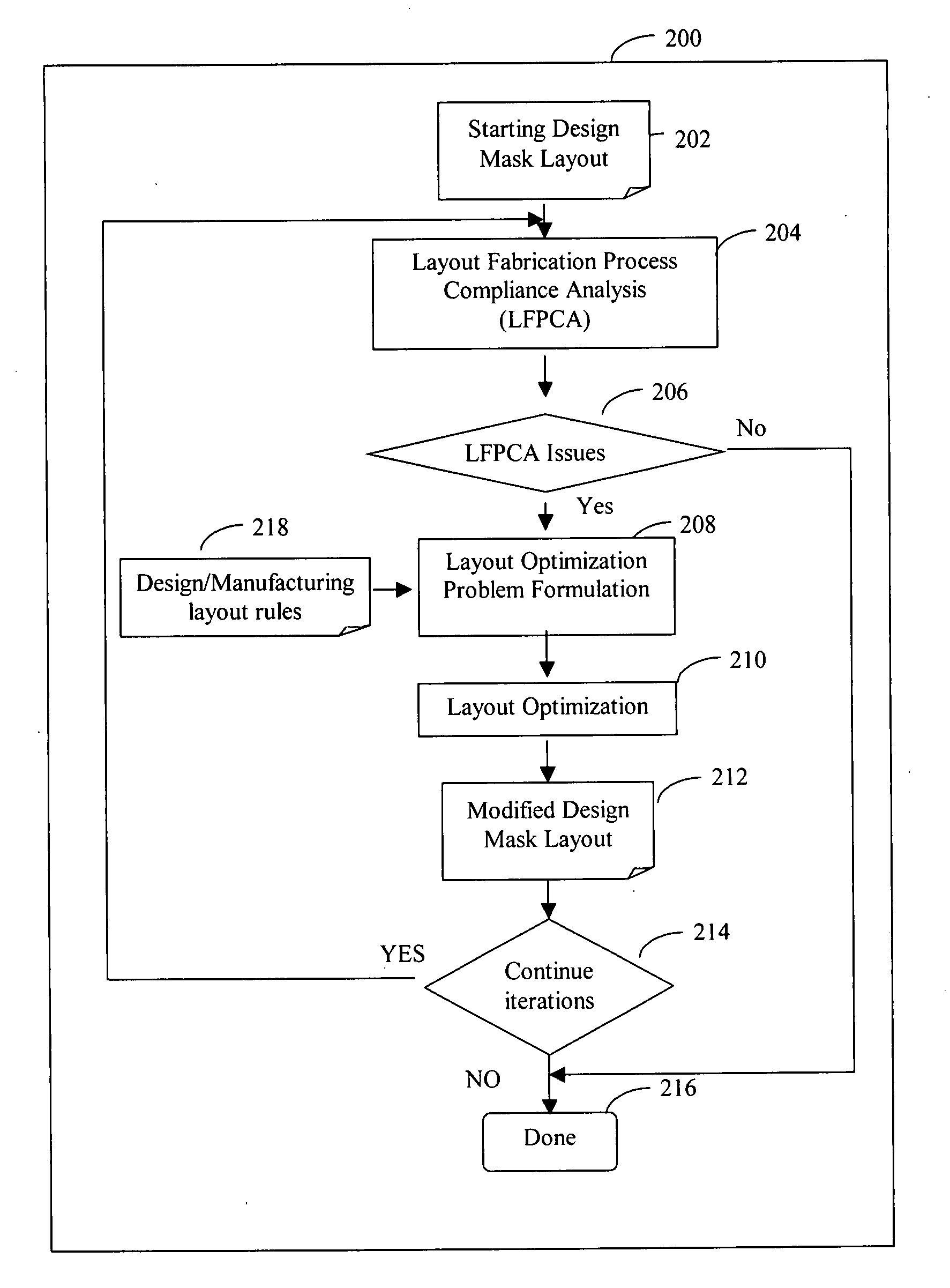
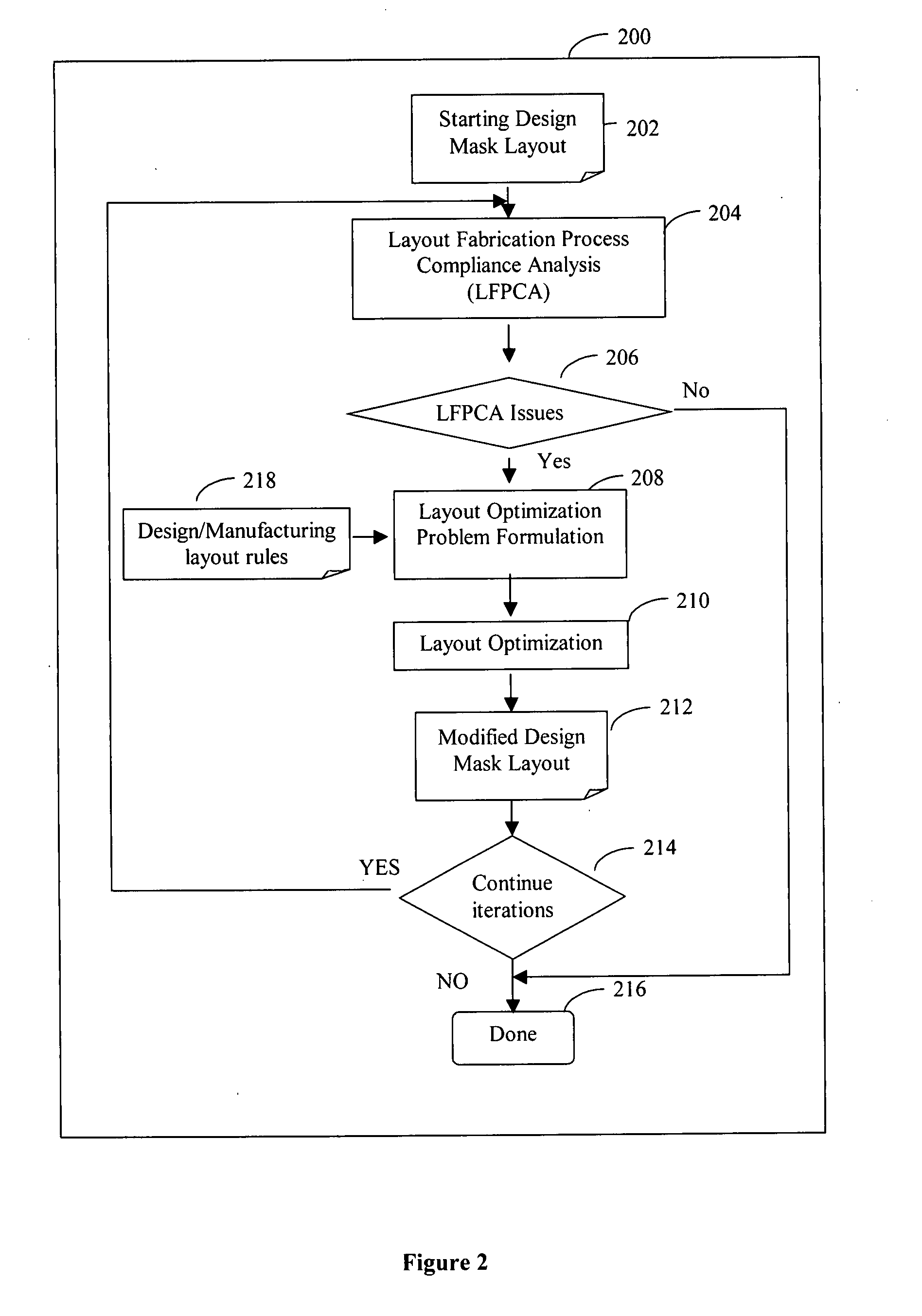
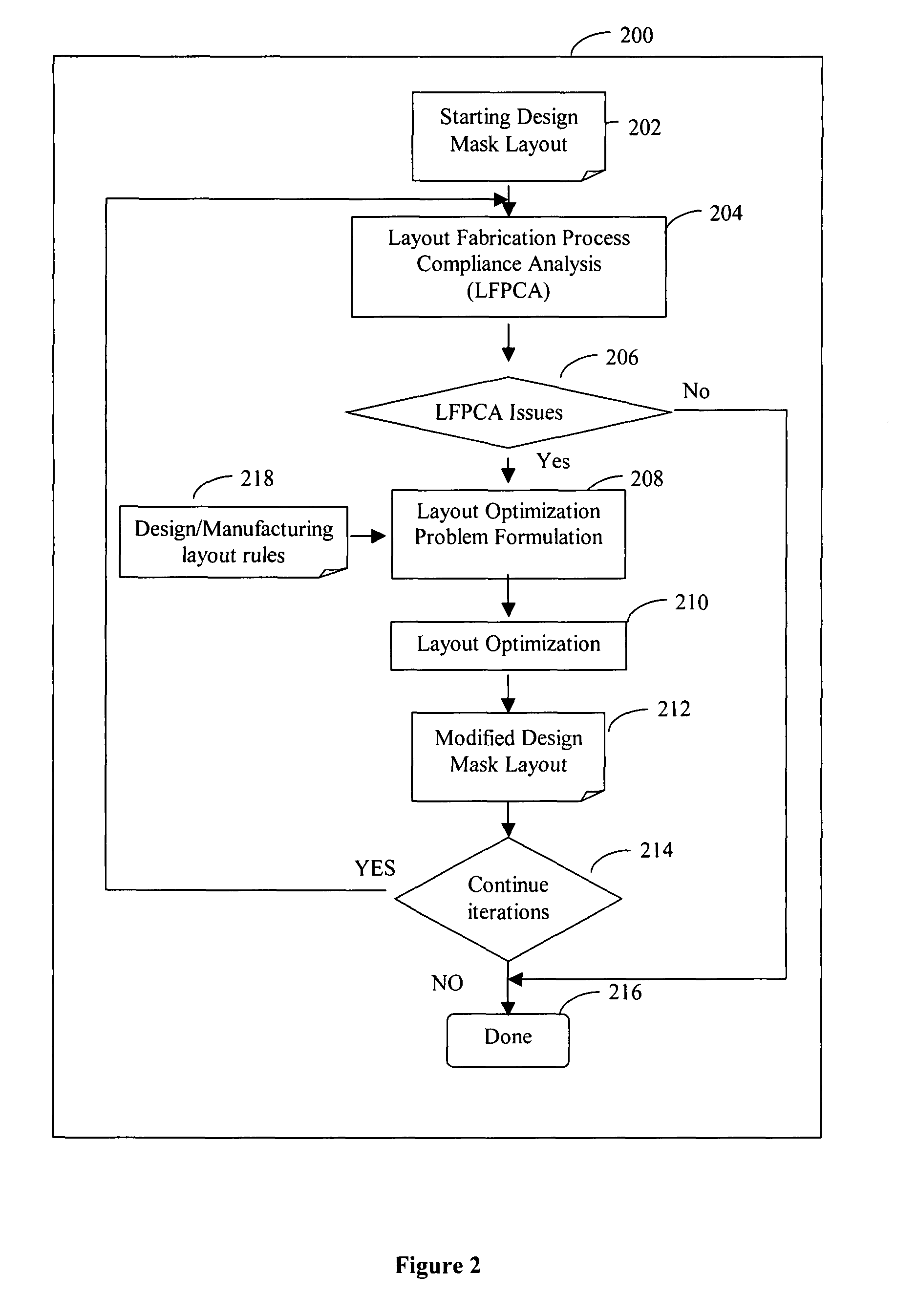
System and method of maximizing integrated circuit manufacturing yield with fabrication process simulation driven layout optimization
InactiveUS20080046846A1Maximizing manufacturing yieldYield maximizationCAD circuit designSoftware simulation/interpretation/emulationIntegrated circuit manufacturingEngineering
A system and a method of maximizing the manufacturing yield of integrated circuit (“IC”) design using IC fabrication process simulation driven layout optimization is described. An IC design layout is automatically modified through formulation of a layout optimization problem utilizing the results of layout fabrication process compliance analysis tools. The modification of layout is performed adaptively and iteratively to make an IC layout less susceptible to yield issues while maintaining design rule correctness and minimal circuit performance impact.
Owner:CHEW MARKO P +1
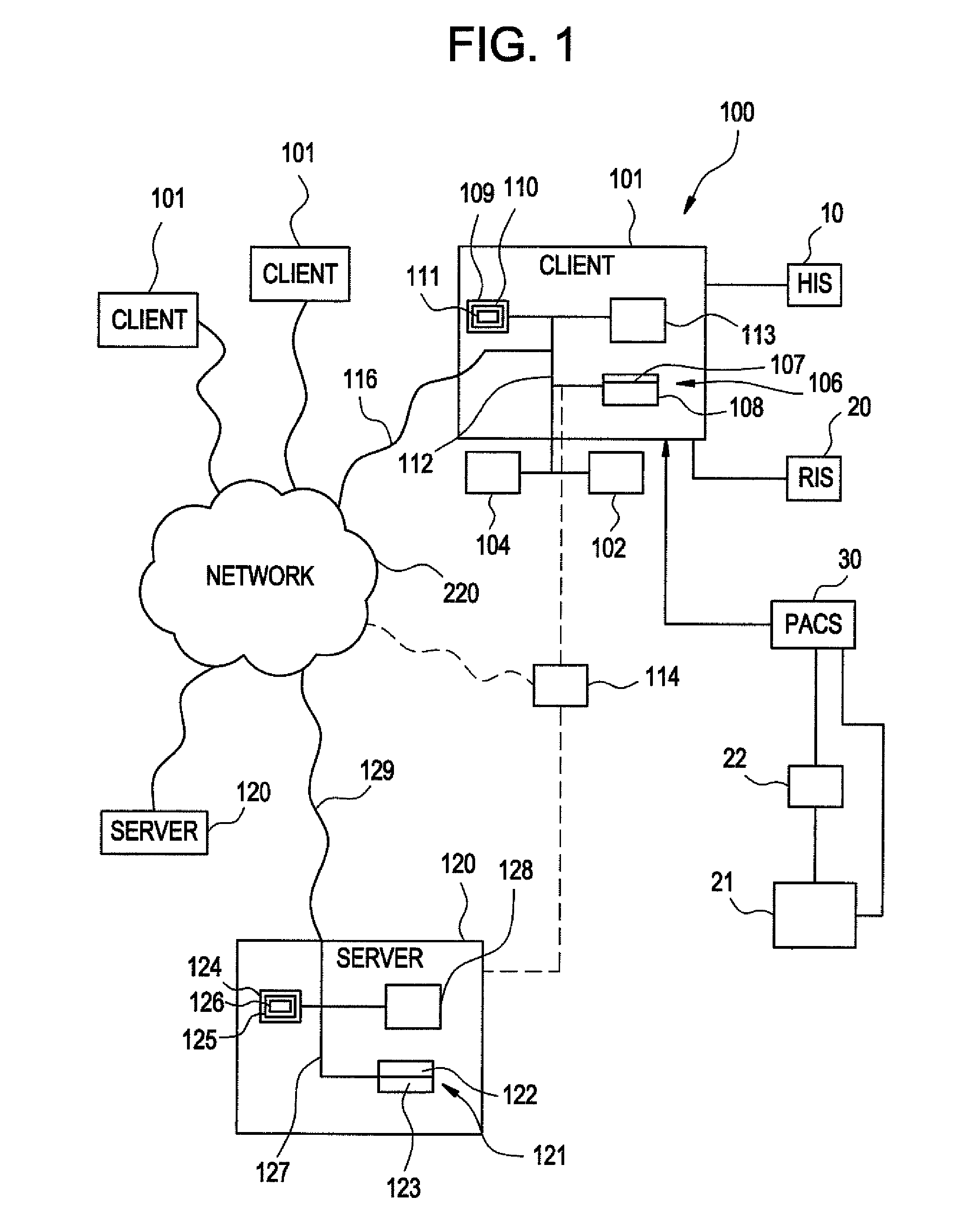
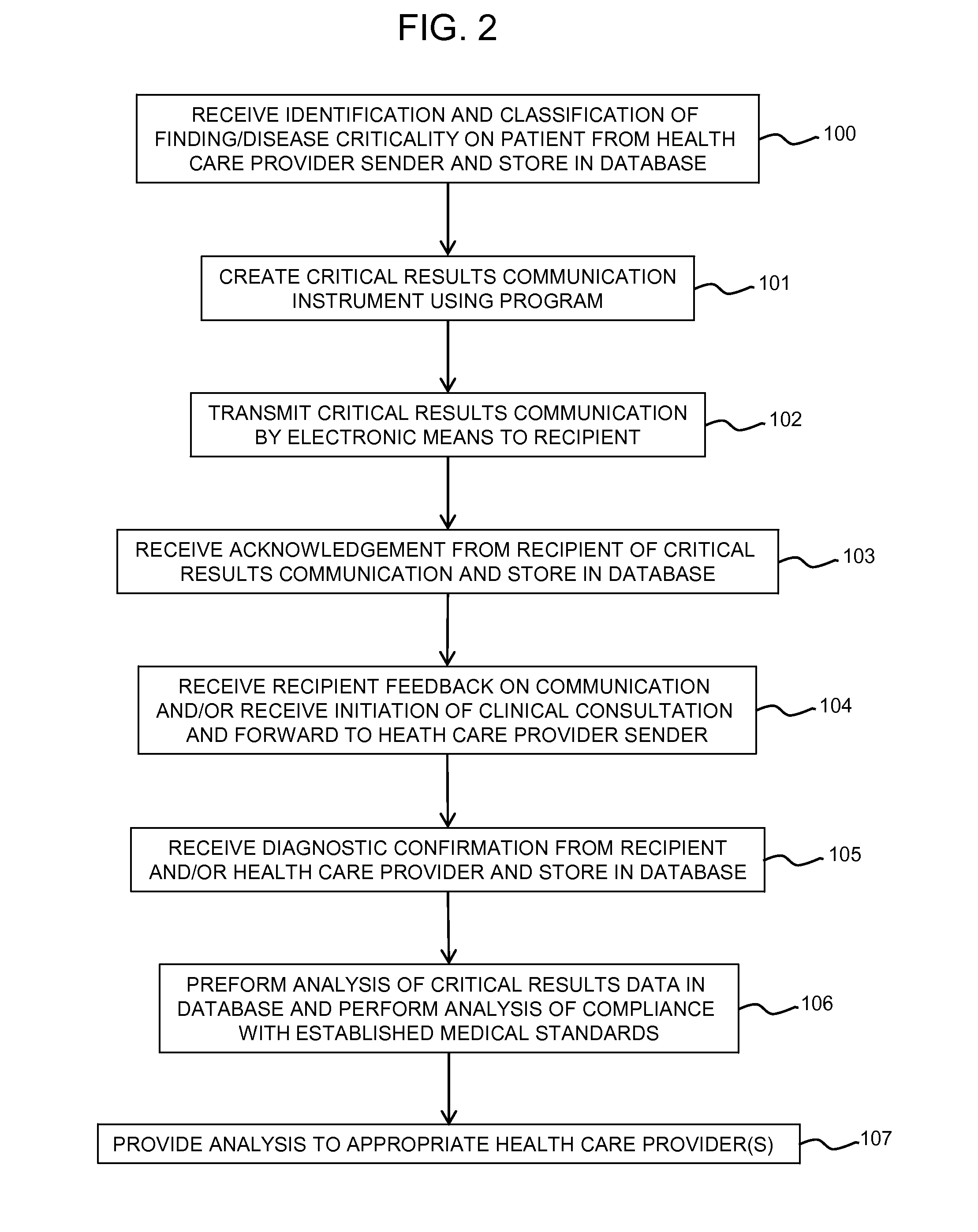
Method and apparatus for data recording, tracking, and analysis in critical results medical communication
InactiveUS20140358585A1Medical communicationData processing applicationsData profilingMedical communication
The present invention relates to an apparatus and method for implementing a medical critical results communication, including: receiving an identification and a classification of a finding of criticality on a patient; creating and transmitting a critical results communication to a recipient by electronic methods; receiving and storing an acknowledgement from the recipient that the critical results communication was received; receiving and storing feedback and / or the initiation of clinical intervention and a follow-up action from the recipient, and transmitting same to the health care provider sender; receiving and storing diagnostic confirmation from the recipient and / or the healthcare provider sender; performing an analysis of critical results data, and performing a compliance analysis with stored established medical standards; and providing the critical results data analysis and the compliance analysis to at least the health care provider sender.
Owner:REINER BRUCE
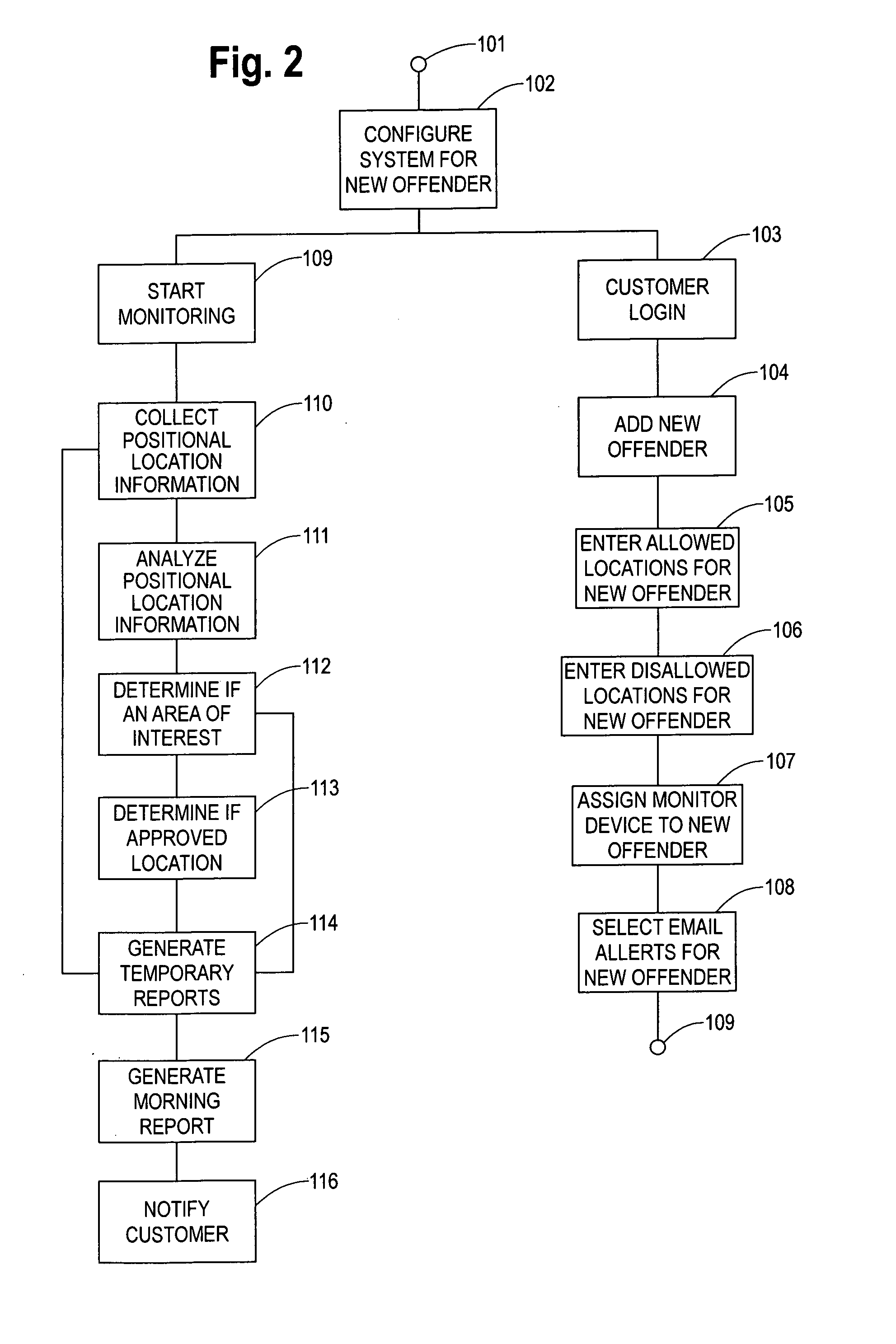
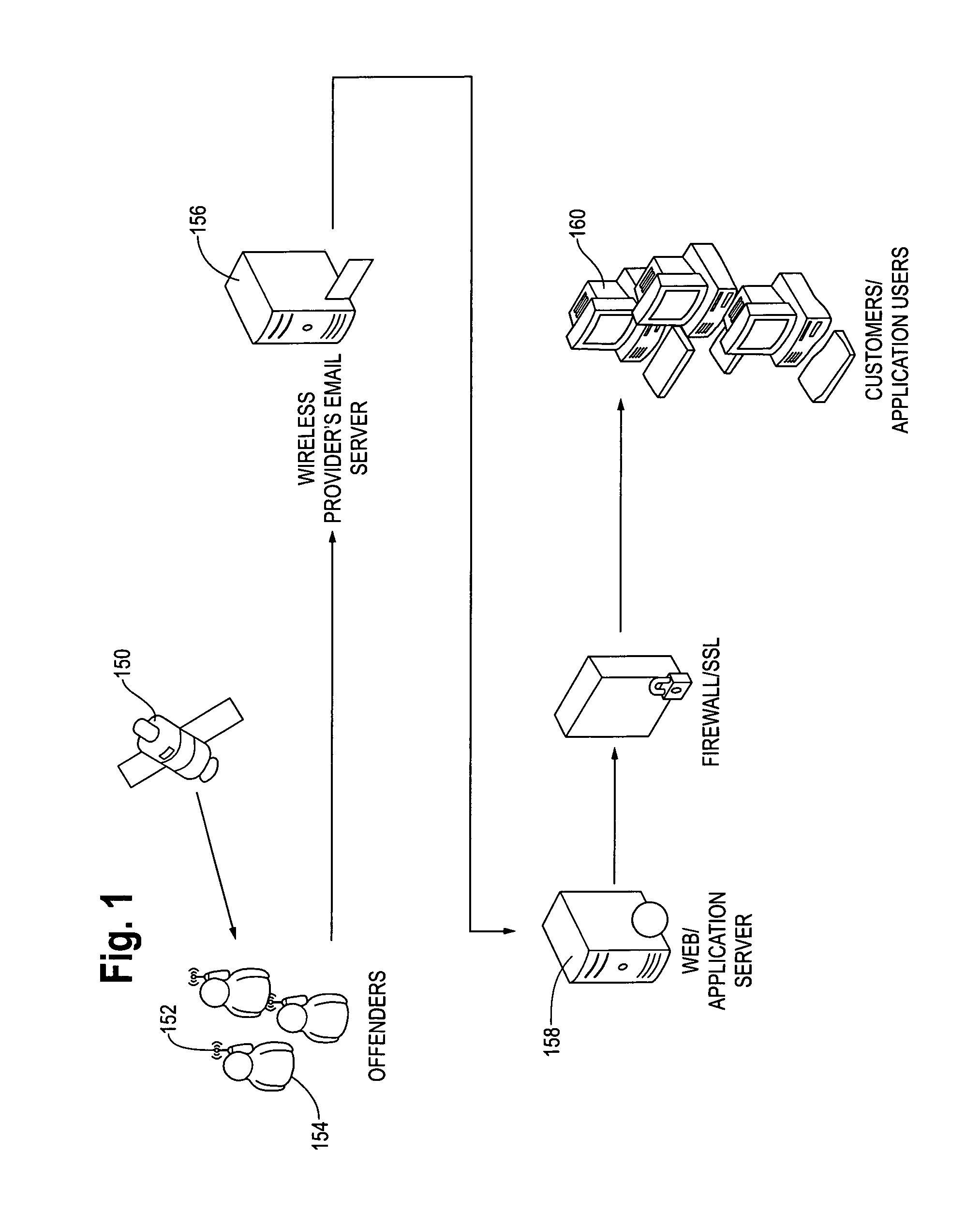
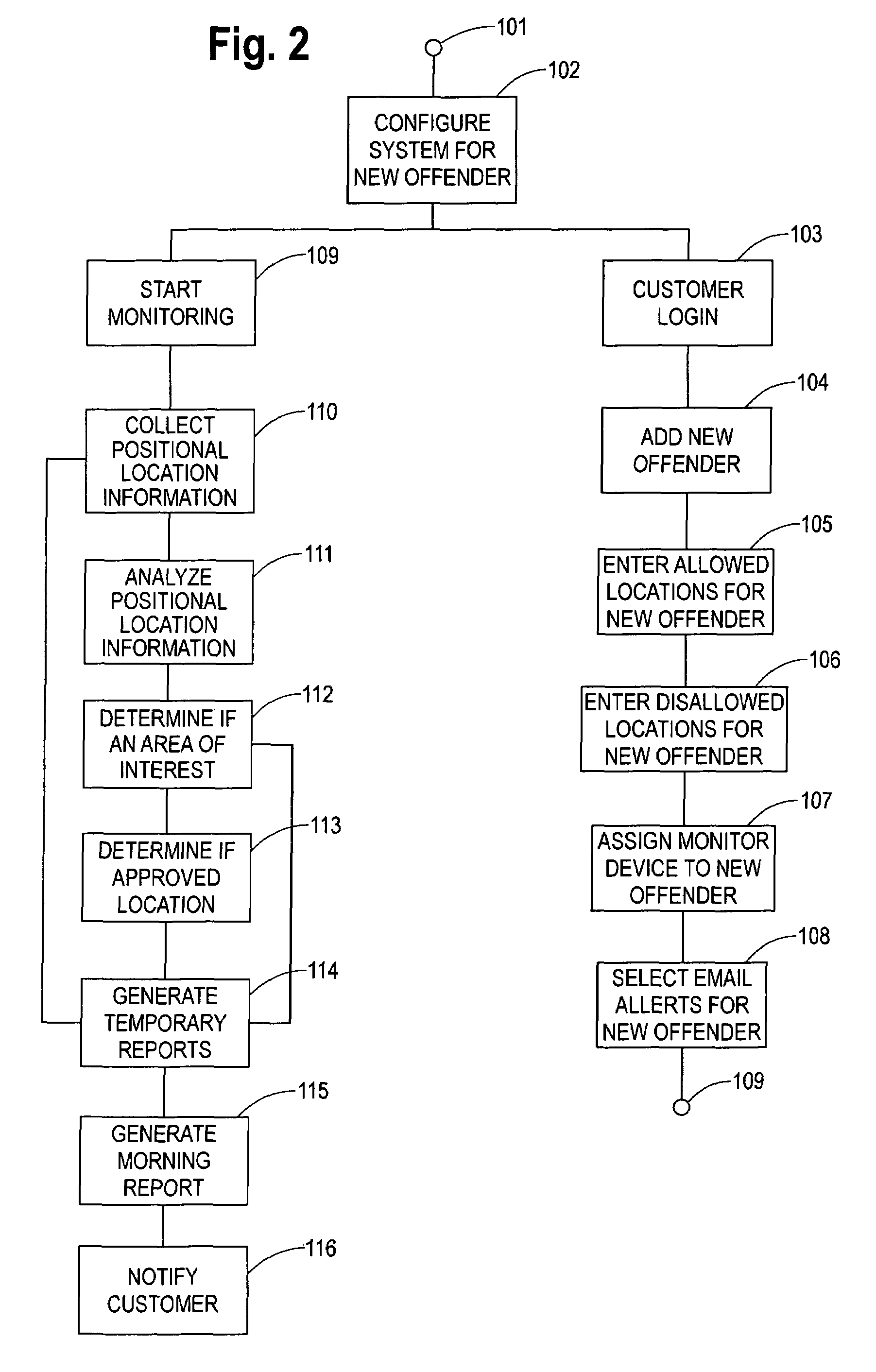
Method and apparatus for monitoring persons
InactiveUS20070159343A1Electric/electromagnetic visible signallingIndividual entry/exit registersRelevant informationMedicine
A method and apparatus for monitoring persons for compliance with a conditional release program from their court ordered confinement. The individual to be monitored is added to the system and assigned a schedule or treatment plan which provides for allowed location and disallowed locations. A monitoring device is used to monitor the positional locations and other relevant information of the individual. This information is collected and analyzed in the system to determine if the individual is in compliance with their schedule or treatment plan. Reports of the results of the analysis of the compliance are created and sent to the customer responsible for the individual during their conditional release program.
Owner:JUSTICE EZ TRAC
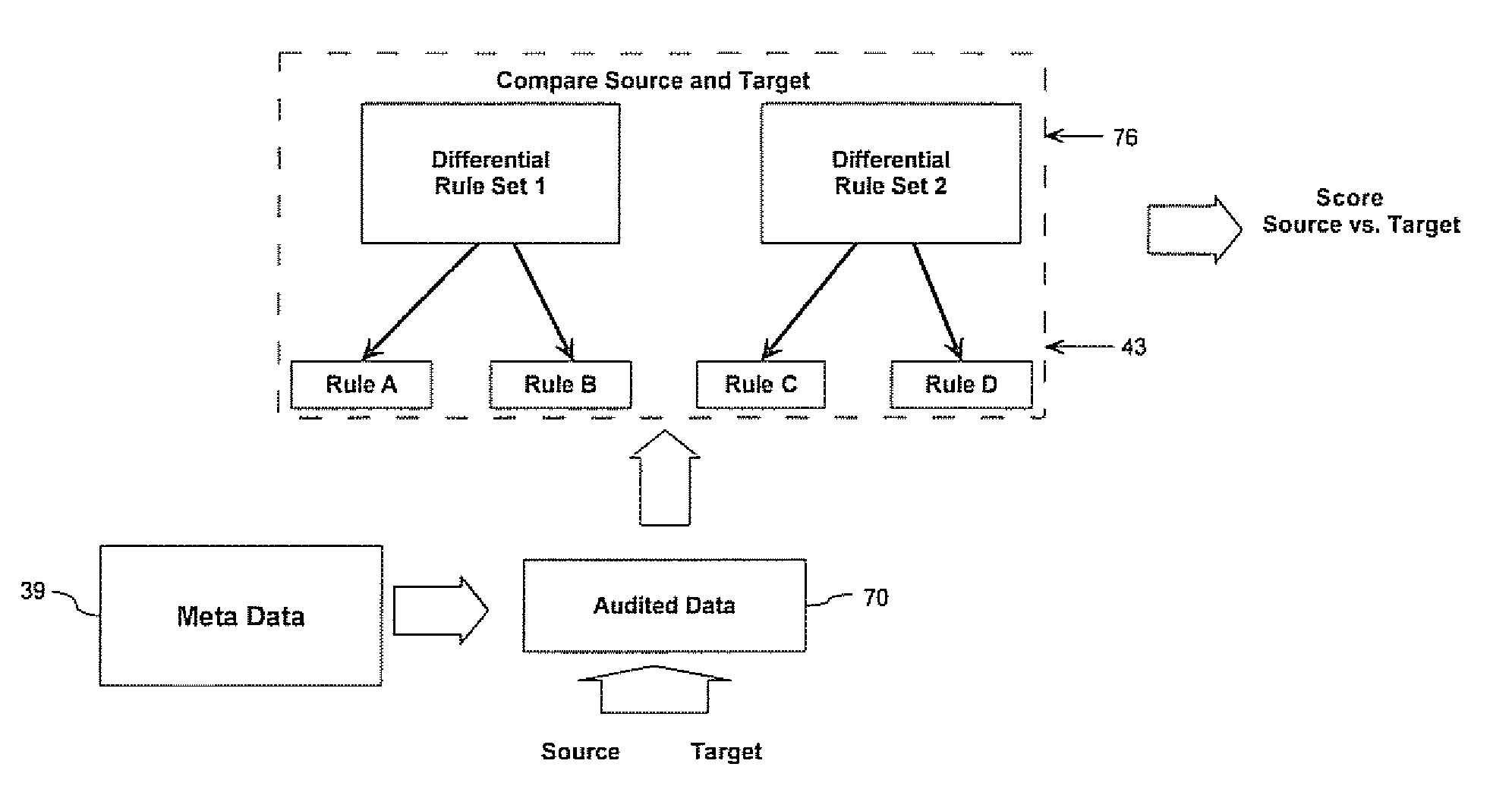
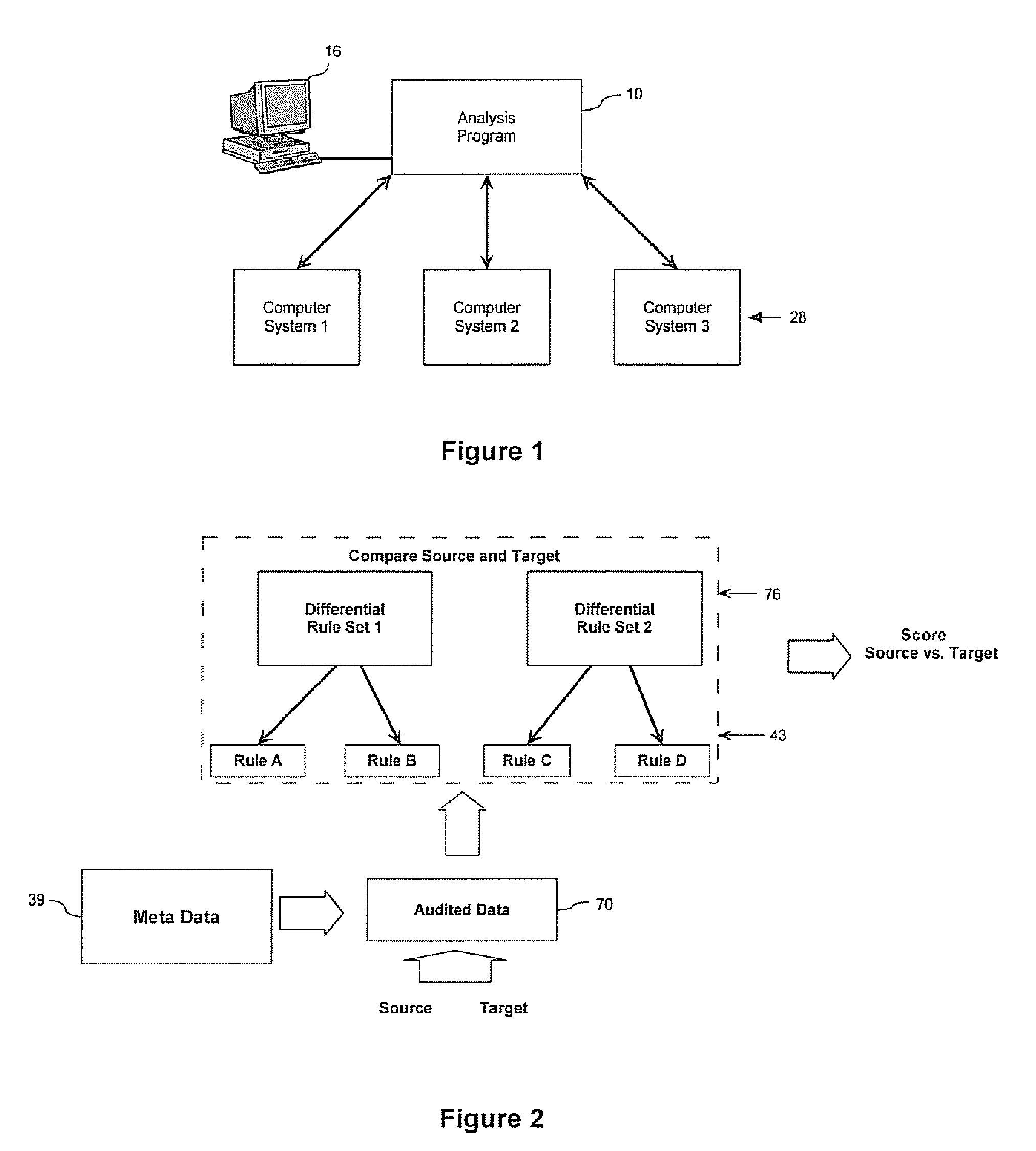
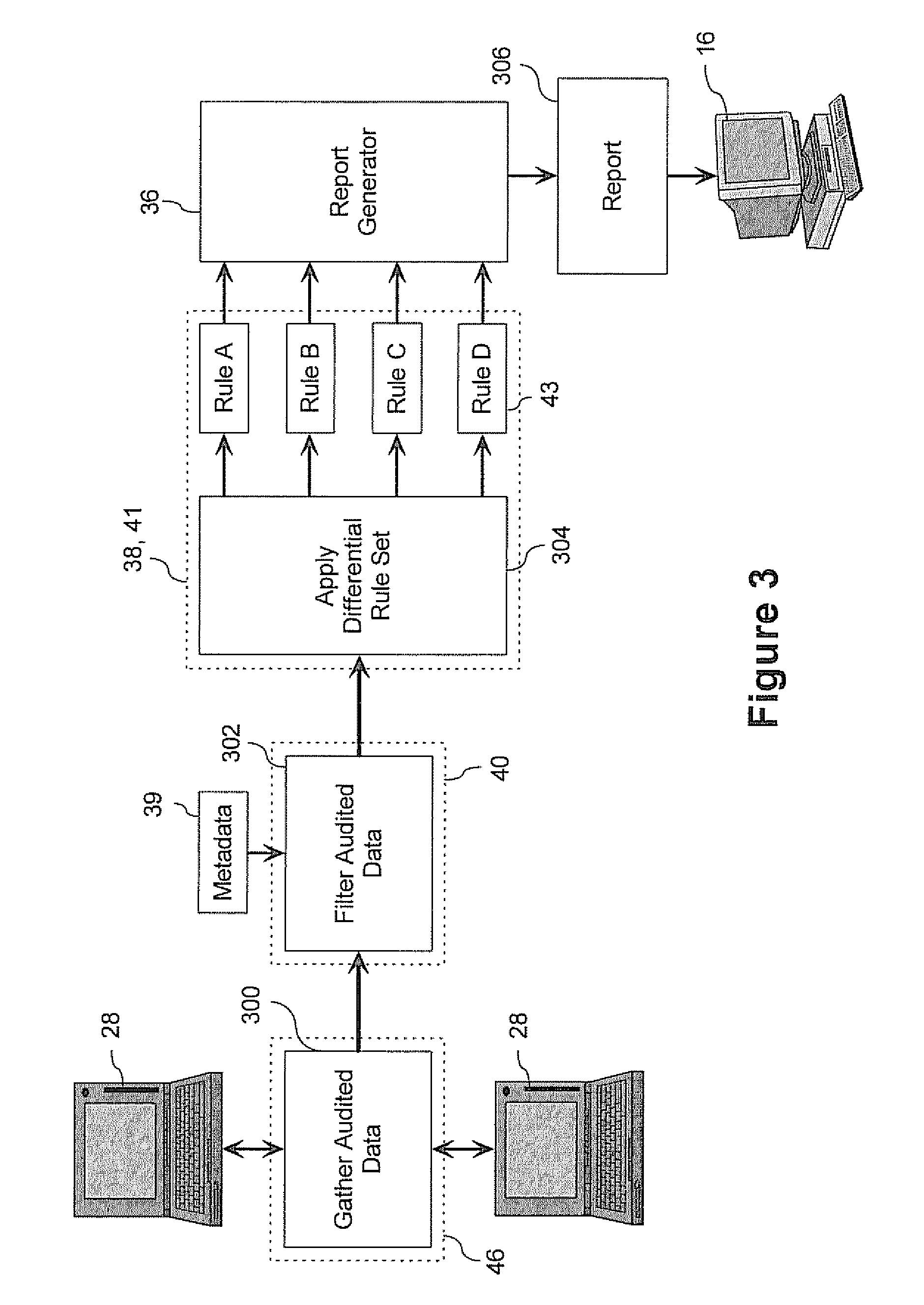
Method For Evaluating Computer Systems
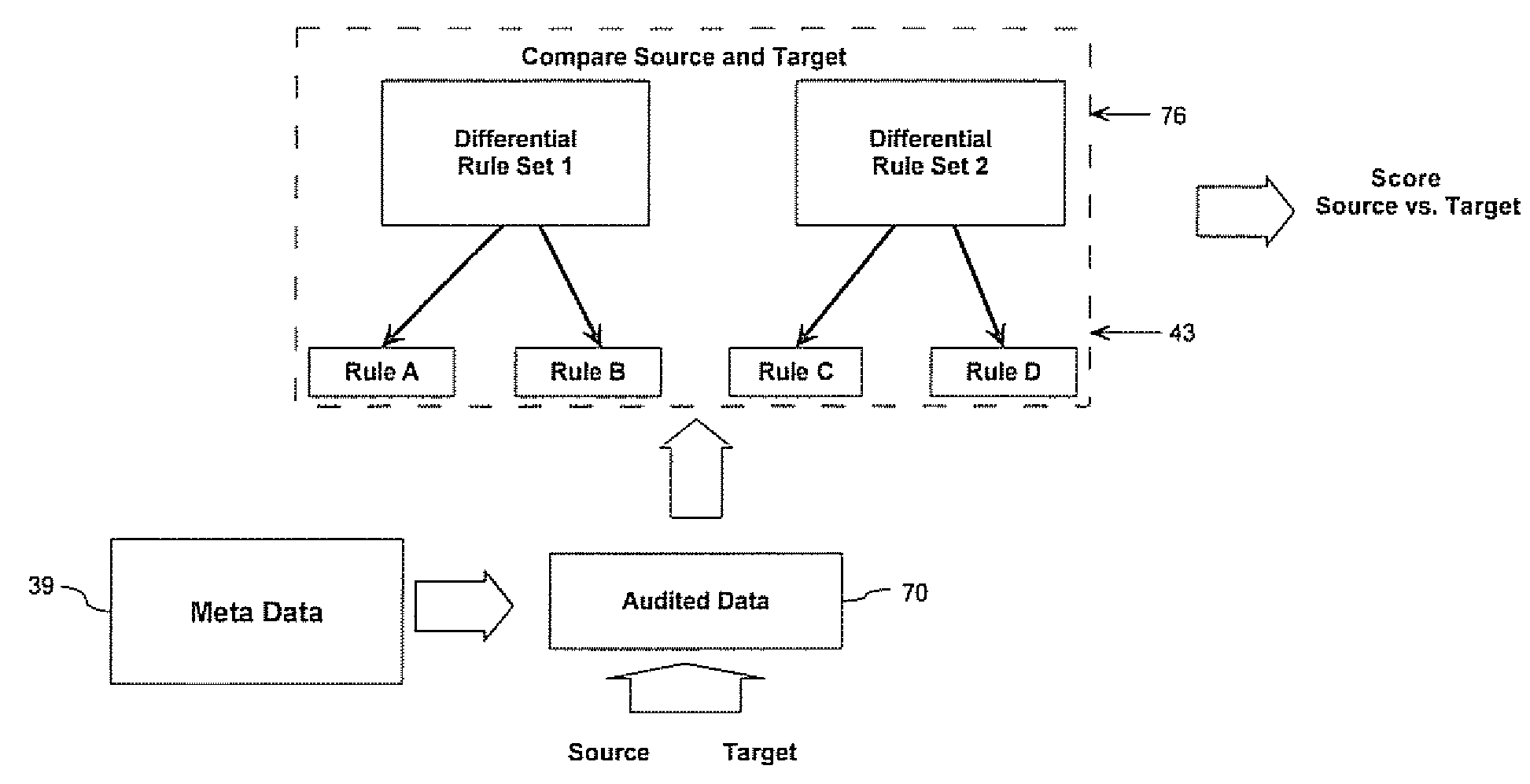
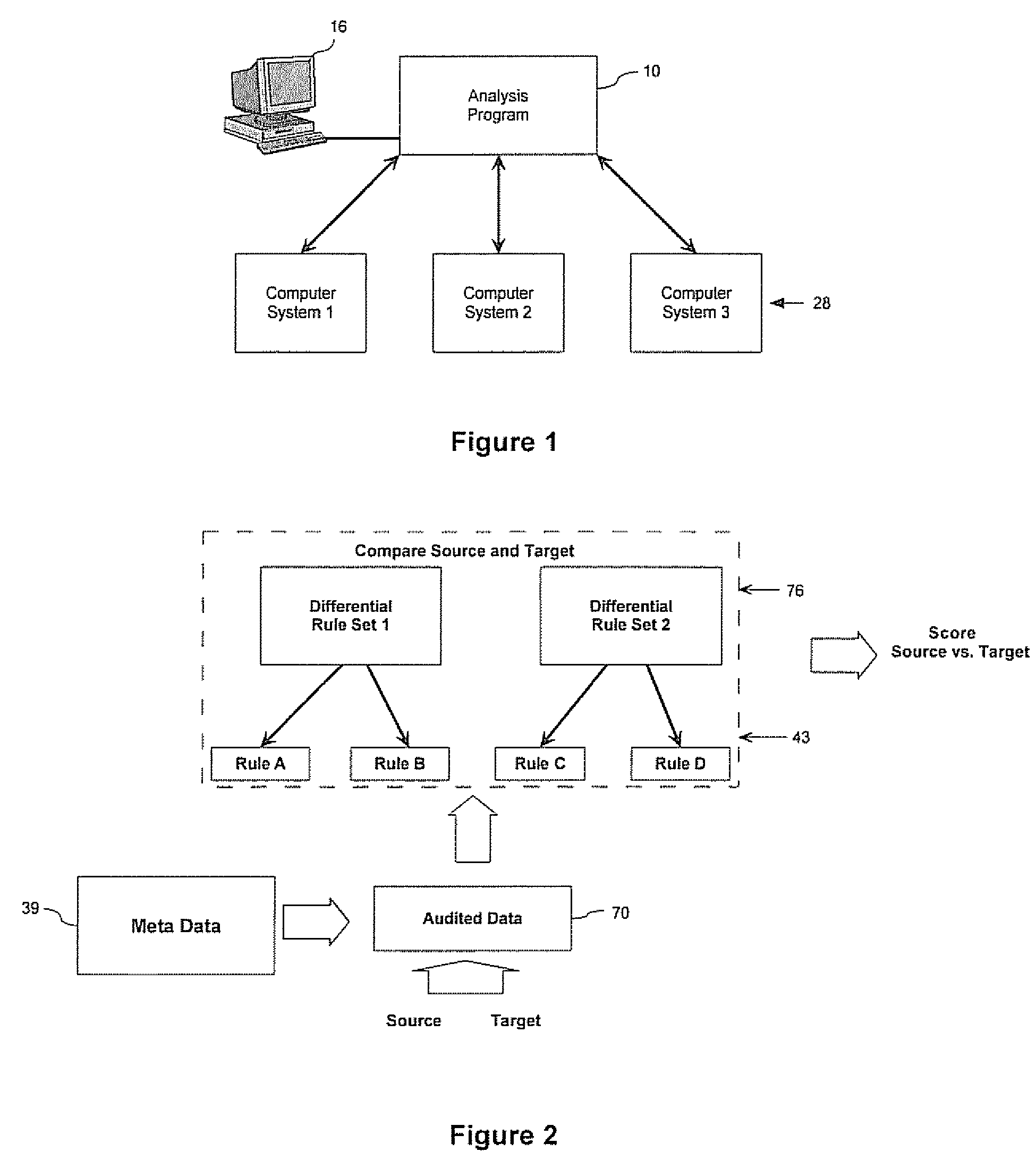
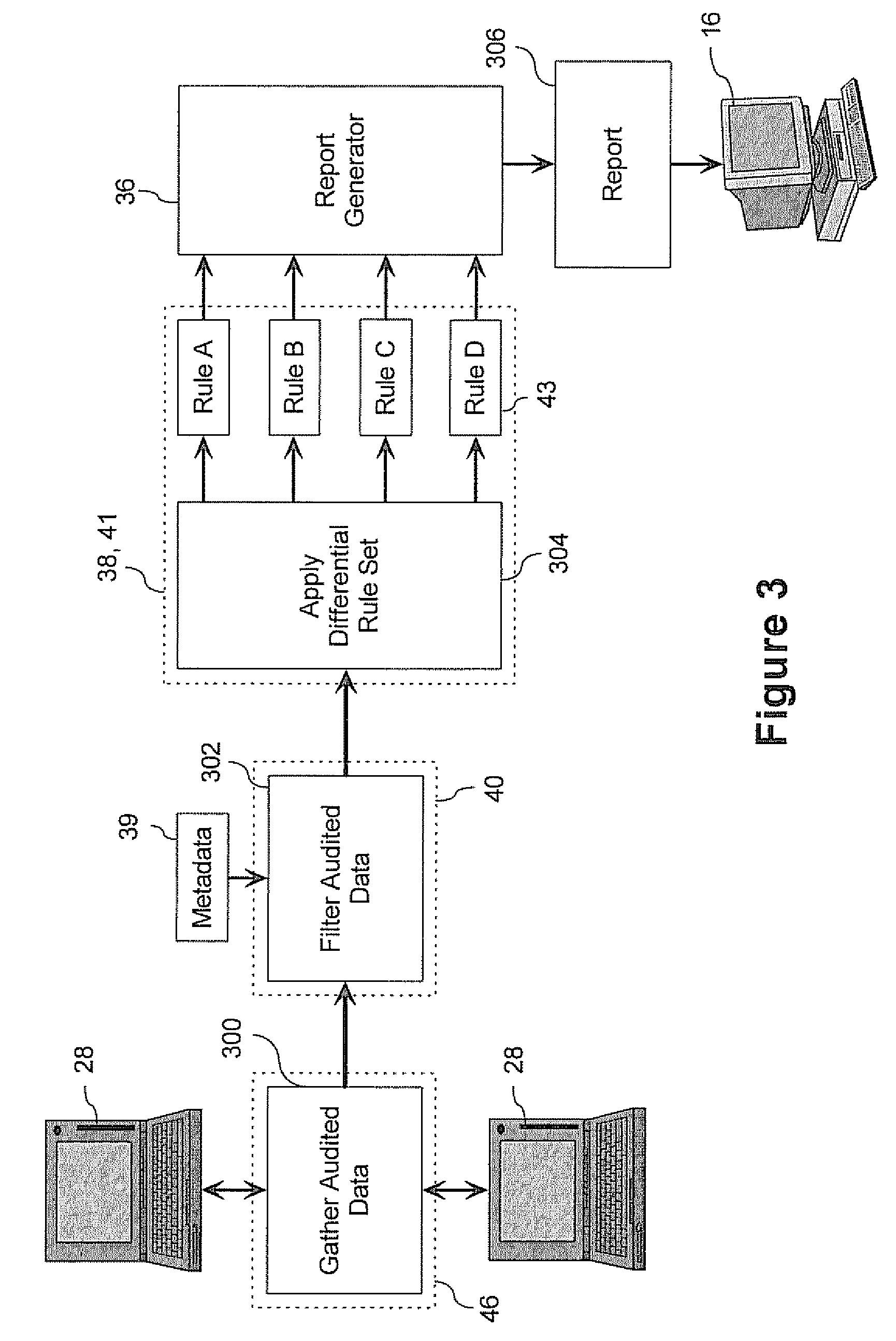
ActiveUS20070250621A1Digital computer detailsKnowledge representationComputer compatibilityCompliance analysis
A method for evaluating the differences between computer systems is provided. The systems are evaluated using one or more differential rule definitions and one or more differential rule sets. The rules evaluate the differences between specific parameters in the computer systems and are used to generate a score that indicates how different the systems are based on these parameters and preferably what the cost to remedy the difference would be. The rules can be used for consolidation analysis, compliance analysis etc. The rules each include a weight that quantifies the importance of the rule to compatibility and the score is affected accordingly. Systems can be evaluated against each other or against themselves at different instances in time.
Owner:CIRBA IP INC
System and method for evaluating differences in parameters for computer systems using differential rule definitions
ActiveUS7680754B2Digital computer detailsKnowledge representationComputer compatibilityCompliance analysis
A method for evaluating the differences between computer systems is provided. The systems are evaluated using one or more differential rule definitions and one or more differential rule sets. The rules evaluate the differences between specific parameters in the computer systems and are used to generate a score that indicates how different the systems are based on these parameters and preferably what the cost to remedy the difference would be. The rules can be used for consolidation analysis, compliance analysis etc. The rules each include a weight that quantifies the importance of the rule to compatibility and the score is affected accordingly. Systems can be evaluated against each other or against themselves at different instances in time.
Owner:CIRBA IP INC
Method and apparatus for monitoring persons
InactiveUS7619533B2Electric/electromagnetic visible signallingIndividual entry/exit registersRelevant informationMedicine
Owner:JUSTICE EZ TRAC
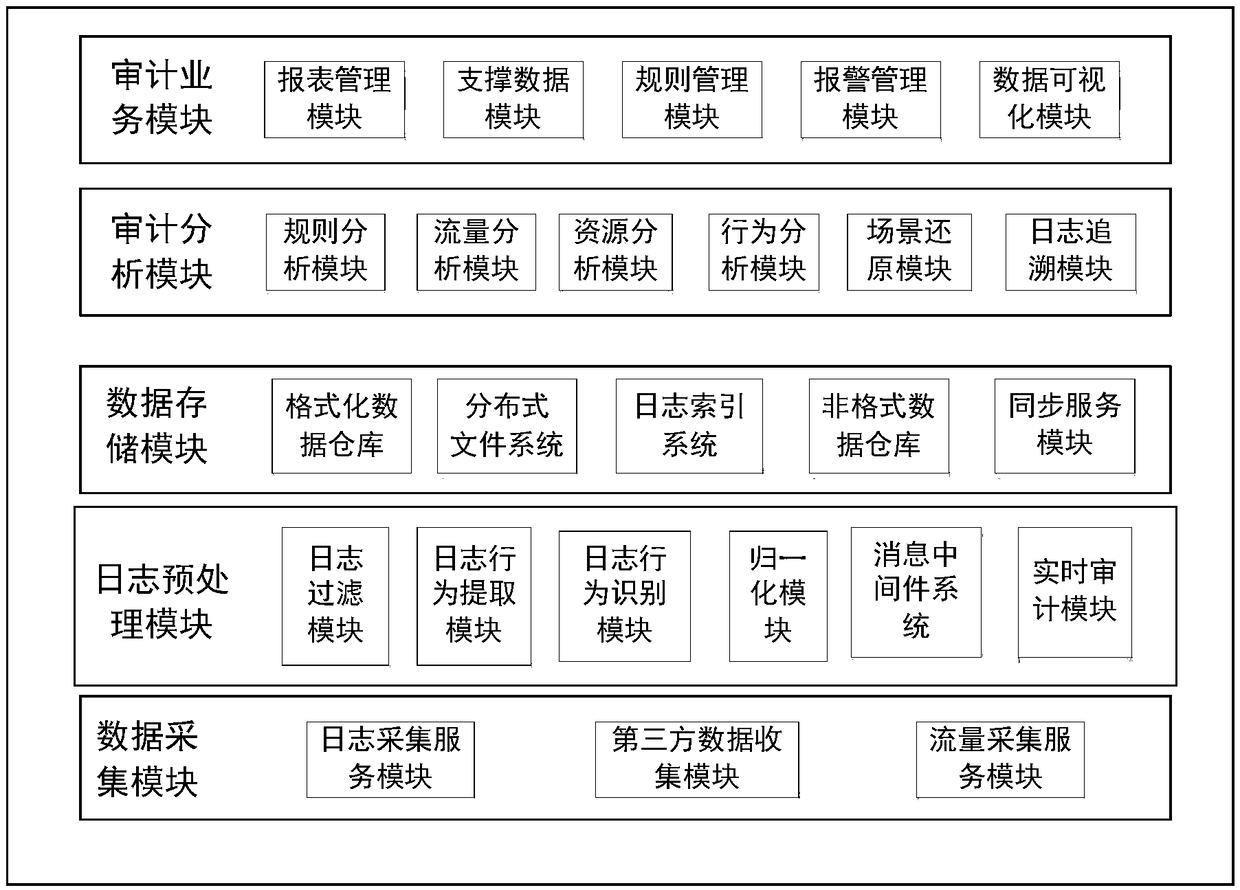
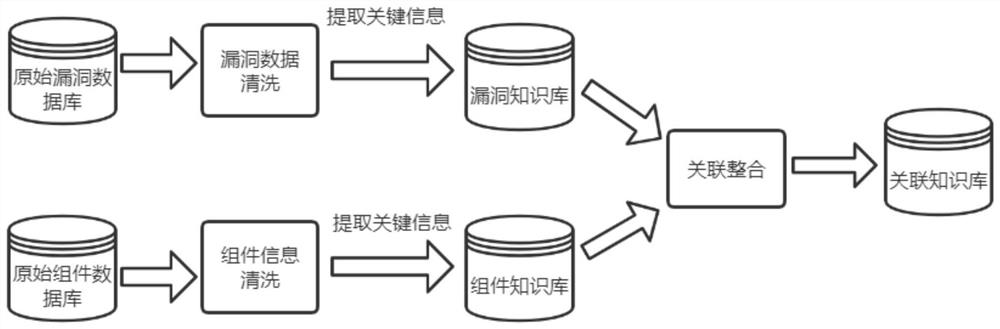
A cloud user behavior audit system and method based on cloud log analysis
InactiveCN109471846AEfficient extractionAccurate extractionSpecial data processing applicationsFile system typesCloud userInto-structure
The cloud user behavior auditing system and the cloud user behavior auditing method based on cloud log analysis provide a unique cloud log processing algorithm, which can efficiently and accurately extract effective information from a mass of original logs with uncertain format, and convert the effective information into structured user operation behavior data which can be used for large data analysis. Based on the operation behavior data, the invention provides the functions of user operation behavior audit, record, multi-dimensional display, violation alarm, compliance analysis, complex process audit, automatic generation of audit strategy and the like, which greatly improves the overall security of the cloud system.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
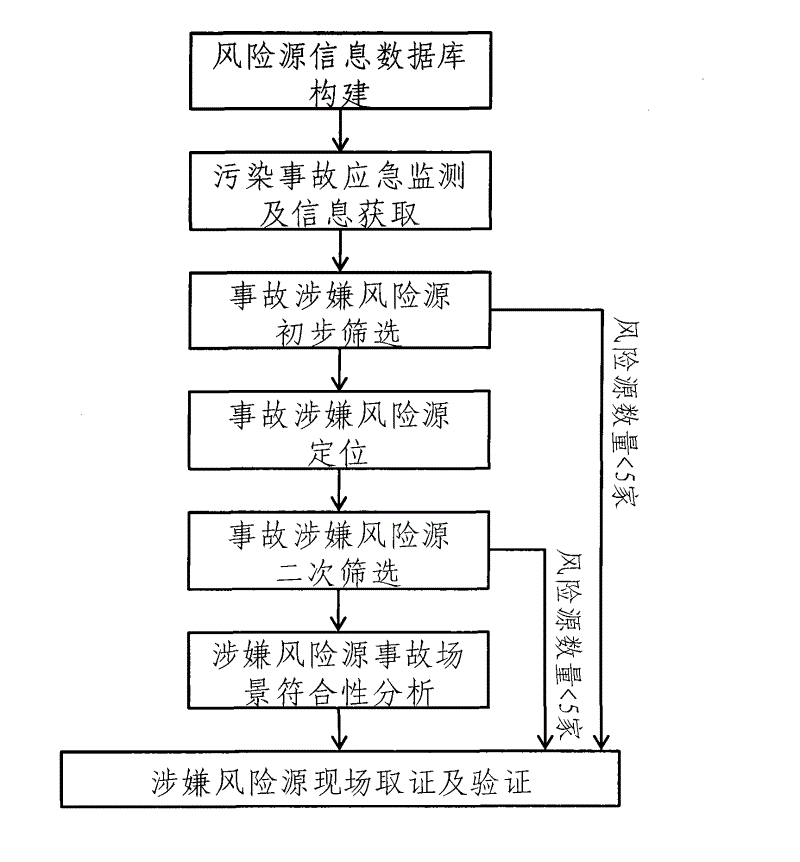
Tracing method for suspected risk sources of sudden water environment pollution accidents
Aiming at the problem that suspected risk sources of sudden water environment pollution accidents are difficult to quickly inspect, the invention discloses a tracing method for the suspected risk sources of the sudden water environment pollution accidents. The tracing method comprises the steps as follows: (1) creating an enterprise risk information database; (2) carrying out pollution accident emergency monitoring and information acquisition; (3) carrying out preliminary screening on the suspected risk sources of the accidents; (4) positioning the suspected risk sources of the sudden accidents; (5) carrying out secondary screening on the suspected risk sources of the accidents; (6) carrying out compliance analysis on the accident scenes of the suspected risk sources; and (7) carrying out scene evidence and validation on the suspected risk sources. According to the created standard inspection method, the problems of subjectivity, lagging and large workload and the like in the process of inspecting the suspected risk sources of the sudden water environment pollution accidents are solved, so that the emergency processes of the water environment pollution accidents can be conveniently standardized by the main environmental-protection agency.
Owner:CHINESE RES ACAD OF ENVIRONMENTAL SCI
System and method of maximizing integrated circuit manufacturing yield with fabrication process simulation driven layout optimization
InactiveUS7886262B2Yield maximizationReduce sensitivityCAD circuit designSoftware simulation/interpretation/emulationIntegrated circuit manufacturingEngineering
A system and a method of maximizing the manufacturing yield of integrated circuit (“IC”) design using IC fabrication process simulation driven layout optimization is described. An IC design layout is automatically modified through formulation of a layout optimization problem utilizing the results of layout fabrication process compliance analysis tools. The modification of layout is performed adaptively and iteratively to make an IC layout less susceptible to yield issues while maintaining design rule correctness and minimal circuit performance impact.
Owner:CHEW MARKO P +1
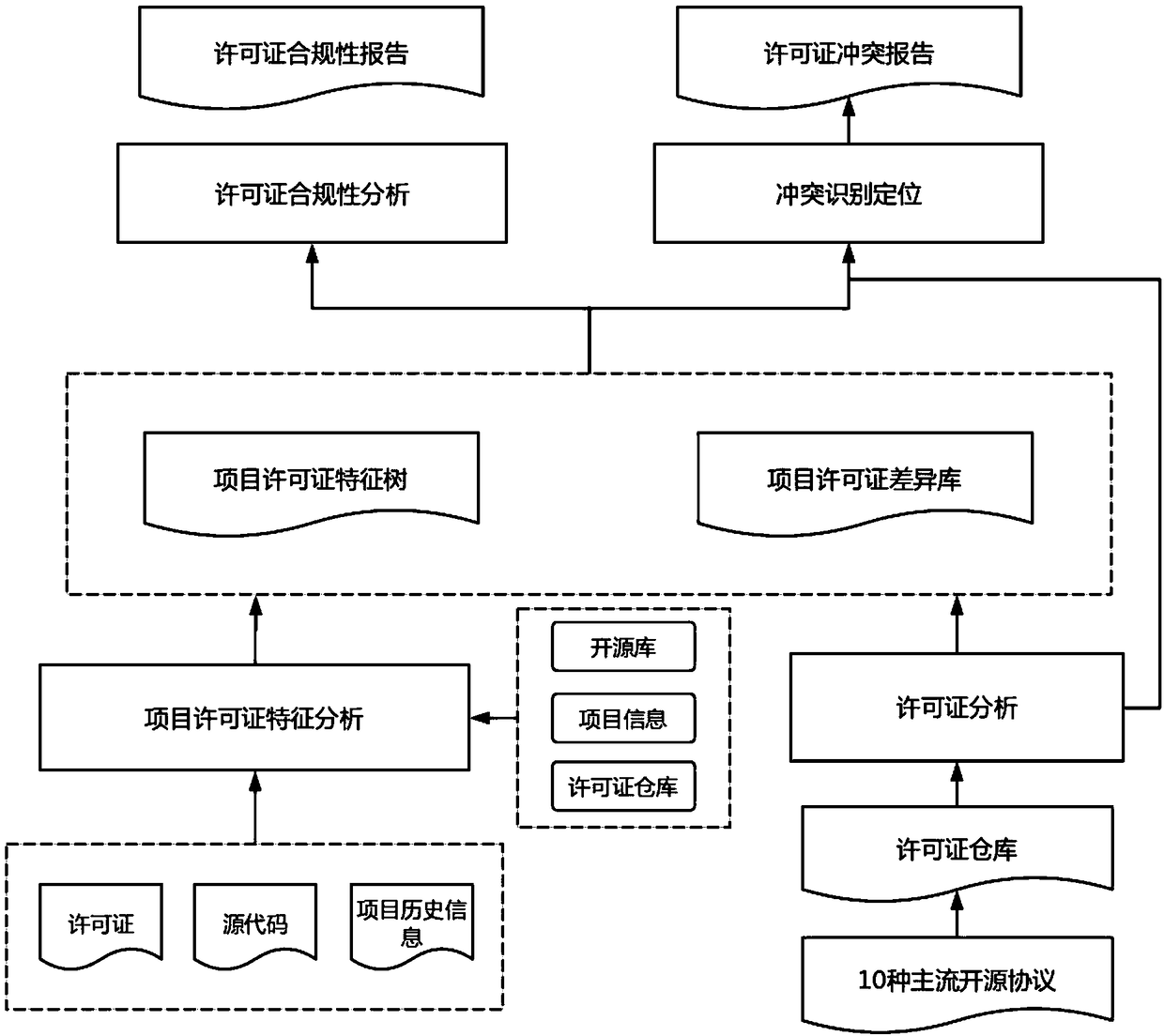
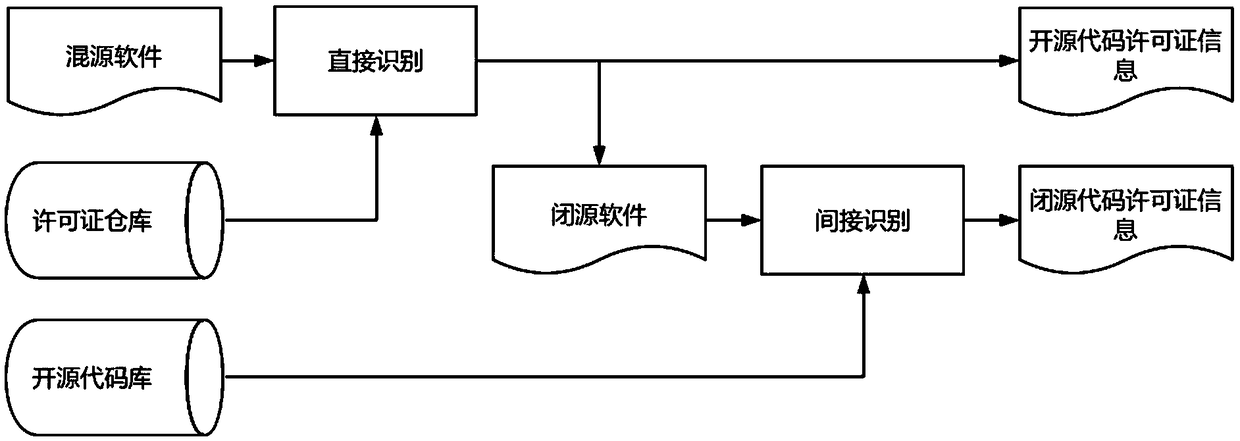
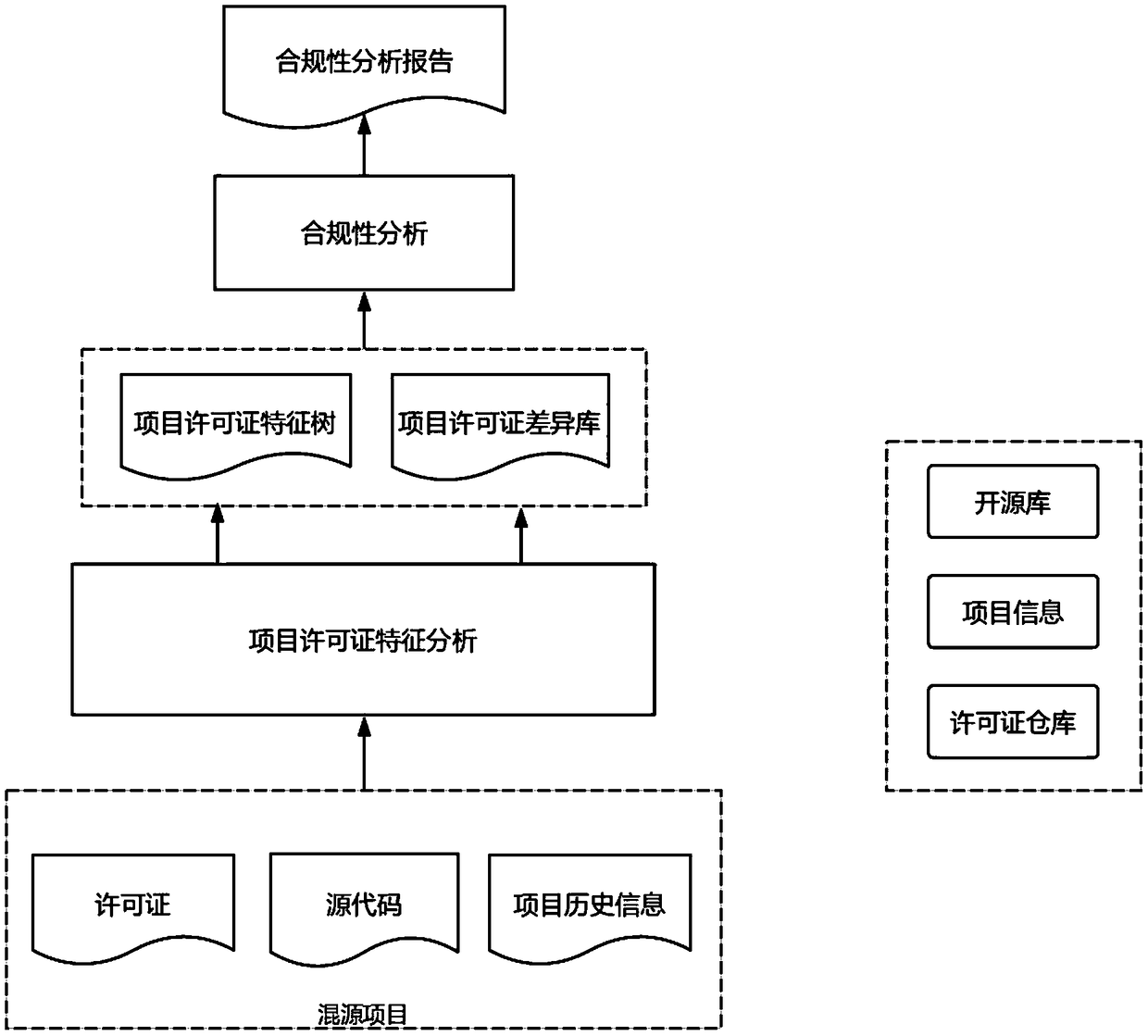
Open source license compliance analysis and conflict detection method
ActiveCN109063421ACheck comprehensivelyImprove scalabilityProgram/content distribution protectionPattern matchingCompliance analysis
The invention relates to an open source license compliance analysis and conflict detection method, which is mainly divided into the following four aspects: a license identification method: one is a direct identification mode adopting a pattern matching heuristic algorithm, and the other is an indirect identification mode adopting a code matching technology. License information extraction and modeling: as a prerequisite for license compliance analysis and conflict identification positioning, feature information associated with the license agreement is collected in the project. Quantitative Analysis of License Compliance: Find out what is consistent and inconsistent with the license agreement in the mixed-source project, based on the license agreement as a standard. License conflict identification positioning: Using license warehouse, from the license name, rights, conditions and restrictions to identify the license conflict between mixed-source project and open-source standard software,and then positioning to specific open-source project and specific location.
Owner:SOUTHEAST UNIV
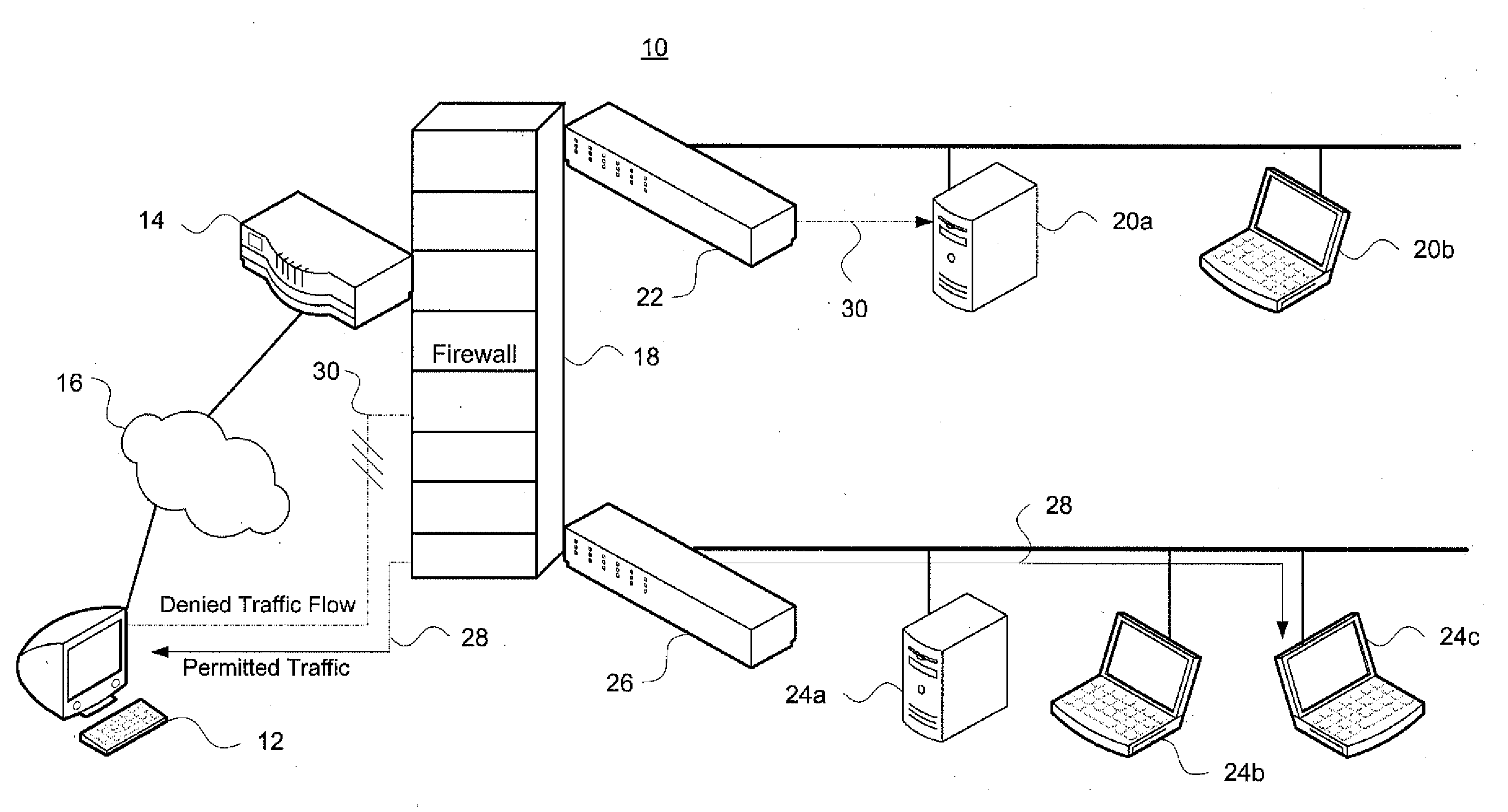
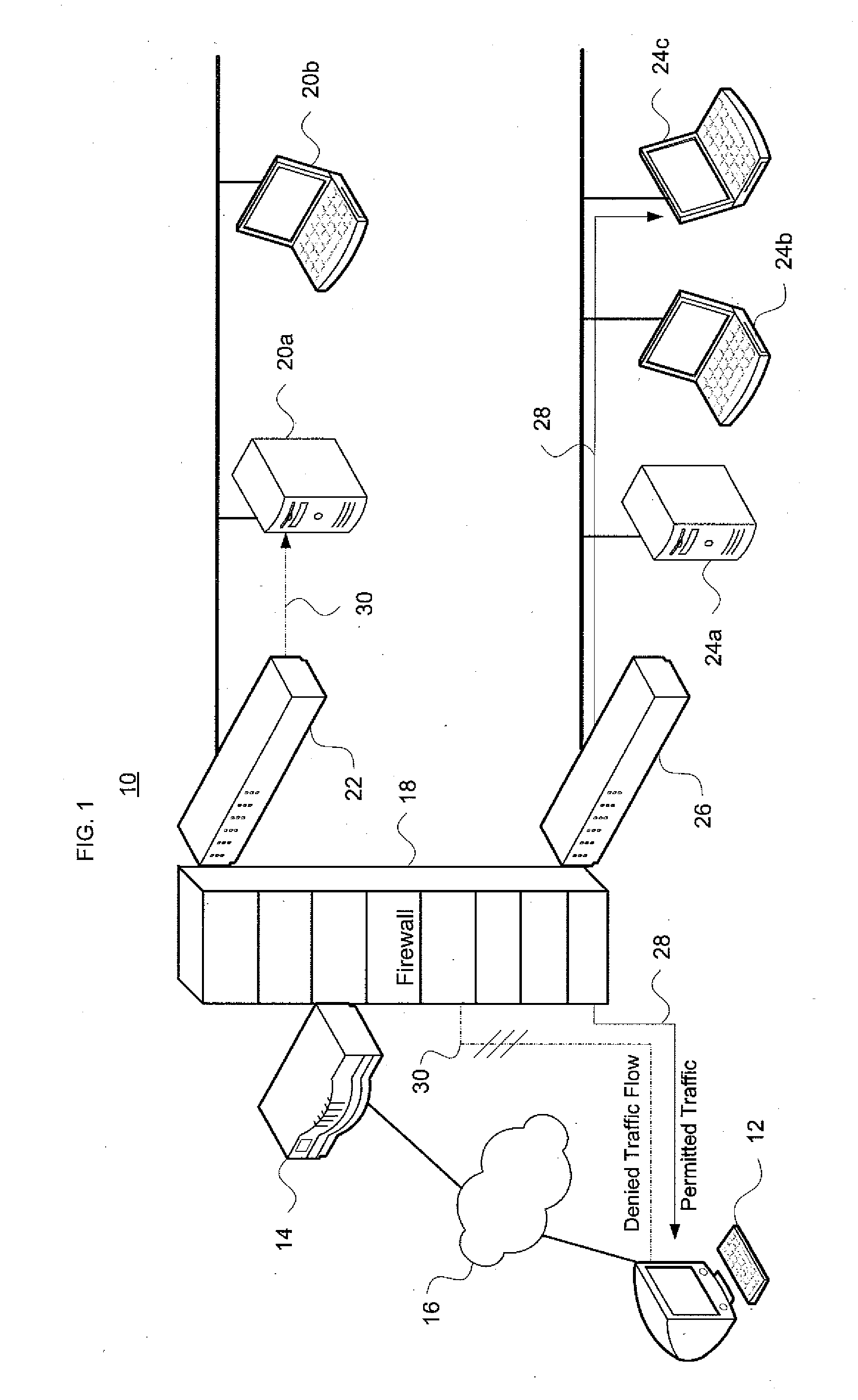
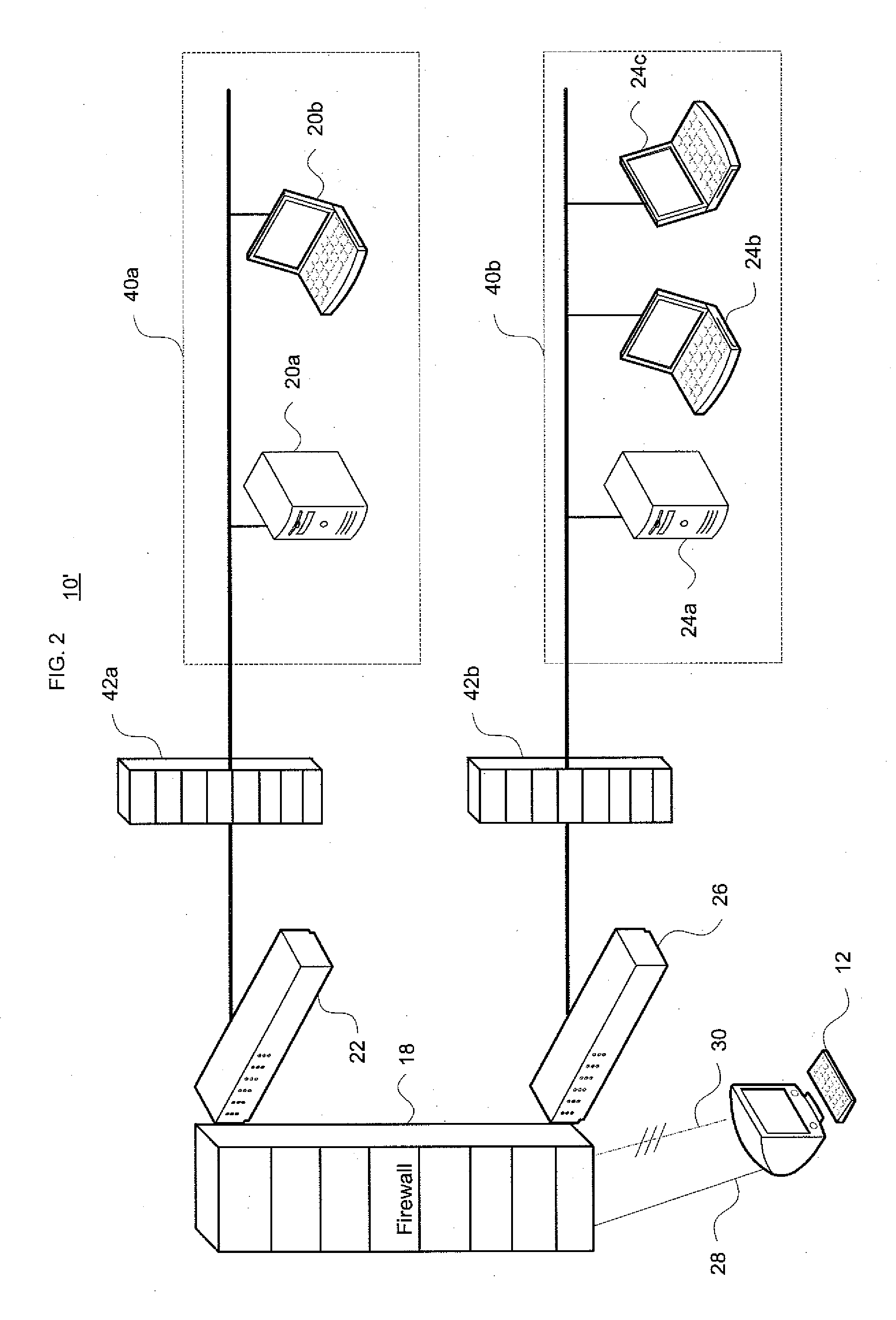
System and method for determining firewall equivalence, union, intersection and difference
InactiveUS20110283348A1Computer security arrangementsMultiple digital computer combinationsNetwork isolationSecurity question
Aspects of the invention pertain to integrated compliance analysis of multiple firewalls and access control lists for network segregation and partitioning. Access control lists may have many individual rules that indicate whether information can be passed between certain devices in a computer network. The access control lists in different firewalls in different network segments within a given network may overlap or have inconsistent rules. Aspects of the invention generate differences between firewalls, analyze equivalency of firewalls, generate the intersection (if any) between a pair of firewalls, and generate the union (if any) between firewalls. Such information provides an integrated analysis of multiple interrelated firewalls, including inbound and outbound access control lists for such firewalls, and may be used to manage firewall operation within the network to ensure consistent operation and maintain network security. It also addresses a wide range of security questions that arise when dealing with multiple firewalls.
Owner:TT GOVERNMENT SOLUTIONS
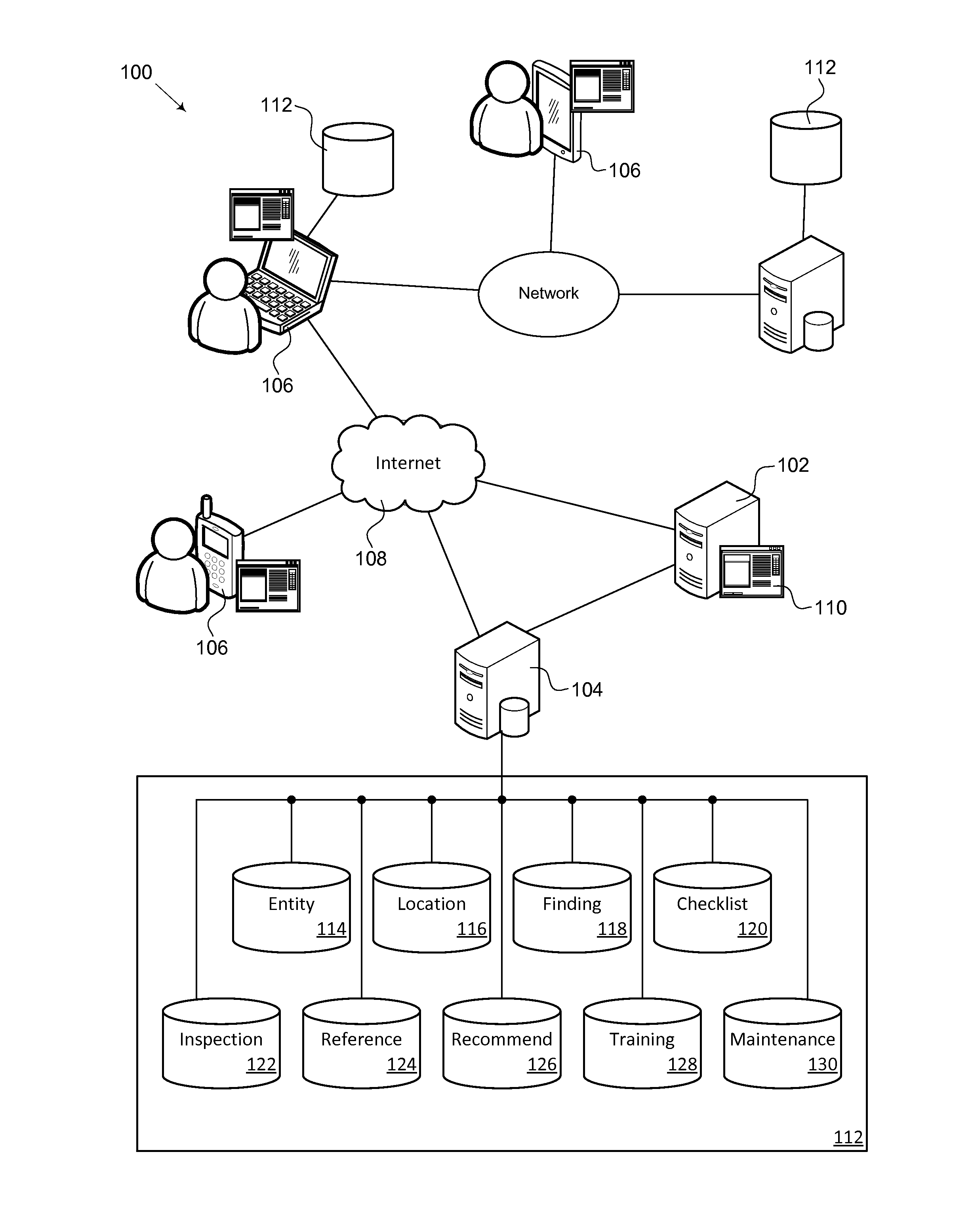
Compliance Analysis System
InactiveUS20140025593A1Easy to analyze and useFollow exactlyCommerceDocumentation procedureCompliance analysis
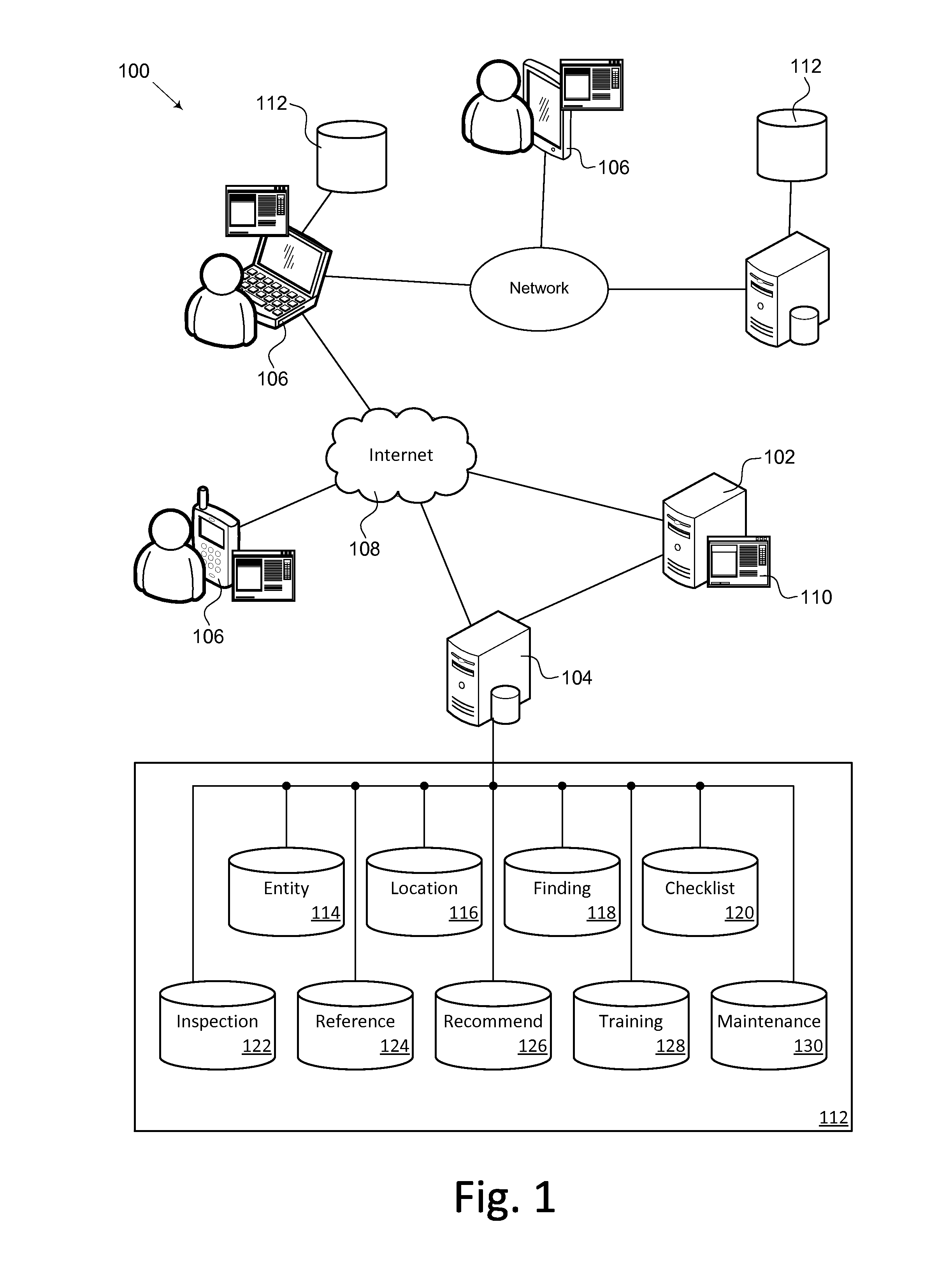
A compliance analysis system. The compliance analysis system is used to evaluate and monitor compliance with a collection of rules applicable to an entity or site. The compliance analysis system uses checklists to insure consistent inspections. The compliance analysis system provides comprehensive documentation of the inspection including reference materials based on the findings of the inspection. The compliance analysis system stores the results of each inspection and allows comparison of the inspection results over time and across sites. Reports and analysis by the compliance analysis system optionally estimate discretionary penalties for violations. User created additions and modifications to the compliance analysis system data collections may be submitted for approval and distribution to other compliance analysis system users. Custom and user specific content is preserved when shared compliance analysis system data collections are updated.
Owner:DLC ENTERPRISES
Automated query compliance analysis
ActiveUS20180182049A1Well formedData processing applicationsKnowledge representationCompliance analysisCompliance problem
Techniques and solutions are described for facilitating the determination of whether a query, such as a database query, may raise a compliance issue, such as whether restricted information associated with a particular database field is provided as an output of the query. A compliance tool receives a query that includes a plurality of query operations. At least one database field associated with a potential compliance issue is received. For example, the at least one database field may be associated with restricted information. The plurality of query operations are analyzed to determine whether information associated with the at least one database field is an output of the query to provide compliance results. The compliance results are output to a user.
Owner:SAP AG
Safety and compliance treatment method suitable for open source component
PendingCN112800430ASupport for VulnerabilitiesSupport automatic repairPlatform integrity maintainanceCompliance analysisOperating system
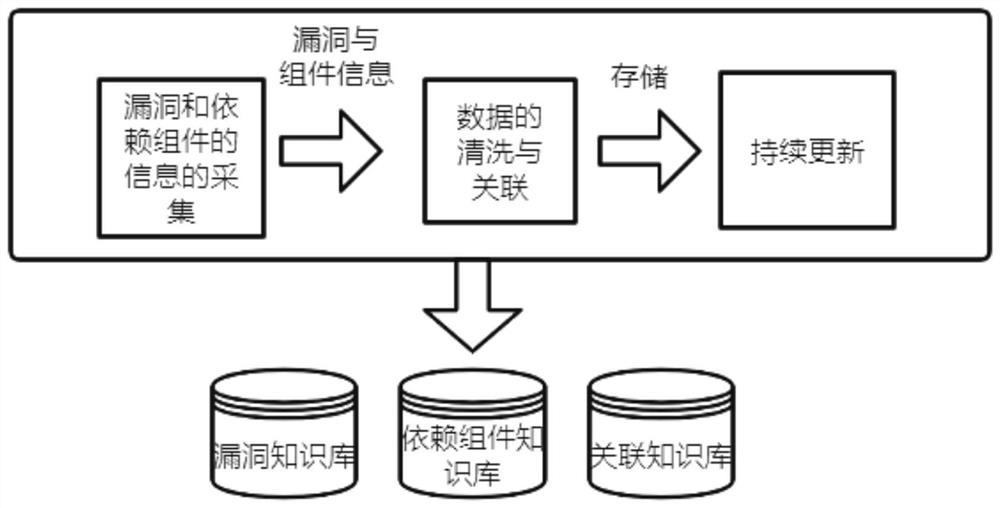
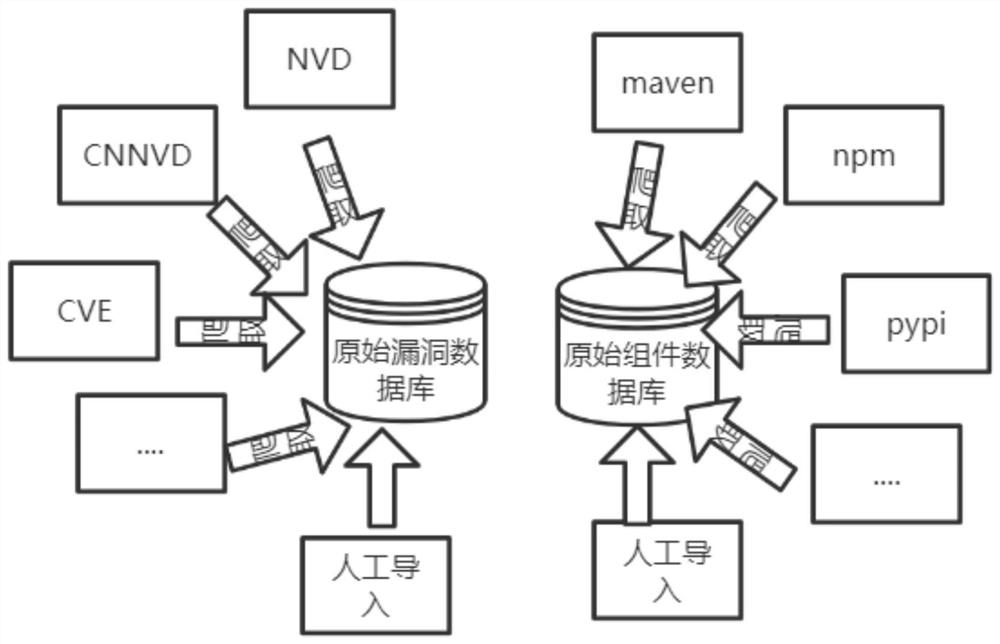
The invention relates to a security and compliance treatment method suitable for an open source component. The method comprises the steps of 1, constructing a knowledge base, scanning a dependency configuration file, forming a component list of the component and establishing a component relation tree, 2, searching a dependency component with vulnerabilities and analyzing the dependency component, and 3, providing a vulnerability repair scheme and a dynamic repair scheme of the component. Therefore, the open source dependent component and the open source license are supported, and automatic identification and safety and compliance analysis can be carried out. And a component relationship tree is established through the dependency relationship among the components, so as to perform examination and management. And detection of vulnerability conditions associated with the component is supported. A dynamic repair scheme can be provided, and meanwhile automatic repair is supported. And vulnerabilities are continuously tracked and monitored, so that the safety of products can be ensured. The method can adapt to agile development, ci / cd tools can be integrated, safe left shift is achieved, the development efficiency is improved, and the development cost is reduced.
Owner:苏州棱镜七彩信息科技有限公司
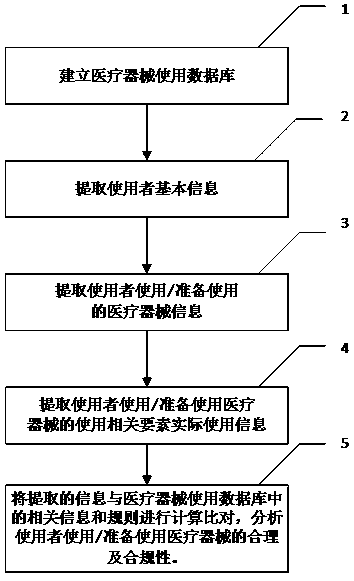
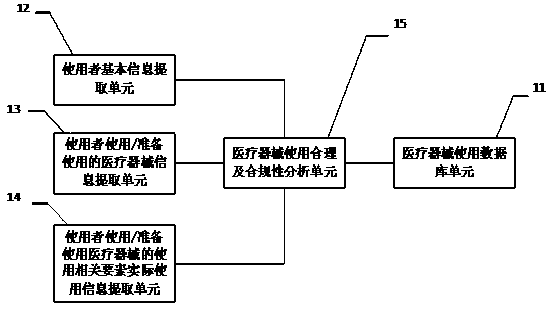
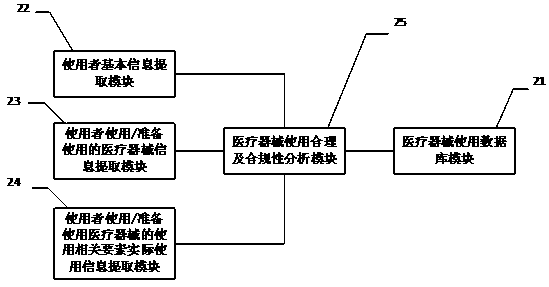
Method, system and equipment for reasonably using and analyzing compliance of medical instrument
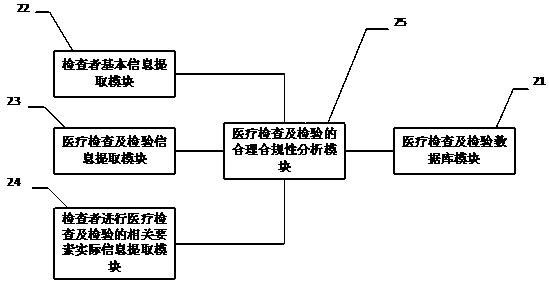
PendingCN110717082AEfficient managementEffective paymentOffice automationOther databases queryingApparatus instrumentsCompliance analysis
The invention discloses a method, a system and equipment for reasonably using and analyzing compliance of a medical instrument. By establishing the medical instrument use database, extracting the userinformation, the used medical instrument information and the actual use information of the related elements when the user uses the medical instrument, and comparing the extracted information with themedical instrument use database, the use reasonability and compliance of the medical instrument can be analyzed. According to the method, the system and the equipment for analyzing the use reasonability and the compliance of the medical instruments, analysis results are provided for different users in different forms, the users are assisted to realize effective management of use of the medical instruments, and the users are helped to use the medical instruments safely, effectively, economically and properly; a medical administrative department, a medical insurance management institution, a medical institution, an insurance company, a market / quality supervision and management department, a commercial circulation management department and a production enterprise are helped to better manageuse, payment, sales and production of medical instruments.
Owner:曹庆恒
Interactive business lifecycle management system
InactiveUS20160098655A1Simplify the viewing processFinanceResourcesCompliance analysisProgram analysis
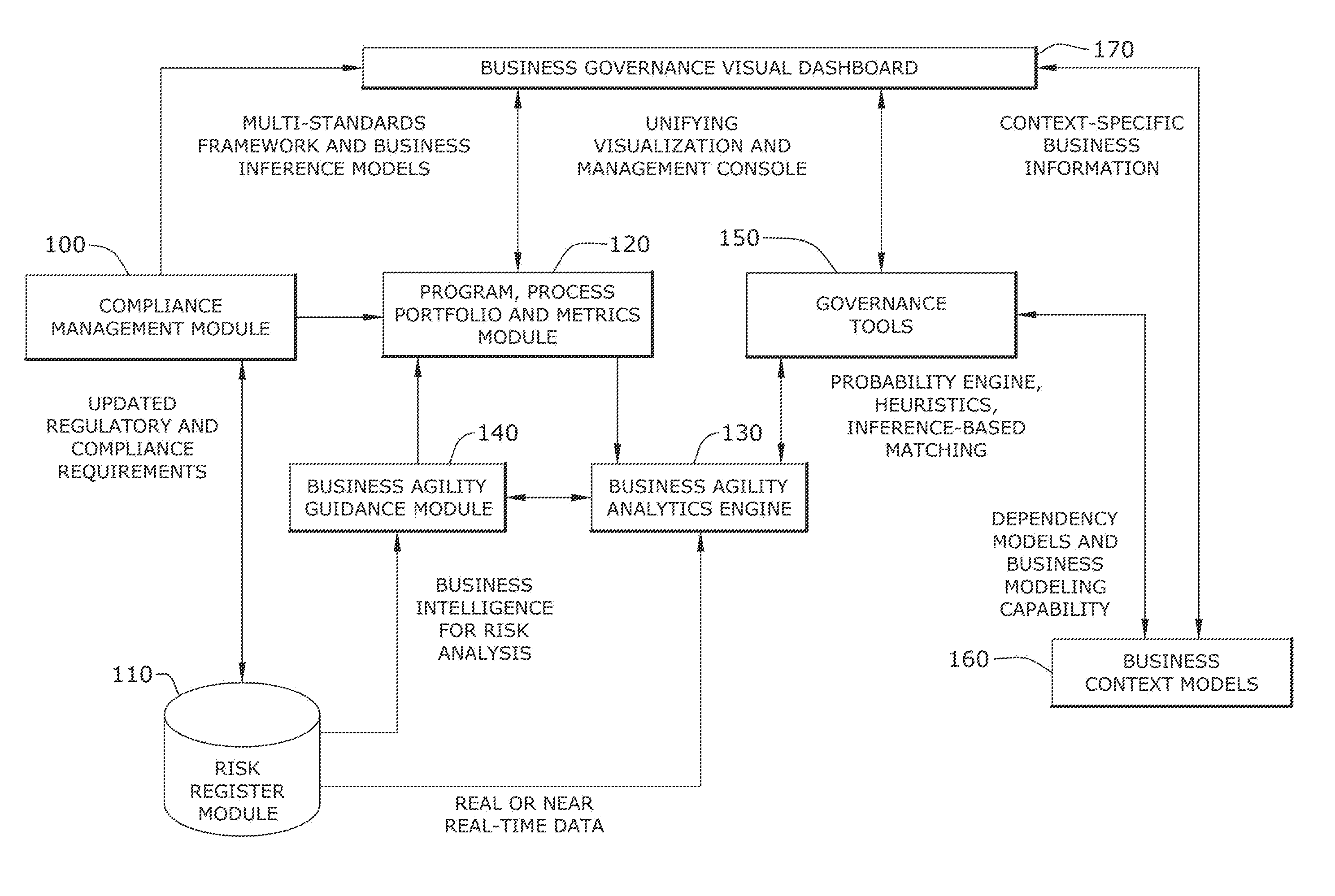
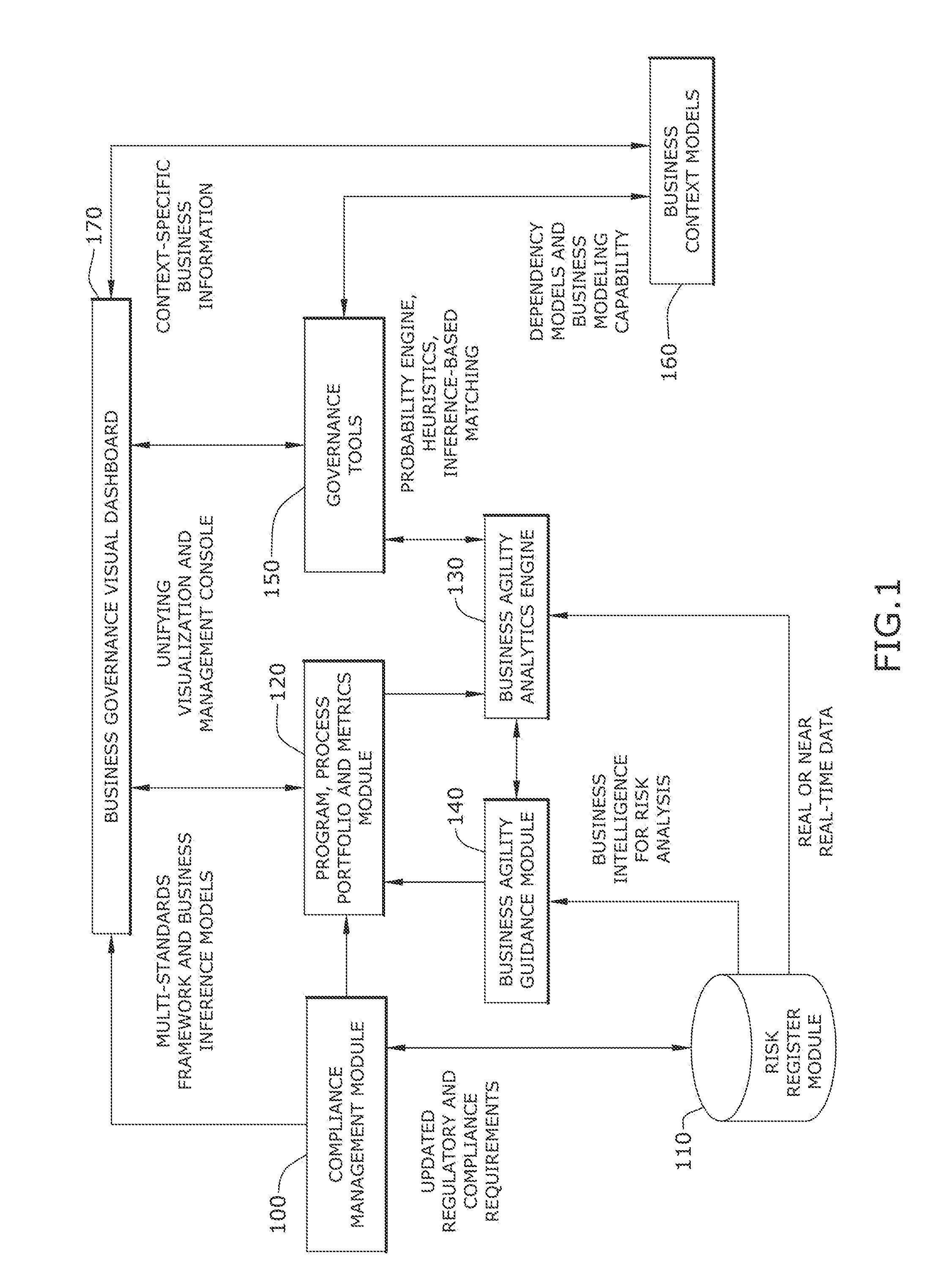
An interactive business lifecycle management system is disclosed which provides intuitive views of business programs, program performance, operations status, and compliance status. The interactive business lifecycle management system provides near real-time status, process analytics, business portfolio management, compliance and governance functions over business operations, and delivers program lifecycle management functions complete with comprehensive business program analysis capabilities and governance program compliance analysis. In this way, the interactive business lifecycle management system enables business leaders to perform business operations while satisfying governance compliance objectives.
Owner:IBM CORP
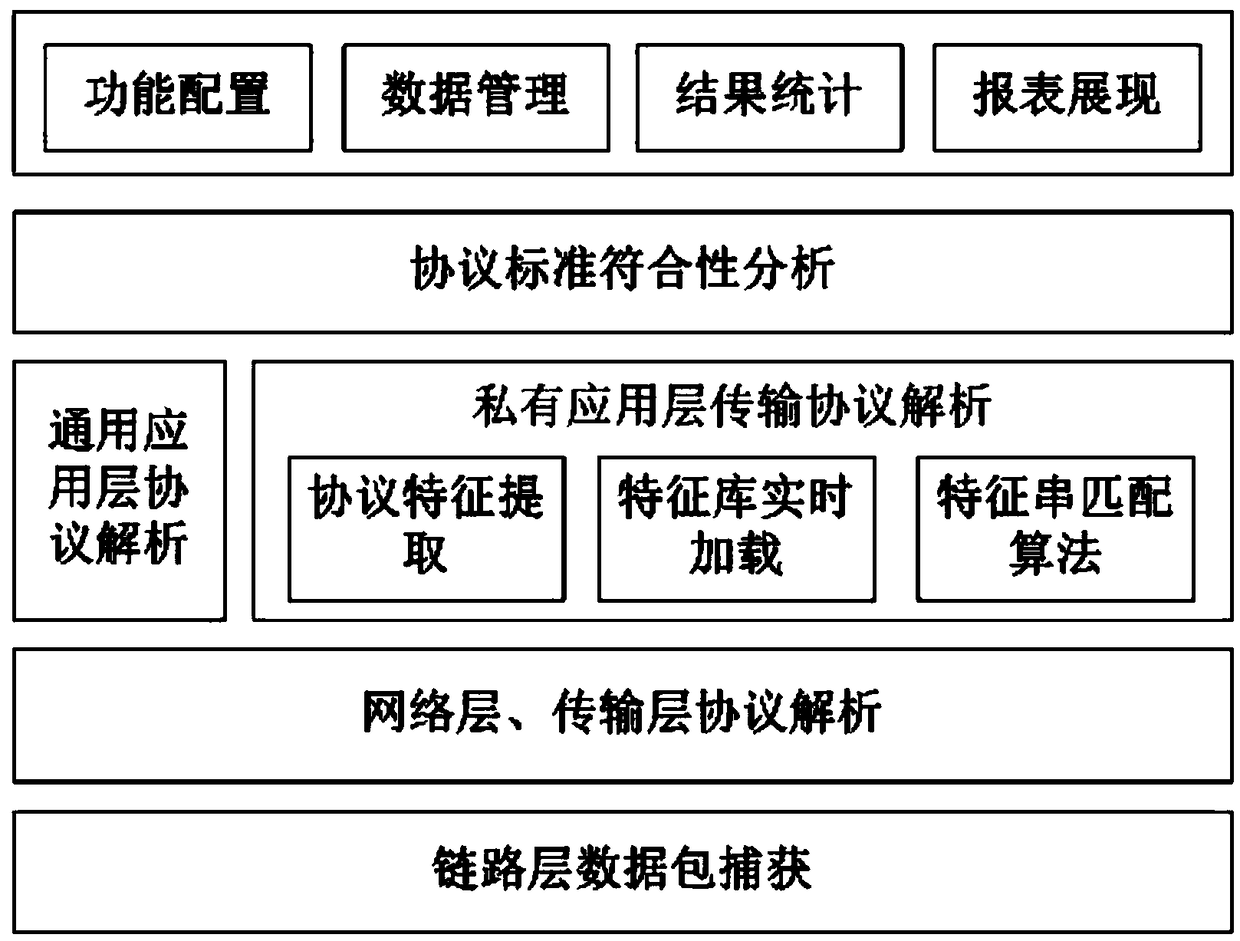
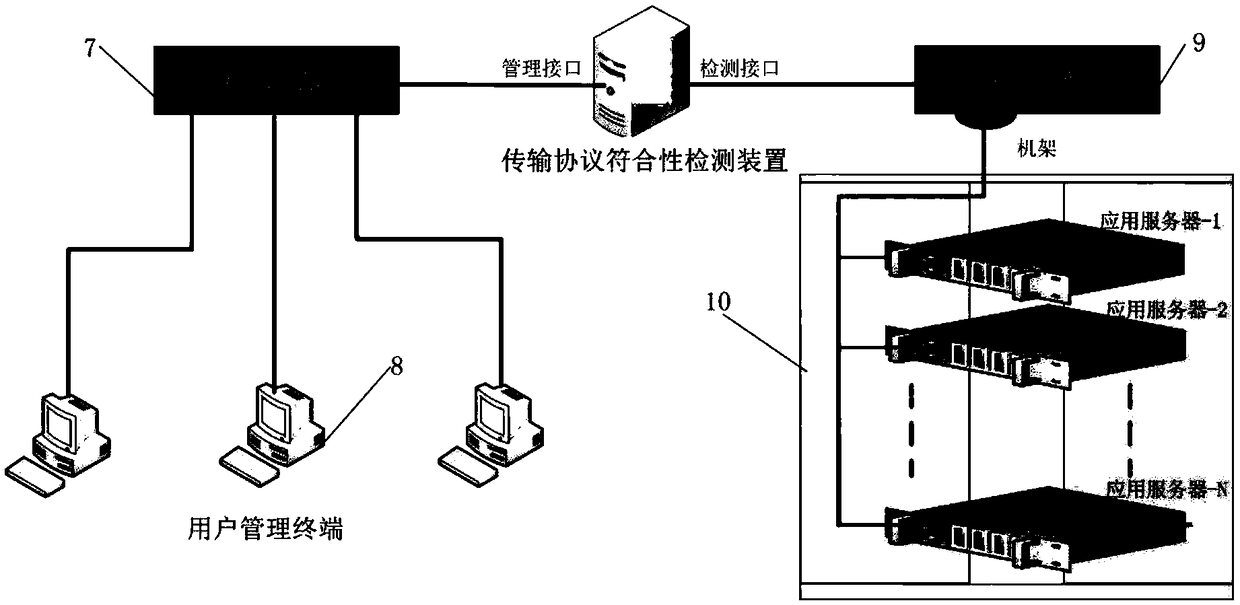
Transmission protocol compliance detection device, system and method
InactiveCN108737212AImprove the ability to identify and expandSupport and promote standardized managementData switching networksTransmission protocolFeature extraction
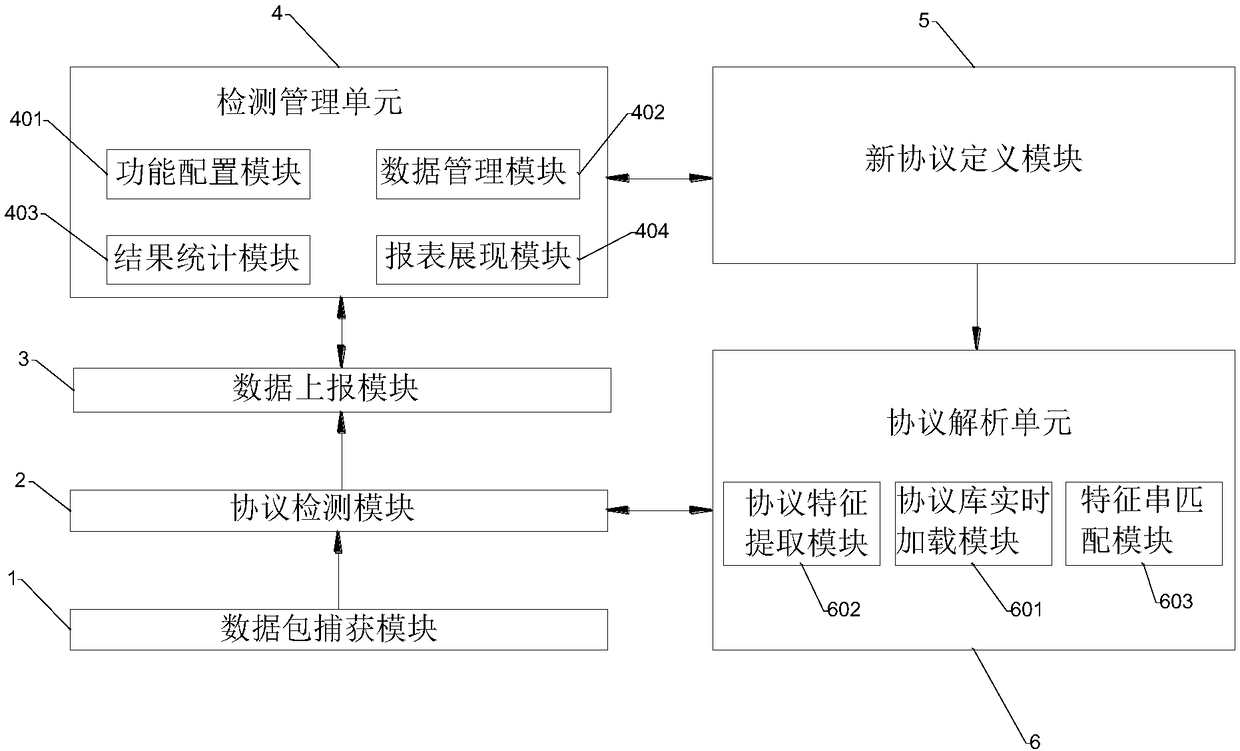
The invention discloses a transmission protocol compliance detection device, system and method. Parsing on various current general protocols is implemented, and a private protocol is subjected to identification detection by the flow of feature extraction, feature loading and feature string matching; a detection result can be subjected to showing, statistics and report export by a uniform interface; a user interface is provided, and the transmission protocol compliance detection device, system and method have functions of defining a new protocol, starting or stopping detection, uploading a file, showing the detection result, exporting the detection result and the like; receiving on a user command and a configuration from Web is implemented; when a detection command is executed, the new protocol is detected according to a defined new standard; and newly added protocol features can be directly subjected to dynamic defining and loading, so that the protocol identification expansion abilityis greatly improved, fine management control on the standard compliance test flow and scientific and fair evaluation on a compliance analysis result are implemented, standardized management of construction of the information communication field is effectively supported and propelled, and the interconnection ability between a network system and equipment is promoted.
Owner:中国人民解放军61062部队科技装备处
System and method of confirming traffic dispatching instruction
InactiveCN106504590AImprove convenience and effectivenessGuaranteed correctnessRailway traffic control systemsSimultaneous traffic control systemsSimulationCompliance analysis
The invention discloses a system and a method of confirming a traffic dispatching instruction. The system uses an instruction confirmation request acquisition device to acquire an instruction confirmation request inputted by an operator and uses a traffic operation information acquisition device to acquire the traffic operation information; and analysis and judgment are carried out by an instruction confirmation request operation requirement compliance analysis device. In a dynamic traffic environment corresponding to the traffic operation information, whether the instruction content corresponding to the instruction confirmation request meets traffic operation requirements in a set time is judged, and thus, an analysis and judgment result of the instruction confirmation request operation requirement compliance analysis device is obtained. The invention also provides a method based on the above system idea. Through the above mode, a dispatching person can judge the correctness of the instruction through analysis and judgment in a technical means before the instruction is issued, the dispatching person can be ensured to issue a correct instruction, and operation safety is ensured.
Owner:WENZHOU YUNHANG INFOMATION TECH LTD
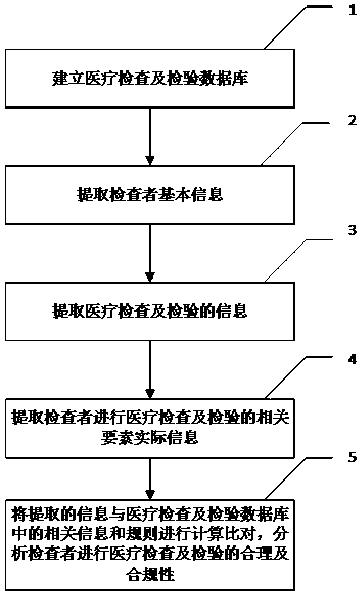
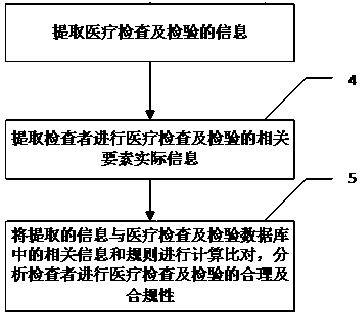
Method, system and device for analyzing reasonability and compliance of medical examination and inspection
PendingCN111028936AEfficient managementEasy to manageMedical data miningMedical equipmentCompliance analysisMedical institution
The invention discloses a method, a system and equipment for analyzing reasonability and compliance of medical examination and inspection. A medical examination and examination database is establishedfor extracting examiner information, medical examination and examination information and actual information of related elements of an examiner for medical examination and examination, and comparing the extracted information with the medical examination and examination database, so that the reasonability and compliance of medical examination and examination can be analyzed. According to method, system and device, analysis results are provided for different users in different forms, users are assisted in achieving effective management of medical examination and examination, and examiners are helped to conduct medical examination and examination safely, effectively, economically and properly; the system helps medical administrative departments, medical insurance management institutions, medical institutions, insurance companies, market / quality supervision and management departments and commercial circulation management departments to better manage medical examination and inspection.
Owner:曹庆恒
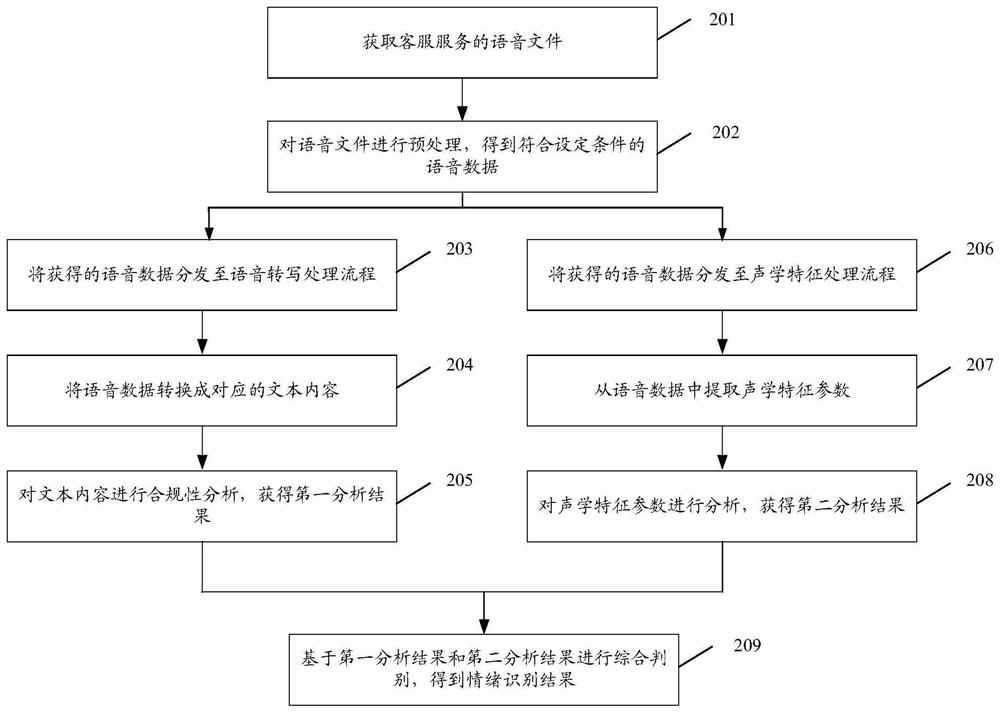
Emotion recognition method and device and storage medium
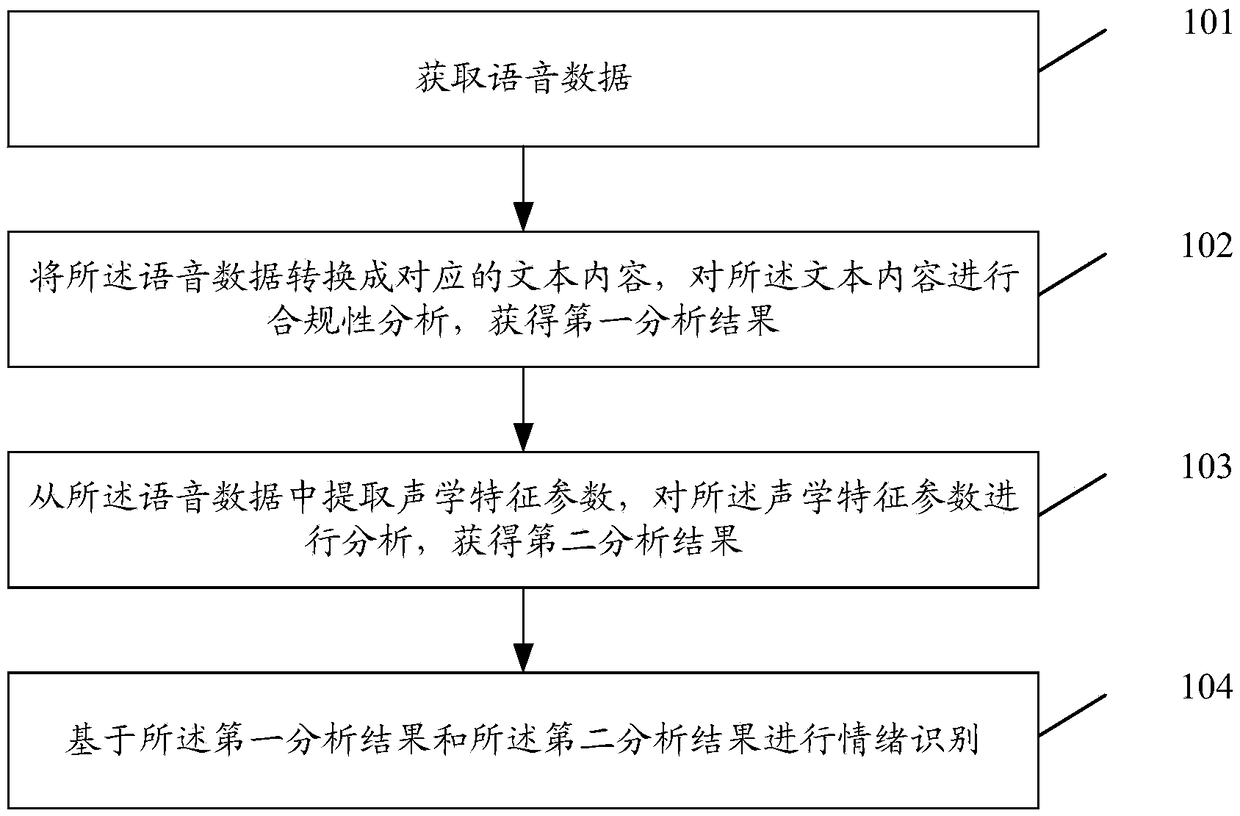
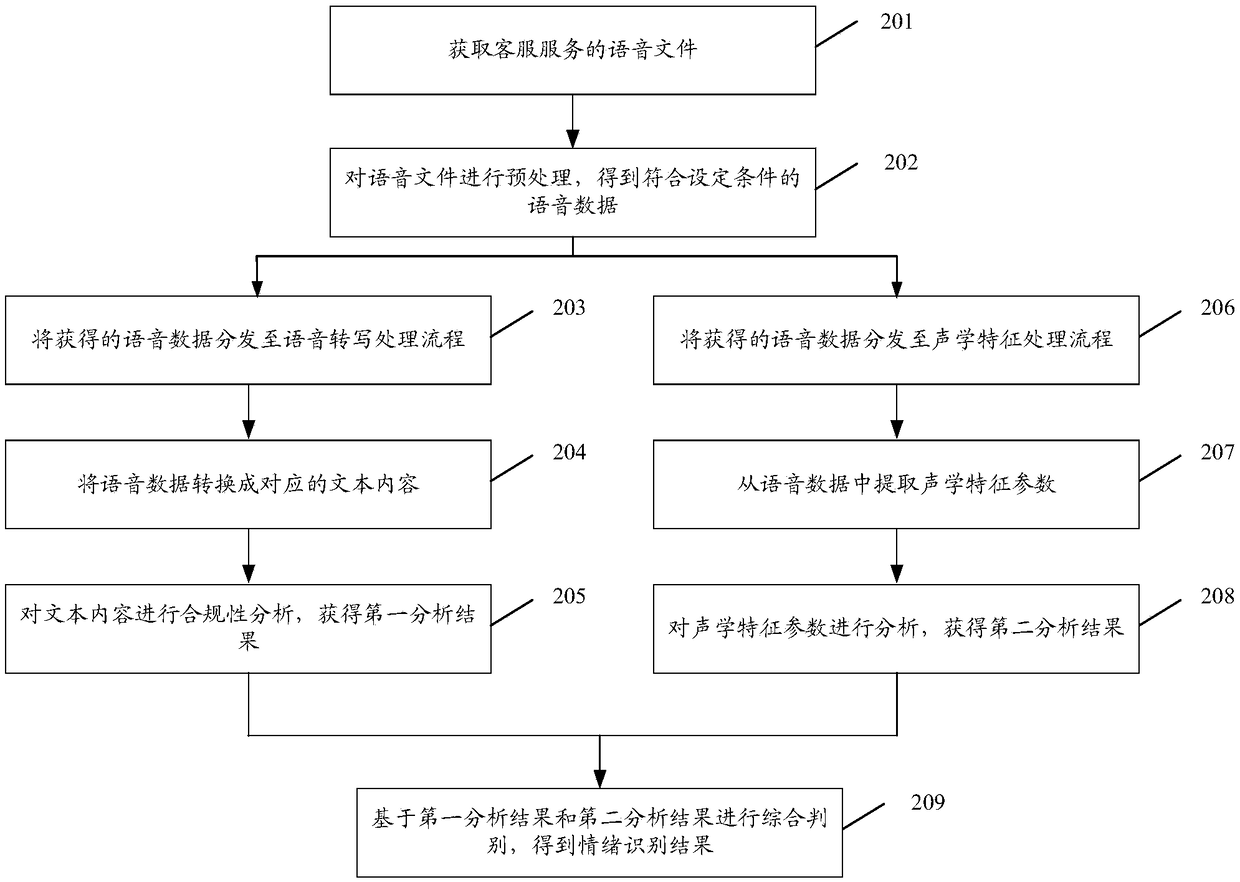
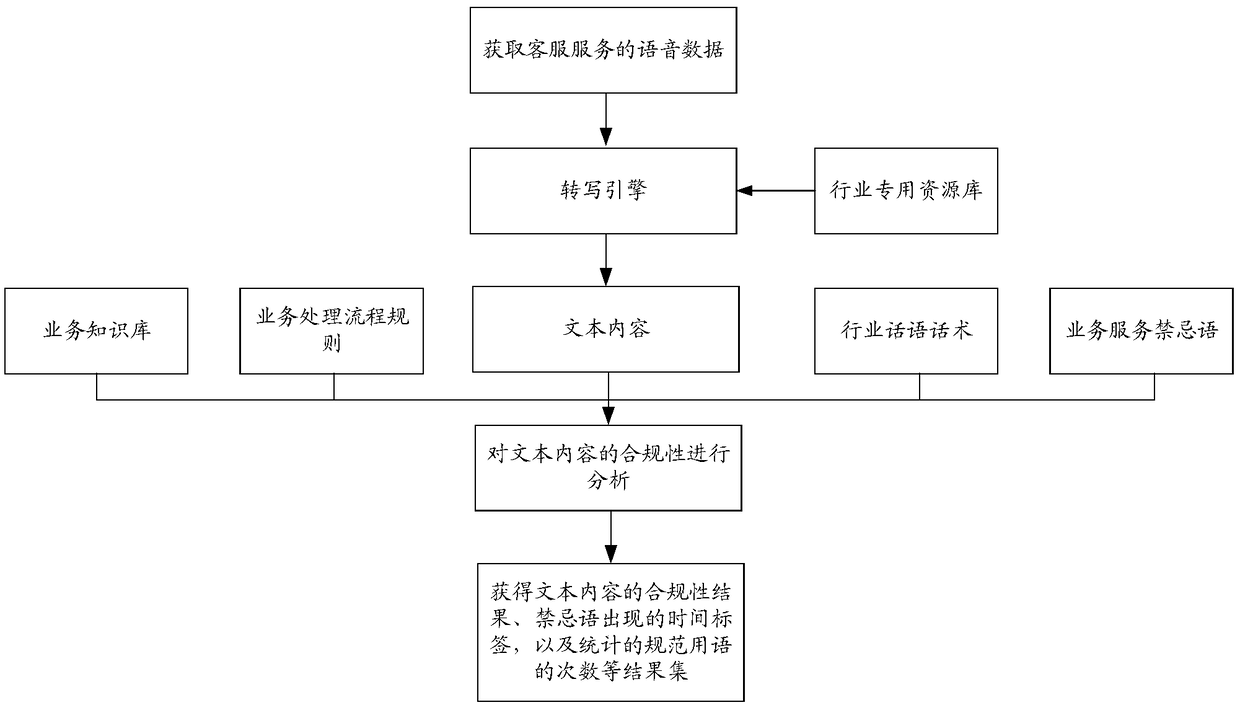
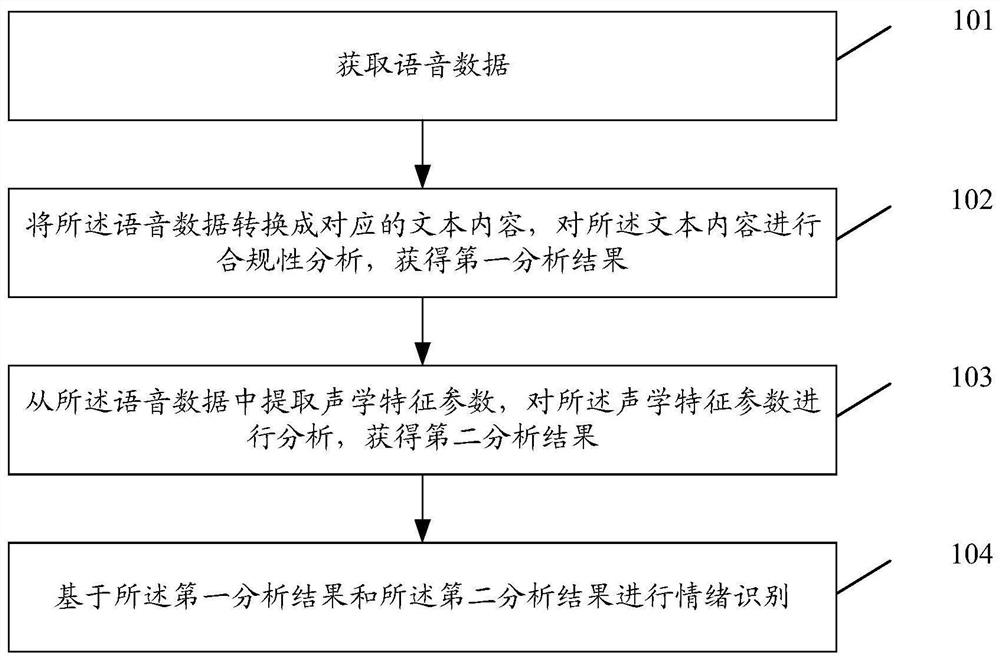
ActiveCN109410986AQuality improvementImprove quality inspection efficiencySpeech recognitionPattern recognitionCompliance analysis
The embodiment of the invention discloses an emotion recognition method, an emotion recognition device and a storage medium. The method comprises the following steps: acquiring voice data; convertingthe voice data into corresponding text content, and carrying out compliance analysis on the text content, thus obtaining a first analysis result; extracting acoustic feature parameters from the voicedata, and analyzing the acoustic feature parameters, thus obtaining a second analysis result; and carrying out emotion recognition on the first analysis result and the second analysis result.
Owner:MIGU DIGITAL MEDIA CO LTD +2
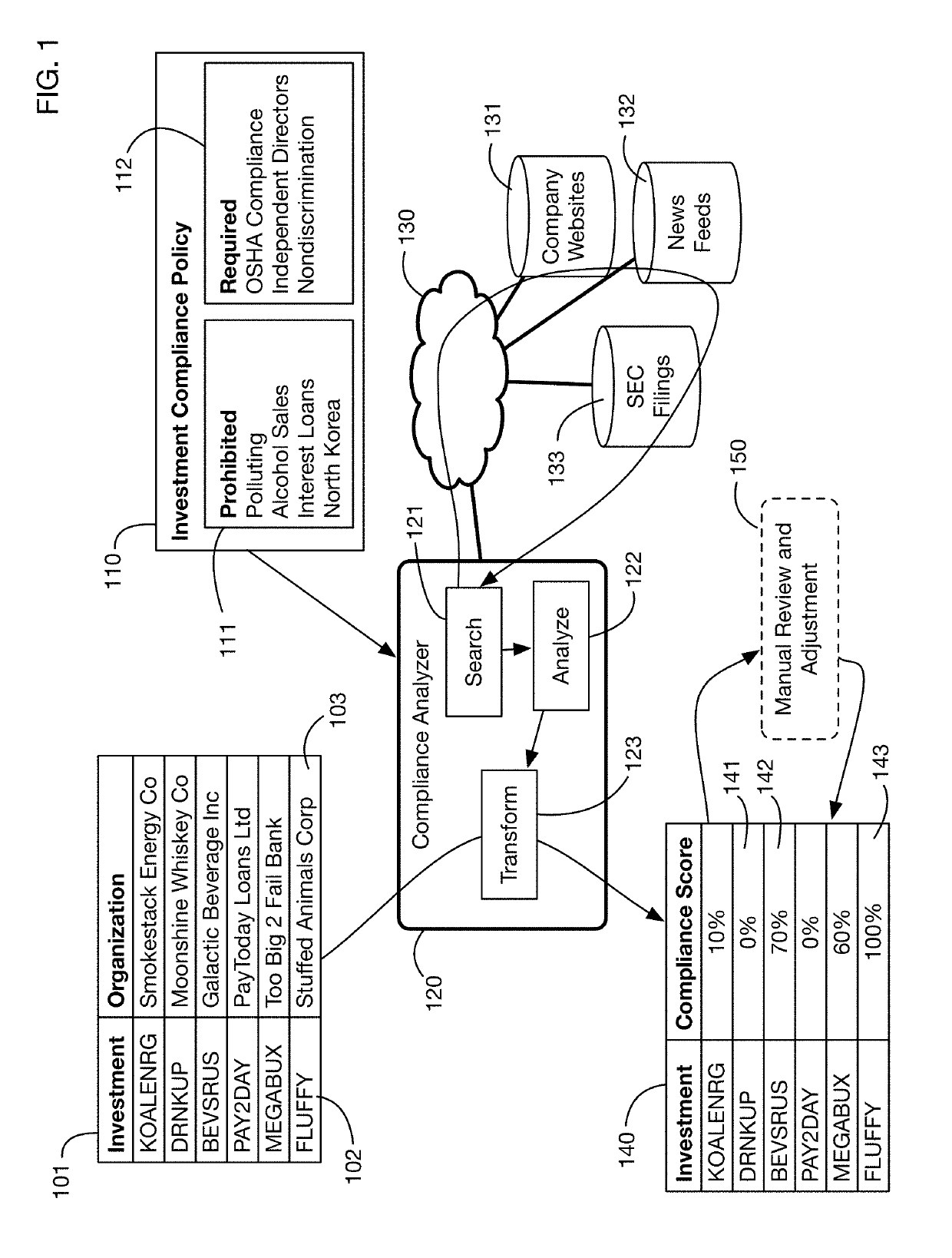
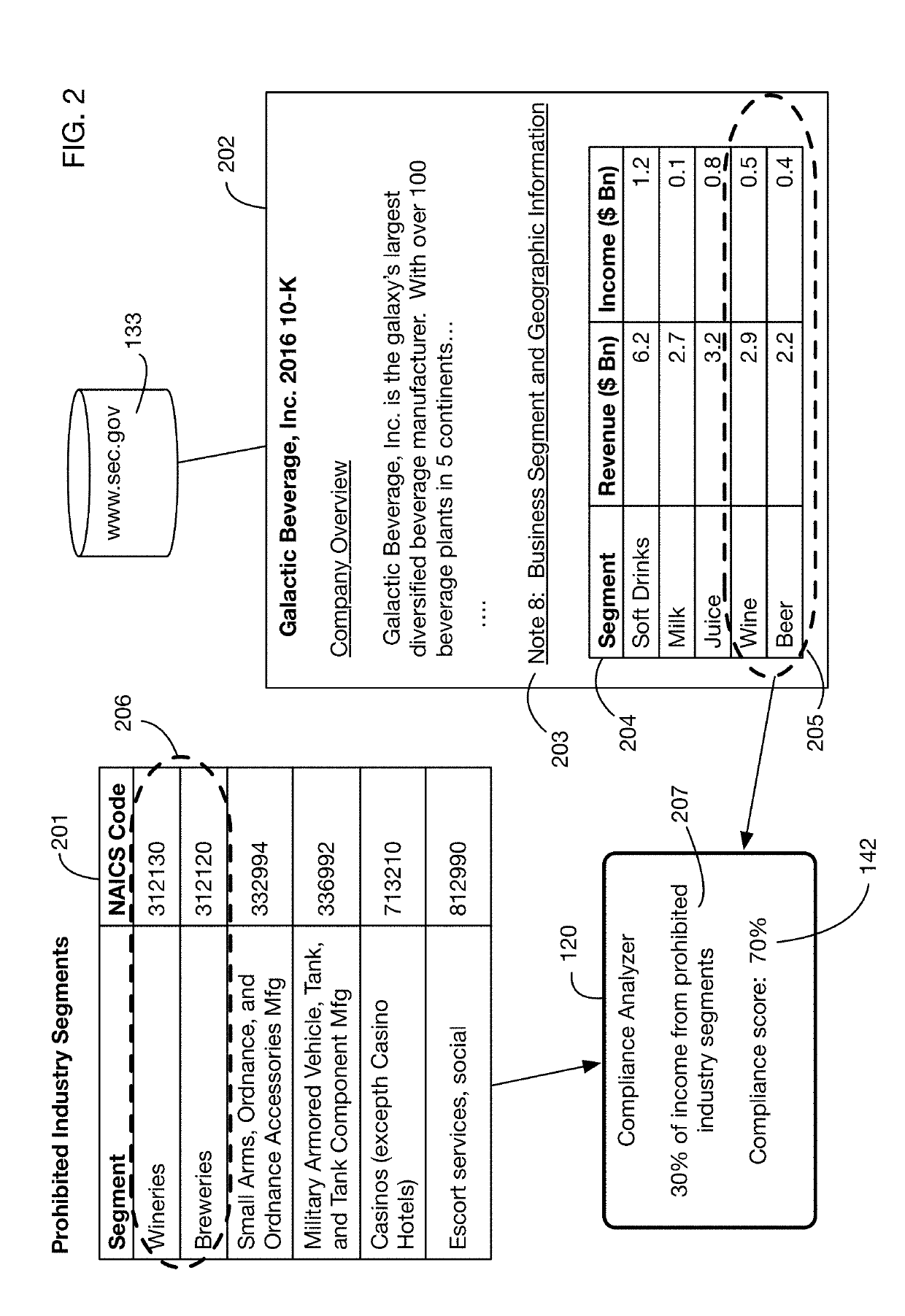
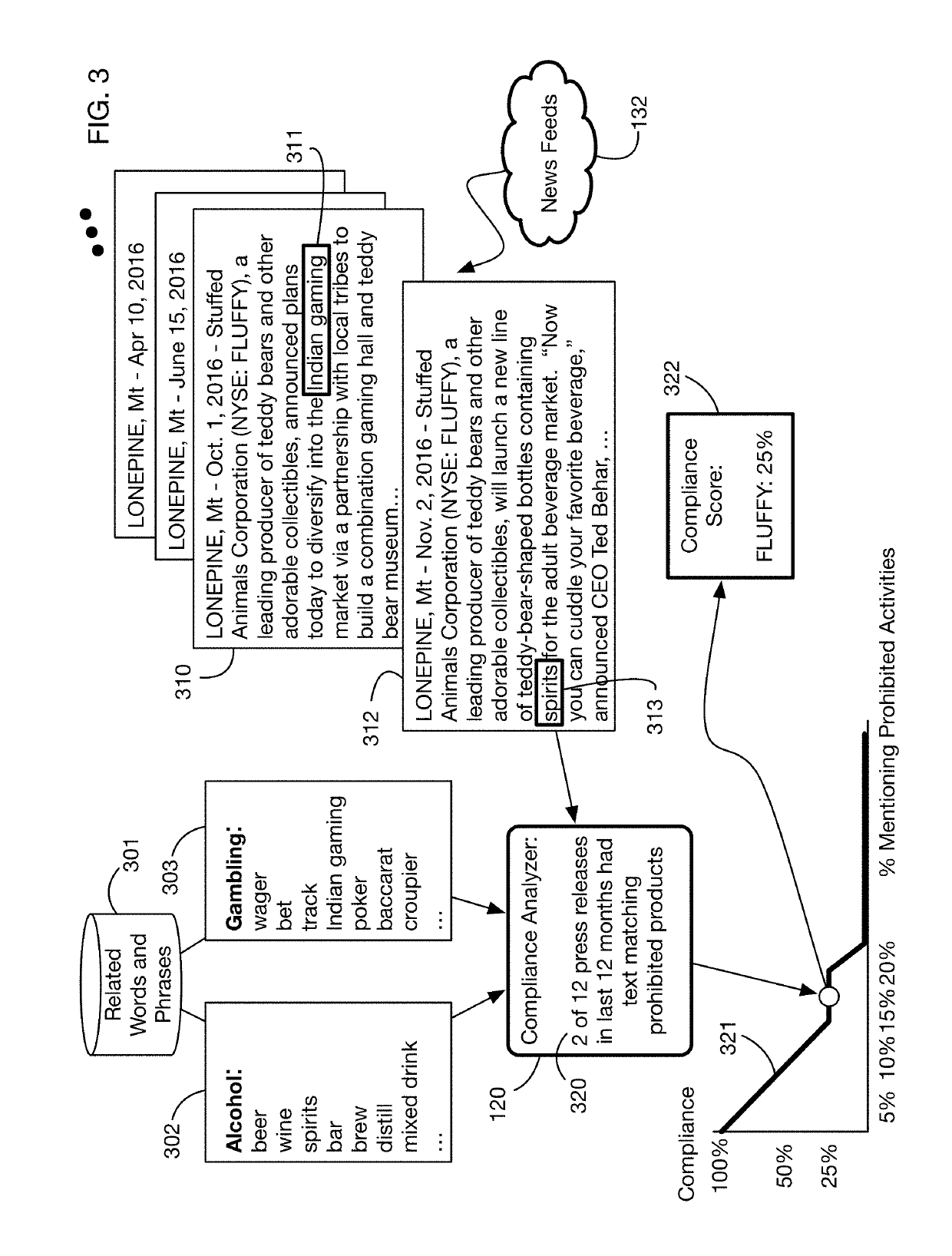
Automated compliance scoring system that analyzes network accessible data sources
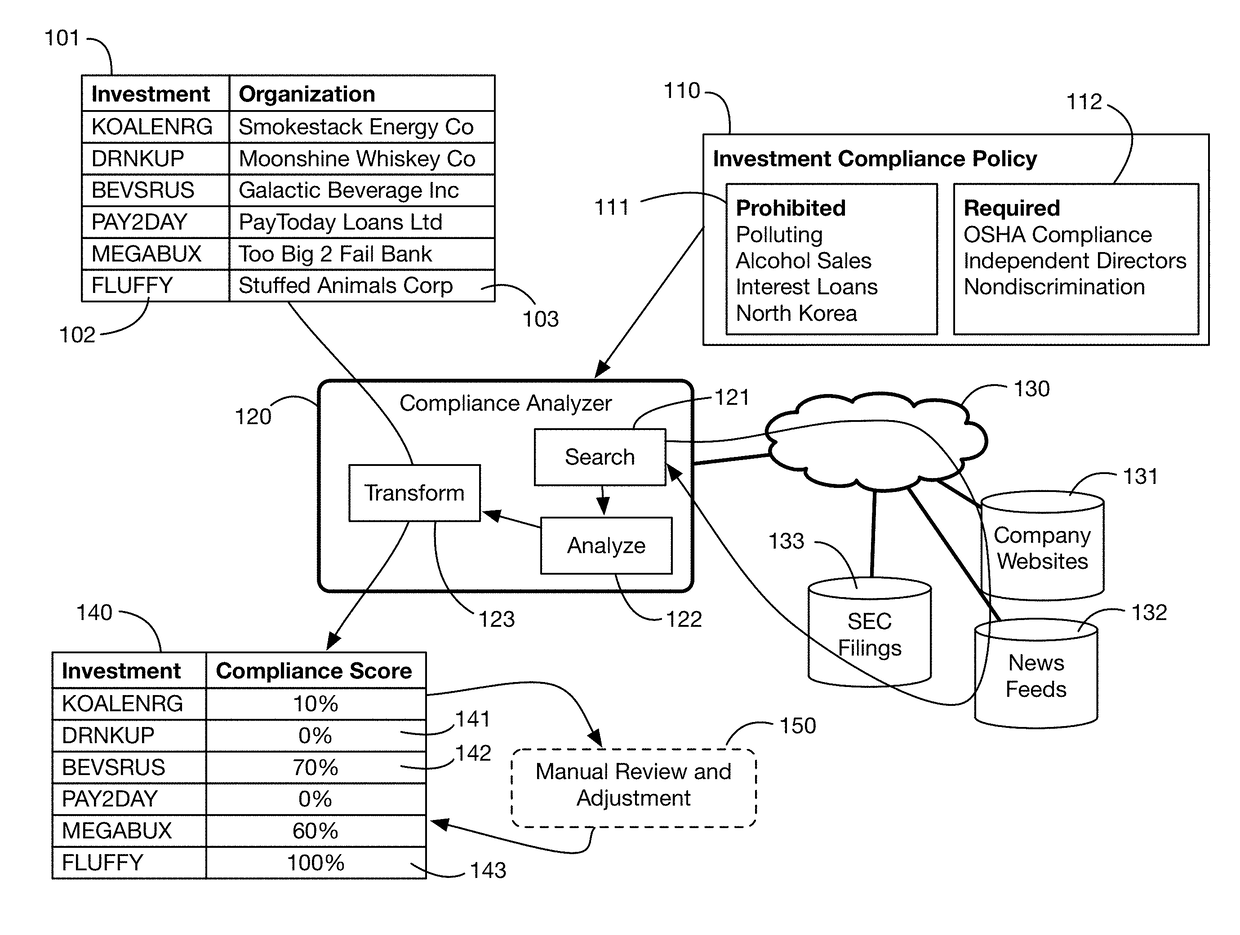
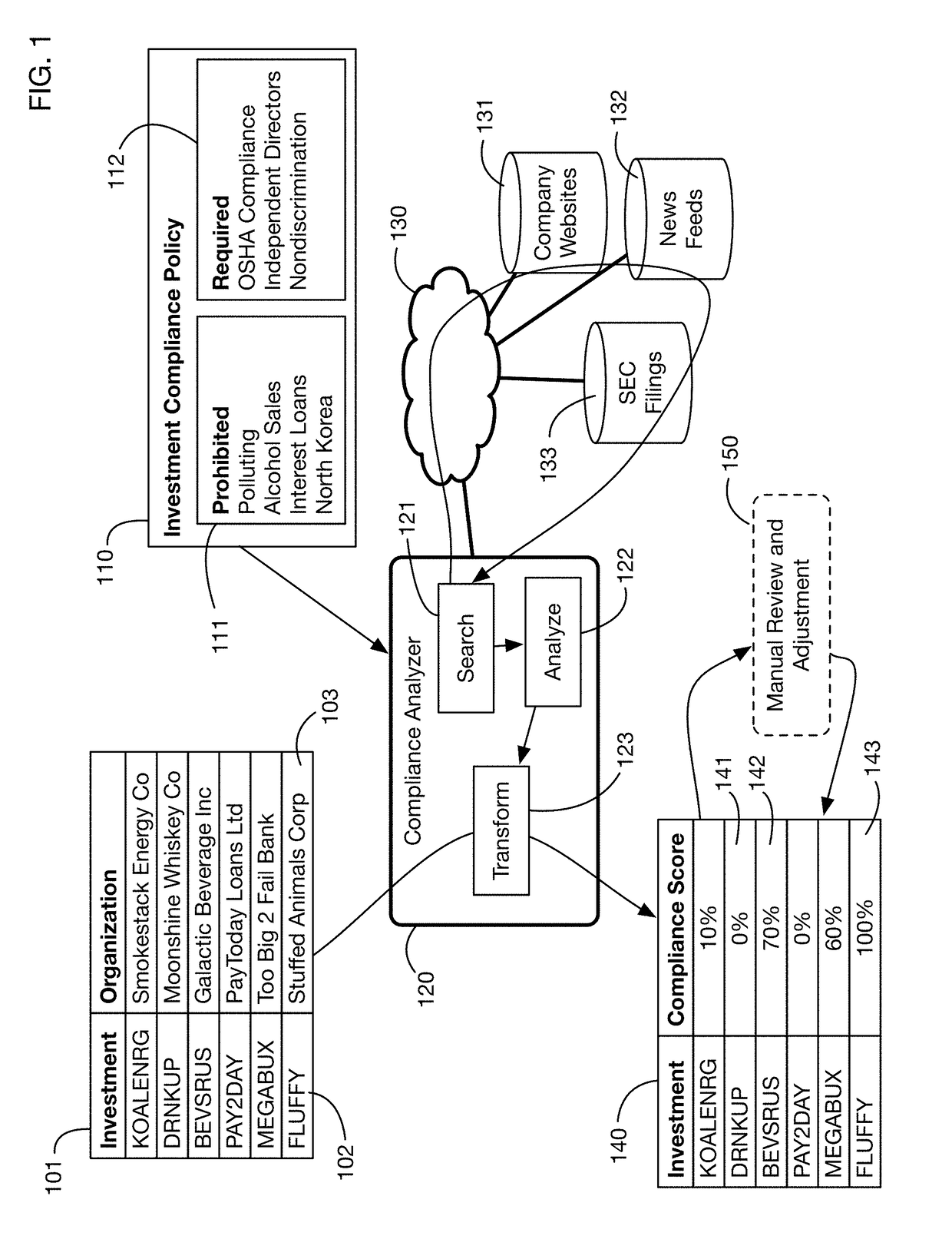
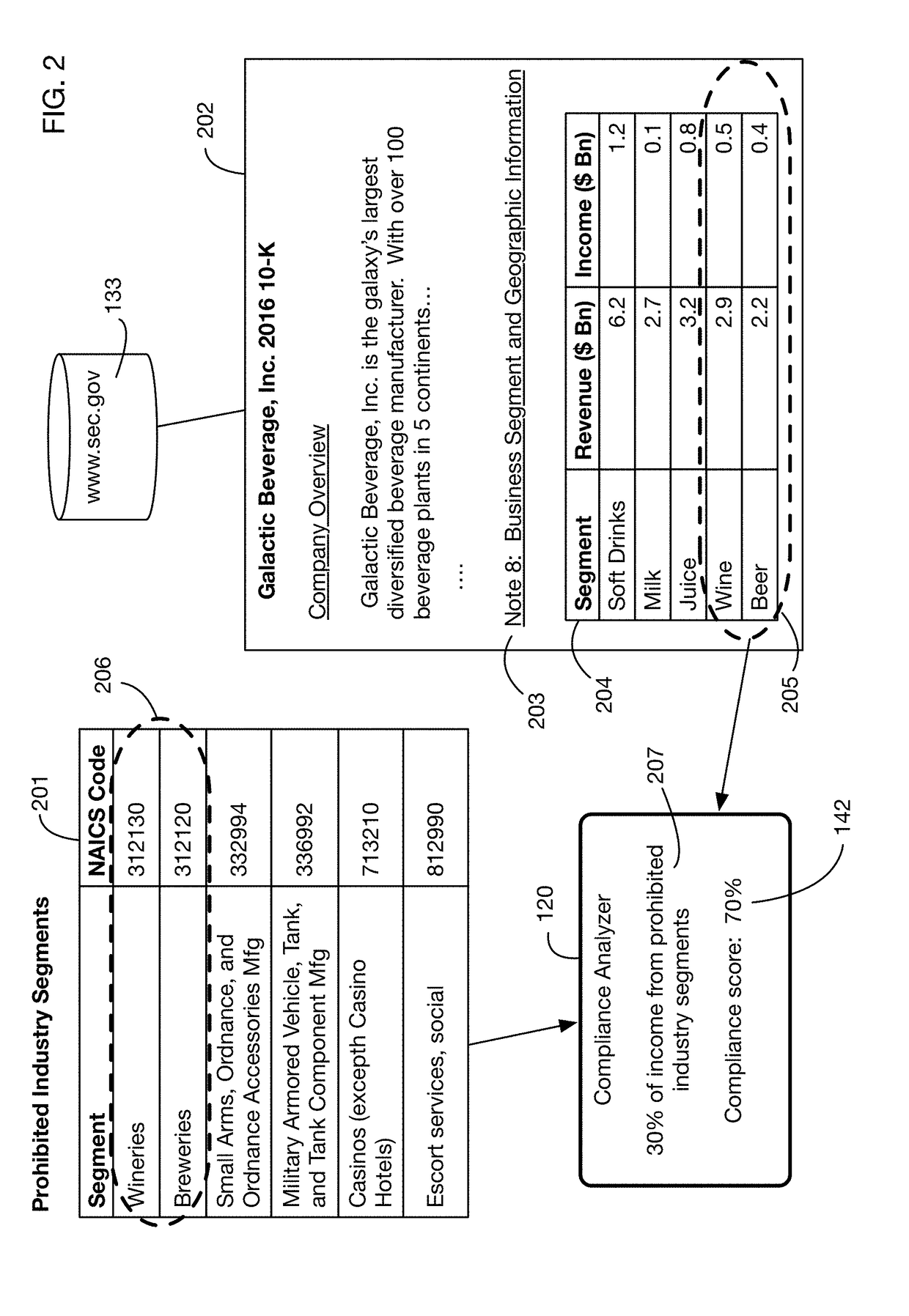
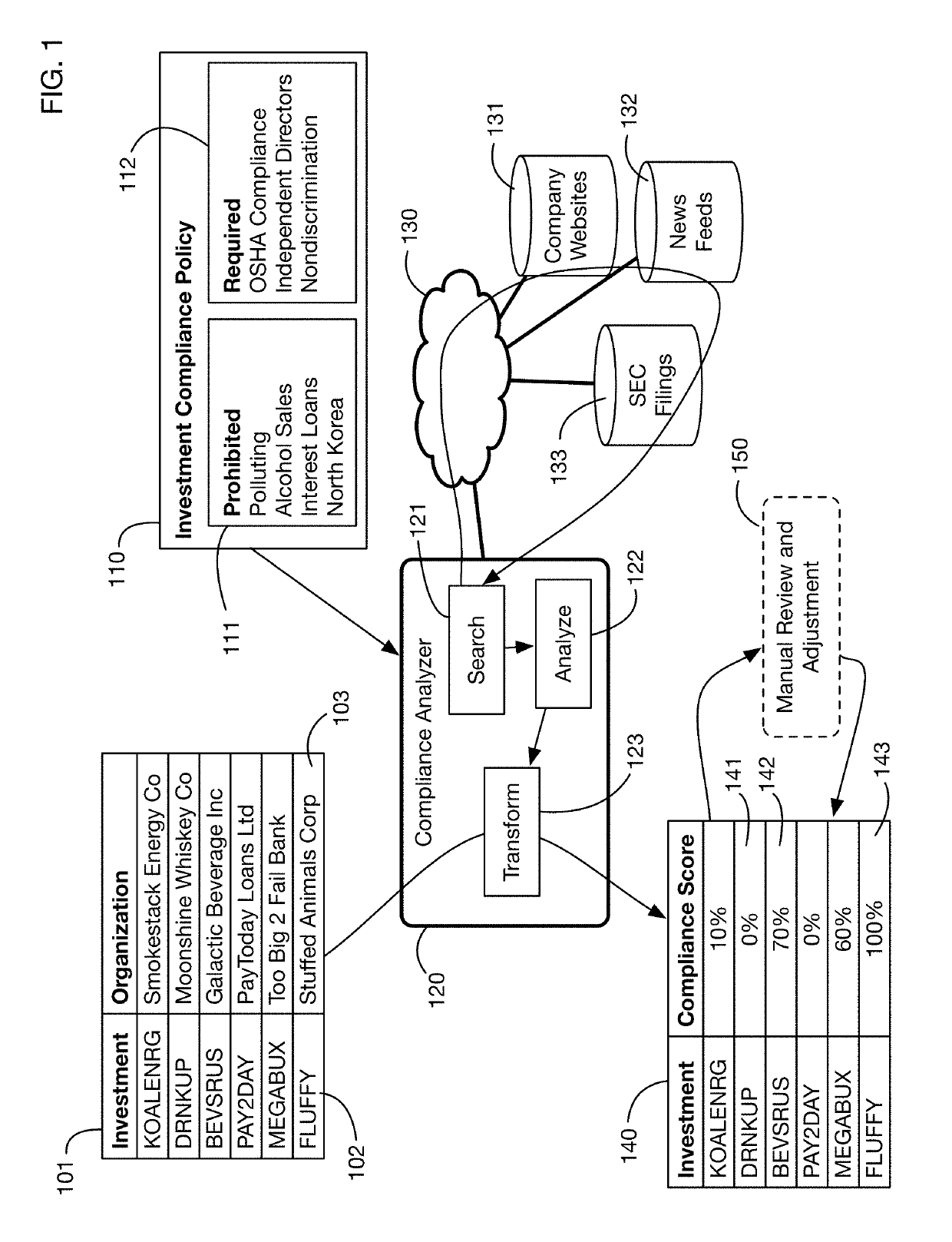
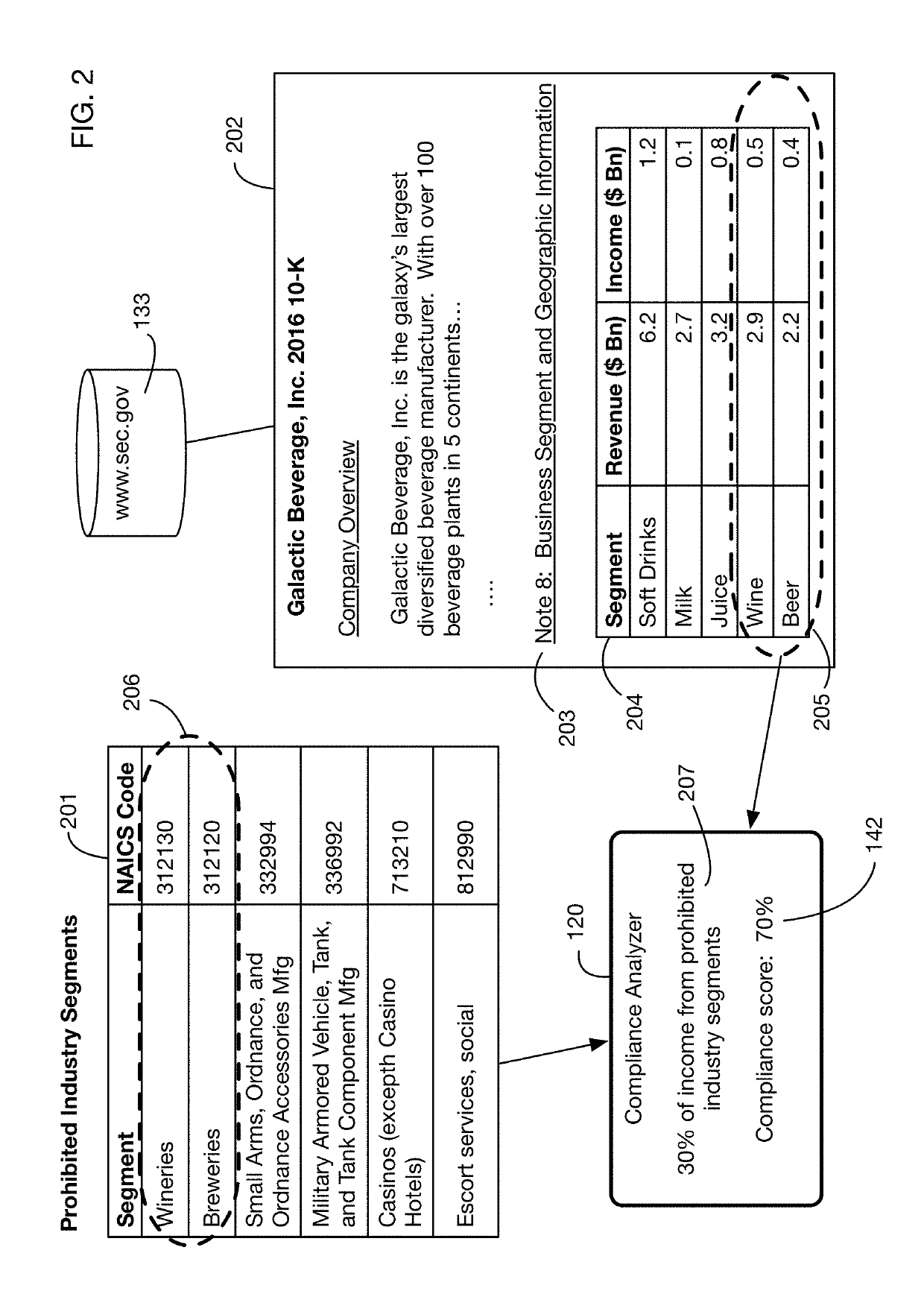
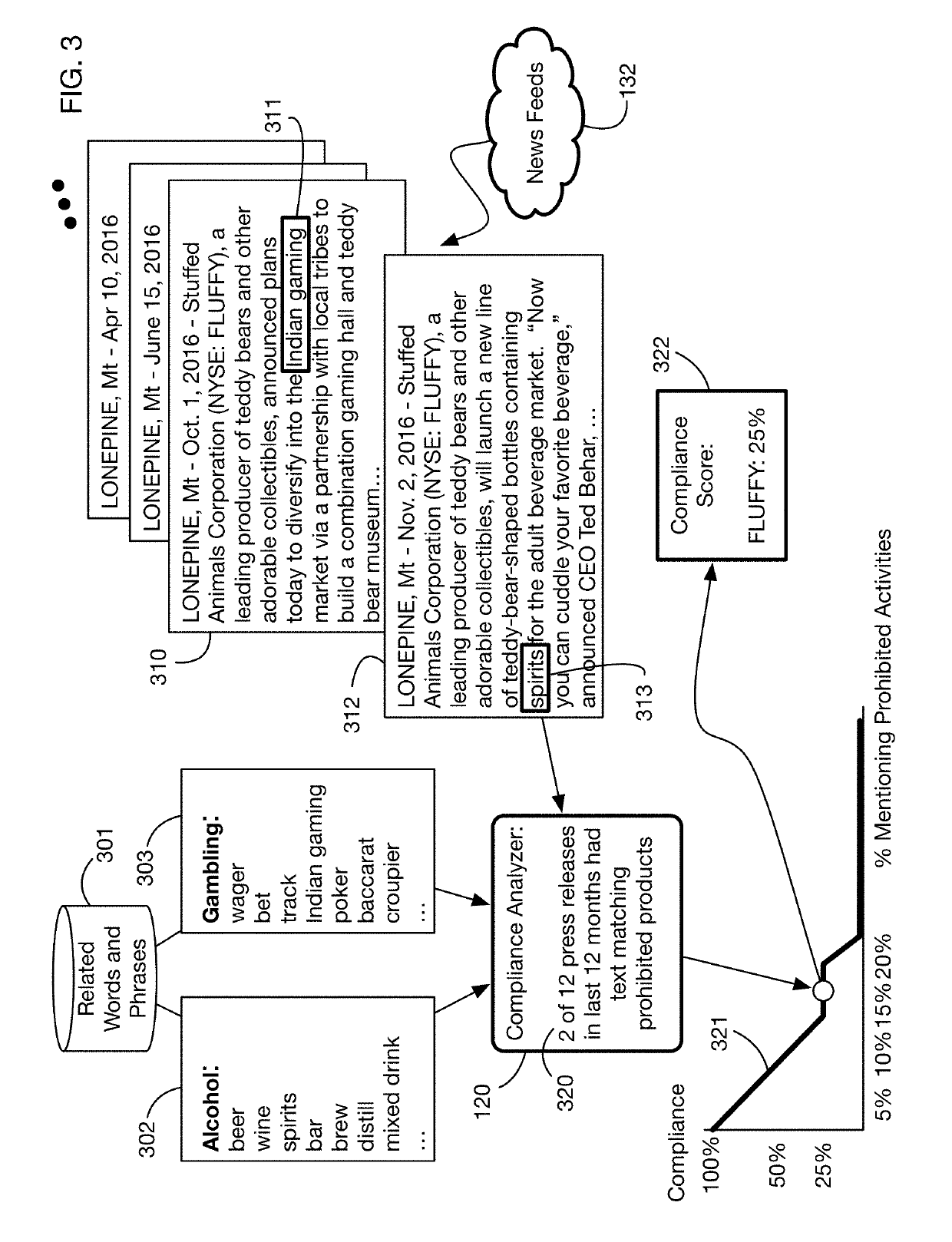
An automated system that analyzes network accessible data sources to determine a score that measures compliance of an investment with a compliance policy. The compliance policy may specify for example ESG (Environment, Social, or Governance) requirements, or prohibitions against selling of certain products and services considered undesirable or unethical by certain investors. Compliance analysis may determine the amount of revenue or income received from prohibited sources, or it may search information for key words and phrases related to these sources. The system may “purify” noncompliant investments by bundling them with charitable contributions that offset the income from prohibited sources. Fund managers may publish and share compliance policy definitions, and may import these shared definitions and customize them for their specific fund requirements.
Owner:IDEALRATINGS INC
Method and system for analyzing user access compliance
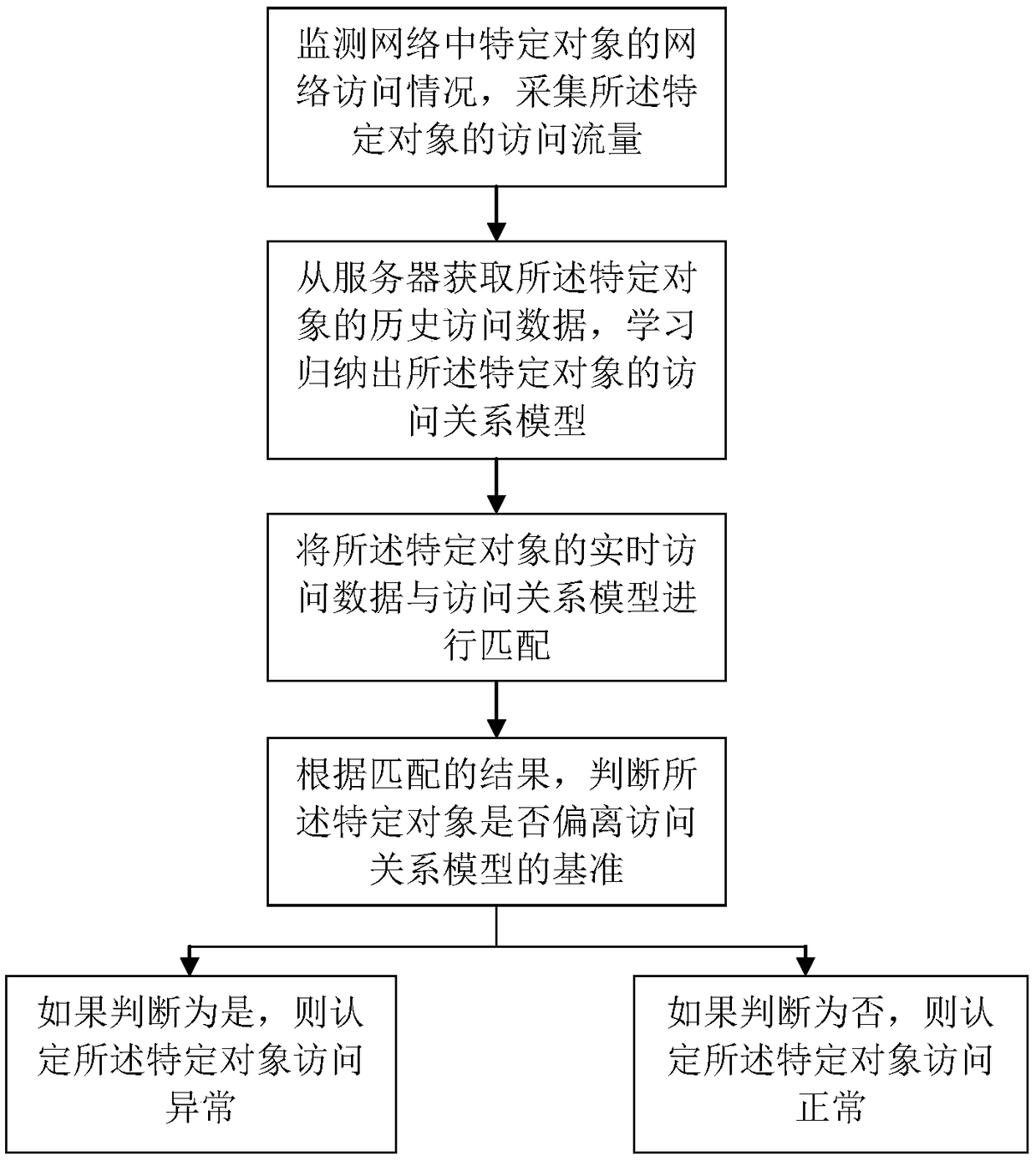
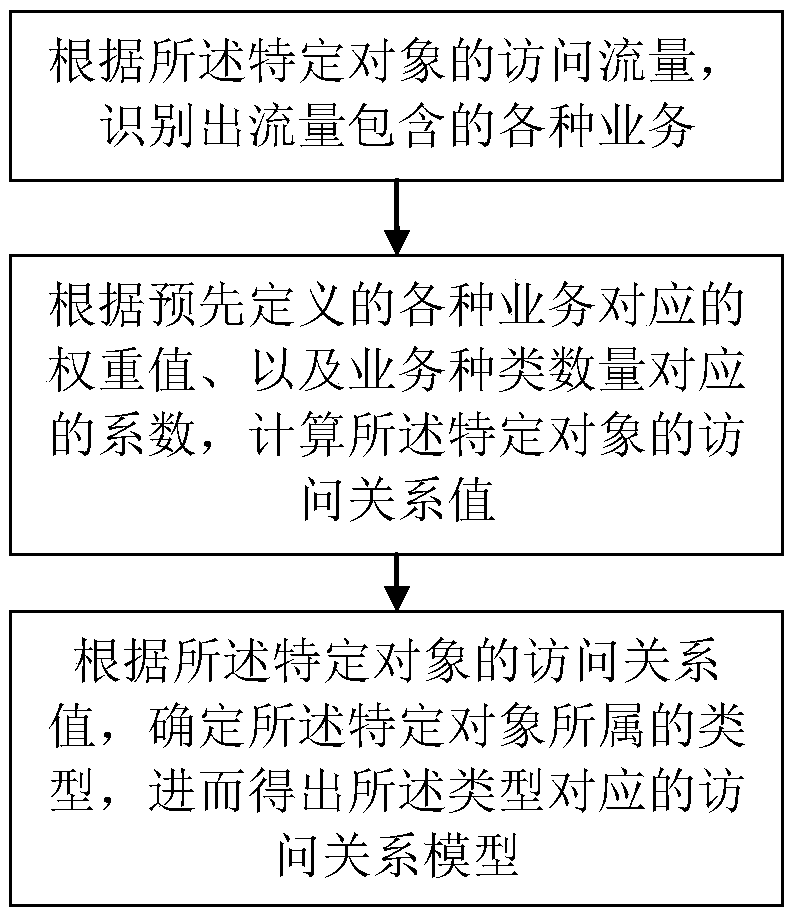
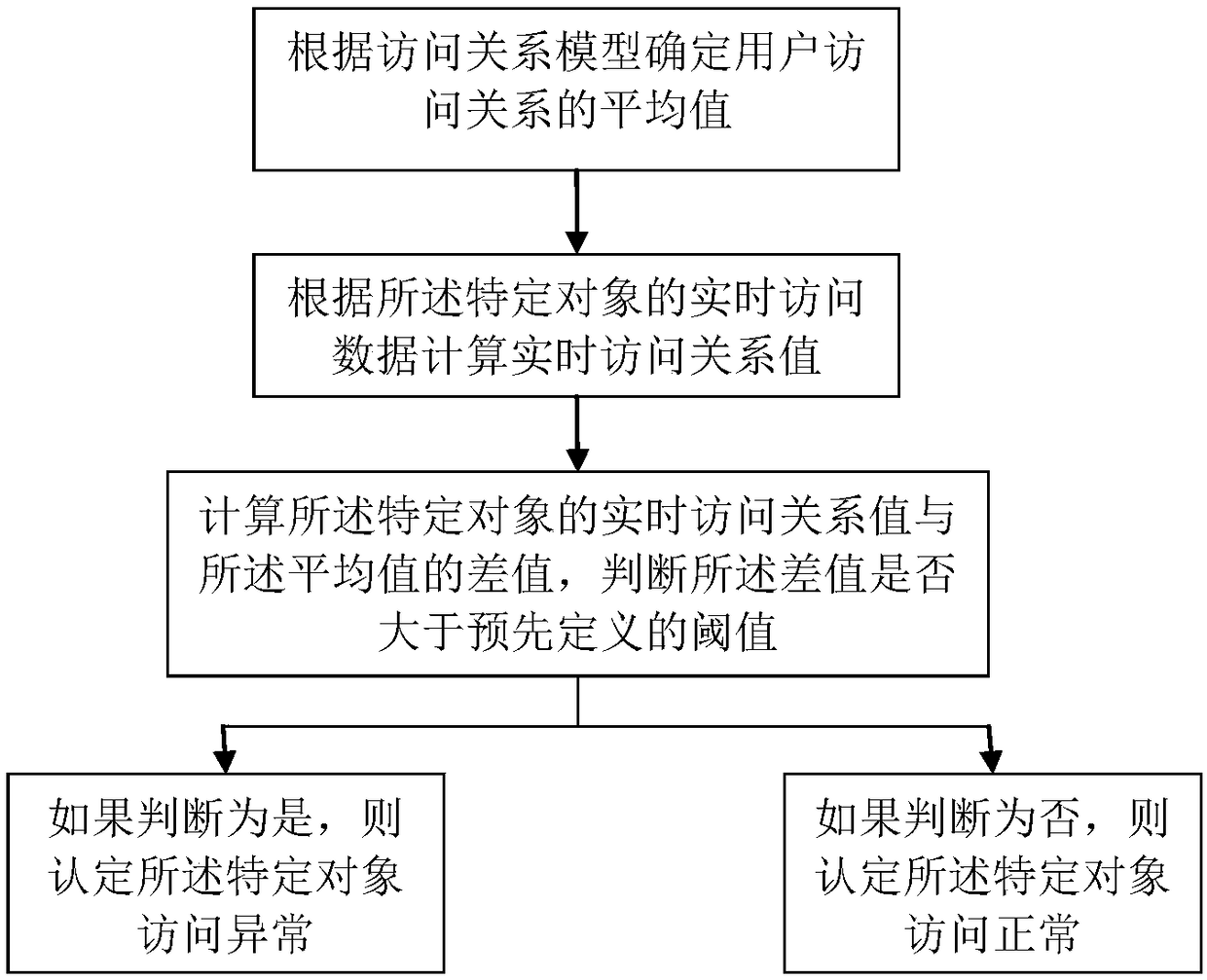
ActiveCN108881275AWhether the access is abnormalDifferentiating attributesDigital data authenticationTransmissionRelational modelCompliance analysis
The invention discloses a method and system for analyzing the user access compliance. The method comprises the following steps: acquiring historical access data of a specific object from a server, learning and summarizing an access relation model of the specific object, matching real-time access data of the specific object with the access relation model, and judging whether the specific object isdeviated from the reference of the access relation model according to a matching result. Therefore, attributes of different users can be distinguished, and whether an access to the specific object isabnormal or not is determined.
Owner:武汉思普崚技术有限公司
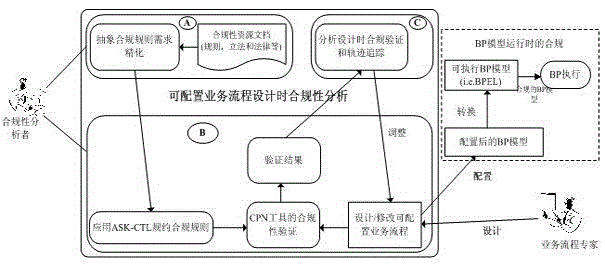
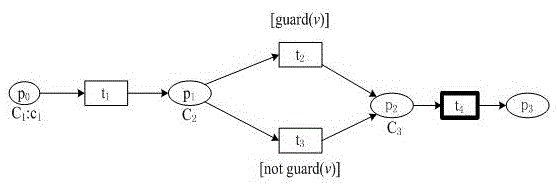
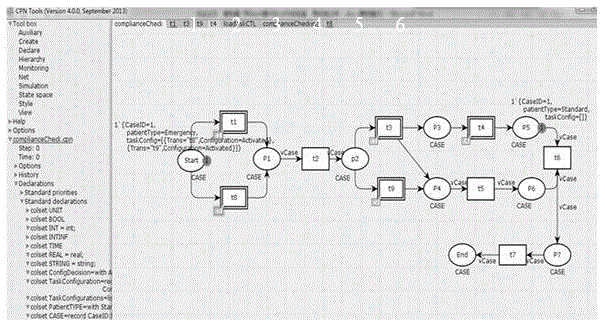
Service process variability configuration management compliance analysis and detection method
The invention discloses a service process variability configuration management compliance analysis and detection method, which comprises the steps of: adopting a CPN as a formal model to express a configurable service process through increasing configuration operation, and adopting an extended CTL formula to express a compliance rule to reflect the compliance requirement of the model; and finally, providing configurable service process compliance analysis and a correctness theorem of compliance constraint in a configurable service process model. According to the service process variability configuration management compliance analysis and detection method, the compliance rule is effectively integrated into the configurable service process, and the compliance correctness of the configurable service process is verified by means of a related tool set provided by the adopted CPN formal model. The analysis and detection method is provided for the consistency of the service process satisfying the service rule during the variability configuration management process, so that an organization or enterprise can comply with the corresponding service rule when providing individualized service process to a user.
Owner:TONGREN UNIV
System and method for analyzing distributed electronic medical record data to determine standards compliance
InactiveUS20160357915A1Large storage capacityLess spacePatient personal data managementSpecial data processing applicationsMedical recordCompliance analysis
The present invention is a system and method for the analysis of the compliance to medical care standards of patient care data retrieved from a plurality of electronic medical records storage systems where the electronic medical records systems are not in direct communication with each other. The system and method is enabled through the use of a plurality of electronic interface appliance devices, each in communication with one of the plurality of electronic medical records systems and also in communication with a medical analytics engine and medical care standards data. The system and method configured so that the retrieval and analysis of patient care data may be performed on a real-time basis to allow a care provider to receive the compliance analysis results during an interaction with a patient.
Owner:HUMANA INC
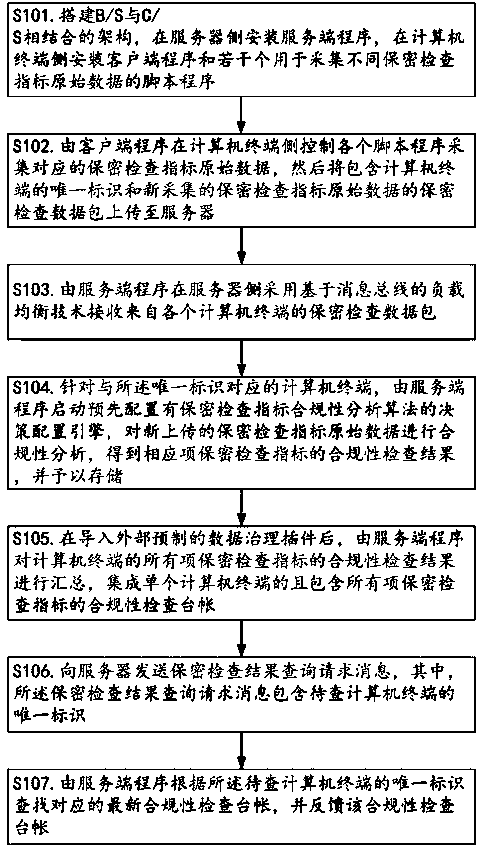
A method for performing security check on a computer terminal
ActiveCN109033840AGuaranteed flexibilityGuaranteed accuracyDigital data protectionPlatform integrity maintainanceConfidentialityOriginal data
The invention relates to the technical field of information security, and discloses a method for performing security check on a computer terminal. In accordance with the present invention, an automated compliance analysis of confidentiality check index raw data from a computer terminal may be provided, and the confidentiality check methods that integrate compliance check results are summarized, that is to say, on the one hand, through the decision-making compliance analysis of the corresponding confidentiality inspection indicators, flexibility and accuracy of compliance results can be ensured, on the other hand, by integrating the compliance check account of a single computer terminal and including all the confidentiality check indexes, the comprehensiveness and integrity of the compliance check results can be ensured, which is beneficial to output the confidentiality check results with guiding significance for the information security management, and further enhance the management value.
Owner:CHENGDU AIRCRAFT INDUSTRY GROUP
Automated compliance scoring system that analyzes network accessible data sources
An automated system that analyzes network accessible data sources to determine a score that measures compliance of an investment with a compliance policy. The compliance policy may specify for example ESG (Environment, Social, or Governance) requirements, or prohibitions against selling of certain products and services considered undesirable or unethical by certain investors. Compliance analysis may determine the amount of revenue or income received from prohibited sources, or it may search information for key words and phrases related to these sources. The system may “purify” noncompliant investments by bundling them with charitable contributions that offset the income from prohibited sources. Fund managers may publish and share compliance policy definitions, and may import these shared definitions and customize them for their specific fund requirements.
Owner:IDEALRATINGS INC
Method for the Utilization of Privately Placed Insurance Contracts as a Cohesive Operational Process for Structurally Efficient Investing, Reified as a Tax Deferred Fund
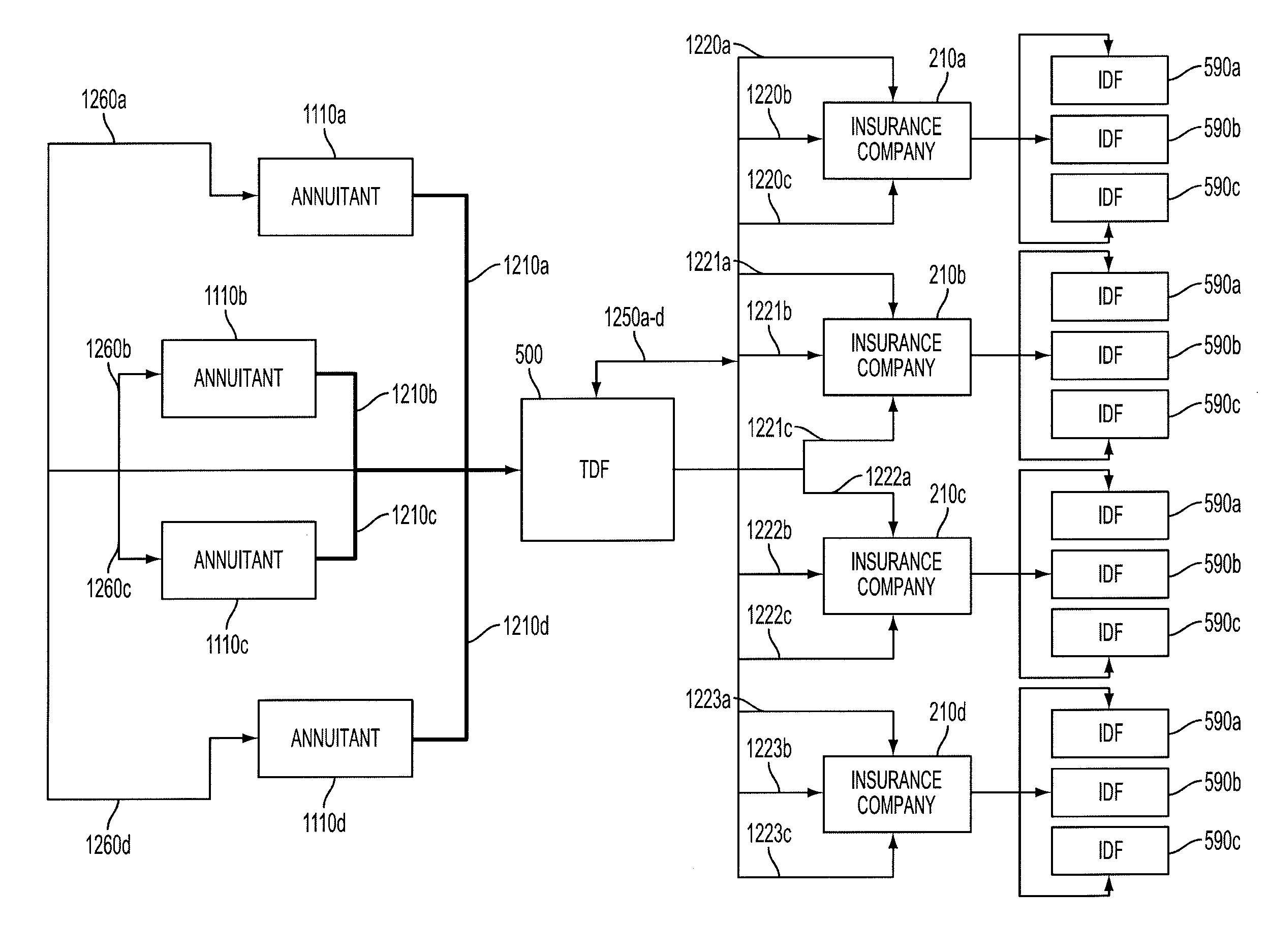
A method performed by a computer of arranging a privately placed variable annuity, including negotiating with at least one life insurance company for a standardized annuity contract; evaluating the standardized annuity contract and a plurality of investments by a plurality of specialists; performing at least one of legal analysis, regulatory analysis, due diligence, and compliance analysis with respect to the plurality of investments; using the computer to provide efficient scalability of the product, and made concrete by embodiment as a privately placed, tax deferred fund (TDF), and the selling by at least one broker of an interest in the TDF to a qualified prospect (Investor Annuitant) who thereby gains exposure to the privately placed variable annuity based on the standardized annuity contract and the plurality of investments.
Owner:MARBLE HILL ADVISORS
Method, device and storage medium for emotion recognition
ActiveCN109410986BQuality improvementImprove quality inspection efficiencySpeech recognitionEmotion identificationCompliance analysis
The embodiment of the present invention discloses an emotion recognition method, device, and storage medium, wherein the method includes: acquiring voice data; converting the voice data into corresponding text content, and performing compliance analysis on the text content , obtaining a first analysis result; extracting acoustic feature parameters from the speech data, analyzing the acoustic feature parameters, and obtaining a second analysis result; performing emotion recognition based on the first analysis result and the second analysis result .
Owner:MIGU DIGITAL MEDIA CO LTD +2
Automated compliance scoring system that analyzes network accessible data sources
An automated system that analyzes network accessible data sources to determine a score that measures compliance of an investment with a compliance policy. The compliance policy may specify for example ESG (Environment, Social, or Governance) requirements, or prohibitions against selling of certain products and services considered undesirable or unethical by certain investors. Compliance analysis may determine the amount of revenue or income received from prohibited sources, or it may search information for key words and phrases related to these sources. The system may “purify” noncompliant investments by bundling them with charitable contributions that offset the income from prohibited sources. Fund managers may publish and share compliance policy definitions, and may import these shared definitions and customize them for their specific fund requirements.
Owner:IDEALRATINGS INC
Special fund monitoring method and device, terminal equipment and storage medium
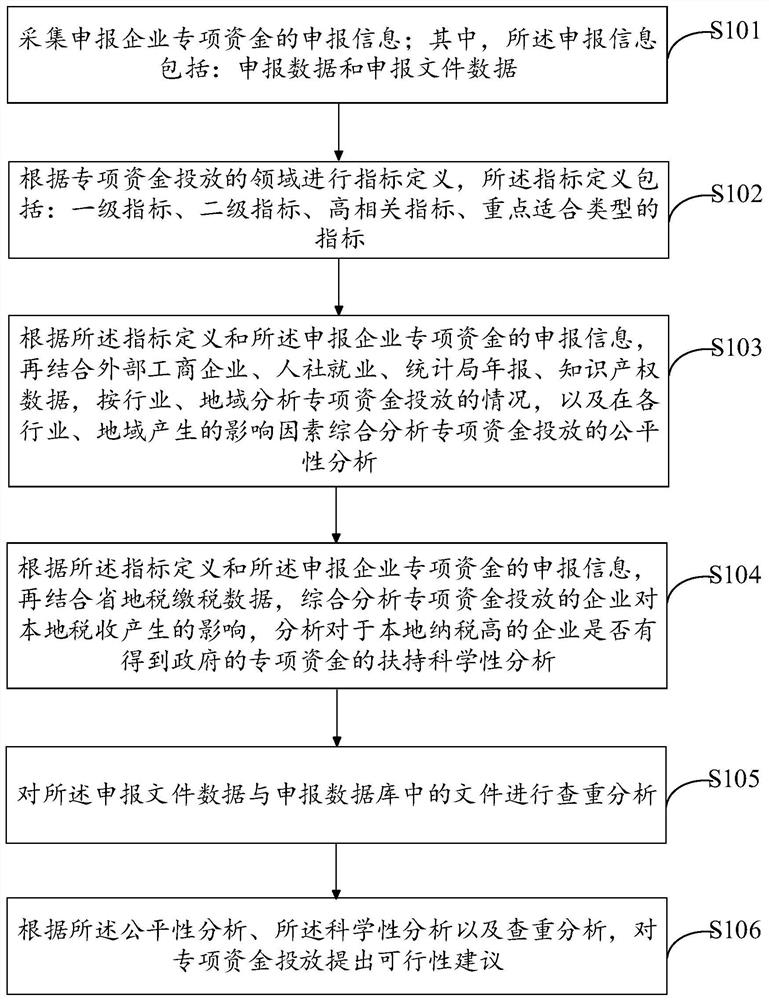
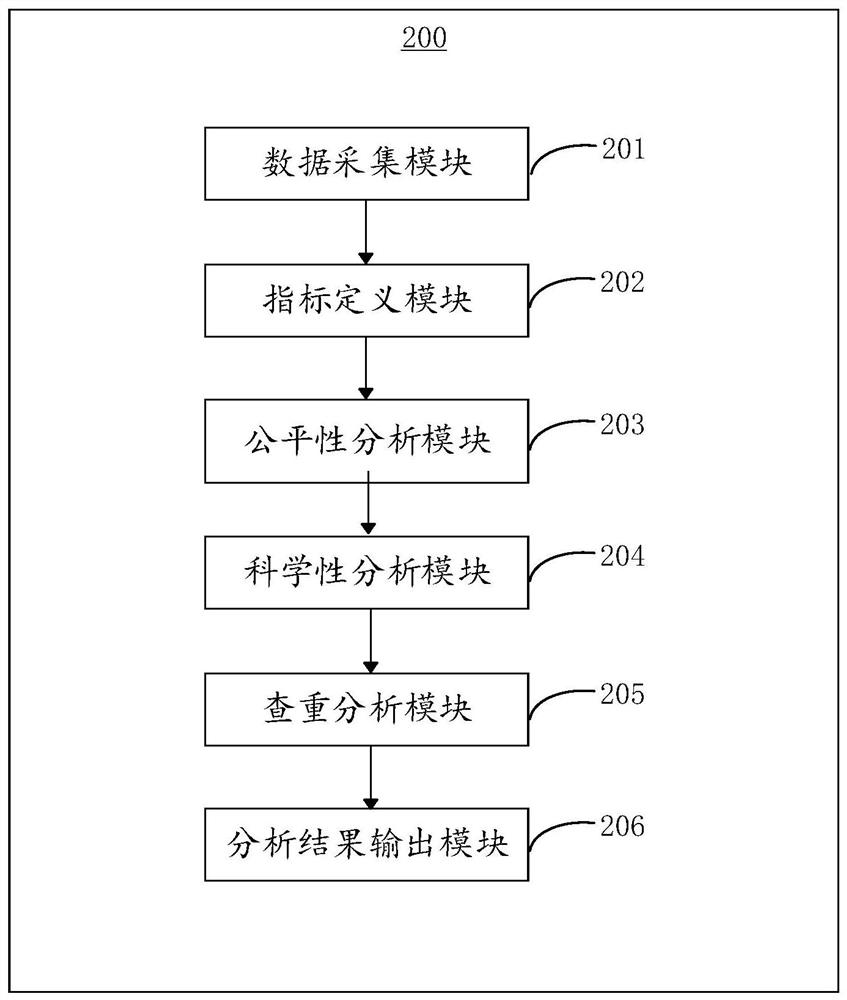
PendingCN111985766AImprove delivery efficiencyImprove application compliance analysisFinanceResourcesBusiness enterpriseTerminal equipment
The invention discloses a special fund monitoring method and apparatus, terminal equipment and a storage medium. The method comprises the steps that declaration information of declaring special fund of an enterprise is collected, wherein the declaration information comprises declaration data and declaration file data; index definition is carried out according to the field of special fund release;according to the index definition and the declaration information of the declaration enterprise special fund, fairness analysis is carried out in combination with related data; according to the indexdefinition and the declaration information of the declaration enterprise special fund, scientific analysis is carried out in combination with related data; duplicate checking analysis is carried out on the declaration file data and files in a declaration database; and according to the fairness analysis, the scientificity analysis and the duplicate checking analysis, feasibility suggestions for special capital investment are proposed. According to the method, the special fund putting benefit and fund application compliance analysis can be improved, and duplicate checking and auditing of the fund application file are assisted, so that the working efficiency and efficiency of a user are improved.
Owner:GUANGDONG GANG XIN SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com