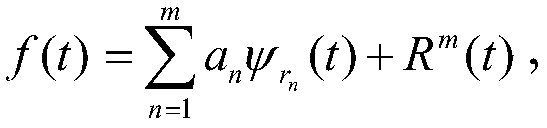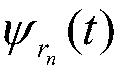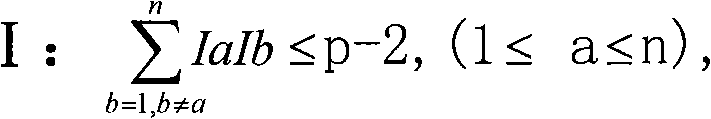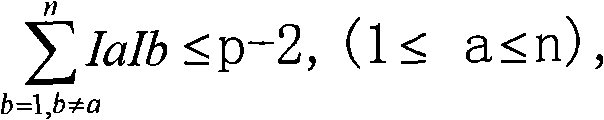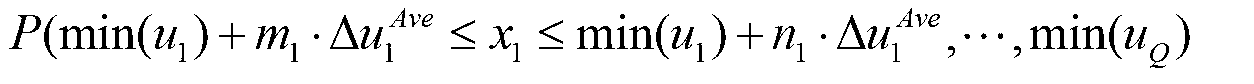Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
97results about How to "The verification method is simple" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
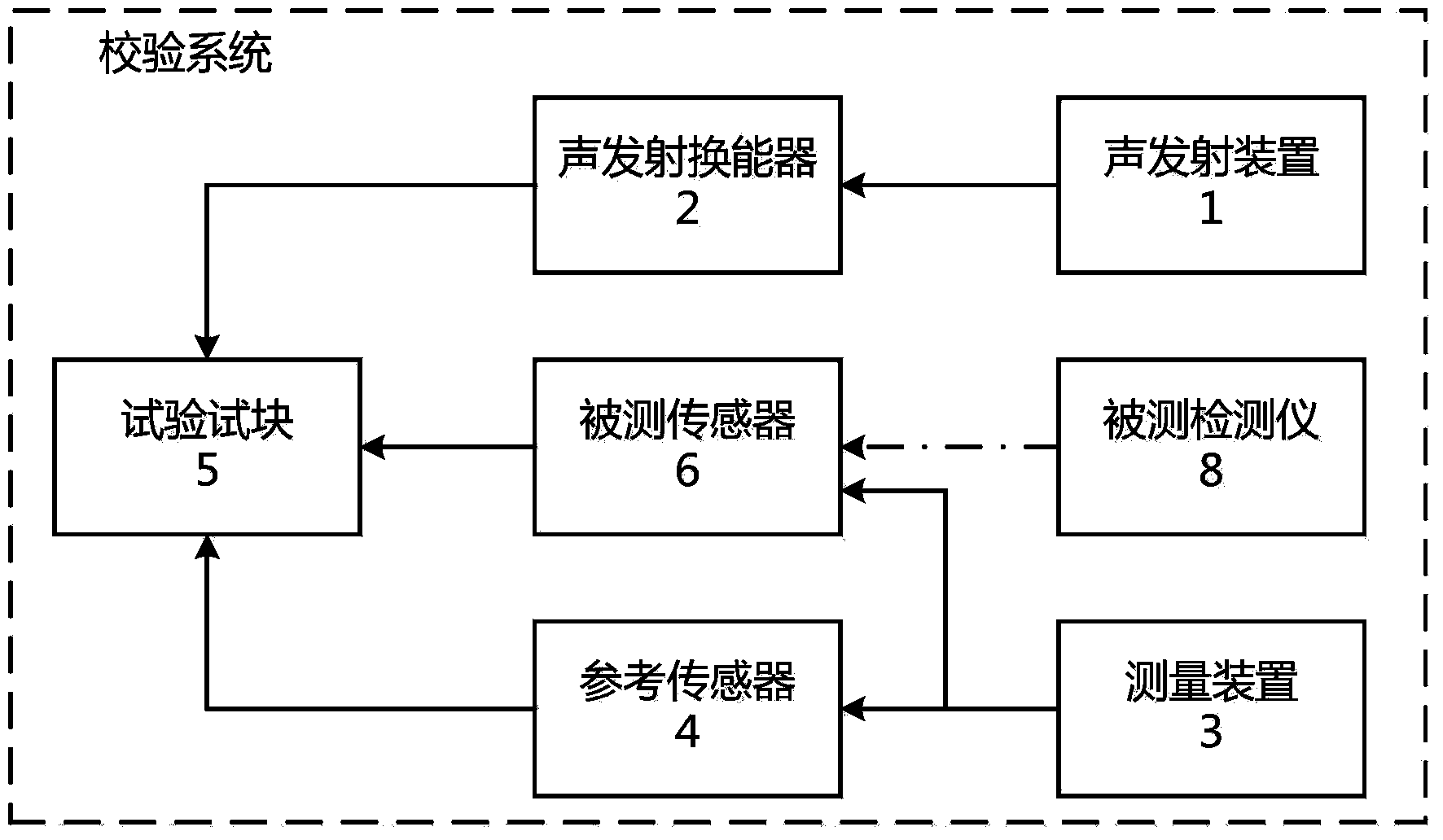
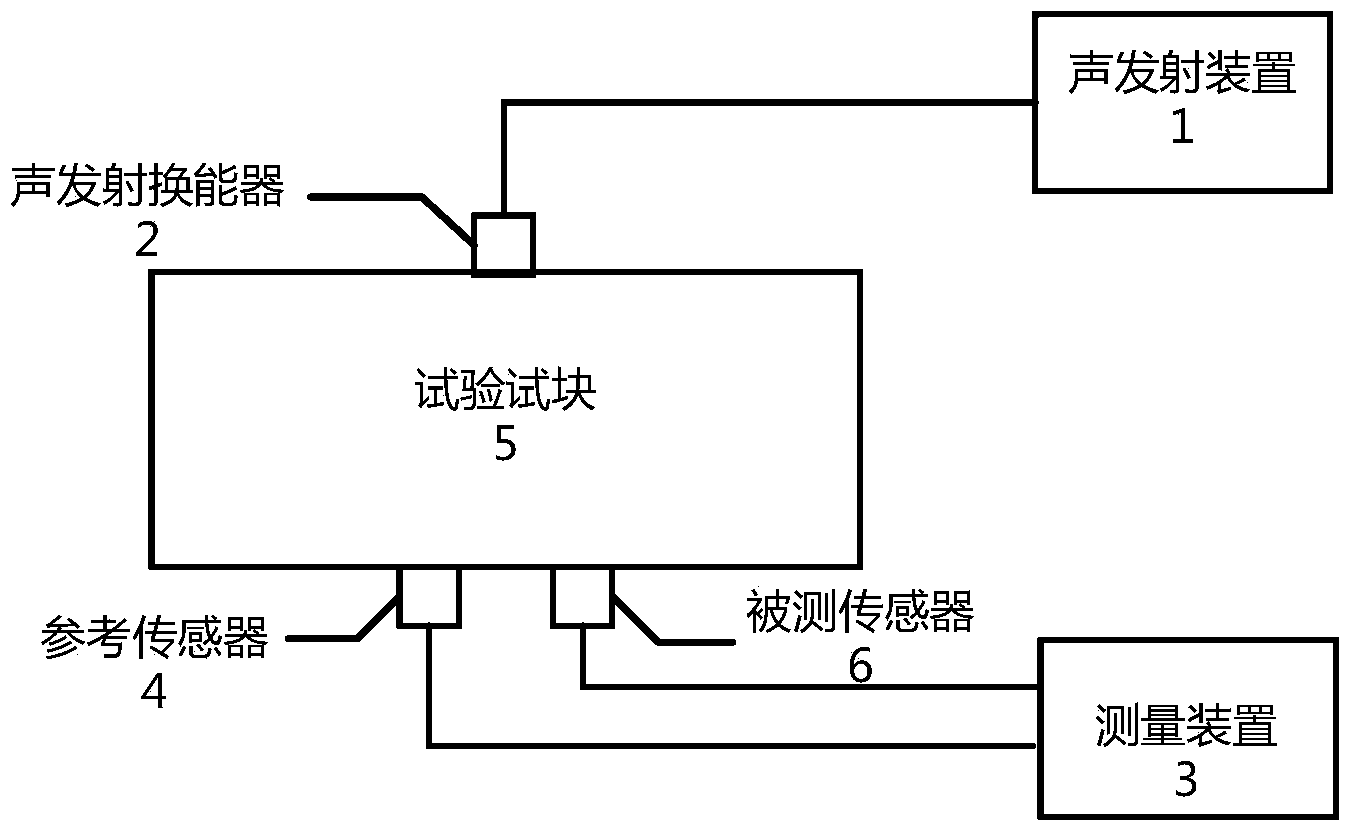
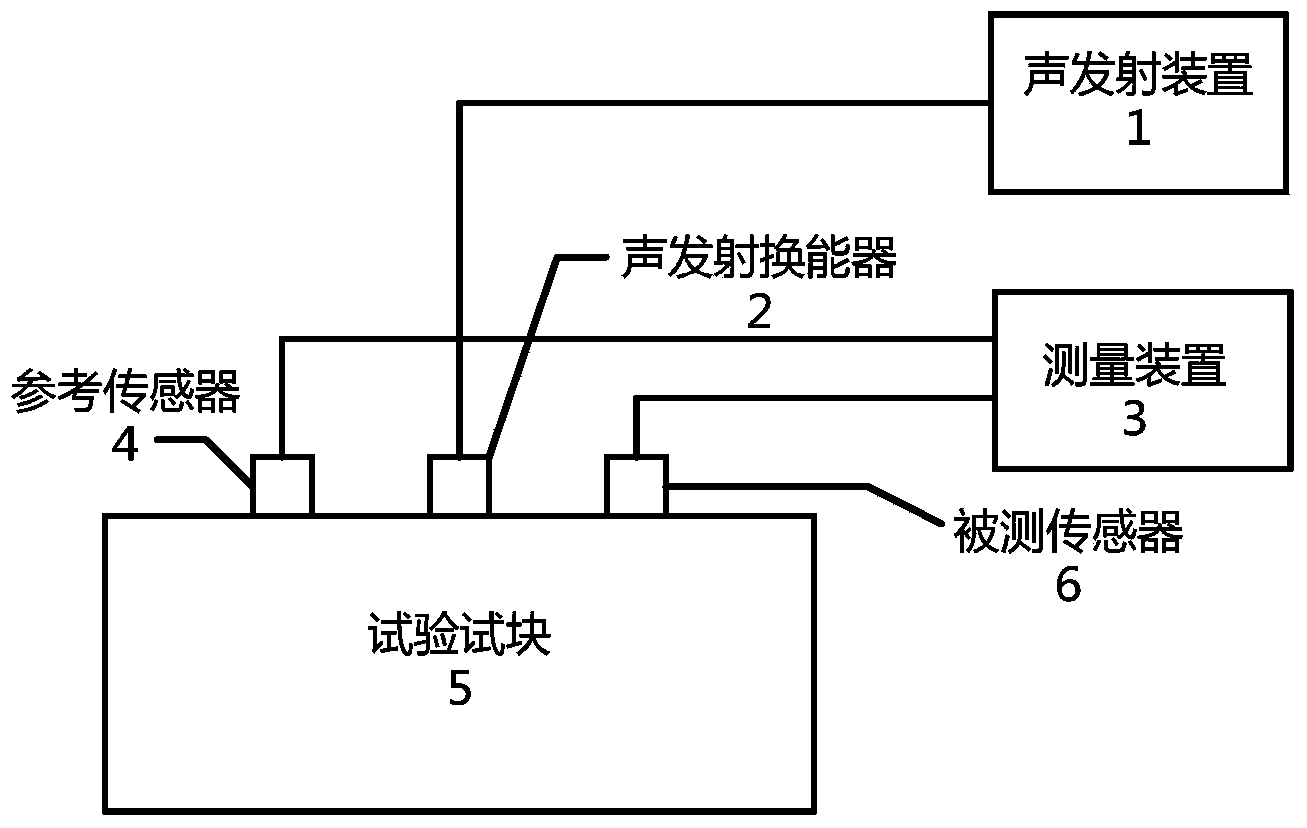
Calibration system of partial discharge supersonic detector
ActiveCN103913714AEasy to implementEasy to check and calibrateElectrical measurementsSurface wavePartial discharge
The invention provides a calibration system of a partial discharge supersonic detector. The calibration system comprises a sound emission device, a sound emission transducer, a measuring device, a reference sensor, a test block, a detector under test and a clamp. The sound emission device is connected with the sound emission transducer, the measuring device is connected with the reference sensor, and the sound emission transducer, the reference sensor and a sensor under test of the detector under test are all arranged on the surface of the test block. The calibration system is used for conducting longitudinal wave sensitivity test, surface wave sensitivity test and pressure field sensitivity test on the detector under test and conducting detection test on the whole machine sensitivity, the whole machine frequency band, whole machine linearity errors and the whole machine repeatability of the detector under test. Compared with the prior art, the calibration system of the partial discharge supersonic detector is easy to implement, good in sound source repeatability, easy to operate, widely applicable to maintaining, testing and calibration of partial discharge supersonic detectors in electric power industry.
Owner:STATE GRID CORP OF CHINA +2
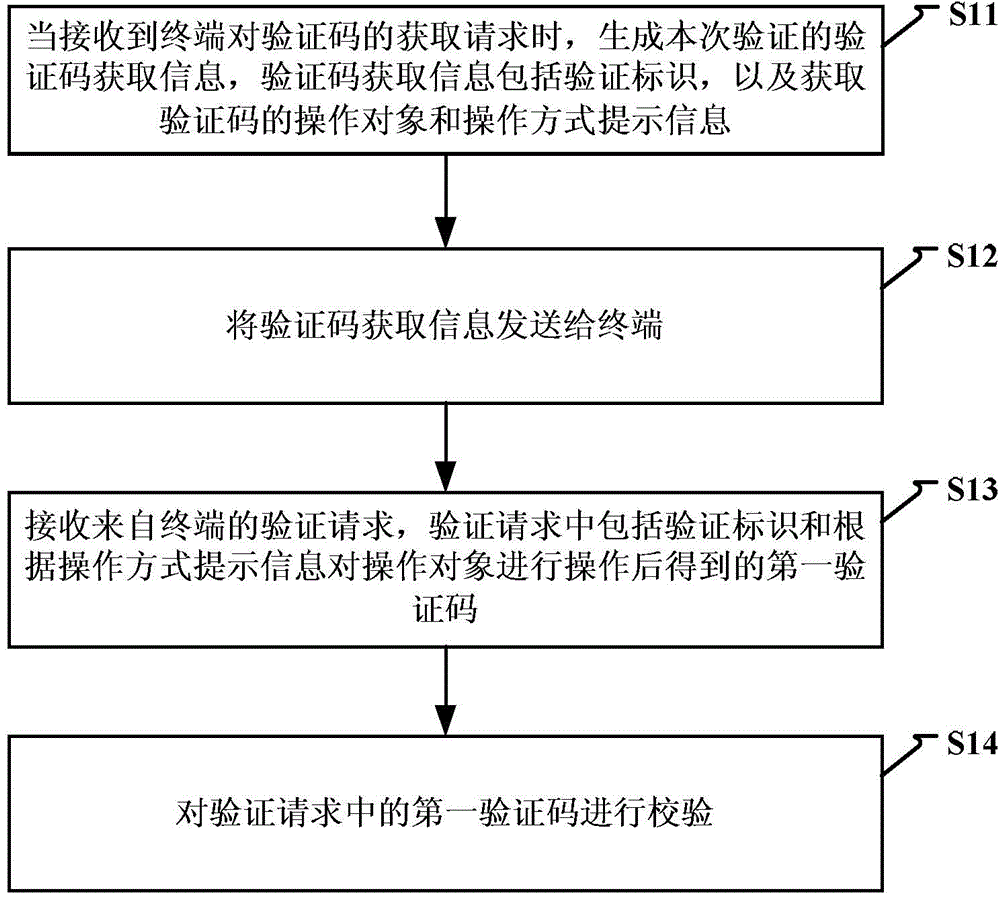
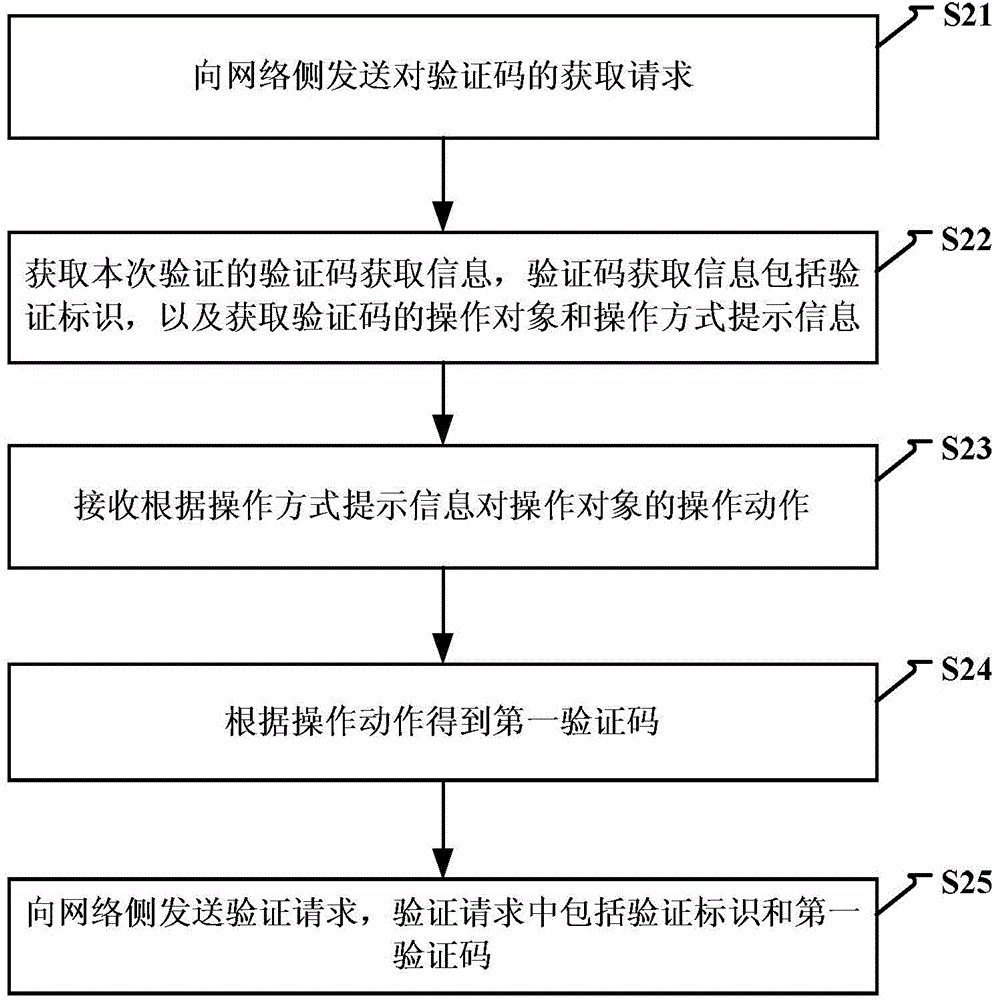
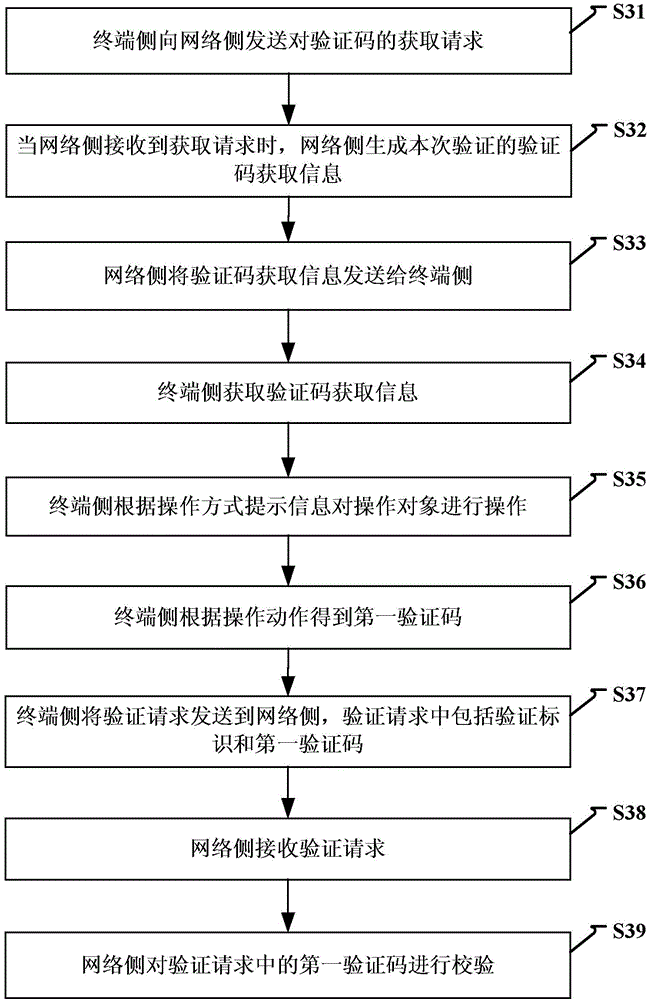
Method and device for identifying by using verification code
InactiveCN104104514AAvoid authentication failuresImprove verification efficiencyUser identity/authority verificationDigital data authenticationObject basedFailure causes
The invention discloses a method and a device for identifying by using a verification code. The method comprises the steps of: when a request of obtaining the verification code from a terminal is received, generating verification code obtaining information including a verification identifier for the verification, and obtaining an operating object of the verification code and operating mode prompting information; sending the verification code obtaining information to the terminal; receiving a verification request from the terminal, wherein the verification request comprises the verification identifier and a first identification code obtained after operation is performed on the operating object based on the operating mode prompting information. A user is unnecessary to input the verification code manually as the operating object is operated based on the operating mode prompting information of the verification code and the result after the operation is verified. Therefore, the verification mode is simplified, verification failure caused by a manual input error of the user is avoided, the verification efficiency of the verification code is improved, and the user experience is increased.
Owner:XIAOMI INC
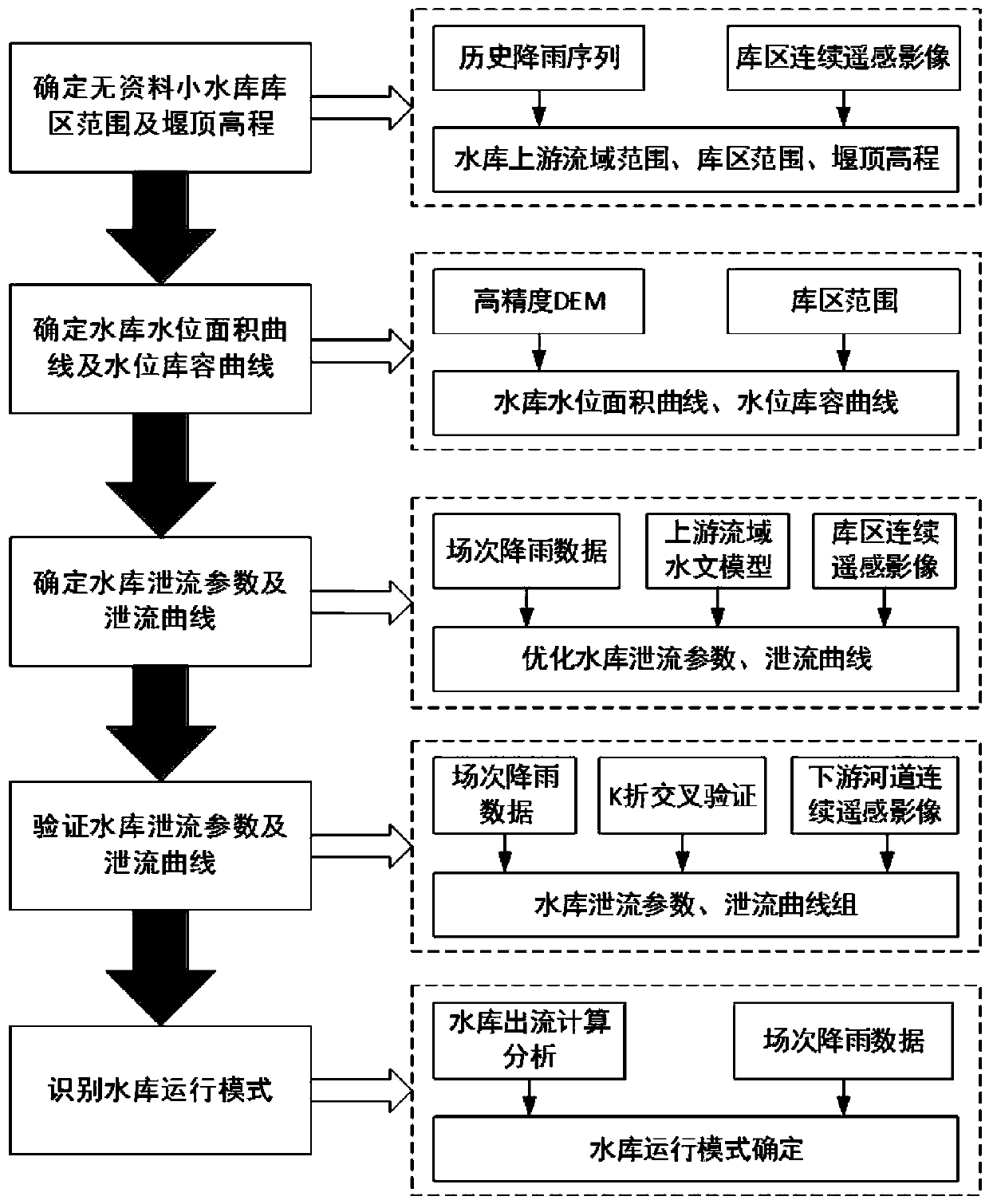
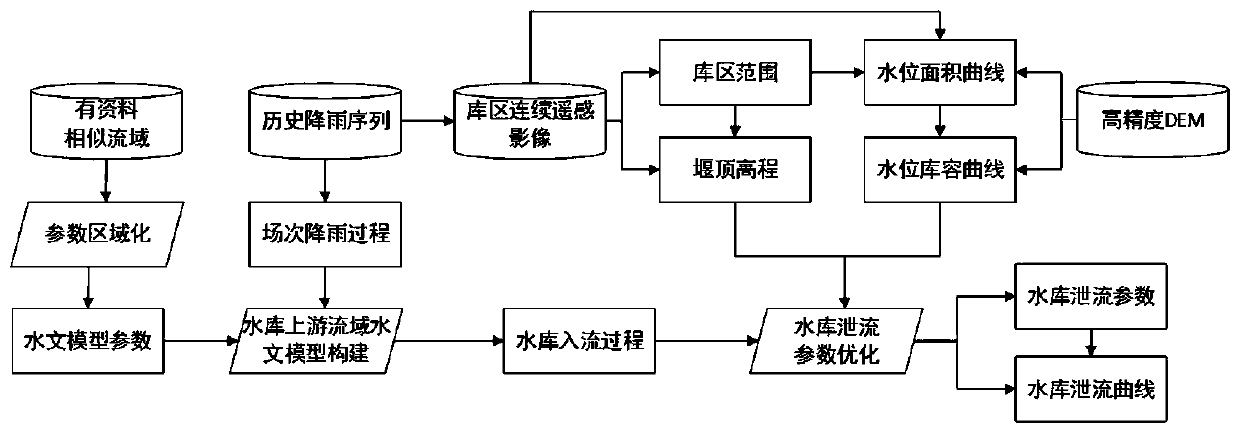
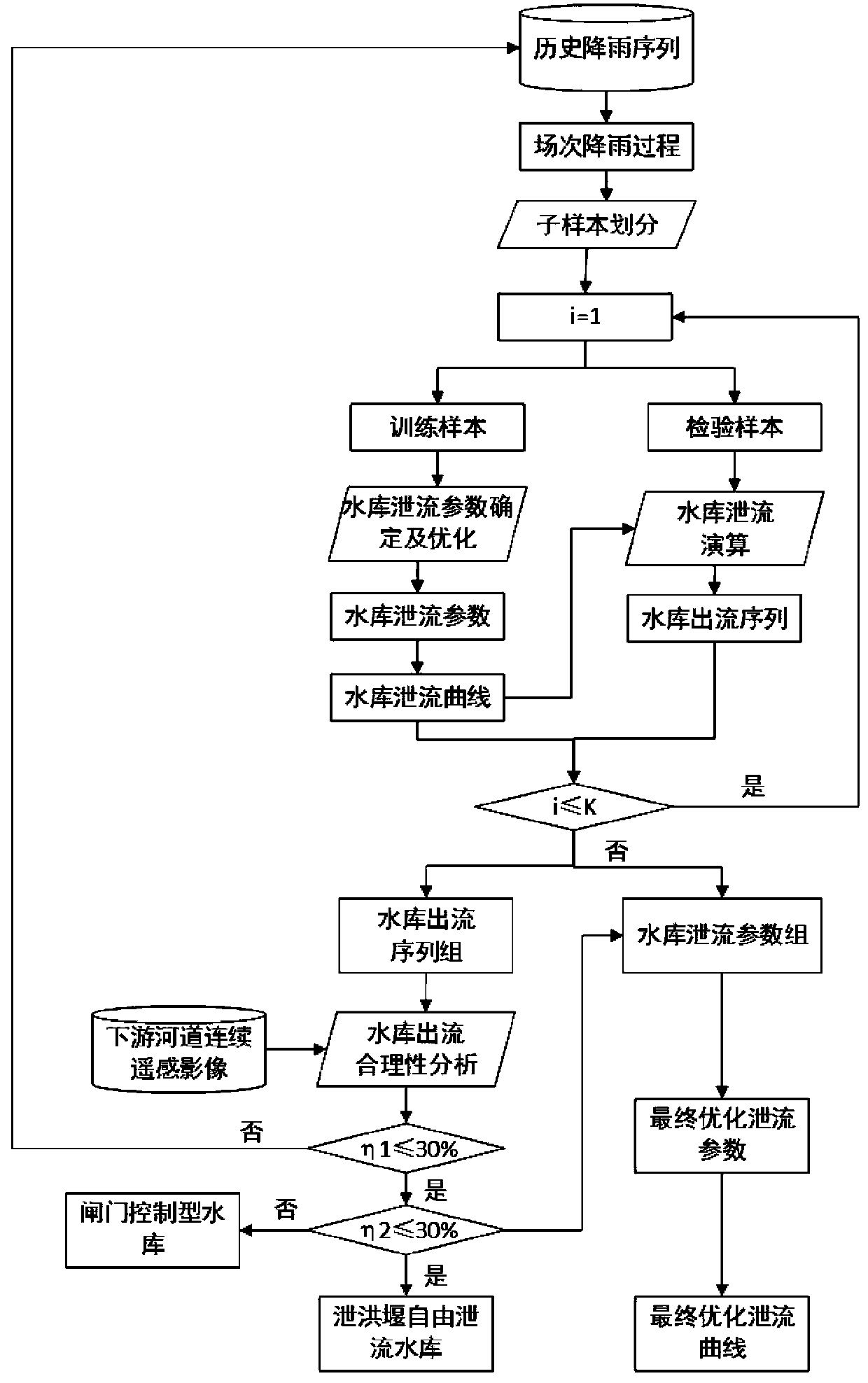
Data-free small reservoir parameter identification method combining hydrological simulation and continuous remote sensing images
ActiveCN109754025AQuick fixEfficient determinationData processing applicationsClimate change adaptationValidation methodsFlood control
The invention relates to a data-free small reservoir parameter identification method combining hydrological simulation and continuous remote sensing images. The method comprises the following steps: step 1, determining a data-free small reservoir area and an upstream basin range; step 2, reservoir discharge parameters and a discharge curve are determined; step 3, verifying the reservoir dischargeparameters and the discharge curve; and step 4, identifying the reservoir operation mode. The data-free small reservoir parameter identification method provided by the invention not only identifies the reservoir area range and the weir crest elevation, but also provides a reservoir discharge parameter and discharge curve determination and verification method, thereby identifying the reservoir operation mode, and providing technical support for small reservoir flood discharge and small basin flood control in a data-free area.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
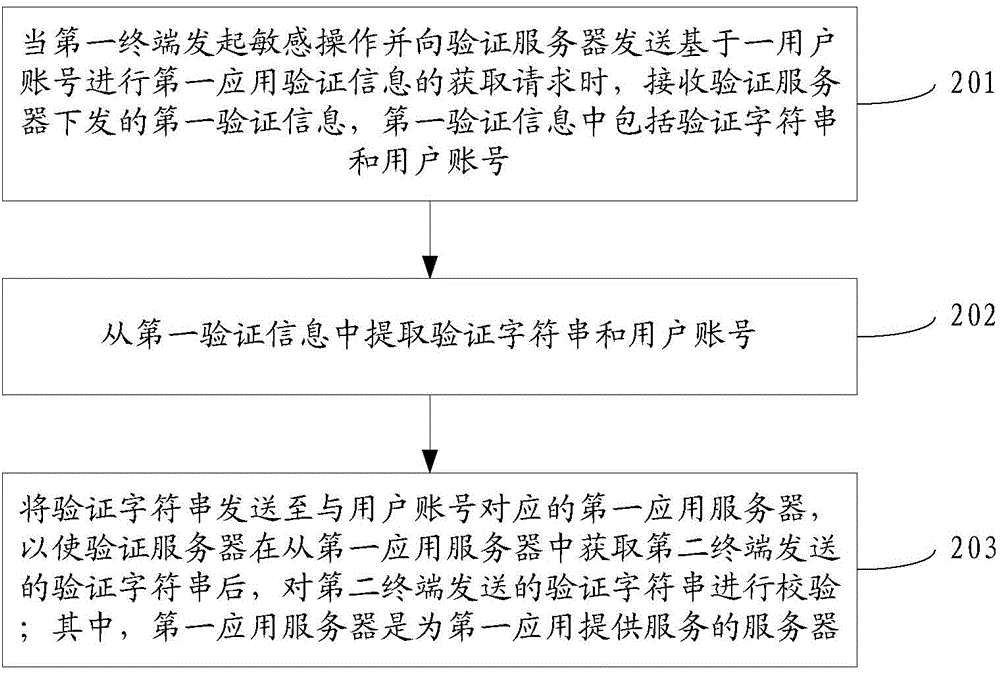
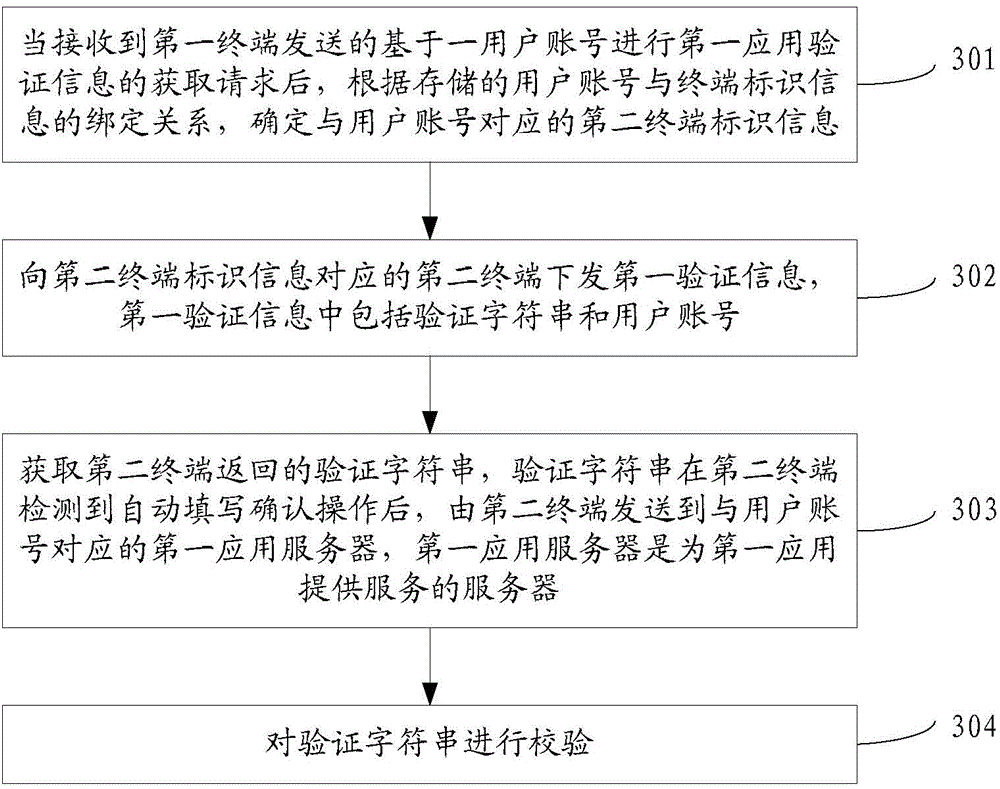
Identity verification method, device and system
ActiveCN105306199AImplement autofillAvoid the error-prone pitfalls of manual entryUser identity/authority verificationInformation processingApplication server
The invention discloses an identity verification method, device and system, belonging to the technical field of information processing. The method comprises the following steps: receiving first verification information sent by a verification server when a first terminal initiates a sensitive operation and sends a request for obtaining first application verification information based on an account number of a user to the verification server, wherein the first verification information comprises a verification character string and the account number of the user; extracting the verification character string and the account number of the user from the first verification information; and sending the verification character string to a first application server relative to the account number of the user, such that the verification server verifies the verification character string sent by a second terminal after obtaining the verification character string sent by the second terminal from the first application server. According to the invention, users are unnecessary to read short messages, fill in the verification information and the like while being verified; therefore, the verification information is automatically filled in; the verification manner is relatively simple; the required time is short; and the disadvantages that mistakes are easily made due to manual input of users can be avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
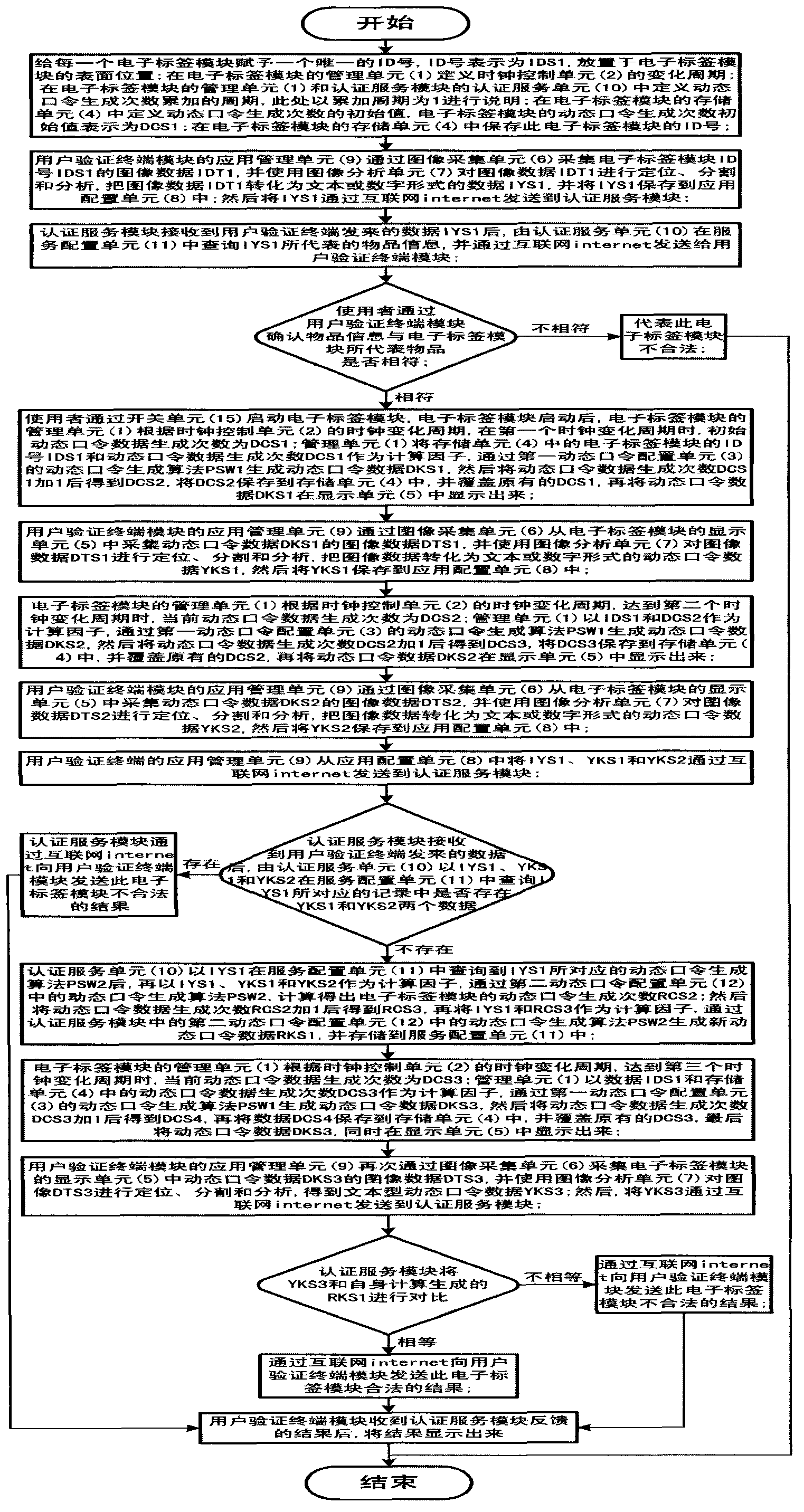
Method for real-time verification of validity of dynamic password
ActiveCN103354499AOvercoming immutability and replicabilityConvenient verification methodUser identity/authority verificationDigital data authenticationComputer hardwareReal time validation
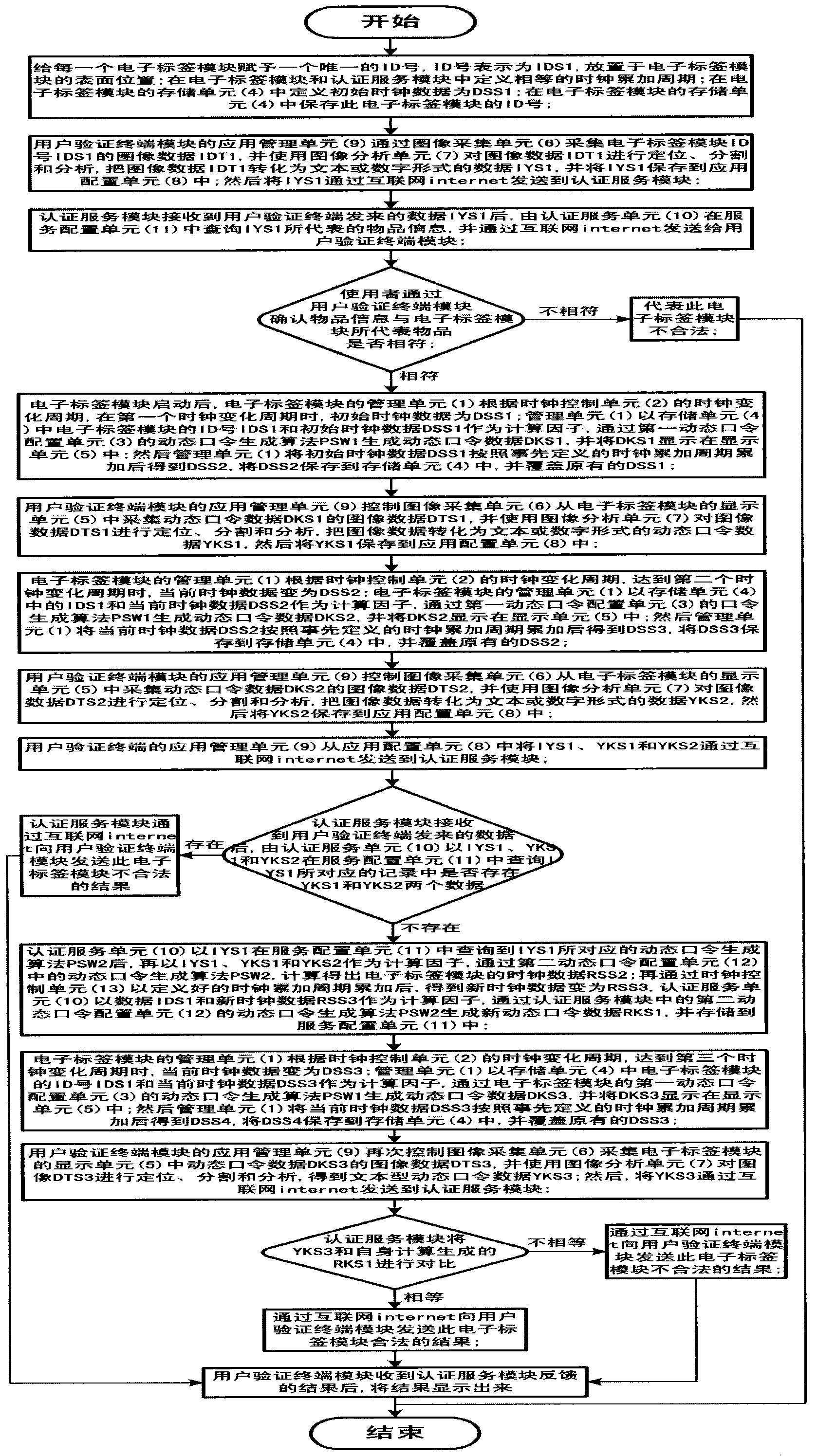
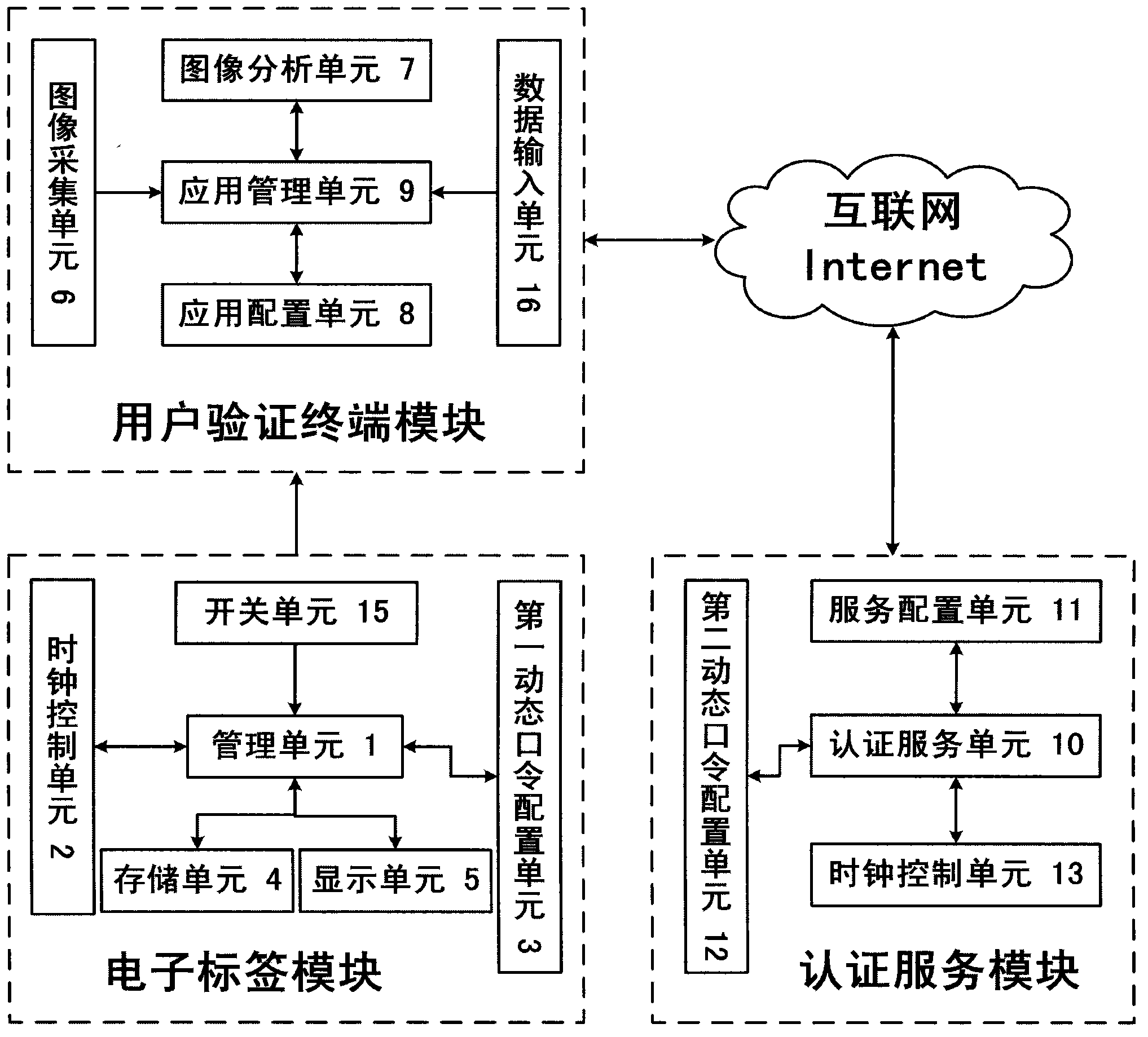
The present invention discloses a method for real-time verification of the validity of a dynamic password. The method is characterized in that a device used in the method comprises an electronic tag module, a user verification terminal module and an authentication service module. The electronic tag module is used for generating dynamic password data and displaying the data. The user verification terminal module collects the dynamic password data generated by the electronic tag module for multiple times and image data of the electronic tag module, obtains textual data after analysis and processing, and sends the textual data to the authentication service module through the Internet. The authentication service module receives the textual data, makes a conclusion that whether a first dynamic password generating algorithm of the electronic tag module is consistent with a second dynamic password generating algorithm of the authentication service module, and returns the conclusion to the user verification terminal module, thereby determining the validity of the electronic tag module.
Owner:樊晓东
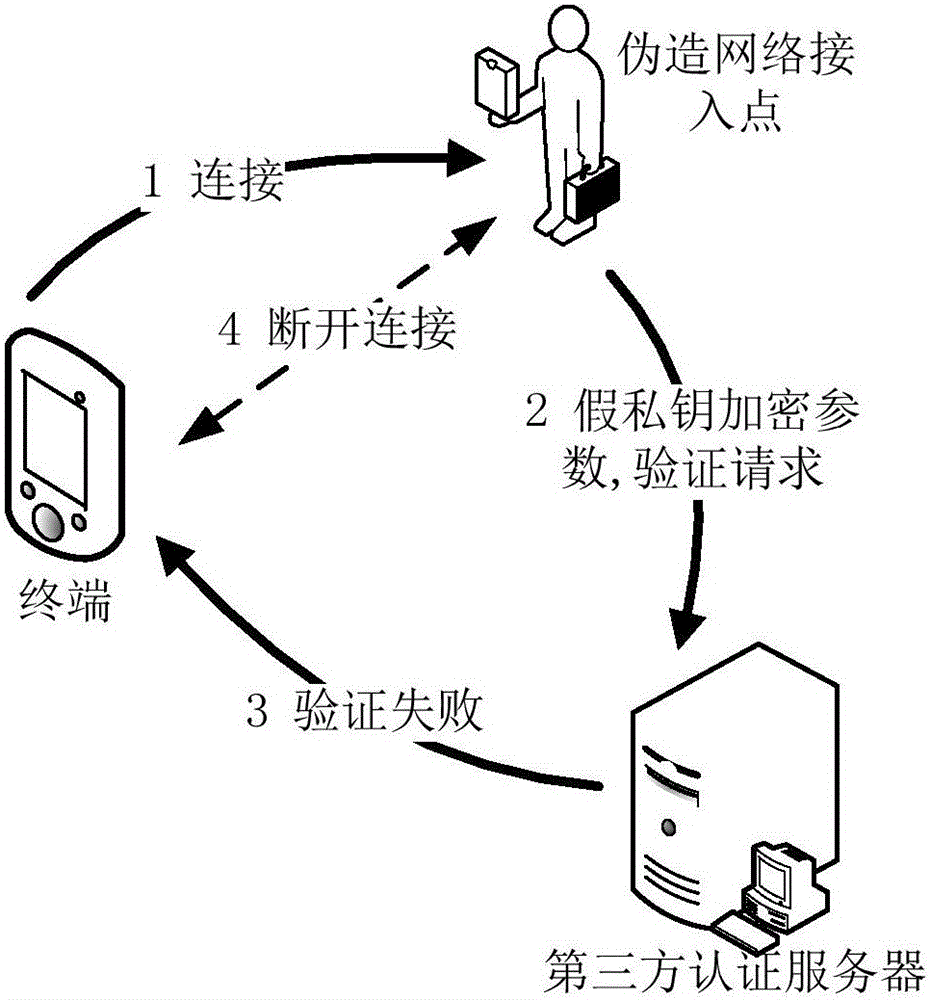
Method for network secure access, terminal device and authentication server
ActiveCN106330828AAvoid safety hazardsEnsure safetyTransmissionSecurity arrangementThird partyTerminal server
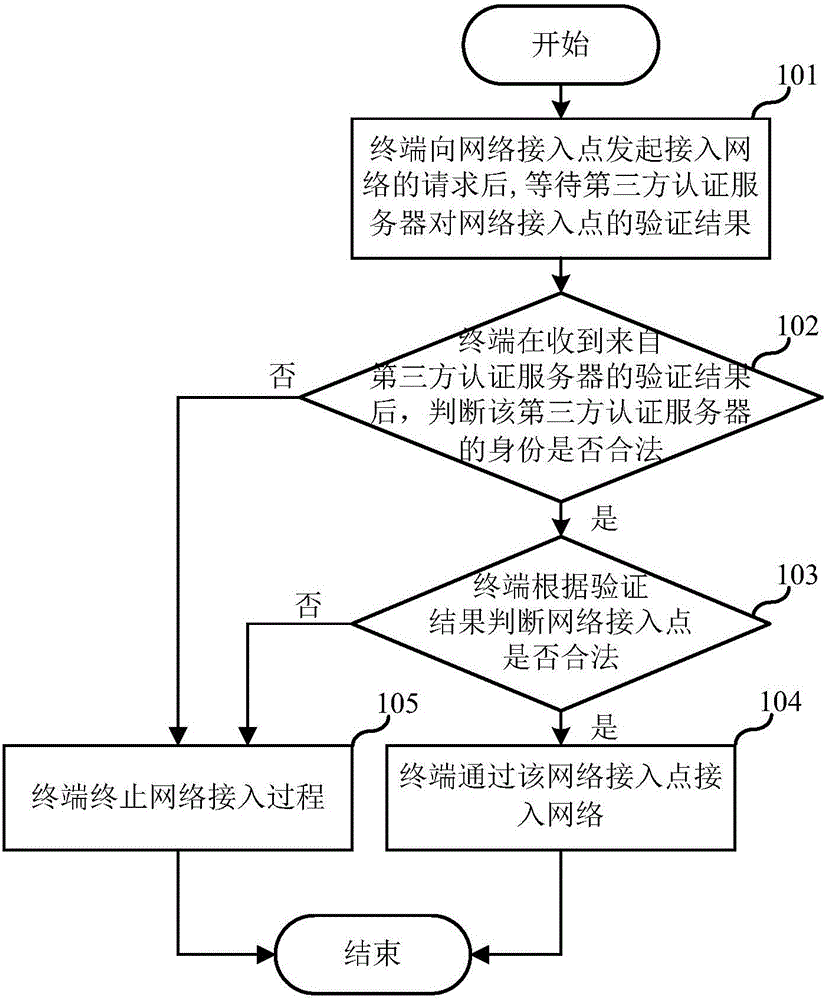
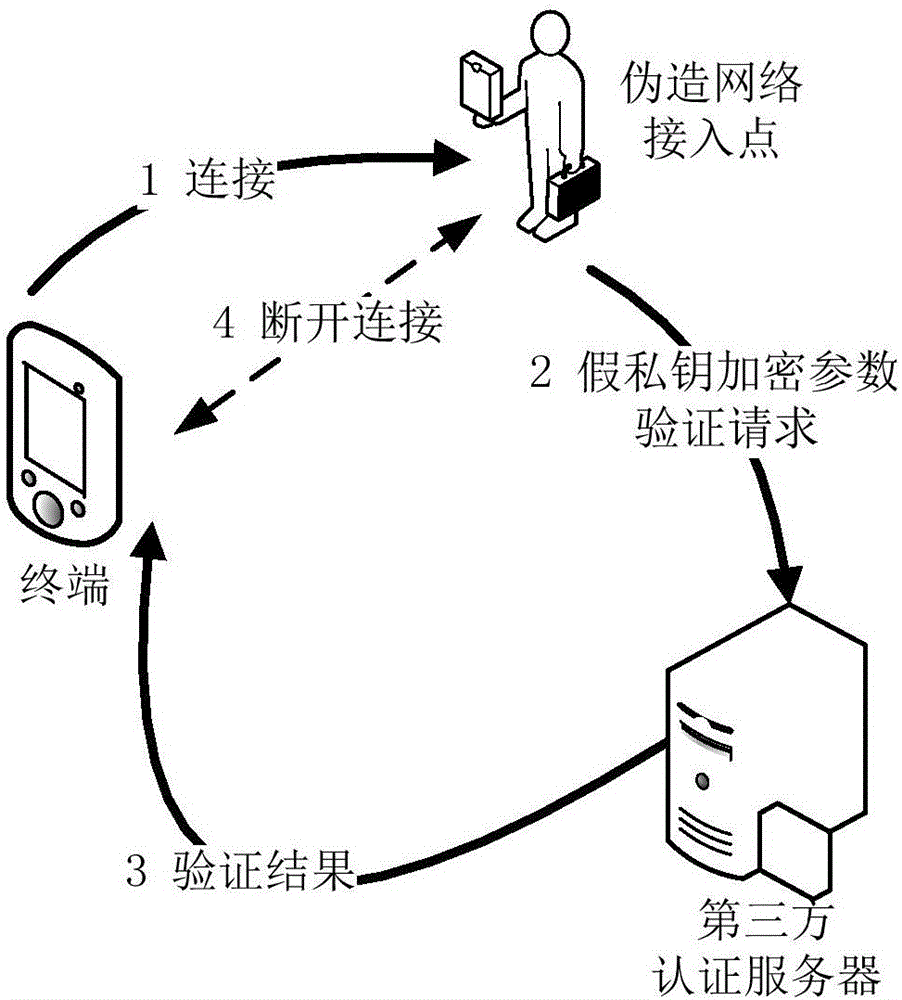
The invention discloses a method for network secure access, a terminal device and an authentication server. According to an embodiment of the invention, the method comprises the following steps: authenticating a network access point by a third party authentication server before a terminal accesses a network through the network access point; and the terminal accesses the network only through the network access point authenticated by the third party authentication server. According to an embodiment of the invention, after the third party authentication server judges that the network access point is a legitimate access point, the terminal accesses the network through the network access point, so that the problem that security risks are caused when the terminal accesses the network through the network access point while the authenticity of the identity of the network access point cannot be judged is solved.
Owner:LEADCORE TECH +1
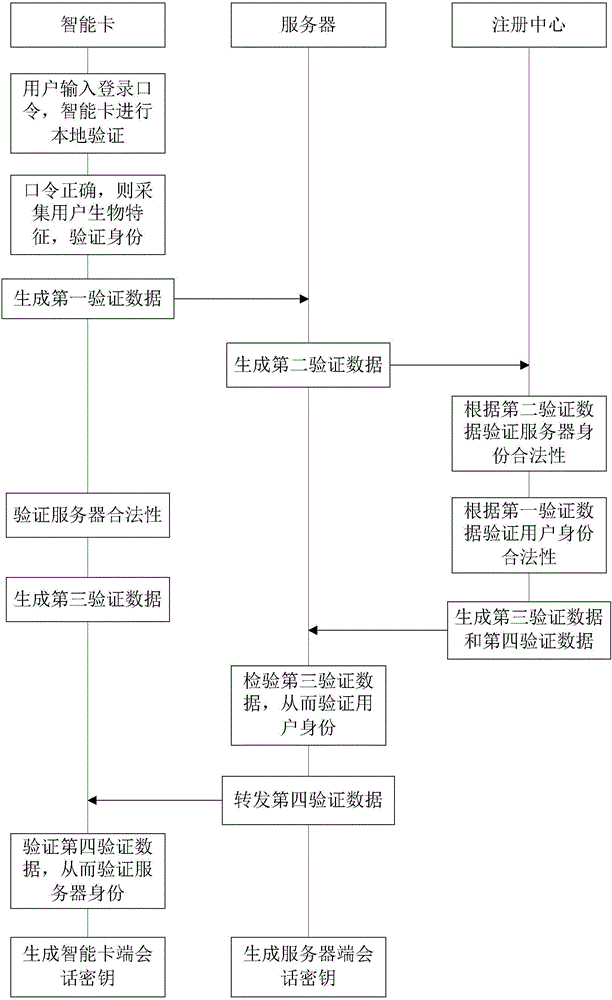
Three-factor remote identity authentication method based on intelligent card
ActiveCN105119721AWon't leakEasy to storeUser identity/authority verificationDigital data authenticationDenial-of-service attackServer log
The invention discloses three-factor remote identity authentication method based on an intelligent card. The method comprises the following steps that a user and a server log in a registration center, wherein the intelligent card comprises encryption information; the user logins; local verification is performed on the intelligent card; the registration center verifies the server and the user; the server verifies the registration center; and the intelligent card verifies the server. By using the method of the invention, user anonymity is realized; and attacking modes of denial of service attacking, eavesdropping attacking, intelligent-card stolen attacking and the like are successfully resisted.
Owner:SHANDONG UNIV OF SCI & TECH
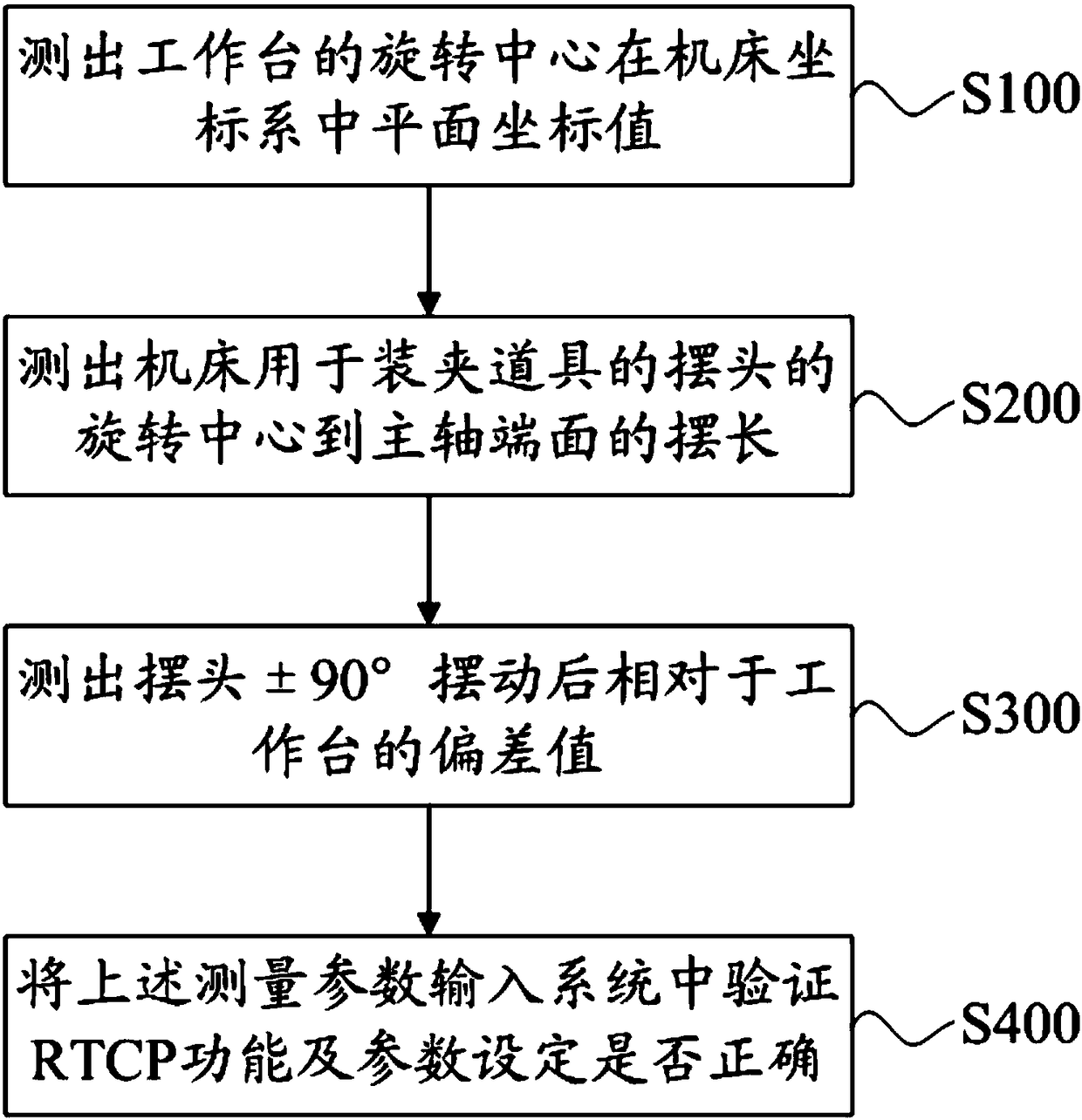
Five-axis RTCP (Rotation Tool Centre Point) measurement method
ActiveCN108490872AImprove machining accuracySimplify programming and machiningProgramme controlComputer controlCentre of rotationProcessing accuracy
The invention discloses a five-axis RTCP (Rotation Tool Centre Point) measurement method. The method includes the following steps that: the plane coordinate value of a rotation center of a worktable in a machine tool coordinate system is measured; the swing length of a distance from the swing head of a machine tool to the end surface of a main shaft is measured, wherein the swing head of the machine tool is used for clamping a cutter; the deviation value of the swing head relative to the worktable after the swing head swings in a range from -90 degrees to +90 degrees is measured; and the abovemeasured parameters are inputted into a system to verify whether RTCP functions and parameter settings are correct. Since the related parameters of an RTCP are measured twice successively; the related parameters are inputted into the system; the RTCP operates, so that whether the RTCP functions and parameter settings are correct can be accurately and effectively verified; and therefore, a good verification method can be provided for RTCP function adjustment and parameter setting, the fast and accurate setting of the RTCP can be realized, the machining accuracy of the machine tool can be improved. The RTCP functions are realized through simple and easy-to-operate data measurement, and five-axis programming processing can be simplified.
Owner:深圳市拓智者科技有限公司
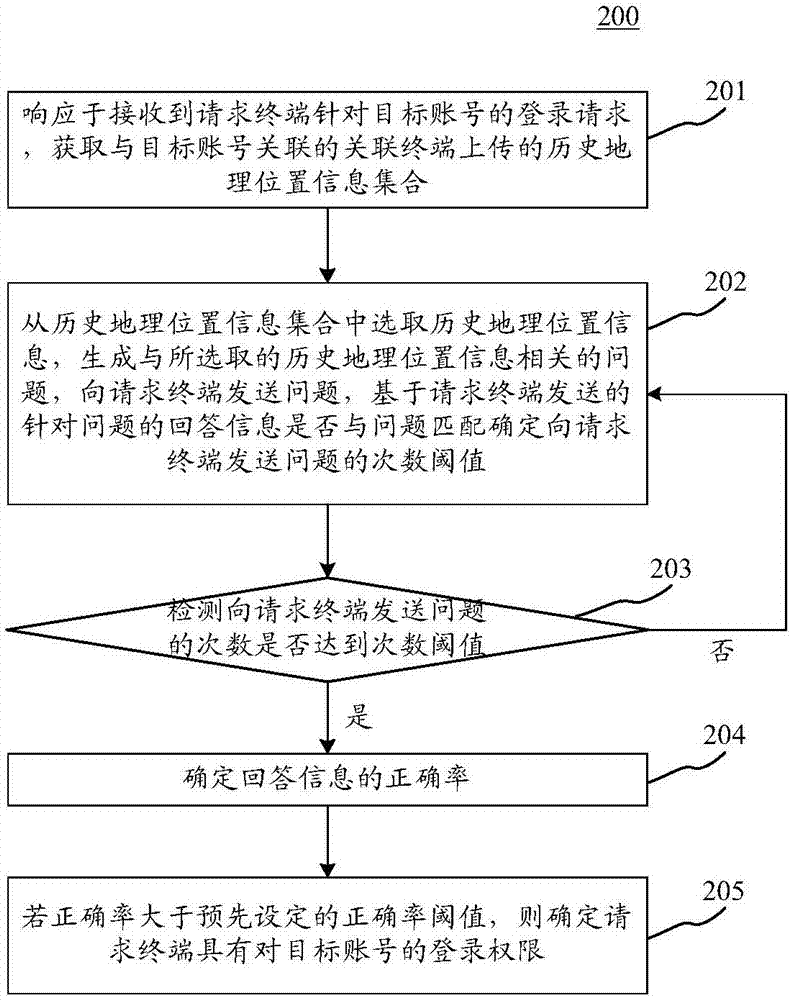
Method and device for determining permission
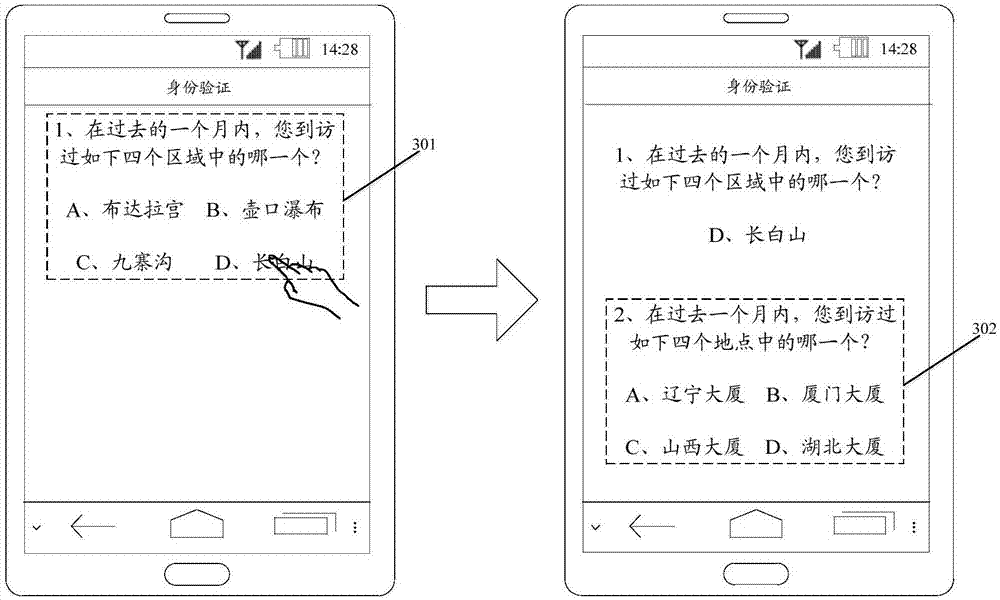
The application discloses a method and device for determining a permission. A specific implementation way of the method comprises the following steps: acquiring historic geographic position information set in response to a received login request aiming at a target account by a request terminal; executing the following authentication steps: selecting historic geographic position information from the historic geographic position information set, generating a problem related to the selected historic geographic position information, sending the problem to the request terminal, determining a frequency threshold value of sending the problem to the request terminal based on a condition whether answer information aiming at the problem and sent by the request terminal is matched with the problem; continuously executing the authentication step in response to the condition that the frequency of sending the problem to the request terminal does not achieve the frequency threshold value; determining an accurate rate of the answer information in response to the condition that the frequency of sending the problem to the request terminal achieves the frequency threshold value; if the accurate rate is greater than a preset accurate rate threshold value, determining that the request terminal has the login permission to the target account. By use of the method disclosed by the embodiment, the degree of accuracy of the identity verification is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
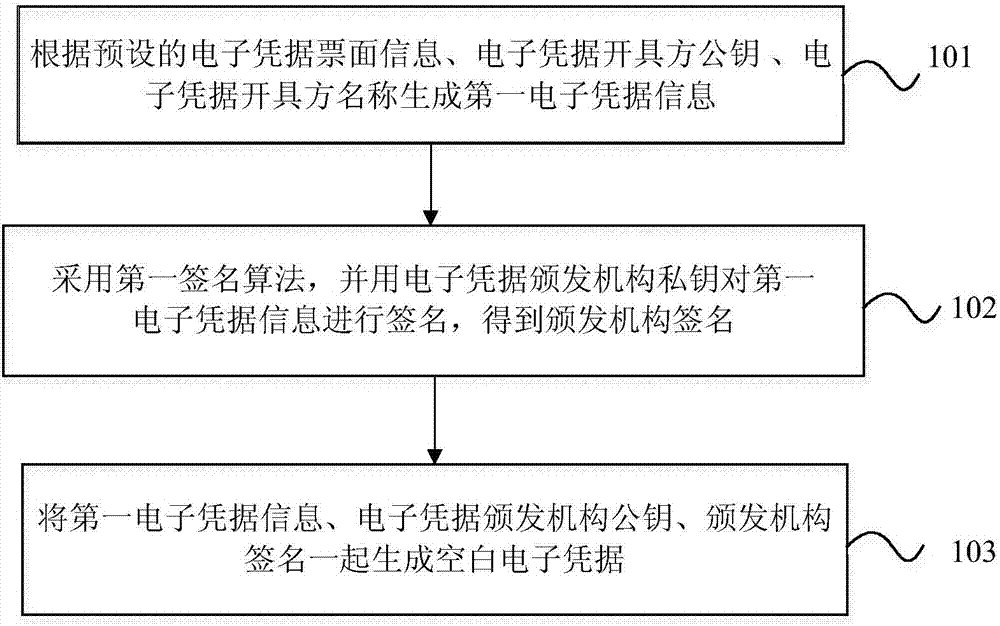
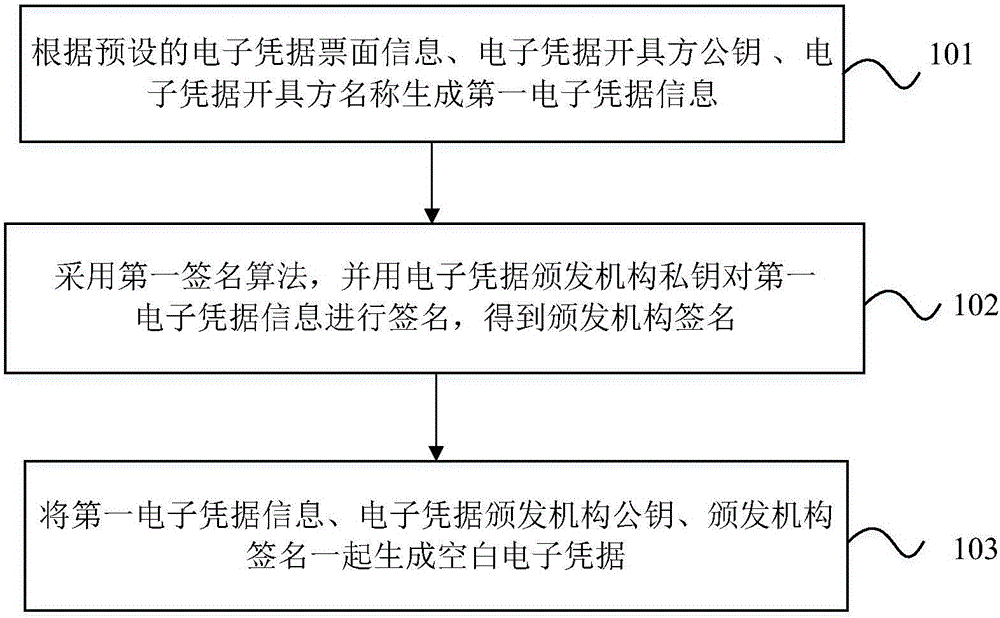
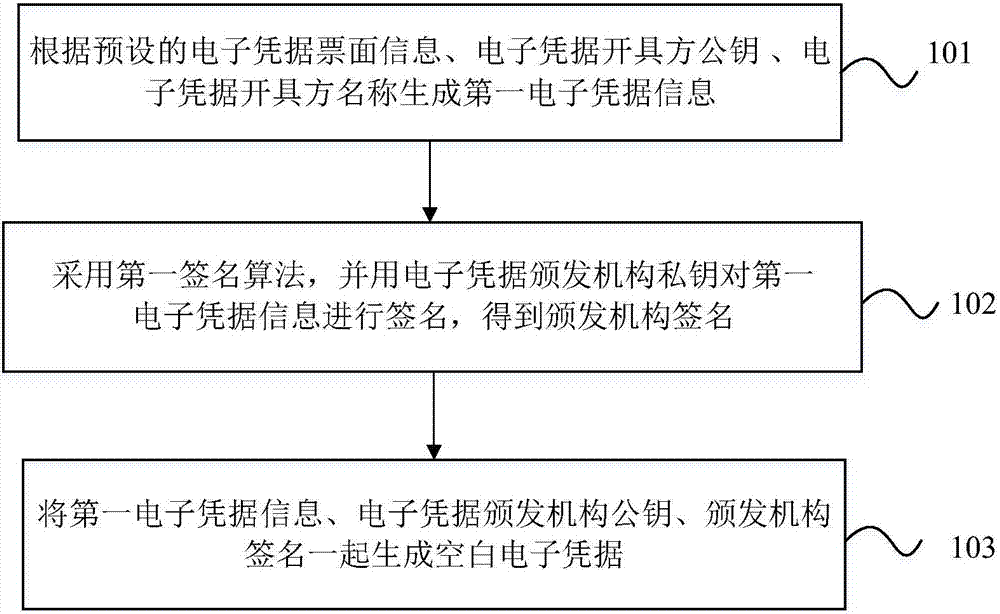
Blank electronic credential generation and blank electronic credential public verification methods, devices and system
ActiveCN106952093AImprove anti-counterfeiting performanceConvenient offline verificationElectronic credentialsValidation methodsComputer security
The invention discloses blank electronic credential generation and blank electronic credential public verification methods, devices and system. The blank electronic credential generation method comprises the following steps: generating first electronic credential information at least according to electronic credential face information among preset electronic credential face information, the public key of an electronic credential accrediting party and the name of the electronic credential accrediting party; using a first signature algorithm and the private key of an electronic credential issuing authority to sign the first electronic credential information to get the signature of the issuing authority; and generating a blank electronic credential according to the first electronic credential information, the public key of the electronic credential issuing authority and the signature of the issuing authority. The anti-counterfeiting property of electronic credentials is enhanced. Mixed use and illegal use of electronic credentials can be prevented. The shortcomings of the prior art, for example, someone pretends to be the credential issuing authority to issue electronic credentials, electronic credentials are used in a mixed way between different electronic credential accrediting parties, and electronic credentials are used illegally, are avoided. The verification difficulty of electronic credentials is reduced. Verification of electronic credentials is easy.
Owner:广州天宁信息技术有限公司
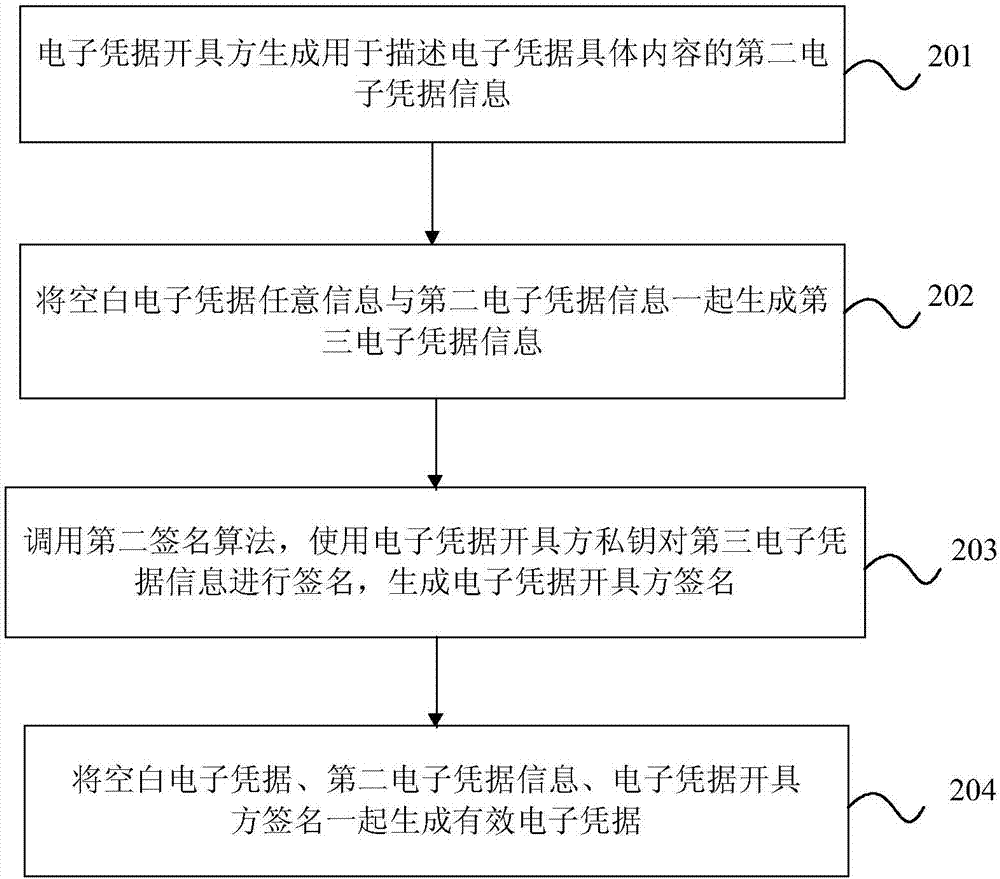
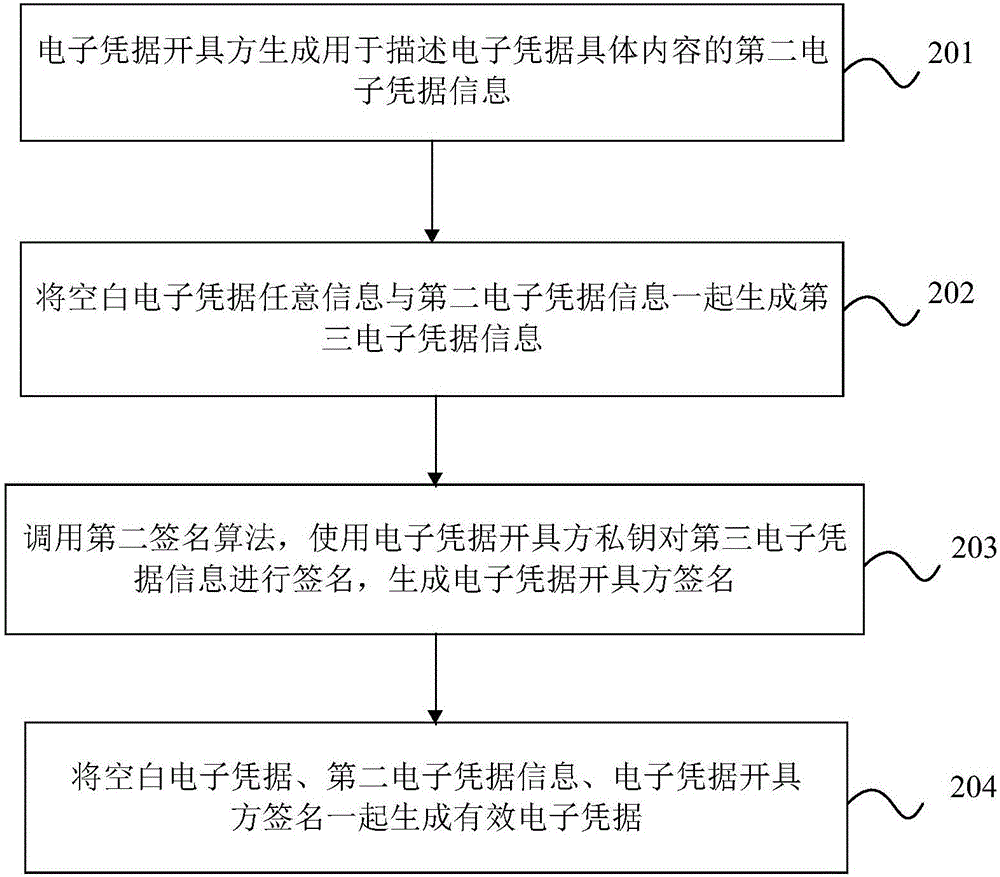
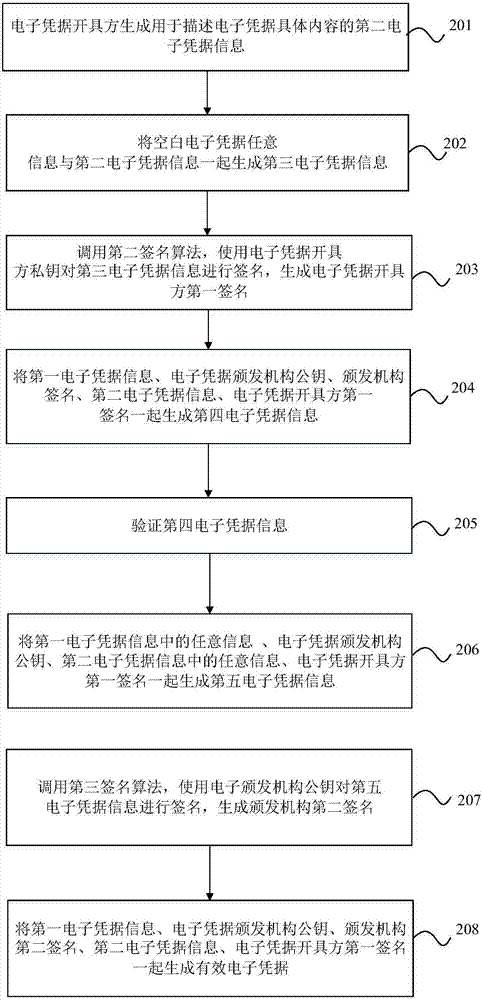
Valid electronic credential generation and public verification method, device and system
ActiveCN106685665AImprove verification efficiencyReduce difficultyUser identity/authority verificationValidation methodsComputer science
The present invention discloses a valid electronic credential generation and public verification method, device and system. The valid electronic credential generation method is configured to generate valid electronic credentials according to blank electronic credentials. The valid electronic credential generation method comprises: a valid electronic credential identification information generation step: an electronic credential issuing party generates second electronic credential information configured to describe the concrete content of the electronic credential, any information of the blank electronic credentials and the second electronic credential information are combined to form third electronic credential information, a second signature algorithm is called to perform signature of the third electronic credential information through adoption of the private key of the electronic credential issuing party and generate the signature of the electronic credential issuing party; and the valid electronic credential generation step: a valid electronic credential is generated according to the blank electronic credentials, the second electronic credential information and the electronic credential issuing party. According to the embodiment of the invention, the valid electronic credential generation and public verification method, device and system enhance the antifalsification of the electronic credentials, have the advantages of sharing usage prevention and unconventional usage prevention, reduce the difficulty of the electronic credential verification and have the easy verification feature.
Owner:北京天宁信安科技有限公司
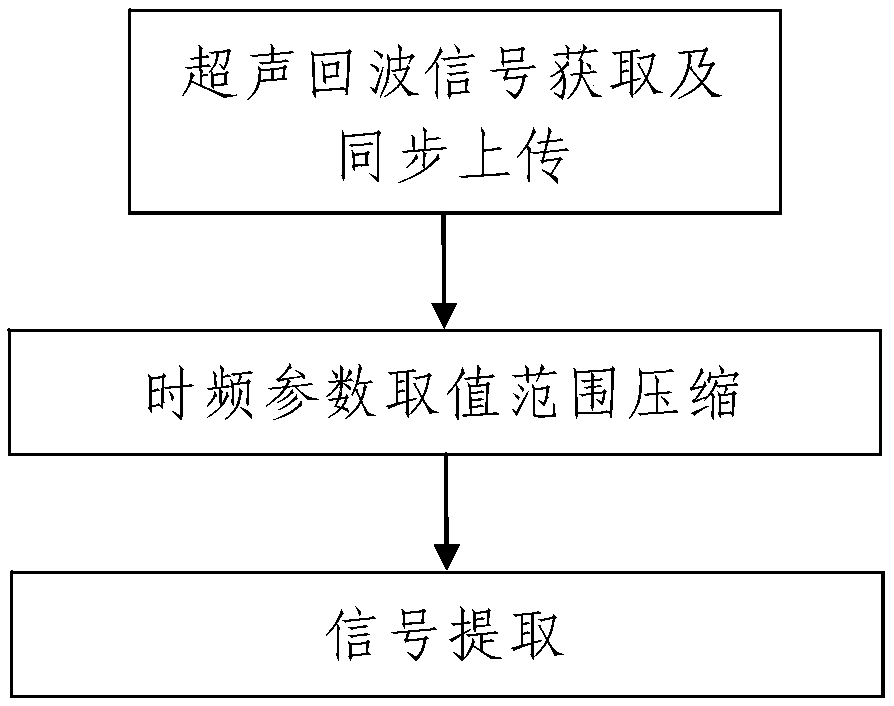
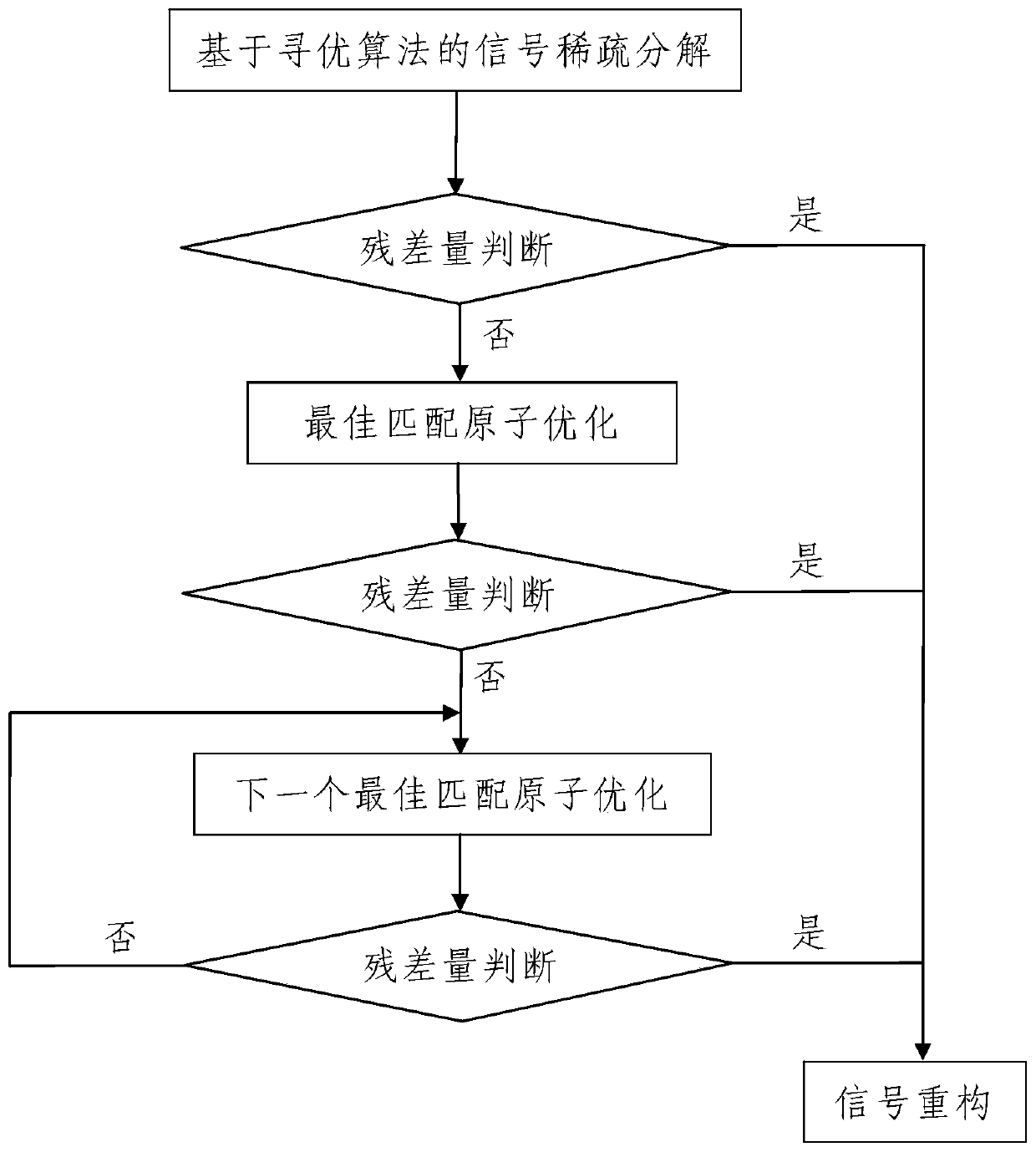
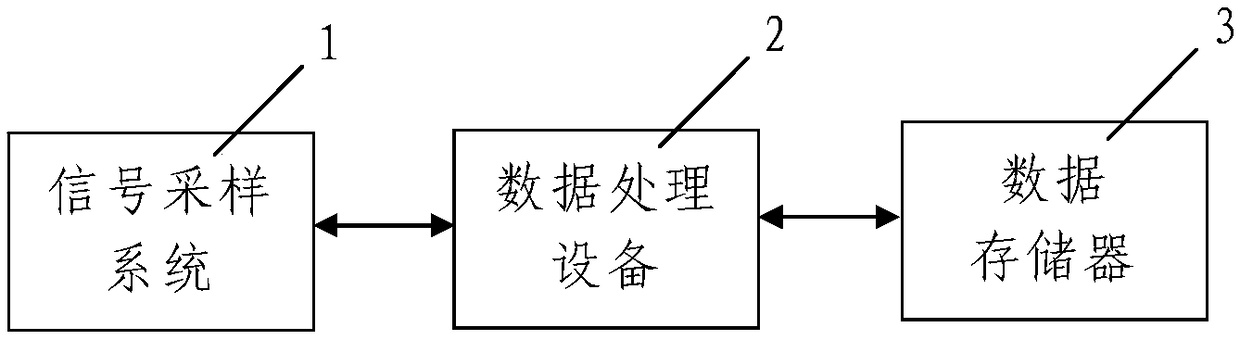
Ultrasonic echo signal extraction method based on multi-scale matching tracking
ActiveCN109632973AThe method steps are simpleReasonable designProcessing detected response signalGabor atomSonification
The invention discloses an ultrasonic echo signal extraction method based on multi-scale matching tracking. The method comprises the following steps: step one, ultrasonic echo signal acquisition and synchronous uploading; step two, time frequency parameter value range compression: compressing value ranges of time frequency parameters of a Garbo atom used for performing sparse decomposition on a to-be-processed signal f(t) by adopting the data processing equipment, wherein the time frequency parameters comprise a scale parameter, a displacement parameter, a frequency parameter and a phase parameter; step three, signal extraction as follows: step 301, signal sparse decomposition based on optimization algorithm; and step 302, signal reconstruction. The method disclosed by the invention is simple in step, reasonable in design, convenient for realization, and good in use effect; the value range of each parameter in the time frequency parameters is compressed, and then the optimal matching atom is searched by adopting the signal sparse decomposition method based on the optimization algorithm, the signal extraction speed can be greatly accelerated, and the signal extraction precision canbe effectively improved.
Owner:XIAN UNIV OF SCI & TECH
Signal dedrying method based on time-frequency analysis
ActiveCN109682892AThe method steps are simpleReasonable designProcessing detected response signalArtificial lifeDecompositionTime–frequency analysis
The invention discloses a signal dedrying method based on time-frequency analysis. The method comprises the steps that 1, a to-be-processed signal is synchronously stored; 2, signal dedrying is conducted, wherein data processing equipment is adopted for dedrying the to-be-processed signal f(t), the process comprises the substeps that 201, signal sparse decomposition based on an optimization algorithm is conducted; when the data processing equipment is adopted for seeking psirn(t), and the time-frequency parameter rn is sought through the following processes of C1, time-frequency parameter optimization; C2, optimal time-frequency parameter determination; 202, signal reconstruction is conducted. The method is simple in step, reasonable in design, convenient to implement and good use effect,a signal sparse decomposition method based on the optimization algorithm is adopted for seeking the optimal matching atom, and meanwhile a fitness value and sparsity are combined for determining the optimal matching atom; the signal dedrying speed can be greatly increased, the dedrying effect can be effectively improved, and the accuracy of the signal obtained after dedrying is guaranteed.
Owner:XIAN UNIV OF SCI & TECH
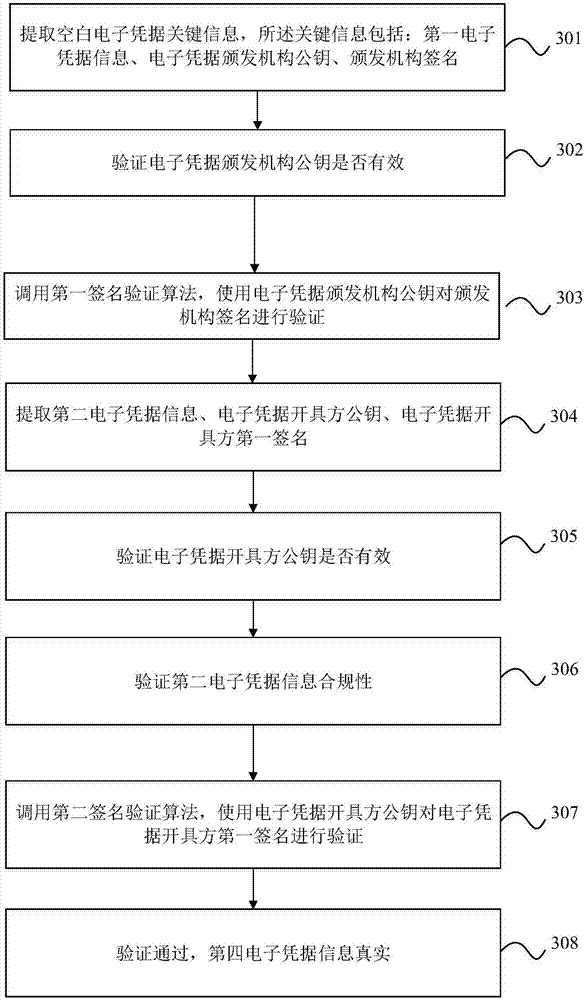
Electronic evidence generation and public verification method, device and system
ActiveCN106934618AImprove anti-counterfeiting performanceSimple processPayment protocolsComputer securityValidation methods
The invention discloses an electronic evidence generation and public verification method, device and system. The electronic evidence generation method comprises a valid electronic evidence identification information generation step, a fourth electronic evidence information generation step, a fourth electronic evidence information verification step, a fifth electronic evidence information generation step, an issuing authority second signature generation step and a valid electronic evidence generation step. According to the method, after an issuing authority is utilized to verify all information, a new signature is made to replace a previous signature, therefore, anti-falsification, sharing prevention and incompliant usage prevention of electronic evidence are improved, the public verification process is simplified, and only the signature of the issuing authority needs to be verified. Through the method, the anti-falsification of the electronic evidence is enhanced, the defects that in the prior art, someone pretends to be the issuing authority to issue the electronic evidence, different electronic evidence issuers share the electronic evidence, and the electronic evidence is used incompliantly are overcome, and the verification difficulty of the electronic evidence is lowered.
Owner:北京天宁信安科技有限公司
Digital signature scheme based on discrete logarithm problem
InactiveCN101635627AOvercoming inefficienciesTo overcome the inability to use the same value k for two different information x <sub>1<</sub> Key distribution for secure communicationUser identity/authority verificationDigital signatureDiscrete logarithm
The invention relates to a digital signature scheme based on a discrete logarithm problem. The technical scheme of the invention comprises the following steps: (1) user private key register and verification phase: a private key management centre publishes one primitive root g of a model p, wherein p is a large prime number, the value of the p determines the difficulty of decoding the private key, thus, the proper value of the p can be selected according to a safety requirement of a system to obtain the balance of safety and efficiency, a registered user registers a personal private key Ii to the private key management centre through a safe path, the private key simultaneously satisfies two conditions as above formula, the private key is stored well to avoid divulging after passing the verification of the private key management centre, and then the own public key g is published on a bulletin board system.
Owner:LANZHOU UNIVERSITY +1
Amplitude value and phase alignment method of high bandwidth oscilloscope
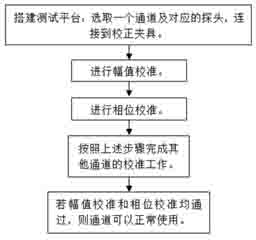
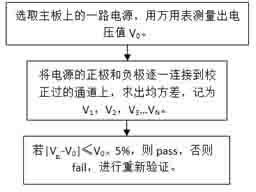
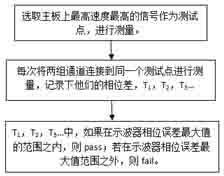
ActiveCN102680933AThe verification method is simpleStrictly control the testing processElectrical measurementsHigh bandwidthPhase alignment
The invention discloses an amplitude value and phase alignment method of a high bandwidth oscilloscope. The method comprises the following steps of: determining channels to be calibrated to be respectively a channel 1, a channel2,...... a channel N, wherein the N is greater than or equal to 2; selecting the channel to be calibrated and corresponding probe, and collecting the probe to a detection point of a calibration clamping apparatus; calibrating the amplitude value and phase of the channel; repeating the step (1) and the step (2), and finishing the amplitude value and the phase alignment of the channel to be calibrated; verifying whether the amplitude value of each channel to be calibrated is success, if not, and calibrating the amplitude value again; and verifying whether the amplitude value of each channel to be calibrated is success, if not, and calibrating the phase again.
Owner:苏州赛克安信息技术有限公司
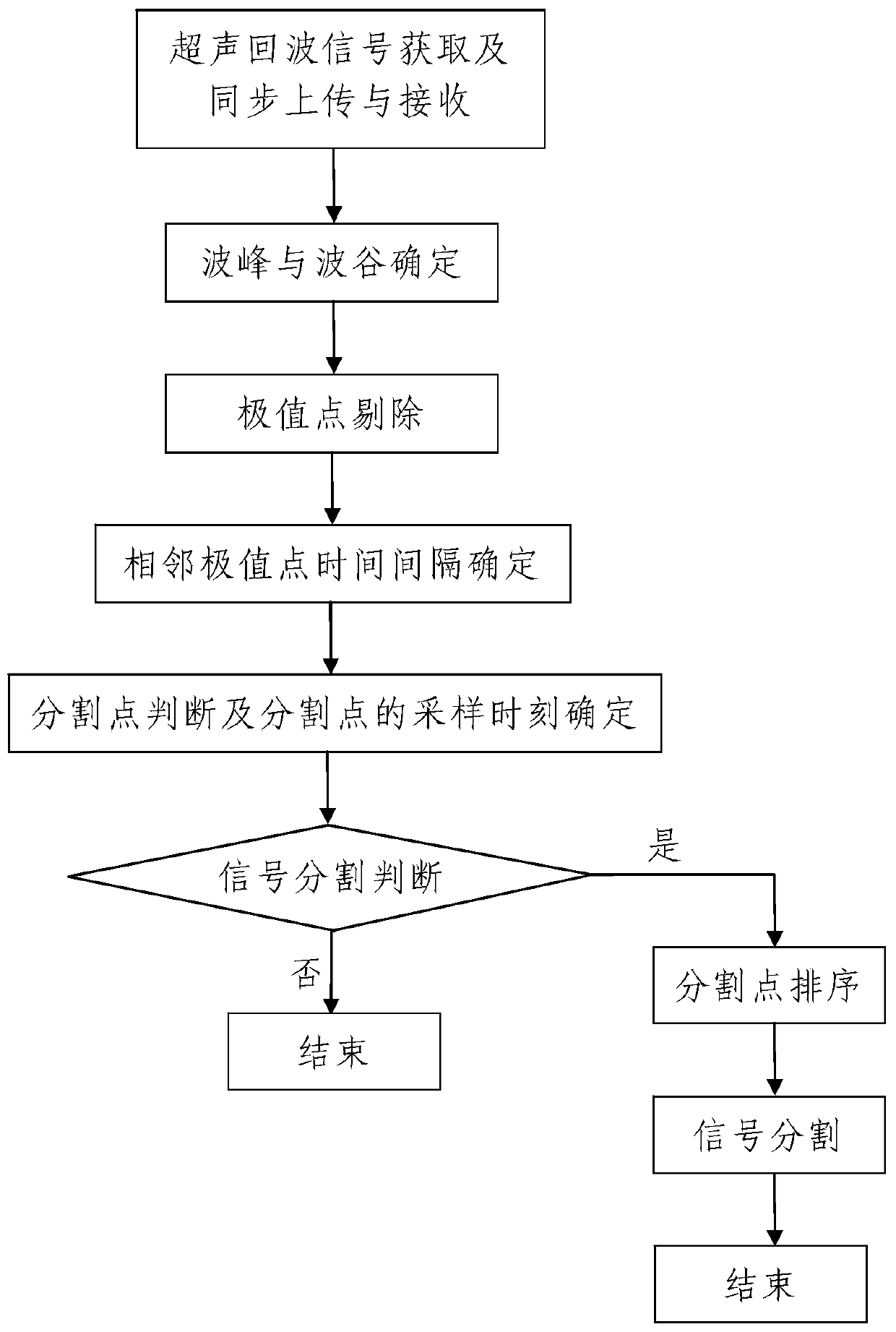
Defect detecting method based on ultrasonic flaw detection
ActiveCN109507304AThe method steps are simpleReasonable designProcessing detected response signalSonificationBlind signal separation
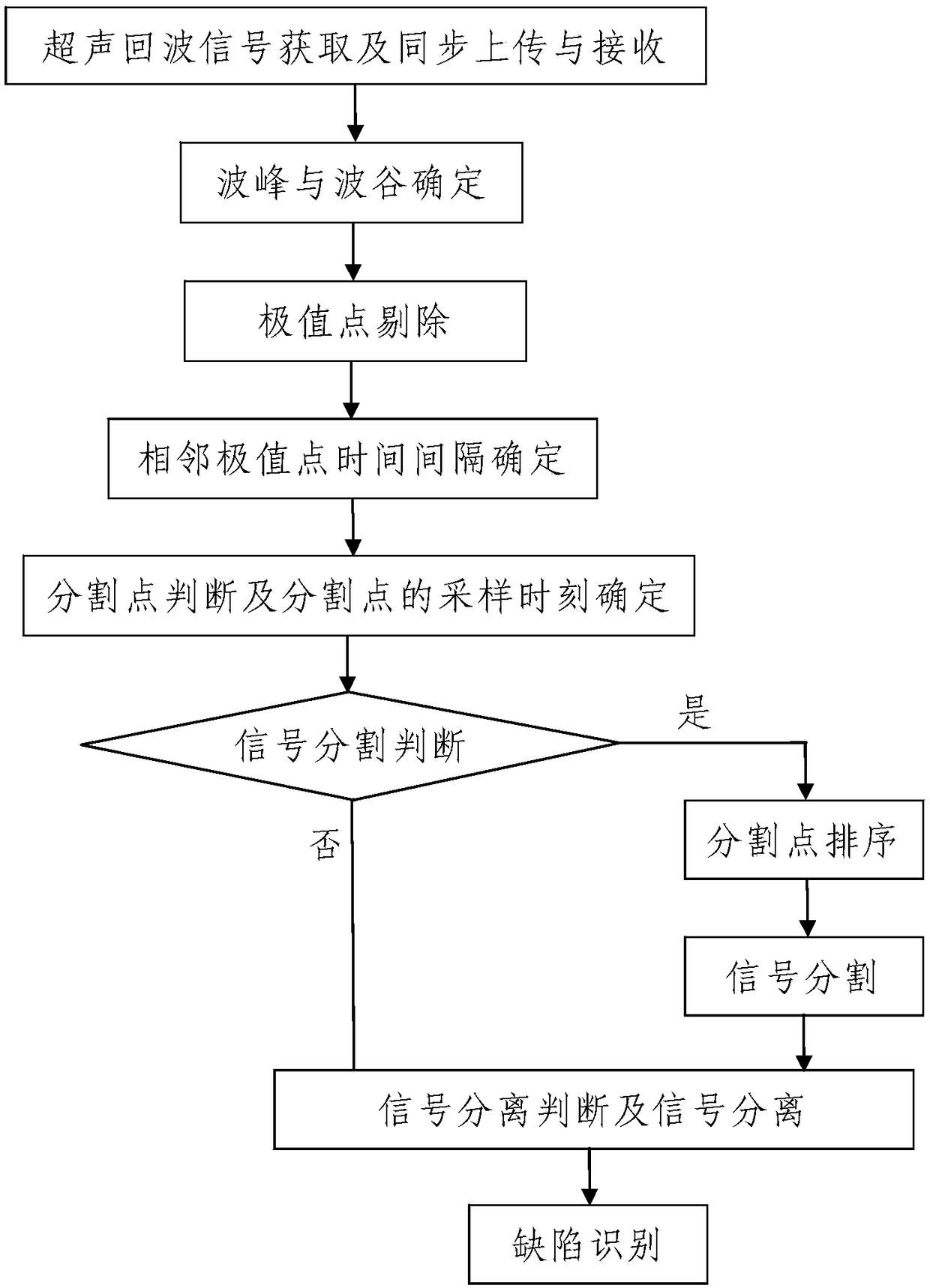
The invention discloses a defect detecting method based on ultrasonic flaw detection. The method comprises the following steps: 1, acquiring an ultrasonic echo signal and uploading the ultrasonic echosignal synchronously; 2, determining wave crests and wave troughs; 3, eliminating extreme points; 4, dividing the signal: determining a time interval between every two adjacent extreme points, judging dividing points, determining sampling moments of the dividing points, judging signal division, sorting the dividing points and dividing the signal; 5, judging signal separation and performing signalseparation; and 6, identifying a defect. The method is simple in steps, reasonable in design, convenient to implement and good in using effect; the judgment of the dividing points and the determination of the sampling moments of the dividing points are achieved by performing threshold judgment on the time interval between every two adjacent extreme points, and the ultrasonic echo signal is divided; then signal separation judgment and signal separation are respectively performed on every divided signal, and independent ultrasonic echo signals at multiple defect positions in the same ultrasonicecho signal can be quickly and accurately identified.
Owner:XIAN UNIV OF SCI & TECH
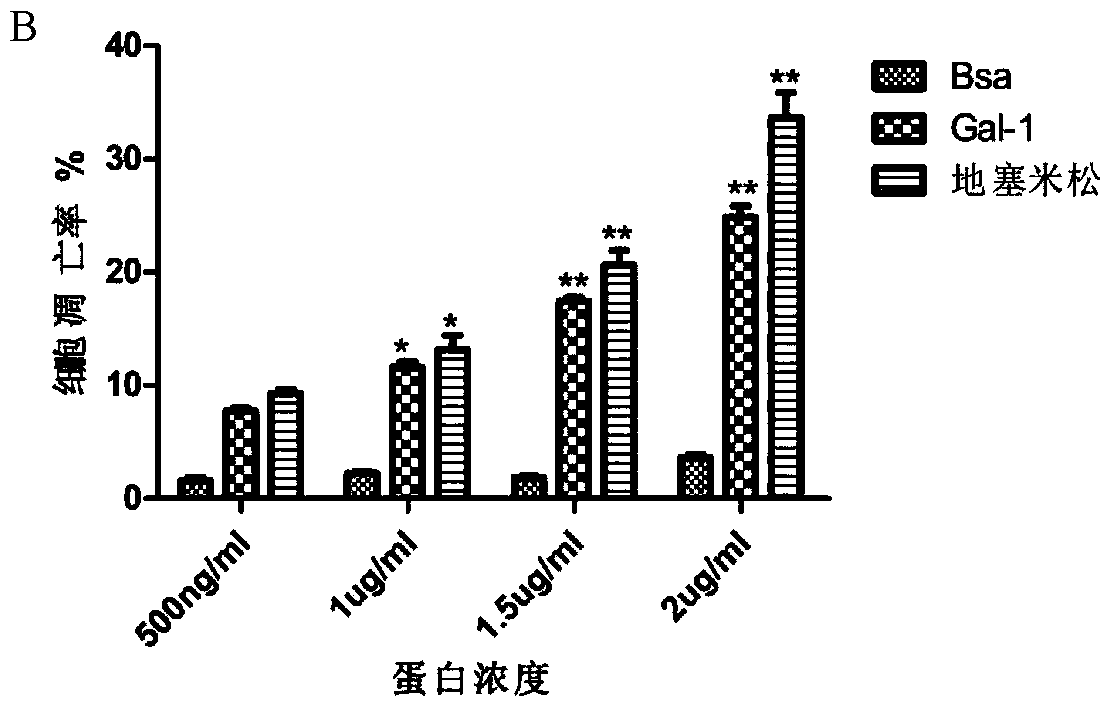
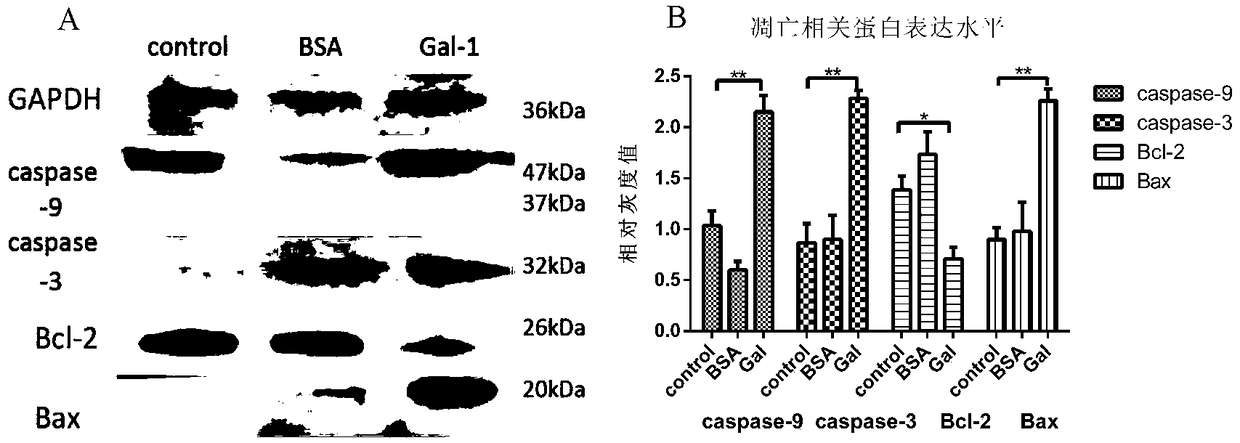
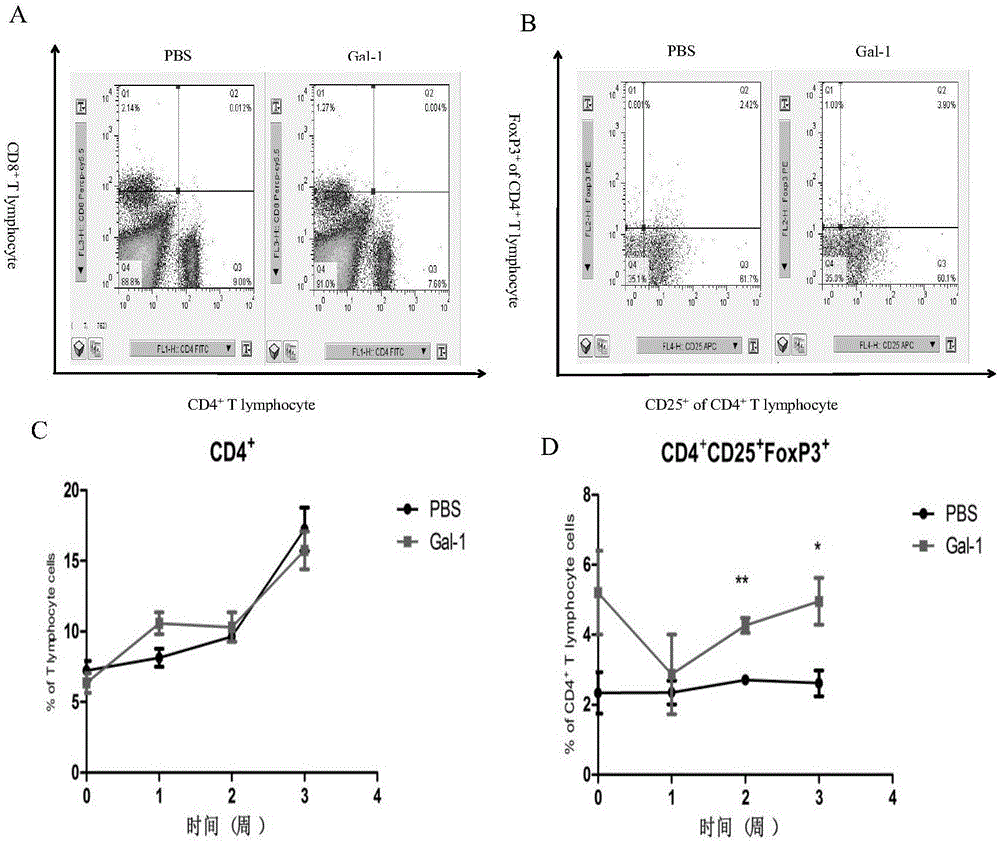
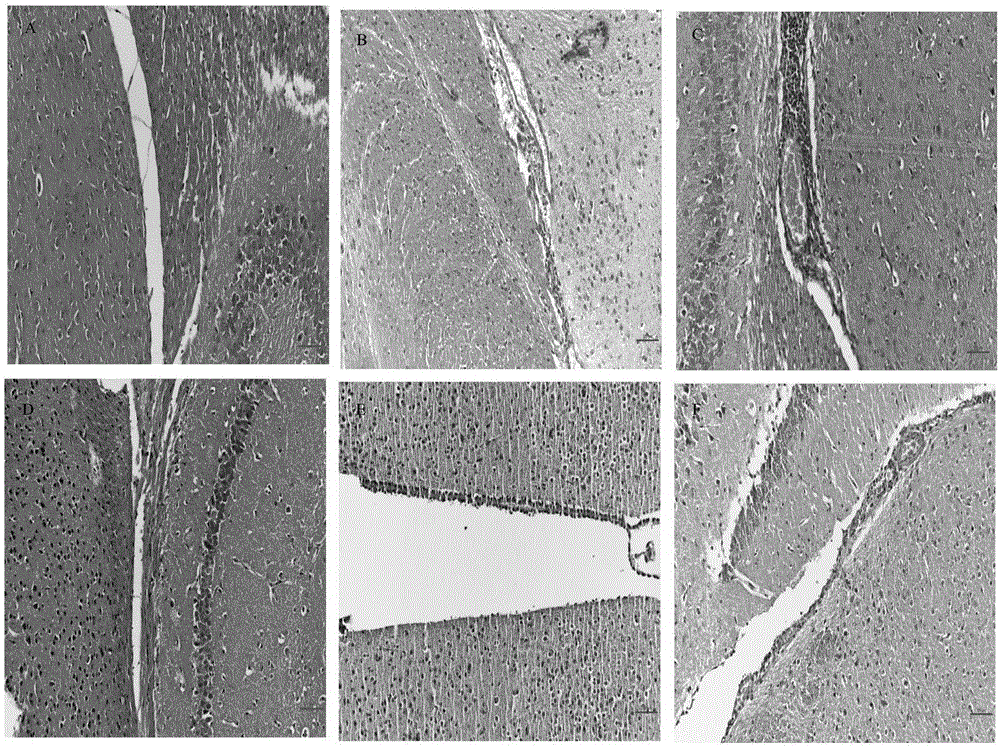
Application of membranin Annexin A2 of cell Thp-1 in Ac-Gal-1 induced apoptosis
ActiveCN109306368AThe verification method is simpleEasy to operateMicrobiological testing/measurementBiological testingApoptosisGalectin-1
The invention relates to application of membranin Annexin A2 of a cell Thp-1 in Angiostrongylus Cantonensis (Ac) protein Galectin-1 induced apoptosis. According to the application of the membranin Annexin A2 of the cell Thp-1 in Ac protein Galectin-1 induced apoptosis, the application provides a theoretical basis for researching applications of a pathogenesis mechanism and control of Ac and treatment of angiostrongyliasis cantonensis and provides a potential acting target, i.e., the Annexin A2 for research and development of treatment drugs; meanwhile, a foundation for research and developmentof angiostrongyliasis cantonensis treatment drugs is laid, and a target is provided for customized treatment of the Ac, so that the application has considerable market prospect and applicability.
Owner:WENZHOU MEDICAL UNIV
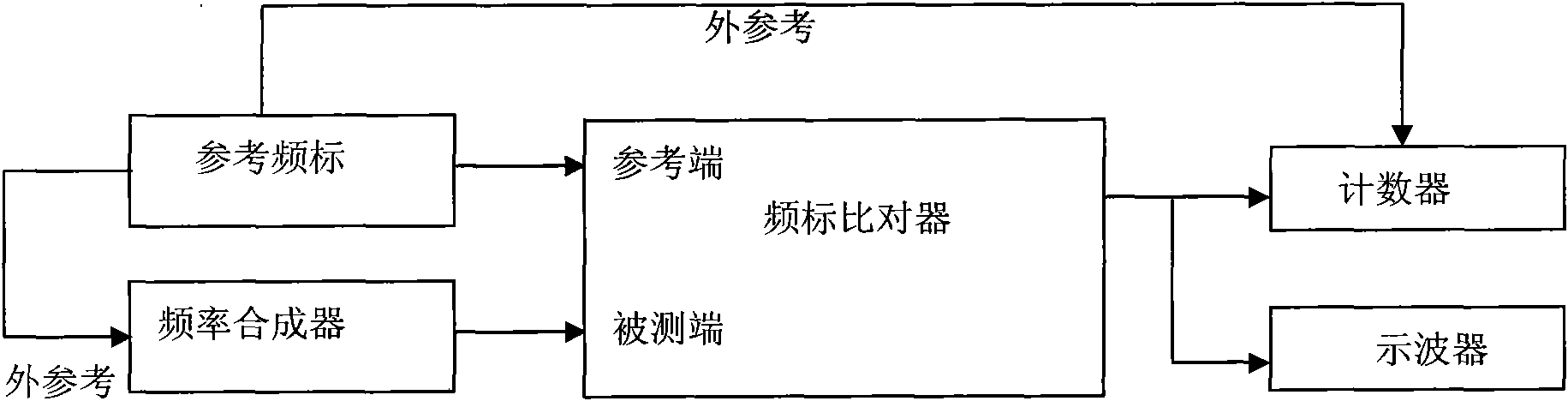
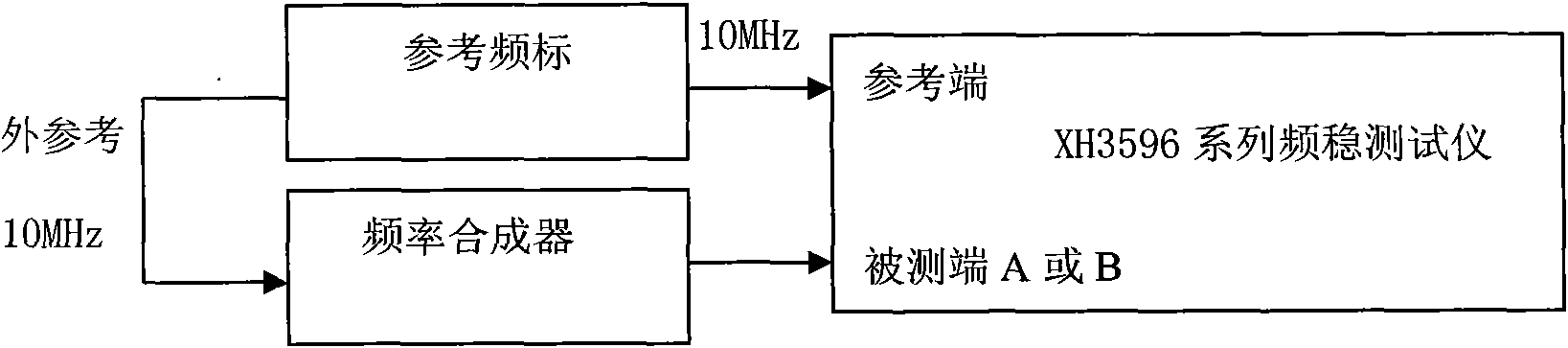
Method for testing frequency stabilization tester
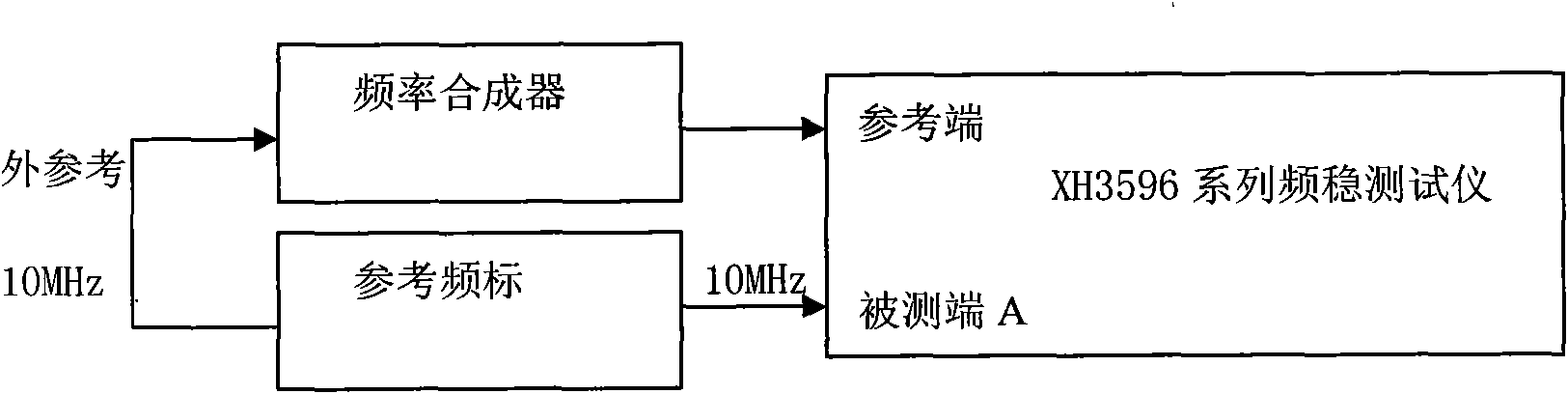
InactiveCN101551448AThe verification method is simpleElectrical measurementsFrequency stabilizationWork performance
A method for testing frequency stabilization tester is especially used for testing XH3596 series frequency stabilization testers belonging to frequency standard comparison instruments. The method is respectively used for testing tested input sensitivity, reference input sensitivity, maximum relative frequency difference, uncertainty of same-frequency correlative comparison and uncertainty of same-source correlative comparison of the frequency stabilization tester. The method comprises the following steps of: 1. checking appearance and normal work performance; 2. connecting equipments involving referential frequency scale and frequency synthesizer; and 3. testing the frequency stabilization tester. The method has the advantages of being capable of testing XH3596 series frequency stabilization testers belonging to frequency standard comparison instruments, accurately obtaining the input sensitivity, maximum relative frequency difference, uncertainty of same-frequency correlative comparison and uncertainty of same-source correlative comparison of the XH3596 series frequency stabilization testers, and having simple testing process.
Owner:SHENYANG AIRCRAFT CORP
Track circuit simulation model checking and varification method on basis of hypothesis test
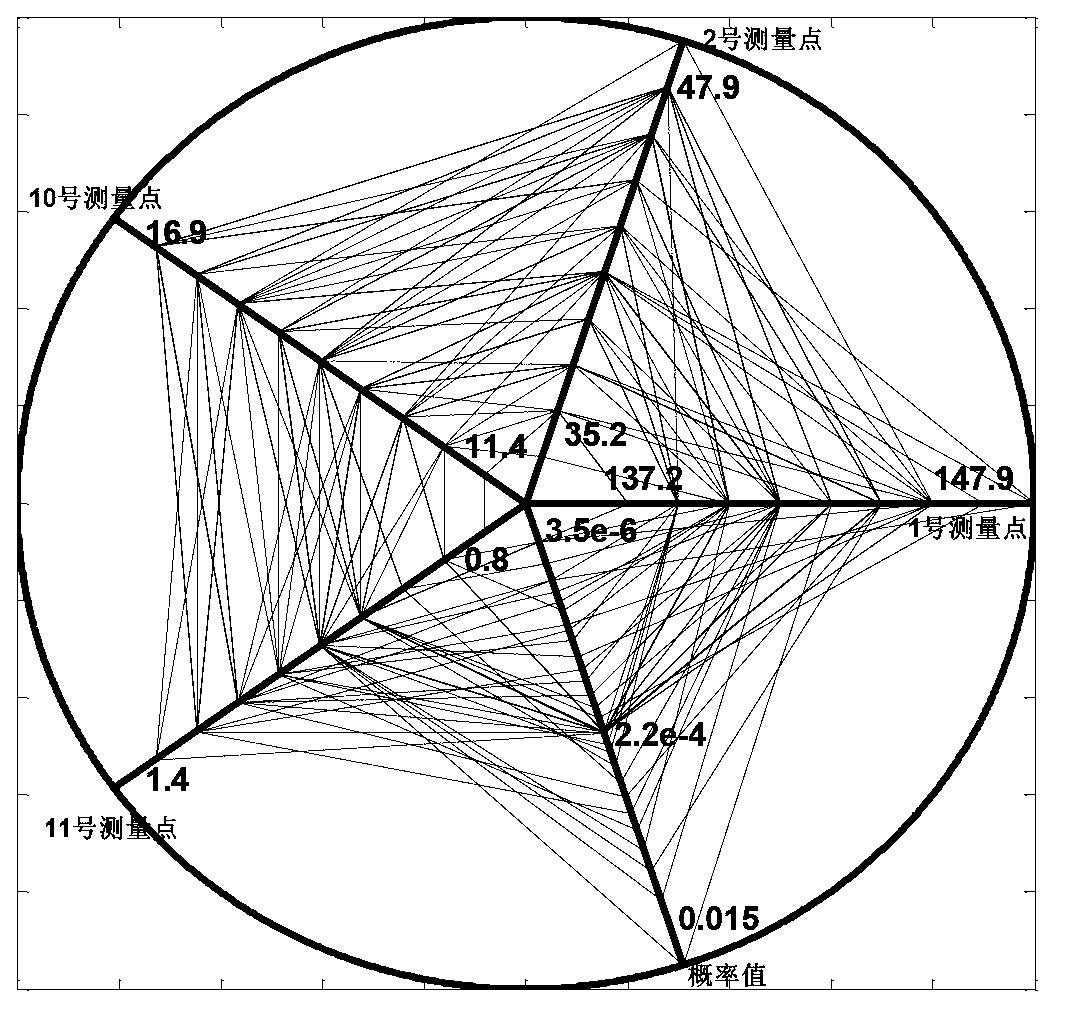
ActiveCN103226657AThe verification method is simpleEasy to operateSpecial data processing applicationsHypothesisMeasurement point
The invention relates to a ZPW2000A track circuit simulation model checking and verification method on basis of a hypothesis testing method, and belongs to the technical field of high speed railway signal systems. The method comprises the following steps: firstly, determining a final measurement point of a ZPW2000A track circuit by calculating the relative sensitivity of a probable measurement point of a simulation model, and meanwhile, calculating the amplitude of the probable measurement point of the simulation model by virtue of the monte carlo method so as to acquire an interval distribution function of test statistics probability; then obtaining an ultra-ellipsoid surface accepted domain of the ZPW2000A track circuit; and finally, testing the conformance of the ZPW2000A track circuit and the simulation model by measuring the signal amplitude of the final measurement point of the ZPW2000A track circuit. The method provided by the invention tests the conformance of the simulation model and the physical model through sample data; the method used for testing is simple and effective, and has strict theoretical foundation and good operability; and the conclusion is highly reliable. The checking and verification method established in the invention can be widely applied to checking and verification of the track circuit simulation system of a high speed railway or a common railway.
Owner:TSINGHUA UNIV +1
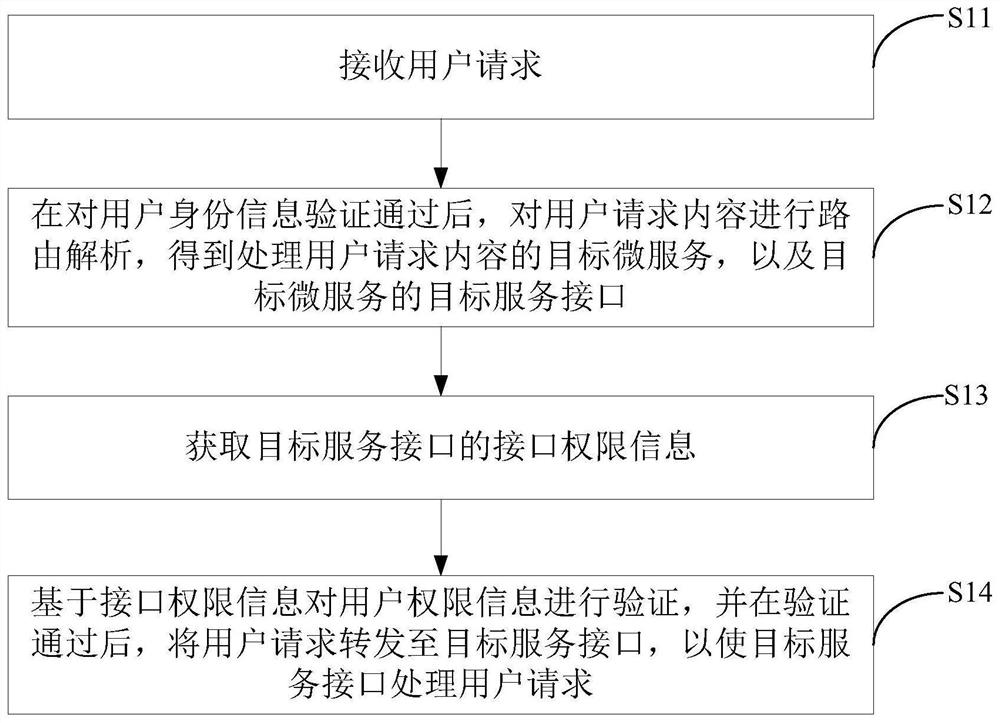
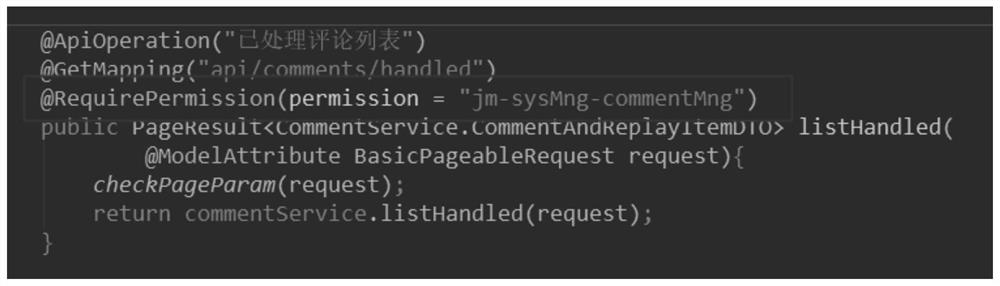
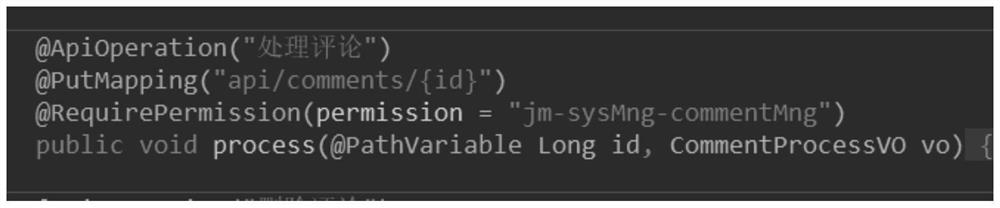
User request processing method and device
PendingCN114692172AImprove programming efficiencyThe verification method is simpleDigital data protectionComputer networkUser Privilege
The invention provides a user request processing method and device, and the method comprises the steps: carrying out the verification of a user permission through a micro-service gateway based on the interface permission information of a target service interface for processing a user request during the verification of the user permission, and forwarding the user request to a target service interface of a target micro-service after the verification is passed, and the target micro-service processes the user request without verifying the user permission. Therefore, when the micro-service is called in a chained manner, the micro-service gateway only needs to verify the user permission once, and each micro-service does not need to verify the user permission any more, so that the verification mode is simplified, and the verification efficiency is improved. Furthermore, according to the invention, the micro-service does not need to perform user permission verification, so that the programming workload during micro-service writing can be reduced, and the micro-service programming efficiency can be improved.
Owner:北京国双千里科技有限公司
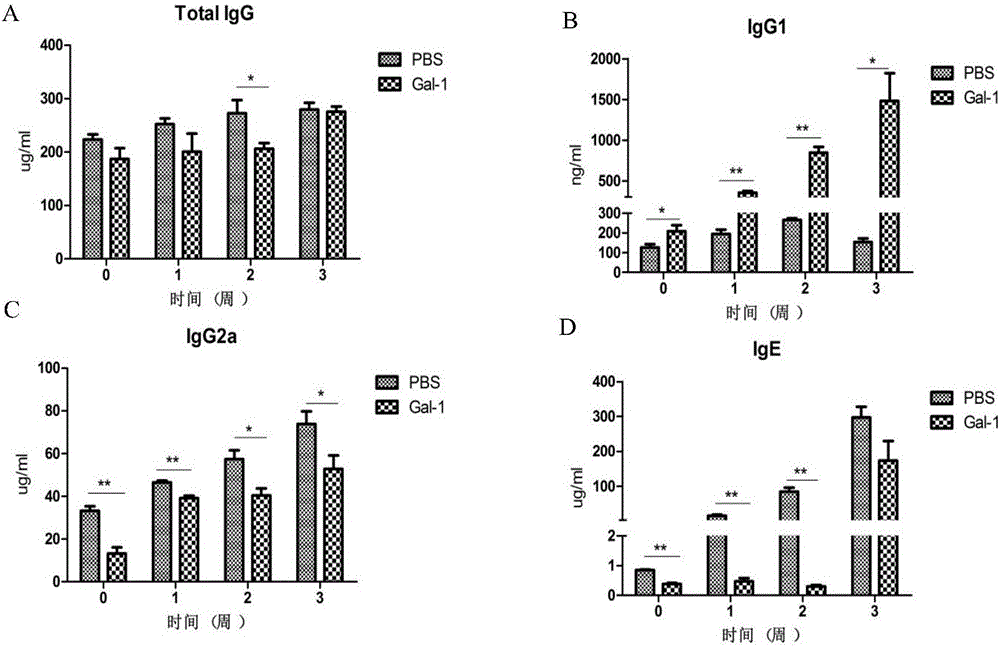
Application of Angiostrongylus Cantonensis protein Galectin-1
ActiveCN106546753AUnderstand the mechanism of diseaseThe verification method is simpleBiological material analysisBiological testingMedicineGalectin-1
The invention relates to an application of Angiostrongylus Cantonensis protein Galectin-1. The application is an immunosuppression effect application the Angiostrongylus Cantonensis protein Galectin-1, and especially is an application of the Angiostrongylus Cantonensis protein Galectin-1 in the preparation of medicines with an immunosuppression effect. The Angiostrongylus Cantonensis protein Galectin-1 provides theoretic basis for treatment of Angiostrongylus cantonensis, provides potential action target for development of treatment medicines, lays foundation for the development of the Angiostrongylus cantonensis treatment medicines, provides target for customized treatment of Angiostrongylus Cantonensis, and has good market prospect and applicability.
Owner:WENZHOU MEDICAL UNIV
Living body detection method based on facial microexpression recognition
InactiveCN109034014AEnsure the uniqueness of special featuresPrevent fraudAcquiring/recognising facial featuresSpoof detectionUser needsPattern recognition
The invention belongs to the technical field of artificial intelligence face recognition and analysis application, and relates to a technology for face recognition application belong to data securityverification technology, in particular to a living body detection method based on facial microexpression recognition. At first, a computer trains an N-type expression through a neural network in advance, and then during log-in for authentication, the computer prompts the user to make M consecutive expressions, and the user needs to follow the computer to make M consecutive expressions; secondly, through judgment by a neural network, K*M pictures are captured during the period of making expressions, where K>= 2, whether K*M faces are the same person is judged, finally Q faces are taken out of K*M pictures, where Q> = 1, and the average result obtained after many times verification is taken to verify the face identity.
Owner:TIANJIN SEWEILANSI TECH +1
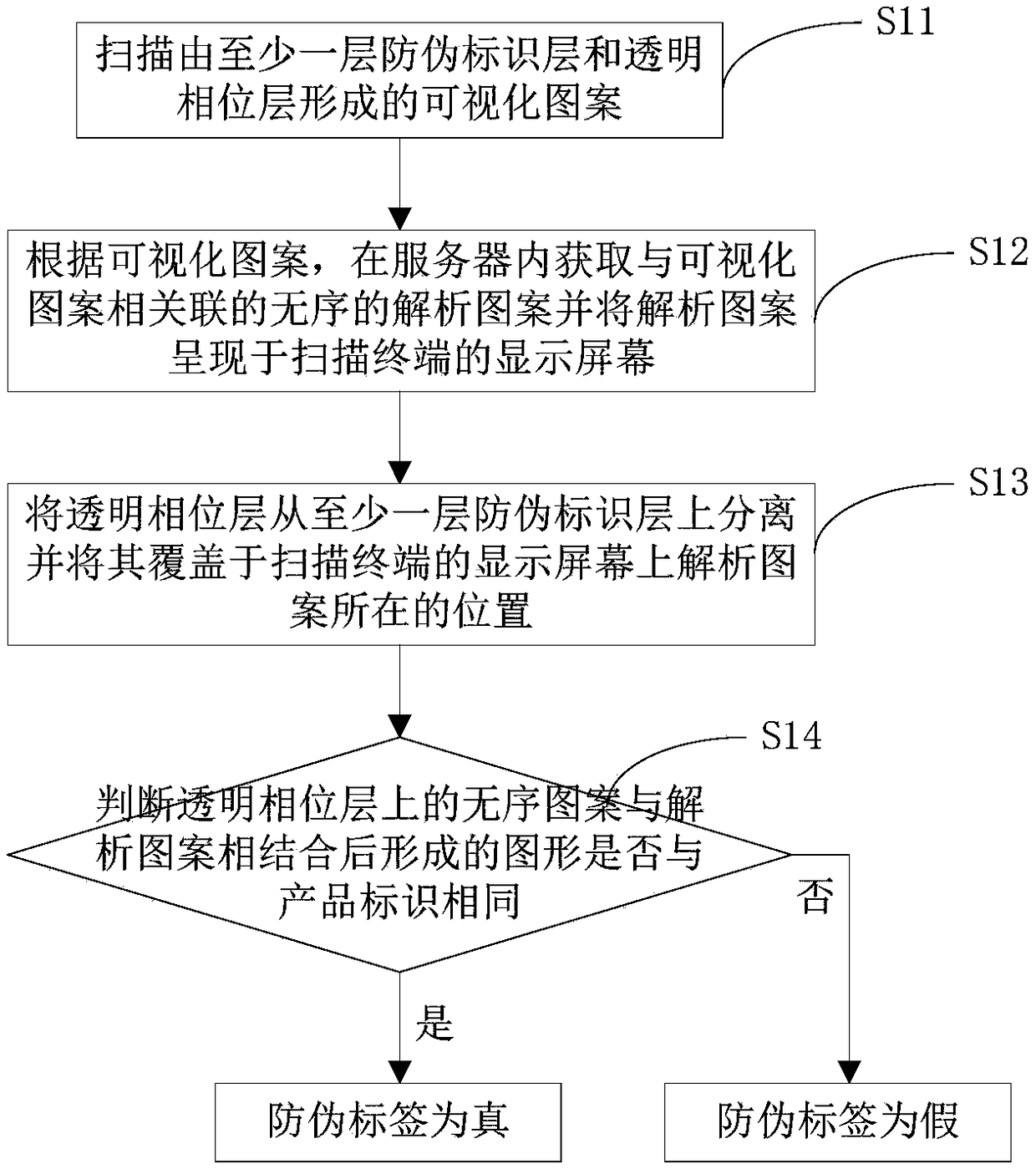
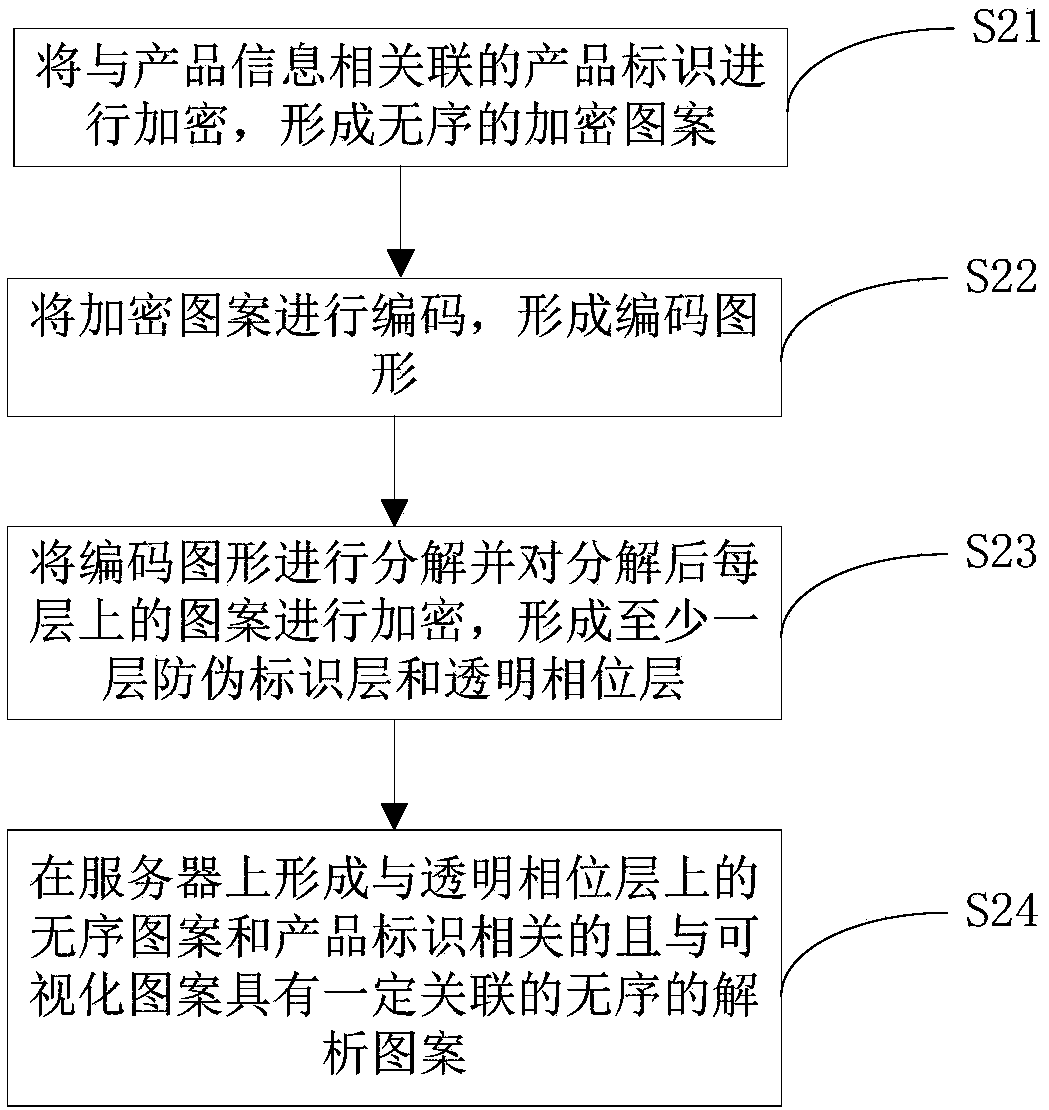
Anti-counterfeit label, verification method of anti-counterfeiting label and generation method of anti-counterfeiting label
ActiveCN108564875AImprove anti-counterfeiting technologyIncrease riskStampsIdentification meansProduct identificationEncryption
The invention provides an anti-counterfeiting label, a verification method of the anti-counterfeiting label and a generation method of the anti-counterfeiting label. The anti-counterfeiting label comprises at least one anti-counterfeiting identification layer and a transparent phase layer. Each anti-counterfeiting identification layer is provided with an identification pattern which is associatedwith product identification and provided with encryption information, and the identification pattern on each anti-counterfeiting identification layer is an encrypted disordered pattern. The transparent phase layers are detachably arranged on the surfaces of the anti-counterfeiting identification layers, each transparent phase layer is provided with an encrypted disordered pattern composed of a plurality of phase points, and the transparent phase layers and the anti-counterfeiting identification layers are combined to form an ordered and identifiable visualized pattern. A scanning terminal scans the visualized pattern, a disordered analytical pattern is displayed on a screen of the scanning terminal after analysis, the transparent phase layers are separated from the anti-counterfeiting identification layers and then pasted to the screen of the scanning terminal, and the disordered patterns on the transparent phase layers are combined with the analytical pattern on the scanning terminalto form product identification.
Owner:李天军
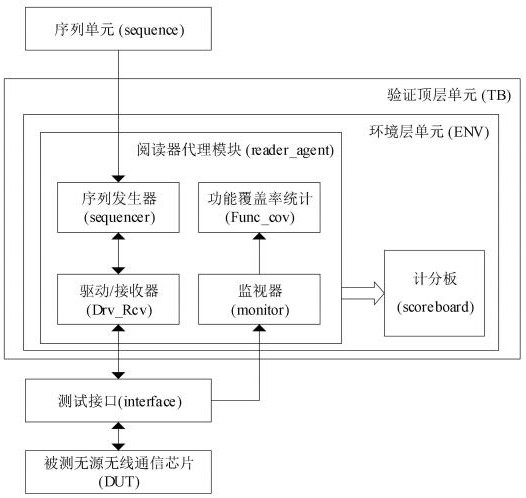
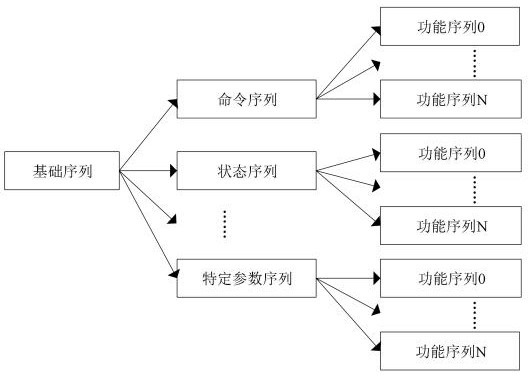
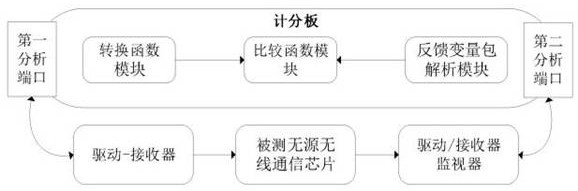
Passive wireless communication chip verification platform, construction method and chip verification method
ActiveCN112100014AImprove quality and efficiencyImprove verification efficiencyHardware monitoringFunctional testingComputer architectureEmbedded system
The invention provides a passive wireless communication chip verification platform, a construction method and a chip verification method. The passive wireless communication chip verification platformcomprises a sequence unit used for providing a three-layer verification sequence for passive wireless communication chip verification; a verification top layer unit used for establishing signal connection between the test interface and the tested passive wireless communication chip and starting simulation verification; an environment layer unit used for sending a target verification sequence to the tested passive wireless communication chip after starting simulation verification and carrying out response result comparison scoring to obtain a verification result; and a test interface used for being connected with the tested passive wireless communication chip. The verification platform is simple in structure and high in operation efficiency, the verification quality and the verification efficiency of the passive wireless communication chip can be effectively improved, three layers of verification sequences provided by the sequence unit can be combined and called according to different verified chips and different environments, a state entering part does not need to be repeatedly compiled, and the verification sequence compiling efficiency is improved.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +1
An ultrasonic signal receiving and processing method based on signal section segmentation
ActiveCN109711333AThe method steps are simpleReasonable designAnalysing solids using sonic/ultrasonic/infrasonic wavesProcessing detected response signalSonificationComputer science
The invention discloses an ultrasonic signal receiving and processing method based on signal section segmentation. The ultrasonic signal receiving and processing method comprises the following steps:1, acquiring and synchronously uploading and receiving an ultrasonic echo signal; 2, determining wave crests and wave troughs; 3, removing extreme points; wherein a data processing device is adopted to segment the ultrasonic echo signal F (t), and the process comprises the following steps that 401, the time interval of adjacent extreme points is determined; 402, judging a segmentation point and determining the sampling time of the segmentation point; 403, performing signal segmentation judgment; 404, sorting the segmentation points; 405, signal segmentation. The method is simple in step, reasonable in design, convenient to implement and good in using effect, segmentation point judgment and segmentation point sampling time determination are achieved by conducting threshold judgment on the time interval of the adjacent extreme points, and ultrasonic echo signals are segmented according to the determined number of segmentation points and the sampling time of all the segmentation points.
Owner:XIAN UNIV OF SCI & TECH
Text generation and evaluation system with emotion tags based on deep learning
PendingCN111914084AGenerated text with good qualitySimple methodCharacter and pattern recognitionNeural architecturesVisualizationVisulation
The invention relates to a text generation and evaluation system with emotion tags based on deep learning, in particular to a text generation and evaluation system with an emotion label based on deeplearning, which is realized by the following technical scheme: generating a comment introduction model through a data introduction model, and finally scoring and realizing visualization so that high-quality text with emotional colors can be generated. Compared with other existing evaluation systems at present, the invention has the advantages that the quality of the generated text is better, the optimal selection of the text is realized, a text visualization interaction terminal is designed, and model optimization and method verification are facilitated.
Owner:BEIHANG UNIV
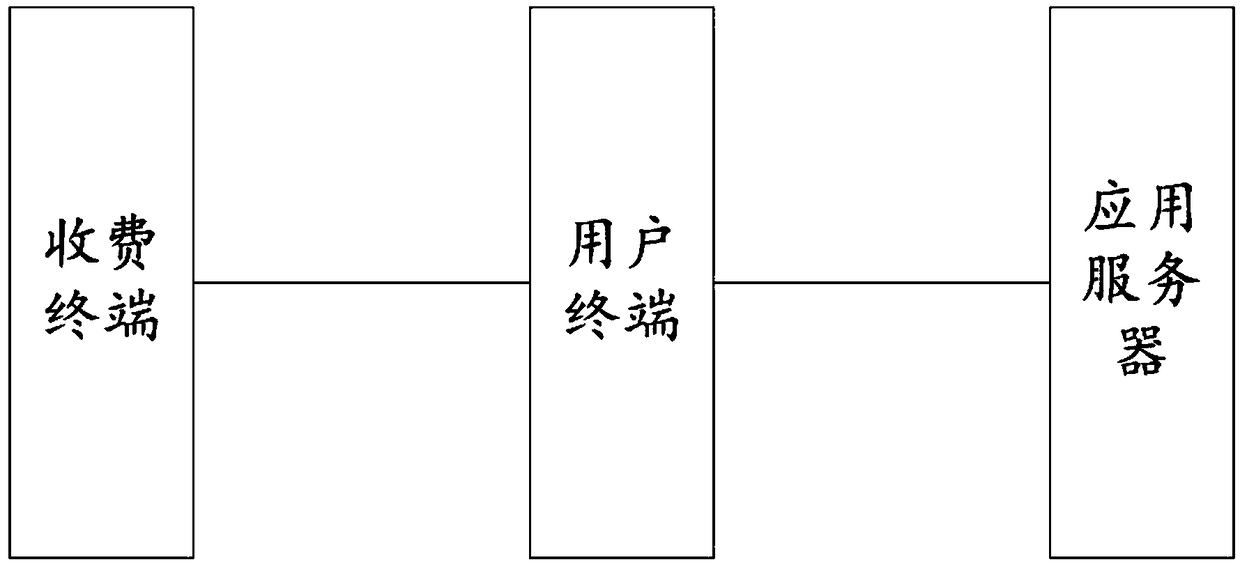
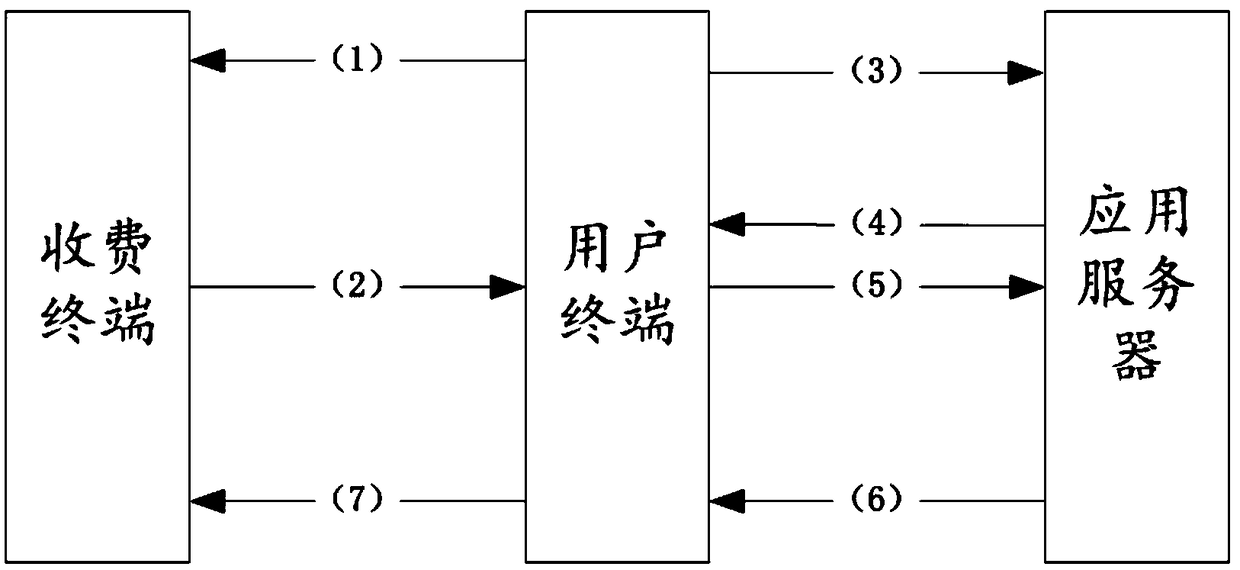
Terminal offline charging service method and system
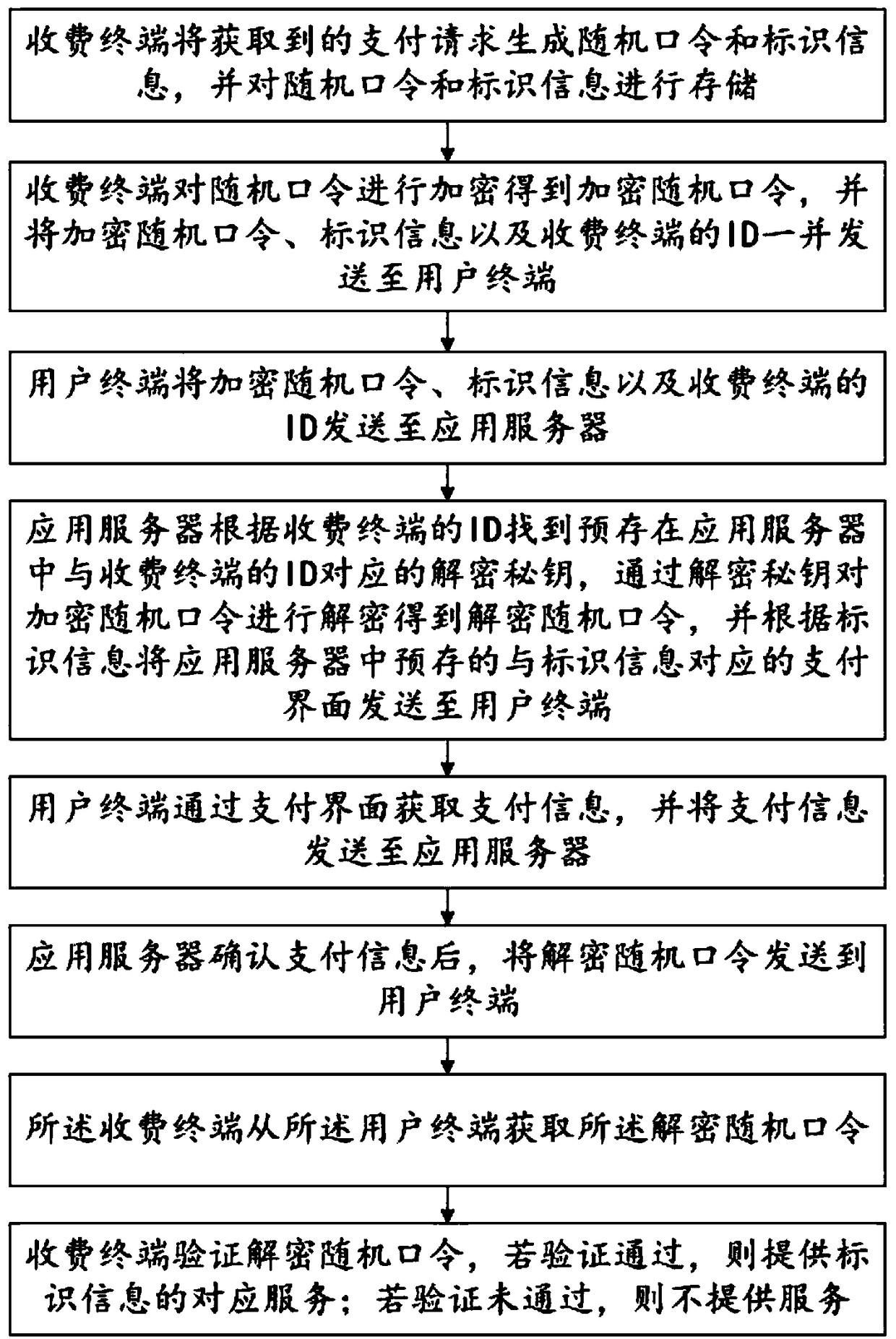
ActiveCN108932619AReduce power consumptionReduce operating costsPayment protocolsPaymentApplication server
The invention relates to a terminal offline charging service method and system. The method includes the following steps: a user requests a service from a charging terminal; the charging terminal generates a random password and related identifier information and encrypts the random password; a user terminal receives the random password encrypted by the charging terminal and the identifier information, and sends the random password and the identifier information to an application server; the server decrypts the encrypted random password and provides a payment interface to the user terminal for the user to make payment; after the application server confirms that the user has made payment, the decrypted random password is sent to the charging terminal through the user terminal; the charging terminal receives the decrypted random password and verifies the decrypted random password, and provides the a corresponding service after the verification is successful. In the whole process of the charging service, the charging terminal is in an offline state, that is to say, the terminal and the server are not connected via a network, so the operation cost of a charging system is greatly saved and the deployment difficulty of the charging terminal is reduced.
Owner:贵州玛迩比特通信科技有限公司
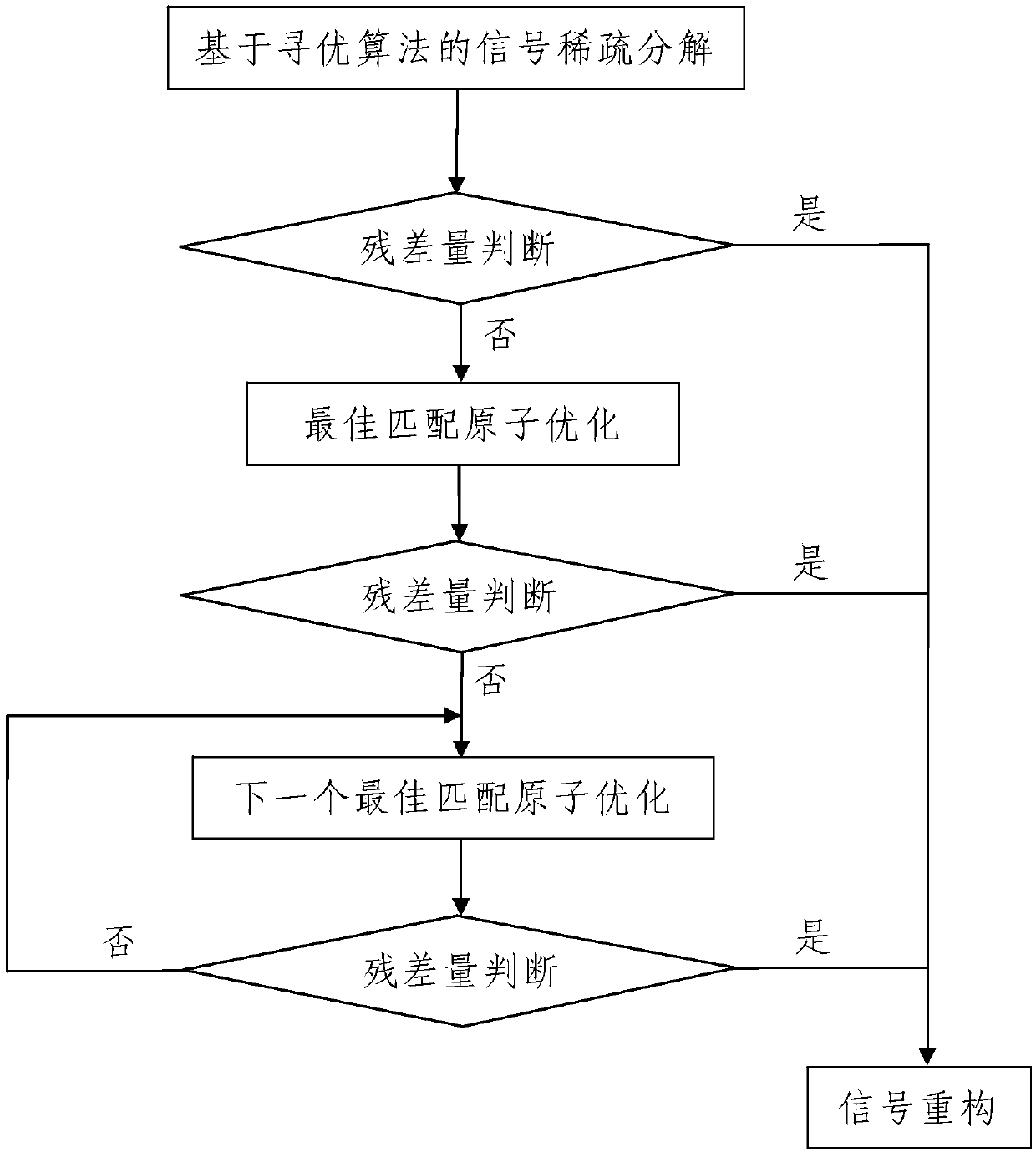
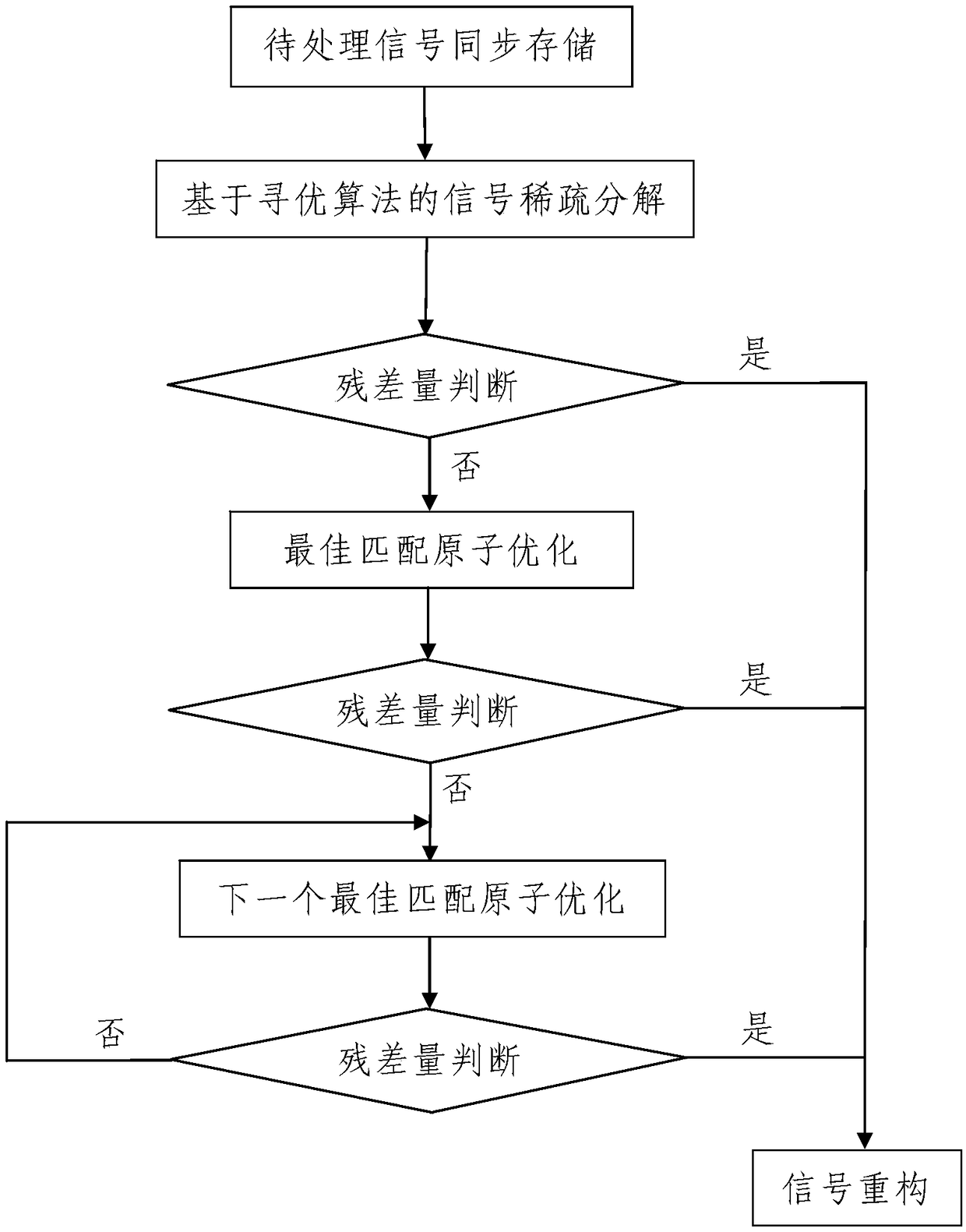
Signal extraction method
ActiveCN109507292AThe method steps are simpleReasonable designAnalysing solids using sonic/ultrasonic/infrasonic wavesDecompositionGreek letter epsilon
The invention discloses a signal extraction method. The signal extraction method comprises the following steps: 1, synchronously storing to-be-processed signals; 2, processing the to-be-processed signals: processing the to-be-processed signal f(t) by using data processing equipment, wherein the process comprises the following steps: 201, performing signal sparse decomposition based on an optimization algorithm; 202, performing residual amount judgment: judging whether ||R<m>(t)||2 obtained after signal sparse decomposition is less than epsilon or not, and if the ||R<m>(t)||2 is greater than orequal to epsilon, entering the step 203, otherwise, entering the step 204; 203, performing best matching atom optimization; 204, performing signal reconstruction. The method is simple in step, reasonable in design, convenient to implement and good in use effect; the best matching atom is searched according to a signal sparse decomposition method based on the optimization algorithm, the signal extraction precision is judged through residual amount judgment, and best matching atom optimization is conducted according to the judgment result, so that the signal extraction speed can be greatly increased and the signal extraction precision can be effectively improved.
Owner:XIAN UNIV OF SCI & TECH
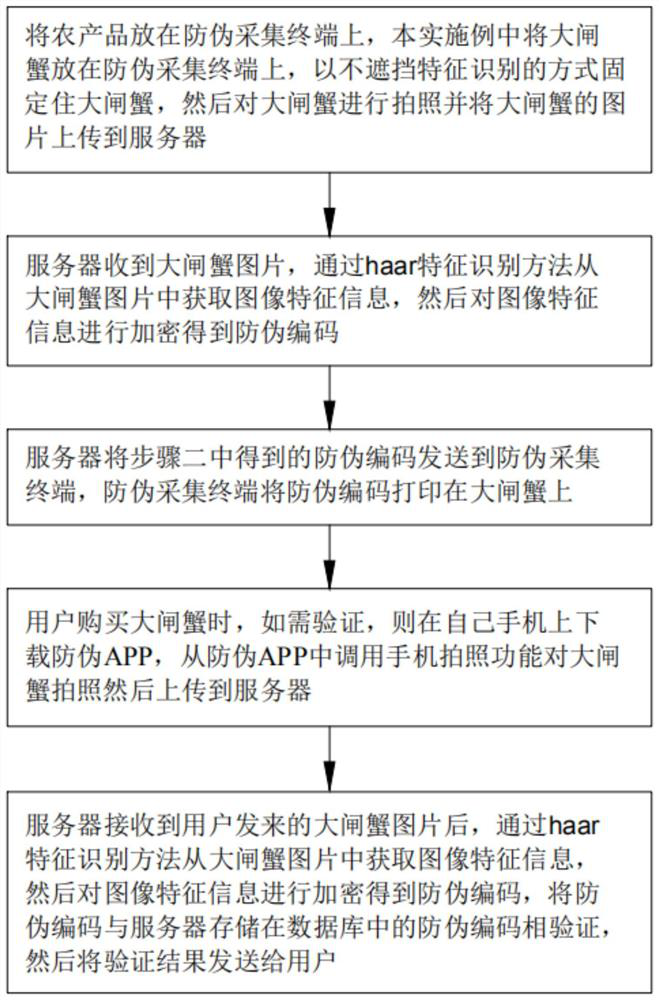
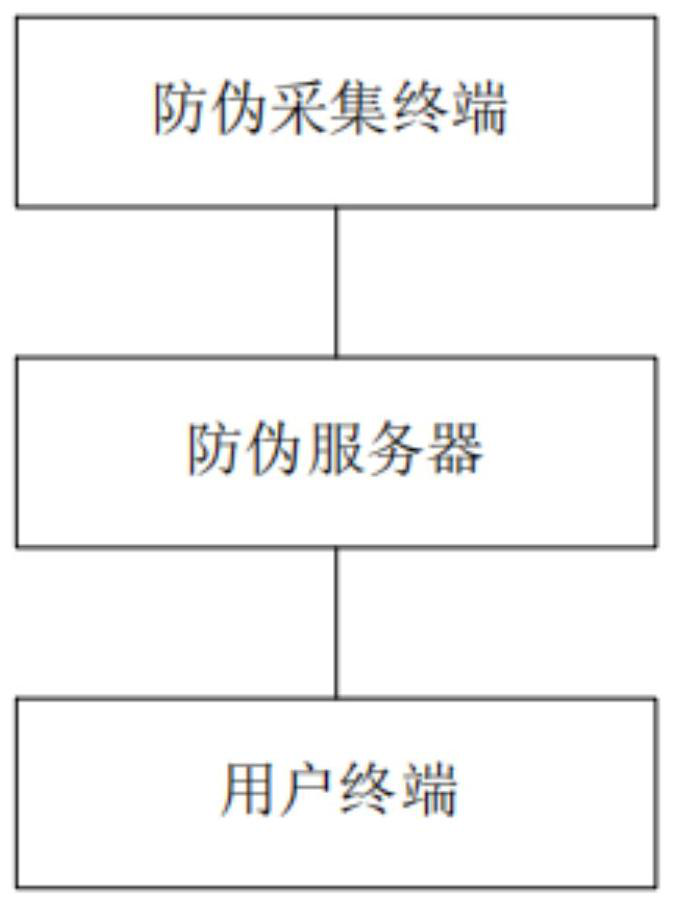
Anti-counterfeiting method and system for high-quality agricultural products
PendingCN112734444AThe verification method is simpleCo-operative working arrangementsCommerceUser verificationAgricultural science
The invention discloses an anti-counterfeiting method and system for high-quality agricultural products. The method comprises the following steps: photographing an agricultural product, and transmitting an agricultural product picture to a server; the server obtains image feature information from the agricultural product picture, and then obtains a corresponding anti-counterfeiting code according to the obtained image feature information; printing the anti-counterfeiting code obtained by the server on an agricultural product; the user photographs the agricultural product and uploads the agricultural product to the server when obtaining the agricultural product, and the server receives the agricultural product picture, verifies the agricultural product picture and sends a verification result to the user. Compared with the prior art, the agricultural product is photographed and then uploaded to the server, the server extracts the image feature information and encrypts the image feature information to obtain the anti-counterfeiting code, a user photographs the agricultural product and uploads the agricultural product to the server when purchasing the agricultural product, and the server sends a verification result to the user after verifying the agricultural product. The user verification mode is simple, and the anti-counterfeiting code cannot be separated from the agricultural product.
Owner:HUNAN INST OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com