Method and device for identifying by using verification code
A verification code and verification request technology, applied in the Internet field, can solve the problems of cumbersome work, easy input errors, waste of user time, etc., to achieve the effect of improving verification efficiency, simplifying verification methods, and avoiding verification failures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0144] In this embodiment, the terminal is a computer using a mouse. like Figure 4 shown, including the following steps:
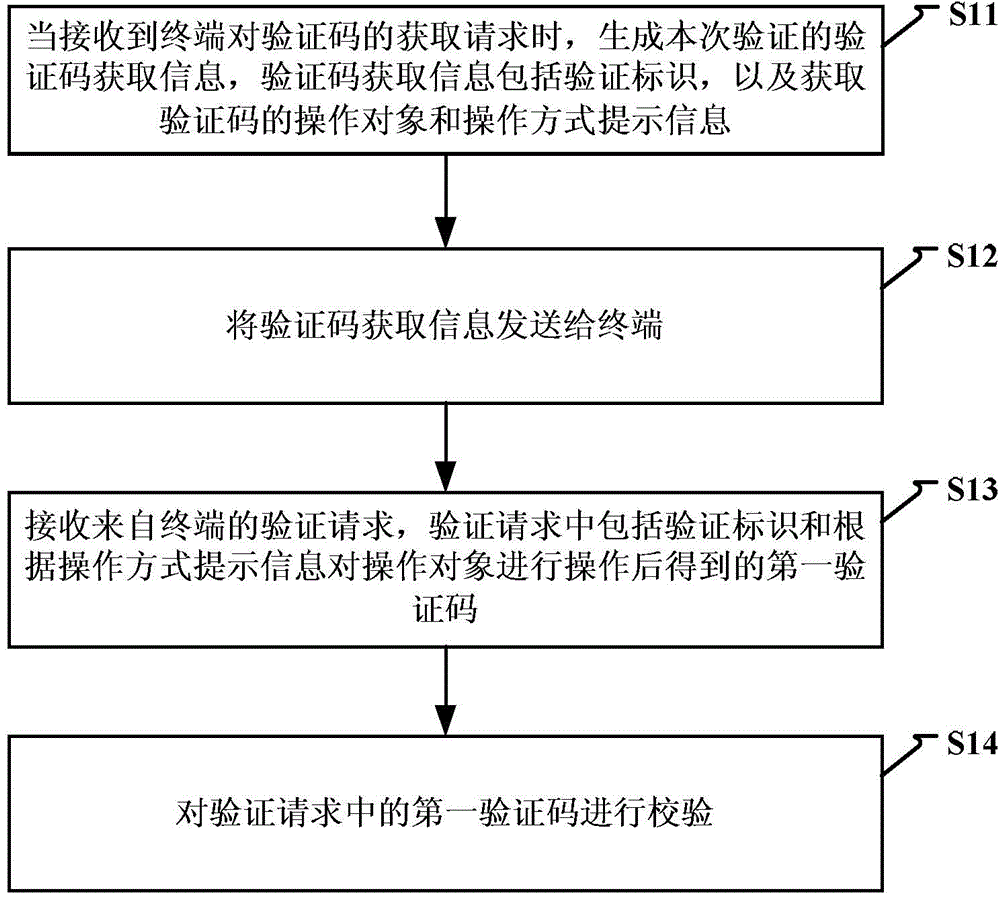
[0145] Step S401, the user sends a request for obtaining a verification code to the server through a click operation;
[0146] Step S402, the server receives the acquisition request sent by the user, and generates the verification code acquisition information for this verification, including the verification identification, the operation object of the verification code, and the operation mode prompt information; for example, the operation object is "A" arranged in sequence in the form of pictures "B" "C" "D" "E" "F" six characters, the corresponding position information is 0x001, 0x002, 0x003, 0x004, 0x005, 0x006, the prompt information of the operation method is: Please drag and drop the exchange character "C" and "D" position;
[0147] Step S403, the server operates the operation object according to the prompt information of the operation mode, and o...
Embodiment 2
[0157] In this embodiment, the terminal is a tablet computer using a touch screen, such as Figure 7 shown, including the following steps:
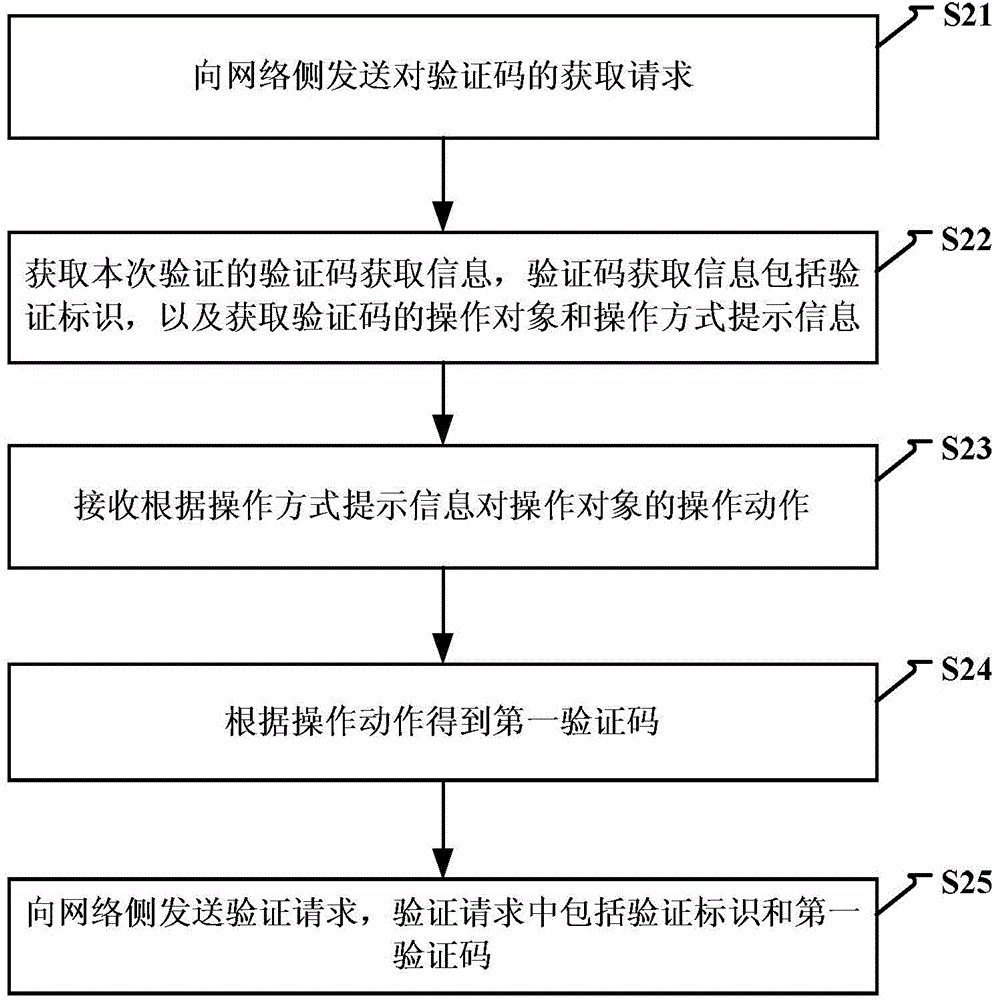
[0158] Step S701, the user sends a request for obtaining a verification code to the server by touching the screen;
[0159] Step S702, the server receives the acquisition request sent by the user, and generates verification code acquisition information, including verification identification, verification code operation object and operation mode prompt information; for example, the operation object is "A" "B" " C", "D", "E" and "F" are six characters, and the prompt message of the operation method is: Please drag and drop to exchange the positions of the characters "C" and "D";
[0160] Step S703, the server sends the generated verification code acquisition information to the terminal;
[0161] Step S704, after receiving the verification code acquisition information, the terminal displays the operation object and operation mode prompt in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com