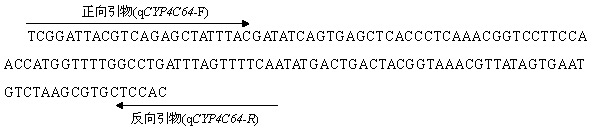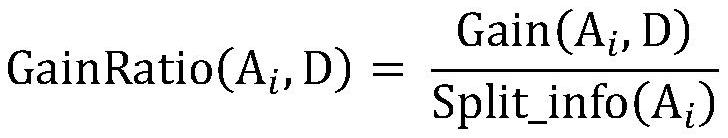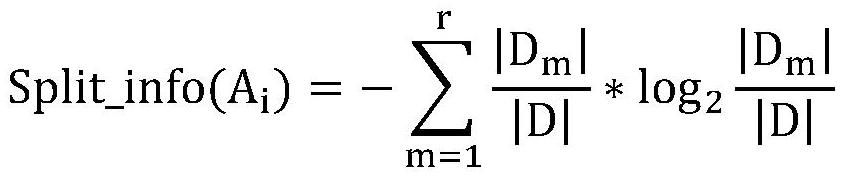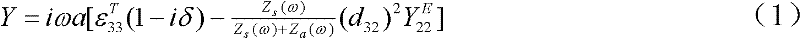Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
56results about How to "Strong uniqueness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Commodity double-layer anti-fake method based on technologies of internet of things
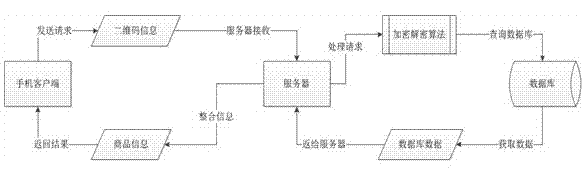
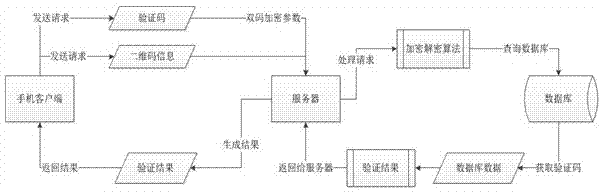
Provided is a commodity double-layer anti-fake method based on technologies of internet of things. The commodity double-layer anti-fake method based on the technologies of the internet of things comprises a plain code layer, a code layer, a mobile terminal, a server and a database. The plain code layer only contains inquiry codes which are used for inquiry of commodity information. A user obtains an inquiry code through the mobile terminal, and the inquiry code is automatically sent to the server. The server obtains a commodity information code through a decipherment algorithm, inquires corresponding commodity information from the database, and then sends the commodity information back to the mobile terminal. The code layer only contains verification codes which are used for verification of authenticity of a commodity, wherein a verification code and a corresponding inquiry code are a pair of rule codes which are bound in a one-to-one correspondence mode. The user obtains the verification code through the mobile terminal which is provided with identification software of two-dimension codes, bar codes or digital codes, and the verification code is automaticlly sent to the server. The server matches the verification code and the inquiry code, and sends a matching result back to the mobile terminal. The commodity double-layer anti-fake method based on the technologies of the internet of things has the advantages of being good in anti-fake performance, providing convenience, and being high in encryption performance, rapid, not prone to being forged, and beneficial for protecting rights and interests of consumers and enterprises.
Owner:HUNAN IOT ONLINE TECH
Vehicle identification data processing method, device and system
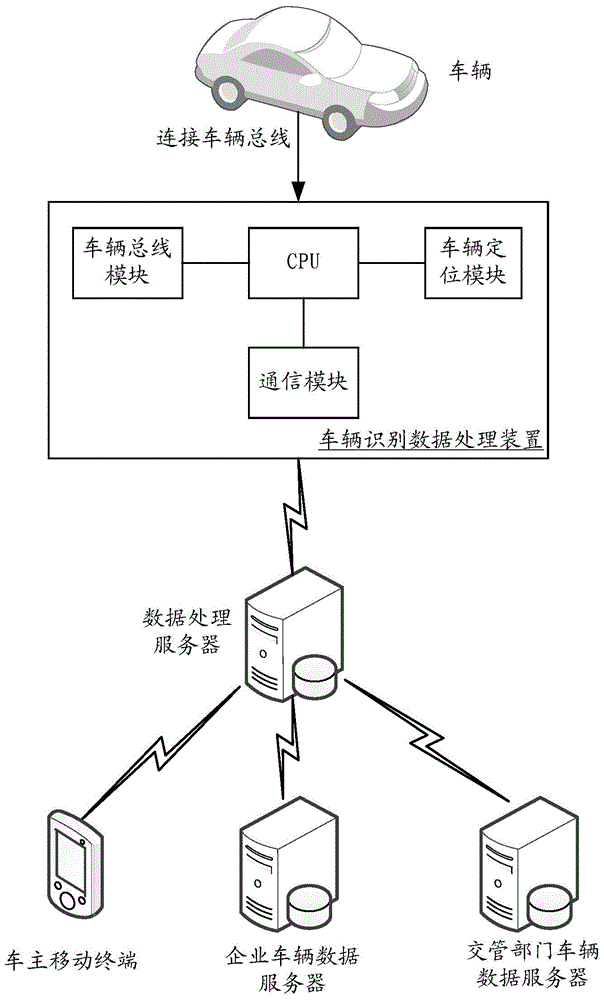
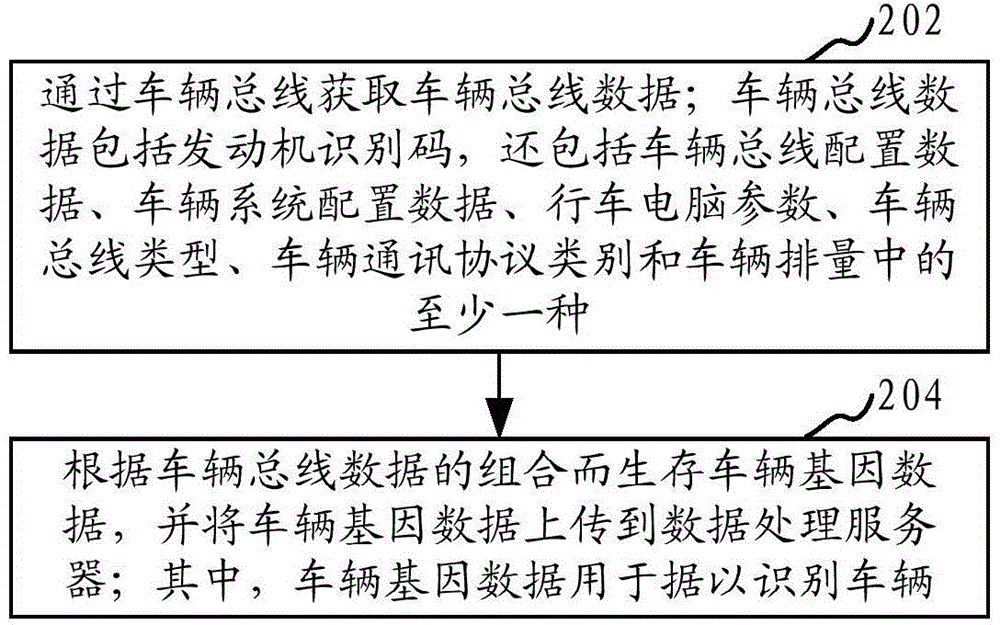
The invention provides a vehicle identification data processing method. The method includes the steps of obtaining vehicle bus data through a vehicle bus, wherein the vehicle bus data include an engine identification code and further include at least one of vehicle bus configuration data, vehicle system configuration data, trip computer parameters, the vehicle bus type, the vehicle communication protocol category and vehicle delivery capacity; generating vehicle genetic data according to the combination of the vehicle bus data, uploading the vehicle genetic data to a data processing server, wherein the vehicle genetic data are used for vehicle identification. According to the vehicle identification data processing method, the vehicle genetic data uploaded to the data processing server have high uniqueness, vehicle identification can be achieved according to the vehicle genetic data so that different vehicles can be distinguished, and the method can be widely applied to various fields such as the traffic management field, the investigation field and the vehicle positioning field. The invention further provides a vehicle identification data processing device and system.
Owner:深圳驾图通信技术有限公司
Method for authenticating identity and device for authenticating identity
InactiveCN104426884AImplement security managementStrong uniqueness and irreproducibilityTransmissionInternet privacyAuthorization
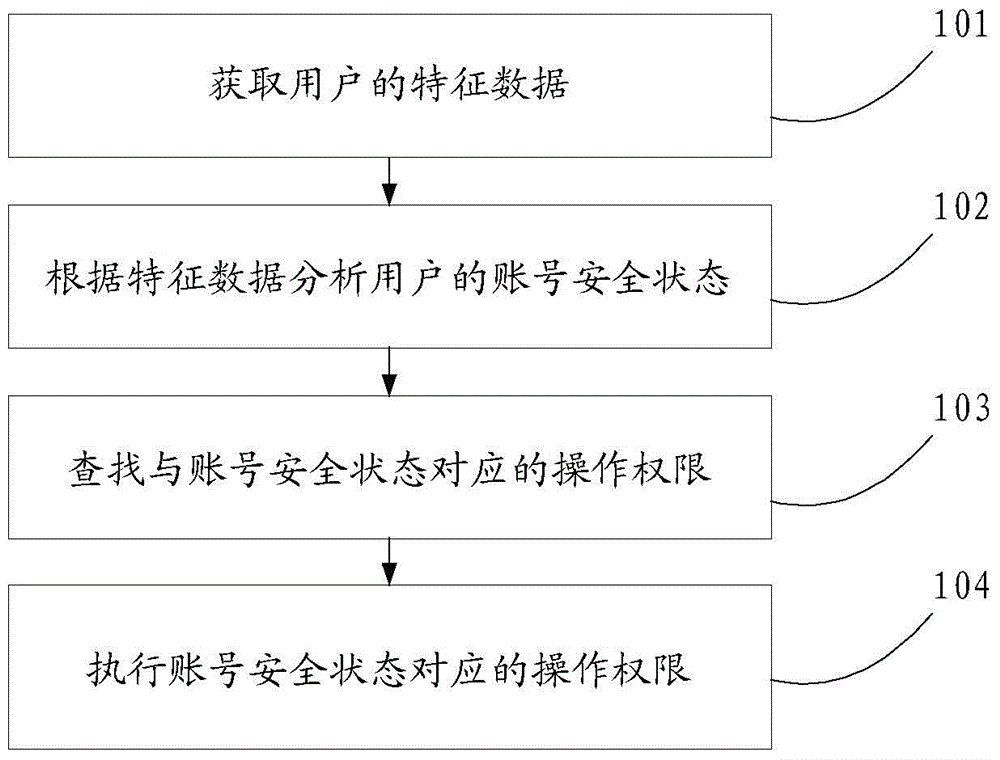
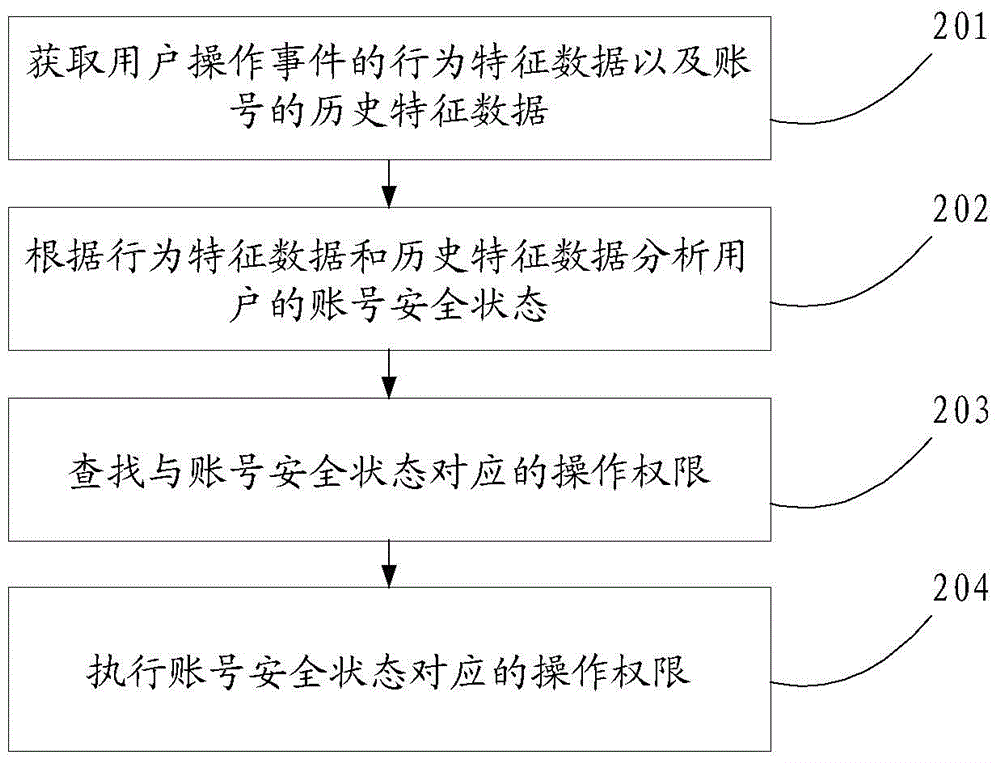
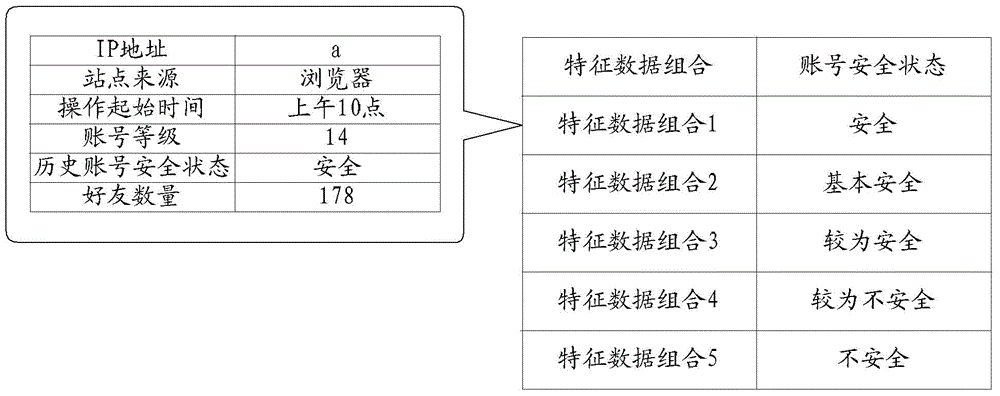
The invention discloses a method for authenticating an identity and a device for authenticating the identity, relates to the technical field of Internet, and can solve the problem that individual accounts in internet application can not be practically protected. The method disclosed by the invention comprises the following steps: obtaining characteristic data of a user; analyzing an account safety state of a user according to the characteristic data; finding an operating authorization corresponding to the account safety state; executing the operating authorization corresponding to the account safety state. The method and the device are mainly applied to an account safety detection process.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Bank exchequer long-distance defense management system
InactiveCN103440691AUniqueness guaranteedStrong uniquenessFinanceIndividual entry/exit registersDatabase serverCentral database
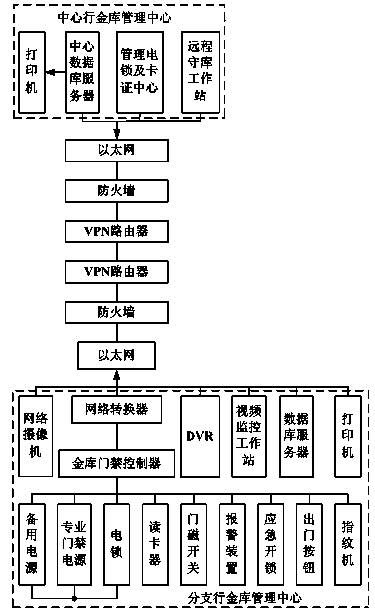
The invention discloses a bank exchequer long-distance defense management system which is technologically characterized by comprising a central exchequer management center, a branch exchequer management center, a communication network, a firewall and a VPN router, wherein the central exchequer management center comprises a central database server, a managing electric lock, a card and certificate center and a long-distance exchequer defense workstation; the branch exchequer management center comprises a database server, a network converter, an exchequer access controller, a fingerprint machine, a professional entrance guard power supply, an electric lock and a warning device; the central exchequer management center is connected with the firewall through the communication network; the firewall is connected with the VPN router; the network converter is connected with the firewall through the communication network; the exchequer access controller is connected with the network converter. The bank exchequer long-distance defense management system combines long-distance defense with local defense, uses the exchequer access controller as the core, has the function of defense in advance, and can avoid internal steal and external steal.
Owner:毛振刚
Port area ship target change detecting method based on remote sensing images
InactiveCN106803070AImprove matching speedStrong uniquenessScene recognitionImaging FeatureFalse alarm
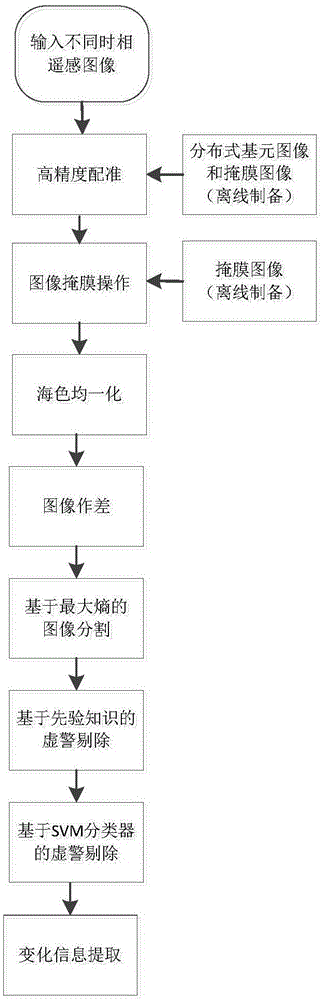
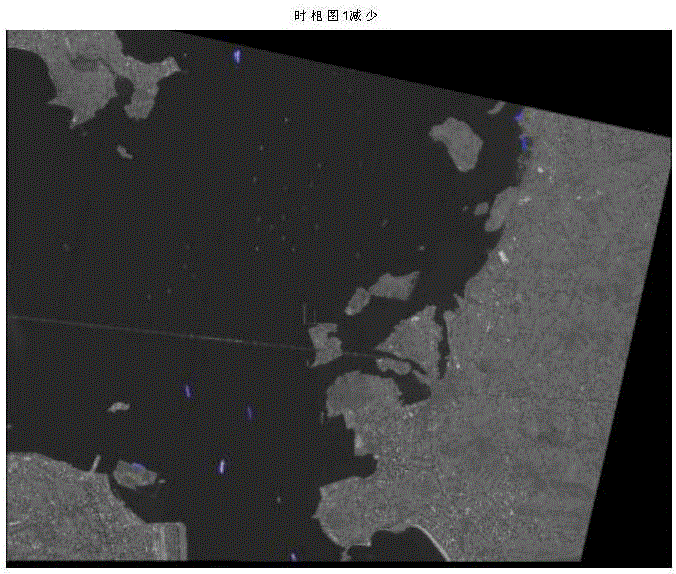
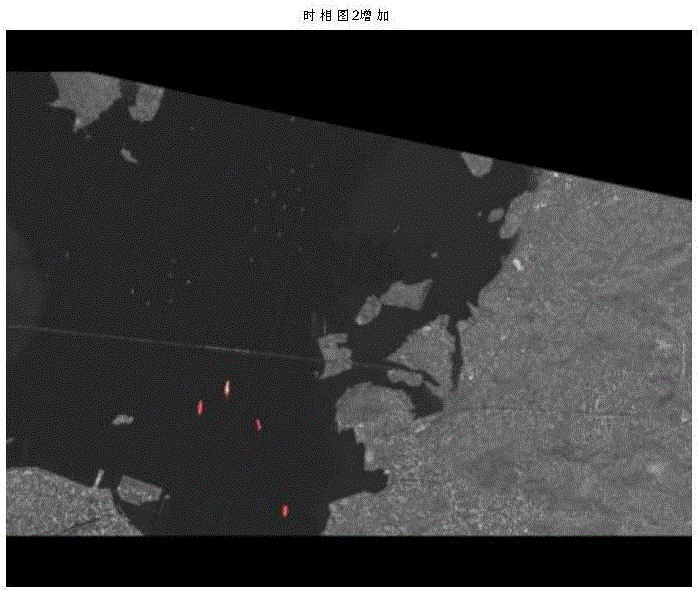
The invention discloses a port area ship target change detecting method based on remote sensing images and belongs to the field of target detection. The method comprises steps of: firstly obtaining two remote sensing images of the same port at different time phases; secondly, registering the two remote sensing images of the same port area acquired at different time; then, using a template image to perform mask operation on the two images, shielding a land area to obtain a sea area, homogenizing sea area image sea colors, and filling the shielded land area with a sea area mean value; making subtraction of the two registered images, and segmenting the subtracted image; finally, extracting the image feature of a slice, removing false alarm, determining the changed ship slices in the slices so as to obtain the changed ship target positions and corresponding information of the two remote sensing images. The method can accurately and quickly eliminate the influence of the cloud and the changed sea background on a final result, reduces a false alarm rate, completely and accurately segments and detects changed ship targets, and improves a detection rate.
Owner:北京理工雷科电子信息技术有限公司
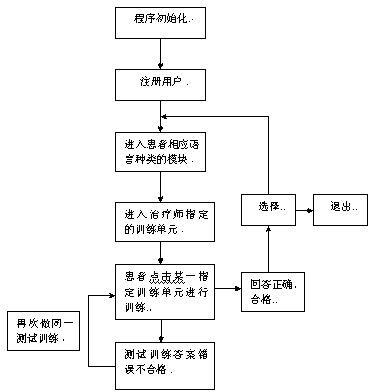
Training system and method for attention dysfunction after cerebral injury
InactiveCN103345853ANot easy to convertImprove training effectElectrical appliancesGraphicsContinuation
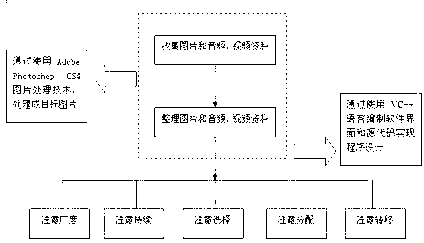
According to a training system for an attention dysfunction after a cerebral injury, a special computer software program is built, and the software is operated through a picture and voice module. 'Attention span' 'attention continuation' 'attention transference' 'selection of attention' 'transference of attention' and 'attention distribution' of a patient are trained through voice and picture hints, a trainee selects the correct answer according to the heard voice and a plurality of seen question graphs, and the training content comprises articles needing to be identified and used by the user in the daily life, and is graded training from the easier to the more difficult. The training system comprises a data processing device, a data input device, a data output device and a video and audio acceptation and processing device. The training system is reasonable in design, high in pertinence, multifunctional, and convenient to use.
Owner:昆明医科大学第二附属医院 +2
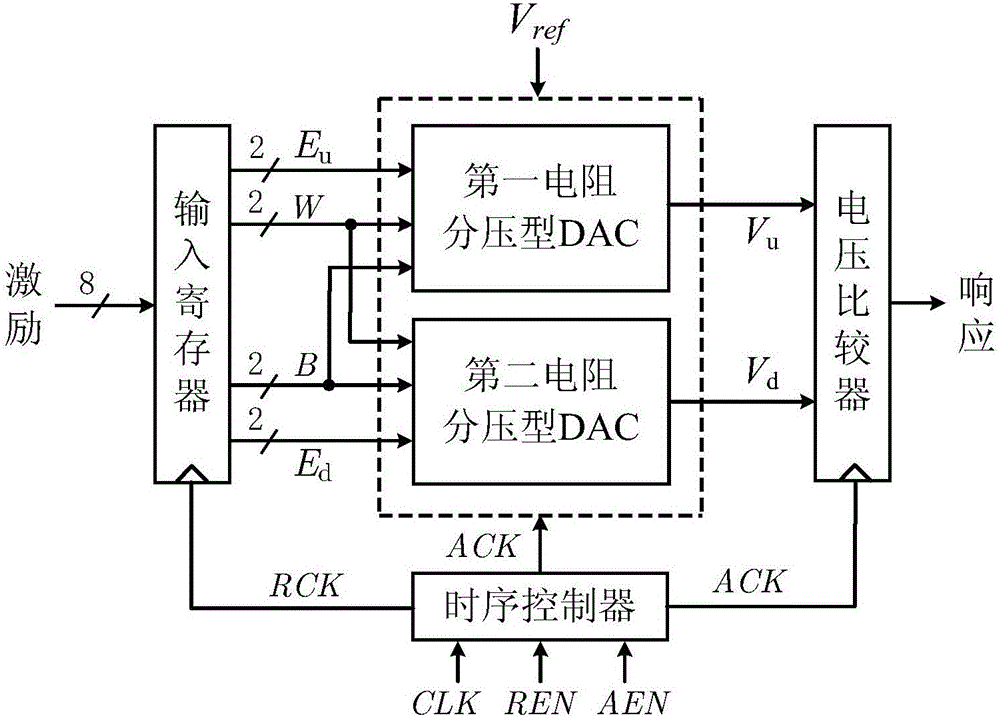
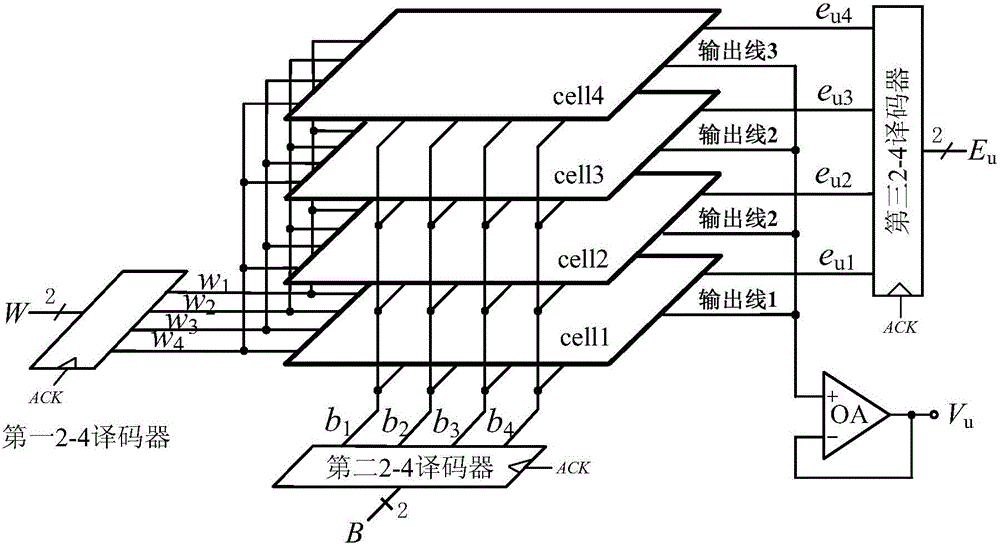
Resistance voltage divider type DAC-PUF circuit
ActiveCN105932996AImplement output key changesStrong uniquenessDigital-analogue convertorsLogic circuitsWorking environmentEngineering
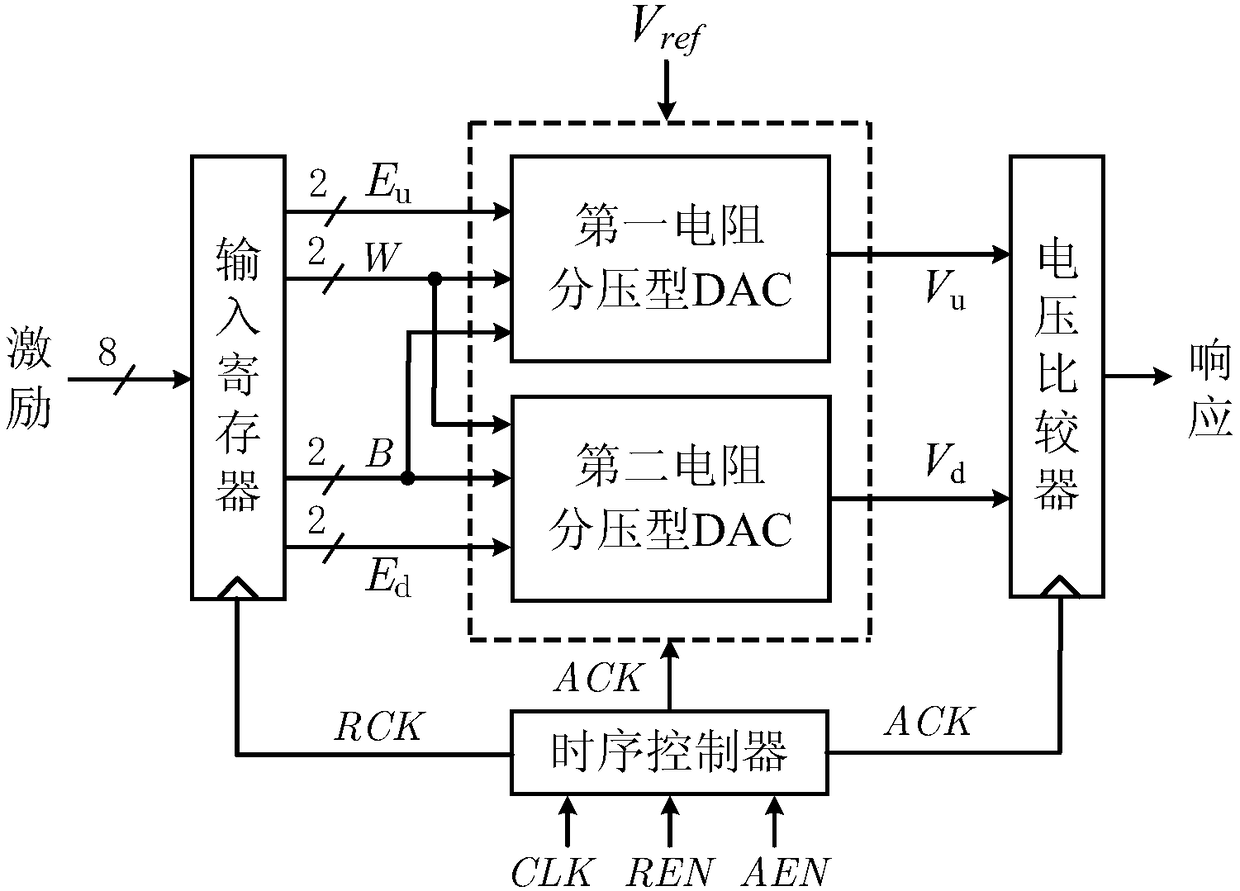
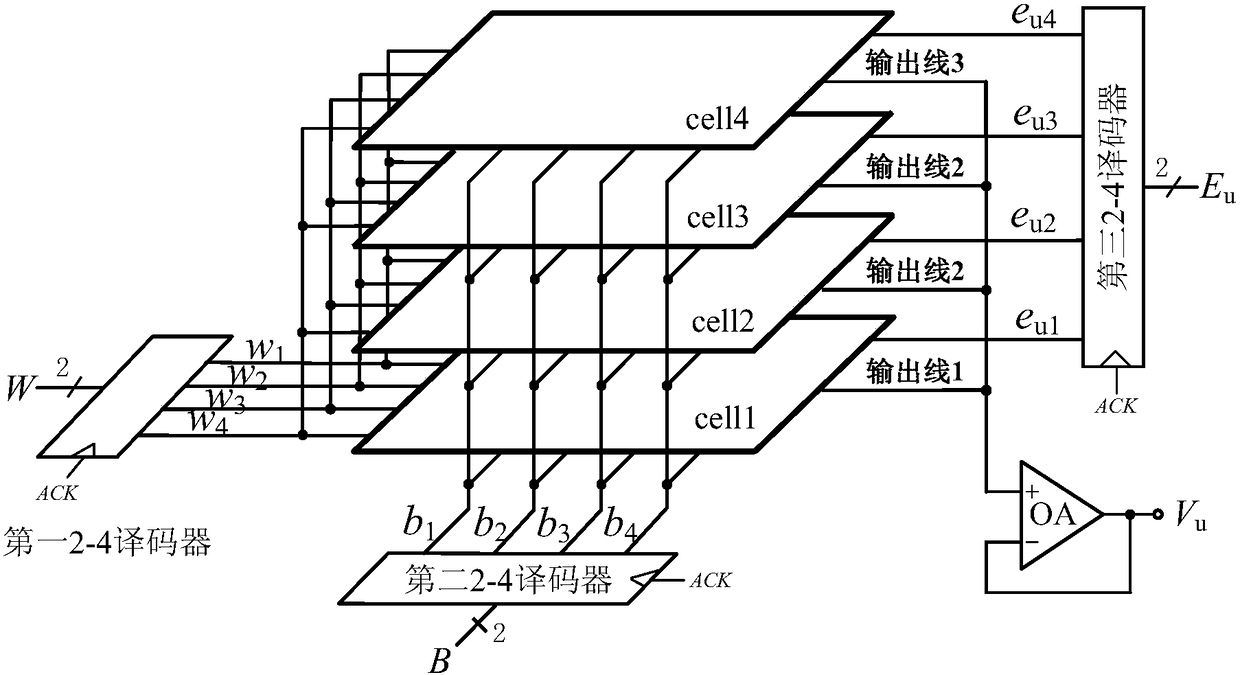
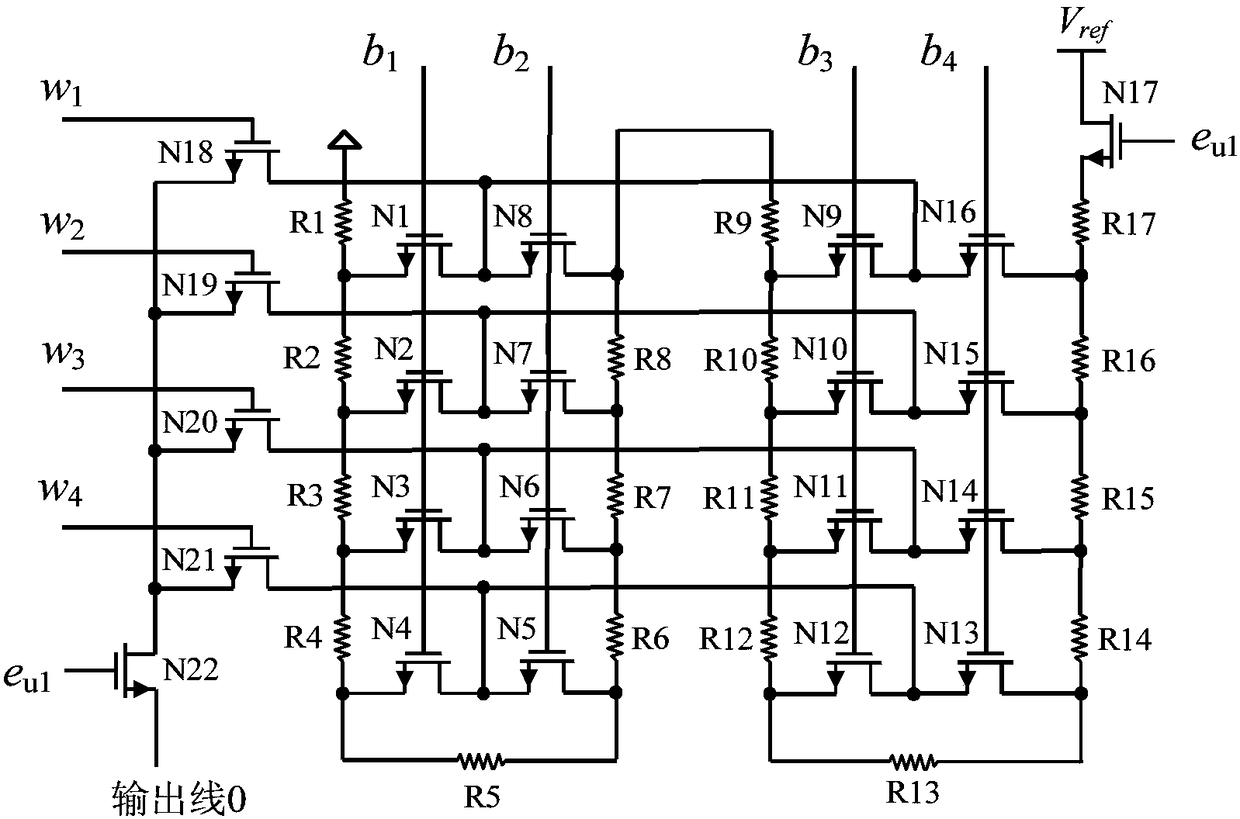
The present invention discloses a resistance voltage divider type DAC-PUF circuit which comprises an input register, a bias voltage generation circuit, a voltage comparator, and a time sequence controller. The bias voltage generation circuit comprises a two resistance voltage divider type DACs with the same structure. Each of the resistance voltage divider type DACs comprises three 2-4 decoded with the same structure, an operational amplifier, and four resistance divider units with the same structure. The resistance divider units comprise 22 NMOS tubes and 17 resistors. The circuit has the advantages that a digital and analog mixing mode is employed, the mismatch of the resistance voltage divider type DAC resistors is used to generate a bias voltage signal, the output key change is realized, in the TSMC-LP 65nm CMOS process, a full customization mode is used to design the circuit layout of the invention, the resistance voltage divider type DAC-PUF circuit is tested, an experimental result shows that the uniqueness of the resistance voltage divider type DAC-PUF circuit is strong, the randomness and reliability in different working environments are larger than 99.1% and 97.8%, and the circuit can be widely applied to the fields of key generation and device authentication.
Owner:NINGBO UNIV
Shadow puppet control robot
InactiveCN102621997AReduce the burden onSimple controlEntertainmentControl using feedbackVertical motionManipulator
A shadow puppet control robot achieves horizontal motion through a spiral transmission mechanism, achieves vertical motion through a crank sliding block mechanism, achieves arm simulation action through an open-loop mechanical arm structure, and transfers arm simulation action to a shadow puppet arm through a parallelogram mechanism so as to achieve the purpose of controlling a shadow puppet to perform. Through mechanical and electrical integrated control, shadow puppet play performance is simpler, load of artists is reduced, accordingly the shadow puppet performance technology heads for automation in true meaning, and the shadow puppet control robot adapts to the modern performance devices and enables shadow puppet culture too be passed on better.
Owner:TSINGHUA UNIV
Three-value PUF unit and circuit realized by using CNFET
ActiveCN106850227AReduce areaStrong randomnessSemiconductor/solid-state device detailsUser identity/authority verificationElectrical and Electronics engineeringMatrix form
Owner:NINGBO UNIV
Finger vein recognition method, apparatus and device
ActiveCN109165639AStrong uniquenessAccurate comparisonSubcutaneous biometric featuresBlood vessel patternsVeinFinger vein recognition
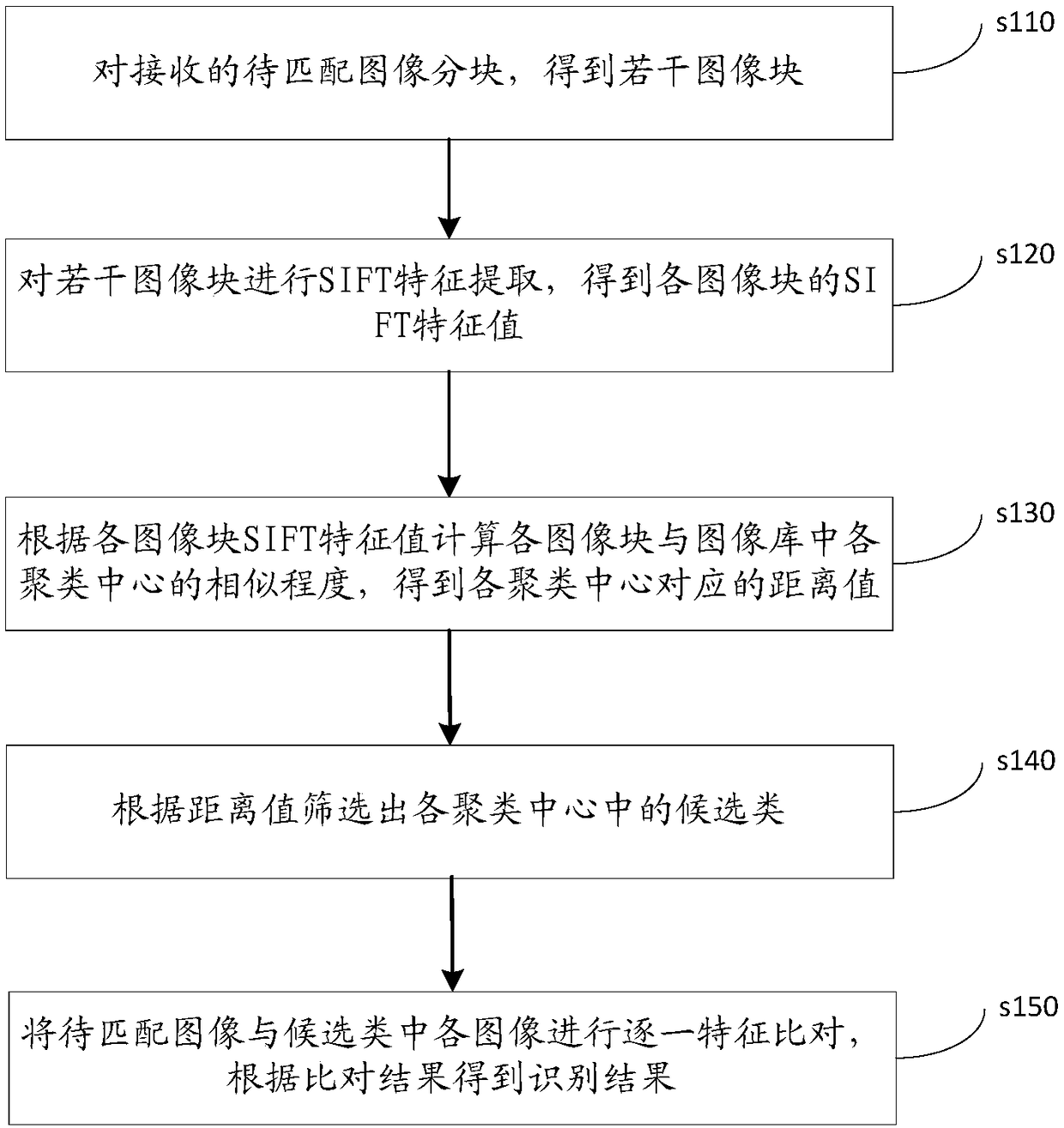
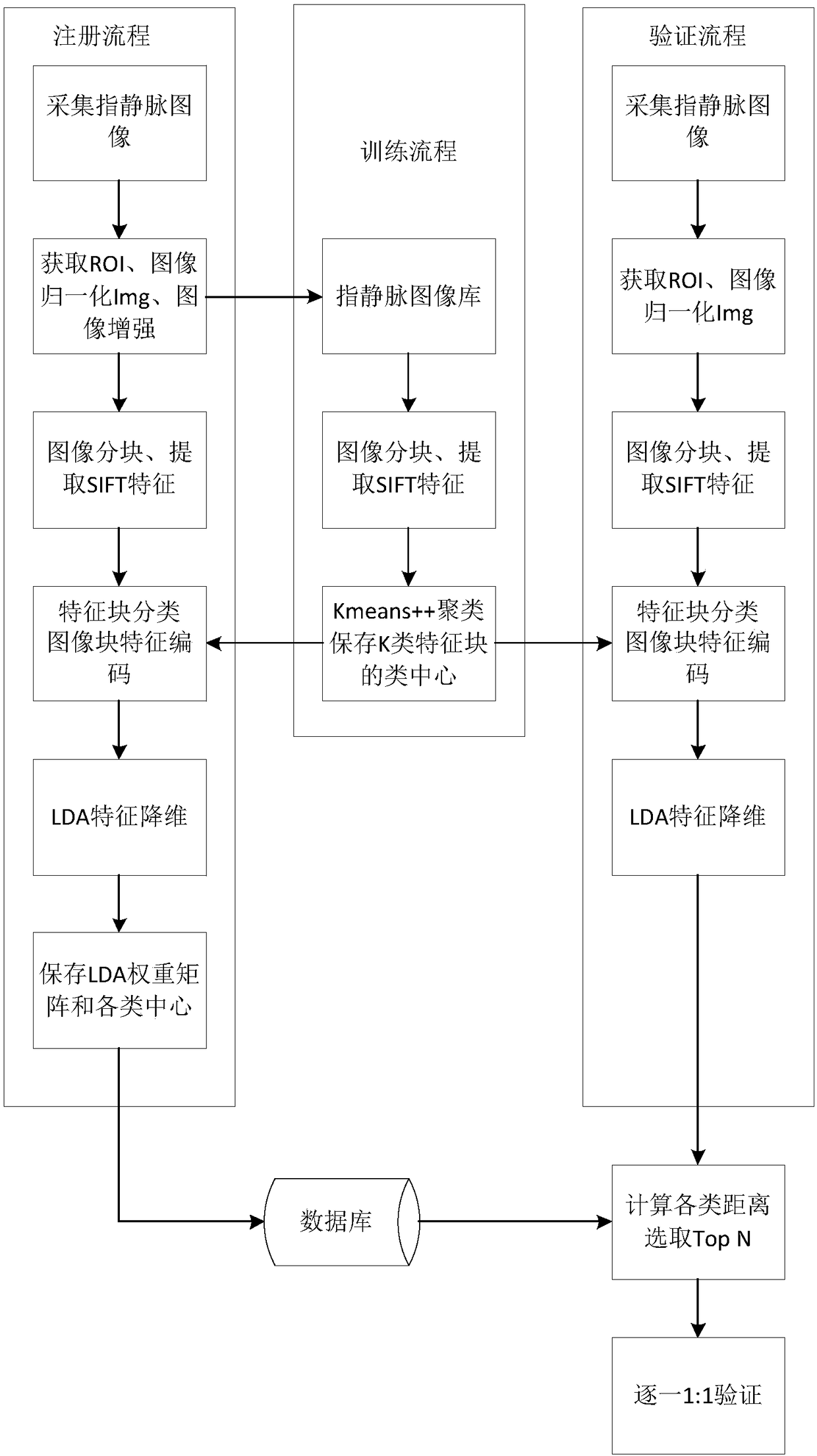
The invention discloses a finger vein identification method, which relates to the field of biometric identification. The method comprises the following steps: the received image to be matched is divided into blocks to obtain an image block; the SIFT eigenvalues of each image block are obtained by extracting the SIFT eigenvalues of several image blocks; according to the SIFT eigenvalue of each image block, the similarity between each image block and each cluster center in the image library is calculated, and the distance value corresponding to each cluster center is obtained, wherein the clustering center is the feature center of all kinds of image blocks of template image in the image library; candidates of clustering centers are selected according to the distance value; the image to be matched is compared with each image in the candidate class one by one, and the recognition result is obtained according to the comparison result. This method can match finger vein image quickly and accurately, and improve the efficiency of finger vein recognition. The invention also discloses a finger vein identification apparatus and device, which have the beneficial effects.
Owner:GRG BAKING EQUIP CO LTD
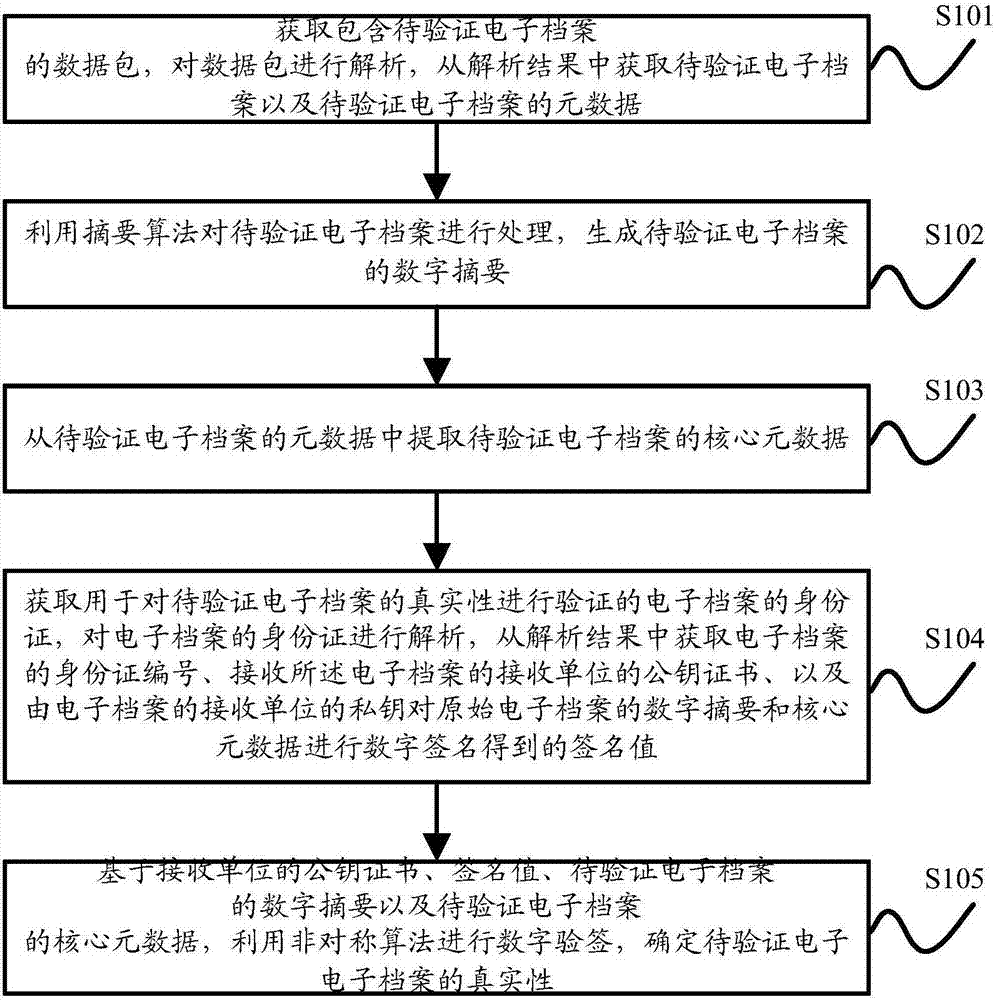
Method and apparatus for verifying authenticity of electronic archives
ActiveCN107171808AGuaranteed accuracyStrong uniquenessUser identity/authority verificationSpecial data processing applicationsComputer securityMetadata
The invention discloses a method and apparatus for verifying the authenticity of electronic archives for solving the problems that the method for verifying the authenticity of electronic archives in the prior art is relatively simple, the security is relatively low, and that the accuracy of the verification results cannot be ensured effectively. The method for verifying the authenticity of electronic archives comprises the following steps: obtaining a to-be-verified electronic archive and metadata of the to-be-verified electronic archive; generating a digital digest of the to-be-verified electronic archive; extracting core metadata of the to-be-verified electronic archive; obtaining an identity card of the electronic archive, analyzing the identity card of the electronic archive, and extracting an identity card serial number of the electronic archive, a public key certificate of a receiving unit receiving the electronic archive and a signature value from the analysis result; and based on the public key certificate of the receiving unit, the signature value, the digital digest of the to-be-verified electronic archive and the core metadata of the to-be-verified electronic archive, performing digital signature verification by using an asymmetric algorithm to determine the authenticity of the to-be-verified electronic archive.
Owner:北京市档案局 +1
Fluorescent quantitative PCR detection method of resistance of bemisia tabaci on thiamethoxam and kit thereof
InactiveCN104031991AStrong specificityHigh sensitivityMicrobiological testing/measurementDNA/RNA fragmentationForward primerNucleotide
The invention discloses a specific PCR (Polymerase Chain Reaction) primer pair for detecting the resistance of (i)Bemisia( / i)(i)tabaci( / i) on thiamethoxam, a kit and a detection method. The forward primer nucleotide sequence of the specific PCR primer pair is as shown in SEQ ID No.1, and the reverse primer nucleotide sequence of the specific PCR primer pair is as shown in SEQ ID No.2. The fluorescent quantitative PCR detection method of the bemisia tabaci on the thiamethoxam, which is disclosed by the invention, has the characteristics of less labour power, small sample quantity, large detection quantity, high sensitivity, high specificity, fastness, simpleness, convenience, accuracy and reliability, thereby effectively detecting the resistance of the bemisia tabaci on the thiamethoxam; the fluorescent quantitative PCR detection method disclosed by the invention is suitable for the early fast diagnosis of the resistance of the bemisia tabaci on the thiamethoxam, can be used for the real-time monitoring, prewarning and prediction of the resistance of the field bemisia tabaci on the thiamethoxam and is wide in application prospect.
Owner:INST OF VEGETABLE & FLOWERS CHINESE ACAD OF AGRI SCI
Circular loop statistic characteristic-based anti-rotation image Hash method
InactiveCN102881008AImprove robustnessRobust Digital ProcessingImage enhancementImage analysisColor imageLow-pass filter
The invention relates to a circular loop statistic characteristic-based anti-rotation image Hash method, which comprises the following steps of: normalizing the size of an image size by using a bilinear interpolation method; processing the image by using a Gaussian low-pass filter; if the image is a color image, converting the image into a YCbCr color space, and representing the color image by using a brightness component; dividing the image into a plurality of circular loops, and extracting statistical data such as an average value, variance, skewness degree and kurtosis of each circular ring as characteristics; normalizing the statistical characteristics; calculating an average value of the statistical data, taking the average value as a reference, calculating Euclidean distances between the statistical characteristics of the circular loops and reference characteristics, and connecting all distance values in series to obtain an image Hah; and when similarity is judged, calculating L2 norms of two Hashes, determining that corresponding images are the same if the similarity is less than a set threshold value, otherwise determining that the corresponding images are different. The method is robust for common digital processing such as image rotation, joint photographic experts group (JPEG) compression, noise jamming, brightness regulation and contrast enhancement, and is high in uniqueness.
Owner:GUANGXI NORMAL UNIV
Anti-counterfeiting mark with holographic tactile structure and preparation method thereof
InactiveCN108648610AGood touchStrong uniquenessStampsSynthetic resin layered productsInformation layerPrinting ink
The invention relates to an anti-counterfeiting mark with a holographic tactile structure and a preparation method thereof, and belongs to the technical field of anti-counterfeiting marks. The anti-counterfeiting mark comprises a peeling layer and a bottom layer, wherein a first PET layer, a permanent mold pressing information layer, a local positioning molding layer, a local positioning washing aluminum ink layer, an aluminum plating layer, a first resin layer, a digital printing ink layer, a film coating glue layer and a second PET layer, a release layer, a second resin layer, a variable information printing ink layer, a film coating glue and grain layer, a fragile layer, a glue adhesive layer and a silicon oil paper layer are sequentially arranged from top to bottom; The anti-counterfeiting mark has the advantages of good anti-counterfeiting effect, good touch feeling and bright color. Meanwhile, the invention also provides the preparation method thereof, which is scientific and reasonable, and is simple and easy to implement.
Owner:SHANDONG TAIBAO PREVENTING COUNTERFEIT
Method for enhancing system reliability based on physical unclonable function
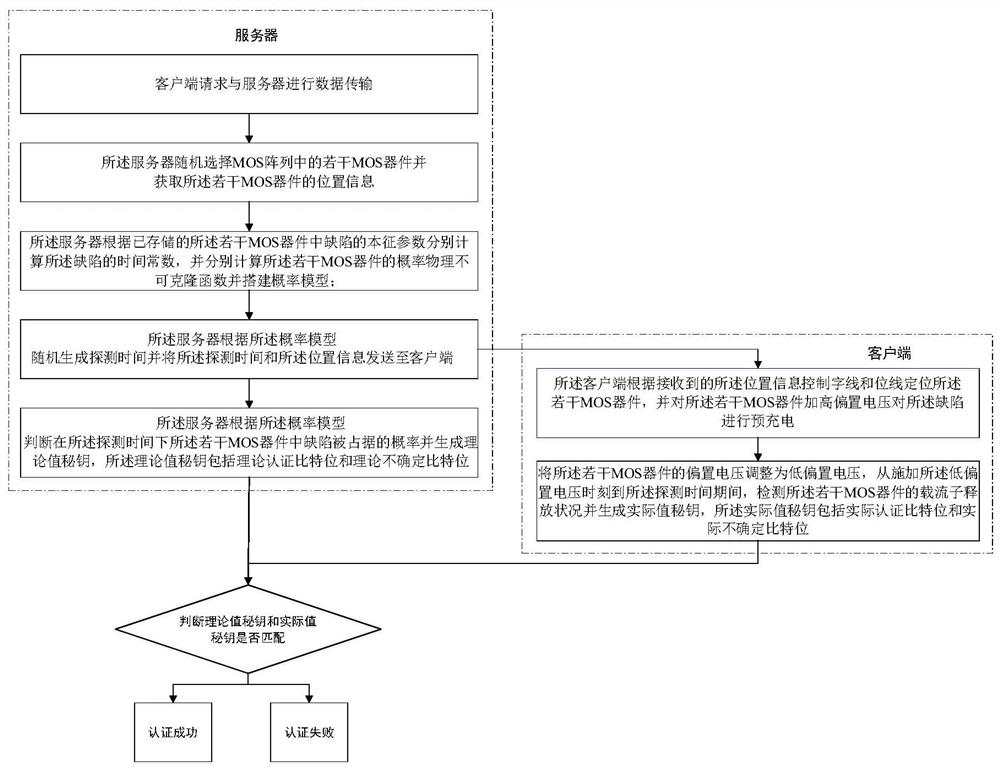
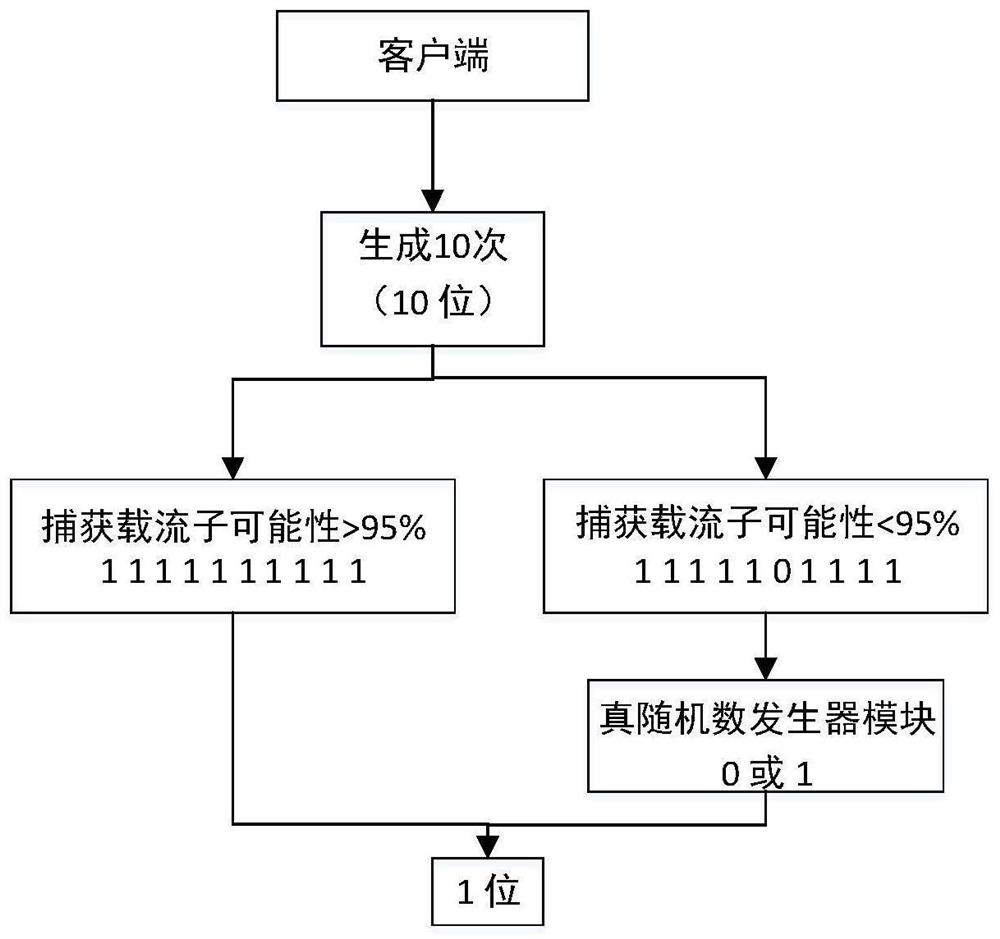
ActiveCN111865617AReduce data storageImprove work efficiencyUser identity/authority verificationDigital storageAlgorithmEngineering
The invention discloses a method for enhancing system reliability based on a physical unclonable function. The method comprises the following steps thata client requests data transmission with a server; the server randomly selects a plurality of MOS devices in the MOS array and acquires position information of the MOS devices; the server calculates the time constants of the defects in the MOS devices according to the stored intrinsic parameters of the defects in the MOS devices, then calculates the probability physical unclonable function that the defects in the MOS devices are occupied by carriers, and builds a probability model; the server randomly generates detection time according to the probability model and sends the detection time and the position information to a client; and the server judges the probability that the defects in the plurality of MOS devices are occupied under the detection time according to the probability model and generates a theoretical value secret key, wherein the theoretical value secret key comprises a theoretical authentication bit and a theoretical uncertain bit.
Owner:SHANGHAI JIAO TONG UNIV
Intelligent steering wheel with human body data monitoring and fingerprint recognition functions
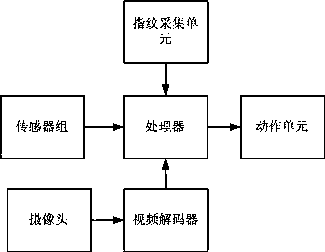
InactiveCN108100018AReal-time detection and monitoring of body temperatureReal-time detection and monitoring of heart rateAnti-theft devicesHand wheelsSteering wheelComputer module
The invention relates to an intelligent steering wheel with human body data monitoring and fingerprint recognition functions. The intelligent steering wheel comprises a steering wheel body and is characterized by further comprising a human body signal collector, an action unit and a control unit, and the human body signal collector, the action unit and the control unit are arranged on the steeringwheel body. The human body signal collector comprises a fingerprint collector, a sensor group and a camera; the control unit comprises a video decoder and a processor, and the processor comprises a human body signal storage module, a data analysis module and an output module; an output end of the camera is connected with an input end of the video decoder, an output end of the video decoder, the sensor group and the fingerprint collector are connected with the human body signal storage module, the data analysis module is connected with the human body signal storage module, an output end of thedata analysis module is connected with the output module, and the output module is connected with the action unit which is used for generating alarms or prompts.
Owner:成都四海万联科技有限公司
Initial and final code Chinese characters input method
InactiveCN101086687AStrong uniquenessLow repetition rateInput/output processes for data processingChinese charactersComputer engineering
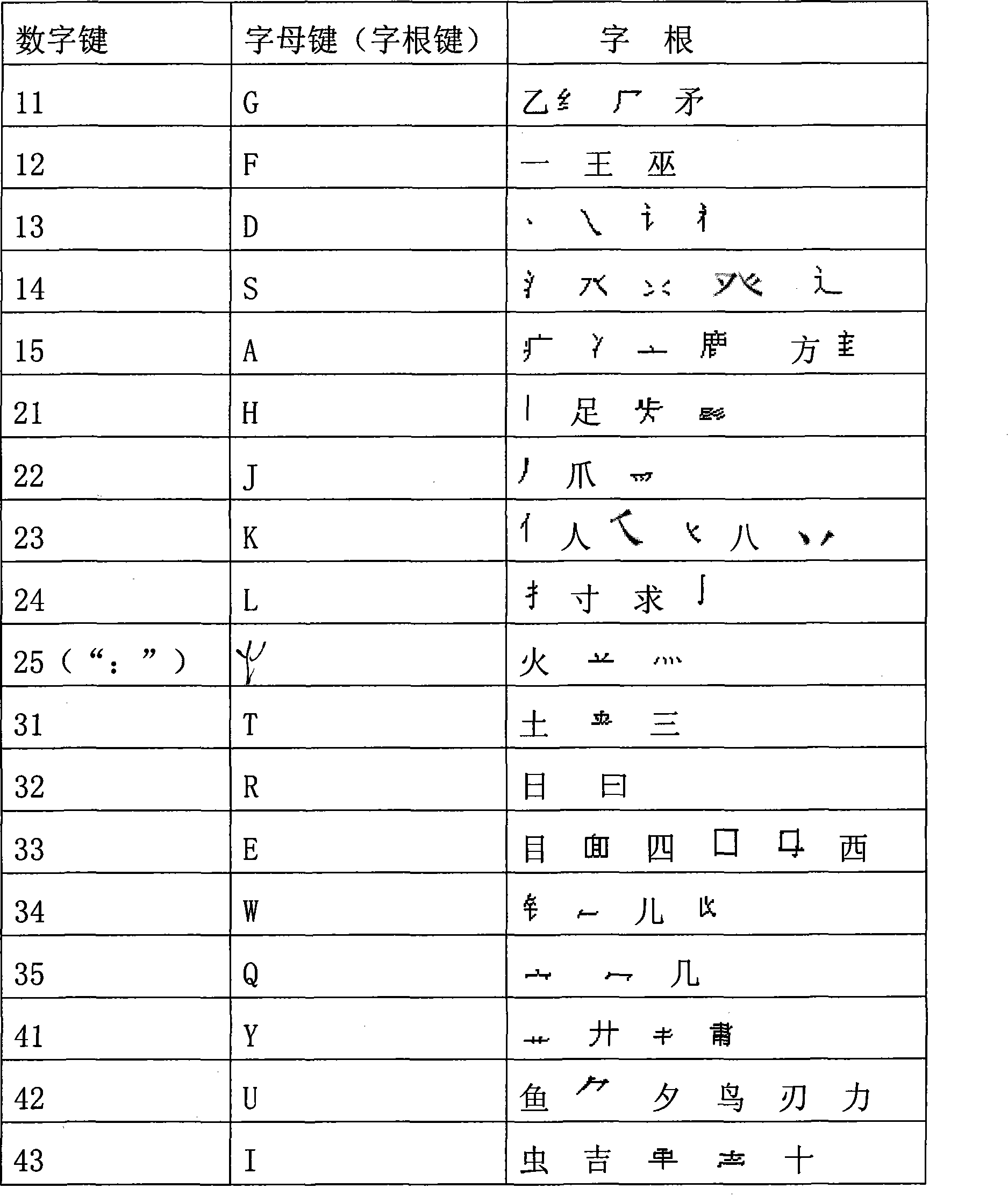
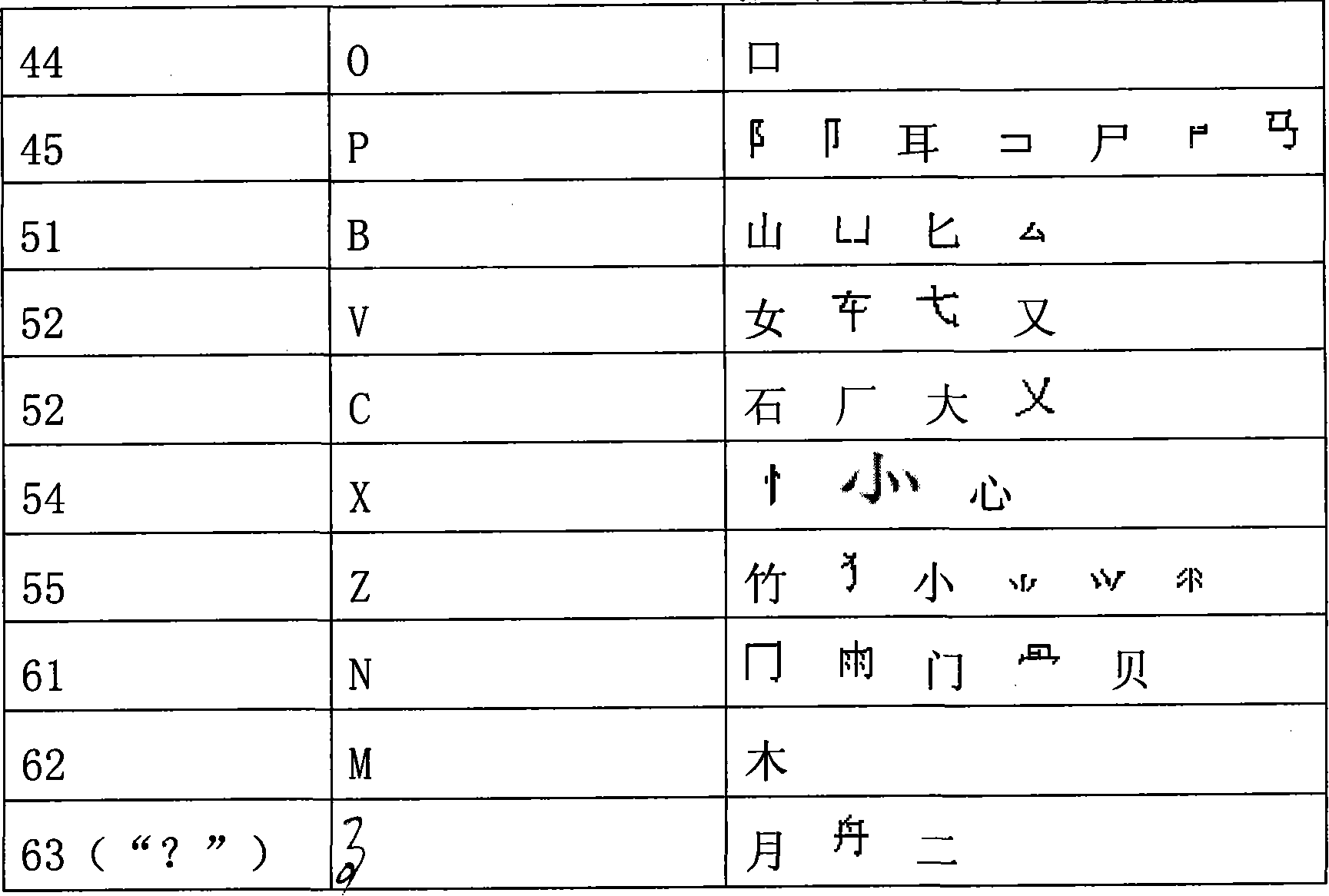
The first and last code Chinese character input selects radicals of 100-130, defined on the letter keys and selected punctuation marks keys, maximizing the first code based on the sequence of writing, and maximizing the last code radical based on the reverse sequence, then maximizing the second radical based on reverse sequence, then the third code. In the sequence of codes, it is based on the sequence of first code, last code, second code and the third code to realize the maximization of the radicals, with the latter giving way to the previous when the strokes of the codes in contradiction. It is easy in character resolution, low in code repetition, visual, easy to remember, and easy to learn.
Owner:刘飞林
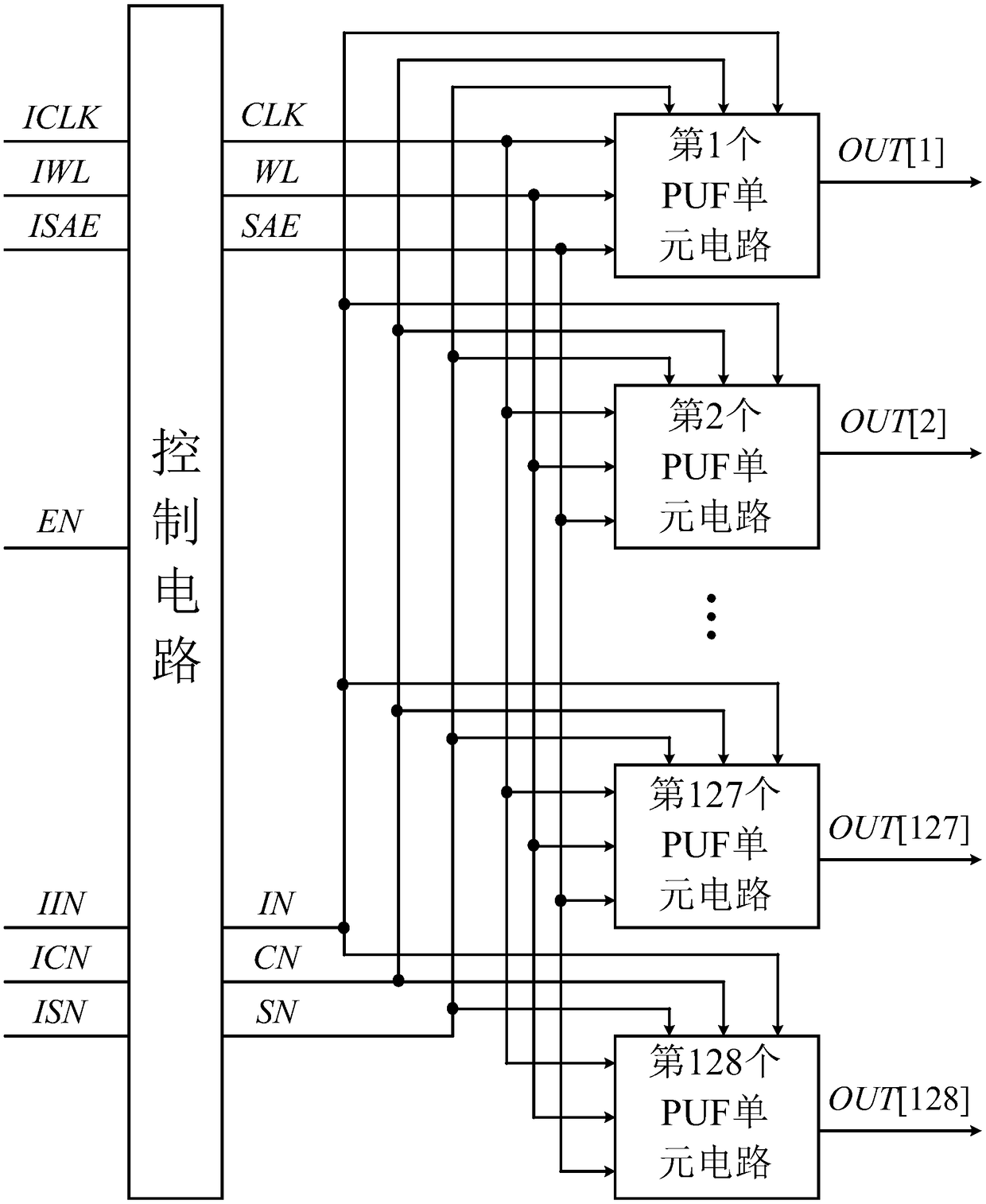
A Strong/Weak Hybrid PUF Circuit Against Model Attack
ActiveCN109086631AIncrease randomnessImprove securityInternal/peripheral component protectionHybrid type16-bit
The invention discloses a strong / weak hybrid PUF circuit for resisting model attack, comprising a control circuit and N PUF unit circuits with the same structure, wherein a PUF cell circuit includes astorage type random source, a linear feedback shift register, a serial-parallel module and an arbiter PUF, the clock side of the linear feedback shift register and the clock side of the serial-parallel block are connected to the clock signal, the input of the arbiter PUF is connected to an input signal, the output of the arbiter PUF is used to output the PUF output response, the 8-bit parallel output of the storage random source is connected to the 8-bit parallel input of the linear feedback shift register, the serial output terminal of the linear feedback shift register is connected with theserial input terminal of the serial-parallel module, the 16-bit parallel output terminal of the serial-parallel module is connected with the 16-bit parallel control terminal of the arbiter PUF, and the memory random source comprises eight memory cells with the same structure; the serial output terminal of the linear feedback shift register is connected with the serial input terminal of the serial-parallel module. The advantages are good randomness, uniqueness and security.
Owner:NINGBO UNIV
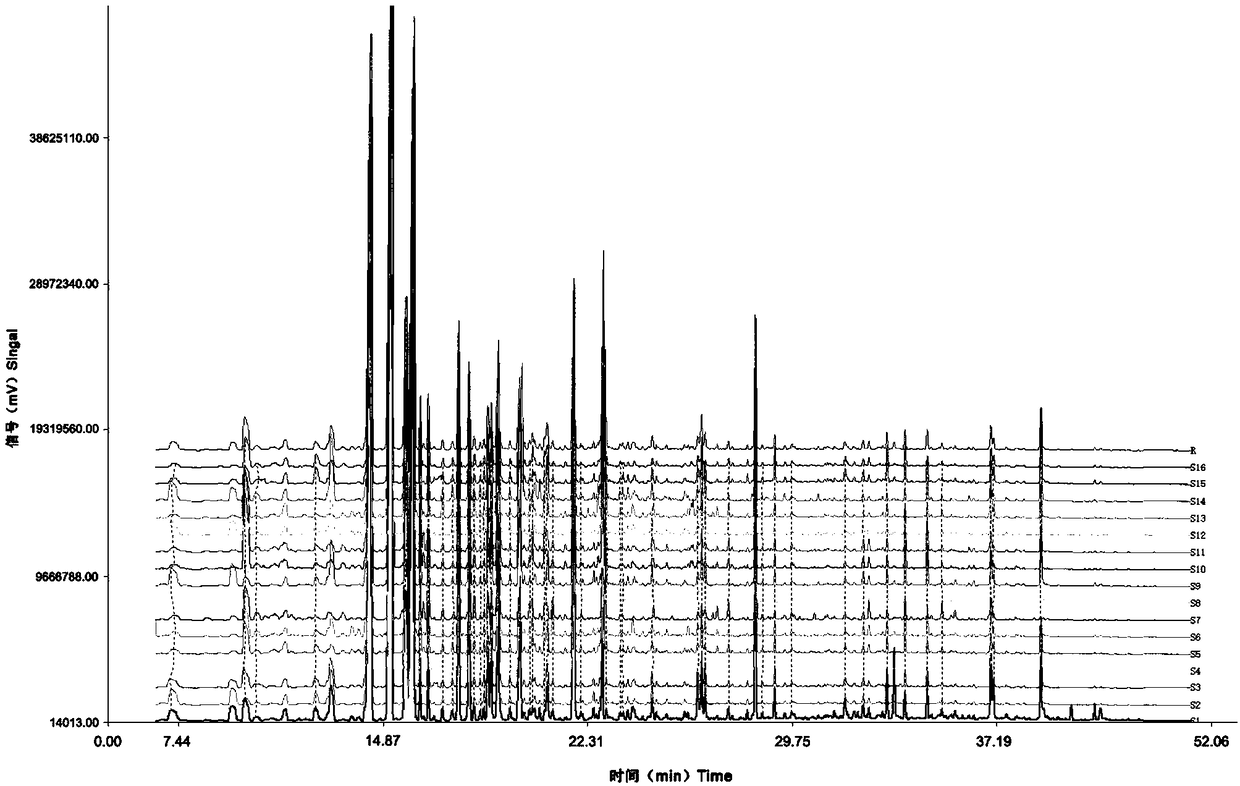
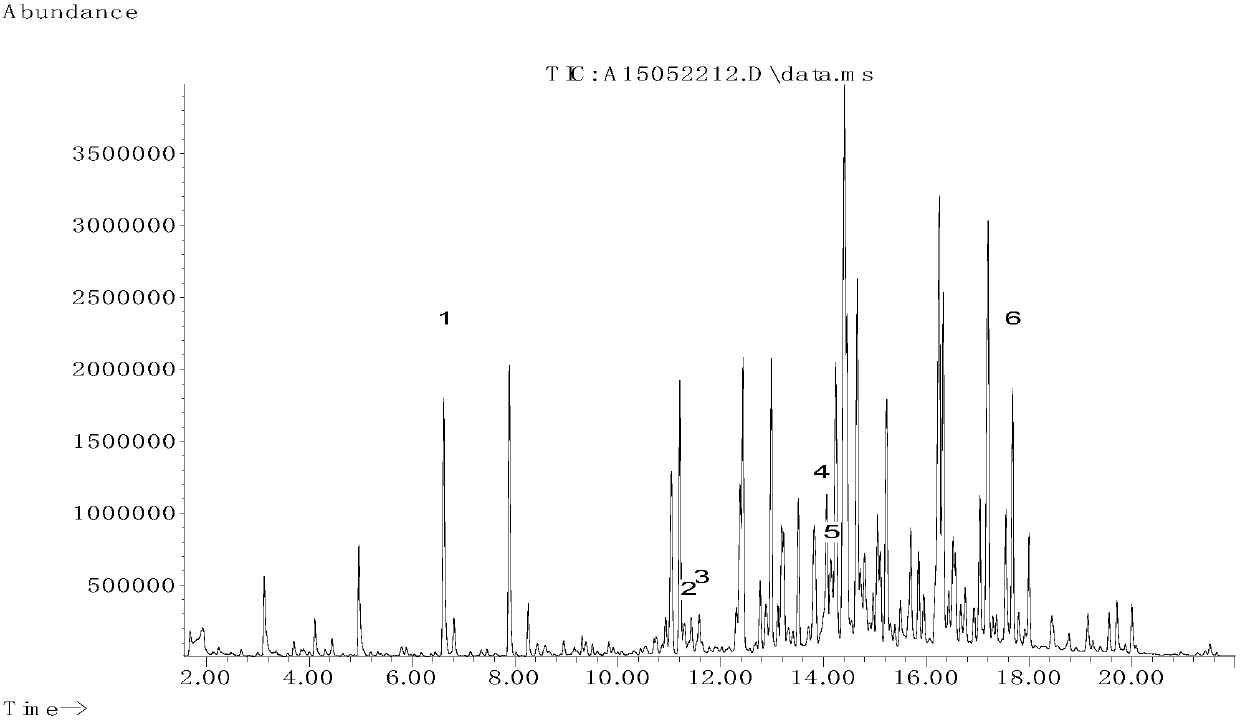
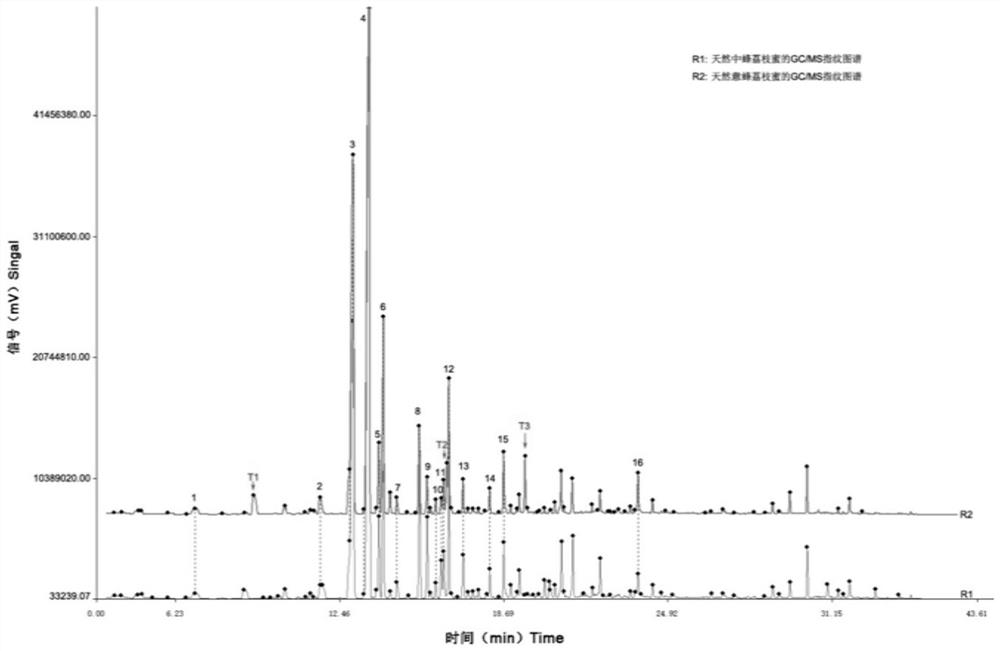
Method for constructing fingerprint spectrums of natural Apis cerana longan honey and natural A.mellifera ligustica longan honey and identification and application of fingerprint spectrums ofnatural Apis cerana longan honey and natural A.mellifera ligustica longan honey
ActiveCN109470785AFix the problem of indistinguishableHigh detection sensitivityComponent separationApis ceranaSocial benefits
The invention discloses a method for constructingfingerprint spectrums of natural Apis cerana longan honey and natural A.mellifera ligustica longan honey and identification and application of the fingerprint spectrums of the natural Apis cerana longan honey and the natural A.mellifera ligustica longan honey. A headspace solid-phase microextraction-gas chromatography-mass spectrometry method and aChinese herbal fingerprint spectrum similarity evaluation system are used to respectively construct GC / MS fingerprint spectrums of the natural Apis cerana longan honey and the natural A.mellifera ligustica longan honey; the GC / MS fingerprint spectrum of the natural Apis cerana longan honey is determined to contain 16 common feature volatile ingredients, and the GC / MS fingerprint spectrum of thenatural A.mellifera ligustica longan honey contains 15 common feature volatile ingredients. By comparing the similarity and the difference of the chemical composition of a total ion chromatogram of a to-be-tested natural longan honey sample and the constructed GC / MS fingerprint spectrum, the natural Apis cerana longan honey and the natural A.mellifera ligustica longan honey are accurately distinguished and identified. The method has the characteristics of small use level of samples, strong characteristics and reliable result, is quite beneficial for solving the problem that the Apis cerana longanhoney and the A.mellifera ligustica longan honey are difficult to distinguish on the market, and has a quite remarkable social benefit.
Owner:INST OF ZOOLOGY GUANGDONG ACAD OF SCI
Parasite egg image registration method
InactiveCN110503669AImprove recognition accuracyGood feature invarianceImage enhancementImage analysisCorrelation coefficientSource image
The invention discloses a parasite egg image registration method, and relates to parasite egg image registration. The parasite egg image registration method comprises a Harris corner point algorithm and an image registration process, and further comprises the following steps: S1, sampling parasite eggs for multiple times, specifically, setting a registration image set of a source image set; S2, carrying out the same preprocessing of the source image and the registered image, carrying out the preliminary image rotation, translation and scale transformation through the basic statistical features, and removing the redundant noise; S3, performing Harris corner detection on the source image and the registration image by using a Harris corner algorithm, and recording corner coordinates; S4, setting a registration area; S5, calculating a correlation coefficient of a registration area of the source image and the registration image; S6, judging the matching degree of the source image and the registration image by using the correlation coefficient; and S7, entering an image registration process. According to the invention, the identification accuracy of parasitic ova is improved by using animage registration method; and the parasite egg image registration method has good feature invariance, uniqueness, stability and independence.
Owner:邵曦
Movable texture anti-counterfeiting method and marker
PendingCN111985592AMovableMaintain stabilityRecord carriers used with machinesPattern recognitionEngineering
The invention provides a movable texture anti-counterfeiting method and a marker. The method comprises the following steps: coding a product, and recording texture information; bonding movable textures formed by individual elements on the base material layer; arranging a transparent protective layer to fix the movable individual elements; collecting the feature information of the immobile individual elements, and filing the feature information into an anti-counterfeiting inspection system database as a texture information file; and checking whether the immovable texture is consistent with thetexture information file or not by using the smart phone so as to identify the authenticity of the product. The method is convenient for the public to discriminate true and false textures by hands, and is high in anti-counterfeiting strength.
Owner:HAINAN PAIPAIKAN INFORMATION TECH CO LTD
Pharmaceutical composition for improving climacteric symptoms and preparation method of pharmaceutical composition
ActiveCN103251793AInnovativeImprove menopausal symptomsAmphibian material medical ingredientsSexual disorderAlcoholMedicine
The invention discloses a pharmaceutical composition for improving climacteric symptoms. The pharmaceutical composition comprises the following materials in parts by weight: 12-20 parts of glossy privet fruits, 12-20 parts of eclipta, 8-15 parts of rhizoma cyperi, 4-10 parts of lilies, 14-25 parts of oysters, 12-20 parts of spina date seeds, 4-14 parts of rhizoma anemarrhenae and 0.1-2.5 parts of oviductus ranae. The preparation method of the pharmaceutical composition comprises the following steps of: extracting and concentrating the glossy privet fruits, the eclipta and the rhizoma cyperi by alcohol to obtain thick extract A; water-extracting and concentrating the lilies, the oysters and the rhizoma anemarrhenae to obtain thick extract B; mixing the thick extract A with the thick extract B, drying, crushing and sieving to dry extract powder; crushing and sieving the oviductus ranae; and mixing the dry extract powder with the oviductus ranae, adding normal auxiliary materials for preparing an oral solid preparation according to a normal process. The pharmaceutical composition disclosed by the invention has the function of improving the climacteric symptoms, and can be used for preparing healthcare food, common food or drugs.
Owner:BEIJING ZHONGYAN TONGRENTANG CHINESE MEDICINE R & D
A resistor divider type dac-puf circuit
ActiveCN105932996BImplement output key changesStrong uniquenessDigital-analogue convertorsLogic circuitsElectrical resistance and conductanceWorking environment
Owner:NINGBO UNIV
Soft PUF based on Camellia encryption algorithm
ActiveCN113268745AAvoid instabilityImprove uniquenessKey distribution for secure communicationDigital data protectionPhysical unclonable functionInformation security
The invention discloses a soft PUF (Physical Unclonable Function) based on a Camellia encryption algorithm, which comprises a hardware platform, the hardware platform is a 128-bit Camellia encryption algorithm hardware circuit, PUF response data is acquired by utilizing path delay deviation in the Camellia encryption algorithm hardware circuit, special hardware overhead is not needed, PUF response acquisition is carried out under a fixed clock frequency, the instability phenomenon caused in the frequency change process is avoided, in addition, the PUF response is subjected to multi-round data randomization of the Camellia encryption algorithm, the uniqueness and randomness are relatively high, the collection difficulty of extracting the PUF response from the output of the Camellia encryption algorithm hardware circuit is low, the number of bits is relatively large, and the security is relatively high. The Soft PUF based on the Camellia encryption algorithm has the advantages of frequency disturbance resistance, high reliability, good uniqueness and randomness and high security, and is beneficial to application in the field of information security.
Owner:WENZHOU UNIVERSITY
Feature Point Extraction Method of Vector Graphics Based on Orientation Feature and Local Uniqueness
ActiveCN113256571BStrong uniquenessImage enhancementImage analysisPattern recognitionComputer vision
The invention discloses a vector graphic feature point extraction method based on direction feature and local uniqueness, which is divided into two parts: direction feature value calculation and local uniqueness screening. In the direction feature value calculation part, the edge feature is calculated through a sliding window; in the local The uniqueness screening part calculates the uniqueness between each region, combines the direction feature and its uniqueness and scores each window region, and sorts in descending order to obtain the top n optimal feature points. A number of alignment feature points can be quickly extracted from the vector map, and the feature points have good uniqueness. At present, this algorithm has been maturely applied to automatic alignment equipment.
Owner:浙江欧威科技有限公司
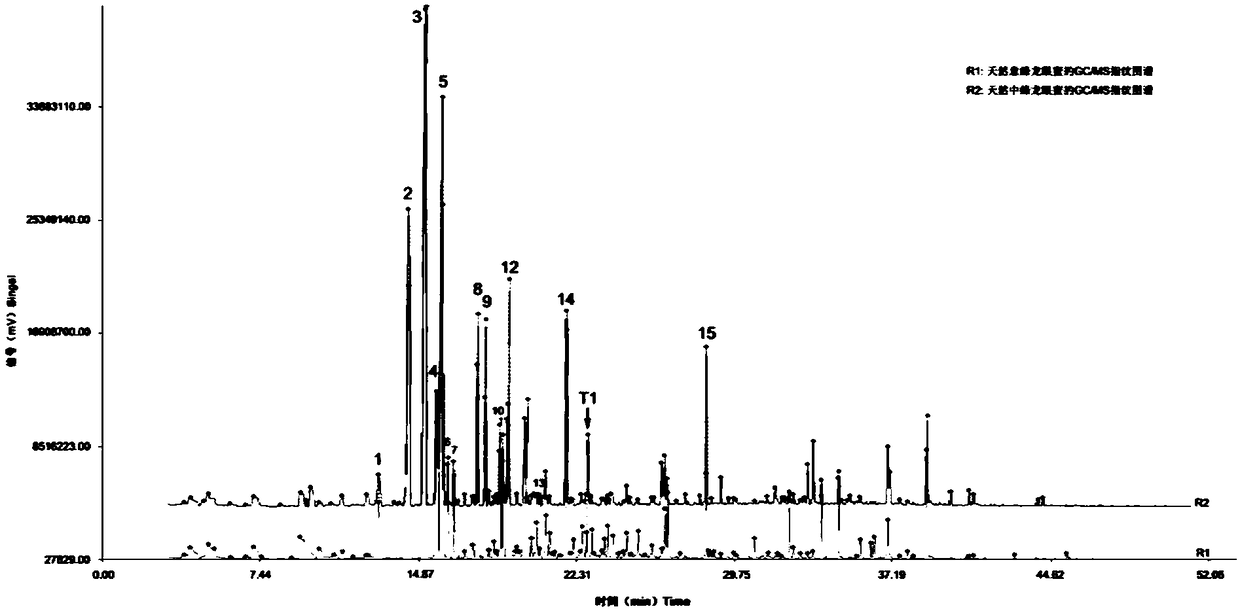
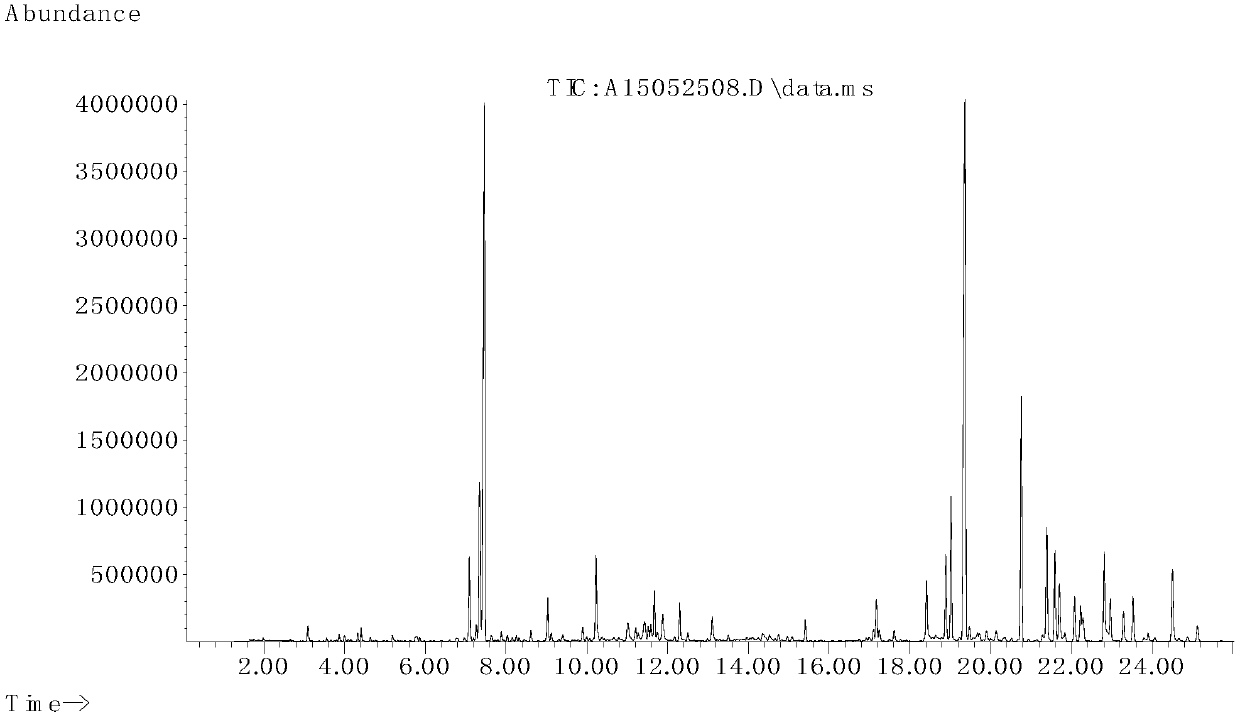
A method for identifying the authenticity of agarwood
ActiveCN106053645BHigh detection sensitivityImprove reliabilityComponent separationAdditive ingredientAgarwood
The invention discloses a method for identifying authenticity of agilawood. According to the method, a GC / MS fingerprint map of a to-be-detected agilawood sample is established, and if the GC / MS fingerprint map of the to-be-detected agilawood sample is basically consistent with that of natural agilawood and the to-be-detected agilawood sample contains six feature ingredients including (1) benzylacetone, (2) p-methoxybenzylacetone, (3) agarofuran, (4) agarospirol, (5) hinesol and (6) baimuxinal, the to-be-detected agilawood sample is natural agilawood; if the GC / MS fingerprint map of the to-be-detected agilawood sample has a bigger difference with that of the natural agilawood and the to-be-detected agilawood sample only contains part of the six feature ingredients or doesn't contain the six feature ingredients, the to-be-detected agilawood sample is fake agilawood. The provided method has the characteristics of small dosage of samples, simplicity, convenience and rapidness in operation, remarkable characteristics and accurate and reliable result and is suitable for identifying the authenticity of agilawood without damaging the overall structure of an agilawood storage product, and the method can be used for identifying the authenticity of the agilawood and agilawood artware.
Owner:INSTITUTE OF ANALYSIS GUANGDONG ACADEMY OF SCIENCES (CHINA NATIONAL ANALYTICAL CENTER GUANGZHOU)
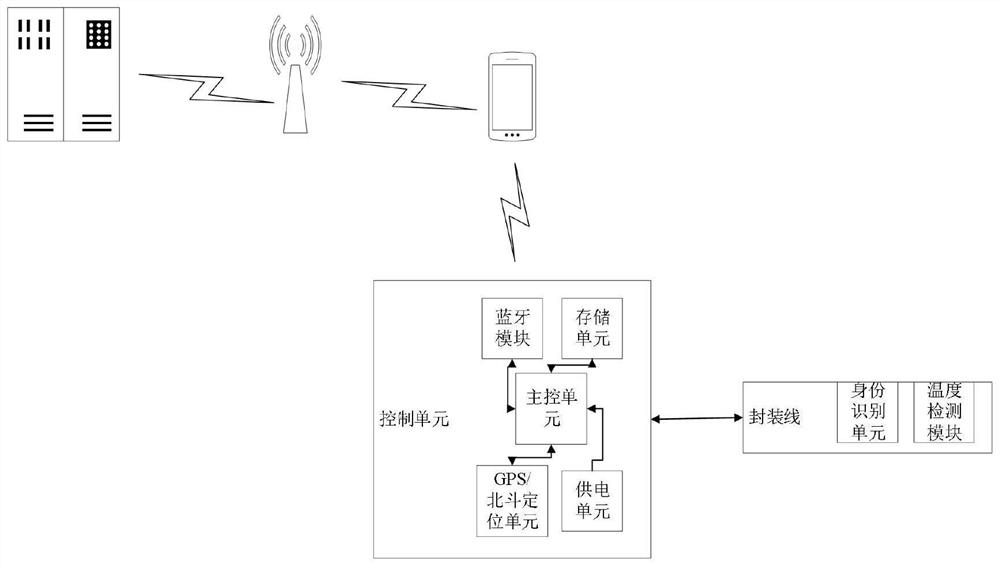
Sealing anti-damage system in article transportation process
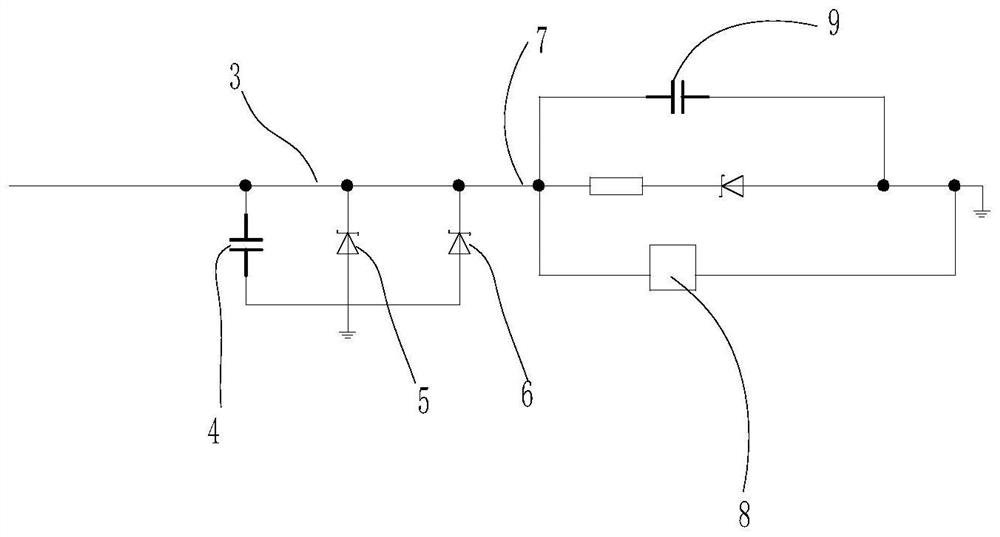
PendingCN114445987AGuaranteed independenceEnsure safetyBurglar alarm with fastening tamperingClosuresCapacitanceCommunication unit
The invention discloses a storage anti-damage system in an article transportation process, which comprises a detection host, a conductive detection line used for packaging an article is connected to the detection host, and two ends of the detection line are respectively connected with the detection host in a locking manner; the detection host comprises a control module, a detection port of the control module is connected with a first link, a first capacitor and a first voltage-regulator tube are connected in parallel on the first link, a second voltage-regulator tube is connected between the first capacitor and the first voltage-regulator tube and between the first link, a cut-off end of the second voltage-regulator tube is connected with the first link, and a cut-off end of the second voltage-regulator tube is connected with the second link. The conducting end of the second voltage-regulator tube is grounded; the first link is conductively connected with the detection line; wherein an identity communication module and a second capacitor are integrated on the detection line, and the second capacitor is connected in parallel with a power supply port of the identity communication unit. Independent work of the marking body effectively guarantees independence and safety of a blocked object, the marking body and the monitoring body work independently, and safety of the whole product is effectively improved.
Owner:河北重优科技有限公司
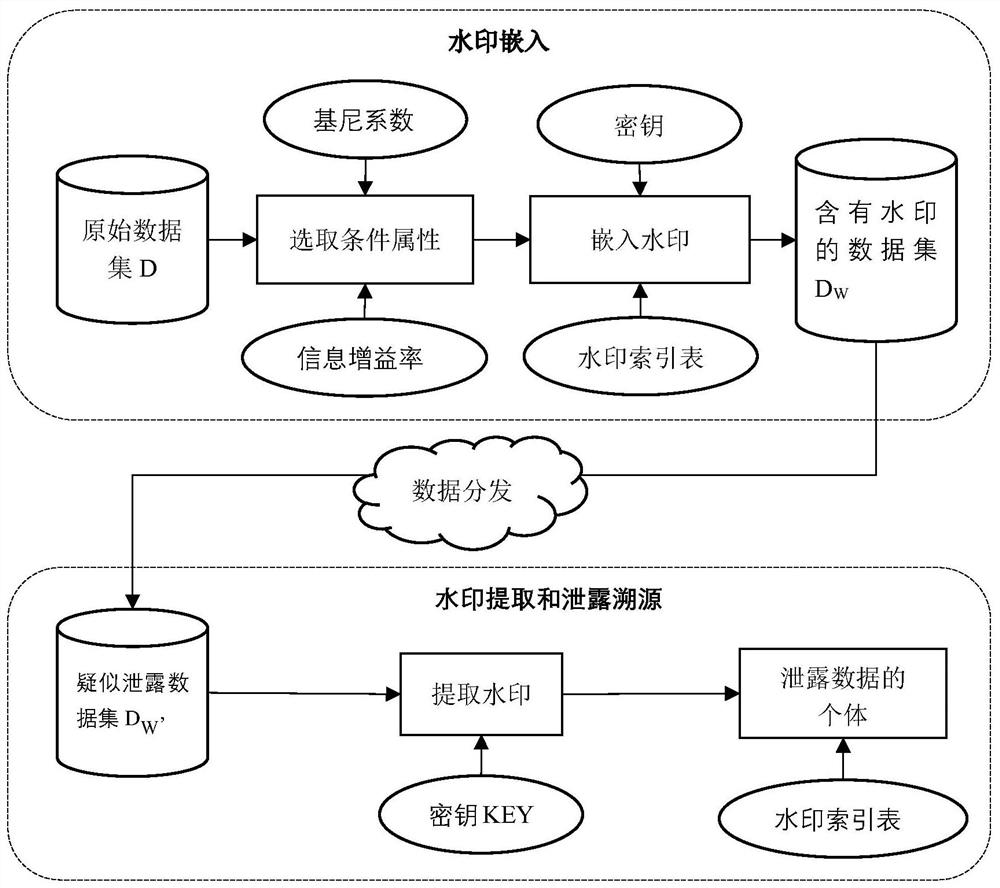
Digital watermark data tracing method based on attribute importance index
PendingCN113704709ATake security into considerationConsider usabilityProgram/content distribution protectionComplete dataDatasheet
The invention discloses a digital watermark data tracing method based on an attribute importance index, and the method specifically comprises the following steps: 1, summarizing original data to be distributed, and extracting a prediction attribute and a class label attribute of each piece of original data to form a data table; 2, creating a watermark index table according to a data receiver of the original data, and generating a key KEY; 3, forming a non-important attribute set attr; 4, embedding a watermark to obtain a data set containing the watermark; 5, distributing the data set containing the watermark according to the information of the data receivers in the watermark index table, and collecting suspected leakage data which is completely or partially leaked in the distribution process or after distribution to form a suspected leakage data set; 6, extracting all sub-watermarks in each piece of data in the suspected leakage data set, and connecting the sub-watermarks with complete watermarks; and 7, extracting the complete watermark, and finding out a corresponding data receiver through the watermark index table, namely an individual with leaked data, so as to complete data leakage traceability.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO LTD MARKETING SERVICE CENT +1
Piezoelectric ceramic novel label, and identification system and identification method for piezoelectric ceramic novel label
InactiveCN102243715AStrong uniquenessEasy to identifySensing record carriersRecord carriers used with machinesImpedance analyzerCeramic
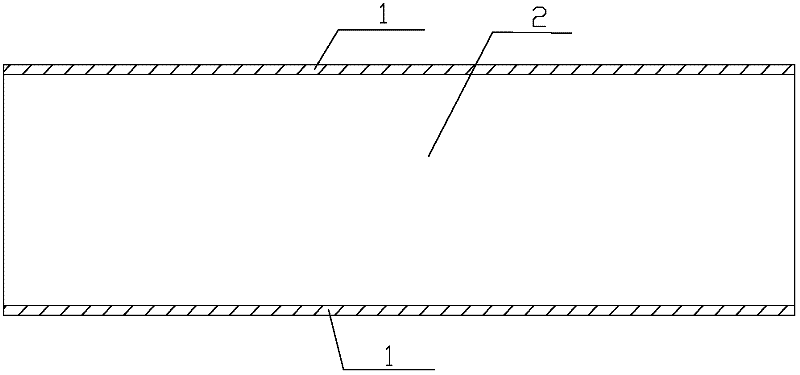
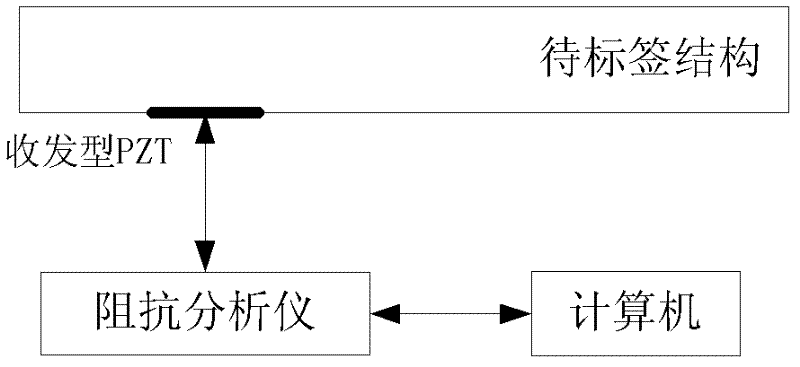
The invention aims to provide a piezoelectric ceramic novel label, and an identification system and an identification method for the piezoelectric ceramic novel label for meeting a protection requirement on special goods. The piezoelectric ceramic novel label has a piezoelectric ceramic sheet, wherein conducting layers are coated on two planes of the piezoelectric ceramic sheet; and the conducting layers on the two planes are not conducted. The identification system comprises the piezoelectric ceramic novel label to be labeled, an impedance analyzer and a computer, wherein the conducting layers on the two planes of the piezoelectric ceramic novel label are connected with the impedance analyzer by leads; and the impedance analyzer is connected to the computer. The impedance characteristic information of the piezoelectric ceramic (lead zirconate titanate (PZT)) label is correlated with PZT materials, glue water, structural physical characteristics and the like, so the PZT label is strong in uniqueness and relatively simple to identify and can be used as a special label.
Owner:中国人民解放军96411部队
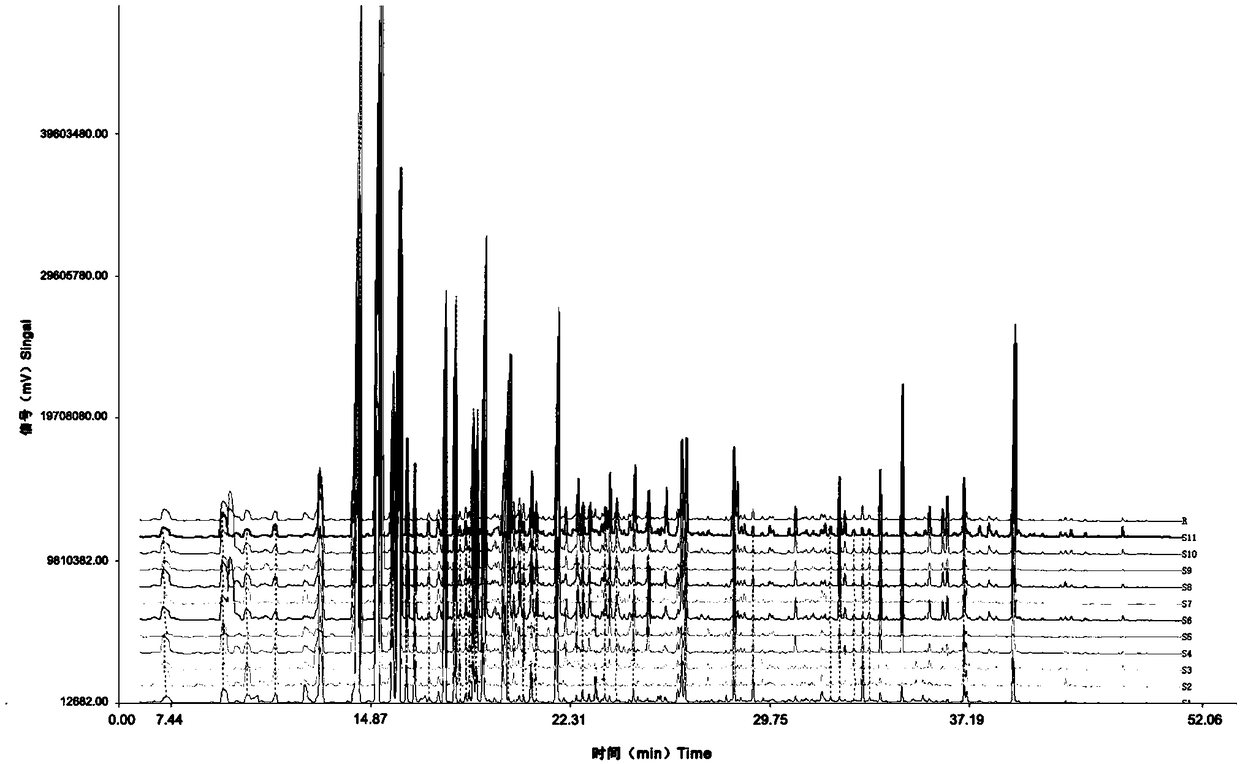
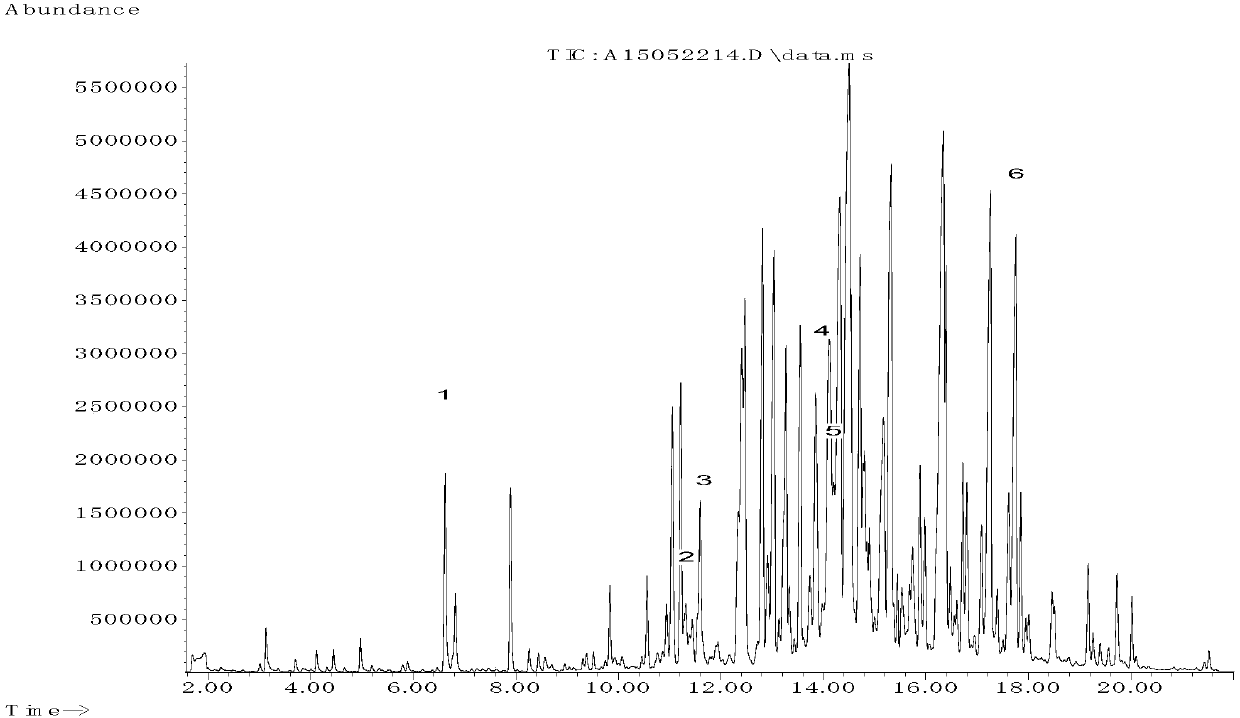
A construction method and identification application of fingerprints of natural Chinese bee lychee honey and natural Italian bee lychee honey
ActiveCN109470779BFix the problem of indistinguishableHigh detection sensitivityComponent separationChemical compositionHoney samples
The invention discloses a method for constructing fingerprints of natural Chinese bee lychee honey and natural Italian bee lychee honey and its identification application. The present invention obtains the GC / MS fingerprints of natural Chinese bee lychee honey and natural Italian bee lychee honey by adopting the method of headspace solid-phase microextraction-gas chromatography-mass spectrometry and the similarity evaluation system of traditional Chinese medicine fingerprints; The GC / MS fingerprint of lychee honey from Zhongfeng contains 19 common characteristic volatile components, and the GC / MS fingerprint of natural Italian lychee honey contains 16 common characteristic volatile components. By comparing the similarity and chemical composition difference between the total ion chromatogram of the tested natural lychee honey sample and the constructed GC / MS fingerprint, the natural Chinese bee lychee honey and natural Italian bee lychee honey can be accurately distinguished. The method of the invention has the characteristics of small amount of samples, strong characteristics and reliable results, is very beneficial to solving the problem that the lichee honey of Chinese Italian bee is difficult to distinguish in the current market, and has very obvious social benefits.
Owner:INST OF ZOOLOGY GUANGDONG ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com