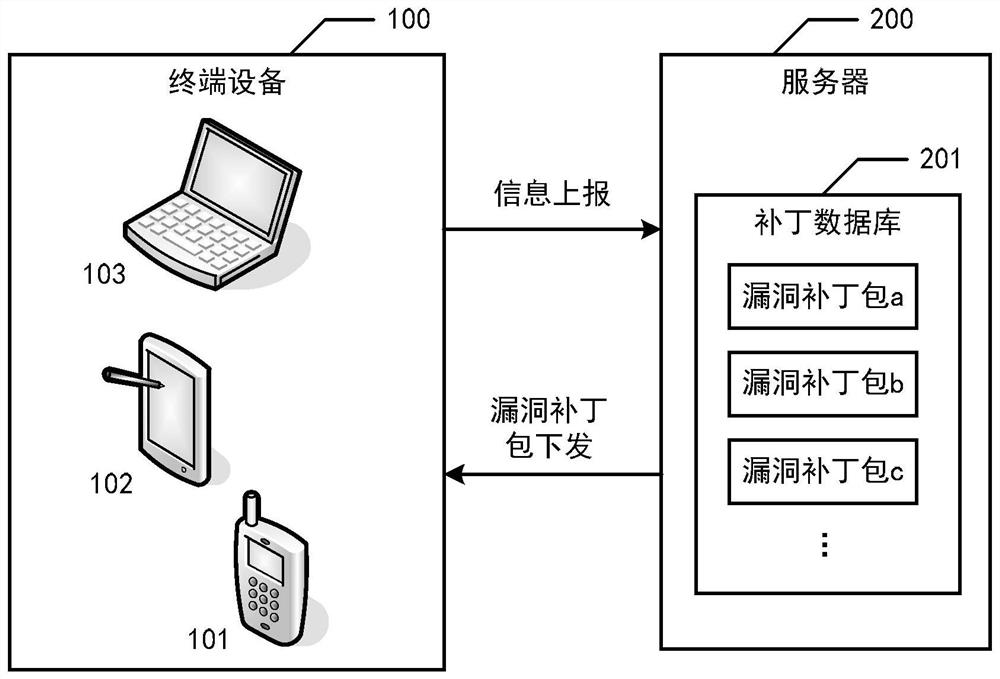
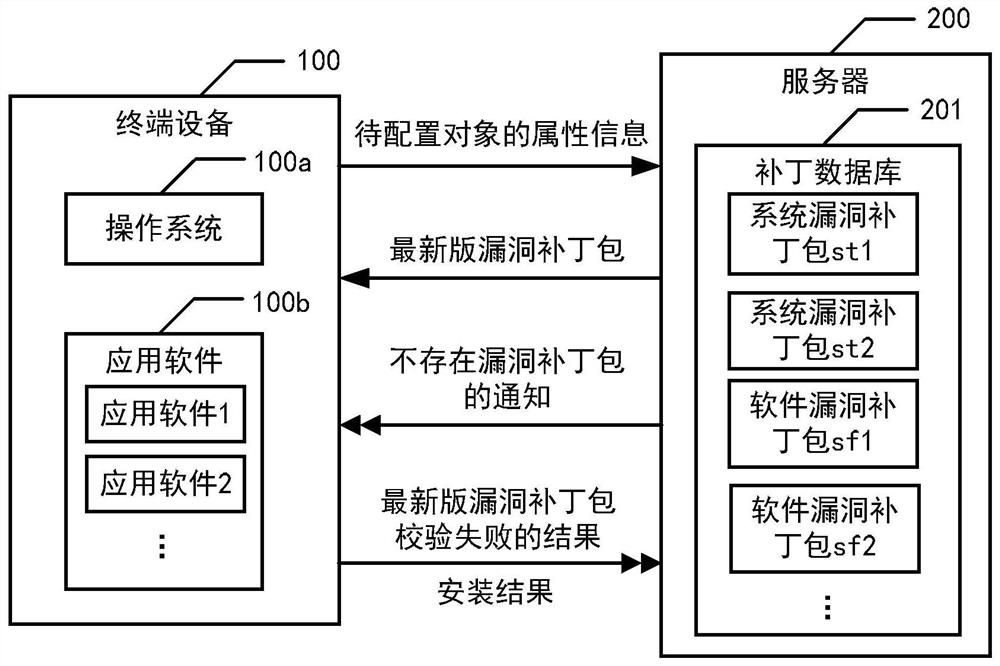
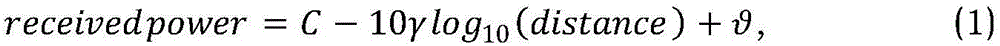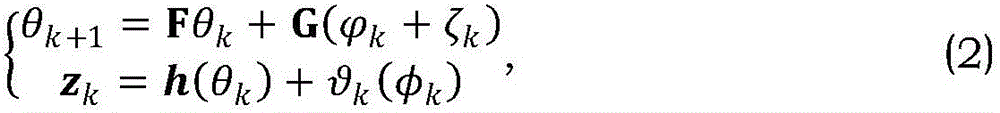Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41results about How to "Solving Information Security Issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
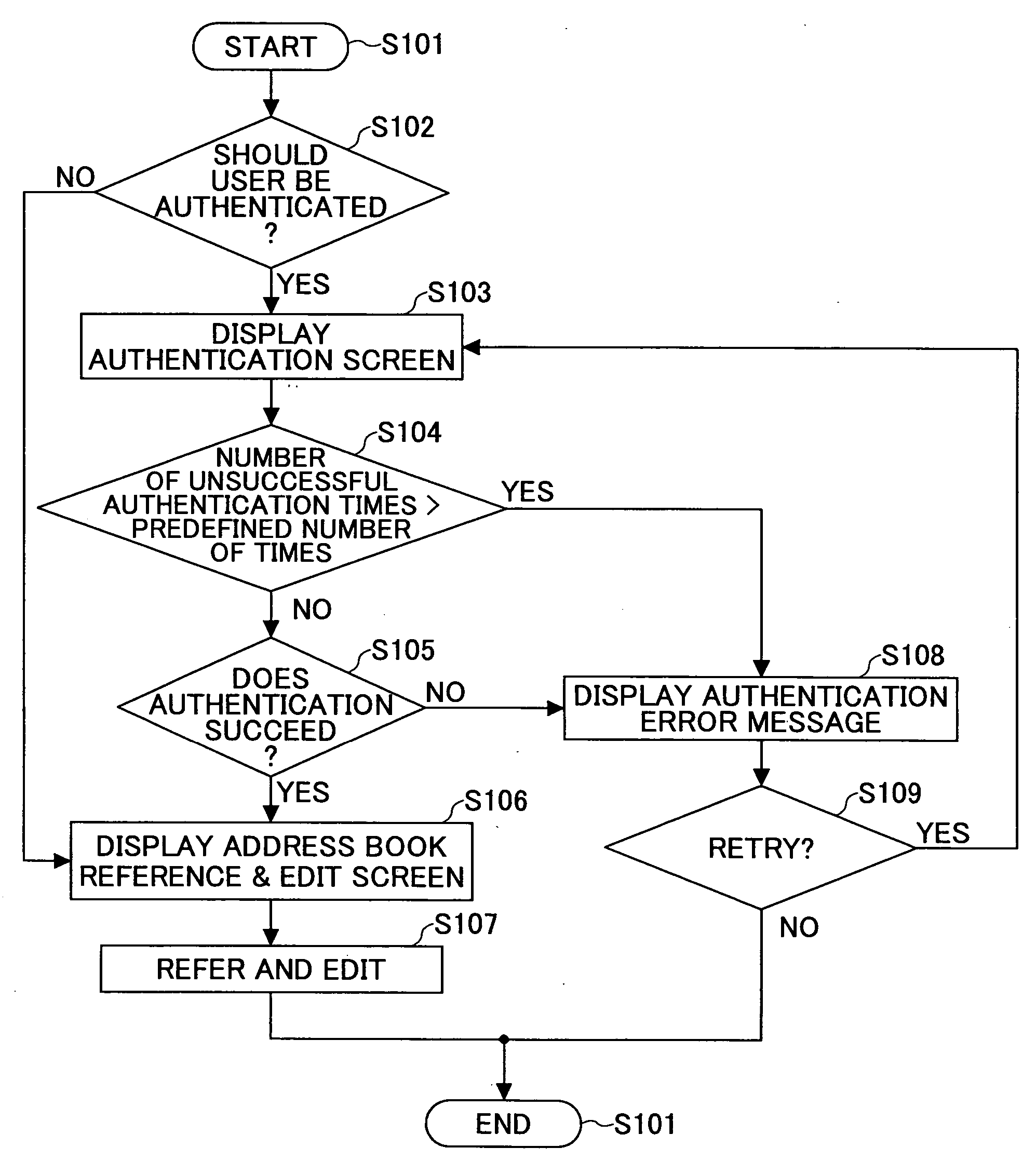
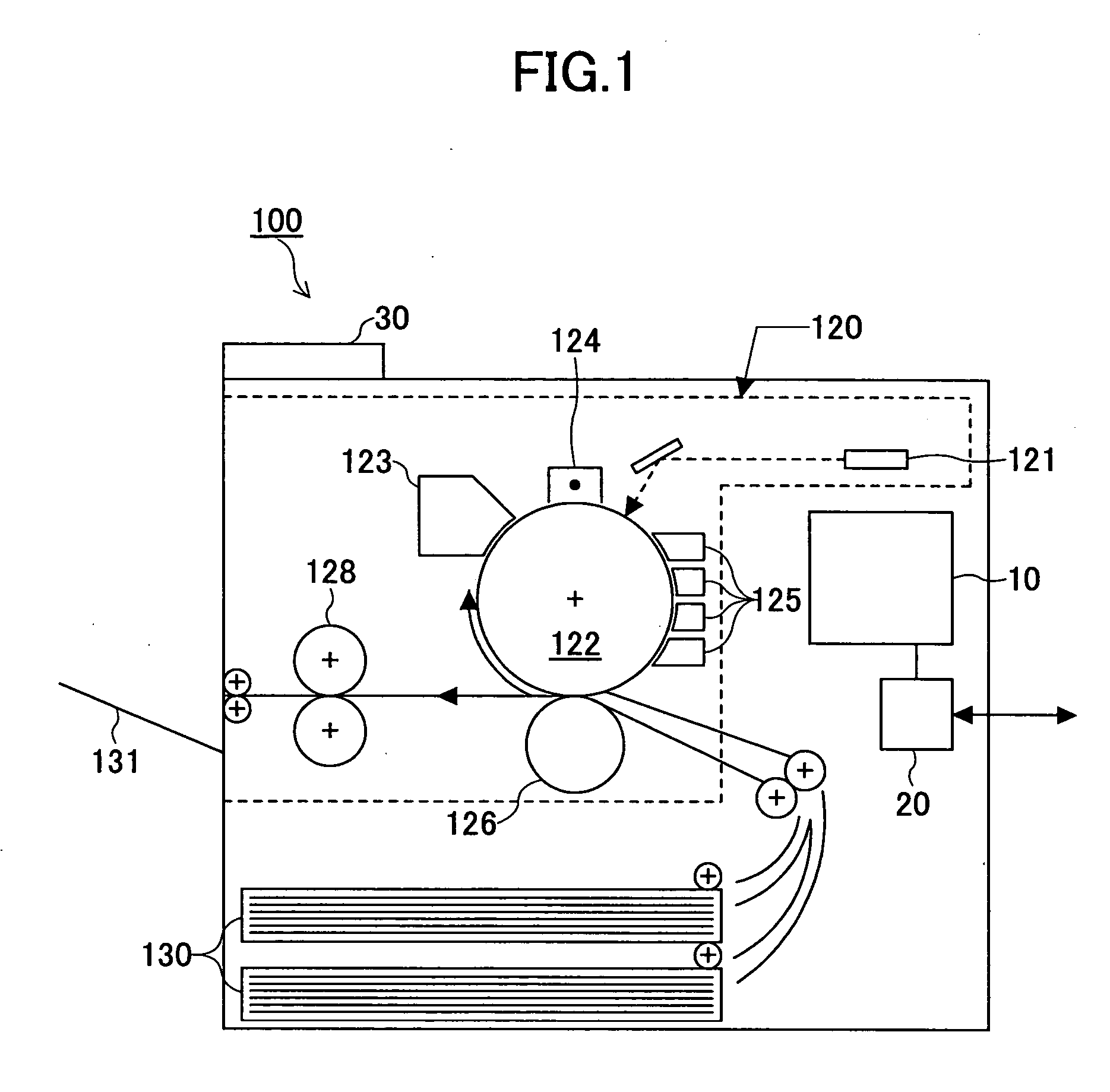
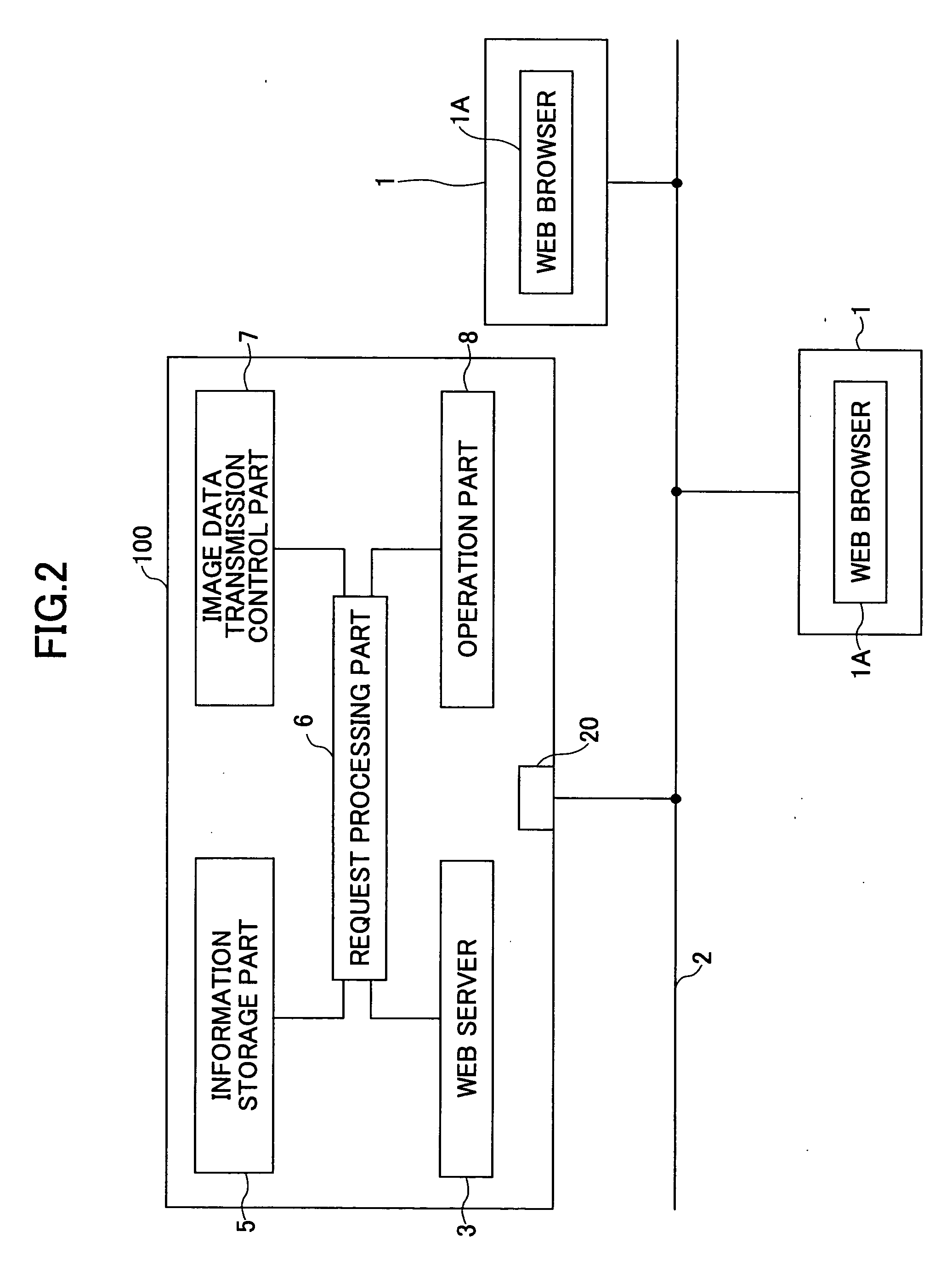
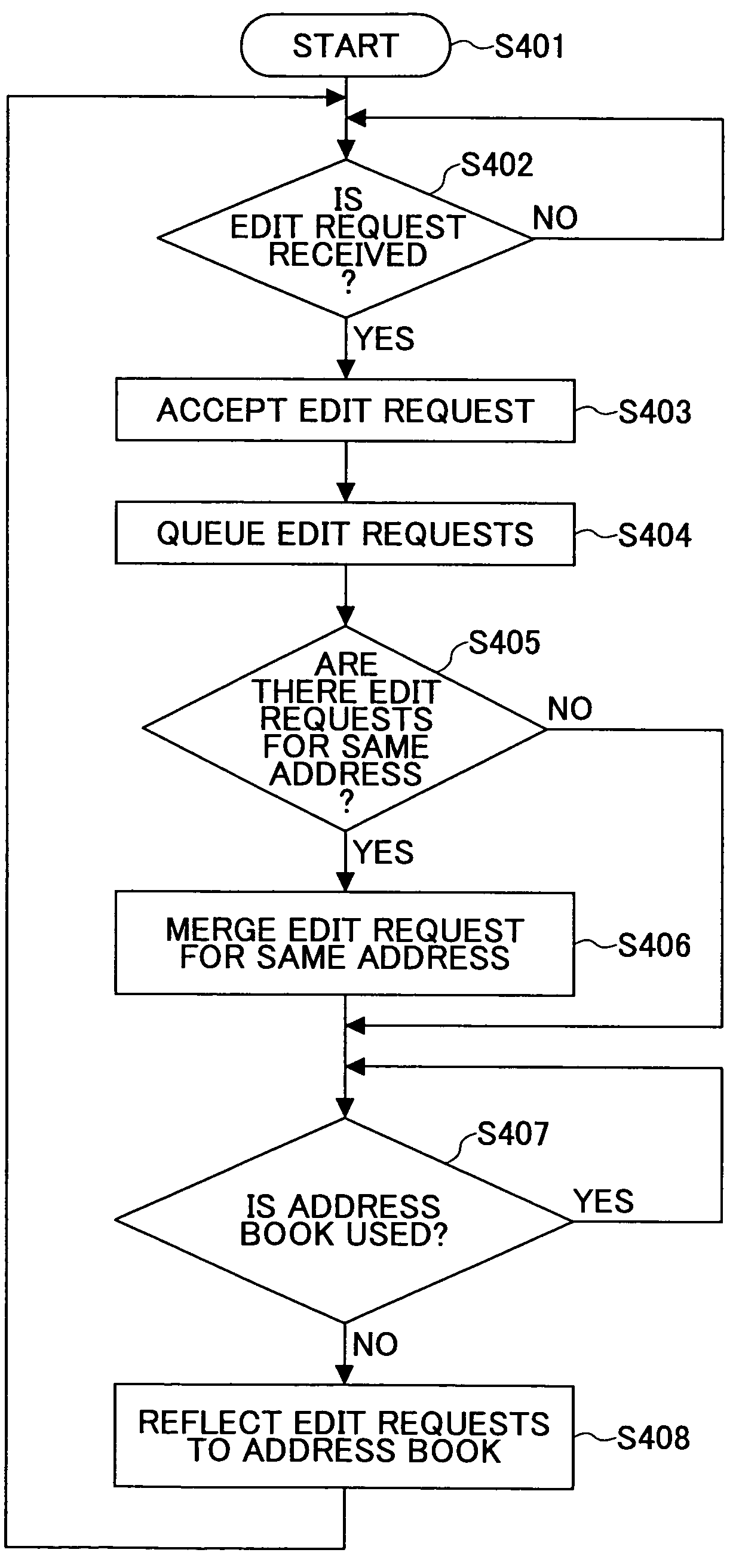
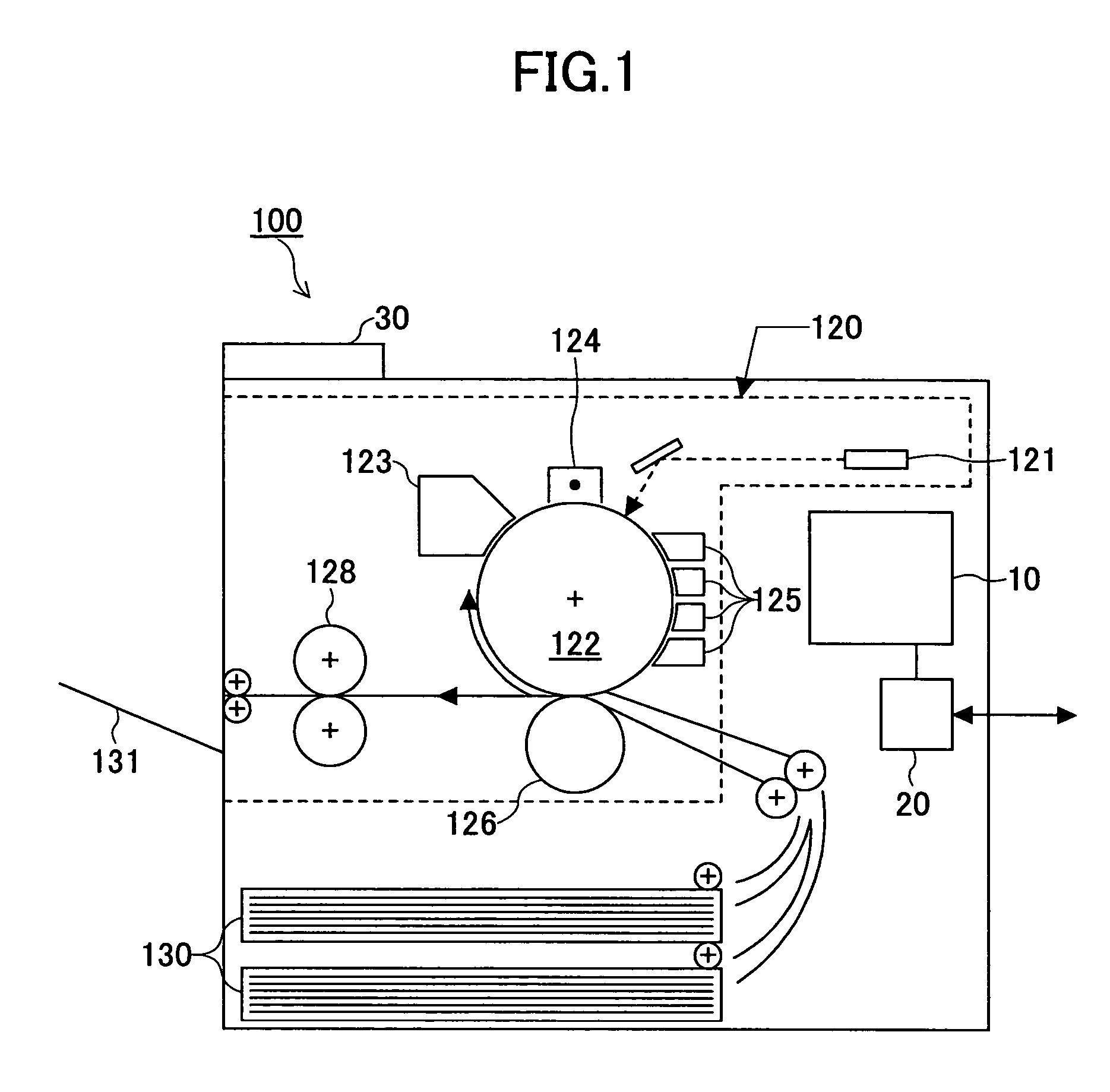
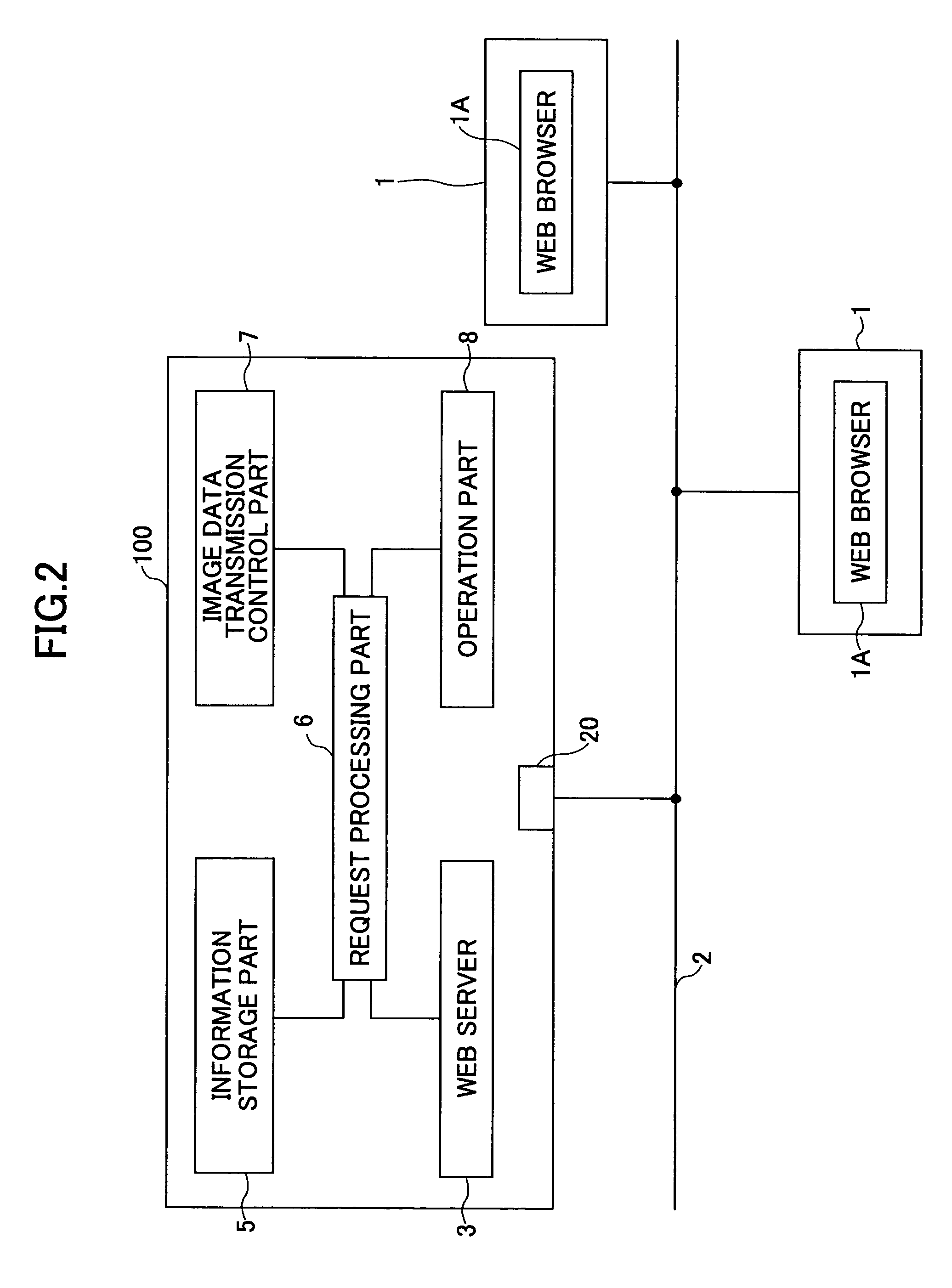
Image forming apparatus and address information processing method
InactiveUS20050002057A1Eliminate the problemSolving Information Security IssuesDigital data processing detailsUser identity/authority verificationInformation processingAddress book
An image forming apparatus and an address book process request processing method are disclosed to improve access security to an address book. The image forming apparatus include an information storage part, a request receipt part and a request processing part. The information storage part stores an address book on users. The request receipt part receives process requests for the address book together with user identification information from users. The request processing part authenticates the users based on the received user identification information and performs operations corresponding to the process requests on the address book in accordance with access authority permitted to the users. The address book includes address information for transmitting data to the users via a network and management information having user identification information of the users.
Owner:RICOH KK
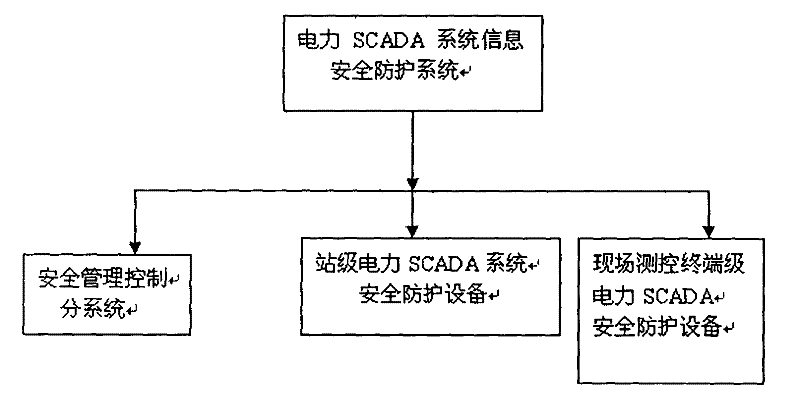
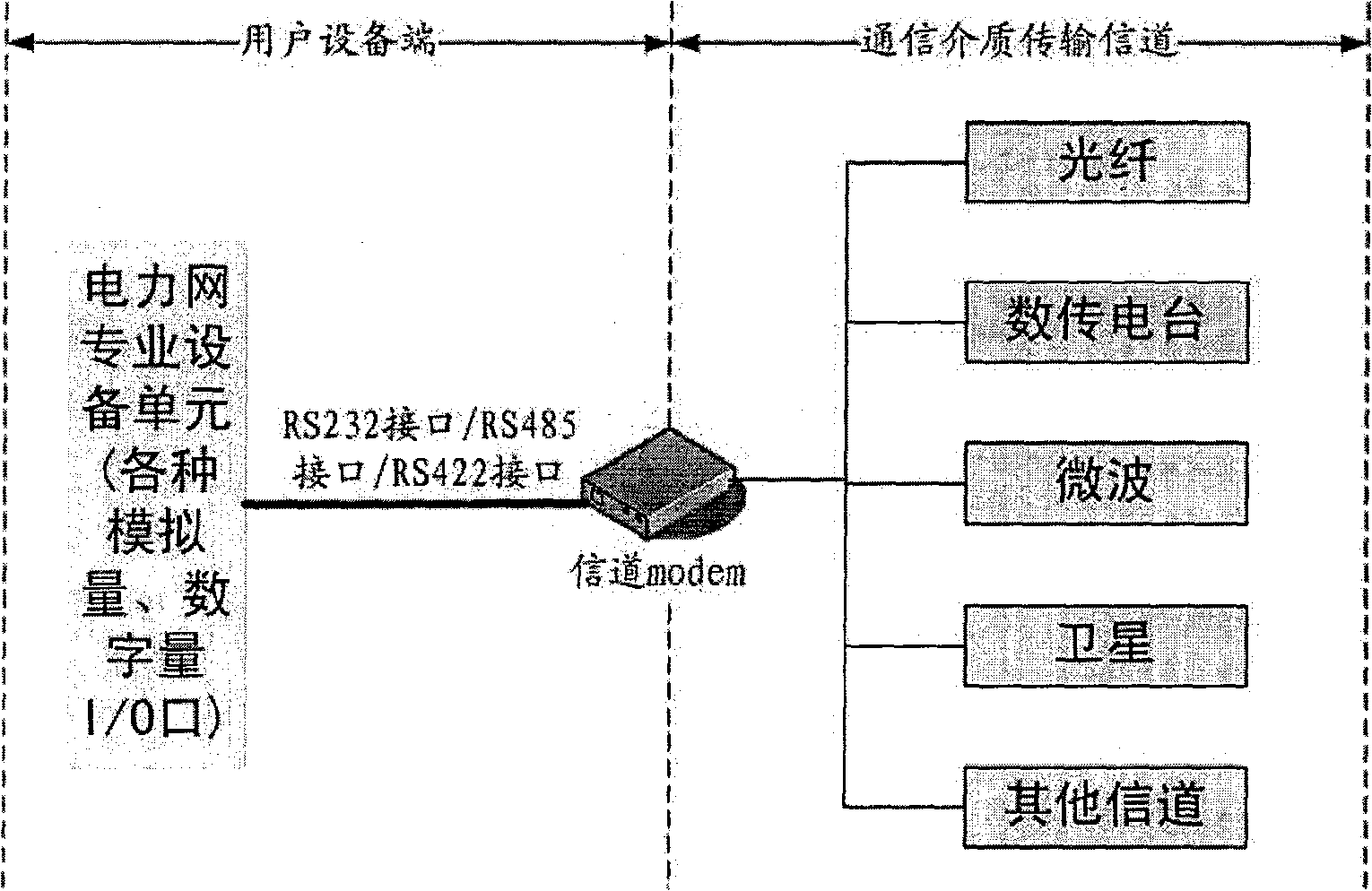
A power scada system information security protection system
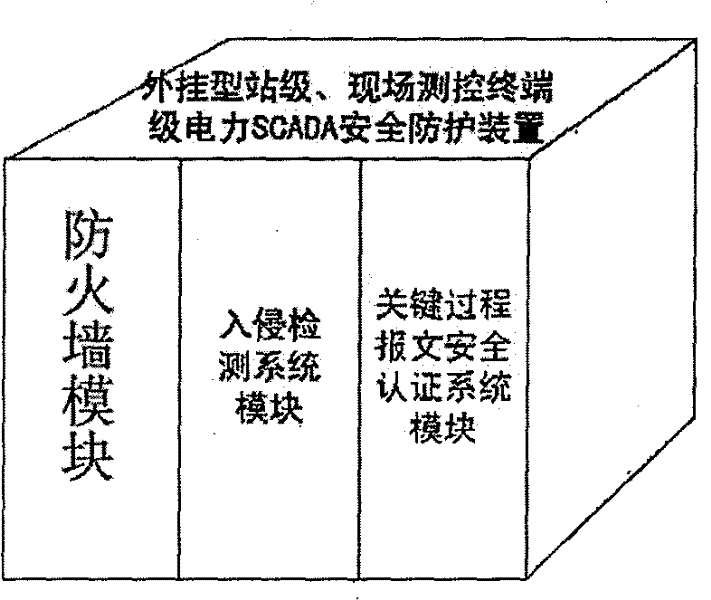
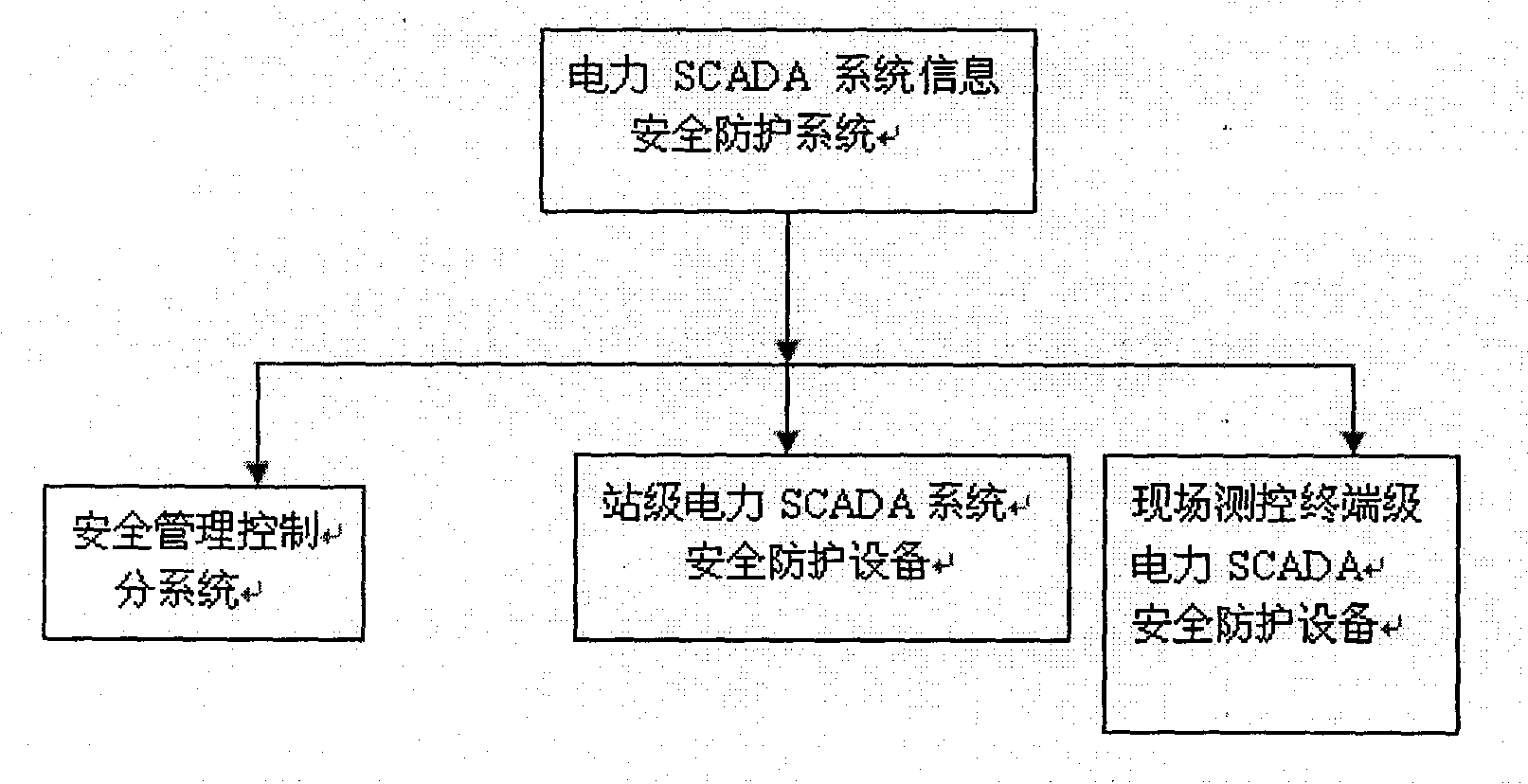
ActiveCN102280929ASolving Information Security IssuesGuarantee the "four remote" function - remote control functionPower network operation systems integrationCircuit arrangementsSafety management systemsData acquisition
The invention discloses a system for information safety protection of an electric power supervisory control and data acquisition (SCADA) system. The system comprises a safety equipment management system, a station level electric power SCADA system safety protection device and an on-site terminal level electric power SCADA system safety protection device, wherein the safety management system is positioned in a power supply control center and becomes one component part of the electric power SCADA system main station system to manage the long-range station level electric power SCADA system safety protection device and the on-site terminal level electric power SCADA system safety protection device. The station level electric power SCADA system safety protection device is placed in a sub-station level electric power SCADA system device of the electric power SCADA system. The on-site terminal level electric power SCADA system safety protection device is placed in an electric power SCADA field device of an electric network field. The system has the main function of providing fine granularity and electric power production control service-based application layer safety protection for the electric power SCADA system, is used for ensuring the safety of 'four-remote functions' including a remote control function, a remote signaling function, a remote sensing function and remote regulatingfunction of the electric power SCADA system, and the safety of a communication channel of the electric power SCADA system, has electric power SCADA system intrusion detection and access control abilities, and has strong electric power service pertinence.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
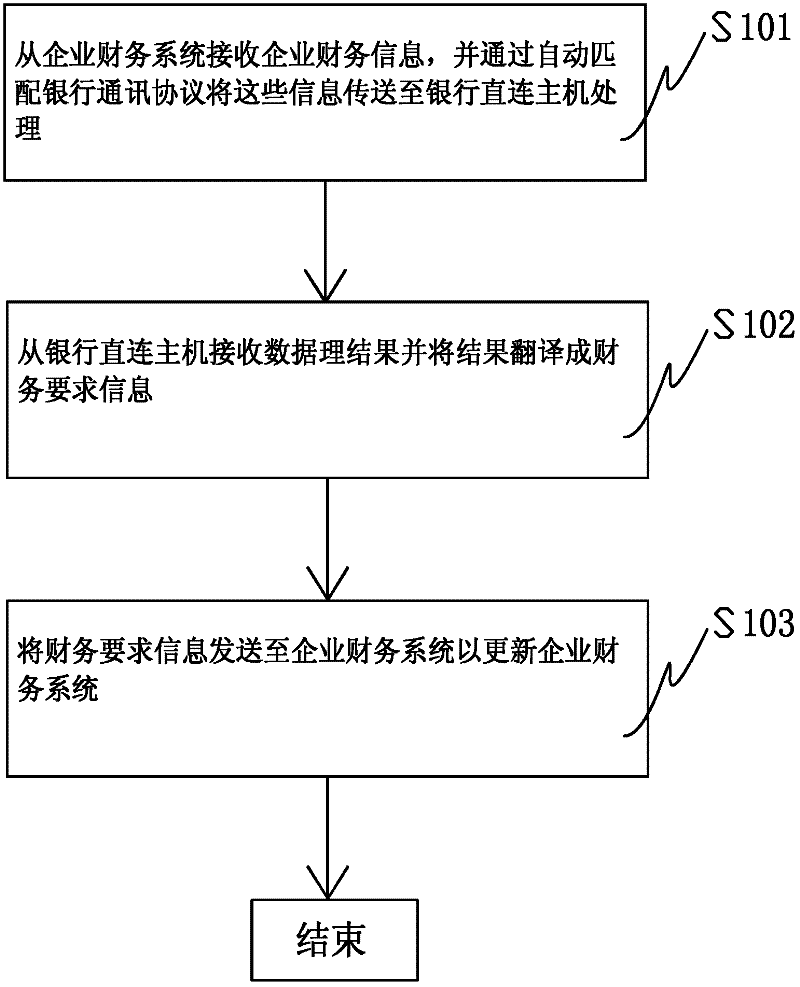
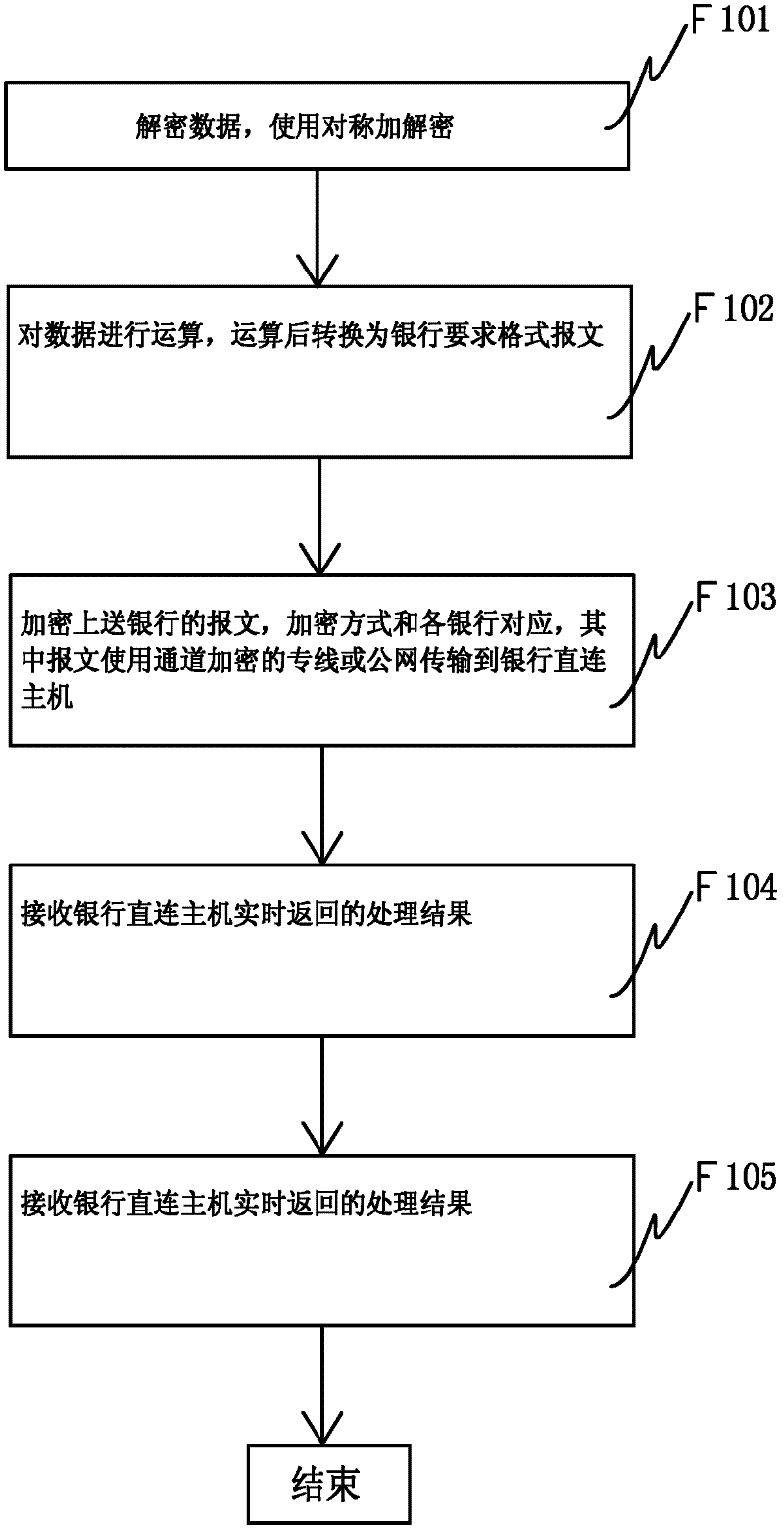
System for directly exchanging financial data by enterprises and banks
InactiveCN102521778AAvoid encrypted transmissionsSave human resourcesFinanceCommunications protocolEnterprise system
The invention relates to a system for directly exchanging financial data by enterprises and banks. The system comprises an enterprise financial system, a bank-enterprise system front-end processor connected with the enterprise financial system, and a bank direct-attached host computer communicated with the bank-enterprise system front-end processor, wherein the bank-enterprise system front-end processor is configured to receive enterprise financial information from the enterprise financial system, transmit the information to the bank direct-attached host computer by automatically matching a bank communication protocol, receive a data processing result from the bank direct-attached host computer, translate the result into financial requirement information, and transmit the financial requirement information to the enterprise financial system so as to update the enterprise financial system.
Owner:CTRIP COMP TECH SHANGHAI
Image forming apparatus and address information processing method
InactiveUS7589857B2Solving Information Security IssuesEnsure safetyDigital data processing detailsUser identity/authority verificationInformation processingAddress book
An image forming apparatus and an address book process request processing method are disclosed to improve access security to an address book. The image forming apparatus include an information storage part, a request receipt part and a request processing part. The information storage part stores an address book on users. The request receipt part receives process requests for the address book together with user identification information from users. The request processing part authenticates the users based on the received user identification information and performs operations corresponding to the process requests on the address book in accordance with access authority permitted to the users. The address book includes address information for transmitting data to the users via a network and management information having user identification information of the users.
Owner:RICOH KK
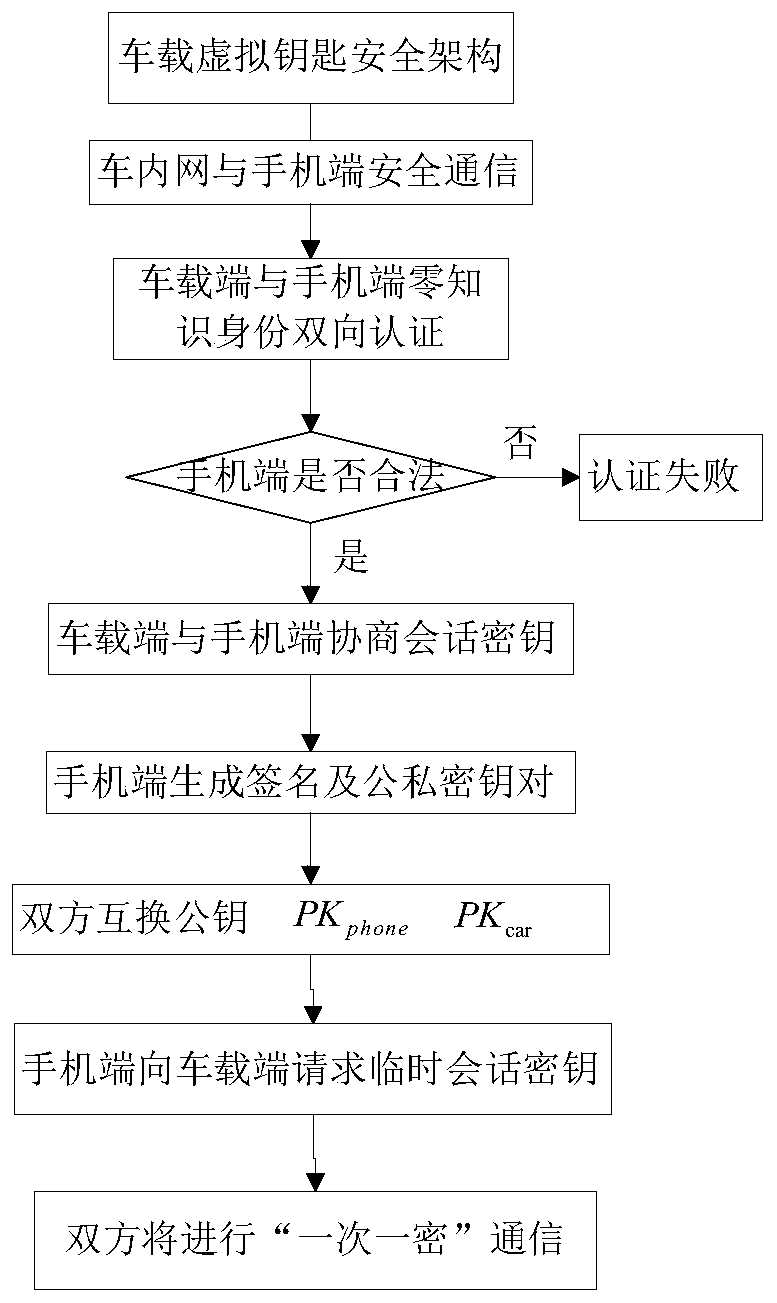
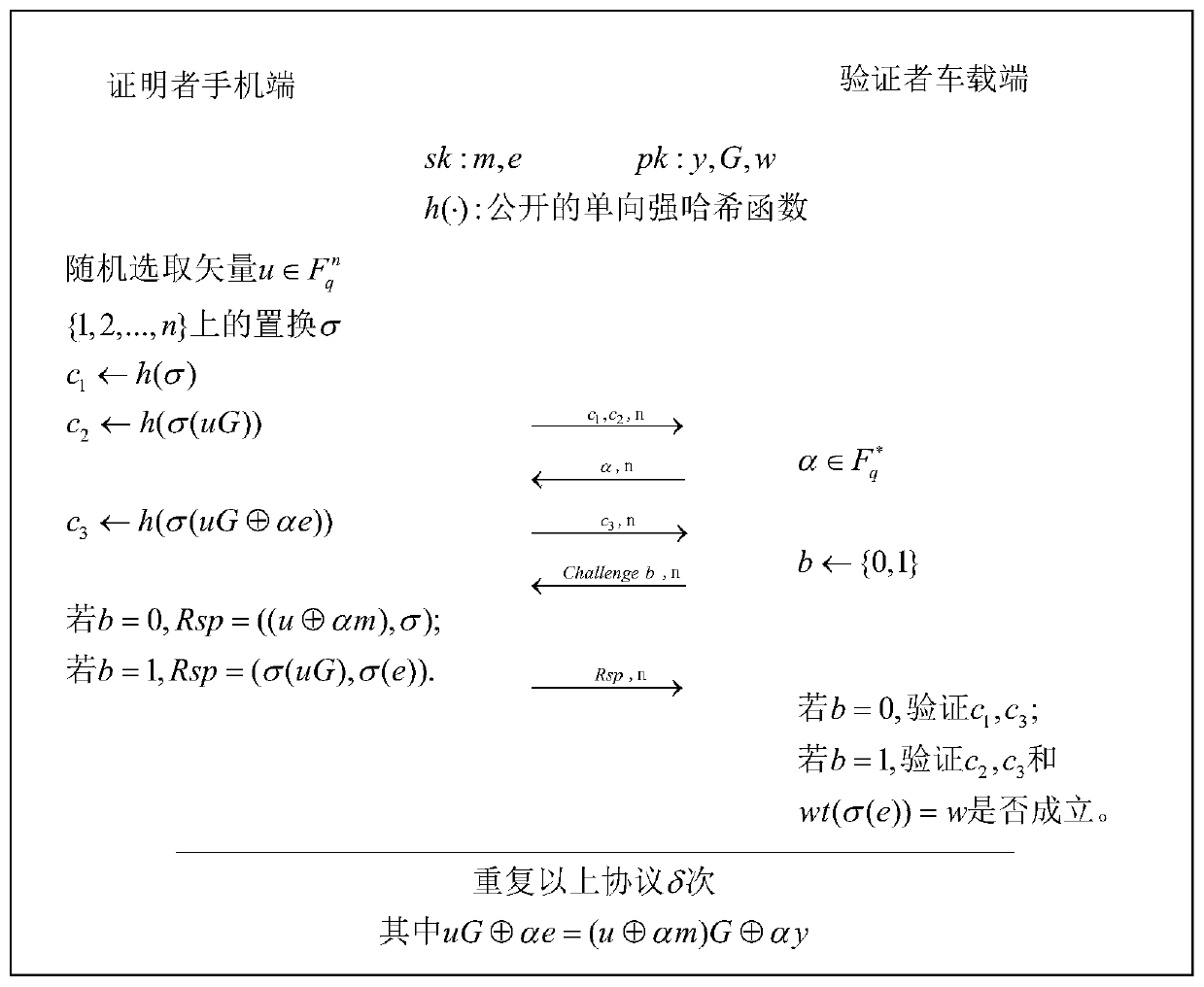
Vehicle-mounted virtual key implementation and communication method
ActiveCN110167021ASolving Information Security IssuesImprove securityKey distribution for secure communicationAnti-theft devicesCiphertextInformation security
The invention provides a vehicle-mounted virtual key realization and communication method, which can improve the security. The method comprises the following steps of: firstly, a zero-knowledge identity authentication protocol based on a quasi-parallel vector error correction code is constructed between a vehicle-mounted terminal and a mobile phone terminal; a mutual authentication mechanism between the vehicle-mounted terminal and the mobile phone terminal is established; and then session key negotiation is carried out between the vehicle-mounted terminal and the mobile phone terminal, then the mobile phone terminal generates a signature and a public and private key pair, and finally, a storage battery voltage random characteristic description and true random number extraction method is adopted to establish a one-time password vehicle-mounted virtual key communication protocol based on ciphertext attributes. The novel vehicle-mounted virtual key communication protocol architecture isestablished on the basis of the novel vehicle-mounted virtual key communication protocol security of the cryptology principle, so that the problem of information security of the vehicle-mounted virtual key is solved, replay attack is prevented, and it is guaranteed that the identity authentication scheme has very high security.
Owner:JIANGSU UNIV
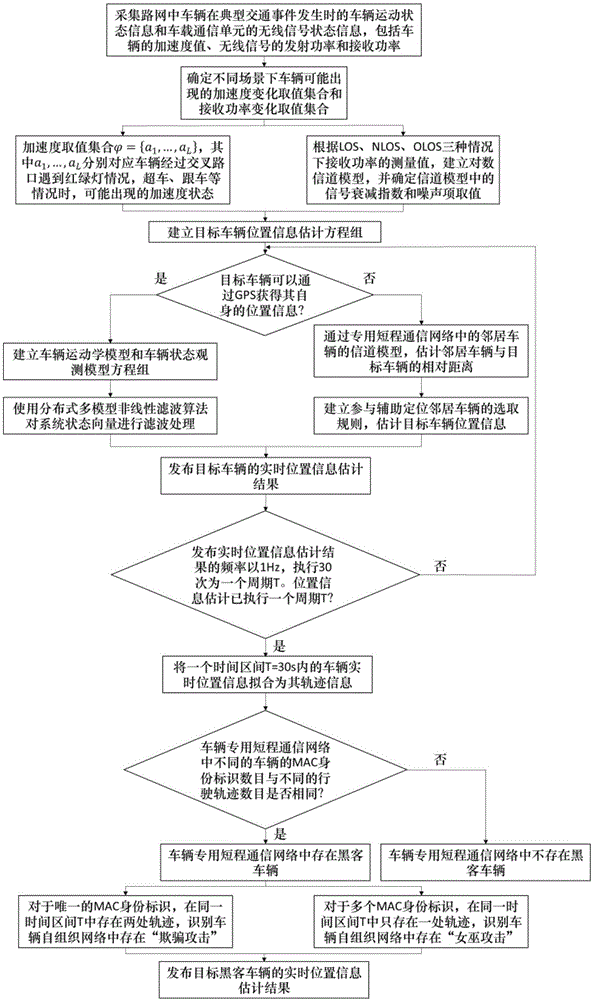
Method for positioning road network unlicensed vehicle based on dedicated short-range communication network
ActiveCN106303968AImprove estimation accuracySolving Information Security IssuesRoad vehicles traffic controlNetwork topologiesIn vehicleService guarantee
The present invention discloses a method for positioning a road network unlicensed vehicle based on a dedicated short-range communication network. With the development of the Internet of vehicles technology, arranging dedicated short-range communication units and satellite positioning devices in vehicles to implement information sharing among a group of vehicles has become a development trend of the Internet of vehicles technology. By fully using the dedicated short-range communication network widely existing an Internet of vehicles system, the resent invention implements recognition and positioning of unlicensed vehicles, thereby providing information security service guarantee for the normal operation of the Internet of vehicles system.
Owner:BEIHANG UNIV
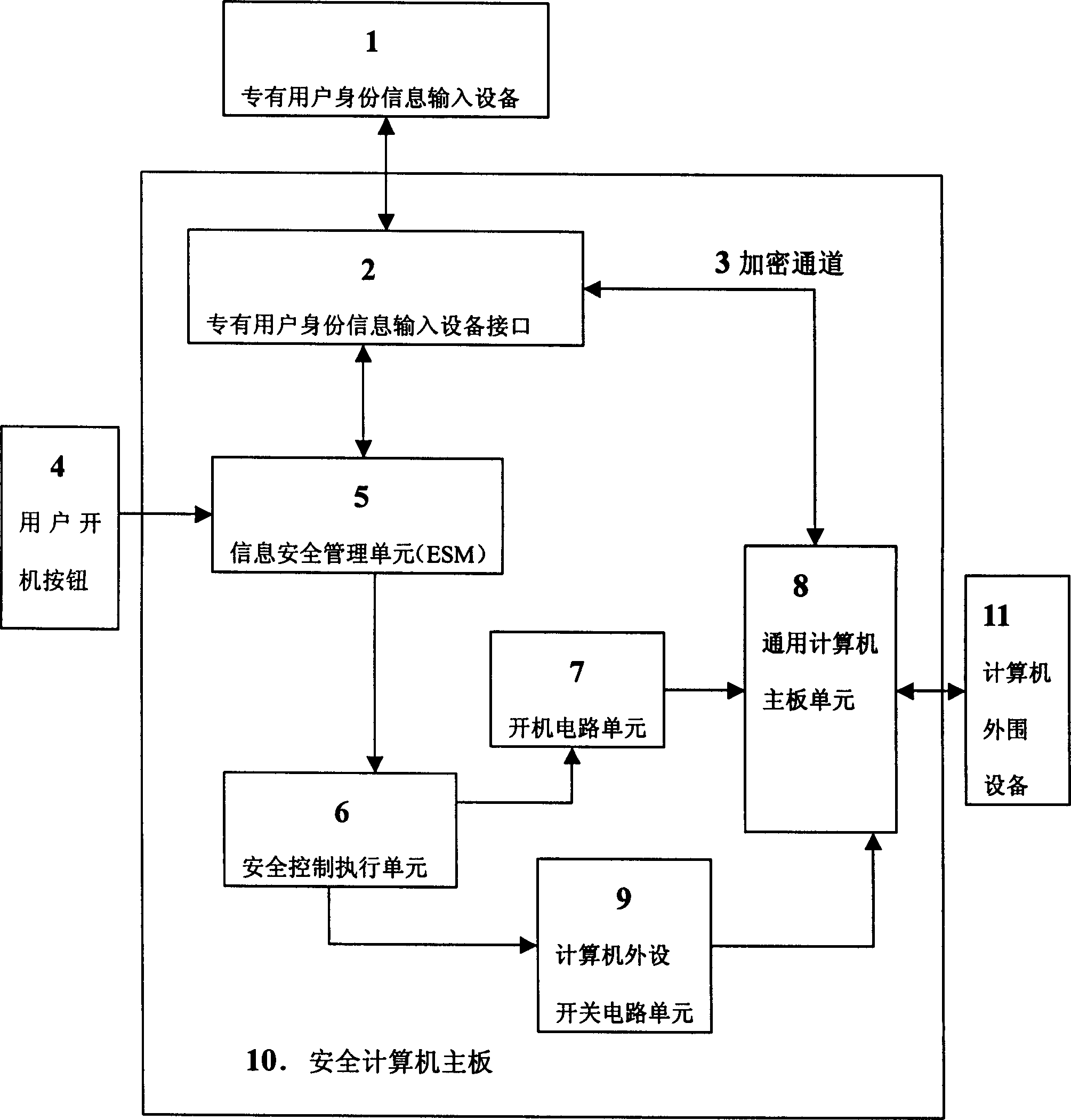
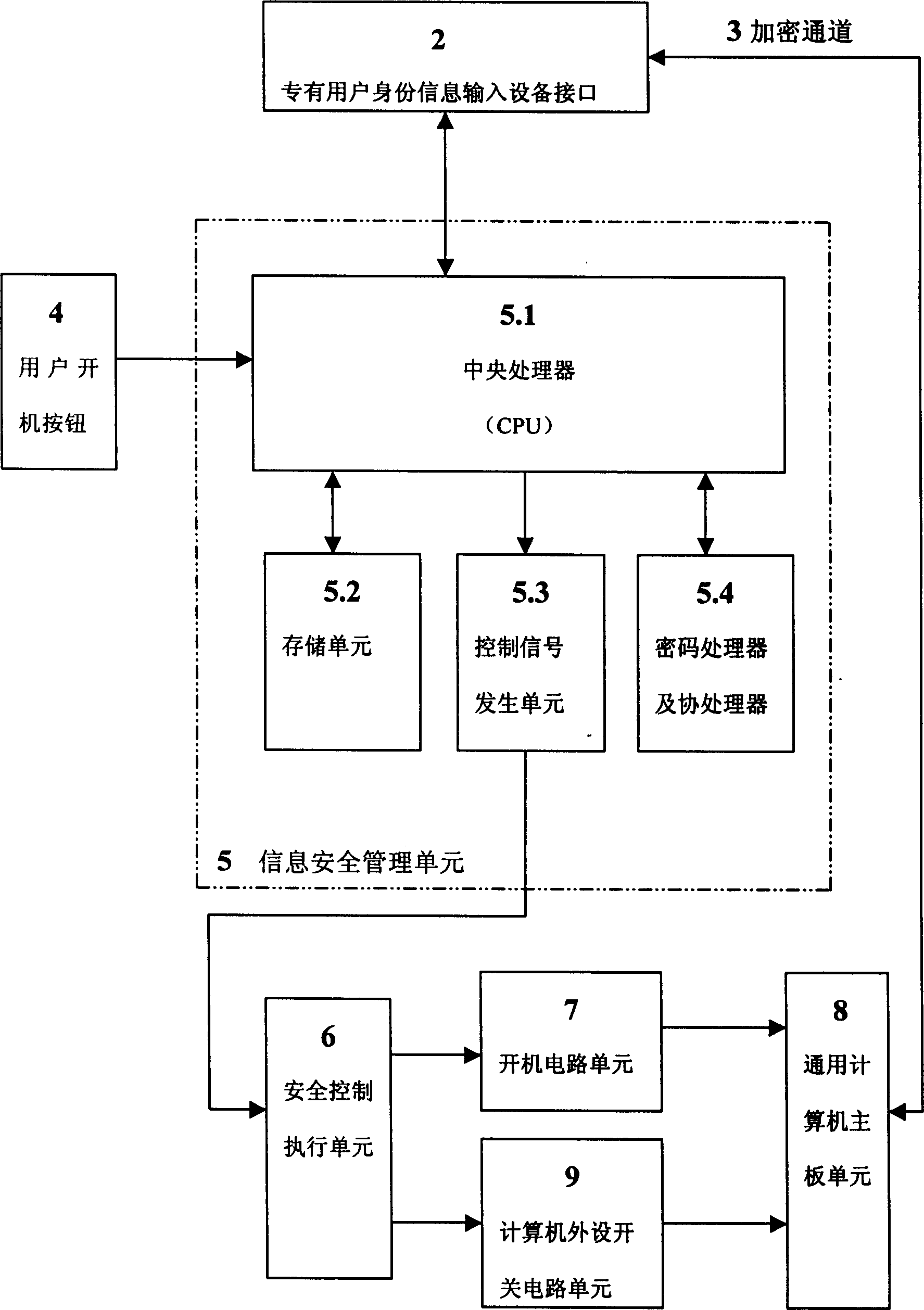
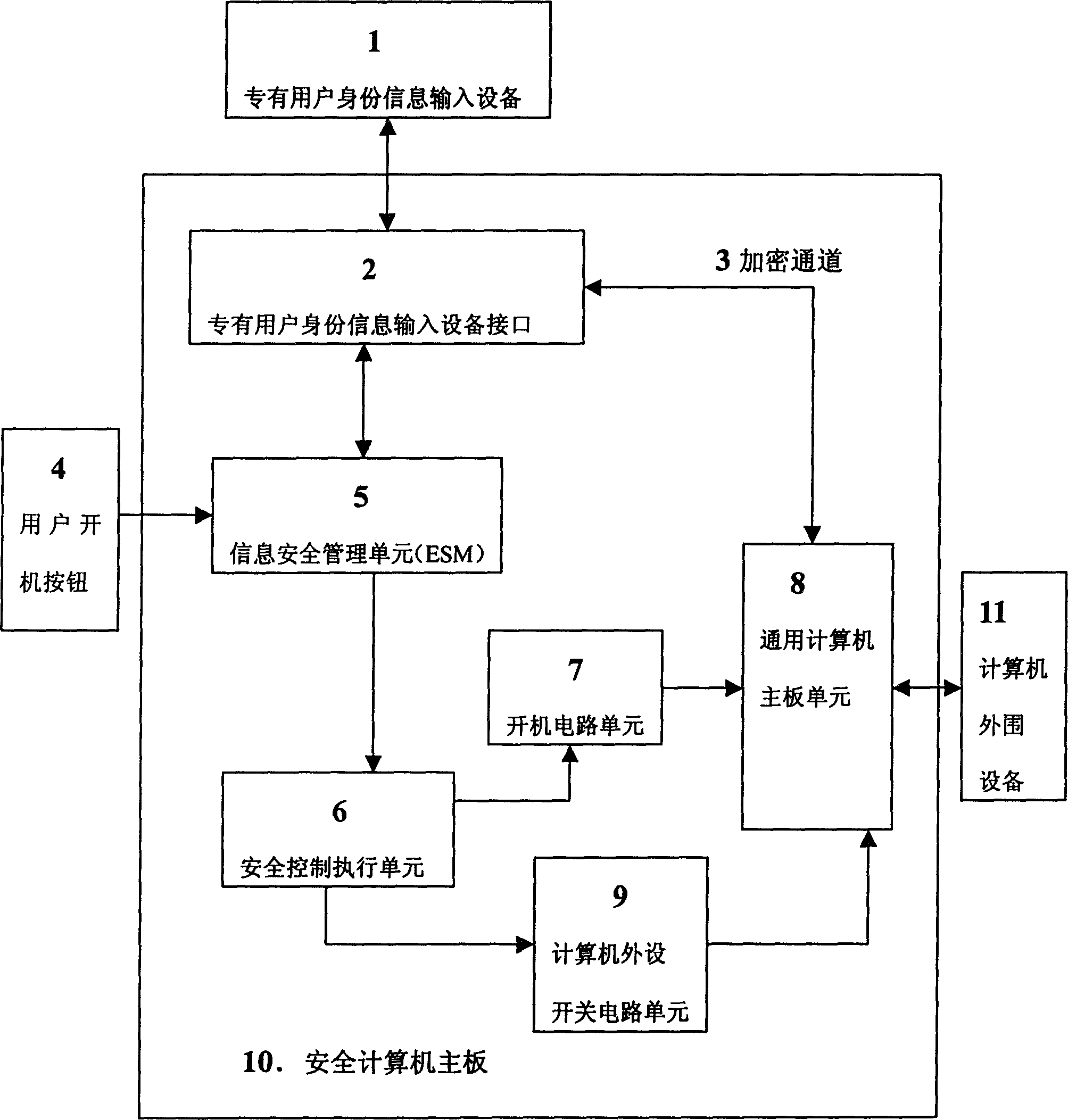
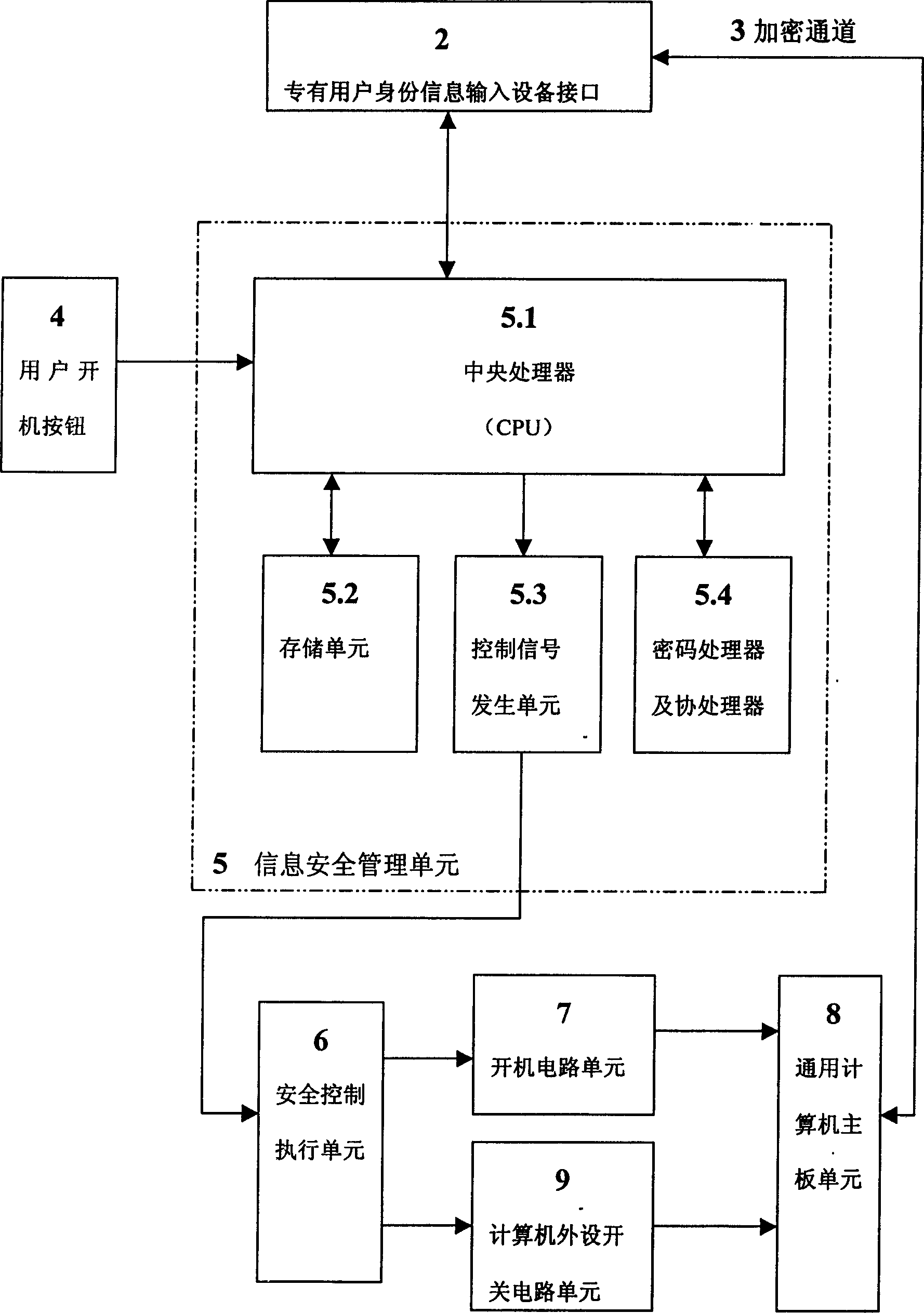
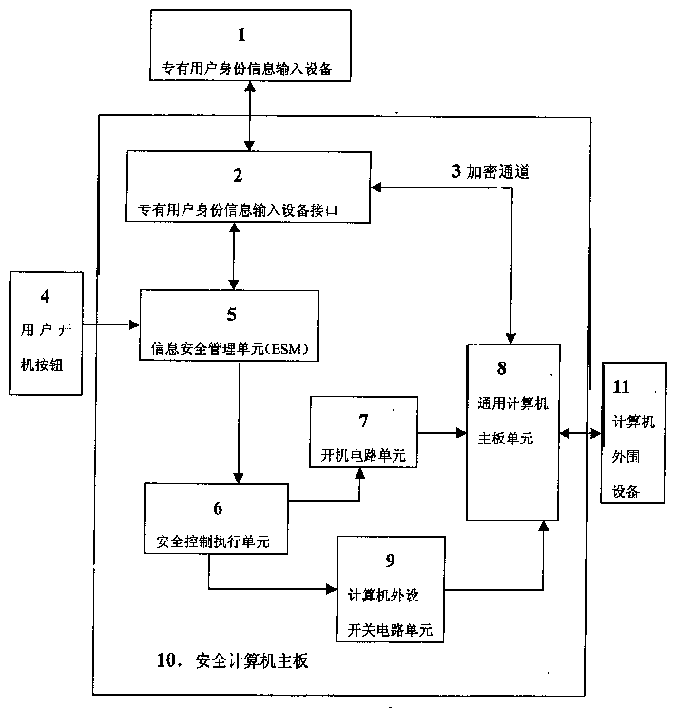
Safety computer with information safety management unit
InactiveCN1423203ASolving Information Security IssuesGuarantee information securityMemory loss protectionUnauthorized memory use protectionManagement unitInformation security
The safety computer comprises the device interface for inputting the identification information, the information safety management unit, the safety control execution element, the starting up circuit unit, the circuit unit for switching computer peripherals and the computer main board unit. The safety management unit in the safety computer can be prepared as the element of the safety module. The invention possesses the advantages of providing the functions of the self-checking and the validation. The management information is controlled from the botton layer of the hardware so as to solve the improve the issue of the safety and the protection of the computer information.
Owner:瑞达信息安全产业股份有限公司
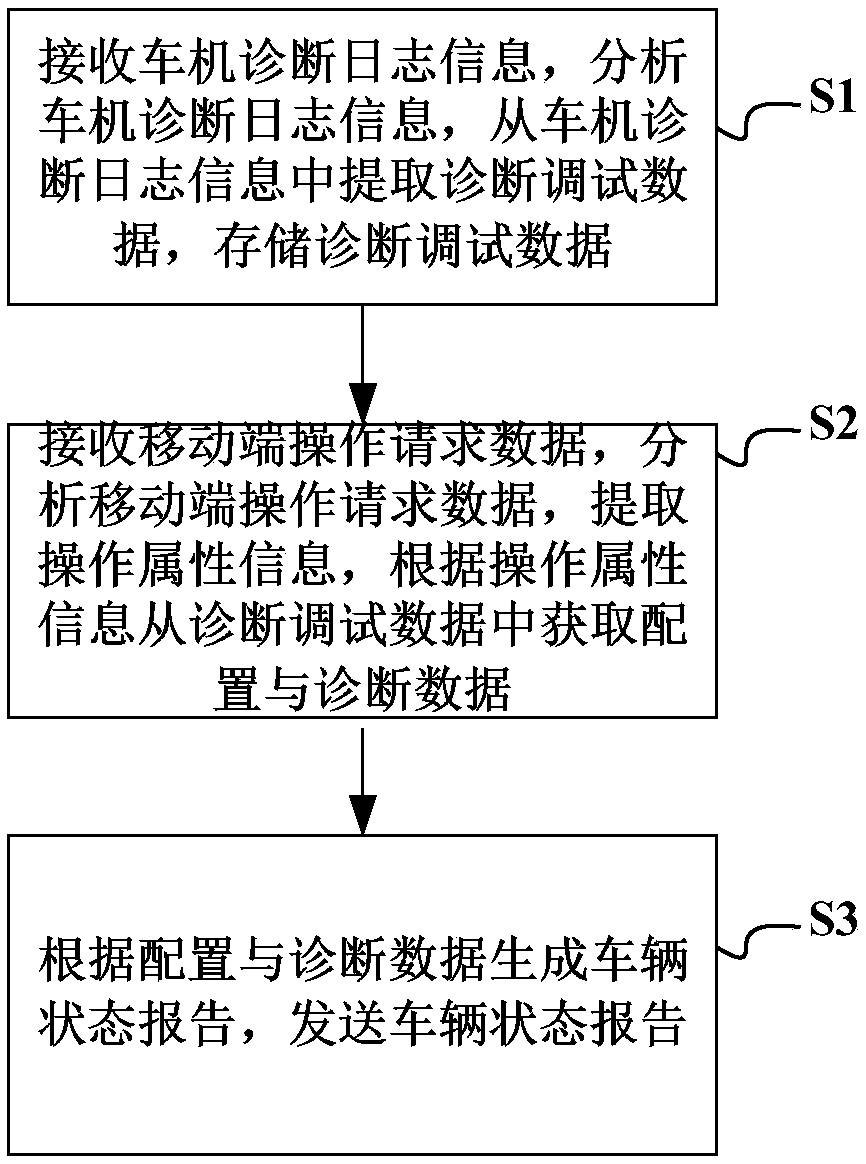
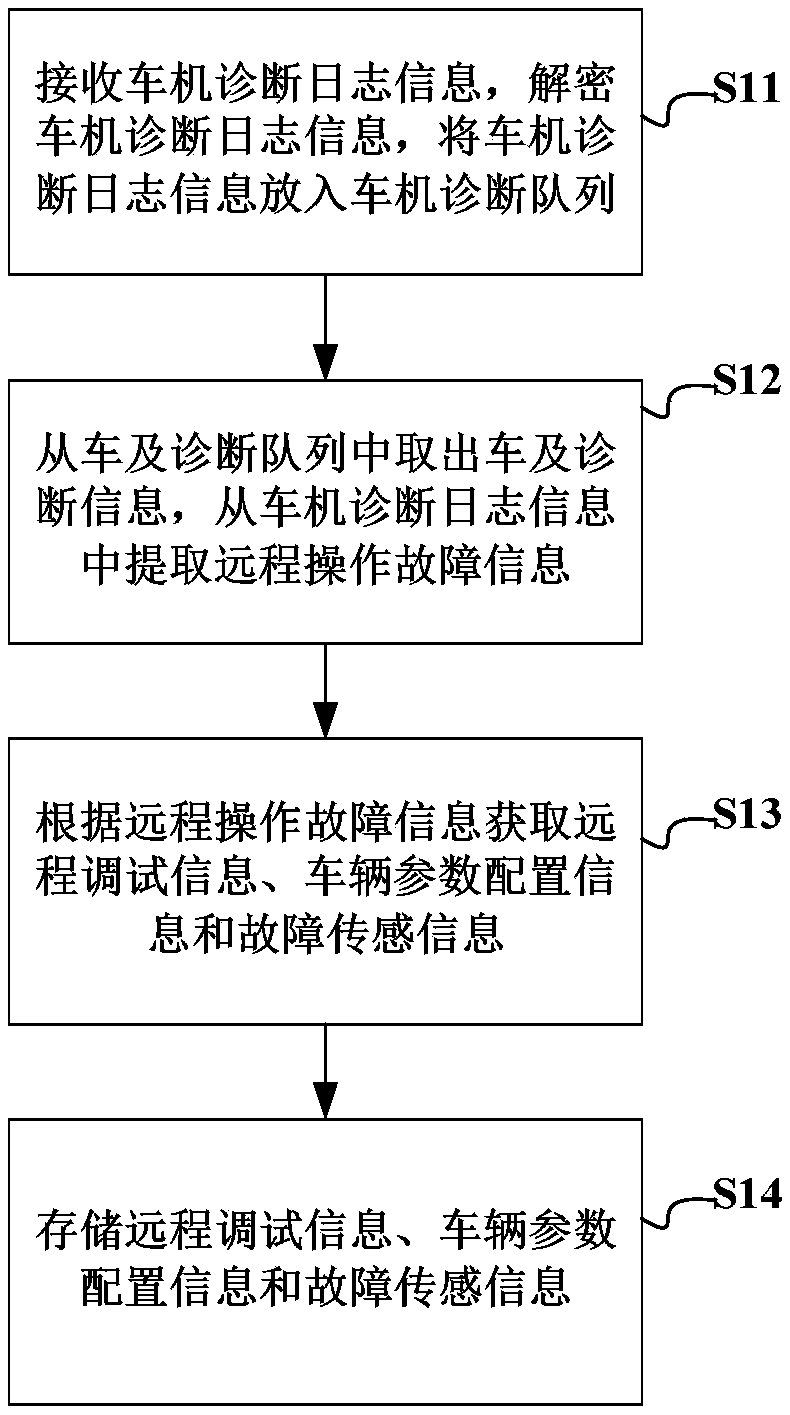
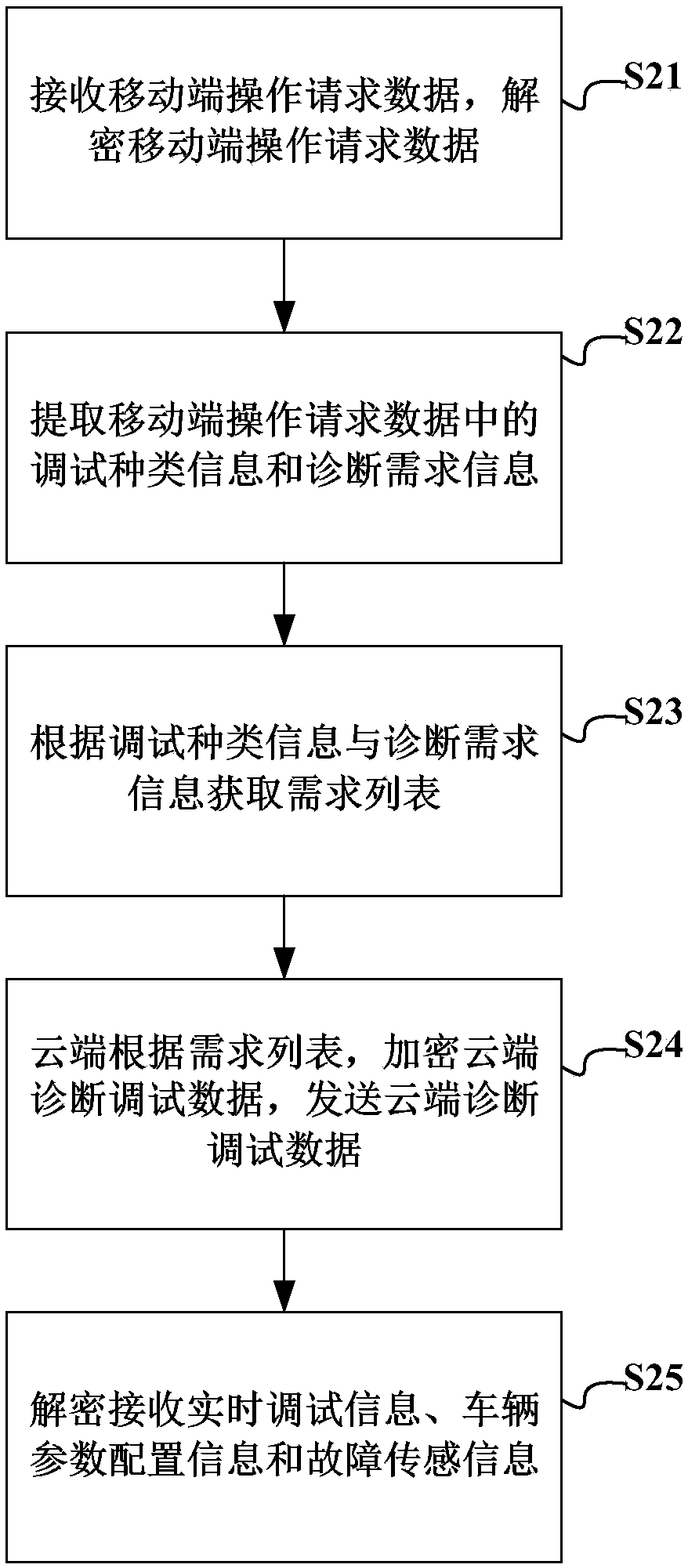
Cloud terminal-based vehicle remote diagnosis method, server end, vehicle end and client end
InactiveCN109240273AAvoid the problem of low efficiency of troubleshooting workReduce couplingElectric testing/monitoringDiagnostic dataCoupling
Disclosed are a cloud terminal-based vehicle remote diagnosis method, server end, vehicle end and client end. The vehicle remote diagnosis method comprises the steps that the diagnosis information ofa vehicle is received, the diagnosis information of the vehicle is analyzed, and diagnosis and debugging data are extracted from the diagnosis information of the vehicle, and the diagnosis and debugging data are stored; operation request data of a mobile terminal is received, the operation request data of the mobile terminal is analyzed, operation attribute information is extracted, and configuration and diagnosis data are obtained from the diagnosis and debugging data according to the operation attribute information; and a vehicle state report is generated according to the configuration and diagnosis data, and the vehicle state report is sent. By virtue of the vehicle remote diagnosis method, the technical problems of low expansibility of vehicle-mounted equipment caused by poor effect, low whole vehicle diagnosis operation efficiency, relatively low remote operation information safety, low diagnosis operation interactivity and over-high coupling degree of a diagnosis system, and relatively poor flexibility caused by single system architecture in the prior art are solved.
Owner:SHANGHAI PATEO INTERNET TECH SERVICE CO LTD
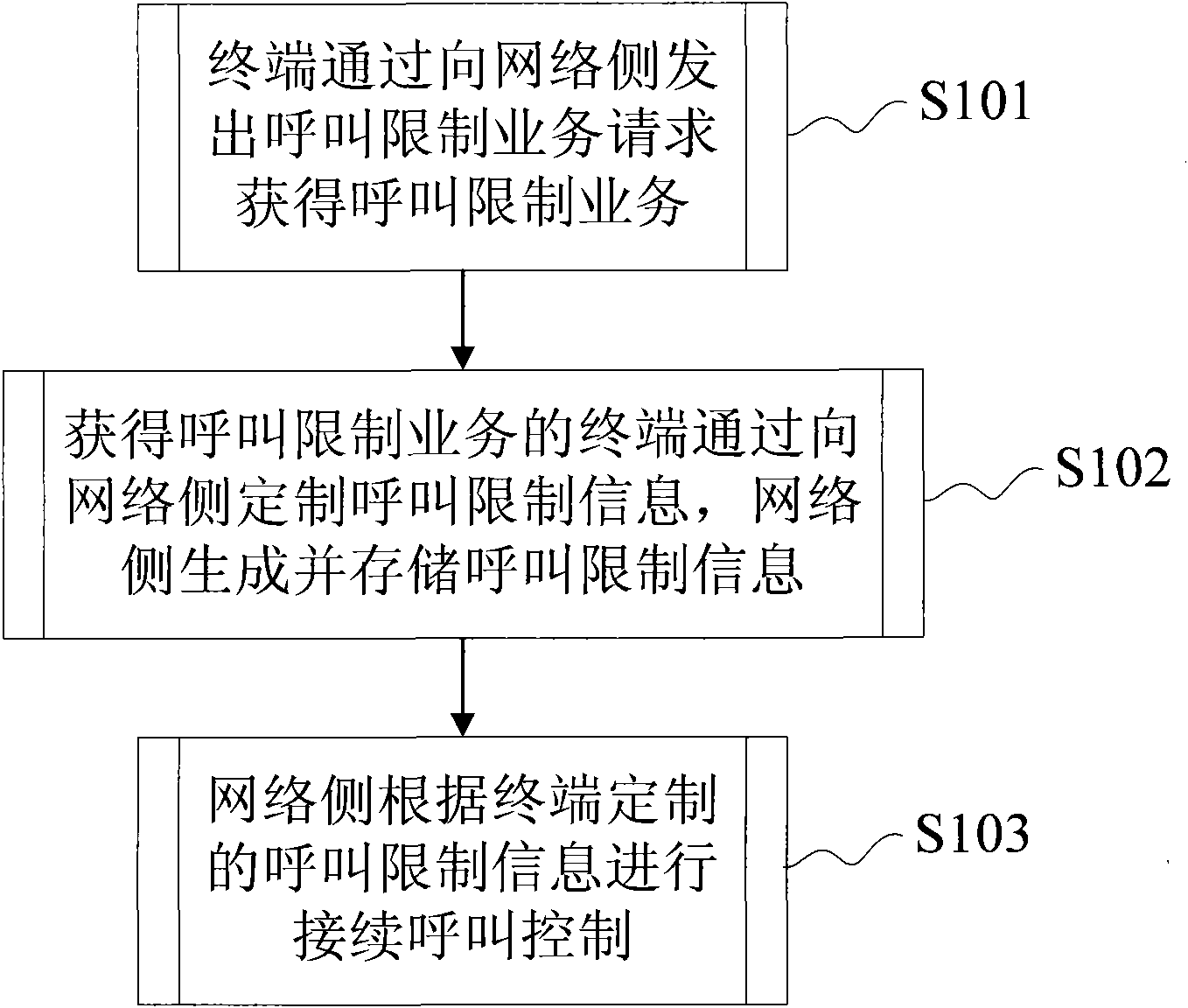
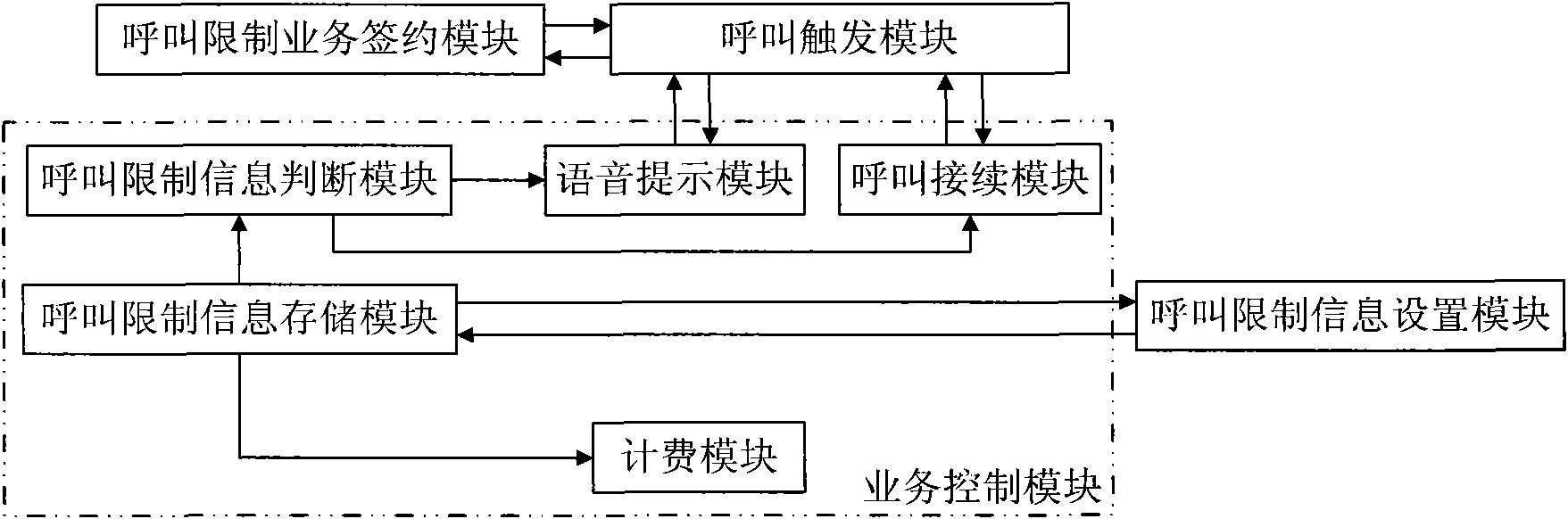
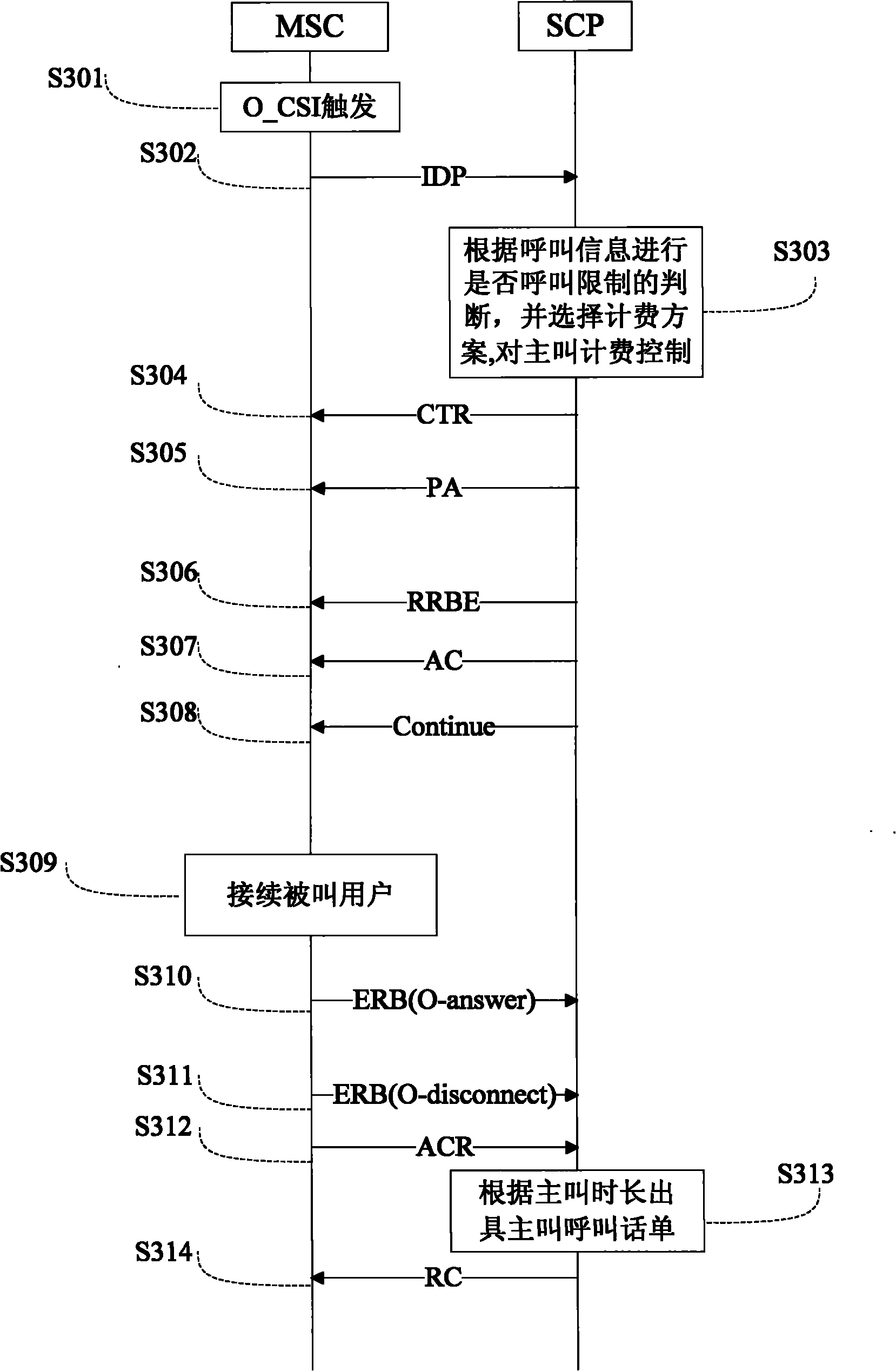
Implementation method and system of call restriction service
InactiveCN101938673ASolving Information Security IssuesAssess restrictionGraded-service arrangementsCall controlInformation security
The invention discloses implementation method and system of a call restriction service. The method comprises the following steps that: a terminal obtains the call restriction service through sending out a call restriction service request to a network side; the terminal obtaining the call restriction service customizes call restriction information to the network side, and the network side generates and stores call restriction information; and the network side carries out the continuous call control according to the call restriction information customized by the terminal. The invention solves the personal and unit information safety problems through carrying out the call restriction on the terminal.
Owner:ZTE CORP
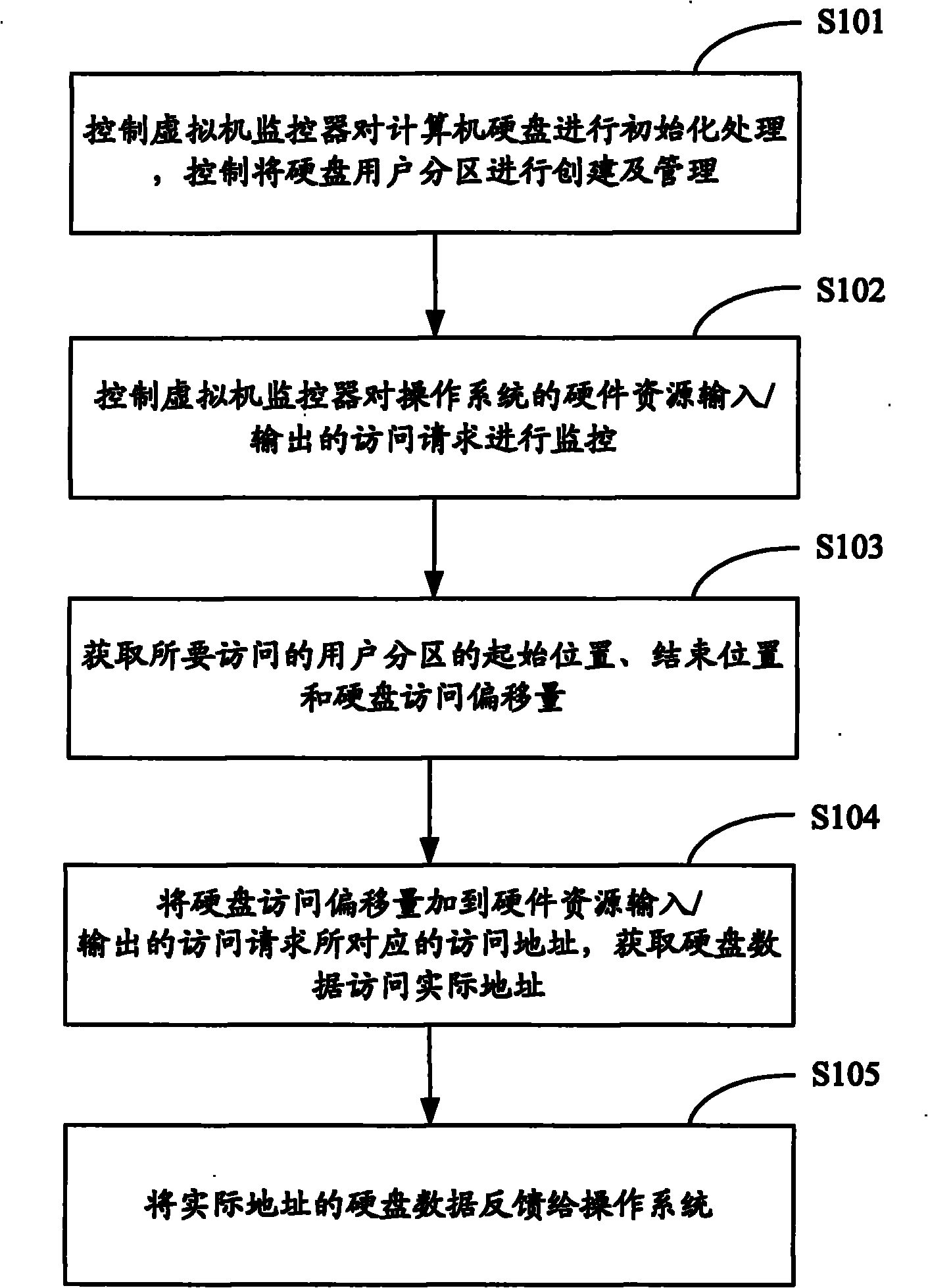
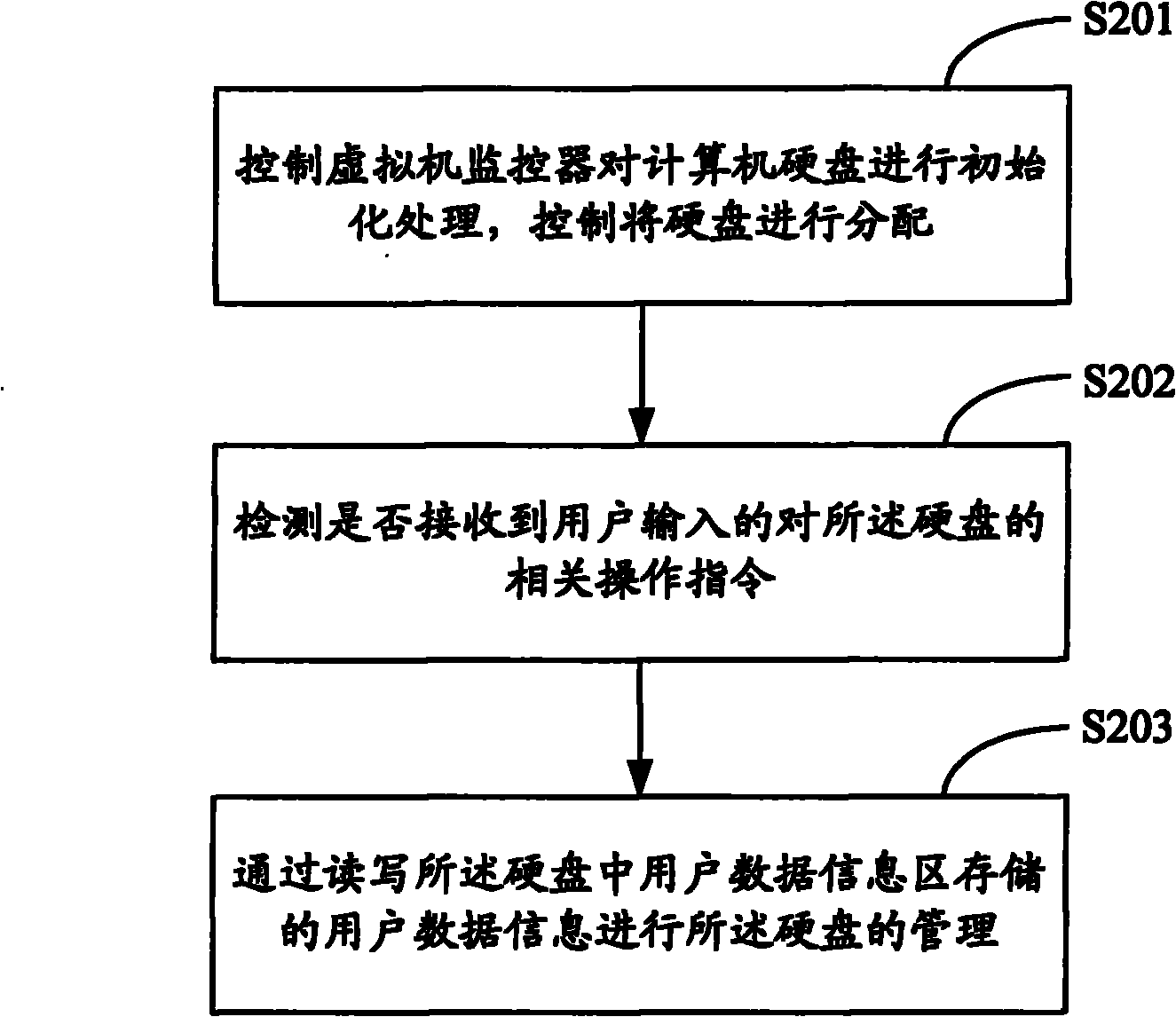
Access method and system for multi-user hard disk data
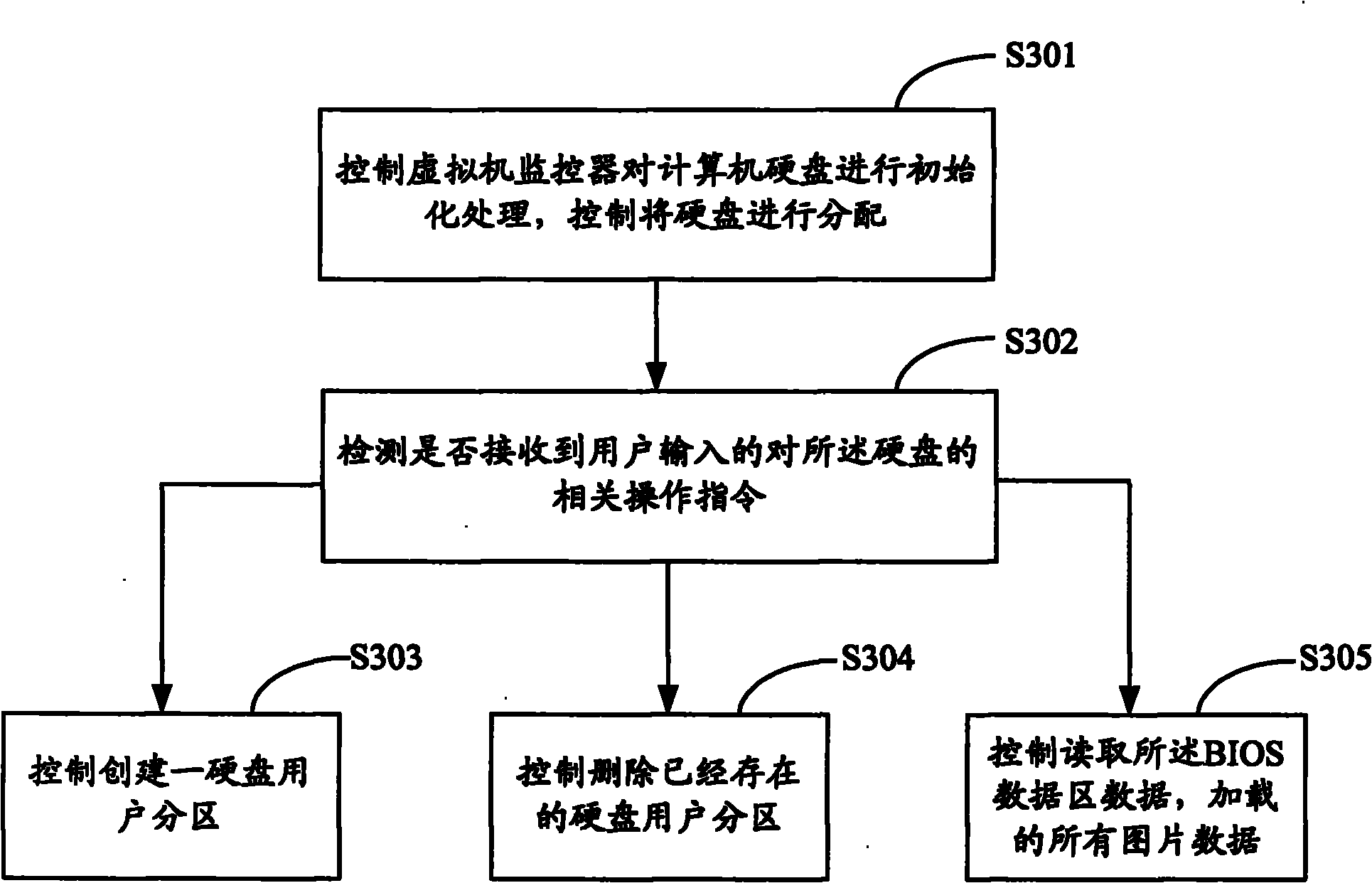
InactiveCN102110059AEasy to useCreate implementationUnauthorized memory use protectionHome positionVirtual machine
The invention is applied in the technical field of computers, and provides an access method and an access system for multi-user hard disk data. The method comprises the following steps of: controlling a virtual machine monitor to initialize a computer hard disk, and controlling creation and management of a hard disk user subarea; controlling the virtual machine monitor to monitor the access request of hardware resource input / output of an operating system; when the input / output access request is monitored, acquiring an initial position and an end position of the accessed user subarea and hard disk access offset; adding the hard disk access offset to an access address corresponding to the access request of the hardware resource input / output of the operating system to acquire an actual address of hard disk data access; and feeding back the hard disk data of the actual address to the operating system. Creation and management of the hard disk multi-user subarea and data access are realized, the data in the hard disk subarea are mutually isolated, the use of users is convenient, and the security of the system can be effectively ensured by offsetting the address on the physical hard disk.
Owner:CHINA GREATWALL TECH GRP CO LTD
Smart socket management system and method based on distributed general account technology
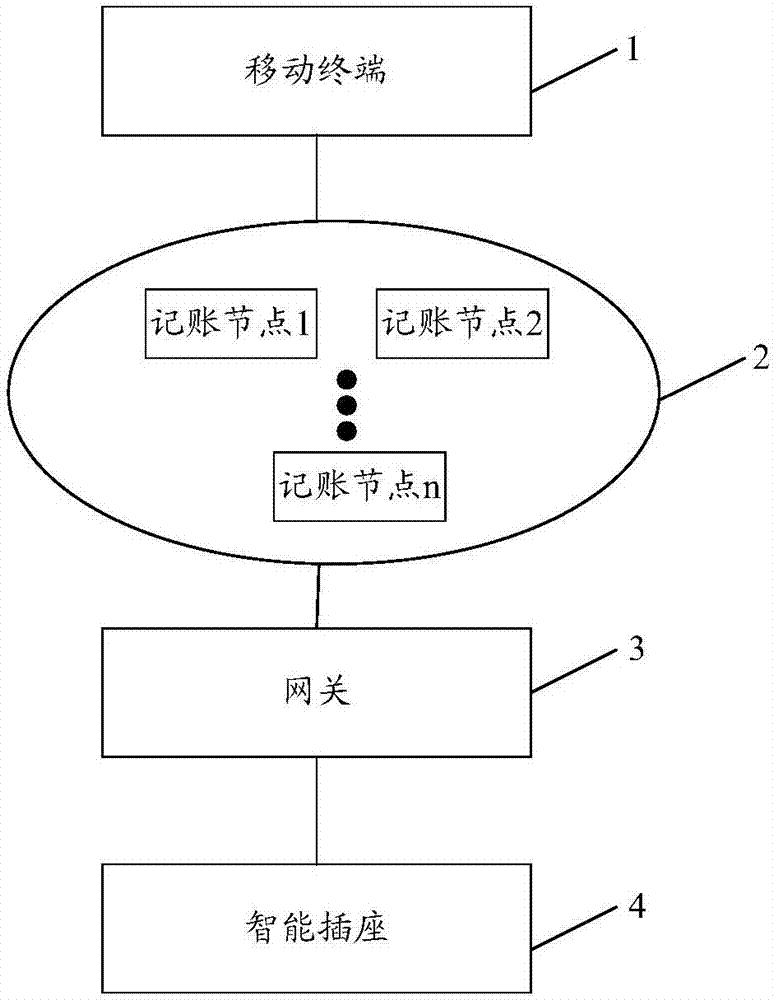
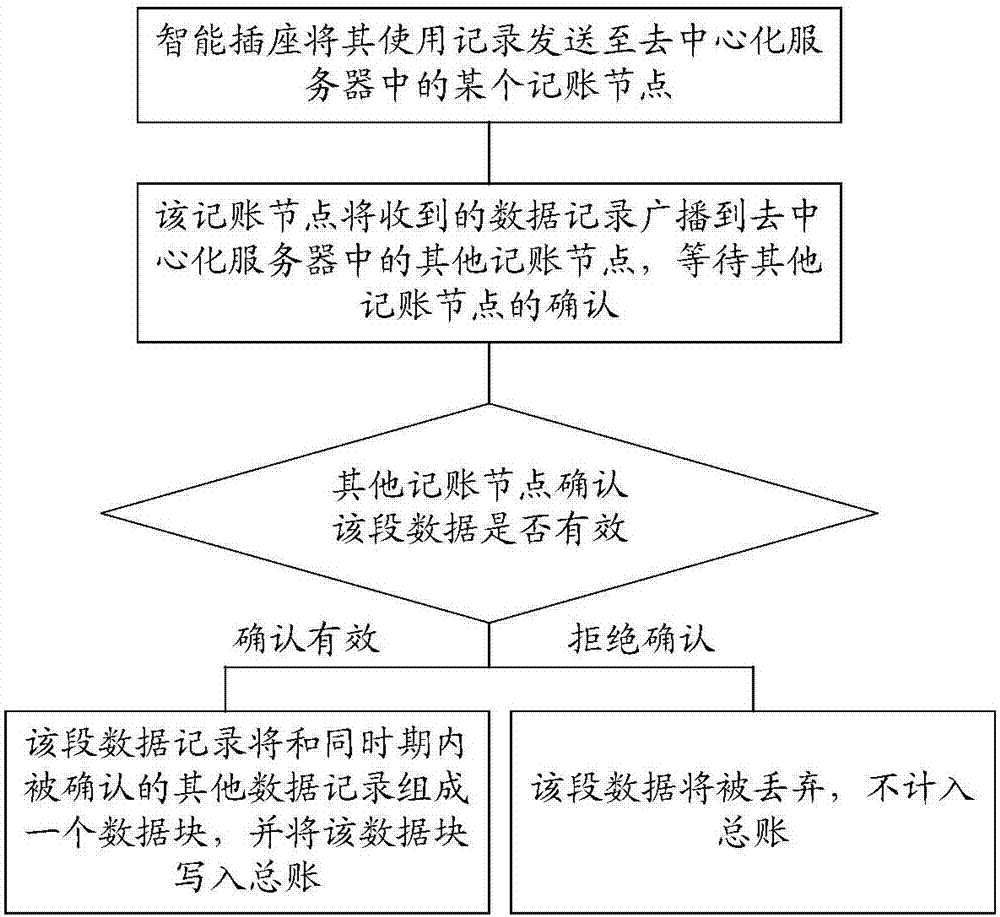
InactiveCN106960166ASolving Information Security IssuesDigital data protectionTransmissionComputer terminalInformation security
The invention discloses a smart socket management system and method based on a distributed general account technology, relates to the technical field of a socket and is used for solving the information security problem in the field of smart socket management. The smart socket management system comprises a mobile terminal, a decentration server, a gateway and the smart socket which are connected in sequence. The decentration server is composed of a plurality of accounting nodes. Each accounting node stores complete general account. All socket utilization records are recorded in the general account. The system and the method are used for ensuring the data completeness and authenticity of the smart socket.
Owner:TSINGHUA UNIV
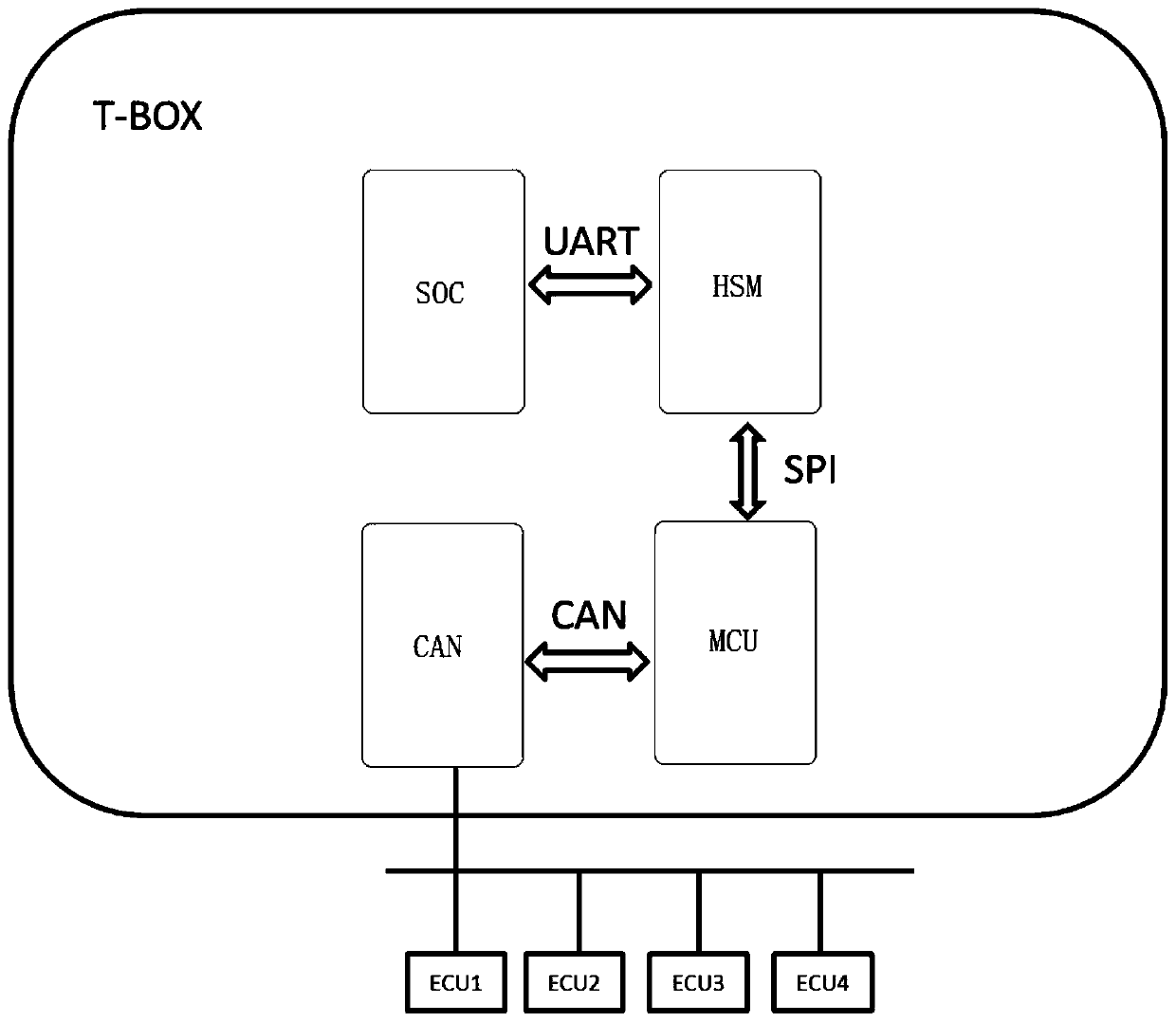
A T-BOX encryption system and method
InactiveCN109743334ASolving Information Security IssuesBus networksComputer hardwareInformation security
The invention discloses a T-BOX encryption system and method. the SOC, the HSM, the MCU and the CAN transceiver form the T-BOX body. a CAN transceiver is used for receiving a CAN network signal of thewhole vehicle and transmitting the signal to the MCU through a CAN network; The MCU encrypts the received network signal through a built-in security suite pair and then transmits the encrypted network signal to the HSM; the HSM is used for carrying out encryption operation on the obtained encrypted signal and then transmitting the encrypted signal to the SOC; And the SOC transmits the signal tothe security operation and maintenance platform through the established security encryption channel. a hardware encryption technology is introduced, a software encryption technology is fused, and theproblem of T-is solved; And the information security problem in the BOX is solved.
Owner:ZOTYE INT AUTOMOBILE TRADING CO LTD
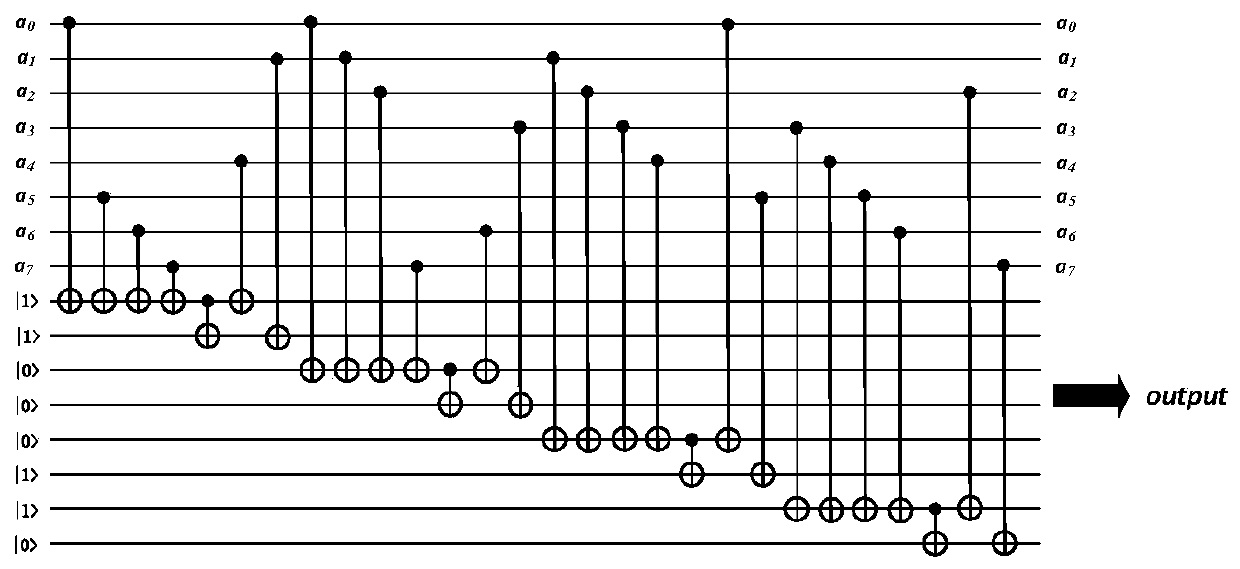
AES hardware encryption system implementation method based on quantum reversible circuit
ActiveCN110120867AGood encryptionShorten the timeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInformation securityMulti interface
The invention provides a realization method of an AES hardware encryption system based on a quantum reversible circuit, and belongs to the technical field of information security. According to the technical scheme, the AES hardware encryption system based on the quantum reversible circuit comprises a quantum reversible circuit encryption and decryption module, a quantum secret key expansion moduleand a multi-interface selection module; the realization method comprises the following steps: realizing hardware setting of the quantum reversible line encryption and decryption module, finishing hardware setting of the quantum secret key expansion module, and setting the multi-interface selection module by adopting an electronic circuit. The method has the beneficial effects that the quantum reversible line-based encryption and decryption module and the quantum secret key expansion module are combined according to algorithm rules to construct the quantum reversible line-based encryption system, and the encryption complexity is (2n-1) times that of a traditional method; in addition, the multi-interface selection module can be connected with devices with various interfaces, and encryptionand decryption operation on various forms of information is completed.
Owner:NANTONG UNIVERSITY
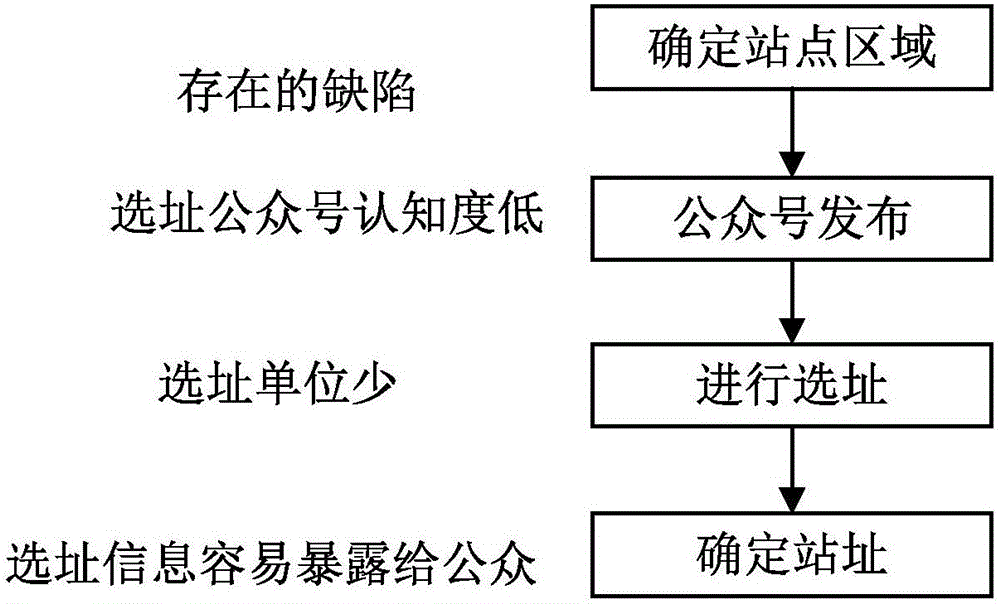
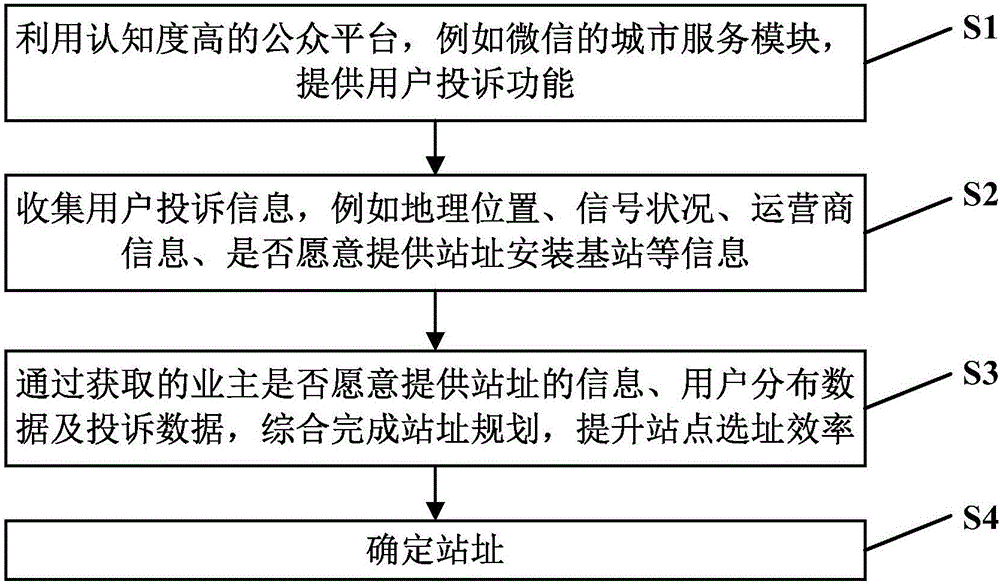
Internet communication base station site selection method and system based on customer complaining
InactiveCN106686610ASolve the difficulty of site selectionAdded complaint processNetwork planningInternet communicationCognition
The invention discloses an internet communication base station site selection method and system based on customer complaining, and relates to the field of communication base station site selection. The method comprises the following steps that 1, a customer complaining function is provided by utilizing a public platform with the high cognition degree; 2, customer complaining information is collected; 3, site selection planning is comprehensively completed according to acquired information whether owners are willing to provide a station site or not, customer distribution data and complaining data, and the station site selection efficiency is improved; 4, the station site is determined. According to the method and system, disputes can be effectively avoided.
Owner:WUHAN FIBERHOME TECHNICAL SERVICES CO LTD
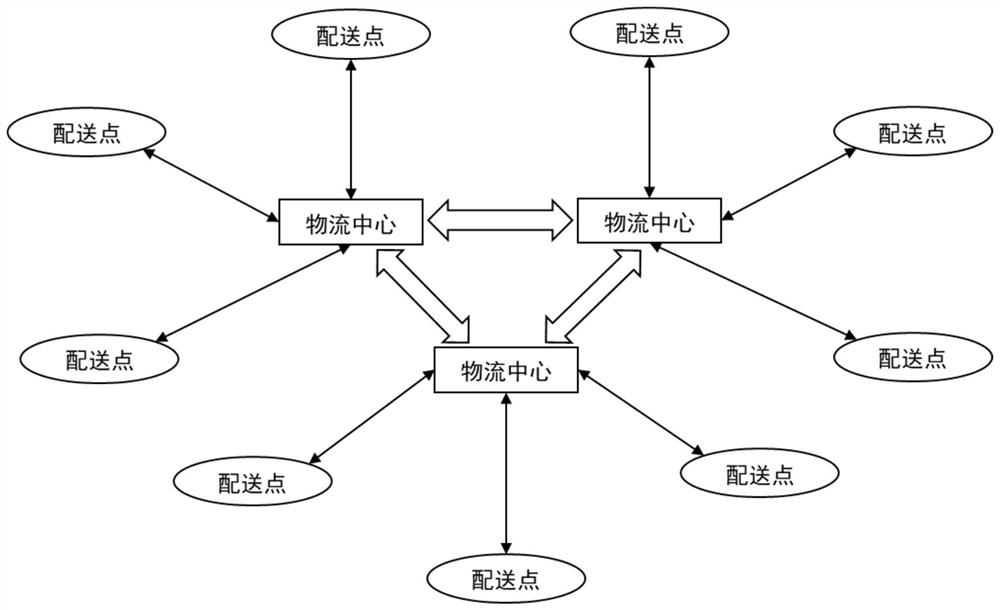
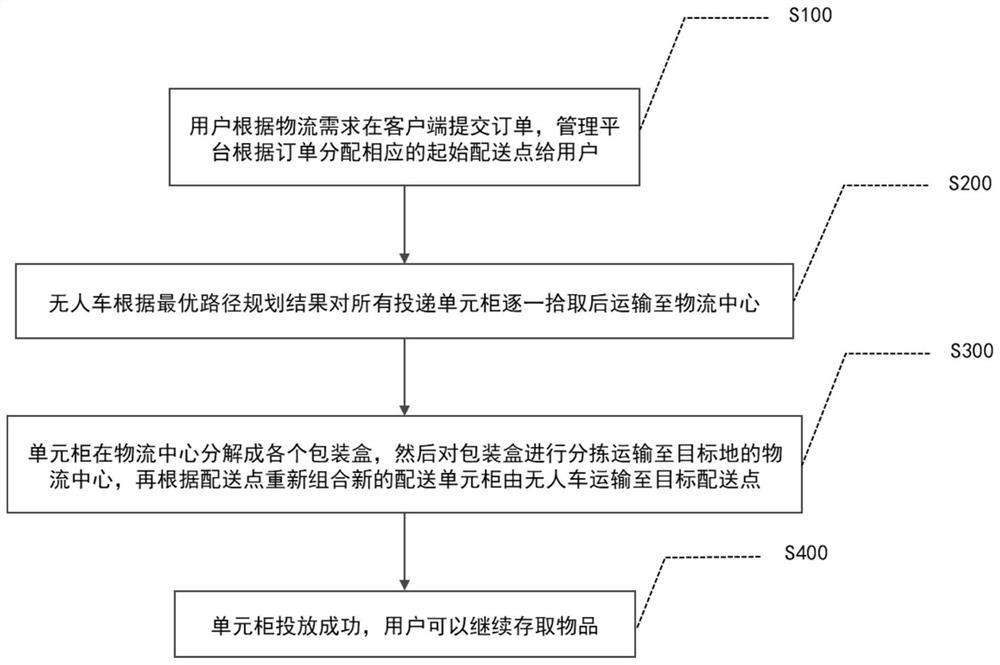
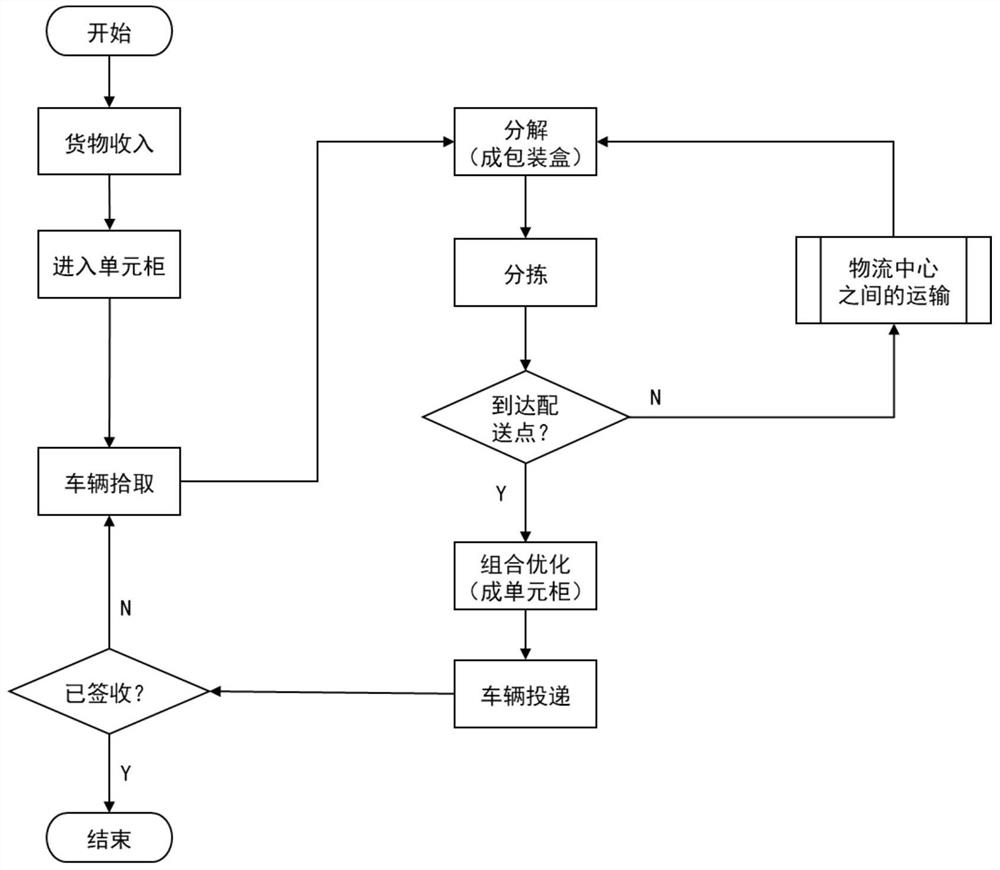
Green and environment-friendly intelligent logistics unmanned distribution method
ActiveCN113112199AImprove experienceImprove the level of management and schedulingForecastingBuying/selling/leasing transactionsTime informationLogistics management
The invention discloses a green and environment-friendly intelligent logistics unmanned distribution method, which comprises the following steps: S100, a user submits an order at a client according to a logistics demand, and a management platform allocates a corresponding initial delivery point to the user according to the order; S200, an unmanned vehicle picks up all the delivery unit cabinets one by one according to the optimal path planning result and then transports the delivery unit cabinets to a logistics center; s300, the unit cabinets are decomposed into packaging boxes in the logistics center, then the packaging boxes are sorted and transported to the logistics center of the destination, new distribution unit cabinets are recombined according to the distribution points, and the new distribution unit cabinets are transported to the target distribution points through the unmanned vehicle; and S400, if the unit cabinets are successfully put, the user can continuously store and take the articles. According to the invention, intelligent logistics modes such as real-time information, path optimization, unmanned vehicle distribution and the like can be adopted for peripheral logistics, so that the labor cost can be effectively saved, the logistics operation efficiency is improved, and the green transformation of express packaging is promoted.
Owner:HEFEI UNIV OF TECH
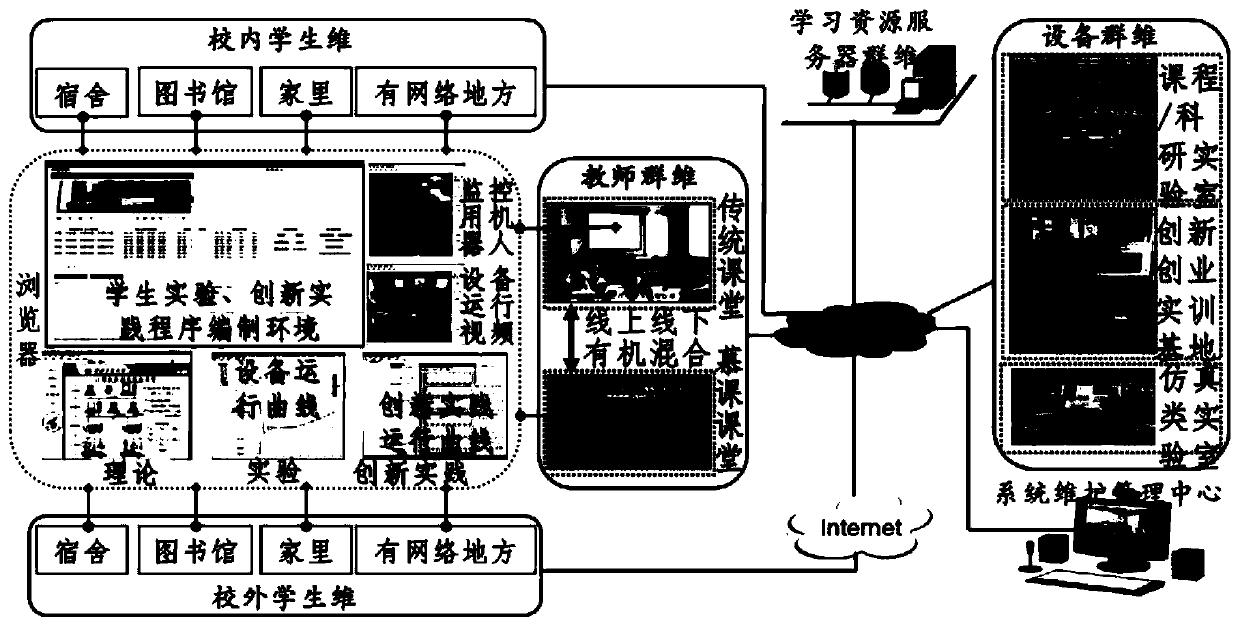
Novel hybrid learning environment teaching platform
InactiveCN110211009AImprove teaching efficiencySolve the random delay problemData processing applicationsTransmissionInterconnectionTraditional classroom
The invention discloses a novel hybrid learning environment teaching platform, relating to the technical field of teaching platforms. The platform comprises an equipment group and a server group whichare both installed in a traditional classroom. Teachers and students are in communication connection with the server group through network equipment, and the traditional classroom and a MOOC classroom jointly carry out teaching and learning resource information interaction through the server group. A set of synchronous teaching platform integrating theories, experiments and innovative practices is established by utilizing a communication interconnection function of a campus network. The four-dimensional integration three-class fusion integrated college classroom teaching function which integrates three teaching links of theories, experiments and innovative practices is achieved. Through a unified browser interface of the platform, a teacher can start experiment and innovative practice equipment of a remote laboratory in a classroom through a campus network, integrated synchronization of three teaching links is achieved, and students can complete three key links of teaching in the classroom on the same interface at the same time.
Owner:南京玖玖教育科技有限公司
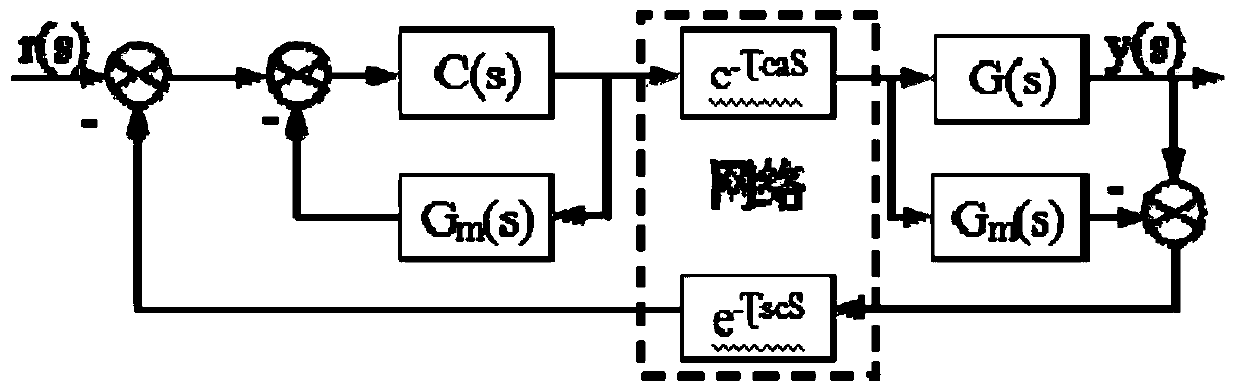
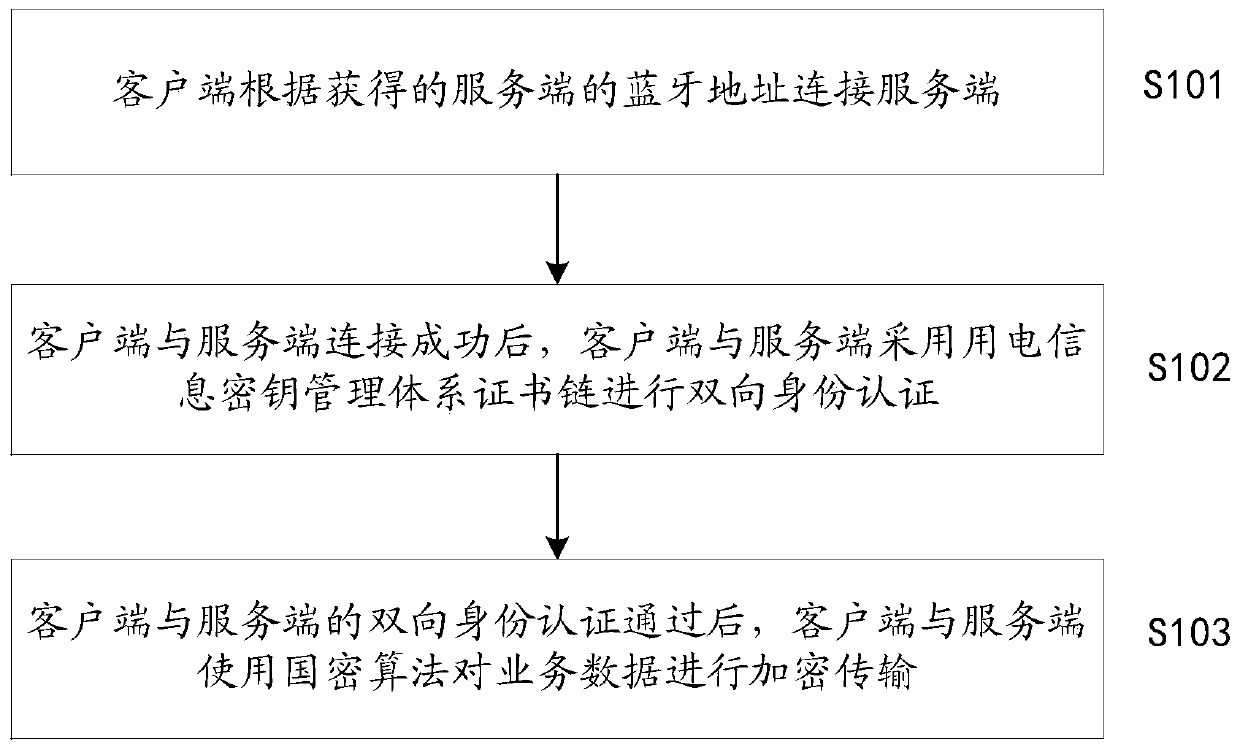
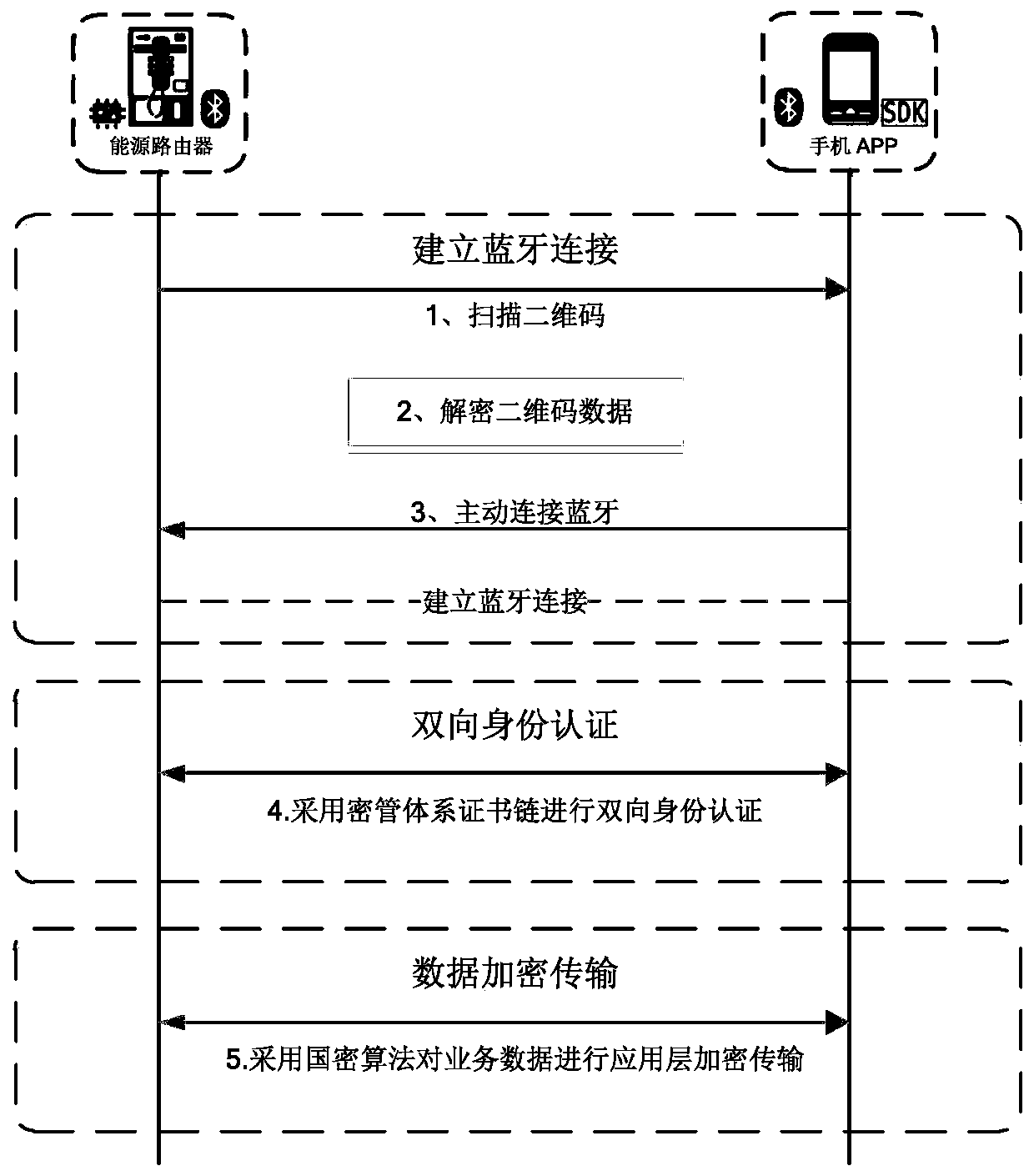
Bluetooth communication safety protection method for electric power marketing major
InactiveCN110691359ASolving Information Security IssuesShort range communication serviceSecurity arrangementTelecommunicationsInformation security
The invention discloses a Bluetooth communication security protection method for an electric power marketing major. The method comprises the steps that a client is connected with a server according toan obtained Bluetooth address of the server; after the client is successfully connected with the server, the client and the server perform bidirectional identity authentication by adopting a certificate chain of a power utilization information key management system; and after the bidirectional identity authentication of the client and the server is passed, the client and the server encrypt and transmit the service data by using a national cryptographic algorithm, so that the information security problem of Bluetooth data communication in the field of power marketing is solved.
Owner:CHINA ELECTRIC POWER RES INST +1
Cross-network area service calling method and system
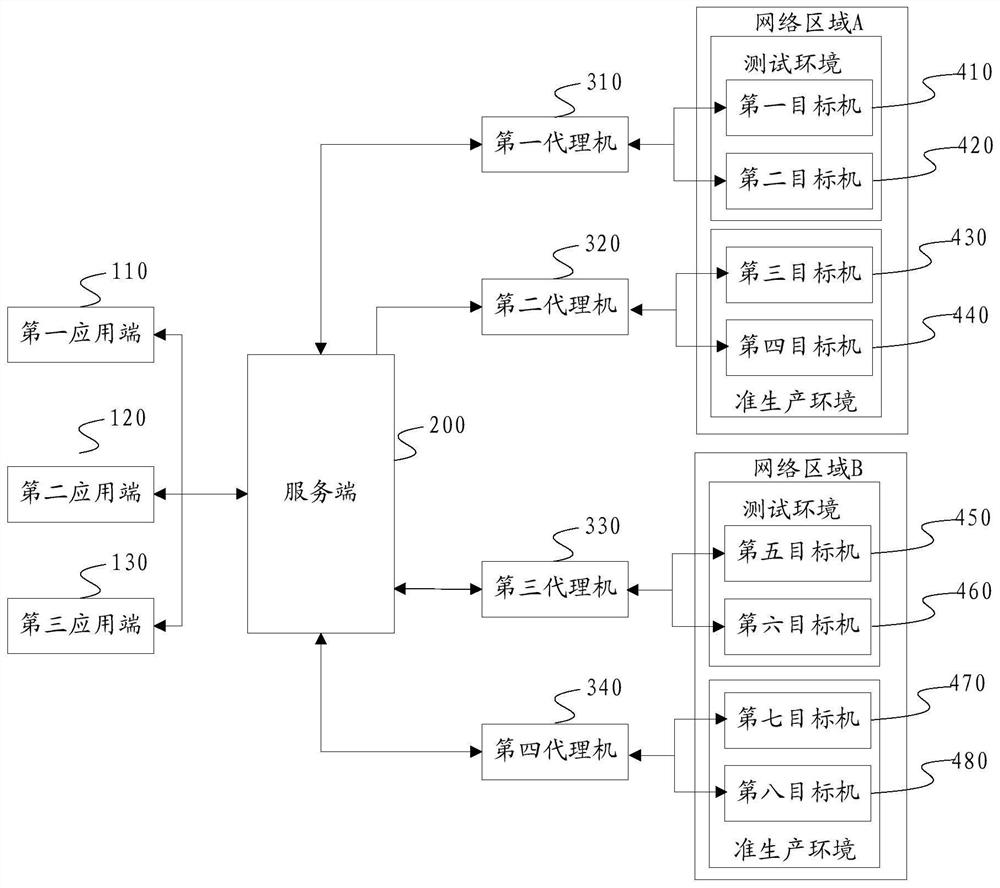
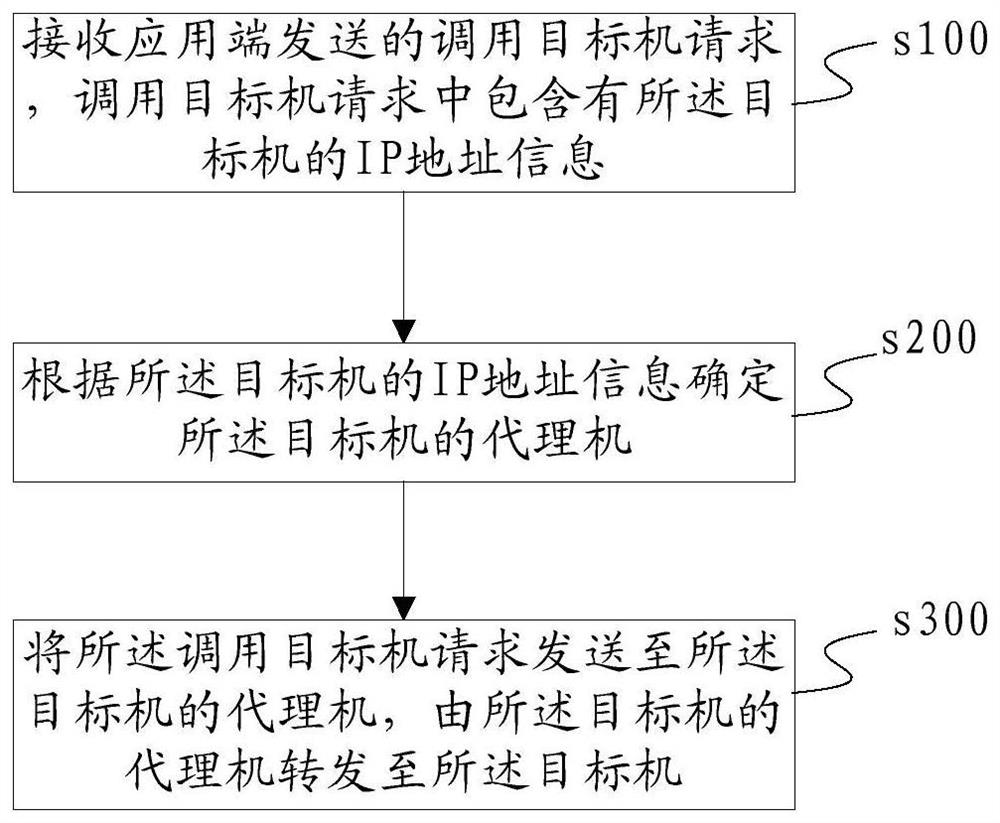
The invention discloses a cross-network area service calling method and system. The method comprises the following steps: receiving a target machine calling request sent by an application end, whereinthe target machine calling request comprises the IP address information of a target machine; determining an agent machine of the target machine according to the IP address information of the target machine, wherein the agent machine is kept open with a firewall between the white list and the corresponding application end; sending the request for calling the target machine to an agent machine of the target machine, forwarding the request to the target machine by the agent machine of the target machine, and correspondingly deploying one agent machine for the target machine in each application environment in each network area. According to the method disclosed in the application, the load of firewall equipment is reduced, firewall opening work is simplified, and an error rate in firewall opening is reduced; meanwhile, direct cross-region transmission communication between the terminal and the background is prevented, a task execution failure rate is reduced, and data capture efficiency is improved.
Owner:SF TECH
Method for realizing connection service
InactiveCN1859243ARealize the establishmentClear logical hierarchyData switching by path configurationService implementationUsability
The present invention relates to a connection service implementation method between end-to-end net element in automatic exchange optical network. It contains originating connection service request from source end to sink end; determining supporting said connection service source end net element to sink end net element end to end logical connection; determining supporting said source net element to sink end net element end to end logical connection plurality of connection section; establishing every connection section connection to complete end to end logical connection establishment, realizing required connection service. The present invention can raise network usability, enhancing network security in network gone wrong.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
An industrial control signal detection system and detection method
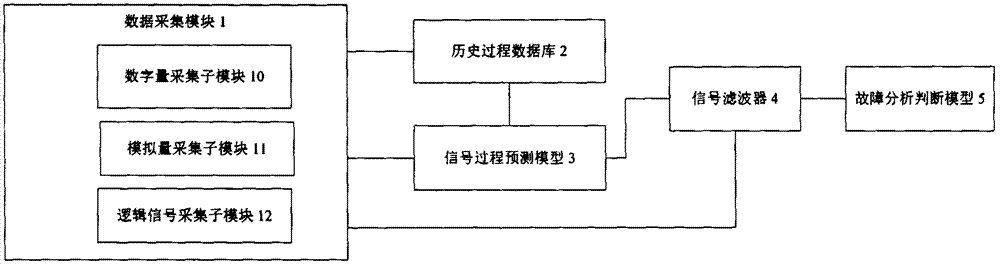
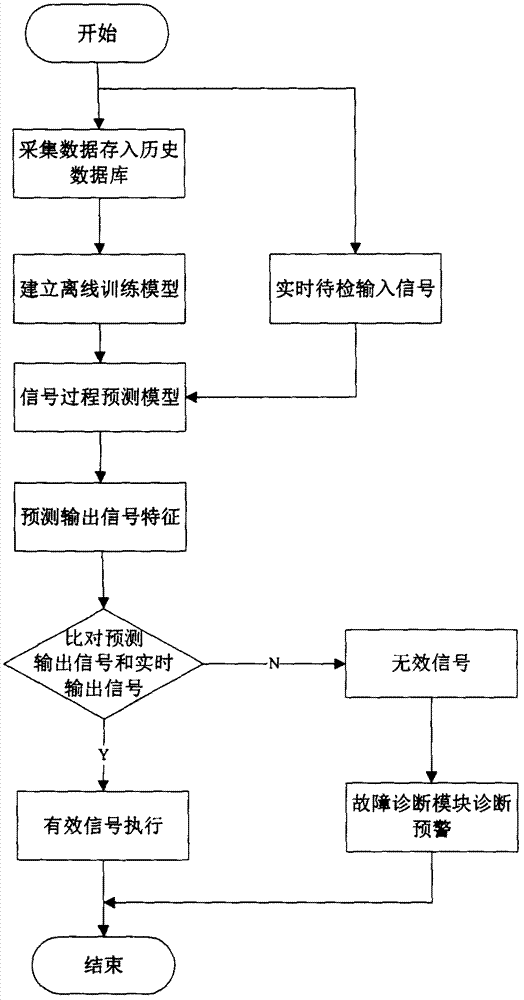
ActiveCN104615122BSolving Information Security IssuesFix security issuesElectric testing/monitoringControl signalComputer module
The invention discloses an industrial control signal detection system and a detection method; the detection system comprises a data collecting module which collects real-time status data of equipment electrical features, and a historical process database which is connected with the data collecting module and used for storing the real-time status data collected by the data collecting module; the detection system further comprises a signal process predicating model which is connected with the historical process database and establishes correspondence between signal input and output in the electrical features based on the data inside the historical process database; the signal process predicating model obtains a predicated output signal based on the real-time input signal collected by the data collecting module, and sends the predicated output signal to a signal filter; the signal filter receivers the predicated output signal from the signal process predicating model and the real-time output signal collected by the data collecting module, and compares the signals, if the feature of the corresponding real-time output signal accords with the feature of the predicated output signal, then the real-time output signal is judged to be an effective executable signal; otherwise, the real-time output signal is judged to be a negative non-executable signal.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Mobile phone terminal APP identity authentication method
ActiveCN111641718AEnsure safetyLow costDigital data authenticationTransmissionInternet privacyPassword
The invention relates to the field of information security, in particular to a mobile phone APP identity authentication method. The method comprises the following steps: when a user needs to perform authentication operation by using a mobile phone APP; the local data read by the APP is read and checked; the probability of operation of the user is calculated; therefore, the information security canbe ensured; the cost generated by calling face recognition is reduced; easy management is realized, according to the invention, all operations can be carried out after a user inputs a login account and a login password in the use of the existing mobile phone APP; after a login account and a login password of a user are leaked, no corresponding secondary identity authentication means is availableduring operation needing to be authenticated, so that the information security problem is caused, and meanwhile, when the operation needing to be authenticated is carried out each time, more expensesare generated due to the fact that identity authentication is carried out by calling face recognition.
Owner:北京弘远博学科技有限公司
The invention discloses a WEB-based method for realizing timed startup and shutdown of a mobile phone
InactiveCN109756617ASolving Information Security IssuesPrevention of crimeSubstation equipmentBroadcastingComputer science
The invention relates to a WEB-based method for realizing timed startup and shutdown of a mobile phone, which comprises the following steps of: adding an interface in a setting program of the mobile phone, so that a user can call the interface at a WEB end to carry out automatic startup and shutdown setting of the mobile phone; The interface setting mode is as follows: a broadcast receiving moduleis defined to receive a custom instruction of automatically turning off a power supply and a custom instruction of automatically turning on the power supply; Defining a service for processing an'automatic power-off 'instruction, and when the broadcast receiving module receives the'automatic power-off' instruction, giving a chance to a user to cancel the current automatic power-off; Displaying a dialogue, prompting a user to automatically shut down, using a timer to count down, shutting down when the user confirms shutdown or the time of the timer is up, otherwise, canceling the current shutdown, and resetting the next automatic shutdown clock.
Owner:CHINA CHANGFENG SCI TECH IND GROUPCORP
Safe network terminal based on single CPU dual bus
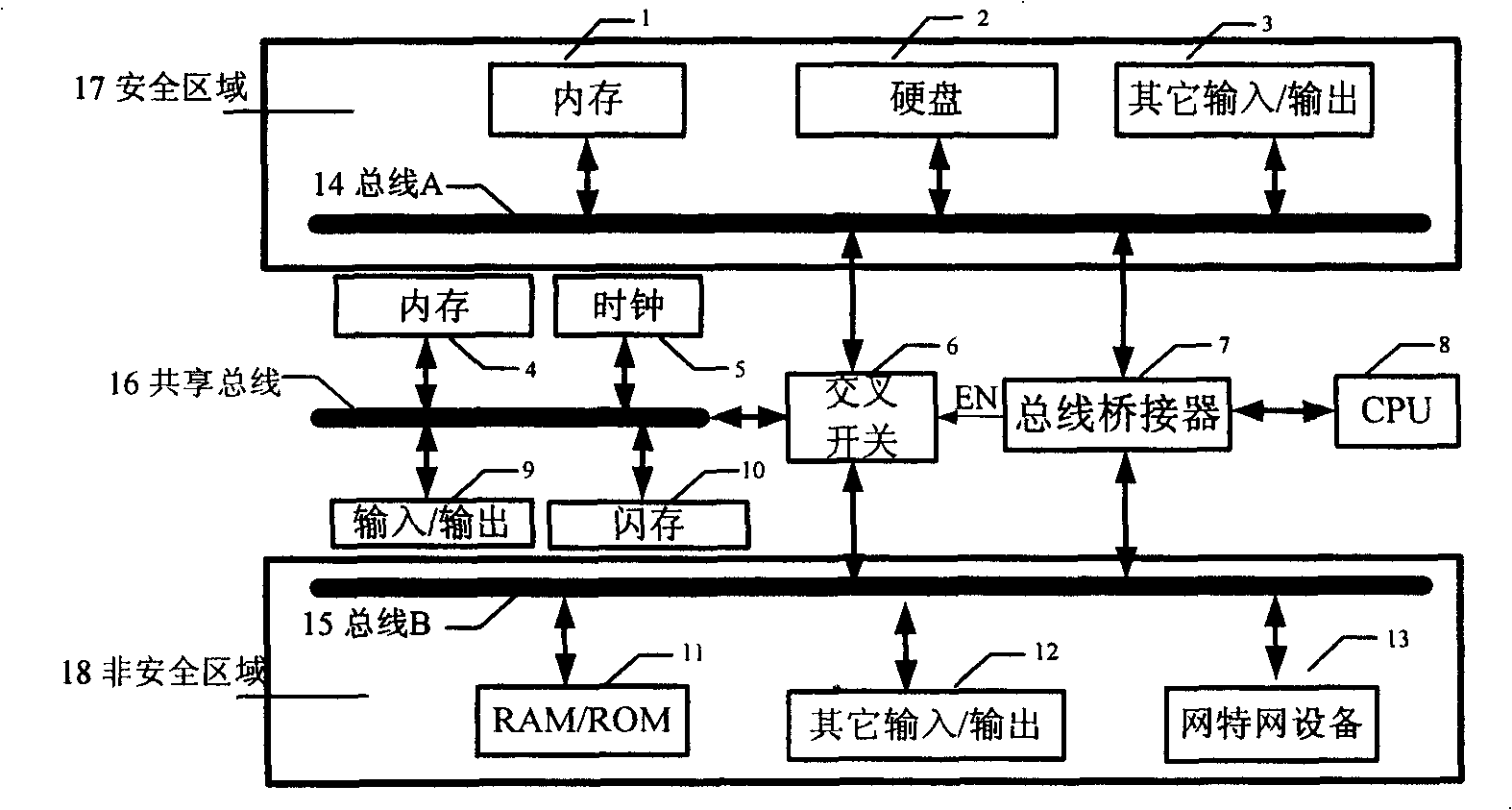
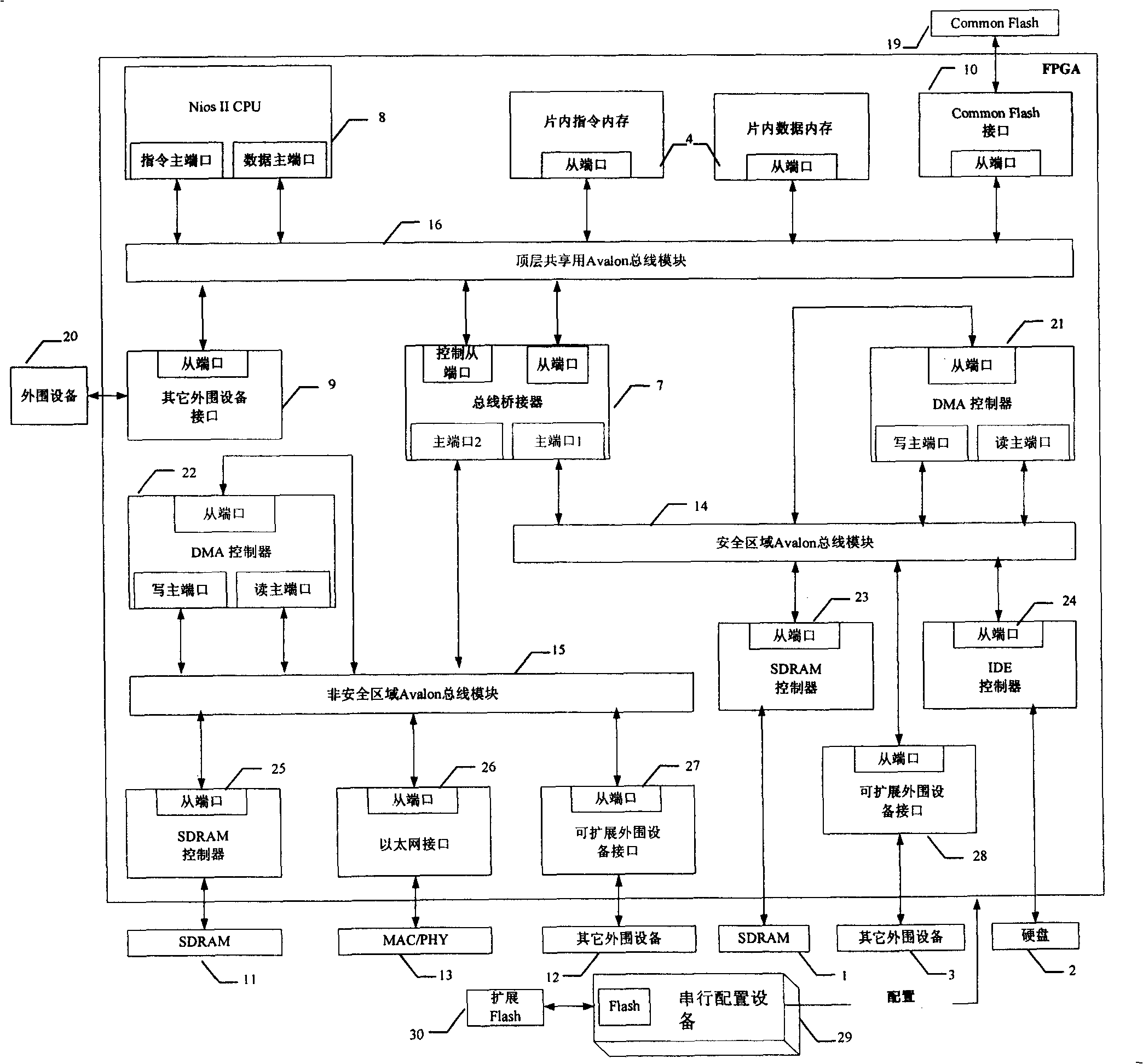
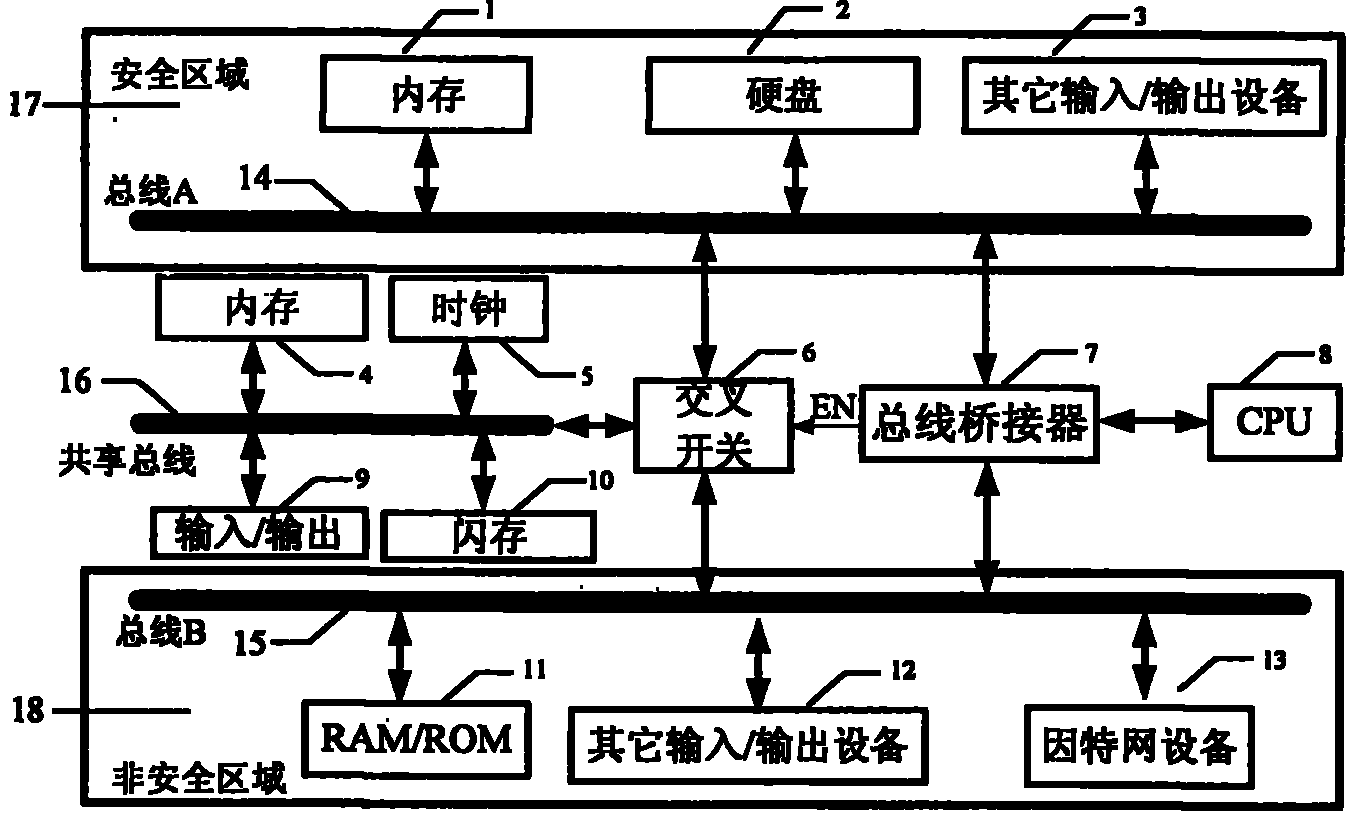
InactiveCN101299228BPrevent intrusionEnsure safetyPlatform integrity maintainanceTransmissionInternet communicationDual bus
The invention relates to a novel safe network terminal based on single CPU double-bus. The novel safe network terminal provides resistance function to the known or unknown network instruction by physical insulation and access control, adopts a single CPU and a safe area system bus and a non-safe area system bus isolated physically, the bus bridge controls the dynamic connection of the CPU and thesystem bus, and realizes the physical insulation of the two system buses; the related internet communication apparatus is only connected to one bus, while the related safe data memory apparatus is connected to the other system bus; one sharing bus is used to share the bus communication between the keyboard, mouse and the other input / output equipment, and the inside and outside system. The invention can effectively prevent the network instruction, guarantee information safety, and have advantages of low cost, strong spreading functional, safety and reliability, and the like.
Owner:QINGDAO UNIV
Data processing method, server end, client end and encryption machine
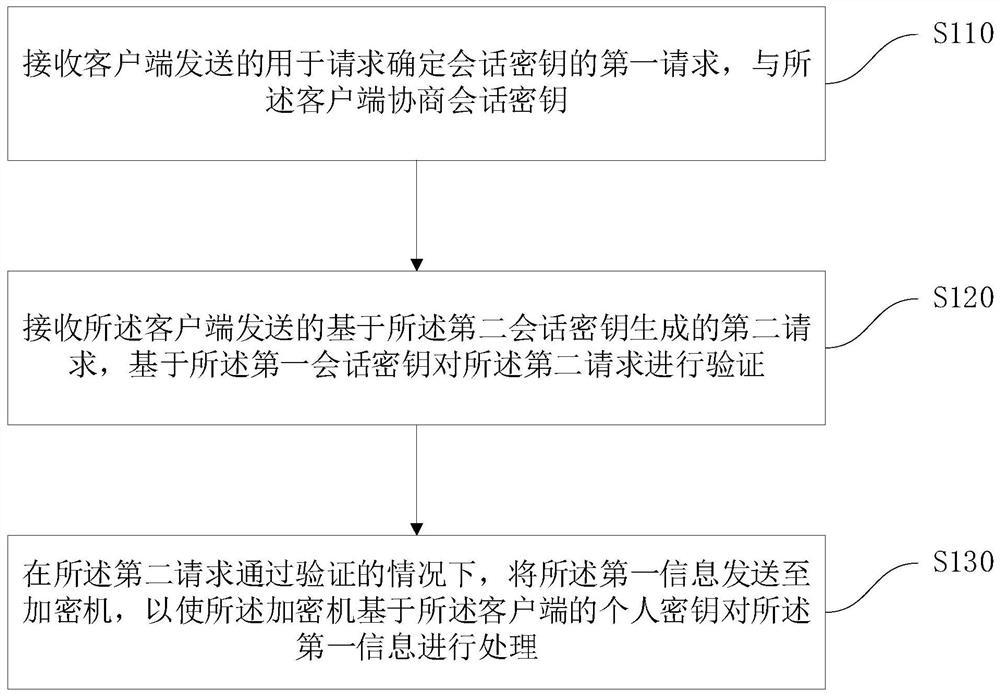
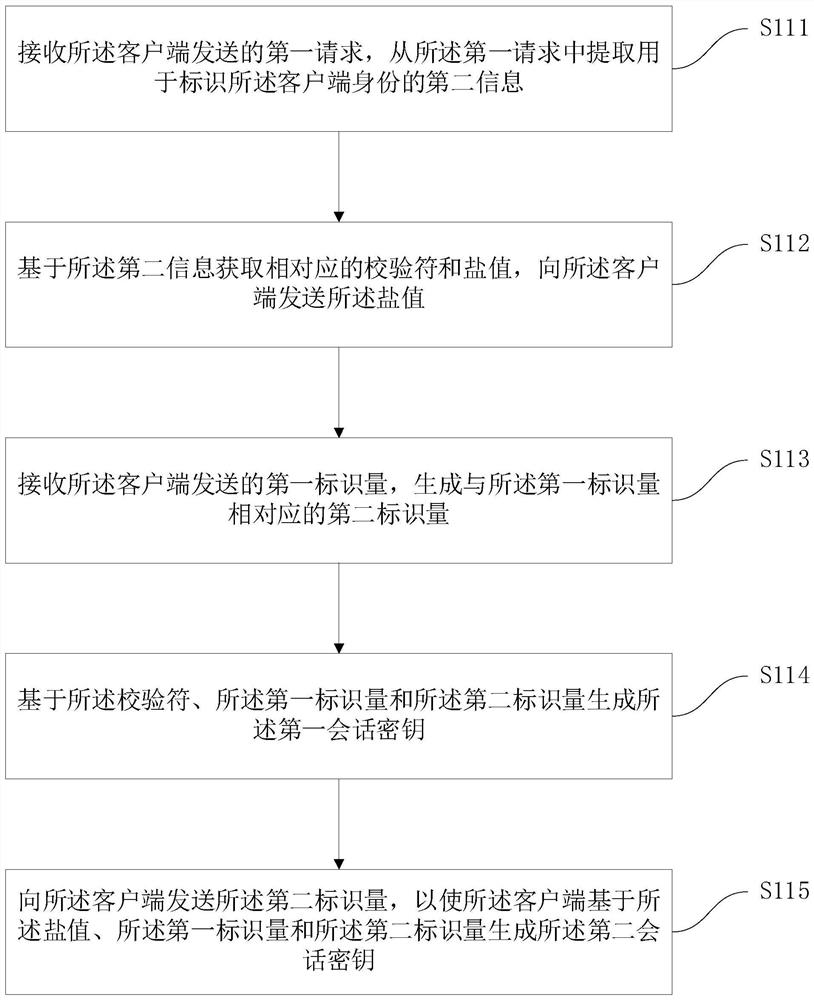
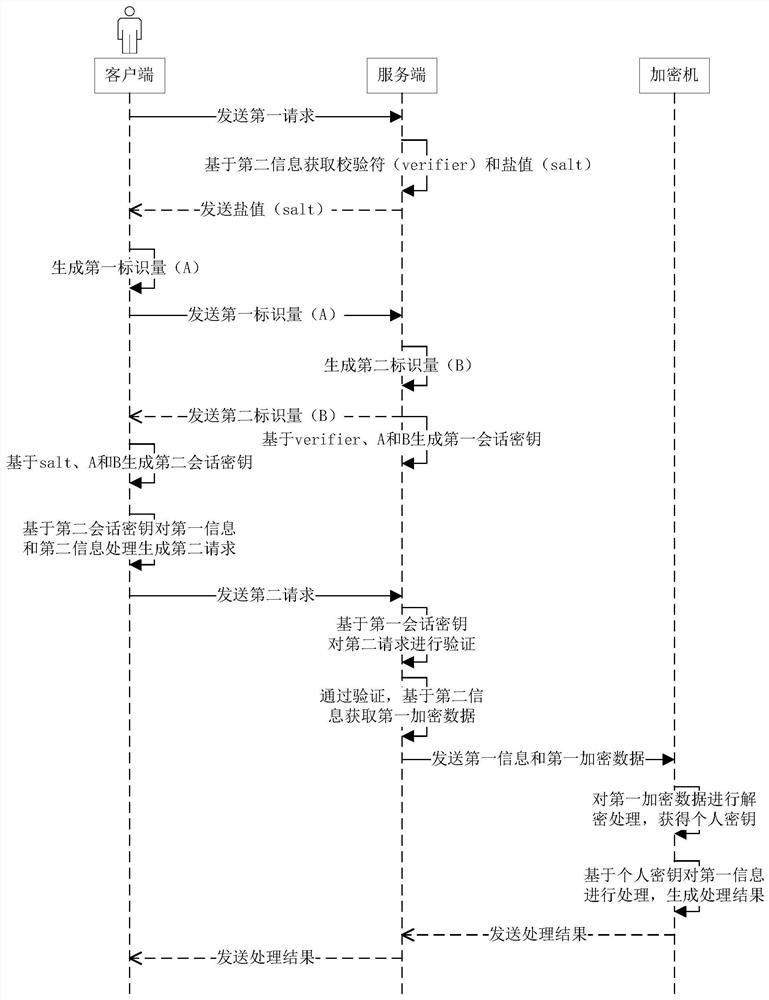
ActiveCN112861148BLost causeSolving Information Security IssuesDigital data protectionInformation processingEngineering
Owner:BEIJING SENSESHIELD TECH
System for information safety protection of electric power supervisory control and data acquisition (SCADA) system
ActiveCN102280929BSolving Information Security IssuesGuarantee the "four remote" function - remote control functionPower network operation systems integrationCircuit arrangementsSafety management systemsData acquisition
The invention discloses a system for information safety protection of an electric power supervisory control and data acquisition (SCADA) system. The system comprises a safety equipment management system, a station level electric power SCADA system safety protection device and an on-site terminal level electric power SCADA system safety protection device, wherein the safety management system is positioned in a power supply control center and becomes one component part of the electric power SCADA system main station system to manage the long-range station level electric power SCADA system safety protection device and the on-site terminal level electric power SCADA system safety protection device. The station level electric power SCADA system safety protection device is placed in a sub-station level electric power SCADA system device of the electric power SCADA system. The on-site terminal level electric power SCADA system safety protection device is placed in an electric power SCADA field device of an electric network field. The system has the main function of providing fine granularity and electric power production control service-based application layer safety protection for the electric power SCADA system, is used for ensuring the safety of 'four-remote functions' including a remote control function, a remote signaling function, a remote sensing function and remote regulatingfunction of the electric power SCADA system, and the safety of a communication channel of the electric power SCADA system, has electric power SCADA system intrusion detection and access control abilities, and has strong electric power service pertinence.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
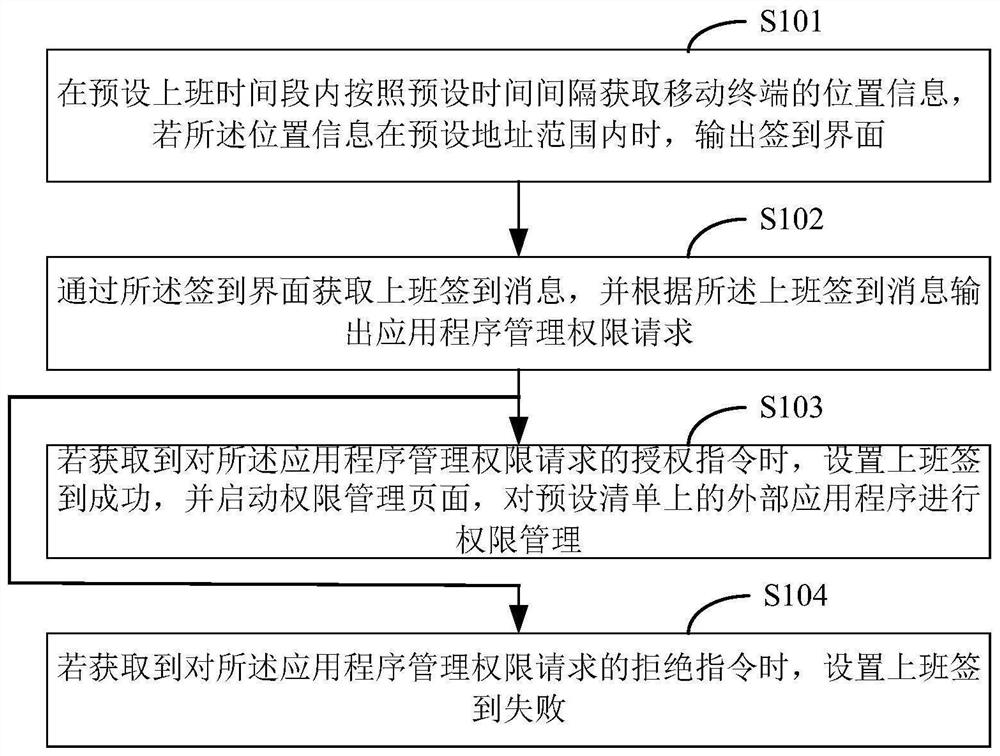
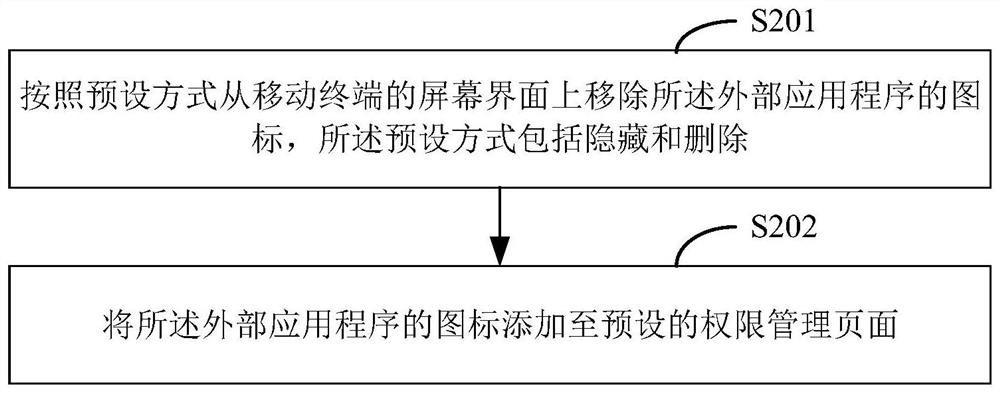
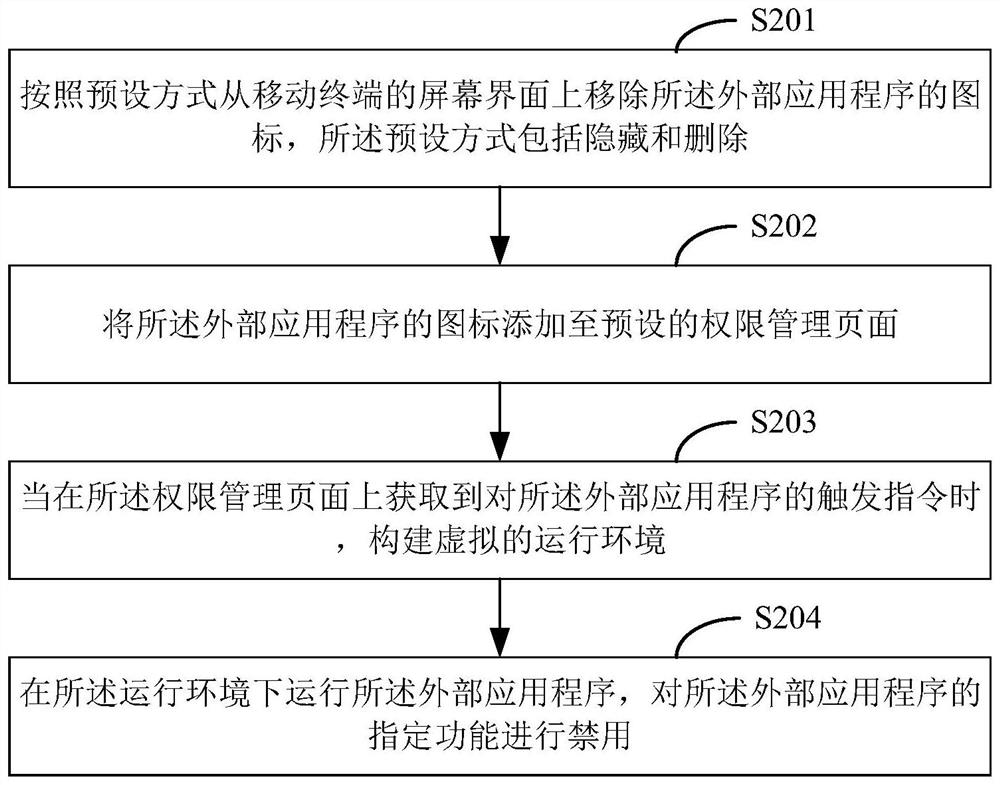
Application program access limiting method and device, equipment and medium
PendingCN112380528AThe impact of reducing productivitySolve problemsComputer security arrangementsOffice automationExternal applicationSoftware engineering
The invention discloses an application program access limiting method, and the method comprises the following steps: acquiring position information of a mobile terminal according to a preset time interval in a preset on-duty time period, and outputting a sign-in interface if the position information is in a preset address range; obtaining an on-duty check-in message through the check-in interface,and outputting an application program management authority request according to the on-duty check-in message; if an authorization instruction for the application program management permission requestis obtained, setting successful attendance check-in, starting a permission management page, and performing permission management on an external application program on a preset list; and if a refusalinstruction for the application program management authority request is obtained, setting that attendance check-in fails. According to the invention, the information security problem of an external application program to an enterprise and the puzzle problem to a user in an on-duty time period are solved.
Owner:PING AN TRUST CO LTD
Vulnerability service pack configuration method, server, terminal equipment and medium
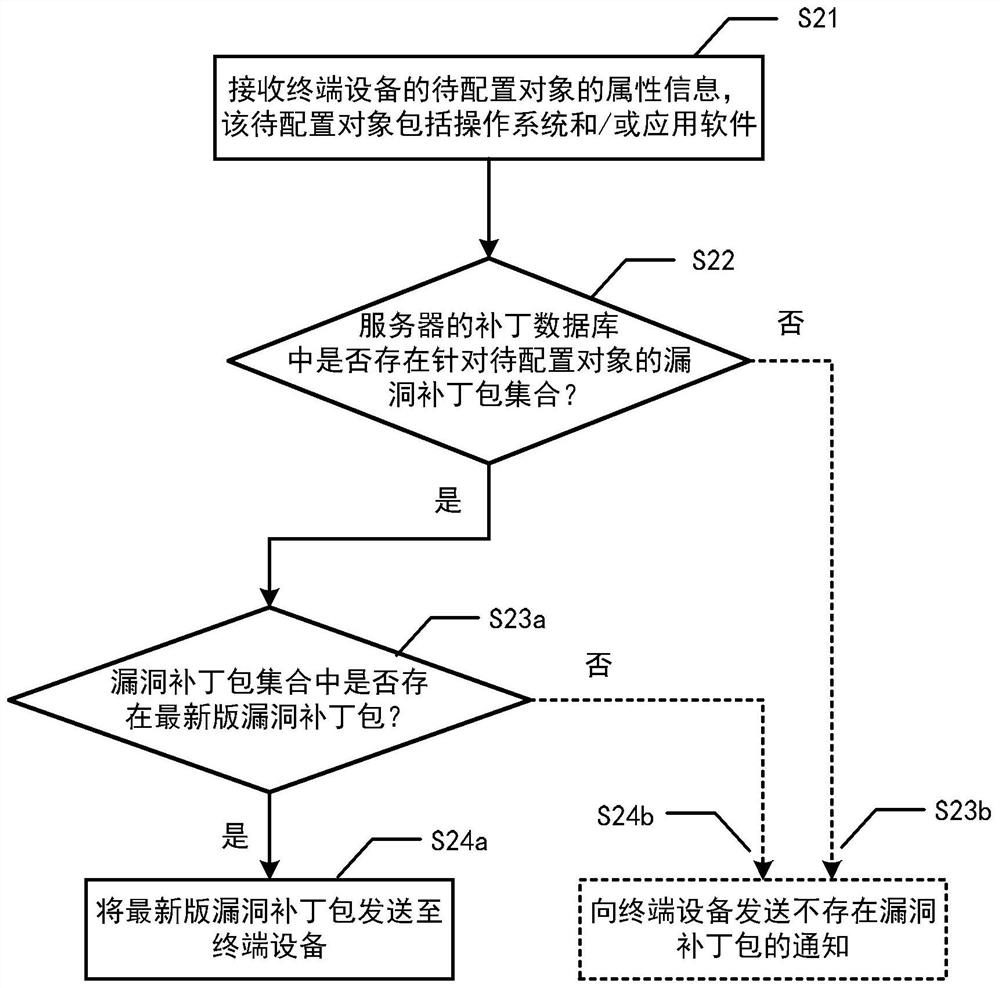
PendingCN113836536ARealize automatic configurationSolve the technical problems of cumbersome configurationVersion controlPlatform integrity maintainanceTerminal equipmentEngineering
The invention provides a vulnerability service pack configuration method, a server, terminal equipment and a medium. The method comprises the following steps: receiving attribute information of a to-be-configured object of the terminal equipment; determining whether a bug service pack set for the to-be-configured object exists in a patch database of the server or not, wherein bug service packs published in real time are stored in the patch database; in response to determining that a vulnerability service pack set for the to-be-configured object exists in the patch database, determining whether a newest version of vulnerability service pack exists in the vulnerability service pack set or not according to attribute information of each vulnerability service pack in the vulnerability service pack set and attribute information of the to-be-configured object; and in response to determining that the latest version of the vulnerability service pack exists in the vulnerability service pack set, sending the latest version of the vulnerability service pack to the terminal equipment. According to the invention, automatic configuration of the vulnerability patch is realized, and the information security problem caused by missing detection during vulnerability detection or untimely installation of the vulnerability patch pack is avoided.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC +1
A realization method of AES hardware encryption system based on quantum reversible circuit
ActiveCN110120867BGood encryptionShorten the timeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInformation securityEmbedded system
The invention provides an implementation method of an AES hardware encryption system based on a quantum reversible circuit, which belongs to the technical field of information security. The technical solution is: an AES hardware encryption system based on a quantum reversible circuit, including a quantum reversible circuit encryption and decryption module, a quantum secret key expansion module and a multi-interface selection module; the implementation method includes the following steps: realizing the quantum reversible circuit encryption and decryption module Hardware setting, complete the hardware setting of the quantum secret key expansion module, and use the electronic circuit to set the multi-interface selection module. The beneficial effects of the present invention are: the encryption and decryption module based on the quantum reversible circuit is combined with the quantum secret key expansion module according to algorithm rules to construct an encryption system based on the quantum reversible circuit, and the complexity of encryption is (2 n -1)! times, improve the encryption effect and anti-attack ability, and the multi-interface selection module can be connected with various interface devices to complete the encryption and decryption operations of various forms of information.
Owner:NANTONG UNIVERSITY
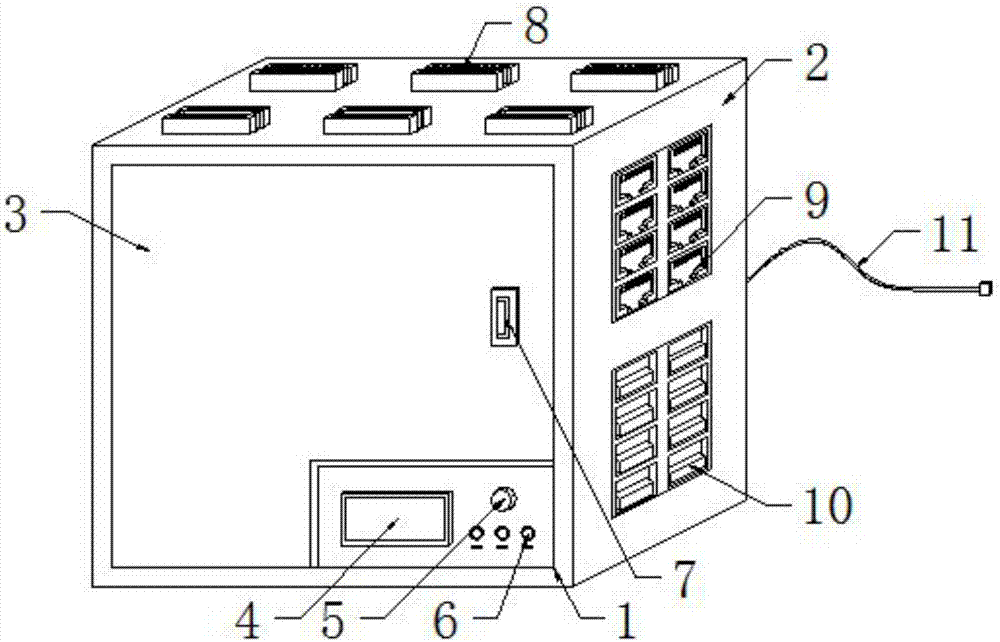
Group office background servo device
The invention discloses a group office background servo device. The device comprises a device body, wherein the device body comprises an enclosure arranged on the side face of the device body and a dust-proof door arranged on the side face of the enclosure, and the dust-proof door and the enclosure are moveably connected through a hinge. In the group office background servo device, a given communication protocol module and a network exchange interface or a USB interface improve information exchange rate and enable servers to exchange information accurately and correctly, also make data furthershared and share resources with external devices easily; a network physical isolation card protects user data thoroughly; a firewall enhances a security policy, prevents exposing overall security ofa user point, and prevents data disclosure and other accidents; and an internet behavior management module can manage the internet behavior of the user, monitor use condition of the network resources,and improve overall working efficiency.
Owner:安徽龙运智能科技有限公司
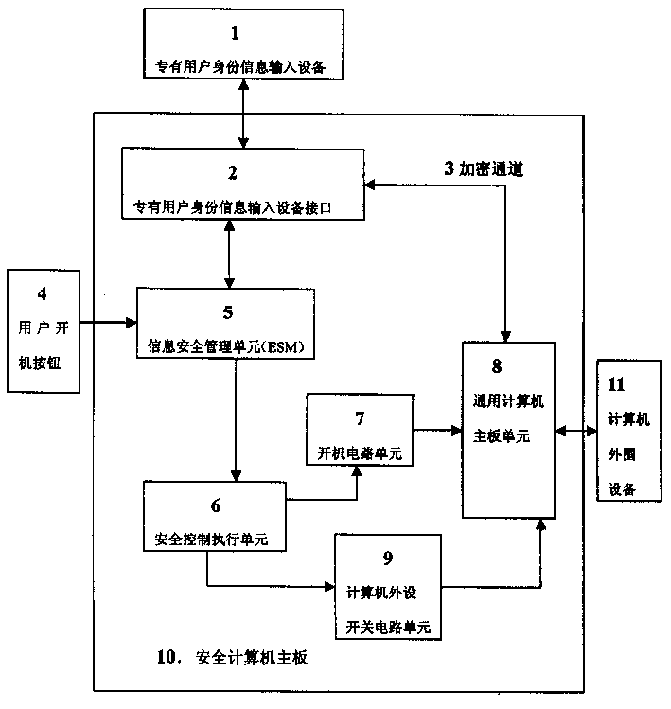
Safety computer with information safety management unit
InactiveCN1208728CSolving Information Security IssuesGuarantee information securityMemory loss protectionUnauthorized memory use protectionSecurity information and event managementManagement unit
Owner:瑞达信息安全产业股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com