Data processing method, server end, client end and encryption machine
A data processing and client-side technology, applied in the computer field, can solve problems such as inability to execute, difficult data synchronization, etc., to achieve the effect of ensuring information security, avoiding information security problems, and avoiding the loss of personal keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
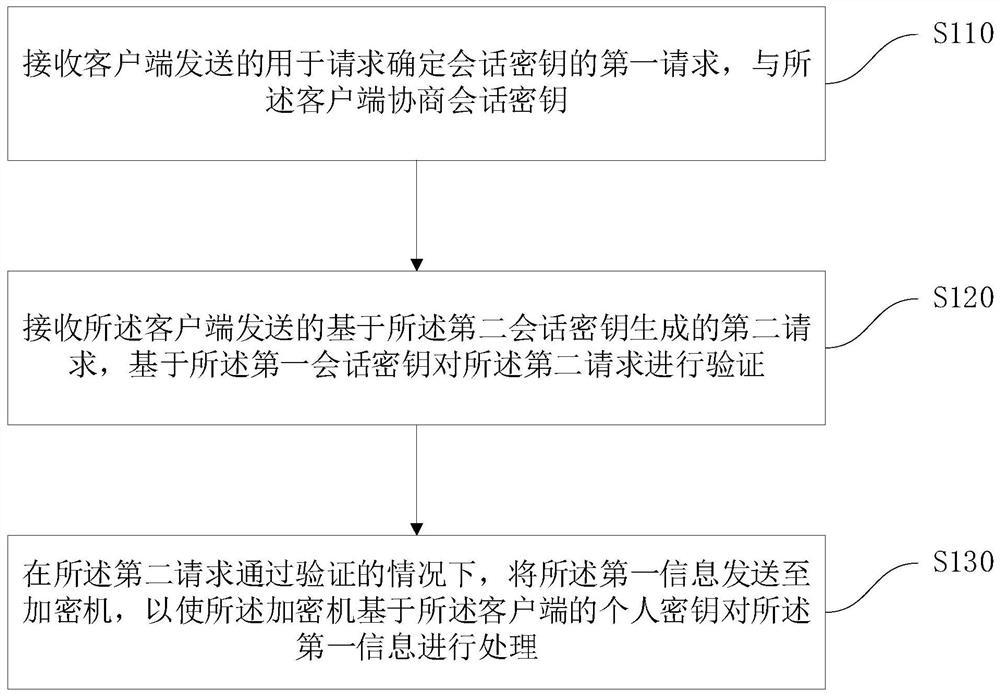
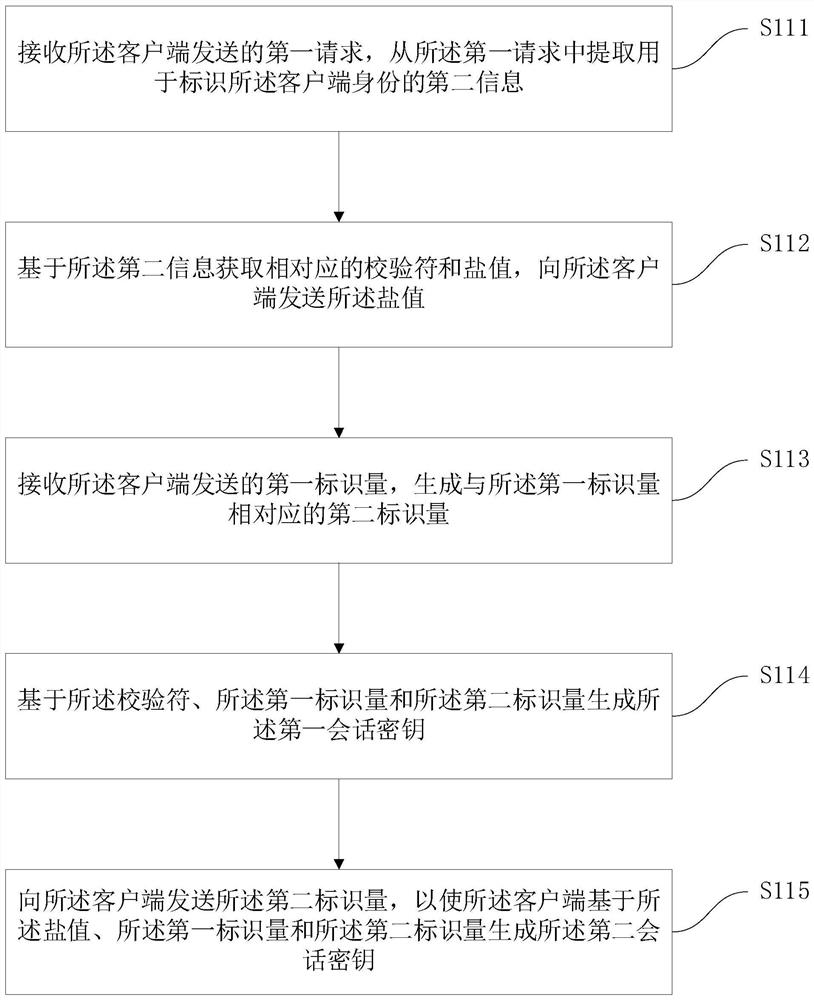
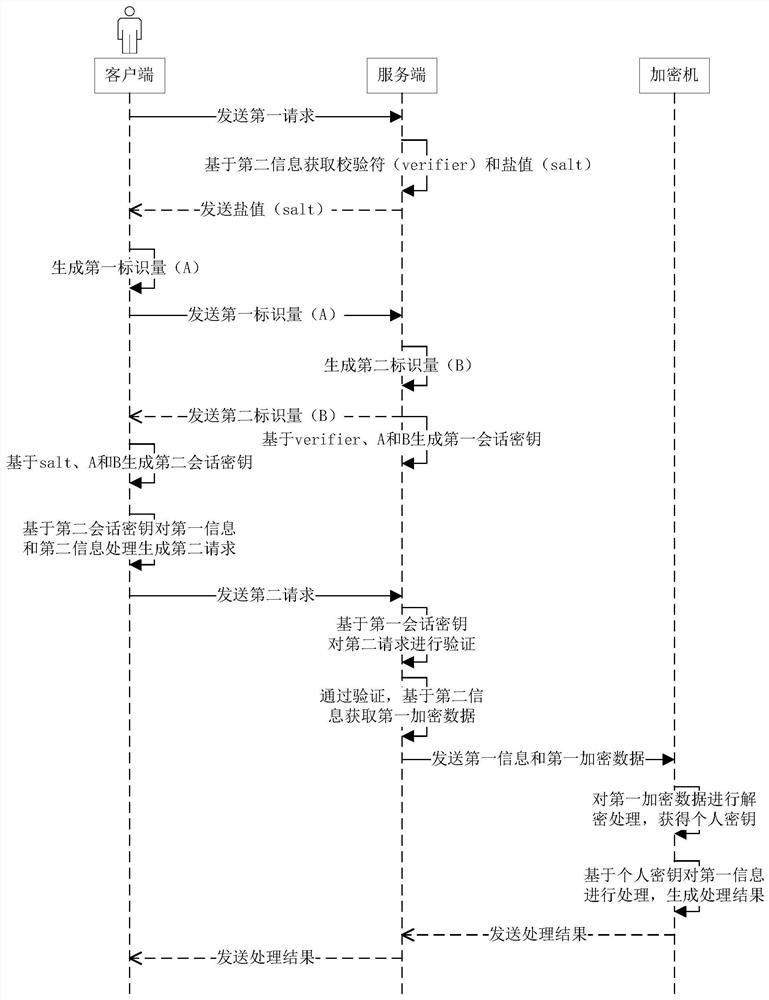
[0046] Various aspects and features of the present application are described herein with reference to the accompanying drawings.
[0047] It should be understood that various modifications may be made to the embodiments applied for herein. Accordingly, the above description should not be viewed as limiting, but only as exemplifications of embodiments. Those skilled in the art will envision other modifications within the scope and spirit of the application.
[0048] The accompanying drawings, which are incorporated in and constitute a part of this specification, illustrate embodiments of the application and, together with the general description of the application given above and the detailed description of the embodiments given below, serve to explain the embodiments of the application. principle.
[0049] These and other characteristics of the present application will become apparent from the following description of preferred forms of embodiment given as non-limiting examp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com