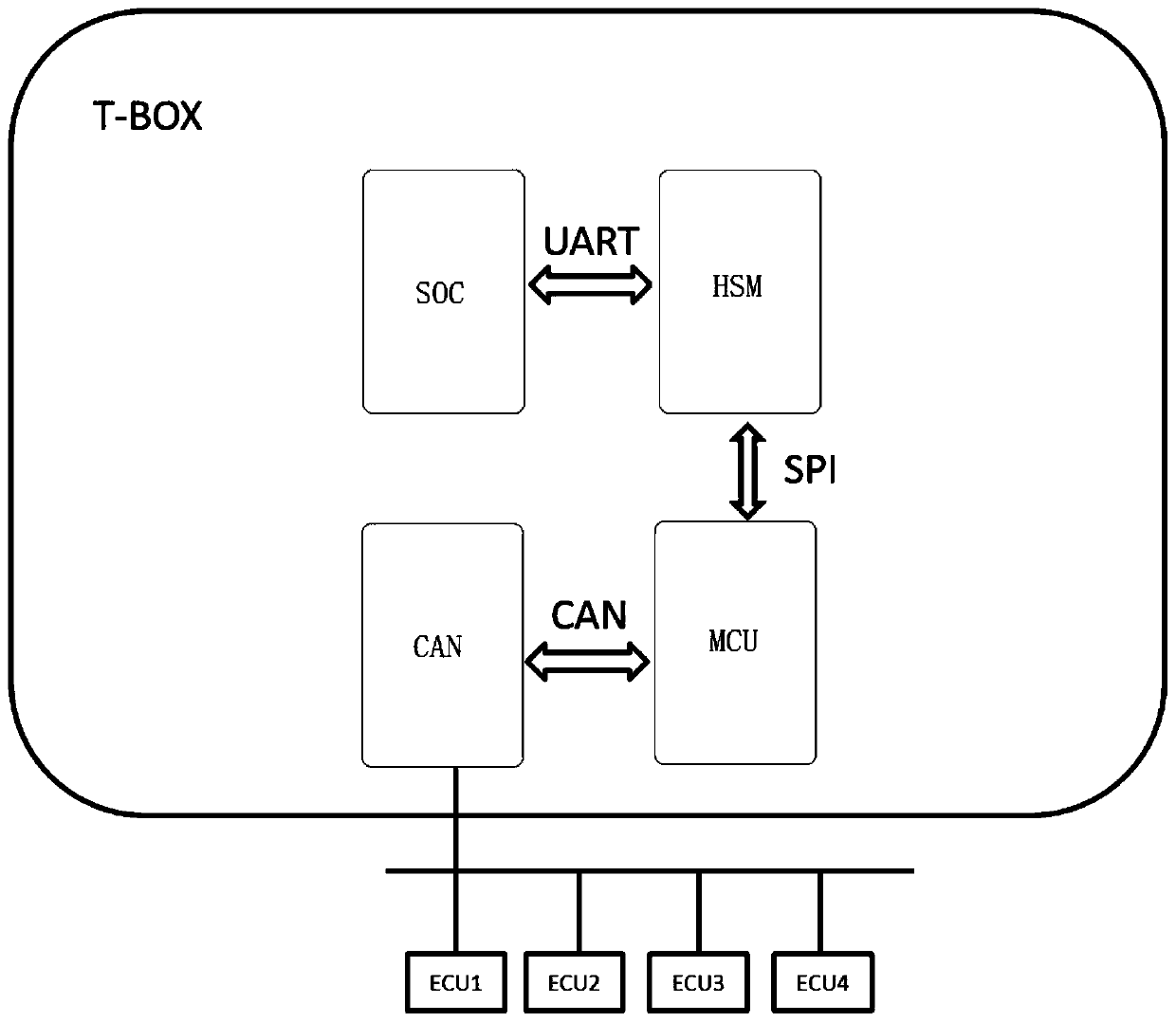
A T-BOX encryption system and method
A technology of T-BOX and encryption system, applied in the transmission system, data exchange through path configuration, electrical components, etc., can solve the problems of no separate protection measures, no data communication encryption protection, no protection against detection and self-destruction, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Referring to the accompanying drawings, through the description of the embodiments, the specific embodiments of the present invention include the shape, structure, mutual position and connection relationship of each part, the function and working principle of each part, and the manufacturing process of the various components involved. And the method of operation and use, etc., are described in further detail to help those skilled in the art have a more complete, accurate and in-depth understanding of the inventive concepts and technical solutions of the present invention.
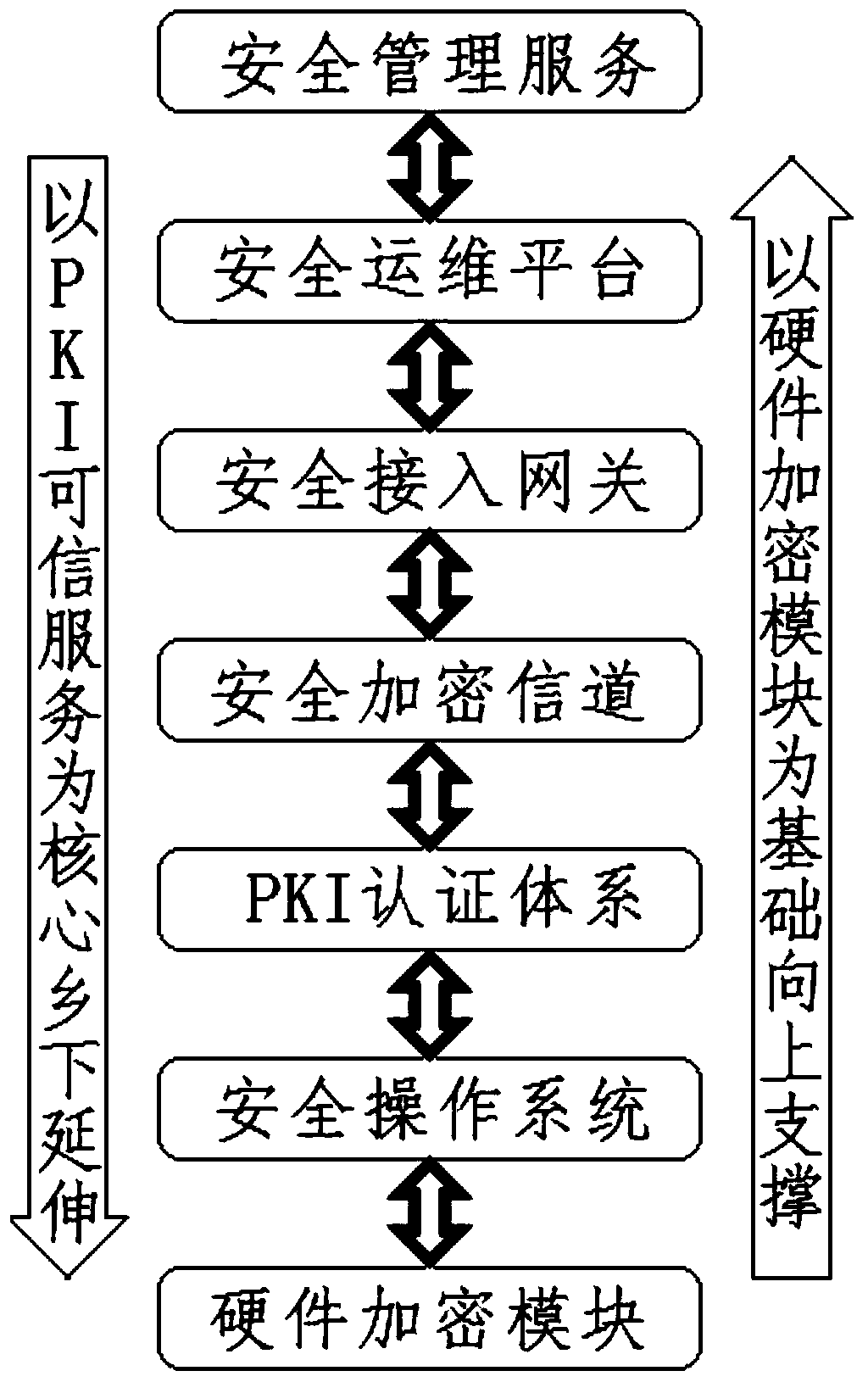
[0037] Such as figure 1 The structure diagram of the encryption method shown, the functions of each module, system, and program are as follows:
[0038] Security management services: provide services such as key generation, identity verification, and certificate management;
[0039] Security operation and maintenance platform: including certificate registration and approval system, secret key manage...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com