Cross-network area service calling method and system
A technology for regional services and network areas, applied in the field of automated operation and maintenance, it can solve problems such as heavy workload, different terminal environment standards, and errors and omissions, so as to solve information security problems, simplify startup work, and reduce error rates.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
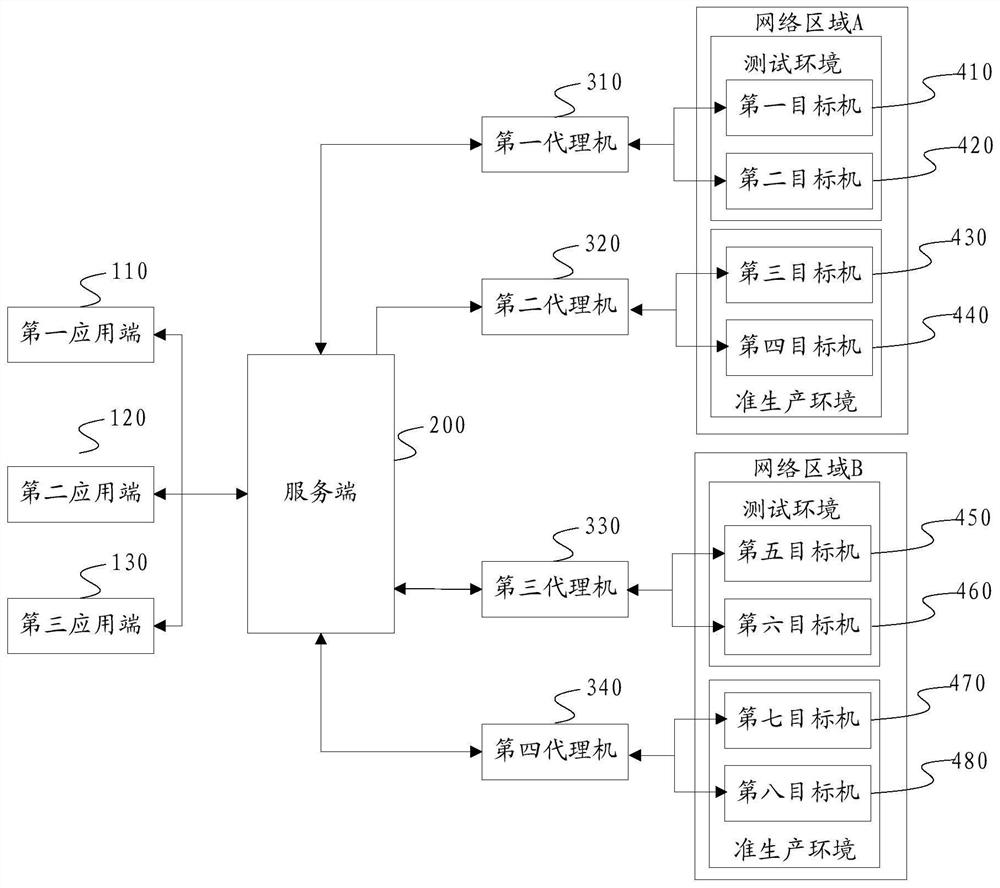
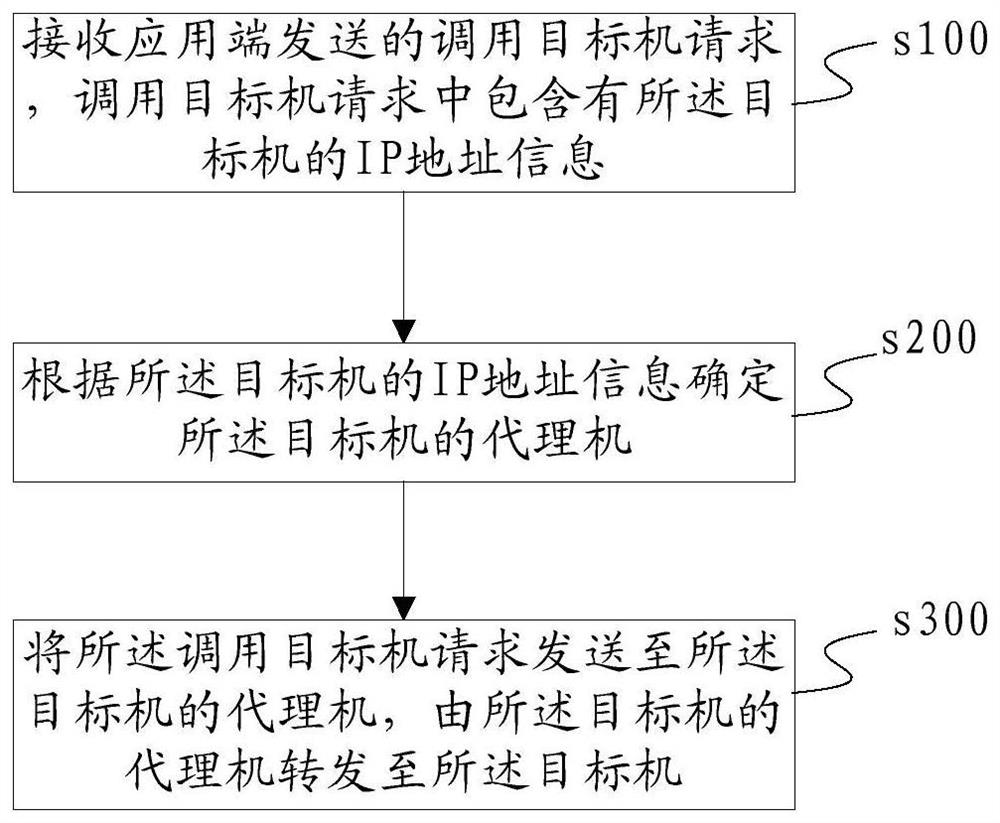
[0067] Please refer to image 3 A flow chart of a cross-network area service invocation method provided by this application, figure 2 When the system shown is deployed, the firewalls between the agents and all whitelists and their corresponding application terminals have been kept open. The whitelist stores a list of safe application terminals corresponding to each agent. The whitelist stores On the server side; since the proxy machine and its target machines are located in the same environment in the same network area, they can communicate with each other; therefore, there is no need to open a firewall between the proxy machine and all the target machines it proxies.
[0068] In the deployment phase, three data tables (such as Table 1 to Table 3 below) are deployed in the server, stored in a database, and initialized according to the application, agent and target machines, as well as the network area and environmental latitude information, using Reserved for query; the thre...
Embodiment 2
[0094] On the basis of Embodiment 1, the above-mentioned method also includes the following steps:
[0095]S400. Update the general network segment agency relationship table according to the network segment table; the network segment table stores all network segment information, environment information and network area information corresponding to the network segment information. The automatic update of the general network segment proxy relationship table can be performed at the same time as scheduled execution and triggered execution, for example, it is updated synchronously every two hours, and it can also be triggered during the execution of the first embodiment. For example Figure 5 As shown, it is triggered according to the execution result of step s220, that is, step s240 is added after step s220;
[0096] s240, judging whether the return result of the agent machine ID is empty;
[0097] That is, when the network segment information is not inquired from the general ag...
Embodiment 3
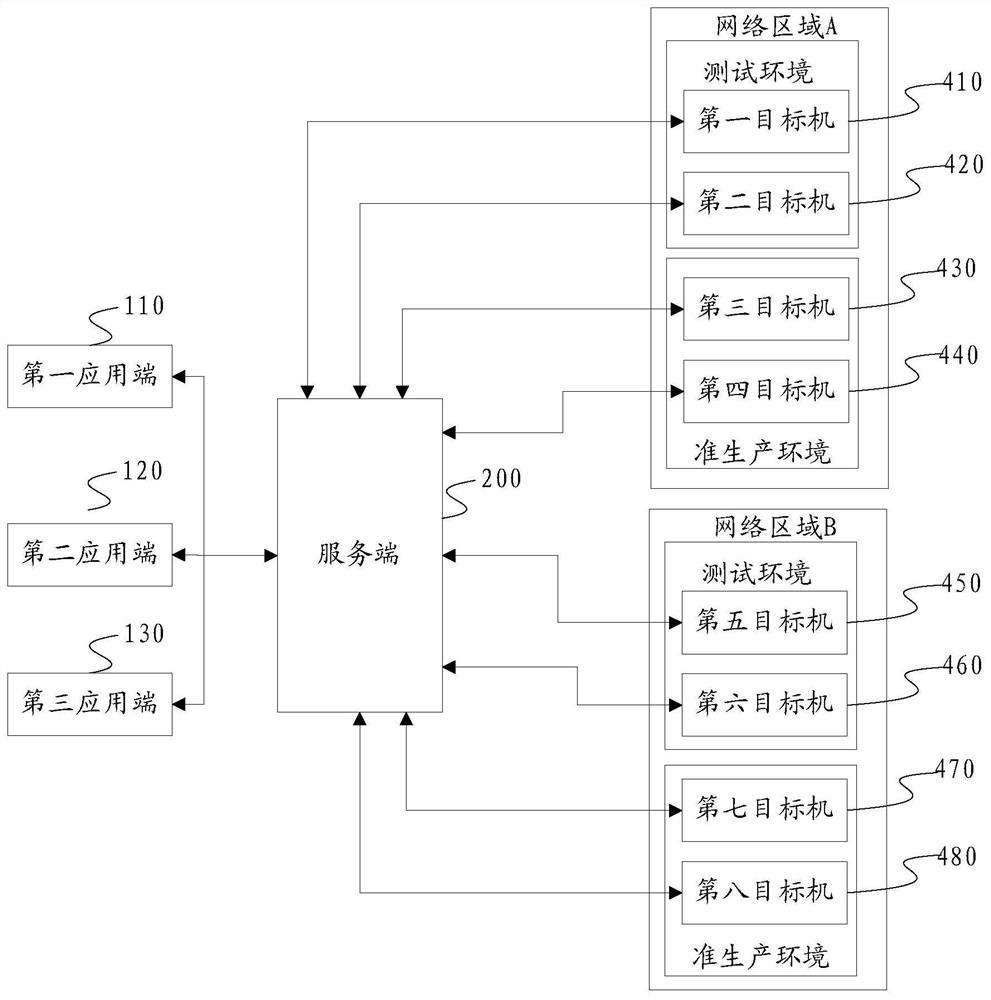
[0116] On the other hand, the embodiment of the present application also provides a cross-network region service invocation system, the system framework of which can be as follows, for example figure 2 or Figure 6 As shown, in the system of this embodiment:
[0117] The application end is configured to send a request for invoking a target machine, and the request for invoking a target machine includes IP address information of the target machine;
[0118] The server is configured to receive the call target machine request, determine the proxy machine of the target machine according to the IP address information of the target machine, and send the call target machine request to the target machine proxy machine; The request for calling the target machine includes the IP address information of the target machine; therefore, the server is specifically configured to: extract the network segment information of the target machine from the IP address information of the target machi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com