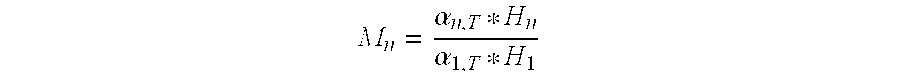Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
58results about How to "Prevent their use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Multiple function electronic cards
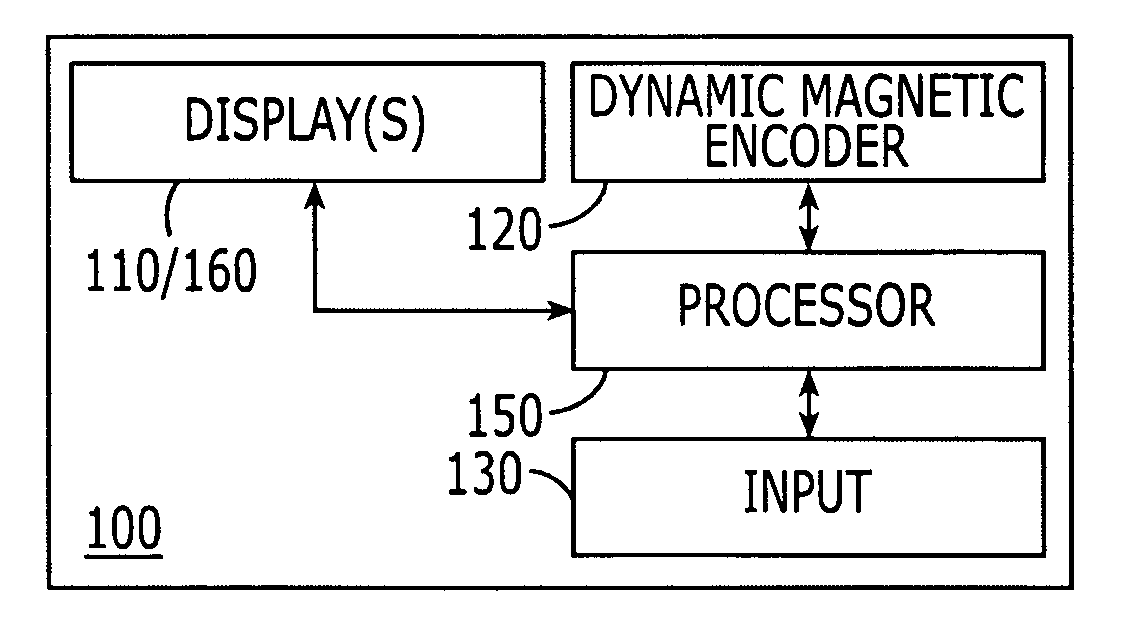
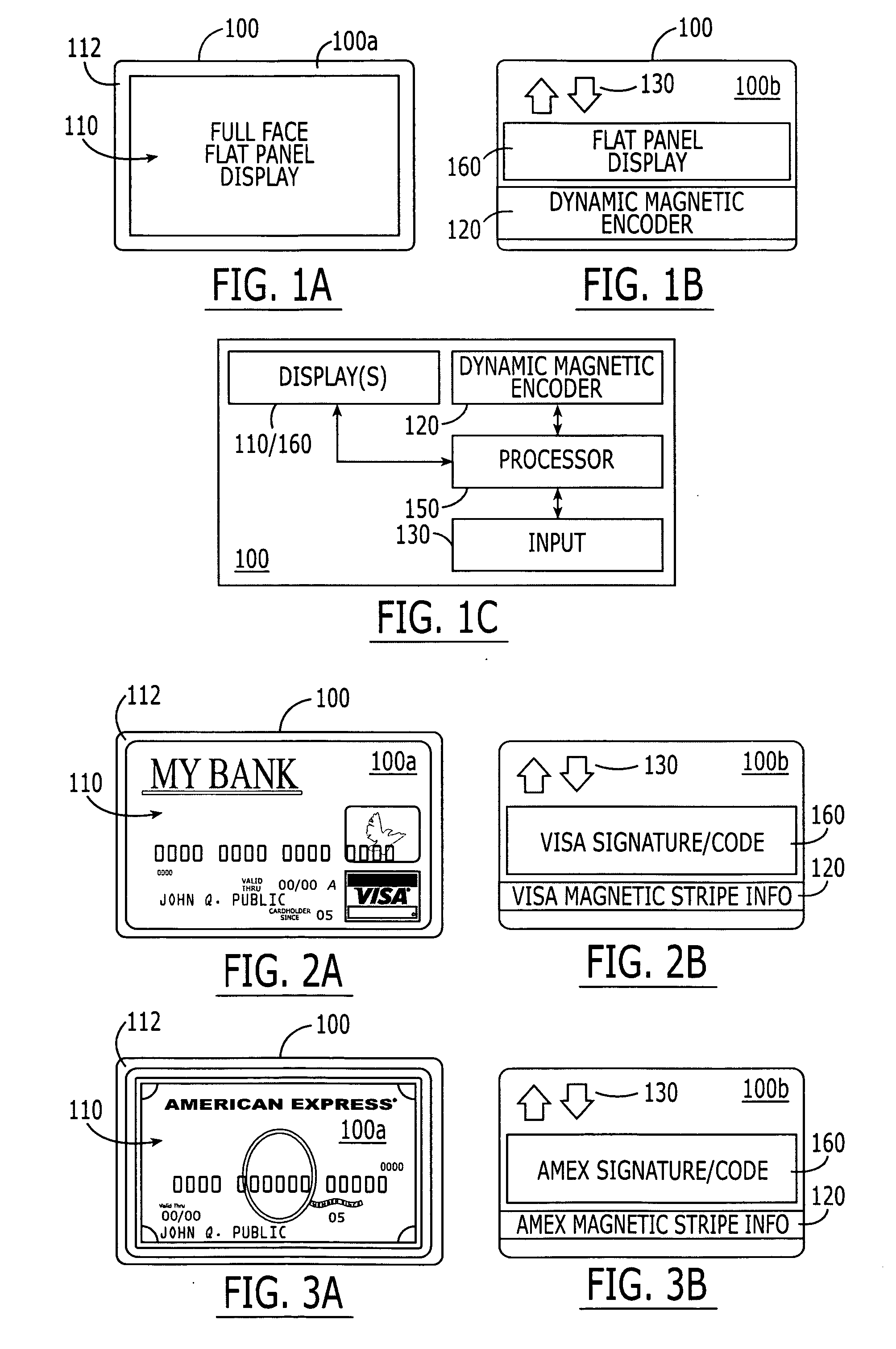
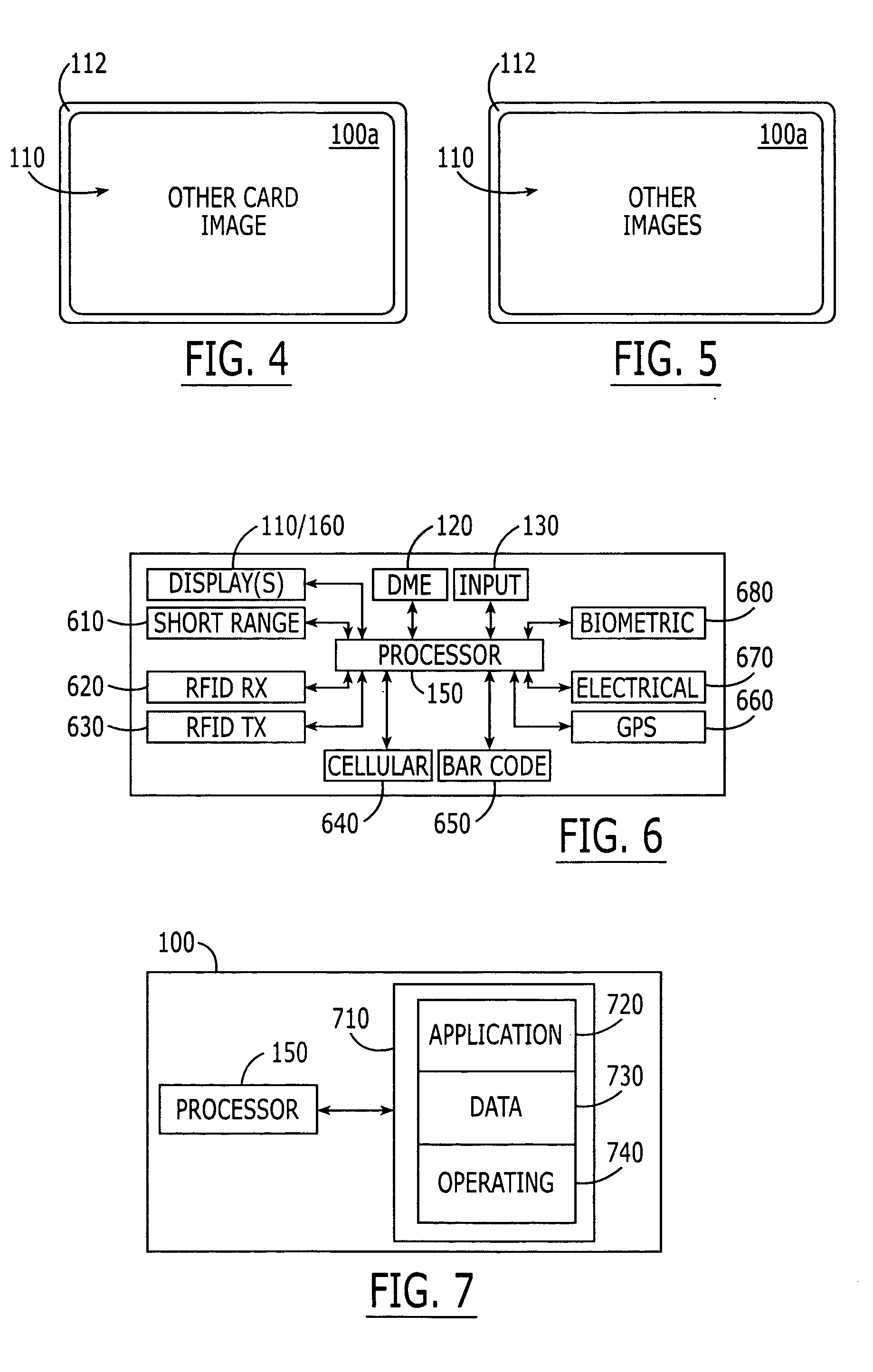
ActiveUS20060091223A1Prevent their useReduce usageAcutation objectsPayment architectureFlat panel displayMultiple function
Electronic cards include a package having vertical and horizontal dimensions of a standard credit card, and including first and second opposing faces. A flat panel display extends over the first face. A dynamic magnetic encoder is provided on the second face. A user input device also is provided on the package. A processor is provided in the package that is configured to display a substantially full size image of a credit card on the flat panel display, and to control the dynamic magnetic encoder to provide magnetic stripe information for the credit card, in response to user selection of the credit card via the user input device. Accordingly, the look (image) of a credit card can be emulated, as well as the magnetic stripe information that would be provided by the credit card, in response to user selection of the credit card.
Owner:BELLSOUTH INTPROP COR
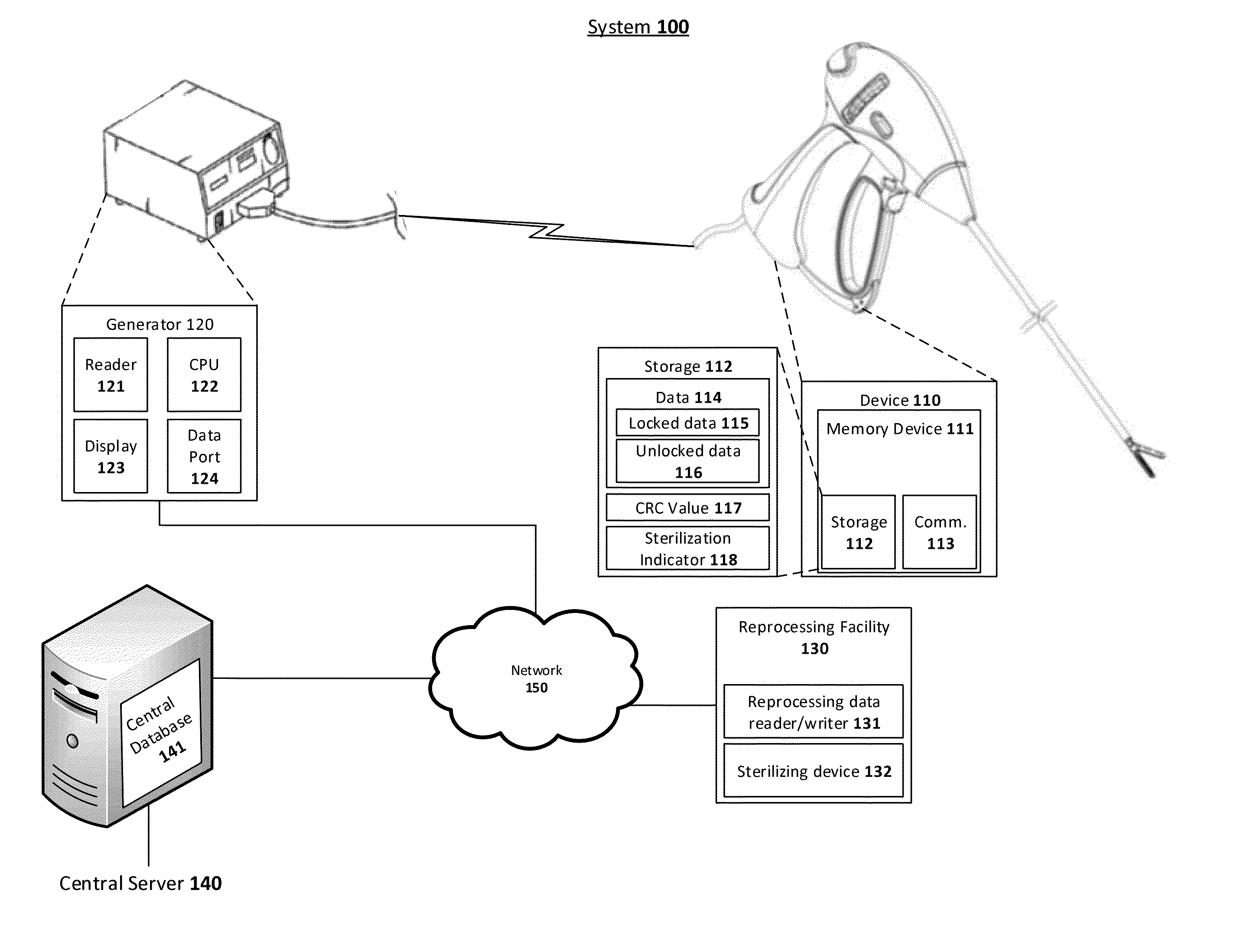
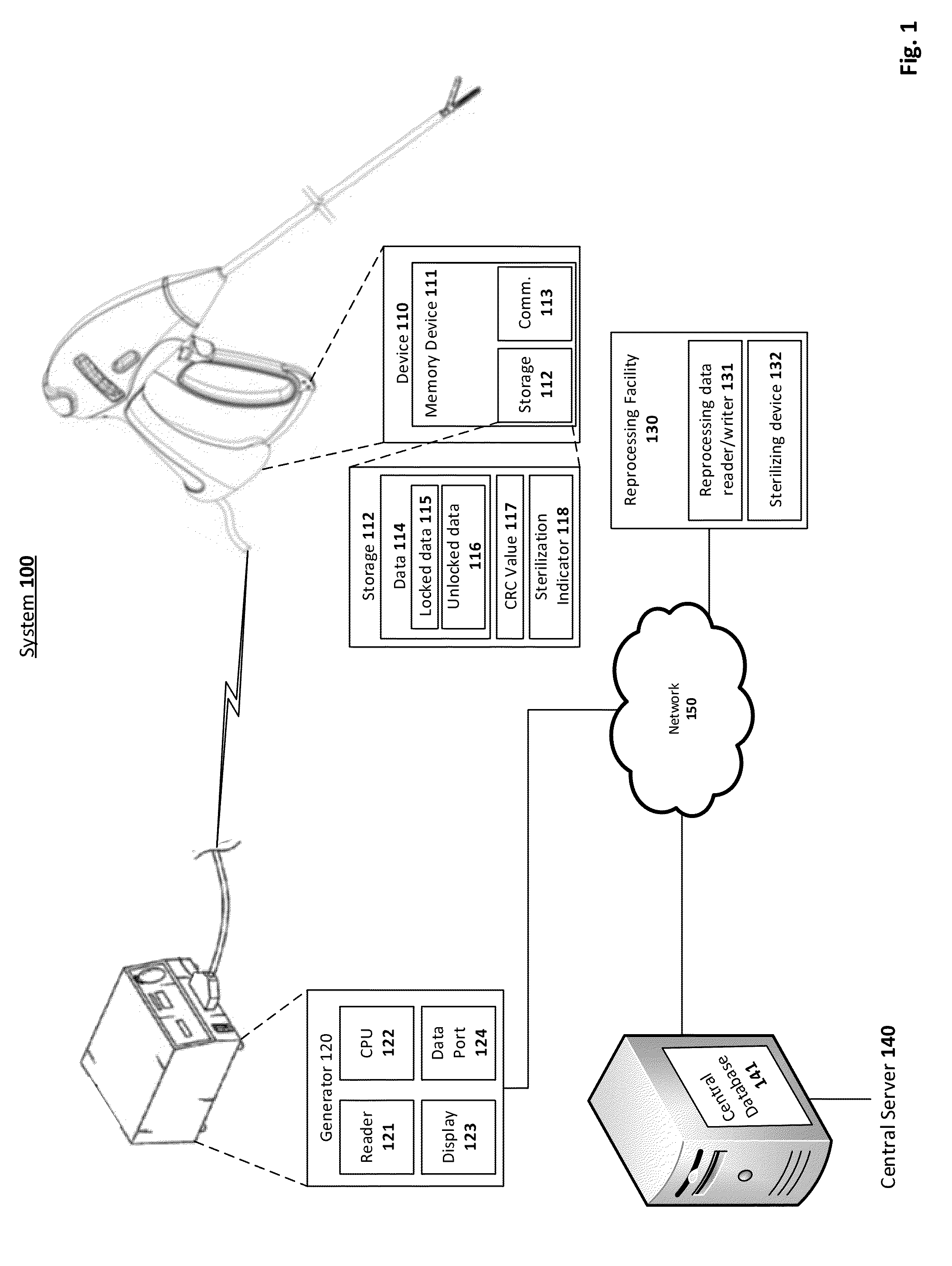
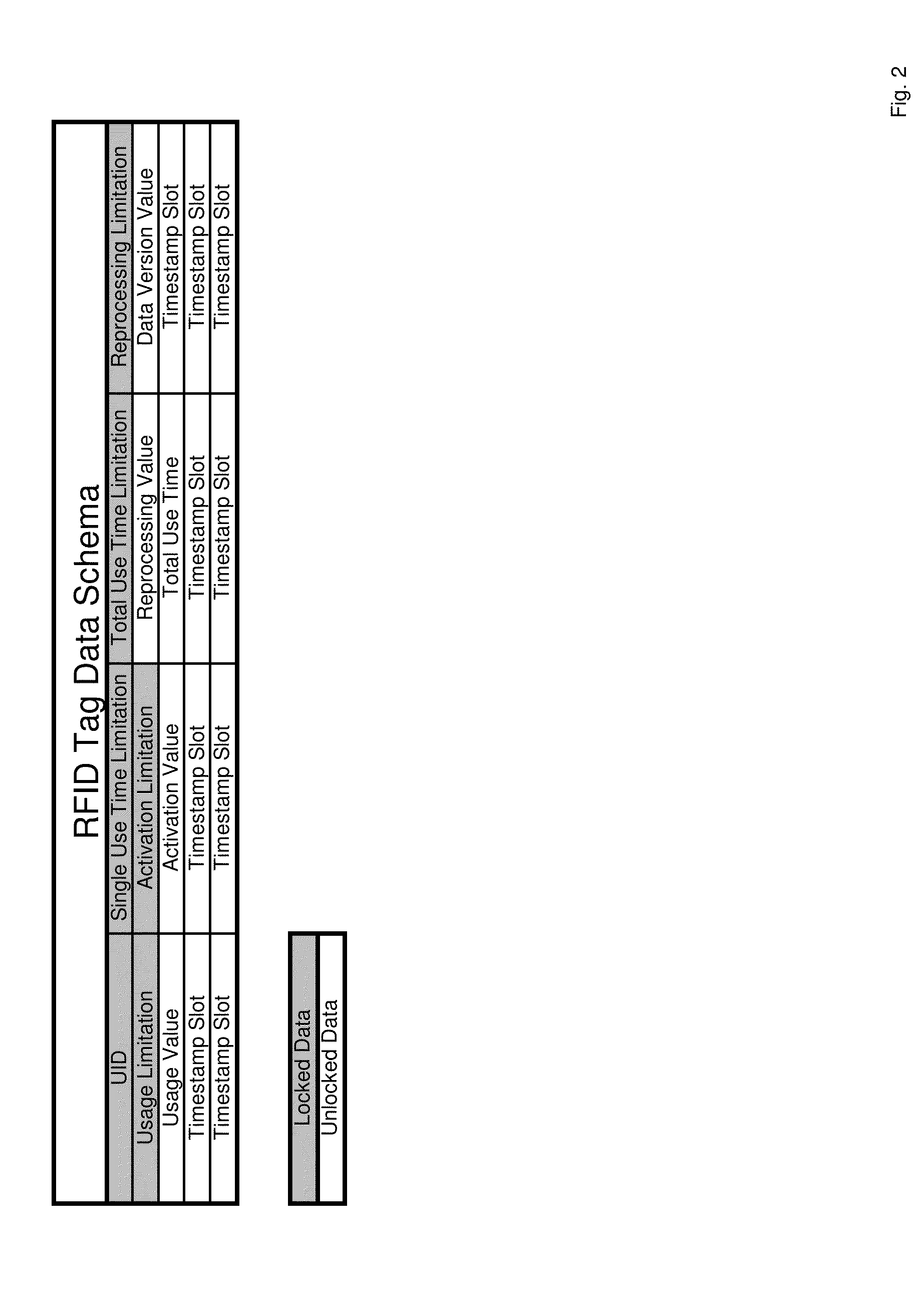
System and method for using RFID tags to determine sterilization of devices
Owner:TYCO HEALTHCARE GRP LP
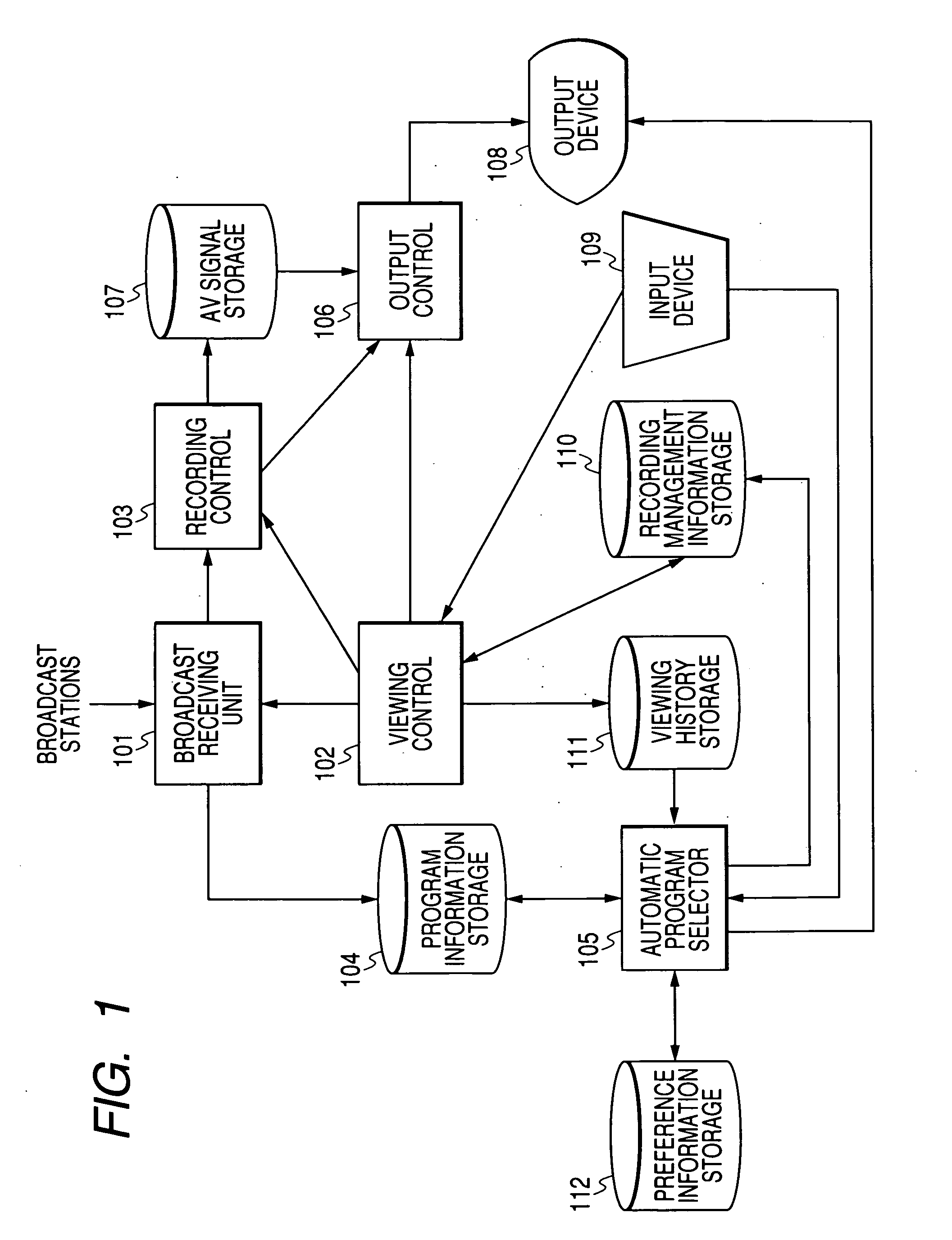
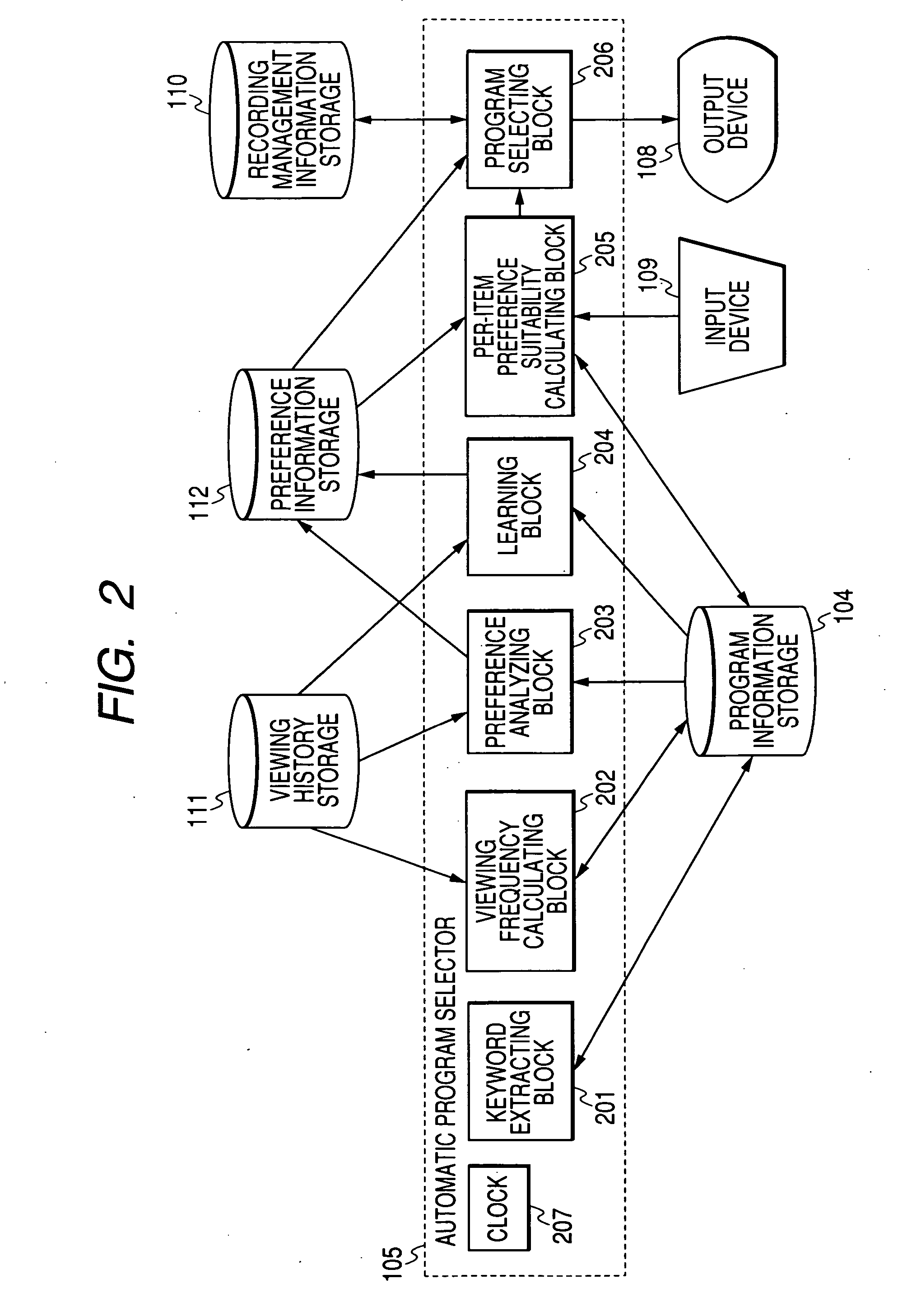
Method and apparatus for ranking broadcast programs
ActiveUS20060010464A1Prevent their useReliably rankingTelevision system detailsSpecific information broadcast systemsRadio programMultimedia
Frequencies of viewing of first weekly broadcast programs by a user are detected in connection with past sections of the first weekly broadcast programs. At least one which has the detected viewing frequency greater than a predetermined threshold value is excluded from the first weekly broadcast programs to get second weekly broadcast programs. Program ranking measures representative of a relation between program attributes and user's preference are generated in response to (1) attributes of the past sections of the second weekly broadcast programs and (2) which of the past sections of the second weekly broadcast programs were viewed by the user. Future sections of the second weekly broadcast programs are ranked in response to (1) the generated program ranking measures and (2) attributes of the future sections of the second weekly broadcast programs.
Owner:RAKUTEN GRP INC
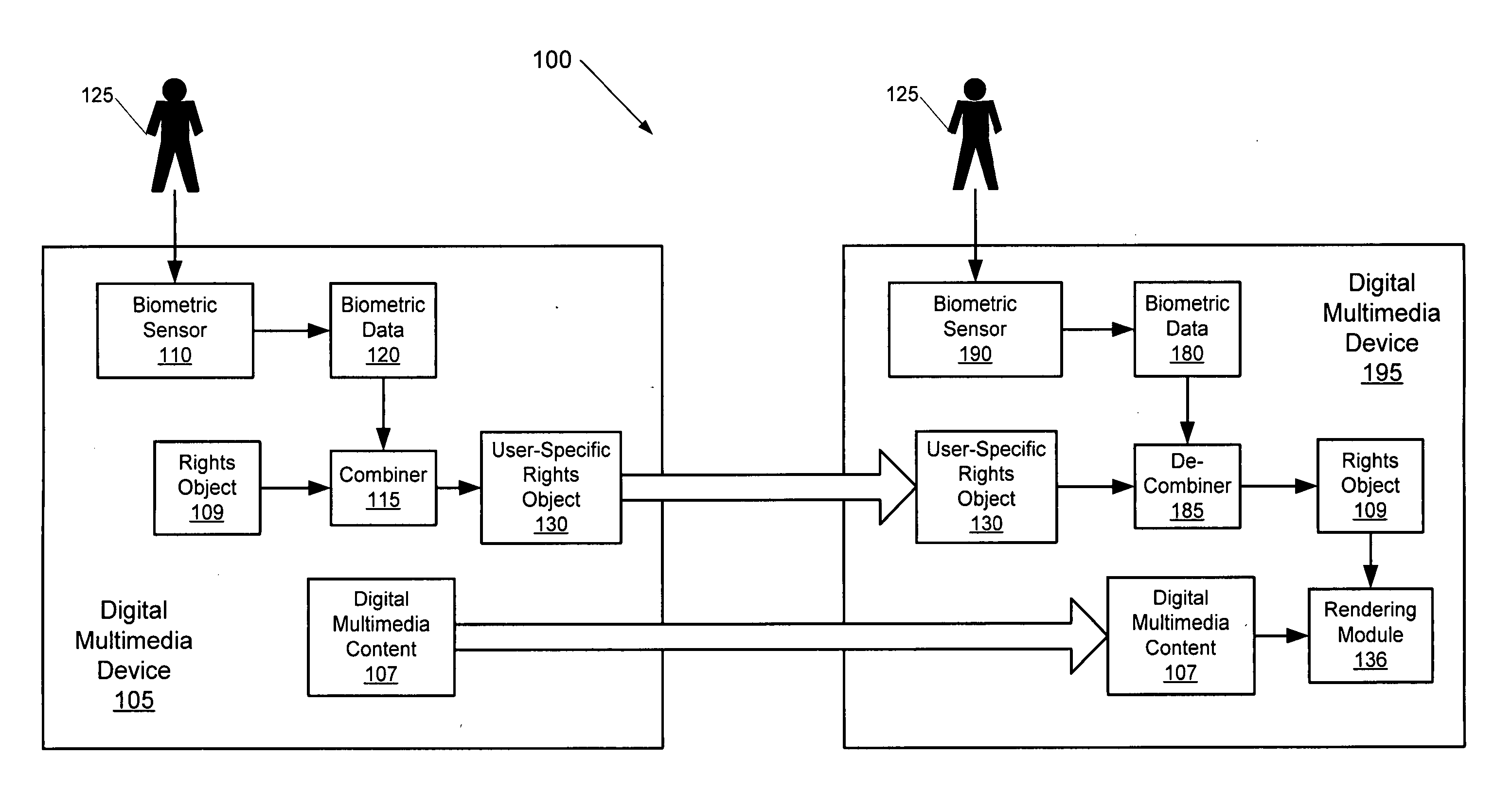
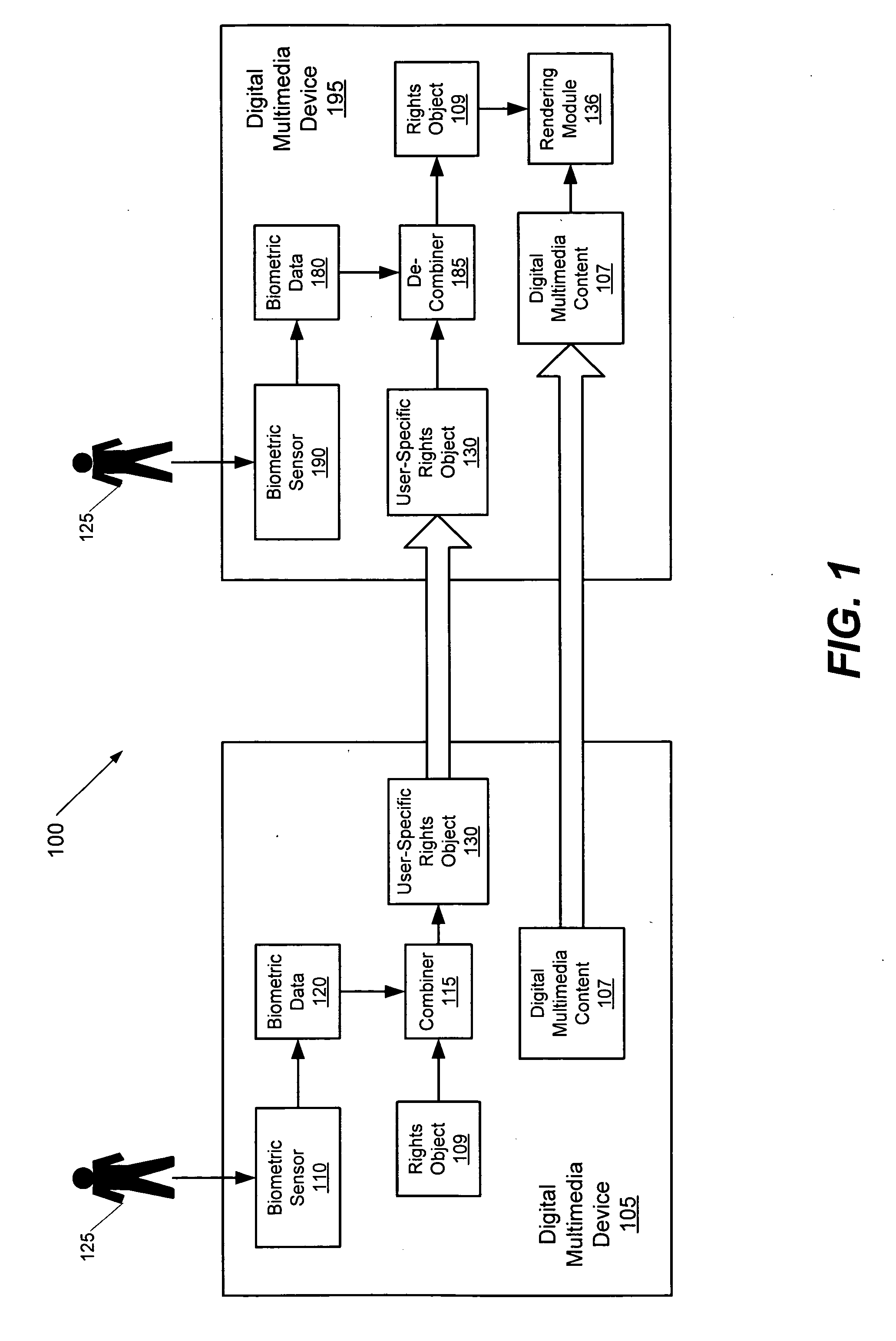
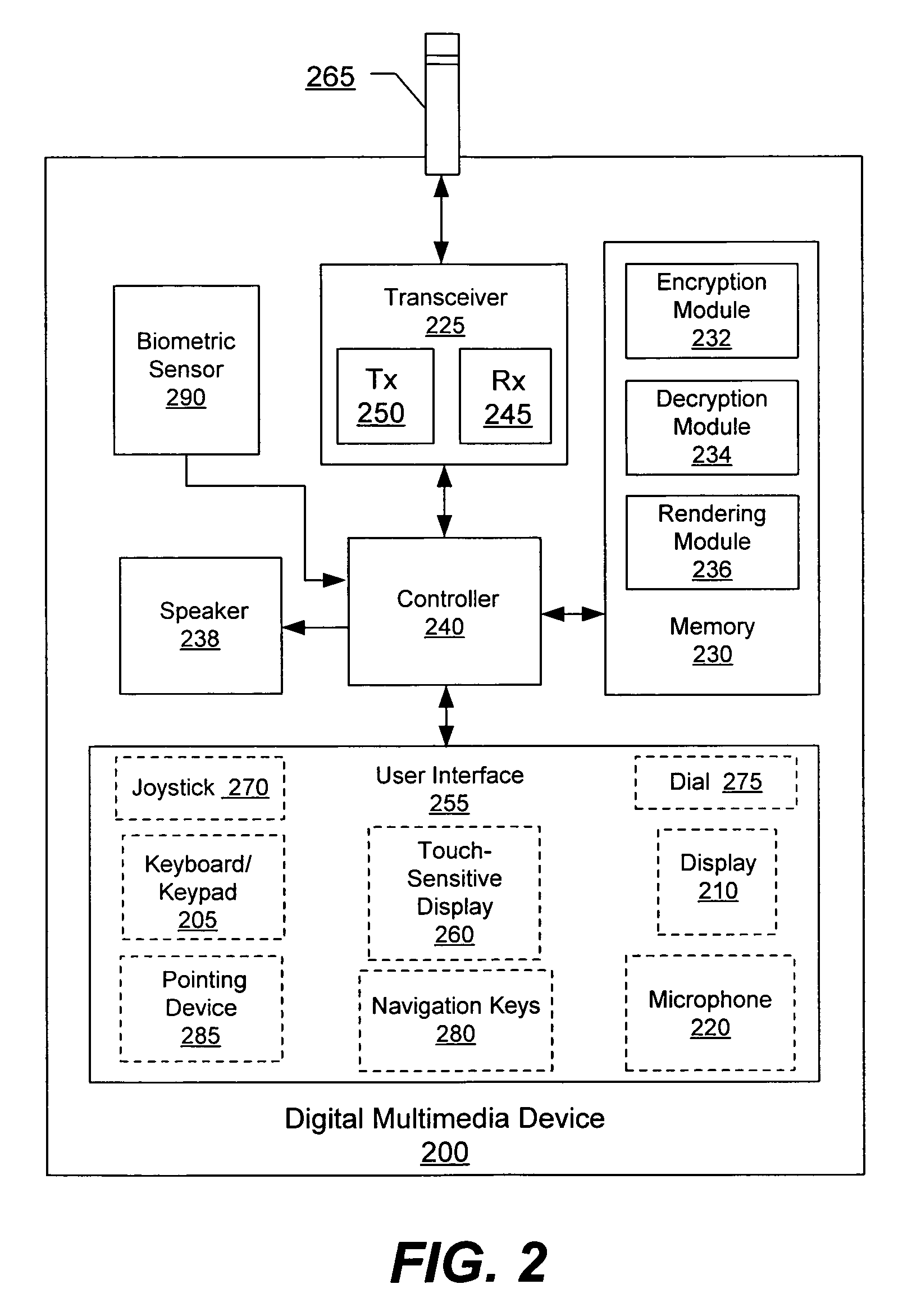
Methods, systems, and computer program products for sharing digital rights management-protected multimedia content using biometric data
InactiveUS20070033414A1Prevent their useReduce usageSecret communicationProgram/content distribution protectionMultiple deviceData sharing
Digital multimedia content having a rights object associated therewith may be shared between multiple devices. A first device includes digital multimedia content and an associated rights object therein. Biometric user data is obtained at the first device via a biometric sensor associated therewith and is combined with the rights object to provide a user-specific rights object. The multimedia content and the user-specific rights object are loaded onto a second device. Biometric user data is obtained at the second device via a biometric sensor associated therewith and is combined with the user-specific rights object to provide the rights object at the second device. The digital multimedia content is rendered on the second device using the rights object.
Owner:SONY ERICSSON MOBILE COMM AB
Certification system, certification apparatus, and certification method
InactiveUS7079922B2Prevent their usePayment architectureAutomatic exchangesInternet privacyThird party
A certification apparatus stores personal information certified to a user to register the user. When a user presented password sent from a portable telephone coincides with a password stored as a part of the personal information and the user who is operating the portable telephone is specified to be the same person as the registered user, adult certification data certifying the user being an adult on the basis of the personal information is sent to the portable telephone. Consequently, it becomes possible to make a portable terminal acquire certification information certifying personal information, and to prevent unfair use of the certification information by a third party almost surely. Thereby, a certification system capable of preventing unfair use by the third party almost surely can be achieved.
Owner:SONY CORP
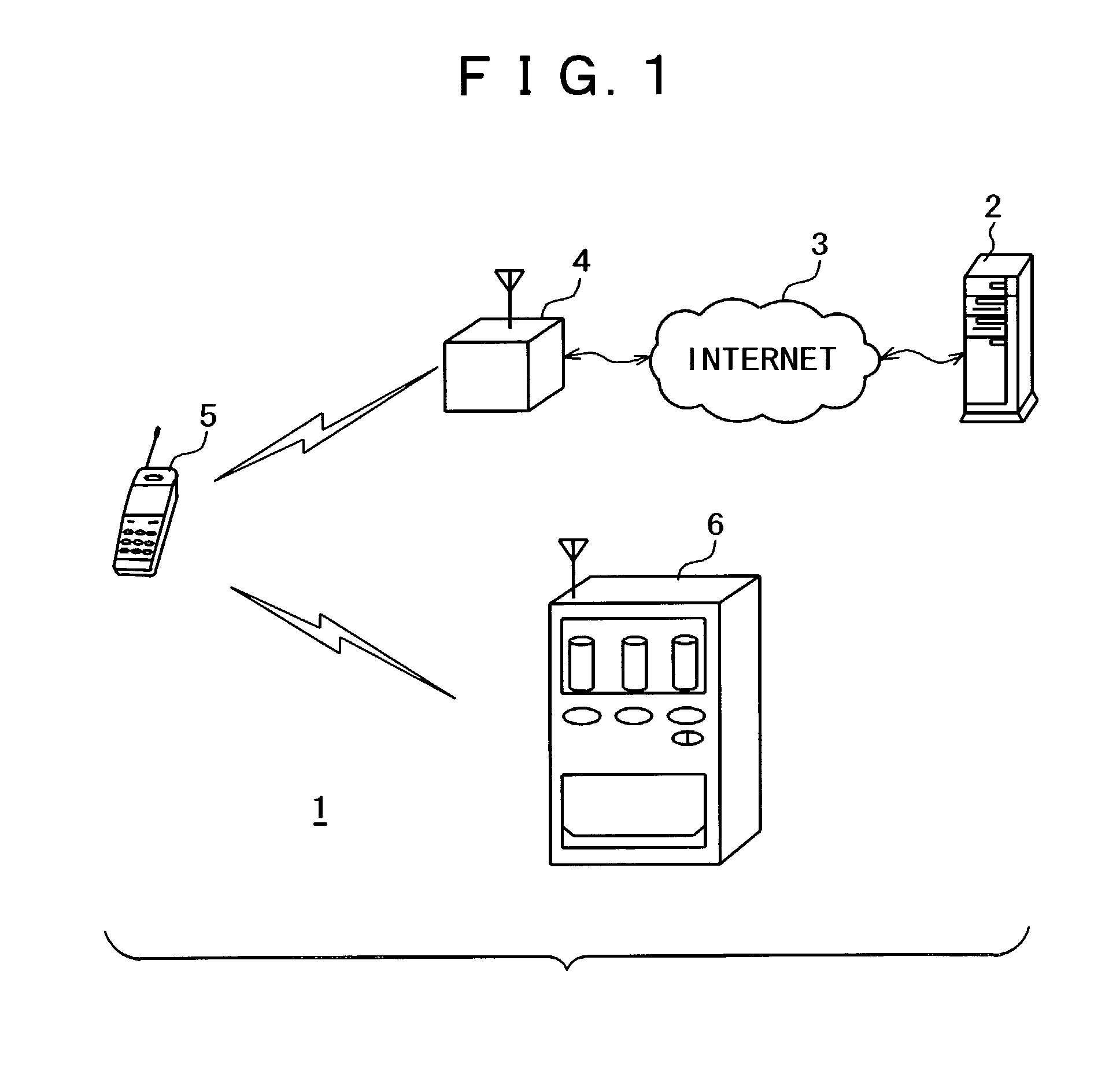
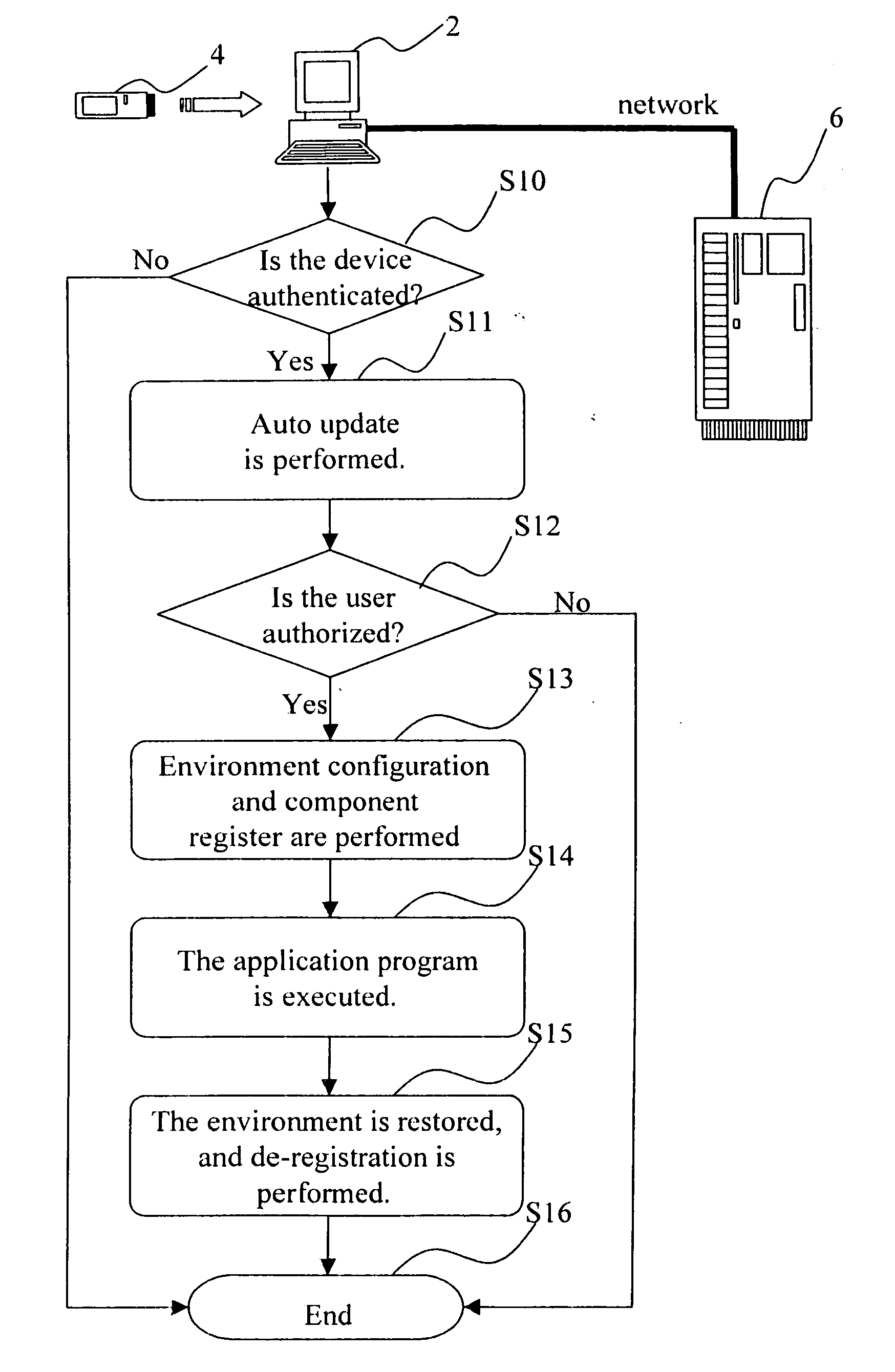
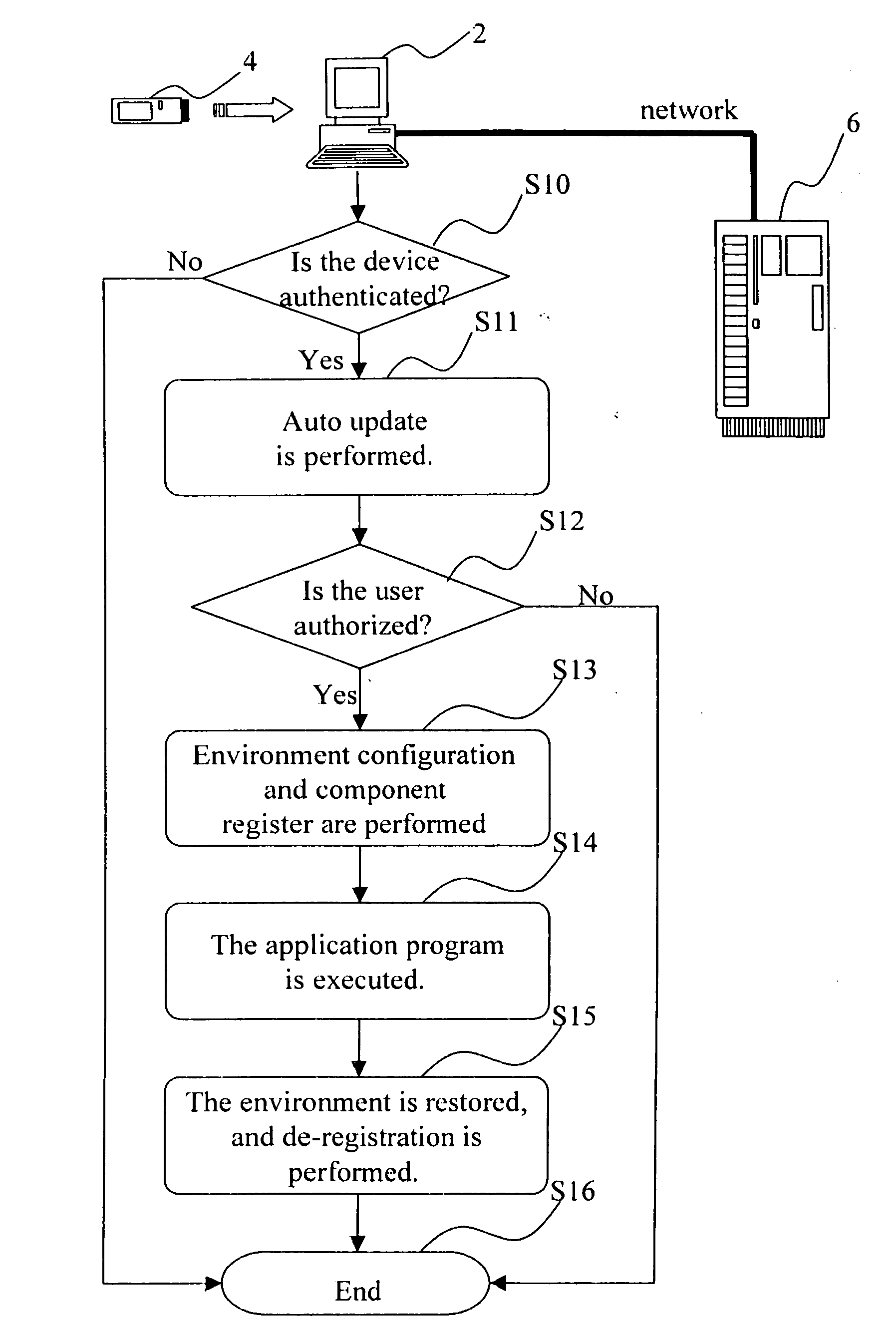
Method for application of portable software
InactiveUS20060218549A1Prevent their useProgram loading/initiatingMemory systemsAuthorizationSystem recovery
A method for application of portable software stores a coordination program and at least an application program in a portable storage device. When the storage device is plugged to a computer system, the coordination program will be automatically run to set up a runtime environment of the application program (including carrying out authentication and authorization to ensure proper use of hardware and software). The application program can thus be executed in the computer system. After the user has finished the tasks, the application program is terminated, and the coordination program will restore the computer system to the original setting and automatically terminate itself. The user can then remove the storage device. In this way, easy usage and better integration can be accomplished, and the advantage of portable software can also be achieved.
Owner:UNISVR GLOBAL INFORMATION TECH CORP
Ocular implant insertion apparatus and methods
An exemplary ocular implant insertion system includes a case and a preloaded ocular implant insertion apparatus. The apparatus includes first and second movable structures that move the ocular implant in a predetermined sequence. The respective configurations of the case and the ocular implant insertion apparatus are such that the ocular implant insertion apparatus is not removable from the case when the ocular implant insertion apparatus is in the pre-use state and is removable after the first movable structure has moved at least a portion of the optical implant.
Owner:HOYA CORP
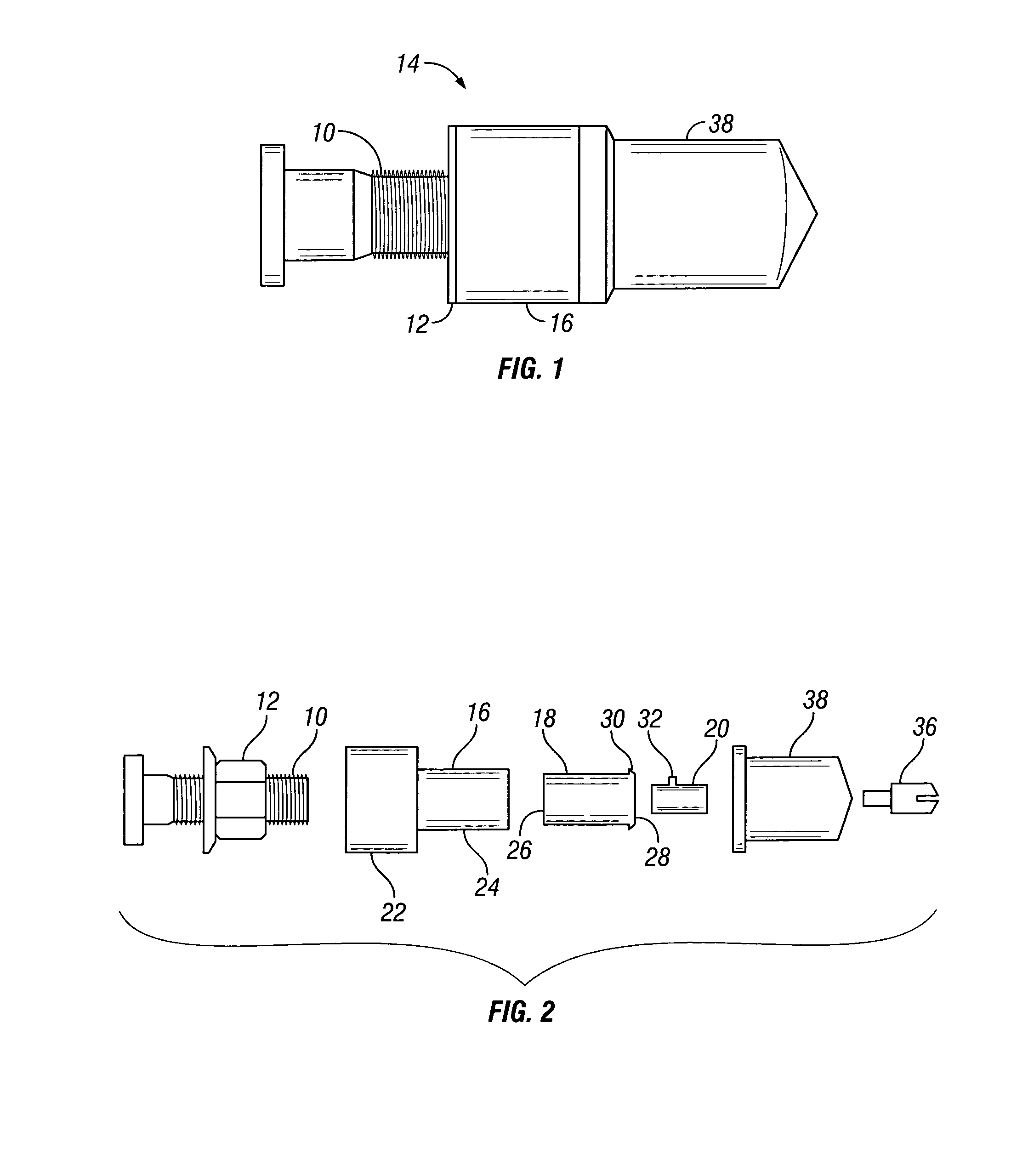
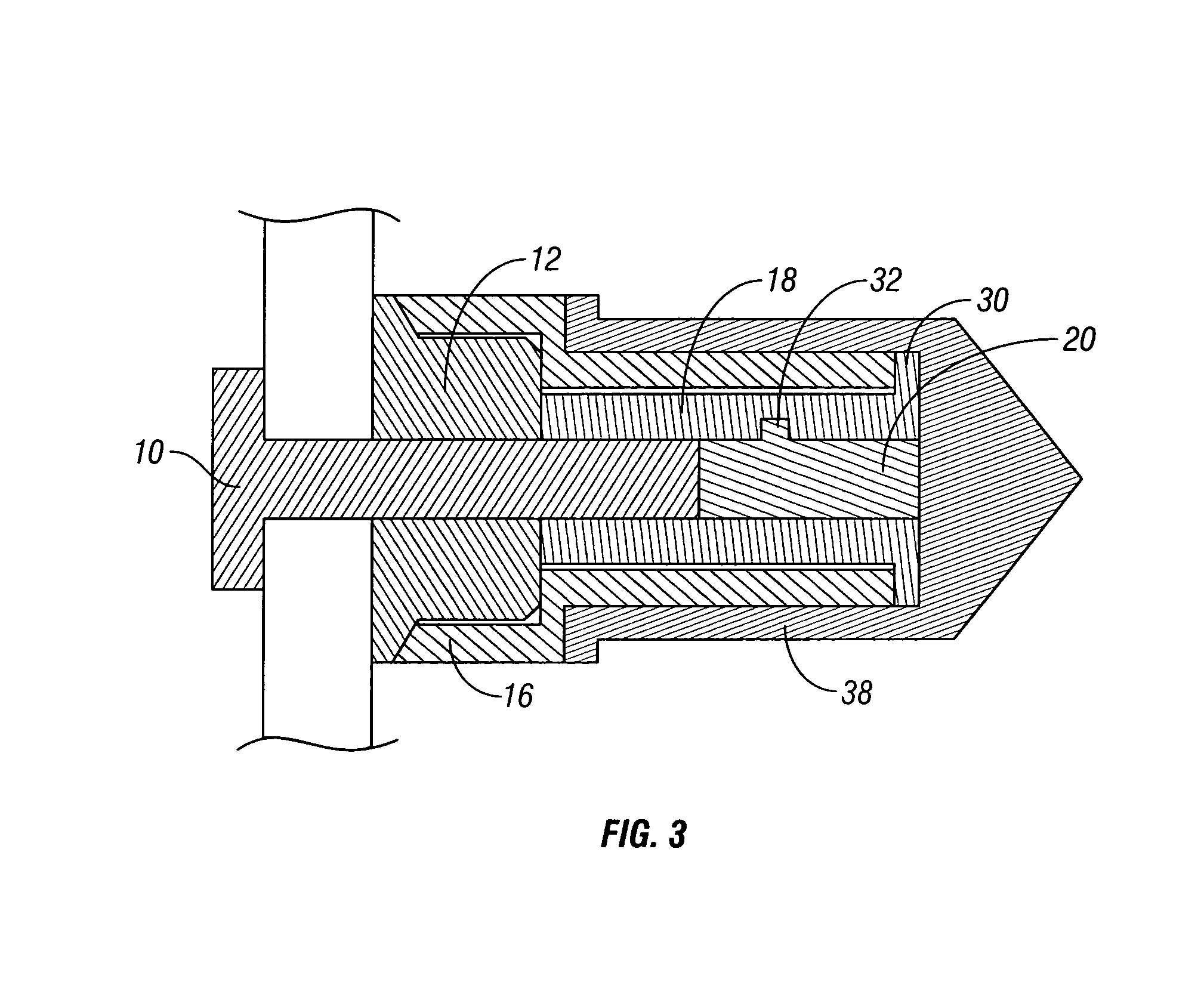
Lug nut locking device
A lug nut locking device is provided to prevent theft of vehicle wheels. The locking device includes a collar adapted to fit over the lug nut. A tube fits within the collar and has a threaded first end to threadably mount onto the lug bolt. The second end of the tube has an opening to receive a tool to tighten the tube onto the lug bolt. A lock cylinder slides into the tube and has a tab extendable by a key into a recess within the tube to lock the cylinder in the tube. A decorative cap frictionally fits over the collar to cover the lock cylinder. The collar and cap spin freely about the lug nut, to prevent use of a wrench while the lock device is mounted on the lug nut and bolt assembly.
Owner:GUMMERT RANDY A
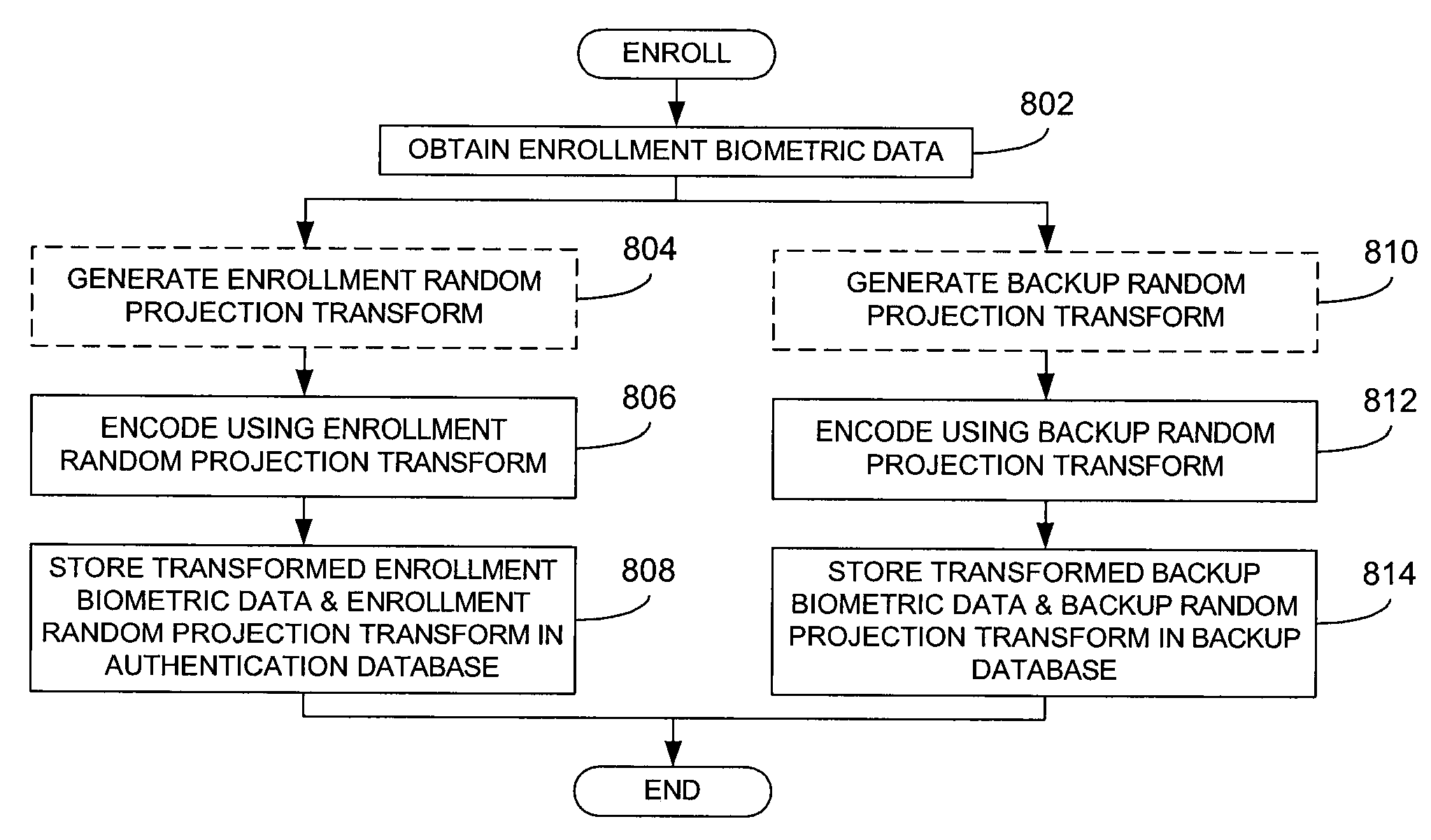
Biometric processing using random projection transforms
ActiveUS20100066493A1Prevent their useProgramme controlElectric signal transmission systemsAuthentication protocolBiometric data
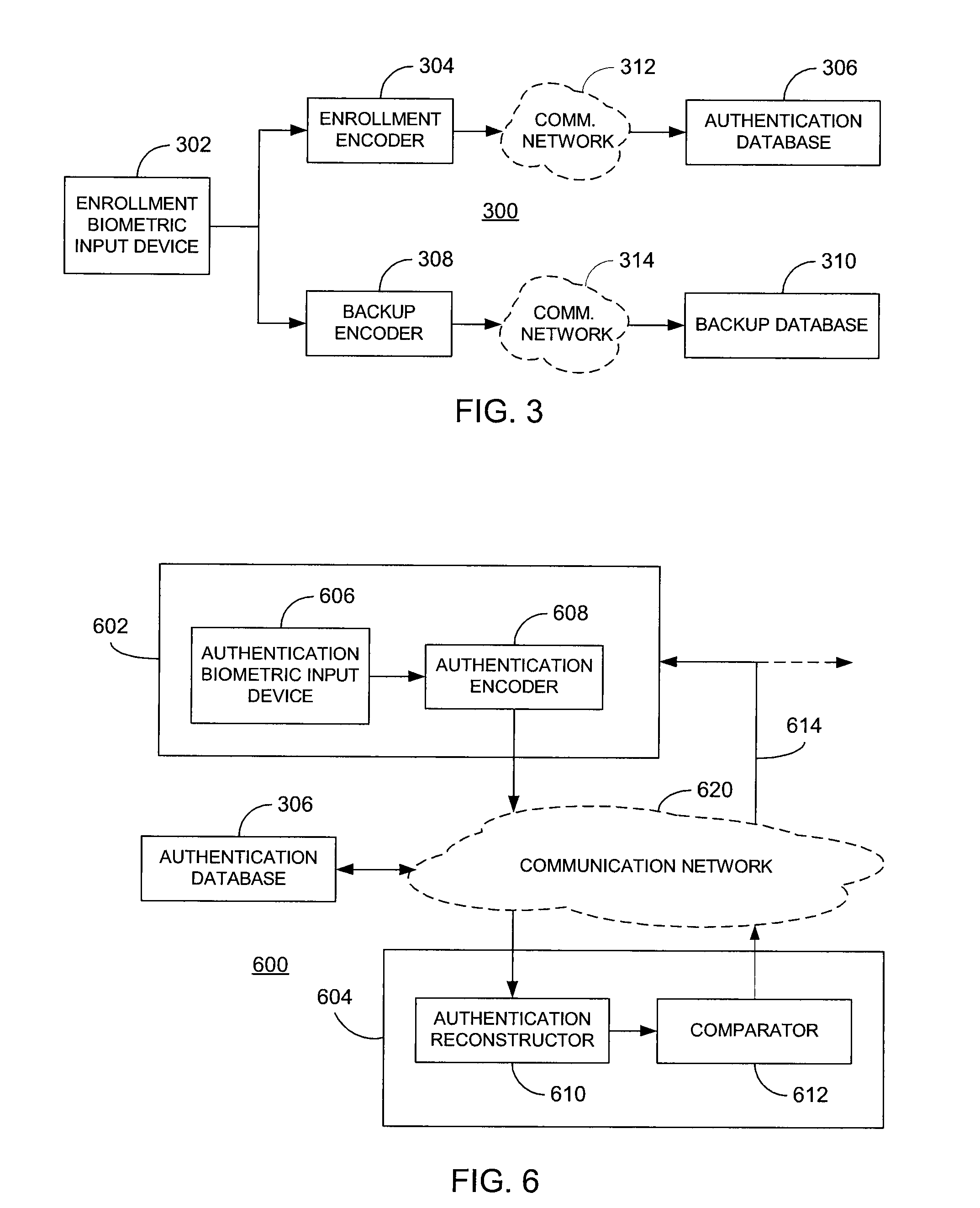
To provide cancelable biometrics, random projection transforms are used to produce transformed biometric data that may be used for authentication purposes. Each random projection transform provides a one-way or irreversible transformation such that the resulting transformed biometric data alone cannot be used to reconstruct the biometric data. Enrollment and backup transforms are produced based on enrollment biometric data. Authentication is possible by similarly transforming authentication biometric and then securely reconstructing the enrollment and authentication biometric data for comparison. In a similar manner, the enrollment and backup transforms may be used to reenroll biometric data when its corresponding transformed biometric data is compromised without requiring further user intervention.
Owner:ACCENTURE GMBH
Electronic cicarette
InactiveUS20160262449A1Increase frictionPrevent their useCigar manufactureTobacco devicesEngineeringElectronic cigarette
An electronic cigarette includes a rod having an atomization device and a battery assembly, wherein the electronic cigarette further includes a jacket, the jacket is arranged on an outer surface of the rod, and an outer surface of the jacket is provided with a friction portion. When using the electronic cigarette, due to the friction portion, fingers of a user may contact the friction portion, which may increase the friction between the fingers and the rod, thereby effectively preventing the electronic cigarette from falling off from the fingers in use.
Owner:KIMREE HI TECH
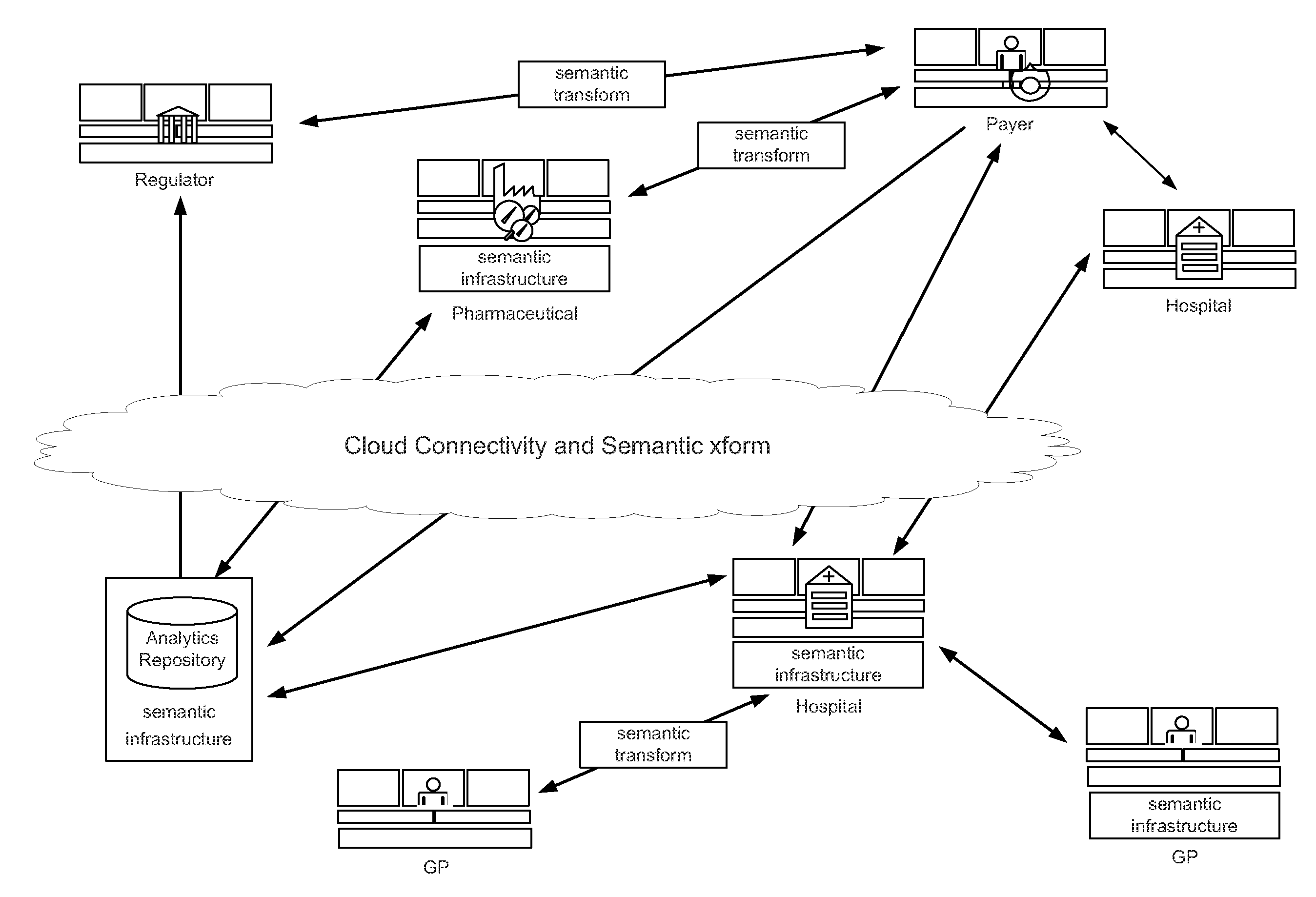
Semantic Interoperability System for Medicinal Information
ActiveUS20130030827A1Prevent their useData processing applicationsMedical automated diagnosisElectronic informationSystem configuration
A system for managing and exchanging electronic information provides a rules management component for executing conceptual rules, an ontology management component, an information model management component, and a system configuration management component. The ontology management component manages at least one ontology and mappings between members of different ontologies. The ontologies may include a code system and a terminology. The ontology management component may manage a value set that is a subset of the terminology. The information model management component manages one or more information model schemas, each defining an information model and comprising information defining at least one slot within the information model. The system configuration management component manages configuration information on the configuration of each system component. The system configuration component utilizes services of the rules management component, information model management component and ontology management component to dynamically bind value sets to slots of the information model.
Owner:CLINERION
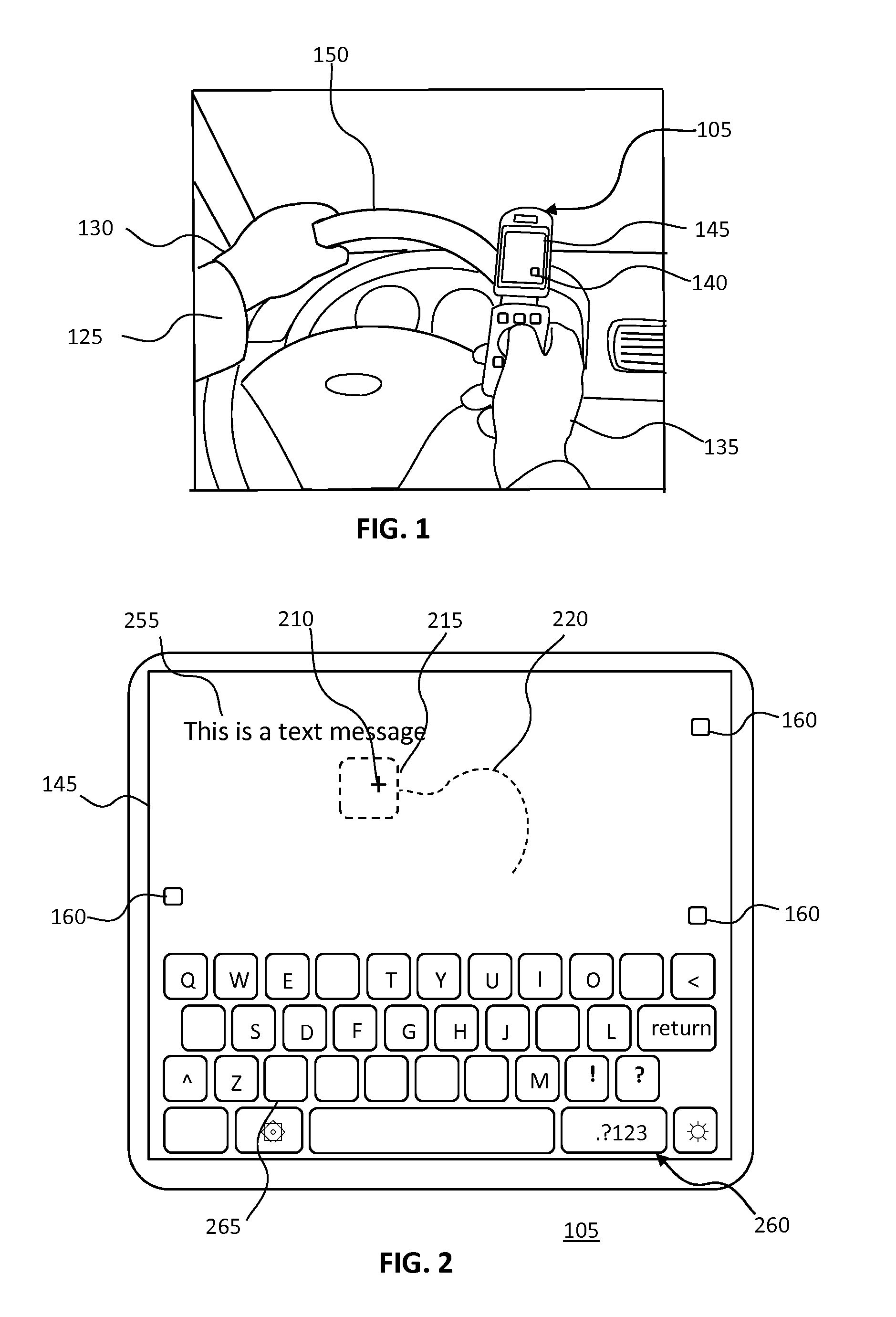
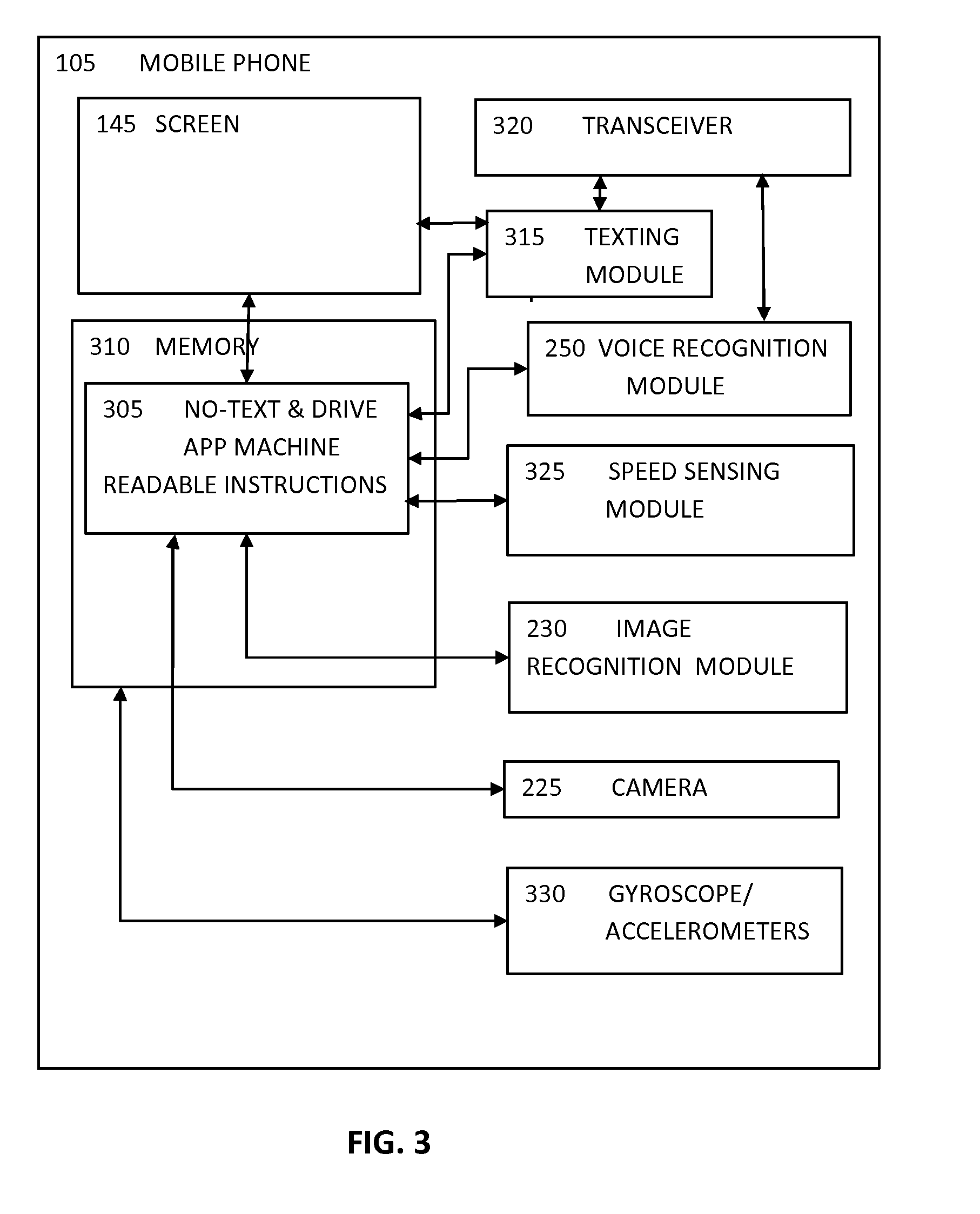
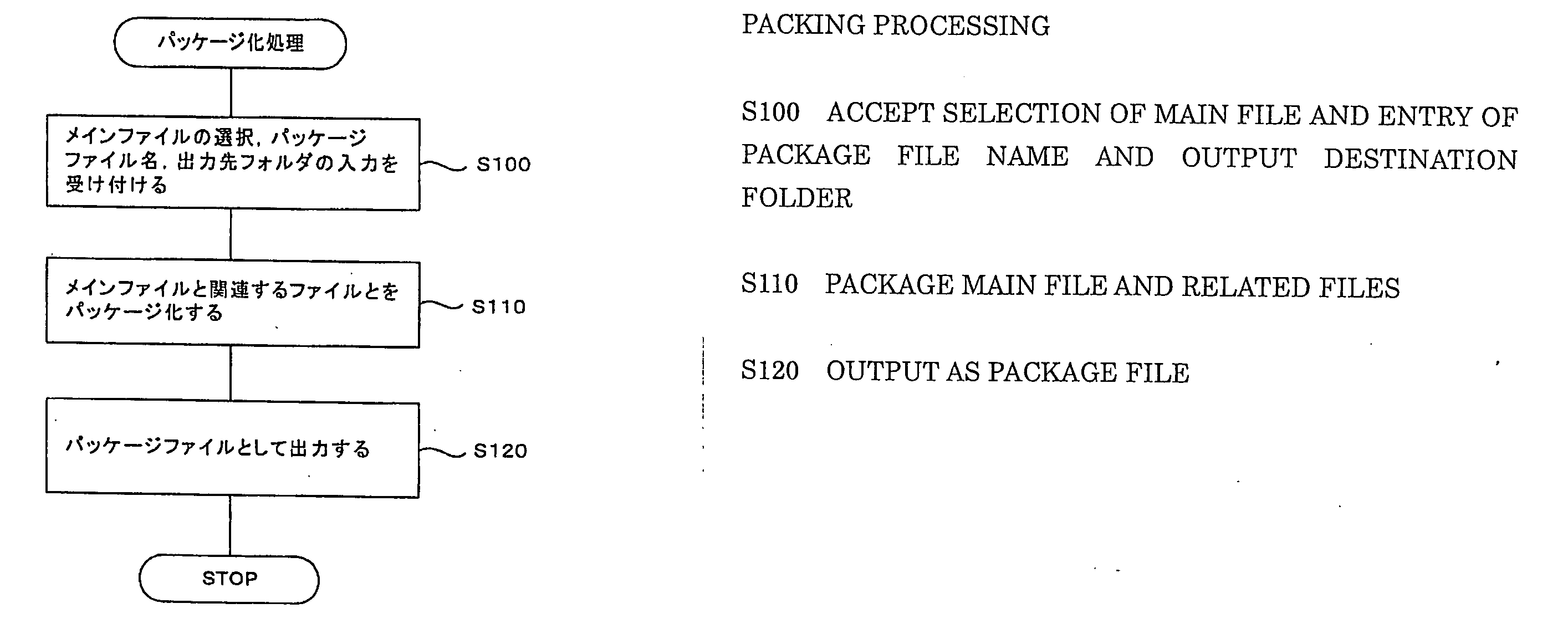
App for Preventing Phone functionality while Driving
InactiveUS20140274023A1Simple but effectivePrevent their useAssess restrictionAutomatic exchangesEmbedded systemApplication software
An app designed to prevent using distracting phone functionality, including texting, on a mobile phone while driving a vehicle is disclosed. The app first detects a speed at which the phone is travelling. If the speed is above a threshold, typically 5 mph the user is given a challenge that require either that both hands, or both eyes, are required on the phone. If the challenge is not met, the user is assumed to be the driver and the distracting phone functionality, including texting, is disabled. If the challenge is met, the user is assumed to be a passenger and the distracting phone functionality, including texting remains enabled.
Owner:RAJEEVALOCHANA ASWIN +1
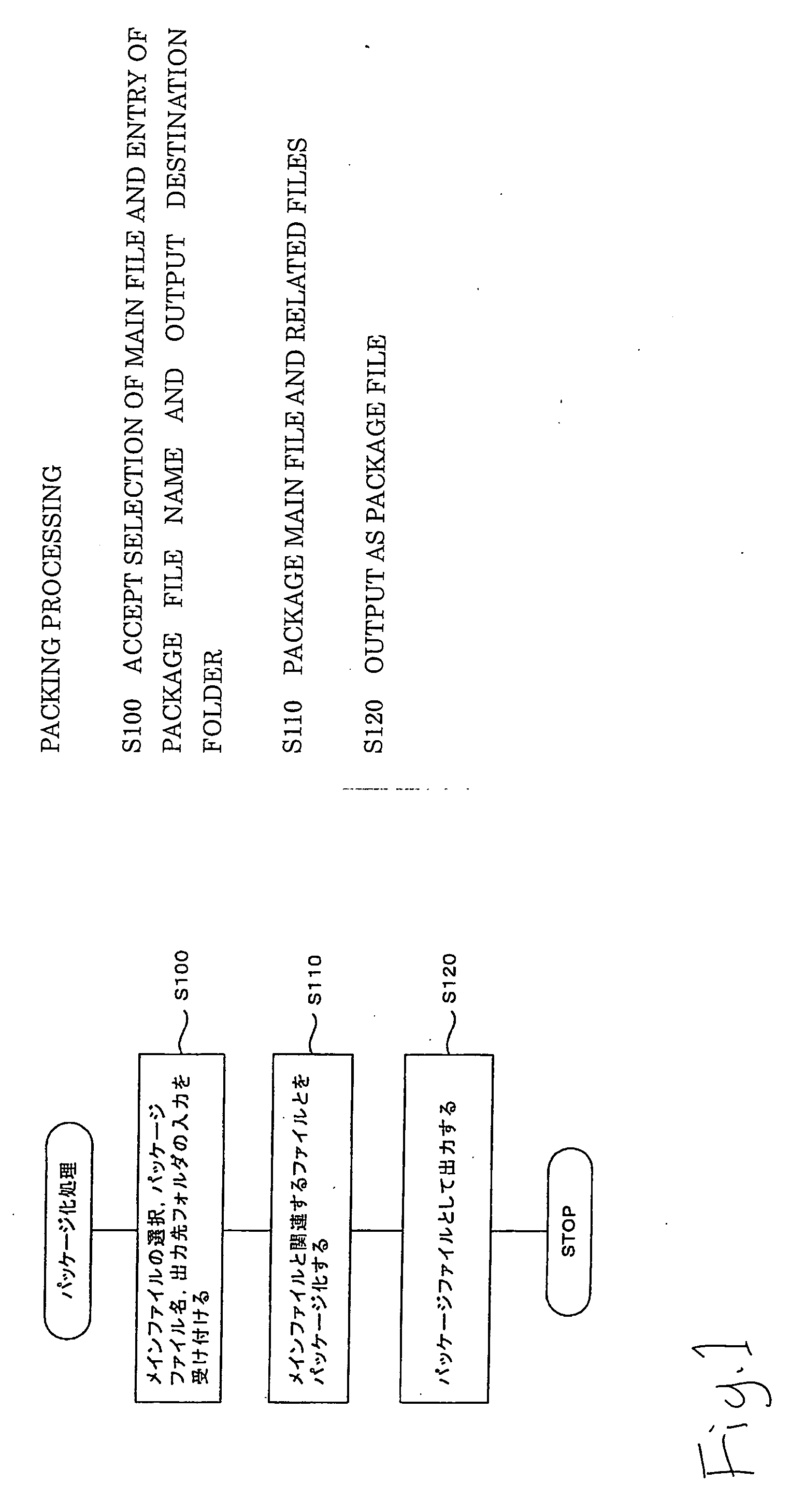
Electronic file operation method and layout edition device
InactiveUS20060155732A1Prevent their useEasy to operateTelevision system detailsProgram control using stored programsObject file
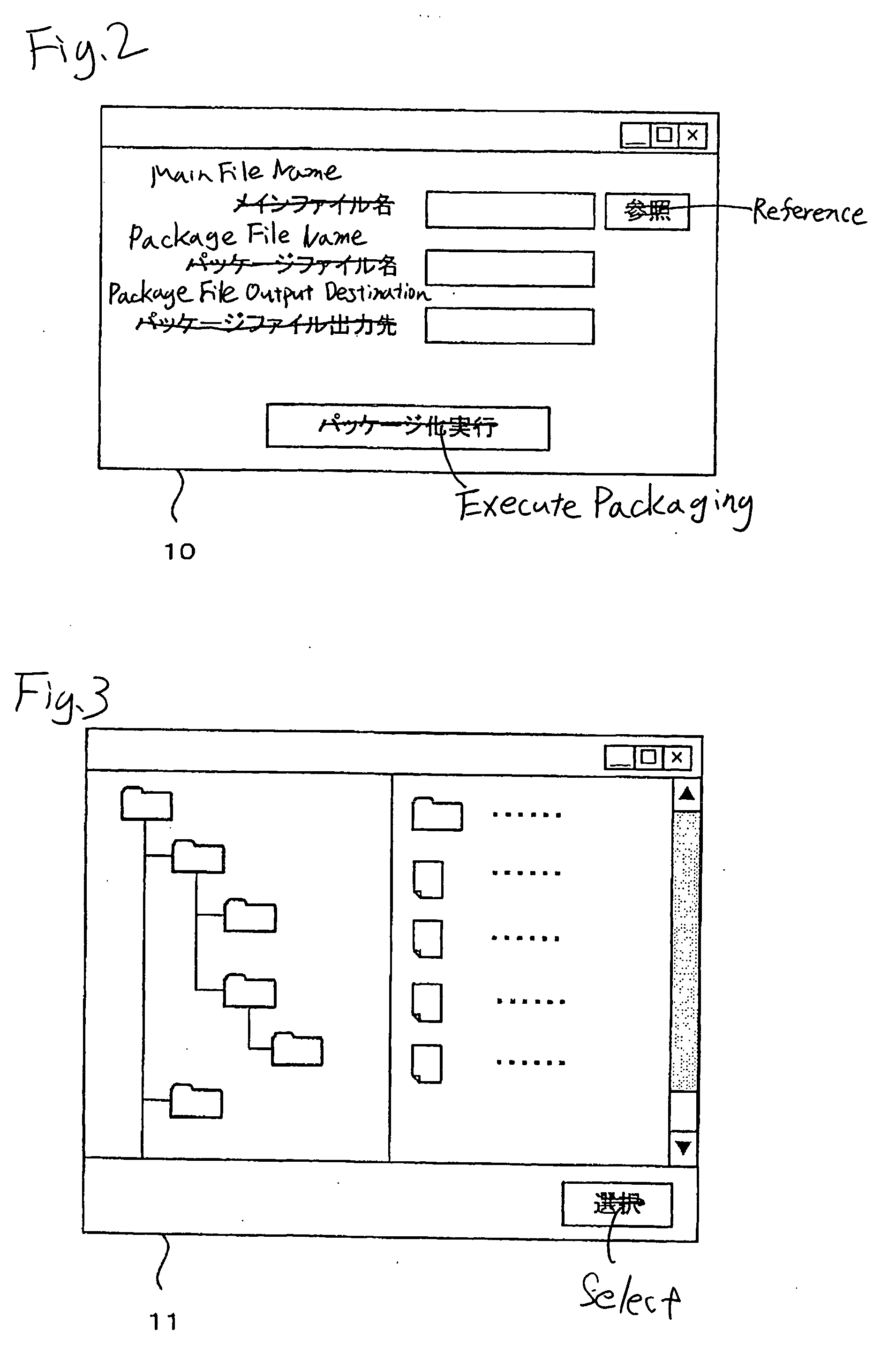
Selection of a main file and entry of the name of a package file, an output destination folder, etc., are accepted (step S100), the files in the folder of the same name as the main file existing in the same folder as the selected main file are packaged as related files (step S110), and the packaged files are output as a package file based on the entered name and the output destination folder (S120). Consequently, a plurality of electronic files can be packaged for easy handling.
Owner:SEIKO EPSON CORP
System and method for authenticating electronic money using a smart card and a communication terminal
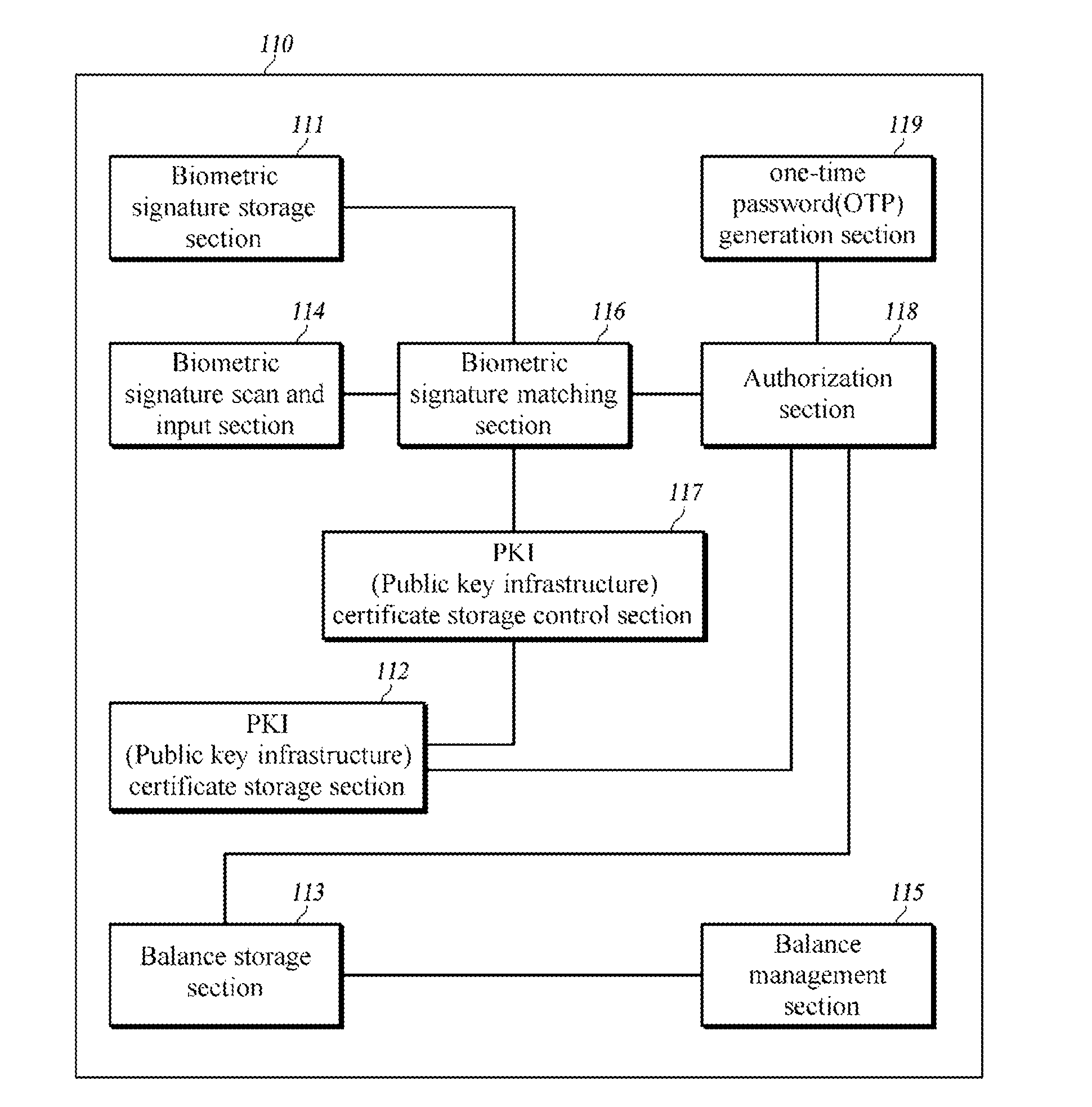
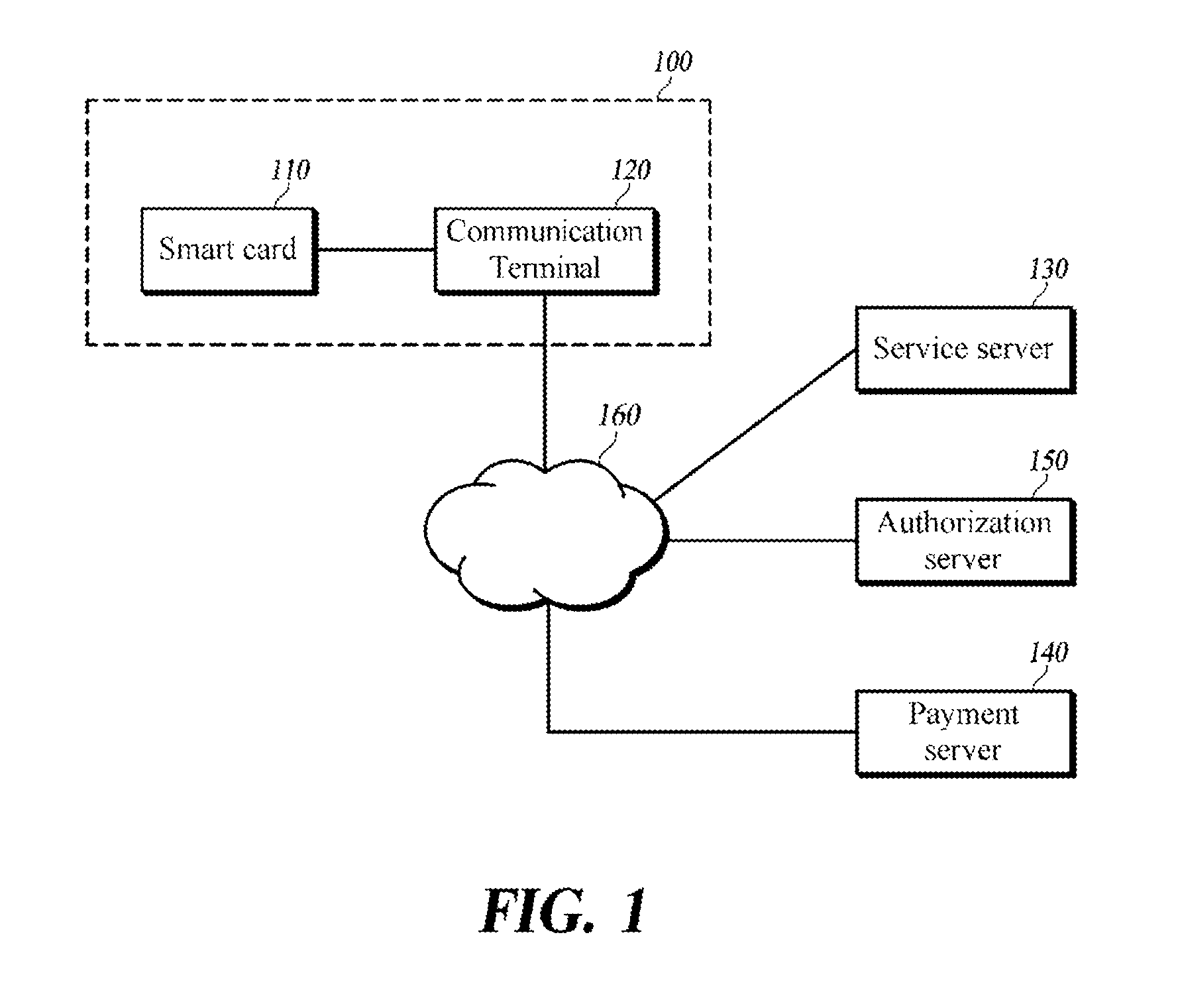
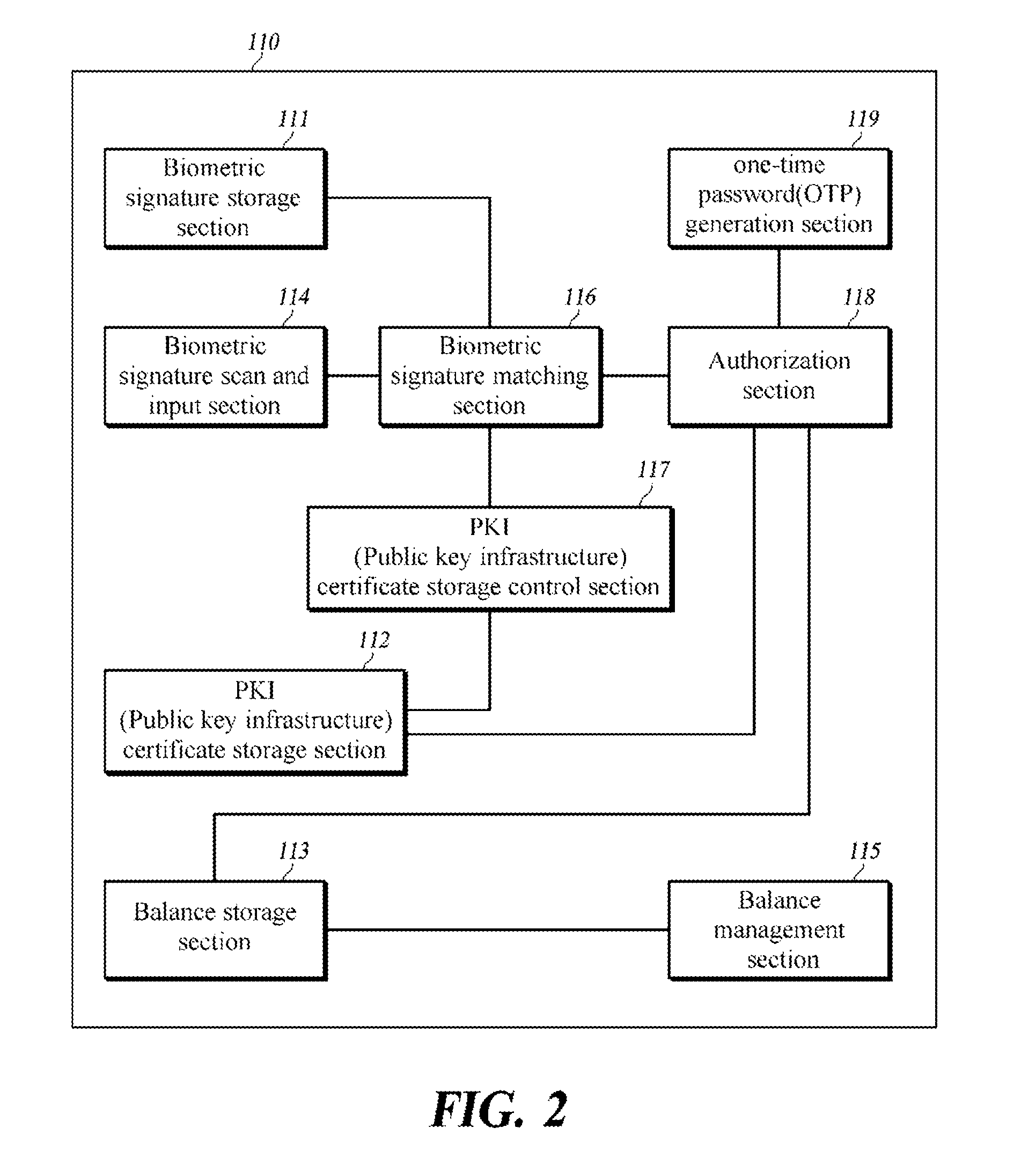
The present invention relates to a system and a method for authenticating an electronic money using a smart card and a communication terminal. The present invention provides a system and a method for authenticating an electronic money, wherein the system comprises a smart card and a communication terminal. The smart card takes biometric signature from a user as an input, transmits recognition completion information to the communication terminal when the biometric signature inputted by the user matches the stored biometric signature, receives an update command from the communication terminal, updates the amount of stored balance data, and transmits an update completion message to the communication terminal. The communication terminal is connected to the smart card in a wired or wireless manner, and transmits the update command to the smart card upon receipt of the recognition completion information.
Owner:CHOI OK
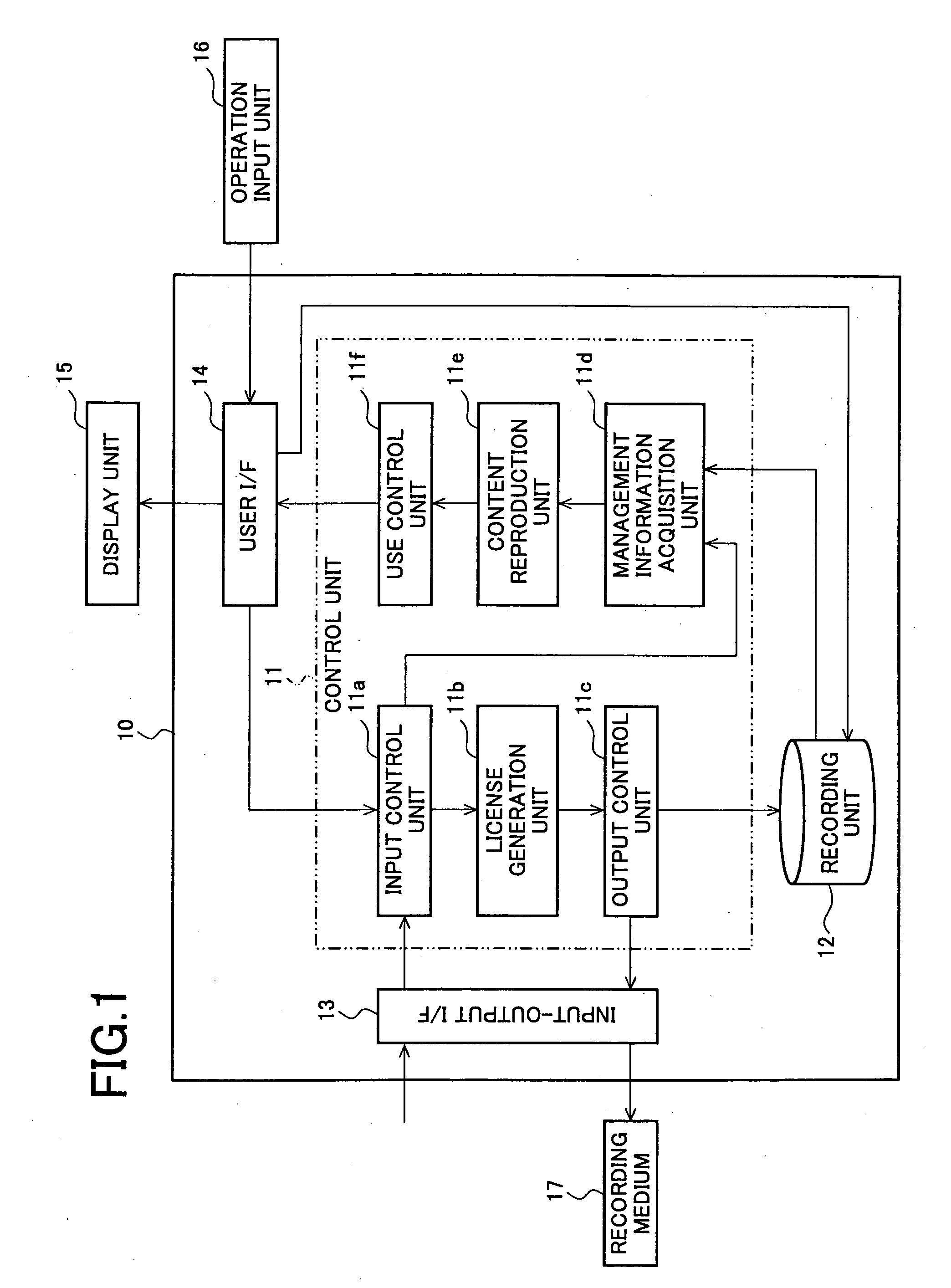
Content use control device, reording device, reproduction device, recording medium, and content use control method
InactiveUS20070124251A1Prevent their useEasily setInput/output to record carriersData processing applicationsInput/outputControl equipment
A collective content consisting of a plurality of partial contents holding license information including a use condition can be appropriately used according to the use condition contained in the license information in each of the partial contents. A content use control device includes an input / output I / F, license generation unit, output control unit, content reproduction unit, and use control unit. The partial content holding the license information including the use condition is inputted via the input / output I / F. License information is assigned to each of the partial contents inputted and constituting a collective content. Single license information collecting the assigned license information and its collective content are outputted to a recording medium. The content use control device reproduces a partial content contained in the collective content recorded on the recording medium and controls the use of the reproduced partial content according to its use condition.
Owner:SHARP KK
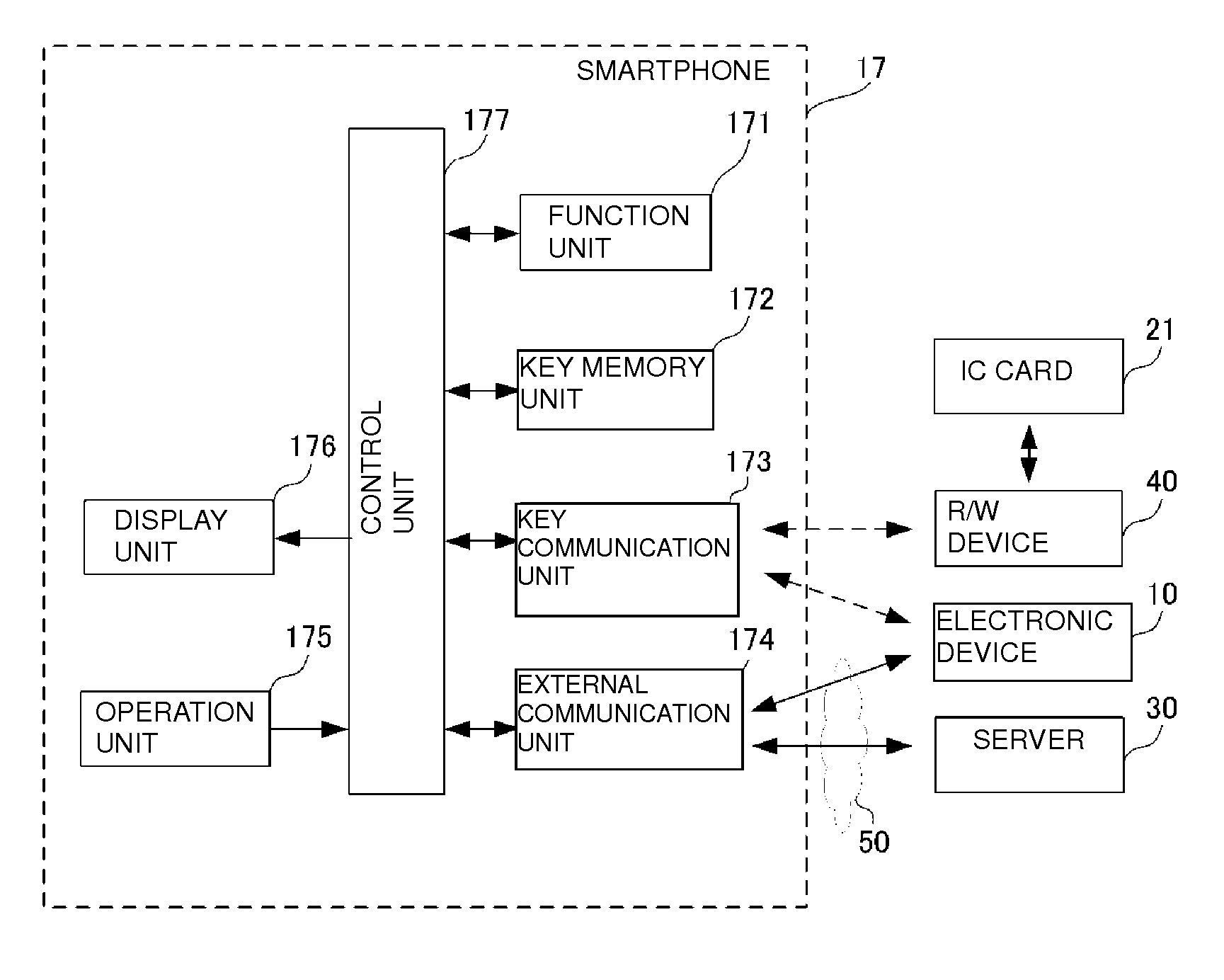
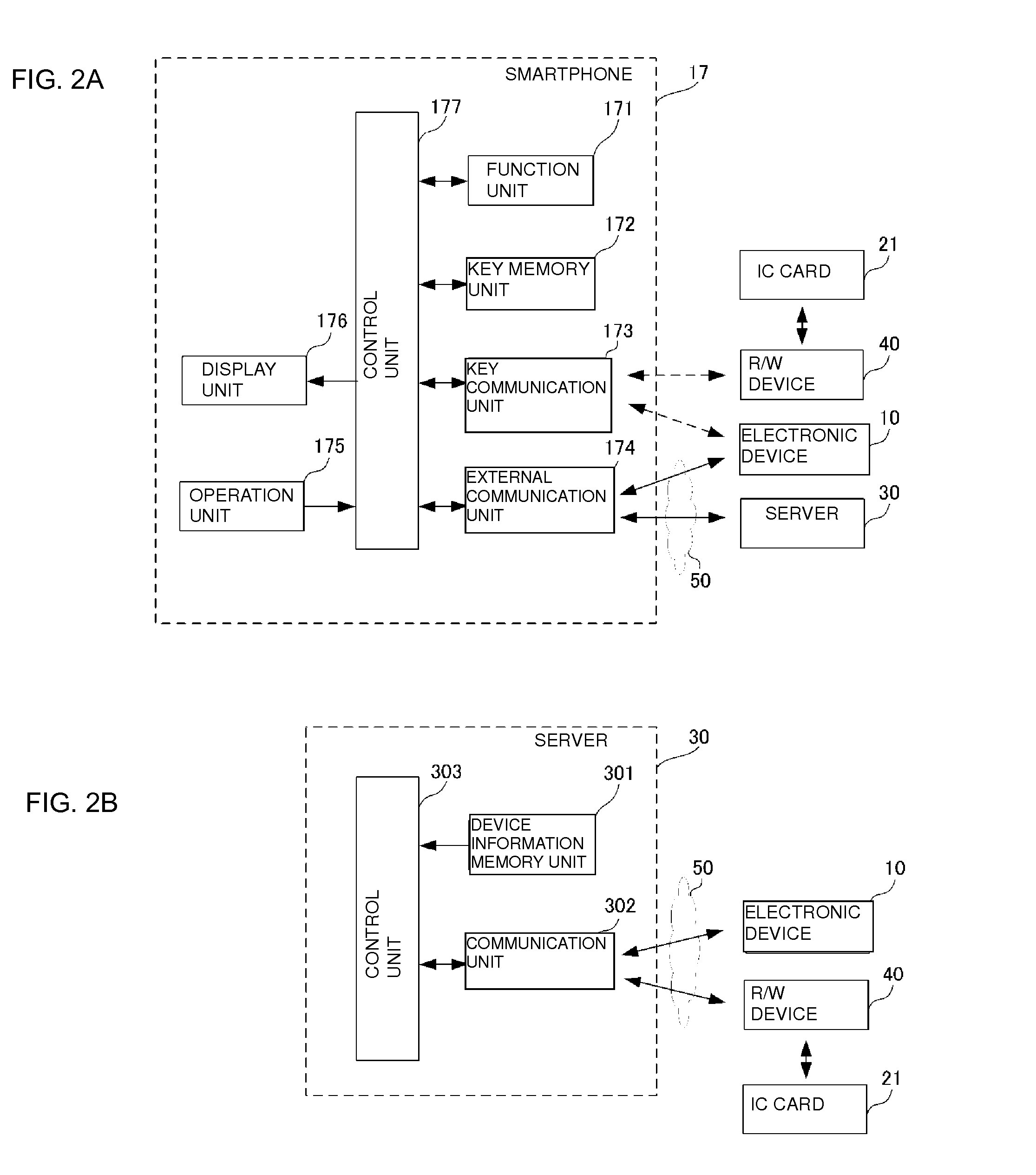
Electronic key system
ActiveUS20150039892A1Prevent their useDisable readingKey distribution for secure communicationUser identity/authority verificationManagement unitElectronic equipment
In a network to which a plurality of electronic devices and a server are connected, an electronic key system controls locking and unlocking of ID information output of each electronic device. Each electronic device includes a switching device that locks or unlocks output of ID information of each electronic device. The server includes an availability changing unit and a management unit. The availability changing unit unlocks only one of the plurality of electronic devices and locks the other electronic devices. The management unit updates a state at which the locking of ID information output and the unlocking of ID information output are swapped between a pair of the electronic devices.
Owner:MURATA MFG CO LTD
Method for universal transport encapsulation for internet protocol network communications
InactiveUS20050058136A1Prevent their usePrevents unauthorized use and interceptionTime-division multiplexData switching by path configurationAsynchronous Transfer ModeTime-division multiplexing
A method for implementing a simple protocol, referred to as the universal transport interface (UTI), that can be used to create high speed Internet Protocol (IP) tunnels for transmitting a variety of different payloads across a network. Payload packets may comprise any currently known packet protocol, including but not limited to time division multiplex data, IP packets, asynchronous transfer mode (ATM) cells, Packet-over-SONET / SDH (POS) packets, and Frame Relay frames. The universal transport interface protocol consists of a predefined set of mappings whereby any known protocol can be packaged into a single, conceptually simple packet format. This format is referred to as the universal transport encapsulation (UTE) format. UTE format packets are, by design, amenable to transport over an IP network without further modification beyond standard IP encapsulation. The disclosed method further implements a security key system to prevent unauthorized use or interception of UTE packets on the network.
Owner:CISCO TECH INC
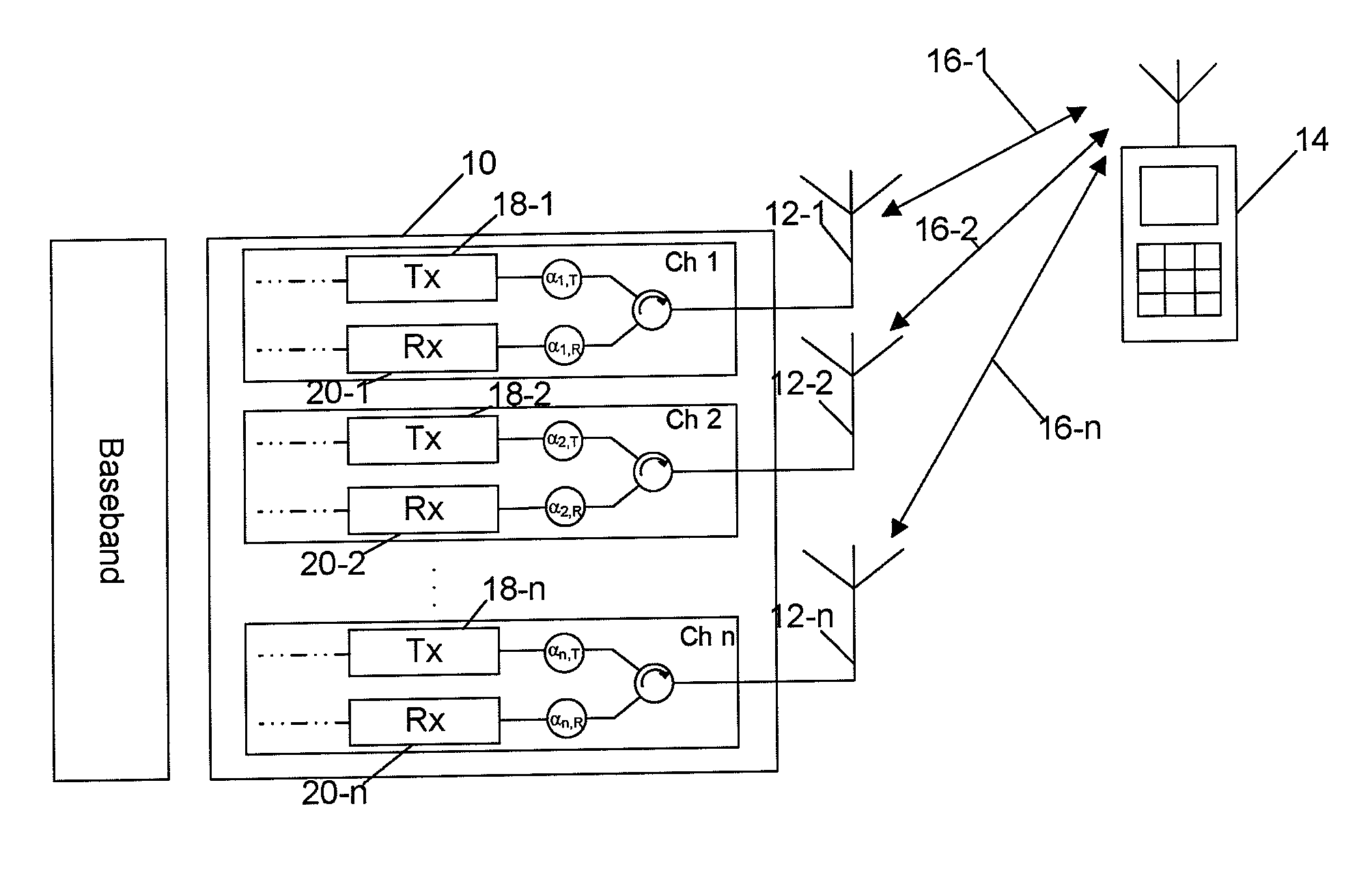
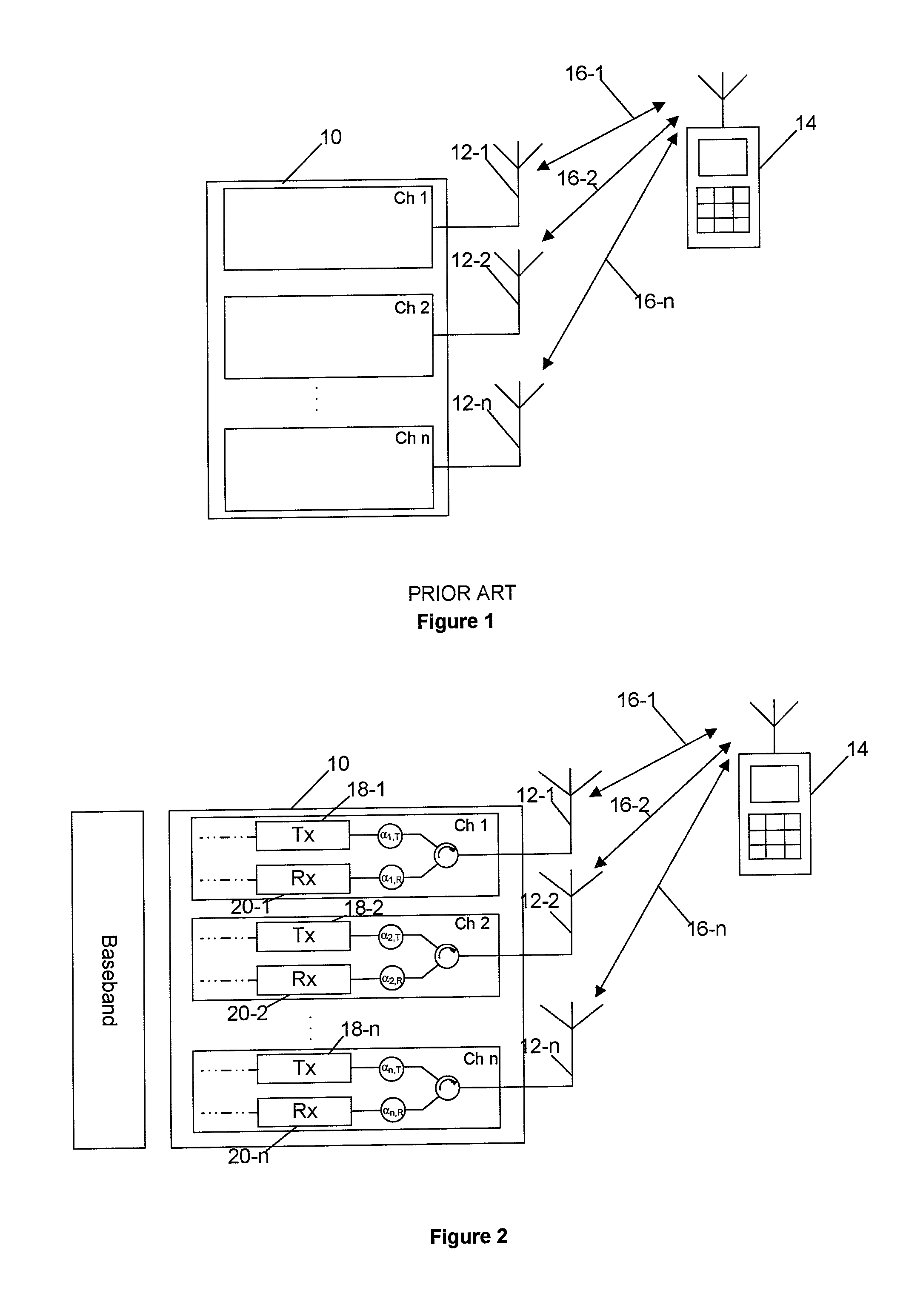
Method for Channel Calibration
InactiveUS20090186590A1Prevent their useTransmitters monitoringReceivers monitoringMultiple antennaPilot signal
The present invention provides an improved method for calibrating transmitter and receiver circuits in a device having multiple antennas. The method involves transmitting pilot signals from the device to a second device and from the second device to the device. Each device determines the relative differences between the signals received by a first antenna and by each of the other antennas. The relative differences can then be used to calculate calibration factors that can be applied to the transmitter and receiver circuits.
Owner:APPLE INC
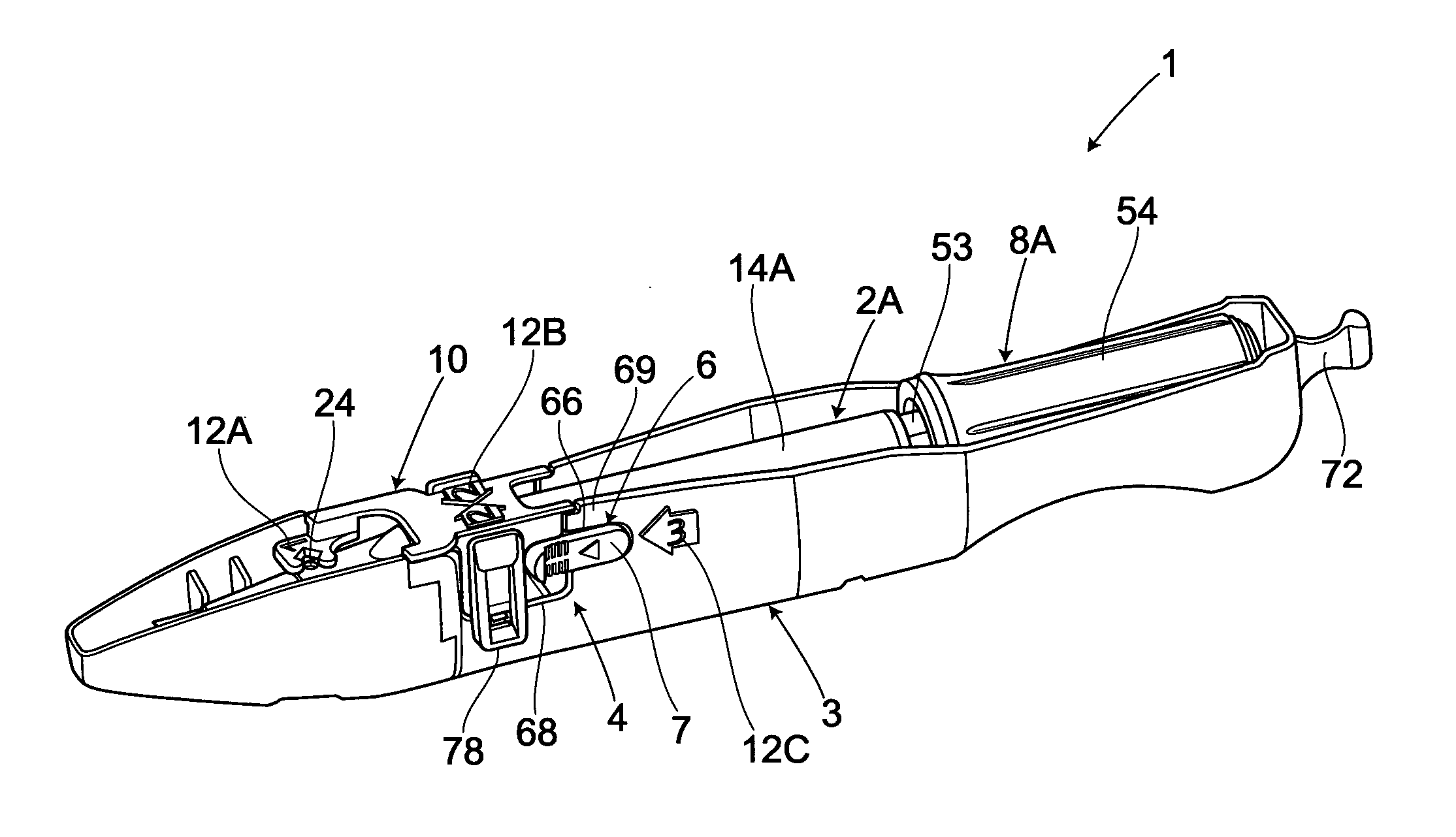
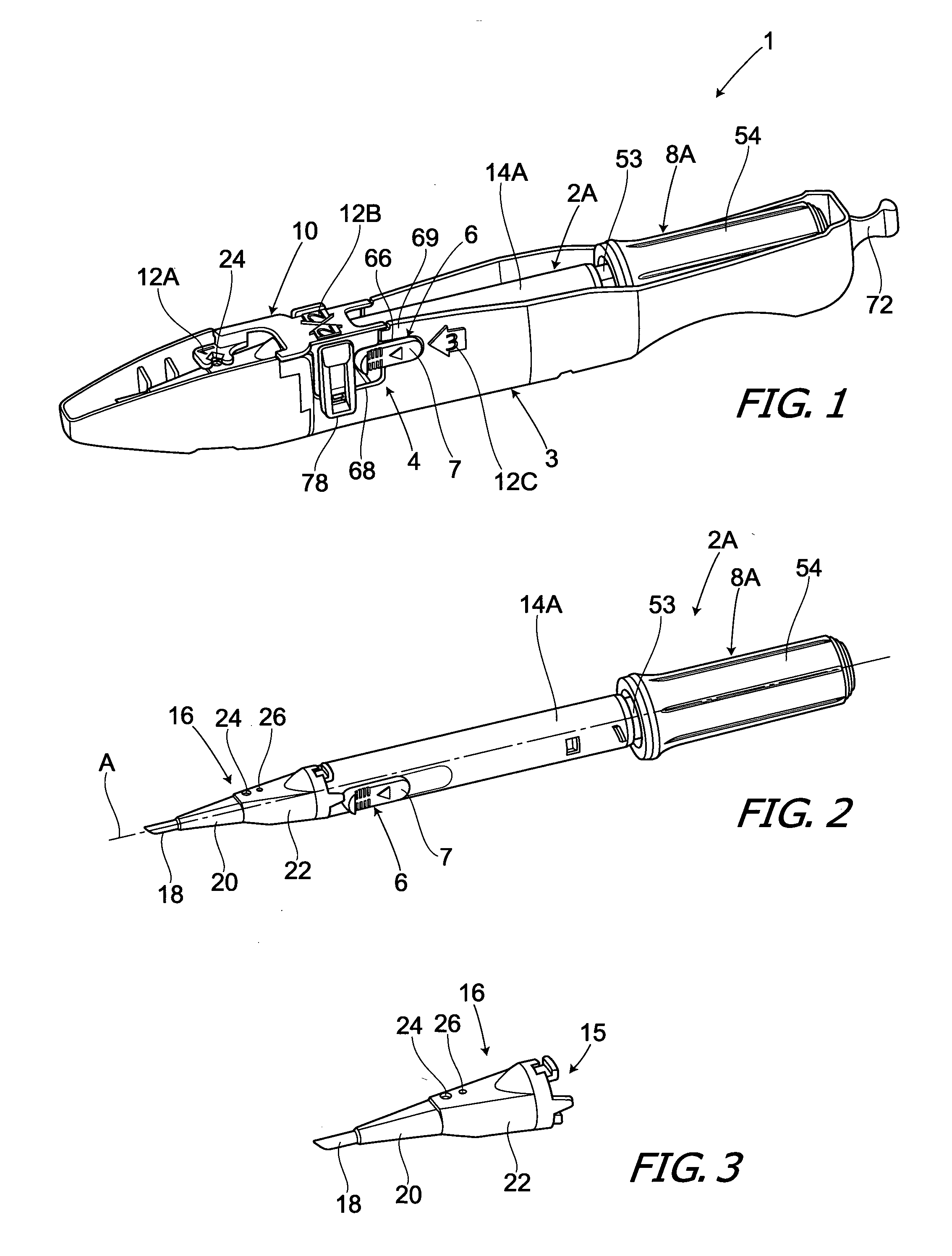
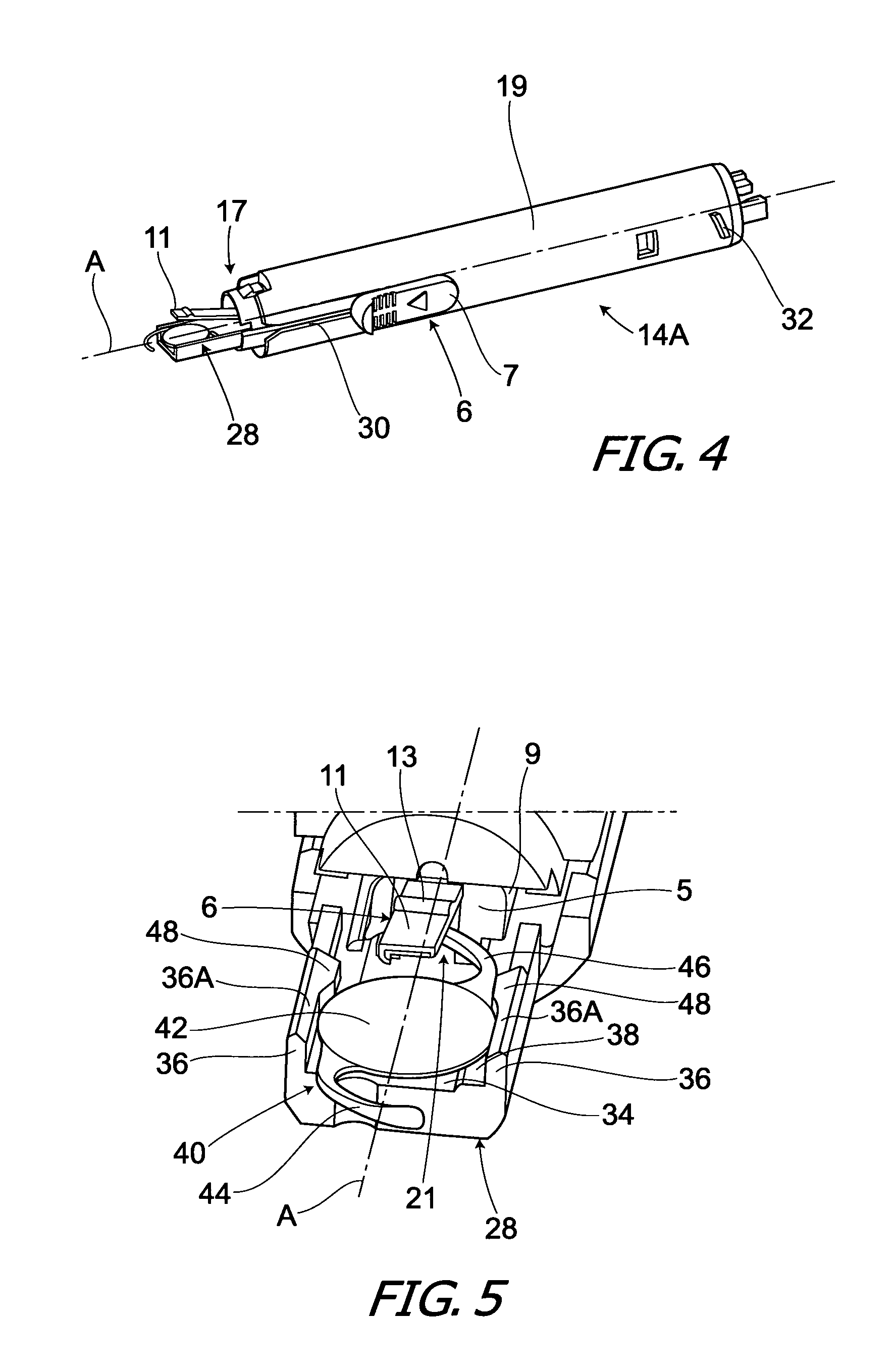
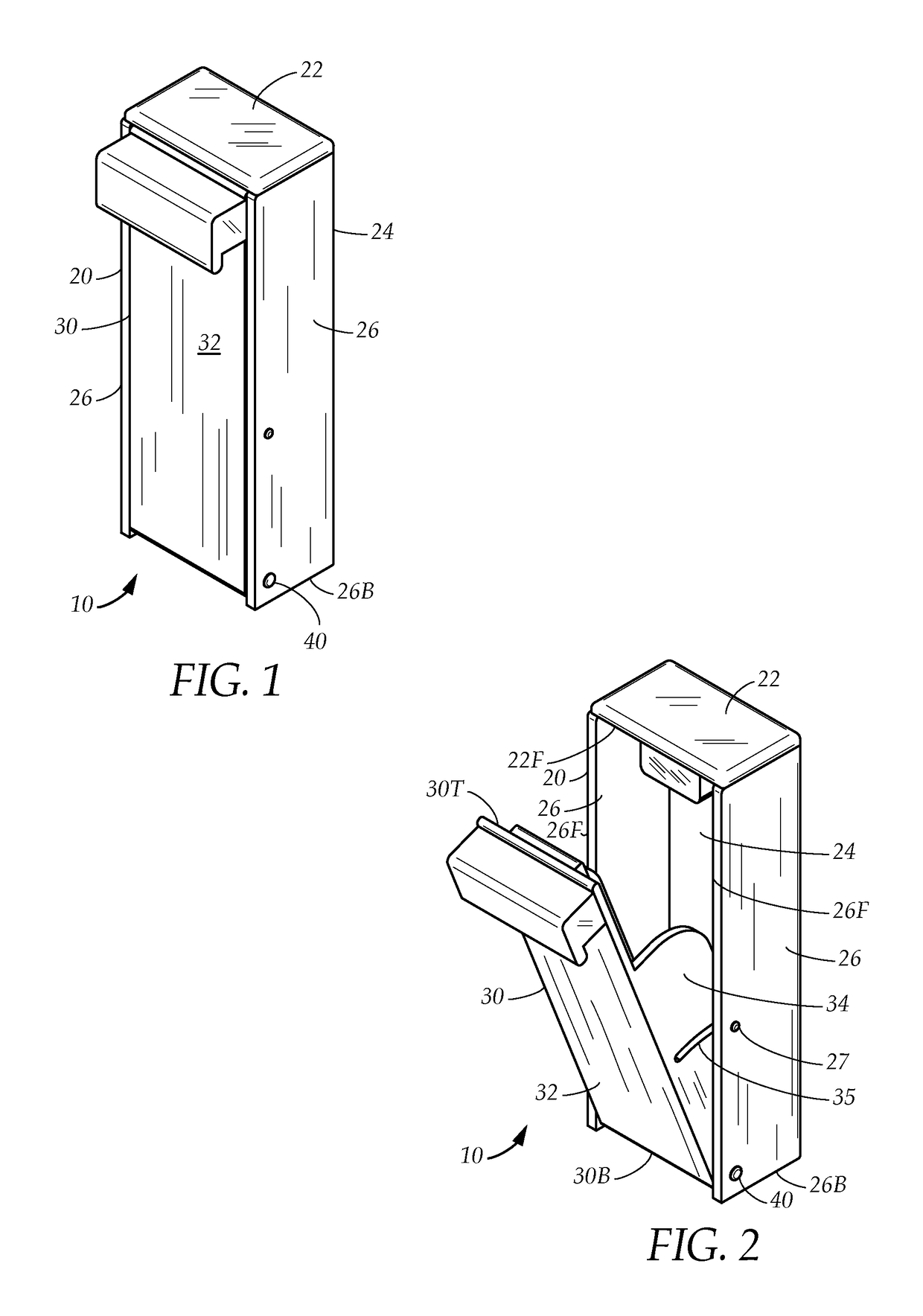
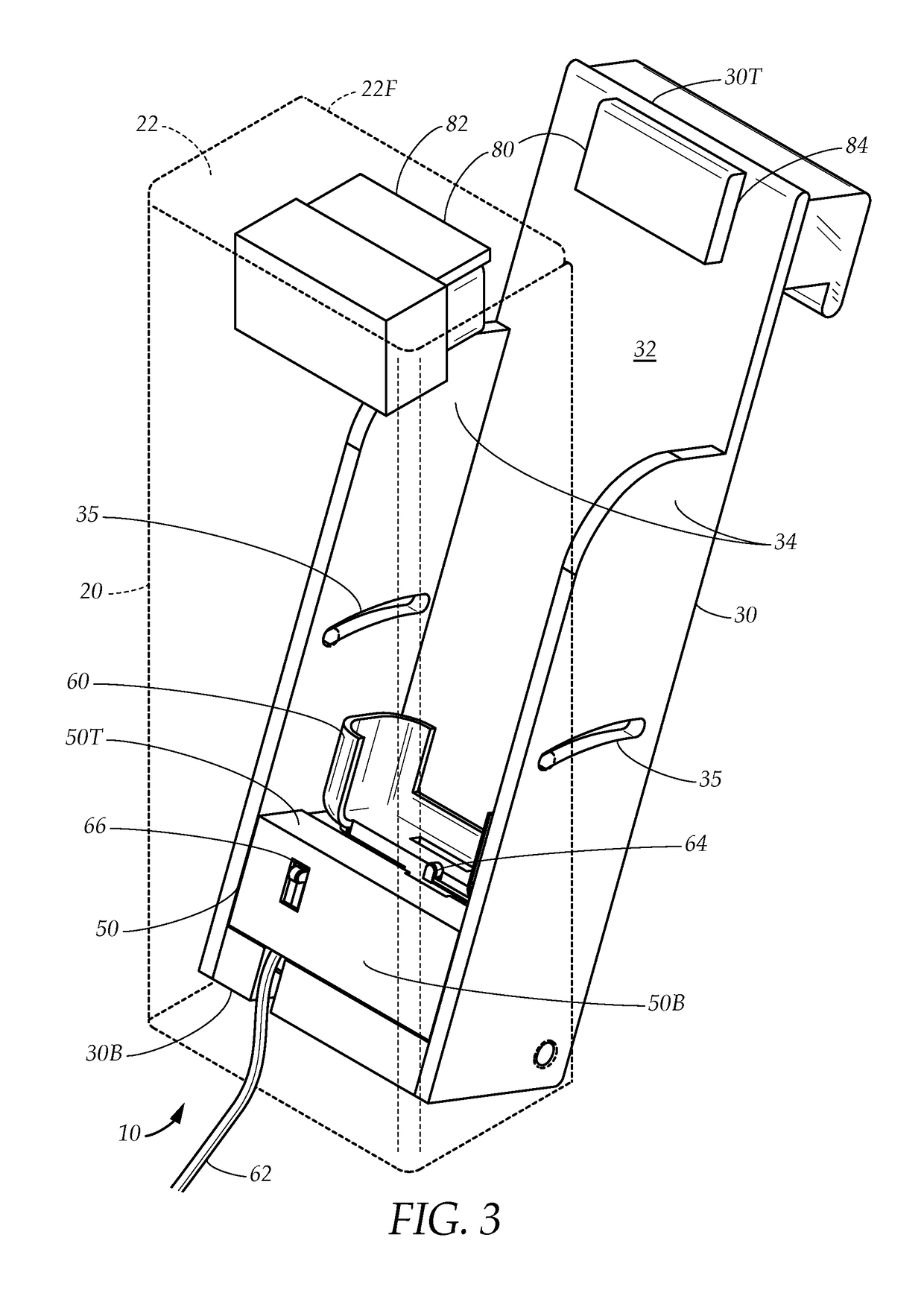
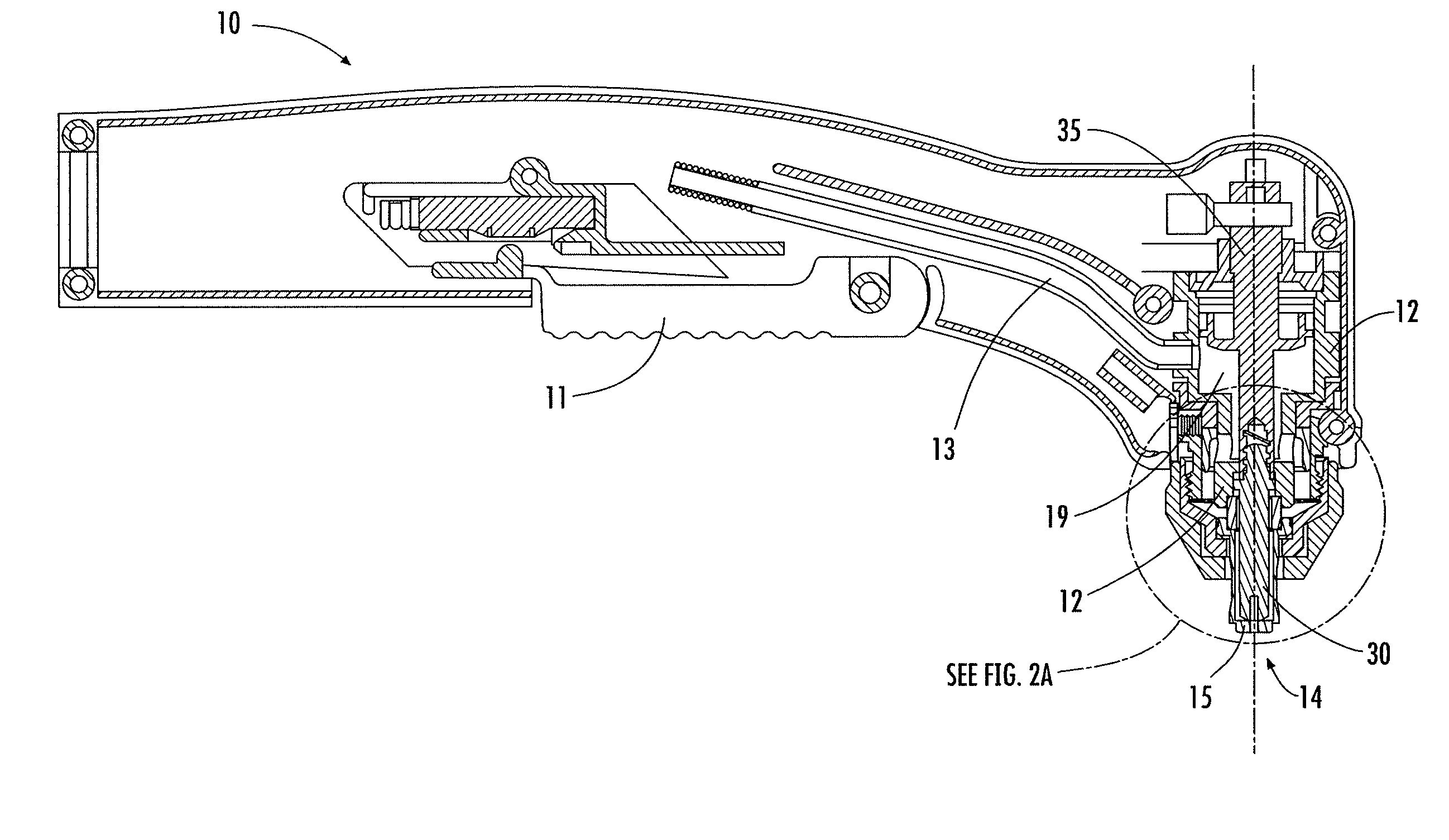
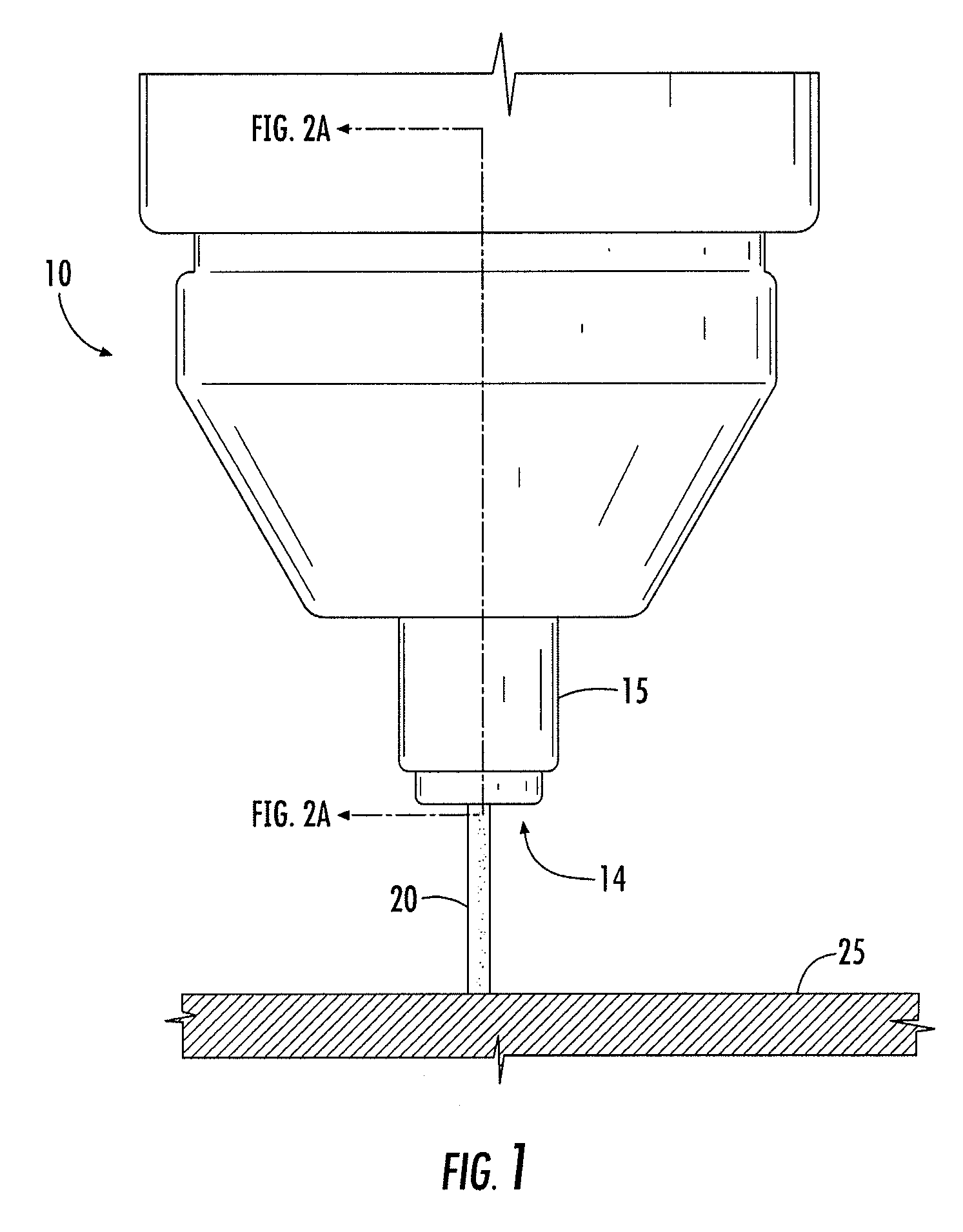
Lock Mechanism for a Dispenser, Roll of Material and End Plug Therefor, and Method for Inserting a Roll of Material Into Such Lock Mechanism
ActiveUS20080229791A1Easily insertPrevent their useBuilding locksAnti-theft devicesEngineeringLocking mechanism
A lock mechanism for a dispenser in combination with an exchangeable roll of material is provided, wherein the roll includes at least one end plug with a bearing pin for mounting the roll to the lock mechanism. The lock mechanism comprises a lock housing with a guide slot for insertion of the bearing pin. The guide slot has a first section with a first width and a second section with a second width which is smaller than the first width. First and second sections are arranged in a direction perpendicular to the longitudinal extension of the guide slot and in a longitudinal direction of the bearing pin. A sliding element is mounted to the lock housing and movable between a first position closing or narrowing the width of the guide slot and a second position opening the guide slot. A lock element is mounted to the sliding element and is rotationally movable about an axis of rotation between a locked position and an unlocked position. The lock element has an engagement portion which, in a locked position, is engaged with a locking geometry of the lock housing.
Owner:GRANGER MAURICE
Vending System and Method
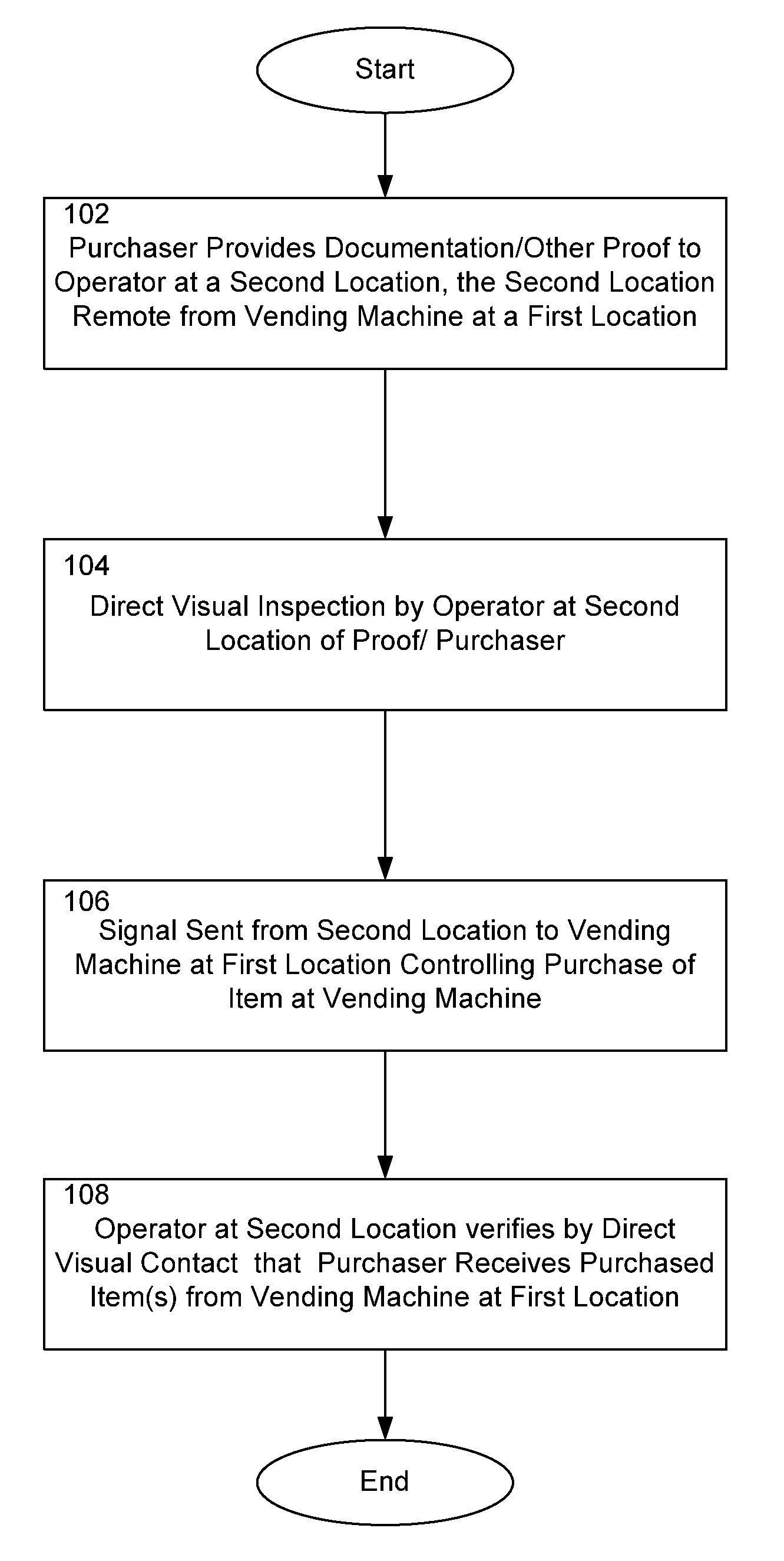
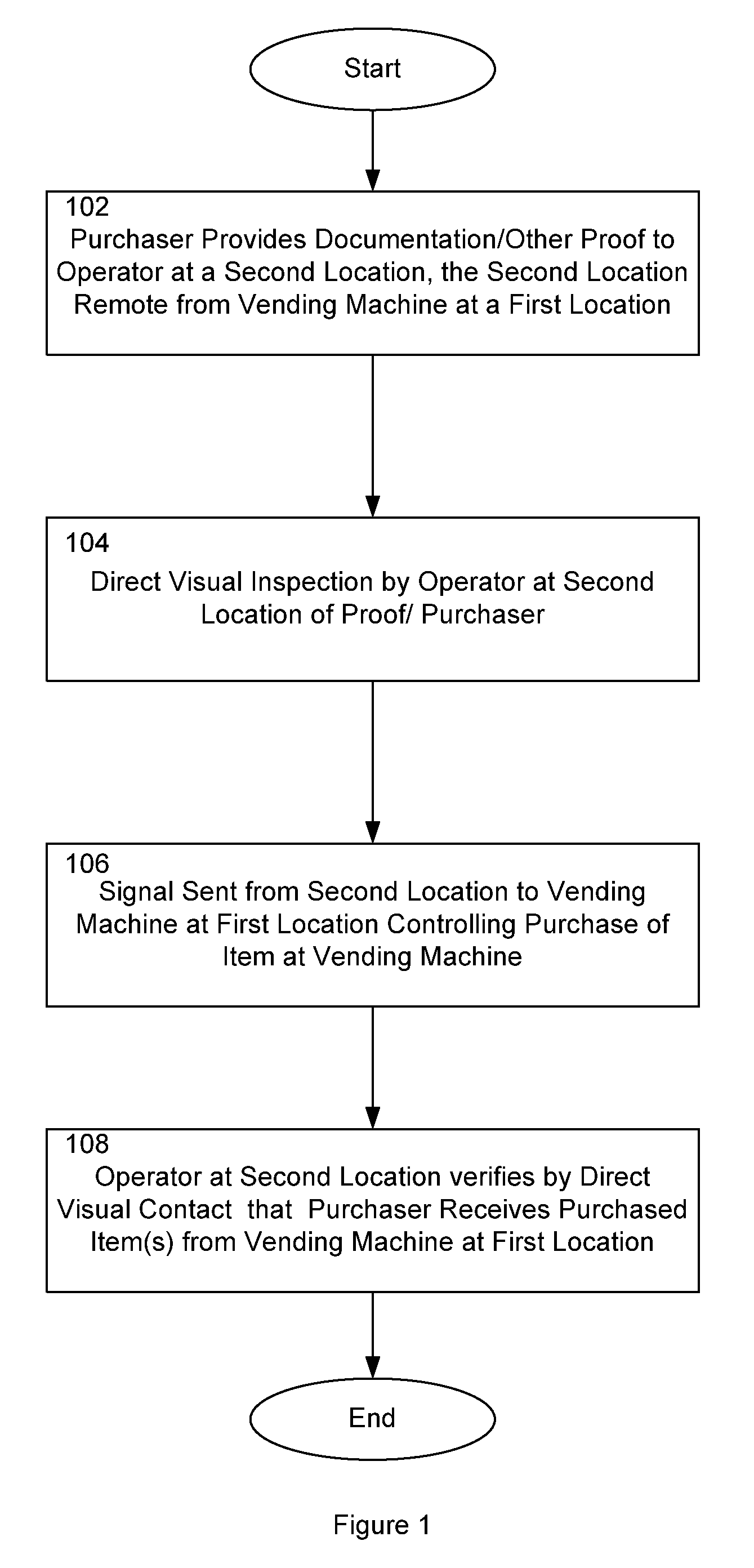
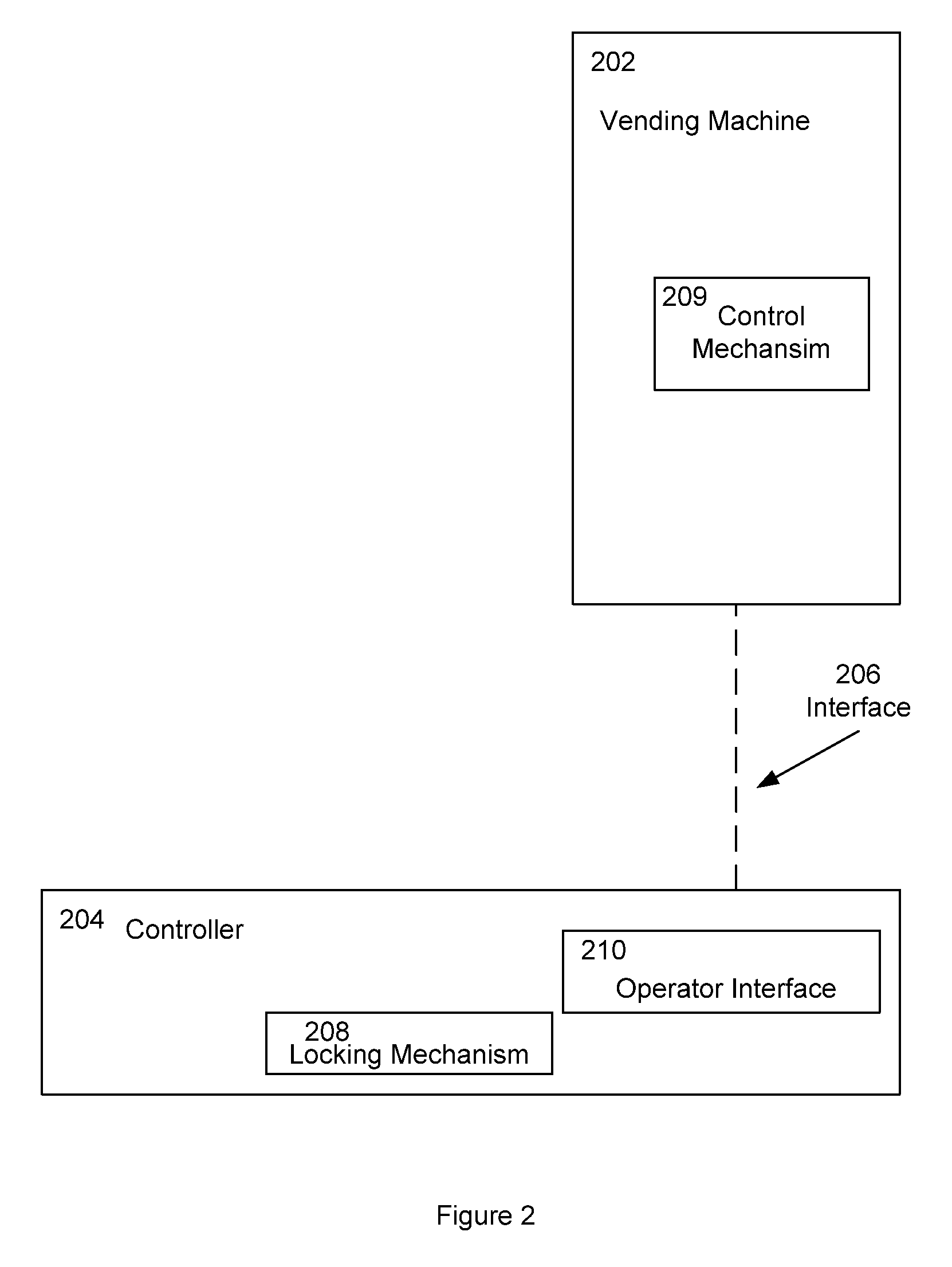
InactiveUS20090276088A1Prevent their useCoin-freed apparatus detailsDe-stacking articlesDocumentation procedureEngineering
A method of dispensing an age-restricted item from a vending machine at a first location is presented. The method includes receiving age documentation from a purchaser at a second location remote from the first location. The age of the purchaser is verified at the second location based on the received age documentation and direct visual inspection of the purchaser. Upon verification, a signal is sent from the second location to the vending machine that allows dispensing of the item. From the second location, it is visually verified that the purchaser receives the item from the vending machine at the first location.
Owner:RUDDY JOHN
Vehicle mounted electronic device enclosure
InactiveUS9900417B1Prevent their useReduce usageVehicle componentsTelephone set constructionsEngineeringElectrical and Electronics engineering
An enclosure for use in a vehicle having an ignition system, for securely holding an electronic device and rendering it inaccessible during operation of the vehicle. The enclosure has a main part and a door. The door has an open position and a closed position and includes a device cradle for holding the electronic device. A device responsive switch is closed when the electronic device is located within the device cradle, and a door responsive switch is closed when the door is in the closed position. When the ignition is on, the door responsive switch and device responsive switch must both be closed for the vehicle to operate. A locking assembly holds the door in the closed position and is activated while the vehicle is in operation to physically prevent access to the electronic device while the vehicle is in operation.
Owner:RUIZ STEVE
Wireless Communications Systems
ActiveUS20080233948A1Prevent their useMinimise useTime-division multiplexMultiple digital computer combinationsWirelessCommunications system
A method for controlling uplink transmissions from a user device to an access point in a wireless telecommunications system is described. Each access point defines a communications cell, and the method comprises monitoring interference in an uplink channel at an access point, performing interference control actions at the access point when monitored interference exceeds a first predetermined level, monitoring occurrences of such control actions at the access point, and if a number of such occurrences exceeds a predetermined level, performing interference control actions with reference to a plurality of cells at a central controller of the telecommunications system, which central controller is operable to control a plurality of access points.
Owner:TELEFON AB LM ERICSSON (PUBL)
Anti-cloning method
ActiveUS7380133B2Prevent their useReduce usageDigital data processing detailsUser identity/authority verificationOperating systemCloning
The objective of the present invention is to propose a method that allows preventing the use of more than one identical security module for the identification and use of resources administered by an operating centre. This objective is achieved by an anti-cloning method based on the memorization of the identification numbers of the user units connected to said security module.During a connection with an operating centre these numbers are transmitted and compared with the numbers of a previous transmission. Differences are accepted as long as new numbers are added to a list previously transmitted. The security module is declared invalid if the numbers previously memorized are not included in the transmitted numbers.
Owner:NAGRAVISION SA
Interlock arrangement for controlling the neutral output of a portable generator
ActiveUS8810081B1Expand usabilityPrevent their useElectric signal transmission systemsTwo pole connectionsElectric energyElectric generator
An interlock arrangement allows a floating neutral electrical generator having a receptacle, such as a duplex receptacle, absent GFCI protection to be used to provide electrical power to the electrical system of a home or other building during utility power interruption. The interlock arrangement includes structure to disable or prevent access to the duplex receptacle when the electrical generator is coupled to the power cord used to transfer electrical power from the generator to the electrical system of the building. Thus, the duplex receptacles cannot be used to power electrical devices when the generator is connected to supply power to the electrical system of the building. Conversely, when the generator is physically disconnected from the electrical system of the building, the interlock arrangement exposes or supplies power to the duplex receptacles, and may be configured to close access to the receptacle used for connecting to a building electrical system.
Owner:RELIANCE CONTROLS
Inflatable exercise apparatus
ActiveUS20100087299A1Increase frictionPrevent their useDollsSpace saving gamesPhysical exerciseRidge
An inflatable exercise apparatus having inflatable bladder segments in fluid communication with each other. The inflatable exercise apparatus includes a valve control mechanism that may control the flow of a fluid between the bladder segments, thereby allowing for the adjustment of the pressure in each bladder segment. Adjusting the pressure in each bladder segment may allow the user to vary the levels of resistance during exercise. The bladder segments may be operably connected to bases. The bladder segments may have a plateau that is configured to accommodate each user's stance dimension, along with ridges to assist in securing the feet of the user in a neutral position. The apparatus may also include band brackets for the attachment of other exercise devices, for example exercise bands or balancing devices. The bases may be pivotably connected so as to allow the apparatus to fold to accommodate a storage state.
Owner:KOREEXTREME
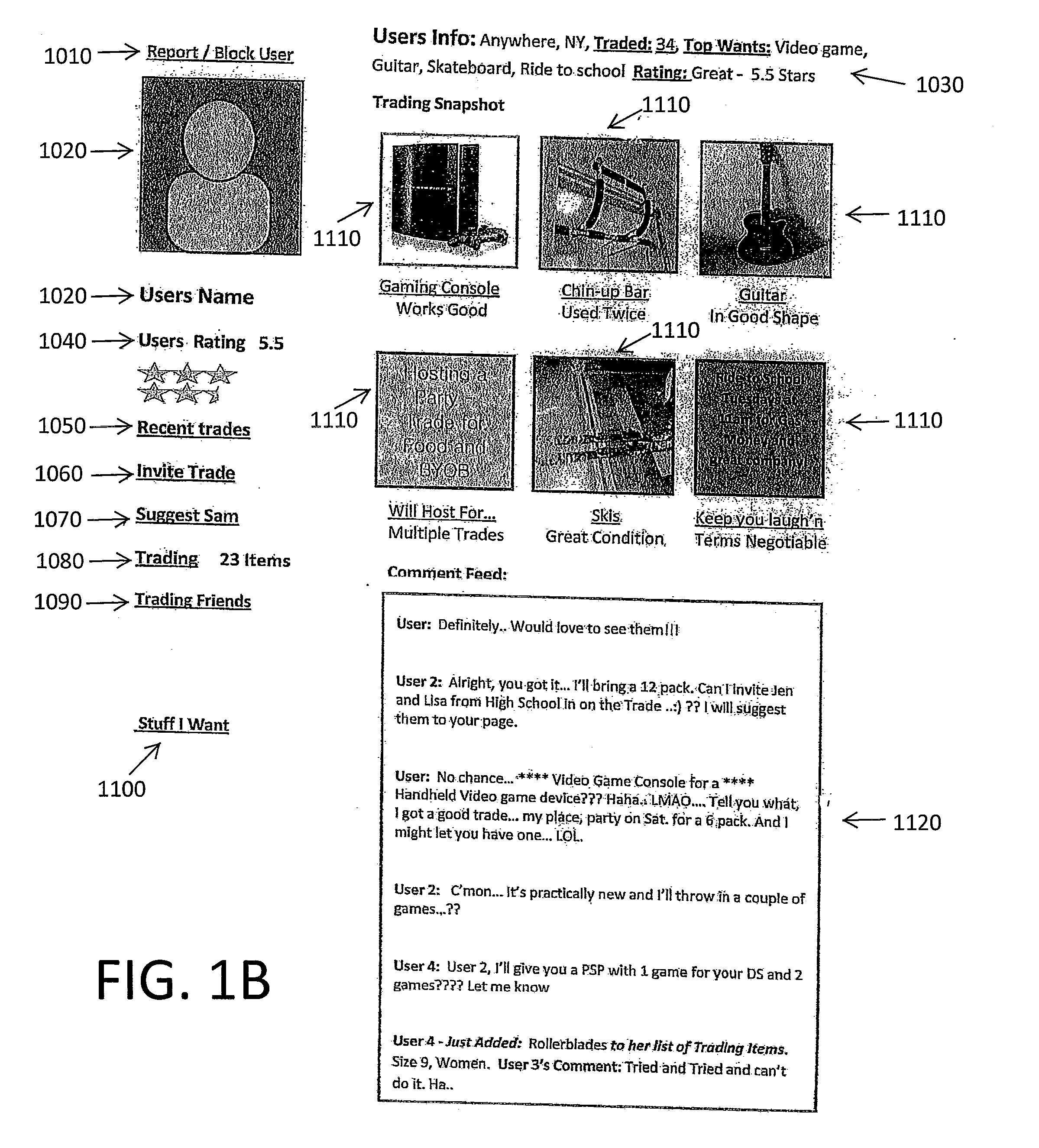
Systems and methods for a website application for the purpose of trading, bartering, swapping, or exchanging personal property through a social networking environment
InactiveUS20120304305A1Prevent their useDigital data processing detailsAnalogue secracy/subscription systemsWebsite localizationSocial web
A system is provided for facilitating a personal property trading system and social networking environment that allows users to interact and create dialogue and socialize in relation to possible trades of personal property or services. This application will allow users who are willing to trade an item, service or favor to obtain similar wants or needs. This form of haggling and the feeling of success are proven to be mentally stimulating, proving another benefit for users. Users will be able to comment and haggle, as well as suggest other users that they believe may have a match on their ‘TRADING ITEMS’ and ‘STUFF I WANT’ lists. The system will promote environmentally conscious trading by bringing unwanted items back to use.
Owner:WERNER SEAN
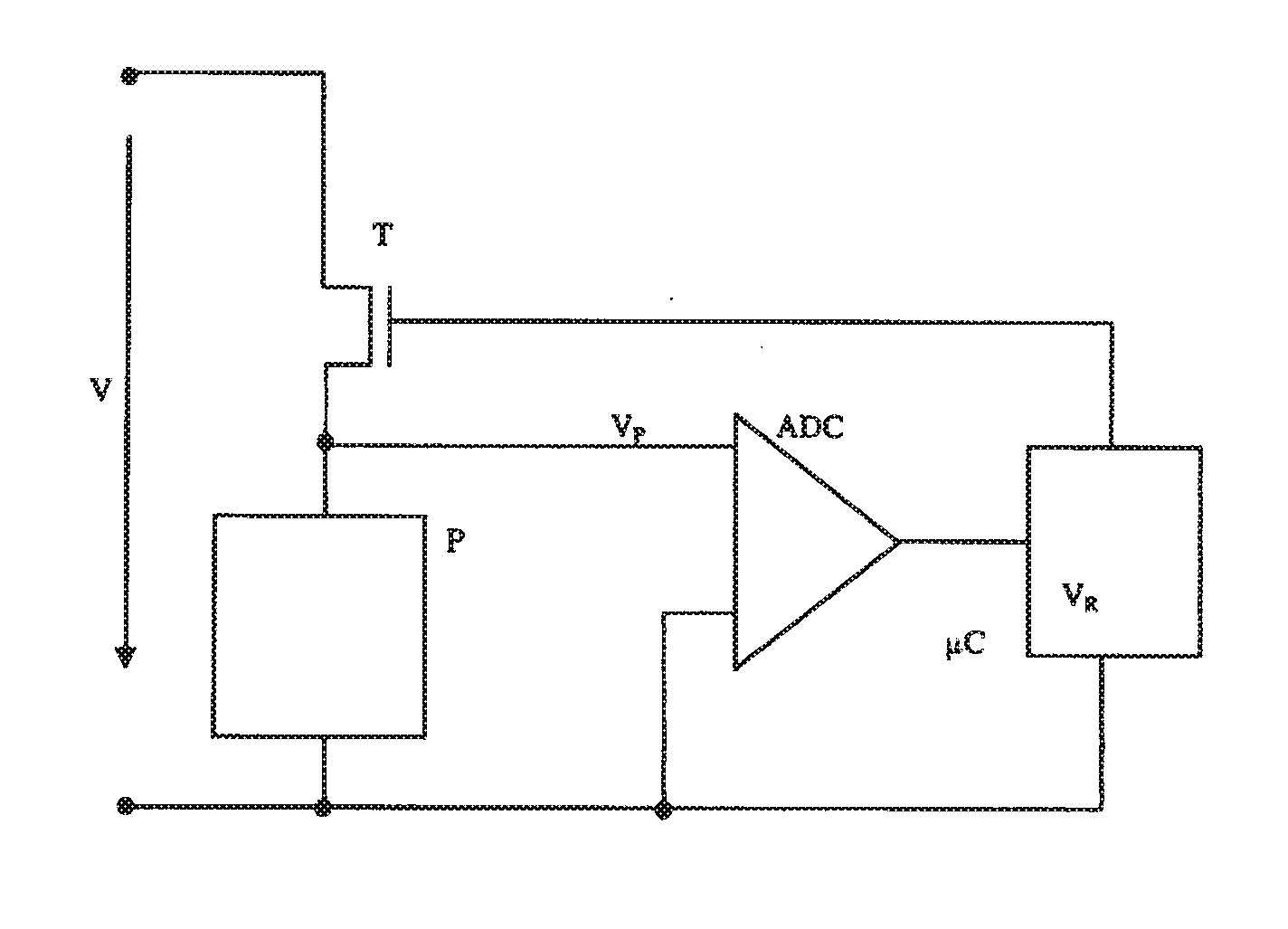
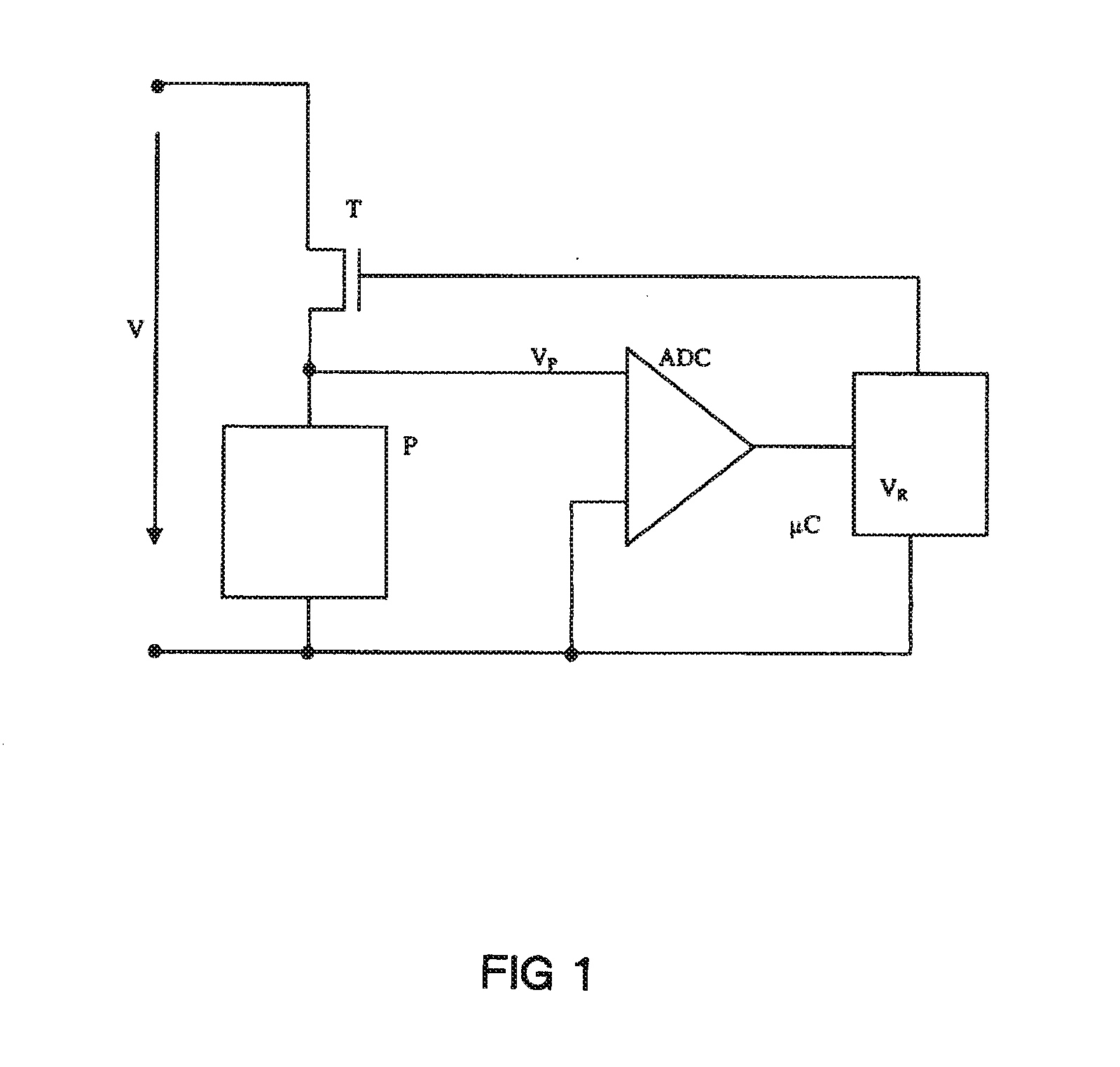
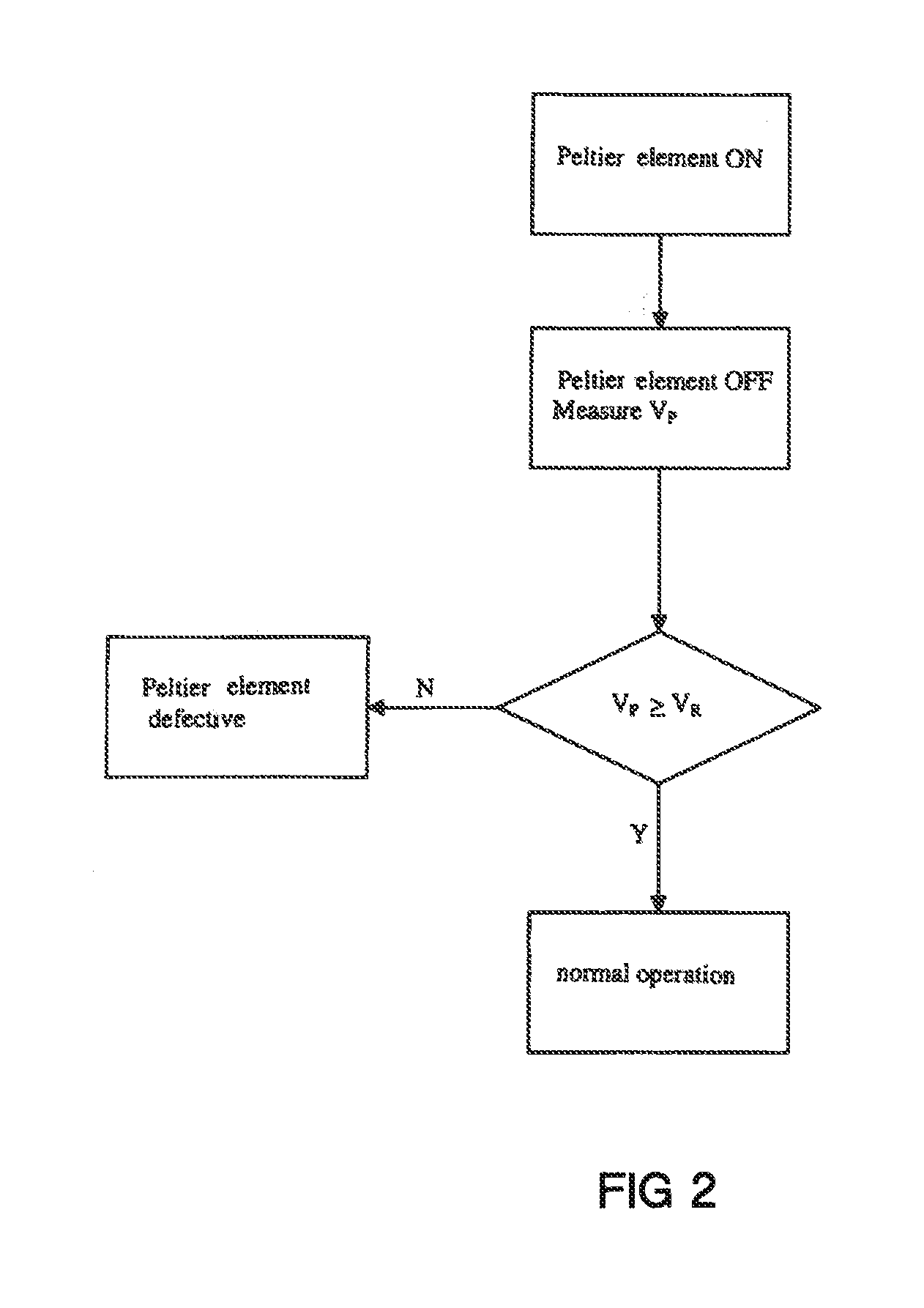
Method for testing a peltier element as well as a small electrical appliance with a peltier element and a safety device
ActiveUS20120234022A1Prevent their useReduce usageMachines using electric/magnetic effectsMaterial thermal analysisEngineeringVoltage
A method with the following steps is described for testing a Peltier element: applying a voltage to the Peltier element; switching off the voltage at the end of a defined period of time; measuring the voltage at the Peltier element; and comparing the measured voltage with a reference value.Furthermore, a small electrical appliance, such as an electric shaver, with a Peltier element is described, which small electrical appliance has a safety device which ensures that a malfunction of the Peltier element cannot result in danger to the user.
Owner:BRAUN GMBH
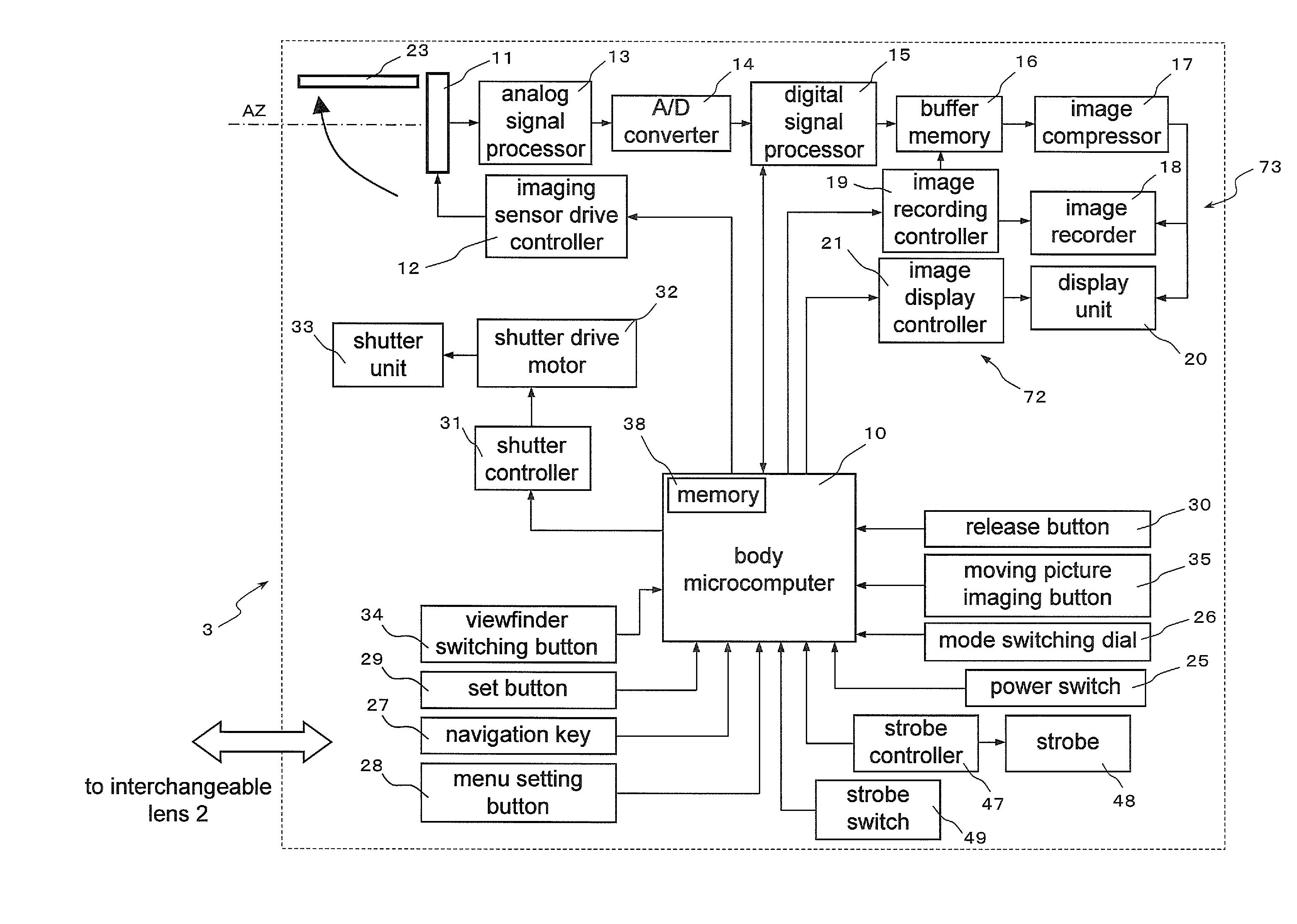
Camera system and interchangeable lens
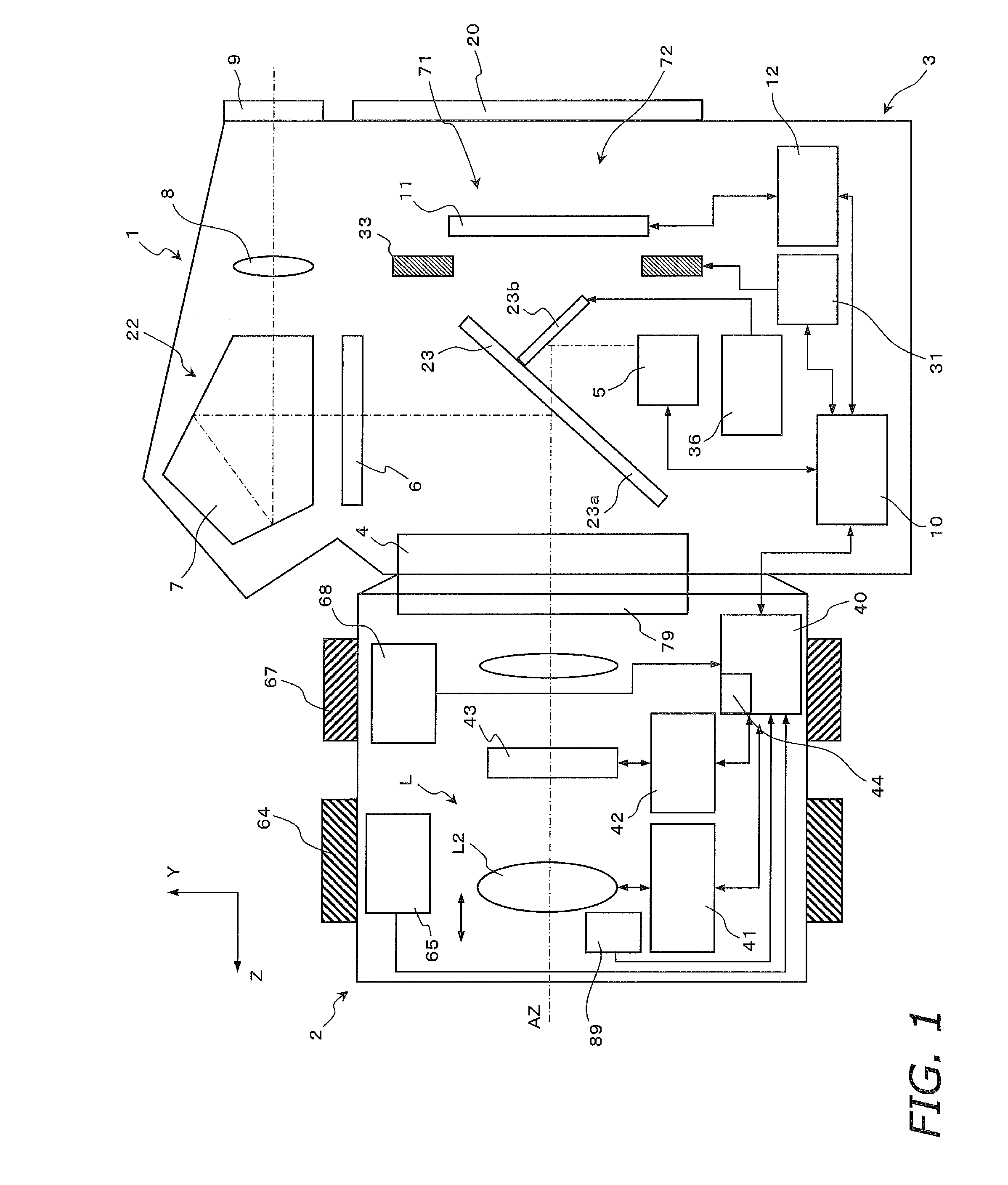
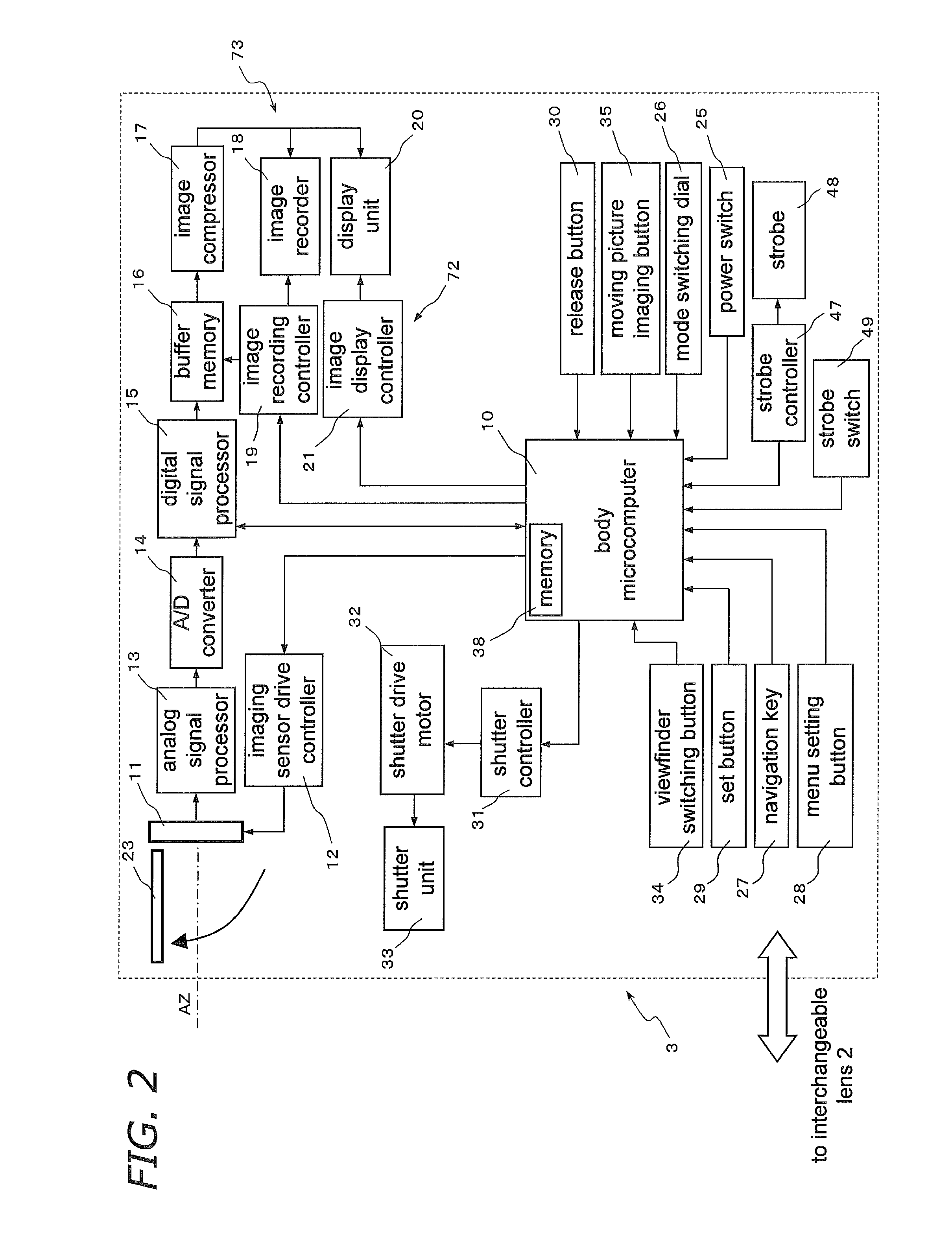
InactiveUS20110109788A1Prevent their useTelevision system detailsProjector focusing arrangementCamera lensMicrocomputer
There are provided a camera system and an interchangeable lens that are compatible with a contrast detection method. A camera system (1) has an interchangeable lens unit (2) and a camera body (3). A lens microcomputer (40) changes the movable range of a second lens group (L2) via a focus lens drive controller (41) depending on whether a second holder (61) is driven by the focus lens drive controller (41) and a focus motor (80) on the basis of angle information inputted to a zoom ring (64) of the interchangeable lens unit (2), or the second holder (61) is driven by the focus lens drive controller (41) on the basis of contrast information.
Owner:PANASONIC CORP
Plasma torch with electrode wear detection system
ActiveUS20110042357A1Prevent their useReduce usagePlasma welding apparatusWelding/cutting media/materialsPlasma torchElectric arc
A plasma arc torch is provided that includes a wear stop designed to detect wear of an electrode and prevent the use of the electrode once the electrode has experienced a certain amount of wear. Either the electrode or the nozzle is movable with respect to the main torch body, and the movable component defines a projection. The wear stop is positioned a predetermined distance from a nozzle of the torch, such that prior to experiencing an excessive amount of wear, the electrode is able to contact the nozzle and initiate a pilot arc for starting a torch operation. Once the length of the electrode becomes shorter than a predetermined length due to wear, the projection of the electrode engages the wear stop, and the wear stop prevents the electrode from contacting the nozzle. In this way, an electrode that is excessively worn cannot be used in subsequent torch operations.
Owner:THE ESAB GROUP
Reusable digital camera that prevents unauthorized use
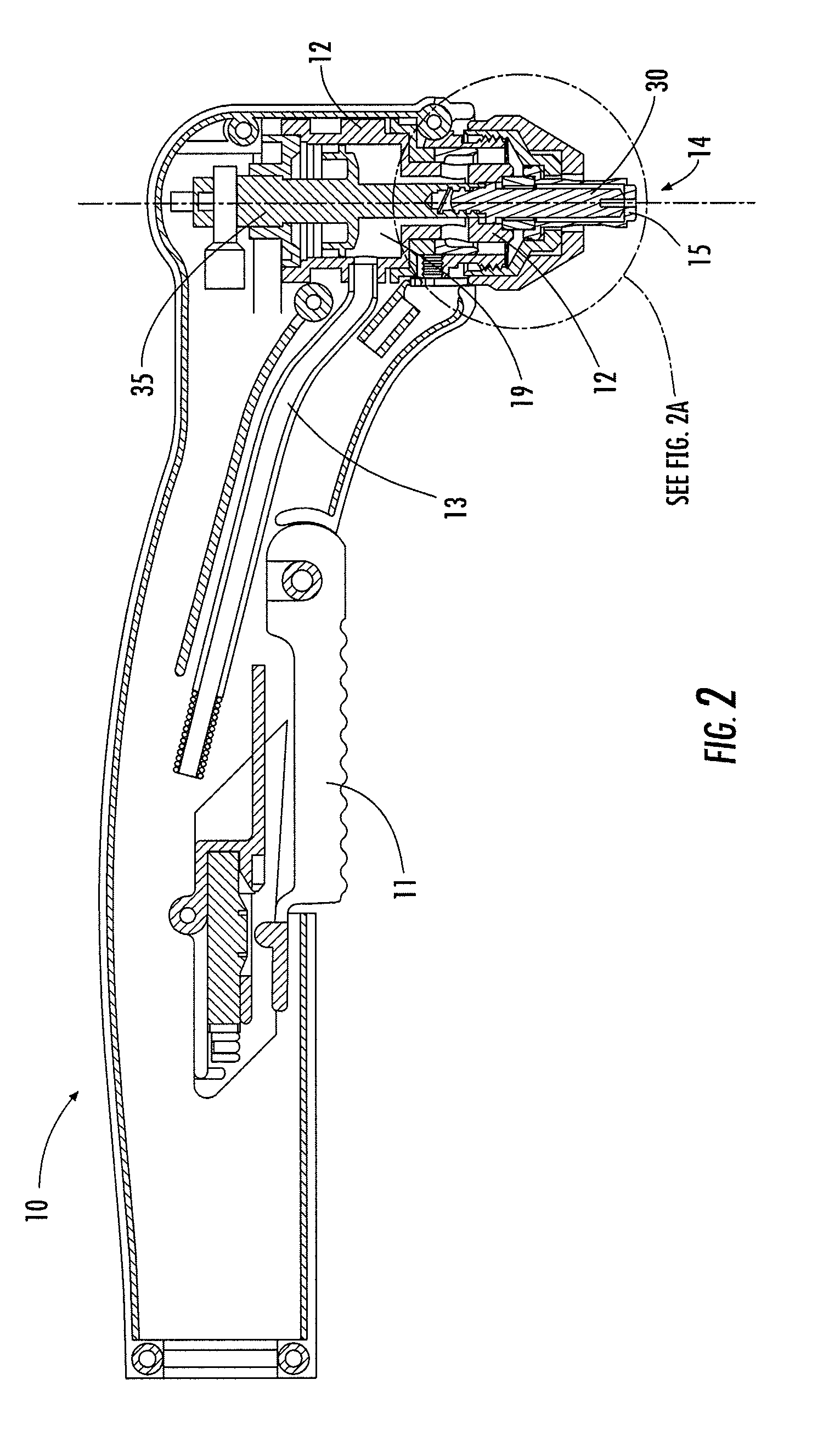
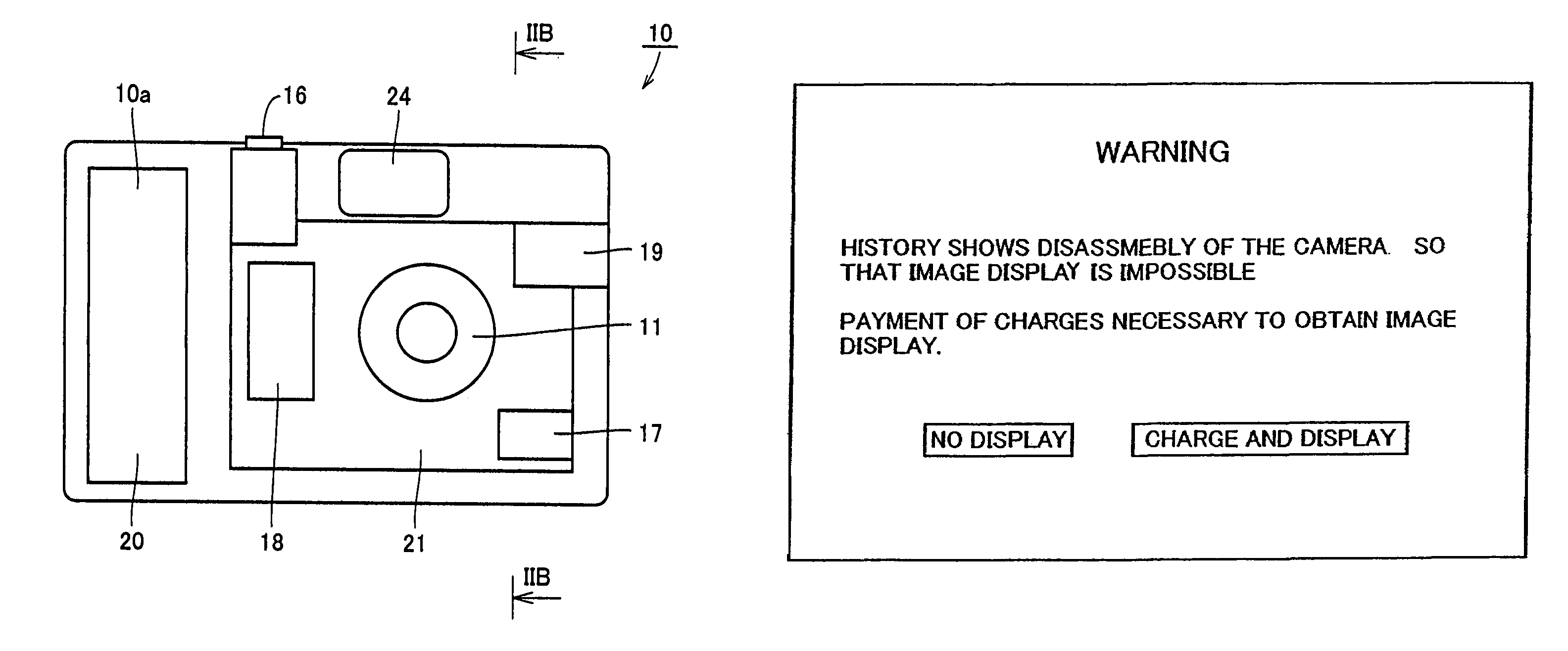
InactiveUS6992701B2Prevent their usePrevent abusive and unauthorized useTelevision system detailsUnauthorized memory use protectionDigital cameraComputer graphics (images)
A reusable digital camera includes a memory storing a picked-up image, and a phototransistor provided in the camera to detect disassembly of the camera. When the user disassembles the digital camera in an unauthorized manner, the phototransistor detects outer light, and the picked-up image stored in the memory is erased. Thus, a digital camera is provided that prevents unauthorized disassembly or unauthorized access.
Owner:SHARP KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com