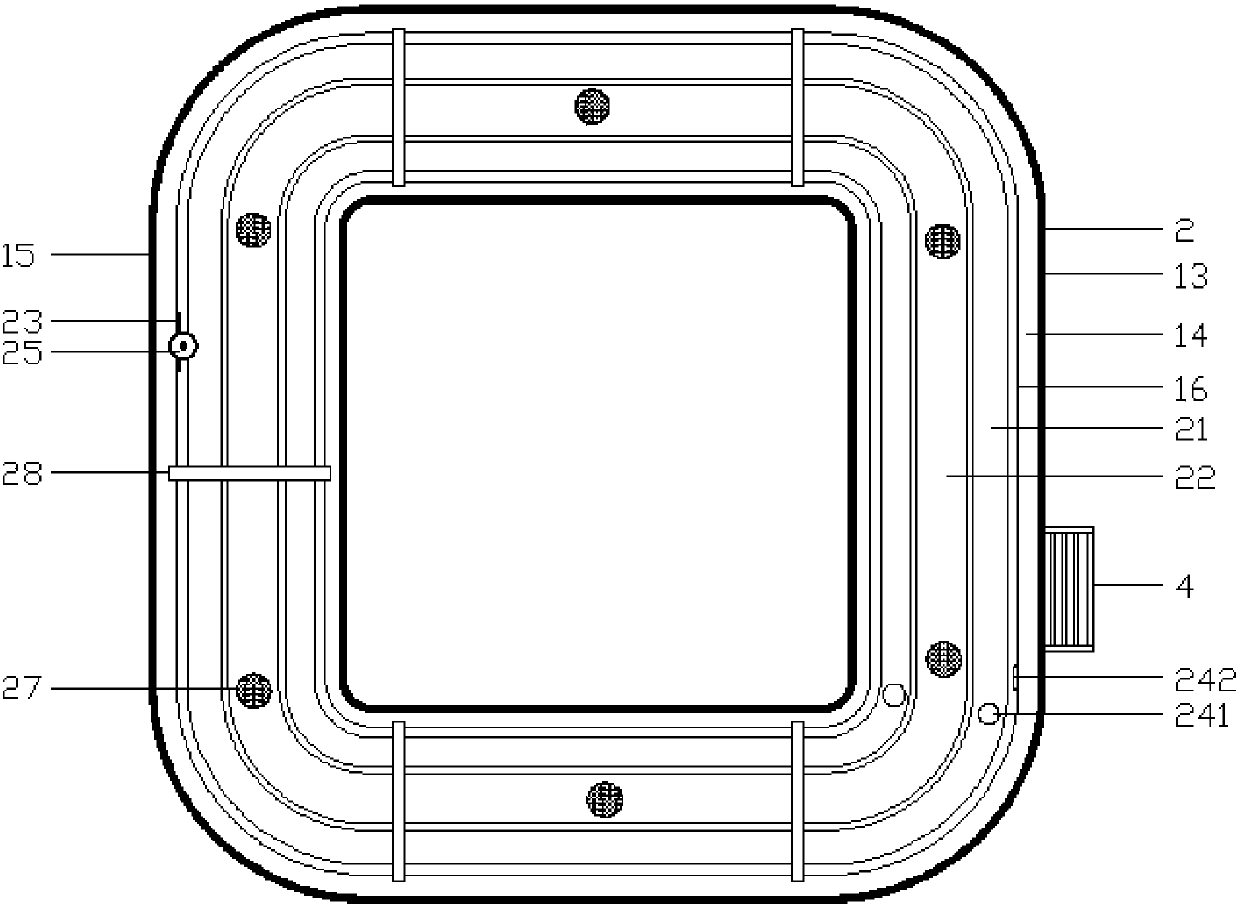
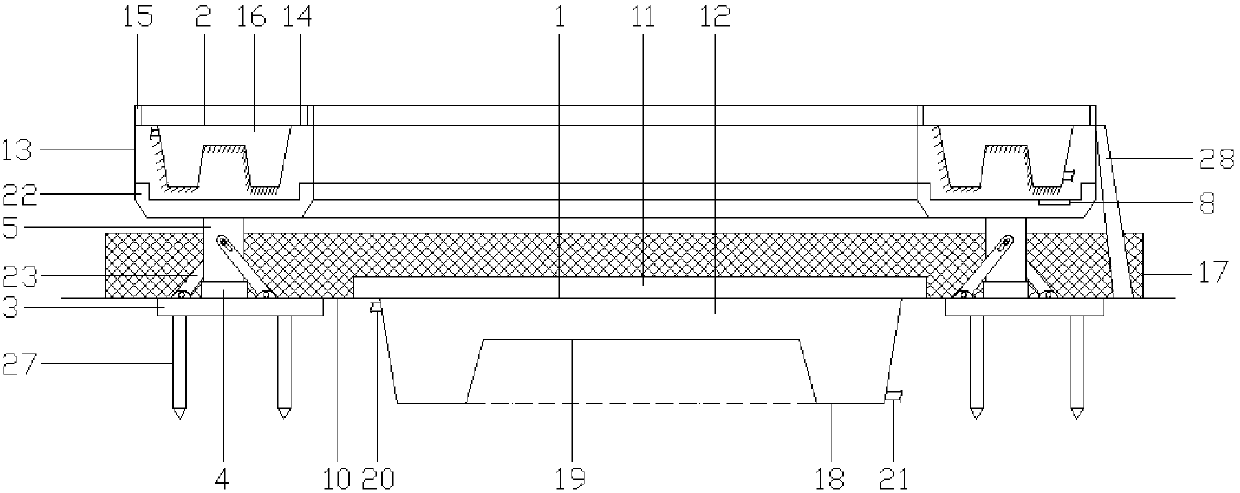
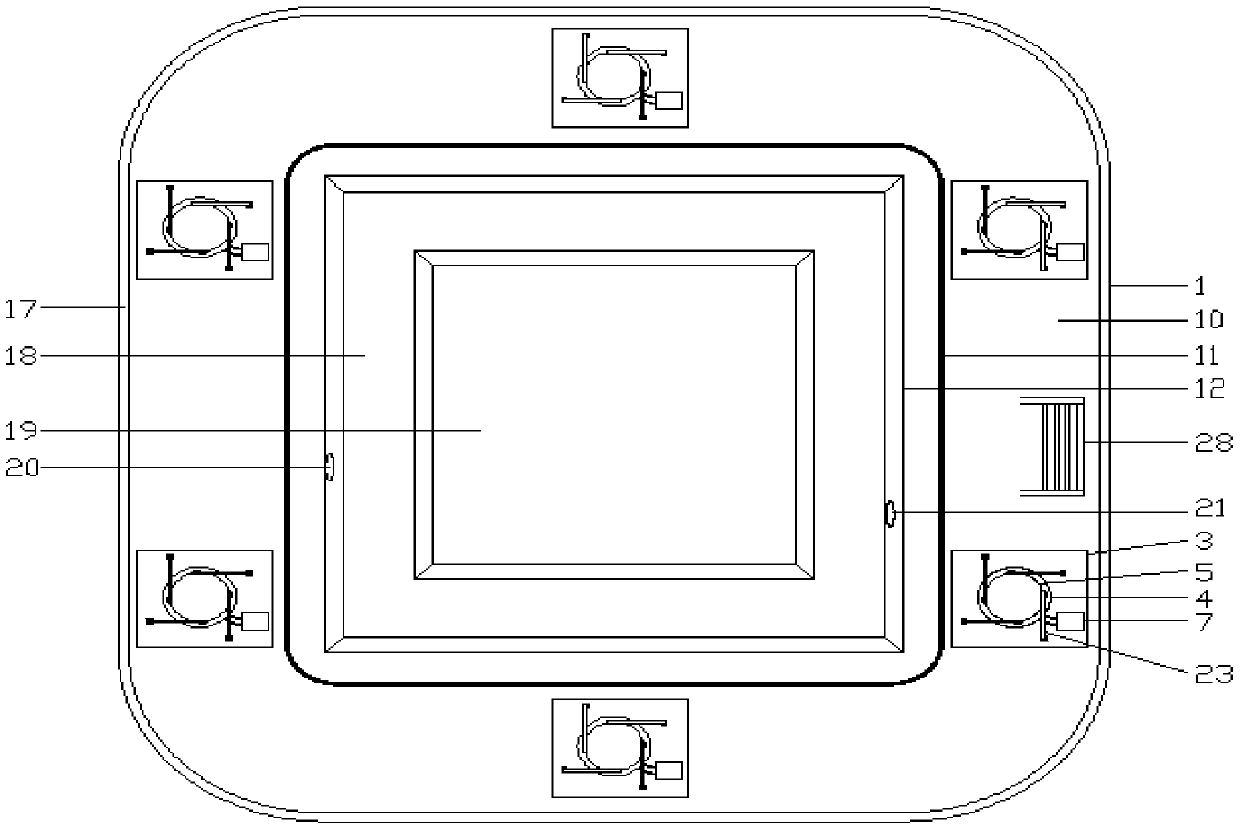
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
56results about How to "Not to be stolen" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
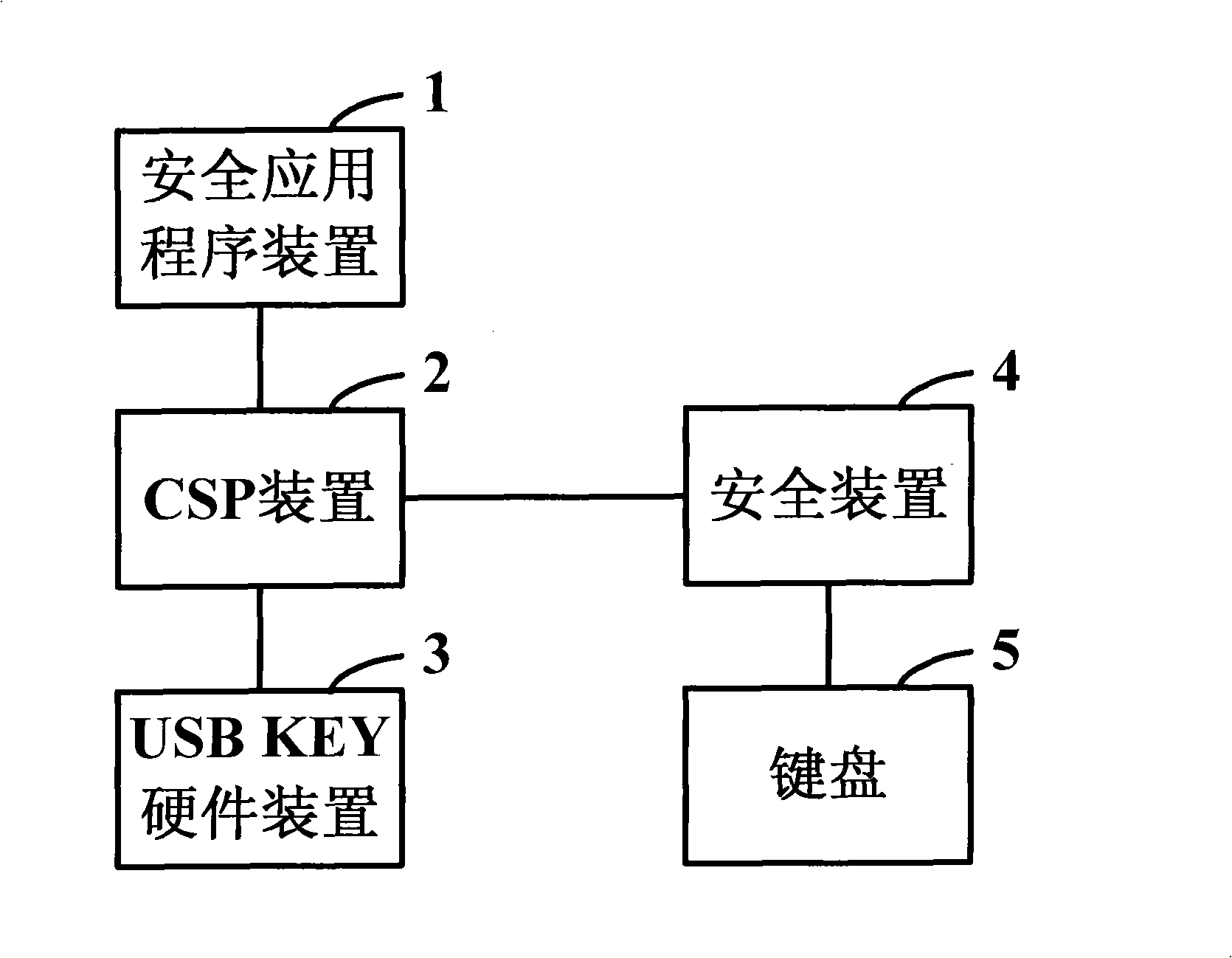
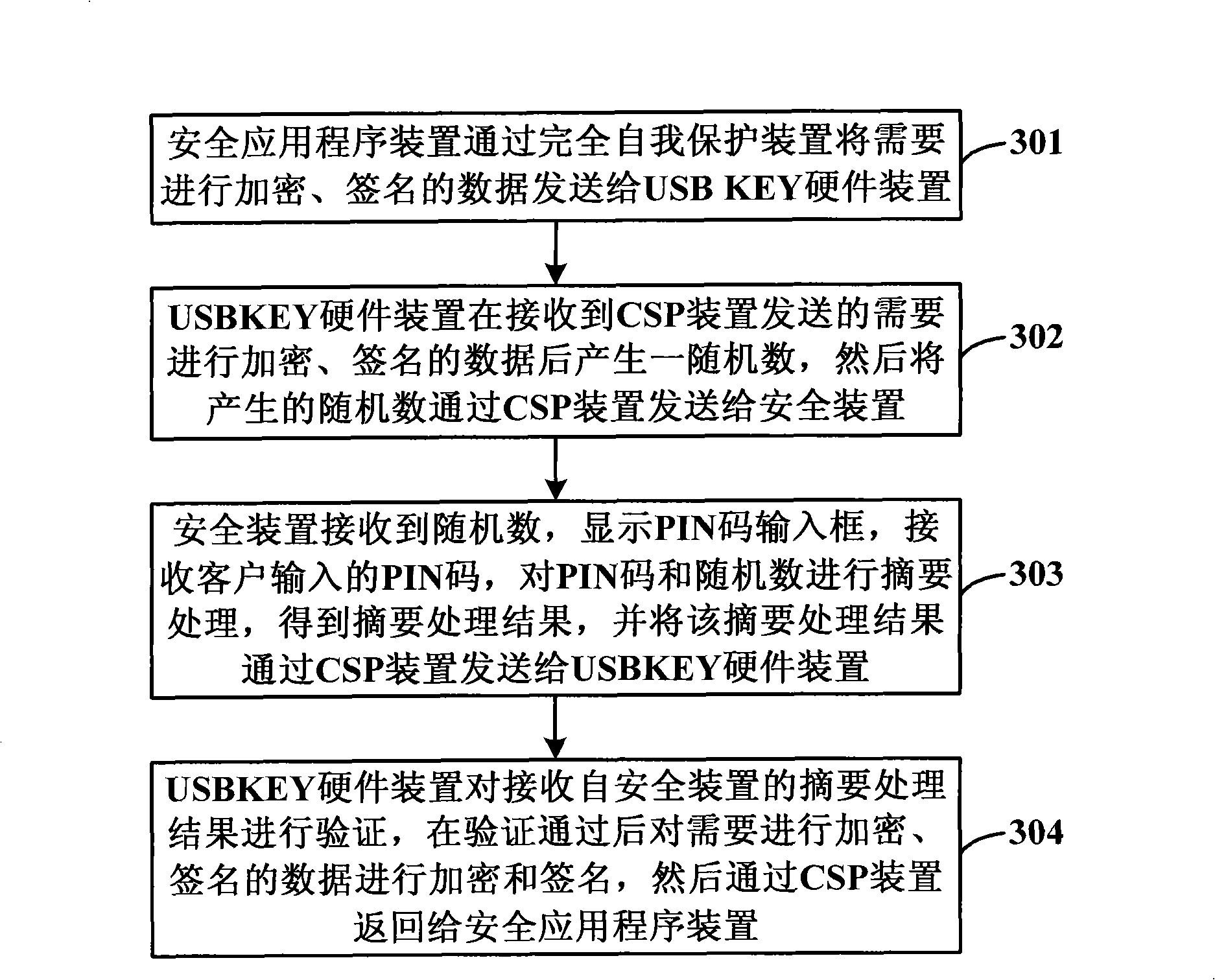
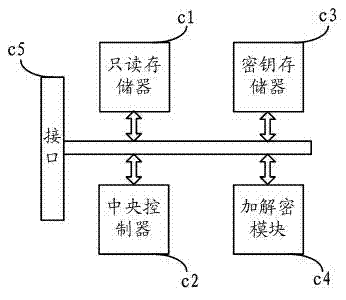
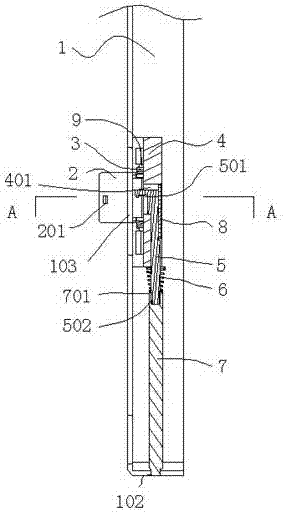
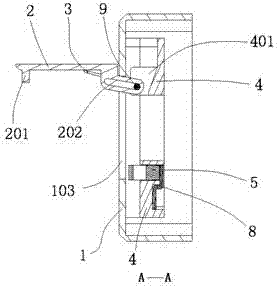
System and method for implementing security protection of PIN code
ActiveCN101494541AImprove securityPrevent replay attacksUser identity/authority verificationMechanically effected encryptionOutcome dataData transmission
The invention discloses a system and a method used for protecting a PIN code. When the PIN code of the user requires verification, USB KEY hardware equipment generates random numbers and submits the numbers to completely-self-protected equipment, and then the completely-self-protected equipment sends the numbers into security equipment. The security equipment pops up a PIN code input prompt box into which the user inputs the PIN code by a keyboard. The security equipment guarantees the safety of data transmission between the user keyboard and the security equipment. After inputting the PIN code, the user clicks OK. The security equipment abstracts and processes the random numbers and the PIN code input by the user, and returns the outcome data after abstracting and processing to the completely-self-protected equipment. The completely-self-protected equipment sends the outcome data after abstracting and processing to the USB KEY hardware equipment for verification. The invention solves the potential safety hazards caused by a plaintext method adopted in the PIN code verification process of the existing USB KEY software equipment, thus realizing effective protection of the PIN code, and improving the safety of USB KEY further.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Mobile payment security system for wireless data private network physical isolation internet
ActiveCN103619020AEnsure safetySafe Payment GuaranteePayment protocolsSecurity arrangementNetwork linkPrivate network
The invention provides a mobile payment security system for the wireless data private network physical isolation internet and aims to provide a mobile payment security system which has the advantages that interactivity is strong, internet invasion can be evaded, payment information is not prone to being stolen by a trojan, internal network data transmission is secure and reliable, internet access is not affected, an SIM card can be prevented from being copied. According to the technical scheme, application systems including a payment server and an authentication device are established in a mobile payment security data network which is isolated from the internet, the mobile payment security data network links with an APN or a VPDN, wherein the APN or the VPDN is isolated from the internet and connected with a GSN mobile gateway, the payment sever account establishment, mobile phone number, IMSI number and password four-in-one binding multiple authentication through a password authentication device and a mobile phone number authentication device; when the mobile payment security data network is networked, an internet access channel is automatically disconnected; after physical isolation of the internet succeeds, graphical verification code information interaction is performed between the mobile payment security system and the mobile payment server through a base station.
Owner:龙岩荣创信息科技有限公司
Method and system for driver identification and supervision
InactiveCN108162975AEnsure consistencyRealize the integrated audit of witnesses and witnessesBelt control systemsDigital data authenticationDriver/operatorSeat belt
The invention discloses a method and system for driver identification and supervision. The method comprises the following steps: (1) inputting driver information; (2) identifying a driver, quickly recognizing the face of the driver through a first camera device, transmitting face information to a security system host which determines whether the face information of the driver is consistent with prestored key information of the face of the driver, authenticating the identity of the driver and performing the step (3) if the face information of the driver is consistent with the prestored key information of the face of the driver, and not authenticating the identity of the driver and forbidding the driver to enter a vehicle if the face information of the driver is not consistent with the prestored key information of the face of the driver; (3) allowing the driver whose identity is authenticated to enter the vehicle and determining whether the driver wears a seat belt through a second camera device for recognizing a whole driving image. The method and system for driver identification and supervision disclosed by the invention can effectively check the consistency of the driver and a driver license and monitor in real time during the driving process so as to ensure driving safety.
Owner:XIAMEN LENZ COMM
Device and method for protecting sensitive information of chip system
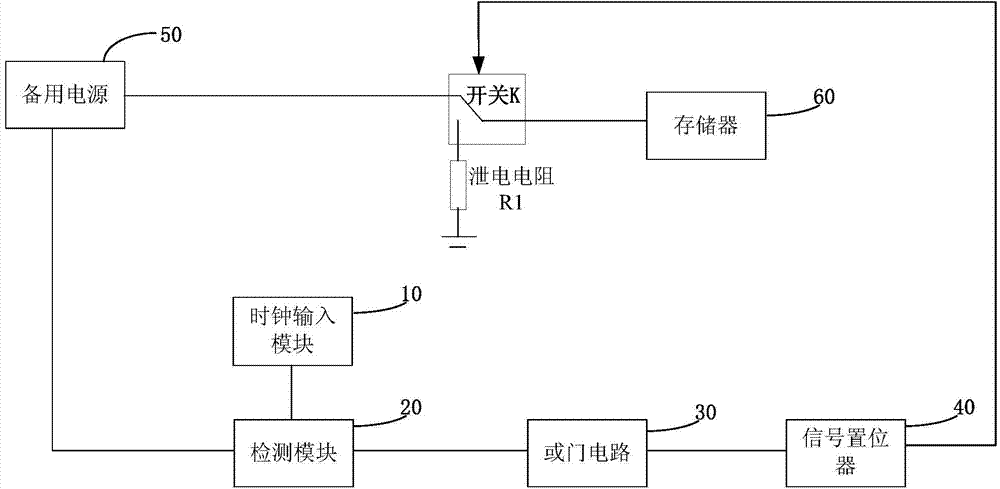
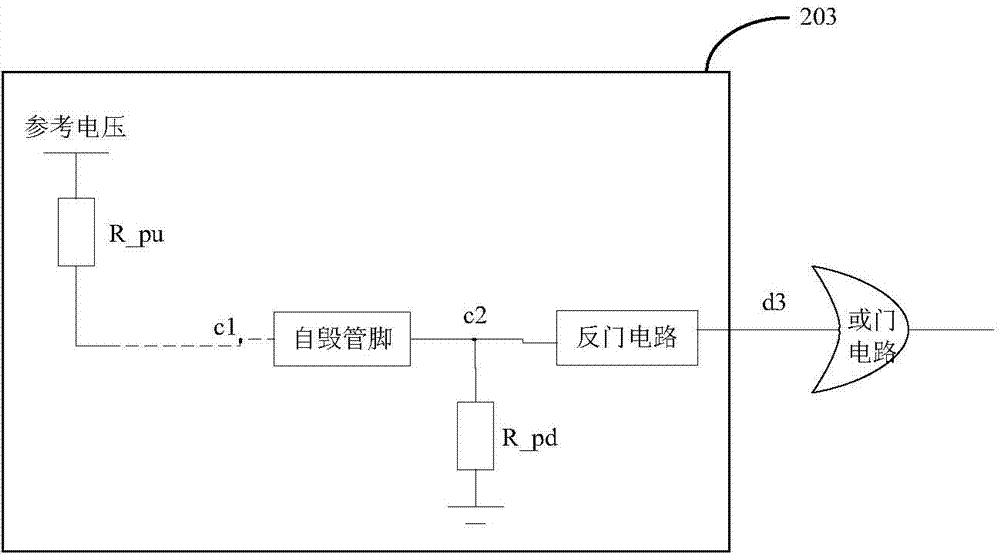
ActiveCN104850805AGuaranteed safe operationSpeed up leakageInternal/peripheral component protectionElectrical resistance and conductanceComputer module
The invention discloses a device and a method for protecting sensitive information of a chip system. The device comprises a clock input module, a detection module, an OR-gate circuit, a signal setting device, a switch, a discharging resistor, a reserve power supply and a storage. The storage stores the sensitive information, and the detection module performs timing completeness detection on temperature, voltage, frequency, light intensity and physical deformation of the chip system to guarantee safety operation of the chip system. When the chip system is attacked and abnormity of the chip system is detected, the OR-gate circuit generates a high level signal; after receiving the high level signal, the signal setting device controls the power input end of the storage to be disconnected from the reserve power supply, and controls the power input end of the storage to be connected with one end of the discharging resistor to form a discharging access between the storage and the ground, so that sensitive data in the storage are cleared away quickly and sensitive information is not stolen by an attacker due to quick clearing.
Owner:BEIJING HUADA INFOSEC TECH
Safety login method based on domestic cryptographic algorithm
The invention discloses a safety login method based on a domestic cryptographic algorithm. Service-end login software and client-end login software are installed on an embedded device and a debugging computer respectively. The embedded device is connected with the debugging computer through a network interface. A client end remotely logs in a device through a network. The login software uses a secret key verification method. A user may log in the device just after a client-end secret key and a service-end secret key pass respective identity verification so as to perform encrypted session. The safety login software is installed on the client end. On the premise that an original function of the device is not changed, a new authentication mode is used and plaintext transmission is converted into cryptograph transmission. Thus, a risk bug in the conventional remote login software is solved, communication security between the network equipment and external environment is improved, and malicious attack to network management is effectively defended.
Owner:成都卫士通信息产业股份有限公司
Edge machine learning system and method based on container cloud platform
ActiveCN111258716ARapid deploymentQuick operation and maintenanceProgram initiation/switchingResource allocationNetwork structureEngineering
The invention discloses an edge machine learning system based on a container cloud platform. The edge machine learning system comprises an infrastructure subsystem, an edge routing subsystem, a storage subsystem, a machine learning computing equipment subsystem and a platform management subsystem. All the subsystems are containerized into edge container cloud platform service, resource scheduling,operation monitoring and the like are achieved in a service mode, and rapid deployment, operation and maintenance and release of the machine learning computing system based on the container cloud technology are achieved. According to the self-organizing cooperation method between the edge machine learning systems, distributed control and a multi-center network structure are achieved through interaction of the edge machine learning systems in a self-organizing communication mode, the identity correctness of the two communication parties is guaranteed through the access authentication technology, and it is guaranteed that important network propagation content is not stolen. The invention further provides a container inner volume collaborative migration method between the edge machine learning systems, data between the container cloud platforms can be migrated mutually through container inner volume collaborative migration, and service integrity and inertness are guaranteed.
Owner:上海雾宇科技有限公司
Network attack path prediction method
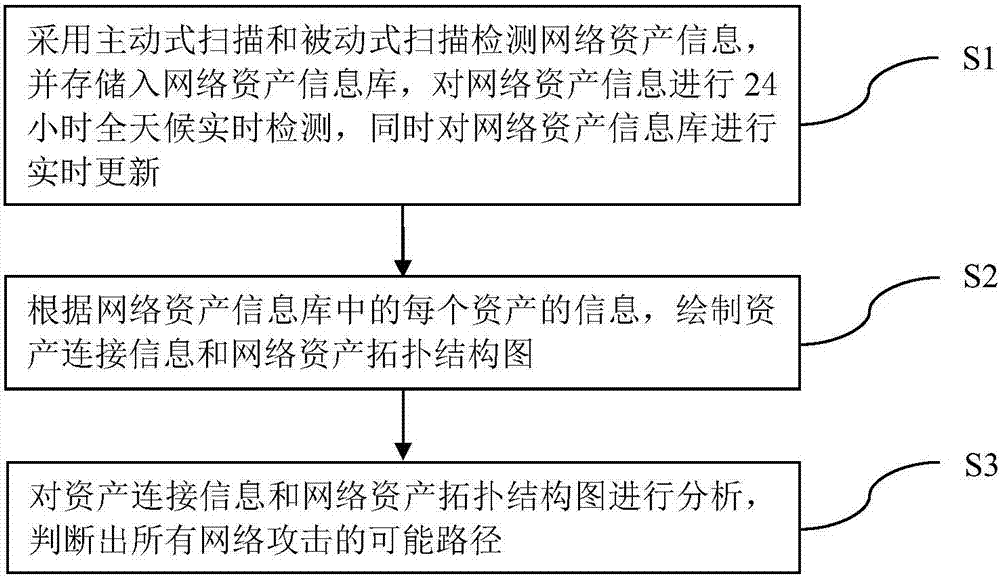
InactiveCN107040552AGrasp the latest developments in real timeNot to be invadedData switching networksNetwork attackNetwork administrator
The invention provides a network attack path prediction method. Because network asset information is monitored in real time throughout the day through active scanning and passive scanning, the latest news of assets can be known in real time. According to the latest network asset information, the connection condition of each asset is identified, and an asset connection information and network asset topology map is drawn. Then, all possible paths of network attack are analyzed and judged, and the network administrator takes measures in advance to defend the network system and the core assets according to all the possible network attack paths predicted. Therefore, through the network attack path prediction method of the invention, network attacks can be prevented, the core data of enterprises can be protected from being invaded and stolen, and the cost of human maintenance can be reduced.
Owner:上海斗象信息科技有限公司
Hand-held equipment data encryption and decryption method and hand-held equipment peripheral equipment thereof
InactiveCN102332077APracticalAvoid the risk of being easily decryptedDigital data protectionSecurity arrangementComputer hardwareEngineering
The invention relates to a hand-held equipment data encryption and decryption method and hand-held equipment peripheral equipment with encryption and decryption functions. In the hand-held equipment data encryption and decryption method, the hand-held equipment peripheral equipment with the encryption and decryption functions is used for encrypting and decrypting private data in the hand-held equipment, when the encryption and the decryption are completed, the hand-held equipment peripheral equipment with the encryption and decryption functions can be physically separated from the hand-held equipment, when the hand-held equipment is not connected with the hand-held equipment peripheral equipment with the encryption and decryption functions, the private data in the hand-held equipment can not be encrypted, and the encrypted data can not be decrypted, so the security of the encrypted data is ensured. A key used during the encryption and the decryption is stored in the hand-held equipment peripheral equipment with the encryption and decryption functions and is bound with the hand-held equipment peripheral equipment, and the security and the uniqueness of the encryption key are ensured.
Owner:NATIONZ TECH INC
Terminal information security method and device
ActiveCN102271332ANot to be stolenSolve problems that are not conducive to protecting the privacy of usersSecurity arrangementSecuring communicationInformation confidentialityPassword
Disclosed is a method for concealing terminal information, comprising: creating a first password and one or more second passwords for terminal information, and setting authorized information and unauthorized information according to the terminal information; when a login user logs in with the second password, on the foreground of the terminal, according to an operation of the login user, displaying information of normal processing of the authorized information and / or unauthorized information, and on the background of the terminal, executing an operation of the login user on the authorized information, and intercepting an operation of the login user on the unauthorized information; when the login user logs in with the first password, on the foreground and the background of the terminal, according to an operation of the login user, displaying and executing normal processing of the authorized information and unauthorized information. Also disclosed is a device for concealing terminal information. The technical solution of the present invention can completely and unnoticeably protect private information in a user terminal from being stolen by others.
Owner:ZTE CORP
Intelligent track flaw detection combined vehicle and a control method
PendingCN108944997AEasy to filterEasy to viewMeasurement devicesRail and road vehiclesRemote controlComputer module
The invention belongs to the technical field of railway construction monitoring, and discloses an intelligent track flaw detection combined vehicle and a control method thereof. The intelligent trackflaw detection combined vehicle and the control method apply the internet of things technology and the modern control technology to realize self-walking, high precision, easy operation and remote control, assist to complete the railway fault detection of the large-scale flaw detection vehicle; Intelligent unmanned operation, self-walking, recording and real-time transmission of damage, mileage andline characteristics signals are realized; The flaw detection signals recorded by computer are processed to realize no take-off and landing or automatic take-off and landing. The invention is provided with two functional modules of manual detection and automatic detection, which can realize self-walking, high precision, easy operation and remote control by using the internet of things technologyand the modern control technology. At the same time, the industrial design elements are designed. It can not only help to complete the railway fault detection of large-scale flaw detection vehicle, but also completely replace the railway maintenance task of manual flaw detection equipment, which can better meet the requirements of track flaw detection.
Owner:SICHUAN UNIVERSITY OF SCIENCE AND ENGINEERING
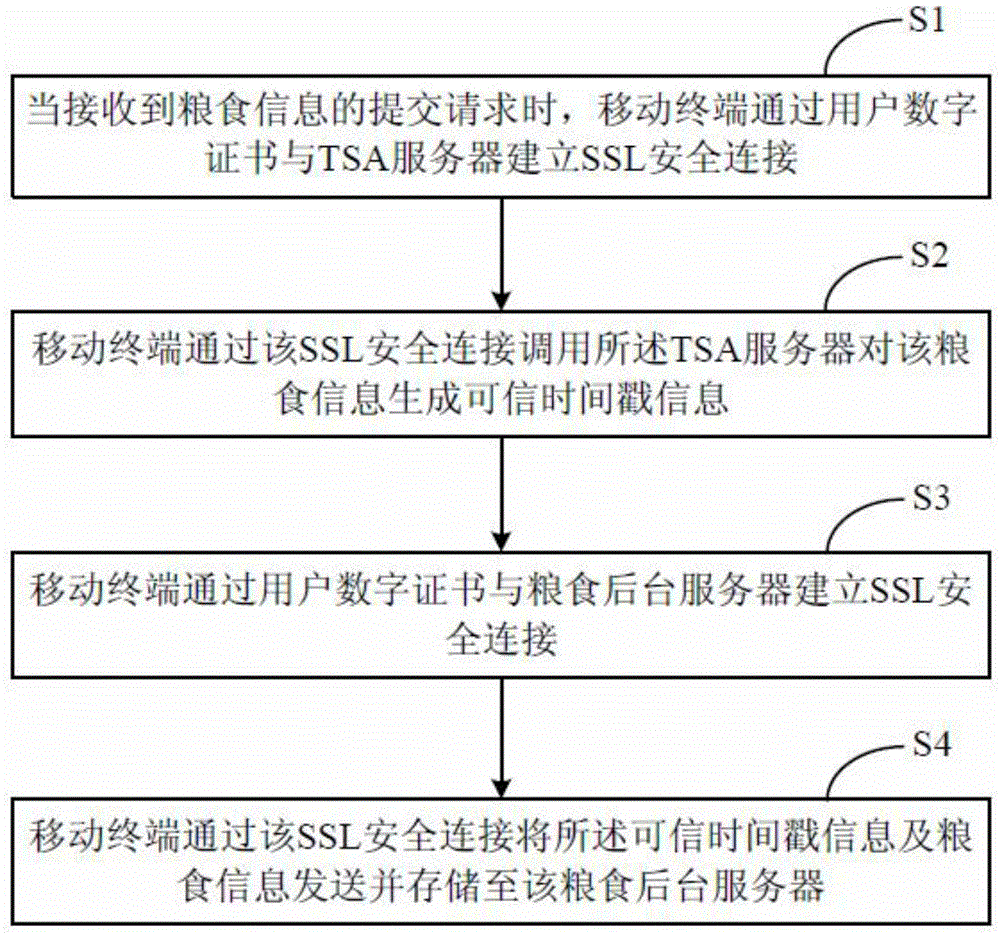
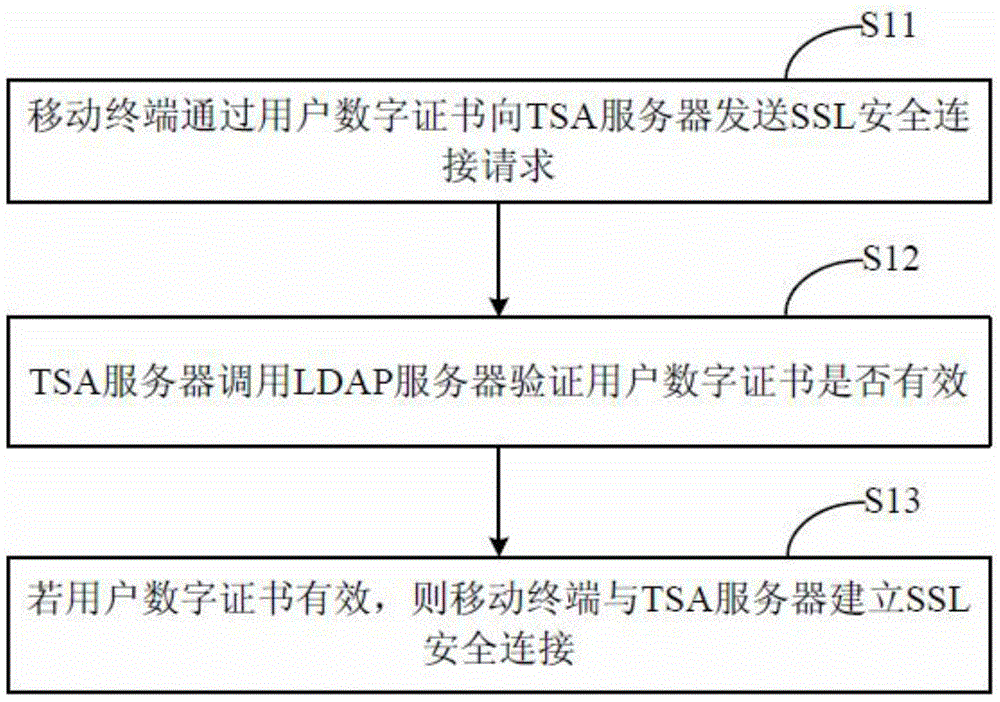
Grain information management method and system
InactiveCN105763506AImprove securityNot interceptedTransmissionTelecommunicationsTrusted timestamping
The invention relates to a grain information management method, and the method comprises the steps that a mobile terminal builds safe cup-joint layer safety connection with a credible time stamp through a user digital certificate when a grain information submitting request is received; the mobile terminal carries out the call of the credible time stamp through the safe cup-joint layer safety connection, so as to generate credible time stamp information for the grain information; the mobile terminal builds safe cup-joint layer safety connection with a grain background server through the user digital certificate; and the mobile terminal enables the credible time stamp information and the grain information to be transmitted and stored in the grain background server through the safe cup-joint layer safety connection. The invention also provides a grain information management system. The method and system can provide reliable basis for the tracking of the quality safety of grains.
Owner:AEROSPACE INFORMATION
Game prop trading method based on blockchains, trading terminal and storage medium
ActiveCN110201400AGuaranteed independenceEnsure safetyFinanceVideo gamesData informationComputer terminal
The invention discloses a game prop trading method based on blockchains, a trading terminal and a storage medium. The game prop trading method based on the blockchains comprises the steps that after auser account is logged in, a trading instruction sent by a user is received, and a trading object account and traded game props are determined according to the trading instruction; and data information of the game props is sent to a blockchain node address corresponding to the trading object account. According to the game prop trading method, it can be ensured that in the trading process of the game props, the data information is always stored in blockchain nodes of the both trading parties, thus it is ensured that the data information is not stolen or modified by other people, and security and authenticity of prop trading are ensured; and a game official department has no modification ability on the data information and cannot intervene in the prop trading process, and thus independenceof game prop trading is guaranteed.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
Static data encryption protection method and system
ActiveCN110990851AImprove key securityImprove securityKey distribution for secure communicationDigital data protectionKey generationDirectory
The invention relates to a static data encryption protection method and system. The static data encryption protection method comprises the steps of: registering information of a server host where a client is located to a server; distributing a master key for a directory or a file of the server host at the server, generating an encryption control strategy and issuing the encryption control strategyto a corresponding client; allowing the client to acquire a corresponding master key from the server according to the encryption control strategy; when data is written into the encrypted directory orfile, randomly generating a data key, and encrypting the directory or file by using the data key so as to obtain an encrypted file; and encrypting the data key by using the master key so as to obtaina key ciphertext, and writing the key ciphertext into the head of the encrypted file so as to finish data writing. According to the invention, the client executes encryption and decryption operationof the file, and the server achieves server host management, secret key management, control strategy management and the like, so encrypted file transparent access and key and strategy unified management are achieved; file management and use permission are separated; and the safety of file protection is improved.
Owner:山东三未信安信息科技有限公司
Internet of Things security system based on cryptographic technology and communication method
ActiveCN110519238AFix security issuesSolve protection problemsKey distribution for secure communicationMultiple keys/algorithms usageInternet of ThingsApplication Identifier
The invention belongs to the technical field of passwords, and discloses an Internet of Things security system and communication method based on a password technology, and the method comprises the steps: registering equipment identifier and an application identifier, and generating a protection secret key, a sign-in secret key, a data secret key, an instruction secret key, a half secret key, a CPKsecret key and an SM9 secret key; encrypting all the generated secret keys and then safely storing the secret keys; sending a request carrying a terminal identifier to the cipher machine, and performing data encryption transmission after the request is authenticated and negotiated by the registration equipment and the cipher machine; and through data encryption transmission, enabling the cipher machine to decrypt the encrypted data after receiving the encrypted data. A symmetric algorithm or an identification cryptographic algorithm is used, a series of software and hardware products are combined, the safety of the Internet of Things is integrally achieved, and the functions of secure channel, secure storage, data encryption, identity authentication, digital signature and the like are rapidly achieved. According to the invention, the data in the Internet of Things is prevented from being stolen and tampered, the identity is credible, and the data can be transmitted secretly.
Owner:北京安御道合科技有限公司
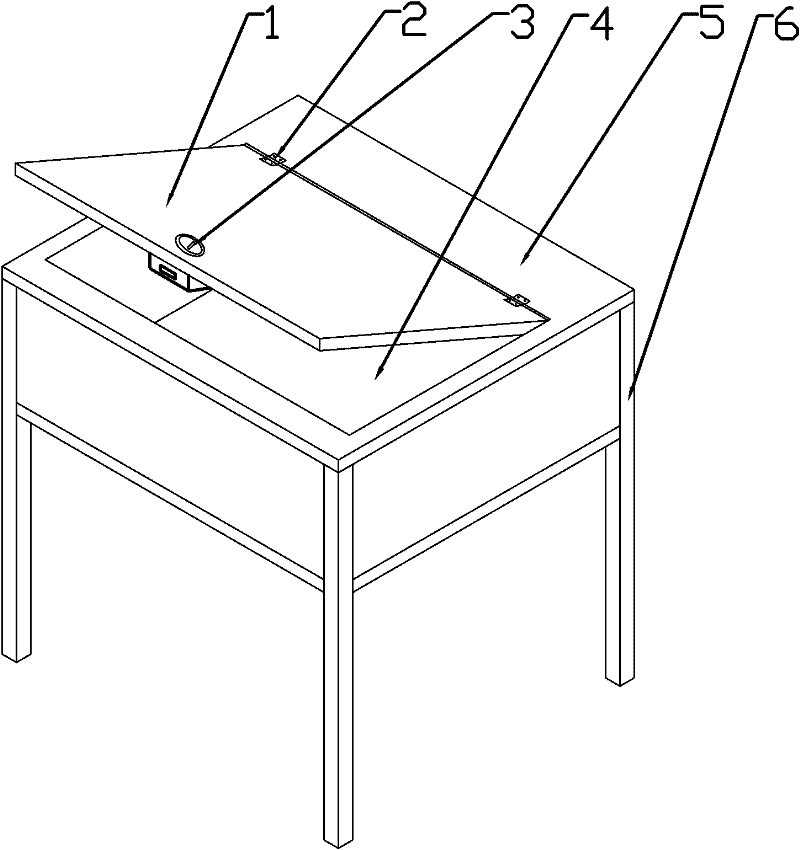
Antitheft computer desk
The invention discloses an antitheft computer desk, mainly solves the problem that the current computer desk cannot be used for safely storing a laptop computer. The structure of the antitheft computer desk comprises a desk top and desk legs; the middle part of the desk top is hinged with a cover plate through a folder; a locker is arranged at the free end of the cover plate, and a storage cavity is arranged at the lower part of the cover plate. The lockable storage cavity can be integrated below the computer desk and is convenient for a user to store the laptop computer inside it; because of the locker, the laptop computer stored in the cavity cannot be stolen illegally and no extra storage cabinet is needed.
Owner:王强
Multi-tier lifting adjustable pond for crab farming
The invention discloses a multi-tier lifting adjustable pond for crab farming, comprising a pond body; the pond body includes a first pond, a second pond and a third pond; the second pond and the third pond are positioned above the first pond and are connected with the same through support posts, the center of the second pond is provided with a through hole, the through hole may be connected and / or disconnected with the third pond, the third pond, the second pond and the first pond may be interconnected through a ladder, the first pond is provided with a foundation, and the foundation is fitted with hydraulic devices connected with the support posts. The multi-tier lifting adjustable pond for crab farming can save farmland, provides multiple tiers of adjustable aerial farming ponds based on existing farming area so that exiting farming area is enlarged and aquaculture income is increased, and is good in structural stability, convenient to use and worthy of popularization.
Owner:泉州市联控自动化科技有限公司
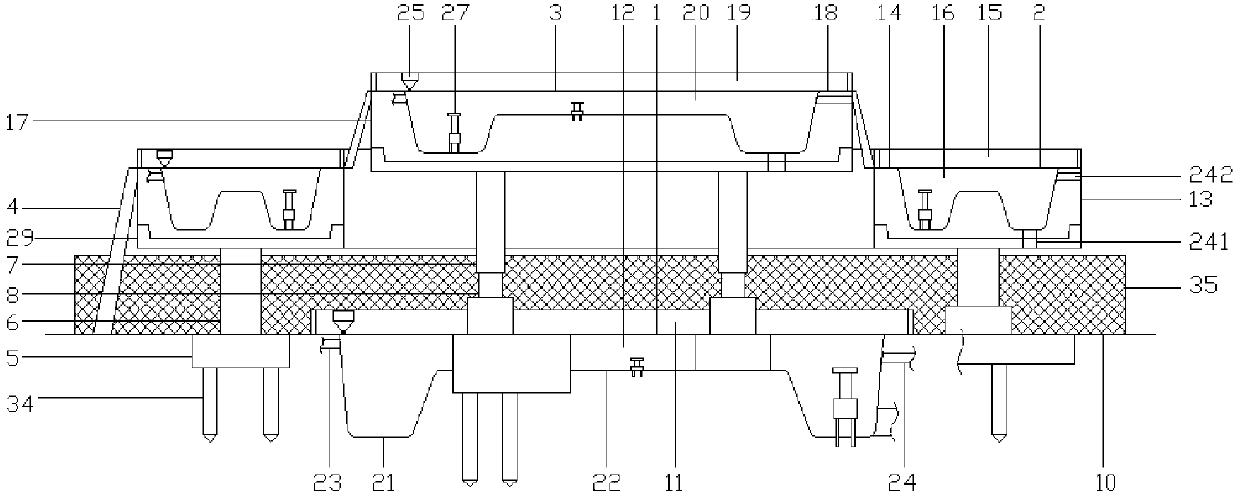
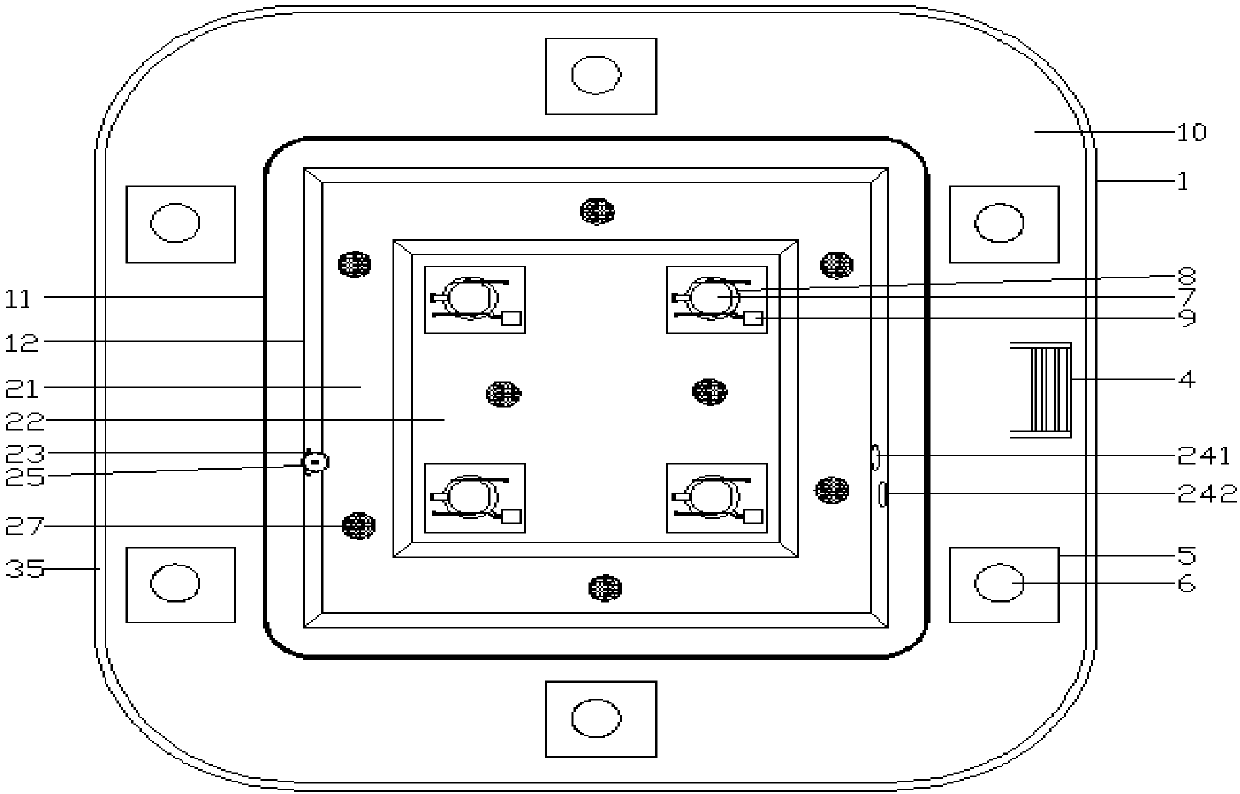
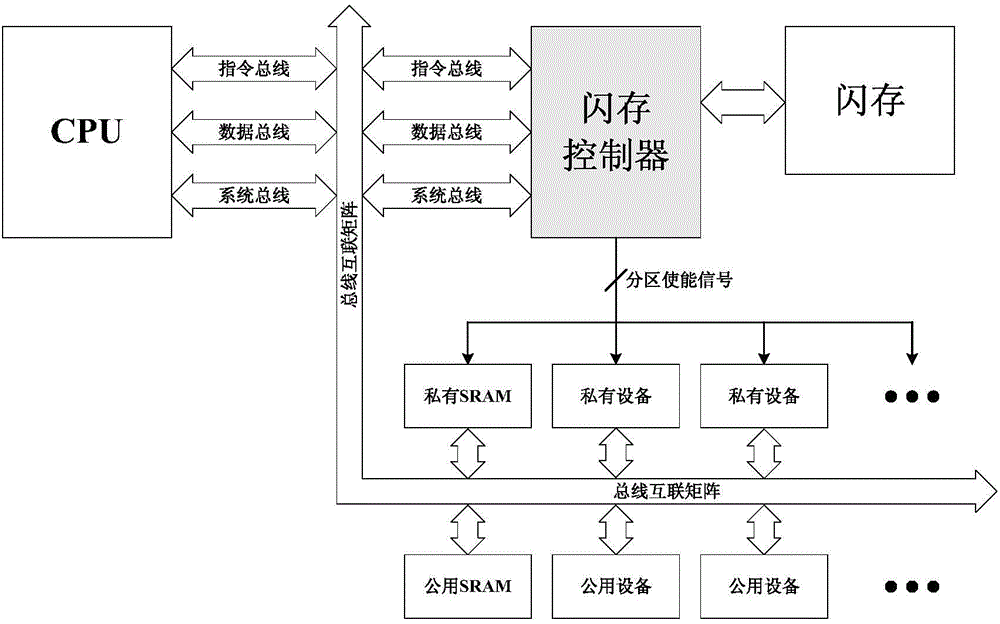
Multi-partition based MCU chip information protection method and device
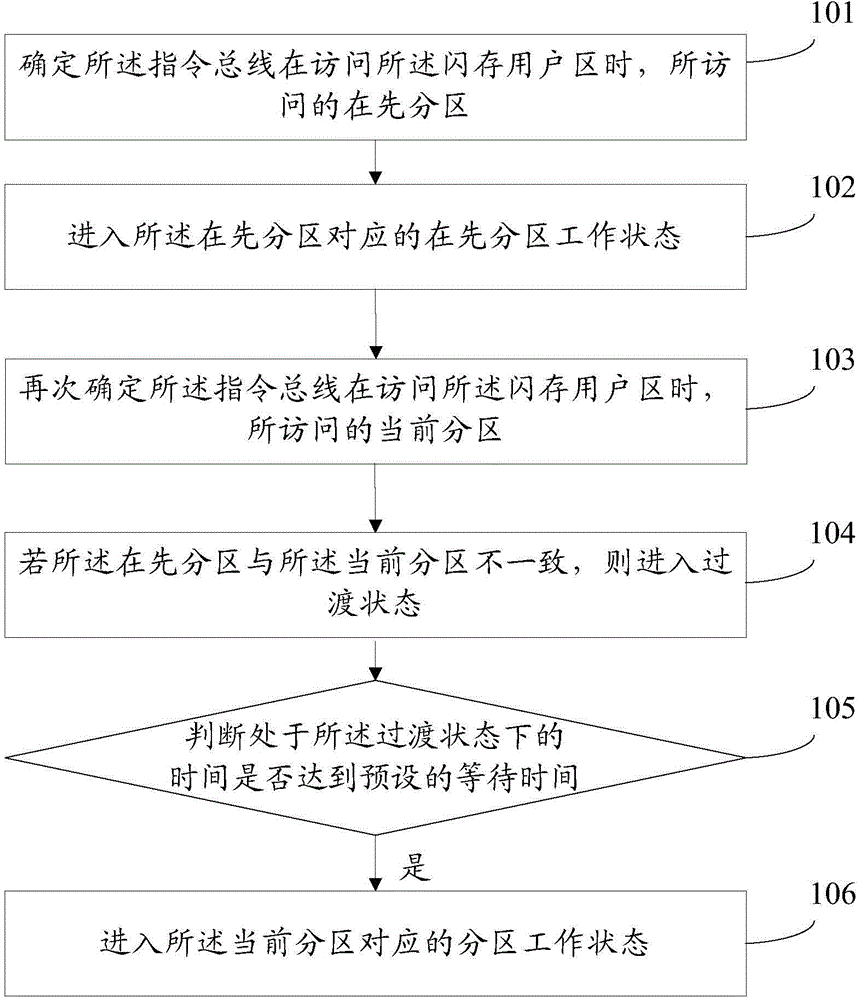
ActiveCN104573421ANot to be stolenProtect development resultsMemory architecture accessing/allocationUnauthorized memory use protectionFlash memory controllerTransition state
The invention provides multi-partition based MCU chip information protection method and device. An MCU chip comprises an instruction bus, a data bus, a flash memory controller and a flash user area. The method comprises the steps of determining the accessed prior partition when the instruction bus accesses the flash user area; entering the prior partition working state corresponding to the prior partition; determining the accessed current partition when the instruction bus accesses the flash user area; entering a transition state in case that the prior area is different from the current partition; determining whether the time under the transition state reaches the preset waiting time; if so, entering the partition working state corresponding to the current partition. With the adoption of the method and device, programs can be protected from being stolen by a user, and meanwhile, the companies cooperating to develop the programs cannot steal programs from each other.
Owner:GIGADEVICE SEMICON (BEIJING) INC
Three-dimensional crab breeding pond capable of being lifted to adjust
PendingCN107873615AIncrease productionExpand the scope of activitiesPisciculture and aquariaMarine engineeringZoology
The invention discloses a three-dimensional crab breeding pond capable of being lifted to adjust. The pond comprises a pond body which comprises a first pond and a second pond, wherein the second pondis located above the first pond and is connected to the first pond through a supporting column; the second pond comprises a concentric-square-shaped pond and / or a round pond; the concentric-square-shaped pond and / or the round pond are located around and / or at the center of the first pond and are connected to the first pond through ladders; and the first pond is provided with a foundation which isprovided with a hydraulic device, the hydraulic device is connected to the supporting column, and the hydraulic device is started, so that the supporting column and the concentric-square-shaped pondand / or the round pond connected to the supporting column ascend or descend. Based on an existing breeding area, an supporting breeding pond capable of being lifted to adjust is additionally arranged for saving the farmland, so that the breeding area is increased and the aquaculture income is increased; and the pond is steady in structure, convenient to use and worth being popularized.
Owner:泉州市联控自动化科技有限公司
A full-text retrieval method based on encryption and decryption algorithm
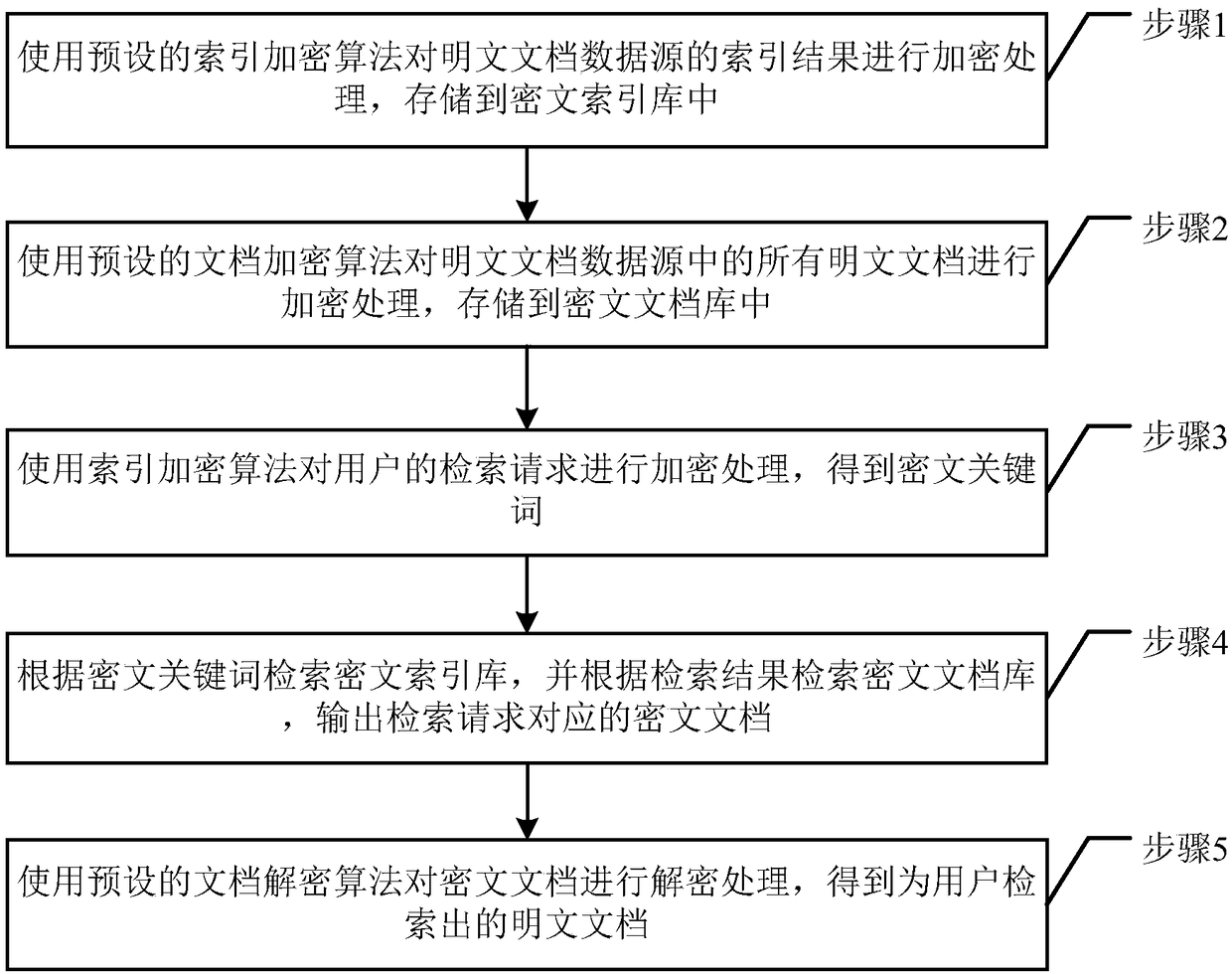
InactiveCN109255248ANot to be stolenImprove securityDigital data protectionFile access structuresPlaintextCiphertext
The invention discloses a full-text retrieval method based on an encryption and decryption algorithm, which is used for realizing the encryption processing of the full-text retrieval index file and improving the security of the full-text retrieval. The invention provides a full-text retrieval method based on an encryption and decryption algorithm. The method comprises the following steps: the index result of a plaintext document data source is encrypted by using a preset index encryption algorithm and stored in a ciphertext index database; a preset document encryption algorithm is used to encrypt all the plaintext documents in the plaintext document data source and store the plaintext documents in a ciphertext document library; the index encryption algorithm is used for encrypting the retrieval request of a user to obtain ciphertext keywords; and the index encryption algorithm is used for encrypting the retrieval request of the user to obtain ciphertext keywords, the ciphertext index library is searched according to the ciphertext keyword, the ciphertext document library is searched according to the searching result, and the ciphertext document corresponding to the searching request is output; a preset document decryption algorithm is used to decrypt the ciphertext document to obtain a plaintext document retrieved for the user.
Owner:福建南威软件有限公司
Heat dissipation anti-theft mobile phone housing
InactiveCN105227706AReduce the temperatureNot to be stolenTelephone set constructionsCooling/ventilation/heating modificationsMobile phoneComputer engineering
Owner:王昊仑 +1
Adjustable lifting multilayer crab culture pond
PendingCN108029620AIncrease productionExpand the scope of activitiesPisciculture and aquariaEngineeringAgriotes
The invention discloses an adjustable lifting multilayer crab culture pond which comprises a pond body. The pond body comprises a first pond, a second pond and a third pond, the third pond and the second pond are positioned above the first pond and connected with the first pond through a supporting column, the third pond is positioned in a through hole formed in the middle of the second pond, thethird pond, the second pond and the first pond can be connected with each other through a ladder, the first pond is provided with a foundation, and a hydraulic device is mounted on the foundation andconnected with the supporting column. The pond can give priority to farmland saving, a plurality of adjustable aerial culture ponds are added based on the area of an existing culture pond, so that thearea of the existing culture pond is increased, aquaculture income is improved, and the adjustable lifting multilayer crab culture pond is stable in structure, convenient to use and worthy of popularization.
Owner:泉州市联控自动化科技有限公司
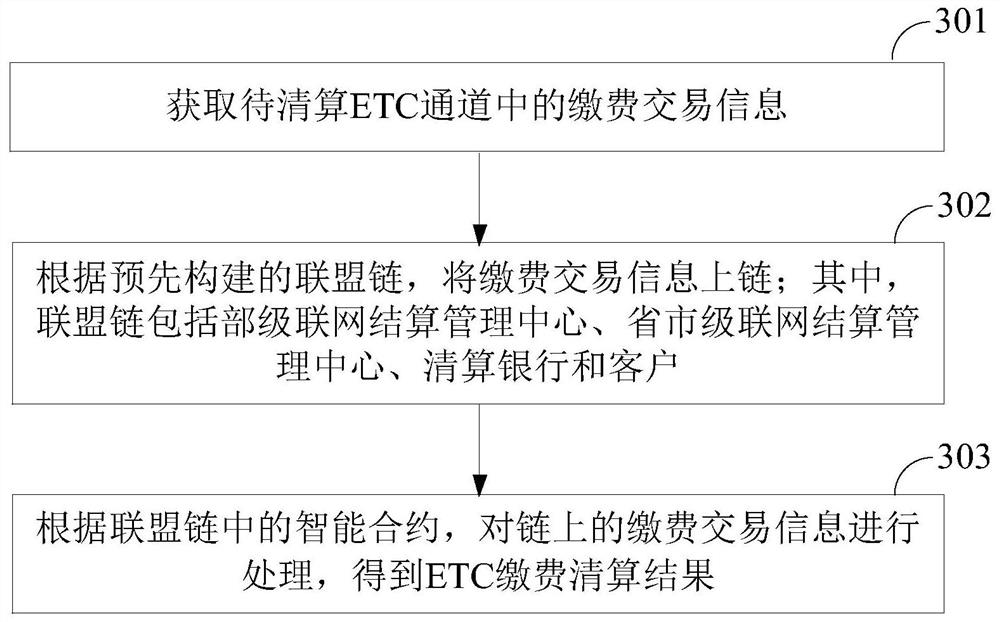
ETC payment clearing method, device and apparatus based on alliance chain
PendingCN112613865AFast and accurate payment and settlementImprove securityTicket-issuing apparatusPayment protocolsComputer securityPayment transaction
The invention discloses an ETC payment and settlement method, device and apparatus based on an alliance chain which can achieve the payment and settlement of ETC more quickly and accurately based on the pre-built alliance chain. The method comprises the steps of firstly obtaining payment transaction information in a to-be-cleared ETC channel, and then uploading the payment transaction information according to a pre-constructed alliance chain; wherein the alliance chain comprises a ministry networking settlement management center, a provincial and municipal networking settlement management center, a clearing bank and a client, and then processing payment transaction information on the chain according to an intelligent contract in the alliance chain to obtain an ETC payment clearing result.
Owner:AGRICULTURAL BANK OF CHINA
Lifting adjustable multi-layer pond for breeding crabs
InactiveCN107897097AImprove yield and feed qualityExpand the scope of activitiesPisciculture and aquariaStructural stabilityEngineering
The invention discloses a multi-layered pond for raising and lowering crabs, which includes a pond body, the pond body includes a first pond and a second pond, the first pond is located on the ground, and the second pond is located in the first pond Above, the first pond is provided with a foundation, the foundation is equipped with a base, the base is equipped with a support column and a hydraulic cylinder, the hydraulic cylinder is connected with the hydraulic pump and the support column, and the support column is connected to the second pond connected, the bottom of the second pond is equipped with a level sensor, the level sensor is connected to the control circuit board, the control circuit board is connected to the power supply, control switch, hydraulic pump and pressure sensor, and the pressure sensor is located at the hydraulic cylinder, And it is connected with the support column, and the pressure sensor is used to detect the bearing pressure of the support column. The pond of the invention can increase the aquaculture area on the basis of the existing aquaculture, increase the income of aquaculture, and has a stable structure and convenient use, and is worth popularizing.
Owner:苏州倍儿壮养殖装备科技有限公司
Lock head cover
Owner:GUANGDONG JINDIAN ATOM LOCK
Separated novel intelligent door lock system and working method thereof
InactiveCN109345665ANot to be stolenPrevent theftBuilding locksIndividual entry/exit registersWorking setEmbedded system
The invention discloses a separated intelligent door lock system and a working method thereof. The system comprises an intelligent door lock. A mechanical switch assembly is provided on the intelligent door lock. A controller controls the operation of the mechanical switch assembly. The system further comprises an unlocking module which is provided separately from the intelligent door lock. A first security chip is provided in the unlocking module, and a second security chip is provided in the intelligent door lock. The first security chip transmits identity authentication information to the second security chip. The door lock system realizes the separation of the unlocking module and the intelligent door lock, the unlocking module can be carried by the locker, thereby greatly improving the security of the door lock system. When the unlocking module is stolen, a thief cannot open the door lock by the unlocking module since the fingerprint information of the thief and the locker are notconsistent, thereby further ensuring the security of the door lock system.
Owner:GOLDPAC GRP LTD
A static data encryption protection method and system
ActiveCN110990851BImprove securityImprove protectionKey distribution for secure communicationDigital data protectionFile allocationCiphertext
The present invention relates to a static data encryption protection method and system. The method includes: registering the information of the server host where the client is located to the server; assigning a master key to the directory or file of the server host at the server, generating an encryption control strategy and downloading Send to the corresponding client; the client obtains the corresponding master key from the server according to the encryption control strategy; when writing data to the encrypted directory or file, a data key is randomly generated, and the directory or file is encrypted using the data key. Encrypt to obtain an encrypted file; use the master key to encrypt the data key to obtain the key ciphertext, and write the key ciphertext to the header of the encrypted file to complete the data writing. In the present invention, the client performs encryption and decryption operations of files, and the server implements server host management, key management, and control strategy management, etc., realizes transparent access to encrypted files, unified management of keys and strategies, and separates file management and use rights, improving file protection security.
Owner:山东三未信安信息科技有限公司
Exhibit protection system
InactiveCN109255915ANot damagedNot to be stolenBurglar alarm by disturbance/breaking stretched cords/wiresMonitoring systemComputer terminal
The invention relates to the field of electronic monitoring equipment, in particular to an exhibit protection system. The invention puts forward the exhibit protection system. The system comprises a vibration sensor, electronic fence monitoring devices and an alarm, wherein the vibration sensor is installed on a display case; the electronic fence monitoring devices are arranged around the displaycase; the triggering end of the alarm is connected with the output end of the vibration sensor and the output ends of the electronic fence monitoring devices; and in addition, the alarm is connected with a wireless communication module. By use of the system, the electronic fence and the vibration sensor serve as dual protection, the alarm can be triggered to emit an alarm signal no matter when theelectronic fence monitoring system monitors exceptions or the vibration sensor detects exceptions, meanwhile, the alarm signal is transmitted to a mobile terminal held by an on-duty monitoring room or security personnel through a network, and relevant personnel are notified in time to process. By use of the system, the exhibits can effectively prevent from being damaged or stolen, and in addition, the system has the advantages of simple structure, convenience in debugging and low cost.
Owner:大连智识科技发展有限公司
Liftable multi-layer pond for breeding crabs
PendingCN108012977AIncrease the farming areaIncrease incomePisciculture and aquariaEngineeringAquaculture
The invention discloses a liftable multi-layer pond for breeding crabs. The pond includes a pond body, the pond body comprises a first pond body and a second pond body, the first pond body is positioned on the ground, and the second pond body is positioned above the first pond body; the first pond body is provided with foundation, and the foundation is provided with a locking mechanism and a hydraulic lifting device; the hydraulic lifting device is connected with supporting columns, the supporting columns are connected with the locking mechanism and the second pond body, the hydraulic liftingdevice can change the height of the second pond body, the locking mechanism can fix the positions of the supporting columns, and foaming partition plates are arranged at the bottom and periphery of the second pond body and can reduce the influences from the exterior temperature, sound waves and light rays on the second pond body. According to the pond, on the basis of the existing breeding area, the breeding area can be further increased, the aquiculture income is augmented, and the pond is firm in structure, convenient to use and worthy of popularization.
Owner:泉州市联控自动化科技有限公司
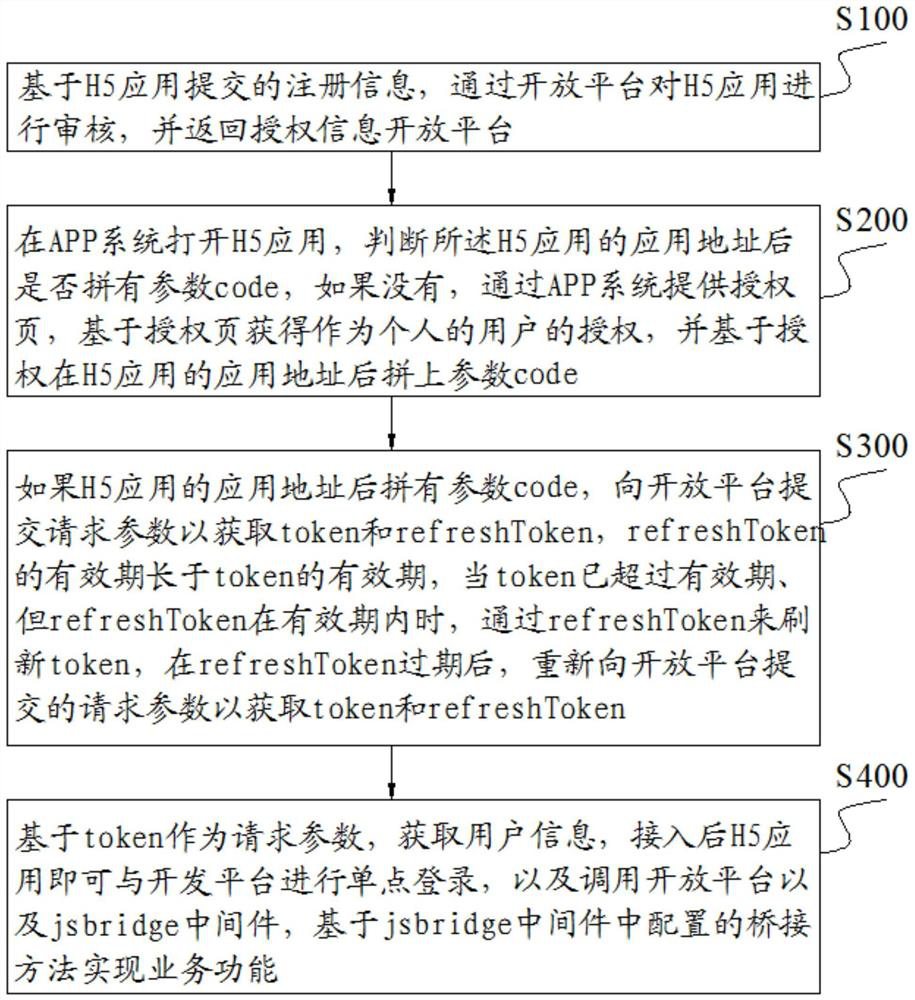
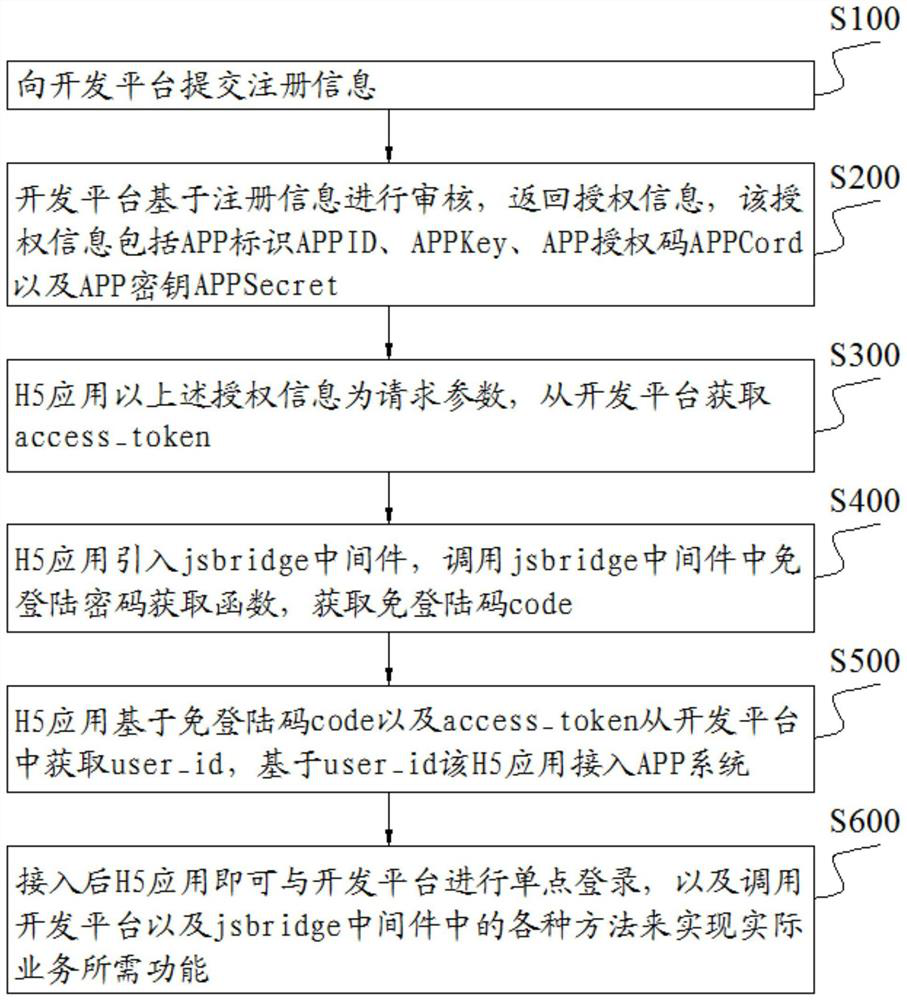
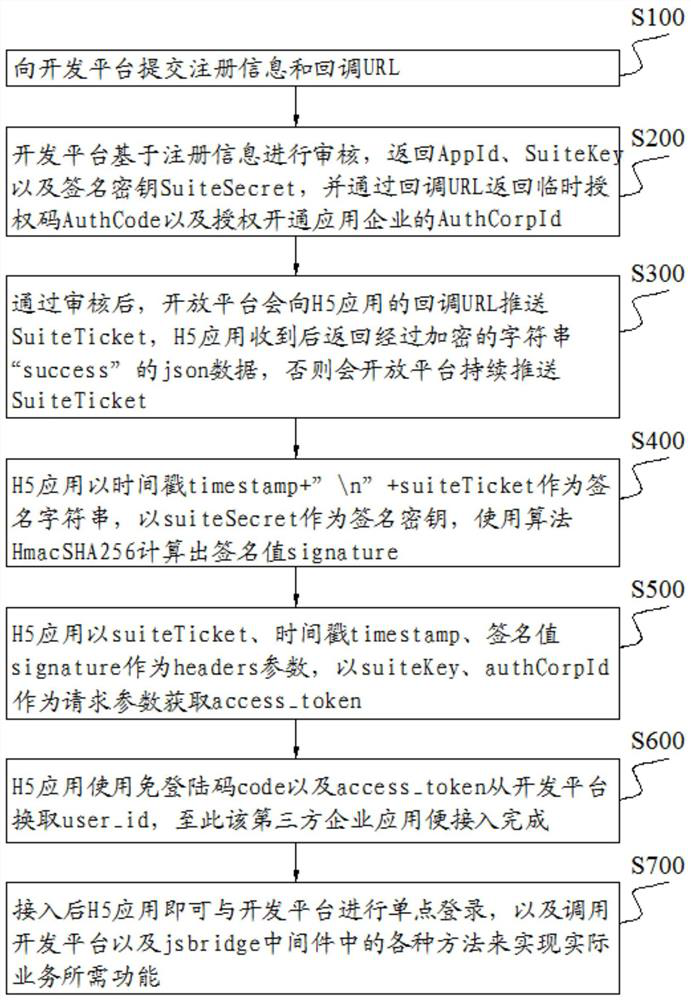
Application access method and system based on jsbridge
PendingCN114462013AIncrease freedomIncrease opennessDigital data authenticationPlatform integrity maintainanceAccess methodOpen platform
The invention discloses an application access method and system based on jsbridge, belongs to the technical field of H5 application access, and aims to solve the technical problem of how to realize interaction between a native H5 application and a native advanced function. For a user as an individual, the method comprises the following steps: checking the H5 application through an open platform based on registration information of the H5 application, and returning authorization information; authorizing the H5 application based on the authorization information; for a user as an enterprise, the method comprises the following steps: checking and authorizing the H5 application through an open platform based on registration information of the H5 application, and returning authorization information; the method comprises the following steps: acquiring a user from an open platform based on a login-free code and an access token, calling the open platform and the jsbridge middleware, and realizing a service function based on a bridging method configured in the jsbridge middleware.
Owner:INSPUR SOFTWARE CO LTD
Terminal information security method and device
ActiveCN102271332BNot to be stolenSolve problems that are not conducive to protecting the privacy of usersSecurity arrangementSecuring communicationPasswordInformation confidentiality
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com