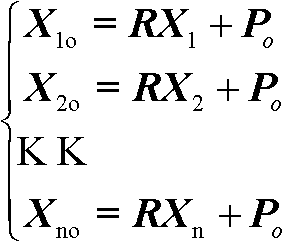Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
63results about How to "Low hardware and software requirements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Firmware program on-line upgrading method and hardware equipment
InactiveCN1991761AConvenient queryReduce the chance of upgrade failureProgram loading/initiatingCommunication interfaceOperational system
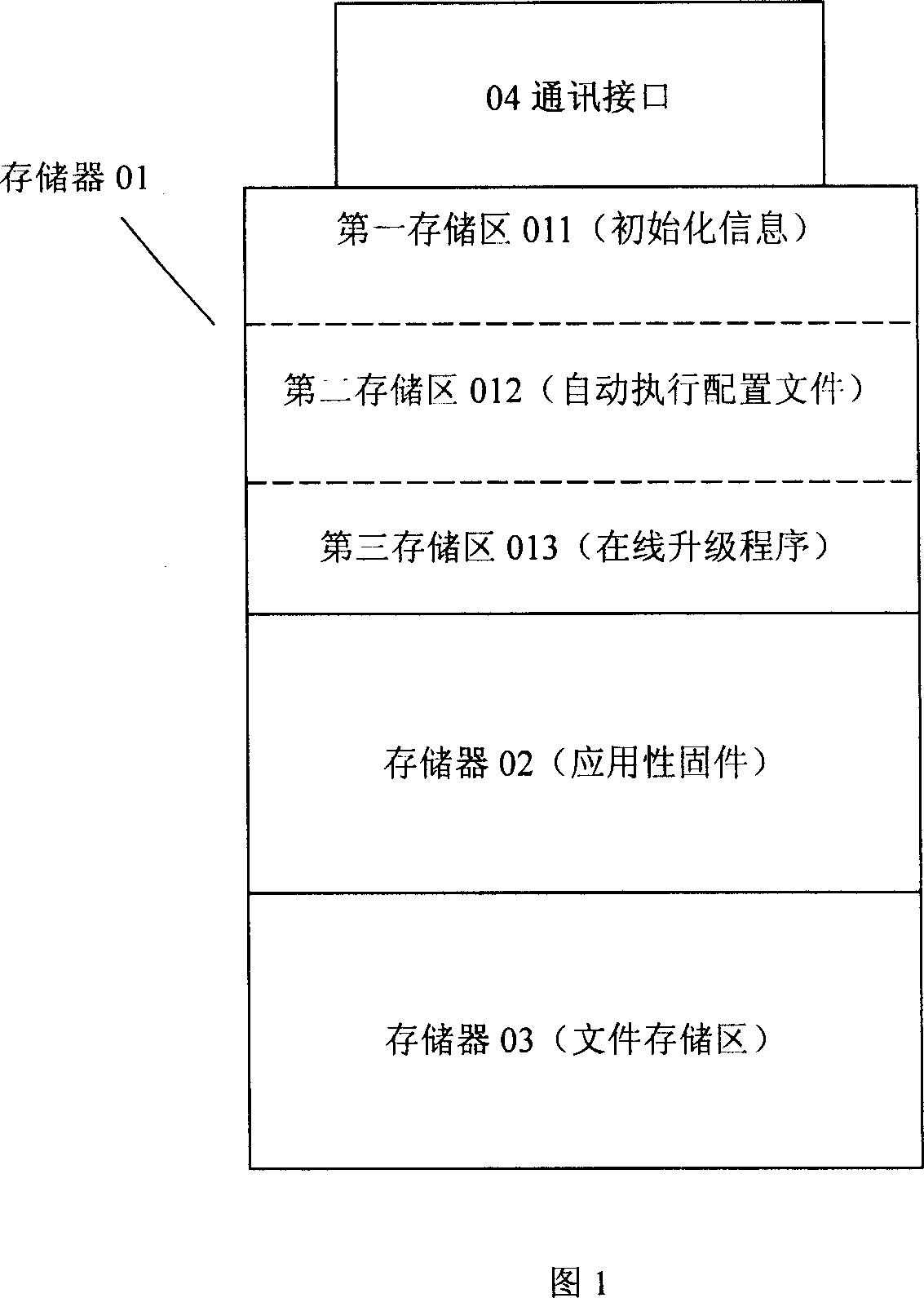
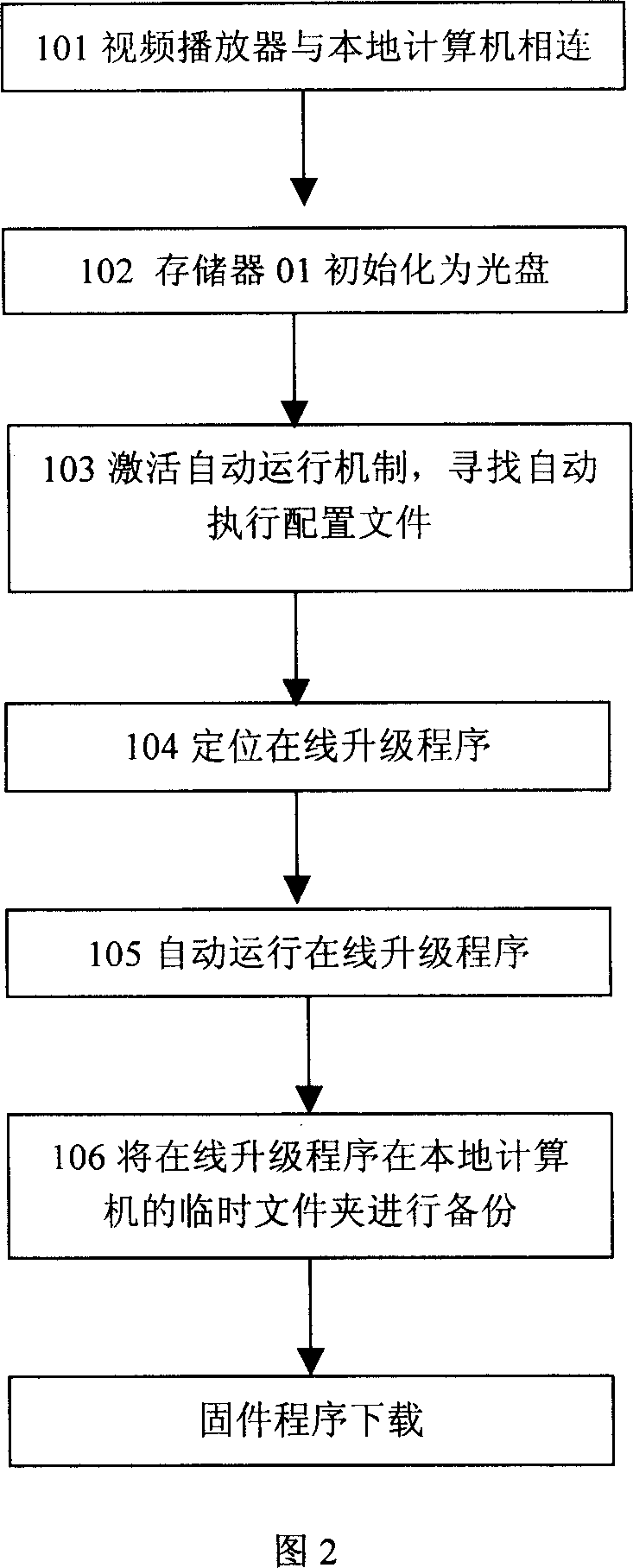
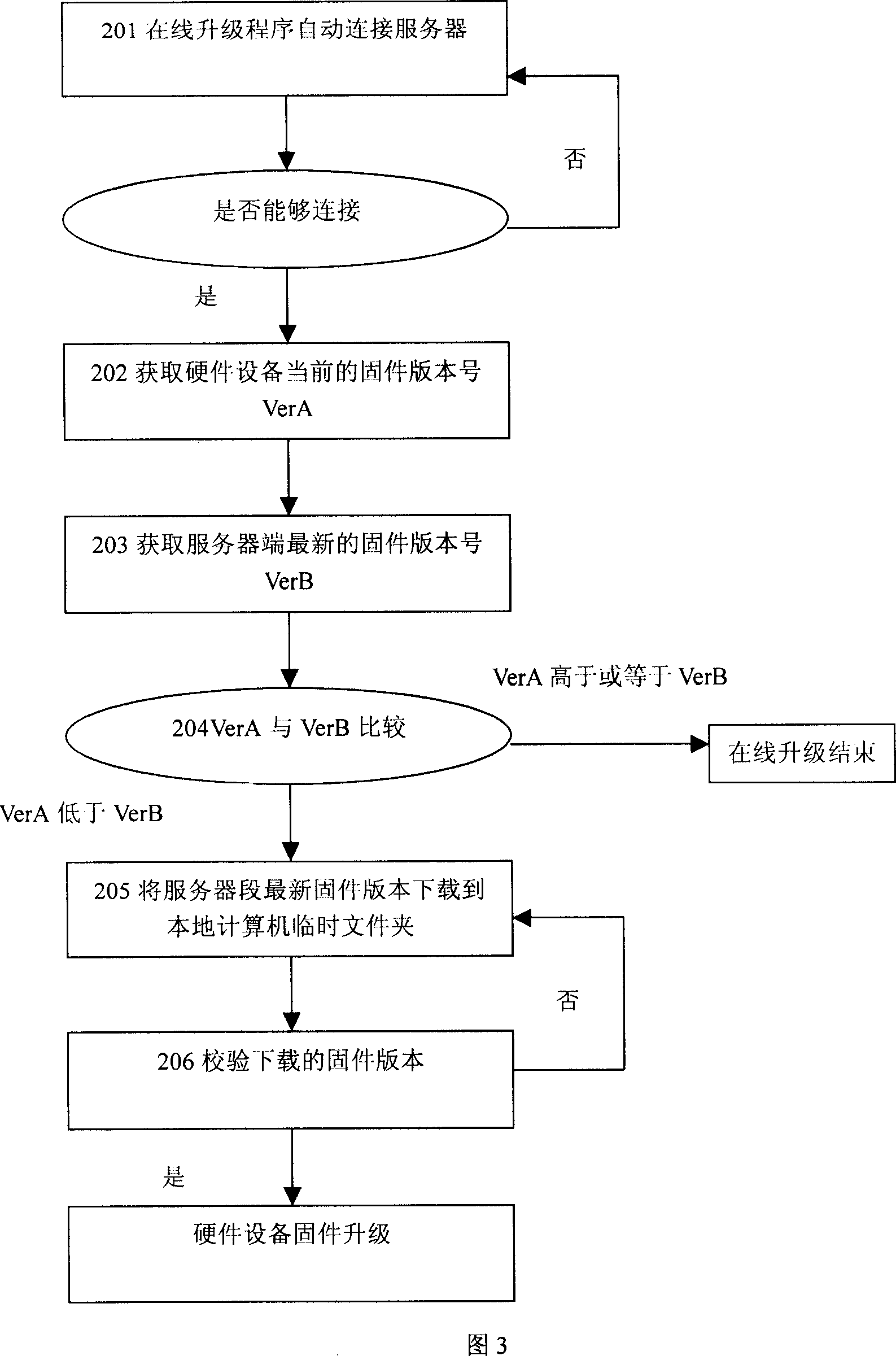
The invention relates to a online upgrading method of firmware program in hard ware that comprises following steps: 1) the hard ware is connected with the computer via communication interface; 2) activating the automatic actuating mechanism of the computer operating system; 3) the operating system executes the online upgrading program stored in memory of hard ware which is appointed by automatic actuating file; 4) the online upgrading program downloads fixed program from the preset server via network; 5) the firmware program downloaded is written into the nonvolatile definite space of memory hard ware to replace the firmware program, so the updating of the firmware program is accomplished. The invention relates to hard equipment which can update the firmware program that includes communication interface and nonvolatile memory which is used to store the firmware program, and initial information memory device, distribution file memory device, online upgrading program memory device.
Owner:AIGO DIGITAL TECHNOLOGY CO LTD
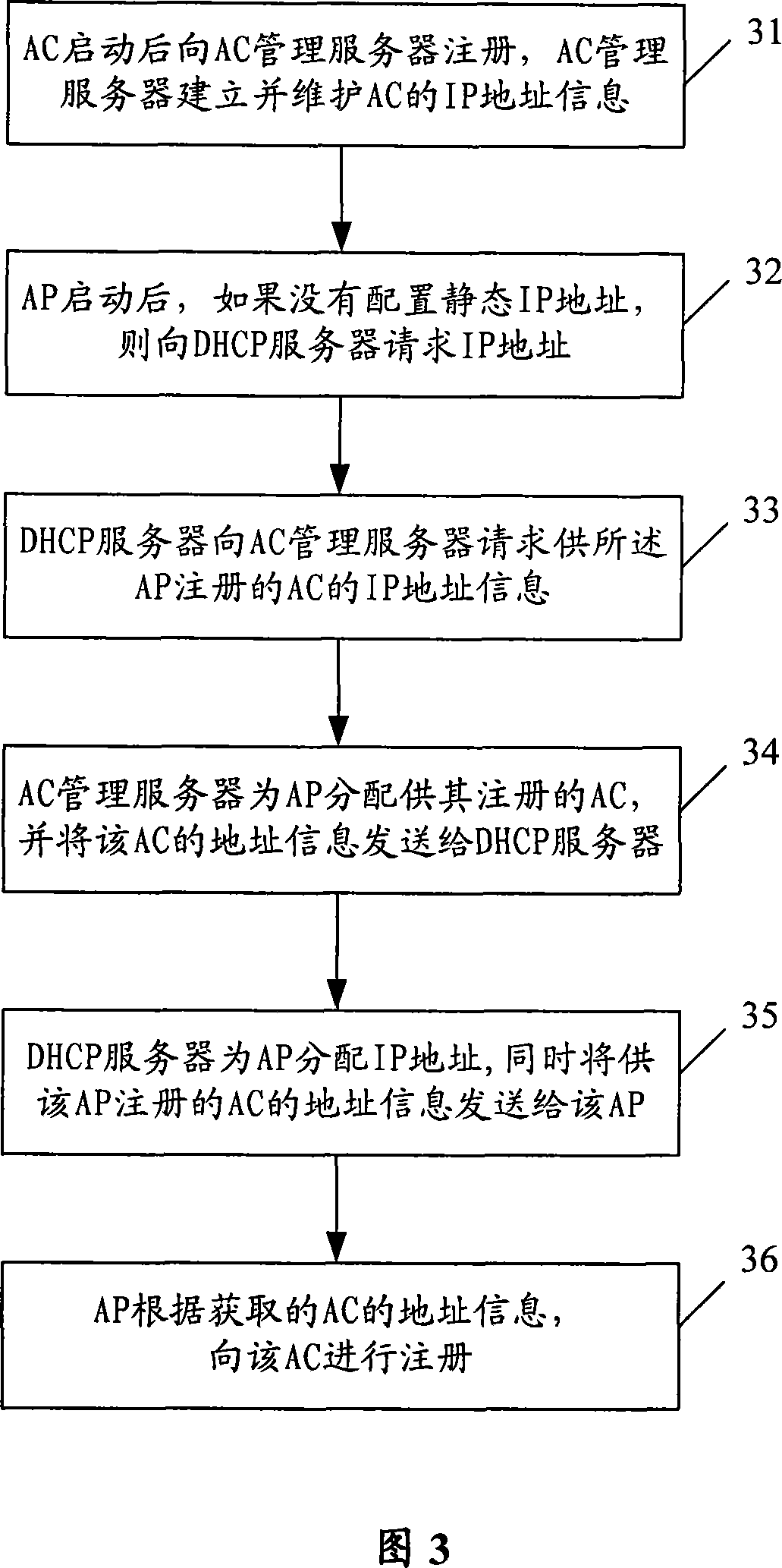
Login method and apparatus for AP
ActiveCN101159646AReduce complexityLow hardware and software requirementsData switching by path configurationRadio/inductive link selection arrangementsDependabilityComputer science
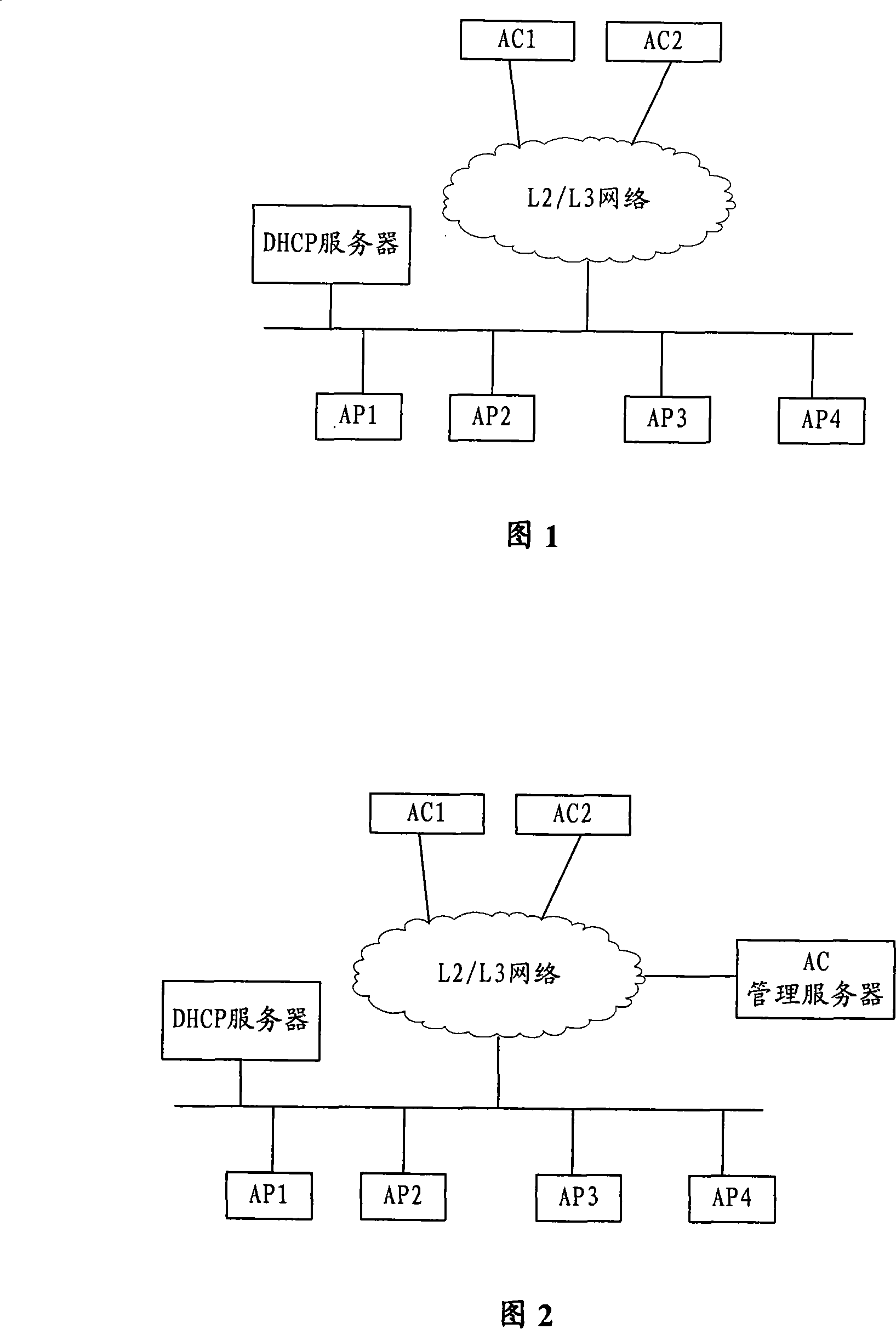
The invention provides a login method and equipment for access point (AP). The login method comprises setting up and maintaining the identification information of an access controller (AC) on an AC management server, and the AC management server allocates proper AC for AP. The inventive method and equipment can reduce the requirements to AP during login process, and improve the flexibility and reliability of login.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method for adjusting poses of airplane components based on 3-2-1 following locator
InactiveCN102514724AOvercome complex difficultiesEasy to implementAircraft assemblyThree degrees of freedomSingle degree of freedom
The invention discloses a method for adjusting poses of airplane components based on a 3-2-1 following locator, which comprises the following steps: firstly, calculating a difference between a current space pose and a target pose of the airplane components to be adjusted according to a measured coordinate and a target coordinate of a measuring point; setting N measuring points on the airplane components to be adjusted; then, calculating a difference between a current space position and a target position of the airplane components to be adjusted; and driving a three-degree of freedom locator, a two-degree of freedom locator and a single-degree of freedom to move according to the difference. The pose adjustment algorithm is simple and easy to implement; and has good adaptability, so that non-rigid body movement cannot occur in the pose adjustment process of the airplane components, and the safety of the pose adjustment process is ensured.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS +1
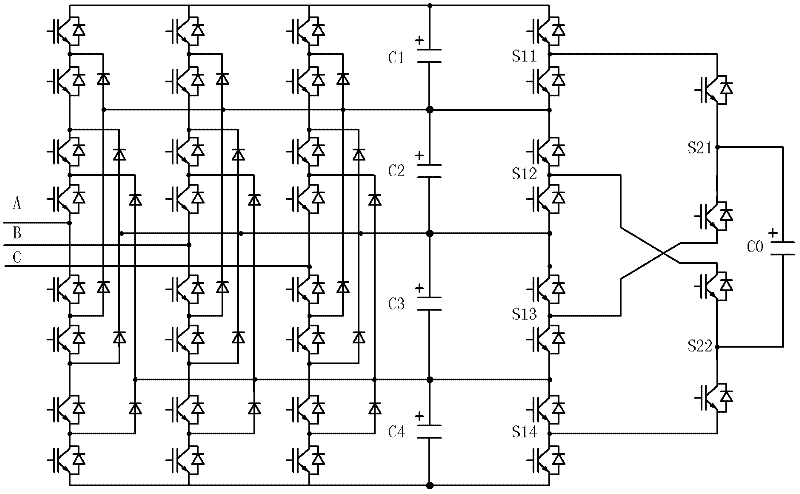
Multi-level converter with DC (direct current) capacitor assisted voltage-sharing circuit
InactiveCN102244477ADoes not affect the main circuitDoes not affect the control principleAc-dc conversionCapacitancePower factor
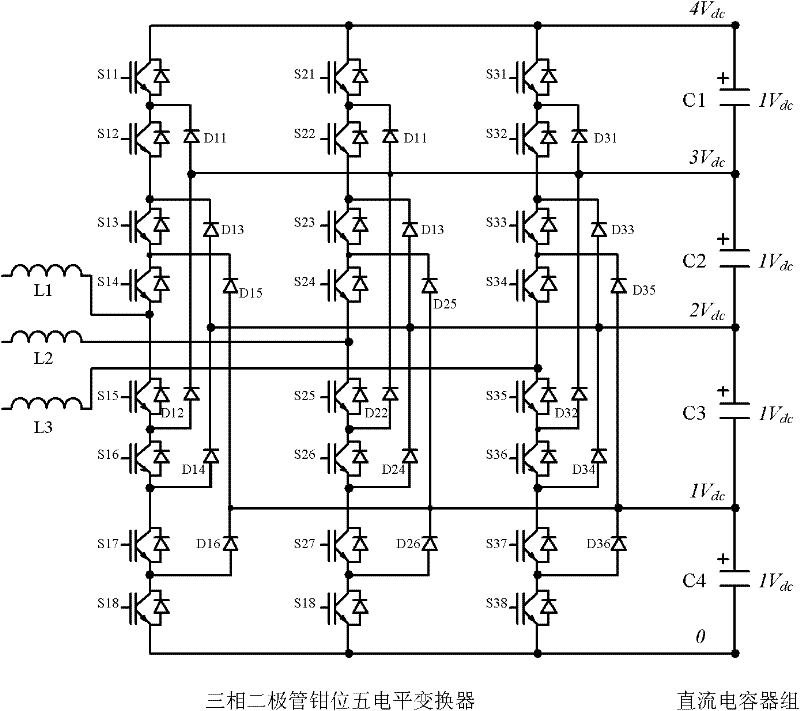
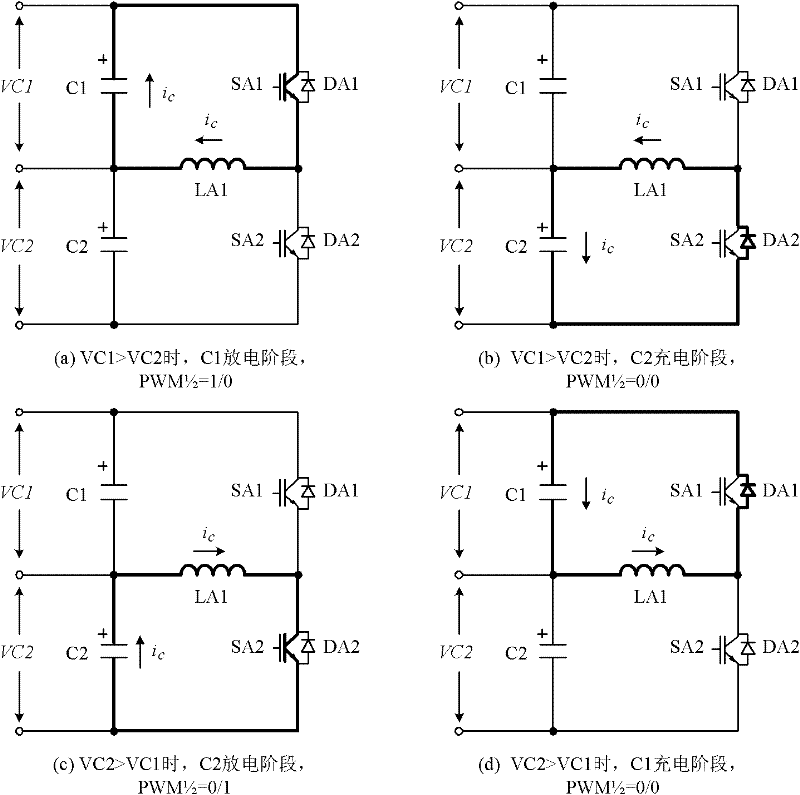
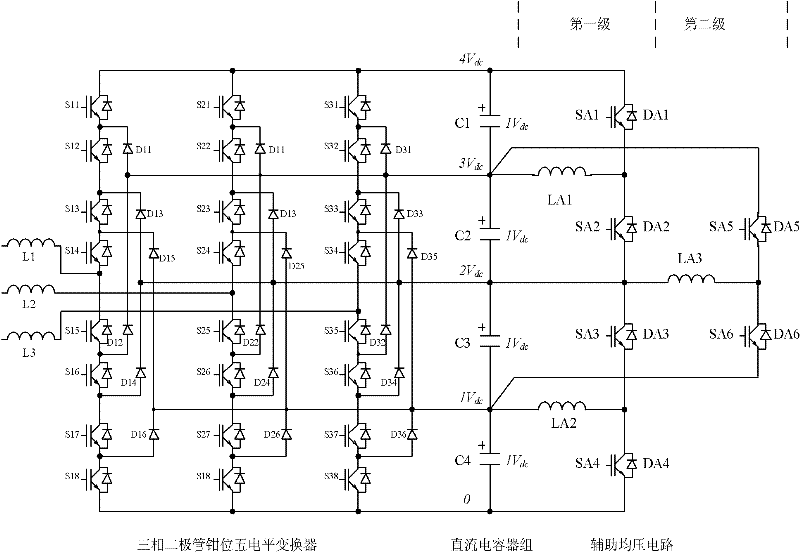
The invention discloses a multi-level converter with a DC (direct current) capacitor assisted voltage-sharing circuit. The voltage-sharing circuit comprises a primary voltage-sharing circuit and a secondary voltage-sharing circuit; for the multi-level converter with N+1 levels and N DC capacitors, the primary voltage-sharing circuit comprises N / 2 inductance voltage-sharing basic circuits; a switching element SA1n and a switching element SA1 (n-1) are connected with a capacitor Cn and a capacitor C (n-1) in parallel and the central connection points between the switching elements and the capacitors are connected by an inductor LA1(n / 2), thus realizing the voltage-sharing of the capacitor Cn and the capacitor C (n-1); the secondary voltage-sharing circuit comprises N / 2-1 groups of inductance voltage-sharing basic circuits to realize the voltage-sharing of the capacitor C (n-1) and a capacitor C (n-2); and finally, the N DC capacitors C realize the equalization of all voltages. The multi-level converter is suitable for the voltage-sharing of any level, does not influence an existing main circuit and a control principle and ensures that a main circuit converter can realize power transmission of any power factor under the condition of any modulation depth. The invention also provides specific circuits of a five-level converter as well as a realization circuit for minimizing the number of the inductors and a control method thereof.
Owner:SOUTHWEST JIAOTONG UNIV
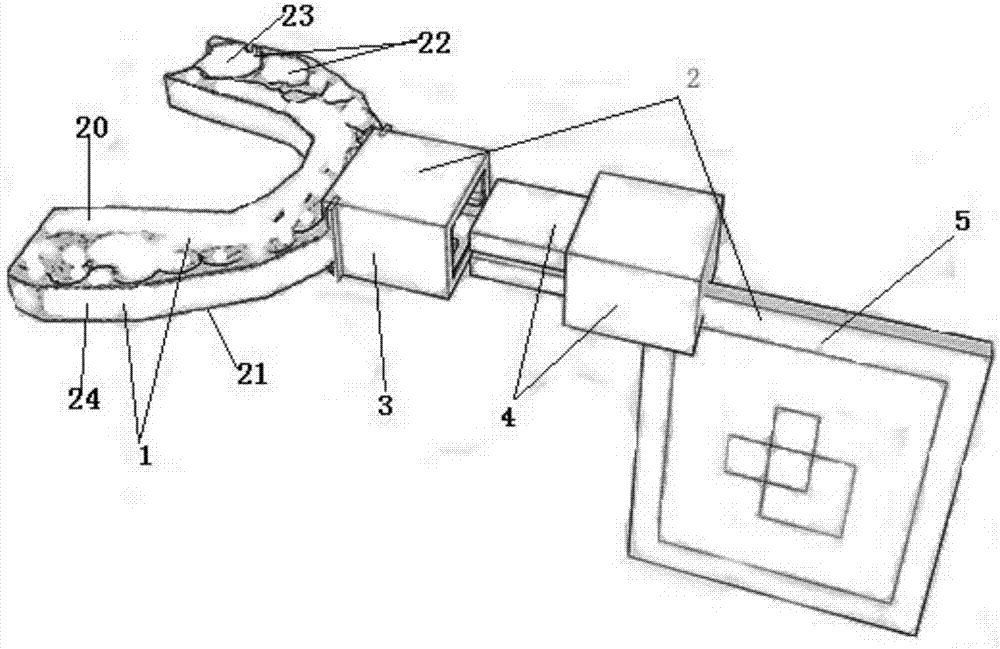
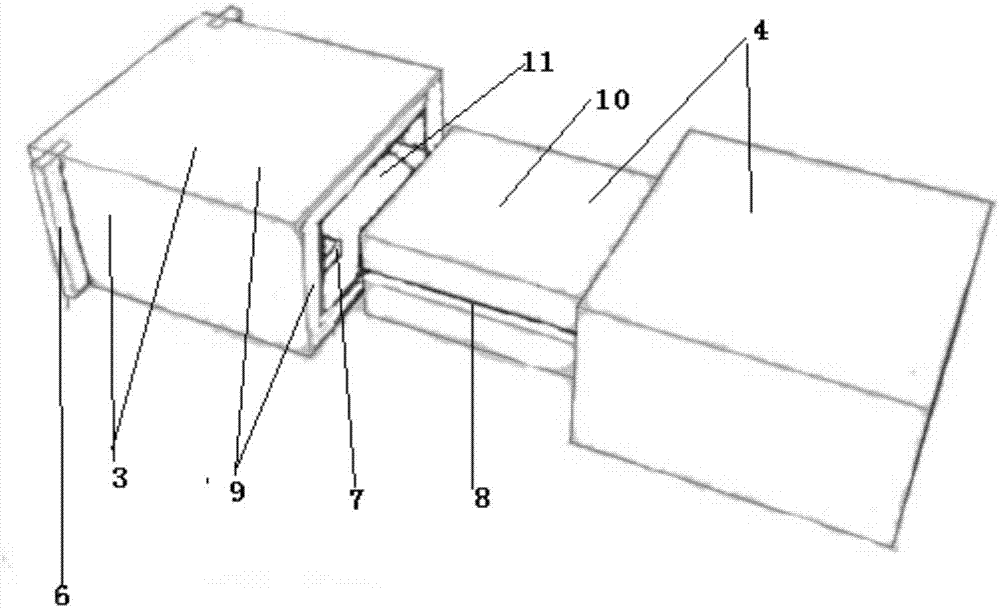
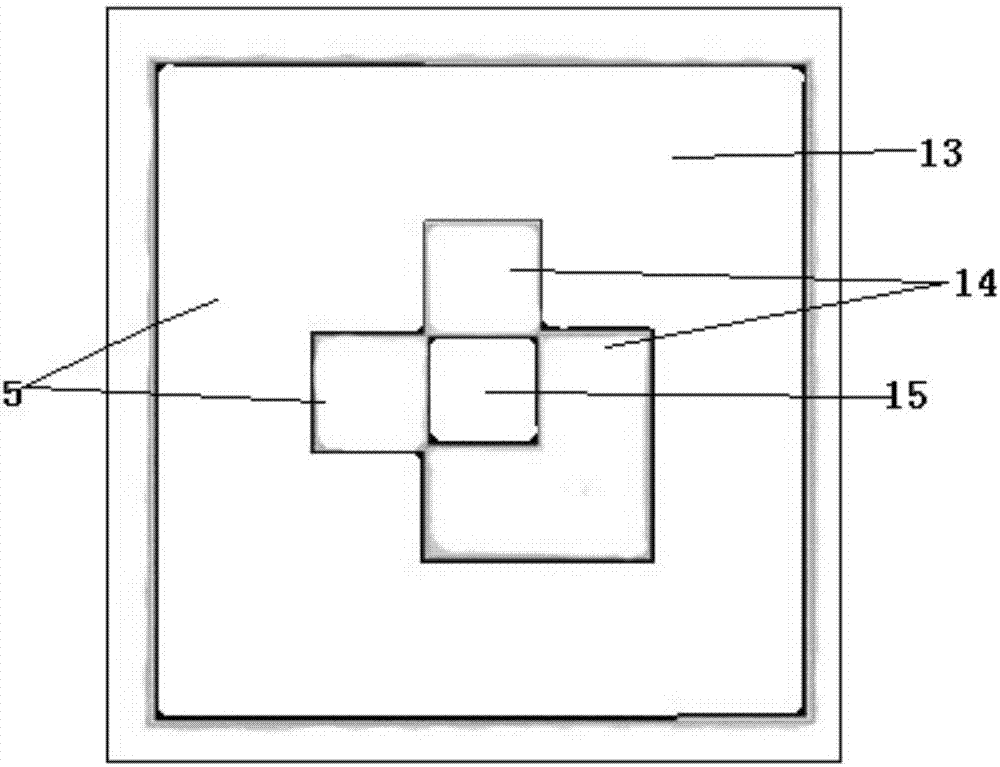
Tooth-borne type maxillofacial augmented reality positioning tracing device based on three-dimensional printing
ActiveCN107951561AImprove 3D dynamic visualizationShorten operation timeAdditive manufacturing apparatusSurgical navigation systems3D printingOral cavity
The invention relates to the related field of oral-maxillofacial surgical medical apparatus and instruments and augmented reality technologies, in particular to a tooth-borne type maxillofacial augmented realitypositioning tracing device based on three-dimensional printing. The device is characterized by comprising an occlusion guide plate and a vision capture marking module, the vision capture marking module is provided with a retention body, a connection body and a replaceable vision capture mark, the occlusion guide plate is connected with the retention body, and the retention body and thereplaceable vision capture mark are integrally connected through the connection body. The tooth-borne type maxillofacial augmented reality positioning tracing device based on three-dimensional printing is simple in structure, convenient to operate, low in cost, portable and efficient, accurate positioning and dynamic visualization are achieved, the device is beneficial for the maxillofacial surgery, and the good effect is achieved.
Owner:SICHUAN UNIV
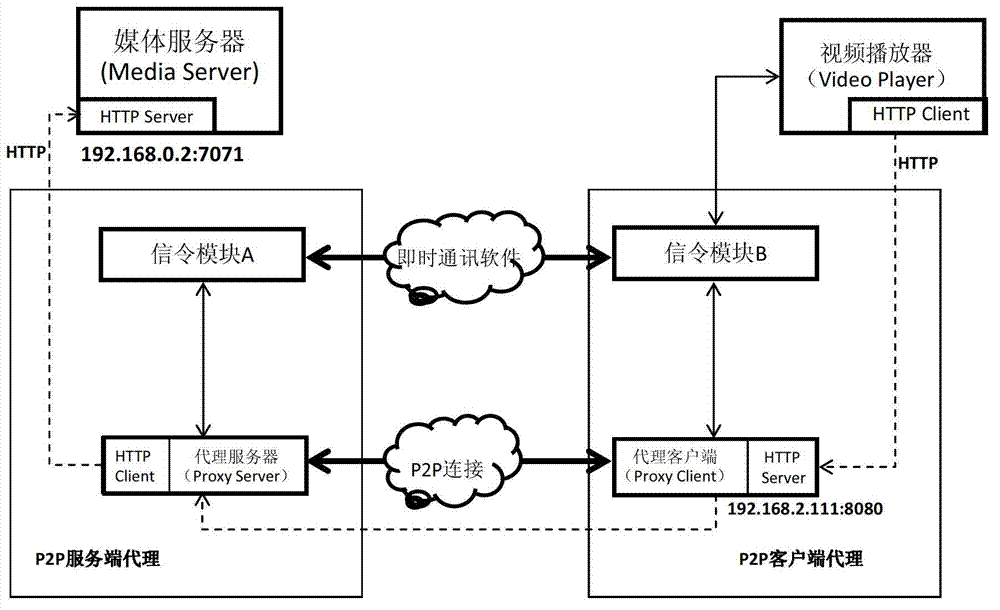
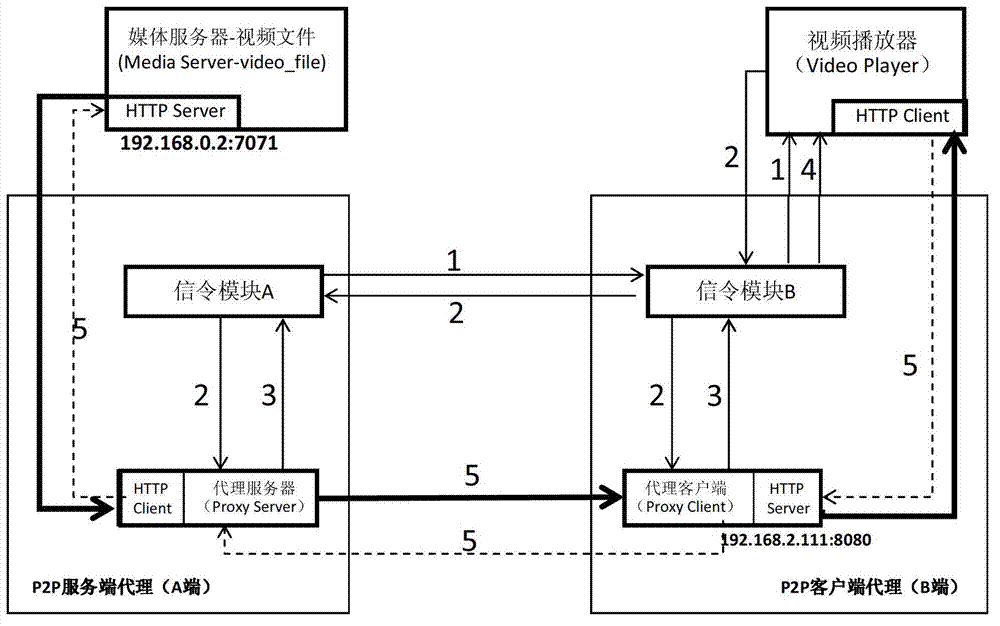
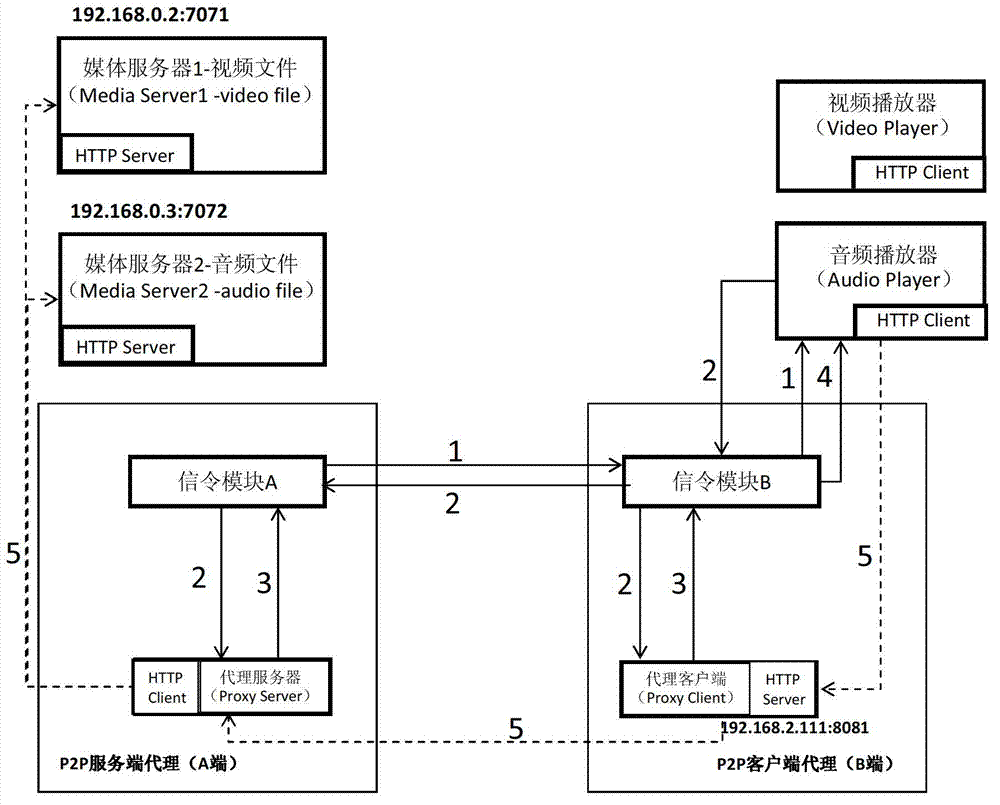
Method and system for transmitting home media resources on the basis of peer-to-peer agent mechanism
ActiveCN103179213ALow hardware and software requirementsReduce overheadTransmissionUser needsClient agent
The invention discloses a method and a system for transmitting home media resources on the basis of a peer-to-peer agent mechanism. The method comprises the following steps of: arranging at least one P2P (Peer-to-Peer) service end agent in a local network of a media resource provider, and providing a uniform P2P connecting inlet for all shared media resources in the local network with the at least one P2P service end agents; arranging at least one P2P client agent in a local network of a media resource user, and providing a uniform remote resource access inlet for all media resource players in the local network with the at least one P2P client agent; and when the media resource players in the local network of the media resource user need to remotely access the shared media resources in the local network of the media resource provider, sending requests to the P2P client agents in the local network with the media resource players by the media resource players, transmitting the required shared media resources to the media resource players through signalling transmission and a P2P connecting channel by the P2P client agents and the remote P2P service end agents.
Owner:深圳市闪联信息技术有限公司
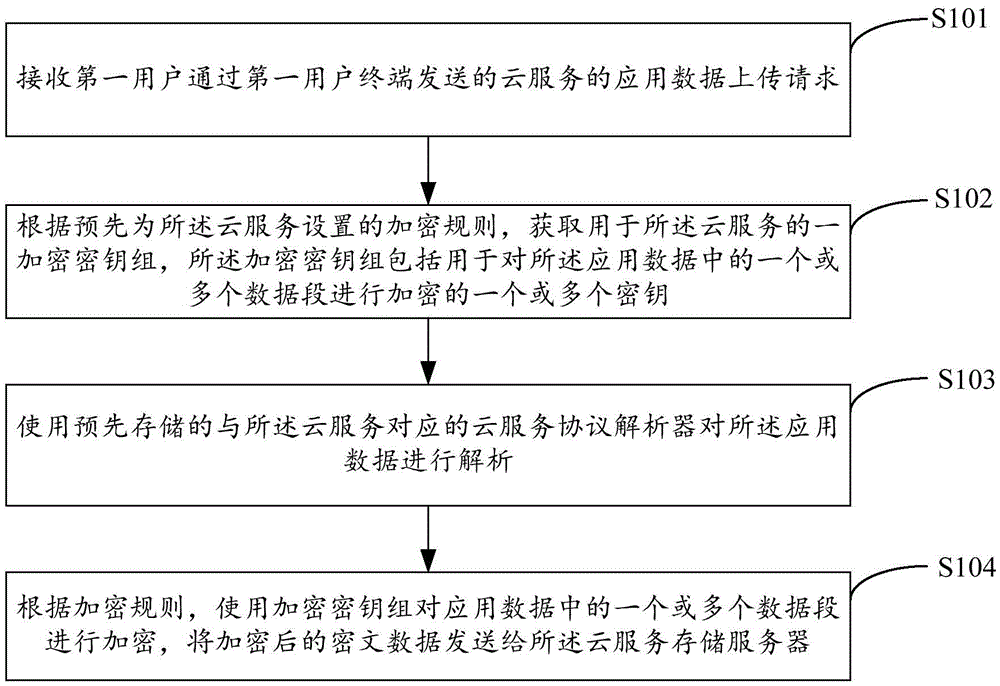
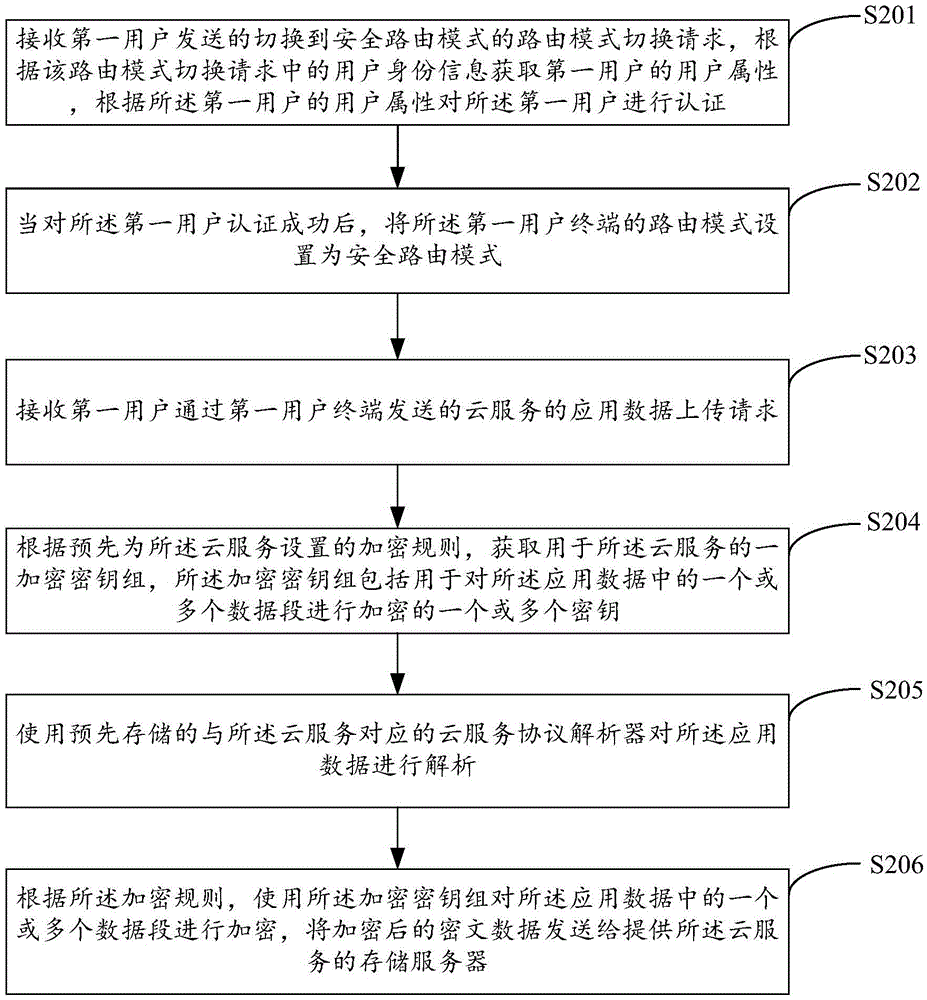
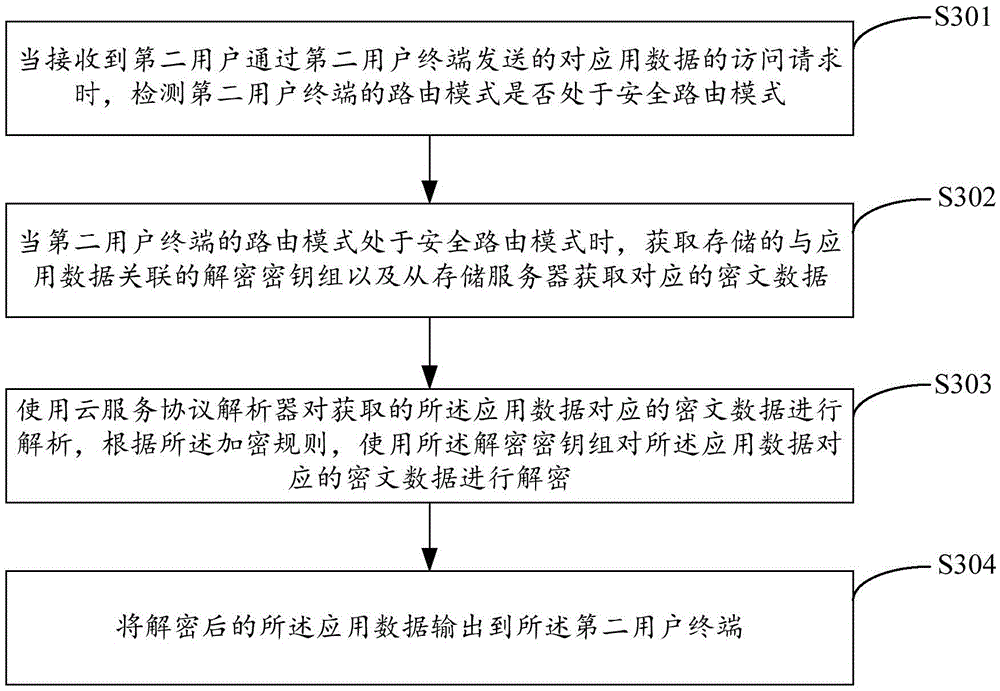
Data routing method and device based on cloud service and system
ActiveCN105610845ALow hardware and software requirementsAchieve sharingTransmissionService protocolComputer hardware
The invention is applicable to the computer technical field, provides a data routing method and device based on cloud service and a system. The method comprises following steps: receiving an application data uploading request of the cloud service, wherein the request is sent by a first user through a first user terminal; obtaining an encryption key set for the cloud service according to an encryption rule preset for the cloud service, wherein the encryption key set comprises one or more keys for encrypting one or more data segments in the application data; analyzing the application data by using a corresponding cloud service protocol parser; encrypting one or more data segments in the application data by using the encryption key set; and sending the encrypted ciphertext data to a storage server providing the cloud service. It is unnecessary to configure a special encryption client or device at the user terminal; the software and hardware demands of the user terminal are reduced; the whole encryption process is transparent to the user; differential encryption can be provided to the cloud service; the differential security is ensured; and the data sharing is realized.
Owner:SHENZHEN YUN AN BAO TECH CO LTD +1
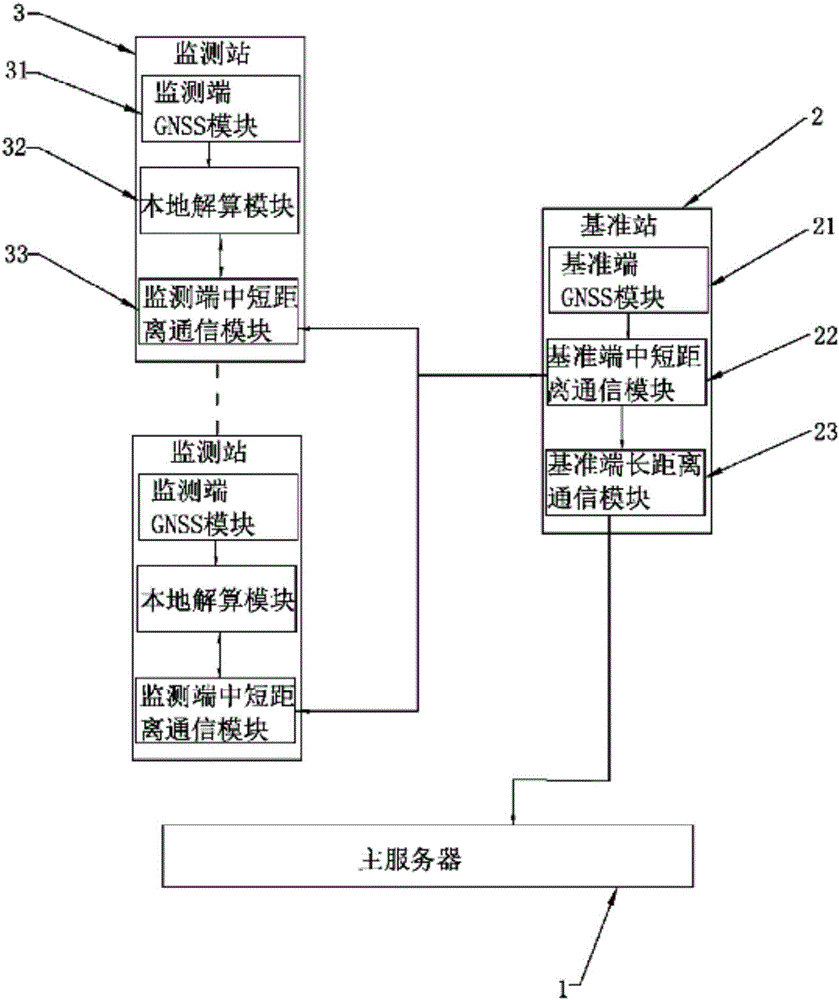
Deformation monitoring reference station based on GNSS technology, monitoring station and system thereof
ActiveCN106767661AAvoid lossLow hardware and software requirementsMeasurement devicesTransmissionShortest distanceDeformation monitoring
The invention relates to the deformation monitoring technology field and especially relates to a deformation monitoring reference station based on a GNSS technology, a monitoring station and a system thereof. The deformation monitoring system comprises a main server, and one reference station and at least one monitoring station are arranged in each detection area. The reference station sends reference end GNSS data monitored by the reference station to the monitoring station via a medium-short distance communication network. The monitoring station calculates a coordinate value and / or an offset amount according to the received reference end GNSS data and monitored monitoring end GNSS data. The monitoring station of the system can communicate with the main server without through long distance communication so that transmission stability of the whole system is increased. Besides, a calculating process is distributed to each monitoring station so as to carry out processing so that software and hardware requirements of a concentrated server are greatly reduced. In addition, by using the system, a data volume transmitted by a long distance communication network with high communication cost is greatly reduced and operation cost is decreased.
Owner:GUANGZHOU HI TARGET SURVEYING INSTRUMENT CO LTD
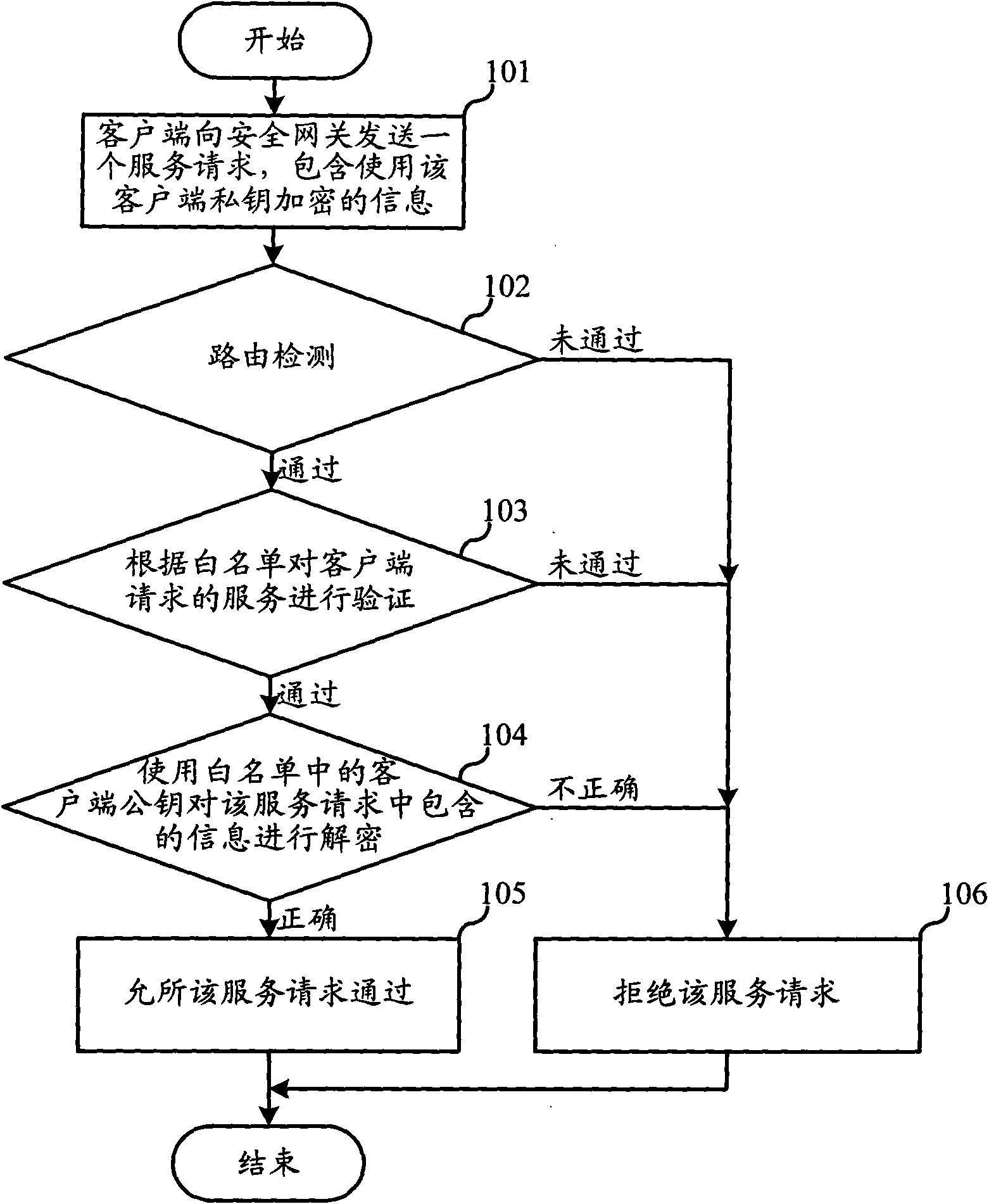
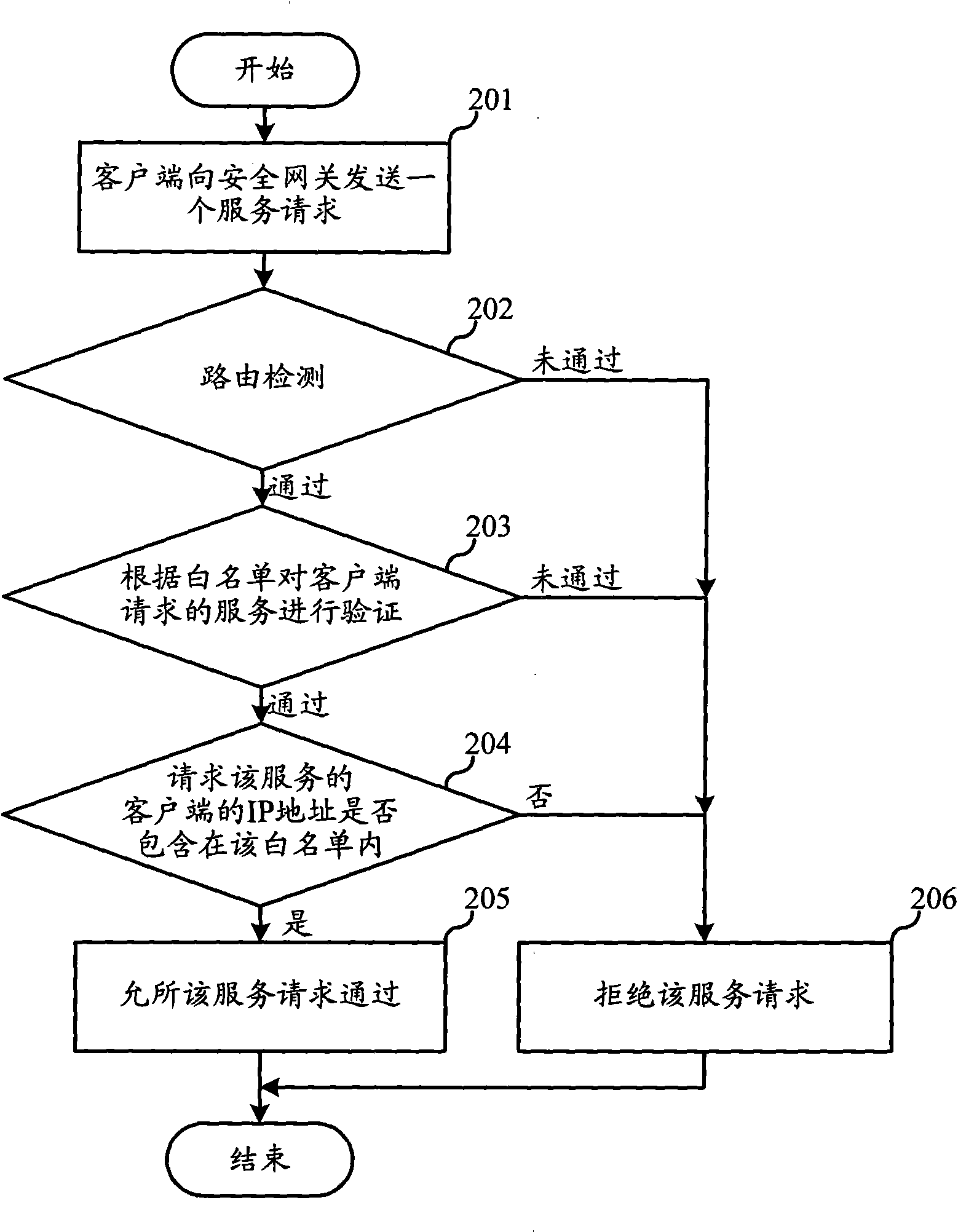
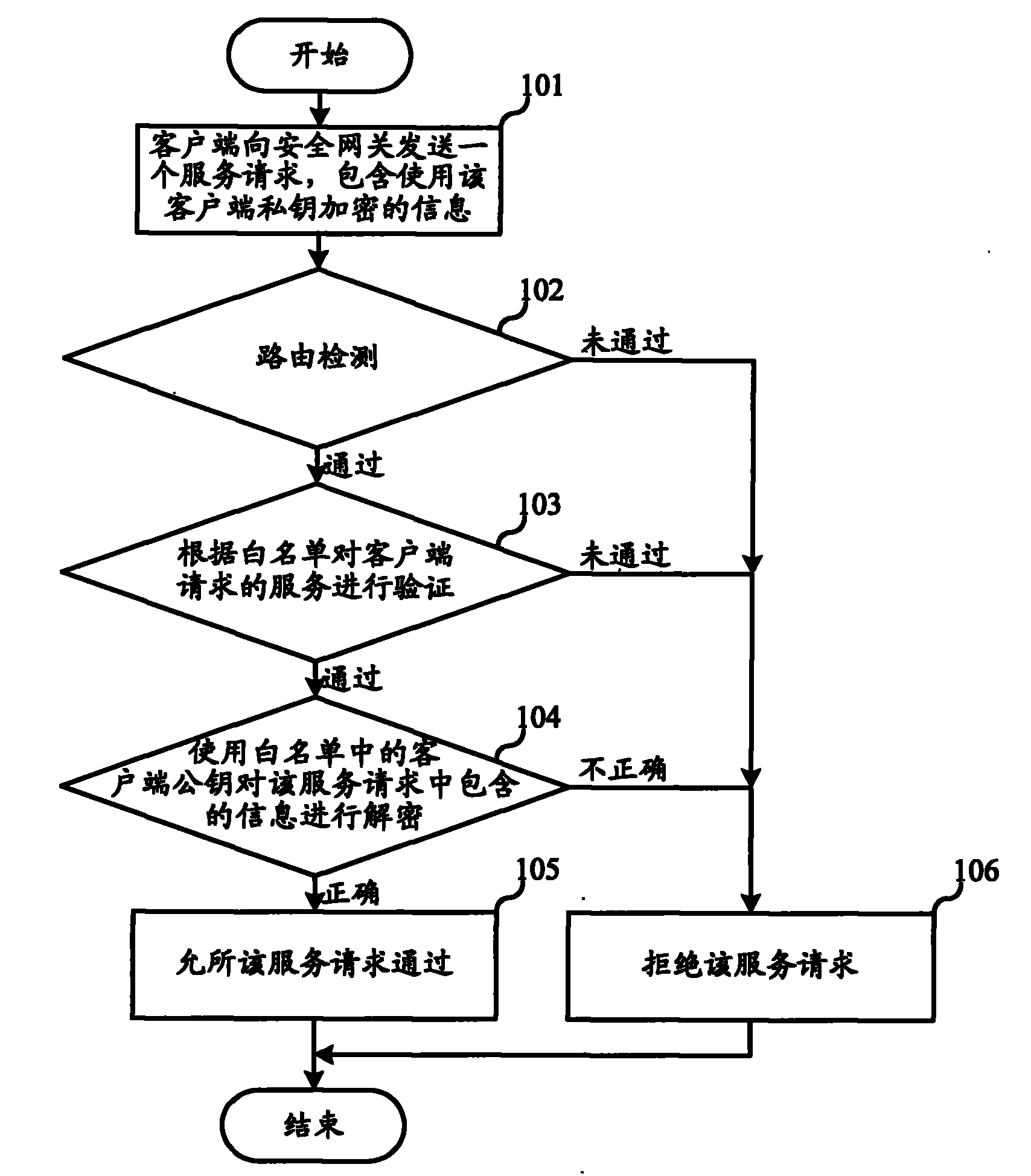
Industrial Internet intrusion detection as well as defense method and device
The invention discloses an industrial Internet intrusion detection as well as defense method and device. In the invention, a white list check method is adopted, i.e. only if the requested service in a service request and the client sending the request conform to those of the white list, the request is accepted; and if not, the request is refused. Compared with the black list mode checking 1 to N, the detection mode does not require a database with a great number of harmful information feature codes and does not require to upgrade the database continuously, thus the detection time is greatly shortened, the demands on software and hardware are very low and the user cost is reduced. In addition, as the industrial Internet is different from the World Wide Web, i,e, the client base of the industrial Internet is limited and fixed and the services provided by the industrial Internet are limited and fixed, the industrial Internet requires to use the data and information of specific applications and can refuse the disrelated data and information request. Therefore, the industrial Internet is extremely suitable for the white list check method; and by adopting the white list mode, the attacks of external undesirable programs on the industrial Internet can be effectively prevented and the safety of the industrial Internet can be ensured.
Owner:ASAT CHINA TECH
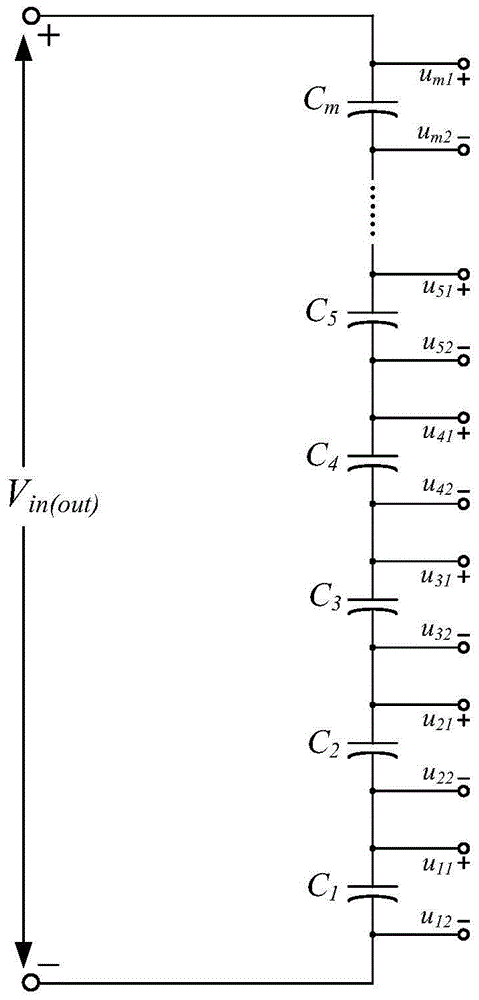
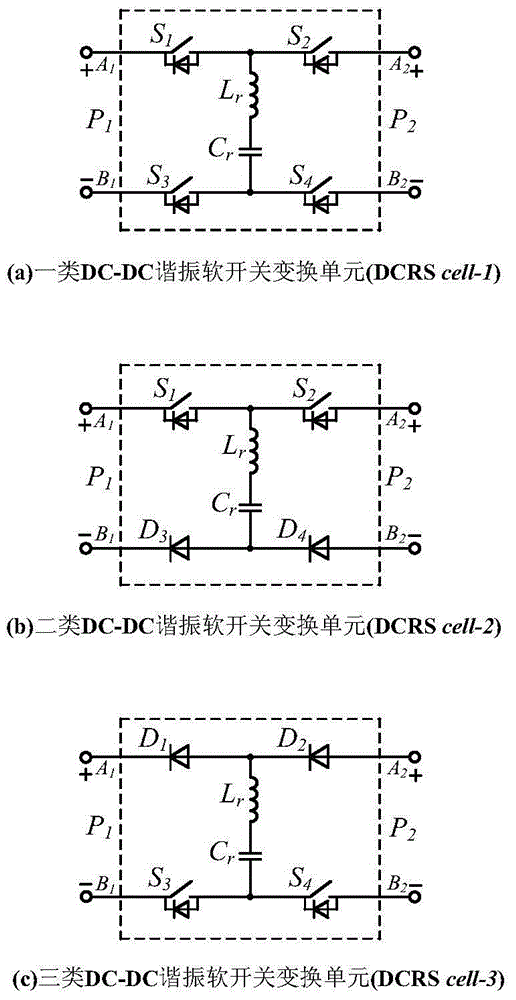
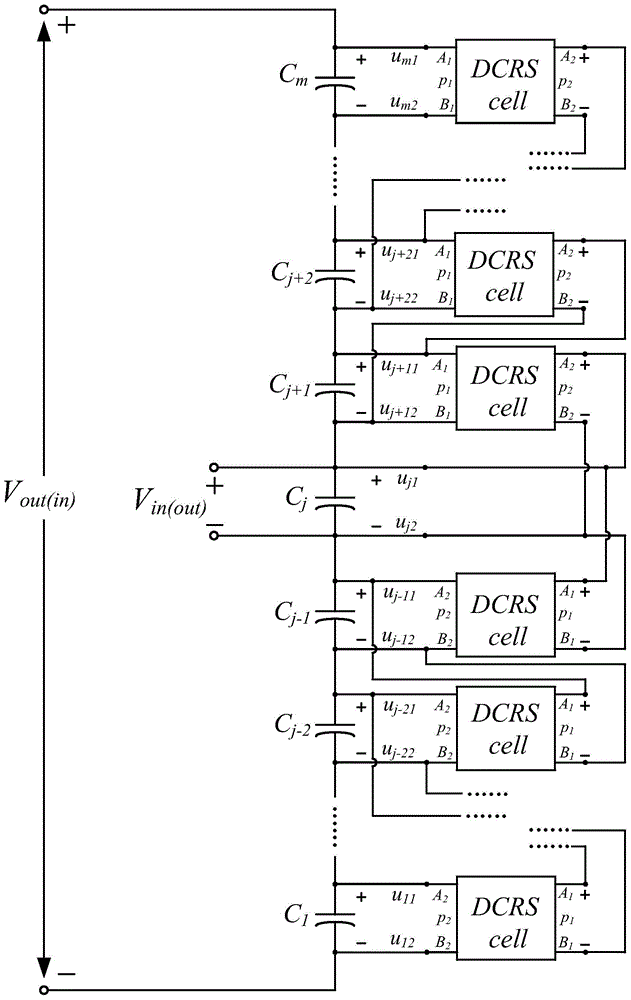
Multi-level equalizing resonance zero current soft switch DC-DC converter
ActiveCN105006964AAchieve pressure equalizationExtend your lifeBatteries circuit arrangementsEfficient power electronics conversionElectricityDc dc converter
The invention relates to a multi-level equalizing resonance zero current soft switch DC-DC converter. The DC-DC converter is composed of a direct current equalizing capacitor group and two-port DC-DC resonance soft switch conversion units connected with capacitors in the direct current equalizing capacitor group. For the converter with a level number of (m+1) (m is an integer and is more than or equal to 2, similarly hereinafter), the direct current equalizing capacitor group is composed of m direct current equalizing capacitors (Cm, C<m-1>,..., C2, C1) in series connection from top to bottom in order, and the potentials of the capacitors (Cm, C<m-1>,..., C2, C1) in the direct current equalizing capacitor group decrease from top to bottom in order. The capacitors in the direct current equalizing capacitor group are connected with at least (m-1) two-port DC-DC resonance soft switch conversion units. The DC-DC converter achieves capacitance and voltage self-balancing, all the switch tubes and diodes achieve zero current switching, the two-port DC-DC resonance soft switch conversion units work without affecting each other and independently mutually, and the whole converter system has characteristics of structure modularization and simple control mode.
Owner:BEIJING JIAOTONG UNIV +1
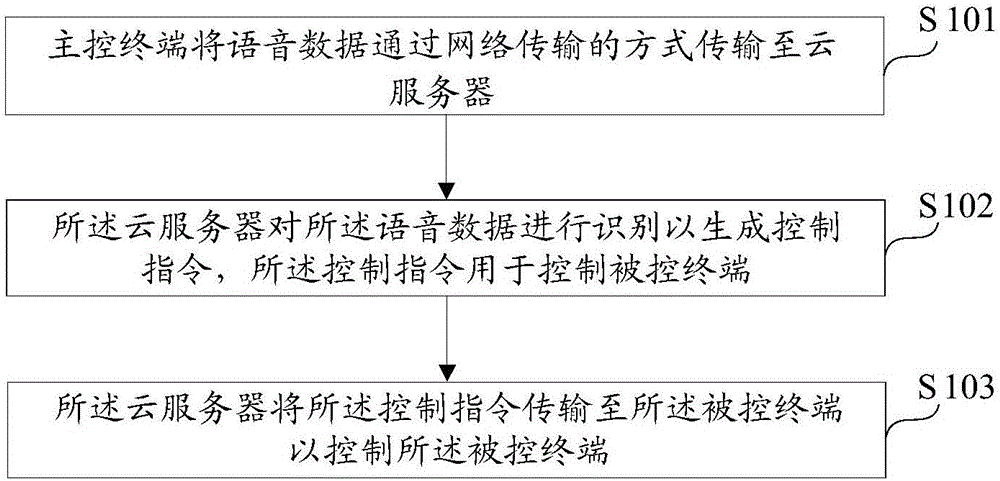
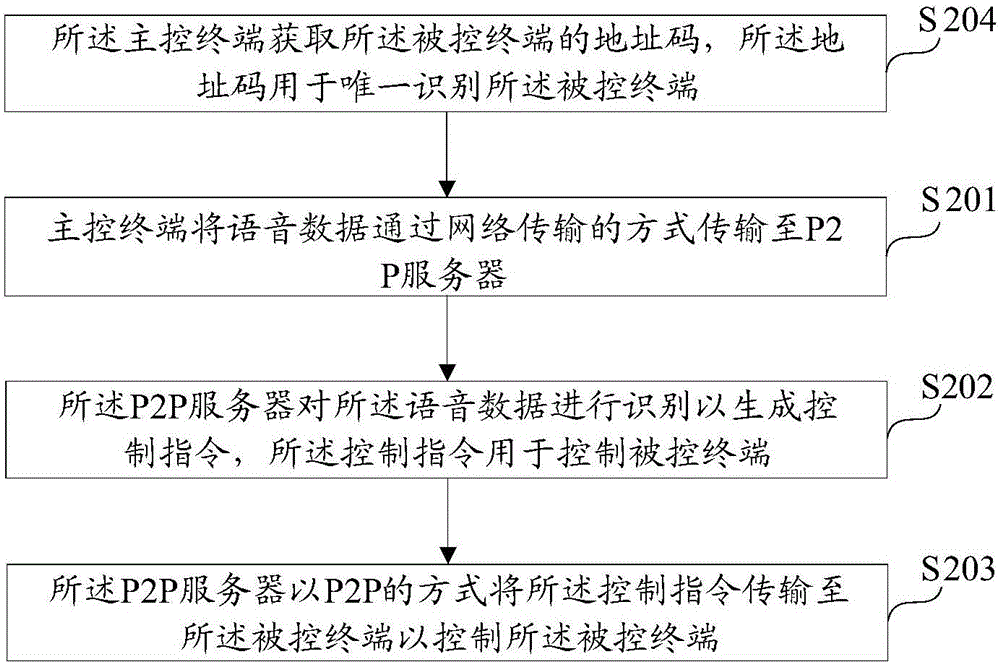
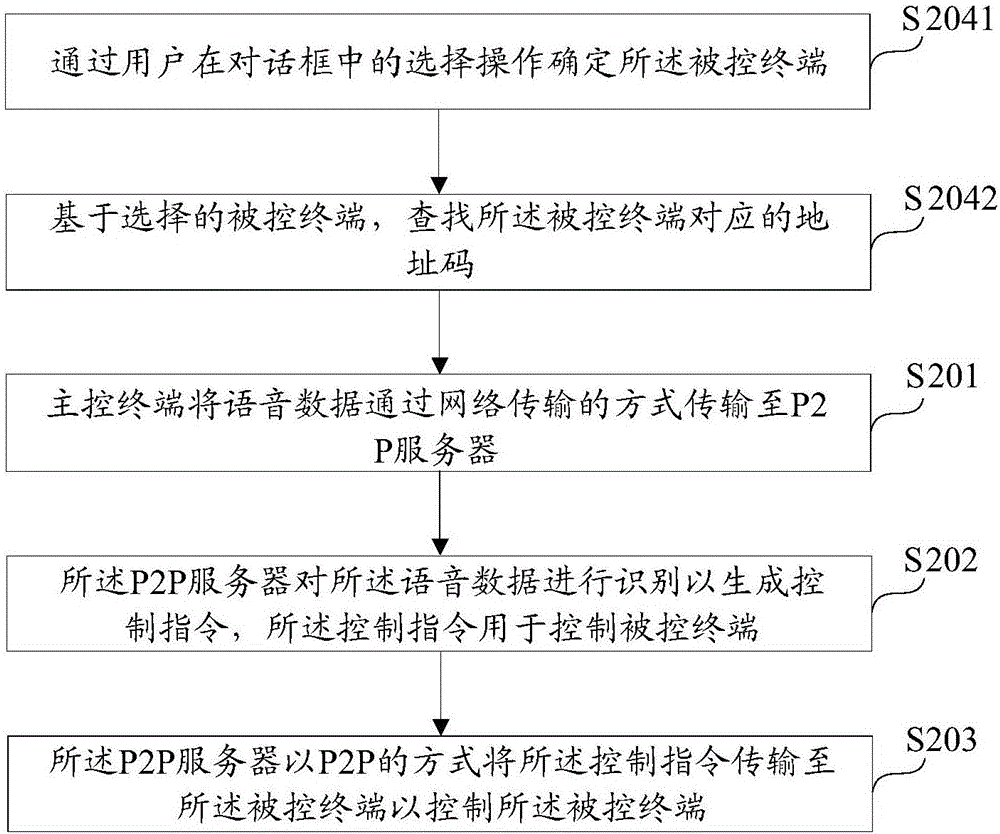
Voice control method and voice control system
InactiveCN106251873AImprove user experienceLow hardware and software requirementsData switching by path configurationSpeech recognitionControl systemRemote control
The invention discloses a voice control method and a voice control system. The voice control method comprises the following steps: transmitting voice data to a cloud server by virtue of a master control terminal in a mode of network transmission; identifying the voice data by virtue of the cloud server so as to generate a control command, wherein the control command is used for controlling a controlled terminal; and by virtue of the cloud server, transmitting the control command to the controlled terminal so as to control the controlled terminal. According to the scheme disclosed by the invention, technical requirement on the controlled terminal can be greatly reduced and the complexity and the cost of the controlled terminal can be reduced; in addition, remote control of the master control terminal on the controlled terminal can be also achieved; and meanwhile, both efficiency and safety are taken into consideration.
Owner:ZHENJIANG HUITONG ELECTRONICS CO LTD
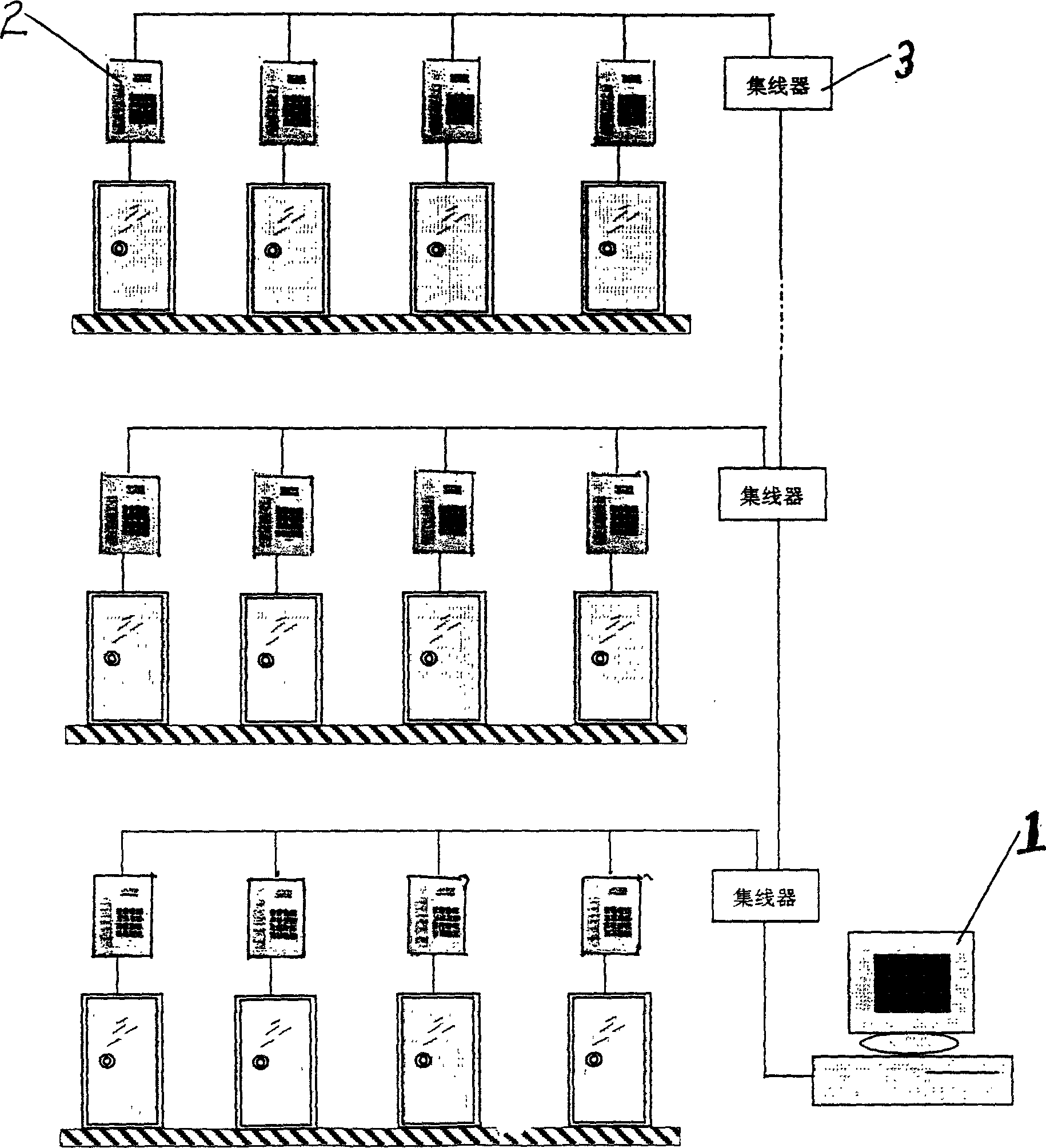
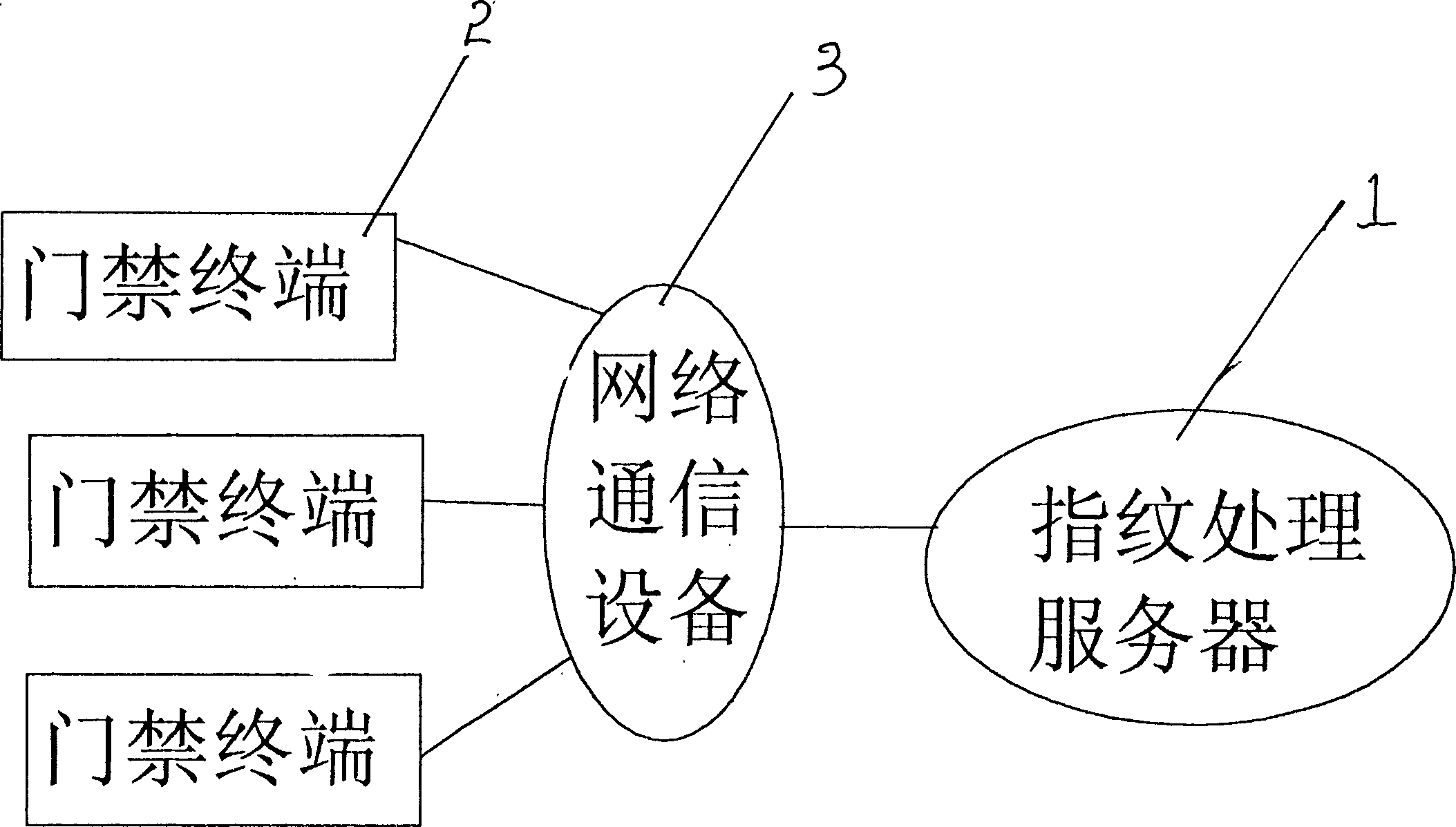
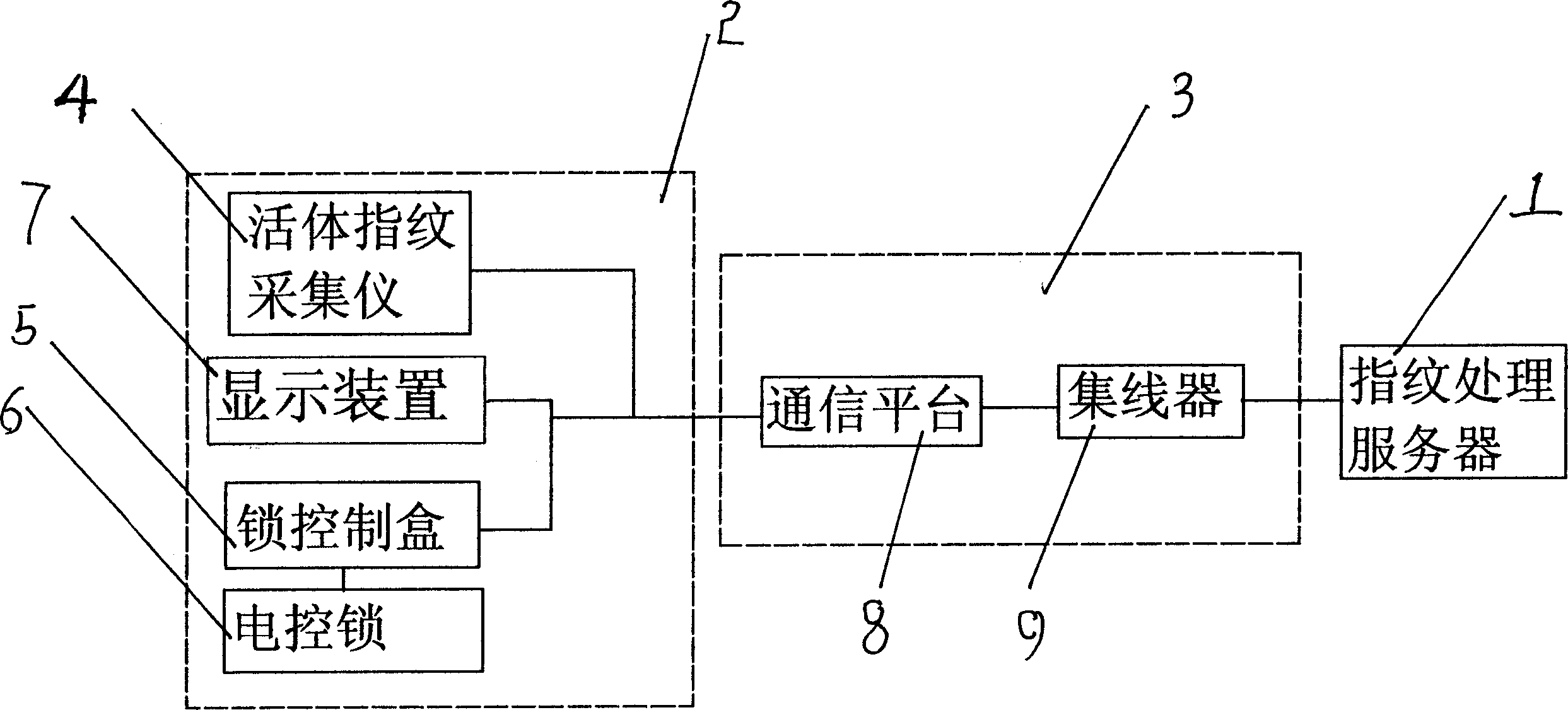
Computer regional network type fingerprint entrance guard system
InactiveCN1462011ALow hardware and software requirementsReduced software and hardware redundancyCharacter and pattern recognitionIndividual entry/exit registersLocal area networkFingerprint database
A computer LAN-type fingerprint-base entrance guard system is composed of hardware and software. Its hardware is composed of fingerprint processing server, multiple entrance guard terminals and network communication equipment. A LAN is composed of said fingerprint processing server and multiple entrance guard terminals. The fingerprint data is acquired, compressed and encrypted by the entrance guard terminals and then transmitted to the fingerprint processing server, where original data is restored by decompression and decryption and compared with the fingerprint data stored in database. The result is transmitted to the entrance guard terminal to open or lock door.
Owner:中山市依纹科技有限公司
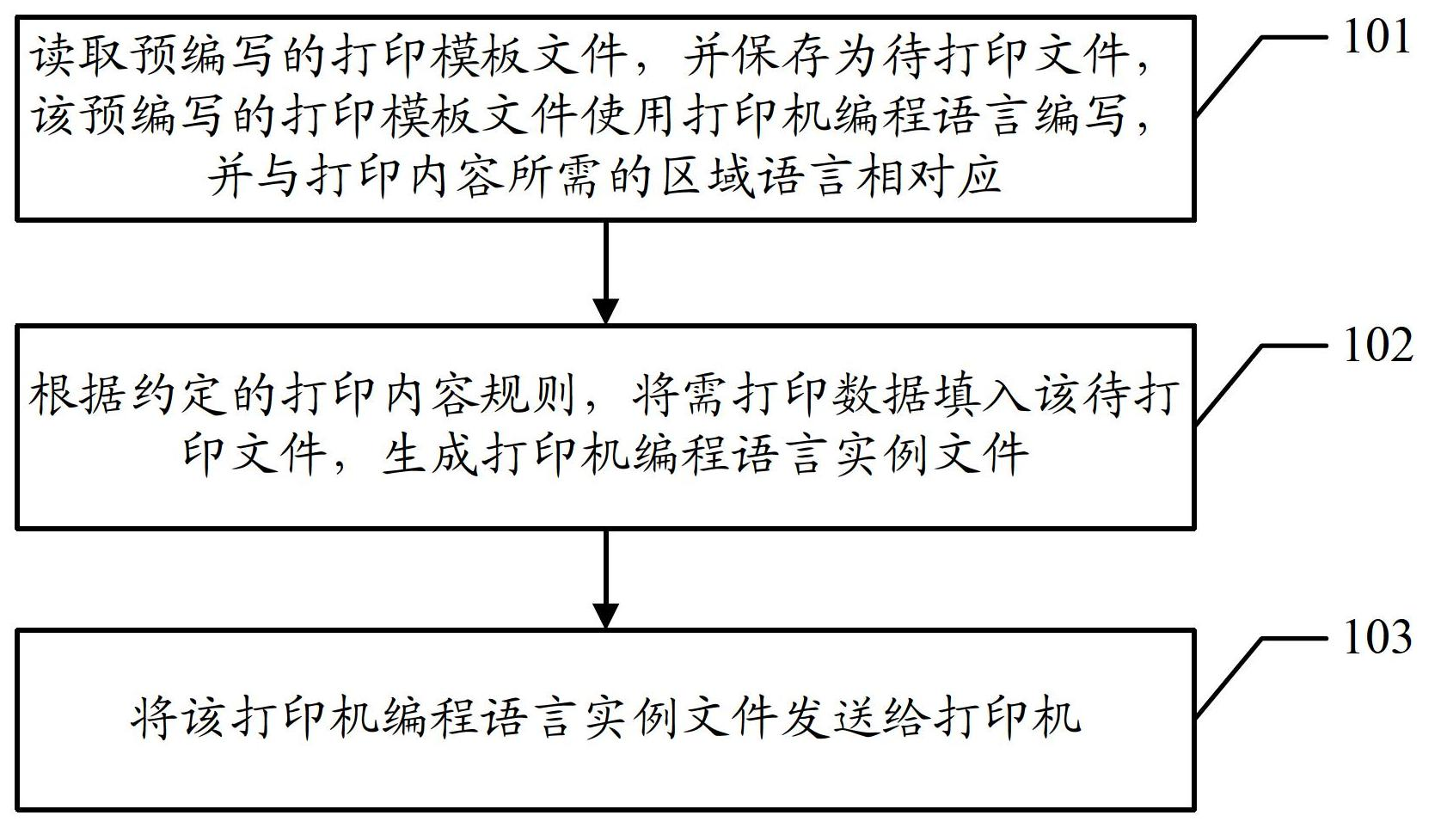
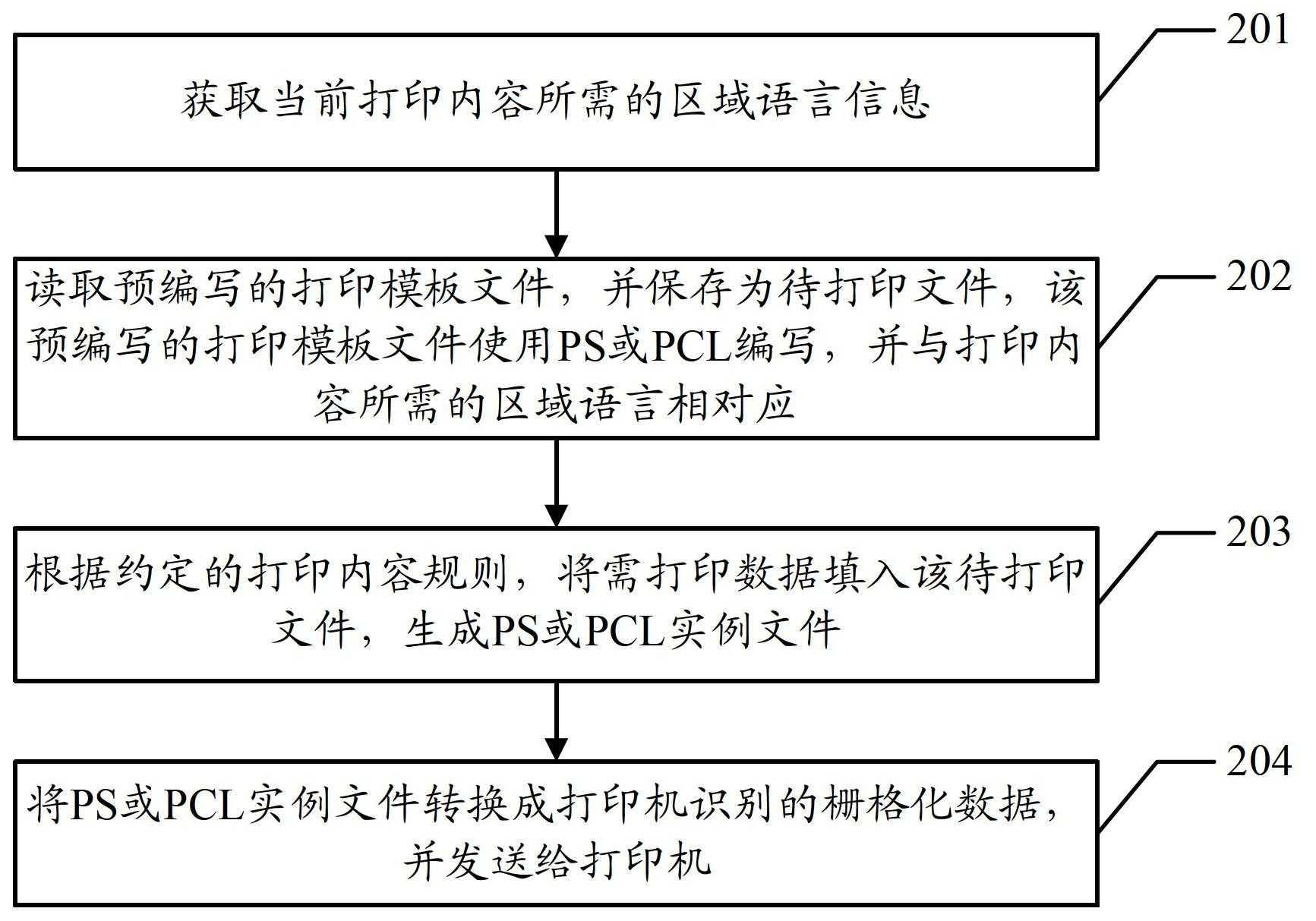
Method and device for printing
InactiveCN102693109AReduce dependenceEasy to transplantDigital output to print unitsPersonalizationEmbedded system
An embodiment of the invention discloses a method and a device for printing. The method and the device for printing are used for realizing individual printing output in an embedded system. The method in the embodiment of the invention comprises reading a pre-written printing template file; storing the pre-written printing template file as a file to be printed; writing the pre-written printing template file by a printer programming language; corresponding the printer programming language with a language of a required region of printed contents; filling data required to be printed into the file to be printed according to an appointed printed content rule; generating a printer programming language example file; and transmitting the printer programming language example file to a printer.
Owner:SONOSCAPE MEDICAL CORP
Ethernet protection switching method
InactiveCN104065546AIncrease contentLow hardware and software requirementsData switching networksTimerComputer science
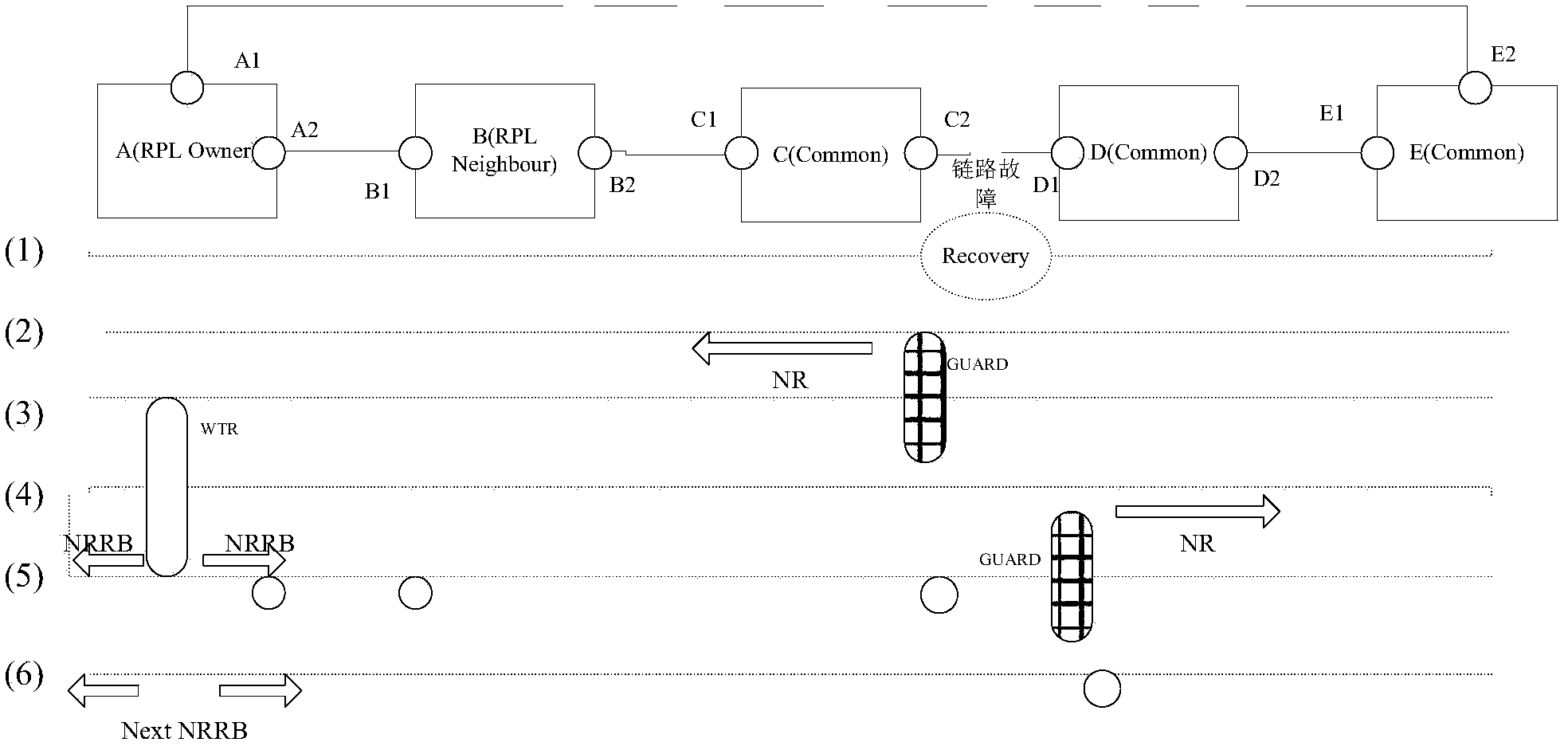
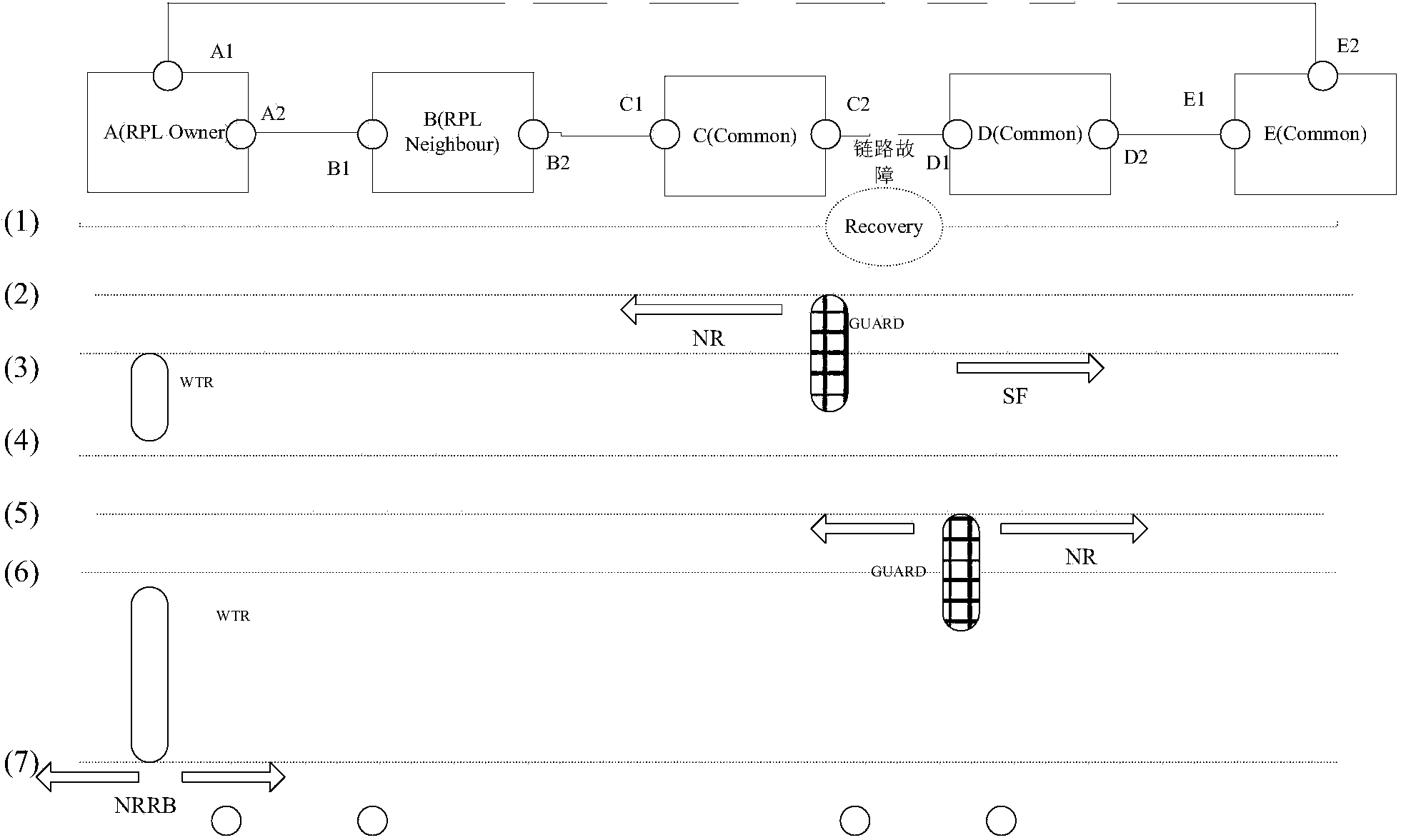
The invention discloses an Ethernet protection switching method. The method includes the steps that after a main node receives an NR frame, a WTR timer is started; at the moment, a second node does not detect that a link corresponding to a D1 port has recovered and thinks that the link is still in the problem state, an SF reminding message is sent after an NR message sent by a first node is received, and other nodes are reminded that the node still has the problem link; the main node receives an SF reminding message sent by the second node, the WTR timer is turned off, and the main node enters a link protection state again; the second node finds that the link corresponding to the D1 port has recovered, a GUARD timer is started, and an NR frame is sent to other nodes; the WTR timer is started after the main node receives the NR frame; an RPL port A2 is blocked by the WTR timer of the main node in an overtime mode, and an NRRB frame is sent to other nodes; the adjacent nodes block an RPL port B1 again after receiving the NRRB frame; the first node and the second node receive the NRRB frame, and a C2 port and the D1 port which are blocked originally because of faults are opened. The Ethernet protection switching method can solve the problem that convergence time is long when the link recovers.
Owner:引通通讯科技(上海)有限公司
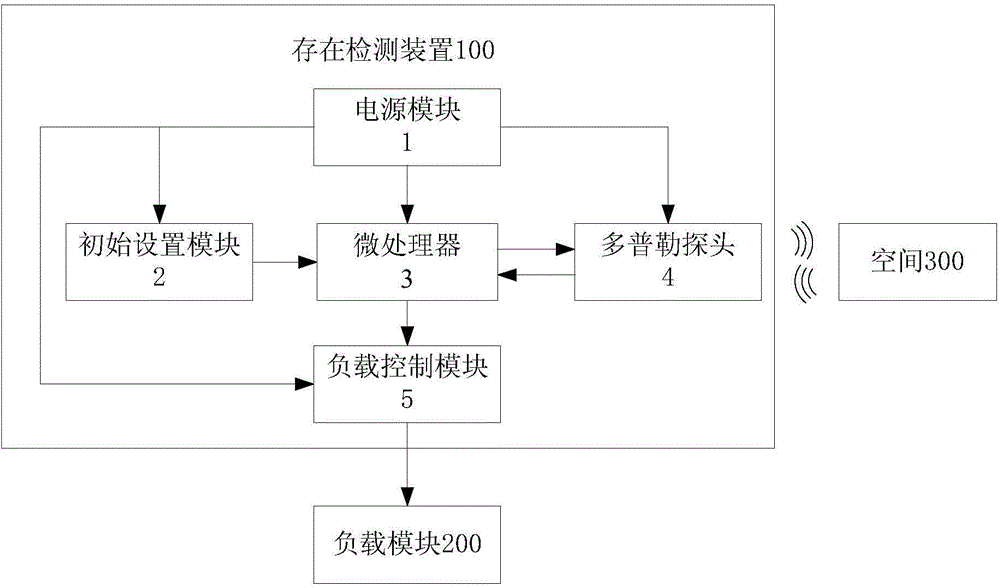
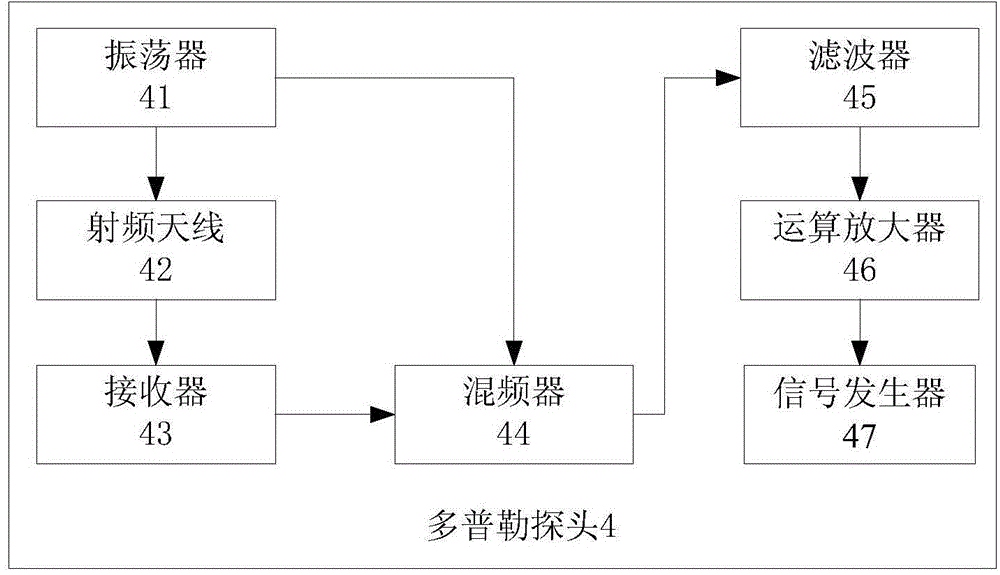
Existence detection method and device
ActiveCN105277991ALow hardware and software requirementsLow costDetection using electromagnetic wavesRadio wave reradiation/reflectionMicrowavePeak value
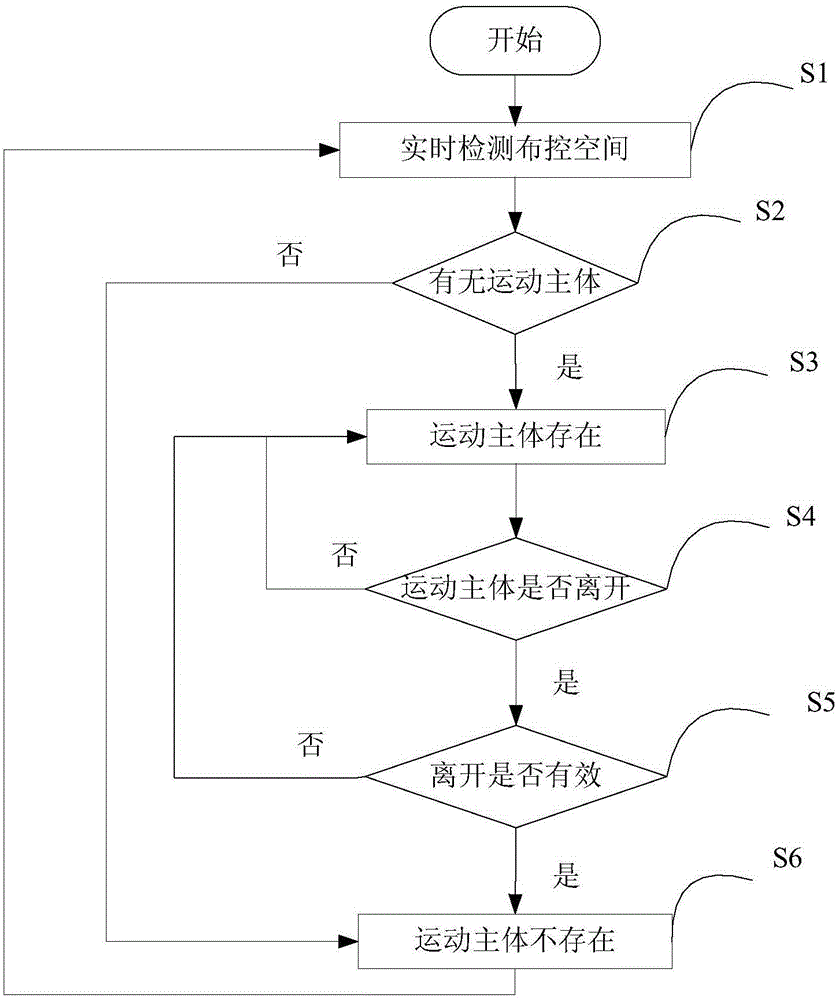
The invention discloses an existence detection method and device. The existence detection method is used for dynamically detecting the existence state of larger moving subjects (e.g. people and automobiles) in a control deploying space. According to the method, the Doppler effect is utilized and the peak value and frequency of received signals are analyzed to judge existence of the larger moving subjects in the control deploying space through a microwave induction detection device, and the detection result is outputted in different signals so that a load is controlled to correspondingly respond to the detection result finally. The beneficial effects of application of the existence detection method and device are that the novel dynamic detection method and device for space existence are provided, and micro-movement of the moving subjects after entering the space can be effectively detected by the method; besides, the Doppler effect is utilized by the detection method so that no material can deliberately avoid detection; and the detection device comprises a Doppler probe and a microprocessor so that the detection device is low in cost and low in the requirement for software and hardware.
Owner:NANCHONG SKY MICROWAVE
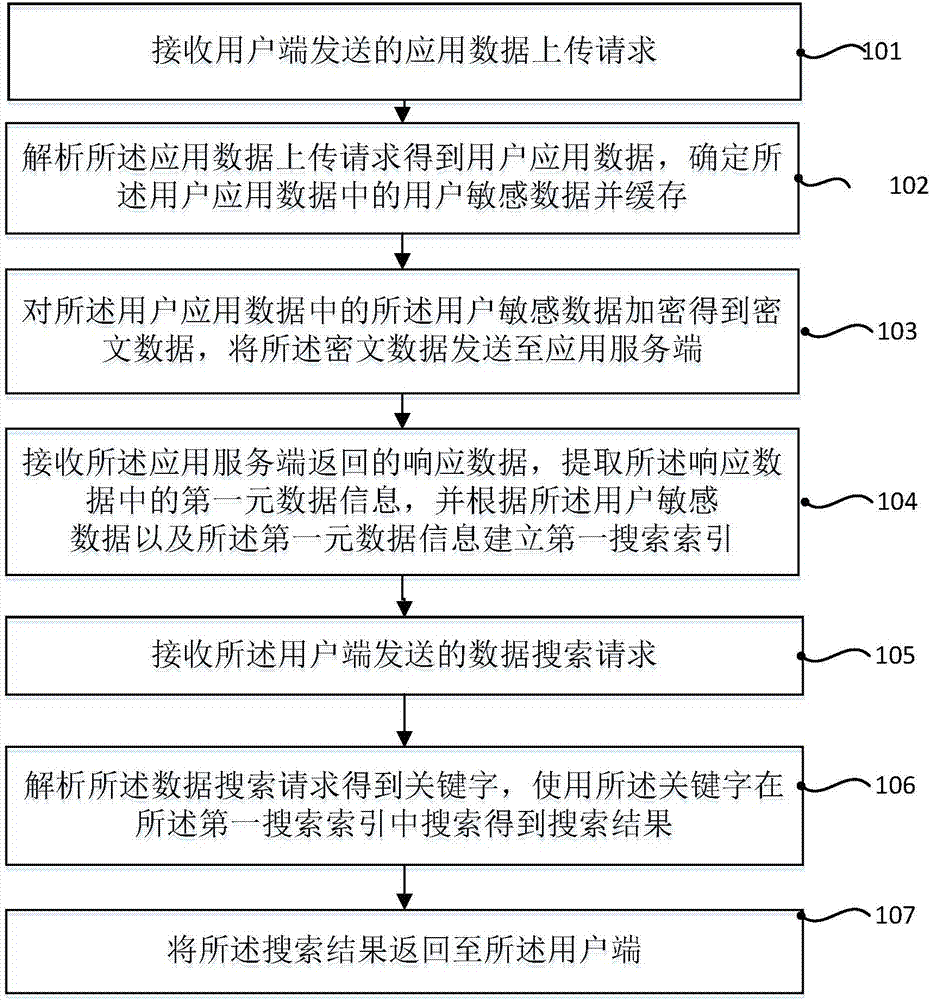
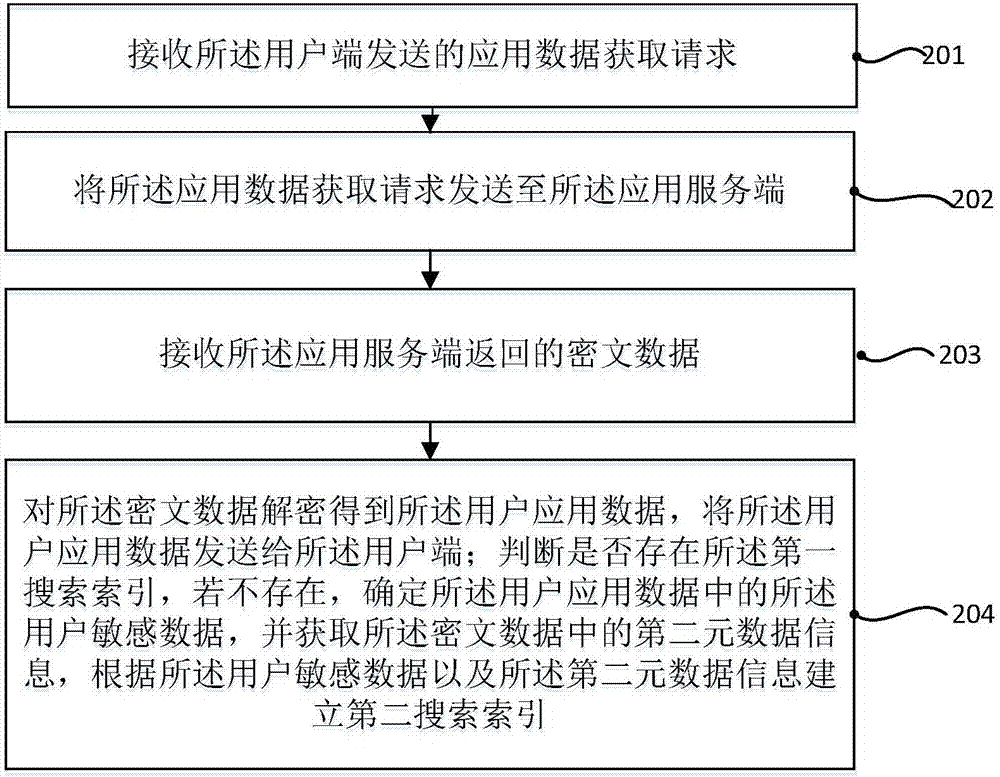
Application-oriented ciphertext search method, apparatus and system, and agent server
ActiveCN107463848AAchieve transparencyLow hardware and software requirementsKey distribution for secure communicationDigital data protectionFull text searchCiphertext
The invention discloses an application-oriented ciphertext search method. The method comprises the steps of receiving an application data uploading request sent by a user end; analyzing the application data uploading request to obtain user application data, determining user sensitive data in the user application data and performing caching; encrypting the user sensitive data in the user application data to obtain ciphertext data, and sending the ciphertext data to an application service end; receiving response data returned by the application service end, extracting first metadata information in the response data, and according to the user sensitive data and the first metadata information, establishing a first search index; receiving a data search request sent by the user end; analyzing the data search request to obtain a keyword, and performing a search in the first search index by using the keyword to obtain a search result; and returning the search result to the user end. According to the method, a special encryption client does not need to be configured; full text search of a ciphertext is supported; transparent data encryption and ciphertext search are realized; and the functionality, efficiency and security of the ciphertext search are ensured.
Owner:BEIJING UNIV OF POSTS & TELECOMM
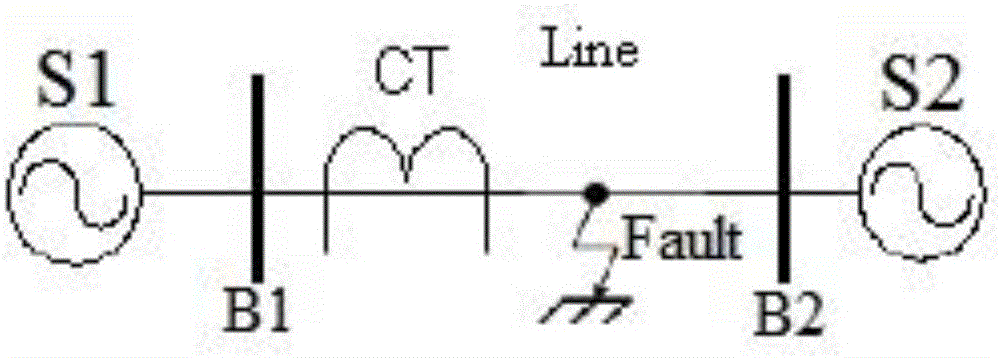
Method for detecting saturation of current transformer (CT) on the basis of third-order central moment
ActiveCN105067906AAvoid defects with a large degree of dispersionLow hardware and software requirementsElectrical testingForm factor measurementsPeak valueMirror image
Provided is a method for detecting the saturation of a current transformer (CT) on the basis of a third-order central moment. The method comprises: sampling current at the secondary side of the CT; acquiring a current waveform from a position near the peak value of a waveform by using a data window in order to obtain a waveform symmetric about the peak value and with less sampling points; computing a dispersion coefficient by using the third-order central moment after the acquired waveform is subjected to waveform mirror image transformation; and outputting a detected result. In the method, a dispersion coefficient after a standard sinusoidal current waveform is subjected to mirror image transformation. By means of analysis and computation, the dispersion coefficient can be considered as a fixed value so as to be used as a comparison basis. The method mainly solves problems of low detection rate and low detection precision when the CT saturation occurs, may fast and accurately detect the generation of the CT saturation just by using sampled data in half cycle so as to improve relay protection reliability to a certain extent and have certain practical significance in the aspect of guaranteeing the accurate and reliable operation of the CT.
Owner:ELECTRIC POWER SCHEDULING CONTROL CENT OF GUIZHOU POWER GRID CO LTD +2
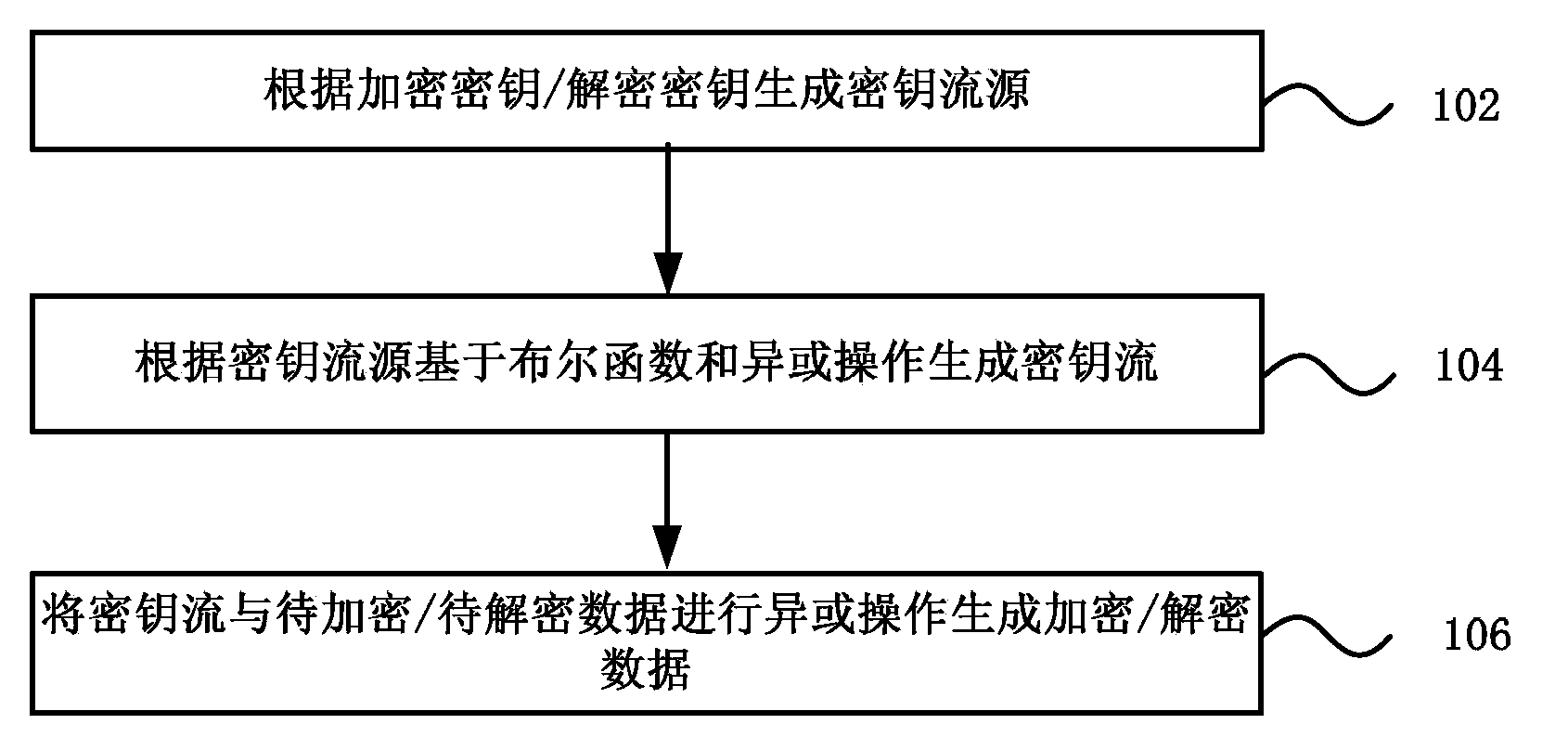
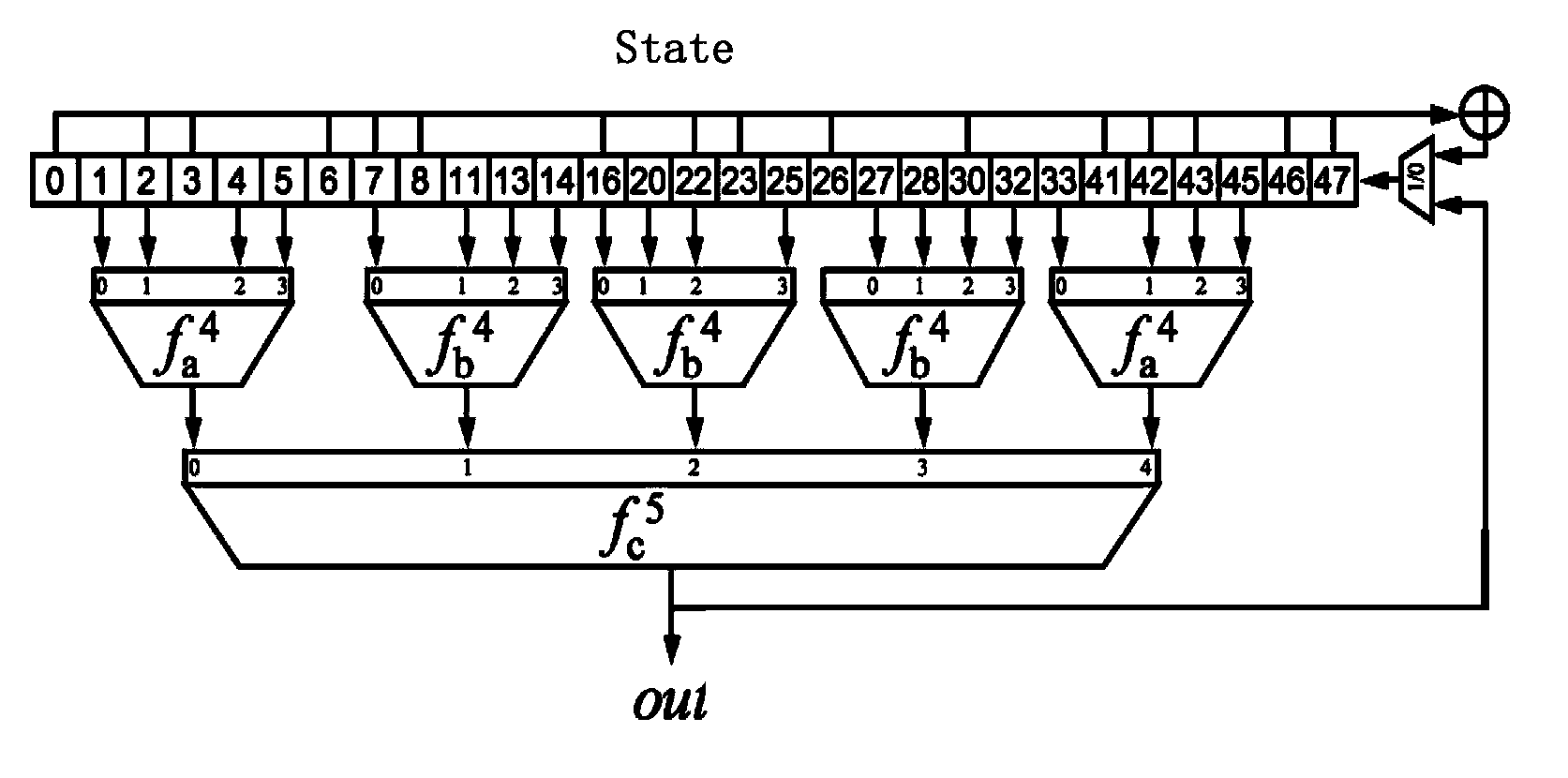
Data encryption and decryption method and device, and mobile terminal
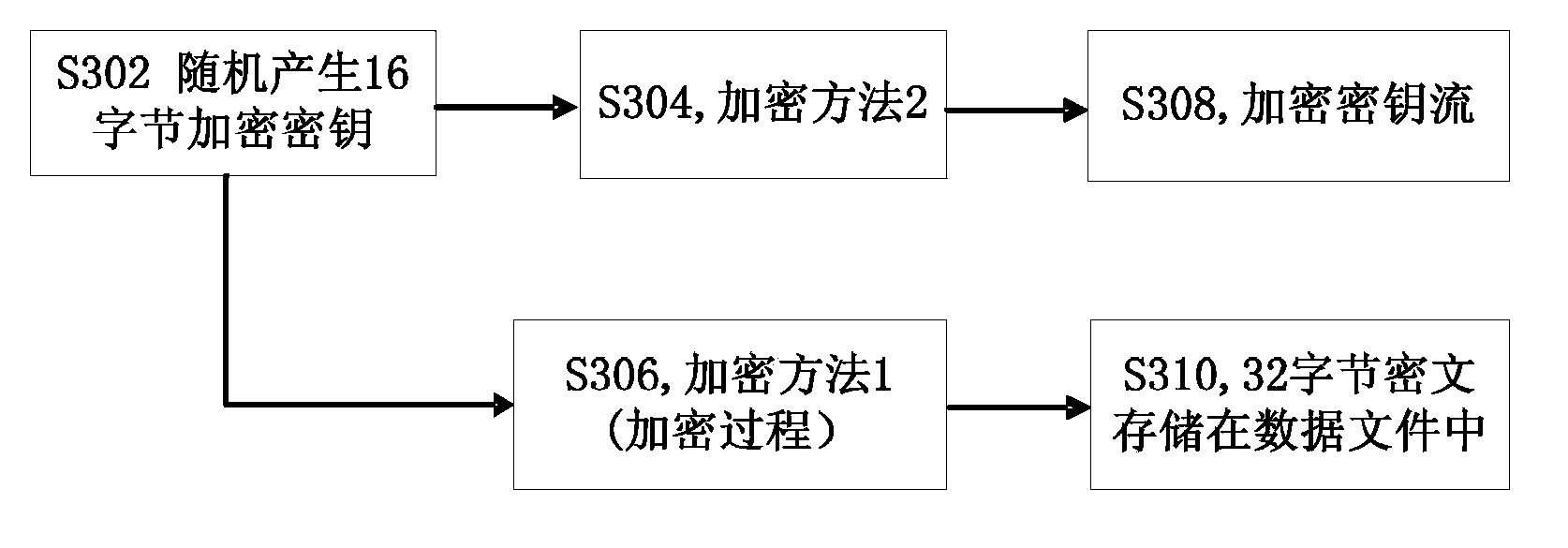
ActiveCN103532706ASimple structureLow hardware and software requirementsEncryption apparatus with shift registers/memoriesComputer hardwareExclusive or
The invention discloses a data encryption and decryption method and device, and a mobile terminal, and relates to the field of encryption technologies. The method comprises: generating, according to an encryption key / decryption key, a key stream source; generating, according to the key stream source and based on the Boolean function and exclusive-or (XOR) operation, a key stream; and generating encryption / decryption data by performing XOR operation on the key stream and data to be encrypted or decrypted. The encryption and decryption method and device structure which are adopted in the invention are quite simple, the requirements for software and hardware are quite low, the method and device can be applied to a low-end apparatus with quite poor calculating capability, and the size of the encrypted data is not increased too much.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Method and system for achieving electronic signature
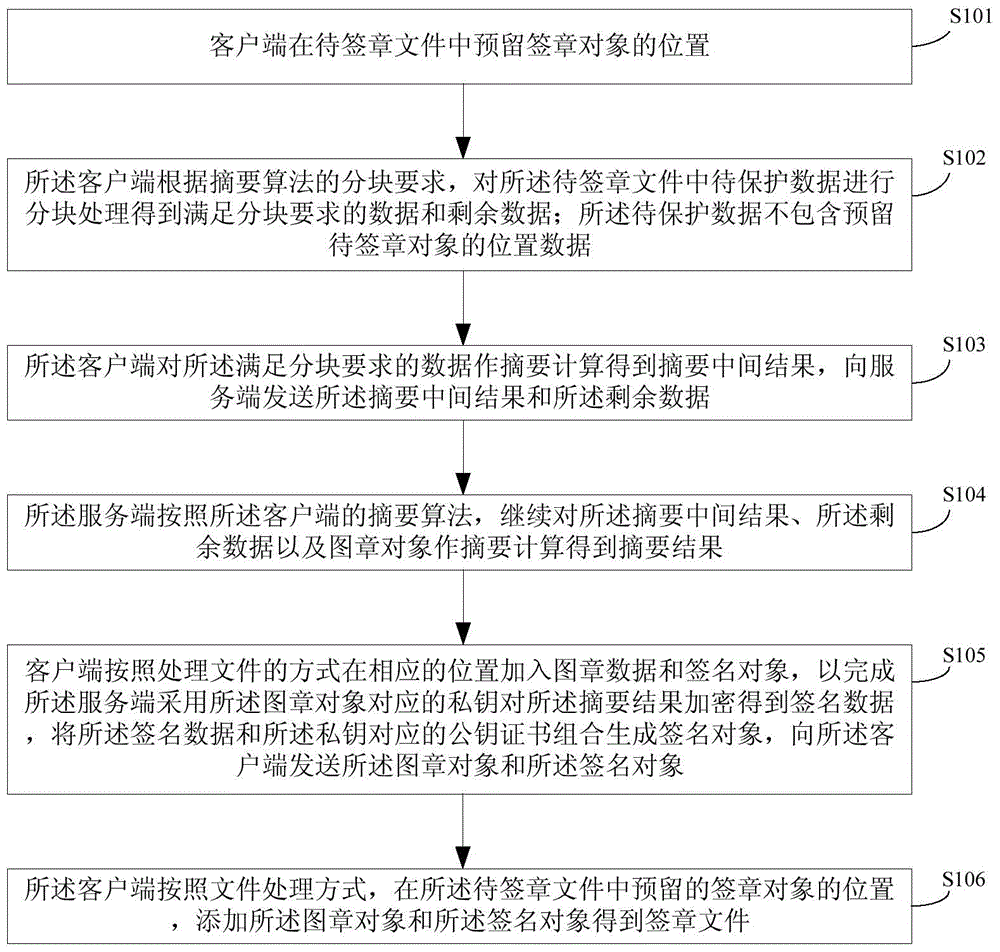
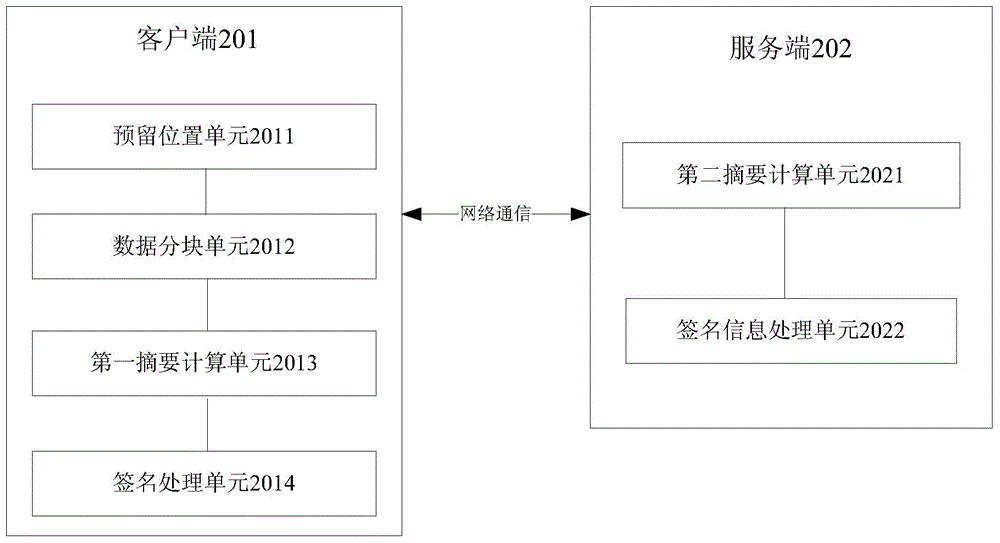
ActiveCN104468120ALow hardware and software requirementsRelieve transmission pressureUser identity/authority verificationDigital signatureClient-side
The invention discloses a method and system for achieving electronic signature. According to the method, the distributed summary computing method is adopted, summary computing is achieved through distributed computing of the client side and distributed computing of the server side, an intermediate result and remainder data of the summary are obtained through primary summary computing by means of the client side and then are sent to the server side, then summary computing of the remainder part is achieved by means of the client side according to the summary computing of the client side to obtain a summary result, digital signature is conducted on the summary result to obtain a signature object which is sent to the client side together with a seal object, and finally the signature object and the seal object are added to a file to be signed through the client side so that signature can be achieved and a signed file can be obtained. The method and system have the advantages of being low in cost, high in efficiency and high in data safety.
Owner:BEIJING CERTIFICATE AUTHORITY
Flow system
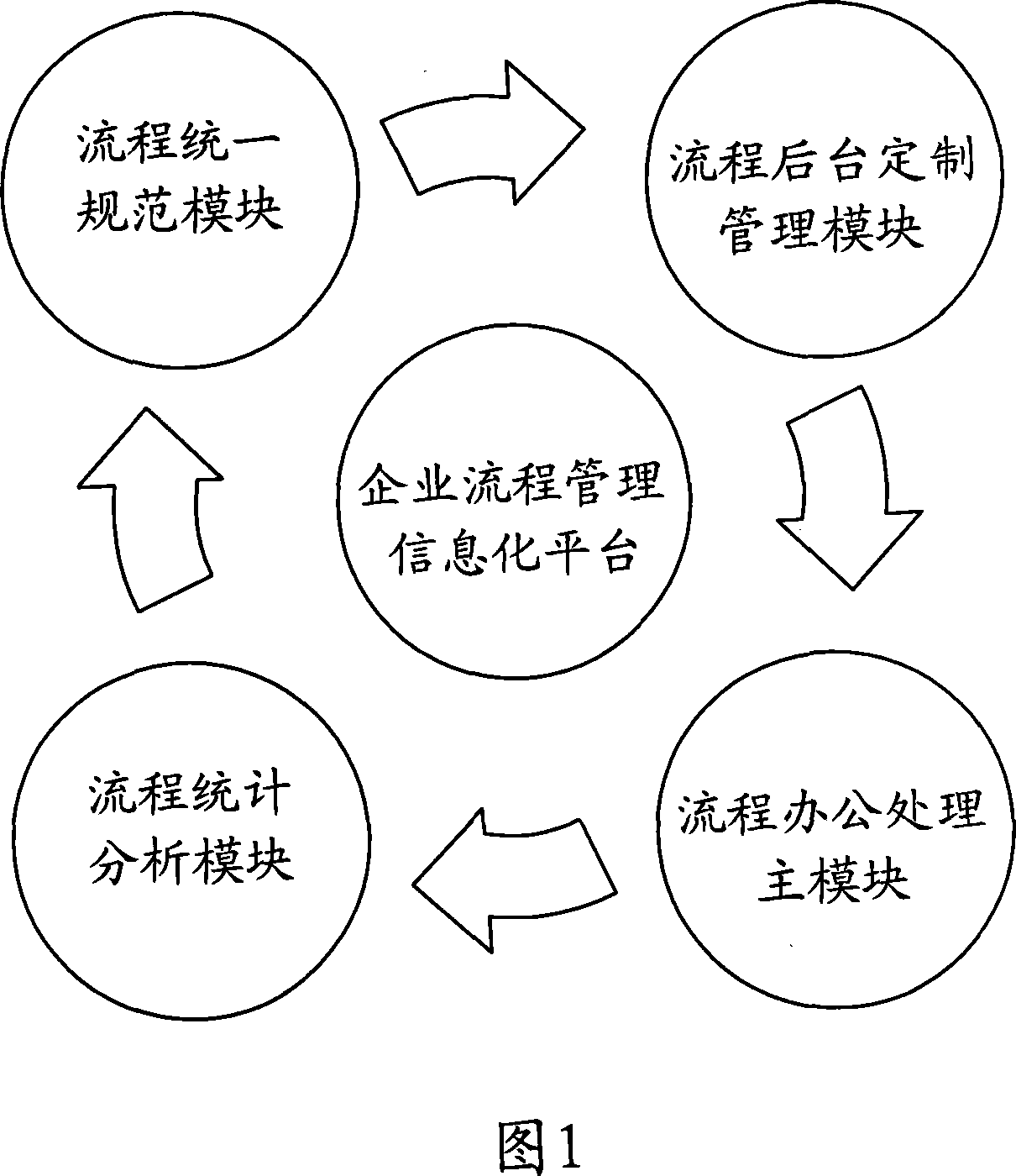
InactiveCN101075311ALower application thresholdLow hardware and software requirementsResourcesWorkflow engineComputer science
A flow system comprises background management module custom-made as per flow, flow master module, flow statistic-analysis module and unified standard module.
Owner:CHINA MOBILE GRP FUJIAN CO LTD
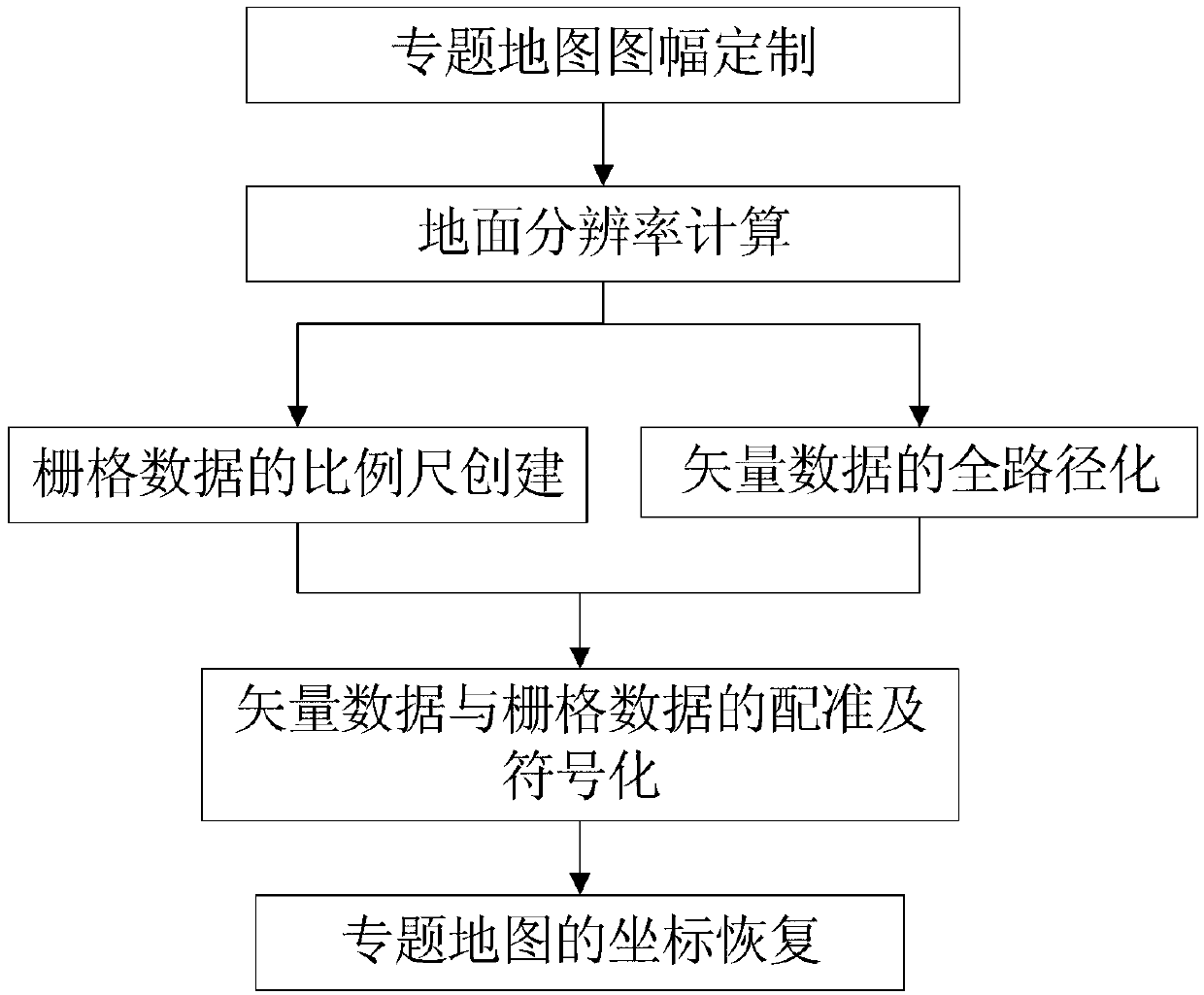
Full-path remote-sensing image thematic charting method
ActiveCN103345769AQuick tokenizationEasy to modify2D-image generationMaps/plans/chartsImage resolutionResolution rate
The invention discloses a full-path remote-sensing image thematic charting method which technically comprises the following steps of determining a thematic map mapsheet, calculating the ground resolution rate, creating a raster data measuring scale, enabling vector data to be in full-path, registering and signifying vector data and raster data, and recovering thematic map coordinates. The P-L formula is used for quickly and accurately calculating the ground resolution rate of a finished map, the raster data measuring scale is created, the vector data is made to be in full-path, vector data of various industries are signified through a more complete symbolic library to achieve automation and lot sizing, and the whole charting process is made to be more smooth and efficient and faster.
Owner:CHINA RAILWAY DESIGN GRP CO LTD
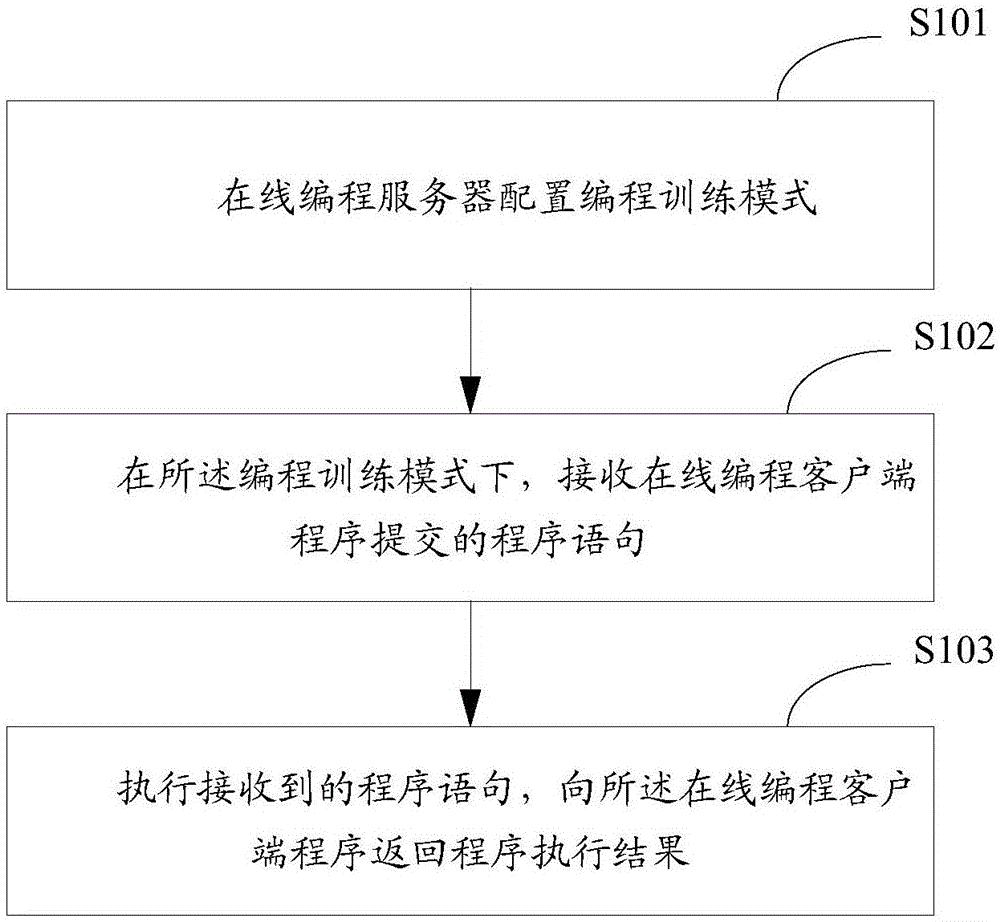
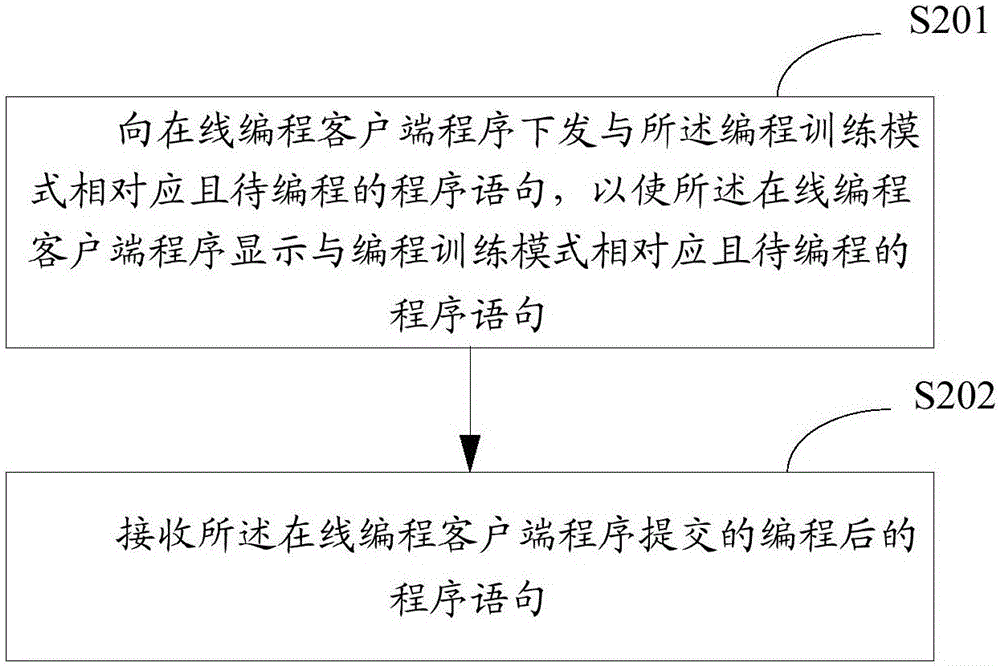
Online programming system implementation method and device
InactiveCN106651697AImprove learning enthusiasmImprove programming performanceData processing applicationsUsabilityClient-side
The invention is suitable for the technical field of network teaching, and provides an online programming system implementation method and device. The online programming system implementation method comprises the steps that an online programming server configures a programming training mode; program statements submitted by online programming client side programs are received under the programming training mode; and the received program statements are performed, and the program performing result is returned to the online programming client side programs, wherein the online programming client side programs include browser programs and Windows client side programs. The problems that online programming and program debugging cannot be performed and integration of online programming learning and programming practice cannot be realized in network teaching of the present programming courses can be solved so that the submitted program statements can be received anytime and anywhere and the program performing result can be returned in real time; besides, the requirements for software and hardware of the client side are extremely low, and programming can be practiced by networking input equipment so that universality and usability of application of the online programming system can be greatly enhanced.
Owner:SHENZHEN INSTITUTE OF INFORMATION TECHNOLOGY +1
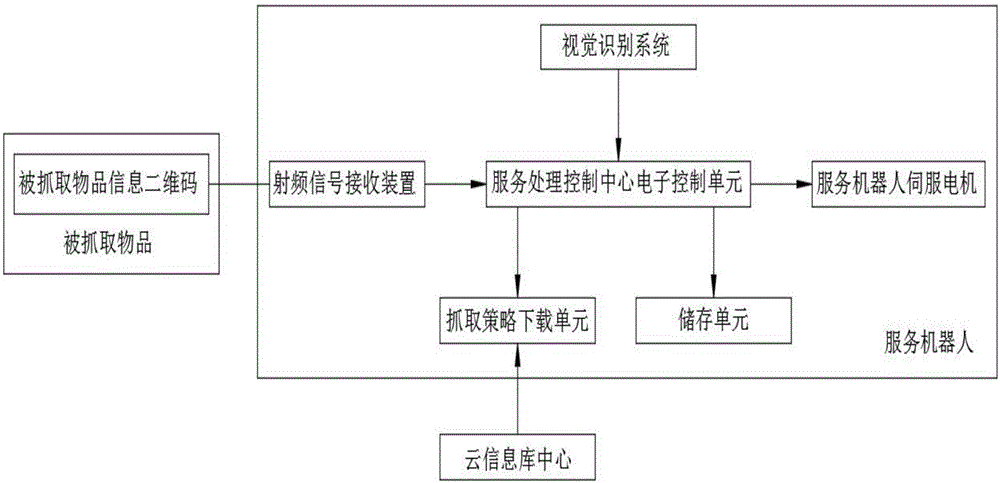
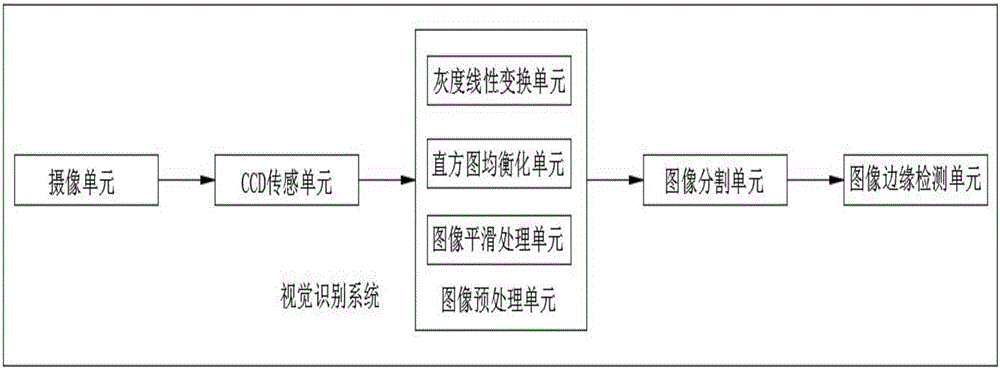
Cloud information bank based service robot gripping system and control method thereof
InactiveCN106737751AImprove adaptabilityImprove stabilityManipulatorRadio frequency signalService robot
The invention discloses a cloud information bank based service robot gripping system and a control method thereof. The system comprises a gripped article and a service robot. A radio-frequency signal receiving device is installed on the service robot. A gripped article information two-dimensional bar code is arranged on the gripped article. The service robot is further provided with a visual identification system, a service processing control center electronic control unit, a storage unit, a gripping strategy download port and a service robot servo motor. According to the cloud information bank based service robot gripping system and the control method thereof, identification of radio-frequency information can be conducted better through the visual identification system, a multifunctional flexible self-adaption gripping strategy is designed according to the variability and uncertainty of tasks of the service robot gripping system, and interaction between the service robot and a product is achieved; and the dynamic adaptability and response stability of the service robot are improved, various uncertain gripping tasks are completed in a self adaption mode, meanwhile, the software and hardware requirement for single service robot is reduced, and the cost of each service robot is reduced.
Owner:禾思凯尔智能科技(东莞)有限公司
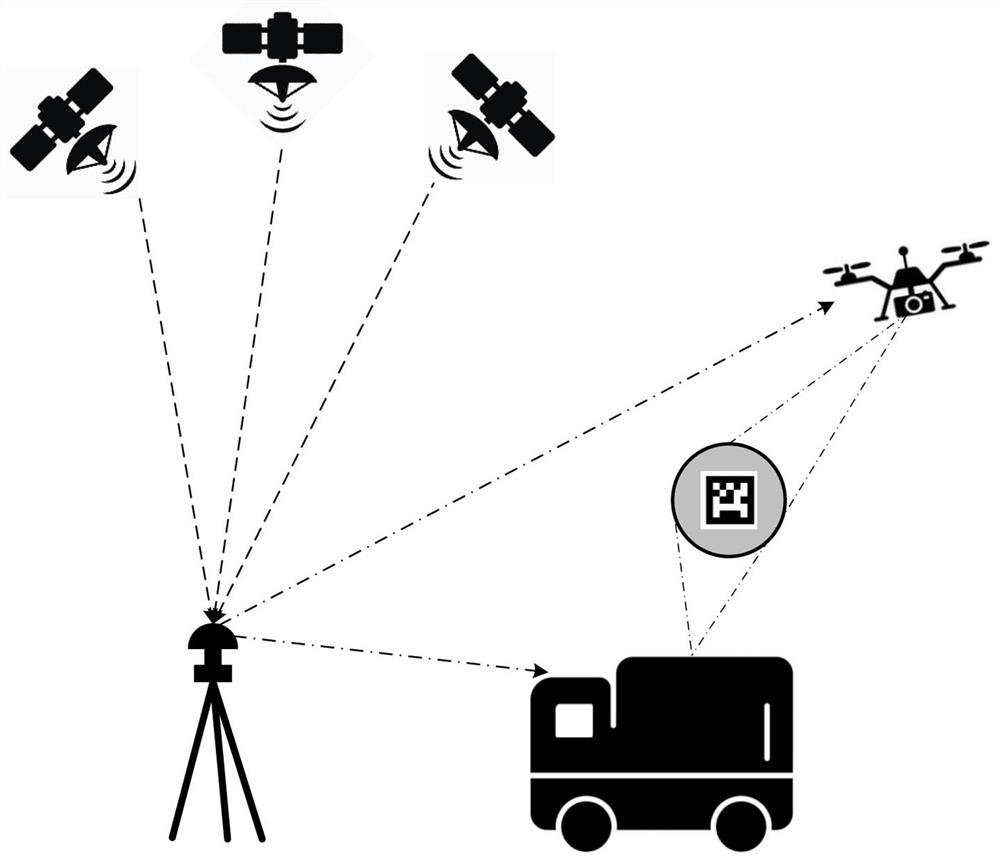
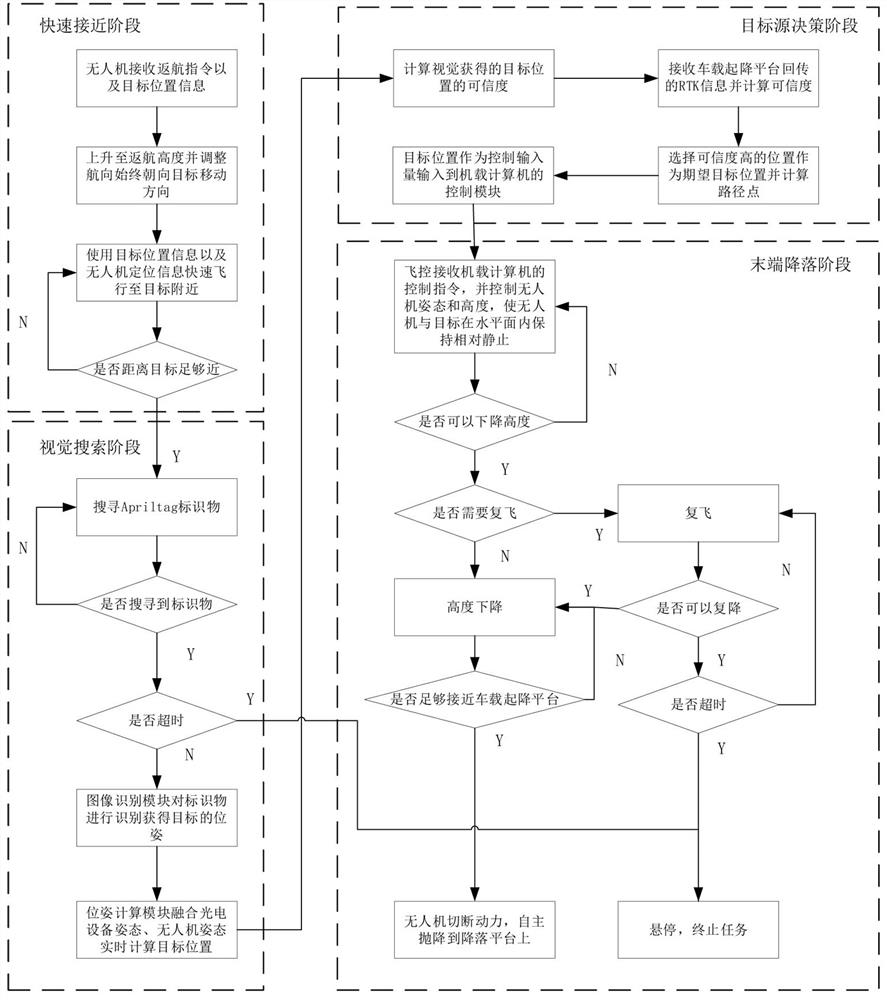
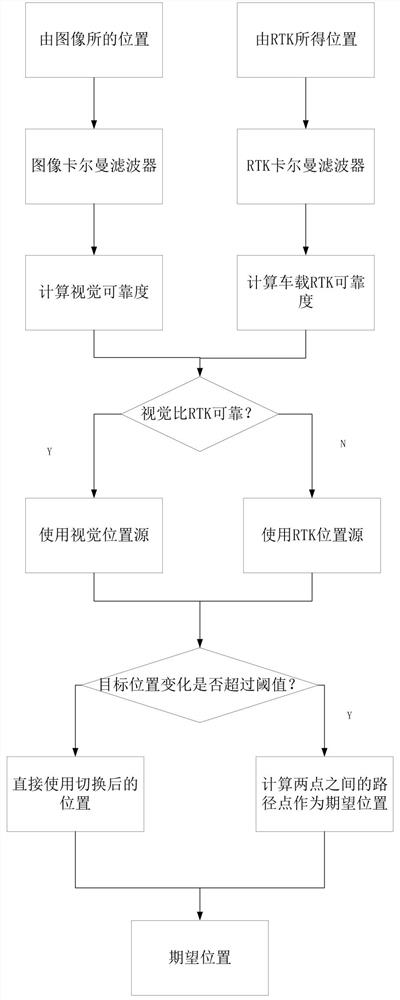
Multi-source fusion vehicle-mounted unmanned aerial vehicle autonomous landing control method and device
ActiveCN114721441AImprove accuracyImprove securityPosition/course control in three dimensionsIn vehicleUncrewed vehicle
The invention discloses a multi-source fusion vehicle-mounted unmanned aerial vehicle autonomous landing control method. In order to solve the problem of autonomous landing of a vehicle-mounted unmanned aerial vehicle in the high-speed moving process of a vehicle-mounted take-off and landing platform, mature RTK positioning and visual positioning are fused, and a complex information fusion algorithm is abandoned; the target position credibility of the RTK positioning module and the visual positioning module is compared, and the target position information of the positioning module with higher target position credibility is selected as a navigation information source for controlling the autonomous landing of the vehicle-mounted unmanned aerial vehicle. The invention further discloses a multi-source fusion vehicle-mounted unmanned aerial vehicle autonomous landing control device. Compared with the prior art, the technical scheme of the invention can greatly improve the autonomous landing accuracy and safety of the vehicle-mounted unmanned aerial vehicle in the moving process of the vehicle-mounted take-off and landing platform, and has the advantages of simple algorithm and low requirements on software and hardware.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Application message processing system and method and application device
ActiveCN106487637AImprove processing efficiencyLow hardware and software requirementsSpecial service provision for substationProgram controlMessage processingEmbedded system
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for detecting definition of document image
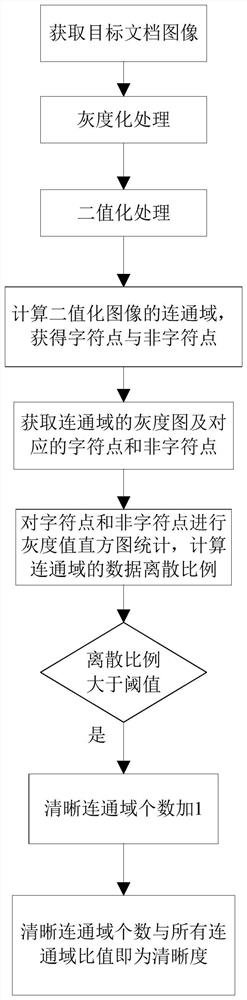
PendingCN114240925ASimplify the processLow hardware and software requirementsImage enhancementImage analysisHistogramGrayscale
The invention relates to a document image definition detection method and system, and the method comprises the steps: obtaining a target document image, carrying out the graying and binarization of the target document image, carrying out the connected domain calculation of a binarized image, obtaining mutually independent connected domains, and carrying out the detection of the definition of a document image according to the coordinates of each pixel of the binarized connected domain image. And obtaining a grayscale image and character points and non-character points corresponding to the connected domain. The method comprises the following steps: respectively carrying out gray value histogram statistics on character points and non-character points of a connected domain grey-scale map, calculating a data discrete proportion of the connected domain grey-scale map, judging whether a current connected domain is a clear connected domain or not according to a relationship between the data discrete proportion and a threshold value, and finally determining the definition of a current image according to a clear connected domain proportion. The definition detection method needs fewer image parameters, is simple and quick, and has low requirements on software and hardware of equipment.
Owner:南京商集智能科技有限公司 +1
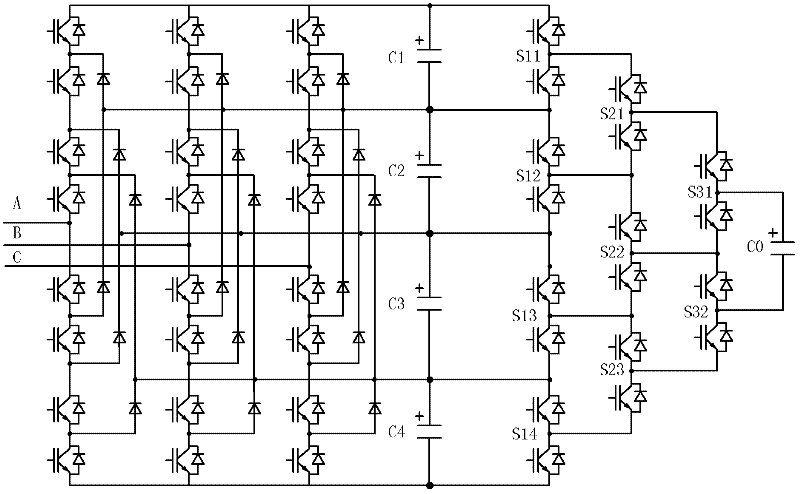
A voltage equalizing circuit and a voltage equalizing method for a DC capacitor voltage of a multilevel converter
ActiveCN102291031AEasy to implementLow hardware and software requirementsAc-dc conversionCapacitancePower flow
The invention discloses a voltage equalization circuit and a voltage equalization method for DC capacitors of a multi-level converter. The voltage equalization circuit is formed in a way that: N DC capacitors Cn on the DC side of a diode-clamped multi-level converter are all connected with the corresponding input ends of a voltage equalizing switch array consisting of a plurality of auxiliary switching devices; n is one of 1, 2, ..., N; the output end of the voltage equalizing switch array is connected with an auxiliary DC capacitor (C0); the control end of each auxiliary switching device in the voltage equalizing switch array is connected with a control device of the multi-level converter; and N is a difference obtained by subtracting 1 from a level number of the multi-level converter. The circuit can realize the voltage equalization and stabilization of the DC capacitors under any power factor condition, particularly in the transmission of active current to free the PWM depth of the converter from the restrictions of DC voltage stabilization conditions and ensure the realization of active or reactive transmission under any modulation depth condition, and has a simple structure, low cost and high reliability.
Owner:成都拓及兴通科技有限公司
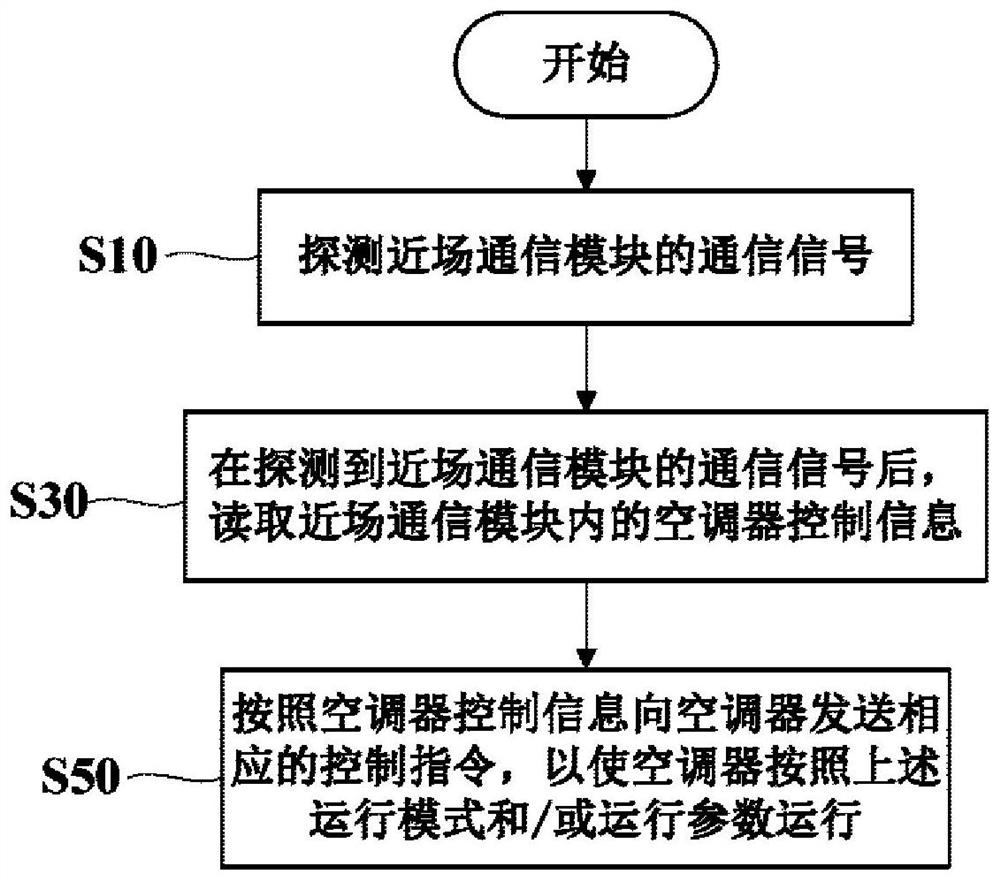
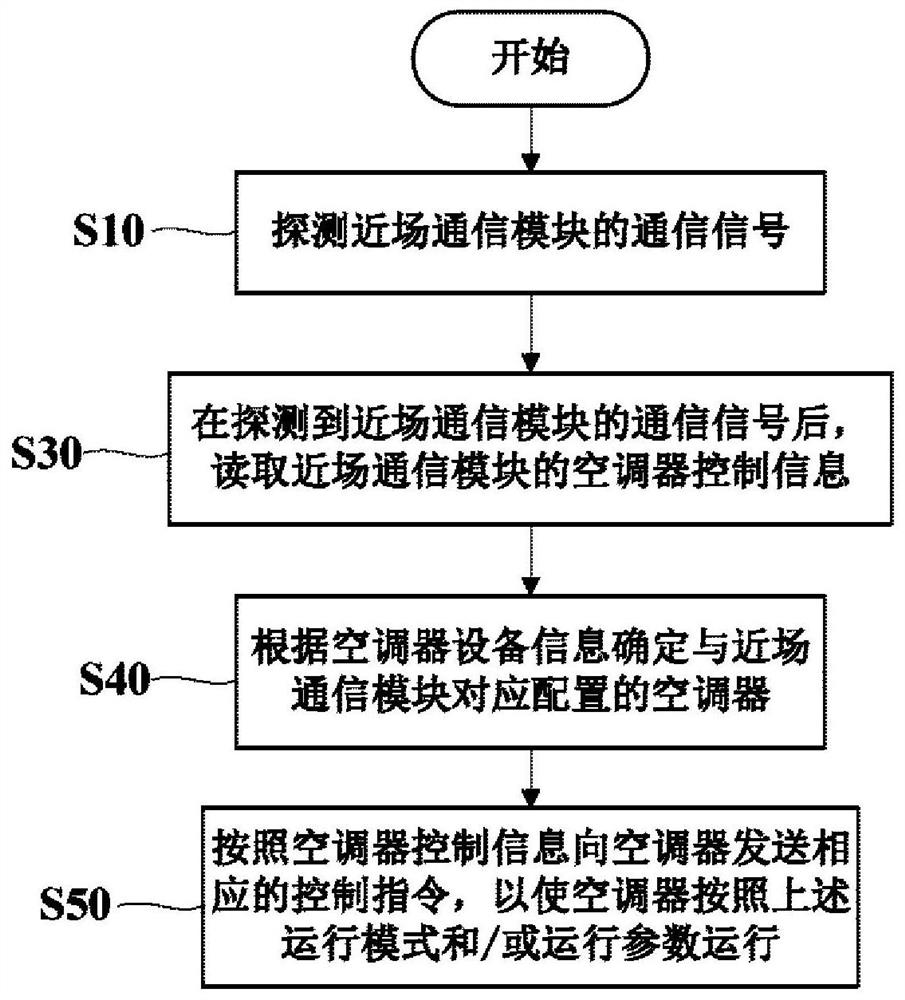
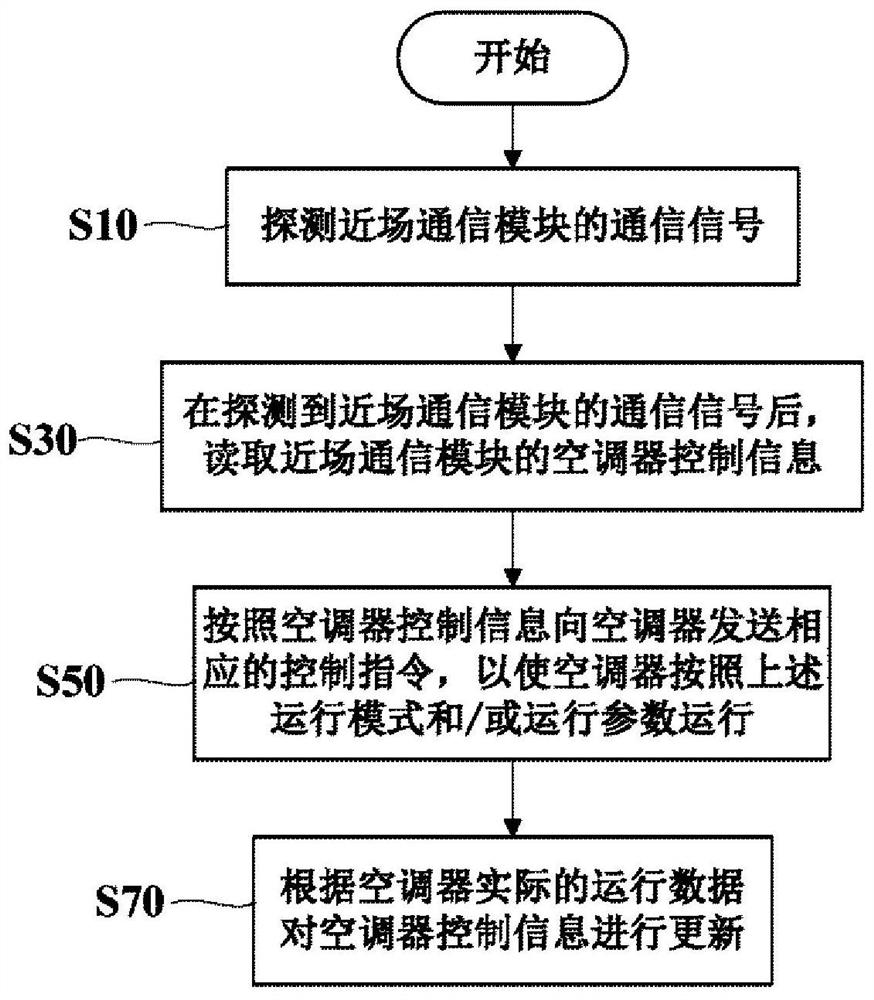
Control method of air conditioner, terminal equipment, server and control system of air conditioner
InactiveCN112665139AEasy to controlRealize high intelligenceMechanical apparatusSpace heating and ventilation safety systemsControl systemControl engineering
The invention relates to a control method of an air conditioner, terminal equipment, a server and a control system of the air conditioner. The air conditioner is correspondingly provided with a near-field communication module, and air conditioner control information including air conditioner operation modes and / or operation parameters is pre-stored in the near-field communication module. The control method comprises the following steps that a communication signal of the near-field communication module is detected; the air conditioner control information in the near-field communication module is read; and a corresponding control instruction is sent to the air conditioner according to the air conditioner control information, so that the air conditioner operates according to the operation mode and / or the operation parameters. A user only needs to make the terminal equipment close to the near-field communication module, the user does not need to manually input the control instruction, the participation degree of the user is reduced, the high intelligence of the whole control process of the air conditioner is achieved, and users at all ages and under all health conditions can easily and conveniently control the air conditioner. Meanwhile, the software and hardware requirements on the terminal equipment are reduced, and the range of applicable terminal equipment is expanded.
Owner:QINGDAO HAIER AIR CONDITIONER GENERAL CORP LTD +2
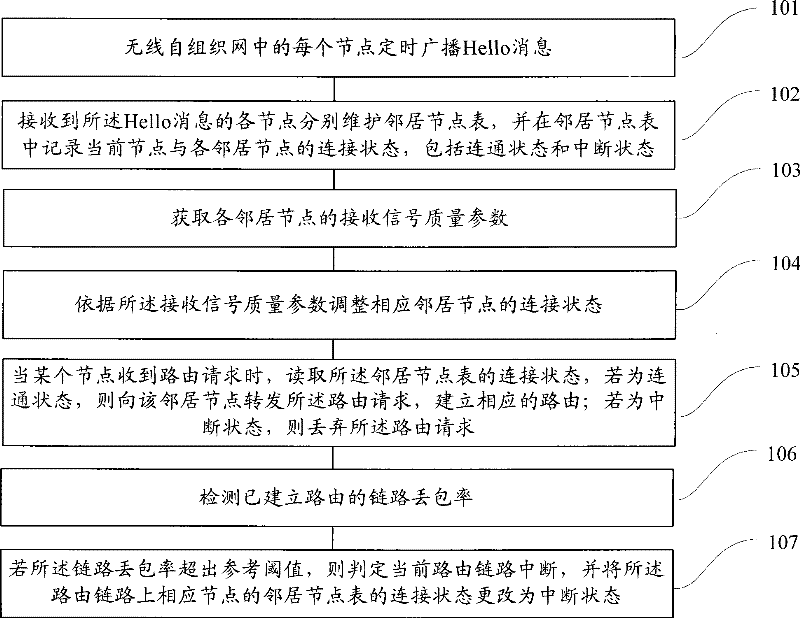
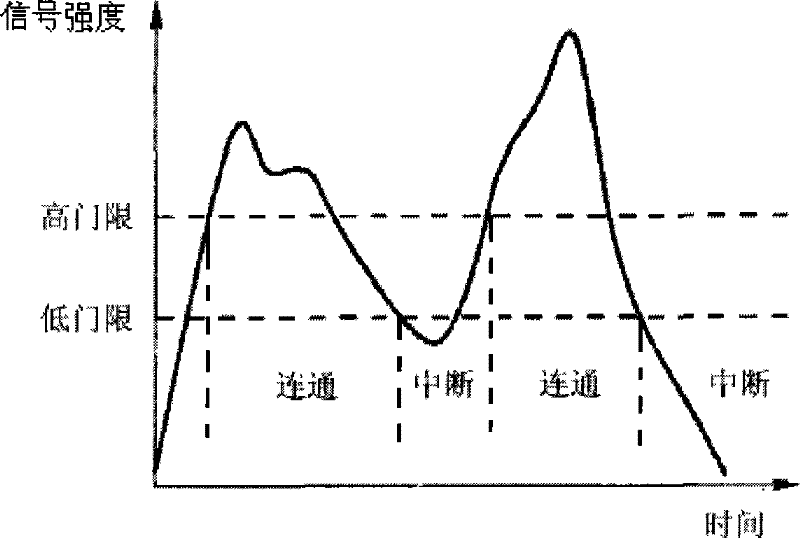
Route establishing and link detecting method and device for mobile Ad hoc network
InactiveCN101394357BImprove stabilityGuarantee the accuracy of judgmentError preventionData switching networksSignal qualityPacket loss
The invention discloses a route setup and link detection method for a wireless Ad hoc network, which comprises the following steps: each node regularly broadcasts a Hello message, and nodes which receive the Hello message all maintain a neighboring node list and records the connection state between the current node and the neighboring nodes including a communication state and a interruption state; received signal quality parameters of the neighboring nodes are acquired and the connection state of the corresponding neighboring node is adjusted in accordance with the signal quality parameters;when a certain node receives a routing request, the routing request is forwarded or discarded according to the connection state of the neighboring node list; the packet loss ratio of a routing link is detected; and the current routing link is judged to be interrupted if the packet loss ratio exceeds a reference threshold, and the connection state of the neighboring node list of the corresponding node is changed to be off state in the routing link. The invention can effectively improve the failure detection of route link, the timeliness and effectiveness of updating.
Owner:PEKING UNIV
Scanning electron microscope sample navigation method
ActiveCN112630242ALow equipment hardware and software requirementsGood universalityMaterial analysis using wave/particle radiationScanning electron microscopeAnalytical chemistry
The invention relates to the field of electron microscope characterization, discloses a scanning electron microscope sample navigation method, and aims to solve the problem that an electron microscope without a navigation device can hardly realize sample navigation. The method comprises the following steps of: marking the four vertexes of a rectangle on a sample table, recording coordinate information of the sample table in an electron microscope when the four vertexes are in the center of a field of view, pasting a sample, exposing the four marking points when the sample is pasted, imaging the sample table after the sample is pasted right above the sample table, reading the coordinate information of the four marking points and the sample in the imaging picture, calculating the coordinate information of the sample position in the scanning electron microscope by utilizing the mathematical coordinate system change, and finally inputting the sample position information into a control panel of the sample table to realize sample navigation. The method is suitable for electron microscope sample navigation.
Owner:CHENGDU ADVANCED METAL MATERIALS IND TECH RES INST CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com