Industrial Internet intrusion detection as well as defense method and device
An industrial Internet and intrusion detection technology, applied in electrical components, transmission systems, etc., can solve the problems that firewalls cannot resist attacking viruses, affect performance, and have high hardware requirements, so as to prevent attacks from external bad programs, shorten detection time, The effect of low hardware and software requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the purpose, technical solution and advantages of the present invention clearer, the following will further describe the implementation of the present invention in detail in conjunction with the accompanying drawings.
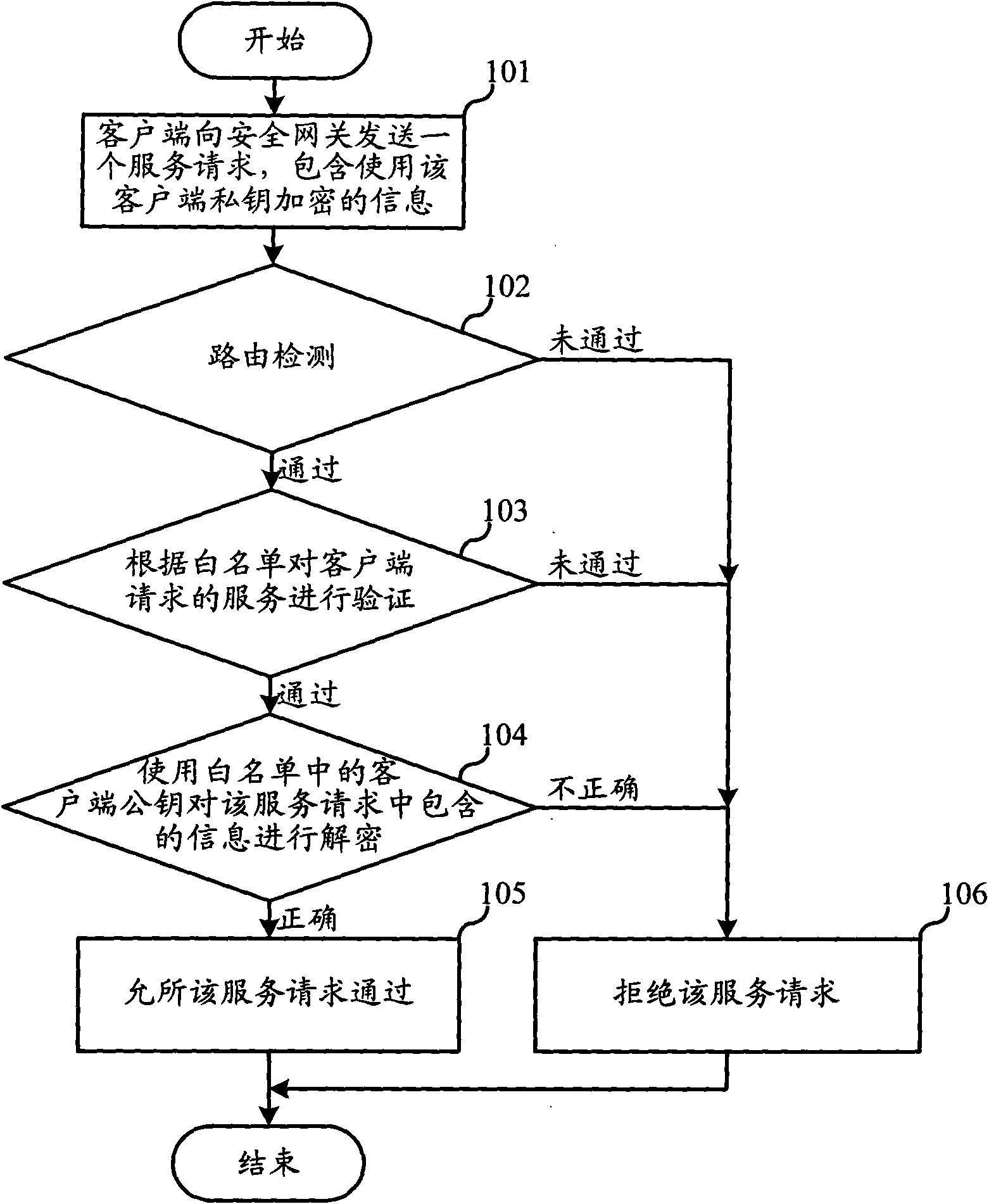
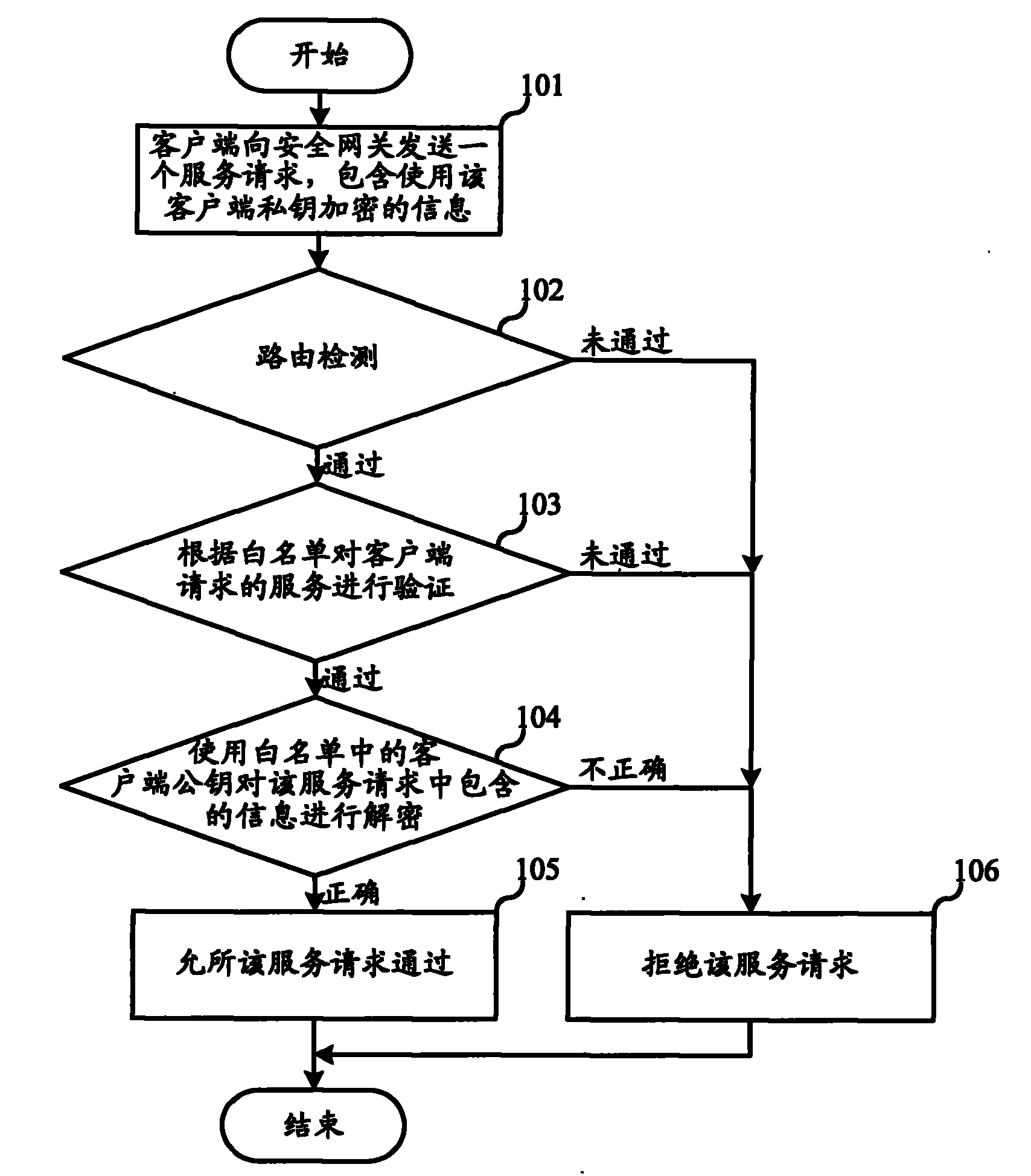
[0036] The first embodiment of the present invention relates to an industrial Internet intrusion detection and defense method. A white list is preset in the security gateway of the industrial Internet, and the white list includes the public key of the client that is allowed to access the industrial Internet, and the allowed services . Intrusion detection and prevention are implemented based on the whitelist. The Industrial Internet here can include enterprise internal networks, such as power supply systems, internal networks of petroleum systems, and so on. Specific methods such as figure 1 Shown:
[0037] In step 101, the client sends a service request to the industrial Internet security gateway, and the service request includes inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com