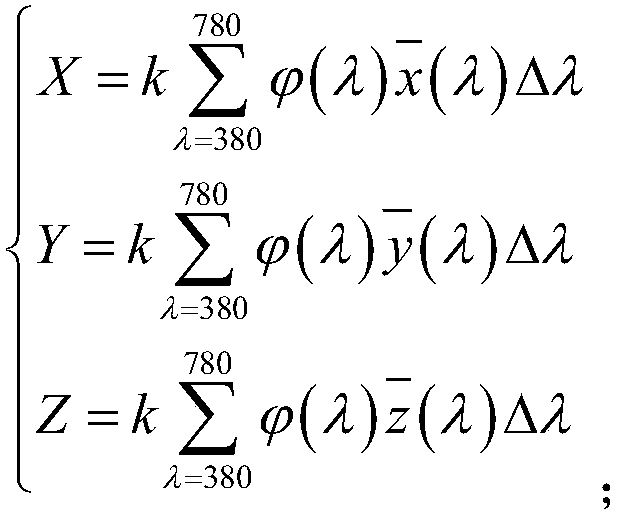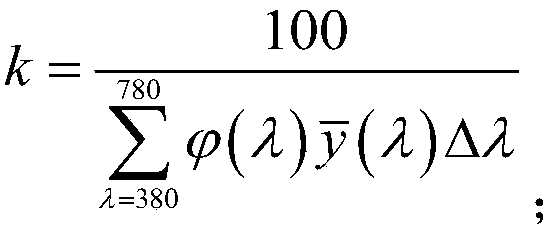Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35results about How to "Implement encryption protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
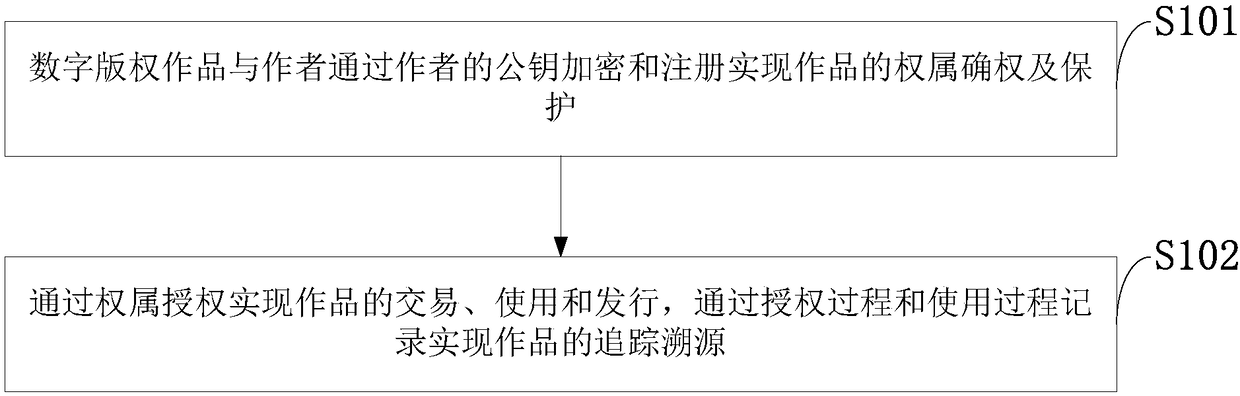
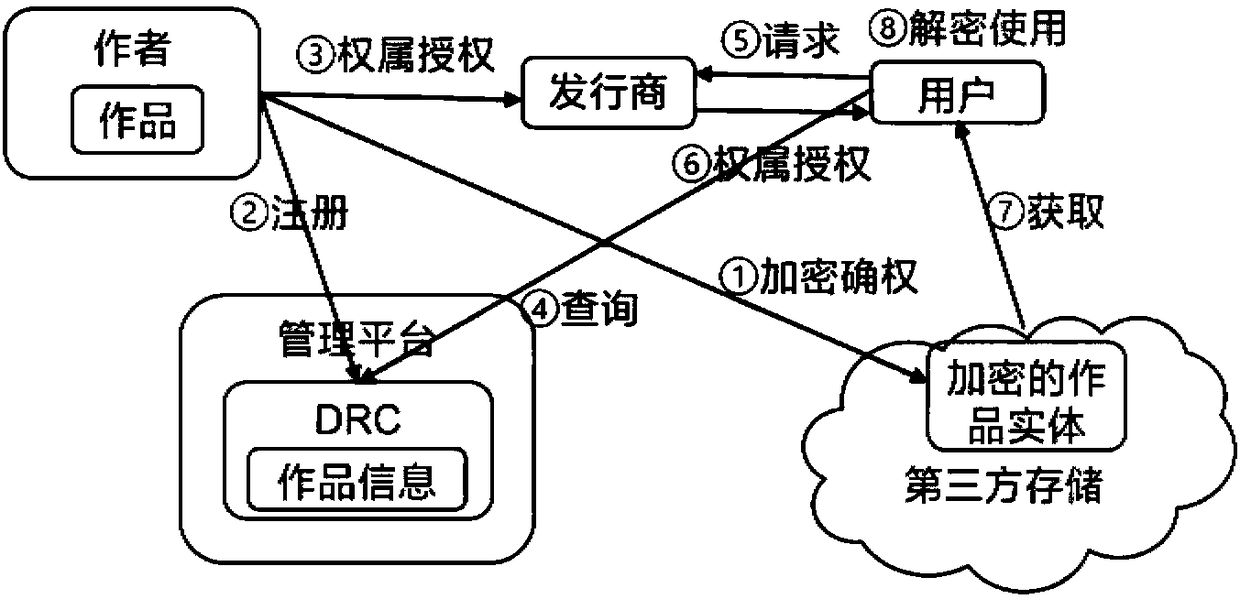
Ownership based digital copyright work protection-transaction-issuing method and system
InactiveCN108389059AProtect interestsProtection of rights and interestsTransmissionCommerceAuthorizationEncryption
The invention discloses an ownership based digital copyright work protection-transaction-issuing method and system, and belongs to the technical field of direction data protection. According to the method, an author declares and protects the ownership of a digital copyright work by public key encryption and registration; and the work is transacted, used and issued by authorization, and the work istracked and traced via recording in authorization and using processes. Via the encrypted ownership declaration and authorization methods, the problem that a traditional digital copyright protection method has deficiency in the aspects of preventing non-authorized use and pirates, help is provided for protection and shared use of the digital copyright work, and benefit and rights of the author canbe protected.
Owner:CHENGDU UNIV
File redirection technology based virtualized security desktop
InactiveCN104318179AOperational securityEasy to operate and controlDigital data protectionPlatform integrity maintainanceVirtualizationFile system
The invention discloses a file redirection technology based virtualized security desktop. Validity in using the security desktop is guaranteed through a login control module; operation behavior results of users can be reliably protected by an encrypted virtual storage file system; the operation behavior results of the users in the virtualized security desktop are 'internally' redirected to the encrypted virtual storage file system through a user operation middle layer and the whole redirection process is encrypted and monitored under a communication encryption module and a black and white list control module. The virtualized security desktop system is 'totally separated' from an original desktop, operations of adhering, copying, shifting and the like of the files cannot be performed between the virtualized security desktop system and the original desktop; the files on an original desktop system are mapped to the same catalog on the virtualized desktop; results (files, register lists, temporary cache and the like) generated from operation of the users in the virtualized desktop are encrypted for redirection treatment, and all the operations in the virtualized desktop are guaranteed to be safe, reliable and controllable.
Owner:中电科网络安全科技股份有限公司
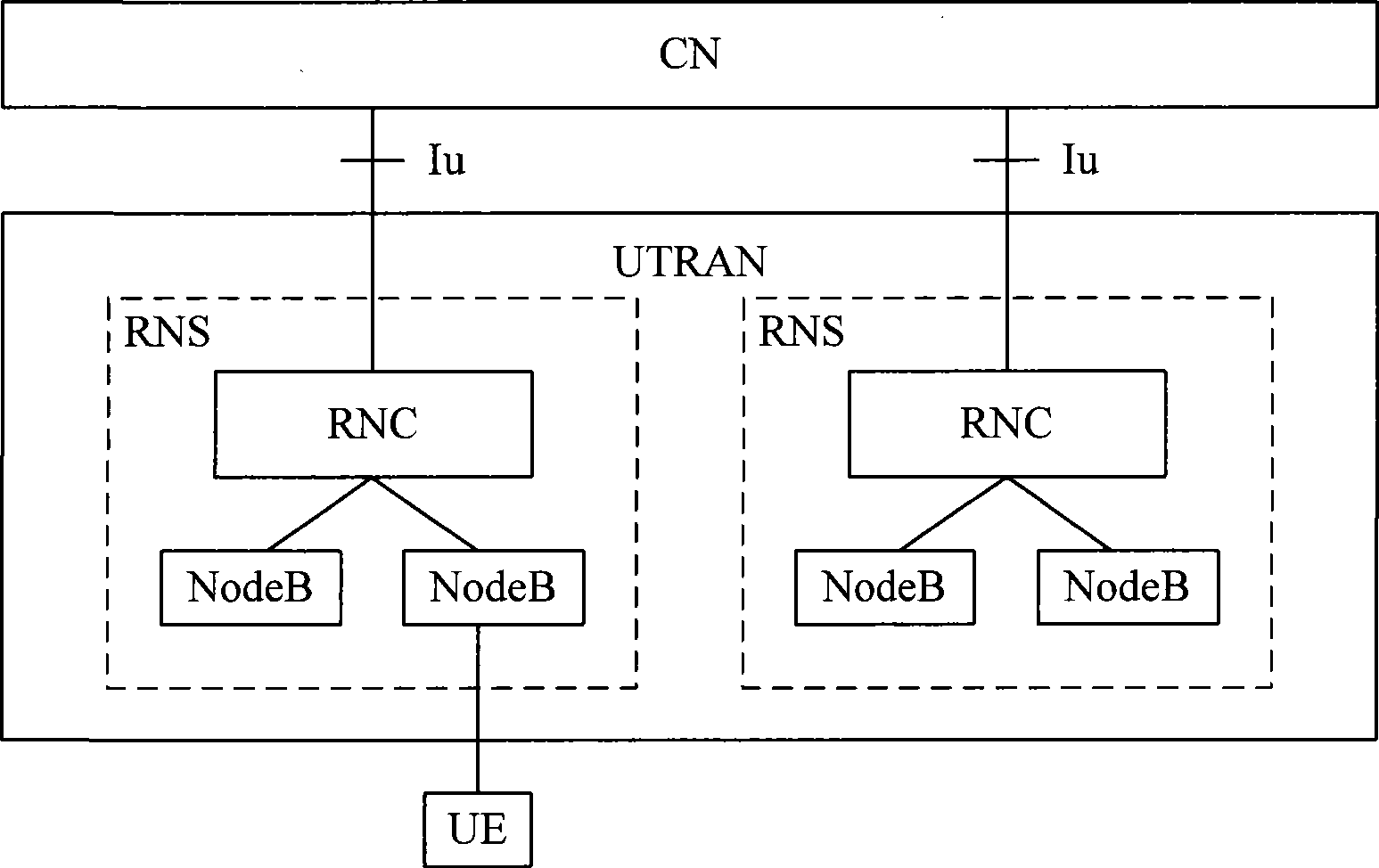
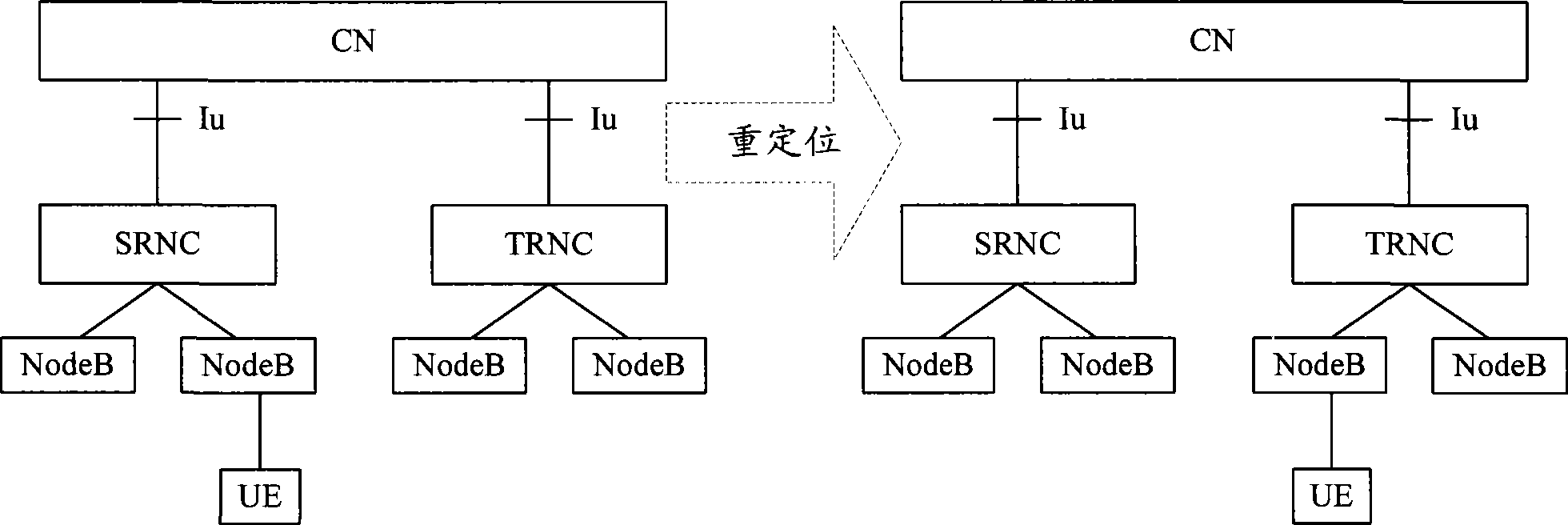
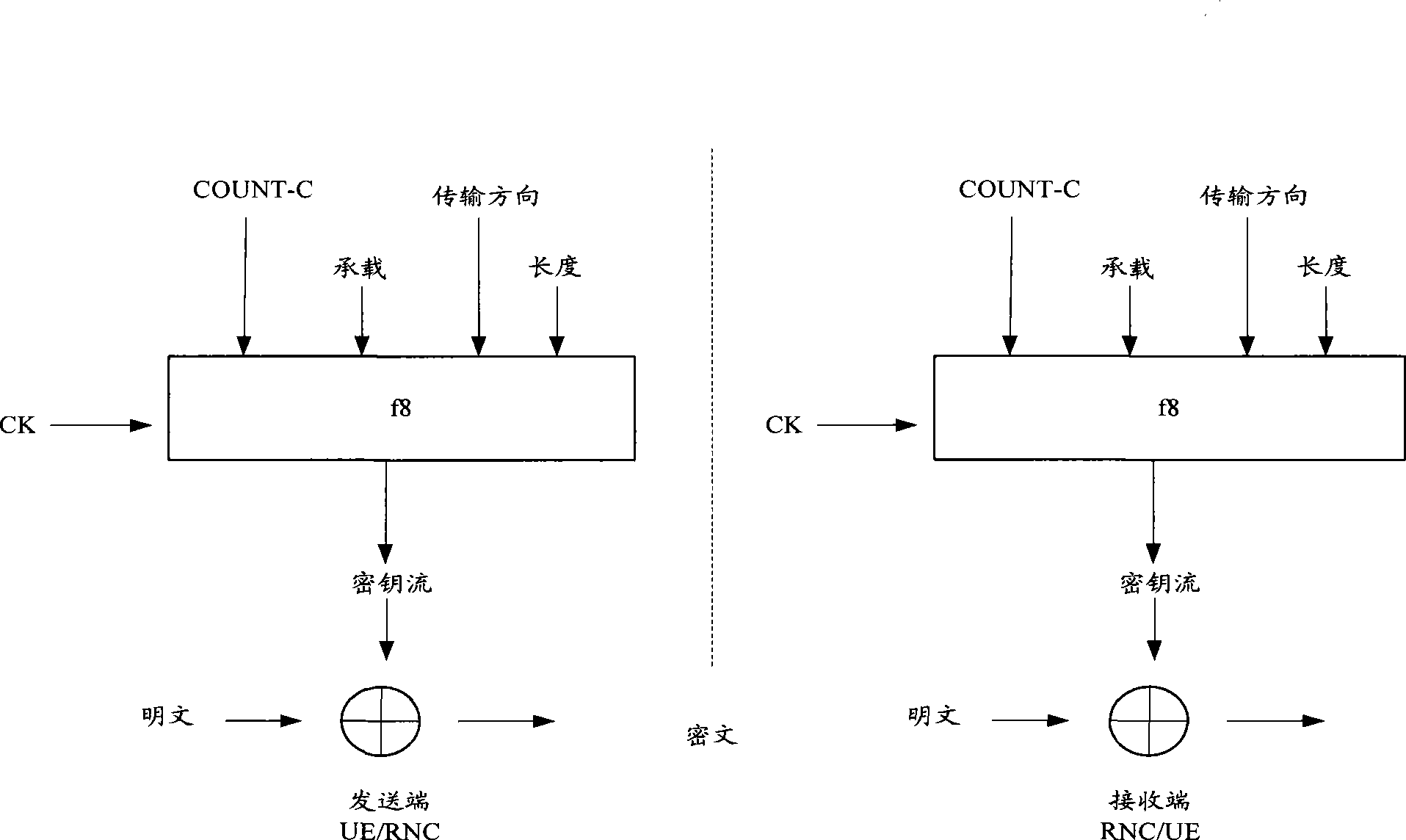
Signaling for reposition and data ciphering method, system and radio network controller
ActiveCN101388829AImplement encryption protectionImplement encrypted communicationData switching by path configurationSecurity arrangementPlaintextRadio Network Controller
The invention discloses a repositioned singling and a method for encrypting data, which comprises the following steps: receiving initial encrypting sequence numbers which are sent by an SRNC by the TPNC, adopting an encrypting RRC singling and user data of the initial encrypting sequence numbers by the TPNC, and then sending an encrypted wireless resource control singling and the user data to a UE. The invention further discloses the repositioned singling and a system with encrypting data, and a wireless network controller. The invention can enable the TPNC to be the same with the encrypting sequence numbers of both ends of the UE, and then can enable the TPNC and the both ends of the UE to obtain clear text data of the other party through decrypting, can guarantee the realization of the encrypting protection of RRC singling and the user data during the repositioning process, and can realize encrypting communication between the UE and the TRNC.
Owner:DATANG MOBILE COMM EQUIP CO LTD
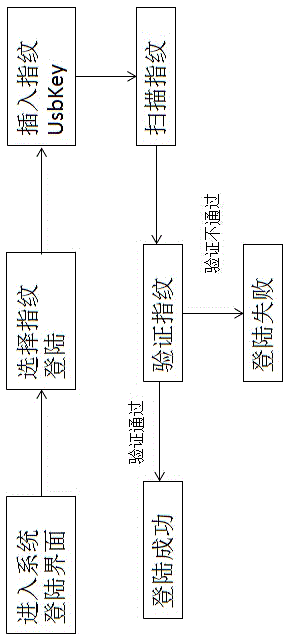
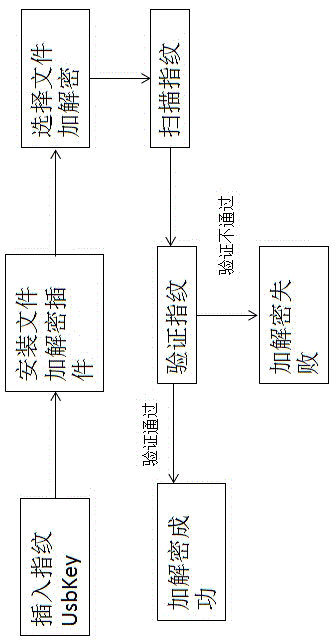
Method for performing identity authentication and file encryption and decryption based on fingerprint UsbKey
InactiveCN104021332AImplement encryption protectionNot easy to loseDigital data authenticationOperational systemEngineering
The invention discloses a method for performing identity authentication and file encryption and decryption based on a fingerprint UsbKey, relating to the field of computer information security. A memory unit, a fingerprint identifier and an indication light are integrated on U disc-like equipment with USB interfaces, configuration management is performed by special PC (personal computer for running Windows, Linux and other normal operation systems) terminal management software, and the U disc-like equipment has a memory function of an ordinary U disc, enables a user to perform identity authentication and file encryption and decryption through fingerprints and also can be taken as the ordinary U disc. Password and key management are performed by the safe and convenient method, and loss caused by the fact that a password or a key is lost is avoided.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
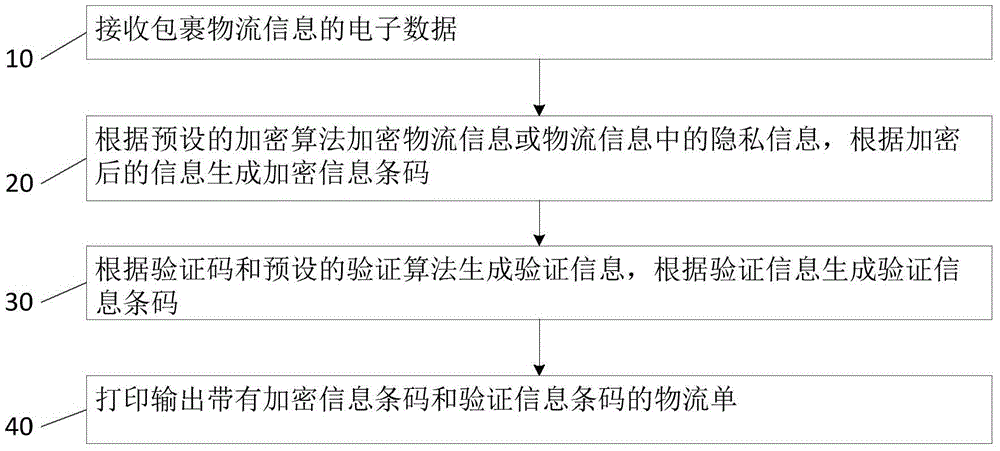
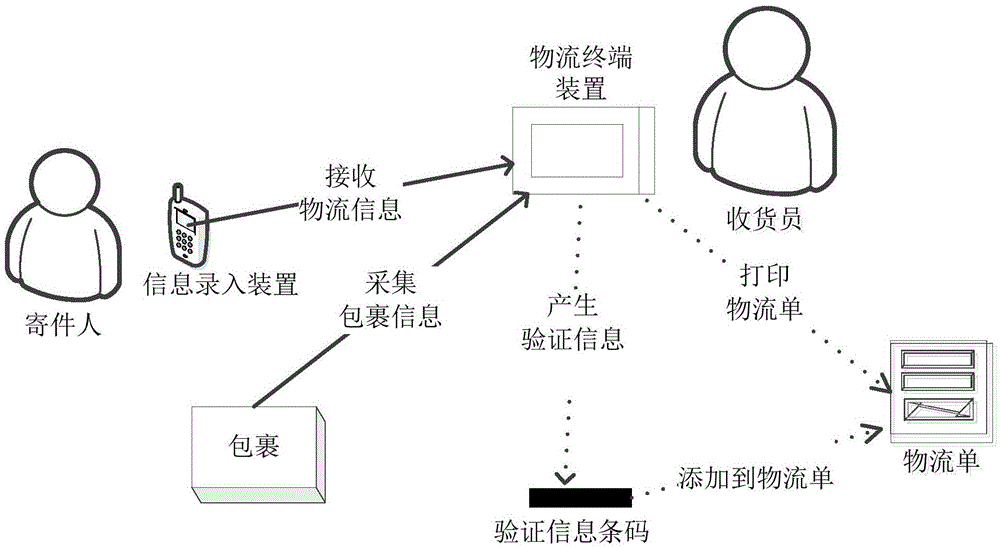
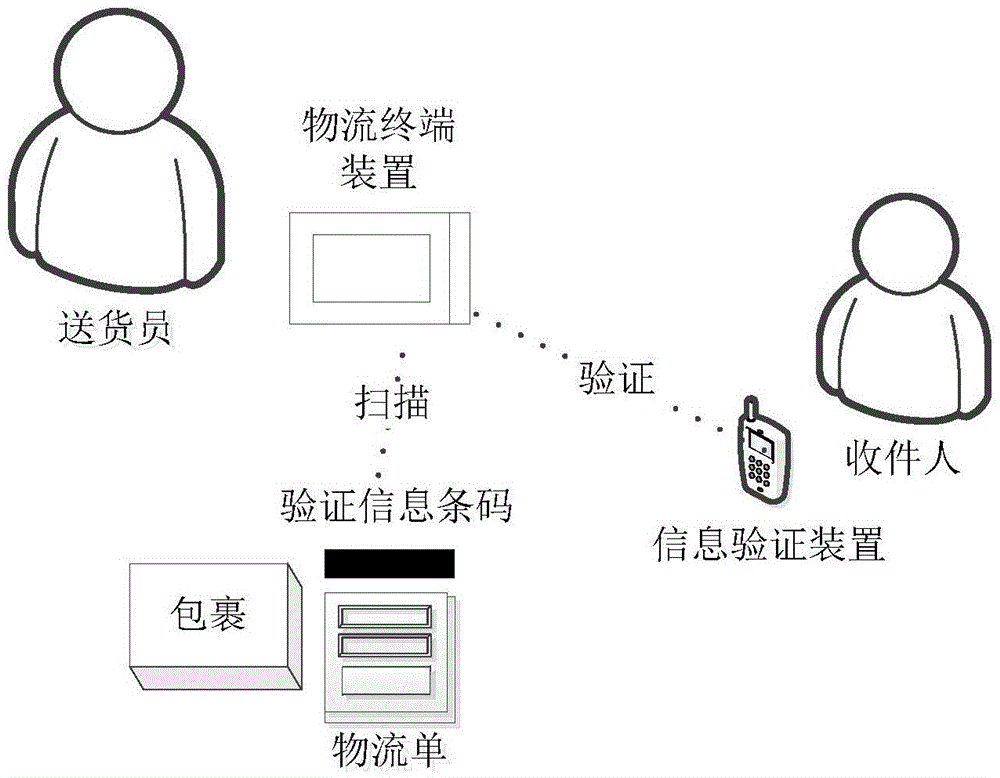
Logistics terminal device and goods-receiving method thereof
InactiveCN105590184AImplement encryption protectionImprove receiving efficiencyLogisticsLogistics managementTerminal equipment
The invention relates to a logistics terminal device and a goods-receiving method thereof. The goods-receiving method of the logistics terminal device comprises a step 10 of receiving electronic data of parcel logistic information; a step 20 of encrypting the logistics information or privacy information in the logistics information according to a preset encryption algorithm, and generating an encrypted information bar code according to the encrypted information; a step 30 of generating verification information according to a verification code and a preset verification algorithm and generating a verification information bar code according to the verification information; and a step 40 of printing and outputting a logistics sheet provided with the encrypted information bar code and the verification information bar code. The invention further provides the corresponding logistics terminal device. According to the logistics terminal device and the goods-receiving method thereof, an encrypted logistics sheet can be generated when goods is received so that logistics data is encrypted and goods can be received without the participation of a logistics center. Therefore, goods-receiving efficiency is increased.
Owner:BEIJING HUAAODA DATA TECH +1
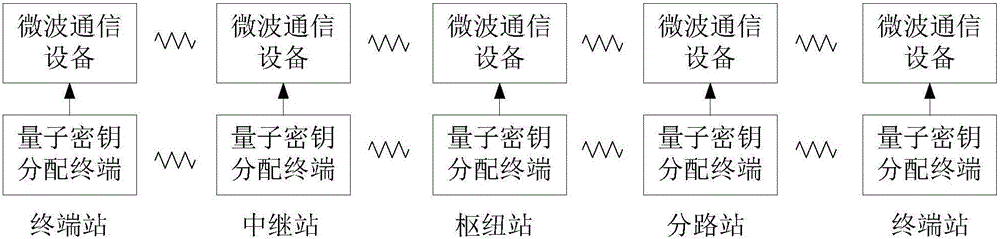
Quantum encryption microwave relay communication system and quantum encryption microwave relay communication method
InactiveCN105915337AImplement relayImplement encryption protectionKey distribution for secure communicationMicrowaveCommunications system
The invention discloses a quantum encryption microwave relay communication system and a quantum encryption microwave relay communication method. The system comprises a terminal station I, a relay station, and a terminal station II. The terminal station I is used for performing encryption operation on a key k with a key k1 to generate a key e1 and sending the key e1 to the relay station. The relay station is used for performing decryption operation on the key e1 with the key k1 to generate the key k, performing encryption operation on the key k with a key k2 to generate a key e2, and sending the key e2 to the terminal station II. The terminal station II is used for performing decryption operation on the key e2 with the key k2 to generate the key k. The key k1 is generated by the terminal station I and the relay station through a quantum key distribution terminal. The key k2 is generated by the terminal station II and the relay station through the quantum key distribution terminal. Finally, the terminal station I and the terminal station II have the same key k. The key k is relayed through the process. Through key relay transfer, transfer of the key k from the terminal station I to the terminal station II is realized.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
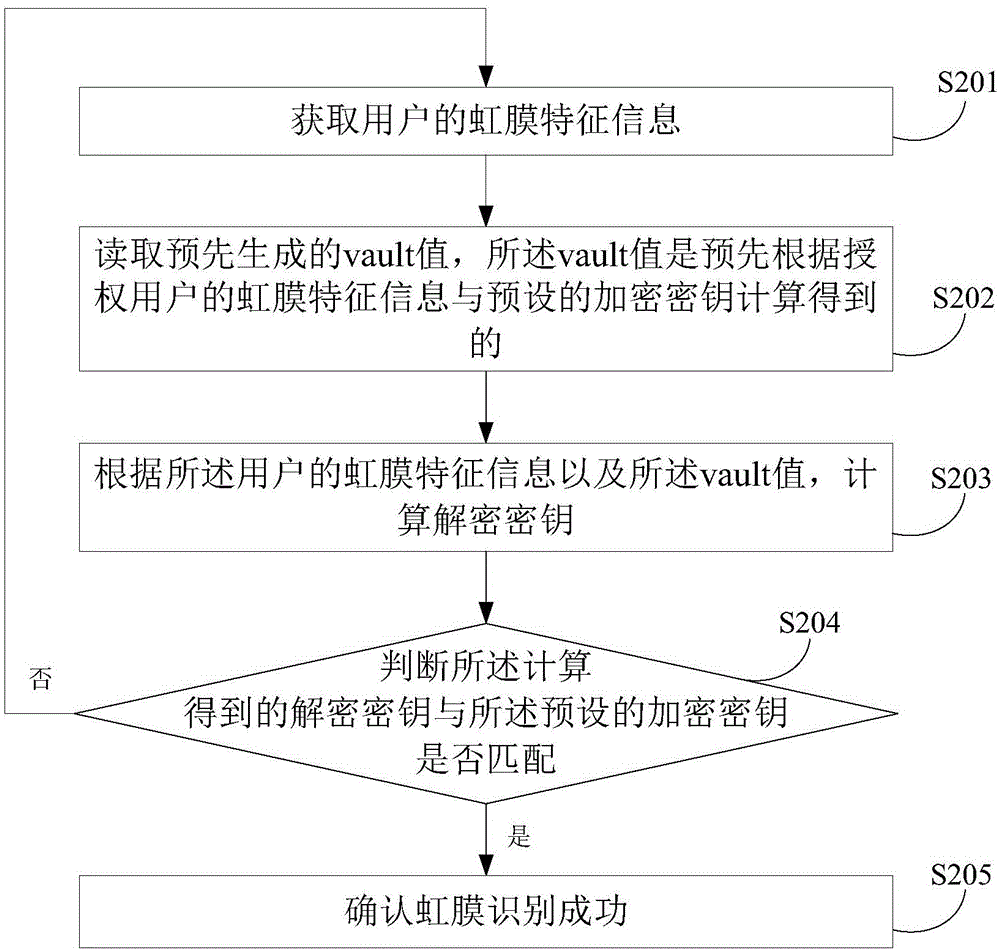
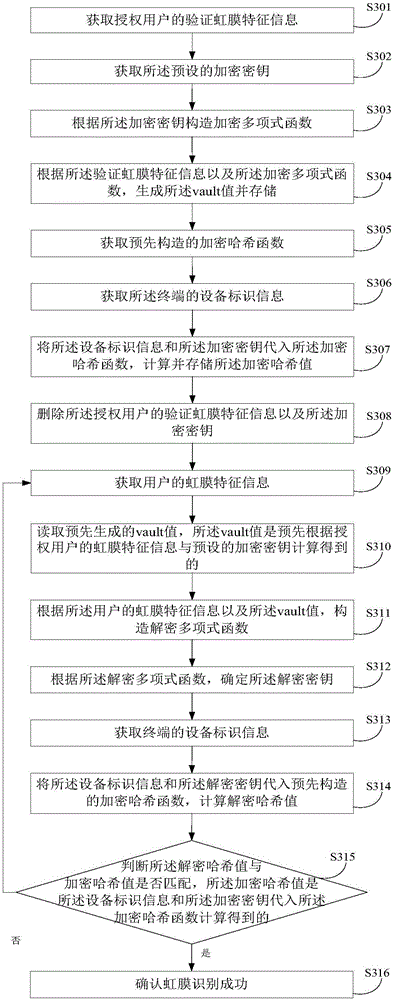
Iris identification method and apparatus
ActiveCN105550626APrevent leakageImplement encryption protectionCharacter and pattern recognitionDigital data protectionIris recognitionEncryption
The embodiment of the invention discloses an iris identification method. The method comprises: iris feature information of a user is obtained; a vault value that is generated in advance is read, wherein the vault value is obtained in advance by calculation based on iris feature information of an authorized user and a preset encrypted secret key; according to the iris feature information of the user as well as the vault value, a decrypted secret key is calculated; whether the decrypted secret key obtained by calculation matches the preset encrypted secret key is determined; and if so, success of the iris identification is confirmed. In addition, the invention also discloses an iris identification apparatus. With the method and apparatus, encryption protection can be carried out on the terminal and leakage of iris feature information can be prevented effectively.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for encrypting fixed-length data capable of carrying effective service information in transmission
InactiveCN107040366AGood effectIncrease the difficulty of crackingEncryption apparatus with shift registers/memoriesData bitsService information
The invention discloses a method for encrypting fixed-length data capable of carrying effective service information in transmission, comprising the following steps: S1, constructing a to-be-encrypted fixed-length original character string; S2, filling specified data bits of the original character string with service information data to get a service information character string; S3, constructing a position exchange code table to disorganize the data bits of the service information character string according to position disorganization rules; S4, inverting the value of the character string after position disorganization; and S5, converting the system of the character string after value inversion according to system conversion rules. Through the method, the problem that the existing popular encryption and decryption algorithm fails to generate a fixed-length character string after encrypting an original character string is solved. According to the method, double modes of encryption in encryption and decryption share encryption and decryption rules and a rule code table, and the rule code table is updated dynamically in variety of ways to increase the cracking difficulty.
Owner:四川智魔王智能科技股份有限公司
Image encryption method and device, image decryption method and device, equipment and readable storage medium
ActiveCN112040086AImplement local encryptionRestrict accessKey distribution for secure communicationDigital data protectionEngineeringEncryption decryption
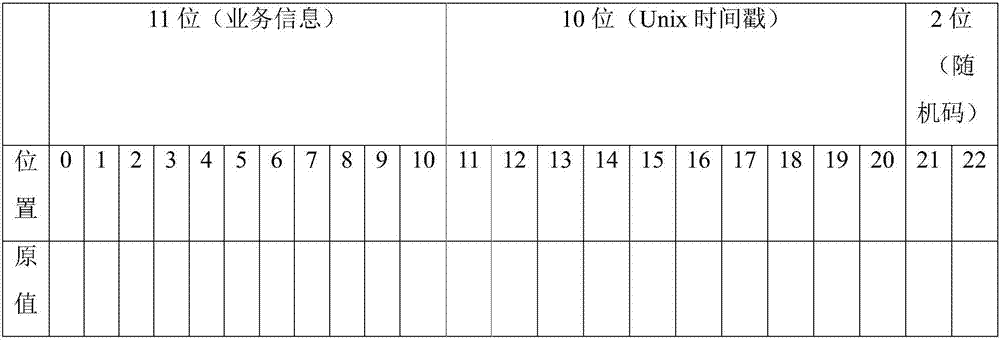
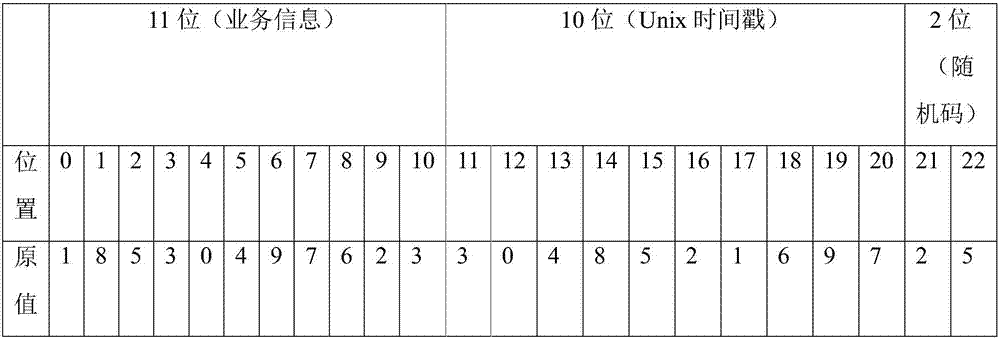
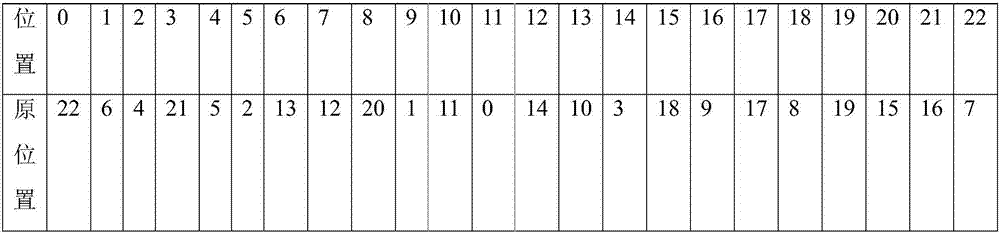
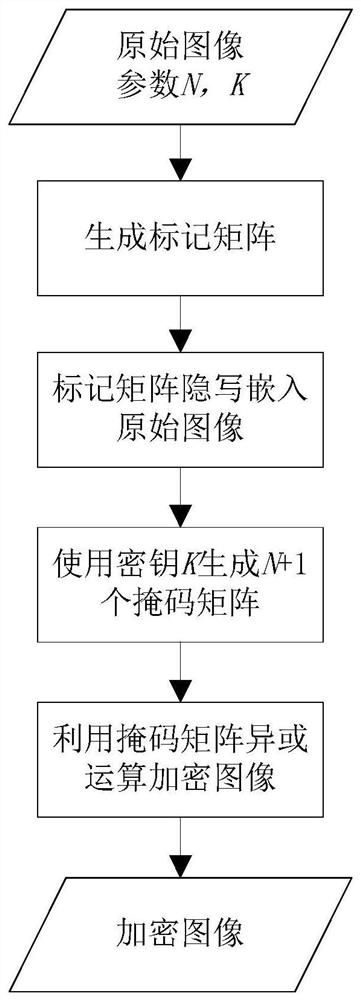
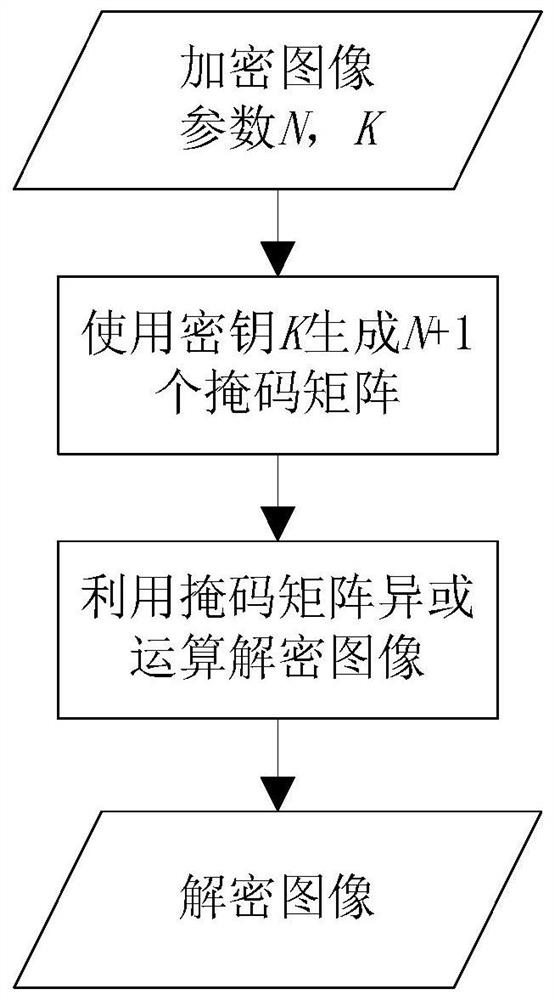
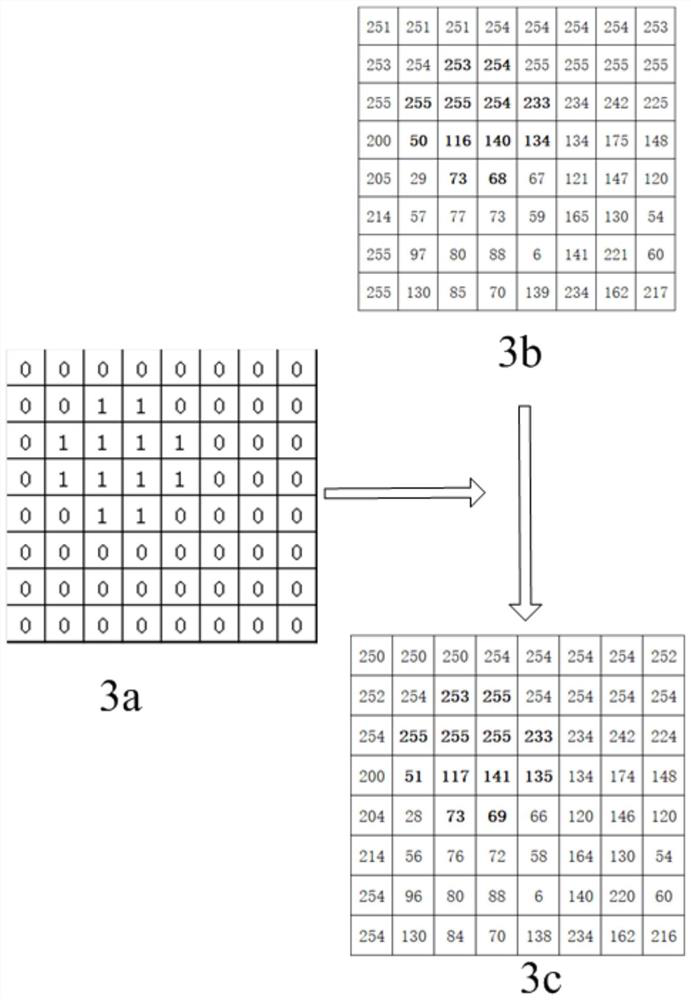
The invention discloses an image encryption method and device, an image decryption method and device, equipment and a readable storage medium. The image encryption method comprises the steps that a binary mark matrix is generated according to image content needing to be encrypted in an original image; marking the original image by using the generated marking matrix; randomly forming an encryptionmatrix by adopting a secret key, and performing AND operation on the encryption matrix and the mark matrix to obtain a mask matrix; and performing exclusive-OR operation on the marked image through the mask matrix to form an encrypted image. During decryption, an encrypted pixel marking matrix is restored on a corresponding bit plane by using exclusive-OR operation, and the corresponding bit planes of all encrypted pixels are subjected to exclusive-OR operation again to restore the encrypted pixel content of the image. According to the invention, a user can restrain the access permission of part of people to part of the image content. When the condition is allowed, the user or an authorized party restores the original content through the protected image.
Owner:湖北微模式科技发展有限公司
Image encryption method and device, image decryption method and device, electronic equipment and storage medium
PendingCN112035847AImplement local encryptionRestrict accessDigital data protectionComputer hardwareEngineering
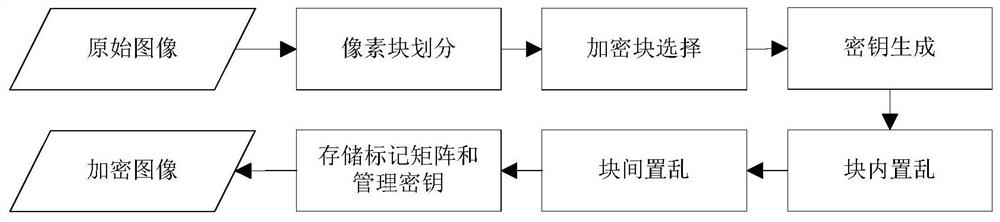
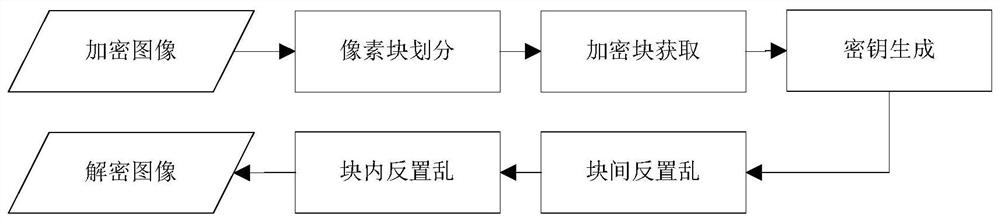
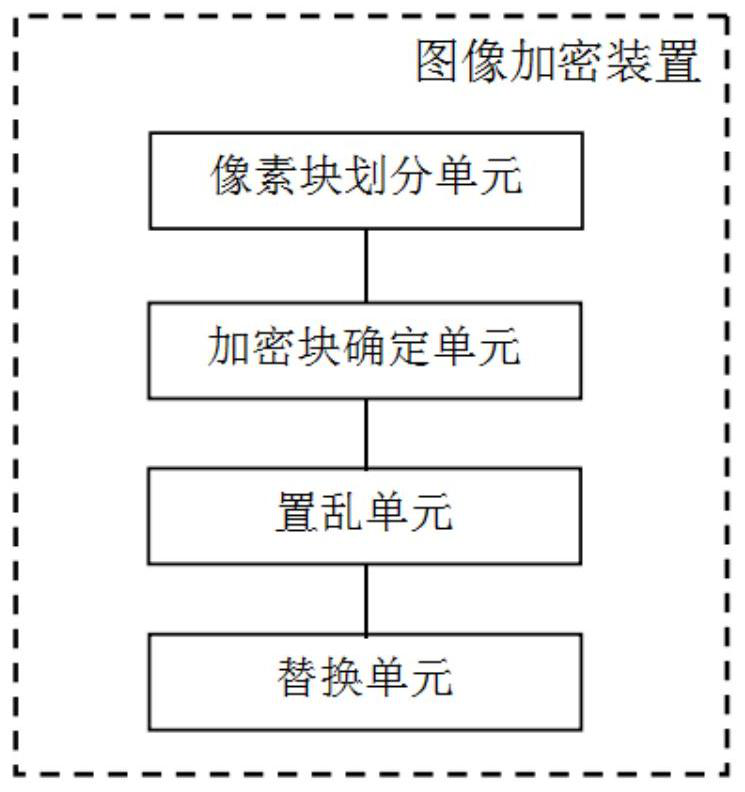
The invention discloses an image encryption method and device, an image decryption method and device, electronic equipment and a storage medium. The image encryption method comprises the following steps: dividing a to-be-encrypted image into a plurality of rectangular pixel blocks with the same size; taking the rectangular pixel block covered by the area needing to be encrypted as an encryption block; sequentially carrying out intra-block pixel scrambling and inter-block scrambling on all the encryption blocks; and replacing the encryption blocks before scrambling with the scrambled encryptionblocks in sequence to form an encrypted image. The image decryption method includes: dividing the image to be decrypted into a plurality of rectangular pixel blocks with the same size during decryption; determining an encryption block from all the rectangular pixel blocks; performing inter-block reverse scrambling and intra-block pixel reverse scrambling on all the encrypted blocks to obtain decrypted pixel blocks; and replacing the corresponding encryption blocks with the decryption pixel blocks in sequence to form a decrypted image. According to the invention, the user can restrain the access permission of part of people to part of image content. When the condition is allowed, the user or the authorized party restores the original content through the protected image.
Owner:湖北微模式科技发展有限公司
Power dependable safety communication system based on dependable computing module
InactiveCN104468591AAchieving Trusted ProtectionFirmly connectedCircuit arrangementsTransmissionInformation securityElectric power
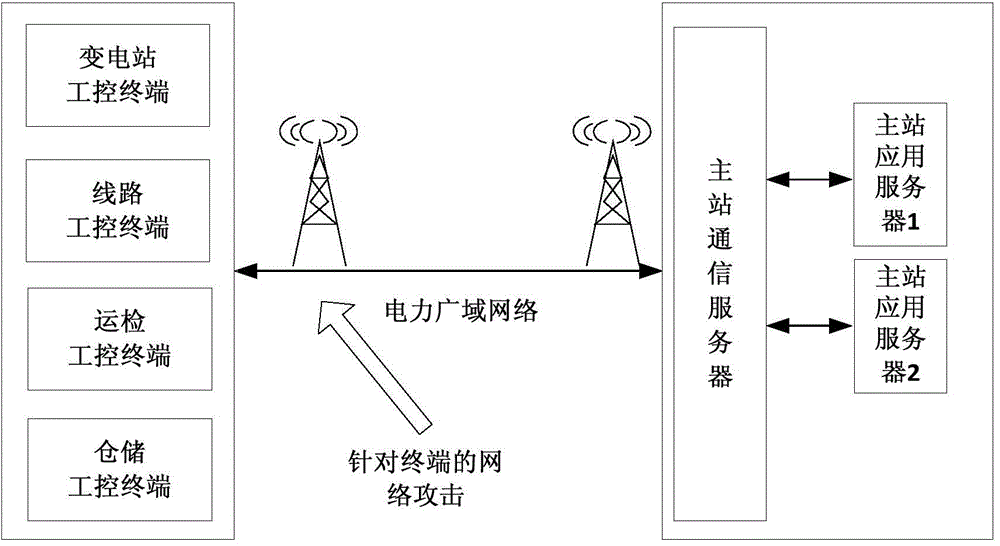
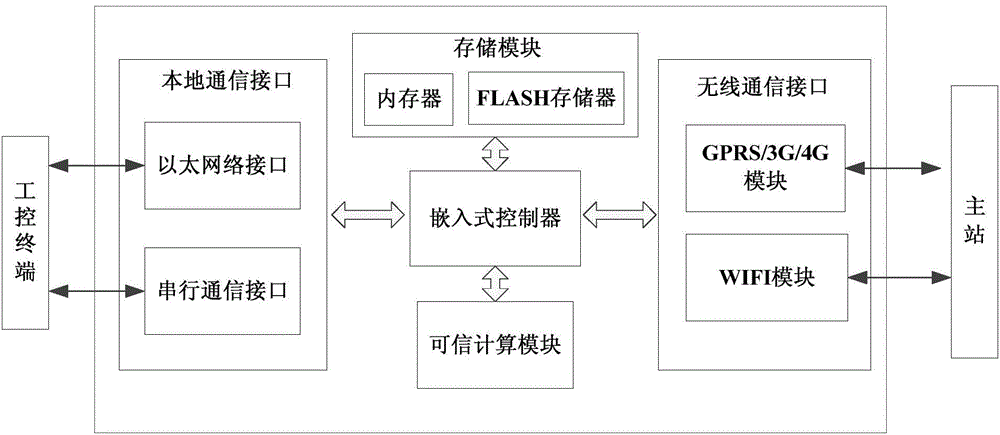
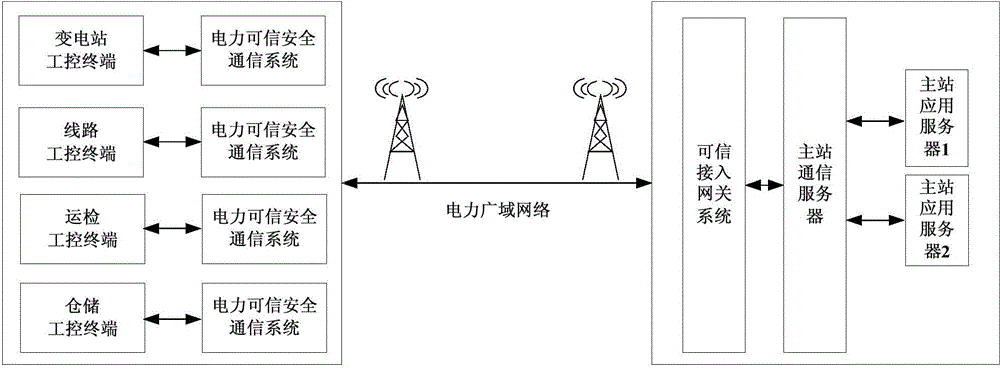
The invention provides a power dependable safety communication system based on a dependable computing module, and belongs to the field of network information safety. The system comprises an embedded type controller, a storage module, the dependable computing module, a local communication interface and a wireless network interface; the storage module, the dependable computing module, the local communication interface and the wireless network interface are in both-way connection with the embedded type controller. According to the power dependable safety communication system based on the dependable computing module, the dependable computing principle and related safety protection technologies are used for power safety communication, the system mainly achieves dependable access of various power embedded type terminals through protection of the power dependable safety communication module, illegal network attacks are prevented, and information safety of the power embedded type terminals is ensured.
Owner:STATE GRID CORP OF CHINA +3
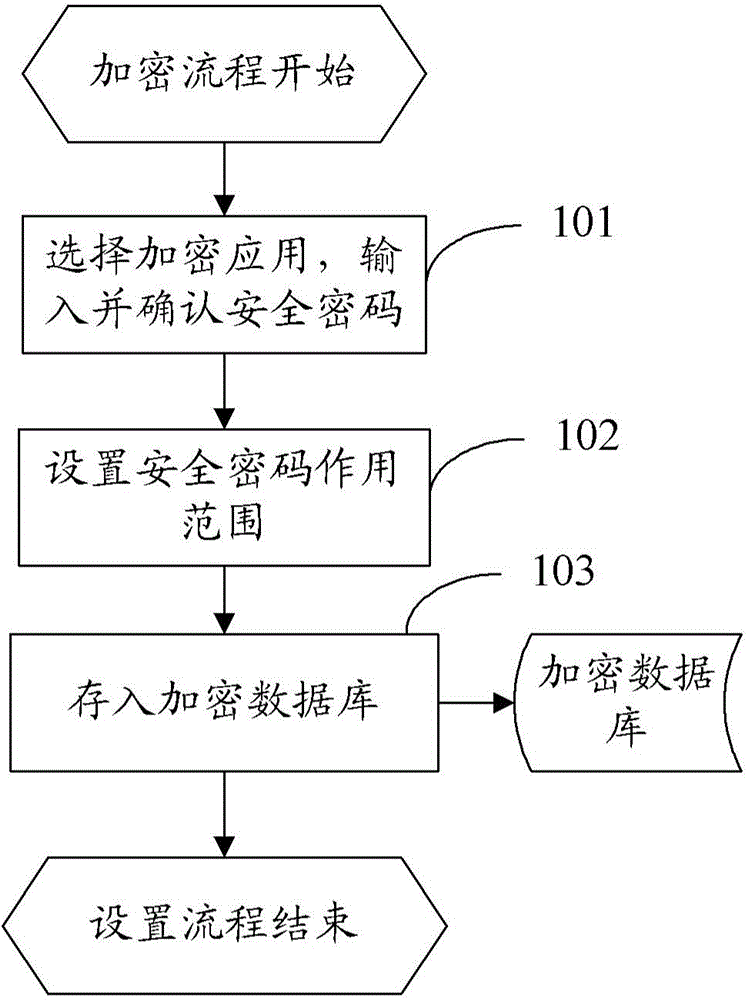
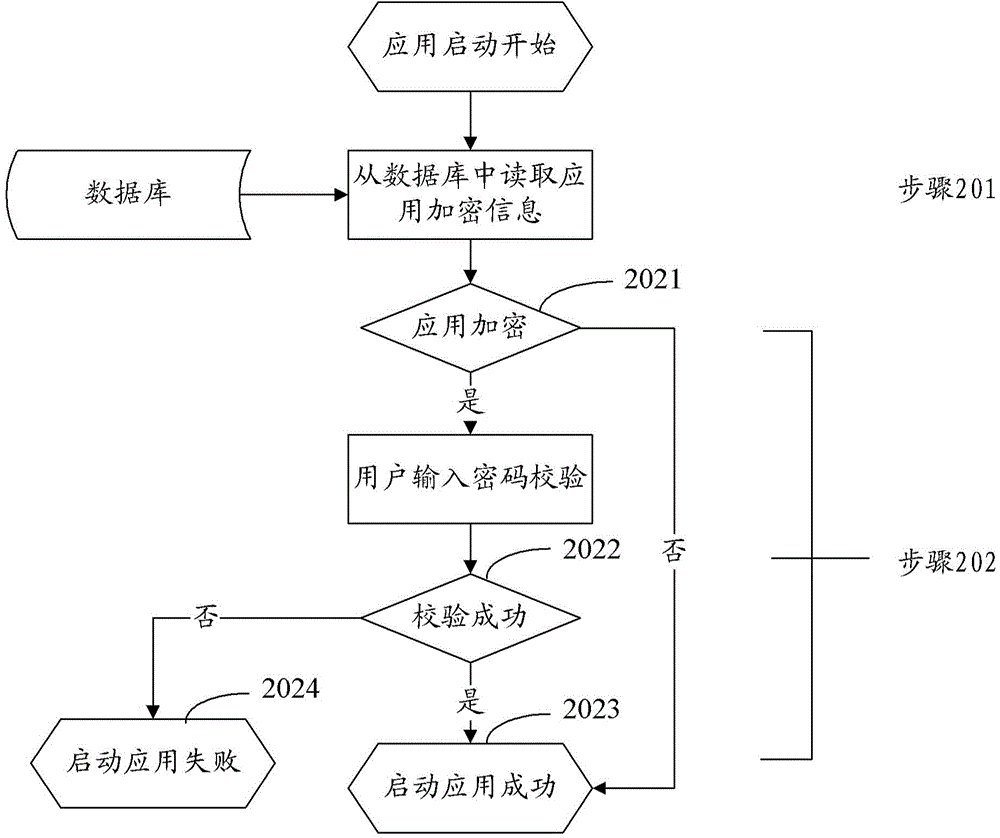
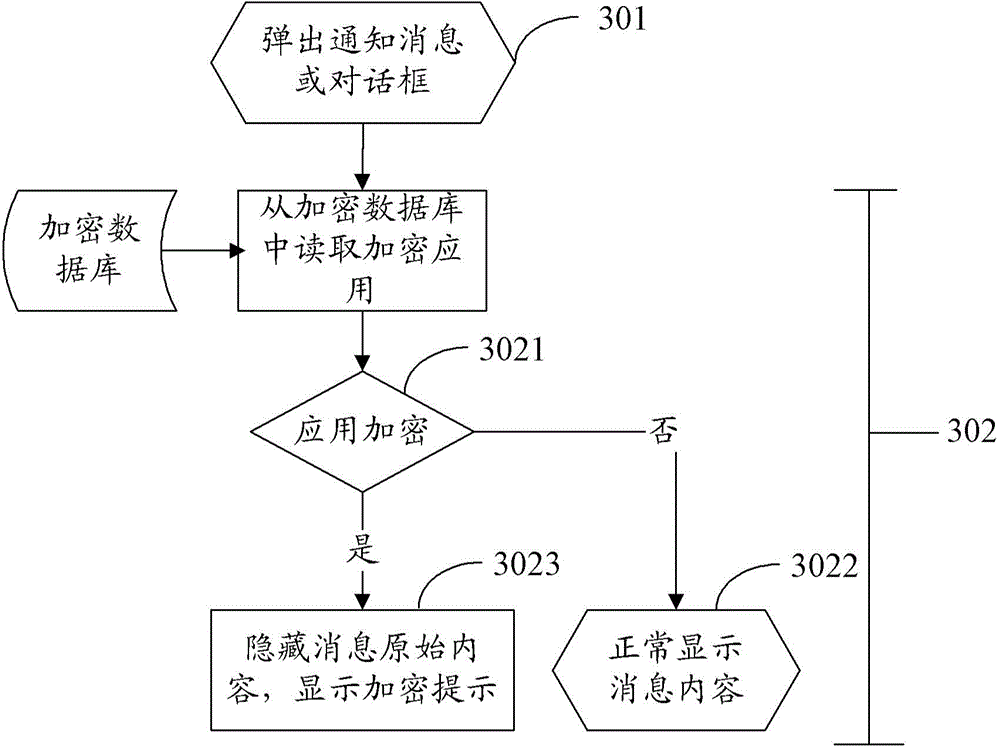
Application encryption method and apparatus
InactiveCN105426712AImplement encryption protectionSolve the problem of leaking user informationDigital data authenticationOperational systemPassword
The invention provides an application encryption method, relates to the field of mobile applications, and solves the problem of user information leakage caused by an operating system of a mobile terminal. The application encryption method comprises the steps of displaying information of an application that is preset to be an encrypted application in an encrypted manner; detecting whether a safety password input by a user is accordant with a safety password corresponding to the application stored in an encrypted database or not; and if so, displaying the application information normally. The technical scheme provided by the invention is applicable to the operating system of the mobile terminal, and the problem of user information leakage caused by the operating system of the mobile terminal is solved.
Owner:ZTE CORP
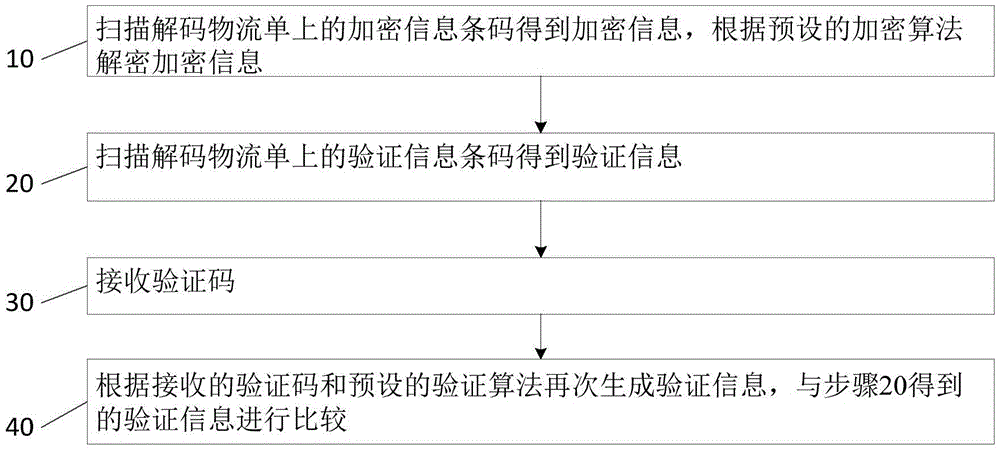
Logistics terminal device and delivery method thereof
InactiveCN105608392AImplement encryption protectionImprove delivery efficiencyDigital data protectionLogisticsComputer hardwareLogistics management
The invention relates to a logistics terminal device and a delivery method thereof. The delivery method of the logistics terminal device comprises the following steps: 10) scanning an encrypted information barcode on a decoding logistics sheet to obtain encrypted information, and decrypting the encrypted information according to a preset encryption algorithm; 20) scanning a verification information barcode on the decoding logistics sheet to obtain verification information; 30) receiving a verification code; and 40) according to the received verification code and the preset verification algorithm, generating the verification information again, and comparing the verification information with the verification information obtained in the S20). The invention also provides a corresponding logistics terminal device. The logistics terminal device and the delivery method of the logistics terminal device can deliver according to the encrypted logistics sheet, realizes the encryption protection of logistics data, can finish delivery without the participation of a logistics center, and improves delivery efficiency.
Owner:BEIJING HUAAODA DATA TECH +1
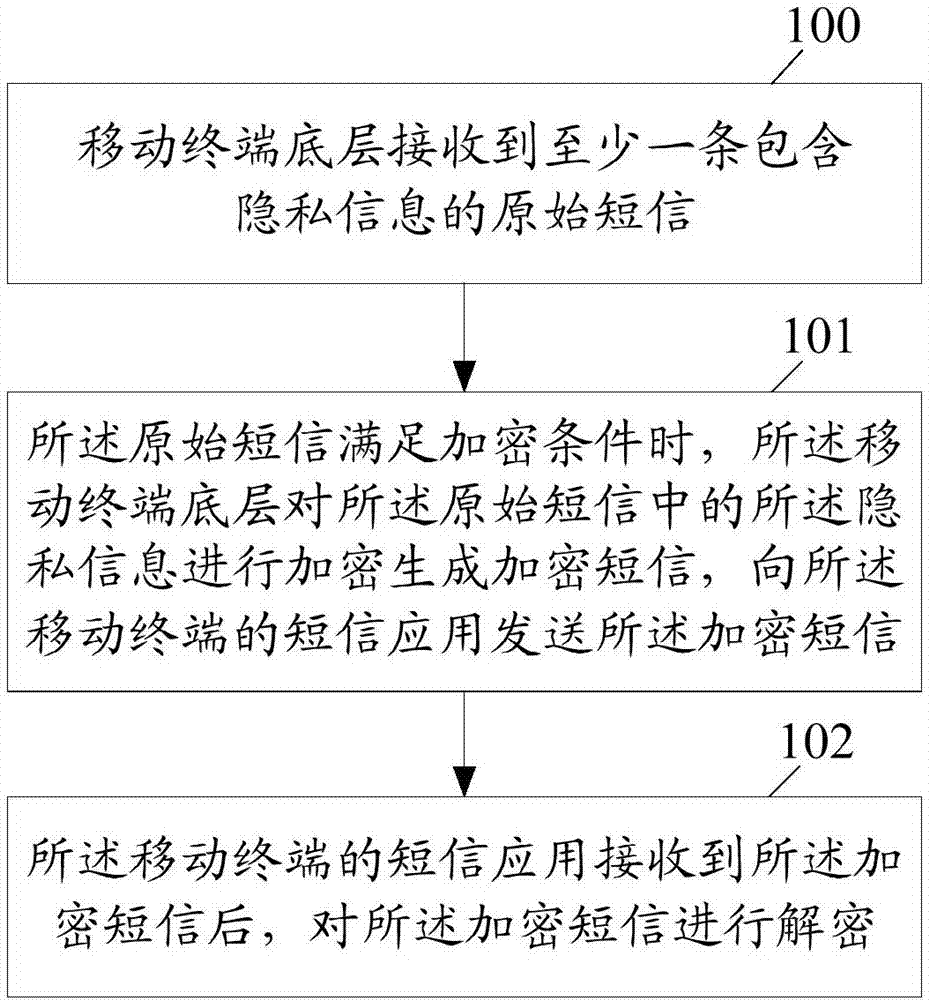
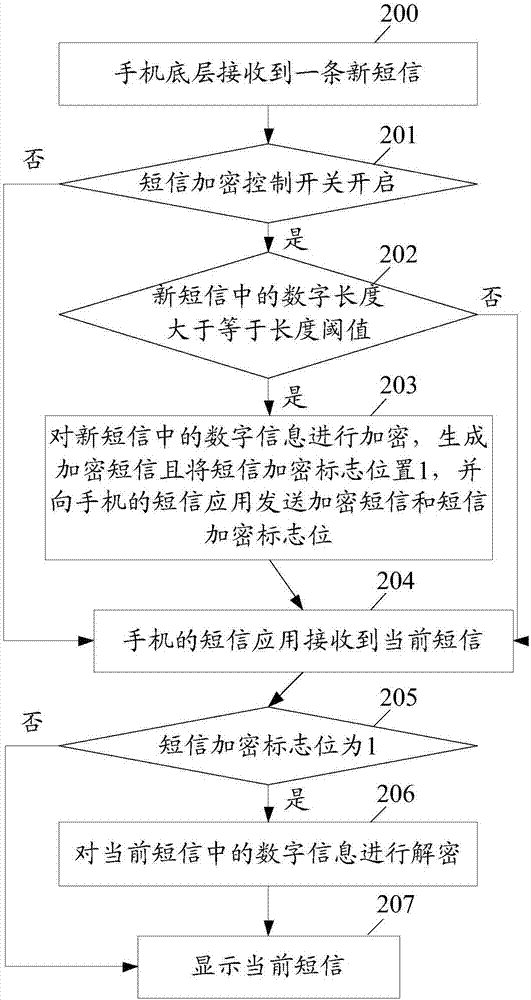
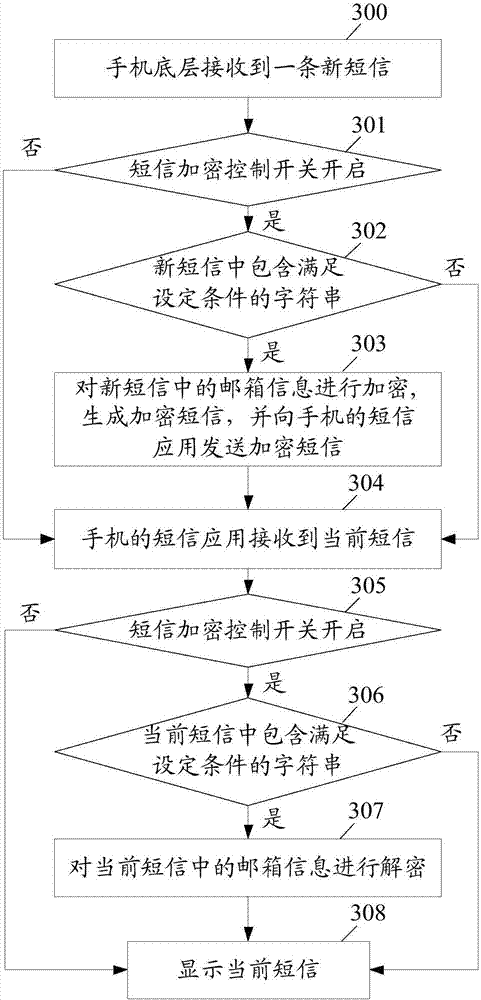
Information encryption and decryption method and apparatus in short message
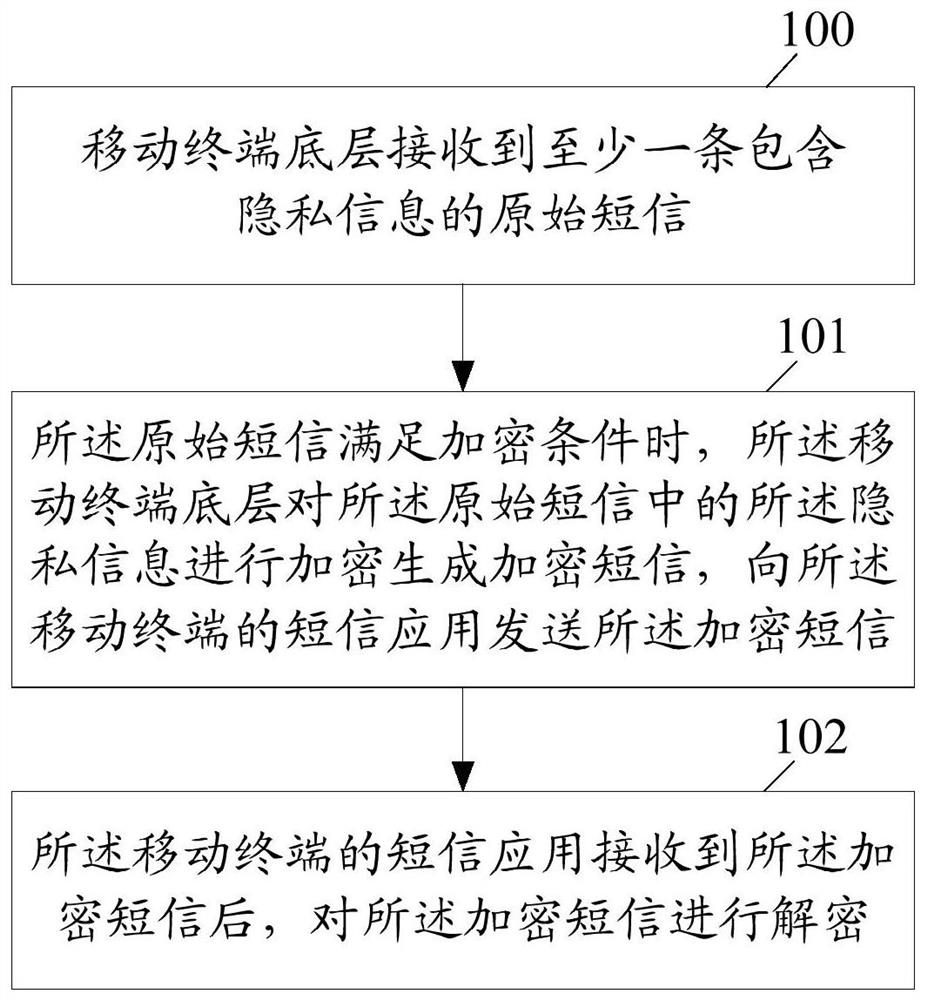
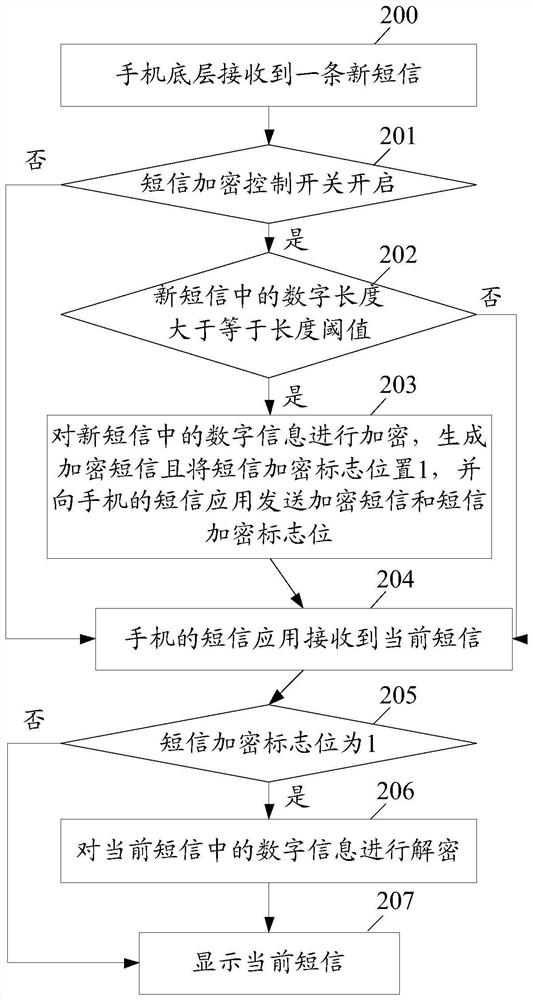
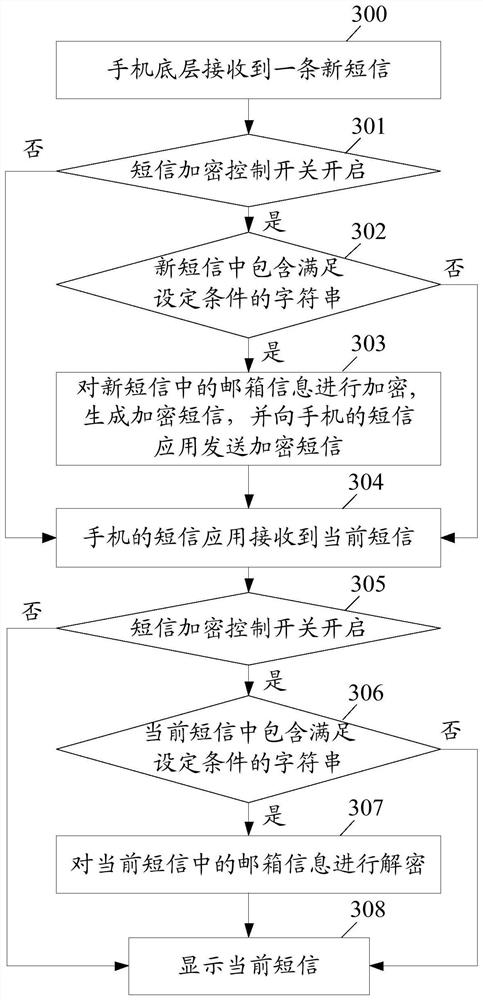
ActiveCN107889102AImplement encryption protectionReduce risk of leakageInformation formatContent conversionText messagingEncryption
The embodiment of the invention discloses an information encryption and decryption method in a short message. The method comprises the following steps: a mobile terminal bottom layer receives at leastone original short message containing privacy information; when the original short message satisfies an encryption condition, the mobile terminal bottom layer encrypts the privacy information in theoriginal short message to generate an encrypted short message, and sends the encrypted short message to a short message application of a mobile terminal; and the short message application of the mobile terminal decrypts the encrypted short message after receiving the encrypted short message. The embodiment of the invention further discloses an information encryption and decryption apparatus in theshort message.
Owner:ZTE CORP
Quick logistics intelligent information encryption method
ActiveCN112184111AImplement encryption protectionAvoid leaking secretsDigital data protectionLogisticsLogistics managementEngineering
The invention relates to a quick logistics intelligent information encryption method. A sender logistics management terminal forms an express waybill number-weather number database containing a corresponding relationship between an express waybill number and a weather condition, and respectively encrypts by using different encryption methods to obtain two pieces of secret embedding information; the weather number corresponding to the current express waybill number and the two secret embedding information are fused to obtain intelligent secret embedding information, and the received intelligentsecret embedding information on the express waybill is sent to a logistics company management system by a receiver logistics management terminal; and the logistics company management system feeds back express waybill information (including sender information and receiver information) corresponding to the intelligent secret embedding information to the receiver logistics management terminal, and the receiver logistics outlet arranges personnel to deliver the express waybill. The sender and receiver information on the express waybill is always presented in an encrypted form of intelligent secret embedding information, and only the logistics company management system and the sender logistics management terminal master the personal information of the sender and the receiver, so that the information encryption protection in the logistics process is effectively realized.
Owner:ZHEJIANG WANLI UNIV
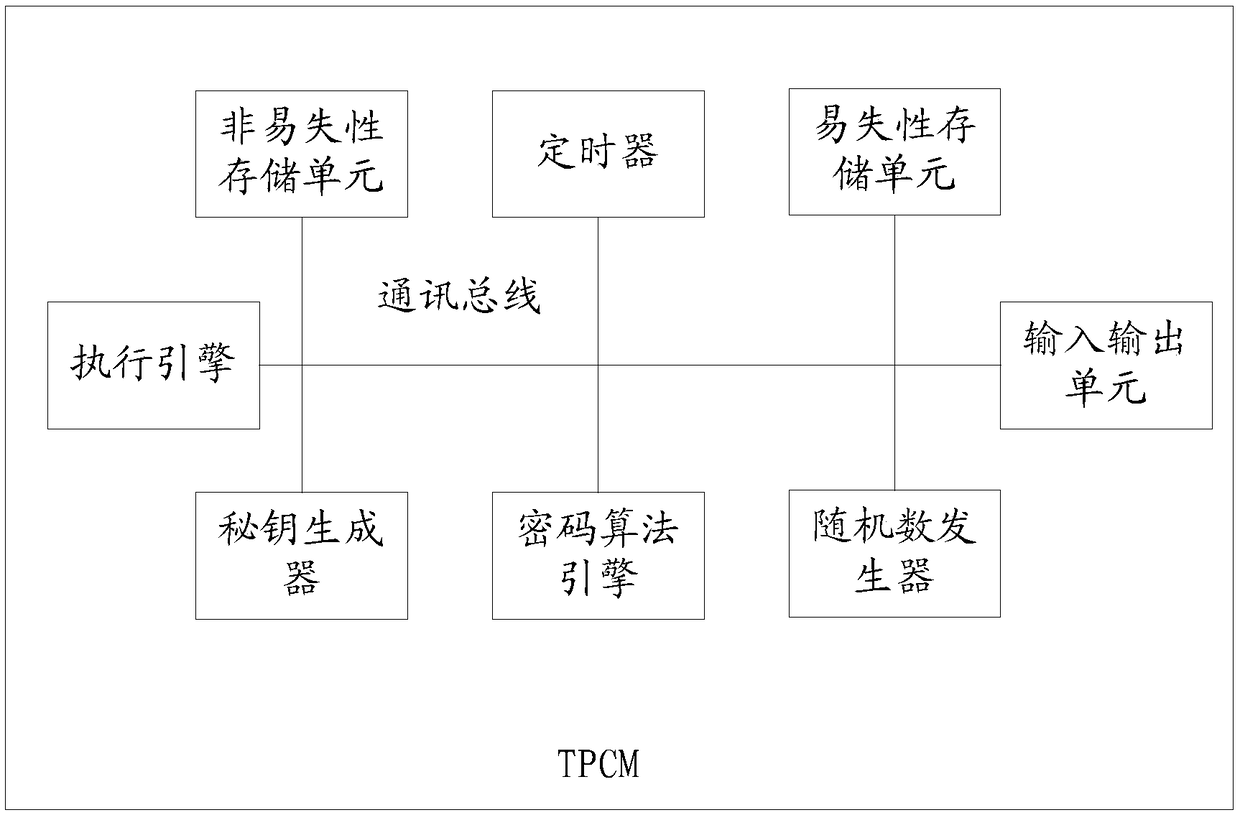
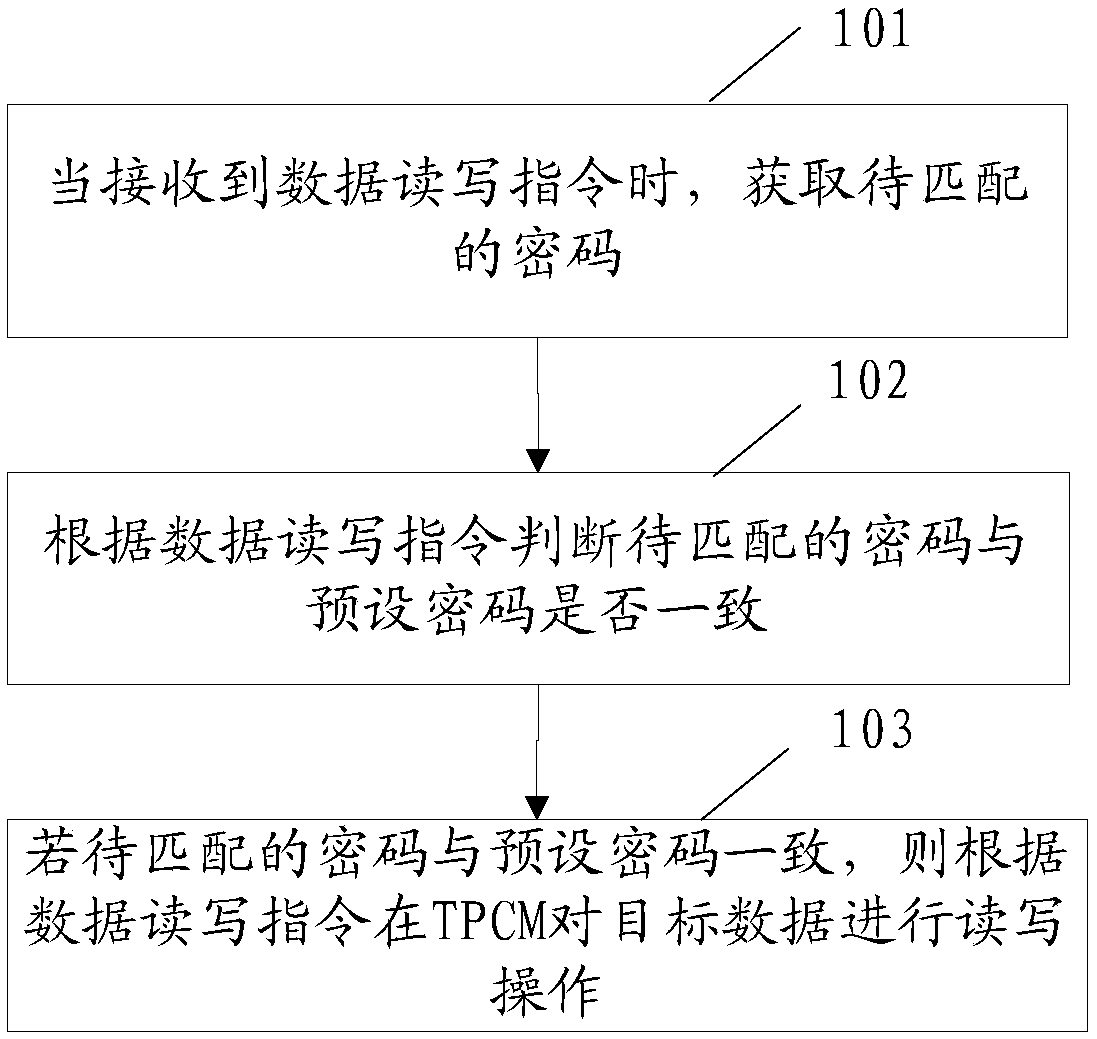
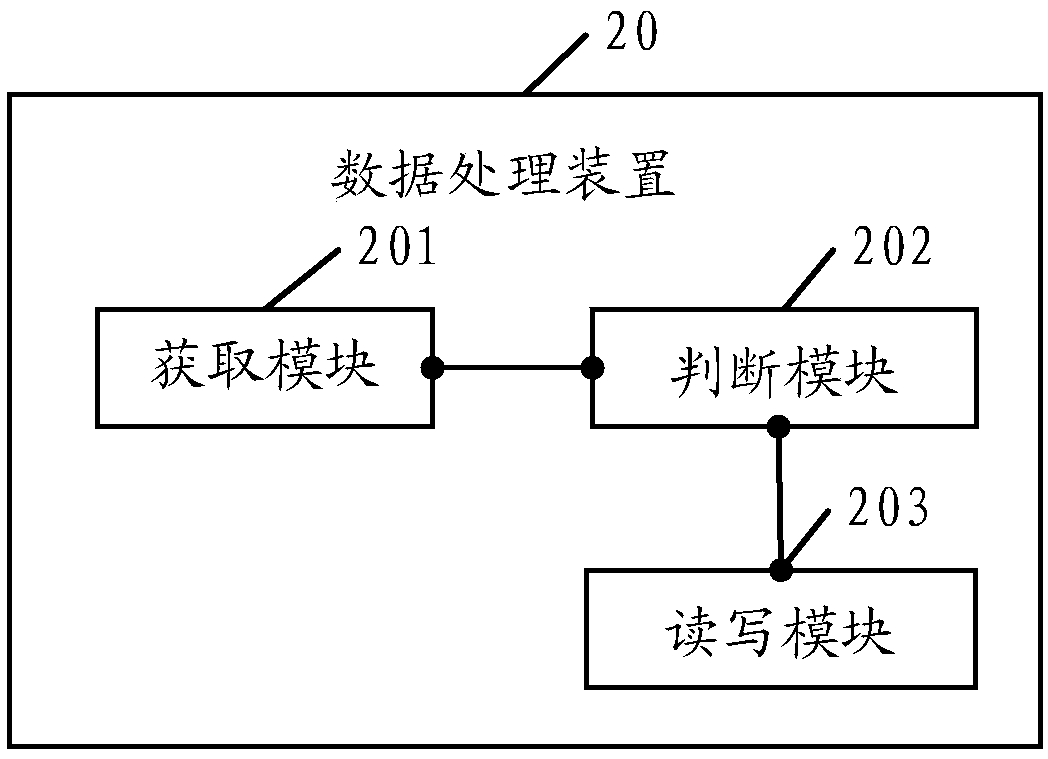
A data processing method and a related apparatus
InactiveCN109145627AImplement encryption protectionImprove securityDigital data protectionPasswordComputer module
The embodiment of the invention discloses a data processing method. The method is applied to a trusted platform control module TPCM. The method comprises the following steps: when receiving a data read-write instruction, obtaining a password to be matched; judging whether the password to be matched is consistent with a preset password according to the data reading and writing instruction; if the password to be matched coincides with the preset password, the target data being read and written in the TPCM according to the data read / write instruction. The embodiment of the invention also discloses a data processing device. The embodiment of the invention provides a method, which realizes the encryption protection of data and improves the security of data.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
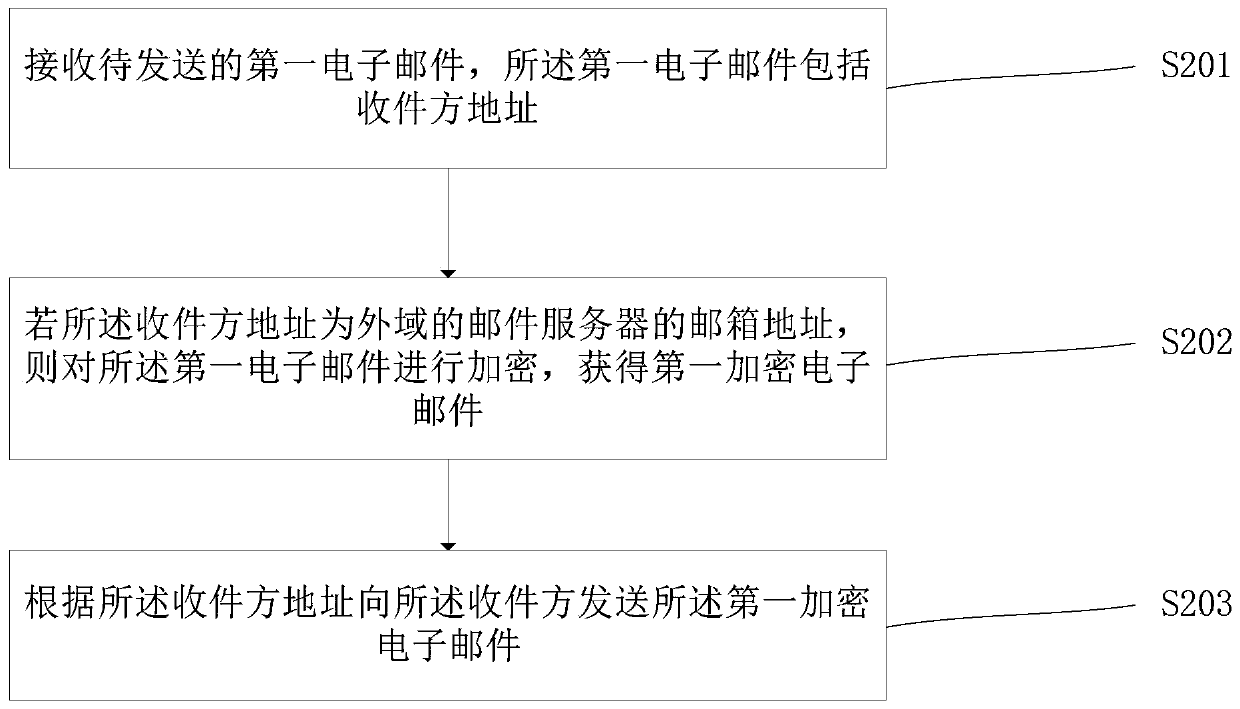
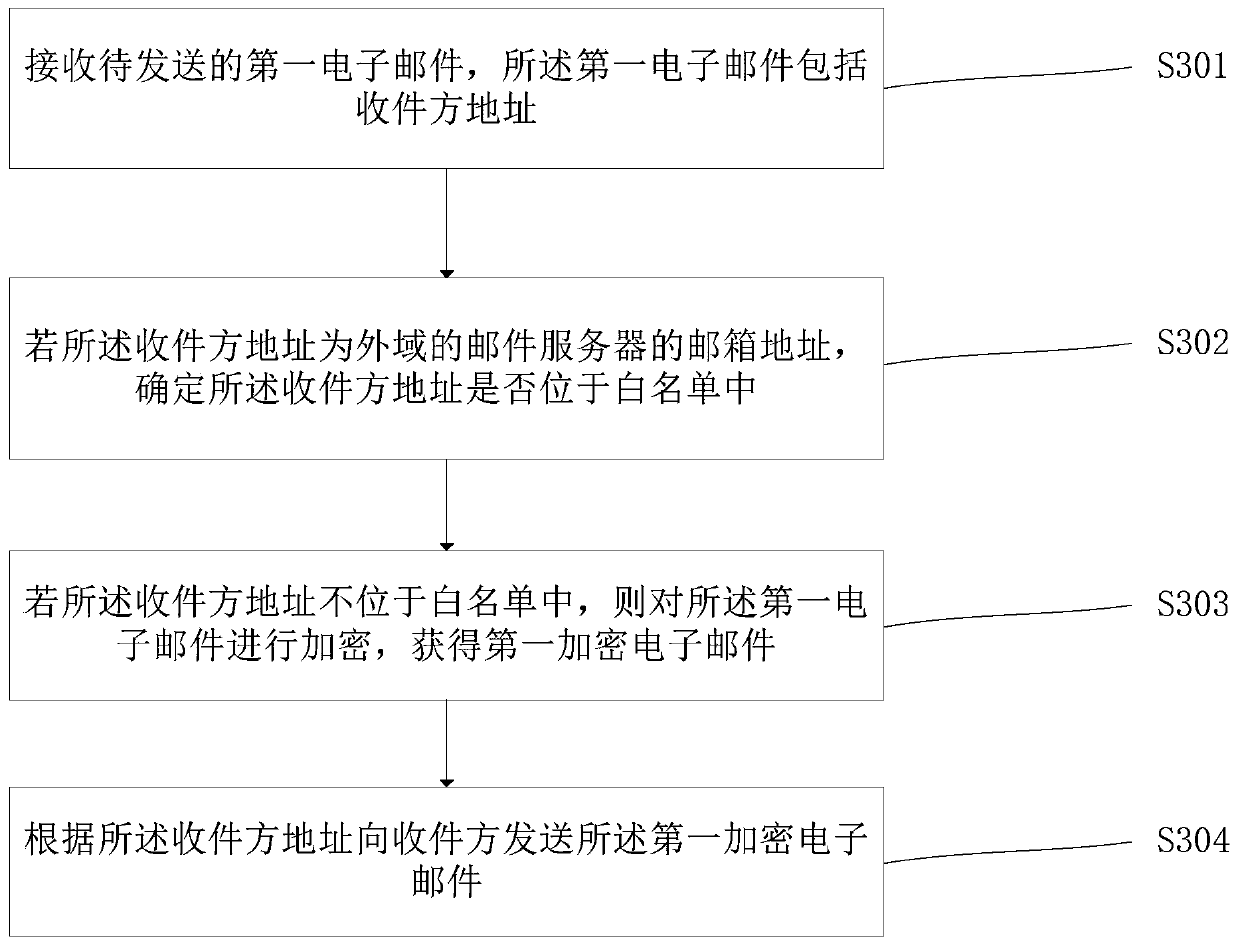
E-mail processing method and processing gateway
InactiveCN110324235AImplement encryption protectionEnsure safetyNetwork connectionsElectronic mailEncryption
The invention provides an E-mail processing method and a processing gateway. The E-mail processing method comprises the steps of receiving a first E-mail to be sent wherein the first E-mail comprisesa receiver address; if the address of the receiver is the mailbox address of a mail server of an external domain, encrypting the first electronic mail to obtain a first encrypted electronic mail; andsending the first encrypted e-mail to a receiver according to the receiver address. According to the embodiment of the invention, encryption protection is carried out on the e-mail sent to the outer domain, the safety of e-mails is improved, and meanwhile, the problems that an e-mail processing method in the prior art is easy to make mistakes, tedious in operation and low in efficiency are solved.
Owner:北京十安赛恩科技有限公司
Supervisable zero-knowledge proof verification method and system in block chain
PendingCN113159774AImplement encryption protectionSupport authenticityPayment protocolsEnergy efficient computingRing signatureData authenticity
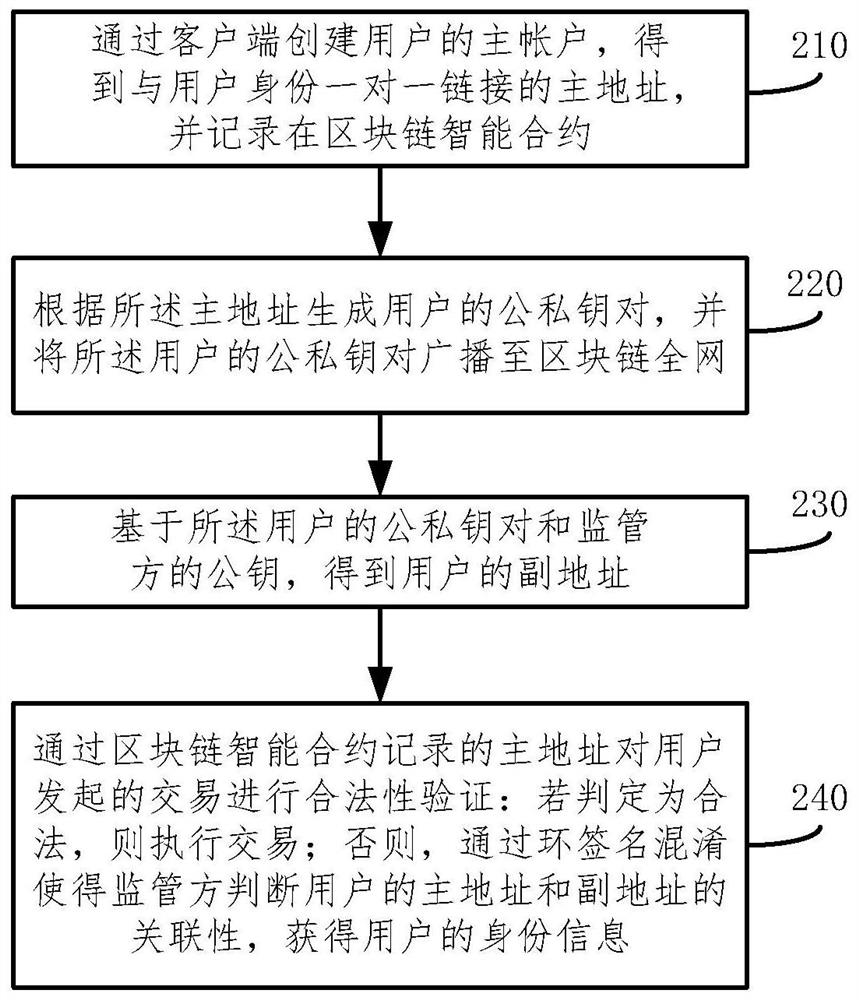
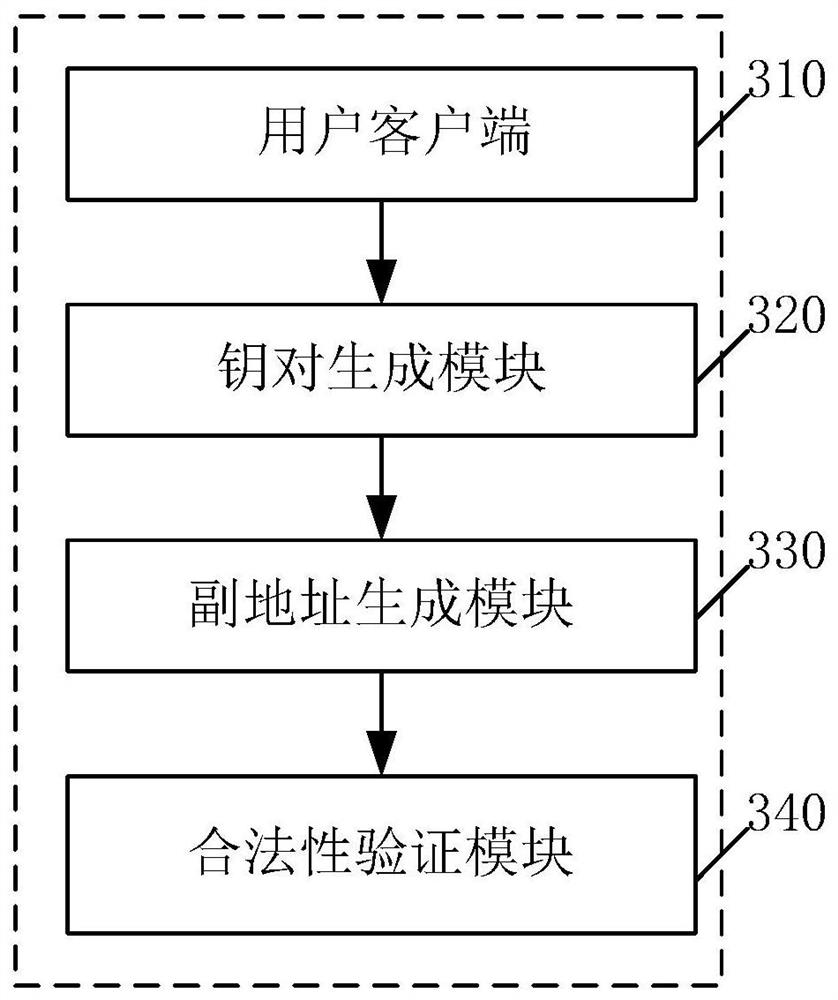
The invention provides a supervisible zero-knowledge proof verification method and system in a block chain, and the method comprises the steps: creating a main account of a user through a client, obtaining a main address which is in one-to-one connection with the identity of the user, and recording the main address in a block chain smart contract; generating a public and private key pair of the user according to the main address, and broadcasting the public and private key pair of the user to the whole block chain network; obtaining a secondary address of the user based on the public and private key pair of the user and the public key of the supervisor; performing legality verification on the transaction initiated by the user through the main address recorded by the block chain smart contract; if it is judged that the transaction is legal, executing the transaction; otherwise, enabling the supervisor to judge the relevance between the primary address and the secondary address of the user through ring signature confusion, and obtaining the identity information of the user. According to the embodiment of the invention, the encryption protection of supervisible anonymous and sensitive data of the user identity is realized, and the verification of data authenticity by a consensus node is supported.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Java application program encryption method and device
InactiveCN111291333AImplement encryption protectionHas the function of interfering with decompilationDigital data protectionPlatform integrity maintainanceJavaTheoretical computer science
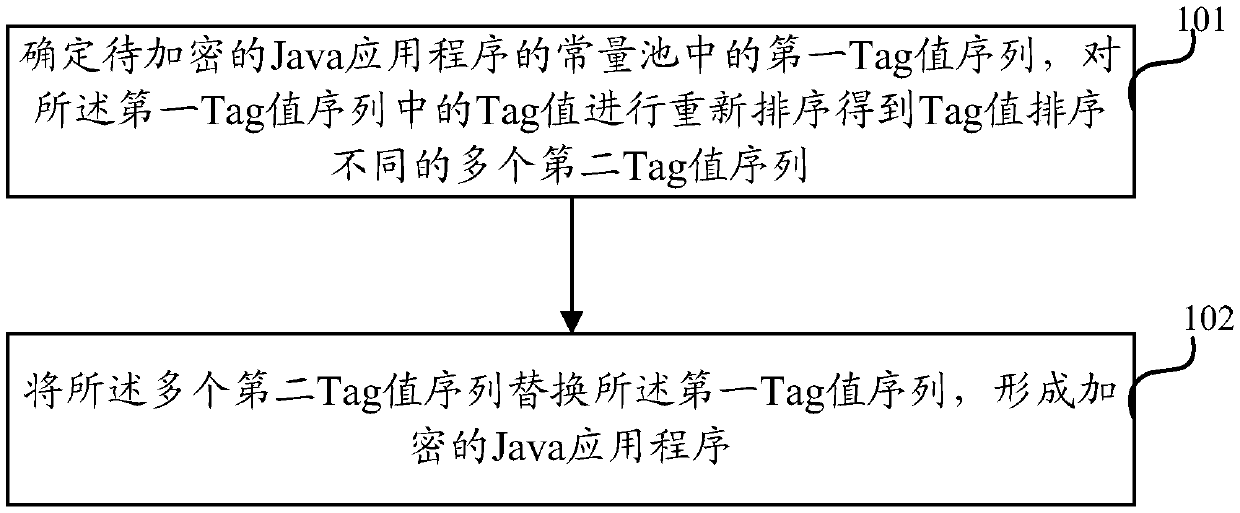
The invention discloses a Java application program encryption method and device, and is applied to the technical field of electronics. The method comprises the following steps: determining a first Tagvalue sequence in a constant pool of a Java application program to be encrypted, and reordering Tag values in the first Tag value sequence to obtain a plurality of second Tag value sequences with different Tag value orders; and replacing the first Tag value sequence with the plurality of second Tag value sequences to form an encrypted Java application program. The technical problems of poor security of the Java application program and leakage of important algorithms and data in the prior art are solved.
Owner:中国移动通信集团陕西有限公司 +1
Database encryption method supporting combinable SQL query
PendingCN113704303AReduce leakageVersatileDatabase updatingDigital data protectionDatabase encryptionData query
The invention discloses a database encryption method supporting combinable SQL query. The scheme mainly comprises the following steps that: (1) based on an encryption method provided by the invention, a user encrypts and preprocesses data, and uploads an encryption result and preprocessed data to a service provider; (2) an SQL query instruction is set and uploaded: the user uploads a query instruction to a service provider according to an actual demand, and uploads an auxiliary parameter used for querying the instruction at the same time; and (3) data query is performed: the service provider performs SQL query according to a query instruction and auxiliary parameters received from the user, stores a calculation result, updates data and returns a query result to the user. The method can be applied to data encryption storage and encrypted data query in actual life and business, and has the advantages of being high in universality, safe, efficient, capable of protecting privacy, easy and convenient to use, high in efficiency, small in memory and time consumption and the like.
Owner:ZHEJIANG UNIV
An information construction method for notarization to participate in judicial auxiliary affairs
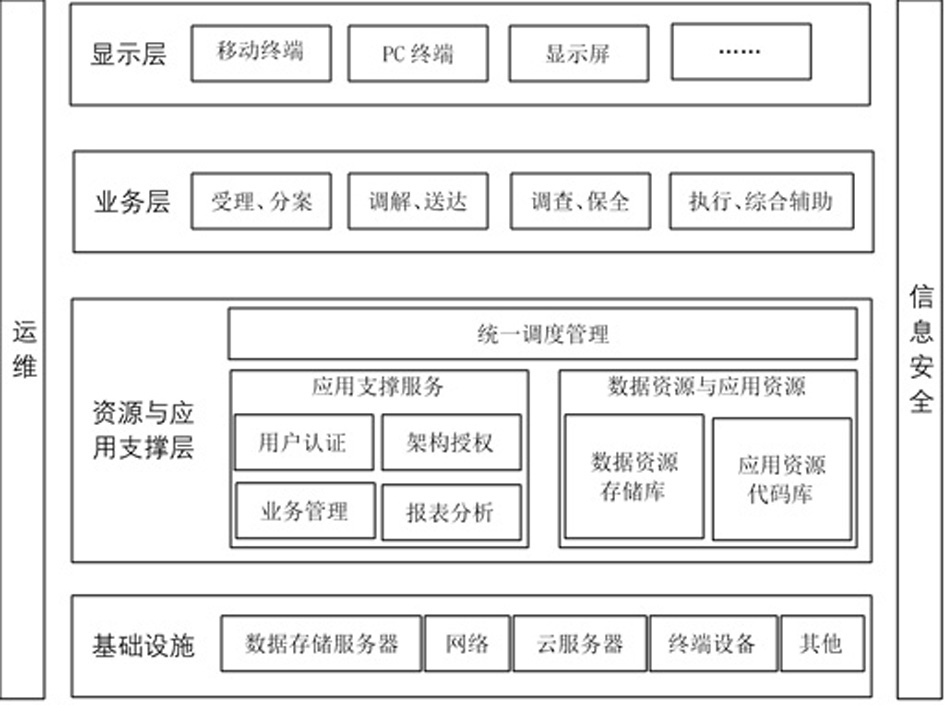
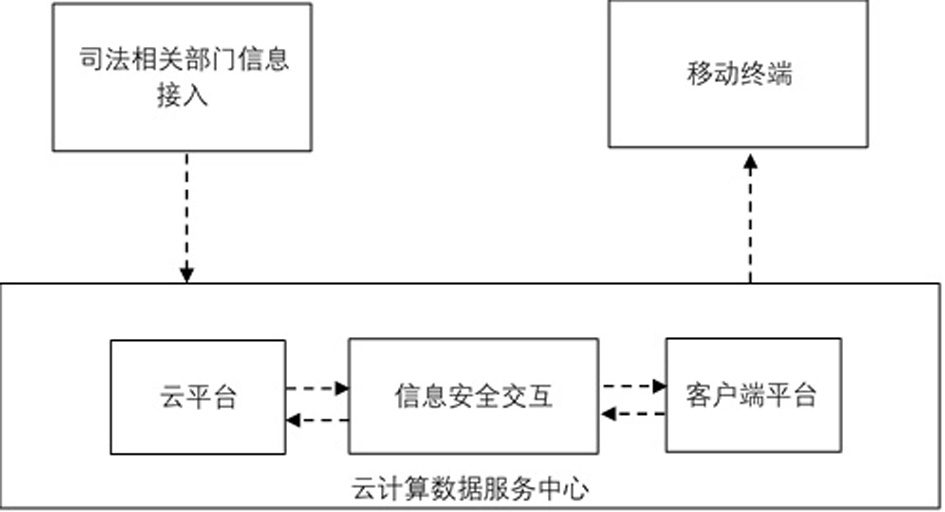
ActiveCN112766917BRealize managementImprove work efficiencyMultimedia data indexingOffice automationInformatizationInformation security
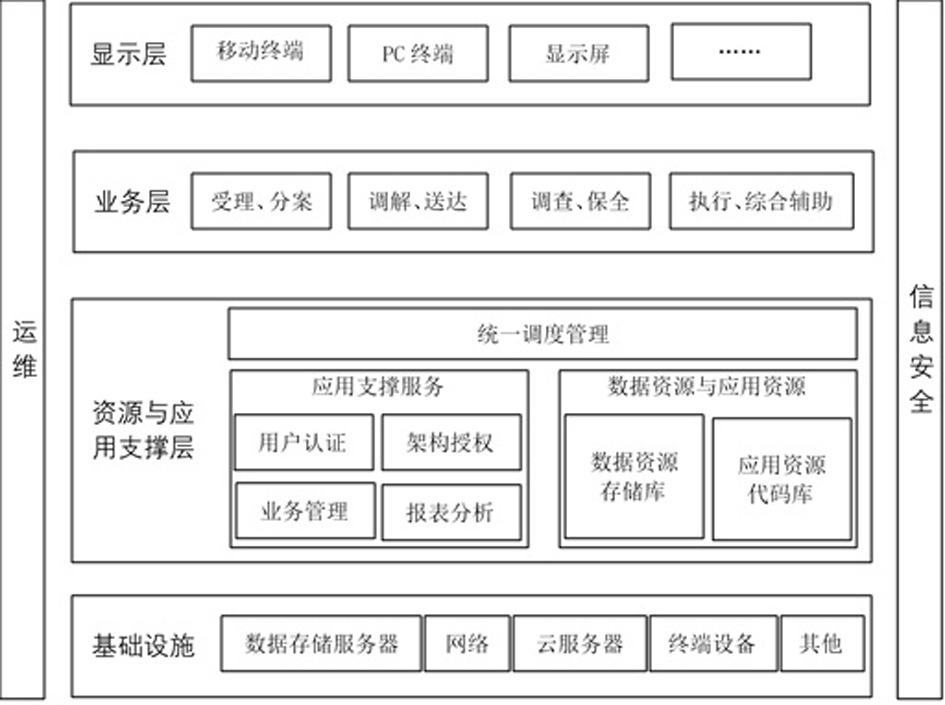
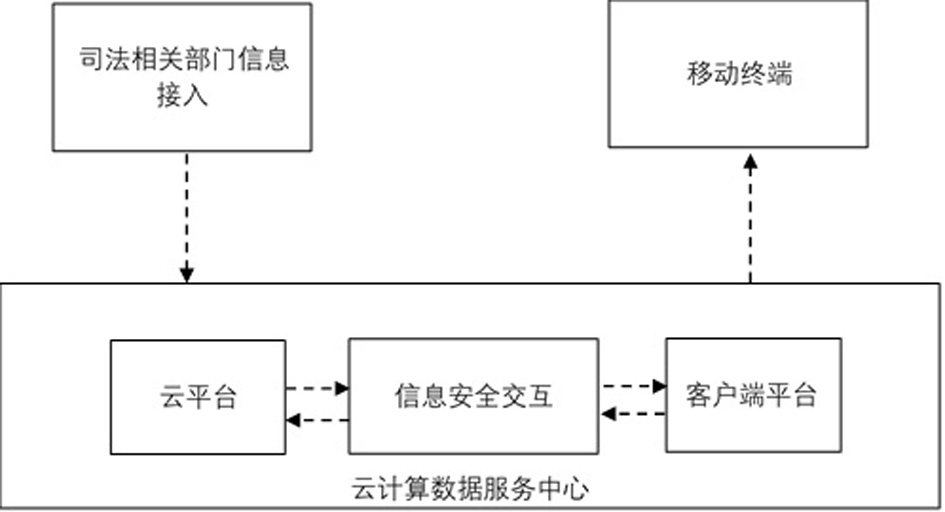
The present invention is an informatization construction method for notarization to participate in judicial auxiliary affairs, which belongs to the technical field of informatization construction methods for notarization in judicial auxiliary affairs; the technical problem to be solved is: to provide an informatization construction method for notarization to participate in judicial auxiliary affairs Improvement; the technical solution adopted to solve the above-mentioned technical problems is: an information construction method for notarization to participate in judicial auxiliary affairs, including the following steps: constructing the overall information architecture of judicial auxiliary affairs: the overall information architecture includes the infrastructure layer, Resource and application support layer, business application layer, display layer, and operation and maintenance management subsystem, information security subsystem, and interface specification subsystem as auxiliary management; build infrastructure layer; build resource and application support layer; build business application layer; Build the display layer; build the operation and maintenance management subsystem; build the information security subsystem; build the interface specification subsystem; the invention is applied to judicial assistance.
Owner:山西瑞呈物联网科技有限公司
Production data processing method and device, computer equipment and storage medium
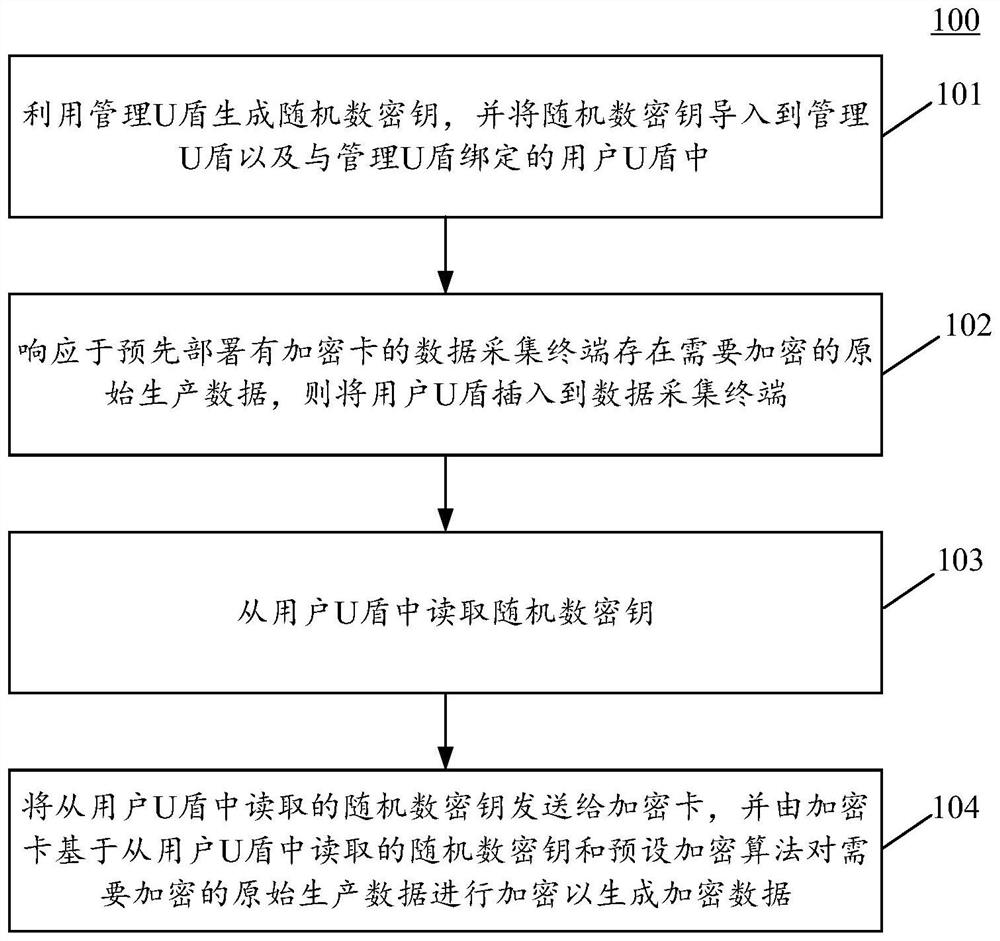
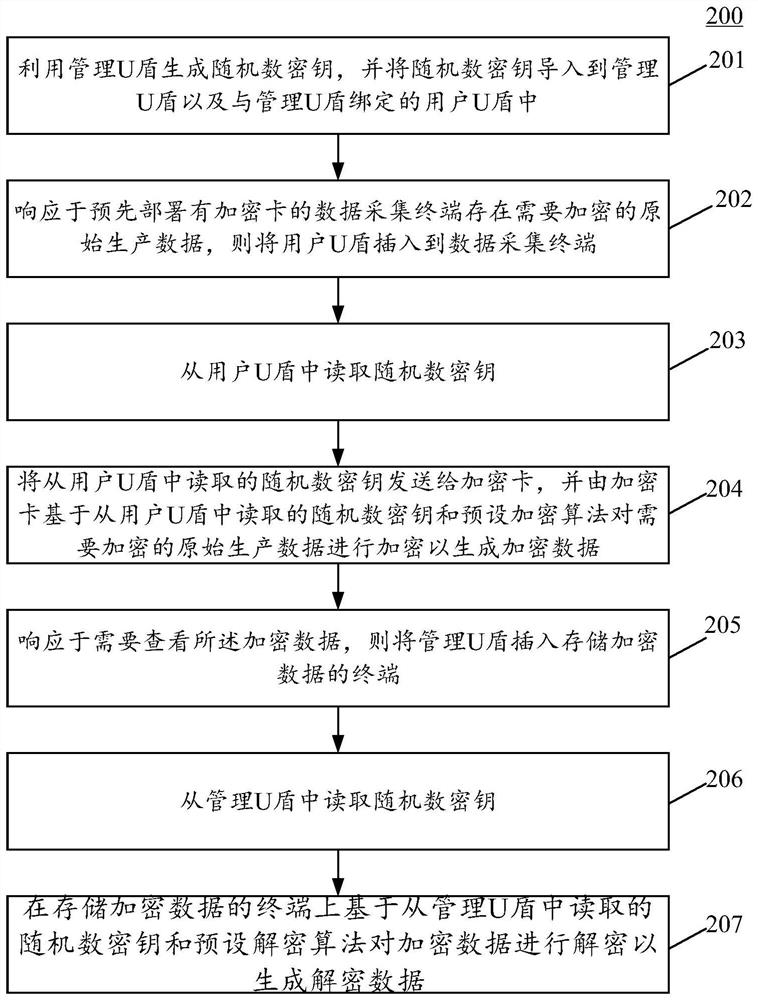
PendingCN114598466AImplement encryption protectionImprove securityKey distribution for secure communicationUser identity/authority verificationSoftware engineeringData acquisition
The invention relates to the field of data processing, in particular to a production data processing method and device, computer equipment and a storage medium. The method comprises the following steps: generating a random number key by utilizing a management U key, and importing the random number key into the management U key and a user U key bound with the management U key; in response to the situation that original production data needing to be encrypted exist in a data acquisition terminal which is pre-deployed with an encryption card, inserting the user USB key into the data acquisition terminal; reading a random number key from the user USB key; and sending the random number key read from the user USB key to an encryption card, and encrypting original production data needing to be encrypted by the encryption card based on the random number key read from the user USB key and a preset encryption algorithm to generate encrypted data. According to the scheme, encryption protection on the production data is realized through the USB key and the encryption card, and the security of the data is improved.
Owner:SHANDONG YUNHAI GUOCHUANG CLOUD COMPUTING EQUIP IND INNOVATION CENT CO LTD
A method and device for encrypting and decrypting information in short messages
ActiveCN107889102BImplement encryption protectionReduce risk of leakageInformation formatContent conversionInternet privacyEncryption
A method and device for encrypting and decrypting information in a short message. The method comprises: a lower layer of a mobile terminal receives at least one original short message comprising private information; when the original short message satisfies an encryption criterion, the lower layer of the mobile terminal encrypts the private information in the original short message to generate an encrypted short message, transmits to a short message application of the mobile terminal the encrypted short message; and upon receiving the encrypted short message, the short message application of the mobile terminal decrypts the encrypted short message.
Owner:ZTE CORP
Trusted cryptographic module security management method and system
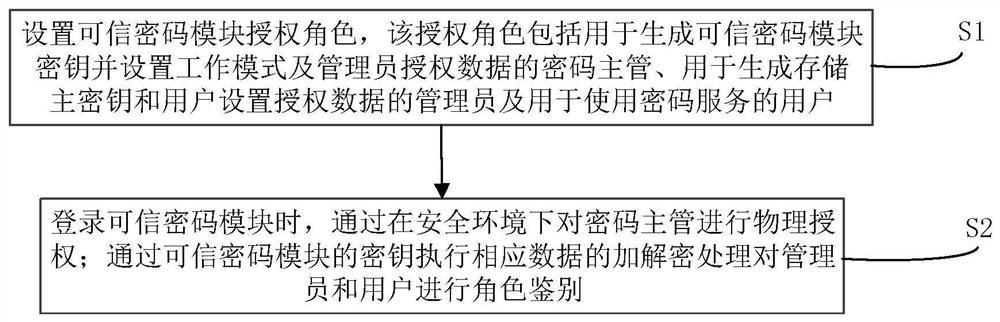
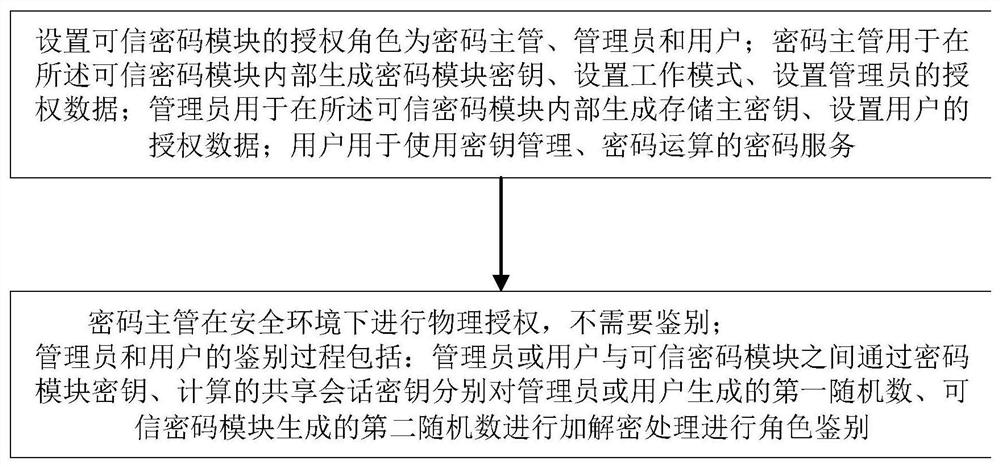
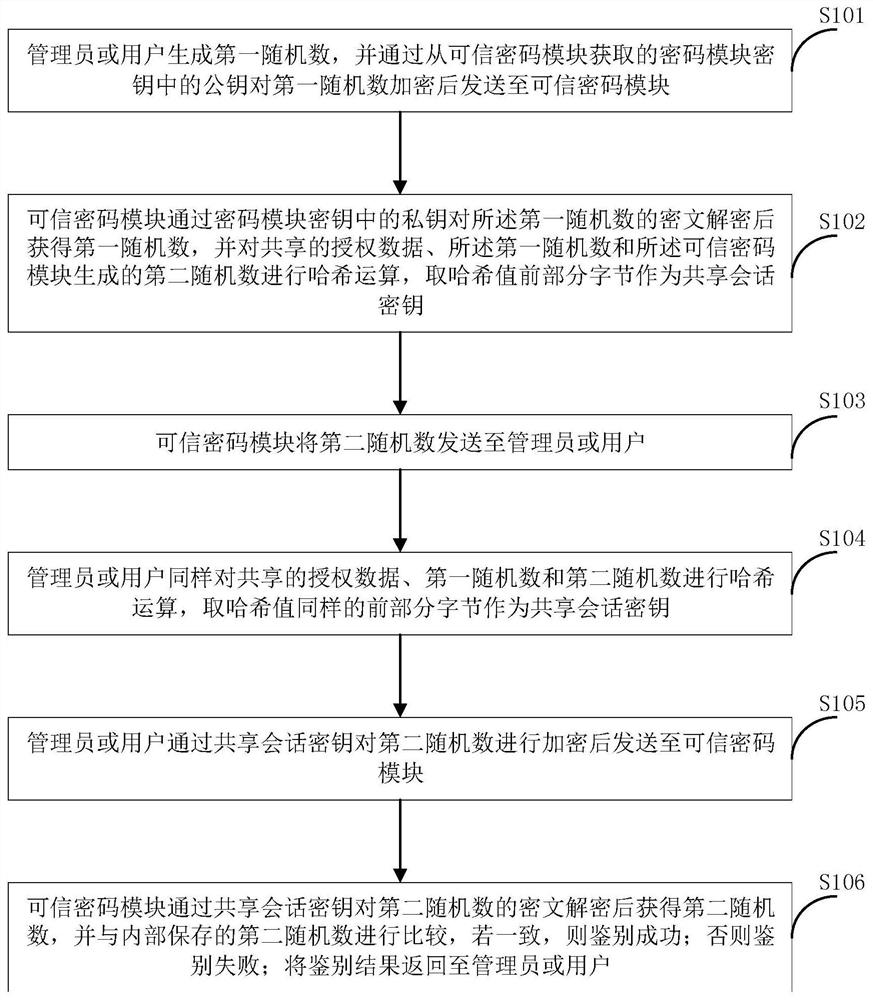
ActiveCN112883396AImplement encryption protectionSafe generationDigital data protectionDigital data authenticationPassword managerAuthorization
The invention relates to the technical field of information security, in particular to a trusted cryptographic module security management method and system. The authorization role comprises a password manager used for generating a trusted password module key and setting a working mode and administrator authorization data, an administrator used for generating a storage main key and user setting authorization data, and a user used for using password service; when the trusted password module is logged in, physical authorization is carried out on a password manager in a safe environment, and role identification is carried out on an administrator and a user by executing data encryption and decryption through the trusted password module. Authorization roles of the trusted password module are set as the password manager, the administrator and the user, different role tasks are distinct, and physical identification under a safe environment is carried out on the password manager, so that role setting and task distinct can be effectively ensured, illegal users are prevented from logging in and accessing the trusted password module, and role and identification security management in the trusted cryptographic module is ensured.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
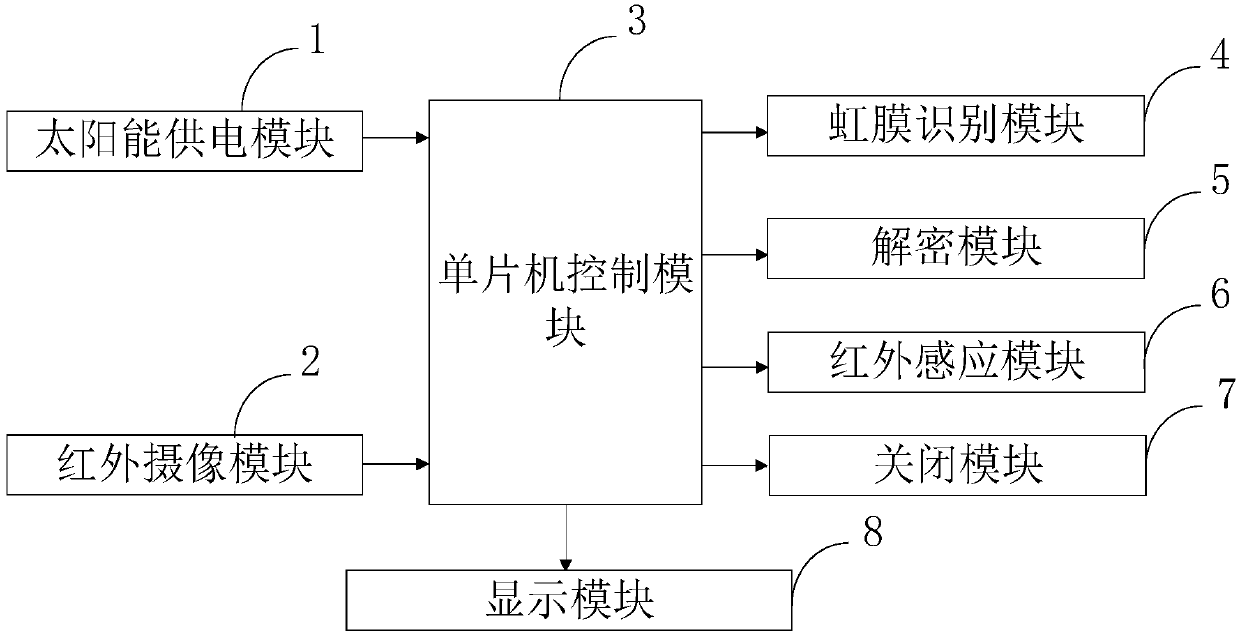
Access control system used for electronic code
InactiveCN108648307AWork lessPrevent leakageAcquiring/recognising eyesDigital data protectionMicrocontrollerElectron
The invention belongs to the technical filed of access control, and discloses an access control system used for an electronic code. The access control system comprises a solar energy power supply module, an infrared shooting module, a single-chip microcomputer control module, an iris recognition module, a decryption module, an infrared induction module, a closure module, and a display module. Thecontinuous solar energy can be obtained through the solar energy power supply module, continuous operation of the access control system can be guaranteed, energy is saved, and the access control system has the advantages of economy and environmental protection; the iris characteristic information of the user can be obtained through the iris identification module, a pre-generated vault value is read, and a decryption secret key is calculated; whether the calculated decryption secret key is matched with a preset encryption key is determined, if the result is positive, the iris identification issuccessfully confirmed, encryption protection is carried out on a terminal, the leakage of the iris characteristic information is effectively prevented, and the security is high.
Owner:QINGDAO TECHN COLLEGE
Data encryption method, system and storage medium of coding technology
ActiveCN114465826BReduce storageDoes not affect accuracyEncryption apparatus with shift registers/memoriesInterval dataDatabase
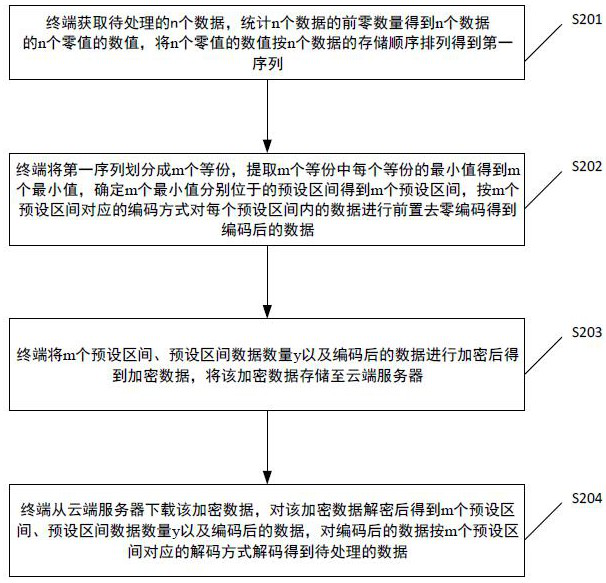
The present application provides a data encryption method, system and storage medium of an encoding technology. The method includes: a terminal obtains n pieces of data to be processed, counts the number of the first zeros of the n pieces of data, and obtains the numerical value of the n pieces of zero values of the n pieces of data, Arrange the n zero-valued values according to the storage order of the n data to obtain the first sequence; the terminal divides the first sequence into m equal parts; the terminal divides the m preset intervals, the preset interval data quantity y, and the encoded After the data is encrypted, encrypted data is obtained, and the encrypted data is stored in the cloud server; the terminal downloads the encrypted data from the cloud server, decrypts the encrypted data, and obtains m preset intervals, the preset interval data quantity y, and the encoded data , and decode the encoded data according to the decoding modes corresponding to the m preset intervals to obtain the data to be processed. The technical solution provided by the present application has the advantage of saving storage space.
Owner:SHENZHEN XINGCHENG TECH CO LTD
Informatization construction method for notarization participation of judicial assistant affairs
ActiveCN112766917ARealize managementImprove work efficiencyMultimedia data indexingOffice automationInformatizationConstruction engineering
The invention discloses an informatization construction method for notarization participation of judicial assistance affairs, and belongs to the technical field of informatization construction methods for notarization participation of judicial assistance affairs. The technical problem to be solved is to provide an improvement of an informatization construction method for notarization participation in judicial assistance affairs. The informatization construction method for notarization participation of judicial assistance affairs, wherein the method comprises the following steps: constructing an informatization overall architecture of judicial assistant affairs, wherein the informatization overall architecture comprises an infrastructure layer, a resource and application support layer, a business application layer, a display layer, and an operation and maintenance management subsystem, an information security subsystem and an interface specification subsystem which are used as assistant management; constructing an infrastructure layer; constructing a resource and application support layer; constructing a business application layer; constructing a display layer; constructing an operation and maintenance management subsystem; constructing an information security subsystem; and constructing an interface specification subsystem. The method is applied to judicial assistance.
Owner:山西瑞呈物联网科技有限公司
Electronic device control method and electronic device
InactiveCN110111718AImplement encryption protectionImprove securityStatic indicating devicesInformation securityEmbedded system
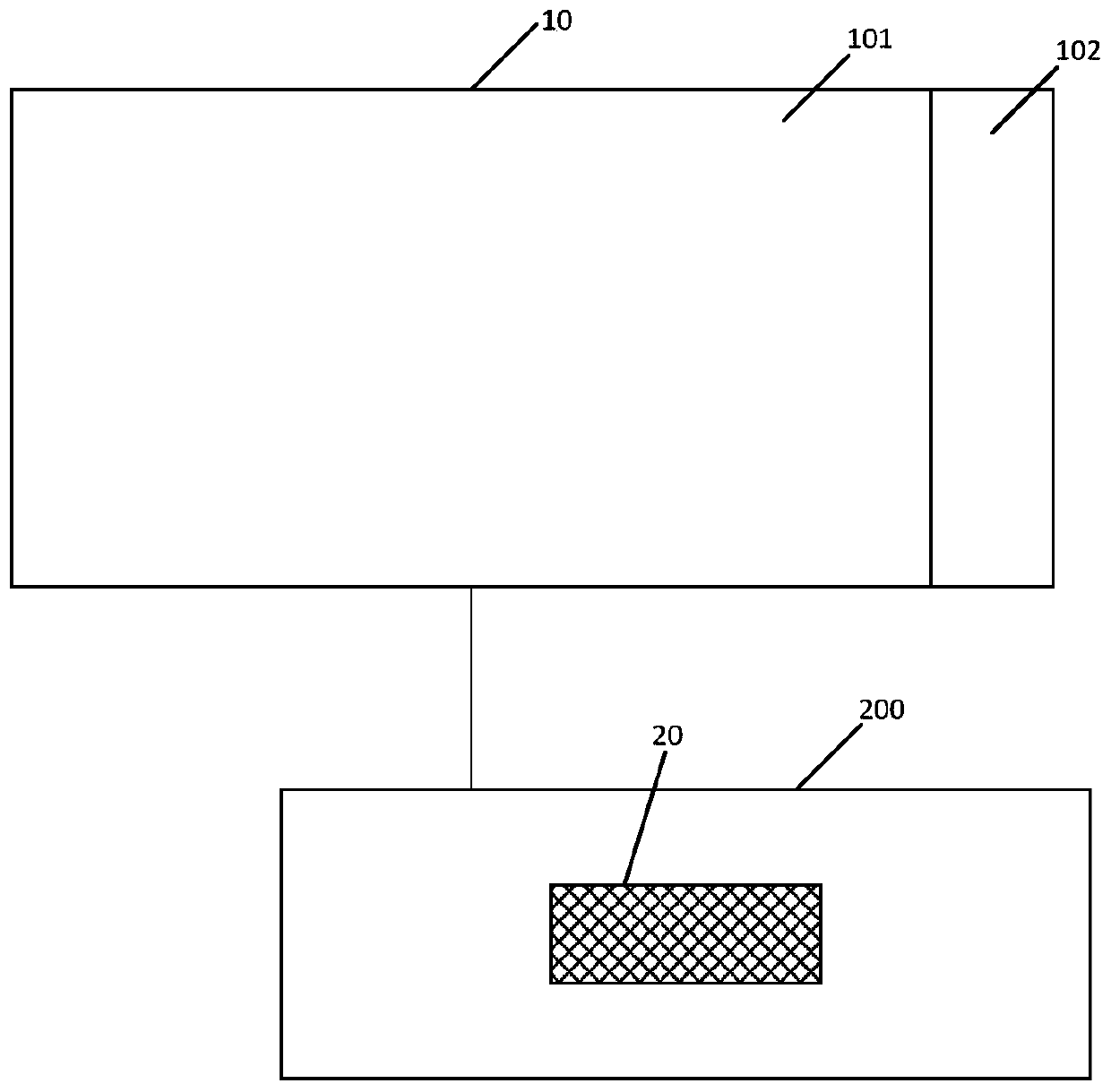
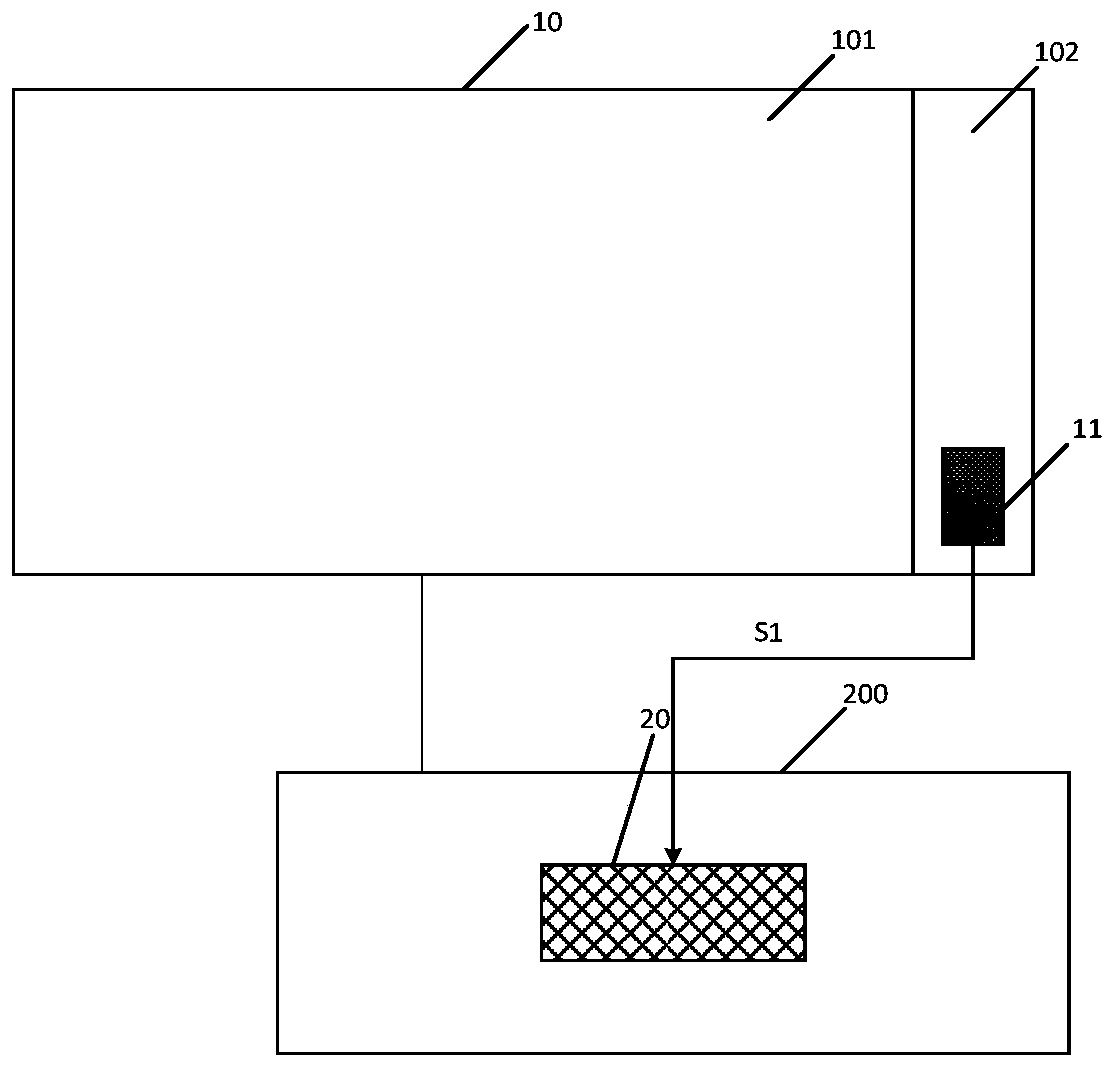
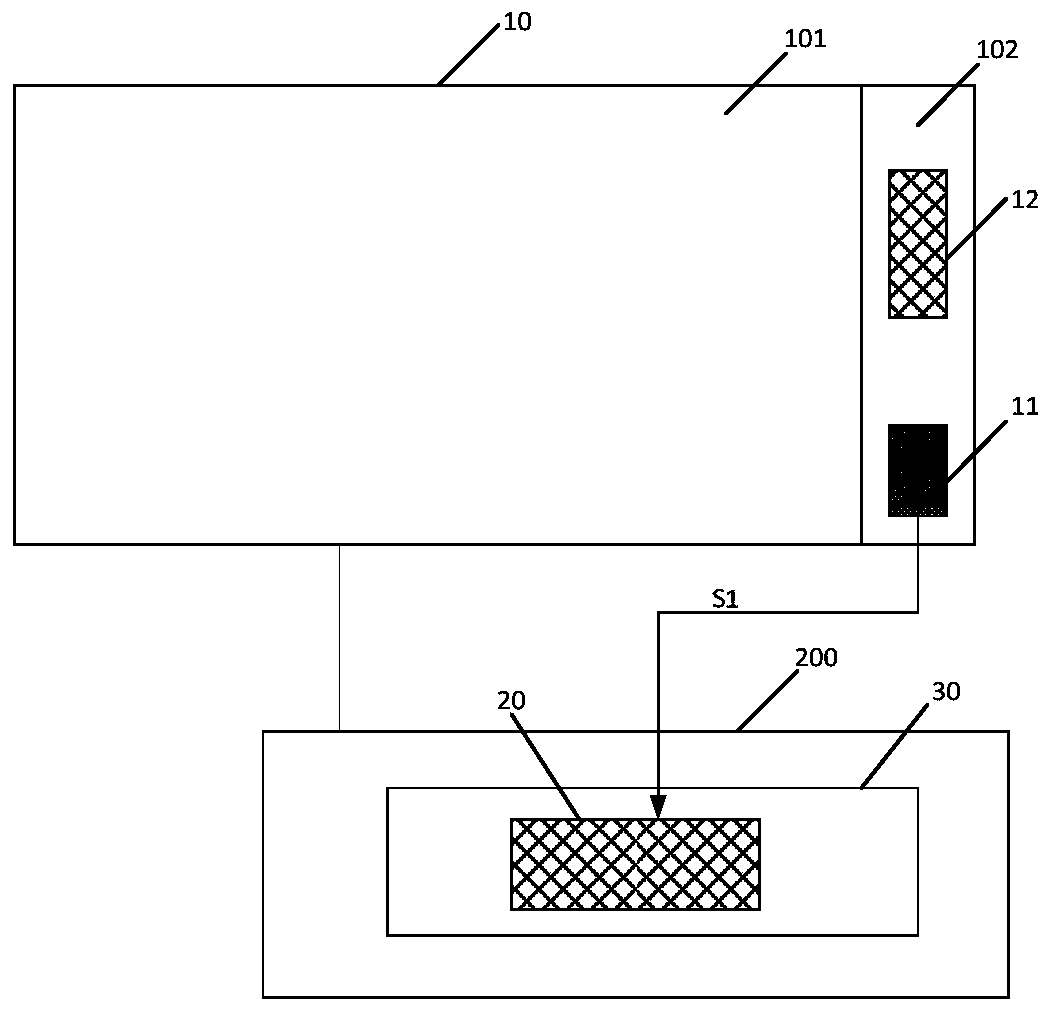
The invention provides an electronic device control method and an electronic device. The electronic device comprises a display panel; a driving assembly arranged outside the display panel, the drivingassembly comprises an optimization module, and reference information is stored in the optimization module in advance; the method comprises the steps that when it is detected that the display panel isstarted, verification information is acquired; when the verification information is matched with the reference information, the optimization module is controlled to be started; and when the verification information is not matched with the reference information, the optimization module is controlled to close. According to the electronic device control method and an electronic device, the information security of the driving assembly can be improved.
Owner:TCL CHINA STAR OPTOELECTRONICS TECH CO LTD
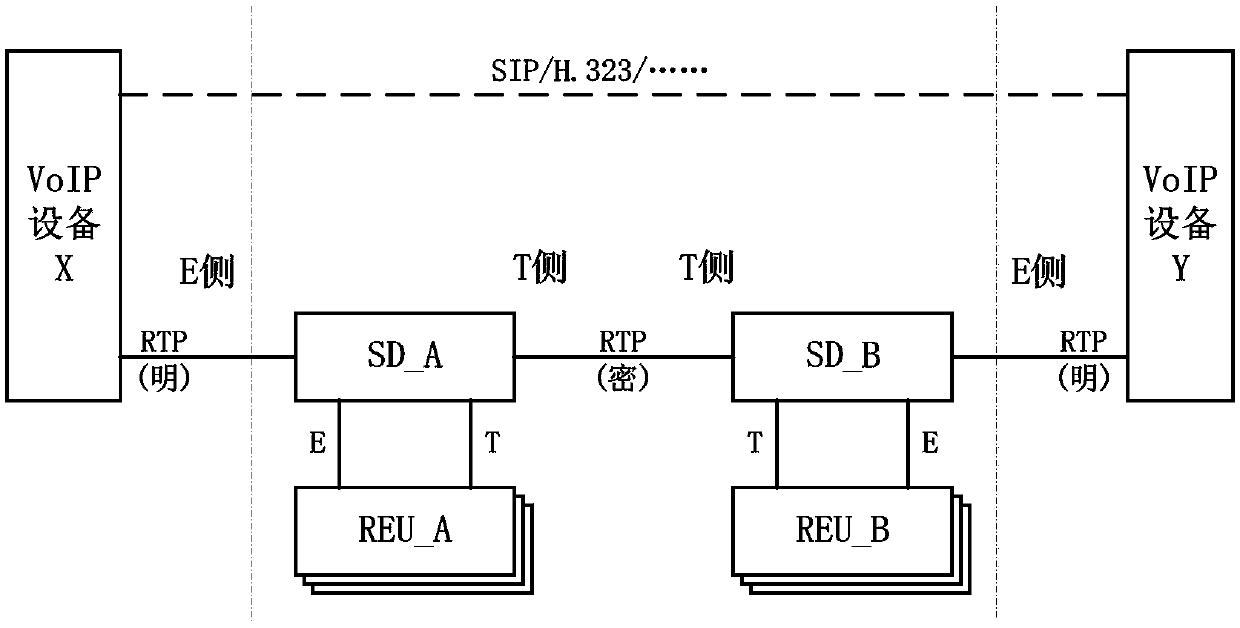
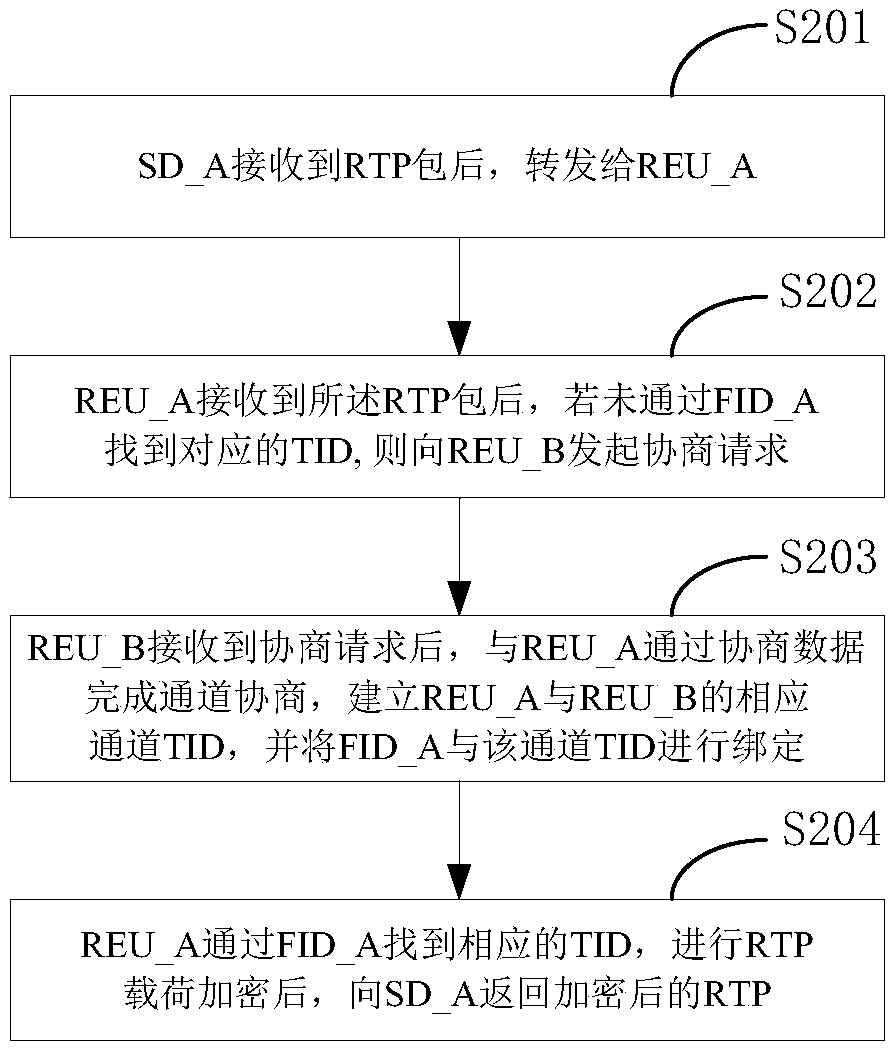
Media data encryption method based on RTP in VoIP communication network
ActiveCN109672692ALow cost of network transformationUser indifferentInterconnection arrangementsTransmissionProtocol for Carrying Authentication for Network AccessComputer hardware
The invention relates to a media data encryption method based on an RTP in a VoIP communication network, and belongs to the technical field of communication. The method comprises the following steps that SD_A receives an RTP packet and forwards the RTP packet to REU_A; after the REU_A receives the RTP packet, if the REU_A does not find a corresponding TID through FID_A, the REU_A initiates a negotiation request to REU_B; after the REU_B receives the negotiation request, the REU_B completes channel negotiation with the REU_A through the negotiation data, establishes a corresponding channel TIDof the REU_A and the REU_B, and binds the FID_A with the channel TID; and the REU_A finds the corresponding TID through the FID_A, carries out RTP load encryption, and returns the encrypted RTP to theSD_A. According to the method, the media data borne on the RTP can be encrypted and protected no matter what communication protocol is adopted by a signaling plane of the VoIP and no matter encryption equipment is deployed at any position of a communication link.
Owner:XINGTANG TELECOMM TECH CO LTD +1
Signaling for reposition and data ciphering method, system and radio network controller
ActiveCN101388829BImplement encryption protectionImplement encrypted communicationData switching by path configurationSecurity arrangementPlaintextRadio Network Controller
The invention discloses a repositioned singling and a method for encrypting data, which comprises the following steps: receiving initial encrypting sequence numbers which are sent by an SRNC by the TPNC, adopting an encrypting RRC singling and user data of the initial encrypting sequence numbers by the TPNC, and then sending an encrypted wireless resource control singling and the user data to a UE. The invention further discloses the repositioned singling and a system with encrypting data, and a wireless network controller. The invention can enable the TPNC to be the same with the encrypting sequence numbers of both ends of the UE, and then can enable the TPNC and the both ends of the UE to obtain clear text data of the other party through decrypting, can guarantee the realization of the encrypting protection of RRC singling and the user data during the repositioning process, and can realize encrypting communication between the UE and the TRNC.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com