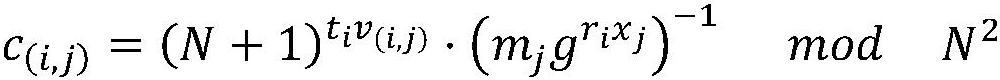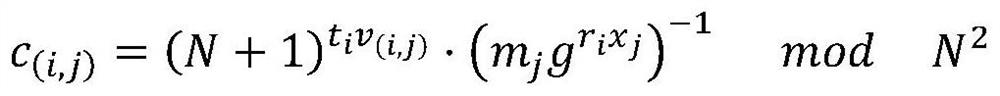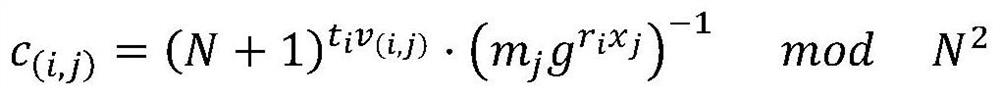Database encryption method supporting combinable SQL query
A database and data technology, which is applied in database update, digital data protection, electronic digital data processing, etc., can solve the problems of insecurity, user privacy exposure to service providers, and safe and efficient operation of unencrypted data. Less time consumption, strong versatility, and the effect of reducing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0082] Assume that user A of the sales company stores his own data set M in a service provider B, and requires service provider B not to obtain any information about M. In addition, user A requires the ability to perform operations on the data set M without revealing privacy (operations include but are not limited to update, insert, delete, add, search for specified keywords, and query specified ranges, such as returning orders with a transaction amount greater than 5,000). In order to solve this situation, utilize a kind of encryption database method that supports combinable SQL inquiry of the present invention, satisfy the requirement of user A, specifically comprise the following steps:
[0083] Step (1) Encrypting and storing data: User A encrypts and preprocesses data M, and uploads the encrypted result and preprocessed data to service provider B, who provides software, devices, and electronic equipment for running the database Or the storage medium is used to store the d...
Embodiment 2
[0149] The present invention discloses an encrypted database system that supports combinable SQL queries, which can perform any secure storage of user data provided by any embodiment of the present invention and support update, insertion, deletion, addition, search for specified keywords and user data. Query the capabilities of the specified range. The encrypted database system supporting combinable SQL queries includes a user device module and a service provider module; the user device module encrypts and preprocesses user data, and uploads the encrypted result and preprocessed data to the service provider module; The user module executes data operation instructions, uploads operation instructions to the service provider module according to actual needs, and the operation instructions include updating, inserting, deleting, summing, searching for specified keywords and querying specified ranges, and uploads auxiliary parameter operation instructions to the service provider mod...
Embodiment 3
[0151] In the field of database, an enterprise runs the database test international standard TPC-C to conduct transactions, that is, a certain cargo warehouse accepts orders from multiple users at the same time, and the warehouse has multiple transactions with these users at the same time. In order to save memory and improve performance, the warehouse encrypts and stores transaction data in the cloud. According to the needs of real-time transactions, the warehouse continuously submits SQL instructions to the encrypted data in the cloud (instructions include update, insert, delete, sum, search for specified keywords and query Specified range), according to the meaning of the order for the actual transaction, the order is divided into five sets:
[0152] 1. New-Order: The customer enters a new order transaction.
[0153] 2. Payment operation (Payment): update the customer account balance and reflect its payment status.
[0154] 3. Delivery (Delivery): delivery (simulating batch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com