Quantum encryption microwave relay communication system and quantum encryption microwave relay communication method
A microwave relay, quantum encryption technology, applied in key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
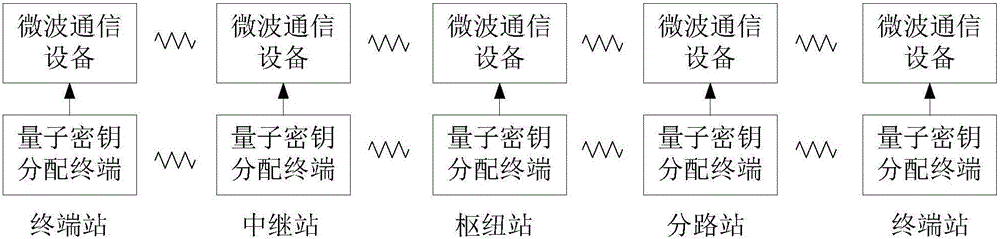
[0021] Such as figure 2 As shown in Fig. 3, this quantum encryption microwave relay communication system includes terminal station one, relay station and terminal station two; terminal station one, relay station and terminal station two are all made up of microwave communication equipment and quantum key distribution terminal; terminal station one It is used to use the key k1 to encrypt the key k to generate the key e1, e1=E(k1,k), and send the key e1 to the relay station; the relay station is used to use the key k1 to decrypt the key e1 Generate a key k, k=D(k1, e1), and use the key k2 to encrypt the key k to generate a key e2, e2=E(k2, k), and the relay station is also used to send the key e2 to Terminal station two; terminal station two is used to use key k2 to decrypt key e2 to generate key k, k=D(k2, e2); key k1 is generated by terminal station one and relay station through quantum key distribution terminal ; The key k2 is generated by the terminal station 2 and the rel...
Embodiment 2
[0023] see figure 2 , the quantum encryption microwave relay communication method, comprising a terminal station one, a relay station and a terminal station two; the terminal station one, the relay station and the terminal station two are all composed of microwave communication equipment and a quantum key distribution terminal; including the following steps:
[0024] 1) The terminal station 1 and the relay station produce the same key k1 through the quantum key distribution terminal;
[0025] 2) The terminal station 2 and the relay station produce the same key k2 through the quantum key distribution terminal;
[0026] 3) When terminal station 1 has key k and needs to be delivered to terminal station 2, first terminal station 1 uses key k1 to encrypt key k to generate key e1, e1=E(k1,k), and then terminal station - send the key e1 to the relay station;
[0027] 4) The relay station uses the key k1 to decrypt the key e1 to generate a key k, k=D(k1, e1), and the relay station ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com